Page 1

p
Configuring Steel-Belted RADIUS Proxy to Send
Grou
Attributes
Page 2

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
Copyright 2007 Sophos Group. All rights
reserved. No part of this publication
may be reproduced, stored in retrieval
system, or transmitted, in any form or
by any means electronic, mechanical,
photocopying, recording or otherwise
unless you are either a valid licensee
where the documentation can be
reproduced in accordance with the license
terms or you otherwise have the prior
permission in writing of the copyright
owner.
All other product and company names
are trademarks or registered trademarks
of their respective owners.
Document version 3.0
Published July 2007
2
Page 3

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
Table of Contents
About this Document.....................................................................................................................4
Configuring the Steel-Belted RADIUS Proxy.................................................................................4
Using the Sophos NAC Agent.....................................................................................................15
3
Page 4
Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
About this Document
The purpose of this document is to configure Steel-Belted RADIUS to pull group information from a remote directory
server and forward that information to Sophos NAC so that the group can be given a Sophos NAC policy without
the Sophos NAC application server having a direct connection to Active Directory or LDAP.
This document requires you to already configured IAS for Remote Proxy as described in the Post-Installation
Requirements in the Sophos NAC Installation Guide. This document also a ssu mes that Steel-Belted RADIUS is
already setup and installed on the server and is running on ports 1812, 1813, 1645 and 1646 (default port s for
Steel-Belted RADIUS). If it is not setup/running on these ports, you must modify these instructions to accommodate
for the changes.
If you plan on using Steel-Belted RADIUS to connect to an Active Directory Domain Controller to pull user/group
information, make sure the Steel-Belted RADIUS server is on the domain or is in a trusted domain for the
account/group information it will be pulling from. Also, make sure to use an account that is a member of the Domain
Admins Group so that you will have access to pull user/group information from AD.
Configuring the Steel-Belted RADIUS Proxy
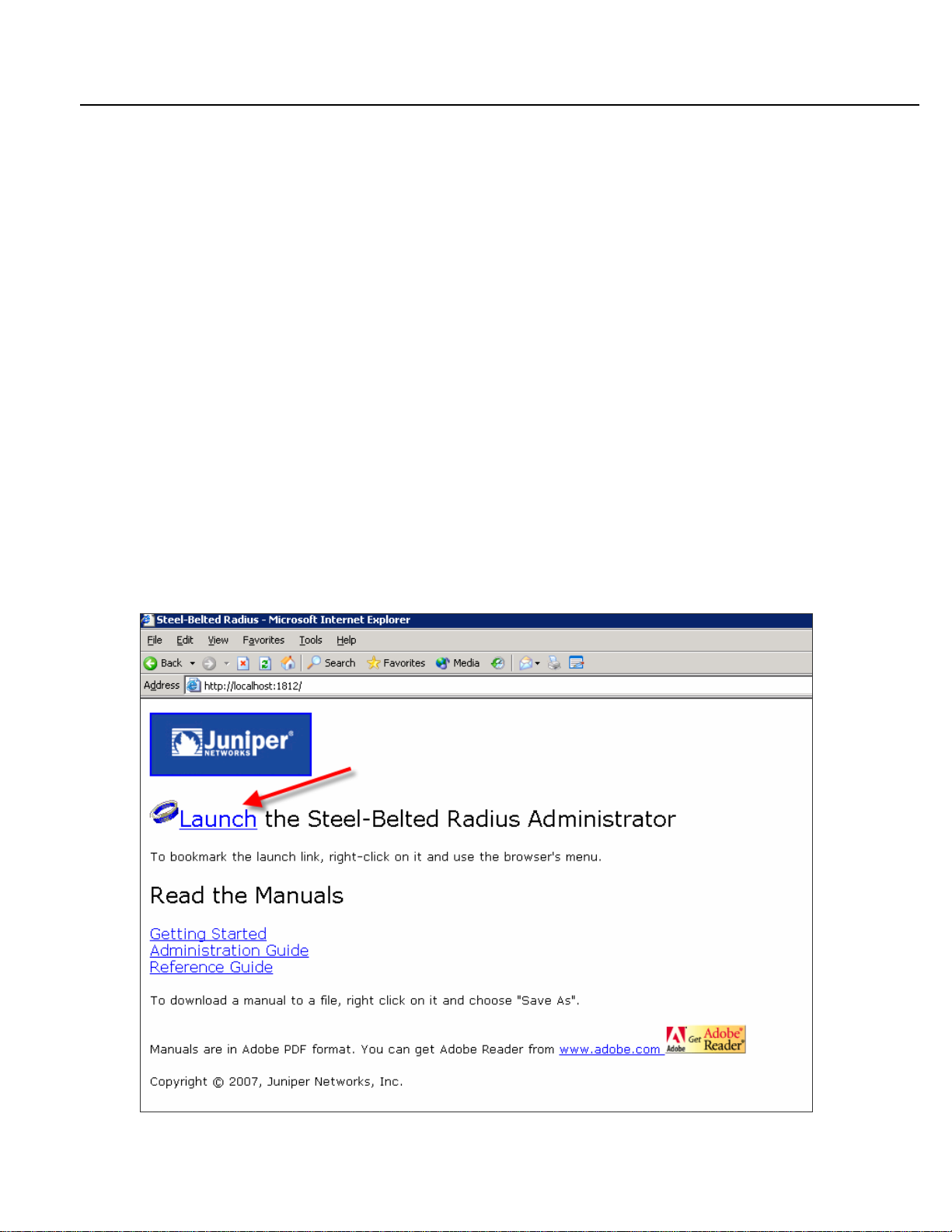
1. Go to http://localhost:1812 and click the Launch link to start Steel-Belted RADIUS.
4
Page 5

