Page 1

HP Medical Archive Solution
audit message reference
Part number: AG583-96009
Fourth edition: October 2007
Page 2

Legal and notice information
© Copyright 2005, 2007 Hewlett-Packard Development Company, L.P.
Hewlett-Packard Company makes no warranty of any kind with regard to this material, including, but not limited to, the implied warranties of
merchantability and fitness for a particular purpose. Hewlett-Packard shall not be liable for errors contained herein or for incidental or consequential
damages in connection with the furnishing, performance, or use of this material.
This document contains proprietary information, which is protected by copyright. No part of this document may be photocopied, reproduced, or
translated into another language without the prior written consent of Hewlett-Packard. The information is provided “as is” without warranty of any
kind and is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements
accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for
technical or editorial errors or omissions contained herein.
Adobe® and Acrobat® are trademarks of Adobe Systems Incorporated.
Microsoft, Windows, Windows NT, and Windows XP are U.S. registered trademarks of Microsoft Corporation.
UNIX® is a registered trademark of The Open Group.
HP Medical Archive Solution audit message reference
Page 3

Contents
About This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Currency . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Intended Audience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Fonts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
HP Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Product Warranties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Subscription Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
HP Web Sites. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Documentation Feedback. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
1 Audit Message Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Overview of Auditing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Audit Message Flow. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Message Retention. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Message Level Filtering. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Audit Log File Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Access via Microsoft Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Audit File Naming Convention . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
2 File and Message Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Audit Log File Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Audit Message Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Data Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Event-Specific Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Common Elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Interpreting a Sample Audit Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
3 Message Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
System Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Object Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Volume Management Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
HTTP Protocol Audit Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
DICOM Audit Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
File System Gateway Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
External Audit Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Audit Message Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
ARCB—Archive Volume Retrieve Begin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
ARCE—Archive Volume Retrieve End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
ASCE—Archive Volume Populate. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
ATCE—Staging Volume Populate. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
BKSB—Backup Store Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
BKSE—Backup Store End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
CBRB—Object Receive Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
CBRE—Object Receive End. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
CBSB—Object Send Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
CBSE—Object Send End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
CDAD—DICOM Study Add . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
DASC—DICOM Association Close . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
DASE—DICOM Association Establish. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
DASF—DICOM Association Fail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
HP Medical Archive Solution audit message reference 3
Page 4

DCFE—DICOM C–FIND End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
DCFS—DICOM C–FIND Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
DCME—DICOM C–MOVE End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
DCMS—DICOM C–MOVE Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
DCMT—DICOM Storage Commitment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
DCPE—DICOM C–STORE End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
DCPS—DICOM C–STORE Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
DCSF—DICOM C–STORE Fail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
ETAF—Security Authentication Failed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
ETCA—TCP/IP Connection Establish . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
ETCC—TCP/IP Connection Close . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
ETCF—TCP/IP Connection Fail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
ETCR—TCP/IP Connection Refused . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
FCRE—File Create . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
FDEL—File Delete. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
FMFY—File Modify . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
FRNM—File Rename . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
FSTG—File Store to Grid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
FSWI—File Swap In. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
FSWO—File Swap Out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
HCPE—HTTP PUT C–STORE End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
HCPS—HTTP PUT C–STORE Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
HDEL—HTTP DELETE Transaction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
HGEE—HTTP GET Transaction End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
HGES—HTTP GET Transaction Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
HHEA—HTTP HEAD Transaction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
HOPT—HTTP OPTIONS Transaction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
HPOE—HTTP POST Transaction End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
HPOS—HTTP POST Transaction Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
HPUE—HTTP PUT Transaction End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
HPUS—HTTP PUT Transaction Start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
HTSC—HTTP Session Close . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
HTSE—HTTP Session Establish. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
OHRP—Object Handle Repoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
RPSB—Replication Session Begin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
RPSE—Replication Session End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
SADD—Security Audit Disable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
SADE—Security Audit Enable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
SCMT—Object Store Commit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
SREM—Object Store Remove . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
SVRF—Object Store Verify Fail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
SVRU—Object Store Verify Unknown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
SYSD—Node Stop. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
SYSU—Node Start. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
TACB—Grid Task Action Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
TACE—Grid Task Action End . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
TSGC—Grid Task Stage Change. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
TSTC—Grid Task State Change. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Figures
1 Audit Message Flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
2 Audit Message Retention . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
3 Default Audit Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Tables
1 Audit Message Filter Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
4
Page 5

2 Data Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
3 Common Elements of Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
4 System Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
5 Object Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
6 Volume Management Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
7 HTTP Protocol Audit Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
8 DICOM Audit Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
9 File System Gateway Audit Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
10 ARCB—Archive Volume Retrieve Begin Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
11 ARCE—Archive Volume Retrieve End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
12 ASCE—Archive Volume Populate Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
13 ATCE—Staging Volume Populate Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
14 BKSB—Backup Store Begin Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
15 BKSE—Backup Store End Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
16 CBRB—Object Receive Begin Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
17 CBRE—Object Receive End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
18 CBSB—Object Send Begin Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
19 CBSE—Object Send End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
20 CDAD—DICOM Study Add Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
21 DASC—DICOM Association Close Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
22 DASE—DICOM Association Establish Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
23 DASF—DICOM Association Fail Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
24 DCFE—DICOM C–FIND End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
25 DCFS—DICOM C–FIND Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
26 DCME—DICOM C–MOVE End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
27 DCMS—DICOM C–MOVE Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
28 DCMT—DICOM Storage Commitment Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
29 DCPE—DICOM C–STORE End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
30 DCPS—DICOM C–STORE Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
31 DCSF—DICOM C–STORE Fail Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
32 ETAF—Security Authentication Failed Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
33 ETCA—TCP/IP Connection Establish Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
34 ETCC—TCP/IP Connection Close Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
35 ETCF—TCP/IP Connection Fail Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
36 ETCR—TCP/IP Connection Refused Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
37 FCRE—File Create Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
38 FDEL—File Delete Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
39 FMFY—File Modify Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
40 FRNM—File Rename Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
41 FSTG—File Store to Grid Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
42 FSWI—File Swap In Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
43 FSWO—File Swap Out Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
44 HCPE—HTTP PUT C–STORE End Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
45 HCPS—HTTP PUT C–STORE Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
46 HDEL—HTTP DELETE Transaction Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43
47 HGEE—HTTP GET Transaction End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
48 HGES—HTTP GET Transaction Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
49 HHEA—HTTP HEAD Transaction Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
50 HOPT—HTTP OPTIONS Transaction Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
51 HPOE—HTTP POST Transaction End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
52 HPOS—HTTP POST Transaction Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
53 HPUE—HTTP PUT Transaction End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
54 HPUS—HTTP PUT Transaction Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
55 HTSC—HTTP Session Close Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
56 HTSE—HTTP Session Establish Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
57 OHRP—Object Handle Repoint Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50
58 RPSB—Replication Session Begin Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
59 RPSE—Replication Session End Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
60 SADD—Security Audit Disable Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
HP Medical Archive Solution audit message reference 5
Page 6

61 SADE—Security Audit Enable Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
62 SCMT—Object Store Commit Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
63 SREM—Object Store Remove Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
64 SVRF—Object Store Verify Fail Fields. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
65 SVRU—Object Store Verify Unknown Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
66 SYSD—Node Stop Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
67 SYSU—Node Start Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
68 TACB—Grid Task Action Begin Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54
69 TACE—Grid Task Action End Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
70 TSGC—Grid Task Stage Change Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
71 TSTC—Grid Task State Change Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
6
Page 7

About This Guide
The Audit Management System (AMS) service stores audit messages of grid activity and events to a set of
text log files. To enable you to read and analyze the audit trail, this document provides information on the
structure and content of the text file log.
The objectives of this document are to:
• Describe how to access the current log file and archived logs
• Describe the text file format
• Provide a reference for common audit messages
Currency
The content is current with the AMS service software version 4.9.0 through 4.11, as included in the
HP Medical Archive system release 7. To find the version number of your AMS service software:
1. Using the NMS interface, select the AMS service, Overview page.
The version number is reported in the Node Information table.
2. To check the software release version, check the SSM service, Services page. The software release
version is reported in the Packages table as the storage-grid-release. The release should be 7.0 or later.
If you have an earlier version of the AMS service, contact HP Support.
Intended Audience
The content of this guide is intended for administrators responsible for producing reports of network activity
and usage that require analysis of the audit messages.
You are assumed to have a sound understanding of the nature of audited activities within the HP Medical
Archive system. To use the text log file, you are assumed to have access to the configured audit share on
the Admin Node server hosting the AMS service.
References
This document assumes familiarity with many terms related to computer operations and programming,
network communications, and operating system file operations. There is wide use of acronyms. To assist
you, there is a glossary at the back of this reference (page 59).
Conventions
This guide adheres to conventions for terminology to avoid confusion or misunderstanding. There are also
conventions for typography to enhance readability and usefulness of the text.
Terminology
There is some room for confusion between common computer network terminology for “server” and “node”
as they are used in HP Medical Archive products and documents.
A server is usually thought of as a piece of computing hardware that provides data services to requesting
network clients; a resource providing network, computational, and storage services. Within the context of
the HP Medical Archive, a server is an entity hosting one or more grid services.
Nodes in a network are usually defined as an independent entity with a unique network identity, running
on a resource. In this text, the use of the phrase “grid node” refers to an addressable entity on the grid that
provides and uses functional services within the grid to perform one or more tasks. Each grid node has a
unique “node ID”. These include: ADC, CMS and LDR. In the HP Medical Archive User Guide and other
user documents these are referred to as “services”.
Fonts
In contrast, the HP Medical Archive packages the grid service modules into “nodes”. For example, the
“Storage Node” usually incorporates the LDR and SSM services on one server.
To assist you in easily picking out the elements of importance, changes from the standard font are used:
HP Medical Archive Solution audit message reference 7
Page 8

• Items upon which you act are shown in bold. These include:
• Sequences of selections from the navigation tree, tabs, and page options, such as: LDR X
Replication X Configuration.
• Buttons or keys to click or press, such as Apply or <Tab>.
• Radio buttons or check buttons to enable or disable, such as Reset DICOM Counts.
• Field prompts, names of windows and dialogs, messages, and other literal text in the interface is shown
as standard text, such as the LDR State pull down menu, or the Sign In... window.
• Items within the narrative that require emphasis appear in italics.
• Coding samples or interactions with a command terminal are shown in the fixed space font:
version=1.0 ?>
Any italicized portion indicates variable data you provide to meet your needs.
Keyboard keys that use words or standard abbreviations are shown within angle brackets, such as <Ctrl>
for the control key, <Tab>, <space>, and <Enter>.
HP Technical Support
Telephone numbers for worldwide technical support are listed on the HP support Web site:
http://www.hp.com/support/
Collect the following information before calling:
• Technical support registration number (if applicable)
• Product serial numbers
• Product model names and numbers
• Applicable error messages
• Operating system type and revision level
• Detailed, specific questions
<?xml
.
For continuous quality improvement, calls may be recorded or monitored.
Product Warranties
For information about HP StorageWorks product warranties, see the warranty information Web site:
http://www.hp.com/go/storagewarranty
Subscription Service
HP strongly recommends that customers sign up online using the Subscriber's choice Web site:
http://www.hp.com/go/e-updates
• Subscribing to this service provides you with e-mail updates on the latest product enhancements, newest
versions of drivers, and firmware documentation updates as well as instant access to numerous other
product resources.
• After signing up, you can quickly locate your products by selecting Business support and then Storage
under Product Category.
HP Web Sites
For other product information, see the following HP web sites:
• http://www.hp.com
• http://www.hp.com/go/storage
• http://www.hp.com/support/
• http://www.docs.hp.com
.
Documentation Feedback
HP welcomes your feedback.
8
Page 9

To make comments and suggestions about product documentation, please send a message to
storagedocsfeedback@hp.com. All submissions become the property of HP.
HP Medical Archive Solution audit message reference 9
Page 10

