Dell Brocade 5300, Brocade 6520, Brocade 6510, Brocade 6505, Brocade 300 Manual
...
53-1003130-01
27 June 2014
Fabric OS
Administrators Guide
Supporting Fabric OS 7.3.0
© 2014, Brocade Communications Systems, Inc. All Rights Reserved.
Brocade, the B-wing symbol, Brocade Assurance, ADX, AnyIO, DCX, Fabric OS, FastIron, HyperEdge, ICX, MLX, MyBrocade, NetIron, OpenScript, VCS, VDX, and Vyatta are registered trademarks, and The Effortless Network and the On-Demand Data Center are trademarks of Brocade Communications Systems, Inc., in the United States and in other countries. Other brands and product names mentioned may be trademarks of others.
Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to this document at any time, without notice, and assumes no responsibility for its use. This informational document describes features that may not be currently available. Contact a Brocade sales office for information on feature and product availability. Export of technical data contained in this document may require an export license from the United States government.
The authors and Brocade Communications Systems, Inc. assume no liability or responsibility to any person or entity with respect to the accuracy of this document or any loss, cost, liability, or damages arising from the information contained herein or the computer programs that accompany it.
The product described by this document may contain open source software covered by the GNU General Public License or other open source license agreements. To find out which open source software is included in Brocade products, view the licensing terms applicable to the open source software, and obtain a copy of the programming source code, please visit http://www.brocade.com/support/oscd.

Contents
Preface................................................................................................................................... |
19 |
Document conventions.................................................................................... |
19 |
Text formatting conventions................................................................ |
19 |
Command syntax conventions............................................................ |
19 |
Notes, cautions, and warnings............................................................ |
20 |
Brocade resources.......................................................................................... |
21 |
Contacting Brocade Technical Support........................................................... |
21 |
Document feedback........................................................................................ |
22 |
About This Document.............................................................................................................. |
23 |
Supported hardware and software.................................................................. |
23 |
What's new in this document........................................................................... |
24 |
Understanding Fibre Channel Services .................................................................................... |
25 |
Fibre Channel services overview.................................................................... |
25 |
Management server........................................................................................ |
26 |
Platform services............................................................................................. |
26 |
Platform services and Virtual Fabrics.................................................. |
26 |
Enabling platform services.................................................................. |
27 |
Disabling platform services ................................................................ |
27 |
Management server database........................................................................ |
27 |
Displaying the management server ACL............................................. |
28 |
Adding a member to the ACL.............................................................. |
28 |
Deleting a member from the ACL ....................................................... |
29 |
Viewing the contents of the management server database ............... |
30 |
Clearing the management server database........................................ |
30 |
Topology discovery......................................................................................... |
30 |
Displaying topology discovery status.................................................. |
31 |
Enabling topology discovery .............................................................. |
31 |
Disabling topology discovery............................................................... |
31 |
Device login..................................................................................................... |
32 |
Principal switch................................................................................... |
32 |
E_Port login process .......................................................................... |
32 |
Fabric login process ........................................................................... |
33 |
Port login process............................................................................... |
33 |
RSCNs................................................................................................ |
33 |
Duplicate Port World Wide Name....................................................... |
34 |
High availability of daemon processes............................................................ |
34 |
Performing Basic Configuration Tasks..................................................................................... |
37 |
Fabric OS overview......................................................................................... |
37 |
Fabric OS command line interface.................................................................. |
38 |
Console sessions using the serial port................................................ |
38 |
Telnet or SSH sessions....................................................................... |
39 |
Getting help on a command................................................................ |
40 |
Viewing a history of command line entries.......................................... |
41 |
Using fosexec to run commands on remote switches or domains...... |
43 |
Fabric OS Administrators Guide |
3 |
53-1003130-01 |
|
Password modification.................................................................................. |
45 |
Default account passwords............................................................... |
45 |
The switch Ethernet interface ....................................................................... |
46 |
Brocade Backbones.......................................................................... |
46 |
Brocade switches.............................................................................. |
46 |
Virtual Fabrics and the Ethernet interface......................................... |
46 |
Management Ethernet port bonding................................................. |
47 |
Displaying the network interface settings.......................................... |
48 |
Static Ethernet addresses................................................................. |
48 |
DHCP activation................................................................................ |
50 |
IPv6 autoconfiguration...................................................................... |
52 |
Date and time settings.................................................................................. |
53 |
Setting the date and time.................................................................. |
53 |
Time zone settings............................................................................ |
53 |
Network time protocol....................................................................... |
55 |
Domain IDs................................................................................................... |
56 |
Domain ID issues.............................................................................. |
56 |
Displaying the domain IDs................................................................ |
56 |
Setting the domain ID........................................................................ |
57 |
Switch names................................................................................................ |
57 |
Customizing the switch name........................................................... |
58 |
Chassis names.............................................................................................. |
58 |
Customizing chassis names.............................................................. |
58 |
Fabric name.................................................................................................. |
58 |
Configuring the fabric name.............................................................. |
59 |
High availability considerations for fabric names.............................. |
59 |
Upgrade and downgrade considerations for fabric names............... |
59 |
Switch activation and deactivation................................................................ |
59 |
Disabling a switch............................................................................. |
60 |
Enabling a switch.............................................................................. |
60 |
Disabling a chassis........................................................................... |
60 |
Enabling a chassis............................................................................ |
61 |
Switch and Backbone shutdown................................................................... |
61 |
Powering off a Brocade switch.......................................................... |
61 |
Powering off a Brocade Backbone.................................................... |
62 |
Basic connections......................................................................................... |
62 |
Device connection............................................................................. |
62 |
Switch connection............................................................................. |
62 |
Performing Advanced Configuration Tasks............................................................................. |
65 |
Port identifiers (PIDs) and PID binding overview.......................................... |
65 |
Core PID addressing mode............................................................... |
65 |
Fixed addressing mode..................................................................... |
66 |
10-bit addressing (mode 0)............................................................... |
66 |
256-area addressing (mode 1 and mode 2)...................................... |
66 |
WWN-based PID assignment........................................................... |
67 |
Ports.............................................................................................................. |
69 |
Port Types......................................................................................... |
69 |
Backbone port blades....................................................................... |
70 |
Setting port names............................................................................ |
71 |
Port identification by slot and port number........................................ |
71 |
Port identification by port area ID...................................................... |
71 |
Port identification by index................................................................ |
71 |
Configuring a device-switch connection ........................................... |
72 |
Swapping port area IDs..................................................................... |
72 |
Enabling a port.................................................................................. |
73 |
Disabling a port................................................................................. |
74 |
4 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
Port decommissioning......................................................................... |
74 |
Setting network interface modes......................................................... |
75 |
Setting port speeds............................................................................. |
76 |
Setting all ports on a switch to the same speed.................................. |
76 |
Setting port speed for a port octet....................................................... |
77 |
Setting maximum auto-negotiated port speed.................................... |
77 |
Blade terminology and compatibility................................................................ |
78 |
CP blades............................................................................................ |
81 |
Core blades......................................................................................... |
82 |
Port and application blade compatibility.............................................. |
82 |
Enabling and disabling blades........................................................................ |
83 |
Enabling blades................................................................................... |
83 |
Disabling blades.................................................................................. |
83 |
Blade swapping............................................................................................... |
84 |
How blades are swapped.................................................................... |
84 |
Swapping blades................................................................................. |
86 |
Disabling switches........................................................................................... |
87 |
Power management........................................................................................ |
87 |
Powering off a port blade or core blade.............................................. |
87 |
Powering on a port blade or core blade.............................................. |
88 |
