Page 1

Wireless LAN Mobility System
Wireless LAN Switch Manager
User’s Guide
3CRWXR10095A, 3CRWX120695A, 3CRWX440095A
http://www.3com.com/
Part No. DUA-WXM10-AAA01
Published June 2005
Page 2

3Com Corporation
350 Campus Drive
Marlborough, MA USA
01752-3064
Copyright © 2005, 3Com Corporation. All rights reserved. No part of this documentation may be reproduced
in any form or by any means or used to make any derivative work (such as translation, transformation, or
adaptation) without written permission from 3Com Corporation.
3Com Corporation reserves the right to revise this documentation and to make changes in content from time
to time without obligation on the part of 3Com Corporation to provide notification of such revision or change.
3Com Corporation provides this documentation without warranty, term, or condition of any kind, either
implied or expressed, including, but not limited to, the implied warranties, terms or conditions of
merchantability, satisfactory quality, and fitness for a particular purpose. 3Com may make improvements or
changes in the product(s) and/or the program(s) described in this documentation at any time.
If there is any software on removable media described in this documentation, it is furnished under a license
agreement included with the product as a separate document, in the hard copy documentation, or on the
removable media in a directory file named LICENSE.TXT or !LICENSE.TXT. If you are unable to locate a copy,
please contact 3Com and a copy will be provided to you.
UNITED STATES GOVERNMENT LEGEND
If you are a United States government agency, then this documentation and the software described herein are
provided to you subject to the following:
All technical data and computer software are commercial in nature and developed solely at private expense.
Software is delivered as “Commercial Computer Software” as defined in DFARS 252.227-7014 (June 1995) or
as a “commercial item” as defined in FAR 2.101(a) and as such is provided with only such rights as are
provided in 3Com’s standard commercial license for the Software. Technical data is provided with limited rights
only as provided in DFAR 252.227-7015 (Nov 1995) or FAR 52.227-14 (June 1987), whichever is applicable.
You agree not to remove or deface any portion of any legend provided on any licensed program or
documentation contained in, or delivered to you in conjunction with, this User Guide.
Unless otherwise indicated, 3Com registered trademarks are registered in the United States and may or may
not be registered in other countries.
3Com is a registered trademark of 3Com Corporation. The 3Com logo is a trademark of 3Com Corporation.
Mobility Domain, Mobility Point, Mobility Profile, Mobility System, Mobility System Software, MP, MSS, and
SentrySweep are trademarks of Trapeze Networks, Inc.
Intel and Pentium are registered trademarks of Intel Corporation. Microsoft, MS-DOS, Windows, Windows XP,
and Windows NT are registered trademarks of Microsoft Corporation.
All other company and product names may be trademarks of the respective companies with which they are
associated.
ENVIRONMENTAL STATEMENT
It is the policy of 3Com Corporation to be environmentally-friendly in all operations. To uphold our policy, we
are committed to:
Establishing environmental performance standards that comply with national legislation and regulations.
Conserving energy, materials and natural resources in all operations.
Reducing the waste generated by all operations. Ensuring that all waste conforms to recognized environmental
standards. Maximizing the recyclable and reusable content of all products.
Ensuring that all products can be recycled, reused and disposed of safely.
Ensuring that all products are labelled according to recognized environmental standards.
Improving our environmental record on a continual basis.
End of Life Statement
3Com processes allow for the recovery, reclamation and safe disposal of all end-of-life electronic components.
Regulated Materials Statement
3Com products do not contain any hazardous or ozone-depleting material.
Environmental Statement about the Documentation
The documentation for this product is printed on paper that comes from sustainable, managed forests; it is
fully biodegradable and recyclable, and is completely chlorine-free. The varnish is environmentally-friendly, and
the inks are vegetable-based with a low heavy-metal content.
Page 3

CONTENTS
ABOUT THIS GUIDE
Conventions 9
Documentation 10
Documentation Comments 11
1 GETTING STARTED
Hardware Requirements for 3WXM Client 13
Hardware Requirements for 3WXM Services 14
Software Requirements 14
Preparing for Installation 15
User Privileges 15
Serial Number, License Key and Activation Key 15
HP OpenView Network Node Manager 16
Resource Allocation 16
3WXM Services Options 16
Installing 3WXM 18
Unpacking Files 18
Using the Installation Wizard 18
Start the 3WXM Services 18
Connect 3WXM Clients to 3WXM Services 19
Configure 3WXM Services 19
3WXM Access Control 21
3WXM Interface 22
Display the Main Window 22
Using Menu Bar and Toolbars 24
Setting Preferences 24
Easy Configuration Using Wizards 25
View Topology 25
Shortcut to Wizards and Editing Properties 26
Getting Help 27
Page 4

2 PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH
3WXM
Overview 29
Which Services To Provide? 30
Network Plan 31
RF Coverage Area 31
RF Auto-Tuning 32
RF Auto-Tuning with Modelling 32
RF Planning 33
Which Planning Method Should I Use? 33
Configuration 35
Wireless Configuration 36
AAA Security Configuration 38
Authentication 38
Authorization 40
Accounting 40
System and Administration Configuration 40
Configure Basic WX Switch Properties 41
Configure WX Switch Connection Information 42
Configure Boot Information 42
Equipment Installation 42
Deployment 43
Management and Monitoring 44
Network Status 44
RF Monitoring 45
Client Monitoring 46
Rogue Detection 46
Event Logging 47
Verification 47
Reporting 47
RF Plan Optimization 49
Page 5

3 CONFIGURING WIRELESS SERVICES
Overview 51
Configure Employee Access Services 52
Tas k Ta bl e 52
Step Summary 56
Example: Configure Employee Access 57
Create a Service Profile 57
Create a Radio Profile 59
Configure RADIUS Servers 61
Specify Network Access Rules 64
Set Up VLANs on WX Switches 66
What’s Next? 68
Configure Guest Access Services 69
Tas k Ta bl e 70
Step Summary 71
Optional: Configure Mobility Profiles 73
Configure Local Authentication 74
What’s Next? 76
Configure Voice over Wireless IP Service 77
Tas k Ta bl e 78
Step Summary 81
Configure Local Authentication 82
Configure Access Control Lists 84
Example: Creating an ACL for SpectraLink Wireless Phones 85
Example: Creating an ACL for Avaya Wireless Phones 87
What’s Next? 90
4 USING RF AUTO-TUNING
Overview 91
Place Your Equipment 92
Configure Initial WX Switch Connectivity 92
Upload the WX Switch Configuration into a 3WXM Network Plan 92
Create a Service Profile 94
Create a Radio Profile and Map the Service Profile to It 95
Create Your MAPs 97
Apply a Radio Profile to Each Radio 98
What’s Next? 98
Page 6

5 USING RF AUTO-TUNING WITH MODELLING
Overview 99
Add Site Information 100
Insert RF Obstacles 104
Create Your RF Coverage Area 106
Create a Wiring Closet 106
Create Your RF Coverage Area 107
Add MAPs 109
Associate MAPs to the Coverage Area 110
What’s Next? 112
6 USING RF PLANNING
Overview 113
Prepare the Floor Drawings 114
Define Site Information 115
Import a Floor Plan 120
Set the Scale 121
Clean Layout 122
Model RF Obstacles 125
Import a Site Survey 127
Plan RF Coverage 127
Add Wiring Closets 127
Create Coverage Areas 129
Compute and Place MAPs 134
Assign Channel Settings 136
Calculate Optimal Power 138
Display Coverage 139
Generate a Work Order 141
Install the Equipment 142
What’s Next? 142
Page 7

7 MANAGING AND MONITORING YOUR NETWORK
Overview 143
Deploy Your Configuration 144
Perform Basic Administrative Tasks 146
Configuring WX Management Services 146
Distributing Image and Configuration Files 147
Using the Image Repository 148
Distributing System Images 148
Distributing WX Configuration Files 149
Saving Versions of Network Plans 150
Importing or Exporting Switch Configuration Files 151
Monitoring Examples 153
Monitor an Individual User 153
Find the User 154
Place User on Watch List 155
Locate the User 155
Display User Activity 157
View Long-Term User Statistics 158
Monitor a Group of Users 161
Monitor a Rogue 163
Configuring Countermeasures 166
8 OPTIMIZING A NETWORK PLAN
Overview 169
Using RF Measurements from MAPs 170
Using RF Measurements from an Ekahau Site Survey 172
Generating an Ekahau Site Survey Work Order 173
Importing RF Measurements from the Ekahau Site Survey 176
Optimizing the RF Coverage Model 179
Locating and Fixing Coverage Holes 181
Displaying the RF Coverage Area 181
Locking Down MAPs 183
Fixing a Coverage Hole 184
Computing and Placing New MAPs 184
Replanning Your Network 184
What’s Next? 185
Page 8

INDEX
Page 9
ABOUT THIS GUIDE
This manual shows you how to plan, configure, deploy, and manage a
Mobility System wireless LAN (WLAN) using the 3Com Wireless LAN
Switch Manager (3WXM).
Read this manual if you are a network administrator or a person
responsible for managing a WLAN.
If release notes are shipped with your product and the information there
differs from the information in this guide, follow the instructions in the
release notes.
Most user guides and release notes are available in Adobe Acrobat
Reader Portable Document Format (PDF) or HTML on the 3Com
World Wide Web site:
http://www.3com.com/
Conventions Table 1 and Table 2 list conventions that are used throughout this guide.
Tab le 1 Notice Icons
Icon Notice Type Description
Information note Information that describes important features or
instructions
Caution Information that alerts you to potential loss of data or
potential damage to an application, system, or device
Page 10

10 CHAPTER : ABOUT THIS GUIDE
This manual uses the following text and syntax conventions:
Tab le 2 Text Conventions
Convention Description
Menu Name >
Command
Monospace text Sets off command syntax or sample commands and system
Bold text Highlights commands that you enter or items you select.
Italic text Designates command variables that you replace with
[ ] (square brackets) Enclose optional parameters in command syntax.
{ } (curly brackets) Enclose mandatory parameters in command syntax.
| (vertical bar) Separates mutually exclusive options in command syntax.
Keyboard key names If you must press two or more keys simultaneously, the key
Words in italics Italics are used to:
Indicates a menu item that you select. For example,
File > New indicates that you select New from the File
menu.
responses.
appropriate values, or highlights publication titles or words
requiring special emphasis.
names are linked with a plus sign (+). Example:
Press Ctrl+Alt+Del
n Emphasize a point.
n Denote a new term at the place where it is defined in the
text.
n Highlight an example string, such as a username or SSID.
Documentation The 3WXM documentation set includes the following documents.
Wireless LAN Switch Manager (3WXM) Release Notes
These notes provide information about the system software release,
including new features and bug fixes.
Wireless LAN Switch and Controller Release Notes
These notes provide information about the system software release,
including new features and bug fixes.
Wireless LAN Switch and Controller Quick Start Guide
This guide provides instructions for performing basic setup of secure
(802.1X) and guest (WebAAA™) access, for configuring a Mobility
Domain for roaming, and for accessing a sample network plan in
3WXM for advanced configuration and management.
Page 11
Documentation Comments 11
Wireless LAN Switch Manager Reference Manual
This manual shows you how to plan, configure, deploy, and manage a
Mobility System wireless LAN (WLAN) using the 3Com Wireless LAN
Switch Manager (3WXM).
Wireless LAN Switch and Controller Installation and Basic
Configuration Guide
This guide provides instructions and specifications for installing a WX
wireless switch in a Mobility System WLAN, and basic instructions for
deploying a secure IEEE 802.11 wireless service.
Wireless LAN Switch and Controller Configuration Guide
This guide provides instructions for configuring and managing the
system through the Mobility System Software (MSS) CLI.
Wireless LAN Switch and Controller Command Reference
This reference provides syntax information for all MSS commands
supported on WX switches.
Documentation Comments
Your suggestions are very important to us. They will help make our
documentation more useful to you. Please e-mail comments about this
document to 3Com at:
pddtechpubs_comments@3com.com
Please include the following information when contacting us:
Document title
Document part number and revision (on the title page)
Page number (if appropriate)
Example:
Wireless LAN Switch and Controller Configuration Guide
Part number 730-9502-0071, Revision B
Page 25
Please note that we can only respond to comments and questions about
3Com product documentation at this e-mail address. Questions related to
Technical Support or sales should be directed in the first instance to your
network supplier.
Page 12

12 CHAPTER : ABOUT THIS GUIDE
Page 13

1
GETTING STARTED
This chapter contains information about recommended system
requirements you should meet for optimum 3WXM performance,
installing 3WXM client and 3WXM Services software, and an introduction
to using the 3WXM interface.
Hardware Requirements for 3WXM Client
Table 3 shows the minimum and recommended requirements to run the
3WXM client in Windows.
Tab le 3 Hardware Requirements for Running 3WXM Client in Windows
Minimum Recommended
Processor Intel Pentium 4 2 GHz or
equivalent
RAM 512 MB 1 GB
Hard drive space
available
Monitor resolution 1024x768 pixels, 24-bit
CD-ROM drive CD-ROM or equivalent CD-ROM
.
100 MB 200 MB
color
Intel Pentium 4 3 GHz or
equivalent
1600x1200 pixels, 32-bit
color
Page 14

14 CHAPTER 1: GETTING STARTED
Hardware Requirements for 3WXM Services
Software Requirements
Table 4 shows the minimum and recommended requirements to run the
3WXM Services in Windows.
Tab le 4 Hardware Requirements for Running 3WXM Services in Windows
Minimum Recommended
Processor Intel Pentium 4 2.4 GHz
or equivalent
RAM 1GB 2GB
Hard drive space available 1GB 2GB
Monitor resolution 1024x768 pixels, 24-bit
color
CD-ROM drive CD-ROM or equivalent CD-ROM
Intel Pentium 4 3.6 GHz
or equivalent
1600x1200 pixels, 32-bit
color
3WXM client and 3WXM Services are each supported on the following
operating systems:
Microsoft Windows Server 2003
Microsoft Windows XP with Service Pack 1 or higher
Microsoft Windows 2000 with Service Pack 4
You must use the English version of the operating system you select.
Operating system versions in other languages are not supported with
3WXM.
The following additional software is required for certain 3WXM features:
HP OpenView Network Node Manager 6.4—Must be installed prior to
3WXM if you plan to use 3WXM in your HP OpenView environment.
Adobe Acrobat Reader 5.x or later (or plug-in)—For reading the
Wireless LAN Switch Manager Reference Manual and release notes.
Web browser (for example, Microsoft Internet Explorer 5.x or 6.x or
Netscape Navigator 6.x or 7.x)—For displaying 3WXM Help, work
orders and inventory reports.
Page 15

