Yealink IEEE 802.1X User Manual

Yealink Technical White Paper 802.1X Authentication
About 802.1X
The IEEE 802.1X standard defines a Port-based Network Access Control (PNAC) and
authentication protocol that restricts unauthorized clients from connecting to a LAN. The IEEE
802.1X defines the encapsulation of the Extensible Authentication Protocol (EAP) defined in
RFC3748 which is known as “EAP over LAN” or EAPOL.
802.1X authentication involves three parties: a supplicant, an authenticator, and an
authentication server. The supplicant is a client device (such as an IP phone) that wishes to
attach to the network. The authenticator is a network device, such as an Ethernet switch. And
the authentication server is typically a host running software supporting the RADIUS and EAP
protocols.
The authenticator acts like a security guard to a protected network. The supplicant is not allowed
access through the authenticator to the protected side of the network until the supplicant’s
identity has been validated and authorized. An analogy to this is like providing a valid visa at the
airport's arrival immigration before being allowed to enter the country. With 802.1X port-based
authentication, the supplicant provides credentials, such as user name, password or digital
certificate for the authenticator, and the authenticator forwards the credentials to the
authentication server for verification. If the authentication server determines the credentials are
valid, the supplicant is allowed to access resources located on the protected side of the network.
Yealink IP Phones Compatible with 802.1X
802.1X is the most widely accepted form of port-based network access control in use and is
available on Yealink IP phones. Yealink IP phones support 802.1X authentication based on
EAP-MD5, EAP-TLS, EAP-PEAP/MSCHAPv2, EAP-TTLS/EAP-MSCHAPv2, EAP-PEAP/GTC,
EAP-TTLS/EAP-GTC, and EAP-FAST protocols.
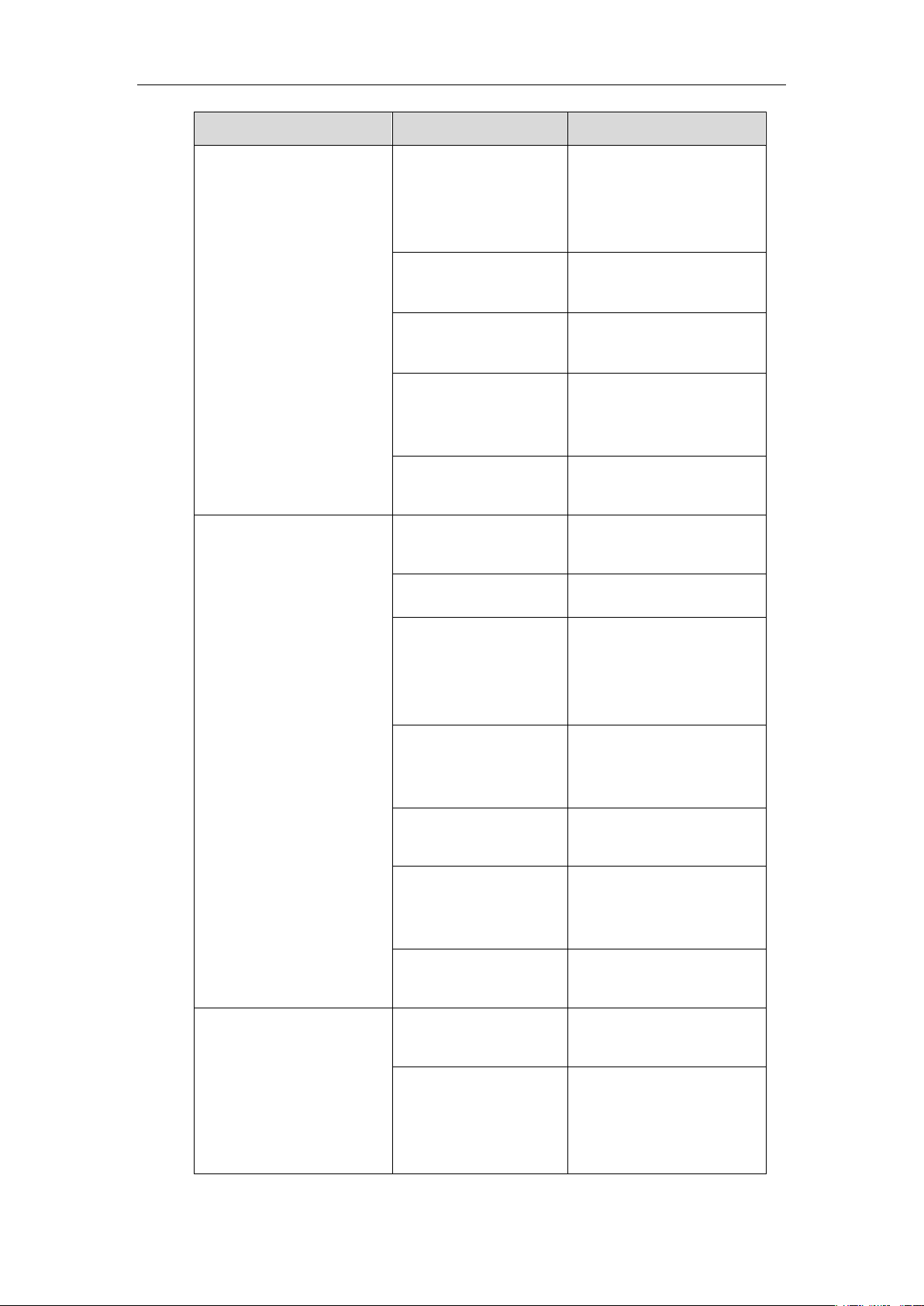
The table below lists the protocols supported by Yealink SIP IP phones with different versions.
