Page 1

Xerox WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Version 2.0
Prepared by:
Larry Kovnat
Xerox Corporation
1350 Jefferson Road
Rochester, New York 14623
Page 2

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
©2010 Xerox Corporation. All rights reserved. Xerox and the sphere of connectivity design are trademarks of
Xerox Corporation in the United States and/or other counties.
Other company trademarks are also acknowledged.
Document Version: 1.00 (May 2010).
Ver. 2.00, March 2011 Page 2 of 50
Page 3

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
1. INTRODUCTION ..................................................................................................................................5
1.1.
Purpose .................................................................................................................................................................................... 5
1.2.
Target Audience ................................................................................................................................................................... 5
1.3.
Disclaimer ............................................................................................................................................................................... 5
2. DEVICE DESCRIPTION .......................................................................................................................6
2.1.
Security-relevant Subsystems ......................................................................................................................................... 6
2.1.1. Physical Partitioning .......................................................................................................................................................................6
2.1.2. Security Functions allocated to Subsystems ........................................................................................................................7
2.2.
Controller ................................................................................................................................................................................ 8
2.2.1. Purpose ................................................................................................................................................................................................8
2.2.2. Memory Components ....................................................................................................................................................................8
2.2.3. External Connections .................................................................................................................................................................. 10
2.2.4. USB Ports ......................................................................................................................................................................................... 10
2.2.
Fax Module .......................................................................................................................................................................... 11
2.3.1. Purpose ............................................................................................................................................................................................. 11
2.3.2. Hardware ......................................................................................................................................................................................... 11
2.4.
Scanner ................................................................................................................................................................................. 11
2.4.1. Purpose ............................................................................................................................................................................................. 11
2.4.2. Hardware ......................................................................................................................................................................................... 11
2.5.
Graphical User Interface (GUI) ................................................................................................................................... 12
2.5.1. Purpose ............................................................................................................................................................................................. 12
2.5.2. Hardware ......................................................................................................................................................................................... 12
2.6.
Marking Engine (also known as the Image Output Terminal or IOT) .......................................................... 13
2.6.1. Purpose ............................................................................................................................................................................................. 13
2.6.2. Hardware ......................................................................................................................................................................................... 13
2.6.3. Control and Data Interfaces .................................................................................................................................................... 13
2.7.
System Software Structure ........................................................................................................................................... 13
2.7.1. Open-source components ......................................................................................................................................................... 13
2.7.2. OS Layer in the Controller ......................................................................................................................................................... 13
2.7.3. Network Protocols ........................................................................................................................................................................ 15
2.8.
Logical Access ..................................................................................................................................................................... 16
2.8.1. Network Protocols ........................................................................................................................................................................ 16
2.8.2. Ports ................................................................................................................................................................................................... 17
2.8.3. IP Filtering ....................................................................................................................................................................................... 21
3. SYSTEM ACCESS ................................................................................................................................ 22
3.1.
Authentication Model ..................................................................................................................................................... 22
Ver. 2.00, March 2011 Page 3 of 50
Page 4

XEROX WorkCentre
3.2.
Login and Authentication Methods ........................................................................................................................... 24
3.2.1. System Administrator Login [All product configurations] ........................................................................................... 24
3.2.2. User authentication ..................................................................................................................................................................... 24
3.3.
System Accounts ............................................................................................................................................................... 26
3.3.1. Printing [Multifunction models only] .................................................................................................................................... 26
3.3.2. Network Scanning [Multifunction models only] .............................................................................................................. 26
3.4.
Diagnostics .......................................................................................................................................................................... 27
3.4.1. Service [All product configurations] ...................................................................................................................................... 27
3.4.2. Alternate Boot via Serial Port .................................................................................................................................................. 27
3.4.3. tty Mode ........................................................................................................................................................................................... 27
3.4.4. Diagnostics via Portable Service Workstation (PSW) Port ........................................................................................... 27
3.4.5. Summary .......................................................................................................................................................................................... 30
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
4. SECURITY ASPECTS OF SELECTED FEATURES ...................................................................... 31
4.1.
Audit Log .............................................................................................................................................................................. 31
4.2.
Xerox Standard Accounting .......................................................................................................................................... 39
4.3.
Automatic Meter Reads ................................................................................................................................................. 40
4.4.
Encrypted Partitions ........................................................................................................................................................ 40
4.5.
Image Overwrite ............................................................................................................................................................... 40
4.5.1. Algorithm ......................................................................................................................................................................................... 41
4.5.2. User Behavior ................................................................................................................................................................................. 41
4.5.3. Overwrite Timing .......................................................................................................................................................................... 41
5. RESPONSES TO KNOWN VULNERABILITIES ......................................................................... 42
5.1.
Security @ Xerox (www.xerox.com/security) .......................................................................................................... 42
6. APPENDICES ....................................................................................................................................... 43
6.1.
Appendix A – Abbreviations ......................................................................................................................................... 43
6.2.
Appendix B – Supported MIB Objects ....................................................................................................................... 45
6.3.
Appendix C –Standards .................................................................................................................................................. 48
6.4.
Appendix E – References ................................................................................................................................................ 50
Ver. 2.00, March 2011 Page 4 of 50
Page 5