10
Page 11
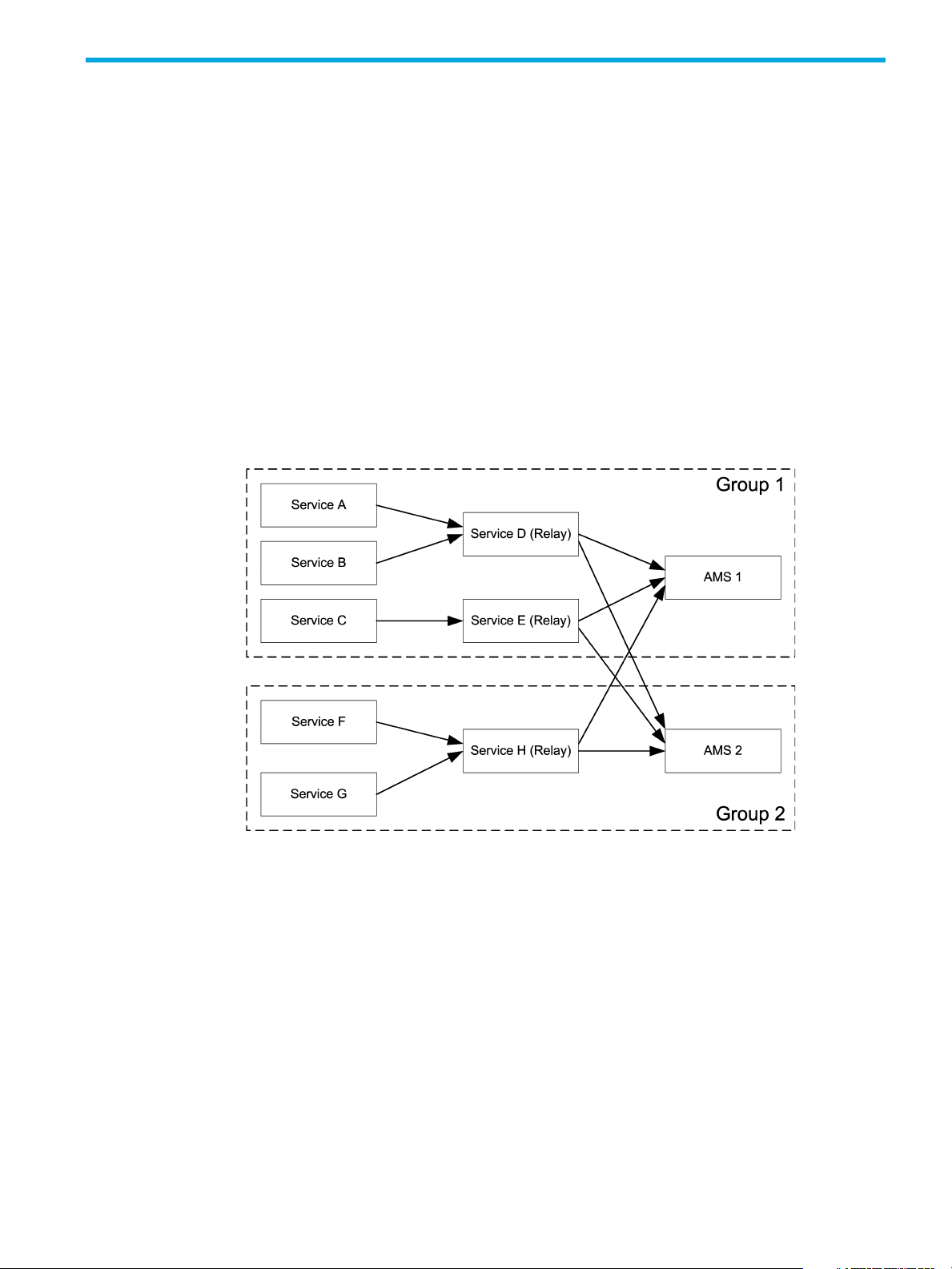
1 Audit Message Overview
Overview of Auditing
As services in the grid perform various activities and process events, audit messages are generated to
retain a record of grid activity. These messages are processed by the Audit Management System (AMS)
service on the Admin Node server, and are stored in the form of text log files. This document provides
information on the structure and content of the text log files to enable you to read and analyze the audit
trail of grid activity.
Audit Message Flow
Audit messages are generated internally by each grid service. All system services generate audit messages
during normal system operation. These messages are sent to all connected AMS services for processing
and storage, so that each AMS maintains a complete record of grid activity.
Some grid services can be designated as audit message relay services. They act as collection points to
reduce the need for every service to send its audit messages to all connected AMS services. Notice in
Figure 1 that each relay service must send messages to all AMS destinations, whereas services can send
messages to just one relay service.
Figure 1 Audit Message Flow
Relay services are designated at the time the grid topology is configured. In an HP Medical Archive grid,
the ADC service is designated as the audit message relay.
Message Retention
Once an audit message is generated, it is stored on the local server of the originating service until it has
been committed to all connected AMS servers, or a designated audit relay service. The relays in turn store
the message until it is committed at all AMS services. This process includes a confirmation (positive
acknowledgment) to ensure no messages are lost.
HP Medical Archive Solution audit message reference 11
Page 12
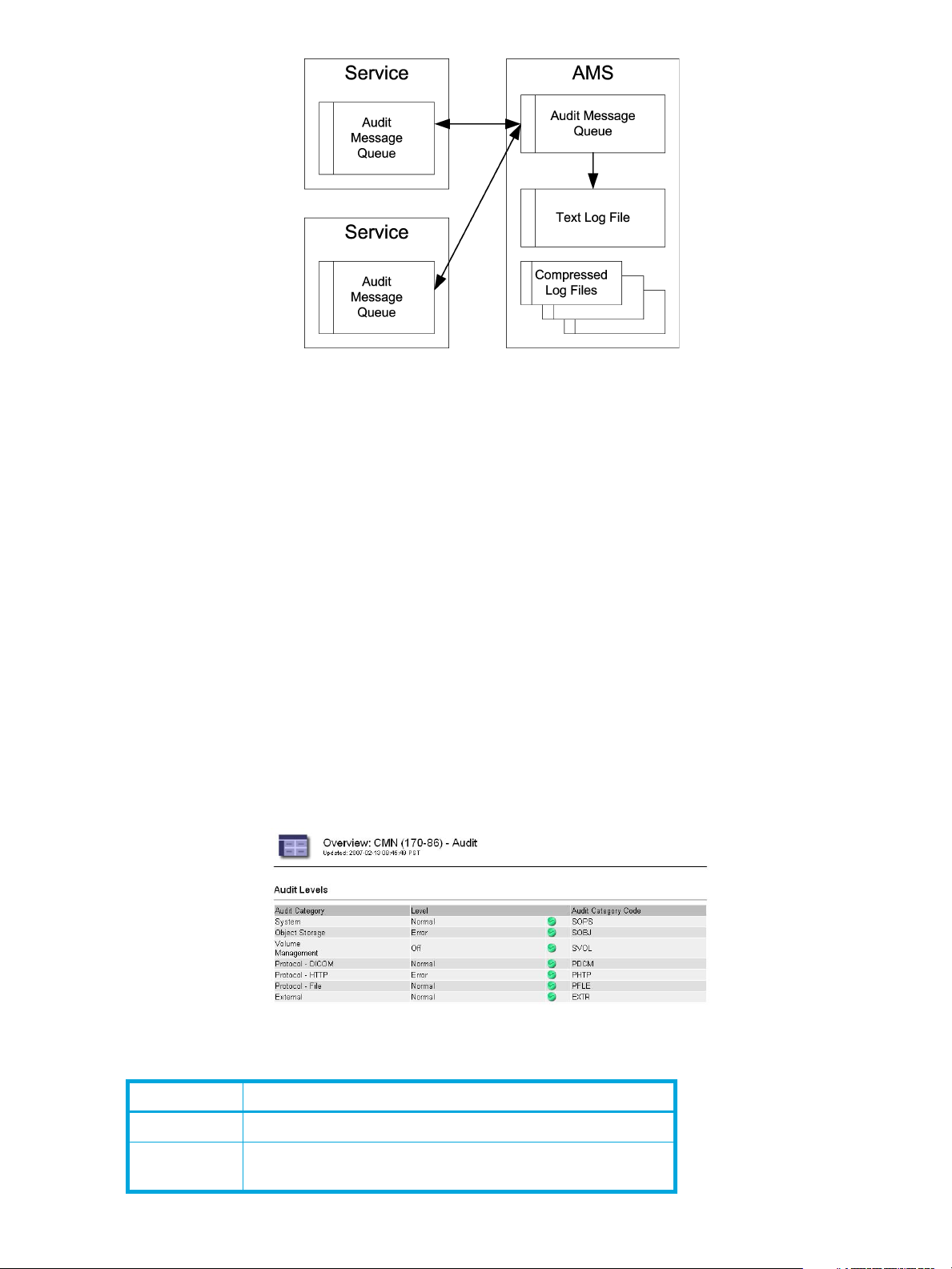
Figure 2 Audit Message Retention
Messages arrive at the AMS and are stored in a queue pending confirmed write to the text log file
audit.log. Confirmation of the arrival of messages is sent to the originating service (or audit relay) to permit
the originator to delete its copy of the message.
Only after a message has been committed to storage at the AMS can it be removed from the queue. The
local message buffer at the audit relay service (ADC) and the AMS each have an alarm (AMQS)
associated with it, in the event the backlog becomes unusually large. At times of peak activity, the rate at
which audit messages are arriving may be faster than they can be relayed to the audit repository on the
AMS or committed to storage in the audit log file, causing a temporary backlog that will clear itself when
grid activity declines.
Once a day the active audit log audit.log is saved to a file named for the date the file is saved (in the
format YYYY-MM-DD.txt) and a new audit.log file is started. Audit logs are compressed when they are
seven days old and are renamed YYYY-MM-DD.txt.gz (where the original date is preserved).
Over very long periods of time, this can result in consumption of the 50 GB of storage available for audit
logs on the server hosting the AMS. Once the audit directory on the AMS is full, the oldest log files in the
directory are automatically deleted until the directory contains less than 50 GB. Depending upon the
regulatory or administrative requirements of your enterprise, you may want to archive the compressed audit
log files to some other media such as DVD-R, or into the grid itself.
Message Level Filtering
The AMS service filters incoming audit messages based on settings made in the CMN X Audit component.
Figure 3 Default Audit Settings
Table 1 Audit Message Filter Levels
Level Description
Off No audit messages from the category are logged.
Error Only error messages are logged; those for which the result
12 Audit Message Overview
code was not “successful” (SUCS).
Page 13

Table 1 Audit Message Filter Levels
Level Description
Normal Standard transactional messages are logged; all messages
listed in this guide for the category.
Debug Trace messages are logged; for troubleshooting only.
The messages included for any particular level in this table includes those that would be logged at the
higher levels. Therefore, the Normal level includes all of the Error messages.
The “Introduction” section of Chapter 3 (page 19) includes tables that sort the audit messages into the
categories shown in the table (that is, System Messages, Object Storage Messages, Volume Management
Messages, DICOM Messages, HTTP Messages, and File System Gateway Messages). The Volume
Management category of audit messages is used only by Enterprise installations of the HP Medical
Archive. The External category of audit message is only used by external custom applications that submit
audit messages using the HPMA HTTP API.
NOTE: Debug level messages are not included in this reference guide.
Audit Log File Access
The audit file share configured on your Admin Node contains the active audit.log file and any compressed
audit log files. Depending upon the configuration at your site, you can access this file share with either an
NFS or CIFS client.
Access via Microsoft Windows
If using Windows to access network file shares, be aware that some versions of Windows do not support
using two different logins (user name and password combinations) to access the same device (IP address).
That means that if you have one login authentication to access the managed file system of a secondary
FSG service on a combined Admin/Gateway Node, and a different login to access the Audit Log on the
same combined Admin/Gateway Node, you may not be able to have both file shares connected at the
same time. You may be required to disconnect the secondary FSG share before you can connect to the
Audit Log, and vice versa.
Audit File Naming Convention
The active audit log file is named:
audit.log
Once a day, the active audit log is closed and saved to an archived log file named:
YYYY-MM-DD.txt
where date stamp in the file name indicates when the file was archived. If more than one audit log file is
manually created in a single day, subsequent files are named YYYY-MM-DD.txt.1,
YYYY-MM-DD.txt.2, etc.
After seven days, these archived log files are compressed, and saved to a file named:
YYYY-MM-DD.txt.gz
where the original date that the file was created is preserved in the file name.
To access a compressed audit log file:
1. Make a local copy of the file to work with.
2. Decompress the file. This process requires a decompression utility. We suggest “7-Zip”, wh ich i s a free
download from:
http://www.7-zip.org/
The next chapter provides details of the file’s internal structure and the syntax of audit messages.
HP Medical Archive Solution audit message reference 13
Page 14

