Page 1

ADMINISTRATOR GUIDE
Linksys Business Series Network Storage System
Models NSS4000 and NSS6000 Series
Linksys Business Series Network Storage System
Administrator Guide
Page 2

© 2007 Copyright 2007, Cisco Systems, Inc.
Specifications are subject to change without notice.
Linksys, the Cisco Systems logo, the Linksys Logo, and the Linksys One logo are registered trademarks of Cisco
Systems, Inc. All other trademarks mentioned in this document are the property of their respective owners.
Page 3

Contents
Network Storage System (NSS) Administrator Guide
Chapter 1: Introduction . . . . . . . . . . . . . . . . . . 4
Using the Help 5
Recommended Disk Drive List 6
Chapter 2: Working with the System . . . . . . . . . . . . . 7
Viewing the Hardware Monitor 11
Viewing and Managing the System Logs 12
Configuring the System for UPS Support 14
NSS-supported UPS Product Families 15
Chapter 3: Managing the Network Options . . . . . . . . . . . 16
Viewing the Network Settings 18
Configuring the Network Link IP 19
Resetting the DHCP Lease on a Link 20
Viewing VLANs Configured on the NSS 21
Allowing a VLAN Access to the NSS 22
Changing a VLAN Configuration 25
Removing a VLAN’s Access to the NSS 26
Configuring the NSS Network Identification 27
Configuring DNS or WINS for Name Resolution 29
Joining the NSS to a Network Information System (NIS) Domain 31
Editing Access Control Lists (ACLs) from Windows Explorer: Restrictions 33
Running Diagnostics of your Physical Links 34
Configuring the Network Ports 35
Setting up the Link Bonding & Advertising Modes 36
Chapter 4: Managing your Storage . . . . . . . . . . . . . . 38
Choosing a RAID Array Level 42
Creating a RAID Array 44
Adding a Disk Drive to an Array 45
Deleting an Array 47
Migrating a RAID Array to another Storage Device 48
Virtualizing Storage within your Network 49
Exporting Storage to your Network 50
Creating Virtualized Storage 51
Unexporting Storage 52
Volume Management 53
Creating a Volume 54
Expanding a Volume 56
Deleting a Volume 58
Viewing the Snapshot Reserve Details 59
Creating a Snapshot for a Volume 61
Taking a Manual Snapshot of a Volume 63
1
Page 4

Contents
Network Storage System (NSS) Administrator Guide
Windows End Users: Accessing a Snapshot for a Share 64
Volume Encryption Overview 65
Locking an Encrypted Volume 66
Unlocking a Locked Volume 67
Changing the Password for an Encrypted Volume 69
Storage Options 71
Setting the RAID Rebuild Priority 72
Setting the Spin Down Time 73
Chapter 5: Administering Access to the NSS. . . . . . . . . . . 74
Managing your NSS Users 75
Creating a User Profile 76
Editing a User Profile 78
Integrating Users from an ADS, NTv4, or NIS Domain 80
Deleting a User Profile 81
Working with Groups 82
Creating a Group 83
Changing the Users Assigned to a Group 85
Integrating Groups from an Active Directory, NTv4, or NIS Domain 86
Deleting a Group 87
Managing Volume Quotas 89
Creating Volume Quota for a User or Group 91
Setting up the Grace Period for a Volume Quota 93
Changing a Volume Quota for a User or Group 94
Clearing a Quota 95
Network Filters Overview 96
Defining the Default Network Policy 97
Creating a Network Filter 98
Available Access Filters 100
Deleting a Network Filter 102
Configuring the User/Group Settings 103
Chapter 6: Managing the Shares. . . . . . . . . . . . . . 104
Creating a Share 105
Editing an Existing Share 108
Adding a DFS Shared Folder 110
Restrictions using Microsoft DFS from the NSS 112
Setting up CIFS Access 113
Setting up Network Filesystem (NFS) Access 114
Configuring the NSS for FTP Access 115
Creating or Running a Backup of a Share 117
Creating a Scheduled Backup for a Share 118
Initiating a Backup for a Share 120
2
Page 5

Contents
Network Storage System (NSS) Administrator Guide
Deleting Backup Images 122
Chapter 7: Managing the Admininstrator Options . . . . . . . 123
Rebooting or Shutting Down the NSS 124
Upgrading the NSS Firmware 126
Restoring the Factory Default Configuration 127
Managing the NSS Configuration 129
Saving the Current Configuration 130
Restoring a Configuration File 132
Deleting a Configuration File 134
Configuring the Timing Settings 135
Configuring SNMP Alerts 137
Changing the Administrator Password 139
Chapter 8: Accessing the NSS’s Storage . . . . . . . . . . . 140
Logging into the CIFS Shares with Administrator Privileges 141
Windows Users: Accessing the NSS Storage using CIFS/SMB 142
Windows Users: Accessing the NSS Storage through FTP 143
Mac Users: Accessing Storage through CIFS/SMB 144
Mac Users: Accessing Storage through FTP 145
UNIX/Linux Users: Accessing Storage through NFS 146
UNIX/Linux Users: Accessing Storage through FTP 147
Chapter 9: Glossary . . . . . . . . . . . . . . . . . . 148
Chapter 10: Troubleshooting . . . . . . . . . . . . . . . 157
LEDs & Buttons 157
Repairing a Degraded Array 160
Working with a Failed Array 162
Free Bound Aggregation Storage when the Master System Fails 163
All CIFS Connections were Unexpectedly Ended 164
Hotplugging the Ethernet Link doesn’t Reset IP or Link Rate 165
Unable to Create a Share or Quota for a Volume 166
Cannot access the NSS through FTP 167
Configuration Page does not Appear in Internet Explorer 168
Handling an Unexpected (Unclean) Shutdown 170
Appendix A: Support Contact Information . . . . . . . . . . 171
3
Page 6

Chapter
Network Storage System (NSS) Administrator Guide
Introduction
Thank you for choosing the Linksys Business Series Network Storage System (NSS).
Administering a network can be a difficult job. Finding low-cost ways to simplify your datamanagement tasks means that you have more resources to dedicate elsewhere. The NSS is a
Network Attached Storage (NAS) unit that appears as a native file server for the various clients
within your network, including Windows, Apple Macintosh, UNIX, and Linux platforms. The biggest
benefit to your users is that they can now access data that might be stored across different physical
platforms as simply as if it were on their own computers. The NSS provides a single repository that
is completely dedicated to storage, ensuring the integrity, reliability, and accessibility of your data
for a relatively low cost.
The NSS lets you install up to four physical disk drives as well as virtualize your storage into one or
more logical, redundant storage units or RAID arrays. The NSS uses the most common file-based
protocols such as NFS, CIFS, and FTP for file sharing.
Benefits
1
The NSS offers the following main advantages to your business:
• Cross-platform File Sharing: Share files easily and inexpensively across heterogeneous
platforms over a cost-effective Ethernet and IP network.
• Easy Installation and Administration: With a basic understanding of networking, the NSS is
easy to get going and to maintain.
• Data Consolidation: Centralize data to reduce management costs and maximize your
investment in existing hardware. This also means better data security.
Chapter 1: Introduction
4
Page 7

Chapter
Network Storage System (NSS) Administrator Guide
Using the Help
The NSS (Network Storage System) help file provides information about using the configuration
interface to configure the NSS. You can access the help topics either through the Help link found in
the Manager Menu or by clicking the Help button at the top-right corner of each configuration
page.
Audience
The information contained in these help pages is intended for use by network administrators. It
assumes a basic understanding of storage-related concepts, including RAID, filesystems, and
networking.
About the NSS Configuration Interface
The NSS configuration interface contains some basic navigation features to help you as you
configure the NSS.
• Manager Menu: The Manager Menu forms the left side of the configuration interface
window. It contains the menu options that represent the major configuration areas for the
NSS. For example, System, Network, Share, Storage, and so on. When you click an option,
a sub-menu of related options appears. Clicking a subtopic opens the associated topic in the
Top ic page in the right side of the window.
1
• Topi c Pa ge: When you select a topic from the Manager Menu, the configuration page for
that topic appears in the right side of the window.
Getting Help
There are two buttons on the NSS configuration interface window that you can click to access help:
•From the Manager Menu click Help to display the full online Administrator Guide. Use the
navigation tools within the help to find information for your chosen topic.
• A context-sensitive help button appears in the upper-right corner of the topic page. Click it to
display help on the specific configuration area. For example, if the current configuration topic
is about the status of your disk drives, click the Help button for information about the details
that appear on the status page.
Chapter 1: Introduction
Using the Help
5
Page 8

Chapter
Network Storage System (NSS) Administrator Guide
Recommended Disk Drive List
If you are purchasing disk drives to install in the NSS, please refer to the product support
information offered on the LinksysOne website for a list of recommended disk drives.
The decision of which disks to purchase also needs to be made based on the RAID levels you want to
create. For example, if you are creating a RAID (versus a JBOD), make sure that each of the disks
used in the array have the same disk capacity. The RAID is built using the capacity of the smallest
disk in the array.
1
Chapter 1: Introduction
Recommended Disk Drive List
6
Page 9

Chapter
Network Storage System (NSS) Administrator Guide
Working with the System
The System Status page provides an overview of the current operating condition of the NSS. For
example, you can view system alert messages such as if a disk drive is failing or has failed, if a
volume is approaching its full capacity, if an array rebuild is complete, and so on. You can also view
the current status of any of the following: storage, shares, backups, volume snapshots, network,
power, and system details. Status pages like the System Status page automatically refresh on a
regular interval and are very helpful for monitoring the progress of certain processes such as
building a RAID.
2
The following sections provide a detailed explanation of the information that appears on the System
Status page.
System Alerts
The System Alerts section shows any system messages issued since the last time they were cleared.
Messages can range in severity from informational to immediate action required.
There are three type of alerts that can appear in this area of the System Status page:
• Error: These types of messages indicate the most severe problem with the NSS. They are
color-coded red and require immediate action. For example, if a disk drive or RAID array is
in a failed condition.
Chapter 2: System
7
Page 10
Chapter
Network Storage System (NSS) Administrator Guide
• Warning: These types of messages indicate there is a problem with the NSS that requires
eventual action. They are color-coded orange. For example, if the amount of storage used for
a volume is over 90%.
• Notification: These types of messages are simply to advise of changes to the NSS. They do
not require action and are color-coded green. For example, the RAID rebuild is complete.
Storage Status
The Storage area displays details about the configured storage on the NSS, including:
• Drives: The number of physical disk drives installed.
• RAID Arrays: The number of configured RAID Arrays.
• Volumes: The number of configured volumes.
• Total Configured Capacity: The total aggregate size of all configured volumes.
• Percent Used: The total amount of the configured capacity used. The percentage is colorcoded according to the current percentage used:
2
- Green: 0 to 74%
- Orange: 75-89%
- Red: 90-100%
Network Status
The Network area displays the following:
• Link 1 & 2: The current status of the physical links. The status of the link can be up (colorcoded green) or down (color-coded red). If the link is not present, the status appears as
"down".
• Bonding Mode: Displays how the bonding mode for the physical links has been configured
on the Network Properties page. (
• VLANs: The number of VLANs configured on the NSS.
• Link 1 IP: The IP address of the first Ethernet link.
• Link 2 IP: The IP address of the second Ethernet link (if installed). If the bonding mode is set to
"active backup" or "802.3ad", the two links appear as a single entity (i.e., "Link 1+2 IP").
see Setting up the Link Bonding & Advertising Modes)
Shares Status
The Shares area displays the status of the following:
• Shares: The number of configured shares.
• Connected Users: The total number of user sessions currently connected to the NSS.
Chapter 2: System
8
Page 11

