Page 1

Switch 8800
Configuration Guide
Version 3.01.01
http://www.3com.com/
Published February 2005
Part No.10014298
Page 2

3Com Corporation
350 Campus Drive
Marlborough, MA
01752-3064
Copyright © 2005, 3Com Corporation. All rights reserved. No part of this documentation may be reproduced
in any form or by any means or used to make any derivative work (such as translation, transformation, or
adaptation) without written permission from 3Com Corporation.
3Com Corporation reserves the right to revise this documentation and to make changes in content from time
to time without obligation on the part of 3Com Corporation to provide notification of such revision or change.
3Com Corporation provides this documentation without warranty, term, or condition of any kind, either
implied or expressed, including, but not limited to, the implied warranties, terms or conditions of
merchantability, satisfactory quality, and fitness for a particular purpose. 3Com may make improvements or
changes in the product(s) and/or the program(s) described in this documentation at any time.
If there is any software on removable media described in this documentation, it is furnished under a license
agreement included with the product as a separate document, in the hard copy documentation, or on the
removable media in a directory file named LICENSE.TXT or !LICENSE.TXT. If you are unable to locate a copy,
please contact 3Com and a copy will be provided to you.
UNITED STATES GOVERNMENT LEGEND
If you are a United States government agency, then this documentation and the software described herein
are provided to you subject to the following:
All technical data and computer software are commercial in nature and developed solely at private expense.
Software is delivered as “Commercial Computer Software” as defined in DFARS 252.227-7014 (June 1995)
or
as a “commercial item” as defined in FAR 2.101(a) and as such is provided with only such rights as are
provided in 3Com’s standard commercial license for the Software. Technical data is provided with limited
rights only as provided in DFAR 252.227-7015 (Nov
applicable. You agree not to remove or deface any portion of any legend provided on any licensed program
or documentation contained in, or delivered to you in conjunction with, this User Guide.
Unless otherwise indicated, 3Com registered trademarks are registered in the United States and may or may
not be registered in other countries.
3Com, the 3Com logo, are registered trademarks of 3Com Corporation.
Intel and Pentium are registered trademarks of Intel Corporation. Microsoft, MS-DOS, Windows, and
Windows NT are registered trademarks of Microsoft
States and other countries, licensed exclusively through X/Open Company, Ltd.
All other company and product names may be trademarks of the respective companies with which they are
associated.
1995) or FAR 52.227-14 (June 1987), whichever is
Corporation. UNIX is a registered trademark in the United
Page 3

CONTENTS
ABOUT THIS GUIDE
Conventions 1
SYSTEM ACCESS
Product Overview 3
Function Features 3
Configuring the Switch 8800 4
Setting Terminal Parameters 5
Configuring Through Telnet 7
Configuring Through a Dial-up Modem 10
Configuring the User Interface 11
Command Line Interface 19
Command Line View 19
Features and Functions of the Command Line 22
PORT CONFIGURATION
Ethernet Port Overview 27
Configuring Ethernet Ports 27
Example: Configuring the Default VLAN ID of the Trunk Port 34
Troubleshooting VLAN Port Configuration 34
Configuring Link Aggregation 34
Load Sharing 35
Port State 36
Configuring Link Aggregation 36
Example: Link Aggregation Configuration 38
VLAN CONFIGURATION
VLAN Overview 39
Configuring VLANs 39
Common VLAN Configuration Tasks 39
Adding Ethernet Ports to a VLAN 40
Configuring GARP/GVRP 42
Configuring GVRP 44
Page 4

NETWORK PROTOCOL OPERATION
Configuring IP Address 49
Subnet and Mask 50
Configuring an IP Address 50
Troubleshooting an IP Address Configuration 52
Configuring Address Resolution Protocol (ARP) 52
Configuring ARP 52
DHCP Relay 54
Configuring DHCP Relay 55
Troubleshooting a DHCP Relay Configuration 58
IP Performance 59
Configuring TCP Attributes 59
Displaying and Debugging IP Performance 59
Troubleshooting IP Performance 60
IPX Configuration 61
IPX Address Structure 61
Routing Information Protocol 61
Service Advertising Protocol 61
IP ROUTING PROTOCOL OPERATION
IP Routing Protocol Overview 63
Selecting Routes Through the Routing Table 64
Routing Management Policy 65
Static Routes 67
Configuring Static Routes 68
Troubleshooting Static Routes 71
RIP 71
Configuring RIP 72
Troubleshooting RIP 81
OSPF 81
Calculating OSPF Routes 81
Configuring OSPF 84
Troubleshooting OSPF 103
IS-IS 105
Two-Level Structure of IS-IS 105
NSAP Structure of IS-IS 107
IS-IS Packets 108
Configuring Integrated IS-IS 109
Integrated IS-IS Configuration Example 123
BGP 125
BGP Messages 126
BGP Routing 126
BGP Peers and Peer Groups 127
Configuring BGP 127
Typical BGP Configuration Examples 145
Troubleshooting BGP 151
Page 5

IP Routing Policy 151
Routing Information Filters 152
Configuring an IP Routing Policy 153
Troubleshooting Routing Policies 159
Route Capacity 159
Limiting Route Capacity 160
Configuring Route Capacity 160
MULTICAST PROTOCOL
IP Multicast Overview 167
Multicast Addresses 168
IP Multicast Protocols 170
Forwarding IP Multicast Packets 171
Applying Multicast 172
Configuring Common Multicast 172
Configuring Common Multicast 172
Configuring IGMP 174
Configuring IGMP 175
IGMP Snooping 181
Configuring IGMP Snooping 184
IGMP Snooping Configuration Example 186
Troubleshooting IGMP Snooping 186
Configuring PIM-DM 187
Configuring PIM-DM 188
PIM-DM Configuration Example 191
Configuring PIM-SM 192
PIM-SM Operating Principles 193
Preparing to Configure PIM-SM 194
Configuring PIM-SM 195
GMRP 203
Configuring GMRP 204
QOS/ACL OPERATION
ACL Overview 207
ACLs Activated Directly on Hardware 207
ACLs Referenced by Upper-level Modules 207
ACLs Supported 208
Configuring ACLs 208
Configuring Time Range 209
Defining and Applying a Flow Template 209
Defining ACLs 211
Activating ACLs 212
Displaying and Debugging ACL Configurations 213
ACL Configuration Example 213
Basic ACL Configuration Example 214
L2 ACL Configuration Example 215
Page 6

QoS Configuration 216
QoS Configuration 219
Configuration Examples 229
Traffic Policing Configuration Example 229
Traffic Shaping Configuration Example 231
Port Mirroring Configuration Example 231
Traffic Priority Configuration Example 232
Traffic Redirection Configuration Example 233
Queue Scheduling Configuration Example 234
WRED Parameters Configuration Example 235
Traffic Statistics Configuration Example 235
Configuring Logon User ACL Control 236
Configuring ACL for Telnet Users 236
Configuration Example 237
Configuring ACL for SNMP Users 238
Configuration Example 239
STP OPERATION
STP Overview 241
Configuring STP 241
Designating Switches and Ports 242
Calculating the STP Algorithm 242
Generating the Configuration BPDU 243
Selecting the Optimum Configuration BPDU 243
Designating the Root Port 243
Configuring the BPDU Forwarding Mechanism 245
MSTP Overview 246
MSTP Concepts 246
MSTP Principles 249
Configuring MSTP 249
Configuring the MST Region for a Switch 250
Specifying the Switch as Primary or Secondary Root Switch 251
Configuring the MSTP Operating Mode 252
Configuring the Bridge Priority for a Switch 253
Configuring the Max Hops in an MST Region 253
Configuring the Switching Network Diameter 254
Configuring the Time Parameters of a Switch 255
Configuring the Max Transmission Speed on a Port 256
Configuring a Port as an Edge Port 257
Configuring the Path Cost of a Port 257
Configuring the Priority of a Port 259
Configuring the Port Connection with the Point-to-Point Link 260
Configuring the mCheck Variable of a Port 261
Configuring the Switch Security Function 262
Enabling MSTP on the Device 263
Enabling or Disabling MSTP on a Port 263
Displaying and Debugging MSTP 264
Page 7

AAA AND RADIUS OPERATION
IEEE 802.1x 265
802.1x System Architecture 265
Configuring 802.1x 267
Configuring the AAA and RADIUS Protocols 274
Configuring AAA 276
Configuring the RADIUS Protocol 279
Troubleshooting AAA and RADIUS 289
RELIABILITY
VRRP Overview 291
Configuring VRRP 292
Enable Pinging the Virtual IP Address 292
Setting Correspondence Between Virtual IP and MAC Addresses 293
Adding and Deleting a Virtual IP Address 293
Configuring the Priority of Switches 294
Configuring Preemption and Delay for a Switch 294
Configuring Authentication Type and Authentication Key 295
Configuring the VRRP Timer 295
Configuring a Switch to Track an Interface 296
Displaying and Debugging VRRP 296
Troubleshooting VRRP 299
SYSTEM MANAGEMENT
File System 301
Using a Directory 301
Managing Files 302
Formatting Storage Devices 302
Setting the Prompt Mode of the File System 302
Configuring File Management 303
FTP 304
TFTP 306
Managing the MAC Address Table 307
Configuring the MAC Address Table 308
Managing Devices 312
Rebooting the Switch 8800 312
Designating the File for the Next Boot 312
Displaying Devices 313
Maintaining and Debugging the System 313
Configuring System Basics 314
Displaying System Information and State 315
Debugging the System 315
Testing Tools for Network Connection 317
Logging Function 318
SNMP 322
Page 8

SNMP Versions and Supported MIB 322
Configuring SNMP 323
RMON 329
Configuring RMON 330
NTP 333
Configuring NTP 335
NTP Configuration Examples 341
Page 9
ABOUT THIS GUIDE
This guide describes the 3Com® Switch 8800 and how to configure it in version
3.0 of the software.
Conventions Ta bl e 1 lists icon conventions that are used throughout this book.
Ta bl e 1 Notice Icons
Icon Notice Type Description
Information
note
Information that describes important features or
instructions.
Caution Information that alerts you to potential loss of data
Warning Information that alerts you to potential personal
or potential damage to an application, system, or
device.
injury.
Ta bl e 2 lists the text conventions used in this book.
Ta bl e 2 Text Conventions
Convention Description
Screen displays This typeface represents information as
Keyboard key names If you must press two or more keys
Press Ctrl+Alt+Del The words “enter” and type”
When you see the word “enter” in this guide, you
must type something, and then press Return or Enter.
Do not press Return or Enter when an instruction
simply says “type.”
Italics are used to: Emphasize a point.
Denote a new term at the place where it is defined in
the text.
Identify menu names, menu commands, and software
button names. Examples:
Click OK. Words in bold
Boldface type is used to highlight command names.
For example, “Use the display user-interface
command to...”
it appears on the screen.
simultaneously, the key names are
linked with a plus sign (+), for example:
Words in italics
Identify command variables.
From the Help menu, select
Contents.
Page 10

2 ABOUT THIS GUIDE
Page 11
SYSTEM ACCESS
1
This chapter covers the following topics:
■ Product Overview
■ Configuring the Switch 8800
■ Setting Terminal Parameters
■ Command Line Interface
Product Overview The 3Com Switch 8800 is a large capacity, modular wire speed Layer 2/Layer 3
switch. It is designed for IP metropolitan area networks (MAN), large-sized
enterprise networks, and campus network users.
The Switch 8800 has an integrated chassis structure. The chassis contains a I/O
module area, fan area, power supply area, and a power distribution area. In the
I/O module area, there are seven, ten, or fourteen slots. Two slots are reserved for
the switch Fabric modules, and the remaining slots are for the I/O modules. You
can install different interface modules for different networks; the slots support a
mixed set of modules.
The Switch 8800 supports the following services:
■ MAN, enterprise/campus networking
■ Multicast service and multicast routing functions and support audio and video
multicast service.
Function Features Ta bl e 1 lists and describes the function features that the Switch 8800 supports.
Ta bl e 1 Function Features
Features Support
VLAN VLANs compliant with IEEE 802.1Q standard
STP protocol Spanning Tree Protocol (STP)
Flow control IEEE 802.3x flow control (full-duplex)
Broadcast suppression Broadcast suppression
Multicast GARP Multicast Registration Protocol (GMRP)
Port-based VLAN
GARP VLAN Registration Protocol (GVRP)
Rapid Spanning Tree Protocol (RSTP)
Multiple Spanning Tree Protocol (MSTP), compliant with IEEE
802.1D/IEEE 802.1s Standard
Back-pressure based flow control (half-duplex)
Internet Group Management Protocol (IGMP) Snooping
Internet Group Management Protocol (IGMP)
Protocol-Independent Multicast-Dense Mode (PIM-DM)
Protocol-Independent Multicast-Sparse Mode (PIM-SM)
Page 12
4 CHAPTER 1: SYSTEM ACCESS
Console port
Table 1 Function Features (continued)
Features Support
IP routing Static route
RIP v1/v2
OSPF
BGP (in advanced software)
IS-IS (in advanced software)
IP routing policy
DHCP Relay Dynamic Host Configuration Protocol (DHCP) Relay
Link aggregation IEEE 802.3ad Link aggregation
Mirror Port-based mirroring (one to one, many to one)
Security features Multi-level user management and password protect
Reliability Virtual Redundancy Routing Protocol (VRRP)
Quality of Service (QoS) Traffic classification
Management and
maintenance
Loading and updating Loading and upgrading software using the XModem protocol
802.1X authentication
Radius authentication
Packet filtering
Bandwidth control
Priority
Queues of different priority on the port
Queue scheduling: supports strict priority (SP), weighted round
robin (WRR), committed access route (CAR) queueing
Command line interface configuration
Configuration through the console and AUX ports
Local or remote configuration by Telnet
Remote configuration by dialing the modem through the AUX port
SNMP
System log
Level alarms
Output of the debugging information
PING and Tracert
Remote maintenance with Telnet and modem
Loading and upgrading software using the File Transfer Protocol
(FTP) and Trivial File Transfer Protocol (TFTP)
Configuring the Switch 8800
On the Switch 8800, you can set up the configuration environment through the
console port. To set up the local configuration environment:
1 Plug the DB-9 or DB-25 female plug of the console cable into the serial port of the
PC or the terminal where the switch is to be configured.
2 Connect the RJ-45 connector of the console cable to the console port of the
switch, as shown in
Figure 1 Setting Up the Local Configuration Environment Through the Console Port
Figure 1.
RS-232 Serial port
Console cable
Page 13
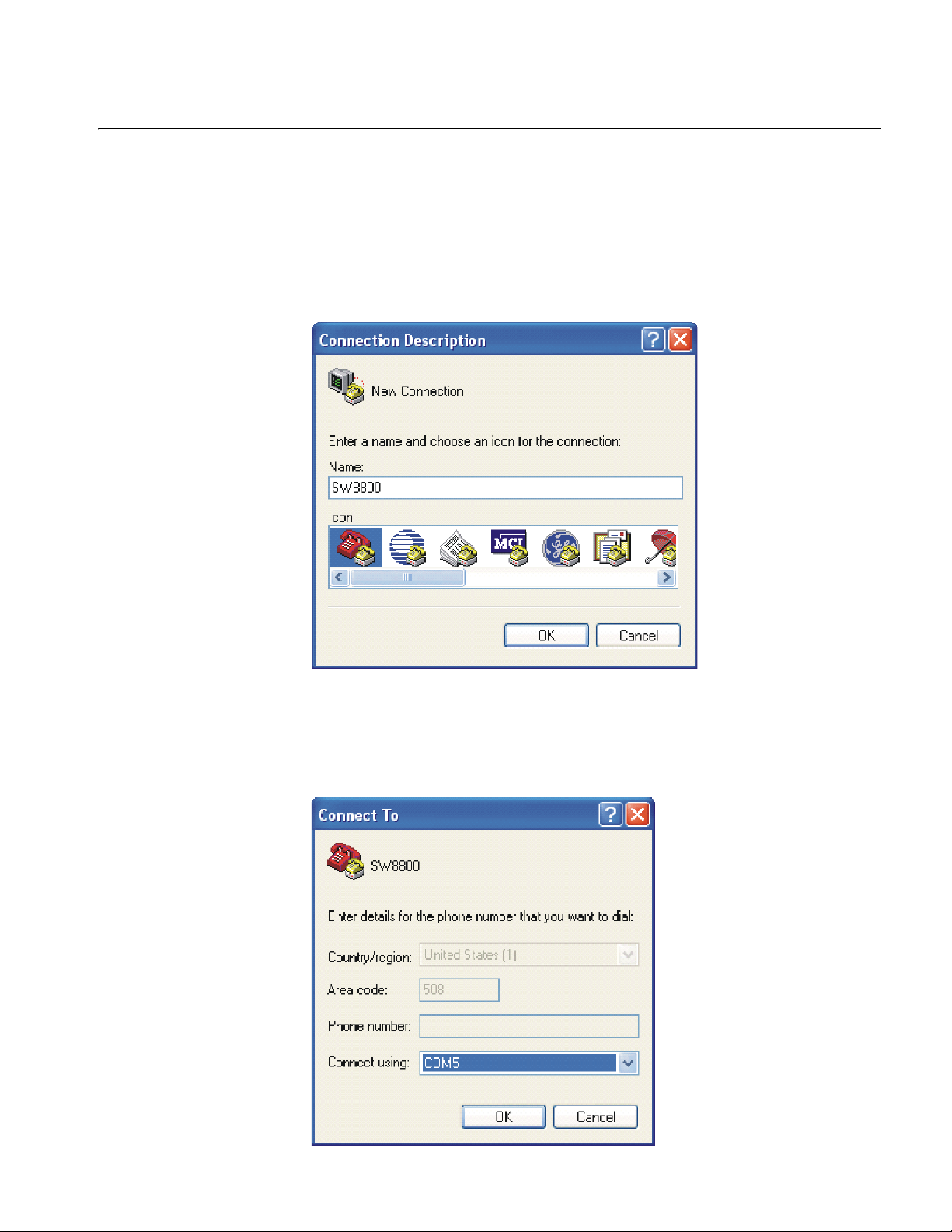
Setting Terminal Parameters 5
Setting Terminal Parameters
To set terminal parameters:
1 Start the PC and select Start > Programs > Accessories > Communications >
HyperTerminal.
2 The HyperTerminal window displays the Connection Description dialog box, as
shown in
Figure 2 Set Up the New Connection
Figure 2.
3 Enter the name of the new connection in the Name field and click OK. The dialog
box, shown in
Figure 3 displays.
4 Select the serial port to be used from the Connect using dropdown menu.
Figure 3 Properties Dialog Box
Page 14
6 CHAPTER 1: SYSTEM ACCESS
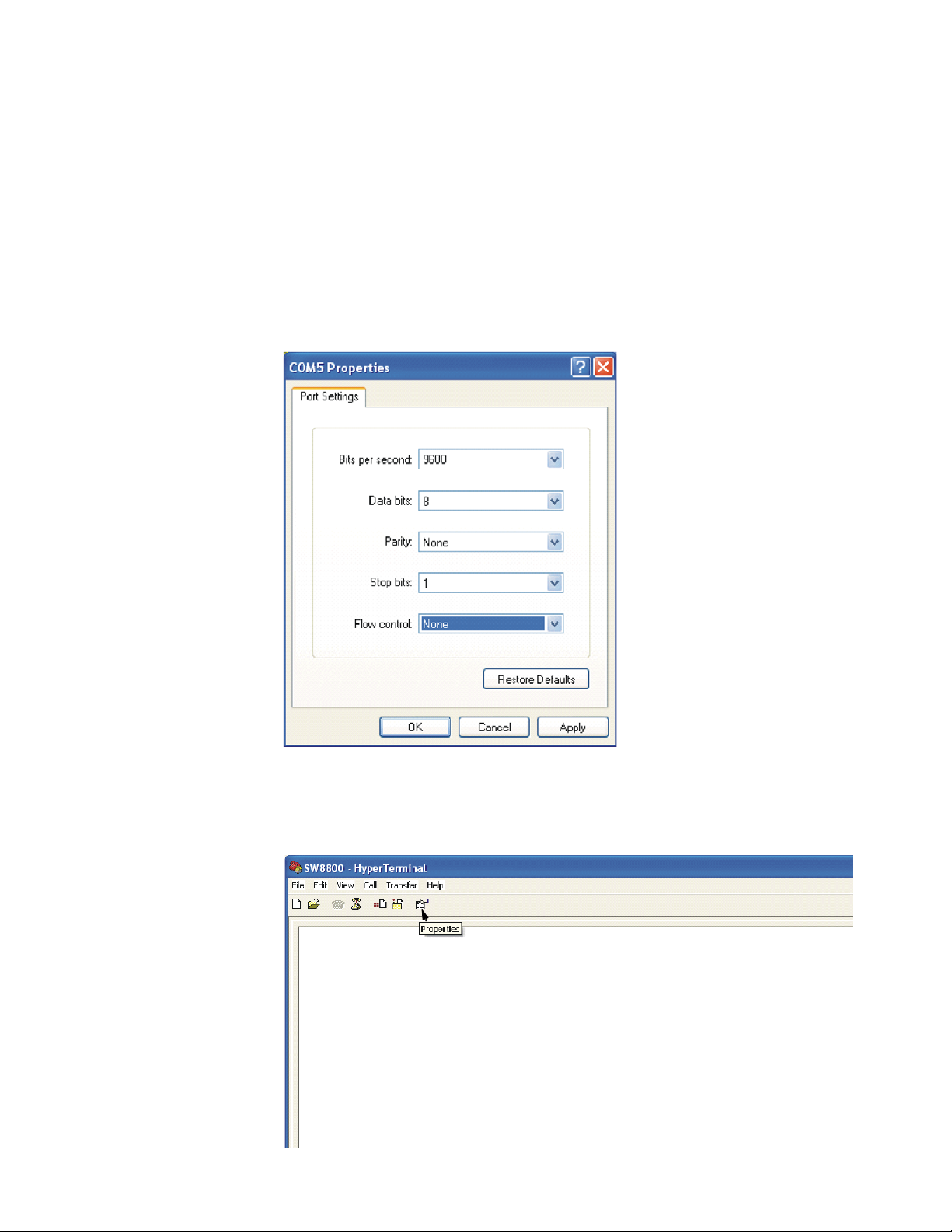
5 Click OK. The Port Settings tab, shown in Figure 4, displays and you can set serial
port parameters. Set the following parameters:
■ Baud rate = 9600
■ Databit = 8
■ Parity check = none
■ Stopbit = 1
■ Flow control = none
Figure 4 Set Communication Parameters
6 Click OK. The HyperTerminal dialogue box displays, as shown in Figure 5.
7 Select Properties.
Figure 5 HyperTerminal Window
Page 15
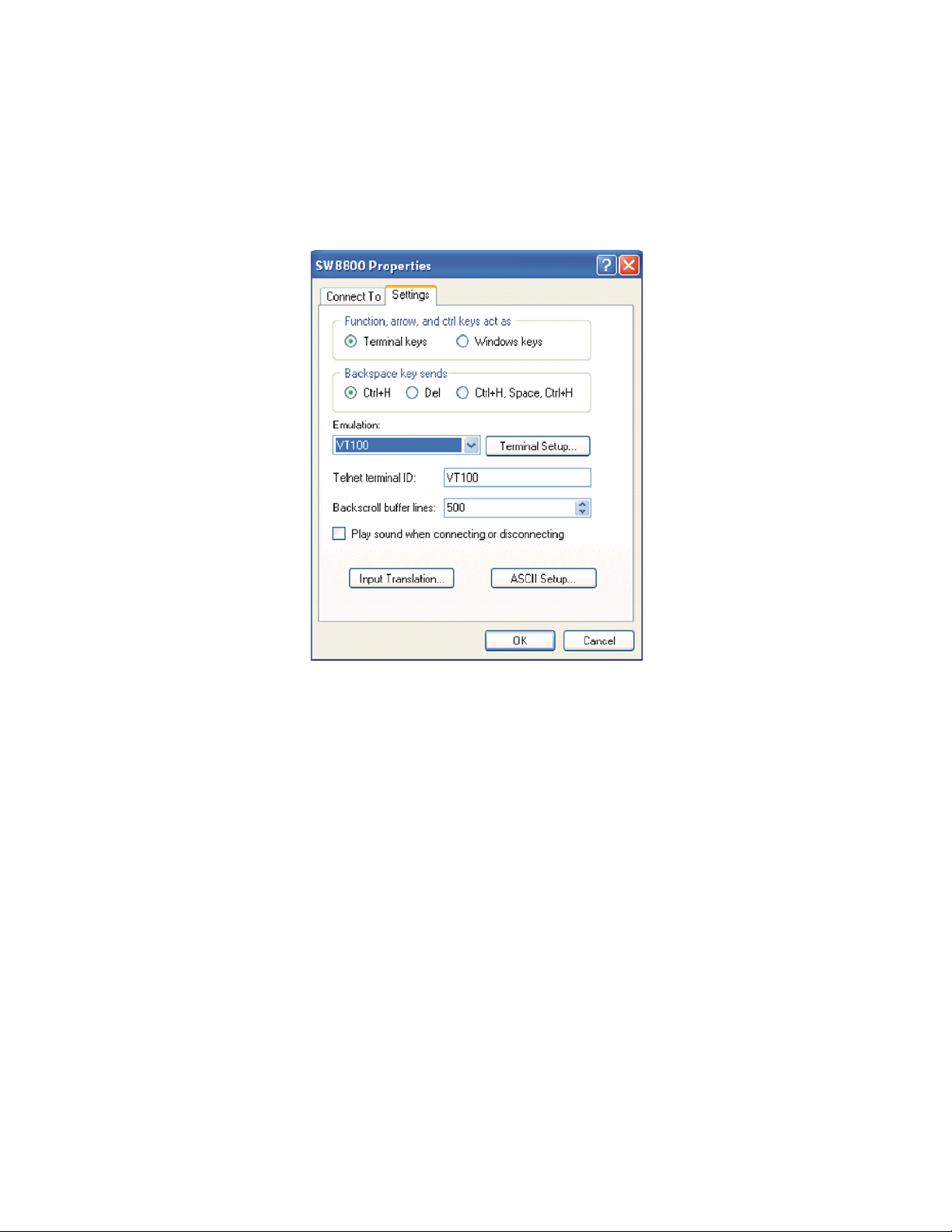
Setting Terminal Parameters 7
8 In the Properties dialog box, select the Settings tab, as shown in Figure 6.
9 Select VT100 in the Emulation dropdown menu.
10 Click OK.
Figure 6 Settings Tab
Configuring Through
Te ln e t
Setting the Terminal Parameters is described in the following sections:
■ Configuring Through Telnet
■ Configuring Through a Dial-up Modem
■ Configuring the User Interface
Before you can telnet to a Switch 8800 and configure it, you must:
1 Configure the IP address of a VLAN interface for the Switch 8800 through the
console port (using the ip address command in VLAN interface view)
2 Add the port (that connects to a terminal) to this VLAN (using the port command
in VLAN view)
3 Log in to the Switch 8800
Tasks for Configuring through Telnet are described in the following sections:
■ Connecting the PC to the Switch 8800
■ Connecting Two Switch 8800 Systems
Page 16
8 CHAPTER 1: SYSTEM ACCESS
1 Authenticate the Telnet user through the console port before the user logs in by
2 Enter system view, return to user view by pressing Ctrl+Z.
3 To set up the configuration environment, connect the Ethernet port of the PC to
Connecting the PC to the Switch 8800
To connect the PC and Switch 8800 through Telnet:
Te ln e t.
By default, a password is required for authenticating the Telnet user to log in the
Switch 8800. If a user logs in by Telnet without a password, the user sees the
message:
<SW8800>system-view
[SW8800]user-interface vty 0 4
[SW8800-ui-vty0]set authentication password simple/cipher xxxx
Login password has not been set!
(xxxx is the preset login password of Telnet user)
that of the Switch 8800 through the LAN. See
Figure 7 Setting Up the Configuration Environment Through Telnet
Figure 7.
Workstation
Switch 8800
Ethernet port
Ethernet
WorkstationServer
4 Run Telnet on the PC by selecting Start > Run from the Windows desktop and
entering Teln et in the Open field, as shown in
Figure 8 Run Telnet
PC (for configuring
the switch through Telnet)
Figure 8. Click OK.
The terminal displays User Access Verification and prompts you for the logon
password.
5 Enter the password. The terminal displays the command line prompt (<SW8800>).
If the message, Too many users! appears, try to reconnect later. At most, 5
Telnet users are allowed to log on to a Switch 8800 simultaneously.
Page 17

