Zyxel VANTAGE REPORT user manual

Vantage Report
User’s Guide
Version 2 .3
Edition 1
2/2006


Vantage Report User’s Guide
Copyright
Copyright © 2006 by ZyXEL Communications Corporation.
The contents of this publication may not be reproduced in any part or as a whole, transcribed,
stored in a retrieval system, translated into any language, or transmitted in any form or by any
means, electronic, mechanical, magnetic, optical, chemical, photocopying, manual, or
otherwise, without the prior written permission of ZyXEL Communications Corporation.
Published by ZyXEL Communications Corporation. All rights reserved.
Note: Refer also to the Open Software Announcements on page 240.
Disclaimer
ZyXEL does not assume any liability arising out of the application or use of any products, or
software described herein. Neither does it convey any license under its patent rights nor the
patent rights of others. ZyXEL further reserves the right to make changes in any products
described herein without notice. This publication is subject to change without notice.
Trademarks
ZyNOS (ZyXEL Network Operating System) is a registered trademark of ZyXEL
Communications, Inc. Other trademarks mentioned in this publication are used for
identification purposes only and may be properties of their respective owners.
Copyright 2

Vantage Report User’s Guide
ZyXEL Limited Warranty
ZyXEL warrants that (a) the Vantage software (henceforth called the SOFTWARE) will
perform substantially in accordance with the accompanying written materials for a period of
ninety (90) days from the date of receipt, and (b) any Support Services provided by ZyXEL
shall be substantially as described in applicable written materials provided to you by ZyXEL,
and ZyXEL support engineers will make commercially reasonable efforts to solve any
problem issues. To the extent allowed by applicable law, implied warranties on the
SOFTWARE, if any, are limited to ninety (90) days.
CUSTOMER REMEDIES.
ZyXEL's and its suppliers' entire liability and your exclusive remedy shall be, at ZyXEL's
option, either (a) return of the price paid, if any, or (b) repair or replacement of the
SOFTWARE that does not meet ZyXEL's Limited Warranty and which is returned to ZyXEL
with a copy of your receipt. This Limited Warranty is void if failure of the SOFTWARE has
resulted from accident, abuse, or misapplication. Any replacement SOFTWARE will be
warranted for the remainder of the original warranty period or thirty (30) days, whichever is
longer. Outside Taiwan, neither these remedies nor any product support services offered by
ZyXEL are available without proof of purchase from an authorized international source.
NO OTHER WARRANTIES.
To the maximum extent permitted by applicable law, ZyXEL and its suppliers disclaim all
other warranties and conditions, either express or implied, including, but not limited to,
implied warranties of merchantability, fitness for a particular purpose, title, and noninfringement, with regard to the SOFTWARE, and the provision of or failure to provide
Support Services. This limited warranty gives you specific legal rights. You may have others,
which vary from state/jurisdiction to state/jurisdiction.
Please read the license screen in the installation wizard. You must accept the terms of the
license in order to install Vantage.
Note: Register your product online to receive e-mail notices of firmware upgrades and
information at www.zyxel.com
North American products.
for global products, or at www.us.zyxel.com for
3 ZyXEL Limited Warranty

Vantage Report User’s Guide
Customer Support
Please have the following information ready when you contact customer support.
• Product model.
• Warranty Information.
• Brief description of the problem and the steps you took to solve it.
METHOD
LOCATION
CORPORATE
HEADQUARTERS
(WORLDWIDE)
CZECH REPUBLIC
DENMARK
FINLAND
FRANCE
GERMANY
HUNGARY
KAZAKHSTAN
NORTH AMERICA
NORWAY
POLAND
SUPPORT E-MAIL TELEPHONE
SALES E-MAIL FAX FTP SITE
support@zyxel.com.tw +886-3-578-3942 www.zyxel.com
sales@zyxel.com.tw +886-3-578-2439 ftp.zyxel.com
info@cz.zyxel.com +420-241-091-350 www.zyxel.cz ZyXEL Communications
info@cz.zyxel.com +420-241-091-359
support@zyxel.dk +45-39-55-07-00 www.zyxel.dk ZyXEL Communications A/S
sales@zyxel.dk +45-39-55-07-07
support@zyxel.fi +358-9-4780-8411 www.zyxel.fi ZyXEL Communications Oy
sales@zyxel.fi +358-9-4780 8448
info@zyxel.fr +33-4-72-52-97-97 www.zyxel.fr ZyXEL France
+33-4-72-52-19-20
support@zyxel.de +49-2405-6909-0 www.zyxel.de ZyXEL Deutschland GmbH.
sales@zyxel.de +49-2405-6909-99
support@zyxel.hu +36-1-3361649 www.zyxel.hu ZyXEL Hungary
info@zyxel.hu +36-1-3259100
http://zyxel.kz/support +7-3272-590-698 www.zyxel.kz ZyXEL Kazakhstan
sales@zyxel.kz +7-3272-590-689
support@zyxel.com 1-800-255-4101
+1-714-632-0882
sales@zyxel.com +1-714-632-0858 ftp.us.zyxel.com
support@zyxel.no +47-22-80-61-80 www.zyxel.no ZyXEL Communications A/S
sales@zyxel.no +47-22-80-61-81
info@pl.zyxel.com +48-22-5286603 www.pl.zyxel.com ZyXEL Communications
+48-22-5206701
A
WEB SITE
REGULAR MAIL
www.europe.zyxel.com
ftp.europe.zyxel.com
www.us.zyxel.com ZyXEL Communications Inc.
ZyXEL Communications Corp.
6 Innovation Road II
Science Park
Hsinchu 300
Ta iw a n
Czech s.r.o.
Modranská 621
143 01 Praha 4 - Modrany
Ceská Republika
Columbusvej
2860 Soeborg
Denmark
Malminkaari 10
00700 Helsinki
Finland
1 rue des Vergers
Bat. 1 / C
69760 Limonest
France
Adenauerstr. 20/A2 D-52146
Wuerselen
Germany
48, Zoldlomb Str.
H-1025, Budapest
Hungary
43, Dostyk ave.,Office 414
Dostyk Business Centre
050010, Almaty
Republic of Kazakhstan
1130 N. Miller St.
Anaheim
CA 92806-2001
U.S.A.
Nils Hansens vei 13
0667 Oslo
Norway
ul.Emilli Plater 53
00-113 Warszawa
Poland
Customer Support 4
Vantage Report User’s Guide
METHOD
LOCATION
RUSSIA
SPAIN
SWEDEN
UKRAINE
UNITED KINGDOM
a. “+” is the (prefix) number you enter to make an international telephone call.
SUPPORT E-MAIL TELEPHONE
SALES E-MAIL FAX FTP SITE
http://zyxel.ru/support +7-095-542-89-29 www.zyxel.ru ZyXEL Russia
sales@zyxel.ru +7-095-542-89-25
support@zyxel.es +34-902-195-420 www.zyxel.es ZyXEL Communications
sales@zyxel.es +34-913-005-345
support@zyxel.se +46-31-744-7700 www.zyxel.se ZyXEL Communications A/S
sales@zyxel.se +46-31-744-7701
support@ua.zyxel.com +380-44-247-69-78 www.ua.zyxel.com ZyXEL Ukraine
sales@ua.zyxel.com +380-44-494-49-32
support@zyxel.co.uk +44-1344 303044
08707 555779 (UK only)
sales@zyxel.co.uk +44-1344 303034 ftp.zyxel.co.uk
A
•
WEB SITE
REGULAR MAIL
Ostrovityanova 37a Str.
Moscow, 117279
Russia
Alejandro Villegas 33
1º, 28043 Madrid
Spain
Sjöporten 4, 41764 Göteborg
Sweden
13, Pimonenko Str.
Kiev, 04050
Ukraine
www.zyxel.co.uk ZyXEL Communications UK
Ltd.,11 The Courtyard,
Eastern Road, Bracknell,
Berkshire, RG12 2XB,
United Kingdom (UK)
5 Customer Support

