Dell Cyber Recovery User Manual

RECOVERING FROM A
DESTRUCTIVE CYBERATTACK
Leveraging Dell EMC Cyber Recovery to Recover the
Lifeline of Your Business
ABSTRACT
Cyber-attacks have become a common
occurrence – and they are growing more
sophisticated and devastating every day. In 2019,
cyber-attacks on businesses cost as much as
$600 billion a year globally . Ransomware attacks
like WannaCry and Petya/NotPetya have cost
organizations tens of millions of dollars in lost
revenue per day. They also inict damage to
reputation and negatively impact stock prices. The
cyber threat is expected to increase as the world
economy continues to digitize operations, supply
chains, business transactions, and employee and
customer services.
Most organizations have strong detection
capabilities in place. But could your organization
recover if an attacker gets through the perimeter
and encrypts or wipes your data? Organizations
need to consider recovery as a vital part of their
overall cyber-security and risk management
strategy. This white paper highlights how Dell EMC
Cyber Recovery, leveraging Dell technologies and
services, can augment your overall cyber-security
posture and provide a way to recover from a
destructive cyber-attack.
March 2020
The information in this publication is provided as is. Dell Inc. makes no representations or warranties of any kind with respect to the
information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose.
Use, copying, and distribution of any software described in this publication requires an applicable software license.
Copyright © 2020 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are
trademarks of Dell Inc. or its subsidiaries. Intel, the Intel logo, the Intel Inside logo and Xeon are trademarks of Intel Corporation in the
U.S. and/or other countries. Other trademarks may be trademarks of their respective owners. Published in the USA.
Dell Inc. believes the information in this document is accurate as of its publication date. The information is subject to change without
notice

TABLE OF CONTENTS
EXECUTIVE SUMMARY 4
DELL EMC Cyber Recovery OVERVIEW 5
USE CASE 1: LARGE MEDIA AND ENTERTAINMENT COMPANY 7
USE CASE 2: LOCAL HEALTH CARE PROVIDER 8
USE CASE 3: GLOBAL RETAIL AND MANUFACTURING CORPORATION 8
CYBER-ATTACK RECOVERY IS NOT TRADITIONAL DISASTER RECOVERY (DR) 9
WHAT DATA TO PROTECT? 10
TECHNOLOGY SELECTION 11
DELL EMC Cyber Recovery DETAILS 12
TECHNOLOGY COMPONENTS 12
AUTOMATED WORKFLOW 13
ANALYTICS IN THE VAULT 14
RECOVERY PROCEDURES 16
SCENARIO #1: RESTORE DATA AND BINARIES IN THE CR VAULT 16
SCENARIO #2: COMPLETE REBUILD FROM CR VAULT 17
CONCLUSION 18
3

EXECUTIVE SUMMARY
Cyber-attacks like WannaCry and Petya/NotPetya have had devastating consequences on organizations
worldwide. The impact of the recent NotPetya attack on a global retail company alone was estimated to be
in the range of $15 million per day in forgone revenue. It took the company almost 5 days to recover. When
also factoring in brand damage, impact on stock price, and the cost to recover, it is clear that the true cost
of ransomware can be signicant.
The attack also highlighted other recurring themes and patterns:
• The velocity with which the malware spreads throughout an environment can be extremely rapid. In this
case, NotPetya spread in seconds after the initial infection.
• The impact on a highly connected business can be signicant. Hundreds of critical servers, desktops,
and phones were rendered useless. Over 10,000 employees were impacted.
• The supply chain impact can be substantial. The production of more than 15 factories was brought to
a halt. This included real-time inventory management systems, where the downtime of these systems
directly impacted the overall supply chain, impacting nal assembly of goods.
• The malware exploited known vulnerabilities in operating systems and found their way into third party
software consumed by the organization. The malware was inserted into a patch of this software.
• Rather than pay the ransom, the organization decided to focus on recovery. Paying ransom is not
recommended and would have not been eective in this case. Hackers promised a decryption key upon
ransom payment, but forensic analysis of the malware determined that a decryption key would not have
allowed the data to be recovered.
• Good detection and prevention strategies were in place, but did not stop the event from occurring. A
good recovery strategy was a critical element in getting this company back on track. Recovery from
tape was ruled out, because it would have taken over 4 weeks.
• There was wide-spread agreement that a better cyber recovery strategy was needed so that the
organization could more quickly and eectively respond in the future.