Equipment status............................................................................................ |
88 |
Checking switch operation.................................................................. |
88 |
Verifying High Availability features (Backbones only)......................... |
88 |
Verifying fabric connectivity................................................................. |
89 |
Verifying device connectivity............................................................... |
89 |
Viewing the switch status policy threshold values............................... |
90 |
Setting the switch status policy threshold values................................ |
90 |
Audit log configuration..................................................................................... |
91 |
Verifying host syslog prior to configuring the audit log........................ |
92 |
Configuring an audit log for specific event classes............................. |
93 |
Duplicate PWWN handling during device login............................................... |
93 |
Setting the behavior for handling duplicate PWWNs.......................... |
95 |
Forward error correction.................................................................................. |
95 |
FEC Limitations................................................................................... |
96 |
Enabling forward error correction........................................................ |
96 |
Disabling forward error correction....................................................... |
97 |
Enabling or disabling FEC for long-distance ports ............................. |
97 |
Routing Traffic........................................................................................................................ |
99 |
Routing overview............................................................................................. |
99 |
Paths and route selection.................................................................... |
99 |
FSPF................................................................................................. |
100 |
Fibre Channel NAT........................................................................... |
101 |
Inter-switch links............................................................................................ |
101 |
Buffer credits..................................................................................... |
102 |
Congestion versus over-subscription................................................ |
103 |
Virtual channels................................................................................. |
103 |
Gateway links................................................................................................ |
104 |
Configuring a link through a gateway................................................ |
105 |
Routing policies............................................................................................. |
106 |
Notes ................................................................................................ |
106 |
Displaying the current routing policy................................................. |
106 |
Port-based routing ............................................................................ |
106 |
Exchange-based routing................................................................... |
107 |
Device-based routing........................................................................ |
107 |
Dynamic Path Selection.................................................................... |
107 |
Route selection............................................................................................. |
107 |
Fabric OS Administrators Guide |
5 |
53-1003130-01 |
|
Dynamic Load Sharing.................................................................... |
108 |
Frame order delivery................................................................................... |
109 |
Forcing in-order frame delivery across topology changes.............. |
109 |
Restoring out-of-order frame delivery across topology changes.... |
109 |
Enabling Frame Viewer................................................................... |
110 |
Using Frame Viewer to understand why frames are dropped ........ |
110 |
Lossless Dynamic Load Sharing on ports................................................... |
112 |
Lossless core.................................................................................. |
113 |
Configuring Lossless Dynamic Load Sharing ................................ |
114 |
Lossless Dynamic Load Sharing in Virtual Fabrics......................... |
114 |
Frame Redirection....................................................................................... |
115 |
Creating a frame redirect zone........................................................ |
115 |
Deleting a frame redirect zone........................................................ |
116 |
Viewing frame redirect zones.......................................................... |
116 |
Buffer-to-Buffer Credits and Credit Recovery....................................................................... |
117 |
Buffer credit management .......................................................................... |
117 |
Buffer-to-buffer flow control............................................................. |
117 |
Optimal buffer credit allocation ....................................................... |
118 |
Fibre Channel gigabit values reference definition........................... |
119 |
Buffer credit allocation based on full-size frames........................... |
119 |
Allocating buffer credits based on average-size frames................. |
121 |
Configuring buffers for a single port directly................................... |
122 |
Configuring buffers using frame size............................................... |
123 |
Calculating the number of buffers required given the distance, |
|
speed, and frame size............................................................... |
123 |
Allocating buffer credits for F_Ports................................................ |
123 |
Monitoring buffers in a port group................................................... |
124 |
Buffer credits per switch or blade model......................................... |
124 |
Maximum configurable distances for Extended Fabrics................. |
126 |
Downgrade considerations.............................................................. |
128 |
Configuring credits for a single VC.................................................. |
128 |
Buffer credit recovery ................................................................................. |
129 |
Buffer credit recovery over an E_Port............................................. |
129 |
Buffer credit recovery over an F_Port............................................. |
130 |
Buffer credit recovery over an EX_Port........................................... |
130 |
Enabling and disabling buffer credit recovery................................. |
130 |
Credit loss................................................................................................... |
131 |
Back-end credit loss detection and recovery support on |
|
Brocade 5300 switches............................................................. |
131 |
Back-end credit loss detection and recovery support on |
|
Brocade 6520 switches............................................................. |
131 |
Enabling back-end credit loss detection and recovery ................... |
132 |
Managing User Accounts.................................................................................................... |
133 |
User accounts overview ............................................................................. |
133 |
Role-Based Access Control............................................................ |
134 |
Management channel...................................................................... |
135 |
Managing user-defined roles........................................................... |
136 |
Local database user accounts.................................................................... |
137 |
Default accounts............................................................................. |
137 |
Local account passwords................................................................ |
139 |
Local user account database distribution.................................................... |
140 |
Distributing the local user database................................................ |
140 |
Accepting distributed user databases on the local switch............... |
140 |
Rejecting distributed user databases on the local switch............... |
140 |
6 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
Password policies......................................................................................... |
140 |
Password strength policy.................................................................. |
141 |
Password history policy..................................................................... |
142 |
Password expiration policy................................................................ |
142 |
Account lockout policy....................................................................... |
143 |
The boot PROM password............................................................................ |
144 |
Setting the boot PROM password for a switch with a recovery |
|
string............................................................................................ |
145 |
Setting the boot PROM password for a Backbone with a recovery |
|
string............................................................................................ |
145 |
Setting the boot PROM password for a switch without a recovery |
|
string............................................................................................ |
146 |
Setting the boot PROM password for a Backbone without a |
|
recovery string............................................................................. |
147 |
Remote authentication.................................................................................. |
148 |
Remote authentication configuration................................................. |
148 |
Setting the switch authentication mode............................................. |
151 |
Fabric OS user accounts................................................................... |
151 |
Fabric OS users on the RADIUS server............................................ |
152 |
Setting up a RADIUS server............................................................. |
155 |
LDAP configuration and Microsoft Active Directory.......................... |
160 |
LDAP configuration and OpenLDAP................................................. |
162 |
TACACS+ service............................................................................. |
166 |
Remote authentication configuration on the switch........................... |
169 |
Configuring local authentication as backup....................................... |
171 |
Configuring Protocols............................................................................................................ |
173 |
Security protocols.......................................................................................... |
173 |
Secure Copy................................................................................................. |
175 |
Setting up SCP for configuration uploads and downloads................ |
175 |
Secure Shell protocol.................................................................................... |
175 |
SSH public key authentication.......................................................... |
176 |
Secure Sockets Layer protocol .................................................................... |
178 |
Browser and Java support................................................................ |
178 |
SSL configuration overview............................................................... |
179 |
The browser ..................................................................................... |
182 |
Root certificates for the Java plugin.................................................. |
183 |
Simple Network Management Protocol......................................................... |
184 |
SNMP Manager................................................................................. |
184 |
SNMP Agent..................................................................................... |
184 |
Management Information Base (MIB)............................................... |
184 |
Basic SNMP operation...................................................................... |
185 |
Understanding MIBs.......................................................................... |
185 |
Access to MIB variables.................................................................... |
186 |
SNMP support .................................................................................. |
187 |
Traps................................................................................................. |
187 |
Loading Brocade MIBs...................................................................... |
190 |
Access Gateway and Brocade MIBs................................................. |
193 |
Firmware upgrades and enabled traps............................................. |
194 |
Support for Administrative Domains.................................................. |
194 |
Support for Role-Based Access Control........................................... |
194 |
Support for IPv6 addressing.............................................................. |
195 |
Support for Virtual Fabrics................................................................ |
195 |
Customized traps.............................................................................. |
196 |
Configuring SNMP using CLI............................................................ |
196 |
Telnet protocol.............................................................................................. |
204 |
Blocking Telnet.................................................................................. |
