
GS-1524 / GS-1548
Web Managed GbE Switch
User’s Guide
Version 1.12
8/2007
Edition 1
www.zyxel.com

About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the Switch using the web
configurator. You should have at least a basic knowledge of TCP/IP networking concepts and
topology.
Related Documentation
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away. It contains
information on setting up your hardware connections.
• Web Configurator Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
" It is recommended you use the web configurator to configure the Switch.
• Supporting Disk
Refer to the included CD for support documents.
• ZyXEL Web Site
Please refer to www.zyxel.com
certifications.
User Guide Feedback
Help us help you. Send all User Guide-related comments, questions or suggestions for
improvement to the following address, or use e-mail instead. Thank you!
The Technical Writing Team,
ZyXEL Communications Corp.,
6 Innovation Road II,
Science-Based Industrial Park,
Hsinchu, 300, Taiwan.
E-mail: techwriters@zyxel.com.tw
for additional support documentation and product
GS-1524/GS-1548 User’s Guide
3
Document Conventions
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
1 Warnings tell you about things that could harm you or your device.
" Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The GS-1524 / GS-1548 may be referred to as the “Switch”, the “device”, or the “system”
in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A key stroke is denoted by square brackets and uppercase text, for example, [ENTER]
means the “enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the [ENTER] key.
“Select” or “choose” means for you to use one of the predefined choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example,
Maintenance > Log > Log Setting means you first click Maintenance in the navigation
panel, then the Log sub menu and finally the Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value. For
example, “k” for kilo may denote “1000” or “1024”, “M” for mega may denote “1000000”
or “1048576” and so on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other words”.
4
GS-1524/GS-1548 User’s Guide

Document Conventions
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The Switch icon is not an
exact representation of your device.
The Switch Computer Notebook computer
Server DSLAM Firewall
Telephone Switch Router
GS-1524/GS-1548 User’s Guide
5

Safety Warnings
Safety Warnings
1 For your safety, be sure to read and follow all warning notices and instructions.
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel should
service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in
North America or 230V AC in Europe).
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the power outlet.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a
new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
6
This product is recyclable. Dispose of it properly.
GS-1524/GS-1548 User’s Guide
Safety Warnings
GS-1524/GS-1548 User’s Guide
7

Safety Warnings
8
GS-1524/GS-1548 User’s Guide

Contents Overview
Contents Overview
Introduction and Hardware Overview ..................................................................................25
Getting to Know Your Switch ..................................................................................................... 27
Hardware Installation and Connection ....................................................................................... 31
Hardware Overview ................................................................................................................... 35
Basic & Advanced Settings .................................................................................................. 41
The Web Configurator ............................................................................................................... 43
System ....................................................................................................................................... 49
Port Settings .............................................................................................................................. 55
System and Port Statistics ......................................................................................................... 57
VLAN ......................................................................................................................................... 61
Trunking ..................................................................................................................................... 65
Mirroring .................................................................................................................................... 67
QoS ........................................................................................................................................... 69
Port Rate Limit and Storm Control ............................................................................................. 79
Layer 2 (L2) Management ......................................................................................................... 83
Cable Diagnostics ...................................................................................................................... 87
Auto Denial of Service (DoS) ..................................................................................................... 89
Auto VoIP ................................................................................................................................... 93
Management and Troubleshooting .....................................................................................95
Event Logging ............................................................................................................................ 97
SNMP ...................................................................................................................................... 105
RMON-Lite ................................................................................................................................119
Dynamic ARP .......................................................................................................................... 135
Troubleshooting ....................................................................................................................... 139
Product Specifications ............................................................................................................. 143
Appendices and Index ......................................................................................................... 147
GS-1524/GS-1548 User’s Guide
9

Contents Overview
10
GS-1524/GS-1548 User’s Guide

Table of Contents
Table of Contents
About This User's Guide ..........................................................................................................3
Document Conventions............................................................................................................4
Safety Warnings........................................................................................................................6
Contents Overview ...................................................................................................................9
Table of Contents....................................................................................................................11
List of Figures .........................................................................................................................17
List of Tables...........................................................................................................................21
Part I: Introduction and Hardware Overview ....................................... 25
Chapter 1
Getting to Know Your Switch.................................................................................................27
1.1 Introduction .......................................................................................................................... 27
1.1.1 Backbone Application ................................................................................................. 27
1.1.2 Bridging Example ....................................................................................................... 28
1.1.3 High Performance Switching Example ....................................................................... 28
1.1.4 IEEE 802.1Q VLAN Application Examples ................................................................ 29
Chapter 2
Hardware Installation and Connection .................................................................................31
2.1 Freestanding Installation ..................................................................................................... 31
2.2 Mounting the Switch on a Rack .......................................................................................... 32
2.2.1 Rack-mounted Installation Requirements .................................................................. 32
2.2.2 Attaching the Mounting Brackets to the Switch .......................................................... 32
2.2.3 Mounting the Switch on a Rack .................................................................................. 33
Chapter 3
Hardware Overview.................................................................................................................35
3.1 Front Panel ........................................................................................................................ 35
3.1.1 Ethernet Ports ............................................................................................................ 36
3.1.2 Mini-GBIC Slots .........................................................................................................36
3.2 LEDs ................................................................................................................................ 38
3.3 Rear Panel ........................................................................................................................... 38
GS-1524/GS-1548 User’s Guide
11

Table of Contents
3.3.1 Power Connector ....................................................................................................... 39
3.4 The RESET Button .............................................................................................................. 39
Part II: Basic & Advanced Settings ...................................................... 41
Chapter 4
The Web Configurator ............................................................................................................43
4.1 Introduction .......................................................................................................................... 43
4.2 System Login .................................................................................................................... 43
4.3 The Status Screen .......................................................................................................... 44
4.3.1 The LED Panel ........................................................................................................... 45
4.3.2 The Navigation Panel ................................................................................................. 45
4.3.3 Change Your Password .......................................................................................... 46
4.4 Saving Your Configuration ................................................................................................... 47
4.5 Switch Lockout .................................................................................................................. 47
4.6 Resetting the Switch ......................................................................................................... 47
4.7 Logging Out of the Web Configurator ................................................................................. 47
4.8 Help ................................................................................................................................... 48
Chapter 5
System .....................................................................................................................................49
5.1 System Screen ................................................................................................................... 49
5.1.1 Configure IP Address ................................................................................................. 50
5.1.2 Layer 2 (L2) Table Aging ............................................................................................ 50
5.1.3 Backup Settings ......................................................................................................... 51
5.1.4 Restore Settings .........................................................................................................51
5.2 System: Change Password .............................................................................................. 52
5.3 Firmware Upgrade ............................................................................................................... 52
5.3.1 System: Restart/Reset ............................................................................................. 53
Chapter 6
Port Settings............................................................................................................................55
6.1 Port Status ......................................................................................................................... 55
6.2 Port Configuration .............................................................................................................. 56
Chapter 7
System and Port Statistics.....................................................................................................57
7.1 Overview .............................................................................................................................. 57
7.2 Statistics Summary .......................................................................................................... 57
7.3 Port Statistics ...................................................................................................................... 58
12
GS-1524/GS-1548 User’s Guide

Table of Contents
Chapter 8
VLAN ........................................................................................................................................61
8.1 Introduction to IEEE 802.1Q Tagged VLANs .................................................................. 61
8.1.1 Forwarding Tagged and Untagged Frames ................................................................ 61
8.2 Static VLAN ......................................................................................................................... 62
8.2.1 IEEE 802.1Q VLAN Screen ....................................................................................... 62
8.2.2 Create IEEE 802.1Q VLAN Screen ........................................................................... 63
8.2.3 Edit IEEE 802.1Q VLAN Screen ............................................................................... 63
Chapter 9
Trunking...................................................................................................................................65
9.1 Trunking Overview .............................................................................................................. 65
9.1.1 Distribution Criteria ..................................................................................................... 65
9.2 Trunk Setting Screen ........................................................................................................... 65
Chapter 10
Mirroring ..................................................................................................................................67
10.1 Port Mirroring Settings ...................................................................................................... 67
Chapter 11
QoS...........................................................................................................................................69
11.1 QoS Overview ................................................................................................................... 69
11.1.1 Weighted Round Robin (WRR) ................................................................................ 69
11.1.2 Strict Priority ............................................................................................................. 69
11.2 QoS Enhancement ............................................................................................................. 70
11.3 Configuring QoS ................................................................................................................ 70
11.3.1 Change Number of Queues ................................................................................... 72
11.4 Advanced QoS Settings ....................................................................................................72
11.4.1 Port Based QoS ....................................................................................................... 72
11.4.2 DSCP Based QoS .................................................................................................... 74
11.4.3 Differentiated Services Code Point (DSCP) Overview ............................................. 74
11.4.4 DSCP Based QoS Screen ........................................................................................ 74
11.4.5 ToS Based QoS ........................................................................................................ 75
11.4.6 IP Address Based QoS ............................................................................................ 76
Chapter 12
Port Rate Limit and Storm Control........................................................................................79
12.1 Port Rate Screen ............................................................................................................. 79
12.1.1 Rate Limit Screen ................................................................................................... 80
12.1.2 Broadcast Storm Control Setup ............................................................................... 81
Chapter 13
Layer 2 (L2) Management....................................................................................................... 83
GS-1524/GS-1548 User’s Guide
13

Table of Contents
13.1 Configuring L2 Management ........................................................................................ 83
13.1.1 Add a Static MAC Address Entry ........................................................................... 84
13.2 Viewing the L2 Address Table ...................................................................................... 84
Chapter 14
Cable Diagnostics...................................................................................................................87
14.1 Diagnostics Overview ....................................................................................................... 87
Chapter 15
Auto Denial of Service (DoS) .................................................................................................89
15.1 About Denial of Service Attacks ....................................................................................... 89
15.1.1 DoS Attacks Summary ............................................................................................. 89
15.2 Global Auto DoS Attack Prevention ................................................................................... 90
15.3 Advanced Auto DoS Attack Prevention ............................................................................ 90
Chapter 16
Auto VoIP ................................................................................................................................. 93
16.1 About Auto VoIP ............................................................................................................... 93
16.2 Auto VoIP Settings ............................................................................................................. 93
Part III: Management and Troubleshooting ........................................ 95
Chapter 17
Event Logging......................................................................................................................... 97
17.1 Event Logging Overview ...................................................................................................97
17.2 Logging Screen ................................................................................................................. 97
17.3 Logging: Add Server ......................................................................................................... 98
17.4 Viewing RAM and Flash Logs ........................................................................................... 99
17.5 Searching RAM and Flash Logs ...................................................................................... 100
17.5.1 Search Results ...................................................................................................... 102
Chapter 18
SNMP......................................................................................................................................105
18.1 About SNMP .................................................................................................................. 105
18.1.1 Supported MIBs ................................................................................................... 106
18.1.2 SNMP Traps ......................................................................................................... 106
18.1.3 SNMP v3 and Authentication ................................................................................. 106
18.1.4 SNMP EngineID .................................................................................................... 107
18.2 SNMP Group .................................................................................................................. 107
18.2.1 SNMP Group: Create ............................................................................................ 108
18.2.2 SNMP Group: Modify ............................................................................................ 109
14
GS-1524/GS-1548 User’s Guide

Table of Contents
18.3 SNMP User ......................................................................................................................110
18.3.1 SNMP User: Create ...............................................................................................110
18.3.2 SNMP User: Modify ................................................................................................111
18.4 SNMP Community ...........................................................................................................112
18.4.1 SNMP Community: Create .....................................................................................113
18.4.2 SNMP Community: Modify .....................................................................................114
18.5 SNMP Notification ...........................................................................................................114
18.6 SNMP Trap Station ..........................................................................................................115
18.6.1 SNMP Trap Station: Create ....................................................................................116
18.6.2 SNMP Trap Station: Modify ....................................................................................117
Chapter 19
RMON-Lite ............................................................................................................................. 119
19.1 RMON-Lite Overview .......................................................................................................119
19.2 RMON Statistics: Overview .............................................................................................119
19.3 RMON-Lite Statistics: Port .............................................................................................. 120
19.4 RMON-Lite History MIB ................................................................................................... 122
19.4.1 RMON History Control: Overview ......................................................................... 122
19.4.2 RMON History Control: Modify .............................................................................. 123
19.4.3 RMON History Statistics: Overview ...................................................................... 124
19.4.4 RMON History Statistics: Control ......................................................................... 125
19.5 RMON Alarm: Overview ................................................................................................. 127
19.5.1 RMON Alarm: Create New Alarm ........................................................................ 128
19.6 RMON Event: Overview ................................................................................................. 129
19.6.1 RMON Event: Create New Event .......................................................................... 130
19.7 RMON Event Log: Overview .......................................................................................... 131
19.7.1 RMON Event Log: Event ....................................................................................... 132
Chapter 20
Dynamic ARP ........................................................................................................................ 135
20.1 ARP Table Overview .......................................................................................................135
20.1.1 ARP Table Entries .................................................................................................. 135
20.1.2 How Dynamic ARP Works ................................................................................... 135
20.2 Enabling Dynamic ARP .................................................................................................. 135
20.3 Viewing ARP Table Entries ........................................................................................... 137
20.4 Adding ARP Table Entries ........................................................................................... 137
Chapter 21
Troubleshooting....................................................................................................................139
21.1 Power, Hardware Connections, and LEDs ...................................................................... 139
21.2 Switch Access and Login ................................................................................................. 139
Chapter 22
Product Specifications.........................................................................................................143
GS-1524/GS-1548 User’s Guide
15

Table of Contents
22.1 General Switch Specifications ......................................................................................... 143
Part IV: Appendices and Index ........................................................... 147
Appendix A IP Addresses and Subnetting ...........................................................................149
Appendix B Legal Information ..............................................................................................157
Appendix C Customer Support............................................................................................. 161
Index.......................................................................................................................................167
16
GS-1524/GS-1548 User’s Guide

List of Figures
List of Figures
Figure 1 Backbone Application .............................................................................................................. 27
Figure 2 Bridging Application ................................................................................................................ 28
Figure 3 High Performance Switched Workgroup Application ............................................................... 29
Figure 4 Shared Server Using VLAN Example ...................................................................................... 29
Figure 5 Attaching Rubber Feet ........................................................................................................... 31
Figure 6 Attaching the Mounting Brackets ............................................................................................. 32
Figure 7 Mounting the Switch on a Rack .............................................................................................. 33
Figure 8 GS-1524 Front Panel ............................................................................................................. 35
Figure 9 GS-1548 Front Panel ............................................................................................................. 35
Figure 10 Transceiver Installation Example ........................................................................................... 37
Figure 11 Installed Transceiver ............................................................................................................. 37
Figure 12 Opening the Transceiver’s Latch Example ............................................................................ 37
Figure 13 Transceiver Removal Example .............................................................................................. 37
Figure 14 GS-1524 Rear Panel .............................................................................................................. 38
Figure 15 GS-1548 Rear Panel .............................................................................................................. 39
Figure 16 Web Configurator: Login ....................................................................................................... 44
Figure 17 Web Configurator Home Screen (System) ............................................................................ 44
Figure 18 LED Panel ............................................................................................................................. 45
Figure 19 Change Administrator Login Password .................................................................................47
Figure 20 Web Configurator: Logout Link .............................................................................................. 48
Figure 21 System .................................................................................................................................. 49
Figure 22 Configure IP Address ............................................................................................................. 50
Figure 23 Configure L2 Table Aging ....................................................................................................... 50
Figure 24 Restore Settings .................................................................................................................... 51
Figure 25 Restore Configuration Error ................................................................................................... 51
Figure 26 System: Password ................................................................................................................. 52
Figure 27 Firmware Upgrade ................................................................................................................ 53
Figure 28 System: Restart/Reset .......................................................................................................... 53
Figure 29 Port Status ............................................................................................................................. 55
Figure 30 Port Configuration ................................................................................................................. 56
Figure 31 Statistics ................................................................................................................................ 57
Figure 32 Status: Port Details ................................................................................................................ 58
Figure 33 VLAN: VLAN Status ............................................................................................................... 62
Figure 34 VLAN: Create VLAN ............................................................................................................. 63
Figure 35 VLAN: Edit VLAN .................................................................................................................. 64
Figure 36 Trunk Setting .......................................................................................................................... 66
Figure 37 Mirror Setting ......................................................................................................................... 67
Figure 38 QoS Setting ........................................................................................................................... 71
GS-1524/GS-1548 User’s Guide
17

