ZyXEL P2612HNUF1F Users Manual
Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
201
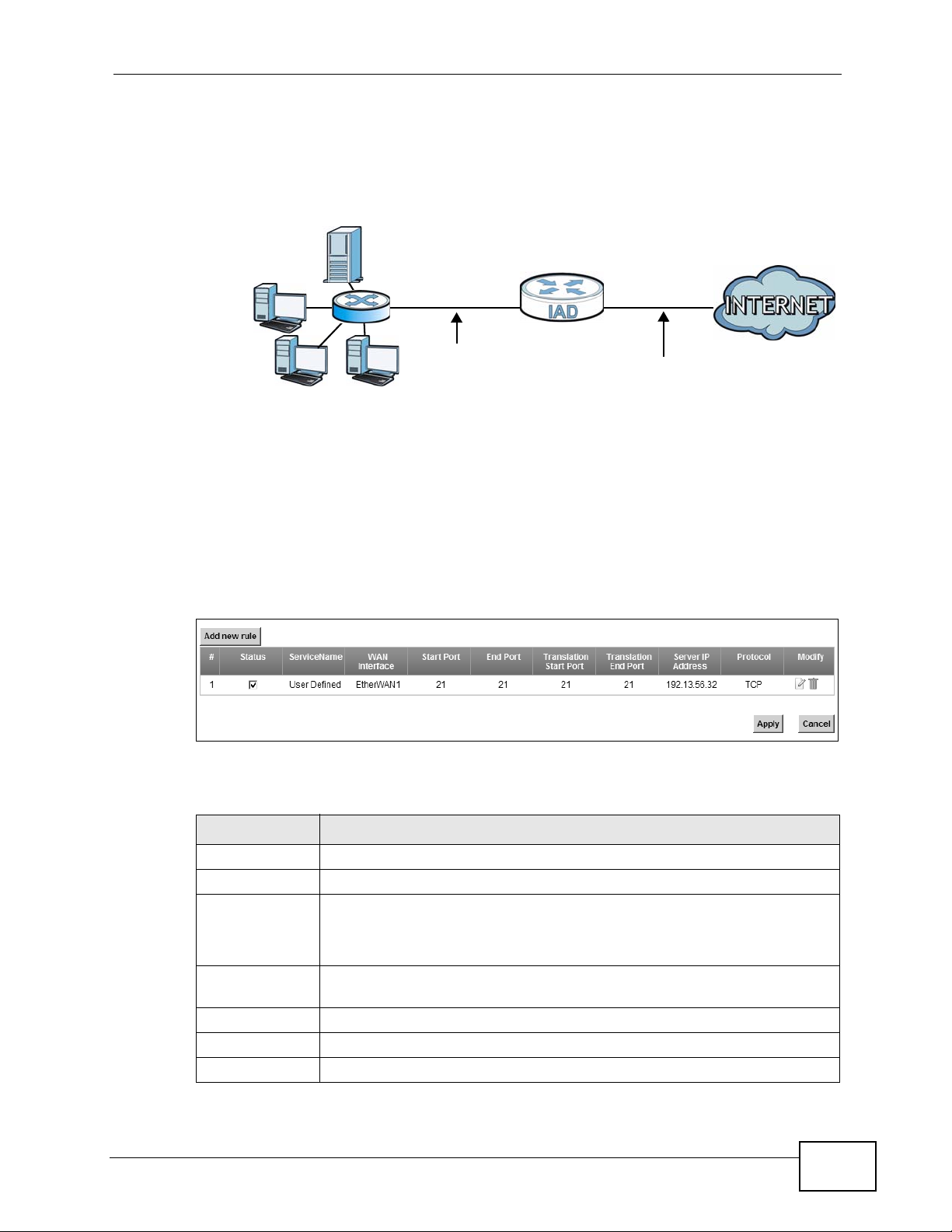
addresses and the ISP assigns the WAN IP address. The NAT network appears as a
single host on the Internet.
Figure 75 Multiple Servers Behind NAT Example
11.2.1 The Port Forwarding Screen
Click Network Setting > NAT to open the Port Forwarding screen.
See Appendix E on page 381 for port numbers commonly used for particular
services.
Figure 76 Network Setting > NAT > Port Forwarding
The following table describes the fields in this screen.
A=192.168.1.33
D=192.168.1.36
C=192.168.1.35
B=192.168.1.34
WAN
LAN
192.168.1.1
IP Address assigned by ISP
Table 44 Network Setting > NAT > Port Forwarding
LABEL DESCRIPTION
Add new rule Click this to add a new port forwarding rule.
# This is the index number of the entry.
Status This field indicates whether the rule is active or not.
Clear the check box to disable the rule. Select the check box to enable
it.
Service Name This is the service’s name. This shows User Defined if you manually
added a service. You can change this by clicking the edit icon.
WAN Interface This shows the WAN interface through which the service is forwarded.
Start Port This is the first external port number that identifies a service.
End Port This is the last external port number that identifies a service.

Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
202
11.2.2 The Port Forwarding Edit Screen
This screen lets you create or edit a port forwarding rule. Click Add new rule in
the Port Forwarding screen or the Edit icon next to an existing rule to open the
following screen.
Figure 77 Port Forwarding: Add/Edit
The following table describes the labels in this screen.
Translation
Start Port
This is the first internal port number that identifies a service.
Translation End
Port
This is the last internal port number that identifies a service.
Server IP
Address
This is the server’s IP address.
Protocol This shows the IP protocol supported by this virtual server, whether it is
TCP, UDP, or TCP/UDP.
Modify Click the Edit icon to edit the port forwarding rule.
Click the Delete icon to delete an existing port forwarding rule. Note
that subsequent address mapping rules move up by one when you take
this action.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 44 Network Setting > NAT > Port Forwarding (continued)
LABEL DESCRIPTION
Table 45 Port Forwarding: Add/Edit
LABEL DESCRIPTION
Service Name Enter a name to identify this rule using keyboard characters (A-Z, a-z, 1-
2 and so on).
WAN Interface Select the WAN interface through which the service is forwarded.
You must have already configured a WAN connection with NAT enabled.

Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
203
11.3 The Sessions Screen
Use the Sessions screen to limit the number of concurrent NAT sessions each
client can use.
Click Network Setting > NAT > Sessions to display the following screen.
Figure 78 Network Setting > NAT > Sessions
Start Port Enter the original destination port for the packets.
To forward only one port, enter the port number again in the External
End Port field.
To forward a series of ports, enter the start port number here and the
end port number in the External End Port field.
End Port Enter the last port of the original destination port range.
To forward only one port, enter the port number in the External Start
Port field above and then enter it again in this field.
To forward a series of ports, enter the last port number in a series that
begins with the port number in the External Start Port field above.
Translation
Start Port
This shows the port number to which you want the ZyXEL Device to
translate the incoming port. For a range of ports, enter the first number
of the range to which you want the incoming ports translated.
Translation End
Port
This shows the last port of the translated port range.
Server IP
Address
Enter the inside IP address of the virtual server here.
Protocol Type Select the protocol supported by this virtual server. Choices are TCP,
UDP, or TCP/UDP.
Apply Click Apply to save your changes.
Back Click Back to return to the previous screen without saving.
Table 45 Port Forwarding: Add/Edit (continued)
LABEL DESCRIPTION
Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
204
The following table describes the fields in this screen.
11.4 Technical Reference
This section provides some technical background information about the topics
covered in this chapter.
11.4.1 NAT Definitions
Inside/outside denotes where a host is located relative to the ZyXEL Device, for
example, the computers of your subscribers are the inside hosts, while the web
servers on the Internet are the outside hosts.
Global/local denotes the IP address of a host in a packet as the packet traverses a
router, for example, the local address refers to the IP address of a host when the
packet is in the local network, while the global address refers to the IP address of
the host when the same packet is traveling in the WAN side.
Note that inside/outside refers to the location of a host, while global/local refers to
the IP address of a host used in a packet. Thus, an inside local address (ILA) is the
IP address of an inside host in a packet when the packet is still in the local
network, while an inside global address (IGA) is the IP address of the same inside
host when the packet is on the WAN side. The following table summarizes this
information.
Table 46 Network Setting > NAT > Sessions
LABEL DESCRIPTION
MAX NAT
Session
Use this field to set a common limit to the number of concurrent NAT
sessions each client computer can have.
If only a few clients use peer to peer applications, you can raise this
number to improve their performance. With heavy peer to peer
application use, lower this number to ensure no single client uses too
many of the available NAT sessions.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 47 NAT Definitions
ITEM DESCRIPTION
Inside This refers to the host on the LAN.
Outside This refers to the host on the WAN.
Local This refers to the packet address (source or destination) as the packet travels
on the LAN.
Global This refers to the packet address (source or destination) as the packet travels
on the WAN.

Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
205
NAT never changes the IP address (either local or global) of an outside host.
11.4.2 What NAT Does
In the simplest form, NAT changes the source IP address in a packet received from
a subscriber (the inside local address) to another (the inside global address)
before forwarding the packet to the WAN side. When the response comes back,
NAT translates the destination address (the inside global address) back to the
inside local address before forwarding it to the original inside host. Note that the
IP address (either local or global) of an outside host is never changed.
The global IP addresses for the inside hosts can be either static or dynamically
assigned by the ISP. In addition, you can designate servers, for example, a web
server and a Telnet server, on your local network and make them accessible to the
outside world. If you do not define any servers, NAT offers the additional benefit of
firewall protection. With no servers defined, your ZyXEL Device filters out all
incoming inquiries, thus preventing intruders from probing your network. For
more information on IP address translation, refer to RFC 1631, The IP Network
Address Translator (NAT).
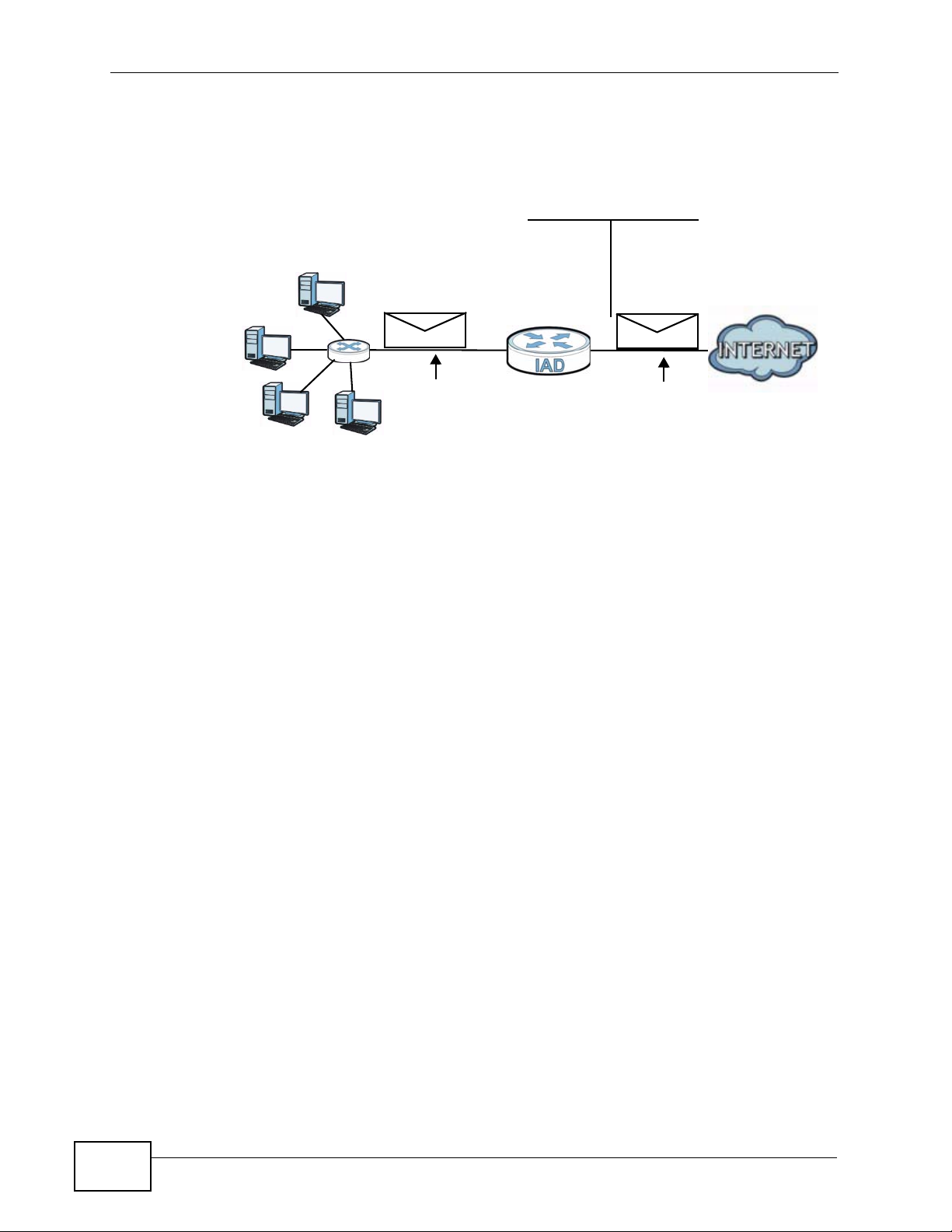
11.4.3 How NAT Works
Each packet has two addresses – a source address and a destination address. For
outgoing packets, the ILA (Inside Local Address) is the source address on the LAN,
and the IGA (Inside Global Address) is the source address on the WAN. For
incoming packets, the ILA is the destination address on the LAN, and the IGA is
the destination address on the WAN. NAT maps private (local) IP addresses to
globally unique ones required for communication with hosts on other networks. It
replaces the original IP source address (and TCP or UDP source port numbers for
Many-to-One and Many-to-Many Overload NAT mapping) in each packet and then
forwards it to the Internet. The ZyXEL Device keeps track of the original addresses
Chapter 11 Network Address Translation (NAT)
P-2612HNU(L)-FxF User’s Guide
206
and port numbers so incoming reply packets can have their original values
restored. The following figure illustrates this.
Figure 79 How NAT Works
192.168.1.13
192.168.1.10
192.168.1.11
192.168.1.12
SA
192.168.1.10
SA
IGA1
Inside Local
IP Address
192.168.1.10
192.168.1.11
192.168.1.12
192.168.1.13
Inside Global
IP Address
IGA 1
IGA 2
IGA 3
IGA 4
NAT Table
WAN
LAN
Inside Local
Address (ILA)
Inside Global
Address (IGA)

P-2612HNU(L)-FxF User’s Guide
207
CH A P T E R 12
Dynamic DNS
12.1 Overview
This chapter discusses how to configure your ZyXEL Device to use Dynamic DNS.
Dynamic DNS allows you to update your current dynamic IP address with one or
many dynamic DNS services so that anyone can contact you (in applications such
as NetMeeting and CU-SeeMe). You can also access your FTP server or Web site on
your own computer using a domain name (for instance myhost.dhs.org, where
myhost is a name of your choice) that will never change instead of using an IP
address that changes each time you reconnect. Your friends or relatives will
always be able to call you even if they don't know your IP address.
First of all, you need to have registered a dynamic DNS account with
www.dyndns.org. This is for people with a dynamic IP from their ISP or DHCP
server that would still like to have a domain name. The Dynamic DNS service
provider will give you a password or key.
12.1.1 What You Need To Know
DYNDNS Wildcard
Enabling the wildcard feature for your host causes *.yourhost.dyndns.org to be
aliased to the same IP address as yourhost.dyndns.org. This feature is useful if
you want to be able to use, for example, www.yourhost.dyndns.org and still reach
your hostname.
If you have a private WAN IP address, then you cannot use Dynamic DNS.

