ZyXEL Communications ZYWALL USG 300 UNIFIED SECURITY GATEWAY, ZYWALL USG 100 UNIFIED SECURITY GATEWAY, ZYWALL USG 1000 UNIFIED SECURITY GATEWAY, ZYWALL USG 200 UNIFIED SECURITY GATEWAY User Manual

Vantage Report
Default Login Details
IP Address http://{Vantage
Report server’s IP
address}:8080/
vrpt
User Name root
Password root
Software Version 3.5
Edition 1, 2/2010
www.zyxel.com
www.zyxel.com
Copyright © 2010
ZyXEL Communications Corporation


About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the Vantage Report
using the web configurator. You should have at least a basic knowledge of TCP/IP
networking concepts and topology.
Related Information
• Download software and documentation (User’s Guide, Quick Start Quide,
Datasheet, Support Notes) from one of the FTP sites:
Europe: ftp://ftp.zyxel.dk/Vantage_Report
Rest of World: ftp://ftp.zyxel.com/Vantage_Report
• Vantage Report Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
•ZyXEL Glossary and Web Site
Please refer to www.zyxel.com
additional support documentation.
for an online glossary of networking terms and
Documentation Feedback
Send your comments, questions or suggestions to: techwriters@zyxel.com.tw
Thank you!
The Technical Writing Team, ZyXEL Communications Corp.,
6 Innovation Road II, Science-Based Industrial Park, Hsinchu, 30099, Taiwan.
Vantage Report User’s Guide
3

About This User's Guide
Need More Help?
More help is available at www.zyx el.com.
• Download Library
Search for the latest product updates and documentation from this link. Read
the Tech Doc Overview to find out how to efficiently use the User Guide, Quick
Start Guide and Command Line Interface Reference Guide in order to better
understand how to use your product.
• Knowledge Base
If you have a specific question about your product, the answer may be here.
This is a collection of answers to previously asked questions about ZyXEL
products.
•Forum
This contains discussions on ZyXEL prod ucts. Learn from others who use ZyXEL
products and share your experiences as well.
Customer Support
Should problems arise that cannot be solved by the methods listed above, you
should conta ct your vendor. If you cannot contact your vendo r, then contact a
ZyXEL office for the region in which you bought the device.
See http://www.zyxel.com/web/contact_us.php for contact information. Please
have the following informatio n ready when you contact an office.
• Product model and serial number.
•Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
4
Vantage Report User’s Guide

Document Conventions
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
Warnings tell you about things that could harm you or your device.
Note: Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The version number on the title page is the version of Vantage Report that is
documented in this User’s Guide.
• Enter means for you to type one or more characters and press the carriage
return. Select or Choose means for you to use one of the predefined choices.
• The choices of a menu item are in Bold Arial font.
• Mouse action sequences are denoted using a right angle bracket (>). For
example, click Report > Traffic > WEB > Top Hosts means first click the
Report main menu and then Traffic, WEB and finally click Top Hosts.
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons.
Computer Server Prestige Device
ZyWALL Device User Internet
VPN Tunnel
Vantage Report User’s Guide
5

Document Conventions
Your product is marked with this symbol, which is known as the WEEE
mark. WEEE stands for Waste Electronics and Electrical Equipment. It
means that used electrical and electronic products should not be mixed with
general waste. Used electrical and electronic equipment should be treated
separately.
6
Vantage Report User’s Guide

Contents Overview
Contents Overview
Introduction ............................................................................................................................17
Introducing Vantage Report ....................................................................................................... 19
The Vantage Report Server .......................................................................................................23
The Web Configurator ...............................................................................................................31
Monitors, Reports and Logs .................................................................................................59
Monitor ...................................... ....................... ...................... ....................... ............................. 61
Traffic .................................................................. .................................................... ...................79
VPN .........................................................................................................................................167
Network Attack ........................................................................................................................ 249
Security Policy ......................................................................................................................... 317
Event .......................................................................................................................................369
EPS ......................................................................................................................................... 379
Schedule Report .............................. ... ... ... ... .... ... ... ... .... ...........................................................383
Logs ....................................... .................................................... .............................................. 401
System Setting, User Management and Troubleshooting ...............................................421
System Setting ......................................... ... .... ............................................. ... ... .... ... ... ...........423
User Management . ... ... ... .... ... ... ... ................................................. ... ... ... .................................. 451
Troubleshooting ..................................................... .................................................................. 459
Appendices and Index .........................................................................................................463
Vantage Report User’s Guide
7