Vantage Report User’s Guide
Table of Contents
Copyright ..................................................................................................................2
ZyXEL Limited Warranty.......................................................................................... 3
Customer Support.................................................................................................... 4
Table of Contents ..................................................................................................... 6
Preface ....................................................................................................................20
Chapter 1
Introducing Vantage Report .................................................................................. 22
1.1 Introduction ........................................................................................................22
1.2 Key Features ......................................................................................................22
1.3 Versions .............................................................................................................23
Chapter 2
The Vantage Report Server ...................................................................................26
2.1 Starting and Stopping the Vantage Report Server ..............................................26
2.2 E-Mail in the Vantage Report Server ..................................................................26
2.3 Time in the Vantage Report Server ....................................................................27
2.4 ZyXEL Device Configuration and Source Data ..................................................28
Chapter 3
The Web Configurator............................................................................................ 30
3.1 Web Configurator Requirements ........................................................................30
3.2 Web Configurator Access ..................................................................................30
3.3 Title Bar ..............................................................................................................32
3.4 Device Window ..................................................................................................32
3.5 Function Window ................................................................................................35
3.6 Report Window ...................................................................................................40
3.6.1 Monitor Layout ..........................................................................................40
3.6.2 Statistical Report Layout ...........................................................................42
Chapter 4
Monitor .................................................................................................................... 44
4.1 Bandwidth Monitor .............................................................................................44
4.2 Service Monitor ..................................................................................................45
4.3 Attack Monitor ....................................................................................................46
4.4 Intrusion Monitor ................................................................................................47
Table of Contents 6

Vantage Report User’s Guide
4.5 Anti-Virus Monitor ...............................................................................................48
4.6 Anti-Spam Monitor ..............................................................................................49
Chapter 5
Traffic ...................................................................................................................... 52
5.1 Bandwidth ..........................................................................................................52
5.1.1 Bandwidth Summary..................................................................................52
5.1.2 Bandwidth Summary Drill-Down ................................................................54
5.1.3 Bandwidth Top Protocols ...........................................................................56
5.1.4 Bandwidth Top Protocols Drill-Down..........................................................58
5.1.5 Top Bandwidth Hosts .................................................................................60
5.1.6 Top Bandwidth Hosts Drill-Down ...............................................................62
5.2 Web Traffic .........................................................................................................63
5.2.1 Top Web Sites............................................................................................63
5.2.2 Top Web Sites Drill-Down ..........................................................................65
5.2.3 Top Web Hosts ..........................................................................................67
5.2.4 Top Web Hosts Drill-Down .........................................................................68
5.3 FTP Traffic ..........................................................................................................70
5.3.1 Top FTP Sites ............................................................................................70
5.3.2 Top FTP Sites Drill-Down...........................................................................72
5.3.3 Top FTP Hosts ...........................................................................................74
5.3.4 Top FTP Hosts Drill-Down .........................................................................75
5.4 Mail Traffic ..........................................................................................................77
5.4.1 Top Mail Sites ............................................................................................77
5.4.2 Top Mail Sites Drill-Down ...........................................................................79
5.4.3 Top Mail Hosts ...........................................................................................81
5.4.4 Top Mail Hosts Drill-Down..........................................................................82
5.5 VPN Traffic .........................................................................................................84
5.5.1 Top VPN Peer Gateways...........................................................................84
5.5.2 Top VPN Peer Gateways Drill-Down .........................................................86
5.5.3 Top VPN Hosts ..........................................................................................88
5.5.4 Top VPN Hosts Drill-Down .........................................................................90
5.6 Other Traffic .......................................................................................................92
5.6.1 Service Settings.........................................................................................92
5.6.2 Top Destinations of Other Traffic ...............................................................93
5.6.3 Top Destinations of Other Traffic Drill-Down..............................................95
5.6.4 Top Sources of Other Traffic ......................................................................97
5.6.5 Top Sources of Other Traffic Drill-Down ....................................................99
Chapter 6
Network Attack ..................................................................................................... 102
6.1 Attack ...............................................................................................................102
6.1.1 Attack Summary ......................................................................................102
7 Table of Contents

