Page 1

D-Link ™ DES-6500
Modular Layer 3 Chassis-based Ethernet Switch
User’s Guide
Page 2

D-Link DES-6500 Stackable Gigabit Ethernet Switch
____________________
Information in this document is subject to change without notice.
© 2004 D-Link Corporation. All rights reserved.
Reproduction in any manner whatsoever without the written permission of D-Link
Corporation is strictly forbidden.
Trademarks used in this text: D-Link, the D-LINK logo are trademarks of D-Link Computer Corporation; Microsoft and Windows are
registered trademarks of Microsoft Corporation.
Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products.
D-Link Computer Corporation disclaims any proprietary interest in trademarks and trade names other than its own.
April 2004 P/N 6DES6500..01
ii
Page 3

CONTENTS
D-Link ™ DES-6500 ................................................................................................................. i
Intended Readers.................................................................................................................................. x
Typographical Conventions................................................................................................................. x
Notes, Notices, and Cautions .................................................................................................. xi
Safety Instructions................................................................................................................... xi
Safety Cautions .............................................................................................................................................. xi
General Precautions for Rack-Mountable Products ...................................................................................... xii
Protecting Against Electrostatic Discharge.................................................................................................. xiv
Introduction .............................................................................................................................. 1
Switch Description............................................................................................................................... 1
Features ............................................................................................................................................................1
DES-6500 chassis contains 9 slots to install the following available modules..............................................................2
DES-6504 12 port 100BASE-FX (SFF) Fast Ethernet Switch module ..........................................................................2
DES-6505 8-port 1000BASE-SX (SC) Gigabit Ethernet Switch module ......................................................................2
DES-6507 12-port 10BASE-T/100BASE-TX/1000BASE-T Switch module ................................................................2
DES-6509 12-port Mini GBIC(SFP) switch module......................................................................................................3
DES-6510 RJ21 connectors provide 24-port 10BASE-T/100BASE-TX Fast Ethernet Switch module.........................3
DES-6508 16-port 10BASE-T/100BASE-TX Fast Ethernet Switch module.................................................................3
DES-6506 Patch Panel ...................................................................................................................................................3
DES-6511 Power Supply Modules.................................................................................................................................3
Front-Panel Components ..................................................................................................................... 4
LED Indicators.................................................................................................................................................4
Management Options........................................................................................................................... 5
Web-based Management Interface...................................................................................................................5
Command Line Console Interface Through the Serial Port or Telnet..............................................................5
SNMP-Based Management..............................................................................................................................5
Installation ................................................................................................................................ 2
Package Contents................................................................................................................................. 2
Switch Installation ............................................................................................................................... 3
Installing the Switch Without the Rack............................................................................................................3
Installing the Switch in a Rack.........................................................................................................................3
Gigabit Combo Ports ........................................................................................................................... 4
Redundant Power System .................................................................................................................... 4
Connecting the Console Port ............................................................................................................... 5
Password Protection............................................................................................................................. 6
SNMP Settings..................................................................................................................................... 7
Page 4

Traps ..............................................................................................................................................................................7
MIBs ..............................................................................................................................................................................8
IP Address Assignment........................................................................................................................ 8
Connecting Devices to the Switch ....................................................................................................... 9
Introduction to Switch Management.................................................................................... 10
Introduction........................................................................................................................................ 10
Login to Web Manager ...................................................................................................................... 10
Web-based User Interface.................................................................................................................. 11
Areas of the User Interface.............................................................................................................................11
Web Pages......................................................................................................................................................13
Basic Setup ........................................................................................................................................ 13
Switch Information.........................................................................................................................................13
Switch IP Settings ..........................................................................................................................................14
Setting the Switch’s IP Address using the Console Interface.......................................................................................16
Security IP Management Stations Configuration...........................................................................................17
User Accounts Management ..........................................................................................................................17
Admin and User Privileges...........................................................................................................................................18
Saving Changes..............................................................................................................................................19
Factory Reset..................................................................................................................................................20
Restart System................................................................................................................................................20
Switch Information ............................................................................................................................ 21
Advanced Settings ............................................................................................................................. 22
Configuration.......................................................................................................................... 24
Configuring Ports............................................................................................................................... 24
Configuring Port Mirroring ............................................................................................................... 26
Configuring Link Aggregation .......................................................................................................... 27
Understanding Port Trunk Groups .................................................................................................................27
Configuring LACP Port Settings ....................................................................................................... 29
Configuring IGMP............................................................................................................................. 30
IGMP Snooping .............................................................................................................................................30
Static Router Ports..........................................................................................................................................32
Configuring Spanning Tree ............................................................................................................... 33
802.1w Rapid Spanning Tree.........................................................................................................................33
Port Transition States ...................................................................................................................................................34
802.1d/802.1w Compatibility.......................................................................................................................................35
STP Switch Settings.......................................................................................................................................35
STP Port Settings ...........................................................................................................................................37
Configuring Forwarding & Filtering ................................................................................................. 39
Page 5

Static Unicast Forwarding..............................................................................................................................39
Static Multicast Forwarding...........................................................................................................................40
Configuring VLANs .......................................................................................................................... 41
Understanding IEEE 802.1p Priority..............................................................................................................41
VLANs ...........................................................................................................................................................41
Notes About VLANs on the DES-6500 .......................................................................................................................42
IEEE 802.1Q VLANs.....................................................................................................................................42
802.1Q VLAN Packet Forwarding...............................................................................................................................43
802.1Q VLAN Tags .....................................................................................................................................................44
Port VLAN ID..............................................................................................................................................................45
Tagging and Untagging................................................................................................................................................46
Ingress Filtering ...........................................................................................................................................................46
Default VLANs............................................................................................................................................................47
VLAN Segmentation....................................................................................................................................................47
VLAN and Trunk Groups.............................................................................................................................................48
Configuring Static VLANs.............................................................................................................................48
GVRP Settings ...............................................................................................................................................51
Configuring Traffic Control (Broadcast/Multicast Storm Control)................................................... 52
Configuring Port Security.................................................................................................................. 53
Configuring QoS................................................................................................................................ 54
Understanding QoS ........................................................................................................................................54
Setting Bandwidth Control.............................................................................................................................55
QoS Scheduling Mechanism Table ................................................................................................................56
QoS Output Scheduling..................................................................................................................................57
802.1p Default Priority...................................................................................................................................58
802.1p User Priority .......................................................................................................................................58
Configuring Traffic Segmentation .................................................................................................................59
The System Log Server...................................................................................................................... 61
Configuring SNTP Settings ............................................................................................................... 62
Time Settings .................................................................................................................................................63
Time Zone and DST.......................................................................................................................................64
Configuring The Access Profile Table .............................................................................................. 66
Configuring The Port Access Entity .................................................................................................. 72
802.1X Port-based Network Access Control..................................................................................................72
Configure Authenticator.................................................................................................................................74
Configuring Local Users ................................................................................................................................76
PAE System Control ......................................................................................................................................76
Port Capability Settings................................................................................................................................................76
Initializing Ports...........................................................................................................................................................77
Page 6

Reauthenticate Port(s) ..................................................................................................................................................78
RADIUS Server .............................................................................................................................................79
Configuring Layer 3 IP Networking.................................................................................................. 81
Setting Up IP Interfaces .................................................................................................................................81
MD5 Key........................................................................................................................................................83
Route Redistribution Settings.........................................................................................................................83
Static ARP Table............................................................................................................................................85
Static/Default Route .......................................................................................................................................86
Routing Information Protocol (RIP)...............................................................................................................87
RIP Version 1 Message Format....................................................................................................................................88
RIP 1 Message..............................................................................................................................................................88
RIP 1 Route Interpretation ...........................................................................................................................................89
RIP Version 2 Extensions.............................................................................................................................................89
RIP2 Message Format..................................................................................................................................................89
Enabling RIP................................................................................................................................................................90
Setting Up RIP .............................................................................................................................................................90
Configuring OSPF..........................................................................................................................................91
OSPF Authentication....................................................................................................................................................91
Message Digest Authentication (MD-5).......................................................................................................................91
Simple Password Authentication..................................................................................................................................91
The Backbone and Area 0 ............................................................................................................................................92
Virtual Links ................................................................................................................................................................92
Areas Not Physically Connected to Area 0 ..................................................................................................................92
Partitioning the Backbone ............................................................................................................................................92
Neighbors.....................................................................................................................................................................92
Adjacencies ..................................................................................................................................................................93
Designated Router Election..........................................................................................................................................93
Building Adjacency......................................................................................................................................................93
Adjacencies on Point-to-Point Interfaces .....................................................................................................................94
OSPF Packet Formats...................................................................................................................................................94
The OSPF Packet Header.............................................................................................................................................94
The Hello Packet..........................................................................................................................................................95
The Database Description Packet.................................................................................................................................97
The Link-State Request Packet ....................................................................................................................................98
The Link-State Update Packet......................................................................................................................................99
The Link-State Acknowledgment Packet...................................................................................................................100
Link-State Advertisement Formats.............................................................................................................................100
The Link State Advertisement Header .......................................................................................................................101
Router Links Advertisements.....................................................................................................................................102
Network Links Advertisements..................................................................................................................................105
Summary Link Advertisements..................................................................................................................................105
Page 7

Autonomous Systems External Link Advertisements ................................................................................................106
General OSPF Settings...............................................................................................................................................107
OSPF Area Setting.....................................................................................................................................................108
OSPF Interface Configuration....................................................................................................................................110
OSPF Virtual Interface Settings.................................................................................................................................112
Area Aggregation Configuration................................................................................................................................114
OSPF Host Route Settings .........................................................................................................................................115
BOOTP/DHCP Relay...................................................................................................................................116
BOOT/DHCP Relay Information...............................................................................................................................116
BOOTP/DHCP Relay Settings...................................................................................................................................117
DNS Relay ...................................................................................................................................................117
Mapping Domain Names to Addresses ......................................................................................................................118
Domain Name Resolution..........................................................................................................................................118
Configuring DNS Relay Information .........................................................................................................................118
DNS Relay Static Table .............................................................................................................................................119
IP Multicasting .............................................................................................................................................119
IGMP Interface Configuration ...................................................................................................................................120
Configuring DVMRP .................................................................................................................................................121
Enabling DVMRP ......................................................................................................................................................122
DVMRP Interface Configuration ...............................................................................................................................122
PIM_DM Interface Configuration..............................................................................................................................123
Enabling PIM-DM .....................................................................................................................................................124
Managing SNMP .................................................................................................................. 126
SNMP Settings................................................................................................................................. 126
Traps ..........................................................................................................................................................................127
MIBs ..........................................................................................................................................................................127
Enabling SNMP Traps ...............................................................................................................................................128
SNMP User Table............................................................................................................................ 128
SNMP View Table........................................................................................................................... 130
SNMP Group Table ......................................................................................................................... 132
SNMP Community Table Configuration ......................................................................................... 134
SNMP Host Table............................................................................................................................ 135
SNMP Engine ID ............................................................................................................................. 136
Monitoring ............................................................................................................................ 137
Port Utilization................................................................................................................................. 137
Packets ............................................................................................................................................. 139
Received(RX)...............................................................................................................................................139
UMB_cast(RX) ............................................................................................................................................141
Transmitted (TX) .........................................................................................................................................143
Errors ............................................................................................................................................... 145
Page 8

Received (RX)..............................................................................................................................................145
Transmitted (TX) .........................................................................................................................................147
Size .................................................................................................................................................. 149
Stacking Information ....................................................................................................................... 151
Device Status ................................................................................................................................... 152
MAC Address .................................................................................................................................. 153
Switch History Log.......................................................................................................................... 156
IGMP Snooping Table ..................................................................................................................... 157
Browse Router Port.......................................................................................................................... 158
Port Access Control ......................................................................................................................... 158
802.1x Diagnostics.......................................................................................................................................158
802.1x Session Statistics ..............................................................................................................................162
802.1x Statistics ...........................................................................................................................................163
Radius Account Client .................................................................................................................................165
Radius Auth Client.......................................................................................................................................167
Layer 3 Monitoring Features ........................................................................................................... 170
Browse IP Address.......................................................................................................................................170
Browse Routing Table..................................................................................................................................171
Browse ARP Table.......................................................................................................................................172
Browse IP Multicast Forwarding Table .......................................................................................................172
Browse IGMP Group Table .........................................................................................................................173
OSPF Monitoring.........................................................................................................................................173
Browse OSPF LSDB Table........................................................................................................................................173
OSPF Neighbor Table ................................................................................................................................................175
OSPF Virtual Neighbor..............................................................................................................................................176
DVMRP Monitoring ....................................................................................................................................176
DVMRP Routing Table..............................................................................................................................................177
DVMRP Neighbor Address Table..............................................................................................................................177
DVMRP Routing Next Hop Table .............................................................................................................................178
PIM Monitoring ...........................................................................................................................................179
PIM Neighbor Address Table.....................................................................................................................................179
Switch Maintenance ............................................................................................................. 180
TFTP Services.................................................................................................................................. 180
Download Firmware.....................................................................................................................................180
Download Configuration File.......................................................................................................................181
Upload Configuration...................................................................................................................................181
Upload Log...................................................................................................................................................181
Ping Test .......................................................................................................................................... 182
Trace Route...................................................................................................................................... 182
Page 9

Save Changes................................................................................................................................... 183
Reset ................................................................................................................................................ 184
Reboot Device.................................................................................................................................. 185
Logout.............................................................................................................................................. 186
Technical Specifications....................................................................................................... 187
Glossary................................................................................................................................. 189
W
ARRANTY AND REGISTRATION FOR ALL COUNTRIES AND REGIONS EXCEPT USA ............... 195
W
ARRANTY AND REGISTRATION INFORMATION FOR USA ONLY............................................ 196
Page 10
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Intended Readers
The DES-6500 User Guide contains information for setup and management and of the DES6500 switch. This guide is intended for network managers familiar with network management
concepts and terminology.
Typographical Conventions
Convention Description
In a command line, square brackets indicate an optional entry. For
[ ]
Bold font
example: [copy filename] means that optionally you can type copy
followed by the name of the file. Do not type the brackets.
Indicates a button, a toolbar icon, menu, or menu item. For example:
Open the File menu and choose Cancel. Used for emphasis. May
also indicate system messages or prompts appearing on your
screen. For example: You have mail. Bold font is also used to
represent filenames, program names and commands. For example:
use the copy command.
Boldface
Typewriter Font
Initial capital letter
Italics
Menu Name > Menu Option
Indicates commands and responses to prompts that must be typed
exactly as printed in the manual.
Indicates a window name. Names of keys on the keyboard have
initial capitals. For example: Click Enter.
Indicates a window name or a field. Also can indicate a variables or
parameter that is replaced with an appropriate word or string. For
example: type filename means that you should type the actual
filename instead of the word shown in italic.
Menu Name > Menu Option Indicates the menu structure.
Device > Port > Port Properties means the Port Properties menu
option under the Port menu option that is located under the Device
menu.
x
Page 11

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Notes, Notices, and Cautions
NOTE: A NOTE indicates important information that helps you
make better use of your device.
NOTICE: A NOTICE indicates either potential damage to
hardware or loss of data and tells you how to avoid the
problem.
CAUTION: A CAUTION indicates a potential for property
damage, personal injury, or death.
Safety Instructions
Use the following safety guidelines to ensure your own personal safety and to help protect
your system from potential damage. Throughout this safety section, the caution icon ( ) is
used to indicate cautions and precautions that you need to review and follow.
Safety Cautions
To reduce the risk of bodily injury, electrical shock, fire, and damage to the equipment,
observe the following precautions.
Observe and follow service markings. Do not service any product except as explained in your
system documentation. Opening or removing covers that are marked with the triangular
symbol with a lightning bolt may expose you to electrical shock. Components inside these
compartments should be serviced only by a trained service technician.
If any of the following conditions occur, unplug the product from the electrical outlet and
replace the part or contact your trained service provider:
– The power cable, extension cable, or plug is damaged.
– An object has fallen into the product.
– The product has been exposed to water.
– The product has been dropped or damaged.
– The product does not operate correctly when you follow the operating instructions.
• Keep your system away from radiators and heat sources. Also, do not block cooling
vents.
• Do not spill food or liquids on your system components, and never operate the product
in a wet environment. If the system gets wet, see the appropriate section in your
troubleshooting guide or contact your trained service provider.
• Do not push any objects into the openings of your system. Doing so can cause fire or
electric shock by shorting out interior components.
xi
Page 12

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
• Use the product only with approved equipment.
• Allow the product to cool before removing covers or touching internal components.
• Operate the product only from the type of external power source indicated on the
electrical ratings label. If you are not sure of the type of power source required, consult
your service provider or local power company.
• To help avoid damaging your system, be sure the voltage selection switch (if
provided) on the power supply is set to match the power available at your location:
– 115 volts (V)/60 hertz (Hz) in most of North and South America and some Far
Eastern countries such as South Korea and Taiwan
– 100 V/50 Hz in eastern Japan and 100 V/60 Hz in western Japan
– 230 V/50 Hz in most of Europe, the Middle East, and the Far East
• Also be sure that attached devices are electrically rated to operate with the power
available in your location.
• Use only approved power cable(s). If you have not been provided with a power cable
for your system or for any AC-powered option intended for your system, purchase a
power cable that is approved for use in your country. The power cable must be rated
for the product and for the voltage and current marked on the product's electrical
ratings label. The voltage and current rating of the cable should be greater than the
ratings marked on the product.
• To help prevent electric shock, plug the system and peripheral power cables into
properly grounded electrical outlets. These cables are equipped with three-prong plugs
to help ensure proper grounding. Do not use adapter plugs or remove the grounding
prong from a cable. If you must use an extension cable, use a 3-wire cable with
properly grounded plugs.
• Observe extension cable and power strip ratings. Make sure that the total ampere
rating of all products plugged into the extension cable or power strip does not exceed
80 percent of the ampere ratings limit for the extension cable or power strip.
• To help protect your system from sudden, transient increases and decreases in
electrical power, use a surge suppressor, line conditioner, or uninterruptible power
supply (UPS).
• Position system cables and power cables carefully; route cables so that they cannot be
stepped on or tripped over. Be sure that nothing rests on any cables.
• Do not modify power cables or plugs. Consult a licensed electrician or your power
company for site modifications. Always follow your local/national wiring rules.
• When connecting or disconnecting power to hot-pluggable power supplies, if offered
with your system, observe the following guidelines:
– Install the power supply before connecting the power cable to the power supply.
– Unplug the power cable before removing the power supply.
– If the system has multiple sources of power, disconnect power from the system by
unplugging all power cables from the power supplies.
• Move products with care; ensure that all casters and/or stabilizers are firmly connected
to the system. Avoid sudden stops and uneven surfaces.
General Precautions for Rack-Mountable Products
xii
Page 13
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Observe the following precautions for rack stability and safety. Also refer to the rack
installation documentation accompanying the system and the rack for specific caution
statements and procedures.
Systems are considered to be components in a rack. Thus, "component" refers to any system
as well as to various peripherals or supporting hardware.
CAUTION: Installing systems in a rack without the front and side stabilizers
installed could cause the rack to tip over, potentially resulting in bodily injury under
certain circumstances. Therefore, always install the stabilizers before installing
components in the rack.
After installing system/components in a rack, never pull more than one component
out of the rack on its slide assemblies at one time. The weight of more than one
extended component could cause the rack to tip over and may result in serious
injury.
• Before working on the rack, make sure that the stabilizers are secured to the rack,
extended to the floor, and that the full weight of the rack rests on the floor. Install front
and side stabilizers on a single rack or front stabilizers for joined multiple racks before
working on the rack.
Safety Instructions (continued)
Always load the rack from the bottom up, and load the heaviest item in the rack first.
Make sure that the rack is level and stable before extending a component from the rack.
Use caution when pressing the component rail release latches and sliding a component into or
out of a rack; the slide rails can pinch your fingers.
After a component is inserted into the rack, carefully extend the rail into a locking position,
and then slide the component into the rack.
Do not overload the AC supply branch circuit that provides power to the rack. The total rack
load should not exceed 80 percent of the branch circuit rating.
Ensure that proper airflow is provided to components in the rack.
Do not step on or stand on any component when servicing other components in a rack.
NOTE: A qualified electrician must perform all connections to DC power and to
safety grounds. All electrical wiring must comply with applicable local or national
codes and practices.
CAUTION: Never defeat the ground conductor or operate the equipment in the
absence of a suitably installed ground conductor. Contact the appropriate electrical
inspection authority or an electrician if you are uncertain that suitable grounding is
available.
CAUTION: The system chassis must be positively grounded to the rack cabinet
frame. Do not attempt to connect power to the system until grounding cables are
connected. Completed power and safety ground wiring must be inspected by a
qualified electrical inspector. An energy hazard will exist if the safety ground cable
is omitted or disconnected.
xiii
Page 14