Chapter 12 Dynamic DNS
P-2612HNU(L)-FxF User’s Guide
208
12.2 The Dynamic DNS Screen
Use the Dynamic DNS screen to enable DDNS and configure the DDNS settings
on the ZyXEL Device. To change your ZyXEL Device’s DDNS, click Network
Setting > DNS. The screen appears as shown.
Figure 80 Network Setting > DNS
The following table describes the fields in this screen.
Table 48 Network Setting > DNS
LABEL DESCRIPTION
Dynamic DNS Configuration
Active
Dynamic DNS
Select this check box to use dynamic DNS.
Service
Provider
Select the name of your Dynamic DNS service provider.
Dynamic DNS
Type
Select the type of service that you are registered for from your Dynamic
DNS service provider.
Host Name Type the domain name assigned to your ZyXEL Device by your Dynamic
DNS provider.
You can specify up to two host names in the field separated by a comma
(",").
User Name Type your user name.
Password Type the password assigned to you.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.
P-2612HNU(L)-FxF User’s Guide
209
CH A P T E R 13
Firewall
13.1 Overview
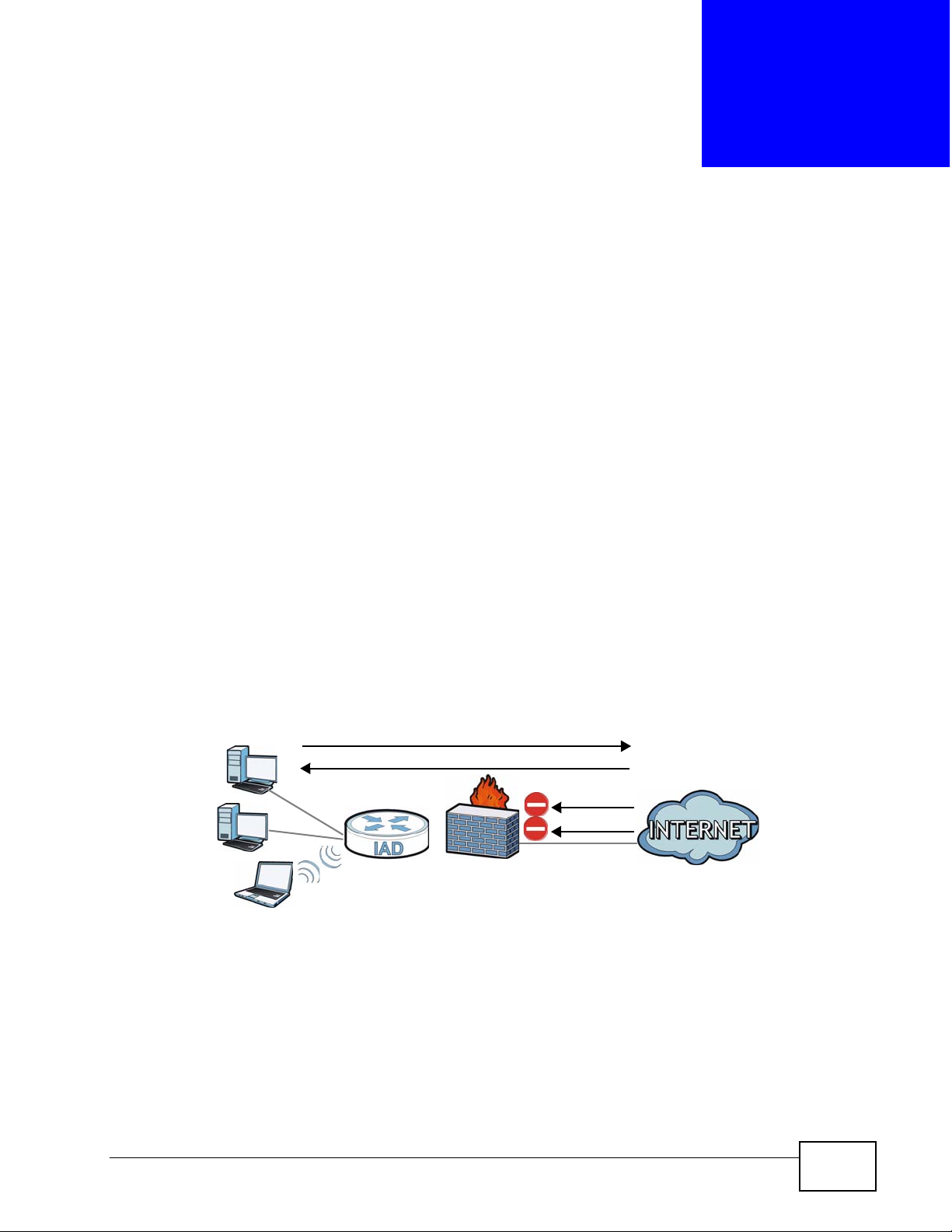
Use the ZyXEL Device firewall screens to enable and configure the firewall that
protects your ZyXEL Device and network from attacks by hackers on the Internet
and control access to it. By default the firewall:
• allows traffic that originates from your LAN and WLAN computers to go to all
other networks.
• blocks traffic that originates on other networks from going to the LAN and
WLAN.
The following figure illustrates the default firewall action. User A can initiate an IM
(Instant Messaging) session from the LAN to the WAN (1). Return traffic for this
session is also allowed (2). However other traffic initiated from the WAN is blocked
(3 and 4).
Figure 81 Default Firewall Action
13.1.1 What You Can Do in this Chapter
• Use the General screen to enable or disable the ZyXEL Device’s firewall
(Section 13.2 on page 211).
• Use the Services screen to view the configured firewall rules and add, edit or
remove a firewall rule (Section 13.3 on page 211).
WAN
LAN
3
4
1
2
A

Chapter 13 Firewall
P-2612HNU(L)-FxF User’s Guide
210
13.1.2 What You Need to Know
Firewall
The ZyXEL Device’s firewall feature physically separates the LAN/WLAN and the
WAN and acts as a secure gateway for all data passing between the networks.
It is designed to protect against Denial of Service (DoS) attacks when activated.
The ZyXEL Device's purpose is to allow a private Local Area Network (LAN) to be
securely connected to the Internet. The ZyXEL Device can be used to prevent
theft, destruction and modification of data, as well as log events, which may be
important to the security of your network.
The ZyXEL Device is installed between the LAN/WLAN and a broadband modem
connecting to the Internet. This allows it to act as a secure gateway for all data
passing between the Internet and the LAN.
The ZyXEL Device has one Ethernet WAN port and four Ethernet LAN ports, which
are used to physically separate the network into two areas.The WAN (Wide Area
Network) port attaches to the broadband (cable or DSL) modem to the Internet.
The LAN (Local Area Network) port attaches to a network of computers, which
needs security from the outside world. These computers will have access to
Internet services such as e-mail, FTP and the World Wide Web. However, "inbound
access" is not allowed (by default) unless the remote host is authorized to use a
specific service.
ICMP
Internet Control Message Protocol (ICMP) is a message control and error-reporting
protocol between a host server and a gateway to the Internet. ICMP uses Internet
Protocol (IP) datagrams, but the messages are processed by the TCP/IP software
and directly apparent to the application user.
Finding Out More
See Section 13.4 on page 213 for advanced technical information on firewall.

Chapter 13 Firewall
P-2612HNU(L)-FxF User’s Guide
211
13.2 The General Screen
Use this screen to enable or disable the ZyXEL Device’s firewall. Click Security >
Firewall to open the General screen.
Figure 82 Security > Firewall > General
The following table describes the labels in this screen.
13.3 The Services Screen
Use this screen to enable service blocking and to maintain the list of services you
want to block. To access this screen, click Security > Firewall > Services.
Table 49 Security > Firewall > General
LABEL DESCRIPTION
Firewall Select Enable to activate the firewall. The ZyXEL Device performs
access control and protects against Denial of Service (DoS) attacks
when the firewall is activated.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.

Chapter 13 Firewall
P-2612HNU(L)-FxF User’s Guide
212
Note: These rules specify which computers on the LAN can access which computers
or services on the WAN.
Figure 83 Security > Firewall > Services
Each field is described in the following table.
Table 50 Security > Firewall > Services
LABEL DESCRIPTION
LAN-to-WAN
Services
Blocking
Select Enable to activate service blocking.
Available
Services
This is a list of pre-defined services (destination ports) you may prohibit
your LAN computers from using. Select the port you want to block, and
click Add to add the port to the Blocked Services field.
A custom port is a service that is not available in the pre-defined
Available Services list. You must define it using the Type and Port
Number fields. See Appendix E on page 381 for some examples of
services.
Blocked
Services
This is a list of services (ports) that are inaccessible to computers on
your LAN when service blocking is effective. To remove a service from
this list, select the service, and click Delete.
Type
Select TCP, UDP or TCP and UDP, based on which one the custom port
uses.
Port Number Enter the range of port numbers that defines the service. For example,
suppose you want to define the Gnutella service. Select TCP type and
enter a port range of 6345-6349.
Add
Click this to add the selected service in Available Services to the
Blocked Services list. Note that the service is blocked immediately
after clicking this.