Organizations
are not worried only about ransomware, even though it is the fastest growing cybercrime
activity. Most Chief Information Security Ocers (CISOs) worry about all types of attacks including slowmoving and sophisticated varieties that target industrial systems and other areas that can put people at risk
of harm. In the case of a prominent media and entertainment company, an organized group is believed to
have attacked data centers in a sophisticated manner. The hackers strategically destroyed server, storage,
and backup assets. It was the rst documented instance of destroying backup infrastructure.
Destroying backup infrastructure is an emerging trend, because hackers think that neutering the backup
system increases the likelihood of payment. The trend of deleting backups was recently seen in the attack
on a municipal rail system in November of 2016 and the April 2017 destruction of backups at a regional
medical center in upstate New York. Any system that is connected to the network is a potential target,
including the backup system.
Because cyber-attacks are becoming more sophisticated and devastating, organizations are considering
new recovery strategies that represent the “last line of defense” for the lifeline of the organization.
Many are considering isolated environments that host business critical data that is sequestered from
the production network. In fact, recent regulatory guidance and government warnings (including FBI)
emphasize that backup and recovery are key components of a good cyber security strategy, preferably with
4
Copyright © 2020 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries.
Other trademarks may be the property of their respective owners. Published in the USA.
a backup or recovery infrastructure that is segregated from other systems. While tape backups can provide
this level of isolation, recovery takes too long and involves too much risk when the daily revenue or mission
critical applications are at stake.
Dell EMC Cyber Recovery provides a solution that combines the benets of isolation and business
continuity. It minimizes the impact of a cyber-attack and provides a faster and higher likelihood of success in