Preparing for Installation 15
Preparing for Installation
User Privileges Before you install 3WXM, make sure that you are logged in as a user who
Serial Number,
License Key and
Activation Key
Before you install 3WXM, make sure you have the appropriate
administrative privileges on the system and a license key if required. If you
plan to install the HP OpenView plug-in for 3WXM, which allows you to
integrate 3WXM into an HP OpenView environment, make sure that HP
OpenView is already installed.
has permission to install software, or as an administrator.
After you install 3WXM, you can configure 3WXM access privileges for
the user accounts on the machine. Likewise, you can configure access
privileges for 3WXM Services, if installed. Access privileges for the 3WXM
client are completely independent of access privileges for 3WXM Services,
and are configured separately.
The serial number is generated automatically when the 3WXM software
is installed.
The license key is included with your 3WXM software packaging. You will
need a separate license key for each host on which you plan to run
3WXM. The license supplied with 3WXM allows you to manage up to 10
wireless switches. If you plan to manage more wireless switches, you will
also need an Unlimited Device license key (3CWXMUPA). You will need a
separate Unlimited Device license key for each host on which you plan to
run 3WXM to manage more than 10 devices.
If you do not have a license key, you can run 3WXM for 30 days. Once
this trial period is over you will need to purchase a license to continue
running the 3WXM software.
When you initially run the 3WXM software, it will ask if it is to be run as a
trial or as a fully licensed version. In the latter case, it will then ask for the
license key. The software will then display the serial number and ask for
an activation key.
To obtain an activation key, you must register the product with 3Com. If
you press the Get Activation Key button, your web browser will be
automatically launched at the correct pages for registering the product.
Once registration is complete, your activation key will then be displayed
and e-mailed to you.
Page 16
16 CHAPTER 1: GETTING STARTED
Once the activation key has been accepted, you may enter an Unlimited
Device license key. This will require its own activation key, which can be
obtained in the same manner.
If you are registering your product using the web browser on a different
host, and you wish to register for the 30-day trial, then you will need to
select 3CWXMA as the software that you are registering. If you have a
license key, then you should select 3CWXM10A. This will register both
the software and the license. The Unlimited Device license is registered as
3CWXMUPA.
HP OpenView
Network Node
Manager
If you want to integrate 3WXM into your HP OpenView environment, you
have the option of installing the HP OpenView plug-in required to use
Network Node Manager with 3Com products. Make sure that HP
OpenView is already installed before installing 3WXM with the plug-in.
Resource Allocation Table 5 contains general recommended guidelines for hardware
requirements and memory allocation based on the number of radios and
WX switches your server will support. A larger number of WX switches
implies more connections and data processing, and consequently, more
CPU is required. A larger number of radios implies more data (including
client sessions) which requires more RAM and storage.
Tab le 5 Recommended Server Hardware Allocation
Number of
Radios 1-25 WX Switches 25-50 WX Switches 50+ WX Switches
1 – 1000 - 2.4 MHz P4
- 500 MB RAM
- 1 GB HD
1000 – 2000 - 2.4 MHz P4
- 1 GB RAM
- 2 GB HD
- 2.8 MHz P4
- 500 MB RAM
- 1 GB HD
- 3.0 GHz P4
- 1 GB RAM
- 2 GB HD
- 3.2 MHz Xeon
- 1 GB RAM
- 1 GB HD
- 3.6 GHz Xeon
- 2 GB RAM
- 2 GB HD
3WXM Services
Options
3WXM Services can be installed either in standalone mode or shared
mode. Standalone mode is when 3WXM client and 3WXM Services are
installed on one machine. Standalone mode is primarily used for trying
out 3WXM, while shared mode is used in a working environment. In
shared mode, the administrator sets up 3WXM Services on a single host
(typically with more resources) and other hosts with the client 3WXM
Page 17
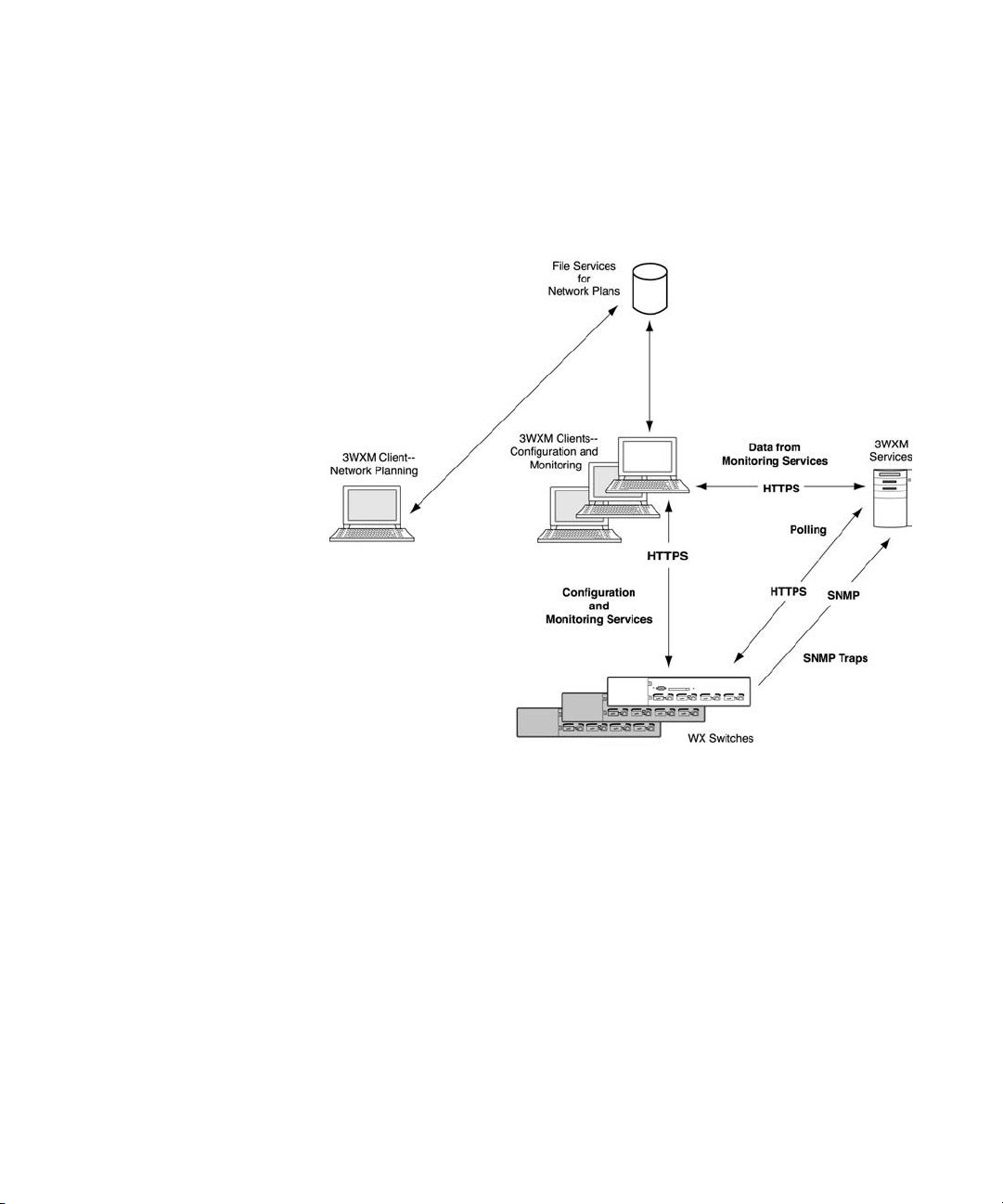
Preparing for Installation 17
application share 3WXM Services to access network plans and monitoring
information. See Figure 1.
Figure 1 3WXM Services in Shared Mode
During the 3WXM installation, you can select to install the 3WXM
Services and 3WXM client, or the client only. If you select the option that
installs 3WXM Services, the services are installed with default settings
that are adequate for getting started.
Network plans are stored on the server. By default, only local access is
allowed. Remote clients cannot access the server unless you enable
remote access.
To learn more about RF monitoring and client monitoring, see
“Managing and Monitoring Your Network” on page 143.
Page 18

18 CHAPTER 1: GETTING STARTED
Installing 3WXM The same 3WXM install program installs either just the 3WXM client or
both the 3WXM client and 3WXM Services.
This section contains information about the following topics:
“Unpacking Files” on page 18
“Using the Installation Wizard” on page 18
Unpacking Files To unpack files on Windows systems:
1 Insert the 3WXM CD in the CD-ROM drive. If Autorun is enabled, wait
briefly for the install program to start. For more information about using
the installation wizard, see “Using the Installation Wizard” below.
If Autorun is disabled, follow these steps:
a In Windows Explorer, navigate to your CD-ROM drive.
b In the Windows\VM directory, double-click install.exe.
The Introduction page of the 3WXM installation wizard appears.
2 Click Next to display the Choose Installation Type page of the installation
wizard, and go to “Using the Installation Wizard”.
Using the Installation
Wizard
To use the Installation Wizard:
1 On the Choose Installation Type page, choose one of the following:
To install both the 3WXM server and the client, click the 3WXM
Services icon.
To install only the 3WXM client, click the 3WXM client icon.
For detailed installation instructions, see “Installing 3WXM” in the
Wireless LAN Switch Manager Reference Manual.
Start the 3WXM Services
The 3WXM Services are automatically started when you install it on a
Windows system.
Page 19
Installing 3WXM 19
Connect 3WXM Clients to 3WXM Services
To connect the client to Services:
1 Select Start > Programs > 3Com > 3WXM > 3WXM. The 3WXM
Services Connection wizard is displayed.
2 Enter the IP address or fully-qualified hostname of the machine on which
the service is installed.
If 3WXM Services is installed on the same machine as the one you are
using to run 3WXM client, enter 127.0.0.1 as the IP address. This is a
standard IP loopback address.
3 Specify the service port, if different from the port number in the Service
Port listbox.
The port number used by the monitoring service must not be used by
another application on the machine where the monitoring service is
installed. If the port number is used by another application, change the
port number on the monitoring service. (See “Configure 3WXM Services”
below.)
4 Click Next to connect to the server.
5 If the Certificate Check dialog is displayed, click Accept.
If you left the Open Network Plan option on the 3WXM Services
Connection dialog selected, the server opens a new (blank) network plan.
Configure 3WXM Services
You can change the properties of 3WXM Services.
If a firewall is enabled on the host where you install 3WXM Services,
3WXM Services will not be able to communicate with 3WXM client or
with WX switches unless the firewall is configured to allow through
traffic for the SSL and SNMP ports (443 and 162 by default).
Page 20
20 CHAPTER 1: GETTING STARTED
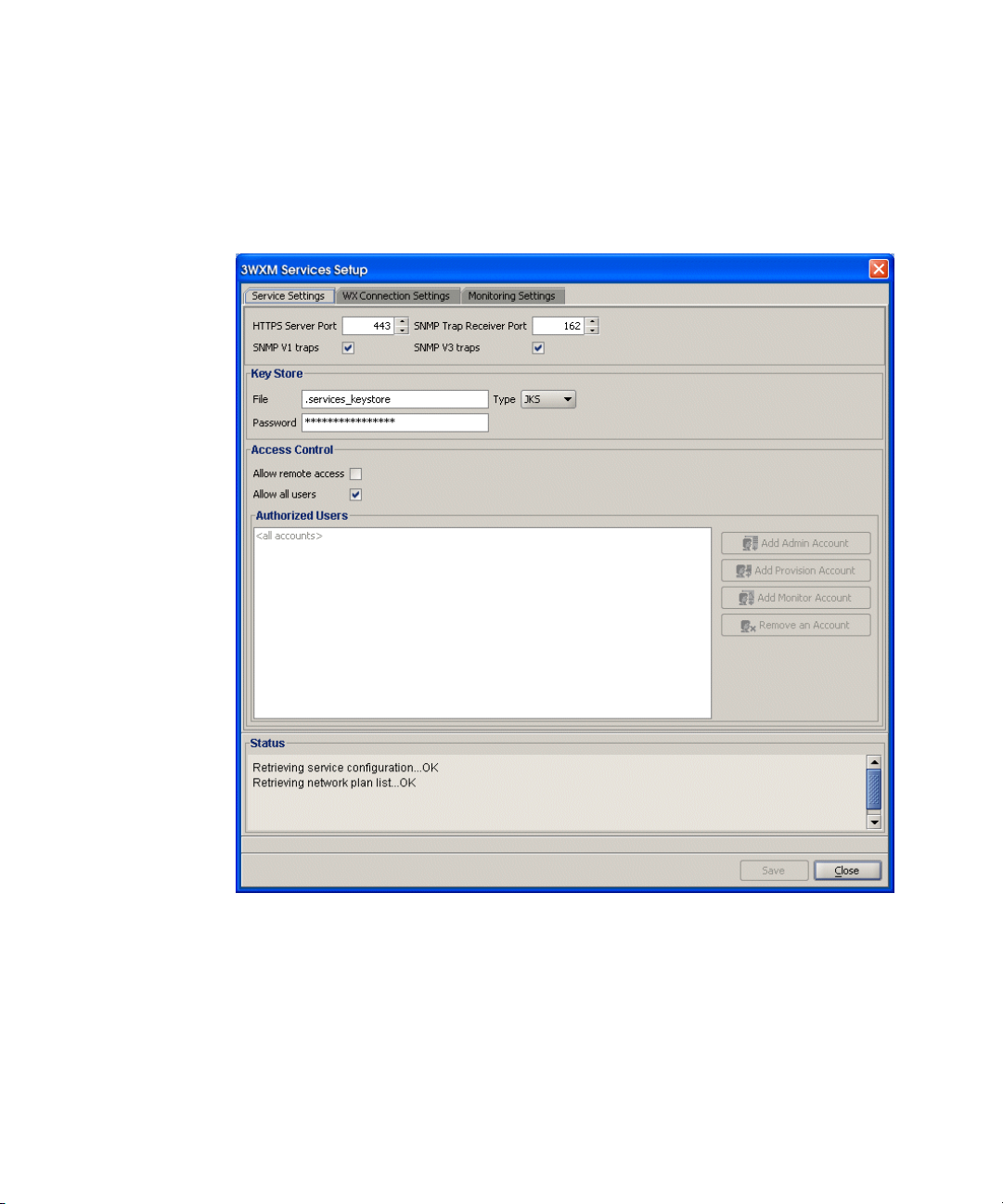
To configure 3WXM Services:
1 Select To ol s > 3WXM Services Setup dialog box from the 3WXM main
tool bar. The 3WXM Services Setup wizard is displayed.
2 You can optionally configure the following:
Select the arrow buttons to change the HTTPS Server Port, which is
the port on which 3WXM Services listens for requests from 3WXM
client.
Select the arrow buttons to change the SNMP Trap Receiver Port,
which is the port on which SNMP traps are received. Also select the
trap type (SNMPv1 or SNMPv3) you want 3WXM Services to receive
from WX switches.
Page 21
Installing 3WXM 21
On each switch in the network plan, you must enable notifications and
configure 3WXM Services as a notification target (trap receiver).
3WXM Services does not start listening for SNMP notifications from
switches until you save the network plan.
From the Key Store area of the window, specify security settings.
From the Access Control area, define user accounts. For more
information about access control, see “3WXM Access Control” on
page 21.
By default, a username and password are not required to access 3WXM
Services from 3WXM client, but only local connections (connections from
client to server on the same host) are allowed. To change these settings,
use the Service Settings tab of the 3WXM Services Setup dialog.
To select monitoring settings:
All monitoring options are enabled by default. You do not need to enable
them and you do not need to specify the switches you want to monitor.
However, for 3WXM Services to receive trap data from WX switches,
SNMP notifications must be enabled on the switches. (See “Deploy Your
Configuration” on page 144.)
To start gathering data for monitoring, deploy your configuration to the
network. For information about deploying your configuration, see
“Deploy Your Configuration” on page 144.
3WXM Access Control You can create a user account with administrator, provision, or monitor
privileges. See Table 6 for privilege definitions.
Tab le 6 User Privilege Levels
Privilege Level Access Control Configuration Monitoring
Administrator yes yes yes
Provision no yes yes
Monitor no no yes
To configure access control:
1 Select To ol s > 3WXM Services Setup from the 3WXM main tool bar.
The 3WXM Services Setup window is displayed.
2 In the Access Control area of the window, deselect Allow all users.
Page 22