Contents Overview
8
Vantage Report User’s Guide

Table of Contents
Table of Contents
About This User's Guide..........................................................................................................3
Document Conventions............................................................................................................5
Contents Overview ...................................................................................................................7
Table of Contents......................................................................................................................9
Part I: Introduction................................................................................. 17
Chapter 1
Introducing Vantage Report...................................................................................................19
1.1 Introduction ......................... ... .... ... ... ... ............................................. .... ... ... ... .... ... ... .............19
1.2 License Versions .......... ... ... ... .... ... ... .................................................................................... 20
1.3 Hardware Requirements ..................................... ................................. ................................20
Chapter 2
The Vantage Report Server....................................................................................................23
2.1 Starting and Stopping the Vantage Report Server .................................. .............................23
2.2 E-Mail in the Vantage Report Server ................................................................................... 24
2.3 Time in the Vantage Report Server ......................................................................................25
2.4 ZyXEL Device Configuration and Source Data .................... ... ... .......................................... 25
2.5 Common Terms ............... ... ... .... ... ... ... ............................................. .... ... ... ... .... ... ................ 28
2.6 Common Icons .......................................... ... ............................................. ... .... ... ... ... ... ....... 29
Chapter 3
The Web Configurator............................................................................................................31
3.1 Web Configurator Requirements ......................................................................................... 31
3.2 Web Configurator Access ....................................................................................................31
3.3 Main Menu Bar .................................................................................................................... 34
3.3.1 The About Screen ........................ .... ... ... ... .... ... ... ... .... ................................................ 34
3.4 Device Window ............................. ... ... ... .... ... ... ... .... ... ..........................................................34
3.5 Menu Panel ............................................... ... ... ... .............................................. ... ... ... .......... 38
3.6 Report and Setting Window ................................................................................................. 47
3.6.1 Device Information Screen ............................... .......................................... ................ 48
3.6.2 Monitors and Statistical Reports .......................................... ... .... ... ... .......................... 49
3.6.3 View Logs ..................... .... ............................................. ... ... ... .................................... 53
3.7 System Dashboard .................................... ... ... ... .... ... ... ... ............................................. ....... 54
Vantage Report User’s Guide
9

Table of Contents
Part II: Monitors, Reports and Logs..................................................... 59
Chapter 4
Monitor.....................................................................................................................................61
4.1 Monitor (Folder) ................................................................................................................... 61
4.1.1 Customize the Column Fields ................ ... .... ... ... ... .... ................................................ 62
4.2 Dashboard Configuration ........... ... ... .................................................................................... 63
4.3 Dashboard Configured ....................................... .... ... ... ... .... ... ... ... ... .... ... ... .......................... 65
4.4 Bandwidth Monitor ........................... ... ... .... ... ... ... .... ............................................................. 66
4.5 CPU Usage Monitor ............... .... ... ... ... ... .... ... ... ... ................................................. ... ... ..........67
4.6 Memory Usage Monitor ................ ... ... ... ................................................. ... ... .... ... ... ... ... .... ...68
4.7 Session Usage Monitor .......................................................................................... ... ... .......69
4.8 Port Usage Monitor ................ .... ... ... ... ... .... ... ... ... ................................................. ... ... ..........70
4.9 Interface Usage Monitor ......................................................................................................71
4.10 Service Monitor .................................................................................................................. 73
4.11 Attack Monitor .................................................................................................................... 74
4.12 Intrusion Monitor ................................................................................................................ 75
4.13 Anti-Virus Monitor .............................................................................................................. 76
4.14 Anti-Spam Monitor ............................................................................................................. 77
Chapter 5
Traffic.......................................................................................................................................79
5.1 Bandwidth ........................... ... .............................................. ... ... ... ... .... ... ............................. 79
5.1.1 Bandwidth Summary ........... ................................................ ... .... ................................ 79
5.1.2 Bandwidth Summary Drill-Down ................................................................................ 83
5.1.3 Bandwidth Top Protocols ............................................................................................ 84
5.1.4 Bandwidth Top Protocols Drill-Down .......................................................................... 88
5.1.5 Top Bandwidth Hosts ................................................................................................. 90
5.1.6 Top Bandwidth Hosts Drill-Down ................................................................................ 94
5.1.7 Top Bandwidth Users .................................................................................................96
5.1.8 Top Bandwidth Users Drill-Down ................................................................................ 99
5.1.9 Top Bandwidth Destinations ..................................................................................... 101
5.1.10 Top Bandwidth Destinations Drill-Down ......................... ... ... .................................. 105
5.2 Web Traffic .............................................................. ... ... ... .... ... ... ........................................ 107
5.2.1 Top Web Sites .......................................................................................................... 107
5.2.2 Top Web Sites Drill-Down .........................................................................................110
5.2.3 Top Web Hosts ..........................................................................................................112
5.2.4 Top Web Hosts Drill-Down ........................................................................................115
5.2.5 Top Web Users .........................................................................................................117
5.2.6 Top Web Users Drill-Down .......................................................................................120
5.3 FTP Traffic ................................................................. ... ... .... ... ........................................... 122
5.3.1 Top FTP Sites ...........................................................................................................122
5.3.2 Top FTP Sites Drill-Down .........................................................................................125
10
Vantage Report User’s Guide