Chapter
Network Storage System (NSS) Administrator Guide
• FTP: FTP access state (enabled or disabled).
• NFS: NFS access state (enabled or disabled).
Backup/Snapshots Status
The Backup/Snapshots area displays the following:
• Snapshots: The total number of volume snapshots configured.
• Last Backup: The date and time of the last backup run. If a backup has never been run on the
system, the word "never" appears.
Power Status
The Power area displays the following:
• UPS: The following options are available depending on the current operating condition of the
UPS. For more information about the functioning of the UPS, refer to the UPS documentation.
2
- No Connection: A UPS is not currently connected to the NSS.
- On Mains: A UPS is connected to the NSS but is not currently being used to power the unit.
The NSS is deriving power from the mains power.
- On Battery (%): The NSS is currently deriving its power from the UPS battery. The
percentage of power still available is also listed and is color-coded according to the amount
of battery remaining.
• RPSU: The following options are available depending on the current operating condition of
the RPSU. For more information about the functioning of the RPSU, refer to the RPSU
documentation.
- No Connection: There is no RPSU installed.
- Ready: An RPSU is installed and is currently available as a backup power source.
- Standby/Fault: An RPSU is installed but is in Standby mode, or, the RPSU is installed and
has some sort of fault condition. For example, the RPSU is connected to the NSS but is
powered off.
- Active: The RPSU is currently being used to provide backup power to the NSS.
- Unavailable: The RPSU is currently providing backup power to another device and is not
available to provide backup power to the NSS.
System Status
The System area displays the following:
• Serial Number: The serial number of the NSS.
• Firmware Version: The current version and date of the firmware installed on the NSS.
Chapter 2: System
9
Page 12
Network Storage System (NSS) Administrator Guide
• Uptime: The number of days the NSS has been running since it was last rebooted.
• Last Boot: The date when the NSS was last rebooted.
Chapter
2
Chapter 2: System
10
Page 13
Chapter
Network Storage System (NSS) Administrator Guide
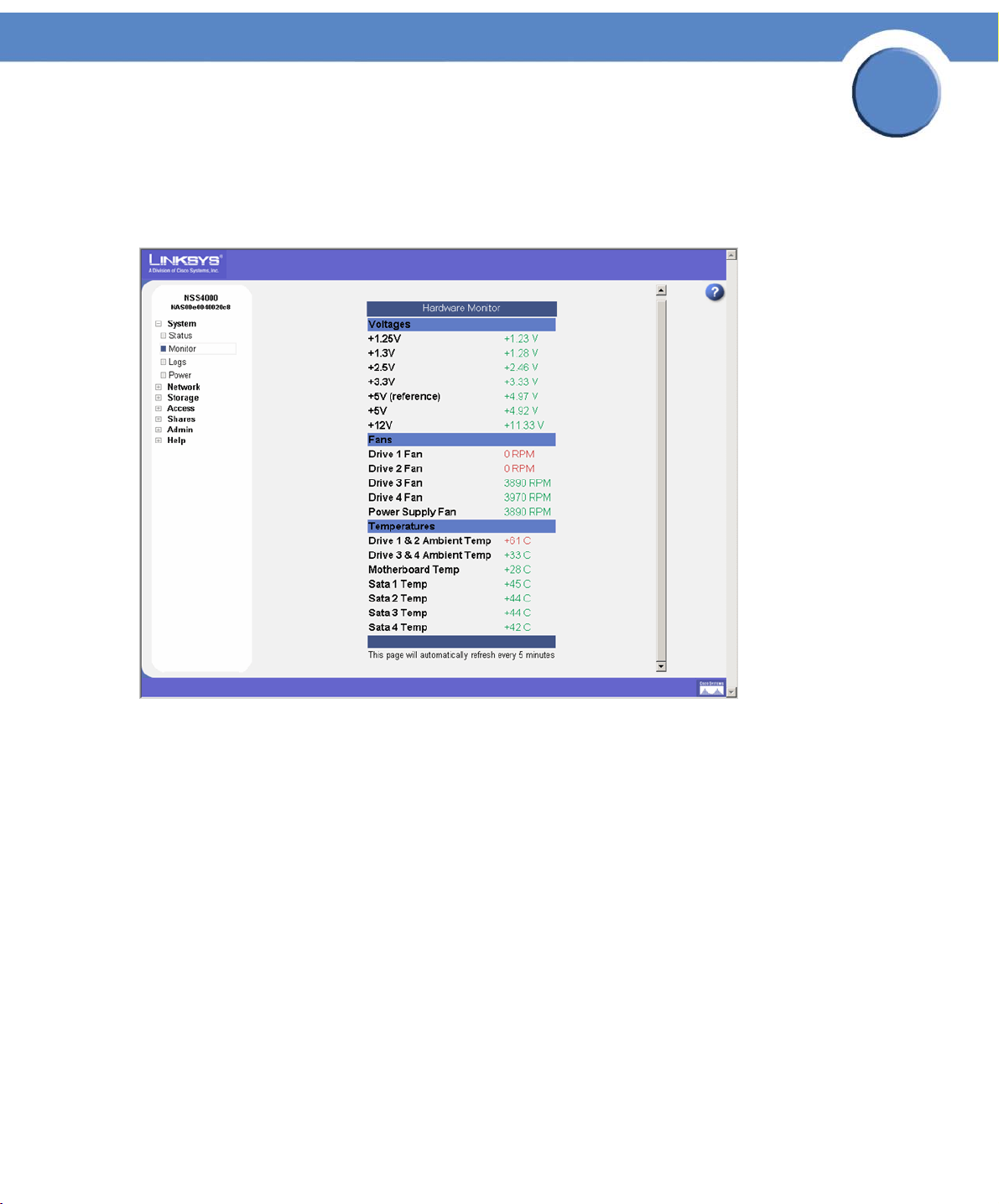
Viewing the Hardware Monitor
The Hardware Monitor page displays details about the following physical conditions related to the
NSS:
2
• Voltages : The current voltage reading for all voltage rails in the system. The reading is colorcoded depending on whether the voltage level is within specification (green) or out of
specification and in need of attention (red).
• Fans: The fan speed for each chassis fan. If the fan has stalled, the reading is color-coded
red. Normal fan operation is color-coded green.
• Tem pe rat ur es : The NSS has temperature sensors located at various parts of the chassis.
Temperature readings are done from these sensors as well as from any installed disks
(provided that the disk has an internal temperature sensor). If a disk does not have a
temperature sensor, the reading appears as "unavailable". If the temperature of the system or
disks is over or under the ideal temperature, the temperature is color-coded red. When the
temperature is within the normal range the color-coding is green.
Chapter 2: System
Viewing the Hardware Monitor
11
Page 14
Chapter
Network Storage System (NSS) Administrator Guide
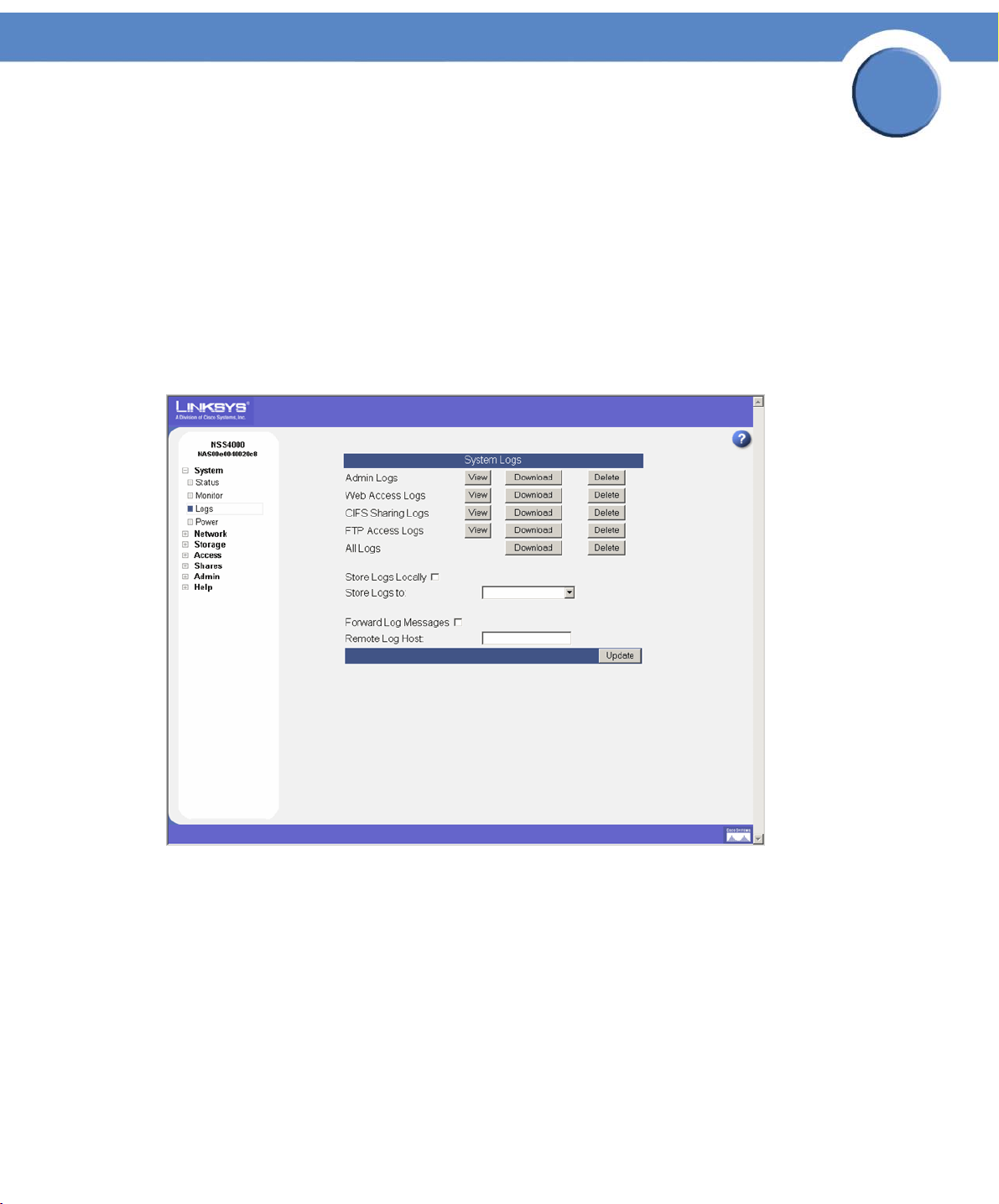
Viewing and Managing the System Logs
The NSS captures various types of information into log files, such as user access details. The logs can
be stored locally or sent to a remote server on the network. Since local space allocated for log files is
limited, the logs are overwritten once the space is filled. Each new event overwrites the oldest event
recorded in the file.
To work with the log files:
1. From the Manager Menu, click System Logs.
The System Logs page appears.
2
2. You can view, download, or delete any of the following types of log files:
• Admin: A full list of time-stamped actions that were initiated through the NSS configuration
interface.
• Web Access: This log displays IP addresses of the systems that accessed the NSS
configuration interface and the date and time of the authentication requests. This information
helps you detect unauthorized attempts to access the NSS configuration interface.
• CIFS Sharing: A time-stamped event log of events initiated by users accessing shares through
CIFS.
• FTP Access: A time-stamped log of FTP actions, including user logins, file transfers, and user
logouts.
Chapter 2: System
Viewing and Managing the System Logs
12
Page 15

Chapter
Network Storage System (NSS) Administrator Guide
• All Logs: A concatenation of all the log files. You can download and save this file to a
location on your network as required.
• Diagnostics: A time-stamped log of the cable diagnostic tests run. You can download and
save this file.
The following screenshot is an example of the Administrator Log:
2
3. Choose where you want to store the log files:
• Locally: To store the log files on the NSS, select Store Logs Locally, and then select the volume
to which you want to store the logs from the options in the Store Logs to drop-down menu.
• Remotely: To store the log files on a remote server, select Forward Log Messages, and then
enter the name or IP address of the server in the Remote Log Host field. Note that the remote
server must be running a syslog server.
4. Click Update.
Chapter 2: System
Viewing and Managing the System Logs
13
Page 16

Chapter
Network Storage System (NSS) Administrator Guide
Configuring the System for UPS Support
You can set up the NSS to use an uninterruptible power supply (UPS) if one is connected directly to
the UPS port on the NSS.
To set up the UPS:
1. From the Manager Menu, click System Power.
The System Power page appears.
2
2. To enable UPS support, select Enable UPS support.
3. Click Update.
Chapter 2: System
Configuring the System for UPS Support
14
Page 17

Network Storage System (NSS) Administrator Guide
NSS-supported UPS Product Families
The NSS supports the following UPS product families:
• APC Back-UPS Pro USB
• APC Back-UPS RS USB
•APC Back-UPS USB
• APC Back-UPS LS USB
• APC Back-UPS ES/CyberFort 350
• APC Smart-UPS USB
Chapter
2
Chapter 2: System
NSS-supported UPS Product Families
15
Page 18

Chapter
Network Storage System (NSS) Administrator Guide
Managing the Network Options
The Network Device Settings page displays the current status of the NSS’s physical and virtual
network interfaces.
3
Physical Interfaces
The Network Device Status table displays the current status of the physical Ethernet links connected
to the NSS.
• Link: The number that appears in this column identifies the link attached to the NSS. It can be
either 1 or 2.
• Status: The status of the physical link. Options include:
- Up: The link is up (color-coded green) and operational.
- Down: The link is down (color-coded red) and not operational. If a cable is actually
connected to the Ethernet port, check the cable integrity and the status of the device (switch,
router, or computer) at the other end of the cable. You can use the NSS’s cable diagnostic
feature (
• Speed: The configured speed, in Mbps, of the physical link. Options include: 10 Mbps, 100
Mbps, 1000 Mbps.
• MAC Address: The Ethernet MAC address for the link.
• MTU: The Maximum Transmission Unit (MTU) in bytes defined for the link. This is set either
manually from the Network Properties page or set via the DHCP server.
• Rx Pkts: The total number of IP packets received since the last boot.
see Running Diagnostics of your Physical Links) to assist you.
• Tx Pkts: The total number of IP packets transmitted since the last boot.
Chapter 3: Network
16
Page 19

Chapter
Network Storage System (NSS) Administrator Guide
• Dropped Pkts: The total number of IP packets dropped since the last boot.
Virtual Interfaces
The VLAN Status area of the Network Status page displays the current status and details regarding
each configured VLAN.
• Link: The number that appears in this column identifies the physical link on which the VLAN is
configured. If there are two physical links, the link appears as either "1" or "2", or, if the two
links are bonded, the number appears as "1+2".
• VLAN: The VLAN number.
• Priority: The 802.1p priority set for the VLAN. Options include 0 through 7 (0 being best
effort data and 7 being network critical data).
• Label: The text description defined for the VLAN.
• Rx Pkts: The total number of IP packets received on the VLAN interface since the last boot.
• Tx Pkts: The total number of IP packets transmitted on the VLAN interface since the last boot.
3
• Dropped Pkts: The total number of IP packets dropped on the VLAN interface since the last
boot.
Chapter 3: Network
17
Page 20

Chapter
Network Storage System (NSS) Administrator Guide
Viewing the Network Settings
The Network Device Settings page displays information about the physical and virtual interfaces
currently configured on the NSS.
NOTE: If you hotplug the Ethernet link after the initial installation of the NSS, wait 15
seconds between the time you unplug the cable and then plug it back in. The NSS
displays the correct new settings within 10 seconds.
3
To dis pla y t he Network Device Settings page, from the Manager Menu, click Network IP. The
Network Device Settings table displays the following:
• Link: "1+ 2" appears in this column.
• VLAN: The ID assigned to the virtual interface. For a physical interface, this column is blank.
• Assign Via: The method used to assign an IP configuration to the physical or virtual interface.
Options include:
- DHCP: The IP configuration was assigned by the DHCP server.
- Manual: A static IP configuration was manually entered through the NSS.
- AutoIP: The interface was configured to use DHCP for IP configuration but no DHCP server
was found. Instead the IP address was assigned by the AutoIP protocol.
• IP Address: The IP address for the physical or virtual interface.
• Netmask: The netmask for the physical or virtual interface.
• Gateway: The address of the gateway for the physical or virtual interface.
Chapter 3: Network
Viewing the Network Settings
18
Page 21

Chapter
Network Storage System (NSS) Administrator Guide
Configuring the Network Link IP
You need to configure the method for assigning an IP configuration to each physical and virtual
interface connected to the NSS.
NOTE: If you hotplug the Ethernet link after the initial installation of the NSS, make sure you
wait 15 seconds between the time you unplug the cable and then plug it back in. The
NSS displays the correct new settings within 10 seconds.
To set the IP address allocation method for an interface:
1. From the Manager Menu, click Network IP.
The Network IP page appears listing each physical and virtual interface.
2. Click Edit on the row of the interface you want to configure.
The Network Link Configuration page appears.
3
3. Select one of the following:
• Obtain IP Address Automatically: Use a DHCP server to retrieve the IP address, netmask,
and gateway address for the interface.
• Use the Following IP Address: Enter the IP configuration details manually, in dotted-quad
notation.
4. Click Update.
Chapter 3: Network
Configuring the Network Link IP
19
Page 22