List of Figures
Figure 39 Change Number of Queues .................................................................................................. 72
Figure 40 Port Based QoS .................................................................................................................... 73
Figure 41 DSCP Based QoS ................................................................................................................. 75
Figure 42 ToS Based QoS ..................................................................................................................... 76
Figure 43 IP Address Based QoS ......................................................................................................... 77
Figure 44 Port Rate Limit ....................................................................................................................... 79
Figure 45 Rate Limit Configuration ........................................................................................................ 80
Figure 46 Broadcast Storm Control ....................................................................................................... 81
Figure 47 L2 Management .................................................................................................................... 83
Figure 48 Add a Static MAC Entry ......................................................................................................... 84
Figure 49 Display L2 Address Table ...................................................................................................... 85
Figure 50 Cable Diagnostic ................................................................................................................... 87
Figure 51 Global Auto DoS Attack Prevention ...................................................................................... 90
Figure 52 Advanced Auto DoS Attack Prevention .................................................................................91
Figure 53 Auto VoIP Settings ................................................................................................................ 94
Figure 54 Logging .................................................................................................................................. 97
Figure 55 Logging: Add Server .............................................................................................................. 98
Figure 56 Logs: RAM/Flash ................................................................................................................... 99
Figure 57 Searching: RAM/Flash Logs ................................................................................................ 101
Figure 58 Logs: Search Results ........................................................................................................... 102
Figure 59 SNMP Management Model ................................................................................................ 105
Figure 60 SNMP EngineID .................................................................................................................. 107
Figure 61 SNMP Group ....................................................................................................................... 108
Figure 62 SNMP Group: Create .......................................................................................................... 108
Figure 63 SNMP Group: Modify .......................................................................................................... 109
Figure 64 SNMP User ..........................................................................................................................110
Figure 65 SNMP User: Create ..............................................................................................................111
Figure 66 SNMP User: Modify ..............................................................................................................111
Figure 67 SNMP Community ................................................................................................................112
Figure 68 SNMP Community: Create ...................................................................................................113
Figure 69 SNMP Community: Modify ...................................................................................................114
Figure 70 SNMP Notification ................................................................................................................115
Figure 71 SNMP Trap Station ...............................................................................................................116
Figure 72 SNMP Trap Station: Create ..................................................................................................116
Figure 73 SNMP Trap Station: Modify ..................................................................................................117
Figure 74 RMON Statistics: Overview ................................................................................................. 120
Figure 75 RMON Statistics: Port .......................................................................................................... 121
Figure 76 RMON History Control: Overview. ........................................................................................ 123
Figure 77 RMON History Control: Modify ............................................................................................. 124
Figure 78 RMON History Statistics: Overview. ..................................................................................... 125
Figure 79 RMON History Statistics: Control ......................................................................................... 126
Figure 80 RMON Alarm: Overview. ...................................................................................................... 127
Figure 81 RMON Alarm: Create New Alarm .........................................................................................128
18
GS-1524/GS-1548 User’s Guide

List of Figures
Figure 82 RMON Event: Overview. ...................................................................................................... 129
Figure 83 RMON Event: Create New Event .........................................................................................131
Figure 84 RMON Event Log: Overview. ............................................................................................... 132
Figure 85 RMON Event Log: Event ...................................................................................................... 132
Figure 86 Dynamic ARP ...................................................................................................................... 136
Figure 87 Viewing ARP Table Entries .................................................................................................. 137
Figure 88 Viewing ARP Table Entries .................................................................................................. 137
Figure 89 Network Number and Host ID .............................................................................................. 150
Figure 90 Subnetting Example: Before Subnetting .............................................................................. 152
Figure 91 Subnetting Example: After Subnetting .................................................................................153
GS-1524/GS-1548 User’s Guide
19

List of Figures
20
GS-1524/GS-1548 User’s Guide

List of Tables
List of Tables
Table 1 Panel Connections .................................................................................................................... 36
Table 2 LEDs ......................................................................................................................................... 38
Table 3 LED Panel ................................................................................................................................. 45
Table 4 Navigation Panel Links ............................................................................................................. 45
Table 5 System ...................................................................................................................................... 49
Table 6 Configure IP Address ................................................................................................................ 50
Table 7 Change Password ..................................................................................................................... 52
Table 8 Port Status ................................................................................................................................ 55
Table 9 Port Configuration ..................................................................................................................... 56
Table 10 Statistics .................................................................................................................................. 57
Table 11 Status: Port Details .................................................................................................................. 58
Table 12 VLAN: VLAN Status ................................................................................................................ 62
Table 13 VLAN: Create VLAN ............................................................................................................... 63
Table 14 VLAN: Edit VLAN .................................................................................................................... 64
Table 15 Trunking: Configuration ........................................................................................................... 66
Table 16 Mirror Setting .......................................................................................................................... 67
Table 17 QoS Setting ............................................................................................................................. 71
Table 18 Port Based QoS ...................................................................................................................... 73
Table 19 DSCP Based QoS ................................................................................................................... 75
Table 20 ToS Based QoS ...................................................................................................................... 76
Table 21 IP Address Based QoS ........................................................................................................... 77
Table 22 Rate Limit and Storm Control .................................................................................................. 79
Table 23 Rate Limit Configuration ......................................................................................................... 80
Table 24 Broadcast Storm Control ......................................................................................................... 82
Table 25 L2 Management ...................................................................................................................... 83
Table 26 Add a Static MAC Entry .......................................................................................................... 84
Table 27 Display L2 Address Table ....................................................................................................... 85
Table 28 Cable Diagnostic ..................................................................................................................... 87
Table 29 DoS Attack Summary .............................................................................................................. 89
Table 30 Global Auto DoS Attack Prevention ........................................................................................ 90
Table 31 Advanced Auto DoS Attack Prevention ..................................................................................91
Table 32 Auto VoIP Settings .................................................................................................................. 94
Table 33 Logging ................................................................................................................................... 98
Table 34 Logging: Add Server ............................................................................................................... 98
Table 35 Logs: RAM/Flash .................................................................................................................... 99
Table 36 Searching: RAM/Flash Logs ................................................................................................. 102
Table 37 Logs: Search Results ............................................................................................................ 102
Table 38 SNMP Commands ................................................................................................................ 106
GS-1524/GS-1548 User’s Guide
21

List of Tables
Table 39 SNMP Traps .......................................................................................................................... 106
Table 40 SNMP EngineID .................................................................................................................... 107
Table 41 SNMP Group ......................................................................................................................... 108
Table 42 SNMP Group: Create ............................................................................................................ 109
Table 43 SNMP Group: Modify ............................................................................................................ 109
Table 44 SNMP User ............................................................................................................................110
Table 45 SNMP User: Create ...............................................................................................................111
Table 46 SNMP User: Modify ...............................................................................................................112
Table 47 SNMP Community .................................................................................................................112
Table 48 SNMP Community: Create .....................................................................................................113
Table 49 SNMP Community: Modify .....................................................................................................114
Table 50 SNMP Notification ..................................................................................................................115
Table 51 SNMP Trap Station ................................................................................................................116
Table 52 SNMP Trap Station: Create ....................................................................................................117
Table 53 SNMP Trap Station: Modify ....................................................................................................117
Table 54 RMON Statistics: Overview ................................................................................................... 120
Table 55 RMON Statistics: Port ........................................................................................................... 121
Table 56 RMON History Control: Overview. ........................................................................................ 123
Table 57 RMON History Control: Modify .............................................................................................. 124
Table 58 RMON History Statistics: Overview ....................................................................................... 125
Table 59 RMON History Statistics: Control .......................................................................................... 126
Table 60 RMON Alarm: Overview ........................................................................................................ 127
Table 61 RMON Alarm: Create New Alarm .........................................................................................129
Table 62 RMON Event: Overview ........................................................................................................ 130
Table 63 RMON Event Configuration Screens .................................................................................... 131
Table 64 RMON Event Log: Overview ................................................................................................. 132
Table 65 RMON Event Log: Event ....................................................................................................... 133
Table 66 ARP Table ............................................................................................................................. 136
Table 67 ARP Table ............................................................................................................................. 137
Table 68 ARP Table ............................................................................................................................. 138
Table 69 Physical and Environmental Specifications ........................................................................... 143
Table 70 General Product Specifications ............................................................................................. 144
Table 71 Management Specifications .................................................................................................. 145
Table 72 Firmware Features ................................................................................................................ 145
Table 73 Subnet Mask Example .......................................................................................................... 150
Table 74 Subnet Masks ....................................................................................................................... 151
Table 75 Maximum Host Numbers ...................................................................................................... 151
Table 76 Alternative Subnet Mask Notation ......................................................................................... 151
Table 77 Subnet 1 ................................................................................................................................ 153
Table 78 Subnet 2 ................................................................................................................................ 154
Table 79 Subnet 3 ................................................................................................................................ 154
Table 80 Subnet 4 ................................................................................................................................ 154
Table 81 Eight Subnets ........................................................................................................................ 154
22
GS-1524/GS-1548 User’s Guide

List of Tables
Table 82 24-bit Network Number Subnet Planning .............................................................................. 155
Table 83 16-bit Network Number Subnet Planning .............................................................................. 155
GS-1524/GS-1548 User’s Guide
23

List of Tables
24
GS-1524/GS-1548 User’s Guide

PART I
Introduction and
Hardware Overview
Getting to Know Your Switch (27)
Hardware Installation and Connection (31)
Hardware Overview (35)
25