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Protecting Against Electrostatic Discharge
Static electricity can harm delicate components inside your system. To prevent static damage,
discharge static electricity from your body before you touch any of the electronic components,
such as the microprocessor. You can do so by periodically touching an unpainted metal
surface on the chassis.
You can also take the following steps to prevent damage from electrostatic discharge (ESD):
1. When unpacking a static-sensitive component from its shipping carton, do not remove
the component from the antistatic packing material until you are ready to install the
component in your system. Just before unwrapping the antistatic packaging, be sure to
discharge static electricity from your body.
2. When transporting a sensitive component, first place it in an antistatic container or
packaging.
3. Handle all sensitive components in a static-safe area. If possible, use antistatic floor
pads and workbench pads and an antistatic grounding strap.
xiv
Page 15

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Section 1
Introduction
Switch Description
Features
Front-Panel Components
Back Panel Description
Plug-in Module Descriptions
Management Options
Switch Description
The DES-6500 is a modular, chassis-based Ethernet backbone switch designed for
adaptability and scalability. This switch provides a management platform with a backplane
switch capacity of 160 Gbps. The chassis contains slots for the DES-6502 CPU management
module and up to 8 modules that can provide up to 192 10/100 Mbps Fast Ethernet ports or up
to 96 1000 Mbps Gigabit Ethernet ports. These modules can be hot-swapped, and the DES6500 chassis allows the installation of a redundant power supply, for maximum reliability and
flexibility. The DES-6511 redundant power supplies operate in a current-sharing mode with
automatic fail-over to ensure constant operation of the switch.
Features
• 160 Gbps switching fabric capacity
• Supports 802.1D STP and 802.1w Rapid Spanning Tree for redundant back up bridge paths
• Supports 802.1Q VLAN, IGMP snooping, 802.1p Priority Queues, port trunking, port mirroring
• Multi-layer Access Control (based on MAC address, IP address, VLAN, Protocol, 802.1p, DSCP)
• Quality of Service (QoS) customized control
• 802.1x (port-based) access control and RADIUS Client support
• Administrator-definable port security
• Per-port bandwidth control
• IEEE 802.3z and IEEE 802.3x compliant Flow Control for all Gigabit ports
• SNMP v.1, v.2, v.3 network management, RMON support
• Support optional external Redundant Power Supply
• Supports Web-based management.
• CLI management support
• DHCP and BOOTP Client support.
• Fully configurable either in-band or out-of-band control via RS-232 console serial connection.
• Telnet remote control console
• TFTP upgrade path for firmware
1
Page 16

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
• Traffic Segmentation
• SysLog support
• Simple Network Time Protocol
• Web GUI Traffic Monitoring
DES-6500 chassis contains 9 slots to install the following available modules
DES-6501 Backplane chassis
DES-6502 Management Module
DES-6506 Patch Panel for 24 port RJ45
DES-6507 12-port 10BASE-T/100BASE-TX/1000BASE-T + Combo 2 SFP
DES-6508 16-port 10/100M Base-T module
DES-6509 12-port mini GBIC Fiber Module
DES-6510 24-port 10/100M RJ21 Module
DES-6504 12-port 100BASE-FX (SFF) Fast Ethernet Switch module
DES-6505 8-port 1000Base-SX SC Fiber Module
DES-6511 Power Supply Module
DES-6504 12 port 100BASE-FX (SFF) Fast Ethernet Switch module
• 12 100BASE-FX (SFF) Fast Ethernet ports
• Fully compliant with IEEE802.3u 100BASE-FX
• IEEE 802.3x compliant Flow Control support for Full-duplex
DES-6505 8-port 1000BASE-SX (SC) Gigabit Ethernet Switch module
• 8 1000BASE-SX (SC) Gigabit Ethernet ports
• Fully compliant with IEEE802.3z
• Support Full Duplex operations
• IEEE 802.3x compliant Flow Control support for full-duplex
DES-6507 12-port 10BASE-T/100BASE-TX/1000BASE-T Switch module
• 12 10BASE-T/100BASE-TX/1000BASE-T ports + Combo 2 SFP
• Fully compliant with IEEE802.3, IEEE802.3a, IEEE802.3u, IEEE802.3z
• All of 10/100/1000Mbps ports support auto-negotiation
• Back pressure Flow Control support for Half-duplex mode
• IEEE 802.3x compliant Flow Control support for Full-duplex
2
Page 17

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
DES-6509 12-port Mini GBIC(SFP) switch module
• 12 Mini GBIC Gigabit Ethernet ports
• Support 1000BASE-SX/LX SFP module
• Fully compliant with IEEE802.3z
• Support Full Duplex operations
• IEEE 802.3x compliant Flow Control support for full-duplex
DES-6510 RJ21 connectors provide 24-port 10BASE-T/100BASE-TX Fast Ethernet Switch module
• 2 RJ21, each support 12-port 10BASE-T/100BASE-TX ports
• Fully compliant with IEEE802.3 10BASE-T, IEEE802.3u 100BASE-TX
• All of 10/100Mbps ports support auto-negotiation
• Back pressure Flow Control support for Half-duplex mode
• IEEE 802.3x compliant Flow Control support for Full-duplex
DES-6508 16-port 10BASE-T/100BASE-TX Fast Ethernet Switch module
• 16 10BASE-T/100BASE-TX ports
• Fully compliant with IEEE802.3 10BASE-T, IEEE802.3u 100BASE-TX
• All of 10/100Mbps ports support auto-negotiation
• Back pressure Flow Control support for Half-duplex mode
• IEEE 802.3x compliant Flow Control support for Full-duplex
DES-6506 Patch Panel
• A patch panel supporting 24 port RJ45 10/100M base-T Interfaces
DES-6511 Power Supply Modules
• Dual power modules design with current sharing design
• Full redundant feature design to ensure continuous operation
• If one power module failed, the other will take over all current supply
automatically.
• Hot-swappable/Hot-pluggable capability
3
Page 18

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
• Power management functions
• Input: 90 ~ 264 VAC, 47 ~ 63Hz
• Output: 3.3V: 4A ~ 80A
• 12V: 0.1A ~ 2A
Front-Panel Components
The front panel of the Switch consists of LED indicators, and an RS-232 communication port.
Figure 1 - 1. Front Panel View of the switch
Comprehensive LED indicators display the status of the switch and the network.
An RS-232 DCE console port for setting up and managing the switch via a connection to a
console terminal or PC using a terminal emulation program.
LED Indicators
The LED indicators of the Switch include Power and System. In addition, there are two
switches to Reset the switch and to turn the switch’s internal alarm off.
The following details the LEDs and Front Panel switchs.
The Power LED will light a constant green to indicate normal operation of the
Power
System
Reset
Alarm Off
Switch’s power supplies. An amber color will be displayed to indicate abnormal
operation of one or more of the Switch’s power supplies.
The System LED will light a constant green to indicate normal operation. An amber
color will be displayed if the switch begins to operate abnormally (usually indicating a
fatal error).
Press this switch to reset the switch.
Press this switch to deactivate the switch’s internal alarm. The internal alarm will
sound if one of the switch’s redundant power supplies fail, or if the safe operating
temperature of one or more of the line cards is exceeded.
4
Page 19

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Management Options
The system may be managed out-of-band through the console port on the front panel or inband using Telnet or a web browser.
Web-based Management Interface
After you have successfully installed the switch, you can configure the switch, monitor the
LED panel, and display statistics graphically using a web browser, such as Netscape
Navigator (version 6.2 and higher) or Microsoft
NOTE: To access the switch through a web browser, the
computer running the web browser must have IP-based
network access to the switch.
Command Line Console Interface Through the Serial Port or Telnet
You can also connect a computer or terminal to the serial console port or use Telnet to access
the switch. The command-line-driven interface provides complete access to all switch
management features. For a full list of commands, see the Command Line Reference, which is
included on the documentation CD.
® Internet Explorer (version 5.0).
SNMP-Based Management
You can manage the switch with an SNMP-compatible console program. The switch is
supports SNMP version 1.0, version 2.0c and version 3.0. The SNMP agent decodes the
incoming SNMP messages and responds to requests with MIB objects stored in the database.
The SNMP agent updates the MIB objects to generate statistics and counters.
The switch supports a comprehensive set of MIB extensions:
• RFC 1213 MIB II
• RFC 1493 Bridge
• RFC 1643 Ether-like MIB
• RFC 1724 (RIPv2)
• RFC 1757 RMON
• RFC 1850 (OSPF)
• RFC 1907 (SNMPv2-MIB)
• D-Link Enterprise MIB
• 802.1p RFC2674
• RFC 2096 (CIDR)
• RFC 2233 Interface MIB
• DVMRP-MIB
• ACLMGT-MIB
• DLKAGENT-MIB
• DLKAUTH-MIB
• DLKEQUIPMENT-MIB
• DLKSYSLOG-MIB
• DLKTIME-MIB
• RSTP-MIB
• RFC 2574 (USM for SNMP)
• L2MGMT-MIB
• L3MGMT-MIB
• LAG-MIB
• RFC 2571 (SNMP Frameworks)
• RFC 2572 (Message Processing for
SNMP)
• RFC 2573 (SNMP Applications)
• RFC 2575 (VACM for SNMP)
• RFC 2576 (Coexistence between SNMPs)
• RFC 2618 (Radius-Auth-Client-MIB)
• RFC 2620 (Radius-Acc-Client-MIB)
• IEEE 8021-PAE-MIB
• RFC 2932 (IPMROUTE)
• RFC 2933 (IGMP)
• RFC 2934 (PIM)
• RFC 2674 (802.1q)
5
Page 20

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Installation
Package Contents
Before You Connect to the Network
Switch Installation
Connecting Stacked Switch Groups
Gigabit Combo Ports
External Redundant Power System
Connecting the Console Port
Password Protection
SNMP Settings
IP Address Assignment
Section 2
Connecting Devices to the Switch
Package Contents
Before you begin installing the switch, confirm that your package contains the following
items:
• One DES-6500 Modular Switch
• Mounting kit: 2 mounting brackets and screws
• Four rubber feet with adhesive backing
• One AC power cord
• This QIG with Registration Card
• CLI Reference
• CD-ROM with User’s Guide and CLI Reference
Before You Connect to the Network
NOTICE: Do not connect the switch to the network until you have established
the correct IP settings.
Before you connect to the network, you must install the switch on a flat surface or in a rack,
set up a terminal emulation program, plug in the power cord, and then set up a password and
IP address.
The switch is supplied with rubber feet for stationing it on a flat surface and mounting
brackets and screws for mounting the switch in a rack.
NOTICE: Do not connect the stacked switch group to the network until you
have properly configured all switches for switch stacking. An improperly configured
switch stack can cause a broadcast storm.
2
Page 21
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Switch Installation
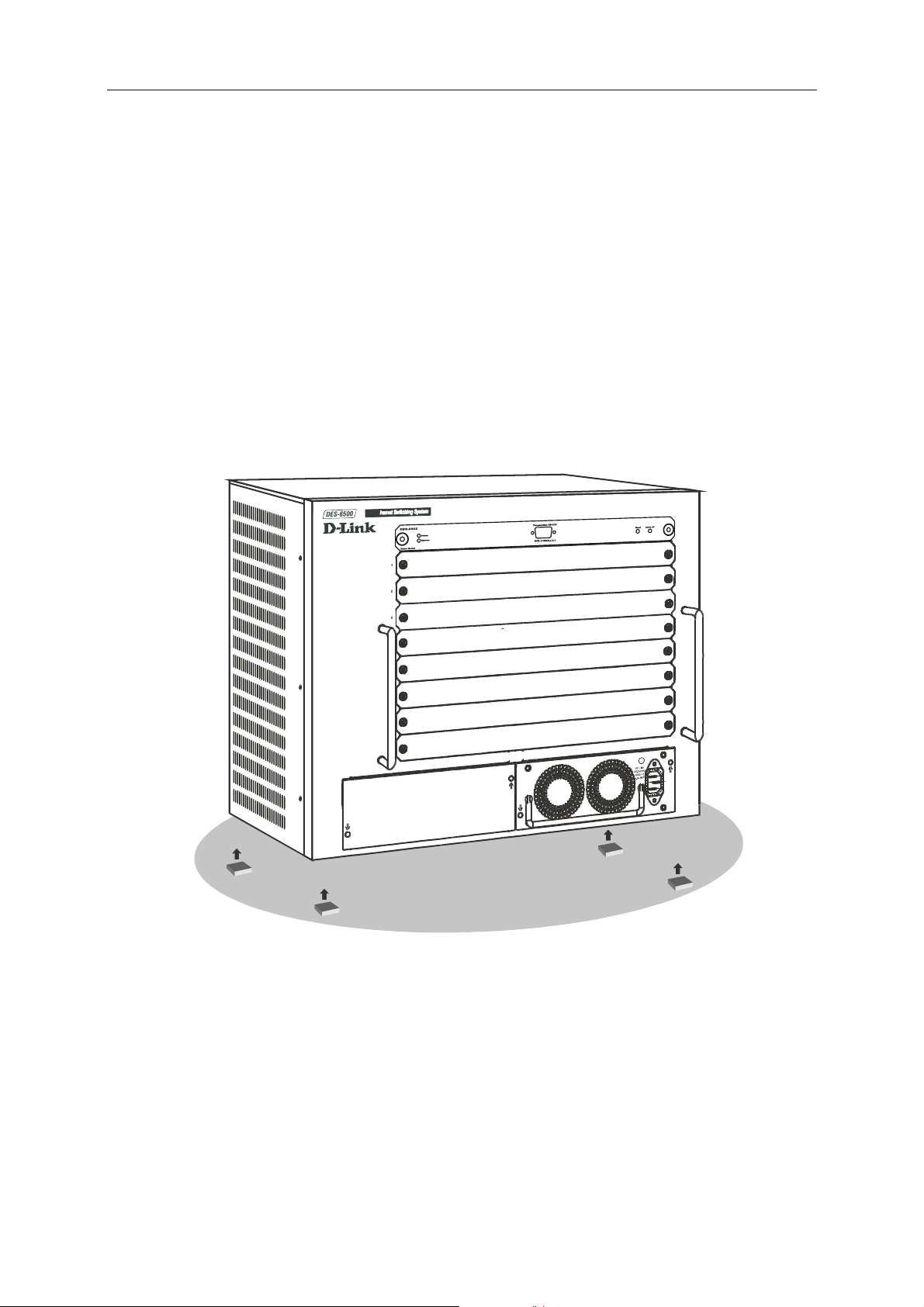
Installing the Switch Without the Rack
1. Install the switch on a level surface that can safely support the weight of the switch
and its attached cables. The switch must have adequate space for ventilation and for
accessing cable connectors.
2. Set the switch on a flat surface and check for proper ventilation. Allow at least 5 cm (2
inches) on each side of the switch and 15 cm (6 inches) at the back for the power
cable.
3. Attach the rubber feet on the marked locations on the bottom of the chassis.
4. The rubber feet, although optional, are recommended to keep the unit from slipping.
Figure 2-1. Install rubber feet for installations with or without a rack
Installing the Switch in a Rack
You can install the switch in most standard 19-inch (48.3-cm) racks. Refer to the illustrations
below.
1. Use the supplied screws to attach a mounting bracket to each side of the switch.
2. Align the holes in the mounting bracket with the holes in the rack.
3
Page 22
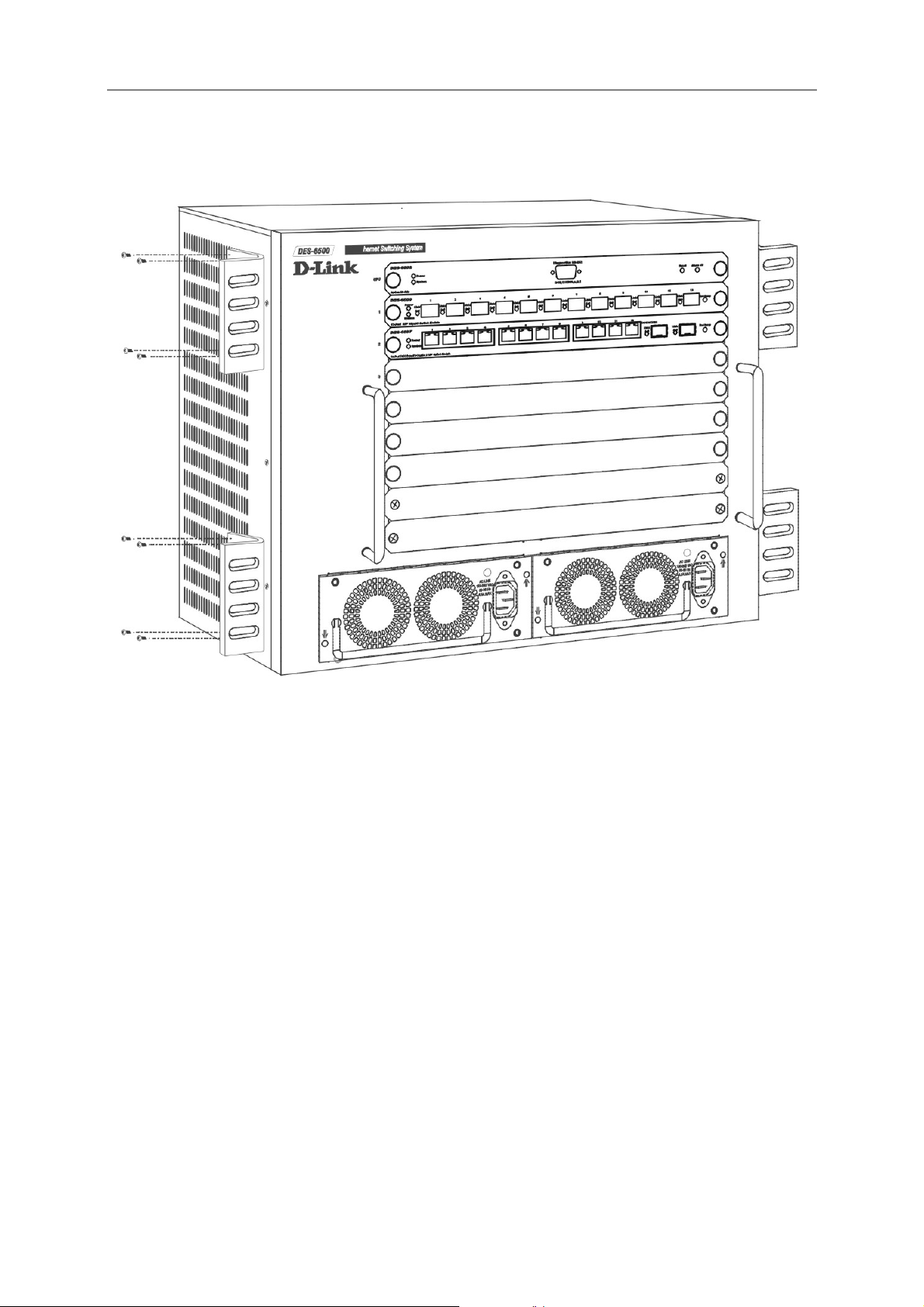
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
3. Insert and tighten two screws through each of the mounting brackets.
Figure 2-2. Attach mounting brackets
Gigabit Combo Ports
In addition to the 24 10/100/1000 Mbps ports, the Switch features four Mini-GBIC Combo
ports. These four ports are 10/100/1000BASE-T copper ports (built-in) and Mini-GBIC ports
(optional). Please note that the Mini-GBIC ports are used instead of the built-in
10/100/1000BASE-T ports. The Mini-GBIC ports will not work simultaneously with its
corresponding 10/100/1000BASE-T port. For example, if port 24x is used on the Mini GBIC
module, port 24 is not available for the 10/100/1000BASE-T built-in port, and vice versa.
Redundant Power System
The switch supports dual, current-sharing, redundant power supplies.
4
Page 23

