Page 1

Quick Start Guide
NXC Series
Wireless LAN Controller
Versions: 2.25, 4.00
Edition 1, 06/2013
CLI Reference Guide
Default Login Details
IP Address https://192.168.1.1
User Name admin
Password 1234
www.zyxel.com
Copyright © 2011
Copyright © 2013 ZyXEL Communications Corporation
ZyXEL Communications Corporation
Page 2
IMPORTANT!
READ CAREFULLY BEFORE USE.
KEEP THIS GUIDE FOR FUTURE REFERENCE.
This is a Reference Guide for a series of products intended for people who want to configure the NXC
via Command Line Interface (CLI).
Some commands or command options in this guide may not be available in your
product. See your product's User’s Guide for a list of supported features. Every effort
has been made to ensure that the information in this guide is accurate.
How To Use This Guide
1 Read Chapter 1 on page 15 for how to access and use the CLI (Command Line Interface).
2 Read Chapter 2 on page 31 to learn about the CLI user and privilege modes.
Do not use commands not documented in this guide.
Related Documentation
• Quick Start Guide
The Quick Start Guide shows how to connect the NXC and access the Web Configurator.
• User’s Guide
The User’s Guide explains how to use the Web Configurator to configure the NXC.
It is recommended you use the Web Configurator to configure the NXC.
Page 3

Contents Overview
Contents Overview
Command Line Interface ........................................................................................................... 15
User and Privilege Modes ......................................................................................................... 31
Object Reference ................ ... ... ... .... ... ... ... ... ....................................... ... .... ... ... ... .... ... ... ... .......... 35
Status ............................................................... ...................... ....................... ............................. 37
Registration ............................................................................................................................... 41
Interfaces ..................................... ....................................................... ....................................... 49
Route ......................................................................................................................................... 65
AP Management ........................................................................................................................ 73
Wireless LAN Profiles ...................... ... ... ... ... .... ...................................... .... ... ... ... .... ... ... ... .......... 77
Rogue AP .................................................................................................................................. 89
Wireless Frame Capture ..................... ... ... ... .... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ............................. 93
Dynamic Channel Selection ......................................................................................................95
Wireless Load Balancing ........................................................................... ... ... ... .... ... ... ... ... ....... 99
Dynamic Guest ........................................................................................................................ 103
Zones .................................. ................... ................... .................... ................... ........................ 107
ALG ..........................................................................................................................................111
Captive Portal ...........................................................................................................................113
RTLS .........................................................................................................................................117
Firewall .....................................................................................................................................119
Application Patrol ..................................................................................................................... 127
Anti-Virus ................................................................................................................................. 137
IDP Commands ....................................................................................................................... 145
Device HA ................................................................................................................................ 163
User/Group .............................................................................................................................. 169
Addresses .............................. ................... .................... ................... ................... ..................... 177
Services ................................. ....................................................... ........................................... 181
Schedules ................................. ................................................. .............................................. 185
AAA Server .............................................................................................................................. 187
Authentication Objects ................. .... ... ... ... ... ....................................... ... .... ... ... ... .... ... ... ... ........ 193
Authentication Server ............................................... .... ... ... ... .... ... ........................................... 197
ENC ......................................................................................................................................... 199
Certificates ................................... ....................... ....................... ...................... ........................ 203
System ................................... ...................... ....................... ....................... .............................. 207
System Remote Management ................................................................................................. 213
File Manager ............................................................................................................................ 223
Logs ....................................... .................................................... .............................................. 241
Reports and Reboot ................................................................................................................ 249
Session Timeout ....................... ... .... ... ... ... ... ....................................... ... .... ... ... ... .... ................. 255
NXC CLI Reference Guide
3
Page 4

Contents Overview
Diagnostics .............................................................................................................................. 257
Packet Flow Explore ................................................................................................................ 259
Maintenance Tools ...................................................................................................................261
Watchdog Timer ....................................................................................................................... 267
Managed AP Commands ................ ... ... ... ... .... ... ... ... .... ... ... ... ....................................... ... ... .... . 271
List of Commands .................................................................................................................... 277
4
NXC CLI Reference Guide
Page 5

Table of Contents
Table of Contents
Contents Overview...............................................................................................................................3
Table of Contents .................................................................................................................................5
Chapter 1
Command Line Interface....................................................................................................................15
1.1 Overview ................... ... ... .... ... ... ... .... ... ....................................... ... ... ... ..............................................15
1.1.1 The Configuration File .............................................................................................................15
1.2 Accessing the CLI .............................................................................................................................15
1.2.1 Console Port .................... ... .... ... ... ... ....................................... ... ... .... ... ... ... ..............................16
1.2.2 Web Configurator Console ......................................................................................................17
1.2.3 Telnet ..... ... .... ... ... ... .... ... ....................................... ...................................... .... ..........................20
1.2.4 SSH (Secure SHell) .................................................................................................................20
1.3 How to Find Commands in this Guide ...............................................................................................21
1.4 How Commands Are Explained ........................................................................................................21
1.4.1 Background Information ..... .... ... ... ... ... .... ... ... ... .... ... ....................................... ... ... ... ... .... ..........21
1.4.2 Command Input Values ...........................................................................................................21
1.4.3 Command Summary ............... ... ... ... ... .... ...................................... .... ... ... ... .... ... ... ... ... .... ..........22
1.4.4 Command Examples .................................... ... ....................................... ... .... ... ... ... .................22
1.4.5 Command Syntax ............................... .... ... ....................................... ... ... ... .... ... ... ....................22
1.4.6 Changing the Password ..........................................................................................................22
1.5 CLI Modes ....... ....................................... ... ... ....................................... ... .... ... ....................................22
1.6 Shortcuts and Help ............................................................................................................................23
1.6.1 List of Available Commands ....................................................................................................23
1.6.2 List of Sub-commands or Required User Input .......................................................................24
1.6.3 Entering Partial Commands ....... ... ... ... .... ... ... ... .... ...................................... .... ... ... ... ... .... ... .......25
1.6.4 Entering a ? in a Command .....................................................................................................25
1.6.5 Command History ............... .... ... ... ....................................... ... ... ... .... ... ... .................................25
1.6.6 Navigation .............. .... ... ... ....................................... ... ... .... ... ... .................................................25
1.6.7 Erase Current Command ................. ... .... ... ..............................................................................25
1.6.8 The no Commands ..................................................................................................................25
1.7 Input Values .................... .... ... ... ... .... ... ....................................... ... ... ... ..............................................26
1.8 Saving Configuration Changes .........................................................................................................29
1.9 Logging Out .................................. .... ...................................... .... ... ... .................................................29
Chapter 2
User and Privilege Modes..................................................................................................................31
2.1 User And Privilege Modes .................................................................................................................31
2.1.1 Debug Commands ........... ... .... ...................................... .... ... ... ... ... .... .......................................33
NXC CLI Reference Guide
5
Page 6

Table of Contents
Chapter 3
Object Reference................................................................................................................................35
3.1 Object Reference Commands ...........................................................................................................35
3.1.1 Object Reference Command Example ....................................................................................36
Chapter 4
Status...................................................................................................................................................37
4.1 Status Show Commands ...................................................................................................................37
Chapter 5
Registration.........................................................................................................................................41
5.1 myZyXEL.com overview ............................... .... ... ... ... .... ... ... ....................................... ... ... .................41
5.1.1 Subscription Services Available on the NXC ...........................................................................41
5.1.2 Maximum Number of Managed APs .......... ... ... .... ... ... ... .... ... ... ... ... .... ... ....................................42
5.2 Registration Commands ............................ ........................................................................................43
5.2.1 Command Examples .................................... ... ....................................... ... .... ... ... ... .................44
5.3 Country Code ............ ... ... .... ...................................... .... ... ... ... .... ... ....................................................44
Chapter 6
Interfaces.............................................................................................................................................49
6.1 Interface Overview ....................... .... ... ... ... ....................................... ... ... .... ... ... ... .... ... .......................49
6.1.1 Types of Interfaces ................................. ... ... ... .... ... ....................................... ... ... ... ... ..............49
6.2 Interface General Commands Summary ...........................................................................................49
6.2.1 Basic Interface Properties and IP Address Commands ..........................................................50
6.2.2 DHCP Setting Commands ............... ....................................... ... ... .... ... ... ... ..............................53
6.2.3 Connectivity Check (Ping-check) Commands .........................................................................57
6.3 Ethernet Interface Specific Commands ............................ ... ... .... ... ... ... ... .... ... ... ... ..............................58
6.3.1 MAC Address Setting Commands ...........................................................................................58
6.4 Port Commands ........................ ... .... ...................................... .... ... ... ... ... ...........................................59
6.5 Port Role Commands ........................................................................................................................60
6.5.1 Port Role Examples .................................................................................................................60
6.6 USB Storage Specific Commands ....................................................................................................60
6.6.1 USB Storage General Commands Example ............................................................................62
6.7 VLAN Interface Specific Commands ...................... ... .... ... ....................................... ... ... ....................62
6.7.1 VLAN Interface Examples .. .... ... ... ... ... .... ...................................... .... ... ... ... .... ... .......................64
Chapter 7
Route....................................................................................................................................................65
7.1 Policy Route ....... .... ...................................... .... ... ... ....................................... ... ... .... ..........................65
7.2 Policy Route Commands ...................................................................................................................65
7.2.1 Assured Forwarding (AF) PHB for DiffServ .............................................................................68
7.2.2 Policy Route Command Example ............................................................................................69
7.3 IP Static Route ..................................................................................................................................69
6
NXC CLI Reference Guide
Page 7

Table of Contents
7.4 Static Route Commands ...................................................................................................................70
7.4.1 Static Route Commands Example ...........................................................................................70
7.5 Learned Routing Information Commands ..................... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... . ...71
7.5.1 show ip route Command Example .......................... .......................... ......................... .............. 71
Chapter 8
AP Management..................................................................................................................................73
8.1 AP Management Overview ...............................................................................................................73
8.2 AP Management Commands .............. ... ... ... .....................................................................................74
8.2.1 AP Management Commands Example ...................................................................................76
Chapter 9
Wireless LAN Profiles ........................................................................................................................77
9.1 Wireless LAN Profiles Overview ......................... ... ... .... ... ... ... .... ... ... ... ..............................................77
9.2 AP & Monitor Profile Commands ..................................... ... ... .... ... ... ... ... .... ... ... ... ..............................77
9.2.1 AP & Monitor Profile Commands Example ....................... ... ... ... ... .... ... ... ... .... ... .......................82
9.3 SSID Profile Commands ........................ ... ... .... ...................................... .... ... ... ... .... ... ... ... .................83
9.3.1 SSID Profile Example ................................ ... ... ....................................... ... .... ... ... ... .................84
9.4 Security Profile Commands .......................... .... ... ... ... .... ... ... ... .... ...................................... .................84
9.4.1 Security Profile Example ........... ... ... ....................................... ... ... .... ... ... ... .... ... ... ... .................87
9.5 MAC Filter Profile Commands ................................ ... .... ...................................... .... ... ... ... ... ..............87
9.5.1 MAC Filter Profile Example .......... ... ... .... ... ... ... .... ... ... ... ....................................... ... ... .... ..........88
Chapter 10
Rogue AP.............................................................................................................................................89
10.1 Rogue AP Detection Overview ........................................................................................................89
10.2 Rogue AP Detection Commands ....................................................................................................89
10.2.1 Rogue AP Detection Examples .............................................................................................90
10.3 Rogue AP Containment Overview ..................................................................................................91
10.4 Rogue AP Containment Commands ...............................................................................................92
10.4.1 Rogue AP Containment Example ..........................................................................................92
Chapter 11
Wireless Frame Capture.....................................................................................................................93
11.1 Wireless Frame Capture Overview .................................................................................................93
11.2 Wireless Frame Capture Commands ..............................................................................................93
11.2.1 Wireless Frame Capture Examples .......................................................................................94
Chapter 12
Dynamic Channel Selection...............................................................................................................95
12.1 DCS Overview .................................................................................................................................95
12.2 DCS Commands .............................................................................................................................95
12.2.1 DCS Examples ......................................................................................................................96
NXC CLI Reference Guide
7
Page 8

Table of Contents
Chapter 13
Wireless Load Balancing...................................................................................................................99
13.1 Wireless Load Balancing Overview ...................... ....... ...... ....... ...... ... ....... ...... ....... ...... ...... ..............99
13.2 Wireless Load Balancing Commands .............................................................................................99
13.2.1 Wireless Load Balancing Examples ....................................................................................101
Chapter 14
Dynamic Guest..................................................................................................................................103
14.1 Dynamic Guest Overview ..............................................................................................................103
14.2 Dynamic Guest Commands ..........................................................................................................103
14.2.1 Dynamic Guest Examples ...................................................................................................105
Chapter 15
Zones.................................................................................................................................................107
15.1 Zones Overview ............................................................................................................................107
15.2 Zone Commands Summary ..........................................................................................................108
15.2.1 Zone Command Examples ..................................................................................................109
Chapter 16
ALG ....................................................................................................................................................111
16.1 ALG Introduction ........................................................................................................................... 111
16.2 ALG Commands ............................................................................................................................112
16.3 ALG Commands Example .............................................................................................................112
Chapter 17
Captive Portal....................................................................................................................................113
17.1 Captive Portal Overview ................................................................................................................113
17.1.1 Web Authentication Policy Commands ........................................... ... ... ... ............................113
17.1.2 page-customization Commands .......................................................................................... 116
Chapter 18
RTLS ..................................................................................................................................................117
18.1 RTLS Introduction .........................................................................................................................117
18.2 RTLS Commands ..........................................................................................................................117
Chapter 19
Firewall ..............................................................................................................................................119
19.1 Firewall Overview ..........................................................................................................................119
19.2 Firewall Commands .............................................................................................................. ........120
19.2.1 Firewall Sub-Commands .....................................................................................................122
19.2.2 Firewall Command Examples ..............................................................................................123
19.3 Session Limit Commands .............................................................................................................124
8
NXC CLI Reference Guide
Page 9

Table of Contents
Chapter 20
Application Patrol.............................................................................................................................127
20.1 Application Patrol Overview ..........................................................................................................127
20.2 Application Patrol Commands Summary ............................. .... ... ... ... ....................................... ... ..128
20.2.1 Pre-defined Application Commands .................................. ... ... ... .........................................128
20.2.2 Rule Commands for Pre-defined Applications .....................................................................128
20.2.3 Exception Commands for Pre-defined Applications ............................................................130
20.2.4 Other Application Commands ..............................................................................................131
20.2.5 Rule Commands for Other Applications ............................ ... ... ... .... ... ... ... ............................132
20.2.6 General Commands for Application Patrol ................................. .... ... ... ... .... ... ... ... ... .... ... ... ..133
Chapter 21
Anti-Virus...........................................................................................................................................137
21.1 Anti-Virus Overview .......................................................................................................................137
21.2 Anti-virus Commands ....................................................................................................................137
21.2.1 General Anti-virus Commands ............................................................................................138
21.2.2 Zone to Zone Anti-virus Rules .............................................................................................138
21.2.3 White and Black Lists ..........................................................................................................140
21.2.4 Signature Search Anti-virus Command ...............................................................................142
21.3 Update Anti-virus Signatures ........................................................................................................142
21.3.1 Update Signature Examples ................................................................................................143
21.4 Anti-virus Statistics ........................................................................................................................143
21.4.1 Anti-virus Statistics Example ...............................................................................................144
Chapter 22
IDP Commands .................................................................................................................................145
22.1 Overview .......................................................................................................................................145
22.2 General IDP Commands ...............................................................................................................145
22.2.1 IDP Activation ......................................................................................................................145
22.3 IDP Profile Commands ..................................................................................................................146
22.3.1 Global Profile Commands ....................................................................................................146
22.3.2 IDP Zone to Zone Rules ......................................................................................................147
22.3.3 Editing/Creating IDP Signature Profiles ......... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ... ... .... ... ... ..148
22.3.4 Editing/Creating Anomaly Profiles ........................... ... .... ... ... ... ... .... ... ... ... .... ........................149
22.3.5 Editing System Protect ........................................................................................................153
22.3.6 Signature Search .................................................................................................................153
22.4 IDP Custom Signatures .................................................................................................................156
22.4.1 Custom Signature Examples ................... ... ... .... ... ... ... .... ...................................... ... .... ... ... ..157
22.5 Update IDP Signatures .................................. ... ... ... .... ... ... ... .... ... ..................................................160
22.5.1 Update Signature Examples ................................................................................................161
22.6 IDP Statistics .................................................................................................................................161
22.6.1 IDP Statistics Example ........................................................................................................162
NXC CLI Reference Guide
9
Page 10

Table of Contents
Chapter 23
Device HA..........................................................................................................................................163
23.1 Device HA Overview .....................................................................................................................163
23.1.1 Before You Begin .................................................................................................................164
23.2 General Device HA Commands ........................ ................................................................ ............164
23.3 Active-Passive Mode Device HA ...................................................................................................164
23.4 Active-Passive Mode Device HA Commands ...............................................................................165
23.4.1 Active-Passive Mode Device HA Commands ......................................................................165
23.4.2 Active-Passive Mode Device HA Command Example ........................................................167
Chapter 24
User/Group........................................................................................................................................169
24.1 User Account Overview .................................................................................................................169
24.1.1 User Types ..........................................................................................................................169
24.2 User/Group Commands Summary .......................... ....................................... ...............................170
24.2.1 User Commands ..................................................................................................................170
24.2.2 User Group Commands .......................................................................................................171
24.2.3 User Setting Commands .....................................................................................................171
24.2.4 MAC Auth Commands .........................................................................................................173
24.2.5 Additional User Commands .................................................................................................174
Chapter 25
Addresses .........................................................................................................................................177
25.1 Address Overview .........................................................................................................................177
25.2 Address Commands Summary .....................................................................................................178
25.2.1 Address Object Commands .................................................................................................178
25.2.2 Address Group Commands ................................................................................................. 179
Chapter 26
Services.............................................................................................................................................181
26.1 Services Overview ........................................................................................................................181
26.2 Services Commands Summary .....................................................................................................181
26.2.1 Service Object Commands ................................ ...................................................... ............181
26.2.2 Service Group Commands ..................................................................................................182
Chapter 27
Schedules..........................................................................................................................................185
27.1 Schedule Overview .......................................................................................................................185
27.2 Schedule Commands Summary ...................................................................................................185
27.2.1 Schedule Command Examples ...........................................................................................186
Chapter 28
AAA Server........................................................................................................................................187
10
NXC CLI Reference Guide
Page 11

Table of Contents
28.1 AAA Server Overview ...................................................................................................................187
28.2 Authentication Server Command Summary ................................ ... ... ... .... ... ..................................187
28.2.1 aaa group server ad Commands .........................................................................................188
28.2.2 aaa group server ldap Commands ......................................................................................189
28.2.3 aaa group server radius Commands ...................................................................................190
28.2.4 aaa group server Command Example .................................................................................192
Chapter 29
Authentication Objects.....................................................................................................................193
29.1 Authentication Objects Overview ..................................................................................................193
29.2 aaa authentication Commands .....................................................................................................193
29.2.1 aaa authentication Command Example ...............................................................................194
29.3 test aaa Command ........................................................................................................................195
29.3.1 Test a User Account Command Example ............................................................................195
Chapter 30
Authentication Server ......................................................................................................................197
30.1 Authentication Server Overview ........................... .................................... .....................................197
30.2 Authentication Server Commands ................................................................................................197
30.2.1 Authentication Server Command Examples ........................................................................198
Chapter 31
ENC ....................................................................................................................................................199
31.1 ENC Overview ...............................................................................................................................199
31.2 ENC-Agent Commands .................................................................................................................199
31.2.1 ENC-Agent Command Examples ........................................................................................201
Chapter 32
Certificates........................................................................................................................................203
32.1 Certificates Overview ....................................................................................................................203
32.2 Certificate Commands ...................................................................................................................203
32.3 Certificates Commands Input Values ............................................. ... ... .... ... ... ... .... ... .....................203
32.4 Certificates Commands Summary .......................... .... ... ... ... .... ... ... ... ... .... ... ... ... .... ... ... ..................204
32.5 Certificates Commands Examples .... ... ... ... .... ... ... ... .... ... ... ... .... ......................................... .... ... ... ..206
Chapter 33
System...............................................................................................................................................207
33.1 System Overview ..........................................................................................................................207
33.2 Customizing the WWW Login Page ..............................................................................................207
33.3 Host Name Commands .................................................................................................................209
33.4 Time and Date ..............................................................................................................................209
33.4.1 Date/Time Commands .................................................... ............................................. ........210
33.5 Console Port Speed .....................................................................................................................211
NXC CLI Reference Guide
11
Page 12

