Page 1

Anti-DDoS
User Guide
Issue 01
Date 2018-08-15
HUAWEI TECHNOLOGIES CO., LTD.
Page 2

Copyright © Huawei Technologies Co., Ltd. 2021. All rights reserved.
No part of this document may be reproduced or transmitted in any form or by any means without prior
written consent of Huawei Technologies Co., Ltd.
Trademarks and Permissions
and other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd.
All other trademarks and trade names mentioned in this document are the property of their respective
holders.
Notice
The purchased products, services and features are stipulated by the contract made between Huawei and
the customer. All or part of the products, services and features described in this document may not be
within the purchase scope or the usage scope. Unless otherwise specied in the contract, all statements,
information, and recommendations in this document are provided "AS IS" without warranties, guarantees
or representations of any kind, either express or implied.
The information in this document is subject to change without notice. Every eort has been made in the
preparation of this document to ensure accuracy of the contents, but all statements, information, and
recommendations in this document do not constitute a warranty of any kind, express or implied.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. i
Page 3

Anti-DDoS
User Guide Contents
Contents
1 Introduction.............................................................................................................................. 1
1.1 Functions.................................................................................................................................................................................... 1
1.2 Application Scenarios............................................................................................................................................................. 2
1.3 Accessing and Using Anti-DDoS.........................................................................................................................................2
1.3.1 How to Access Anti-DDoS.................................................................................................................................................2
1.3.2 How to Use Anti-DDoS...................................................................................................................................................... 3
1.3.3 Related Services.................................................................................................................................................................... 3
1.3.4 User Permissions.................................................................................................................................................................. 4
2 Operation Guide...................................................................................................................... 5
2.1 Enabling Anti-DDoS................................................................................................................................................................5
2.2 Enabling Alarm Notication................................................................................................................................................ 7
2.3 Adjusting Security Settings.................................................................................................................................................. 8
2.4 Viewing a Monitoring Report........................................................................................................................................... 11
2.5 Viewing an Interception Report....................................................................................................................................... 12
3 FAQs.......................................................................................................................................... 14
3.1 What Is Anti-DDoS?............................................................................................................................................................. 14
3.2 What Services Can Anti-DDoS Protect?........................................................................................................................ 14
3.3 How Do I Use Anti-DDoS?................................................................................................................................................. 14
3.4 What Kinds of Attacks Does Anti-DDoS Defend Against?......................................................................................14
3.5 Will I Be Promptly
Notied When an Attack Is Detected?..................................................................................... 15
A Change History...................................................................................................................... 16
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. ii
Page 4