Authentication Protocol
IP Phone Models
Firmware Version
EAP-MD5
All IP phones
All Versions
EAP-TLS
T46G, T42G, T41P,
CP860
Firmware version 71 or later
T48G
Firmware version 72 or later
Yealink Technical White Paper 802.1X Authentication
2
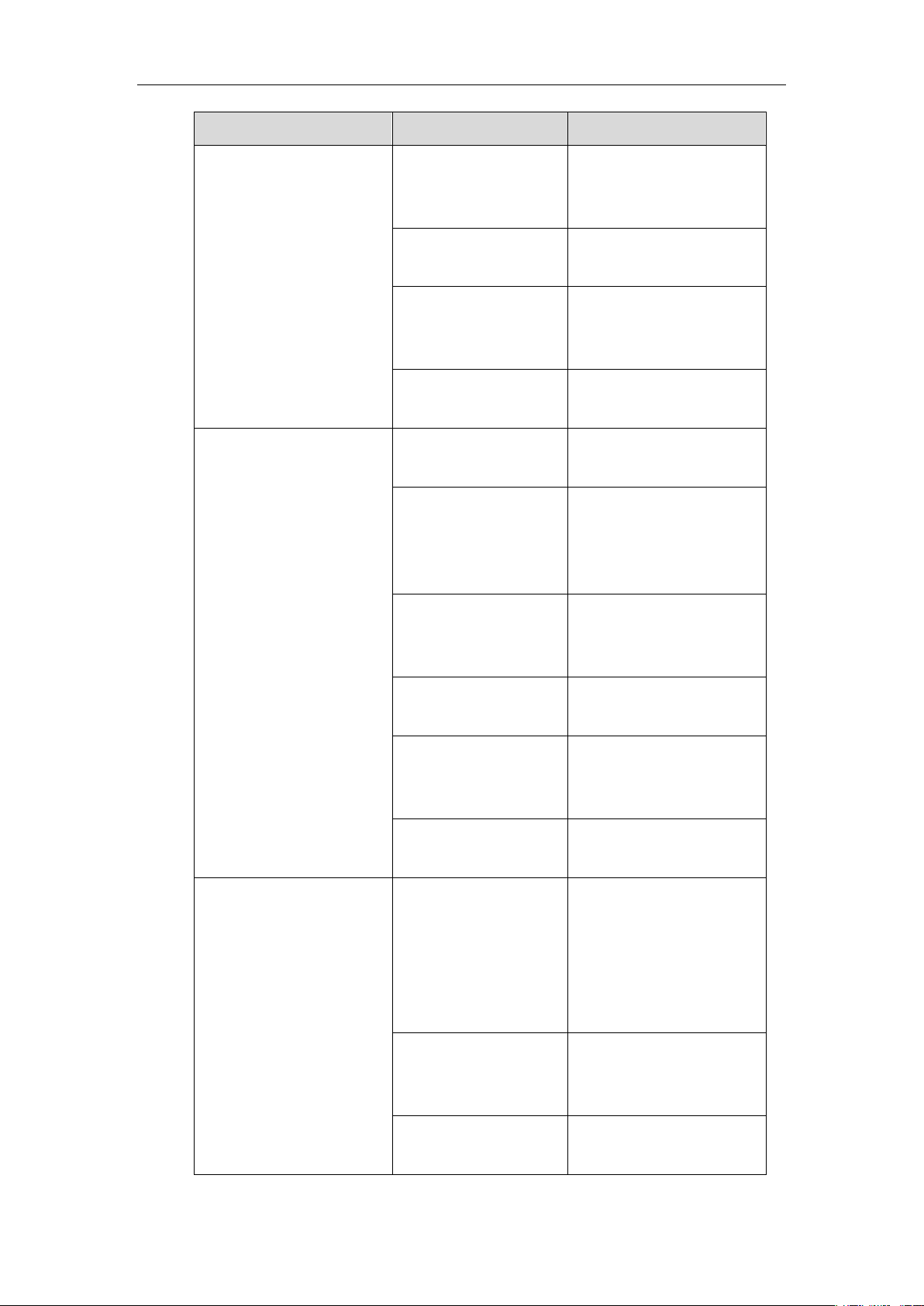
Authentication Protocol
IP Phone Models
Firmware Version
T58A T49G, T40P, T29G,
T23P/G, T21(P) E2,
T19(P) E2, CP960, and
W56P
Firmware version 80 or later
T48S, T46S, T42S, T41S,
T40G, T27G, W52P
Firmware version 81 or later
VP59, W53P, and
CP930W-Base
Firmware version 83 or later
T57W, T54W, T53W, T53,
T48U, T46U, T43U and
T42U
Firmware version 84 or later
T33P, T33G, T31P, T31G,
T31, T30P and T30
Firmware version 85 or later
EAP-TTLS/EAP-MSCHAPv2
T46G, T42G, T41P,
CP860
Firmware version 71 or later
T48G
Firmware version 72 or later
T58A, T49G, T40P, T29G,
T23P/G, T21(P) E2,
T19(P) E2, CP960, and
W56P
Firmware version 80 or later
T48S, T46S, T42S, T41S,
T40G, T27G, W52P,
W60P and CP920
Firmware version 81 or later
VP59, W53P, and
CP930W-Base
Firmware version 83 or later
T57W, T54W, T53W, T53,
T48U, T46U, T43U and
T42U
Firmware version 84 or later
T33P, T33G, T31P, T31G,
T31, T30P and T30
Firmware version 85 or later
EAP-PEAP/GTC
T48G, T46G, T42G,
T41P
Firmware version 73 or later
T58A T49G, T40P, T29G,
T23P/G, T21(P) E2,
T19(P) E2, CP860,
CP960 and W56P
Firmware version 80 or later
Yealink Technical White Paper 802.1X Authentication
3
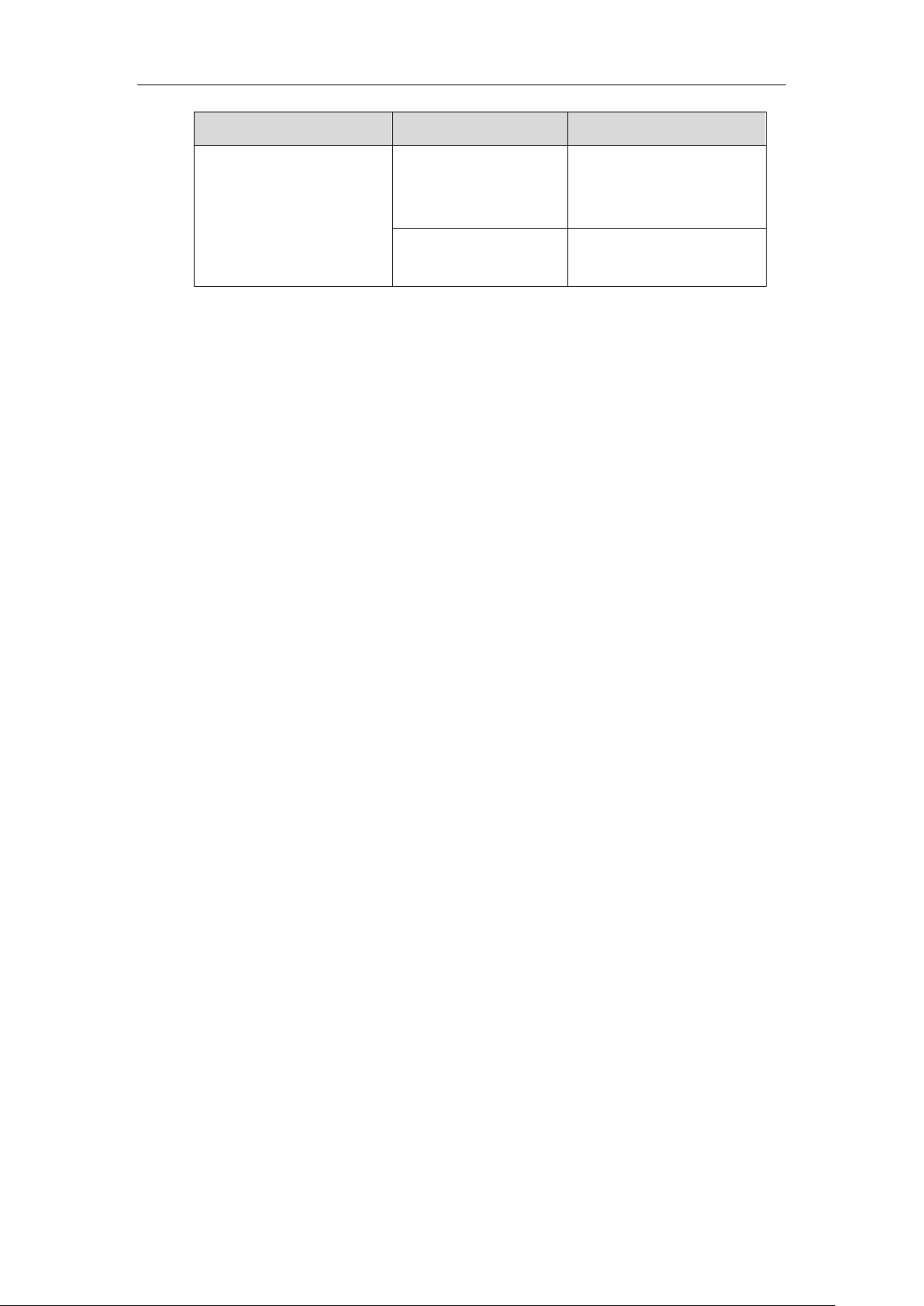
Authentication Protocol
IP Phone Models
Firmware Version
T48S, T46S, T42S, T41S,
T40G, T27G, W52P,
W60P and CP920
Firmware version 81 or later
VP59, W53P, and
CP930W-Base
