Page 1

USER GUIDE
Wireless-N Home ADSL2 + Modem Router
Models: RAN201
Page 2

About This Guide
bou
W
a
:
cates that there is
should
.
.
y
.
s
address because most current web
dd
h
.
l
y
y
l
t
t
.
A
t This Guide
Icon Descriptions
hile reading through the User Guide you may see
various icons that call attention to specific items. Below is
description of these icons
NOTE: This check mark indi
a note of interest and is something that you
pay special attention to while using the
roduct
WARNING: This exclamation point indicates
that there is a caution or warning of potential
risk of bodily injury and/or it is something that
ould damage your property or product
WEB: This globe icon indicates a noteworth
website address or e-mail address
Copyright and Trademarks
inksys, Cisco and the Cisco Logo
are registered trademarks or
trademarks of Cisco Systems, Inc.
and/or its affiliates in the U.S. and certain
ther countries. Other brands and product
names are trademarks or registered
trademarks of their respective holders.
Copyright © 2009 Cisco Systems, Inc. All
rights reserved
nline Resource
ebsite addresses in this document are listed without
ttp:// in front of the
rowsers do not require it. If you use an older web browser,
ou may have to a
Resource Website
inksys
nternational
work
ecurit
eb Technica
uppor
ttp://in front of the web address
ww.linksysbycisco.com/internationa
ww.linksysbycisco.com/securit
ww.linksysbycisco.com/suppor
i
Page 3

Table of Contents
Chapter 1:
Product Overview 1
Front Panel.................................................. 1
Back Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Placement Positions............................................ 2
Chapter 2:
Wireless Security Checklist 3
General Network Security Guidelines ................................. 3
Additional Security Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Chapter 3:
Advanced Conguration 4
How to Access the Utility......................................... 4
Using the Utility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
List of Screens in the Utility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
Setup Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Wireless Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Storage Tab (WAG320N Only) ...................................... 5
Security Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Access Restrictions Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Applications & Gaming Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Administration Tab............................................. 6
Status Tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Appendix A:
Troubleshooting 8
Appendix B:
Specications 9R
RAN201
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Appendix C:
Regulatory Information 11
European Union . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
Australia . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
New Zealand . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
United States of America.........................................18
Canada . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
ii
Page 4

Chapter 1
T
.
d)
Th
s
(
s.
each of the number
.
:
d
p
d
T
.
)
Th
ected to the
.
ess
ed. It flashes
k.
afu
ection.
.
.
l
ces.
b-
p
gpg
,
b.
ode
outer to a hard d
-
.
on
e
.
.
ff.
Product Overview
apter 1:
roduct Overview
hank you for choosing the Wireless ADSL2+ Modem
Router. This device lets you access the Internet via a
wireless connection or through one of its four switched
orts. You can also use it to share resources such as
computers, printers and files. A variety of security features,
such as WPA2
irewall and NAT technology, help to protect your data
nd your privacy while online. Configuration is easy using
the provided browser-based utility
Front Panel
Power
s continuously lit gn while the device i
or red (WAG160N v2 and WAG320N) if a POST
Power On Self Test) failure or device malfunction
Ethernet 1-4
Modem Router’s back panel, serve two purposes.
If the LED is continuously lit, the Modem Router is
successfully connected to a device through that
that port.
Wi-Fi Protected Setup™ Button
Green/Amber; WAG160N v2 and WAG320N
Green) Press this button to have Wi-Fi Protecte
continuously lit green when a Wi-Fi Protecte
security, a Stateful Packet Inspection (SPI)
: Green/Amber; WAG160Nv2
nd WAG320N: Green/Re
owered on. The LED is lit amber
r
Green)These numbered LEDs,
ne for
ort. It flashes to indicate network activity over
NOTE: The Ethernet 1 LED is lit amber
en the WAN link is established on that
port
etu
etup™-supported wireless device. The LED is
etup™ connection is successfully established.
he LED blinks slowly while Wi-Fi Protected
etup™ is setting up a connection, and is lit amber
AG320N) if an error occurs. The LED is off when
i-Fi Protected Setup™ is idle
search for your Wi-Fi Protected
N20) or blinks rapidly (WAG160Nv2 and
e Power LED
ports on the
USB (WAG320N only)
lights up when a USB device is
Modem Router through the USB port
Wireless
when the wirel
when the Modem Router is actively sending or
eceiving data over the networ
DSL
here is
lashes green while the Modem Router is
establishing the ADSL connection
Internet The Internet LED lights up
en and stays on when a connection is made
through the Internet port. It flashes to indicate
etwork activity over the Internet port. The LED
s lit red when an authentication error occurs
Back Pane
DSLThe DSL port connects to the ADSL line.
Ethernet 4, 3, 2, 1 The Ethernet ports (4, 3, 2, 1)
nd other Ethernet network devi
USB (WAG320N only) The USB port connects
he M
ased USB storage device
ResetThere are two ways to reset the Modem
Router’s factory defaults. Either press and
hold the Reset button for approximately five
seconds, or restore the defaults from the
Administrati
Modem Router’s web-based utility
PowerThe Power port is where you will connect
e power adapter
On/Off Button Press the On/Off button to turn
ower to the device on or o
Green
Green)The Wireless LED lights up
re is enabl
Green)The DSL LED lights up whenever
l DSL conn
t the Modem Router to wired computers
NOTE: The Ethernet 1 port can
lso be configured as the WAN
port. To do this, access the We
based utility (refer to
en select the Setup > Ethernet ta
m R
actory Defaults screen
e USB LED
nn
The LED
rive or flash
th
)
NOTE:
that makes it easy to configure your
wireless network and its security settings.
Wi-Fi Protected Setup™ is a feature
1
Page 5
Chapter 1
.
.
p
.
ace the wa
ots
de
Th
lly
T
.
T
.
T
.
The d
T
.
3
0
scale.
.
Product Overview
Placement Positions
ere are two ways to physica
irst way is to place the device horizontally on a surface.
he second way is to mount the device on a wall
he best place for the device is usually at the center of
our wireless network, within range of all of your wireless
devices
Horizontal Placement
he device has four rubber feet on its bottom panel. Place
the device on a level surface near an electrical outlet
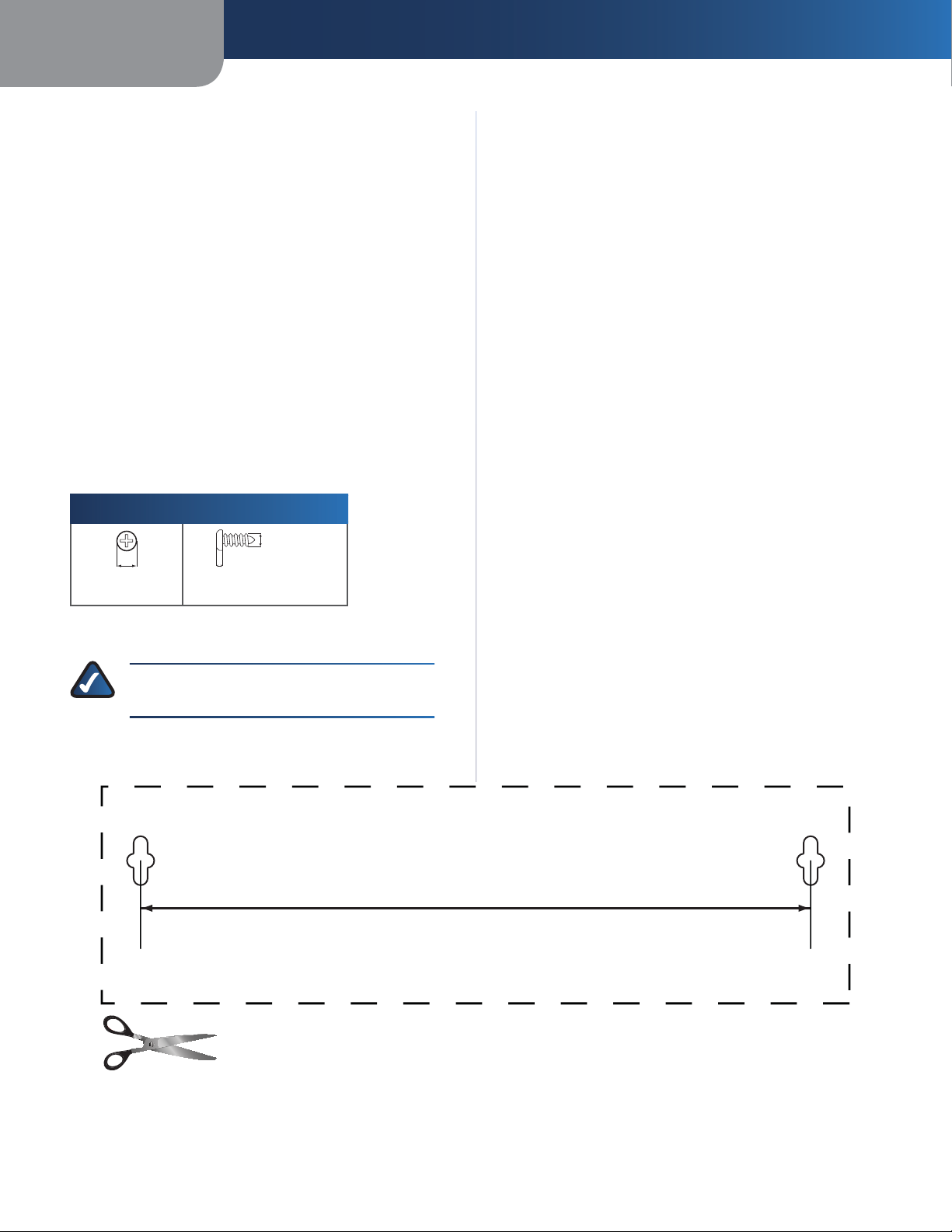
Wall-Mounting Placement
evice has two wall-mount slots on its bottom
anel. The distance between the slots is 152 mm
(6 inches).
wo screws are needed to mount the device
Suggested Mounting Hardware
install the device. The
mm
,
,5-
Follow these instructions:
Determine where you
sure that the wall you use is smooth, flat, dry, and
sturdy. Also make sure the location is within reach of
n electrical outlet.
Drill two holes int the wall. Make sure the holes are
52 mm (6 inches) apart
Insert a screw into each hole and leave 3 mm
(0,12 inches) of its head exposed
Maneuver the device so the wall-mount slots line u
with the two screws
Pl
the device down until the screws fit snugly into the
wall-mount slots.
ll-mount sl
ant to mount the device. Make
ver the screws and sli
ote: Mounting hardware illustrations are not
rue to
NOTE: Cisco is not responsible for damages
incurred by insecure wall-mounting hardware
152 mm
all Mounting Template
2
Page 6