204 |
Fabric OS Administrators Guide |
7 |
53-1003130-01 |
|
Unblocking Telnet........................................................................... |
205 |
Listener applications................................................................................... |
205 |
Ports and applications used by switches.................................................... |
206 |
Port configuration............................................................................ |
207 |
Configuring Security Policies............................................................................................... |
209 |
ACL policies overview................................................................................. |
209 |
How the ACL policies are stored..................................................... |
209 |
Policy members............................................................................... |
210 |
ACL policy management............................................................................. |
210 |
Displaying ACL policies................................................................... |
211 |
Saving changes without activating the policies............................... |
211 |
Activating ACL policy changes........................................................ |
211 |
Deleting an ACL policy.................................................................... |
211 |
Adding a member to an existing ACL policy................................... |
212 |
Removing a member from an ACL policy....................................... |
212 |
Abandoning unsaved ACL policy changes..................................... |
212 |
FCS policies................................................................................................ |
213 |
FCS policy restrictions.................................................................... |
213 |
Ensuring fabric domains share policies .......................................... |
214 |
Creating an FCS policy................................................................... |
215 |
Modifying the order of FCS switches.............................................. |
215 |
FCS policy distribution.................................................................... |
216 |
Device Connection Control policies............................................................ |
216 |
Virtual Fabrics considerations .................................................... |
217 |
DCC policy restrictions.................................................................... |
217 |
Creating a DCC policy..................................................................... |
217 |
Deleting a DCC policy..................................................................... |
218 |
DCC policy behavior with Fabric-Assigned PWWNs...................... |
219 |
SCC Policies............................................................................................... |
220 |
Virtual Fabrics considerations for SCC policies ....................... |
220 |
Creating an SCC policy................................................................... |
221 |
Authentication policy for fabric elements.................................................... |
221 |
Virtual Fabrics considerations .................................................... |
222 |
E_Port authentication...................................................................... |
222 |
Device authentication policy............................................................ |
224 |
AUTH policy restrictions.................................................................. |
225 |
Authentication protocols.................................................................. |
226 |
Secret key pairs for DH-CHAP........................................................ |
227 |
FCAP configuration overview.......................................................... |
228 |
Fabric-wide distribution of the authorization policy......................... |
230 |
IP Filter policy.............................................................................................. |
231 |
Virtual Fabrics considerations for IP Filter policy .................... |
231 |
Creating an IP Filter policy.............................................................. |
231 |
Cloning an IP Filter policy............................................................... |
232 |
Displaying an IP Filter policy........................................................... |
232 |
Saving an IP Filter policy................................................................. |
232 |
Activating an IP Filter policy............................................................ |
232 |
Deleting an IP Filter policy.............................................................. |
233 |
IP Filter policy rules......................................................................... |
233 |
IP Filter policy enforcement............................................................. |
236 |
Adding a rule to an IP Filter policy.................................................. |
237 |
Deleting a rule from an IP Filter policy............................................ |
237 |
Aborting an IP Filter transaction...................................................... |
237 |
IP Filter policy distribution............................................................... |
237 |
Policy database distribution........................................................................ |
238 |
Database distribution settings......................................................... |
239 |
8 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
ACL policy distribution to other switches........................................... |
240 |
Fabric-wide enforcement................................................................... |
241 |
Notes on joining a switch to the fabric............................................... |
242 |
Management interface security..................................................................... |
244 |
Configuration examples.................................................................... |
245 |
IPsec protocols.................................................................................. |
246 |
Security associations........................................................................ |
247 |
Authentication and encryption algorithms......................................... |
247 |
IPsec policies.................................................................................... |
248 |
IKE policies....................................................................................... |
248 |
Creating the tunnel............................................................................ |
250 |
Example of an end-to-end transport tunnel mode............................. |
251 |
Maintaining the Switch Configuration File............................................................................. |
255 |
Configuration settings................................................................................... |
255 |
Configuration file format ................................................................... |
256 |
Configuration file backup............................................................................... |
257 |
Uploading a configuration file in interactive mode............................. |
257 |
Configuration file restoration......................................................................... |
258 |
Restrictions....................................................................................... |
258 |
Configuration download without disabling a switch........................... |
260 |
Configurations across a fabric....................................................................... |
261 |
Downloading a configuration file from one switch to another |
|
switch of the same model............................................................ |
262 |
Security considerations..................................................................... |
262 |
Configuration management for Virtual Fabrics.............................................. |
262 |
Uploading a configuration file from a switch with Virtual Fabrics |
|
enabled........................................................................................ |
262 |
Restoring a logical switch configuration using configDownload........ |
263 |
Restrictions....................................................................................... |
264 |
Brocade configuration form........................................................................... |
264 |
Managing Virtual Fabrics...................................................................................................... |
267 |
Virtual Fabrics overview................................................................................ |
267 |
Logical switch overview................................................................................. |
268 |
Default logical switch......................................................................... |
268 |
Logical switches and fabric IDs......................................................... |
270 |
Port assignment in logical switches.................................................. |
271 |
Logical switches and connected devices.......................................... |
272 |
Management model for logical switches....................................................... |
274 |
Logical fabric overview.................................................................................. |
274 |
Logical fabric and ISLs...................................................................... |
274 |
Base switch and extended ISLs........................................................ |
276 |
Account management and Virtual Fabrics.................................................... |
279 |
Setting up IP addresses for a logical switch.................................................. |
279 |
Supported platforms for Virtual Fabrics......................................................... |
280 |
Supported port configurations in the fixed-port switches.................. |
281 |
Supported port configurations in Brocade Backbones...................... |
281 |
Virtual Fabrics interaction with other Fabric OS features.............................. |
282 |
Limitations and restrictions of Virtual Fabrics................................................ |
283 |
Restrictions on XISLs........................................................................ |
284 |
Restrictions on moving ports ............................................................ |
284 |
Enabling Virtual Fabrics mode...................................................................... |
285 |
Disabling Virtual Fabrics mode..................................................................... |
285 |
Configuring logical switches to use basic configuration values..................... |
286 |
Creating a logical switch or base switch....................................................... |
287 |
Fabric OS Administrators Guide |
9 |
53-1003130-01 |
|
Executing a command in a different logical switch context......................... |
288 |
Deleting a logical switch.............................................................................. |
289 |
Adding and moving ports on a logical switch.............................................. |
290 |
Displaying logical switch configuration........................................................ |
291 |
Changing the fabric ID of a logical switch................................................... |
291 |
Changing a logical switch to a base switch................................................. |
292 |
Configuring a logical switch for XISL use ................................................... |
293 |
Changing the context to a different logical fabric........................................ |
294 |
Creating a logical fabric using XISLs.......................................................... |
294 |
Administering Advanced Zoning.......................................................................................... |
297 |
Zone types.................................................................................................. |
297 |
Zoning overview.......................................................................................... |
298 |
Approaches to zoning..................................................................... |
299 |
Zone objects.................................................................................... |
300 |
Zone configurations......................................................................... |
301 |
Zoning enforcement........................................................................ |
302 |
Considerations for zoning architecture........................................... |
302 |
Best practices for zoning................................................................. |
303 |
Broadcast zones......................................................................................... |
303 |
Broadcast zones and Admin Domains............................................ |
304 |
Broadcast zones and FC-FC routing............................................... |
305 |
High availability considerations with broadcast zones.................... |
305 |
Loop devices and broadcast zones................................................ |
305 |
Broadcast zones and default zoning mode..................................... |
305 |
Zone aliases................................................................................................ |
306 |
Creating an alias............................................................................. |
306 |
Adding members to an alias............................................................ |
307 |
Removing members from an alias.................................................. |
307 |
Deleting an alias.............................................................................. |
308 |
Viewing an alias in the defined configuration.................................. |
308 |
Zone creation and maintenance................................................................. |
