Page 1
NS4802-24P-4S-2X User
Manual
P/N 1073040 • REV A • ISS 27AUG15
Page 2
2
Copyright
©
Interlogix is part of UTC Building & Industrial Systems, a unit of
reserved
Tradema
rks and
patents
Trade names used in this document may be trademarks or registered
trademarks of the manufacturers or vendors of the respective products.
Manufacturer
Interlogix
2955 Red Hill Avenue, Costa Mesa, CA 92626
Authorized EU manufactu
UTC Fire & Security B.V.
Kelvinstraat 7, 6003 DH Weert, The Netherlands
FCC compliance
Class A:
for a Class A digital device, pursuant to part 15 of the FCC Rules. Th
are designed to provide reasonable protection against harmful interference
when the equipment is operated in a commercial environment. This equipment
generates, uses, and can radiate radio frequency energy and, if not installed
and used in accor
interference to radio communications. Operation of this equipment in a
residential area is likely to cause harmful interference in which case the user will
be required to correct the interference at his
Canada
This Class A digital apparatus complies with Canadian ICES
Cet appareil mumérique de la classe A est conforme à la norme NMB
Canada.
Notice!
cause radio interference in which case the user may be required to take
adequate measures.
Certification
EU directives
2004/108/EC (EMC directive)
device is in compliance or with the es
provisions of Directive 2004/108/EC
2012/19/EU (WEEE directive):
disposed of as unsorted municipal waste in the European Union. For proper
recycling, return this produc
equivalent new equipment, or dispose of it at designated collection points. For
more information see: www.recyclethis.info.
2006/66/EC (battery directive):
dis
product documentation for specific battery information. The battery is marked
with this symbol, which may include lettering to indicate cadmium (Cd), lead
(Pb), or mercury (Hg). For proper recycling, return the battery to your supplier or
to a designated collection point. For more information see: www.recyclethis.info.
Contact information
For contact information, see
www.utcfssecurityproducts.eu
2015 UTC. All rights reserved.
UTC. All rights
-5923, USA
ring representative:
This equipment has been tested and found to comply with the limits
ese limits
dance with the instruction manual, may cause harmful
own expense.
-003.
-003 du
ACMA compliance
This is a Class A product. In a domestic environment this product may
posed of as unsorted municipal waste in the European Union. See the
N4131
: Hereby, UTC Fire & Security declares that this
sential requirements and other relevant
.
Products marked with this symbol cannot be
t to your local supplier upon the purchase of
This product contains a battery that cannot be
www.interlogix.com or
.
Page 3

3
TABLE OF CONTENTS
1. INTRODUCTION .................................................................................................................. 10
1.1 Packet Contents ......................................................................................................................................... 10
1.2 Product Description ................................................................................................................................... 11
1.3 How to Use This Manual ............................................................................................................................ 15
1.4 Product Features ........................................................................................................................................ 16
1.5 Product Specifications .............................................................................................................................. 19
2. INSTALLATION ................................................................................................................... 22
2.1 Hardware Description ................................................................................................................................ 22
2.1.1 Switch Front Panel .............................................................................................................................................. 22
2.1.2 LED Indications ................................................................................................................................................... 23
2.1.3 Switch Rear Panel ............................................................................................................................................... 24
2.2 Installing the Switch ................................................................................................................................... 25
2.2.1 Desktop Installation ............................................................................................................................................. 25
2.2.2 Rack Mounting ..................................................................................................................................................... 26
2.2.3 Installing the SFP/SFP+ Transceiver ................................................................................................................... 26
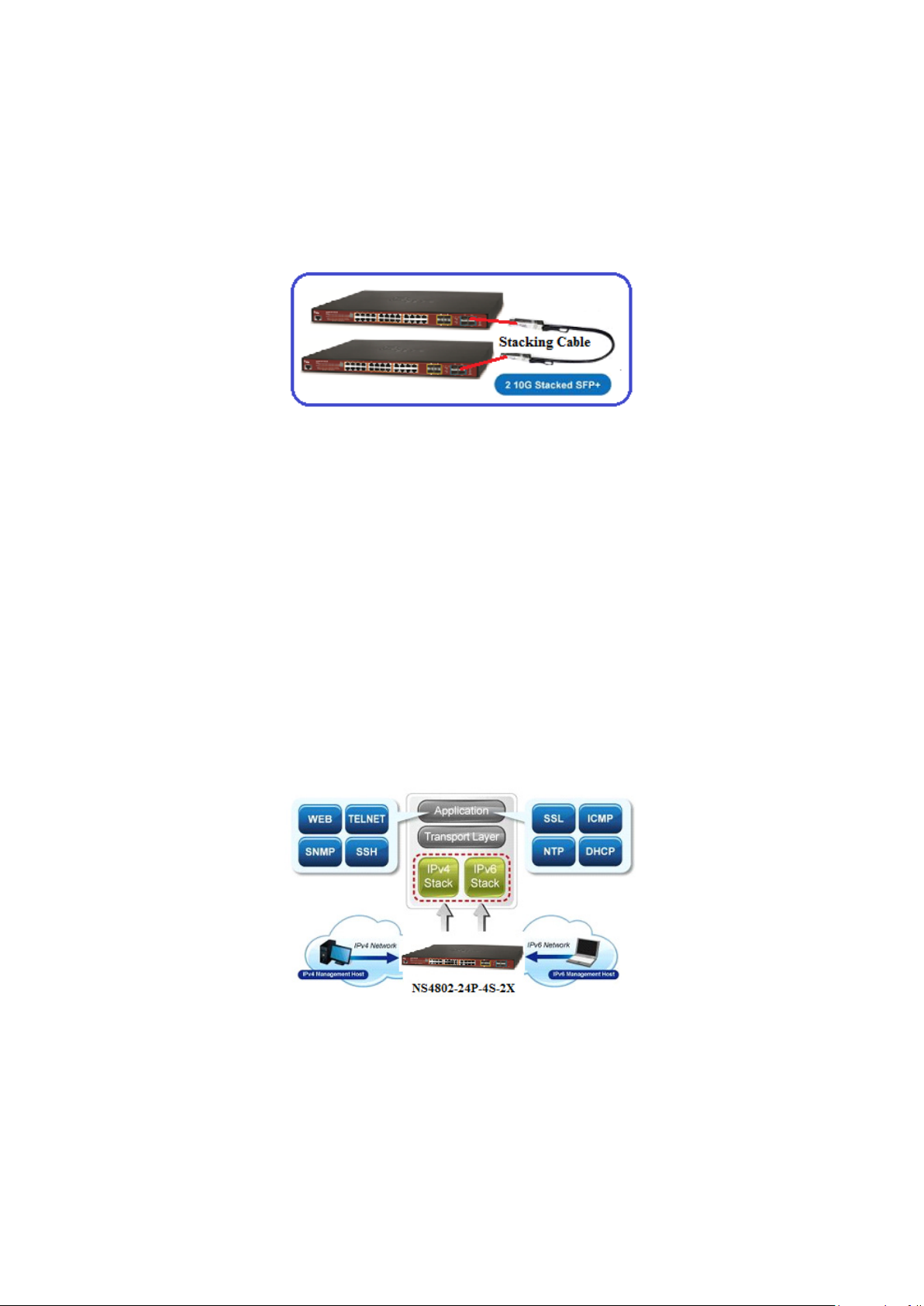
2.3 Stack Installation ........................................................................................................................................ 29
2.3.1 Connecting Stacking Cable .................................................................................................................................. 31
2.3.2 Management Stacking ......................................................................................................................................... 32
3. SWITCH MANAGEMENT .................................................................................................... 34
3.1 Requirements .............................................................................................................................................. 34
3.2 Management Access Overview ................................................................................................................. 35
3.3 Administration Console ............................................................................................................................. 36
3.4 Web Management ....................................................................................................................................... 37
3.5 SNMP-based Network Management ......................................................................................................... 37
4. WEB CONFIGURATION ...................................................................................................... 39
4.1 Main Web Page ........................................................................................................................................... 41
4.2 System ......................................................................................................................................................... 43
4.2.1 System Information .............................................................................................................................................. 44
Page 4

4
4.2.2 IP Configuration ................................................................................................................................................... 45
4.2.3 IP Status .............................................................................................................................................................. 47
4.2.4 Users Configuration ............................................................................................................................................. 48
4.2.5 Privilege Levels ................................................................................................................................................... 51
4.2.6 NTP Configuration ............................................................................................................................................... 52
4.2.7 Time Configuration .............................................................................................................................................. 53
4.2.8 UPnP ................................................................................................................................................................... 55
4.2.9 DHCP Relay ........................................................................................................................................................ 56
4.2.10 DHCP Relay Statistics ....................................................................................................................................... 58
4.2.11 CPU Load .......................................................................................................................................................... 60
4.2.12 System Log ........................................................................................................................................................ 61
4.2.13 Detailed Log ...................................................................................................................................................... 62
4.2.14 Remote Syslog .................................................................................................................................................. 63
4.2.15 SMTP Configuration .......................................................................................................................................... 64
4.2.16 Web Firmware Upgrade ..................................................................................................................................... 65
4.2.17 TFTP Firmware Upgrade ................................................................................................................................... 66
4.2.18 Save Startup Config ........................................................................................................................................... 67
4.2.19 Configuration Download .................................................................................................................................... 67
4.2.20 Configuration Upload ......................................................................................................................................... 68
4.2.21 Configuration Activate ........................................................................................................................................ 68
4.2.22 Configuration Delete .......................................................................................................................................... 69
4.2.23 Image Select ...................................................................................................................................................... 69
4.2.24 Factory Default .................................................................................................................................................. 70
4.2.25 System Reboot .................................................................................................................................................. 71
4.3 Simple Network Management Protocol .................................................................................................... 72
4.3.1 SNMP Overview .................................................................................................................................................. 72
4.3.2 SNMP System Configuration ............................................................................................................................... 73
4.3.3 SNMP Trap Configuration .................................................................................................................................... 75
4.3.4 SNMP System Information .................................................................................................................................. 77
4.3.5 SNMPv3 Configuration ........................................................................................................................................ 78
4.3.5.1 SNMPv3 Communities .............................................................................................................................. 78
4.3.5.2 SNMPv3 Users .......................................................................................................................................... 79
4.3.5.3 SNMPv3 Groups ........................................................................................................................................ 80
4.3.5.4 SNMPv3 Views .......................................................................................................................................... 81
4.3.5.5 SNMPv3 Access ........................................................................................................................................ 82
4.4 Port Management ....................................................................................................................................... 84
4.4.1 Port Configuration ................................................................................................................................................ 84
4.4.2 Port Statistics Overview ....................................................................................................................................... 86
4.4.3 Port Statistics Detail ............................................................................................................................................. 87
Page 5

5
4.4.4 SFP Module Information ...................................................................................................................................... 89
4.4.5 Port Mirror ............................................................................................................................................................ 90
4.5 Link Aggregation ........................................................................................................................................ 93
4.5.1 Static Aggregation ................................................................................................................................................ 95
4.5.2 LACP Configuration ............................................................................................................................................. 96
4.5.3 LACP System Status ........................................................................................................................................... 98
4.5.4 LACP Port Status ................................................................................................................................................. 99
4.5.5 LACP Port Statistics ............................................................................................................................................. 99
4.6 VLAN .......................................................................................................................................................... 101
4.6.1 VLAN Overview ................................................................................................................................................. 101
4.6.2 IEEE 802.1Q VLAN ........................................................................................................................................... 101
4.6.3 VLAN Port Configuration ................................................................................................................................... 105
4.6.4 VLAN Membership Status .................................................................................................................................. 111
4.6.5 VLAN Port Status ............................................................................................................................................... 112
4.6.6 Port Isolation ...................................................................................................................................................... 11 4
4.6.7 VLAN setting example: ...................................................................................................................................... 11 6
4.6.7.1 Two Separate 802.1Q VLANs .................................................................................................................. 116
4.6.7.2 VLAN Trunking between two 802.1Q aware switches ............................................................................. 11 8
4.6.7.3 Port Isolate .............................................................................................................................................. 121
4.6.8 MAC-based VLAN ............................................................................................................................................. 122
4.6.9 Protocol-based VLAN ........................................................................................................................................ 123
4.6.10 Protocol-based VLAN Membership ................................................................................................................. 124
4.7 Spanning Tree Protocol ........................................................................................................................... 126
4.7.1 Theory ............................................................................................................................................................... 126
4.7.2 STP System Configuration ................................................................................................................................ 132
4.7.3 Bridge Status ..................................................................................................................................................... 134
4.7.4 CIST Port Configuration ..................................................................................................................................... 135
4.7.5 MSTI Priorities ................................................................................................................................................... 138
4.7.6 MSTI Configuration ............................................................................................................................................ 139
4.7.7 MSTI Ports Configuration .................................................................................................................................. 140
4.7.8 Port Status ......................................................................................................................................................... 142
4.7.9 Port Statistics ..................................................................................................................................................... 143
4.8 Multicast .................................................................................................................................................... 144
4.8.1 IGMP Snooping ................................................................................................................................................. 144
4.8.2 Profile Table ....................................................................................................................................................... 148
4.8.3 Address Entry .................................................................................................................................................... 149
4.8.4 IGMP Snooping Configuration ........................................................................................................................... 150
4.8.5 IGMP Snooping VLAN Configuration ................................................................................................................. 152
Page 6

6
4.8.6 IGMP Snooping Port Group Filtering ................................................................................................................. 154
4.8.7 IGMP Snooping Status ...................................................................................................................................... 155
4.8.8 IGMP Group Information .................................................................................................................................... 156
4.8.9 IGMPv3 Information ........................................................................................................................................... 157
4.8.10 MLD Snooping Configuration ........................................................................................................................... 158
4.8.11 MLD Snooping VLAN Configuration................................................................................................................. 159
4.8.12 MLD Snooping Port Group Filtering ................................................................................................................. 161
4.8.13 MLD Snooping Status ...................................................................................................................................... 162
4.8.14 MLD Group Information ................................................................................................................................... 163
4.8.15 MLDv2 Information .......................................................................................................................................... 164
4.8.16 MVR (Multicaset VLAN Registration) ............................................................................................................... 165
4.8.17 MVR Status ...................................................................................................................................................... 168
4.8.18 MVR Groups Information ................................................................................................................................. 169
4.8.19 MVR SFM Information ..................................................................................................................................... 169
4.9 Quality of Service ..................................................................................................................................... 171
4.9.1 Understanding QoS ........................................................................................................................................... 171
4.9.2 Port Policing ...................................................................................................................................................... 172
4.9.3 Port Classification .............................................................................................................................................. 172
4.9.4 Port Scheduler ................................................................................................................................................... 174
4.9.5 Port Shaping ...................................................................................................................................................... 175
4.9.5.1 QoS Egress Port Schedule and Shapers ................................................................................................ 176
4.9.6 Port Tag Remarking ........................................................................................................................................... 177
4.9.6.1 QoS Egress Port Tag Remarking ............................................................................................................. 178
4.9.7 Port DSCP ......................................................................................................................................................... 179
4.9.8 DSCP-based QoS ............................................................................................................................................. 180
4.9.9 DSCP Translation .............................................................................................................................................. 181
4.9.10 DSCP Classification ......................................................................................................................................... 182
4.9.11 QoS Control List............................................................................................................................................... 183
4.9.11.1 QoS Control Entry Configuration ........................................................................................................... 185
4.9.12 QCL Status ...................................................................................................................................................... 187
4.9.13 Storm Control Configuration ............................................................................................................................ 188
4.9.14 WRED.............................................................................................................................................................. 189
4.9.15 QoS Statistics .................................................................................................................................................. 192
4.9.16 Voice VLAN Configuration ............................................................................................................................... 192
4.9.17 Voice VLAN OUI Table ..................................................................................................................................... 195
4.10 Access Control Lists .............................................................................................................................. 196
4.10.1 Access Control List Status ............................................................................................................................... 196
4.10.2 Access Control List Configuration .................................................................................................................... 198
4.10.3 ACE Configuration ........................................................................................................................................... 200
Page 7

7
4.10.4 ACL Ports Configuration .................................................................................................................................. 210
4.10.5 ACL Rate Limiter Configuration ....................................................................................................................... 212
4.11 Authentication ......................................................................................................................................... 213
4.11.1 Understanding IEEE 802.1X Port-Based Authentication .................................................................................. 214
4.11.2 Authentication Configuration ............................................................................................................................ 217
4.11.3 Network Access Server Configuration .............................................................................................................. 218
4.11.4 Network Access Overview ............................................................................................................................... 229
4.11.5 Network Access Statistics ................................................................................................................................ 230
4.11.6 RADIUS ........................................................................................................................................................... 237
4.11.7 TACACS+ ........................................................................................................................................................ 239
4.11.8 RADIUS Overview ........................................................................................................................................... 240
4.11.9 RADIUS Details ............................................................................................................................................... 242
4.11.10 Windows Platform RADIUS Server Configuration .......................................................................................... 248
4.11.11 802.1X Client Configuration ........................................................................................................................... 253
4.12 Security ................................................................................................................................................... 256
4.12.1 Port Limit Control ............................................................................................................................................. 256
4.12.2 Access Management ....................................................................................................................................... 260
4.12.3 Access Management Statistics ........................................................................................................................ 261
4.12.4 HTTPs ............................................................................................................................................................. 262
4.12.5 SSH ................................................................................................................................................................. 263
4.12.6 Port Security Status ......................................................................................................................................... 263
4.12.7 Port Security Detail .......................................................................................................................................... 266
4.12.8 DHCP Snooping .............................................................................................................................................. 267
4.12.9 Snooping Table ................................................................................................................................................ 268
4.12.10 IP Source Guard Configuration ...................................................................................................................... 269
4.12.11 IP Source Guard Static Table ......................................................................................................................... 270
4.12.12 ARP Inspection .............................................................................................................................................. 271
4.12.13 ARP Inspection Static Table ........................................................................................................................... 272
4.1 Address Table ........................................................................................................................................... 274
4.13.1 MAC Table Configuration ................................................................................................................................. 274
4.13.2 MAC Address Table Status .............................................................................................................................. 276
4.13.3 Dynamic ARP Inspection Table ........................................................................................................................ 277
4.13.4 Dynamic IP Source Guard Table ...................................................................................................................... 278
4.14 LLDP ........................................................................................................................................................ 280
4.14.1 Link Layer Discovery Protocol ......................................................................................................................... 280
4.14.2 LLDP Configuration ......................................................................................................................................... 280
4.14.3 LLDP MED Configuration ................................................................................................................................ 283
4.14.4 LLDP-MED Neighbor ....................................................................................................................................... 289
Page 8

