Page 1

ED5000
User Manual
Page 2

FCC NOTICE (Class A)
This device complies with Part 15 of the FCC Rules. Operation is subject to the following
two conditions: (1) this device may not cause harmful interference, and (2) this device must
accept any interference received, including interference that may cause undesired
operation.
Federal Communications Commission Statement
NOTE- This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a residential installation. This equipment generates uses and can
radiate radio frequency energy and, if not installed and used in accordance with the instructions, may
cause harmful interference to radio communications. However, there is no guarantee that interference
will not occur in a particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by tuning the equipment off and on, the user is
encouraged to try to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna.
Increase the separation between the equipment and receiver.
Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
Consult the dealer or an experienced radio/television technician for help.
Class A ITE
Class A ITE is a category of all other ITE which satisfies the class A ITE limits but not the class B ITE
limits. Such equipment should not be restricted in its sale but the following warning shall be included in
the instructions for use:
Warning -This is a class A product. In a domestic environment this product may cause radio
interference in which case the user may be required to take adequate measures.
European Community Compliance Statement (Class A)
This product is herewith confirmed to comply with the requirements set out in the Council
Directives on the Approximation of the laws of the Member States relating to
Electromagnetic Compatibility Directive 2004/108/EC.
Warning - This is a Class A product. In a domestic environment this product may cause radio
interference in which case the user may be required to take adequate measures to correct this
interference.
COPYRIGHT
© 2014 AVer Information Inc. All rights reserved.
All rights of this object belong to AVer Information Inc. Reproduced or transmitted in any
form or by any means without the prior written permission of AVer Information Inc. is
prohibited. All information or specifications are subject to change without prior notice.
Trademark
“AVer” is a trademark owned by AVer Information Inc. Other trademarks used herein for
description purpose only belong to each of their companies.
NOTICE
SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT PRIOR NOTICE. THE
INFORMATION CONTAINED HEREIN IS TO BE CONSIDERED FOR REFERENCE ONLY.
Page 3

Table of Contents
PACKAGE CONTENTS ....................................................................................................... 1
CAMERA PARTS ................................................................................................................. 1
IP CAMERA INSTALLATION ............................................................................................... 2
MOUNT THE IP CAMERA ...................................................................................................... 2
EXTERNAL SPEAKER LINE INSTALLATION ............................................................................... 3
USING THE IP CAMERA BROWSER INTERFACE ............................................................ 4
LIVE VIEW .......................................................................................................................... 4
SYSTEM > GENERAL ........................................................................................................... 7
SYSTEM > GENERAL > MAINTENANCE ................................ ................................................... 7
TO UPGRADE THE IP CAMERA FIRMWARE ......................................................................... 8
SYSTEM > GENERAL > DATE & TIME ..................................................................................... 9
SYSTEM > GENERAL > SYSTEM LOG .................................................................................. 10
SYSTEM > USER MANAGEMENT ......................................................................................... 11
SYSTEM > USER MANAGEMENT > ACCOUNT ........................................................................ 11
To Create a User Account ........................................................................................ 11
To Delete or Edit a User Account .............................................................................. 12
SYSTEM > USER MANAGEMENT > CONNECTION................................................................... 13
SYSTEM > NETWORK ........................................................................................................ 14
Page 4

SYSTEM > NETWORK > SETTING ........................................................................................ 14
SYSTEM > NETWORK > SERVER ......................................................................................... 16
SYSTEM > NETWORK > STEAMING...................................................................................... 17
SYSTEM > NETWORK > QOS ............................................................................................. 18
SYSTEM > NETWORK > OTHERS ........................................................................................ 19
SYSTEM > SECURITY ........................................................................................................ 21
SYSTEM > SECURITY > IP FILTER ....................................................................................... 21
TO ADD FILTER ............................................................................................................ 21
SYSTEM > SECURITY > 802.1X ......................................................................................... 23
SYSTEM > SECURITY > RTSP AUTH. .................................................................................. 24
SYSTEM > IMAGE .............................................................................................................. 25
SYSTEM > IMAGE > OSD .................................................................................................. 25
SYSTEM > IMAGE > PREFERENCE ....................................................................................... 26
SYSTEM > IMAGE > EXPOSURE .......................................................................................... 27
SYSTEM > IMAGE > ADVANCED........................................................................................... 29
SYSTEM > IMAGE > PRIVACY MASK .................................................................................... 30
SYSTEM > VIDEO STREAM ................................................................................................. 31
SMART STREAM ............................................................................................................... 33
SYSTEM > AUDIO .............................................................................................................. 34
Page 5