Vantage Report User’s Guide
6.1.2 Attack Summary Drill-Down.....................................................................104
6.1.3 Top Attack Sources ..................................................................................106
6.1.4 Top Attack Sources Drill-Down ................................................................107
6.1.5 Top Attack Categories..............................................................................109
6.1.6 Top Attack Categories Drill-Down ............................................................ 111
6.2 Intrusion ........................................................................................................... 113
6.2.1 Intrusion Summary................................................................................... 113
6.2.2 Intrusion Summary Drill-Down .................................................................115
6.2.3 Top Intrusion Signatures .......................................................................... 117
6.2.4 Top Intrusion Signatures Drill-Down ........................................................119
6.2.5 Top Intrusion Sources ..............................................................................121
6.2.6 Top Intrusion Sources Drill-Down ............................................................123
6.2.7 Top Intrusion Destinations .......................................................................125
6.2.8 Top Intrusion Destinations Drill-Down ......................................................127
6.2.9 Intrusion Severities ..................................................................................129
6.2.10 Intrusion Severities Drill-Down...............................................................131
6.3 AntiVirus ...........................................................................................................133
6.3.1 Virus Summary ........................................................................................133
6.3.2 Virus Summary Drill-Down.......................................................................135
6.3.3 Top Viruses ..............................................................................................137
6.3.4 Top Viruses Drill-Down ............................................................................139
6.3.5 Top Virus Sources....................................................................................141
6.3.6 Top Virus Sources Drill-Down ..................................................................143
6.3.7 Top Virus Destinations .............................................................................145
6.4 AntiSpam ..........................................................................................................147
6.4.1 Spam Summary .......................................................................................147
6.4.2 Spam Summary Drill-Down......................................................................149
6.4.3 Top Spam Senders ..................................................................................151
6.4.4 Top Spam Sources...................................................................................153
6.4.5 Top Spam Scores.....................................................................................155
Chapter 7
Security Policy ..................................................................................................... 158
7.1 Blocked Web Accesses ....................................................................................158
7.1.1 Web Block Summary ...............................................................................158
7.1.2 Web Block Summary Drill-Down..............................................................160
7.1.3 Top Blocked Web Sites ............................................................................162
7.1.4 Top Blocked Web Sites Drill-Down ..........................................................163
7.1.5 Top Blocked Web Hosts...........................................................................165
7.1.6 Top Blocked Web Hosts Drill-Down .........................................................167
7.1.7 Top Blocked Web Categories ..................................................................169
7.1.8 Top Blocked Web Categories Drill-Down .................................................170
7.2 Allowed Web Accesses ....................................................................................172
Table of Contents 8

Vantage Report User’s Guide
7.2.1 Web Allowed Summary ...........................................................................172
7.2.2 Web Allowed Summary Drill-Down..........................................................174
7.2.3 Top Allowed Web Sites ............................................................................176
7.2.4 Top Allowed Web Sites Drill-Down ..........................................................177
7.2.5 Top Allowed Web Hosts ...........................................................................179
7.2.6 Top Allowed Web Hosts Drill-Down .........................................................181
Chapter 8
Authentication ...................................................................................................... 184
8.1 Successful Login Screen ..................................................................................184
8.2 Failed Login Screen .........................................................................................185
Chapter 9
Log Viewer ............................................................................................................ 188
9.1 Regular Log Viewer ..........................................................................................188
9.2 Critical Log Viewer ...........................................................................................190
Chapter 10
Schedule Report................................................................................................... 194
10.1 Scheduled Report Summary Screen ..............................................................194
10.2 Customize Daily Report Screen .....................................................................195
10.3 Customize Weekly Report Screen .................................................................197
10.4 Customize Overtime Report Screen ..............................................................199
Chapter 11
System .................................................................................................................. 202
11.1 General Configuration Screen ........................................................................202
11.2 Server Configuration Screen ..........................................................................203
11.3 User Maintenance Screens ............................................................................204
11.3.1 User Maintenance Summary Screen.....................................................205
11.3.2 Add/Edit User Account Screen ..............................................................205
11.4 Data Maintenance Screens ............................................................................206
11.4.1 Data Backup and Data Restore Screen .................................................207
11.4.2 Device List Export and Device List Import Screen.................................207
11.5 Upgrade Screen .............................................................................................208
11.6 Registration Screens ......................................................................................209
11.6.1 Registration Summary Screen...............................................................209
11.6.2 Registration Screen ...............................................................................211
11.7 About Screen ..................................................................................................212
Appendix A
Troubleshooting................................................................................................... 214
Appendix B
9 Table of Contents

Vantage Report User’s Guide
Product Specifications ........................................................................................ 216
Appendix C
Setting up Your Computer’s IP Address............................................................ 218
Windows 2000/NT/XP ............................................................................................ 218
Verifying Settings ................................................................................................... 222
Appendix D
Log Descriptions.................................................................................................. 224
Appendix E
Open Software Announcements......................................................................... 240
Notice ..................................................................................................................... 240
Index...................................................................................................................... 276
Table of Contents 10

Vantage Report User’s Guide
11 Table of Contents

Vantage Report User’s Guide
List of Figures
Figure 1 Typical Vantage Report Application ...................................................................... 22
Figure 2 Web Configurator Login Screen ............................................................................ 31
Figure 3 Web Configurator Main Screen ............................................................................. 31
Figure 4 Device Window ..................................................................................................... 33
Figure 5 Add Device, Edit Device, and Device Information Screens .................................. 34
Figure 6 Device Window Right-Click Menu ......................................................................... 35
Figure 7 Function Window .................................................................................................. 35
Figure 8 Function Window Right-Click Menu ...................................................................... 39
Figure 9 Report Window: Monitor and Statistical Report Examples .................................... 40
Figure 10 Typical Monitor Layout ........................................................................................ 41
Figure 11 Report Window Right-Click Menu ....................................................................... 42
Figure 12 Typical Statistical Report Layout ......................................................................... 42
Figure 13 Report Window Right-Click Menu ....................................................................... 43
Figure 14 Monitor > Bandwidth ........................................................................................... 44
Figure 15 Monitor > Service ................................................................................................ 45
Figure 16 Monitor > Attack .................................................................................................. 47
Figure 17 Monitor > Intrusion .............................................................................................. 48
Figure 18 Monitor > AntiVirus .............................................................................................. 49
Figure 19 Monitor > AntiSpam ............................................................................................ 50
Figure 20 Traffic > Bandwidth > Summary .......................................................................... 53
Figure 21 Traffic > Bandwidth > Summary > Drill-Down ..................................................... 55
Figure 22 Traffic > Bandwidth > Top Protocol ..................................................................... 57
Figure 23 Traffic > Bandwidth > Top Protocol > Drill-Down ................................................. 59
Figure 24 Traffic > Bandwidth > Top Hosts ......................................................................... 60
Figure 25 Traffic > Bandwidth > Top Hosts > Drill-Down ..................................................... 62
Figure 26 Traffic > WEB > Top Sites ................................................................................... 64
Figure 27 Traffic > WEB > Top Sites > Drill-Down .............................................................. 66
Figure 28 Traffic > WEB > Top Hosts .................................................................................. 67
Figure 29 Traffic > WEB > Top Hosts > Drill-Down ............................................................. 69
Figure 30 Traffic > FTP > Top Sites .................................................................................... 71
Figure 31 Traffic > FTP > Top Sites > Drill-Down ................................................................ 73
Figure 32 Traffic > FTP > Top Hosts ................................................................................... 74
Figure 33 Traffic > FTP > Top Hosts > Drill-Down ............................................................... 76
Figure 34 Traffic > MAIL > Top Sites ................................................................................... 78
Figure 35 Traffic > MAIL > Top Sites > Drill-Down .............................................................. 80
Figure 36 Traffic > MAIL > Top Hosts .................................................................................. 81
List of Figures 12