Table of Contents
33.6 DNS Overview ..............................................................................................................................211
33.6.1 DNS Commands ..................................................................................................................211
33.6.2 DNS Command Example ....................................................................................................212
Chapter 34
System Remote Management..........................................................................................................213
34.1 Remote Management Overview .................................................................................................... 213
34.1.1 Remote Management Limitations ........................................................................................213
34.1.2 System Timeout ...................................................................................................................213
34.2 Common System Command Input Values ....................................................................................214
34.3 HTTP/HTTPS Commands .............................................................................................................214
34.3.1 HTTP/HTTPS Command Examples ....................................................................................215
34.4 SSH ...............................................................................................................................................216
34.4.1 SSH Implementation on the NXC ........................................................................................216
34.4.2 Requirements for Using SSH ................................... ... .... ... ... ... ... .........................................216
34.4.3 SSH Commands ..................................................................................................................216
34.4.4 SSH Command Examples ...................................................................................................217
34.5 Telnet ............................................................................................................................................217
34.6 Telnet Commands .........................................................................................................................218
34.6.1 Telnet Commands Examples ................................................... ............................................ 218
34.7 Configuring FTP ...........................................................................................................................219
34.7.1 FTP Commands ..................................................................................................................219
34.7.2 FTP Commands Examples ..................................................................................................219
34.8 SNMP ...........................................................................................................................................220
34.8.1 Supported MIBs ...................................................................................................................220
34.8.2 SNMP Traps ........................................................................................................................220
34.8.3 SNMP Commands ...............................................................................................................221
34.8.4 SNMP Commands Examples ..............................................................................................222
34.9 Language Commands ...................................................................................................................222
Chapter 35
File Manager......................................................................................................................................223
35.1 File Directories ..............................................................................................................................223
35.2 Configuration Files and Shell Scripts Overview ............... ....................................... ... ..................223
35.2.1 Comments in Configuration Files or Shell Scripts ...............................................................224
35.2.2 Errors in Configuration Files or Shell Scripts .......................................................................225
35.2.3 NXC Configuration File Details ................................ ............................................................225
35.2.4 Configuration File Flow at Restart .......................................................................................226
35.3 File Manager Commands Input Values .........................................................................................226
35.4 File Manager Commands Summary .............................................................................................227
35.5 File Manager Command Example ........................ ....... ...... ... ....... ...... ....... ...... ....... ...... ...... .... ........228
35.6 FTP File Transfer ..........................................................................................................................228
35.6.1 Command Line FTP File Upload .........................................................................................228
12
NXC CLI Reference Guide
Page 13

Table of Contents
35.6.2 Command Line FTP Configuration File Upload Example ....................................................229
35.6.3 Command Line FTP File Download .....................................................................................229
35.6.4 Command Line FTP Configuration File Download Example ...............................................230
35.7 NXC File Usage at Startup ............................................................................................................230
35.8 Notification of a Damaged Recovery Image or Firmware .............................................................231
35.9 Restoring the Recovery Image (NXC5200 Only) ..........................................................................232
35.10 Restoring the Firmware ...............................................................................................................234
35.11 Restoring the Default System Database .....................................................................................236
35.11.1 Using the atkz -u Debug Command (NXC5200 Only) .......................................................238
Chapter 36
Logs...................................................................................................................................................241
36.1 Log Commands Summary ............................................................................................................241
36.1.1 Log Entries Commands .......................................................................................................242
36.1.2 System Log Commands ......................................................................................................242
36.1.3 Debug Log Commands ........................................................................................................243
36.1.4 E-mail Profile Log Commands .............................................................................................244
36.1.5 Console Port Log Commands .............................................................................................246
36.1.6 Access Point Logging Commands .............................. ....................... ...................... ............246
Chapter 37
Reports and Reboot..........................................................................................................................249
37.1 Report Commands Summary ........................................................................................................249
37.1.1 Report Commands ..............................................................................................................249
37.1.2 Report Command Examples ...............................................................................................250
37.1.3 Session Commands ............................................................................................................250
37.2 Email Daily Report Commands ............................ .........................................................................251
37.2.1 Email Daily Report Example .......................... .......................................................... ............253
37.3 Reboot ...........................................................................................................................................254
Chapter 38
Session Timeout...............................................................................................................................255
Chapter 39
Diagnostics .......................................................................................................................................257
39.1 Diagnostics ....................................................................................................................................257
39.2 Diagnosis Commands ...................................................................................................................257
39.3 Diagnosis Commands Example ....................................................................................................257
Chapter 40
Packet Flow Explore.........................................................................................................................259
40.1 Packet Flow Explore .....................................................................................................................259
40.2 Packet Flow Explore Commands ...................... ............................................................................259
40.3 Packet Flow Explore Commands Example ...................................................................................260
NXC CLI Reference Guide
13
Page 14

Table of Contents
Chapter 41
Maintenance Tools............................................................................................................................261
41.1 Maintenance Tools Commands ................................................................................................ .....261
41.1.1 Command Examples ...........................................................................................................263
Chapter 42
Watchdog Timer................................................................................................................................267
42.1 Hardware Watchdog Timer .................. ... ... .... ...................................... .... ... ... ... .... ... ... ... ... ............267
42.2 Software Watchdog Timer .............................................................. ... ... .... ... ... ... .... ... ... ... ...............267
42.3 Application Watchdog ...................................................................................................................268
42.3.1 Application Watchdog Commands Example ........................................................................269
Chapter 43
Managed AP Commands..................................................................................................................271
43.1 Managed Series AP Commands Overview ...................................................................................271
43.2 Accessing the AP CLI ...................................................................................................................271
43.3 CAPWAP Client Commands .........................................................................................................272
43.3.1 CAPWAP Client Commands Example .................................................................................273
43.4 DNS Server Commands ................................................................................................................274
43.4.1 DNS Server Commands Example ....................................................................................... 274
43.4.2 DNS Server Commands and DHCP ........................ ....................................................... .....275
List of Commands ............................................................................................................................277
14
NXC CLI Reference Guide
Page 15
CHAPTER 1
Command Line Interface
This chapter describes how to access and use the CLI (Command Line Interface).
1.1 Overview
If you have problems with your NXC, customer support may request that you issue some of
these commands to assist them in troubleshooting.
Use of undocumented commands or misconfiguration can damage the NXC
and possibly render it unusable.
1.1.1 The Configuration File
When you configure the NXC using either the CLI (Command Line Interface) or the web
configurator, the settings are saved as a series of commands in a configuration file on the
NXC. You can store more than one configuration file on the NXC. However, only one
configuration file is used at a time.
You can perform the following with a configuration file:
• Back up NXC configuration once the NXC is set up to work in your network.
• Restore NXC configuration.
• Save and edit a configuration file and upload it to multiple NXCs in your network to have
the same settings.
You may also edit a configuration file using a text editor.
1.2 Accessing the CLI
You can access the CLI using a terminal emulation program on a computer connected to the
console port, from the web configurator or access the NXC using Telnet or SSH (Secure
SHell).
NXC CLI Reference Guide
15
Page 16
Chapter 1 Command Line Interface
The NXC might force you to log out of your session if reauthentication time,
lease time, or idle timeout is reached. See Chapter 24 on page 169 for more
information about these settings.
1.2.1 Console Port
The default settings for the console port are as follows.
Table 1 Managing the NXC: Console Port
SETTING VALUE
Speed 115200 bps
Data Bits 8
Parity None
Stop Bit 1
Flow Control Off
When you turn on your NXC, it performs several internal tests as well as line initialization.
You can view the initialization information using the console port.
• Garbled text displays if your terminal emulation program’s speed is set lower than the
NXC’s.
• No text displays if the speed is set higher than the NXC’s.
• If changing your terminal emulation program’s speed does not get anything to display,
restart the NXC.
• If restarting the NXC does not get anything to display, contact your local customer
support.
Figure 1 Console Port Power-on Display
Flash: 8 MiB
BootModule Version: V0.9.1 | 2012-12-28 13:01:22
DRAM: Size = 1024 Mbytes
DRAM POST: Testing: 262144K
After the initialization, the login screen displays.
16
Figure 2 Login Screen
Welcome to NXC
Username:
NXC CLI Reference Guide
Page 17
Chapter 1 Command Line Interface
Enter the user name and password at the prompts.
The default login username is admin and password is 1234. The username
and password are case-sensitive.
1.2.2 Web Configurator Console
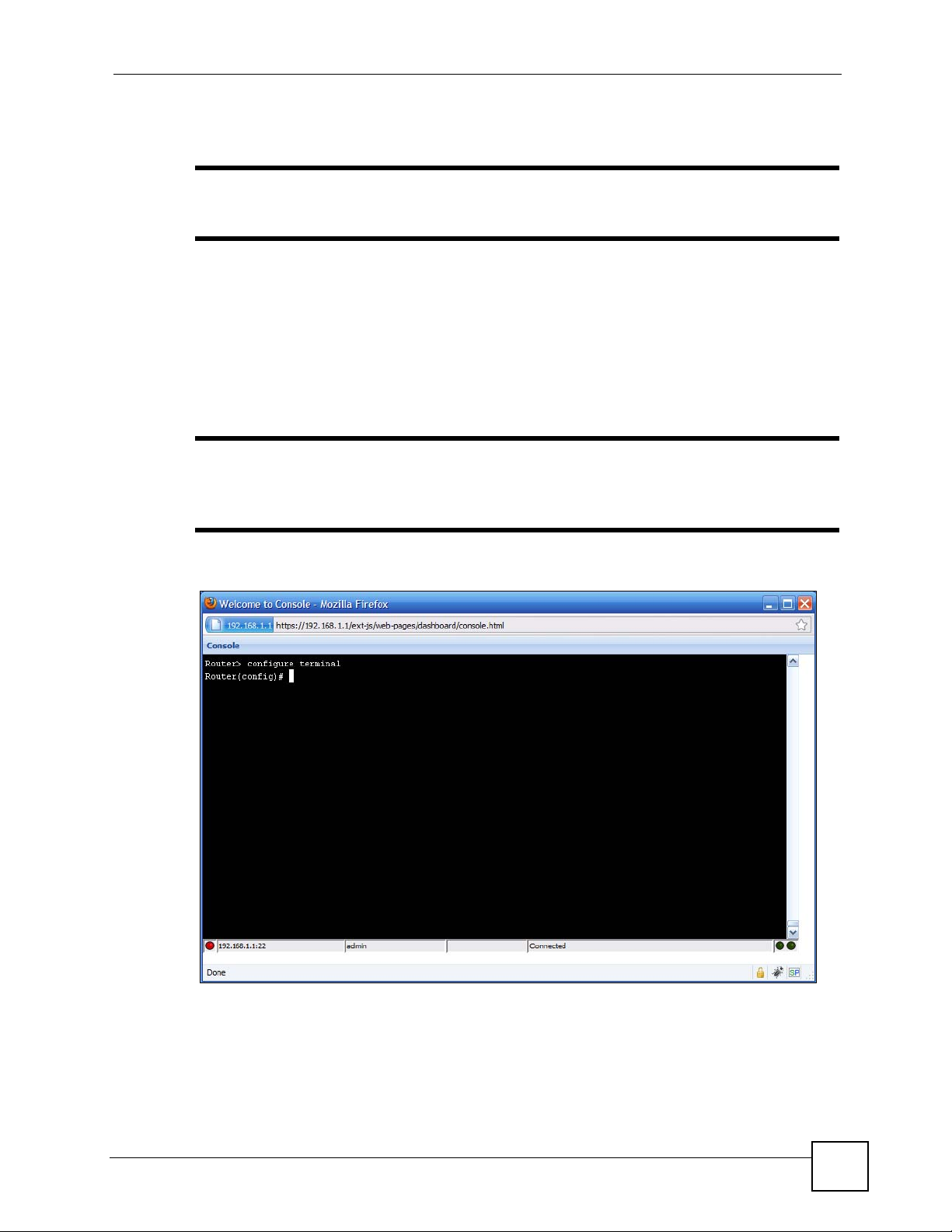
The Console allows you to use CLI commands from directly within the Web Configurator
rather than having to use a separate terminal program. In addition to logging in directly to the
NXC’s CLI, you can also log into other devices on the network through this Console. It uses
SSH to establish a connection.
To view the functions in the Web Configurator user interface that correspond
directly to specific NXC CLI commands, use the CLI Messages window
(described in the User’s Guide) in tandem with this one.
Figure 3 Console
NXC CLI Reference Guide
17
Page 18
Chapter 1 Command Line Interface
The following table describes the elements in this screen.
Table 2 Console
LABEL DESCRIPTION
Command Line
Enter commands for the device that you are currently logged into here. If you are
logged into the NXC, see the CLI Reference Guide for details on using the
command line to configure it.
Device IP
Address
This is the IP address of the device that you are currently logged into.
Logged-In User
This displays the username of the account currently logged into the NXC through
the Console Window.
Y ou can log into the Web Configurator with a different account than used to log into
the NXC through the Console.
Connection
Status
This displays the connection status of the account currently logged in.
If you are logged in and connected, then this displays ‘Connected’.
If you lose the connection, get disconnected, or logout, then this displays ‘Not
Connected’.
Tx/RX Activity
Monitor
This displays the current upload / download activity. The faster and more frequently
an LED flashes, the faster the data connection.
Before you use the Console, ensure that:
• Your web browser of choice allows pop-up windows from the IP address assigned to your
NXC.
• Your web browser allows Java programs.
• You are using the latest version of the Java program (http://www.java.com).
To login in through the Console:
1 Click the Console button on the Web Configurator title bar.
18
NXC CLI Reference Guide
Page 19
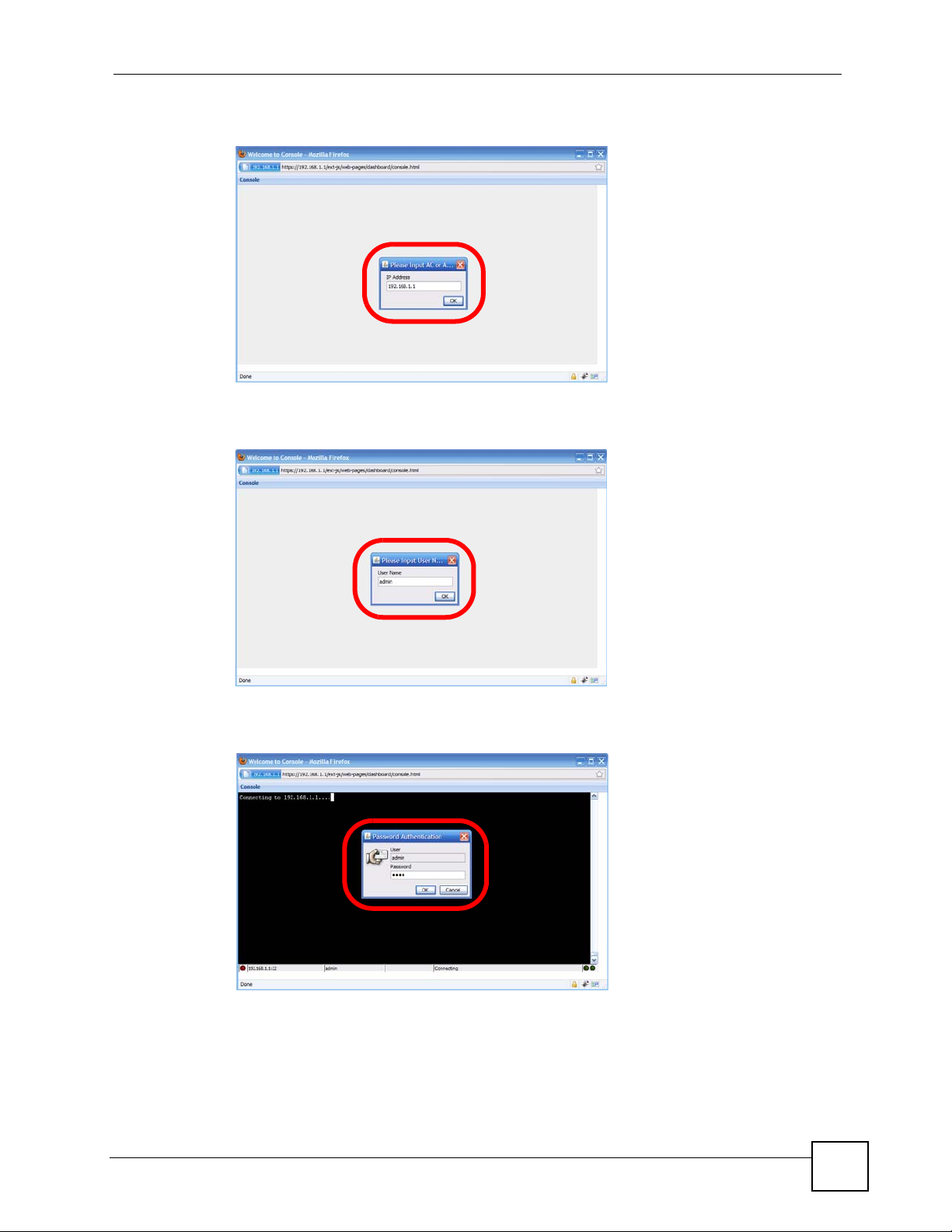
Chapter 1 Command Line Interface
2 Enter the IP address of the NXC and click OK.
3 Next, enter the user name of the account being used to log into your target device and
then click OK.
4 You may be prompted to authenticate your account password, depending on the type of
device that you are logging into. Enter the password and click OK.
NXC CLI Reference Guide
19
Page 20

Chapter 1 Command Line Interface
5 If your login is successful, the command line appears and the status bar at the bottom of
the Console updates to reflect your connection state.
1.2.3 Telnet
Use the following steps to Telnet into your NXC.
1 If your computer is connected to the NXC over the Internet, skip to the next step. Make
sure your computer IP address and the NXC IP address are on the same subnet.
2 In Windows, click Start (usually in the bottom left corner) and Run. Then type
and the NXC’s IP address. For example, enter telnet 192.168.1.1 (the default
management IP address).
3 Click OK. A login screen displays. Enter the user name and password at the prompts.
telnet
The default login username is admin and password is 1234. The username
and password are case-sensitive.
1.2.4 SSH (Secure SHell)
You can use an SSH client program to access the CLI. The following figure shows an example
using a text-based SSH client program. Refer to the documentation that comes with your SSH
program for information on using it.
The default login username is admin and password is 1234. The username
and password are case-sensitive.
20
NXC CLI Reference Guide
Page 21
Figure 4 SSH Login Example
C:\>ssh2 admin@192.168.1.1
Host key not found from database.
Key fingerprint:
xolor-takel-fipef-zevit-visom-gydog-vetan-bisol-lysob-cuvun-muxex
You can get a public key's fingerprint by running
% ssh-keygen -F publickey.pub
on the keyfile.
Are you sure you want to continue connecting (yes/no)? yes
Host key saved to C:/Documents and Settings/user/Application Data/SSH/
hostkeys/
ey_22_192.168.1.1.pub
host key for 192.168.1.1, accepted by user Tue Aug 09 2005 07:38:28
admin's password:
Authentication successful.
1.3 How to Find Commands in this Guide
Chapter 1 Command Line Interface
You can simply look for the feature chapter to find commands. In addition, you can use the
List of Commands at the end of the guide. This section lists the commands in alphabetical
order that they appear in this guide.
If you are looking at the CLI Reference Guide electronically, you might have additional
options (for example, bookmarks or Find...) as well.
1.4 How Commands Are Explained
Each chapter explains the commands for one keyword. The chapters ar e divided into the
following sections.
1.4.1 Background Information
See the User’s Guide for background information about most features.
This section provides background information about features that you cannot configure in the
web configurator. In addition, this section identifies related commands in other chapters.
1.4.2 Command Input Values
This section lists common input values for the commands for the feature in one or more tables
NXC CLI Reference Guide
21
Page 22

Chapter 1 Command Line Interface
1.4.3 Command Summary
This section lists the commands for the feature in one or more tables.
1.4.4 Command Examples
This section contains any examples for the commands in this feature.
1.4.5 Command Syntax
The following conventions are used in this guide.
• A command or keyword in courier new must be entered literally as shown. Do not
abbreviate.
• Values that you need to provide are in italics.
• Required fields that have multiple choices are enclosed in curly brackets
• A range of numbers is enclosed in angle brackets
• Optional fields are enclosed in square brackets
•The
| symbol means OR.
{}.
<>.
[].
For example, look at the following command to create a TCP/UDP service object.
service-object object-name {tcp | udp} {eq <1..65535> | range <1..65535>
<1..65535>}
1 Enter service-object exactly as it appears.
2 Enter the name of the object where you see object-name.
3 Enter
tcp or udp, depending on the service object you want to create.
4 Finally , do one of the following.
•Enter
•Enter
eq exactly as it appears, followed by a number between 1 and 65535.
range exactly as it appears, followed by two numbers between 1 and 65535.
1.4.6 Changing the Password
It is highly recommended that you change the password for accessing the NXC. See Section
24.2 on page 170 for the appropriate commands.
1.5 CLI Modes
You run CLI commands in one of several modes.
Table 3 CLI Modes
USER PRIVILEGE CONFIGURATION SUB-COMMAND
What Guest users
can do
What User users
can do
Unable to access Unable to access Unable to access Unable to access
• Look at (but not
run) available
commands
Unable to access Unable to access Unable to access
22
NXC CLI Reference Guide
Page 23
Chapter 1 Command Line Interface
Table 3 CLI Modes (continued)
USER PRIVILEGE CONFIGURATION SUB-COMMAND
What LimitedAdmin users can
do
What Admin
users can do
How you enter it Log in to the NXC Type enable in User
What the prompt
looks like
How you exit it Type exit Type disable Type exit Type exit
• Look at system
information (like
Status screen)
• Run basic
diagnostics
• Look at system
information (like
Status screen)
• Run basic
diagnostics
Router> Router# Router(config)# (varies by part)
• Look at system
information (like
Status screen)
• Run basic
diagnostics
• Look at system
information (like
Status screen)
• Run basic
diagnostics
mode
Unable to access Unable to access
• Configure simple
features (such as
an address
object)
• Create or remove
complex parts
(such as an
interface)
Type configure
terminal in User or
Privilege mode
• Configure
complex parts
(such as an
interface) in the
NXC
Type the command
used to create the
specific part in
Configuration mode
Router(zone)#
Router(configif-ge)#
...
See Chapter 24 on page 169 for more information about the user types. User users can only
log in, look at (but not run) the available commands in User mode, and log out. Limited-
Admin users can look at the configuration in the web configurator and CLI, and they can run
basic diagnostics in the CLI. Admin users can configure the NXC in the web configurator or
CLI.
At the time of writing, there is not much difference between User and Privilege mode for
admin users. This is reserved for future use.
1.6 Shortcuts and Help
1.6.1 List of Available Commands
A list of valid commands can be found by typing ? or [TAB] at the command prompt. To view a
list of available commands within a command group, enter
[TAB].
<command> ? or <command>
NXC CLI Reference Guide
23
Page 24