Firmware version 83 or later
T57W, T54W, T53W, T53,
T48U, T46U, T43U and
T42U
Firmware version 84 or later
T33P, T33G, T31P, T31G,
T31, T30P and T30
Firmware version 85 or later
EAP-TTLS/EAP-GTC
T48G, T46G, T42G,
T41P
Firmware version 73 or later
T58A T49G, T40P, T29G,
T23P/G, T21(P) E2,
T19(P) E2, CP860,
CP960 and W56P
Firmware version 80 or later
T48S, T46S, T42S, T41S,
T40G, T27G, W52P,
W60P and CP920
Firmware version 81 or later
VP59, W53P, and
CP930W-Base
Firmware version 83 or later
T57W, T54W, T53W, T53,
T48U, T46U, T43U and
T42U
Firmware version 84 or later
T33P, T33G, T31P, T31G,
T31, T30P and T30
Firmware version 85 or later
EAP-FAST
T58A T29G, T23P/G,
T21(P) E2, T19(P) E2,
T49G, T48G, T46G,
T42G, T41P, T40P,
CP860, CP960 and
W56P
Firmware version 80 or later
T48S, T46S, T42S, T41S,
T40G, T27G, W52P,
W60P and CP920
Firmware version 81 or later
VP59, W53P, and
CP930W-Base
Firmware version 83 or later
Yealink Technical White Paper 802.1X Authentication
4
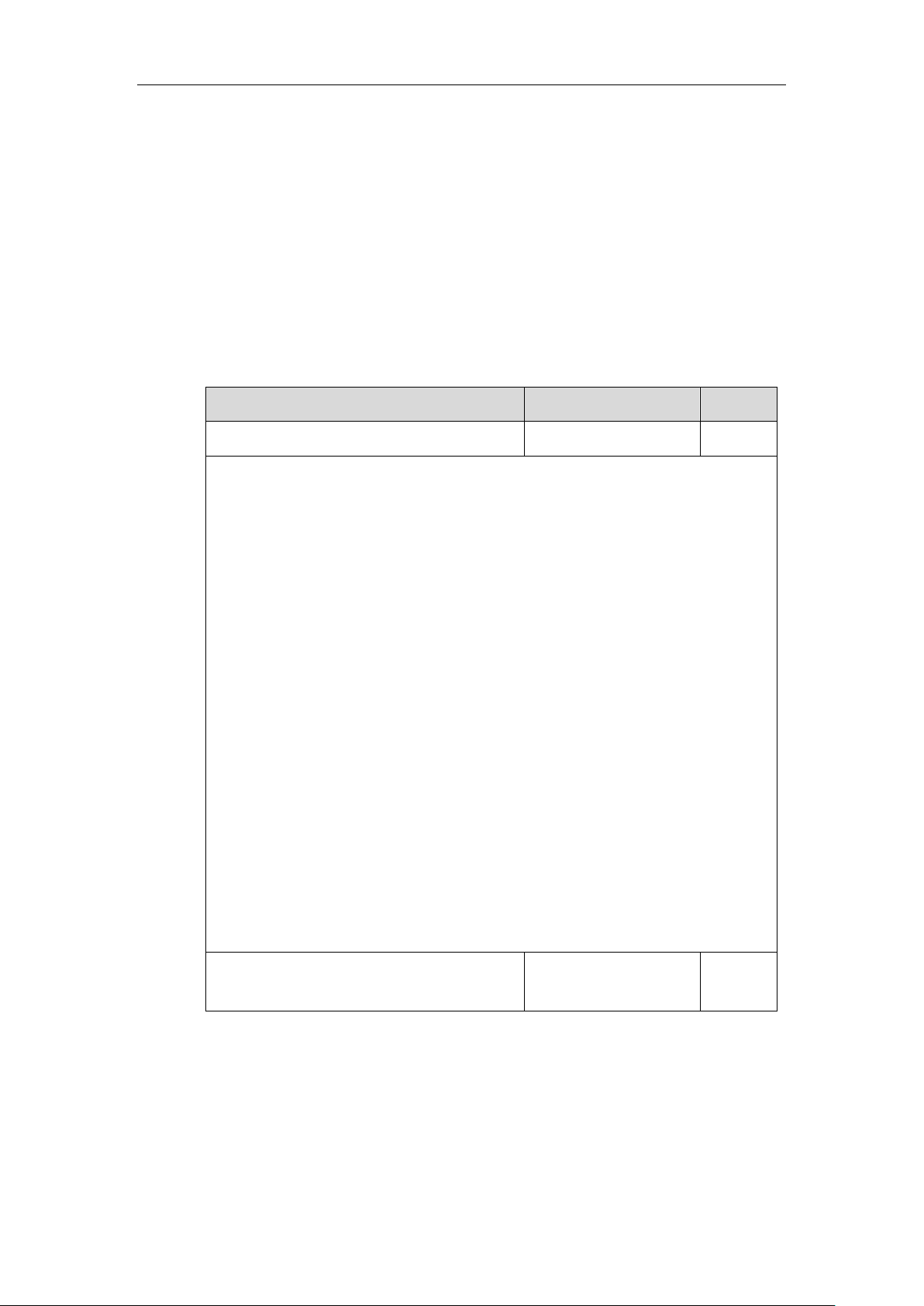
Authentication Protocol
IP Phone Models
Firmware Version
T57W, T54W, T53W, T53,
T48U, T46U, T43U and
T42U
Firmware version 84 or later
T33P, T33G, T31P, T31G,
T31, T30P and T30
Firmware version 85 or later
Yealink IP phones support 802.1X as a supplicant, both Pass-thru Mode and Pass-thru Mode
with Proxy Logoff. When the device connected to the phone disconnects from the PC port, the
Yealink IP phone can provide additional security by sending an EAPOL Logoff message to the
Ethernet switch. This functionality, also known as proxy logoff, prevents another device from
using the port without first authenticating via 802.1X.