Vantage Report User’s Guide
Figure 37 Traffic > MAIL > Top Hosts > Drill-Down ............................................................. 83
Figure 38 Traffic > VPN > Top Peer Gateways ................................................................... 85
Figure 39 Traffic > VPN > Top Peer Gateways > Drill-Down .............................................. 87
Figure 40 Traffic > VPN > Top Hosts ................................................................................... 89
Figure 41 Traffic > VPN > Top Hosts > Drill-Down .............................................................. 91
Figure 42 Service > Customization > Customization .......................................................... 92
Figure 43 Traffic > Customization > Top Destinations ......................................................... 94
Figure 44 Traffic > Customization > Top Destinations > Drill-Down .................................... 96
Figure 45 Traffic > Customization > Top Sources ............................................................... 97
Figure 46 Traffic > Customization > Top Sources > Drill-Down .......................................... 99
Figure 47 Network Attack > Attack > Summary .................................................................. 103
Figure 48 Network Attack > Attack > Summary > Drill-Down .............................................. 105
Figure 49 Network Attack > Attack > Top Sources .............................................................. 106
Figure 50 Network Attack > Attack > Top Sources > Drill-Down ......................................... 108
Figure 51 Network Attack > Attack > By Category .............................................................. 110
Figure 52 Network Attack > Attack > By Category > Drill-Down ......................................... 112
Figure 53 Network Attack > Intrusion > Summary .............................................................. 114
Figure 54 Network Attack > Intrusion > Summary > Drill-Down .......................................... 116
Figure 55 Network Attack > Intrusion > Top Intrusions ....................................................... 118
Figure 56 Network Attack > Intrusion > Top Intrusions > Drill-Down ................................... 120
Figure 57 Network Attack > Intrusion > Top Sources .......................................................... 122
Figure 58 Network Attack > Intrusion > Top Sources > Drill-Down ..................................... 124
Figure 59 Intrusion > Top Destinations ............................................................................... 126
Figure 60 Network Attack > Intrusion > Top Destinations > Drill-Down ............................... 128
Figure 61 Network Attack > Intrusion > By Severity ............................................................ 130
Figure 62 Network Attack > Intrusion > By Severity > Drill-Down ....................................... 132
Figure 63 Network Attack > AntiVirus > Summary .............................................................. 134
Figure 64 Network Attack > AntiVirus > Summary > Drill-Down ......................................... 136
Figure 65 Network Attack > AntiVirus > Top Viruses ........................................................... 138
Figure 66 Network Attack > AntiVirus > Top Viruses > Drill-Down ...................................... 140
Figure 67 Network Attack > AntiVirus > Top Sources ......................................................... 142
Figure 68 Network Attack > AntiVirus > Top Sources > Drill-Down ..................................... 144
Figure 69 Network Attack > AntiVirus > Top Destinations ................................................... 146
Figure 70 Network Attack > AntiSpam > Summary ............................................................. 148
Figure 71 Network Attack > AntiSpam > Summary > Drill-Down ........................................ 150
Figure 72 Network Attack > AntiSpam > Top Senders ........................................................ 152
Figure 73 Network Attack > AntiSpam > Top Sources ........................................................ 154
Figure 74 Network Attack > AntiSpam > By Score .............................................................. 156
Figure 75 Security Policy > WEB Blocked > Summary ....................................................... 159
Figure 76 Security Policy > WEB Blocked > Summary > Drill-Down .................................. 161
Figure 77 Security Policy > WEB Blocked > Top Sites ....................................................... 162
Figure 78 Security Policy > WEB Blocked > Top Sites > Drill-Down ................................... 164
Figure 79 Security Policy > WEB Blocked > Top Hosts ...................................................... 166
13 List of Figures

Vantage Report User’s Guide
Figure 80 Security Policy > WEB Blocked > Top Hosts > Drill-Down .................................. 168
Figure 81 Security Policy > WEB Blocked > By Category .................................................. 169
Figure 82 Security Policy > WEB Blocked > By Category > Drill-Down .............................. 171
Figure 83 Security Policy > WEB Allowed > Summary ....................................................... 173
Figure 84 Security Policy > WEB Allowed > Summary > Drill-Down .................................. 175
Figure 85 Security Policy > WEB Allowed > Top Sites ........................................................ 176
Figure 86 Security Policy > WEB Allowed > Top Sites > Drill-Down ................................... 178
Figure 87 Security Policy > WEB Allowed > Top Hosts ...................................................... 180
Figure 88 Security Policy > WEB Allowed > Top Hosts > Drill-Down .................................. 182
Figure 89 Event > Device Login > Successful Login ........................................................... 184
Figure 90 Event > Device Login > Failed Login .................................................................. 185
Figure 91 Log Viewer > All Logs ......................................................................................... 189
Figure 92 Log Viewer > Critical Logs .................................................................................. 191
Figure 93 Schedule Reports > Schedule Reports ............................................................... 194
Figure 94 Schedule Reports > Schedule Reports > Add (Daily Report) ............................. 196
Figure 95 Schedule Reports > Schedule Reports > Add (Weekly Report) ......................... 198
Figure 96 Schedule Reports > Schedule Reports > Add (Overtime Report) ...................... 200
Figure 97 System > General Configuration ......................................................................... 203
Figure 98 System > Server Configuration ........................................................................... 204
Figure 99 System > User Maintenance ............................................................................... 205
Figure 100 Add/Edit User Account Screen ......................................................................... 206
Figure 101 System > Data Maintenance > Configuration Backup & Restore ..................... 207
Figure 102 System > Data Maintenance > Device List Import & Export ............................. 208
Figure 103 System > Upgrade ............................................................................................ 209
Figure 104 System > Registration ....................................................................................... 210
Figure 105 Registration Screen .......................................................................................... 211
Figure 106 System > About ................................................................................................ 212
Figure 107 Windows XP: Start Menu .................................................................................. 219
Figure 108 Windows XP: Control Panel .............................................................................. 219
Figure 109 Windows XP: Control Panel: Network Connections: Properties ....................... 220
Figure 110 Windows XP: Local Area Connection Properties .............................................. 220
Figure 111 Windows XP: Advanced TCP/IP Settings .......................................................... 221
Figure 112 Windows XP: Internet Protocol (TCP/IP) Properties ......................................... 222
List of Figures 14