Chapter 1 Command Line Interface
Figure 5 Help: Available Commands Example 1
Router> ?
<cr>
apply
atse
clear
configure
------------------[Snip]-------------------shutdown
telnet
test
traceroute
write
Router>
Figure 6 Help: Available Command Example 2
Router> show ?
<wlan ap interface>
aaa
access-page
account
ad-server
address-object
------------------[Snip]-------------------wlan
workspace
zone
Router> show
1.6.2 List of Sub-commands or Required User Input
To view detailed help information for a command, enter <command> <sub command> ?.
Figure 7 Help: Sub-command Information Example
Router(config)# ip telnet server ?
;
<cr>
port
rule
|
Router(config)# ip telnet server
Figure 8 Help: Required User Input Example
Router(config)# ip telnet server port ?
<1..65535>
Router(config)# ip telnet server port
24
NXC CLI Reference Guide
Page 25

1.6.3 Entering Partial Commands
The CLI does not accept partial or incomplete commands. You may enter a unique part of a
command and press
[TAB] to have the NXC automatically display the full command.
Chapter 1 Command Line Interface
For example, if you enter
config and press [TAB] , the full command of configure
automatically displays.
If you enter a partial command that is not unique and press
commands that start with the partial command.
Figure 9 Non-Unique Partial Command Example
Router# c [TAB]
clear configure copy
Router# co [TAB]
configure copy
1.6.4 Entering a ? in a Command
Typing a ? (questio n mark) usually displays help information. However, some commands
allow you to input a ?, for example as part of a string. Press [CTRL+V] on your keyboard to
enter a ? without the NXC treating it as a help query.
1.6.5 Command History
The NXC keeps a list of commands you have entered for the current CLI session. You can use
any commands in the history again by pressing the up () or down () arrow key to scroll
through the previously used commands and press
[TAB], the NXC displays a list of
[ENTER].
1.6.6 Navigation
Press [CTRL]+A to move the cursor to the beginning of the line. Press [CTRL]+E to move the
cursor to the end of the line.
1.6.7 Erase Current Command
Press [CTRL]+U to erase whatever you have currently typed at the prompt (before pressing
[ENTER]).
1.6.8 The no Commands
When entering the no commands described in this document, you may not need to type the
whole command. For example, with the “[no] mss <536..1452>” command, you use
“mss 536” to specify the MSS value. But to disable the MSS setting, you only need to type
“no mss” instead of “no mss 536”.
NXC CLI Reference Guide
25
Page 26
Chapter 1 Command Line Interface
1.7 Input Values
You can use the ? or [TAB] to get more information about the next input value that is required
for a command. In some cases, the next input value is a string whose length and allowable
characters may not be displayed in the screen. For example, in the following example, the next
input value is a string called
Router# configure terminal
Router(config)# interface ge1
Router(config-if-ge)# description
<description>
<description>.
The following table provides more information about input values like
<description>.
Table 4 Input-Value Formats for Strings in CLI Commands
TAG # VALUES LEGAL VALUES
* 1*
all -- ALL
authentication key 32-40
16-20
Used in MD5 authentication keys and text authentication key
0-16 alphanumeric or _Used in text authentication keys
0-8 alphanumeric or _-
certificate name 1-31 alphanumeric or ;`~!@#$%^&()_+[\]{}',.=-
community string 0-63 alphanumeric or .-
connection_id 1+ alphanumeric or -_:
contact 1-61 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-.
country code 0 or 2 alphanumeric
custom signature file
name
description Used in keyword criteria for log entries
distinguished name 1-511 alphanumeric, spaces, or .@=,_-
domain name 0+ lower-case letters, numbers, or .-
email 1-63 alphanumeric or .@_-
0-30 alphanumeric or _-.
1-64 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-.
Used in other commands
1-61 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-
Used in ip dns server
1-248 alphanumeric or .-
Used in domainname, ip dhcp pool, and ip domain
1-255 alphanumeric or ._-
“0x” or “0X” + 32-40 hexadecimal values
alphanumeric or ;|`~!@#$%^&*()_+\\{}':,./<>=-
first character: alphanumeric or -
first character: letter
first character: alphanumeric or -
first character: alphanumeric or -
26
NXC CLI Reference Guide
Page 27
Chapter 1 Command Line Interface
Table 4 Input-Value Formats for Strings in CLI Commands (continued)
TAG # VALUES LEGAL VALUES
e-mail 1-64 alphanumeric or .@_-
encryption key 16-64
8-32
file name 0-31 alphanumeric or _-
filter extension 1-256 alphanumeric, spaces, or '()+,/:=?;!*#@$_%.-
fqdn Used in ip dns server
1-253 alphanumeric or .-
Used in ip, time server, device HA, certificates, and
interface ping check
1-255 alphanumeric or .-
full file name 0-256 alphanumeric or _/.-
hostname Used in hostname command
1-64 alphanumeric or .-_
Used in other commands
1-253 alphanumeric or .-
import configuration
file
import shell script 1-
initial string 1-64 alphanumeric, spaces, or '()+,/:=!*#@$_%-.&
key length -- 512, 768, 1024, 1536, 2048
license key 25 “S-” + 6 upper-case letters or numbers + “-” + 16
mac address -- aa:bb:cc:dd:ee:ff (hexadecimal)
mail server fqdn lower-case letters, numbers, or -.
name 1-31 alphanumeric or _-
notification message 1-81 alphanumeric, spaces, or '()+,/:=?;!*#@$_%-
password: less than 15
chars
password: less than 8
chars
126+”.conf”
26+”.zysh”
1-15 alphanumeric or `~!@#$%^&*()_\-+={}|\;:'<,>./
1-8 alphanumeric or ;/?:@&=+$\.-_!~*'()%,#$
“0x” or “0X” + 16-64 hexadecimal values
alphanumeric or ;\|`~!@#$%^&*()_+\\{}':,./<>=-
first character: alphanumeric or -
first character: alphanumeric or -
first character: alphanumeric or -
first character: alphanumeric or alphanumeric or ;`~!@#$%^&()_+[]{}',.=-
add “.conf” at the end
alphanumeric or ;`~!@#$%^&()_+[]{}',.=-
add “.zysh” at the end
upper-case letters or numbers
NXC CLI Reference Guide
27
Page 28
Chapter 1 Command Line Interface
Table 4 Input-Value Formats for Strings in CLI Commands (continued)
TAG # VALUES LEGAL VALUES
password Used in user and ip
1-63 alphanumeric or `~!@#$%^&*()_-+={}|\;:'<,>./
Used in e-mail log profile SMTP authentication
1-63 alphanumeric or `~!@#$%^&*()_-+={}|\;:'<>./
Used in device HA synchronization
1-63 alphanumeric or ~#%^*_-={}:,.
Used in registration
6-20 alphanumeric or .@_-
phone number 1-20 numbers or ,+
preshared key 16-64 “0x” or “0X” + 16-64 hexadecimal values
alphanumeric or ;|`~!@#$%^&*()_+\{}':,./<>=-
profile name 1-31 alphanumeric or _-
first character: letters or _-
proto name 1-16 lower-case letters, numbers, or -
protocol name 1-31 alphanumeric or _-
first character: letters or _-
quoted string less
than 255 chars
quoted string less
than 63 chars
quoted string 0+ alphanumeric, spaces, or punctuation marks
realm 1-253 alphanumeric or -_
service name 0-63 alphanumeric or -_@$./
spi 2-8 hexadecimal
string less than 15
chars
string: less than 63
chars
string 1+ alphanumeric or -_@
subject 1-61 alphanumeric, spaces, or '()+,./:=?;!*#@$_%-
system type 0-2 hexadecimal
timezone [-+]hh -- -12 through +12 (with or without “ +”)
url 1-511 alphanumeric or '()+,/:.=?;!*#@$_%-
url “http://”+
user name 1-31 alphanumeric or _-
1-255 alphanumeric, spaces, or ;/?:@&=+$\.-_!~*'()%,
1-63 alphanumeric, spaces, or ;/?:@&=+$\.-_!~*'()%
enclosed in double quotation marks (“)
must put a backslash (\) before double quotation
marks that are part of input value itself
first character: alphanumeric or -_
used in domain authentication
1-15 alphanumeric or -_
1-63 alphanumeric or `~!@#$%^&*()_-+={}|\;:'<,>./
alphanumeric or ;/?:@&=+$\.-_!~*'()%,
“https://”+
starts with “http://” or “https://”
may contain one pound sign (#)
first character: letters or _-
28
NXC CLI Reference Guide
Page 29
Chapter 1 Command Line Interface
Table 4 Input-Value Formats for Strings in CLI Commands (continued)
TAG # VALUES LEGAL VALUES
username 1-31 alphanumeric or _-
first character: alphanumeric or _domain authorization
username 6-20 alphanumeric or .@_-
registration
user name 1+ alphanumeric or -_.
logging commands
user@domainname 1-80 alphanumeric or .@_-
vrrp group name: less
than 15 chars
week-day sequence,
i.e. 1=first,2=second
xauth method 1-31 alphanumeric or _-
xauth password 1-31 alphanumeric or ;|`~!@#$%^&*()_+\{}':,./<>=-
mac address 0-12 (even
1-15 alphanumeric or _-
11-4
hexadecimal
number)
for example: xx-xx-xx-xx-xx-xx
1.8 Saving Configuration Changes
Use the write command to save the current configuration to the NXC.
Always save the changes before you log out after each management session.
All unsaved changes will be lost after the system restarts.
1.9 Logging Out
Enter the exit or end command in configure mode to go to privilege mode.
Enter the
exit command in user mode or privilege mode to log out of the CLI.
NXC CLI Reference Guide
29
Page 30

Chapter 1 Command Line Interface
30
NXC CLI Reference Guide
Page 31

CHAPTER 2
User and Privilege Modes
This chapter describes how to use these two modes.
2.1 User And Privilege Modes
This is the mode you are in when you first log into the CLI. (Do not confuse ‘user mode’ with
types of user accounts the NXC uses. See Chapter 24 on page 169 for more information about
the user types. ‘User’ type accounts can only run ‘exit’ in this mode. However, they may need
to log into the device in order to be authenticated for ‘user-aware’ policies, for example a
firewall rule that a particular user is exempt from.)
Type ‘enable’ to go to ‘privilege mode’. No password is required. All commands can be run
from here except those marked with an asterisk. Many of these commands are for troubleshooting purposes, for example the htm (hardware test module) and debug commands.
Customer support may ask you to run some of these commands and send the results if you
need assistance troubleshooting your device.
For admin logins, all commands are visible in ‘user mode’ but not all can be run there. The
following table displays which commands can be run in ‘user mode’. All commands can be
run in ‘privilege mode’.
The htm and psm commands are for ZyXEL’s internal manufacturing process.
Table 5 User (U) and Privilege (P) Mode Commands
COMMAND MODE DESCRIPTION
apply P Applies a configuration file.
atse U/P Displays the seed code
clear U/P Clears system or debug logs or DHCP binding.
configure U/P Use ‘configure terminal’ to enter configuration mode.
copy P Copies configuration files.
debug (*) U/P For support personnel only! The device needs to have the debug flag enabled.
delete P Deletes configuration files.
details P Performs diagnostic commands.
diag P Provided for support personnel to collect internal system information. It is not
recommended that you use these.
NXC CLI Reference Guide
31
Page 32

Chapter 2 User and Privilege Modes
Table 5 User (U) and Privilege (P) Mode Commands (continued)
COMMAND MODE DESCRIPTION
diag-info P Has the NXC create a new diagnostic file.
dir P Lists files in a directory.
disable U/P Goes from privilege mode to user mode
enable U/P Goes from user mode to privilege mode
exit U/P Goes to a previous mode or logs out.
htm U/P Goes to htm (hardware test module) mode for testing hardware components. You
may need to use the htm commands if your customer support Engineer asks you
to during troubleshooting.
Note: These commands are for ZyXEL’s internal manufacturing
process.
interface U/P Dials or disconnects an interface.
no packet-trace U/P Turns of packet tracing.
nslookup U/P Resolves an IP add ress to a host name and vice -versa.
packet-trace U/P Performs a packet trace.
ping U/P Pings an IP address or host name.
psm U/P Goes to psm (product support module) mode for setting product parameters. You
may need to use the htm commands if your customer support Engineer asks you
to during troubleshooting.
Note: These commands are for ZyXEL’s internal manufacturing
process.
reboot P Restarts the device.
release P Releases DHCP information from an interface.
rename P Renames a configuration file.
renew P Renews DHCP information for an interface.
run P Runs a script.
setenv U/P Turns stop-on-error on (terminates booting if an error is found in a configuration
file) or off (ignores configuration file errors and continues booting).
show U/P Displays command statistics. See the associated command chapter in this guide.
shutdown P Writes all d data to disk and stops the system processes. It does not turn off the
power.
telnet U/P Establishes a connection to the TCP port number 23 of the specified host name or
IP address.
test aaa U/P Tests whether the specified user name can be successfully authenticated by an
traceroute P Traces the route to the specified host name or IP address.
write P Saves the current configuration to the NXC. All unsaved changes are lost after the
external authentication server.
NXC restarts.
Subsequent chapters in this guide describe the configuration commands. User/privilege mode
commands that are also configuration commands (for example, ‘show’) are described in more
detail in the related configuration command chapter.
32
NXC CLI Reference Guide
Page 33

Chapter 2 User and Privilege Modes
2.1.1 Debug Commands
Debug commands marked with an asterisk (*) are not available when the debug flag is on and
are for ZyXEL service personnel use only. The debug commands follow a syntax that is
Linux-based, so if there is a Linux equivalent, it is displayed in this chapter for your reference.
You must know a command listed here well before you use it. Otherwise, it may cause
undesired results.
Table 6 Debug Commands
COMMAND SYNTAX DESCRIPTION LINUX COMMAND EQUIVALENT
debug alg FTP/SIP ALG debug commands
debug app Application patrol debug command
debug app show l7protocol
(*)
debug ca (*) Certificate debug commands
debug device-ha (*) Device HA debug commands
debug force-auth (*) Authentication policy debug commands
debug gui (*) Web Configurator related debug
debug hardware (*) Hardware debug commands
debug idp IDP debug commands
debug idp-av IDP and Anti-Virus debug commands
debug interface Interface debug commands
debug interface ifconfig
[interface]
debug ip dns DNS debug commands
debug ip virtual-server Virtual Server (NAT) debug commands.
debug logging System logging debug commands
debug manufacture Manufacturing related debug
debug network arpignore (*) Enable/Display the ignoring of ARP
debug no registration
server (*)
debug policy-route (*) Policy route debug command
debug service-register Service registration debug command
debug show ipset Lists the NXC‘s received cards
debug show registration-
server status
debug [cmdexec|corefile|ip
|kernel|mac-idrewrite|observer|switch
|system|zyinetpkt|zysh-iptop] (*)
debug update server (*) Update server debug command
Shows app patrol protocol list > cat /etc/l7_protocols/
protocol.list
commands
Shows system interfaces detail > ifconfig [interface]
commands
responses for interfaces which don't
own the IP address
Set the myZyXEL.com registration/
update server to the official site
myZyXEL.com debug commands
ZLD internal debug commands
cat /proc/sys/net/ipv4/
conf/*/arp_ignore
NXC CLI Reference Guide
33
Page 34

Chapter 2 User and Privilege Modes
34
NXC CLI Reference Guide
Page 35

CHAPTER 3
Object Reference
This chapter describes how to use object reference commands.
3.1 Object Reference Commands
The object reference commands are used to see which configuration settings reference a
specific object. You can use this table when you want to delete an object because you have to
remove references to the object first.
Table 7 show reference Commands
COMMAND DESCRIPTION
show reference object username
[username]
show reference object address
[profile]
show reference object service
[profile]
show reference object schedule
[profile]
show reference object aaa
authentication [default |
auth_method]
show reference object ca
category {local|remote}
[cert_name]
show reference object zone
[profile]
show reference object-group
username [username]
show reference object-group
address [profile]
show reference object-group
service [profile]
show reference object-group
interface [profile]
show reference object-group aaa
ad [group_name]
show reference object-group aaa
ldap [group_name]
Displays which configuration settings reference the
specified user object.
Displays which configuration settings reference the
specified address object.
Displays which configuration settings reference the
specified service object.
Displays which configuration settings reference the
specified schedule object.
Displays which configuration settings reference the
specified AAA authentication object.
Displays which configuration settings reference the
specified authentication method object.
Displays which configuration settings reference the
specified zone object.
Displays which configuration settings reference the
specified user group object.
Displays which configuration settings reference the
specified address group object.
Displays which configuration settings reference the
specified service group object.
Displays which configuration settings reference the
specified trunk object.
Displays which configuration settings reference the
specified AAA AD group object.
Displays which configuration settings reference the
specified AAA LDAP group object.
NXC CLI Reference Guide
35
Page 36

Chapter 3 Object Reference
Table 7 show reference Commands (continued)
COMMAND DESCRIPTION
show reference object-group aaa
radius [group_name]
show reference object [wlan-
radio-profile]
show reference object [wlan-
monitor-profile]
show reference object [wlan-
ssid-profile]
show reference object [wlan-
security-profile]
show reference object [wlan-
macfilter-profile]
Displays which configuration settings reference the
specified AAA RADIUS group object.
Displays the specified radio profile object.
Displays the specified monitor profile object.
Displays the specified SSID profile object.
Displays the specified security profile object.
Displays the specified macfilter profile object.
3.1.1 Object Reference Command Example
This example shows how to check which configuration is using an address object named
LAN1_SUBNET. For the command output, firewall rule 3 named LAN1-to-NXC is using the
address object.
Router(config)# show reference object address LAN1_SUBNET
LAN1_SUBNET References:
Category
Rule Priority Rule Name
Description
===========================================================================
Firewall
3 N/A
LAN1-to-NXC
Router(config)#
36
NXC CLI Reference Guide
Page 37

CHAPTER 4
Status
This chapter explains some commands you can use to display information about the NXC’s
current operational state.
4.1 Status Show Commands
The following table describes the commands available for NXC system status.
Table 8 Status Show Commands
COMMAND DESCRIPTION
show boot status Displays details about the NXC’s startup state.
show comport status Displays whether the console and auxiliary ports are on or off.
show cpu status Displays the CPU utilization.
show disk Displays the disk utilization.
show extension-slot Displays the status of the extension card slot and the USB ports and the names of
show fan-speed Displays the current fan speed.
show led status Displays the status of each LED on the NXC.
show mac Displays the NXC’s MAC address.
show mem status Displays what percentage of the NXC’s memory is currently being used.
show ram-size Displays the size of the NXC’s on-board RAM.
show serial-number Displays the serial number of this NXC.
show socket listen Displays the NXC’s listening ports
show socket open Displays the ports that are open on the NXC.
show system uptime Displays how long the NXC has been running since it last restarted or was turned
show version Displays the NXC’s model, firmware and build information.
any connected devices.
on.
NXC CLI Reference Guide
37
Page 38

Chapter 4 Status
Here are examples of the commands that display the CPU and disk utilization.
Router(config)# show cpu status
CPU utilization: 0 %
CPU utilization for 1 min: 0 %
CPU utilization for 5 min: 0 %
Router(config)# show disk
; <cr> |
Router(config)# show disk
No. Disk Size(MB) Usage
===========================================================================
1 image 67 83%
2 onboard flash 163 15%
Here are examples of the commands that display the fan speed, MAC address, memory usage,
RAM size, and serial number.
Router(config)# show fan-speed
FAN1(F00)(rpm): limit(hi)=6500, limit(lo)=1400, max=6650, min=6642, avg=6644
FAN2(F01)(rpm): limit(hi)=6500, limit(lo)=1400, max=6809, min=6783, avg=6795
FAN3(F02)(rpm): limit(hi)=6500, limit(lo)=1400, max=6683, min=6666, avg=6674
FAN4(F03)(rpm): limit(hi)=6500, limit(lo)=1400, max=6633, min=6617, avg=6627
Router(config)# show mac
MAC address: 28:61:32:89:37:61-28:61:32:89:37:67
Router(config)# show mem status
memory usage: 39%
Router(config)# show ram-size
ram size: 1024MB
Router(config)# show serial-number
serial number: S132L06160030
Here is an example of the command that displays the listening ports.
Router(config)# show socket listen
No. Proto Local_Address Foreign_Address State
===========================================================================
1 tcp 0.0.0.0:2601 0.0.0.0:0 LISTEN
2 tcp 0.0.0.0:2602 0.0.0.0:0 LISTEN
3 tcp 127.0.0.1:10443 0.0.0.0:0 LISTEN
4 tcp 0.0.0.0:2604 0.0.0.0:0 LISTEN
5 tcp 0.0.0.0:80 0.0.0.0:0 LISTEN
6 tcp 127.0.0.1:8085 0.0.0.0:0 LISTEN
7 tcp 1.1.1.1:53 0.0.0.0:0 LISTEN
8 tcp 172.16.13.205:53 0.0.0.0:0 LISTEN
9 tcp 10.0.0.8:53 0.0.0.0:0 LISTEN
10 tcp 172.16.13.240:53 0.0.0.0:0 LISTEN
11 tcp 192.168.1.1:53 0.0.0.0:0 LISTEN
12 tcp 127.0.0.1:53 0.0.0.0:0 LISTEN
13 tcp 0.0.0.0:21 0.0.0.0:0 LISTEN
14 tcp 0.0.0.0:22 0.0.0.0:0 LISTEN
15 tcp 127.0.0.1:953 0.0.0.0:0 LISTEN
16 tcp 0.0.0.0:443 0.0.0.0:0 LISTEN
17 tcp 127.0.0.1:1723 0.0.0.0:0 LISTEN
38
NXC CLI Reference Guide
Page 39