Configuring 802.1X Settings
The 802.1X authentication on Yealink IP phones is disabled by default. You can configure the
802.1X authentication in one of the following three ways:
⚫ Configuring 802.1X Using Configuration Files
⚫ Configuring 802.1X via Web User Interface
⚫ Configuring 802.1X via Phone User Interface
For detailed descriptions of the authentication parameters in configuration files, you can refer to
Configuring 802.1X Using Configuration Files. When setting up a large number of IP phones,
Yealink recommends using the boot file (for new auto provisioning mechanism) and
configuration files. If you are provisioning a few phones, you can use the web user interface or
phone user interface to configure the 802.1X feature.
If the EAP-TLS, EAP-PEAP/MSCHAPv2, EAP-TTLS/EAP-MSCHAPv2, EAP-PEAP/GTC,
EAP-TTLS/EAP-GTC or EAP-FAST protocol is preferred in your 802.1X environment, make
sure that the firmware running on your new phone supports the protocol.
The followings provide the system administrator with the procedures to successfully configure
Yealink IP phones in a secure 802.1X environment.
Configuring 802.1X Using Configuration Files
The following IP phones use the new auto provisioning mechanism:
⚫ SIP-T58A/CP960 IP phones running firmware version 80 or later
⚫ SIP-T48G/T48S/T46G/T46S/T42G/T42S/T41P/T41S/T40P/T40G/T29G/T27G/T23P/T23
G/T21(P) E2/T19(P) E2, CP860, CP920, W60P, W52P and W56P IP phones running
firmware version 81 or later
⚫ VP59, W53P and CP930W-Base IP phones running firmware version 83 or later
Yealink Technical White Paper 802.1X Authentication
5
⚫ SIP-T57W/T54W/T53W/T53/T48U/T46U/T43U/T42U IP phones running firmware
version 84 or later
⚫ SIP-T33P/T33G/T31P/T31G/T31/T30P/T30 IP phones running firmware version 85 or
later
Other IP phones or the IP phones listed above running old firmware version use the old auto
provisioning mechanism.
For Old Auto Provisioning Mechanism
1. Add/Edit 802.1X authentication parameters in the configuration file.
The following table shows the information of parameters:
Parameters
Permitted Values
Default
network.802_1x.mode
0, 1, 2, 3, 4, 5, 6 or 7
0
Description:
Configures the 802.1x authentication method.
0-Disabled
1-EAP-MD5
2-EAP-TLS
3-EAP-PEAP/MSCHAPv2
4-EAP-TTLS/EAP-MSCHAPv2
5-EAP-PEAP/GTC
6-EAP-TTLS/EAP-GTC
7-EAP-FAST
Note: If you change this parameter, the IP phone will reboot to make the change take
effect.
Web User Interface:
Network->Advanced->802.1x->802.1x Mode
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin) ->Network->802.1x
Settings->802.1x Mode
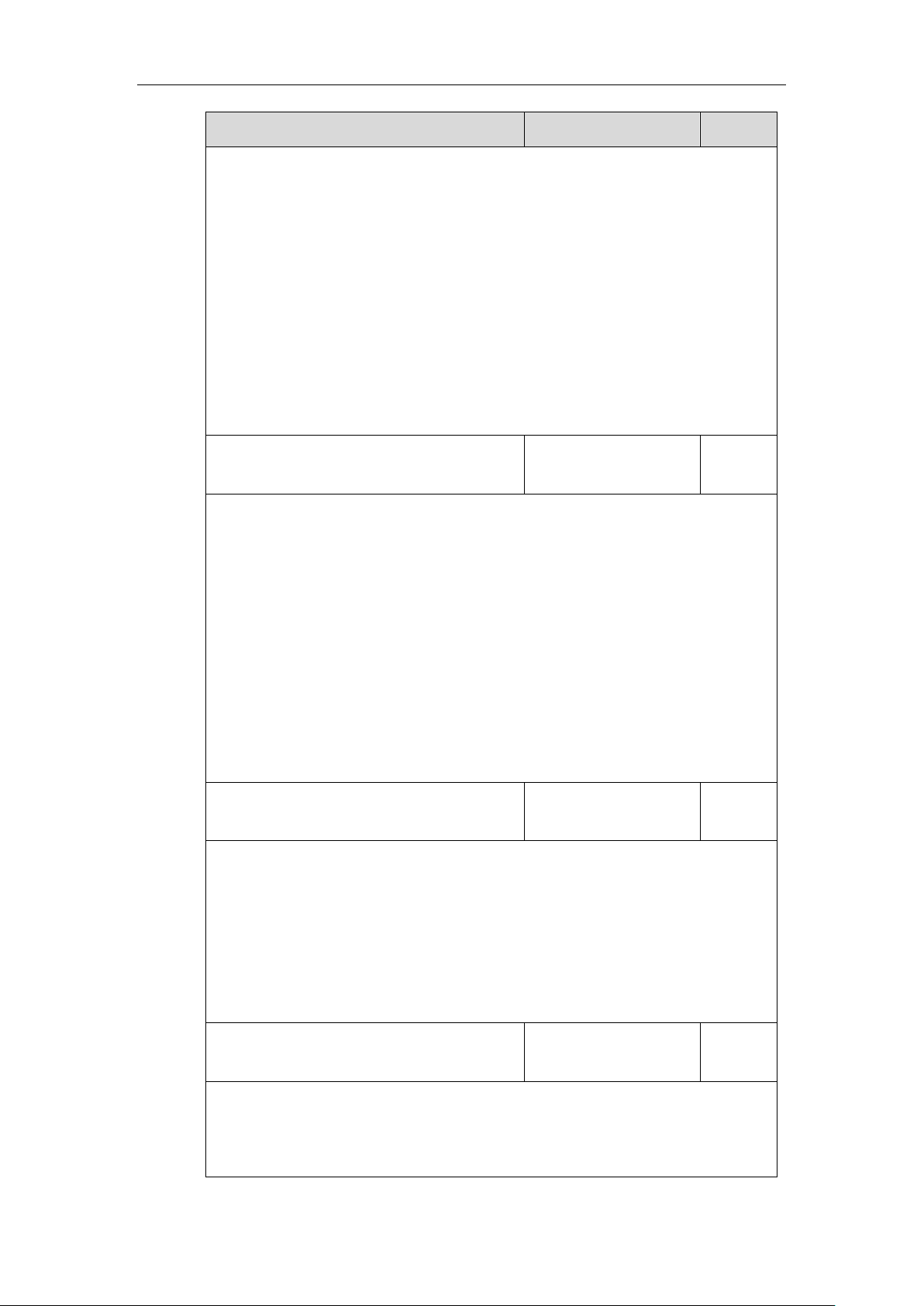
network.802_1x.identity
String within 32
characters
Blank
Yealink Technical White Paper 802.1X Authentication
6
Parameters
Permitted Values
Default
Description:
Configures the user name for 802.1x authentication.