26
CHAPTER 1
Getting to Know Your Switch
This chapter introduces the main features and applications of the Switch.
1.1 Introduction
Your Switch is an intelligent layer 2 switch with 1000BASE-T RJ-45 ports and mini-GBIC
slots for fiber-optic transceivers. The Switch features dual-personality ports, each of which
consists of one 1000BASE-T RJ-45 port and one mini-GBIC slot, with either interface active
at one time.
• The GS-1524 has 20 1000BASE-T RJ-45 ports, and four dual-personality ports.
• The GS-1548 has 44 1000BASE-T RJ-45 ports, and four dual-personality ports.
With its built-in web configurator, managing and configuring the Switch is easy. See Appendix
A on page 141 for a full list of software features available on the Switch.
1.1.1 Backbone Application
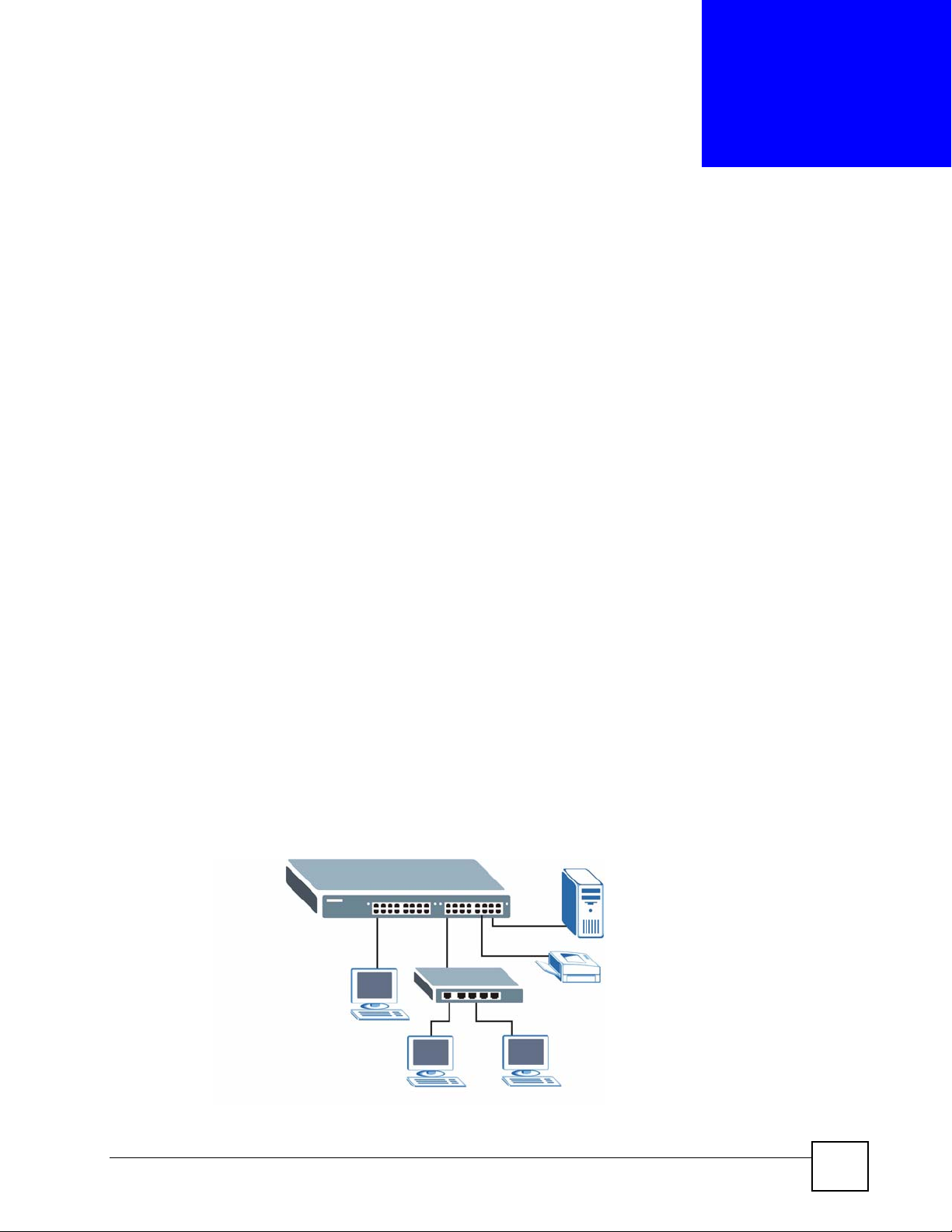
The Switch is an ideal solution for small networks where rapid growth can be expected in the
near future. The Switch can be used standalone for a group of heavy traffic users. You can
connect computers and servers directly to the Switch’s port or connect other switches to the
Switch.
In this example, all computers can share high-speed applications on the server. To expand the
network, simply add more networking devices such as switches, routers, computers, print
servers etc.
Figure 1 Backbone Application
GS-1524/GS-1548 User’s Guide
27
Chapter 1 Getting to Know Your Switch
1.1.2 Bridging Example
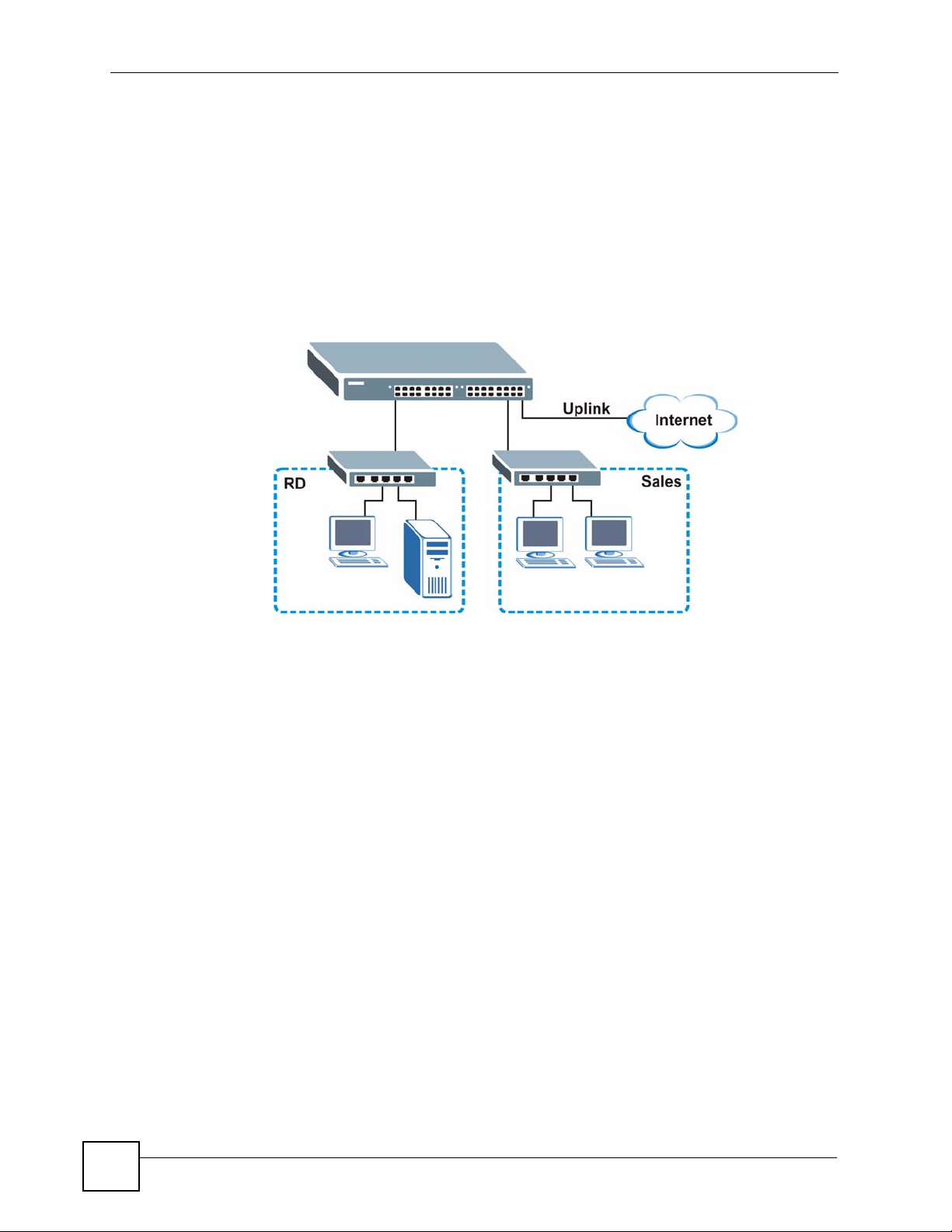
In this example application the Switch connects different company departments (RD and
Sales) to the corporate backbone. It can alleviate bandwidth contention and eliminate server
and network bottlenecks. All users that need high bandwidth can connect to high-speed
department servers via the Switch. You can provide a super-fast uplink connection by using a
Gigabit Ethernet/mini-GBIC port on the Switch.
Moreover, the Switch eases supervision and maintenance by allowing network managers to
centralize multiple servers at a single location.
Figure 2 Bridging Application
1.1.3 High Performance Switching Example
The Switch is ideal for connecting two networks that need high bandwidth. In the following
example, use trunking to connect these two networks.
Switching to higher-speed LANs such as ATM (Asynchronous Transmission Mode) is not
feasible for most people due to the expense of replacing all existing Ethernet cables and
adapter cards, restructuring your network and complex maintenance. The Switch can provide
the same bandwidth as ATM at much lower cost while still being able to use existing adapters
and switches. Moreover, the current LAN structure can be retained as all ports can freely
communicate with each other.
28
GS-1524/GS-1548 User’s Guide
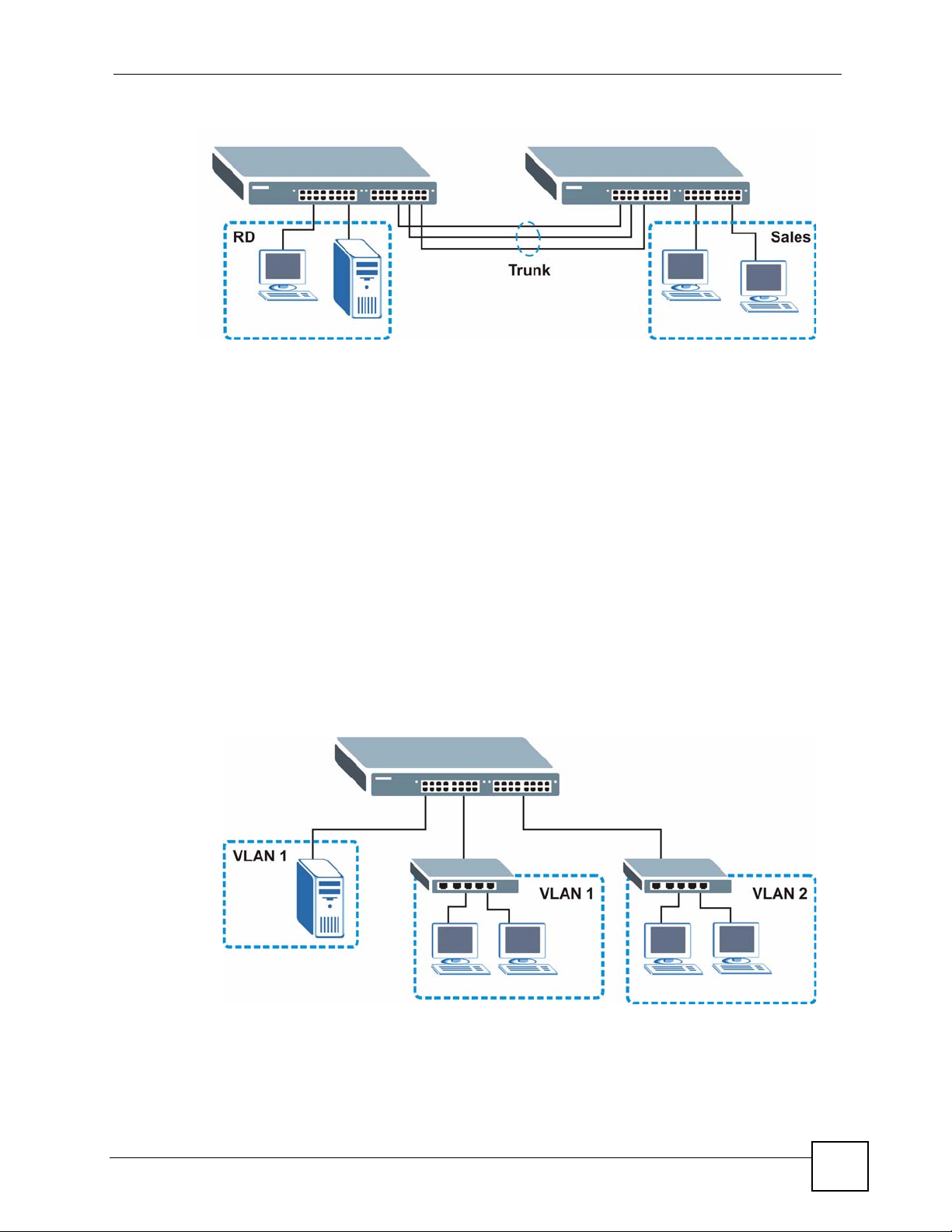
Chapter 1 Getting to Know Your Switch
Figure 3 High Performance Switched Workgroup Application
1.1.4 IEEE 802.1Q VLAN Application Examples
A VLAN (Virtual Local Area Network) allows a physical network to be partitioned into
multiple logical networks. Stations on a logical network belong to one group. A station can
belong to more than one group. With VLAN, a station cannot directly talk to or hear from
stations that are not in the same group(s) unless such traffic first goes through a router.
For more information on VLANs, refer to Chapter 8 on page 61.
1.1.4.1 Tag-based VLAN Example
Ports in the same VLAN group share the same frame broadcast domain thus increase network
performance through reduced broadcast traffic. VLAN groups can be modified at any time by
adding, moving or changing ports without any re-cabling.
Shared resources such as a server can be used by all ports in the same VLAN as the server. In
the following figure only ports that need access to the server need to be part of VLAN 1. Ports
on the Switch can belong to other VLAN groups too.
Figure 4 Shared Server Using VLAN Example
GS-1524/GS-1548 User’s Guide
29

Chapter 1 Getting to Know Your Switch
30
GS-1524/GS-1548 User’s Guide

CHAPTER 2
Hardware Installation and
Connection
This chapter shows you how to install and connect the Switch.
2.1 Freestanding Installation
1 Make sure the Switch is clean and dry.
2 Set the Switch on a smooth, level surface strong enough to support the weight of the
Switch and the connected cables. Make sure there is a power outlet nearby.
3 Make sure there is enough clearance around the Switch to allow air circulation and the
attachment of cables and the power cord.
4 Remove the adhesive backing from the rubber feet.
5 Attach the rubber feet to each corner on the bottom of the Switch. These rubber feet help
protect the Switch from shock or vibration and ensure space between devices when
stacking.
Figure 5 Attaching Rubber Feet
GS-1524/GS-1548 User’s Guide
31

Chapter 2 Hardware Installation and Connection
" Do NOT block the ventilation holes. Leave space between devices when
stacking.
For proper ventilation, allow at least 4 inches (10 cm) of clearance at the front
and 3.4 inches (8 cm) at the back of the Switch. This is especially important for
enclosed rack installations.
2.2 Mounting the Switch on a Rack
This section lists the rack mounting requirements and precautions and describes the
installation steps.
2.2.1 Rack-mounted Installation Requirements
• Two mounting brackets.
• Eight M3 flat head screws and a #2 Philips screwdriver.
• Four M5 flat head screws and a #2 Philips screwdriver.
" Failure to use the proper screws may damage the unit.
2.2.1.1 Precautions
• Make sure the rack will safely support the combined weight of all the equipment it
contains.
• Make sure the position of the Switch does not make the rack unstable or top-heavy. Take
all necessary precautions to anchor the rack securely before installing the unit.
2.2.2 Attaching the Mounting Brackets to the Switch
1 Position a mounting bracket on one side of the Switch, lining up the four screw holes on
the bracket with the screw holes on the side of the Switch.
Figure 6 Attaching the Mounting Brackets
32
GS-1524/GS-1548 User’s Guide

2 Using a #2 Philips screwdriver, install the M3 flat head screws through the mounting
bracket holes into the Switch.
3 Repeat steps 1 and 2 to install the second mounting bracket on the other side of the
Switch.
4 You may now mount the Switch on a rack. Proceed to the next section.
2.2.3 Mounting the Switch on a Rack
1 Position a mounting bracket (that is already attached to the Switch) on one side of the
rack, lining up the two screw holes on the bracket with the screw holes on the side of the
rack.
Figure 7 Mounting the Switch on a Rack
Chapter 2 Hardware Installation and Connection
2 Using a #2 Philips screwdriver, install the M5 flat head screws through the mounting
bracket holes into the rack.
3 Repeat steps 1 and 2 to attach the second mounting bracket on the other side of the rack.
GS-1524/GS-1548 User’s Guide
33

Chapter 2 Hardware Installation and Connection
34
GS-1524/GS-1548 User’s Guide

CHAPTER 3
Hardware Overview
This chapter describes the front panel and rear panel of the Switch and shows you how to
make the hardware connections.
3.1 Front Panel
The figures below show the front panel of the Switch.
Figure 8 GS-1524 Front Panel
LEDs
Figure 9 GS-1548 Front Panel
RJ-45 Gigabit Ethernet Ports
LEDs
Mini-GBIC Slots
Mini-GBIC Slots
GS-1524/GS-1548 User’s Guide
RJ-45 Gigabit Ethernet Ports
35

Chapter 3 Hardware Overview
The following table describes the ports on the panels.
Table 1 Panel Connections
CONNECTOR DESCRIPTION
RJ-45 Gigabit
Ethernet Ports
Mini-GBIC
Slots
3.1.1 Ethernet Ports
The GS-1524 has 24 auto-negotiating, auto-crossover RJ-45 Gigabit Ethernet ports.
The GS-1548 has 48 auto-negotiating, auto-crossover RJ-45 Gigabit Ethernet ports.
The speed of the Gigabit Ethernet ports can be 10 Mbps, 100Mbps or 1000Mbps and the
duplex mode can be half duplex (at 100 Mbps) or full duplex.
An auto-negotiating port can detect and adjust to the optimum Ethernet speed (100/
1000Mpbs) and duplex mode (full duplex or half duplex) of the connected device.7
An auto-crossover (auto-MDI/MDI-X) port automatically works with a straight-through or
crossover Ethernet cable.
Connect these Gigabit Ethernet ports to high-bandwidth backbone network Ethernet
switches or use them to daisy-chain other switches.
Use mini-GBIC transceivers in these slots for fiber-optic connections to backbone
Ethernet switches.
3.1.1.1 Default Ethernet Settings
The factory default negotiation settings for the Ethernet ports on the Switch are:
• Speed: Auto
• Duplex: Auto
• Flow control: Off
3.1.2 Mini-GBIC Slots
There are four mini-GBIC (Gigabit Interface Converter) slots for mini-GBIC transceivers. A
transceiver is a single unit that houses a transmitter and a receiver. The Switch does not come
with transceivers. You must use transceivers that comply with the SFP Transceiver
MultiSource Agreement (MSA). See the SFF committee’s INF-8074i specification Rev 1.0 for
details.
You can change transceivers while the Switch is operating. You can use different transceivers
to connect to Ethernet switches with different types of fiber-optic connectors.
• Type: SFP connection interface
• Connection speed: 1 Gigabit per second (Gbps)
" To avoid possible eye injury, do not look into an operating fiber-optic module’s
connectors.
3.1.2.1 Transceiver Installation
Use the following steps to install a mini GBIC transceiver (SFP module).
36
GS-1524/GS-1548 User’s Guide

Chapter 3 Hardware Overview
1 Insert the transceiver into the slot with the exposed section of PCB board facing down.
Figure 10 Transceiver Installation Example
2 Press the transceiver firmly until it clicks into place.
3 The Switch automatically detects the installed transceiver. Check the LEDs to verify that
it is functioning properly.
Figure 11 Installed Transceiver
3.1.2.2 Transceiver Removal
Use the following steps to remove a mini GBIC transceiver (SFP module).
1 Open the transceiver’s latch (latch styles vary).
Figure 12 Opening the Transceiver’s Latch Example
2 Pull the transceiver out of the slot.
Figure 13 Transceiver Removal Example
GS-1524/GS-1548 User’s Guide
37