Chapter 4 Status
Here is an example of the command that displays the open ports.
Router(config)# show socket open
No. Proto Local_Address Foreign_Address State
===========================================================================
1 tcp 172.16.13.240:22 172.16.13.10:1179 ESTABLISHED
2 udp 127.0.0.1:64002 0.0.0.0:0
3 udp 0.0.0.0:520 0.0.0.0:0
4 udp 0.0.0.0:138 0.0.0.0:0
5 udp 0.0.0.0:138 0.0.0.0:0
6 udp 0.0.0.0:138 0.0.0.0:0
7 udp 0.0.0.0:138 0.0.0.0:0
8 udp 0.0.0.0:138 0.0.0.0:0
9 udp 0.0.0.0:138 0.0.0.0:0
10 udp 0.0.0.0:138 0.0.0.0:0
11 udp 0.0.0.0:32779 0.0.0.0:0
12 udp 192.168.1.1:4500 0.0.0.0:0
13 udp 1.1.1.1:4500 0.0.0.0:0
14 udp 10.0.0.8:4500 0.0.0.0:0
15 udp 172.16.13.205:4500 0.0.0.0:0
16 udp 172.16.13.240:4500 0.0.0.0:0
17 udp 127.0.0.1:4500 0.0.0.0:0
18 udp 127.0.0.1:63000 0.0.0.0:0
19 udp 127.0.0.1:63001 0.0.0.0:0
20 udp 127.0.0.1:63002 0.0.0.0:0
21 udp 0.0.0.0:161 0.0.0.0:0
22 udp 127.0.0.1:63009 0.0.0.0:0
23 udp 192.168.1.1:1701 0.0.0.0:0
24 udp 1.1.1.1:1701 0.0.0.0:0
25 udp 10.0.0.8:1701 0.0.0.0:0
26 udp 172.16.13.205:1701 0.0.0.0:0
27 udp 172.16.13.240:1701 0.0.0.0:0
28 udp 127.0.0.1:1701 0.0.0.0:0
29 udp 127.0.0.1:63024 0.0.0.0:0
30 udp 127.0.0.1:30000 0.0.0.0:0
31 udp 1.1.1.1:53 0.0.0.0:0
32 udp 172.16.13.205:53 0.0.0.0:0
33 udp 10.0.0.8:53 0.0.0.0:0
34 udp 172.16.13.240:53 0.0.0.0:0
35 udp 192.168.1.1:53 0.0.0.0:0
36 udp 127.0.0.1:53 0.0.0.0:0
37 udp 0.0.0.0:67 0.0.0.0:0
38 udp 127.0.0.1:63046 0.0.0.0:0
39 udp 127.0.0.1:65097 0.0.0.0:0
40 udp 0.0.0.0:65098 0.0.0.0:0
41 udp 192.168.1.1:500 0.0.0.0:0
42 udp 1.1.1.1:500 0.0.0.0:0
43 udp 10.0.0.8:500 0.0.0.0:0
44 udp 172.16.13.205:500 0.0.0.0:0
45 udp 172.16.13.240:500 0.0.0.0:0
46 udp 127.0.0.1:500 0.0.0.0:0
NXC CLI Reference Guide
39
Page 40

Chapter 4 Status
Here are examples of the commands that display the system uptime and model, firmware, and
build information.
Router> show system uptime
system uptime: 04:18:00
Router> show version
ZyXEL Communications Corp.
model : NXC5200
firmware version: 2.20(AQQ.0)b3
BM version : 1.08
build date : 2009-11-21 01:18:06
This example shows the current LED states on the NXC. The SYS LED lights on and green.
Router> show led status
sys: green
Router>
40
NXC CLI Reference Guide
Page 41

CHAPTER 5
Registration
This chapter introduces myzyxel.com and shows you how to register the NXC for IDP/
AppPatrol and anti-virus using commands.
5.1 myZyXEL.com overview
myZyXEL.com is ZyXEL’s online services center where you can register your NXC and
manage subscription services available for the NXC.
You need to create an account before you can register your device and
activate the services at myZyXEL.com.
You can directly create a myZyXEL.com account, register your NXC and activate a service
using the Licensing > Registration screens. Alternatively, go to http://www.myZyXEL.com
with the NXC’s serial number and LAN MAC address to register it. Refer to the web site’s online help for details.
To activate a service on a NXC, you need to access myZyXEL.com via that
NXC.
5.1.1 Subscription Services Available on the NXC
The NXC can use anti-virus and IDP/AppPatrol (Intrusion Detection and Prevention and
application patrol) subscription services.
• The NXC’s anti-virus packet scanner uses the signature files on the NXC to detect virus
files. Your NXC scans files transmitting through the enabled interfaces into the network.
Subscribe to signature files for ZyXEL’s anti-virus engine or one powered by Kaspersky.
After the service is activated, the NXC can download the up-to-date signature files from
the update server.
NXC CLI Reference Guide
41
Page 42

Chapter 5 Registration
When using the trial, you can switch from one engine to the other in the Registration
screen. There is no limit on the number of times you can change the anti-virus engine
selection during the trial, but you only get a total of one anti-virus trial period (not a
separate trial period for each anti-virus engine). After the service is activated, the NXC
can download the up-to-date signature files from the update server.
After the trial expires, you need to purchase an iCard for the anti-virus engine you want to
use and enter the PIN number (license key) in the Registration > Service screen. You
must use the ZyXEL anti-virus iCard for the ZyXEL anti-virus engine and the Kaspersky
anti-virus iCard for the Kaspersky anti-virus engine. If you were already using an iCard
anti-virus subscription, any remaining time on your earlier subscription is automatically
added to the new subscription. Even if the earlier iCard anti-virus subscription was for a
different anti-virus engine. For example, suppose you purchase a one-year Kaspersky
engine anti-virus service subscription and use it for six months. Then you purchase a oneyear ZyXEL engine anti-virus service subscription and enter the iCard’s PIN number
(license key) in the Registration > Service screen. The one-year ZyXEL engine anti-virus
service subscription is automatically extended to 18 months.
• The IDP and application patrol features use the IDP/AppPatrol si gnature files on the NXC.
IDP detects malicious or suspicious packets and responds immediately. Application patrol
conveniently manages the use of various applications on the network. After the service is
activated, the NXC can download the up-to-date signature files from the update server.
• You will get automatic e-mail notification of new signature releases from mySecurityZone
after you activate the IDP/AppPatrol service. You can also check for new signatures at
http://mysecurity.zyxel.com.
See the respective chapters for more information about these features.
5.1.2 Maximum Number of Managed APs
The NXC2500 is initially configured to support up to 8 managed APs (such as the NWA5123NI). You can increase this by subscribing to additional licenses. As of this writing, each
license upgrade allows an additional 8 managed APs while the maximum number of APs a
single NXC2500 can support is 24.
The NXC5200 is initially configured to support up to 48 managed APs (such as the
NWA5160N). You can increase this by subscribing to additional licenses. As of this writing,
each license upgrade allows an additional 48 managed APs while the maximum number of
APs a single NXC5200 can support is 240.
To update the signature file or use a subscription service, you have to register
the NXC and activate the corresponding service at myZyXEL.com (through the
NXC).
42
NXC CLI Reference Guide
Page 43

Chapter 5 Registration
5.2 Registration Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 9 Input Values for General Registration Commands
LABEL DESCRIPTION
user_name The user name of your myZyXEL.com account. You may use six to 20
password The password for the myZyXEL.com account. You may use six to 20
The following table describes the commands available for registration. You must use the
configure terminal command to enter the configuration mode before you can use these
commands.
Table 10 Command Summary: Registration
COMMAND DESCRIPTION
device-register checkuser user_name Checks if the user name exists in the
device-register username user_name password
password [e-mail user@domainname country-code
country_code] [reseller-name
reseller_name][reseller-mail user@domainname]
[reseller-phone reseller_phonenumber][vat
vat_number]
service-register checkexpire Gets information of all service subscriptions from
service-register service-type standard licensekey key_value
service-register service-type trial service
{all|av|idp}
service-register service-type trial service all
{kav|zav}
service-register service-type trial service av
{kav|zav}
service-register service-type trial av-engine
{kav|zav}
show device-register status Displays whether the device is registered and
show service-register status {all|idp|av|maps} Displays service license information.
alphanumeric characters (and the underscore). Spaces are not allowed.
alphanumeric characters (and the underscore). Spaces are not allowed.
myZyXEL.com database.
Registers the device with an existing account or
creates a new account and registers the device at
one time.
country_code: see Table 11 on page 44
vat_number: your seller’s Value-Added Tax
number, if you bought your NXC from Europe.
myZyXEL.com and updates the status table.
Activates a standard service subscription with the
license key.
Activates the content filter or IDP trial service
subscription.
Activates all of the trial service subscriptions,
including Kaspersky or ZyXEL anti-virus.
Activates a Kaspersky or ZyXEL anti-virus trial
service subscription.
Changes from one anti-virus engine to the other.
account information.
NXC CLI Reference Guide
43
Page 44

Chapter 5 Registration
5.2.1 Command Examples
The following commands allow you to register your device with an existing account or create
a new account and register the device at one time, and activate a trial service subscription.
Router# configure terminal
Router(config)# device-register username alexctsui password 123456
Router(config)# service-register service-type trial service idp
The following command displays the account information and whether the device is
registered.
Router# configure terminal
Router(config)# show device-register status
username : alexctsui
password : 123456
device register status : yes
expiration self check : no
The following command displays the service registration status and type and how many days
remain before the service expires.
Router# configure terminal
Router(config)# show service-register status all
Service Status Type Count Expiration
===========================================================================
IDP Signature Licensed Standard N/A 698
Anti-Virus Licensed Standard N/A 698
MAPS Licensed Standard 240 N/A
5.3 Country Code
The following table displays the number for each country.
Table 11 Country Codes
COUNTRY CODE COUNTRY NAME COUNTRY CODE COUNTRY NAME
001 Afghanistan 002 Albania
003 Algeria 004 American Samoa
005 Andorra 006 Angola
007 Anguilla 008 Antarctica
009 Antigua & Barbuda 010 Argentina
011 Armenia 012 Aruba
013 Ascension Island 014 Australia
015 Austria 016 Azerbaijan
017 Bahamas 018 Bahrain
44
NXC CLI Reference Guide
Page 45

Chapter 5 Registration
Table 11 Country Codes (continued)
COUNTRY CODE COUNTRY NAME COUNTRY CODE COUNTRY NAME
019 Bangladesh 020 Barbados
021 Belarus 022 Belgium
023 Belize 024 Benin
025 Bermuda 026 Bhutan
027 Bolivia 028 Bosnia and Herzegovina
029 Botswana 030 Bouvet Island
031 Brazil 032 British Indian Ocean Territory
033 Brunei Darussalam 034 Bulgaria
035 Burkina Faso 036 Burundi
037 Cambodia 038 Cameroon
039 Canada 040 Cape Verde
041 Cayman Islands 042 Central African Republic
043 Chad 044 Chile
045 China 046 Ch ristmas Island
047 Cocos (Keeling) Islands 048 Colombia
049 Comoros 050 Congo, Democratic Republic of the
051 Congo, Republic of 052 Cook Islands
053 Costa Rica 054 Cote d'Ivoire
055 Croatia/Hrvatska 056 Cyprus
057 Czech Republic 058 Denmark
059 Djibouti 060 Dominica
061 Dominican Republic 062 East Timor
063 Ecuador 064 Egypt
065 El Salvador 066 E quatorial Guinea
067 Eritrea 068 Estonia
069 Ethiopia 070 Falkland Islands (Malvina)
071 Faroe Islands 072 F iji
073 Finland 074 France
075 France (Metropolitan) 076 French Guiana
077 French Polynesia 078 French Southern Territories
079 Gabon 080 Gambia
081 Georgia 082 Germany
083 Ghana 084 Gibraltar
085 Great Britain 086 Greece
087 Greenland 088 Grenada
089 Guadeloupe 090 Guam
091 Guatemala 092 Guernsey
093 Guinea 094 Guinea-Bissau
NXC CLI Reference Guide
45
Page 46

Chapter 5 Registration
Table 11 Country Codes (continued)
COUNTRY CODE COUNTRY NAME COUNTRY CODE COUNTRY NAME
095 Guyana 096 Haiti
097 Heard and McDonald Islands 098 Holy See (City Vatican State)
099 Honduras 100 Hong Kong
101 Hungary 102 Iceland
103 India 104 Indonesia
105 Ireland 106 Isle of Man
107 Italy 108 Jamaica
109 Japan 110 Jersey
111 Jordan 112 Kazakhstan
113 Kenya 114 Kiribati
115 Korea, Republic of 116 Kuwait
117 Kyrgyzstan 118 Lao People’s Democratic Republic
119 Latvia 120 Lebanon
121 Lesotho 122 Liberia
123 Liechtenstein 124 Lithuania
125 Luxembourg 126 Macau
127 Macedonia, Former Yugoslav
Republic
129 Malawi 130 Malaysia
131 Maldives 132 Mali
133 Malta 13 4 Marshall Islands
135 Martinique 136 Mauritania
137 Mauritius 138 Mayotte
139 Mexico 140 Micronesia, Federal State of
141 Moldova, Republic of 142 Monaco
143 Mongolia 144 Montserrat
145 Morocco 146 Mozambique
147 Namibia 148 Nauru
149 Nepal 150 Netherlands
151 Netherlands Antilles 152 New Caledonia
153 New Zealand 154 Nicaragua
155 Niger 156 Nigeria
157 Niue 158 Norfolk Island
159 Northern Mariana Islands 160 Norway
161 Not Determined 162 Oman
163 Pakistan 164 Palau
165 Panama 166 Papua New Guinea
167 Paraguay 168 Peru
169 Philippines 170 Pitcairn Island
128 Madagascar
46
NXC CLI Reference Guide
Page 47

Chapter 5 Registration
Table 11 Country Codes (continued)
COUNTRY CODE COUNTRY NAME COUNTRY CODE COUNTRY NAME
171 Poland 172 Portugal
173 Puerto Rico 174 Qatar
175 Reunion Island 176 Romania
177 Russian Federation 178 Rwanda
179 Saint Kitts and Nevis 180 Saint Lucia
181 Saint Vincent and the Grenadines 182 San Marino
183 Sao Tome and Principe 184 Saudi Arabia
185 Senegal 186 Seychelles
187 Sierra Leone 188 Singapore
189 Slovak Republic 190 Slovenia
191 Solomon Islands 192 Somalia
193 South Africa 194 South Georgia and the South
185 Spain 196 Sri Lanka
197 St Pierre and Miquelon 198 St. Helena
199 Suriname 200 Svalbard and Jan Mayen Islands
201 Swaziland 202 Sweden
203 Switzerland 204 Taiwan
205 Tajikistan 206 Tanzania
207 Thailand 208 Togo
209 Tokelau 210 Tonga
211 Trinidad and Tobago 212 Tunisia
213 Turkey 214 Turkmenistan
215 Turks and Caicos Islands 216 Tuvalu
217 US Minor Outlying Islands 218 Ug anda
219 Ukraine 220 United Arab Emirates
221 United Kingdom 222 United States
223 Uruguay 224 Uzbekistan
225 Vanuatu 226 Venezuela
227 Vietnam 228 Virgin Islands (British)
229 Virgin Islands (USA) 230 Wallis And Futuna Islands
231 Western Sahara 232 Western Samoa
233 Yemen 234 Yugoslavia
235 Zambia 236 Zimbabwe
Sandwich Islands
NXC CLI Reference Guide
47
Page 48

Chapter 5 Registration
48
NXC CLI Reference Guide
Page 49

CHAPTER 6
Interfaces
This chapter shows you how to use interface-related commands.
6.1 Interface Overview
In general, an interface has the following characteristics.
• An interface is a logical entity through which (layer-3) packets pass.
• An interface is bound to a physical port or another interface.
• Many interfaces can share the same physical port.
• An interface is bound to one zone at most.
• Many interface can belong to the same zone.
• Layer-3 virtualization (IP alias, for example) is a kind of interface.
Some characteristics do not apply to some types of interfaces.
6.1.1 Types of Interfaces
You can create several types of interfaces in the NXC:
• Ethernet interfaces are the foundation for defining other interfaces and network policies.
RIP and OSPF are also configured in these interfaces.
• VLAN interfaces receive and send tagged frames. The NXC automatically adds or
removes the tags as needed.
6.2 Interface General Commands Summary
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 12 Input Values for General Interface Commands
LABEL DESCRIPTION
interface_name The name of the interface.
Ethernet interface: gex, x = 1 - N, where N equals the highest numbered Ethernet
interface for your NXC model.
VLAN interface: vlanx, x = 0 - 4094
NXC CLI Reference Guide
49
Page 50

Chapter 6 Interfaces
Table 12 Input Values for General Interface Commands (continued)
LABEL DESCRIPTION
profile_name The name of the DHCP pool. You may use 1-31 alphanumeric characters,
underscores(
value is case-sensitive.
domain_name Fully-qualified domain name. You may up to 254 alphanumeric characters,
dashes (-), or periods (.), but the first character cannot be a period.
_), or dashes (-), but the first character cannot be a number. This
The following sections introduce commands that are supported by several types of interfaces.
6.2.1 Basic Interface Properties and IP Address Commands
This table lists basic properties and IP address commands.
Table 13 interface General Commands: Basic Properties and IP Address Assignment
COMMAND DESCRIPTION
show interface {ethernet | vlan} status Displays the connection status of the specified type
of interfaces.
show interface {interface_name | ethernet |
vlan | all}
show interface send statistics interval Displays the interval for how often the NXC
show interface summary all Displays basic information about the interfaces.
show interface summary all status Displays the connection status of the interfaces.
[no] interface interface_name Creates the specified interface if necessary and
[no] description description Specifies the description for the specified interface.
[no] downstream <0..1048576> This is reserved for future use.
exit Leaves the sub-command mode.
[no] ip address dhcp Makes the specified interface a DHCP client; the
[no] ip address ip subnet_mask Assigns the specified IP address and subnet mask
[no] ip gateway ip Adds the specified gateway using the specified
ip gateway ip metric <0..15> Sets the priority (relative to every gateway on every
Displays information about the specified interface,
specified type of interfaces, or all interfaces.
refreshes the sent packet statistics for the
interfaces.
enters sub-command mode. The
deletes the specified interface.
The no command clears the description.
description: You can use alphanumeric and
no command
()+/:=?!*#@$_%- characters, and it can be up
to 60 characters long.
Specifies the downstream bandwidth for the
specified interface. The
downstream bandwidth to 1048576.
DHCP server gives the specified interface its IP
address, subnet mask, and gateway. The
command makes the IP address static IP address
for the specified interface. (See the next command
to set this IP address.)
to the specified interface. The
the IP address and the subnet mask.
interface. The
interface) for the specified gateway. The lower the
number, the higher the priority.
no command removes the gateway.
no command sets the
no
no command clears
50
NXC CLI Reference Guide
Page 51

Chapter 6 Interfaces
Table 13 interface General Commands: Basic Properties and IP Address Assignment (continued)
COMMAND DESCRIPTION
[no] mss <536..1460> Specifies the maximum segment size (MSS) the
interface is to use. MSS is the largest amount of
data, specified in bytes, that the interface can
handle in a single, unfragmented piece. The
command has the interface use its default MSS.
[no] mtu <576..1500> Specifies the Maximum Transmission Unit, which is
[no] shutdown Deactivates the specified interface. The
traffic-prioritize {tcp-ack|dns} bandwidth
<0..1048576> priority <1..7> [maximizebandwidth-usage];
traffic-prioritize {tcp-ack|dns}
deactivate
[no] upstream <0..1048576> Specifies the upstream bandwidth for the specified
interface send statistics interval <15..3600> Sets how often the NXC sends interface statistics
show interface-name Displays all Ethernet interface system name and
interface-name ethernet_interface
user_defined_name
the maximum number of bytes in each packet
moving through this interface. The NXC divides
larger packets into smaller fragments. The
command resets the MTU to 1500.
command activates it.
Applies traffic priority when the interface sends
TCP-ACK traffic, or traffic for resolving domain
names. It also sets how much bandwidth the traffic
can use and can turn on maximize bandwidth
usage.
Turns off traffic priority settings for when the
interface sends the specified type of traffic.
interface. The
bandwidth to 1048576.
to external servers. For example, a syslog server.
user-defined name mappings.
Specifies a name for an Ethernet interface. It can
use alphanumeric characters, hyphens, and
underscores, and it can be up to 11 characters
long.
ethernet_interface: This must be the system
name of an Ethernet interface. Use the show
interface-name command to see the system
name of interfaces.
user_defined_name:
• This name cannot be one of the follows:
"ethernet", "ppp", "vlan", "bridge", "virtual",
"wlan", "cellular", "aux", "tunnel", "status",
"summary", "all"
• This name cannot begin with one of the follows
either: "ge", "ppp", "vlan", "wlan-", "br",
"cellular", "aux", "tunnel".
no command sets the upstream
no
no
no
6.2.1.1 Basic Interface Properties Command Examples
The following commands make Ethernet interface ge1 a DHCP client.
Router# configure terminal
Router(config)# interface ge1
Router(config-if)# ip address dhcp
Router(config-if)# exit
NXC CLI Reference Guide
51
Page 52