14 Audit Message Overview
Page 15
2 File and Message Format
Audit Log File Format
The audit log file at the AMS contains a collection of individual audit messages. Each audit message
contains:
• the UTC time of the event that triggered the audit message (ATIM) in ISO 8601 format (that is,
YYYY-MM-DDTHH:MM:SS.UUUUUU where UUUUUU are microseconds), followed by a space.
• the audit message itself, enclosed within square brackets “[]” and beginning with “AUDT:”. The
message structure is discussed in more detail in the next section.
The following is part of a sample log file. Messages are wrapped within the boundaries shown, ending
after the ASES attribute and double closing brackets “]]”. The “\n” (line feed) characters at the end of each
message are not shown.
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5ddbc/0/44a198def43f13f69f4649980193f7a
9_254"][UUID(CSTR):"F2485A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(FC32):SUCS][AVER(UI
32):5][ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32)
:FSGC][ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146600838125065
]]
2006-05-03T01:40:37.787159
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5ddbc/0/44a198def43f13f69f4649980193f7a
9_249"][UUID(CSTR):"11BA3243-AC7A-43CC-B925-178528780365"][RSLT(FC32):SUCS][AVER(UI
32):5][ATIM(UI64):1146620437787159][ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32)
:FSGC][ATID(UI64):1940194281971359843][ASQN(UI64):13658][ASES(UI64):114660083812506
5]]
2006-05-03T01:40:37.799230
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5ddbc/0/44a198def43f13f69f4649980193f7a
9_257"][UUID(CSTR):"B93B1D96-22E9-47D8-B099-8F32A1A94FB9"][RSLT(FC32):SUCS][AVER(UI
Audit Message Format
Audit messages exchanged within the grid include some standard information common to all messages,
and specific content describing the event or activity being reported.
The following is a sample audit message as it might appear in the audit.log file:
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5ddbc/0/44a198def43f13f69f4649980193f
7a9_254"]
[UUID(CSTR):"F2485A1A-9E84-49C6-98A1-1FF59D500E1B"]
[RSLT(FC32):SUCS][AVER(UI32):5][ATIM(UI64):1146620437775242]
[ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32):FSGC]
[ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146600838125065]]
Each audit message is logged as a string composed of attribute elements that are:
• Enclosed in square brackets “[ ]”
• Introduced by the string “AUDT”, indicating an audit message
• Do not have delimiters (no commas or spaces) between attributes
• Terminated by a line feed character (“\n”)
Each element includes: an attribute code, data type, and value. It takes the format:
[ATTR(type):value][ATTR(type):value]...
[ATTR(type):value]\n
Where:
HP Medical Archive Solution audit message reference 15
Page 16
The number of attribute elements in the message depends on the event type of the message.
See “Interpreting a Sample Audit Message” on page 17 for a step-by-step description of how to interpret
an audit message.
Data Types
The data types encountered in the audit messages are:
Table 2 Data Types
Type Description
UI32 Unsigned long integer (32 bits); it can store the numbers
UI64 Unsigned double long integer (64 bits); it can store the numbers
FC32 Four Character Constant; a 32-bit unsigned integer value
• ATTR is a four-character code for the attribute being reported. These attributes can either be related
to event-specific messages (as described in Chapter 3, starting on page 19), or may be attributes
common to all audit messages (as described later in this chapter, on page 17).
•
type is a four-character identifier of the programming data type of the value, such as: UI64, FC32,
and so on. See “Data Types” on page 16. The type is enclosed in brackets “( )”.
•
value is the content of the attribute, typically a numeric or text value. Values always follow a colon
“:”. Values of data type CSTR are surrounded by double quotes “ “.
0–4,294,967,295.
0– 18,446,744,073,709,551,615.
represented as four ASCII characters such as: “ABCD”.
IP32 IP Address; a 32-bit IP address representation.
CSTR A string; a variable length array of UTF-8 characters. In brief, the
most relevant escaping rules state:
• characters may be replaced by their hexadecimal equivalents
• double quotes are represented as \"
• backslashes are represented as \\
Event-Specific Data
Following the opening “[AUDT:” container that identifies the message itself, the next set of attributes are
items related to the event or action described by the audit message. These attributes are identified in italics
in the sample message below:
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshareCT_1200_1_5ddbce950bc640d1ed6a21d5005fb802/044a1
98def43f13f69f4649980193f7a9_254"][UUID(CSTR):"F2485A1A-9E84-49C6-98A1-1FF59D500E
1B"][RSLT(FC32):SUCS]
[AVER(UI32):5][ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][
AMID(FC32):FSGC][ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146
600838125065]]
The event that these attributes describe is identified using the ATYP element described in “Common
Elements” below. The attributes for each event are described in Chapter 3, “Message Reference” on
page 19.
(in the format \xHH, where HH is the hexadecimal value
representing the character)
16 File and Message Format
Page 17
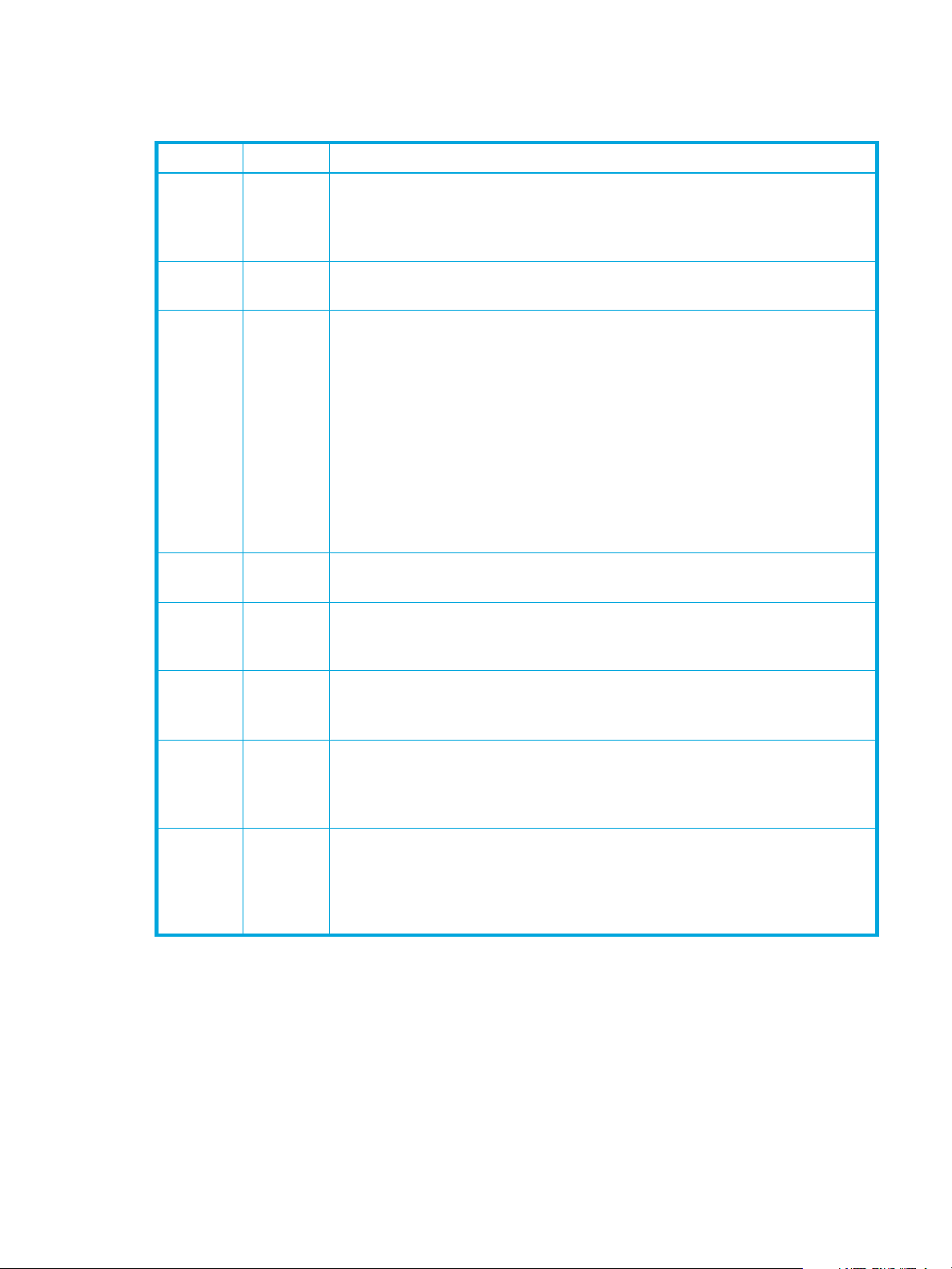
Common Elements
After the event-specific information is a set of elements common to all audit messages:
Table 3 Common Elements of Audit Messages
Code Type Description
AVER UI32 Version—The version of the audit message. As the HP Medical Archive
ATYP FC32 Event Type—A four-character identifier of the event being logged. This governs
ATIM UI64 Timestamp—The time the event was generated that triggered the audit
software evolves, new versions of services may incorporate new features in
audit reporting. This field enables backward compatibility in the AMS to
process messages from older versions of services.
the “payload” content of the message—the attributes which are included.
message, measured in microseconds since the operating system epoch
(00:00:00 UTC on 1 January, 1970). Note that most available tools for
converting the timestamp to local date and time are based on milliseconds.
Rounding or truncation of the logged timestamp may be required.
The human-readable time that appears at the beginning of the audit message
in the audit.log file is the ATIM attribute in ISO 8601 format. (That is, the date
and time is represented as YYYY-MM-DDTHH:MM:SS.UUUUUU, where the T is
a literal string character indicating the beginning of the time segment of the
date. UUUUUU are microseconds).
ATID UI64 Trace ID—An identifier that is shared by the set of messages that were
triggered by a single event.
ANID UI32 Node ID—The grid node ID assigned to the service that generated the
message. Each service is allocated a unique identifier at the time the
HP Medical Archive is configured and installed. This ID cannot be changed.
AMID FC32 Module ID—A four-character identifier of the module ID that generated the
message. This indicates the code segment within which the audit message was
generated.
ASQN UI64 Sequence Count—A counter that is incremented for each generated audit
message on the grid node (ANID). This counter is reset to zero at service
restart. It can be used for consistency checks to ensure that no audit messages
have been lost.
ASES UI64 Audit Session Identifier—Indicates the time at which the audit system was
initialized after the service started up. This time value is measured in
microseconds since the operating system epoch (00:00:00 UTC on 1 January,
1970). It can be used to identify which messages were generated during a
given runtime session.
Interpreting a Sample Audit Message
The following is a sample audit message, as it might appear in the audit.log file:
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5d/044a198def43f1_254"][UUID(CSTR):"F
2485A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(FC32):SUCS][AVER(UI32):5]
[ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32):FSG
C][ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146600838125065]]
The audit message contains information about the event being recorded, as well as information about the
audit message itself.
HP Medical Archive Solution audit message reference 17
Page 18

To identify which event is recorded by the audit message, look for the ATYP attribute (highlighted below):
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5d/0/44a198def43f1_254"][UUID(CSTR):"
F2485A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(FC32):SUCS][AVER(UI32):5]
[ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32):FSGC]
[ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146600838125065]]
The value of this attribute is FSWO. Consult Chapter 3 to discover that FSWO represents a File Swap Out
event, which logs the removal of a file from the FSG local cache. The table in “FSWO—File Swap Out” on
page 43 documents the attributes reported for FSWO. From this list you can discover, for example, that the
UUID attribute in the audit message records the unique identifier of the file that was swapped out of the
FSG cache:
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5d/0/44a198def43f1_254"][UUID(CSTR):"F24
85A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(FC32):SUCS]
[AVER(UI32):5][ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][
AMID(FC32):FSGC][ATID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146
600838125065]]
To discover when the swap-out event occurred, look at the UTC time stamp at the beginning of the audit
message. This value is a human-readable version of the ATIM attribute of the audit message itself
(described in “Common Elements” on page 17):
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5d/0/44a198def43f1_254"][UUID(CSTR):"
F2485A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(FC32):SUCS][AVER(UI32):5]
[ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):9990056][AMID(FC32):FSGC][A
TID(UI64):619557531566285967][ASQN(UI64):13657][ASES(UI64):1146600838125065]]
ATIM records the time, in microseconds, since the beginning of the UNIX epoch. The value
1146620437775242 translates to Wed, 03 May 2006 01:40:37 UTC.
18 File and Message Format
Page 19
3 Message Reference
A comprehensive listing of generated audit messages.
Introduction
This chapter provides detailed descriptions of event-specific audit messages, and the attributes reported for
these messages.
Each audit message is first listed in a table that groups related messages by the class of activity that the
message represents. These groupings are useful both for understanding the types of activities that are
audited, and for selecting the desired type of audit message filtering (as described on page 12).
The audit messages are also listed alphabetically by their four-character codes (starting on page 23). This
alphabetic listing facilitates finding information about a specific message of interest.
The four-character codes used throughout this chapter are the ATYP values found in the audit messages, as
shown in the sample message below:
2006-05-03T01:40:37.775242
[AUDT:[FPTH(CSTR):"/fsg/cifsshare/CT_1200_1_5d/0/44a198def43f1_
254"][UUID(CSTR):"F2485A1A-9E84-49C6-98A1-1FF59D500E1B"][RSLT(F
C32):SUCS][AVER(UI32):5]
[ATIM(UI64):1146620437775242][ATYP(FC32):FSWO][ANID(UI32):99900
56][AMID(FC32):FSGC][ATID(UI64):619557531566285967][ASQN(UI64):
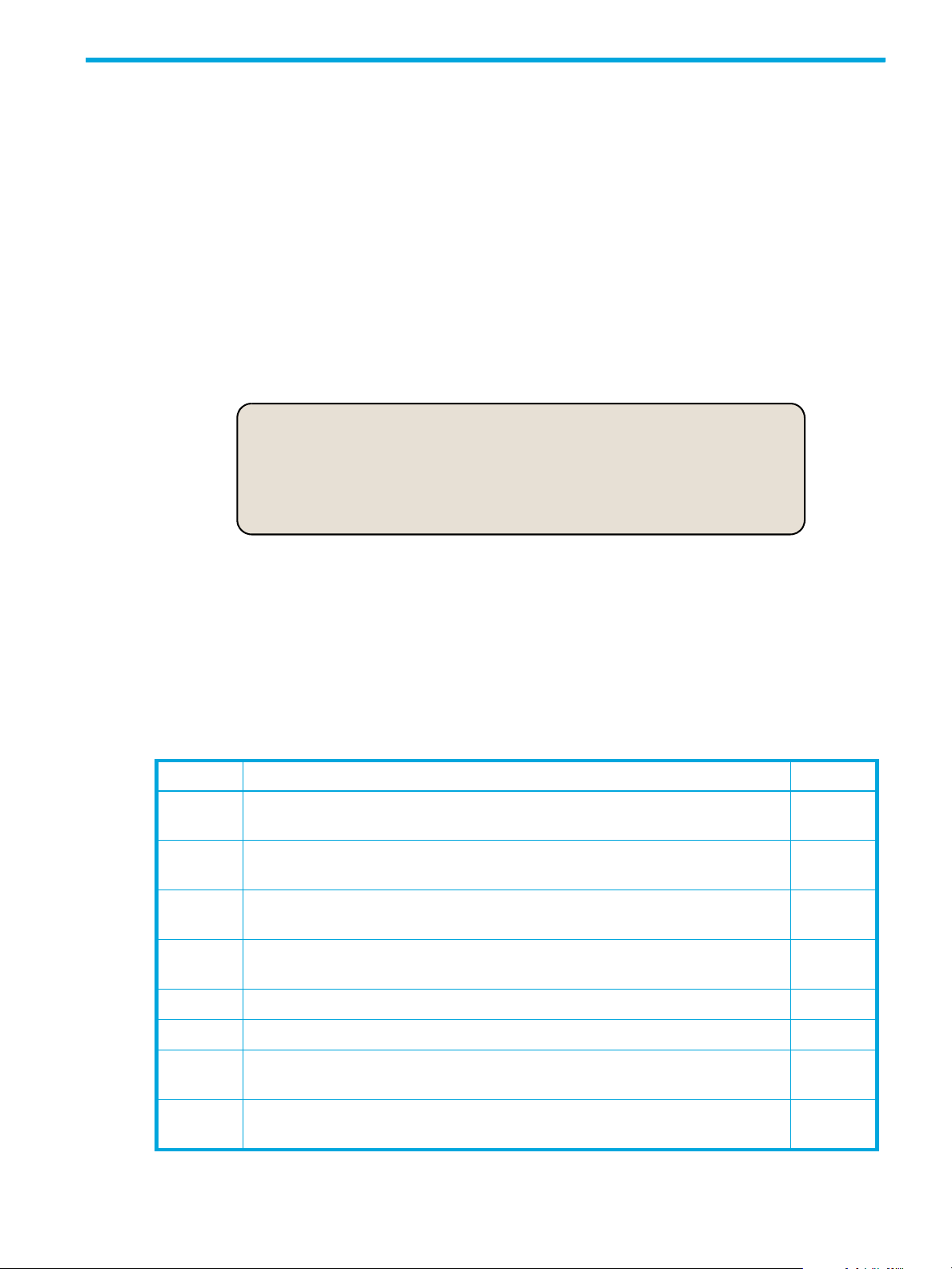
System Audit Messages
This group of messages belong to the System audit category and are for events related to:
• The auditing system itself
• Grid node states
• Grid-wide task activity (Grid Tasks)
• Service backup operations
• File System Gateway (FSG) replications
Table 4 System Audit Messages
Code Description Page
ETCA TCP/IP Connection Establish—An incoming or outgoing TCP/IP connection
was successfully established.
ETCC TCP/IP Connection Close—An established connection has been closed by
either side of the connection (normally or abnormally).
ETCF TCP/IP Connection Fail—An outgoing connection attempt failed at the lowest
level, due to communication problems.
ETCR TCP/IP Connection Refused— An incoming TCP/IP connection attempt was
not allowed.
SADD Security Audit Disable—Audit message logging has been turned off. 53
38
39
39
40
SADE Security Audit Enable—Audit message logging has been turned on. 54
ETAF Security Authentication Failed—A connection attempt using Transport Layer
Security (TLS) has failed.
SYSU Node Start—An HP Medical Archive grid service started; the nature of the
previous shutdown is indicated in the message.
HP Medical Archive Solution audit message reference 19
37
56
Page 20

Table 4 System Audit Messages (continued)
Code Description Page
SYSD Node Stop—An HP Medical Archive grid service has been gracefully
stopped.
TSTC Grid Task State Change—A grid task has been added, started, paused,
canceled, or completed.
TSGC Grid Task Stage Change—The stage of a grid task has changed. 57
TACB Grid Task Action Begin—A grid task action has begun. 56
TACE Grid Task Action End—A grid task action has completed. 57
BKSB Backup Store Begin—A service has begun a backup operation. 26
BKSE Backup Store End—A service has completed a backup operation. 26
RPSB Replication Session Begin—A service has begun a replication operation to a
secondary service.
RPSE Replication Session End—A service has completed a replication operation to
a secondary service.
Object Audit Messages
Object storage category audit messages represent events related to the storage and management of
objects within the grid. These include:
• Object storage/retrieval
• Node-to-node transfer
• Verification
Table 5 Object Audit Messages
56
58
52
53
Code Description Page
CBSB Object Send Begin—The source entity initiated a node-to-node data transfer
operation on a single piece of content.
CBSE Object Send End—The source entity completed a node-to-node data transfer
operation.
CBRB Object Receive Begin—The destination entity initiated a node-to-node data
transfer operation on a single piece of content.
CBRE Object Receive End—The destination entity completed a node-to-node data
transfer operation.
OHRP Object Handle Repoint—Indicates that the object referenced by an object
handle was changed.
SCMT Object Store Commit—A content block was completely stored and verified,
and can now be requested.
SREM Object Store Remove—A content block was deleted from a node, and can no
longer be requested directly.
SVRF Object Store Verify Fail—A content block failed verification checks. 55
SVRU Object Store Verify Unknown—Unexpected file(s) detected in the object store. 55
28
29
27
27
51
54
54
20 Message Reference
Page 21