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Connecting the Console Port
The switch provides an RS-232 serial port that enables a connection to a computer or terminal
for monitoring and configuring the switch. This port is a DB-9 connector, implemented as a
DCE connection.
To use the console port, you need the following equipment:
• A terminal or a computer with both a serial port and the ability to emulate a terminal
• A RS-232 cable with a female DB-9 connector for the console port on the switch
To connect a terminal to the console port:
1. Connect the RS-232 cable directly to the console port on the switch, and tighten the
captive retaining screws.
2. Connect the other end of the cable to a terminal or to the serial connector of a
computer running terminal emulation software. Set the terminal emulation software as
follows:
1. Select the appropriate serial port (COM port 1 or COM port 2).
3. Set the data rate to 115200 baud.
4. Set the data format to 8 data bits, 1 stop bit, and no parity.
5. Set flow control to
none.
6. Under Properties, select VT100 for Emulation mode.
7. Select Terminal keys for Function, Arrow, and Ctrl keys. Ensure that you
select Terminal keys (not Windows keys).
NOTICE: When you use HyperTerminal with the Microsoft® Windows® 2000
operating system, ensure that you have Windows 2000 Service Pack 2 or later
installed. Windows 2000 Service Pack 2 allows you to use arrow keys in
HyperTerminal’s VT100 emulation. See www.microsoft.com for information on
Windows 2000 service packs.
8. After you have correctly set up the terminal, plug the power cable into the
power receptacle on the back of the switch. The boot sequence appears in the
terminal.
9. After the boot sequence completes, the console login screen displays.
10. If you have not logged into the command line interface (CLI) program, press
the Enter key at the User name and password prompts. There is no default user
name and password for the switch, user names and passwords must first be
created by the administrator. If you have previously set up user accounts, log in
and continue to configure the Switch.
11. Enter the commands to complete your desired tasks. Many commands require
administrator-level access privileges. Read the next section for more
information on setting up user accounts. See the Command Line Reference on
the documentation CD for a list of all commands and additional information on
using the CLI.
12. When you have completed your tasks, exit the session with the logout
command or close the emulator program.
5
Page 24
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Password Protection
The DES-6500 does not have a default user name and password. One of the first tasks when
settings up the switch is to create user accounts. If you log in using a predefined
administrator-level user name you have privileged access to the switch’s management
software.
After your initial login, define new passwords for both default user names to prevent
unauthorized access to the switch, and record the passwords for future reference.
To create an administrator-level account for the switch, do the following:
1. At the CLI login prompt, enter create account admin followed by the <user
name> and press the Enter key.
2. You will be asked to provide a password. Type the <password> used for the
administrator account being created and press the Enter key.
3. You will be prompted to enter the same password again to verify it. Type the
same password and press the Enter key.
4. Successful creation of the new administrator account will be verified by a
Success message.
User names and passwords can be up to 15 characters in
length.
The sample below illustrates a successful creation of a
new administrator-level account with the user name “newmanager”.
NOTE:
Passwords are
case sensitive.
DES-6500:4#create account admin newmanager
Command: create account admin newmanager
Enter a case-sensitive new password:********
Enter the new password again for confirmation:********
Success.
DES-6500:4#
NOTICE: CLI configuration commands only modify the
running configuration file and are not saved when the switch
is rebooted. To save all your configuration changes in
nonvolatile storage, you must use the save command to copy
the running configuration file to the startup configuration.
6
Page 25

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
SNMP Settings
Simple Network Management Protocol (SNMP) is an OSI Layer 7 (Application Layer)
function designed specifically for managing and monitoring network devices. SNMP enables
network management stations to read and modify the settings of gateways, routers, switches,
and other network devices. Use SNMP to configure system features for proper operation,
monitor performance and detect potential problems in the switch, switch group or network.
Managed devices that support SNMP include software (referred to as an agent), which runs
locally on the device. A defined set of variables (managed objects) is maintained by the
SNMP agent and used to manage the device. These objects are defined in a Management
Information Base (MIB), which provides a standard presentation of the information controlled
by the on-board SNMP agent. SNMP defines both the format of the MIB specifications and
the protocol used to access this information over the network.
The DES-6500 supports the SNMP versions 1, 2c, and 3. You can specify which version of
the SNMP you want to use to monitor and control the switch. The three versions of SNMP
vary in the level of security provided between the management station and the network
device.
In SNMP v.1 and v.2c, user authentication is accomplished using ‘community strings’, which
function like passwords. The remote user SNMP application and the switch SNMP must use
the same community string. SNMP packets from any station that has not been authenticated
are ignored (dropped).
The default community strings for the switch used for SNMP v.1 and v.2c management access
are:
public - Allows authorized management stations to retrieve MIB objects.
private - Allows authorized management stations to retrieve and modify MIB objects.
SNMP v.3 uses a more sophisticated authentication process that is separated into two parts.
The first part is to maintain a list of users and their attributes that are allowed to act as SNMP
managers. The second part describes what each user on that list can do as an SNMP manager.
The switch allows groups of users to be listed and configured with a shared set of privileges.
The SNMP version may also be set for a listed group of SNMP managers. Thus, you may
create a group of SNMP managers that are allowed to view read-only information or receive
traps using SNMP v.1 while assigning a higher level of security to another group, granting
read/write privileges using SNMP v.3.
Using SNMP v.3 individual users or groups of SNMP managers can be allowed to perform or
be restricted from performing specific SNMP management functions. The functions allowed
or restricted are defined using the Object Identifier (OID) associated with a specific MIB. An
additional layer of security is available for SNMP v.3 in that SNMP messages may be
encrypted. To read more about how to configure SNMP v.3 settings for the switch read the
next section, Management.
Traps
Traps are messages that alert network personnel of events that occur on the Switch. The
events can be as serious as a reboot (someone accidentally turned OFF the Switch), or less
serious like a port status change. The Switch generates traps and sends them to the trap
recipient (or network manager). Typical traps include trap messages for Authentication
Failure, and Topology Change.
7
Page 26
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
MIBs
Management and counter information are stored by the switch in the Management
Information Base (MIB). The Switch uses the standard MIB-II Management Information Base
module. Consequently, values for MIB objects can be retrieved from any SNMP-based
network management software. In addition to the standard MIB-II, the Switch also supports
its own proprietary enterprise MIB as an extended Management Information Base. The
proprietary MIB may also be retrieved by specifying the MIB Object Identifier. MIB values
can be either read-only or read-write.
IP Address Assignment
Each Switch must be assigned its own IP Address, which is used for communication with an
SNMP network manager or other TCP/IP application (for example BOOTP, TFTP). The
switch’s default IP address is 10.90.90.90. You can change the default Switch IP address to
meet the specification of your networking address scheme.
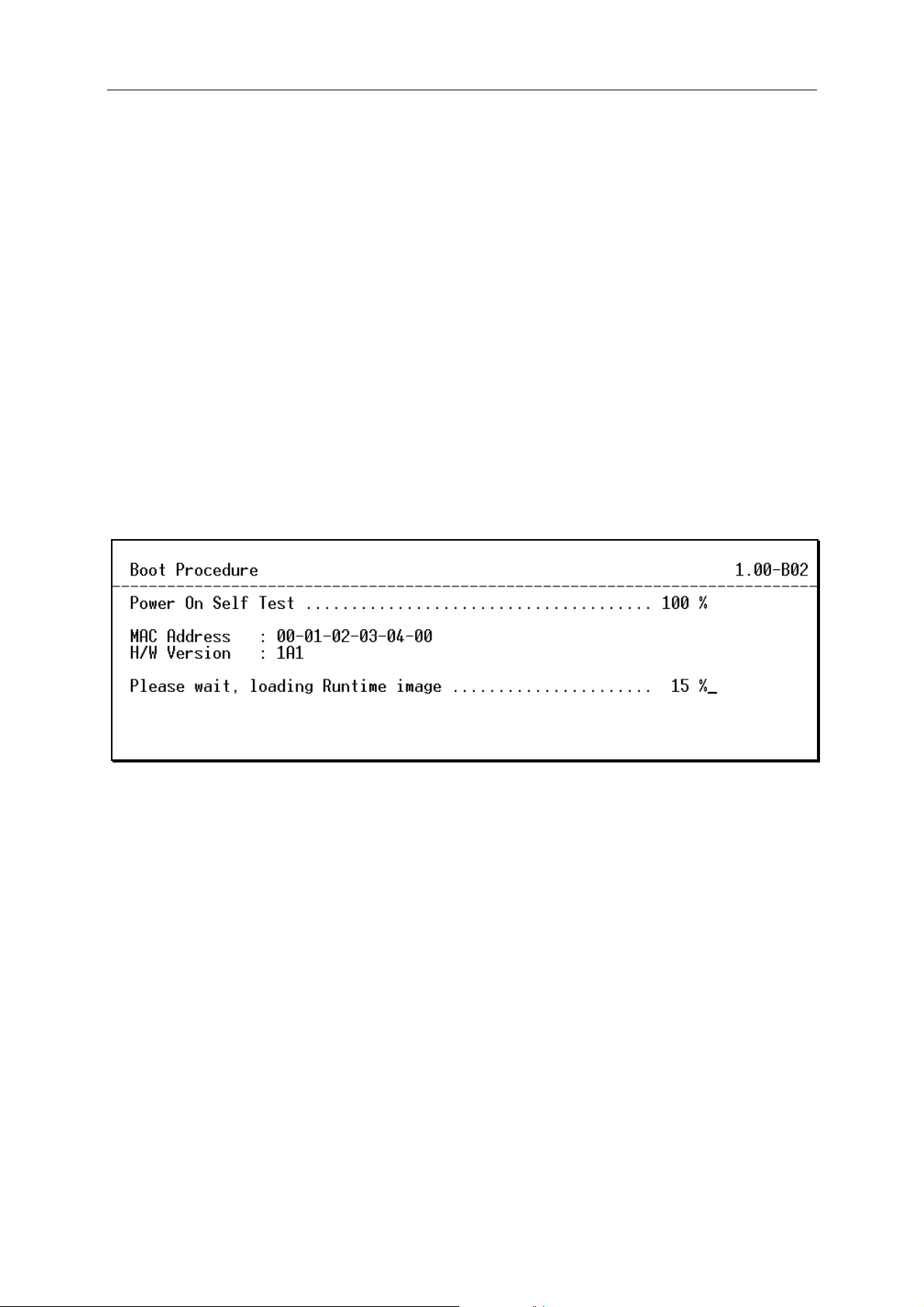
The switch is also assigned a unique MAC address by the factory. This MAC address cannot
be changed, and can be found from the initial boot console screen – shown below.
Figure 2 - 3. Boot Screen
The switch’s MAC address can also be found from the Web management program on the
Switch Information (Basic Settings) window on the Configuration menu.
The IP address for the switch must be set before it can be managed with the Web-based
manager. The switch IP address can be automatically set using BOOTP or DHCP protocols, in
which case the actual address assigned to the switch must be known.
The IP address may be set using the Command Line Interface (CLI) over the console serial
port as follows:
1. Starting at the command line prompt, enter the commands config ipif System
ipaddress xxx.xxx.xxx.xxx/yyy.yyy.yyy.yyy. Where the x’s represent the IP address
to be assigned to the IP interface named System and the y’s represent the
corresponding subnet mask.
2. Alternatively, you can enter config ipif System ipaddress xxx.xxx.xxx.xxx/z. Where
the x’s represent the IP address to be assigned to the IP interface named System and
the z represents the corresponding number of subnets in CIDR notation.
8
Page 27

