Comtrend NL3240U User Manual
6.9 IP Tunnel
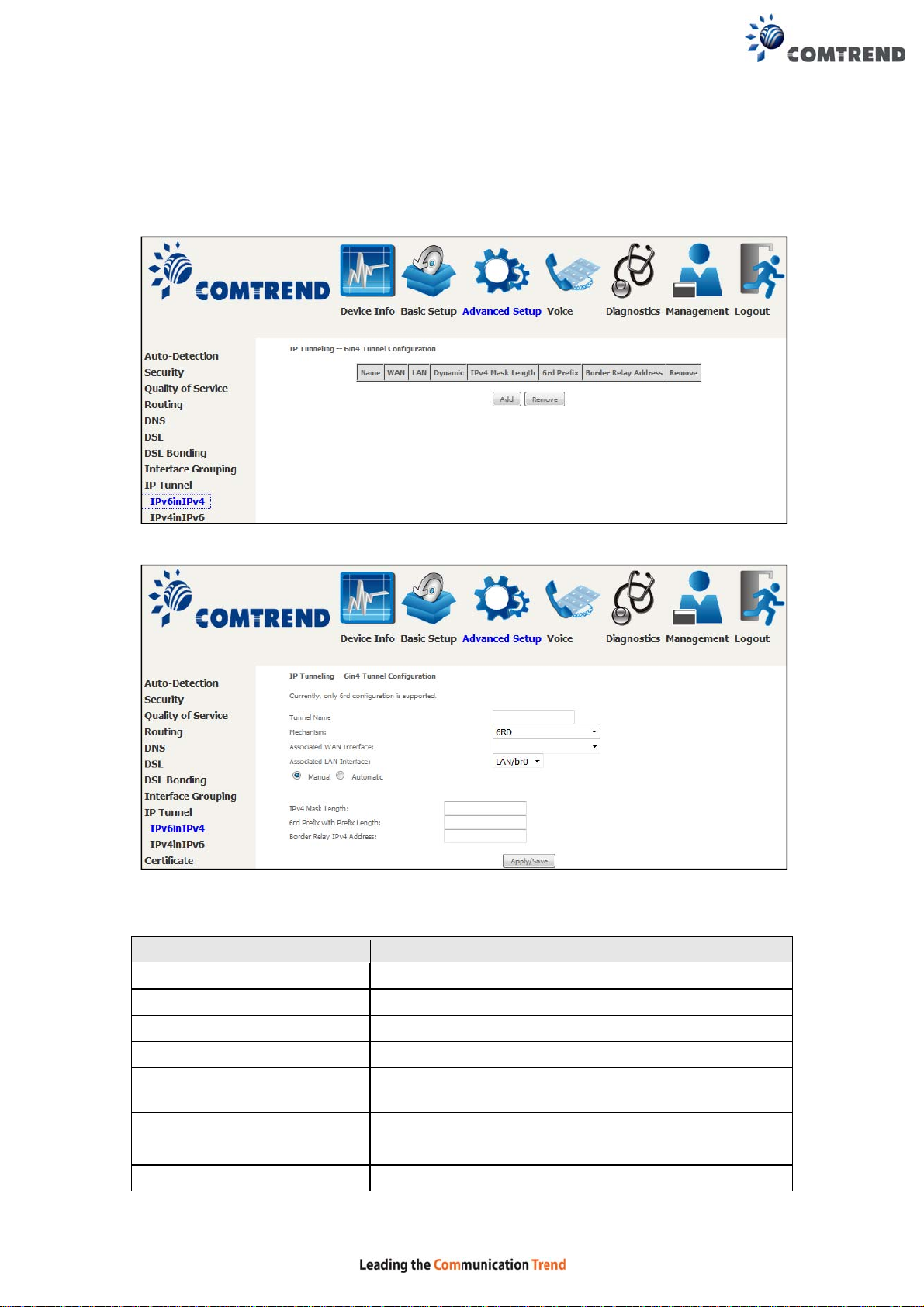
6.9.1 IPv6inIPv4
Configure 6in4 tunneling to encapsulate IPv6 traffic over explicitly-configured IPv4
links.
Click the Add button to display the following.
Click Apply/Save to apply and save the settings.
Options Description
Tunnel Name Input a name for the tunnel
Mechanism Mechanism used by the tunnel deployment
Associated WAN Interface Select the WAN interface to be used by the tunnel
Associated LAN Interface Select the LAN interface to be included in the tunnel
Manual/Automatic Select automatic for point-to-multipoint tunneling /
manual for point-to-point tunneling
IPv4 Mask Length The subnet mask length used for the IPv4 interface
6rd Prefix with Prefix Length Prefix and prefix length used fo r the IPv6 interface
Border Relay IPv4 Address Input the IPv4 address of the other device
103
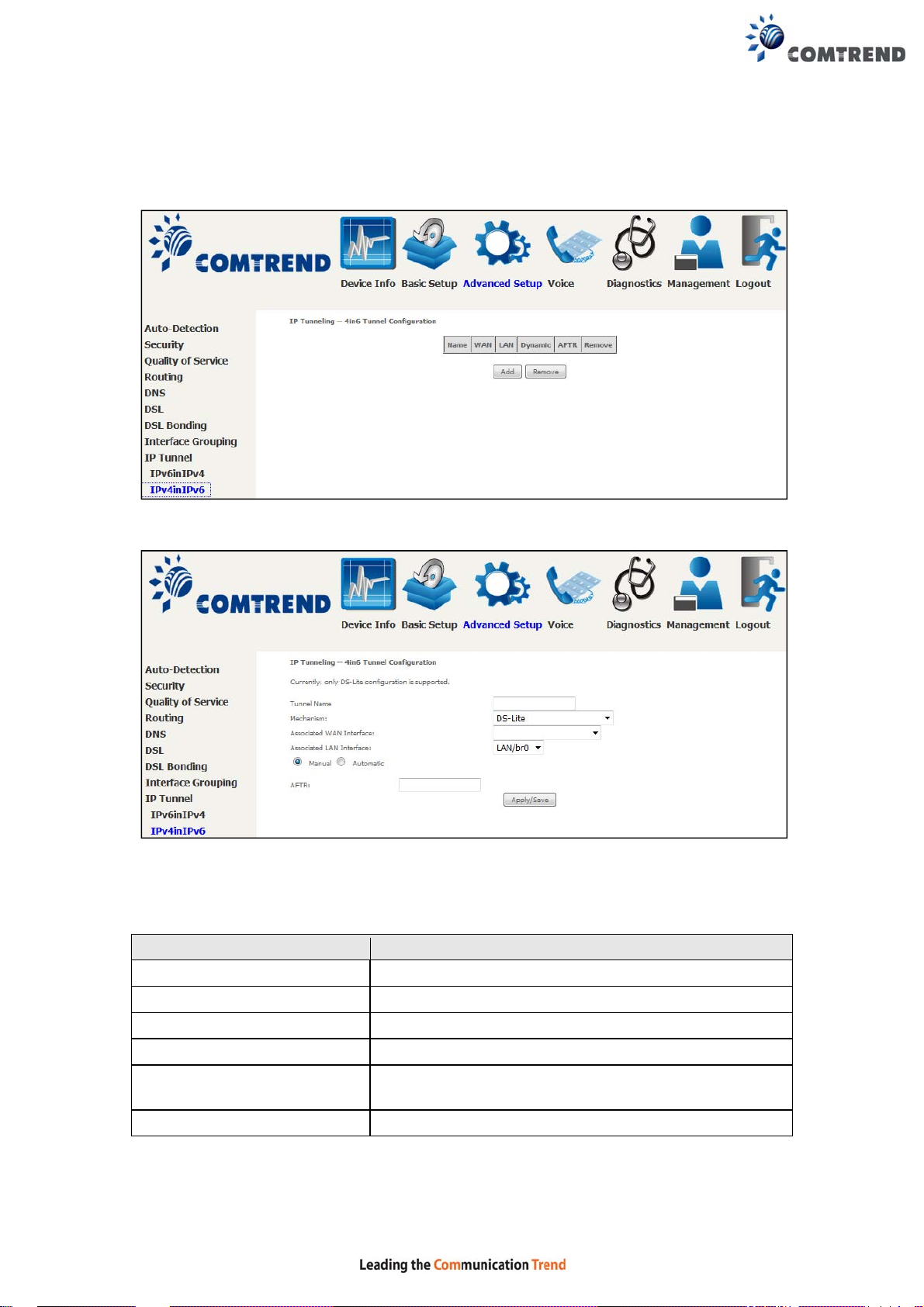
6.9.2 IPv4inIPv6
Configure 4in6 tunneling to encapsulate IPv4 traffic over an IPv6-onl y environment.
Click the Add button to display the following.
Click Apply/Save to apply and save the settings.
Options Description
Tunnel Name Input a name for the tunnel
Mechanism Mechanism used by the tunnel deployment
Associated WAN Interface Select the WAN interface to be used by the tunnel
Associated LAN Interface Select the LAN interface to be included in the tunnel
Manual/Automatic Select automatic for point-to-multipoint tunneling /
manual for point-to-point tunneling
AFTR Address of Address Family Translation Router
104
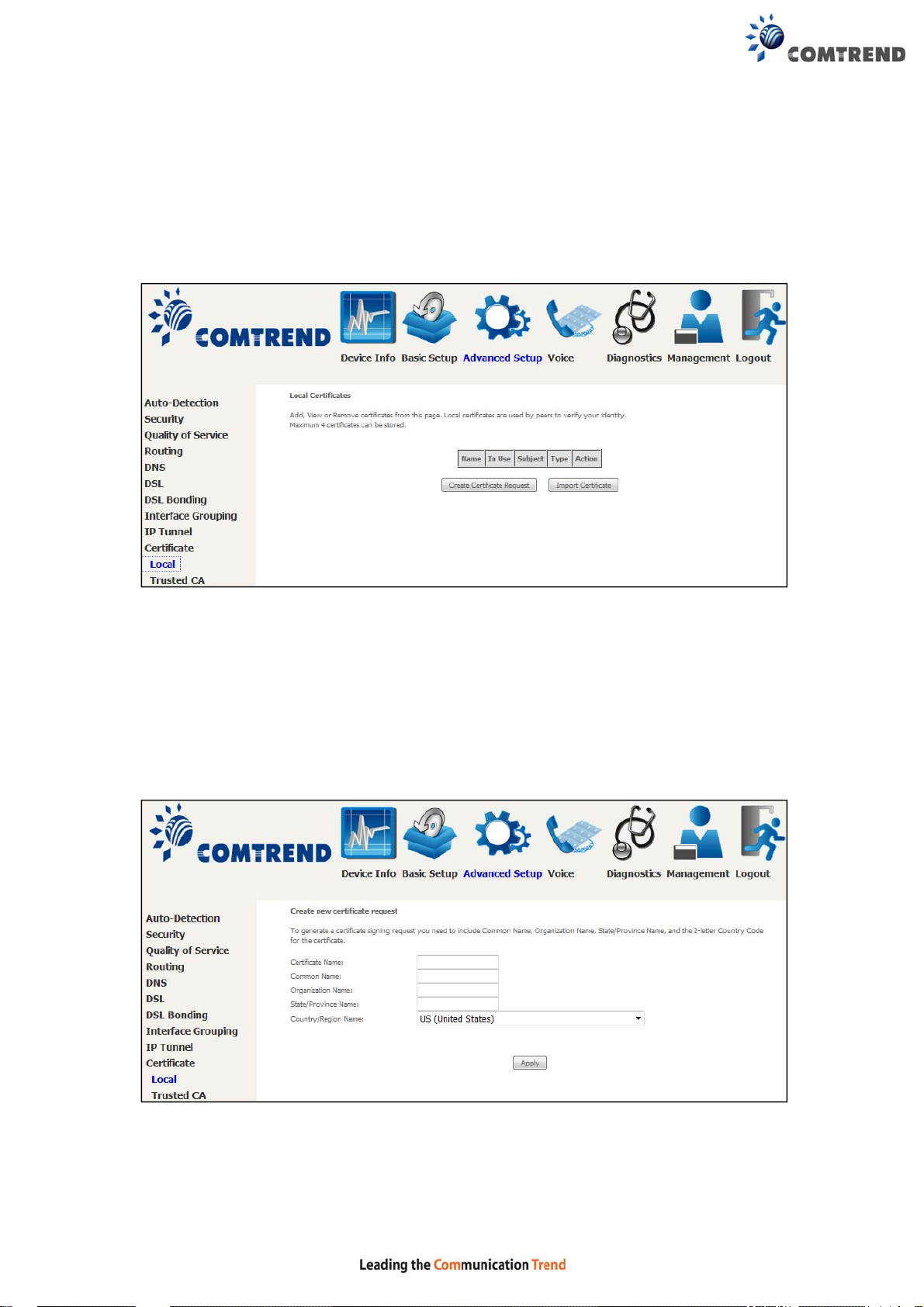
6.10 Certificate
A certificate is a public key, attached with its owner’s information (company name,
server name, personal real name, contact e-mail, postal address, etc) and digital
signatures. There will be one or more digital signatures attached to the certificate,
indicating that these entities have verified that this certificate is valid.
6.10.1 Local
CREATE CERTIFICATE REQUEST
Click Create Certificate Request to generate a certificate-signing request.
The certificate-signing request can be submitted to the vendor/ISP/ITSP to apply for
a certificate. Some information must be included in the certificate-signing request.
Your vendor/ISP/ITSP will ask you to provide the information they require and to
provide the information in the format they regulate. Enter the required information
and click Apply to generate a private key and a certificate-signing request.
The following table is provided for your reference.
105
Field Description
Certificate Name A user-defined name for the certificate.
Common Name Usually , the fully qualified domain name for the machine.
Organization Name The exact legal name of your organization.
Do not abbreviate.