8
4.14.5 Neighbor .......................................................................................................................................................... 293
4.14.6 Port Statistics ................................................................................................................................................... 294
4.15 Network Diagnostics .............................................................................................................................. 296
4.15.1 Ping ................................................................................................................................................................. 297
4.15.2 IPv6 Ping ......................................................................................................................................................... 298
4.15.3 Remote IP Ping Test ........................................................................................................................................ 299
4.15.4 Cable Diagnostics ............................................................................................................................................ 300
4.16 Power over Ethernet .............................................................................................................................. 302
4.16.1 Power over Ethernet Powered Device ............................................................................................................. 302
4.16.2 System Configuration ...................................................................................................................................... 304
4.16.3 Power Over Ethernet Configuration ................................................................................................................. 305
4.16.4 Port Sequential ................................................................................................................................................ 307
4.16.5 Port Configuration ............................................................................................................................................ 308
4.16.6 PoE Status ....................................................................................................................................................... 310
4.16.7 PoE Schedule .................................................................................................................................................. 312
4.16.8 LLDP PoE Neighbours ..................................................................................................................................... 315
4.17 Loop Protection ...................................................................................................................................... 316
4.17.1 Configuration ................................................................................................................................................... 316
4.17.2 Loop Protection Status..................................................................................................................................... 317
4.18 RMON ....................................................................................................................................................... 319
4.18.1 RMON Alarm Configuration ............................................................................................................................. 319
4.18.2 RMON Alarm Status......................................................................................................................................... 321
4.18.3 RMON Event Configuration ............................................................................................................................. 322
4.18.4 RMON Event Status......................................................................................................................................... 323
4.18.5 RMON History Configuration ........................................................................................................................... 324
4.18.6 RMON History Status....................................................................................................................................... 325
4.18.7 RMON Statistics Configuration ........................................................................................................................ 326
4.18.8 RMON Statistics Status .................................................................................................................................... 327
4.19 Stack ........................................................................................................................................................ 329
4.19.1 Stack ................................................................................................................................................................ 331
4.19.1.1 Switch IDs ........................................................................................................................................... 331
4.19.1.2 Master Election ................................................................................................................................... 332
4.19.1.3 Stack Redundancy .............................................................................................................................. 332
4.19.1.4 Shortest Path Forwarding ................................................................................................................... 333
4.19.2 Stack Configuration.......................................................................................................................................... 333
4.19.3 Stack Information ............................................................................................................................................. 337
4.19.4 Stack Port State Overview ............................................................................................................................... 338
4.19.5 Stack Example ................................................................................................................................................. 338
Page 9

9
5. SWITCH OPERATION ....................................................................................................... 342
5.1 Address Table ........................................................................................................................................... 342
5.2 Learning .................................................................................................................................................... 342
5.3 Forwarding & Filtering ............................................................................................................................. 342
5.4 Store-and-Forward ................................................................................................................................... 342
5.5 Auto-Negotiation ...................................................................................................................................... 343
6. TROUBLESHOOTING ....................................................................................................... 344
APPENDIX A: Networking Connection ............................................................................... 345
A.1 PoE RJ-45 Port Pin Assignments ........................................................................................................... 345
A.2 Switch's Data RJ-45 Pin Assignments - 1000Mbps, 1000BASE-T ...................................................... 345
A.3 10/100Mbps, 10/100BASE-TX .................................................................................................................. 345
APPENDIX B : GLOSSARY .................................................................................................. 347
Page 10

10
1. INTRODUCTION
Thank you for purchasing a NS4802-24P-4S-2X L2+ 24-Port 10/100/1000T 802.3at PoE + 4-Port Shared SFP + 2-Port 10G
SFP+ Managed Stackable Switch. NS4802-24P-4S-2X, comes with the multi-port Gigabit Ethernet Switch and SFP fiber optic
connectibility and robust layer 2 features. The description of this model is shown below:
NS4802-24P-4S-2X L2+ 24-Port 10/100/1000T 802.3at PoE + 4-Port Shared SFP + 2-Port 10G SFP+ Managed
Stackable Switch
“Managed Switch” “NS4802” is used as an alternative name in this user’s manual.
1.1 Packet Contents
Open the box of the Managed Switch and carefully unpack it. The box should contain the following items:
Managed Switch x 1
Quick Installation Guide x 1
RJ45 to RS232 Cable x 1
SFP Dusty Cap x 8
Rubber Feet x 4
Rack-mount Accessory Kit x 1
Power Cord x 1
If any of these are missing or damaged, please contact your dealer immediately; if possible, retain the carton including the
original packing material, and use them again to repack the product in case there is a need to return it to us for repair.
Page 11

11
1.2 Product Description
High-Density, Resilient Deployment Switch Solution for Gigabit Networking of Enterprise, Campus and Data Center
For the growing Gigabit network and IoT (Internet of Things) demand, IFS has launched a new-generation Stackable Gigabit
PoE+ Switch solution, the NS4802-24P-4S-2X, to meet the needs of IP surveillance, enterprises, telecoms and campuses for a
large-scale network deployment. The NS4802-24P-4S-2X is Layer 2+ Managed Stackable Gigabit PoE+ Switch, which supports
both IPv4 and IPv6 protocols and hardware Layer 3 static routing capability, and provides 24 10/100/1000Mbps Gigabit
Ethernet ports, 4 shared Gigabit SFP slots, 2 10G SFP+ uplink slots and another 2 dedicated 10G SFP+ stacked
interfaces for stacking the switch. Up to 16 units, 384 Gigabit Ethernet ports and 32 10Gbps SFP+ slots can be managed by a
stacking group and you can add ports and functionality as needed.
Efficient Single IP Management
The NS4802-24P-4S-2X applies the advantage of the stacking technology to managing the stack group with one single IP
address, which helps network managers to easily manage a stack of switches instead of connecting and setting each unit one
by one. The stacking technology also enables the chassis-based switches to be integrated into the NS4802-24P-4S-2X
Managed Switch at an inexpensive cost.
Page 12
12
Highly-reliable Stacking Ability
Through its up to 40Gbps, bi-directional high bandwidth tunnel and stacking technology, the NS4802 gives the enterprises,
service providers and telecoms flexible control over port density, uplinks and switch stack performance. The stack redundancy
of the NS4802 ensures that data integrity is retained even if one switch in the stack fails. You can even hot-swap switches
without disrupting the network, which greatly simplifies the tasks of upgrading the LAN for catering to increasing bandwidth
demands.
Cost-effective 10Gbps Uplink Capacity
10G Ethernet is a big leap in the evolution of Ethernet. The two 10G SFP+ slot of the NS4802 supports Dual-speed,
10GBASE-SR/LR or 1000BASE-SX/LX, meaning the administrator now can flexibly choose the suitable SFP/SFP+ transceiver
according to the transmission distance or the transmission speed required to extend the network efficiently. They greatly support
SMB network to achieve 10Gbps high performance in a cost-effective way because 10GbE interface usually could be available
in Layer 3 Switch but Layer 3 Switch could be too expensive to SMBs. (Small Businesses)
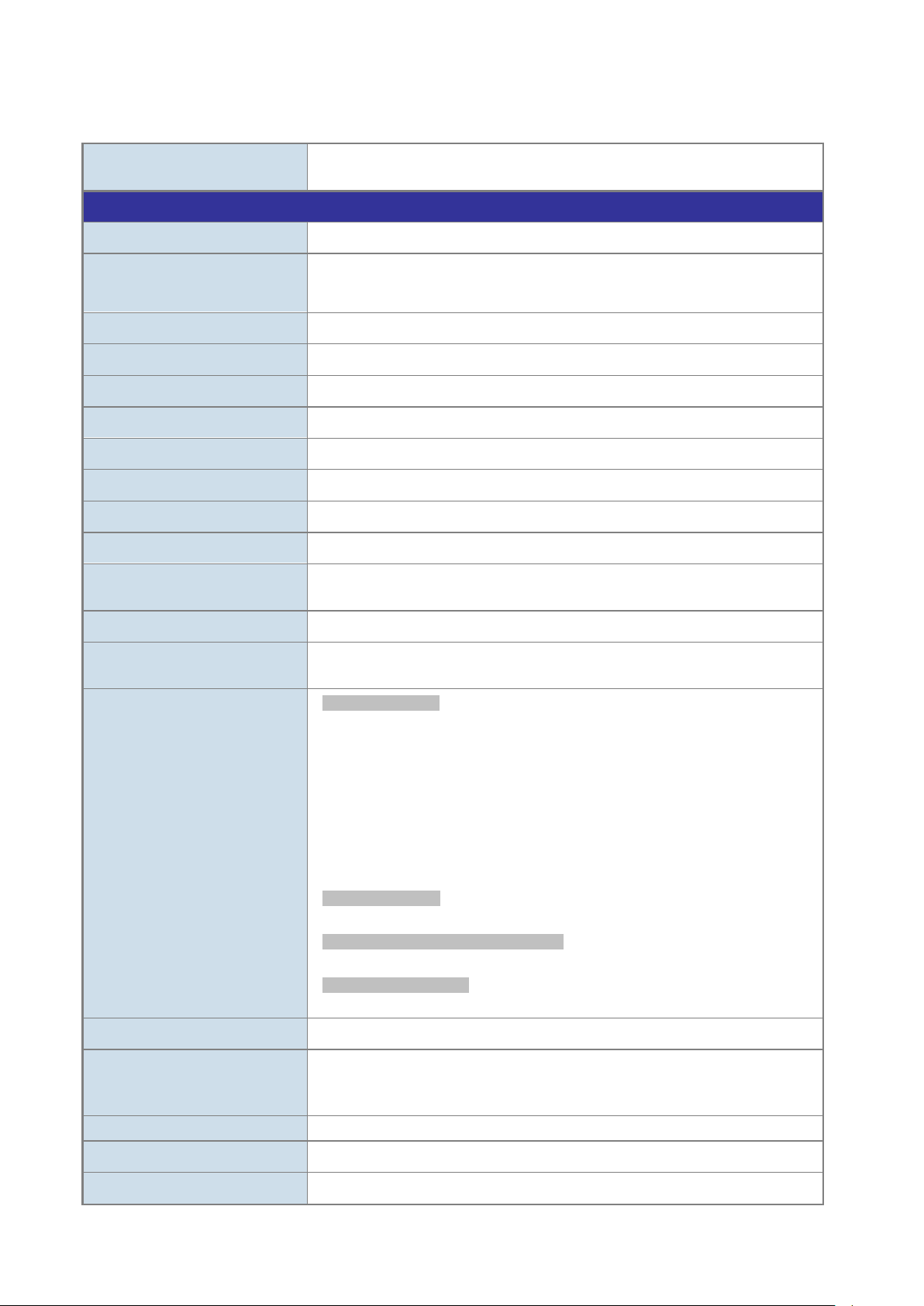
Solution for IPv6 Networking
By supporting IPv6 / IPv4 dual stack and plenty of management functions with easy and friendly management interfaces, the
NS4802 is the best choice for IP surveillance, VoIP and wireless service providers to connect with the IPv6 network. It also helps
the SMB to step in the IPv6 era with the lowest investment but not necessary to replace the network facilities while the ISP
constructs the IPv6 FTTx edge network.
IPv4 and IPv6 VLAN Routing for Secure and Flexible Management
To help customers stay on top of their businesses, the NS4802 not only provides ultra high transmission performance and
excellent layer 2 technologies, but also offers IPv4/IPv6 VLAN routing feature which allows crossing over different VLANs and
different IP addresses for the purpose of having a highly secured, flexible management and simpler networking application.
Robust Layer2 Features
Page 13

13
The NS4802 can be programmed for advanced switch management function, such as dynamic port link aggregation, Q-in-Q
VLAN, Multiple spanning tree protocol (MSTP), Layer 2/4 QoS, bandwidth control and IGMP/MLD snooping. The NS4802
allows the operation of a high-speed trunk combining multiple ports. It enables up to 3 groups of 6 ports for trunk maximum and
supports connection fail-over as well.
Powerful Security
The NS4802-24P-4S-2X offers comprehensive layer2 to layer4 access control list (ACL) for enforcing security to the edge. It
can be used to restrict to network access by denying packets based on source and destination IP address, TCP/UDP port
number or defined typical network applications. Its protection mechanism also comprises 802.1x Port-based and MAC-based
user and device authentication. With the private VLAN function, communication between edge ports can be prevented to
ensure user privacy.
Enhanced Security and Traffic Control
The NS4802-24P-4S-2X also provides DHCP Snooping, IP Source Guard and Dynamic ARP Inspection functions to prevent
IP snooping from attack and discard ARP packets with invalid MAC address. The network administrator can now construct
highly secured corporate networks with considerably less time and effort than before.
User-friendly Secure Management
For efficient management, the NS4802-24P-4S-2X managed switch is equipped with console, web and SNMP management
interfaces. With the built-in web-based management interface, the NS4802-24P-4S-2X offers an easy-to-use, platform
independent management and configuration facility. The NS4802-24P-4S-2X supports SNMP and it can be managed via any
management software based on standard of SNMP v1 and v2 protocol. For reducing product learning time, the
NS4802-24P-4S-2X offers Cisco-like command via Telnet or console port and customer doesn’t need to learn new command
from these switches. Moreover, the NS4802-24P-4S-2X offers remote secure management by supporting SSH, SSL and
SNMPv3 connection which can be encrypted the packet content at each session.
Flexible and Extendable Solution
The 4 mini-GBIC SFP slots built in the NS4802-24P-4S-2X support dual speed as it features 100BASE-FX and
1000BASE-SX/LX SFP (Small Form-factor Pluggable) fiber-optic modules. Now the administrator can flexibly choose the
suitable SFP transceiver according to not only the transmission distance, but also the transmission speed required. The
distance can be extended from 550 meters to 2km (multi-mode fiber) and up to above 10/20/30/40/50/70 kilometers
(single-mode fiber or WDM fiber). They are well suited for applications within the enterprise data centers and distributions.
Intelligent SFP Diagnosis Mechanism
The NS4802 supports SFP-DDM (Digital Diagnostic Monitor) function that greatly helps network administrator to easily
monitor real-time parameters of the SFP and SFP+ transceivers, such as optical output power, optical input power, temperature,
laser bias current, and transceiver supply voltage.
Page 14

14
Centralized Power Management for Gigabit Ethernet PoE Networking
To fulfill the needs of higher power required PoE network applications with Gigabit speed transmission, the NS4802 features
high-performance Gigabit IEEE 802.3af PoE (up to 15.4 watts) and IEEE 802.3at PoE+ (up to 30 watts) on all ports. It perfectly
meets the power requirement of PoE VoIP phone and all kinds of PoE IP cameras such as IR, PTZ, speed dome cameras or
even box type IP cameras with built-in fan and heater for high power consumption.
The NS4802’s PoE capabilities also help to reduce deployment costs for network devices as a result of freeing from restrictions
of power outlet locations. Power and data switching are integrated into one unit, delivered over a single cable and managed
centrally. It thus eliminates cost for additional AC wiring and reduces installation time.
Built-in Unique PoE Functions for Surveillance Management
As a managed PoE Switch for surveillance network, the NS4802 features intelligent PoE Management functions:
Scheduled Power Recycling
SMTP/SNMP Trap Event Alert
PoE Schedule
Scheduled Power Recycling
The NS4802 allows each of the connected PD (Powered Device) to reboot in a specific time each week. Therefore, it will reduce
the chance of PD (Powered Device) crash resulting from buffer overflow.
SMTP/SNMP Trap Event alert
Though most NVR or camera management software offer SMTP email alert function, the NS4802 further provides event alert
function to help to diagnose the abnormal device owing to whether or not there is a break of the network connection, loss of PoE
power or the rebooting response by PD Alive Check process.
PoE Schedule for Energy Saving
Besides being used for IP surveillance, theNS4802 is certainly applicable to construct any PoE network including VoIP and
wireless LAN. Under the trend of energy saving worldwide and contributing to the environmental protection on the Earth, the
NS4802 can effectively control the power supply besides its capability of giving high watts power. The “PoE schedule” function
helps you to enable or disable PoE power feeding for each PoE port during specified time intervals and it is a powerful function
to help SMBs or enterprises save power and money.
Page 15

15
1.3 How to Use This Manual
This User’s Manual is structured as follows:
Section 2, INSTALLATION
The section explains the functions of the Managed Switch and how to physically install the Managed Switch.
Section 3, SWITCH MANAGEMENT
The section contains the information about the software function of the Managed Switch.
Section 4, WEB CONFIGURATION
The section explains how to manage the Managed Switch by Web interface.
Section 5, SWITCH OPERATION
The chapter explains how to do the switch operation of the Managed Switch.
Section 6, POWER over ETHERNET OVERVIEW
The chapter introduces the IEEE 802.3af / 802.3at PoE standard and PoE provision of the Managed Switch.
Section 7, TROUBLESHOOTING
The chapter explains how to do troubleshooting of the Managed Switch.
Appendix A
The section contains cable information of the Managed Switch.
Page 16

16
1.4 Product Features
Physical Port
24-Port 10/100/1000BASE-T RJ45 copper with IEEE 802.3at / 802.3af Power over Ethernet Injector function
4 100/1000BASE-X mini-GBIC/SFP slots, shared with Port-21 to Port-24 compatible with 100BASE-FX SFP
2 10GBASE-SR/LR SFP+ slots, compatible with 1000BASE-SX/LX/BX SFP
2 10GBASE-SR/LR SFP+ stacking slots
RJ45 console interface for basic management and setup
Stacking Features
■ Physical stacking up to 16 units, 384 Gigabit ports, 32 10 Gigabit ports
■ Single IP address stack management
■ Stacking architecture supports Chain and Ring mode
■ Plug and Play connectivity
■ Mirror across stack
■ Link Aggregation groups spanning multiple switches in a stack
■ Physical MAC address learning with MAC table synchronization across stack
Layer 2 Features
■ Prevents packet loss with back pressure (half-duplex) and IEEE 802.3x pause frame flow control (full-duplex)
■ High performance of Store-and-Forward architecture and runt/CRC filtering eliminates erroneous packets to optimize
the network bandwidth
■ Storm Control support
− Broadcast / Multicast / Unknown unicast
■ Supports VLAN
− IEEE 802.1Q tagged VLAN
− Up to 255 VLANs groups, out of 4094 VLAN IDs
− Supports provider bridging (VLAN Q-in-Q, IEEE 802.1ad)
− Private VLAN Edge (PVE)
− Protocol-based VLAN
− MAC-based VLAN
− Voice VLAN
■ Supports Spanning Tree Protocol
− STP, IEEE 802.1D Spanning Tree Protocol
− RSTP, IEEE 802.1w Rapid Spanning Tree Protocol
− MSTP, IEEE 802.1s Multiple Spanning Tree Protocol, spanning tree by VLAN
− BPDU Guard
■ Supports Link Aggregation
− 802.3ad Link Aggregation Control Protocol (LACP)
− Cisco ether-channel (Static Trunk)
− Maximum 10 trunk groups, up to 16 ports per trunk group
− Up to 32Gbps bandwidth (full duplex mode)
■ Provides port mirror (many-to-1)
■ Port mirroring to monitor the incoming or outgoing traffic on a particular port
■ Loop protection to avoid broadcast loops
Layer 3 IP Routing Features
Supports maximum 128 VLAN interfaces
32 static routing entries
Quality of Service
Page 17