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
1. Introduction
The
WorkCentre 5735/5740/5745/5755/5765/5775/5790 multifunction systems
versions of Xerox copier and multifunction devices for the general office.
1.1. Purpose
The purpose of this document is to disclose information for the WorkCentre products with respect to device security.
Device Security, for this paper, is defined as how image data is stored and transmitted, how the product behaves in a
networked environment, and how the product may be accessed, both locally and remotely. Please note that the
customer is responsible for the security of their network and the WorkCentre products do not establish security for
any network environment.
The purpose of this document is to inform Xerox customers of the design, functions, and features of the WorkCentre
products relative to Information Assurance (IA).
This document does NOT provide tutorial level information about security, connectivity, PDLs, or WorkCentre
products features and functions. This information is readily available elsewhere. We assume that the reader has a
working knowledge of these types of topics. However, a number of references are included in the Appendix.
Information Assurance Disclosure Paper
are among the latest
1.2. Target Audience
The target audience for this document is Xerox field personnel and customers concerned with IT security.
1.3. Disclaimer
The information in this document is accurate to the best knowledge of the authors, and is provided without warranty
of any kind. In no event shall Xerox Corporation be liable for any damages whatsoever resulting from user's use or
disregard of the information provided in this document including direct, indirect, incidental, consequential, loss of
business profits or special damages, even if Xerox Corporation has been advised of the possibility of such damages.
Ver. 2.00, March 2011 Page 5 of 50
Page 6
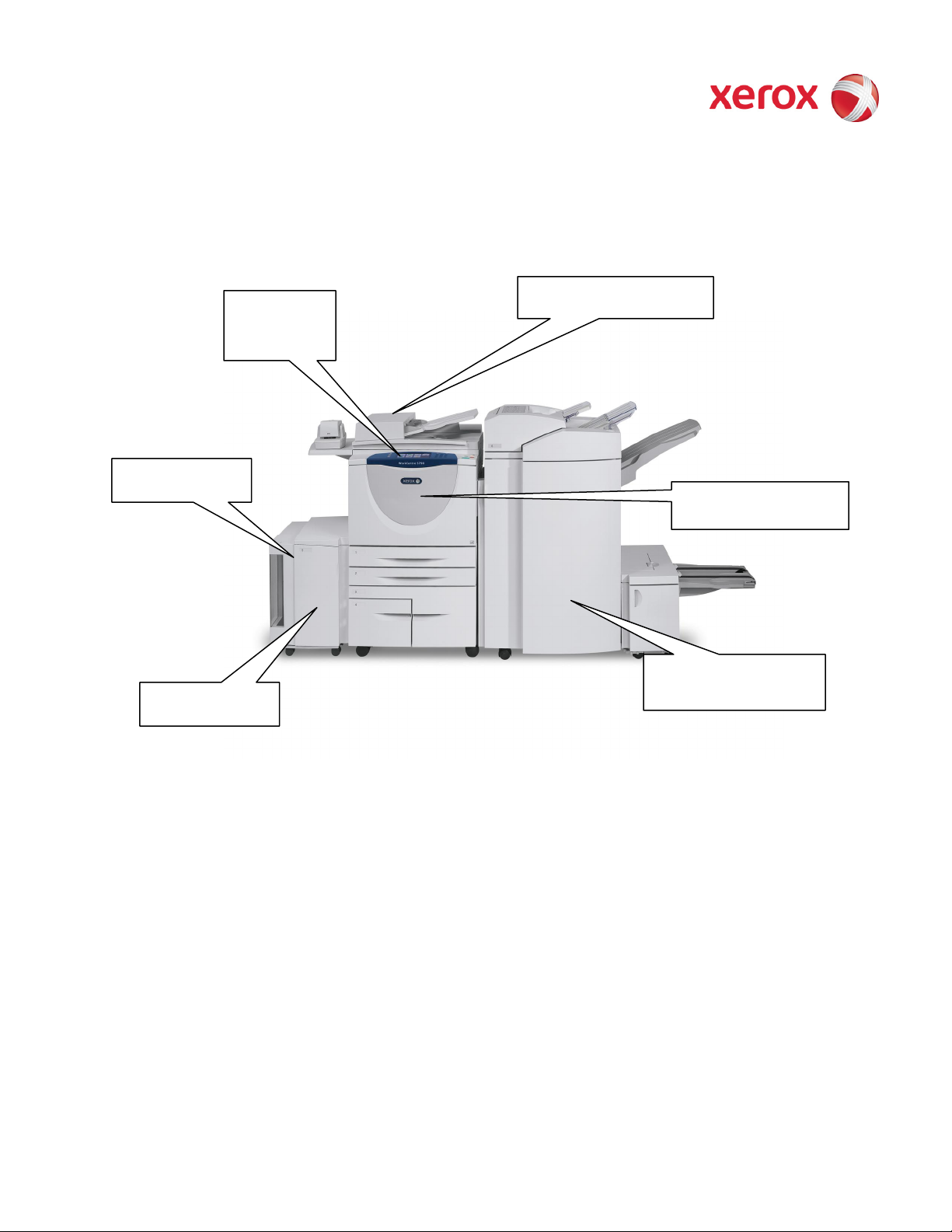
XEROX WorkCentre
(IIT)
Marking Engine (IOT)
feeder accessory
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2. Device Description
This product consists of an in put document handler and scanner, marking engine including paper path, controller,
and user interface.
Paper Trays
Graphical User
Interface
(GUI)
Document Feeder & Scanner
High-volume finisher and
High-capacity
Figure 2-1 WorkCentre Multifunction System
booklet maker accessories
2.1. Security-relevant Subsystems
2.1.1. Physical Partitioning
The security-relevant subsystems of the product are partitioned as shown in Figure 2-2.
Ver. 2.00, March 2011 Page 6 of 50
Page 7
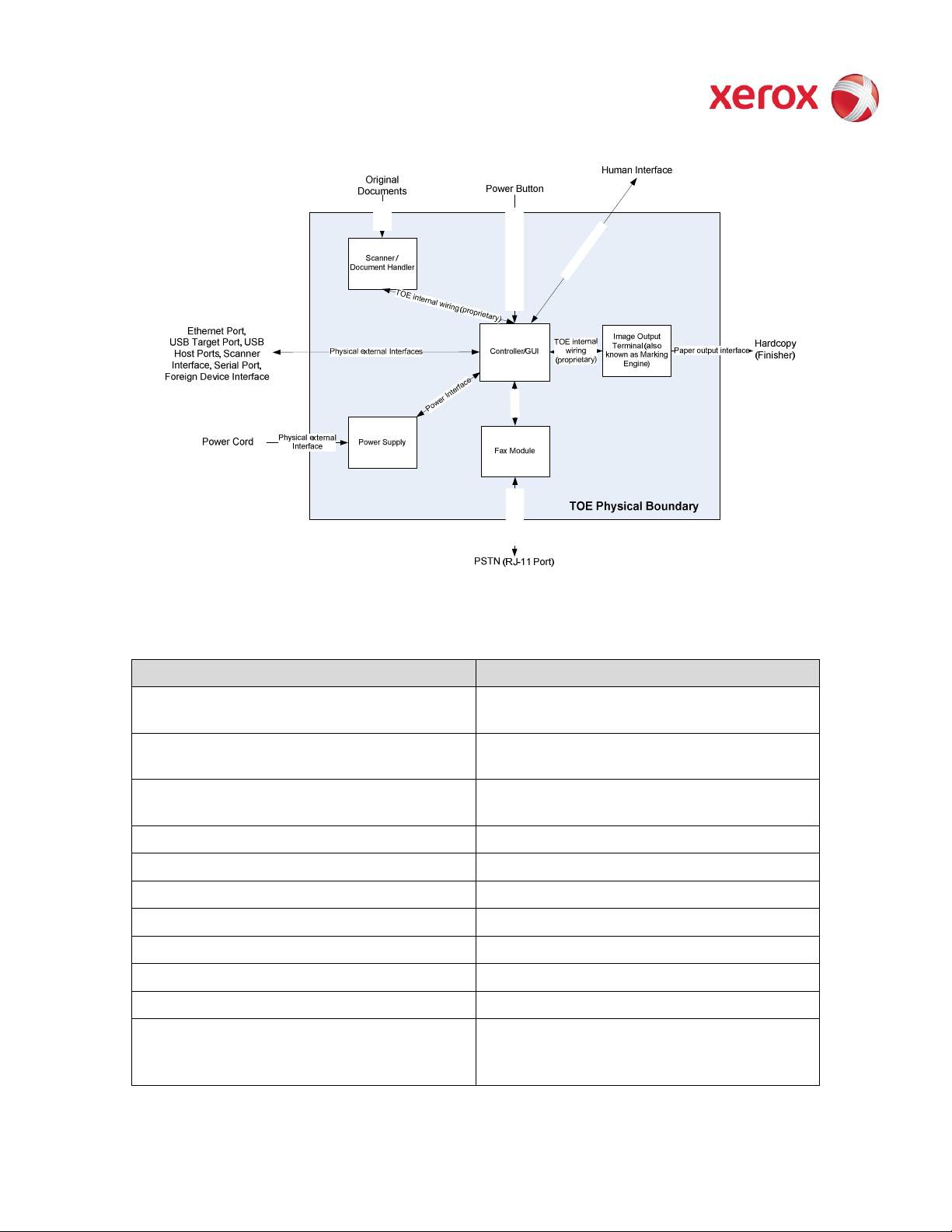
XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
interface
Optical
y
a
l
p
s
i
D
d
n
a
s
n
o
t
t
u
B
(proprietary)
Button and TOE internal wiring
s
u
B
I
C
P
l
a
n
r
e
e
t
c
x
a
e
f
l
r
a
e
t
c
i
n
i
s
y
h
P
Figure 2-2 System functional block diagram
2.1.2. Security Functions allocated to Subsystems
Security Function Subsystem
Image Overwrite
System Authentication
Network Authentication
Security Audit
Cryptographic Operations
User Data Protection – SSL
User Data Protection – IP Filtering
User Data Protection – IPSec
User Data Protection – Disk Encryption
Network Management Security
Fax Flow Security
Controller
Graphical User Interface
Controller
Graphical User Interface
Controller
Graphical User Interface
Controller
Controller
Controller
Controller
Controller
Controller
Controller
Fax Module
Controller
Graphical User Interface
Ver. 2.00, March 2011 Page 7 of 50
Page 8
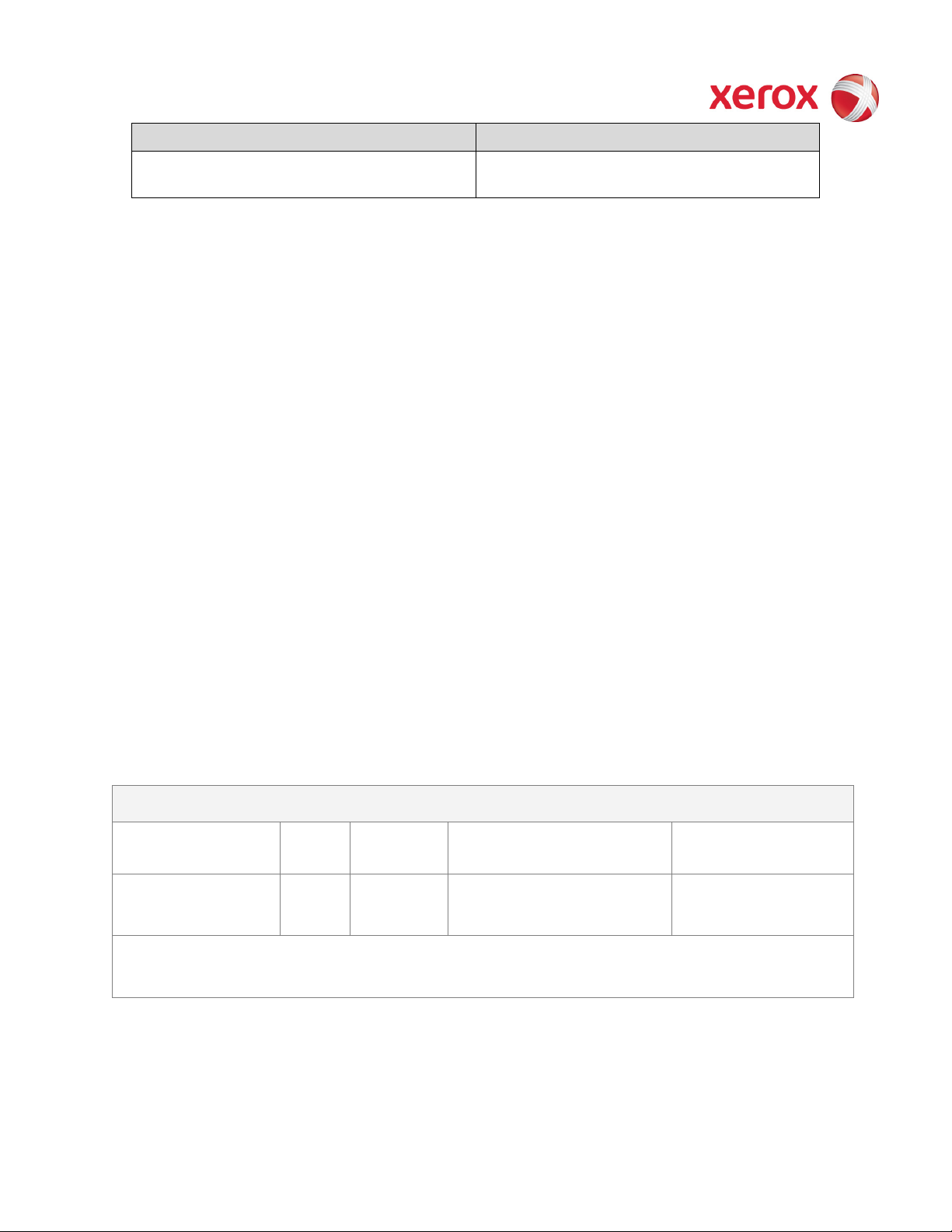
XEROX WorkCentre
Type (SRAM, DRAM,
Size User
Function or Use
Process to Sanitize
5735/5740/5745/5755/5765/5775/5790
Security Function Subsystem
Security Management
2.2. Controller
2.2.1. Purpose
The controller provides both network and direct-connect external interfaces, and enables copy, print, email, network
scan, server fax, internet FAX, and LanFAX functionality. Network scanning, server fax, internet fax, and LanFax, are
standard features.
NOTE: The Copier only version includes a hard drive which is used to hold Operating System software, printing
applications, and jam clearance videos. Job Image data is not stored on this disk.
Image Overwrite, which is included as a standard feature, enables both Immediate and On-Demand overwrite of any
temporary image data created on disk. The controller also incorporates an open-source web server (Apache) that
exports a Web User Interface (WebUI) through which users can submit jobs and check job and machine status, and
through which system administrators can remotely administer the machine.
The controller contains the image path, which uses proprietary hardware and algorithms to process the scanned
images into high-quality reproductions. Scanned images may be temporarily buffered in DRAM to enable electronic
pre-collation, sometimes referred to as scan-once/print-many. When producing multiple copies of a document, the
scanned image is processed and buffered in the DRAM in a proprietary format. Extended buffer space for very large
documents is provided on the network disk. The buffered bitmaps are then read from DRAM and sent to the Image
Output Terminal (IOT) for marking on hardcopy output. For long documents, the production of hardcopy may begin
before the entire original is scanned, achieving a level of concurrency between the scan and mark operations.
The controller operating system is Wind River Linux, kernel v. 2.6.20+. (Note: Consistent with Flaw Remediation, this
baseline may be updated as indicated by the ‘+’ sign. Unnecessary services such as rsh, telnet and finger are disabled
in the OS. FTP is used in client-only mode by the network scanning feature for the filing of scanned images and the
retrieval of Scan Templates; however the controller does not contain an FTP server.
The controller works with the Graphical User Interface (GUI) assembly to provide system configuration functions. A
System Administrator PIN must be entered at the GUI in order to access these functions.
Information Assurance Disclosure Paper
Controller
Graphical User Interface
Table 1 Security Functions allocated to Subsystems
2.2.2. Memory Components
Volatile Memory
etc)
DDR2 SDRAM
Upgradeable to
1GB
2GB
Additional Information:
manipulation (Reduce/Enlarge, etc.), and all have no data retention capability. When power is removed all data is lost.
These buffers are typically built into the ASICs. Typical bleed down time for all volatile memory is 10 seconds.
Ver. 2.00, March 2011 Page 8 of 50
Modifiable
(Y/N)
N Single Board Controller
(System and user image stored)
There are also a number of RAM buffers in the video path that are used for image
Subsequent jobs overwrite
the data and all images are
lost at power off or reboot.
Page 9
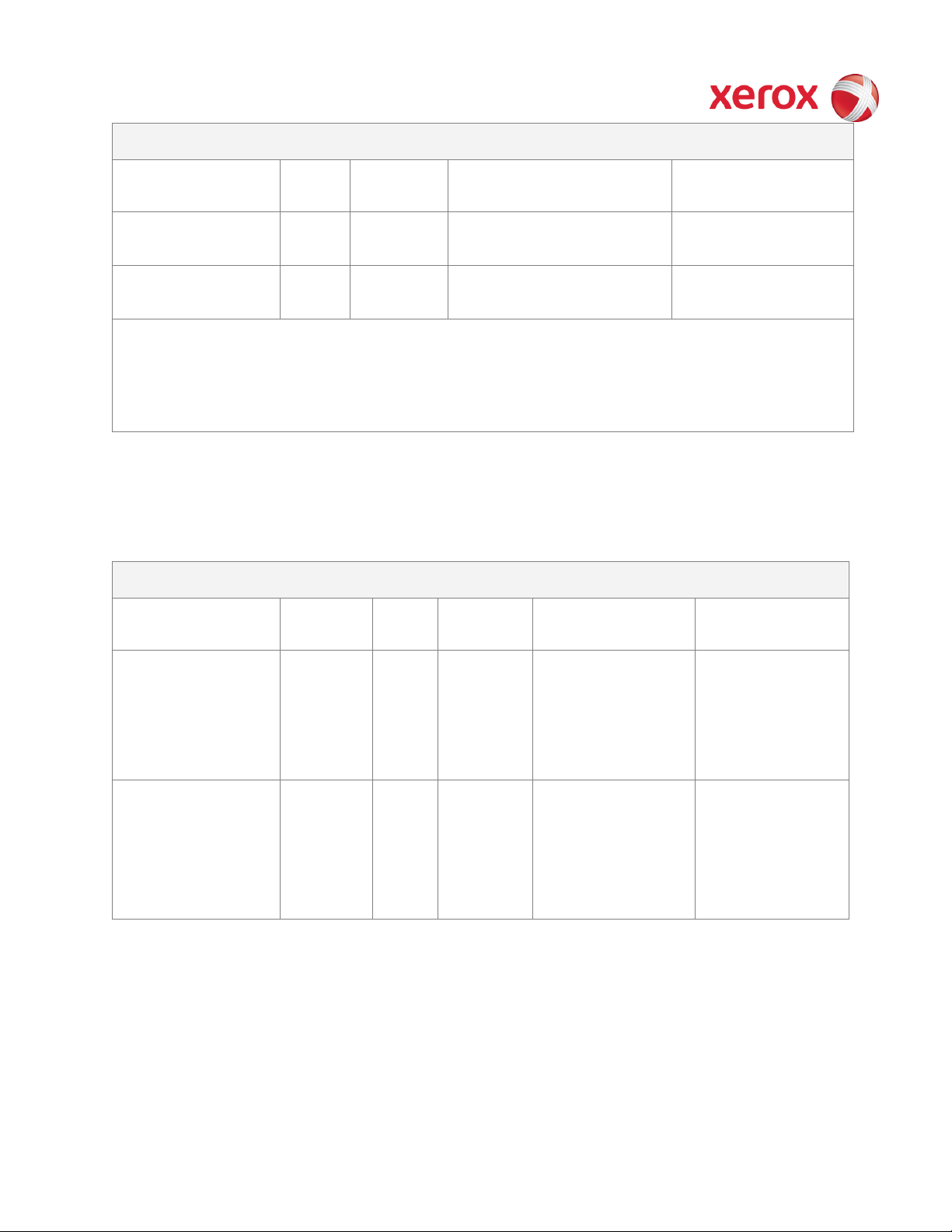
XEROX WorkCentre
Type (Flash, EEPROM,
Size User
Function or Use
Process to Sanitize
Type (disk drives,
Removable
Size: User
Function:
Process to Sanitize:
5735/5740/5745/5755/5765/5775/5790
Non-Volatile Memory
Information Assurance Disclosure Paper
etc)
Modifiable
(Y/N)
Flash ROM 128MB N Single Board Controller
(Boot code and system file)
NVRAM 128KB N Single Board Controller
(Xerographic set points)
Additional Information:
low level I/O control. Some examples of this distributed control are:
• Power distribution, Photoreceptor and main drive motors control
• Raster Output Scanner (ROS)
• Paper Registration
•
Finisher
tape drives, CF/SD/XD
memory cards, etc.):
Disk drive N 80GB N Network Controller
There are other non volatile memory devices in the system, but these are used solely for
Table 2 Controller memory components
Y / N
Media and Storage
Modifiable:
Y / N
Application and Copy
Controller Application
software. Image
storage, processing and
Overflow EPC image
storage.
No user image data stored
No user image data stored.
On Demand Image
Overwrite
Fax Card N 512MB N User FAX image data
Ver. 2.00, March 2011 Page 9 of 50
stored
Table 3 Hard Disk Drives
User image data
overwritten at the
completion of each fax
job.
Overwritten by
Standard or Full
ODIO operation
Page 10
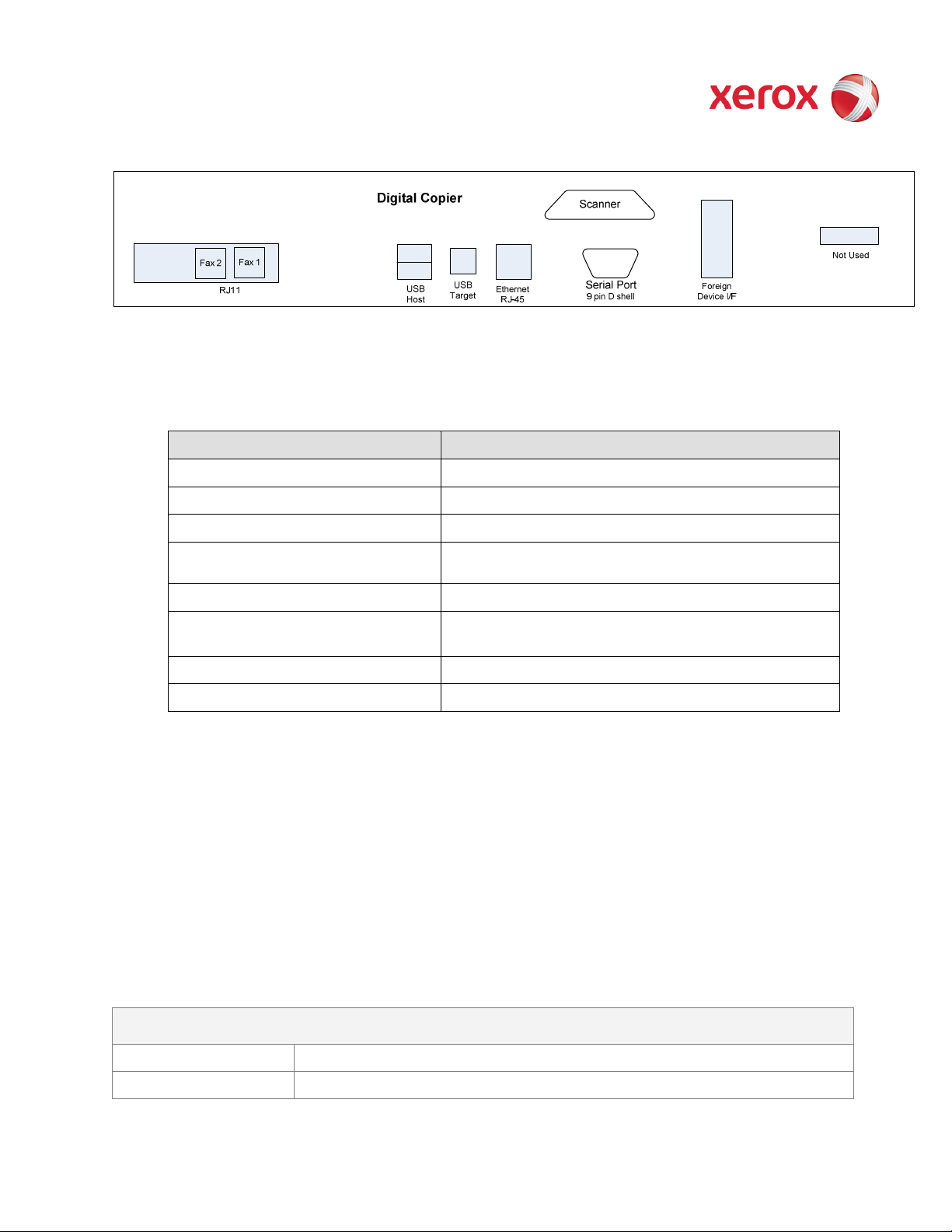
XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
2.2.3. External Connections
Interface Description / Usage
FAX line 1, RJ-11 Supports FAX Modem T.30 protocol only
FAX line 2, RJ-11 Supports FAX Modem T.30 protocol only
USB Host Port
PSW USB Target Port
Information Assurance Disclosure Paper
Figure 2-3 Back panel connections
Software upgrade
Direct-connect printing; Xerox diagnostic tools (PSW and CAT)
and Xerox copier assistant
Ethernet 10/100/1000 Network connectivity
Scanner Proprietary connection between the scanner and controller
Serial Port Engineering development debug; default state is disabled
Foreign Device Interface (FDI) Allows connection of optional access control hardware
2.2.4. USB Ports
The WorkCentre contains a host connector for a USB flash drive, enabling upload of software upgrades and
download of network logs or machine settings files.
Autorun is disabled on this port. No executable files will be accepted by the port.
Modifying the software upgrade, network logging or saved machine settings files will make the files unusable on a
WorkCentre .
The data in the network logging file is encrypted and can only be decrypted by Xerox service.
The machine settings that can be saved and restored by a service technician are limited to controller and fax
parameters that are needed for normal operation. For example, the fax address book can be saved and restored by a
service technician.
There is no method for a user, administrator or technician to move image data from the WorkCentre to a USB device.
carrying power and communications
Table 4 Controller External Connections
USB
USB port and location Purpose
USB Host ports Software upgrade
Ver. 2.00, March 2011 Page 10 of 50
Page 11