Note: It works only if the value of the parameter “network.802_1x.mode” is set to 1, 2, 3, 4,
5, 6 or 7. If you change this parameter, the IP phone will reboot to make the change take
effect.
Web User Interface:
Network->Advanced->802.1x->Identity
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin) ->Network->802.1x
Settings->Identity
network.802_1x.md5_password
String within 32
characters
Blank
Description:
Configures the password for 802.1x authentication.
Note: It works only if the value of the parameter “network.802_1x.mode” is set to 1, 3, 4, 5,
6 or 7. If you change this parameter, the IP phone will reboot to make the change take
effect.
Web User Interface:
Network->Advanced->802.1x->MD5 Password
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin) ->Network->802.1x
Settings->MD5 Password
network.802_1x.root_cert_url
URL within 511
characters
Blank
Description:
Configures the access URL of the CA certificate.
Note: It works only if the value of the parameter “network.802_1x.mode” is set to 2, 3, 4, 5,
6 or 7. The format of the certificate must be *.pem, *.crt, *.cer or *.der.
Web User Interface:
Network->Advanced->802.1x->CA Certificates
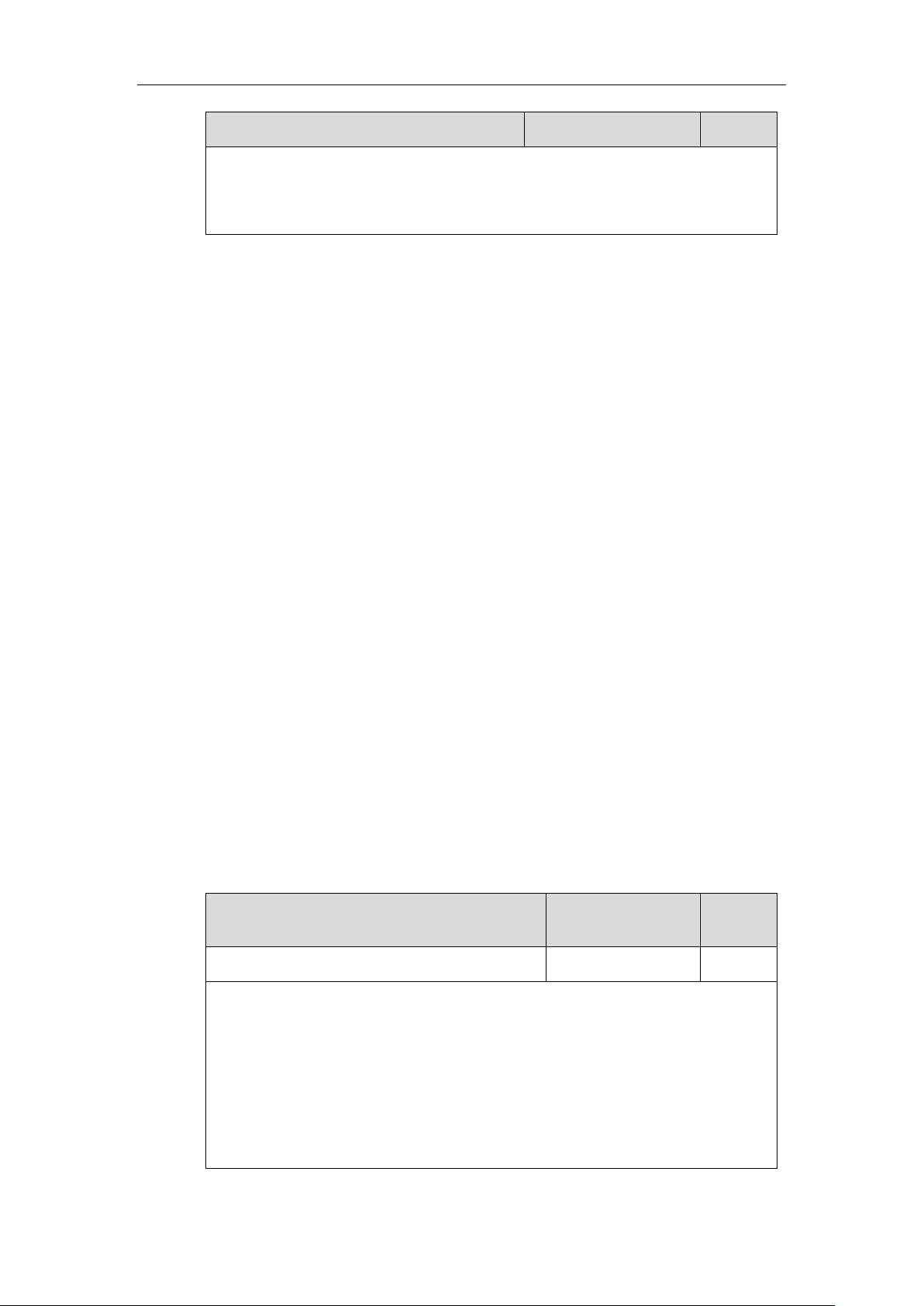
network.802_1x.client_cert_url
URL within 511
characters
Blank
Description:
Configures the access URL of the device certificate.
Note: It works only if the value of the parameter “network.802_1x.mode” is set to 2
Yealink Technical White Paper 802.1X Authentication
7
Parameters
Permitted Values
Default
(EAP-TLS). The format of the certificate must be *.pem.
Web User Interface:
Network->Advanced->802.1x->Device Certificates
The following shows an example of the EAP-TLS protocol for 802.1X authentication in
configuration files:
network.802_1x.mode = 2
network.802_1x.identity = yealink
network.802_1x.root_cert_url = http://192.168.1.8:8080/ca.crt
network.802_1x.client_cert_url = http://192.168.1.8:8080/client.pem
2. Upload the configuration files, CA certificate and client certificate to the root directory of the
provisioning server.
Applying the Configuration Files to Your Phone
Once you have edited and configuration file (e.g., y0000000000xx.cfg) using the parameters
introduced above, you need to do the following to apply the files to your phone:
1. Connect your phone to a network that is not 802.1X-enabled.
2. Perform the auto provisioning process to apply the configuration files to the phone.
Then the IP phone will reboot to make the settings effective.
For more information on auto provisioning, refer to
Yealink_SIP-T2 Series_T19(P)
E2_T4_Series_CP860_W56P_IP_Phones_Auto_Provisioning_Guide
.
3. Connect the phone to the 802.1X-enabled network and reboot the phone.
You can make a phone call to verify whether the phone is authenticated.