17
■ Ingress Shaper and Egress Rate Limit per port bandwidth control
■ 8 priority queues on all switch ports
■ Traffic classification
- IEEE 802.1p CoS
- TOS / DSCP / IP Precedence of IPv4/IPv6 packets
- IP TCP/UDP port number
- Typical network application
■ Strict priority and Weighted Round Robin (WRR) CoS policies
■ Supports QoS and In/Out bandwidth control on each port
■ Traff ic-policing policies on the switch port
■ DSCP remarking
Multicast
Supports IGMP Snooping v1, v2 and v3
Supports MLD Snooping v1 and v2
Querier mode support
IGMP Snooping port filtering
MLD Snooping port filtering
Multicast VLAN Registration (MVR) support
Security
Authentication
- IEEE 802.1x Port-based / MAC-based network access authentication
- Built-in RADIUS client to co-operate with the RADIUS servers
- TACACS+ login users access authentication
- RADIUS / TACACS+ users access authentication
Access Control List
- IP-based Access Control List (ACL)
- MAC-based Access Control List
Source MAC / IP address binding
DHCP Snooping to filter un-trusted DHCP messages
Dynamic ARP Inspection discards ARP packets with invalid MAC address to IP address binding
IP Source Guard prevents IP spoofing attacks
IP address access management to prevent unauthorized intruder
Management
IPv4 and IPv6 dual stack management
Switch Management Interfaces
- Console / Telnet Command Line Interface
- Web switch management
- SNMP v1, v2c, and v3 switch management
- SSH / SSL secure access
IPv6 IP Address / NTP / DNS management
Built-in Trivial File Transfer Protocol (TFTP) client
BOOTP and DHCP for IP address assignment
System Maintenance
- Firmware upload/download via HTTP / TFTP
- Reset button for system reboot or reset to factory default
- Dual Images
DHCP Relay
Page 18

18
DHCP Option82
User Privilege levels control
NTP (Network Time Protocol)
Link Layer Discovery Protocol (LLDP) and LLDP-MED
Network Diagnostic
- ICMPv6 / ICMPv4 Remote Ping
- Cable Diagnostic technology provides the mechanism to detect and report potential cabling issues
SMTP / Syslog remote alarm
Four RMON groups (history, statistics, alarms and events)
SNMP trap for interface Link Up and Link Down notification
System Log
IFS Smart Discovery Utility for deploy management
Power over Ethernet
■ Complies with IEEE 802.3at High Power over Ethernet End-Span PSE
■ Complies with IEEE 802.3af Power over Ethernet End-Span PSE
■ Up to 24 ports of IEEE 802.3af / 802.3at devices powered
■ Supports PoE Power up to 30.8 Watts for each PoE ports
■ Auto detects powered device (PD)
■ Circuit protection prevents power interference between ports
■ Remote power feeding up to 100 meters
■ PoE Management
− Total PoE power budget control
− Per port PoE function enable/disable
− PoE Port Power feeding priority
− Per PoE port power limitation
− PD classification detection
− PD alive-check
− PoE schedule
− PD power recycling schedule
Page 19
19
1.5 Product Specifications
Back pressure for half-duplex
> 5 sec: Factory Default
10G (Green), 1G (Orange)
ESD Protection
Model NS4802-24P-4S-2X
Hardware Specifications
Copper Ports 24 10/ 100/1000BASE-T RJ-45 Auto-MDI/MDI-X ports
10/100/1000Mbps / SFP Combo
Interfaces
10Gbps Fiber Uplink Ports
10Gbps Fiber Stackable Ports
Console 1 x RJ45 serial port (115200, 8, N, 1)
Switch Architecture Store-and-Forward
Switch Fabric 128Gbps / non-blocking
Throughput 95.2Mpps@64Bytes
Address Table 16K entries, automatic source address learning and ageing
Shared Data Buffer 4 megabits
Flow Control
Jumbo Frame 9K bytes
Reset Button
LED
4 10/100/1000Mbps TP and SFP shared combo interfaces, SFP (Mini-GBIC)
supports 100/1000Mbps Dual mode DDM, shared with Port-21 to Port-24
2 1/10GBASE-SR/LR SFP+ slots
2 10GBASE-SR/LR SFP+ slots
IEEE 802.3x pause frame for full-duplex
< 5 sec: System reboot
System/Alert/Stack:
PWR (Green)
Master (Green)
PWR1 Alert (Green)
PWR2 Alert (Green)
Fan1 Alert (Green)
Fan2 Alert (Green)
STX1 (Green)
STX2 (Green)
Ethernet Interfaces (Port 1 to Port 24):
LNK/ACT (Green), PoE (Orange)
100/1000Mbps SFP Combo Interfaces (Port 21 to Port 24):
LNK/ACT (Green)
1/10G SFP+ Interfaces (Port 25 to Port 26):
Power Requirements
Power Consumption
(Full Loading)
Dimensions (W x D x H)
Weight
100~240V AC, 50/60Hz
440 watts maximum, (220W for ports 1 thru 12 and 220W for ports 13 thru 24)
6KV DC
440 x 300 x 44.5 mm, 1U height
4887g
Page 20
20
Stacking Functions
Flow Control disable / enable
negotiation status, trunk status
Many-to-1 monitor
Up to 255 VLAN groups, out of 4094 VLAN IDs
Supports 3 groups of 6-Port trunk (Fiber Port Supported Only)
- DSCP/TOS field in IP Packet
Stacking Ports
Stacking Numbers
Stacking Bandwidth
Stack ID Display
Stack Topology
Power over Ethernet
PoE Standard
PoE Power Supply Type
PoE Power Output
Power Pin Assignment
PoE Power Budget
PoE Ability PD @ 7 watts
PoE Ability PD @ 15.4 watts
PoE Ability PD @ 30.8 watts
Layer2 Management Function
2 SFP+ slots
16
40Gbps full duplex
7-Segment LED display (1~9, A~F, 0)
Ring / Chain / Back-to-Back
IEEE 802.3af / 802.3at PoE / PSE
End-span
Per Port 56V DC, Max. 30 watts per port (Max.7 per each side)
1/2(+), 3/6(-)
380 watts (max.) @ 50 degrees C
24 units
24 units
14 units (Max.7 per each side)
Basic Management Interfaces Console, Telnet, Web Browser, SNMP v1, v2c
Secure Management Interfaces SSH, SSL, SNMP v3
Port disable / enable
Port Configuration
Port Status
Port Mirroring
VLAN
Link Aggregation
Auto-negotiation 10/100/1000Mbps full and half duplex mode selection
Display each port’s speed duplex mode, link status, flow control status, auto
TX / RX / Both
802.1Q tagged based VLAN, up to 255 VLAN groups
Q-in-Q tunneling
Private VLAN Edge (PVE)
MAC-based VLAN
Protocol-based VLAN
Voice VLAN
MVR (Multicast VLAN Registration)
IEEE 802.3ad LACP / Static Trunk
Traffic classification based, Strict priority and WRR
8-Level priority for switching
QoS
- Port Number
- 802.1p priority
- 802.1Q VLAN tag
Page 21
21
IGMP Snooping
IGMP Querier mode support
MLD Querier mode support
Up to 256 entries
Bandwidth Control
Per port ingress / egress bandwidth control
RFC 2737 Entity MIB
PoE-Ethernet MIB
IPv6 hardware static routing
FRC 3810 MLD version 2
Environments
Relative Humidity: 5 ~ 95% (non-condensing)
Relative Humidity: 5 ~ 95% (non-condensing)
IGMP (v1/v2/v3) Snooping, up to 255 multicast Groups
MLD Snooping
Access Control List
SNMP MIBs
Layer3 Function
IP Interfaces
Routing Table
Routing Protocols
Standards Conformance
Regulation Compliance FCC Part 15 Class A, CE
MLD (v1/v2) Snooping, up to 255 multicast Groups
IP-based ACL / MAC-based ACL
RFC 1213 MIB-II
IF-MIB
RFC 1493 Bridge MIB
RFC 1643 Ethernet MIB
RFC 2863 Interface MIB
RFC 2665 Ether-Like MIB
Max. 128 VLAN interfaces
Max. 32 routing entries
IPv4 hardware static routing
RFC 2819 RMON MIB (Group 1, 2, 3 and 9)
RFC 2618 RADIUS Client MIB
RFC 3411 SNMP-Frameworks-MIB
IEEE 802.1X PAE
LLDP
MAU-MIB
Standards Compliance
Operating
Storage
IEEE 802.1Q VLAN tagging
IEEE 802.1x Port Authentication Network Control
IEEE 802.1ab LLDP
IEEE 802.3af Power over Ethernet
IEEE 802.3at Power over Ethernet PLUS
RFC 768 UDP
RFC 793 TFTP
RFC 791 IP
RFC 792 ICMP
RFC 2068 HTTP
RFC 1112 IGMP version 1
RFC 2236 IGMP version 2
RFC 3376 IGMP version 3
RFC 2710 MLD version 1
Temperature: 0 ~ 50 degrees C
Temperature: -10 ~ 70 degrees C
Page 22

22
2. INSTALLATION
This section describes the hardware features and installation of the Managed Switch on the desktop or rack mount. For easier
management and control of the Managed Switch, familiarize yourself with its display indicators, and ports. Front panel
illustrations in this chapter display the unit LED indicators. Before connecting any network device to the Managed Switch, please
read this chapter completely.
2.1 Hardware Description
2.1.1 Switch Front Panel
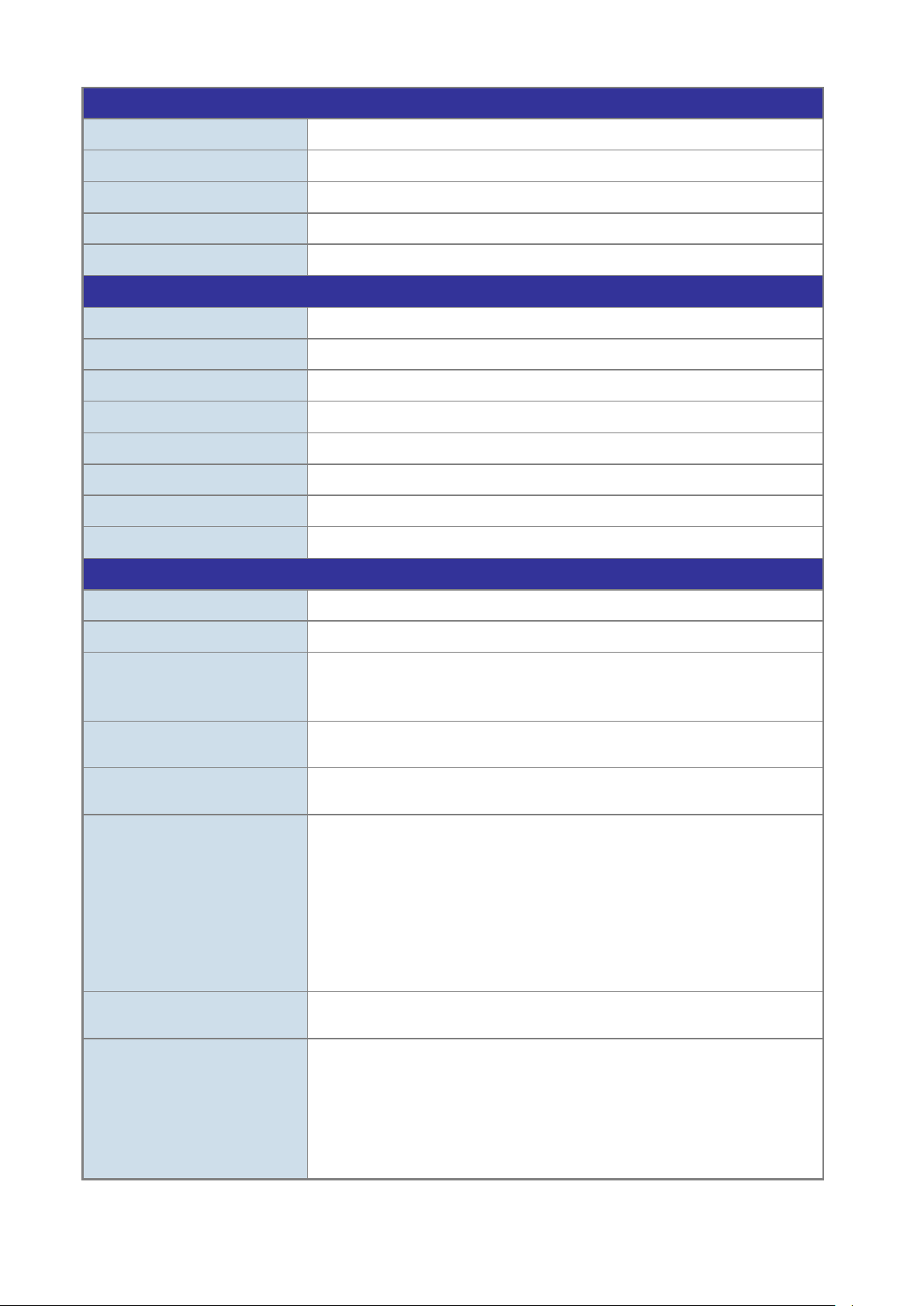
The front panel provides a simple interface monitoring the Managed Switch. Figure 2-1-1 shows the front panel of the Managed
Switch.
NS4802-24P-4S-2X Front Panel
Figure 2-1-1: Front Panel of NS4802
■ Gigabit TP interface
10/100/1000BASE-T Copper, RJ45 twisted-pair: Up to 100 meters.
■ SFP slot
100/1000BASE-X mini-GBIC slot, SFP (Small-form Factor Pluggable) transceiver module: From 550 meters to 2km
(multi-mode fiber), up to above 10/20/30/40/50/70/120 kilometers (single-mode fiber).
■ 10 Gigabit SFP+ slot
10GBASE-SR/LR mini-GBIC slot, SFP+ Transceiver Module supports from 300 meters (multi-mode fiber) to up to 10
kilometers (single-mode fiber)
■ 10 Gigabit Stacked SFP+ slot
10GBASE-SR/LR mini-GBIC slot, SFP+ Transceiver Module supports from 300 meters (multi-mode fiber) to up to 10
kilometers (single-mode fiber)
■ Console Port
The console port is an RJ45 port connector. It is an interface for connecting a terminal directly. Through the console port, it
provides rich diagnostic information including IP address setting, factory reset, port management, link status and system
setting. Users can use the attached DB9 to RJ45 console cable in the package and connect to the console port on the
device. After the connection, users can run any terminal emulation program (Hyper Terminal, ProComm Plus, Telix,
Page 23
23
Winterm and so on) to enter the startup screen of the device.
Reset Button Pressed and Released
Function
Default Gateway: 192.168.0.254
■ Reset button
At the right of the front panel, the reset button is designed for rebooting the Managed Switch without turning off and on the
power. The following is the summary table of reset button functions:
< 5 sec: System Reboot Reboot the Managed Switch.
Reset the Managed Switch to Factory Default configuration.
The Managed Switch will then reboot and load the default
settings as shown below:
> 5 sec: Factory Default
。 Default Username: admin
。 Default Password: admin
。 Default IP address: 192.168.0.100
。 Subnet mask: 255.255.255.0
。
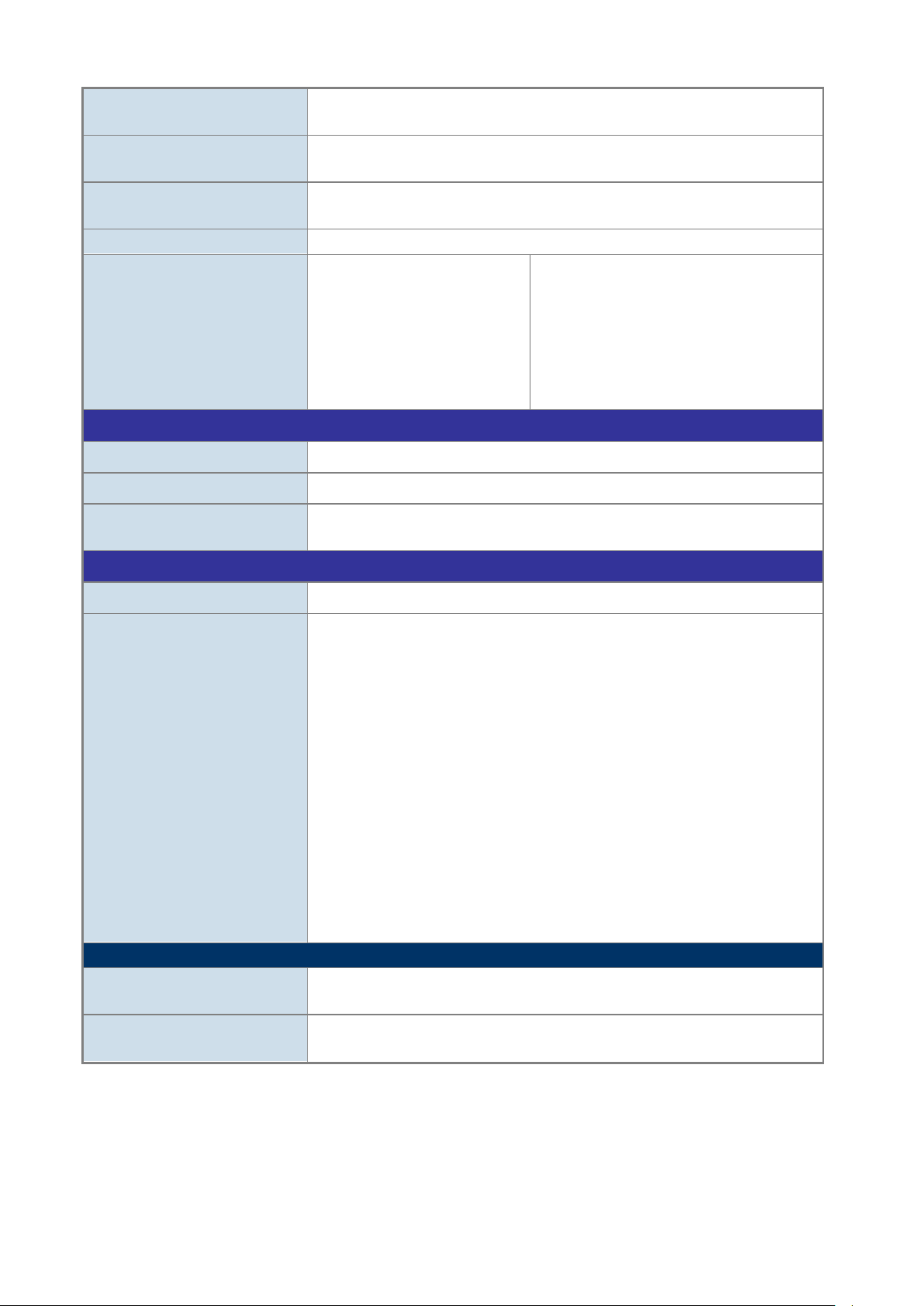
2.1.2 LED Indications
The front panel LEDs indicate instant status of power and system status, fan status, port links / PoE in-use and data activity;
they help monitor and troubleshoot when needed. Figure 2-1-2 shows the LED indications of the Managed Switch.
NS4802-24P-4S-2X LED Indication
Figure 2-1-2: Front Panel LEDs of NS4802-24P-4S-2X
NS4802-24P-4S-2X LED Indication Table
LED definition
System / Alert / Stack
LED Color Function
PWR Green
Master Green Lights to indicate that the Switch is the Master of the stack group.
FAN1
FAN2
PWR1
PWR2
Green
Green
Green
Green
Lights to indicate that the Switch is powered on.
Blinks to indicate the System is running under booting procedure.
Lights to indicate fan1 has failed.
Lights to indicate fan2 has failed.
Lights to indicate power supply 1 has failed.
Lights to indicate power supply 2 has failed.
Page 24