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The IP interface named System on the switch can be assigned an IP address and subnet mask
which can then be used to connect a management station to the switch’s Telnet or Web-based
management agent.
Figure 2 - 4. Assigning the Switch an IP Address
In the above example, the switch was assigned an IP address of 10.52.19.13 with a subnet
mask of 255.0.0.0. The system message Success indicates that the command was executed
successfully. The switch can now be configured and managed via Telnet and the CLI or via
the Web-based management.
Connecting Devices to the Switch
After assigning IP addresses to the switch, you can connect devices to the switch.
To connect a device to an SFP transceiver port:
1. Use your cabling requirements to select an appropriate SFP transceiver type.
2. Insert the SFP transceiver (sold separately) into the SFP transceiver slot.
3. Use the appropriate network cabling to connect a device to the connectors on the SFP
transceiver.
NOTICE: When the SFP transceiver acquires a link, the
associated integrated 10/100/1000BASE-T port is disabled.
9
Page 28
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Section 3
Introduction to Switch Management
Login to Web Manager
Web-based User Interface
Basic Setup
Switch Information
IP Address
User Accounts
Saving Changes
Factory Reset
Restart System
Introduction
All software functions of the DES-6500 can be managed, configured and monitored via the
embedded web-based (HTML) interface. The switch can be managed from remote stations
anywhere on the network through a standard browser such as Netscape
Navigator/Communicator or Microsoft Internet Explorer. The browser acts as a universal
access tool and can communicate directly with the Switch using the HTTP protocol.
The Web-based management module and the Console program (and Telnet) are different ways
to access the same internal switching software and configure it. Thus, all settings encountered
in web-based management are the same as those found in the console program.
Login to Web Manager
To begin managing your Switch simply run the browser you have installed on your computer
and point it to the IP address you have defined for the device. The URL in the address bar
should read something like: http://123.123.123.123, where the numbers 123 represent the IP
address of the switch.
NOTE: The Factory default IP address for the switch is
10.90.90.90.
In the page that opens, click on the Login to make a setup button at the top of the window:
Figure 3-1. Login Page
This opens the management module’s main page.
The switch management features available in the web-based manager are explained below.
10
Page 29
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
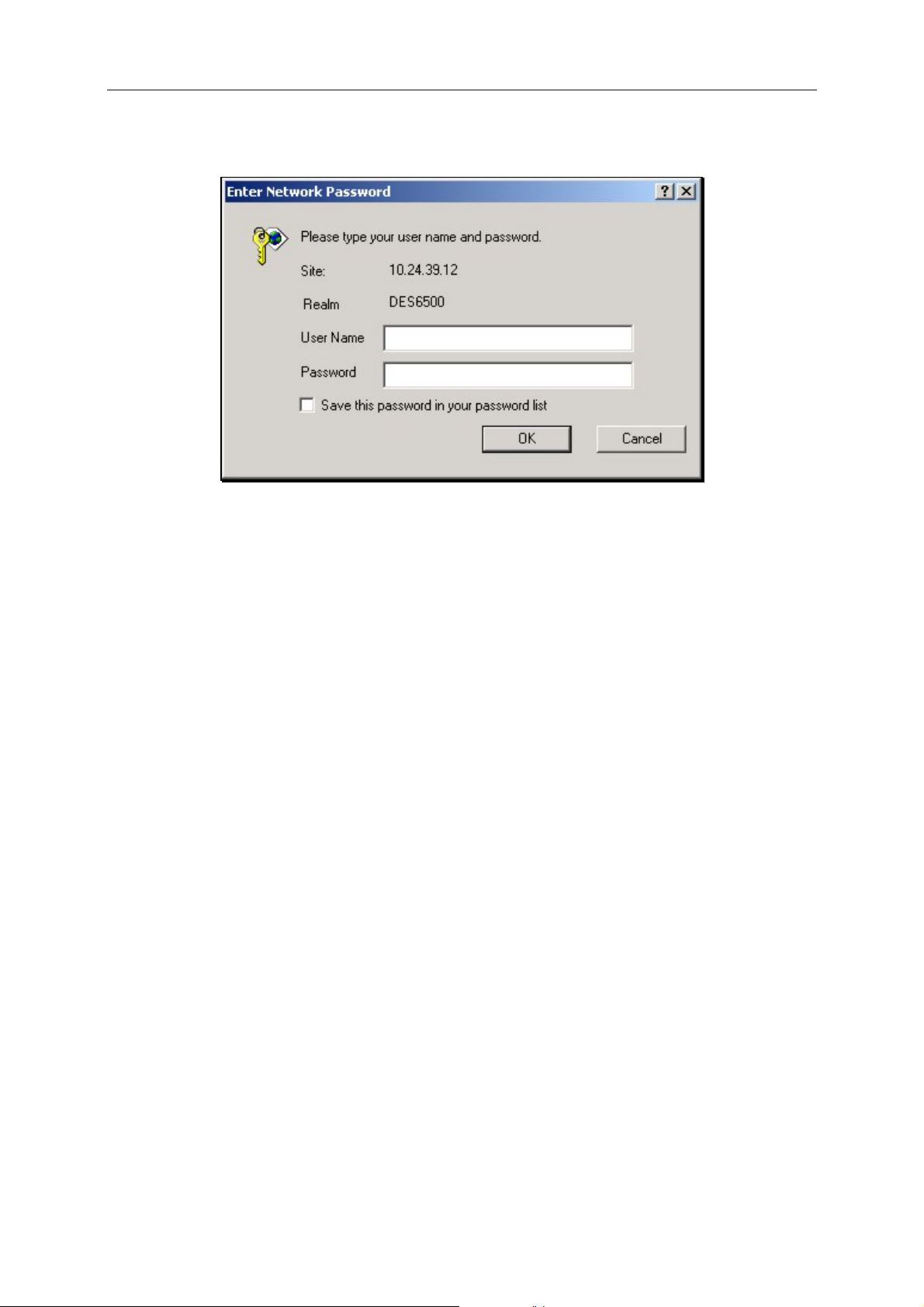
This opens the management module’s user authentication window, as shown below.
Leave both the User Name field and the Password field blank and click OK. This will open
the Web-based user interface. The Switch management features available in the web-based
manager are explained below.
Web-based User Interface
The user interface provides access to various switch configuration and management screens,
allows you to view performance statistics, and permits you to graphically monitor the system
status.
Areas of the User Interface
The figure below shows the user interface. The user interface is divided into 3 distinct areas
as described in the table.
11
Page 30
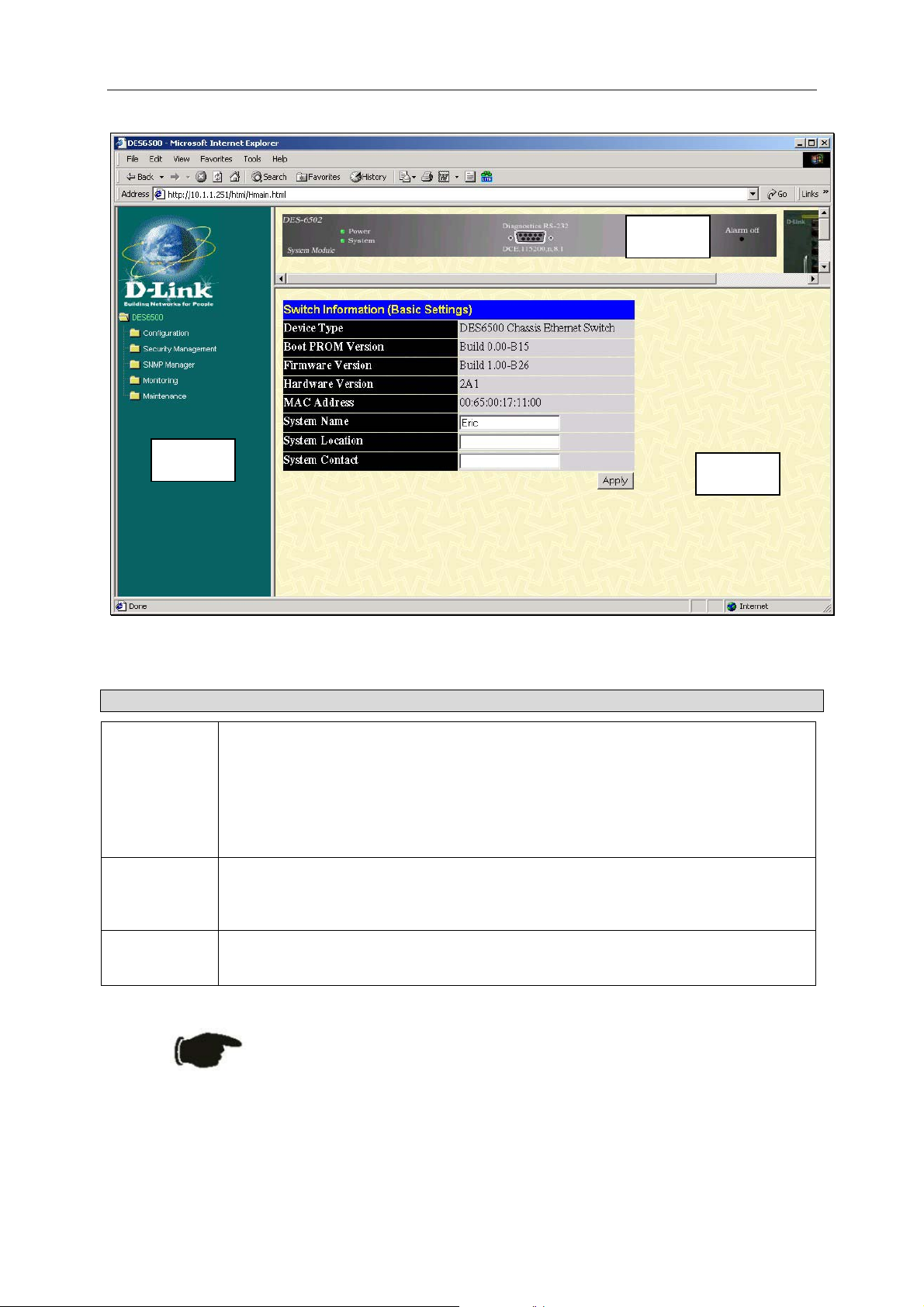
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Area 1
Area 2
Area Function
Presents a graphical near real-time image of the front panel of the switch. This area
displays the switch’s ports and expansion modules, showing port activity, duplex
1
2
mode, or flow control, depending on the specified mode. To the right of the Switch’s
front panel is the current stacking configuration.
Various areas of the graphic can be selected for performing management functions,
including port configuration.
Select the menu or window to be displayed. The folder icons can be opened to
display the hyperlinked menu buttons and subfolders contained within them. Click
the D-Link logo to go to the D-Link website.
Area 3
Figure 3-2. Main Web-Manager Screen
3
Presents switch information based on your selection and the entry of configuration
data.
NOTICE: Any changes made to the switch configuration
during the current session must be saved in the Save
Changes web menu (explained below) or use the command
line interface (CLI) command save.
12
Page 31

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Web Pages
When you connect to the management mode of the switch with a web browser, a login screen
is displayed. Enter a user name and password to access the switch’s management mode.
Below is a list and description of the main folders available in the web interface:
Configuration folder: includes menus for port configuration, bandwidth control, link
aggregation, port mirroring, VLANs configuration, Spanning Tree Protocol setup, forwarding
& filtering configuration, Quality of Service, broadcast/multicast storm controls (Traffic
Control), IGMP snooping, static router ports setup, SysLog server setup, port security, SNTP
settings and the access profile table. This also contains the Advanced Settings menu which is
used to configure miscellaneous settings such as for the serial port, MAC address aging time,
and to enable/disable the following: RMON, IGMP snooping, Telnet and web management
access, traffic segmentation, and 802.1x. The Switch Information page is used to enter system
contact and physical location information and lists basic information such as the switch’s
MAC address, current firmware version and the modules installed.
Security Management: contains 802.1x settings including Radius server information and
PAE setup and security management IP station setup.
SNMP Manager: contains menus for establishing the switch IP settings, user accounts
configuration and SNMP setup including SNMP v.3 configuration.
Monitoring: includes menus for monitoring switch performance monitors, MAC address
table information, router port information, IGMP Snooping information and 802.1x related
information.
Maintenance: contains menus for upgrading firmware and saving configuration files (TFTP
Services), saving configuration changes, resetting and rebooting the switch, Ping test and
logging out of the web manager.
NOTE: Be sure to configure the user name and password in the User Accounts
menu before connecting the switch to the greater network.
Basic Setup
The subsections below describe how to change some of the basic settings for the switch such
as changing IP settings and assigning user names and passwords for management access
privileges, as well as how to save the changes and restart the switch.
Switch Information
Click the Switch Information link in the Configuration menu.
13
Page 32

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 3-3. Switch Information – Basic Settings
The Switch Information window shows the switch’s MAC Address (assigned by the factory
and unchangeable). In addition, the Boot PROM and Firmware Version numbers are shown.
This information is helpful to keep track of PROM and Firmware updates and to obtain the
switch’s MAC address for entry into another network device’s address table – if necessary.
You may assign a System Name, System Location, and System Contact. If any changes or
additions are made, click Apply.
Switch IP Settings
Switch IP settings may initially be set using the console interface prior to connecting to it
through the Ethernet. If the switch IP address has not yet been changed, read the Introduction
of the CLI Reference or skip ahead to the end of this section for a quick description of how to
use the console port and CLI IP settings commands to establish IP settings for the switch.
To change IP settings using the web manager you must access the IP Address menu located
in the Configuration folder.
To configure the switch’s IP address:
Open the Configuration folder and click the IP Address link. The web manager will display
the Switch IP Settings menu below.
14
Page 33

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 3-4. Configure Switch IP Settings
NOTE: the switch’s factory default IP address is 10.90.90.90
with a subnet mask of 255.0.0.0 and a default gateway of
0.0.0.0.
To manually assign the switch’s IP address, subnet mask, and default gateway address:
-Select Manual from the Get IP From drop-down menu.
-Enter the appropriate IP address and subnet mask.
-If you want to access the switch from a different subnet from the one it is installed on, enter
the IP address of the gateway. If you will manage the switch from the subnet on which it is
installed, you can leave the default address (0.0.0.0) in this field.
If no VLANs have been previously configured on the switch, you can use the default VLAN
Name “default”. The default VLAN contains all of the switch ports as members. If VLANs
have been previously configured on the switch, you will need to enter the VLAN Name of the
VLAN that contains the port connected to the management station that will access the switch.
The switch will allow management access from stations with the same VLAN Name listed
here.
To use the BOOTP or DHCP protocols to assign the switch an IP address, subnet mask,
and default gateway address:
Use the Get IP From: <Manual> pull-down menu to choose from BOOTP or DHCP. This
selects how the switch will be assigned an IP address on the next reboot.
The Switch IP Settings options are:
Parameter Description
BOOTP
The switch will send out a BOOTP broadcast request when it is powered up.
The BOOTP protocol allows IP addresses, network masks, and default
gateways to be assigned by a central BOOTP server. If this option is set, the
Switch will first look for a BOOTP server to provide it with this information
before using the default or previously entered settings.
DHCP
Manual
The switch will send out a DHCP broadcast request when it is powered up.
The DHCP protocol allows IP addresses, network masks, and default
gateways to be assigned by a DHCP server. If this option is set, the switch
will first look for a DHCP server to provide it with this information before using
the default or previously entered settings.
Allows the entry of an IP address, Subnet Mask, and a Default Gateway for
15
Page 34

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
the switch. These fields should be of the form xxx.xxx.xxx.xxx, where each
xxx is a number (represented in decimal form) between 0 and 255. This
address should be a unique address on the network assigned for use by the
network administrator. The fields which require entries under this option are
as follows:
Subnet Mask
Default Gateway
VLAN Name
A Bitmask that determines the extent of the subnet that the Switch is on.
Should be of the form xxx.xxx.xxx.xxx, where each xxx is a number
(represented in decimal) between 0 and 255. The value should be 255.0.0.0
for a Class A network, 255.255.0.0 for a Class B network, and 255.255.255.0
for a Class C network, but custom subnet masks are allowed.
IP address that determines where packets with a destination address outside
the current subnet should be sent. This is usually the address of a router or a
host acting as an IP gateway. If your network is not part of an intranet, or you
do not want the Switch to be accessible outside your local network, you can
leave this field unchanged.
This allows the entry of a VLAN Name from which a management station will
be allowed to manage the switch using TCP/IP (in-band via web manager or
Telnet). Management stations that are on VLANs other than the one entered
in the VLAN Name field will not be able to manage the switch in-band unless
their IP addresses are entered in the Security IP Management menu. If
VLANs have not yet been configured for the switch, The default VLAN Name
contains all of the switch’s ports. There are no entries in the Security IP
Management table, by default − so any management station that can connect
to the switch can access the switch until either a management VLAN is
specified or Management Station IP Addresses are assigned.
Setting the Switch’s IP Address using the Console Interface
Each Switch must be assigned its own IP Address, which is used for communication with an
SNMP network manager or other TCP/IP application (for example BOOTP, TFTP). The
switch’s default IP address is 10.90.90.90. You can change the default Switch IP address to
meet the specification of your networking address scheme.
The IP address for the switch must be set before it can be managed with the Web-based
manager. The switch IP address can be automatically set using BOOTP or DHCP protocols, in
which case the actual address assigned to the switch must be known.
The IP address may be set using the Command Line Interface (CLI) over the console serial
port as follows:
Starting at the command line prompt, enter the commands config ipif System ipaddress
xxx.xxx.xxx.xxx/yyy.yyy.yyy.yyy. Where the x’s represent the IP address to be assigned to
the IP interface named System and the y’s represent the corresponding subnet mask.
Alternatively, you can enter config ipif System ipaddress xxx.xxx.xxx.xxx/z. Where the x’s
represent the IP address to be assigned to the IP interface named System and the z represents
the corresponding number of subnets in CIDR notation.
The IP interface named System on the switch can be assigned an IP address and subnet mask
which can then be used to connect a management station to the switch’s Telnet or Web-based
management agent.
The system message Success indicates that the command was executed successfully. The
switch can now be configured and managed via Telnet and the CLI or via the Web-based
management agent using the above IP address to connect to the switch.
16
Page 35

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Security IP Management Stations Configuration
Go to the Security Management folder and click on Security IP; the following screen will
appear.
Figure 3-5. Security IP Management Setup
Use the Management Station IP Settings to select up to three management stations used to
manage the Switch. If you choose to define one or more designated management stations,
only the chosen stations, as defined by IP address, will be allowed management privilege
through the web manager or Telnet session. To define a management station IP setting, type in
the IP address and click on the Apply button.
User Accounts Management
Use the User Accounts Control Table to control user privileges. To view existing User
Accounts, open the Security Management folder and click on the User Accounts link. This
will open the User Account Management page, as shown below.
Figure 3-6. User Accounts Management Table
To add a new user, click on the Add button. To modify or delete an existing user, click on the
Modify button for that user.
17
Page 36

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 3-7. Add User Accounts Modify Table
Add a new user by typing in a User Name, and New Password and retype the same password
in the Confirm New Password. Choose the level of privilege (Admin or User) from the
Access Right drop-down menu. To add a user account using the CLI commands use create
account and config account.
Figure 3-8. Modify User Accounts
Modify or delete an existing user account in the User Account Control Table – Edit. To delete
the user account, click on the Delete button. To change the password, type in the New
Password and retype it in the Confirm New Password entry field. Choose the level of
privilege (Admin or User) from the Access Right drop-down menu. To delete a user account
using CLI use the command delete account. To change an existing account use config
account.
From the Main Menu, highlight Setup User Accounts and press Enter, then the User
Account Management menu appears.
Admin and User Privileges
There are two levels of user privileges: Admin and User. Some menu selections available to
users with Admin privileges may not be available to those with User privileges.
The following table summarizes the Admin and User privileges:
Management Admin User
Configuration
Yes Read Only
18
Page 37

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Network Monitoring
Community Strings and Trap Stations
Update Firmware and Configuration Files
System Utilities
Factory Reset
User Account Management
Add/Update/Delete User Accounts
View User Accounts
Admin and User Privileges
Yes Read Only
Yes Read Only
Yes No
Yes Ping Only
Yes No
Yes No
Yes No
After establishing a User Account with Admin-level privileges, be sure to save the changes
(see below).
Saving Changes
Changes made to the switch’s configuration must be saved in order to retain them. Access the
Save Configuration by clicking the Save Changes button located in the Maintenance folder.
Figure 3-9. Save Configuration window
The switch has two levels of memory, normal RAM and non-volatile or NV-RAM. To save
all the changes made in the current session to the Switch’s flash memory, click the Save
Configuration button. Click the OK button in the new dialog box that appears to continue.
When this is done, the settings will be immediately applied to the switching software in RAM,
and will immediately take effect. Once the switch configuration settings have been saved to
NV-RAM, they become the default settings for the switch. These settings will be used every
time the switch is rebooted.
Some settings, though, require you to restart the switch before they will take effect. Restarting
the switch erases all settings in RAM and reloads the stored settings from the NV-RAM.
Thus, it is necessary to save all setting changes to NV-RAM before rebooting the switch.
To save settings using CLI the command is save.
19
Page 38

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Factory Reset
Click the Reset link in the Maintenance folder to bring up the reset menu.
Figure 3-10. Factory Reset to Default Value
Reset − returns all configuration settings except the switch’s IP address, subnet mask, default
gateway, log, user account and stack information settings to the factory default settings.
Reset Config − returns all configuration settings except the stack information settings to the
factory default settings, but does not save the settings or reboot the switch. If you select this
option the switch configuration will be returned to the factory default settings for the current
session only. When the switch is rebooted, it will return to the last configuration saved to the
switch’s NV-RAM using the Save Changes option.
Reset System − returns switch configuration to the factory default settings and then saves the factory default
configuration to the switch’s NV-RAM. The switch will then reboot. When the switch has rebooted, it will have
the same configuration as when it was delivered from the factory.
Restart System
The following menu is used to restart the switch. Access this menu by clicking on the Reboot
Device link in the Maintenance folder.
Click the Yes after Do you want to save the settings? to instruct the switch to save the
current configuration to non-volatile RAM before restarting the switch.
Clicking the No option instructs the switch not to save the current configuration before
restarting the switch. All of the configuration information entered since the last time Save
Changes was executed will be lost.
Click the Restart button to restart the switch.
20
Page 39

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 3-11. Restart System
NOTE: Clicking Yes is equivalent to executing Save
Changes and then restarting the switch.
Switch Information
The first page displayed upon logging in presents the System Information menu. This page
can be accessed at any time by clicking the Switch Information button in the Configuration
folder.
Figure 3-12. Switch Information
21
Page 40

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The System Information page displays general information about the Switch including its
MAC Address, Hardware Boot PROM and Firmware versions, and other optional
information.
You can also enter or change a System Name, System Location, and the name and telephone
number of the responsible administrator in the System Contact. It is recommended that the
person responsible for the maintenance of the network system be listed here. Click on the
Apply button to make the changes effective.
To view this information using Telnet use CLI command show switch.
Advanced Settings
The Advanced Settings window contains the main settings for all major functions for the
Switch. To view the Advanced Settings window, click its link in the Configuration folder.
This will enable the following window to be viewed and configured.
Figure 3-13. Switch Information − Advanced Settings
The Advanced Settings menu options are summarized in the table below.
Variables in the Advanced Settings menu of the Web Manager and their corresponding CLI
command groups are the following:
Parameter Description
Serial Port Auto
Logout
Select the logout time used for the console interface. This automatically
logs the user out after an idle period of time as defined. Choose from the
22
Page 41

