Page 1

Cisco Small Business
RVS4000 4-Port Gigabit Security Router with VPN
ADMINISTRATION
GUIDE
Page 2

CCDE, CCENT, Cisco Eos, Cisco HealthPresence, the Cisco logo, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, Cisco TelePresence, Cisco WebEx, DCE, and Welcome to the
Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are service marks; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting
To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems,
Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare,
GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, iQuick Study, IronPort, the IronPort logo, LightStream, Linksys, MediaTone, MeetingPlace, MeetingPlace Chime Sound,
MGX, Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The
Fastest Way to Increase Your Internet Quotient, TransPath, WebEx, and the WebEx logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and
certain other countries.
All other trademarks mentioned in this document or website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between
Cisco and any other company. (0812R)
© 2009 Cisco Systems, Inc. All rights reserved. OL-19755-01
Page 3
Contents
About This Document 1
How to Use This Guide 1
Organization 1
Finding Information in PDF Files 2
Finding Text in a PDF 3
Finding Text in Multiple PDF Files 3
Chapter 1: Introduction 6
Chapter 2: Networking and Security Basics 7
An Introduction to LANs 7
The Use of IP Addresses 7
The Intrusion Prevention System (IPS) 9
Chapter 3: Planning Your Virtual Private Network (VPN) 11
Why do I need a VPN? 11
1) MAC Address Spoofing 12
2) Data Sniffing 12
3) Man in the middle attacks 12
What is a VPN? 12
VPN Router to VPN Router 13
Computer (using the Cisco QuickVPN Client software) to VPN Router 14
Chapter 4: Getting Started with the RVS4000 Router 16
Front Panel 16
Back Panel 17
Placement Options 18
Desktop Option 18
Stand Option 18
Wall Option 19
Installing the Router 20
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide iii
Page 4
Contents
Configuring the Router 21
Chapter 5: Setting Up and Configuring the Router 24
Setup 25
Setup > Summary 26
Setup > WAN 28
Setup > LAN 36
Setup > DMZ 40
Setup > MAC Address Clone 40
Setup > Advanced Routing 41
Setup > Time 43
Setup > IP Mode 44
Firewall 44
Firewall > Basic Settings 45
Firewall > IP Based ACL 46
Firewall > Internet Access Policy 50
Firewall > Single Port Forwarding 53
Firewall > Port Range Forwarding 54
Firewall > Port Range Triggering 55
ProtectLink 56
ProtectLink > ProtectLink Purchase 56
VPN 57
VPN > Summary 57
VPN > IPSec VPN 58
VPN > VPN Client Accounts 63
VPN > VPN Passthrough 65
QoS 65
QoS > Bandwidth Management 66
QoS > QoS Setup 68
QoS > DSCP Setup 69
Administration 70
Administration > Management 70
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide iv
Page 5
Router Access 70
Administration > Log 72
Administration > Diagnostics 74
Administration > Backup & Restore 75
Administration > Factory Default 76
Administration > Reboot 77
Administration > Firmware Upgrade 77
Contents
IPS 78
IPS > Configuration 78
IPS > P2P/IM 79
IPS > Report 80
IPS > Information 82
L2 Switch 82
L2 > Create VLAN 82
L2 > VLAN Port Setting 84
L2 > VLAN Membership 85
L2 > RADIUS 86
L2 > Port Setting 87
L2 > Statistics 88
L2 > Port Mirroring 89
L2 > RSTP 90
Status 91
Status > Gateway 91
Status > Local Network 93
Chapter 6: Using the VPN Setup Wizard 95
VPN Setup Wizard 95
Before You Begin 95
Running the VPN Router Software Wizard 96
Building Your VPN Connection Remotely 105
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide v
Page 6
Contents
Appendix A: Troubleshooting 113
Frequently Asked Questions 126
Appendix B: Using Cisco QuickVPN for Windows 2000, XP, or Vista 130
Overview 130
Before You Begin 130
Installing the Cisco QuickVPN Software 131
Installing from the CD-ROM 131
Downloading and Installing from the Internet 133
Using the Cisco QuickVPN Software 134
Distributing Certificates to QuickVPN Users 136
Appendix C: Configuring IPSec with a Windows 2000 or XP Computer 138
Introduction 138
Environment 139
Windows 2000 or Windows XP 139
RVS4000 139
How to Establish a Secure IPSec Tunnel 139
Establishing a Secure IPSec Tunnel 140
Appendix D: Gateway-to-Gateway VPN Tunnel 162
Overview 162
Before You Begin 162
Configuration when the Remote Gateway Uses a Static IP Address 163
Configuration when the Remote Gateway Uses a Dynamic IP Address 167
Configuration When Both Gateways Use Dynamic IP Addresses 172
Appendix E: Trend Micro ProtectLink Gateway Service 178
Overview 178
How to Access the Web-Based Utility 178
How to Purchase, Register, or Activate the Service 179
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide vi
Page 7
ProtectLink 179
Contents
How to Use the Service 181
ProtectLink > Web Protection 182
ProtectLink > Email Protection 186
ProtectLink > License 186
Appendix F: Specifications 188
Specifications 188
Performance 188
Setup/Config 188
Management 189
Security Features 189
QoS 189
Network 190
VPN 190
Routing 190
Layer 2 190
Environmental 191
Appendix G: Where to Go From Here 192
Product Resources 192
Related Documentation 193
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide vii
Page 8

About This Document
!
The focus of this guide is on the hardware and software features found on the
Cisco Small Business RVS4000 4-Port Gigabit Security Router with VPN.
Advanced configuration settings and security options are covered in this
administration guide.
How to Use This Guide
This administration guide has been designed to make understanding the router
easier. Look for the following items when reading this guide:
Preface
CAUTION This exclamation point indicates that caution should be used when performing a
NOTE This checkmark indicates there is a note of interest and is something you should
Organization
step or a serious error may occur.
pay special attention to while using the router.
This table describes the contents of each chapter in this document.
Chapter Title Description
Chapter 1 Introduction Introduces the product and this user
manual.
Chapter 2 Networking and
Security Basics
Introduces basic networking and
security concepts.
Chapter 3 Planning Your Virtual
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 1
Private Network (VPN)
Describes how to connect the
product.
Page 9
Chapter Title Description
Preface
Chapter 4 Getting Started with the
RVS4000 Router
Chapter 5 Setting Up and
Configuring the Router
Chapter 6 Using the VPN Setup
Wizard
Appendix A Troubleshooting Provides solutions to problems that
Appendix B Using Cisco QuickVPN
for Windows 2000, XP, or
Vista
Appendix C Configuring IPSec with a
Windows 2000 or XP
Computer
Describes the physical features of
the RVS4000 router and provides
information for installing the router.
Describes how to set up the product
software.
Describes how to configure a
gateway-to-gateway VPN tunnel
between two VPN routers.
may occur during the installation and
operation of the router.
Explains how to install and use the
Cisco QuickVPN software
Explains how to establish a secure
IPSec tunnel using preshared keys to
join a private network inside the
router and a Windows 2000 or XP
computer.
Appendix D Gateway-to-Gateway
VPN Tunnel
Appendix E Trend Micro ProtectLink
Gateway Service
Appendix F Specifications Provides product specifications.
Explains how to configure an IPSec
VPN tunnel between two VPN
routers by example.
Explains how to use the Trend Micro
ProtectLink Gateway service
Finding Information in PDF Files
The Cisco RVS4000 router documents are published as PDF files. The PDF Find/
Search tool within Adobe® Reader® lets you find information quickly and easily
online. You can perform the following tasks:
• Search an individual PDF file.
• Search multiple PDF files at once (for example, all PDFs in a specific folder
or disk drive).
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 2
Page 10
Preface
• Perform advanced searches.
Finding Text in a PDF
Follow this procedure to find text in a PDF file.
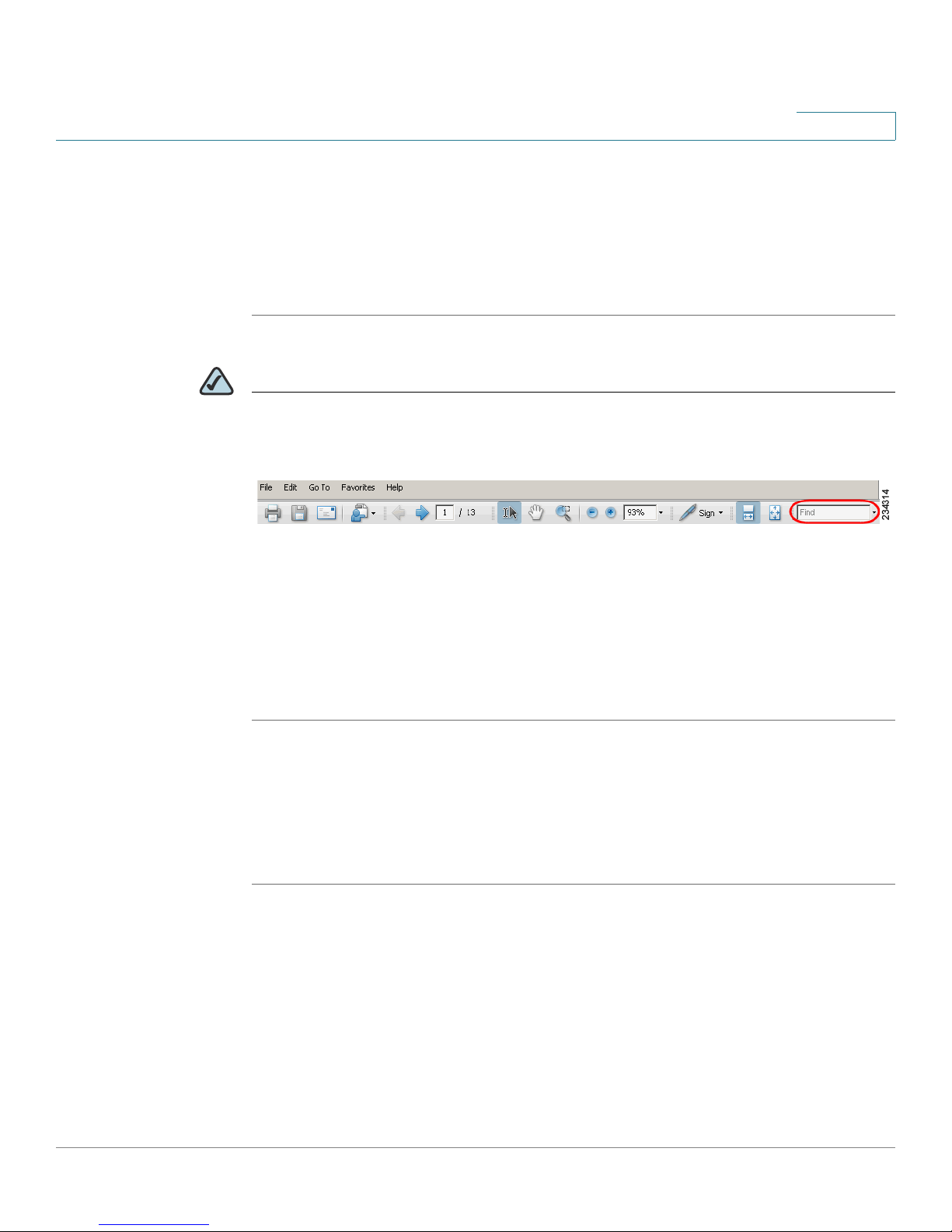
STEP 1 Enter your search terms in the Find text box on the toolbar.
NOTE By default, the Find tool is available at the right end of the Acrobat toolbar. If the
Find tool does not appear, choose Edit > Find.
STEP 2 Optionally, click the arrow next to the Find text box to refine your search by
choosing special options such as Whole Words Only.
STEP 3 Press Enter.
STEP 4 Acrobat displays the first instance of the search term.
STEP 5 Press Enter again to continue to more instances of the term.
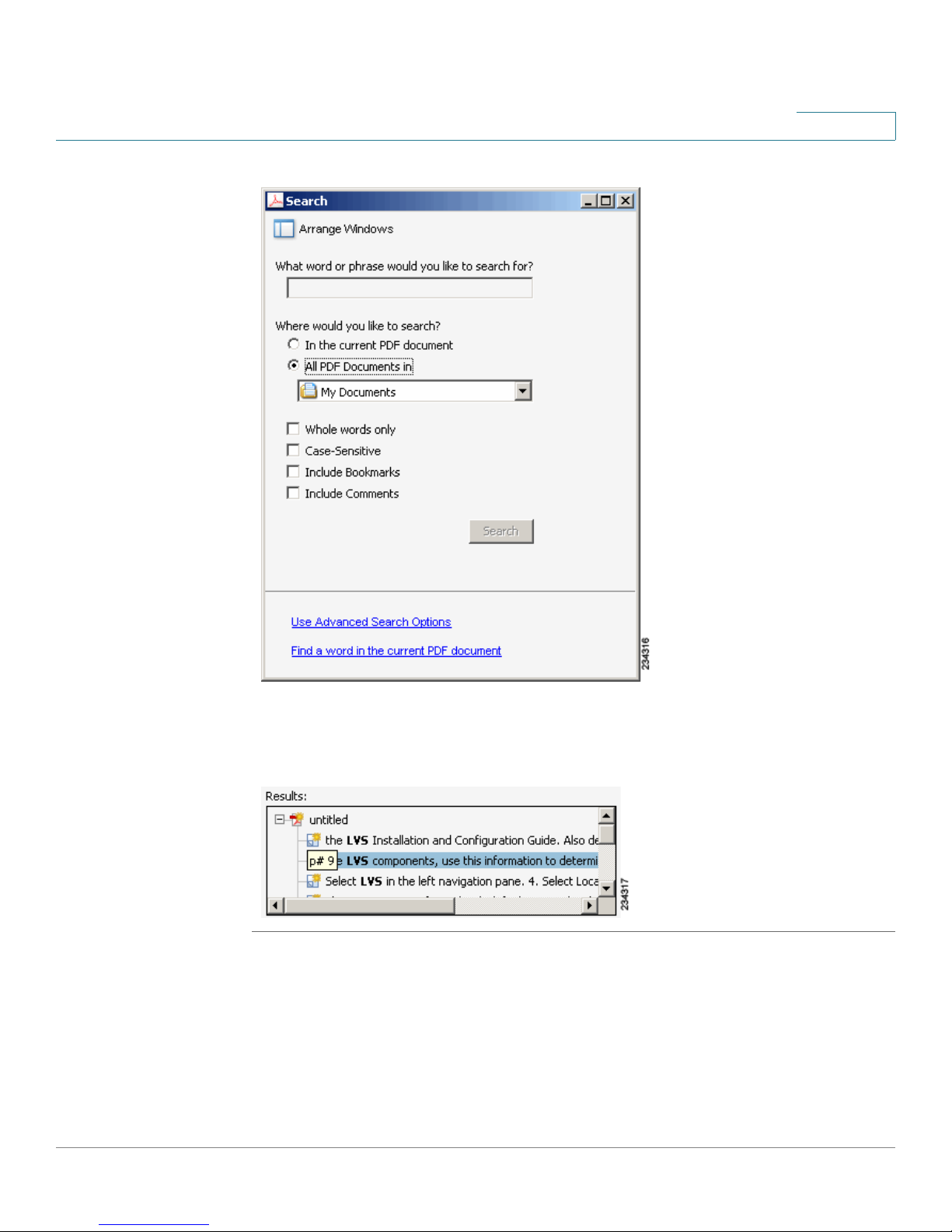
Finding Text in Multiple PDF Files
The
Search
on your computer or local network. The PDF files do not need to be open.
STEP 1 Start Acrobat Professional or Adobe Reader.
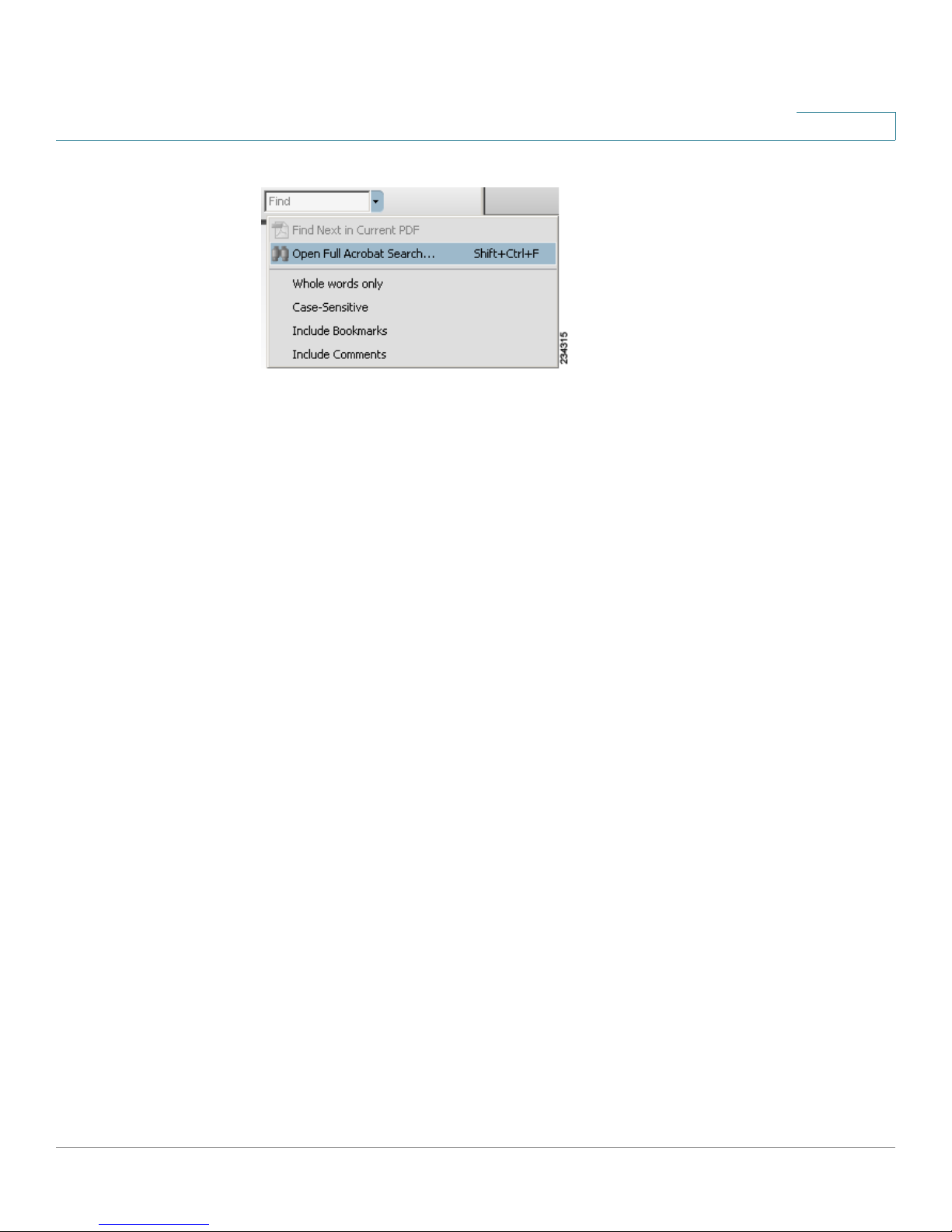
STEP 2 Choose Edit > Search, or click the arrow next to the
Open Full Acrobat Search.
window lets you search for terms in multiple PDF files that are stored
Find
box and then choose
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 3
Page 11
Preface
STEP 3 In the
a. Enter the text that you want to find.
b. Choose All PDF Documents in.
From the drop-down box, choose Browse for Location. Then choose the
location on your computer or local network, and click OK.
c. If you want to specify additional search criteria, click Use Advanced Search
Options, and choose the options you want.
d. Click Search.
Search
window, complete the following steps:
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 4
Page 12
Preface
STEP 4 When the Results appear, click + to open a folder, and then click any link to open
the file where the search terms appear.
For more information about the Find and Search functions, see the Adobe Acrobat
online help.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 5
Page 13