State/Province Name The state or province where your organization is located.
It cannot be abbreviated.
Country/Region Name The two-letter ISO abbreviation for your country.
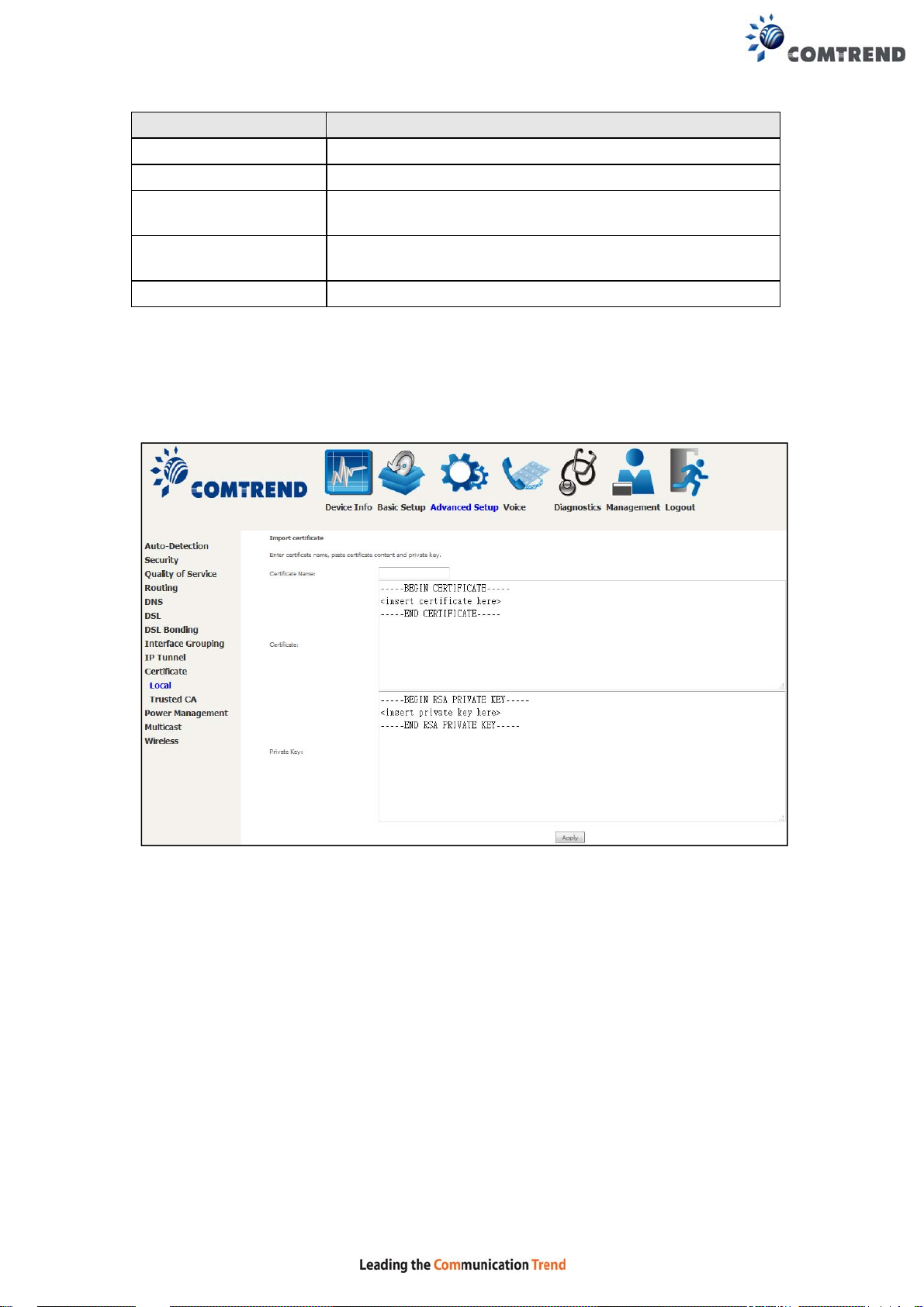
IMPORT CERTIFICATE
Click Import Certificate to paste the certificate content and the private key
provided by your vendor/ISP/ITSP into the corresponding boxes shown below.
Enter a certificate name and click the Apply button to import the certificate and its
private key.
106
6.10.2 Trusted CA
CA is an abbreviation for Certificate Authority, which is a part of the X.509 system.
It is itself a certificate, attached with the owner inf o rmation of this certificate
authority; but its purpose is not encryption/decryption. Its purpose is to sign and
issue certificates, in order to prove that these certificates are valid.
Click Import Certificate to paste the certificate content of your trusted CA. The
CA certificate content will be provided by your vendor/ISP /ITSP and is used to
authenticate the Auto-Configuration Server (ACS) that the CPE will connect to.
Enter a certificate name and click Apply to import the CA certificate.
107
6.11 Power Management
This screen allows for control of hardware modules to evaluate power consumpti on.
Use the buttons to select the desired option, click Apply and check the response.
108
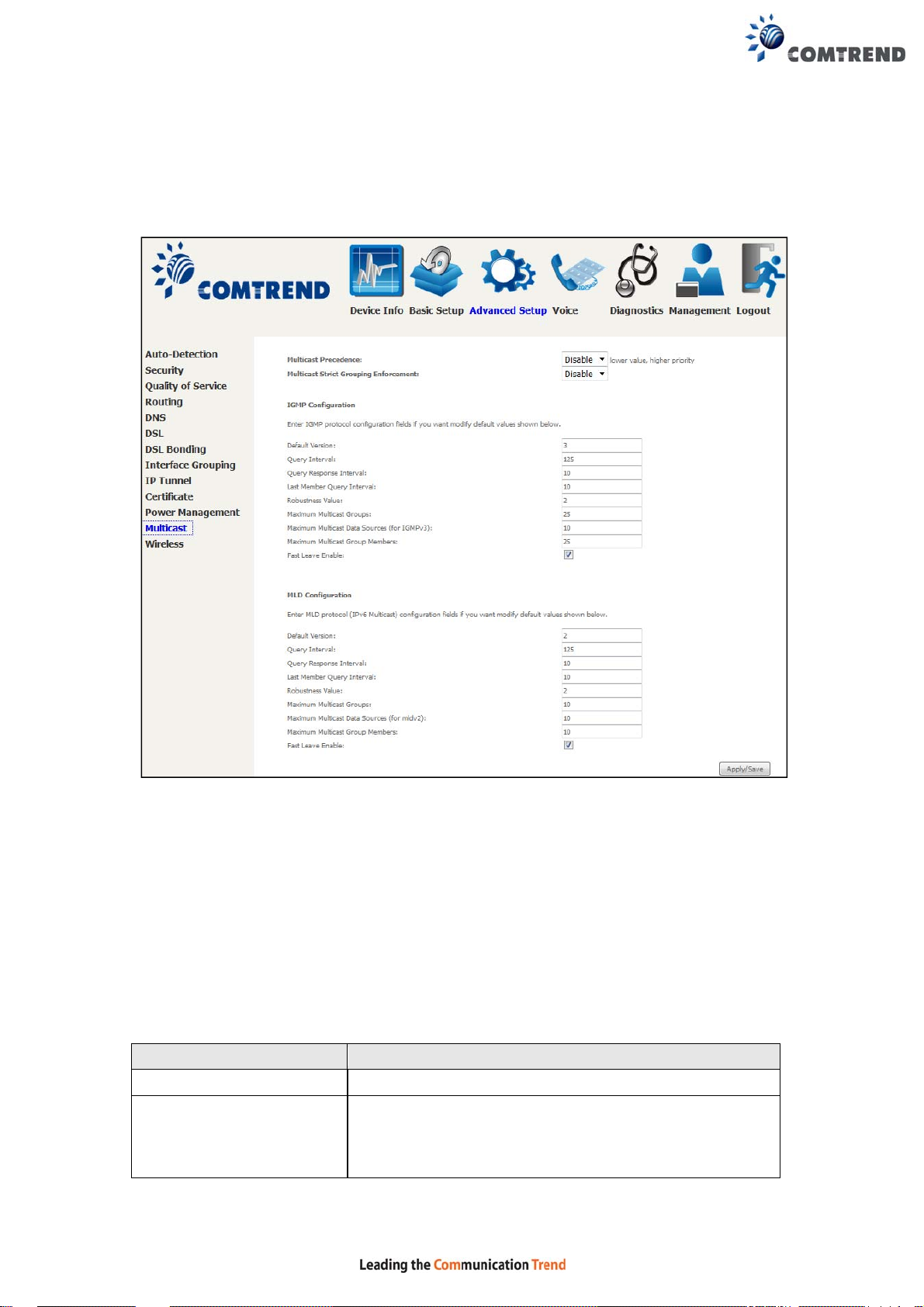
6.12 Multicast
Input new IGMP or MLD protocol configuration fields if you want modify default
values shown. Then click Apply/Save.
Multicast Precedence:
Select precedence of multicast packets.
Multicast Strict Grouping Enforcement:
Enable/Disable multicast strict grouping.
Field Description
Default Version Define IGMP using version with video server.
Query Interval The query interval is the amount of time in seconds
between IGMP General Query messages sent by the
router (if the router is the querier on this subnet). The
default query interval is 125 seconds.
109
Field Description
Query Response Interval The query response interval is the maximum amount
of time in seconds that the IGMP router waits to
receive a response to a General Query message. The
query response interval is the Maximum Response
Time field in the IGMP v2 Host Membership Query
message header. The default query response interval
is 10 seconds and must be less than the query
interval.
Last Member Query
Interval
The last member query interval is the amount of time
in seconds that the IGMP router waits to receive a
response to a Group-Specific Query message. The last
member query interval is also the amount of time in
seconds between successive Group-Specific Query
messages. The default last member query interval is
10 seconds.
Robustness Value The robustness variable is a way of indicating how
susceptible the subnet is to lost packets. IGMP can
recover from robustness variable minus 1 lost IGMP
packets. The robustness variable should be set to a
value of 2 or greater. The default robustness variable
value is 2.
Maximum Multicast
Setting the maximum number of Multicast groups.
Groups
Maximum Multicast Data
Define the maximum multicast video stream number.
Sources (for IGMPv3)
Maximum Multicast
Group Members
Setting the maximum number of groups that ports
can accept.
Fast Leave Enable When you enable IGMP fast-leave processing, the
switch immediately removes a port when it detects an
IGMP version 2 leave message on that port.