Table of Contents
5.3.3 Top FTP Hosts ......................................................................................................... 127
5.3.4 Top FTP Hosts Drill-Down ........................................................................................ 130
5.3.5 Top FTP Users .........................................................................................................132
5.3.6 Top FTP Users Drill-Down ........................................................................................ 135
5.4 Mail Traffic .................................................................................... ... .... ... ... ... .... ... ..............137
5.4.1 Top Mail Sites ...........................................................................................................137
5.4.2 Top Mail Sites Drill-Down ......................................................................................... 140
5.4.3 Top Mail Hosts ..........................................................................................................142
5.4.4 Top Mail Hosts Drill-Down ........................................................................................145
5.4.5 Top Mail Users ......................................................................................................... 147
5.4.6 Top Mail Users Drill-Down ....................................................................................... 150
5.5 Other Traffic ..... ... ... ... .... ............................................. ... ... .... .............................................. 152
5.5.1 Platform Selection ............................................... ............................................. ... .... . 152
5.5.2 Service Settings ......................................................................................................153
5.5.3 Top Destinations of Other Traffic .............................................................................. 154
5.5.4 Top Destinations of Other Traffic Drill-Down ............................................................ 156
5.5.5 Top Sources of Other Traffic .................................................................................... 158
5.5.6 Top Sources of Other Traffic Drill-Down ................................................................... 160
5.5.7 Top Other Traffic Users ............................................................................................ 162
5.5.8 Top Users of Other Traffic Drill-Down ....................................................................... 164
Chapter 6
VPN.........................................................................................................................................167
6.1 VPN Site-to-Site .................................................................................. ... ... ... .... ... ... ...........167
6.1.1 VPN Link Status ....................................................................................................... 167
6.1.2 VPN Traffic Monitor .................................................................................................. 169
6.1.3 Top VPN Peer Gateways ......................................................................................... 170
6.1.4 Top VPN Peer Gateways Drill-Down ........................................................................ 172
6.1.5 Top VPN Sites .......................................................................................................... 174
6.1.6 Top VPN Sites Drill-Down ........................................................................................177
6.1.7 Top VPN Tunnels ..................................................................................................... 179
6.1.8 Top VPN Tunnels Drill-Down .................................................................................... 182
6.1.9 Top VPN Protocols ................................................................................................... 184
6.1.10 Top VPN Protocols Drill-Down ............................................................................... 187
6.1.11 Top VPN Hosts ........................... .............................................. ... ... ... .... ................. 189
6.1.12 Top VPN Hosts Drill-Down ..................................................................................... 192
6.1.13 Top VPN Users ....................................................................................................... 194
6.1.14 Top VPN Users Drill-Down ..................................................................................... 197
6.1.15 Top VPN Destinations ............................................................................................ 198
6.1.16 Top VPN Destinations Drill-Down ............................. ............ ............. ................ ..... 201
6.2 VPN Remote Access (IPSec) ............................................................................................ 203
6.2.1 VPN User Status ...................................................................................................... 203
6.2.2 VPN User Status Drill-Down .....................................................................................206
Vantage Report User’s Guide
11

Table of Contents
6.2.3 Top VPN Protocols ................................................................................................... 208
6.2.4 Top VPN Protocols Drill-Down ..................................................................................211
6.2.5 Top VPN Destinations .............................................................................................. 213
6.2.6 Top VPN Destinations Drill-Down ............................................................................. 216
6.2.7 VPN Top Users .........................................................................................................218
6.2.8 VPN Top Users Drill-Down .......................................................................................221
6.3 VPN Remote Access (SSL) ............................................................................................... 223
6.3.1 VPN User Status ...................................................................................................... 223
6.3.2 VPN User Status Drill-Down .....................................................................................226
6.3.3 Top VPN Protocols ................................................................................................... 227
6.3.4 Top VPN Protocols Drill-Down ............................................. 230
6.3.5 Top VPN Destinations .............................................................................................. 231
6.3.6 Top VPN Destinations Drill-Down ............................................................................. 234
6.3.7 Top VPN Applications ............................................................................................... 236
6.3.8 Top VPN Applications Drill-Down .............................................................................239
6.3.9 VPN Top Users .........................................................................................................241
6.3.10 VPN Top Users Drill-Down ..................................................................................... 243
6.4 Xauth ............... ... ... ... .... ... ............................................. ... .... ... ... ... ... .................................. 245
6.4.1 VPN Successful Login .............................................................................................. 245
6.4.2 VPN Failed Login ..................................................................................................... 247
Chapter 7
Network Attack......................................................................................................................249
7.1 Attack ........... .... ............................................. ... ... .... ... ........................................................249
7.1.1 Attack Summary ............................................................................ ... ... .... ... ... ... ... .....249
7.1.2 Attack Summary Drill-Down .......................................................... ... ... .... ... ... ... ... .... . 252
7.1.3 Top Attacks ................... .... ... ... ... ............................................. .... .............................. 253
7.1.4 Top Attacks Drill-Down ..... ... ... ... ... .............................................. ... ... ... .... ... ... ........... 256
7.1.5 Top Attack Sources ..................................................................................................257
7.1.6 Top Attack Sources Drill-Down ................................................................................. 260
7.1.7 Attack Types .................................................. ... ... ... .... ... ... ........................................262
7.1.8 Attack Types Drill-Down ......................... ............................................. .... ... ... ... ... .... . 264
7.2 Intrusion .............................. ... .... ... ... ... ... .... ... ... ... ...............................................................265
7.2.1 Intrusion Summary .... ... .... ... ... ... ... .... ........................................................................ 265
7.2.2 Intrusion Summary Drill-Down ................................................................................. 268
7.2.3 Top Intrusion Signatures ........................................................ .... ... ... ... ..................... 2 70
7.2.4 Top Intrusion Signatures Drill-Down .................................... ... .... .............................. 273
7.2.5 Top Intrusion Sources ................................................ ... ... ... ... .................................. 275
7.2.6 Top Intrusion Sources Drill-Down .................................. ... ... ... .... ... ... ... .... ................. 278
7.2.7 Top Intrusion Destinations ................................... ... .... ... ........................................... 280
7.2.8 Top Intrusion Destinations Drill-Down ...................................................................... 283
7.2.9 Intrusion Severities .......................... ... ... ... .... ........................................................... 285
7.2.10 Intrusion Severities Drill-Down ............................................................................... 288
12
Vantage Report User’s Guide