Introduction
Thank you for choosing the Cisco RVS4000 4-Port Gigabit Security Router with
VPN. The 4-Port Gigabit Security Router with VPN is an advanced Internet-sharing
network solution for your small business needs. Like any router, it lets multiple
computers in your office share an Internet connection.
The 4-Port Gigabit Security Router with VPN also features a built-in 4-Port fullduplex 10/100/1000 Ethernet switch to connect four PCs directly, or you can
connect more hubs and switches to create as big a network as you need.
The Virtual Private Network (VPN) capability creates encrypted “tunnels” through
the Internet, allowing up to 5 remote offices and 5 traveling users to securely
connect into your office network from off-site. Users connecting through a VPN
tunnel are attached to your company’s network — with secure access to files, email, and your intranet — just as if they were in the building. You can also use the
VPN capability to allow users on your small office network to securely connect out
to a corporate network. The QoS features provide consistent voice and video
quality throughout your business.
1
The 4-Port Gigabit Security Router with VPN can serve as a DHCP Server, and has
a powerful SPI firewall and Intrusion Prevention System (IPS) to protect your PCs
against intruders and most known Internet attacks. It can be configured to filter
internal users’ access to the Internet, and has IP and MAC address filtering so you
can specify exactly who has access to your network. Configuration is a snap with
the web browser-based configuration utility.
This administration guide will give you all the information you need to connect, set
up, and configure your router.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 6
Page 14

Networking and Security Basics
This chapter describes networking and security basics. It includes the following
sections:
• An Introduction to LANs, page 7
• The Use of IP Addresses, page 7
• The Intrusion Prevention System (IPS), page 9
An Introduction to LANs
2
A router is a network device that connects two networks together.
The router connects your local area network (LAN), or the group of PCs in your
home or office, to the Internet. The router processes and regulates the data that
travels between these two networks.
The router’s Network Address Translation (NAT) technology protects your network
of PCs so users on the Internet cannot “see” your PCs. This is how your LAN
remains private. The router protects your network by inspecting the first packet
coming in through the Internet port before delivery to the final destination on one
of the Ethernet ports. The router inspects Internet port services like the web
server, ftp server, or other Internet applications, and, if allowed, it will forward the
packet to the appropriate PC on the LAN side.
The Use of IP Addresses
IP stands for Internet Protocol. Every device in an IP-based network, including PCs,
print servers, and routers, requires an IP address to identify its location, or
address, on the network. This applies to both the Internet and LAN connections.
There are two ways of assigning IP addresses to your network devices.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 7
Page 15
Networking and Security Basics
The Use of IP Addresses
A static IP address is a fixed IP address that you assign manually to a PC or other
device on the network. Since a static IP address remains valid until you disable it,
static IP addressing ensures that the device assigned it will always have that same
IP address until you change it. Static IP addresses are commonly used with
network devices such as server PCs or print servers.
If you use the router to share your cable or DSL Internet connection, contact your
ISP to find out if they have assigned a static IP address to your account. If so, you
will need that static IP address when configuring the router. You can get the
information from your ISP.
A dynamic IP address is automatically assigned to a device on the network. These
IP addresses are called dynamic because they are only temporarily assigned to
the PC or other device. After a certain time period, they expire and may change. If
a PC logs onto the network (or the Internet) and its dynamic IP address has
expired, the DHCP server will assign it a new dynamic IP address.
2
A DHCP server can either be a designated PC on the network or another network
device, such as the router. By default, the router’s Internet Connection Type is
Obtain an IP automatically (DHCP).
The PC or network device obtaining an IP address is called the DHCP client. DHCP
frees you from having to assign IP addresses manually every time a new user is
added to your network.
For DSL users, many ISPs may require you to log on with a user name and
password to gain access to the Internet. This is a dedicated, high-speed
connection type called Point to Point Protocol over Ethernet (PPPoE). PPPoE is
similar to a dial-up connection, but PPPoE does not dial a phone number when
establishing a connection. It also will provide the router with a dynamic IP address
to establish a connection to the Internet.
By default, a DHCP server (on the LAN side) is enabled on the router. If you already
have a DHCP server running on your network, you MUST disable one of the two
DHCP servers. If you run more than one DHCP server on your network, you will
experience network errors, such as conflicting IP addresses. To disable DHCP on
the router, see the Basic Setup section in Chapter 5, “Setting Up and Configuring
the Router.”
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 8
Page 16
Networking and Security Basics
The Intrusion Prevention System (IPS)
NOTE Since the router is a device that connects two networks, it needs two IP
addresses—one for the LAN, and one for the Internet. In this Administration
Guide, you’ll see references to the “Internet IP address” and the “LAN IP
address”.
Since the router uses NAT technology, the only IP address that can be seen
from the Internet for your network is the router’s Internet IP address.
However, even this Internet IP address can be blocked so the router and
network seem invisible to the Internet.
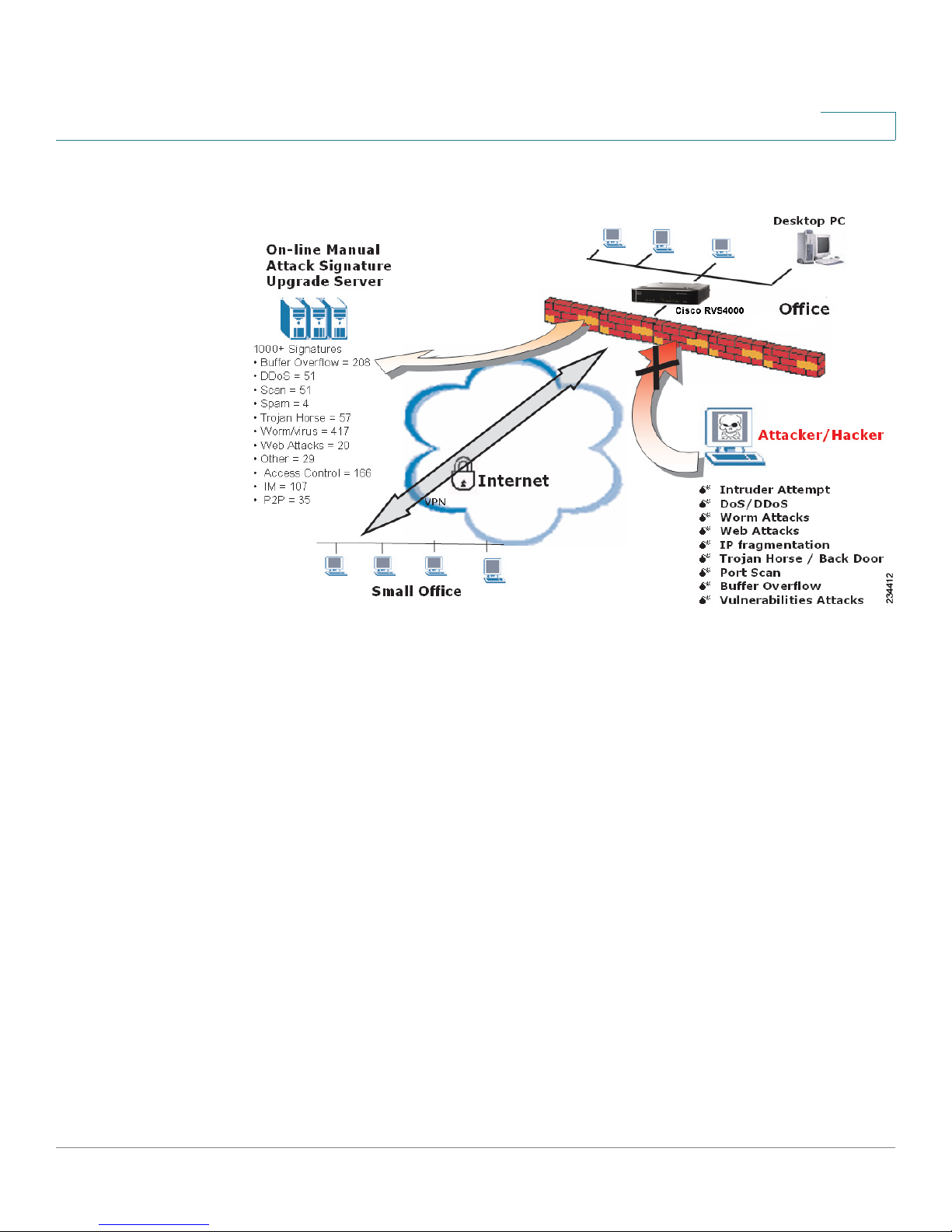
The Intrusion Prevention System (IPS)
2
IPS is an advanced technology to protect your network from malicious attacks. IPS
works together with your SPI Firewall, IP Based Access Control List (ACL),
Network Address Port Translation (NAPT), and Virtual Private Network (VPN) to
achieve the highest level of security. IPS works by providing real-time detection
and prevention as an in-line module in a router.
The RVS4000 has hardware-based acceleration for real-time pattern matching for
detecting malicious attacks. It actively filters and drops malicious TCP/UDP/ICMP/
IGMP packets and can reset TCP connections. This protects your client PCs and
servers running various operating systems including Windows, Linux, and Solaris
from network worm attacks. However, this system does not prevent viruses
contained in e-mail attachments.
The P2P (Peer-to-Peer) and IM (Instant Messaging) control allows the system
administrator to prevent network users from using those protocols to
communicate with people over the Internet. This helps the administrators to set up
company policies on how to use the Internet bandwidth wisely.
The signature file is the heart of the IPS system. It is similar to the Virus definition
file on your PC’s Anti-Virus software. IPS uses this file to match against packets
coming into the router and performs actions accordingly. The RVS4000 is shipped
with a signature file containing 1000+ rules, which cover the following categories:
DDoS, Buffer Overflow, Access Control, Scan, Trojan Horse, Misc., P2P, IM, Virus,
Worm, and Web Attacks.
Customers are encouraged to update their IPS signature file regularly to prevent
any new types of attacks on the Internet.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 9
Page 17
Networking and Security Basics
The Intrusion Prevention System (IPS)
IPS Scenarios
2
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 10
Page 18