110
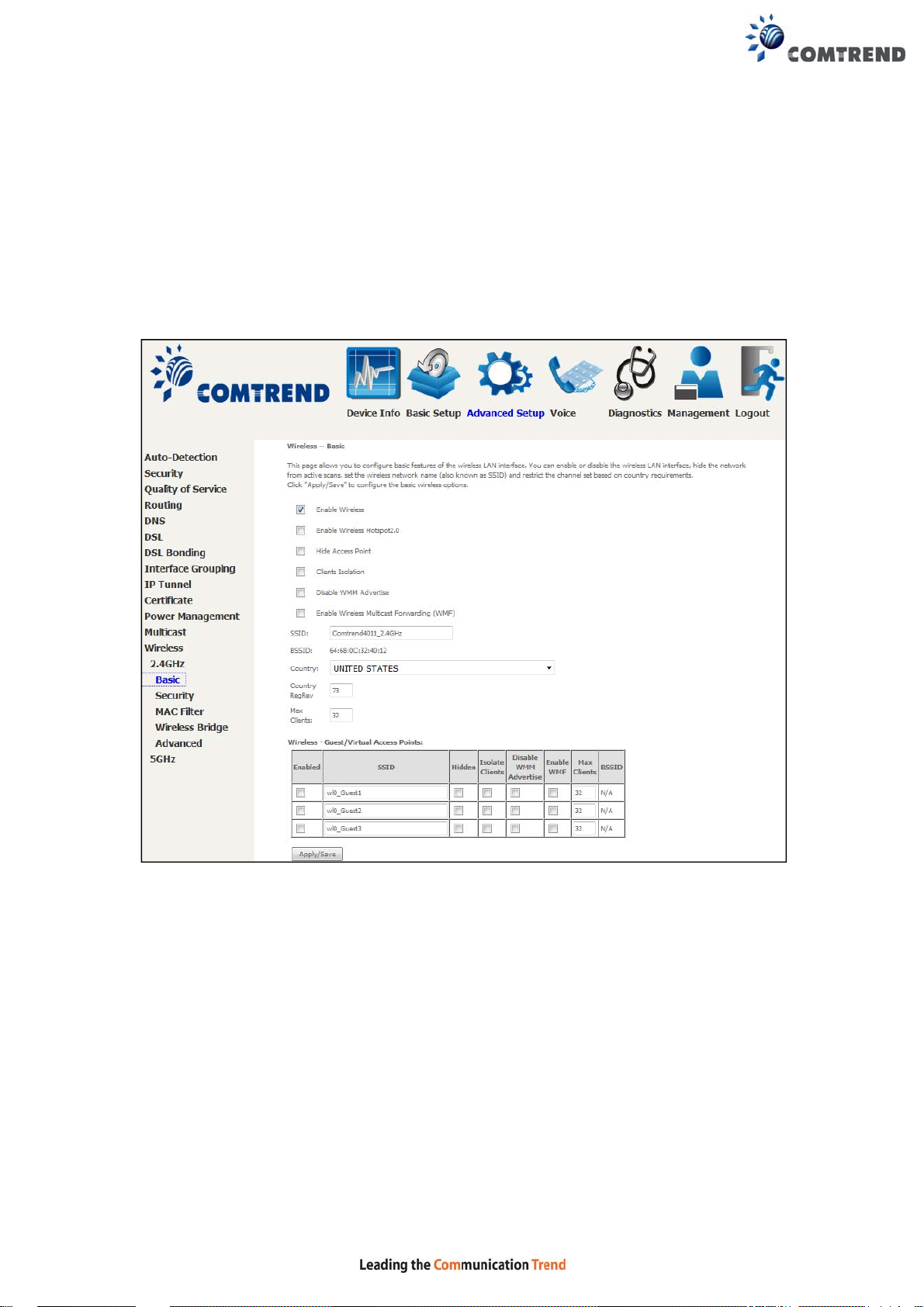
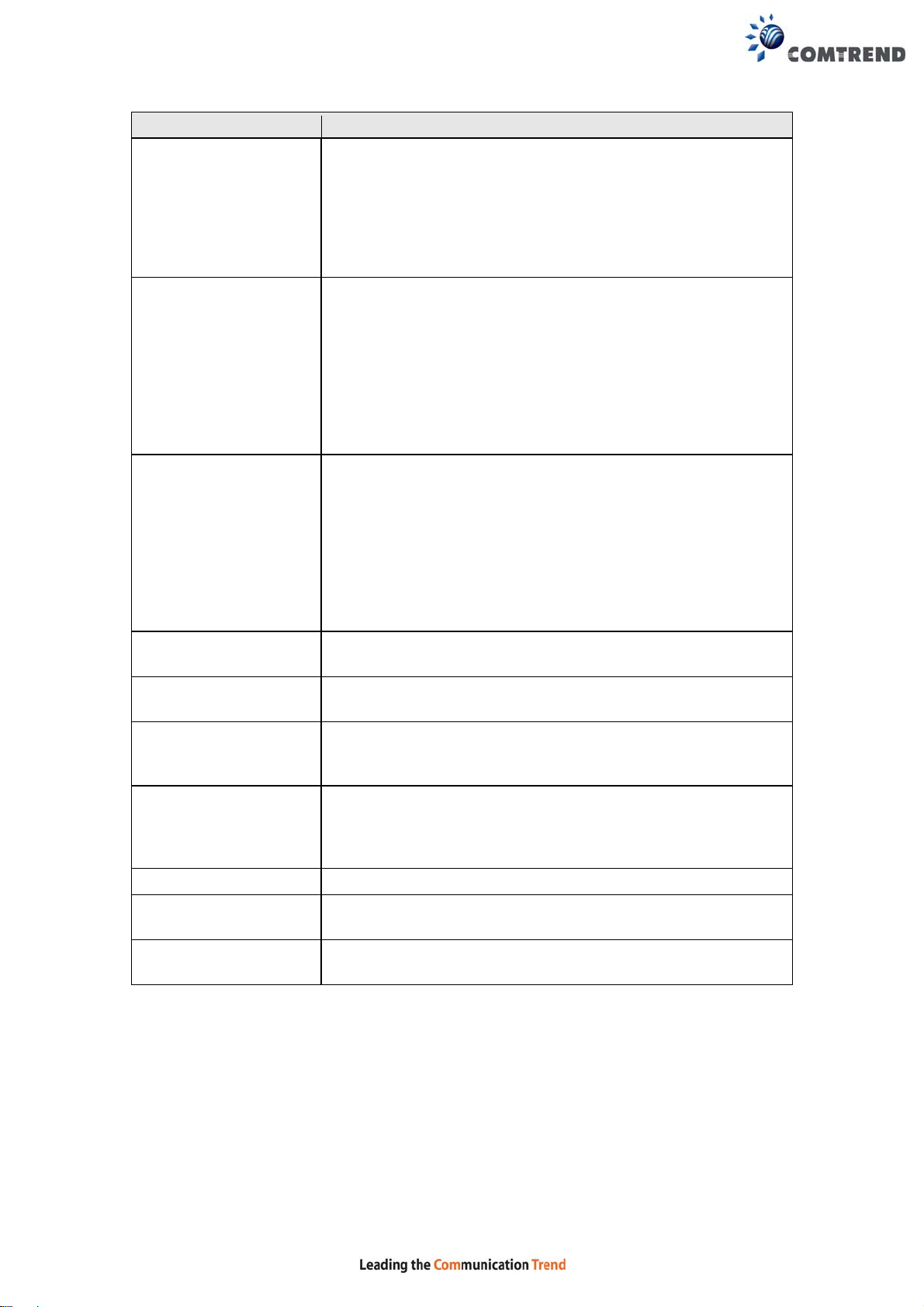
6.13 Wireless
6.13.1 Basic 2.4GHz
The Basic option allows you to configure basic features of the wireless LAN interface.
Among other things, you can enable or disable the wireless LAN interface, hide the
network from active scans, set the wireless network name (also known as SSID)
and restrict the channel set based on country requirements.
Click Apply/Save to configure the basic wireless options.
Consult the table below for descriptions of these options.
111
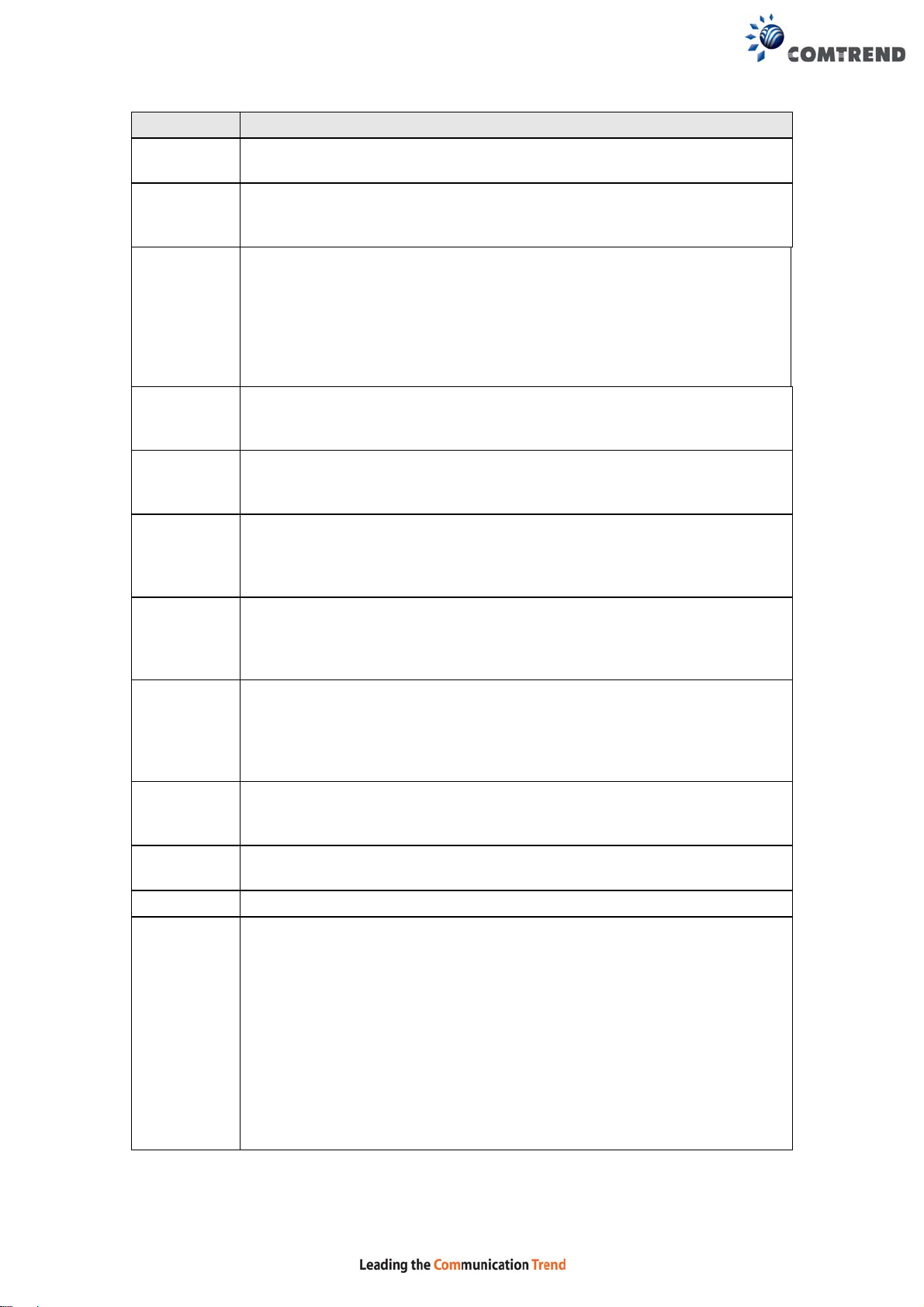
Option Description
Enable
Wireless
Enable
Wireless
Hotspot2.0
Hide Access
Point
A checkbox that enables or disables the wireless LAN interface.
When selected, a set of basic wireless options will appear.
Enable Wireless Hotspot 2.0 (Wi-Fi Certified Passpoint) on the
wireless interface.
Select Hide Access Point to protect the access point from detection by
wireless active scans. To check AP status in Windows XP, open
Network Connections from the start Menu and select View
Available Network Connections. If the access point is hidden, it
will not be listed there. To connect a client to a hidden access point,
the station must add the access point manually to its wireless
configuration.
Clients
Isolation
When enabled, it prevents client PCs from seeing one another in My
Network Places or Network Neighborhood. Also, prevents one
wireless client communicating with another wireless client.
Disable
WMM
Advertise
Enable
Stops the router from ‘advertising’ its Wireless Multimedia (WMM)
functionality , which provides basic quality of service for time-sensitive
applications (e.g. VoIP, Video).
Select the checkbox to enable this function.
Wireless
Multicast
Forwarding
SSID
[1-32
characters]
Sets the wireless network name. SSID stands for Service Set
Identifier. All stations must be configured with the correct SSID to
access the WLAN. If the SSID does not match, that user will not be
granted access.
BSSID The BSSID is a 48-bit identity used to identify a particular BSS (Basic
Service Set) within an area. In Infrastructure BSS networks, the
BSSID is the MAC (Media Access Control) address of the AP (Access
Point); and in Independent BSS or ad hoc networks, the BSSID is
generated randomly.
Country A drop-down menu that permits worldwide and specific national
settings. Local regulations limit channel range:
US= worldwide, Japan=1-14, Jordan= 10-13, Israel= 1-13
Country
Wireless country code for transmit power limit.
RegRev
Max Clients The maximum number of clients that can access the router.
Wireless -
Guest /
Virtual
Access
Points
This router supports multiple SSIDs called Guest SSIDs or Virtual
Access Points. To enable one or more Guest SSIDs select the
checkboxes in the Enabled column. T o hide a Guest SSID select its
checkbox in the Hidden column.
Do the same for Isolate Clients and Disable WMM Advertise. For
a description of these two functions, see the previous entries for
“Clients Isolation” and “Disable WMM Advertise”. Similarly , for Enable
WMF, Max Clients and BSSID, consult the matching entries in this
table.
NOTE: Remote wireless hosts cannot scan Guest SSIDs.
112
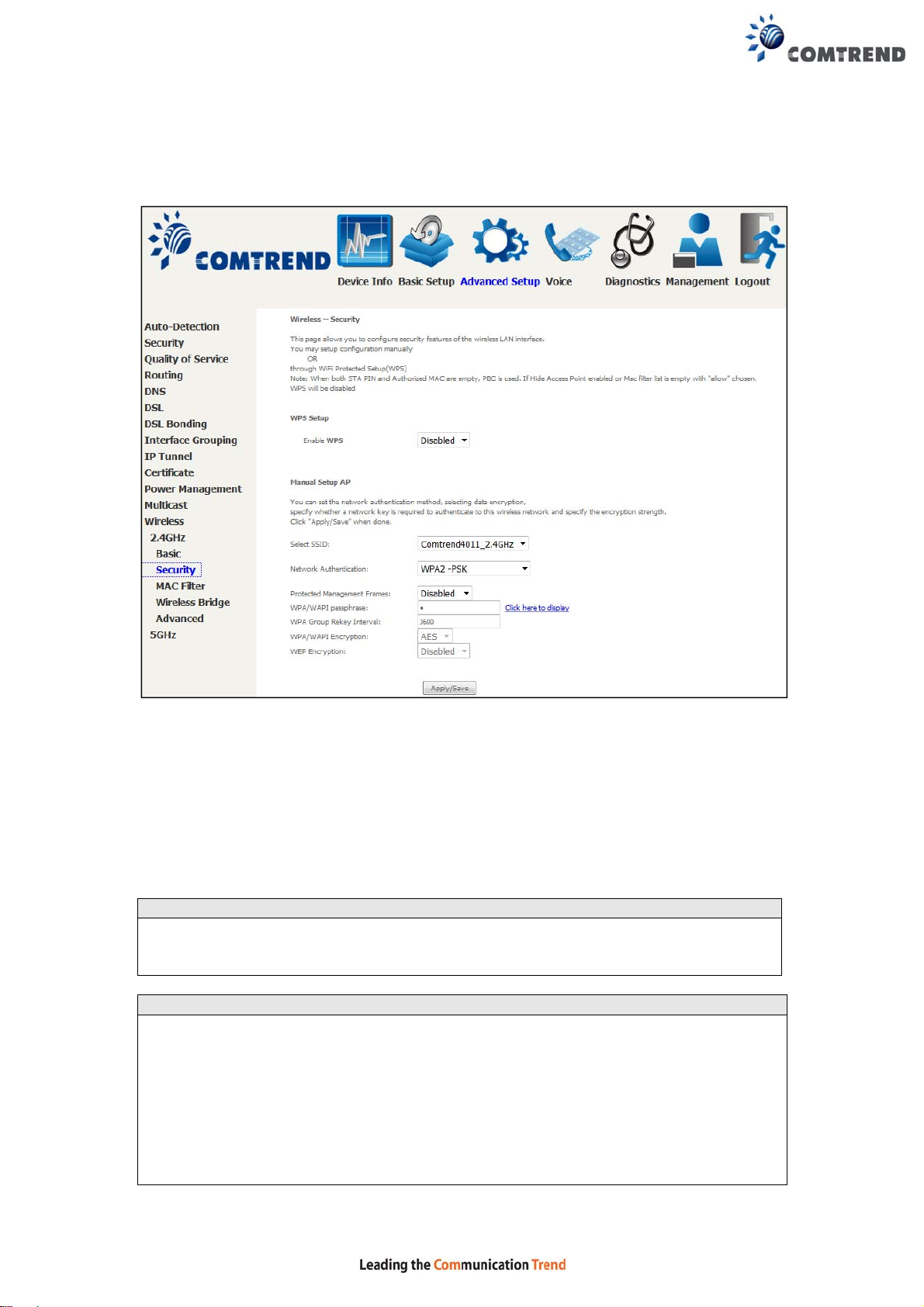
6.13.2 Security 2.4GHz
The following screen appears when Wireless Security is selected. The options shown
here allow you to configure security features of the wireless LAN interface.