SYSTEM > SD/MICROSD CARD > MANAGEMENT ................................................................. 35
SYSTEM > SD/MICROSD CARD > FILE SEARCH ................................................................... 36
APPLICATION > MOTION DETECTION ................................................................................... 37
TO SET THE MOTION DETECTION ................................................................................... 37
APPLICATION > IVA ........................................................................................................... 38
APPLICATION > IVA > CROSS DETECTION ....................................................................... 38
APPLICATION > IVA > TAMPERING .................................................................................. 40
APPLICATION > IVA > MISSING OBJECT .......................................................................... 41
APPLICATION > IVA > SUSPICIOUS OBJECT..................................................................... 42
APPLICATION > TRACKING ................................................................................................. 43
EVENT SETTING ............................................................................................................... 44
TO SETUP THE EVENT .................................................................................................. 44
STATUS INFORMATION ....................................................................................................... 47
Page 6
1
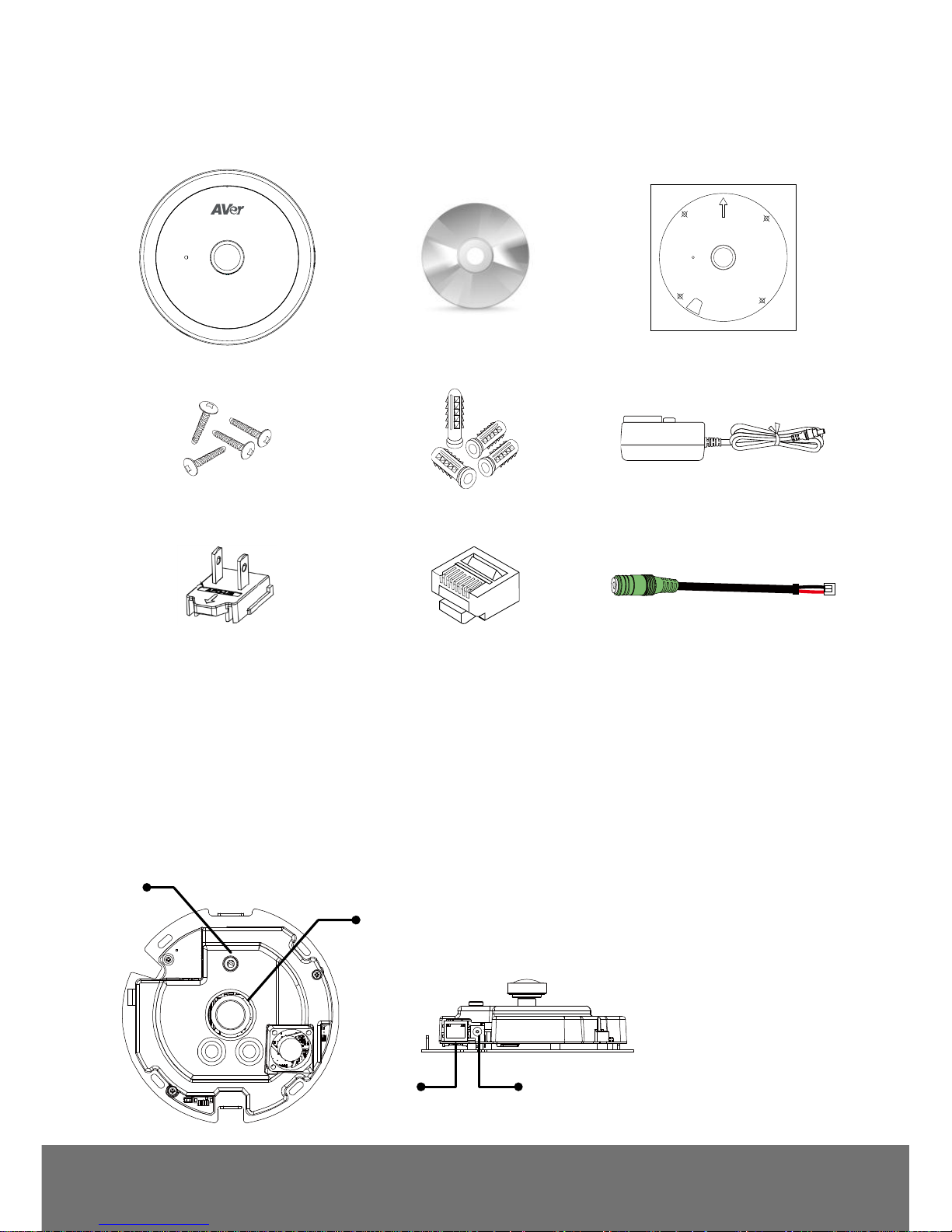
Package Contents
The following items are included in the package.
Microphone
TOP
(for wall mount)
ED5000
Software & Manual CD
Alignment Sticker
4 Screws
4 Plastic Anchors
Power Adapter
Power plug**
RJ-45 header
External speaker line
**The power plug will vary
depending on the standard power
outlet of the country where it is
sold.
Camera Parts
(2)
(3) (4)
(1)
(1) MIC
(2) Lens
(3) RJ45 Ethernet Port
(4) Power DC
Page 7
2
IP Camera Installation
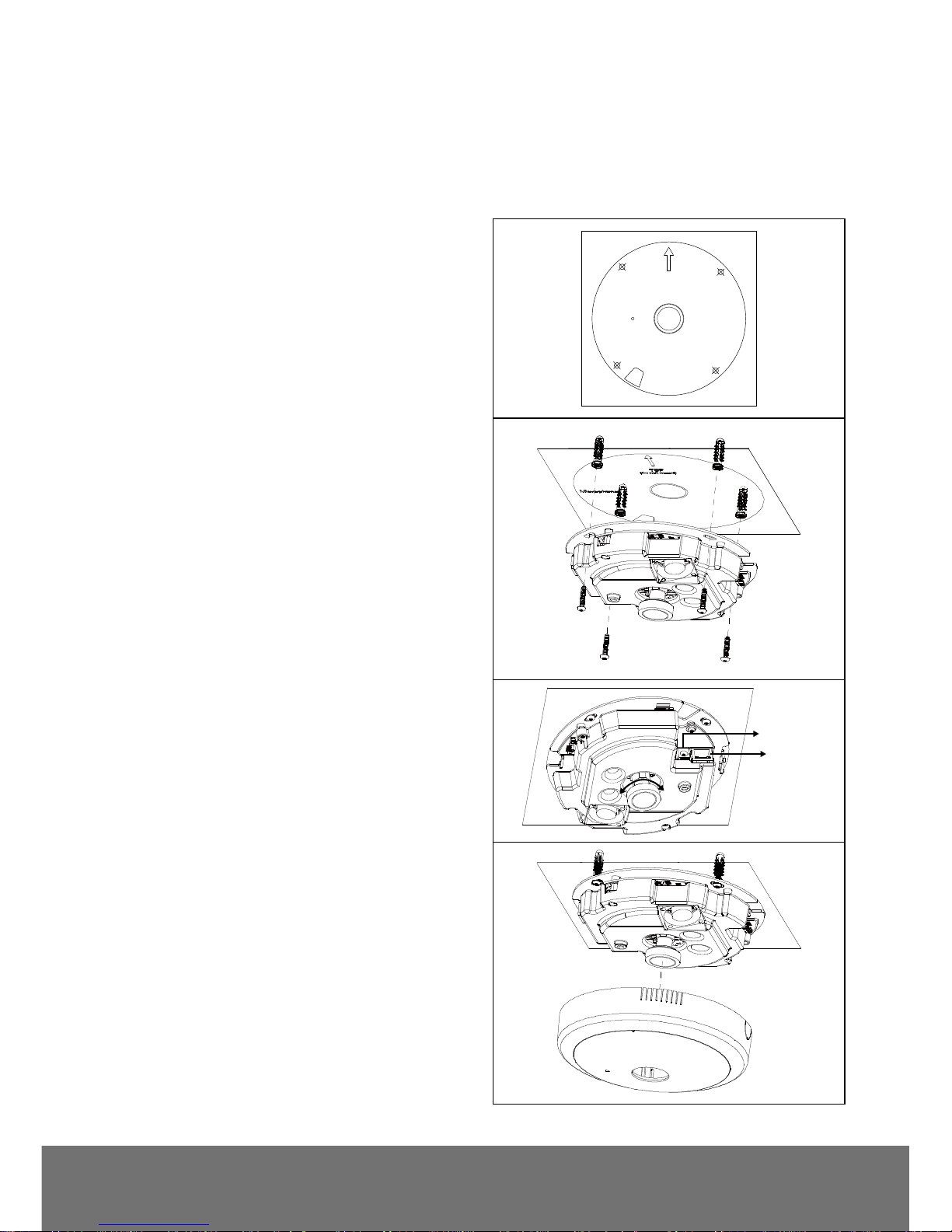
Mount the IP Camera
User can install the camera on the ceiling or on the wall. The following steps are describing how to
install the camera on the ceiling and wall.
1. Place the alignment sticker on the wall surface.
Then spot the mark and drill the 4 holes
indicated on the sticker.
[Note] If the camera is installed on ceiling, no need
to follow the arrow position on alignment sticker.
Microphone
TOP
(for wall mount)
2. Insert the 4 plastic anchors in the ceiling or
wall. Next, hook the Camera and use the
screws to secure the camera.
3. Connect the power and Ethernet to the
camera.
4. Next, adjust the focus manually.
Ethernet
Power
Adjust focus
5. After adjusting the focus, secure the cover
case of camera.
Page 8