For New Auto Provisioning Mechanism
1. Add/Edit 802.1X authentication parameters in the configuration file (e.g., static.cfg).
The following table shows the information of parameters:
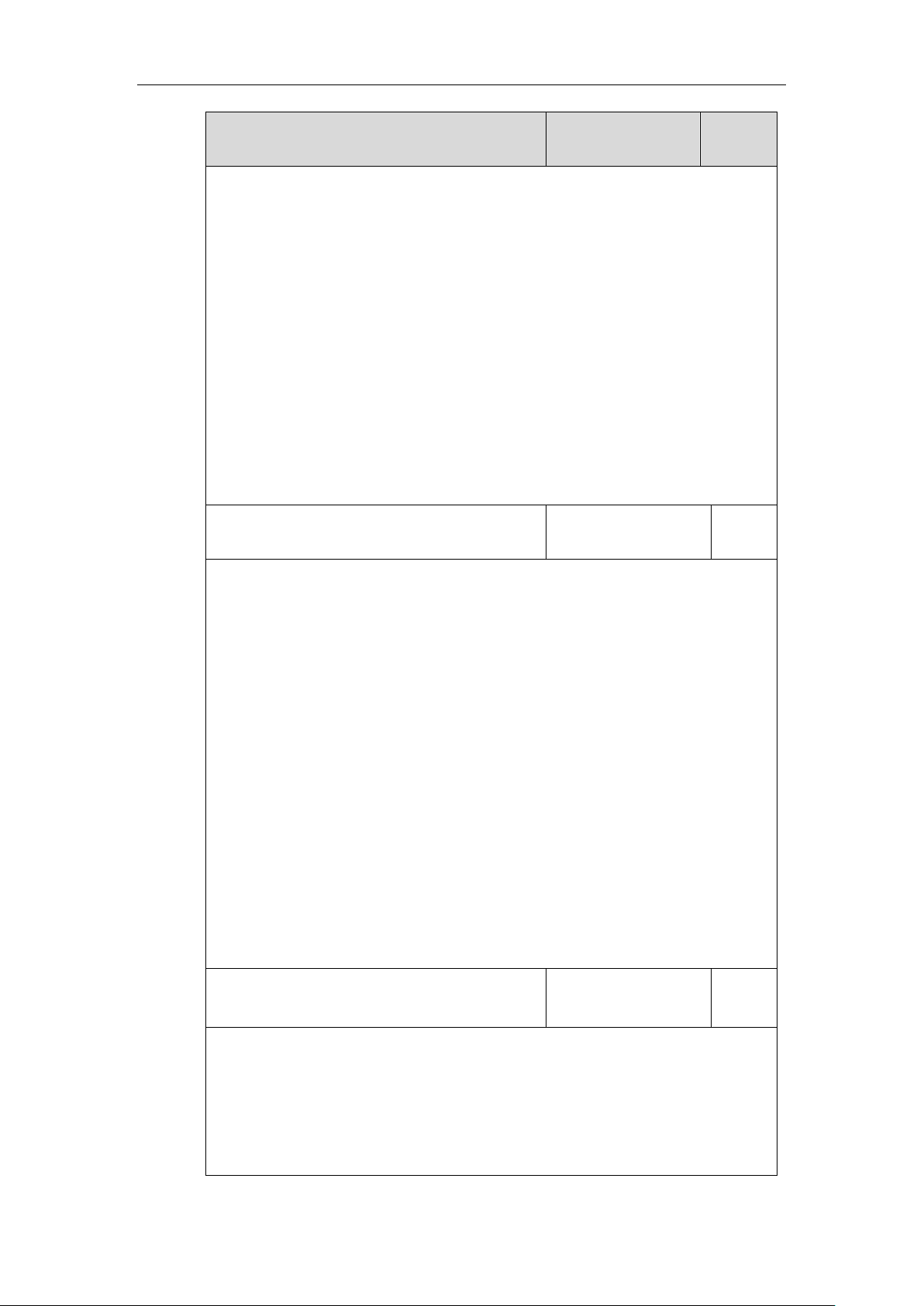
Parameters
Permitted Values
Default
static.network.802_1x.mode
0, 1, 2, 3, 4, 5, 6 or 7
0
Description:
Configures the 802.1x authentication method.
0-EAP-None
1-EAP-MD5
2-EAP-TLS
3-EAP-PEAP/MSCHAPv2
Yealink Technical White Paper 802.1X Authentication
8
Parameters
Permitted Values
Default
4-EAP-TTLS/EAP-MSCHAPv2
5-EAP-PEAP/GTC
6-EAP-TTLS/EAP-GTC
7-EAP-FAST
If it is set to 0 (EAP-None), 802.1x authentication is not required.
Note: If you change this parameter, the IP phone will reboot to make the change take
effect.
Web User Interface:
Network->Advanced->802.1x->802.1x Mode
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin)
->Network->802.1x->802.1x Mode
static.network.802_1x.eap_fast_provision_mode
0 or 1
0
Description:
Configures the EAP In-Band provisioning method for EAP-FAST.
0-Unauthenticated Provisioning
1-Authenticated Provisioning
If it is set to 0 (Unauthenticated Provisioning), EAP In-Band provisioning is enabled by
server unauthenticated PAC (Protected Access Credential) provisioning using anonymous
Diffie-Hellman key exchange.
If it is set to 1 (Authenticated Provisioning), EAP In-Band provisioning is enabled by server
authenticated PAC provisioning using certificate-based server authentication.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 7
(EAP-FAST). If you change this parameter, the IP phone will reboot to make the change
take effect.
Web User Interface:
Network->Advanced->802.1x->Provisioning Mode
static.network.802_1x.anonymous_identity
String within 512
characters
Blank
Description:
Configures the anonymous identity (user name) for 802.1X authentication.