22 CHAPTER 1: GETTING STARTED
3 Select Add Admin Account, Add Provision Account, or Add Monitor
Account. A dialog box is displayed.
4 Enter the account name and the password and click OK.
5 To remove an account, click Remove Account.
3WXM Interface This section contains the following topics:
“Display the Main Window” on page 22
“Using Menu Bar and Toolbars” on page 24
“Setting Preferences” on page 24
“Easy Configuration Using Wizards” on page 25
“View Topology” on page 25
“Shortcut to Wizards and Editing Properties” on page 26
“Shortcut to Wizards and Editing Properties” on page 26
“Getting Help” on page 27
Display the Main
Window
When you open a network plan or create a network plan using the
Network Planning wizard, 3WXM displays the Main window. The Main
window is divided into four panels (see Figure 2 on page 23):
1 Organizer panel displays a network tree representing your WLAN’s
devices and configurations on those devices. You can use it to navigate to
Policy configurations, Equipment within your network, and network Sites.
When you select a device or configuration in the tree, the
context-sensitive information about the device or configuration is
displayed to the right in the Content and Information panels. Select the
Details checkbox at the top of the Organizer panel to display detailed
configuration information about items in the tree.
2 Content panel displays context-sensitive information about the device or
configuration selected from the tree in the Organizer panel. From the
Content panel, view 3Com devices and their status, verify 3Com device
configurations in the network plan and in the network, and display event
logs and Rogue detection results.
3 Alerts panel displays a summary of alerts, including network and
configuration verification, Rogue detection, and local and network
changes. Click on a summary to display details.
Page 23
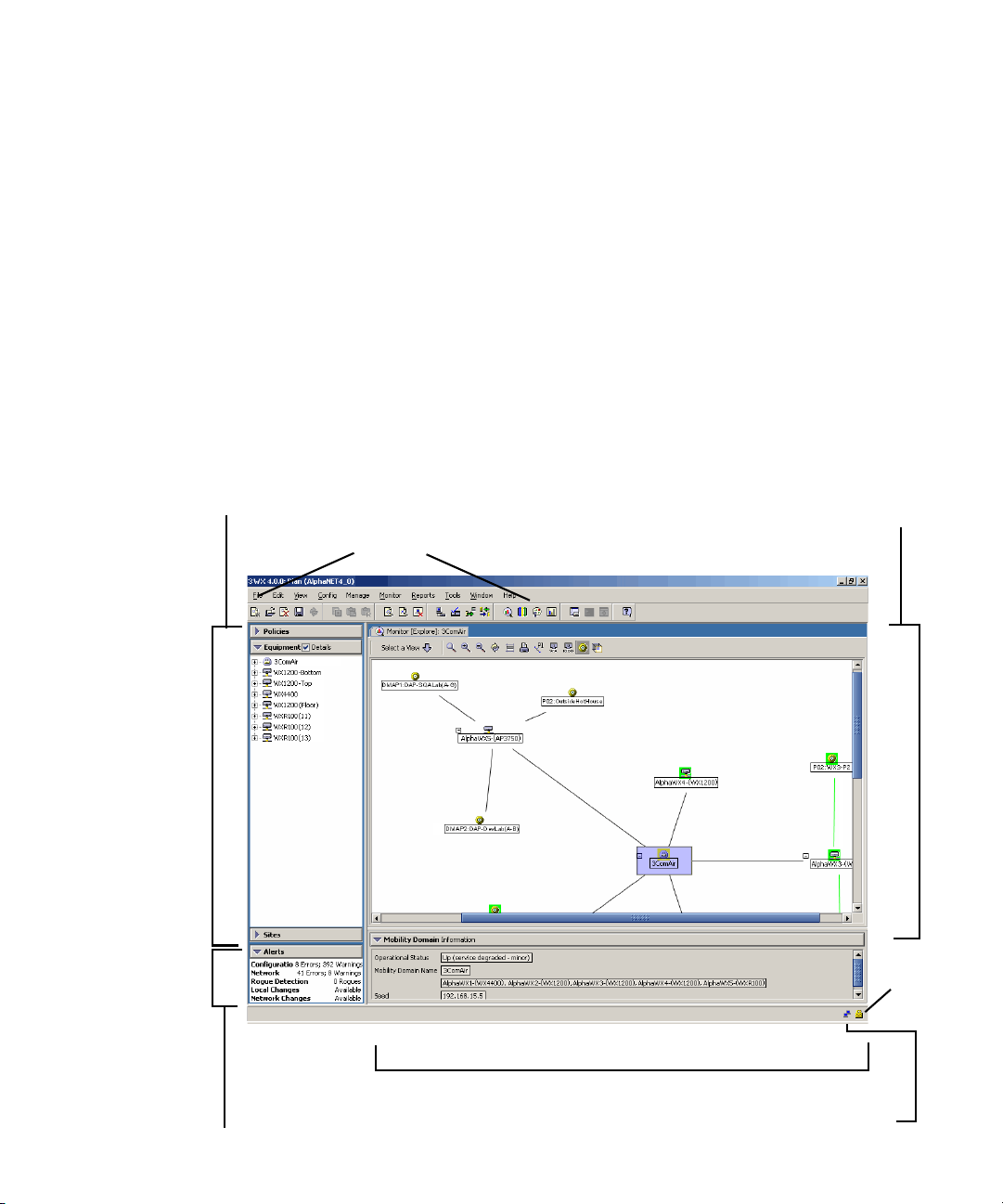
3WXM Interface 23
4 Information panel displays information about an object you select from
the navigation tree under the Organizer panel. The information is
dependent upon the object selected.
The Network Activity icon displays statistics for management traffic
between 3WXM and the WX switches in the network plan. You can click
on the icon to display more details.
The Lock icon indicates whether the network plan has been locked.
When you make changes to a network plan, 3WXM locks it on the server.
The lock prevents other clients who open the network plan from
modifying it while you are making changes. The network plan remains
locked until you save your changes, after which the lock is released.
Figure 2 3WXM Main Window
Organizer panel
Content panel
Toolbar
Lock
icon
Alerts panel
Object Details panel (hidden by default)
Network Activity icon
Page 24
24 CHAPTER 1: GETTING STARTED
Using Menu Bar and
Toolbars
The Main window and individual panels have a menu bar at the top to
select certain actions. Select an item from the menu bar, then select an
action from the dropdown menu. See Figure 3.
Figure 3 Menu Bar with Dropdown Menu
Setting Preferences You can set network and user interface preferences, as well as
preferences for save interval and autosave, certificate handling,
RF monitoring, and logging.
1 Select To ol s > Preferences from the 3WXM main tool bar.
The Preferences wizard is displayed.
Figure 4 Preferences Wizard
2 Select any of the tabs, make modifications in the fields, and select
Reset All to reset preferences.
Page 25
3WXM Interface 25
Easy Configuration
Using Wizards
Wizards help walk administrators through configuration steps. There are
several wizards in the 3WXM application.
Enter the required fields and click Next at the bottom of the wizard to
display the next step. Click Cancel to discard any changes made with the
wizard. When you are done, click Finish to save changes.
You can right-click on many objects to display the Insert option. Select
Insert to create a new object that is a “child” of the selected object.
View Topology You can display a topology view of managed devices in your WLAN and
their relationships to each other. You can also click on the devices in the
topology view to display summary monitoring information about each
one.
To display a topology view of your network:
1 In the Equipment section of the Organizer panel, select a mobility domain
or a WX switch.
2 From the main 3WXM window, select Monitor > New Monitor.
3 Select Explore from the drop-down list in the Monitor tab. The topology
view of the selected object is displayed.
Page 26
26 CHAPTER 1: GETTING STARTED
Shortcut to Wizards
and Editing
Properties
Shortcuts are built into the 3WXM interface to quickly access wizards and
for editing properties for selected objects.
To use shortcuts:
1 Right-click an object from the topology tree in the Organizer panel.
2 Select one of the options displayed. You can select Edit to edit object
properties, or Insert to display a wizard that assists you to create a new
object.
Page 27
3WXM Interface 27
Getting Help Click Help from the Main menu bar to access different types of help:
1 Select Help > 3WXM Help to display HTML help about configuring and
using 3WXM.
2 Select Help > Licensing to view product licensing information, or to add
an Unlimited Device license to the installation.
3 Select Help > Report Problem to report a problem to 3Com Technical
Support.
4 Select Help > About 3WXM to display information about 3WXM and to
display the Release Notes. You also can click Force GC (garbage
collection) to free resources.
Page 28

28 CHAPTER 1: GETTING STARTED
Page 29
PLANNING AND MANAGING YOUR
S
2
WIRELESS NETWORK WITH
3WXM
This chapter contains information about planning and managing your
wireless network with 3WXM. Planning your wireless network is highly
recommended because it not only helps you configure and deploy it, but
also aids in scaling and monitoring your network. 3Com provides you
with flexible tools to assist with network planning.
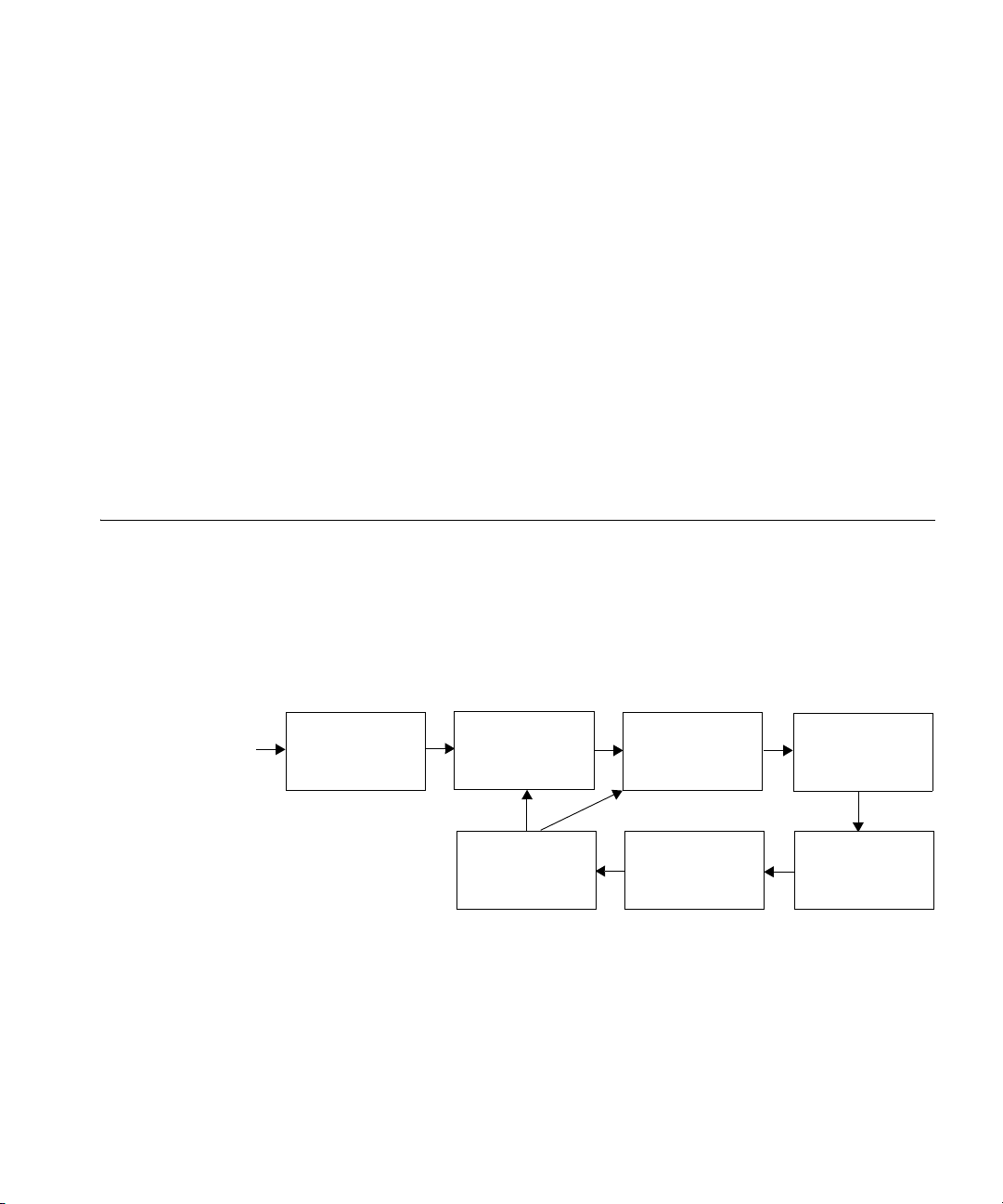
Overview You plan your wireless network to support the services you want to offer
your employees, guests, or customers. Figure 5 describes the process you
will follow to establish services in your company or organization,
beginning with determining the services you want to offer. Each step in
the process is described in this chapter.
Figure 5 Process to Establish Wireless Services
Determine which
TART order and install
services to
provide
Configure
services
Optimize
services
Plan for network
equipment and
coverage
Monitor
services
Generate work
equipment
Deploy
services
Page 30

30 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Which Services To Provide?
A service is a concept (not a selectable item in the 3WXM interface) that
represents a set of options you configure and deploy on your wireless
network.
You configure services to support the different levels of network access
you need to provide. For example, a service configured to support
employee access will have different options configured to provide greater
access to the network. In contrast, a service configured for guest access
typically restricts users to limited or no internal network access, but easily
provides a gateway connection to the Internet.
A service can be fully isolated and independent of other services on the
network (multi-hosted access is typically isolated), or you can reuse part of a
service configuration for another service you want to provide. Each service
has potential authentications (802.1X, web page, MAC address, or “last
resort”) and potential encryptions (802.11i, WPA, WEP, or unencrypted).
The purpose of this section is to provide information about services that you
can configure using 3WXM. Understanding the services you can configure
with 3WXM is the first step in planning and configuring your network.
The first step you need to do when planning your wireless network is to
determine which services your organization requires. The three common
types of services are:
Employee access
Guest access
Voice over Wireless IP (VoWIP)
Employee access is typically secure, encrypted access to the wireless
network. Guest access is access (possibly unencrypted) for visitors at your
location. If you intend to resell services to other providers, you will need
to provide multi-hosted access.
Determining the services you will need at the beginning of the planning
process results in configuration data. The configuration data is used to
create service profiles and AAA rules for each service. A service profile is a
subset of a radio profile. A radio profile is a common set of configuration
parameters that can be applied to many MAP radios.
See “Create a Service Profile” on page 94 for information about
configuring services.
Page 31

Network Plan 31
Network Plan A network plan is the workspace in 3WXM you use to design a wireless
network.
You can better manage and visualize your network topology by creating
a detailed and accurate network plan.
You can start by creating a device-oriented (WX switches and MAPs) view
of your network without any geographic information about your site—no
floor dimensions, building material information, or RF obstacle
information. You can go a step further and provide some geographic
information by adding floor dimensions, your RF coverage area, and
some attenuation information, such as elevator shafts or internal
concrete walls. If you want to enjoy the full benefits of network
monitoring and visualization, you can create a detailed network plan. This
is done by importing detailed building and floor plans into 3WXM,
defining RF obstacles, and defining the quality of coverage (traffic
engineering parameters) you want for specific RF coverage areas.
RF Coverage Area An RF coverage area is the geographical area in which IEEE 802.11 radios
provide wireless services.
This section describes the three techniques you can use for RF coverage.
By understanding available RF coverage planning techniques, you can use
the technique that meets your organization’s requirements.
There are three techniques you can use to get your wireless network
started:
RF Auto-Tuning lets you use the default auto tuning feature to select
power and channel settings for RF signals in your RF coverage area.
You upload the WX switches into 3WXM, configure the MAPs, enable
RF Auto-Tuning, and deploy.
Page 32