Chapter 3 Hardware Overview
3.2 LEDs
The following table describes the LEDs.
Table 2 LEDs
LED STATUS DESCRIPTION
PWR Green On The system is turned on.
Off The system is off.
SYS Green On The system is on and functioning properly.
Off The system is off or is malfunctioning.
Gigabit Ethernet Ports (GS-1524 ONLY)
LINK/ACT Green On The link to a 10/1000 Mbps Ethernet network is up.
Amber On The link to a 100 Mbps Ethernet network is up.
Blinking The port is transmitting/receiving data.
Off The link to an Ethernet network is down.
FDX Amber On The port is negotiating in full-duplex mode.
Gigabit Ethernet Ports (GS-1548 ONLY)
1 ~ 48 Green On The link to a 10/1000 Mbps Ethernet network is up.
Amber On The link to a 100 Mbps Ethernet network is up.
Blinking The port is transmitting/receiving data.
Off The link to an Ethernet network is down.
GBIC Slots
LNK Green On The port has a successful connection.
ACT Green Blinking The port is receiving or transmitting data.
Off The port is negotiating in half-duplex mode and no collisions are
occurring.
Off No Ethernet device is connected to this port.
Off The link to an Ethernet network is down.
3.3 Rear Panel
The following figures show the rear panels of the AC power input model Switch. The rear
panel contains a receptacle for the power cord, and the RESET button.
Figure 14 GS-1524 Rear Panel
38
GS-1524/GS-1548 User’s Guide

Figure 15 GS-1548 Rear Panel
3.3.1 Power Connector
Make sure you are using the correct power source as shown on the panel.
To connect the power to the Switch, insert the female end of the power cord into the power
receptacle on the rear panel. Connect the other end of the supplied power cord to a 100~240V
AC, 50/60 Hz power outlet capable of supplying at least 0.9A (G-1524) or 1.4A (GS-1548).
3.4 The RESET Button
Reset the Switch to its factory default configuration via the RESET button. Press the RESET
button for one second and release. The Switch automatically reboots and reloads its factory
default configuration file.
Chapter 3 Hardware Overview
" When you use the RESET button all of your configuration settings will be lost.
Use the default IP address (192.168.1.1) and user name (admin) and
password (1234) to log back into the Switch. It may take up to 2 minutes for
the Switch to restart when you reload the default configuration file.
GS-1524/GS-1548 User’s Guide
39

Chapter 3 Hardware Overview
40
GS-1524/GS-1548 User’s Guide

PART II
Basic & Advanced
Settings
The Web Configurator (43)
System (49)
Port Settings (55)
System and Port Statistics (57)
VLAN (61)
Trunking (65)
Mirroring (67)
QoS (69)
Port Rate Limit and Storm Control (79)
Layer 2 (L2) Management (83)
Cable Diagnostics (87)
Auto Denial of Service (DoS) (89)
Auto VoIP (93)
41

42

CHAPTER 4
The Web Configurator
This section introduces the configuration and functions of the web configurator.
4.1 Introduction
The web configurator is an HTML-based management interface that allows easy setup and
management of the Switch via Internet browser. Use Internet Explorer 6.0 and later or
Netscape Navigator 7.0 and later versions. The recommended screen resolution is 1024 by 768
pixels.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by
default in Windows XP SP (Service Pack) 2.
• JavaScript (enabled by default).
• Java permissions (enabled by default).
" This User’s Guide shows screens from the GS-1524, unless otherwise
specified.
4.2 System Login
1 Start your web browser.
2 Type “http://” and the IP address of the Switch (for example, the default is 192.168.1.1)
in the Location or Address field. Press [ENTER].
3 The login screen appears. The default username is admin and the associated default
password is 1234.
GS-1524/GS-1548 User’s Guide
43

Chapter 4 The Web Configurator
Figure 16 Web Configurator: Login
4 Click Login to view the first web configurator screen.
4.3 The Status Screen
The System screen is the first screen that displays when you access the web configurator.
The following figure shows the navigating components of the web configurator screen.
Figure 17 Web Configurator Home Screen (System)
B
A
D
C
44
A - The LED panel displays the port status.
B - The navigation panel has links to screens that let you configure the Switch’s features.
C - The function frame allows you to view and edit individual feature settings.
D - Use the Help link to find out more information about the fields in the screen you are
configuring.
GS-1524/GS-1548 User’s Guide

4.3.1 The LED Panel
Use the LED panel to view the status of the individual ports. The LED panel in the web
configurator updates automatically every 5 seconds.
Figure 18 LED Panel
The following table describes the labels in this screen.
Table 3 LED Panel
LABEL DESCRIPTION
1G This LED is green if the corresponding port has a 1 Gbps connection.
100 This LED is amber if the corresponding port has a 100 Mbps connection.
Full This LED is green if the corresponding port is transmitting in full duplex
Link This LED is green if the corresponding port has an Ethernet connection. It
1...24 (GS-1524)
1...48 (GS-1548)
Chapter 4 The Web Configurator
mode.
is orange if the port has been disabled.
This number indicates the port number on the Switch.
4.3.2 The Navigation Panel
Navigate to individual feature configuration screens from the navigation panel.
The following table describes the links in the navigation panel.
Table 4 Navigation Panel Links
LINK DESCRIPTION
System Use these screens to view general system information such as firmware version, IP
address and so on. You can also use this screen to backup and restore your
configuration.
Status Use this screen to view general system information.
Password Use this screen to change the system login password
Firmware Use this screen to perform firmware upgrades
Restart/
Reset
Port Use these screens to view the status and configure settings for individual ports on
Statistics Use these screen to view system statistics such as the number of packets received
VLAN Use these screens to create new IEEE 802.1Q VLANs as well as view the status
Trunk Groups Use these screens to create trunk groups and add/remove ports from existing trunk
Use this screen to reboot the Switch or to restore the default configuration of the
Switch.
the Switch.
on the Switch, collisions and errors and to view statistics for individual ports on the
Switch.
and edit existing IEEE 802.1Q VLANs on the Switch.
groups.
GS-1524/GS-1548 User’s Guide
45

Chapter 4 The Web Configurator
Table 4 Navigation Panel Links (continued)
LINK DESCRIPTION
Mirror Use this screen to copy traffic from one port or ports to another port in order that
you can examine the traffic from the first port without interference.
QoS Use these screens to configure queuing with associated queue weights for the
Switch.
Rate Use these screens to specify bandwidth limits and storm control limits for the
Switch.
Port Rate Use this screen to cap the maximum bandwidth allowed from specified source(s) to
specified destination(s).
Storm
Control
L2 Address Use these screens to view and manage the MAC address table.
Management Use this screen to add, delete or look up MAC addresses in the MAC address
Display Use this screen to view the entries in the MAC address table.
Cable Diagnostic Use this screen to perform cable testing on individual ports.
Auto DoS Use these screens to activate security features against Denial of Service (DoS)
Auto VoIP Use these screens to configure settings that automatically give higher priority to
Logging Use these screens to configure log settings and view system logs.
Settings Use this screen to configure which events the Switch should log.
RAM Logs Use this screen to configure logs which are saved to volatile memory. These logs
Flash Logs Use this screen to configure logs which are saved to non-volatile memory. These
SNMP Use these screens to configure SNMP management settings.
Engine ID Use this screen to configure SNMP engine ID.
Group Use this screen to configure groups with different access rights for SNMP
User Use this screen to create users and assign them to pre-defined SNMP groups.
Community Use this screen to define security parameters for SNMP v1 and SNMP v2c.
Trap Station Use this screen to configure settings that define when notifications are sent to an
RMON-Lite Use this screen to configure Remote Network Monitoring Management Information
Dynamic ARP Use these screens to enable and configure ARP table settings.
Settings Use this screen to configure ARP table settings.
ARP Entries Use this screen to enter and view MAC address to IP address mappings.
Logout Click this to logout of the web configurator.
Use this screen to cap the rate of broadcast, multicast and unknown unicast
packets the Switch will allow on individual ports.
table.
attacks.
Voice over Internet Protocol (VoIP) traffic.
are cleared when the Switch is rebooted.
logs can be seen even after the Switch is rebooted.
management.
external management station.
Base (RMON MIB) settings.
4.3.3 Change Your Password
After you log in for the first time, it is recommended you change the default administrator
password. Click System, Password to display the next screen.
46
GS-1524/GS-1548 User’s Guide

Figure 19 Change Administrator Login Password
4.4 Saving Your Configuration
When you are done modifying the settings in a screen, click Apply to save your changes back
to the Switch.
4.5 Switch Lockout
Chapter 4 The Web Configurator
You could block yourself (and all others) from using the web configurator if you:
1 Remove all the ports from the default VLAN (default is VLAN 1) when no other
VLANs exist.
2 Disable all ports.
3 Forget the password and/or IP address.
4 Enable Dynamic ARP without entering the proper MAC to IP address binding.
4.6 Resetting the Switch
If you lock yourself (and others) from the Switch or forget the administrator password, you
will need to reset the Switch back to the factory defaults.
Use the RESET button on the front panel of the Switch to reset the Switch back to factory
defaults. Press and hold the RESET button for one second. The Switch will reload its factory
defaults.
The Switch is now reinitialized with a default configuration file including the default
administrator username (admin) and password (1234). The IP address of the Switch also
reverts to the default 192.168.1.1.
4.7 Logging Out of the Web Configurator
Click Logout in the navigation panel to exit the web configurator. You have to log in with
your password again after you log out. This is recommended after you finish a management
session for security reasons.
GS-1524/GS-1548 User’s Guide
47

Chapter 4 The Web Configurator
Figure 20 Web Configurator: Logout Link
4.8 Help
The web configurator’s online help has descriptions of individual screens and some
supplementary information.
Click the Help link from a web configurator screen to view an online help description of that
screen.
48
GS-1524/GS-1548 User’s Guide

CHAPTER 5
System
This chapter describes the system screens.
5.1 System Screen
The home screen of the web configurator displays general system information and allows you
to perform system maintenance. Click System > Status in the navigation panel to view device
specific information such as system name, firmware version and so on.
Figure 21 System
The following table describes the labels in this screen.
Table 5 System
LABEL DESCRIPTION
Device Name This read-only field displays the name of your Switch.
Firmware
Ver si on
Build Date This field displays the date of the currently installed firmware.
MAC Address This field displays the MAC (Media Access Control) address of the Switch.
IP Address This field indicates the IP address of the Switch.
Subnet Mask This field indicates the subnet mask of the Switch.
Gateway This field indicates the IP address of the default gateway.
L2 Table Aging This field displays whether the L2 Table Aging is enabled or disabled. Click Enabled/
GS-1524/GS-1548 User’s Guide
This field displays the version number of the Switch 's current firmware. Click
Upgrade to go to the firmware upgrade screen. See Section 5.3 on page 52.
You can click the existing IP address to change it. See Section 5.1.1 on page 50.
Disabled to change the L2 Table Aging settings.
49

Chapter 5 System
Table 5 System (continued)
LABEL DESCRIPTION
Backup settings Click this link to create and save a backup configuration file. See Section 5.1.3 on
page 51.
Restore
settings
Click this link to upload an existing configuration file to the Switch. See Section 5.1.4
on page 51.
5.1.1 Configure IP Address
Use the Configure IP Address screen to set up the IP address manually. The following screen
appears when you click the existing IP address in the System > Status screen.
Figure 22 Configure IP Address
The following table describes the labels in this screen.
Table 6 Configure IP Address
LABEL DESCRIPTION
IP Address Enter the IP address of your Switch in dotted decimal notation.
For example, 192.168.1.1.
Network Submask Enter the IP subnet mask of your Switch in dotted decimal
Gateway Enter the IP address of the default outgoing gateway in dotted
notation for example 255.255.255.0.
decimal notation, for example 192.168.1.5.
5.1.2 Layer 2 (L2) Table Aging
L2 Table Aging defines the aging time of the Address Resolution Logic (ARL) table. This
table learns and remembers MAC addresses of devices sending information through it. See
Chapter 13 on page 83 for more background information. Click the link in the L2 Table Aging
field to see the screen as shown next.
Figure 23 Configure L2 Table Aging
50
GS-1524/GS-1548 User’s Guide

Select the Enable L2 Table Aging checkbox and enter the amount of time in seconds (up to
1048575) that the Switch remembers MAC address entries. Select “0” to disable L2 table
aging. Click Apply to save your configuration changes.
5.1.3 Backup Settings
Backing up your Switch configurations allows you to create various “snap shots” of your
device from which you may restore at a later date.
Back up your current Switch configuration to a computer using the Backup Settings link.
Follow the steps below to back up the current Switch configuration.
1 Click Backup.
2 Click Save to display the Save As screen.
3 Choose a location to save the file on your computer from the Save in drop-down list box
and type a descriptive name for it in the File name list box. Click Save to save the
configuration file to your computer.
5.1.4 Restore Settings
Chapter 5 System
Restore a previously saved configuration from your computer to the Switch using the Restore
Settings screen.
Figure 24 Restore Settings
Type the path and file name of the configuration file you wish to restore in the Please select a
saved configuration file text box or click Browse to display the Choose File screen from
which you can locate it. After you have specified the file, click Restore.
Make sure you are using the proper configuration when you are restoring your configuration.
The file name extension should be “.cfg”. If you attempt to restore a wrong configuration file
the following error message appears.
Figure 25 Restore Configuration Error
You can click Retry to locate the proper configuration file.
GS-1524/GS-1548 User’s Guide
51

Chapter 5 System
5.2 System: Change Password
Use the Change Password screen to change the administrator username and password for the
Switch. Click System > Password to view the screen as shown.
Figure 26 System: Password
The following table describes the labels in this screen.
Table 7 Change Password
LABEL DESCRIPTION
Old Password Type the existing system password (1234 is the default password when shipped).
New Password Enter your new system password. Enter up to 15 alpha-numeric characters; spaces
are allowed.
Confirm New
Password
Retype your new system password for confirmation
5.3 Firmware Upgrade
Make sure you have downloaded (and unzipped) the correct model firmware and version to
your computer before uploading to the device.
1 Be sure to upload the correct model firmware as uploading the wrong model
firmware may damage your device.
From the System screen, click Upgrade in the Firmware Version field to display the screen as
shown next.
52
GS-1524/GS-1548 User’s Guide

Figure 27 Firmware Upgrade
Type the path and file name of the firmware file you wish to upload to the Switch in the File
Path text box or click Browse to locate it. After you have specified the file, click Upgrade.
After the firmware upgrade process is complete, see the System > Status screen to verify your
current firmware version number.
5.3.1 System: Restart/Reset
Click System > Restart/Reset to perform a system restart (keep current configuration) or a
system reset (restore the Switch’s default configuration settings). Follow the instructions in the
screen below to reset or restart the Switch.
Chapter 5 System
Figure 28 System: Restart/Reset
GS-1524/GS-1548 User’s Guide
53

Chapter 5 System
54
GS-1524/GS-1548 User’s Guide

CHAPTER 6
Port Settings
This chapter describes how to view and configure the port settings on the Switch.
6.1 Port Status
Use this screen to view Switch port settings. Click Port in the navigation panel to display the
Port Status screen.
Figure 29 Port Status
The following table describes the labels in this screen.
Table 8 Port Status
LABEL DESCRIPTION
Refresh Click this to update the PORT Status screen.
Port This identifies the Ethernet port. Click a port number to display the Port
Configuration screen (refer to Section 6.2 on page 56).
Link Status This field displays the link status of the port. Up, if the port is enabled and active or
Down, if the port is disabled or not connected to any device.
Speed Duplex This field displays the speed either 10Mbps, 100Mbps or 1000Mbps and the duplex
mode Full or Half.
Flow Control Enables access to buffering resources for the port thus ensuring lossless operation
across network switches. This field displays either Enabled or Disabled.
PVID The PVID field specifies what tag the incoming untagged frames receive on that port
so that the frames are forwarded to the VLAN group that the tag defines.
GS-1524/GS-1548 User’s Guide
55