Table of Contents
7.3 AntiVirus ...... .... ... ... ... .............................................. ... ... ... .... .............................................. 289
7.3.1 Virus Summary .................... ... ... ... .... ............................................. ... ... .... ... ... ... ........289
7.3.2 Virus Summary Drill-Down ....................................................................................... 292
7.3.3 Top Viruses ...................................................... ... ... .... ... ...........................................293
7.3.4 Top Viruses Drill-Down ............................................................................................. 296
7.3.5 Top Virus Sources .................................................................................................... 297
7.3.6 Top Virus Sources Drill-Down .................................................................................300
7.3.7 Top Virus Destinations ............................................................................................. 302
7.3.8 Top Virus Destinations Drill-Down ............................................................................ 304
7.4 AntiSpam ...................................... ............................................. ... ... .... .............................. 305
7.4.1 Spam Summary ................................................... ... .... ............................................. . 305
7.4.2 Spam Summary Drill-Down .................................... .... .............................................. 308
7.4.3 Top Spam Senders ........................... ... ............................................. ... .... ... ... ... ... .... . 309
7.4.4 Top Spam Sources ................................. ... .... ... ............................................. ... ... .... . 312
7.4.5 Spam Scores ....................... ............................................. ... ... .... ... ... ... ..................... 315
Chapter 8
Security Policy......................................................................................................................317
8.1 Firewall Access Control .....................................................................................................317
8.1.1 Top Users Blocked ...................... .............................................. ... ... ... .... ................. 317
8.1.2 Top Packets Blocked ................................................................................................ 320
8.2 Application Access Control ................................................................................................ 322
8.2.1 Top Applications Blocked ......................................................................................... 322
8.2.2 Top Users Blocked .................... ............................................. .... ... ... ... ..................... 325
8.2.3 Top Applications Allowed .........................................................................................328
8.3 Blocked Web Accesses ...................................... .... ... ... ... .... ... ........................................... 331
8.3.1 Web Block Summary ................................................................................................331
8.3.2 Web Block Summary Drill-Down ..............................................................................333
8.3.3 Top Blocked Web Sites ............................................................................................335
8.3.4 Top Blocked Web Sites Drill-Down ........................................................................... 338
8.3.5 Top Blocked Web Hosts ........................................................................................... 339
8.3.6 Top Blocked Web Hosts Drill-Down .......................................................................... 342
8.3.7 Top Blocked Web Users ........................................................................................... 343
8.3.8 Top Blocked Web Users Drill-Down ......................................................................... 346
8.3.9 Blocked Web Categories .......................................................................................... 347
8.3.10 Blocked Web Categories Drill-Down ...................................................................... 3 50
8.4 Allowed Web Accesses ..................................................................................................... 351
8.4.1 Web Allowed Summary ............................................................................................ 351
8.4.2 Web Allowed Summary Drill-Down .......................................................................... 353
8.4.3 Top Allowed Web Sites ............................................................................................ 355
8.4.4 Top Allowed Web Sites Drill-Down ........................................................................... 358
8.4.5 Top Allowed Web Hosts ........................................................................................... 359
8.4.6 Top Allowed Web Hosts Drill-Down ..................... ... .... ... ........................................... 362
Vantage Report User’s Guide
13

Table of Contents
8.4.7 Top Allowed Web Users ........................................................................................... 363
8.4.8 Top Allowed Web Users Drill-Down ......................................................................... 366
Chapter 9
Event......................................................................................................................................369
9.1 Successful Logins ............ .................................................................................................. 369
9.2 Failed Logins ............ .... ... ... ... .... ............................................. ... ... ... .... ... ... ........................ 371
9.3 Top Sessions Per Host .......... .... ... ... ... ... .... ... .....................................................................372
9.4 Top Sessions Per User ....................................... .... ... ... ... .... ..............................................375
Chapter 10
EPS.........................................................................................................................................379
10.1 Overview .......................................................................................................................... 379
10.1.1 What Endpoint Security Can Check .......................................................................379
10.2 EPS Summary ................................................................................................................. 380
10.3 View Logs ........................................................................................................................ 381
Chapter 11
Schedule Report ...................................................................................................................383
11.1 Scheduled Report Summary Screen ............................................................................... 383
11.2 Customize Daily Report Screen ....................................................................................... 384
11.3 Customize Weekly Report Screen ................................................................................... 391
11.4 Customize Overtime Report Screen ................................................................................ 393
11.5 Configure Template List ...................................................................................................395
11.6 Template Add/Edit ............................................................................................................ 396
11.7 Logo Template ................................................................................................................. 396
11.8 Logo Template Add/Edit ................................................................................................... 397
Chapter 12
Logs .......................................................................................................................................401
12.1 Log Viewer ................... ... ... .... ............................................. ... ... ... .... ... ... ........................ 401
12.2 Log Receiver ................................................................................................................... 405
12.2.1 By Day (Summary) ................................................................................................. 405
12.3 By Device ....................................................................................................................... 408
12.3.1 Log Receiver > By Device > By Category Screen ................................................. 410
12.4 VRPT System Logs .........................................................................................................410
12.5 Log Archiving ................................................................................................................... 413
12.5.1 File Archiving Settings ................................. ............. ............ ............. .......... ........... 413
12.5.2 View Archived Files ................................................................................................ 416
12.5.3 Log Transfer ........................................................................................................... 418
12.6 Log Remove ....................................................................................................................419
14
Vantage Report User’s Guide