Volume Management Audit Messages
NOTE: The Volume Management category of audit messages is supported only by Enterprise installations
of the HP Medical Archive.
The Volume Management audit messages represent events related to the operation of a Tape Node,
including the writing of objects to staging volumes in preparation for writing them to removable media,
and the writing and retrieval of archive volumes from removable media.
Note that logical Tape Node volumes do not correspond to physical volumes on the Removable Storage
Media Device.
Table 6 Volume Management Audit Messages
Code Description Page
ATCE Staging Volume Populate— A content block has been staged to a volume in
preparation for archiving.
ASCE Archive Volume Populate—A content block has been written to the archive
media, and the ARC reports the status of the write operation.
ARCB Archive Volume Retrieve Begin—The ARC begins the retrieval of a specified
content block from removable archival media.
ARCE Archive Volume Retrieve End—The content block has been retrieved from
archive media, and the ARC reports the status of the retrieval operation.
HTTP Protocol Audit Messages
HTTP Protocol audit messages (the Protocol – HTTP category) represent events related to interactions with
internal and external system components using the HTTP protocol. These include:
• Session establishment/breakdown
• Object storage
• Retrieval
• Query
Table 7 HTTP Protocol Audit Messages
Code Description Page
HTSE HTTP Session Establish—A remote host successfully established an HTTP
session to the node.
25
24
23
24
51
HTSC HTTP Session Close—An HTTP client closed a previously-established HTTP
session.
HHEA HTTP HEAD Transaction—Information about a piece of content was requested
by an HTTP client.
HGES HTTP GET Transaction Start—A request for a GET transaction to transfer
content to an HTTP client was initiated.
HGEE HTTP GET Transaction End—A GET transaction to transfer content to an HTTP
client completed.
HPUS HTTP PUT Transaction Start—A PUT transaction to transfer content from an
HTTP client was initiated.
HPUE HTTP PUT Transaction End—A PUT transaction to transfer content from an
HTTP client completed.
HP Medical Archive Solution audit message reference 21
51
47
46
46
50
49
Page 22

Table 7 HTTP Protocol Audit Messages (continued)
Code Description Page
HPOS HTTP POST Transaction Start—An HTTP client initiated a query for stored
content.
HPOE HTTP POST Transaction End—An HTTP client completed a query for stored
content.
HDEL HTTP DELETE Transaction—Logs the result of a request to delete content. 45
HOPT HTTP OPTIONS Transaction—Logs the result of a request for information about
the transactions that can be performed on content.
HCPS HTTP PUT C–STORE Start—A PUT transaction to transfer content between hosts
was initiated.
HCPE HTTP PUT C–STORE End—A PUT transaction to transfer content between hosts
completed.
DICOM Audit Messages
The Protocol – DICOM audit messages log activity related to interactions with external systems using the
DICOM protocol. These include:
• Association establishment
• C–STORE
• C–FIND
• C–MOVE
• N–ACTION (storage commitment)
Table 8 DICOM Audit Messages
49
48
48
45
44
Code Description Page
DASE DICOM Association Establish—A successful inbound or outbound DICOM
association was established with a remote host.
DASC DICOM Association Close—An established DICOM association with a remote
host closed.
DASF DICOM Association Fail—An association attempt failed (remote host cannot
process the DICOM protocol, or the request was rejected).
DCPS DICOM C–STORE Start—A transfer of content between hosts over a DICOM
association has started.
DCPE DICOM C–STORE End—A transfer of content between hosts over a DICOM
association has completed.
DCSF DICOM C–STORE Fail—A transfer of content between hosts over a DICOM
association has failed.
DCFS DICOM C–FIND Start—A remote DICOM host initiated a query for
DICOM-related content.
DCFE DICOM C–FIND End—A remote DICOM host completed a query for
DICOM-related content.
DCMS DICOM C–MOVE Start—A remote DICOM host initiated a transfer of DICOM
instances to a remote Application Entity.
30
30
31
36
35
36
32
32
33
DCME DICOM C–MOVE End—A remote DICOM host completed a transfer of
22 Message Reference
33
DICOM instances to a remote Application Entity.
Page 23

Table 8 DICOM Audit Messages (continued)
Code Description Page
DCMT DICOM Storage Commitment—A remote DICOM host initiated an operation
to check if content was previously stored.
CDAD DICOM Study Add—A new study (not previously recorded by the CMS) or a
new instance (image) has been added to a known study.
File System Gateway Audit Messages
This set of messages (the Protocol – File category) log activity related to interactions with external systems
via the File System Gateway (FSG) interface to the grid.
Table 9 File System Gateway Audit Messages
Code Description Page
FCRE File Create—Logs the addition of new files (not directories) to the FSG. 41
FDEL File Delete—Logs deletion of a file from the FSG directory tree (not from the
grid).
FRNM File Rename—Logs changes to the name or path of an existing file. 42
FMFY File Modify—Logs changes to the content of an existing file. 42
FSTG File Store to Grid—Logs the storage of content from the FSG local cache to the
grid.
FSWO File Swap Out—Logs the deletion of a file from the FSG local cache (but not
from the directory tree or grid).
34
30
41
42
43
FSWI File Swap In—Logs the retrieval of a file from the grid to the FSG local cache. 43
As content is added to the grid via the FSG, the content is first stored locally in a cache on the FSG server.
The FSG manages ingesting the content to the grid. The content in the cache can be purged if space is
needed for new content, either inbound or outbound. As the cache content is changed, additional audit
messages are logged.
Any changes made to the name or content of a file previously entered in the FSG are also logged, as are
file deletions from the FSG.
External Audit Messages
It is possible to develop a custom application using the HPMA HTTP API that saves messages generated by
an external application to the audit log file. These audit messages must follow the format of grid-generated
messages, but the meaning of these messages and their codes are controlled by the external application.
For more information on external audit messages, contact your local HP team.
Audit Message Reference
ARCB—Archive Volume Retrieve Begin
When a request is made to retrieve content stored on removable media, this message is generated as the
retrieval process begins.
HP Medical Archive Solution audit message reference 23
Page 24

Retrieval requests are processed immediately, but can be reordered to improve efficiency of retrieval from
linear media such as tape.
Table 10 ARCB—Archive Volume Retrieve Begin Fields
Code Field Description
CBID Content Block ID The unique identifier of the Content Block to be retrieved from the
archive media.
RSLT Result Indicates the result of starting the archive retrieval process.
Currently defined values are:
SUCS—the content request was received and queued for retrieval.
This audit message marks the time of an archive volume retrieval. It allows you to match the message with
a corresponding ARCE end message to determine the duration of archived content retrieval, and whether
the operation was successful.
ARCE—Archive Volume Retrieve End
When an attempt to retrieve content from removable media completes, this message is generated. If
successful, the message indicates that the data has been completely read from the archive location, and
was successfully verified. Once content has been retrieved and verified, it is delivered to the requesting
node and is cached on the Tape Node.
Table 11 ARCE—Archive Volume Retrieve End Fields
Code Field Description
CBID Content Block ID The unique identifier of the Content Block to be retrieved from the
VLID Volume Identifier The identifier of the volume on which the data was archived.
RSLT Retrieval Result The completion status of the archive retrieval process:
Matching this message with the corresponding ARCB message can indicate the time taken to perform the
archive retrieval. This message indicates whether the retrieval was successful, and in the case of failure, the
cause of the failure to retrieve the content block.
ASCE—Archive Volume Populate
This message is generated after a content block is completely written to the archive location, optionally
retrieved and verified, and the CMS notified of the location of the content block.
Table 12 ASCE—Archive Volume Populate Fields
archive media.
If an archive location for the content is not found, a Volume ID of
0 is returned.
SUCS—successful
VRFL—failed (object verification failure)
ARUN—failed (archive middleware unavailable)
CANC—failed (retrieval operation cancelled)
GERR—failed (general error)
Code Field Description
CBID Content Block Identifier The identifier of the content block stored on the archive
VLID Volume ID The unique identifier of the archive volume to which the data is
24 Message Reference
destination.
written.
Page 25

Table 12 ASCE—Archive Volume Populate Fields (continued)
Code Field Description
VREN Verification Enabled Indicates if verification is performed for content blocks. Currently
RSLT Result Indicates the result of archive process. Currently defined values
This audit message means that the specified content block has been written to archive media. If the write
fails, the result provides basic troubleshooting information about where the failure occurred. More detailed
information about archive failures can be found by examining Tape Node attributes in the NMS.
ATCE—Staging Volume Populate
This message indicates that specified content block has been written to the staging volume in preparation
for consolidation and writing to removable media.
defined values are:
VENA—verification is enabled
VDSA—verification is disabled
are:
SUCS—successful (archiving process succeeded)
VRFL—failed (object verification failed)
ARUN—failed (archive middleware was unavailable)
GERR—failed (general error)
When the CMS decides that content should be stored on a given Tape Node, the first step of the archiving
process is to temporarily save it to a staging volume on that node. The content is consolidated and
archived to removable media when a triggering condition is met (such as the number of objects or age of
the staging volume).
Table 13 ATCE—Staging Volume Populate Fields
Code Field Description
CBID Content Block ID The unique identifier of the Content Block that is staged for
archiving.
VLID Volume ID The unique identifier of the staging volume to which the content
block is written.
If the staging operation fails, a Volume ID of 0 is returned.
RSLT Result Indicates the result of the transfer of the content block to the
staging volume. Currently defined values are:
SUCS—success (content block staged successfully)
EXIS— ignored (content block was already staged)
ISFD—failed (insufficient disk space)
STER—failed (error retrieving or storing the CBID)
OFFL—failed (archiving is offline)
This message indicates that the Tape Node has staged a given content block.
HP Medical Archive Solution audit message reference 25
Page 26

BKSB—Backup Store Begin
When a service begins a backup operation—storing private structured data to the grid—this message is
generated.
Table 14 BKSB—Backup Store Begin Fields
Code Field Description
BKSI Backup Session ID The unique identifier of the backup session that is being started.
BKOI Backup Source Entity The type of entity that is performing the backup; typically one of:
BKEE Entries to Backup The number of entries (objects) the entity expects to include in this
RSLT Backup Initiation Status This field indicates status at the time the backup store was
This message marks the time of a backup session. It allows you to match the message with a corresponding
BKSE end message to determine that backups are happening as planned and whether they are successful.
BKSE—Backup Store End
When a service completes a backup operation, this message is generated.
Table 15 BKSE—Backup Store End Fields
BFSG, BCMS, or BNMS.
backup session. If the value is unknown, this field is set to zero
(0).
initiated:
SUCS—the backup store started successfully.
Code Field Description
BKSI Backup Session ID The unique identifier of the backup session that has been
completed.
BKOI Backup Source Entity The type of entity that performed the backup; typically one of:
BFSG, BCMS, or BNMS.
BKEA Entries Backed Up The actual number of entries (objects) that were included in this
backup session. You can compare this to BKEE in the BKSB
message.
UUID Backup UUID The Universal Unique IDentifier assigned to the backup by the
grid. If the backup session fails or is aborted, this value is the
NULL UUID.
RSLT Backup Result The completion status of the backup session:
SUCS—The backup completed successfully.
ABRT—The backup was aborted.
FAIL—The backup failed before completion.
STFL—The backup data could not be stored in the grid.
Matching this message with the corresponding BKSB message can indicate the time it took to perform the
backup. This message indicates whether the backup was successful and the UUID of the backup data
within the grid, should a restoration be needed.
26 Message Reference
Page 27

CBRB—Object Receive Begin
During normal system operations, content blocks are continuously transferred between different nodes as
data is accessed, replicated and retained. When transfer of a content block from one node to another is
initiated, this message is issued by the destination entity.
Table 16 CBRB—Object Receive Begin Fields
Code Field Description
CNID Connection Identifier The unique identifier of the node-to-node content block transfer.
CBID Content Block Identifier The unique identifier of the content block being transferred.
CTDR Transfer Direction Indicates if the CBID transfer was push-initiated or pull-initiated:
CTSR Source Entity The node ID of the source (sender) of the CBID transfer.
CTDS Destination Entity The node ID of the destination (receiver) of the CBID transfer.
CTSS Start Sequence Count Indicates the first sequence count requested. If successful, the
PUSH—the transfer operation was requested by the sending
entity.
PULL—the transfer operation was requested by the receiving
entity.
transfer begins from this sequence count.
CTES Expected End
Sequence Count
RSLT Transfer Start Status Status at the time the transfer was started:
This audit message means a node-to-node data transfer operation was initiated on a single piece of
content, as identified by its Content Block Identifier. The operation requests data from “Start Sequence
Count” to “Expected End Sequence Count”. Sending and receiving nodes are identified by their node IDs.
This information can be used to track system data flow, and when combined with storage audit messages,
to verify replica counts.
CBRE—Object Receive End
When transfer of a content block from one node to another is completed, this message is issued by the
destination entity.
Table 17 CBRE—Object Receive End Fields
Code Field Description
CNID Connection Identifier The unique identifier of the node-to-node content block transfer.
CBID Content Block Identifier The unique identifier of the content block being transferred.
CTDR Transfer Direction Indicates if the CBID transfer was push-initiated or pull-initiated:
Indicates the last sequence count requested. If successful, the
transfer is considered complete when this sequence count has
been received.
SUCS—transfer started successfully.
PUSH—the transfer operation was requested by the sending
entity.
PULL—the transfer operation was requested by the receiving
entity.
CTSR Source Entity The node ID of the source (sender) of the CBID transfer.
CTDS Destination Entity The node ID of the destination (receiver) of the CBID transfer.
CTSS Start Sequence Count Indicates the sequence count on which the transfer started.
HP Medical Archive Solution audit message reference 27
Page 28

Table 17 CBRE—Object Receive End Fields (continued)
Code Field Description
CTAS Actual End Sequence
Count
RSLT Transfer Result The result of the transfer operation (from the perspective of the
This audit message means a node-to-node data transfer operation was completed. If the Transfer Result
was successful, the operation transferred data from “Start Sequence Count” to “Actual End Sequence
Count”. Sending and receiving nodes are identified by their node IDs. This information can be used to
track system data flow and to locate, tabulate, and analyze errors. When combined with storage audit
messages, it can also be used to verify replica counts.
CBSB—Object Send Begin
Indicates the last sequence count successfully transferred. If the
Actual End Sequence Count is the same as the Start Sequence
Count, and the Transfer Result was not successful, no data was
exchanged.
sending entity):
SUCS—transfer successfully completed; all requested sequence
counts were sent.
CONL—connection lost during transfer
CTMO—connection timed-out during establishment
UNRE—destination node ID unreachable
CRPT—transfer ended due to reception of corrupt or invalid data
(may indicate tampering)
During normal system operations, content blocks are continuously transferred between different nodes as
data is accessed, replicated and retained. When transfer of a content block from one node to another is
initiated, this message is issued by the source entity.
Table 18 CBSB—Object Send Begin Fields
Code Field Description
CNID Connection Identifier The unique identifier of the node-to-node content block transfer.
CBID Content Block Identifier The unique identifier of the content block being transferred.
CTDR Transfer Direction Indicates if the CBID transfer was push-initiated or pull-initiated:
PUSH—the transfer operation was requested by the sending
entity.
PULL—the transfer operation was requested by the receiving
entity.
CTSR Source Entity The node ID of the source (sender) of the CBID transfer.
CTDS Destination Entity The node ID of the destination (receiver) of the CBID transfer.
CTSS Start Sequence Count Indicates the first sequence count requested. If successful, the
transfer begins from this sequence count.
CTES Expected End
Sequence Count
Indicates the last sequence count requested. If successful, the
transfer is considered complete when this sequence count has
been received.
RSLT Transfer Start Status Status at the time the transfer was started:
28 Message Reference
SUCS—transfer started successfully.
Page 29