Vantage Report User’s Guide
15 List of Figures

Vantage Report User’s Guide
List of Tables
Table 1 Differences Between Standard Version and Professional Version ........................ 24
Table 2 Processing Times by Menu Item ........................................................................... 27
Table 3 Configuration Requirements for ZyXEL Devices by Menu Item ............................ 28
Table 4 Title Bar ................................................................................................................. 32
Table 5 Device Window ...................................................................................................... 33
Table 6 Function Window ................................................................................................... 36
Table 7 Typical Monitor Features ....................................................................................... 41
Table 8 Typical Statistical Report Features ........................................................................ 42
Table 9 Monitor > Bandwidth .............................................................................................. 44
Table 10 Monitor > Service ................................................................................................ 46
Table 11 Monitor > Attack ................................................................................................... 47
Table 12 Monitor > Intrusion ............................................................................................... 48
Table 13 Monitor > AntiVirus .............................................................................................. 49
Table 14 Monitor > AntiSpam ............................................................................................. 50
Table 15 Traffic > Bandwidth > Summary .......................................................................... 53
Table 16 Traffic > Bandwidth > Summary > Drill-Down ...................................................... 55
Table 17 Traffic > Bandwidth > Top Protocol ...................................................................... 57
Table 18 Traffic > Bandwidth > Top Protocol > Drill-Down ................................................. 59
Table 19 Traffic > Bandwidth > Top Hosts .......................................................................... 61
Table 20 Traffic > Bandwidth > Top Hosts > Drill-Down ..................................................... 63
Table 21 Traffic > WEB > Top Sites .................................................................................... 64
Table 22 Traffic > WEB > Top Sites > Drill-Down ............................................................... 66
Table 23 Traffic > WEB > Top Hosts .................................................................................. 68
Table 24 Traffic > WEB > Top Hosts > Drill-Down .............................................................. 69
Table 25 Traffic > FTP > Top Sites ..................................................................................... 71
Table 26 Traffic > FTP > Top Sites > Drill-Down ................................................................ 73
Table 27 Traffic > FTP > Top Hosts .................................................................................... 75
Table 28 Traffic > FTP > Top Hosts > Drill-Down ............................................................... 76
Table 29 Traffic > MAIL > Top Sites ................................................................................... 78
Table 30 Traffic > MAIL > Top Sites > Drill-Down ............................................................... 80
Table 31 Traffic > MAIL > Top Hosts .................................................................................. 82
Table 32 Traffic > MAIL > Top Hosts > Drill-Down .............................................................. 83
Table 33 Traffic > VPN > Top Peer Gateways .................................................................... 85
Table 34 Traffic > VPN > Top Peer Gateways > Drill-Down ............................................... 87
Table 35 Traffic > VPN > Top Hosts ................................................................................... 89
Table 36 Traffic > VPN > Top Hosts > Drill-Down ............................................................... 91
List of Tables 16

Vantage Report User’s Guide
Table 37 Service > Customization > Customization ........................................................... 93
Table 38 Traffic > Customization > Top Destinations ......................................................... 94
Table 39 Traffic > Customization > Top Destinations > Drill-Down .................................... 96
Table 40 Traffic > Customization > Top Sources ................................................................ 98
Table 41 Traffic > Customization > Top Sources > Drill-Down ........................................... 99
Table 42 Network Attack > Attack > Summary ................................................................... 103
Table 43 Network Attack > Attack > Summary > Drill-Down .............................................. 105
Table 44 Network Attack > Attack > Top Sources .............................................................. 107
Table 45 Network Attack > Attack > Top Sources > Drill-Down .......................................... 108
Table 46 Network Attack > Attack > By Category .............................................................. 110
Table 47 Network Attack > Attack > By Category > Drill-Down .......................................... 112
Table 48 Network Attack > Intrusion > Summary ............................................................... 114
Table 49 Network Attack > Intrusion > Summary > Drill-Down .......................................... 116
Table 50 Network Attack > Intrusion > Top Intrusions ........................................................ 118
Table 51 Network Attack > Intrusion > Top Intrusions > Drill-Down ................................... 120
Table 52 Network Attack > Intrusion > Top Sources .......................................................... 122
Table 53 Network Attack > Intrusion > Top Sources > Drill-Down ...................................... 124
Table 54 Intrusion > Top Destinations ................................................................................ 126
Table 55 Network Attack > Intrusion > Top Destinations > Drill-Down ............................... 128
Table 56 Network Attack > Intrusion > By Severity ............................................................ 130
Table 57 Network Attack > Intrusion > By Severity > Drill-Down ........................................ 132
Table 58 Network Attack > AntiVirus > Summary ............................................................... 134
Table 59 Network Attack > AntiVirus > Summary > Drill-Down .......................................... 136
Table 60 Network Attack > AntiVirus > Top Viruses ........................................................... 138
Table 61 Network Attack > AntiVirus > Top Viruses > Drill-Down ...................................... 140
Table 62 Network Attack > AntiVirus > Top Sources .......................................................... 142
Table 63 Network Attack > AntiVirus > Top Sources > Drill-Down ..................................... 144
Table 64 Network Attack > AntiVirus > Top Destinations ................................................... 146
Table 65 Network Attack > AntiSpam > Summary ............................................................. 148
Table 66 Network Attack > AntiSpam > Summary > Drill-Down ......................................... 150
Table 67 Network Attack > AntiSpam > Top Senders ......................................................... 152
Table 68 Network Attack > AntiSpam > Top Sources ......................................................... 154
Table 69 Network Attack > AntiSpam > By Score .............................................................. 156
Table 70 Security Policy > WEB Blocked > Summary ....................................................... 159
Table 71 Security Policy > WEB Blocked > Summary > Drill-Down ................................... 161
Table 72 Security Policy > WEB Blocked > Top Sites ........................................................ 163
Table 73 Security Policy > WEB Blocked > Top Sites > Drill-Down ................................... 164
Table 74 Security Policy > WEB Blocked > Top Hosts ....................................................... 166
Table 75 Security Policy > WEB Blocked > Top Hosts > Drill-Down .................................. 168
Table 76 Security Policy > WEB Blocked > By Category ................................................... 170
Table 77 Security Policy > WEB Blocked > By Category > Drill-Down .............................. 171
Table 78 Security Policy > WEB Allowed > Summary ........................................................ 173
Table 79 Security Policy > WEB Allowed > Summary > Drill-Down ................................... 175
17 List of Tables