Chapter 6 Interfaces
This example shows how to modify the name of interface ge4 to “VIP”. First you have to
check the interface system name (ge4 in this example) on the NXC. Then change the name and
display the result.
Router> show interface-name
No. System Name User Defined Name
===========================================================================
1 ge1 ge1
2 ge2 ge2
3 ge3 ge3
4 ge4 ge4
5 ge5 ge5
Router> configure terminal
Router(config)# interface-name ge4 VIP
Router(config)# show interface-name
No. System Name User Defined Name
===========================================================================
1 ge1 ge1
2 ge2 ge2
3 ge3 ge3
4 ge4 VIP
5 ge5 ge5
Router(config)#
This example shows how to restart an interface. You can check all interface names on the
NXC. Then use either the system name or user-defined name of an interface (ge4 or Customer
in this example) to restart it.
Router> show interface-name
No. System Name User Defined Name
===========================================================================
1 ge1 ge1
2 ge2 ge2
3 ge3 ge3
4 ge4 Customer
5 ge5 ge5
Router> configure terminal
Router(config)# interface reset ge4
Router(config)# interface reset Customer
Router(config)#
52
NXC CLI Reference Guide
Page 53

Chapter 6 Interfaces
6.2.2 DHCP Setting Commands
This table lists DHCP setting commands. DHCP is based on DHCP pools. Create a DHCP
pool if you want to assign a static IP address to a MAC address or if you want to specify the
starting IP address and pool size of a range of IP addresses that can be assigned to DHCP
clients. There are different commands for each configuration. Afterwards, in either case, you
have to bind the DHCP pool to the interface.
Table 14 interface Commands: DHCP Settings
COMMAND DESCRIPTION
show ip dhcp dhcp-options Shows the DHCP extended option settings.
show ip dhcp pool [profile_name] Shows information about the specified DHCP poo l
ip dhcp pool rename profile_name profile_name Renames the specified DHCP pool from the first
[no] ip dhcp pool profile_name Creates a DHCP pool if necessary and enters sub-
show Shows information about the specified DHCP pool.
[no] host ip Specifies the static IP address the NXC should
or about all DHCP pools.
profile_name to the second profile_name.
command mode. You can use the DHCP pool to
create a static entry or to set up a range of IP
addresses to assign dynamically.
About the sub-command settings:
• If you use the
this DHCP pool as a static DHCP entry.
• If you do not use the
the network command, the NXC treats this
DHCP pool as a pool of IP addresses.
• If you do not use the
host command, the NXC treats
host command and use
host command or the
network command, the DHCP pool is not
properly configured and cannot be bound to
any interface.
The no command removes the specified DHCP
pool.
Use the following commands if you want to create
a static DHCP entry. If you do not use the
command, the commands that are not in this
section have no effect, but you can still set them.
assign. Use this command, along with
host
hardware-address, to create a static DHCP
entry.
Note: The IP address must be in the
same subnet as the interface to
which you plan to bind the DHCP
pool.
When this command is used, the NXC treats this
DHCP pool like a static entry, regardless of the
network setting. The no command clears this
field.
[no] hardware-address mac_address Reserves the DHCP pool for the specified MAC
address. Use this command, along with host, to
create a static DHCP entry. The
clears this field.
NXC CLI Reference Guide
no command
53
Page 54

Chapter 6 Interfaces
Table 14 interface Commands: DHCP Settings (continued)
COMMAND DESCRIPTION
[no] client-identifier mac_address Specifies the MAC address that appears in the
DHCP client list. The
[no] client-name host_name Specifies the host name that appears in the DHCP
client list. The
host_name: You may use 1-31 alphanumeric
characters, underscores(
first character cannot be a number. This value is
case-sensitive.
Use the following commands if you want to create
a pool of IP addresses. These commands have no
effect if you use the host command. You can still
set them, however.
dhcp-option <1..254> option_name {boolean
<0..1>| uint8 <0..255> | uint16 <0..65535>
| uint32 <0..4294967295> | ip ipv4 [ ipv4 [
ipv4]] | fqdn fqdn [ fqdn [ fqdn]] | text
text | hex hex | vivc enterprise_id hex_s
[enterprise_id hex_s ] | vivs
enterprise_id hex_s [enterprise_id hex_s ]
no dhcp-option <1..254> Removes the DHCP extended option for the
network IP/<1..32>
network ip mask
no network
Adds or edits a DHCP extended option for the
specified DHCP pool.
text: String of up to 250 characters
hex: String of up to 250 hexadecimal pairs.
vivc: Vendor-Identifying Vendor Class option. A
DHCP client may use this option to unambiguously
identify the vendor that manufactured the hardware
on which the client is running, the software in use,
or an industry consortium to which the vendor
belongs.
enterprise_id: Number <0..4294967295>.
hex_s: String of up to 120 hexadecimal pairs.
vivs: Vendor-Identifying Vendor-Specific option.
DHCP clients and servers may use this option to
exchange vendor-specific information.
specified DHCP pool.
Specifies the IP address and subnet mask of the
specified DHCP pool. The subnet mask can be
written in w.x.y.z format or in /<1..32> format.
no command clears this field.
no command clears this field.
_), or dashes (-), but the
54
Note: The DHCP pool must have the
same subnet as the interface to
which you plan to bind it.
The no command clears these fields.
[no] default-router ip Specifies the default gateway DHCP clients should
use. The
[no] description description Specifies a description for the DHCP pool for
identification. The
description.
[no] domain-name domain_name Specifies the domain name assigned to DHCP
clients. The
no command clears this field.
no command removes the
no command clears this field.
NXC CLI Reference Guide
Page 55

Chapter 6 Interfaces
Table 14 interface Commands: DHCP Settings (continued)
COMMAND DESCRIPTION
[no] starting-address ip pool-size
<1..65535>
Sets the IP start address and maximum pool size of
the specified DHCP pool. The final pool size is
limited by the subnet mask.
Note: You must specify the network
number
first, and the start address
must be in the same subnet.
The no command clears the IP start address and
maximum pool size.
[no] first-dns-server {ip | interface_name
{1st-dns | 2nd-dns | 3rd-dns} |
EnterpriseWLAN}
[no] second-dns-server {ip |
interface_name {1st-dns | 2nd-dns | 3rddns} | EnterpriseWLAN}
[no] third-dns-server {ip | interface_name
{1st-dns | 2nd-dns | 3rd-dns} |
EnterpriseWLAN}
[no] first-wins-server ip Specifies the first WINS server IP address to
[no] second-wins-server ip Specifies the second WINS server IP address to
[no] lease {<0..365> [<0..23> [<0..59>]] |
infinite}
interface interface_name Enters sub-command mode.
[no] ip dhcp-pool profile_name Binds the specified interface to the specified DHCP
[no] ip helper-address ip Creates the specified DHCP relay. You have to
release dhcp interface-name Releases the TCP/IP configuration of the specified
renew dhcp interface-name Renews the TCP/IP configuration of the specified
show ip dhcp binding [ip] Displays information about DHCP bindings for the
clear ip dhcp binding {ip | *} Removes the DHCP bindings for the specified IP
Sets the first DNS server to the specified IP
address, the specified interface’s first, second, or
third DNS server, or the NXC itself. The
command resets the setting to its default value.
Sets the second DNS server to the specified IP
address, the specified interface’s first, second, or
third DNS server, or the NXC itself. The
command resets the setting to its default value.
Sets the third DNS server to the specified IP
address, the specified interface’s first, second, or
third DNS server, or the NXC itself. The
command resets the setting to its default value.
assign to the remote users. The no command
removes the setting.
assign to the remote users. The no command
removes the setting.
Sets the lease time to the specified number of
days, hours, and minutes or makes the lease time
infinite. The
server setting to its default value.
pool. You have to remove any DHCP relays first.
The
no command removes the binding.
remove the DHCP pool first, if the DHCP pool is
bound to the specified interface. The
removes the specified DHCP relay.
interface. The interface must be a DHCP client.
This command is available in privilege mode, not
configuration mode.
interface. The interface must be a DHCP client.
This command is available in privilege mode, not
configuration mode.
specified IP address or for all IP addresses.
address or for all IP addresses.
no command resets the first DNS
no
no
no
no command
NXC CLI Reference Guide
55
Page 56

Chapter 6 Interfaces
6.2.2.1 DHCP Setting Command Examples
The following example uses these commands to configure DHCP pool DHCP_TEST.
Router# configure terminal
Router(config)# ip dhcp pool DHCP_TEST
Router(config-ip-dhcp-pool)# network 192.168.1.0 /24
Router(config-ip-dhcp-pool)# domain-name zyxel.com
Router(config-ip-dhcp-pool)# first-dns-server 10.1.5.1
Router(config-ip-dhcp-pool)# second-dns-server ge1 1st-dns
Router(config-ip-dhcp-pool)# third-dns-server 10.1.5.2
Router(config-ip-dhcp-pool)# default-router 192.168.1.1
Router(config-ip-dhcp-pool)# lease 0 1 30
Router(config-ip-dhcp-pool)# starting-address 192.168.1.10 pool-size 30
Router(config-ip-dhcp-pool)# hardware-address 00:0F:20:74:B8:18
Router(config-ip-dhcp-pool)# client-identifier 00:0F:20:74:B8:18
Router(config-ip-dhcp-pool)# client-name TWtester1
Router(config-ip-dhcp-pool)# exit
Router(config)# interface ge1
Router(config-if)# ip dhcp-pool DHCP_TEST
Router(config-if)# exit
Router(config)# show ip dhcp server status
binding interface : ge1
binding pool : DHCP_TEST
56
NXC CLI Reference Guide
Page 57

Chapter 6 Interfaces
6.2.3 Connectivity Check (Ping-check) Commands
Use these commands to have an interface regularly check the connection to the gateway you
specified to make sure it is still available. You specify how often the interface checks the
connection, how long to wait for a response before the attempt is a failure, and how many
consecutive failures are required before the NXC stops routing to the gateway. The NXC
resumes routing to the gateway the first time the gateway passes the connectivity check.
This table lists the ping-check commands
Table 15 interface Commands: Ping Check
COMMAND DESCRIPTION
show ping-check [interface_name | status] Displays information about ping check settings for
the specified interface or for all interfaces.
status: displays the current connectivity check
status for any interfaces upon which it is activated.
show ping-check [interface_name] Displays information about ping check settings for
the specified interface or for all interfaces.
[no] connectivity-check continuous-log
activate
show connectivity-check continuous-log status Displays the continuous log setting about
interface interface_name Enters sub-command mode.
[no] ping-check activate Enables ping check for the specified interface. The
ping-check {domain_name | ip | defaultgateway}
ping-check {domain_name | ip | defaultgateway} period <5..30>
ping-check {domain_name | ip | defaultgateway} timeout <1..10>
ping-check {domain_name | ip | defaultgateway} fail-tolerance <1..10>
ping-check {domain_name | ip | defaultgateway} method {icmp | tcp}
ping-check {domain_name | ip | defaultgateway} port <1..65535>
Use this command to have the NXC logs
connectivity check result continuously. The no
command disables the setting.
connectivity check.
no command disables ping check for the specified
interface.
Specifies what the NXC pings for the ping check;
you can specify a fully-qualified domain name, IP
address, or the default gateway for the interface.
Specifies what the NXC pings for the ping check
and sets the number of seconds between each
ping check.
Specifies what the NXC pings for the ping check
and sets the number of seconds the NXC waits for
a response.
Specifies what the NXC pings for the ping check
and sets the number of times the NXC times out
before it stops routing through the specified
interface.
Sets how the NXC checks the connection to the
gateway.
icmp: ping the gateway you specify to make sure it
is still available.
tcp: perform a TCP handshake with the gateway
you specify to make sure it is still available.
Specifies the port number to use for a TCP
connectivity check.
NXC CLI Reference Guide
57
Page 58

Chapter 6 Interfaces
6.2.3.1 Connectivity Check Command Example
The following commands show you how to set the WAN1 interface to use a TCP handshake
on port 8080 to check the connection to IP address 1.1.1.2
Router# configure terminal
Router(config)# interface wan1
Router(config-if-wan1)# ping-check 1.1.1.2 method tcp port 8080
Router(config-if-wan1)# exit
Router(config)# show ping-check
Interface: wan1
Check Method: tcp
IP Address: 1.1.1.2
Period: 30
Timeout: 5
Fail Tolerance: 5
Activate: yes
Port: 8080
Router(config)#
6.3 Ethernet Interface Specific Commands
This section covers commands that are specific to Ethernet interfaces.
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 16 Input Values for Ethernet Interface Commands
LABEL DESCRIPTION
interface_name The name of the interface.
Ethernet interface: gex, x = 1 - N, where N equals the highest numbered
Ethernet interface for your NXC model.
VLAN interface: vlanx, x = 0 - 4094.
6.3.1 MAC Address Setting Commands
This table lists the commands you can use to set the MAC address of an interface..
Table 17 interface Commands: MAC Setting
COMMAND DESCRIPTION
interface interface_name Enters sub-command mode.
no mac Has the interface use its default MAC address.
mac mac Specifies the MAC address the interface is to use.
58
NXC CLI Reference Guide
Page 59

Chapter 6 Interfaces
Table 17 interface Commands: MAC Setting (continued)
COMMAND DESCRIPTION
type {internal|external|general} Sets which type of network you will connect this
interface. The NXC automatically adds default
route and SNAT settings for traffic it routes from
internal interfaces to external interfaces; for
example LAN to WAN traffic.
internal: Set this to connect to a local network.
Other corresponding configuration options: DHCP
server and DHCP relay. The NXC automatically
adds default SNAT settings for traffic flowing from
this interface to an external interface.
external: Set this to connect to an external
network (like the Internet). The NXC automatically
adds this interface to the default WAN trunk.
general: Set this if you want to manually
configure a policy route to add routing and SNAT
settings for the interface.
no use-defined-mac Has the interface use its default MAC address.
use-defined-mac Has the interface use a MAC address that you
specify.
6.4 Port Commands
This section covers commands that are specific to ports.
In CLI, representative interfaces are also called representative ports.
Table 18 Basic Interface Setting Commands
COMMAND DESCRIPTION
no port <1..x> Removes the specified physical port from its
current representative interface and adds it to its
default representative interface (for example, port x
--> gex).
port status Port<1..x> Enters a sub-command mode to configure the
specified port’s settings.
[no] duplex <full | half> Sets the port’s duplex mode. The no command
returns the default setting.
exit Leaves the sub-command mode.
[no] negotiation auto Sets the port to use auto-negotiation to determine
the port speed and duplex. The no command turns
off auto-negotiation.
[no] speed <100,10> Sets the Ethernet port’s connection speed in Mbps.
The no command returns the default setting.
show port setting Displays the Ethernet port negotiation, duplex, and
show port status Displays statistics for the Ethernet ports.
speed settings.
NXC CLI Reference Guide
59
Page 60

Chapter 6 Interfaces
6.5 Port Role Commands
The following table describes the commands available for port role identification. You must
use the
these commands.
Table 19 Command Summary: Port Role
COMMAND DESCRIPTION
show port type Displays the type of cable connection for each physical
show module type Display the type of module for each physical interface on
6.5.1 Port Role Examples
The following are two port role examples..
configure terminal command to enter the configuration mode before you can use
interface on the device.
the device.
Router(config)# show port type
Port Type
===========================================================================
1 Copper
2 Down
3 Down
4 Down
5 Down
6 Down
7 Down
8 Down
Router(config)# show module type
Port Type
===========================================================================
1 Copper
2 Copper
3 Copper
4 Copper
5 Fiber
6 Fiber
7 Fiber
8 Fiber
6.6 USB Storage Specific Commands
Use these commands to configure settings that apply to the USB storage device connected to
the NXC.
60
NXC CLI Reference Guide
Page 61

Chapter 6 Interfaces
For the NXC which supports more than one USB ports, these commands only
apply to the USB storage device that is first attached to the NXC.
Table 20 USB Storage General Commands
COMMAND DESCRIPTION
show usb-storage Displays the status of the connected USB storage device.
[no] usb-storage activate Enables or disables the connected USB storage service.
usb-storage warn number
<percentage|megabyte>
usb-storage mount Mounts the connected USB storage device.
usb-storage umount Unmounts the connected USB storage device.
[no] logging usb-storage Sets to have the NXC log or not log any information about the connected
logging usb-storage category
category level <all|normal>
logging usb-storage category
category disable
logging usb-storage
flushThreshold <1..100>
[no] diag-info copy usbstorage
[no] corefile copy usbstorage
show corefile copy usbstorage
show diag-info copy usbstorage
show logging status usbstorage
Sets a number and the unit (percentage or megabyte) to have the NXC
send a warning message when the remaining USB storage space is less
than the set value.
percentage: 10 to 99
megabyte: 100 to 9999
USB storage device(s) for the system log.
Configures the logging settings for the specified category for the connected
USB storage device.
Stops logging for the specified category to the connected USB storage
device.
Configures the maximum storage space (in percentage) for storing system
logs on the connected USB storage device.
Sets to have the NXC save or stop saving the current system diagnostics
information to the connected USB storage device. You may need to send
this file to customer support for troubleshooting.
Sets to have the NXC save or not save a process’s core dump to the
connected USB storage device if the process terminates abnormally
(crashes). You may need to send this file to customer support for
troubleshooting.
Displays whether (enable or disable) the NXC saves core dump files to the
connected USB storage device.
Displays whether (enable or disable) the NXC saves the current system
diagnostics information to the connected USB storage device.
Displays the logging settings for the connected USB storage device.
NXC CLI Reference Guide
61
Page 62

Chapter 6 Interfaces
6.6.1 USB Storage General Commands Example
This example shows how to display the status of the connected USB storage device.
Router> show usb-storage
USBStorage Configuration:
Activation: enable
Criterion Number: 100
Criterion Unit: megabyte
USB Storage Status:
Device description: N/A
Usage: N/A
Filesystem: N/A
Speed: N/A
Status: none
Detail: none
6.7 VLAN Interface Specific Commands
A Virtual Local Area Network (VLAN) divides a physical network into multiple logical
networks. The standard is defined in IEEE 802.1q.
In the NXC, each VLAN is called a VLAN interface. As a router, the NXC routes traffic
between VLAN interfaces, but it does not route traffic within a VLAN interface.
vlan0 is the default VLAN interface. It cannot be deleted and its VID cannot
changed.
Otherwise, VLAN interfaces are similar to other interfaces in many ways. They have an IP
address, subnet mask, and gateway used to make routing decisions. They restrict bandwidth
and packet size. They can provide DHCP services, and they can verify the gateway is
available.
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 21 Input Values for VLAN Interface Commands
LABEL DESCRIPTION
virtual_interface The VLAN interface name. You may use 0 - 511 alphanumeric
characters, underscores (
be a number. This value is case-sensitive.
gateway The gateway IP address of the interface. Enter a standard IPv4 IP
address (for example, 127.0.0.1).
ip_address The netwo rk mask IP address. Enter a standard IPv4 IP address.
netmask The network subnet mask. For example, 255.255.255.0.
_), or dashes (-), but the first character cannot
62
NXC CLI Reference Guide
Page 63

Chapter 6 Interfaces
Table 21 Input Values for VLAN Interface Commands (continued)
LABEL DESCRIPTION
description Sets the description of the interface. Y ou may use 0 - 511 alphanumeric
characters, underscores (
be a number. This value is case-sensitive.
profile_name The DHCP pool name.
_), or dashes (-), but the first character cannot
The following table describes the commands available for VLAN interface management. You
must use the
configure terminal command to enter the configuration mode before you
can use these commands.
Table 22 Command Summary: VLAN Interface Profile
COMMAND DESCRIPTION
[no] interface virtual_interface Enters configuration mode for the specified interface. Use
vlanid <1..4094> Sets the interface’s VLAN identification number.
[no] ip address ip_address netmask Sets the interface’s IP address and netmask address.
[no] ip address dhcp [metric <0..15>] Sets the interface to use the DHCP to acquire an IP
mtu <576..1500> Sets the maximum size of each data packet, in bytes, that
no mtu Disables the mtu feature for this interface.
[no] ip gateway gateway [metric
<0..15>]
join <interface_name> <tag|untag> Links the VLAN to the specified physical interface and
no join <interface_name> Disa ssociates the specified physical interface from the
upstream <0..1048576> Sets the maximum amount of traffic, in kilobits per
no upstream Disables the upstream bandwidth limit.
downstream <0..1048576> Sets the maximum amount of traffic, in kilobits per
no downstream Disables the downstream bandwidth limit.
the no command to remove the specified VLAN interface.
Use the no command to remove these values from this
interface.
address. Enter the metric (priority) of the gateway (if any)
on this interface. The NXC decides which gateway to use
based on this priority. The lower the number, the higher
the priority. If two or more gateways have the same
priority, the NXC uses the one that was configured first.
can move through this interface. If a larger packet arrives,
the NXC divides it into smaller fragments.
Enter the IP address of the gateway. The NXC sends
packets to the gateway when it does not know how to
route the packet to its destination. The gateway should be
on the same network as the interface.
Also enter the metric (priority) of the gateway (if any) on
this interface. The NXC decides which gateway to use
based on this priority. The lower the number, the higher
the priority. If two or more gateways have the same
priority, the NXC uses the one that was configured first.
also sets this interface to send packets with or without a
VLAN tag.
VLAN.
second, the NXC can send through the interface to the
network.
second, the NXC can receive from the network through
the interface.
NXC CLI Reference Guide
63
Page 64