32 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
RF Auto-Tuning with Modelling, as with the RF Auto-Tuning
technique, lets you set the auto tuning feature to adjust power and
channel settings to provide RF signals to the coverage area for your
users. Enhance the auto tuning feature by providing modelling
information about your geographic location. By providing some
information about your buildings and floors, you add enough details
into 3WXM so that your can better visualize your network topology
and support improved monitoring at your site.
RF Planning is a technique you can use to create a detailed network
plan that provides powerful monitoring and visualization benefits.
Unlike RF Auto-Tuning or RF Auto-Tuning with Modelling, you do not
rely on the auto tuning feature. Instead, you fully model your
geographic location with detailed information about your floors, and
specify your RF coverage areas and your RF obstacles.
Each of these methods is described in the sections that follow.
RF Auto-Tuning To use the RF Auto-Tuning technique:
Physically place WX switches and the MAPs in their desired locations.
RF Auto-Tuning with
Modelling
Upload a WX switch configuration and deploy it
Enable the RF Auto-Tuning feature
This is a great way to install a WX switch and some MAPs, and observe
how the network operates. The RF Auto-Tuning plan is best suited to
networks containing fewer MAPs.
To use the RF Auto-Tuning with Modelling technique, you add to the RF
Auto-Tuning technique by providing some geographical modelling about
your building, floors, and RF coverage area. You also add RF obstacle
information for major obstacles (like concrete walls, windows, and
elevator shafts) that affect attenuation—the quality of RF signals emitted
from and received by the MAPs.
By adding geographical modelling, you will be able to manage your
network in the context of that geographical information. For example,
you will be able to manage your network overlaid on a floor plan, versus
managing an abstract logical group of switches and MAPs.
Page 33

RF Coverage Area 33
RF Planning To do RF Planning, you provide detailed information about your site and
buildings by importing AutoCAD DXF™, AutoCAD DWG, JPEG, or GIF
floor plan files of the buildings into 3WXM.
As you import the floor plans, you can modify them to add or remove RF
obstacles. 3WXM includes a library of attenuators for building obstacles.
The library includes doors, walls, ceilings, and other physical obstructions
that you can select. Attenuators can be defined by height, width, type of
building material. 3WXM factors in the impact these objects have on how
the radio frequency (RF) signals flow through a given site.
If the network contains third-party APs, you can enter information for
these APs so that 3WXM takes the APs into account when calculating the
placement (and optionally, the channel and power settings) of the 3Com
MAPs.
By using this technique, you receive these substantial benefits:
Instead of you making a “best guess” as to how many MAPs you
require for the desired coverage and where MAPs should be placed,
3WXM automatically calculates how many MAPs you need and where
to place MAPs for optimal positioning.
Which Planning
Method Should I Use?
You can generate a deployable work order to help installers place WX
switches and MAPs.
You automatically receive a deployable configuration that includes
optimum power and channel settings.
You enjoy more accurate monitoring options and network
visualization based on the additional geographic modelling
information loaded into 3WXM.
The more detailed your network plan, the better you will be able to
manage and monitor the network. However, there are other
requirements organizations should consider.
3Com suggests you use the RF Auto-Tuning technique if you are
installing MAPs without consideration to blanket coverage, throughput
concerns, or the number of users for whom service will be provided. RF
Auto-Tuning is ideal for small areas; for example, coverage that only
requires a few MAPs, or widely dispersed areas in a building, such as
conference rooms.
Page 34

34 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Use the RF Auto-Tuning with Modelling technique if you want to
better monitor your wireless network in terms of buildings, floors, or
coverage areas. You may only be able to locate inaccurate or incomplete
building and floor plans (perhaps only a JPEG file), but with even a bit
more geographic modelling of your site, you boost your ability to manage
and visualize your network.
Use RF Planning when you want to use all the tools provided in 3WXM
to deploy, manage, and monitor your network. You likely have multiple
constituencies of users you need to consider; for example, sets of users
that are mobile and wireless that have specific throughput and
bandwidth needs. One group of users may be mobile and require high
throughput performance (a higher bandwidth), while another group of
users are more stationary and require less throughput. Additionally, you
may be planning for future capacity, and need to add as much detailed
information as you can about your site in order to plan for the future.
See Table 7 for some guidelines to help you determine what planning
technique is right for your organization.
Tab le 7 Planning Techniques to Use
Concern If yes, use If No, use
Do I have adequate time to add
geographic modelling and RF
obstacle information?
Can I locate accurate building
and floor plans?
Do I need to plan for capacity of
users or quality of coverage
(traffic engineering concerns) for
certain users?
Do I need to visualize coverage
accurately?
Do I need to locate users? RF Planning or RF
RF Auto-Tuning with
Modelling
RF Planning or
RF Auto-Tuning with
Modelling
RF Planning RF Auto-Tuning or RF
RF Planning RF Auto-Tuning or RF
Auto-Tuning with
Modelling
RF Auto-Tuning
RF Auto-Tuning with
Modelling
Auto-Tuning with
Modelling
Auto-Tuning with
Modelling
RF Auto-Tuning
Page 35

Configuration 35
Tab le 7 Planning Techniques to Use
Concern If yes, use If No, use
Do I need to locate rogue APs? RF Planning or RF
Auto-Tuning with
Modelling
Do I want to better monitor my
wireless network in terms of
buildings, floors, or coverage
areas?
RF Planning or RF
Auto-Tuning with
Modelling
RF Auto-Tuning
RF Auto-Tuning
If RF Planning does not fit your requirements now, you can always use the
RF Planning technique in the future when you have the need, the time,
and the necessary floor plans available. You also can leverage the data in
RF Auto-Tuning and convert these RF measurements to configured
baseline values for planning.
Configuration This section describes the main areas of the 3Com network (WX switch
and MAPs) you will configure in 3WXM. It provides you with overview
information about the software so that you can plan a configuration to
support the services you require.
You will configure the wireless configuration and AAA security
configuration for each service you provide on your wireless network. You
also create a basic configuration for the WX switch.
Figure 6 Configuration Required for Each Service
Wireless Service
Wireless Configuration
- Radio Profile
- Service Profile
- Encryption Choices
AAA Security Configuration
- AAA methods
- Rules
- Authentication choices
Page 36

36 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
This section contains information about:
“Wireless Configuration” on page 36
“AAA Security Configuration” on page 38
“System and Administration Configuration” on page 40
Wireless
Configuration
Wireless configuration focuses on the configuration tasks (radio
configuration and AAA configuration) you do to deliver the virtual
wireless services you want to provide on your network. You enable the
MAPs to operate according to your planned RF coverage requirements.
Most of the wireless configuration is done as you plan your RF coverage
and create your radio profiles and service profiles.
A radio profile is used to apply common settings to multiple radios, and
each radio profile can support up to 32 service profiles, one for each
service you want to support. You specify in the service profile an SSID for
each service and the type of encryption mechanisms to be used by the
MAP radios. This gives the radio the potential to look like 32 different and
independent MAPs. See Figure 7.
AP7250, AP8250, and AP8750 support up to eight service profiles per
radio. AP2750 and AP3750 support up to 32 service profiles per radio.
Figure 7 Radio and Service Profiles
Radio 1
MAP 1
MAP 2
Radio 2
Radio 1
Radio 2
Radio Profile “default” applied to MAP 1, Radio 1
and Radio 2 and MAP2, Radio 1
Service Profiles 1-32
Radio Profile “EBC” applied to MAP2, Radio 2
Service Profile, 1-32
SSID
SSID
Page 37

Configuration 37
You must configure a radio profile to set attributes that you can apply to
multiple radios. Rather than configuring each radio individually, you
create a radio profile and apply it to multiple radios that you select. You
can also create a radio profile as part of a domain policy and apply it to
MAP access points on different WX switches.
The radio profile can contain RF Auto-Tuning settings and IEEE 802.11
settings that control how the data is received and transmitted. You can
select RF Auto-Tuning in the radio profile to apply AutoRF settings
(enable or disable auto tuning of power and channels) to radios en masse
via the radio profile. AutoRF enabled through the radio profile to multiple
radios can be easily disabled, too, should you want to go to full RF
planning. You can set specific IEEE 802.11 settings, such as beacon, DTIM
intervals, and the fragment threshold to control how packets are
transmitted.
A default radio profile named “default” is provided and cannot be
deleted.
For each service you want to provide, you configure the following items
in a service profile:
The SSID name
SSID advertisement (whether the SSID name is beaconed)
Whether the SSID name is encrypted or clear (not encrypted)
Web page (if using WebAAA)
Multiple encryption choices (Dynamic/static WEP, WPA, WEP + WPA,
802.11i)
You also must configure AAA security configuration items for each
service. For more information, see “AAA Security Configuration” on
page 38.
Which encryption you use depends on the type of services you’re
offering. Employee access is typically encrypted, guest access is typically
clear (no encryption), and multi-host or “multiple virtualized services”
service can be encrypted, with each SSID being matched with its own
service profile.
Page 38

38 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
If services are being used for customer corporate entities (e.g. different
airlines on an airport wireless net), then they would probably use 802.1X
and strong encryption with web guest access for their airport club guests.
If the services are being used to advertise multiple wireless service
TM
providers (WISP), such as T-Mobile
, Wayport ®, and Boingo WirelessTM,
then these services would probably be completely open. However, they
would likely be assigned to their own dedicated subnet containing their
proxy server/billing gateway.
AAA Security
Configuration
An administrator can control the way in which users access the network.
For each service you provide, you can configure unique authentication,
authorization, and accounting (AAA) security features, creating an
entirely virtualized wireless service. For each service, you configure:
Multiple authentication choices (802.1X, Web, AAA, MAC
authentication, Bonded Auth, open)
AAA methods (up to four RADIUS server groups, or a local database
on the WX switch)
Authentication
Authentication is the method of determining whether a user is allowed
access to your network. Users can be authenticated by a RADIUS server
(pass-through) or by the WX switch local database (local). The WX switch
can also assist the RADIUS server by performing the Extensible
Authentication Protocol (EAP) processing for the server (offload).
To authenticate users, you will need to configure users either in the local
database or on RADIUS servers. Each user will have a username,
password, and RADIUS and/or vendor-specific attributes (VSAs). You will
also need to configure authentication rules (802.1X, MAC, last-resort, or
web authentication).
See Figure 8 on page 39 to see a flowchart representing the
authentication process. Generally, 802.1X authentication is attempted
first. If the user fails, then MAC authentication is attempted. If this fails,
then last resort and web authentication is used. For a service profile, you
specify either web authentication, last-resort, or none in the
auth-fall-thru box. You can only select one.
Page 39

Figure 8 Authentication Flowchart for Network Users
Client associates with 3Com radio
or requests access from wired authentication port
Configuration 39
Client requests
encrypted SSID?
No
last-resort?
802.1X rule that
Yes
No
matches SSID?
MAC rule that
matches SSID?
Use fallthru authentication
Ye s
No
No
Client
Yes
Last-resort rule that
matches SSID?
responds
to 802.1X?
No
Refuse
Client
No
Yes
Yes
Authent.
succeeds?
No
Refuse
Client
Authent.
succeeds?
No
Authent.
succeeds?
No
Refuse
Client
Yes
Yes
Yes
Allow
Client
Allow
Client
Allow
Client
web?
none?
No
Yes
Yes
Refuse
Client
Web Auth rule that
matches SSID?
No
Refuse
Client
Yes
Authent.
succeeds?
No
Refuse
Client
Yes
Allow
Client
Page 40

40 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Authorization
Authorization is the method for providing users with specific rights to the
network by associating attribute-value (AV) pairs to the user. AAA
authorization works by assembling a set of attributes that describe what
the user is authorized to perform. These attributes are compared to the
information contained in a local database or on a RADIUS server for a
given user and the result is returned to the WX switch to determine the
user’s actual capabilities and restrictions.
You can configure attributes, such as the time of day or specific VLAN
access. You can also control access using security access control lists
TM
(ACLs), Mobility Profiles
, and Location Policies. Security ACLs permit or
deny traffic based on IP protocol, IP addresses and, optionally, TCP or
UDP port. They also can be used to set type-of-service (ToS) and
class-of-service (CoS) values in a packet. Mobility Profiles contain
attributes to allow or deny access to specific parts of the network for a
specific user or group of users. Location Policies are an ordered list of
location policy rules based on a user glob, VLAN, and/or ports. A Location
Policy can be configured if you need to override the configured AAA user
authorization attributes locally for a specific WX.
System and
Administration
Configuration
Accounting
Accounting collects and sends information used for billing, auditing, and
reporting—for example, user identities, connection start and stop times,
the number of packets received and sent, and the number of bytes
transferred. You can track sessions through accounting information
stored locally or on a remote RADIUS server. As network users roam
throughout the network, accounting records track them and their
network usage.
A Mobility Domain is a collection of WX switches that work together to
support roaming users. One of the WX switches is defined as a seed
device, which distributes information to the other WX switches defined in
the Mobility Domain.
A Mobility Domain allows users to roam geographically from one WX
switch to another without losing network connectivity. Users connect as
a member of a VLAN through their authorized identities.
Page 41

Configuration 41
Using the default Mobility Domain or one you create, add a WX switch to
the network plan that is a member or seed device of the Mobility
Domain. You can then configure that WX, or you can just add it to the
network plan, and configure it later. After you configure the WX switch
and verify its configuration, you can deploy it to the network.
You can create the following types of WX switches:
WX4400—Provides four dual-interface gigabit Ethernet ports. Each
port has a 1000BASE-TX copper interface and a Gigabit interface
converter (GBIC) slot for insertion of a 1000BASE-SX or 1000BASE-LX
fiber-optic interface.
WX1200—Provides eight 10/100 Ethernet ports, six of which support
PoE.
WXR100—Provides two 10/100 Ethernet ports, one of which supports
PoE.
You perform the following tasks to create and initially configure a WX
switch:
Configure basic WX switch properties.
Configure WX switch connection information.
Configure boot information.
Configure Basic WX Switch Properties
To configure basic WX switch properties, you specify a name, select a
model, select its location by wiring closet, and select the Mobility System
Software (MSS) you want to run on the switch. Optionally, you can select
an MSS image to download when you deploy changes to the WX.
You also can specify if the switch is managed. A WX switch that is
physically installed as well as configured can be managed. You can
deploy configuration changes only to managed devices, and 3WXM
periodically checks the managed WX switches in the network for
changes. You also can fully configure a switch without it being physically
installed (unmanaged). Having an unmanaged device in your network
plan may be useful for predeployment purposes.
Page 42

42 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Basic configuration also includes specifying how you will manage the
switch. You can manage it through HTTPS, telnet, and Secure Shell (SSH).
You also can enable monitoring using the Simple Network Management
Protocol (SNMP) to exchange information about network activity
between your network devices.
For more information about configuring basic WX switch properties, see
“Perform Basic Administrative Tasks” on page 146.
For detailed information about configuring basic WX switch properties,
see the Wireless LAN Switch and Controller Quick Start Guide.
Configure WX Switch Connection Information
You need to supply connection information for the WX switch on both
the WX switch and in 3WXM when you make the WX a managed device.
Connection information includes the IP address of the switch and how it
will connect to the backbone; for example, by means of a VLAN or a port.
Configure Boot Information
You select the software image that the WX will use when reset, or
optionally, the configuration file the WX will use when reset.
Equipment Installation
To physically install a WX switch:
1 Unpack and rack the WX switch in the wiring closet or data center
location.
2 Plug the WX switch electrical cord into a power outlet.
3 Connect a network access cable from your existing network to one of the
Ethernet ports on the switch (10/100 or Gigabit Ethernet, depending on
the WX model and available interfaces on the network).
Remember the port number you used. You will need to know this when
performing the initial setup of the switch.
4 Connect a serial interface to the console port of the WX switch to access
the console’s CLI for initial setup.
Page 43