Vantage Report User’s Guide
Table 80 Security Policy > WEB Allowed > Top Sites ........................................................ 177
Table 81 Security Policy > WEB Allowed > Top Sites > Drill-Down .................................... 178
Table 82 Security Policy > WEB Allowed > Top Hosts ....................................................... 180
Table 83 Security Policy > WEB Allowed > Top Hosts > Drill-Down .................................. 182
Table 84 Event > Device Login > Successful Login ........................................................... 184
Table 85 Event > Device Login > Failed Login ................................................................... 186
Table 86 Log Viewer > All Logs .......................................................................................... 189
Table 87 Log Viewer > Critical Logs ................................................................................... 192
Table 88 Schedule Reports > Schedule Reports ............................................................... 195
Table 89 Schedule Reports > Schedule Reports > Add (Daily Report) .............................. 197
Table 90 Schedule Reports > Schedule Reports > Add (Weekly Report) .......................... 199
Table 91 Schedule Reports > Schedule Reports > Add (Overtime Report) ....................... 201
Table 92 System > General Configuration ......................................................................... 203
Table 93 System > Server Configuration ........................................................................... 204
Table 94 System > User Maintenance ............................................................................... 205
Table 95 Add/Edit User Account Screen ............................................................................ 206
Table 96 System > Data Maintenance > Configuration Backup & Restore ........................ 207
Table 97 System > Data Maintenance > Device List Import & Export ................................ 208
Table 98 System > Upgrade ............................................................................................... 209
Table 99 System > Registration ......................................................................................... 210
Table 100 Registration Screen ........................................................................................... 211
Table 101 Web Configurator Specifications ....................................................................... 216
Table 102 System Notifications Specifications ................................................................... 216
Table 103 Feature Specifications ....................................................................................... 216
Table 104 System Maintenance Logs ................................................................................ 224
Table 105 System Error Logs ............................................................................................. 225
Table 106 Access Control Logs .......................................................................................... 225
Table 107 TCP Reset Logs ................................................................................................ 226
Table 108 Packet Filter Logs .............................................................................................. 226
Table 109 ICMP Logs ......................................................................................................... 226
Table 110 CDR Logs .......................................................................................................... 227
Table 111 PPP Logs ........................................................................................................... 227
Table 112 UPnP Logs ......................................................................................................... 228
Table 113 Content Filtering Logs ........................................................................................ 228
Table 114 Attack Logs ........................................................................................................ 229
Table 115 IPSec Logs ........................................................................................................ 230
Table 116 IKE Logs ............................................................................................................230
Table 117 PKI Logs ............................................................................................................233
Table 118 Certificate Path Verification Failure Reason Codes ........................................... 234
Table 119 802.1X Logs ....................................................................................................... 235
Table 120 ACL Setting Notes ............................................................................................. 236
Table 121 ICMP Notes ....................................................................................................... 236
Table 122 Syslog Logs ....................................................................................................... 237
List of Tables 18

Vantage Report User’s Guide
Table 123 RFC-2408 ISAKMP Payload Types ................................................................... 237
19 List of Tables

Vantage Report User’s Guide
Preface
Vantage Report is a cost-effective, browser-based global management solution that allows an
administrator from any location to easily manage, monitor and gather statistics on ZyXEL
devices located worldwide.
About This User's Guide
This manual is designed to guide you through the configuration of Vantage Report for its
various applications.
Related Documentation
• Included CD
Refer to the included CD for support documents.
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away.
• Vantage Report Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
• ZyXEL Glossary and Web Site
Please refer to www.zyxel.com
support documentation.
for an online glossary of networking terms and additional
User Guide Feedback
Help us help you! E-mail all User Guide-related comments, questions or suggestions for
improvement to techwriters@zyxel.com.tw or send regular mail to The Technical Writing
Team, ZyXEL Communications Corp., 6 Innovation Road II, Science-Based Industrial Park,
Hsinchu, 300, Taiwan. Thank you!
Syntax Conventions
• The version number on the title page is the version of Vantage Report that is documented
in this User’s Guide.
• Enter means for you to type one or more characters and press the carriage return. Select
or Choose means for you to use one of the predefined choices.
• The choices of a menu item are in Bold Arial font.
• Mouse action sequences are denoted using a right angle bracket (>). For example, click
Traffic > WEB > Top Hosts means first click Traffic, then click WEB and finally click
Top Hos t s .
Preface 20

Vantage Report User’s Guide
21 Preface
Introducing Vantage Report
Please see the Quick Start Guide for Vantage Report setup requirements, installation, and
access. This chapter introduces Vantage Report and its key features.
1.1 Introduction
With Vantage Report, you can monitor network access, enhance security, and anticipate future
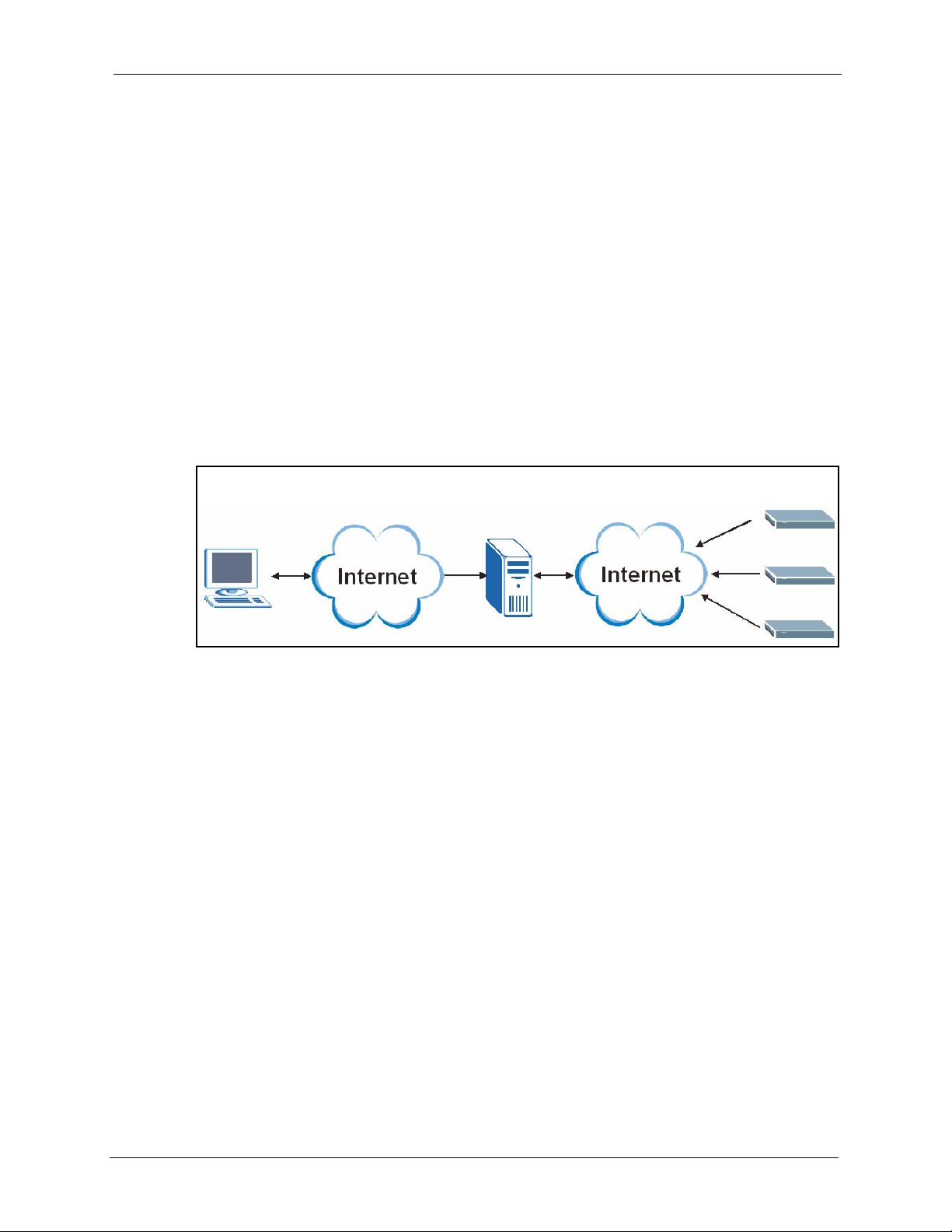
bandwidth needs. A typical application is illustrated in Figure 1.
Figure 1 Typical Vantage Report Application
Vantage Report User’s Guide
CHAPTER 1
A
In this example, you use the web configurator (A) to set up the Vantage Report server (B).
You also configure the ZyXEL devices (C) to send their logs and traffic statistics to the
Vantage Report Server. The Vantage Report server collects this information. Then, you can
• monitor the whole network
• look at historical reports about network performance and events
• examine device logs
The Vantage Report server can also send statistical reports to you by e-mail.
1.2 Key Features
B
C
• Device Monitors and Logs
Monitor the status of all your ZyXEL devices in one application. You can also look at the
logs for all your ZyXEL devices in Vantage Report. In normal operation, this information
should be no older than thirty minutes, worst-case.
• Statistical Reports
Chapter 1 Introducing Vantage Report 22