Chapter 2
t
uders than a traditiona
.
g
y
d
otected Access
A
/
.
A
/
A
/
A
s
.
.
s
T
.
g
f
Wireless Security Checklist
apter 2:
Wireless Security Checklis
ireless networks are convenient and easy to install, so
homes with high-speed Internet access are adopting them
t a rapid pace. Because wireless networking operates by
sending information over radio waves, it can be more
vulnerable to intr
Like signals from your cellular or cordless phones, signals
rom your wireless network can also be intercepted. Since
ou cannot physically prevent someone from connecting
to your wireless network, you need to take some additional
steps to keep your network secure.
1. Change the default wireless
network name or SSID
ireless devices have a default wireless network name
or Service Set Identifier (SSID) set by the factory. This is
the name of your wireless network, and can be up to 32
characters in length. Linksys by Cisco wireless products
inksys as the default wireless network name. You
should change the wireless network name to somethin
nique to distinguish your wireless network from other
wireless networks that may exist around you, but do not
se personal information (such as your Social Securit
umber) because this information may be available for
nyone to see when browsing for wireless networks.
2. Change the default password
For wireless products such as access points, routers, an
odem routers, you will be asked for a password when
you want to change their settings. These devices have a
default password set by the factory. The default password
min. Hackers know these defaults and may try to
se them to access your wireless device and change your
etwork settings. To thwart any unauthorized changes,
customize the device’s password so it will be hard to
guess.
l wired network
4. Enable encryption
Encryption protects data transmitted over a wireless
work. Wi-Fi Pr
ired Equivalency Privacy (WEP) offer different levels of
security for wireless communication
network encrypted with WP
secure than a network encrypted with WEP, because
P
WPA2 uses dynamic key encryption. To protect
the information as it passes over the airwaves, you should
enable the highest level of encryption supported by your
etwork equipment.
EP is an older encryption standard and may be the
only option available on some older devices that do not
support WP
(WP
WPA2
WPA2 is more
and
General Network Security Guideline
ireless network security is useless if the underlying
etwork is not secure.
Password protect all computers on the network and
ndividually password protect sensitive files
Change passwords on a regular basis
Install anti-virus software and personal firewall
software.
Disable file sharing (peer-to-peer). Some applications
ay open file sharing without your consent and/or
knowledge.
Additional Security Tip
Keep wireless routers, access points, or modem routers
way from exterior walls and windows.
urn wireless routers, access points, or modem routers
off when they are not being used (at night, during
vacations)
Use strong passphrases that are at least eight characters
n length. Combine letters and numbers to avoid usin
standard words that can be found in the dictionary.
3. Enable MAC address filtering
Linksys by Cisco routers and modem routers give you
the ability to enable Media Access Control (MAC) address
iltering. The MAC address is a unique series of numbers
nd letters assigned to every networking device. With
MAC address filtering enabled, wireless network access
s provided solely for wireless devices with specific MAC
ddresses. For example, you can specify the MAC address
of each computer in your home so that only those
computers can access your wireless network.
WEB: For more in
isitwww.linksysbycisco.com/security
ormation on wireless security,
3
Page 7

Chapter 3
.
efer to
ote
pp
.
y
Add
s
ter
y
.
T
.
Th
lly
)
b
p
t
g
ab
s
y
ess
ess
ter
s
ly)
r
n
r
b
ll
h
b
y
b
g
g
g
Z
S
ab
t
g
s
e
s
e
e
ab
ode
outer
k
eless Network
ection
Advanced Configuration
apter 3:
Advanced Configuration
ter you finish running the Setup Wizard on the Setup
CD-ROM, the device is ready for use. To change the device’s
dvanced settings, access the Configuration Utility via a
web browser on a computer connected to the device
NOTE FOR USERS IN NEW ZEALAND: R
he N
setup instructions specific to your country
How to Access the Utilit
Launch the web browser on your computer, and enter the
device’s default IP address,92.168.1.1 in the
ield. Then, press
login screen appears. Use the default user name and
assword,
an the Setup Wizard. (You can set a new user name and
assword from the Administration tab’s
screen.) Click
in
n
min, unless you changed them when you
to continue.
for
res
anagement
List of Screens in the Utility
e screens are organized hierarchica
(Some screens may not apply to all models.
Setup Ta
etup > Basic Setu
etup > Etherne
etup > DDNS
etup > MAC Address Clone
etup > Advanced Routin
ireless T
ireless > Basic Wireless Setting
ireless > Wireless Securit
irel
> Wirel
ireless > Advanced Wireless Setting
Storage Tab (WAG320N On
torage > Disk Management
torage > Shared Folde
torage > Administratio
torage > Media Serve
Security Ta
ecurity > Firewa
ecurity > VPN Passthroug
MAC Fil
as listed below.
ogin
If you are unable to log in, press the Reset button on the
ack panel for at least 5 seconds, then wait for the device
to reset and try again.
Using the Utility
Immediately after login, the Basic Setup screen appears.
Near the top of the screen is a bar with selectable tabs.
Use these tabs to navigate within the Utility. The
indicate the Utility’s main configuration categories.
Each primary tab has one or more secondary tabs that
rovide access to the primary tab’s configuration screens
rimary Tabs
Access
Setup Wireless Storage Security
Basic Setup Ethernet DDNS MAC Address Clone Advanced Routing
Secondary Tabs
o access a screen, click the appropriate primary tab,
then click the appropriate secondary tab. The screen will
ppear, with its primary and secondary tabs highlighted
Restrictions
Navigation Tabs
Applications &
Gaming
Administration Status
rimar
Access Restrictions Ta
ccess Restrictions > Internet Access Polic
Applications & Gaming Ta
pplications & Gaming > Single Port Forwardin
pplications & Gaming > Port Range Forwardin
pplications & Gaming > Port Range Triggerin
pplications & Gaming > DM
pplications & Gaming > Qo
Administration T
ministration > Managemen
ministration > Reportin
dministration > Diagnostic
ministration > Back Up & Restor
dministration > Factory Default
dministration > Firmware Upgrad
ministration > Languag
Status T
> M
tatus > Local Networ
> Wir
> DSL Conn
m R
4
Page 8