Anti-DDoS
User Guide 1 Introduction
1 Introduction
1.1 Functions
The Anti-DDoS trac cleaning service (Anti-DDoS for short) defends elastic IP
addresses (EIPs) against network- and application-layer distributed denial of
service (DDoS) attacks and sends alarms immediately when detecting an attack.
In addition, Anti-DDoS improves the utilization of bandwidth and ensures the
stable running of users' services.
Anti-DDoS monitors the service
trac in real time. It then cleans attack trac according to user-congured
defense policies so that services run as normal. In addition, monitoring reports are
generated, presenting users with clear network security evaluations.
Anti-DDoS helps users cope with trac attacks with ease. It can precisely identify
connection exhaustion and slow-connection attacks and can help users defend
against the following attacks:
● Web server attacks
Such as SYN
connection attacks
● Game attacks
Such as User Datagram Protocol (UDP)
Protocol (TCP), and fragment attacks
● HTTPS server attacks
Such as SSL DoS and DDoS attacks
ood, HTTP ood, Challenge Collapsar (CC), and slow-
trac from the Internet to EIPs to detect attack
ood, SYN ood, Transmission Control
● DNS server attacks
Such as attacks targeted at vulnerabilities in the Domain Name Server (DNS)
protocol stack, DNS reection attacks, DNS ood attacks, and DNS cachemiss attacks
Anti-DDoS also provides the following functions:
● Providing monitoring records for each EIP, including the current defense
status, current defense
abnormalities.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 1
congurations, and the last 24 hours' trac and
Page 5
Anti-DDoS
User Guide 1 Introduction
● Providing attack statistics reports on all protected EIPs, covering the trac
cleaning frequency, cleaned trac amount, top 10 attacked EIPs, and number
of blocked attacks.
1.2 Application Scenarios
Anti-DDoS defends only EIPs against DDoS attacks.
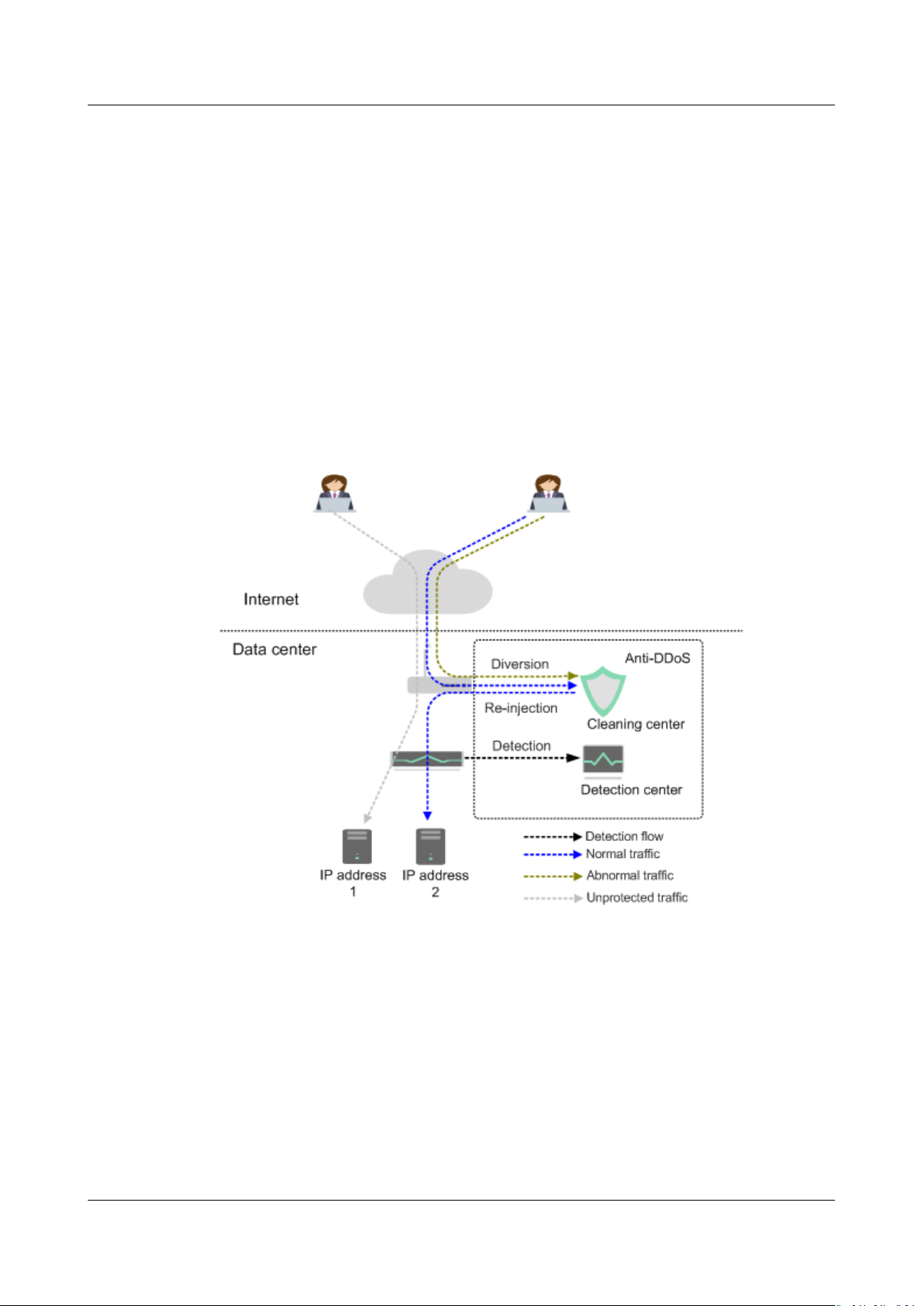
Anti-DDoS devices are deployed at egresses of data centers. Figure 1-1 shows the
network topology.
The detection center detects network access
security policies. If an attack is detected, data is diverted to cleaning devices for
real-time defense. Abnormal
Figure 1-1 Network topology
trac is cleaned, and normal trac is forwarded.
trac according to user-congured
1.3 Accessing and Using Anti-DDoS
1.3.1 How to Access Anti-DDoS
Anti-DDoS provides a web-based service management platform. You can access
Anti-DDoS using the management console or HTTPS-based application
programming interfaces (APIs).
● Management console
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 2
Page 6
Anti-DDoS
User Guide 1 Introduction
If you have registered an account, you can log in to the management console
directly. On the home page, choose Security > Anti-DDoS to access the AntiDDoS service.
● HTTPS-compliant APIs
You can access Anti-DDoS using APIs. For details, see the
Reference
.
Anti-DDoS API
1.3.2 How to Use Anti-DDoS
Description:
● Anti-DDoS defends IP addresses against DDoS attacks after you enable it.
● Enable alarm notication, which sends notications by SMS or email when an
IP address is under a DDoS attack.
● Adjust security settings based on service needs during defense.
● View monitoring and interception reports after the defense is enabled to
check network security situations.
● You can disable Anti-DDoS defense as required.
1.3.3 Related Services
CTS
Cloud Trace Service (CTS) provides you with a history of Anti-DDoS operations.
After enabling CTS, you can view all generated traces to review and audit
performed Anti-DDoS operations. For details, see the
.
Guide
● Anti-DDoS operations that can be recorded by CTS
Table 1-1 Anti-DDoS operations that can be recorded by CTS
Operation
Enabling Anti-DDoS openAntiddos
Disabling Anti-DDoS deleteAntiddos
Adjusting Anti-DDoS security settings updateAntiddos
● Using CTS to view Anti-DDoS audit logs
a. Log in to the management console.
b. Select Cloud Trace Service under Management & Deployment.
c. In the left navigation pane, choose Trace List.
d. You can use lters to query traces. The following four lters are available:
Cloud Trace Service User
Trace Name
▪ Trace Source, Resource Type, and Search By
○ Select query conditions from the drop-down list, for example,
choose Anti-DDoS > anti-ddos > Trace name > openAntiddos
to query all Anti-DDoS enabling operations.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 3
Page 7