This audit message means a node-to-node data transfer operation was initiated on a single piece of
content, as identified by its Content Block Identifier. The operation requests data from “Start Sequence
Count” to “Expected End Sequence Count”. Sending and receiving nodes are identified by their node IDs.
This information can be used to track system data flow, and when combined with storage audit messages,
to verify replica counts.
CBSE—Object Send End
When transfer of a content block from one node to another is completed, this message is issued by the
source entity.
Table 19 CBSE—Object Send End Fields
Code Field Description
CNID Connection Identifier The unique identifier of the node-to-node content block transfer.
CBID Content Block Identifier The unique identifier of the content block being transferred.
CTDR Transfer Direction Indicates if the CBID transfer was push-initiated or pull-initiated:
CTSR Source Entity The node ID of the source (sender) of the CBID transfer.
PUSH—the transfer operation was requested by the sending
entity.
PULL—the transfer operation was requested by the receiving
entity.
CTDS Destination Entity The node ID of the destination (receiver) of the CBID transfer.
CTSS Start Sequence Count Indicates the sequence count on which the transfer started.
CTAS Actual End Sequence
Count
RSLT Transfer Result The result of the transfer operation (from the perspective of the
This audit message means a node-to-node data transfer operation was completed. If the Transfer Result
was successful, the operation transferred data from “Start Sequence Count” to “Actual End Sequence
Count”. Sending and receiving nodes are identified by their node IDs. This information can be used to
track system data flow and to locate, tabulate, and analyze errors. When combined with storage audit
messages, it can also be used to verify replica counts.
Indicates the last sequence count successfully transferred. If the
Actual End Sequence Count is the same as the Start Sequence
Count, and the Transfer Result was not successful, no data was
exchanged.
sending entity):
SUCS—transfer successfully completed; all requested sequence
counts were sent.
CONL—connection lost during transfer
CTMO—connection timed-out during establishment
UNRE—destination node ID unreachable
CRPT—transfer ended due to reception of corrupt or invalid data
(may indicate tampering)
HP Medical Archive Solution audit message reference 29
Page 30

CDAD—DICOM Study Add
When a new DICOM study ID is ingested, or when new images are added to an existing study, this logs
the addition.
Table 20 CDAD—DICOM Study Add Fields
Code Field Description
STDY Study GUID The unique DICOM study identifier.
SIMC Number of Images The number of instances (images) in the study.
RSLT Result Indicates the result of the operation that added the study or
This audit message appears for each new study instance (image) that is added to the grid. As a new study
appears, the message indicates the new study is now known to the grid. As images are added to the study,
the message appears with the new count of images.
DASC—DICOM Association Close
When an established DICOM association with a remote host is closed, this message is issued.
Table 21 DASC—DICOM Association Close Fields
Code Field Description
image and notified the CMS of the addition. Current values are:
SUCS—operation was successful
ASID Association Identifier The unique identifier assigned to the DICOM association.
RSLT Closing State Indicates how the association closed:
SUCS—closed normally without errors
TOUT—timed-out by the node due to inactivity
ERRC—lost connection
ABRT—aborted
GERR—general data processing error
This audit message means the DICOM association specified by the Association Identifier is no longer
established. The DASC message always corresponds with a previous DASE (Association Establish)
message. DASC should be monitored to determine if there are excessive problems during attempts to
establish an association. Problems could indicate communications or interoperability issues related to
DICOM implementation.
DASE—DICOM Association Establish
When a DICOM association is established between a node and a host, this message is issued.
Table 22 DASE—DICOM Association Establish Fields
Code Field Description
CNID Connection Identifier The unique identifier assigned to the connection over which the
DICOM association was established.
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR Association Direction Indicates whether the association was opened by the grid node
30 Message Reference
or by a remote host:
INBO—initiated by a remote host connecting to the grid node
OUTB—initiated by the grid node connecting to a remote host
Page 31

Table 22 DASE—DICOM Association Establish Fields (continued)
Code Field Description
RMAE External Application
Entity
GRAE Grid Application Entity The Application Entity Title of the grid.
RSLT Result Indicates the result of opening the association. Currently defined
This audit message means a successful inbound or outbound DICOM association was established with a
remote host. It can be used to track hosts communicating with the system via DICOM.
The Grid Application Entity field allows identification of related configuration and coerce tag profiles, if
applicable. The Association Identifier can be used to trace the progress of a single transaction, such as a
C-MOVE or a C-FIND, from initiation to completion.
DASF—DICOM Association Fail
When an attempt by a DICOM service to establish an association fails, this message is issued. This can
occur if the remote host cannot process the DICOM protocol, or when either side of the communication
rejects the association request.
Table 23 DASF—DICOM Association Fail Fields
Code Field Description
CNID Connection Identifier The unique identifier assigned to the connection over which the
The Application Entity Title of the remote device.
values are:
SUCS—association was opened successfully
DICOM association was established.
DIDR Association Direction Indicates whether the association was opened by the grid node
or by a remote host:
INBO—initiated by a remote host connecting to the grid node
OUTB—initiated by the grid node connecting to a remote host
RMAE External Application
Entity
GRAE Grid Application Entity The Application Entity Title of the grid.
RSLT Failure Code Reason for the failure:
This audit message should be monitored to determine if there are repetitive or excessive problems during
attempts to establish an association. Problems could indicate communications or interoperability issues
related to DICOM implementation, or incorrectly configured external DICOM devices.
The Application Entity Title of the remote device (if unknown, this
field contains a null string).
ERRC—connection closed by remote host before an association
could be established
TOUT—timeout period expired
REJT—association rejected
PERM—calling AE Title denied permission to connect
CONF—unexpected AE Title for called entity
COMP—suitable presentation context could not be negotiated
GERR—unknown data received from remote host
Note that the result codes for PERM and CONF depend whether the association is inbound (INBO) or
outbound (OUTBO). For example, if the association is inbound, the calling AE is the remote host, and
HP Medical Archive Solution audit message reference 31
Page 32

PERM refers to the AE title of the remote host. If the association is outbound, the grid is the calling AE, and
PERM refers to the AE title of the grid.
The Grid Application Entity field allows identification of related configuration and coerce tag profiles, if
applicable.
DCFE—DICOM C–FIND End
When a DICOM association completes a C–FIND operation to query available content, this message is
issued.
Table 24 DCFE—DICOM C–FIND End Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–FIND Direction Indicates whether the C–FIND was initiated by the grid node or
ROOT DICOM Query Root The query root specified in the C–FIND.
LEVL DICOM Query Level The query level specified in the C–FIND.
RSFD Results Found The number of DICOM objects found matching the query.
RSLT Result Code The result of the C–FIND operation:
by a remote host:
INBO—initiated by a remote host
This audit message means a remote DICOM host initiated and completed a query for DICOM-related
content. It can be monitored to determine the content being queried. The “Result Code” field can be used
to determine when errors occur.
The time interval between the C–FIND Start and C–FIND End audit messages tells you how long the
related C–FIND operations are taking to complete.
DCFS—DICOM C–FIND Start
When a DICOM association initiates a C–FIND operation to query available content, this message is
issued.
Table 25 DCFS—DICOM C–FIND Start Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–FIND Direction Indicates whether the C–FIND was initiated by the grid node or
SUCS—successful
CANC—cancelled by the Service Class User
GERR—general error processing the C–FIND command
by a remote host:
INBO—initiated by a remote host
ROOT DICOM Query Root The query root specified in the C–FIND.
LEVL DICOM Query Level The query level specified in the C–FIND.
RSLT Result Indicates the result of staging the C-FIND operation. Currently
This audit message means a remote DICOM host initiated a query for DICOM-related content. It can be
monitored to determine the content being queried.
32 Message Reference
defined values are:
SUCS—C-FIND was started successfully.
Page 33

The time interval between the C–FIND Start and C–FIND End audit messages tells you how long the
related C–FIND operations are taking to complete.
DCME—DICOM C–MOVE End
When a DICOM association completes a C–MOVE operation to query and retrieve found content over a
second association, this message is issued.
Table 26 DCME—DICOM C–MOVE End Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–MOVE Direction Indicates whether the C–MOVE was initiated by the grid node or
ROOT DICOM Query Root The query root specified in the C–MOVE.
LEVL DICOM Query Level The query level specified in the C–MOVE.
by a remote host:
INBO—initiated by a remote host
SAET Source Application
Entity (AE) Title
DAET Destination AE-Title The destination AE-Title for the C–MOVE operation.
RSFD Results Found The number of DICOM objects retrieved matching the query.
RSLT Result Code The result of the C–MOVE operation:
This audit message means a remote DICOM host initiated and completed a a C–MOVE operation to
transfer DICOM content. It can be monitored to determine the content being queried/transferred. The
“Result Code” field can be used to determine when errors occur.
The time interval between the C–MOVE Start and C–MOVE End audit messages tells you how long the
related C–MOVE operations are taking to complete.
DCMS—DICOM C–MOVE Start
When a DICOM association initiates a C–MOVE operation to query and transfer DICOM content over a
second association, this message is issued.
Table 27 DCMS—DICOM C–MOVE Start Fields
The source AE-Title for the C–MOVE operation.
SUCS—successful
CANC—cancelled by the Service Class User
GERR—general error processing the C–MOVE command
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–MOVE Direction Indicates whether the C–MOVE was initiated by the grid node or
by a remote host:
INBO—initiated by a remote host
ROOT DICOM Query Root The query root specified in the C–MOVE.
LEVL DICOM Query Level The query level specified in the C–MOVE.
SAET Source Application
Entity (AE) Title
The source AE-Title for the C–MOVE operation.
HP Medical Archive Solution audit message reference 33
Page 34

Table 27 DCMS—DICOM C–MOVE Start Fields (continued)
Code Field Description
DAET Destination AE-Title The destination AE-Title for the C–MOVE operation.
RSLT Result Indicates the result of starting the C-MOVE operation. Currently
defined values are:
SUCS—successful.
This audit message means a remote DICOM host initiated a C–MOVE operation to transfer DICOM
instances to a remote Application Entity. It can be monitored to identify the content being retrieved as the
C–STORE audit messages that use the same association (i.e. the same Association Identifier) as the
C–MOVE correspond to the retrieved objects.
The time interval between the C–MOVE Start and C–MOVE End audit messages tells you how long the
related C–MOVE operations are taking to complete.
DCMT—DICOM Storage Commitment
When a DICOM association initiates a Storage Commitment operation to determine if content has been
successfully received and stored, this message is issued.
Table 28 DCMT—DICOM Storage Commitment Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR Storage
Commitment Direction
ISTR Items Requested The number of items requested for storage verification.
ISTS Items Stored The number of items requested for verification which have been
ISTN Items not Stored The number of items requested for verification which have not
RSLT Result Code Result of the Storage Commitment operation:
This audit message means that a Storage Commitment operation was initiated (usually by a a remote
DICOM host) to check whether content has been previously stored. It can be used to discover situations
where a discrepancy exists between content storage requests and what was in fact successfully stored.
Indicates whether the Storage Commit operation was initiated by
the grid node or by a remote host:
INBO—initiated by a remote host
OUTB—initiated by the node
successfully stored.
been successfully stored.
SUCS—successful
GERR—an error occurred during Storage Commitment processing
34 Message Reference
Page 35

DCPE—DICOM C–STORE End
When a DICOM association completes a C–STORE operation to transfer content from one host to another,
this message is issued.
Table 29 DCPE—DICOM C–STORE End Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–STORE Direction Indicates whether the C–STORE was initiated by the grid node or
STUG Study Instance UID The Study Identifier of the data being transferred.
SERG Series Instance UID The Series Identifier of the data being transferred.
IMGG SOP Instance UID The Image Identifier of the data being transferred.
STCL SOP Class The SOP Class of the instance.
STTX Transfer Syntax The Transfer Syntax of the instance.
CBID Content Block Identifier The identifier of the content block being transferred.
CSIZ Content Size The size of the original content stored, in bytes.
by a remote host:
INBO—initiated by a remote host
OUTB—initiated by the node
BSIZ Object Size The size of the managed fixed content object (after compression),
in bytes.
RSLT Result Code The result of the C–STORE operation:
SUCS—successful
CANC—canceled
TOUT—timed-out due to inactivity
COMP—presentation contexts not accepted
ERRC—lost connection
ERFH—failure message sent by remote application entity
CTNF—content to be transferred was not found
CVRF—content to be transferred failed verification
GERR—general error processing content
This audit message means a transfer of content between hosts over a DICOM association completed. The
message can be monitored to determine the content sent to particular systems. The “Result Code” field can
be used to determine when errors occurred.
HP Medical Archive Solution audit message reference 35
Page 36

DCPS—DICOM C–STORE Start
When a DICOM association initiates a C–STORE operation to transfer content from one host to another,
this message is issued.
Table 30 DCPS—DICOM C–STORE Start Fields
Code Field Description
ASID Association Identifier The unique identifier assigned to the DICOM association.
DIDR C–STORE Direction Indicates whether the C–STORE was initiated by the grid node or
STUG Study Instance UID The Study Identifier of the data being transferred.
SERG Series Instance UID The Series Identifier of the data being transferred.
IMGG SOP Instance UID The Image Identifier of the data being transferred.
STCL SOP Class The SOP Class of the instance.
STTX Transfer Syntax The Transfer Syntax of the instance.
CBID Content Block Identifier The identifier of the content block being transferred.
RSLT Result Indicates the result of starting the C-STORE operation. Currently
by a remote host:
INBO—initiated by a remote host
OUTB—initiated by the node
defined values are:
This audit message means a transfer of content between hosts over a DICOM association has started. The
message can be monitored to determine the content sent to particular systems.
DCSF—DICOM C–STORE Fail
When an association to perform a requested C–STORE cannot be established, or the information required
to establish an association to perform a C–STORE cannot be located, the C–STORE operation cannot be
initiated, and this message is issued.
Table 31 DCSF—DICOM C–STORE Fail Fields
Code Field Description
SVIP Destination Service Port The destination port for the C–STORE operation. If unknown, this
DAIP Destination IP Address The destination IP address for the C–STORE operation. If
RMAE External Application
Entity (AE)
DIDR C–STORE Direction Indicates whether the C–STORE was initiated by the grid node or
SUCS—C-STORE started successfully.
field is omitted from the audit message output.
unknown, this field is omitted from the audit message output.
The AE-Title of the destination device. If unknown, this field is
omitted from the audit message output.
by a remote host:
INBO—initiated by a remote host
STUG Study Instance UID The Study Identifier of the data being transferred. If unknown, this
SERG Series Instance UID The Series Identifier of the data being transferred. If unknown, this
36 Message Reference
OUTB—initiated by the node
field is omitted from the audit message output.
field is omitted from the audit message output.
Page 37