Chapter 3
T
.
p
T
A
outed
A
s
s
y
:
ccess the
p
sc
.
.
tual Cir
.
ing
ect Mu
ode
odulatio
assword details
The
et
screen allows you to configure the device’s
S
Th
ce.
ess
access the
et.
y
.
g
The
.
ab
T
.
gs
T
.
y
Th
screen allows you to configure the
.
eless
eless
lter
T
ess
ter
.
The
.
t
T
t
screen displays information on an
attached disk.
r
The
r
screen allows you to manage the shared
Advanced Configuration
etup Tab
he Setup tab provides the device’s basic setup functions.
For detailed information on the Setup tab, refer to the
Utility’s online help pages
Setup > Basic Setu
he Basic Setup screen allows you to change the device’s
general settings. The following connection types
(encapsulations) are available:
RFC2364PPPo
RFC2516PPPoE
RFC2684R
IPo
RFC2684 Bridged-Dynamic IP Addres
RFC2684 Bridged-Static IP Addres
Bridge Mode Onl
NOTE FOR USERS IN NEW ZEALAND:To set up
he device, follow these instructions
A
.Select
Encapsulation drop-down menu
For the Vir
nd00 for the VCI
l
rop-down menu.
Enter your User Name
from your ISP.
7.
ickSave Settings
etup > Basic Setu
FC 2364 PPPoAfr
cuit ID, enter
VC for Multiplex
ltim
from theDSL M
.
nd P
r
n
m the
for the VPI
n
Setup > Advanced Routin
Advanced Routingscreen allows you to configure the
device’s advanced routing functions, such as operating
ode, dynamic mode, and static routing
Wireless T
he Wireless tab allows you to configure the device’s
wireless functions.
For detailed information on the Wireless tab, refer to the
Utility’s online help pages
Wireless > Basic Wireless Settin
he
asic Wireless Settingsscreen allows you to set up a
etwork with Wi-Fi Protected Setup™, change the radio
and, select the network mode, change the wireless
etwork name (SSID), change the wireless channel and
isable the SSID broadcast
Wireless > Wireless Securit
e
security of your wireless network(s). It allows you to select
rom a number of security modes, such as WPA2
Wir
he Wirel
or allow) Internet access by individual devices on your
wireless network by specifying their MAC addresses
Wireless > Advanced Wireless Settings
configure the device’s advanced wireless functions
> Wir
MAC Fil
Advanced Wireless Settingsscreen allows you to
MAC Fi
creen allows you to control (block
Setup > Ethernet
Ethern
Ethernet settings. It also allows you to set up the first
Ethernet port as a WAN port.
Setup > DDN
e DDNS screen allows you to assign a fixed host and
domain name to a network computer that has been
ssigned a dynamic Internet IP address. This is useful
when you are hosting your own website, FTP server, or
her server behind the devi
Setup > MAC Address Clone
ome service providers require you to register a MAC
r
in order to
Clonescreen lets you use the MAC address of a device that
has already been registered with your service provider, b
copying that MAC address to the device
Intern
TheAC Address
Storage > Disk Managemen
he Disk Managemen
ttached USB storage device, and allows you to perform
asic management functions on the device. It also
rovides information on the attached USB disk, allows for
blank disk to be formatted, and enables safe removal of
he
Storage > Shared Folde
Shared Folde
olders on an external USB storage device. A shared folder
5
Page 9

Chapter 3
n
Th
.
r
The
r
screen allows you to configure the
.
b
T
.
ll
T
l
screen allows you to configure a firewall that
oca
.
h
The
.
T
,
y
The
k.
b
T
.
g
Th
.
g
Th
g
Th
.
T
g
.
S
The
y
affic.
b
T
s.
.
t
Th
y.
Advanced Configuration
s a directory on the device that a user can access through
the network.
Storage > Administratio
e Administrationscreen allows you to configure basic
storage settings and manage the device’s users
Storage > Media Serve
edia Serve
device’s built-in media server, and to select the folders to
scan for content
ecurity Ta
he Security tab allows you to enhance the security of
our network.
For detailed information on the Security tab, refer to the
Utility’s online help pages
Security > Firewa
he
irewal
can filter out various types of unwanted traffic on the
vice’s l
Security > VPN Passthroug
device’s VPN passthrough feature. This feature lets VPN
tunnels using the IPSec, L2TP, or PPTP protocols to pass
through the device’s firewall
l network
PN Passthroughscreen allows you to configure the
For detailed information on the Applications & Gaming
tab, refer to the Utility’s online help pages
Applications & Gaming > Single Port Forwardin
e Single Port Forwarding screen allows you to set up
ort forwarding for a single port. You should assign static
IP addresses to the destination computers before you use
this feature
Applications & Gaming > Port Range Forwardin
e Port Range Forwarding
ort forwarding for a range of ports. You should assign
static IP addresses to the destination computers before
ou use this feature.
creen allows you to set up
Applications & Gaming > Port Range Triggerin
e Port Range Triggering screen allows you to set up port
triggering. When port triggering is configured, the device
watches for specified port numbers in outgoing data.
hen a match is found, the device records the sending
computer’s IP address so that when the requested data
eturns, it can be sent to the proper computer
Applications & Gaming > DMZ
he
MZscreen allows you to expose one network user
to the Internet for use of a special-purpose service such
as Internet gaming or video conferencing. DMZ hostin
orwards all the ports at the same time to one computer.
You should assign static IP addresses to the destination
computers before you use this feature
Access Restrictions Tab
he Access Restrictions tab allows you to configure
the Internet access restrictions for each device in your
etwork.
For detailed information on the Access Restrictions tab
efer to the Utility’s online help pages.
Access Restrictions > Internet Access Polic
nternet Access Policy screen allows you to define
olicies that are used to block or allow specific kinds
of Internet usage and traffic, such as Internet access,
designated applications, websites, and inbound traffic
during specific days and times, and for a specified list of
evices in your networ
Applications & Gaming Ta
he Applications & Gaming tab allows you to configure
unctions such as port forwarding and quality of service
that may be necessary for special applications such as
hosting web servers, ftp servers, and e-mail servers on on
our network, or other specialized internet applications
such as videoconferencing or online gaming.
Applications & Gaming > Qo
oS
creen allows you to specify priorities for different
types of traffic. Lower priority traffic will be slowed down
to allow greater throughput or less delay for high priorit
r
Administration Ta
he Administration tab allows you to configure the device’s
ministrative function
For detailed information on the Administration tab, refer
to the Utility’s online help pages
Administration > Managemen
e
anagementcreen allows you to manage specific
unctions for access and securit
6
Page 10

Chapter 3
.
.
g
Th
attac
detected.
s
The
.
e
Th
d
.
s
Th
t
de
Th
e.
The
.
b
T
.
.
r
T
.
k
T
k
Th
about the
ess netwo
ce.
on
The
Advanced Configuration
NOTE ON CISCO WEB ASSISTANT OPTION
(not on all models): If you see an “error code
404” message (indicating that you entered an
invalid web address), the Cisco Web Assistant
will appear and automatically run a search
ased on the keywords in the web address. This
eature can be enabled or disabled from this
reen
NOTE ON TREND MICRO OPTION (not on all
models): Trend Micro ProtectLink Gateway
is a hosted security service that stops spam
and filters URLS to prevent unwanted content
rom passing through your router. The Email
rotection is the hosted messaging security
olution provided by Trend Micro InterScan
essaging Hosted Security (IMHS). This feature
an be enabled or disabled from this screen
Administration > Reportin
e
eporting
logging and to configure sending of e-mail alerts when a
Denial of Service
creen allows you to configure system event
k is
tatus Ta
he Status tab allows you to display status information
For detailed information on the Status tab, refer to the
Utility’s online help pages
Status > Modem Route
he
odem Router
device and its current settings. The on-screen information
ill vary depending on the Internet Connection Type you
se
Status > Local Networ
he Local Network screen displays the status of your Local
rea Network.
Status > Wireless Networ
e
ireless Network screen displays some basic
nformation
Status > DSL Connecti
L Connection screen displays the status of your DSL
connection.
creen displays information about the
wirel
rk of the devi
Administration > Diagnostic
iagnostics screen allows you to perform a ping test
to check the status of your Internet connection
Administration > Back Up & Restor
e Back Up & Restore
estore the configuration settings of your device
creen allows you to back up an
Administration > Factory Default
e Fac tory Defaults
actory defaults of the device. All savings you have saved
will be los
NOTE: Restoring the factory defaults causes all
ettings you have previously saved to be lost.
creen allows you to restore the
Administration > Firmware Upgra
e Firmware Upgrade screen allows you to upgrade the
vice’s firmwar
Administration > Language
anguage
language for the utility
creen allows you to select an available
7
Page 11

Appendix A
g
:
g.
r
.
:
ls
>
s
tab.
n
k
t.
lly
.
y
.
.
.
e
and fields
s
t
Troubleshooting
Appendix A:
Troubleshootin
our computer cannot connect to the Internet.
Follow the instructions until your computer can connect
to the Internet
Make sure that the Modem Router is powered on. The
Power LED should be green and not flashin
If the Power LED is flashing, then power off all of
our network devices, including the Modem Router
nd computers. Then power on each device in the
ollowing order:
Modem Route
omputer
Check the LEDs on the device’s front panel. Make sure
the Power, DSL, and at least one of the numbered
Ethernet LEDs are lit. If they are not, then check
the cable connections. The computer should be
connected to one of the Ethernet ports numbered
-4 on the device, and the device’s DSL port must be
connected to the ADSL line.
ou need to modify the basic settings on the
eviceRouter.
Run the Setup Wizard on the Setup CD-ROM
ou need to modify the advanced settings on the
evice
Open the web browser (for example, Internet Explorer or
Firefox), and enter the device’s IP address in the address
ield (the default IP address is
rompted, complete the
(the default user name and password is
ppropriate tab to change the setting
ser nam
92.168.1.1. When
dmin
. Click the
WEB: If your questions are not
addressed here, refer to the website,
ww.linksysbycisco.com/suppor
When you double-click the web browser, you are
prompted for a user name and password. If you want to
get rid of the prompt, follow these instructions
Launch the web browser and perform the following steps
(these steps are specific to Internet Explorer but are similar
or other browsers)
elect To o
lick thennections
elect
Clic
ou are using a static IP address and cannot cnnec
Refer to Windows Help and change your Internet Protocol
(TCP/IP) Properties to Obtain an IP address automatica
The computer cannot connect wirelessly to the network
Make sure the wireless network name or SSID is the same
on both the computer and the device. If you have enabled
ireless security, then make sure the same securit
ethod and key are used by both the computer and the
evice
nternet Option
ever dial a connecio
.
8
Page 12