3
External Speaker Line Installation
1. Un-screw the screws as figure shown.
2. Open the black cover.
3. Connect the external speaker line to the
camera.
4. Close the black cover and screw it tight.
5. Finally, close camera case cover and security
it.
Page 9
4
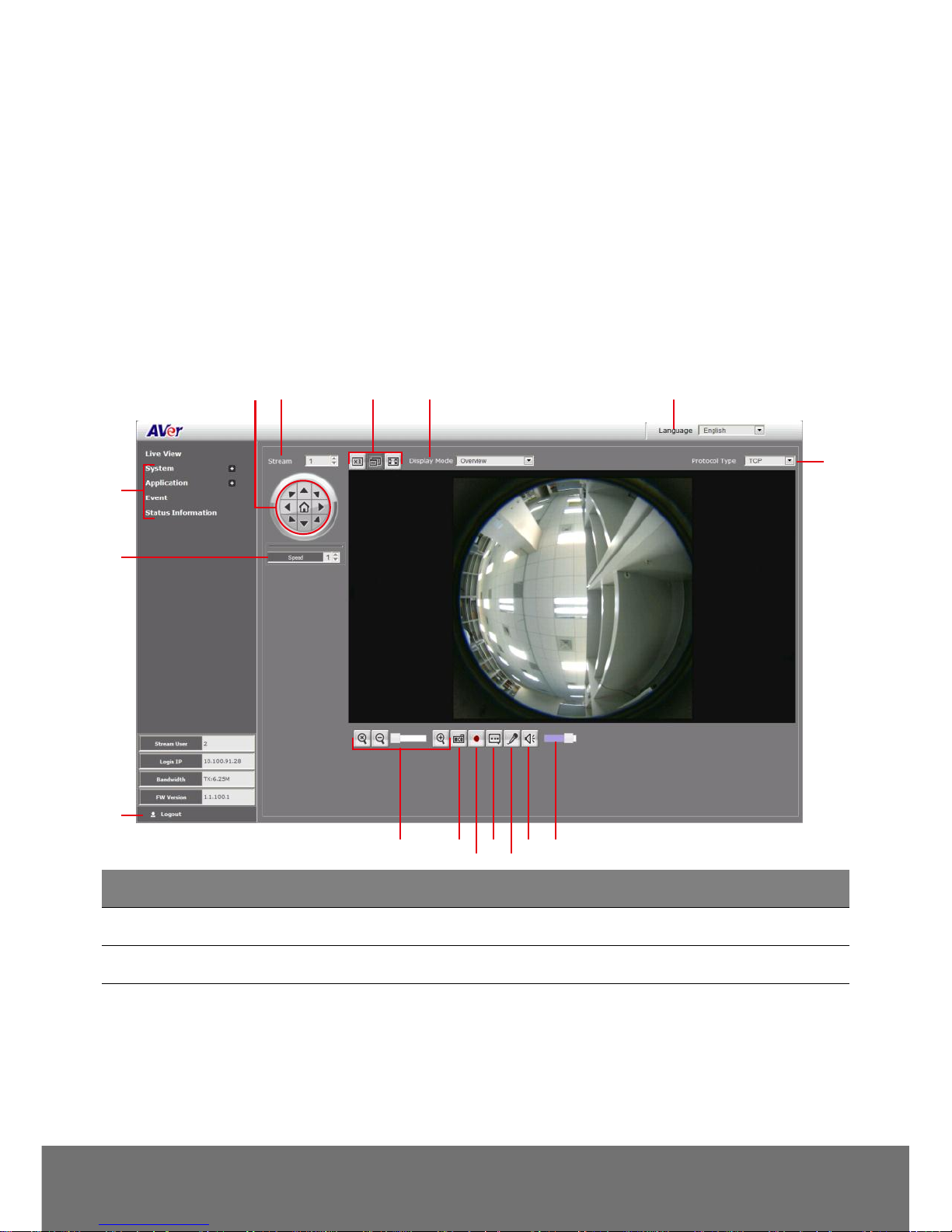
Using the IP Camera Browser Interface
The admin have the full access to the IP camera browser interface. The menu on the left, you can
expand and navigate to access all the features.
Open the IE browser and enter the IP address of IP camera to access the IP camera Web
configuration interface. In login dialog, enter the ID and Password (default is admin/admin).
Live View
In the Live View page, all three user levels can view and change the language setting, the IP camera
video stream setting, capture screen shot, record video, turn on/off 2-way talk, mic and volume, and
adjust the zoom and volume level.
(7)
(8)
(9)
(5)(6) (4) (3) (2)
(1)
(11)(10)
(12)
(13)
(14)
(16)(15)
Name
Function
(1) Protocol Type
Select the protocol for the live view video stream.
(2) Language
Select the browser interface language.
Page 10
5
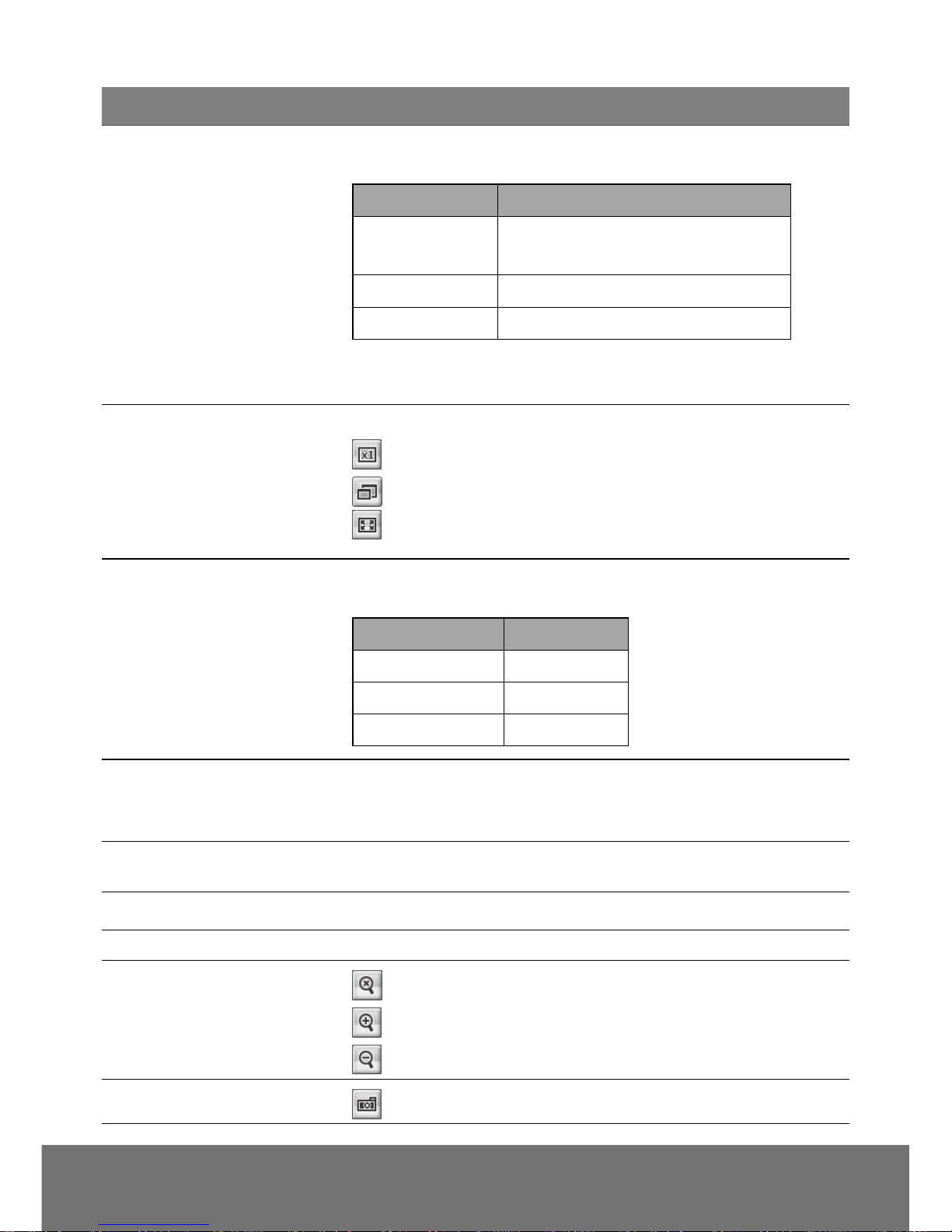
Name
Function
(3) Display mode
The display modes are depended on the Stream mode that user
has selected; they will have different type of display modes
Stream mode
Display mode
Normal ceiling
Overview/Panoramic/Dual
Panoramic/Quad/Dual Panoramic
Quad ceiling
Area1/Area2/Area3/Area4/Overview
Wall mode
Panoramic
[Note] Stream mode setup is in System > Video Stream.
(4) Video screen
Change the video screen display.
Display the actual video pixel size.
Display the video screen in compact size.
Display the video on the entire screen. Press ESC to exit full
screen mode.
(5) Stream
Switch to view the different video stream. The number of video
streams are depended on Stream mode that user has selected.
Stream mode
Stream
Normal ceiling
1/2/5
Quad ceiling
1/2/3/4/5
Wall mode
1/2
(6) Direction buttons
Use to move the position of the view point while in zoom mode.
[Note] When object tracking is enabled, the PTZ function of upper
left channel is disabled.
(7) System/Application/
Event/Status Information
Set up IP camera’s configuration.
(8) Speed control
Set the speed when panning, tilting, or zooming.
(9) Logout
Exit the application
(10) Zoom control
Reset zoom level.
Increase zoom level.
Decrease zoom level.
(11) Capture
Capture and save the image on the screen in *.bmp format.
Page 11