Table 31 DCSF—DICOM C–STORE Fail Fields (continued)
Code Field Description
IMGG SOP Instance UID The Image Identifier of the data being transferred. If unknown,
this field is omitted from the audit message output.
STCL SOP Class The SOP Class of the instance. If unknown, this field is omitted
from the audit message output.
CBID Content Block Identifier The identifier of the content block being transferred.
RSLT Result Code Why the C–STORE was unable to complete:
CBLK—the CBID associated with the image could not be
referenced
CBNM—CBID associated with the image did not contain
metadata, or had invalid metadata in the CMS
ASOF—an association could not be established for the C-STORE
request.
CSDI—extraction error while processing incoming C-STORE
transaction data.
This audit message means a transfer of content between hosts over a DICOM association failed. This can
be symptomatic of network problems, or indicate attempts to send data to systems that do not support the
image SOP Class.
If the attempt could be initiated but the transfer failed, an DCSF message is not generated. Instead, there is
a DCPS (page 36) and DCPE (page 35) pair of messages which indicate the start and end of the transfer,
with result codes that identify the cause of the failure.
ETAF—Security Authentication Failed
A connection attempt using Transport Layer Security (TLS) has failed.
Table 32 ETAF—Security Authentication Failed Fields
Code Field Description
CNID Connection Identifier The unique grid identifier for the TCP/IP connection over which
the authentication failed.
RUID User Identity A service dependent identifier representing the identity of the
remote user.
RSLT Reason Code The reason for the failure:
SCNI—Secure connection establishment failed.
CERM—Certificate was missing.
CERT—Certificate was invalid.
CERE—Certificate was expired.
CERR—Certificate was revoked.
CSGN—Certificate signature was invlid.
CSGU—Certificate signer was unknown.
UCRM—User credentials were missing.
UCRI—User credentials were invalid.
UCRU—User credentials were disallowed.
TOUT—Authentication timed out.
HP Medical Archive Solution audit message reference 37
Page 38

When a connection is established to a secure service that uses TLS, the credentials of the remote entity are
verified using the TLS profile and additional logic built into the service. If this authentication fails due to
invalid, unexpected, or disallowed certificates or credentials, an audit message is logged. This enables
queries for unauthorized access attempts and other security-related connection problems.
The message could result from a remote entity having an incorrect configuration, or from attempts to
present invalid or disallowed credentials to the system. This audit message should be monitored to detect
attempts to gain unauthorized access to the system.
ETCA—TCP/IP Connection Establish
When a connection to a service running on a node is permitted, this message is generated.
Table 33 ETCA—TCP/IP Connection Establish Fields
Code Field Description
SEID Service Identifier The unique identifier of the service to which the connection was
established. Values of interest include:
DING: DICOM Ingest Service
DCLN: DICOM Query/Retrieve Service
HING: HTTP Ingest Service
HCLN: HTTP Query/Retrieve Service
NCON: Neighbor Connection Service
CNDR Connection Direction Indicates whether the connection was opened by the grid node or
by a remote host:
INBO—connection initiated by a remote host, which connected to
the node
OUTB—connection initiated by the grid node, which connected to
a remote host
SVIP Destination Service Port The port the connection was established to.
DAIP Destination IP Address The IP address the connection was established to.
SAIP Source IP Address The IP address the connection was established from (local IP
address).
CNID Connection Identifier The unique identifier of the connection.
RSLT Result Code Connection status:
SUCS—connection successfully established
This audit message means an incoming or outgoing TCP/IP connection was successfully established. This
does not indicate the corresponding user was permitted to use the service - just that they were not rejected.
Typically, each service implements additional authentication mechanisms specific to the service type
(DICOM, HTTP etc.).
This message can be used to report on external hosts communicating with the system, and to correlate
higher level protocol messages back to the IP address initiating the activity. The “Connection Identifier”
field allows correlation of audit messages related to actions performed during a session.
38 Message Reference
Page 39

ETCC—TCP/IP Connection Close
When the system on either side of an established connection closes the connection (either normally or
abnormally), this message is generated.
Table 34 ETCC—TCP/IP Connection Close Fields
Code Field Description
CNID Connection Identifier The unique identifier of the connection.
INIE Initiating Entity The entity causing the connection to be closed:
RSLT Result Code Why the connection was closed:
LOCL—the node closed the connection
RMOT—the remote entity closed the connection
SUCS—connection closed at an expected point
CLIN—client (remote side) closed the connection at an expected
point
LOST—connection closed by the remote entity at an unexpected
point
UNEX—connection closed by the remote entity at an unexpected
point
TOUT—connection timed-out and was closed
This audit message means a TCP/IP connection was closed. When this message is generated, the
corresponding connection ID no longer exists, and the associated TCP/IP connection is no longer
established.
This message can be used to detect problems within the system, such as network issues over a WAN, or
interoperability problems between systems. The “Connection Identifier” field allows correlation of audit
messages related to actions performed during a session.
ETCF—TCP/IP Connection Fail
When an attempt to establish a connection to a remote service fails during establishment, this message is
generated.
Table 35 ETCF—TCP/IP Connection Fail Fields
Code Field Description
SEID Service Identifier The unique identifier of the service to which the connection was
CNDR Connection Direction Indicates whether the connection was opened by the grid node or
attempted. Values of interest include:
• DING: DICOM Ingest Service
• DCLN: DICOM Query/Retrieve Service
• HING: HTTP Ingest Service
• HCLN: HTTP Query/Retrieve Service
• NCON: Neighbor Connection Service
by a remote host:
INBO—connection initiated by a remote host connecting to the
node
OUTB—connection initiated by the grid node, attempting a
connection to a remote host
SVIP Destination Service Port The port to which the connection attempt was made.
HP Medical Archive Solution audit message reference 39
Page 40

Table 35 ETCF—TCP/IP Connection Fail Fields (continued)
Code Field Description
DAIP Destination IP Address The IP address to which the connection attempt was made
(remote IP address).
SAIP Source IP Address The IP address from which the connection attempt was made
(local IP address).
CNID Connection Identifier The unique identifier of the attempted connection.
RSLT Result Code Why the attempted connection failed:
IPAR—inbound IP address was not from allowed range
CRFU—outgoing connection refused by remote host
UNRE—destination (remote host) unreachable
ATHF—TCP/IP connection level authentication failure
This audit message means an outgoing connection attempt failed at the lowest level, due to communication
problems - the corresponding service was unable to access the remote host, and the TCP/IP connection
was not established.
This message can be used to detect system problems such as configuration errors where content is being
pushed to unreachable hosts, or where routing problems result in inaccessibility of hosts.
The message can also be used to report on the hosts to which content was pushed. The “Connection
Identifier” field allows correlation of audit messages related to actions performed during a session.
ETCR—TCP/IP Connection Refused
The Connection Refused Audit Message indicates that an incoming TCP/IP connection attempt was not
allowed.
When a remote client needs to communicate with a service running on a node, it attempts to create a
connection to that node. If the node refuses the connection, this message is generated. Failures of inbound
connections can result from a variety of reasons, which are described in the entry below for the Result field.
Table 36 ETCR—TCP/IP Connection Refused Fields
Code Field Description
SEID Service Identifier The unique identifier of the service to which the connection was
CNDR Connection Direction Indicates that the connection was opened by a remote host:
attempted. Values of interest include:
• DING: DICOM Ingest Service
• DCLN: DICOM Query/Retrieve Service
• HING: HTTP Ingest Service
• HCLN: HTTP Query/Retrieve Service
• NCON: Neighbor Connection Service
INBO—connection initiated by a remote host connecting to the
node
SVIP Destination Service Port The port to which the connection attempt was made.
DAIP Destination IP Address The IP address to which the connection attempt was made
SAIP Source IP Address The IP address from which the connection attempt was made
40 Message Reference
(remote IP address).
(local IP address).
Page 41

Table 36 ETCR—TCP/IP Connection Refused Fields (continued)
Code Field Description
CNID Connection Identifier The unique identifier of the attempted connection.
RSLT Result Code Why the attempted connection was refused:
For incoming connections, this audit message means that a connection was not successfully established at
the lowest level due to a security violation. When this message is received, the corresponding user was not
able to access the service and the TCP/IP Connection was closed. The most common reporting use of this
message is to detect unauthorized attempts to access services running on the system from foreign IP
Address that have not been explicitly given access to the service.
FCRE—File Create
When a new file (not a directory) is created on the FSG, this logs the creation.
Table 37 FCRE—File Create Fields
Code Field Description
FPTH File Path The complete path and name of the file that has been created.
RSLT Result Indicates the result of creating the file. Currently defined values
IPAR—inbound IP address was not from allowed range
ATHF—TCP/IP connection level authentication failure
are:
This audit message means a new file entry has been added to the FSG directory tree. The content of the file
resides on the local FSG cache, and the process of storing it within the grid has initiated.
NOTE: Directory creation operations on the FSG do not generate audit messages.
FDEL—File Delete
When an existing file entry in the FSG is deleted, this logs the deletion.
Table 38 FDEL—File Delete Fields
Code Field Description
FPTH File Path The complete path and name of the file that has been deleted.
RSLT Result Indicates the result of deleting the file. Currently defined values
This audit message means an existing file entry has been deleted from the FSG directory tree. The content
of the file residing within the grid is not affected, however the file becomes inaccessible through the FSG.
SUCS—file created successfully.
are:
SUCS—file deleted successfully.
NOTE: Deletion of empty directories on the FSG do not generate audit messages.
Deleting a directory triggers an audit message for each enclosed file that is deleted.
HP Medical Archive Solution audit message reference 41
Page 42

FMFY—File Modify
The FMFY message indicates that the indicated UUID is no longer associated with the file identified in the
message. This can occur when an existing file is modified (such that the original file is overwritten), or
when the file is deleted.
Table 39 FMFY—File Modify Fields
Code Field Description
FPTH File path The complete path and name of the file being modified.
UUID Universal Unique ID The identifier of the original version of the file within the grid.
RSLT Result Indicates the result of modifying the file. Currently defined values
If file purging is not enabled for the grid, the original content of the modified file is retained within the grid,
but can no longer be accessed through the FSG. The content is available through other direct grid
interfaces via a query on object metadata.
If file purging is enabled, the original content of the file is deleted as needed to free grid storage.
FRNM—File Rename
When an existing file entry in the FSG is renamed, this logs the change.
Table 40 FRNM—File Rename Fields
are:
SUCS—file modified successfully
Code Field Description
OLDP Original file path The complete path and name of the (original) file being renamed.
NEWP New file path The complete path and name being assigned to the file.
RSLT Result Indicates the result of renaming the file. Currently defined values
An existing file entry in the FSG directory tree is changing. The content of the file residing within the grid is
not affected, however metadata associating the file path and name is changed.
Renaming a directory does not trigger any audit messages. The metadata recorded for any enclosed files
remains unchanged, indicating the original ingest location only.
FSTG—File Store to Grid
When new content is stored via the FSG, the content is cached locally by the FSG server and is copied into
the grid. When the grid confirms it has stored the copy (and is processing it under its business rules for
replication), this message is issued.
Table 41 FSTG—File Store to Grid Fields
Code Field Description
FPTH File path The complete path and name of the file being stored.
are:
SUCS—file renamed sucessfully.
FLTP File Type Indicates the type of object storage, as processed by the grid’s
42 Message Reference
file type detection.
Page 43

Table 41 FSTG—File Store to Grid Fields (continued)
Code Field Description
UUID Universal Unique ID The identifier of the file content within the grid.
RSLT Result Code The result of the storage operation:
If a failure is logged, the FSG initiates a new storage attempt. Retries continue until successful.
FSWI—File Swap In
A file has been retrieved from the grid for storage in the FSG local cache. Content still resides in the grid.
Table 42 FSWI—File Swap In Fields
Code Field Description
FPTH File path The complete path and name of the file added to the FSG local
SUCS—Successfully stored.
FTER—Failed extended type verification (will be re-ingested as a
generic object).
TOUT—Failed due to timeout.
ERRC—Failed due to lost connection.
GERR—A general error occurred while storing content.
cache.
UUID Universally Unique ID The identifier of the file content within the grid.
RSLT Result Code The result of the file retrieve operation:
The original content of the file (along with its associated path and file name metadata) is retained within
the grid at the UUID provided.
This message indicates that a file not stored in the FSG local cache has been accessed using the FSG. That
access may be for the purpose of modification, in which case the FMFY message should also appear in the
audit log.
FSWO—File Swap Out
A file has been purged from the FSG local cache. Content still resides in the grid and can be accessed
using the FSG.
Table 43 FSWO—File Swap Out Fields
Code Field Description
FPTH File path The complete path and name of the file dropped from the FSG
SUCS—Successfully retrieved.
TOUT—Failed due to timeout.
ERRC—Failed due to lost connection.
GERR—A general error occurred while retrieving the content.
local cache.
UUID Universal Unique ID The identifier of the file content within the grid.
RSLT Result Indicates the result of the swap out operation. Currently defined
values are:
SUCS—file successfully swapped out.
HP Medical Archive Solution audit message reference 43
Page 44

The original content of the file (along with its associated path and file name metadata) is retained within
the grid at the UUID provided. The FSG interface can be used to retrieve the content from the grid.
HCPE—HTTP PUT C–STORE End
An object can be stored into the /DICOM namespace over an established HTTP session by initiating a PUT
transaction to process and store the content as a DICOM object in the grid. When DICOM object storage
has completed, this message is issued.
Table 44 HCPE—HTTP PUT C–STORE End Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
STUG Study Instance UID The Study Identifier of the data being stored.
SERG Series Instance UID The Series Identifier of the data being stored.
IMGG SOP Instance UID The Image Identifier of the data being stored.
STCL SOP Class The SOP Class of the instance.
STTX Transfer Syntax The Transfer Syntax of the instance.
CBID Content Block Identifier The identifier of the corresponding content block for the
the node.
successfully stored content. If the store operation was not
successful, this field is set to 0.
UUID Content UUID The Universal Unique IDentifier assigned to the successfully stored
content. If the UUID was not specified, or the store operation
failed, this field is set to the NULL UUID.
CSIZ Content Size The size of the original content stored, in bytes.
BSIZ Object Size The size of the managed fixed content object (after compression),
in bytes.
RSLT Result Code The result of the DICOM Store operation:
SUCS—successful
TOUT—timed-out due to inactivity
ERRS—session closed or lost while the C–STORE transaction was
being performed
CTNF—content to be transferred was not found
CVRF—content to be transferred failed verification
GERR—general error processing content
This audit message means a transfer of content between hosts over an HTTP session completed. This
message is generated prior to, and in addition to, the “HTTP PUT Transaction End” audit message.
44 Message Reference
Page 45