Please see 6.13.3 for WPS setup instructions.
Click Apply/Save to implement new configuration settings.
WIRELESS SECURITY
Setup requires that the user configure these settings using the Web User Interface
(see the table below).
Select SSID
Select the wireless network name from the drop-down menu. SSID stands for
Service Set Identifier. All stations must be configured with the correct SSID to
access the WLAN. If the SSID does not match, that client will not be gr anted access.
Network Authentication
This option specifies whether a network key is used for authenticat ion to the
wireless network. If network authe ntication is set to Open, then no authenti cation
is provided. Despite this, the iden tity of the client is still verified.
Each authentication type has its own settings. For example, selecting 802.1X
authentication will reveal the RADIUS Server IP address, Port and Key fields. WEP
Encryption will also be enabled as shown below.
Different authentication type pops up different settings requests.
113
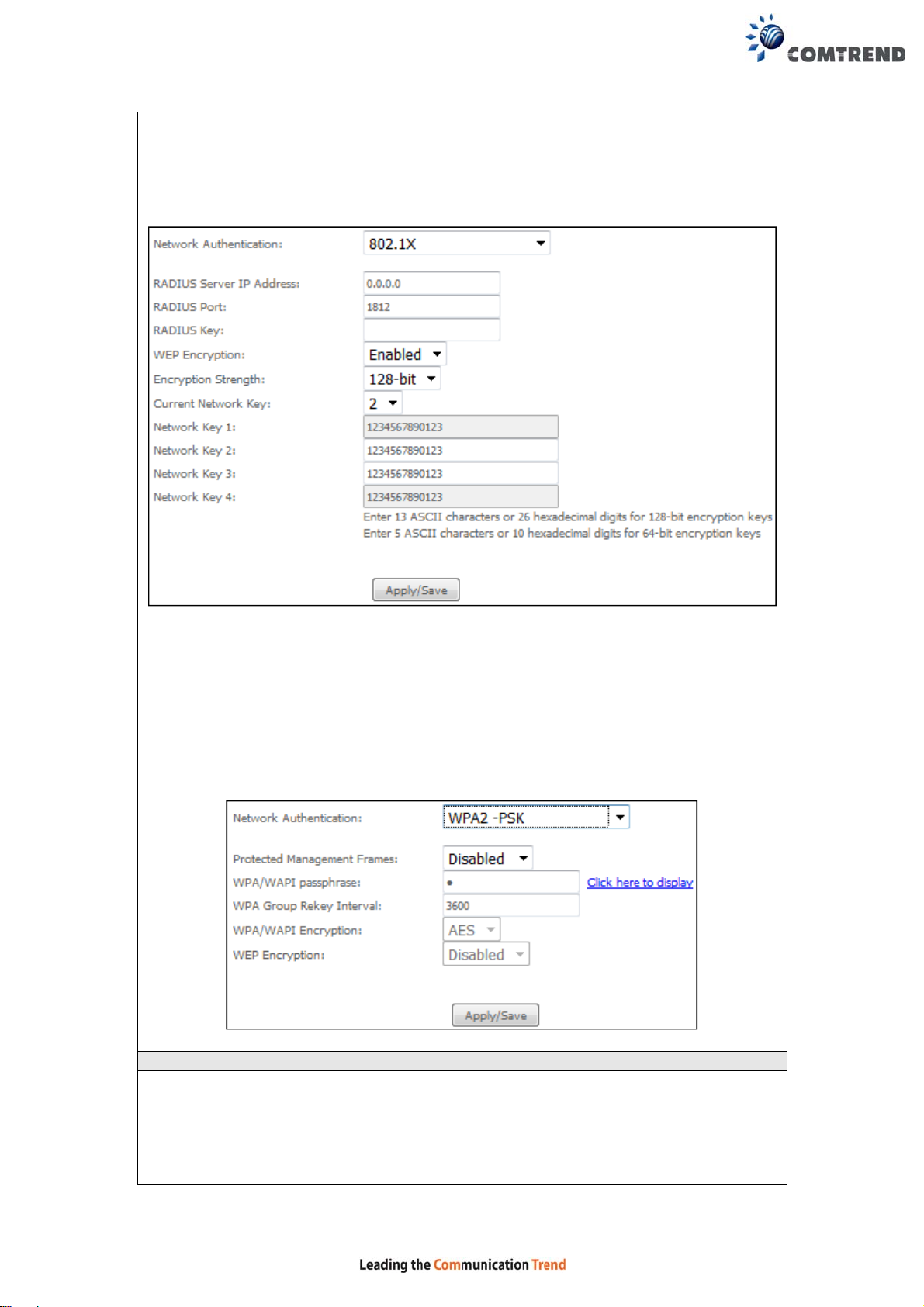
Choosing 802.1X, enter RADIUS Server IP address, RADIUS P ort, RADIUS key and
Current Network Key.
Also, enable WEP Encryption and select Encryption Strength.
Select the Current Network Key and enter 13 ASCII characters or 26 hexadecimal
digits for 128-bit encryption keys and enter 5 ASCII characters or 10 hexadecimal
digits for 64-bit encryption keys.
Choosing WPA2-PSK, you must enter WPA Pre-Shared Key and Group Rekey
Interval.
WEP Encryption
This option specifies whether data sent over the network is encrypted. The same
network key is used for data encryption and network authentication. Four network
keys can be defined although only one can be used at any one time. Use the Current
Network Key list box to select the appropriate network key.
114
Security options include authentication and encryption services based on the wire d
equivalent privacy (WEP) algorithm. WEP is a set of security services used to
protect 802.11 networks from unauthorized access, such as eavesdropping; in this
case, the capture of wireless network traffic.
When data encryption is enabled, secret shared encryption keys are generated and
used by the source station and the destination station to alter frame bits, thus
avoiding disclosure to eavesdroppers.
Under shared key authentication, each wire less station is assumed to have received
a secret shared key over a secure channel that is independent from the 802.11
wireless network communications channel.
Encryption Strength
This drop-down list box will display when WEP Encryption is en abled. The key
strength is proportional to the number of binary bits comprising the key. This
means that keys with a greater number of bits have a grea ter degree of security and
are considerably more difficult to crack. Encryption strength can be set to either
64-bit or 128-bit. A 64-bit key is equivalent to 5 ASCII characters or 10