XEROX WorkCentre
Type (SRAM, DRAM, etc)
Size User Modifiable
Function or Use
Process to Clear:
Additional Information:
Type (Flash, EEPROM, etc)
Size User Modifiable
Function or Use
Process to Clear:
Additional Information:
USB Target port Direct-connect printing; Xerox diagnostic tools (PSW and CAT) and Xerox copier assistant
5735/5740/5745/5755/5765/5775/5790
Table 5 USB Ports
Information Assurance Disclosure Paper
2.2. Fax Module
2.3.1. Purpose
The embedded FAX service uses the installed embedded fax card to send and receive images over the telephone
interface.
2.3.2. Hardware
The Fax module contains the fax modem and RJ-11 connector. The Fax modem implements the T.30 fax protocol.
The Fax module contains a CPU, BIOS, RAM, and Non-Volatile Memory.
Volatile Memory Description
(Y/N)
SDRAM 80MB N FAX Card volatile memory No user image data
stored
All memory listed above contains code for execution and configuration information. No user or job data is permanently stored
in this location.
Non-Volatile Memory Description
(Y/N)
Flash ROM
All memory listed above contains code for execution and configuration information. No user or job data is stored in this location.
4MB
N
Table 6 Fax Module memory components
FAX executable code.
No user image data
stored.
2.4. Scanner
2.4.1. Purpose
The purpose of the scanner is to provide mechanical transport of hardcopy originals and to convert hardcopy
originals to electronic data.
2.4.2. Hardware
The scanner converts the image from hardcopy to electronic data. An optional document handler moves originals
into a position to be scanned. The scanner provides enough image processing for signal conditioning and
formatting. The scanner does not store scanned images. All other image processing functions are in the copy
controller.
The DADF/Scanner contains a CPU, BIOS, RAM, and Non-Volatile Memory
.
Ver. 2.00, March 2011 Page 11 of 50
Page 12
XEROX WorkCentre
Type (SRAM, DRAM, etc)
Size User Modifiable
Function or Use
Process to Clear:
Additional Information:
Type (Flash, EEPROM, etc)
Size User Modifiable
Function or Use
Process to Clear:
Additional Information:
Type (SRAM, DRAM, etc)
Size User Modifiable
Function or Use
Process to Clear:
Additional Information:
Type (Flash, EEPROM, etc)
Size User Mo
difiable
Function or Use
Process to Clear:
Additional Information:
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Volatile Memory Description
(Y/N)
SRAM 6KB N Scanner volatile memory; no user
image data stored
All memory listed above contains code for execution and configuration information. No user or job data is permanently stored in this location.
Power Off System
Non-Volatile Memory Description
(Y/N)
Flash ROM 128MB N Scanner executable code No user image data
stored
All memory listed above contains code for execution and configuration information. No user or job data is stored in these locations.
Table 7 Scanner memory components
2.5. Graphical User Interface (GUI)
2.5.1. Purpose
The GUI detects soft and hard button actuations, and provides text and graphical prompts to the user. The GUI is
sometimes referred to as the Local UI (LUI) to distinguish it from the WebUI, which is exported by the web service
that runs in theccontroller. Images are not transmitted to or stored in the GUI. The Start hard button is located on
the GUI panel.
2.5.2. Hardware
The user interface contains a FPGA that contains RAM and Non-Volatile Memory
Volatile Memory Description
(Y/N)
DRAM 2KB N User Interface volatile memory; no
user image data stored
All memory listed above contains code for execution and configuration information. No user or job data is permanently stored in this location.
.
Power Off System
Non-Volatile Memory Description
Flash ROM 32KB N no user image data stored No user image data
All memory listed above contains code for execution and configuration information. No user or job data is stored in this location.
Ver. 2.00, March 2011 Page 12 of 50
(Y/N)
stored
Page 13