Chapter 13 Firewall
P-2612HNU(L)-FxF User’s Guide
213
13.4 Firewall Technical Reference
This section provides some technical background information about the topics
covered in this chapter.
13.4.1 Guidelines For Enhancing Security With Your Firewall
1 Change the default password via web configurator.
2 Think about access control before you connect to the network in any way.
3 Limit who can access your ZyXEL Device.
4 Don't enable any local service (such as Telnet or FTP) that you don't use. Any
enabled service could present a potential security risk. A determined hacker might
be able to find creative ways to misuse the enabled services to access the firewall
or the network.
5 For local services that are enabled, protect against misuse. Protect by configuring
the services to communicate only with specific peers, and protect by configuring
rules to block packets for the services at specific interfaces.
6 Keep the firewall in a secured (locked) room.
13.4.2 Security Considerations
Note: Incorrectly configuring the firewall may block valid access or introduce security
risks to the ZyXEL Device and your protected network. Use caution when
creating or deleting firewall rules and test your rules after you configure them.
Consider these security ramifications before creating a rule:
1 Does this rule stop LAN users from accessing critical resources on the Internet?
For example, if IRC is blocked, are there users that require this service?
Delete Select a service in the Blocked Services, and click this to remove the
service from the list.
Clear All Click this to remove all the services in the Blocked Services list.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.
Table 50 Security > Firewall > Services (continued)
LABEL DESCRIPTION

Chapter 13 Firewall
P-2612HNU(L)-FxF User’s Guide
214
2 Is it possible to modify the rule to be more specific? For example, if IRC is blocked
for all users, will a rule that blocks just certain users be more effective?
3 Does a rule that allows Internet users access to resources on the LAN create a
security vulnerability? For example, if FTP ports (TCP 20, 21) are allowed from the
Internet to the LAN, Internet users may be able to connect to computers with
running FTP servers.
4 Does this rule conflict with any existing rules?
Once these questions have been answered, adding rules is simply a matter of
entering the information into the correct fields in the web configurator screens.

P-2612HNU(L)-FxF User’s Guide
215
CH A P T E R 14
MAC Filter
14.1 Overview
This chapter discusses MAC address filtering.
You can configure the ZyXEL Device to permit access to clients based on their MAC
addresses in the MAC Filter screen. This applies to wired and wireless
connections.
14.1.1 What You Need to Know
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC
address is assigned at the factory and consists of six pairs of hexadecimal
characters, for example, 00:A0:C5:00:00:02. You need to know the MAC address
of the devices to configure this screen.
Chapter 14 MAC Filter
P-2612HNU(L)-FxF User’s Guide
216
14.2 The MAC Filter Screen
Use the MAC Filter screen to allow wireless clients access to the ZyXEL Device. To
change your ZyXEL Device’s MAC filter settings, click Security > MAC Filter. The
screen appears as shown.
Figure 84 Security > MAC Filter
The following table describes the labels in this menu.
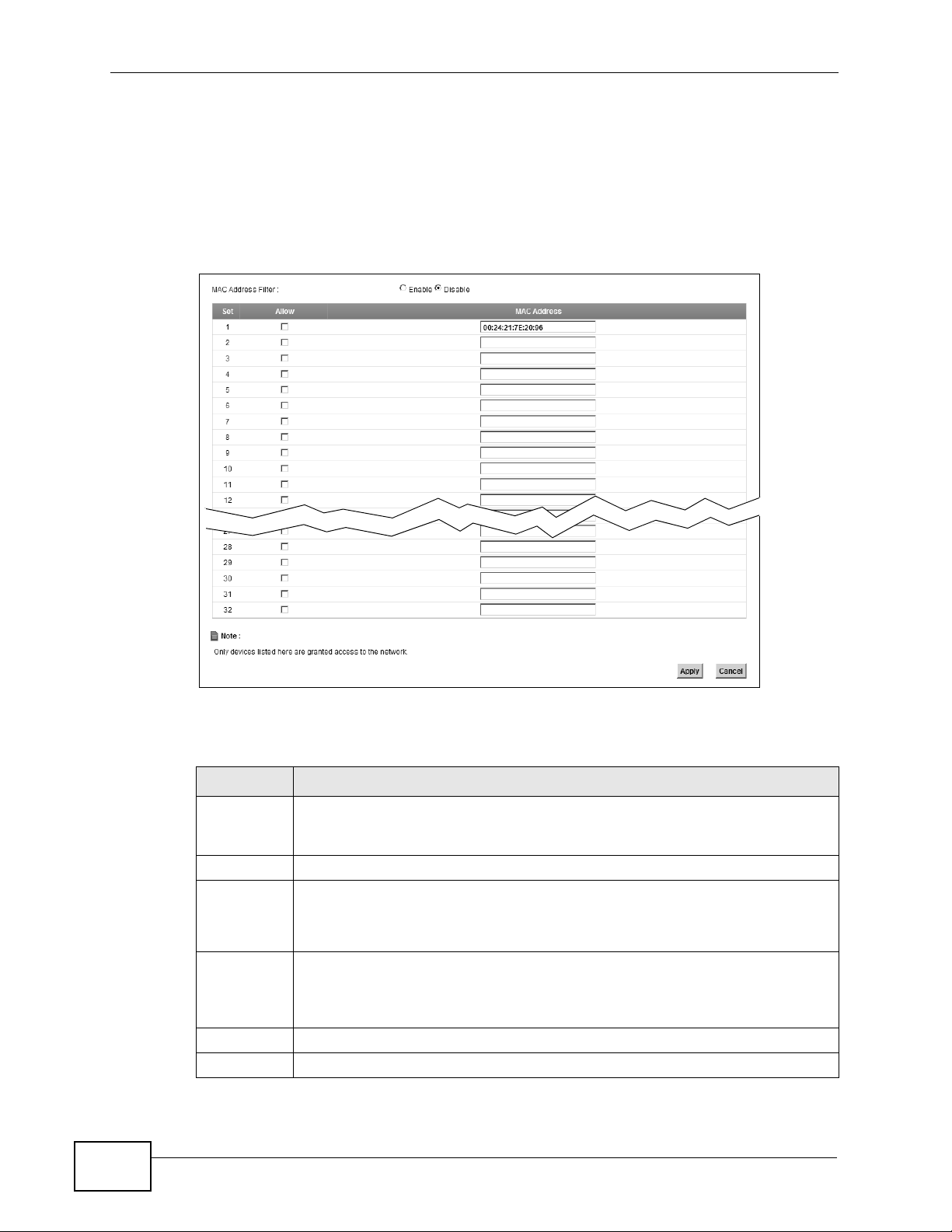
Table 51 Security > MAC Filter
LABEL DESCRIPTION
MAC
Address
Filter
Select Enable to activate MAC address filtering.
Set This is the index number of the MAC address.
Allow Select Allow to permit access to the ZyXEL Device. MAC addresses not
listed will be denied access to the ZyXEL Device.
If you clear this, the MAC Address field for this set clears.
MAC
Address
Enter the MAC addresses of the wireless station that are allowed access to
the ZyXEL Device in these address fields. Enter the MAC addresses in a
valid MAC address format, that is, six hexadecimal character pairs, for
example, 12:34:56:78:9a:bc.
Apply Click Apply to save your changes.
Cancel Click Cancel to restore your previously saved settings.

P-2612HNU(L)-FxF User’s Guide
217
CH A P T E R 15
Certificates
15.1 Overview
The ZyXEL Device can use certificates (also called digital IDs) to authenticate
users. Certificates are based on public-private key pairs. A certificate contains the
certificate owner’s identity and public key. Certificates provide a way to exchange
public keys for use in authentication.
15.1.1 What You Can Do in this Chapter
• Use the Local Certificate screens to view and import the ZyXEL Device’s CAsigned certificates (Section 15.2 on page 220).
• Use the Trusted CA screens to save the certificates of trusted CAs to the ZyXEL
Device. You can also export the certificates to a computer (Section 15.3 on page
222).
15.1.2 What You Need to Know
The following terms and concepts may help as you read this chapter.
Certification Authorities
A Certification Authority (CA) issues certificates and guarantees the identity of
each certificate owner. There are commercial certification authorities like
CyberTrust or VeriSign and government certification authorities.
Public and Private Keys
When using public-key cryptology for authentication, each host has two keys. One
key is public and can be made openly available; the other key is private and must
be kept secure. Public-key encryption in general works as follows.
1 Tim wants to send a private message to Jenny. Tim generates a public-private key
pair. What is encrypted with one key can only be decrypted using the other.
2 Tim keeps the private key and makes the public key openly available.

Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
218
3 Tim uses his private key to encrypt the message and sends it to Jenny.
4 Jenny receives the message and uses Tim’s public key to decrypt it.
5 Additionally, Jenny uses her own private key to encrypt a message and Tim uses
Jenny’s public key to decrypt the message.
The ZyXEL Device uses certificates based on public-key cryptology to authenticate
users attempting to establish a connection. The method used to secure the data
that you send through an established connection depends on the type of
connection. For example, a VPN tunnel might use the triple DES encryption
algorithm.
The certification authority uses its private key to sign certificates. Anyone can then
use the certification authority’s public key to verify the certificates.
Certification Path
A certification path is the hierarchy of certification authority certificates that
validate a certificate. The ZyXEL Device does not trust a certificate if any
certificate on its path has expired or been revoked.
Certificate Directory Servers
Certification authorities maintain directory servers with databases of valid and
revoked certificates. A directory of certificates that have been revoked before the
scheduled expiration is called a CRL (Certificate Revocation List). The ZyXEL
Device can check a peer’s certificate against a directory server’s list of revoked
certificates. The framework of servers, software, procedures and policies that
handles keys is called PKI (public-key infrastructure).
Advantages of Certificates
Certificates offer the following benefits.
• The ZyXEL Device only has to store the certificates of the certification
authorities that you decide to trust, no matter how many devices you need to
authenticate.
• Key distribution is simple and very secure since you can freely distribute public
keys and you never need to transmit private keys.
Certificate File Formats
The certification authority certificate that you want to import has to be in one of
these file formats:

Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
219
• Binary X.509: This is an ITU-T recommendation that defines the formats for
X.509 certificates.
• PEM (Base-64) encoded X.509: This Privacy Enhanced Mail format uses 64
ASCII characters to convert a binary X.509 certificate into a printable form.
• Binary PKCS#7: This is a standard that defines the general syntax for data
(including digital signatures) that may be encrypted. The ZyXEL Device
currently allows the importation of a PKS#7 file that contains a single
certificate.
• PEM (Base-64) encoded PKCS#7: This Privacy Enhanced Mail (PEM) format uses
64 ASCII characters to convert a binary PKCS#7 certificate into a printable
form.
Note: Be careful not to convert a binary file to text during the transfer process. It is
easy for this to occur since many programs use text files by default.
15.1.3 Verifying a Certificate
Before you import a trusted CA or trusted remote host certificate into the ZyXEL
Device, you should verify that you have the actual certificate. This is especially
true of trusted CA certificates since the ZyXEL Device also trusts any valid
certificate signed by any of the imported trusted CA certificates.
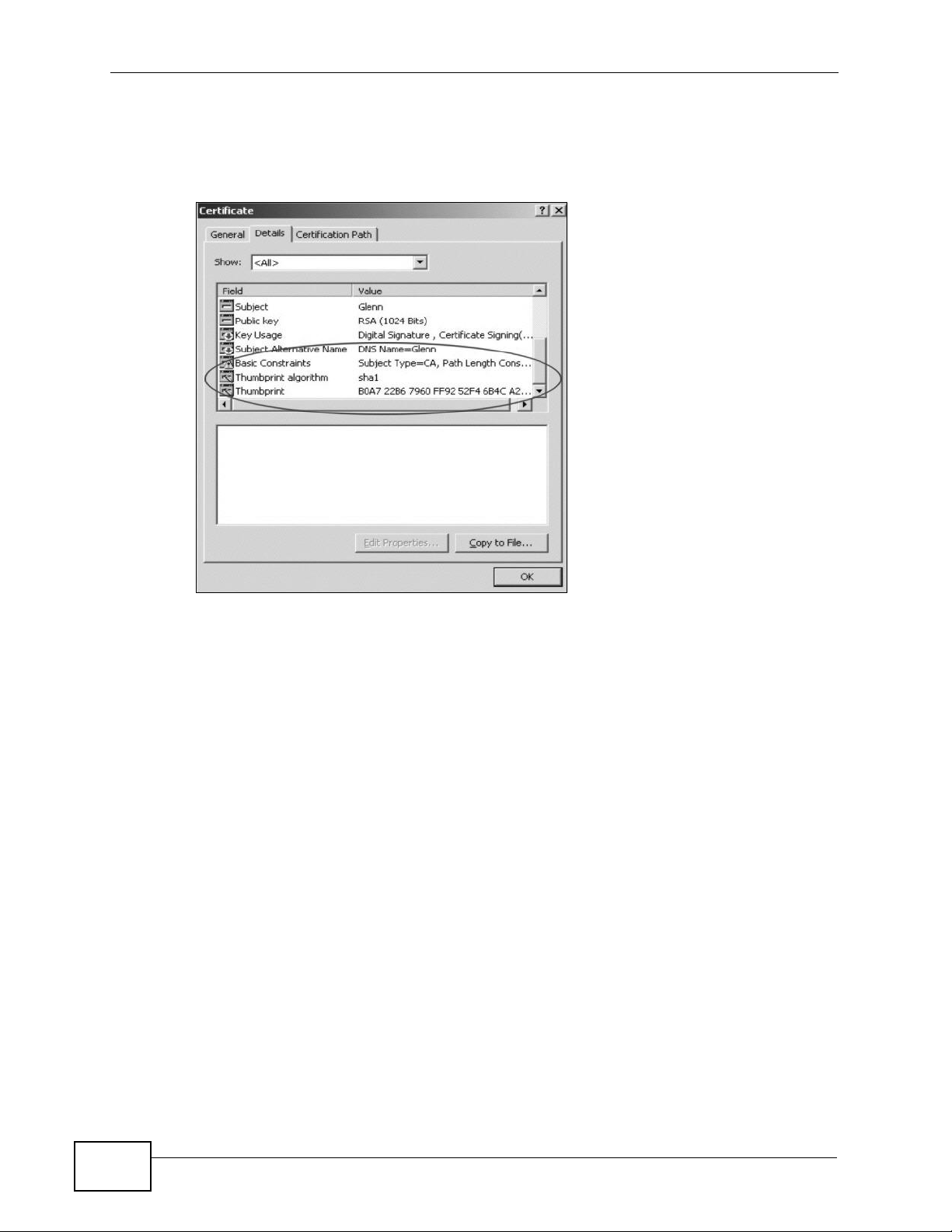
You can use a certificate’s fingerprint to verify it. A certificate’s fingerprint is a
message digest calculated using the MD5 or SHA1 algorithms. The following
procedure describes how to check a certificate’s fingerprint to verify that you have
the actual certificate.
1 Browse to where you have the certificate saved on your computer.
2 Make sure that the certificate has a “.cer” or “.crt” file name extension.
Figure 85 Certificates on Your Computer
Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
220
3 Double-click the certificate’s icon to open the Certificate window. Click the
Details tab and scroll down to the Thumbprint Algorithm and Thumbprint
fields.
Figure 86 Certificate Details
4 Use a secure method to verify that the certificate owner has the same information
in the Thumbprint Algorithm and Thumbprint fields. The secure method may
very based on your situation. Possible examples would be over the telephone or
through an HTTPS connection.
15.2 Local Certificates
Use this screen to view the ZyXEL Device’s summary list of certificates and
certification requests. You can import the following certificates to your ZyXEL
Device:
• Web Server - This certificate secures HTTP connections.
• SIP TLS - This certificate secures VoIP connections.
• SSH/SCP/SFTP - This certificate secures remote connections.
Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
221
Click Security > Certificates to open the Local Certificates screen.
Figure 87 Security > Certificates > Local Certificates
The following table describes the labels in this screen.
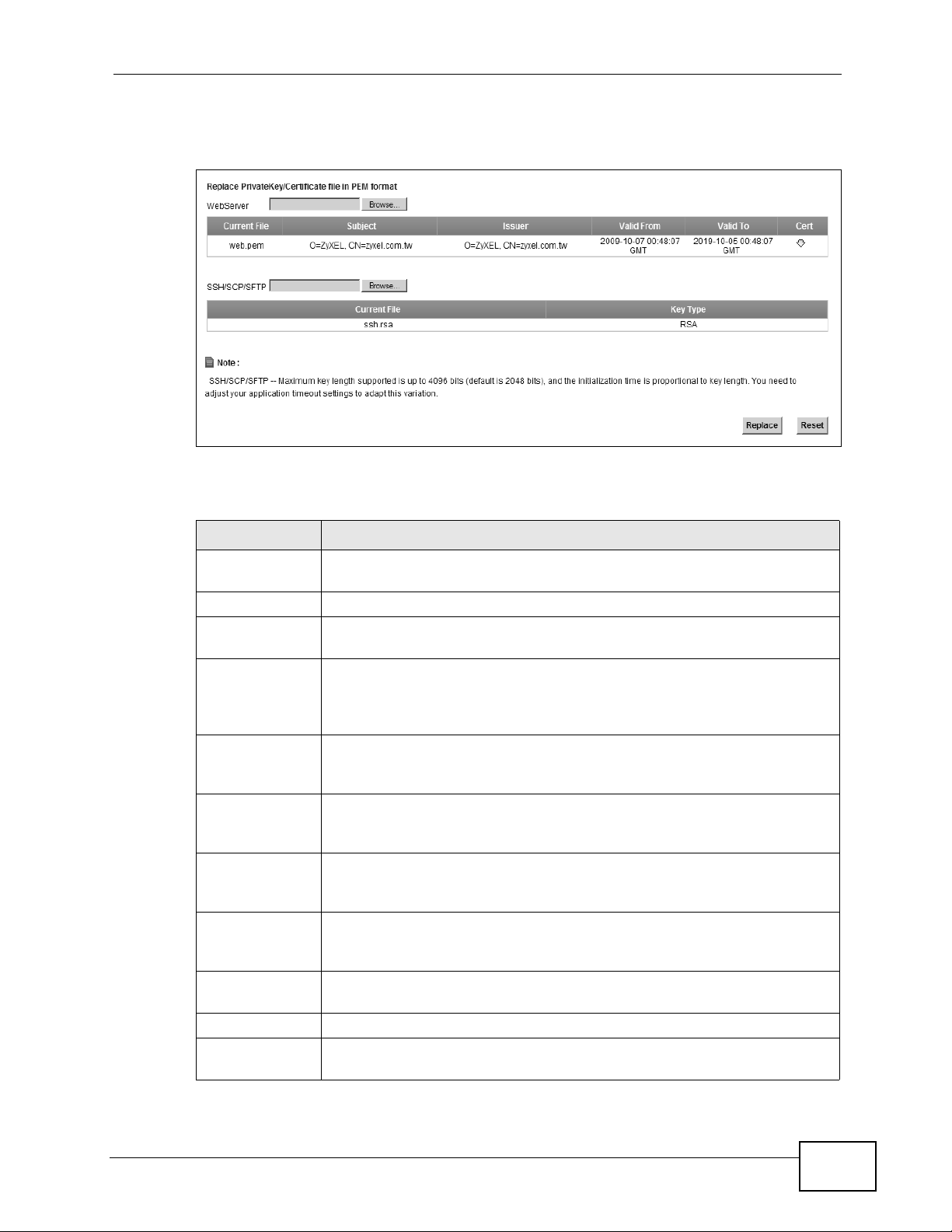
Table 52 Security > Certificates > Local Certificates
LABEL DESCRIPTION
Web Server Type in the location of the Web Server certificate file you want to
upload in this field or click Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
Current File This field displays the name used to identify this certificate. It is
recommended that you give each certificate a unique name.
Subject This field displays identifying information about the certificate’s owner,
such as CN (Common Name), OU (Organizational Unit or department),
O (Organization or company) and C (Country). It is recommended that
each certificate have unique subject information.
Issuer This field displays identifying information about the certificate’s issuing
certification authority, such as a common name, organizational unit or
department, organization or company and country.
Valid From This field displays the date that the certificate becomes applicable. The
text displays in red and includes a Not Yet Valid! message if the
certificate has not yet become applicable.
Valid To This field displays the date that the certificate expires. The text displays
in red and includes an Expiring! or Expired! message if the certificate
is about to expire or has already expired.
Cert Click this button and then Save in the File Download screen. The
Save As screen opens, browse to the location that you want to use and
click Save.
SSH/SCP/SFTP Type in the location of the SSH/SCP/SFTP certificate file you want to
upload in this field or click Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
Current File This field displays the name used to identify this certificate. It is
recommended that you give each certificate a unique name.

Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
222
15.3 Trusted CA
Use this screen to view a summary list of certificates of the certification authorities
that you have set the ZyXEL Device to accept as trusted. The ZyXEL Device
accepts any valid certificate signed by a certification authority on this list as being
trustworthy; thus you do not need to import any certificate that is signed by one
of these certification authorities.
Click Security > Certificates > Trusted CA to open the Trusted CA screen.
Figure 88 Security > Certificates > Trusted CA
The following table describes the labels in this screen.
Key Type This field applies to the SSH/SCP/SFTP certificate.
This shows the
file format of the current certificate.
Replace Click this to replace the certificate(s) and save your changes back to the
ZyXEL Device.
Reset Click this to clear your settings.
Table 52 Security > Certificates > Local Certificates (continued)
LABEL DESCRIPTION
Table 53 Security > Certificates > Trusted CA
LABEL DESCRIPTION
Import
Certificate
Click this button to open a screen where you can save the certificate of
a certification authority that you trust to the ZyXEL Device.
Name This field displays the name used to identify this certificate.
Subject This field displays information that identifies the owner of the
certificate, such as Common Name (CN), OU (Organizational Unit or
department), Organization (O), State (ST) and Country (C). It is
recommended that each certificate have unique subject information.
Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
223
15.4 Trusted CA Import
Click Import Certificate in the Trusted CAs screen to open the Import
Certificate screen. You can save a trusted certification authority’s certificate to
the ZyXEL Device.
Note: You must remove any spaces from the certificate’s filename before you can
import the certificate.
Figure 89 Trusted CA > Import
The following table describes the labels in this screen.
Type This field displays general information about the certificate. ca means
that a Certification Authority signed the certificate.
Action Click the View icon to open a screen with an in-depth list of information
about the certificate (or certification request).
Click the Delete icon to delete the certificate (or certification request).
You cannot delete a certificate that one or more features is configured
to use.
Table 53 Security > Certificates > Trusted CA (continued)
LABEL DESCRIPTION
Table 54 Security > Certificates > Trusted CA > Import
LABEL DESCRIPTION
Certificate
File Path
Type in the location of the file you want to upload in this field or click
Browse to find it.
Browse Click Browse to find the certificate file you want to upload.
Apply Click Apply to save the certificate on the ZyXEL Device.
Back Click Back to return to the previous screen.
Chapter 15 Certificates
P-2612HNU(L)-FxF User’s Guide
224
15.5 View Certificate
Use this screen to view in-depth information about the certification authority’s
certificate, change the certificate’s name and set whether or not you want the
ZyXEL Device to check a certification authority’s list of revoked certificates before
trusting a certificate issued by the certification authority.
Click Security > Certificates > Trusted CA to open the Trusted CA screen.
Click the View icon to open the View Certificate screen.
Figure 90 Trusted CA: View
The following table describes the labels in this screen.
Table 55 Trusted CA: View
LABEL DESCRIPTION
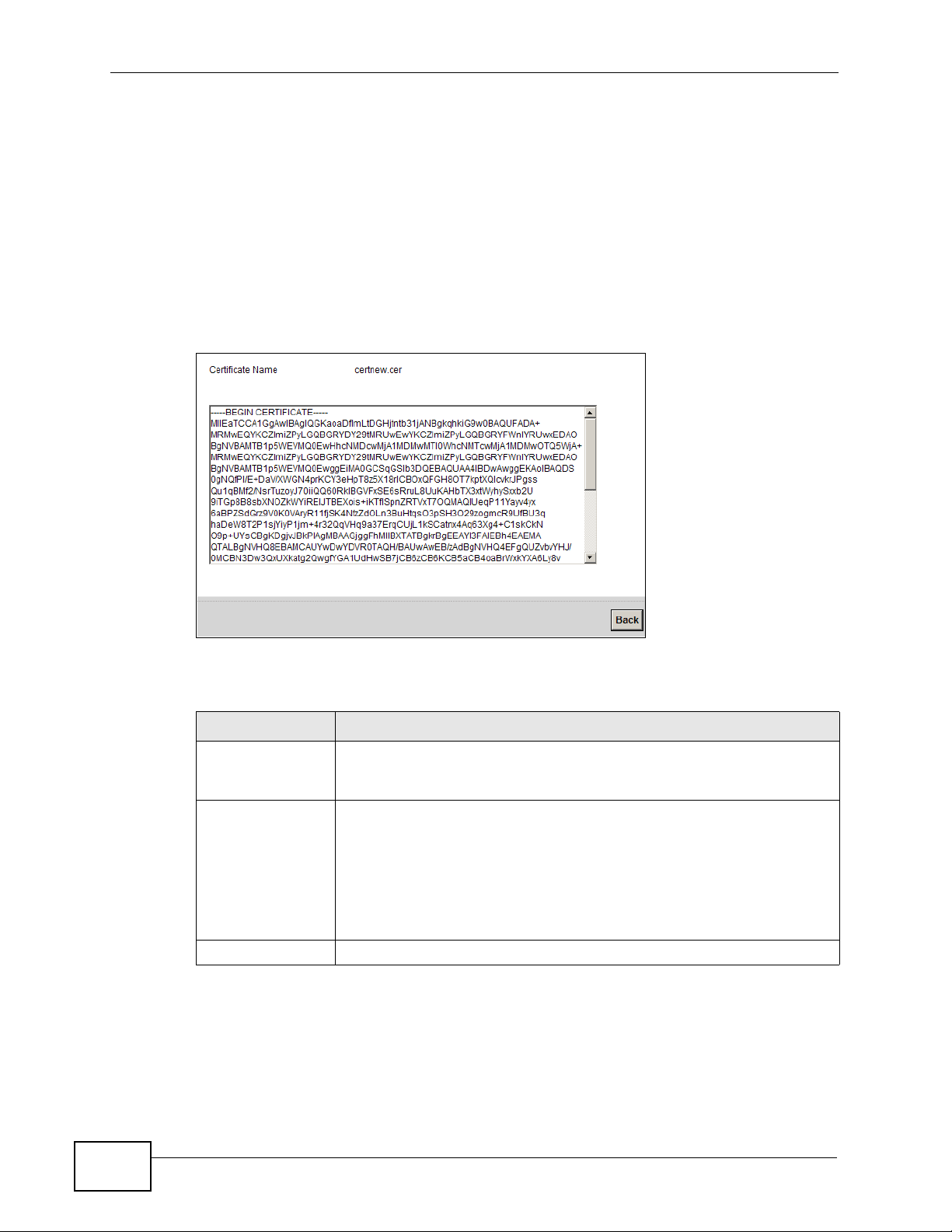
Certificate Name This field displays the identifying name of this certificate. If you want
to change the name, type up to 31 characters to identify this key
certificate. You may use any character (not including spaces).
Certificate Detail This read-only text box displays the certificate or certification request
in Privacy Enhanced Mail (PEM) format. PEM uses 64 ASCII characters
to convert the binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to
friends or colleagues or you can copy and paste the certificate into a
text editor and save the file on a management computer for later
distribution (via floppy disk for example).
Back Click this to return to the previous screen.