Chapter 6 Port Settings
6.2 Port Configuration
Use this screen to configure individual port settings.Click a port number in the Port Status
screen to access this screen.
Figure 30 Port Configuration
The following table describes the labels in this screen.
Table 9 Port Configuration
LABEL DESCRIPTION
Port This is the port index number.
Admin Select Enable to activate the port or Disable to deactivate the port.
Auto Negotiate Select Enable and the port will negotiate the speed, duplex mode and flow control
settings with the peer port. If the peer port does not support auto-negotiation or turns
off this feature, the Switch determines the connection speed by detecting the signal
on the cable and using half duplex mode.
Select Disable to configure the port settings manually. When the Switch’s autonegotiation is turned off, a port uses the pre-configured speed and duplex mode when
making a connection, thus requiring you to make sure that the settings of the peer
port are the same in order to connect.
Speed Duplex Select the speed and the duplex mode of the Ethernet connection on this port.
Flow Control A concentration of traffic on a port decreases port bandwidth and overflows buffer
Default Priority This priority value is added to incoming frames without a priority queue tag.
PVID Enter a number identifying an existing VLAN. The Switch tags the incoming untagged
Apply Click Apply to save your changes.
Choices are 10Mbps Half, 10Mbps Full, 100Mbps Half, 100Mbps Full and 1Gbps
Full.
memory causing packet discards and frame losses. Flow Control is used to regulate
transmission of signals to match the bandwidth of the receiving port.
The Switch uses IEEE802.3x flow control in full duplex mode and backpressure flow
control in half duplex mode.
IEEE802.3x flow control is used in full duplex mode to send a pause signal to the
sending port, causing it to temporarily stop sending signals when the receiving port
memory buffers fill.
Back Pressure flow control is typically used in half duplex mode to send a "collision"
signal to the sending port (mimicking a state of packet collision) causing the sending
port to temporarily stop sending signals and resend later. Select Enable to turn this
feature on or select Disable to turn it off.
frames on that port so that the frames are forwarded to the VLAN group that the tag
defines.
56
GS-1524/GS-1548 User’s Guide

CHAPTER 7
System and Port Statistics
This chapter describes the overview and individual port statistics screens.
7.1 Overview
The statistics screen of the web configurator displays a port statistical summary with links to
each port showing statistical details.
7.2 Statistics Summary
Click Statistics in the navigation panel to view the screen as shown. Use this screen to view
the traffic counters for the Switch.
Figure 31 Statistics
The following table describes the labels in this screen.
Table 10 Statistics
LABEL DESCRIPTION
Clear Counters Click this to reset all counters to zero.
Refresh Click this to retrieve the current information from the Switch and update this screen.
Port This identifies the Ethernet port. Click a port number to display the Port Details
screen (refer to Figure 32 on page 58).
GS-1524/GS-1548 User’s Guide
57

Chapter 7 System and Port Statistics
Table 10 Statistics (continued)
LABEL DESCRIPTION
Tx This field shows the number of transmitted frames on this port.
Rx This field shows the number of received frames on this port.
7.3 Port Statistics
Click a number in the Port column in the Statistics screen to display individual port statistics.
Use this screen to check status and detailed performance data about an individual port on the
Switch.
Figure 32 Status: Port Details
58
The following table describes the labels in this screen.
Tabl e 11 Status: Port Details
LABEL DESCRIPTION
Refresh Click this to retrieve the current information from the Switch and update this
screen.
Port This field displays the port number you are viewing.
TX
The following fields display detailed information about packets transmitted.
Octets This field shows the number of octets transmitted.
UnicastPkts This field shows the number unicast packets transmitted.
NonUnicastPkts This field shows the number of non-unicast packets transmitted.
GS-1524/GS-1548 User’s Guide

Chapter 7 System and Port Statistics
Tabl e 11 Status: Port Details (continued)
LABEL DESCRIPTION
Discards This field shows the number discarded (dropped) packets.
Errors This field shows the number of packets for which transmission failed because of
QLength This field shows the number of packets currently buffered.
RX
The following fields display detailed information about packets received.
Octets This field shows the number of octets received.
UnicastPkts This field shows the number unicast packets received.
NonUnicastPkts This field shows the number of non-unicast packets received.
Discards This field shows the number discarded (dropped) packets.
Errors This field shows the number of undersize, oversize, fragmented or FCS error
UnknownProtos This field shows the number of packets received with unknown protocols.
Summary
The following fields display a summary of types of errors and size of packets transmitted/received.
Drop Events This is a count of dropped packets due to GBP or backpressure (buffer
MulticastPkts This is a count of transmitted/received multicast packets.
BroadcastPkts This is a count of transmitted/received broadcast packets.
UndersizePkts This is a count of transmitted/received packets with length less than the
OversizePkts This is a count of transmitted/received packets with length more than the
Fragments This is a count of transmitted/received packets that were too short (shorter than
Jabbers This is a count of transmitted/received packets that which exceeded maximum
Collision This is a count of transmitted collision packets.
CRCAlignErr This is a count of transmitted/received packets that were too short (shorter than
TotalOctets This is a count of all transmitted/received packets that which exceeded
TotalPkts This is a count of transmitted/received packets (including bad packets, all
64 BytePkts This field shows the number of packets (including bad packets) received that
65-127 BytePkts This field shows the number of packets (including bad packets) received that
128-255
BytePkts
256-511
BytePkts
excessive collision.
packets received.
overflow).
minimum packet size.
maximum packet size.
64 octets) with invalid FCS or alignment errors.
size to receive frame length.
64 octets) with invalid FCS or alignment errors.
maximum size to receive frame length.
unicast, broadcast, multicast and MAC control packets).
were 64 octets in length.
were between 65 and 127 octets in length.
This field shows the number of packets (including bad packets) received that
were between 128 and 255 octets in length.
This field shows the number of packets (including bad packets) received that
were between 256 and 511 octets in length.
GS-1524/GS-1548 User’s Guide
59

Chapter 7 System and Port Statistics
Tabl e 11 Status: Port Details (continued)
LABEL DESCRIPTION
512-1023
BytePkts
1024-1518
BytePkts
This field shows the number of packets (including bad packets) received that
were between 512 and 1023 octets in length.
This field shows the number of packets (including bad packets) received that
were between 1024 and 1522 octets in length.
60
GS-1524/GS-1548 User’s Guide

CHAPTER 8
VLAN
This chapter shows you how to configure IEEE 802.1Q tagged VLANs.
8.1 Introduction to IEEE 802.1Q Tagged VLANs
A tagged VLAN uses an explicit tag (VLAN ID) in the MAC header to identify the VLAN
membership of a frame across bridges - they are not confined to the switch on which they were
created. The VLANs can be created statically by hand or dynamically through GVRP. The
VLAN ID associates a frame with a specific VLAN and provides the information that switches
need to process the frame across the network. A tagged frame is four bytes longer than an
untagged frame and contains two bytes of TPID (Tag Protocol Identifier, residing within the
type/length field of the Ethernet frame) and two bytes of TCI (Tag Control Information, starts
after the source address field of the Ethernet frame).
The CFI (Canonical Format Indicator) is a single-bit flag, always set to zero for Ethernet
switches. If a frame received at an Ethernet port has a CFI set to 1, then that frame should not
be forwarded as it is to an untagged port. The remaining twelve bits define the VLAN ID,
giving a possible maximum number of 4,096 VLANs. Note that user priority and VLAN ID
are independent of each other. A frame with VID (VLAN Identifier) of null (0) is called a
priority frame, meaning that only the priority level is significant and the default VID of the
ingress port is given as the VID of the frame. Of the 4096 possible VIDs, a VID of 0 is used to
identify priority frames and value 4095 (FFF) is reserved, so the maximum possible VLAN
configurations are 4,094.
TPID
2 Bytes
User Priority
3 Bits
CFI
1 Bit
VLAN ID
12 bits
8.1.1 Forwarding Tagged and Untagged Frames
Each port on the Switch is capable of passing tagged or untagged frames. To forward a frame
from an 802.1Q VLAN-aware switch to an 802.1Q VLAN-unaware switch, the Switch first
decides where to forward the frame and then strips off the VLAN tag. To forward a frame from
an 802.1Q VLAN-unaware switch to an 802.1Q VLAN-aware switch, the Switch first decides
where to forward the frame, and then inserts a VLAN tag reflecting the ingress port's default
VID. The default PVID is VLAN 1 for all ports, but this can be changed.
A broadcast frame (or a multicast frame for a multicast group that is known by the system) is
duplicated only on ports that are members of the VID (except the ingress port itself), thus
confining the broadcast to a specific domain.
GS-1524/GS-1548 User’s Guide
61

Chapter 8 VLAN
8.2 Static VLAN
Use a IEEE 802.1Q VLAN to decide whether an incoming frame on a port should be
• sent to a VLAN group as normal depending on its VLAN tag.
• sent to a group whether it has a VLAN tag or not.
You can also tag all outgoing frames (that were previously untagged) from a port with the
specified VID.
8.2.1 IEEE 802.1Q VLAN Screen
Use this screen to display IEEE 802.1Q VLAN status. Click VLAN in the navigation panel to
display the IEEE 802.1Q VLAN screen as shown next.
Figure 33 VLAN: VLAN Status
The following table describes the labels in this screen.
Table 12 VLAN: VLAN Status
LABEL DESCRIPTION
VLAN ID Select which VLAN you want to configure or click Create New VLAN to go to the
VLAN Status
Ta ble
VLAN ID Click on the VLAN ID to go to the VLAN edit screen.
Member Ports All the ports participating in the VLAN are listed here. The ports show up in two
Previous Page Click this button to view VLANs with lower identification numbers. This field is only
Next Page Click this button to view VLANs with higher identification numbers. This field is only
new VLAN configuration screen.
This table shows you the existing VLANs and their configurations.
different colors:
• (Orange) When the packet leaves this member port, the VLAN tag is
added.
• (Turquoise) When the packet leaves this member port, the VLAN tag is
removed.
active if there are more VLANs than can be displayed on one screen.
active if there are more VLANs than can be displayed on one screen.
62
GS-1524/GS-1548 User’s Guide
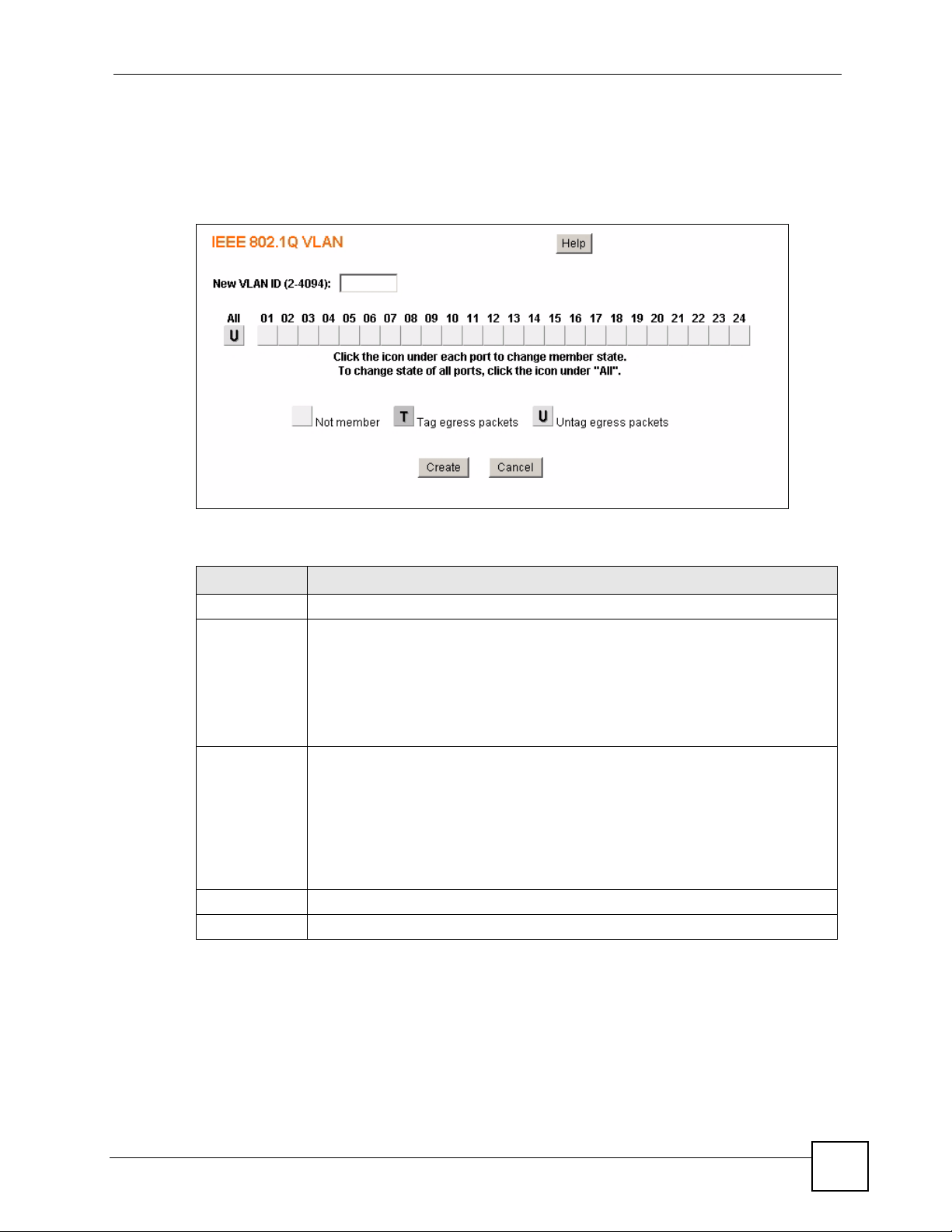
8.2.2 Create IEEE 802.1Q VLAN Screen
See Section 8.1 on page 61 for more information on VLANs. Click VLAN in the navigation
panel to display the IEEE 802.1Q VLAN screen as shown next.
Figure 34 VLAN: Create VLAN
Chapter 8 VLAN
The following table describes the labels in this screen.
Table 13 VLAN: Create VLAN
LABEL DESCRIPTION
New VLAN ID Enter the VLAN ID of the VLAN you want to create.
ALL This button allows you to configure all the ports at once. Click this button to change
1...52 These buttons allow you to specify whether the individual ports are members of this
Create Click Create to add this VLAN to the Switch.
Cancel Click Cancel to return to the VLAN status screen without making any changes.
the state of all the ports at once. The possible states are:
empty - This indicates that the port is not part of the VLAN.
T - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is added.
U - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is removed.
VLAN. Click the buttons below the numbers to change the state of the ports. The
possible states are:
empty - This indicates that the port is not part of the VLAN.
T - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is added.
U - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is removed.
8.2.3 Edit IEEE 802.1Q VLAN Screen
See Section 8.1 on page 61 for more information on VLANs. Click VLAN in the navigation
panel to display the IEEE 802.1Q VLAN screen as shown next.
GS-1524/GS-1548 User’s Guide
63