Appendix B
G
,
b
u
,
),
B
ts
s
p™
,
t
e
)
as
al
odulations
Transmit Power
s
;
ll
s
t
e
r
p
)
s
)
t
)
r
A
cation
,
2
p
)
g
y
g
g
IEEE802.11bmode:19.83dBm
IEEE802.11gmode:17.45dBm
draft802.11nstandard‑20MHzChannelmode:18.70dBm
draft802.11nWide‑40MHzChannelmode:15.47dBm
IEEE802.11bmode:DSSS
IEEE802.11gmode:OFDM
draft802.11nStandard‑20MHzChannelmode:OFDM
draft802.11nWide‑40MHzChannelmode:OFDM
PCBAntennaGain:1.5dBi
PIFAAntennaGain:2dBi
Specifications
Appendix B:
ecifications
A
120N RAN201
tandards
Por
n
LEDs Power, Ethernet (1-4), Security
Cabling Typ
ntenn
M
LAN: 802.11n draft 2.0, 802.11g
2.11
Ethernet: 802.3, 802.3
DSL: T1.413i2, G.992.1 (G.DMT)
G.992.2 (G.Lite), G.992.3 (ADSL2
G.992.5 (ADSL2+) for Annex A, B, M, L,
U-R2 for Annex
DSL, Ethernet (1-4), Power
On/O, Reset, Wi-Fi Protected Setu
ireless, DSL, Interne
CAT5, RJ-11 (for Annex A),
RJ-45 (for Annex B
2 Intern
perating Temp.0 to 40°C (32 to 104°F
torage Temp. -20 to 70°C (-4 to 158°F)
Operatin
Humidit
0 to 85% Noncondensin
torage Humidity to 90% Noncondensin
Receive Sensitivity-80 dBm (typical) @ 11 Mbps
-70 dBm (typical) @ 54 Mbps
-61 dBm (typical) @ 130 Mbps
-61 dBm (typical) @ 270 Mbp
ntenna Gain
ecurity FeaturesWPA2/WPA Personal and Enterprise
28, 64 bits WEP;
MAC Address Filtering;
PI Firewa
S Requirement
(to run th
indows XP, Vista, or Vista 64-bi
edition with latest updates (fo
Setup CD) Network Magic and Setup Wizard);
Mac OS X 10.4 or higher (for Setu
Wizard
Environmental
Dimension
eigh
owe
rti
202 x 34 x 160 mm (8,0” x 1,3” x 6,3”
62 g (12,8 oz
2VDC, 1
FCC, CE, Telepermit, K.21, UL, CB
i-Fi (802.11b/g), WPA WPA
MM, Wi-Fi Protected Setu
9
Page 13

Appendix C
T
.
(
)
Т
T
est
e.
T
τ
k
]
T
T
T
Regulatory Information
Appendix C:
egulatory Information
European Union
he following information applies if you use the product
within the European Union
Declaration of Conformity with Regard to EU
Directive 1999/5/EC
Compliance Information for 2,4-GHz Wireless
Products Relevant to the EU and Other Countries
Following the EU Directive 1999/5/EC (R&TTE Directive
ългарски
Bulgarian]
esky
Czech]:
nsk
Danish]:
h
German]:
E
i
Estonian]:
nglish:
spañol
Spanish]:
λληνική
Greek]:
rançais
French]:
ова оборудване отговаря на съществените
зисквания и приложими клаузи на
иректива 1999/5/ЕС.
oto zařízení je v souladu se základními
ožadavky a ostatními odpovídajícími
stanoveními Směrnice 1999/5/EC.
ette udstyr er i overensstemmelse med
e væsentlige krav og andre relevante
estemmelser i Direktiv 1999/5/EF.
ieses Gerät entspricht den grundlegenden
nforderungen und den weiteren
ntsprechenden Vorgaben der Richtlinie
999/5/EU.
ee seade vastab direktiivi 1999/5/EÜ
lulistele nõuetele ja teistele asjakohastele
his equipment is in compliance with the
ssential requirements and other relevant
rovisions of Directive 1999/5/EC.
ste equipo cumple con los requisitos
senciales asi como con otras disposiciones
e la Directiva 1999/5/CE.
υτός ο εξοπλισµός είναι σε συµµόρφωση µε
ις ουσιώδεις απαιτήσεις και άλλες σχετικές
ιατάξεις της Οδηγίας 1999/5/EC.
et appareil est conforme aux exigences
ssentielles et aux autres dispositions
ertinentes de la Directive 1999/5/EC.
R&TTE Directive)
l
slenska
Icelandic]:
taliano
Italian]:
atviski
Latvian]:
etuvių
Lithuanian]:
ederlands
Dutch]:
alti
Maltese]:
agyar
Hungarian]:
ors
Norwegian]:
olski
Polish]:
ortuguês
Portuguese]:
omână
Romanian
ovensko
Slovenian]:
ovensky
Slovak]:
uomi
Finnish]:
venska
Swedish]:
etta tæki er samkvæmt grunnkröfum og
rum viðeigandi ákvæðum Tilskipunar
999/5/EC.
uesto apparato é conforme ai requisiti
ssenziali ed agli altri principi sanciti dalla
irettiva 1999/5/CE.
ī iekārta atbilst Direktīvas 1999/5/
K būtiskajām prasībām un citiem ar to
aistītajiem noteikumiem.
is įrenginys tenkina 1999/5/EB Direktyvos
sminius reikalavimus ir kitas šios direktyvos
uostatas.
it apparaat voldoet aan de essentiele eisen
n andere van toepassing zijnde bepalingen
an de Richtlijn 1999/5/EC.
an l-apparat huwa konformi mal-ħtiġiet
ssenzjali u l-provedimenti l-oħra rilevanti
ad-Direttiva 1999/5/EC.
z a készülék teljesíti az alapvető
övetelményeket és más 1999/5/EK
rányelvben meghatározott vonatkozó
endelkezéseket.
ette utstyret er i samsvar med de
runnleggende krav og andre relevante
estemmelser i EU-direktiv 1999/5/EF.
rządzenie jest zgodne z ogólnymi
ymaganiami oraz szczególnymi warunkami
reślonymi Dyrektywą UE: 1999/5/EC.
ste equipamento está em conformidade com
s requisitos essenciais e outras provisões
elevantes da Directiva 1999/5/EC.
cest echipament este in conformitate
u cerintele esentiale si cu alte prevederi
elevante ale Directivei 1999/5/EC.
a naprava je skladna z bistvenimi zahtevami
n ostalimi relevantnimi pogoji Direktive
999/5/EC.
oto zariadenie je v zhode so základnými
ožiadavkami a inými príslušnými
ariadeniami direktív: 1999/5/EC.
ämä laite täyttää direktiivin 1999/5/EY
ennaiset vaatimukset ja on siinä asetettujen
uiden laitetta koskevien määräysten
ukainen.
enna utrustning är i överensstämmelse med
e väsentliga kraven och andra relevanta
estämmelser i Direktiv 1999/5/EC.
11
Page 14

Appendix C
.
.
t
yy
and
.
/
.
)
T
:
4
g
/
)
T
:
ble
1
s
Th
:
-
:
:
.
T
.
T
e
pp
pp
.
Regulatory Information
For all products, the Declaration of Conformity (DofC) is
vailable through one or more of these options:
s
pdf file is included on the product’s CD
print copy is included with the product
pdf file is available on the product’s webpage.
Visi
select your country or region. Then select your product
If you need any other technical documentation, see the
Technical Documents on www.linksysbycisco.com
nternational” section, as shown later in this appendix
on-Wireless Equipment (ADSL Modems/Gateways
he following standards were applied during the
ssessment of the product against the requirements of
the Directive 1999/5/EC
EMC: EN 55 022 and EN 55 02
afety: EN 60950-1
CE Markin
For the Linksys products such as the ADSL modems
gateways, the following CE mark is added to the
equipment.
nessuna limitazione, eccetto per i paesi menzionati di
seguito
as Produkt kann in allen EU Staaten ohne Einschränkungen
ingesetzt werden (sowie in anderen Staaten die der EU
irektive 1999/5/CE folgen) mit Außnahme der folgenden
aufgeführten Staaten:
In the majority of the EU and other European countries,
the 2,4-GHz bands have been made available for
the use of wireless local area networks (LANs). Later in
this document you will find an overview of countries in
which additional restrictions or requirements or both are
pplicable
he requirements for any country may evolve. Linksys
ecommends that you check with the local authorities for
the latest status of their national regulations for both the
2,4- GHz wireless LANs
he following countries have restrictions and/or
equirements in addition to those given in the table
labeled “
verview of Regulatory Requirements for Wireless
s
Wireless Equipment (Wireless-N/G/A/B Products
he following standards were applied during the
ssessment of the product against the requirements of
the Directive 1999/5/EC
Radio: EN 300 328 and/or EN 301 893 as applica
EMC: EN 301 489-1, EN 301 489-17
afety: EN 60950-1 and either EN 50385 or EN 5037
For the Linksys Wireless-N, -G, -B, and/or -A products, the
ollowing CE mark, and class 2 identifier are added to the
equipment.
National Restriction
is product may be used in all EU countries (and other
countries following the EU directive 1999/5/EC) without
ny limitation except for the countries mentioned below
Ce produit peut être utilisé dans tous les pays de l’UE (et dans
tous les pays ayant transposés la directive 1999/5/CE) sans
aucune limitation, excepté pour les pays mentionnés ci
essous
ranc
For 2,4 GHz, the product should not be used outdoors
n the band 2454 - 2483,5 MHz. There are no restrictions
when used in other parts of the 2,4 GHz band OR when
sed indoors. Check
etails.
Pour la bande 2,4 GHz, l’ équipement ne doit pas être
tilisé en extérieur dans la bande 2454- 2483,5 MHz. Il
’y a aucune restriction pour son utilisation dans d’autres
arties de la bande des 2,4 GHz ainsi que pour une
tilisation en intérieur. Consultez
our de plus amples détails
for more
Questo prodotto è utilizzabile in tutte i paesi EU (ed in tutti
gli altri paesi che seguono le direttive EU 1999/5/EC) senza
12
Page 15