3
Planning Your Virtual Private Network (VPN)
This chapter provides information for planning your VPN and includes the
following sections:
• Why do I need a VPN?, page 11
• What is a VPN?, page12
Why do I need a VPN?
Computer networking provides a flexibility not available when using an archaic,
paper-based system. With this flexibility, however, comes an increased risk in
security. This is why firewalls were first introduced. Firewalls help to protect data
inside of a local network. But what do you do once information is sent outside of
your local network, when e-mails are sent to their destination, or when you have to
connect to your company’s network when you are out on the road? How is your
data protected?
That is when a VPN can help. VPNs are called Virtual Private Networks because
they secure data moving outside of your network as if it were still within that
network.
When data is sent out across the Internet from your computer, it is always open to
attacks. You may already have a firewall, which will help protect data moving
around or held within your network from being corrupted or intercepted by entities
outside of your network, but once data moves outside of your network—when you
send data to someone via e-mail or communicate with an individual over the
Internet—the firewall will no longer protect that data.
At this point, your data becomes open to hackers using a variety of methods to
steal not only the data you are transmitting but also your network login and
security data. Some of the most common methods are as follows:
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 11
Page 19
Planning Your Virtual Private Network (VPN)
What is a VPN?
1) MAC Address Spoofing
Packets transmitted over a network, either your local network or the Internet, are
preceded by a packet header. These packet headers contain both the source and
destination information for that packet to transmit efficiently. A hacker can use this
information to spoof (or fake) a MAC address allowed on the network. With this
spoofed MAC address, the hacker can also intercept information meant for
another user.
2) Data Sniffing
Data “sniffing” is a method used by hackers to obtain network data as it travels
through unsecured networks, such as the Internet. Tools for just this kind of activity,
such as protocol analyzers and network diagnostic tools, are often built into
operating systems and allow the data to be viewed in clear text.
3
What is a VPN?
3) Man in the middle attacks
Once the hacker has either sniffed or spoofed enough information, he can now
perform a “man in the middle” attack. This attack is performed, when data is being
transmitted from one network to another, by rerouting the data to a new
destination. Even though the data is not received by its intended recipient, it
appears that way to the person sending the data.
These are only a few of the methods hackers use and they are always developing
more. Without the security of your VPN, your data is constantly open to such
attacks as it travels over the Internet. Data travelling over the Internet will often
pass through many different servers around the world before reaching its final
destination. That’s a long way to go for unsecured data and this is when a VPN
serves its purpose.
A VPN, or Virtual Private Network, is a connection between two endpoints—a VPN
router, for instance—in different networks that allows private data to be sent
securely over a shared or public network, such as the Internet. This establishes a
private network that can send data securely between these two locations or
networks.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 12
Page 20
Planning Your Virtual Private Network (VPN)
What is a VPN?
This is done by creating a “tunnel”. A VPN tunnel connects the two PCs or
networks and allows data to be transmitted over the Internet as if it were still
within those networks. Not a literal tunnel, it is a connection secured by encrypting
the data sent between the two networks.
VPN was created as a cost-effective alternative to using a private, dedicated,
leased line for a private network. Using industry standard encryption and
authentication techniques—IPSec, short for IP Security—VPN creates a secure
connection that, in effect, operates as if you were directly connected to your local
network. VPN can be used to create secure networks linking a central office with
branch offices, telecommuters, and/or professionals on the road (travelers can
connect to a VPN router using any computer with the Cisco QuickVPN Client
software.)
There are two basic ways to create a VPN connection:
• VPN router to VPN router
3
• Computer (using the Cisco QuickVPN Client software) to VPN router
The VPN router creates a “tunnel” or channel between two endpoints, so that data
transmissions between them are secure. A computer with the Cisco QuickVPN
Client software can be one of the two endpoints (refer to Appendix B, “Using
Cisco QuickVPN for Windows 2000, XP, or Vista”). If you choose not to run the VPN
client software, any computer with the built-in IPSec Security Manager (Microsoft
2000 and XP) allows the VPN router to create a VPN tunnel using IPSec (refer to
Appendix C, “Configuring IPSec with a Windows 2000 or XP Computer”). Other
versions of Microsoft operating systems require additional, third-party VPN client
software applications that support IPSec to be installed.
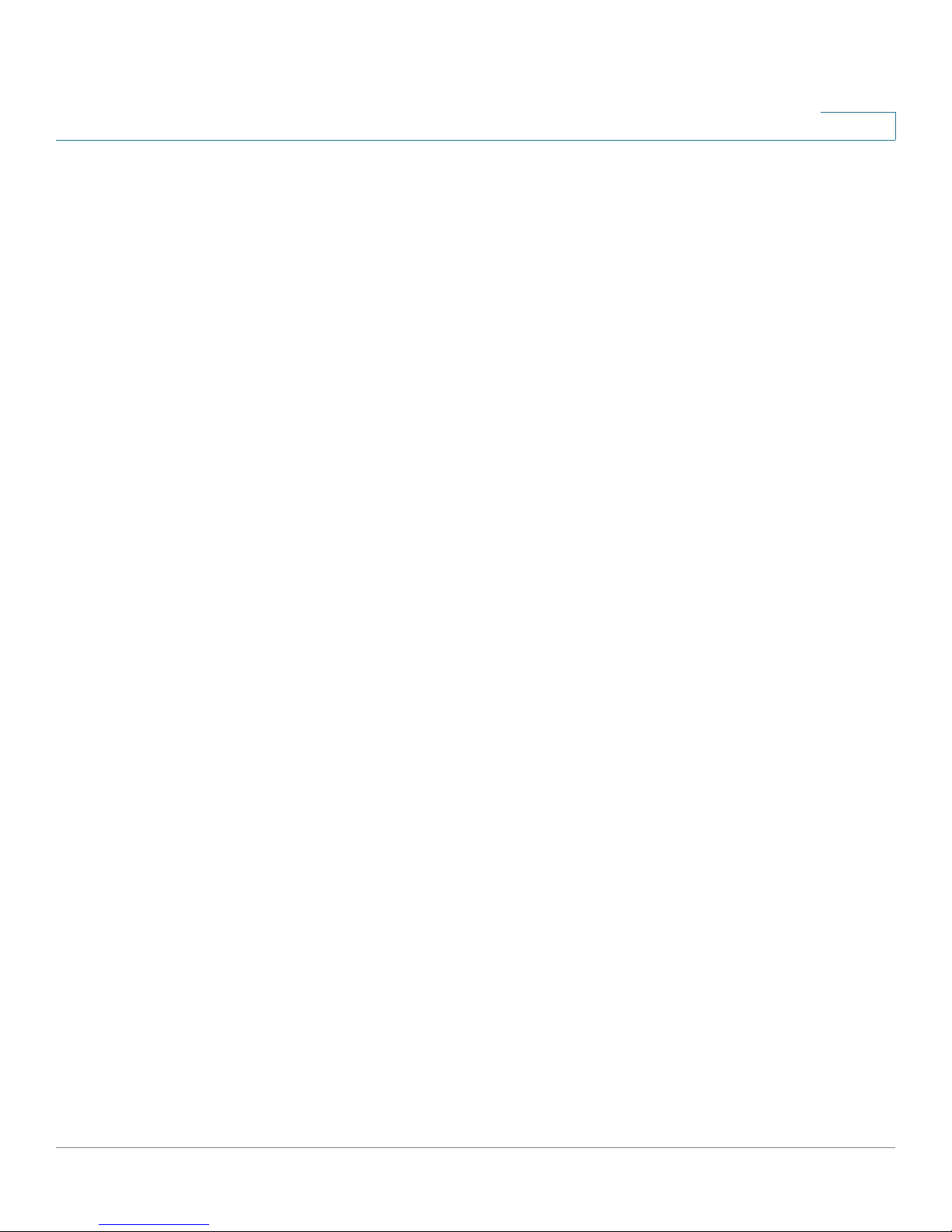
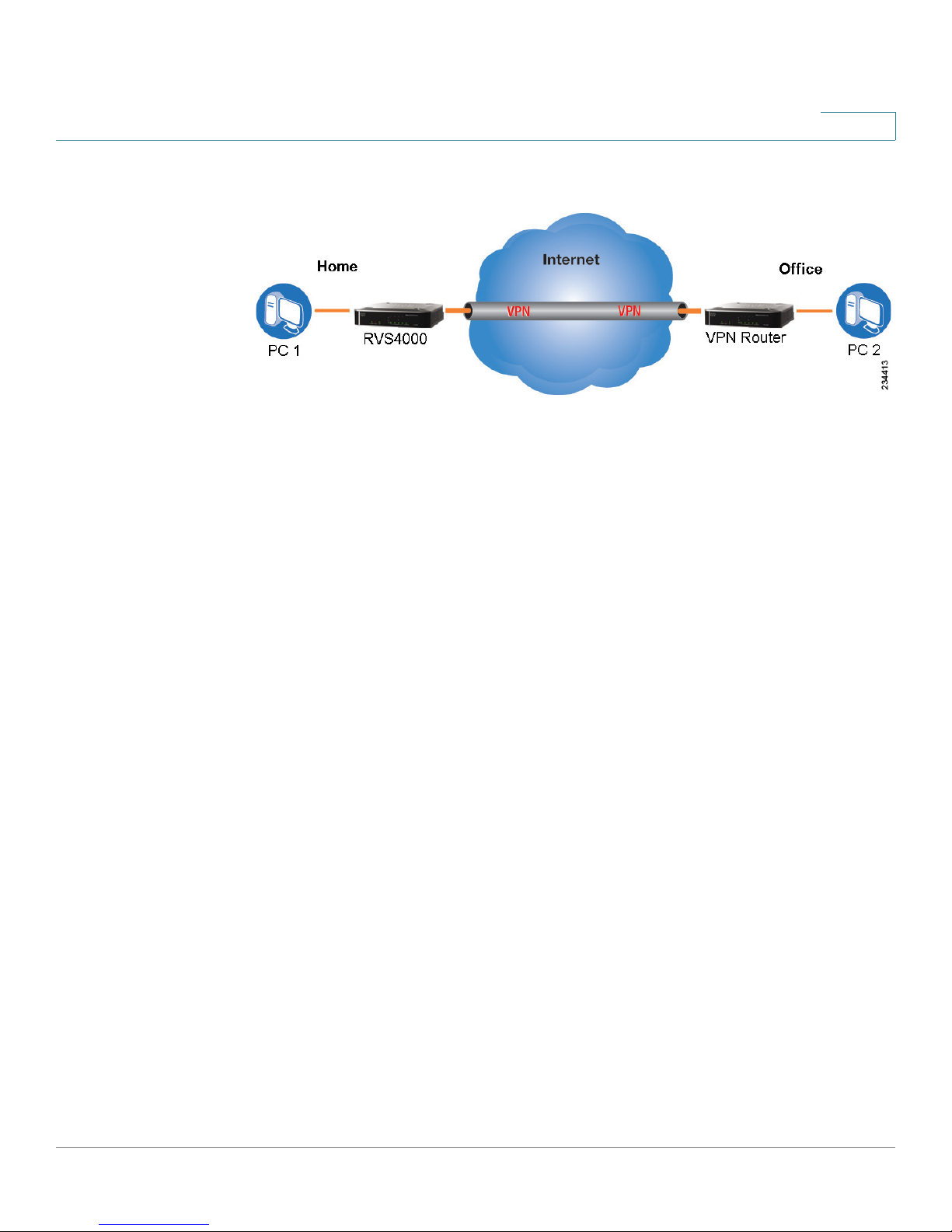
VPN Router to VPN Router
An example of a VPN router-to-VPN router VPN would be as follows. At home, a
telecommuter uses his VPN router for his always-on Internet connection. His router
is configured with his office’s VPN settings. When he connects to his office’s router,
the two routers create a VPN tunnel, encrypting and decrypting data. As VPNs
utilize the Internet, distance is not a factor. Using the VPN, the telecommuter now
has a secure connection to the central office’s network, as if he were physically
connected. For more information, refer to Appendix D, “Gateway-to-Gateway VPN
Tunnel.”
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 13
Page 21
Planning Your Virtual Private Network (VPN)
What is a VPN?
VPN Router to VPN Router
Computer (using the Cisco QuickVPN Client software) to VPN
Router
3
The following is an example of a computer-to-VPN router VPN. In her hotel room, a
traveling businesswoman connects to her ISP. Her notebook computer has the
Cisco QuickVPN Client software, which is configured with her office’s IP address.
She accesses the Cisco QuickVPN Client software and connects to the VPN
router at the central office. As VPNs utilize the Internet, distance is not a factor.
Using the VPN, she now has a secure connection to the central office’s network, as
if she were physically connected.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 14
Page 22
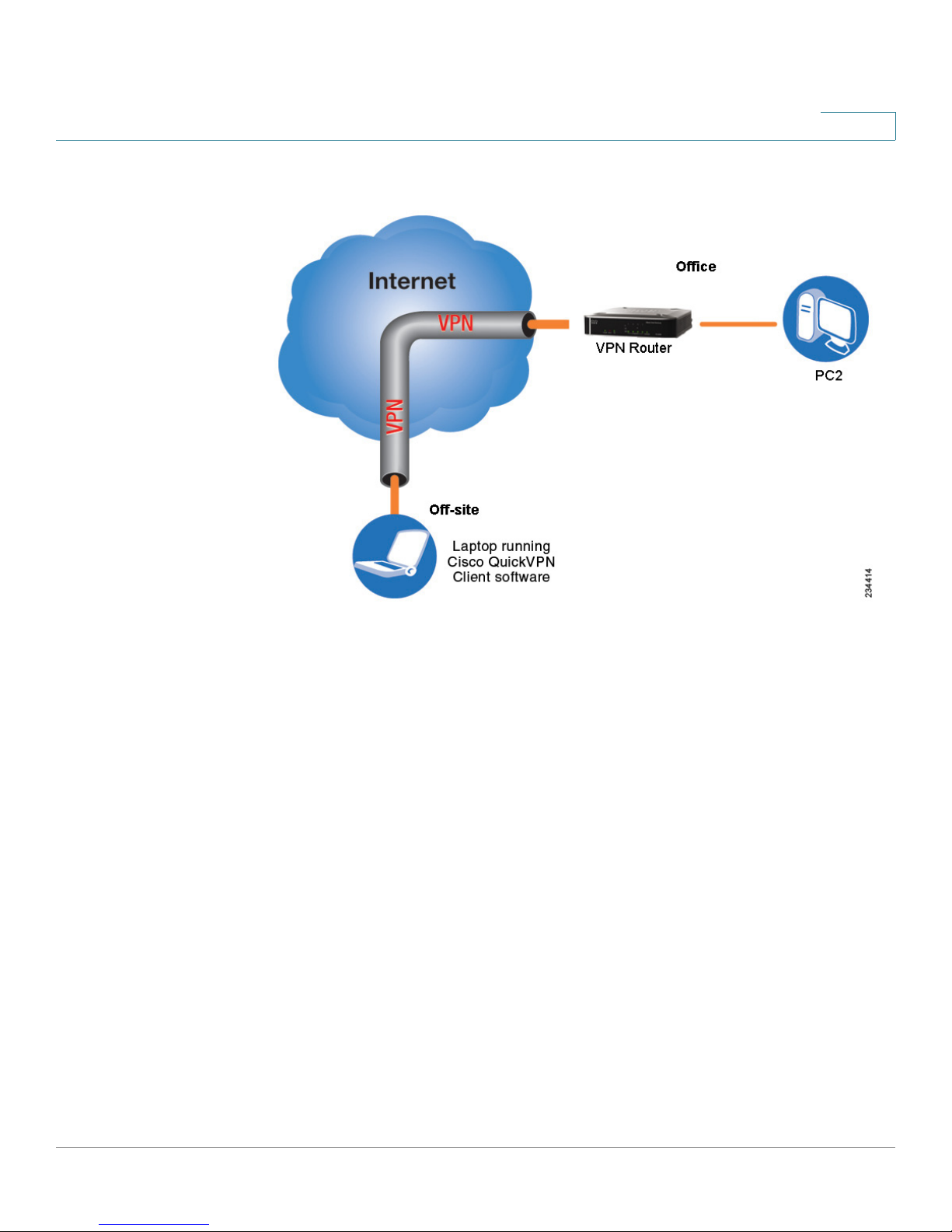
Planning Your Virtual Private Network (VPN)
What is a VPN?
Computer to VPN Router
3
For additional information and instructions about creating your own VPN, please
visit www.cisco.com. You can also refer to Appendix B, “Using Cisco QuickVPN for
Windows 2000, XP, or Vista”, Appendix C, “Configuring IPSec with a Windows
2000 or XP Computer” and Appendix D, “Gateway-to-Gateway VPN Tunnel.”
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 15
Page 23