Chapter 8 VLAN
Figure 35 VLAN: Edit VLAN
The following table describes the labels in this screen.
Table 14 VLAN: Edit VLAN
LABEL DESCRIPTION
VLAN ID Select which VLAN you want to configure. Click Remove This VLAN to remove this
VLAN from the Switch.
Note: VLAN 1 cannot be removed.
Display All
VLAN
ALL This button allows you to configure all the ports at once. Click this button to change
1...52 These buttons allow you to specify whether the individual ports are members of this
Apply Click Apply to create the VLAN or update the VLAN’s configuration.
Click this button to go back to the VLAN status screen.
the state of all the ports at once. The possible states are:
empty - This indicates that the port is not part of the VLAN.
T - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is added.
U - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is removed.
VLAN. Click the buttons below the numbers to change the state of the port. The
possible states are:
empty - This indicates that the port is not part of the VLAN.
T - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is added.
U - This indicates that this port is a member of the VLAN. When the packet leaves
the member port, the VLAN tag is removed.
64
GS-1524/GS-1548 User’s Guide

CHAPTER 9
Trunking
This chapter shows you how to logically aggregate physical links to form one logical, higherbandwidth link.
9.1 Trunking Overview
Trunking is the grouping of physical ports into one logical higher-capacity link. You may want
to trunk ports if for example, it is cheaper to use multiple lower-speed links than to underutilize a high-speed, but more costly, single-port link.
However, the more ports you aggregate then the fewer available ports you have. A trunk group
is one logical link containing multiple ports.
9.1.1 Distribution Criteria
The Switch uses a traffic distribution algorithm to balance traffic between trunk members. The
Switch allows you to specify what criterion it should use to calculate the most efficient
distribution of traffic. The choices are Source MAC Address (SA), Destination MAC Address
(DA) or both (SA + DA). The best choice of distribution criteria depends on your specific
network environment.
9.2 Trunk Setting Screen
Use this screen to aggregate groups of physical ports into one higher capacity link. Click
Trunk Groups in the navigation panel to display the Trunk Setting screen.
GS-1524/GS-1548 User’s Guide
65

Chapter 9 Trunking
Figure 36 Trunk Setting
The following table describes the labels in this screen.
Table 15 Trunking: Configuration
LABEL DESCRIPTION
Distribution
Criterion
Modify Trunk
Group
Member
Trunk id Select the trunk you want to modify or select a trunk id which is not yet configured to
Port Select the port you want to add or delete.
Add Click this to add the port to the trunk group you selected in the Trunk id field.
Del Click this to delete the port from the trunk group you selected in the Trunk id field.
Trunk 1 ...
Trunk 6
Apply Click Apply to save your changes.
Trunking uses a distribution algorithm to balance traffic between trunk members.
Select the traffic distribution algorithm between trunk member ports. Your choices are:
• SA (Source MAC Address)
• DA (Destination MAC Address)
• SA + DA
Configure the following settings to create and modify trunk groups.
create a new trunk group.
This summary table lists all the trunks. Trunk Group Member column indicates which
ports are members of the trunk group.
66
GS-1524/GS-1548 User’s Guide

CHAPTER 10
Mirroring
This chapter discusses port mirroring.
10.1 Port Mirroring Settings
Port mirroring allows you to copy traffic flow to a monitor port (the port you copy the traffic
to) in order that you can examine the traffic from the mirrored port without interference.
Click Mirror in the navigation panel to display the Mirror Setting screen. Use this screen to
select a monitor port and specify the traffic flow to be copied to the monitor port.
Figure 37 Mirror Setting
The following table describes the labels in this screen.
Table 16 Mirror Setting
LABEL DESCRIPTION
Mode Select Enabled to turn on port mirroring or select Disabled to turn it off.
Ingress
Mirror
Egress
Mirror
Mirror To The Mirror To (monitor) port is the port you copy the traffic to in order to examine it in
Apply Click Apply to save your changes.
GS-1524/GS-1548 User’s Guide
Select the ports for which you want to monitor the ingress (incoming) traffic.
Select the ports for which you want to monitor the egress (outgoing) traffic.
more detail without interfering with the traffic flow on the original port(s). Select the
monitor port.
67

Chapter 10 Mirroring
68
GS-1524/GS-1548 User’s Guide

CHAPTER 11
QoS
This chapter introduces the quality of service (QoS) parameters you can configure on the
Switch.
11.1 QoS Overview
QoS is used to help solve performance degradation when there is network congestion. Use the
QoS Setting screen to configure queuing algorithms for outgoing traffic.
Queuing algorithms allow switches to maintain separate queues for packets from each
individual source or flow and prevent a source from monopolizing the bandwidth.
11.1.1 Weighted Round Robin (WRR)
Round Robin scheduling services queues on a rotating basis and is activated only when a port
has more traffic than it can handle. A queue is given an amount of bandwidth irrespective of
the incoming traffic on that port. This queue then moves to the back of the list. The next queue
is given an equal amount of bandwidth, and then moves to the end of the list; and so on,
depending on the number of queues being used. This works in a looping fashion until a queue
is empty.
Weighted Round Robin (WRR) scheduling uses the same algorithm as round robin scheduling,
but services queues based on their priority and queue weight (the number you configure in the
queue Weight field) rather than a fixed amount of bandwidth. WRR is activated only when a
port has more traffic than it can handle. Queues with larger weights get more service than
queues with smaller weights. This queuing mechanism is highly efficient in that it divides any
available bandwidth across the different traffic queues and returns to queues that have not yet
emptied.
11.1.2 Strict Priority
Strict priority scheduling singles out the highest priority queue and ensures all queued traffic
in this queue is transmitted before servicing the lower priority queues. Strict priority
scheduling services the remaining queues using WRR. As traffic comes into the Switch, traffic
on the highest priority queue, Queue 3 is transmitted first. Only when that queue empties,
traffic on the lower priority queues is transmitted using WRR scheduling.
GS-1524/GS-1548 User’s Guide
69

Chapter 11 QoS
11.2 QoS Enhancement
You can configure the Switch to prioritize traffic even if the incoming packets are not marked
with IEEE 802.1p priority tags or change the existing priority tags based on the criteria you
select. The Switch allows you to choose one of the following methods for assigning priority to
incoming packets on the Switch:
Port Based QoS - Assign priority to packets based on the incoming port on the Switch. See
Section 11.4.1 on page 72.
DSCP Based QoS - Assign priority to packets based on their Differentiated Services Code
Points (DSCPs). See Section 11.4.2 on page 74.
ToS Based QoS - Assign priority to packets based on their Type of Service (ToS) tagging. See
Section 11.4.5 on page 75.
IP Address Based QoS - Assign priority to packets based on their IP address. See Section
11.4.6 on page 76.
" Advanced QoS methods only affect the internal priority queue mapping for the
Switch. The Switch does not modify the IEEE 802.1p value for the egress
frames.
You can choose one of these ways to alter the way incoming packets are prioritized or you can
choose not to use any QoS enhancement setting on the Switch.
11.3 Configuring QoS
Use the QoS Setting screen to specify a queuing method and configure queue weights for the
Switch. Click QoS in the navigation panel to view the following screen.
70
GS-1524/GS-1548 User’s Guide

Chapter 11 QoS
Figure 38 QoS Setting
The following table describes the labels in this screen.
Table 17 QoS Setting
LABEL DESCRIPTION
Advanced Click this link to configure QoS settings based on port number, IP address or configure
DSCP or ToS priority to 802.1p priority mappings.
Number of
queues
Scheduling
Method
This field displays the number of queues configurable on the Switch. Click Change to
edit the number of queues on the Switch.
Select Strict Priority or Weighted Round Robin.
Strict Priority scheduling singles out the highest priority queue and ensures all queued
traffic in this queue is transmitted before servicing the lower priority queues. Strict
Priority scheduling services the remaining queues using WRR.
Note: Queue weights can only be changed when Weighted Round
Weighted Round Robin scheduling services queues on a rotating basis based on their
queue weight (the number you configure in the queue Weight field). Queues with larger
weights get more service than queues with smaller weights.
Priority This value indicates packet priority and is retrieved from the priority tag field of incoming
packets. The values range from 0 (lowest priority) to 7 (highest priority). Click the options
below the priority values to send packets of a specific priority to a particular queue. You
can also set this priority based on criteria you configure in the Advanced QoS screens.
See the sections later in this chapter for more information.
Queue 0 ...
Queue 3
GS-1524/GS-1548 User’s Guide
This field indicates which Queue (0 to 3) you are configuring. Queue 0 has the lowest
priority and Queue 3 the highest priority.
Robin is selected.
71

Chapter 11 QoS
Table 17 QoS Setting (continued)
LABEL DESCRIPTION
Weight You can only configure the queue weights when Weighted Round Robin is selected.
Bandwidth is divided across the different traffic queues according to their weights.
Note: If you want to use Strict Priority but want to change the weights
for the queues, configure them with Weighted Round Robin
selected first and then change the scheduling method to Strict
Priority.
Apply Click Apply to save your changes.
11.3.1 Change Number of Queues
Use the Change Number of Queues screen to edit the number of queues on the Switch. Click
Change in the QoS Setting screen to view the following screen.
Figure 39 Change Number of Queues
Select the number of queues from the Number of Queues drop down list box and click Apply
to save your settings to the Switch.
11.4 Advanced QoS Settings
The following sections describe additional methods for setting priority for incoming packets
on the ports. The Switch allows you to choose one of the following methods:
" Advanced QoS methods only affect the internal priority queue mapping for the
Switch. The Switch does not modify the IEEE 802.1p value for the egress
frames.
11.4.1 Port Based QoS
You can configure the Switch to assign a IEEE 802.1p priority to packets based on the ingress
(incoming) port of the packet. Select Port Based QoS in the QoS Enhancement Setting
screen to view the following screen.
72
GS-1524/GS-1548 User’s Guide
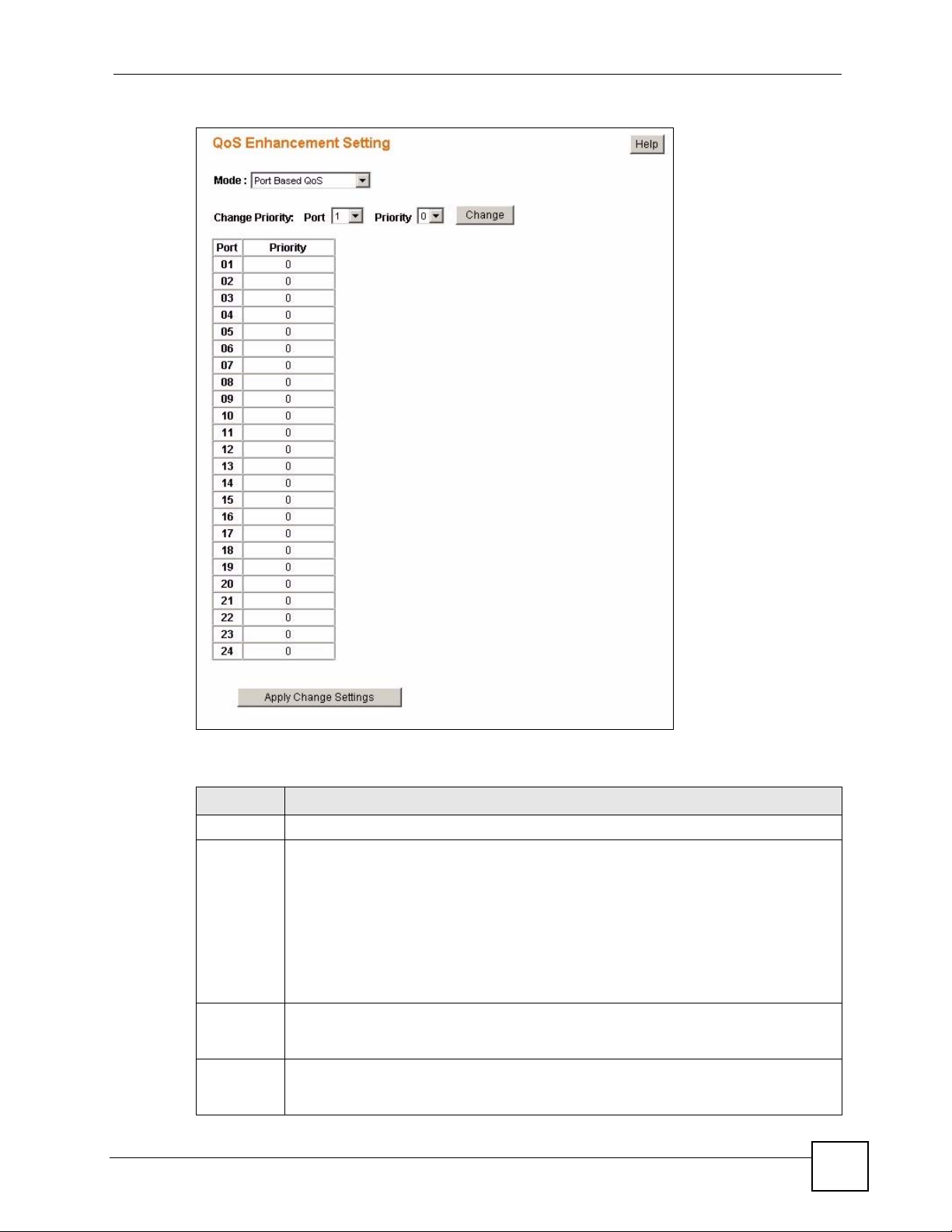
Figure 40 Port Based QoS
Chapter 11 QoS
The following table describes the labels in this screen.
Table 18 Port Based QoS
LABEL DESCRIPTION
Mode Select Port Based QoS to specify priority rules based on the port of incoming packets.
Change
Priority
Configure the following:
• Port - Select the number of the port for which you want to assign IEEE 802.1p priority
to incoming frames.
• Priority - Select the IEEE 802.1p priority you want to assign to the packets coming
into the Switch on the port specified in the Port field.
Click Change to view your changed settings.
Note: The changes are not applied until you click Apply Change
Port,
Priority
Apply
Change
Settings
GS-1524/GS-1548 User’s Guide
This is a summary table of your port to IEEE 802.1p priority mappings. The Port column
indicates the port number of the incoming packets and the Priority column indicates
what IEEE 802.1p priority gets assigned to those packets.
Click this when you have reviewed the changes you want to make and you want to save
them to the Switch’s memory.
Settings.
73

Chapter 11 QoS
11.4.2 DSCP Based QoS
The Switch allows you to create a mapping table between Differentiated Services Code Points
(DSCPs) tags and IEEE 802.1p priority tags.
11.4.3 Differentiated Services Code Point (DSCP) Overview
Differentiated Services (DiffServ) is a class of service (CoS) model that marks packets so that
they receive specific per-hop treatment at DiffServ-compliant network devices along the route
based on the application types and traffic flow. Packets are marked with DiffServ Code Points
(DSCPs) indicating the level of service desired. This allows the intermediary DiffServcompliant network devices to handle the packets differently depending on the code points
without the need to negotiate paths or remember state information for every flow. In addition,
applications do not have to request a particular service or give advanced notice of where the
traffic is going.
DiffServ defines a new DS (Differentiated Services) field to replace the Type of Service (ToS)
field in the IP header. The DS field contains a 2-bit unused field and a 6-bit DSCP field which
can define up to 64 service levels.
You can configure the DSCP to IEEE 802.1p mapping to allow the Switch to prioritize all
traffic based on the incoming DSCP value according to the DiffServ to IEEE 802.1p mapping
table.
11.4.4 DSCP Based QoS Screen
You can configure the Switch to assign a IEEE 802.1p priority to packets coming into the
Switch with DSCPs assigned to them. Select DSCP Based QoS in the QoS Enhancement
Setting screen to view the following screen.
74
GS-1524/GS-1548 User’s Guide