Deployment 43
To physically install MAPs:
1 Instruct the cabling installer to run the Cat. 5 Ethernet cable from the
closest wiring closet to intended location of the MAP.
2 Unpack the MAP, and select the appropriate mounting kit for your
installation location.
3 Install the MAP at the indicated location on the floor.
4 Connect the Cat 5. Ethernet cable(s) to the MAP.
5 At the wiring closet, connect the MAP to the infrastructure equipment:
a If you are directly connecting the MAP to a WX switch, plug the other
cable end(s) to the indicated port(s).
b If you are indirectly connecting the WX to the switch, plug the other
cable end(s) to an available network port on the wiring closet switch.
If the switch does not supply PoE, then ensure that a mid-span PoE
device is inserted in-line with the connection.
Deployment Deployment is when WX configuration information in the 3WXM
network plan is sent to your WX switch.
Configuration changes are collected in 3WXM when you save them, but
are not applied to WX switches until you send the configuration to the
WX switch and deploy the configuration to your network. Any changes
you make to your network in 3WXM are saved, but not applied to your
network until they are deployed. This method makes it easy to apply
configurations simultaneously to multiple WX switches, or you can deploy
changes to a single WX switch.
Page 44

44 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Management and Monitoring
Network Status 3WXM provides summary status on devices in the network at the mobility
Understanding the management and monitoring tools available in 3WXM
can help you to quickly identify and correct problems in your wireless
network, as well as to provide you with the statistics and reporting
information you need to optimize your network.
This section discusses the following management and monitoring
features:
Network Status
RF monitoring
Client monitoring
Rogue detection
Event logging
Verification
Reporting
domain, switch or MAP level. View the summary status as the initial step
in monitoring. Summary status displays the operational status of WX
switches, MAP access points, and their radios (whether they are up or
down).
In addition, 3WXM collects network statistics for devices, including
system-level events and statistics for the wired network.
The Alerts panel in the bottom, left panel in 3WXM displays top-level
status information. The Alerts panel provides you with summary error and
warning information for the following areas:
Configuration—indicates network plan configuration issues
Network—indicates managed network issues
Rogue detection—identifies the number of rogue APs detected
Local changes—indicates changes in 3WXM that can be deployed to
the network
Network changes—indicates configuration changes in the network
Page 45

Management and Monitoring 45
You can display a topology view of your network, including the state and
relationship of devices. You can right-mouse click on a device in the
topology to display the status of that device. The display can include the
wired network, third-party APs, and rogue access points (access points
that are not authorized to operate in your network).
You also can set thresholds for events. If the threshold is crossed, the
affected device is flagged, and a star is placed beside the parameter that
triggered the threshold.
RF Monitoring RF monitoring provides you with current and historical information about
your radio health and activity. Data collected for the RF environment and
the RF neighborhood includes the following items:
RF environment
Channel
Noise
CRC errors
PHY errors
Packet retransmissions
Percent utilization
RF neighborhood
Transmitters (heard by this radio)
Listeners (who heard this radio)
Neighbors
BSSID to SSID mapping
Channel
RSSI
Statistics collected for the RF environment provides data on a per-channel
basis. You can view noise levels, cyclic redundancy check (CRC) and PHY
errors, packet retransmissions and percent utilization.
Data collected for the RF neighborhood displays the neighboring radios.
This information can be viewed as a list of radios heard by a particular
radio, as well as a list of radios who can hear a particular radio.
Page 46

46 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
You also can display trending information on a per-radio basis. Trending
collects radio statistics and charts them on a time basis. For example, you
could display average throughput rates for the previous 30 days, week, or
day. You can display and print the charts from 3WXM, as well as
generate a report.
Client Monitoring Client monitoring provides current and historical information about the
clients using your network, including client activity, watch list clients,
current client sessions, and the ability to locate clients at your site. 3WXM
displays the data that WX switches collect on user sessions—either for a
single user, users associated with a MAP, users associated with a specific
radio, or users added to a watch list.
By viewing monitoring information for a user or a group of users, you can
troubleshoot problems originating from bandwidth constraints or
roaming patterns. You can collect statistics and view reports on:
Client associations, authentication, and authorization failures
Client activity, such as roaming and successful authorization
Current session status, location history, and statistics
Specifics on users over a period of time; information can be gathered
up to 30 days for session status, location history, client errors, and
client activity on users you place on the watch list
Rogue Detection A rogue AP is an access point that is not authorized to operate in or near
your network. You can use RF countermeasures to deny service to or
from a targeted rogue AP, and render them ineffective. Once a rogue AP
is detected and reported, the closest 3Com MAP is assigned to perform
RF countermeasures. By spoofing various 802.11 control messages, the
MAP’s countermeasures disrupt association and authentication attempts
to the rogue AP by any new clients. This also disrupts any active
communications between any existing client and rogue AP.
You can collect and statistics and view reports on:
Current rogue list, aggregated for the whole network
Current hour rogue list
Current day rogue list
30 days of rogue history, using best listener data
Page 47

Management and Monitoring 47
Rogue lifecycle events (when the rogue was first seen, by whom, and
when it went away)
Counter-measure activity
The number of currently detected rogues is conveniently displayed in the
Alerts panel.
Event Logging 3WXM incorporates a powerful and flexible display interface for all
events collected by the system. Events are stored on a per-WX basis and
are collected continuously. Customizable filters can be created to easily
drill down to specific information the event log database. You can filter
events based on:
Category
Severity
Date and time ranges
WX switch
3WXM client and services log
Specific text string matches
Verification Both configuration verification and network verification rules are checked
for any inconsistencies or problems. Verification rules include “instant
fix” resolutions. Instant fix resolutions are errors that can be automatically
fixed, or alternatively providing a hot link to the object containing the
error.
You can selectively disable any rule. Disabling a rule is useful if you wish
to ignore a warning and do not want to see it displayed anymore. The
number of configuration and network errors or warnings are
conveniently displayed in the Alerts panel.
Reporting 3WXM uses a database to collect and store client, RF, and other system
dynamic data, such as statistics, status, events, and traps. You can
generate reports from the monitoring and configuration data collected in
the database. A report can have a selectable scope and a selectable time
period and in some cases, query filter parameters. See Table 8 for a listing
and description of the reports you can generate in 3WXM.
Page 48

48 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Tab le 8 3WXM Reports
Report Description
Configuration Reports
Inventory Report Provides information about the WX
switches and MAPs in your network.
Mobility domain configuration Provides a configuration overview,
Wireless Switch (WX) Configuration Provides details on a WX configuration.
Site Survey Order Provides a map of your site that can be
Work Order Provides information installers use to
Monitoring Reports
Client Session Summary Displays summary data for sessions in the
Client Session Details Displays detailed session information.
Client Errors Provides data on client-related health in
Watch List Clients Contains detailed information for the
Network Usage Provides information about network
RF Summary Provides information about overall
Radio Details Provides a detailed set of statistical
Rogue Details Provides current and historical
Rogue Summary Provides information for all visible rogues
providing data that spans multiple WX
switches. For example, it contains
information about the AAA/RADIUS
setup, SSIDs, and where they are
configured.
used to guide a site survey.
physically install WX switches and MAPs.
selected scope.
the network over time; for example, if
there is a large number of association
failures in some area of the network.
clients on the Watch List.
resource usage and client activity.
network health using selected radio
statistics. It can be used to compare RF
environments across the network and
isolate potential problem areas.
information for each radio in the selected
MAP.
information for a selected rogue.
for a selected time.
Page 49

RF Plan Optimization 49
RF Plan Optimization
RF Plan Optimization is the importing of RF measurement data into an RF
model to improve the accuracy of the model.
A network plan contains the configuration settings that determine the
performance of your wireless network. Optimization of the RF model
leads to a more successful RF plan. The ultimate result is an accurate
visualization of your RF coverage, better-defined statistics for monitoring,
and the ability to more accurately plan for and improve network
performance.
You can optimize your network based on user and network statistics
gathered from:
The monitoring data in 3WXM
A site survey
Based on RF measurement data you gather in 3WXM to optimize the RF
model of a floor, you can make configuration changes in the software to
improve signal strength and coverage for groups or individuals, modify
MAP locations, or add additional equipment to your wireless network if
statistics indicate your network has outgrown the support provided by its
current deployment of WX switches and MAPs.
You also can import RF measurement data based on a site survey done
outside of 3WXM. See the “Using RF Measurements from MAPs” on
page 170 for general guidelines about performing a site survey.
Page 50

50 CHAPTER 2: PLANNING AND MANAGING YOUR WIRELESS NETWORK WITH 3WXM
Page 51

CONFIGURING WIRELESS SERVICES
3
Overview A service is a concept (not a selectable item in the 3wxm interface) that
represents a set of options you configure and deploy on your wireless
network.
Services are configured to provide various levels of wireless network
access to users, such as secure employee access, guest access,
multi-hosted access, or Voice over Wireless IP (VoWIP) access.
You can configure a service to be independent of other services on your
wireless network, or you may be able to share configuration components
among services. For example, multi-hosted access is typically fully isolated
from other services (no shared configuration), while services that provide
for guest and employee access in a single corporation may share a
common radio profile. In this way, you can reuse part of the service
configuration for other services you want to provide. You could configure
a service for employee access; then reuse part of the configuration to
provide services for guest access. Each service has potential
authentications (802.1X, web page, MAC address, or “last resort”) and
potential encryptions (802.11i, WPA, WEP, or unencrypted).
This chapter contains examples to help you configure the following types
of service sets:
Employee access (802.1X)
Guest access (WebAAA)
Voice over IP (MAC AAA)
Page 52

52 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Configure Employee Access Services
Tas k Ta b l e Table 9 contains the tasks you need to perform to create a service for
Services for Employee access are typically configured to provide secure,
encrypted access to the wireless network.
The following sections provide information about how to configure
Employee access:
“Task Table” on page 52
“Step Summary” on page 56
“Example: Configure Employee Access” on page 57
Table 9 on page 53 contains the tasks you need to perform to configure
Employee access services. The summary provides the configurable options
you should set. The section “Example: Configure Employee Access” on
page 57 guides you through the primary wizards and pages in 3WXM to
configure Employee access services.
employee access. For a summary of configurable items, see “Step
Summary” on page 56. For detailed steps about how to perform each of
these tasks, see “Example: Configure Employee Access” on page 57.
Page 53

Configure Employee Access Services 53
.
Tab le 9 Creating a Service for Employee Access
Task Path Primary Parameters to Configure
“Step
Summary” on
page 56
Expand the WX switch icon
in the Organizer panel;
right-click Service Profiles
> Insert > Service Profile.
The Service Profile wizard is
displayed
1 From the Create Service Profile
wizard:
SSID name: enter name
SSID type: select encrypted
Beacon: select yes (to advertise the
SSID)
2 Click Encryption tab:
Security mode: select WPA
802.1X Auth Enabled: select yes
TKIP enabled: select yes
Click Finish
“Create a
Radio Profile”
on page 59
Expand the WX switch icon
in the Organizer panel;
right-click Radio Profiles >
Insert > Radio Profile.
1 From the Create Radio Profile
wizard:
Radio profile name: enter a name
2 From the Service Profile tab:
Select the employee service profile
in the Available Service Profiles list.
Click Add; then click Finish
Page 54

54 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Tab le 9 Creating a Service for Employee Access (continued)
Task Path Primary Parameters to Configure
“Configure
RADIUS
Servers” on
page 61
Expand the WX switch icon
in the Organizer panel,
right-click AAA > Edit;
then click RADIUS
1 From RADIUS Server tab:
Click New RADIUS server
Name: enter server name
IP Address: enter server IP address
Key: enter key
Authorization password: enter
password
Click Next
2 From RADIUS Server Group tab:
Click New RADIUS Server Group
Name: enter a group name
Click Choose Available: select a
server
Click Finish; then click Finish again
3 Configure the AAA backend from a
RADIUS server (not in 3WXM):
Setup each WX switch as a RADIUS
client.
Define the 3Com vendor-specific
attributes (VSAs) in the RADIUS
server’s dictionary.
Configure each user record with
authorization rules (username and
password).
Configure each user with either the
Vlan-Name attribute (3Com VSA)
or the RADIUS
Tunnel-Private-Group-ID to assign
users to VLANs.
Configure authentication rules
(802.1X, MAC, last-resort, or web
authentication).
Page 55

Configure Employee Access Services 55
Tab le 9 Creating a Service for Employee Access (continued)
Task Path Primary Parameters to Configure
“Specify
Network
Access Rules”
on page 64
Expand the AAA icon in the
Organizer panel; right-click
Network Access Rules >
Insert > 802.1X Network
Access.
1 From 802.1X Network Access
tab:
User Glob: enter **
SSID: enter SSID name
2 From 802.1X Policy tab:
Select Enabled
EAP type: Pass-Through
Optionally for an offload
configuration
EAP type: PEAP, EAP Sub-Protocol:
MSCHAPV2
EAP certificate: install or generate
by means of the CLI
Click Choose Available:
Select the RADIUS server group
Click Finish
“Set Up
VLANs on WX
Switches” on
page 66
Expand the WX switch icon
in the Organizer panel,
right-click VLANs > Insert >
VLAN
1 From VLAN Setup tab:
VLAN ID: select number
VLAN Name: enter name
IP Address: enter IP Address
2 From VLAN Member Selection
tab:
Available Members: select port(s);
click Add
If the port is connected to an
802.1Q trunk line, select the Tag
checkbox and change the tag value
(if necessary)
Select PVST+ (if you wish to enable
it)
3 From Spanning Tree tab:
Select STP options
4 From Spanning Tree Port Setup
tab:
Select STP port options
Click Finish
Page 56

56 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Step Summary The following list summarizes the fields selected or configuration items
entered in the example that follows to configure Employee access:
1 Create a service profile.
From the Service Profile wizard, enter “Employees” as the Name of
the service profile and “Employees” as the SSID.
Select SSID Type Encrypted. Select Beacon. Select the Fall Through
Authentication as None.
Select Encryption. Select WPA for the Security Mode. Click Finish.
2 Create a radio profile.
From the Radio Profile wizard, enter “RadioProfile1” as the Name of
the radio profile.
Select Service Profile Selection. Select the Employees service profile.
Click Add. Click Finish.
3 Configure the RADIUS server in 3WXM.
From the Create Radius wizard, enter “sg1” as the Name of the
server, server’s IP address, secret for Key. Click Next.
Click New RADIUS Server Group. Enter “Group1.” Click Finish.
Click Finish.
4 Configure the RADIUS server.
Configure the RADIUS server for 802.1X. Use the recommended EAP
method, PEAP + MS-CHAPv2.
Setup each WX switch as a RADIUS client.
Define any desired 3Com vendor-specific attributes (VSAs).
Configure each user record with either the VLAN-Name attribute or
the RADIUS Tunnel-Private-Group-ID.
Configure authentication rules (802.1X, MAC, last-resort, or web
authentication.)
5 Specify network access rules.
From the 802.1X Web Network Access wizard, click the Web
Network Access tab.
For the User Glob value, enter “**”.
For the SSID, enter the SSID name.
Page 57