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
following options: 2 Minutes, 5 Minutes, 10 Minutes, 15 Minutes or Never.
Serial Port Baud
Rate
MAC Address Aging
Time
IGMP Snooping
Multicast Router
Only
GVRP
Telnet Status
Fixed at 115200.
This field specifies the length of time a learned MAC Address will remain in
the forwarding table without being accessed (that is, how long a learned
MAC Address is allowed to remain idle). The default age-out time for the
Switch is 300 seconds. To change this, type in a different value
representing the MAC address age-out time in seconds. The Aging Time
can be set to any value between 10 and 1,000,000 seconds.
To enable system-wide IGMP Snooping capability select Enabled. IGMP
snooping is Disabled by default. Enabling IGMP snooping allows you to
specify use of a multicast router only (see below). To configure IGMP
Snooping for individual VLANs, use the IGMP Snooping page under the
IGMP folder.
If this option is enabled and IGMP Snooping is also enabled, the switch
forwards all multicast traffic to a multicast-enabled router only. Otherwise,
the switch will forward all multicast traffic to any IP router.
Use this pull-down menu to Enable or Disable GVRP on the switch.
Telnet configuration is Enabled by default. If you do not want to allow
configuration of the system through Telnet choose Disabled.
Web Status
RMON Status
Link Aggregation
Algorithm
Switch 802.1x
Auth Protocol
HOL State
Jumbo Frame
Syslog State
Web-based management is Enabled by default. If you choose to disable
this by selecting Disabled, you will lose the ability to configure the system
through the web interface as soon as these settings are applied.
Remote monitoring (RMON) of the switch is Enabled or Disabled here.
The algorithm that the switch uses to balance the load across the ports that
make up the port trunk group is defined by this definition. Choose Source
Address, Destination Address or Both. (See Link Aggregation).
Enables or disables 802.1x VLANs; default is Disabled.
You can select between Radius Eap or Local.
Enables or disables HOL (Head of Line) prevention; default is Enabled.
Enables or disables Jumbo Frame acceptance; default is Disabled.
Enables or disables Syslog State; default is Disabled.
23
Page 42

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuration
Configuring Ports
Configuring Port Mirroring
Configuring Link Aggregation
Configuring IGMP
Configuring The Spanning Tree
Configuring Forwarding and Filtering
Configuring VLANs
Configuring Traffic Control
Configuring Port Security
Configuring QoS
The System Log Server
Section 4
Configuring SNTP Settings
Configuring The Access Profile Table
Configuring The Port Access Entity
Configuring Layer 3 IP Networking
Configuring Ports
This section contains information for configuring various attributes and properties for
individual physical ports, including port speed and flow control. Clicking on Port
Configurations in the Configuration menu will display the following window for the user.
The Unit pull-down menu refers to the module installed in the DES-6500 chassis that you
want to configure ports for. The modules are numbered from 1 at the top (just below the
DES-6502 CPU module) to 8 at the bottom (the slot farthest from the CPU module).
24
Page 43

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
g
Figure 4- 1. Port Configuration menu
To configure switch ports:
1. Choose the Unit from the pull-down menu. The Unit pull-down menu refers to the
module installed in the DES-6500 chassis that you want to configure ports for. The
modules are numbered from 1 at the top (just below the DES-6502 CPU module) to 8
at the bottom (the slot farthest from the CPU module)
2. Choose the port or sequential range of ports using the From…To… port pull-down
menus.
3. Use the remaining pull-down menus to configure the parameters described below:
Parameter Description
State <Enabled> Toggle the State <Enabled> field to either enable or disable a given
port.
Speed/Duplex
<Auto>
Toggle the Speed/Duplex <Auto> field to either select the speed and
duplex/half-duplex state of the port. Auto – auto-negotiation between
10 and 1000 Mbps devices, full- or half-duplex. The Auto setting
allows the port to automatically determine the fastest settings the
device the port is connected to can handle, and then to use those
settings. The other options are auto, 10M/Half, 10M/Full, 100M/Half,
100M/Full, 1000M/Full Master, and 1000M/Full Slave. There is no
automatic adjustment of port settings with any option other than Auto.
Flow Control
Displays the flow control scheme used for the various port
configurations. Ports configured for full-duplex use 802.3x flow
control, half-duplex ports use backpressure flow control, and Auto
ports use an automatic selection of the two. The default is Disabled.
Learning
Enable or disable MAC address learning for the selected ports. When
Enabled, destination and source MAC addresses are automatically
listed in the forwardin
table. When learning is Disabled, MAC
25
Page 44

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
addresses must be manually entered into the forwarding table. This is
sometimes done for reasons of security or efficiency. See the section
on Forwarding/Filtering for information on entering MAC addresses
into the forwarding table.
Configuring Port Mirroring
The Switch allows you to copy frames transmitted and received on a port and redirect the
copies to another port. You can attach a monitoring device to the mirrored port, such as a
network sniffer or an RMON probe, to view details about the packets passing through the first
port. This is useful for network monitoring and troubleshooting purposes. To view the Setup
Port Mirroring window, click Port Mirroring in the Configuration folder.
Figure 4- 2. Setup port Mirroring window
To configure a mirror port:
1. Select the Source Port from where you want to copy frames and the Target Port,
which receives the copies from the source port.
2. Select the Source Direction, Ingress, Egress, or Both and change the Status dropdown menu to Enabled. None is equivalent to Disabled in the Status pull-down
menu.
3. Click Apply to let the changes take effect.
26
Page 45

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
NOTE: You cannot mirror a fast port onto a slower port. For
example, if you try to mirror the traffic from a 100 Mbps port onto a
10 Mbps port, this can cause throughput problems. The port you are
copying frames from should always support an equal or lower speed
than the port to which you are sending the copies. Also, the target
port for the mirroring cannot be a member of a trunk group. Please
note a target port and a source port cannot be the same port.
Configuring Link Aggregation
Understanding Port Trunk Groups
Port trunk groups are used to combine a number of ports together to make a single highbandwidth data pipeline.
The Switch treats all ports in a trunk group as a single port. Data transmitted to a specific host
(destination address) will always be transmitted over the same port in a trunk group. This
allows packets in a data stream to arrive in the same order they were sent.
Link aggregation allows several ports to be grouped together and to act as a single link. This
gives a bandwidth that is a multiple of a single link’s bandwidth.
Link aggregation is most commonly used to link a bandwidth intensive network device or
devices, such as a server, to the backbone of a network.
All ports in the group must be a member of the same VLAN and their STP status
configuration, static multicast entries, traffic control, traffic segmentation and 802.1p default
priority, must be identical. Also, port locking, port mirroring and 802.1X must not be enabled
on the trunk group. Further, the aggregated links must all be of the same speed and should be
configured as full-duplex.
The Master Port of the group, becomes the configuration for all of the ports in the aggregation
group and all configuration options, including the VLAN configuration, that can be applied to
the Master Port are applied to the entire link aggregation group.
Load balancing is automatically applied to the ports in the aggregated group, and a link failure
within the group causes the network traffic to be directed to the remaining links in the group.
The Spanning Tree Protocol will treat a link aggregation group as a single link, on the switch
level. On the port level, the STP will use the port parameters of the Master Port in the
calculation of port cost and in determining the state of the link aggregation group. If two
redundant link aggregation groups are configured on the switch, STP will block one entire
group, in the same way STP will block a single port that has a redundant link.
To configure port trunking, click on the Link Aggregation hyperlink in the Configuration
folder to bring up the Current Link Aggregation Group Entries table:
Note: If ports become disconnected within a trunk group,
intended packets will be load shared to the other up-linked
ports of the link aggregation group.
27
Page 46

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 3. Port Trunking Group Entry Table
To configure port trunk groups, click the Add button to add a new trunk group and use the
menu Link Aggregation Group Configuration menu (see example below) to set up trunk
groups. To modify a port trunk group, double-click on it to bring up the Link Aggregation
Group Configuration menu. To delete a port trunk group, click the Delete option in the
Current Link Aggregation Group Entries table.
Figure 4- 4. Link Aggregation Group Configuration
The user-changeable parameters are as follows:
Parameter Description
Group ID
Group Name
Type
State
Select an ID number for the group.
Type in a name for the group (optional).
This pull-down menu allows you to select between Static and LACP (Link
Aggregation Control Protocol.) LACP allows for the automatic detection of
links in a Port Trunking Group.
Trunk groups can be toggled between Enabled and Disabled. This is used
28
Page 47

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
to turn a port trunking group on or off. This is useful for diagnostics, to
quickly isolate a bandwidth intensive network device or to have an absolute
backup aggregation group that is not under automatic control.
Master Port
Choose Member
Ports
Flooding Port
Choose the Master port for the trunk group.
Choose the members of a trunked group. Up to 8 ports per group can be
assigned to a group.
A trunking group must designate one port to allow transmission of
broadcasts and unknown unicasts.
Configuring LACP Port Settings
To configure the LACP port settings, click the LACP Port Settings link to open the Lacp
Settings menu, as shown below.
Figure 4- 5. LACP Configuration
The user-changeable parameters are as follows:
Parameter Description
29
Page 48

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Unit
From
To
Mode
Select the module that contains the ports you want to configure LACP for.
The modules are numbered from 1 at the top (just below the CPU module),
to 8 (the slot farthest from the CPU module).
Select the first in a group of ports you want to configure LACP for.
Select the last in a group of ports you want to configure LACP for.
You can choose between Passive and Active LACP modes.
In the Passive mode, the port does not initiate the exchange of LACP
packets, but does understand the incoming LACP packets. Links can only
be formed with ports that are running LACP in the Active mode.
In the Active mode, the port initiates the negotiation and will form links with
other ports if the other end is running LACP.
Configuring IGMP
Internet Group Management Protocol (IGMP) snooping allows the Switch to recognize
IGMP queries and reports sent between network stations or devices and an IGMP host. When
enabled for IGMP snooping, the Switch can open or close a port to a specific device based on
IGMP messages passing through the Switch.
In order to use IGMP Snooping it must first be enabled for the entire Switch (see Advanced
Settings). You may then fine-tune the settings for each VLAN using the IGMP Snooping
link in the Configuration folder. When enabled for IGMP snooping, the Switch can open or
close a port to a specific Multicast group member based on IGMP messages sent from the
device to the IGMP host or vice versa. The Switch monitors IGMP messages and discontinues
forwarding multicast packets when there are no longer hosts requesting that they continue.
IGMP Snooping
Use the IGMP Snooping Group Entry Table to view IGMP Snooping status. To modify
settings, click the Modify button for the VLAN ID you want to change.
Figure 4- 6. Current IGMP Snooping Group Entries
Clicking the Modify button will bring up the IGMP Snooping Settings menu.
30
Page 49

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 7. IGMP Snooping Settings window
The following parameters may be viewed or modified:
Parameter Description
Query Interval
Max Response Time
Robustness Variable
Last Member Query
Interval
The Query Interval field is used to set the time (in seconds) between
transmitting IGMP queries. Entries between 1 and 9,999 seconds are
allowed. Default = 125.
This determines the maximum amount of time in seconds allowed before
sending an IGMP response report. The Max Response Time field allows
an entry between 1 and 25 (seconds). Default = 10.
Adjust this variable according to expected packet loss. If packet loss on
the VLAN is expected to be high, the Robustness Variable should be
increased to accommodate increased packet loss. This entry field allows
an entry of 2 to 255. Default = 2.
Specifies the maximum amount of time between group-specific query
messages, including those sent in response to leave group messages.
Default = 1.
Host Timeout
Route Timeout
This is the maximum amount of time in seconds allowed for a host to
continue membership in a multicast group without the Switch receiving a
host membership report. Default = 260.
This is the maximum amount of time in seconds a route is kept in the
forwarding table without receiving a membership report. Default = 260.
31
Page 50

Leave Timer
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
This specifies the maximum amount of time in seconds between the
Switch receiving a leave group message from a host, and the Switch
issuing a group membership query. If no response to the membership
query is received before the Leave Timer expires, the (multicast)
forwarding entry for that host is deleted.
Querier State
State
Choose Querier to enable transmitting IGMP Query packets or NonQuerier to disable. The default value is Non-Querier.
Select Enabled to implement IGMP Snooping. This is Disabled by
default.
Static Router Ports
A static router port is a port that has a multicast router attached to it. Generally, this router
would have a connection to a WAN or to the Internet. Establishing a router port will allow
multicast packets coming from the router to be propagated through the network, as well as
allowing multicast messages (IGMP) coming from the network to be propagated to the router.
A router port has the following behavior:
• All IGMP Report packets will be forwarded to the router port.
• IGMP queries (from the router port) will be flooded to all ports.
• All UDP multicast packets will be forwarded to the router port. Because routers do not
send IGMP reports or implement IGMP snooping, a multicast router connected to the
router port of the Layer 3 switch would not be able to receive UDP data streams unless
the UDP multicast packets were all forwarded to the router port.
A router port will be dynamically configured when IGMP query packets, RIPv2 multicast,
DVMRP multicast, PIM-DM multicast packets are detected flowing into a port.
Open the IGMP folder and the click on the Static Router Ports Entry link to open the
Current Static Router Ports Entries page, as shown below.
Figure 4- 8. Current Static Router Ports Entries window
The Current Static Router Ports Entries page (shown above) displays all of the current
entries to the Switch’s static router port table. To add or modify an entry, click the Modify
button. This will open the Static Router Ports Settings page, as shown below.
32
Page 51

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 9. Static Router Ports Settings window
The following parameters can be set:
Parameter Description
VID (VLAN ID)
VLAN Name
Slot
Member Ports
This is the VLAN ID that, along with the VLAN name, identifies the VLAN
where the multicast router is attached.
This is the name of the VLAN where the multicast router is attached.
This is the Unit ID of the switch in a switch stack for which you are creating
an entry into the switch’s static router port table.
There are the ports on the switch that will have a multicast router attached
to them.
Configuring Spanning Tree
The switch supports 802.1d Spanning Tree Protocol (STP) and 802.1w Rapid Spanning Tree
Protocol (RSTP). 802.1d STP will be familiar to most networking professionals. However
since 802.1w RSTP has been recently introduced to D-Link managed Ethernet switches, a
brief introduction to the technology is provided below followed by a description of how to set
up 802.1 d STP and 802.1w RSTP.
802.1w Rapid Spanning Tree
The Switch implements two versions of the Spanning Tree Protocol, the Rapid Spanning Tree
Protocol (RSTP) as defined by the IEEE 802.1w specification and a version compatible with
the IEEE 802.1d STP. RSTP can operate with legacy equipment implementing IEEE 802.1d,
however the advantages of using RSTP will be lost.
The IEEE 802.1w Rapid Spanning Tree Protocol (RSTP) evolved from the 802.1d STP
standard. RSTP was developed in order to overcome some limitations of STP that impede the
function of some recent switching innovations, in particular, certain Layer 3 function that are
33
Page 52

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
increasingly handled by Ethernet switches. The basic function and much of the terminology is
the same as STP. Most of the settings configured for STP are also used for RSTP. This section
introduces some new Spanning Tree concepts and illustrates the main differences between the
two protocols.
Port Transition States
An essential difference between the two protocols is in the way ports transition to a
forwarding state and the in the way this transition relates to the role of the port (forwarding or
not forwarding) in the topology. RSTP combines the transition states disabled, blocking and
listening used in 802.1d and creates a single state Discarding. In either case, ports do not
forward packets; in the STP port transition states disabled, blocking or listening or in the
RSTP port state discarding there is no functional difference, the port is not active in the
network topology. Table 5-7 below compares how the two protocols differ regarding the port
state transition.
Both protocols calculate a stable topology in the same way. Every segment will have a single
path to the root bridge. All bridges listen for BPDU packets. However, BPDU packets are sent
more frequently – with every Hello packet. BPDU packets are sent even if a BPDU packet
was not received. Therefore, each link between bridges are sensitive to the status of the link.
Ultimately this difference results faster detection of failed links, and thus faster topology
adjustment. A drawback of 802.1d is this absence of immediate feedback from adjacent
bridges.
802.1d STP
802.1w
RSTP
Forwarding? Learning?
Disabled Discarding No No
Blocking Discarding No No
Listening Discarding No No
Learning Learning No Yes
Forwarding Forwarding Yes Yes
Comparing Port States
RSTP is capable of more rapid transition to a forwarding state – it no longer relies on timer
configurations – RSTP compliant bridges are sensitive to feedback from other RSTP
compliant bridge links. Ports do not need to wait for the topology to stabilize before
transitioning to a forwarding state. In order to allow this rapid transition, the protocol
introduces two new variables: the edge port and the point-to-point (P2P) port.
Edge Port
The edge port is a configurable designation used for a port that is directly connected to a
segment where a loop cannot be created. An example would be a port connected directly to a
single workstation. Ports that are designated as edge ports transition to a forwarding state
immediately without going through the listening and learning states. An edge port loses its
status if it receives a BPDU packet, immediately becoming a normal spanning tree port.
34
Page 53

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
P2P Port
A P2P port is also capable of rapid transition. P2P ports may be used to connect to other
bridges. Under RSTP, all ports operating in full-duplex mode are considered to be P2P ports,
unless manually overridden through configuration.
802.1d/802.1w Compatibility
RSTP can interoperate with legacy equipment and is capable of automatically adjusting
BPDU packets to 802.1d format when necessary. However, any segment using 802.1 STP will
not benefit from the rapid transition and rapid topology change detection of RSTP. The
protocol also provides for a variable used for migration in the event that legacy equipment on
a segment is updated to use RSTP.
STP Switch Settings
The Spanning Tree Protocol (STP) operates on two levels: on the switch level, the settings are
globally implemented. On the port level, the settings are implemented on a per user-defined
Group of ports basis. To open the following window, open the Spanning Tree folder in the
Configuration menu and click the STP Switch Settings link.
Figure 4- 10. STP Switch Settings
35
Page 54

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configure the following parameters and click the Apply button to implement them:
Parameter Description
Spanning Tree
Protocol <Disabled>
Max Age: (6 - 40 sec)
<20 >
Hello Time: (1 - 10
sec) < 2 >
Forward Delay: (4 30 sec) <15 >
Priority: (0 - 61440)
<32768>
STP Version<RSTP >
This field can be toggled between Enabled and Disabled using the pulldown menu. This will enable or disable the Spanning Tree Protocol (STP),
globally, for the switch.
The Max. Age can be set from 6 to 40 seconds. At the end of the Max.
Age, if a BPDU has still not been received from the Root Bridge, your
Switch will start sending its own BPDU to all other Switches for permission
to become the Root Bridge. If it turns out that your Switch has the lowest
Bridge Identifier, it will become the Root Bridge.
The Hello Time can be set from 1 to 10 seconds. This is the interval
between two transmissions of BPDU packets sent by the Root Bridge to
tell all other Switches that it is indeed the Root Bridge.
The Forward Delay can be from 4 to 30 seconds. This is the time any port
on the Switch spends in the listening state while moving from the blocking
state to the forwarding state.
A Priority for the switch can be set from 0 to 61440. This number is used
in the voting process between switches on the network to determine which
switch will be the root switch. A low number indicates a high priority, and a
high probability that this switch will be elected as the root switch.
Choose RSTP (default) or STP Compatibility. Both versions use STP
parameters in the same way. RSTP is fully compatible with IEEE 802.1d
STP and will function with legacy equipment.
Tx Hold Count <3 >
Forwarding BPDU
<Enabled >
This is the maximum number of Hello packets transmitted per interval. The
count can be specified from 1 to 10. Default value = 3.
This field can enabled or disabled. When it is enabled it allows the
forwarding of STP BPDU packets from other network devices when STP is
disabled on the switch. The default is enabled.
Note: The Hello Time cannot be longer than the Max. Age.
Otherwise, a configuration error will occur.
Observe the following formulas when setting the above
parameters:
Max. Age ≤ 2 x (Forward Delay - 1 second)
Max. Age ≥ 2 x (Hello Time + 1 second)
36
Page 55