Table of Contents
Part III: System Setting, User Management and Troubleshooting .. 421
Chapter 13
System Setting......................................................................................................................423
13.1 General Configuration Screen ......................................................................................... 423
13.1.1 Configuring for Hostname Reverse ........................................................................ 425
13.2 Server Configuration Screen ........................................................................................... 428
13.3 Data Maintenance Screens ............................................................................................. 429
13.3.1 Data Backup and Data Restore Screen ................................................................. 429
13.3.2 Device List Screen ................................................................................................. 430
13.4 Upgrade Screen .............................................................................................................. 431
13.5 Registration Screens .......................................................................................................432
13.5.1 Registration Summary Screen ............................................................................... 433
13.5.2 Registration > Upgrade Screen ................................ ......................... ..................... 434
13.6 Notification ....................................................................................................................... 435
13.6.1 Add/Edit a Notification ................................. .......................................... ................. 437
13.7 Rule-Based Alert ............................................................................................................. 439
13.7.1 Add/Edit a Rule-based Alert ...................................................................................440
Chapter 14
User Management.................................................................................................................451
14.1 Group Screen .................................................................................................................. 451
14.1.1 Group > Add/Edit Group Screen ............................................................................452
14.2 Account Screen ............................................................................................................... 453
14.2.1 Account > Add/Edit User Account Screen ............................................................. 454
Chapter 15
Troubleshooting....................................................................................................................459
Part IV: Appendices and Index ........................................................... 463
Appendix A Product Specifications.......................................................................................465
Appendix B Setting up Your Computer’s IP Address............................................................473
Appendix C ZyNOS Log Descriptions..................................................................................481
Appendix D ZyWALL 1050 and ZyWALL USG Series Log Descriptions..............................507
Appendix E Open Software Announcements.......................................................................553
Appendix F Legal Information ..............................................................................................591
Index.......................................................................................................................................593
Vantage Report User’s Guide
15

Table of Contents
16
Vantage Report User’s Guide

PART I
Introduction
Introducing Vantage Report (19)
The Vantage Report Server (23)
The Web Configurator (31)
17

18

CHAPTER 1
Introducing Vantage Report
Please see the Quick Start Guide for Vantage Report setup requirements,
installation, and access. This chapter introduces Vantage Report. See Appendix A
on page 465 for a list of key features.
1.1 Introduction
Vantage Report is a cost-effective, browser-based global management solution
that allows an administrator from any location to easily manage, monitor and
gather statistics on ZyXEL devices located worldwide. With Vantage Report, you
can monitor network access, enhance security, and anticipate future bandwidth
needs. A typical applica t ion is illustrated in Figure 1.
Figure 1 Typical Vantage Report Application
A
C
B
In this example, you use the web configurator (A) to set up the Vantage
Report server (B). You also configure the ZyXEL devices (C) to send their logs
and traffic statistics to the Vantage Report Server. The Vantage Report server
collects this information. Then, you can
• monitor the whole network
• look at historical reports about network performance and events
• examine device logs
Vantage Report User’s Guide
19

Chapter 1 Introducing Vantage Repo rt
The Vantage Report server can also send statistical reports to you by e-mail.
1.2 License Versions
This is independent from the version number, 3.1 for example. There are two
versions of Vantage Report, the basic version and the full version. When you
install Vantage Report, you get the basic version. The full version requires a
license key, which you usually have to purchase.
Note: This User’s Guide discusses the features in the full version.
The following table shows differences between the basic and full versions.
Table 1 Differences Between Basic Version and Full Version
FEATURE BASIC FULL
Number of supported devices 1 up to 100
Supported formats for scheduled reports PDF PDF, HTML
Drill-down reports 1 layer 2 layers
Reverse DNS lookup no yes
Reverse Hostname lookup no yes
Web usage by category no yes
AntiVirus no yes
AntiSpam no yes
Dashboard no yes
Number of scheduled reports 20 20 per device
Customizable scheduled report templates no yes
Schedule Report Format PDF PDF, HTML
Reports for the ZyWALL 1050/Z yWALL USG
series
no yes
There is also a free trial of the full version. The trial version is the same as the full
version except that it only supports one device. You can get the trial version by
registering Vantage Report. See Section 13.5 on page 432 for more information.
1.3 Hardware Requirements
Minimum hardware requirements:
• Intel Pentium 4 processor 1 GHz
• 512 Mb RAM
20
Vantage Report User’s Guide