HCPS—HTTP PUT C–STORE Start
An object can be stored into the /DICOM namespace over an established HTTP session by initiating a PUT
transaction to process and store the content as a DICOM object in the grid. When DICOM object storage
has been initiated, this message is issued.
Table 45 HCPS—HTTP PUT C–STORE Start Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
STUG Study Instance UID The Study Identifier of the data being stored.
SERG Series Instance UID The Series Identifier of the data being stored.
IMGG SOP Instance UID The Image Identifier of the data being stored.
STCL SOP Class The SOP Class of the instance.
STTX Transfer Syntax The Transfer Syntax of the instance
RSLT Result Code Status at the time the C–STORE operation was initiated:
This audit message means a transfer of content between hosts over an HTTP session has been initiated.
This message is generated after, and in addition to, the “HTTP PUT Transaction Start” audit message.
the node.
SUCS—C–STORE transaction successfully initiated
HDEL—HTTP DELETE Transaction
When an HTTP client issues a DELETE transaction, a request is made to remove the specified stored
content, and this message is issued by the server.
Table 46 HDEL—HTTP DELETE Transaction Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the object to be removed resides.
OBPA Object Path The path to the object to be removed.
OBNA Object Name The name of the object to be removed.
UUID Content UUID The Universal Unique IDentifier assigned to the content requested
RSLT Result Code Result of the DELETE transaction:
the node.
for removal.
SUCS—successful
ERRS—session closed or lost while the DELETE transaction was
being performed
CTNF—content to be deleted not found
BRQT—malformed DELETE transaction
GERR—general error processing content
This audit message indicates the result of a request to delete content. If the specified content exists, it can
be identified via the “Content UUID” field (which contains the save value as OBNA, given that deletion
occurs in the UUID namespace). If deletion occurs via the FSG, the FMFY message (page 42) can be used
to identify the file name. The “Result Code” field can be used to determine when errors occurred.
HP Medical Archive Solution audit message reference 45
Page 46

HGEE—HTTP GET Transaction End
When an HTTP client completes a GET transaction to transfer content from the HTTP server to the HTTP
client, this message is issued.
Table 47 HGEE—HTTP GET Transaction End Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the requested object resides.
OBPA Object Path The path to the requested object.
OBNA Object Name The name of the requested object.
CBID Content Block Identifier The unique identifier of the corresponding content block
UUID Content UUID The Universal Unique IDentifier corresponding to the requested
RSLT Result Code Result of the GET transaction:
the node.
requested. If the CBID is unknown, this field is set to 0.
content. If the UUID is unknown, this field is set to the NULL UUID.
SUCS—successful
TOUT—timed-out due to inactivity
This audit message means a transfer of content to an HTTP client completed. It can be monitored to
determine the content sent to particular systems. The “Result Code” field can be used to determine when
errors occurred.
HGES—HTTP GET Transaction Start
When an HTTP client initiates a GET transaction to transfer content from the HTTP server to the HTTP client,
this message is issued.
Table 48 HGES—HTTP GET Transaction Start Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
ERRS—session closed or lost while the GET transaction was being
performed
CTNF—content to be transferred not found or generated (404)
error
CTRD—content requested resulted in a redirect operation
CVRF—content to be transferred failed validation
AUTH—transaction terminated due to authorization failure
GERR—general error processing content
the node.
OBNS Object Namespace The namespace within which the requested object resides.
OBPA Object Path The path to the requested object.
OBNA Object Name The name of the requested object.
CBID Content Block Identifier The unique identifier of the corresponding content block
46 Message Reference
requested. If the CBID is unknown, this field is set to 0.
Page 47

Table 48 HGES—HTTP GET Transaction Start Fields (continued)
Code Field Description
UUID Content UUID The Universal Unique IDentifier corresponding to the requested
RSLT Result Code Status at the time the request for the GET transaction was
This audit message means a request for transfer of content to an HTTP client has been initiated. It can be
monitored to determine the content sent to particular systems.
HHEA—HTTP HEAD Transaction
When an HTTP client initiates a HEAD transaction to request information about stored content, this
message is issued.
Table 49 HHEA—HTTP HEAD Transaction Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
content. If the UUID is unknown, this field is set to the NULL UUID.
initiated:
SUCS—GET transaction successfully initiated
BRQT—GET transaction malformed
the node.
OBNS Object Namespace The namespace within which the requested object resides.
OBPA Object Path The path to the requested object.
OBNA Object Name The name of the requested object.
CBID Content Block Identifier The unique identifier of the corresponding content block about
which information is being requested. If the CBID is unknown, this
field is set to 0.
UUID Content UUID The Universal Unique IDentifier corresponding to the content
about which information is being requested. If the UUID is
unknown, this field is set to the NULL UUID.
RSLT Result Code Result of the HEAD transaction:
SUCS—successful
CTNF—specified content was not found, or generated (404) error
CTRD—content requested resulted in a redirect operation
AUTH—transaction terminated due to authorization failure
ERRS—session closed or lost while the HEAD transaction was
being performed
BRQT—HEAD transaction malformed
GERR—general error processing content
This audit message means information about a given piece of content was requested by an HTTP client. It
can be monitored to determine the content inspected by clients. The “Result Code” field can be used to
determine when errors occurred.
HP Medical Archive Solution audit message reference 47
Page 48

HOPT—HTTP OPTIONS Transaction
When an HTTP client initiates an OPTIONS transaction to discover which HTTP transactions can be
performed on a given piece of content, this message is issued.
Table 50 HOPT—HTTP OPTIONS Transaction Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the specified object resides.
OBPA Object Path The path to the specified object.
OBNA Object Name The name of the specified object.
RSLT Result Code Result of the OPTIONS transaction:
the node.
SUCS—successful
ERRS—session closed or lost while the OPTIONS transaction was
being performed
AUTH—transaction terminated due to authorization failure
BRQT—OPTIONS transaction malformed
GERR—general error processing content
This audit message indicates the result of a request for information about the transactions that can be
performed on content. The OPTIONS transaction is typically performed to discover if content can be
deleted, created, and so on.
HPOE—HTTP POST Transaction End
When a POST transaction initiated by an HTTP client to query available content completes, this message is
issued.
Table 51 HPOE—HTTP POST Transaction End Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the query is performed.
RSFD Results Found The number of found objects matching the query.
RSLT Result Code Result of the POST query operation:
the node.
SUCS—successful
TOUT—timed-out due to inactivity
ERRS—session closed or lost while the POST transaction was
being performed
CMLF—malformed query parameters received from client
This audit message means an HTTP client has initiated and completed a query for stored content in the
specified namespace. If the query cannot be started (HPOS fails), then no HPOE message is generated.
48 Message Reference
AUTH—transaction terminated due to authorization failure
BRQT—invalid POST query (bad request)
GERR—general error processing content
Page 49

HPOE can be monitored to determine the content being queried. The “Result Code” field can be used to
determine when errors occurred.
The time between the “HTTP POST Transaction Start” and “HTTP POST Transaction End” audit messages
tells you how long particular query operations are taking to complete.
HPOS—HTTP POST Transaction Start
When a POST transaction is initiated by an HTTP client to query available content, this message is issued.
Table 52 HPOS—HTTP POST Transaction Start Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
the node.
OBNS Object Namespace The namespace within which the query is performed.
RSLT Result Code Status at the time the request for the POST transaction was
initiated:
SUCS—POST transaction initiated successfully
BRQT—failure (bad request, usually malformed POST transaction)
This audit message means an HTTP client initiated a query for stored content in the specified namespace. It
can be monitored to determine the content being queried.
The time between the “HTTP POST Transaction Start” and “HTTP POST Transaction End” audit messages
tells you how long particular query operations are taking to complete.
HPUE—HTTP PUT Transaction End
When an HTTP client completes a PUT transaction to transfer content from the HTTP client to the HTTP
server (the node), this message is issued.
Table 53 HPUE—HTTP PUT Transaction End Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the stored object was handled.
OBPA Object Path The path used to store the object.
OBNA Object Name The name of the stored object.
CBID Content Block Identifier The identifier of the corresponding content block for the
UUID Content UUID The Universal Unique IDentifier assigned to the successfully stored
the node.
successfully-stored content. If the store operation was not
successful, this field is set to 0.
content. If the UUID was not specified, or the store operation
failed, this field is set to ““.
CSIZ Content Size The size of the original content stored, in bytes.
HP Medical Archive Solution audit message reference 49
Page 50

Table 53 HPUE—HTTP PUT Transaction End Fields (continued)
Code Field Description
BSIZ Object Size The size of the managed fixed content object (after compression),
in bytes.
RSLT Result Code The result of the PUT transaction:
SUCS—successful
TOUT—timed-out due to inactivity
ERRS—session closed or lost while the PUT transaction was being
performed
CMLF—malformed content received from the client
STER—storing the content failed
AUTH—transaction terminated due to authorization failure
CANC—cancelled by client
GERR—general error processing content
This audit message means a transfer of content from an HTTP client completed. If content was successfully
stored, the CBID and/or UUID fields identify it.
This audit message can be monitored to determine the content sent to particular systems. The “Result Code”
field can be used to determine when errors occurred.
HPUS—HTTP PUT Transaction Start
When an HTTP client initiates a PUT transaction to transfer content from the HTTP client to the HTTP server
(the node), this message is issued.
Table 54 HPUS—HTTP PUT Transaction Start Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
OBNS Object Namespace The namespace within which the stored object should be
OBPA Object Path The path to use when storing the object.
OBNA Object Name The name of the object to store.
RSLT Result Code The status at the time the request for the PUT transaction was
This audit message means a transfer of content from an HTTP client has initiated. It can be monitored to
determine the content stored using HTTP.
the node.
handled.
initiated:
SUCS—PUT transaction initiated successfully
BRQT—malformed PUT transaction
50 Message Reference
Page 51

HTSC—HTTP Session Close
When an HTTP client finishes communicating with a remote host and closes the previously-established HTTP
session, this message is issued.
Table 55 HTSC—HTTP Session Close Fields
Code Field Description
HSID Session Identifier The unique identifier assigned to the HTTP session established to
RSLT Result Code Why the session was closed:
This audit message means an HTTP client closed a previously-established HTTP session. “HTTP Session
Close” always corresponds with a previously-issued “HTTP Session Establish” message.
the node.
SUCS—session closed normally, without errors
TOUT—timed-out by the node, due to inactivity
ERRC—lost the connection over which the session was established
ERRT—session terminated due to an error occurring on a
transaction
AUTH—session terminated due to a failed transaction
authorization
GERR—a general error occurred, causing the session to close
This message should be monitored to determine if there are any repetitive or excessive problems in
attempting to establish a session. This could indicate potential communications or interoperability problems
related to HTTP client or server implementations.
HTSE—HTTP Session Establish
When an HTTP client establishes an HTTP session, this message is issued.
Table 56 HTSE—HTTP Session Establish Fields
Code Field Description
CNID Connection Identifier The unique identifier for the connection over which the HTTP
HSID Session Identifier The unique identifier assigned to the HTTP session established to
RSLT Result Code Status at the time the session was established:
This audit message means a remote host (client) successfully established an HTTP session to the node. It
can be used to track which hosts the system is communicating with via the HTTP protocol.
OHRP—Object Handle Repoint
This message is generated when the content handle of an object (UUID) is updated to reference a different
object (CBID).
session was established.
the node.
SUCS—session successfully established
HP Medical Archive Solution audit message reference 51
Page 52

When the CMS determines that two objects ingested into the grid are identical, it repoints the content
handle (UUID) of one of them so that both content handles refer to the same object (CBID). The CMS
repoints content handles as part of the GE Optimized Store (deduplication) feature.
Table 57 OHRP—Object Handle Repoint Fields
Code Field Description
RCHN Repointed Content
Handle
OCBI Original CBID The CBID that the content handle pointed to originally.
RCBI Repointed CBID The CBID that the content handle points to after the operation is
When a content handle is updated to point to a different CBID, the original CBID will no longer have any
content handles pointing to it. Depending on the retention rules for the grid, the CBID may be deleted from
the system.
RPSB—Replication Session Begin
When a service begins a replication operation—replicating private structured data to a secondary
service—this message is generated.
Table 58 RPSB—Replication Session Begin Fields
Code Field Description
RPSI Replication Session ID The unique identifier of the replication session being started.
RPPI Previous Session ID The identifier of the previous replication session (if one exists);
RPSE Replication Source
Entity
The content handle (UUID) of the object that was pointed to
another CBID.
complete.
zero otherwise.
The node ID of the service that is generating the replication
session.
RPDE Replication Destination
Entity
RPSC Start Sequence Count The replication sequence count of FSG transactions at which the
RSSS Session Start Reason The status of the replication session:
RSLT Operation Result The status of the replication operation:
This message indicates a replication session is either starting or being resumed. It identifies the primary
(originating) and secondary (accepting) services by their node IDs. Both the source and destination
services report this message.
The node ID of the service that is accepting the replication
session.
session starts or resumes.
NEWS—A new session is being established.
CONT—A new session is being resumed.
RSUM—A previous session is being resumed.
SUCS—The replication session started successfully.
52 Message Reference
Page 53

RPSE—Replication Session End
When a service completes a replication session, this message is generated.
Table 59 RPSE—Replication Session End Fields
Code Field Description
RPSI Replication Session ID The unique identifier of the replication session that has ended.
RPPI Next Session ID The identifier of the next replication session (if known). If the next
session ID is not known, this value is zero (0).
RPSE Replication Source
Entity
RPDE Replication Destination
Entity
RPSC End Sequence Count The replication sequence count of FSG transactions that would be
RSSS Session End Reason The completion status of the replication session:
RSLT Session Result The result of the replication session:
Matching this message with the corresponding RPSB message can indicate the time it took to perform the
replication. This message indicates whether the replication session closed normally. Both the source and
destination services report this message.
The node ID of the service that is generating the replication
session.
The node ID of the service that is accepting the replication
session.
the next value (in another session).
SUCS—The replication session was closed successfully.
UNEX—The session was closed unexpectedly.
PAUS—The session was paused (the FSG was shut down).
CKPT—The session was stopped for a checkpoint such as a
backup. A new session handles remaining replication.
SUCS—The replication session completed successfully.
FAIL—The replication session did not complete successfully.
SADD—Security Audit Disable
This message indicates the originating service (node ID) has turned off audit message logging; audit
messages are no longer being collected or delivered.
Table 60 SADD—Security Audit Disable Fields
Code Field Description
AETM Enable Method The method used to disable the audit.
AEUN User Name The user name that executed the command to disable audit
The message implies that logging was previously enabled but has now been disabled. This is typically only
used during bulk ingest to improve system performance. Following the bulk activity, auditing is restored
(SADE) and the capability to disable auditing is then permanently blocked.
logging.
HP Medical Archive Solution audit message reference 53
Page 54