the recovery of mission critical systems. This technology provides innovative automation and workow tools
to ensure gold copies of critical data are available so business processes can be resumed in the event of a
destructive cyber-attack.
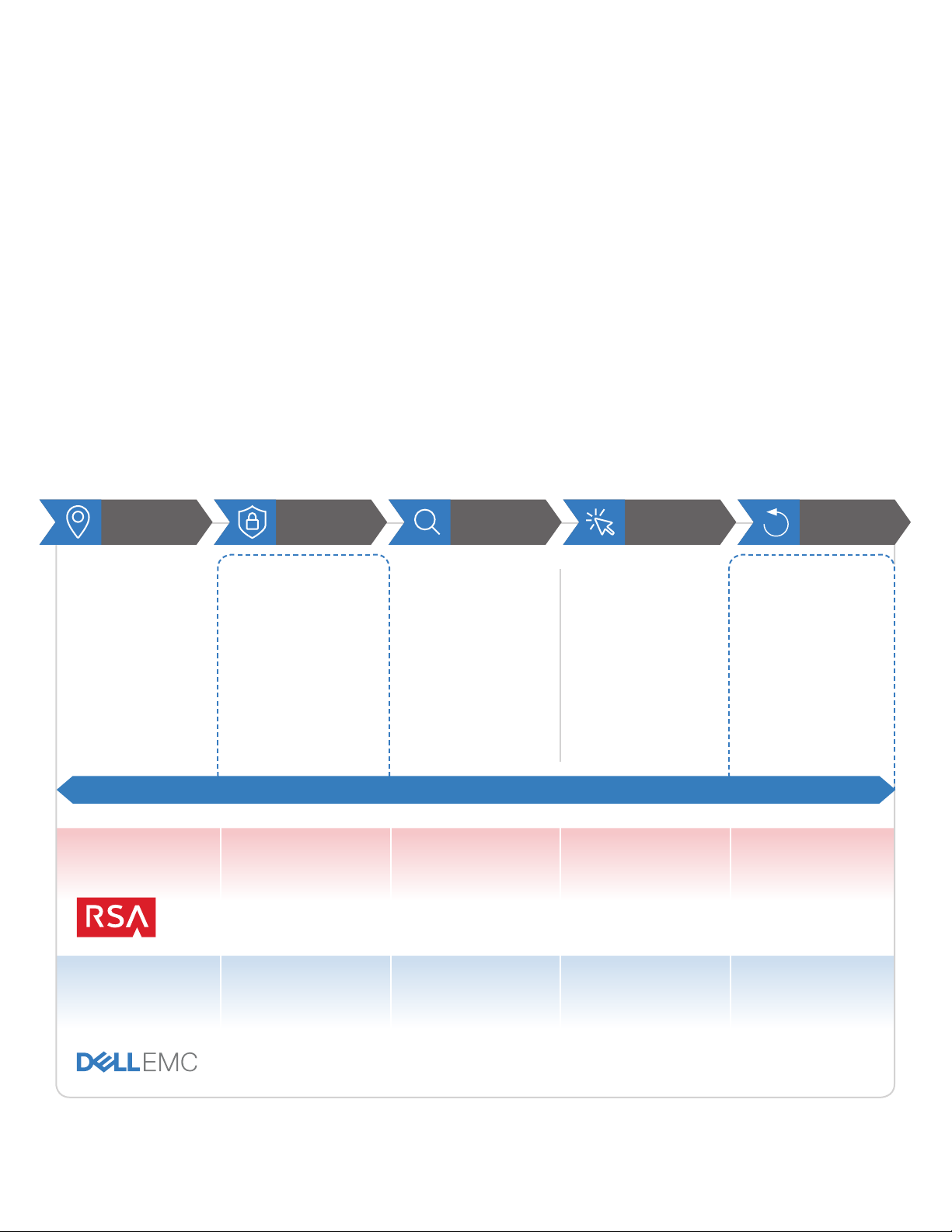
DELL EMC CYBER RECOVERY OVERVIEW
A robust and comprehensive cyber security strategy should leverage frameworks like the National Institute
of Standards and Technology (NIST) Cybersecurity Framework (CSF), which can help outline an end-toend cyber-attack defense continuum. Dell Technologies has strong capabilities in each category. It leverages
technology and services from RSA, SecureWorks, VMware, Dell EMC Information Systems Group, Dell EMC
Cyber Solutions Group, and Dell EMC Services.
ProtectIdentify Detect Respond Recover
Asset Management
Business Environment
Governance
Risk Assessment
Risk Management
Strategy
Supply Chain Risk
Management
Risk Management
RSA Incident Discovery
Governance and
Measurement Program
Access Control
Awareness and Training
Data Security (Integrity
Checking)
Information Protection
Processes and
Procedures
Maintenance
Protective Technology
Anomolies and Events
Security Continuous
Monitoring
Detection Processes
Signature-based
behavioral analysis
engines
Measurement Program
Identity Management RSA NetWitness
Security Analytics
Data Protection
Hardening Services
Cyber Recovery
Logging Monitoring
Cyber Security
Solutions Group
Response Planning
Communications
Analysis
Mitigation
Improvements
®
Incident Response
Retainer
Advanced Cyber
Defense
Disaster / Cyber
Recovery Planning
Recovery Planning
Isolation / Air-gap
CR Vault Security
Analytics
Recovery Management
RSA NetWitness
Forensics / RSA
®
Archer
Recovery Management
Cyber Recovery
Cyber Security
Solutions Group, 3rd
Party
®
5
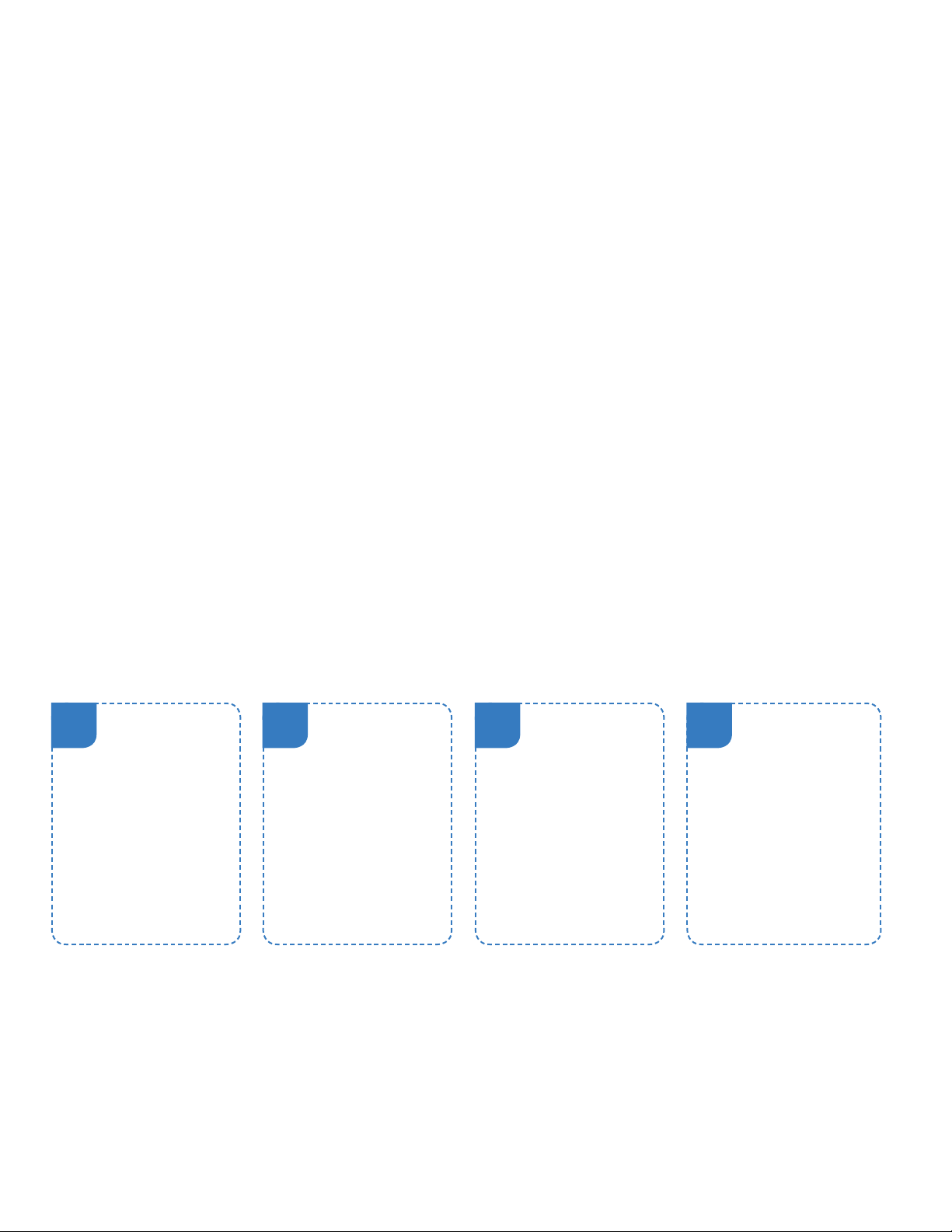
Dell EMC Cyber Recovery focuses on the protection and recovery pillars of the cyber security continuum
and leverages a combination of professional services and technology that provide the following four key
elements:
1. Planning and Design – Assess mission critical systems and applications, current infrastructure, cyber-