Chapter 1 Introducing Vantage Report
• 8 GB free hard disk space
The following table shows the recommended hardware specifications. The more
powerful your computer, the more devices you can manage.
Table 2 Hardware Specification Recommendations
NUMBER
OF
DEVICES
0 - 5 0 - 75 Intel P4 2.6
5 - 50 75 - 750 Intel P4 2.6
50 - 100 750 - 1500 Intel P4 3.2
LOG HANDLING
CAPABILITY (LOGS/
SEC)
CPU SPEC
(GHZ)
GHz
GHz
GHz
MEMOR
Y
SPEC
512 MB 0 - 1
1 GB 1 - 12
1 GB 12 - 24
LOG SPACE
REQUIRED (GB/
DAY)
Vantage Report User’s Guide
21

Chapter 1 Introducing Vantage Repo rt
22
Vantage Report User’s Guide

CHAPTER 2
The Vantage Report Server
This chapter explains several characteristics of the Vantage Report server.
2.1 Starting and Stopping the Vantage Report
Server
Note: Make sure the port Vantage Report uses for web services is not used by other
applications, especially web servers.
The Vantage Report server runs as a service on the Vantage Report server. By
default, this service starts automatically when you log in to the Vantage Report
server. You can use the services management screen to start, stop, or configure
this service. To open this screen,ì
1 In Windows 2000, click Start > Settings > Control Panel > Administrative
Tools > Services. The Services screen opens.
2 In Windows XP, click Start > Control Panel > Performance and Maintenance
> Administrative Tools > Services. The Services screen opens.
Vantage Report User’s Guide
23

Chapter 2 The Vantage Report Server
3 In Windows Vista or Windows 7, click Start > Control Panel > Administrative
Tools > Services. The Services screen opens.
4 Right-click on Vantage Report. A menu appears.
5 Select Start or Stop to start or stop the Vantage Report service. Select
Properties to configure the service.
2.2 E-Mail in the Vantage Report Server
Note: Before the Vantage Report server can send e-mail to anyone, you have to
configure the SMTP mail server. See Section 13.2 on page 428 for more
information.
The Vantage Report server can use e-mail to send information in several
situations. In some situations, it sends e-mail to the e-mail address that is
associated with a specific user (see Section 13.3 on page 429). In other
situations, it sends e-mail to any valid e-mail address.
• scheduled report - The Vantage R eport server can send one or more statist ical
reports regularly or one-time to any valid e-mail address. See Chapter 11 on
page 383 for more information.
• system notifications - When certain system parameters cross a threshold
(minimum or maximum) value, the Vantage Report server sends e-mail to the
Vantage Report administrator (the e-mail address associated with the root
account). Some of these messages are warnings; in some situations, however,
the Vantage R e port server starts or stops receive logs. See Appendix A on page
465 for a list of parameters and threshold values. One of the threshold values
can be configured. See Section 13.1 on page 423.
24
Vantage Report User’s Guide

Chapter 2 The Vantage Report Server
• forgotten password - A user clicks Forget Password? in the Login screen.
In this case, the Vantage Report server sends the account information to the email address associated with the specified user name. See Section 3.2 on page
31 for an example of the Login screen.
• test message - The Vantage Report administrator tests the SMTP mail server
settings. The Vantage Report server sends an e-mail message to the e-mail
address associated with the root account. See Section 13.2 on page 428 for
more information.
2.3 Time in the Vantage Report Server
• In Vantage Report, clock time is the time the Vantage Report server receives
information (log entries or traffic statistics) from the ZyXEL devices, not the
time the device puts in the entry . As soon as the V antage R eport server receives
information, it replaces device times with the current time in the Vantage Report
server.
• The Vantage Report server processes log entries and traffic statistics b efore the
information is available in any screen (including log viewers). For performance
reasons, the Vantage Report server does not process this information right
away. Instead, the processing time depend s on the way the information is used
in Vantage Report. See the following table for processing times for each menu
item.
Table 3 Processing Times by Menu Item
MENU ITEM TIME (MIN)
Monitor 5
Report (Traffic, Network Attack, Security Policy, Authentication) 5
Logs (Log Viewer) 5
2.4 ZyXEL Device Configuration and Source Data
The following table identifies the configuration required in ZyXEL devices for each
screen in Vantage Report.
Table 4 ZyNOS-based ZyWALL Configuration Requirements by Menu Item
VANTAGE REPORT MENU ITEM(S)
Monitor > Bandwidth traffic statistics -- -Monitor > Service traffic statistics -- -Monitor > Attack log entries Attack -Monitor > Intrusion log entries IDP IDP >
Vantage Report User’s Guide
ZYNOS-BASED ZYWALL
SOURCE
DATA
LOG
SETTINGS*
ADDITIONAL
Signature
25