Getting Started with the RVS4000 Router
This chapter describes the physical features of the RVS4000 router and provides
information for installing the router. The following sections are included:
• Front Panel, page16
• Back Panel, page17
• Placement Options, page18
• Installing the Router, page 20
• Configuring the Router, page 21
4
Front Panel
The LEDs are located on the front panel of the router.
Front Panel
POWER LED—Lights up green to indicate the router is powered on. The LED
flashes when the router is running a diagnostic test.
DIAG LED—If this light is off, the system is ready. The Diag LED blinks red
during firmware upgrades.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 16
Page 24

Getting Started with the RVS4000 Router
Back Panel
IPS LED—The IPS LED lights up when the Intrusion Prevention System (IPS)
function is enabled. If the LED is off, then IPS functions are disabled. The IPS
LED flashes green when an external attack is detected. It flashes red when an
internal attack is detected.
Ethernet Port LEDs 1-4—For each LAN port, there are three LEDs. If a port
LED is continuously lit green, the router is connected to a device at the speed
indicated through the corresponding port (1, 2, 3, or 4). The LED flashes green
when a router is actively sending or receiving data on that port.
INTERNET LED—The Internet LED lights up green to indicate the line speed of
the device attached to the Internet port. If the router is connected to a cable or
DSL modem, typically the 100 LED will be the only LED lit up, indicating
100 Mbps. Flashing indicates activity.
Back Panel
4
The Ethernet ports, Internet port, Reset button, and Power port are on the back panel of
the router.
Back Panel
RESET Button—The Reset button can be used in two ways:
• If the router is having problems connecting to the Internet, press
the Reset button for just a second with a paper clip or a pencil tip.
This is similar to pressing the reset button on your PC to reboot it.
• If you are experiencing extreme problems with the router and
have tried all other troubleshooting measures, press and hold in
the Reset button for 10 seconds. This will restore the factory
defaults and clear all of the router settings, such as port
forwarding or a new password.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 17
INTERNET Port—Provides a WAN connection to a cable modem or DSL
modem.
Page 25

Getting Started with the RVS4000 Router
274946
POWER DIAG IPS ETHERNET
RVS4000
10
100
1000
1 2 3 4
INTERNET
Placement Options
ETHERNET Ports 1-4—Provide a LAN connection to network devices,
such as PCs, print servers, or additional switches.
POWER Port—Connects the router to power via the supplied AC power
adapter.
Placement Options
You can place the router horizontally on the rubber feet, mount it in the stand, or
mount it on the wall.
Desktop Option
4
For desktop placement, place the Cisco RVS4000 router horizontally on a surface
so it sits on its four rubber feet.
Stand Option
To install the router vertically in the supplied stands, follow the steps below.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 18
Page 26

Getting Started with the RVS4000 Router
193817
Wall
mount
slots
2-9/16
Placement Options
To place the router vertically, follow these steps.
STEP 1 Locate the left side panel of the router.
STEP 2 With the two large prongs of one of the stands facing outward, insert the short
prongs into the little slots in the router and push the stand upward until the stand
snaps into place.
4
STEP 3 Repeat step 2 with the other stand.
Wall Option
To mount the Cisco RVS4000 router on the wall, follow these steps.
STEP 1 Determine where you want to mount the router and install two screws (not
supplied) that are 2-9/16 in. apart (approximately 64.5 mm).
STEP 2 With the back panel pointing up (if installing vertically), line up the router so that the
wall-mount crisscross slots on the bottom of the access point line up with the two
screws.
STEP 3 Place the wall-mount slots over the screws and slide the router down until the
screws fit snugly into the wall-mount slots.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 19
Page 27

Getting Started with the RVS4000 Router
Installing the Router
Installing the Router
To prepare the router for installation do the following:
• Obtain the setup information for your specific type of Internet connection
from your Internet Service Provider (ISP).
• Power off all of your network hardware, including the router, PCs, and cable
modem or DSL modem.
Perform the steps in this section to install the hardware.
STEP 1 Connect one end of an Ethernet network cable to one of the LAN ports
(labeled 1-4) on the back of the router. Connect the other end to an Ethernet port
on a PC.
4
STEP 2 Repeat step 1 to connect up to four PCs, switches, or other network devices to the
router.
STEP 3 Connect an Ethernet network cable from your cable modem or DSL modem to the
Internet port on the back panel of the router.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 20
Page 28

Getting Started with the RVS4000 Router
Configuring the Router
STEP 4 Power on the cable or DSL modem.
STEP 5 Connect the power adapter to the router’s Power port and plug the other end into
an electrical outlet.
4
STEP 6 The Power and Internet LEDs on the front panel will light up green as soon as the
power adapter is connected.
STEP 7 Power on the PCs.
The router hardware installation is now complete.
Configuring the Router
To configure the RVS4000, plug a PC into the router and launch the web-based
configuration utility.
NOTE Before setting up the router, make sure your PCs are configured to obtain an IP (or
TCP/IP) address automatically from the router.
STEP 1 Launch a web browser, such as Internet Explorer or Mozilla Firefox.
STEP 2 In the Address field enter http://192.168.1.1 and press Enter.
STEP 3 In the User Name and Password fields, enter admin.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 21
Page 29
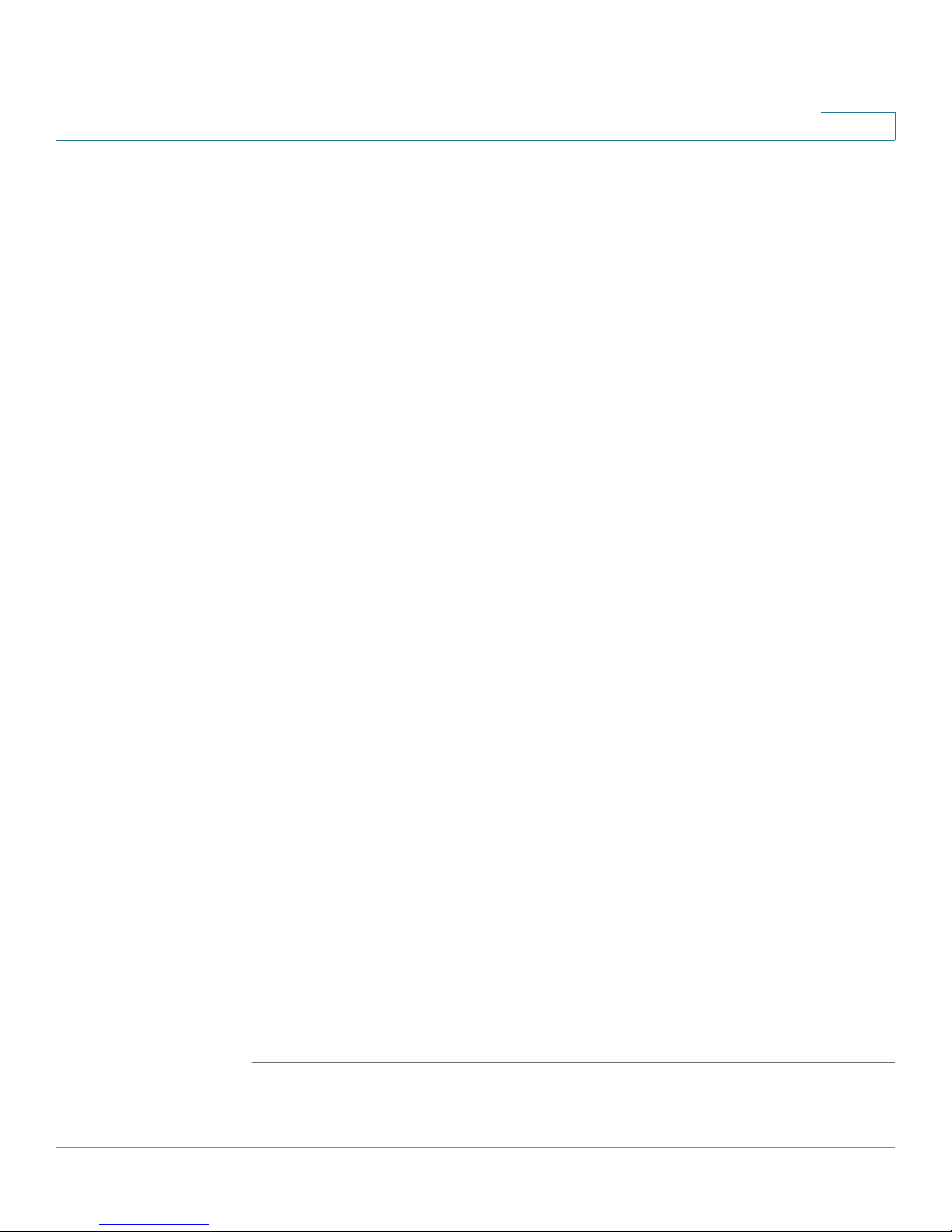
Getting Started with the RVS4000 Router
Configuring the Router
The default user name and password is admin.
STEP 4 Click OK.
For added security, you should later set a new password using the
Administration > Management window of the web-based utility.
STEP 5 The web-based utility will appear with the Setup menu and Summary selected.
Click WAN under the Setup menu.
STEP 6 If requested by your ISP (usually cable ISPs), complete the Host Name and Domain
Name fields, and the MTU and MTU Size fields. Otherwise, leave the defaults.
STEP 7 In the WAN screen, choose an Internet Connection Type from the
drop-down menu. Depending on which Internet connection type you select,
addtional setup may be required.
The Internet Connection Types are:
4
Automatic Configuration - DHCP: If you are connecting through DHCP or a
dynamic IP address from your ISP, keep this default setting.
Static IP: If your ISP assigns you a static IP address, select Static IP from the
drop-down menu. Complete the Internet IP Address, Subnet Mask, Default
Gateway, and DNS fields. Enter at least one DNS address.
PPPoE: If you are connecting through PPPoE, select PPPoE from the drop-down
menu. Complete the User Name and Password fields.
PPTP: PPTP is a service used in Europe only. If you are using a PPTP
connection, check with your ISP for the necessary setup information.
Heartbeat Signal: Heartbeat Signal is used primarily in Australia. Check with
your ISP for the necessary setup information.
L2TP: L2TP is used mostly in Europe. Check with your ISP for the necessary
setup information.
STEP 8 When you are finished entering your Internet connection settings, click Save.
STEP 9 Restart or power on your PC to obtain the new router setting.
STEP 10 Test the setup by opening your web browser from any computer and entering
http://www.cisco.com/smb.
Congratulations! The installation of the router is complete.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 22
Page 30
Getting Started with the RVS4000 Router
Configuring the Router
NOTE For more information about advanced settings and security options, refer to
Chapter 5, “Setting Up and Configuring the Router.”
4
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 23
Page 31

Setting Up and Configuring the Router
This chapter includes information for configuring the following router functions:
• Setup, page 25
• Firewall, page 44
• ProtectLink, page 56
• VPN, page 57
• QoS, page 65
• Administration, page 70
• IPS, page 78
5
• L2 Switch, page 82
• Status, page 91
The router is configured using the built-in web-based configuration utility. To
access the web-based configuration utility of the router, open your web browser
and enter http://192.168.1.1 into the Address field. Press the Enter key and the
Login window will appear.
Address Bar of Web Browser
NOTE The default IP address is 192.168.1.1. If the IP address has been changed
using DHCP or via the console interface, enter the assigned IP address
instead of the default.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 24
Page 32

Setting Up and Configuring the Router
Setup
The first time you open the web-based utility, enter admin (the default username)
in the Username field and enter admin in the Password field. Click the OK button.
You can change the password later from the Administration > Management
window.
Login Window
5
Setup
After you log in, the web-based utility starts. The utility’s main functions are
indicated by nine menu items that appear in the left panel: Setup, Firewall,
ProtectLink, VPN, QoS, Administration, IPS, L2 Switch, and Status. After you
select a menu, a list of windows is displayed below the menu bar. To perform a
specific function, you select a menu, then select the appropriate window. By
default, the Setup menu’s Summary window is displayed following login.
The utility’s menus and windows are described below. For brevity, window names
are listed using the notation: MenuName > WindowName.
The Setup menu is used to access all of the router’s basic setup functions. The
device can be used in most network settings without changing any of the default
values. Some users may need to enter additional information in order to connect to
the Internet through an ISP (Internet Service Provider) or broadband (DSL, cable
modem) carrier
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 25
Page 33

Setting Up and Configuring the Router
Setup
Setup > Summary
The Setup > Summary window displays a read-only summary of the router’s
basic information. Clicking on a hyperlink (underlined text) takes you directly to the
related page where you can update the information.
Setup > Summary
5
System Information
Firmware version Displays the router’s current firmware version.
CPU Displays the router’s CPU type.
System up time Displays the length of time that has elapsed since the router was
last reset.
DRAM Displays the amount of DRAM installed in the router.
Flash Displays the amount of flash memory installed in the router.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 26
Page 34

Setting Up and Configuring the Router
Setup
Port Statistics
This section displays the following color-coded status information on the router’s
Ethernet ports:
• Green Indicates that the port has a connection.
• Black Indicates that the port has no connection.
Network Setting Status
LAN IP Displays the IP address of the router’s LAN interface.
WAN IP Displays the IP address of the router’s WAN interface. If this address was
assigned using DHCP, click DHCP > Release to release the address, or click
DHCP > Renew to renew the address.
Mode Displays the operating mode, Gateway or Router.
5
Gateway Displays the Gateway address, which is the IP address of your ISP’s
server.
DNS 1-2 The IP addresses of the Domain Name System (DNS) server(s) that the
router is using.
DDNS Indicates whether the Dynamic Domain Name System (DDNS) feature is
enabled.
DMZ Host Indicates whether the DMZ Hosting feature is enabled.
Firewall Setting Status
DoS (Denial of Service) Indicates whether the DoS Protection feature is enabled
to block DoS attacks.
Block WAN Request Indicates whether the Block WAN Request feature is
enabled.
Remote Management Indicates whether the Remote Management feature is
enabled.
IPSec VPN Setting Status
IPSec VPN Summary Click the IPSec VPN Summary hyperlink to display the
VPN > Summary window.
Tunnel(s) Used Displays the number of VPN tunnels currently being used.
Tunnel(s) Available Displays the number of VPN tunnels that are available.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 27
Page 35

Setting Up and Configuring the Router
Setup
Log Setting Status
E-mail If this displays Email cannot be sent because you have not specified an
outbound SMTP server address, then you have not set up the mail server. Click
the E-mail hyperlink to display the Administration > Log window where you can
configure the SMTP mail server.
Setup > WAN
Internet Connection Type
The router supports six types of connections. Each Setup > WAN window and
available features will differ depending on what kind of connection type you
select.
Automatic Configuration - DHCP
5
By default, the router’s Configuration Type is set to Automatic Configuration DHCP, and it should be kept only if your ISP supports DHCP or you are connecting
through a dynamic IP address.
Automatic Configuration - DHCP
Static IP
If your connection uses a permanent IP address to connect to the Internet, then
select Static IP.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 28
Page 36