Figure 41 DSCP Based QoS
Chapter 11 QoS
The following table describes the labels in this screen.
Table 19 DSCP Based QoS
LABEL DESCRIPTION
Mode Select DSCP Based QoS to specify mapping rules between DSCP priority and IEEE
802.1p priority for incoming packets on the Switch.
Change
Priority
Configure the following:
• DSCP - Select the DSCP priority for which you want to change a priority mapping.
• Priority - Select the IEEE 802.1p priority you want to assign to the packets with the
DSCP priority you specified in the DSCP field.
Click Change to view your changed settings.
Note: The changes are not applied until you click Apply Change
DSCP,
Priority
Apply
Change
Settings
This is a summary table of your DSCP to IEEE 802.1p priority mappings. The DSCP
column indicates the DSCP values of the incoming packets and the Priority column
indicates what IEEE 802.1p priority gets assigned to those packets.
Click this when you have reviewed the changes you want to make and you want to save
them to the Switch’s memory.
11.4.5 ToS Based QoS
You can configure the Switch to assign a IEEE 802.1p priority to packets coming into the
Switch with Type of Service (ToS) priority assigned to them. Select ToS Based QoS in the
QoS Enhancement Setting screen to view the following screen.
Settings.
GS-1524/GS-1548 User’s Guide
75

Chapter 11 QoS
Figure 42 ToS Based QoS
The following table describes the labels in this screen.
Table 20 ToS Based QoS
LABEL DESCRIPTION
Mode Select ToS Based QoS to specify mapping rules between ToS priority and IEEE 802.1p
Change
Priority
priority for incoming packets on the Switch.
Configure the following:
• TOS - Select the ToS priority for which you want to change a priority mapping.
• Priority - Select the IEEE 802.1p priority you want to assign to the packets with the
ToS priority you specified in the TOS field.
Click Change to view your changed settings.
Note: The changes are not applied until you click Apply Change
Settings.
TOS,
Priority
Apply
Change
Settings
This is a summary table of your ToS priority to IEEE 802.1p priority mappings. The TOS
column indicates the ToS priority of the incoming packets and the Priority column
indicates what IEEE 802.1p priority gets assigned to those packets.
Click this when you have reviewed the changes you want to make and you want to save
them to the Switch’s memory.
11.4.6 IP Address Based QoS
You can configure the Switch to assign a higher priority to packets coming into the Switch
from specific IP addresses. Select IP Address Based QoS in the QoS Enhancement Setting
screen to view the following screen.
76
GS-1524/GS-1548 User’s Guide

Chapter 11 QoS
Figure 43 IP Address Based QoS
The following table describes the labels in this screen.
Table 21 IP Address Based QoS
LABEL DESCRIPTION
Mode Select IP Address Based QoS to give higher or lower priority to packets coming into the
Switch from a specified source IP address.
Add Entry Enter the IP address and the subnet mask of the source whose traffic you want to assign
a priority to in the IP and MASK fields respectively. Select the Priority value and click
Add.
Change
Priority
Use these fields to edit existing IP address based QoS entries. Select the index of an
existing IP address based QoS entry. (This is the same value as listed in the ID column
of this screen.) Select the Priority you want to assign to this entry. Click Change to view
your changed settings.
ID, IP,
MASK,
Priority,
Delete
Apply
Change
Settings
Note: The changes are not applied until you click Apply Change
Settings.
This is a summary table of your IP address based QoS settings. This table updates when
you click the Change button in this screen. Click DELETE in the Delete column to
remove this IP address based QoS entry from the Switch.
Click this when you have reviewed the changes you want to make and you want to save
them to the Switch’s memory.
GS-1524/GS-1548 User’s Guide
77

Chapter 11 QoS
78
GS-1524/GS-1548 User’s Guide
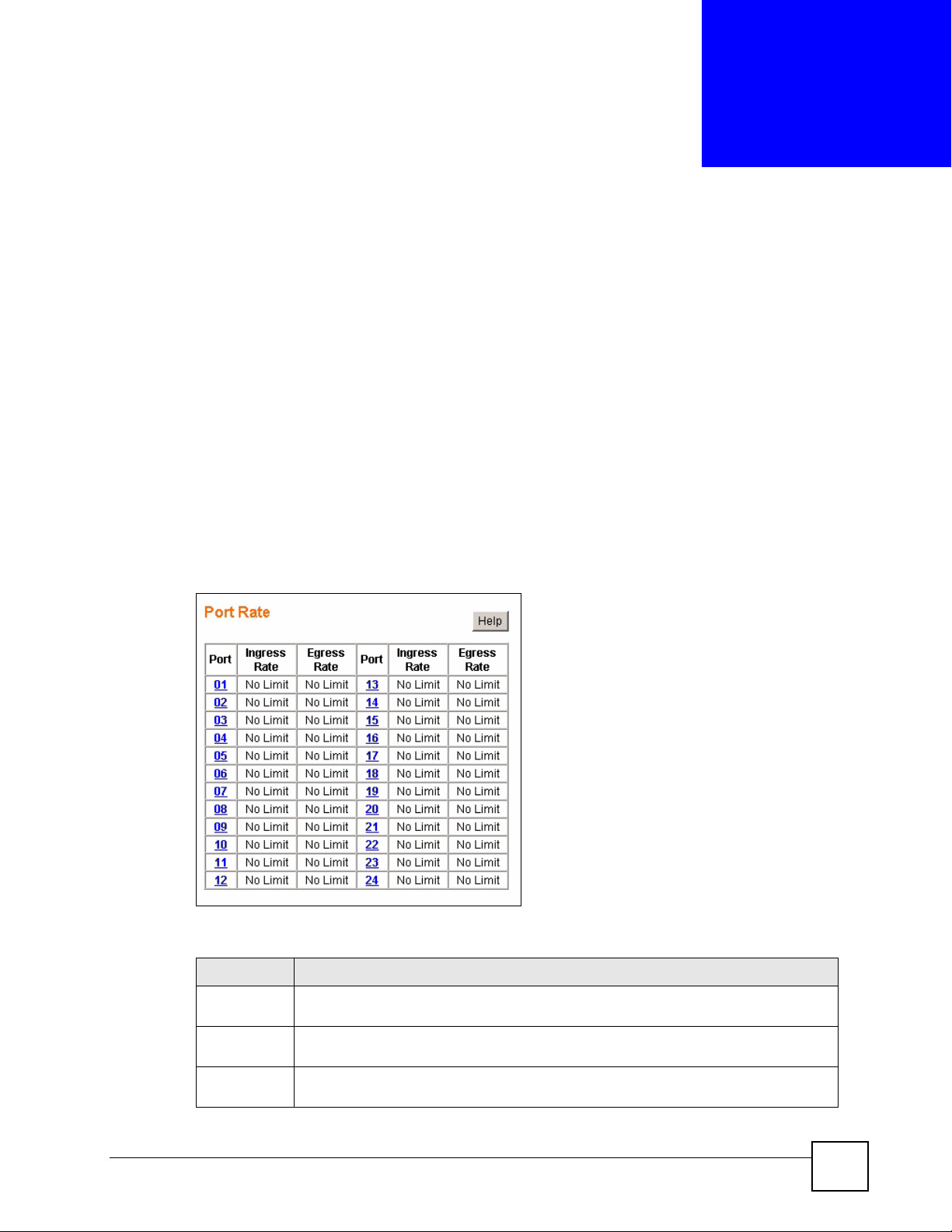
CHAPTER 12
Port Rate Limit and Storm
Control
This chapter shows you how you can manage bandwidth on each port and set up broadcast
storm control settings using the Port Rate and Storm Control screens.
12.1 Port Rate Screen
Rate control means defining a maximum allowable bandwidth for incoming and/or out-going
traffic flows on a port. Click Rate > Port Rate in the navigation panel to bring up the screen
as shown next.
Figure 44 Port Rate Limit
The following table describes the related labels in this screen.
Table 22 Rate Limit and Storm Control
LABEL DESCRIPTION
Port This field displays the port number. Click on an individual port number to configure rate
limits on that port.
Ingress Rate Displays the maximum bandwidth allowed in kilobits per second (Kbps) for the
Egress Rate Displays the maximum bandwidth allowed in kilobits per second (Kbps) for the out-
incoming traffic flow on a port.
going traffic flow on a port.
GS-1524/GS-1548 User’s Guide
79

Chapter 12 Port Rate Limit and Storm Control
12.1.1 Rate Limit Screen
Click a port number in the Port Rate screen to bring up the screen as shown next.
Figure 45 Rate Limit Configuration
The following table describes the related labels in this screen.
Table 23 Rate Limit Configuration
LABEL DESCRIPTION
Ingress Rate Specify the maximum bandwidth allowed in kilobits per second (Kbps) for the incoming
traffic flow on a port.
Egress Traffic
Shaping
Rate This is a read only field indicating the rate limit of outgoing traffic on the port in Kbps.
Tokens
Added Per
Interval
Burst Size The burst size specifies the maximum amount of traffic that can be allowed out the port
Apply Click this to save your changes to the Switch.
Select Disabled to not have any bandwidth limits for outgoing traffic on the port or
select Enabled to enable bandwidth limits for outgoing traffic on the port.
This value changes depending on the number of Tokens Added Per Interval.
The Switch uses a “Token Bucket” algorithm to limit the outgoing rate on the ports and
to limit the largest amount of packets that can leave the port in any one instance.
In this algorithm each “token” represents an allowed amount of bandwidth to be sent
out on the port.
The “bucket” holds the tokens. In other words, the number of tokens in the bucket
represents the maximum allowed bandwidth to go out on the port. The size of the
bucket is specified by the “burst size” (see below).
Every time traffic goes out on the port, tokens (representing used up bandwidth) are
removed from the bucket, thus limiting the amount of traffic allowed to go out on the
port. Tokens are also added to the bucket every Token Update Interval, thus resetting
the amount of bandwidth allowed to go out. If the bucket is empty, the data packets are
dropped until more tokens are added to the bucket.
Select the number of tokens that should be added to the bucket per Token Update
Interval. Each token represents .5 bit in bandwidth allowed to go out on the port.
at any one instance. In the “Token Bucket” algorithm this is referred to as the size of
the bucket as this value limits the number of tokens that can accumulate in the bucket.
80
GS-1524/GS-1548 User’s Guide

12.1.2 Broadcast Storm Control Setup
Broadcast storm control limits the number of broadcast, multicast and unknown unicast (also
referred to as Destination Lookup Failure or DLF) packets the Switch receives per second on
the ports. When the maximum number of allowable broadcast, multicast and unknown unicast
packets is reached per second, the subsequent packets are discarded. Enable this feature to
reduce broadcast, multicast and unknown unicast packets in your network.
Click Rate > Storm Control in the navigation panel to display the screen as shown next.
Figure 46 Broadcast Storm Control
Chapter 12 Port Rate Limit and Storm Control
GS-1524/GS-1548 User’s Guide
81

Chapter 12 Port Rate Limit and Storm Control
The following table describes the labels in this screen.
Table 24 Broadcast Storm Control
LABEL DESCRIPTION
Port Select the port number for which you want to configure storm control settings or
Storm Control
Type
Storm Control
Rate
Apply Click Apply to save your changes.
select Apply settings to all ports to configure all the ports at once.
Select
Disabled - to turn off this feature.
Broadcast only - to only specify a limit for the amount of broadcast packets
received per second.
Broadcast and multicast - to specify a limit for the amount of broadcast and
multicast packets received per second.
Broadcast and unknown unicast - to specify a limit for the amount of broadcast
and DLF packets received per second.
Broadcast, multicast and unknown unicast - to specify a limit for the amount of
broadcast, multicast and DLF (Destination Lookup Failure) packets received per
second.
Select the number of packets (of the type specified in the Storm Control Type field)
per second the Switch can receive per second.
82
GS-1524/GS-1548 User’s Guide

CHAPTER 13
Layer 2 (L2) Management
Use these screens to add, delete and view entries in the Layer 2 (L2) address table.
13.1 Configuring L2 Management
Layer 2 (L2) management refers to management based on the Media Access Control (MAC)
address of networking devices. A static Media Access Control (MAC) address is an address
that has been manually entered in the MAC address table. Static MAC addresses do not age
out. When you set up static MAC address rules, you are setting static MAC addresses for a
port. This may reduce the need for broadcasting.
Click L2 Address > Management in the navigation panel to display the configuration screen
as shown.
Figure 47 L2 Management
The following table describes the labels in this screen.
Table 25 L2 Management
LABEL DESCRIPTION
Address
Lookup:
Static
Address:
ADD Click this to add a static MAC address entry to the MAC address table.
Item This is the index number of the static MAC address entry.
Source MAC This field displays the MAC address of a manually entered MAC address entry.
VID This field displays the VID of a manually entered MAC address entry.
Enter the MAC address and the corresponding Vlan ID in the MAC and VID fields
respectively. Click Lookup to search for the MAC address entry in the MAC address
table.
This section allows you to add or delete static MAC address entries.
GS-1524/GS-1548 User’s Guide
83

Chapter 13 Layer 2 (L2) Management
Table 25 L2 Management (continued)
LABEL DESCRIPTION
Port This field displays the port number of a manually entered MAC address entry.
Delete Click DELETE to remove this manually entered MAC address entry from the MAC
address table.
13.1.1 Add a Static MAC Address Entry
Click Add in the L2 Address Management screen to display the configuration screen as
shown.
Figure 48 Add a Static MAC Entry
The following table describes the labels in this screen.
Table 26 Add a Static MAC Entry
LABEL DESCRIPTION
MAC Address Enter the MAC address in valid MAC address format, that is, six hexadecimal
character pairs.
Note: Static MAC addresses do not age out.
VID Enter the VLAN identification number.
Port Select the port where the traffic with the destination MAC address entered in the
MAC Address field will be automatically forwarded.
Add Address Click this to add this entry into the MAC address table.
13.2 Viewing the L2 Address Table
Use the L2 Address Table screen to view entries in the MAC address table. Click L2 Address
> Display in the navigation panel to display the screen as shown.
84
GS-1524/GS-1548 User’s Guide

Figure 49 Display L2 Address Table
Chapter 13 Layer 2 (L2) Management
The following table describes the labels in this screen.
Table 27 Display L2 Address Table
LABEL DESCRIPTION
Reload
Address Table
Item This is the index number of the MAC address entry.
Source MAC This field displays the MAC address.
VID This field displays the VID of a manually entered MAC address entry.
Port This field displays the port number of a MAC address entry or it displays HOST if its
Type This field displays whether this entry was entered manually into the L2 address table
Previous
Page/
Next Page
Click this to update all the fields in the L2 Address table.
the entry for the Switch itself.
- static or whether it was learned by the Switch - dynamic.
Use these navigation links to browse all L2 learned entries.
GS-1524/GS-1548 User’s Guide
85