Chapter 6 Interfaces
Table 22 Command Summary: VLAN Interface Profile (continued)
COMMAND DESCRIPTION
description description Sets the description of this interface. It is not used
elsewhere. You can use alphanumeric and ()+/
:=?!*#@$_%- characters, and it can be up to 60
characters long.
no description Removes the VLAN description.
[no] shutdown Exits this sub-command mode, saving all changes but
[no] ip dhcp-pool profile_name Sets the DHCP server pool. The no command removes
[no] ip helper-address ip_address Sets the IP helper address. The no command removes
exit Exits configuration mode for this interface.
without enabling the VLAN.
the specified DHCP pool.
the IP address.
6.7.1 VLAN Interface Examples
This example creates a VLAN interface called ‘vlan0’..
Router(config)# interface vlan0
Router(config-if-vlan)# vlanid 100
Router(config-if-vlan)# join ge2 untag
Router(config-if-vlan)# ip address 1.2.3.4 255.255.255.0
Router(config-if-vlan)# ip gateway 2.2.2.2 metric 11
Router(config-if-vlan)# mtu 598
Router(config-if-vlan)# upstream 345
Router(config-if-vlan)# downstream 123
Router(config-if-vlan)# description I am vlan0
Router(config-if-vlan)# exit
Router(config)#
This example changes VLAN interface ‘vlan0’ to use DHCP..
Router(config)# interface vlan0
Router(config-if-vlan)# vlanid 100
Router(config-if-vlan)# join ge1 untag
Router(config-if-vlan)# ip address dhcp metric 4
Router(config-if-vlan)# exit
Router(config)#
64
NXC CLI Reference Guide
Page 65

CHAPTER 7
Route
This chapter shows you how to configure policies for IP routing and static routes on your
NXC.
7.1 Policy Route
Traditionally, routing is based on the destination address only and the NXC takes the shortest
path to forward a packet. IP Policy Routing (IPPR) provides a mechanism to override the
default routing behavior and alter the packet forwarding based on the policy defined by the
network administrator. Policy-based routing is applied to incoming packets on a per interface
basis, prior to the normal routing.
7.2 Policy Route Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 23 Input Values for General Policy Route Commands
LABEL DESCRIPTION
address_object The name of the IP address (group) object. You may use 1-31 alphanumeric
interface_name The name of the interface.
policy_number The number of a policy route. 1 - x where x is the highest number of policy
schedule_object The name of the schedule. You may use 1-31 alphanumeric characters,
service_name The name of the service (group). You may use 1-31 alphanumeric characters,
user_name The name of a user (group). You may use 1-31 alphanumeric characters,
characters, underscores(
number. This value is case-sensitive.
Ethernet interface: gex, x = 1 - N, where N equals the highest numbered
Ethernet interface for your NXC model.
routes the NXC model supports. See the NXC’s User’s Guide for details.
underscores(
value is case-sensitive.
underscores(
value is case-sensitive.
underscores(
value is case-sensitive.
_), or dashes (-), but the first character cannot be a number. This
_), or dashes (-), but the first character cannot be a number. This
_), or dashes (-), but the first character cannot be a number. This
_), or dashes (-), but the first character cannot be a
NXC CLI Reference Guide
65
Page 66

Chapter 7 Route
The following table describes the commands available for policy route. You must use the
configure terminal command to enter the configuration mode before you can use these
commands.
Table 24 Command Summary: Policy Route
COMMAND DESCRIPTION
[no] bwm activate Globally enables bandwidth management. You
policy {policy_number | append | insert
policy_number}
[no] auto-disable When you set interface as the next-hop type
[no] bandwidth <1..1048576> priority
<1..1024> [maximize-bandwidth-usage]
[no] deactivate Disables the specified policy. The
[no] description description Sets a descriptive name for the policy. The
[no] destination {address_object|any} Sets the destination IP address the matched
[no] dscp {any | <0..63>} Sets a custom DSCP code point (0~63). This is
[no] dscp class {default | dscp_class} Sets a DSCP class. Use default to apply this
dscp-marking <0..63> Sets a DSCP value to have the NXC apply that
dscp-marking class {default | dscp_class} Sets how the NXC handles the DSCP value of
must globally activate bandwidth management to
have individual policy routes or application patrol
policies apply bandwidth management. The
command globally disables bandwidth
management.
Enters the policy-route sub-command mode to
configure, add or insert a policy.
(using the next-hop interface) for this route,
you can use this command to have the NXC
automatically disable this policy route when the
next-hop’s connection is down. The no command
disables the setting.
Sets the maximum bandwidth and priority for the
policy. The no command removes bandwidth
settings from the rule. You can also turn
maximize bandwidth usage on or off.
no command
enables the specified policy.
command removes the name for the policy.
packets must have. The no command resets the
destination IP address to the default (any). any
means all IP addresses.
the DSCP value of incoming packets to which
this policy route applies. any means all DSCP
value or no DSCP marker.
policy route to incoming packets that are marked
with DSCP value 0. Use one of the pre-defined
AF classes (including af11~af13, af21~af23,
af31~af33, and af41~af43) to apply this policy
route to incoming packets that are marked with
the DSCP AF class.
The “af” entries stand for Assured Forwarding.
The number following the “af” identifies one of
four classes and one of three drop preferences.
DSCP value to the route’s outgoing packets.
the outgoing packets that match this route. Set
this to default to have the NXC set the DSCP
value of the packets to 0. Set this to an “af” class
(including af11~af13, af21~af23, af31~af33, and
af41~af43) which stands for Assured Forwarding.
The number following the “af” identifies one of
four classes and one of three drop preferences.
no
no
66
NXC CLI Reference Guide
Page 67

Chapter 7 Route
Table 24 Command Summary: Policy Route (continued)
COMMAND DESCRIPTION
no dscp-marking Use this command to have the NXC not modify
the DSCP value of the route’s outgoing packets.
[no] interface {interface_name |
EnterpriseWLAN}
[no] next-hop {auto|gateway address object |
interface interface_name}
[no] schedule schedule_object Sets the schedule. The no command removes
[no] service {service_name|any} Sets the IP protocol. The
[no] snat {outgoing-interface|pool
{address_object}}
[no] source {address_object|any} Sets the source IP address that the matched
[no] trigger <1..8> incoming service_name
trigger service_name
trigger append incoming service_name trigger
service_name
trigger delete <1..8> Removes a port triggering rule.
trigger insert <1..8> incoming service_name
trigger service_name
trigger move <1..8> to <1..8> Moves a port trigge ring rule to the number that
[no] user user_name Sets the user name. The
policy default-route Enters the policy-route sub-command mode to
policy delete policy_number Removes a routing policy.
policy flush Clears the policy routing table.
policy list table Displays all policy route settings.
policy move policy_number to policy_number Moves a routing policy to the number that you
[no] policy override-direct-route activate Use this command to have the NXC forward
show policy-route [policy_number] Displays all or specified policy route settings.
Sets the interface on which the incoming packets
are received. The
incoming interface to the default (
means all interfaces.
EnterpriseWLAN: the packets are coming from
the NXC itself.
Sets the next-hop to which the matched packets
are routed. The
settings to the default (
the schedule setting to the default (
means any time.
no command resets the
any). any
no command resets next-hop
auto).
none). none
no command resets
service settings to the default (
all services.
Sets the source IP address of the matched
packets that use SNAT. The no command
removes source NAT settings from the rule.
packets must have. The no command resets the
source IP address to the default (
means all IP addresses.
Sets a port triggering rule. The
removes port trigger settings from the rule.
Adds a new port triggering rule to the end of the
list.
Adds a new port triggering rule before the
specified number.
you specified.
any). any means
any). any
no command
no command resets the
user name to the default (
users.
set a route with the name “default-route”.
specified.
packets that match a policy route according to
the policy route instead of sending the packets to
a directly connected network. Use the no
command to disable it.
any). any means all
NXC CLI Reference Guide
67
Page 68

Chapter 7 Route
Table 24 Command Summary: Policy Route (continued)
COMMAND DESCRIPTION
show policy-route begin policy_number end
policy_number
show policy-route override-direct-route Displays whether or not the NXC forwards
show policy-route rule_count Displays the number of policy routes that have
show policy-route underlayer-rules Displays all policy route rule details for advanced
show bwm activation Displays whether or not the global setting for
show bwm-usage < [policy-route policy_number] |
[interface interface_name]
Displays the specified range of policy route
settings.
packets that match a policy route according to
the policy route instead of sending the packets to
a directly connected network.
been configured on the NXC.
debugging.
bandwidth management on the NXC is enabled.
Displays the specified policy route or interface’s
bandwidth allotment, current bandwidth usage,
and bandwidth usage statistics.
7.2.1 Assured Forwarding (AF) PHB for DiffServ
Assured Forwarding (AF) behavior is defined in RFC 2597. The AF behavior group defines
four AF classes. Inside each class, packets are given a high, medium or low drop precedence.
The drop precedence determines the probability that routers in the network will drop packets
when congestion occurs. If congestion occurs between classes, the traffic in the higher class
(smaller numbered class) is generally given priority. Combining the classes and drop
precedence produces the following twelve DSCP encodings from AF11 through AF43. The
decimal equivalent is listed in brackets.
Table 25 Assured Forwarding (AF) Behavior Group
CLASS 1 CLASS 2 CLASS 3 CLASS 4
Low Drop Precedence AF11 (10) AF21 (18) AF31 (26) AF41 (34)
Medium Drop Precedence AF12 (12) AF22 (20) AF32 (28) AF42 (36)
High Drop Precedence AF13 (14) AF23 (22) AF33 (30) AF43 (38)
68
NXC CLI Reference Guide
Page 69

7.2.2 Policy Route Command Example
The following commands create two address objects (TW_SUBNET and GW_1) and insert a
policy that routes the packets (with the source IP address TW_SUBNET and any destination
IP address) through the interface ge1 to the next-hop router GW_1. This route uses the IP
address of the outgoing interface as the matched packets’ source IP address.
Router(config)# address-object TW_SUBNET 192.168.2.0 255.255.255.0
Router(config)# address-object GW_1 192.168.2.250
Router(config)# policy insert 1
Router(policy-route)# description example
Router(policy-route)# destination any
Router(policy-route)# interface ge1
Router(policy-route)# next-hop gateway GW_1
Router(policy-route)# snat outgoing-interface
Router(policy-route)# source TW_SUBNET
Router(policy-route)# exit
Router(config)# show policy-route 1
index: 1
active: yes
description: example
user: any
schedule: none
interface: ge1
tunnel: none
sslvpn: none
source: TW_SUBNET
destination: any
DSCP code: any
service: any
nexthop type: Gateway
nexthop: GW_1
nexthop state: Not support
auto destination: no
bandwidth: 0
bandwidth priority: 0
maximize bandwidth usage: no
SNAT: outgoing-interface
DSCP marking: preserve
amount of port trigger: 0
Router(config)#
Chapter 7 Route
7.3 IP Static Route
The NXC has no knowledge of the networks beyond the n e twork that is directly connected to
the NXC. For instance, the NXC knows about network N2 in the following figure through
gateway R1. However, the NXC is unable to route a packet to network N3 because it doesn't
know that there is a route through the same gateway R1 (via gateway R2). The static routes are
for you to tell the NXC about the networks beyond the network connected to the NXC directly.
NXC CLI Reference Guide
69
Page 70

Chapter 7 Route
Figure 10 Example of Static Routing Topolo gy
7.4 Static Route Commands
The following table describes the commands available for static route. You must use the
configure terminal command to enter the configuration mode before you can use these
commands.
Table 26 Command Summary: Static Route
COMMAND DESCRIPTION
[no] ip route {w.x.y.z} {w.x.y.z}
{interface|w.x.y.z} [<0..127>]
ip route replace {w.x.y.z} {w.x.y.z}
{interface|w.x.y.z} [<0..127>] with {w.x.y.z}
{w.x.y.z} {interface|w.x.y.z} [<0..127>]
show ip route-settings Displays static route information. Use show ip
show ip route control-virtual-server-rules Displays whether or not static routes have priority
Sets a static route. The no command disables a
static route.
Changes an existing route’s settings.
route to see learned route information.
over NAT virtual server rules (1-1 SNAT).
7.4.1 Static Route Commands Example
The following command sets a static route with IP address 10.10.10.0 and subnet mask
255.255.255.0 and with the next-hop interface ge1. Then use the show command to display
the setting.
Router(config)# ip route 10.10.10.0 255.255.255.0 ge1
Router(config)#
Router(config)# show ip route-settings
Route Netmask Nexthop Metric
===========================================================================
10.10.10.0 255.255.255.0 ge1 0
70
NXC CLI Reference Guide
Page 71

Chapter 7 Route
7.5 Learned Routing Information Commands
This table lists the commands to look at learned routing information.
Table 27 ip route Commands: Learned Routing Information
COMMAND DESCRIPTION
show ip route [kernel | connected | static] Displays learned routing and other routing information.
7.5.1 show ip route Command Example
The following example shows learned routing information on the NXC.
Router> show ip route
Flags: A - Activated route, S - Static route, C - directly Connected
O - OSPF derived, R - RIP derived, G - selected Gateway
! - reject, B - Black hole, L - Loop
IP Address/Netmask Gateway IFace Metric Flags
Persist
===========================================================================
127.0.0.0/8 0.0.0.0 lo 0 ACG -
192.168.1.0/24 0.0.0.0 vlan0 0 ACG -
Router>
NXC CLI Reference Guide
71
Page 72

Chapter 7 Route
72
NXC CLI Reference Guide
Page 73

CHAPTER 8
A
B
C
D
AP Management
This chapter shows you how to configure wireless AP management options on yo ur NXC.
8.1 AP Management Overview
The NXC allows you to remotely manage all of the wireless station Access Points (APs) on
your network. You can manage a number of APs without having to configure them
individually as the NXC automatically handles basic configuration for you.
The commands in this chapter allow you to add, delete, and edit the APs managed by the NXC
by means of the CAPWAP protocol. An AP must be moved from the wait list to the
management list before you can manage it. If you do not want to use this registration
mechanism, you can disable it and then any newly connected AP is registered automatically.
Figure 11 Example AP Management
In this example, the NXC (A) connects up to a number of Power over Ethernet switches, such
as the ES-2025 PWR (B). They connect to the NWA5160N Acc ess Points (C), which in turn
provide access to the network for the wireless clients within their broadcast radius.
Let’s say one AP (D) starts giving you trouble. You can log into the NXC via console or T eln et
and troubleshoot, such as viewing its traffic statistics or reboot it or even remove it altogether
from the list of viable APs that stations can use.
NXC CLI Reference Guide
73
Page 74

Chapter 8 AP Management
8.2 AP Management Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 28 Input Values for General AP Management Commands
LABEL DESCRIPTION
ap_mac The Ethernet MAC address of the managed AP. Enter 6 hexidecimal pairs
ap_model The model name of the managed AP , such as NWA5160N, NWA5560-N,
slot_name The slot name for the AP’s on-board wireless LAN card. Use either slot1 or
profile_name The wireless LAN radio profile name. You may use 1-31 alphanumeric
ap_description The AP description. This is strictly used for reference purposes and has no
sta_mac The MAC address of the wireless client. Enter 6 hexidecimal pairs separated by
separated by colons. You can use 0-9, a-z and A-Z.
NWA5550-N, NWA5121-NI or NWA5123-NI.
slot2. (The NWA5560-N supports up to 2 radio slots.)
characters, underscores(
number. This value is case-sensitive.
effect on any other settings. You may use 1-31 alphanumeric characters,
underscores(
value is case-sensitive.
colons. You can use 0-9, a-z and A-Z.
_), or dashes (-), but the first character cannot be a number. This
_), or dashes (-), but the first character cannot be a
The following table describes the commands available for AP management. You must use the
configure terminal command to enter the configuration mode before you can use these
commands.
Table 29 Command Summary: AP Management
COMMAND DESCRIPTION
capwap manual-add {enable | disable} Allows the NXC to either automatically add new APs to
show capwap manual-add Displays the current manual add option.
capwap ap add ap_mac [ap_model] Adds the specified AP to the NXC for management. If
capwap ap kick {all | ap_mac} Removes the specified AP (ap_mac) or all connected
capwap ap reboot ap_mac Forces the specified AP (ap_mac) to restart. Doing this
capwap ap ap_mac Enters the sub-command mode for the specified AP.
slot_name ap-profile profile_name Sets the radio (slot_name) to AP mode and assigns a
no slot_name ap-profile Remove s the AP mode profile assignment for the
the network (disable) or wait until you manually confirm
them (enable).
manual add is disabled, this command can still be used; if
you add an AP before it connects to the network, then this
command simply preconfigures the management list with
that AP’s information.
APs (all) from the management list. Doing this removes
the AP(s) from the management list.
If the NXC is set to automatically add new APs to the AP
management list, then any kicked APs are added back to
the management list as soon as they reconnect.
severs the connections of all associated stations.
created profile to the radio.
specified radio (slot_name).
74
NXC CLI Reference Guide
Page 75

Chapter 8 AP Management
Table 29 Command Summary: AP Management (continued)
COMMAND DESCRIPTION
slot_name monitor-profile
profile_name
no slot_name monitor-profile Removes the monitor mode profile assignment for the
description ap_description Sets the description for the specified AP.
[no] force vlan Sets whether or not the NXC changes the AP’s
vlan <1..4094> {tag | untag} Sets the VLAN ID for the specified AP as well as whether
exit Exits the sub-command mode for the specified AP.
show capwap ap wait-list Displays a list of connected but as-of-yet unmanaged
show capwap ap {all | ap_mac} Displays the management list (all) or whether the
show capwap ap all statistics Displays radio statistics for all APs on the manageme nt
show capwap ap ap_mac slot_name detail Displays details for the specified radio (slot_name) on
show capwap ap {all | ap_mac} config
status
show capwap station all Displays information for all stations connected to the APs
capwap station kick sta_mac Forcibly disconnects the specified station from the
Sets the specified radio (slot_name) to monitor mode
and assigns a created profile to the radio. Monitor mode
APs act as wireless monitors, which can detect rogue
APs and help you in building a list of friendly ones. See
also Section 9.2 on page 77.
specified radio (slot_name).
management VLAN to match the one you configure using
the vlan sub-command. The management VLAN on the
NXC and AP must match for the NXC to manage the AP.
This takes priority over the AP’s CAPWAP client
commands described in Chapter 43 on page 271.
packets sent to and from that ID are tagged or untagged.
APs. This is known as the ‘wait list’.
specified AP is on the management list (ap_mac).
list.
the specified AP (ap_mac).
Displays whether or not any AP’s configuration or the
specified AP’s configuration is in conflict with the NXC’s
settings for the AP and displays the settings in conflict if
there are any.
on the management list.
network.
NXC CLI Reference Guide
75
Page 76

Chapter 8 AP Management
8.2.1 AP Management Commands Example
The following example shows you how to add an AP to the management list, and then edit it.
Router# show capwap ap wait-list
index: 1
IP: 192.168.1.35, MAC: 00:11:11:11:11:FE
Model: NWA5160N, Description: AP-00:11:11:11:11:FE
index: 2
IP: 192.168.1.36, MAC: 00:19:CB:00:BB:03
Model: NWA5160N, Description: AP-00:19:CB:00:BB:03
Router# configure terminal
Router(config)# capwap ap add 00:19:CB:00:BB:03
Router(config)# capwap ap 00:19:CB:00:BB:03
Router(AP 00:19:CB:00:BB:03)# slot1 ap-profile approf01
Router(AP 00:19:CB:00:BB:03)# exit
Router(config)# show capwap ap all
index: 1
Status: RUN
IP: 192.168.1.37, MAC: 40:4A:03:05:82:1E
Description: AP-404A0305821E
Model: NWA5160N
R1 mode: AP, R1Prof: default
R2 mode: AP, R2Prof: n/a
Station: 0, RadioNum: 2
Mgnt. VLAN ID: 1, Tag: no
WTP VLAN ID: 1, WTP Tag: no
Force VLAN: disable
Firmware Version: 2.25(AAS.0)b2
Recent On-line Time: 08:43:04 2012/07/24
Last Off-line Time: N/A
Router(config)# show capwap ap 40:4A:03:05:82:1E slot1 detail
index: 1
SSID: ZyXEL, BSSID: 40:4A:03:05:82:1F
SecMode: NONE, Forward Mode: Local Bridge, Vlan: 1
Router(config)# show capwap ap all statistics
index: 1
Status: RUN, Loading: AP MAC: 40:4A:03:05:82:1E
Radio: 1, OP Mode: AP
Profile: default, MAC: 40:4A:03:05:82:1F
Description: AP-404A0305821E
Model: NWA5160N
Band: 2.4GHz, Channel: 6
Station: 0
RxPkt: 4463, TxPkt: 38848
RxFCS: 1083323, TxRetry: 198478
76
NXC CLI Reference Guide
Page 77