SADE—Security Audit Enable
This message indicates that the originating service (node ID) has restored audit message logging; audit
messages are again being collected and delivered.
Table 61 SADE—Security Audit Enable Fields
Code Field Description
AETM Enable Method The method used to enable the audit.
AEUN User Name The user name that executed the command to enable audit
The message implies that logging was previously disabled (SADD) but has now been restored. This is
typically only used during bulk ingest to improve system performance. Following the bulk activity, auditing
is restored and the capability to disable auditing is then permanently blocked.
SCMT—Object Store Commit
Grid content is not made available or recognized as being stored until it has been committed - meaning it
has been stored persistently. Persistently-stored content has been completely written to disk, and has passed
related integrity checks. When a content block is committed to storage, this message is issued.
Table 62 SCMT—Object Store Commit Fields
Code Field Description
CBID Content Block Identifier The unique identifier of the content block committed to permanent
logging.
storage.
RSLT Result Code Status at the time the object was stored to disk:
This message means a given content block has been completely stored and verified, and can now be
requested. It can be used to track data flow within the system.
SREM—Object Store Remove
When grid content is removed, it is either downgraded to transient status (“removed”) or completely wiped
from the system such that no parts of the content remain (“purged”). If content is downgraded to transient
status, it may still be accessed until purged from the system.
When a content block is deleted from permanent storage (either removed or purged), this message is
issued.
Table 63 SREM—Object Store Remove Fields
Code Field Description
CBID Content Block Identifier The unique identifier of the content block deleted from permanent
RSLT Result Code How the content was deleted:
SUCS - object successfully stored
storage.
SUCS - content removed (downgraded to transient status)
PURG -content purged from the node
This audit message means a given content block has been deleted from a node and can no longer be
requested directly. The message can be used to track the flow of deleted content within the system.
54 Message Reference
INTL - the operation succeeded and the content is no longer
accessible - but not erased, as the purge interlock is enabled
Page 55

SVRF—Object Store Verify Fail
Each time content is read from or written to disk, several verification and integrity checks are performed to
ensure data being sent to the requesting user is identical to the data originally ingested into the system. If
any of these checks fail, the system automatically removes the corrupt data to prevent it from being
retrieved again.
When a content block fails the verification process, this message is issued.
Table 64 SVRF—Object Store Verify Fail Fields
Code Field Description
CBID Content Block Identifier The unique identifier of the content block which failed verification.
RSLT Result Code Verification failure type:
CRCF - content CRC checks failed
HMAC - content HMAC checks failed
EHSH - unexpected encrypted content hash
PHSH - unexpected original content hash
SEQC - incorrect data sequence on disk
PERR - invalid structure of disk file
DERR - disk error
NOTE: The “SVRF - Object Store Verify Fail” audit message should be monitored closely. It means a given
content block failed verification checks, which can indicate attempts to tamper with content or impending
hardware failures.
SVRU—Object Store Verify Unknown
The Local Distribution Router (LDR) storage component continuously scans all files in the object store to
schedule content verification. If it detects a file or directory does not match expected naming conventions,
it moves the unexpected file(s) to the “garbage” directory, where they can be automatically or manually
removed (depending on LDR configuration).
When an unknown or unexpected file is detected in the object store and moved to the “garbage” directory,
this message is issued.
Table 65 SVRU—Object Store Verify Unknown Fields
Code Field Description
FPTH File Path The full path to the unexpected file’s original location.
NOTE: The “SVRU - Object Store Verify Unknown” audit message should be monitored closely. It means
unexpected files were detected in the object store. This situation should be investigated immediately to
determine how the files were created, as it can indicate attempts to tamper with content or impending
hardware failures.
HP Medical Archive Solution audit message reference 55
Page 56

SYSD—Node Stop
When an HP Medical Archive grid service is stopped gracefully, this message is generated to indicate the
shutdown was requested. Typically this message is sent only after a subsequent restart as the audit
message queue is not cleared prior to shutdown.
Table 66 SYSD—Node Stop Fields
Code Field Description
RSLT Clean Shutdown The nature of the shutdown:
The message does not indicate if the host server is being stopped, only the reporting service. The RSLT of a
SYSU cannot indicate a “dirty” shutdown, as the message is only generated by “clean” shutdowns.
SYSU—Node Start
When an HP Medical Archive grid service is restarted, this message is generated to indicate if the previous
shutdown was clean (commanded) or disorderly (unexpected).
Table 67 SYSU—Node Start Fields
Code Field Description
RSLT Clean Shutdown The nature of the shutdown:
SUCS—System was cleanly shutdown.
SUCS—System was cleanly shutdown.
The message does not indicate if the host server was started, only the reporting service.
This message can be used to:
• Detect discontinuity in the audit trail.
• Determine if a service is failing during operation (as the distributed nature of the grid can mask these
failures). The Server Manager restarts a failed service automatically.
TACB—Grid Task Action Begin
When a grid task action begins, this message is generated.
Table 68 TACB—Grid Task Action Begin Fields
Code Field Description
TSID Task ID The unique identifier of the task used to manage the task over its
TTYP Task Type The type of task.
TSFC Task Stage The current stage of the task.
ACNT Task Action Node ID The service node ID being requested to perform the task.
ACTT Task Action The action being started.
DSDN—System was not cleanly shutdown.
life cycle.
RSLT Action Status Status at the time the task action begins:
Matching this message with the corresponding TACE message can indicate the time it took to perform a
task action.
56 Message Reference
SUCS—The task stage started successfully.
Page 57

TACE—Grid Task Action End
When a grid task action completes, this message is generated.
Table 69 TACE—Grid Task Action End Fields
Code Field Description
TSID Task ID The unique identifier of the task used to manage the task over its
TTYP Task Type The type of task.
TSFC Task Stage The current stage of the task.
ACNT Task Action Node ID The service node ID being requested to perform the task.
ACTT Task Action The action that is being ended.
RSLT Action Result The completion status of the task action:
Matching this message with the corresponding TACB message can indicate the time it took to perform a
task action.
life cycle.
SUCS—completed successfully
ABRT—aborted
FAIL—failed before completion
TSGC—Grid Task Stage Change
This message indicates the stage of a grid task has changed; either the task is progressing to the next
stage, was aborted, or has failed.
Table 70 TSGC—Grid Task Stage Change Fields
Code Field Description
TSID Task ID The unique identifier of the task used to manage the task over its
TTYP Task Type The type of task.
TSDC Task Stage Description A text description of the next task stage (starting).
TSFC Task Stage The current stage of the task.
RSLT Task Stage Result The completion status of the previous task stage:
All actions within a task stage must complete before the stage can complete.
When a new grid task starts, this message is generated with RSLT = SUCS.
life cycle.
SUCS—completed successfully
ABRT—aborted
FAIL—failed before completion
HP Medical Archive Solution audit message reference 57
Page 58

TSTC—Grid Task State Change
When a grid task is added, started, paused, canceled, or completed, this message is issued to audit the
change in task state.
Table 71 TSTC—Grid Task State Change Fields
Code Field Description
TSID Task ID The unique identifier of the task used to manage the task over its
TTYP Task Type The type of task.
TDSC Task Description A text description of the task.
TSRC Task Source A text identification of the issuer of the task.
TSTS Task State The current state of the task:
life cycle.
NEWT—Newly added
PEND—Pending
ACTV—Active (running)
PAUS—Paused
ROLA—Aborting; performing a rollback
ROLF—Rollback failed
HIST—Historical (task completed, cancelled, or expired)
RMVD—Task is now removed
RSLT Task Status The status of the grid task:
SUCS—The task successfully entered the current state.
ABRT—The task was aborted (rollback if possible).
FAIL—The task has failed (rollback if possible).
CANC—The task was cancelled (never started).
EXPR—The task expired (never started).
IVLD—The task is invalid.
AUTH—The task is unauthorized.
DUPL—The task is a duplicate.
This message is used to determine what tasks have been added, run, and completed, and the result of the
completion.
The Task Status serves to indicate why the task is in the current state. If a task ends abnormally (is aborted
or fails) and requires a rollback, the reason is retained in the task status (TCTS). The status of the rollback
itself is noted within the state (TSTS). The sequence of messages would indicate either:
• ROLA > HIST if the rollback is successful, or
• ROLA > ROLF > HIST if the rollback failed.
58 Message Reference
Page 59

Glossary
ADC Administrative Domain Controller—a unit of the HP Medical Archive software that authenticates
grid nodes (certificates), manages interconnections, maintains information about grid topology,
and acts as an audit relay.
AE title Application Entity Title—the identifier of a DICOM node communicating with other DICOM
Application Entities.
AMS Audit Management System—a unit of the HP Medical Archive software that monitors and logs
all audited system events and transactions.
ARC ARChive Service—a unit of the HP Medical Archive software that manages interactions with a
tape storage archive or other long-term offline storage device.
association A connection protocol between two DICOM Application Entities (AEs), typically a local and
remote AE. The AEs use the Association Establishment to negotiate the type of data to exchange
and the format of data encoding.
audit message Information about an event occurring in the HP Medical Archive system that is captured and
logged to a file.
CBID Content Block Identifier—a number that uniquely identifies a piece of content within the
HP Medical Archive system.
CMS Content Management System—a unit of the HP Medical Archive software that manages a
distributed database catalog of the grid content (metadata) and duplicates data according to
business rules to provide Information Lifecycle Management (ILM).
C-STORE A DICOM operation to send data between devices.
CSTR Null-terminated, variable length string.
DICOM Digital Imaging and COmmunications in Medicine—a standard developed by ACR-NEMA (an
alliance of the American College of Radiology and the National Electrical Manufacturer’s
Association) for communications between medical imaging devices.
FCS Fixed Content Storage—a class of stored data where the data, once captured, is rarely
changed and must be retained for long periods of time in its original form. Typically this
includes image data, audit data, and other data where alterations would reduce the value of
the stored information.
FSG File System Gateway—a unit of the HP Medical Archive software that enables standard
network file systems to interface with the grid.
HTTP Hyper-Text Transfer Protocol—A simple, text based client/server protocol for requesting
hypertext documents from a server. This protocol has evolved into the primary protocol for
delivery of information on the World Wide Web.
instance A DICOM term for an image. One or more instances for a single patient are collected in a
“study”. For example, each “slice” of an MRI is an instance; together, the full set of slices is a
study.
LDR Local Distribution Router—a unit of the HP Medical Archive software that manages the storage
and transmission of content within the grid.
metadata Data that provides information about other data. In the HPMA system, this includes things like
block size and content block ID that describe specific object data entities.
HP Medical Archive Solution audit message reference 59
Page 60

namespace A set whose elements are unique names. There is no guarantee that a name in one namespace
is not repeated in a different namespace.
NMS Network Management System—a unit of the HP Medical Archive software for alarm monitoring
and system administration. It provides a web-based interface for managing and monitoring the
HP Medical Archive system, as well as viewing and reporting on statistics regarding network,
DICOM, storage, and many other related attributes for each of the various services and servers.
PDF Portable Document Format—a file format (developed by Adobe Systems and based on the
postscript language) for exchanging documents between computer systems that may have
differing operating systems. It is designed to preserve the appearance of the document
regardless of the system used to render it.
presentation context A combination of a DICOM SOP Class and a transfer syntax; the type and format of a DICOM
transaction.
release The edition of the complete HP Medical Archive system. Contrast with “version” and “revision”.
revision The edition of a document. Contrast with “version” and “release”.
service A unit of the HP Medical Archive software such as the ADC, CMS, or SSM.
SCP Storage Class Provider—a device that provides images (a storage class) to a DICOM compliant
system. Contrast with “SCU”.
SCU Storage Class User—a device that receives (uses) images (a storage class) from a DICOM
compliant system. Contrast with “SCP”.
SOP class Service-Object Pair Class—the combination of an information object description (IOD) and the
set of Services that are useful for a given purpose.
SOP instance Service-Object Pair (SOP) Instance—a specific occurrence of an Information Object.
SQL Structured Query Language—an industry standard interface language for managing relational
databases. An SQL database is one that supports the SQL interface.
SSM Service Status Monitor—a unit of the HP Medical Archive software that monitors hardware
conditions and reports to the NMS. Every server in the grid runs an instance of the SSM.
study A DICOM term for a collection of images (instances) related to an individual patient or subject.
TCP/IP Transmission Control Protocol / Internet Protocol—a process of encapsulating and transmitting
packet data over a network. It includes positive acknowledgement of transmissions.
transfer syntax The parameters, such as the byte order and compression method, needed to exchange data
between systems.
UUID Universally Unique Identifier— a unique identifier for each piece of content in the HP Medical
Archive. UUIDs provide client applications with a content handle that permits them to access
grid content in a way that does not interfere with the grid’s management of that same content.
URI Universal Resource Identifier—a generic set of all names or addresses used to refer to resources
that can be served from a computer system. These addresses are represented as short text
strings.
URL Universal Resource Location—a URI that can be typed into a browser or other client program in
order to retrieve/access an object, such that the client software is able to understand how to
perform the requested action. (The client, typically a “browser”, often uses a Domain Name
Server (DNS) to resolve a URL into an IP address and URI combination.)
60 Glossary
Page 61

UTC A language-independent international abbreviation, UTC is neither English nor French. It means
both “Coordinated Universal Time” and “Temps Universel Coordonné”. UTC refers to the
standard time common to every place in the world. It is derived from International Atomic Time
(TAI) by the addition of a whole number of “leap seconds” to synchronize it with Universal Time
(UT1). UTC is expressed using a 24-hour clock and uses the Gregorian calendar.
version The edition of a service within the HP Medical Archive system. Contrast with “release” and
“revision”.
HP Medical Archive Solution audit message reference 61
Page 62

62 Glossary
Page 63

Index
A
AMQS 12
association, definition
audit message
data types
flow
format
relay service
retention
timestamp
16
11
15
11
17
59
11
B
BKSE 26
C
CBID, definition 59
CDAD
30
conventions
fonts
7
terminology
7
D
data types 16
E
ETAF 37
F
FCRE 41
FCS, definition
FDEL
41
FMFY
42
format
audit message
log file
FRNM
42
FSG audit messages
FSTG
42
FSWI
43
FSWO
43
59
15
15
20, 21, 23
G
grid node (definition) 7
grid task audit messages
H
help, obtaining 8
HP
storage web site
Subscriber’s choice web site
technical support
8
8
20
8
L
log file
accessing
compression
format
naming
13
12
15
12
M
metadata, definition 59
N
namespace, definition 60
node (definition)
7
R
release, definition 60
revision
revision, definition
RPSB
RPSE
7
60
52
53
S
SADD 53
SADE
54
Subscriber’s choice, HP
SYSD
56
SYSU
56
8
T
TACB 56
TACE
57
technical support, HP
terminology
conventions
timestamp, audit message
TSGC
57
TSTC
58
7
8
U
URI, definition 60
URL, definition
60
V
version
history
7
number
version, definition
7
61
W
web sites
HP storage
HP Subscriber’s choice
8
17
8
HP Medical Archive Solution audit message reference 63
 Loading...
Loading...