P-2612HNU(L)-FxF User’s Guide
225
CH A P T E R 16
VoIP
16.1 Overview
Use this chapter to:
• Connect an analog phone to the ZyXEL Device.
• Make phone calls over the Internet, as well as the regular phone network.
• Configure settings such as speed dial.
• Configure network settings to optimize the voice quality of your phone calls.
16.1.1 What You Can Do in this Chapter
These screens allow you to configure your ZyXEL Device to make phone calls over
the Internet and your regular phone line, and to set up the phones you connect to
the ZyXEL Device.
• Use the SIP Service Provider screen to configure the SIP server information,
QoS for VoIP calls, the numbers for certain phone functions (Section 16.3 on
page 231).
• Use the SIP Account screen to set up information about your SIP account,
control which SIP accounts the phones connected to the ZyXEL Device use and
configure audio settings such as volume levels for the phones connected to the
ZyXEL Device (Section 16.3 on page 231).
• Use the Common screen to configure RFC3262 support on the ZyXEL Device
(Section 16.4 on page 236).
• Use the Phone Device screen to control which SIP accounts the phones
connected to the ZyXEL Device use (Section 16.6 on page 239).
• Use the Region screen to change settings that depend on the country you are
in (Section 16.7 on page 241).
• Use the Call Rule screen to set up shortcuts for dialing frequently-used (VoIP)
phone numbers (Section 16.9 on page 243).
• Use the FXO screen to set up the PSTN line used to make regular phone calls
which do not use the Internet (Section 16.9 on page 243).

Chapter 16 VoIP
P-2612HNU(L)-FxF User’s Guide
226
You don’t necessarily need to use all these screens to set up your account. In fact,
if your service provider did not supply information on a particular field in a screen,
it is usually best to leave it at its default setting.
16.1.2 What You Need to Know
The following terms and concepts may help as you read this chapter.
VoIP
VoIP stands for Voice over IP. IP is the Internet Protocol, which is the messagecarrying standard the Internet runs on. So, Voice over IP is the sending of voice
signals (speech) over the Internet (or another network that uses the Internet
Protocol).
SIP
SIP stands for Session Initiation Protocol. SIP is a signalling standard that lets one
network device (like a computer or the ZyXEL Device) send messages to another.
In VoIP, these messages are about phone calls over the network. For example,
when you dial a number on your ZyXEL Device, it sends a SIP message over the
network asking the other device (the number you dialed) to take part in the call.
SIP Accounts
A SIP account is a type of VoIP account. It is an arrangement with a service
provider that lets you make phone calls over the Internet. When you set the
ZyXEL Device to use your SIP account to make calls, the ZyXEL Device is able to
send all the information about the phone call to your service provider on the
Internet.
Strictly speaking, you don’t need a SIP account. It is possible for one SIP device
(like the ZyXEL Device) to call another without involving a SIP service provider.
However, the networking difficulties involved in doing this make it tremendously
impractical under normal circumstances. Your SIP account provider removes these
difficulties by taking care of the call routing and setup - figuring out how to get
your call to the right place in a way that you and the other person can talk to one
another.
Voice Activity Detection/Silence Suppression
Voice Activity Detection (VAD) detects whether or not speech is present. This lets
the ZyXEL Device reduce the bandwidth that a call uses by not transmitting “silent
packets” when you are not speaking.