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
2. Login to Steel-Belted RADIUS.
3. Right-click RADIUS Clients and select Add.
5
Page 6

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
4. Type the appropriate information in the fields.
▪ Name (1)
▪ Description (2)
▪ IP Address for the remote RADIUS client (3) (IP of the Sophos NAC application server)
▪ Shared Secret (4) (This must be the same password that was used in IAS when setting up the RADIUS
Proxy.)
5. Select Standard RADIUS from the Make or model (5) list box.
6. Click OK (6) to save your changes.
6
Page 7

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
7. Select RADIUS Clients to verify the new entry.
8. Open c:\program files\Juniper Networks\Steel-Belted RADIUS\Service. This is the default location for radius.dct
file.
9. Open the radius.dct file.
7
Page 8

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
10. In the radius.dct file, add the following lines for the following Sophos Dictionary attributes.
###################################################################
# SOPHOS.dct – SOPHOS Dictionary File
@radius.dct
MACRO ENDFORCE-VSA(t,s) 26 [vid=5428 type1=%t% len1=+2 data=%s%]
ATTRIBUTE EF-GroupResponse ENDFORCE-VSA(20, string) r
###################################################################
You can add all of the vendor-specific attributes, as shown below, but the one Sophos requires for configuration
is shown in this step.
11. Save the radius.dct file.
12. Restart the Steel-Belted RADIUS Service for the changes to take effect.
8
Page 9

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
13. Log into the Steel-Belted RADIUS Admin application.
14. Right-click Profiles and select Add.
15. Type a name (1) and description (2) for the profile in the appropriate fields.
a
9
Page 10

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
16. Click the Return List tab (3).
Note: You complete this step because you want RADIUS to send back the group attribute to the Sophos NAC
application server.
17. Click Add (4).
18. Locate and select the EF-Group Response (5).
19. Type in the group name that you want to pull for this profile (6), and click Add to add the Return List Attribute
20. Click Close.
Note: That attribute is not a Multi-valued Attribute. Sophos NAC Advanced only supports single-valued
attributes.
21. Verify that your new Return List Attribute displays, and click OK.
22. Verify that the new profile displays in the profiles section.
10
Page 11

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
23. Map the new profile to the domain group that the users are apart of in Active Directory. To do this, expand the
Users section, right-click Domains and click Add.
24. Click Browse to look for the possible users/groups to add (1).
11
Page 12

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
25. Select the domain (2).
26. Click the Groups tab (3).
27. Select the appropriate group from the list (4) and click OK (5) to add the new group.
28. Verify that the Domain (1), User (2), and Name (3) are correct.
29. Type a description (4), and select the Use Profile check box (5).
12
Page 13

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
30. Select the name of the profile you just created from the list box (6), and click OK (7).
Note: You can see the added Group and its corresponding profile. By configuring groups/profiles in this
manner, you can apply policies to whole groups of users, and then send the group attribute back to the Sophos
NAC application server using IAS so that a NAC policy can be applied to that group.
31. Open the radius.ini file located in c:\program files\Juniper Networks\Steel-B elted RADIUS\Service and add
authenticate only=0 in the configuration settings.
Note: This step forces Steel-Belted RADIUS to pass the attributes you created back to IAS.
13
Page 14

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
32. Remove the null termination in the radius.ini file by setting the NoNullTermination = 1.
Note: Null termination must be turned off for NAC to map the policy with the group correctly.
33. Restart the Steel-Belted RADIUS service for the changes to take effect.
14
Page 15

Configuring Steel-Belted RADIUS Proxy to Send Group Attributes
Using the Sophos NAC Agent
When you use the Sophos NAC Agent with a valid username and password that exists in the domain users group in
Active Directory, an entry for this user appears in the Manage > Endpoints area of the Sophos NAC Web interface.
15
 Loading...
Loading...