Setting Terminal Parameters 9
6 Use the appropriate commands to configure the Switch 8800 or to monitor the
operational state. Enter
? to get immediate help. For details on specific
commands, refer to the chapters in this guide.
When configuring the Switch 8800 by Telnet, do not modify the IP address unless
necessary, because the modification might terminate the Telnet connection. By
default, after passing the password authentication and logging on, a Telnet user
can access the commands at login level 0.
Connecting Two Switch 8800 Systems
Before you can telnet the Switch 8800 to another Switch 8800, as shown in
Figure 9, you must:
1 Configure the IP address of a VLAN interface for the Switch 8800 through the
console port (using the ip address command in VLAN interface view)
2 Add the port (that connects to a terminal) to this VLAN (using the port command
in VLAN view)
3 Log in to the Switch 8800
After you telnet to a Switch 8800, you can run the telnet command to log in and
configure another Switch 8800.
Figure 9 Provide Telnet Client Service
PC
Telnet client
Telnet server
1 Authenticate the Telnet user through the console port on the Telnet Server (Switch
8800) before login.
By default, a password is required for authenticating the Telnet user to log in the
Switch 8800. If a user logs into Telnet without password, the system displays the
following message:
Login password has not been set!
2 Enter system view, return to user view by pressing Ctrl+Z.
<SW8800>system-view
[SW8800]user-interface vty 0
[SW8800-ui-vty0]set authentication password simple/cipher xxxx (xxxx
is the preset login password of Telnet user)
3 Log in to the Telnet client (Switch 8800). For the login process, see “Connecting
the PC to the Switch 8800”.
4 Perform the following operations on the Telnet client:
<SW8800>telnet xxxx
(XXXX can be the hostname or IP address of the Telnet Server. If it is the hostname,
you need to use the ip host command to specify it).
5 Enter the preset login password. The Switch 8800 prompt (<SW8800>) displays. If
the message,
Too many users! displays, try to connect later.
Page 18
10 CHAPTER 1: SYSTEM ACCESS
6 Use the appropriate commands to configure the Switch 8800 or view its
operational state. Enter
? to get immediate help. For details on a specific
command, refer to the appropriate chapter in this guide.
Configuring Through a
Dial-up Modem
To configure your router with a dial-up modem through the AUX port:
1 Authenticate the modem user through the console port of the Switch 8800 before
the user logs in to the switch through a dial-up modem.
By default, a password is required for authenticating the modem user to log in to
the Switch 8800. If a user logs in through the modem without a password, the
user sees the message,
Password required, but none set.
a Enter system view, return user view with Ctrl+Z.
<SW8800>system-view
[SW8800]user-interface aux 0
[SW8800-ui-aux0]set authentication password simple/cipher xxxx (xxxx
is the preset login password of the Modem user.)
b Using the modem command, you can configure the console port to modem
mode.
[SW8800-ui-aux0]modem
2 To set up the remote configuration environment, connect the modems to a PC (or
a terminal) serial port and to the Switch 8800 console port, as shown in
Set Up
Remote Configuration Environment.
Figure 10 Set Up Remote Configuration Environment
Modem serial port line
Modem
Telephone line
PST
Console port
Modem
Remote telephone:
555-5555
3 Dial for a connection to the switch, using the terminal emulator and modem on
the remote end. Dial the telephone number of the modem connected to the
Switch 8800. See
Figure 11 and Figure 12.
Page 19
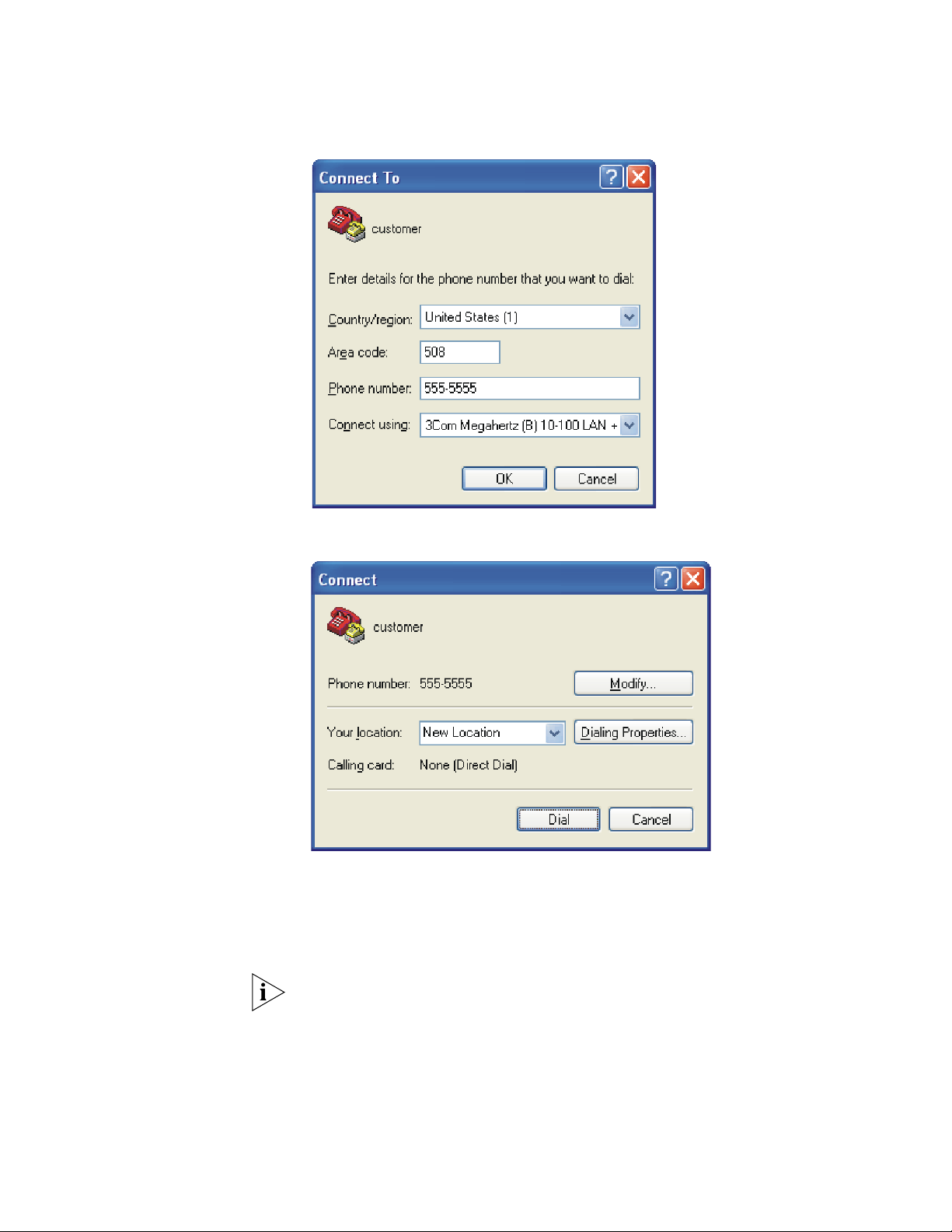
Figure 11 Set the Dialed Number
Setting Terminal Parameters 11
Figure 12 Dial the Remote PC
4 Enter the preset login password on the remote terminal emulator and wait for the
<SW8800>prompt.
5 Use the appropriate commands to configure the Switch 8800 or view its
operational state. Enter
? to get immediate help. For details on a specific
command, refer to the appropriate chapter in this guide.
Configuring the User
Interface
By default, after login, a modem user can access the commands at Level 0.
User interface configuration is another way to configure and manage port data.
The Switch 8800 supports the following configuration methods:
■ Local configuration through the console port
■ Remote configuration through Telnet on the Ethernet port
Page 20
12 CHAPTER 1: SYSTEM ACCESS
■ Remote configuration through a modem through the console port.
There are two types of user interfaces:
■ AUX user interface is used to log in the Switch 8800 through a dial-up modem.
A Switch 8800 can only have one AUX port.
■ VTY user interface is used to telnet the Switch 8800.
For the Switch 8800, the AUX port and Console port are the same port. There is
only the type of AUX user interface.
The user interface is numbered by absolute number or relative number.
To number the user interface by absolute number:
■ The AUX user interface is the first interface — user interface 0.
■ The VTY is numbered after the AUX user interface. The absolute number of the
first VTY is the AUX user interface number plus 1.
To number the user interface by relative number, represented by interface +
number assigned to each type of user interface:
■ AUX user interface = AUX 0.
■ The first VTY interface = VTY 0, the second one = VTY 1, and so on.
Tasks for configuring the user interface are described in the following sections:
■ Entering the User Interface View
■ Configuring the Attributes of the AUX (Console) Port
■ Configuring the Terminal Attributes
■ Managing Users
■ Configuring the Attributes of a Modem
■ Configuring Redirection
■ Displaying and Debugging User Interface
Entering the User Interface View
Use the user-interface command (see Tab le 2) to enter a user interface view. You
can enter a single user interface view or multi-user interface view to configure one
or more user interfaces.
Perform the following configuration in system view.
Ta bl e 2 Enter User Interface View
Operation Command
Enter a single user interface view or multi user
interface views
user-interface [ type ] first-number [
last-number ]
Configuring the Attributes of the AUX (Console) Port
Use the speed, flow control, parity, stop bit, and data bit commands (see
Ta bl e 3) to configure these attributes of the AUX (Console) port.
Page 21

Setting Terminal Parameters 13
Perform the following configurations in user interface (AUX user interface only)
view.
Ta bl e 3 Configure the Attributes of the AUX (Console) Port
Operation Command
Configure the transmission speed on AUX
(Console) port. By default, the transmission
speed is 9600bps
Restore the default transmission speed on
AUX (Console) port
Configure the flow control on AUX (Console)
port. By default, no flow control is performed
on the AUX (Console) port
Restore the default flow control mode on AUX
(Console) port
Configure parity mode on the AUX (Console)
port. By default, there is no parity bit on the
AUX (Console) port
Restore the default parity mode undo parity
Configure the stop bit of AUX (Console) port.
By default, AUX (Console) port supports 1
stop bit
Restore the default stop bit of AUX (Console)
port
Configure the data bit of AUX (Console) port.
By default, AUX (Console) port supports 8
data bits.
Restore the default data bit of AUX (Console)
port
speed speed-value
undo speed
flow-control { hardware | none |
software }
undo flow-control
parity { even | mark | none | odd | space }
stopbits { 1 | 1.5 | 2 }
undo stopbits
databits { 7 | 8 }
undo databits
Configuring the Terminal Attributes
The following commands can be used for configuring the terminal attributes,
including enabling/disabling terminal service, disconnection upon timeout,
lockable user interface, configuring terminal screen length and history command
buffer size.
Perform the following configuration in user interface view. Perform the lock
command in user view.
Enabling and Disabling Terminal Service After the terminal service is
disabled on a user interface, you cannot log in to the Switch 8800 through the
user interface. However, if a user logged in through the user interface before
disabling the terminal service, the user can continue operation. After the user logs
out, the user cannot log in again. In this case, the user can log in to the Switch
through the user interface only when the terminal service is enabled again. Use
the commands described in
Ta bl e 4 Enabling and Disabling Terminal Service
Operation Command
Enable terminal service shell
Disable terminal service undo shell
Ta bl e 4 to enable or disable terminal service.
Page 22

14 CHAPTER 1: SYSTEM ACCESS
By default, terminal service is enabled on all the user interfaces.
Note the following points:
■ For the sake of security, the undo shell command can only be used on the user
interfaces other than the AUX user interface.
■ You cannot use this command on the user interface through which you log in.
■ You must confirm your privilege before using the undo shell command in any
legal user interface.
Configuring idle-timeout By default, idle-timeout is enabled and set to 10
minutes on all the user interfaces. The idle-timeout command is described in
Ta bl e 5.
Ta bl e 5 Idle Timeout
Operation Command
Configure idle-timeout idle-timeout minutes [ seconds ]
(idle-timeout 0 means disabling
idle-timeout.)
Restore the default idle-timeout undo idle-timeout
Locking the User Interface The lock command locks the current user interface
and prompts the user to enter a password. This makes it impossible for others to
operate in the interface after the user leaves. The lock command is described in
Ta bl e 6.
Ta bl e 6 Lock User Interface
Operation Command
Lock user interface lock
Setting the Screen Length If a command displays more than one screen of
information, you can use the screen length command to determine how many
lines are displayed on a screen so that information can be separated in different
screens and you can view it more conveniently. The screen-length command is
described in
Ta bl e 7 Setting Screen Length
Operation Command
Set the screen length screen-length screen-length (screen-length
Restore the default screen length undo screen-length
Ta bl e 7.
0 indicates to disable screen display separation
function.)
By default, the terminal screen length is 24 lines.
Setting the History-Command Buffer Size
Ta bl e 8 describes the history-command max-size command.
By default, the size of the history-command max-size command buffer is 10.
Ta bl e 8 Set the History Command Buffer Size
Operation Command
Set the history command buffer size history-command max-size value
Page 23
Setting Terminal Parameters 15
Table 8 Set the History Command Buffer Size
Operation Command
Restore the default history command buffer
size
undo history-command max-size
Managing Users
The management of users includes, the setting of the user logon authentication
method, the level of command a user can use after logging on, the level of
command a user can use after logging on from the specific user interface, and the
command level.
Configuring the Authentication Method The authentication-mode
command configures the user login authentication method that allows access to
an unauthorized user.
Ta bl e 9 describes the authentication-mode command.
Perform the following configuration in user interface view.
Ta bl e 9 Configure Authentication Method
Operation Command
Configure the authentication method authentication-mode { password | scheme
}
Configure no authentication authentication-mode none
By default, terminal authentication is not required for users who log in through
the console port, whereas a password is required for authenticating modem and
Telnet users when they log in.
To configure authentication for modem and Telnet users:
1 Configure local password authentication for the user interface.
When you set the password authentication mode, you must also configure a login
password to log in successfully.
Ta bl e 10 describes the set authentication
password command.
Perform the following configuration in user interface view.
Ta bl e 10 Configure the Local Authentication Password
Operation Command
Configure the local authentication password set authentication password { cipher |
Remove the local authentication password undo set authentication password
simple } password
Configure for password authentication when a user logs in through a VTY 0 user
interface and set the password to 3Com:
[SW8800]user-interface vty 0
[SW8800-ui-vty0]authentication-mode password
[SW8800-ui-vty0]set authentication password simple 3Com
2 Configure the local or remote authentication username and password.
Use the authentication-mode scheme command to perform local or remote
authentication of username and password. The type of the authentication
depends on your configuration. For detailed information, see
“AAA and RADIUS
Operation”
Page 24
16 CHAPTER 1: SYSTEM ACCESS
3 Set the Switch 8800 to allow user access without authentication.
Perform username and password authentication when a user logs in through the
VTY 0 user interface and set the username and password to zbr and 3Com
respectively:
[SW8800-ui-vty0]authentication-mode scheme
[SW8800-ui-vty0]quit
[SW8800]local-user zbr
[SW8800-luser-zbr]service-type telnet
[SW8800-luser-zbr]password simple 3Com
[SW8800-ui-vty0]authentication-mode none
By default, the password is required for authenticating the modem and Telnet
users when they log in. If the password has not been set, when a user logs in, the
following message displays,
Login password has not been set!
If the authentication-mode none command is used, the modem and Telnet
users are not required to enter a password.
Set the Command Level after Login The following command is used for
setting the command level used after a user logs in.
Perform the following configuration in local-user view.
Ta bl e 11 Set Command Level Used After a User Logs In
Operation Command
Set the command level used after a user
logging in
Restore the default command level used after
a user logging in
service-type { level level | telnet [ level level
] ] | telnet [ level level ] }
undo service-type { level | telnet [ level ] ] |
telnet [ level ] }
By default, a Telnet user can access the commands at Level 1 after logon.
Setting the Command Level Used after a User Logs in from a User Interface
Use the user privilege level command to set the command level, after a user
logs in from a specific user interface, so that a user is able to execute the
commands at that command level.
Ta bl e 12 describes the user privilege level
command.
Perform the following configuration in user interface view.
Ta bl e 12 Set Command Level After User Login
Operation Command
Set command level used after a user logging
in from a user interface
Restore the default command level used after
a user logging in from a user interface
user privilege level level
undo user privilege level
By default, a user can access the commands at Level 3 after logging in through the
AUX user interface, and the commands at Level 0 after logging in through the VTY
user interface.
Page 25
Setting Terminal Parameters 17
When a user logs in to the switch, the command level that the user can access
depends on two points. One is the command level that the user can access, the
other is the set command level of the user interface. If the two levels are different,
the former is taken. For example, the command level of VTY 0 user interface is 1,
however, user Tom has the right to access commands of level 3; if Tom logs in from
VTY 0 user interface, he can access commands of level 3 and lower.
Setting Command Priority The command-privilege level command sets the
priority of a specified command in a certain view. The command levels include
visit, monitoring, configuration, and management, which are identified with
command level 0 through 3, respectively. An administrator assigns authority
according to user requirements. See
Ta bl e 13.
Perform the following configuration in system view.
Ta bl e 13 Set Command Priority
Operation Command
Set the command priority in a specified view. command-privilege level level view view
command
Restore the default command level in a
specified view.
undo command-privilege view view
command
Configuring the Attributes of a Modem
You can use the commands described in Tab le 14 to configure the attributes of a
modem when logging in to the Switch through the modem.
Perform the following configuration in user interface view.
Ta bl e 14 Configure Modem
Operation Command
Set the interval since the system receives the
RING until CD_UP
Restore the default interval since the system
receives the RING until CD_UP
Configure auto answer modem auto-answer
Configure manual answer undo modem auto-answer
Configure to allow call-in modem call-in
Configure to bar call-in undo modem call-in
Configure to permit call-in and call-out. modem both
Configure to disable call-in and call-out undo modem both
modem timer answer seconds
undo modem timer answer
Configuring Redirection
The send Command can be used for sending messages between user
interfaces. See
Ta bl e 15.
Page 26
18 CHAPTER 1: SYSTEM ACCESS
Perform the following configuration in user view.
Ta bl e 15 Configure to Send Messages Between User Interfaces
Operation Command
Configure to send messages between
different user interfaces.
send { all | number | type number }
The auto-execute Command is used to run a command automatically after
you log in. The command is automatically executed when you log in again. See
Ta bl e 16.
This command is usually used to execute the telnet command automatically on a
terminal, which connects the user to a designated device.
Perform the following configuration in user interface view.
Ta bl e 16 Configure Automatic Command Execution
Operation Command
Configure to automatically run the command auto-execute command text
Configure not to automatically run the
command
undo auto-execute command
After applying the auto-execute command, the user interface can no longer be
used to carry out the routine configurations for the local system.
Make sure that you will be able to log in to the system in some other way and
cancel the configuration before you use the auto-execute command and save
the configuration.
Telnet 10.110.100.1 after the user logs in through VTY0 automatically.:
[SW8800-ui-vty0]auto-execute command telnet 10.110.100.1
When a user logs on by VTY 0, the system will run telnet 10.110.100.1
automatically.
Displaying and Debugging User Interface
After creating the previous configuration, execute the display command in all
views to display the user interface configuration, and to verify the effect of the
configuration. Execute the free command in user view to clear a specified user
interface.
Ta bl e 17 Display and Debug User Interface
Operation Command
Clear a specified user interface free user-interface [ type ] number
Display the user application information of the
user interface
Display the physical attributes and some
configurations of the user interface
display users [ all ]
display user-interface [ type number ] [
number ] [summary]
See Ta bl e 17.
Page 27