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Table 8 User Interface memory components
Information Assurance Disclosure Paper
2.6. Marking Engine (also known as the Image
Output Terminal or IOT)
2.6.1. Purpose
The Marking Engine performs copy/print paper feeding and transport, image marking and fusing, and document
finishing. Images are not stored at any point in these subsystems.
2.6.2. Hardware
The marking engine is comprised of paper supply trays and feeders, paper transport, laser scanner, xerographics, and
paper output and finishing. The marking engine contains a CPU, BIOS, RAM and Non-Volatile Memory.
2.6.3. Control and Data Interfaces
Images and control signals are transmitted from the copy controller to the marking engine across a proprietary
interface.
2.7. System Software Structure
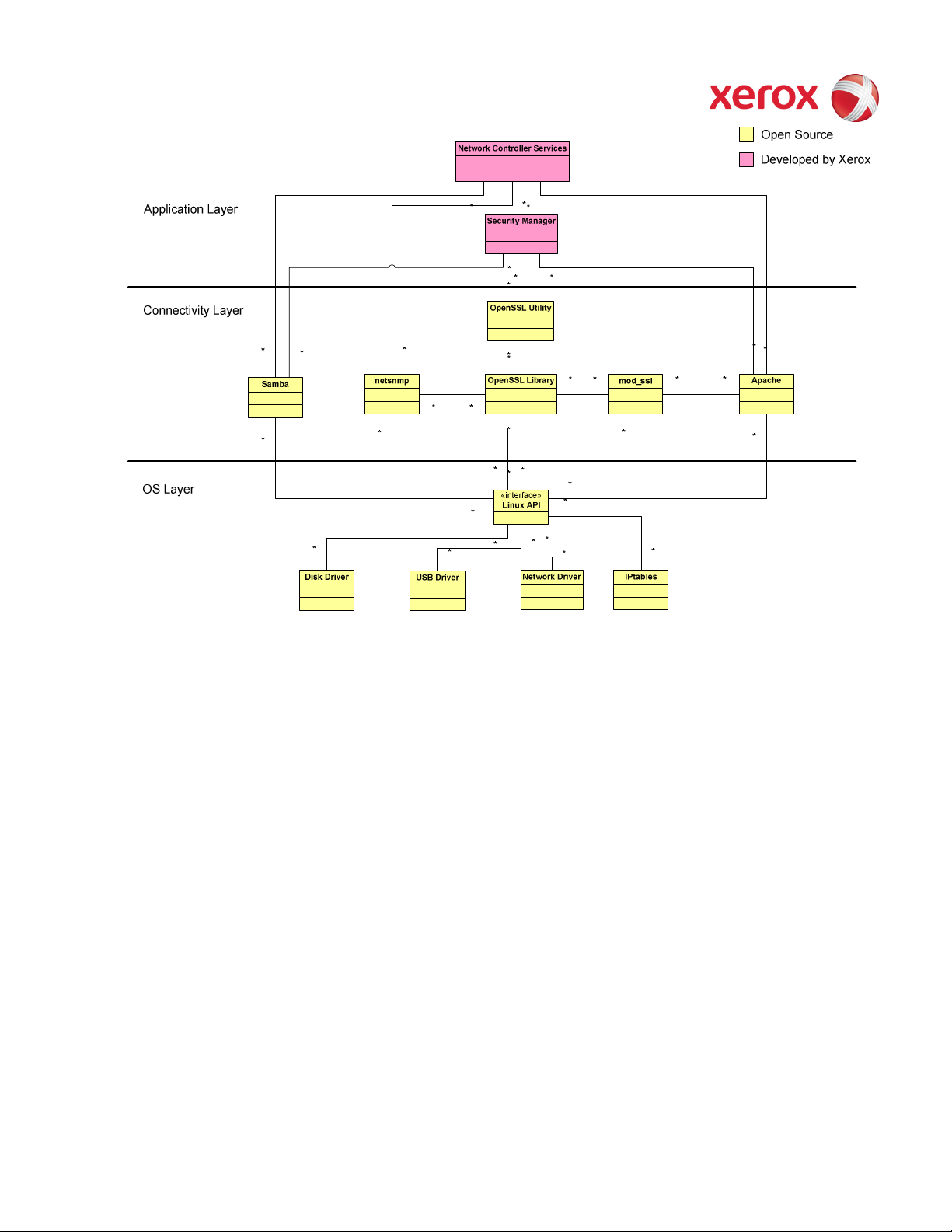
2.7.1. Open-source components
Open-source components in the connectivity layer implement high-level protocol services. The security-relevant
connectivity layer components are:
• Apache 2.2.11, with mod_ssl integrated (http and https)
• PHP 5.3.1
• OpenSSL 0.9.8l (SSL)
• SAMBA 3.0.30 (SMB)
• Netsnmp 5.0.9 (SNMPv3)
2.7.2. OS Layer in the Controller
The OS layer includes the operating system, network and physical I/O drivers. The controller operating system is
Wind River Linux, kernel v. 2.6.20+. Xerox may issue security patchesfor the OS, in which case the Xerox portion of
the version number (i.e.. after the ‘+’ sign) will be incremented.
The crypto library for IPSec is provided by the kernel.
IP Filtering is also provided by the kernel.
Ver. 2.00, March 2011 Page 13 of 50
Page 14
XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Figure 2-4 Controller Operating System layer components
Ver. 2.00, March 2011 Page 14 of 50
Page 15
XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
2.7.3. Network Protocols
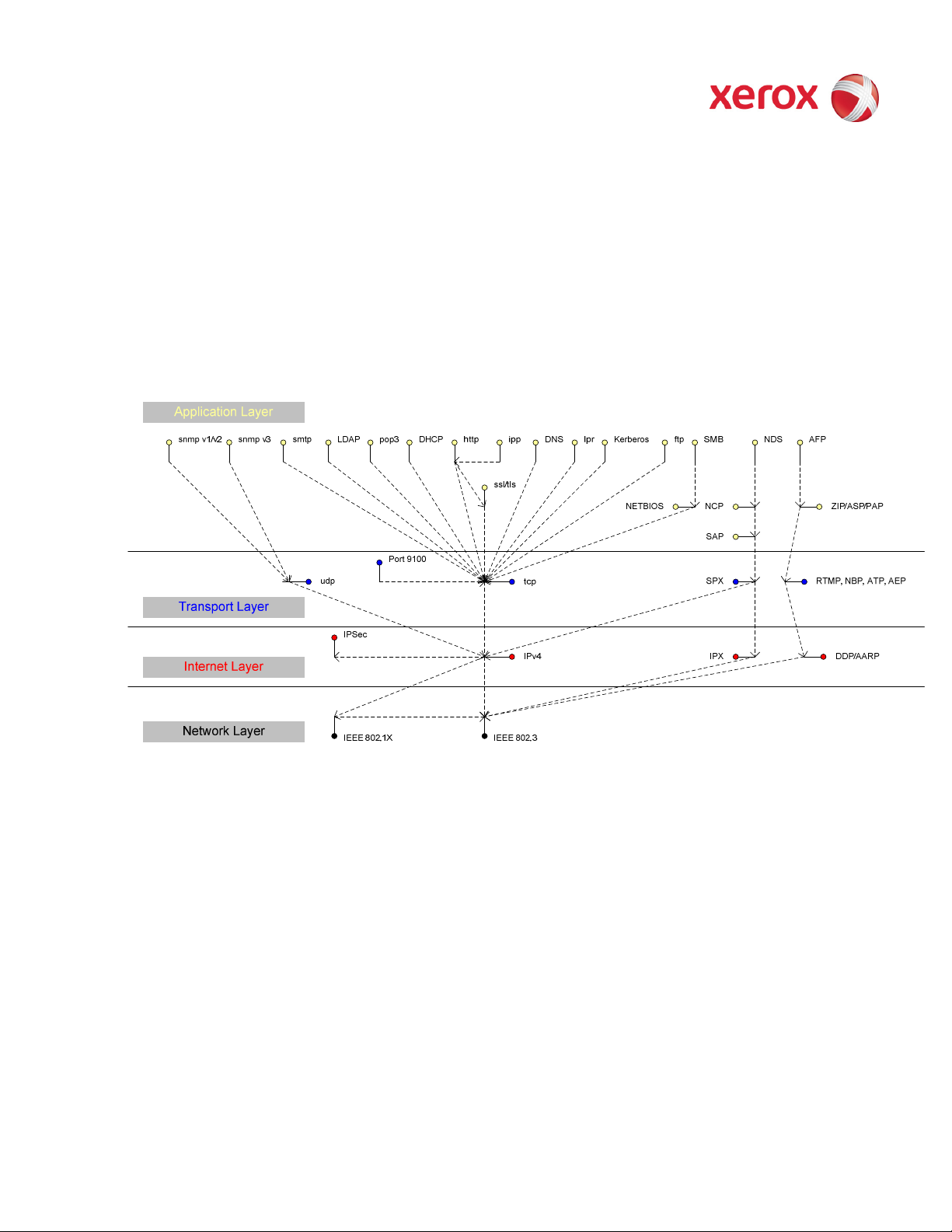
Figure 2-5 is an interface diagram depicting the protocol stacks supported by the device, annotated according to the
DARPA model.
Information Assurance Disclosure Paper
Figure 2-5 IPv4 Network Protocol Stack
Ver. 2.00, March 2011 Page 15 of 50
Page 16

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Figure 2-6 IPv6 Network Protocol Stack
2.8. Logical Access
2.8.1. Network Protocols
The supported network protocols are listed in Appendix D and are implemented to industry standard specifications
(i.e. they are compliant to the appropriate RFC) and are well-behaved protocols. There are no ‘Xerox unique’
additions to these protocols.
2.8.1.1. IPSec
The device supports IPSec tunnel mode. The print channel can be secured by establishing an IPSec association
between a client and the device. A shared secret is used to encrypt the traffic flowing through this tunnel. SSL must
be enabled in order to set up the shared secret.
When an IPSec tunnel is established between a client and the machine, the tunnel will also be active for
administration with SNMPv2 tools (HP Open View, etc.), providing security for SNMP SETs and GETS with an
otherwise insecure protocol. SNMP Traps may not be secure if either the client or the device has just been rebooted.
IP Filtering can be useful to prevent SNMP calls from non-IPSec clients.
Once an IPSec channel is established between two points, it stays open until one end reboots or goes into power
saver,. Only network clients and servers will have the ability to establish an IPSec tunnel with the machine. Thus
Ver. 2.00, March 2011 Page 16 of 50
Page 17

XEROX WorkCentre
device-initiated operations (like scanning) cannot assume the existence of the tunnel unless a print job (or other
client initiated action) has been previously run since the last boot at either end of the connection.
2.8.2. Ports
The following table summarizes all potential open ports and subsequent sections discuss each port in more detail.
Default
Port #
1900
3003
9100
25
53
68
80
88
110
137
138
139
161
162
389
396
427
443
515
631
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Type Service name
TCP SMTP
UDP DNS
UDP BOOTP/DHCP
TCP HTTP
UDP Kerberos
TCP POP-3 client
UDP NETBIOS- Name Service
UDP NETBIOS-Datagram Service; SMB filing and Scan template retrieval
TCP NETBIOS; SMB filing and Scan template retrieval
UDP SNMP
UDP SNMP trap
UDP LDAP
TCP Netware
UDP SLP
TCP SSL
TCP LPR
TCP IPP
UDP SSDP
TCP http/SNMP reply
TCP raw IP
Table 9 Network Ports
Please note that there is no ftp port in this list. ftp is only used to export scanned images and to retrieve Scan Job
Templates, and will open port 21 on the remote device. An ftp port is never open on the controller itself.
2.8.2.1. Port 25, SMTP
This unidirectional port is open only when Scan to E-mail or Internet Fax (I-Fax) is exporting images to an SMTP
server, or when email alerts are being transmitted. SMTP messages & images are transmitted to the SMTP server
from the device.
2.8.2.2. Port 53, DNS
Designating a DNS server will allow the device to resolve domain names. This can be configured via the LocalUI or
WebUI.
2.8.2.3. Port 68, DHCP
This port is used only when performing DHCP, and is not open all of the time. To permanently close this port, DHCP
must be explicitly disabled. This is done in User Tools via the Local User Interface or via the TCP/IP page in the
Properties tab on the WebUI.
Ver. 2.00, March 2011 Page 17 of 50
Page 18

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2.8.2.4. Port 80, HTTP
The embedded web pages communicate to the machine through a set of unique APIs and do not have direct access
Network Controller
I
n
request
http
server
Network
to machine information:
The HTTP port can only access the HTTP server residing in the controller. The embedded HTTP server is Apache. The
purpose of the HTTP server is to:
• Give users information of the status of the device;
response
t
e
r
n
a
l
response
A
P
I
request
machine
information
• View the job queue within the device and delete jobs;
• Allow users to download print ready files and program Scan to File Job Templates;
• Allow remote administration of the device. Many settings that are on the Local UI are replicated in the
device’s web pages. Users may view the properties of the device but not change them without logging into the
machine with administrator privileges.
The HTTP server can only host the web pages resident on the hard disk of the device. It does not and cannot act as a
proxy server to get outside of the network the device resides on. Hence the server cannot access any networks (or
web servers) outside of the customer firewall.
When the device is configured with an IP address, it is as secure as any device inside the firewall. The web pages are
accessible only to authorized users of the network inside the firewall.
This service (and port) may be disabled in User Tools via the Local User Interface or via the TCP/IP page in the
Properties tab on the WebU. Please note that when this is disabled, IPP Port 631 is also disabled.
HTTP may be secured by enabling Secure Sockets Layer.
2.8.2.4.1. Proxy Server
The device can be configured to communicate through a proxy server. Features that can make use of a proxy server
include the Automatic Meter Read feature, scanning to a remote repository, or retrieving scan templates from a
remote template pool.
Ver. 2.00, March 2011 Page 18 of 50
Page 19

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2.8.2.5. Port 88, Kerberos
This port is only open when the device is communicating with the Kerberos server to authenticate a user, and is only
used only to authenticate users in conjunction with the Network Scanning feature. To disable this port,
authentication must be disabled, and this is accomplished via the Local User Interface.
This version of software has Kerberos 5.1.1 with DES (Data Encryption Standard) and 64-bit encryption. The Kerberos
code is limited to user authentication, and is used to authenticate a user with a given Kerberos server as a valid user
on the network. Please note that the Kerberos server (a 3rd party device) needs to be set up for each user. Once the
user is authenticated, the Kerberos software has completed its task. This code will not and cannot be used to encrypt
or decrypt documents or other information.
This feature is based on the Kerberos program from the Massachusetts Institute of Technology (MIT). The Kerberos
network authentication protocol is publicly available on the Internet as freeware at
http://web.mit.edu/kerberos/www/. Xerox has determined that there are no export restrictions on this version of the
software. However, there are a few deviations our version of Kerberos takes from the standard Kerberos
implementation from MIT. These deviations are:
1) The device does not keep a user’s initial authentication and key after the user has been authenticated. In a
standard Kerberos implementation, once a user is authenticated, the device holds onto the authentication for a
programmed timeout (the usual default is 12 hours) or until the user removes it (prior to the timeout period). In
the Xerox implementation, all traces of authentication of the user are removed once they have been
authenticated to the device. The user can send any number of jobs until the user logs off the system, either
manually or through system timeout.
2) The device ignores clock skew errors. In a standard implementation of Kerberos, authentication tests will fail if a
device clock is 5 minutes (or more) different from the Kerberos server. The reason for this is that given enough
time, someone could reverse engineer the authentication and gain access to the network. With the 5-minute
timeout, the person has just 5 minutes to reverse engineer the authentication and the key before it becomes
invalid. It was determined during the implementation of Kerberos for our device that it would be too difficult for
the user/SA to keep the device clock in sync with the Kerberos server, so the Xerox instantiation of Kerberos has
the clock skew check removed. The disadvantage is that this gives malicious users unlimited time to reverse
engineer the user’s key. However, since this key is only valid to access the Network Scanning features on a
device, possession of this key is of little use for nefarious purposes.
3) The device ignores much of the information provided by Kerberos for authenticating. For the most part, the
device only pays attention to information that indicates whether authentication has passed. Other information
that the server may return (e.g. what services the user is authenticated for) is ignored or disabled in the Xerox
implementation. This is not an issue since the only service a user is being authenticated for is access to an email directory. No other network services are accessible from the Local UI.
Xerox has received an opinion from its legal counsel that the device software, including the implementation of a
Kerberos encryption protocol in its network authentication feature, is not subject to encryption restrictions based on
Export Administration Regulations of the United States Bureau of Export Administration (BXA). This means that it
can be exported from the United States to most destinations and purchasers without the need for previous approval
from or notification to BXA. At the time of the opinion, restricted destinations and entities included terroristsupporting states (Cuba, Iran, Libya, North Korea, Sudan and Syria), their nationals, and other sanctioned entities
such as persons listed on the Denied Parties List. Xerox provides this information for the convenience of its customers
and not as legal advice. Customers are encouraged to consult with legal counsel to assure their own compliance with
applicable export laws.
2.8.2.6. Port 110, POP-3 Client
This unidirectional port is used when receiving an Internet Fax (I-Fax) or E-Mail. These jobs may only be printed, and
the port is only open if I-Fax is enabled and while receiving the job. It is not configurable.
Ver. 2.00, March 2011 Page 19 of 50
Page 20