It is used for constructing a secure tunnel for 802.1X authentication.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 2,
3, 4, 5, 6 or 7. If you change this parameter, the IP phone will reboot to make the change
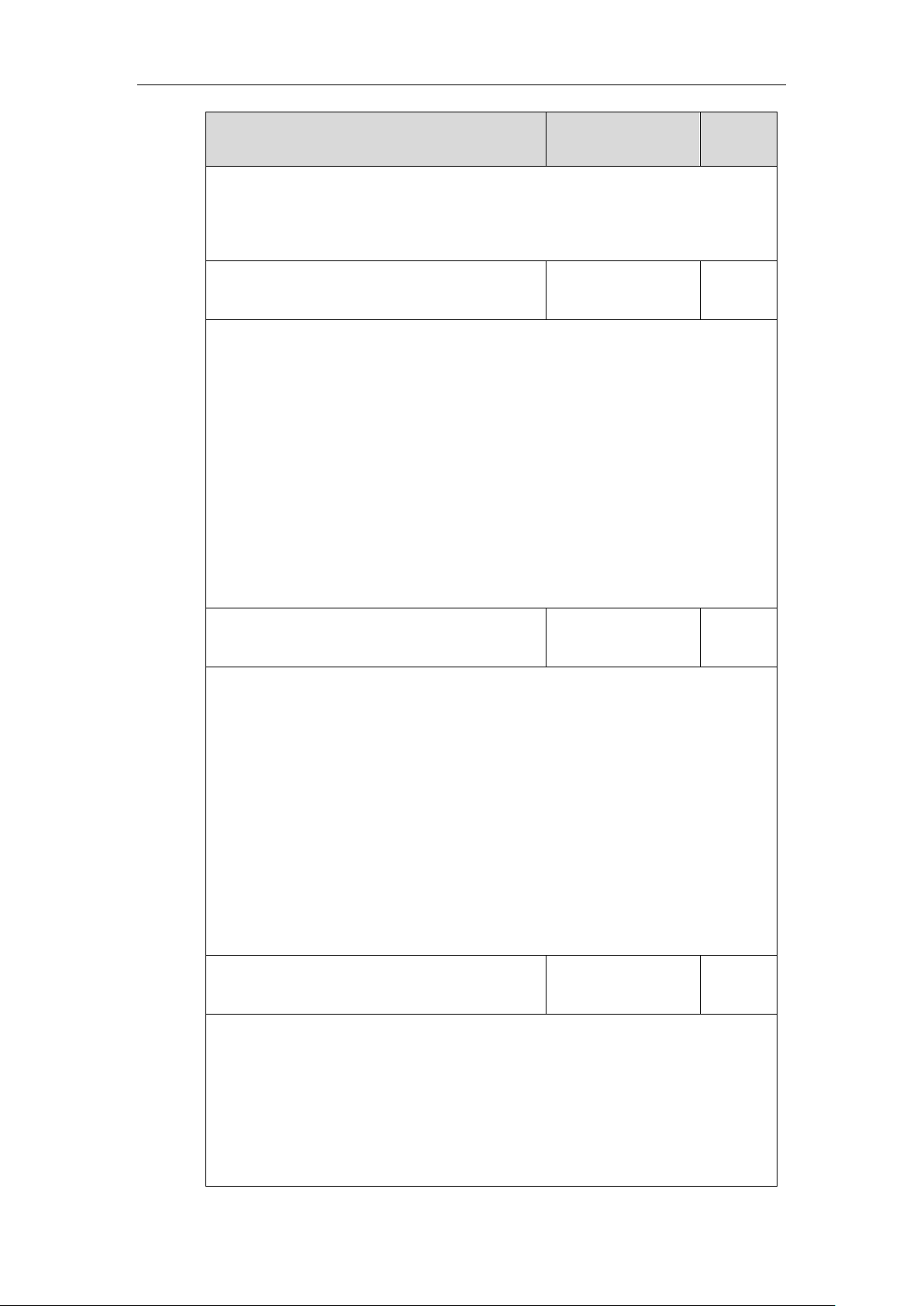
Yealink Technical White Paper 802.1X Authentication
9
Parameters
Permitted Values
Default
take effect.
Web User Interface:
Network->Advanced->802.1x->Anonymous Identity
static.network.802_1x.identity
String within 32
characters
Blank
Description:
Configures the user name for 802.1x authentication.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 1,
2, 3, 4, 5, 6 or 7. If you change this parameter, the IP phone will reboot to make the change
take effect.
Web User Interface:
Network->Advanced->802.1x->Identity
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin)
->Network->802.1x->Identity
static.network.802_1x.md5_password
String within 32
characters
Blank
Description:
Configures the password for 802.1x authentication.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 1,
3, 4, 5, 6 or 7. If you change this parameter, the IP phone will reboot to make the change
take effect.
Web User Interface:
Network->Advanced->802.1x->MD5 Password
Phone User Interface:
Menu->Settings->Advanced Settings (default password: admin) ->Network->802.1x->MD5
Password
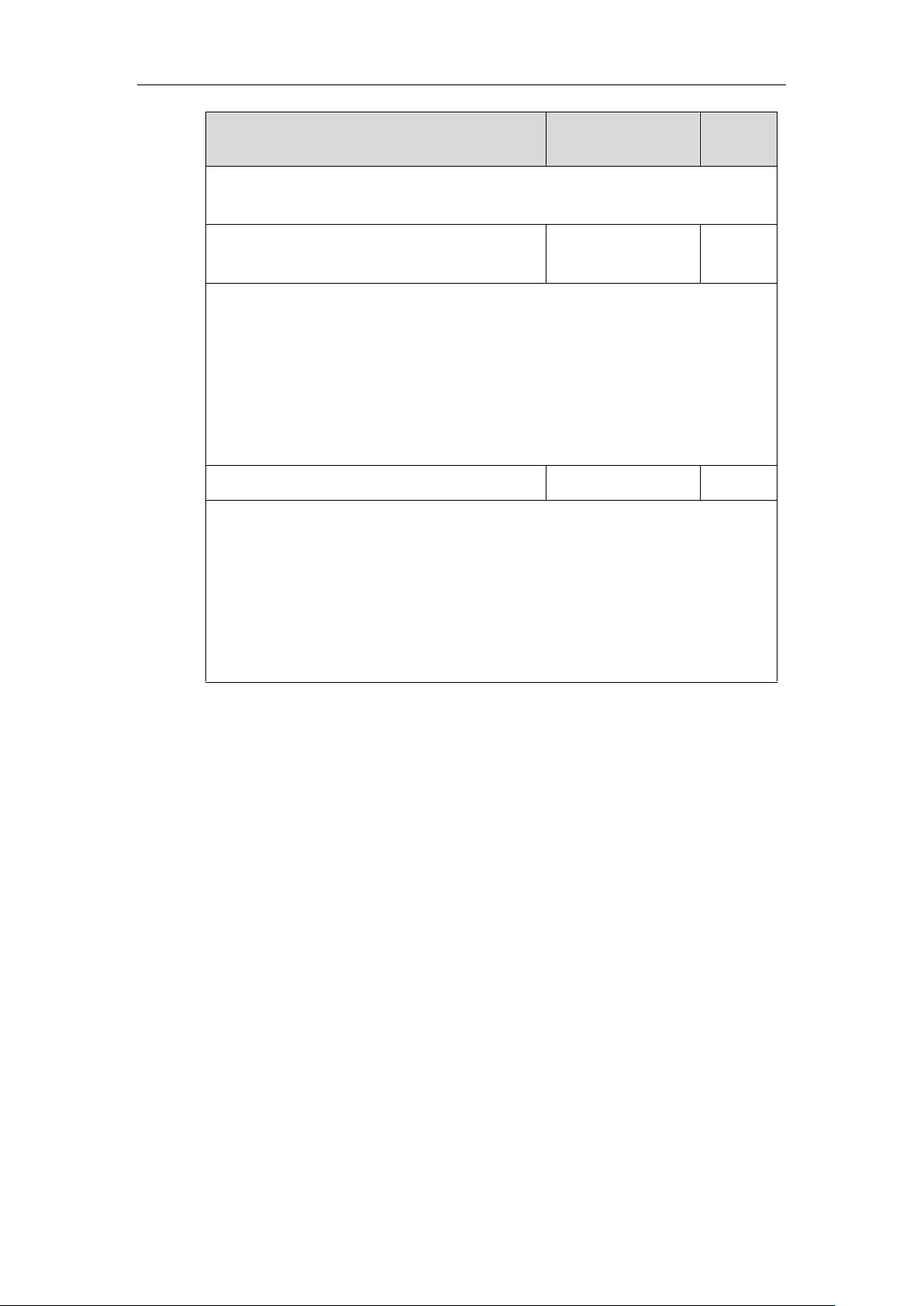
static.network.802_1x.root_cert_url
URL within 511
characters
Blank
Description:
Configures the access URL of the CA certificate.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 2,
3, 4, 5, 6 or 7. If the authentication method is EAP-FAST, you also need to set the value of
the parameter “static.network.802_1x.eap_fast_provision_mode” to 1 (Authenticated
Provisioning). The format of the certificate must be *.pem, *.crt, *.cer or *.der.