Chapter
Network Storage System (NSS) Administrator Guide
Resetting the DHCP Lease on a Link
You can force a renewal of the DHCP lease on a physical link or VLAN that is configured for DHCP:
1. From the Manager Menu, click Network IP.
The Network IP page appears listing each physical and virtual interface.
2. Click Edit on the row of the link IP you want to reset.
The Network Link Configuration page appears.
3
3. Click Update.
Chapter 3: Network
Resetting the DHCP Lease on a Link
20
Page 23

Chapter
Network Storage System (NSS) Administrator Guide
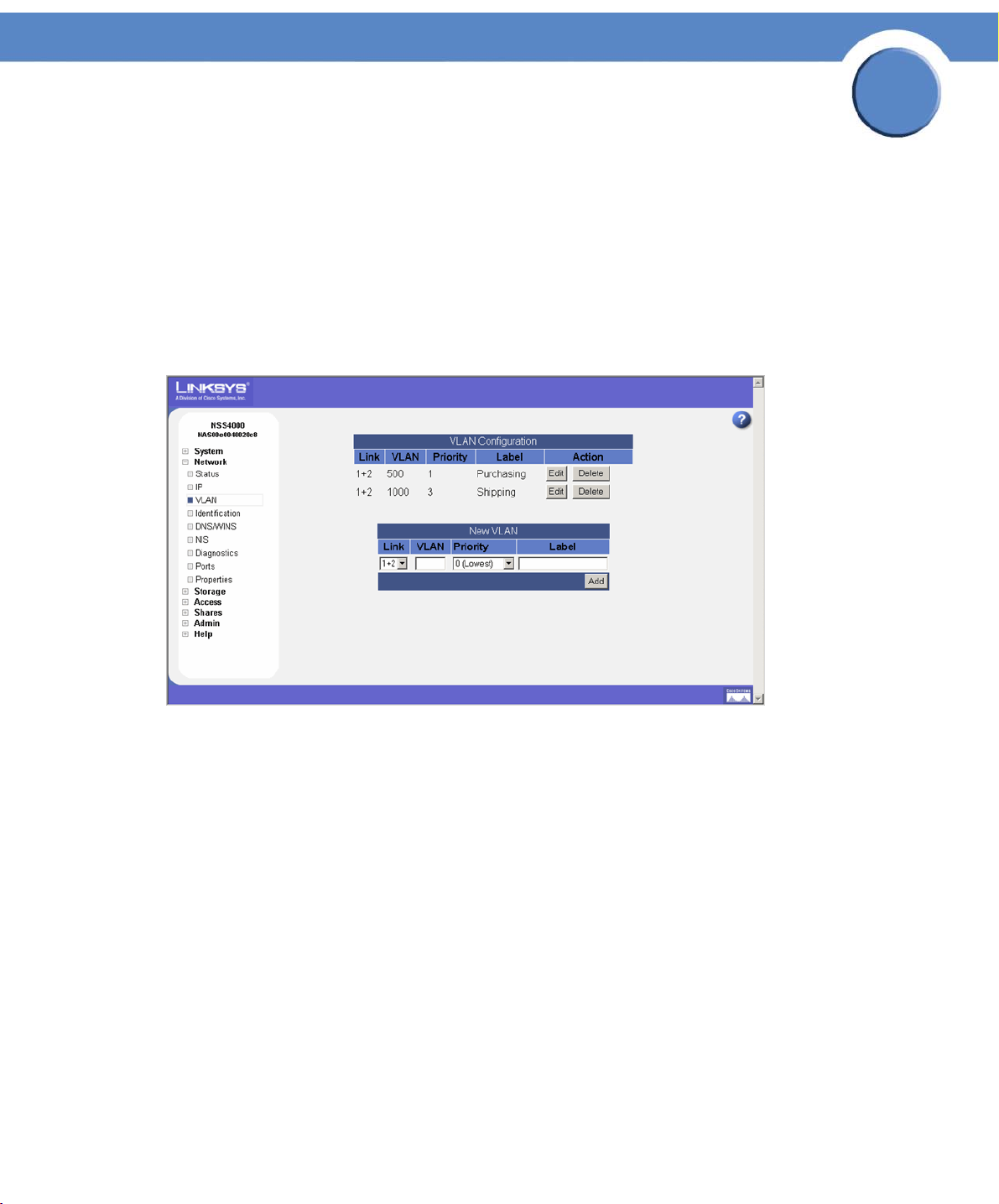
Viewing VLANs Configured on the NSS
When you first display the Network VLAN page, the currently configured VLANs appear.
Configuring a VLAN to connect to the NSS depends if it is trunk-based or port-based. To configure a
trunk-based VLAN, follow the steps provided next. To configure a port-based VLAN, configure the
switch to assign the port to which the NSS is connected to the desired VLAN. In this case, no
configuration changes are required on the NSS.
To view the VLANs currently configured on the NSS:
1. From the Manager Menu, click Network VLAN.
The VLAN Configuration page appears.
3
2. View the following details for each existing VLAN that appears in the VLAN Configuration
table:
• Link: The link on which the VLAN is configured. The status appears as "1+2".
• VLAN: The ID of the VLAN. This is configured when the VLAN is added to the NSS and
should match the ID of the VLAN as it is configured in your network. The range of valid VLAN
IDs is from 0 to 4095.
• Priority: The quality of service (QoS) as defined in the IEEE 802.1p standard for the VLAN
traffic. VLAN Ethernet frames contain a three-bit priority tag ranging from 0 to 7 (where 0 is
best effort and 7 is network-critical traffic).
• Label: A text description for the VLAN (for example, "Data," "Voice," "Video," and so on).
This description is used solely as a reference within the NSS interface and does not affect its
operation.
Chapter 3: Network
Viewing VLANs Configured on the NSS
21
Page 24

Network Storage System (NSS) Administrator Guide
Allowing a VLAN Access to the NSS
To set up a network VLAN to access the NSS:
1. From the Manager Menu, click Network VLAN.
The VLAN Configuration page appears.
Chapter
3
2. In the New VLAN area of the page, set up the following fields:
• Link: Select the Ethernet link on which you want the VLAN to connect to the NSS. Available
options depend on the configuration of your Ethernet link(s).
• VLAN: Enter the ID of the VLAN as it is defined within your network. The range of valid VLAN
IDs is from 0 to 4095.
• Priority: Select the QoS priority for the VLAN traffic as it is defined for your network. Valid
options range from 0 to 7 (as defined by the IEEE 802.1p standard). VLAN Ethernet frames
contain a three-bit priority tag ranging from 0 to 7 (where 0 is best effort and 7 is networkcritical traffic).
Chapter 3: Network
Allowing a VLAN Access to the NSS
22
Page 25

Chapter
Network Storage System (NSS) Administrator Guide
• Label: Enter a text description for the VLAN (for example, "Data", "Voice", "Video", etc.). It
can be made up of alphanumeric characters. Note that this description is used solely as a
reference within the NSS interface and does not affect its operation.
3
3. Click Add.
The newly added VLAN appears in the VLAN Configuration table. The VLAN configuration
ONLY takes effect after you configure the IP address for the VLAN. A message appears to
advise that the VLAN does not take effect until you configure the IP address.
4. Click OK.
The Network IP page appears. The newly added VLAN appears in the list.
5. Click Edit for the VLAN.
Chapter 3: Network
Allowing a VLAN Access to the NSS
23
Page 26

The Network Configuration page appears.
Chapter
Network Storage System (NSS) Administrator Guide
3
6. Click one of the following, depending on how you want to assign the VLAN IP addressing:
• Obtain IP Address Automatically: Use a DHCP server to retrieve the IP address, netmask
address, and gateway address for the VLAN.
• Use the Following IP address: Enter the IP configuration details manually.
7. Click Update.
Chapter 3: Network
Allowing a VLAN Access to the NSS
24
Page 27

Network Storage System (NSS) Administrator Guide
Changing a VLAN Configuration
After you set up a VLAN to access the NSS, you can change its configuration details.
To edit a VLAN configuration:
1. From the Manager Menu, click Network VLAN.
The VLAN Configuration page appears.
Chapter
3
2. Click Edit for the VLAN you want to change.
The VLAN Configuration page appears.
3. Make changes to any of the VLAN configuration fields as required.
4. Click Update.
Chapter 3: Network
Changing a VLAN Configuration
25
Page 28
Chapter
Network Storage System (NSS) Administrator Guide
Removing a VLAN’s Access to the NSS
All connected VLANs appear when you first display the VLAN Configuration page. You can delete
the connection between a VLAN and the NSS. Note that deleting the VLAN only affects the VLAN’s
ability to access the NSS. It does not impact the VLANs operation within your network.
To disconnect a VLAN’s access to the NSS:
1. From the Manager Menu, click Network VLAN.
The VLAN Configuration page appears.
3
2. From the VLAN Configuration table, click Delete for the VLAN you want to remove.
The VLAN disappears from the VLAN Configuration table and no longer has access to the NSS.
Chapter 3: Network
Removing a VLAN’s Access to the NSS
26
Page 29
Chapter
Network Storage System (NSS) Administrator Guide
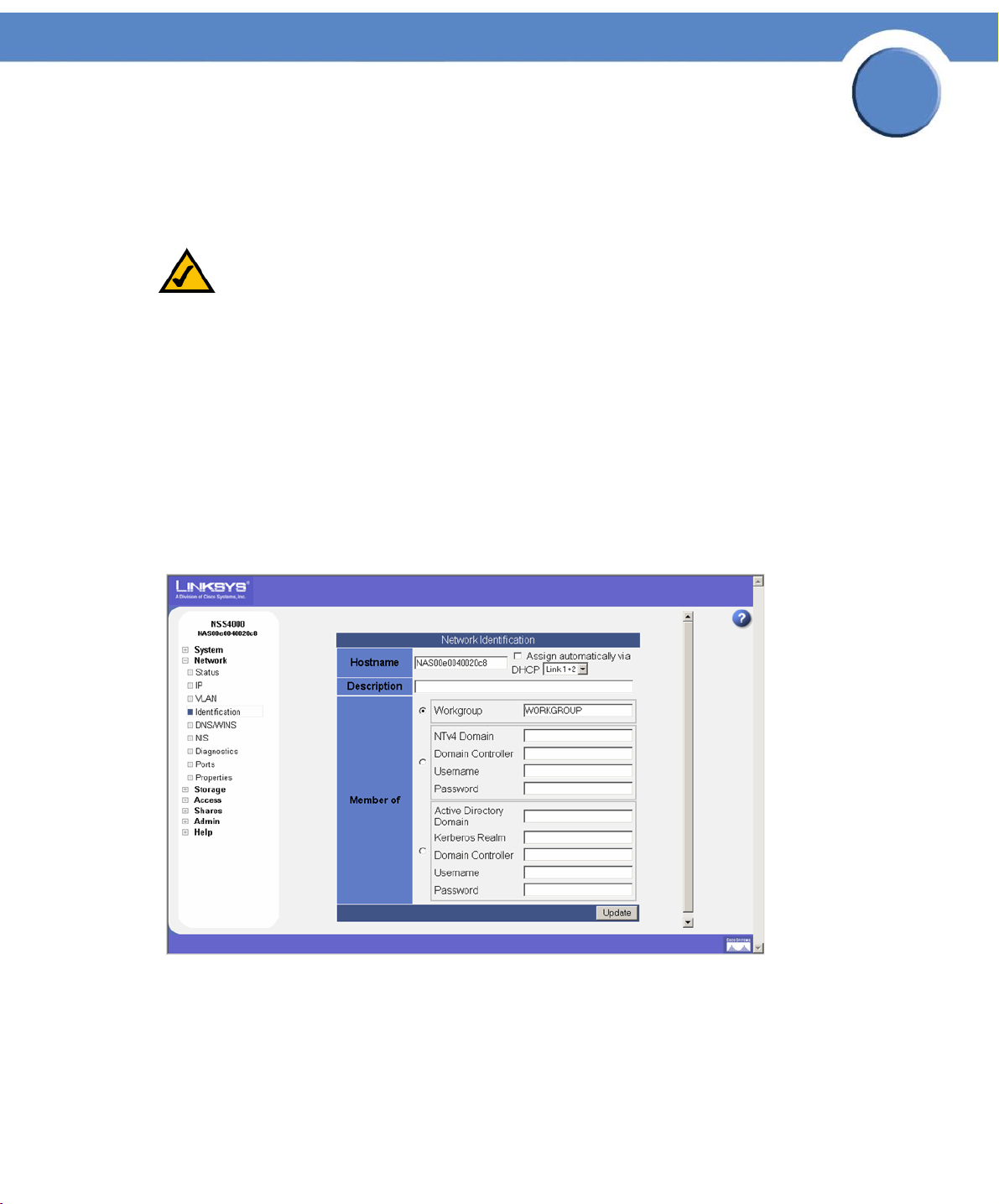
Configuring the NSS Network Identification
The Network Identification page is where you configure the network identity of the NSS, including
the hostname and domain membership.
NOTE: Before you join the NSS to an NTv4 or Active Directory Service (ADS) domain, make
sure you do the following:
• Configure the IP and DNS information.
3
• Set up your user and group ID ranges on the User/Group Settings page. (
User/Group Settings) You cannot make changes to the User or Group ID range after the
domain is joined.
To configure the NSS network identity:
1. From the Manager Menu, click Network Identification.
The Network Identification page appears.
see Configuring the
2. In the Hostname field, enter the name you want to use for the NSS. Note any special naming
restrictions or conventions enforced by the domain(s) into which the NSS is being joined.
Chapter 3: Network
Configuring the NSS Network Identification
27
Page 30