Chapter 2 The Vantage Report Server
Table 4 ZyNOS-based ZyWALL Configuration Requirements by Menu Item
VANTAGE REPORT MENU ITEM(S)
Monitor > AntiVirus log entries Anti-Virus Anti-Virus >
Monitor > AntiSpam log entries Anti-Spam -Report > Traffic traffic statistics -- -Report > VPN log entries IPSec -Report > Network Attack > Attack log entries Attack -Report > Network Attack > Intrusion log entries IDP IDP >
Report > Network Attack > AntiVirus log entries Anti-Virus Anti-Virus >
Report > Network Attack > AntiSpam log entries A nti-Spam -Report > Security Policy > Firewall
Access Control
Report > Security Policy > Application
Access Control
Report > Security Policy > WEB Blocked log entries Blocked Web
Report > Security Policy > WEB Allowed log entries Forward Web
Report > Event > Login log entries System
Report > Event > Session Per Host log entries Access
Report > EPS N/A N/A N/A
Logs > Log Viewer log entries ** **
ZYNOS-BASED ZYWALL
SOURCE
DATA
log entries Access
N/A N/A N/A
LOG
SETTINGS*
Control
Sites
Sites
Maintenance
Control
ADDITIONAL
General
Signature
General
--
--
--
--
--
* - The names of categories may be different for different devices. Use the category that is appropriate for each
device.
** - The log viewers display whatever log entries the ZyXEL devices record, including log entries that may not
be used in other reports.
Table 5 ZLD-based ZyWALL Configuration Requirements by Menu Item
VANTAGE REPORT MENU ITEM(S)
Monitor > CPU Usage traffic
Monitor > Memory Usage traffic
Monitor > Session Usage traffic
26
ZLD-BASED ZYWALL
SOURCE
DATA
statistics
statistics
statistics
LOG
SETTINGS*
-- --
-- --
-- --
Vantage Report User’s Guide
ADDITIONAL

Chapter 2 The Vantage Report Server
Table 5 ZLD-based ZyWALL Configuration Requirements by Menu Item
ZLD-BASED ZYWALL
VANTAGE REPORT MENU ITEM(S)
Monitor > Port Usage traffic
Monitor > Interface Usage traffic
Monitor > Service traffic
Monitor > Attack log entries IDP -Monitor > Intrusion log entries IDP IDP > Signature
Monitor > AntiVirus N/A N/A N/A
Monitor > AntiSpam N/A N/A N/A
Report > Traffic traffic
Report > VPN log entries IPSec, User -Report > VPN > Remote Access (SSL) log entries SSL VPN,
Report > Network Attack > Attack log entries IDP -Report > Network Attack > Intrusion log entries IDP IDP > Signature
Report > Network Attack > AntiVirus N/A N/A N/A
Report > Network Attack > AntiSpam N/A N/A N/A
Report > Security Policy > Firewall Access
Control
Report > Security Policy > Application
Access Control
Report > Security Policy > WEB Blocked log entries Blocked web
Report > Security Policy > WEB Allowed log entries Forward
Report > Event > Login log entries User -Report > Event > Session Per Host log entries Sessions
Report > EPS log entries EPS, Auth.
Logs > Log Viewer log entries ** **
SOURCE
DATA
statistics
statistics
statistics
statistics
log entries
log entries Firewall --
log entries Application
LOG
SETTINGS*
-- --
-- --
-- --
-User
User
Patrol
sites
web sites
Limit, User
Policy, SSL
VPN
ADDITIONAL
--
--
--
--
--
--
* - The names of categories may be different for different devices. Use the category that is appropriate for each
device.
** - The log viewers display whatever log entries the ZyXEL devices record, including log entries that may not
be used in other reports.
Vantage Report User’s Guide
27
Chapter 2 The Vantage Report Server
• Source Data - Some screens use log entries; some screens use traffic
statistics. Some ZyXEL devices do not track traffic statistics. If Vantage Report
does not get one of these, the screens are empty. See the Quick Start Guide for
detailed instructions.
• Log Settings - If ZyXEL devices do not record some categories of log entries,
Vantage R eport does not ha v e any information to displa y either. For example, if
you want to look at VPN traffic for a particular device, the device has to record
log entries for IPSec.
For most devices, go to the Logs > Log Settings screen, and select the
appropriate categories. You may also use the command-line interface.
• Additional - In some cases, it is possible to control what log entries are
recorded in even more detail. For example, in some ZyXEL devices, it is possible
to control what attack types are logged.
For most devices, go to the screen indicated to select the appropriate log
entries. You may also use the command-line interface.
2.5 Common Terms
The following table describes the terms that appear frequently in this document.
Table 6 Common Terms
TERM DESCRIPTION
ZLD-based ZyXEL
Devices
ZyNOS-based ZyXEL
Devices
Drill-down Report Click a link in a report to display details in another screen. For
Host A host represents a computer with an IP address.
Remote User A user login the device with a legal user’s account.
ZLD (ZyXEL Linux Distribution) is ZyXEL's platform based on
Linux. ZLD models include ZyWALL 1050 and ZyWALL USG
series.
ZyNOS is ZyXEL's Networking Operating Sy stem. ZyNOS
models include ZyWALL 5, ZyWALL 35, and ZyWALL 70, etc.
example, click VPN > Remote Access (IPSec) > User
Status, then click a user’s link to display a report of the
services for which the user sent the most traffic.
Figure 2 Remote User
28
Vantage Report User’s Guide