Setting Up and Configuring the Router
Setup
Static IP
5
Internet IP Address This is the router’s IP address, when seen from the WAN, or
the Internet. Your ISP will provide you with the IP Address you need to specify
here.
Subnet Mask This is the router’s Subnet Mask, as seen by external users on the
Internet (including your ISP). Your ISP will provide you with the Subnet Mask.
Default Gateway Your ISP will provide you with the Default Gateway Address,
which is the ISP server’s IP address.
Primary DNS (Required) and Secondary DNS (Optional) Your ISP will provide
you with at least one DNS (Domain Name System) Server IP Address.
When you have finished making changes, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
PPPoE
Some DSL-based ISPs use PPPoE (Point-to-Point Protocol over Ethernet) to
establish Internet connections. If you are connected to the Internet through a DSL
line, check with your ISP to see if they use PPPoE. If they do, you will have to
enable PPPoE.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 29
Page 37

Setting Up and Configuring the Router
Setup
PPPoE
5
User Name and Password Enter the User Name and Password provided by your
ISP.
Connect on Demand: Max Idle Time
Internet connection after it has been inactive for a specified period of time (Max
Idle Time), and then automatically re-establish the connection as soon as you
attempt to access the Internet again. To activate Connect on Demand, select the
Connect on Demand option and enter in the Max Idle Time field the number of
minutes of inactivity that must elapse before your Internet connection is
terminated automatically.
Keep Alive: Redial period If you select this option, the router will periodically
check your Internet connection. If you are disconnected, then the router will
automatically re-establish your connection. To use this option, click the radio
button next to Keep Alive. In the Redial Period field, specify how often you want
the router to check the Internet connection. The default Redial Period is 30
seconds.
When you have finished making changes, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
You can configure the router to cut the
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 30
Page 38

Setting Up and Configuring the Router
Setup
PPTP
Point-to-Point Tunneling Protocol (PPTP) is a service that applies to
connections in Europe and Israel only.
PPTP
5
IP Address This is the router’s IP address, when seen from the WAN, or the
Internet. Your ISP will provide you with the IP Address you need to specify here.
Subnet Mask This is the router’s Subnet Mask, as seen by external users on the
Internet (including your ISP). Your ISP will provide you with the Subnet Mask.
Default Gateway Your ISP will provide you with the Default Gateway Address.
PPTP Server Enter the IP address of the PPTP server.
User Name and Password Enter the User Name and Password provided by your
ISP.
Connect on Demand: Max Idle Time You can configure the router to cut the
Internet connection after it has been inactive for a specified period of time (Max
Idle Time), and then automatically re-establish the connection as soon as you
attempt to access the Internet again. To activate Connect on Demand, select the
Connect on Demand option and enter in the Max Idle Time field the number of
minutes of inactivity that must elapse before your Internet connection is
terminated automatically.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 31
Page 39

Setting Up and Configuring the Router
Setup
Keep Alive: Redial period If you select this option, the router will periodically
check your Internet connection. If you are disconnected, then the router will
automatically re-establish your connection. To use this option, click the radio
button next to Keep Alive. In the Redial Period field, specify how often you want
the router to check the Internet connection. The default Redial Period is 30
seconds.
When you have finished making changes, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
Heart Beat Signal
Heart Beat Signal is a service used in Australia. Check with your ISP for the
necessary setup information.
Heart Beat Signal
5
User Name and Password Enter the User Name and Password provided by your
ISP.
Heart Beat Server Enter the IP address of the Heart Beat server.
Connect on Demand: Max Idle Time You can configure the router to cut the
Internet connection after it has been inactive for a specified period of time (Max
Idle Time), and then automatically re-establish the connection as soon as you
attempt to access the Internet again. To activate Connect on Demand, select the
Connect on Demand option and enter in the Max Idle Time field the number of
minutes of inactivity that must elapse before your Internet connection is
terminated automatically.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 32
Page 40

Setting Up and Configuring the Router
Setup
Keep Alive: Redial period If you select this option, the router will periodically
check your Internet connection. If you are disconnected, then the router will
automatically re-establish your connection. To use this option, click the radio
button next to Keep Alive. In the Redial Period field, specify how often you want
the router to check the Internet connection. The default Redial Period is 30
seconds.
When you have finished making changes, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
L2TP
Layer 2 Tunneling Protocol (L2TP) is a service that tunnels Point-to-Point
Protocol (PPP) across the Internet. It is used mostly in European countries. Check
with your ISP for the necessary setup information.
L2TP
5
IP Address This is the router’s IP address, when seen from the WAN, or the
Internet. Your ISP will provide you with the IP Address you need to specify here.
Subnet Mask This is the router’s Subnet Mask, as seen by external users on the
Internet (including your ISP). Your ISP will provide you with the Subnet Mask.
Gateway Your ISP will provide you with the Default Gateway Address.
L2TP Server Enter the IP address of the L2TP server.
User Name and Password Enter the User Name and Password provided by your
ISP.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 33
Page 41

Setting Up and Configuring the Router
Setup
Connect on Demand: Max Idle Time You can configure the router to cut the
Internet connection after it has been inactive for a specified period of time (Max
Idle Time), and then automatically re-establish the connection as soon as you
attempt to access the Internet again. To activate Connect on Demand, select the
Connect on Demand option and enter in the Max Idle Time field the number of
minutes of inactivity that must elapse before your Internet connection is
terminated automatically.
Keep Alive: Redial period If you select this option, the router will periodically
check your Internet connection. If you are disconnected, then the router will
automatically re-establish your connection. To use this option, click the radio
button next to Keep Alive. In the Redial Period field, you specify how often you
want the router to check the Internet connection. The default Redial Period is 30
seconds.
When you have finished making changes, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
5
Optional Settings (Required by some ISPs)
Some of these settings may be required by your ISP. Verify with your ISP before
making any changes.
Optional Settings
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 34
Page 42

Setting Up and Configuring the Router
Setup
Host Name Some ISPs, usually cable ISPs, require a host name as identification.
You may have to check with your ISP to see if your broadband Internet service has
been configured with a host name. In most cases, leaving this field blank will work.
Domain Name Some ISPs, usually cable ISPs, require a domain name as
identification. You may have to check with your ISP to see if your broadband
Internet service has been configured with a domain name. In most cases, leaving
this field blank will work.
MTU MTU is the Maximum Transmission Unit. It specifies the largest packet size
permitted for Internet transmission. Select Manual if you want to manually enter
the largest packet size that will be transmitted. To have the router select the best
MTU for your Internet connection, keep the default setting, Auto.
Size When Manual is selected in the MTU field, this option is enabled. It is
recommended that you set this value within the range of 1200 to 1500, but the
value can be defined between 128 and 1500.
5
DDNS Service DDNS Service is disabled by default. To enable DDNS Service,
follow these instructions:
STEP 1 Sign up for DDNS Service
• DynDNS - Sign up for DDNS service at www.dyndns.org and write down
your User Name, Password, and Host Name information.
• TZO - Sign up for DDNS service at www.tzo.com and write down your E-
mail Address, Password and Domain Name information.
STEP 2 Select the DDNS service provider whose service you are using.
STEP 3 Configure the following fields:
• User Name (DynDNS) or E-mail address (TZO).
• Password
• Host Name (DynDNS) or Domain name (TZO)
• Custom DNS (DynDNS)
STEP 4 Click Save Settings.
The router will now advise the DDNS Service of your current WAN (Internet) IP
address whenever this address changes. If using TZO, you should NOT use the
TZO software to perform this “IP address update”.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 35
Page 43

Setting Up and Configuring the Router
Setup
Connect The Connect button is displayed when DDNS is enabled. This button is
used to contact the DDNS server to manually update your IP address information.
The Status area on this window is also updated.
Setup > LAN
The Setup > LAN window allows you to change the router’s local network
settings.
5
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 36
Page 44

Setting Up and Configuring the Router
Setup
Setup > LAN
5
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 37
Page 45

Setting Up and Configuring the Router
Setup
VLAN Select the VLAN for the DHCP server from the drop-down menu.
NOTE This option appears only if you have created at least one VLAN from the L2 Switch
> Create VLAN window.
IPv4
The router’s Local IP Address and Subnet Mask are shown here. In most cases,
you can keep the defaults.
Local IP Address The default value is 192.168.1.1.
Subnet Mask The default value is 255.255.255.0.
5
Server Settings (DHCP)
The router can be used as your network’s DHCP (Dynamic Host Configuration
Protocol) server, which automatically assigns an IP address to each PC on your
network. Unless you already have one, it is highly recommended that you leave the
router enabled as a DHCP server.
DHCP Server DHCP is already enabled by factory default. If you already have a
DHCP server on your network, or if you don’t want a DHCP server, then select
Disabled (no other DHCP features will be available). If you already have a DHCP
server on your network, and you want this router to act as a Relay for that DHCP
Server, select DHCP Relay, then enter the DHCP Server IP Address. If you disable
DHCP, assign a static IP address to the router.
Starting IP Address Enter a value for the DHCP server to start with when issuing
IP addresses. This value must be 192.168.1.2 or greater, but smaller than
192.168.1.254, because the default IP address for the router is 192.168.1.1, and
192.168.1.255 is the broadcast IP address.
Maximum Number of DHCP Users Enter the maximum number of PCs that you
want the DHCP server to assign IP addresses to. This number cannot be greater
than 253. In order to determine the DHCP IP Address range, add the starting IP
address (e.g., 100) to the number of DHCP users.
Client Lease Time This is the amount of time a DHCP client can keep the assigned
IP address before it sends a renewal request to the DHCP server.
Static DNS 1-3 If applicable, enter the IP address(es) of your DNS server(s).
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 38
Page 46

Setting Up and Configuring the Router
Setup
WINS The Windows Internet Naming Service (WINS) provides name resolution
service (similar to DNS) in Windows networks. If you use a WINS server, enter that
server’s IP Address here. Otherwise, leave this blank.
Static IP Mapping
Static IP Mapping is used to bind a specific IP address to a specific MAC address.
This helps external (WAN) users to access LAN servers that are advertised
through NAPT port forwarding. You can define up to 50 entries.
Static IP Address Enter the IP address to be mapped.
MAC Address Enter the MAC address to be mapped.
Host Name Enter the host name to be mapped.
Click Add to create the entry and add it to the list. To modify an existing entry,
select it from the list, edit the appropriate field(s), and then click Modify. To delete
an entry, select it and click Remove.
5
IPv6
IPv6 Address If your network has implemented IPv6, enter the proper IPv6
address in this field.
Prefix Length Enter the appropriate IPv6 prefix length.
Router Advertisement Enabling this option allows IPv6 hosts to configure their IP
addresses automatically using the IPv6 prefix broadcast by the router.
DHCPv6
To enable the DHCP v6 feature, select Enable. To disable DHCP v6, select Disable.
Lease time Enter the lease time in minutes.
DHCP6 address range start Enter the starting DHCP v6 IP address.
DHCP6 address range end Enter the ending DHCP v6 IP address.
Primary DNS Enter the Primary DHCP v6 DNS server address.
Secondary DNS Enter the Secondary DHCP v6 DNS server address.
Click Save Settings to save your changes, or click Cancel Changes to undo your
changes.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 39
Page 47

Setting Up and Configuring the Router
Setup
Setup > DMZ
The DMZ window allows one local PC to be exposed to the Internet for use of a
special-purpose service such as Internet gaming and videoconferencing.
Whereas Port Range Forwarding can only forward a maximum of 10 ranges of
ports, DMZ hosting forwards all the ports for one PC at the same time.
Setup > DMZ
DMZ Hosting This feature allows one local PC to be exposed to the Internet for
use of a special-purpose service such as Internet gaming and videoconferencing.
To use this feature, select Enable. To disable the DMZ feature, select Disable.
5
DMZ Host IP Address To expose one PC, enter the computer’s IP address.
Click Save Settings to save your changes, or click Cancel Changes to undo your
changes.
Setup > MAC Address Clone
Some ISPs require that you register a MAC address. This feature “clones” your
network adapter’s MAC address onto the router, and prevents you from having to
call your ISP to change the registered MAC address to the router’s MAC address.
The router’s MAC address is a 12-digit code assigned to a unique piece of
hardware for identification.
Setup > MAC Address Clone
MAC Address Clone Select Enabled or Disabled from the drop-down menu.
MAC Address Enter the MAC Address registered with your ISP in this field.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 40
Page 48

Setting Up and Configuring the Router
Setup
Clone My PC’s MAC When MAC Address Clone is enabled, click this button to
copy the MAC address of the network adapter in the computer that you are using
to connect to the Web interface.
Click Save Settings to save the MAC Cloning settings or click Cancel Changes to
undo your changes.
Setup > Advanced Routing
Setup > Advanced Routing
5
Operating Mode
Operation Mode Select the Operating mode in which this router will function.:
• Gateway This is the normal mode of operation. This allows all devices on
your LAN to share the same WAN (Internet) IP address. In Gateway mode,
the NAT (Network Address Translation) mechanism is enabled.
• Router You either need another router to act as the Internet Gateway, or all
PCs on your LAN must be assigned (fixed) Internet IP addresses. In Router
mode, the NAT mechanism is disabled.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 41
Page 49

Setting Up and Configuring the Router
Setup
Dynamic Routing
The router’s dynamic routing feature can be used to automatically adjust to
physical changes in the network’s layout. The router can use the dynamic RIP
protocol to calculate the most efficient route for the network’s data packets to
travel between the source and the destination, based upon the shortest paths. The
RIP protocol regularly broadcasts routing information to other routers on the
network.
RIP (Routing Information Protocol) If you want the router to use the RIP protocol,
select Enabled; otherwise, keep the default setting, Disabled.
RIP Send Packet Version Choose the TX protocol you want for transmitting data
on the network: RIPv1 or RIPv2. This should match the version supported by
other routers on your LAN.
RIP Recv Packet Version Choose the RX protocol you want for receiving data
from the network: RIPv1 or RIPv2. This should match the version supported by
other routers on your LAN.
5
Static Routing
Sometimes you will prefer to use static routes to build your routing table instead of
using dynamic routing protocols. Static routes do not require CPU resources to
exchange routing information with a peer router. You can also use static routes to
reach peer routers that do not support dynamic routing protocols. Static routes
can be used together with dynamic routes. Be careful not to introduce routing
loops in your network.
To set up static routing, you should add route entries in the routing table that tell
the router where to forward packets to specific IP destinations.
Enter the following data to create a static route entry:
Select Set Number Select the set number (routing table entry number) that you
wish to view or configure. If necessary, click Delete This Entry to clear the entry.
Destination IP Address Enter the network address of the remote LAN segment.
For a standard Class C IP domain, the network address is the first three fields of
the Destination LAN IP, while the last field should be zero.
Subnet Mask Enter the Subnet Mask used on the destination LAN IP domain. For
Class C IP domains, the Subnet Mask is 255.255.255.0.
Gateway If this router is used to connect your network to the Internet, then your
gateway IP is the router’s IP Address. If you have another router handling your
network’s Internet connection, enter the IP Address of that router instead.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 42
Page 50