Appendix C
a
T
p
f
.
f
p
otes:
.
T
.
s
T
.
T
cable.
.
T
.
l
:
py
oducts
tab.
.
l
Regulatory Information
Third-Party Software or Firmware
he use of software or firmware not supported/provided
Linksys may result that the equipment is no longer
compliant with the regulatory requirements
tvi
he outdoor usage of the 2,4 GHz band requires an
uthorization from the Electronic Communications Office.
Please check
2,4 GHz frekveču joslas izmantošanai ārpus telpām
epieciešama atļauja no Elektronisko sakaru direkcijas.
Vairāk in
N
ormācijas:
lthough Norway, Switzerland and Liechtenstein are
ot EU member states, the EU Directive 1999/5/EC has
lso been implemented in those countries
he regulatory limits
specified in EIRP. The EIRP level (in dBm) of a device can
e calculated by adding the gain of the antenna used
(specified in dBi) to the output power available at the
connector (specified in dBm)
or maximum output power are
or more details
Product Usage Restriction
his product is designed for indoor usage only. Outdoor
sage is not recommended, unless otherwise noted.
Outdoor usage may even be prohibited (see below)
echnical Documents on
ww.linksysbycisco.com/internationa
Follow these steps to access technical documents
Enter
n your web browser.
2.elect the country or region in which you live.
lick thePr
elect the appropriate produc category.
elect the product sub-catgory, if necessary.
elect the product
.
elect the type of documentation you want from the More
Information section.The document will open in PDF format
you have Adobe Acrobat installed on your computer.
NOTE: If you have questions regarding
the compliance of this product or you
cannot find the information you need,
lease contact your local sales office or visit
www.linksysbycisco.com/internationa
2,4 GHz Restrictions
his product is designed for use with the standard, integral
or dedicated (external) antenna(s) that is/are shipped
together with the equipment. However, some applications
ay require the antenna(s), if removable, to be separated
rom the product and installed remotely from the device
y using extension cables. For these applications, Linksys
offers an R SMA extension cable (AC9SMA) and an R-TNC
extension cable (AC9TNC). Both of these cables are 9
eters long and have a cable loss (attenuation) of 5 dB. To
compensate for the attenuation, Linksys also offers higher
ain antennas, the HGA7S (with R-SMA connector) and
HGA7T (with R-TNC connector). These antennas have a
gain of 7 dBi and may only be used with either the R-SMA
r R-TNC extension
Combinations of extension cables and antennas resulting
n a radiated power level exceeding 20 dBm (100 mW)
EIRP (2,4 GHz band) are illegal
13
Page 16

Appendix C
odu
d
d
)
T
y
:
n
e
bol
U
lek
n
Regulatory Information
ser Information for Consumer Pr
cts Covere
y EU Directive 2002/96/EC on Waste Electric an
Electronic Equipment (WEEE
his document contains important information for users
with regards to the proper disposal and recycling of
Linksys products. Consumers are required to compl
with this notice for all electronic products bearing the
ollowing symbol
he European Unio
European Directive 2002/96/EC requires that the equipment
bearing this symbol
ot be disposed of with unsorted municipal waste. The symbol
ndicates that this product should be disposed of separately
rom regular household waste streams. It is your responsibility to
ispose of this and other electric and electronic equipment via
esignated collection facilities appointed by the government or
ocal authorities. Correct disposal and recycling will help prevent
otential negative consequences to the environment and
uman health. For more detailed information about the disposal
f your old equipment, please contact your local authorities,
aste disposal service, or the shop where you purchased the
roduct.
Български (Bulgarian) - Информация относно
пазването на околната среда за потребители в
Европейския съюз
Европейска директива 2002/96/EC изисква уредите, носещи
този символ
се изхвърля т с несортирани битови отпадъци. Символът
обозначава, че изделието трябва да се изхвърля отделно от
сметосъбирането на обикновените битови отпадъци. Ваша
е отговорността този и другите електрически и електронни
реди да се изхвърлят в предварително определени от
държавните или общински органи специализирани пунктове
за събиране. Правилното изхвърляне и рециклиране
ще спомогнат да се предотвратят евентуални вредни за
околната среда и здравето на населението последствия. За
по-подробна информация относно изхвърлянето на вашите
стари уреди се обърнете към местните власти, службите за
сметосъбиране или магазина, от който сте закупили уреда.
eština (Czech) - Informace o ochraně životního
prostředí pro zákazníky v zemích Evropské uni
Evropská směrnice 2002/96/ES zakazuje, aby zařízení označené
tímto sym
netříděným komunálním odpadem. Tento symbol udává,
e daný produkt musí být likvidován odděleně od běžného
omunálního odpadu. Odpovídáte za likvidaci tohoto produktu
dalších elektrických a elektronických zařízení prostřednictvím
rčených sběrných míst stanovených vládou nebo místními
řady. Správná likvidace a recyklace pomáhá předcházet
otenciálním negativním dopadům na životní prostředí a lidské
draví. Podrobnější informace o likvidaci starého vybavení si
askavě vyžádejte od místních úřadů, podniku zabývajícího se
ikvidací komunálních odpadů nebo obchodu, kde jste produkt
akoupili.
em
Dansk (Danish) - Miljøinformation for kunder i E
EU-direktiv 2002/96/EF kræver, at udstyr der bærer dette symbol
usorteret kommunalt affald. Symbolet betyder, at dette produkt
skal bortskaffes adskilt fra det almindelige husholdningsaffald.
Det er dit ansvar at bortskaffe dette og andet elektrisk og
tronisk udstyr via bestemte indsamlingssteder udpeget
e
af staten eller de lokale myndigheder. Korrekt bortskaffelse
og genvinding vil hjælpe med til at undgå mulige skader for
miljøet og menneskers sundhed. Kontakt venligst de lokale
myndigheder, renovationstjenesten eller den butik, hvor du
har købt produktet, angående mere detaljeret information om
bortskaffelse af dit gamle udstyr.
Deutsch (German) - Umweltinformation für Kunden
innerhalb der Europäischen Unio
Die Europäische Richtlinie 2002/96/EC verlangt, dass technische
Ausrüstung, die direkt am Gerät und/oder an der Verpackung mit
iesem Symbol versehen ist
emeindeabfall entsorgt werden darf. Das Symbol weist darauf
in, dass das Produkt von regulärem Haushaltmüll getrennt
ntsorgt werden sollte. Es liegt in Ihrer Verantwortung, dieses
erät und andere elektrische und elektronische Geräte über
ie dafür zuständigen und von der Regierung oder örtlichen
ehörden dazu bestimmten Sammelstellen zu entsorgen.
rdnungsgemäßes Entsorgen und Recyceln trägt dazu bei,
otentielle negative Folgen für Umwelt und die menschliche
esundheit zu vermeiden. Wenn Sie weitere Informationen zur
ntsorgung Ihrer Altgeräte benötigen, wenden Sie sich bitte an
ie örtlichen Behörden oder städtischen Entsorgungsdienste
er an den Händler, bei dem Sie das Produkt erworben haben.
14
Page 17