6
Name
Function
(12) Record
Start/stop audio and video recording. The recorded video will
be saved in *.mp4 format.
(13) 2-way talk
Enable/disable mic from IP camera browser side.
(14) Mic
Enable/disable mic from the IP camera side.
(15) Sound
Enable/disable audio from the IP camera side.
(16) Volume bar
Adjust the volume.
Page 12

7
System > General
In this section, only admin level is authorized to configure the IP camera general settings. There are 3
tabs in General settings: Maintenance, Date & Time, and System Log.
System > General > Maintenance
In the Maintenance tab, the admin can easily backup and restore the IP camera setting, reboot the IP
camera, reset all the settings to factory default, and upgrade the IP camera firmware.
(1)
(2)
(3)
(4)
(5)
(6)
(7)
Name
Function
(1) Reboot
Restart the IP camera.
(2) Information
Displays the explanation of Reboot, Reset, and Factory default.
(3) Reset
Set all the configuration settings back to default except the user
management and network settings.
(4) Factory Default
Set all the configuration settings back to factory default.
(5) Export
Backup all the configuration settings.
Page 13
8
Name
Function
(6) Import Settings
Restore or replace the current settings with the backup file.
(7) Firmware Upgrade
Upgrade the firmware to the latest version.
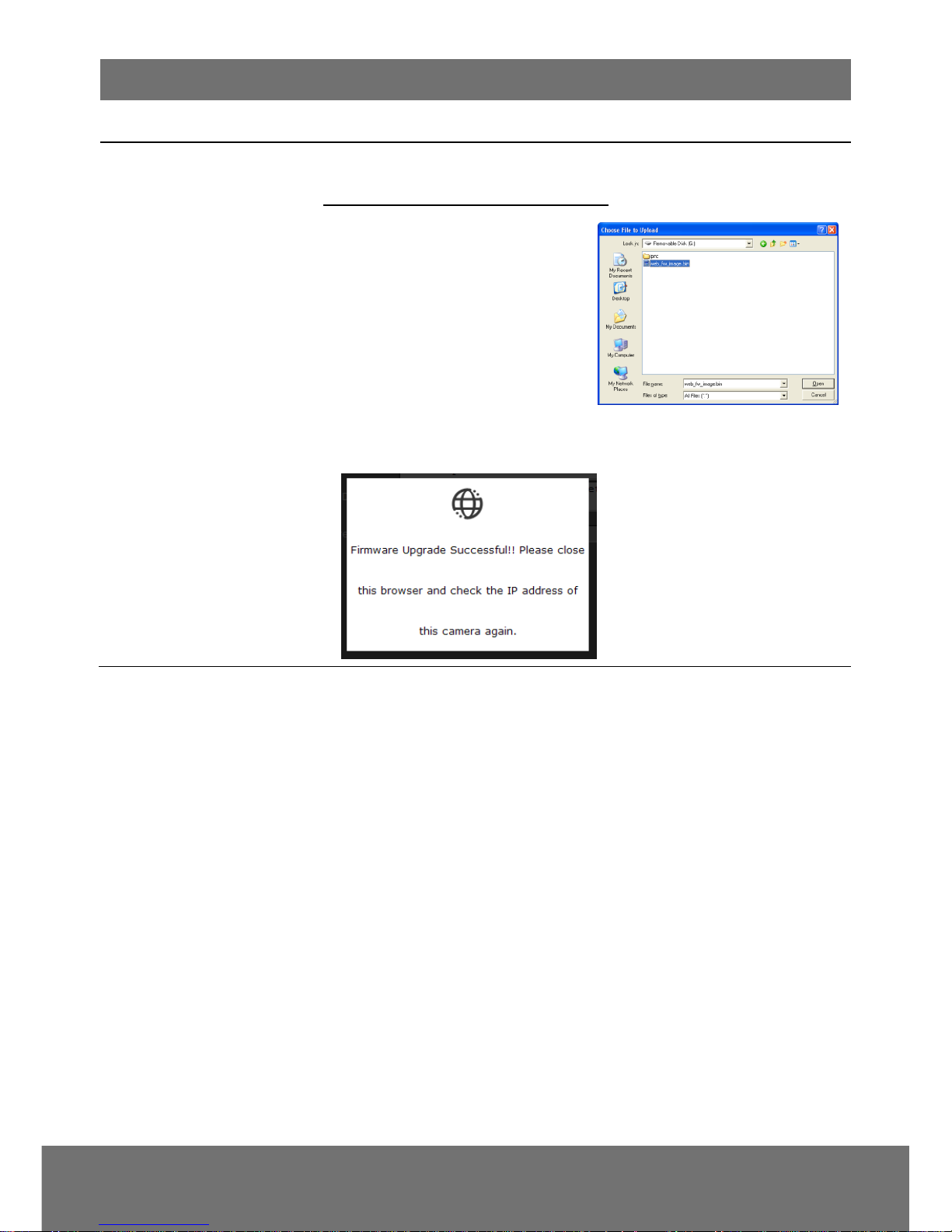
To Upgrade the IP Camera Firmware
1. Download the file from our
website and save it in your
computer hard disk.
2. Click Browse. Locate and
select the file and click Open.
3. Click Apply. Wait till you see the
massage “Firmware Upgrade
OK!!”. You may now click the IE browser refresh button or press F5.
The login page will appear.
Page 14
9
System > General > Date & Time
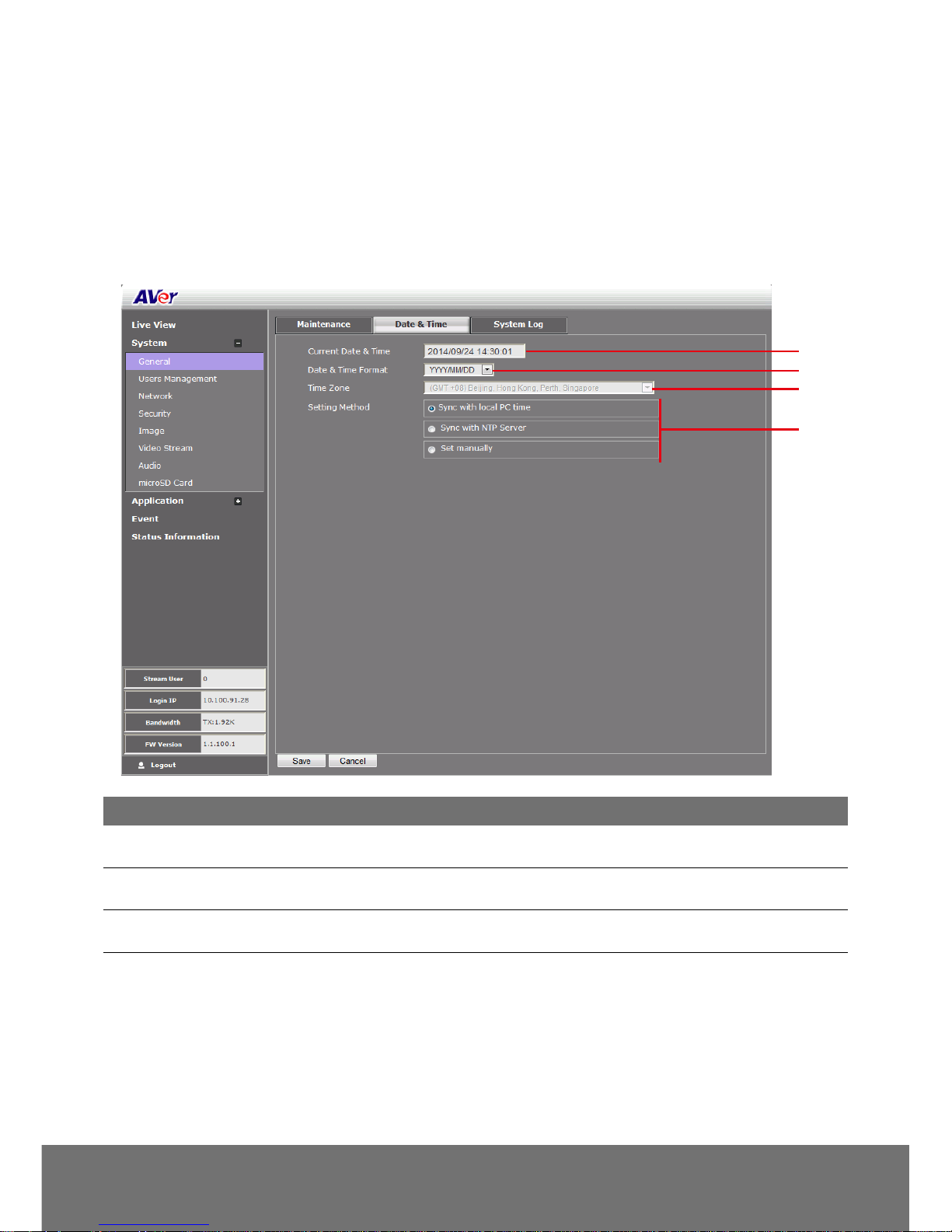
In the Date & Time tab, admin can manually set the date and time setting or synchronize it with the
Internet time server or the computer date and time setting. This is used to record the time whenever