Anti-DDoS
User Guide 1 Introduction
○ Trace name: This option allows you to select a trace name, such
as openAntiddos.
○ Resource ID: This option allows you to select or manually enter
the ID of the instance for which you want to view audit logs.
○ Resource name: This option allows you to select or manually
enter the name of the instance for which you want to view audit
logs.
IAM
SMN
▪ Operator: Select a
level).
specic operator (at user level rather than tenant
▪ Trace Status: Available options include All trace statuses, normal,
warning, and incident. You can only select one of them.
▪ Start time and end time: You can specify the time period to query
traces.
e. Click
f. In the row containing the desired record, click View Trace.
Identity and Access Management (IAM) provides the permission management
function for Anti-DDoS. Only users who have Anti-DDoS Administrator
permissions can use Anti-DDoS. To apply for Anti-DDoS Administrator permissions,
contact a user with Security Administrator permissions. For details, see the
and Access Management User Guide
The Simple Message Notication (SMN) service provides the notication function.
When alarm notication is enabled in Anti-DDoS, you will receive alarm messages
by SMS or email if your IP address is under a DDoS attack.
on the left of the record to be queried to extend its details.
Identity
.
For details about SMN, see the
Simple Message Notication User Guide
.
1.3.4 User Permissions
The public cloud system provides two types of permissions by default: user
management and resource management.
● User management refers to the management of users, user groups, and user
group rights.
● Resource management refers to the control operations that can be performed
by users on cloud service resources.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 4
Page 8