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
STP Port Settings
For stacked switch installations, first select the Unit to be configured.
Figure 4- 11. STP Port Settings
In addition to setting Spanning Tree parameters for use on the switch level, the switch allows
for the configuration of groups of ports, each port-group of which will have its own spanning
tree, and will require some of its own configuration settings. An STP Group will use the
switch-level parameters entered above, with the addition of Port Priority and Port Cost.
An STP Group spanning tree works in the same way as the switch-level spanning tree, but the
root bridge concept is replaced with a root port concept. A root port is a port of the group that
is elected on the basis of port priority and port cost, to be the connection to the network for the
group. Redundant links will be blocked, just as redundant links are blocked on the switch
level.
The STP on the switch level blocks redundant links between switches (and similar network
devices). The port level STP will block redundant links within an STP Group.
It is advisable to define an STP Group to correspond to a VLAN group of ports.
The following fields can be set:
Parameter Description
Unit
This is the Unit ID of a switch in a switch stack. 15 indicates a DES-6500
switch in standalone mode.
From/To < Port 1 >
A consecutive group of ports may be configured starting with the selected
port.
37
Page 56

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
State < Disabled >
Cost < 0 >
Priority <0>
Migration <No>
Edge <No>
This drop-down menu allows you to Enable or Disable STP for the
selected group of ports.
A Port Cost can be set from 1 to 200000000. The lower the number, the
greater the probability the port will be chosen to forward packets.
Default port cost:
100Mbps port = 200000
Gigabit ports = 20000
A Port Priority can be from 0 to 240. The lower the number, the greater the
probability the port will be chosen as the Root Port.
Select Yes or No. Choosing Yes will enable the port to migrate from 802.1d
STP status to 802.1w RSTP status. RSTP can coexist with standard STP,
however the benefits of RSTP are not realized on a port where an 802.1d
network connects to an 802.1w enabled network. Migration should be
enabled (yes) on ports connected to network stations or segments that will
be upgraded to 802.1w RSTP on all or some portion of the segment.
Select Yes or No. Choosing Yes designates the port as an edge port. Edge
ports cannot create loops, however an edge port can lose edge port status
if a topology change creates a potential for a loop. An edge port normally
should not receive BPDU packets. If a BPDU packet is received it
automatically loses edge port status. No indicates the port does not have
edge port status.
P2P <No>
Select Yes or No. Choosing Yes indicates a point-to-point (p2p) shared
link. These are similar to edge ports however they are restricted in that a
p2p port must operate in full duplex. Like edge ports, p2p ports transition to
a forwarding state rapidly thus benefiting from RSTP.
38
Page 57

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuring Forwarding & Filtering
Static Unicast Forwarding
Open the Forwarding & Filtering folder in the Configuration menu and click on the
Unicast Forwarding link. This will open the Setup Static Unicast Forwarding Table, as
shown below.
Figure 4- 12. Static Unicast Forwarding Setup
To add or edit an entry, define the following parameters and then click Add/Modify:
Parameter Description
VLAN ID
MAC Address
Unit
Port
The VLAN ID number of the VLAN on which the above Unicast MAC
address resides.
The MAC address to which packets will be statically forwarded. This must
be a unicast MAC address.
Allows the designation of the module on which the above MAC address
resides.
Allows the selection of the port number on which the MAC address entered
above resides.
39
Page 58

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Static Multicast Forwarding
The following figure and table describe how to set up Multicast forwarding on the switch.
Open the Forwarding & Filtering folder and click on the Multicast Forwarding link to see
the entry screen below:
Figure 4- 13. Setup Static Multicast Forwarding Table
The Static Multicast Forwarding Settings page displays all of the entries made into the
switch’s static multicast forwarding table. Click the Add button to open the Setup Static
Multicast Forwarding Table, as shown below.
Figure 4- 14. Setup Static Multicast Forwarding Table
The following parameters can be set:
Parameter Description
VID
Multicast MAC
Address
Port Settings
The VLAN ID of the VLAN the above MAC address belongs to.
The MAC address of the static source of multicast packets. This must be a
multicast MAC address.
Allows the selection of ports that will be members of the static multicast
group.
The options are:
None – no restrictions on the port dynamically joining the multicast group,
Egress – the port is a static member of the multicast group.
40
Page 59

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuring VLANs
Understanding IEEE 802.1p Priority
Priority tagging is a function defined by the IEEE 802.1p standard designed to provide a
means of managing traffic on a network where many different types of data may be
transmitted simultaneously. It is intended to alleviate problems associated with the delivery of
time critical data over congested networks. The quality of applications that are dependent on
such time critical data, such as video conferencing, can be severely and adversely affected by
even very small delays in transmission.
Network devices that are in compliance with the IEEE 802.1p standard have the ability to
recognize the priority level of data packets. These devices can also assign a priority label or
tag to packets. Compliant devices can also strip priority tags from packets. This priority tag
determines the packet’s degree of expeditiousness and determines the queue to which it will
be assigned.
Priority tags are given values from 0 to 7 with 0 being assigned to the lowest priority data and
7 assigned to the highest. The highest priority tag 7 is generally only used for data associated
with video or audio applications, which are sensitive to even slight delays, or for data from
specified end users whose data transmissions warrant special consideration.
The Switch allows you to further tailor how priority tagged data packets are handled on your
network. Using queues to manage priority tagged data allows you to specify its relative
priority to suit the needs of your network. There may be circumstances where it would be
advantageous to group two or more differently tagged packets into the same queue. Generally,
however, it is recommended that the highest priority queue, Queue 1, be reserved for data
packets with a priority value of 7. Packets that have not been given any priority value are
placed in Queue 0 and thus given the lowest priority for delivery.
A weighted round robin system is employed on the Switch to determine the rate at which the
queues are emptied of packets. The ratio used for clearing the queues is 4:1. This means that
the highest priority queue, Queue 1, will clear 4 packets for every 1 packet cleared from
Queue 0.
Remember, the priority queue settings on the Switch are for all ports, and all devices
connected to the Switch will be affected. This priority queuing system will be especially
beneficial if your network employs switches with the capability of assigning priority tags.
VLANs
A Virtual Local Area Network (VLAN) is a network topology configured according to a
logical scheme rather than the physical layout. VLANs can be used to combine any collection
of LAN segments into an autonomous user group that appears as a single LAN. VLANs also
logically segment the network into different broadcast domains so that packets are forwarded
only between ports within the VLAN. Typically, a VLAN corresponds to a particular subnet,
although not necessarily.
41
Page 60

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
VLANs can enhance performance by conserving bandwidth, and improve security by limiting
traffic to specific domains.
A VLAN is a collection of end nodes grouped by logic instead of physical location. End nodes
that frequently communicate with each other are assigned to the same VLAN, regardless of
where they are physically on the network. Logically, a VLAN can be equated to a broadcast
domain, because broadcast packets are forwarded to only members of the VLAN on which the
broadcast was initiated.
Notes About VLANs on the DES-6500
No matter what basis is used to uniquely identify end nodes and assign these nodes VLAN
membership, packets cannot cross VLANs without a network device performing a routing
function between the VLANs.
The DES-6500 supports IEEE 802.1Q VLANs. The port untagging function can be used to
remove the 802.1Q tag from packet headers to maintain compatibility with devices that are
tag-unaware.
The Switch’s default is to assign all ports to a single 802.1Q VLAN named “default.”
The “default” VLAN has a VID = 1.
IEEE 802.1Q VLANs
Some relevant terms:
Tagging – The act of putting 802.1Q VLAN information into the header of a packet.
Untagging – The act of stripping 802.1Q VLAN information out of the packet header.
Ingress port – A port on a switch where packets are flowing into the switch and VLAN
decisions must be made.
Egress port – A port on a switch where packets are flowing out of the switch, either to
another switch or to an end station, and tagging decisions must be made.
IEEE 802.1Q (tagged) VLANs are implemented on the Switch. 802.1Q VLANs require
tagging, which enables them to span the entire network (assuming all switches on the network
are IEEE 802.1Q-compliant).
VLANs allow a network to be segmented in order to reduce the size of broadcast domains. All
packets entering a VLAN will only be forwarded to the stations (over IEEE 802.1Q enabled
switches) that are members of that VLAN, and this includes broadcast, multicast and unicast
packets from unknown sources.
VLANs can also provide a level of security to your network. IEEE 802.1Q VLANs will only
deliver packets between stations that are members of the VLAN.
Any port can be configured as either tagging or untagging. The untagging feature of IEEE
802.1Q VLANs allows VLANs to work with legacy switches that don’t recognize VLAN tags
in packet headers. The tagging feature allows VLANs to span multiple 802.1Q-compliant
42
Page 61
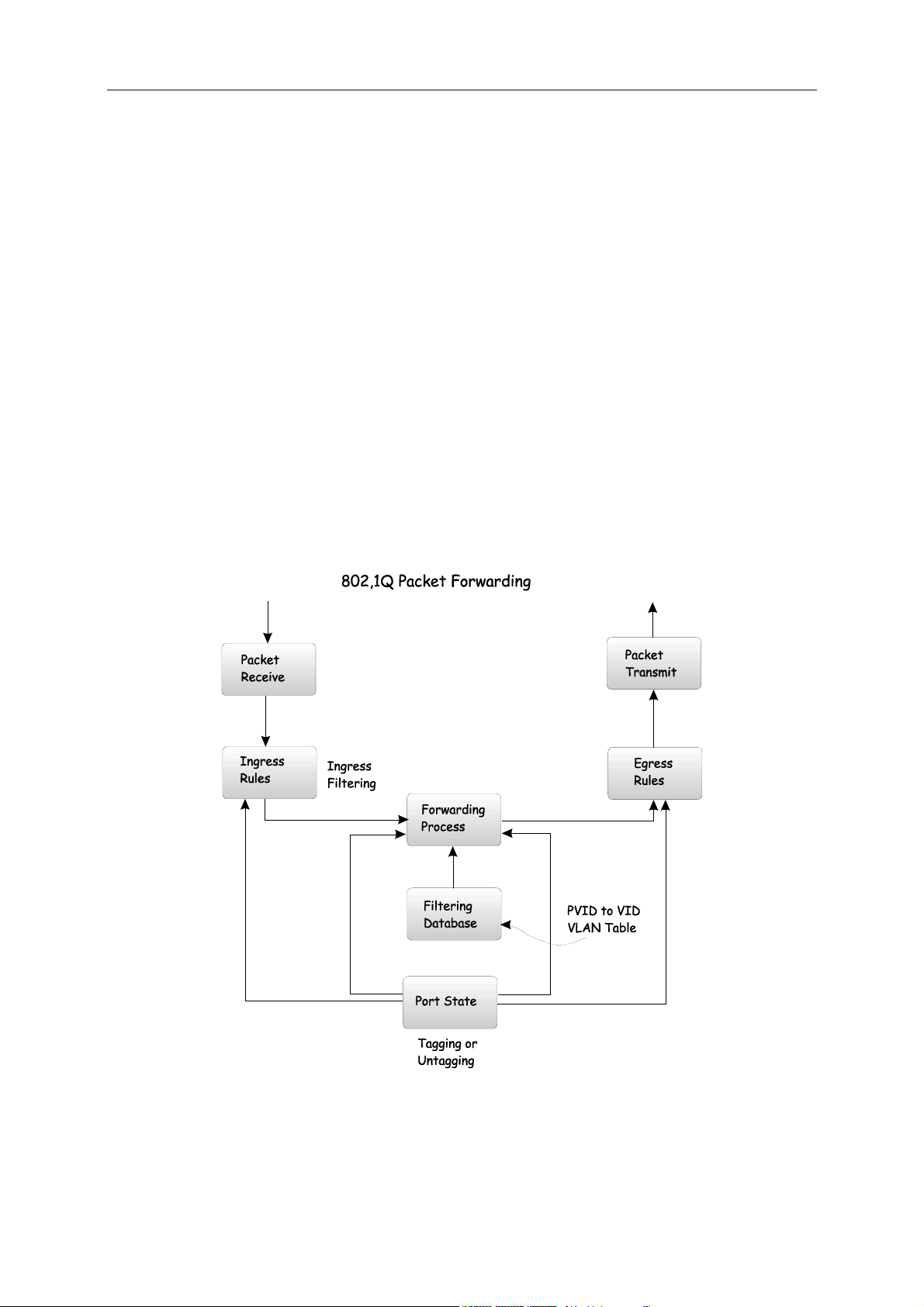
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
switches through a single physical connection and allows Spanning Tree to be enabled on all
ports and work normally.
The IEEE 802.1Q standard restricts the forwarding of untagged packets to the VLAN the
receiving port is a member of.
The main characteristics of IEEE 802.1Q are as follows:
• Assigns packets to VLANs by filtering.
• Assumes the presence of a single global spanning tree.
• Uses an explicit tagging scheme with one-level tagging.
802.1Q VLAN Packet Forwarding
Packet forwarding decisions are made based upon the following three types of rules:
• Ingress rules – rules relevant to the classification of received frames belonging to a
VLAN.
• Forwarding rules between ports – decides whether to filter or forward the packet.
• Egress rules – determines if the packet must be sent tagged or untagged.
Figure 4- 15. IEEE 802.1Q Packet Forwarding
43
Page 62

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
802.1Q VLAN Tags
The figure below shows the 802.1Q VLAN tag. There are four additional octets inserted after
the source MAC address. Their presence is indicated by a value of 0x8100 in the EtherType
field. When a packet’s EtherType field is equal to 0x8100, the packet carries the IEEE
802.1Q/802.1p tag. The tag is contained in the following two octets and consists of 3 bits of
user priority, 1 bit of Canonical Format Identifier (CFI – used for encapsulating Token Ring
packets so they can be carried across Ethernet backbones), and 12 bits of VLAN ID (VID).
The 3 bits of user priority are used by 802.1p. The VID is the VLAN identifier and is used by
the 802.1Q standard. Because the VID is 12 bits long, 4094 unique VLANs can be identified.
The tag is inserted into the packet header making the entire packet longer by 4 octets. All of
the information originally contained in the packet is retained.
Figure 4- 16. IEEE 802.1Q Tag
The EtherType and VLAN ID are inserted after the MAC source address, but before the
original EtherType/Length or Logical Link Control. Because the packet is now a bit longer
than it was originally, the Cyclic Redundancy Check (CRC) must be recalculated.
44
Page 63

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 17. Adding an IEEE 802.1Q Tag
Port VLAN ID
Packets that are tagged (are carrying the 802.1Q VID information) can be transmitted from
one 802.1Q compliant network device to another with the VLAN information intact. This
allows 802.1Q VLANs to span network devices (and indeed, the entire network, if all network
devices are 802.1Q compliant).
Unfortunately, not all network devices are 802.1Q compliant. These devices are referred to as
tag-unaware. 802.1Q devices are referred to as tag-aware.
Prior to the adoption of 802.1Q VLANs, port-based and MAC-based VLANs were in
common use. These VLANs relied upon a Port VLAN ID (PVID) to forward packets. A
packet received on a given port would be assigned that port’s PVID and then be forwarded to
the port that corresponded to the packet’s destination address (found in the switch’s
forwarding table). If the PVID of the port that received the packet is different from the PVID
of the port that is to transmit the packet, the switch will drop the packet.
Within the switch, different PVIDs mean different VLANs (remember that two VLANs
cannot communicate without an external router). So, VLAN identification based upon the
PVIDs cannot create VLANs that extend outside a given switch (or switch stack).
Every physical port on a switch has a PVID. 802.1Q ports are also assigned a PVID, for use
within the switch. If no VLANs are defined on the switch, all ports are then assigned to a
default VLAN with a PVID equal to 1. Untagged packets are assigned the PVID of the port on
which they were received. Forwarding decisions are based upon this PVID, in so far as
VLANs are concerned. Tagged packets are forwarded according to the VID contained within
the tag. Tagged packets are also assigned a PVID, but the PVID is not used to make packet
forwarding decisions, the VID is.
Tag-aware switches must keep a table to relate PVIDs within the switch to VIDs on the
network. The switch will compare the VID of a packet to be transmitted to the VID of the port
that is to transmit the packet. If the two VIDs are different, the switch will drop the packet.
Because of the existence of the PVID for untagged packets and the VID for tagged packets,
tag-aware and tag-unaware network devices can coexist on the same network.
45
Page 64

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
A switch port can have only one PVID, but can have as many VIDs as the switch has memory
in its VLAN table to store them.
Because some devices on a network may be tag-unaware, a decision must be made at each
port on a tag-aware device before packets are transmitted – should the packet to be transmitted
have a tag or not? If the transmitting port is connected to a tag-unaware device, the packet
should be untagged. If the transmitting port is connected to a tag-aware device, the packet
should be tagged.
Tagging and Untagging
Every port on an 802.1Q compliant switch can be configured as tagging or untagging.
Ports with tagging enabled will put the VID number, priority and other VLAN information
into the header of all packets that flow into and out of it. If a packet has previously been
tagged, the port will not alter the packet, thus keeping the VLAN information intact. The
VLAN information in the tag can then be used by other 802.1Q compliant devices on the
network to make packet-forwarding decisions.
Ports with untagging enabled will strip the 802.1Q tag from all packets that flow into and out
of those ports. If the packet doesn’t have an 802.1Q VLAN tag, the port will not alter the
packet. Thus, all packets received by and forwarded by an untagging port will have no 802.1Q
VLAN information. (Remember that the PVID is only used internally within the switch).
Untagging is used to send packets from an 802.1Q-compliant network device to a noncompliant network device.
Ingress Filtering
A port on a switch where packets are flowing into the switch and VLAN decisions must be
made is referred to as an ingress port. If ingress filtering is enabled for a port, the switch will
examine the VLAN information in the packet header (if present) and decide whether or not to
forward the packet.
If the packet is tagged with VLAN information, the ingress port will first determine if the
ingress port itself is a member of the tagged VLAN. If it is not, the packet will be dropped. If
the ingress port is a member of the 802.1Q VLAN, the switch then determines if the
destination port is a member of the 802.1Q VLAN. If it is not, the packet is dropped. If the
destination port is a member of the 802.1Q VLAN, the packet is forwarded and the destination
port transmits it to its attached network segment.
If the packet is not tagged with VLAN information, the ingress port will tag the packet with
its own PVID as a VID (if the port is a tagging port). The switch then determines if the
destination port is a member of the same VLAN (has the same VID) as the ingress port. If it
does not, the packet is dropped. If it has the same VID, the packet is forwarded and the
destination port transmits it on its attached network segment.
This process is referred to as ingress filtering and is used to conserve bandwidth within the
switch by dropping packets that are not on the same VLAN as the ingress port at the point of
46
Page 65