there is a significant occurrence listed in system log and is also used in event scheduling. After
completing the setting, click Save to apply the new setting and Cancel to keep the old setting.
(1)
(2)
(3)
(4)
Name
Function
(1) Current Date & Time
Display the current date and time setting.
(2) Date Format
Select the date display format.
(3) Time Zone
Set the local time zone.
Page 15
10
Name
Function
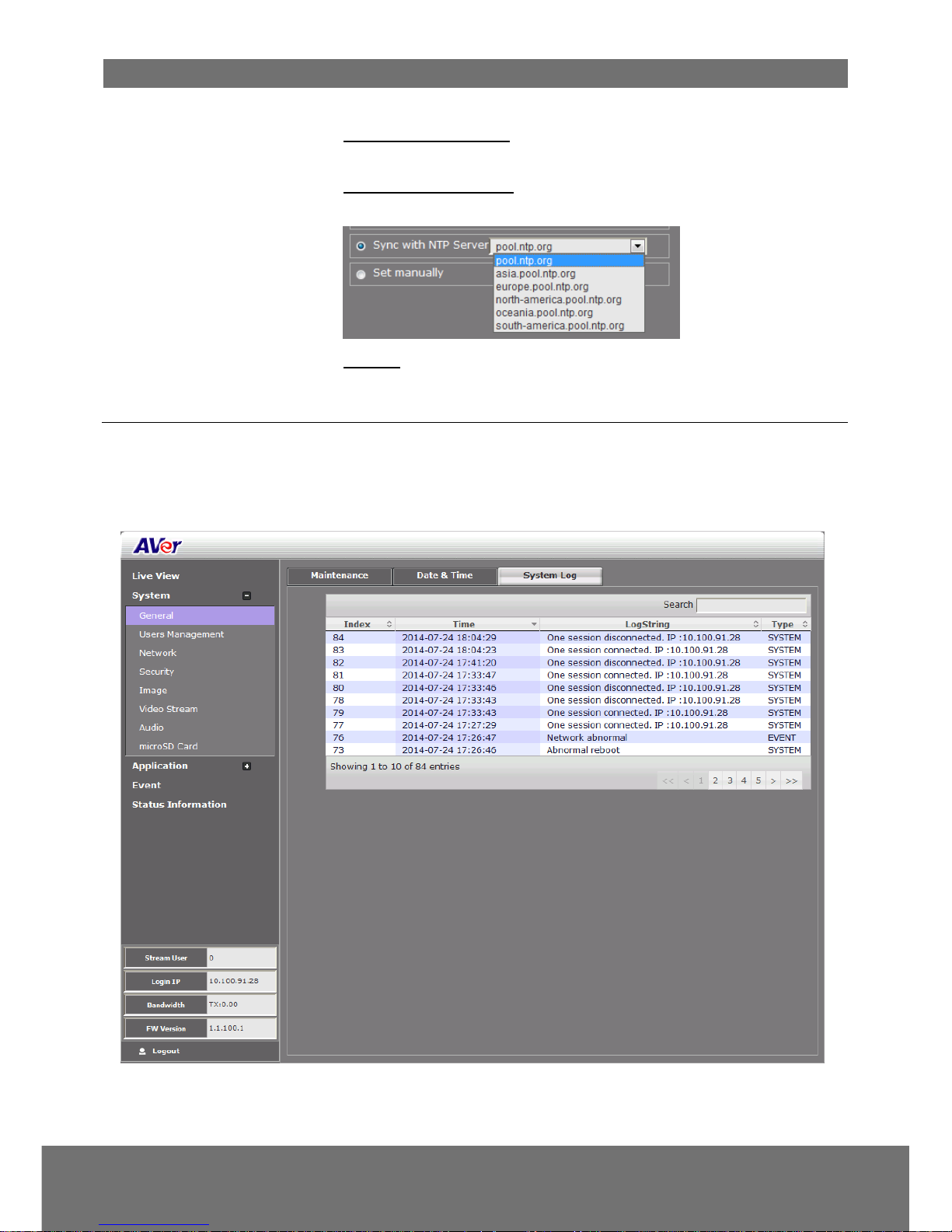
(4) Setting Method
Select the date & time setting method.
Sync with current PC: obtain the date and time setting on the
current login computer.
Sync with NTP Server: obtain the date and time setting from NTP
server. In the drop-down list, select the NTP host name.
Manual: manually set the date and time. Click Now to set the date
base on the computer time setting and Done to close the date and
time interface.
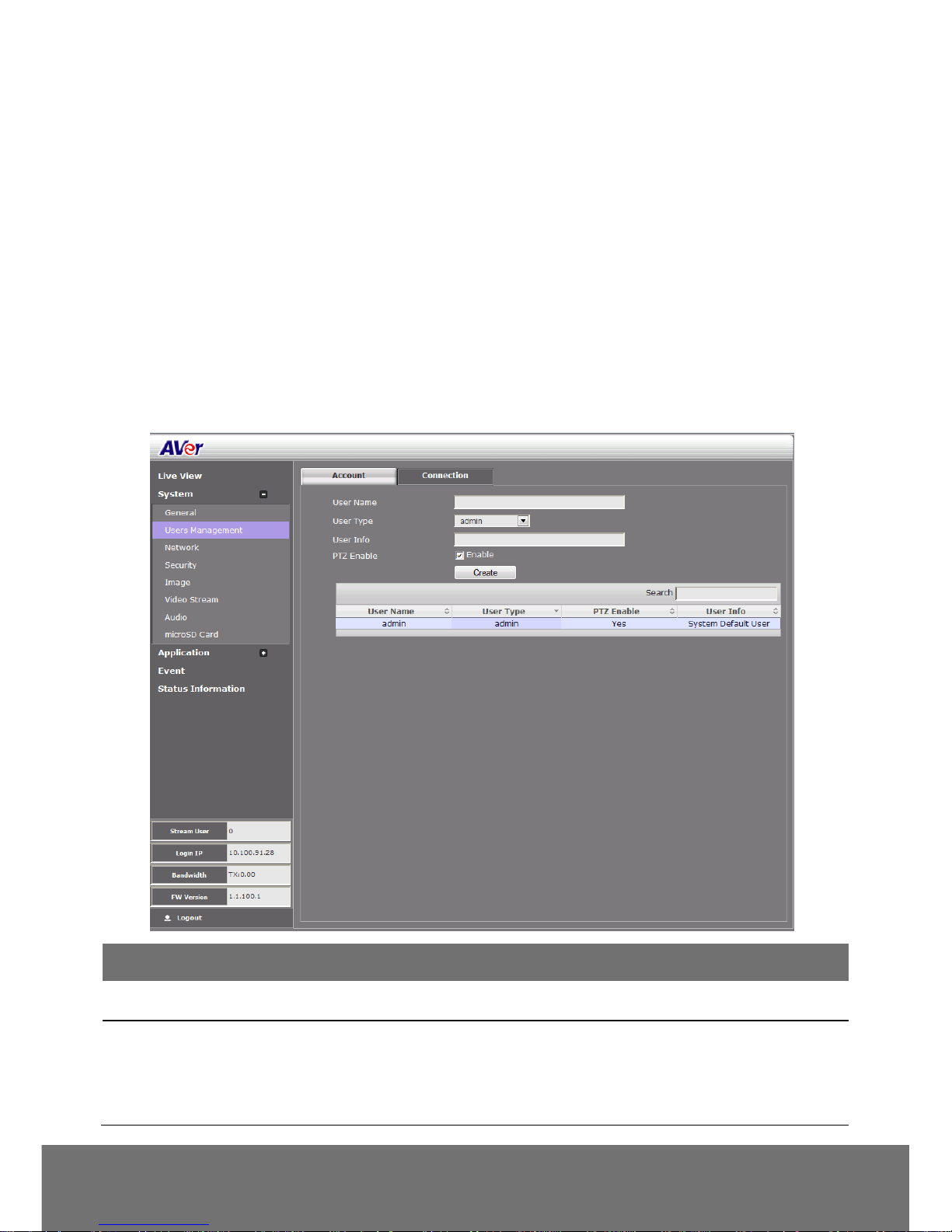
System > General > System Log
In the System Log, admin can view and search the significant event occurred in the IP camera.
Page 16
11
System > User Management
In User Management, only admin level is authorized to create, delete, and edit account to connect to
the IP camera and configure the client connection setting. There are 2 tabs in User Management
setting: Account and Connection.
System > User Management > Account
In Account page, admin can create, delete and set the access level of the user account.
To Create a User Account
1. Click System > User Management > Account tab.
2. Enter the User Name, User Info, and select the User Type. Then, click Create.
User Type
Access rights
Admin
Allow to access all the configuration pages.
Operator
Allow to preview live image, modify and adjust certain settings; except in
System > General, User Management, Network, and SD/microSD Card >
Management. As for the I/O Control, admin could enable/disable to allow
operator to access it.
Page 17