309 |
Displaying existing zones ............................................................... |
309 |
Creating a zone............................................................................... |
310 |
Adding devices (members) to a zone.............................................. |
310 |
Removing devices (members) from a zone.................................... |
311 |
Replacing zone members............................................................... |
312 |
Deleting a zone............................................................................... |
314 |
Viewing a zone in the defined configuration................................... |
314 |
Viewing zone configuration names without case distinction........... |
315 |
Validating a zone............................................................................. |
316 |
Default zoning mode................................................................................... |
319 |
Setting the default zoning mode..................................................... |
319 |
Viewing the current default zone access mode.............................. |
320 |
Zone database size..................................................................................... |
320 |
Zone configurations..................................................................................... |
321 |
Creating a zone configuration......................................................... |
321 |
Adding zones to a zone configuration............................................. |
322 |
Removing members from a zone configuration.............................. |
322 |
Enabling a zone configuration......................................................... |
323 |
Disabling a zone configuration........................................................ |
323 |
Deleting a zone configuration......................................................... |
324 |
Abandoning zone configuration changes........................................ |
324 |
Viewing all zone configuration information...................................... |
324 |
Viewing selected zone configuration information............................ |
325 |
Viewing the configuration in the effective zone database............... |
325 |
Clearing all zone configurations...................................................... |
326 |
10 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
Zone object maintenance.............................................................................. |
326 |
Copying a zone object....................................................................... |
326 |
Deleting a zone object....................................................................... |
327 |
Renaming a zone object................................................................... |
328 |
Zone configuration management.................................................................. |
328 |
Security and zoning....................................................................................... |
329 |
Zone merging................................................................................................ |
329 |
Fabric segmentation and zoning....................................................... |
331 |
Zone merging scenarios.................................................................... |
331 |
Concurrent zone transactions....................................................................... |
338 |
Viewing zone database transactions................................................. |
339 |
Traffic Isolation Zoning.......................................................................................................... |
341 |
Traffic Isolation Zoning overview................................................................... |
341 |
TI zone failover ............................................................................................. |
342 |
Additional considerations when disabling failover............................. |
343 |
FSPF routing rules and traffic isolation............................................. |
344 |
Enhanced TI zones....................................................................................... |
346 |
Illegal configurations with enhanced TI zones.................................. |
346 |
Traffic Isolation Zoning over FC routers........................................................ |
348 |
TI zones within an edge fabric.......................................................... |
349 |
TI zones within a backbone fabric..................................................... |
350 |
Limitations of TI zones over FC routers............................................ |
351 |
Fabric-Level Traffic Isolation in a backbone fabric........................................ |
352 |
Fabric-Level TI zones........................................................................ |
353 |
Failover behavior for Fabric-Level TI zones...................................... |
354 |
Creating a separate TI zone for each path........................................ |
354 |
Creating a single TI zone for all paths............................................... |
355 |
General rules for TI zones............................................................................. |
356 |
Traffic Isolation Zone violation handling for trunk ports..................... |
357 |
Supported configurations for Traffic Isolation Zoning.................................... |
358 |
Additional configuration rules for enhanced TI zones....................... |
358 |
Trunking with TI zones...................................................................... |
358 |
Limitations and restrictions of Traffic Isolation Zoning.................................. |
359 |
Admin Domain considerations for Traffic Isolation Zoning............................ |
360 |
Virtual Fabrics considerations for Traffic Isolation Zoning............................ |
360 |
Traffic Isolation Zoning over FC routers with Virtual Fabrics........................ |
362 |
Creating a TI zone......................................................................................... |
363 |
Creating a TI zone in a base fabric................................................... |
365 |
Modifying TI zones........................................................................................ |
366 |
Changing the state of a TI zone.................................................................... |
368 |
Deleting a TI zone......................................................................................... |
368 |
Displaying TI zones....................................................................................... |
369 |
Troubleshooting TI zone routing problems.................................................... |
370 |
Setting up TI zones over FCR (sample procedure)....................................... |
370 |
Optimizing Fabric Behavior................................................................................................... |
375 |
Adaptive Networking overview...................................................................... |
375 |
Ingress Rate Limiting.................................................................................... |
376 |
Virtual Fabrics considerations........................................................... |
376 |
Limiting traffic from a particular device.............................................. |
376 |
Disabling Ingress Rate Limiting......................................................... |
377 |
QoS............................................................................................................... |
377 |
License requirements for QoS.......................................................... |
378 |
CS_CTL-based frame prioritization............................................................... |
378 |
Supported configurations for CS_CTL-based frame prioritization..... |
379 |
Fabric OS Administrators Guide |
11 |
53-1003130-01 |
|
High availability considerations for CS_CTL-based frame |
|
prioritization............................................................................... |
379 |
Enabling CS_CTL-based frame prioritization on ports.................... |
379 |
Disabling CS_CTL-based frame prioritization on ports................... |
380 |
Using CS_CTL auto mode at the chassis level............................... |
380 |
Considerations for using CS_CTL-based frame prioritization......... |
380 |
QoS zone-based traffic prioritization........................................................... |
381 |
QoS zones.................................................................................................. |
381 |
QoS on E_Ports.............................................................................. |
383 |
QoS over FC routers....................................................................... |
383 |
Virtual Fabrics considerations for QoS zone-based traffic |
|
prioritization............................................................................... |
384 |
High-availability considerations for QoS zone-based traffic |
|
prioritization............................................................................... |
385 |
Supported configurations for QoS zone-based traffic prioritization.385 |
|
Limitations and restrictions for QoS zone-based traffic |
|
prioritization............................................................................... |
386 |
Setting QoS zone-based traffic prioritization............................................... |
386 |
Setting QoS zone-based traffic prioritization over FC routers..................... |
387 |
Disabling QoS zone-based traffic prioritization........................................... |
388 |
Bottleneck Detection.......................................................................................................... |
389 |
Bottleneck detection overview ................................................................... |
389 |
Types of bottlenecks....................................................................... |
390 |
How bottlenecks are reported......................................................... |
390 |
Supported configurations for bottleneck detection...................................... |
391 |
Limitations of bottleneck detection.................................................. |
391 |
High availability considerations for bottleneck detection................. |
391 |
Upgrade and downgrade considerations for bottleneck detection.. 391 |
|
Trunking considerations for bottleneck detection............................ |
391 |
Virtual Fabrics considerations for bottleneck detection................... |
392 |
Access Gateway considerations for bottleneck detection............... |
392 |
Enabling bottleneck detection on a switch.................................................. |
392 |
Displaying bottleneck detection configuration details................................. |
393 |
Setting bottleneck detection alerts ............................................................. |
394 |
Setting both a congestion alert and a latency alert......................... |
395 |
Setting only a congestion alert........................................................ |
396 |
Setting only a latency alert.............................................................. |
396 |
Changing bottleneck detection parameters................................................ |
397 |
Examples of applying and changing bottleneck detection |
|
parameters................................................................................ |
398 |
Adjusting the frequency of bottleneck alerts .................................. |
400 |
Logging frame timeouts due to bottlenecking............................................. |
400 |
Advanced bottleneck detection settings...................................................... |
401 |
Excluding a port from bottleneck detection................................................. |
402 |
Displaying bottleneck statistics................................................................... |
404 |
MAPS and bottleneck detection.................................................................. |
404 |
Disabling bottleneck detection on a switch................................................. |
404 |
In-flight Encryption and Compression.................................................................................. |
407 |
In-flight encryption and compression overview........................................... |
407 |
Supported ports for in-flight encryption and compression............... |
408 |
In-flight encryption and compression restrictions............................ |
408 |
How in-flight encryption and compression are enabled.................. |
410 |
Authentication and key generation for encryption and |
|
compression.............................................................................. |
411 |
12 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
Availability considerations for encryption and compression.............. |
411 |
Virtual Fabrics considerations for encryption and compression........ |
412 |
In-flight compression on long-distance ports..................................... |
412 |
Compression ratios for compression-enabled ports.......................... |
412 |
Configuring in-flight encryption and compression on an EX_Port................. |
413 |
Configuring in-flight encryption and compression on an E_Port................... |
413 |
Viewing the encryption and compression configuration................................ |
414 |
Configuring and enabling authentication for in-flight encryption................... |
415 |
Enabling in-flight encryption.......................................................................... |
417 |
Enabling in-flight compression...................................................................... |
418 |
Disabling in-flight encryption......................................................................... |
418 |
Disabling in-flight compression..................................................................... |
419 |
Diagnostic Port..................................................................................................................... |