Setting Up and Configuring the Router
Setup
Hop Count This value gives the number of nodes that a data packet passes
through before reaching its destination. A node is any device on the network, such
as switches, PCs, etc. The maximum hop count value is 16.
Show Routing Table Click this button to show the routing table established either
through dynamic or static routing methods.
Inter-VLAN Routing
Inter-VLAN Routing Select Enable to allow packets to be routed between VLANs
that are in different subnets. The default is Enable.
Click Save Settings to save the Routing settings or click Cancel Changes to undo
your changes.
Setup > Time
5
Setup > Time
Set the local time Manually If you wish to enter the time and date manually, select
this option, then select the Date from the drop-down fields and enter the hour,
minutes, and seconds in the Time fields using 24-hour format. For example, for
10:00 pm, enter 22 in the hours field, 0 in the minutes field, and 0 in the seconds
field.
Set the local time using Network Time Protocol (NTP) Automatically If you wish
to use a Network Time Protocol server to set the time and date, select this option,
then complete the following fields.
Time Zone Select the time zone for your location and your time setting is
synchronized over the Internet.
Auto Daylight Saving If your location observes daylight savings time, select the
Enable option.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 43
Page 51

Setting Up and Configuring the Router
Firewall
User-defined NTP Server To specify a user-defined NTP server, select the Enable
option, then enter the NTP Server’s IP address in the NTP Server IP field.
NTP Server IP If the User-defined NTP Server option is set to Enable, enter the IP
address of the NTP server.
Click Save Settings to save your settings or click Cancel Changes to undo your
changes.
Setup > IP Mode
Setup > IP Mode
5
Firewall
IPv4 Only
Dual-Stack IP Select this option to use IPv4 on the Internet and IPv4 and IPv6 on
the local network. IPv6 hosts in the LAN are connected to remote IPv6 islands over
6to4 tunnels (per RFC3056).
Click Save Settings to save your settings or click Cancel Changes to undo your
changes.
From the Firewall menu, you can configure the router to deny or allow specific
internal users from accessing the Internet. You can also configure the router to
deny or allow specific Internet users from accessing the internal servers. You can
set up different packet filters for different users that are located on internal (LAN)
side or external (WAN) side based on their IP addresses or their network Port
number.
Select this option to use IPv4 on the Internet and local network.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 44
Page 52

Setting Up and Configuring the Router
Firewall
Firewall > Basic Settings
Firewall > Basic Settings
5
Firewall When this feature is enabled, the router’s NAT firewall feature is enabled.
DoS Protection When this feature is enabled, the router will block DoS (Denial of
Service) attacks. A DoS attack does not attempt to steal data or damage your PCs,
but overloads your Internet connection so you can not use it.
Block WAN Request When this feature is enabled, the router filters out
anonymous requests from the WAN.
Remote Management This feature allows you to use an http or https port to
remotely manage the router. To enable this feature, select Enable and enter the
port number in the Port field, then configure the HTTPS and Remote IP address
settings that appear below.
HTTPS This option limits access to the web-based utility from the WAN to https
sessions only. An https session uses SSL encryption, providing better protection
for your remote session than http. The default is Enable.
• Remote IP address Select the appropriate value to specify which external
IP address(es) can access the router.
• Any IP Address Allows access from any external IP address.
• Single IP Address Allows access from the single IP address that you enter
in the field provided.
• IP Range Allows access from a range of IP addresses that you enter in the
field provided.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 45
Page 53

Setting Up and Configuring the Router
Firewall
• Subnet Allows access from the Subnet that you enter in the field provided.
Remote Upgrade This option allows you to upgrade the router remotely. To allow
remote upgrade, select Enable. The Remote Management feature must be set to
Enable as well. The default is Disable.
Multicast Passthrough If an IGMP Proxy running on the router, set this to Enable to
cause the router to allow IP Multicast traffic to come in from the Internet. The
default is Disable.
SIP Application Layer Gateway When this feature is enabled, the SIP Application
Layer Gateway (ALG) allows Session Initiation Protocol (SIP) packets (used for
Voice over IP) to traverse the NAT firewall. This feature can be disabled if the VoIP
service provider is using other NAT traversal solutions such as STUN, TURN, and
ICE.
Block Place a checkmark next to the Web features that you wish to restrict.
5
• Java Java is a programming language for websites. If you deny Java, you
run the risk of not having access to Internet sites created using this
programming language.
• Cookies A cookie is data stored on your PC and used by Internet sites
when you interact with them, so you may not want to deny cookies.
• ActiveX ActiveX is a Microsoft (Internet Explorer) programming language
for websites. If you deny ActiveX, you run the risk of not having access to
Internet sites using this programming language. Also, Windows Update
uses ActiveX, so if this is blocked, Windows update will not work.
• Access to Proxy HTTP Server If local users have access to WAN proxy
servers, they may be able to circumvent the router’s content filters and
access Internet sites blocked by the router. Denying Proxy will block access
to any WAN proxy servers.
Firewall > IP Based ACL
The IP-Based ACL window allows you to create an Access Control List (ACL) with
up to 50 rules. Each ACL rule denies or allows access to the network based on
various criteria including priority, service type, interface, source IP address,
destination IP address, day of the week, and time of day.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 46
Page 54

Setting Up and Configuring the Router
Firewall
Firewall > IP Based ACL
Priority This is the rule’s priority.
Enable This indicates whether the rule is enabled or disabled.
Action This is the rule’s action, either Allow or Deny.
5
Service This is the service(s) to which the rule applies.
Source Interface This is the source interface, either WAN, LAN, or ANY.
Source This is the source IP address, which can be one specific IP address, ANY
(all IP addresses), a range of IP addresses, or a specific IP subnet.
Destination This is the destination IP address, which can be one specific IP
address, ANY (all IP addresses), a range of IP addresses, or a specific IP subnet.
Time The time of day when the rule is in effect, either Any Time (24 hours) or a
specific start and end time.
Day The day(s) of the week when the rule is in effect. This may be Any Day or a
user-specified set of days.
Edit button Click Edit at the end of a row to edit the associated rule.
Delete button Click Delete at the end of a row to delete the associated rule.
To add a new rule to the ACL rule table, click Add New Rule and the Edit IP ACL
Rule window appears. Follow the instructions in the section below to create a new
ACL rule. To disable all the rules without deleting them, click Disable All Rules. To
delete all the rules from the table, click Delete All Rules.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 47
Page 55

Setting Up and Configuring the Router
Firewall
Editing IP ACL Rules
Editing IP ACL Rules
5
Action Select the desired action, Allow or Deny, from the drop-down menu.
Service Select the service types to which the rule will apply. You can either select
one of the predefined services in the drop-down menu; select ALL to allow or
deny all types of IP traffic; or define a new service by clicking Service
Management to bring up the Service Management window, then the new
service’s Name, select the Type (TCP, UDP, or TCP/UDP), enter the Start Port and
Finish Port, then click Save. The new service will then appear in the drop-down
menu on the Edit IP ACL Rule window.
Log Select this option to log all traffic that is filtered by this rule.
Log Prefix Enter a text string that will be prepended to each matched event in the
log.
Source Interface Select the source interface, WAN, LAN, or ANY, from the drop-
down menu.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 48
Page 56

Setting Up and Configuring the Router
Firewall
Source IP To apply the rule to one source IP address, select Single from the drop-
down menu, then enter the address in the field. To apply the rule to all source IP
addresses, select ANY from the drop-down menu. To apply the rule to a range of
IP addresses, select Range and enter the starting and ending IP addresses. To
apply the rule to a subnet, select Net and enter the IP address and subnet mask.
Destination IP To apply the rule to one destination IP address, select Single from
the drop-down menu, then enter the address in the field. To apply the rule to all
destination IP addresses, select ANY from the drop-down menu. To apply the rule
to a range of IP addresses, select Range and enter the starting and ending IP
addresses. To apply the rule to a subnet, select Net and enter the IP address and
subnet mask.
Days To make the rule apply on a daily basis, select Everyday. To make the rule
apply on specific days of the week only, select the desired days.
Time To make the rule apply for an entire day, select 24 Hours. To make the rule
apply only during a specific period of the day, enter the starting time in the From
field and the ending time in the To field.
5
Click Save Settings to save your settings. Click Cancel Changes to cancel your
changes. Click Return to return to the IP-Based ACL window.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 49
Page 57

Setting Up and Configuring the Router
Firewall
Firewall > Internet Access Policy
Firewall > Internet Access Policy
5
Access can be managed by a policy. Use the settings on this window to establish
an access policy. Selecting a policy from the drop-down menu will display that
policy’s settings. You can then perform the following operations:
• Create a Policy—see instructions below.
• Delete the current policy—click Delete.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 50
Page 58

Setting Up and Configuring the Router
Firewall
• View all policies—click Summary to display the Internet Policy Summary
popup which lists all of the Internet access policies and includes the
following information: No., Policy Name, Days, Time, and a checkbox to
delete (clear) the policy. To delete a policy, check the checkbox in the
Delete column, and click Delete.
• View or change the PCs covered by the current policy—click Edit List of
PCs to display the List of PCs popup.
Internet Policy Summary
5
List of PCs
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 51
Page 59

Setting Up and Configuring the Router
Firewall
On the List of PCs popup, you can define PCs by MAC Address or IP Address. You
can also enter a range of IP Addresses if you want this policy to affect a group of
PCs.
To create an Internet Access policy:
STEP 1 Select the desired policy number from the Internet Access Policy drop-down
menu.
STEP 2 Enter a Policy Name in the field provided.
STEP 3 To enable this policy, set the Status option to Enable.
STEP 4 Click Edit List of PCs to select which PCs will be affected by the policy. The List
of PCs popup will appear. You can select a PC by MAC Address or IP Address.
You can also enter a range of IP Addresses if you want this policy to affect a group
of PCs. After making your changes, click Save Settings to apply your changes.
5
STEP 5 Click the appropriate option, Deny or Allow, depending on whether you want to
block or allow Internet access for the PCs you listed on the List of PCs popup.
STEP 6 Decide which Days and what Times you want this policy to be enforced. Select
the individual days during which the policy will be in effect, or select Everyday.
Enter a range of hours and minutes during which the policy will be in effect, or
select 24 Hours.
STEP 7 If you wish to block access to websites, use the Website Blocking by URL
Address or Website Blocking by Keyword feature.
• Website Blocking by URL Address. Enter the URL or Domain Name of the
websites you wish to block.
• Website Blocking by Keyword. Enter the keywords you wish to block in the
fields provided. If any of these Keywords appears in the URL of a website,
access to the site will be blocked. Note that only the URL is checked, not the
content of each Web page.
Click Save Settings to save the policy settings you have entered. Click Cancel
Changes to cancel any changes you have entered.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 52
Page 60

Setting Up and Configuring the Router
Firewall
Firewall > Single Port Forwarding
Firewall > Single Port Forwarding
5
Application Enter the name of the application you wish to configure.
External Port This is the port number used by the server or Internet application.
Internet users must connect using this port number. Check with the software
documentation of the Internet application for more information.
Internal Port This is the port number used by the router when forwarding Internet
traffic to the PC or server on your LAN. Normally, this is the same as the External
Port number. If it is different, the router performs a “Port Translation”, so that the
port number used by Internet users is different from the port number used by the
server or Internet application.
For example, you could configure your Web Server to accept connections on both
port 80 (standard) and port 8080. Then enable Port Forwarding, and set the
External Port to 80, and the Internal Port to 8080. Now, any traffic from the Internet
to your Web server will be using port 8080, even though the Internet users used
the standard port, 80. (Users on the local LAN can and should connect to your Web
Server using the standard port 80.)
Protocol Select the protocol used for this application, TCP and/or UDP.
IP Address For each application, enter the IP address of the PC running the
specific application.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 53
Page 61

Setting Up and Configuring the Router
Firewall
Enabled Click the Enabled checkbox to enable port forwarding for the relevant
application.
Click Save Settings to save the settings you have entered. Click Cancel Changes
to cancel any changes you have entered.
Firewall > Port Range Forwarding
Firewall > Port Range Forwarding
5
Application Enter the name of the application you wish to configure.
Start This is the beginning of the port range. Enter the beginning of the range of
port numbers (external ports) used by the server or Internet application. Check
with the software documentation of the Internet application for more information if
necessary.
End This is the end of the port range. Enter the end of the range of port numbers
(external ports) used by the server or Internet application. Check with the software
documentation of the Internet application for more information if necessary.
Protocol Select the protocol(s) used for this application, TCP and/or UDP.
IP Address For each application, enter the IP address of the PC running the
specific application.
Enabled Click the Enabled checkbox to enable port range forwarding for the
relevant application.
Click Save Settings to save the settings you have entered. Click Cancel Changes
to cancel any changes you have entered.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 54
Page 62

Setting Up and Configuring the Router
Firewall
Firewall > Port Range Triggering
Firewall > Port Range Triggering
5
Application Name Enter the name of the application you wish to configure.
Triggered Range For each application, list the triggered port number range.
These are the ports used by outgoing traffic. Check with the Internet application
documentation for the port number(s) needed. In the first field, enter the starting
port number of the Triggered Range. In the second field, enter the ending port
number of the Triggered Range.
Forwarded Range For each application, list the forwarded port number range.
These are the ports used by incoming traffic. Check with the Internet application
documentation for the port number(s) needed. In the first field, enter the starting
port number of the Forwarded Range. In the second field, enter the ending port
number of the Forwarded Range.
Enabled Click the Enabled checkbox to enable port range triggering for the
relevant application.
Click Save Settings to save the settings you have entered. Click Cancel Changes
to cancel any changes you have entered.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 55
Page 63

Setting Up and Configuring the Router
ProtectLink
ProtectLink
ProtectLink > ProtectLink Purchase
ProtectLink > ProtectLink Purchase
5
The optional Trend Micro ProtectLink Gateway service provides security for your
network. For more information, see Appendix E, “Trend Micro ProtectLink Gateway
Service.”
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 56
Page 64

Setting Up and Configuring the Router
VPN
VPN
VPN > Summary
VPN > Summary
5
Tunnels Used Displays the number of tunnels used.
Tunnel(s) Available Displays the number of available tunnels.
Detail button Click Detail to display more tunnel information.
Tunnel Status
No. Displays the number of the tunnel.
Name Displays the name of the tunnel, as defined by the Tunnel Name field on the
VPN > IPSec VPN window.
Status Displays the tunnel’s status: Connected, Hostname Resolution Failed,
Resolving Hostname, or Waiting for Connection.
Phase2 Enc/Auth. Displays the Phase 2 Encryption type (3DES), Authentication
type (MD5 or SHA1), and Group (768-bit, 1024-bit, or 1536-bit) that you chose in
the VPN > IPSec VPN window.
Local Group Displays the IP address and subnet of the local group.
Remote Group Displays the IP address and subnet of the remote group.
Remote Gateway Displays the IP address of the remote gateway.
Tunnel Test Click Connect to verify the tunnel status; the test result is updated in
the Status column. If the tunnel is connected, you can disconnect the IPSec VPN
connection by clicking Disconnect.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 57
Page 65