Chapter
Network Storage System (NSS) Administrator Guide
Warning: If you change the hostname, any current CIFS connections to shares on the NSS will
be disconnected.
3. To assign the hostname for the NSS using the DHCP server, select Assign automatically via
DHCP. If the DHCP server is not available or if it is not configured to supply a hostname, the NSS
hostname is assigned using the information entered in the Hostname field.
4. In the Description field, enter the textual description for the NSS as you want it to appear in the
file manager window for your users.
5. Select the type of network into which you are making the NSS a member from the following
options:
• Workgroup: Make the NSS part of a peer-to-peer network.
• NTv4 Domain: Make the NSS a part of a pre-Windows 2000 domain. If you select this
option, set up the following fields:
- NTv4 Domain: Enter the domain name.
- Domain Controller: Enter the hostname or IP address of the domain controller.
3
- Username: Enter the username of an account that has administrator privileges for this
domain.
- Password: Enter the password for the administrator account.
• Member of Active Directory domain: Make the NSS part of an Active Directory (ADS)
domain. If you select this option, set up the following fields:
- Active Directory Domain: Enter the domain name.
- Domain Controller: Enter the hostname or IP address of the domain controller.
- Kerberos Realm: Enter the name of your Kerberos realm. If you are not sure what to enter
here, enter the domain name. In most standard Windows domain installations, this is the
correct value.
- Username: Enter the username of an account that has administrator privileges for this
domain.
- Password: Enter the password for the administrator account.
6. Click Update.
If you configured the NSS to join a domain, when you click Update, the domain join occurs. The
NSS configuration interface displays the status of the domain join (i.e., successful or not
successful).
Chapter 3: Network
Configuring the NSS Network Identification
28
Page 31

Chapter
Network Storage System (NSS) Administrator Guide
Configuring DNS or WINS for Name Resolution
Within a network, DNS and WINS are used to translate hostnames into IP addresses. For example,
the hostname "myserver" might translate to 172.1.135.6. Configuring how the NSS works with name
resolution depends on what type of servers exist within your network.
To configure the DNS or WINS server addresses for your network:
1. From the Manager Menu, click Network DNS/WINS.
The Network Name Resolution page appears.
3
2. Based on your network setup, configure the following fields:
• Search Domain: Enter the address of the DNS search domain accessible by the NSS.
• Primary DNS Server: Enter the IP address of the primary DNS server on your network.
• Alternate DNS Server: Enter the IP address of a second DNS server to be used should the
primary DNS server become unavailable. This field is optional.
• Assign automatically via DHCP: Select this to assign the IP address for the DNS server using
the DHCP server. If the DHCP server cannot be found or times out, the DNS server IP address
is assigned the IP address manually entered in the Primary or Alternate DNS Server fields.
• Primary WINS server: If your network has a WINS server, enter its address. This field is
optional.
• Alternate WINS server: If your network has a secondary WINS server, enter its address. This
field is optional.
Chapter 3: Network
Configuring DNS or WINS for Name Resolution
29
Page 32

Chapter
Network Storage System (NSS) Administrator Guide
• Assign automatically via DHCP: Select this to assign the IP address for the WINS server using
the DHCP server. If the DHCP server cannot be found or times out, the DNS server IP address
is assigned the IP address manually entered in the Primary or Alternate WINS Server fields.
3. Click Update.
3
Chapter 3: Network
Configuring DNS or WINS for Name Resolution
30
Page 33

Chapter
Network Storage System (NSS) Administrator Guide
Joining the NSS to a Network Information System (NIS)
Domain
To join the NSS to a NIS domain, you need to configure and enable it.
NOTE:Before you join a NIS domain, make sure you set up or make changes to the NIS domain
users and groups ID range on the User/Groups Settings page. (
User/Group Settings) This minimizes the risk of collisions of user or group IDs within
your network.
To configure the NSS for NIS:
1. From the Manager Menu, click Network NIS.
The NIS Configuration page appears.
see Configuring the
3
2. Select Enable NIS.
3. Enter the NIS domain name in the NIS Domain Name field.
4. Set the bind state by clicking one of the following:
• Broadcast for NIS Server: Click this option to have the NSS search until it finds the NIS server
on the network.
• Use the following NIS Servers: To manually identify the NIS server you want the NSS to use,
click this option, and then enter the address of up to three different NIS servers.
Chapter 3: Network
Joining the NSS to a Network Information System (NIS)
31
Page 34

Network Storage System (NSS) Administrator Guide
The Bind State field shows the current bind status of the NSS.
Chapter
3
5. Click Update.
Chapter 3: Network
Joining the NSS to a Network Information System (NIS)
32
Page 35

Chapter
Network Storage System (NSS) Administrator Guide
Editing Access Control Lists (ACLs) from Windows Explorer:
Restrictions
Access Control Lists (ACLs) are used to set user and group access privileges for specific files and
folders stored on the NSS. There are certain restrictions to be aware of as you work with ACLs
through Windows Explorer:
• Group versus User ACLs: You can only set up an ACL for individual users. You cannot set up
a group ACL.
• NIS domain: You cannot create or edit ACLs for NIS domain users; they do not appear in the
Security tab in Windows Explorer.
3
Chapter 3: Network
Editing Access Control Lists (ACLs) from Windows Ex-
33
Page 36

Chapter
Network Storage System (NSS) Administrator Guide
Running Diagnostics of your Physical Links
The NSS lets you test the physical network cables attached to Ethernet links 1 and 2 for certain fault
conditions. You must manually initiate a test to update the results shown on the Network Diagnostics
page.
NOTE: When you initiate a test on an Ethernet link, you take down the link for the duration
of the test. Any current user connections on the link are dropped. If you have two
links installed, any connections through the untested link remain unaffected.
To test the physical link:
1. From the Manager Menu, click Network Diagnostics.
The Network Diagnostics page appears.
3
2. Click Tes t for the cable you want to test.
After the test completes, the test results appear in the Link Status area. The test results also
appear on the System Status page. If the cable is in sufficient working condition, the link is
again accessible to your users.
Chapter 3: Network
Running Diagnostics of your Physical Links
34
Page 37

Chapter
Network Storage System (NSS) Administrator Guide
Configuring the Network Ports
By default the NSS runs network services on their well known (IETF defined) port numbers. You can
change the port on which any particular service runs. When you disable WAN access for a given
service, only hosts on the same subnet as the NSS may connect to that service. This is in essence a
shortcut to manually defining an equivalent network filter.
To set up the network services:
1. From the Manager Menu, click Network Ports.
The Network Ports Configuration page appears.
3
2. Change the port assignment for any of the following service types:
• FTP/FTPS Port: The well-known port setting is 21. Select Disable WAN Access to disallow FTP
and FTPS protocol access to the NSS from a WAN.
• Web Ser ver Port: The well-known port setting is 80. Note that to access the NSS GUI, you
must have either the HTTP port or HTTPS port enabled. Select Disable WAN Access to
disallow HTTP protocol access to the NSS from a WAN.
• SSL Web Server Port: The well-known port setting is 443. Select Disable WAN Access to
disallow HTTPS protocol access to the NSS from a WAN.
3. Click Update.
Chapter 3: Network
Configuring the Network Ports
35
Page 38

Chapter
Network Storage System (NSS) Administrator Guide
Setting up the Link Bonding & Advertising Modes
The Network Properties page is where you configure the bonding mode for the physical Ethernet
link(s) attached to the NSS. It also lets you determine how you want to advertise the presence of the
NSS within your network.
To configure the network properties:
1. From the Manager Menu, click Network Properties.
The Network Properties page appears.
3
2. To set the bonding mode of your physical links, click one of the following:
• 802.3ad Link Aggregation (failover and load sharing): Select this option to aggregate the
two Ethernet connections using the IEEE 802.3ad standard. This technology is also known as
trunking or bonding.
• Active backup (failover): This is the default option when you first install the NSS or when you
restore the factory default settings by resetting the NSS. Select this option to define one link as
the active link and one link as the backup. Should the active link become unusable (either
disconnected or significantly degraded), the backup link automatically becomes the active
link.
3. Set the Maximum Transmission Unit (MTU), in bytes, in the MTU field. This is the largest Ethernet
frame that your network can handle. The default MTU size is 1500 bytes. MTU sizes greater
than 1500 bytes are considered "jumbo frames".
4. To assign the link MTU size automatically using the DHCP server, click Assign automatically via
DHCP. In this case, the value entered in the MTU field is used as a backup if the DHCP server
does not provide an MTU value or if the server cannot be reached.
5. Based on your network requirements, enable any of the following:
• Advertise using UPnP: The NSS is advertised within the network using UPnP.
Chapter 3: Network
Setting up the Link Bonding & Advertising Modes
36
Page 39

Network Storage System (NSS) Administrator Guide
• Advertise using Zeroconf/Bonjour: The NSS is advertised within the network using
Zeroconf/Bonjour.
6. Click Update.
Chapter
3
Chapter 3: Network
Setting up the Link Bonding & Advertising Modes
37
Page 40

Chapter
Network Storage System (NSS) Administrator Guide
Managing your Storage
The Storage Status page is where you can view the current state of the disk drives, arrays, and
volumes currently installed or exported to the NSS. You can also view the S.M.A.R.T. health report
for each physical disk. To display the Storage Status page, from the Manager Menu, click Storage
Status. Status pages like the Storage Status page automatically refresh on a regular interval and
are very helpful for monitoring the progress of certain processes such as checking the condition of a
drive.
4
Disk Status Table
The Disk Status table lists each of the physical disks installed in the NSS. The table is made up of the
following columns:
• Port: The port number on the NSS in which the disk is installed.
• Model: The model of the disk drive. This information is read from the disk drive.
• Capacity: The size of the disk drive.
Chapter 4: Storage
38
Page 41

Chapter
Network Storage System (NSS) Administrator Guide
• Health: The system monitors each disk drive and reports the condition of the disk drive.
Options include:
- Passed: The disk drive has passed the S.M.A.R.T. test and is considered fully operational.
The Error LED on the disk drive is off.
- Failing: The disk drive has failed the S.M.A.R.T. test and is predicated to fail. The red Error
LED on the disk drive is blinking.
- Failed: The disk drive is not operational (has failed). The red Error LED on the disk drive is
on solid.
• Status: The state of use for the disk drive. Options include:
- Online: The disk drive is spun up.
- Standby: The disk drive is idle and is spun down.
- Offline: The disk drive is failed.
• Action: There are available action buttons associated with each installed disk drive:
4
- Get Details: View the current, detailed S.M.A.R.T. report for the disk drive.
- Locate: Send a locate request to the applicable disk drive. The white disk drive LED on the
front of the NSS chassis blinks for the targeted disk drive. (Note that only one locate request
can be sent at a time to ensure that you can easily spot the desired disk drive. Disk drives
Chapter 4: Storage
39
Page 42

Chapter
Network Storage System (NSS) Administrator Guide
are numbered from 1 to 4 from left to right on the chassis (when facing the chassis front
panel) and correspond with the port number.
- Cancel Locate: There is currently a locate request set up for the applicable disk drive. Click
Cancel Locate to cancel the locate request. This lets you send a locate request for another
disk drive.
RAID Arrays Table
The RAID Arrays table lists each array (either RAID or JBOD) currently configured. The table is
made up of the following:
• Label: The name assigned to the array.
• RAID Level: The configured RAID level.
• Size: The size allocated for the array. The amount of available storage for an array depends
on the number of drives in the array, the size of the smallest drive, as well as the RAID level
assigned. The calculation for an array, according to RAID level, is as follows. (Where "n" =
the number of drives in the array and "s" = the size of the smallest drive in the array.)
4
- JBOD = sum(size of each drive)
- RAID0 = n * s
- RAID1 = s
- RAID5 = (n-1) * s
- RAID10 = n * s /2
• Status: The current condition of the RAID array. Options include:
- Clean: The array is in a normal state. This status is color-coded green.
- Degraded: For RAID arrays with redundancy (i.e., RAID levels 1, 5, 10), one or more of the
redundant disk drives has been removed from the system or has failed. In this state, the
array is fully recoverable. This status is color-coded orange.
- Failed: One or more disk drives have been removed or are unrecoverable from a RAID0 or
a JBOD array. For RAID levels 1, 5, 10, it indicates a loss of all the redundant disks in the
array plus at least one more drive. In this state, the array is unrecoverable.
- Rebuilding: A RAID level with redundancy is being rebuilt. Note that during a rebuild, the
RAID array is still fully usable. This status is color-coded orange. During the rebuild, the LED
for the disk drive slowly blinks green.
- Stopped: A RAID array has been stopped by the system (through degraded mode
management) due to it being in degraded mode for the amount of time configured in the
Storage Options page. Volumes associated with a stopped array are unmounted and
unusable. To start the RAID array, click the Start button.
Chapter 4: Storage
40
Page 43
Chapter
Network Storage System (NSS) Administrator Guide
Volumes Table
The Volumes table provides a list of the existing volumes. The table is made up of the following:
• Location: The name of the RAID array on which the volume is configured.
• Volume: The name assigned to the volume.
• Total Space: The amount of space configured for the volume.
• Used Space: The amount of space used on the volume.
• Avail. Space: The amount of unused space on the volume.
• % Used: The percentage of available space that is used.
• Encrypted: Whether the volume is encrypted or unencrypted.
• Locked: The encrypted volume has been locked and is not currently inaccessible. To make the
volume accessible, the volume must be unlocked.
4
USB Storage Status
If you mount a USB flash device by inserting it into the AUX-1 port on the front of the chassis, the
USB Storage Status table appears. If there is no USB flash device mounted, the USB Storage Status
table does not appear. The USB flash device can be used to save a backup of the configuration file
see Saving the Current Configuration). When you finish using the USB flash device, click Unmount
(
before you remove it from the AUX-1 port. (The AUX-1 LED on the front of the chassis must be off
before you can safely remove the USB flash device.) If you remove the USB flash device in a
mounted state, you risk corrupting the files or filesystem.
The USB Storage Status table provides the following details about the mounted USB flash device:
• Disk: The type of disk in this case is the USB flash.
• Total Space: The total amount of space (both used and available) on the USB flash device.
• Used Space: The amount of space taken up on the USB flash device.
• Available Space: The amount of unused space on the USB flash device.
• %Used: The percentage of space used on the USB flash device.
• Action: The Unmount button unmounts the USB flash device so that it can be safely removed
from the AUX-1 port.
Chapter 4: Storage
41
Page 44