Command Line Interface 19
Command Line Interface
The Switch 8800 provides a series of configuration commands and command line
interfaces for configuring and managing the Switch 8800. The command line
interface has the following features.
■ Local configuration through the console and AUX ports.
■ Local or remote configuration through Telnet.
■ Remote configuration through a dial-up Modem through the AUX port to log
in to the Switch 8800.
■ Hierarchy command protection to prevent unauthorized users from accessing
the switch.
■ Access to online Help by entering ?.
■ Network test commands, such as Tracert and Ping, for rapid troubleshooting of
the network.
■ Detailed debugging information to help with network troubleshooting.
■ Ability to log in and manage other Switch 8800s directly, using the telnet
command.
■ FTP service for the users to upload and download files.
■ Ability to view previously executed commands.
■ The command line interpreter that searches for a target not fully matching the
keywords. You can enter the whole keyword or part of it, as long as it is unique
and not ambiguous.
Configuring a Command Line Interface is described in the following sections:
■ Command Line View
■ Features and Functions of the Command Line
Command Line View The Switch 8800 provides hierarchy protection for the command lines to prevent
unauthorized users from accessing the switch illegally.
There are four levels of commands:
■ Visit level — involves commands for network diagnosis tools (such as ping and
tracert), command of the switch between different language environments of
user interface (language-mode) and the telnet command. Saving the
configuration file is not allowed on this level of commands.
■ Monitoring level — includes the display command and the debugging
command for system maintenance, service fault diagnosis, and so on. Saving
the configuration file is not allowed on this level of commands.
■ Configuration level — provides service configuration commands, such as the
routing command and commands on each network layer that are used to
provide direct network service to the user.
■ Management level — influences the basic operation of the system and the
system support module which plays a support role for service. Commands at
this level involve file system commands, FTP commands, TFTP commands,
XModem downloading commands, user management commands, and level
setting commands.
Page 28

20 CHAPTER 1: SYSTEM ACCESS
Login users are also classified into four levels that correspond to the four
command levels. After users of different levels log in, they can only use commands
at their own, or lower, levels.
To prevent unauthorized users from illegal intrusion, users are identified when
switching from a lower level to a higher level with the super [ level ] command.
User ID authentication is performed when users at a lower level switch to users at
a higher level. Only when correct password is entered three times, can the user
switch to the higher level. Otherwise, the original user level remains unchanged.
Command views are implemented according to requirements that are related to
one another. For example, after logging in to the Switch 8800, you enter user
view, in which you can only use some basic functions, such as displaying the
operating state and statistics information. In user view, key in system-view to
enter system view, in which you can key in different configuration commands and
enter the corresponding views.
The command line provides the following views:
■ User view
■ System view
■ Ethernet Port view
■ VLAN view
■ VLAN interface view
■ Local-user view
■ User interface view
■ FTP client view
■ PIM view
■ RIP view
■ OSPF view
■ OSPF area view
■ Route policy view
■ Basic ACL view
■ Advanced ACL view
■ Layer-2 ACL view
■ RADIUS server group view
■ ISP domain view
■ BGP view
■ ISIS view
The relation diagram of the views is shown in Figure 13.
Page 29
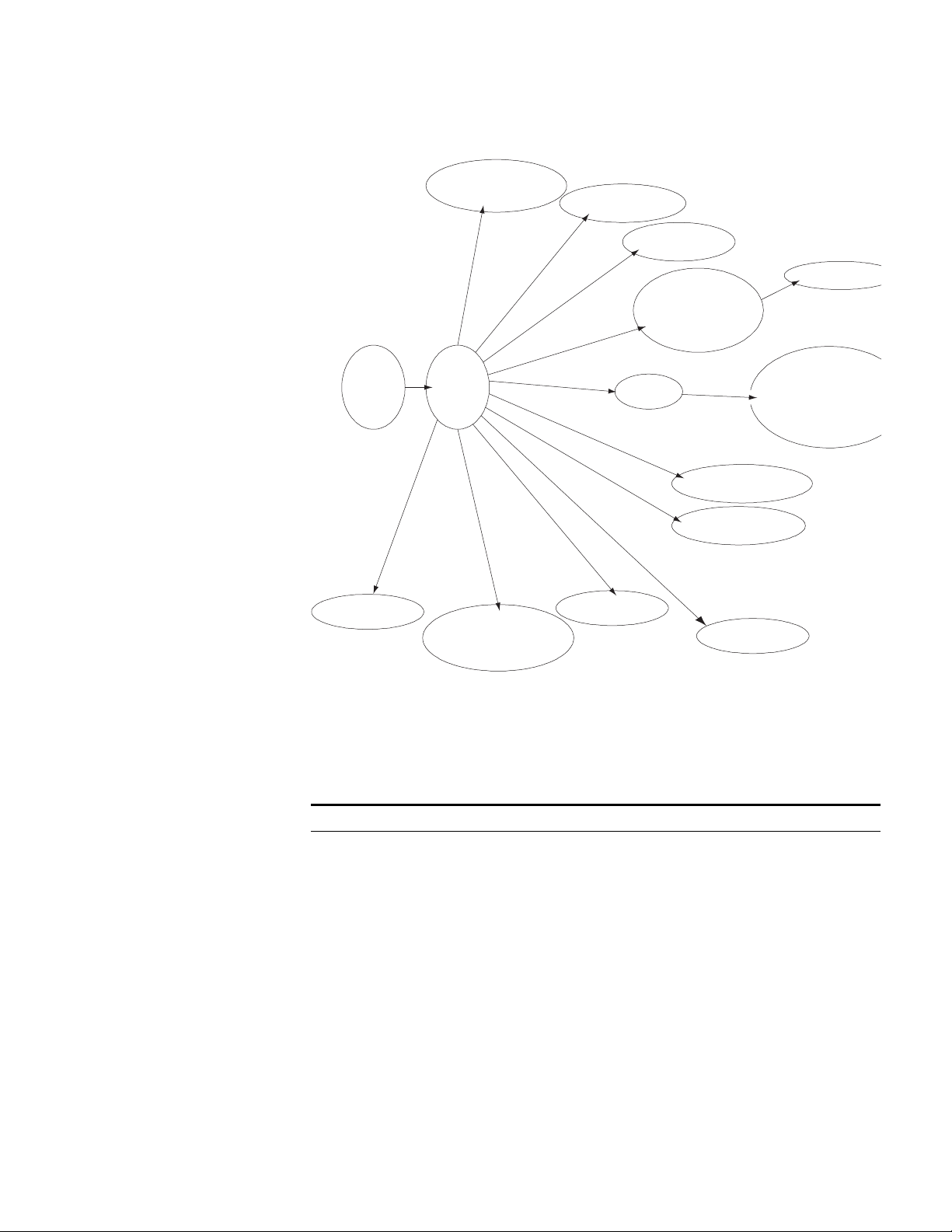
Figure 13 Relation Diagram of the Views
Ethernet port view
User interface view
VLAN view
VLAN interface view
User view
System
view
RIP view
OSPF view
Route policy view
OSPF area view
Basic ACL view
Advanced ACL view
Interface-based ACL view
Layer-2 ACL view
FTP client view
Local-user view
PIM view
RADIUS server group view
Command Line Interface 21
ACL
IS-IS view
Ta bl e 18 describes the function features of different views.
For all views, use the quit command to return to system view and use the return
command to return to user view.
Ta bl e 18 Function Feature of Command View
Command view Function Prompt Command to enter
User view Show basic infor-
System view Configure system
Ethernet Port view Configure Ethernet
VLAN view Configure VLAN
VLAN interface view Configure IP interface
mation about
operation and
statistics
parameters
port parameters
parameters
parameters for a
VLAN or a VLAN
aggregation
BGP view
<SW8800> Enter right after
connecting the switch
[SW8800] Key in system-view
in user view
[SW8800-Gigabit
Ethernet1/1/1]
[SW8800-Gigabit
Ethernet1/1/1]
[SW8800Vlan1]
[SW8800-Vlan-in
terface1]
100M Ethernet port
view
Gigabit Ethernet port
view
Enter vlan 1 in
System view
Enter interface
vlan-interface 1
in
System view
Page 30

22 CHAPTER 1: SYSTEM ACCESS
Table 18 Function Feature of Command View (continued)
Command view Function Prompt Command to enter
Local-user view Configure local user
parameters
User interface view Configure user
interface parameters
FTP Client view Configure FTP Client
[SW8800-useruser1]
Enter local-user
user1 in System view
[SW8800-ui0] Enter user-interface
0 in System view
[ftp] Enter ftp in user view
parameters
PIM view Configure PIM
parameters
RIP view Configure RIP
parameters
OSPF view Configure OSPF
parameters
OSPF area view Configure OSPF area
parameters
Route policy view Configure route policy
parameters
[SW8800-PIM] Enter pim in System
view
[SW8800-rip] Enter rip in System
view
[SW8800-ospf] Enter ospf in System
view
[SW8800-ospf-0.
0.0.1]
[SW8800-routepolicy]
Enter area 1 in OSPF
view
Enter route-policy
policy1 permit node
10 in System view
Basic ACL view Define the rule of
basic ACL
Advanced ACL view Define the rule of
advanced ACL
Layer-2 ACL view Define the rule of
layer-2 ACL
RADIUS server group
view
Configure radius
parameters
ISP domain view Configure ISP domain
parameters
[SW8800-aclbasic-2000]
[SW8800-acl-adv
-3000]
[SW8800-acllink-4000]
Enter acl number
2000 in System view
Enter acl number
3000 in System view
Enter acl number
4000 in System view
[SW8800-radius-1]Enter radius scheme
1 in System view
[SW8800-isp-163
.net]
Enter domain
isp-163.net in System
view
Features and Functions
of the Command Line
Tasks for configuring the features and functions of the command line are
described as follows:
■ Online Help
■ Common Command Line Error Messages
■ History Command
■ Editing Features of the Command Line
■ Displaying Features of the Command Line
Online Help
The command line interface provides full and partial online Help modes.
You can get the help information through these online help commands, which are
described as follows.
■ Enter ? in any view to get all the commands in it and corresponding
descriptions.
<SW8800>?
User view commands:
language-mode Specify the language environment
ping Ping function
Page 31

Command Line Interface 23
quit Exit from current command view
super Enter the command workspace with specified user priority
level
telnetEstablish one TELNET connection
tracertTrace route function
■ Enter a command with a ?, separated by a space. If this position is for
keywords, then all the keywords and the corresponding brief descriptions will
be listed.
<SW8800>ping ?
-a Select source IP address
-c Specify the number of echo requests to send
-d Specify the SO_DEBUG option on the socket being used
-h Specify TTL value for echo requests to be sent
-I Select the interface sending packets
-n Numeric output only. No attempt will be made to lookup host
addresses for symbolic names
-p No more than 8 "pad" hexadecimal characters to fill out the sent
packet. For example, -p f2 will fill the sent packet with f and 2
repeatedly
-q Quiet output. Nothing is displayed except the summary lines at
startup time and when finished
-r Record route. Includes the RECORD_ROUTE option in the ECHO_REQUEST
packet and displays the route
-s Specifies the number of data bytes to be sent
-t Timeout in milliseconds to wait for each reply
-v Verbose output. ICMP packets other than ECHO_RESPONSE that are
received are listed
STRING<1-20> IP address or hostname of a remote system
Ip IP Protocol
■ Enter a command with a ?, separated by a space. If this position is for
parameters, all the parameters and their brief descriptions will be listed.
[SW8800]garp timer leaveall ?
INTEGER<65-32765> Value of timer in centiseconds
(LeaveAllTime > (LeaveTime [On all ports]))
Time must be multiple of 5 centiseconds
[SW8800]garp timer leaveall 300 ?
<cr>
<cr> indicates no parameter in this position. The next command line repeats
the command, you can press Enter to execute it directly.
■ Enter a character string with a ?, and list all the commands beginning with this
character string.
<SW8800>p?
ping
■ Input a command with a character string and ?, and list all the key words
beginning with this character string in the command.
<SW8800>display ver?
version
Page 32

24 CHAPTER 1: SYSTEM ACCESS
Common Command Line Error Messages
All the commands that are entered by users can be correctly executed if they have
passed the grammar check. Otherwise, error messages are reported to users.
Common error messages are listed in
Ta bl e 19 Common Command Line Error Messages
Error messages Causes
Unrecognized command Cannot find the command.
Cannot find the keyword. Wrong parameter type.
The value of the parameter exceeds the range. Incomplete command
The command is incomplete. Too many parameters
You entered too many parameters. Ambiguous command
The parameters you entered are not specific.
Ta bl e 19.
History Command
The command line interface provides a function similar to DosKey. The commands
entered by users can be automatically saved by the command line interface and
you can invoke and execute them at any time. By default, the history command
buffer can store 10 history commands for each user. The operations are shown in
Ta bl e 20.
Ta bl e 20 Retrieve History Command
Operation Key Result
Display history command display history-command Displays history commands
Retrieve the previous history
command
Retrieve the next history
command
Up cursor key <> or <Ctrl+P> Retrieves the previous history
Down cursor key <> or
<Ctrl+N>
by the user who is entering
them.
command, if there is any.
Retrieves the next history
command, if there is any.
Editing Features of the Command Line
The command line interface provides a basic command editing function and
supports editing multiple lines. A command cannot be longer than 256 characters.
Ta bl e 21.
See
Ta bl e 21 Editing Functions
Key Function
Common keys Inserts at the cursor position and the cursor
moves to the right, if the edition buffer still
has free space.
Backspace Deletes the character preceding the cursor
and the cursor moves backward.
Left cursor key < or Ctrl+B Moves the cursor a character backward
Right cursor key > or Ctrl+F Moves the cursor a character forward
Up cursor key ^ or Ctrl+P
Down cursor key v or Ctrl+N
Retrieves the history command.
Page 33

Command Line Interface 25
Table 21 Editing Functions
Key Function
Tab Press Tab after typing the incomplete key
word and the system will execute the partial
help: If the key word matching the typed one
is unique, the system will replace the typed
one with the complete key word and display it
in a new line. If there is not a matched key
word or the matched key word is not unique,
the system will do no modification but
displays the originally typed word in a new
line.
Displaying Features of the Command Line
If information to be displayed exceeds one screen, the pause function allows users
three choices, as described in
Ta bl e 22 Display Functions
Key or Command Function
Press Ctrl+C when the display pauses Stop displaying and executing command.
Enter a space when the display pauses Continue to display the next screen of
Press Enter when the display pauses Continue to display the next line of
Tab le 22.
information.
information.
Page 34

26 CHAPTER 1: SYSTEM ACCESS
Page 35

2
PORT CONFIGURATION
This chapter covers the following topics:
■ Ethernet Port Overview
■ Configuring Link Aggregation
Ethernet Port Overview
Configuring Ethernet
Ports
The following features are found in the Ethernet ports of the Switch 8800:
■ 10GBASE-X-XENPAK 10-Gigabit Ethernet ports work in 10-gigabit full duplex
mode.
■ 10GBASE-X-XFP operates in 10 Gbps full duplex mode, which needs no
configuring.
■ 1000BASE-X-SFP Gigabit Ethernet ports work in gigabit full duplex mode.
■ 10/100/1000BASE-T Gigabit Ethernet ports support MDI/MDI-X auto-sensing,
and the modes are 1000 Mbps full duplex, 100 Mbps half/full duplex, and 10
Mbps half/full duplex. These modules also support auto-negotiation
Configuring an Ethernet port is described in the following sections:
■ Configuring Ethernet Ports
■ Example: Configuring the Default VLAN ID of the Trunk Port
■ Troubleshooting VLAN Port Configuration
Tasks for configuring Ethernet ports are described in the following sections:
■ Entering Ethernet Port View
■ Enabling and Disabling Ethernet Ports
■ Setting the Description Character String for an Ethernet Port
■ Setting the Duplex Attribute of the Ethernet Port
■ Setting the Speed of the Ethernet Port
■ Setting the Cable Type for an Ethernet Port
■ Setting Flow Control for an Ethernet Port
■ Permitting/Forbidding Jumbo Frames on the Ethernet port
■ Setting the Maximum MAC Addresses an Ethernet Port Can Learn
■ Setting the Link Type for an Ethernet Port
■ Adding an Ethernet Port to a VLAN
■ Setting the Default VLAN ID for an Ethernet Port
■ Copying a Port Configuration to Other Ports
Page 36

28 CHAPTER 2: PORT CONFIGURATION
■ Displaying and Debugging Ethernet Ports
Entering Ethernet Port View
Before configuring the Ethernet port, enter Ethernet port view.
Perform the following configuration in system view.
Ta bl e 1 Enter Ethernet Port View
Operation Command
Enter Ethernet port view interface { Gigabit | Ethernet }
The subslot on the Fabric is always set to 1.
Enabling and Disabling Ethernet Ports
The following command can be used for disabling or enabling the port. After
configuring the related parameters and protocol of the port, you can use the
following command to enable the port.
Perform the following configuration in Ethernet port view.
slot/subslot/port
Ta bl e 2 Enable/Disable an Ethernet Port
Operation Command
Disable an Ethernet port shutdown
Enable an Ethernet port undo shutdown
By default, the port is enabled.
Setting the Description Character String for an Ethernet Port
You can use the following command to identify the Ethernet ports.
Perform the following configuration in Ethernet port view.
Ta bl e 3 Set Description Character String for Ethernet Port
Operation Command
Set description character string for Ethernet
port.
Delete the description character string of
Ethernet.
description text
undo description
By default, the port description is a null character string.
Setting the Duplex Attribute of the Ethernet Port
Set the port to full duplex to send and receive data packets at the same time. Set
the port to half-duplex to either send or receive only. If the port has been set to
auto-negotiation mode, the local and peer ports will automatically negotiate the
duplex mode.
Page 37

Ethernet Port Overview 29
Perform the following configuration in Ethernet port view.
Ta bl e 4 Set the Duplex Attribute for an Ethernet Port
Operation Command
Set the duplex attribute for an Ethernet port. duplex {auto | full | half}
Restore the default duplex attribute of
Ethernet port.
undo duplex
The Gigabit Ethernet Base-T ports can operate in full duplex, half duplex, or
auto-negotiation mode. When the ports operate at 1000 Mbps, the duplex mode
can be set to full (full duplex) or auto (auto-negotiation).
By default, the port is in auto (auto-negotiation) mode.
Setting the Speed of the Ethernet Port
You can use the following command to set the speed on the Ethernet port. If the
speed is set to auto (auto-negotiation) mode, the local and peer ports will
automatically negotiate the port speed.
Perform the following configuration in Ethernet port view.
Ta bl e 5 Set Speed on Ethernet Port
Operation Command
Set Ethernet port speed speed {10 | 100 | 1000 | auto}
Restore the default speed on Ethernet port undo speed
The Gigabit Ethernet BASE-T port can operate at 10 Mbps, 100 Mbps, or 1000
Mbps. However in half duplex mode, the port cannot operate at 1000 Mbps. The
Gigabit optical Ethernet port supports1000 Mbps; the 10 Gigabit optical Ethernet
port supports 10000 Mbps, which does not need to be configured.
Setting the Cable Type for an Ethernet Port
The Ethernet port supports the straight-through (MDI) and cross-over (MDIX)
network cables. The Switch 8800 only supports auto (auto-sensing). If you set
some other type, you will see an error message. By default, the cable type is auto
(auto-recognized). The system will automatically recognize the type of cable
connecting to the port.
Perform the following configuration in Ethernet port view. The settings only take
effect on 10/100/1000 Mbps electrical ports.
Ta bl e 6 Set the Type of the Cable Connected to the Ethernet Port
Operation Command
Set the type of the cable connected to the
Ethernet port.
Restore the default type of the cable
connected to the Ethernet port.
mdi { auto }
undo mdi
Setting Flow Control for an Ethernet Port
If flow control is enabled on both the local and the peer switch and congestion
occurs in the local switch, the local switch can instruct its peer to temporarily stop
sending packets. Once the peer switch receives this message, it stops sending
Page 38