Appendix C
le
l
f
este símbolo
y
y
obtene
detallada sobre la e
ηψη
τ
e
l
l
l
ll
h
.
a
essere smaltito
estici.
ā
Regulatory Information
Eesti (Estonian) - Keskkonnaalane informatsioon
Euroopa Liidus asuvatele klientide
Euroopa Liidu direktiivi 2002/96/EÜ nõuete kohaselt on
seadmeid, millel on tootel või pakendil käesolev sümbol
eelatud kõrvaldada koos sorteerimata olmejäätmetega. See
sümbol näitab, et toode tuleks kõrvaldada eraldi tavalistest
olmejäätmevoogudest. Olete kohustatud kõrvaldama käesoleva
ja ka muud elektri- ja elektroonikaseadmed riigi või kohalike
ametiasutuste poolt ette nähtud kogumispunktide kaudu.
Seadmete korrektne kõrvaldamine ja ringlussevõtt aitab vältida
võimalikke negatiivseid tagajärgi keskkonnale ning inimeste
e. Vanade seadmete kõrvaldamise kohta täpsema
tervise
informatsiooni saamiseks võtke palun ühendust kohalike
ametiasutustega, jäätmekäitlus
toote ostsite.
irmaga või kauplusega, kust te
Español (Spanish) - Información medioambiental para
lientes de la Unión Europea
La Directiva 2002/96/CE de la UE exige que los equipos que
lleven
no deben eliminarse junto con otros residuos urbanos no
seleccionados. El símbolo indica que el producto en cuestión
debe separarse de los residuos domésticos convencionales con
vistas a su eliminación. Es responsabilidad suya desechar este y
cualesquiera otros aparatos eléctricos y electrónicos a través de
los puntos de recogida que ponen a su disposición el gobierno y
las autoridades locales. Al desechar y reciclar correctamente estos
aparatos estará contribu
negativas para el medio ambiente
segura de su aparato usado, consulte a las autoridades locales,
al servicio de recogida y eliminación de residuos de su zona o
pregunte en la tienda donde adquirió el producto.
endo a evitar posibles consecuencias
r información más
la salud de las personas. Si
liminación
Ελληνικά (Greek) - Στοιχεία περιβαλλοντικής
προστασίας για πελάτες εντός της Ευρωπαϊκής
Ένωσης
Σύμφωνα με την Κοινοτική Οδηγία 2002/96/EC, ο εξοπλισμός που
έρει αυτό το σύμβολο
εν πρέπει να απορρίπτεται μαζί με τα μη διαχωρισμένα αστικά
πορρίμματα. Το σύμβολο υποδεικνύει ότι αυτό το προϊόν θα
ρέπει να απορρίπτεται ξεχωριστά από τα συνήθη οικιακά
πορρίμματα. Είστε υπεύθυνος για την απόρριψη του παρόντος
αι άλλου ηλεκτρικού και ηλεκτρονικού εξοπλισμού μέσω των
αθορισμένων εγκαταστάσεων συγκέντρωσης απορριμμάτων,
ι οποίες ορίζονται από το κράτος ή τις αρμόδιες τοπικές αρχές.
σωστή απόρριψη και ανακύκλωση συμβάλλει στην πρόλ
νδεχόμενων αρνητικών επιπτώσεων στο περιβάλλον και την
γεία. Για περισσότερες πληροφορίες σχετικά με την απόρριψη
ου παλαιού σας εξοπλισμού, επικοινωνήστε με τις τοπικές
ρχές, τις υπηρεσίες αποκομιδής απορριμμάτων ή το κατάστημα
πό το οποίο αγοράσατε το προϊόν.
Français (French) - Informations environnementales
pour les clients de l’Union européenn
La directive européenne 2002/96/CE exige que l’équipement
equel est apposé ce symbole
sur
emballage ne soit pas jeté avec les autres ordures ménagères. Ce
symbole indique que le produit doit être éliminé dans un circuit
istinct de celui pour les déchets des ménages. Il est de votre
responsabilité de jeter ce matériel ainsi que tout autre matériel
é
ectrique ou électronique par les moyens de collecte indiqués
e gouvernement et les pouvoirs publics des collectivités
par
territoriales. L’élimination et le recyclage en bonne et due forme
ont pour but de lutter contre l’impact néfaste potentiel de ce
type de produits sur l’environnement et la santé publique. Pour
plus d’informations sur le mode d’élimination de votre ancien
équipement, veui
ocaux, le service de traitement des déchets, ou l’e ndroit où vous
avez ac
eté le produit
ez prendre contact avec les pouvoirs publics
Italiano (Italian) - Informazioni relative all’ambiente
er i clienti residenti nell’Unione Europe
La direttiva europea 2002/96/EC richiede che le apparecchiature
contrassegnate con questo simbolo
ull’imballaggio non siano smaltite insieme ai rifiuti urbani
on differenziati. Il simbolo indica che questo prodotto non
ve
esponsabilità del proprietario smaltire sia questi prodotti sia
e altre apparecchiature elettriche ed elettroniche mediante
e specifiche strutture di raccolta indicate dal governo o dagli
nti pubblici locali. Il corretto smaltimento ed il riciclaggio
iuteranno a prevenire conseguenze potenzialmente negative
er l’ambiente e per la salute dell’essere umano. Per ricevere
nformazioni più dettagliate circa lo smaltimento delle vecchie
pparecchiature in Vostro possesso, Vi invitiamo a contattare gli
nti pubblici di competenza, il servizio di smaltimento rifiuti o il
egozio nel quale avete acquistato il prodotto.
insieme ai normali rifiuti dom
È
Latviešu valoda (Latvian) - Ekoloģiska informācija
lientiem Eiropas Savienības jurisdikcij
Direktīvā 2002/96/EK ir prasība, ka aprīkojumu, kam pievienota
zīme
zmest nešķirotā veidā kopā ar komunālajiem atkritumiem
tiem, ko rada vietēji iedzīvotāji un uzņēmumi). Šī zīme nozīmē
o, ka šī ierīce ir jāizmet atkritumos tā, lai tā nenonāktu kopā ar
arastiem mājsaimniecības atkritumiem. Jūsu pienākums ir šo
n citas elektriskas un elektroniskas ierīces izmest atkritumos,
zmantojot īpašus atkritumu savākšanas veidus un līdzekļus, ko
odrošina valsts un pašvaldību iestādes. Ja izmešana atkritumos
n pārstrāde tiek veikta pareizi, tad mazinās iespējamais
aitējums dabai un cilvēku veselībai. Sīkākas ziņas par
ovecojuša aprīkojuma izmešanu atkritumos jūs varat saņemt
ietējā pašvaldībā, atkritumu savākšanas dienestā, kā arī veikalā,
ur iegādājāties šo izstrādājumu.
15
Page 18

Appendix C
s
bend
k
k
a
u
j
j
j
a
e
d
f
f
l
f
U
duk
y
odowiska
duk
ład
Regulatory Information
Lietuvškai (Lithuanian) - Aplinkosaugos informacija,
irta Europos Sąjungos vartotojam
Europos direktyva 2002/96/EC numato, kad įrangos, kuri ir
negalima šalinti kartu su nerūšiuotomis komunalinėmis
atliekomis. Šis simbolis rodo, kad gaminį reikia šalinti atskirai
nuo
ši ir kita elektros ar elektroninė įranga būtų šalinama per tam
ti
sistemas. Tin
galimos žalos aplinkai ir žmonių sveikatai. Daugiau informacijos
apie jūsų senos įrangos šalinimą gali pateikti vietinės valdžios
institucijos, atliekų šalinimo tarnybos arba parduotuvės, kuriose
sigijote tą gaminį.
ro buitinių atliekų srauto. Jūs privalote užtikrinti, kad
ras nacionalinės ar vietinės valdžios nustatytas atliekų rinkimo
amai šalinant ir perdirbant atliekas, bus išvengta
alti (Maltese) - Informazzjoni Ambjentali għal
Klijenti fl-Unjoni Ewrope
Id-Direttiva Ewropea 2002/96/KE titlob li t-tagħmir li jkun fih
is-simbol
intrema ma’ skart muniċipali li ma ġiex isseparat. Is-simbolu
indika li dan il-prodott għandu jintrema separatament minn ma’
-iskart domestiku regolari. Hija responsabbiltà tiegħek li tarmi
an it-tagħmir u kull tagħmir ieħor ta’ l-elettriku u elettroniku
ermezz ta’ faċilitajiet ta’ ġbir appuntati apposta mill-gvern jew
ill-awtoritajiet lokali. Ir-rimi b’mod korrett u r-riċiklaġġ jgħin
ipprevjeni konsegwenzi negattivi potenzjali għall-ambjent u
ħas-saħħa tal-bniedem. Għal aktar informazzjoni dettaljata
war ir-rimi tat-tagħmir antik tiegħek, jekk jogħġbok ikkuntattja
ill-awtoritajiet lokali tiegħek, is-servizzi għar-rimi ta’ l-iskart, jew
l-ħanut minn fejn xtrajt il-prodott.
Nederlands (Dutch) - Milieu-informatie voor klanten
in de Europese Uni
De Europese Richtlijn 2002/96/EC schrijft voor dat apparatuur die
is voorzien van
niet mag worden ingezameld met niet-gescheiden huishoudelijk
afval. Dit symbool geeft aan dat het product apart moet worden
ingezameld. U bent zel
van deze en andere elektrische en elektronische apparatuur via de
daarvoor door de landelijke o
ingskanalen. De juiste vernietiging en recycling van
inzame
eze apparatuur voorkomt mogelijke negatieve gevolgen voor
het milieu en de gezondheid. Voor meer informatie over het
vernietigen van uw oude apparatuur neemt u contact op met
de plaatselijke autoriteiten of afvalverwerkingsdienst, of met de
winkel waar u het product hebt aangescha
it symbool
verantwoordelijk voor de vernietiging
plaatselijke overheid aangewezen
t.
Norsk (Norwegian) - Miljøinformasjon for kunder i E
EU-direktiv 2002/96/EF krever at utstyr med følgende symbol
sammen med usortert avfall. Symbolet indikerer at dette
produktet skal håndteres atskilt fra ordinær avfallsinnsamling
for husholdningsavfall. Det er ditt ansvar å kvitte deg med
ette produktet og annet elektrisk og elektronisk avfall via egne
innsamlingsordninger slik myndighetene eller kommunene
bestemmer. Korrekt avfallshåndtering og gjenvinning vil
være med på å forhindre mulige negative konsekvenser for
miljø og helse. For nærmere informasjon om håndtering av
et kasserte utstyret ditt, kan du ta kontakt med kommunen,
en innsamlingsstasjon for avfall eller butikken der du kjøpte
tet.
pro
agyar (Hungarian) - Környezetvédelmi információ az
urópai uniós vásárlók számár
A 2002/96/EC számú európai uniós irányelv megkívánja,
ogy azokat a termékeket, amelyeken, és/vagy amelyek
csomagolásán az alábbi címke
szelektálatlan lakossági hulladékkal együtt kidobni. A címke
azt jelöli, hogy az adott termék kidobásakor a szokványos
áztartási hulladékelszállítási rendszerektõl elkülönített eljárást
kell alkalmazni. Az Ön felelõssége, hogy ezt, és más elektromos
és elektronikus berendezéseit a kormányzati vagy a helyi
atóságok által kijelölt gyűjtõredszereken keresztül számolja
el. A megfelelõ hulladékfeldolgozás segít a környezetre és az
emberi egészségre potenciálisan ártalmas negatív hatások
megelõzésében. Ha elavult berendezéseinek felszámolásához
további részletes információra van szüksége, kérjük, lépjen
kapcsolatba a helyi hatóságokkal, a hulladékfeldolgozási
szolgálattal, vagy azzal üzlettel, ahol a terméket vásárolta.
Polski (Polish) - Informacja dla klientów w Unii
Europejskiej o przepisach dotyczących ochron
r
Dyrektywa Europejska 2002/96/EC wymaga, aby sprzęt
oznaczony symbolem
ub jego opakowaniu nie był wyrzucany razem z innymi
niesortowanymi odpadami komunalnymi. Symbol ten wskazuje,
że pro
odpadami z gospodarstw domowych. Na Państwu spoczywa
obowiązek wyrzucania tego i innych urządzeń elektrycznych
oraz elektronicznych w punktach odbioru wyznaczonych
przez w
we właściwy sposób i jego recykling pomogą zapobiec
potencjalnie negatywnym konsekwencjom dla środowiska i
zdrowia ludzkiego. W celu uzyskania szczegółowych informacji
o usuwaniu starego sprzętu, prosimy zwrócić się do lokalnych
władz, służb oczyszczania miasta lub sklepu, w którym produkt
został nabyty.
t nie powinien być usuwany razem ze zwykłymi
ze krajowe lub lokalne. Pozbywanie się sprzętu
16
Page 19