Configure Employee Access Services 57
Click 802.1X Policy tab. Select Enabled. Set EAP Type to
Pass-Through.
Click Choose Available. Select the RADIUS server group.
Click Finish. Click Finish again.
6 Setup VLANs on the WX switches.
From the Create VLANs wizard, click VLAN Setup. Select the VLAN ID
number. Enter the VLAN name and the IP address.
Click VLAN Member Selection tab. From Available Members, select
port(s). Click Add
Click Spanning Tree tab. Select STP options.
Click Spanning Tree Port Setup tab. Select STP port options. Click
Finish.
Example: Configure
Employee Access
The following detailed steps provide an example of how to configure
Employee services. You will:
“Create a Service Profile” on page 57
“Create a Radio Profile” on page 59
“Configure RADIUS Servers” on page 61
“Specify Network Access Rules” on page 64
“Set Up VLANs on WX Switches” on page 66
In general, these same steps are required to configure other services, too.
You can refer back to this section, using the summary list or the task
table, with configuration options for “Configure Guest Access Services”
on page 69 or “Configure Voice over Wireless IP Service” on page 77.
Create a Service Profile
A service profile contains the configuration for the service you want to
offer, such as employee access, guest access, or VoWIP.
For more information about service profiles, see “Wireless
Configuration” on page 36. For more information about service sets, see
“Which Services To Provide?” on page 30.
Page 58

58 CHAPTER 3: CONFIGURING WIRELESS SERVICES
To create a service profile:
1 Expand the WX switch icon in the Organizer panel, and select
Service Profiles > Insert > Service Profile.
The Create Service Profile wizard is displayed.
2 Enter the service profile and SSID names, and select SSID Type Encrypted.
3 Select Beacon (to advertise this SSID).
4 Select None for the type of Fall Through Authentication.
Authentication is generally attempted in the following order: 802.1X
authentication, MAC authentication, then fall through authentication.
For more information about authentication, see “AAA Security
Configuration” on page 38.
5 Click Next. The Encryption wizard is displayed.
Page 59

Configure Employee Access Services 59
6 Click next to WPA to enable it.
The 802.1X Auth Enabled and TKIP Enabled options are automatically
selected when you enable WPA.
7 Click Finish.
The service profile Employees is displayed in the Organizer panel.
Create a Radio Profile
You configure a radio profile to set attributes that you can apply to
multiple radios. Rather than configuring each radio individually, the radio
profile is applied to multiple radios that you select. Service profiles are
mapped to radio profiles.
The radio profile can contain RF Auto-Tuning settings and IEEE 802.11
settings that control how the data is received and transmitted.
Page 60

60 CHAPTER 3: CONFIGURING WIRELESS SERVICES
MAPs (and consequently, radios) need to be added to 3WXM after
creating a radio profile. For more information about adding radios, refer
to one of the following:
“Using RF Auto-Tuning” on page 91
“Using RF Auto-Tuning with Modelling” on page 99
“Using RF Planning” on page 113
To create a radio profile and map a service profile to it:
1 Expand the WX switch in the tree topology to which you want to add a
radio profile.
2 Right-click Radio Profiles > Insert.
The Create Radio Profiles wizard is displayed.
3 From the Radio Profile tab, enter the name of the radio profile. Click
Service Profile Selection at the top of the wizard.
4 Select the employee service profile in the Available Service Profiles list.
Click Add.
Page 61

Configure Employee Access Services 61
5 Click Finish to save the changes and close the wizard.
Configure RADIUS Servers
Remote Authentication Dial-In User Service (RADIUS) is a client-server
security protocol that provides authentication, authorization, and
accounting for network users and devices. A RADIUS server stores user
profiles, which include usernames, passwords, and other user attributes.
To configure RADIUS servers, you must:
Configure RADIUS server attributes in 3WXM
Configure attributes on the RADIUS server
Configure RADIUS Server in 3WXM To configure RADIUS in 3WXM,
you define RADIUS server groups (named sets of RADIUS servers). You
must create at least one server group. RADIUS server groups can
authenticate administrators and network users.
Page 62

62 CHAPTER 3: CONFIGURING WIRELESS SERVICES
To configure the RADIUS server in 3WXM:
1 Expand the WX switch icon in the Organizer panel, right-click on AAA,
and select Edit.
The Modify AAA wizard is displayed.
2 Click RADIUS to display the Modify RADIUS wizard, and click Next.
The Create RADIUS Server wizard is displayed.
3 Type the name, IP address, key, and authorization password for the
server; then click Finish.
4 Click Next to display the RADIUS Server Group page.
5 Click New RADIUS Server Group.
6 Type a name for the group, then click Choose Available and select the
server from the dropdown list.
7 Click Finish to close the Create RADIUS Server Group page.
8 Click Finish again to redisplay the Modify AAA wizard.
Page 63

Table 10 3Com VSAs
Type,
Vendor
ID,
Attribute
VLAN-Name 26,
Mobility-Profile 26,
Encryption-Type 26,
Time-Of-Day 26,
SSID 26,
Vendor
Type
43,
2
43,
3
43,
4
43,
5
43,
6
Configure Employee Access Services 63
Configure Attributes on the RADIUS Server To authenticate users,
you will need to configure users either in the local database or on RADIUS
servers. To configure services for Employee access, the following items
should be configured on the RADIUS server.
To configure the RADIUS server:
1 Configure RADIUS server to perform 802.1X using the recommended
EAP method PEAP + MS ChapV2.
2 Setup each WX switch as a RADIUS client.
3 Define any desired 3Com vendor-specific attributes (VSAs) in the RADIUS
server’s dictionary.
The vendor-specific attributes (VSAs) created by 3Com are embedded
according to the procedure recommended in RFC 2865, with Vendor-ID
set to 14525. Table 10 describes the 3Com VSAs, listed in order by
vendor type number.
Rcv in
Access
Resp?
Yes No Yes Name of the VLAN to which the client belongs.
Yes No No Name of the Mobility Profile used by the authorized
Yes No No Type of encryption used to authenticate the client.
Yes No No Day(s) and time(s) during which a user can log into
Yes No Yes Name of the SSID you want the user to use. The
Sent in
Access
Reqst?
Sent in
Acct
Reqst? Description
client.
the network.
SSID must be configured in a service profile, and the
service profile must be used by a radio profile
assigned to 3Com radios in the Mobility Domain.
Page 64

64 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Table 10 3Com VSAs (continued)
Type,
Vendor
ID,
Vendor
Attribute
End-Date 26,
Start-Date 26,
URL 26,
Type
43,
7
43,
8
43,
9
Rcv in
Access
Resp?
Yes No No Date and time after which the user is no longer
Yes No No Date and time at which the user becomes eligible to
YesNoNoURL to which the user is redirected after successful
Sent in
Access
Reqst?
4 Configure each user record with authorization rules (username and
password) and with either the Vlan-Name attribute (3Com VSA) or the
RADIUS Tunnel-Private-Group-ID to assign users to VLANs.
Sent in
Acct
Reqst? Description
allowed to be on the network. Use the following
format:
YY/MM/DD-HH:MM
access the network. Use the following format:
YY/MM/DD-HH:MM
Web authentication. Use the following format:
http://www.example.com
Other attributes are optional.
Specify Network Access Rules
To specify network access rules:
1 Expand the AAA icon in the Organizer panel; right-click Network Access
Rules > Insert > 802.1X Network Access.
2 Enter ** as a wildcard in the Matching User Glob field.
“**” is a reserved keyword that matches on all user names.
3 Enter any as a wildcard in the SSID field.
“Any” is a reserved keyword that matches on all SSID names. Click Next.
Page 65

Configure Employee Access Services 65
4 From the 802.1X Policy tab, select Enabled and Pass-Through as the
EAP Type.
This option uses the RADIUS servers to perform all the EAP and AAA
processing. An EAP certificate does not need to be installed on the WX
switch.
5 Click Finish.
You can also create an offload configuration. An offload configuration
allows a WX switch to offload some of the work from the RADIUS
servers. The WX switch will perform EAP processing on behalf of the
RADIUS servers. If you use an offload option, you will need to use the CLI
to generate or install an EAP certificate on the WX switch. To specify an
offload configuration, select PEAP as the EAP Type, and MSCHAPV2 as
the EAP Sub-Protocol.
Page 66

66 CHAPTER 3: CONFIGURING WIRELESS SERVICES
6 Click Choose Available and select the RADIUS server group from the
dropdown list.
7 Click Finish to close the Modify AAA wizard.
Set Up VLANs on WX Switches
WX switches in a Mobility Domain contain a user’s traffic within the
VLAN the user is assigned to. For example, if you assign a user to VLAN
red, the WX switches in the Mobility Domain contain the user’s traffic
within VLAN red configured on the switches. The VLANs you set up for
service sets support wireless users—they don’t serve as management
VLANs.
If an WX is connected to the network by only one IP subnet, the WX must
have at least one VLAN configured. Optionally, each VLAN can have its
own IP address. However, no two IP addresses on the switch can belong
to the same IP subnet. User VLANs must be defined on at least on WX
switch within the Mobility Domain.
Page 67

Configure Employee Access Services 67
You can configure the Spanning Tree Protocol (STP) on a VLAN. STP is
used to maintain a loop-free network; meaning, devices will recognize a
loop in the topology and block one or more redundant paths, creating a
loop-free path.
The Mobility System Software (MSS) supports Per-VLAN Spanning Tree
protocol (PVST+). PVST+ allows a separate spanning tree in each VLAN.
STP, disabled by default on all VLANS, is configurable for individual
VLANs. STP does not run on MAP ports or wired authentication ports and
does not affect traffic flow on these port types.
To set up a VLAN on a WX switch:
1 Expand the WX switch icon in the Organizer panel, right-click on VLANs >
Insert > VLAN.
The Create VLAN wizard is displayed.
2 Select the VLAN ID number and enter the VLAN Name.
3 (Optional) To assign an IP interface to the VLAN, type the IP address or
select DHCP Client.
Page 68

68 CHAPTER 3: CONFIGURING WIRELESS SERVICES
4 Click Next. The VLAN Member Selection page is displayed.
5 From the Available Members pane, select the network ports that will be
used to reach the router interface and click Add.
If the network port is an 802.1Q tagged trunk link, select the Tag
checkbox for the port or port group. By default, the checkbox is not
selected.
To remove a tag for a port or port. Double-click the Tag Value column
for the port or port group. Change the tag value.
If you specify a tag value, 3Com recommends that you use the same
value as the VLAN number. 3Com wireless switches do not require the
VLAN number and tag value to be the same, but other devices may do so.
6 (Optional) If you want to add STP to a VLAN, select the Spanning Tree
tab and set options.
7 (Optional) For STP, select the Spanning Tree Port Setup tab and set
options.
What’s Next? After you create Employee services, you can create additional services.
For information about configuring additional services, refer to:
“Configure Guest Access Services” on page 69
“Configure Voice over Wireless IP Service” on page 77
After you have created additional services, you can create your RF
environment, and deploy your configuration and enable monitoring.
For information about creating your RF environment, refer to:
“Using RF Auto-Tuning” on page 91
“Using RF Auto-Tuning with Modelling” on page 99
“Using RF Planning” on page 113
For information about deploying your configuration and enabling
monitoring your network, refer to:
“Managing and Monitoring Your Network” on page 143.
Page 69

Configure Guest Access Services 69
Configure Guest Access Services
Guest access is access for visitors at your location and is typically clear (no
encryption).
This section contains the following information about how to configure
Guest access services:
“Task Table” on page 70
“Step Summary” on page 71
“Optional: Configure Mobility Profiles” on page 73
Table 11 on page 70 contains the tasks you must perform to configure
Guest access services.
The “Step Summary” provides the configurable options you should set.
The table contains references to the section “Example: Configure
Employee Access” on page 57. The references are provided in case you
want to refer back to detailed steps. However, be sure to use the
configurable options for Guest access services set forth in the “Step
Summary” on page 71.
Also, you can optionally configure mobility profiles for your Guest access
services to limit access based on criteria, such as RF coverage area or time
of day.
Page 70

70 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Tas k Ta b l e Table 11 contains the tasks you need to perform to create Guest access
services. For a summary of configurable items, see “Step Summary” on
page 71.
Table 11 Creating a Service for Guest Access
Task Path Primary Parameters to Configure
“Step Summary”
on page 56
“Create a Radio
Profile” on
page 59
“Configure Local
Authentication”
on page 74
“Specify
Network Access
Rules” on
page 64
Expand the WX switch icon in the
Organizer panel; right-click Service
Profiles > Insert > Service Profile.
The Create Service Profile wizard is
displayed.
Expand the WX switch icon in the
Organizer panel; right-click Radio
Profiles > Insert > Radio Profile.
Expand the WX switch icon in the
Organizer panel, right-click > AAA >
Edit; click Local User Database. The
Modify Local User Database wizard is
displayed.
Configuring authentication can be
done more easily by first adding a user
group and associating or creating users
for that group.
Expand the AAA icon in the Organizer
panel; right-click Network Access
Rules > Insert > Web Network
Access.
1 From the Create Service Profiles wizard:
Name: enter Guests
SSID: enter Guests
SSID type: select clear
Beacon: select yes (to advertise the SSID)
Fall Through Auth: Web Portal or Last Resort (to
allow guest access without authentication)
1 From Create Radio Profiles wizard:
Radio profile name: enter a name
2 From Service Profile tab:
Select the Guest service profile in the Available
Service Profiles list.
Click Add; then click Finish
1 Click User Group tab
Select New > User Group
Enter: User group name
Enter: VLAN name
2 Click Choose Available or New
Create a new user or select a user
Click Next
Click User Attributes:
3 Select User Attributes
Click Finish; click Finish again.
4 Repeat steps 1 – 3 for all Guests.
1 From Web Network Access tab:
User Glob: enter **
SSID: enter SSID name
From Authentication tab:
Select Choose Available > Local server
Click Finish
Page 71

Configure Guest Access Services 71
Table 11 Creating a Service for Guest Access
Task Path Primary Parameters to Configure
“Set Up VLANs
on WX
Switches” on
page 66
Expand the WX switch icon in the
Organizer panel, right-click VLANs >
Insert > VLAN
Setup guest VLAN on an WX switch that can access the
external DMZ subnet.
1 From VLAN Setup tab:
VLAN ID: select number (must be unique)
VLAN Name: enter name (must be unique)
IP Address: enter IP Address
2 From VLAN Member Selection tab:
Available Members: select port(s) that connect to the
DMZ; click Add
3 From Spanning Tree tab:
Select STP options
4 From Spanning Tree Port Setup tab:
Select STP port options
Click Finish
“Optional:
Configure
Mobility Profiles”
on page 73
Expand the WX switch icon in the
Organizer panel, right-click on a WX
switch; select Edit. Click AAA >
Mobility Profile.
1 Click New Mobility Profile:
Enter a Profile Name
Enter: selected
Select the Ports or Distributed MAPs
Click Finish
Step Summary The following list summarizes the fields selected or configuration items
entered configure Guest access.
1 Create a service profile.
From the Service Profile wizard, enter “GuestsSrvcProf” as the Name
of the service profile and “Guests” as the SSID.
Select SSID Type Clear. Select Beacon. Select the Fall Through
Authentication as “Web Portal”.
2 Create a radio profile.
From the Radio Profile wizard, enter the name of the radio profile.
Select Service Profile Selection. Select the Guests service profile.
Click Add. Click Finish.
Page 72