Chapter 2 The Vantage Report Server
TERM DESCRIPTION
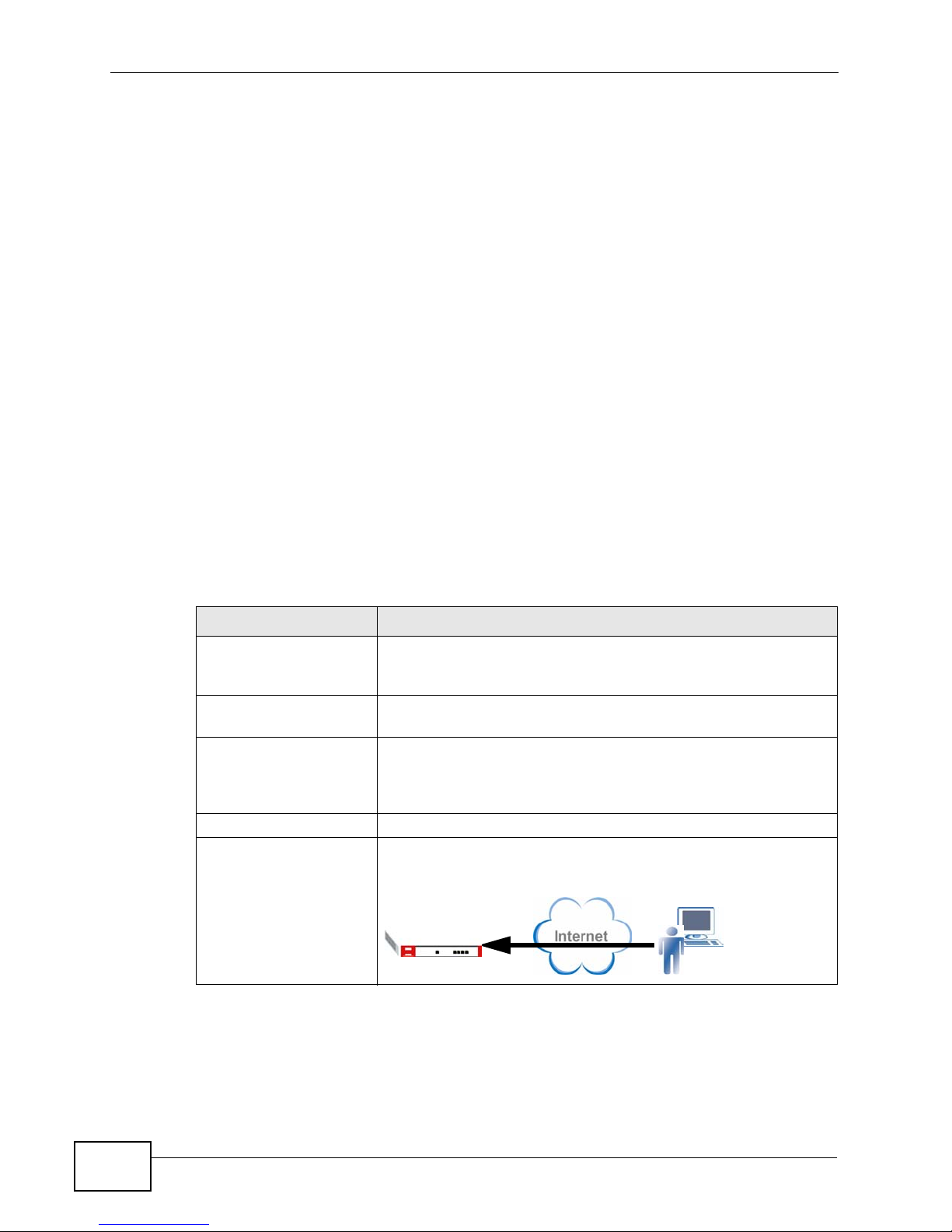
Remote VPN User A VPN user is a user who is allowed to send traffic through VPN
tunnel.
Figure 3 Remote VPN User
Incoming VPN Traffic A diagram is referred to in following figure. In this example,
incoming VPN traffic is encrypted data that the ZyXEL Device
receives from VPN tunnels (A) and the traffic sent back (B).
Figure 4 Incoming VPN Traffic
A
Outgoing VPN Traffic A diagram is referred to in following figure. In this example,
outgoing VPN traffic is encrypted data that the ZyXEL Device
forwards through VPN tunnels (A) and the returned traffic (B).
Figure 5 Outgoing VPN Traffic
2.6 Common Icons
The following table describes common icons.
Table 7 Common Icons
ICON DESCRIPTION
The View Detail icon (in the Dashboard) lets you focus on an individual
monitor report.
The Settings icons open a screen where you can modify the report display
settings.
The Print icon opens a screen for printing the screen.
B
A
B
Vantage Report User’s Guide
29

Chapter 2 The Vantage Report Server
Table 7 Common Icons
ICON DESCRIPTION
The Pie View icon displays the statistical report in a pie chart.
The Bar View icon displays the statistical report in a bar chart.
The Refresh icon updates the information in the screen.
30
Vantage Report User’s Guide
 Loading...
Loading...