24
Lights to indicate the link through that SFP+ stacking port
is successfully established with
Off to indicate that the port is link down.
is successfully established with
Off to indicate that the port is link down.
Blinks to indicate that the switch is actively sending or receiving data over that port.
Blinks to indicate that the switch is actively sending or receiving data over that port.
Blinks to indicate that the switch is actively sending or receiving data over that port.
active all the time, please consider using UPS (Uninterrupted Power Supply) for your device.
Switch from being damaged by unregulated
STX1
STX2
Per 10/100/1000BASE-T interfaces (Port-1 to Port-24)
LED Color Function
LNK/ACT Green
Green
Green
speed 10Gbps.
Lights to indicate the link through that SFP+ stacking port
speed 10Gbps.
Lights to indicate the link through that port is successfully established at
10/100/1000Mbps.
PoE Orange
Per 10G uplink SFP+ interface (Port-25 to Port-26)
LED Color Function
10G
LNK/ACT
1G
LNK/ACT
Green
Orange
Lights to Indicate the port is providing 56V DC in-line power.
Blinks to indicate the connected device is not a PoE Powered Device (PD).
Lights to indicate the port is running in 10Gbps speed and successfully established.
Lights to indicate the port is running in 1Gbps speed and successfully established.
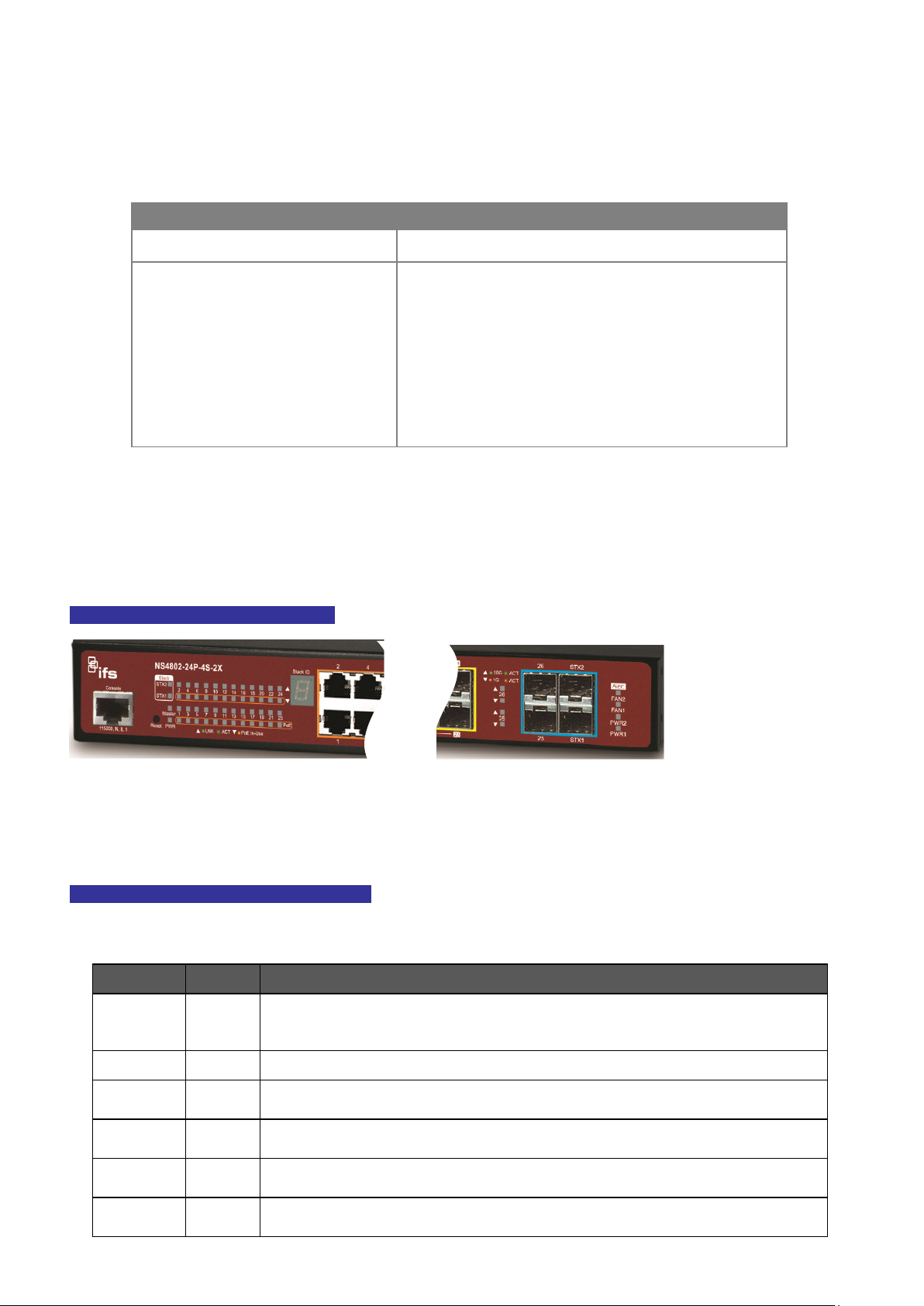
2.1.3 Switch Rear Panel
The rear panel of the Managed Switch indicates an AC inlet power socket, which accepts input power from 100 to 240V AC,
50-60Hz. Figure 2-1-3 shows the rear panel of the Managed Switch.
NS4802-24P-4S-2X Rear Panel
Figure 2-1-3: Rear Panel of NS4802-24P-4S-2X
■ AC Power Receptacle
For compatibility with electric service in most areas of the world, the Managed Switch’s power supply automatically adjusts
line power in the range of 100-240V AC and 50/60 Hz.
Plug the female end of the power cord firmly into the receptalbe on the rear panel of the Managed Switch and the other end
of the power cord into an electric service outlet and the power will be ready.
The device is a power-required device, which means it will not work till it is powered. If your networks
should be
Power Notice:
It will prevent you from network data loss or network downtime. In some areas, installing a surge
suppression device may also help to protect your Managed
surge or current to the Switch or the power adapter.
Page 25
25
Chapter 1,
2.2 Installing the Switch
This section describes how to install your Managed Switch and make connections to the Managed Switch. Please read the
following topics and perform the procedures in the order being presented. To install your Managed Switch on a desktop or shelf,
simply complete the following steps.
2.2.1 Desktop Installation
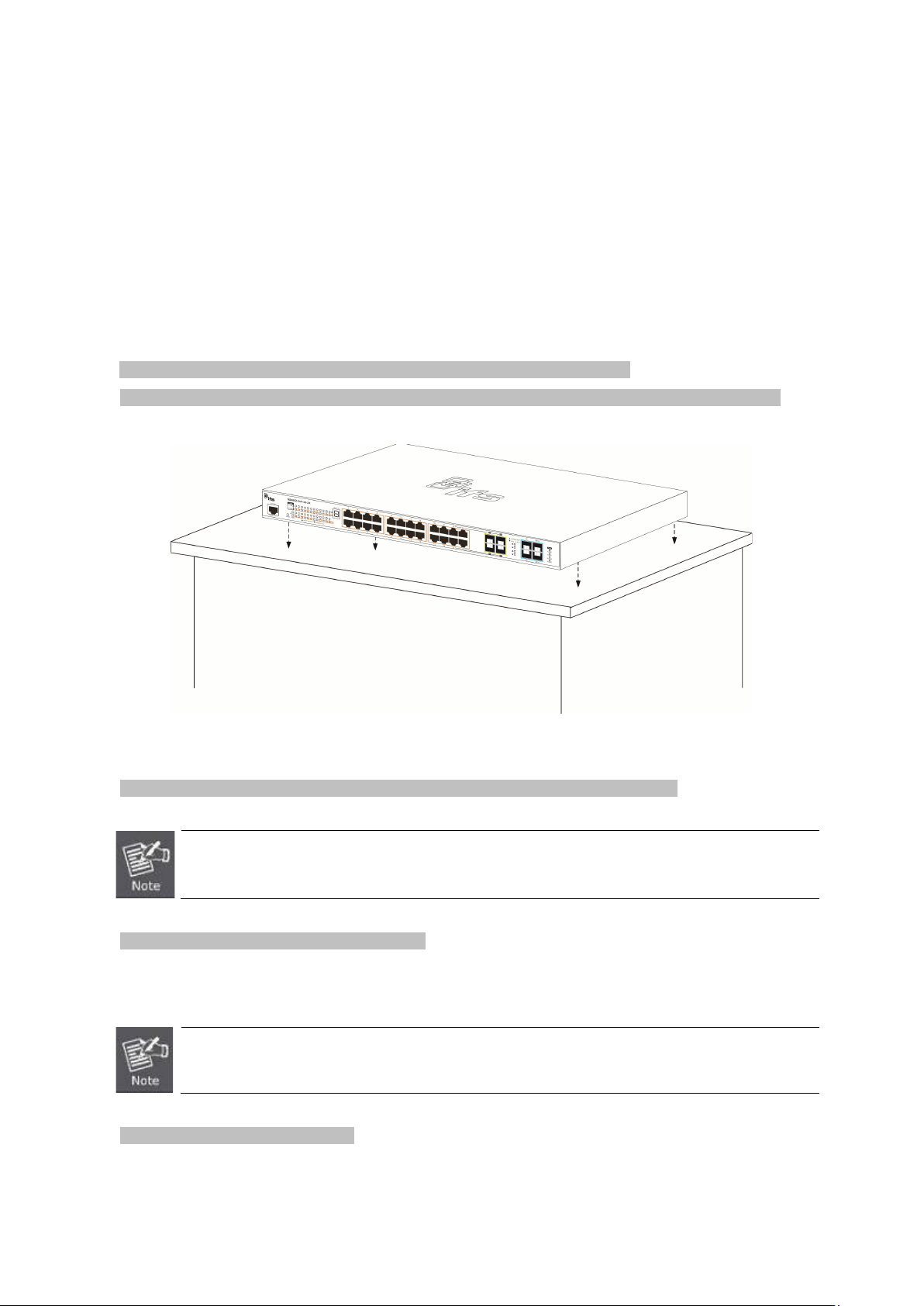
To install the Managed Switch on desktop or shelf, please follow these steps:
Step 1: Attach the rubber feet to the recessed areas on the bottom of the Managed Switch.
Step 2: Place the Managed Switch on the desktop or the shelf near an AC power source, as shown in Figure 2-2-1.
Figure 2-2-1: Place the Managed Switch on the Desktop
Step 3: Keep enough ventilation space between the Managed Switch and the surrounding objects.
When choosing a location, please keep in mind the environmental restrictions discussed in
Section 4, and specifications.
Step 4: Connect the Managed Switch to network devices.
Connect one end of a standard network cable to the 10/100/1000 RJ-45 ports on the front of the Managed Switch.
Connect the other end of the cable to the network devices such as printer server, workstation or router.
Connection to the Managed Switch requires UTP Category 5e network cabling with RJ-45 tips. For
more information, please see the Cabling Specification in Appendix A.
Step 5: Supply power to the Managed Switch.
Connect one end of the power cable to the Managed Switch.
Connect the power plug of the power cable to a standard wall outlet.
When the Managed Switch receives power, the Power LED should remain solid Green.
Page 26
26
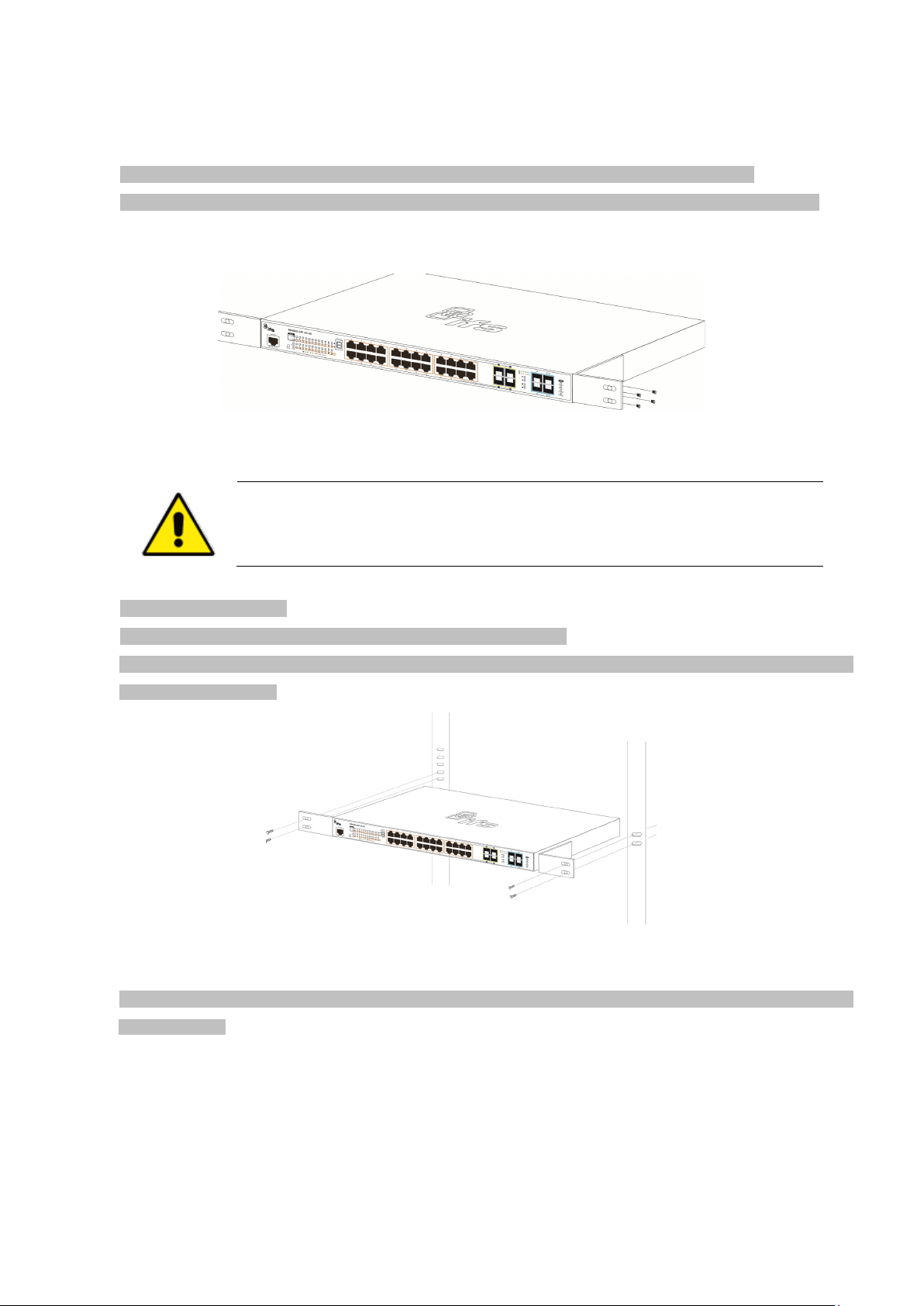
2.2.2 Rack Mounting
st use the screws supplied with the mounting brackets. Damage caused to the parts by
To install the Managed Switch in a 19-inch standard rack, please follow the instructions described below.
Step 1: Place the Managed Switch on a hard flat surface, with the front panel positioned towards the front side.
Step 2: Attach the rack-mount bracket to each side of the Managed Switch with supplied screws attached to the package.
Figure 2-2-2 shows how to attach brackets to one side of the Managed Switch.
Figure 2-2-2: Attach Brackets to the Managed Switch.
You mu
using incorrect screws would invalidate the warranty.
Step 3: Secure the brackets tightly.
Step 4: Follow the same steps to attach the second bracket to the opposite side.
Step 5: After the brackets are attached to the Managed Switch, use suitable screws to securely attach the brackets to the rack,
as shown in Figure 2-2-3.
Figure 2-2-3: Mounting Managed Switch in a Rack
Step 6: Proceed with Steps 4 and 5 of session 2.2.1 Desktop Installation to connect the network cabling and supply power to the
Managed Switch.
2.2.3 Installing the SFP/SFP+ Transceiver
The sections describe how to insert an SFP/SFP+ transceiver into an SFP/SFP+ slot. The SFP/SFP+ transceivers are
hot-pluggable and hot-swappable. You can plug in and out the transceiver to/from any SFP/SFP+ port without having to power
down the Managed Switch, as the Figure 2-2-4 shows..
Page 27
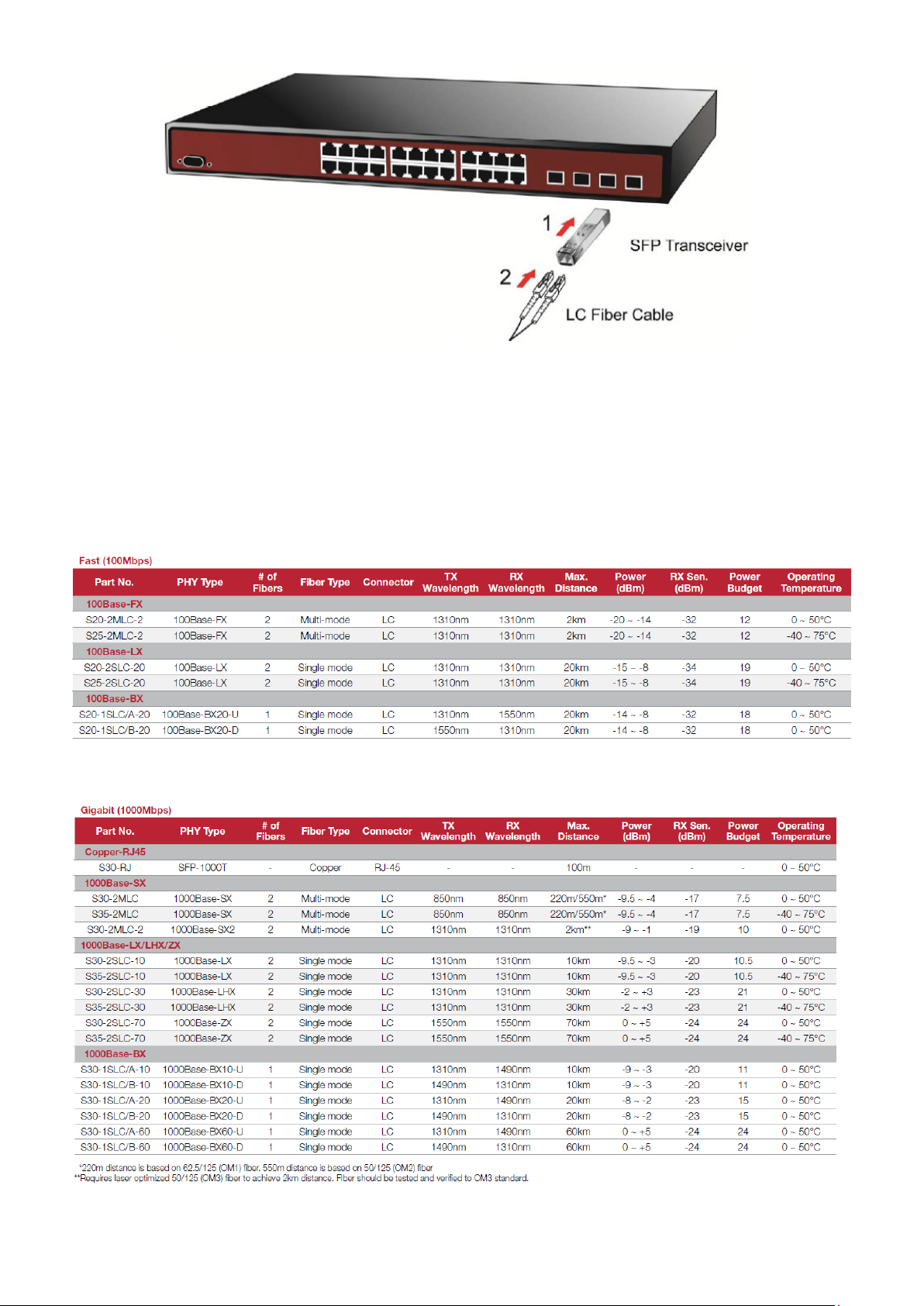
27
Figure 2-2-4: Plug-in the SFP/SFP+ Transceiver
Approved IFS SFP/SFP+ Transceivers
IFS Managed Switch supports both single mode and multi-mode SFP/SFP+ transceiver. The following list of approved IFS
SFP/SFP+ transceivers is correct at the time of publication:
Fast Ethernet Transceiver (100Base-X SFP)
Gigabit Ethernet Transceiver (1000BASX-LX-BX, Fiber Bi-Directional SFP)
Page 28