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2.8.2.7. Ports 137, 138, 139, NETBIOS
For print jobs, these ports support the submission of files for printing as well as support Network Authentication
through SMB. Port 137 is the standard NetBIOS Name Service port, which is used primarily for WINS. Port 138
supports the CIFS browsing protocol. Port 139 is the standard NetBIOS Session port, which is used for printing. Ports
137, 138 and 139 may be configured in the Properties tab of the device’s web page.
For Network Scanning features, ports 138 and 139 are used for both outbound (i.e. exporting scanned images and
associated data) and inbound functionality (i.e. retrieving Scan Templates). In both instances, these ports are only
open when the files are being stored to the server or templates are being retrieved from the Template Pool. For these
features, SMB protocol is used.
2.8.2.8. Ports 161, 162, SNMP
These ports support the SNMPv1, SNMPv2c, and SNMPv3 protocols. Please note that SNMP v1 does not have any
password or community string control. SNMPv2 relies on a community string to keep unwanted people from
changing values or browsing parts of the MIB. This community string is transmitted on the network in clear text so
anyone sniffing the network can see the password. Xerox strongly recommends that the customer change the
community string upon product installation. SNMP is configurable, and may be explicitly enabled or disabled in the
Properties tab of the device’s web pages.
SNMP traffic may be secured if an IPSec tunnel has been established between the agent (the device) and the
manager (i.e. the user’s PC).
The device supports SNMPv3, which is an encrypted version of the SNMP protocol that uses a shared secret. Secure
Sockets Layer must be enabled before configuring the shared secret needed for SNMPv3.
2.8.2.9. Port 389, LDAP
This is the standard LDAP port used for address book queries in the Scan to Email feature.
2.8.2.10. Port 396, Netware
This configurable port is used when Novell Netware is enabled to run over IP.
2.8.2.11. Port 427, SLP
When activated, this port is used for service discovery and advertisement. The device will advertise itself as a printer
and also listen for SLP queries using this port. It is not configurable. This port is explicitly enabled / disabled in the
Properties tab of the device’s web pages.
2.8.2.12. Port 443, SSL
This is the default port for Secure Sockets Layer communication. This port can be configured via the device’s web
pages. SSL must be enabled before setting up either SNMPv3 or IPSec or before retrieving the audit log (see Sec.
4.1). SSL must also be enabled in order to use any of the Web Services (Scan Template Management, Automatic
Meter Reads, or Network Scanning Validation Service).
SSL should be enabled so that the device can be securely administered from the web UI. When scanning, SSL can be
used to secure the filing channel to a remote repository.
SSL uses X.509 certificates to establish trust between two ends of a communication channel. When storing scanned
images to a remote repository using an https: connection, the device must verify the certificate provided by the
remote repository. A Trusted Certificate Authority certificate should be uploaded to the device in this case.
To securely administer the device, the user’s browser must be able to verify the certificate supplied by the device. A
certificate signed by a well-known Certificate Authority (CA) can be downloaded to the device, or the device can
generate a self-signed certificate. In the first instance, the device creates a Certificate Signing Request (CSR) that
can be downloaded and forwarded to the well-known CA for signing. The signed device certificate is then uploaded
to the device. Alternatively, the device will generate a self-signed certificate. In this case, the generic Xerox root CA
certificate must be downloaded from the device and installed in the certificate store of the user’s browser.
The device supports only server authentication.
Ver. 2.00, March 2011 Page 20 of 50
Page 21

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2.8.2.13. Port 515, LPR
This is the standard LPR printing port, which only supports IP printing. It is a configurable port, and may be explicitly
enabled or disabled in the Properties tab of the device’s web pages.
2.8.2.14. Port 631, IPP
This port supports the Internet Printing Protocol. It is not configurable. This is disabled when the http server is
disabled.
2.8.2.15. Port 1900, SSDP
This port behaves similarly to the SLP port. When activated, this port is used for service discovery and advertisement.
The device will advertise itself as a printer and also listen for SSDP queries using this port. It is not configurable. This
port is explicitly enabled / disabled in the Properties tab of the device’s web pages.
2.8.2.16. Port 3003, http/SNMP reply
This port is used when the http server requests device information. The user displays the Web User Interface
(WebUI) and goes to a page where the http server must query the device for settings (e.g. Novell network settings).
The http server queries the machine via an internal SNMP request (hence this port can only open when the http
server is active). The machine replies back to the http server via this port. It sends the reply to the loopback address
(127.0.0.0), which is internally routed to the http server. This reply is never transmitted on the network. Only SNMP
replies are accepted by this port, and this port is active when the http server is active (i.e. if the http server is disabled,
this port will be closed). If someone attempted to send an SNMP reply to this port via the network, the reply would
have to contain the correct sequence number, which is highly unlikely, since the sequence numbers are internal to the
machine.
2.8.2.17. Port 9100, raw IP
This allows downloading a PDL file directly to the interpreter. This port has limited bi-directionality (via PJL back
channel) and allows printing only. This is a configurable port, and may be disabled in the Properties tab of the
device’s web pages.
2.8.3. IP Filtering
The devices contain a static host-based firewall that provides the ability to prevent unauthorized network access
based on IP address and/or port number. Filtering rules can be set by the SA using the WebUI. An authorized SA can
create rules to (Accept / Reject / Drop) for ALL or a range of IP addresses. In addition to specifying IP addresses to
filter, an authorized SA can enable/disable all traffic over a specified transport layer port.
Ver. 2.00, March 2011 Page 21 of 50
Page 22

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
3. System Access
3.1. Authentication Model
The authentication model allows for both local and network authentication and authorization. In the
local and network cases, authentication and authorization take place as separate processes: a user must
be authenticated before being authorized to use the services of the device.
If the device is set for local authentication, user account information will be kept in a local accounts
database (see the discussion in Chapter 4 of Xerox Standard Accounting) and the authentication process
will take place locally. The system administrator can assign authorization privileges on a per user basis.
User access to services will be provided based on the privileges set for each user in the local accounts
database. .
When the device is set for network authentication, the user’s network credentials will be used to
authenticate the user at the network domain controller.
Users can be authorized on an individual basis to access one or any combination of the following services:
Copy, Fax, Server Fax, Reprint Saved Jobs, Email, Internet Fax, Workflow Scanning Server.
Also users can be authorized to access one or any combination of the following machine pathways:
Services, Job Status, or Machine Status.
Information Assurance Disclosure Paper
Assignment of users to the System Administrator role or the Accounting Administrator is managed by
groups set up at the LDAP or Active Directory server. Any user listed in the System Administrator group
will be granted sys admin privileges at the device. Likewise any user listed in the Accounting
Administrator group will be granted the privileges for that role. Use of network credentials for system
administrator login provides more security than the legacy model based on a sys admin PIN, allowing for
better tracking of sys admin logins by individual users.
Figure 3-1 provides a schematic view of the authentication and authorization subsystem. Use of the local
accounts database or the network can be set independently for both authentication and authorization,
meaning that it is possible to enable network authentication and local authorization, or vice versa.
Usually the device will be set for both authentication and authorization to take place against the same
database, either local or network.
Ver. 2.00, March 2011 Page 22 of 50
Page 23

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Figure 3-1 Authentication and Authorization schematic
Ver. 2.00, March 2011 Page 23 of 50
Page 24

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
3.2. Login and Authentication Methods
There are a number of methods for different types of users to be authenticated. In addition, the
connected versions of the product also log into remote servers. A description of these behaviors follows.
3.2.1. System Administrator Login [All product configurations]
Users must authenticate themselves to the device. To access the User Tools via the Local UI, a numerical
PIN is required. The customer can set the PIN to anywhere from 3 to 31digits in length. This PIN is
stored in the controller NVM and is inaccessible to the user. Xerox strongly recommends that this PIN be
changed from its default value immediately upon product installation. The PIN should be set to a
minimum of 8 characters in length and changed at least once per month. Longer PINs can be changed
less frequently; a 9-digit PIN would be good for a year. The same PIN is used to access the
Administration screens in the Web UI.
3.2.2. User authentication
Users may authenticate to the device using Kerberos, LDAP, SMB Domain, or NDS authentication
protocols. Once the user is authenticated to the device, the user may proceed to use the Network
Scanning features listed above.
The WebUI allows an SA to set up a default authentication domain and as many as 8 additional
alternate authentication domains. The device will attempt to authenticate the user at each domain
server in turn until authentication is successful, or the list is exhausted.
3.2.2.1. Kerberos Authentication (Solaris or Windows 2000/Windows 2003)
This is an option that must be enabled on the device, and is used in conjunction with all Network
Scanning features (Scan to File, Scan to E-mail, internet fax, and Scan to Fax Server). The authentication
steps are:
1) A User enters a user name and password at the device in the Local UI. The device sends an
authentication request to the Kerberos Server.
2) The Kerberos Server responds with the encrypted credentials of the user attempting to sign on.
3) The device attempts to decrypt the credentials using the entered password. The user is
authenticated if the credentials can be decrypted.
4) The device then logs onto and queries the LDAP server trying to match an email address against the
user’s Login Name. The user’s email address will be retrieved if the personalization option has been
selected on the Authentication Configuration page.
5) If the LDAP Query is successful, the user’s email address is placed in the From: field. Otherwise, the
user’s login name along with the system domain is used in the From: field.
6) The user may then add recipient addresses by accessing the Address Book on the LDAP server. Please
see the User Manual for details. Each addition is a separate session to the LDAP server.
3.2.2.2. SMB Authentication (Windows NT 4 or Windows 2000/Windows 2003)
This is also an option that may be enabled on the device, and is used in conjunction with all Network
Scanning features (Scan to File, Scan to E-mail, internet fax, and Scan to Fax Server). The authentication
steps vary somewhat, depending on the network configuration. Listed below are 3 network
configurations and the authentication steps.
Basic Network Configuration: Device and Domain Controller are on the same Subnet
Authentication Steps:
1) The device broadcasts an authentication request that is answered by the Domain Controller.
Ver. 2.00, March 2011 Page 24 of 50
Page 25

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
2) The Domain Controller responds back to the device whether or not the user was successfully
authenticated.
If (2) is successful, steps 3 – 5 proceed as described in steps 4 – 6 of the Kerberos section.
Device and Domain Controller are on different Subnets, SA defines IP Address of Domain Controller
Authentication Steps:
1) The device sends an authentication request directly to the Domain Controller through the
router using the IP address of the Domain Controller.
2) The Domain Controller responds back to the device through the router whether or not the user
was successfully authenticated.
If (2) is successful, steps 3 – 5 proceed as described in 4 - 6 of Kerberos section.
Router
Subnet 1
1
2 2
1
Domain Controller LDAP Server
Subnet 2
WorkCentre or
WorkCentre Pro
3
4
5
Device and Domain Controller are on different Subnets, SA defines Hostname of Domain Controller
Authentication Steps:
1) The device sends the Domain Controller hostname to the DNS Server.
Router
Subnet 1
33
4 4
Domain Controller LDAP Server
Subnet 2
WorkCentre or
WorkCentre Pro
1
DNS Server
2
5
6
7
2) The DNS Server returns the IP Address of the Domain Controller
Ver. 2.00, March 2011 Page 25 of 50
Page 26