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
reception. This eliminates the subsequent processing of packets that will just be dropped by
the destination port.
Default VLANs
The Switch initially configures one VLAN, VID = 1, called “default.” The factory default
setting assigns all ports on the Switch to the “default.” As new VLANs are configured in Portbased mode, their respective member ports are removed from the “default.”
Packets cannot cross VLANs. If a member of one VLAN wants to connect to another VLAN,
the link must be through an external router.
Note: If no VLANs are configured on the switch, then all
packets will be forwarded to any destination port. Packets with
unknown source addresses will be flooded to all ports.
Broadcast and multicast packets will also be flooded to all
ports.
An example is presented below:
VLAN Name VID Switch Ports
System (default) 1 5, 6, 7, 8, 21, 22, 23, 24
Engineering 2 9, 10, 11, 12
Marketing 3 13, 14, 15, 16
Finance 4 17, 18, 19, 20
Sales 5 1, 2, 3, 4
Table 4- 1. VLAN Example – Assigned Ports
VLAN Segmentation
Take for example a packet that is transmitted by a machine on Port 1 that is a member of
VLAN 2. If the destination lies on another port (found through a normal forwarding table
lookup), the switch then looks to see if the other port (Port 10) is a member of VLAN 2 (and
can therefore receive VLAN 2 packets). If Port 10 is not a member of VLAN 2, then the
packet will be dropped by the switch and will not reach its destination. If Port 10 is a member
of VLAN 2, the packet will go through. This selective forwarding feature based on VLAN
criteria is how VLANs segment networks. The key point being that Port 1 will only transmit
on VLAN 2.
Network resources such as printers and servers however, can be shared across VLANs. This is
achieved by setting up overlapping VLANs. That is ports can belong to more than one VLAN
group. For example, setting VLAN 1 members to ports 1, 2, 3, and 4 and VLAN 2 members
to ports 1, 5, 6, and 7. Port 1 belongs to two VLAN groups. Ports 8, 9, and 10 are not
configured to any VLAN group. This means ports 8, 9, and 10 are in the same VLAN group.
47
Page 66

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
VLAN and Trunk Groups
The members of a trunk group have the same VLAN setting. Any VLAN setting on the
members of a trunk group will apply to the other member ports.
Note: In order to use VLAN segmentation in conjunction with
port trunk groups, you can first set the port trunk group(s), and
then you may configure VLAN settings. If you wish to change
the port trunk grouping with VLANs already in place, you will
not need to reconfigure the VLAN settings after changing the
port trunk group settings. VLAN settings will automatically
change in conjunction with the change of the port trunk group
settings.
Configuring Static VLANs
To create or modify an 802.1Q VLAN:
In the Configuration folder, open the VLAN folder and click the Static VLAN Entry link to
open the following window:
Figure 4- 18. 802.1Q Static VLANs
The 802.1Q Static VLANs menu lists all previously configured VLANs by VLAN ID and
name. To delete an existing 802.1Q VLAN, click the corresponding Delete button.
To create a new 802.1Q VLAN, click the Add button in the Static VLANs menu. A new
menu will appear, as shown below, to configure the port settings and to assign a unique name
and number to the new VLAN. See the table below for a description of the parameters in the
new menu.
48
Page 67

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 19. 802.1Q Static VLANs Entry Settings – Add
To change an existing 802.1Q VLAN entry, double-click on the selected entry in the 802.1Q
Static VLANs menu. A new menu appears, use this to configure the port settings and to assign
a unique name and number to the new VLAN. See the table below for a description of the
parameters in the new menu.
Figure 4- 20. 802.1Q Static VLANs Entry Settings – Modify
49
Page 68

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The following fields can then be set in either the Add or Modify 802.1Q Static VLANs
menus:
Parameter Description
Unit
VID (VLAN ID) Allows the entry of a VLAN ID in the Add dialog box, or displays the VLAN
VLAN Name
Advertisement
Port
Tag
None
Egress
Displays the Unit ID of the switch − within the switch stack − that the VLAN
will be created on.
ID of an existing VLAN in the Edit dialog box. VLANs can be identified by
either the VID or the VLAN name.
Allows the entry of a name for the new VLAN in the Add dialog box, or for
editing the VLAN name in the Edit dialog box.
Enabling this function will allow the switch to send out GVRP packets to
outside sources, notifying that they may join the existing VLAN.
Allows an individual port to be specified as member of a VLAN.
Specifies the port as either 802.1Q tagging or 802.1Q untagged. Checking
the box will designate the port as Tagged.
Allows an individual port to be specified as a non-VLAN member.
Select this to specify the port as a static member of the VLAN. Egress
member ports are ports that will be transmitting traffic for the VLAN. These
ports can be either tagged or untagged.
Forbidden
Select this to specify the port as not being a member of the VLAN and that
the port is forbidden from becoming a member of the VLAN dynamically.
50
Page 69

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
GVRP Settings
In the Configuration menu, open the VLANs folder and click GVRP Setting.
The Port VLAN ID (PVID) dialog box, shown below, allows you to determine whether the
switch will share its VLAN configuration information with other GARP VLAN Registration
Protocol (GVRP) enabled switches. In addition, Ingress Checking can be used to limit
traffic by filtering incoming packets whose PVID does not match the PVID of the port.
Results can be seen in the table under the configuration settings, as seen below.
Figure 4- 21. GVRP Setting
The following fields can be set:
Parameter Description
Unit
From/To
State
Ingress Check
Displays the Unit ID of the switch − within the switch stack − that the VLAN
will be created on.
These two fields allow you to specify the range of ports that will be
included in the Port-based VLAN that you are creating using the 802.1Q
Port Settings page.
The Group VLAN Registration Protocol (GVRP) enables the port to
dynamically become a member of a VLAN. GVRP is disabled by default.
This field can be toggled using the space bar between Enabled and
Disabled. Enabled enables the port to compare the VID tag of an incoming
packet with the PVID number assigned to the port. If the two are different,
the port filters (drops) the packet. Disabled disables Ingress filtering.
51
Page 70

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Ingress Checking is disabled by default.
This read only field in the GVRP Table shows the current
PVID assignment for each port. The switch’s default is to
assign all ports to the Default VLAN with a VID of 1.
The PVID is used by the port to tag outgoing, untagged packets, and to
make filtering decisions about incoming packets. If the port is specified to
accept only tagged frames − as tagging, and an untagged packet is
PVID
forwarded to the port for transmission, the port will add an 802.1Q tag
using the PVID to write the VID in the tag. When the packet arrives at its
destination, the receiving device will use the PVID to make VLAN
forwarding decisions.
If a packet is received by the port, and Ingress filtering is enabled, the port
will compare the VID of the incoming packet to its PVID. If the two are
unequal, the port will drop the packet. If the two are equal, the port will
receive the packet.
Configuring Traffic Control (Broadcast/Multicast Storm
Control)
Use the Traffic Control menu to enable or disable storm control and adjust the threshold for
multicast and broadcast storms, as well as DLF (Destination Look Up Failure). Traffic control
settings are applied to individual Switch modules.
Figure 4- 22. Traffic Control Settings window
Traffic or storm control is used to stop broadcast, multicast or ARP request storms that may
result when a loop is created. The Destination Look Up Failure control is a method of shutting
52
Page 71

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
down a loop when a storm is formed because a MAC address cannot be located in the
Switch’s forwarding database and it must send a packet to all ports or all ports on a VLAN.
To configure Traffic Control, select the Unit (Unit ID of a switch in a switch) you want to
configure. Broadcast Storm, Multicast Storm and Destination Unknown may be Enabled
or Disabled. The Threshold value is the upper threshold at which the specified traffic control
is switched on. This is the number of Broadcast, Multicast or DLF packets, in Kbps, received
by the switch that will trigger the storm traffic control measures. The Threshold value can be
set from 0 to 255 packets. The Default setting is 128.
Configuring Port Security
A given port’s (or a range of ports’) dynamic MAC address learning can be locked such that
the current source MAC addresses entered into the MAC address forwarding table can not be
changed once the port lock is enabled. The port can be locked by using the Learn <Disabled>
pull-down menu to Enabled, and clicking Apply.
This is a security feature that prevents unauthorized computers (with source MAC addresses
unknown to the switch prior to locking the port (or ports) from connecting to the switch’s
locked ports and gaining access to the network.
Figure 4- 23. Port Security Settings window
53
Page 72

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The following parameters can be set:
Parameter Description
Unit
From/To
Admin State
Max.Addr(0-64)
Mode
Allows you to specify a switch in a switch stack using that switch’s Unit ID.
A consecutive group of ports may be configured starting with the selected
port.
This pull-down menu allows you to Enable or Disable Port Security
(locked MAC address table for the selected ports.)
The number of MAC addresses that will be in the MAC address forwarding
table for the selected switch and group of ports.
This pull-down menu allows you to select how the MAC address table
locking will be implemented on the switch, for the selected group of ports.
The options are DeleteOnReset and DeleteOnTimeout.
Configuring QoS
Understanding QoS
The DES-6500 supports 802.1p priority queuing. The switch has two priority queues. These
priority queues are labeled as 0, the high queue, and 6, the low queue. These priority queues,
specified in IEEE 802.1p are mapped to the switch’s priority queues as follows:
• Priority 0 is assigned to the Switch’s Q2 queue.
• Priority 1 is assigned to the Switch’s Q0 queue.
• Priority 2 is assigned to the Switch’s Q1 queue.
• Priority 3 is assigned to the Switch’s Q3 queue.
• Priority 4 is assigned to the Switch’s Q4 queue.
• Priority 5 is assigned to the Switch’s Q5 queue.
• Priority 6 is assigned to the Switch’s Q6 queue.
• Priority 7 is assigned to the Switch’s Q6 queue.
For strict priority-based scheduling, any packets residing in the higher priority queues are
transmitted first. Only when these queues are empty, are packets of lower priority transmitted.
For weighted round-robin queuing, the number of packets sent from each priority queue
depends upon the assigned weight.
For a configuration of 8 CoS queues, A~H with their respective weight value: 8~1, the
packets are sent in the following sequence: A1, B1, C1, D1, E1, F1, G1, H1, A2, B2, C2, D2,
E2, F2, G2, A3, B3, C3, D3, E3, F3, A4, B4, C4, D4, E4, A5, B5, C5, D5, A6, B6, C6, A7,
B7, A8, A1, B1, C1, D1, E1, F1, G1, H1.
For weighted round-robin queuing, if each CoS queue has the same weight value, then each
CoS queue has an equal opportunity to send packets just like round-robin queuing.
54
Page 73

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
For weighted round-robin queuing, if the weight for a CoS is set to 0, then it will continue
processing the packets from this CoS until there are no more packets for this CoS. The other
CoS queues that have been given a nonzero value, and depending upon the weight, will follow
a common weighted round-robin scheme.
Remember that the DES-6500 has 8 priority queues (and seven Classes of Service) for each
port on the switch.
Setting Bandwidth Control
The bandwidth control settings are used to place a ceiling on the transmitting and receiving
data rates for any selected port. In the Configuration folder open the QoS folder and click
Bandwidth Control, to view the screen shown below.
Figure 4- 24. Bandwidth Settings window
The following parameters can be set or are displayed:
Parameter Description
Unit
From/To
Type
Allows you to specify a switch in a switch stack using that switch’s Unit ID.
A consecutive group of ports may be configured starting with the selected
port.
This drop-down menu allows you to select between RX (receive,) TX
(transmit,) and Both. This setting will determine whether the bandwidth
ceiling is applied to receiving, transmitting, or both receiving and
55
Page 74

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
transmitting packets.
no_limit
Rate
This drop-down menu allows you to specify that the selected port will have
no bandwidth limit. Enabled disables the limit.
This field allows you to enter the data rate, in kb/s, that will be the limit for
the selected port.
Results of the Bandwidth Settings will be displayed directly below, in the Port Bandwidth
Table
QoS Scheduling Mechanism Table
This drop-down menu allows you to select between a Weight Fair and a Strict mechanism
for emptying the priority queues. In the Configuration folder open the QoS folder and click
QoS Scheduling Mechanism, to view the screen shown below.
Figure 4- 25. Scheduling Mechanism Configuration window
Click Apply to let your changes take effect.
The Scheduling Mechanism has the following parameters.
Parameter Description
Strict
The highest queue is the first to process traffic. That is, the highest
queue should be finished at first.
Weight fair
Use the weight fair algorithm to handle packets in an even distribution
in priority queues.
56
Page 75

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
QoS Output Scheduling
QoS can be customized by changing the output scheduling used for the hardware queues in
the Switch. As with any changes to QoS implementation, careful consideration should be
given to how network traffic in lower priority queues is affected. Changes in scheduling may
result in unacceptable levels of packet loss or significant transmission delay. If you choose to
customize this setting, it is important to monitor network performance, especially during peak
demand, as bottlenecks can quickly develop if the QoS settings are not suitable. In the
Configuration folder open the QoS folder and click QoS Output Scheduling, to view the
screen shown below.
Figure 4- 26. QoS Output Scheduling Configuration window
Once you have assigned a priority to the port groups on the switch, you can then assign this
Class to each of the 7 levels of 802.1p priorities.
Note: The settings you assign to the queues, numbers 0-7,
represent the IEEE 802.1p priority tag number. Do not
confuse these settings with port numbers.
57
Page 76
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
802.1p Default Priority
The switch allows the assignment of a default 802.1p priority to each port on the switch. In
the Configuration folder open the QoS folder and click 802.1p Default Priority, to view the
screen shown below.
Figure 4- 27. 802.1p Default Priority window
This page allows you to assign a default 802.1p priority to any given port on the switch. The
priority queues are numbered from 0 − the lowest priority − to 7 − the highest priority.
802.1p User Priority
The DES-6500 allows the assignment of a User Priority to each of the 802.1p priorities. In the Configuration
folder open the QoS folder and click 802.1p User Priority, to view the screen shown below.
58
Page 77

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 28. User Priority Configuration window
Once you have assigned a priority to the port groups on the switch, you can then assign this
Class to each of the 8 levels of 802.1p priorities.
Configuring Traffic Segmentation
Traffic segmentation is used to limit traffic flow from a single port to a group of ports on
either a single switch (in standalone mode) or a group of ports on another switch in a switch
stack. This method of segmenting the flow of traffic is similar to using VLANs to limit traffic,
but is more restrictive. It provides a method of directing traffic that does not increase the
overhead of the Master switch CPU.
In the Configuration folder open the QoS folder and click Traffic Segmentation, to view
the screen shown below.
Figure 4- 29. Traffic Segmentation window
59
Page 78
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Click on the Setup button to open the Setup Forwarding ports page, as shown below.
Figure 4- 30. Setup Forwarding Ports window
This page allows you to determine which port on a given switch in a switch stack will be
allowed to forward packets to other ports on that switch.
Configuring traffic segmentation on the DES-6500 is accomplished in two parts. First you
specify a switch from a switch stack, and then a port from that switch. Then you specify a
second switch from the switch stack, and then you select which ports (or different ports on the
same switch,) on that switch that you want to be able to receive packets from the switch and
port you specified in the first part.
In the example above, the switch is Unit 1 and port 5 is selected as the transmitting port. Ports
1-3 and 9-24 are selected as being able to receive packets from port 5.
Clicking the Apply button will enter the combination of transmitting port and allowed
receiving ports into the switch’s Traffic Segmentation table.
The Unit drop-down menu at the top of the page allows you to select a switch from a switch
stack using that switch’s Unit ID. The Port drop-down menu allows you to select a port from
that switch. This is the port that will be transmitting packets.
The Unit drop-down menu under the Setup Forwarding ports heading allows you to select a
switch from a switch stack using that switch’s Unit ID. The Forward Port click boxes allow
you to select which of the ports on the selected switch will be able to forward packets. These
are the ports that will be allowed to receive packets from the port specified above.
Click Apply to enter the settings into the Switch’s Traffic Segmentation table.
60
Page 79

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The System Log Server
The Switch can send Syslog messages to up to four designated servers using the System Log
Server. In the Configuration folder click System Log Server, to view the screen shown
below.
Figure 4- 31. System Log Server window
The parameters configured for adding and editing System Log Server settings are the same.
See the table below for a description.
Figure 4- 32. System Log Servers − Add
The following parameters can be set:
Parameter Description
Index
Server IP
Severity
Facility
Syslog server settings index (1-4).
The IP address of the Syslog server.
This drop-down menu allows you to select the level of messages that will
be sent. The options are Warning, Informational, and All.
Some of the operating system daemons and processes have been
assigned Facility values. Processes and daemons that have not been
explicitly assigned a Facility may use any of the "local use" facilities or they
may use the "user-level" Facility. Those Facilities that have been
designated are shown in the following: Bold font means the facility values
that the switch currently now.
61
Page 80

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Numerical Facility
Code
0 kernel messages
1 user-level messages
2 mail system
3 system daemons
4 security/authorization messages
5 messages generated internally by syslog line printer subsystem
7 network news subsystem
8 UUCP subsystem
9 clock daemon
10 security/authorization messages
11 FTP daemon
12 NTP subsystem
13 log audit
14 log alert
15 clock daemon
16 local use 0 (local0)
17 local use 1 (local1)
18 local use 2 (local2)
19 local use 3 (local3)
20 local use 4 (local4)
21 local use 5 (local5)
22 local use 6 (local6)
23 local use 7 (local7)
UDP Port (6000-
65535)
Status
Type the UDP port number used for sending Syslog messages. The
default is 514.
Choose Enabled or Disabled to activate or deactivate this
Configuring SNTP Settings
The Simple Network Time Protocol (SNTP) {an adaptation of the Network Time Protocol
(NPT)} is configured on the switch using the following pages.
62
Page 81

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Time Settings
To configure the time settings for the Switch, open the Configuration folder, then The SNTP
folder and click on the Time Setting link, revealing the following screen for the user to
configure.
Figure 4- 33. Time Settings Page
The following parameters can set or are displayed:
Parameter Description
System Boot Time
System Current Time
Time Source
SNTP State
SNTP Primary
Server
SNTP Secondary
Server
SNTP Poll Interval in
Seconds
Displays the time when the Switch was initially started for this session.
Displays the current time.
Displays the time source for the system.
Use this pull-down menu to Enable or Disable SNTP.
This is the primary server the SNTP information will be taken from.
This is the secondary server the SNTP information will be taken from.
This is the interval, in seconds, between requests for updated SNTP
information.
63
Page 82

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Year
Month
Day
Time in HH MM SS
Enter the current year, if you want to update the system clock.
Enter the current month, if you would like to update the system clock.
Enter the current day, if you would like to update the system clock.
Enter the current time in hours, minutes and seconds if you would like
to update the system clock.
Time Zone and DST
The following are screens used to configure time zones and Daylight Savings time settings for
SNTP. Open the Configuration folder, then the SNTP folder and click on the Time Zone
and DST link, revealing the following screen.
Figure 4- 34. Time Zone and DST Settings Page
64
Page 83