421 |
Diagnostic Port.............................................................................................. |
421 |
Supported platforms for D_Port.................................................................... |
421 |
Licensing requirements for D_Port................................................................ |
422 |
Understanding D_Port................................................................................... |
422 |
Advantages of D_Port....................................................................... |
423 |
D_Port configuration modes and nature of test................................. |
424 |
General limitations and considerations for D_Port............................ |
425 |
Supported topologies.................................................................................... |
426 |
Topology 1: ISLs............................................................................... |
426 |
Topology 2: ICLs............................................................................... |
427 |
Topology 3: Access Gateways.......................................................... |
428 |
Topology 4: HBA to switch................................................................ |
429 |
Using D_Port in static-static mode between switches................................... |
430 |
Enabling D_Port in static mode......................................................... |
430 |
Disabling D_Port in static mode........................................................ |
431 |
Pre-provisioning D_Ports.................................................................. |
432 |
Using D_Port between switches and HBAs.................................................. |
432 |
Enabling D_Port in static mode between a switch and an HBA........ |
433 |
BCU D_Port commands.................................................................... |
433 |
Limitations and considerations for D_Port with HBAs....................... |
433 |
Using D_Port in dynamic mode..................................................................... |
434 |
Using D_Port in on-demand mode ............................................................... |
434 |
Example test scenarios and output............................................................... |
435 |
Confirming SFP and link status with an HBA.................................... |
435 |
Starting and stopping D_Port testing................................................ |
435 |
NPIV..................................................................................................................................... |
439 |
NPIV overview............................................................................................... |
439 |
Upgrade considerations.................................................................... |
440 |
Fixed addressing mode..................................................................... |
440 |
10-bit addressing mode..................................................................... |
440 |
Configuring NPIV.......................................................................................... |
441 |
Enabling and disabling NPIV......................................................................... |
442 |
Base device logout........................................................................................ |
442 |
Difference in the device logout behaviors......................................... |
443 |
Enabling base device logout............................................................. |
443 |
Use cases and dependencies........................................................... |
444 |
Viewing base device logout setting................................................... |
446 |
Viewing NPIV port configuration information................................................. |
447 |
Viewing virtual PID login information................................................. |
448 |
Fabric OS Administrators Guide |
13 |
53-1003130-01 |
|
Fabric-Assigned PWWN....................................................................................................... |
449 |
Fabric-Assigned PWWN overview.............................................................. |
449 |
Userand auto-assigned FA-PWWN behavior .......................................... |
450 |
Configuring an FA-PWWN for an HBA connected to an Access Gateway. 451 |
|
Configuring an FA-PWWN for an HBA connected to an edge switch......... |
452 |
Supported switches and configurations for FA-PWWN.............................. |
452 |
Configuration upload and download considerations for FA-PWWN........... |
453 |
Security considerations for FA-PWWN....................................................... |
453 |
Restrictions of FA-PWWN........................................................................... |
454 |
Access Gateway N_Port failover with FA-PWWN....................................... |
454 |
Managing Administrative Domains...................................................................................... |
455 |
Administrative Domains overview............................................................... |
455 |
Admin Domain features................................................................... |
457 |
Requirements for Admin Domains.................................................. |
457 |
Admin Domain access levels.......................................................... |
458 |
User-defined Admin Domains......................................................... |
458 |
System-defined Admin Domains..................................................... |
458 |
Home Admin Domains and login..................................................... |
460 |
Admin Domain member types......................................................... |
461 |
Admin Domains and switch WWNs................................................. |
462 |
Admin Domain compatibility, availability, and merging................... |
464 |
SAN management with Admin Domains..................................................... |
464 |
CLI commands in an AD context..................................................... |
465 |
Executing a command in a different AD context............................. |
465 |
Displaying an Admin Domain configuration.................................... |
465 |
Switching to a different Admin Domain context.............................. |
466 |
Admin Domain interactions with other Fabric OS features............. |
467 |
Admin Domains, zones, and zone databases................................. |
468 |
Admin Domains and LSAN zones................................................... |
469 |
Configuration upload and download in an AD context.................... |
470 |
Admin Domain management for physical fabric administrators.................. |
471 |
Setting the default zoning mode for Admin Domains...................... |
471 |
Creating an Admin Domain............................................................. |
472 |
User assignments to Admin Domains............................................. |
473 |
Removing an Admin Domain from a user account......................... |
474 |
Activating an Admin Domain........................................................... |
474 |
Deactivating an Admin Domain....................................................... |
475 |
Adding members to an existing Admin Domain.............................. |
476 |
Removing members from an Admin Domain.................................. |
476 |
Renaming an Admin Domain.......................................................... |
477 |
Deleting an Admin Domain............................................................. |
477 |
Deleting all user-defined Admin Domains....................................... |
478 |
Deleting all user-defined Admin Domains non-disruptively............. |
478 |
Validating an Admin Domain member list....................................... |
481 |
Inter-chassis Links.............................................................................................................. |
483 |
Inter-chassis links ....................................................................................... |
483 |
License requirements for ICLs........................................................ |
484 |
ICLs for the Brocade DCX 8510 Backbone family...................................... |
484 |
ICL trunking on the Brocade DCX 8510-8 and DCX 8510-4........... |
485 |
ICLs for the Brocade DCX Backbone family............................................... |
486 |
ICL trunking on the Brocade DCX and DCX-4S............................. |
487 |
Virtual Fabrics considerations for ICLs....................................................... |
487 |
14 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
Supported topologies for ICL connections.................................................... |
487 |
Mesh topology................................................................................... |
487 |
Core-edge topology........................................................................... |
489 |
Monitoring Fabric Performance............................................................................................. |
491 |
Advanced Performance Monitoring overview................................................ |
491 |
Types of monitors.............................................................................. |
491 |
Restrictions for installing monitors.................................................... |
492 |
Virtual Fabrics considerations for Advanced Performance |
|
Monitoring.................................................................................... |
492 |
Access Gateway considerations for Advanced Performance |
|
Monitoring.................................................................................... |
493 |
End-to-end performance monitoring............................................................. |
493 |
Maximum number of EE monitors..................................................... |
493 |
Supported port configurations for EE monitors................................. |
494 |
Adding EE monitors.......................................................................... |
494 |
Setting a mask for an EE monitor..................................................... |
495 |
Deleting EE monitors........................................................................ |
496 |
Displaying EE monitor counters........................................................ |
496 |
Clearing EE monitor counters........................................................... |
497 |
Frame monitoring.......................................................................................... |
497 |
License requirements for frame monitoring....................................... |
498 |
Creating frame types to be monitored............................................... |
498 |
Creating a frame monitor.................................................................. |
499 |
Deleting frame types......................................................................... |
499 |
Adding frame monitors to a port........................................................ |
500 |
Removing frame monitors from a port............................................... |
500 |
Saving a frame monitor configuration............................................... |
500 |
Displaying frame monitors................................................................. |
501 |
Clearing frame monitor counters....................................................... |
501 |
Top Talker monitors...................................................................................... |
501 |
Top Talker monitors and FC-FC routing........................................... |
503 |
Limitations of Top Talker monitors.................................................... |
505 |
Adding a Top Talker monitor to a port (port mode)........................... |
505 |
Adding Top Talker monitors on all switches in the fabric (fabric |
|
mode).......................................................................................... |
505 |
Displaying the top bandwidth-using flows on a port (port mode)...... |
506 |
Displaying top talking flows for a given domain ID (fabric mode)...... |
506 |
Deleting a Top Talker monitor on a port (port mode)........................ |
506 |
Deleting all fabric mode Top Talker monitors.................................... |
507 |
Trunk monitoring........................................................................................... |
507 |
Trunk monitoring considerations....................................................... |
507 |
Saving and restoring monitor configurations................................................. |
507 |
Performance data collection.......................................................................... |
508 |
Managing Trunking Connections........................................................................................... |
509 |
Trunking overview......................................................................................... |
509 |
Types of trunking............................................................................... |
509 |
Masterless trunking........................................................................... |
510 |
License requirements for trunking..................................................... |
510 |
Port groups for trunking..................................................................... |
511 |
Supported platforms for trunking................................................................... |
511 |
Supported configurations for trunking........................................................... |
511 |
High Availability support for trunking................................................. |
512 |
Requirements for trunk groups...................................................................... |
512 |
Recommendations for trunk groups.............................................................. |
512 |
Fabric OS Administrators Guide |
15 |
53-1003130-01 |
|