hexadecimal numbers. A 128-bit key contains 13 ASCII characters or 26
hexadecimal numbers. Each key contains a 24-bit header (an initiation vector)
which enables parallel decoding of multiple streams of encrypted data.
115
6.13.3 WPS 2.4GHz
Wi-Fi Protected Setup (WPS) is an industry standard that simplifies wireless security
setup for certified network devices. Every WPS certified device has both a PIN
number and a push button, located on the device or accessed through device
software. The NexusLink 3240 has a WPS button on the device.
Devices with the WPS logo (shown here)
support WPS. If the WPS logo is not present
on your device it still may support WPS, in
this case, check the device documentation
for the phrase “Wi-Fi Protected Setup”.
NOTE: WPS is only available in Open, WPA-PSK, WPA2-PSK and Mixed
WPA2/WPA-PSK network authentication modes. Other authentication
modes do not use WPS so they must be configured manually.
To configure security settings with WPS, follow the procedures below .
I. Setup
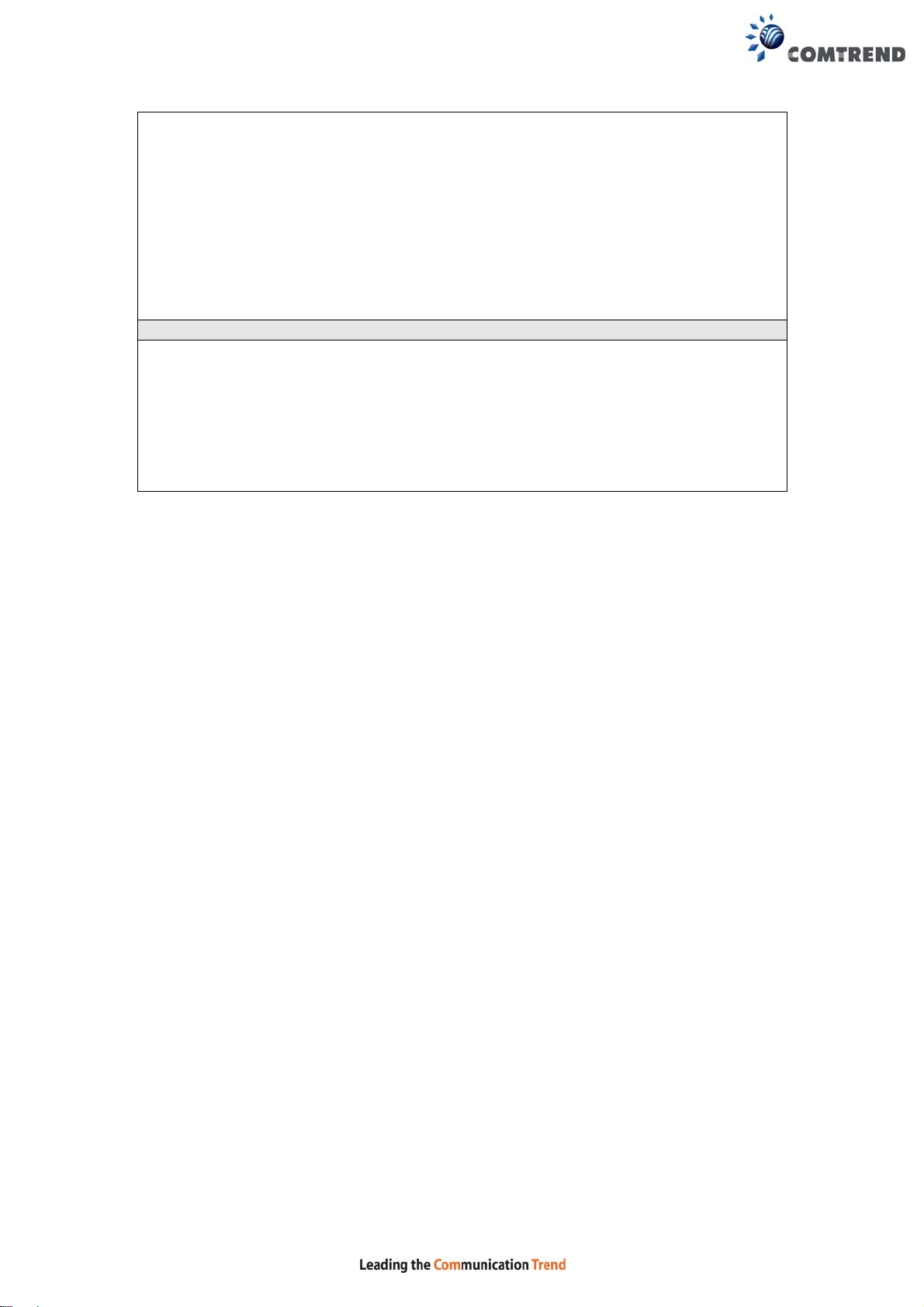
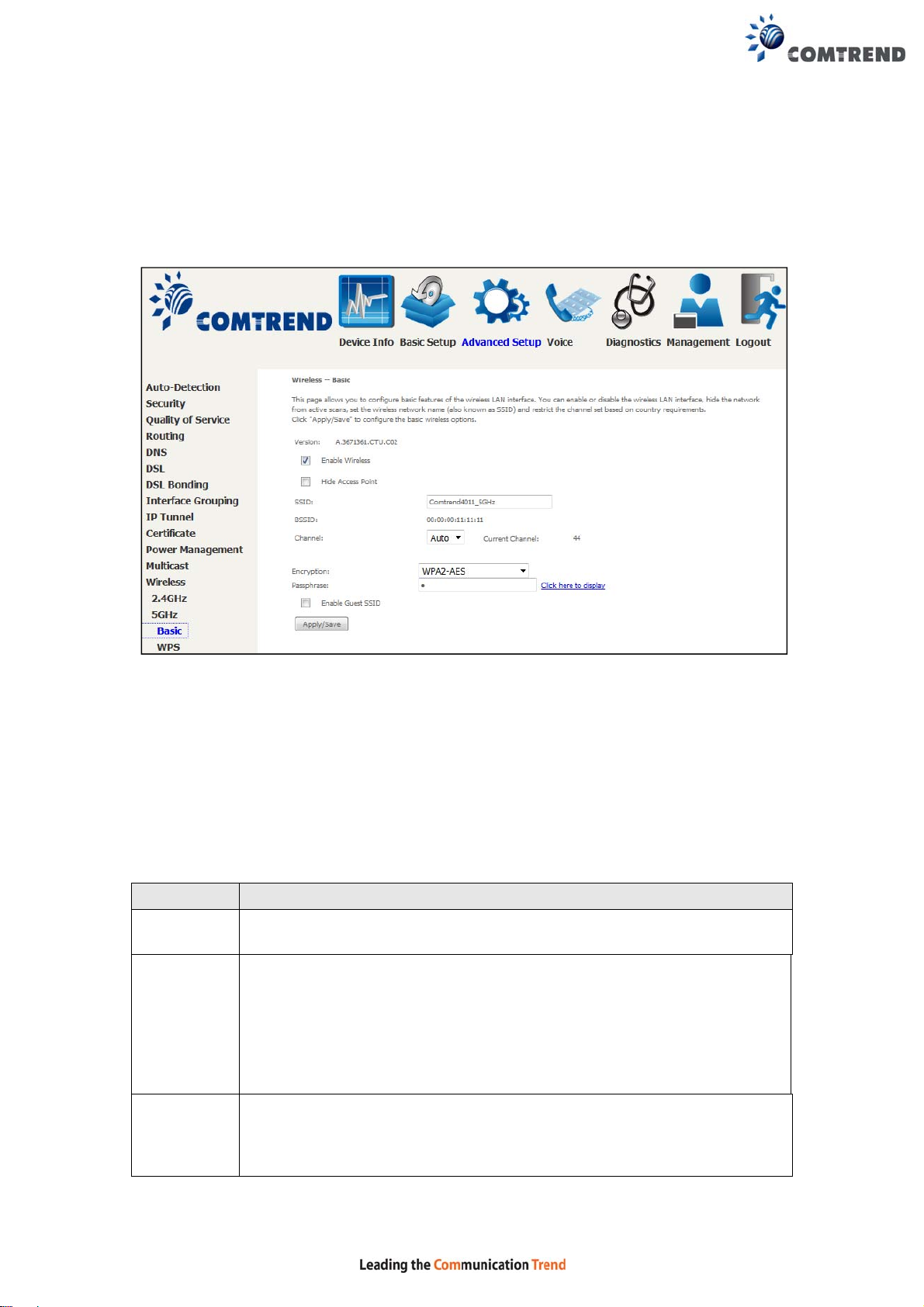
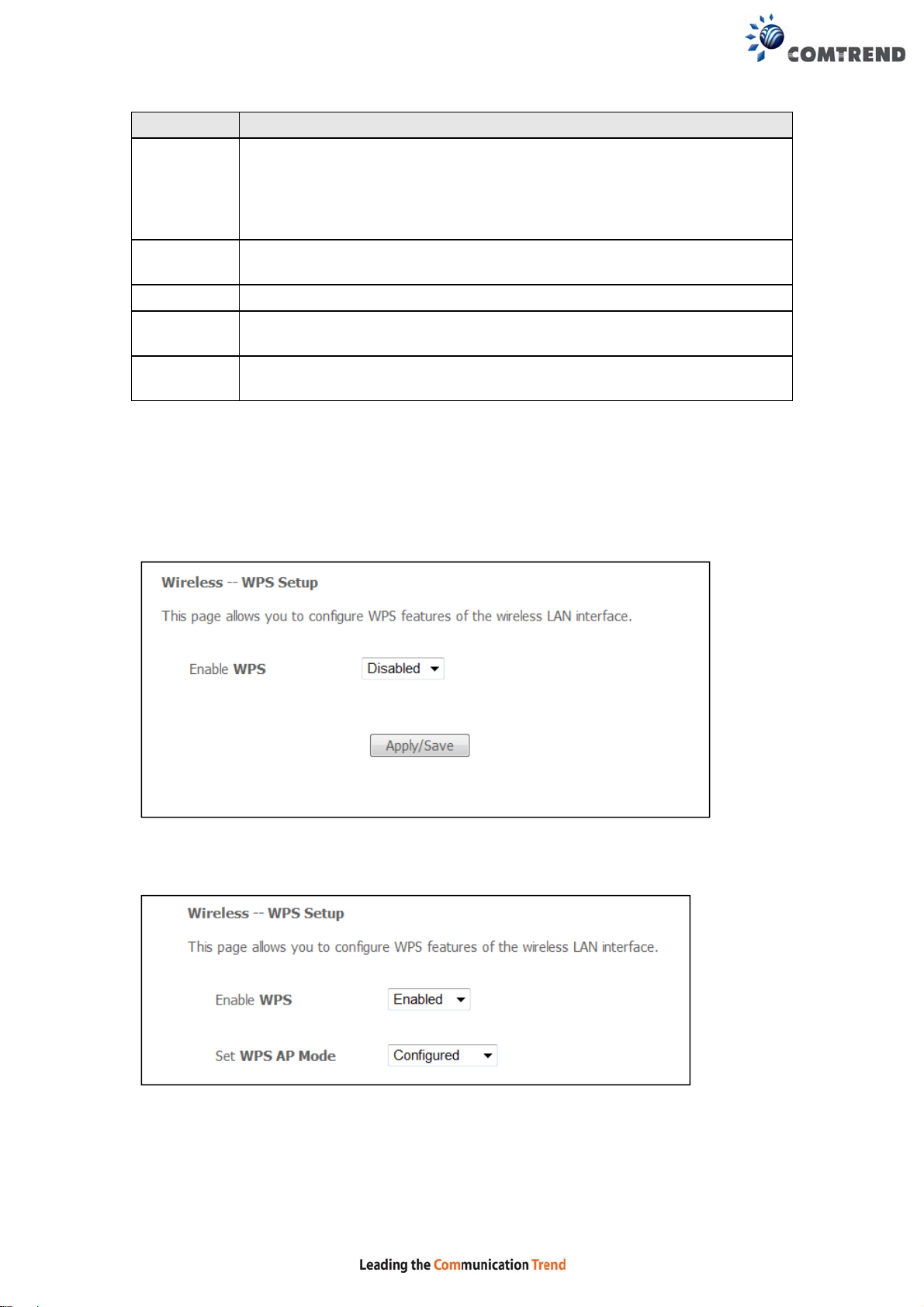
Step 1: Enable WPS by selecting Enabled from the drop down list box shown.
Step 2: Set the WPS AP Mode. Configured is used when the NexusLink 3240 will
assign security settings to clients. Unconfigured is used when an
external client assigns security settings to the NexusLink 3240.
NOTES: Your client may or may not have the ability to provide security settings to
the NexusLink 3240. If it does not, then you must set the WPS AP mode
to Configured. Consult the device documentation to check its capabilities.
116
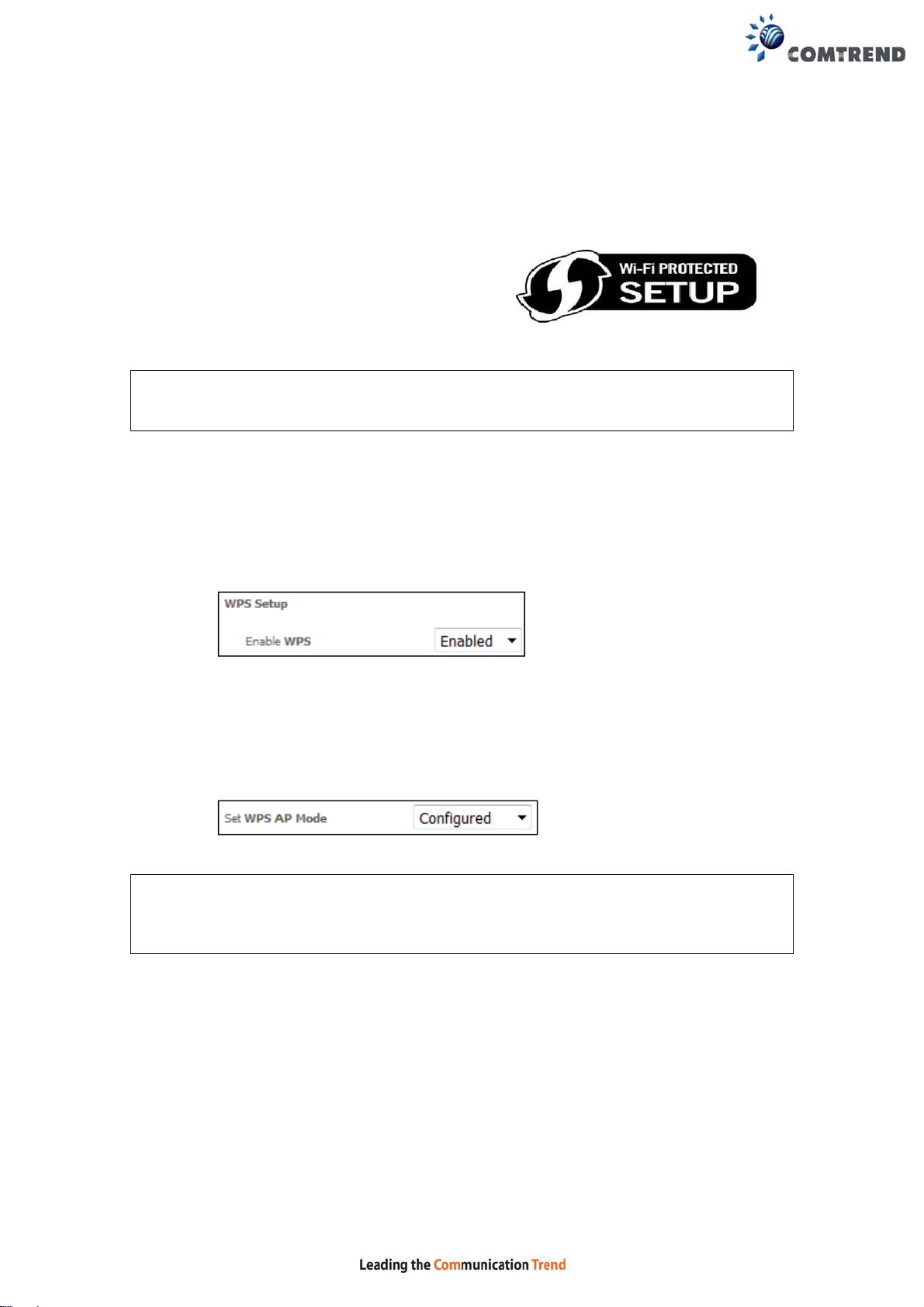
IIa. PUSH-BUTTON CONFIGURATION
The WPS push-button configuration provides a semi-automated configuration
method. The WPS button on the front panel of the router can be used for this
purpose.
The WPS push-button configuration is described in the procedure below. It is
assumed that the Wireless function is Enabled and that the router is configured as
the Wireless Access Point (AP) of your WLAN. In addition, the wireless client must
also be configured correctly and turned on, with WPS function enabled.
NOTE: The wireless AP on the router searches for 2 minutes. If the router stops
searching before you complete Step 4, return to Step 3.
Step 3: Press WPS button
Press the WPS button on the front panel of the router. The WPS LED will
blink to show that the router has begun searching for the client.
Step 4: Go to your WPS wireless client and activate the push-button function.
A typical WPS client screenshot is shown below as an example.
Now go to Step 7 (part III. Check Connection) to check the WPS connection.
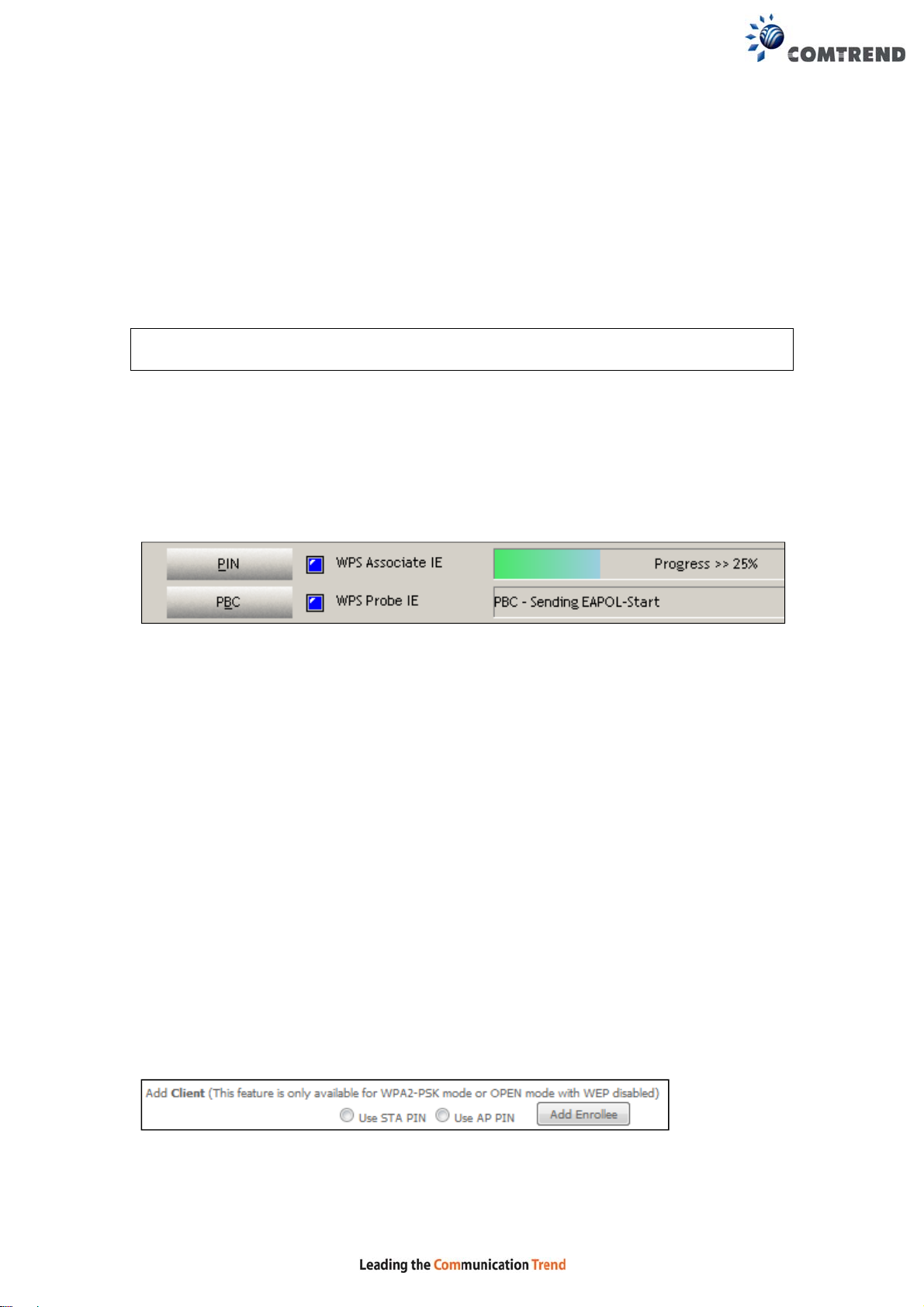
IIb. WPS – PIN CONFIGURATION
Using this method, security settings are configured with a personal identification
number (PIN). The PIN can be found on the device itself or within the software.