28
Connector
Interface
Operating Temp.
transceiver that is
Gigabit SFP transceiver.
10Gigabit Ethernet Transceiver (10GBASE-X SFP+)
■ 10 Gigabit Stacked SFP+ slot
10GBASE-SR/LR mini-GBIC slot, SFP+ Transceiver Module supports from 300 meters (multi-mode fiber) to up to 10
kilometers (single-mode fiber)
Model Speed (Mbps)
S40-2MLC 10G LC Multi Mode 300m 850nm
S40-2SLC-10 10G LC Single Mode 10km 1310nm
Fiber Mode Distance Wavelength (nm)
0 ~ 60 ℃
0 ~ 60 ℃
1. It is recommended to use IFS SFP on the Managed Switch. If you insert an SFP
not supported, the Managed Switch will not recognize it.
2. Port 21 to Port 24 are a shared SFP slot that supports the Gigabit and Fast Ethernet SFP
transceiver.
3. Port 25 to Port 26 are a shared SFP+ slot that supports the 10 Gigabit SFP+ transceiver and
1. Before we connect the NS4802 to the other network device, we have to make sure both sides of the SFP transceivers are
with the same media type, for example: 1000BASE-SX to 1000BASE-SX, 1000Bas-LX to 1000BASE-LX.
2. Check whether the fiber-optic cable type matches with the SFP transceiver requirement.
To connect to 1000BASE-SX SFP transceiver, please use the multi-mode fiber cable with one side being the male
duplex LC connector type.
To c onnect to 1000BASE-LX SFP transceiver, please use the single-mode fiber cable with one side being the male
duplex LC connector type.
Connect the Fiber Cable
1. Insert the duplex LC connector into the SFP/SFP+ transceiver.
2. Connect the other end of the cable to a device with SFP/SFP+ transceiver installed.
3. Check the LNK/ACT LED of the SFP/SFP+ slot on the front of the Managed Switch. Ensure that the SFP/SFP+
transceiver is operating correctly.
4. Check the Link mode of the SFP/SFP+ port if the link fails. To function with some fiber-NICs or Media Converters, user
has to set the port Link mode to “10GForce”, “1000 Force” or “100 Force”.
Remove the Transceiver Module
1. Make sure there is no network activity anymore.
2. Remove the Fiber-Optic Cable gently.
3. Lift up the lever of the SFP module and turn it to a horizontal position.
4. Pull out the module gently through the lever.
Page 29

29
rizontal
module
Figure 2-2-5: How to Pull Out the SFP/SFP+ Transceiver
Never pull out the module without lifting up the lever of the module and turning it to a ho
position. Directly pulling out the module could damage the module and the SFP/SFP+
slot of the Managed Switch.
2.3 Stack Installation
NS4802-24P-4S-2X
The NS4802 Managed Switch series provides a switch stacking function to manage up to 16 switches using a single IP address.
And up to 320 Gigabit Ethernet ports, 64 Gigabit TP/SFP ports and 32 high-capacity 10G SFP+ ports can be managed by a
stacking group and you can add ports and functionality as needed. You can add the NS4802 switch as needed to support more
network clients, knowing that your switching fabric will scale to meet increasing traffic demands.
Two types of stack topologies are supported by the NS4802.
Chain topology (same as a disconnected ring)
Ring topology
Page 30
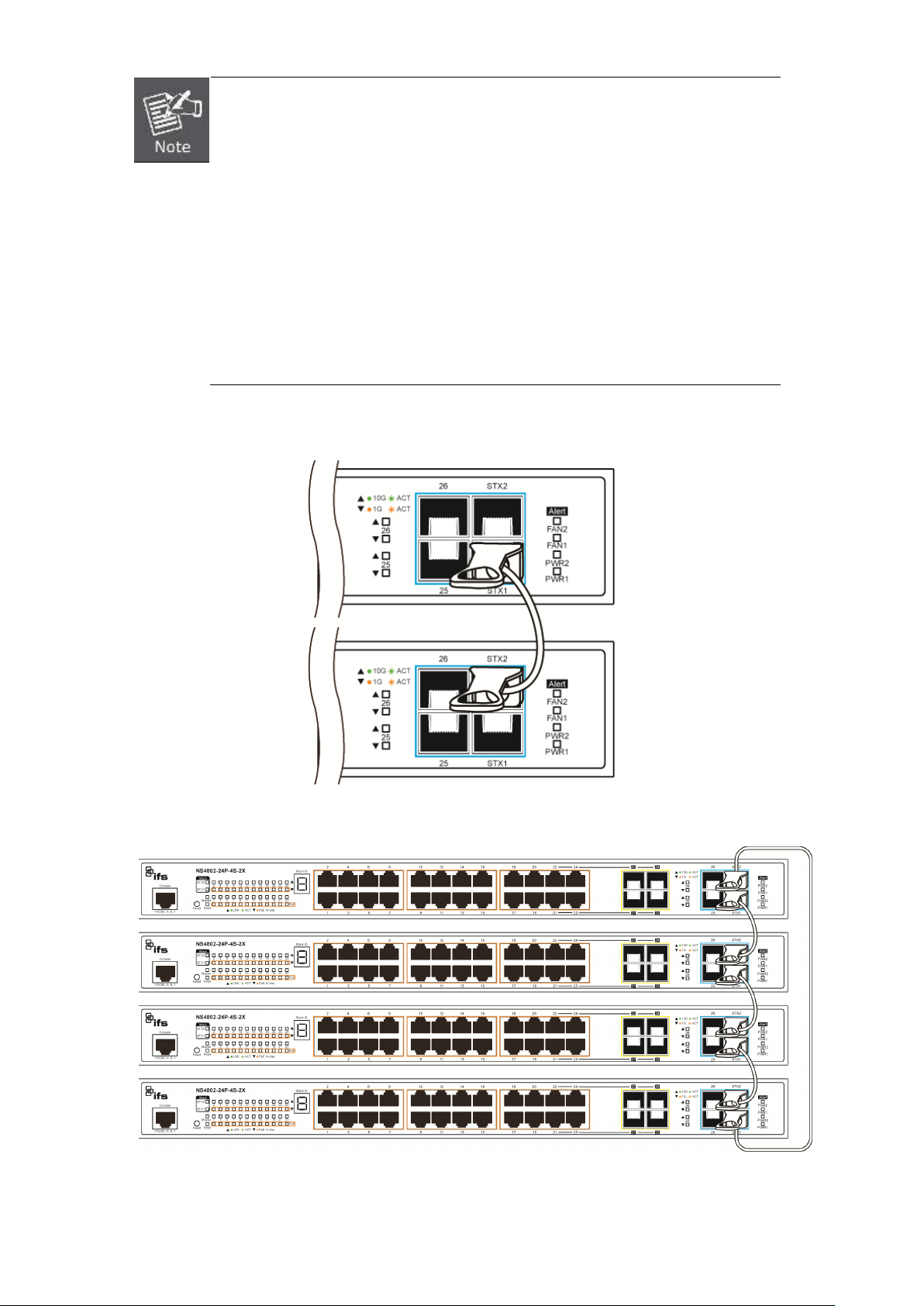
30
,
stacking ports are on the front panel, but the stacking cable
before you make
1. Please note that from now on the stacking example images are coming from NS4802
however, as NS4802-24P
connection rule is totally same with NS3601.
2. if you remove one of switch from stacking group and causes stacking ID without
sequence, please re-assign stacking ID from “Stack Configuration“
the other operation.
3. Stack ports are port27 and port28 and the stacking ports could be used for stacking
only, it can’t be set to “uplink”.
Please find the following picture for sample connection.
Figure 2-21 Chain Stack topology
Figure 2-22 Ring Stack topology
Page 31

31
stackable
2.3.1 Connecting Stacking Cable
Before attempting to connect stacking ports, verify that you have the required stack cables. The following cables are used to
connect stacked switches:
• NS-10G-CBL-50: 10G SFP+ Directly-attached Copper Cable (0.5M in length)
• NS-10G-CBL-2M: 10G SFP+ Directly-attached Copper Cable (2M in length)
• SFP+ Port 10GBASE-LR mini-GBIC Module (single-mode / 1310nm / max. 10km).
• SFP+ Port 10GBASE-SR mini-GBIC Module (multi-mode / 850nm / max. 300m)
• Standard 10GBASE-LR/SR mini-GBIC SFP+ Module.
There are two high-performance SFP+ stacked ports on the front panel for proprietary management stack.
Step 1: Plug one end of the cable into the “STX1” port and the other end into the ”STX2” port of the next device.
Step 2: Repeat the step for every device in the stack cluster, and then ending with the last switch.
Figure 2-23 Stacking Connection
Step 3: If you wish to implement stack redundancy, use the long stack cable to connect the stack port marked “STX1” on the
bottom switch to the port marked “STX2” on the top switch of the stack.
The stack port is for management and data packets to be transmitted between other IFS-5220
switch series. The stack ports can’t be configured with Layer 2 features via management interface.
Step 4: Power up the stack switches.
Page 32

32
nly
2.3.2 Management Stacking
The stack operation of the IFS Managed Switch supports Plug and Play Stacking connection and auto stack configuration.
Step 5: Once the stack starts operation, the Stack master will be automatically elected without any configuration. The Stack
master is indicated by a lit green “Master” LED on the front panel as Figure 2-24 shows.
Figure 2-24 Stack Master with “Master” LED lit
Step 6: When an IFS Switch is added to the stack, a Switch ID is automatically assigned to the IFS Switch. The automatic SID
assignment can be modified by choosing a different Switch ID on the Stack Configuration page. This method allows
Switch IDs to be assigned so that it is easier for the user to remember the ID of each switch.
1. The stack switch with the least priority ID or MAC Address number will become Master. O
Master switch’s management interface (console, Telnet, Web and SNMP) is accessible.
Page 33

33
2m stack cable
2m stack cable
.5m stack cable
It allows to build a stack of up to 16 NS4802 Switches. If there is the space limitation or power issue and you wish to stack all the
switches in different racks, use long stack cables to connect two stacks.
Figure 2-26 Cabling for multiple Stack ring connection
Page 34

34
3. SWITCH MANAGEMENT
This chapter explains the methods that you can use to configure management access to the Managed Switch. It describes the
types of management applications and the communication and management protocols that deliver data between your
management device (workstation or personal computer) and the system. It also contains information about port connection
options.
This chapter covers the following topics:
Requirements
Management Access Overview
Administration Console Access
Web Management Access
SNMP Access
Standards, Protocols, and Related Reading
3.1 Requirements
Workstations running Windows 2000/XP, 2003, Vista/7/8, 2008, MAC OS9 or later, or Linux, UNIX , or other
platforms compatible with TCP/IP protocols.
Workstation is installed with Ethernet NIC (Network Interface Card)
Serial Port connect (Terminal)
• The above PC with COM Port (DB9 / RS-232) or USB-to-RS-232 converter
Ethernet Port connect
• Network cables - Use standard network (UTP) cables with RJ45 connectors.
The above workstation is installed with WEB Browser and JAVA runtime environment Plug-in
It is recommended to use Internet Explore 8.0 or above to access Managed Switch.
Page 35

35
3.2 Management Access Overview
The Managed Switch gives you the flexibility to access and manage it using any or all of the following methods:
An administration console
Web browser interface
An external SNMP-based network management application
The administration console and Web browser interface support are embedded in the Managed Switch software and are
available for immediate use. Each of these management methods has their own advantages. Table 3-1 compares the three
management methods.
Method Advantages Disadvantages
Console
Web Browser
SNMP Agent
• No IP address or subnet needed
• Te xt -based
• Telnet functionality and HyperTerminal
built into Windows
95/98/NT/2000/ME/XP operating
systems
• Secure
• Ideal for configuring the switch remotely
• Compatible with all popular browsers
• Can be accessed from any location
• Most visually appealing
• Communicates with switch functions at
the MIB level
• Based on open standards
• Must be near the switch or use dial-up
connection
• Not convenient for remote users
• Modem connection may prove to be unreliable
or slow
• Security can be compromised (hackers need
only know the IP address and subnet mask)
• May encounter lag times on poor connections
• Requires SNMP manager software
• Least visually appealing of all three methods
• Some settings require calculations
• Security can be compromised (hackers need
only know the community name)
Table 3-1 Comparison of Management Methods
Page 36

36
3.3 Administration Console
The administration console is an internal, character-oriented, and command line user interface for performing system
administration such as displaying statistics or changing option settings. Using this method, you can view the administration
console from a terminal, personal computer, Apple Macintosh, or workstation connected to the Managed Switch's console
(serial) port.
Figure 3-1-1: Console Management
Direct Access
Direct access to the administration console is achieved by directly connecting a terminal or a PC equipped with a
terminal-emulation program (such as HyperTerminal) to the Managed Switch console (serial) port. When using this
management method, a straight DB9 RS-232 cable is required to connect the switch to the PC. After making this connection,
configure the terminal-emulation program to use the following parameters:
The default parameters are:
115200 bps
8 data bits
No parity
1 stop bit
Figure 3-1-2: Terminal Parameter Settings
You can change these settings, if desired, after you log on. This management method is often preferred because you can
remain connected and monitor the system during system reboots. Also, certain error messages are sent to the serial port,
regardless of the interface through which the associated action was initiated. A Macintosh or PC attachment can use any
Page 37

37
terminal-emulation program for connecting to the terminal serial port. A workstation attachment under UNIX can use an emulator
such as TIP.
3.4 Web Management
The Managed Switch offers management features that allow users to manage the Managed Switch from anywhere on the
network through a standard browser such as Microsoft Internet Explorer. After you set up your IP address for the switch, you can
access the Managed Switch's Web interface applications directly in your Web browser by entering the IP address of the
Managed Switch.
Figure 3-1-3: Web Management
You can then use your Web browser to list and manage the Managed Switch configuration parameters from one central location,
just as if you were directly connected to the Managed Switch's console port. Web Management requires either Microsoft
Internet Explorer 7.0 or later, Safari or Mozilla Firefox 1.5 or later.
Figure 3-1-4: Web Main Screen of Managed Switch
3.5 SNMP-based Network Management
You can use an external SNMP-based application to configure and manage the Managed Switch, such as SNMP Network
Manager, HP Openview Network Node Management (NNM) or What’s Up Gold. This management method requires the SNMP
Page 38

38
agent on the switch and the SNMP Network Management Station to use the same community string. This management
different LAN card
method, in fact, uses two community strings: the get community string and the set community string. If the SNMP Net-work
management Station only knows the set community string, it can read and write to the MIBs. However, if it only knows the get
community string, it can only read MIBs. The default getting and setting community strings for the Managed Switch is public.
Figure 3-1-5: SNMP Management
If there are two LAN cards or above in the same administrator PC, choose a
by using the “Select Adapter” tool.
Page 39

39
4. WEB CONFIGURATION
.0 or later version does not allow Java Applets to open sockets. The user has to explicitly
This section introduces the configuration and functions of the Web-based management from Managed Switch.
About Web-based Management
The Managed Switch offers management features that allow users to manage the Managed Switch from anywhere on the
network through a standard browser such as Microsoft Internet Explorer.
The Web-based Management supports Internet Explorer 8.0. It is based on Java Applets with an aim to reduce network
bandwidth consumption, enhance access speed and present an easy viewing screen.
By default, IE8
modify the browser setting to enable Java Applets to use network ports.
The Managed Switch can be configured through an Ethernet connection, making sure the manager PC must be set on the same
IP subnet address with the Managed Switch.
For example, the default IP address of the Managed Switch is 192.168.0.100, then the manager PC should be set at
192.168.0.x (where x is a number between 1 and 254, except 100), and the default subnet mask is 255.255.255.0.
If you have changed the default IP address of the Managed Switch to 192.168.1.1 with subnet mask 255.255.255.0 via console,
then the manager PC should be set at 192.168.1.x (where x is a number between 2 and 254) to do the relative configuration on
manager PC.
Figure 4-1-1: Web Management
Logging on the Managed Switch
1. Use Internet Explorer 7.0 or above Web browser. Enter the factory-default IP address to access the Web interface. The
factory-default IP Address is shown as follows:
http://192.168.0.100
2. When the following login screen appears, please enter the default username "admin" with password “admin” (or the
username/password you have changed via console) to login the main screen of Managed Switch. The login screen in
Figure 4-1-2 appears.
Page 40

40
Figure 4-1-2: Login Screen
Default User name: admin
Default Password: admin
After entering the username and password, the main screen appears as shown in Figure 4-1-3.
Figure 4-1-3: Web Main Page
Now, you can use the Web management interface to continue the switch management or manage the Managed Switch by Web
interface. The Switch Menu on the left of the web Page lets you access all the commands and statistics the Managed Switch
provides.
Page 41

41
1. It is recommended to use Internet Explore 8.0 or above to access Managed Switch.
(Port 27~28)
2. The changed IP address takes effect immediately after clicking on the Save button. You need to
use the new IP address to access the Web interface.
3. For security reason, please change and memorize the new password after this first setup.
4. Only accept command in lowercase letter under web interface.
4.1 Main Web Page
The Managed Switch provides a Web-based browser interface for configuring and managing it. This interface allows you to
access the Managed Switch using the Web browser of your choice. This chapter describes how to use the Managed Switch’s
Web browser interface to configure and manage it.
Main Functions Menu
Help Button
Copper Port Link Status
SFP/SFP+ Port Link Status
(Port 25~26)
Stack Port Link Status
Figure 4-1-4: Web Main Page
Page 42