30 CHAPTER 2: PORT CONFIGURATION
packets and packet loss is reduced. The flow control function of the Ethernet port
can be enabled or disabled using the following commands.
Perform the following configuration in Ethernet port view.
Ta bl e 7 Set Flow Control for Ethernet Port
Operation Command
Enable Ethernet port flow control flow-control
Disable Ethernet port flow control undo flow-control
By default, Ethernet port flow control is disabled.
Permitting/Forbidding Jumbo Frames on the Ethernet port
Using the jumbo frame enable command, you can allow jumbo frames (1523 to
to 9216 bytes) to pass through the specified Ethernet port. Note that packets of
1518 to 1522 bytes, including the IEEE 802.1Q tagging are always allowed to pass
through Ethernet ports.
Jumbo frames are only allowed for Ethernet Type II frames. Most network
equipment, including NICs, switches, and routers are not capable of supporting
jumbo frames and will always discard these packets.
Perform the following configuration in Ethernet port view.
Ta bl e 8 Permitting/Forbidding Jumbo Frames to Pass Through the Ethernet Port
Operation Command
Permit jumbo frame to pass through the
Ethernet port.
Forbid jumbo frame to pass through the
Ethernet port.
jumboframe enable [ jumboframe_value ]
undo jumboframe enable
By default, jumbo frames are disabled.
Setting the Maximum MAC Addresses an Ethernet Port Can Learn
Use the following command to set a limit on the number of MAC addresses that
an Ethernet port will learn.
Perform the following configuration in Ethernet port view.
Ta bl e 9 Set a Limit on the Number of MAC Addresses Learned by an Ethernet Port
Operation Command
Set a limit on the number of MAC addresses
learned by an Ethernet port
Restore the default limit on MAC addresses
learned by the Ethernet port
mac-address max-mac-count count
undo mac-address max-mac-count
If the count parameter is set to 0, the port is not permitted to learn MAC address.
By default, there is no limit to the amount of the MAC addresses that an Ethernet
port can learn. However the number of MAC addresses a port can learn is still
restricted by the size of the MAC address table.
Page 39

Ethernet Port Overview 31
Setting the Ethernet Port Broadcast Suppression Ratio
You can use the following commands to restrict the broadcast traffic. Once the
broadcast traffic exceeds the value set by the user, the system maintains an
appropriate broadcast packet ratio by discarding the overflow traffic. This is done
to suppress broadcast storm, avoid congestion, and ensure good traffic flow.
The parameter indicates the maximum wire speed ratio of the broadcast traffic
allowed on the port. The smaller the ratio, the smaller the amount of broadcast
traffic allowed. If the ratio is 100%, broadcast storm suppression is not performed
on the port.
Perform the following configuration in Ethernet port view.
Ta bl e 10 Setting the Ethernet Port Broadcast Suppression Ratio
Operation Command
Set the Ethernet port broadcast suppression
ratio
Restore the default Ethernet port broadcast
suppression ratio
broadcast-suppression pct
undo broadcast-suppression
By default, 100% broadcast traffic is allowed to pass through and no broadcast
suppression is performed.
Setting the Link Type for an Ethernet Port
An Ethernet port can operate in three different link modes, access, hybrid, and
trunk. The management access port carries one VLAN only and is used for
connecting to the user’s computer.
A trunk port can belong to more than one VLAN and can transmit packets on
multiple VLANs. A hybrid port can also belong to more than one VLAN and
transmit packets on multiple VLANs.
However, the hybrid port allows packets from multiple VLANs to be sent without
tags but the trunk port only allows packets from the default VLAN to be sent
without tags.
Perform the following configuration in Ethernet port view.
Ta bl e 11 Set the Link Type for an Ethernet Port
Operation Command
Configure the port as an access port port link-type access
Configure the port as a hybrid port port link-type hybrid
Configure the port as a trunk port port link-type trunk
Restore the default link type, that is, the
access port.
undo port link-type
A port on a switch can be configured as an access port, a hybrid port, or a trunk
port. However, to reconfigure between hybrid and trunk link types, you must first
restore the default, or access link type.
The default port link type is the access link type.
Page 40

32 CHAPTER 2: PORT CONFIGURATION
Adding an Ethernet Port to a VLAN
The following commands are used for adding an Ethernet port to a specified
VLAN. Access ports can be added to only one VLAN, while hybrid and trunk ports
can be added to multiple VLANs.
Perform the following configuration in Ethernet port view.
Ta bl e 12 Adding an Ethernet Port to Specified VLANs
Operation Command
Add the current access port to a specified
VLAN
Add the current hybrid port to specified
VLANs
Add the current trunk port to specified VLANs port trunk permit vlan {vlan_id_list | all}
Remove the current access port from to a
specified VLAN.
Remove the current hybrid port from to
specified VLANs.
Remove the current trunk port from specified
VLANs.
port access vlan vlan_id
port hybrid vlan vlan_id_list {tagged |
untagged}
undo port access vlan
undo port hybrid vlan vlan_id_list
undo port trunk permit vlan {vlan_id_list |
all}
The access port will be added to an existing VLAN other than VLAN 1. The VLAN
to which a Hybrid port is added must exist. The VLAN to which a Trunk port is
added cannot be VLAN 1.
After adding the Ethernet port to the specified VLANs, the local port can forward
packets from these VLANs. The hybrid and trunk ports can be added to multiple
VLANs, thereby, implementing the VLAN intercommunication between peers. For
the hybrid port, you can tag VLAN packets to process packets in different ways,
depending on the target device.
Setting the Default VLAN ID for an Ethernet Port
An access port can only be included in one VLAN so its default VLAN is the VLAN
to which it belongs.
The hybrid port and the trunk port can be included in several VLANs but a default
VLAN ID must be configured. If the default VLAN ID has been configured, the
packets without a VLAN tag are forwarded to the port that belongs to the default
VLAN. When the system sends packets with a VLAN tag, if the VLAN ID of the
packet is identical to the default VLAN ID of the port, the system will remove the
VLAN tag before sending this packet.
Perform the following configuration in Ethernet port view.
Ta bl e 13 Set the Default VLAN ID for the Ethernet Port
Operation Command
Set the default VLAN ID for the hybrid port. port hybrid pvid vlan vlan_id
Set the default VLAN ID for the trunk port port trunk pvid vlan vlan_id
Restore the default VLAN ID of the hybrid port
to the default value
Restore the default VLAN ID of the trunk port
to the default value
undo port hybrid pvid
undo port trunk pvid
Page 41

Ethernet Port Overview 33
To guarantee proper packet transmission, the default VLAN ID of local hybrid port
or Trunk port should be identical to that of the hybrid port or Trunk port on the
peer switch. The VLAN of hybrid port and trunk port is VLAN 1 by default. The
access port is the VLAN to which it belongs.
Copying a Port Configuration to Other Ports
To keep the configuration of other ports consistent with a specified port, you can
copy the configuration of that specified port to other ports. Port configuration
involves the following settings:
■ STP setting — includes STP enabling/disabling, link attribute (point-to-point or
not), STP priority, path cost, max transmission speed, loop protection, root
protection, edge port or not.
■ QoS setting — includes traffic limiting, priority marking, default 802.1p priority,
bandwidth assurance, congestion avoidance, traffic redirection, traffic
statistics.
■ VLAN setting — includes permitted VLAN types, default VLAN ID.
■ Port setting — includes port link type, port speed, duplex mode.
Perform the following configuration in system view.
Ta bl e 14 Copying a Port Configuration to Other Ports
Operation Command
Copy port configuration to other ports copy configuration source { interface-type
interface-number | interface-name |
aggregation-group agg-id } destination {
interface_list [ aggregation-group agg-id ] |
aggregation-group agg-id }
Note that if the copy source is an aggregation group, use the port with the lowest
ID as the source. If the copy destination is an aggregation group, make the
configurations of all group member ports identical with that of the source.
Displaying and Debugging Ethernet Ports
After configuration, execute the display command in all views to display the
current configuration of Ethernet port parameters, and to verify the configuration.
Use the reset command in user view to clear the statistics from the port.
Use the loopback command in Ethernet port view to configure the Ethernet port
in internal loop mode. Use the undo loopback command in Ethernet port view to
cancel the loop setting.
Ta bl e 15 Display and Debug Ethernet Port
Operation Command
Display all the information of the port display interface {interface_type |
Display hybrid port or trunk port display port {hybrid | trunk}
Clear the statistics information of the port reset counters interface [interface_type |
interface_type interface_num |
interface_name}
interface_type interface_num |
interface_name]
Page 42

34 CHAPTER 2: PORT CONFIGURATION
Example: Configuring
the Default VLAN ID of
the Trunk Port
In this example, Switch A is connected to the peer, Switch B, through the trunk
port GigabitEthernet2/1/1. Configure the trunk port with a default VLAN ID, so
that the port can forward packets to the member ports belonging to the default
VLAN when it receives them without a VLAN tag. When it sends the packets with
VLAN tag and the packet VLAN ID is the default VLAN ID, the trunk port removes
the packet VLAN tag and forward the packet.
Figure 1 Configure the Default VLAN for a Trunk Port
Switch A
Switch B
The following configurations are used for Switch A, configure Switch B in a similar
way:
1 Enter the Ethernet port view of Ethernet2/1/1.
[SW8800]interface gigabitethernet2/1/1
2 Set the GigabitEthernet2/1/1 to be a trunk port which allows VLAN 2, 6 through
50, and 100 to pass through.
[SW8800-GigabitEthernet2/1/1]port link-type trunk
[SW8800-GigabitEthernet2/1/1]port trunk permit vlan 2 6 to 50 100
Troubleshooting VLAN
Port Configuration
Configuring Link Aggregation
3 Create the VLAN 100.
[SW8800]vlan 100
4 Configure the default VLAN ID of GigabitEthernet2/1/1 as 100.
[SW8800-GigabitEthernet2/1/1]port trunk pvid vlan 100
If the default VLAN ID configuration fails, take the following steps:
1 Execute the display interface or display port command to check if the port is a
trunk port or a hybrid port. If it is neither, configure it as a trunk port or a hybrid
port.
2 Then configure the default VLAN ID.
Link aggregation means aggregating several ports together to implement the
outgoing/incoming payload balance among the member ports and to enhance
connection reliability.
For the member ports in an aggregation group, their basic configurations must be
the same. That is, if one is a trunk port, others must be trunk ports also. If a port
turns into an access port, then others must change to access ports.
Basic configuration includes:
■ STP setting
■ STP enabling and disabling
■ Link attribute (point-to-point or not)
Page 43

■ STP priority
■ Path cost
■ Maximum transmission speed
■ Loop protection
■ Root protection
■ Type of port (edge)
■ QoS setting
■ Traffic limiting
■ Priority marking
■ Default 802.1p priority
■ Bandwidth assurance
■ Congestion avoidance
■ Traffic redirection
■ Traffic statistics.
■ VLAN setting
Configuring Link Aggregation 35
■ Permitted VLAN types
■ Default VLAN ID
■ Port setting
■ Port link type
The Switch 8800 supports a maximum of 31 link aggregation groups, with a
maximum of eight ports in each group.
Load Sharing Link aggregation may be load balancing aggregation or non-load balancing
aggregation. In general, the system only provides limited load balancing
aggregation resources, so the system needs to rationally allocate these resources
among aggregation groups. The system will always allocate hardware aggregation
resources to the aggregation groups with higher priority levels. When the load
sharing aggregation resources are used up for existing aggregation groups,
newly-created aggregation groups will be non-load sharing groups. The priority
levels (in descending order) for allocating load sharing aggregation resources are
aggregation groups that:
■ Include special ports which require hardware aggregation resources
■ Are likely to reach the maximum rate after the resources are allocated to them
■ Have the minimum master port numbers if they reach an equal rate with other
groups after the resources are allocated to them
When aggregation groups of higher priority levels appear, the aggregation groups
of lower priority levels release their hardware resources. For single-port
aggregation groups, if they can transmit packets normally without occupying
hardware resources, they cannot occupy the resources.
Page 44

36 CHAPTER 2: PORT CONFIGURATION
Port State In an aggregation group, ports may be in selected or standby state and only the
selected ports can transmit user service packets. The selected port with the
minimum port number serves as the master port, while others serve as sub-ports.
In an aggregation group, the system sets the ports to selected or standby state
based on these rules:
■ The system sets the port with the highest priority to selected state, and sets
■ The system sets to standby state the ports which cannot aggregate with the
■ The system sets to standby state the ports with basic configurations different
others to standby state based on the descending order of priority levels, as
follows:
■ full duplex/high speed
■ full duplex/low-speed
■ half duplex/high speed
■ half duplex/low speed
selected port with the lowest port number, due to hardware limits.
from that of the selected port with the lowest port number.
Configuring Link
Aggregation
Only a defined number of ports can be supported in an aggregation group, so if
the selected ports in an aggregation group exceed the port quantity threshold for
that group, the system sets some ports with smaller port numbers (in ascending
order) as selected ports and others as standby ports. The selected ports can
transmit user service packets, but standby ports cannot.
A load sharing aggregation group may contain several selected ports, but a
non-load sharing aggregation group can only have one selected port, while others
are standby ports.
The Switch 8800 only supports link aggregation for ports on the same I/O module.
A maximum number of 8 ports can be selected in a link aggregation. For modules
that have fewer than 8 ports, such as the 2-port 10GBASE-X module, only two
ports can be selected members of a link aggregation.
Link aggregation configuration includes tasks described in the following sections:
■ Creating or Deleting an Aggregation Group
■ Adding or Deleting Ethernet Ports to or from an Aggregation Group
■ Setting or Deleting an Aggregation Group Descriptor
■ Displaying and Debugging Link Aggregation
Creating or Deleting an Aggregation Group
You can use the following command to create a manual aggregation group. You
can also delete an existing aggregation group. When you delete a manual
aggregation group, all its member ports are removed from the aggregation.
Page 45

Configuring Link Aggregation 37
Perform the following configuration in system view.
Ta bl e 16 Create or Delete an Aggregation Group
Operation Command
Create an aggregation group link-aggregation group agg-id mode {
manual }
Delete an aggregation group undo link-aggregation group agg-id
Adding or Deleting Ethernet Ports to or from an Aggregation Group
You can use the following commnad to add or delete ports into/from a manual
aggregation group.
Perform the following configuration in corresponding view.
Ta bl e 17 Adding or Deleting an Ethernet Port to or from an Aggregation Group
Operation Command
Add an Ethernet port into the aggregation
group (Ethernet port view)
Delete an Ethernet port from the aggregation
port (Ethernet port view)
Aggregate Ethernet ports (System view) link-aggregation interface_name1 to
port link-aggregation group agg-id
undo port link-aggregation group
interface_name2 [ both ]
Note that you must delete the aggregation group, instead of the port, if the
manual aggregation group contains only one port.
Setting or Deleting an Aggregation Group Descriptor
Perform the following configuration in system view.
Ta bl e 18 Setting or Deleting an Aggregation Group Descriptor
Operation Command
Set aggregation group descriptor link-aggregation group agg-id description
Delete aggregation group descriptor undo link-aggregation group agg-id
alname
description
By default, an aggregation group has no descriptor.
Displaying and Debugging Link Aggregation
After you have completed your configuration, execute the display command in
any view to display the link aggregation configuration, and to verify the effect of
the configuration.
Ta bl e 19 Display and Debug Link Aggregation
Operation Command
Display summary information of all
aggregation groups
Display detailed information of a specific
aggregation group
display link-aggregation summary
display link-aggregation verbose agg-id
Page 46

38 CHAPTER 2: PORT CONFIGURATION
Table 19 Display and Debug Link Aggregation (continued)
Operation Command
Display detailed link aggregation information
at the port
Disable/enable debugging link aggregation
errors
Disable/enable debugging link aggregation
events
display link-aggregation interface {
interface-type interface-number |
interface-name } [ to { interface-type
interface-num | interface-name } ]
[ undo ] debugging link-aggregation error
[ undo ] debugging link-aggregation
event
Example: Link
Aggregation
Configuration
Switch A connects switch B with three aggregation ports, numbered as
GigabitEthernet2/1/1 to GigabitEthernet2/1/3, so that the incoming and outgoing
loads can be balanced among the member ports.
Figure 2 Networking For Link Aggregation
Link aggregation
Switch A Switch B
The following code example lists only the configuration for switch A. The
configuration for switch B is similar.
1 Configure aggregation group 1.
[SW8800]link-aggregation group 1 mode manual
Add Ethernet ports GigabitEthernet2/1/1 to GigabitEthernet2/1/3 into
aggregation group 1.
[SW8800]interface gigabitethernet2/1/1
[SW8800-GigabitEthernet2/1/1]port link-aggregation group 1
[SW8800-GigabitEthernet2/1/1]interface ethernet2/1/2
[SW8800-GigabitEthernet2/1/2]port link-aggregation group 1
[SW8800-GigabitEthernet2/1/2]interface ethernet2/1/3
[SW8800-GigabitEthernet2/1/3]port link-aggregation group 1
Page 47

VLAN CONFIGURATION
3
This chapter covers the following topics:
■ VLAN Overview
■ Configuring VLANs
■ Configuring GARP/GVRP
VLAN Overview A virtual local area network (VLAN) creates logical groups of LAN devices into
segments to implement virtual workgroups.
Using VLAN technology, you can logically divide the physical LAN into different
broadcast domains. Every VLAN contains a group of workstations with the same
resource requirements. However, the workstations of a VLAN do not have to
belong to the same physical LAN segment.
Within a VLAN, broadcast and unicast traffic is not forwarded to other VLANs.
Therefore, VLAN configurations are very helpful in controlling network traffic,
simplifying network management, and improving security.
The Switch 8800 supports port-based VLANs, which define VLAN members
according to switch ports. This is the simplest and most efficient way to create
VLANs.
Configuring VLANs The following sections describe how to configure VLANs:
■ Common VLAN Configuration Tasks
Common VLAN
Configuration Tasks
The following sections discuss the common tasks for configuring a VLAN:
■ Creating or Deleting a VLAN
■ Adding Ethernet Ports to a VLAN
■ Setting or Deleting the VLAN Description Character String
■ Specifying or Removing VLAN Interfaces
■ Shutting Down or Enabling a VLAN Interface
■ Displaying and Debugging a VLAN
Creating or Deleting a VLAN
Use the following command to create or delete a VLAN.
Page 48

40 CHAPTER 3: VLAN CONFIGURATION
Perform the following configurations in system view.
Ta bl e 1 Creating or Deleting a VLAN
Operation Command
Create and enter a VLAN view vlan vlan_id
Delete the specified VLAN undo vlan { vlan_id [ to vlan_id ] / all }
The command creates the VLAN then enters the VLAN view. If the VLAN already
exists, the command enters the VLAN view directly.
Note that the default VLAN, VLAN 1, cannot be deleted.
Adding Ethernet Ports to
a VLAN
Use the port interface_list command to add the Ethernet ports to a VLAN.
Perform the following configuration in VLAN view.
Ta bl e 2 Adding Ethernet Ports to a VLAN
Operation Command
Add Ethernet ports to a VLAN port interface_list
Remove Ethernet ports from a VLAN undo port interface_list
By default, the system adds all the ports to a default VLAN, whose ID is 1.
You can add or delete trunk port and hybrid ports to or from a VLAN by the port
and undo port commands in Ethernet port view, but not in VLAN view.
Setting or Deleting the VLAN Description Character String
You can use the following command to set or delete the VLAN description
character string.
You can use description character strings, such as workgroup_name and
department_name, to distinguish the different VLANs.
Perform the following configuration in VLAN view.
Ta bl e 3 Setting and Deleting VLAN Description Character String
Operation Command
Set the description character string for the
specified VLAN
Delete the description character string of the
specified VLAN
description string
undo description
By default, the VLAN description character string is the VLAN ID of the VLAN,
VLAN 0001. The VLAN interface description character string is the VLAN interface
name, for example, 3Com, Switch 8800, Vlan-interface1 Interface.
Specifying or Removing VLAN Interfaces
You can use the following command to specify or remove the VLAN interfaces. To
implement the network layer function on a VLAN interface, the VLAN interface
should be configured with an IP address and mask. For the corresponding
configuration, refer to
“Network Protocol Operation” on page 49.
Page 49

Configuring VLANs 41
Perform the following configurations in system view.
Ta bl e 4 Specifying and Removing VLAN interfaces
Operation Command
Create a new VLAN interface
and enter VLAN interface view
Remove the specified VLAN
interface
interface vlan-interface vlan_id
undo interface vlan-interface vlan_id
Create a VLAN before creating an interface for it.
Shutting Down or Enabling a VLAN Interface
Use the following command to shut down or enable a VLAN interface.
Perform the following configuration in VLAN interface view.
Ta bl e 5 Shutting Down or Enabling a VLAN Interface
Operation Command
Shut down the VLAN interface shutdown
Enable the VLAN interface undo shutdown
Example: VLAN
Configuration
The operation of shutting down or enabling the VLAN interface has no effect on
the UP/DOWN status of the Ethernet ports in the VLAN.
By default, when the status of all Ethernet ports in a VLAN is DOWN, the status of
the VLAN interface is DOWN also so the VLAN interface is shut down. When the
status of one or more Ethernet ports is UP, the status of the VLAN interface is UP
also, so the VLAN interface is enabled.
Displaying and Debugging a VLAN
After the configuring a VLAN, execute the display command in any view to
display the VLAN configuration, and to verify the effect of the configuration.
Ta bl e 6 Displaying and Debugging a VLAN
Operation Command
Display the information about a VLAN
interface
Display the information about a VLAN display vlan [ vlan_id | all | static | dynamic ]
display interface vlan-interface [ vlan_id ]
Create VLAN2 and VLAN3. Add GigabitEthernet3/1/1 and GigabitEthernet4/1/1 to
VLAN2 and add GigabitEthernet3/1/2 and GigabitEthernet4/1/2 to VLAN3.
Page 50

42 CHAPTER 3: VLAN CONFIGURATION
Figure 1 VLAN Configuration Example
Switch 8800
Configuring GARP/GVRP
E3/1/1
VLAN2
E4/1/1
E3/1/2
VLAN3
E4/1/2
1 Create VLAN 2 and enter its view.
[SW8800]vlan 2
2 Add GigabitEthernet3/1/1 and GigabitEthernet4/1/1 to VLAN2.
[SW8800-vlan2]port GigabitEthernet3/1/1 GigabitEthernet4/1/1
3 Create VLAN 3 and enters its view.
[SW8800-vlan2]vlan 3
4 Add GigabitEthernet3/1/2 and GigabitEthernet4/1/2 to VLAN3.
[SW8800-vlan3]port GigabitEthernet3/1/2 GigabitEthernet4/1/2
Generic Attribute Registration Protocol (GARP), allows members in the same
switching network to distribute, propagate, and register information, such as
VLAN and multicast addresses.
GARP does not exist in a switch as an entity. A GARP participant is called a GARP
application. The main GARP applications are GVRP and GMRP. GVRP is described
Configuring GARP/GVRP and GMRP is described in “GMRP” on page 203.
in
When a GARP participant is on a port of the switch, each port corresponds to a
GARP participant.
Through GARP, configuration information on one GARP member is advertised to
the entire switching network. A GARP member can be a terminal workstation or a
bridge. A GARP member can notify other members to register or remove its
Page 51