XEROX WorkCentre
3) The device sends an authentication request directly to the Domain Controller through the
router using the IP address of the Domain Controller.
4) The Domain Controller responds back to the device through the router whether or not the user
was successfully authenticated.
If (4) is successful, steps 5 – 7 proceed as described in steps 4 - 6 of the Kerberos section.
5735/5740/5745/5755/5765/5775/5790
3.2.2.3. DDNS
The implementation in the device does not support any security extensions.
3.3. System Accounts
3.3.1. Printing [Multifunction models only]
The device may be set up to connect to a print queue maintained on a remote print server. The login
name and password are sent to the print server in clear text. IPSec should be used to secure this channel.
3.3.2. Network Scanning [Multifunction models only]
Network Scanning may require the device to log into a server. The instances where the device logs into a
server are detailed in the following table. Users may also need to authenticate for scanning. This
authentication is detailed in subsequent sections.
Information Assurance Disclosure Paper
3.3.2.1. Device log on
Scanning feature Device behavior
Scan to File, Public Template The device logs in to the scan repository as set up by the SA in User
Tools.
Scan to E-mail, I-Fax
Scan to Fax Server The device logs in to the Fax Server as set up by the SA in User Tools on
Please note that when the device logs into any server the device username and password are sent over
the network in clear text unless SSL has been enabled or IPSec has been configured to encrypt the traffic.
The device logs into an SMTP Server as set up by the SA in User
Tools. It will only log into the Server when a user attempts to use
the scan-to-email feature. At the time the LDAP server must be
accessed, the device will log into the LDAP server.
The device uses simple authentication on the SMTP server. A network
username and password must be assigned to the device. The device
logs in as a normal user, with read only privileges. User credentials are
not used for this authentication step, and are never transmitted over the
network.
the Local UI or from the Properties tab on the WebUI.
3.3.2.2. Scan Template Management
This is a web service that allows the SA to manage templates stored in a remote template pool. The
connection to the remote pool can be secured with SSL.
Ver. 2.00, March 2011 Page 26 of 50
Page 27

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
3.4. Diagnostics
3.4.1. Service [All product configurations]
To access onboard diagnostics from the local user interface, Xerox service representatives must enter a
unique 4-digit password. This PIN is the same for all product configurations and cannot be changed.
For additional security, a Xerox authorized service representative can enable a “secure diagnostics” mode.
In this mode, the service representative must enter two PINs to access onboard diagnostics. When
enabling the secure diagnostics mode for the first time, the service representative should change the PIN
to something known only to him or his local team. On subsequent logins, the secure diagnostics PIN must
be entered followed by the standard diagnostics PIN in order to gain access to the diagnostics menu.
3.4.2. Alternate Boot via Serial Port
Alternate Boot (Alt-boot) is a means for the Portable Service Workstation (PSW) to directly connect to the
controller. The primary purpose of Alternate Boot is to provide the capability to boot the controller in
case of hard disk failure, to perform system diagnostics, and load controller software, independent of
other sub-systems.
Information Assurance Disclosure Paper
To enter this mode a user must strike any key on the PSW within 10 seconds of power on. If the 10
seconds times out, then the normal boot sequence occurs and the serial port acts as a typical tty (see
next section). However, if this mode is entered, a Xerox unique serial protocol is used to communicate to
the alt-boot code. All commands are DOS-type menu driven (i.e. type in a number to start a command).
If a PSW is connected, the application on the PSW cannot be accessed without logging on with a
password (see next section).
If the PSW is used and is successfully logged on, then the Ethernet port is used to download executable
files. The serial port is used for commands and status. Again, please refer to the PSW section for details.
3.4.3. tty Mode
When the controller has completed booting a login line will be displayed. This mode is a typical tty
window, and is password protected. This password changes with each major software release. The
password is stored on the controller hard disk in an encrypted format similarly to how UNIX encrypts and
stores passwords. Through this port a user can gain information and access to any files or information
stored in the controller DRAM or controller hard disk. However, this mode is only used by a CSE if directed
by a Field Engineer when all other diagnostics fail to solve a problem. The written repair procedures that
direct the CSE never employ this mode.
3.4.4. Diagnostics via Portable Service Workstation (PSW) Port
When connected to the PSW Port, the PSW provides an extensive suite of diagnostic functions for use by
the Xerox Customer Service Engineer (CSE). The over-the-wire protocol is Xerox proprietary. This port
cannot process any other protocol except this proprietary protocol used for machine diagnosis. Also, the
PSW must have an application loaded to connect to and communicate with the device.
Customer documents or files cannot be accessed during a diagnostic session, nor are network servers
accessible through this port.
Ver. 2.00, March 2011 Page 27 of 50
Page 28

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
3.4.4.1. Access
The Xerox Service Technician must be authenticated twice:
1. The first password, called the PSW Lock Facility, is obtained by calling a Xerox service location and
providing the CSE employee number and the serial number of the PSW. The password is then given to
the Xerox Service Technician, and is valid for 90 days. When the password expires, the Xerox Service
Technician must call in again. This password is unique to the client application running on that particular
PSW, and is required to log onto the PSW prior to initiating communications with the machine.
2. Once the application is running, the PSW supplies the second password (different from the first) to
authenticate the session to the device. This embedded password is automatically passed from the
application to the machine, and is never seen by anyone. It is hardcoded in the software of the Marking
Engine and the PSW application, and is common to all products. It is not encrypted. Many of the
diagnostic routines will require this password in order to function.
3.4.4.2. Communication Protocol
The communication process uses a Xerox proprietary protocol. Each packet passing back and forth will
have a unique identifier (session key) with it for authentication and tracking purposes. All protocols are
API based – very little information is directly transferred. For example, in order to run any given
diagnostic test, the ‘Start Test XXX’ command is sent to the Marking Engine. The Marking Engine runs
the test and responds with a “Test XXX passed (or failed)’ reply. This is illustrated in the following
diagram:
Network
Network Controller Marking Engine
Marking Engine information may be
retrieved; no image data may be accessed
PSW (Laptop computer)
3.4.4.3. Network Diagnostics executed from the PSW
The PSW allows the technician to execute certain Network diagnostic tests by connecting directly to the
serial port on the controller. These tests are executed with the device disconnected from the customer’s
LAN.
The tests that are available are echo tests for the various protocols (e.g. IP, IPX), where the controller
sends a dummy message to itself to test the transmit and receive capabilities of its own connectivity
stacks. Each protocol is tested individually and each test must be invoked separately. The diagnostic
sequence is as follows:
1) After the PSW and Marking Engine have established a connection, the PSW must send the expected
synchronization message to the machine.
2) The Marking Engine will respond with an acknowledge message containing its serial number.
Ver. 2.00, March 2011 Page 28 of 50
Page 29

XEROX WorkCentre
3) The PSW will send a request for Diagnostic service and a password.
4) Assuming the password is authentic, the Marking Engine will either execute a Marking Engine diagnostic, or
else forward the diagnostic request to the controller. If this is a network diagnostic, the controller will
execute the diagnostic and report results back to the Marking Engine.
5) The Marking Engine will report diagnostic results back to the PSW.
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
3.4.4.4. Accessible Data
The only files that are accessible are various log files (fault log, internal event log, complete job log,
configuration log and a debug log). The customer’s network is accessible for diagnostic purposes only.
However, there is one diagnostic routine (Get Network Connectivity Data), where the device will collect
data about the network it is on and transmit the data. The CSE is expected to seek permission from the
customer before connecting the device to the LAN and performing this diagnostic.
The Novell test will only collect information for devices on the local network. It will not provide
information for any devices across a router. The following data will be stored on the controller:
• Frame Type (local network devices only)
• Server Name
• Server internal network number
• Server node (Media Access Control) address
• Server NOS version number
• Hop count to device (local net)
The IP test will collect data from all responding IP routers and lpd hosts. The following data will be stored
on the controller:
• controller Interface where host discovered (Ethernet, Token Ring, etc.)
• Device subnet mask
• Device IP address
• Device Media Access Control (MAC) address
The Novell test will NOT collect:
• Print Queue Name
• Attached to File Server status
• Attached to Print Queue status
The IP test will NOT collect:
• Device Name
• Gateway IP address
• Destination Network number
• Hop count to device
Ver. 2.00, March 2011 Page 29 of 50
Page 30

XEROX WorkCentre
3.4.5. Summary
As stated above, accessibility of customer documents, files or network resources is impossible via the
PSW. In the extremely unlikely event that someone did spoof the Xerox proprietary protocols, only
diagnostic activities can be executed.
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Ver. 2.00, March 2011 Page 30 of 50
Page 31

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
4. Security Aspects of
Selected Features
4.1. Audit Log
The device maintains a security audit log. Recording of security audit log data can be enabled or disabled
by the SA. The audit log is implemented as a circular log containing a maximum of 15000 event entries,
meaning that once the maximum number of entries is reached, the log will begin overwriting the earliest
entry. Only an SA will be authorized to download the log from the device. The log may only be exported
over an https: connection, so SSL must be set up before retrieving the log. The log is exported in MS-Excel
comma-separated file format. The log does not clear when it is disabled, and will persist through power
cycles.
Information Assurance Disclosure Paper
The following table lists the events that are recorded in the log:
ID
1 System startup Device name
Device serial number
2 System shutdown Device name
Device serial number
3 Manual ODIO Standard started Device name
Device serial number
4 Manual ODIO Standard complete Device name
Device serial number
Overwrite Status
5 Print job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
6 Network scan job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-net-destination
net-destination.
7 Server fax job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
net-destination.
Ver. 2.00, March 2011 Page 31 of 50
Page 32

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
8 IFAX
9
10 Audit Log Disabled Device name
11 Audit Log Enabled Device name
12 Copy Job name
13 Efax Job name
14 Lan Fax Job Job name
15 Data Encryption enabled Device name
16 Manual ODIO Full started Device name
17 Manual ODIO Full complete Device name
20 Scan to Mailbox job Job name or Dir name
21 Delete File/Dir Job name or Dir name
Email job
Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-of-smtp-recipients
smtp-recipients
Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-of-smtp-recipients
smtp-recipients
Device serial number
Device serial number
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
Device serial number
Device serial number
Device serial number
Overwrite Status
User Name
Completion Status
IIO status
User Name
Completion Status
IIO status
Ver. 2.00, March 2011 Page 32 of 50
Page 33

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
22 USB Thumbdrive UserName
Device name
Device serial number
USB port
Completion Status (Enabled/Disabled)
23 Scan to Home UserName
Device name
Device serial number
Completion Status (Enabled/Disabled)
24 Scan to Home job Job name or Dir name
User Name
Completion Status (Normal/Error)
IIO status
25 Copy store job Job name or Dir name
User Name
Completion Status (Normal/Error)
IIO status
26 PagePack login Device name
Device serial number
Completion Status (Success, Failed)
Locked out (if Max attempts exceed 5)
Time remaining
27 Postscript Passwords Device name
Device serial number
StartupMode (enabled/disabled)
System Params Password (changed or failed)
Start Job Password (changed or failed)
Completion Status (Success, Failed)
29 Network User Login UsereName
Device name
Device serial number
Completion Status (Success, Failed)
30 SA login Device name
Device serial number
Completion Status (Success or Failed)
31 User Login UserName
Device name
Device serial number
Completion Status (Success or Failed)
32 Service Login Diagnostics Service name
Device name
Device serial number
Completion status (Success or Failed).
33 Audit log download UserName
Device name
Device Serial Number
Completion status (Success or Failed).
34 IIO feature status UserName
Device name
Device serial number
IIO Status (enabled or disabled)
35 SA pin changed UserName
Device name
Device serial number
Completion status
36 Audit log Transfer UserName
Device name
Device serial number
Completion status
Ver. 2.00, March 2011 Page 33 of 50
Page 34

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
ID
37 SSL UserName
Device name
Device serial number
Completion status (Enabled/Disabled).
38 X509 certificate UserName
Device name
Device serial number
Completion Status (Created/uploaded/Downloaded).
39 IP sec UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
40 SNMPv3 UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
41 IP Filtering Rules UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
42 Network Authentication UserName
Device name
Device serial number
Completion Status (Enabled/Disabled)
43 Device clock UserName
Device name
Device serial number
Completion Status (time changed/date changed)
44 SW upgrade Device name
Device serial number
Completion Status (Success, Failed)
45 Cloning Device name
Device serial number
Completion Status (Success, Failed)
46 Secure scanning Device name
Device serial number
Completion Status (Certificate Validation success,
certificate validation failed)
47 Secure authentication Device name
Device serial number
Completion status (completed w errors).
48 Service login copy mode Service name
Device name
Device serial number
Completion Status (Success, Failed)
49 Smartcard access UserName
Device name
Device serial number
Completion Status (Success, Failed)
50 Process terminated Device name
Device serial number
Process name
51 ODIO scheduled Device name
Device serial number
ODIO type (Full or Standard)
Scheduled time
ODIO status (Started/Completed/canceled)
Completion Status (Success/Failed/Canceled)
Information Assurance Disclosure Paper
Ver. 2.00, March 2011 Page 34 of 50
Page 35