CHAPTER 9
Wireless LAN Profiles
This chapter shows you how to configure wireless LAN profiles on your NXC.
9.1 Wireless LAN Profiles Overview
The NWA5160N Access Points designed to work explicitly with your NXC do not have onboard configuration files, you must create “profiles” to manage them. Profiles are preset
configurations that are uploaded to the APs and which manage them. They include: Radio and
Monitor profiles, SSID profiles, Security profiles, and MAC Filter profiles. Altogether, these
profiles give you absolute control over your wireless network.
9.2 AP & Monitor Profile Commands
The radio profile commands allow you to set up configurations for the radios onboard your
various APs. The monitor profile commands allow you to set up monitor mode configurations
that allow your APs to scan for other APs in the vicinity.
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 30 Input Values for General Radio and Monitor Profile Commands
LABEL DESCRIPTION
radio_profile_name The radio profile name. You may use 1-31 alphanumeric characters,
underscores (
number. This value is case-sensitive.
monitor_profile_name The monitor profile name. You may use 1-31 alphanumeric characters,
underscores (
number. This value is case-sensitive.
wlan_role Sets the wireless LAN radio operating mode. At th e time of writing, you
can use ap for Access Point.
wireless_channel_2g Sets the 2 GHz channel used by this radio profile. The channel range is
1 ~ 14.
Note: Your choice of channel may be restricted by
wireless_channel_5g Sets the 5 GHz channel used by this radio profile. The channel range is
36 ~ 165.
_), or dashes (-), but the first character cannot be a
_), or dashes (-), but the first character cannot be a
regional regulations.
NXC CLI Reference Guide
Note: Your choice of channel may be restricted by
regional regulations.
77
Page 78

Chapter 9 Wireless LAN Profiles
Table 30 Input Values for General Radio and Monitor Profile Commands (continued)
LABEL DESCRIPTION
wlan_hctw Sets the HT channel width. Select either auto or 20m.
wlan_htgi Sets the HT guard interval. Select either long or short.
wlan_2g_basic_speed Sets the basic band rate for 2.4 GHz. The available band rates are
wlan_2g_support_speed Sets the support rate for the 2.4 GHz band. The available band rates
wlan_mcs_speed Sets the HT MCS rate. The available rates are: 0, 1, 2, 3, 4, 5,
wlan_5g_basic_speed Sets the basic band rate for 5 GHz. The available band rates are: 6.0,
wlan_5g_support_speed Sets the support rate for the 5 GHz band. The available band rates are:
chain_mask Sets the network traffic chain mask. The range is 1 ~ 7.
wlan_power Sets the radio output power. Select 100%, 50%, 25%, or 12.5%.
scan_method Sets the radio’s scan method while in Monitor mode. Select manual or
wlan_interface_index Sets the radio interface index number. The range is 1 ~ 8.
ssid_profile Sets the associated SSID profile name. This name must be an existing
1.0, 2.0, 5.5, 11.0, 6.0, 9.0, 12.0, 18.0, 24.0,
36.0, 48.0, 54.0.
are: 1.0, 2.0, 5.5, 11.0, 6.0, 9.0, 12.0, 18.0, 24.0,
36.0, 48.0, 54.0.
6, 7, 8, 9, 10, 11, 12, 13, 14, 15.
9.0, 12.0, 18.0, 24.0, 36.0, 48.0, 54.0.
6.0, 9.0, 12.0, 18.0, 24.0, 36.0, 48.0, 54.0
auto.
SSID profile. You may use 1-31 alphanumeric characters, underscores
(
_), or dashes (-), but the first character cannot be a number. This value
is case-sensitive.
The following table describes the commands available for radio and monitor profile
management. You must use the
configure terminal command to enter the configuration
mode before you can use these commands.
Table 31 Command Summary: Radio Profile
COMMAND DESCRIPTION
show wlan-radio-profile {all |
radio_profile_name}
wlan-radio-profile rename
radio_profile_name1 radio_profile_name2
[no] wlan-radio-profile
radio_profile_name
[no] activate Makes this profile active or inactive.
role wlan_role Sets the role of this profile.
rssi-dbm <-20~-76> When using the RSSI threshold, set a minimum client
[no] rssi-thres Sets whether or not to use the Received Signal Strength
Displays the radio profile(s).
all: Displays all profiles for the selected operating mode.
radio_profile_name: Displays the specified profile for
the selected operating mode.
Gives an existing radio profile (radio_profile_name1)
a new name (radio_profile_name2).
Enters configuration mode for the specified radio profile.
Use the no parameter to remove the specified profile.
signal strength for connecting to the AP. -20 dBm is the
strongest signal you can require and -76 is the weakest.
Indication (RSSI) threshold to ensure wireless clients
receive good throughput. This allows only wireless clients
with a strong signal to connect to the AP.
78
NXC CLI Reference Guide
Page 79

Chapter 9 Wireless LAN Profiles
Table 31 Command Summary: Radio Profile (continued)
COMMAND DESCRIPTION
band {2.4G |5G} band-mode
{11n | bg | a}
2g-channel wireless_channel_2g Sets the broadcast band for this profile in the 2.4 GHz
5g-channel wireless_channel_5g Sets the broadcast band for this profile in the 5 GHz
[no] disable-dfs-switch Makes the DFS switch active or inactive. By default this is
[no] dot11n-disable-coexistence Fixes the channel bandwidth as 40 MHz. The no
[no] ctsrts <0..2347> Sets or removes the RTS/CTS value for this profile.
[no] frag <256..2346> Sets or removes the fragmentation value for this profile.
dtim-period <1..255> Sets the DTIM period for this profile.
Sets the radio band (2.4 GHz or 5 GHz) and band mode
for this profile. Band mode details:
For 2.4 GHz, 11n lets IEEE 802.11b, IEEE 802.11g, and
IEEE 802.11n clients associate with the AP.
For 2.4 GHz, bg lets IEEE 802.11b and IEEE 802.11g
clients associate with the AP.
For 5 GHz, 11n lets IEEE 802.11a and IEEE 802.11n
clients associate with the AP.
For 5 GHz, a lets only IEEE 802.11a clients associate
with the AP.
frequency range. The default is 6.
frequency range. The default is 36.
inactive.
command has the AP automatically choose 40 MHz if all
the clients support it or 20 MHz if some clients only
support 20 MHz.
Use RTS/CTS to reduce data collisions on the wireless
network if you have wireless clients that are associated
with the same AP but out of range of one another. When
enabled, a wireless client sends an RTS (Request To
Send) and then waits for a CTS (Clear To Send) before it
transmits. This stops wireless clients from transmitting
packets at the same time (and causing data collisions).
A wireless client sends an RTS for all packets larger than
the number (of bytes) that you enter here. Set the RTS/
CTS equal to or higher than the fragmentation threshold
to turn RTS/CTS off.
The default is 2347.
The threshold (number of bytes) for the fragmentation
boundary for directed messages. It is the maximum data
fragment size that can be sent.
The default is 2346.
Delivery Traffic Indication Message (DTIM) is the time
period after which broadcast and multicast packets are
transmitted to mobile clients in the Active Power
Management mode. A high DTIM value can cause clients
to lose connectivity with the network. This value can be
set from 1 to 255.
The default is 1.
NXC CLI Reference Guide
79
Page 80

Chapter 9 Wireless LAN Profiles
Table 31 Command Summary: Radio Profile (continued)
COMMAND DESCRIPTION
beacon-interval <40..1000> Sets the beacon interval for this profile.
When a wirelessly networked device sends a beacon, it
includes with it a beacon interval. This specifies the time
period before the device sends the beacon again. The
interval tells receiving devices on the network how long
they can wait in low-power mode before waking up to
handle the beacon. This value can be set from 40ms to
1000ms. A high value helps save current consumption of
the access point.
The default is 100.
[no] ampdu Activates MPDU frame aggregation for this profile. Use
limit-ampdu < 100..65535> Sets the maximum frame size to be aggregated.
subframe-ampdu <2..64> Sets the maximum number of frames to be aggregated
[no] amsdu Activates MPDU frame aggregation for this profile. Use
limit-amsdu <2290..4096> Sets the maximum frame size to be aggregated.
[no] multicast-to-unicast “Multicast to unicast” broadcasts wireless multicast traffic
[no] block-ack Makes block-ack active or inactive. Use the no
ch-width wlan_htcw Sets the channel width for this profile.
guard-interval wlan_htgi Sets the guard interval for this profile.
2g-basic-speed wlan_2g_basic_speed Sets the 2.4 GHz basic band rates.
the no parameter to disable it.
Message Protocol Data Unit (MPDU) aggregation collects
Ethernet frames along with their 802.11n headers and
wraps them in a 802.11n MAC header. This method is
useful for increasing bandwidth throughput in
environments that are prone to high error rates.
By default this is enabled.
By default this is 50000.
each time.
By default this is 32.
the no parameter to disable it.
Mac Service Data Unit (MSDU) aggregation collects
Ethernet frames without any of their 802.11n headers and
wraps the header-less payload in a single 802.11n MAC
header. This method is useful for increasing bandwidth
throughput. It is also more efficient than A-MPDU except
in environments that are prone to high error rates.
By default this is enabled.
The default is 4096.
to all wireless clients as unicast traffic to provide more
reliable transmission. The data rate changes dynamically
based on the application’s bandwidth requirements.
Although unicast provides more reliable transmission of
the multicast traffic, it also produces duplicate packets.
The no command turns multicast to unicast off to send
wireless multicast traffic at the rate you specify with the
2g-multicast-speed or 5g-multicast-speed
command.
parameter to disable it.
The default for this is short.
The default is 1.0 2.0 5.5 11.0.
80
NXC CLI Reference Guide
Page 81

Chapter 9 Wireless LAN Profiles
Table 31 Command Summary: Radio Profile (continued)
COMMAND DESCRIPTION
2g-support-speed {disable |
wlan_2g_support_speed}
2g-mcs-speed {disable |
wlan_mcs_speed}
2g-multicast-speed
wlan_2g_support_speed
5g-basic-speed wlan_5g_basic_speed Sets the 5 GHz basic band rate.
5g-support-speed {disable |
wlan_5g_support_speed}
5g-mcs-speed {disable |
wlan_mcs_speed}
5g-multicast-speed
{wlan_5g_basic_speed}
tx-mask chain_mask Sets the outgoing chain mask rate.
rx-mask chain_mask Sets the incoming chain mask rate.
[no] htprotection Activates HT protection for this profile. Use the no
output-power wlan_power Sets the output power for the radio in this profile.
[no] ssid-profile
wlan_interface_index ssid_profile
exit Exits configuration mode for this profile.
show wlan-monitor-profile {all |
monitor_profile_name}
wlan-monitor-profile rename
monitor_profile_name1
monitor_profile_name2
[no] wlan-monitor-profile
monitor_profile_name
[no] activate Makes this profile active or inactive.
scan-method scan_method Sets the channel scanning method for this profile.
[no] 2g-scan-channel
wireless_channel_2g
[no] 5g-scan-channel
wireless_channel_5g
scan-dwell <100..1000> Sets the duration in milliseconds that the device using
exit Exits configuration mode for this profile.
Disables or sets the 2.4 GHz support rate.
The default is 1.0~54.0.
Disables or sets the 2.4 GHz HT MCS rate.
The default is 0~15.
When you disable
command to set the data rate
Mbps for 2.4 GHz multicast traffic.
The default is 6.0 12.0 24.0.
Disables or sets the 5 GHz support rate.
The default is 6.0~54.0.
Disables or sets the 5 GHz HT MCS rate.
The default is 0~15.
When you disable
command to set the data rate
Mbps for 5 GHz multicast traffic.
parameter to disable it.
By default, this is disabled.
The default is 100%.
Assigns an SSID profile to this radio profile. Requires an
existing SSID profile. Use the no parameter to disable it.
Displays all monitor profiles or just the specified one.
Gives an existing monitor profile
(monitor_profile_name1) a new name
(monitor_profile_name2).
Enters configuration mode for the specified monitor
profile. Use the no parameter to remove the specified
profile.
By default, this is enabled.
Sets the broadcast band for this profile in the 2.4 Ghz
frequency range. Use the no parameter to disable it.
Sets the broadcast band for this profile in the 5 GHz
frequency range. Use the no parameter to disable it.
this profile scans each channel.
multicast to unicast, use this
{ 1.0 | 2.0 | … } in
multicast to unicast, use this
{ 6.0 | 9.0 | … } in
NXC CLI Reference Guide
81
Page 82

Chapter 9 Wireless LAN Profiles
9.2.1 AP & Monitor Profile Commands Example
The following example shows you how to set up the radio profile named ‘RADIO01’, activate
it, and configure it to use the following settings:
• 2.4G band with channel 6
• channel width of 20MHz
• a DTIM period of 2
• a beacon interval of 100ms
• AMPDU frame aggregation enabled
• an AMPDU buffer limit of 65535 bytes
• an AMPDU subframe limit of 64 frames
• AMSDU frame aggregation enabled
• an AMSDU buffer limit of 4096
• block acknowledgement enabled
• a short guard interval
• an output power of 100%
It will also assign the SSID profile labeled ‘default’ in order to create WLAN VAP (wlan-1-1)
functionality within the radio profile.
Router(config)# wlan-radio-profile RADIO01
Router(config-profile-radio)# activate
Router(config-profile-radio)# band 2.4G
Router(config-profile-radio)# 2g-channel 6
Router(config-profile-radio)# ch-width 20m
Router(config-profile-radio)# dtim-period 2
Router(config-profile-radio)# beacon-interval 100
Router(config-profile-radio)# ampdu
Router(config-profile-radio)# limit-ampdu 65535
Router(config-profile-radio)# subframe-ampdu 64
Router(config-profile-radio)# amsdu
Router(config-profile-radio)# limit-amsdu 4096
Router(config-profile-radio)# block-ack
Router(config-profile-radio)# guard-interval short
Router(config-profile-radio)# tx-mask 5
Router(config-profile-radio)# rx-mask 7
Router(config-profile-radio)# output-power 100%
Router(config-profile-radio)# ssid-profile 1 default
82
NXC CLI Reference Guide
Page 83

9.3 SSID Profile Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 32 Input Values for General SSID Profile Commands
LABEL DESCRIPTION
ssid_profile_name The SSID profile name. You may use 1-31 alphanumeric characters,
underscores (
number. This value is case-sensitive.
ssid The SSID broadcast name. You may use 1-32 alphanumeric
characters, underscores (_), or dashes (-). This value is case-sensitive.
wlan_qos Sets the type of QoS the SSID should use.
disable: Turns off QoS for this SSID.
wmm: Turns on QoS for this SSID. It automatically assigns Access
Categories to packets as the device inspects them in transit.
wmm_be: Assigns the “best effort” Access Category to all traffic moving
through the SSID regardless of origin.
wmm_bk: Assigns the “background” Access Category to all traffic
moving through the SSID regardless of origin.
wmm_vi: Assigns the “video” Access Category to all traffic moving
through the SSID regardless of origin.
wmm_vo: Assigns the “voice” Access Category to all traffic moving
through the SSID regardless of origin.
vlan_iface The VLAN interface name of the controller (in this case, it is NXC5200).
The maximum VLAN interface number is product-specific; for the NXC,
the number is 512.
securityprofile Assigns an existing security profile to the SSID profile. You may use 1-
31 alphanumeric characters, underscores (
character cannot be a number. This value is case-sensitive.
macfilterprofile Assigns an existing MAC filter profile to the SSID profile. You may use
1-31 alphanumeric characters, underscores (_), or dashes (-), but the
first character cannot be a number. This value is case-sensitive.
description2 Sets the description of the profile. You may use up to 60 alphanumeric
characters, underscores (_), or dashes (-). This value is case-sensitive.
Chapter 9 Wireless LAN Profiles
_), or dashes (-), but the first character cannot be a
_), or dashes (-), but the first
The following table describes the commands available for SSID profile management. You
must use the
configure terminal command to enter the configuration mode before you
can use these commands.
Table 33 Command Summary: SSID Profile
COMMAND DESCRIPTION
show wlan-ssid-profile {all |
ssid_profile_name}
wlan-ssid-profile rename
ssid_profile_name1 ssid_profile_name2
[no] wlan-ssid-profile ssid_profile_name Enters configuration mode for the specified SSID profile.
[no] block-intra Enables intra-BSSID traffic blocking. Use the no
NXC CLI Reference Guide
Displays the SSID profile(s).
all: Displays all profiles for the selected operating mode.
ssid_profile_name: Displays the specified profile for
the selected operating mode.
Gives an existing SSID profile (ssid_profile_name1)
a new name (ssid_profile_name2).
Use the no parameter to remove the specified profile.
parameter to disable it in this profile.
By default this is disabled.
83
Page 84

Chapter 9 Wireless LAN Profiles
Table 33 Command Summary: SSID Profile (continued)
COMMAND DESCRIPTION
[no] hide Prevents the SSID from being publicly broadcast. Use the
no parameter to re-enable public broadcast of the SSID
in this profile.
By default this is disabled.
ssid Sets the SSID. This is the name visible on the network to
wireless clients. Enter up to 32 characters, spaces and
underscores are allowed.
The default SSID is ‘ZyXEL’.
qos wlan_qos Sets the type of QoS used by this SSID.
data-forward {localbridge | tunnel
vlan_iface}
vlan-id <1..4094> Appl ies to each SSID profile that uses localbridge. If
security securityprofile Assign s the specified security profile to this SSID profile.
[no] macfilter macfilterprofile Assigns the specified MAC filtering profile to this SSID
exit Exits configuration mode for this profile.
Sets the data forwarding mode used by this SSID.
The default is localbridge.
the VLAN ID is equal to the AP’s native VLAN ID then
traffic originating from the SSID is not tagged.
The default VLAN ID is 1.
profile. Use the no parameter to remove it.
By default, no MAC filter is assigned.
9.3.1 SSID Profile Example
The following example creates an SSID profile with the name ‘ZyXEL’. It makes the
assumption that both the security profile (SECURITY01) and the MAC filter profile
(MACFILTER01) already exist.
Router(config)# wlan-ssid-profile SSID01
Router(config-ssid-radio)# ssid ZyXEL
Router(config-ssid-radio)# qos wmm
Router(config-ssid-radio)# data-forward localbridge
Router(config-ssid-radio)# security SECURITY01
Router(config-ssid-radio)# macfilter MACFILTER01
Router(config-ssid-radio)# exit
Router(config)#
9.4 Security Profile Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 34 Input Values for General Security Profile Commands
LABEL DESCRIPTION
security_profile_name The security profile name. You may use 1-31 alphanumeric characters,
underscores (
number. This value is case-sensitive.
wep_key Sets the WEP key encryption strength. Select either 64bit or 128bit.
_), or dashes (-), but the first character cannot be a
84
NXC CLI Reference Guide
Page 85

Chapter 9 Wireless LAN Profiles
Table 34 Input Values for General Security Profile Commands (continued)
LABEL DESCRIPTION
wpa_key Sets the WPA/WPA2 pre-shared key in ASCII. You may use 8~63
alphanumeric characters. This value is case-sensitive.
wpa_key_64 Sets the WPA/WPA2 pre-shared key in HEX. You muse use 64
alphanumeric characters.
secret Sets the shared secret used by your network’s RADIUS server.
auth_method The authentication method used by the security profile.
The following table describes the commands available for security profile management. You
must use the
configure terminal command to enter the configuration mode before you
can use these commands.
Table 35 Command Summary: Security Profile
COMMAND DESCRIPTION
show wlan-security-profile {all |
security_profile_name}
wlan-security-profile rename
security_profile_name1
security_profile_name2
[no] wlan-security-profile
security_profile_name
[no] mac-auth activate MAC authentication has the AP use an external server to
mac-auth auth-method auth_method Sets the authentication method for MAC authentication.
mac-auth case account {upper | lower} Sets the case (upper or lower) the external server
mac-auth case calling-station-id
{upper | lower}
mac-auth delimiter account {colon |
dash | none}
Displays the security profile(s).
all: Displays all profiles for the selected operating mode.
security_profile_name: Displays the specified
profile for the selected operating mode.
Gives existing security profile
(security_profile_name1) a new name,
(security_profile_name2).
Enters configuration mode for the specified security
profile. Use the no parameter to remove the specified
profile.
authenticate wireless clients by their MAC addresses.
Users cannot get an IP address if the MAC authentication
fails. The no parameter turns it off.
RADIUS servers can require the MAC address in the
wireless client’s account (username/password) or Calling
Station ID RADIUS attribute. See Section 24.2.4.1 on
page 173 for a MAC authentication example.
requires for using MAC addresses as the account
username and password.
For example, use mac-auth case account upper
and mac-auth delimiter account dash if you
need to use a MAC address formatted like 00-11-AC-01A0-11 as the username and password.
Sets the case (upper or lower) the external server
requires for letters in MAC addresses in the Calling
Station ID RADIUS attribute.
Specify the separator the external server uses for the
two-character pairs within MAC addresses used as the
account username and password.
For example, use mac-auth case account upper
and mac-auth delimiter account dash if you
need to use a MAC address formatted like 00-11-AC-01A0-11 as the username and password.
NXC CLI Reference Guide
85
Page 86