Anti-DDoS
User Guide 2 Operation Guide
2 Operation Guide
2.1 Enabling Anti-DDoS
Scenarios
Prerequisites
Procedure
Step 1 Log in to the management console.
Step 2 Click
Step 3 Under Security, choose Anti-DDoS. The Security Console is displayed.
Step 4 Choose Instances. On the displayed page, locate the row that contains the
The Anti-DDoS service then protects your IP addresses against DDoS attacks.
● You have obtained an account and its password to log in to the management
console.
● You have not enabled Anti-DDoS for your IP addresses.
in the upper left corner and select the desired region or project.
unprotected IP address, and click Enable Anti-DDoS in the Operation column, as
shown in Figure 2-1.
Figure 2-1 Instance IP Address
Step 5 In the displayed Enable Anti-DDoS dialog box, set required parameters and click
OK.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 5
Page 9

Anti-DDoS
User Guide 2 Operation Guide
Figure 2-2 Enabling Anti-DDoS
Table 2-1 Parameters for enabling Anti-DDoS
Parameter
Trac
Cleaning
Threshold
Description
Anti-DDoS scrubs trac when detecting that the incoming
trac of an IP address exceeds the threshold.
If service trac triggers scrubbing, only attack trac is
intercepted. If service trac does not trigger scrubbing, no
trac is intercepted.
Set this parameter based on the actual service access
You are advised to set a value close to, but not exceeding, the
purchased bandwidth.
trac.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 6
Page 10

Anti-DDoS
User Guide 2 Operation Guide
Parameter Description
CC Defense ● Disable: disables the defense.
● Enable: enables the defense.
NOTE
CC defense is available only for clients supporting the full HTTP
protocol stack because This is because CC defense works in
redirection or redirection+verication code mode. If your client does
not support the full HTTP protocol stack, you are advised to disable
CC defense.
● HTTP Request Rate:
This option is available only when CC defense is enabled.
You are advised to set this parameter to the maximum
number of HTTP requests that can be processed by the
deployed service. Anti-DDoS automatically scrubs
the total number of detected requests exceeds this
threshold. If the value is too large, CC defense will not be
triggered promptly.
– If the actual HTTP request rate is smaller than the
congured value, the deployed service is able to process
all HTTP requests, and Anti-DDoS does not need to be
involved.
– If the actual HTTP request rate is greater than or equal
to the
to analyze and check each request, which
responses to normal requests.
congured value, Anti-DDoS triggers CC defense
trac if
aects
Step 6 Click OK to save the
----End
congurations and enable protection.
2.2 Enabling Alarm Notication
Scenarios
The alarm notication function sends you alarm notications (by SMS or email) if
a DDoS attack is detected. If you do not enable this function, you have to log in to
the management console to view alarms.
Prerequisites
You have obtained an account and its password to log in to the management
console.
Procedure
Step 1 Log in to the management console.
Step 2 Click
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 7
in the upper left corner and select the region or project.
Page 11

Anti-DDoS
User Guide 2 Operation Guide
Step 3 Under Security, choose Anti-DDoS. The Security Console is displayed.
Step 4 In the upper right corner, click Congure Alarm Notication.
Figure 2-3 Conguring alarm notications
Table 2-2 Parameter description
Parameter Description Exampl
Anti-DDoS Indicates whether the alarm notication
function is enabled. There are two values:
● : enabled
● : disabled
If the function is in disabled state, click
Topic You can select an existing topic or click View
Topic to create a topic.
For details about topics, see the
Message Notication User Guide
Step 5 Click OK to enable alarm
----End
e Value
to set it to .
N/A
Simple
.
notication.
2.3 Adjusting Security Settings
Scenarios
You can adjust security settings after Anti-DDoS is enabled.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 8
Page 12