Chapter
Network Storage System (NSS) Administrator Guide
Choosing a RAID Array Level
RAID (Redundant Array of Inexpensive Disks) is a technology that enables multiple low-cost hard
drives to be used together in a way that increases performance and/or reliability compared to that
of a single drive. The component devices in a RAID array appear as a single logical storage device.
There are various types of RAID, referred to as RAID levels. Some RAID levels increase the
performance of the array, some increase the reliability, and others do a mixture of both. The NSS
supports the following RAID levels: 0, 1, 5 and 10. The NSS also supports JBOD (Just a Bunch of
Disks), which is not technically a RAID level.
The following variables are used in formulas below which explain how to calculate the total capacity
of each RAID level:
• m – capacity of the smallest disk in the array
• n – number of disks in the array
RAID0: RAID0 stripes the data written to the array across the component disks. The data is broken
into chunks and each chunk is written to a different disk. Reads and writes to each disk occur in
parallel, speeding up the total read and write performance of the array.
4
• Minimum Number of Disks: 2
• Total capacity: m x n
• Advantages: Increased read and write performance.
• Disadvantages: Decreased reliability. A failure of any component disk in the array causes the
entire array to fail.
RAID1: RAID1 writes the same data to each disk in the array. The disks are referred to as “mirrors”
because each one mirrors the data stored on the others. As long as one disk in the array is intact, all
data can be read back from the array. If a disk fails in the array and is subsequently replaced, the
array must copy the entire contents of a good disk to the new disk. This process is referred to as
“resynching”. During a resync, the array continues to be available for reads and writes. When an
array contains a failed disk, it is said to be operating in “degraded” mode. This reflects the
decreased performance and reliability of the array when it is missing disks.
• Minimum Number of Disks: 2
• Total capacity: m
• Advantages: Increased reliability. The array can sustain the loss of all but one disk without
any data loss. Each mirror disk added to the array increases the reliability (for example, a
two-disk RAID1 is half as likely to fail, a three-disk RAID1 is one-third as likely to fail, and so
on). Increased read performance
• Disadvantages: Decreased aggregate storage capacity (each mirror disk does not contribute
to the total capacity of the array). Decreased write performance. I/O intensive when
resynching mirrors.
RAID5: RAID5 stripes data written to the array like RAID0, except that, unlike RAID0, RAID5
generates parity information that also gets striped across the array. This parity information is used to
Chapter 4: Storage
Choosing a RAID Array Level
42
Page 45
Chapter
Network Storage System (NSS) Administrator Guide
reconstruct the data lost when a drive fails in the array. When a failed disk is subsequently replaced,
the array must regenerate and rewrite the parity information of the array. This process is referred to
as “rebuilding”. During a rebuild, the array continues to be available for reads and writes. If the
parity information in the array gets out of synch with the data in the array, usually as the result of an
unexpected loss of power to the system, the array must be rebuilt. Like RAID1, if a disk is missing
from the array, the array is said to be operating in “degraded” mode.
• Minimum Number of Disks: 3
• Total capacity: m x (n-1)
• Advantages: Increased reliability; The RAID array can sustain the loss of any single disk
without any data loss; Increased read and write performance.
• Disadvantages: Decreased aggregate storage capacity (you lose the equivalent capacity of a
single disk); CPU intensive calculation of parity, especially during rebuild operation; I/O
intensive during rebuild operation.
RAID10: RAID10 is a combination of RAID1 and RAID0. The NSSimplements RAID10 as two, 2-disk
RAID1 mirrors, which are then used to build a RAID0 array. RAID10 can be thought of as “mirror,
then stripe”.
4
• Minimum Number of Disks: 4
• Total capacity: 2 x m
• Advantages: Increased read and write performance; increased reliability; the RAID array
can sustain the loss of any single disk without data loss; depending on which disks fail, the
array can lose up to two disks without data loss.
• Disadvantages: Decreased aggregate storage capacity (you lose half of the storage space)
JBOD: JBOD lets you combine multiple disks of mixed capacities into a single logical storage device.
The capacity of the JBOD array is the sum of the total capacities of the individual component disks
(that is, it does not have the limitation of RAID0 where you lose some capacity when using mixed
sized disks). JBOD offers no performance increase compared to the component disks. It has lower
reliability than the component disks, as the failure of a single disk results, in general, in the failure of
the whole array. Depending on how you create volumes on the JBOD array, you may be able to
recover data when one or more disks in the JBOD fail. This, however, is not guaranteed.
• Minimum Number of Disks: 1
• Total capacity: sum of capacities of component disks
• Advantages: Maximal storage capacity, especially when using mixed size disks
• Disadvantages: Decreased reliability
Chapter 4: Storage
Choosing a RAID Array Level
43
Page 46

Chapter
Network Storage System (NSS) Administrator Guide
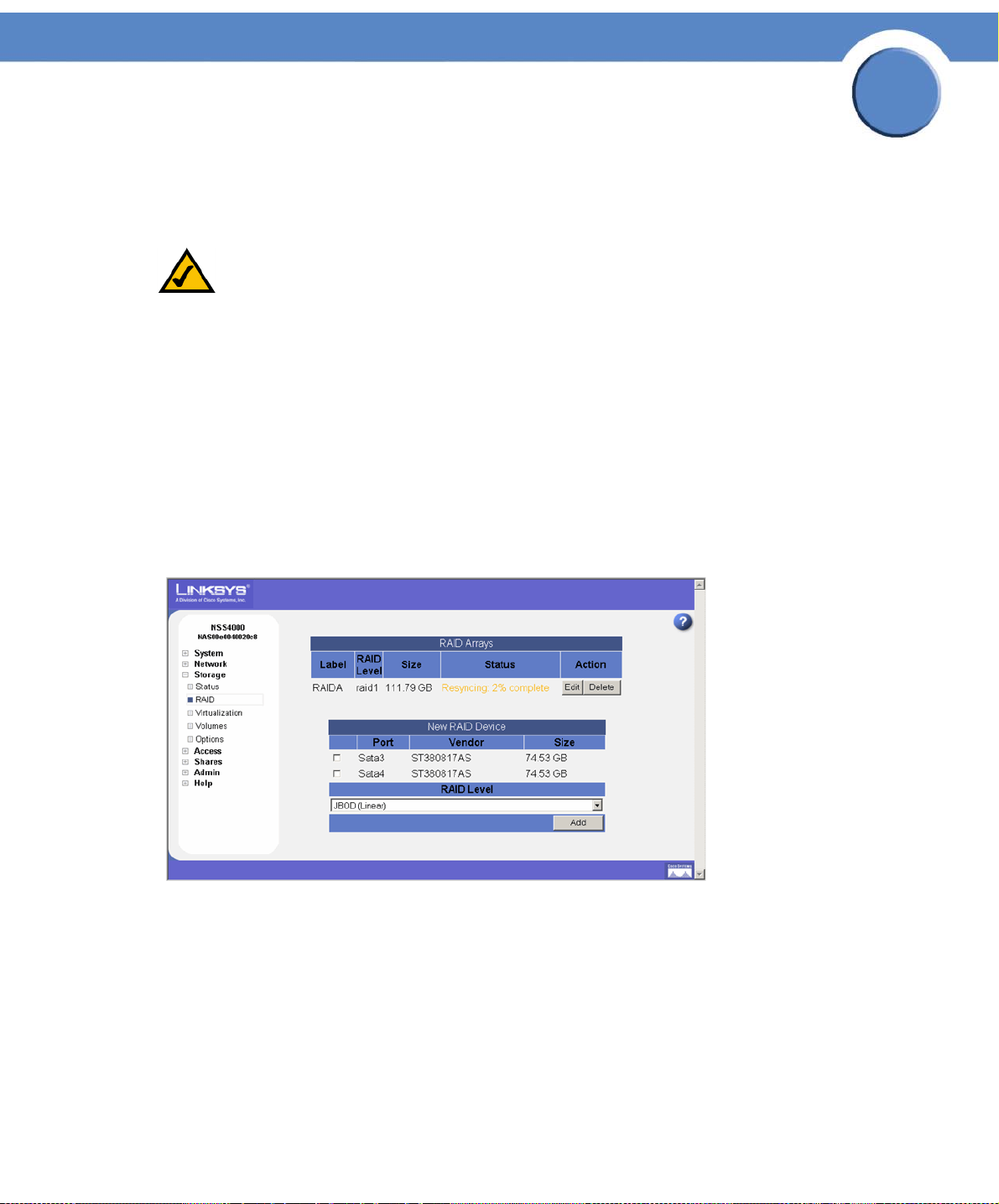
Creating a RAID Array
After you install the physical disks, you can create the RAID arrays. Before you create a RAID array,
either for the first time, or when you are rebuilding it as a result of failed disks in the array, it is a
good idea to set the Rebuild Priority (
want to allocate the system resources for the rebuild.
NOTE: When adding disks to an array, we recommend you use the same model of disk with
the same capacity. With the exception of a JBOD, RAIDs are configured to use the
maximum of the smallest disk capacity in the array for each additional disk in the
array. For example, if you install two, 250 GB disks and one 500 GB disk in a
RAID0 array, the total capacity is only 750 GB.
To create an array:
1. From the Manager Menu, click Storage RAID.
The RAID page appears:
see Setting the RAID Rebuild Priority) to determine how you
4
2. The available disks appear in the New RAID Device table. Select each disk that you want to
include in the array.
3. From the RAID Level drop-down menu, click the RAID level of the RAID array you want to create.
4. Click Add.
The RAID creation can take some time to complete (depending on the size of the disks and the
selected RAID level). When the build is finished, the array appears in the RAID Arrays table. The
disks used in the array are no longer available for creating additional arrays.
Chapter 4: Storage
Creating a RAID Array
44
Page 47
Chapter
Network Storage System (NSS) Administrator Guide
Adding a Disk Drive to an Array
You can add additional disks to an existing RAID1, RAID5, and RAID10. As long as the array is clean,
these disks then become spares.
NOTE: When adding disks to an array, we recommend you use the same model of disk with
the same capacity. The new disk must have at least the same capacity of the smallest
disk currently in the array. With the exception of a JBOD, RAIDs are configured to
use the maximum of the smallest disk capacity in the array for each additional disk
in the array. For example, if you install two, 250 GB disks and one 500 GB disk, the
total capacity is 750 GB.
To add a disk to an array:
1. If not already installed in the chassis, insert the disk in the NSS.
2. From the Manager Menu, click Storage RAID.
4
The RAID page appears.
3. In the RAID Arrays table, click Edit for the applicable RAID array.
Chapter 4: Storage
Adding a Disk Drive to an Array
45
Page 48

Chapter
Network Storage System (NSS) Administrator Guide
The RAID Configuration page appears.
4. Available disk drives appear in the listing. Click Add to add the disk drive to the array.
4
The RAID array is rebuilt for the added or changed redundant disk drive. While the rebuild
continues, the array can still be used. After the rebuild process completes, the disk becomes part
of the redundant storage. You can monitor the progress of the rebuild through the System Status
page.
Chapter 4: Storage
Adding a Disk Drive to an Array
46
Page 49

Chapter
Network Storage System (NSS) Administrator Guide
Deleting an Array
You can remove an existing array and release the disks used in the array back into available storage.
Note that deleting an array also deletes any existing data on the array (including the volumes, shares,
and quotas). If you delete an array that contains the volume that is used as the location of your users’
Home Directories, note that you must assign a new volume as the Home Directory location.
To delete an existing array:
1. From the Manager Menu, click Storage RAID.
The RAID page appears.
4
2. Click Delete in the row of the RAID array that you want to delete.
A warning message appears.
3. To continue, click OK.
The deleted array disappears from the list of existing arrays. The disks used in the array are
released back into available storage and appear in the New RAID Device table.
Chapter 4: Storage
Deleting an Array
47
Page 50

Chapter
Network Storage System (NSS) Administrator Guide
Migrating a RAID Array to another Storage Device
If you are migrating a RAID array from the NSS to another network NSS, ensure that you coldplug
the RAID array (versus hotplug it) into the new system as per the following:
1. Power down the NSS (from which you are removing the RAID array).
2. Remove each of the disk drives that make up the RAID array to be moved.
3. Power down the NSS to which you are migrating the RAID array.
4. Insert each of the disk drives in the RAID array into the new NSS.
NOTE: You can install the drives into the new NSS in any order (that is, you do not need to
install them in the same order or slots that they were installed in the original NSS.
5. When all the disk drives are installed, power up the NSS.
4
Chapter 4: Storage
Migrating a RAID Array to another Storage Device
48
Page 51

Chapter
Network Storage System (NSS) Administrator Guide
Virtualizing Storage within your Network
The NSS virtualization feature lets you create storage physically located on other network NSS units
into one logical storage unit. The recommended network configuration for using virtualization is to
use an NSS6000 series to operate as the "master" storage device (the "slave" devices can either be
NSS6000 series or NSS4000 series devices). This configuration setup means that you export
storage (must be an unused disk drive or configured array) from the slave NSS and then import the
storage into the master NSS. The supported RAID level for virtualized storage is JBOD (although the
JBOD can consist of concatenated exported arrays).
4
Currently Exported Storage
The Currently Exported Storage table shows the details for any exported disks or arrays:
• Device: The name of the exported disk or array.
• Size: The size of the exported storage.
• Imported by: The serial number of the NSS that has imported the storage. If the exported disk
or array has not yet been imported by the master NSS, "None" appears in this column.
• Action: Click the Unexport button to stop the NSS from exporting the associated drive or
array. This frees up the drive or array for use in local RAID arrays.
Currently Imported Storage
For the master NSS to access a disk from another NSS on the network, the network device that
contains the storage must first export its storage. Once the exported storage is involved in an array
on the master device it appears in the Currently Imported Storage table. Until the exported storage
is used to build a JBOD, the storage appears in the list of available disks in the New RAID Device
table on the RAID page.
• Device: The name of the imported disk or array.
• Size: The size of the imported disk or array.
• Exported by: The serial number of the network device that exported the storage to the
network.
Chapter 4: Storage
Virtualizing Storage within your Network
49
Page 52

Chapter
Network Storage System (NSS) Administrator Guide
Exporting Storage to your Network
If you have multiple NSS units in your network, you can easily export the storage to form a large,
logical storage unit that can be managed from the master NSS). The first step in creating virtualized
storage is to export the disk(s) or array to the network. Note that when you export storage, you need
to consider how things like rebooting an NSS might impact users of the virtualized storage. While the
logical storage is controlled from the master NSS, the physical device (including the disk drives) is still
controlled through the slave’s configuration interface as well as is affected by the conditions of the
physical unit.
To export storage to the network:
1. Log into the configuration interface for the device from which you are exporting storage.
2. From the Manager Menu, click Storage Virtualization.
The Storage Virtualization page appears.
4
3. From the Export a device area, select each device that you want to export from the list of
available devices.
4. From the Link field, select the physical link that you want to use to export the storage.
5. Click Export.
The selected disk(s) disappear from the available list of arrays and appears in the Currently
Exported Storage
virtualized storage (
Chapter 4: Storage
Exporting Storage to your Network
table at the top of the page. Follow the steps to create a JBOD from
see Creating Virtualized Storage) to use the exported storage.
50
Page 53