Yealink Technical White Paper 802.1X Authentication
10
Parameters
Permitted Values
Default
Web User Interface:
Network->Advanced->802.1x->CA Certificates
static.network.802_1x.client_cert_url
URL within 511
characters
Blank
Description:
Configures the access URL of the device certificate.
Note: It works only if the value of the parameter “static.network.802_1x.mode” is set to 2
(EAP-TLS). The format of the certificate must be *.pem.
Web User Interface:
Network->Advanced->802.1x->Device Certificates
static.network.802_1x.proxy_eap_logoff.enable
0 or 1
0
Description:
Enables or disables the 802.1x-logoff feature for the PC port.
0-Disabled
1-Enabled
If it is set to 1 (Enabled), the 802.1x logoff message is sent to the authenticator when the
PC is disconnected.
The following shows an example of the EAP-TLS protocol for 802.1X authentication in
configuration files:
static.network.802_1x.mode = 2
static.network.802_1x.anonymous_identity = Anonymous
static.network.802_1x.identity = yealink
static.network.802_1x.root_cert_url = http://192.168.1.8:8080/ca.crt
static.network.802_1x.client_cert_url = http://192.168.1.8:8080/client.pem
static.network.802_1x.proxy_eap_logoff.enable = 1
2. Reference the configuration file in the boot file (e.g., y000000000000.boot).
Example:
include:config “http://10.2.1.158/static.cfg”
3. Upload the boot file, configuration file, CA certificate and client certificate to the root
directory of the provisioning server.
Applying the Configuration Files to Your Phone
Once you have edited a boot file (e.g., y000000000000.boot) and configuration file (e.g.,
static.cfg) using the parameters introduced above, you need to do the following to apply the files
to your phone:
Yealink Technical White Paper 802.1X Authentication
11
1. Connect your phone to a network that is not 802.1X-enabled.
2. Perform the auto provisioning process to apply the configuration files to the phone.
Then the IP phone will reboot to make the settings effective.
For more information on auto provisioning, refer to the latest Auto Provisioning Guide on
Yealink Technical Support.
3. Connect the phone to the 802.1X-enabled network and reboot the phone.
You can make a phone call to verify whether the phone is authenticated.
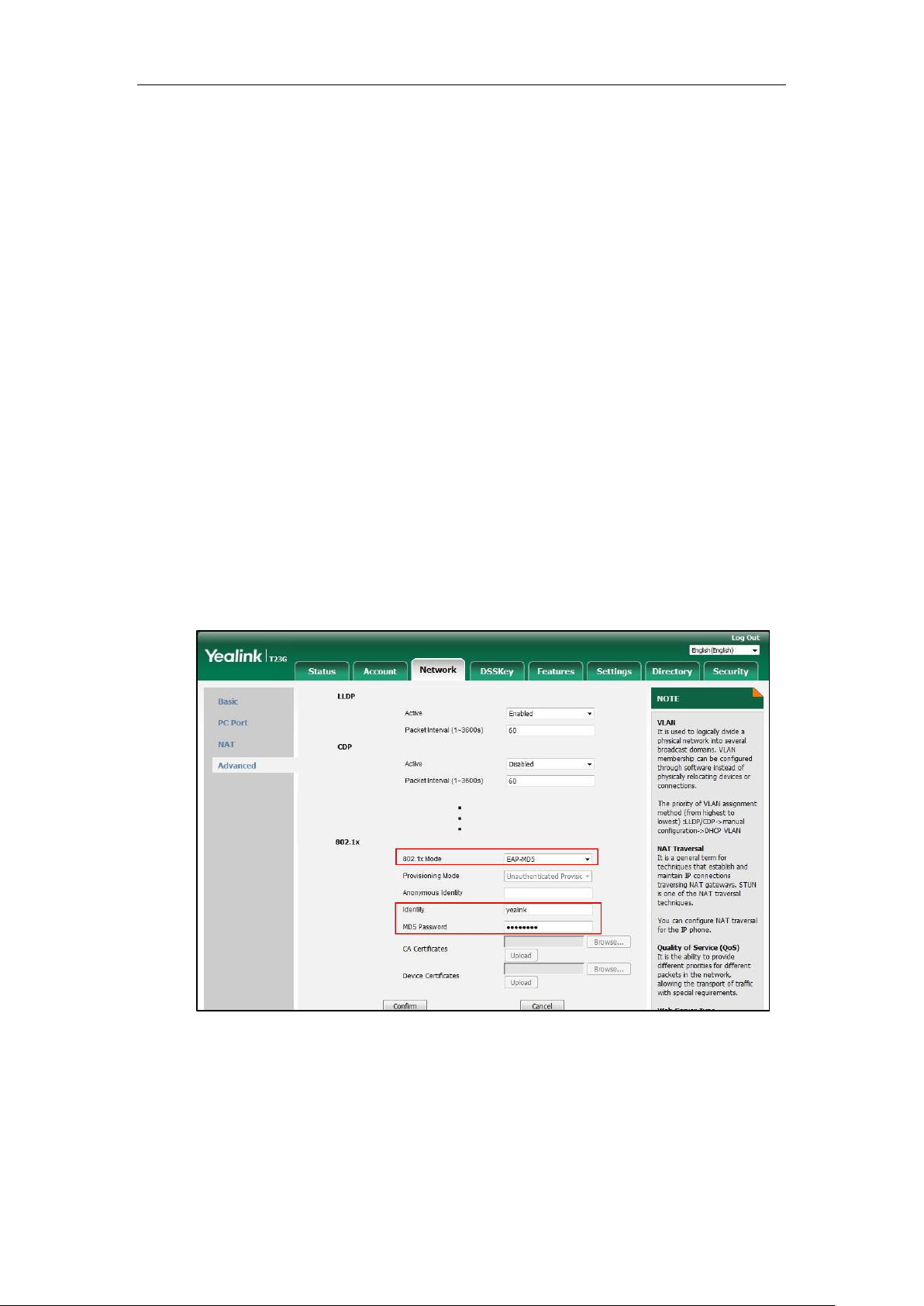
Configuring 802.1X via Web User Interface
The following takes a SIP-T23G IP phone running firmware version 81 as an example.
1. Connect your phone to a network that is not 802.1X-enabled.
2. Login to the web user interface of the phone.
3. Click on Network->Advanced.
4. In the 802.1x block, select the desired protocol from the pull-down list of 802.1x Mode.
a) If you select EAP-MD5:
1) Enter the user name for authentication in the Identity field.
2) Enter the password for authentication in the MD5 Password field.
b) If you select EAP-TLS:
1) (Optional.) Enter the anonymous user name for authentication in the
Anonymous Identity field.
2) Enter the user name for authentication in the Identity field.
3) Leave the MD5 Password field blank.
4) In the CA Certificates field, click Browse to select the desired CA certificate
 Loading...
Loading...