42
Panel Display
The web agent displays an image of the Managed Switch’s ports. The Mode can be set to display different information for the
ports, including Link up or Link down. Clicking on the image of a port opens the Port Statistics Page.
The port status are illustrated as follows:
State Disabled Down Link
RJ-45 Ports
SFP Ports
Main Menu
Using the onboard web agent, you can define system parameters, manage and control the Managed Switch, and all its ports, or
monitor network conditions. Via the Web-Management, the administrator can set up the Managed Switch by selecting the
functions those listed in the Main Function. The screen in Figure 4-1-5 appears.
Figure 4-1-5: Managed Switch Main Functions Menu
Page 43

43
4.2 System
v4/IPv6 interface and IP routes
provides an overview of the current users. Currently the only way
Managed
the
Use the System menu items to display and configure basic administrative details of the Managed Switch. Under the System, the
following topics are provided to configure and view the system information. This section has the following items:
■ System Information The Managed Switch system information is provided here.
■ IP Configuration Configures the Managed Switch-managed IP
on this Page.
■ IP Status This page displays the status of the IP protocol layer. The status is defined
by the IP interfaces, the IP routes and the neighbour cache (ARP cache)
status.
■ Users Configuration
This Page
to login as another user on the web server is to close and reopen the
browser.
■ Privilege Levels
■ NTP Configuration Configure NTP server on this Page.
■ Time Configuration Configure time parameter on this Page.
■ UPnP Configure UPnP on this Page.
■ DHCP Relay Configure DHCP Relay on this Page.
■ DHCP Relay Statistics This Page provides statistics for DHCP relay.
■ CPU Load This Page displays the CPU load, using an SVG graph.
■ System Log The Managed Switch system log information is provided here.
■ Detailed Log The Managed Switch system detailed log information is provided here.
■ Remote Syslog Configure remote syslog on this Page.
■ SMTP Configuration Configuration SMTP parameters on this Page.
■ Web Firmware Upgrade This Page facilitates an update of the firmware controlling the
■ TFTP Firmware Upgrade Upgrade the firmware via TFTP server
■ Save Startup Config
■ Configuration Download
This Page provides an overview of the privilege levels.
Switch.
This copies running-config to startup-config, thereby ensuring that the
currently active configuration will be used at the next reboot.
You can download the files on the switch.
■ Configuration Upload
■ Configuration Activate
■ Configuration Delete
■ Image Select
■ Factory Default
■ System Reboot You can restart the Managed Switch on this Page. After restarting,
You can upload the files to the switch.
You can activate the configuration file present on the switch.
You can delete the writable files which stored in flash.
Configuration active or alternate firmware on this Page.
You can reset the configuration of the Managed Switch on this Page. Only
the IP configuration is retained.
Managed Switch will boot normally.
Page 44

44
4.2.1 System Information
The System Infomation Page provides information for the current device information. System Information Page helps a switch
administrator to identify the hardware MAC address, software version and system uptime. The screen in Figure 4-2-1 appears.
The Page includes the following fields:
Object Description
• Contact
• Name
• Location
• MAC Address
• Temperature
• System Date
• System Uptime
• Switch ID
• Model
• Software Version
The system contact configured in SNMP | System Information | System Contact.
The system name configured in SNMP | System Information | System Name.
The system location configured in SNMP | System Information | System Location.
The MAC Address of this Managed Switch.
Indicates chipset temperature.
The current (GMT) system time and date. The system time is obtained through the
configured NTP Server, if any.
The period of time the device has been operational.
The stacked ID of the stack group.
Display the switch model name.
The software version of the Managed Switch.
Figure 4-2-1: System Information Page Screenshot
Buttons
Auto-refresh : Check this box to refresh the Page automatically. Automatic refresh occurs every 3 seconds.
: Click to refresh the Page; any changes made locally will be undone.
Page 45

45
4.2.2 IP Configuration
The IP Configuration includes the IP Configuration, IP Interface and IP Routes. The configured column is used to view or
change the IP configuration. The maximum number of interfaces supported is 128 and the maximum number of routes is 32.
The screen in Figure 4-2-2 appears.
Figure 4-2-2: IP Configuration Page Screenshot
The current column is used to show the active IP configuration.
Object Description
• IP Configurations Mode
DNS Server
Configure whether the IP stack should act as a Host or a Router. In
Host mode, IP traffic between interfaces will not be routed. In Router
mode traffic is routed between all interfaces.
This setting controls the DNS name resolution done by the switch. The
following modes are supported:
From any DHCP interfaces
The first DNS server offered from a DHCP lease to a DHCP-enabled
interface will be used.
No DNS server
No DNS server will be used.
Configured
Explicitly provide the IP address of the DNS Server in dotted decimal
notation.
From this DHCP interface
Specify from which DHCP-enabled interface a provided DNS server
Page 46

46
should be preferred.
, and reply as a DNS resolver to the client
The VLAN associated with the IP interface. Only ports in this VLAN will be
0.0.0.0
DNS Proxy
• IP Address Delete
VLAN
IPv4
DHCP
IPv4 Address
IPv6 Address
Enabled
Fallback
Current Lease
Mask Length
When DNS proxy is enabled, system will relay DNS requests to the
currently configured DNS server
devices on the network.
Select this option to delete an existing IP interface.
able to access the IP interface. This field is only available for input when
creating an new interface.
Enable the DHCP client by checking this box.
The number of seconds for trying to obtain a DHCP lease.
For DHCP interfaces with an active lease, this column show the current
interface address, as provided by the DHCP server.
Provide the IP address of this Managed Switch in dotted decimal notation.
The IPv4 network mask, in number of bits (prefix length). Valid values are
between 0 and 30 bits for a IPv4 address.
Provide the IP address of this Managed Switch. A IPv6 address is in
128-bit records represented as eight fields of up to four hexadecimal
• IP Routes Delete
Network
Mask Length
Gateway
Next Hop VLAN
Buttons
: Click to add a new IP interface. A maximum of 128 interfaces is supported.
Mask Length
digits with a colon separating each field (:).
The IPv6 network mask, in number of bits (prefix length). Valid values are
between 1 and 128 bits for a IPv6 address.
Select this option to delete an existing IP route.
The destination IP network or host address of this route. Valid format is
dotted decimal notation
the value
The destination IP network or host mask, in number of bits (prefix length).
The IP address of the IP gateway. Valid format is dotted decimal notation
or a valid IPv6 notation. Gateway and Network must be of the same type.
The VLAN ID (VID) of the specific IPv6 interface associated with the
gateway.
or a valid IPv6 notation. A default route can use
or IPv6 :: notation.
: Click to add a new IP route. A maximum of 32 routes is supported.
: Click to apply changes.
: Click to undo any changes made locally and revert to previously saved values.
Page 47

47
4.2.3 IP Status
LINK
IPv4
IP Status displays the status of the IP protocol layer. The status is defined by the IP interfaces, the IP routes and the neighbour
cache (ARP cache) status. The screen in Figure 4-2-3 appears.
Figure 4-2-3: IP Stat us Page Screenshot
The Page includes the following fields:
Object Description
• IP Interfaces
• IP Routes
• Neighbor Cache
Buttons
Interface The name of the interface.
Type
Address The current address of the interface (of the given type).
Status The status flags of the interface (and/or address).
Network The destination IP network or host address of this route.
Gateway The gateway address of this route.
Status The status flags of the route.
IP Address The IP address of the entry.
Link Address The Link (MAC) address for which a binding to the IP address given exist.
The address type of the entry. This may be
or
.
Auto-refresh : Check this box to refresh the Page automatically. Automatic refresh occurs every 3 seconds.
: Click to refresh the Page.
Page 48

48
4.2.4 Users Configuration
groups, i.e. that is granted the fully control of the device. But others value need to
This Page provides an overview of the current users. Currently the only way to login as another user on the web server is to
close and reopen the browser. After setup is completed, press “Apply” button to take effect. Please login web interface with
new user name and password, the screen in Figure 4-2-4 appears.
Figure 4-2-4: Users Configuration Page Screenshot
The Page includes the following fields:
Object Description
Buttons
• User Name
• Privilege Level
The name identifying the user. This is also a link to Add/Edit User.
The privilege level of the user.
The allowed range is 1 to 15. If the privilege level value is 15, it can access all
refer to each group privilege level. User's privilege should be same or greater
than the group privilege level to have the access of that group.
By default setting, most groups privilege level 5 has the read-only access and
privilege level 10 has the read-write access. And the system maintenance
(software upload, factory defaults and etc.) need user privilege level 15.
Generally, the privilege level 15 can be used for an administrator account,
privilege level 10 for a standard user account and privilege level 5 for a guest
account.
: Click to add a new user.
Page 49

49
Add / Edit User
groups, i.e. that is granted the fully control of the device. But others value need to
This Page configures a user – add, edit or delete user.
Figure 4-2-5: Add / Edit User Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Username
• Password
• Password (again)
• Privilege Level
A string identifying the user name that this entry should belong to. The allowed
string length is 1 to 31. The valid user name is a combination of letters, numbers
and underscores.
The password of the user. The allowed string length is 1 to 31.
Please enter the user’s new password here again to confirm.
The privilege level of the user.
The allowed range is 1 to 15. If the privilege level value is 15, it can access all
refer to each group privilege level. User's privilege should be same or greater
than the group privilege level to have the access of that group.
By default setting, most groups privilege level 5 has the read-only access and
privilege level 10 has the read-write access. And the system maintenance
(software upload, factory defaults and etc.) need user privilege level 15.
Generally, the privilege level 15 can be used for an administrator account,
privilege level 10 for a standard user account and privilege level 5 for a guest
account.
Buttons
: Click to apply changes.
: Click to undo any changes made locally and revert to previously saved values.
: Click to undo any changes made locally and return to the Users.
: Delete the current user. This button is not available for new configurations (Add new user)
Page 50

50
he
mode.
Once the new user is added, the new user entry shown in the Users Configuration Page.
Figure 4-2-6: User Configuration Page Screenshot
If you forget the new password after changing the default password, please press the “Reset”
button on the front panel of the Managed Switch for over 10 seconds and then release it. T
current setting including VLAN will be lost and the Managed Switch will restore to the default
Page 51

51
4.2.5 Privilege Levels
This Page provides an overview of the privilege levels. After setup is completed, please press “Apply” button to take effect.
Please login web interface with new user name and password and the screen in Figure 4-2-7 appears.
Figure 4-2-7: Privilege Levels Configuration Page Screenshot
Page 52

52
The Page includes the following fields:
consists of a single module (e.g. LACP, RSTP or QoS), but a few of them contain
: Authentication, System Access Management, Port (contains Dot1x
Object Description
• Group Name
• Privilege Level
The name identifying the privilege group. In most cases, a privilege level group
more than one. The following description defines these privilege level groups in
details:
System: Contact, Name, Location, Timezone, Log.
Security
port, MAC based and the MAC Address Limit), ACL, HTTPS, SSH, ARP
Inspection and IP source guard.
IP: Everything except 'ping'.
Port: Everything except 'VeriPHY'.
Diagnostics: 'ping' and 'VeriPHY'.
Maintenance: CLI- System Reboot, System Restore Default, System
Password, Configuration Save, Configuration Load and Firmware Load.
Web- Users, Privilege Levels and everything in Maintenance.
Debug: Only present in CLI.
Every privilege level group has an authorization level for the following sub
groups:
Configuration read-only
Configuration/execute read-write
Status/statistics read-only
Status/statistics read-write (e.g. for clearing of statistics).
Buttons
: Click to apply changes.
: Click to undo any changes made locally and revert to previously saved values.
4.2.6 NTP Configuration
Configure NTP on this Page. NTP is an acronym for Network Time Protocol, a network protocol for synchronizing the clocks of
computer systems. NTP uses UDP (data grams) as transport layer. You can specify NTP Servers. The NTP Configuration
screen in Figure 4-2-8 appears.
Page 53

53
the agent forward and to transfer NTP messages between the clients and the
The Page includes the following fields:
Object Description
Figure 4-2-8: NTP Configuration Page Screenshot
Buttons
• Mode
• Server #
: Click to apply changes.
Indicates the NTP mode operation. Possible modes are:
Enabled: Enable NTP mode operation. When enable NTP mode operation,
server when they are not on the same subnet domain.
Disabled: Disable NTP mode operation.
Provide the NTP IPv4 or IPv6 address of this switch. IPv6 address is in 128-bit
records represented as eight fields of up to four hexadecimal digits with a colon
separates each field (:).
For example, 'fe80::215:c5ff:fe03:4dc7'. The symbol '::' is a special syntax that
can be used as a shorthand way of representing multiple 16-bit groups of
contiguous zeros; but it can only appear once. It also used a following legally
IPv4 address. For example, '::192.1.2.34'.
: Click to undo any changes made locally and revert to previously saved values.
4.2.7 Time Configuration
Configure Time Zone on this Page. A Time Zone is a region that has a uniform standard time for legal, commercial, and social
purposes. It is convenient for areas in close commercial or other communication to keep the same time, so time zones tend to
follow the boundaries of countries and their subdivisions. The Time Zone Configuration screen in Figure 4-2-9 appears
Page 54

54
The Page includes the following fields:
s various Time Zones world wide. Select appropriate Time Zone from the drop
Object Description
Figure 4-2-9: Time Configuration Page Screenshot
• Time Zone
• Acronym
• Daylight Saving Time
• Start Time Settings • Week - Select the starting week number.
List
down and click Save to set.
User can set the acronym of the time zone. This is a User configurable acronym
to identify the time zone. ( Range : Up to 16 characters )
This is used to set the clock forward or backward according to the configurations
set below for a defined Daylight Saving Time duration. Select 'Disable' to disable
the Daylight Saving Time configuration. Select 'Recurring' and configure the
Daylight Saving Time duration to repeat the configuration every year. Select
'Non-Recurring' and configure the Daylight Saving Time duration for single time
configuration. ( Default : Disabled ).
• Day - Select the starting day.
Page 55

55
• Month - Select the starting month.
• Hours - Select the starting hour.
• Minutes - Select the starting minute.
• End Time Settings • Week - Select the ending week number.
• Day - Select the ending day.
• Month - Select the ending month.
• Hours - Select the ending hour.
• Minutes - Select the ending minute
• Offset Settings
Buttons
: Click to apply changes.
: Click to undo any changes made locally and revert to previously saved values.
Enter the number of minutes to add during Daylight Saving Time. ( Range: 1 to
1440 )
4.2.8 UPnP
Configure UPnP on this Page. UPnP is an acronym for Universal Plug and Play. The goals of UPnP are to allow devices to
connect seamlessly and to simplify the implementation of networks in the home (data sharing, communications, and
entertainment) and in corporate environments for simplified installation of computer components. The UPnP Configuration
screen in Figure 4-2-10 appears.
Figure 4-2-10: UPnP Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Mode
Indicates the UPnP operation mode. Possible modes are:
Enabled: Enable UPnP mode operation.
Disabled: Disable UPnP mode operation.
Page 56

56
When the mode is enabled, two ACEs are added automatically to trap UPnP
DP packets, is used to inform a control point or control
related packets to CPU. The ACEs are automatically removed when the mode is
disabled.
Buttons
• TTL
• Advertising Duration
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
The TTL value is used by UPnP to send SSDP advertisement messages.
Valid values are in the range of 1 to 255.
The duration, carried in SS
points how often it or they should receive a SSDP advertisement message from
this switch. If a control point does not receive any message within the duration, it
will think that the switch no longer exists. Due to the unreliable nature of UDP, in
the standard it is recommended that such refreshing of advertisements to be
done at less than one-half of the advertising duration. In the implementation, the
switch sends SSDP messages periodically at the interval one-half of the
advertising duration minus 30 seconds. Valid values are in the range 100 to
86400.
Figure 4-2-11: UPnP devices show on Windows My Network Place
4.2.9 DHCP Relay
Configure DHCP Relay on this Page. DHCP Relay is used to forward and to transfer DHCP messages between the clients and
the server when they are not on the same subnet domain.
Page 57

57
The DHCP option 82 enables a DHCP relay agent to insert specific information into a DHCP request packets when forwarding
client DHCP packets to a DHCP server and remove the specific information from a DHCP reply packets when forwarding server
DHCP packets to a DHCP client. The DHCP server can use this information to implement IP address or other assignment
policies. Specifically the option works by setting two sub-options:
Circuit ID (option 1)
Remote ID (option2).
The Circuit ID sub-option is supposed to include information specific to which circuit the request came in on.
The Remote ID sub-option was designed to carry information relating to the remote host end of the circuit.
The definition of Circuit ID in the switch is 4 bytes in length and the format is "vlan_id" "module_id" "port_no". The parameter of
"vlan_id" is the first two bytes representing the VLAN ID. The parameter of "module_id" is the third byte for the module ID (in
standalone switch it always equals 0; in stackable switch it means switch ID). The parameter of "port_no" is the fourth byte and it
means the port number.
The Remote ID is 6 bytes in length, and the value equals the DHCP relay agent’s MAC address. The DHCP Relay Configuration
screen in Figure 4-2-12 appears.
Figure 4-2-12 DHCP Relay Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Relay Mode
• Relay Server
• Relay Information
Mode
Indicates the DHCP relay mode operation. Possible modes are:
Enabled: Enable DHCP relay mode operation. When enabling DHCP relay
mode operation, the agent forwards and transfers DHCP messages between
the clients and the server when they are not on the same subnet domain.
And the DHCP broadcast message won't flood for security considered.
Disabled: Disable DHCP relay mode operation.
Indicates the DHCP relay server IP address. A DHCP relay agent is used to
forward and transfer DHCP messages between the clients and the server when
they are not on the same subnet domain.
Indicates the DHCP relay information mode option operation. Possible modes
are:
Enabled: Enable DHCP relay information mode operation. When enabling
DHCP relay information mode operation, the agent inserts specific
Page 58

58
information (option82) into a DHCP message when forwarding to DHCP
contains relay agent information. It will enforce the policy. And it only works under
server and removing it from a DHCP message when transferring to DHCP
client. It only works under DHCP relay operation mode enabled.
Disabled: Disable DHCP relay information mode operation.
Buttons
• Relay Information
Policy
Indicates the DHCP relay information option policy. When enabling DHCP relay
information mode operation, if agent receives a DHCP message that already
DHCP relay information operation mode enabled. Possible policies are:
Replace: Replace the original relay information when receiving a DHCP
message that already contains it.
Keep: Keep the original relay information when receiving a DHCP message
that already contains it.
Drop: Drop the package when receiving a DHCP message that already
contains relay information.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.2.10 DHCP Relay Statistics
This Page provides statistics for DHCP relay. The DHCP Relay Statistics screen in Figure 4-2-13 appears.
Figure 4-2-13: DHCP Relay Statistics Page Screenshot
The Page includes the following fields:
Server Statistics
Object Description
• Transmit to Server
The packets number that relayed from client to server.
Page 59