Chapter
Network Storage System (NSS) Administrator Guide
Creating Virtualized Storage
After you export storage from a slave storage unit, it becomes available to other storage units in your
network. The recommended way to use virtualized storage is to assign a master storage unit (the
master must be a NSS6000 series model). The designated master unit then becomes the configuration
point for all your storage-related management. Exported storage can be used to create a JBOD,
which can then be used to set up volumes and shares. Keep in mind that although the storage is
managed through the master unit, the physical device that contains the exported storage is still
managed through the applicable slave unit. If you affect the physical disk drives (e.g., shut down the
power to the unit), this affects any logical storage built using those disk drives.
To create a JBOD with exported disks:
1. Log in to the configuration interface from the master unit.
2. From the Manager Menu, click Storage RAID.
The RAID page appears.
4
Exported disks from other NSS units in the network appear in the New RAID Device table.
3. From the New RAID Device table, click the disks or arrays that you want to include in the JBOD.
4. Select JBOD as the RAID level.
5. Click Add.
The JBOD appears in the RAID Arrays listing. You can now create volumes from the virtualized
JBOD.
Chapter 4: Storage
Creating Virtualized Storage
51
Page 54

Chapter
Network Storage System (NSS) Administrator Guide
Unexporting Storage
You can choose to unexport pieces of the storage currently exported to the network. Note that you
can only unexport storage that has not yet been used.
To unexport a piece of storage:
1. From the Manager Menu, click Storage Virtualization.
The Storage Virtualization page appears.
4
2. Click Unexport for the device you want to release from the network.
The disk drive(s) or array no longer appears in the Currently Exported Storage list. It now
appears in the Export a device list and is again available for use.
Chapter 4: Storage
Unexporting Storage
52
Page 55

Chapter
Network Storage System (NSS) Administrator Guide
Volume Management
A volume is a way to partition storage space available on an array. The Storage Volumes page is
where you can view the following details about configured volumes, or create additional volumes.
4
The Volumes table displays the following:
• Volume: The name of the volume.
• Location: The array on which the volume is located.
• Total Space: The amount of space allocated for the volume (in MB or GB).
• % Used: The amount of space, as a percentage, that is currently used.
• Crypto: Whether the volume is encrypted or not.
• Action: Click Edit to make changes to the current volume. Click Delete to remove the volume
(and any saved data on the volume) from the array. If the volume is encrypted, you can either
click Unlock to unlock it and make it usable, or click Lock to manually lock it.
Chapter 4: Storage
Volume Management
53
Page 56

Chapter
Network Storage System (NSS) Administrator Guide
Creating a Volume
After you define at least one RAID array, you can create a volume. You need to create at least one
volume before you can create users, groups, or shares.
To create a volume:
1. From the Manager Menu, click Storage Volu mes.
The Storage Volumes page appears.
4
2. From the New Volume area, set up the following fields:
• Array: Click the drop-down menu to select the array on which you want to create the volume.
• Name: Enter the name you want to give the volume. The volume name must consist of at least
one alphanumeric character, must begin with a letter, but cannot contain any spaces.
• Size (in MB): Enter the size for the volume. The unit is in megabytes (MB). The final size of the
shared volume will be less than the size you enter in this field due to filesystem overhead. The
minimum volume size is 32 MB. Volume sizes are rounded down to the nearest 32 MB
increment.
NOTE: Once the volume is created, you can expand the volume but you cannot reduce its
size.
3. To encrypt the volume, select Encrypted. To create an unencrypted volume, go to step 6.
Chapter 4: Storage
Creating a Volume
54
Page 57

Chapter
Network Storage System (NSS) Administrator Guide
NOTE: You can encrypt the volume only when the volume is first created. After a volume is
created, you cannot change whether it is encrypted or unencrypted. Expect slower
Read/Write performance when using encrypted volumes.
4. Enter a password in the Password field using a minimum of eight alphanumeric characters. The
password must consist of at least three of the following: lower-case character, upper-case
character, number (0-9), or a special character (such as #@*&^). The password must be entered
to unlock an encrypted volume when the NSS is started up following a power interruption,
shutdown, or reboot, or, if the volume was manually locked through the NSS configuration
interface.
WAR NI NG : Because you need the password to decrypt a locked volume, keep a secure backup
of the password to ensure that it is accessible when required. There is no way to unlock the
volume without the password. (If the password is forgotten, the only way to retrieve the
password is if the password was saved in a configuration file. See Restoring the Configuration
see Restoring a Configuration File) for help on this.)
(
4
5. Re-enter the password in the Confirm Password field.
6. Click Add.
Chapter 4: Storage
Creating a Volume
55
Page 58

Chapter
Network Storage System (NSS) Administrator Guide
Expanding a Volume
After a volume is created, you can increase its size, provided there is available space on the array.
To increase the size of a volume:
1. From the Manager Menu, click Storage Volu mes.
The Volumes page appears.
4
2. Click Edit for the volume you want to expand.
The Grow File System page appears for the selected volume.
3. In the Resize by field, select one of the following:
Chapter 4: Storage
Expanding a Volume
56
Page 59

Chapter
Network Storage System (NSS) Administrator Guide
• Grow By: Select this option to add the space allocated in the Size field to the existing space
for the volume. For example, if the volume currently has 224 MB of space and you want to
add another 224 MB, select "Grow By" and then enter 224 in the Size field. Note: The
system rounds up the total space to the nearest 32 MB boundary.
• Resulting Size: Select this option to resize the volume to the space entered in the Size field.
For example, if the volume currently has 224 MB of space and you want it to have 928 MB,
select "Resulting Size" and then enter 928 in the Size field. Note: The system rounds up the
total space to the nearest 32 MB boundary.
4. Depending on your choice in the previous step, enter the new number in the Size field. If you
selected "Grow By", the new number is added to the existing volume size. If you selected
"Resulting Size", the new number becomes the total size for the volume.
5. Click OK.
4
Chapter 4: Storage
Expanding a Volume
57
Page 60

Chapter
Network Storage System (NSS) Administrator Guide
Deleting a Volume
You can choose to delete a volume at any time. WAR N IN G: Deleting the volume removes any shares
or data currently saved to that volume. If the volume was assigned as the users’ Home Directory
Location, you must reassign the Home Directory Location to another volume.
To delete a volume:
1. From the Manager Menu, click Storage Volu mes.
The Storage Volumes page appears.
4
2. From the Existing Volumes area, click Delete for the volume you want to delete.
Chapter 4: Storage
Deleting a Volume
58
Page 61
Chapter
Network Storage System (NSS) Administrator Guide
Viewing the Snapshot Reserve Details
You can configure the NSS6000 series NAS to take snapshots of the data on an existing volume.
When you create a snapshot, a backup of each of the shares on the volume is created and is
available within the file directory to which the end user has access. The advantage of a snapshot
over a backup is that a snapshot is user-accessible and can be used for quick file recovery resulting
from end user error (such as, an accidentally deleted file). A backup is only accessible to the
administrator through the NSS configuration interface and restoring data through the backup can
be timely. Backups are usually used to restore the system from a major system failure.
Snapshots can be taken at various time intervals (such as hourly, daily, and so on). Each time a
snapshot is taken, the previous snapshot is overwritten. You can also configure multiple snapshots to
occur at different time intervals for the same volume. For example, you might want to capture a
snapshot each hour, weekly, and bi-weekly. In this case, the volume has three separate snapshots.
Each snapshot is overwritten when the next snapshot of the same frequency is taken. To ensure data
integrity, during the creation of the snapshot (the duration is approximately a few seconds), no
writes can occur to the share.
The snapshot reserve is the amount of space that you want to allocate to the snapshot on the
associated array. Once set, this space is not available for other storage use. The recommended
amount of a reserve is generally between 10 to 20% of the total volume size. Note that if the period
of time between snapshots is greater, the amount of the reserve should be greater. Or, if there is a
heavy amount of activity on the volume, set a higher reserve. This is due to the snapshot reserve
being used to store the changes to the volume contents since the last time the snapshot was taken.
4
NOTE: This feature is only available on the NSS6000 series NAS.
Chapter 4: Storage
Viewing the Snapshot Reserve Details
59
Page 62

Chapter
Network Storage System (NSS) Administrator Guide
Maintaining Active Snapshots
You can view the list of configured snapshots by displaying the Storage Snapshots page. The
Currently Active Snapshots area lists each snapshot set up for all the volumes on your NSS6000
series NAS.
4
The following column headings provide details about the snapshot:
• Volume: The name of the volume for which the snapshot is set up.
• Frequency: The time interval of the snapshot. If the time interval is set up to occur at a certain
time of the week, day, or hour, it is also listed. For example, daily @ 10:30 means that the
snapshot occurs each day at 10:30 a.m.
• Size: The size of the snapshot reserve.
• Current Usage: The percent of the space allocated for the snapshot currently taken up by the
snapshot.
Chapter 4: Storage
Viewing the Snapshot Reserve Details
60
Page 63

Chapter
Network Storage System (NSS) Administrator Guide
Creating a Snapshot for a Volume
As part of your backup strategy, you can configure the NSS6000 series NAS to capture snapshots
of the data stored on a volume. You can define a snapshot to occur at various frequencies (such as
hourly, daily, weekly, and so on). Individual snapshots are overwritten by the subsequent snapshot
for the same interval. For example, if you set up an hourly snapshot, the 10:00 a.m. snapshot is
replaced by the 11:00 a.m. snapshot (and so on). You can also configure multiple snapshots for the
same volume. For example, you might set up an hourly snapshot, another snapshot to occur every
four hours, and a daily snapshot. Each of these three snapshots is maintained separately and is only
overwritten by the subsequent snapshot of its own frequency type. The snapshot(s) reside in the
reserve area allocated for each snapshot. When a snapshot is created, the end user can access it by
logging into the NSS with their username and password. Each snapshot appears as a copy of the
share accessible by the end user.
4
The snapshot reserve is the amount of space that you want to allocate on the array to the snapshot.
Once set, this space is not available for other storage use. The recommended amount of a reserve is
generally between 10 to 20% of the total volume size. Note that if the period of time between
snapshots is greater, the amount of the reserve should be greater. Or, if there is a heavy amount of
activity on the volume, set a higher reserve
NOTE: This feature is only available on NSS6000 series NAS units.
To create a snapshot for a volume:
1. From the Manager Menu, click Storage Snapshots.
Chapter 4: Storage
Creating a Snapshot for a Volume
61
Page 64

The Storage Snapshots page appears.
Chapter
Network Storage System (NSS) Administrator Guide
4
2. From the New Snapshot table, click the volume for which you are creating the snapshot.
3. Depending on the frequency, use the first part of the Every field to enter a unit of time. Tab to the
second part of the Every field, and then click the snapshot frequency (that is, hours or days). For
example, set the first part of the field to "7", and the second part to "Days" to take a snapshot
once every week.
4. Use the At: fields to set up the timing for the snapshot. For example, if the frequency is set to
Days, set the hour and minute of the day at which you want the snapshot to be taken. Note:
When entering the hour, use the 24-hour clock. For example, 3 p.m. should be entered as
15:00. When the frequency is set to Hours, you can only edit the minutes part of the At: field.
5. In the Reserve Size field, enter the amount of space (in MB) that you want to allocate to the
snapshot. This space becomes unavailable for any other storage on the array. Note that you
must enter a minimum of 32 MB in this field.
NOTE: The snapshot is built at the array level. The Volume column currently shows the
amount of space left on the array on which the volume is located. To calculate the
reserve size, refer to the applicable volume size as listed on the Volume page.
6. Click Add to save the snapshot.
The snapshot details appear in the Currently Active Snapshots area at the top of the page.
Chapter 4: Storage
Creating a Snapshot for a Volume
62
Page 65

Chapter
Network Storage System (NSS) Administrator Guide
Taking a Manual Snapshot of a Volume
There might be times when you want to take a snapshot of a volume that falls outside of the regularly
scheduled snapshot times. When you take a snapshot of a volume using the resnap function, the
newly taken snapshot overwrites the previously existing one for the specified interval. For example,
if you have a snapshot set up to occur hourly and then click Resnap, a new snapshot is built that
overwrites the existing hourly snapshot.
NOTE: This feature is only available on NSS6000 series NAS units.
To take a manual snapshot:
1. From the Manager Menu, click Storage Snapshots.
The Storage Snapshots page appears.
4
2. Click Resnap next to the volume for which you want to take a snapshot.
The snapshot takes seconds to complete. To ensure data integrity, no writes can occur to the
share until the snapshot is complete.
Chapter 4: Storage
Taking a Manual Snapshot of a Volume
63
Page 66

Chapter
Network Storage System (NSS) Administrator Guide
Windows End Users: Accessing a Snapshot for a Share
After a snapshot is created for a volume, a file folder appears in the end user’s file directory for each
share to which the end user has access. Snapshots are saved with the name of the share followed by
an underscore and then the term "snap". Each file folder contains a subfolder for each snapshot
interval (for example, hourly, daily, etc.).
To access a snapshot for a share:
1. There are a variety of ways to access the NSS:
•From the My Computer window, type \\<hostname> or IP address in the Address bar.
(Where the <hostname> refers to your NSS hostname. For example, \\NAS).
• Browse for the NSS from the My Network Places window.
• Map the NSS to a network drive.
The Log In window appears.
4
2. Enter your NSS user name and password.
3. Click OK.
The Windows Explorer window opens with a directory listing of the folders for the shares
available on the user’s home directory
4. Snapshots are read-only. To work with a snapshot, locate it, take a copy of it, and then place the
copy in a working directory.
Chapter 4: Storage
Windows End Users: Accessing a Snapshot for a Share
64
Page 67

Chapter
Network Storage System (NSS) Administrator Guide
Volume Encryption Overview
The Volumes page lists both the encrypted and unencrypted volumes and lets you create a volume,
and lock, unlock, or change the password for encrypted volumes.
4
Chapter 4: Storage
Volume Encryption Overview
65
Page 68

Chapter
Network Storage System (NSS) Administrator Guide
Locking an Encrypted Volume
You can manually lock an encrypted volume at any time. Locking a volume means that it becomes
unmounted and is unusable (you cannot create or use shares stored on the locked volume). This
provides an extra layer of security against the theft of data.
To lock a volume:
1. From the Manager Menu, click Storage Volu mes.
The Volumes page appears.
4
The Crypto column displays whether the volume is encrypted (Yes) or not encrypted (No).
2. Click Lock to lock the volume.
Chapter 4: Storage
Locking an Encrypted Volume
66
Page 69