Vantage Report User’s Guide
Generate reports for historical analysis. These reports include bandwidth usage, service
usage, VPN usage, web filter (blocked sites), attack, intrusion, anti-virus, anti-spam, and
authentication reports. (Some reports are not available for every ZyXEL device.)
• Drill-Down Reports
In most statistical reports, look at more details for clearer understanding and better
decisions. For example, when you look at the top web sites, you can look at which users
are accessing each one.
• Report Formats
Generate statistical reports in PDF or HTML format.
• Reverse DNS Lookup
Where possible, see domain names, instead of IP addresses, in statistical reports.
• Scheduled Reports
Set up regular times to generate and e-mail statistical reports.
• Registration, Activation, and Upgrades
Register and activate on myZyXEL.com through Vantage Report. This makes getting the
trial version and upgrading simpler.
• System Service
Run and manage Vantage Report as a system service.
• Administration
Create separate accounts for network administrators and device administrators. These
accounts do not give access to administration screens for Vantage Report.
• File Management and Data Maintenance
Backup Vantage Report configurations, including various statistical "snapshots," and
restore them later.
1.3 Versions
There are two versions of Vantage Report, standard version and professional version. When
you install Vantage Report, you get the standard version. The professional version requires a
license key, which you usually have to purchase.
Note: This User’s Guide discusses the features in the professional version.
23 Chapter 1 Introducing Vantage Report
Vantage Report User’s Guide
The following table shows some of the differences between the standard and professional
version.
Table 1 Differences Between Standard Version and Professional Version
FEATURE STANDARD PROFESSIONAL
number of supported devices 1 up to 25
number of scheduled reports 20 500
supported formats for scheduled reports PDF PDF, HTML
drill-down reports no yes
reverse DNS lookup no yes
web usage by category no yes
AntiVirus no yes
AntiSpam no yes
There is also a free trial of the professional version. The trial version is the same as the
professional version except that it only supports one device. You can get the trial version by
registering Vantage Report. See section 11.6 on page 209 for more information
Chapter 1 Introducing Vantage Report 24

Vantage Report User’s Guide
25 Chapter 1 Introducing Vantage Report
Vantage Report User’s Guide
CHAPTER 2
The Vantage Report Server
This chapter explains several characteristics of the Vantage Report server.
2.1 Starting and Stopping the Vantage Report Server
Note: Make sure the port Vantage Report uses for web services is not used by other
applications, especially web servers.
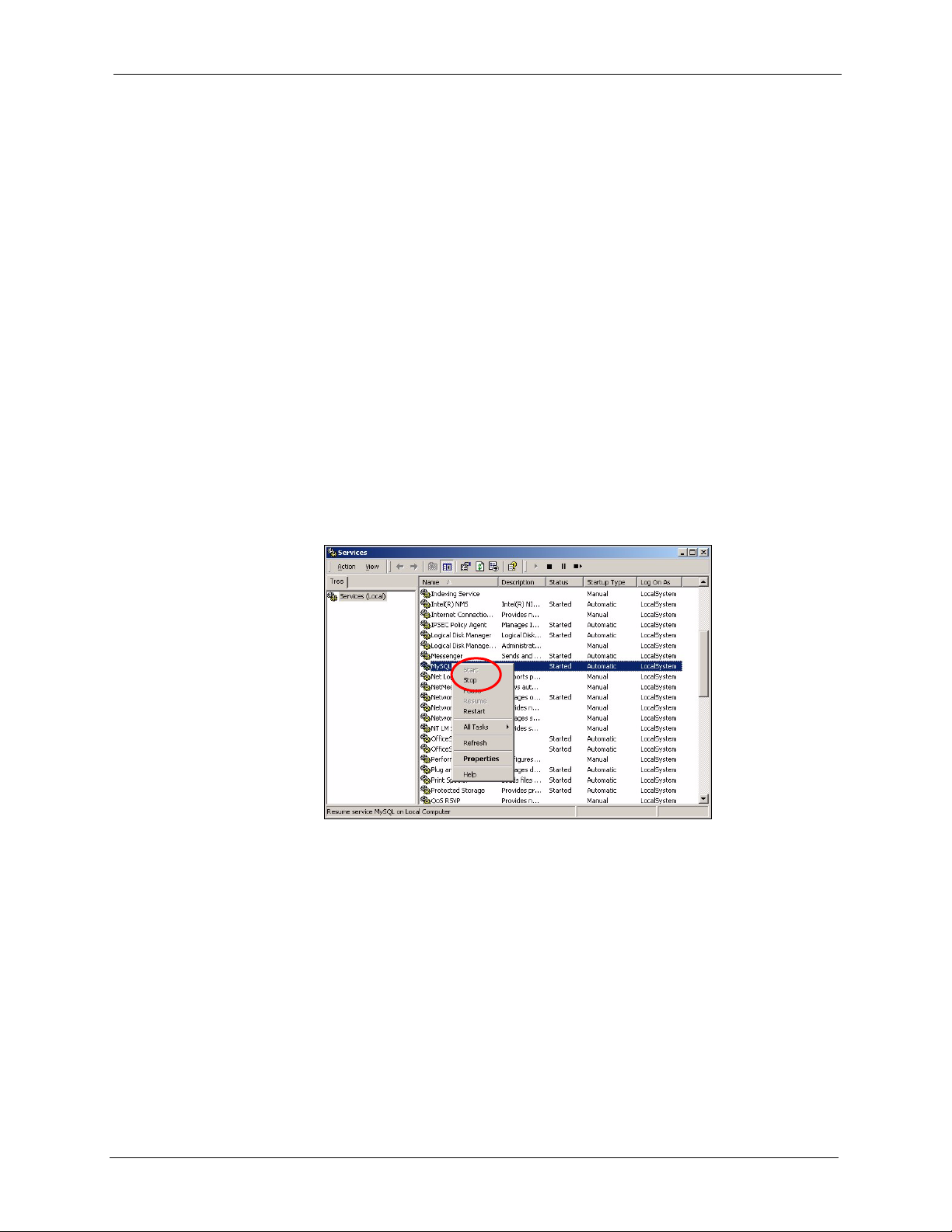
The Vantage Report server runs as a service on the Vantage Report server. By default, this
service starts automatically when you log in to the Vantage Report server. You can use the
services management screen to start, stop, or configure this service. To open this screen,
1 In Windows 2000, click Start > Settings > Control Panel > Administrative Tools >
Services. The Services screen opens.
2 Right-click on Vantage Report. A menu appears.
3 Select Start or Stop to start or stop the Vantage Report service. Select Properties to
configure the service.
2.2 E-Mail in the Vantage Report Server
Note: Before the Vantage Report server can send e-mail to anyone, you have to
configure the SMTP mail server. See section 11.2 on page 203 for more
information.
Chapter 2 The Vantage Report Server 26