attack recovery time and recovery objectives in order to tailor a solution deployment. Dell EMC Advisory
Services can help organizations determine their business critical systems and create dependency
mappings with associated foundation services, metadata, and other components needed to bring them
back online. Today, our consulting services experts work with organizations to determine their recovery
objectives and design solutions with matching technologies to economically meet organizational
requirements.
2. Isolation and Replication – Based on the outcome of the Planning and Design phase, a custom
implementation of Dell EMC replication technologies will be completed. These technologies synchronize
data between the production environment and the air-gapped Cyber Recovery Vault (CR Vault). Within
the CR Vault, the created immutable restore points can be leveraged for recovery and analytics.
3. Analytics – CR Vault oers distinct advantages for analytics in an oine and controlled environment but
it is also not intended to be a substitute for good end-point and cyber security tools. Organizations have
the ability to leverage a variety of existing, Dell Technologies, and third-party tools for analytics in the CR
Vault.
4. Restore and Recovery – Recovery procedures mostly follow standard processes, but special
considerations apply across a variety of dierent scenarios. The steps usually follow invoking a cyber
incident response plan, performing forensics and damage assessment, preparing the recovery, cleaning
out the malware or rebuilding systems from gold-copy images of application and OS binaries, and then
recovering the data back into the production environment.
Plan and Design Analyze Data Restore and
1 2 3 4
Isolate and
Replicate
Asset Management
Business Environment
Governance
Risk Assessment
Risk Management Strategy
Supply Chain Risk
Management
6
Access Control
Awareness and Training
Data Security (Integrity
Checking)
Information Protection
Processes and Procedures
Maintenance
Protective Technology
Anomolies and Events
Security Continuous
Monitoring
Detection Processes
Signature-based behavioral
analysis engines
Recover
Response Planning
Communications
Analysis
Mitigation
Improvements
 Loading...
Loading...