Appendix C
a
b
ă
ţ
ţ
ţ
i
i
bol
-
y
tuote tai tuotteet
ste
y
n
.
l
Regulatory Information
Português (Portuguese) - Informação ambiental para
ientes da União Europei
A Directiva Europeia 2002/96/CE exige que o equipamento
que exi
ocais. A eliminação e reciclagem correctas ajudarão a prevenir
orma de eliminar o seu equipamento antigo, contacte as
e este símbolo
ão seja eliminado junto com os resíduos municipais não
eparados. O símbolo indica que este produto deve ser
iminado separadamente dos resíduos domésticos regulares.
da sua responsabilidade eliminar este e qualquer outro
quipamento eléctrico e electrónico através das instalações
e recolha designadas pelas autoridades governamentais ou
s consequências negativas para o ambiente e para a saúde
umana. Para obter informações mais detalhadas sobre a
utoridades locais, os serviços de eliminação de resíduos ou o
stabelecimento comercial onde adquiriu o produto.
Română (Romanian) - Informaţii de mediu pentru
lienţii din Uniunea European
Directiva europeană 2002/96/CE impune ca echipamentele care
rezintă acest simbol
nu fie casate împreună cu gunoiul menajer municipal. Simbolul
indică faptul că acest produs trebuie să fie casat separat de
gunoiul menajer obişnuit. Este responsabilitatea dvs. să casaţi
acest produs şi alte echipamente electrice şi electronice prin
intermediul unită
sau de autorită
la prevenirea poten
mediului şi a oamenilor. Pentru mai multe informaţii detaliate
cu privire la casarea acestui echipament vechi, contactaţi
autorităţile locale, serviciul de salubrizare sau magazinul de la
care aţi achiziţionat produsul.
ilor de colectare special desemnate de guvern
ile locale. Casarea şi reciclarea corecte vor ajuta
ialelor consecinţe negative asupra sănătăţii
Slovenčina (Slovak) - Informácie o ochrane životného
prostredia pre zákazníkov v Európskej úni
Podľa európskej smernice 2002/96/ES zariadenie s týmto
symbolom
ikvidované spolu s netriedeným komunálnym odpadom.
ymbol znamená, že produkt by sa mal likvidovať oddelene
d bežného odpadu z domácností. Je vašou povinnosťou
ikvidovať toto i ostatné elektrické a elektronické zariadenia
rostredníctvom špecializovaných zberných zariadení určených
ádou alebo miestnymi orgánmi. Správna likvidácia a recyklácia
omôže zabrániť prípadným negatívnym dopadom na životné
rostredie a zdravie ľudí. Ak máte záujem o podrobnejšie
nformácie o likvidácii starého zariadenia, obráťte sa, prosím, na
iestne orgány, organizácie zaoberajúce sa likvidáciou odpadov
ebo obchod, v ktorom ste si produkt zakúpili.
Slovenščina (Slovene) - Okoljske informacije za
tranke v Evropski unij
Evropska direktiva 2002/96/ES prepoveduje odlaganje opreme s
tem sim
omunalnimi odpadki. Ta simbol opozarja, da je treba izdelek
avreči ločeno od preostalih gospodinjskih odpadkov. Vaša
govornost je, da to in preostalo električno in elektronsko
premo oddate na posebna zbirališča, ki jih določijo državne
stanove ali lokalne oblasti. S pravilnim odlaganjem in
ecikliranjem boste preprečili morebitne škodljive vplive na
kolje in zdravje ljudi. Če želite izvedeti več o odlaganju stare
preme, se obrnite na lokalne oblasti, odlagališče odpadkov ali
rgovino, kjer ste izdelek kupili.
om
Suomi (Finnish) - Ympäristöä koskevia tietoja EU
alueen asiakkaille
EU-direktiivi 2002/96/EY edellyttää, että jos laitteistossa on tämä
mboli
s
ei saa hävittää lajittelemattoman yhdyskuntajätteen mukana.
Symboli merkitsee sitä, että tämä tuote on hävitettävä erillään
tavallisesta kotitalousjätteestä. Sinun vastuullasi on hävittää
tämä elektroniikkatuote ja muut vastaavat elektroniikkatuotteet
viemällä
spisteeseen. Laitteiston oikea hävittäminen estää
kerä
mahdolliset kielteiset vaikutukset ympäristöön ja ihmisten
terveyteen. Lisätietoja vanhan laitteiston oikeasta hävitystavasta
saa paikallisilta viranomaisilta, jätteenhävityspalvelusta tai siitä
myymälästä, josta ostit tuotteen.
viranomai
n määräämään
Svenska (Swedish) - Miljöinformation för kunder i
Europeiska unione
Det europeiska direktivet 2002/96/EC kräver att utrustning med
enna symbol
astas med osorterat kommunalt avfall. Symbolen visar att denna
produkt bör kastas efter att den avskiljts från vanligt hushållsavfall.
Det faller på ditt ansvar att kasta denna och annan elektrisk och
lektronisk utrustning på fastställda insamlingsplatser utsedda
av regeringen eller lokala myndigheter. Korrekt kassering och
tervinning skyddar mot eventuella negativa konsekvenser
ör miljön och personhälsa. För mer detaljerad information om
assering av din gamla utrustning kontaktar du dina lokala
myndigheter, avfallshanteringen eller butiken där du köpte
produkten
WEB: For additional information, please visit
www.linksysbycisco.com/internationa
17
Page 20