Configuring trunk groups............................................................................. |
513 |
Enabling trunking........................................................................................ |
513 |
Disabling trunking........................................................................................ |
514 |
Displaying trunking information................................................................... |
514 |
Trunk Area and Admin Domains................................................................. |
515 |
Example of Trunk Area assignment on port domain,index ............ |
515 |
ISL trunking over long-distance fabrics....................................................... |
516 |
EX_Port trunking......................................................................................... |
516 |
Masterless EX_Port trunking........................................................... |
517 |
Supported configurations and platforms for EX_Port trunking........ |
517 |
Configuring EX_Port trunking.......................................................... |
518 |
Displaying EX_Port trunking information......................................... |
518 |
F_Port trunking............................................................................................ |
518 |
F_Port trunking for Access Gateway............................................... |
519 |
F_Port trunking for Brocade adapters............................................. |
521 |
F_Port trunking considerations....................................................... |
521 |
F_Port trunking in Virtual Fabrics.................................................... |
524 |
Displaying F_Port trunking information....................................................... |
525 |
Disabling F_Port trunking............................................................................ |
525 |
Enabling the DCC policy on a trunk area.................................................... |
526 |
Managing Long-Distance Fabrics........................................................................................ |
527 |
Long-distance fabrics overview................................................................... |
527 |
Extended Fabrics device limitations............................................................ |
528 |
Long-distance link modes........................................................................... |
528 |
Configuring an extended ISL...................................................................... |
529 |
Enabling long distance when connecting to TDM devices ............. |
530 |
Forward error correction on long-distance links.......................................... |
530 |
Enabling FEC on a long-distance link............................................. |
531 |
Disabling FEC on a long-distance link............................................ |
531 |
Using FC-FC Routing to Connect Fabrics.............................................................................. |
533 |
FC-FC routing overview.............................................................................. |
533 |
License requirements for FC-FC routing......................................... |
534 |
Supported platforms for FC-FC routing........................................... |
534 |
Supported configurations for FC-FC routing................................... |
535 |
Network OS connectivity limitations ............................................... |
535 |
Fibre Channel routing concepts.................................................................. |
535 |
Proxy devices.................................................................................. |
539 |
FC-FC routing topologies................................................................ |
540 |
Phantom domains........................................................................... |
540 |
FC router authentication ................................................................. |
543 |
Setting up FC-FC routing............................................................................ |
544 |
Verifying the setup for FC-FC routing............................................. |
544 |
Backbone fabric IDs.................................................................................... |
545 |
Assigning backbone fabric IDs........................................................ |
546 |
Assigning alias names to fabric IDs............................................................ |
546 |
FCIP tunnel configuration............................................................................ |
547 |
Inter-fabric link configuration....................................................................... |
548 |
Configuring an IFL for both edge and backbone connections........ |
548 |
Configuring EX_Ports on an ICL..................................................... |
551 |
FC router port cost configuration................................................................. |
553 |
Port cost considerations.................................................................. |
553 |
Setting router port cost for an EX_Port........................................... |
554 |
Shortest IFL cost configuration................................................................... |
554 |
Configuring shortest IFL cost.......................................................... |
556 |
16 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
EX_Port frame trunking configuration........................................................... |
558 |
LSAN zone configuration.............................................................................. |
559 |
Use of Admin Domains with LSAN zones and FC-FC routing.......... |
559 |
Zone definition and naming............................................................... |
559 |
LSAN zones and fabric-to-fabric communications............................ |
560 |
Controlling device communication with the LSAN............................. |
560 |
Configuring backbone fabrics for interconnectivity............................ |
562 |
Setting the maximum LSAN count.................................................... |
562 |
HA and downgrade considerations for LSAN zones......................... |
563 |
LSAN zone policies using LSAN tagging.......................................... |
563 |
LSAN zone binding........................................................................... |
568 |
Proxy PID configuration................................................................................ |
572 |
Fabric parameter considerations................................................................... |
573 |
Inter-fabric broadcast frames........................................................................ |
573 |
Displaying the current broadcast configuration................................. |
573 |
Enabling broadcast frame forwarding............................................... |
574 |
Disabling broadcast frame forwarding............................................... |
574 |
Resource monitoring..................................................................................... |
574 |
FC-FC routing and Virtual Fabrics................................................................ |
575 |
Logical switch configuration for FC routing....................................... |
576 |
Backbone-to-edge routing with Virtual Fabrics................................. |
577 |
Upgrade and downgrade considerations for FC-FC routing......................... |
578 |
How replacing port blades affects EX_Port configuration................. |
578 |
Displaying the range of output ports connected to xlate domains................. |
579 |
Port Indexing........................................................................................................................ |
581 |
Hexadecimal Conversion....................................................................................................... |
585 |
Hexadecimal overview.................................................................................. |
585 |
Example conversion of the hexadecimal triplet Ox616000............... |
585 |
Decimal-to-hexadecimal conversion table........................................ |
586 |
Index.................................................................................................................................... |
589 |
Fabric OS Administrators Guide |
17 |
53-1003130-01 |
|
18 |
Fabric OS Administrators Guide |
|
53-1003130-01 |

Preface
● Document conventions.................................................................................................... |
19 |
● Brocade resources.......................................................................................................... |
21 |
● Contacting Brocade Technical Support........................................................................... |
21 |
● Document feedback........................................................................................................ |
22 |
Document conventions
The document conventions describe text formatting conventions, command syntax conventions, and important notice formats used in Brocade technical documentation.
Text formatting conventions
Text formatting conventions such as boldface, italic, or Courier font may be used in the flow of the text to highlight specific words or phrases.
Format
bold text
italic text
Courier font
Description
Identifies command names
Identifies keywords and operands
Identifies the names of user-manipulated GUI elements Identifies text to enter at the GUI
Identifies emphasis
Identifies variables and modifiers
Identifies paths and Internet addresses
Identifies document titles
Identifies CLI output
Identifies command syntax examples
Command syntax conventions
Bold and italic text identify command syntax components. Delimiters and operators define groupings of parameters and their logical relationships.
Convention |
Description |
bold text |
Identifies command names, keywords, and command options. |
italic text |
Identifies a variable. |
Fabric OS Administrators Guide |
19 |
53-1003130-01 |
|

Notes, cautions, and warnings
Convention |
Description |
value |
In Fibre Channel products, a fixed value provided as input to a command |
|
option is printed in plain text, for example, --show WWN. |
[ ] |
Syntax components displayed within square brackets are optional. |
|
Default responses to system prompts are enclosed in square brackets. |
{ x | y | z }
x | y
< >
...
\
A choice of required parameters is enclosed in curly brackets separated by vertical bars. You must select one of the options.
In Fibre Channel products, square brackets may be used instead for this purpose.
A vertical bar separates mutually exclusive elements.
Nonprinting characters, for example, passwords, are enclosed in angle brackets.
Repeat the previous element, for example, member[member...].
Indicates a “soft” line break in command examples. If a backslash separates two lines of a command input, enter the entire command at the prompt without the backslash.
Notes, cautions, and warnings
Notes, cautions, and warning statements may be used in this document. They are listed in the order of increasing severity of potential hazards.
NOTE
A Note provides a tip, guidance, or advice, emphasizes important information, or provides a reference to related information.
ATTENTION
An Attention statement indicates a stronger note, for example, to alert you when traffic might be interrupted or the device might reboot.
CAUTION
A Caution statement alerts you to situations that can be potentially hazardous to you or cause damage to hardware, firmware, software, or data.
DANGER
A Danger statement indicates conditions or situations that can be potentially lethal or extremely hazardous to you. Safety labels are also attached directly to products to warn of these conditions or situations.
20 |
Fabric OS Administrators Guide |
|
53-1003130-01 |

Brocade resources
Brocade resources
Visit the Brocade website to locate related documentation for your product and additional Brocade resources.
You can download additional publications supporting your product at www.brocade.com. Select the Brocade Products tab to locate your product, then click the Brocade product name or image to open the individual product page. The user manuals are available in the resources module at the bottom of the page under the Documentation category.
To get up-to-the-minute information on Brocade products and resources, go to MyBrocade. You can register at no cost to obtain a user ID and password.
Release notes are available on MyBrocade under Product Downloads.
White papers, online demonstrations, and data sheets are available through the Brocade website.
Contacting Brocade Technical Support
As a Brocade customer, you can contact Brocade Technical Support 24x7 online, by telephone, or by e- mail. Brocade OEM customers contact their OEM/Solutions provider.
Brocade customers
For product support information and the latest information on contacting the Technical Assistance Center, go to http://www.brocade.com/services-support/index.html.
If you have purchased Brocade product support directly from Brocade, use one of the following methods to contact the Brocade Technical Assistance Center 24x7.
Online |
Telephone |
|
|
|
|
Preferred method of contact for nonurgent issues:
Required for Sev 1-Critical and Sev support@brocade.com
2-High issues:
Please include:
• My Cases through MyBrocade |
• Continental US: 1-800-752-8061 |
• Software downloads and licensing |
• Europe, Middle East, Africa, and |
tools |
Asia Pacific: +800-AT FIBREE |
• Knowledge Base |
(+800 28 34 27 33) |
|
• For areas unable to access toll |
|
free number: +1-408-333-6061 |
|
• Toll-free numbers are available in |
|
many countries. |
•Problem summary
•Serial number
•Installation details
•Environment description
Brocade OEM customers
If you have purchased Brocade product support from a Brocade OEM/Solution Provider, contact your OEM/Solution Provider for all of your product support needs.
•OEM/Solution Providers are trained and certified by Brocade to support Brocade® products.
•Brocade provides backline support for issues that cannot be resolved by the OEM/Solution Provider.