Configuring GARP/GVRP 43
attribute information by sending join declarations or withdrawal declarations. It
can also register or remove the attribute information of other GARP members
according to the join declarations or withdrawal declarations that it receives from
them.
GARP members exchange information by sending GARP messages. There are three
main types of GARP messages, including join, leave, and leaveall. When a GARP
participant wants to register its attribute information on other switches, it sends a
join message. When the GARP participant wants to remove its attribute
information from other switches, it sends a leave message. The leaveall timer is
started at the same time that each GARP participant is enabled and a leaveall
message is sent out when the leaveall timer times out. The join and leave
messages cooperate to ensure the logout and the re-registration of a message. By
exchanging messages, all the attribute information to be registered can be
propagated to all the switches in the same switching network.
The destination MAC addresses of the packets of the GARP participants are
specific multicast MAC addresses. A switch that supports GARP classifies the
packets that it receives from GARP participants and processes them with the
corresponding GARP applications (GVRP or GMRP).
GARP and GMRP are described in detail in the IEEE 802.1p standard. The Switch
8800 fully supports GARP compliant with the IEEE standards.
■ The value of the GARP timer is used in all GARP applications, including GVRP
and GMRP, that are running in a switched network.
■ In one switched network, GARP timers on all the switching devices should be
set to the same value.
Setting the GARP Timers
GARP timers include the hold, join, and leaveall timers.
The GARP participant sends join message regularly when the join timer times out
so that other GARP participants can register its attribute values.
When the GARP participant wants to remove attribute values, it sends a leave
message. When the leave message arrives, the receiving GARP participant starts
the leave timer. If the receiving participant does not receive a join message from
the sender before the leave timer expires, the receiving participant removes the
sender’s GARP attribute values.
The leaveall timer is started as soon as a GARP participant joins. A leaveall message
is sent at timeout so that other GARP participants remove all the attribute values
of this participant. Then, the leaveall timer is restarted and a new cycle begins.
When a switch receives GARP registration information, it does not send a join
message immediately. Instead, it enables a hold timer and sends the join message
outward when the hold timer times out. In this way, all the VLAN registration
Page 52

44 CHAPTER 3: VLAN CONFIGURATION
information received within the time specified by the hold timer can be sent in one
frame to save bandwidth.
Ta bl e 7 Setting the GARP Timers
Operation Command
Configure the hold, join, and leave timers in Ethernet port view.
Set the GARP hold, join, and leave
timers
Restore the default GARP hold,
join, and leave timer settings
Configure the leaveall timer in system view.
Set GARP leaveall timer garp timer leaveall timer_value
Restore the default GARP leaveall
timer settings.
The value of the join timer should be no less than twice the value of the hold
timer, and the value of the leave timer should be greater than twice the value of
the join timer and smaller than the leaveall timer value. Otherwise, the system
displays an error message.
garp timer { hold | join | leave } timer_value
undo garp timer { hold | join | leave }
undo garp timer leaveall
Join timer > 2 x hold timer > leave timer < leavall timer
GARP timers have the following default values:
■ Hold timer — 10 centiseconds
■ Join timer — 20 centiseconds,
■ Leave timer — 60 centiseconds
■ Leaveall timer — 1000 centiseconds.
Displaying and Debugging GARP
After you configure the GARP timer, use the display command in all views to
display the GARP configuration, and to verify the effect of the configuration.
Execute the reset command in user view to reset the GARP configuration.
Execute the debugging command in user view to debug the GARP configuration.
Ta bl e 8 Display and Debug GARP
Operation Command
Display GARP statistics information display garp statistics [ interface interface-list ]
Display GARP timer display garp timer [ interface interface-list ]
Reset GARP statistics information reset garp statistics [ interface interface-list ]
Enable GARP event debugging debugging garp event
Disable GARP event debugging undo debugging garp event
Configuring GVRP GARP VLAN Registration Protocol (GVRP) is a GARP application. GVRP is based on
the GARP, and maintains the dynamic VLAN registration information in the switch
and distributes the information to other switches. All the GVRP-supporting
switches can receive VLAN registration information from other switches and can
Page 53

Configuring GARP/GVRP 45
dynamically update local VLAN registration information, including the active
members and the port through which each member can be reached.
All the switches that support GVRP can distribute their local VLAN registration
information to other switches so that VLAN information is consistent on all GVRP
devices in the same network. The VLAN registration information that is distributed
by GVRP includes both the local static registration information that is configured
manually and the dynamic registration information received from other switches.
GVRP is described in the IEEE 802.1Q standard. The Switch 8800 fully supports
GARP compliant with the IEEE standards.
GVRP configuration steps include tasks described in the following sections:
■ Enabling or Disabling Global GVRP
■ Enabling or Disabling Port GVRP
■ Setting the GVRP Registration Type
When you configure GVRP, you need to enable it globally and for each port
participating in GVRP. Similarly, the GVRP registration type can take effect only
after you configure port GVRP. In addition, you must configure GVRP on the trunk
port.
Enabling or Disabling Global GVRP
Use the following commands to enable or disable global GVRP.
Perform the following configurations in system view.
Ta bl e 9 Enabling/Disabling Global GVRP
Operation Command
Enable global GVRP gvrp
Disable global GVRP undo gvrp
By default, GVRP is disabled on a port.
Enabling or Disabling Port GVRP
Use the following commands to enable or disable GVRP on a port.
Perform the following configurations in Ethernet port view.
Ta bl e 10 Enabling/Disabling Port GVRP
Operation Command
Enable port GVRP gvrp
Disable port GVRP undo gvrp
You should enable GVRP globally before you enable it on the port. GVRP can only
be enabled or disabled on a trunk port.
By default, global GVRP is disabled.
Page 54

46 CHAPTER 3: VLAN CONFIGURATION
Setting the GVRP Registration Type
The GVRP includes normal, fixed, and forbidden registration types (see IEEE
802.1Q).
■ When an Ethernet port registration type is set to normal, the dynamic and
■ When one trunk port registration type is set to fixed, the system adds the port
■ When an Ethernet port registration type is set to forbidden, all the VLANs
Perform the following configurations in Ethernet port view.
Ta bl e 11 Setting the GVRP Registration Type
Operation Command
Set GVRP registration type gvrp registration { normal | fixed | forbidden }
Set the GVRP registration type back
to the default setting
manual creation, registration, and logout of VLAN are allowed on this port.
to the VLAN if a static VLAN is created on the switch and the trunk port allows
VLAN passing. GVRP also adds this VLAN item to the local GVRP database, one
link table for GVRP maintenance. However, GVRP cannot learn dynamic VLAN
through this port.
except VLAN1 are removed and no other VLANs can be created or registered
on this port.
undo gvrp registration
Example: GVRP
Configuration Example
By default, the GVRP registration type is normal.
Displaying and Debugging GVRP
After you set the GVRP registration type, execute the display command in all
views to display the GVRP configuration and to verify the effect of the
configuration.
Execute the debugging command in user view to debug the configuration of
GVRP.
Ta bl e 12 Displaying and Debugging GVRP
Operation Command
Display GVRP statistics information display gvrp statistics [ interface interface-list ]
Display GVRP global status
information
Enable GVRP packet or event
debugging
Disable GVRP packet or event
debugging
display gvrp status
debugging gvrp { packet | event}
undo debugging gvrp { packet | event}
Set network requirements to dynamically register and update VLAN information
among switches.
Page 55

Figure 2 GVRP Configuration Example
Configuring GARP/GVRP 47
E3/1/1
E4/1/1
Switch A
Switch B
Configure Switch A:
1 Set GigabitEthernet3/1/1 as a trunk port and allow all the VLANs to pass through.
[SW8800]interface GigabitEthernet3/1/1
[SW8800-GigabitEthernet3/1/1]port link-type trunk
[SW8800-GigabitEthernet3/1/1]port trunk permit vlan all
2 Enable GVRP on the trunk port.
[SW8800-GigabitEthernet3/1/1]gvrp
Configure Switch B:
1 Enable GVRP globally.
[SW8800]gvrp
2 Set Gigabit Ethernet4/1/1 as a trunk port and allow all the VLANs to pass
through.
[SW8800]interface GigabitEthernet4/1/1
[SW8800-GigabitEthernet4/1/1]port link-type trunk
[SW8800-GigabitEthernet4/1/1]port trunk permit vlan all
3 Enable GVRP on the trunk port.
[SW8800-GigabitEthernet4/1/1]gvrp
Page 56

48 CHAPTER 3: VLAN CONFIGURATION
Page 57

4
NETWORK PROTOCOL OPERATION
This chapter covers the following topics:
■ Configuring IP Address
■ Configuring Address Resolution Protocol (ARP)
■ DHCP Relay
■ IP Performance
Configuring IP Address
IP address is a 32-bit address represented by four octets. IP addresses are divided
into five classes, A, B, C, D and E. The octets are set according to the first few bits
of the first octet.
The rule for IP address classification is described as follows:
■ Class A addresses are identified with the first bit of the first octet being 0.
■ Class B addresses are identified with the first bits of the first octet being 10.
■ Class C addresses are identified with the first bits of the first octet being 110.
■ Class D addresses are identified with the first bits of the first octet being 1110.
■ Class E addresses are identified with the first bits of the first octet being 11110.
Addresses of Classes A, B and C are unicast addresses. The Class D addresses are
multicast addresses and Class E addresses are reserved for future uses.
At present, IP addresses are mostly Class A, Class B and Class C. IP addresses of
Classes A, B and C are composed of two parts, network ID and host ID. Their
network ID lengths are different.
■ Class A IP addresses use only the first octet to indicate the network ID.
■ Class B IP addresses use the first two octets to indicate the network ID.
■ Class C IP addresses use the first three octets to indicate the network ID.
At most, there are: 28 =128 Class A addresses, 216=16384 Class B addresses and
224=2,097,152 Class C addresses.
The IP address is in dotted decimal format. Each IP address contains 4 integers in
dotted decimal notation. Each integer corresponds to one byte,
e.g.,10.110.50.101.
Configuring an IP Address is described in the following sections:
■ Subnet and Mask
■ Configuring an IP Address
Page 58

50 CHAPTER 4: NETWORK PROTOCOL OPERATION
■ Troubleshooting an IP Address Configuration
Subnet and Mask IP protocol allocates one IP address for each network interface. Multiple IP
addresses can only be allocated to a device which has multiple network interfaces.
IP addresses on a device with multiple interfaces have no relationship among
themselves.
With the rapid development of the Internet, IP addresses are depleting very fast.
The traditional IP address allocation method uses up IP addresses with little
efficiency. The concept of mask and subnet was proposed to make full use of the
available IP addresses.
A mask is a 32-bit number corresponding to an IP address. The number consists of
1s and 0s. Principally, these 1s and 0s can be combined randomly. However, the
first consecutive bits are set to 1s when designing the mask. The mask is divided
into two parts, the subnet address and host address. The 1 bits and the mask
indicate the subnet address, and the other bits indicate the host address.
If there is no sub-net division, then the sub-net mask is the default value and the
length of “1” indicates the net-id length. Therefore, for IP addresses of classes A,
B and C, the default values of the corresponding sub-net mask is 255.0.0.0 for
Class A, 255.255.0.0 for Class B, and 255.255.255.0 for Class C.
Configuring an IP
Address
The mask can be used to divide a Class A network containing more than
16,000,000 hosts or a Class B network containing more than 60,000 hosts into
multiple small networks. Each small network is called a subnet. For example, for
the Class A network address 10.110.0.0, the mask 255.255.224.0 can be used to
divide the network into 8 subnets: (10.110.0.0, 10.110.32.0, 10.110.64.0, and so
on). Each subnet can contain more than 8000 hosts.
The following sections describe the tasks for configuring an IP address:
■ Configure the Host IP Address and HostName for a Host
■ Configuring the IP Address of the VLAN Interface
■ Displaying and Debugging an IP Address
Configure the Host IP Address and HostName for a Host
This command creates correspondence between the name and the IP address of
the host. When you use applications like Telnet, you can use the host name
without having to memorize the IP address because the system translates the
name to the IP address automatically.
Perform the following configuration in System view.
Ta bl e 1 Configure the Host Name and the Corresponding IP Address
Operation Command
Configure the host name and the
corresponding IP address
Delete the host name and the corresponding
IP address
ip host hostname ip-address
undo ip host hostname [ ip-address ]
By default, there is no host name associated to any host IP address.
Page 59

Configuring IP Address 51
Configuring the IP Address of the VLAN Interface
You can configure a maximum of ten IP addresses for a VLAN interface.
Perform the following configuration in VLAN interface view.
Ta bl e 2 Configure IP Address for a VLAN Interface
Operation Command
Configure IP address for a VLAN interface ip address ip-address net-mask [ sub ]
Delete the IP address of a VLAN interface [ undo ] ip address [ ip-address { net-mask |
mask-length } [ sub ] ]
The network ID of an IP address is identified by the mask. For example, the IP
address of a VLAN interface is 129.9.30.42 and the mask is 255.255.0.0. After
performing the AND operation for the IP address and the mask, you can assign
that device to the network segment 129.9.0.0.
Generally, it is sufficient to configure one IP address for an interface. However, you
can also configure more than one IP address for an interface so that it can be
connected to several subnets. Among these IP addresses, one is the primary IP
address and all others are secondary.
Example: Configuring
an IP Address
By default, the IP address of a VLAN interface is null.
Displaying and Debugging an IP Address
Use the display command in all views to display the IP address configuration on
interfaces, and to verify configuration.
Ta bl e 3 Display and Debug IP Address
Operation Command
Display all hosts on the network and the
corresponding IP addresses
Display the configurations of each interface display ip interface vlan-interface vlan-id
display ip hosts
Configure the IP address as 129.2.2.1 and sub-net mask as 255.255.255.0 for the
VLAN interface 1 of the Switch 8800.
Figure 1 IP Address Configuration Networking
Switch
Console cable
PC
1 Enter VLAN interface 1.
[SW8800]interface vlan 1
2 Configure the IP address for VLAN interface 1.
[SW8800-vlan-interface1]ip address 129.2.2.1 255.255.255.0
Page 60

52 CHAPTER 4: NETWORK PROTOCOL OPERATION
Troubleshooting an IP
Address Configuration
Configuring Address Resolution Protocol (ARP)
If the Switch 8800 cannot ping a certain host on the LAN, proceed as follows:
1 Determine which VLAN includes the port connected to the host. Check whether
the VLAN has been configured with the VLAN interface. Determine whether the IP
address of the VLAN interface and the host are on the same network segment.
2 If the configuration is correct, enable ARP debugging on the switch from user
level, and check whether or not the switch can correctly send and receive ARP
packets. If it can only send but not receive the ARP packets, there are probably
errors at the Ethernet physical layer.
An IP address cannot be directly used for communication between network
devices, because devices can only identify MAC addresses. An IP address is the
address of a host at the network layer. To send data packets through the network
layer to the destination host, the physical address of the host is required. So the IP
address must be resolved to a physical address.
When two hosts in Ethernet communicate, they must know each other’s MAC
address. Every host maintains an IP-MAC address translation table, which is known
as the ARP mapping table. A series of maps between IP addresses and MAC
addresses of other hosts are stored in the ARP mapping table. When a dynamic
ARP mapping entry is not in use for a long time, the host will remove it from the
mapping table to save memory space and shorten the search interval.
Example: IP Address
Resolution
Host A and Host B are on the same network segment. The IP address of Host A is
IP_A and the IP address of Host B is IP_B. Host A wants to transmit packets to Host
B. Host A checks its own ARP mapping table first to make sure that there are
corresponding ARP entries of IP_B in the table. If the corresponding MAC address
is found, Host A will use the MAC address in the ARP mapping table to
encapsulate the IP packet in an Ethernet frame and send it to Host B. If the
corresponding MAC address is not found, Host A will store the IP packet in the
queue waiting for transmission, and broadcast an ARP request to attempt to
resolve the MAX address of Host B.
The ARP request packet contains the IP address of Host B and the IP address and
MAC address of Host A. Since the ARP request packet is broadcast, all hosts on
the network segment receive the request. However, only the requested host (i.e.,
Host B) needs to process the request. Host B will first store the IP address and the
MAC address of the request sender (Host A) from the ARP request packet in its
own ARP mapping table. Host B will then generate an ARP reply packet and add
the MAC address of Host B before sending it to Host A. The reply packet will be
sent directly to Host A instead of being broadcast. Upon receiving the reply
packet, Host A will extract the IP address and the corresponding MAC address of
Host B and add them to its own ARP mapping table. Then Host A will send Host B
all the packets standing in the queue.
Normally, dynamic ARP executes and automatically attempts to resolve the IP
address to an Ethernet MAC address with no intervention from the administrator.
Configuring ARP The ARP mapping table can be maintained dynamically or manually. Addresses
that are mapped manually are referred to as static ARP. The user can display, add,
or delete the entries in the ARP mapping table through manual commands.
Page 61

Configuring Address Resolution Protocol (ARP) 53
ARP configuration includes tasks described in the following sections:
■ Manually Adding/Deleting Static ARP Mapping Entries
■ Learning Gratuitous ARPs
■ Configuring the Dynamic ARP Aging Timer
■ Displaying and Debugging ARP
Manually Adding/Deleting Static ARP Mapping Entries
Perform the following configuration in System view.
Ta bl e 4 Manually Adding/Deleting Static ARP Mapping Entries
Operation Command
Manually add a static ARP mapping entry arp static ip-address mac-address VLANID {
interface_type interface_num | interface_name
}
Manually delete a static ARP mapping entry undo arp static ip-address
Static ARP mapping entries will not time out, however dynamic ARP mapping
entries time out after 20 minutes.
The ARP mapping table is empty and the address mapping is obtained through
dynamic ARP by default.
Learning Gratuitous ARPs
Perform the following configuration in System view.
Ta bl e 5 Learning Gratuitous ARPs
Operation Command
Enable the switch to learn gratuitous ARPs gratuitous-arp-learning enable
Prevent the switch from learning gratuitous
ARPs
undo gratuitous-arp-learning enable
By default, the switch does not learn gratuitous ARPs.
Configuring the Dynamic ARP Aging Timer
The following commands assign a dynamic ARP aging period to enable flexible
configurations. When the system learns a dynamic ARP entry, its aging period is
based on the currently configured value.
Perform the following configuration in system view.
Ta bl e 6 Configure the Dynamic ARP Aging Timer
Operation Command
Configure the dynamic ARP aging timer arp timer aging aging-time
Restore the default dynamic ARP aging time undo arp timer aging
By default, the aging time of the dynamic ARP aging timer is 20 minutes.
Displaying and Debugging ARP
After the previous configuration, execute display command in all views to display
the operation of the ARP configuration, and to verify the effect of the
Page 62

54 CHAPTER 4: NETWORK PROTOCOL OPERATION
DHCP clients
Switch
Intranet
DHCP client
DHCP server
Ethernet
Ethernet
configuration. Execute the debugging command in user view to debug the ARP
configuration.
Ta bl e 7 Display and Debug ARP
Operation Command
Display ARP mapping table display arp [ ip-address | [ static | dynamic ] [
{ begin | include | exclude } text ] ]
Display the current setting of the dynamic
ARP map aging timer
Enable ARP information debugging debugging arp { error | info | packet }
Disable ARP information debugging undo debugging arp { error | info | packet }
display arp timer aging
By default, all ARP mapping entries of the Ethernet switch are displayed.
DHCP Relay Dynamic Host Configuration Protocol (DHCP) offers dynamic IP address
assignment. DHCP works in Client-Server mode. With this protocol, the DHCP
Client can dynamically request configuration information and the DHCP server can
configure the information for the Client.
The DHCP relay serves as conduit between the DHCP Client and the server located
on different subnets. The DHCP packets can be relayed to the destination DHCP
server (or Client) across network segments. The DHCP clients on different
networks can use the same DHCP server. This is economical and convenient for
centralized management.
Figure 2 DHCP Relay Schematic Diagram
DHCP client
Ethernet
Intranet
DHCP clients
Switch
Ethernet
DHCP server
When the DHCP Client performs initialization, it broadcasts the request packet on
the local network segment. If there is a DHCP server on the local network segment
(e.g. the Ethernet on the right side of the figure), then the DHCP can be
configured directly without the relay. If there is no DHCP server on the local
network segment, DHCP relay will process the received broadcast packets and
forward them to remote DHCP servers. The server configures the clients based on
the information provided in the DHCP request packet and in the server setup.
Then the server transmits the configuration information to the clients through the
DHCP relay, thereby, completing the dynamic configuration of the client.
Page 63

DHCP Relay 55
Configuring DHCP is described in the following sections:
■ Configuring DHCP Relay
■ Troubleshooting a DHCP Relay Configuration
Configuring DHCP Relay DHCP relay configuration includes tasks described in the following sections:
■ Configuring a DHCP Server IP Address in a DHCP Server Group
■ Configuring the DHCP Server Group for the VLAN Interface
■ Configuring the Address Table Entry
■ Enabling/Disabling DHCP Security Features
■ Enabling/Disabling DHCP Pseudo-server Detection
■ Displaying and Debugging DHCP Relay
The server IP address is associated , through its DHCP server group, with a specific
VLAN interface. This implementation differs from others in which the server IP is a
global parameter.
Configuring a DHCP Server IP Address in a DHCP Server Group
You can set master and slave DHCP servers on a network segment to promote the
reliability of the device. The master and slave DHCP servers form a DHCP server
group. You can specify the IP addresses of the two servers using the following
command.
Perform the following configuration in System view.
Ta bl e 8 Configure/Delete the IP Address of the DHCP Server
Operation Command
Configure the IP address for a DHCP Server dhcp-server groupNo ip ipaddress1 [
Remove all the IP addresses of the DHCP
Server (set the IP addresses of the primary and
secondary servers to 0).
ipaddress2 ]
undo dhcp-server groupNo
The backup server IP address cannot be configured independently, instead, it has
to be configured together with the master server IP address.
By default, the IP address of the DHCP Server is not configured. The DHCP Server
address must be configured before DHCP relay can be used.
Configuring the DHCP Server Group for the VLAN Interface
Perform the following configuration in VLAN interface view.
Ta bl e 9 Configure/Delete the Corresponding DHCP Server Group of VLAN Interface
Operation Command
Configure the DHCP server group for the
VLAN interface
Delete the DHCP server group for the VLAN
interface
dhcp-server groupNo
undo dhcp-server
Page 64