Chapter 16 VoIP
P-2612HNU(L)-FxF User’s Guide
227
Comfort Noise Generation
When using VAD, the ZyXEL Device generates comfort noise when the other party
is not speaking. The comfort noise lets you know that the line is still connected as
total silence could easily be mistaken for a lost connection.
Echo Cancellation
G.168 is an ITU-T standard for eliminating the echo caused by the sound of your
voice reverberating in the telephone receiver while you talk.
Use this screen to maintain basic information about each SIP account. You can
also enable and disable each SIP account, configure the volume, echo cancellation
and VAD (Voice Activity Detection) settings for each individual phone port on the
ZyXEL Device.
How to Find Out More
See Chapter 3 on page 37 for a tutorial showing how to set up these screens in an
example scenario.
See Section 16.10 on page 244 for advanced technical information on SIP.
16.1.3 Before You Begin
• Before you can use these screens, you need to have a VoIP account already set
up. If you don’t have one yet, you can sign up with a VoIP service provider over
the Internet.
• You should have the information your VoIP service provider gave you ready,
before you start to configure the ZyXEL Device.
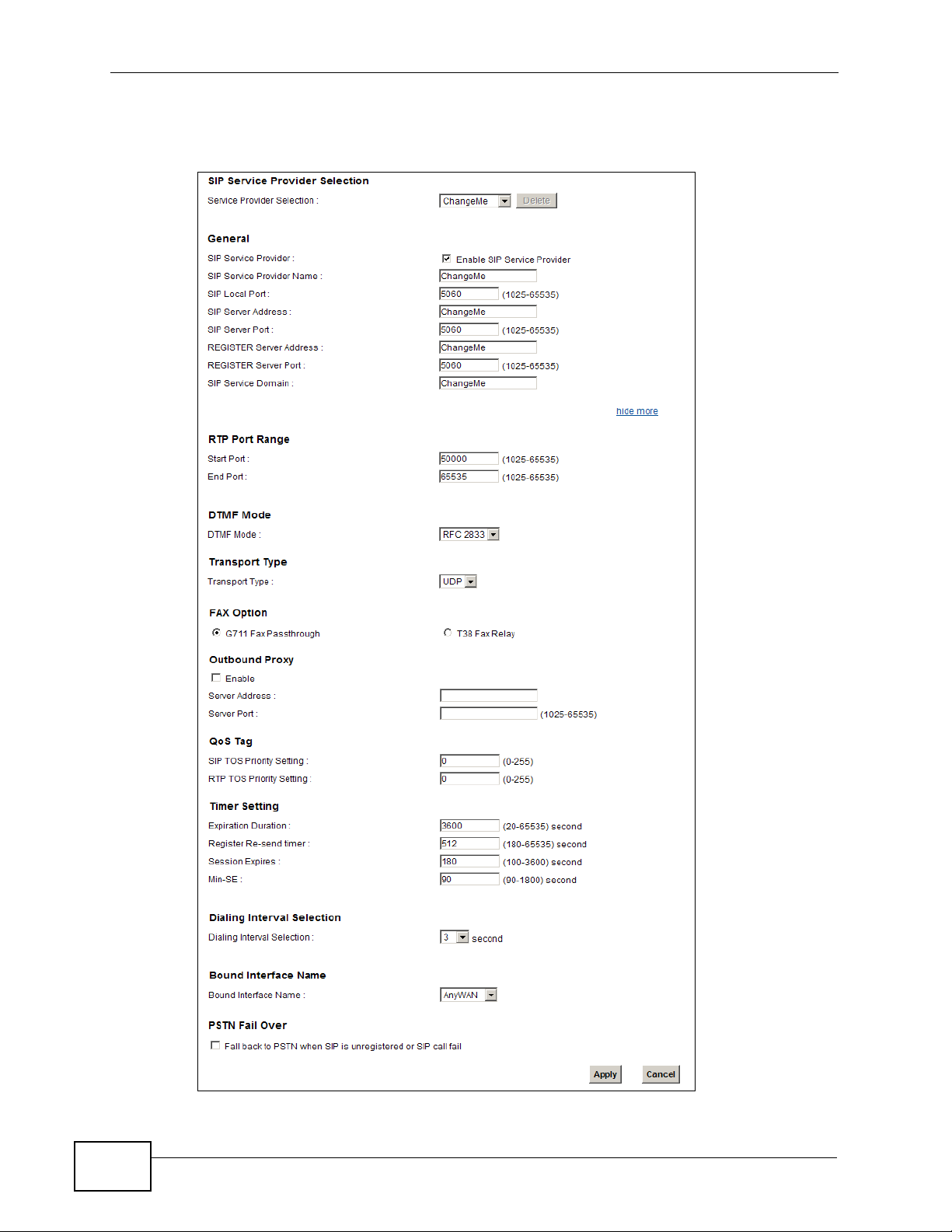
16.2 The SIP Service Provider Screen
Use this screen to configure the SIP server information, QoS for VoIP calls, the
numbers for certain phone functions and dialing plan. Click VoIP > SIP to open
the SIP Service Provider screen.
Note: Click more... to see all the fields in the screen. You don’t necessarily need to
use all these fields to set up your account. Click hide more to see and
configure only the fields needed for this feature.
Chapter 16 VoIP
P-2612HNU(L)-FxF User’s Guide
228
Figure 91 VoIP > SIP > SIP Service Provider
Chapter 16 VoIP
P-2612HNU(L)-FxF User’s Guide
229
The following table describes the labels in this screen.
Table 56 VoIP > SIP > SIP Service Provider
LABEL DESCRIPTION
SIP Service Provider Selection
Service
Provider
Selection
Select the SIP service provider profile you want to use for the SIP
account you configure in this screen. If you change this field, the screen
automatically refreshes. If you want to configure a new service
provider, select Add New.
General
SIP Service
Provider
Select this if you want the ZyXEL Device to use this SIP provider. Clear
it if you do not want the ZyXEL Device to use this SIP provider.
SIP Service
Provider Name
Enter the name of your SIP service provider.
SIP Local Port Enter the ZyXEL Device’s listening port number, if your VoIP service
provider gave you one. Otherwise, keep the default value.
SIP Server
Address
Enter the IP address or domain name of the SIP server provided by
your VoIP service provider. You can use up to 95 printable ASCII
characters. It does not matter whether the SIP server is a proxy,
redirect or register server.
SIP Server Port Enter the SIP server’s listening port number, if your VoIP service
provider gave you one. Otherwise, keep the default value.
REGISTER
Server Address
Enter the IP address or domain name of the SIP register server, if your
VoIP service provider gave you one. Otherwise, enter the same address
you entered in the SIP Server Address field. You can use up to 95
printable ASCII characters.
REGISTER
Server Port
Enter the SIP register server’s listening port number, if your VoIP
service provider gave you one. Otherwise, enter the same port number
you entered in the SIP Server Port field.
SIP Service
Domain
Enter the SIP service domain name. In the full SIP URI, this is the part
after the @ symbol. You can use up to 127 printable ASCII Extended
set characters.
RTP Port Range
Start Port
End Port
Enter the listening port number(s) for RTP traffic, if your VoIP service
provider gave you this information. Otherwise, keep the default values.
To enter one port number, enter the port number in the Start Port and
End Port fields.
To enter a range of ports,
• enter the port number at the beginning of the range in the Start
Port field.
• enter the port number at the end of the range in the End Port field.
Chapter 16 VoIP
P-2612HNU(L)-FxF User’s Guide
230
DTMF Mode Control how the ZyXEL Device handles the tones that your telephone
makes when you push its buttons. You should use the same mode your
VoIP service provider uses.
RFC2833 - send the DTMF tones in RTP packets.
PCM - send the DTMF tones in the voice data stream. This method
works best when you are using a codec that does not use compression
(like G.711). Codecs that use compression (like G.729 and G.726) can
distort the tones.
SIP INFO - send the DTMF tones in SIP messages.
Transport Type
Transport Type
Select the transport layer protocol (TCP, UDP or TCP) used for SIP.
FAX Option This field controls how the ZyXEL Device handles fax messages.
G711 Fax
Passthrough
Select this if the ZyXEL Device should use G.711 to send fax messages.
The peer devices must also use G.711.
T38 Fax Relay Select this if the ZyXEL Device should send fax messages as UDP or
TCP/IP packets through IP networks. This provides better quality, but it
may have inter-operability problems. The peer devices must also use
T.38.
Outbound Proxy
Enable Select this if your VoIP service provider has a SIP outbound server to
handle voice calls. This allows the ZyXEL Device to work with any type
of NAT router and eliminates the need for STUN or a SIP ALG. Turn off
any SIP ALG on a NAT router in front of the ZyXEL Device to keep it
from re-translating the IP address (since this is already handled by the
outbound proxy server).
Server Address Enter the IP address or domain name of the SIP outbound proxy server.
Server Port Enter the SIP outbound proxy server’s listening port, if your VoIP
service provider gave you one. Otherwise, keep the default value.
QoS Tag
SIP TOS Priority
Setting
Enter the DSCP (DiffServ Code Point) number for SIP message
transmissions. The ZyXEL Device creates Class of Service (CoS) priority
tags with this number to SIP traffic that it transmits.
RTP TOS
Priority Setting
Enter the DSCP (DiffServ Code Point) number for RTP voice
transmissions. The ZyXEL Device creates Class of Service (CoS) priority
tags with this number to RTP traffic that it transmits.
Timer Setting
Expiration
Duration
Enter the number of seconds your SIP account is registered with the
SIP register server before it is deleted. The ZyXEL Device automatically
tries to re-register your SIP account when one-half of this time has
passed. (The SIP register server might have a different expiration.)
Register Resend timer
Enter the number of seconds the ZyXEL Device waits before it tries
again to register the SIP account, if the first try failed or if there is no
response.
Session Expires Enter the number of seconds the ZyXEL Device lets a SIP session
remain idle (without traffic) before it automatically disconnects the
session.
Table 56 VoIP > SIP > SIP Service Provider (continued)
LABEL DESCRIPTION
 Loading...
Loading...