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The following parameters can set:
Parameter Description
Daylight Saving
Time State
Daylight Saving
Time Offset in
Minutes
Time Zone Offset
from GMT in +/HH:MM
DST Repeating
Settings
From: Which Day
From: Day of Week
From: Month
From: time in HH:MM
Use this pull-down menu to Enable or Disable the DST Settings.
Use this pull-down menu to specify the amount of time that will
constitute your local DST offset − 30, 60, 90, or 120 minutes.
Use these pull-down menus to specify your local time zone’s offset
from Greenwich Mean Time (GMT.)
Repeating - Using repeating mode will enable DST seasonal time
adjustment. Repeating mode requires that the DST beginning and
ending date be specified using a formula. For example, specify to
begin DST on Saturday during the second week of April and end DST
on Sunday during the last week of October.
Should be From: Which Week. Enter the week of the month that DST
will start.
Enter the day of the week that DST will start on.
Enter the month DST will start on.
Enter the time of day that DST will start on.
To: Which Day
To: Day of Week
To: Month
To: time in HH:MM
DST Annual Settings
From: Month
From: Day
From: time in HH:MM
To: Month
To: Day
To: time in HH:MM
Should be be To: Which Week. Enter the week of the month the DST
will end.
Enter the day of the week that DST will end.
Enter the month that DST will end.
Enter the time DST will end.
Annual - Using annual mode will enable DST seasonal time
adjustment. Annual mode requires that the DST beginning and ending
date be specified concisely. For example, specify to begin DST on
April 3 and end DST on October 14.
Enter the month DST will start on, each year.
Enter the day of the week DST will start on, each year.
Enter the time of day DST will start on, each year.
Enter the month DST will end on, each year.
Enter the day of the week DST will end on, each year.
Enter the time of day that DST will end on, each year.
65
Page 84

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuring The Access Profile Table
Access profiles allow you to establish criteria to determine whether or not the switch will
forward packets based on the information contained in each packet’s header. These criteria
can be specified on a basis of VLAN, MAC address or IP address.
Creating an access profile is divided into two basic parts. The first is to specify which part or
parts of a frame the switch will examine, such as the MAC source address or the IP
destination address. The second part is entering the criteria the switch will use to determine
what to do with the frame. The entire process is described below in two parts.
To display the currently configured Access Profiles on the switch, open the Configuration
folder and click on the Access Profile Table link. This will open the Access Profile Table
page, as shown below.
Figure 4- 35. Access Profile Table
To add an entry to the Access Profile Table, click the Add button. This will open the Access
Profile Configuration page, as shown below. There are two Access Profile Configuration
pages − one for Ethernet (or MAC address-based) profile configuration, and one for IP
address-based profile configuration. You can switch between the two Access Profile
Configuration pages by using the Type drop-down menu, and clicking on the Apply button.
The page shown below is the Ethernet Access Profile Configuration page.
Figure 4- 36. Access Profile Table (Ethernet)
66
Page 85

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
The following parameters can be set:
Parameter Description
Profile ID (1-8)
Type
Vlan
Source Mac
Destination Mac
802.1p
Ethernet type
Type in a unique identifier number for this profile set. This value can be set
from 1 – 8.
Select profile based on Ethernet (MAC Address) or IP address. This will
change the menu according to the requirements for the type of profile.
Select Ethernet to instruct the switch to examine the layer 2 part of each
packet header. Select IP to instruct the switch to examine the IP address in
each frame’s header.
Selecting this option instructs the switch to examine the VLAN part of each
packet header and use this as the full or partial criterion for forwarding.
Source MAC Mask - Enter a MAC address mask for the source MAC
address.
Destination MAC Mask - Enter a MAC address mask for the destination
MAC address.
Selecting this option instructs the switch to examine the 802.1p priority
value of each packet header and use this as the, or part of the criterion for
forwarding.
Selecting this option instructs the switch to examine the Ethernet type
value in each frame’s header.
To add an entry to the Access Profile Table, click the Add button. This will open the Access
Profile Configuration page, as shown below. There are two Access Profile Configuration
pages − one for Ethernet (or MAC address-based) profile configuration, and one for IP
address-based profile configuration. You can switch between the two Access Profile
Configuration pages by using the Type drop-down menu, and clicking on the Apply button.
The page shown below is the IP Access Profile Configuration page.
67
Page 86

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 37. Access Profile Configuration (IP)
The following parameters can be set:
Parameter Description
Profile ID(1-8)
Type
Vlan
Source IP Mask
Destination IP Mask
Type in a unique identifier number for this profile set. This value can be set
from 1 – 8.
Select profile based on Ethernet (MAC Address) or IP address. This will
change the menu according to the requirements for the type of profile.
Select Ethernet to instruct the switch to examine the layer 2 part of each
packet header. Select IP to instruct the switch to examine the IP address in
each frame’s header.
Selecting this option instructs the switch to examine the VLAN part of each
packet header and use this as the, or part of the criterion for forwarding.
Source IP Mask - Enter an IP address mask for the source IP network
address.
Destination IP Mask - Enter an IP address mask for the destination IP
network address.
Dscp
Selecting this option instructs the switch to examine the DiffServ Code part
of each packet header and use this as the, or part of the criterion for
forwarding.
68
Page 87

Protocol
D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Selecting this option instructs the switch to examine the protocol type value
in each frame’s header. You must then specify what protocol(s) to include
according to the following guidelines:
Select ICMP to instruct the switch to examine the Internet Control Message
Protocol (ICMP) field in each frame’s header.
Select Type to further specify that the access profile will apply an ICMP
type value, or specify Code to further specify that the access profile will
apply an ICMP cod value.
Select IGMP to instruct the switch to examine the Internet Group
Management Protocol (ICMP) field in each frame’s header.
Select Type to further specify that the access profile will apply an IGMP
type value
Select TCP to use the TCP port number contained in an incoming packet
as the forwarding criterion. Selecting TCP requires that you specify a
source port mask and/or a destination port mask.
src port mask − Specify a TCP port mask for the source port in hex form
(hex 0x0-0xffff).
dest port mask − Specify a TCP port mask for the destination port in hex
form (hex 0x0-0xffff).
Select UDP to use the UDP port number contained in an incoming packet
as the forwarding criterion. Selecting UDP requires that you specify a
source port mask and/or a destination port mask.
src port mask − Specify a TCP port mask for the source port in hex form
(hex 0x0-0xffff).
dest port mask − Specify a TCP port mask for the destination port in hex
form (hex 0x0-0xffff).
protocol id − Specify a Layer 4 port mask for the destination port in hex
form (hex 0x0-0xffffffff).
To modify the rule for a previously created Access Profile:
In the Configuration folder, click the Access Profile Table link opening the Access Profile
Table. Under the heading Access Rule, click Modify. This will open the following window.
Figure 4- 38. Access Rule Table window
If you want to modify an access rule, click the Modify button. This will open the following
screen (for IP access profiles − a corresponding screen will be opened for Ethernet profiles):
69
Page 88

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 39. Access Rule Configuration window − Modify
To modify a rule set for the access profile enter the new settings in the appropriate fields.
This screen is the only place you can specify whether a rule will Permit or Deny access. Click
the Apply button to make the changes current. Remember to Save the settings to the switch’s
NV-RAM.
Configure the following Access Rule Configuration settings:
Parameter Description
Profile ID
Access ID
Permit/Deny
Type
This is the identifier number for this profile set.
Type in a unique identifier number for this access. This value can be set
from 1 – 50.
Specify if packets that match this Access profile will be permitted or denied
access.
Select profile based on Ethernet (MAC Address) or IP address. This will
change the menu according to the requirements for the type of profile.
Select Ethernet to instruct the switch to examine the layer 2 part of each
packet header. Select IP to instruct the switch to examine the layer 3 (IP
address) in each frame’s header.
Priority (0-7)
Replace Dscp (0-63)
This instructs the switch to examine the priority tag of incoming packets to
determine if they match the value specified. The replace priority click-box
instructs the switch to replace the 802.1p priority tag with a DSCP value,
as specified below.
Selecting this option instructs the switch to replace the DiffServ Code part
of each packet header that meets the criteria of this access profile with the
specified value, if the replace priority click-box is clicked (above).
70
Page 89

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Vlan Name
Source IP
Destination IP
Dscp (0-63)
Protocol
Protocol ID
User define
This instructs the switch to examine the VLAN tag in the header of
incoming packets to determine if they meet the specified name.
Source IP Mask - Enter an IP address mask for the source IP network
address.
Destination IP Mask - Enter an IP address mask for the destination IP
network address.
Selecting this option instructs the switch to examine the DiffServ Code part
of each packet header and use this as the, or part of the criterion for
forwarding.
This allows you to specify a value − in hex − that the switch will compare
with the value in the Protocol field in the header of incoming packets. If the
switch finds a match, then the actions specified in this access profile will be
taken.
71
Page 90

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuring The Port Access Entity
802.1X Port-based Network Access Control
The Switch is an implementation of the server side of IEEE 802.1X-Port Based Network
Access Control. Through this mechanism, users have to be authorized before being able to
access the network. See the following figure:
Figure 4- 40. Typical 802.1X Configuration Prior to User Authentication
Once the user is authenticated, the switch unblocks the port that is connected to the user as
shown in the next figure.
72
Page 91

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 41. Typical 802.1X Configuration with User Authentication
The user’s information, including account number, password, and configuration details such
as IP address and billing information, is stored in a centralized RADIUS server.
Figure 4- 42. Typical Configuration with 802.1X Fully Implemented
73
Page 92

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Port Timers state machine
Authenticator PAE state machine
The Authenticator Key Transmit state machine
Reauthentication Timer state machine
Backend Authentication state machine
Controlled Directions state machine
The Key Receive state machine
Conformance to IEEE 802.1X Standards
Configure Authenticator
State Machine Name
To display the current 802.1X Authenticator Settings on the switch, open the Configuration
folder, and then the Port Access Entity folder and finally click on the Configure
Authenticator link. This will open the 802.1X Authenticator Settings page, as shown
below.
Figure 4- 43. 802.1x Authenticator Settings window
To configure the 802.1X Authenticator Settings for a given port, click on the blue port
number under the Port heading. This will open the 802.1X Authenticator Settings page, as
shown below.
74
Page 93

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 44. 802.1x Authenticator Settings modify window
This window allows you to set the following features:
Parameter Description
Unit
From [ ] To [ ]
AdmDir
Port Control
TxPeriod
Allows you to select a switch from a switch stack using that switch’s Unit ID.
Enter the port or ports to be set.
From the pull-down menu, select whether a controlled Port that is
unauthorized will exert control over communication in both (both) receiving
and transmitting directions, or just the receiving direction (in). The default is
both.
Displays the administrative control over the port’s authorization status.
forceAuthorized forces the Authenticator of the port to become Authorized.
forceUnauthorized forces the port to become Unauthorized. Auto means the
port state reflects the outcome of the authentication exchange between
supplicant, authenticator, and authentication. The default is forceAuthorized.
Select the time to wait for a response from a supplicant (user) to send EAP
Request/Identity packets. The default is 30 seconds.
Quiet Period
SuppTimeout
Select the time interval between authentication failure and the start of a new
authentication attempt. The default is 60 seconds.
Select the time to wait for a response from a supplicant (user) for all EAP
packets, except for the Request/Identity packets. The default is 30 seconds
75
Page 94

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Server Timeout
Max Req
ReAuthPeriod
ReAuth
Select the length of time to wait for a response from a RADIUS server. The
default is 30 seconds.
Select the maximum number of times to retry sending packets to the
supplicant. The default is 2.
Select the time interval between successive re-authentications. The default is
3600 seconds.
Enable or disable reauthentication. The default is Disabled.
Configuring Local Users
In the configuration folder, open the Port Access Entity folder and click Local users to open
the 802.1x Local User Table Configuration window. This window will allow the user to set
different local users on the Switch.
Figure 4- 45. 802.1x Local User Table Configuration window
Enter a User Name, Password and confirmation of that password. Properly configured local
users will be displayed in the 802.1x Local Users Table in the same window.
PAE System Control
Port Capability Settings
Existing 802.1x port settings are displayed and can be configured using the window below.
Click Port Capability Settings on the PAE Access Entity folder on the Configuration menu
to open the 802.1X Capability Settings window:
76
Page 95

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 46. 802.1x Capability Settings and Table window
To set up the switch’s 802.1x port-based authentication, select which ports are to be
configured in the From and To fields. Next, enable the ports by selecting Authenticator from
the drop-down menu under Capability. Click Apply to let your change take effect.
Configure the following 802.1x capability settings:
Parameter Description
Unit
From and To Ports being configured for 802.1x settings.
Capability
Allows you to select a switch from a switch stack using that switch’s Unit ID.
Two role choices can be selected:
Authenticator − A user must pass the authentication process to gain access
to the network.
None − The port is not controlled by the 802.1x functions.
Initializing Ports
Existing 802.1x port settings are displayed and can be configured using the window below.
Click Initialize Port(s) on the PAE Access Entity folder on the Configuration menu to open
the 802.1x Port Initial window:
77
Page 96

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 47. 802.1x Port Initial and Port Authentication state window
This window allows you to initialize a port or group of ports. The Initialize Port Table in the
bottom half of the window displays the current status of the port(s) once you have clicked
Apply.
This window displays the following information:
Parameter Description
Unit
From and To
Port
Auth PAE State
Backend State
Port Status
Allows you to select a switch from a switch stack using that switch’s Unit ID.
Ports selected to be initialized.
A read only field indicating a port on the switch.
The Authenticator PAE State will display one of the following: Initialize,
Disconnected, Connecting, Authenticating, Authenticated, Aborting, Held,
ForceAuth, ForceUnauth, and N/A.
The Backend Authentication State will display one of the following: Request,
Response, Success, Fail, Timeout, Idle, Initialize, and N/A.
The status of the controlled port can be authorized, unauthorized, or N/A.
Reauthenticate Port(s)
This window allows you to reauthenticate a port or group of ports. The Reauthenticate Port
Table displays the current status of the port(s) once you have clicked Apply.
Click Reauthenticate Port(s) on the PAE Access Entity folder on the Configuration menu
to open the Reauthenticate Port(s) window:
78
Page 97

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 48. Reauthenticate Port and Reauthenticate Port Table window
This window displays the following information:
Parameter Description
Port
MAC Address
Auth State
BackendState
Oper Dir
PortStatus
The port number.
The MAC address of the switch where the port resides.
The Authenticator State will display one of the following: Initialize,
Disconnected, Connecting, Authenticating, Authenticated, Aborting, Held,
ForceAuth, ForceUnauth, and N/A.
The Backend State will display one of the following: Request, Response,
Success, Fail, Timeout, Idle, Initialize, and N/A.
The Operational Controlled Directions are both and in.
The status of the controlled port can be authorized, unauthorized, or N/A.
RADIUS Server
The RADIUS feature of the switch allows you to facilitate centralized user administration as
well as providing protection against a sniffing, active hacker. The Web Manager offers three
windows.
Click the Radius Server folder on the Configuration menu, and then click the Authentic
Radius Server link to open the Authentic Radius Server Setting window:
79
Page 98

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 49. Authentic Radius Server Setting and Table window
This window displays the following information:
Parameter Description
Succession <First>
Radius Server
<10.53.13.94>
Authentic Port <1812>
Accounting Port
<1813>
Key
Confirm Key
Status
Choose the desired RADIUS server to configure: First, Second or Third.
Set the RADIUS server IP.
Set the RADIUS authentic server(s) UDP port. The default is 1812.
Set the RADIUS account server(s) UDP port. The default is 1813.
Set the key the same as that of the RADIUS server.
Confirm the shared key is the same as that of the RADIUS server.
This allows you to set the RADIUS Server as either Valid or Invalid.
80
Page 99

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Configuring Layer 3 IP Networking
To access the Layer 3 IP Networking links, open the Configuration folder and then the
Layer 3 IP Networking folder.
Setting Up IP Interfaces
Each VLAN must be configured prior to setting up the VLAN’s corresponding IP interface.
An example is presented below:
VLAN Name VID Switch Ports
System (default) 1 5, 6, 7, 8, 21, 22, 23, 24
Engineer 2 9, 10, 11, 12
Marketing 3 13, 14, 15, 16
Finance 4 17, 18, 19, 20
Sales 5 1, 2, 3, 4
Backbone 6 25, 26
Table 4- 2. VLAN Example – Assigned Ports
In this case, 6 IP interfaces are required, so a CIDR notation of 10.32.0.0/11 (or a 11-bit)
addressing scheme will work. This addressing scheme will give a subnet mask of
11111111.11100000.00000000.00000000 (binary) or 255.224.0.0 (decimal).
Using a 10.xxx.xxx.xxx IP address notation, the above example would give 6 network
addresses and 6 subnets.
Any IP address from the allowed range of IP addresses for each subnet can be chosen as an IP
address for an IP interface on the switch.
For this example, we have chosen the next IP address above the network address for the IP
interface’s IP Address:
VLAN Name VID Network Number IP Address
System (default) 1 10.32.0.0 10.32.0.1
Engineer 2 10.64.0.0 10.64.0.1
Marketing 3 10.96.0.0 10.96.0.1
Finance 4 10.128.0.0 10.128.0.1
Sales 5 10.160.0.0 10.160.0.1
Backbone 6 10.192.0.0 10.192.0.1
Table 4- 3. VLAN Example – Assigned IP Interfaces
The 6 IP interfaces, each with an IP address (listed in the table above), and a subnet mask of
255.224.0.0 can be entered into the IP Interfaces Table window.
To setup IP Interfaces on the switch:
Go to the Configuration folder, and click on the Layer 3 IP Networking folder, and then
click on the IP Interface Table link to open the following dialog box:
81
Page 100

D-Link DES-6500 Layer 3 Stackable Gigabit Ethernet Switch
Figure 4- 50. IP Interface Table window
To setup a new IP interface, click the Add button. To edit an existing IP Interface entry, click
on an entry under the Interface Name heading. Both actions will result in the same screen, as
shown below.
Figure 4- 51. IP Interface Configuration window
Choose a name for the interface to be added and enter it in the Interface Name field (if you
are editing an IP Interface, the Interface Name will already be in the top field as seen in the
window above). Enter the interface’s IP address and subnet mask in the corresponding fields.
Pull the Active pull-down menu to Yes and click Apply to enter to make the IP interface
effective. Use the Save Changes dialog box from the Basic Setup folder to enter the changes
into NV-RAM.
The following fields can be set:
Parameter Description
Interface Name
IP Address
Subnet Mask
VLAN Name
This field displays the name for the IP interface. The default IP interface is
named “System”.
This field allows the entry of an IP address to be assigned to this IP
interface.
This field allows the entry of a subnet mask to be applied to this IP interface.
This field allows the entry of the VLAN Name for the VLAN the IP interface
belongs to.
State <Disabled>
This field may be altered between Enabled and Disabled using the pull
down menu. This entry determines whether the interface will be active or
not.
82
 Loading...
Loading...