XEROX WorkCentre
Event
Event description
Entry Data
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
53 CPSR Backup File Name
User Name
Completion Status (Normal / Error)
IIO Status
54 CPSR Restore File Name
User Name
Completion Status (Normal / Error)
IIO Status
55 SA Tools Access Admin Device serial number
Completion Status (Locked/Unlocked)
60 Device Clock NTP Enable/Disable Device Name
Device serial number
Enable/Disable NTP
NTP Server IP Address
Completion Status (Success/Failed)
61 Grant / Revoke Admin Device Name
Device Serial Number
User Name (of target user)
Grant or Revoke (the admin right)
Completion Status (Success/Failed)
62 Smartcard (CAC/PIV)
Enable/Disable/Configure
63 IPv6
Enable/Disable/Configure
64 802.1x
Enable/Disable/Configure
65 Abnormal System Termination Device Name
66 Local Authentication UserName
67 Web User Interface Authentication
(Enable Network or Local)
69 Xerox Secure Access Login UserName
73 System Log Download Username
106 SA PIN Reset Device serial number
UserName
Device Name
Device Serial Number
Completion Status (Success/Failed)
UserName
Device Name
Device Serial Number
Completion Status (Success/Failed)
UserName
Device Name
Device Serial Number
Completion Status (Success/Failed)
Device Serial Number
Device Name
Device Serial Number
Completion Status (Enabled/Disabled)
UserName
Device Name
Device Serial Number
Authentication Method Enabled (Network/Local)
Device Name
Device Serial Number
Completion Status (Success/Failed)
IP of requesting device (if available)
File names downloaded
Destination (IP address or USB device)
Completion status (Success/failed)
Completion Status (Success/Failed)
ID
1 System startup Device name
Device serial number
Ver. 2.00, March 2011 Page 35 of 50
Page 36

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
ID
2 System shutdown Device name
Device serial number
3 Manual ODIO Standard
started
4 Manual ODIO Standard
complete
5 Print job Job name
6 Network scan job Job name
7 Server fax job Job name
8 IFAX
9
10 Audit Log Disabled Device name
11 Audit Log Enabled Device name
12 Copy Job name
Email job
Device name
Device serial number
Device name
Device serial number
Overwrite Status
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-net-destination
net-destination.
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
net-destination.
Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-of-smtp-recipients
smtp-recipients
Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-of-smtp-recipients
smtp-recipients
Device serial number
Device serial number
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
Information Assurance Disclosure Paper
Ver. 2.00, March 2011 Page 36 of 50
Page 37

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
13 Efax Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
14 Lan Fax Job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
15 Data Encryption enabled Device name
Device serial number
16 Manual ODIO Full started Device name
Device serial number
17 Manual ODIO Full complete Device name
Device serial number
Overwrite Status
20 Scan to Mailbox job Job name or Dir name
User Name
Completion Status
IIO status
21 Delete File/Dir Job name or Dir name
User Name
Completion Status
IIO status
22 USB Thumbdrive UserName
Device name
Device serial number
USB port
Completion Status (Enabled/Disabled)
23 Scan to Home UserName
Device name
Device serial number
Completion Status (Enabled/Disabled)
24 Scan to Home job Job name or Dir name
User Name
Completion Status (Normal/Error)
IIO status
25 Copy store job Job name or Dir name
User Name
Completion Status (Normal/Error)
IIO status
26 PagePack login Device name
Device serial number
Completion Status (Success, Failed)
Locked out (if Max attempts exceed 5)
Time remaining
27 Postscript Passwords Device name
Device serial number
StartupMode (enabled/disabled)
System Params Password (changed or failed)
Start Job Password (changed or failed)
Completion Status (Success, Failed)
Ver. 2.00, March 2011 Page 37 of 50
Page 38

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
29 Network User Login UsereName
Device name
Device serial number
Completion Status (Success, Failed)
30 SA login Device name
Device serial number
Completion Status (Success or Failed)
31 User Login UserName
Device name
Device serial number
Completion Status (Success or Failed)
32 Service Login Diagnostics Service name
Device name
Device serial number
Completion status (Success or Failed).
33 Audit log download UserName
Device name
Device Serial Number
Completion status (Success or Failed).
34 IIO feature status UserName
Device name
Device serial number
IIO Status (enabled or disabled)
35 SA pin changed UserName
Device name
Device serial number
Completion status
36 Audit log Transfer UserName
Device name
Device serial number
Completion status
37 SSL UserName
Device name
Device serial number
Completion status (Enabled/Disabled).
38 X509 certificate UserName
Device name
Device serial number
Completion Status (Created/uploaded/Downloaded).
39 IP sec UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
40 SNMPv3 UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
41 IP Filtering Rules UserName
Device name
Device serial number
Completion Status (Configured/enabled/disabled).
42 Network Authentication UserName
Device name
Device serial number
Completion Status (Enabled/Disabled)
43 Device clock UserName
Device name
Device serial number
Completion Status (time changed/date changed)
Ver. 2.00, March 2011 Page 38 of 50
Page 39

XEROX WorkCentre
Event
Event description
Entry Data
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
ID
44 SW upgrade Device name
Device serial number
Completion Status (Success, Failed)
45 Cloning Device name
Device serial number
Completion Status (Success, Failed)
46 Secure scanning Device name
Device serial number
Completion Status (Certificate Validation success, certificate
validation failed)
47 Secure authentication Device name
Device serial number
Completion status (completed w errors).
48 Service login copy mode Service name
Device name
Device serial number
Completion Status (Success, Failed)
49 Smartcard access UserName
Device name
Device serial number
Completion Status (Success, Failed)
50 Process terminated Device name
Device serial number
Process name
51 ODIO scheduled Device name
Device serial number
ODIO type (Full or Standard)
Scheduled time
ODIO status (Started/Completed/canceled)
Completion Status (Success/Failed/Canceled)
4.2. Xerox Standard Accounting
Xerox Standard Accounting (XSA), intended primarily for use as an accounting service, can be used as an
internal authorization service. XSA tracks copy, scan (including filing and email), print and fax usage by
individual user1. The system administrator can enable/disable the feature via the LUI or Web UI, add or
delete users, and set usage limits by service for each user. If XSA is enabled, a walk-up user must enter a
valid XSA ID before being allowed access to the device. The device will confirm that the entered XSA ID
matches an authorized user, and that the usage limits for the selected service have not been exceeded. In
this sense, XSA acts as an authorization service. The system administrator can limit access to device
services by setting the usage limits on specific services to zero for users that should not have rights to use
the feature. After each job is performed, the user’s balance is updated by the number of impressions or
scans performed. Services become unavailable to the user when the usage limits are exceeded.
When XSA is enabled in the print driver or on the Web UI, before a print job is submitted, an XSA ID must
also be entered. The ID is sent to the controller for validation. If the submitted ID is valid, the job will print,
and the user’s balance will be updated by the number of impressions performed. If the submitted ID is
invalid, the job is deleted and an error sheet is printed in its place.
1
On color machines XSA can track color copy or color print usage.
Ver. 2.00, March 2011 Page 39 of 50
Page 40

XEROX WorkCentre
On demand, the SA will be able to download a report that shows activity for all of the users. The SA can
add, modify or remove users and their allocations at any point.
An end user will be able to review their balances by entering a User ID at the LUI or web UI.
5735/5740/5745/5755/5765/5775/5790
4.3. Automatic Meter Reads
Automatic Meter Reads (AMR) is a service that allows devices to electronically report meter readings back
to Xerox. The Systems Administrator sets up the attributes for the AMR service via the web UI, including
registering the device with the Xerox AMR server. Once enabled, the device will poll the Xerox AMR server
daily over the network. The server will check whether it is time in the monthly billing cycle to update the
meter readings. If so, the server will request reads from the device, and the device will then respond by
sending the meter reads back to the server.
This communication process means that the device initiates all communication between it and Xerox. Only
device ID and meter read information is transferred. The information is sent in clear text.
The device can be set to communicate via a proxy server on the customer’s network. The proxy server
address is set up using the WebUI.
Information Assurance Disclosure Paper
4.4. Encrypted Partitions
When enabled by the customer, the controller disk is encrypted using the AES algorithm with a 128-bit key.
256-bit encryption is available via SPAR – please contact Xerox Customer Support and request SPAR 85669.
The key is generated dynamically on each boot, and is kept only in volatile memory. Encryption is installed
but must be enabled by the customer.
4.5. Image Overwrite
The Image Overwrite Security feature provides both Immediate Image Overwrite (IIO) and On-Demand
Image Overwrite (ODIO) functions. Immediately before a job is considered complete, IIO will overwrite any
temporary files associated with print, network scan, internet fax, network fax, or e-mail jobs that had been
created on the controller Hard Disk. The ODIO feature can be executed at any time by the SA and will
overwrite the entire document image partitions of the controller Hard disk. ODIO may also be scheduled to
run at regular times. A standard ODIO will overwrite all image data from memory and disks except for Jobs
and Folders stored in the Reprint Saved Jobs feature; Jobs stored in the Scan to Mailbox feature (if
installed); Fax Dial Directories (if fax card is installed); and Fax Mailbox contents (if fax card is installed). A
full ODIO will overwrite all image data from memory and disks as well as the items excluded from a
standard ODIO.
Ver. 2.00, March 2011 Page 40 of 50
Page 41

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
4.5.1. Algorithm
The overwrite mechanism for both IIO and ODIO conforms to the U.S. Department of Defense Directive
5200.28-M (Section 7, Part 2, paragraph 7-2022.
The algorithm for the Image Overwrite feature is:
Step 1: Pattern #1 is written to the sectors containing temporary files (IIO) or to the entire spooling
area of the disks (ODIO). (hex value 0x35 (ASCII “5”)).
Step 2: Pattern #2 is written to the sectors containing temporary files (IIO) or to the entire spooling
area of the disks (ODIO). (hex value 0xCA (ASCII compliment of 5)).
Step 3: Pattern #3 is written to the sectors containing temporary files (IIO) or to the entire spooling
area of the disks (ODIO). (hex value 0x97 (ASCII “ú”)).
Step 4: 10% of the overwritten area is sampled to ensure Pattern #3 was properly written. The 10%
sampling is accomplished by sampling a random 10% of the overwritten area.
4.5.2. User Behavior
IIO can be enabled at the local UI only.
completion of a print, network scan, internet fax, network fax, or e-mail job. If IIO completes successfully,
status is displayed in the Job Queue. However, if IIO fails, a popup will appear on the Local UI
recommending that the user run ODIO, and a failure sheet will be printed.
ODIO may be invoked either from the Local UI in Tools Pathway or from the CentreWare Internet Services
Web UI. Network functions will be delayed until the overwrite is completed. Copying is unavailable while
the overwrite itself is underway, but copies may be made while the controller is booting.
Upon completion and verification of the ODIO process, a confirmation sheet is printed which indicates the
status of the overwrite. The completion status can be successful, failed, cancelled, or timed-out.
Please note that invocation of ODIO will cause currently processing print jobs to be aborted. However, scan
jobs will not be aborted and so ODIO might fail. The user should insure that all scan jobs have been
completed before invoking ODIO.
Please refer to the customer documentation for a description on how failures are logged.
Once enabled, IIO is invoked automatically immediately prior to the
4.5.3. Overwrite Timing
The ODIO overwrite time is dependent on the type of hard disk in the product. The overwrite and reset
average time is 10 minutes, but longer times are possible.
IIO is performed as a background operation, with no user-perceivable reduction in copy, print or scan
performance.
2
http://www.dtic.mil/whs/directives/corres/archives/520028m_0173/p520028m.pdf
Ver. 2.00, March 2011 Page 41 of 50
Page 42

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
5. Responses to Known
Vulnerabilities
5.1. Security @ Xerox
(www.xerox.com/security)
Xerox maintains an evergreen public web page that contains the latest security information pertaining to its products.
Please see www.xerox.com/security.
Ver. 2.00, March 2011 Page 42 of 50
Page 43

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Paper
Information Assurance Disclosure
6. APPENDICES
6.1. Appendix A – Abbreviations
API Application Programming Interface
AMR Automatic Meter Reads
ASIC Application-Specific Integrated Circuit. This is a custom integrated circuit that is
unique to a specific product.
CAT Customer Administration Tool
CSE Customer Service Engineer
DADF/DADH Duplex Automatic Document Feeder/Handler
DHCP Dynamic Host Configuration Protocol
DNS Domain Name Server. A centralized database that maps host names to static IP
addresses.
DDNS Dynamic Domain Name Server. Maps host names to dynamic static IP addresses.
DRAM Dynamic Random Access Memory
EEPROM Electrically erasable programmable read only memory
EGP Exterior Gateway Protocol
GB Gigabyte
HP Hewlett-Packard
HTTP Hypertext transfer protocol
IBM International Business Machines
ICMP Internet Control Message Protocol
IETF Internet Engineering Task Force
IFAX Internet Fax
IIO Immediate Image Overwrite
IIT Image Input Terminal (the scanner)
IT Information Technology
IOT Image Output Terminal (the marking engine)
IP Internet Protocol
IPSec Internet Protocol Security
IPX Internet Protocol Exchange
LAN Local Area Network
LDAP Lightweight Directory Access Protocol
LDAP Server Lightweight Directory Access Protocol Server. Typically the same server that is used
for email. It contains information about users such as name, phone number, and
email address. It can also include a users login alias.
LED Light Emitting Diode
LPR Line Printer Request
MAC Media Access Control
MIB Management Information Base
n/a not applicable
NDPS Novell Distributed Print Services
NETBEUI NETBIOS Extended User Interface
NETBIOS Network Basic Input/Output System
NOS Network Operating System
Ver. 2.00, March 2011 Page 43 of 50
Page 44