The PIN may be generated randomly in the latter case. To obtain a PIN number for
your client, check the device documentation for specific instructions.
The WPS PIN configuration is described in the procedure below. It is assumed that
the Wireless function is Enabled and that the router is conf igured as the Wireless
Access Point (AP) of your wireless LAN. In addition, the wireless client must also be
configured correctly and turned on, with WPS function enabled.
Step 5: Select the PIN radio button in the WSC Setup section of the Wireless
Security screen, as shown in A or B below , and then click the appropriate
button based on the WSC AP mode selected in step 2.
A - For Configured mode, click the Add Enrollee button.
117
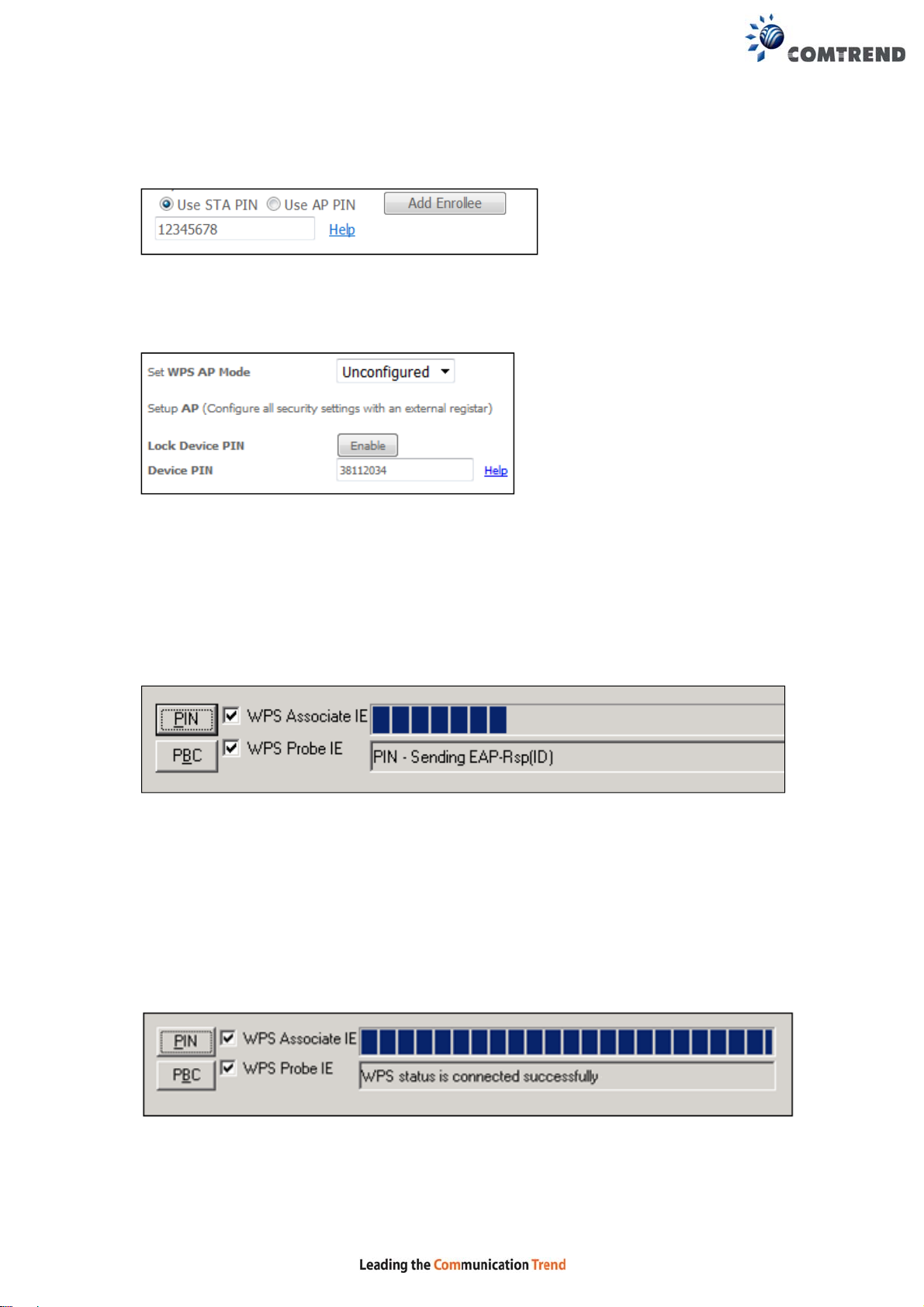
Enter STA PIN: a Personal Identification N umber (PIN) has to be read from either
a sticker or the display on the new wireless device. This PIN must then be inputted
at representing the network, usually the Access Point of the network.
B - For Unconfigured mode, click the Config AP button.
Step 6: Activate the PIN functio n on the wi reless client. For Configured mode,
the client must be configured as an Enrollee. For Unconfigured mode,
the client must be configured as the Registr ar. This is different from the
External Registrar function provided in Windows Vista.
The figure below provides an example of a WPS client PIN function in-progress.
III. CHECK CONNECTION
Step 7: If the WPS setup method was successful, you will be able access the
wireless AP from the client. The client software should show the status.
The example below shows that the connection established successfully.
You can also double-click the Wirele ss Network Connection icon from the
Network Connections window (or the system tr ay) to confirm the status of
the new connection.
118
6.13.4 MAC Filter 2.4GHz
This option allows access to the router to be restricted based upon MAC addresses.
To add a MAC Address filter, click the Add button shown below. To delete a filter,
select it from the MAC Address table below and click the Remove button.
Option Description
Select
SSID
MAC
Restrict
Mode
MAC
Address
After clicking the Add button, the following screen appears.
Select the wireless network name from the drop-down menu. SSID
stands for Service Set Identifier. All stations must be configured with the
correct SSID to access the WLAN. If the SSID does not mat ch, that user
will not be granted access.
Disabled: MAC filtering is disabled.
Allow: Permits access for the specified MAC addresses.
Deny: Rejects access for the specified MAC addresses.
Lists the MAC addresses subject to the MAC Restrict Mode. A maximum
of 60 MAC addresses can be added. Every network device has a unique
48-bit MAC address. This is usually shown as xx.xx.xx. xx.xx.xx, where
xx are hexadecimal numbers.
119
Enter the MAC address in the box provided and click Apply/Save.
120
6.13.5 Wireless Bridge 2.4GHz
This screen allows for the configuration of wireless bridge features of the WiFi
interface. See the table below for detailed explanations of the various options.
Click Apply/Save to implement new configuration settings.
Feature Description
Bridge Restrict Selecting Disabled disables wireless bridge restriction, which
means that any wireless bridge will be granted access.
Selecting Enabled or Enabled (Scan) enables wireless bridge
restriction. Only those bridges selected in the Remote Bridges
list will be granted access. Click Refresh to update the station
list when Bridge Restrict is enabled.
Remote
Bridges MAC
Address
Enter the list of MAC addresses allowed to act as wireless bridge
clients.
121
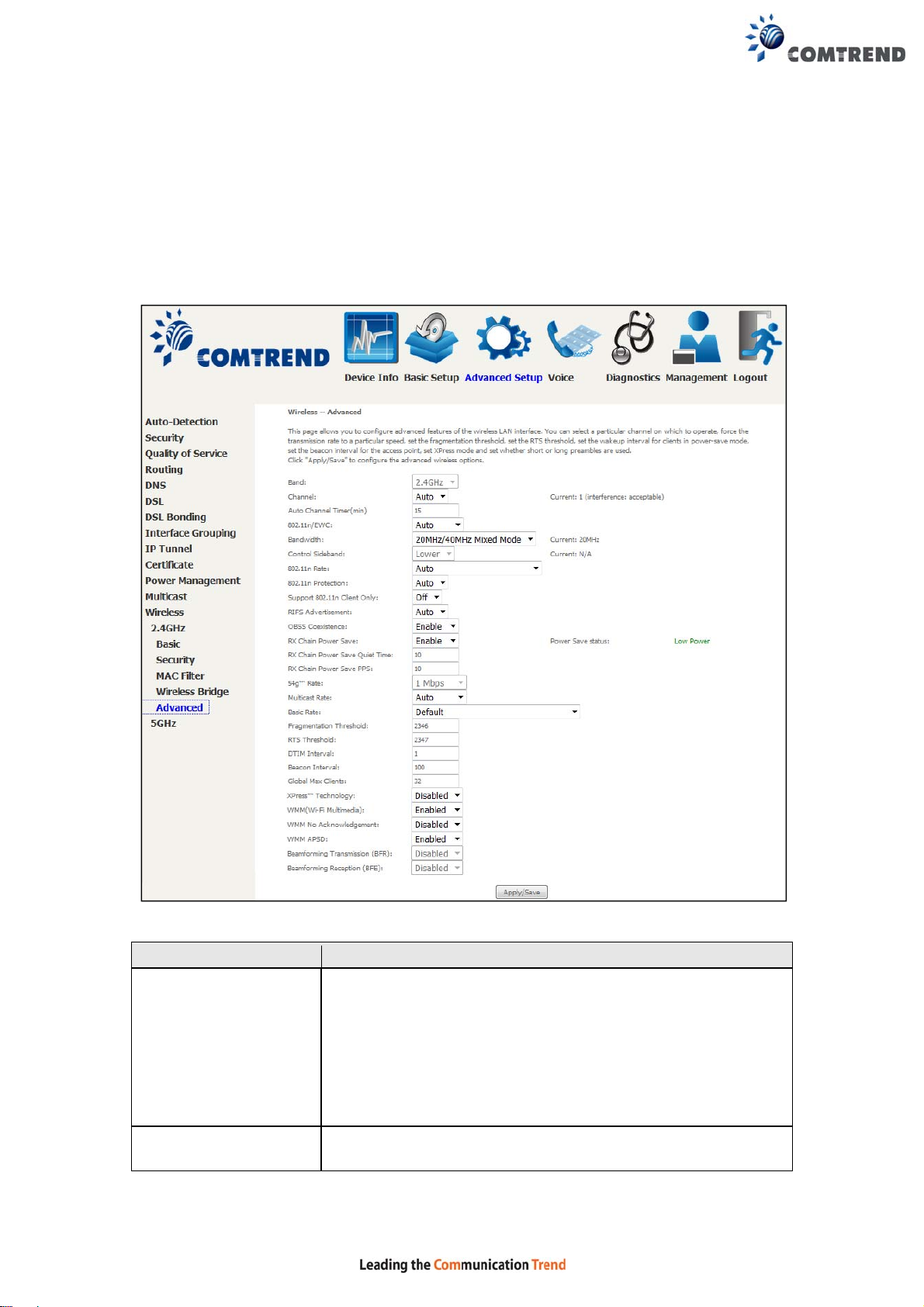
6.13.6 Advanced 2.4GHz
The Advanced screen allows you to configure advanced features o f the wireless LAN
interface. You can select a particular channel on which to operate, force the
transmission rate to a particular speed, set the fragmentation threshold, set the RTS
threshold, set the wakeup interval for clients in power-save mode, set the beacon
interval for the access point, set XPress mode and set whether short or long
preambles are used. Click Apply/Save to set new advanced wireless options.
Field Description
Band Set to 2.4 GHz for compatibility with IEEE 802.11x
standards. The new amendment allows IEEE 802.11n units
to fall back to slower speeds so that legacy IEEE 802.11x
devices can coexist in the same network. IEEE 802.11g
creates data-rate parity at 2.4 GHz with the IEEE 802.11a
standard, which has a 54 Mbps rate at 5 GHz. (IEEE
802.11a has other differences compared to IEEE 802.11b
or g, such as offering more channels.)
Channel Drop-down menu that allows selection of a specific
channel.
122
Field Description
Auto Channel Timer
Auto channel scan timer in minutes (0 to disable)
(min)
802.11n/EWC An equipment interoperability standard setting based on
IEEE 802.11n Draft 2.0 and En hanced Wireless Consortium
(EWC)
Bandwidth Select 20MHz or 40MHz bandwidth. 40MHz bandwidth uses
two adjacent 20MHz bands for increased data throughput.
Control Sideband Select Upper or Lower sideband when in 40MHz mode.
802.11n Rate Set the physical transmission rate (PHY).
802.11n Protection Turn Off for maximized throughput.
Turn On for greater security.
Support 802.11n
Client Only
Turn Off to allow 802.11b/g clients access to the router.
T ur n On to prohibit 802.11b/g client’s access to the ro uter.
RIFS Advertisement One of several draft-n features designed to improve
efficiency. Provides a shorter delay between OFDM
transmissions than in802.11a or g.
OBSS Co-Existence Co-existence between 20 MHZ AND 40 MHZ overlapping
Basic Service Set (OBSS) in WLAN.