59
• Transmit Error
The packets number that errors sending packets to clients.
• Receive from Server
• Receive Missing Agent
Option
• Receive Missing
Circuit ID
• Receive Missing
Remote ID
• Receive Bad Circuit ID
Receive Bad Remote ID The packets number that the Remote ID option did not match known Remote ID.
Client Statistics
Object Description
• Transmit to Client
• Transmit Error
The packets number that received packets from server.
The packets number that received packets without agent information options.
The packets number that received packets which the Circuit ID option was
missing.
The packets number that received packets which Remote ID option was missing.
The packets number that the Circuit ID option did not match known circuit ID.
The packets number that relayed packets from server to client.
The packets number that erroneously sent packets to servers.
• Receive from Client
• Receive Agent Option
• Replace Agent Option
• Keep Agent Option
• Drop Agent Option
Buttons
Auto-refresh : Check this box to refresh the Page automatically. Automatic refresh occurs every 3 seconds.
: Click to refresh the Page immediately.
: Clears all statistics.
The packets number that received packets from server.
The packets number that received packets with relay agent information option.
The packets number that replaced received packets with relay agent information
option.
The packets number that kept received packets with relay agent information
option.
The packets number that dropped received packets with relay agent information
option.
Page 60

60
4.2.11 CPU Load
This Page displays the CPU load, using a SVG graph. The load is measured as average over the last 100ms, 1sec and 10
seconds intervals. The last 120 samles are graphed, and the last numbers are displayed as text as well. In order to display the
SVG graph, your browser must support the SVG format. Consult the SVG Wiki for more information on browser support.
Specifically, at the time of writing, Microsoft Internet Explorer will need to have a plugin installed to support SVG. The CPU Load
screen in Figure 4-2-14 appears.
Figure 4-2-14: CPU Load Page Screenshot
Buttons
Auto-refresh : Check this box to refresh the Page automatically. Automatic refresh occurs every 3 seconds.
If your browser cannot display anything on this Page, please download Adobe SVG tool and
install it in your computer.
Page 61

61
4.2.12 System Log
The Managed Switch system log information is provided here. The System Log screen in Figure 4-2-15 appears.
Figure 4-2-15: System Log Page Screenshot
The Page includes the following fields:
Buttons
Object Description
• ID
• Level
The ID (>= 1) of the system log entry.
The level of the system log entry. The following level types are supported:
Info: Information level of the system log.
Warning: Warning level of the system log.
Error: Error level of the system log.
All: All levels.
• Clear Level
To clear the system log entry level. The following level types are supported:
Info: Information level of the system log.
Warning: Warning level of the system log.
Error: Error level of the system log.
All: All levels.
• Time
• Message
The time of the system log entry.
The message of the system log entry.
Auto-refresh : Check this box to refresh the Page automatically. Automatic refresh occurs every 3 seconds.
: Updates the system log entries, starting from the current entry ID.
: Flushes the selected log entries.
: Hides the selected log entries.
: Downloads the selected log entries.
Page 62

62
: Updates the system log entries, starting from the first available entry ID.
: Updates the system log entries, ending at the last entry currently displayed.
: Updates the system log entries, starting from the last entry currently displayed.
: Updates the system log entries, ending at the last available entry ID.
4.2.13 Detailed Log
The Managed Switch system detailed log information is provided here. The Detailed Log screen in Figure 4-2-16 appears.
The Page includes the following fields:
Object Description
• ID
• Message
Buttons
: Download the system log entry to the current entry ID.
: Updates the system log entry to the current entry ID.
: Updates the system log entry to the first available entry ID.
: Updates the system log entry to the previous available entry ID.
: Updates the system log entry to the next available entry ID.
Figure 4-2-15: Detailed Log Page Screenshot
The ID (>= 1) of the system log entry.
The message of the system log entry.
: Updates the system log entry to the last available entry ID.
: Print the system log entry to the current entry ID.
Page 63

63
4.2.14 Remote Syslog
UDP communication and received on UDP port 514 and the syslog server will not
Configure remote syslog on this Page. The Remote Syslog screen in Figure 4-2-17 appears.
Figure 4-2-17: Remote Syslog Page Screenshot
The Page includes the following fields:
Object Description
Buttons
• Mode
• Syslog Server IP
• Syslog Level
Indicates the server mode operation. When the mode operation is enabled, the
syslog message will send out to syslog server. The syslog protocol is based on
send acknowledgments back sender since UDP is a connectionless protocol and
it does not provide acknowledgments. The syslog packet will always send out
even if the syslog server does not exist. Possible modes are:
Enabled: Enable remote syslog mode operation.
Disabled: Disable remote syslog mode operation.
Indicates the IPv4 host address of syslog server. If the switch provides DNS
feature, it also can be a host name.
Indicates what kind of message will send to syslog server. Possible modes are:
Info: Send information, warnings and errors.
Warning: Send warnings and errors.
Error: Send errors.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Page 64

64
4.2.15 SMTP Configuration
Name
Password
E-mail 1 To
This Page facilitates an SMTP Configuration on the switch. The SMTP Configure screen in Figure 4-2-18 appears.
Figure 4-2-18: SMTP Configuration Page Screenshot
The Page includes the following fields:
Object Description
• SMTP Mode
• SMTP Server
• SMTP Port
• SMTP Authentication
• Authentication User
• Authentication
• E-mail From
• E-mail Subject
•
• E-mail 2 To
Controls whether SMTP is enabled on this switch.
Type the SMTP server name or the IP address of the SMTP server.
Set port number of SMTP service.
Controls whether SMTP authentication is enabled If authentication is required
when an e-mail is sent.
Type the user name for the SMTP server if Authentication is Enable.
Type the password for the SMTP server if Authentication is Enable.
Type the sender’s E-mail address. This address is used for reply e-mails.
Type the subject/title of the e-mail.
Type the receiver’s e-mail address.
Buttons
: Send a test mail to mail server to check this account is available or not.
: Click to save changes.
Page 65

65
: Click to undo any changes made locally and revert to previously saved values.
4.2.16 Web Firmware Upgrade
This Page facilitates an update of the firmware controlling the switch. The Web Firmware Upgrade screen in Figure 4-2-19
appears.
Figure 4-2-19: Web Firmware Upgrade Page Screenshot
To open Firmware Upgrade screen, perform the following:
1. Click System -> Web Firmware Upgrade.
2. The Firmware Upgrade screen is displayed as in Figure 4-2-19.
3. Click the “
4. Select on the firmware then click “
5. Once the software is loaded to the system successfully, the following screen appears. The system will load the new
software after reboot.
“button of the Main Page, the system would pop up the file selection menu to choose firmware.
”, the Software Upload Progress would show the file with upload status.
Figure 4-2-20: Software Successfully Loaded Notice Screen
DO NOT Power OFF the Managed Switch until the update progress is complete.
Do not quit the Firmware Upgrade Page without pressing the “OK” button after the image is
loaded. Or the system won’t apply the new firmware. User has to repeat the firmware
upgrade processes.
Page 66

66
4.2.17 TFTP Firmware Upgrade
The Firmware Upgrade Page provides the functions to allow a user to update the Managed Switch firmware from the TFTP
server in the network. Before updating, make sure you have your TFTP server ready and the firmware image is on the TFTP
server. The TFTP Firmware Upgrade screen in Figure 4-2-21 appears.
Figure 4-2-20: TFTP Firmware Update Page Screenshot
The Page includes the following fields:
Object Description
Buttons
• TFTP Server IP
• Firmware File Name
: Click to upgrade firmware.
DO NOT Power OFF the Managed Switch until the update progress is complete.
Do not quit the Firmware Upgrade Page without pressing the “OK” button after the image is
loaded. Or the system won’t apply the new firmware. User has to repeat the firmware
upgrade processes.
Fill in your TFTP server IP address.
The name of firmware image.
(Maximum length : 24 characters)
Page 67

67
4.2.18 Save Startup Config
This function allows save the current configuration, thereby ensuring that the current active configuration can be used at the
next reboot screen in Figure 4-2-22 appears. After saving the configuratioin, the screen Figure 4-2-23 will appear.
Figure 4-2-22: Configuration Save Page Screenshot
Figure 4-2-23: Finish Saving Page Screenshot
4.2.19 Configuration Download
The switch stores its configuration in a number of text files in CLI format. The files are either virtual (RAM-based) or stored in
flash on the switch.
There are three system files:
• running-config: A virtual file that represents the currently active configuration on the switch. This file is volatile.
• startup-config: The startup configuration for the switch, read at boot time.
• default-config: A read-only file with vendor-specific configuration. This file is read when the system is restored to default
settings.
It is also possible to store up to two other files and apply them to running-config, thereby switching configuration.
Configuration Download page allows the download the running-config, startup-config and default-config on the switch. Please
refer to the Figure 4-2-24 shown below.
Figure 4-2-24: Configuration Download Page Screenshot
Page 68

68
4.2.20 Configuration Upload
Configuration Upload page allows the upload the running-config and startup-config on the switch. Please refer to the Figure
4-2-25 shown below.
Figure 4-2-25: Configuration Upload Page Screenshot
If the destination is running-config, the file will be applied to the switch configuration. This can be done in two ways:
• Replace mode: The current configuration is fully replaced with the configuration in the uploaded file.
• Merge mode: The uploaded file is merged into running-config.
If the file system is full (i.e. contains the three system files mentioned above plus two other files), it is not possible to create new
files, but an existing file must be overwritten or another deleted first.
4.2.21 Configuration Activate
Configuration Activate page allows to activate the startup-config and default-config files present on the switch. Please refer to
the Figure 4-2-26 shown below.
Figure 4-2-26: Configuration Activate Page Screenshot
Page 69

69
It is possible to activate any of the configuration files present on the switch, except for running-config which represents the
n. In this
The firmware version and date information may be empty for older firmware releases. This does
currently active configuration.
Select the file to activate and click
configuration with that of the selected file.
. This will initiate the process of completely replacing the existing
4.2.22 Configuration Delete
Configuration Delete page allows to delete the startup-config and default-config files which stored in FLASH. If this is done and
the switch is rebooted without a prior Save operation, this effectively resets the switch to default configuration. Please refer to
the Figure 4-2-27 shown below.
Figure 4-2-27: Configuration Delete Page Screenshot
4.2.23 Image Select
This Page provides information about the active and alternate (backup) firmware images in the device, and allows you to revert
to the alternate image. The web Page displays two tables with information about the active and alternate firmware images. The
Image Select screen in Figure 4-2-28 appears.
In case the active firmware image is the alternate image, only the "Active Image" table is show
case, the Activate Alternate Image button is also disabled.
1. If the alternate image is active (due to a corruption of the primary image or by manual
intervention), uploading a new firmware image to the device will automatically use the primary
image slot and activate this.
2.
not constitute an error.
Page 70

70
Figure 4-2-28: Software Image Selection Page Screenshot
The Page includes the following fields:
Object Description
• Image
• Version
• Date
Buttons
: Click to use the alternate image. This button may be disabled depending on system state.
The flash index name of the firmware image. The name of primary (preferred)
image is image, the alternate image is named image.bk.
The version of the firmware image.
The date where the firmware was produced.
4.2.24 Factory Default
You can reset the configuration of the Managed Switch on this Page. Only the IP configuration is retained. The new
configuration is available immediately, which means that no restart is necessary. The Factory Default screen in Figure 4-2-29
appears.
Page 71

71
Figure 4-2-29: Factory Default Page Screenshot
To reset the Managed Switch to the Factory default setting, you can also press the hardware reset button
completely or
on, you can use
Buttons
: Click to reset the configuration to Factory Defaults.
: Click to return to the Port State Page without resetting the configuration.
at the front panel about 10 seconds. After the device be rebooted. You can login the management WEB
interface within the same subnet of 192.168.0.xx.
4.2.25 System Reboot
The Reboot Page enables the device to be rebooted from a remote location. Once the Reboot button is pressed, user have to
re-login the WEB interface about 60 seconds later, the System Reboot screen in Figure 4-2-30 appears.
Buttons
Figure 4-2-30: System Reboot Page Screenshot
: Click to reboot the system.
: Click to return to the Port State Page without rebooting the system.
You can also check the SYS LED at the front panel to identify whether the System is loaded
not. If the SYS LED is blinking, then it is in the firmware load stage; if the SYS LED light is
the WEB browser to login the Managed Switch.
Page 72

72
4.3 Simple Network Management Protocol
:
4.3.1 SNMP Overview
The Simple Network Management Protocol (SNMP) is an application layer protocol that facilitates the exchange of management
information between network devices. It is part of the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite.
SNMP enables network administrators to manage network performance, find and solve network problems, and plan for network
growth.
An SNMP-managed network consists of three key components: Network management stations (NMSs), SNMP agents,
Management information base (MIB) and network-management protocol:
■ Network management stations (NMSs)
that monitor and control network elements. Physically, NMSs are usually engineering workstation-caliber computers with
fast CPUs, megapixel color displays, substantial memory, and abundant disk space. At least one NMS must be present in
each managed environment.
■ Agents:Agents are software modules that reside in network elements. They collect and store management information
such as the number of error packets received by a network element.
■ Management information base (MIB):A MIB is a collection of managed objects residing in a virtual information store.
Sometimes called consoles, these devices execute management applications
Collections of related managed objects are defined in specific MIB modules.
■ Network-management protocol:A management protocol is used to convey management information between agents
and NMSs. SNMP is the Internet community's de facto standard management protocol.
SNMP Operations
SNMP itself is a simple request/response protocol. NMSs can send multiple requests without receiving a response.
■ Get -- Allows the NMS to retrieve an object instance from the agent.
■ Set -- Allows the NMS to set values for object instances within an agent.
■ Trap -- Used by the agent to asynchronously inform the NMS of some event. The SNMPv2 trap message is designed to
replace the SNMPv1 trap message.
SNMP community
Page 73

73
An SNMP community is the group that devices and management stations running SNMP belong to. It helps define where
information is sent. The community name is used to identify the group. A SNMP device or agent may belong to more than one
SNMP community. It will not respond to requests from management stations that do not belong to one of its communities. SNMP
default communities are:
。 Write = private
。 Read = public
Use the SNMP Menu to display or configure the Managed Switch's SNMP function. This section has the following items:
System Configuration Configure SNMP on this Page.
Trap Configuration Configure SNMP trap on this Page.
System Information The system information is provided here.
SNMPv3 Communities Configure SNMPv3 communities table on this Page.
SNMPv3 Users Configure SNMPv3 users table on this Page.
SNMPv3 Groups Configure SNMPv3 groups table on this Page.
SNMPv3 Views Configure SNMPv3 views table on this Page.
SNMPv3 Access Configure SNMPv3 accesses table on this Page.
4.3.2 SNMP System Configuration
Configure SNMP on this Page. The SNMP System Configuration screen in Figure 4-3-1 appears.
Figure 4-3-1: SNMP System Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Mode
Indicates the SNMP mode operation. Possible modes are:
Enabled: Enable SNMP mode operation.
Disabled: Disable SNMP mode operation.
• Version
Indicates the SNMP supported version. Possible versions are:
SNMP v1: Set SNMP supported version 1.
SNMP v2c: Set SNMP supported version 2c.
Page 74

74
SNMP v3: Set SNMP supported version 3.
SNMP version is SNMPv3, the community string will be associated with SNMPv3
• Read Community
• Write Community
Indicates the community read access string to permit access to SNMP agent.
The allowed string length is 0 to 255, and the allowed content is the ASCII
characters from 33 to 126.
The field is applicable only when SNMP version is SNMPv1 or SNMPv2c. If
communities table. It provides more flexibility to configure security name than a
SNMPv1 or SNMPv2c community string. In addition to community string, a
particular range of source addresses can be used to restrict source subnet.
Indicates the community write access string to permit access to SNMP agent.
The allowed string length is 0 to 255, and the allowed content is the ASCII
characters from 33 to 126.
The field is applicable only when SNMP version is SNMPv1 or SNMPv2c. If
SNMP version is SNMPv3, the community string will be associated with SNMPv3
communities table. It provides more flexibility to configure security name than a
SNMPv1 or SNMPv2c community string. In addition to community string, a
Buttons
particular range of source addresses can be used to restrict source subnet.
• Engine ID
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Indicates the SNMPv3 engine ID. The string must contain an even number
between 10 and 64 hexadecimal digits, but all-zeros and all-'F's are not allowed.
Change of the Engine ID will clear all original local users.
Page 75

75
4.3.3 SNMP Trap Configuration
Configure SNMP trap on this Page. The SNMP Trap Configuration screen in Figure 4-3-2 appears.
Figure 4-3-2: SNMP Trap Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Tr ap Config
• Trap Mode
Indicates which trap Configuration's name for configuring. The allowed string
length is 0 to 255, and the allowed content is ASCII characters from 33 to 126.
Indicates the SNMP trap mode operation. Possible modes are:
Enabled: Enable SNMP trap mode operation.
Disabled: Disable SNMP trap mode operation.
• Trap Version
Indicates the SNMP trap supported version. Possible versions are:
Page 76

76
SNMP v1: Set SNMP trap supported version 1.
allowed string length is 0 to 255, and the allowed content is the ASCII characters
Indicates the SNMP trap destination port. SNMP Agent will send SNMP message
SNMP v2c: Set SNMP trap supported version 2c.
SNMP v3: Set SNMP trap supported version 3.
• Trap Community
• Trap Destination
Address
• Trap Destination Port
• Trap Inform Mode
• Trap Inform Timeout
(seconds)
• Trap Inform Retry
Times
• Trap Probe Security
Engine ID
Indicates the community access string when send SNMP trap packet. The
from 33 to 126.
Indicates the SNMP trap destination address.
via this port, the port range is 1~65535.
Indicates the SNMP trap inform mode operation. Possible modes are:
Enabled: Enable SNMP trap authentication failure.
Disabled: Disable SNMP trap authentication failure.
Indicates the SNMP trap inform timeout.
The allowed range is 0 to 2147.
Indicates the SNMP trap inform retry times.
The allowed range is 0 to 255.
Indicates the SNMPv3 trap probe security engine ID mode of operation. Possible
values are:
• Trap Security Engine
ID
• Trap Security Name
• System
• Interface
Enabled: Enable SNMP trap probe security engine ID mode of operation.
Disabled: Disable SNMP trap probe security engine ID mode of operation.
Indicates the SNMP trap security engine ID. SNMPv3 sends traps and informs
using USM for authentication and privacy. A unique engine ID for these traps and
informs is needed. When "Trap Probe Security Engine ID" is enabled, the ID will
be probed automatically. Otherwise, the ID specified in this field is used. The
string must contain an even number(in hexadecimal format) with number of digits
between 10 and 64, but all-zeros and all-'F's are not allowed.
Indicates the SNMP trap security name. SNMPv3 traps and informs using USM
for authentication and privacy. A unique security name is needed when traps and
informs are enabled.
Enable/disable that the Interface group's traps. Possible traps are:
Warm Start: Enable/disable Warm Start trap.
Cold Start: Enable/disable Cold Start trap.
Indicates that the Interface group's traps. Possible traps are:
Link Up: Enable/disable Link up trap.
Link Down: Enable/disable Link down trap.
LLDP: Enable/disable LLDP trap.
• AAA
Indicates that the AAA group's traps. Possible traps are:
Authentication Fail : Enable/disable SNMP trap authentication failure trap.
Page 77