XEROX WorkCentre
NVRAM Non-Volatile Random Access Memory
NVM Non-Volatile Memory
ODIO On-Demand Image Overwrite
PCL Printer Control Language
PDL Page Description Language
PIN Personal Identification Number
PSW Portable Service Workstation
PWBA Printed Wire Board Assembly
PWS Common alternative for PSW
RFC Required Functional Capability
SA System Administrator
SLP Service Location Protocol
SNMP Simple Network Management Protocol
SRAM Static Random Access Memory
SSDP Simple Service Discovery Protocol
SSL Secure Sockets Layer
TCP Transmission Control Protocol
TIFF Tagged Image File Format
UI User Interface
URL Uniform Resource Locator
UDP User Datagram Protocol
WebUI Web User Interface – the web pages resident in the WorkCentre Pro. These are
XCMI Xerox Common Management Interface
XSA Xerox Standard Accounting
5735/5740/5745/5755/5765/5775/5790
Paper
accessible through any browser using the machine’s IP address as the URL.
Information Assurance Disclosure
Ver. 2.00, March 2011 Page 44 of 50
Page 45

XEROX WorkCentre
"supported"
all MIB objects exists a
nd are populated w/ meaningful data that is consistent w/ the
"supported w/ caveats"
all MIB objects exists, however, 2 major bugs or less may exists w/ some of the objects that
"not supported"
MIB o
bjects do not exist/implementation was not planned
"not fully supported"
MIB objects exists, HOWEVER, are NOT populated w/ meaningful data OR provide only default
"optional, *"
optional group that is NOT required by
the RFC, however, an implementation may exist; some
SNMPv1 (RFC 1157)
supported
SNMPv2P (RFCs 140x)
not supported
SNMPv2C (RFCs 190x)
supported
SNMPv3 (RFCs
1902, 2572, 2574)
supported
SNMP over UDP (IP)
supported
SNMP over IPX (Netware)
supported
SNMP over NETBEUI (Microsoft Networking)
not supported (implemented but never delivered)
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure
Paper
6.2. Appendix B – Supported MIB
Objects
NOTES :
(1) The number of objects shown per MIB group represents the number of objects defined by the IETF
standard for that MIB group. It does not represent the instantiation of the MIB group which may
contain many more objects.
(2) Some MIB objects defined within Input and Output groups of the Printer MIB (RFC 1759) have a
MAX-ACCESS of RW. However, the Printer MIBv2 defines a MIB-ACCESS of RO for these MIB objects
within the Input and Output groups and all machines assessed support RO access. Therefore, RO
access to these MIB objects is considered IETF compliant.
(3) It is assumed that mandatory IETF string-related MIB objects shall contain meaningful data; not
blank strings
(4) The "(C)" notation indicates that the previously stated item is a true caveat condition. The "(I)"
notation indicates that the previous stated item should be regarded as information only.
(5) MIB objects that CANNOT be populated with meaningful data (e.g. a machine may not have paper
level sensors, hence, can only support "0" or "-3 for more than 1 sheet" for prtInputCurrentLevel) will
be considered a caveat, denoted as "(C)".
(6) The Printer MIB requires a few groups from RFC 1213 and RFC 1514 to be supported. Therefore, this
assessment will indicate that these groups are "supported" as long as the basic MIB structures have
been implemented.
Support Definitions
Term Definition
hardware installed within the machine.
were not fixed
values OR contain 3 or more major bugs
MIB objects may not be populated w/ meaningful data
SNMP version / Network Transport support WorkCentre
Ver. 2.00, March 2011 Page 45 of 50
Page 46

XEROX WorkCentre
RFC 1213
- Syst
em group
supported
RFC 1213
- Interface group
supported
RFC 1514
- Storage group
supported
RFC 1514
- Device group
supported
7 objects
supported
3 objects
supported w/ caveats = Finisher cover is shown as open when only
the
4 objects
supported w/ caveats = only US English language supported
supported
4 objects
supported
12 objects
supported
supported
supported
6 objects
supported w/ caveats = only "
-
3" (i.e. can accept 1 or more sheets) can
supported
supported
supported
15 objects
supported
supported
supported
11 objects
supported
8 objects
supported
12 objects
supported
4 objects
supported w/ cav
eats = prtConsoleDisable is hardcoded to enabled(3),
2 objects
supported w/ caveats = limited local UI messaging captured within table
5 objects
supported w/ caveats = only the Power Saver LED is supported, the other
objects
supported
supported
7 objects
supported
8 objects
supported
6 objects
supported w/ caveats = hrDeviceStatus for xcmHrDeviceScanner
does
not work, hrDeviceErrors for xcmHrDeviceScanner does not work, all other
2 objects
supported
1 object
supported
2 objects
suppor
ted
4 objects
supported
5 objects
supported
9 objects
supported w/ caveats = hrFSLastFullBackupDate &
optional, not supported
optional, not supported
optional, not supported
7 objects
s
upported
23 objects
supported w/ caveats = ifInUnknownProtos does not work
3 objects
supported, but this group has been DEPRICATED by the IETF
42 objects
supported
26 objects
suppor
ted
19 objects
supported
6 objects
supported
20 objects
not applicable because Exterior Gateway Protocol not supported by
RFC 1759 - Printer MIB Group WorkCentre
5735/5740/5745/5755/5765/5775/5790
Paper
Information Assurance Disclosure
General group [
Covers group [
Localization group [
Responsible Party group [2 objects] - OPTIONAL
System Resources group [
Input group [
Extended Input group [7 objects] - OPTIONAL
Input Media group [4 objects] - OPTIONAL
Output group [
Extended Output group [7 objects] - OPTIONAL
Output Dimensions group [5 objects] OPTIONAL
Output Features group [6 objects] - OPTIONAL
Marker group [
Marker Supplies group [9 objects] - OPTIONAL
Marker Colorant group [5 objects] - OPTIONAL
Media Path group [
Channels group [
Interpreter group [
Console group [
Console Display Buffer group [
Console Display Light group [
Alert Table group [8
Alert Time group [1 object] - OPTIONAL
]
]
]
]
]
]
]
]
]
]
]
]
]
]
RFC 1514 – Host Resources MIB group WorkCentre
System group [
Storage group [
Devices group [
]
]
]
Front Door is open due to detection limitation of status condition
be supported for the Top Tray (C)
prtConsoleLocalization hardcoded to 1
(C), local UI button selection messages are not captured within table
LEDs were not implemented because they represent local UI menu
activations (I)
Processor Table [
Network Interface Table [
Printer Table [
Disk Storage Table [
Partition Table [
File System Table [
Software Running group [7 objects] – OPTIONAL
Software Running Performance group [2 objects] – OPTIONAL
Software Installed group [7 objects] – OPTIONAL
]
]
]
]
]
]
device error counts AND hrDeviceStatus are not supported ©
hrFSLastPartialBackupDate are not supported ©
RFC 1213 - MIB-II for TCP/IP group WorkCentre
System group [
Interfaces group [
Address Translation group [
IP group [
ICMP group [
TCP group [
UDP group [
EGP group [
]
]
]
]
]
]
]
]
machine
Ver. 2.00, March 2011 Page 46 of 50
Page 47

XEROX WorkCentre
0 objects
not applicable because the group has not yet been defin
ed by the IETF
28 objects
supported
8
supported
ability to change GET, SET, TRAP PDU community names
supported, default
values : GET="public", SET="private",
Printer MIB traps
supported = printerV1Alert, printerV2Alert
SNMP Generic Traps
supported = coldStart, warmStart, authenticationFailure
Vendor
-
specific Traps
supported = xcmJobV1AlertNew, xcmJobV2A
lertNew for job monitoring
set trap destination address(es) for any 3rd party Net Mgmt
supported via Web UI
polling for IETF status objects using any 3rd party Net Mgmt
supported
walking IETF MIB tree structure using any 3rd party Net
Mgmt
supported
New type 2 enumerations from next generation Host
optional, not support because Host Resources MIBv2 has NOT entered
New type 2 enumerations fro
m next generation Printer MIB
supported
New Printer MIBv2 objects implemented
optional, not support because Printer MIBv2 has NOT entered the
IETF AppleTalk MIB (RFC ?) implemented
not supported
Job monitoring via MIBs
supporte
d via Xerox MIBs
Vendor
-
specific MIBs implemented
supported = Network Connectivity, Job Monitoring, Scan
-to-
File, and
Vendor
-
specific MIBs provided to customer
supported w/ caveat = planned support within
2 - 3Q00 via Xerox web
Vendor
-
specific client application(s) provided
CentreWare Services
required Windows2000 MIB objects supported
supported
Embedded Web Server support
supported
Xerox PrinterMap application support
support
ed
Xerox PrintXchange support
supported
Novell Distributed Print Services support
supported = w/ Xerox NDPS Gateway solution w/ improved device status
Dazel Output Management Environment
supported
HP OpenView snap
-
in module
supported
CA Unicenter snap
-
in module
supported
IBM/Tivoli NetView snap
-
in module
supported
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure
Paper
RFC 1213 - MIB-II for TCP/IP group WorkCentre
Transmission group [
SNMP group [
System Object Resources Table/objects per RFC 1907 [
objects]
]
]
Additional Capabilities / Application Support WorkCentre
TRAP="SNMP_trap"
alerts
apps.
apps.
app. (e.g. HP OpenView, etc.) / shareware program
Resources MIB supported
supported
the standards track
standards track
Scan-to-LAN FAX features supported via Xerox MIBs
site, URL = www.xerox.com
Ver. 2.00, March 2011 Page 47 of 50
Page 48

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Paper
Information Assurance Disclosure
6.3. Appendix C –Standards
Controller Hardware
PCI Specification (PCI Local Bus Specification Revision 2.1)
100 Megabit Ethernet (IEEE 802.3)
Universal Serial Bus 1.1
Parallel (IEEE 1284)
IEEE 1394a (FireWire)
Controller Software
Function
Internet Protocol 950
Internet standard subnetting procedure 919
Broadcasting internet datagrams 922
IP Version 6 2460
IP Version 6 Addressing Architecture 2373
ICMP Version 6 Protocol 2463
Transition Mechanisms for IPv6 Hosts and Routers 1933
Transmission Control Protocol (TCP) 793
User Datagram Protocol 768
Standard for the transmission of IP datagrams over Ethernet
networks
Standard for the transmission of IP datagrams over IEEE802
networks
ICMP – ICMP Echo, ICMP Time, ICMP Echo Reply, and ICMP
Destination Unreachable message.
Reverse Address Resolution Protocol (RARP) 903
Bootstrap Protocol (BOOTP) 951
Clarifications and Extensions for the Bootstrap Protocol (BOOTP) 1542
X.500 Distinguished Name RFC references 1779, 2253, 2297, 2293
SLP 2608
Dynamic Host Configuration Protocol (DHCP) 2131
DHCP Options and BOOTP Vendor Extensions 2132
X.509 Certificate RFC references 2247, 2293, 2459, 2510, 2511, 3280
Hyper Text Transfer Protocol version 1.1 (HTTP) 2616
Line Printer Daemon (LPR/LPD) 1179
File Transfer Protocol (FTP) 959
SNMPv1 1157
SNMPv2 1901, 1905, 1906, 1908, 1909
SNMPv3
Structure of Management Information (SMI) for SNMPv1 1155, 1212
Structure of Management Information (SMI) for SNMPv2 1902, 1903, 1904
IETF MIBs:
MIB II
Host Resources
RFC 1759 (Printer), Printer MIB V2
SNMP Traps
RFC/Standard
894
1042
792
1902, 2572, 2574
1213
1514
1759
1215
Ver. 2.00, March 2011 Page 48 of 50
Page 49

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Paper
Information Assurance Disclosure
Function
Document Printing Application (DPA)
Appletalk
Printing Description Languages
Postscript Language Reference, Third Edition
PCL6 (PCL5E 5SI emulation)
PCL6 (PCLXL 5M emulation)
TIFF 6.0
JPEG
Portable Document Format Reference Manual Version 1.3
RFC/Standard
10175
Inside Appletalk, Second Edition
Ver. 2.00, March 2011 Page 49 of 50
Page 50

XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Paper
Information Assurance Disclosure
6.4. Appendix E – References
Kerberos FAQ http://www.nrl.navy.mil/CCS/people/kenh/kerberos-
faq.html
IP port numbers http://www.iana.org/assignments/port-numbers
Ver. 2.00, March 2011 Page 50 of 50
 Loading...
Loading...