12
User Type
Access rights
Viewer
Only allow to access the preview and status information pages.
3. Enter the same password in Password and Confirm Password column. Then click Add.
To Delete or Edit a User Account
Select the user account that you want to delete or edit.
Click Cancel to cancel the operation.
Click Modify to apply the new changes. Make sure to edit the account before clicking the
Modify button.
Click Remove to delete the account.
Page 18

13
System > User Management > Connection
In Connection page, admin can set the total number of user for accessing the IP camera, and filtering
the IP address to allow or deny accessing the IP camera.
Http Connection: Select the connection type. For higher security data transmission level, select
http & https or http only. The authenticated and encrypted the data is over the SSL (Secure
Socket Layer).
Maximum Number of Clients: Select the max number of users to simultaneously access the IP
camera.
Page 19

14
System > Network
In this section, only admin level is authorized to configure the Network settings.
System > Network > Setting
In Setting page, you can configure the type of network connection for IP camera and assign name for
the IP camera. Depending on the network connection, IP camera can be accessed from the computer
within the same local area network (LAN) or anywhere with Internet connection. After completing the
setting, click Save to apply the new setting and Cancel to keep the old setting.
(1)
(2)
(3)
Name
Function
(1) Device Name
Assign name for the IP camera.
Page 20

15
Name
Function
(2) Network Type
Select the type of IP camera network connection.
DHCP: select this option to automatically obtain an IP address from the
DHCP server, whenever the IP camera is connected to the network.
You can use the IP camera UPnP Discovery software in the CD to
easily setup the IP camera network.
Static IP: select this option to manually assign a fix IP address to the
IP camera.
PPPoE: select this option to access the IP camera anywhere with
Internet connection. To use this option, this requires an account
provided by the ISP. Set this setting while connected to the LAN and
click Save. Connect the IP camera directly to DSL or cable modem.
(3) IPv6 Settings
Enable IPv6 support
Select “Manually set the IP address” to specify IP address manually.
Page 21

16
System > Network > Server
In Server page, you can configure the Email, FTP, and NAS setting. It is necessary to configure the
server settings so that IP camera can perform the task in the Event setting when a trigger is activated.
You can configure either one or all of it. After completing the setting, click Save to apply the new
setting and Cancel to keep the old setting.
Page 22

17
System > Network > Steaming
In Streaming page, you can configure the HTTP/HTTP/RTSP port and multicast setting.
HTTP Port: Setup web page connecting port and video transmitting port (Default is 80).
HTTPS Port: AVer IP Camera supports encrypted browsing using HTTPS.
RTSP Port: Setup port for RTSP transmitting (Default is 554).
Multicast group address 1/2/3: Set multicast group address.
Multicast video port 1/2/3: Set multicast video port number.
Multicast RTCP video port 1/2/3: Set multicast RTCP video port number.
Multicast TTL 1/2/3: Set multicast TTL value.
Page 23

18
System > Network > QoS
In QoS page, you can configure the Quality of Service setting. Enabling the QoS allows you to set the
parameter and prioritize the IP camera to provide stable streaming performance at a certain level in a
traffic network.
Page 24

19
System > Network > Others
In Others page, you can enable/disable the UPnP setting, DDNS, and SMNP function. If your router
does not support UPnP function, you can enable the UPnP forwarding and set the port mapping. Click
Save button to apply the settings.
UPnP Support: The IP camera supports UPnP, if this service is enabled on your computer.
[Note] UPnP must be enabled on your PC.
UPnP Port Forwarding: If the IP camera is installed behind the firewall, please select ON to
enable it.
DDNS setting: Setup DDNS server.
a. Mark “Enabled DDNS” to enable DDNS function.
b. Enter the DDNS Provider, Domain Name, User Name, and Password that the user has
registered on the DDNS service provider in the appropriate columns.
c. DDNS Status displays the DDNS function current status.
SNMP
(Simple Network Management Protocol) provides a simple framework for
administering networked hardware. SNMPv1, SNMPv2c, and SNMPv3 can be
enabled simultaneously.
Page 25

20
SNMPv1 and SNMPv2: The term "Community name" in SNMPv1 and SNMPv2 can be
roughly regarded as key. The person who has the community name has the authority to read
or edit the information of IP camera via SNMP. Check the box to enable SNMPv1 and
SNMPv2 protocol, and specify the community name for Read/Write and Read only
community. The user who uses read community name to access the IP camera cannot
modify any data of this camera
SNMPv3: For data security reason, the authentication and encryption assurances are added
when developing SNMPv3. The user has to give not only the security name (the same as
"community name" in v1&v2, or sometimes we call it "context name") but the password in
order to access the IP camera. Please set Security name, Authentication type,
Authentication password, Encryption type, Encryption password of Write/Read and
Read Only respectively. The password must be 8~64 bits in length.
Page 26