72 CHAPTER 3: CONFIGURING WIRELESS SERVICES
3 Configure local authentication.
From the Local User Database wizard, click User Group. Select
New > User Group, and enter a group name and a VLAN name.
Add users to the group. Click Choose Available or New to add
users. Click Next.
Click User Attributes. Select User Attributes. Click Finish.
Although normally, setting the VLAN is required, the special web-portal
user that MSS creates for WebAAA assigns the VLAN instead. Setting the
VLAN for an individual WebAAA user has no effect.
4 Modify the VLAN assigned to the special user “web-portal-Guests”,
which MSS created when you created the “Guests” SSID with Fall
Through Authentication “Web Portal”. Change the VLAN from default to
the VLAN you assigned to the WebAAA users.
From the Local User Database wizard, click Users. Select
“web-portal-Guests”, and click Modify.
Edit the name in the VLAN Name box. Click Finish.
5 Specify network access rules.
From the Web Network Access wizard, click the Web Network
Access tab. For the User Glob value, enter “**”.
For the SSID, enter the SSID name.
Click Authentication. Select Choose Available > Local server.
6 Set up VLANs on the WX switches.
From the Create VLANs wizard, click VLAN Setup. Select the VLAN ID
number. Enter the VLAN name and the IP address.
Click VLAN Member Selection tab. From Available Members, select
port(s). Click Add
Click Spanning Tree tab. Select STP options.
Click Spanning Tree Port Setup tab. Select STP port options. Click Finish.
7 Optional: Configure a Mobility Profile.
From New Mobility Profile wizard, enter the Profile Name.
Select “Selected.”
Choose the Ports or Distributed MAPs to which you’ll restrict guest
users to certain geographic areas of your network.
Click Finish.
Page 73

Configure Guest Access Services 73
For detailed information about the steps, see the cross-references in the
“Task Table” on page 70. New configuration items that were not part of
the example “Configure Employee Access Services” on page 52 are
included in the following sections.
Optional: Configure
Mobility Profiles
Mobility Profile™ attributes allow or deny access to the network for a
specific user or group of users. When you create a Mobility Profile, you
specify which MAP ports, Distributed MAPs, or wired authentication ports
are to be included. Typically, you include ports that are defined as MAP
ports or Distributed MAPs. You can specify that all or no ports are
included, or you can specify a list of ports to be included.
When you apply the Mobility Profile, it guests have access only through
specific areas of your WLAN—if they roam outside of a designated area
supported by an WX switch or certain MAPs, they no longer have access
to the Internet.
After creating a Mobility Profile, you can assign it to users created in the
local WX user database, or users who are authenticated and authorized
by a RADIUS server. To assign it to users in the WX user database, you
add the Mobility Profile name when you create or modify a user or user
group. To add this on a RADIUS server, you assign the name of the
Mobility Profile by using the Mobility-Profile RADIUS attribute, which is a
3Com vendor-specific attribute (VSA).
To create a Mobility Profile:
1 Right-click on a WX switch in the Organizer panel. Select Edit.
2 Select AAA at the top of the wizard, if not already selected.
3 Select Mobility Profile from the organizer list on the left side of the
page, if not already selected.
4 Click New Mobility Profile.
The Create Mobility Profile wizard appears.
5 In the Profile Name box, type the name of the Mobility Profile.
The name can be up to 16 alphanumeric characters, and it cannot
contain tabs.
The Mobility Profile Name has to be defined as an authorization attribute
in the defined users or user groups in the local database.
6 In the Ports list, specify ports to include in the Mobility Profile:
Page 74

74 CHAPTER 3: CONFIGURING WIRELESS SERVICES
All—Include all MAP or wired authentication ports. Go to step 13.
Selected—Include a selected list of ports. Go to the next step.
None—Include no ports. Go to step 13.
7 Click Choose Available. The Physical Port Selection dialog box appears.
8 Select the ports to be included in the Mobility Profile. To make multiple
selections. press Shift (for contiguous items) or Control (for
noncontiguous items) while clicking items.
9 In the Distributed MAPs list, specify the Distributed MAPs to include in
the Mobility Profile:
All—Include all Distributed MAPs. Go to step 13.
Selected—Include a selected list of Distributed MAPs. Go to the
next step.
None—Include no Distributed MAPs. Go to step 13.
10 Click Choose Available.
11 Select the Distributed MAPs to be included in the Mobility Profile.
12 Click Close. The Create Mobility Profiles dialog box is active.
Configure Local
Authentication
13 Click Finish to save the changes and close the wizard.
The WX switch contains a local database that can store user information
for a 3Com WLAN. You can use the local database to create users and
authenticate them, or you can use the local database in conjunction with
a RADIUS server. For example, although you might use a RADIUS server
to manage most users, you could define IT staff as users in the local
database in the event that the RADIUS server is unavailable.
You can create two types of users in the local database:
Named users—These users are authenticated by username and
password and are assigned to specific VLANs. Users include
administrators and network users. You can group these users by
creating user groups, in order to simplify configuration.
Page 75

Configure Guest Access Services 75
MAC address users—These users are authenticated by a MAC
address. For example, devices such as PDAs or cellular phones that do
not support 802.1X authentication are identified when the WX switch
discovers the MAC addresses of these devices from received frames.
The MAC address is the username and is authenticated by the local
database. You can group these users by creating user groups. MAC
address users and user groups cannot be assigned administrative
access to the WX switch.
To create a user group and named Guest users:
1 Expand the WX switch icon in the Organizer panel, right-click on
AAA > Edit. Click Local User Database.
The Modify Local Database User wizard is displayed.
2 Click User Group. Enter the Name for the user group. Click New.
Also specify the VLAN name, unless the group is for WebAAA users.
If the group is for WebAAA users, do not specify the VLAN name. The
VLAN name is instead associated with the special web-portal user that
MSS creates for WebAAA assigns the VLAN. Setting the VLAN for an
individual WebAAA user or user group has no effect.
The Create User Group wizard is displayed.
Page 76

76 CHAPTER 3: CONFIGURING WIRELESS SERVICES
3 Click Choose Available to select users to add to the user group, or click
Create to create new users.
4 Enter the user’s Name and user’s Password. Select the User Group to
which the user belongs. Click Next.
The Create User wizard is displayed.
5 Select any User Attributes you would like applied to the user.
6 Click Finish.
What’s Next? After you create Guest services, you can create another service.
For information about configuring an additional service, refer to:
“Configure Voice over Wireless IP Service” on page 77
You can create your RF environment, and deploy your configuration and
enable monitoring.
For information about creating your RF environment, refer to:
“Using RF Auto-Tuning” on page 91
“Using RF Auto-Tuning with Modelling” on page 99
“Using RF Planning” on page 113
Page 77

Configure Voice over Wireless IP Service 77
For information about deploying your configuration and enabling
monitoring your network, refer to:
“Managing and Monitoring Your Network” on page 143.
Configure Voice over Wireless IP Service
Voice over Wireless IP (VoWIP) is a new technology, merging VoIP (Voice
over IP) with 802.11 wireless LANs to create a wireless telephone system.
Organizations that add VoWIP to their wireless LANs can deploy and
manage voice and data over a single wireless backbone, reserving some
portion of network bandwidth to support real-time voice
communications.
For a Voice over Wireless IP (VoWIP) service (sometimes also referred to
simply as VoIP, or Voice over IP), you can configure either local or RADIUS
server authentication, and add Access Lists (ACLs) to restrict user access.
This section contains the following information about how to configure
VoWIP services:
“Task Table” on page 78
“Step Summary” on page 81
“Configure Local Authentication” on page 82
“Configure Access Control Lists” on page 84
Table 12 on page 78 contains the tasks you must perform to configure
Guest access services. The table contains references to the section
“Example: Configure Employee Access” on page 57. The references are
provided in case you want to refer back to detailed steps. However, be
sure to use the configurable options for VoWIP access services set forth in
the “Step Summary” on page 81. The “Step Summary” provides the
configurable options you should set.
Page 78

78 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Tas k Ta b l e Table 12 contains the tasks you need to perform to create VoWIP access
services. For a summary of configurable items, see “Step Summary” on
page 81.
Table 12 Creating a Service for VoWIP Access
Task Path Primary Parameters to Configure
“Step Summary”
on page 56
“Create a Radio
Profile” on
page 59
Expand the WX switch icon in the
Organizer panel; right-click Service
Profiles > Insert > Service Profile
Expand the WX switch icon in the
Organizer panel; right-click Radio
Profiles > Insert > Radio Profile
1 From Service Profile tab:
SSID name: enter name
SSID type: select Encrypted
Beacon: not selected (hide presence of SSID for
marginally improved security)
Fall Through Auth: None
2 From Encryption tab:
Security mode: select WEP or WPA/PSK (provides higher
level of security)
3 If you select WEP:
802.1X Auth Enabled: select yes
TKIP enabled: select no
Click Finish
4 If you select WPA/PSK (Must be supported by your
VoWIP device):
802.1X Auth Enabled: select no
PSK Auth: select enabled
Pre-shared Key: (64 Hex characters) or enter a pass
phrase and click Generate Key
TKIP enabled: select yes
Click Finish
1 From Radio Profile tab:
Radio profile name: enter a name
2 From Service Profile tab:
Select the VoWIP service profile in the Available Service
Profiles list.
Click Add; then click Finish
Page 79

Configure Voice over Wireless IP Service 79
Table 12 Creating a Service for VoWIP Access (continued)
Task Path Primary Parameters to Configure
“Configure Local
Authentication”
on page 82
or
Configure
authentication
using RADIUS
Expand the WX switch icon in the
Organizer panel, right-click > AAA
> Edit; click Local User Database
1 Click User:
Select New MAC Address User
2 Click User:
User MAC Address: enter user’s VoWIP device MAC
address
(Optional)
MAC User Group: select a group
Click Next
3 From User Attributes tab:
Select User Attributes
Click Finish
“Configure
RADIUS Server in
3WXM” on
page 61
or
Configure local
authentication
Expand the WX switch icon in the
Organizer panel, right-click AAA >
Edit > RADIUS
1 From RADIUS Server tab:
Click New RADIUS server
Name: enter server name
IP Address: enter server IP address
Key: enter key
Authorization password: enter password (required)
Click Next
2 From RADIUS Server Group tab:
Click New RADIUS Server Group
Name: enter a group name
Click Choose Available: select a server
Click Finish; then click Finish again
“Configure
Attributes on the
RADIUS Server”
on page 63
N/A Configure the AAA backend from a RADIUS server (not in
3WXM):
1 Setup each WX switch as a RADIUS client.
2 Define the 3Com vendor-specific attributes (VSAs) in
the RADIUS server’s dictionary.
3 Configure user record, where user name is the MAC
address (entered with dashes)
4 Configure user password, where the password is the
authorization password defined in your WX RADIUS
configuration (with dashes), and password
authorization rules (username and password)
5 Configure each user with the Vlan-Name attribute and
other optional attributes
Page 80

80 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Table 12 Creating a Service for VoWIP Access (continued)
Task Path Primary Parameters to Configure
“Specify
Network Access
Rules” on
page 64
Expand the AAA icon in the
Organizer panel; right-click Network
Access Rules > Insert > MAC
Network Access
1 From MAC Network Access page:
Matching user Glob: enter **
SSID: enter SSID name
2 From Authentication tab:
Select Choose Available > RADIUS or Local
Click Finish; then click Finish again
“Set Up VLANs
on WX
Switches” on
page 66
Expand the WX switch icon in the
Organizer panel, right-click VLANs
> Insert > VLAN
Note: 3Com recommends
completely isolating the VoWIP VLAN
as a best practice procedure in your
WLAN.
Setup VoWIP VLAN.
1 From VLAN Setup tab:
VLAN ID: select number (must be unique)
VLAN Name: enter name (must be unique)
IP Address: enter IP Address
2 From VLAN Member Selection tab:
VLAN Name: enter VLAN name for the VoWIP phones
Available Members: select port(s) to reach other ports
on the VoWIP VLAN or the VoWIP gateway/PBX; click
Add
3 From Spanning Tree tab:
Select STP options
4 From Spanning Tree Port Setup tab:
Select STP port options
5 From VLAN IGMP tab:
Uncheck Enabled
Click Finish
“Configure
Access Control
Lists” on
page 84
Expand the WX switch icon in the
Organizer panel, right-click on ACLs
> Insert
1 From ACL Setup tab:
Click New; select an ACE
Enter ACE set up information
Click Finish
2 From ACL Map tab:
Map ACL to VoWIP VLAN
Click Finish
Page 81

Configure Voice over Wireless IP Service 81
Step Summary The following list summarizes the fields selected or configuration items
entered in the example that follows to configure VoWIP access:
1 Create a service profile.
From the Service Profile wizard, enter “VoWIP” as the Name of the
service profile and “VoWIP” as the SSID.
Select SSID Type Encrypted. Do not select Beacon. Select the Fall
Through Authentication as None.
Select Encryption. Select WEP or WPA/PSK for the Security Mode,
and click Finish.
WEP—802.1X Auth Enabled is yes, TKIP Enabled is no.
WPA/PSK—802.1X Auth Enabled is no, PSK Auth is enabled TKIP
Enabled is yes. Enter a 64 Hex character key for Preshared key, or
enter a pass phrase and click Generate Key.
2 Create a radio profile.
From the Radio Profile wizard, enter “VoWIP1” as the Name of the
radio profile.
Select Service Profile Selection. Select the VoWIP service profile. Click
Add. Click Finish.
3 Configure local authentication (or configure the RADIUS server in
3WXM).
From the Local Database User wizard, click User.
Select New MAC Address User. Click User. Enter user’s VoWIP device
MAC address. Click Next.
From Attributes tab, select User Attributes. Click Finish.
4 Create a new MAC Network Access rule.
For the User Glob value, enter “**”.
For the SSID, enter VoWIP.
From Authentication tab, select Choose Available > Local.
Click Finish. Click Finish again.
5 Setup VLANs on the WX switches.
From the Create VLANs wizard, click VLAN Setup. Select the VLAN ID
number (must be unique). Enter the VLAN name and the IP address.
Page 82

82 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Click VLAN Member Selection tab. From Available Members, select
the VLAN name for the VoWIP phones.
Select port(s) to reach other ports on the VoWIP VLAN or the VoWIP
gateway/PBX. Click Add.
Click Spanning Tree tab. Select STP options.
Click Spanning Tree Port Setup tab. Select STP port options.
Click VLAN IGMP tab. Uncheck enabled.
Click Finish.
6 Create ACLs.
From the Create ACL wizard, enter a name for the ACL. The example
uses “svp” for SpectraLink or “voice” for Avaya).
Add ACEs to the ACL.
See “Example: Creating an ACL for SpectraLink Wireless Phones”
on page 85 for ACE details.
See “Example: Creating an ACL for Avaya Wireless Phones” on
page 87 for ACE details.
Configure Local
Authentication
Click Finish.
The WX switch contains a local database that can store user information
for a 3Com WLAN. You can use the local database to create users and
authenticate them, or you can use the local database in conjunction with
a RADIUS server. For example, although you might use a RADIUS server
to manage most users, you could define IT staff as users in the local
database in the event that the RADIUS server is unavailable.
You can create two types of users in the local database:
Named users—These users are authenticated by username and
password and are assigned to specific VLANs. Users include
administrators and network users. You can group these users by
creating user groups, in order to simplify configuration.
Page 83