Fabric OS Administrators Guide |
21 |
53-1003130-01 |
|
Document feedback
•Brocade Supplemental Support augments your existing OEM support contract, providing direct access to Brocade expertise. For more information, contact Brocade or your OEM.
•For questions regarding service levels and response times, contact your OEM/Solution Provider.
Document feedback
To send feedback and report errors in the documentation you can use the feedback form posted with the document or you can e-mail the documentation team.
Quality is our first concern at Brocade and we have made every effort to ensure the accuracy and completeness of this document. However, if you find an error or an omission, or you think that a topic needs further development, we want to hear from you. You can provide feedback in two ways:
•Through the online feedback form in the HTML documents posted on www.brocade.com.
•By sending your feedback to documentation@brocade.com.
Provide the publication title, part number, and as much detail as possible, including the topic heading and page number if applicable, as well as your suggestions for improvement.
22 |
Fabric OS Administrators Guide |
|
53-1003130-01 |

About This Document
● Supported hardware and software.................................................................................. |
23 |
● What's new in this document........................................................................................... |
24 |
Supported hardware and software
In those instances in which procedures or parts of procedures documented here apply to some switches but not to others, this list identifies exactly which switches are supported and which are not.
Although many different software and hardware configurations are tested and supported by Brocade Communications Systems, Inc. for Fabric OS 7.3.0, documenting all possible configurations and scenarios is beyond the scope of this document.
The following hardware platforms are supported by this release of Fabric OS:
TABLE 1 Brocade Fixed-port switches
Gen 4 platform (8-Gpbs) |
Gen 5 platform (16-Gbps) |
|
|
Brocade 300 switch |
Brocade 6505 switch |
|
|
Brocade 5100 switch |
Brocade M6505 embedded switch |
|
|
Brocade 5300 switch |
Brocade 6510 switch |
|
|
Brocade 5410 embedded switch |
Brocade 6520 switch |
|
|
Brocade 5424 embedded switch |
Brocade 6547 embedded switch |
|
|
Brocade 5430 embedded switch |
Brocade 6548 embedded switch |
|
|
Brocade 5431 embedded switch |
Brocade 7840 extension switch |
|
|
Brocade 5432 embedded switch |
|
|
|
Brocade 5450 embedded switch |
|
|
|
Brocade 5460 embedded switch |
|
|
|
Brocade 5470 embedded switch |
|
|
|
Brocade 5480 embedded switch |
|
|
|
Brocade NC-5480 embedded switch |
|
|
|
Brocade 7800 extension switch |
|
|
|
Brocade VA-40FC |
|
|
|
Brocade Encryption Switch |
|
|
|
Fabric OS Administrators Guide |
23 |
53-1003130-01 |
|

What's new in this document
TABLE 2 Brocade DCX Backbone family
Gen 4 platform (8-Gpbs) |
Gen 5 platform (16-Gbps) |
|
|
Brocade DCX |
Brocade DCX 8510-4 |
|
|
Brocade DCX-4S |
Brocade DCX 8510-8 |
|
|
What's new in this document
This document includes new and modified information for the Fabric OS 7.3.0 release.
The following content has been removed from this book and moved to other books:
•Removed the chapter "Installing and Maintaining Firmware". The information in this chapter is now in the Fabric OS Upgrade Guide.
•Removed the chapter "Administering Licensing". The information in this chapter is now in the Fabric OS Software Licensing Guide.
•Removed the chapter "FIPS Support". The information in this chapter is now in the Fabric OS FIPS Configuration Guide.
The following content is new or significantly revised for this release of this document:
•Added support for the Brocade 7840 Extension Switch and the FC16-64 port blade.
•Added Using fosexec to run commands on remote switches or domains on page 43.
•Added note that Frame discards can be logged as audit messages using the Fabric OS syslog facility to the chapter Routing Traffic on page 99.
•Added Enabling Frame Viewer on page 110.
•Updated Buffer-to-Buffer Credits and Credit Recovery on page 117 with the Brocade 7840 and the FC16-64 port blade information.
•Updated the supported OpenSSH version, in the section Secure Shell protocol on page 175.
•Updated snmpconfig --set snmpv3 command output to indicate AES-256 support, in the section Configuring SNMPv3 user/traps on page 197.
•Removed AP policy section from the chapter Configuring Security Policies on page 209.
•Added zone merging scenarios tables to the section Zone merging scenarios on page 331.
•Added description of support for two new discard frame types, destination unreachable (DU) and un-routable (UNRTBL), to Frame Viewer (Frame Discard Log) to the Bottleneck Detection on page 389 chapter.
•Added description of the -type option to the framelog -–enable and --disable command so that the type of discard frame to be enabled or disabled can be specified. This applies to Gen 5 platforms only. (In the chapter Bottleneck Detection on page 389.)
•Added information on setting lossless DLS to the chapter Routing Traffic on page 99.
•Updated the following sections for FCAP support:
Authentication and key generation for encryption and compression on page 411
Configuring and enabling authentication for in-flight encryption on page 415
•Added dynamic and on-demand D_Port modes information to the chapter Diagnostic Port on page 421.
•Added the section Base device logout on page 442.
•Added information about setting the FID alias, in the section Assigning alias names to fabric IDs on page 546.
24 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
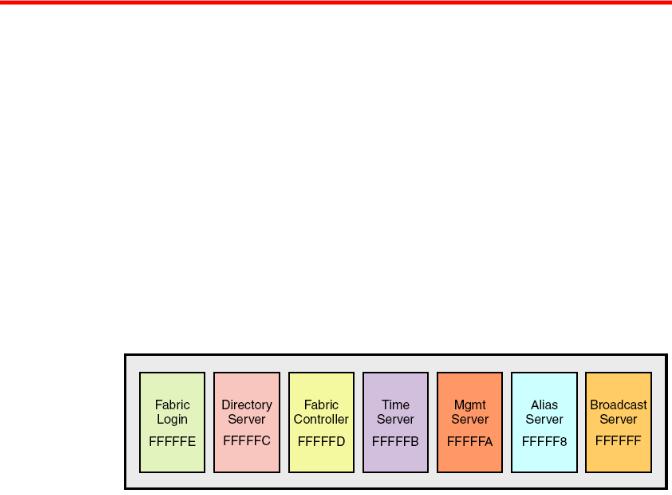
Understanding Fibre Channel Services
● Fibre Channel services overview.................................................................................... |
25 |
● Management server........................................................................................................ |
26 |
● Platform services............................................................................................................. |
26 |
● Management server database........................................................................................ |
27 |
● Topology discovery......................................................................................................... |
30 |
● Device login..................................................................................................................... |
32 |
● High availability of daemon processes............................................................................ |
34 |
Fibre Channel services overview
Fibre Channel services define service functions that reside at well-known addresses. A well-known address is a reserved three-byte address for each service. Services are provided to either nodes or management applications in the fabric.
FIGURE 1 Well-known addresses
Fabric Login -- The Fabric Login server assigns a fabric address to a fabric node, which allows it to communicate with services on the switch or other nodes in the fabric. The fabric address is a 24-bit address (0x000000) containing three 3-byte nodes. Reading from left to right, the first node (0x00 0000) represents the domain ID, the second node (0x0000 00) the port area number of the port where the node is attached, and the third node (0x000000 ) the arbitrated loop physical address (AL_PA), if applicable.
Directory server -- The directory server or name server registers fabric and public nodes and conducts queries to discover other devices in the fabric.
Fabric controller -- The fabric controller provides State Change Notifications (SCNs) to registered nodes when a change in the fabric topology occurs.
Time server -- The time server sends the time to the member switches in the fabric from either the principal switch or, if configured, the primary fabric configuration server (FCS) switch. Refer to Configuring Security Policies on page 209 for additional information on FCS policies.
Management server -- The management server provides a single point for managing the fabric. This is the only service that users can configure. Refer to Management server on page 26 for more details
Alias server -- The alias server keeps a group of nodes registered as one name to handle multicast groups.
Fabric OS Administrators Guide |
25 |
53-1003130-01 |
|

Management server
Broadcast server -- The broadcast server is optional. When frames are transmitted to this address, they are broadcast to all operational N_ and NL_Ports.
When registration and query frames are sent to a well-known address, a different protocol service, Fibre Channel Common Transport (FC-CT), is used. This protocol provides a simple, consistent format and behavior when a service provider is accessed for registration and query purposes.