Anti-DDoS
User Guide 2 Operation Guide
Prerequisites
You have obtained an account and its password to log in to the management
console.
Procedure
Step 1 Log in to the management console.
Step 2 Click
Step 3 Under Security, choose Anti-DDoS. The Security Console is displayed.
Step 4 On the Anti-DDoS > Instances page, locate the target IP address and click
Advanced Settings in the Operation column, as shown in Figure 2-4.
Figure 2-4 Instance IP address list
Step 5 In the displayed Advanced Settings dialog box, set required parameters.
Figure 2-5 Page for setting protection parameters
in the upper left corner and select the desired region or project.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 9
Page 13

Anti-DDoS
User Guide 2 Operation Guide
Table 2-3 Parameter description
Parameter Description
Trac
Cleaning
Threshold
Anti-DDoS scrubs trac when detecting that the incoming
trac of an IP address exceeds the threshold.
Set this parameter based on the actual service access trac.
You are advised to set a value close to, but not exceeding, the
purchased bandwidth.
NOTE
If your service trac is larger than the value of Trac Cleaning
Threshold you set,
intercepted. If service trac does not trigger scrubbing, no trac is
intercepted.
trac scrubbing is triggered. Only attack trac is
CC Defense CC defense is available only for clients supporting the full HTTP
protocol stack because CC defense works in redirection or
redirection+verication code mode. If your client does not
support the full HTTP protocol stack, you are advised to disable
CC defense.
HTTP Request
Threshold
This parameter is required only when CC Defense is set to
Enable. The unit is qps (short for queries per second). QPS is a
common measure of the amount of search trac an
information retrieval system, such as a search engine or a
database, receives during one second.
This parameter is used to defend against a large number of
malicious requests targeting websites. Defense against CC
attacks, which aim to exhaust server resources by sending
specially crafted GET or POST requests, is triggered when the
HTTP request rate on a site reaches the selected value. In EIP
protection, the maximum recommended value is 5000. In ELB
protection, the value can be larger
You are advised to set this parameter to the maximum number
of HTTP requests that can be processed by the deployed
service. Anti-DDoS will automatically scrub
trac if detecting
that the total number of requests exceeds the congured HTTP
request threshold. If the value is too large, CC defense will not
be triggered promptly.
● If the actual HTTP request rate is smaller than the
congured value, the deployed service is able to process all
HTTP requests, and Anti-DDoS does not need to be involved.
● If the actual HTTP request rate is greater than or equal to
congured value, Anti-DDoS triggers CC defense to
the
analyze and check each request, which aects responses to
normal requests.
Step 6 Click OK to save the settings.
----End
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 10
Page 14

Anti-DDoS
User Guide 2 Operation Guide
2.4 Viewing a Monitoring Report
Scenarios
This section describes how to view the monitoring report of an instance IP address,
covering the current protection status, protection settings, and the
anomalies within the last 24 hours.
Prerequisites
You have obtained an account and its password to log in to the management
console.
Procedure
Step 1 Log in to the management console.
trac and
Step 2
Step 3 Under Security, choose Anti-DDoS. The Security Console is displayed.
Step 4 On the Anti-DDoS > Instances page, locate the IP addresses for which Anti-DDoS
Step 5 On the Monitoring Report page, view monitoring details about an instance IP
Click
has been enabled and click the IP address in the Instance IP Address or View
Monitoring Report in the Operation column.
Figure 2-6 Viewing a monitoring report
address.
● You can view information such as the current protection status, protection
● A 24-hour defense
● The attack event list within one day records DDoS attacks on the ECS within
in the upper left corner and select the region or project.
settings, and the
minute intervals. It includes the following information:
Trac (Kbps) displays the trac status of the selected ECS, including
–
the incoming attack trac and normal trac.
– Packet Rate (pps) displays the packet rate of the selected ECS, including
the attack packet rate and normal incoming packet rate.
one day, including cleaning events and black hole events.
trac and anomalies within the last 24 hours.
trac chart is generated from data points taken in ve-
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 11
Page 15