Chapter
Network Storage System (NSS) Administrator Guide
Unlocking a Locked Volume
When an encrypted volume is locked, either automatically as a result of the NSS being rebooted or
manually locked through the configuration interface, you must unlock it before it c an be used for tasks
such as creating shares or quotas.
To unlock a volume:
1. From the Manager Menu, click Storage Volu mes.
The Volumes page appears.
4
2. Click Unlock for the volume you want to unlock.
Chapter 4: Storage
Unlocking a Locked Volume
67
Page 70

Network Storage System (NSS) Administrator Guide
The Unlock Volume page appears.
3. Enter the password for the volume in the Password field.
4. Click OK.
Chapter
4
The Volume En cr yption page appears. The volume is now unlocked.
Chapter 4: Storage
Unlocking a Locked Volume
68
Page 71

Network Storage System (NSS) Administrator Guide
Changing the Password for an Encrypted Volume
Chapter
4
A password must be set up when you create an encrypted volume (
volume is created, you can change the password at any time. The password must be entered under
two conditions: when the NSS is started up after a power interruption, or, the volume has been
manually locked. WAR NI NG : Because the password is required to de-crypt a locked volume, keep a
backup of the password to ensure that it is accessible when required. There is no way to unlock the
volume without the password. (If the password is forgotten, the only way to retrieve the password is
if the password was saved in a configuration file. See Restoring the Configuration (
Configuration File) for help on this.)
To change the password on an existing encrypted volume:
1. From the Manager Menu, click Storage Volumes.
The Volumes page appears.
see Creating a Volume). After the
see Restoring a
Chapter 4: Storage
Changing the Password for an Encrypted Volume
69
Page 72

2. Click Edit for the volume you want to change.
Chapter
Network Storage System (NSS) Administrator Guide
4
3. In Current Password field, enter the password.
4. In the New Password field, enter the new password. Note: The password must be at least eight
characters of which at least three of the following characteristics are included: lower-case
character, upper-case character, integer (0 to 9), and a special character (such as @#$%^*&).
5. Re-enter the new password in the Confirm Password field.
6. Click Update.
Chapter 4: Storage
Changing the Password for an Encrypted Volume
70
Page 73

Network Storage System (NSS) Administrator Guide
Storage Options
The Storage Options page lets you define the following:
Chapter
4
• Idle Drive Spin Down: (
the disk drives after a predefined time of inactivity.
• RAID Rebuild Priority: (
prioritizes the RAID rebuild and allocates the system resources based on the current workload
and need for responsiveness.
• Degraded Mode Grace Period: Set the period of time after which the system automatically
shuts down degraded arrays. You can manually restart RAID arrays automatically stopped by
using degraded mode management. Warning messages are sent out periodically while the
RAID array is degraded.
• Enable Global Spares: Allow RAID arrays defined in the system to share spare drives. If this
option is disabled, a RAID array can only use a spare that has been added to that particular
array. If this option is enabled, spare drives added to one RAID array may be reallocated by
the NSS to another RAID array. For example, if RAID A is a two-drive RAID1 that is not
degraded and RAID B is a degraded two-drive RAID1, if you add a spare drive to RAID A,
the NSS automatically gives the spare drive to RAID B to enable RAID B to resync. This option
is only relevant when you use network disks (via storage virtualization). A system limited to
local disks lets you only build up to two, two-disk RAID arrays, but have no spares.
see Setting the Spin Down Time) Configure the NSS to spin down
see Setting the RAID Rebuild Priority) Control how the system
Chapter 4: Storage
Storage Options
71
Page 74

Chapter
Network Storage System (NSS) Administrator Guide
Setting the RAID Rebuild Priority
During normal operation, the CPU switches between tasks to service all active tasks on the system.
Creating a RAID array or rebuilding an existing array can take up a significant amount of the
available percentage of CPU processing power. You can control how the system prioritizes the rebuild
and allocates the system’s resources based on your system’s current workload and need for
responsiveness.
To configure the RAID rebuild priority:
1. From the Manager Menu, click Storage Options.
The Storage Options page appears.
4
2. From the RAID Rebuild Priority menu, select the allocation of CPU processing power to the RAID
rebuild task.
• High: The CPU focuses on the RAID rebuilding process. This setting allows for the fastest
possible RAID rebuild at the expense of other system tasks. File-sharing throughput is
adversely affected during RAID rebuild when this setting is chosen.
• Medium: This option gives a balance between the rebuild process and other system tasks. The
rebuild process takes longer than if it was set to High.
• Low: The CPU focuses on other tasks versus the RAID rebuild process. This results in a longer
rebuild time on a busy system. However, if the workload on the system is low, the CPU
services the rebuild process well. Note that if you are repairing an array, this option leaves
the array vulnerable until the rebuild is complete.
3. Click Update.
Chapter 4: Storage
Setting the RAID Rebuild Priority
72
Page 75

Chapter
Network Storage System (NSS) Administrator Guide
Setting the Spin Down Time
You can configure the NSS to spin down the disk drives after a predefined time of inactivity. This
reduces the power consumption of the system and can possibly increase the lifespan of drives.
Because of the potential risks and benefits of spinning down a disk versus leaving it running in an idle
condition, we recommend you consult the disk drive manufacturer documentation for the optimum
way to handle the disk.
To configure the disk drives for spin down:
1. From the Manager Menu, click Storage Options.
The Storage Options page appears.
4
2. In the Idle Drive Spin Down field, select the period of time that the disk drive must be idle before
it is spun down. (Select "Never" to ensure that the drives are never spun down.)
3. Click Update.
Chapter 4: Storage
Setting the Spin Down Time
73
Page 76
Chapter
Network Storage System (NSS) Administrator Guide
Administering Access to the NSS
The Access Status page lets you view the current end-user connections to the NSS, grouped by the
file-sharing protocol used. The page displays the username, the name of the host from which the
user is currently connected, and the share or path that the user is accessing. Status pages like the
Access Status page automatically refresh on a regular interval and are very helpful for monitoring
the progress of certain processes such as the current end user connections to the NSS.
5
Chapter 5: Access
74
Page 77

Chapter
Network Storage System (NSS) Administrator Guide
Managing your NSS Users
You can create, view, and maintain the list of users who can access the NSS. The Configured Users
page displays the Configured Users table. This table lists each defined user whether the user was
created locally via the NSS configuration interface or imported from an NTv4, Active Directory, or
NIS domain. Note that users not created locally via the NSS are read-only. Once a user profile is
created, you cannot rename the username. To rename an existing user profile, delete the user profile
and then create a new one. User profiles are maintained by the administrator. Users cannot make
changes to their passwords.
5
Chapter 5: Access
Managing your NSS Users
75
Page 78
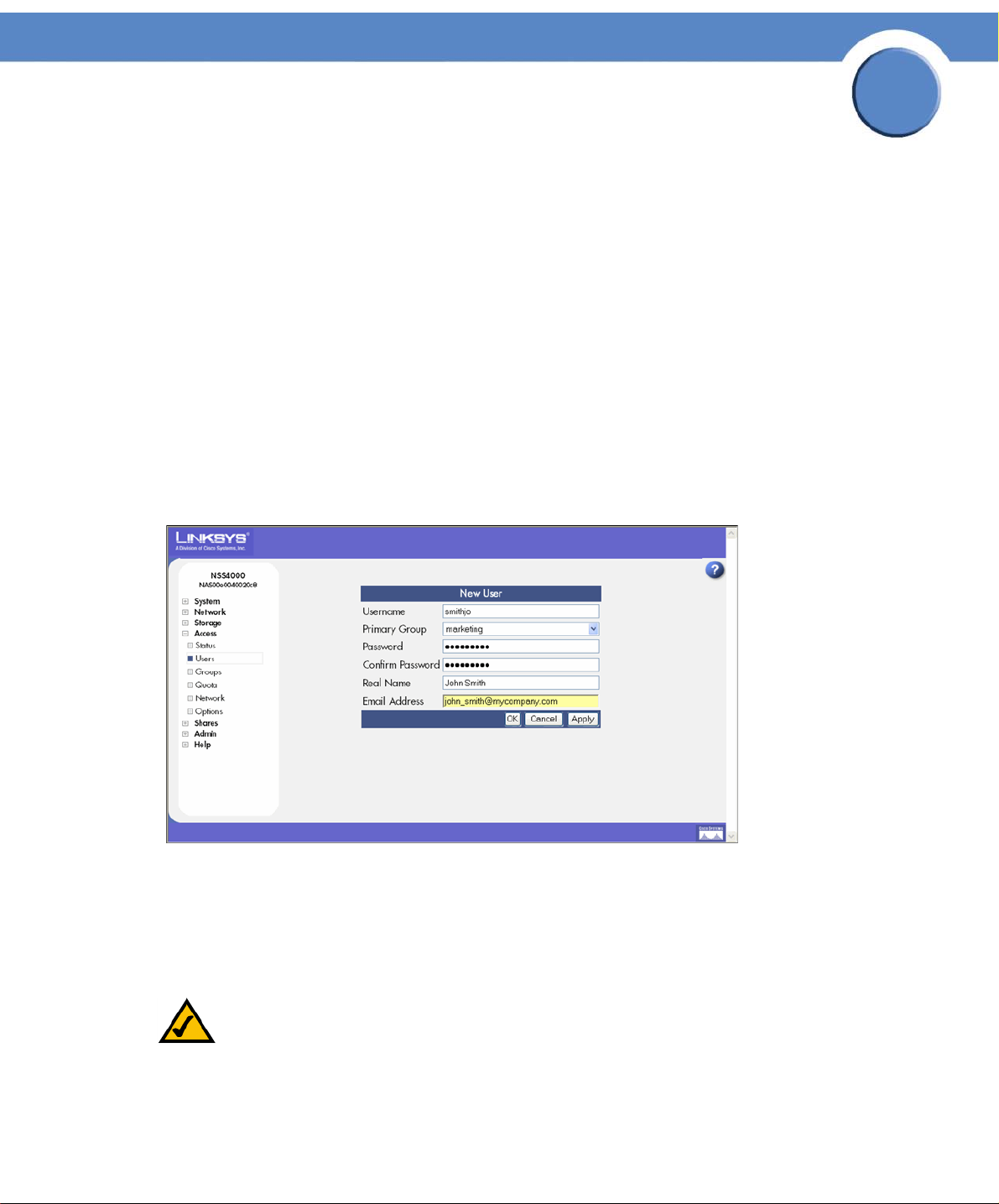
Chapter
Network Storage System (NSS) Administrator Guide
Creating a User Profile
Depending on your network setup, you might administer users and groups locally or via the domain
controller. The NSS configuration interface gives you read-only access to users and groups provided
by NTv4, Active Directory, or NIS domains. You can also create and manage local users from the
NSS configuration interface. Before you can create a user profile, you must configure the volume you
want to use as the home directory location for your users on the Access Options page (from the
Manager Menu, click Access > Options).
To add a local user:
1. From the Manager Menu, click Access Users.
The Configured Users page appears. Users created from the NSS configuration interface and
provided by the ADS, NTv4, or NIS domain appear in the Configured Users table.
2. Click Add to create a user.
The New User page appears.
5
3. In the Username field, type the username. The name must be made up of alphanumeric
characters (that is, a-z, 0-9), any case, to a maximum of 32 characters. This field is required.
4. Select the group you want to assign as the user’s primary group from the Primary Group field. If
there are no groups configured, the only available choice is the default group "nasusers". This
field is required.
NOTE: Although you can assign the user to multiple groups (through the Add Group or Edit
Group page), the primary group is the group against which quota charges for the
user’s storage usage are made and is the group that defines the group ownership for
all files created by the user. The primary group applies to users set up locally on the
Chapter 5: Access
Creating a User Profile
76
Page 79

Chapter
Network Storage System (NSS) Administrator Guide
NSS. A domain user’s primary group is set up from the domain and is not derived
from the Primary Group field in the NSS user profile.
5. Assign a password by entering any valid (ASCII table) characters in the Password field. The
password is required.
6. To verify the password, re-enter it in the Confirm Password field.
NOTE: All password changes to end-user accounts set up through the NSS configuration
pages must be made by the administrator.
7. To record the user’s full name, enter it in the Real Name field. This field is optional. Note that you
cannot enter the "/" character in this field.
8. To record the user’s email address, enter it in the Email Address field. This field is optional.
9. Click OK to create the user and exit the New User page. Click Apply to create the user and then
add another new user.
5
Chapter 5: Access
Creating a User Profile
77
Page 80

Chapter
Network Storage System (NSS) Administrator Guide
Editing a User Profile
You can change certain aspects of the user’s profile. Note that once you create a username, the only
way to "rename" that user is to delete the existing user profile and then create a new one. If the user
profile resides on an ADS, NTv4, or NIS domain, you need to edit the profile from the applicable
domain manager. All password changes for end-user accounts set up directly through the NSS
configuration pages must be done by the Administrator.
To edit an existing user profile:
1. From the Manager Menu, click Access Users.
The Configured Users page appears.
5
The existing users appear in the Configured Users table.
2. Select the user from the list, and then click Edit.
Chapter 5: Access
Editing a User Profile
78
Page 81

Chapter
Network Storage System (NSS) Administrator Guide
The end user’s profile appears in the Edit User page.
3. The username is read-only. You can make changes to any of the other fields in the user’s profile.
5
4. Click Update.
Chapter 5: Access
Editing a User Profile
79
Page 82

Chapter
Network Storage System (NSS) Administrator Guide
Integrating Users from an ADS, NTv4, or NIS Domain
Overview
When the NSS is joined to an ADS, NTv4, or NIS domain, a list of existing domain users is
imported into the Configured Users list. You can view the entire user list from the Configured Users
page but can only edit or delete locally created users (not domain users). The naming conventions
use the NetBIOS format with the domain name as a prefix of the username. The primary group for
users set up within the ADS, NTv4 or NIS domain is taken from the user’s domain profile versus the
Primary Group field in the NSS user profile.
NOTE: It is important to set up your User and Group ID ranges before you join the NSS to
an ADS, NTv4, or NIS domain. After you join the NSS to a domain, you should not
make changes to the range as this might lead to an ID collision.
Logging Into the NSS as a Local User
5
When the NSS is joined to an NTv4 or ADS domain, local users must prefix their username with the
hostname of the NSS. Users who log in without the hostname prefix are automatically assumed to be
domain users. For example, if the NSS hostname is "NASadmin" and the local username is "bob",
the user would need to log in as "NASadmin\bob" in the login dialog.
Chapter 5: Access
Integrating Users from an ADS, NTv4, or NIS Domain
80
Page 83