Setting Up and Configuring the Router
VPN
Config Click Edit to change the tunnel’s settings. Click Trash to delete all of the
tunnel’s settings.
Tunnel(s) Enabled Displays the total number of currently enabled tunnels.
Tunnel(s) Defined Displays the number of tunnels currently defined. This number
will be greater than the Tunnels Enabled field if any defined tunnels have been
disabled.
VPN Clients Status
No. Displays the user number from 1 to 5.
Username. Displays the username of the VPN Client.
Status Displays the connection status of the VPN Client.
Start Time Displays the start time of the most recent VPN session for the
specified VPN Client.
5
End Time Displays the end time of a VPN session if the VPN Client has
disconnected.
Duration Displays the total connection time of the latest VPN session.
Disconnect Check the Disconnect checkbox at the end of each row in the VPN
Clients Table and click the Disconnect button to disconnect a VPN Client session.
VPN > IPSec VPN
The VPN > IPSec VPN window is used to create and configure a Virtual Private
Network (VPN) tunnel.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 58
Page 66

Setting Up and Configuring the Router
VPN
VPN > IPSec VPN
5
Select Tunnel Entry To create a new tunnel, select new. To configure an existing
tunnel, select it from the drop-down menu.
Delete Click this button to delete all settings for the selected tunnel.
Summary Clicking this button shows the settings and status of all enabled tunnels.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 59
Page 67

Setting Up and Configuring the Router
VPN
IPSec VPN Tunnel Check the Enable option to enable this tunnel.
Tunnel Name Enter a name for this tunnel, such as “Anaheim Office”.
Local Group Setup
Local Security Gateway Type This has two settings, IP Only and IP + Domain
Name (FQDN) Authentication.
• IP Only If this is selected, the RVS4000’s WAN IP address automatically
appears in the IP Address field.
• IP + Domain Name (FQDN) Authentication This is the same as IP Only, but
includes a domain name for greater security. Enter an arbitrary domain
name in the Domain Name field. The router’s WAN IP address automatically
appears in the IP Address field.
Local Security Group Type Select the local LAN user(s) behind the router that can
use this VPN tunnel. This may be a single IP address or Sub-network. Notice that
the Local Security Group Type must match the other router’s Remote Security
Group Type.
5
IP Address Enter the IP address on the local network.
Subnet Mask If the Local Security Group Type is set to Subnet, enter the mask to
determine the IP addresses on the local network.
Remote Group Setup
Remote Security Gateway Type Select either IP Only or IP + Domain Name
(FQDN) Authentication. The setting should match the Local Security Gateway
Type for the VPN device at the other end of the tunnel.
• IP Only Select this to specify the remote device that will have access to the
tunnel. Then either select IP Address from the drop-down menu and enter
the remote gateway’s WAN IP address in the IP Address field, or select IP
by DNS Resolved from the drop-down menu and enter the remote
gateway’s domain name in the Domain Name field.
• IP + Domain Name (FQDN) Authentication This is the same as IP Only but
includes a domain name for greater security. Enter an arbitrary domain
name in the Domain Name field. Then select either IP Address or IP by
DNS Resolved from the drop-down menu, and fill in the IP Address field or
Domain Name field.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 60
Page 68

Setting Up and Configuring the Router
VPN
Remote Security Group Type Select the remote LAN user(s) behind the remote
gateway who can use this VPN tunnel. This may be a single IP address or a Subnetwork. Note that the Remote Security Group Type must match the other router’s
Local Security Group Type.
IP Address Enter the IP address on the remote network.
Subnet Mask If the Remote Security Group Type is set to Subnet, enter the mask
to determine the IP addresses on the remote network.
IPSec Setup
Keying Mode The router supports both automatic and manual key management.
When choosing automatic key management, IKE (Internet Key Exchange)
protocols are used to negotiate key material for SA (Security Association). If
manual key management is selected, no key negotiation is needed. Basically,
manual key management is used in small static environments or for
troubleshooting purposes. Note that both sides must use the same Key
Management method.
5
Phase 1
• Encryption The Encryption method determines the length of the key used
to encrypt/decrypt ESP packets. Only 3DES is supported. Notice that both
sides must use the same Encryption method.
• Authentication Authentication determines a method to authenticate the
ESP packets. Either MD5 or SHA1 may be selected. Notice that both sides
(VPN endpoints) must use the same Authentication method.
• MD5 A one-way hashing algorithm that produces a 128-bit digest.
• SHA1 A one-way hashing algorithm that produces a 160-bit digest.
• Group The Diffie-Hellman (DH) group to be used for key exchange. Select
the 768-bit (Group 1), 1024-bit (Group 2), or 1536-bit (Group 5) algorithm.
Group 5 provides the most security, Group 1 the least.
• Key Life Time This specifies the lifetime of the IKE-generated key. If the
time expires, a new key will be renegotiated automatically. Enter a value
from 300 to 100,000,000 seconds. The default is 28800 seconds.
Phase 2
• Encryption The Encryption method determines the length of the key used
to encrypt/decrypt ESP packets. Only 3DES is supported. Note that both
sides must use the same Encryption method.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 61
Page 69

Setting Up and Configuring the Router
VPN
• Authentication Authentication determines a method to authenticate the
ESP packets. Either MD5 or SHA1 may be selected. Note that both sides
(VPN endpoints) must use the same Authentication method.
• MD5 A one-way hashing algorithm that produces a 128-bit digest.
• SHA1 A one-way hashing algorithm that produces a 160-bit digest.
• Perfect Forward Secrecy If PFS is enabled, IKE Phase 2 negotiation will
generate a new key material for IP traffic encryption and authentication.
Note that both sides must have this selected.
• Preshared Key IKE uses the Preshared Key field to authenticate the remote
IKE peer. Both character and hexadecimal values are acceptable in this
field; e.g., “My_@123” or “0x4d795f40313233”. Note that both sides must
use the same Preshared Key.
• Group The Diffie-Hellman (DH) group to be used for key exchange. Select
the 768-bit (Group 1), 1024-bit (Group 2), or 1536-bit (Group 5) algorithm.
Group 5 provides the most security, Group 1 the least.
5
• Key Life Time This specifies the lifetime of the IKE-generated key. If the
time expires, a new key will be renegotiated automatically. Enter a value
from 300 to 100,000,000 seconds. The default is 3600 seconds.
Status
Status Displays the connection status for the selected tunnel. The state is either
connected or disconnected.
Connect Click this button to establish a connection for the current VPN tunnel. If
you have made any changes, click Save Settings first to apply your changes.
Disconnect Click this button to break a connection for the current VPN tunnel.
View Log Click this button to view the VPN log, which shows details of each tunnel
established.
Advanced Click this button to display the following additional settings.
Aggressive Mode This is used to specify the type of Phase 1 exchange, Main
mode or Aggressive mode. Check the box to select Aggressive Mode or leave the
box unchecked (default) to select Main mode. Aggressive mode requires half of
the main mode messages to be exchanged in Phase 1 of the SA exchange. If
network security is preferred, select Main mode.
NetBios Broadcasts Check the box to enable NetBIOS traffic to pass through the
VPN tunnel. By default, the RVS4000 blocks these broadcasts.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 62
Page 70

Setting Up and Configuring the Router
VPN
Click Save Settings to save the settings you have entered. Click Cancel Changes
to cancel any changes you have entered.
VPN > VPN Client Accounts
Use this window to administer your VPN Client users. Enter the information at the
top of the window and the users you’ve entered will appear in the list at the
bottom, showing their status. This will work with the Cisco QuickVPN client only.
(The router supports up to five Cisco QuickVPN Clients by default. Additional
QuickVPN Client licenses can be purchased separately. See www.cisco.com for
more information.)
VPN > VPN Client Accounts
5
Username Enter the username using any combination of keyboard characters.
Password Enter the password you would like to assign to this user.
Re-enter to Confirm Retype the password to ensure it has been entered
correctly.
Allow User to Change Password This option determines whether the user is
allowed to change their password.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 63
Page 71

Setting Up and Configuring the Router
VPN
VPN Client List Table
No. Displays the user number.
Active When checked, the designated user can connect, otherwise the VPN client
account is disabled.
Username Displays the username.
Edit This button is used to modify the username or password, and to allow/deny
the user permission to change their password.
Remove This button is used to delete a user account.
Certificate Management
This section allows you to manage the certificate used for securing the
communication between the router and QuickVPN clients.
5
Generate Click this button to generate a new certificate to replace the existing
certificate on the router.
Export for Admin Click this button to export the certificate for administrator. A
dialog will ask you to specify where you want to store your certificate. The default
file name is “RVS4000_Admin.pem” but you can use another name. The certificate
for administrator contains the private key and needs to be stored in a safe place as
a backup. If the router’s configuration is reset to the factory default, this certificate
can be imported and restored on the router.
Export for Client Click this button to export the certificate for client. A dialog will
ask you where you want to store your certificate. The default file name is
“RVS4000_Client.pem” but you can use another name. For QuickVPN users to
securely connect to the router, this certificate needs to be placed in the install
directory of the QuickVPN client.
Import Click this button to import a certificate previously saved to a file using
Export for Admin or Export for Client. Enter the file name in the field or click
Browse to locate the file on your computer, then click Import.
Certificate Last Generated or Imported This displays the date and time when a
certificate was last generated or imported.
Click Save Settings to save your settings. Click Cancel Changes to cancel any
changes you have entered.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 64
Page 72

Setting Up and Configuring the Router
QoS
VPN > VPN Passthrough
VPN > VPN Passthrough
IPSec PassThrough Internet Protocol Security (IPSec) is a suite of protocols used
to implement secure exchange of packets at the IP layer. IPSec Passthrough is
enabled by default to allow IPSec tunnels to pass through the router. To disable
IPSec Passthrough, select Disabled.
PPTP PassThrough Point-to-Point Tunneling Protocol (PPTP) allows the Point-to-
Point Protocol (PPP) to be tunneled through an IP network. PPTP Passthrough is
enabled by default. To disable it, select Disabled.
5
QoS
L2TP PassThrough Layer 2 Tunneling Protocol is the method used to enable
Point-to-Point sessions via the Internet on the Layer 2 level. L2TP Passthrough is
enabled by default. To disable L2TP Passthrough, select Disabled.
Click Save Settings to save your settings. Click Cancel Changes to cancel any
changes you have entered.
QoS (Quality of Service) allows you to perform Bandwidth Management, by either
Rate Control or Priority. You can also configure QoS Trust Mode and the DSCP
settings.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 65
Page 73

Setting Up and Configuring the Router
QoS
QoS > Bandwidth Management
QoS > Bandwidth Management - Rate Control
5
Bandwidth
This section lets you specify the maximum bandwidth provided by the ISP on the
WAN interface, for both the upstream and downstream directions.
Bandwidth Management Type
Type The desired type of bandwidth management, either Rate Control or Priority
(default). Depending on your selection, the lower portion of the window displays
either the Rate Control section or the Priority section.
Rate Control
Service Select the service from the drop-down menu. If it does not contain the
service you need, click Service Management to add the service.
IP Enter the IP address or IP range you need to control. The default is zero which
includes all internal IP addresses.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 66
Page 74

Setting Up and Configuring the Router
QoS
Direction Select Upstream for outbound traffic or Downstream for inbound
traffic.
Mini. Rate Enter the minimum rate for the guaranteed bandwidth.
Max. Rate Enter the maximum rate for the guaranteed bandwidth.
Enable Check this box to enable this Rate Control Rule.
Add to list After a rule is set up, click this button to add it to the list. The list can
contain a maximum of 15 entries.
Delete selected application Click this button to delete a rule from the list.
Priority
QoS > Bandwidth Management - Priority
5
Service Select the service from the drop-down menu. If it does not contain the
service you need, click Service Management to add the service.
Direction Select Upstream for outbound traffic or Downstream for inbound
traffic from the drop-down menu.
Priority Select High, Medium, Normal, or Low priority for the service. The default
is Medium.
Enable Check this box to enable this Priority Rule.
Add to list After a rule is set up, click this button to add it to the list. The list can
contain a maximum of 15 entries.
Delete selected application Click this button to delete a rule from the list.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 67
Page 75

Setting Up and Configuring the Router
QoS
Click Save Settings to save your settings. Click Cancel Changes to cancel any
changes you have entered.
QoS > QoS Setup
The QoS Setup window allows users to configure QoS Trust Mode for each LAN
port.
QoS > QoS Setup
5
Port ID The number of the LAN port.
Trust Mode Select either Port, CoS, or DSCP. The default is Port.
Default CoS/Port Priority If Trust Mode is set to Port, select the port priority from
1 to 4 from the drop-down menu, where 4 is the highest priority. If Trust Mode is
set to CoS, select the default CoS priority from 0 to 7 from the drop-down menu.
CoS Setup
Priority The CoS priority from 0 to 7.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 68
Page 76

Setting Up and Configuring the Router
QoS
Queue Select the traffic forwarding queue, 1 to 4, to which the CoS priority is
mapped. Queue 4 has the highest priority.
Click Save Settings to save your settings. Click Cancel Changes to cancel any
changes you have entered.
QoS > DSCP Setup
QoS > DSCP Setup
5
DSCP The Differentiated Services Code Point value in the incoming packet.
Queue Select the traffic forwarding queue, 1 to 4, to which the DSCP priority is
mapped. Queue 4 has the highest priority.
Restore Defaults Click this button to restore the default DSCP values.
Click Save Settings to save your settings. Click Cancel Changes to cancel any
changes you have entered.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 69
Page 77

Setting Up and Configuring the Router
Administration
Administration
The Administration menu provides access to system administration settings and
tools. It includes the following windows:
Administration > Management
Administration > Management
5
Router Access
Router Userlist Select the desired router user list.
Router Username Enter the user name here.
Router Password Enter the password.
Re-enter to Confirm Retype the password in this field.
SNMP
SNMP Select Enable if you wish to use SNMP. To use SNMP, you need SNMP
software on your PC.
System Name Enter a suitable name. This name will be used to identify this
device, and will be displayed by your SNMP software.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 70
Page 78

Setting Up and Configuring the Router
Administration
System Contact Enter contact information for the system.
System Location Enter the location of the system.
Read Community Enter the SNMP community name for SNMP “Get” commands.
Write Community Enter the SNMP community name for SNMP “Set” commands.
Trap Community Enter the SNMP community name for SNMP “Trap” commands.
Trap To Enter the IP Address of the SNMP Manager to which traps will be sent. If
desired, this may be left blank.
UPnP
Universal Plug and Play (UPnP) can be used to set up public services on your
network. When the UPnP function is enabled, Windows XP can add or delete
entries to the underlined UPnP Forwarding Table. Some Internet games require
enabling UPnP.
5
UPnP If you want to use UPnP, keep the default setting, Enable. Otherwise, select
Disable.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 71
Page 79

Setting Up and Configuring the Router
Administration
Administration > Log
Administration > Log
5
Log Setting
Log Level Select the log level(s) that the router should record. Log levels and their
meanings are:
Log Levels
Level Severity Name Description
7 LOG_DEBUG Debug-level message
6 LOG_INFO Informational messages only
5 LOG_NOTICE Normal but significant condition
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 72
Page 80