21
System > Security
Only admin levels can adjust the Image setting. There are 2 function tabs: IP Filter, 802.1x, RSTP
Auth...
System > Security > IP Filter
Enable Filter List: Select to turn the IP address filtering on or off.
Filter Type: Select to allow or deny the IP address in the filter list to access the IP camera.
Filter List: Create and display the filtered IP address.
To Add Filter
1. Click System > Security > IP Filter tab, then, click Add Filter.
2. In Rule drop down list, select from the 3 types of rules: Single, Network and Range.
Page 27

22
Single – add an IP address
Network – assign a network address and the corresponding subnet mask to be filtered.
Range – assign a range of IP address to be filtered.
3. Click Save to add the created data in the filter list or click Cancel to exit and without saving
data.
IPv6 Filter: Please follow the IPv4 filter rules to set up IPv6 filter. The IPv6 setting needs to be
enabled first (System > Network > Setting).
Page 28

23
System > Security > 802.1X
IEEE 802.1X is an IEEE Standard for port-based Network Access Control. It provides
an authentication mechanism to devices wishing to attach to a LAN or WLAN.
Mark the check box to Enable 802.1X protocol. Select the EAPOL (EAP over LAN) version,
Authentication method and enter the ID and Password.
Page 29

24
System > Security > RTSP Auth.
Enable/disable RTST authentication. After completing the setting, click Save to apply the new setting.
Page 30

25
System > Image
Both admin and operator levels can adjust the Image setting. There are 5 function tabs: OSD,
Preference, Exposure, Advanced, and Privacy Mask.
System > Image > OSD
In OSD page, you can enable/disable overlaying time stamp, text title and add logo.
(1)
(2)
(3)
(4)
(5)
Name
Function
(1) Time Stamp
Select the location of the Time Stamp. Click the checkbox to
enable/disable display the date and time stamp.
(2) Customize Title
Select the location of the Text Title. Click the checkbox to enable/disable
display the text title.
(3) Title Text
Enter the title text, e.g. AVer.
(4) Logo
Select the location of the logo image file. Click the checkbox to
enable/disable display the logo.
(5) Customize Logo
Upload your company logo. The maximum size is 64 x 64 pixels.
Page 31

26
System > Image > Preference
In Preference page, you can tune the IP camera white balance, select display color or black & white,
set the flicker frequency, change the video orientation, and adjust the brightness and contrast.
Page 32

27
System > Image > Exposure
In Exposure page, you can set the exposure zone, exposure mode, and calibrate the DC Iris.
(1)
(2)
(3)
(4)
Name
Function
(1) Exposure Area
Select the exposure area to define the light distribution and bring out
more details.
Entire screen: measure the entire screen to adjust the exposure.
Customize: measure the exposure to where the adjustable and movable
frame on the screen is located. Move the spot to dark zone to adjust the
light condition.
Backlight compensation: measure the exposure at the center of the
screen.
Page 33

28
Name
Function
(2) Exposure Mode
Select to automatically or manually adjust the exposure.
Auto: adjust exposure level from -2.0 to +2.0
Manual: adjust max shutter and gain control
(3) AE Profile
Select the auto exposure scenes – Indoor, Outdoor, or ManualIRIS.
(4) Low light priority
Select the one you want to prioritize during low light mode image quality
or frame rate.
Page 34

29
System > Image > Advanced
In Advanced page, you can configure the Wide Dynamic Range, Denoise, and AE profile.
(1)
(2)
Name
Function
(1) Wide Dynamic
Range
WDR effectively balances the video image on the screen in both bright
and dark areas making it possible to see clear details. There are 3
levels for your choice or disable WDR.
(2) Denoise
Select Disable/2D/3D/Auto to reduce the excessive noise on the video
image.
Auto: automatically switch between 2D, 3D, and Disable.
Page 35

30
System > Image > Privacy Mask
In Privacy Mask page, you can enable 4 privacy masks. Simply adjust the size and position the mask
on the area you want to conceal. The viewer will not be able to see the masked area. It will cover the
video screen with black frame. After completing the setting, click Save to apply the new setting and
Cancel to keep the old setting.
Page 36

31
System > Video Stream
Both admin and operator levels can configure the Video Stream. After configuring the video stream
setting, click Save to apply the new setting and Cancel to keep the old setting.
(1)
(2)
(3)
(4)
(5)
(6)
(7)
(8)
Name
Function
(1) Stream Mode
The ED5000 supports 3 stream mode – Normal ceiling, Quad ceiling,
and Wall mode. Each stream mode has supported different type of
display mode; refer to (2) Display mode.
(2) Display mode
According to stream mode, display mode supports are different.
Stream mode
Display mode
Normal ceiling
Overview/Panoramic/Dual
Panoramic/Quad/Dual Panoramic
Quad ceiling
Area1/Area2/Area3/Area4
Wall mode
Panoramic
Page 37

32
Name
Function
(3) Stream Type
According to stream mode, stream type supports are different.
(4) Stream
Select the streaming source. According to stream mode, stream
supports are different.
Stream mode
Stream
Normal ceiling
1/2/5
Quad ceiling
1/2/3/4/5
Wall mode
1/2
(5) Output Resolution
Select the video size. According to stream mode, output resolution
supports are different.
(6) Frame Rate
Select frame rate per second of video.
(7) Intra Frame Period
Select frame internal time period.
(8) Code Type
Select the type of video compression codec. The supported codec is
H.264, MPEG4, and MJPEG. On each stream, adjust rate control and
video quality setting.
VBR (Variable Bit Rate): by default use this setting if there is a need to
maintain the image quality whenever there is lot of activities on the
scene or no motion. This setting keeps the video stream constant as
possible which increases the bandwidth requirement when there is high
motion and decreases when there is no motion. The bandwidth must be
able to accommodate high throughputs.
CBR (Constant Bit Rate): use this setting if there is bandwidth
concern. This setting is restricted to keep the bit rate setting. This could
affect the image quality and frame rate if there is high activity that result
in a bit rate that is higher than the set bit rate.
Page 38

33
Smart Stream
(1)
(2)
Name
Function
(1) Stream
Select the streaming source. This option is only applied to H.264.
(2) Quality
High: video quality of selected area is better than that of un-selected
area.
Low: video quality of selected area is worse than that of un-selected
area.
Page 39

34
System > Audio
Both admin and operator levels can configure the IP camera audio setting. After configuring the Audio
setting, click Save to apply the new setting and Cancel to keep the old setting.
(1)
(2)
(3)
(4)
Name
Function
(1) Audio
Select to enable/disable the IP camera built-in mic and mic port.
(2) Internal/External
MIC gain
Select to boost up the internal/external mic gain or set to normal.
(3) Audio Codec
Select the audio protocol, algorithm, and audio bit rate.
G.711: uses Pulse code modulation (PCM) of voice.
G.726: uses 40, 32, 24, 16 kbit/s adaptive differential pulse code
modulation (ADPCM)
AAC: uses AAC codec
(4) Alarm Audio
Select to choose from 2 types of alarms sound or customer alarm to
use the uploaded alarm sound. The supported sound format are in
*.wav (PCM 8KHz/16bit Mono, 10 seconds).
Page 40