Deleting a User Profile
To delete an existing user profile:
1. From the Manager Menu, click Access Users.
The Configured Users page appears.
Chapter
Network Storage System (NSS) Administrator Guide
5
2. Click the username and then click Delete. To delete multiple users, use the following mouse-key
combinations:
• Shift-click: To select a contiguous group of users that you want to delete, hold down the Shift
key, and then click the first user and then last user in the series. Click Delete to delete the
highlighted users.
• Ctrl-click: To select a non-contiguous group of users that you want to delete, hold down the
Ctrl key, and then click each user from the list. Click Delete to delete the highlighted users.
The selected user(s) disappear from the list of available users.
Chapter 5: Access
Deleting a User Profile
81
Page 84

Chapter
Network Storage System (NSS) Administrator Guide
Working with Groups
Groups are an easy way to manage users with the same storage needs and privileges. A group
consists of one or more users. You can add or remove users from a group at any time. The user’s
primary group (the group to which quota charges for storage usage are applied) is set up in the
Primary Group field of the user’s profile.
A group called "nasusers" is automatically created when you first install the NSS. This group is the
default primary group when you create new users.
5
Chapter 5: Access
Working with Groups
82
Page 85

Chapter
Network Storage System (NSS) Administrator Guide
Creating a Group
Groups let you specify the share access privileges for a set of users. After you create a group, you
can define the group’s access privileges on a per-share basis. You can add or remove users to and
from the group at any time. Note that each user is assigned a primary group within their user profile.
When a user creates a file, the group ownership is automatically set to the user’s primary group. The
user’s storage usage is charged to the user’s primary group for the purposes of volume quota
accounting. Group membership, other than the primary group, is defined in either the Add Group or
Edit Group page and is used only to control access to shares and files.
NOTE: You cannot add a group to file ACL on a CIFS share.
To create a group:
1. From the Manager Menu, click Access Groups.
The Configured Groups page appears.
5
2. Click Add.
Chapter 5: Access
Creating a Group
83
Page 86

Chapter
Network Storage System (NSS) Administrator Guide
The New Group page appears.
3. In the Group Name field, type the name you want to assign to the group. The name can only
contain lower-case alphanumeric characters and underscores (i.e., a-z, 0-9, _) to a maximum of
32 characters.
5
4. Move the users you want to assign to the group from the Users Available list to the Users in
Group list. Note that a user can be assigned to multiple groups. (The single angled bracket "<"
or ">" moves the selection in the direction of the bracket. The double angled bracket "<<" or
">>" moves the entire list in the direction of the bracket.)
5. Click OK to save the current group and display the Configured Groups page. Click Apply to
save the current group and remain in the New Group page to add another group.
Chapter 5: Access
Creating a Group
84
Page 87

Chapter
Network Storage System (NSS) Administrator Guide
Changing the Users Assigned to a Group
After you create a group, you can delete or add to the list of users that belong to that group.
NOTE: When you delete an end user from a group, the end user must log out of their client
machine before the change takes effect. This means that users no longer assigned to
a group maintain full group privileges (i.e., access to shares) until they log off/log
on to their computer.
To change the group membership:
1. From the Manager Menu, click Access Groups.
The Configured Groups page appears.
2. From the list of configured groups, select the group to which you want to change.
3. Click Edit.
5
The Edit Group page appears.
4. Set up the Users in Group list as required. (The single angled bracket "<" or ">" moves the
selection in the direction of the bracket. The double angled bracket "<<" or ">>" moves the
entire list in the direction of the bracket.)
5. Click Update.
Chapter 5: Access
Changing the Users Assigned to a Group
85
Page 88

Chapter
Network Storage System (NSS) Administrator Guide
Integrating Groups from an Active Directory, NTv4, or NIS
Domain
When the NSS is joined to an Active Directory, NTv4, or NIS domain, domain groups are imported
into the Configured Groups list. Group membership for imported domain groups are read-only. The
naming conventions use the NetBIOS format with the domain name as a prefix of the group name.
For example, "DOMAINNAME\GroupName"
NOTE: It is important to set up your User and Group ID ranges before you join the NSS to
an ADS, NTv4, or NIS domain. After you join the NSS to a domain, you should not
make changes to the range as this might lead to an ID collision.
5
Chapter 5: Access
Integrating Groups from an Active Directory, NTv4, or
86
Page 89

Network Storage System (NSS) Administrator Guide
Deleting a Group
When you delete a group, the group is automatically removed from having access to any
configured shares.
To delete a group:
1. From the Manager Menu, click Access Groups.
The Configured Groups page appears.
Chapter
5
2. You can delete a group from two locations in the NSS configuration interface:
• Groups page: Highlight the group you want to delete from the Configured Groups table, and
then click Delete. To delete multiple groups, use the following key-mouse combination:
- Shift-click: To select a contiguous list of groups that you want to delete, hold down the Shift
key, and then click the first group and then last group in the series. Click Delete to delete the
highlighted groups.
- Ctrl-click: To select a non-contiguous set of groups that you want to delete, hold down the
Ctrl key, and then click each group from the list. Click Delete to delete the highlighted
groups.
Chapter 5: Access
Deleting a Group
87
Page 90

Chapter
Network Storage System (NSS) Administrator Guide
• Edit Groups page: Select the group you want to edit, and then click Edit. The Edit Groups
page appears. Click Delete to remove the group.
5
Chapter 5: Access
Deleting a Group
88
Page 91

Chapter
Network Storage System (NSS) Administrator Guide
Managing Volume Quotas
You can set up specific space limits for each user or group who has write access to a volume.
Defining a user or group’s quota means that you can set a space limit (referred to as a soft quota)
that, when reached, sends a warning to the administrator and initiates a countdown of the defined
grace period. The user has the amount of time in the grace period to reduce the amount of space
used to below the soft quota limit. Users who do not reduce the space in the allotted grace period, or
who reach their hard quota limit, no longer have write access to the volume until they reduce their
usage to below their soft quota limit.
NOTE: Before you create or edit a quota located on an encrypted volume, make sure the
volume is unlocked. You also need to set up the Warn For time for each volume from
the Volume Quota page. The Warn For time only affects individual quota that was
created after the Warn For time was set.
Changing the User’s Primary Group
5
Quotas are charged to the group assigned as the user’s primary group at the time of file creation. If
the user’s primary group changes, files created under the previous group continue to be charged
against that group. Note that if the user’s primary group changes while the user is connected to the
NSS, the previous primary group continues to be the group charged until the user’s connection is
closed. The new primary group becomes the group charged only after the connection is re-opened.
NOTE: If the user is created within a domain, the primary group defined in the user profile
from the domain, not the Primary Group field in the NSS user profile.
Chapter 5: Access
Managing Volume Quotas
89
Page 92

Chapter
Network Storage System (NSS) Administrator Guide
About the Volume Quota Page
The Volume Quota page is where you manage user and group quotas for each volume. To display
the Volume Quota page, from the Manager Menu, click Access Quota.
5
Chapter 5: Access
Managing Volume Quotas
90
Page 93

Chapter
Network Storage System (NSS) Administrator Guide
Creating Volume Quota for a User or Group
You can set up a quota on a volume for each user or group. This quota limits the user or group to the
allocated amount of space within the volume. To give certain users or groups assigned to a volume
full access to the space on the volume, do not create a quota for that user or group.
NOTE: Before you can create quota on an encrypted volume, make sure it is unlocked. You
also need to set up the Warn For time for each volume from the Volume Quota
page. The Warn For time only affects individual quota that was created after the
Warn For time was set.
To create a quota for a user or group:
1. From the Manager Menu, click Access Quota.
The Volume Quota page appears.
5
2. Click New Quota.
Chapter 5: Access
Creating Volume Quota for a User or Group
91
Page 94

Chapter
Network Storage System (NSS) Administrator Guide
The New Volume Quota page appears.
3. Select the volume on which you want to set the quota from the New Quota on FS drop-down list.
5
4. Select the user or group for which you are creating the quota from the For User/Group dropdown list.
5. In the Warning at (MB) field, enter the threshold of space that, when exceeded, triggers a
warning that the quota is close to being used up. When the threshold is exceeded, the grace
period set up for the volume begins. The user has the amount of time set in the grace period to
reduce the amount of space used to below the space set in the Warning at (MB) field or they will
not be allowed to write further data to the volume. Another way to think about this field is as a
"soft quota".
6. In the Space Limit (MB) field, enter the amount of space that the user or group has available to
use. Another way to think about this field is as the "hard quota". If the user reaches the space
limit, the user can no longer write data to the volume until they either reduce the amount of
space used to below the limit by deleting files or have the quota increased.
7. Click Update.
Chapter 5: Access
Creating Volume Quota for a User or Group
92
Page 95

Chapter
Network Storage System (NSS) Administrator Guide
Setting up the Grace Period for a Volume Quota
You can set up a limit on the amount of space available to your users or groups. This limit can be set
as a soft quota and hard quota. When the user reaches their "soft quota", a warning is issued and
the grace period begins. The user then has the amount of time set in the grace period to either reduce
the amount of spaced used by deleting files, or have the quota increased. If the amount of space is
not reduced before the grace period expires or the user reaches the hard quota, the user is
automatically denied write access to the volume.
NOTE: Before you create quotas for a user or group, make sure you set up the Warn For
time for each volume from the Filesystem Quota page. The Warn For time only
affects individual quota that was created after the Warn For time was set.
To set up the grace period for a volume:
1. From the Manager Menu, click Access Quota.
The Filesystem Quota page appears.
5
2. To set up the grace period, after which if the soft limit set for the user or group is still exceeded,
the user or group is denied write access, enter the time period in the Warn for <time period>
before denying access field. Enter the number in the first part of the field, and the time unit in
the second part of the field. For example, to warn the user or group that they have reached their
soft limit and have three days to reduce it, enter "3" and then select "days". Normally, when the
quota is under the limit, it appears in black type. When a user reaches their soft quota limit, the
amount listed on Filesystem Quota page turns red.
3. Click Update.
4. Repeat steps 2 and 3 for each applicable volume.
Chapter 5: Access
Setting up the Grace Period for a Volume Quota
93
Page 96

Chapter
Network Storage System (NSS) Administrator Guide
Changing a Volume Quota for a User or Group
After a quota is created, you can increase or decrease it. You can also change the limit at which the
user or group receives a warning message and the grace period begins.
To change the quota limit or warning limit:
1. From the Manager Menu, click Access Quota.
The Filesystem Quota page appears.
5
2. Click Edit for the user or group for which you want to change the quota.
The Edit Quota page appears.
3. Make the required changes to the soft (warning) or hard quota (space limit) limits.
4. Click OK.
Chapter 5: Access
Changing a Volume Quota for a User or Group
94
Page 97

Chapter
Network Storage System (NSS) Administrator Guide
Clearing a Quota
After a quota has been set up, you can clear it. Clearing a quota means that the user or group no
longer has a space limitation on their use of the associated volume (other than the actual unused
storage space on the volume).
To delete a quota for a user or group:
1. From the Manager Menu, click Access Quota.
The Volume Quota page appears.
5
Quotas are displayed according to their associated volume.
2. Click Clear for the user or group whose quota you want to remove.
Chapter 5: Access
Clearing a Quota
95
Page 98

Chapter
Network Storage System (NSS) Administrator Guide
Network Filters Overview
In addition to providing storage for your data, the NSS provides a configurable firewall to protect
that data. Defining network filters lets you specify which network hosts have access to the NSS via the
various supported protocols.
To view the network filters:
1. From the Manager Menu, click Access Network.
The Network Filters page appears.
5
2. You can do any of the following:
• Set the default network policy (
happens to traffic not explicitly covered by defined filters.
• View or delete the existing filters (
Active Network Access Filters table.
• Create a new filter (
range of IP addresses.
Chapter 5: Access
Network Filters Overview
see Creating a Network Filter) based on an IP or MAC address or a
see Defining the Default Network Policy) to control what
see Network Filters Overview) defined for the NSS from the
96
Page 99

Chapter
Network Storage System (NSS) Administrator Guide
Defining the Default Network Policy
The default network policy is the overarching policy that defines the gateway for communication to
the NSS. It specifies how traffic that is not covered by defined filters is handled. The default policy can
be defined to either accept or reject such traffic.
To define the default network policy:
1. From the Manager Menu, click Access Network.
The Network Filters page appears.
5
2. From the Default Network Policy drop-down menu, click one of the following:
• Accept Traffic: Allow the NSS to communicate with all initiating hosts. Select this option if you
have a limited number of systems that you want to disallow. When you set up your individual
filters, select those filters that "disallow" (i.e., drop or reject) certain types of connections. For
example, you might want to disallow CIFS connections but allow all other types.
• Drop Traffic: Disallow the NSS from communicating with any initiating systems. Select this
option if you have a limited number of systems that you want to allow to communicate with
the NSS. When you set up your filters, select those filters that "allow" certain types of
connections. For example, you might only want to allow FTP connections.
3. Click Change Policy.
Chapter 5: Access
Defining the Default Network Policy
97
Page 100

Chapter
Network Storage System (NSS) Administrator Guide
Creating a Network Filter
The Active Network Access Filters table on the Network Filters page displays currently defined filters.
These filters control if access to the NSS from specified hosts is granted or denied on a per-protocol
basis. Each device in your network is assigned a fixed 48-bit MAC address and changeable 32-bit
IP address. When you define a filter, it grants or denies access via the specified protocol from the
specified IP/MAC address or range of IP addresses.
To add a network filter:
1. From the Manager Menu, click Access Network.
The Network Filters page appears.
5
2. From the New Network Access Filter table, type the IP/MAC address to which you are applying
the filter, in the IP/MAC address field. You can also enter addresses for the following:
• An IP Address Range: Type the range according to the following format:
address. (Where the first IP address in the range is entered first, followed by a hyphen, and
then the last IP address in the range.)
• A Subnet: Enter the subnet to set a filter for all the addresses within the subnet. The format
should appear as shown in the following example: 192.168.1.0/24 (where the digits
following the slash represent the number of bits in the network portion of the IP address).
Chapter 5: Access
Creating a Network Filter
first address-last
98
 Loading...
Loading...