Management server
The Brocade Fabric OS management server (MS) allows a SAN management application to retrieve information and administer interconnected switches, servers, and storage devices. The management server assists in the autodiscovery of switch-based fabrics and their associated topologies.
A client of the management server can find basic information about the switches in the fabric and use this information to construct topology relationships. The management server also allows you to obtain certain switch attributes and, in some cases, modify them. For example, logical names identifying switches can be registered with the management server.
The management server provides several advantages for managing a Fibre Channel fabric:
•It is accessed by an external Fibre Channel node at the well-known address FFFFFAh , so an application can access information about the entire fabric management with minimal knowledge of the existing configuration.
•It is replicated on every Brocade switch within a fabric.
•It provides an unzoned view of the overall fabric configuration. This fabric topology view exposes the internal configuration of a fabric for management purposes; it contains interconnect information about switches and devices connected to the fabric. Under normal circumstances, a device (typically an FCP initiator) queries the name server for storage devices within its member zones. Because this limited view is not always sufficient, the management server provides the application with a list of the entire name server database.
Platform services
By default, all management services except platform services are enabled; the MS platform service and topology discovery are disabled.
You can activate and deactivate the platform services throughout the fabric. Activating the platform services attempts to activate the MS platform service for each switch in the fabric. The change takes effect immediately and is committed to the configuration database of each affected switch. MS activation is persistent across power cycles and reboots.
NOTE
The commands msplMgmtActivate and msplMgmtDeactivate are allowed only in AD0 and AD255.
Platform services and Virtual Fabrics
Each logical switch has a separate platform database. All platform registrations done to a logical switch are valid only in that particular logical switch’s Virtual Fabric.
Activating the platform services on a switch activates the platform services on all logical switches in a Virtual Fabric. Similarly, deactivating the platform services deactivates the platform service on all
26 |
Fabric OS Administrators Guide |
|
53-1003130-01 |

Enabling platform services
logical switches in a Virtual Fabric. The msPlatShow command displays all platforms registered in a Virtual Fabric.
Enabling platform services
When FCS policy is enabled, the msplMgmtActivate command can be issued only from the primary FCS switch.
The execution of the msplMgmtActivate command is subject to Admin Domain restrictions that may be in place.
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msCapabilityShow command to verify that all switches in the fabric support the MS platform service; otherwise, the next step fails.
3.Enter the msplMgmtActivate command, as in the following example.
switch:admin> msplmgmtactivate
Request to activate MS Platform Service in progress......
*Completed activating MS Platform Service in the fabric!
Disabling platform services
Use the following procedure to disable platform services:
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msplMgmtDeactivate command.
3.Enter y to confirm the deactivation, as in the following example. switch:admin> msplmgmtdeactivate
MS Platform Service is currently enabled.
This will erase MS Platform Service configuration information as well as database in the entire fabric.
Would you like to continue this operation? (yes, y, no, n): [no] y
Request to deactivate MS Platform Service in progress......
*Completed deactivating MS Platform Service in the fabric!
Management server database
You can control access to the management server database.
An access control list (ACL) of WWN addresses determines which systems have access to the management server database. The ACL typically contains those WWNs of host systems that are running management applications.
If the list is empty (the default), the management server is accessible to all systems connected in-band to the fabric. For more access security, you can specify WWNs in the ACL so that access to the management server is restricted to only those WWNs listed.
NOTE
The management server is logical switch-capable. All management server features are supported within a logical switch.
Fabric OS Administrators Guide |
27 |
53-1003130-01 |
|
Displaying the management server ACL
Displaying the management server ACL
Use the following procedure to display the management server ACL:
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msConfigure command. The command becomes interactive.
3.At the "select" prompt, enter 1 to display the access list.
A list of WWNs that have access to the management server is displayed. The following is an example of an empty access list
switch:admin> msconfigure
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 1
MS Access list is empty.
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 0
done ...
Adding a member to the ACL
Use the following procedure to add a member to the ACL:
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msConfigure command. The command becomes interactive.
3.At the "select" prompt, enter 2 to add a member based on its port/node WWN.
4.At the "Port/Node WWN" prompt, enter the WWN of the host to be added to the ACL.
5.At the "select" prompt, enter 1 to display the access list so you can verify that the WWN you entered was added to the ACL.
6.After verifying that the WWN was added correctly, enter 0 at the prompt to end the session.
7.At the "Update the FLASH?" prompt, enter y .
8.Press Enter to update the nonvolatile memory and end the session.
The following is an example of adding a member to the management server ACL
switch:admin> msconfigure
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 2
Port/Node WWN (in hex): [00:00:00:00:00:00:00:00] 20:00:00:20:37:65:ce:aa
*WWN is successfully added to the MS ACL.
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN
28 |
Fabric OS Administrators Guide |
|
53-1003130-01 |

Deleting a member from the ACL
select : (0..3) [2] 1
MS Access List consists of (14): { 20:00:00:20:37:65:ce:aa 20:00:00:20:37:65:ce:bb 20:00:00:20:37:65:ce:ff 20:00:00:20:37:65:ce:11 20:00:00:20:37:65:ce:22 20:00:00:20:37:65:ce:33 20:00:00:20:37:65:ce:44 10:00:00:60:69:04:11:24 10:00:00:60:69:04:11:23 21:00:00:e0:8b:04:70:3b 10:00:00:60:69:04:11:33 20:00:00:20:37:65:ce:55 20:00:00:20:37:65:ce:66 00:00:00:00:00:00:00:00
}
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 0
done ...
Update the FLASH? (yes, y, no, n): [yes] y *Successfully saved the MS ACL to the flash.
Deleting a member from the ACL
When you delete a member from the ACL, that member no longer has access to the management server.
NOTE
If you delete the last member of the ACL, leaving the ACL list is empty, then the management server will be accessible to all systems connected in-band to the fabric.
1.Connect to the switch and log in using an account with admin permissions.
2.Enter the msConfigure command. The command becomes interactive.
3.At the "select" prompt, enter 3 to delete a member based on its port/node WWN.
4.At the "Port/Node WWN" prompt, enter the WWN of the member to be deleted from the ACL.
5.At the "select" prompt, enter 1 to display the access list so you can verify that the WWN you entered was deleted from the ACL.
6.After verifying that the WWN was deleted correctly, enter 0 at the "select" prompt to end the session.
7.At the "Update the FLASH?" prompt, enter y .
8.Press Enter to update the nonvolatile memory and end the session.
The following is an example of deleting a member from the management server ACL
switch:admin> msconfigure
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 3
Port/Node WWN (in hex): [00:00:00:00:00:00:00:00] 10:00:00:00:c9:29:b3:84
*WWN is successfully deleted from the MS ACL.
0Done
1 Display the access list
Fabric OS Administrators Guide |
29 |
53-1003130-01 |
|

Viewing the contents of the management server database
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [3] 1
MS Access list is empty
0Done
1Display the access list
2Add member based on its Port/Node WWN
3 Delete member based on its Port/Node WWN select : (0..3) [1] 0
Viewing the contents of the management server database
Use the following procedure to view the contents of the management server database:
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msPlatShow command.
Example of viewing the contents of the management server platform database switch:admin> msplatshow
-----------------------------------------------------------
Platform Name: [9] "first obj" Platform Type: 5 : GATEWAY Number of Associated M.A.: 1
[35] "http://java.sun.com/products/plugin" Number of Associated Node Names: 1 Associated Node Names: 10:00:00:60:69:20:15:71
-----------------------------------------------------------
Platform Name: [10] "second obj" Platform Type: 7 : HOST_BUS_ADAPTER Number of Associated M.A.: 1 Associated Management Addresses:
[30] "http://java.sun.com/products/1" Number of Associated Node Names: 1 Associated Node Names: 10:00:00:60:69:20:15:75
Clearing the management server database
Use the following procedure to clear the management server database:
NOTE
The command msPlClearDB is allowed only in AD0 and AD255.
1.Connect to the switch and log in using an account assigned to the admin role.
2.Enter the msplClearDb command.
3.Enter y to confirm the deletion.
The management server platform database is cleared.
Topology discovery
The topology discovery feature can be displayed, enabled, and disabled; it is disabled by default. The commands mstdEnable and mstdDisable are allowed only in AD0 and AD255.
30 |
Fabric OS Administrators Guide |
|
53-1003130-01 |
 Loading...
Loading...