Chapter 13 Layer 2 (L2) Management
86
GS-1524/GS-1548 User’s Guide

CHAPTER 14
Cable Diagnostics
This chapter explains the Cable Diagnostics screen.
14.1 Diagnostics Overview
The cable diagnostics function works with systems using CAT-5 twisted-pair cables.
The Switch can perform basic cable diagnostics. Click Cable Diagnostic in the navigation
panel to view the screen as shown.
Figure 50 Cable Diagnostic
The following table describes the labels in this screen.
Table 28 Cable Diagnostic
LABEL DESCRIPTION
Port to diagnose Select the port you want to test.
Apply Click this to perform cable testing on the specified port.
Diagnostic for Port
01:
Status This field displays the results of the test:
Pair A .. Pair D This field displays the whether the twisted pair has a good connection - Ok, or it
GS-1524/GS-1548 User’s Guide
This field displays the number of wired pairs the port is communicating over.
Ok - the cable is working properly.
Open - there is no cable connected to the port or the cable is damaged.
Short - there is a short along the cable.
Short-between-pair - there is a short between two twisted pairs of cable.
displays the type of fault the Switch has detected: Open, Short or Shortbetween-pair. It also displays the length of total twisted pair length or the
distance to the detected fault depending whether the cable tested Ok or a fault
was found.
87

Chapter 14 Cable Diagnostics
88
GS-1524/GS-1548 User’s Guide

CHAPTER 15
Auto Denial of Service (DoS)
This chapter shows you how to configure automatic Denial of Service prevention on the
Switch.
15.1 About Denial of Service Attacks
Denial of Service (DoS) attacks try to disable a device or network so users no longer have
access to network resources. The Switch has features which automatically detect and thwart
currently known DoS attacks.
15.1.1 DoS Attacks Summary
The following table summarizes the types of attacks the Switch can prevent.
Table 29 DoS Attack Summary
ATTACK DESCRIPTION
Land Attacks These attacks result from sending a specially crafted packet to a machine
where the source host IP address is the same as the destination host IP
address. The system attempts to reply to itself, resulting in system lockup.
Blat Attacks These attacks result from sending a specially crafted packet to a machine
where the source host port is the same as the destination host port. The
system attempts to reply to itself, resulting in system lockup.
SYNFIN scans SYNchronization (SYN), ACKnowledgment (ACK) and FINish (FIN)
packets are used to initiate, acknowledge and conclude TCP/IP
communication sessions. The following scans exploit weaknesses in the
TCP/IP specification and try to illicit a response from a host to identify ports
for an attack:
Scan SYNFIN - SYN and FIN bits are set in the packet.
Xmascan - TCP sequence number is zero and the FIN, URG and PSH bits
are set.
NULL Scan - TCP sequence number is zero and all control bits are zeroes.
SYN with port < 1024 - SYN packets with source port less than 1024.
Smurf Attacks This attack uses Internet Control Message Protocol (ICMP) echo requests
packets (pings) to cause network congestion or outages.
Ping Flooding This attack floods the target network with ICMP packets.
SYN/SYN-ACK Flooding This attack floods the target network with SYN or SYN/ACK packets.
GS-1524/GS-1548 User’s Guide
89

Chapter 15 Auto Denial of Service (DoS)
15.2 Global Auto DoS Attack Prevention
Use the Global Auto DoS Attack Prevention screen to configure DoS attack prevention
settings for the Switch. Click Auto DoS in the navigation panel to open the following screen.
Figure 51 Global Auto DoS Attack Prevention
The following table describes the labels in this screen.
Table 30 Global Auto DoS Attack Prevention
LABEL DESCRIPTION
Advanced Click this link to configure advance Auto DoS settings.
Denial of
Service
Prevention
Apply Click Apply to save your changes.
Select the types of attacks you want to prevent or choose Select All to prevent all
types of attacks and scans supported by the Switch. See Section 15.1.1 on page 89
for more information on specific types of attacks.
15.3 Advanced Auto DoS Attack Prevention
Use the Advanced Auto DoS Attack Prevention screen to configure DoS attack prevention
settings for individual ports. Click the Advanced link in the Global Auto DoS Attack
Prevention screen to view the following screen.
90
GS-1524/GS-1548 User’s Guide

Chapter 15 Auto Denial of Service (DoS)
Figure 52 Advanced Auto DoS Attack Prevention
The following table describes the labels in this screen.
Table 31 Advanced Auto DoS Attack Prevention
LABEL DESCRIPTION
Global Click this link to view the Global Auto DoS Attack Prevention screen.
Port Select the port you want to configure or select Apply settings to all ports to
configure all the ports on the Switch.
Denial of
Service
Prevention
Parameter For Ping and SYN/SYN-ACK Flooding attacks you can specify thresholds for
Apply Click Apply to save your changes.
Select the types of attacks you want to prevent or choose Select All to prevent all
types of attacks and scans supported by the Switch. See Section 15.1.1 on page 89
for more information on specific types of attacks.
triggering the dropping of packets by the Switch. Select:
• 64 kbps - the Switch will drop packets when the rate of incoming Ping or SYN/
SYN-ACK packets reaches this limit.
• 128 kbps - the Switch will drop packets when the rate of incoming Ping or SYN/
SYN-ACK packets reaches this limit.
GS-1524/GS-1548 User’s Guide
91

Chapter 15 Auto Denial of Service (DoS)
92
GS-1524/GS-1548 User’s Guide

CHAPTER 16
Auto VoIP
This chapter shows you how to give higher priority to Voice over Internet Protocol (VoIP)
packets over other data packets as they pass through the Switch.
16.1 About Auto VoIP
Voice over Internet Protocol (VoIP) allows telephone calls to be made over a data network like
the Internet. With the increased prominence of delay-sensitive applications (voice, video, and
other multimedia applications) deployed in networks today, proper QoS configuration ensures
high-quality application performance.
The Auto VoIP feature is intended to provide an easy classification mechanism for voice
packets so that they can be given high priority in order to provide better transmission resulting
in higher sound quality for the end users.
The AutoVoIP feature explicitly matches VoIP packets in Ethernet switches and provides them
with the highest class of service. The AutoVoIP feature provides the capability to assign the
highest priority for the following VoIP packets:
• SIP – Session Initiation Protocol is an internationally recognized standard for
implementing VoIP. SIP is an application-layer control (signaling) protocol that handles
the setting up, altering and tearing down of voice and multimedia sessions over the
Internet.
• MGCP – Media Gateway Control Protocol is a control and signal standard for the
conversion of audio signals carried on telephone circuits (PSTN) to data packets carried
over the Internet or other packet networks.
• SCCP – Skinny Client Control Protocol is a Cisco proprietary protocol used between call
managers and VoIP phones.
16.2 Auto VoIP Settings
Use the Auto VoIP Settings to enable automatic assignment of high priority to VoIP packets
passing through the Switch. Click Auto VoIP in the navigation panel to view the following
screen.
GS-1524/GS-1548 User’s Guide
93

Chapter 16 Auto VoIP
Figure 53 Auto VoIP Settings
The following table describes the labels in this screen.
Table 32 Auto VoIP Settings
LABEL DESCRIPTION
Profiles Select Disable if you don’t want to give higher priority to VoIP traffic or select IP
Apply Click Apply to save your changes.
Phone to give the highest priority to SIP, MGCP and SCCP packets passing through
the Switch.
94
GS-1524/GS-1548 User’s Guide

PART III
Management and
Troubleshooting
Event Logging (97)
SNMP (105)
RMON-Lite (119)
Dynamic ARP (135)
Troubleshooting (139)
Product Specifications (143)
95

96

CHAPTER 17
Event Logging
This chapter shows you different ways to inspect logs and how to configure an external log
server.
17.1 Event Logging Overview
You can configure the Switch to save specific events in different log targets:
RAM - This log is saved into the Switch’s volatile memory. The logs are cleared when the
Switch is rebooted.
Flash - This log is saved into the switch’s non-volatile memory. You can view the logs even
after the switch is rebooted. Due to the space limitations on the switch the oldest log entries are
overwritten as new events are recorded.
Server - You can configure syslog servers to store system events from the Switch. The Switch
uses UDP protocol to send log messages to the remote servers. The syslog servers must be
Berkeley Software Distribution (BSD) syslog protocol compliant.
17.2 Logging Screen
Use this screen to specify which system events should be recorded and where the log messages
should be saved. Click Logging > Settings in the navigation panel to view the screen as
shown.
Figure 54 Logging
GS-1524/GS-1548 User’s Guide
97

Chapter 17 Event Logging
The following table describes the labels in this screen.
Table 33 Logging
LABEL DESCRIPTION
Add Server Click this to configure a new syslog server.
Logging Target Click the RAM or Flash link to view the logs stored on the Switch.
Apply Click Apply to save your changes.
Use the columns on the right to select the types of system events each logging
target should record. Select:
• Error - to record system failures, such as events which will cause the Switch to
malfunction and events such as invalid user input in the web configurator.
• Warning - to record non critical errors on the Switch. The Switch will continue to
function when warnings are recorded.
• Info - to record regular system events, such as configuration changes or logins.
• Debug - to record events which can be helpful for engineering debugging of the
Switch’s function. This field is not recommended to track as it creates many
messages not helpful to typical users.
For RAM and Flash logs, you can also hit Clear to delete all log entries.
For each Server log you configured you can hit Delete to remove this syslog server
from logging system events for the Switch.
17.3 Logging: Add Server
Use this screen to configure a new syslog entry. Click Add Server in the Logging screen to
view the screen as shown.
Figure 55 Logging: Add Server
The following table describes the labels in this screen.
Table 34 Logging: Add Server
LABEL DESCRIPTION
Name Enter a short descriptive name for identifying this server. You can use 1-12 printable
IP Address Enter the IP address in dotted decimal notation of the syslog server you want to add.
Port Specify the UDP port for sending log messages to this server. Typically port 514 is
Facility The log facility allows you to send logs to different files in the syslog server. Refer to
Add Click Add to save this entry to the Switch and return to the Logging screen.
ASCII characters. Spaces are allowed.
used with syslog.
the documentation of your syslog server for more details.
98
GS-1524/GS-1548 User’s Guide
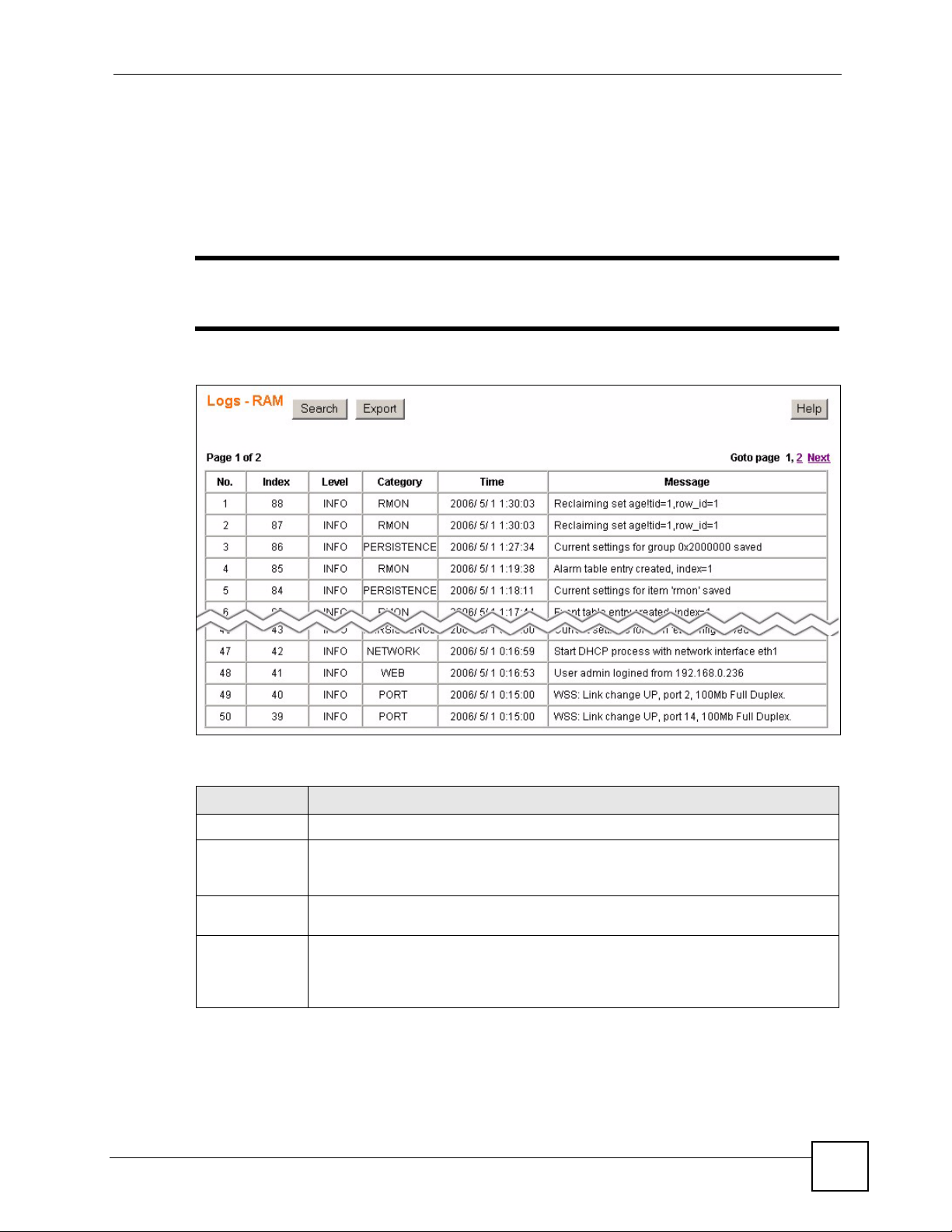
Chapter 17 Event Logging
17.4 Viewing RAM and Flash Logs
Use these screens to view or export RAM or Flash logs.
Click RAM Logs or Flash Logs in the navigation panel to view the Logs - RAM or Logs -
Flash screen.
" The RAM Logs and Flash Logs screen contain the same fields as the Logs -
RAM or Logs - Flash screen in the following figure.
Figure 56 Logs: RAM/Flash
The following table describes the labels in this screen.
Table 35 Logs: RAM/Flash
LABEL DESCRIPTION
Search Click this to search for specific log entries.
Export Click this to export (save) the log. The logs default name is “events.csv”. A .csv
(Comma Separated Values) file can be viewed by most spreadsheet software such
as Microsoft’s Excel.
No. This is the number of the log entry. The log entries with the lowest numerical value
are the most recent.
Index This field indicates the index number of the log. This number doesn’t change even if
some logs are deleted from the Switch due to memory limits. The index number
increments by one for each recorded event. The largest number represents the most
recent log event.
GS-1524/GS-1548 User’s Guide
99

Chapter 17 Event Logging
Table 35 Logs: RAM/Flash (continued)
LABEL DESCRIPTION
Level This field displays the severity level of the log event. The possible severity levels are:
Category This field displays what category the log entry fits. The categories are based on
Time This field specifies the time when the Switch recorded the log event. The Switch
Message This field displays an explanation for the log entry.
Goto page Click Next, Previous or click on a page number to browse through the log pages.
• Error - to record system failures, such as events which will cause the Switch to
malfunction and events such as invalid user input in the web configurator.
• Warning - to record non critical errors on the Switch. The Switch will continue to
function when warnings are recorded.
• Info - to record regular system events, such as configuration changes or logins.
• Debug - to record events which can be helpful for engineering debugging of the
Switch’s function. This field is not recommended to track as it creates many
messages not helpful to typical users.
software and hardware features of the Switch. For example the category AUTODOS
records events which deal with the Auto Denial of Service features you set up and
the category SYSTEM records events which deal with the overall operation of the
Switch.
resets its internal clock when it is restarted.
17.5 Searching RAM and Flash Logs
Use these screens to search RAM and Flash logs based on level and category. Click the Search
link in the Logs - RAM or Logs - Flash screen to view the screen as shown.
100
GS-1524/GS-1548 User’s Guide
 Loading...
Loading...