Appendix C
T
ustralia.
e
h
.
aland
T
d.
t
Th
ll
ceed 100 metres.
g
T
ection to its network.
cates no endorsement
y
Telecom’s netwo
ces.
ices
T
y
.
y
T
T
d
y
occur.
eco
e
s
d
.
a
T
.
FCC Caution: Any changes or modifications not expressly
approved by the party responsible for compliance could
void the user’s authority to operate this equipment.
FCC Radiation Exposure Statement
This equipment complies with FCC radiation exposure limits
set forth for an uncontrolled environment. This equipment
should be installed and operated with minimum distance
20cm between the radiator and your body.
This equipment has been tested and found to comply with the
limits for a Class B digital device, pursuant to part 15 of the
FCC rules. These limits are designed to provide reasonable
protection against harmful interference in a residential
installation. This equipment generates, uses and can radiate
radio frequency energy and, if not installed and used in
accordance with the instructions, may cause harmful
interference to radio communications. However, there is no
guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference
to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try
to correct the interference by one or more of the following
measures:
-Reorient or relocate the receiving antenna.
-Increase the separation between the equipment and receiver.
-Connect the equipment into an outlet on a circuit different
from that to which the receiver is connected.
-Consult the dealer or an experienced radio/TV technician for
help.
Regulatory Information
Australia
he following information applies if you use the product
within A
Safety Notic
WARNING: To ensure compliance wit
exposure limits to radiofrequency fields, the
antenna of the device should be no closer than
20 cm from the body during use
New Ze
he following information applies if you use the product
within New Zealan
elepermit Statemen
e cabling between the phone port and the phone sha
ex
PTC200 General Warnin
he grant of a Telepermit for any item of terminal
equipment indicates only that Telecom has accepted
that the item complies with minimum conditions for
nn
of the product by Telecom, nor does it provide any sort
of warranty. Above all, it provides no assurance that an
tem will work correctly in all respects with another item
of Telepermitted equipment of a different make or model,
or does it imply that any product is compatible with all of
rk servi
It indi
isco-Linksys ADSL2+ Devices on Long Line
DSL2+ devices may not achieve the type of “high speed”
operation expected when attached to a line that is longer
than intended by the ITU-T Rec. G.996.1 ADSL standar
.e. >3 km of 0.4mm cable or a shorter cable length with
several tails or multiples. If the device is installed in such
conditions and does not give the expected “download”
erformance, then do not refer the matter to the Telecom
Fault Service or ADSL Helpdesk
United States of Americ
he following information applies if you use the product
within the United States of America
FCC Statement
Wireless Connectivity Security on Cisco-Linksys
ADSL2+ Dev
etting up the security of the wireless connection
ssociated with ADSL2+ device is the user’s responsibility.
elecom will take no responsibility for charges made to
ser’s accounts due to poorly organized wireless securit
llowing unknown users to connect to the Internet via this
device. Do not complain to the Telecom Fault Service or
Jetstream Helpdesk should this occur
eneral Warning for Cisco-Linksys ADSL2+
Devices and ADSL2+ Capabilit
his device has been tested and found suitable to connect
to the Telecom ADSL2+ capability. This indicates only that
elecom has accepted that this device complies with the
spectrum management plan for ADSL2+ on copper cable
nd with simple voiceband compatibility tests include
n PTC273. It does not indicate that this device is full
compatible with all services accessed via the ADSL2+
capability. Contact the supplier of the device when
Do not call the Tel
Jetstream Helpdesk.
m Fault Service or th
18
Page 21

Appendix C
T
.
T
g
y.
T
.
h
leph
k.
T
l
.
.
Th
.
T
.
y
.
s
y
d.
l.
g.
h
oser tha
.
Regulatory Information
his transmitter must not be co-located or operating in
conjunction with any other antenna or transmitter. IEEE
802.11b or 802.11g operation of this product in the USA is
irmware-limited to channels 1 through 11
Part 68 Statement
his equipment complies with Part 68 of the FCC Rules. A
label is attached to the equipment that contains, amon
other information, its FCC registration number and ringer
equivalence number. If requested, this information must
e provided to the telephone compan
his equipment uses the following USOC Jack: RJ-11
n FCC compliant telephone cord and modular plug
s provided with this equipment. This equipment is
designed to be connected to the telephone network or
remises wiring using a compatible modular jack, whic
s FCC Part 68 compliant. Connection to the telephone
etwork should be made by using the standard modular
te
one jac
he REN is useful to determine the quantity of devices
that may be connected to the telephone line and still have
ll of those devices ring when your telephone number is
called. In most, but not all areas, the sum of RENs should
ot exceed 5. To be certain of the number of devices that
ay be connected to the line, as determined by the tota
RENs, contact the telephone company to determine the
aximum REN for the calling area
No repairs may be done by the customer. If trouble is
experienced with this equipment, please contact your
uthorized support provider for repair and warrant
nformation. If the trouble is causing harm to the
telephone network, the telephone company may request
ou remove the equipment from the network until the
roblem is resolved. This equipment cannot be used on
telephone company provided coin service. Connection to
Party Line Service is subject to state tariffs
Safety Notice
WARNING: To reduce the risk of fire, use onl
o.26 AWG or larger telecommunication line
cor
WARNING: Do not use this product near water,
or example, in a wet basement or near a
wimming poo
WARNING: Avoid using this product during an
electrical storm. There may be a remote risk of
electric shock from lightnin
WARNING: This equipment will be inoperable
when main power fails.
If this equipment causes harm to the telephone network,
the telephone company may discontinue your service
temporarily. If advance notice is not practical, the
telephone company will notify the customer as soon as
ossible. Also, you will be advised of your right to file a
complaint with the FCC if you believe it is necessary
e telephone company may make changes in its
acilities, equipment, operations, or procedures that could
ffect the operation of the equipment. If this happens, the
telephone company will provide advance notice in order
or you to make the necessary modifications in order to
aintain uninterrupted service
In the event this equipment should fail to operate
roperly, disconnect the unit from the telephone line.
ry using another FCC approved device in the same
telephone jack. If the trouble persists, call the telephone
company repair service bureau. If the trouble does not
ersist and appears to be with this unit, disconnect the
nit from the telephone line and discontinue use of the
nit until it is repaired. Please note that the telephone
company may ask that you disconnect the equipment
rom the telephone network until the problem has been
corrected or until you are sure that the equipment is not
alfunctioning. The user must use the accessories and
cables supplied by the manufacturer to get optimum
erformance from the product
WARNING: To ensure compliance wit
explosure limits to radiofrequency fields, the
ntenna of the device should be no cl
20 cm from the body during use
n
19
Page 22

Appendix C
atériel doit être
stallé
,
T
.
-
l
.
T
ada.
t
T
.
:
T
d
T
T
:
T
y.
T
.
dustrie Canada.
:
ctement
sation d’antennes dont le
éduire le r
.
4
Regulatory Information
Canada
he following information applies if you use the product
within Can
Industry Canada Statemen
his device complies with Industry Canada ICES-003 and
RSS210 rules
Operation is subject to the following two conditions
his device may not cause interfernce an
his device must accept
nterference that may cause undesired operation of
the device. This device has been designed to operate
with an antenna having a maximum gain of 2dBi.
ntenna having a higher gain is strictly prohibited per
egulations of Industry Canada. The required antenna
mpedance is 50 ohms.
o reduce potential radio interference to other users,
the antenna type and its gain should be so chosen
that the EIRP is not more than required for successful
communication.
ndustry Canada Radiation Exposure Statement
his equipment complies with IC radiation exposure limits
set forth for an uncontrolled environment. This equipment
should be installed and operated with minimum distance
20cm between the radiator & your bod
his transmitter must not be co-located or operating in
conjunction with any other antenna or transmitter
Avis d’Industrie Canada
Cet appareil est conforme aux normes NMB003 et RSS210
’In
L’utilisation de ce dispositif est autorisée seulement aux
conditions suivantes
ny interference, including
vis d’Industrie Canada concernant l’exposition aux radio-
réquences :
Ce matériel est conforme aux limites établies par IC
en matière d’exposition aux radiofréquences dans un
nvironnement non contrôlé. Ce m
et utilisé à une distance d’au moins 20 cm entre l’antenne
et le corps de l’utilisateur.
L’émetteur ne doit pas être placé près d’une autre antenne
ou d’un autre émetteur
ntenne ou un autre émetteur.
ou fonctionner avec une autre
in
Wireless Disclaimer
he maximum performance for wireless is derived from
IEEE Standard 802.11 specifications. Actual performance
can vary, including lower wireless network capacity,
data throughput rate, range and coverage. Performance
depends on many factors, conditions and variables,
ncluding distance from the access point, volume of
etwork traffic, building materials and construction,
operating system used, mix of wireless products used,
nterference and other adverse conditions
Avis de non-responsabilité concernant les appar
eils sans fi
Les performances maximales pour les réseaux sans fil
sont tirées des spécifications de la norme IEEE 802.11.
Les performances réelles peuvent varier, notamment
en fonction de la capacité du réseau sans fil, du débit
de la transmission de données, de la portée et de la
couverture. Les performances dépendent de facteurs,
conditions et variables multiples, en particulier de la
distance par rapport au point d’accès, du volume du trafic
éseau, des matériaux utilisés dans le bâtiment et du
type de construction, du système d’exploitation et de la
combinaison de produits sans fil utilisés, des interférences
et de toute autre condition défavorable
l ne doit pas produire de brouillage et
l doit accepter tout brouillage radioélectrique reçu,
ême si ce brouillage est susceptible de compromettre
le fonctionnement du dispositif. Le dispositif a été
conçu pour fonctionner avec une antenne ayant un gain
aximum de 2 dBi. Les règlements d’Industrie Canada
nterdisent stri
gain est supérieur à cette limite. L’impédance requise
e l’antenne est de 50 ohms.
in de r
tilisateurs, le type d’antenne et son gain doivent
être choisis de façon à ce que la puissance isotrope
ayonnée équivalente (p.i.r.e.) ne soit pas supérieure
u niveau requis pour obtenir une communication
satisfaisante
l’utili
isque d’interférence aux autres
90605-10_20-10C-AI3425-0141
20
 Loading...
Loading...