Vantage Report User’s Guide
The Vantage Report server can use e-mail to send information in several situations. In some
situations, it sends e-mail to the e-mail address that is associated with a specific user (see
section 11.3 on page 204). In other situations, it sends e-mail to any valid e-mail address.
• scheduled report - The Vantage Report server can send one or more statistical reports
regularly or one-time to any valid e-mail address. See Chapter 10 on page 194 for more
information.
• system notifications - When certain system parameters cross a threshold (minimum or
maximum) value, the Vantage Report server sends e-mail to the Vantage Report
administrator (the e-mail address associated with the
messages are warnings; in some situations, however, the Vantage Report server starts or
stops receive logs. See Appendix B on page 216 for a list of parameters and threshold
values. One of the threshold values can be configured. See section 11.1 on page 202.
• forgotten password - A user clicks Forget Password? in the Login screen. In this case,
the Vantage Report server sends the account information to the e-mail address associated
with the specified user name. See section 3.2 on page 30 for an example of the Login
screen.
• test message - The Vantage Report administrator tests the SMTP mail server settings.
The Vantage Report server sends an e-mail message to the e-mail address associated with
root account. See section 11.2 on page 203 for more information.
the
root account). Some of these
2.3 Time in the Vantage Report Server
• In Vantage Report, clock time is the time the Vantage Report server receives information
(log entries or traffic statistics) from the ZyXEL devices, not the time the device puts in
the entry. As soon as the Vantage Report server receives information, it replaces device
times with the current time in the Vantage Report server.
• The Vantage Report server processes log entries and traffic statistics before the
information is available in any screen (including log viewers). For performance reasons,
the Vantage Report server does not process this information right away. Instead, the
processing time depends on the way the information is used in Vantage Report. See the
following table for processing times for each menu item.
Table 2 Processing Times by Menu Item
MENU ITEM TIME (MIN)
Monitor 5
Traffic, Network Attack, Security Policy,
Authentication
Log Viewer > All Logs 30
Log Viewer > Critical Logs 1
5
27 Chapter 2 The Vantage Report Server
Vantage Report User’s Guide
2.4 ZyXEL Device Configuration and Source Data
The following table identifies the configuration required in ZyXEL devices for each
screen in Vantage Report.
Table 3 Configuration Requirements for ZyXEL Devices by Menu Item
MENU ITEM(S) SOURCE DATA LOG SETTINGS* ADDITIONAL
Monitor > Bandwidth traffic statistics -- --
Monitor > Service traffic statistics -- --
Monitor > Attack log entries Attack --
Monitor > Intrusion log entries IDP IDP > Signature
Monitor > AntiVirus log entries Anti-Virus Anti-Virus > General
Monitor > AntiSpam log entries Anti-Spam --
Traffic (except VPN) traffic statistics -- --
Traffic > VPN log entries IPSec --
Network Attack > Attack log entries Attack --
Network Attack > Intrusion log entries IDP IDP > Signature
Network Attack > AntiVirus log entries Anti-Virus Anti-Virus > General
Network Attack > AntiSpam log entries Anti-Spam --
Security Policy > WEB Blocked log entries Blocked Web Sites --
Security Policy > WEB Allowed log entries Forward Web Sites --
Event > Device Login log entries System Maintenance --
Log Viewer > All Logs log entries ** **
Log Viewer > Critical Logs log entries ** **
* - The names of categories may be different for different devices. Use the category that is
appropriate for each device.
** - The log viewers display whatever log entries the ZyXEL devices record, including log entries
that may not be used in other reports.
• Source Data - Some screens use log entries; some screens use traffic statistics. Some
ZyXEL devices do not track traffic statistics. If Vantage Report does not get one of these,
the screens are empty. See the Quick Start Guide for detailed instructions.
• Log Settings - If ZyXEL devices do not record some categories of log entries, Vantage
Report does not have any information to display either. For example, if you want to look
at VPN traffic for a particular device, the device has to record log entries for IPSec.
For most devices, go to the Logs > Log Settings screen, and select the appropriate
categories. You may also use the command-line interface.
• Additional - In some cases, it is possible to control what log entries are recorded in even
more detail. For example, in some ZyXEL devices, it is possible to control what attack
types are logged.
For most devices, go to the screen indicated to select the appropriate log entries. You may
also use the command-line interface.
Chapter 2 The Vantage Report Server 28

Vantage Report User’s Guide
29 Chapter 2 The Vantage Report Server
 Loading...
Loading...