56 CHAPTER 4: NETWORK PROTOCOL OPERATION
When associating a VLAN interface to a new DHCP server group, you can
configure the association without disassociating it from the previous group.
By default, VLAN interfaces have no associated DHCP server group.
Configuring the Address Table Entry
To check the address of users who have valid and fixed IP addresses in the VLAN
(with DHCP enabled), it is necessary to add an entry in the static address table.
Perform the following configuration in system view.
Ta bl e 10 Configure/Delete the Address Table Entry
Operation Command
Add an entry to the address table dhcp-security static ip_address mac_address
Delete an entry from the address table undo dhcp-security { ip_address | all |
Enabling/Disabling DHCP Security Features
Enabling DHCP security features starts an address check on the VLAN interface,
while disabling DHCP security features cancels an address check.
{ dynamic | static }
dynamic | static }
Perform the following configuration in VLAN interface view.
Ta bl e 11 Enable/Disable DHCP Security on VLAN Interfaces
Operation Command
Enable DHCP security features address-check enable
Disable DHCP security features on VLAN
interface
address-check disable
By default, DHCP security features function are disabled.
Enabling/Disabling DHCP Pseudo-server Detection
Suppose there is a DHCP server placed on a network without permission. When
there is a user request for an IP address, the DHCP server will interact with the
DHCP client, leading the user to get a wrong IP address. In this case, the user will
be unable to access the network. Such a DHCP server is called DHCP
pseudo-server.
After a DHCP pseudo-server detection-enabled, switch will record the information
of the DHCP servers such as their IP addresses so that the administrator can
discover the DHCP pseudo-servers.
Perform the following configuration in system view.
Ta bl e 12 Enabling and Disabling DHCP Pseudo-server Detection
Operation Command
Enable DHCP pseudo-server detection dhcp-server detect
Disable DHCP pseudo-server detection undo dhcp-server detect
By default, DHCP pseudo-server detection is disabled.
Page 65

DHCP Relay 57
Displaying and Debugging DHCP Relay
Execute display command in all views to display the current DHCP Relay
configuration, and to verify the effect of the configuration. Execute the
debugging command in user view to debug DHCP Relay configuration.
Ta bl e 13 Displaying and Debugging DHCP Relay
Operation Command
Display the information about the DHCP
server group
Display the information about the DHCP
server group corresponding to the VLAN
interface.
Enable DHCP relay debugging debugging dhcp-relay
Disable DHCP relay debugging undo debugging dhcp-relay
Display address information for all the legal
clients of the DHCP Server group.
display dhcp-server groupNo
display dhcp-server interface
vlan-interface vlan-id
display dhcp-security [ ip_address |
dynamic | static ]
Example: Configuring
DHCP Relay
Configure the VLAN interface corresponding to the user and the related DHCP
server so as to use DHCP relay.
Figure 3 Networking Diagram of Configuring DHCP Relay
1.99.255.36
Server Group 1
VLAN 2
VLAN 3
Switch
VLAN
4000
VLAN
3001
1.99.255.35
IP Network
1.88.255.36
Server Group 2
1.88.255.35
1 Configure the DHCP Server IP addresses into DHCP Server Group 1.
[SW8800]dhcp-server 1 ip 1.99.255.36 1.99.255.35
2 Associate DHCP Server Group 1 with VLAN interface 2.
[SW8800-VLAN-Interface2]dhcp-server 1
3 Configure the IP address corresponding to DHCP server group 2.
[SW8800]dhcp-server 2 ip 1.88.255.36 1.88.255.35
4 Associate the DHCP Server Group 2 with VLAN interface 3.
[SW8800-VLAN-Interface3]dhcp-server 2
5 Configure the corresponding interface and gateway address of VLAN2.
[SW8800]vlan 2
[SW8800-vlan2]port GigabitEthernet 1/1/2
[SW8800]interface vlan 2
[SW8800-VLAN-Interface2]ip address 1.1.2.1 255.255.0.0
Page 66

58 CHAPTER 4: NETWORK PROTOCOL OPERATION
6 Configure the corresponding interface and gateway address of VLAN3.
[SW8800]vlan 3
[SW8800-vlan3]port GigabitEthernet 1/1/3
[SW8800]interface vlan 3
[SW8800-VLAN-Interface3]ip address 21.2.2.1 255.255.0.0
7 It is necessary to configure a VLAN for the servers. The corresponding interface
VLAN of the DHCP server group 1 is configured as 4000, and that of the group 2
is configured as 3001.
[SW8800]vlan 4000
[SW8800-vlan4000]port GigabitEthernet 1/1/4
[SW8800]interface vlan 4000
[SW8800-VLAN-Interface4000]ip address 1.99.255.1 255.255.0.0
[SW8800]vlan 3001
[SW8800-vlan3001]port GigabitEthernet 1/1/5
[SW8800]interface vlan 3001
[SW8800-VLAN-Interface3001]ip address 1.88.255.1 255.255.0.0
In this example, clients on VLAN2 will receive IP addresses from the servers in
DHCP server group 1 (VLAN 4000). Clients on VLAN3 will receive IP addresses
from the servers in DHCP server group 2 (VLAN 3001).
Troubleshooting a DHCP
Relay Configuration
8 Show the configuration of DHCP server groups in User view.
<SW8800>display dhcp-server 1
9 Show the DHCP Server Group number corresponding to the VLAN interface in
User view.
<SW8800>display dhcp-server interface vlan-interface 2
<SW8800>display dhcp-server interface vlan-interface 3
Perform the following procedure if a user cannot apply for an IP address
dynamically:
1 Use the display dhcp-server groupNo command to check if the IP address of the
corresponding DHCP server has been configured.
2 Use the display VLAN and display IP commands to check if the VLAN and the
corresponding interface IP address have been configured.
3 Ping the configured DHCP Server to ensure that the link is connected.
4 Ping the IP address of the VLAN interface of the switch to where the DHCP user is
connected from the DHCP server to make sure that the DHCP server can correctly
find the route of the network segment the user is on. If the ping execution fails,
check if the default gateway of the DHCP server has been configured as the
address of the VLAN interface that it locates on.
5 If no problems are found in the last two steps, use the display dhcp-server
groupNo command to view the packet that has been received. If you only see the
Discover packet and there is no response packet, it means the DHCP Server has
not sent the message to the Switch 8800. In this case, check if the DHCP Server
has been configured properly. If the numbers of request and response packets are
normal, enable the debugging dhcp-relay in User view and then use the terminal
debugging command to output the debugging information to the console. In
this way, you can view the detailed information of all DHCP packets on the
console while applying for the IP address, thereby, conveniently locating the
problem.
Page 67

IP Performance IP performance configuration includes:
■ Configuring TCP Attributes
■ Displaying and Debugging IP Performance
■ Troubleshooting IP Performance
IP Performance 59
Configuring TCP
Attributes
The TCP attributes that can be configured include:
■ synwait timer: When sending the syn packets, TCP starts the synwait timer. If
response packets are not received before synwait timeout, the TCP connection
will be terminated. The timeout of synwait timer ranges 2 to 600 seconds and
it is 75 seconds by default.
■ finwait timer: When the TCP connection state turns from FIN_WAIT_1 to
FIN_WAIT_2, finwait timer will be started. If FIN packets are not received before
finwait timer timeout, the TCP connection will be terminated. Finwait ranges
76 to 3600 seconds and it is 675 seconds by default.
■ The receiving/sending buffer size of connection-oriented Socket is in the range
from 1 to 32K bytes and is 4K bytes by default.
Perform the following configuration in System view.
Ta bl e 14 Configure TCP Attributes
Operation Command
Configure synwait timer time for TCP
connection establishment
Restore synwait timer time for TCP connection
establishment to default value
Configure FIN_WAIT_2 timer time of TCP tcp timer fin-timeout time-value
Restore FIN_WAIT_2 timer time of TCP to
default value
Configure the Socket receiving/sending buffer
size of TCP
Restore the socket receiving/sending buffer
size of TCP to default value
tcp timer syn-timeout time-value
undo tcp timer syn-timeout
undo tcp timer fin-timeout
tcp window window-size
undo tcp window
Displaying and
Debugging IP
Performance
By default, the TCP finwait timer is 675 seconds, the synwait timer is 75 seconds,
and the receiving/sending buffer size of connection-oriented Socket is 4K bytes.
After the previous configuration, display the operation of the IP Performance
configuration in all views, and verify the effect of the configuration. Execute the
debugging command in user view to debug IP Performance configuration.
Ta bl e 15 Display and Debug IP Performance
Operation Command
Display TCP connection state display tcp status
Display TCP connection statistics data display tcp statistics
Display IP statistics information display ip statistics
Display ICMP statistics information display icmp statistics
Display the summary of the FIB display fib
Page 68

60 CHAPTER 4: NETWORK PROTOCOL OPERATION
Table 15 Display and Debug IP Performance
Operation Command
Display the FIB entries matching the
destination IP address (range)
Display the FIB entries that match a specific
ACL
Display the FIB entries which are output from
the buffer according to regular expression and
related to the specific character string
Display the FIB entries matching the specific
prefix list
Display the total number of FIB entries display fib statistics
Reset IP statistics information reset ip statistics
Reset TCP statistics information reset tcp statistics
display fib ip_address1 [ { mask1 |
mask-length1 } [ ip_address2 { mask2 |
mask-length2 } | longer ] | longer ]
display fib acl { number | name }
display fib | { { begin | include | exclude }
text }
display fib ip-prefix listname
Troubleshooting IP
Performance
If the IP layer protocol works normally, but TCP and UDP do not work normally,
you can enable the corresponding debugging information output to view the
debugging information.
■ Use the terminal debugging command to output the debugging information
to the console.
■ Use the debugging udp packet command to enable the UDP debugging to
trace the UDP packet. When the router sends or receives UDP packets, the
content format of the packet can be displayed in real time. You can locate the
problem from the contents of the packet.
The following are the UDP packet formats:
UDP output packet:
Source IP address:202.38.160.1
Source port:1024
Destination IP Address 202.38.160.1
Destination port: 4296
■ Use the debugging tcp packet or debugging tcp transaction command to
enable the TCP debugging to trace the TCP packets. There are two available
ways for debugging TCP.
■ Debug and trace the packets of the TCP connection that take this device as one
end.
Operations include:
<SW8800>terminal debugging
<SW8800>debugging tcp packet
The TCP packets, received or sent can be checked in real time. Specific packet
formats include:
TCP output packet:
Source IP address:202.38.160.1
Source port:1024
Destination IP Address 202.38.160.1
Destination port: 4296
Sequence number :4185089
Ack number: 0
Flag :SYN
Page 69

IPX Configuration 61
Packet length :60
Data offset: 10
■ Debug and trace the packets located in SYN, FIN or RST.
Operations include:
<SW8800>terminal debugging
<SW8800>debugging tcp transact
The TCP packets received or sent can be checked in real time, and the specific
packet formats are the same as those mentioned above.
IPX Configuration Internetwork Packet Exchange (IPX) protocol is a network layer protocol in the
NetWare protocol suite. It is similar to IP in the TCP/IP protocol suite. IPX functions
to address, route and forward packets.
IPX is a connectionless protocol. Though an IPX packet includes a destination IPX
address in addition to the data, there is no guarantee of successful delivery. Packet
acknowledgement and connection control must be provided by protocols above
IPX. Each IPX packet is considered an independent entity that has no logical or
sequential relationship with any other IPX packets.
IPX Address Structure IPX and IP use different address structures. An IPX address comprises two parts:
the network number and the node address; it is in the format of network.node.
A network number identifies the network where a site is located. It is four bytes
long and expressed by eight hexadecimal numbers. A node address identifies a
node on the network. Like a MAC address, it is six bytes long and written with the
bytes being separated into three 2-byte parts by “-”. The node address cannot be
a broadcast or multicast address. For example, in the IPX address bc.0-0cb-47, bc
(or 000000bc) is the network number and 0-0cb-47 (0000-00cb-0047) is the node
address. You can also write an IPX address in the form of N.H-H-H, where N is the
network number and H-H-H is the node address.
Routing Information
Protocol
IPX uses the Routing Information Protocol (RIP) to maintain and advertise dynamic
routing information. With IPX enabled, the switch exchanges routing information
with other neighbors through RIP to maintain an internetwork routing information
database (also known as a routing table) to accommodate to the network
changes. When the switch receives a packet, it looks up the routing table for the
next site and if there is any, forwards the packet. The routing information can be
configured statically or collected dynamically.
This chapter introduces RIP in IPX. For the RIP configurations on an IP network,
refer to the routing protocol section in this manual.
Service Advertising
Protocol
The Service Advertising Protocol (SAP) advertises the services provided by servers
and their addresses. It is used by IPX to maintain and advertise dynamic service
information. With SAP, a server broadcasts its services when it starts and the
termination of the services when it goes down.
With IPX enabled, the switch creates and maintains an internetwork service
information database (or the service information table) through SAP. It helps you
learn what services are available on the networks and where they are provided.
Page 70

62 CHAPTER 4: NETWORK PROTOCOL OPERATION
The servers periodically broadcast their services and addresses to the networks
directly connected to them. Users cannot use such information directly, however.
Instead, the information is collected by the SAP agents of the switches on the
networks and saved in their server information tables.
Page 71

5
IP ROUTING PROTOCOL OPERATION
This chapter covers the following topics:
■ IP Routing Protocol Overview
■ Static Routes
■ RIP
■ OSPF
■ IS-IS
■ BGP
■ IP Routing Policy
■ Route Capacity
IP Routing Protocol Overview
Routers select an appropriate path through a network for an IP packet according
to the destination address of the packet. Each router on the path receives the
packet and forwards it to the next router. The last router in the path submits the
packet to the destination host.
In a network, the router regards a path for sending a packet as a logical route unit,
and calls it a hop. For example, in
goes through 3 networks and 2 routers and the packet is transmitted through two
hops and router segments. Therefore, when a node is connected to another node
through a network, there is a hop between these two nodes and these two nodes
are considered adjacent in the Internet. Adjacent routers are two routers
connected to the same network. The number of route segments between a router
and hosts in the same network count as zero. In
represent the hops. A router can be connected to any physical link that constitutes
a route segment for routing packets through the network.
When a switch runs a routing protocol, it can perform router functions. In this
guide, a router and its icon represent a generic router or a switch running routing
protocols.
Figure 1, a packet sent from Host A to Host C
Figure 1, the bold arrows
Page 72

64 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Figure 1 About Hops
A
Route
Segment
C
R
R
B
R
R
R
Networks can have different sizes, so, the segment lengths connected between
two different pairs of routers are also different.
If a router in a network is regarded as a node and a route segment in the Internet
is regarded as a link, message routing in the Internet works in a similar way as the
message routing in a conventional network. Routing a message through the
shortest route may not always be the optimal route. For example, routing through
three LAN route segments may be much faster than a route through two WAN
route segments.
Selecting Routes
Through the Routing
Ta bl e
Configuring the IP Routing Protocol Overview is described in the following
sections:
■ Selecting Routes Through the Routing Table
■ Routing Management Policy
For the router, a routing table is the key to forwarding packets. Each router saves a
routing table in its memory, and each entry in this table specifies the physical port
of the router through which a packet is sent to a subnet or a host. The packet can
reach the next router over a particular path or reach a destination host through a
directly connected network.
A routing table has the following key entries:
■ A destination address — Identifies the destination IP address or the destination
network of the IP packet, which is 32 bits in length.
■ A network mask — Is made up of several consecutive 1s, which can be
expressed either in the dotted decimal format, or by the number of the
consecutive 1s in the mask. Combined with the destination address, the
network mask identifies the network address of the destination host or router.
With the destination address and the network mask, you have the address of
the network segment where the destination host or router is located. For
example, if the destination address is 129.102.8.10, the address of the
network where the host or the router with the mask 255.255.0.0 is located is
129.102.0.0.
Page 73

IP Routing Protocol Overview 65
■ The output interface — Indicates an interface through which an IP packet
should be forwarded.
■ The next hop address — Indicates the next router that an IP packet will pass
through.
■ The priority added to the IP routing table for a route — Indicates the type of
route that is selected. There may be multiple routes with different next hops to
the same destination. These routes can be discovered by different routing
protocols, or they can be the static routes that are configured manually. The
route with the highest priority (the smallest numerical value) is selected as the
current optimal route.
Types of routes are divided into the following types, subnet routes, in which the
destination is a subnet, or host routes, in which the destination is a host.
In addition, depending on whether the network of the destination host is directly
connected to the router, there are the following types of routes:
■ Direct route: The router is directly connected to the network where the
destination is located.
■ Indirect route: The router is not directly connected to the network where the
destination is located.
To limit the size of the routing table, an option is available to set a default route.
All the packets that fail to find a suitable table entry are forwarded through this
default route.
In a complicated Internet, as shown in the following figure, the number in each
network is the network address. The router R8 is connected to three networks, so
it has three IP addresses and three physical ports. Its routing table is shown in
Figure 2.
Figure 2 The Routing Table
15.0.0.1
14.0.0.1
15.0.0.2
15.0.0.0
R2
14.0.0.0
12.0.0.3
16.0.0.2
R6
16.0.0.2
13.0.0.2
14.0.0.2
13.0.0.1
12.0.0.2
R1
16.0.0.3
16.0.0.0
R5
13.0.0.0
R3
12.0.0.0
16.0.0.3
13.0.0.3
13.0.0.4
R7
10.0.0.1
11.0.0.1
11.0.0.2
R4
10.0.0.2
10.0.0.0
R8
11.0.0.0
Destination
host
location
10.0.0
11.0.0
12.0.0
13.0.0
14.0.0
15.0.0
16.0.0
Forwarding
router
Directly
Directly
11.0.0.2
Directly
13.0.0.2
10.0.0.2
10.0.0.2
Port
passed
2
1
1
3
3
2
2
Routing Management
Policy
12.0.0.1
The Switch 8800 supports the configuration of a series of dynamic routing
protocols such as RIP, OSPF, as well as static routes. The static routes configured by
Page 74

66 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
the user are managed together with the dynamic routes as detected by the
routing protocol. The static routes and the routes learned or configured by routing
protocols can be shared with each other.
Routing protocols (as well as the static configuration) can generate different
routes to the same destination, but not all these routes are optimal. In fact, at a
certain moment, only one routing protocol can determine a current route to a
single destination. Thus, each routing protocol (including the static configuration)
has a set preference, and when there are multiple routing information sources, the
route discovered by the routing protocol with the highest preference becomes the
current route. Routing protocols and the default preferences (the smaller the
value, the higher the preference) of the routes that they learn are shown in
Ta bl e 1.
Ta bl e 1 Routing Protocols and the Default Preferences for Routes
Routing protocol or route type
DIRECT 0
OSPF 10
ISIS 15
STATIC 60
RIP 100
OSPF ASE 150
OSPF NSSA 150
IBGP 256
EBGP 256
UNKNOWN 255
The preference of the corresponding
route
In the table, 0 indicates a direct route, and 255 indicates any route from an
unreliable source.
Except for direct routing and BGP (IBGP and EBGP), the preferences of various
dynamic routing protocols can be manually configured to meet the user
requirements. The preferences for individual static routes can be different.
Supporting Load Sharing and Route Backup
The Switch 8800 supports load sharing and route backup.
Load sharing is supported by configuring multiple routes that reach the same
destination and use the same precedence. The same destination can be reached
by multiple different paths, whose precedences are equal. When there is no route
that can reach the same destination with a higher precedence, the multiple routes
will be adopted by IP, which will forward the packets to the destination by these
paths to implement load sharing.
Route backup allows the system to automatically switch to a backup route when
main route has failed to improve network reliability.
To achieve route backup, the user can configure multiple routes to the same
destination according to actual situation. One of the routes has the highest
precedence and is called as main route. The other routes have descending
precedence and are called backup routes. Normally, the router sends data by the
Page 75

Static Routes 67
main route. When the line fails, the main route hides itself and the router chooses
one from the remaining routes as a backup route whose precedence is higher than
others' to send data. When the main route recovers, the router restores it and
re-selects a route. As the main route has the highest precedence, the router
chooses the main route to send data. This process is the automatic switchover
from the backup route to the main route.
For the same destination, a specified routing protocol may find multiple different
routes. If the routing protocol has the highest precedence among all active routing
protocols, these multiple routes will be regarded as currently valid routes. Thus,
load sharing of IP traffic is ensured in terms of routing protocols. The Switch 8800
supports four routes to implement load sharing.
Routes Shared Between Routing Protocols
As the algorithms of various routing protocols are different, different protocols can
generate different routes. This situation creates the problem of how to resolve
different routes being generated by different routing protocols. The Switch 8800
supports an operation to import the routes generated by one routing protocol into
another routing protocol. Each protocol has its own route redistribution
mechanism. For details, refer to
“Enabling RIP to Import Routes of Other
Protocols”, “Configuring OSPF to Import the Routes of Other Protocols”, or
“Importing Routing Information Discovered by Other Routing Protocols”.
Static Routes A static route is a route that is manually configured by the network administrator.
You can set up an interconnected network using static routes. However, if a fault
occurs in the network, the static route cannot change automatically to steer
packets away from the fault without the help of the administrator.
In a relatively simple network, you only need to configure static routes to make the
router work normally. The proper configuration and usage of the static route can
improve network performance and ensure bandwidth for important applications.
The following routes are static routes:
■ Reachable route — The normal route in which the IP packet is sent to the next
hop towards the destination. It is a common type of static route.
■ Unreachable route — When a static route to a destination has the reject
attribute, all the IP packets to this destination are discarded, and the originating
host is informed that the destination is unreachable.
■ Blackhole route — When a static route to a destination has the blackhole
attribute, all the IP packets to this destination are discarded, and the originating
host is not informed.
The attributes reject and blackhole are usually used to control the range of
reachable destinations of this router, and to help troubleshoot the network.
Default Route
A default route is also a static route. A default route is used only when no suitable
routing table entry is found. In a routing table, the default route is in the form of
the route to the network 0.0.0.0 (with the mask 0.0.0.0). You can determine
whether a default route has been set by viewing the output of the display ip
routing-table command. If the destination address of a packet fails to match any
Page 76

68 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
entry of the routing table, the router selects the default route to forward this
packet. If there is no default route and the destination address of the packet fails
to match any entry in the routing table, the packet is discarded, and an Internet
Control Message Protocol (ICMP) packet is sent to the originating host to indicate
that the destination host or network is unreachable.
In a typical network that consists of hundreds of routers, if you used multiple
dynamic routing protocols without configuring a default route then significant
bandwidth would be consumed. Using the default route can provide appropriate
bandwidth, but not high bandwidth, for communications between large numbers
of users.
Configuring Static Routes is described in the following sections:
■ Configuring Static Routes
■ Troubleshooting Static Routes
Configuring Static
Routes
Static route configuration tasks are described in the following sections:
■ Configuring a Static Route
■ Configuring a Default Route
■ Deleting All Static Routes
■ Displaying and Debugging Static Routes
Configuring a Static Route
Perform the following configurations in system view.
Ta bl e 2 Configuring a Static Route
Operation Command
Add a static route ip route-static ip-address {mask |
mask-length } { interface-name |
gateway-address } [ preference value ] [
reject | blackhole ]
Delete a static route undo ip route-static ip-address {mask |
mask-length } { interface-name |
gateway-address} [ preference value ]
The parameters are explained as follows:
■ IP address and mask
The IP address and mask use a decimal format. Because the 1s in the 32-bit
mask must be consecutive, the dotted decimal mask can also be replaced by
the mask-length which refers to the digits of the consecutive 1s in the mask.
■ Transmitting interface or next hop address
When you configure a static route, you can specify either the interface-type
port-number to designate a transmitting interface, or the gateway-address to
decide the next hop address, depending on the actual conditions.
You can specify the transmitting interfaces in the cases below:
■ For the interface that supports resolution from the network address to the link
layer address (such as the Ethernet interface that supports ARP), when
ip-address and mask (or mask-length) specifies a host address, and this
Page 77