RX Chain Power Save Enabling this feature turns off one of the Receive chains,
going from 2x2 to 2x1 to save power.
RX Chain Power Save
Quiet Time
The number of seconds the traffic must be below the PPS
value below before the Rx Chain Power Save feature
activates itself.
RX Chain Power Save
PPS
The maximum number of packets per seconds that can be
processed by the WLAN interface for a duration of Quiet
Time, described above, before the Rx Chain Power Sa v e
feature activates itself.
54g Rate Drop-down menu that specifies the following fixed rates:
Auto: Default. Uses the 11 Mbps data rate when possible
but drops to lower rates when necessary. 1 Mbps, 2Mbps,
5.5Mbps, or 11Mbps fixed rates. The appropriate setting
is dependent on signal strength.
Multicast Rate Setting for multicast packet transmit rate (1-54 Mbps)
Basic Rate Setting for basic transmission rate.
Fragmentation
Threshold
A threshold, specified in bytes, that determines whether
packets will be fragmented and at what size. On an
802.11 WLAN, packets that exceed the fragmentation
threshold are fragmented, i.e., split into, smaller units
suitable for the circuit size. Packets smaller than the
specified fragmentation threshold value are not
fragmented. Enter a value between 256 and 2346. If you
experience a high packet error rate, try to slightly increase
your Fragmentation Threshold. The value should remain
at its default setting of 2346. Setting the Fragmentation
Threshold too low may result in poor performance.
123
Field Description
RTS Threshold Request to Send, when set in bytes, specifies the packet
size beyond which the WLAN Card invokes its RTS/CTS
mechanism. Packets that exceed the specified RTS
threshold trigger the RTS/CTS mechanism. The NIC
transmits smaller packet without using RTS/CTS. The
default setting of 2347 (maximum length) disables RTS
Threshold.
DTIM Interval Delivery T raffic Indication Message (DTIM) is also known as
Beacon Rate. The entry range is a value between 1 and
65535. A DTIM is a countdown variable that informs clients
of the next window for listening to broadcast and multicast
messages. When the AP has buffered broadcast or
multicast messages for associated clients, it sends the next
DTIM with a DTIM Interval value. AP Clients hear the
beacons and awaken to receive the broadcast and
multicast messages. The default is 1.
Beacon Interval The amount of time between beacon transmissions in
milliseconds. The default is 100 ms and the acceptable
range is 1 – 65535. The beacon transmissions identify the
presence of an access point. By default, network devices
passively scan all RF channels listening for beacons coming
from access points. Before a station enters power save
mode, the station needs the beacon interval to know when
to wake up to receive the beacon (and learn whether there
are buffered frames at the access point).
Global Max Clients The maximum number of clients that can connect to the
router.
Xpress
TM
Technology Xpress Technology is compliant with draft specifications of
two planned wireless industry standards.
WMM (Wi-Fi
Multimedia)
The technology maintains the priority of audio, video and
voice applications in a Wi-Fi network. It allows multimedia
service get higher priority.
WMM No
Acknowledgement
Refers to the acknowledge policy used at the MAC level.
Enabling no Acknowledgement can result in more efficient
throughput but higher error rates in a noisy Radio
Frequency (RF) environment.
WMM APSD This is Automatic Power Save Delivery. It saves power.
Beamforming
Transmission (BFR)
Beamforming
Reception (BFE)
Enable beamforming signal enhance for wireless
transmission.
Enable beamforming signal enhance for wireless reception.
124
6.13.7 Basic 5GHz
The Basic option allows you to configure basic features of the wireless LAN interface.
Among other things, you can enable or disable the wireless LAN interface, hide the
network from active scans, set the wireless network name (also known as SSID)
and restrict the channel set based on country requirements.
Click Apply/Save to configure the basic wireless options.
Consult the table below for descriptions of these options.
Option Description
Enable
Wireless
Hide Access
Point
SSID
[1-32
characters]
A checkbox that enables or disables the wireless LAN interface.
When selected, a set of basic wireless options will appear.
Select Hide Access Point to protect the access point from detection by
wireless active scans. To check AP status in Windows XP, open
Network Connections from the start Menu and select View
Available Network Connections. If the access point is hidden, it
will not be listed there. To connect a client to a hidden access point,
the station must add the access point manually to its wireless
configuration.
Sets the wireless network name. SSID stands for Service Set
Identifier. All stations must be configured with the correct SSID to
access the WLAN. If the SSID does not match, that user will not be
granted access.
125
Option Description
BSSID The BSSID is a 48-bit identity used to identify a particular BS S (Basic
Service Set) within an area. In Infrastructure BSS networks, the
BSSID is the MAC (Media Access Control) address of the AP (Access
Point); and in Independent BSS or ad hoc networks, the BSSID is
generated randomly.
Channel Drop-down menu that allows selection of a specific channel.
Encryption The encryption mode used for the wireless LAN interface.
Passphrase Enter a passphrase of at least 8 digits is required for WP A2 mode and
mixed mode wireless encryption.
Enable
Guest SSID
Click Enable Guest SSID to enable an additional SSID to provide
varied access.
6.13.8 WPS 5GHz
Refer to 6.13.3 for WPS setup procedure.
WPS can be disabled / enabled by selecting the corresponding option and click
“Apply/Save”
a. When enabled in configured mode, use Push button or PIN to allow client
connection.
To activate Push button, click on the “Add Enrollee PBC” button or use the 5G Wifi
On/Off & WPS button on the front panel.
126
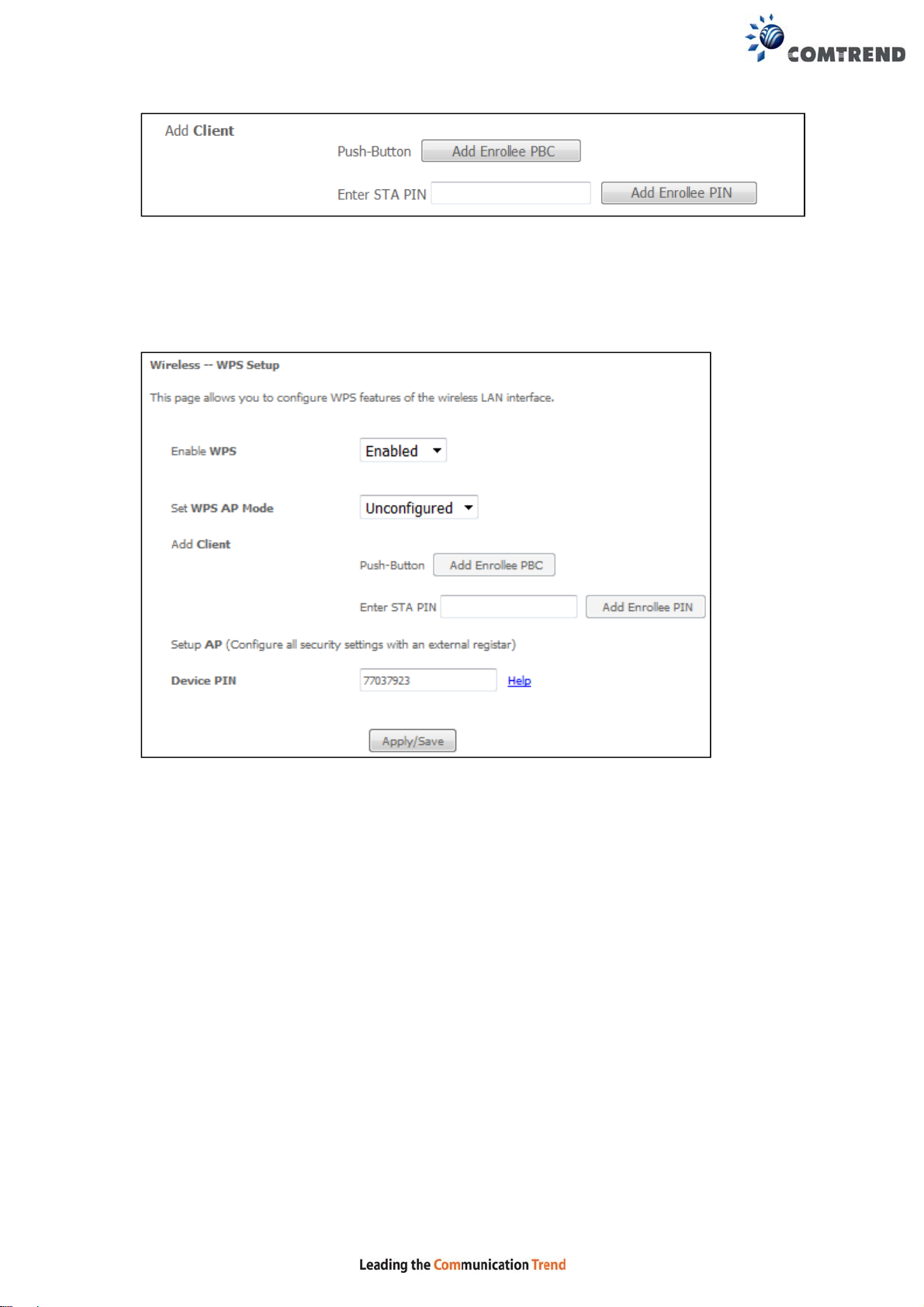
Enter the STA PIN and click the “Add Enrollee PIN” button to active PIN mode
connection
b. When enabled in unconfigured mode, enter the Device PIN to the external
registrar for PIN mode setup.
127
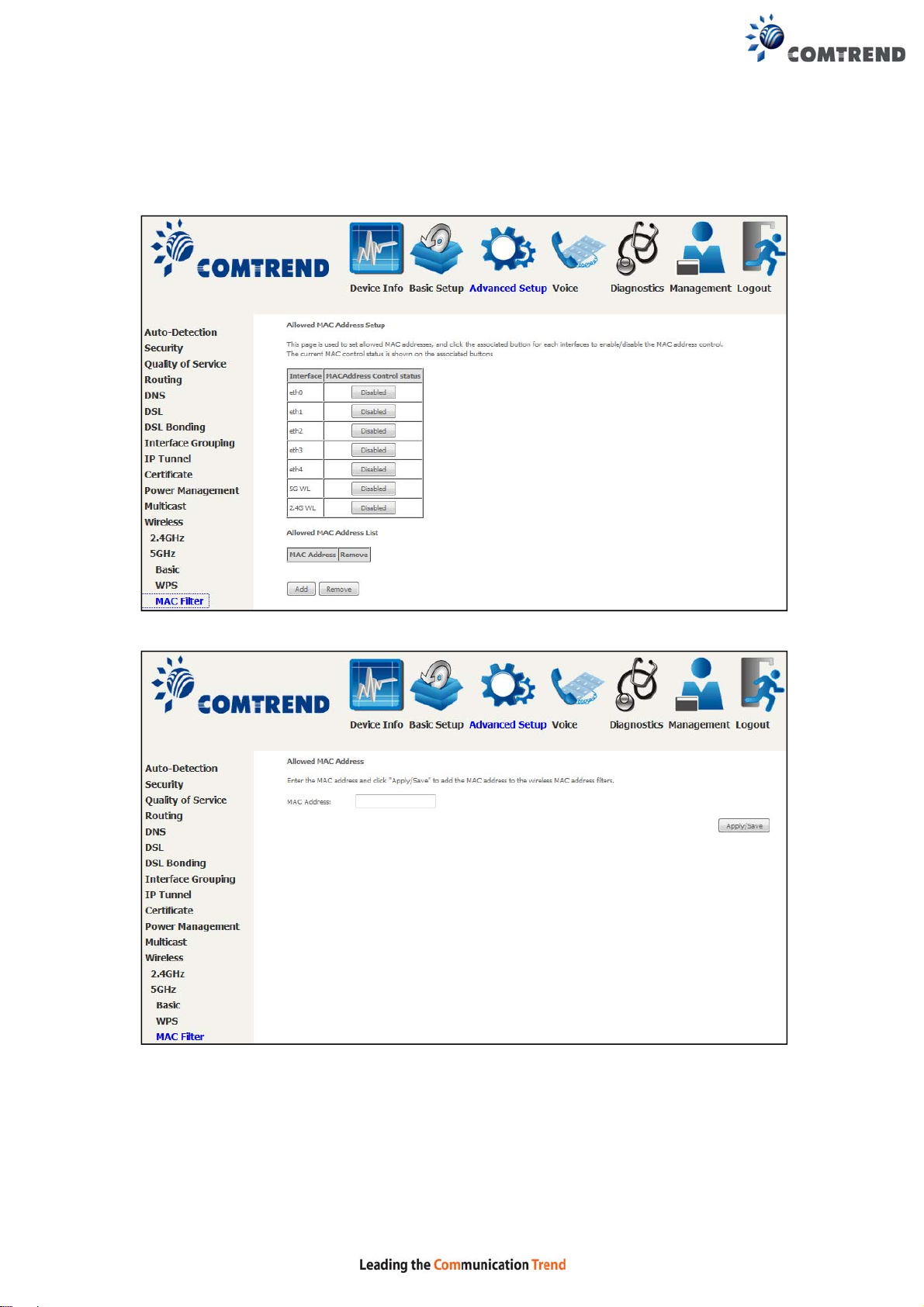
6.13.9 MAC Filter 5GHz
This page is used to set allowed MAC addresses, and click the associated button for
each interface to enable/disable the MAC address control.
The current MAC control status is shown on the associated buttons.
After clicking the Add button, the following screen appears.
Enter the MAC address in the box provided and click Apply/Save.