35
System > SD/microSD Card > Management
Both admin and operator levels can manage the SD/microSD Card local storage. After managing the
SD/microSD Card setting, click Save to apply the new setting and Cancel to keep the old setting. We
recommend formatting the SD/microSD card when using it for the first time.
(1)
(2)
(3)
(4)
(5)
Name
Function
(1) SD/microSD Card
Info
Shows the SD/microSD card details. No details will appear if
SD/microSD Card is not inserted.
(2) Storage Overwrite
Enable/disable cycle recording. The old file in the SD/microSD card will
be overwritten with the latest one when it has reached the maximum
capacity.
(3) Automatic Cleanup
Enable/disable automatic clear the data in SD/microSD card. The file
will be deleted when it reached the number of days set in Delete data
after [xx] days.
(4) Delete data after
Enter the number of days you wish to retain a file.
(5) Format
To delete all the data in the SD/microSD card.
Page 41

36
System > SD/microSD Card > File Search
Use this to search the captured image in the SD/microSD card.
Page 42

37
Application > Motion Detection
Both admin and operator levels can specify up to 3 areas on the screen to monitor the motion. In the
motion detection page, the frame will blink when the motion detected has reached the percentage
threshold setting. This feature can be utilized to trigger a response in Event setting.
To Set the Motion Detection
1. Click Application > Motion Detection.
2. Enable the region check box (Region 1, Region 2, Region 3) to create a motion detection frame.
3. Move and adjust the frame to the area you want to detect the motion.
4. Adjust the sensitivity and percentage. Sensitivity detects the motion on the screen and assesses
the changes in pixel thru percentage. The motion detection will activate when the Monitor level
reaches the defined percentage.
5. Click Save to apply the new setting and Cancel to keep the old setting.
Page 43

38
Application > IVA
If IVA function has been disabled, the all corresponded functions are disabled.
Application > IVA > Cross Detection
Cross detection function detects moving objects that cross the virtual lines that user has set up in IP
camera application and to trigger the alarm.
1. Click Application > IVA, select Cross Detection from the drop-down list.
2. Enable Cross Detection Area 1/2 check box
3. You will see the red/green line is shown on the video screen.
4. Drag the red line (area 1) or green line (area 2) to set the area for cross detection. You can set
both lines for cross detection or one of the lines. There is no priority for the 2 lines; the color is just
for you to differentiate when both lines are set.
5. After setting the cross detection area, click the arrow to set cross detect direction. The arrow point
is the direction of cross way.
6. Click Save to save the setting.
7. Go to System > Image > Cross Detection Display to set the display lines of cross detection on
live view screen when cross detection is triggered. If user wants to see the cross detection line(s)
always display on the screen, select always. If user only wants to see the cross detection line(s)
when the cross detection has triggered, select the time in second (1s, 2s, 3s, 4s, or 5s) to display
the cross line(s) on the screen. The cross detection line(s) only can be viewed in Quad mode in
stream 5.
Page 44

39
8. To set the cross detection alarm, please go to the Event Setting.
Page 45

40
Application > IVA > Tampering
Alarm triggers when the following situation has occurred.
Spray-painting: Alarm is triggered when the camera has detected the painting sprayed on the
camera’s view for over 2 seconds.
Intention Block /Cover: Alarm is triggered when the camera has detected the camera’s view
being blocked intentionally over 2 seconds.
Accidental redirection: Alarm is triggered when someone re-directs the position or direction of
camera accidentally.
Defocusing: Alarm is triggered when the camera has lost focus.
1. Click Application > IVA, select the Tampering from the drop-down list.
2. Click Save to enable the Tampering function.
3. Go to Event setting and mark Tampering to enable tampering alarm.
4. When alarm has been triggered, there will be a red-frame flashing on the live video screen for 30
seconds.
Page 46

41
Application > IVA > Missing Object
Select a certain object on the screen for the camera system to detect; System gives alarm when the
object disappears.
1. Click Application > IVA, select the Missing Object from the drop-down list.
2. A red frame will show up on the screen. Click and drag the red frame to the object position and click
the frame to adjust the size of frame.
3. Sensitivity: Set the degree of response of detection.
4. Detection Duration: Set the lasting time for camera system to detect the object.
5. Alert Duration: Set the alarm lasting time after alarm has been triggered.
6. Click Save to save the settings.
7. Go to System > Image > Missing Object Display to set the display missing object frame on live
view screen when the missing object is triggered.
8. Go to Event setting and mark Missing Object to enable the alarm.
Page 47

42
Application > IVA > Suspicious Object
Suspicious Object is an unusual object appears on the screen.
1. Click Application > IVA, select the Suspicious Object from the drop-down list.
2. A red frame and green frame will show up on the screen. The red frame is defined as detecting
zone and green frame is defined as object size frame. Click and drag the red frame to the position
and click the frame to adjust the size of frame. Next, click and drag the green frame the detecting
zone and adjust the size of object for detection.
3. Sensitivity: Set the degree of response of detection.
4. Detection Duration: Set the lasting time for camera system to detect the object.
5. Alert Duration: Set the alarm lasting time after alarm has been triggered.
6. Click Save to save the settings.
7. Go to System > Image > Suspicious Object Display, mark Enable to display suspicious object
frame on live view screen when suspicious object is triggered.
Page 48

43
8. Go to Event setting and mark Suspicious Object to enable the alarm.
Application > Tracking
Enable to track the moving object. The camera lens will track the moving object and display on
left-corner screen view.
Sensitivity: Select the sensitivity level of tracking object – High, Medium, or Low.
Return to original position while object stops moving for: Set the time for camera lens reset
back to pre-position.
Page 49

44
Event Setting
Both admin and operator levels can configure the Event setting. In this section, the IP camera can be
configured to perform an action when an event is triggered at the specified time.
To Setup the Event
1. Click Event.
2. On the time table, click-drag to select the time period to specify the period of the event.
3. Type a name for the event. The naming rule is no space between each character and number and
no special character. The length of name is 20 in both characters and numbers.
4. Select the color to represent the event
5. Set the schedule. You can set the time period and choose another day(s) to apply the same event
setting.
Page 50

45
6. Enable the type of event for the IP camera to trigger.
- Alarm Interval
This triggers the IP camera based on the time that use has set in Minutes column. The
interval time rage is 1~60 minutes.
- Motion Detection Region 1/2/3
This triggers the IP camera when a motion is detected on the motion detection region.
- Alarm Cross Detection Area 1/2
This triggers the IP camera when a cross detection is detected on the cross detection area.
- Tampering
This triggers the IP camera when tampering situation has met (Spray-painting, Intention Block
/Cover, Accidental redirection, or Defocusing). The tampering alarm selection will display only
when tampering function has enabled.
- Missing Object
This triggers the IP camera when a missing object is occurred. The missing object alarm
selection will display only when missing object function has enabled.
Page 51

46
- Suspicious Object
This triggers the IP camera when a suspicious object is occurred. The suspicious object alarm
selection will display only when suspicious object function has enabled.
- Digital Input
This triggers the IP camera when the external digital input device or sensor is activated.
- SD Card / microSD Card
This triggers the IP camera when the SD/microSD card is removed.
- Network
This triggers the IP camera when the Internet connection is disconnected.
7. Select the type of action for the IP camera to perform when a trigger is activated. Set the duration.
Choose digital output to send recorded video or still image, or Alarm Audio to sound the alarm.
Then select the type of server/media to where to send the file. To configure the FTP and NAS
setting, go to System > Network > Server tab.
[Note]
a. Snapshot and System log support sending the file thru Mail, and storing in FTP, NAS or
SD/microSD card. You can enable multiple options to send and save the captured image.
b. Video Clip supports storing in FTP, NAS or SD/microSD card. You can only select one
storage option to save the video file. For better performance, we recommend to set the
video stream is default value.
8. Click OK to add the event setting, Delete to remove, and Cancel to without save and close the
event setting.
Page 52

47
Status Information
Show the information about the device and network setting.
 Loading...
Loading...