NO TE
Anti-DDoS
User Guide 2 Operation Guide
Figure 2-7 Monitoring report
On the Monitoring Report page, click to download the monitoring report about the
instance IP address.
----End
2.5 Viewing an Interception Report
Scenarios
This topic describes how to view the protection statistics, including the trac
cleaning frequency, cleaned trac amount, weekly top 10 attacked instance IP
addresses, and total number of intercepted attacks of all instance IP addresses of
a user.
Prerequisites
You have obtained an account and its password to log in to the management
console.
Procedure
Step 1 Log in to the management console.
Step 2 Click
in the upper left corner and select the desired region or project.
Step 3 Under Security, choose Anti-DDoS. The Security Console is displayed.
Step 4 On the Anti-DDoS > Security Report page, view the protection statistics of all
instance IP addresses of a user, as shown in Figure 2-8.
You can set Report Date to view the security report within a
(one week long). You can query statistics of the last four weeks, including the
number of cleaning times, cleaned
addresses, and total number of intercepted attacks.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 12
trac volume, top 10 attacked public IP
specied time range
Page 16

NO TE
Anti-DDoS
User Guide 2 Operation Guide
Figure 2-8 Interception report
On the Statistics page, click to download monitoring reports to view protection
statistics of a certain period of time.
----End
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 13
Page 17

Anti-DDoS
User Guide 3 FAQs
3 FAQs
3.1 What Is Anti-DDoS?
The Anti-DDoS trac cleaning service (Anti-DDoS for short) defends elastic IP
addresses (EIPs) against network- and application-layer distributed denial of
service (DDoS) attacks and sends alarms immediately when detecting an attack.
In addition, Anti-DDoS improves the utilization of bandwidth and ensures the
stable running of users' services.
Anti-DDoS monitors the service
trac in real time. It then cleans attack trac according to user-congured
defense policies so that services run as normal. In addition, monitoring reports are
generated, presenting users with clear network security evaluations.
trac from the Internet to EIPs to detect attack
3.2 What Services Can Anti-DDoS Protect?
Anti-DDoS provides the
by users.
trac cleaning function for public IP addresses purchased
3.3 How Do I Use Anti-DDoS?
The Anti-DDoS protection is automatically enabled for the elastic IP addresses you
purchased. If the protection is not enabled for any IP address, enable it by
following the instructions in Enabling Anti-DDoS.
3.4 What Kinds of Attacks Does Anti-DDoS Defend Against?
Anti-DDoS helps users cope with
connection exhaustion and slow-connection attacks and can help users defend
against the following attacks:
● Web server attacks
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 14
trac attacks with ease. It can precisely identify
Page 18

Anti-DDoS
User Guide 3 FAQs
Such as SYN ood, HTTP ood, Challenge Collapsar (CC), and slowconnection attacks
● Game attacks
Such as User Datagram Protocol (UDP) ood, SYN ood, Transmission Control
Protocol (TCP), and fragment attacks
● HTTPS server attacks
Such as SSL DoS and DDoS attacks
● DNS server attacks
Such as attacks targeted at vulnerabilities in the Domain Name Server (DNS)
protocol stack, DNS
miss attacks
reection attacks, DNS ood attacks, and DNS cache-
3.5 Will I Be Promptly Notied When an Attack Is
Detected?
You will be promptly
alarm notication.
On the Anti-DDoS console page, click Congure Alarm Notication in the upper
right corner to enable the alarm notication function. Then you will receive
notications (by SMS or email) if a DDoS attack is detected.
notied when an attack is detected after you have enabled
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 15
Page 19

Anti-DDoS
User Guide A Change History
A Change History
Released On Description
2018-08-15 This issue is the rst ocial release.
Issue 01 (2018-08-15) Copyright © Huawei Technologies Co., Ltd. 16
 Loading...
Loading...