128
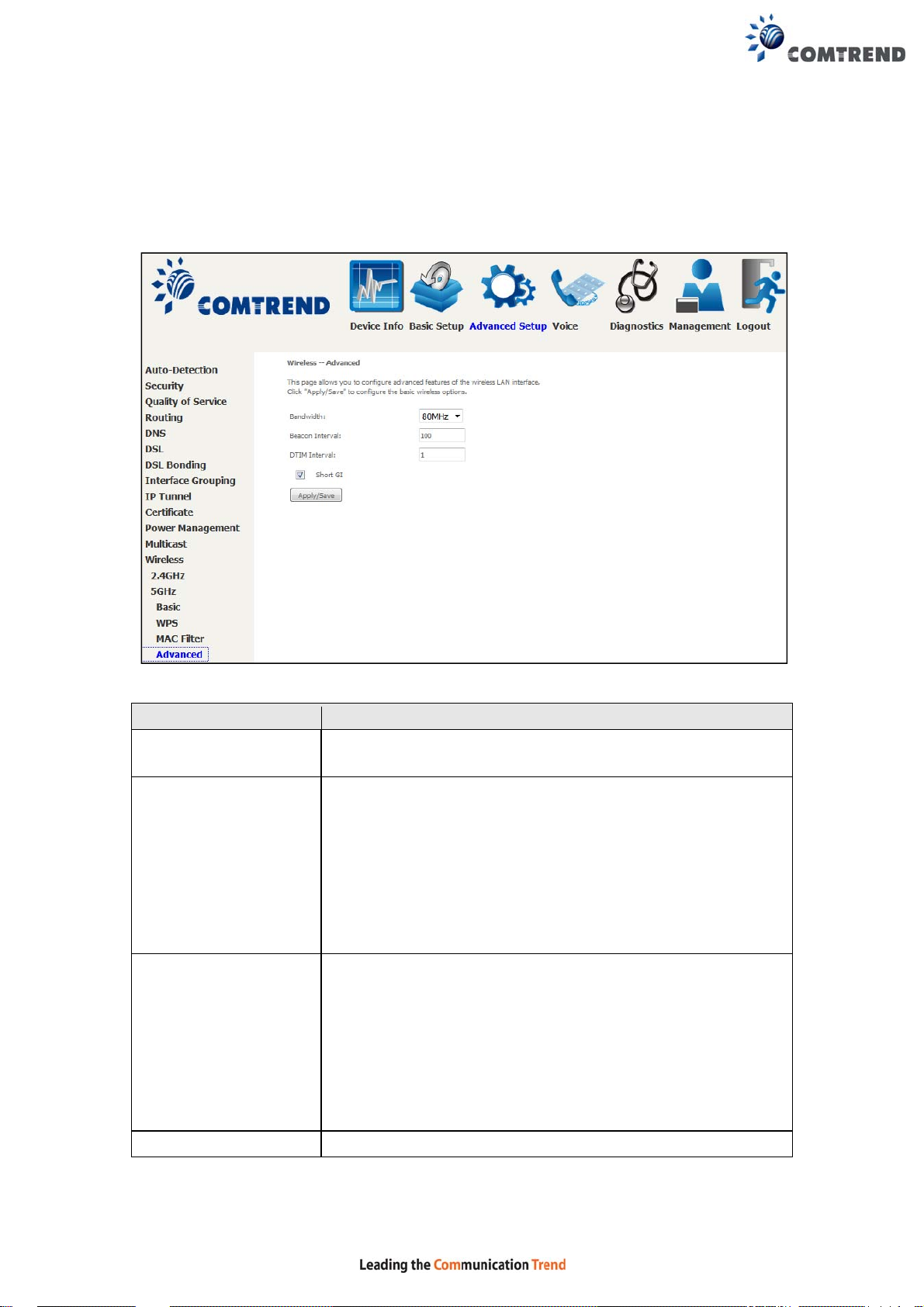
6.13.10 Advanced 5GHz
This page allows you to configure advanced features of the wireless LAN int erface.
Click Apply/Save to configure the basic wireless options.
Field Description
Bandwidth
Beacon Interval The amount of time between beacon transmissions in
DTIM Interval Delivery T raffic Indication Message (DTIM) is also known as
Short GI Enable/Disable use of short guard interval.
Select the bandwidth used on the 5G interface. 80MHz is
selected by default.
milliseconds. The default is 100 ms and the acceptable
range is 1 – 65535. The beacon transmissions identify the
presence of an access point. By default, network devices
passively scan all RF channels listening for beacons coming
from access points. Before a station enters power save
mode, the station needs the beacon interval to know when
to wake up to receive the beacon (and learn whether there
are buffered frames at the access point).
Beacon Rate. The entry range is a value between 1 and
65535. A DTIM is a countdown variable that informs clients
of the next window for listening to broadcast and multicast
messages. When the AP has buffered broadcast or
multicast messages for associated clients, it sends the next
DTIM with a DTIM Interval value. AP Clients hear the
beacons and awaken to receive the broadcast and
multicast messages. The default is 1.
129
Chapter 7 Voice
This chapter first describes the various options for configuration of the SIP voice
service. It then provides detailed instructions for making telephone calls using VoIP
(Voice over IP) or PSTN (Public Switched Telephone Network) services. Session
Initiation Protocol (SIP) is a peer-to-peer protocol used for Internet conferencing,
telephony, events notification, presence and instant messaging.
SIP is designed to address the functions of signaling and session management
within a packet telephony network. Signaling allows call information to be carried
across network boundaries. Session management provides the ability to control
the attributes of an end-to-end call.
NOTE: The SIP standard is set by the Internet Engineering Task Force (IETF).
The SIP standard defines the following agents/servers:
• User Agents (UA) - SIP phone clients (hardware or software)
• Proxy Server – relays data between UA and external servers
• Registrar Server - a server that accepts register requests from UA
• Redirect Server – provides an address lookup service to UA
The following subsections present Basic, Advanced and Debug SIP screens.
Each screen provides various options for customizing the SIP configuration.
130
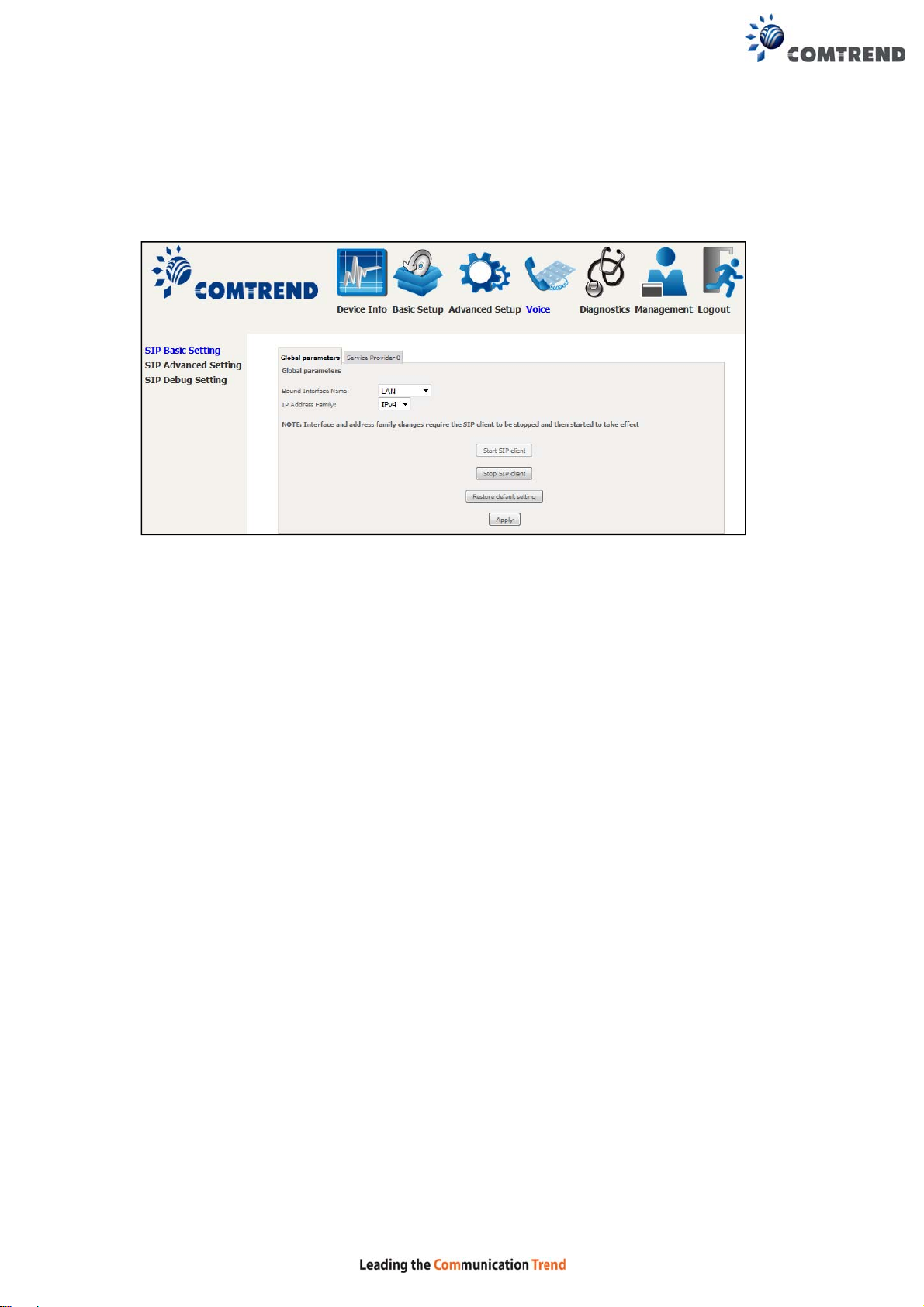
7.1 SIP Basic Setting – Global Parameters
A common parameter setting.
Bound Interface Name:
Select a WAN interface to send SIP control messages.
IP Address Family:
Select to use IPv4 or IPv6 for VoIP messages.
131
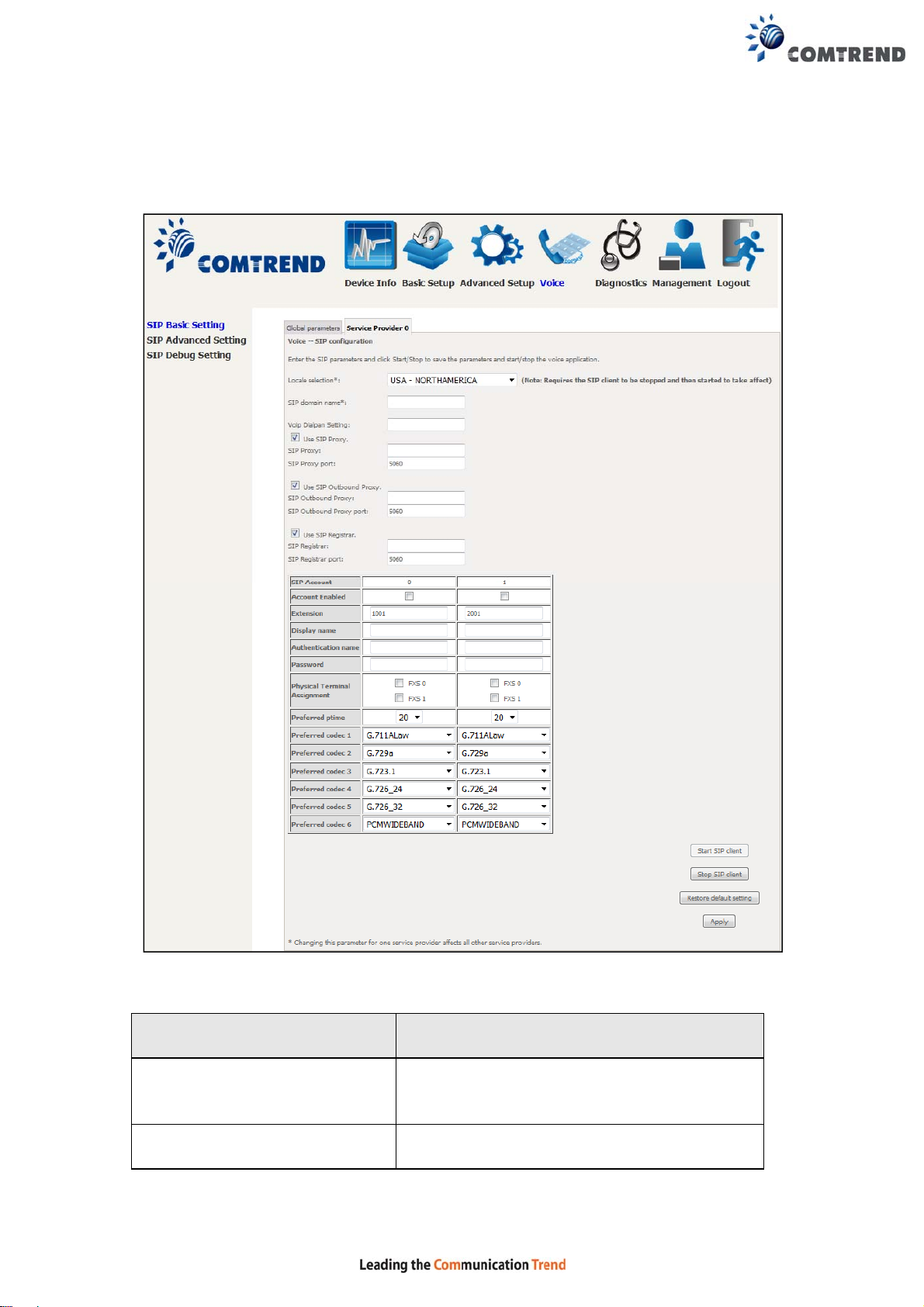
7.2 SIP Basic Setting – Service Provider
Enter the SIP parameters and click Start/Stop to save the parameters and start/stop
the voice application.
Once settings are configured click Apply to begin using the service.
Field Description
Locale Selection Sets tone, ring type and physical
characteristics for specific countries.
SIP domain name Provided by your VoIP provider.
132
 Loading...
Loading...