Static Routes 69
destination address is in the directly connected network, the transmitting
interface can be specified.
■ For a P2P interface, the address of the next hop defines the transmitting
interface because the address of the opposite interface is the address of the
next hop of the route.
In fact, for all routing items, the next hop address must be specified. When the
IP layer transmits a packet, it first searches the matching route in the routing
table, depending on the destination address of the packet. Only when the next
hop address of the route is specified, can the link layer find the corresponding
link layer address, and then forward the packet.
■ For different configurations of preference-value, you can flexibly apply the
routing management policy.
■ The reject and blackhole attributes indicate the unreachable route and the
blackhole route.
Configuring a Default Route
Perform the following configurations in system view.
Ta bl e 3 Configuring a Default Route
Operation Command
Configure a default route ip route-static 0.0.0.0 { 0.0.0.0 | 0 } {
interface-name | gateway-address } [
preference value ] [ reject | blackhole ]
Delete a default route undo ip route-static 0.0.0.0 { 0.0.0.0 | 0 } {
interface-name | gateway-address } ]
Parameters for default route are the same as for static route.
Deleting All Static Routes
You can use the undo ip route-static command to delete one static route. The
Switch 8800 also provides the delete static-route all command for you to delete
all static routes at one time, including the default routes.
Perform the following configuration in system view.
Ta bl e 4 Deleting All Static Routes
Operation Command
Delete all static routes delete static-routes all
Displaying and Debugging Static Routes
After you configure static and default routes, execute the display command in all
views, to display the static route configuration, and to verify the effect of the
configuration.
Ta bl e 5 Displaying and Debugging the Routing Table
Operation Command
View routing table summary display ip routing-table
View routing table details display ip routing-table verbose
View the detailed information of a specific
route
display ip routing-table ip-address
Page 78

70 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Table 5 Displaying and Debugging the Routing Table
Operation Command
View the route filtered through specified basic
access control list (ACL)
View the route information that through
specified ip prefix list
View the routing information found by the
specified protocol
View the tree routing table display ip routing-table radix
View the integrated routing information display ip routing-table statistics
display ip routing-table acl { acl-number |
acl-name } [ verbose ]
display ip routing-table ip-prefix
ip-prefix-number [ verbose ]
display ip routing-table protocol protocol [
inactive | verbose ]
Example: Typical Static
Route Configuration
As shown in the Figure 3, the masks of all the IP addresses in the figure are
255.255.255.0. All the hosts or switches must be interconnected in pairs, by
configuring static routes.
Figure 3 Static Route Configuration
C
Host 1.1.5.1
1.1.5.2/24
1.1.3.1/24
1.1.2.1/24
1.1.1.2/24
A
Switch A
Host 1.1.1.1
Switch C
1.1.3.2/24
Switch B
1.1.4.1/24
Host 1.1.4.2
B
1 Configure the static route for Switch A:
[Switch A]ip route-static 1.1.3.0 255.255.255.0 1.1.2.2
[Switch A]ip route-static 1.1.4.0 255.255.255.0 1.1.2.2
[Switch A]ip route-static 1.1.5.0 255.255.255.0 1.1.2.2
2 Configure the static route for Switch B:
[Switch B]ip route-static 1.1.2.0 255.255.255.0 1.1.3.1
[Switch B]ip route-static 1.1.5.0 255.255.255.0 1.1.3.1
[Switch B]ip route-static 1.1.1.0 255.255.255.0 1.1.3.1
3 Configure the static route for Switch C:
[Switch C]ip route-static 1.1.1.0 255.255.255.0 1.1.2.1
[Switch C]ip route-static 1.1.4.0 255.255.255.0 1.1.3.2
4 Configure the default gateway of the Host A to be 1.1.5.2
5 Configure the default gateway of the Host B to be 1.1.4.1
Page 79

RIP 71
6 Configure the default gateway of the Host C to be 1.1.1.2
Using this procedure, all the hosts or switches in Figure 3 can be interconnected in
pairs.
Troubleshooting Static
Routes
The Switch 8800 is not configured with any dynamic routing protocols enabled.
Both the physical status and the link layer protocol status of the interface are
enabled, but the IP packets cannot be forwarded normally.
■ Use the display ip routing-table protocol static command to view
whether the corresponding static route is correctly configured.
■ Use the display ip routing-table command to view whether the
corresponding route is valid.
RIP Routing Information Protocol (RIP) is a simple, dynamic routing protocol, that is
Distance-Vector (D-V) algorithm-based. It uses hop counts to measure the distance
to the destination host, which is called routing cost. In RIP, the hop count from a
router to its directly connected network is 0. The hop count to a network which
can be reached through another router is 1, and so on. To restrict the time to
converge, RIP prescribes that the cost value is an integer that ranges from 0 to 15.
The hop count equal to or exceeding 16 is defined as infinite, or the destination
network or host is unreachable.
RIP exchanges routing information using UDP packets. RIP sends a routing refresh
message every 30 seconds. If no routing refresh message is received from one
network neighbor in 180 seconds, RIP tags all routes of the network neighbor as
unreachable. If no routing refresh message is received from one network neighbor
in 300 seconds, RIP removes the routes of the network neighbor from the routing
table. RIP v2 has the MD5 cipher authentication function while RIP v1 does not.
To improve performance and avoid routing loops, RIP supports split horizon,
poison reverse, and allows for importing routes discovered by other routing
protocols.
Each router that is running RIP manages a route database, which contains routing
entries to all the reachable destinations in the network. These routing entries
contain the following information:
■ Destination address — The IP address of a host or network.
■ Next hop address — The address of the next router that an IP packet will pass
through to reach the destination.
■ Output interface — The interface through which the IP packet should be
forwarded.
■ Cost — The cost for the router to reach the destination, which should be an
integer in the range of 0 to 15.
■ Timer — The length of time from the last time that the routing entry was
modified until now. The timer is reset to 0 whenever a routing entry is
modified.
■ Route tag — The indication whether the route is generated by an interior
routing protocol, or by an exterior routing protocol.
Page 80

72 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
The whole process of RIP startup and operation can be described as follows:
1 If RIP is enabled on a router for the first time, the router broadcasts a request
packet to adjacent routers. When they receive the request packet, adjacent routers
(on which RIP is also enabled) respond to the request by returning response
packets containing information about their local routing tables.
2 After receiving the response packets, the router that sent the request modifies its
own routing table.
3 RIP broadcasts its routing table to adjacent routers every 30 seconds. The adjacent
routers maintain their own routing tables after receiving the packets and elect an
optimal route, then advertise the modification information to their adjacent
network to make the updated route globally available. Furthermore, RIP uses
timeout mechanism to handle timed-out routes to ensure the timeliness and
validity of the routes. With these mechanisms, RIP, an interior routing protocol,
enables the router to learn the routing information of the entire network.
RIP has become one of the most popular standards of transmitting router and host
routes. It can be used in most campus networks and regional networks that are
simple, yet extensive. RIP is not recommended for larger and more complicated
networks.
Configuring RIP is described in the following sections:
■ Configuring RIP
■ Troubleshooting RIP
Configuring RIP Only after RIP is enabled can other functional features be configured. But the
configuration of the interface-related functional features is not dependent on
whether RIP has been enabled.
After RIP is disabled, the interface-related features also become invalid.
The RIP configuration tasks are described in the following sections:
■ Enabling RIP and Entering the RIP View
■ Enabling the RIP Interface
■ Configuring Unicast RIP Messages
■ Specifying the RIP Version
■ Configuring RIP Timers
■ Configuring RIP-1 Zero Field Check of the Interface Packet
■ Specifying the Operating State of the Interface
■ Disabling Host Route
■ Enabling RIP-2 Route Aggregation
■ Setting RIP-2 Packet Authentication
■ Configuring Split Horizon
■ Enabling RIP to Import Routes of Other Protocols
■ Configuring the Default Cost for the Imported Route
■ Setting the RIP Preference
Page 81

RIP 73
■ Setting Additional Routing Metrics
■ Configuring Route Filtering
■ Displaying and Debugging RIP
Enabling RIP and Entering the RIP View
Perform the following configurations in system view.
Ta bl e 6 Enabling RIP and Entering the RIP View
Operation Command
Enable RIP and enter the RIP view rip
Disable RIP undo rip
By default, RIP is not enabled.
Enabling the RIP Interface
For flexible control of RIP operation, you can specify the interface and configure
the network where it is located in the RIP network, so that these interfaces can
send and receive RIP packets.
Perform the following configurations in RIP view.
Ta bl e 7 Enabling RIP Interface
Operation Command
Enable RIP on the specified network interface network network-address
Disable RIP on the specified network interface undo network network-address
After the RIP interface is enabled, you should also specify its operating network
segment, because RIP only operates on the interface when the network segment
has been specified. RIP does not receive or send routes for an interface that is not
on the specified network, and does not forward its interface route.
The network-address parameter is the address of the enabled or disabled network,
and it can also be configured as the IP network address of the appropriate
interfaces.
When a network command is used for an address, the effect is to enable the
interface of the network with the address. For example, for network
129.102.1.1, you can see network 129.102.0.0 using either the display
current-configuration command or the display rip command.
Configuring Unicast RIP Messages
RIP is a broadcast protocol. To exchange route information with the non-broadcast
network, the unicast transmission mode must be adopted.
Perform the following configuration in the RIP view.
Ta bl e 8 Configuring Unicast RIP Messages
Operation Command
Configure unicast RIP messages peer ip-address
Cancel unicast RIP messages undo peer ip-address
Page 82

74 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
By default, RIP does not send messages to unicast addresses.
Usually, this command is not recommended because the opposite side does not
need to receive two of the same messages at a time. It should be noted that the
peer command should also be restricted by the rip work, rip output, rip input
and network commands.
Specifying the RIP Version
RIP has two versions, RIP-1 and RIP-2. You can specify the version of the RIP packet
processed by the interface.
RIP-1 broadcasts the packets. RIP-2 can transmit packets by both broadcast and
multicast. By default, multicast is adopted for transmitting packets. In RIP-2, the
default multicast address is 224.0.0.9. The advantage of transmitting packets in
the multicast mode is that the hosts in the same network that do not run RIP, do
not receive RIP broadcast packets. In addition, this mode prevents the hosts that
are running RIP-1 from incorrectly receiving and processing the routes with subnet
mask in RIP-2. When an interface is running RIP-2, it can also receive RIP-1
packets.
Perform the following configuration in VLAN interface view.
Ta bl e 9 Specifying RIP Version of the Interface
Operation Command
Specify the interface version as RIP-1 rip version 1
Specify the interface version as RIP-2 rip version 2 [ broadcast | multicast ]
Restore the default RIP version running on the
interface
undo rip version { 1 | 2 }
By default, the interface receives and sends RIP-1 packets. It transmits packets in
multicast mode when the interface RIP version is set to RIP-2.
Configuring RIP Timers
As stipulated in RFC1058, RIP is controlled by three timers, period update,
timeout, and garbage-collection:
■ Period update is triggered periodically to send all RIP routes to all the
neighbors.
■ If a RIP route has not been updated when the timeout timer expires, the route
will be considered unreachable.
■ If the garbage-collection timer times out before the unreachable route is
updated by the update packets from the neighbors, the route will be deleted
completely from the routing table.
Modification of these timers can affect the convergence speed of RIP.
Page 83

RIP 75
Perform the following configuration in RIP view.
Ta bl e 10 Configuring RIP Timers
Operation Command
Configure RIP timers timers { update update-timer-length |
timeout timeout-timer-length }*
Restore the default settings of RIP undo timers { update | timeout } *
The modification of RIP timers takes effect immediately.
By default, the values of period update and timeout timers are 30 seconds and
180 seconds. The value of garbage-collection timer is four times that of period
update timer, 120 seconds.
In fact, you may find that the timeout time of garbage-collection timer is not fixed.
If period update timer is set to 30 seconds, garbage-collection timer might range
from 90 to 120 seconds.
Before RIP completely deletes an unreachable route from the routing table, it
advertises the route by sending four update packets with route metric of 16, to let
all the neighbors knows that the route is unreachable. Routes do not always
become unreachable when a new period starts so the actual value of the
garbage-collection timer is 3 to 4 times the value of the period update timer.
You must consider network performance when adjusting RIP timers, and configure
all the routes that are running RIP, to avoid unnecessary traffic or network
oscillation.
Configuring RIP-1 Zero Field Check of the Interface Packet
According to the RFC1058, some fields in the RIP-1 packet must be 0. When an
interface version is set to RIP-1, the zero field check must be performed on the
packet. If the value in the zero field is not zero, processing is refused. There are no
zero fields in RIP-2 packets so configuring a zero field check is invalid for RIP-2.
Perform the following configurations in RIP view.
Ta bl e 11 Configuring Zero Field Check of the Interface Packet
Operation Command
Configure zero field check on the RIP-1 packet checkzero
Disable zero field check on the RIP-1 packet undo checkzero
By default, RIP-1 performs zero field check on the packet.
Specifying the Operating State of the Interface
In the VLAN interface view, you can specify whether RIP update packets are sent
and received on the interface. In addition, you can specify whether an interface
sends or receives RIP update packets.
Page 84

76 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Perform the following configuration in VLAN interface view.
Ta bl e 12 Specifying the Operating State of the Interface
Operation Command
Enable the interface to run RIP rip work
Disable RIP on the interface undo rip work
Enable the interface to receive RIP update
packets
Disable receipt of RIP update packets on the
interface
Enable the interface to send RIP update
packets
Disable transmission of RIP packets on the
interface
The rip work command is functionally equivalent to both rip input and rip
output commands.
By default, all interfaces except loopback interfaces both receive and transmit RIP
update packets.
rip input
undo rip input
rip output
undo rip output
Disabling Host Route
In some cases, the router can receive many host routes from the same segment,
and these routes are of little help in route addressing but consume a lot of
network resources. Routers can be configured to reject host routes by using undo
host-route command.
Perform the following configurations in RIP view.
Ta bl e 13 Disabling Host Routes
Operation Command
Enable receiving host routes host-route
Disable receiving host routes undo host-route
By default, the router receives the host route.
Enabling RIP-2 Route Aggregation
Route aggregation means that different subnet routes in the same natural
network can be aggregated into one natural mask route for transmission when
they are sent to other outside networks. Route aggregation can be performed to
reduce the routing traffic on the network, as well as to reduce the size of the
routing table.
RIP-1 only sends the routes with natural mask, that is, it always sends routes in the
route aggregation form.
RIP-2 supports subnet mask and classless inter-domain routing. To advertise all the
subnet routes, the route aggregation function of RIP-2 can be disabled.
Page 85

RIP 77
Perform the following configurations in RIP view.
Ta bl e 14 Enabling Route Aggregation
Operation Command
Enable the automatic aggregation function of
RIP-2
Disable the automatic aggregation function of
RIP-2
summary
undo summary
By default, RIP-2 uses the route aggregation function.
Setting RIP-2 Packet Authentication
RIP-1 does not support packet authentication. However, you can configure packet
authentication on RIP-2 interfaces.
RIP-2 supports two authentication modes:
■ Simple authentication — This mode does not ensure security. The key is not
encrypted and can be seen in a network trace so simple authentication should
not be applied when there are high security requirements
■ MD5 authentication — This mode uses two packet formats: One format
follows RFC1723 (RIP Version 2 Carrying Additional Information); the other
format follows RFC2082 (RIP-2 MD5 Authentication).
Perform the following configuration in VLAN interface view
Ta bl e 15 Setting RIP-2 Packet Authentication
Operation Command
Configure RIP-2 simple authentication key rip authentication-mode simple
password-string
Configure RIP-2 MD5 authentication with
packet type following RFC 1723
Configure RIP-2 MD5 authentication with
packet type following RFC 2082
Set the packet format type of RIP-2 MD5
authentication
Cancel authentication of RIP-2 packet undo rip authentication-mode
rip authentication-mode { simple password
| md5 { usual key-string | nonstandard
key-string key-id } }
rip authentication-mode { simple password
| md5 { usual key-string | nonstandard
key-string key-id } }
rip authentication-mode { simple password
| md5 { usual key-string | nonstandard
key-string key-id } }
The usual packet format follows RFC1723 and nonstandard follows RFC2082.
Configuring Split Horizon
Split horizon means that the route received through an interface will not be sent
through this interface again. The split horizon algorithm can reduce the
generation of routing loops, but in some special cases, split horizon must be
disabled to obtain correct advertising at the cost of efficiency. Disabling split
horizon has no effect on the P2P connected links but is applicable on the Ethernet.
Page 86

78 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Perform the following configuration in VLAN interface view.
Ta bl e 16 Configuring Split Horizon
Operation Command
Enable split horizon rip split-horizon
Disable split horizon undo rip split-horizon
By default, split horizon of the interface is enabled.
Enabling RIP to Import Routes of Other Protocols
RIP allows users to import the route information of other protocols into the
routing table.
RIP can import direct, static, OSPF, BGP, and IS-IS routes.
BGP and IS-IS require the advanced version of the software on the Switch 8800.
Perform the following configurations in RIP view.
Ta bl e 17 Enabling RIP to Import Routes of Other Protocols
Operation Command
Enable RIP to import routes of other protocols import-route protocol [ cost value ]
Disable route imports from other protocols undo import-route protocol
[route-policy route-policy-name ]
By default, RIP does not import the route information of other protocols.
Configuring the Default Cost for the Imported Route
When you use the import-route command to import the routes of other
protocols, you can specify their cost. If you do not specify the cost of the imported
route, RIP will set the cost to the default cost, specified by the default cost
parameter.
Perform the following configurations in RIP view.
Ta bl e 18 Configuring the Default Cost for the Imported Route
Operation Command
Configure default cost for the imported route default cost value
Restore the default cost of the imported
route.
undo default cost
By default, the cost value for the RIP imported route is 1.
Setting the RIP Preference
Each routing protocol has its own preference by which the routing policy selects
the optimal one from the routes of different protocols. The greater the preference
value, the lower the preference. The preference of RIP can be set manually.
Page 87

RIP 79
Perform the following configurations in RIP view.
Ta bl e 19 Setting the RIP Preference
Operation Command
Set the RIP Preference preference value
Restore the default value of RIP preference undo preference
By default, the preference of RIP is 100.
Setting Additional Routing Metrics
The additional routing metric, is the input or output routing metric added to a RIP
route. It does not change the metric value of the route in the routing table, but
adds a specified metric value when the interface receives or sends a route.
Perform the following configuration in VLAN interface view.
Ta bl e 20 Setting Additional Routing Metric
Operation Command
Set the additional routing metric of the route
when the interface receives an RIP packet
Disable the additional routing metric of the
route when the interface receives an RIP
packet
Set the additional routing metric of the route
when the interface sends an RIP packet
Disable the additional routing metric of the
route when the interface sends an RIP packet
rip metricin value
undo rip metricin
ip metricout value
undo rip metricout
By default, the additional routing metric added to the route when RIP sends the
packet is 1. The additional routing metric when RIP receives the packet is 0.
Configuring Route Filtering
The router provides the route filtering function. You can configure the filter policy
rules by specifying the ACL and ip-prefix for route redistribution and distribution.
To import a route, the RIP packet of a specific router can also be received by
designating a neighbor router.
Perform the following configurations in RIP view.
Ta bl e 21 Configuring RIP to Filter Routes
Operation Command
Configure filtering the received routing
information distributed by the specified
address
Cancel filtering the received routing
information distributed by the specified
address
Configure filtering the received global
routing information
Cancel filtering the received global routing
information
filter-policy gateway ip-prefix-name import
undo filter-policy gateway ip-prefix-name
import
filter-policy { acl-number | ip-prefix
ip-prefix-name } import
undo filter-policy { acl-number | ip-prefix
ip-prefix-name } import
Page 88

80 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
By default, RIP does not filter received and distributed routing information.
Displaying and Debugging RIP
After configuring RIP, execute the display command in all views to display the RIP
configuration, and to verify the effect of the configuration. Execute the
debugging command in user view to debug the RIP module. Execute the reset
command in RIP view to reset the system configuration parameters of RIP.
Ta bl e 22 Displaying and Debugging RIP
Operation Command
Display the current RIP state and configuration
information.
Enable the RIP debugging information debugging rip packets
Enable the debugging of RIP receiving packet. debugging rip receive
Enable the debugging of RIP sending packet. debugging rip send
Restore the default RIP settings reset
display rip
Example: Typical RIP
Configuration
As shown in Figure 4, the Switch C connects to the subnet 117.102.0.0 through
the Ethernet port. The Ethernet ports of Switch A and Switch B are connected to
the network 155.10.1.0 and 196.38.165.0. Switch C, Switch A, and Switch B are
connected by Ethernet 110.11.2.0. Correctly configure RIP to ensure that Switch
C, Switch A, and Switch B can interconnect.
Figure 4 RIP Configuration
Network address:
155.10.1.0/24
Switch A
Network address:
110.11.2.2/24
Switch B
Network address:
196.38.165.0/24
Ethernet
Switch C
Network address:
117.102.0.0/16
Interface address:
155.10.1.1/24
Interface address:
110.11.2.1/24
Interface address:
117.102.0.1/16
Interface address:
196.38.165.1/24
The following configuration only shows the operations related to RIP. Before
performing the following configuration, verify that the Ethernet link layer works
normally.
1 Configure RIP on Switch A:
[Switch A]rip
[Switch A-rip]network 110.11.2.0
[Switch A-rip]network 155.10.1.0
2 Configure RIP on Switch B:
[Switch B]rip
[Switch B-rip]network 196.38.165.0
Page 89