Setting Up and Configuring the Router
Administration
Log Levels
Level Severity Name Description
4 LOG_WARNING Warning conditions
3 LOG_ERR Error conditions
2 LOG_CRIT Critical conditions
1 LOG_ALERT Immediate action needed
0 LOG_EMERG System unusable
Outgoing Log Select Enable to cause all outgoing packets to be logged. You can
then click View Outgoing Table to display information on the outgoing packets
including Source IP, Destination IP, and Service/Port number.
5
Incoming Log Select Enable to cause all incoming packets to be logged. You can
then click View Incoming Table to display information on incoming packets
including Source IP, Destination IP, and Service/Port number.
Email Alerts
Email Alerts Select Enable to cause an e-mail to be sent immediately if a DoS
(Denial of Service) attack is detected. If enabled, fill in the e-mail address
information in the remaining fields in this section.
Denial of Service Thresholds Enter the number of DoS (Denial of Service) attacks
which need to be blocked by the built-in Firewall before an e-mail alert is sent. The
minimum value is 20, the maximum value is 100.
Log Queue Length The default is 50 entries (Router will e-mail the log if there are
more than 50 entries).
Log Time Threshold The default is 10 minutes (Router will e-mail the log every 10
minutes).
SMTP Mail Server Enter the address (domain name) or IP address of the SMTP
(Simple Mail Transport Protocol) Server you use for outgoing e-mail.
Email Address for Alert Logs Enter the e-mail address the Log is to be sent to.
Return Email Address The e-mail will show this address as the Sender’s address.
Enable SMTP Authentication If your SMTP server requires Authentication, you
can enable it here, and enter the Username and Password.
E-mail Log Now Press this button to cause the log to be e-mailed immediately.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 73
Page 81

Setting Up and Configuring the Router
Administration
Syslog
Enable Syslog Select the checkbox if you want to use this feature.
Syslog Server Enter the IP Address in this field when Enable Syslog is checked.
Local Log
Local Log Enable this if you want to see a log of all incoming and outgoing URLs or
IP addresses.
View Log Click this button when you wish to view the logs. A new window will
appear with the log data.
Administration > Diagnostics
5
Administration > Diagnostics
Ping Test Parameters
Ping Target IP Enter the IP address or URL that you want to ping.
Ping Size Enter the size of the packet you want to use.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 74
Page 82

Setting Up and Configuring the Router
Administration
Number of Pings Enter the number of times you wish to ping the target device.
Ping Interval Enter the time period (milliseconds) between each ping.
Ping Timeout Enter the desired time period (milliseconds). If a response is not
received within the defined ping period, the ping is considered to have failed.
Start Test Click this button to begin the test. A new window will appear and
display the test results.
Ping Result Displays the Ping status.
Traceroute Test Parameters
Traceroute Target Enter the target IP address for the traceroute test.
Start Test Click this button to begin the test. A new window will appear and
display the test results.
5
Cable Diagnostics
Port Select the port number from the drop-down menu.
Pair Identifies a specific pair (A, B, C, or D) in the cable. Each cable consists of 8
pins (4 pairs).
Cable Length Displays the length of the cable in meters.
Status Displays the status of the pair.
Administration > Backup & Restore
Administration > Backup & Restore
To download a copy of the current configuration and store the file on your PC,
click Backup to start the download.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 75
Page 83

Setting Up and Configuring the Router
Administration
Restore Configuration
To restore a previously saved config file back to the router, enter the file name in
the field or click Browse to select the config file, then click Restore to upload the
config file.
Administration > Factory Default
Administration > Factory Default
5
Restore Factory Defaults Click this button to reset all configuration settings to
their factory default values. Any settings that have been saved will be lost when
the default settings are restored. After clicking the button, another window will
appear. Click OK to continue. Another window will appear while the system
reboots.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 76
Page 84

Setting Up and Configuring the Router
Administration
Administration > Reboot
Administration > Reboot
5
Reboot Click this button to reboot the router. This operation will not cause the
router to lose any of its stored settings.
Administration > Firmware Upgrade
Administration > Firmware Upgrade
To upgrade firmware, download the latest firmware for the product. For the
firmware download link, see Appendix G, “Where to Go From Here.” Extract the
firmware to your computer and perform the steps below.
File Type in the name of the extracted firmware upgrade file or click Browse to
locate the file.
Start to Upgrade Once you have selected the appropriate file, click Start to
Upgrade and follow the on-screen instructions to upgrade your firmware.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 77
Page 85

Setting Up and Configuring the Router
IPS
IPS
IPS > Configuration
IPS > Configuration
5
Figure1 IPS > Configuration
IPS Function Select Enable to enable or Disable to disable the IPS Function.
Anomaly Detection
HTTP Web attack signature is matched. HTTP request decoder will decode UTF-
8 (1, 2, and 3 byte) code and normalize URI (according to those evasion methods
mentioned in whisker) before pattern match.
FTP FTP Bounce Detection and Inserting telnet opcodes into FTP command
stream Detection.
TELNET Normalization of Telnet negotiation strings.
RPC RPC record fragging detection.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 78
Page 86

Setting Up and Configuring the Router
IPS
Signature Update Before upgrading the firmware, download and extract the
router firmware upgrade file from the Cisco website. For the firmware download
link, see Appendix G, “Where to Go From Here.” Enter the firmware upgrade file
name in the Signature Update field, or click Browse to find the file. Then click
Update and follow the on-screen instructions.
IPS > P2P/IM
Peer To Peer
5
Peer to Peer
Peer-to-peer file sharing applications can be blocked (Block) or allowed (NonBlock). The preconfigured file sharing networks are GNUTELLA (EZPEER),
FASTTRACK, KURO, EDONKEY2000, BITTORRENT, DIRECTCONNECT, PIGO, and
WINMX.
Instant Messenger
Instant messaging applications can be blocked (Block) or allowed (Non-Block).
The preconfigured instant messaging applications are MSN, ICQ,
YAHOO_MESSENGER, SKYPE, IRC, ODIGO, REDIFF, GOOGLE_TALK, and IM_QQ.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 79
Page 87

Setting Up and Configuring the Router
IPS
IPS > Report
Provides a graphical representation of the level of network traffic and attacks
during the last twenty four hours.
Attacker
Displays the IP Address of attackers and the frequency (number of times) of the
attacks.
Attack Category
Displays the category (type) of attack and the frequency (number of times) of the
attacks.
5
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 80
Page 88

Setting Up and Configuring the Router
IPS
IPS > Report
5
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 81
Page 89

Setting Up and Configuring the Router
L2 Switch
IPS > Information
IPS > Information
5
L2 Switch
Signature Version Displays the version of the signature patterns in the router that
protects against malicious threats.
Last Time Upload This displays when the signature patterns in the router were
last updated.
Protect Scope Lists the types of attacks that the router’s IPS feature protects
against.
L2 > Create VLAN
VLANs are logical subgroups of a Local Area Network (LAN) created via software
rather than defining a hardware solution. VLANs combine user stations and
network devices into a single domain regardless of the physical LAN segment to
which they are attached. VLANs allow network traffic to flow more efficiently
within subgroups. VLANs managed through software reduce the amount of time in
which network changes are implemented.
VLANs have no minimum number of ports, and can be created per unit, per device,
per stack, or any other logical connection combination, as VLANs are software
based and not defined by physical attributes.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 82
Page 90

Setting Up and Configuring the Router
L2 Switch
VLANs function at layer 2. Since VLANs isolate traffic within the VLAN, a Layer 3
router is needed to allow traffic flow between VLANs. Layer 3 routers identify
segments and coordinate with VLANs.
VLANs are broadcast and multicast domains. Broadcast and multicast traffic is
transmitted only in the VLAN in which the traffic is generated.
The RVS4000 supports up to 4 VLANs, including the default VLAN.
L2 Switch > Create VLAN
5
VLAN ID The VLAN ID number. This can be any number from 2 to 3290, or from
3293 to 4094. (VLAN ID 1 is reserved for the default VLAN, which is used for
untagged frames received on the interface. VLAN IDs 3291-3292 are reserved
and cannot be used.) To create a VLAN, enter the ID number and click Add VLAN.
VLAN ID Range To create multiple VLANs with a range of ID numbers, enter the
starting and ending ID numbers and click Add Range.
Delete Selected VLAN To delete a VLAN, select it form the VLAN list and click
Delete Selected VLAN.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 83
Page 91

Setting Up and Configuring the Router
L2 Switch
L2 > VLAN Port Setting
L2 Switch > VLAN Port Setting
Port ID Displays the port number from 1 to 4.
Mode Select the mode of the port, either Trunk, Untagged, or Tagged. The
default is Untagged. In Trunk mode, incoming and outgoing frames can be either
tagged or untagged; incoming untagged frames are tagged with the default PVID
(Port VLAN ID). In Untagged mode, all incoming and outgoing frames are untagged.
In Tagged mode, all incoming and outgoing frames must be tagged; all untagged
frames are dropped.
5
PVID The Port VLAN ID (PVID) assigned to untagged frames received on the
interface. The default is 1. If the Mode is Tagged, the port will receive only tagged
frames and so the port will have no PVID.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 84
Page 92

Setting Up and Configuring the Router
L2 Switch
L2 > VLAN Membership
L2 Switch > VLAN Membership
5
VLAN ID Select the VLAN whose membership you want to configure.
Description Enter a VLAN group name of up to 50 characters.
Function/Port table The top half of the table indicates each port’s current mode
(Untagged, Tagged, or Trunk). The lower half of the table is used to assign port
membership for the selected VLAN. The default for each port is Exclude (the port
is not a member of the VLAN). To make a port a member of the VLAN, select the
applicable mode(s). For example, if the port mode is Untagged, select Untagged; if
the mode is Tagged, select Tagged; if the mode is Trunk, select either Tagged or
Untagged.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 85
Page 93

Setting Up and Configuring the Router
L2 Switch
L2 > RADIUS
L2 Switch > RADIUS
5
Mode Select Enabled or Disabled from the drop-down menu to enable or disable
RADIUS.
RADIUS IP Enter the Server IP address.
RADIUS UDP Port Enter the UDP port. The UDP port is used to verify the RADIUS
server authentication.
RADIUS Secret Enter the Key string used for authenticating and encrypting all
RADIUS communications between the device and the RADIUS server. This key
must match the RADIUS server encryption key. If no host-specific value is
specified, the global value applies to each host.
Administration State Specifies the port authorization state. The possible field
values are:
• Auto The controlled port state is set by the Authentication method.
• Force Authorized The controlled port state is set to Force-Authorized
(forward traffic).
• Force Unauthorized The controlled port state is set to Force-Unauthorized
(discard traffic).
Port State Displays the state of the selected port.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 86
Page 94

Setting Up and Configuring the Router
L2 Switch
L2 > Port Setting
L2 Switch > Port Setting
Port Displays the physical port number.
5
Link Displays the port duplex mode and speed. Full Duplex indicates that the
interface supports transmission between the device and its link partner in both
directions simultaneously. Half Duplex indicates that the interface supports
transmission between the device and the client in only one direction at a time.
Mode Select the port duplex mode and speed from the drop-down menu. You can
also select Auto Negotiation, which is a protocol between two link partners that
enables a port to advertise its transmission rate, duplex mode and flow control
abilities to its partner.
Flow Control Displays the flow control status on the port. Operates when port is in
Full duplex mode.
MaxFrame Displays the maximum frame size the port can receive and send.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 87
Page 95

Setting Up and Configuring the Router
L2 Switch
L2 > Statistics
L2 Switch > Statistics
Statistics Overview
5
Tx Bytes Displays the number of Bytes transmitted from the selected port.
Tx Frames Displays the number of Frames transmitted from the selected port.
Rx Bytes Displays the number of Bytes received on the selected port.
Rx Frames Displays the number of Frames received on the selected port.
Tx Errors Displays the number of error packets transmitted from the selected
port.
Rx Errors Displays the number of error packets received from the selected port.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 88
Page 96

Setting Up and Configuring the Router
L2 Switch
L2 > Port Mirroring
L2 Switch > Port Mirroring
5
Mirror Source Use this to enable or disable source port mirroring for each port on
the router. To enable source port mirroring on a port, check the box next to that
port. To disable source port mirroring on a port, leave the box unchecked. The
default is disabled.
Mirror Port Select the mirror destination port from the drop-down menu.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 89
Page 97

Setting Up and Configuring the Router
L2 Switch
L2 > RSTP
L2 Switch > RSTP
5
The RSTP (Rapid Spanning Tree Protocol) protocol prevents loops in the network
and dynamically reconfigures which physical links in a switch should forward
frames.
System Priority Enter the system priority from 0 to 61440 in increments of 4096.
Valid values are 0, 4096, 8192, 12288, 16384, 20480, 24576, 28672, 32768,
40960, 45056, 49152, 53248, 57344, and 61440. The lower the system priority,
the more likely the router is to become the root in the Spanning Tree. The default is
32768.
Hello Time Enter a number from 1 to 10. The default is 2.
Max Age Enter a number from 6 to 40. The default is 20.
Forward Delay Enter a number from 4 to 30. The default is 15.
Force Version This is the default protocol version to use. Select Normal (use
RSTP) or Compatible (compatible with old STP). The default is Normal.
Protocol Enable Check this box to enable RSTP on the associated port. The
default is unchecked (RSTP disabled).
Edge Check this box to specify that the associated port is an edge port (end
station). Uncheck the box to specify that the associated port is a link (bridge) to
another STP device. The default is checked (edge port).
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 90
Page 98

Setting Up and Configuring the Router
Status
Path Cost This is the RSTP path cost for the designated ports. Enter a number
from 1 to 200000000, or auto (autogenerated path cost). The default is auto.
Status
Status > Gateway
Status > Gateway
5
Firmware Version Displays the Gateway’s current firmware.
MAC Address Displays the Gateway MAC Address, as seen by your ISP.
Current Time Displays the time, based on the time zone you selected on the
Setup menu.
Internet Connection
Connection Type Displays the type of the connection.
Interface Displays the Gateway Internet Interface.
IP Address Displays the Gateway Internet IP Address.
Subnet Mask Displays the Subnet Mask that is associated with the IP address
above.
Default Gateway Displays your ISP’s Gateway.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 91
Page 99

Setting Up and Configuring the Router
Status
DNS 1-2 Displays the DNS (Domain Name System) IP addresses currently used
by this Gateway.
IP Conntrack Click this button to display the IP Conntrack window.
IP Conntrack
The IP Conntrack (Connection Tracking) window displays information about TCP/
UDP connections, such as source and destination IP address and port number
pairs (known as socket pairs), protocol types (TCP/UDP/ICMP), connection state
and timeouts. To see more information, click Next Page or Previous Page, or
select the page from the Goto Page drop-down menu. To see the latest
information, click Refresh. Click Close to return to the Status > Gateway window.
Status > Gateway > IP Conntrack
5
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 92
Page 100

Setting Up and Configuring the Router
Status
Status > Local Network
Status > Local Network
5
Current IP address System This shows the current system.
MAC Address This is the router MAC Address, as seen on your local, Ethernet
network.
IP Address The Internet IP Address is displayed here.
Subnet Mask This Subnet Mask is associated with the IP address above.
IPv6 Address This shows the IPv6 IP address, if applicable.
DHCP Server The status of the router’s DHCP server function is displayed here.
Start IP Address This shows the beginning of the range of IP addresses used by
the DHCP Server.
End IP Address This shows the end of the range of IP addresses used by the
DHCP Server.
DHCP Client Table Clicking this button will open a window showing you which
PCs are utilizing the router as a DHCP server. On the DHCP Client Table window,
you will see a list of DHCP clients (PCs and other network devices) with the
following information: Client Names, Interfaces, IP Addresses, MAC Addresses,
and the length of time before their assigned IP addresses expire.
Cisco RVS4000 4-Port Gigabit Security Router with VPN Administration Guide 93
 Loading...
Loading...