Chapter 9 Wireless LAN Profiles
Table 35 Command Summary: Security Profile (continued)
COMMAND DESCRIPTION
mac-auth delimiter calling-station-id
{colon | dash | none}
mode {none | wep | wpa | wpa2 | wpa2mix}
wep <64 | 128> default-key <1..4> Sets the WEP encryption strength (64 or 128) and the
wep-auth-type {open | share} Sets the authentication key type to either open or share.
wpa-encrypt {tkip | aes | auto} Sets the WPA/WPA2 encryption cipher type.
wpa-psk {wpa_key | wpa_key_64} Sets the WPA/WPA2 pre-shared key.
[no] wpa2-preauth Enables pre-au thentication to allow wireless clients to
[no] reauth <30..30000> Sets the interval (in seconds) between authentication
idle <30..30000> Sets the idle interval (in seconds) that a client can be idle
group-key <30..30000> Sets the interval (in seconds) at which the AP updates the
[no] dot1x-eap Enables 802.1x secure authentication. Use the no
Select the separator the external server uses for the pairs
in MAC addresses in the Calling Station ID RADIUS
attribute.
Sets the security mode for this profile.
default key value (1 ~ 4).
If you select WEP-64 enter 10 hexadecimal digits in the
range of “A-F”, “a-f” and “0-9” (for example,
0x11AA22BB33) for each Key used; or enter 5 ASCII
characters (case sensitive) ranging from “a-z”, “A-Z” and
“0-9” (for example, MyKey) for each Key used.
If you select WEP-128 enter 26 hexadecimal digits in the
range of “A-F”, “a-f” and “0-9” (for example,
0x00112233445566778899AABBCC) for each Key used;
or enter 13 ASCII characters (case sensitive) ranging
from “a-z”, “A-Z” and “0-9” (for example,
MyKey12345678) for each Key used.
You can save up to four different keys. Enter the
default-key (1 ~ 4) to save your WEP to one of those
four available slots.
auto: This automatically chooses the best available
cipher based on the cipher in use by the wireless client
that is attempting to make a connection.
tkip: This is the Temporal Key Integrity Protocol
encryption method added later to the WEP encryption
protocol to further secure. Not all wireless clients may
support this.
aes: This is the Advanced Encryption Standard
encryption method, a newer more robust algorithm than
TKIP Not all wireless clients may support this.
switch APs without having to re-authenticate their
network connection. The RADIUS server puts a
temporary PMK Security Authorization cache on the
wireless clients. It contains their session ID and a preauthorized list of viable APs.
Use the no parameter to disable this.
requests.
The default is 0.
before authentication is discontinued.
The default is 300.
group WPA/WPA2 encryption key.
The default is 1800.
parameter to disable it.
86
NXC CLI Reference Guide
Page 87

Chapter 9 Wireless LAN Profiles
Table 35 Command Summary: Security Profile (continued)
COMMAND DESCRIPTION
eap {external | internal auth_method} Sets the 802.1x authentication method.
[no] server-auth <1..2> activate Activates server authentication. Use the no parameter to
server-auth <1..2> ip address
ipv4_address port <1..65535> secret
secret
[no] server-auth <1..2> Clears the server authentication setting.
exit Exits configuration mode for this profile.
deactivate.
Sets the IPv4 address, port number and shared secret of
the RADIUS server to be used for authentication.
9.4.1 Security Profile Example
The following example creates a security profile with the name ‘SECURITY01’..
Router(config)# wlan-security-profile SECURITY01
Router(config-security-profile)# mode wpa2
Router(config-security-profile)# wpa-encrypt aes
Router(config-security-profile)# wpa-psk 12345678
Router(config-security-profile)# idle 3600
Router(config-security-profile)# reauth 1800
Router(config-security-profile)# group-key 1800
Router(config-security-profile)# exit
Router(config)#
9.5 MAC Filter Profile Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 36 Input Values for General MAC Filter Profile Commands
LABEL DESCRIPTION
macfilter_profile_name The MAC filter profile name. You may use 1-31 alphanumeric
characters, underscores (
cannot be a number. This value is case-sensitive.
description2 Sets the description of the profile. You may use up to 60
alphanumeric characters, underscores (
is case-sensitive.
_), or dashes (-), but the first character
_), or dashes (-). This value
NXC CLI Reference Guide
87
Page 88

Chapter 9 Wireless LAN Profiles
The following table describes the commands available for security profile management. You
must use the
configure terminal command to enter the configuration mode before you
can use these commands.
Table 37 Command Summary: MAC Filter Profile
COMMAND DESCRIPTION
show wlan-macfilter-profile {all |
macfilter_profile_name}
wlan-macfilter-profile rename
macfilter_profile_name1
macfilter_profile_name2
[no] wlan-macfilter-profile
macfilter_profile_name
filter-action {allow | deny} Permits the wireless client with the MAC addresses in this
[no] MAC description description2 Sets the description of this profile. Enter up to 60
exit Exits configuration mode for this profile.
Displays the security profile(s).
all: Displays all profiles for the selected operating mode.
macfilter_profile_name: Displays the specified
profile for the selected operating mode.
Gives an existing security profile
(macfilter_profile_name1) a new name
(macfilter_profile_name2).
Enters configuration mode for the specified MAC filter
profile. Use the no parameter to remove the specified
profile.
profile to connect to the network through the associated
SSID; select deny to block the wireless clients with the
specified MAC addresses.
The default is set to deny.
characters. Spaces and underscores allowed.
9.5.1 MAC Filter Profile Example
The following example creates a MAC filter profile with the name ‘MACFILTER01’..
Router(config)# wlan-macfilter-profile MACFILTER01
Router(config-macfilter-profile)# filter-action deny
Router(config-macfilter-profile)# MAC 01:02:03:04:05:06 description MAC01
Router(config-macfilter-profile)# MAC 01:02:03:04:05:07 description MAC02
Router(config-macfilter-profile)# MAC 01:02:03:04:05:08 description MAC03
Router(config-macfilter-profile)# exit
Router(config)#
88
NXC CLI Reference Guide
Page 89

CHAPTER 10
Rogue AP
This chapter shows you how to set up Rogue Access Point (AP) detection and containment.
10.1 Rogue AP Detection Overview
Rogue APs are wireless access points operating in a network’s coverage area that are not under
the control of the network’s administrators, and can potentially open holes in the network
security. Attackers can take advantage of a rogue AP’s weaker (or non-existent) security to
gain illicit access to the network, or set up their own rogue APs in order to capture information
from wireless clients.
Conversely, a friendly AP is one that the NXC network administrator regards as nonthreatening. This does not necessarily mean the friendly AP must belong to the network
managed by the NXC; rather, it is any unmanaged AP within range of the NXC’ s own wireless
network that is allowed to operate without being contained. This can include APs from
neighboring companies, for example, or even APs maintained by your company’s employees
that operate outside of the established network.
10.2 Rogue AP Detection Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 38 Input Values for Rogue AP Detection Commands
LABEL DESCRIPTION
ap_mac Specifies the MAC address (in XX:XX:XX:XX:XX:XX format) of the AP
to be added to either the rogue AP or friendly AP list. The no command
removes the entry.
description2 Sets the description of the AP. You may use 1-60 alphanumeric
characters, underscores (
The following table describes the commands available for rogue AP detection. You must use
configure terminal command to enter the configuration mode before you can use
the
these commands.
Table 39 Command Summary: Rogue AP Detection
COMMAND DESCRIPTION
rogue-ap detection Enters sub-command mode for rogue AP detection.
[no] activate Activates rogue AP detection. Use the no parameter to
deactivate rogue AP detection.
_), or dashes (-). This value is case-sensitive.
NXC CLI Reference Guide
89
Page 90

Chapter 10 Rogue AP
Table 39 Command Summary: Rogue AP Detection (continued)
COMMAND DESCRIPTION
rogue-ap ap_mac description2 Sets the device that owns the specified MAC address as
a rogue AP. You can also assign a description to this
entry on the rogue AP list.
no rogue-ap ap_mac Removes the device that owns the specified MAC
address from the rogue AP list.
friendly-ap ap_mac description2 Sets the device that owns the specified MAC address as
no friendly-ap ap_mac Removes the device that owns the specified MAC
exit Exits configuration mode for rogue AP detection.
show rogue-ap detection monitoring Displays a table of detected APs and information about
show rogue-ap detection list {rogue |
friendly| all}
show rogue-ap detection status Displays whether rogue AP detection is on or off.
show rogue-ap detection info Displays a summary of the number of detected devices
a friendly AP. You can also assign a description to this
entry on the friendly AP list.
address from the friendly AP list.
them, such as their MAC addresses, when they were last
seen, and their SSIDs, to name a few.
Displays the specified rogue/friendly/all AP list.
from the following categories: rogue, friendly, ad-hoc,
unclassified, and total.
10.2.1 Rogue AP Detection Examples
This example sets the device associated with MAC address 00:13:49:11:11:11 as a rogue AP,
and the device associated with MAC address 00:13:49:11:11:22 as a friendly AP. It then
removes MAC address from the rogue AP list with the assumption that it was misidentified.
Router(config)# rogue-ap detection
Router(config-detection)# rogue-ap 00:13:49:11:11:11 rogue
Router(config-detection)# friendly-ap 00:13:49:11:11:22 friendly
Router(config-detection)# no rogue-ap 00:13:49:11:11:11
Router(config-detection)# exit
This example displays the rogue AP detection list.
Router(config)# show rogue-ap detection list rogue
no. mac description
contain
===========================================================================
1 00:13:49:18:15:5A
0
90
NXC CLI Reference Guide
Page 91

Chapter 10 Rogue AP
This example shows the friendly AP detection list.
Router(config)# show rogue-ap detection list friendly
no. mac description
===========================================================================
1 11:11:11:11:11:11 third floor
2 00:13:49:11:22:33
3 00:13:49:00:00:05
4 00:13:49:00:00:01
5 00:0D:0B:CB:39:33 dept1
This example shows the combined rogue and friendly AP detection list.
Router(config)# show rogue-ap detection list all
no. role mac description
===========================================================================
1 friendly-ap 11:11:11:11:11:11 third floor
2 friendly-ap 00:13:49:11:22:33
3 friendly-ap 00:13:49:00:00:05
4 friendly-ap 00:13:49:00:00:01
5 friendly-ap 00:0D:0B:CB:39:33 dept1
6 rogue-ap 00:13:49:18:15:5A
This example shows both the status of rogue AP detection and the summary of detected APs.
Router(config)# show rogue-ap detection status
rogue-ap detection status: on
Router(config)# show rogue-ap detection info
rogue ap: 1
friendly ap: 4
adhoc: 4
unclassified ap: 0
total devices: 0
10.3 Rogue AP Containment Overview
These commands enable rogue AP containment. You can use them to isolate a device that is
flagged as a rogue AP. They are global in that they apply to all managed APs on the network
(all APs utilize the same containment list, but only APs set to monitor mode can actively
engage in containment of rogue APs). This means if we add a MAC address of a device to the
containment list, then every AP on the network will respect it.
NXC CLI Reference Guide
91
Page 92

Chapter 10 Rogue AP
Containing a rogue AP means broadcasting unviable login data at it,
preventing legitimate wireless clients from connecting to it. This is a kind of
Denial of Service attack.
10.4 Rogue AP Containment Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 40 Input Values for Rogue AP Containment Commands
LABEL DESCRIPTION
ap_mac Specifies the MAC address (in XX:XX:XX:XX:XX:XX format) of the AP
to be contained. The no command removes the entry.
The following table describes the commands available for rogue AP containment. You must
use the
these commands.
configure terminal command to enter the configuration mode before you can use
Table 41 Command Summary: Rogue AP Containment
COMMAND DESCRIPTION
rogue-ap containment Enters sub-command mode for rogue AP containment.
[no] activate Activates rogue AP containment. Use the no parameter
to deactivate rogue AP containment.
[no] contain ap_mac Isolates the device associated with the specified MAC
address. Use the no parameter to remove this device
from the containment list.
exit Exits configuration mode for rogue AP containment.
show rogue-ap containment list Displays the rogue AP containment list.
10.4.1 Rogue AP Containment Example
This example contains the device associated with MAC address 00:13:49:11:11:12 then
displays the containment list for confirmation.
Router(config)# rogue-ap containment
Router(config-containment)# activate
Router(config-containment)# contain 00:13:49:11:11:12
Router(config-containment)# exit
Router(config)# show rogue-ap containment list
no. mac
=====================================================================
1 00:13:49:11:11:12
92
NXC CLI Reference Guide
Page 93
CHAPTER 11
Wireless Frame Capture
This chapter shows you how to configure and use wireless frame capture on the NXC.
11.1 Wireless Frame Capture Overview
Troubleshooting wireless LAN issues has always been a challenge. Wireless sniffer tools like
Ethereal can help capture and decode packets of information, which can then be analyzed for
debugging. It works well for local data traffic, but if your devices are spaced increasingly
farther away then it often becomes correspondingly difficult to attempt remote debugging.
Complicated wireless packet collection is arguably an arduous and perplexing process. The
wireless frame capture feature in the NXC can help.
This chapter describes the wireless frame capture commands, which allows a network
administrator to capture wireless traffic information and download it to an Ethereal/Tcpdump
compatible format packet file for analysis.
11.2 Wireless Frame Capture Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 42 Input Values for Wireless Frame Capture Commands
LABEL DESCRIPTION
ip_address The IP address of the Access Point (AP) that you want to monitor. Enter
a standard IPv4 IP address (for example, 192.168.1.2).
mon_dir_size The total combined size (in kbytes) of all files to be captured. The
maximum you can set is 50 megabtyes (52428800 bytes.)
file_name The file name prefix for each captured file. The default prefix is monitor
while the default file name is monitor.dump.
You can use 1-31 alphanumeric characters, underscores or dashes but
the first character cannot be a number. This string is case sensitive.
NXC CLI Reference Guide
93
Page 94

Chapter 11 Wireless Frame Capture
The following table describes the commands available for wireless frame capture. You must
use the
configure terminal command to enter the configuration mode before you can use
these commands.
Table 43 Command Summary: Wireless Frame Capture
COMMAND DESCRIPTION
frame-capture configure Enters sub-command mode for wireless frame capture.
src-ip {add|del} {ipv4_address |
local}
file-prefix file_name Sets the file name prefix for each captured file. Enter up
files-size mon_dir_size Sets the total combined size (in kbytes) of all files to be
exit Exits configuration mode for wireless frame capture.
[no] frame-capture activate Starts wireless frame capture. Use the no parameter to
show frame-capture status Displays whether frame capture is running or not.
show frame-capture config Displays the frame capture configuration.
Sets or removes the IPv4 address of an AP controlled by
the NXC that you want to monitor. You can use this
command multiple times to add additional IPs to the
monitor list.
to 31 alphanumeric characters. Spaces and underscores
are not allowed.
captured.
turn it off.
11.2.1 Wireless Frame Capture Examples
This example configures the wireless frame capture parameters for an AP located at IP address
192.168.1.2.
Router(config)# frame-capture configure
Router(frame-capture)# src-ip add 192.168.1.2
Router(frame-capture)# file-prefix monitor
Router(frame-capture)# files-size 1000
Router(frame-capture)# exit
Router(config)#
This example shows frame capture status and configuration.
Router(config)# show frame-capture status
capture status: off
Router(config)# show frame-capture config
capture source: 192.168.1.2
file prefix: monitor
file size: 1000
94
NXC CLI Reference Guide
Page 95

CHAPTER 12
Dynamic Channel Selection
This chapter shows you how to configure and use dynamic channel selection on the NXC.
12.1 DCS Overview
Dynamic Channel Selection (DCS) is a feature that allows an AP to automatically select the
radio channel upon which it broadcasts by passively listening to the area around it and
determining what channels are currently being broadcast on by other devices.
When numerous APs broadcast within a given area, they introduce the possibility of
heightened radio interference, especially if some or all of them are broadcasting on the same
radio channel. This can make accessing the network potentially rather difficult for the stations
connected to them. If the interference becomes too great, then the network administrator must
open his AP configuration options and manually change the channel to one that no other AP is
using (or at least a channel that has a lower level of interference) in order to give the connected
stations a minimum degree of channel interference.
12.2 DCS Commands
The following table identifies the values required for many of these commands. Other input
values are discussed with the corresponding commands.
Table 44 Input Values for DCS Commands
LABEL DESCRIPTION
interval Enters the dynamic channel selection interval time. The range is 10 ~
The following table describes the commands available for dynamic channel selection. You
must use the
can use these commands.
Table 45 Command Summary: DCS
COMMAND DESCRIPTION
[no] dcs activate Starts dynamic channel selection. Use the no parameter
dcs 2g-selected-channel 2.4g_channels Sets the channels that are available in the 2.4 GHz band
configure terminal command to enter the configuration mode before you
1440 minutes.
to turn it off.
when you manually configure the channels an AP can
use.
NXC CLI Reference Guide
95
Page 96

Chapter 12 Dynamic Channel Selection
Table 45 Command Summary: DCS (continued)
COMMAND DESCRIPTION
dcs 5g-selected-channel 5g_channels Sets the channels that are available in the 5 GHz band
when you manually configure the channels an AP can
use.
dcs dcs-2g-method {auto|manual} Sets the AP to automatically search for available
channels or manually configures the channels the AP
uses in the 2.4 GHz band.
dcs dcs-5g-method {auto|manual} Sets the AP to automatically search for available
channels or manually configures the channels the AP
uses in the 5 GHz band.
dcs time-interval interval Sets the interval that specifies how often DCS should run.
dcs sensitivity-level {high| medium |low} Sets how sensitive DCS is to radio channel changes in
the vicinity of the AP running the scan.
dcs client-aware {enable|disable} When enabled, this ensures that an AP will not change
channels as long as a client is connected to it. If disabled,
the AP may change channels regardless of whether it has
clients connected to it or not.
dcs channel-deployment {3-channel|4channel}
dcs dfs-aware {enable|disable} Enables this to allow an AP to avoid phase DFS channels
show dcs config Displays the current DCS configura ti o n.
Sets either a 3-channel deployment or a 4-channel
deployment.
In a 3-channel deployment, the AP running the scan
alternates between the following channels: 1, 6, and 11.
In a 4-channel deployment, the AP running the scan
alternates between the following channels: 1, 4, 7, and 11
(FCC) or 1, 5, 9, and 13 (ETSI).
Sets the option that is applicable to your region. (Channel
deployment may be regulated differently between
countries and locales.)
below the 5 GHz spectrum.
12.2.1 DCS Examples
This example creates a DCS configuration.
Router(config)# dcs time-interval 720
Router(config)# dcs sensitivity-level high
Router(config)# dcs client-aware enable
Router(config)# dcs channel-deployment 3-channel
Router(config)# dcs dfs-aware enable
96
NXC CLI Reference Guide
Page 97

Chapter 12 Dynamic Channel Selection
This example displays the DCS configuration created in the previous example.
Router(config)# show dcs config
dcs activate: no
dcs time interval: 720
dcs sensitivity level: high
dcs client-aware: enable
dcs 2.4-ghz selection method: auto
dcs 2.4-ghz selected channels: none
dcs 2.4-ghz channel deployment: 3-channel
dcs 5-ghz selection method: auto
dcs 5-ghz selected channels: none
dcs 5-ghz DFS-aware: enable
NXC CLI Reference Guide
97
Page 98

Chapter 12 Dynamic Channel Selection
98
NXC CLI Reference Guide
Page 99

CHAPTER 13
Wireless Load Balancing
This chapter shows you how to configure wireless load balancing.
13.1 Wireless Load Balancing Overview
Wireless load balancing is the process whereby you limit the number of connections allowed
on an wireless access point (AP) or you limit the amount of wireless traffic transmitted and
received on it. Because there is a hard upper limit on the AP’s wireless bandwidth, this can be
a crucial function in areas crowded with wireless users. Rather than let every user connect and
subsequently dilute the available bandwidth to the point where each connecting device
receives a meager trickle, the load balanced AP instead limits the incoming connections as a
means to maintain bandwidth integrity.
13.2 Wireless Load Balancing Commands
The following table describes the commands available for wireless load balancing. You must
use the
these commands.
Table 46 Command Summary: Load Balancing
COMMAND DESCRIPTION
[no] load-balancing kickout Enables an overloaded AP to disconnect (“kick”) idle
load-balancing mode {station | traffic} Enables load balancing based on either number of
load-balancing max sta <1..127> If load balancing by the number of stations/wireless
load-balancing traffic level {high | low |
medium}
load-balancing alpha <1..255> Sets the load balancing alpha value.
configure terminal command to enter the configuration mode before you can use
clients or clients with noticeably weak connections.
stations (also known as wireless clients) or wireless traffic
on an AP.
clients, this sets the maximum number of devices allowed
to connect to a load-balanced AP.
If load balancing by traffic threshold, this sets the traffic
threshold level.
When the AP is balanced, then this setting delays a
client’s association with it by this number of seconds.
Note: This parameter has been optimized for
the NXC and should not be changed
unless you have been specifically
directed to do so by ZyXEL support.
NXC CLI Reference Guide
99
Page 100

Chapter 13 Wireless Load Balancing
Table 46 Command Summary: Load Balancing (continued)
COMMAND DESCRIPTION
load-balancing beta <1..255> Sets the load balancin g beta value.
When the AP is overloaded, then this setting delays a
client’s association with it by this number of seconds.
Note: This parameter has been optimized for
the NXC and should not be changed
unless you have been specifically
directed to do so by ZyXEL support.
load-balancing sigma <51..100> Sets the load balancing sigma value.
This value is algorithm parameter used to calculate
whether an AP is considered overloaded, balanced, or
underloaded. It only applies to ‘by traffic mode’.
Note: This parameter has been optimized for
the NXC and should not be changed
unless you have been specifically
directed to do so by ZyXEL support.
load-balancing timeout <1..255> Sets the length of time that an AP retains load balancing
information it receives from other APs within its range.
load-balancing liInterval <1..255> Sets the interval in seconds that each AP communicates
with the other APs in its range for calculating the load
balancing algorithm.
Note: This parameter has been optimized for
the NXC and should not be changed
unless you have been specifically
directed to do so by ZyXEL support.
load-balancing kickInterval <1..255> Enables the kickout feature for load balancing and also
sets the kickout interval in seconds. While load balancing
is enabled, the AP periodically disconnects stations at
intervals equal to this setting.
This occurs until the load balancing threshold is no longer
exceeded.
show load-balancing config Displays the load balancing configuration.
[no] load-balancing activate Enables load balancing. Use the no parameter to disable
it.
100
NXC CLI Reference Guide
 Loading...
Loading...