OSPF 81
[Switch B-rip]network 110.11.2.0
3 Configure RIP on Switch C:
[Switch C]rip
[Switch C-rip]network 117.102.0.0
[Switch C-rip]network 110.11.2.0
Troubleshooting RIP The Switch 8800 cannot receive update packets when the physical connection to
the peer routing device is normal.
■ RIP does not operate on the corresponding interface (for example, if the undo
rip work command is executed) or this interface is not enabled through the
network command.
■ The peer routing device is configured for multicast mode (for example, the rip
version 2 multicast command is executed) but the multicast mode has not
been configured on the corresponding interface of the local switch.
OSPF Open Shortest Path First (OSPF) is an Interior Gateway Protocol (IGP). At present,
OSPF version 2 (RFC2328) is used, which has the following features:
■ Scope — Supports networks of various sizes and can support several hundred
routers
■ Fast convergence — Transmits the update packets instantly after the network
topology changes so the change is synchronized in the AS
■ Loop-free — Calculates routes using the shortest path tree algorithm,
according to the collected link states so that no loop routes are generated from
the algorithm itself
■ Area partition — Allows the network of AS to be divided into different areas
for management convenience, so that the routing information that is
transmitted between the areas is further abstracted to reduce network
bandwidth consumption
■ Equal-cost multi-route — Supports multiple equal-cost routes to a destination
■ Routing hierarchy — Supports a four-level routing hierarchy that prioritizes
routes into intra-area, inter-area, external type-1, and external type-2 routes.
■ Authentication — Supports the interface-based packet authentication to
guarantee the security of the route calculation
■ Multicast transmission — Uses multicast addresses to send updates.
Configuring OSPF is described in the following sections:
■ Calculating OSPF Routes
■ Configuring OSPF
■ Troubleshooting OSPF
Calculating OSPF Routes The OSPF protocol calculates routes in the following way:
■ Each OSPF-capable router maintains a Link State Database (LSD), which
describes the topology of the entire AS. According to the network topology
around itself, each router generates a Link State Advertisement (LSA). The
routers on the network transmit the LSAs among themselves by transmitting
Page 90

82 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
the protocol packets to each other. Thus, each router receives the LSAs of other
routers and all these LSAs constitute its LSD.
■ LSA describes the network topology around a router, so the LSD describes the
network topology of the entire network. Routers can easily transform the LSD
to a weighted directed graph, which actually reflects the topology of the whole
network. All the routers have the same graph.
■ A router uses the SPF algorithm to calculate the shortest path tree which shows
the routes to the nodes in the autonomous system. In this tree, the router is the
root. The external routing information is a leaf node. A router that advertises
the routes, also tags them and records the additional information of the
autonomous system. Therefore, the routing tables obtained from different
routers are different.
OSPF supports interface-based packet authentication to guarantee the security of
route calculation. OSPF also transmits and receives packets by IP multicast.
OSPF Packets
OSPF uses five types of packets:
■ Hello Packet
The Hello packet is the most common packet sent by the OSPF protocol. A
router periodically sends it to its neighbor. It contains the values of some
timers, DR, BDR and the known neighbor.
■ Database Description (DD) Packet
When two routers synchronize their databases, they use the DD packets to
describe their own Link State Databases (LSDs), including the digest of each
LSA. The digest refers to the HEAD of an LSA, which can be used to uniquely
identify the LSA. Synchronizing databases with DD packets reduces the traffic
size transmitted between the routers, since the HEAD of an LSA only occupies a
small portion of the overall LSA traffic. With the HEAD, the peer router can
judge whether it has already received the LSA.
■ Link State Request (LSR) Packet
After exchanging the DD packets, the two routers know which LSAs of the
peer routers are missing from the local LSD’s. In this case, they send LSR
packets to the peers, requesting the missing LSAs. The packets contain the
digests of the missing LSAs.
■ Link State Update (LSU) Packet
The LSU packet is used to transmit the needed LSAs to the peer router. It
contains a collection of multiple LSAs (complete contents).
■ Link State Acknowledgment (LSAck) Packet
The packet is used for acknowledging received LSU packets. It contains the
HEAD(s) of LSA(s) requiring acknowledgement.
Basic Concepts Related to OSPF
■ Router ID
To run OSPF, a router must have a router ID. If no ID is configured, the system
automatically selects an IP address from the IP addresses of the current
interface as the router ID.
Page 91

OSPF 83
■ Designated Router (DR)
In a broadcast network, in which all routers are directly connected, any two
routers must establish adjacency to broadcast their local status information to
the whole AS. In this situation, every change that a router makes results in
multiple transmissions, which is not only unnecessary but also wastes
bandwidth. To solve this problem, OSPF defines a “designated router” (DR). All
routers send information only to the DR for broadcasting the network link
states to the network. This reduces the number of router adjacent relations on
the multi-access network.
When the DR is not manually specified, the DR is elected by all the routers in
the segment. See
■ Backup Designated Router (BDR)
“Setting the Interface Priority for DR Election”
If the DR fails, a new DR must be elected and synchronized with the other
routers on the segment. This process takes a relatively long time, during which
the route calculation is incorrect. To shorten the process, OSPF creates a BDR as
backup for the DR. A new DR and BDR are elected in the meantime. The
adjacencies are also established between the BDR and all the routers on the
segment, and routing information is also exchanged between them. After the
existing DR fails, the BDR becomes a DR immediately.
■ Area
If all routers on a large network are running OSPF, the large number of routers
results in an enormous LSD, which consumes storage space, complicates the
SPF algorithm, and adds CPU. Furthermore, as a network grows larger, the
topology becomes more likely to change. Hence, the network is always in
“turbulence”, and a large number of OSFP packets are generated and
transmitted in the network. This shrinks network bandwidth. In addition, each
change causes all the routers on the network to recalculate the routes.
OSPF solves this problem by dividing an AS into different areas. Areas logically
group the routers, which form the borders of each area. Thus, some routers
may belong to different areas. A router that connects the backbone area and a
non-backbone area is called an area border router (ABR). An ABR can connect
to the backbone area physically or logically.
■ Backbone Area
After the area division of OSPF, one area is different from all the other areas. Its
area-id is 0 and it is usually called the backbone area.
■ Virtual link
Since all the areas should be connected logically, virtual link is adopted so that
the physically separated areas can still maintain logical connectivity.
■ Route summary
An AS is divided into different areas that are interconnected through OSPF
ABRs. The routing information between areas can be reduced by use of a route
summary. Thus, the size of routing table can be reduced and the calculation
speed of the router can be improved. After finding an intra-area route of an
area, the ABR looks in the routing table and encapsulates each OSPF route into
an LSA and sends it outside the area.
Page 92

84 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Configuring OSPF You must first enable OSPF then specify the interface and area ID before
configuring other functions. However, the configuration of functions that are
related to the interface does not depend on whether OSPF is enabled. However, if
OSPF is disabled, the OSPF-related interface parameters become invalid.
OSPF configuration includes tasks that are described in the following sections:
■ Enabling OSPF and Entering OSPF View
■ Entering OSPF Area View
■ Specifying the Interface
■ Configuring Router ID
■ Configuring the Network Type on the OSPF Interface
■ Configuring the Cost for Sending Packets on an Interface
■ Setting the Interface Priority for DR Election
■ Setting the Peer
■ Setting the Interval of Hello Packet Transmission
■ Setting a Dead Timer for the Neighboring Routers
■ Configuring an Interval Required for Sending LSU Packets
■ Setting an Interval for LSA Retransmission Between Neighboring Routers
■ Setting a Shortest Path First (SPF) Calculation Interval for OSPF
■ Configuring the OSPF STUB Area
■ Configuring NSSA of OSPF
■ Configuring the Route Summarization of OSPF Area
■ Configuring OSPF Virtual Link
■ Configuring Summarization of Imported Routes by OSPF
■ Configuring the OSPF Area to Support Packet Authentication
■ Configuring OSPF Packet Authentication
■ Configuring OSPF to Import the Routes of Other Protocols
■ Configuring Parameters for OSPF to Import External Routes
■ Configuring OSPF to Import the Default Route
■ Setting OSPF Route Preference
■ Configuring OSPF Route Filtering
■ Configuring Filling the MTU Field When an Interface Transmits DD Packets
■ Disabling the Interface to Send OSPF Packets
■ Configuring OSPF and Network Management System (NMS)
■ Resetting the OSPF Process
■ Displaying and Debugging OSPF
Page 93

OSPF 85
Enabling OSPF and Entering OSPF View
Perform the following configurations in system view.
Ta bl e 23 Enabling the OSPF Process
Operation Command
Enable the OSPF process ospf [ process-id [[ router-id router-id ]]
Disable the OSPF process undo ospf [ process-id ]
By default, OSPF is not enabled.
Entering OSPF Area View
Perform the following configurations in OSPF view.
Ta bl e 24 Entering OSPF Area View
Operation Command
Enter an OSPF area view area area-id
Delete a designated OSPF area undo area area-id
Specifying the Interface
OSPF divides the AS into different areas. You must configure each OSPF interface
to belong to a particular area, identified by an area ID. The areas transfer routing
information between them through the ABRs.
In addition, parameters of all the routers in the same area should be identical.
Therefore, when configuring the routers in the same area, please note that most
configurations should be based on the area. An incorrect configuration can disable
the neighboring routers from transmitting information, and lead to congestion or
self-loop of the routing information.
Perform the following configuration in OSPF Area view.
Ta bl e 25 Specifying Interface
Operation Command
Specify an interface to run OSPF network ip-address ip-mask
Disable OSPF on the interface undo network ip-address ip-mask
You must specify the segment to which the OSPF will be applied after enabling the
OSPF tasks.
Configuring Router ID
A router ID is a 32-bit unsigned integer that uniquely identifies a router within an
AS. A router ID can be configured manually. If a router ID is not configured, the
system selects the IP address of an interface automatically. When you set a router
ID manually, you must guarantee that the IDs of any two routers in the AS are
unique. A common undertaking is to make the router ID the same as the IP
address of an interface on the router.
Page 94

86 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Perform the following configurations in system view.
Ta bl e 26 Configuring Router ID
Operation Command
Configure router ID router id router-id
Remove the router ID undo router id
To ensure the stability of OSPF, you must determine the division of router IDs and
manually configure them when implementing network planning.
Configuring the Network Type on the OSPF Interface
The route calculation of OSPF is based on the topology of the adjacent network of
the local router. Each router describes the topology of its adjacent network and
transmits it to all the other routers.
OSPF divides networks into four types by link layer protocol:
■ Broadcast: If Ethernet or FDDI is adopted, OSFP defaults the network type to
broadcast.
■ Non-Broadcast Multi-access (NBMA): If Frame Relay, ATM, HDLC or X.25 is
adopted, OSPF defaults the network type to NBMA.
■ Point-to-Multipoint (P2MP): OSPF does not default the network type of any link
layer protocol to P2MP. The general undertaking is to change a partially
connected NBMA network to P2MP network, if the NBMA network is not
fully-meshed.
■ Point-to-point (P2P): If PPP, LAPB or POS is adopted, OSPF defaults the network
type to P2P.
As you configure the network type, consider the following points:
■ NBMA means that a network is non-broadcast and multi-accessible. ATM is a
typical example. You can configure the polling interval for hello packets before
the adjacency of neighboring routers is formed.
■ Configure the interface type to nonbroadcast on a broadcast network without
multi-access capability.
■ Configure the interface type to P2MP if not all the routers are directly
accessible on an NBMA network.
■ Change the interface type to P2P if the router has only one peer on the NBMA
network.
The differences between NBMA and P2MP are listed below:
■ In OSPF, NBMA refers to the networks that are fully connected, non-broadcast
and multi-accessible. However, a P2MP network is not required to be fully
connected.
■ DR and BDR are required on a NBMA network but not on a P2MP network.
■ NBMA is the default network type. For example, if ATM is adopted as the link
layer protocol, OSPF defaults the network type on the interface to NBMA,
regardless of whether the network is fully connected. P2MP is not the default
network type. No link layer protocols are regarded as P2MP. You must change
Page 95

OSPF 87
the network type to P2MP manually. The most common method is to change a
partially connected NBMA network to a P2MP network.
■ NBMA forwards packets by unicast and requires neighbors to be configured
manually. P2MP forward packets by multicast.
Perform the following configuration in VLAN interface view.
Ta bl e 27 Configuring a Network Type on the Interface that Starts OSPF
Operation Command
Configure network type on the interface ospf network-type { broadcast | NBMA |
P2MP | P2P }
Restore the default network type of the OSPF
interface
undo ospf network-type
After the interface has been configured with a new network type, the original
network type is removed automatically.
Configuring the Cost for Sending Packets on an Interface
The user can control the network traffic by configuring different message sending
costs for different interfaces. Otherwise, OSPF automatically calculates the cost
according to the baud rate on the current interface.
Perform the following configuration in VLAN interface view.
Ta bl e 28 Configuring the Cost for Sending Packets on the Interface
Operation Command
Configure the cost for sending packets on
interface
Restore the default cost for packet
transmission on the interface
ospf cost value
undo ospf cost
Setting the Interface Priority for DR Election
The priority of the router interface determines the qualification of the interface for
DR election. A router of higher priority is considered first if there is a collision in the
election.
DR is not designated manually, instead, it is elected by all the routers on the
segment. Routers with priorities > 0 in the network are eligible candidates. Among
all the routers self-declared to be the DR, the one with the highest priority is
elected. If two routers have the same priority, the one with the highest router ID is
elected DR. Each router writes the expected DR in the packet and sends it to all the
other routers on the segment. If two routers attached to the same segment
concurrently declare themselves to be the DR, the one with the higher priority
wins. If the priorities are the same, the router with higher router ID wins. If the
priority of a router is 0, it is not eligible to be elected DR or BDR.
If a DR fails, the routers on the network must elect a new DR and synchronize with
the new DR. The process takes a relatively long time, during which, route
calculation can become incorrect. To speed up this DR replacement process, OSPF
implements the BDR as a backup for DR. The DR and BDR are elected at the same
time. The adjacencies are also established between the BDR and all the routers on
the segment, and routing information is exchanged between them. When the DR
Page 96

88 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
fails, the BDR becomes the DR instantly. Since no re-election is needed and the
adjacencies have already been established, the process is very short. But in this
case, a new BDR must be elected. Although it also takes a long time, it does not
affect the route calculation.
Note that:
■ The DR on the network is not necessarily the router with the highest priority.
Likewise, the BDR is not necessarily the router with the second highest priority.
If a new router is added after DR and BDR election, it is impossible for the
router to become the DR even if it has the highest priority.
■ The DR is based on the router interface in a certain segment. Maybe a router is
a DR on one interface, but it can be a BDR or DROther on another interface.
■ DR election is only required for broadcast or NBMA interfaces. For the P2P or
P2MP interfaces, DR election is not required.
Perform the following configuration in VLAN interface view.
Ta bl e 29 Setting the Interface Priority for DR Election
Operation Command
Configure the interface with a priority for DR
election
Restore the default interface priority undo ospf dr-priority
ospf dr-priority priority_num
By default, the priority of the interface is 1 in the DR election. The value can be set
from 0 to 255.
Setting the Peer
For an NBMA network, some special configurations are required. Since an NBMA
interface on the network cannot discover the adjacent router through
broadcasting the Hello packets, you must manually specify an IP address for the
adjacent router of the interface, and whether the adjacent router is eligible for
election. This can be done by configuring the peer ip-address command. If
dr-priority-number is not specified, the adjacent router will be regarded as
ineligible.
Perform the following configuration in OSPF view.
Ta bl e 30 Configuring the Peer
Operation Command
Configure a peer for the NBMA interface. peer ip-address [ dr-priority
dr-priority-number ]
Remove the configured peer for the NBMA
interface
undo peer ip-address
By default, the preference for the neighbor of NBMA interface is 1.
Setting the Interval of Hello Packet Transmission
Hello packets are the most frequently sent packets. They are periodically sent to
the adjacent router for discovering and maintaining adjacency, and for electing a
DR and BDR. The user can set the hello timer.
Page 97

OSPF 89
According to RFC2328, the consistency of hello intervals between network
neighbors should be kept. The hello interval value is in inverse proportion to the
route convergence rate and network load.
Perform the following configuration in VLAN interface view.
Ta bl e 31 Setting Hello Timer and Poll Interval
Operation Command
Set the hello interval of the interface ospf timer hello seconds
Restore the default hello interval of the
interface
Set the poll interval on the NBMA interface ospf timer poll seconds
Restore the default poll interval undo ospf timer poll
undo ospf timer hello
By default, P2P and broadcast interfaces send Hello packets every 10 seconds, and
P2MP and NBMA interfaces send the packets every 30 seconds.
Setting a Dead Timer for the Neighboring Routers
If hello packets are not received from a neighboring router, that router is
considered dead. The dead timer of neighboring routers refers to the interval after
which a router considers a neighboring router dead. You can set a dead timer for
the neighboring routers.
Perform the following configuration in VLAN interface view.
Ta bl e 32 Setting a Dead Timer for the Neighboring Routers
Operation Command
Configure a dead timer for the neighboring
routers
Restore the default dead interval of the
neighboring routers
ospf timer dead seconds
undo ospf timer dead
By default, the dead interval for the neighboring routers of P2P or broadcast
interfaces is 40 seconds and for the neighboring routers of P2MP or NBMA
interfaces is 120 seconds.
Both hello and dead timers restore the default values if you modify the network
type.
Configuring an Interval Required for Sending LSU Packets
Trans-delay seconds should be added to the aging time of the LSA in an LSU
packet. Setting the parameter like this, the time duration that the interface
requires for transmitting the packet, is considered.
You can configure the interval for sending LSU messages. More attention should
be paid to this item on low speed networks.
Page 98

90 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
Perform the following configuration in VLAN interface view.
Ta bl e 33 Configuring an Interval for LSU packets
Operation Command
Configure an interval for sending LSU packets ospf trans-delay seconds
Restore the default interval of sending LSU
packets
By default, LSU packets are transmitted by seconds.
Setting an Interval for LSA Retransmission Between Neighboring Routers
If a router transmits an LSA to the peer, it requires the acknowledgement packet
from the peer. If it does not receive the acknowledgement packet within the
retransmission, it retransmits this LSA to the neighbor. You can configure the value
of the retransmission interval.
Perform the following configuration in VLAN interface view.
Ta bl e 34 Setting Retransmit Timer
undo ospf trans-delay
Operation Command
Configure the interval of LSA retransmission
for the neighboring routers
Restore the default LSA retransmission interval
for the neighboring routers
ospf timer retransmit interval
undo ospf timer retransmit
By default, the interval for neighboring routers to retransmit LSAs is five seconds.
The value of the interval should be bigger than the interval in which a packet can
be transmitted and returned between two routers.
An LSA retransmission interval that is too small will cause unnecessary
retransmission.
Setting a Shortest Path First (SPF) Calculation Interval for OSPF
Whenever the OSPF LSDB changes, the shortest path requires recalculation.
Calculating the shortest path after a change consumes enormous resources and
affects the operating efficiency of the router. Adjusting the SPF calculation interval,
however, can restrain the resource consumption caused by frequent network
changes.
Perform the following configuration in OSPF view.
Ta bl e 35 Setting the SPF Calculation Interval
Operation Command
Set the SPF calculation interval spf-schedule-interval seconds
Restore the SPF calculation interval undo spf-schedule-interval seconds
By default, the interval for SPF recalculation is 5 seconds.
Page 99

OSPF 91
Configuring the OSPF STUB Area
STUB areas are special LSA areas in which the ABRs do not propagate the learned
external routes of the AS. In these areas, the routing table sizes of routers and the
routing traffic are significantly reduced.
The STUB area is an optional configuration attribute, but not every area conforms
to the configuration condition. Generally, STUB areas, located at the AS
boundaries, are those non-backbone areas with only one ABR. Even if this area has
multiple ABRs, no virtual links are established between these ABRs.
To insure that routes to the destinations outside the AS are still reachable, the ABR
in this area generates a default route (0.0.0.0) and advertises it to the non-ABR
routers in the area.
Note the following items when you configure a STUB area:
■ The backbone area cannot be configured as a STUB area, and virtual links
cannot pass through the STUB area.
■ If you want to configure an area as a STUB area, all the routers in this area
should be configured with the stub command.
■ No ASBR can exist in a STUB area and the external routes of the AS cannot be
propagated in the STUB area.
Perform the following configuration in OSPF Area view.
Ta bl e 36 Configuring an OSPF STUB Area
Operation Command
Configure an area as the STUB area stub [no-summary]
Remove the configured STUB area undo stub
Set the cost of the default route to the STUB
area
Remove the cost of the default route to the
STUB area
default-cost value
undo default-cost
By default, the STUB area is not configured, and the cost of the default route to a
STUB area is 1.
Configuring NSSA of OSPF
An NSSA is similar to a STUB area. However, NSSA does not allow importing
AS-External-LSAs (type-5 LSAs) although it does allow importing
NSSA-External-LSAs (type-7 LSAs). ASBRs can be configured to convert type-5
LSAs to type-7 LSAs to allow advertising of type-5 LSAs within the NSSA. Similarly,
ABRs can be configured to reconvert the type-7 LSAs to type-5 LSAs as these LSAs
leave the NSSA.
For example, in Figure 5, the AS running OSPF includes three areas: Area 1, Area 2
and Area 0. Among them, Area 0 is the backbone area. Also, there are other two
ASs running RIP. Area 1 is defined as an NSSA. After RIP routes of Area 1 are
propagated to the NSSA ASBR, the NSSA ASBR generates type-7 LSAs which are
propagated in Area 1. When the type-7 LSAs reach the NSSA ABR, the NSSA ABR
translates it into a type-5 LSA, which is propagated to Area 0 and Area 2. On the
other hand, RIP routes of the AS running RIP are translated into type-5 LSAs that
Page 100

92 CHAPTER 5: IP ROUTING PROTOCOL OPERATION
are propagated in the OSPF AS. However, the type-5 LSAs do not reach Area 1
because Area 1 is an NSSA. NSSAs and STUB areas have the same approach in this
aspect.
Similar to a STUB area, the NSSA cannot be configured with virtual links.
Figure 5 NSSA
RIP
Area 2
Perform the following configuration in OSPF Area view.
Ta bl e 37 Configuring NSSA of OSPF
Area 0
NSSA
ABR
Area 1
NSSA
NSSA
ASBR
RIP
Operation Command
Configure an area to be the NSSA area nssa [ default-route-advertise ] [
Cancel the configured NSSA undo nssa
Configure the default cost value of the route
to the NSSA
Restore the default cost value of the route to
the NSSA area
no-import-route ] [ no-summary ]
default-cost cost
undo default-cost
All routers connected to the NSSA must use the nssa command to configure the
area with the NSSA attribute.
The default-route-advertise parameter is used to generate the default type-7
LSAs. The default type-7 LSA route is generated on the ABR, even though the
default route 0.0.0.0 is not in the routing table. On an ASBR, however, the default
type-7 LSA route can be generated only if the default route 0.0.0.0 is in the
routing table.
Executing the no-import-route command on the ASBR prevents the external
routes that OSPF imported through the import-route command from advertising
to the NSSA. Generally, if an NSSA router is both ASBR and ABR, this argument is
used.
The default-cost command is used on the ABR attached to the NSSA. Using this
command, you can configure the default route cost on the ABR to NSSA.
By default, the NSSA is not configured, and the cost of the default route to the
NSSA is 1.
Configuring the Route Summarization of OSPF Area
Route summary means that ABR can aggregate information of the routes of the
same prefix and advertise only one route to other areas. An area can be
configured with multiple aggregate segments allowing OSPF to summarize them.
 Loading...
Loading...