Configure Voice over Wireless IP Service 83
MAC address users—These users are authenticated by a MAC
address. For example, devices such as PDAs or cellular phones that do
not support 802.1X authentication are identified when the WX switch
discovers the MAC addresses of these devices from received frames.
The MAC address is the username and is authenticated by the local
database. You can group these users by creating user groups. MAC
address users and user groups cannot be assigned administrative
access to the WX switch.
To create MAC users
1 Expand the WX switch icon in the Organizer panel, right-click on AAA >
Edit.
2 Click Local User Database.
3 Click New. Select New MAC Address User. The Create User wizard
appears.
4 Enter the User MAC Address and the VLAN Name to which the user
belongs.
You can also specify that the user be part of a MAC User Group. Click
Next.
5 Select any User Attributes you would like applied to the user.
6 Click Finish.
Page 84

84 CHAPTER 3: CONFIGURING WIRELESS SERVICES
Configure Access
Control Lists
You can control access using security access control lists (ACLs). Security
ACLs permit or deny traffic based on IP protocol, IP addresses and,
optionally, TCP or UDP port. They also can be used to set type-of-service
(TOS) and class-of-service (CoS) values in a packet.
Suggested uses for ACLs include restricting guest access from your
intranet, or restricting guests from communicating with each other (using
an IP access control entry).
You create an ACL by defining a series of access control entries (ACEs).
ACEs are processed in the order in which they are added to the ACL.
Generally, more specific checks are performed before general checks.
Because of this, the order of the ACE is important within the ACL.
You can add the following types of ACEs to an ACL:
IP—Filters packets by source and destination IP addresses, type of
TOS, or precedence.
TCP—Filters packets by established TCP connections, source and
destination IP addresses, TOS, precedence, or TCP source and
destination ports.
ICMP—Filters packets by source and destination IP addresses, TOS,
precedence, ICMP type, or ICMP code.
UDP—Filters packets by source and destination IP addresses, TOS,
precedence, or UDP source and destination ports.
Layer 4 Protocol—Filters packets by source and destination IP
addresses, TOS, precedence, or Layer 4 protocol.
After creating an ACL, you can assign it to users created in the local WX
user database or users who are authenticated and authorized by a
RADIUS server. You assign the name of the ACL by using the Filter-Id.in
and Filter-Id.out RADIUS attributes. Assign the Filter-Id.in RADIUS
attribute with the name of an ACL that filters incoming packets. Assign
the Filter-Id.out RADIUS attribute with the name of an ACL that filters
outgoing packets. The ACL name must have an .in or .out suffix.
Page 85

Configure Voice over Wireless IP Service 85
Example: Creating an ACL for SpectraLink Wireless Phones
The following example illustrates how to define an ACL on a WX switch
in an environment where SpectraLink® wireless phones are used.
To define an ACL on a WX switch and add ACEs:
1 Expand the WX switch icon in the Organizer panel; right-click on
ACLs > Insert > ACL. The Create ACL wizard is displayed.
2 Enter the name for the ACL in the ACL Name field.
3 Click New. Select New L4 Protocol ACE. Create an ACE that matches
the SVP protocol (SpectraLink’s proprietary protocol).
Select 7 for the CoS value to map the ACL to an elevated priority.
If Wi-Fi Multimedia (WMM) support is disabled, use 6 or 7 for SVP, and
use 4 or 5 for other VoWIP types. When WMM is disabled, the MAP
forwarding queue that maps to CoS values 6 and 7 is optimized for SVP.
If WMM support is disabled, use 6 or 7 for all types of VoWIP.
Select 119 for the Protocol ID value (representing the SVP protocol).
Click Finish. The Create ACL wizard is displayed again.
Page 86

86 CHAPTER 3: CONFIGURING WIRELESS SERVICES
4 Click New. Select IP ACE. Create a second ACE as a “catch-all” ACE,
permitting other traffic to pass at a normal priority through the WLAN.
5 Click Finish.
The Create ACL wizard is displayed again with the two ACEs displayed.
Page 87

6 Click Finish to save the ACL.
Configure Voice over Wireless IP Service 87
7 Click ACL Map at the top of the Create ACL wizard to map the ACL.
Map the ACL to ports (or port groups), VLANs, or virtual ports. You
cannot map an ACL to an MAP port or a wired authentication port.
Example: Creating an ACL for Avaya Wireless Phones
The following example illustrates how to define an ACL for an
environment where Avaya® wireless phones are using Avaya Media
Servers and Call Controllers in a WLAN.
To define an ACL on a WX switch and add ACEs:
1 Expand the WX switch icon in the Organizer panel; right-click on
ACLs > Insert.
The Create ACL wizard is displayed.
2 Enter a name for the ACL in the ACL Name field.
3 Create the following ACEs for the ACL.
a Click New. Select IP ACE.
Page 88

88 CHAPTER 3: CONFIGURING WIRELESS SERVICES
This ACE (as well as the next one) matches the DiffServ codepoints
that Avaya equipment uses for call setup and call control traffic.
Select 7 for the CoS value to map the ACL to an elevated priority.
If Wi-Fi Multimedia (WMM) support is disabled, use 6 or 7 for SVP, and
use 4 or 5 for other VoWIP types. When WMM is disabled, the MAP
forwarding queue that maps to CoS values 6 and 7 is optimized for SVP.
If WMM support is disabled, use 6 or 7 for all types of VoWIP.
Select 4 for the Precedence value. This value specifies that packets
with flash override precedence are filtered.
Select 4 for the type of service (TOS) value.
Click Finish.
b Click New. Select IP ACE.
Select 7 for the CoS value to map the ACL to an elevated priority.
Select 5 for the Precedence value. This value specifies that packets
with critical precedence are filtered.
Select 12 for the TOS value.
Click Finish.
c Click New. Select UDP Ace.
This ACE roughly matches the RTP protocol used by Avaya IP
Softphones for voice traffic.
Select 7 for the CoS value to map the ACL to an elevated priority.
Select Range for the Source Port and specify a range. The range in
the example is 2048 to 65535.
Click Finish
Page 89

Configure Voice over Wireless IP Service 89
d Click New. Select New IP ACE.
This ACE is a generic “catch-all,” permitting other traffic to pass at a
normal priority through the WLAN.
Click Finish.
4 The ACL properties are displayed.
5 Click Finish to save the ACL.
6 Map the ACL to ports (or port groups), VLANs, or virtual ports. Click ACL
Map at the top of the Create ACL wizard to map the ACL.
You cannot map an ACL to a MAP port or a wired authentication port.
Page 90

90 CHAPTER 3: CONFIGURING WIRELESS SERVICES
What’s Next? After you create VoWIP access services, you can create another service.
For information about configuring an additional service, refer to:
“Configure Guest Access Services” on page 69
You can create your RF environment, and deploy your configuration and
enable monitoring.
For information about creating your RF environment, refer to:
“Using RF Auto-Tuning” on page 91
“Using RF Auto-Tuning with Modelling” on page 99
“Using RF Planning” on page 113
For information about deploying your configuration and enabling
monitoring your network, refer to:
“Managing and Monitoring Your Network” on page 143.
Page 91

USING RF AUTO-TUNING
4
Overview RF Auto-Tuning is a technique you can use to configure your RF (radio)
network. RF Auto-Tuning is a quick method that requires minimal
configuration and no RF planning or site surveys, and instead, relies on
the AutoTune feature to set MAP channels and power settings.
This is a great way to quickly install a WX switch and MAPs, and observe
how the network operates. The RF Auto-Tuning technique is best suited
to networks containing fewer MAPs.
To learn more about the benefits of RF Auto-Tuning, see “RF
Auto-Tuning” on page 32.
To use this technique:
1 Physically place your equipment (WX switches and MAPs) in their desired
locations.
2 Configure initial WX switch connectivity (configure IP addresses and
install certificates).
3 Upload the WX switch configuration into a 3WXM network plan.
4 Create a service profile.
5 Create a radio profile (or use the default radio profile).
6 Map your service profile to your radio profile.
7 Create your MAPs.
8 Apply a radio profile to each radio on a MAP.
9 Deploy your configuration.
Page 92

92 CHAPTER 4: USING RF AUTO-TUNING
Place Your Equipment
Configure Initial WX Switch Connectivity
Upload the WX Switch Configuration into a 3WXM Network Plan
You will need to unpack and physically install your WX switches and
MAPs. For information about installing your equipment, see “Equipment
Installation” on page 42.
After installing a WX switch, you must use the command-line interface
(CLI) to prepare it for configuration and management by 3WXM. Use the
Web Quick Start (if available), or enter the quickstart command at the
CLI prompt. From there, you will:
Configure IP connectivity between the WX and 3WXM.
Enable secure communication between the WX and 3WXM or the
Web browser by installing certificates from a certificate authority (CA)
or a self-generated certificate.
For more information about configuring initial WX switch connectivity,
see the Wireless LAN Switch and Controller Installation and Basic
Configuration Guide.
Retrieve the basic configuration information you added to the WX switch
and upload it into 3WXM.
Page 93

Upload the WX Switch Configuration into a 3WXM Network Plan 93
To upload the WX switch configuration into a 3WXN network plan:
1 From the main 3WXM window, select File > New. The Options wizard
appears.
2 Enter a name for your network plan, select a Country Code, and click
Finish.
3 Select Manage > Managed Devices from the main menu bar; then click
Upload.
The Upload Wireless Switch wizard is displayed.
4 Enter the IP address and the enable password for the WX switch
containing the configuration.
5 Click Next.
Page 94

94 CHAPTER 4: USING RF AUTO-TUNING
6 The certificate is verified, and the WX switch added to 3WXM.
7 The WX switch is now visible in the Equipment section of the Organizer
panel on the left side of the 3WXM main window.
Create a Service Profile
A service profile contains the configuration for the service you want to
offer, such as employee access, guest access, or multi-hosted access.
For more information about service profiles, see “Wireless
Configuration” on page 36. For more information about wireless
services, see “Which Services To Provide?” on page 30.
To create a service profile:
1 Right-click the WX switch you added, and select Edit. The Modify Switch
wizard is displayed.
Page 95

Create a Radio Profile and Map the Service Profile to It 95
2 Click Wireless. Click Service Profile and select New Service Profile.
3 Enter the name and SSID for the service profile, and the type of
encryption.
4 Select whether you want to Beacon (advertise) this SSID.
5 Select the type of Fall Through Authentication. Select None for no
authentication, Web Portal for web authentication, or Last Resort.
Authentication is attempted in the following order: 802.1X
authentication, MAC authentication, then fall through authentication.
For more information about authentication, see “AAA Security
Configuration” on page 38.
6 Click Finish.
The service profile you created is displayed in the center of the Modify
Switch wizard.
Create a Radio Profile and Map the Service Profile to It
To create a radio profile and map a service profile to it:
1 Right-click the WX switch you added, and select Edit.
The Modify Switch wizard is displayed.
2 Click Wireless at the top of the wizard. Select Radio Profile on the left
side; then click New Radio Profile on the right side. The Create Radio
Profile wizard is displayed.
3 Enter the name of the radio profile.
4 Click the Auto-Tune tab. Tune Channel is enabled by default. Select
Tune Transmit Power.
Page 96

96 CHAPTER 4: USING RF AUTO-TUNING
5 Click the Service Profile Selection tab.
6 Select the service profile that you want to map to the radio profile, and
click Add.
7 Click Finish to save the radio profile configuration.
8 Click Finish again to close the Modify Switch wizard.
Page 97

Create Your MAPs 97
Create Your MAPs Depending on how your MAPs are connected to a WX switch, you need
to create a direct connect MAP or a distributed MAP in your network plan
in 3WXM.
A direct connect MAP is connected to the wired network through a direct
10/100 Ethernet connection to a WX switch. A distributed MAP is
connected to the WX switch indirectly through other Layer 2 or Layer 3
wired networking devices.
To create a directly connected MAP in 3WXM:
1 In the Equipment area of the Organizer panel, expand the WX switch.
2 Right-click on Port/MAPs, right-click on a port, and select Edit. The
Modify Ports/MAPs wizard is displayed.
3 Select the MAP enabled checkbox to the left of the Port number that
will connect to the MAP.
4 Click Finish.
The MAP appears under Ports/MAPs for the switch, in the Organizer
panel.
To create a Distributed MAP in 3WXM:
1 In the Equipment area of the Organizer panel, right-click on Distributed
MAPs under the WX switch, and select Insert > Distributed MAP. The
Create Distributed MAPs wizard is displayed.
2 Enter the MAP name and the MAP serial number.
3 Enter the fingerprint. This is a hash value of the MAP’s public encryption
key, and may be printed on the back of the MAP. Alternatively, you also
can display the fingerprint in the CLI, by typing display dap status.
4 Click Finish.
The MAP appears under Distributed MAPs for the switch, in the
Organizer panel.
Page 98

98 CHAPTER 4: USING RF AUTO-TUNING
Apply a Radio Profile to Each Radio
When you create a MAP, a new radio (or radios, depending upon the
type of MAP created) are added into 3WXM. The radios use the default
radio profile in 3WXM unless you create a new radio profile and apply it
to each radio on the MAP.
For more information about creating a radio profile, see “Create a Radio
Profile and Map the Service Profile to It” on page 95. For more
information about creating a MAP, see “Create Your MAPs” on page 97.
To apply a radio profile to a radio:
1 In the Equipment area of the Organizer panel, expand the switch, then
expand the MAP.
2 Right-click on the radio and select Edit.
3 Click the down arrow beside the Radio Profile box, and select the radio
profile.
4 Click Finish.
You have completed the necessary steps for configuring your RF
environment.
What’s Next? After you create your services (“Configuring Wireless Services” on
page 51) and following the instructions in this chapter to create your RF
environment, you need to deploy your configuration and enable
monitoring. Optionally, you can improve your network monitoring
options by modelling your floor and defining RF obstacles.
For information about monitoring your network, see “Managing and
Monitoring Your Network” on page 143.
For information about enhancing RF Auto-Tuning with modelling to
better define your site and improve monitoring options, see “Using RF
Auto-Tuning with Modelling” on page 99.
Page 99

USING RF AUTO-TUNING WITH
5
MODELLING
Overview RF Auto-Tuning with modelling is a technique you can use to configure
and implement your network that builds on the RF Auto-Tuning method.
You will, as the name implies, still use RF Auto-Tuning (auto tuning) to
adjust power and channel settings to provide RF signals to the coverage
area for your users. You’ll then enhance the auto tuning feature by
providing modelling information about your geographic location.
To use this technique, you will complete the tasks described in “Using RF
Auto-Tuning” on page 91. Then, you’ll complete the following steps in
your network plan:
1 Add site information (buildings and floors) or import a floor drawing
2 Add RF obstacles (optional)
3 Add an RF coverage area
By providing some information about your buildings and floors, you add
enough details into 3WXM so that you can better visualize your network
topology and support improved monitoring at your site.
To learn more about the benefits of RF Auto-Tuning with modelling, see
“RF Auto-Tuning with Modelling” on page 32.
Page 100

100 CHAPTER 5: USING RF AUTO-TUNING WITH MODELLING
Add Site Information
By adding minimal information about your buildings and floors at your
site, you support improved monitoring for your network. You can
manually add building and floor information or you can import a floor.
For information about importing a floor plan, see “Import a Floor Plan”
on page 120.
To add site information:
1 Without selecting any object in the Organizer panel, select Config >
Insert > Site from the main 3WXM menu. The Create Site wizard
appears.
2 In the Site Name box, type a name for the site (1 to 80 alphanumeric
characters, with no spaces or tabs).
3 In the Number Of Buildings box, specify how many buildings are in your
site.
When you specify the number of buildings a site contains and save the
site, 3WXM creates each building using the default settings. You can edit
the buildings 3WXM creates or you can add new buildings.
 Loading...
Loading...