77
• Switch
An administratively assigned name for this managed node. By convention, this is
the first or last character must not be a minus sign. The allowed string length is 0
string length is 0 to 255, and the allowed content is the ASCII characters from 32
Indicates that the Switch group's traps. Possible traps are:
STP: Enable/disable STP trap.
RMON: Enable/disable RMON trap.
Buttons
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.3.4 SNMP System Information
The switch system information is provided here. The SNMP System Information screen in Figure 4-3-3 appears.
Figure 4-3-3: System Information Configuration Page Screenshot
The Page includes the following fields:
Object Description
• System Contact
• System Name
• System Location
The textual identification of the contact person for this managed node, together
with information on how to contact this person. The allowed string length is 0 to
255, and the allowed content is the ASCII characters from 32 to 126.
the node's fully-qualified domain name. A domain name is a text string drawn
from the alphabet (A-Za-z), digits (0-9), minus sign (-). No space characters are
permitted as part of a name. The first character must be an alpha character. And
to 255.
The physical location of this node(e.g., telephone closet, 3rd floor). The allowed
to 126.
Page 78

78
4.3.5 SNMPv3 Configuration
allowed string length is 1 to 32, and the allowed content is ASCII characters from
4.3.5.1 SNMPv3 Communities
Configure SNMPv3 communities table on this Page. The entry index key is Community. The SNMPv3 Communities screen in
Figure 4-3-4 appears.
Figure 4-3-4: SNMPv3 Communities Configuration Page Screenshot
The Page includes the following fields:
Object Description
Buttons
• Delete
• Community
• Source IP
• Source Mask
: Click to add a new community entry.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Check to delete the entry. It will be deleted during the next save.
Indicates the community access string to permit access to SNMPv3 agent. The
33 to 126. The community string will be treated as security name and map a
SNMPv1 or SNMPv2c community string.
Indicates the SNMP access source address. A particular range of source
addresses can be used to restrict source subnet when combined with source
mask.
Indicates the SNMP access source address mask.
Page 79

79
4.3.5.2 SNMPv3 Users
string must contain an even number(in hexadecimal format) with number of digits
value. The value can also take the value of the snmpEngineID of a remote SNMP
Configure SNMPv3 users table on this Page. The entry index keys are Engine ID and User Name. The SNMPv3 Users screen
in Figure 4-3-5 appears.
Figure 4-3-5: SNMPv3 Users Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Delete
• Engine ID
• User Name
• Security Level
Check to delete the entry. It will be deleted during the next save.
An octet string identifying the engine ID that this entry should belong to. The
between 10 and 64, but all-zeros and all-'F's are not allowed. The SNMPv3
architecture uses the User-based Security Model (USM) for message security
and the View-based Access Control Model (VACM) for access control. For the
USM entry, the usmUserEngineID and usmUserName are the entry's keys.
In a simple agent, usmUserEngineID is always that agent's own snmpEngineID
engine with which this user can communicate. In other words, if user engine ID
equal system engine ID then it is local user; otherwise it's remote user.
A string identifying the user name that this entry should belong to. The allowed
string length is 1 to 32, and the allowed content is ASCII characters from 33 to
126.
Indicates the security model that this entry should belong to. Possible security
models are:
NoAuth, NoPriv: None authentication and none privacy.
Auth, NoPriv: Authentication and none privacy.
Auth, Priv: Authentication and privacy.
• Authentication
Protocol
The value of security level cannot be modified if entry already exist. That means
must first ensure that the value is set correctly.
Indicates the authentication protocol that this entry should belong to. Possible
authentication protocol are:
None: None authentication protocol.
Page 80

80
MD5: An optional flag to indicate that this user using MD5 authentication
allowed string length is 8 to 40. The allowed content is the ASCII characters from
protocol.
SHA: An optional flag to indicate that this user using SHA authentication
protocol.
The value of security level cannot be modified if entry already exist. That means
must first ensure that the value is set correctly.
Buttons
• Authentication
Password
• Privacy Protocol
• Privacy Password
: Click to add a new user entry.
A string identifying the authentication pass phrase. For MD5 authentication
protocol, the allowed string length is 8 to 32. For SHA authentication protocol, the
33 to 126.
Indicates the privacy protocol that this entry should belong to. Possible privacy
protocol are:
None: None privacy protocol.
DES: An optional flag to indicate that this user using DES authentication
protocol.
AES: An optional flag to indicate that this user uses AES authentication
protocol.
A string identifying the privacy pass phrase. The allowed string length is 8 to 32,
and the allowed content is the ASCII characters from 33 to 126.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.3.5.3 SNMPv3 Groups
Configure SNMPv3 groups table on this Page. The entry index keys are Security Model and Security Name. The SNMPv3
Groups screen in Figure 4-3-6 appears.
Figure 4-3-6: SNMPv3 Groups Configuration Page Screenshot
Page 81

81
The Page includes the following fields:
Object Description
Buttons
• Delete
• Security Model
• Security Name
• Group Name
: Click to add a new group entry.
Check to delete the entry. It will be deleted during the next save.
Indicates the security model that this entry should belong to. Possible security
models are:
v1: Reserved for SNMPv1.
v2c: Reserved for SNMPv2c.
usm: User-based Security Model (USM).
A string identifying the security name that this entry should belong to.
The allowed string length is 1 to 32, and the allowed content is the ASCII
characters from 33 to 126.
A string identifying the group name that this entry should belong to.
The allowed string length is 1 to 32, and the allowed content is the ASCII
characters from 33 to 126.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.3.5.4 SNMPv3 Views
Configure SNMPv3 views table on this Page. The entry index keys are View Name and OID Subtree. The SNMPv3 Views
screen in Figure 4-3-7 appears.
Figure 4-3-7: SNMPv3 Views Configuration Page Screenshot
Page 82

82
The Page includes the following fields:
eneral, if a view entry's view type is 'excluded', it should be exist another view
Object Description
Buttons
• Delete
• View Name
• V iew Type
• OID Subtree
Check to delete the entry. It will be deleted during the next save.
A string identifying the view name that this entry should belong to. The allowed
string length is 1 to 32, and the allowed content is the ASCII characters from 33
to 126.
Indicates the view type that this entry should belong to. Possible view type are:
included: An optional flag to indicate that this view subtree should be
included.
excluded: An optional flag to indicate that this view subtree should be
excluded.
In g
entry which view type is 'included' and it's OID subtree overstep the 'excluded'
view entry.
The OID defining the root of the subtree to add to the named view. The allowed
OID length is 1 to 128. The allowed string content is digital number or asterisk(*).
: Click to add a new view entry.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.3.5.5 SNMPv3 Access
Configure SNMPv3 accesses table on this Page. The entry index keys are Group Name, Security Model and Security Level.
The SNMPv3 Access screen in Figure 4-3-8 appears.
Figure 4-3-8: SNMPv3 Accesses Configuration Page Screenshot
The Page includes the following fields:
Page 83

83
Object Description
• Delete
• Group Name
• Security Model
• Security Level
• Read View Name
Check to delete the entry. It will be deleted during the next save.
A string identifying the group name that this entry should belong to. The allowed
string length is 1 to 32, and the allowed content is the ASCII characters from 33
to 126.
Indicates the security model that this entry should belong to. Possible security
models are:
any: Accepted any security model (v1|v2c|usm).
v1: Reserved for SNMPv1.
v2c: Reserved for SNMPv2c.
usm: User-based Security Model (USM)
Indicates the security model that this entry should belong to. Possible security
models are:
NoAuth, NoPriv: None authentication and none privacy.
Auth, NoPriv: Authentication and none privacy.
Auth, Priv: Authentication and privacy.
The name of the MIB view defining the MIB objects for which this request may
Buttons
request the current values. The allowed string length is 1 to 32, and the allowed
content is the ASCII characters from 33 to 126.
• Write View Name
: Click to add a new access entry.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
The name of the MIB view defining the MIB objects for which this request may
potentially SET new values. The allowed string length is 1 to 32, and the allowed
content is the ASCII characters from 33 to 126.
Page 84

84
4.4 Port Management
Use the Port Menu to display or configure the Managed Switch's ports. This section has the following items:
Port Configuration Configures port connection settings
Port Statistics Overview Lists Ethernet and RMON port statistics
Port Statistics Detail Lists Ethernet and RMON port statistics
SFP Module Information Display SFP information
Port Mirror Sets the source and target ports for mirroring
4.4.1 Port Configuration
This Page displays current port configurations. Ports can also be configured here. The Port Configuration screen in Figure 4-4-1
appears.
Figure 4-4-1: Port Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Port
• Port Description
• Link
This is the logical port number for this row.
Indicates the per port description.
The current link state is displayed graphically. Green indicates the link is up and
red that it is down.
Page 85

85
• Current Link Speed
The
Provides the current link speed of the port.
• Configured Link Speed
• Flow Control
Select any available link speed for the given switch port. Draw the menu bar to
select the mode.
Auto - Setup Auto negotiation for copper interface.
10Mbps HDX - Force sets 10Mbps/Half-Duplex mode.
10Mbps FDX - Force sets 10Mbps/Full-Duplex mode.
100Mbps HDX - Force sets 100Mbps/Half-Duplex mode.
100Mbps FDX - Force sets 100Mbps/Full-Duplex mode.
1Gbps FDX - Force sets 10000Mbps/Full-Duplex mode.
Auto Fiber (10G) – Setup 10G firber port for negotiation
automatically.
Disable - Shutdown the port manually.
When Auto Speed is selected on a port, this section indicates the flow control
capability that is advertised to the link partner.
When a fixed-speed setting is selected, that is what is used. The Current Rx
column indicates whether pause frames on the port are obeyed, and the Current
Tx column indicates whether pause frames on the port are transmitted. The Rx
and Tx settings are determined by the result of the last Auto-Negotiation.
Buttons
Check the configured column to use flow control. This setting is related to the
setting for Configured Link Speed.
• Maximum Frame Size
• Excessive Collision
Mode
When set each port to run at 100M Full, 100M Half, 10M Full, and 10M Half-speed modes.
Auto-MDIX function will disable.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Enter the maximum frame size allowed for the switch port, including FCS. The
allowed range is 1518 bytes to 10056 bytes.
Configure port transmit collision behavior.
Discard: Discard frame after 16 collisions (default).
Restart: Restart back off algorithm after 16 collisions.
: Click to refresh the Page. Any changes made locally will be undone.
Page 86

86
4.4.2 Port Statistics Overview
This Page provides an overview of general traffic statistics for all switch ports. The Port Statistics Overview screen in Figure
4-4-2 appears.
The displayed counters are:
Object Description
• Port
• Packets
• B ytes
• Errors
• Drops
• Filtered
Buttons
: Download the Port Statistics Overview result as EXECL file.
Figure 4-4-2: Port Statistics Overview Page Screenshot
The logical port for the settings contained in the same row.
The number of received and transmitted packets per port.
The number of received and transmitted bytes per port.
The number of frames received in error and the number of incomplete
transmissions per port.
The number of frames discarded due to ingress or egress congestion.
The number of received frames filtered by the forwarding process.
: Click to refresh the Page immediately.
: Clears the counters for all ports.
: Print the Port Statistics Overview result.
Auto-refresh : Check this box to enable an automatic refresh of the Page at regular intervals.
Page 87

87
4.4.3 Port Statistics Detail
This Page provides detailed traffic statistics for a specific switch port. Use the port select box to select which switch port details
to display. The selected port belong to the currently selected stack unit, as reflected by the Page header. The displayed counters
are the totals for receive and transmit, the size counters for receive and transmit, and the error counters for receive and transmit.
The Port Statistics Detail screen in Figure 4-4-3 appears.
Figure 4-4-3: Detailed Port Statistics Port 1 Page Screenshot
The Page includes the following fields:
Receive Total and Transmit Total
Object Description
• Rx and Tx Packets
• Rx and Tx Octets
• Rx and Tx Unicast
• Rx and Tx Multicast
• Rx and Tx Broadcast
• Rx and Tx Pause
The number of received and transmitted (good and bad) packets
The number of received and transmitted (good and bad) bytes, including FCS,
but excluding framing bits.
The number of received and transmitted (good and bad) unicast packets.
The number of received and transmitted (good and bad) multicast packets.
The number of received and transmitted (good and bad) broadcast packets.
A count of the MAC Control frames received or transmitted on this port that has
an opcode indicating a PAUSE operation.
Page 88

88
Receive and Transmit Size Counters
The number of received and transmitted (good and bad) packets split into categories based on their respective frame
sizes.
Receive and Transmit Queue Counters
The number of received and transmitted packets per input and output queue.
Receive Error Counters
Object Description
• Rx Drops
• Rx CRC/Alignment
• Rx Undersize
• Rx Oversize
• Rx Fragments
• Rx Jabber
• Rx Filtered
The number of frames dropped due to lack of receive buffers or egress
congestion.
The number of frames received with CRC or alignment errors.
The number of short frames received with valid CRC.
The number of long frames received with valid CRC.
The number of short frames received with invalid CRC.
The number of long frames received with invalid CRC.
The number of received frames filtered by the forwarding process.
Short frames are frames that are smaller than 64 bytes.
Long frames are frames that are longer than the configured maximum
frame length for this port.
1 Short frames are frames that are smaller than 64 bytes.
2 Long frames are frames that are longer than the configured maximum frame length for this port.
Transmit Error Counters
Object Description
• Tx Drops
• Tx Late/Exc. Coll.
Buttons
: Click to refresh the Page immediately.
: Clears the counters for all ports.
Auto-refresh : Check this box to enable an automatic refresh of the Page at regular intervals.
The number of frames dropped due to output buffer congestion.
The number of frames dropped due to excessive or late collisions.
Page 89

89
4.4.4 SFP Module Information
100BASE-FX
se this column to check if the wavelength values of two nodes
The WGSW-48040HP has supported the SFP module with digital diagnostics monitoring (DDM) function, this feature is also
known as digital optical monitoring (DOM). You can check the physical or operational status of an SFP module via the SFP
Module Information Page. This Page shows the operational status, such as the transceiver type, speed, wavelength, optical
output power, optical input power, temperature, laser bias current and transceiver supply voltage in real time. You can also use
the hyperlink of port no. to check the statistics on a speficic interface. The SFP Module Information screen in Figure 4-4-4
appears.
Figure 4-4-4: SFP Module Information for Switch Page Screenshot
The Page includes the following fields:
Object Description
• Type
• Speed
• Wave Length(nm)
Display the type of current SFP module, the possible types are:
10GBASE-SR
10GBASE-LR
1000BASE-SX
1000BASE-LX
Display the spedd of current SFP module, the speed value or description is get
from the SFP module. Different vendors SFP modules might shows different
speed information.
Display the wavelength of current SFP module, the wavelength value is get from
the SFP module. U
are the matched while the fiber connection is failed.
• Distance(m)
• Temperature(C)
– SFP DDM Module Only
Display the supports distance of current SFP module, the distance value is get
from the SFP module.
Display the temperature of current SFP DDM module, the temperature value is
get from the SFP DDM module.
Page 90

90
• Voltage(V)
Display the voltage of current SFP DDM module, the voltage value is get from the
– SFP DDM Module Only
• Current(mA)
– SFP DDM Module Only
• TX power(dBm)
– SFP DDM Module Only
• RX power(dBm)
– SFP DDM Module Only
Buttons
SFP Monitor Event Alert:
Warning Temperature:
Check SFP Monitor Event Alert box; it will be in accordance with your warning temperature setting and allows users to
record message out via SNMP Trap.
Auto-refresh
: Check this box to enable an automatic refresh of the Page at regular intervals.
SFP DDM module.
Display the Ampere of current SFP DDM module, the Ampere value is get from
the SFP DDM module.
Display the TX power of current SFP DDM module, the TX power value is get
from the SFP DDM module.
Display the RX power of current SFP DDM module, the RX power value is get
from the SFP DDM module.
send trap
degrees C
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
: Click to refresh the Page immediately.
4.4.5 Port Mirror
Configure port Mirroring on this Page. This function provide to monitoring network traffic that forwards a copy of each incoming
or outgoing packet from one port of a network Switch to another port where the packet can be studied. It enables the manager to
keep close track of switch performance and alter it if necessary.
• To debug network problems, selected traffic can be copied, or mirrored, to a mirror port where a frame analyzer can be
attached to analyze the frame flow.
• The Managed Switch can unobtrusively mirror traffic from any port to a monitor port. You can then attach a protocol
analyzer or RMON probe to this port to perform traffic analysis and verify connection integrity.
Page 91

91
Figure 4-4-7: Port Mirror Application
The traffic to be copied to the mirror port is selected as follows:
• All frames received on a given port (also known as ingress or source mirroring).
• All frames transmitted on a given port (also known as egress or destination mirroring).
Mirror Port Configuration
The Port Mirror screen in Figure 4-4-8 appears.
Figure 4-4-8: Mirror Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Port to mirror on
Frames from ports that have either source (rx) or destination (tx) mirroring enabled are
mirrored to this port. Disabled disables mirroring.
Page 92

92
• Port
It is therefore not possible to mirror Tx frames on
The logical port for the settings contained in the same row.
Buttons
• Mode
For a given port, a frame is only transmitted once.
the mirror port. Because of this, mode for the selected mirror port is limited to Disabled or Rx only.
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Select mirror mode.
■ Rx only: Frames received at this port are mirrored to the mirroring port. Frames
transmitted are not mirrored.
■ Tx only: Frames transmitted from this port are mirrored to the mirroring port. Frames
received are not mirrored.
■ Disabled: Neither frames transmitted or frames received are mirrored.
■ Both: Frames received and frames transmitted are mirrored to the mirror port.
Page 93

93
4.5 Link Aggregation
Port Aggregation optimizes port usage by linking a group of ports together to form a single Link Aggregated Groups (LAGs). Port
Aggregation multiplies the bandwidth between the devices, increases port flexibility, and provides link redundancy.
Each LAG is composed of ports of the same speed, set to full-duplex operations. Ports in a LAG, can be of different media types
(UTP/Fiber, or different fiber types), provided they operate at the same speed.
Aggregated Links can be assigned manually (Port Trunk) or automatically by enabling Link Aggregation Control Protocol
(LACP) on the relevant links.
Aggregated Links are treated by the system as a single logical port. Specifically, the Aggregated Link has similar port attributes
to a non-aggregated port, including auto-negotiation, speed, Duplex setting, etc.
The device supports the following Aggregation links :
Static LAGs (Port Trunk) – Force aggregared selected ports to be a trunk group.
Link Aggregation Control Protocol (LACP) LAGs - LACP LAG negotiate Aggregated Port links with other LACP
ports located on a different device. If the other device ports are also LACP ports, the devices establish a LAG
between them.
Figure 4-5-1: Link Aggregation
Page 94

94
The Link Aggregation Control Protocol (LACP) provides a standardized means for exchanging information between Partner
Systems that require high speed redundant links. Link aggregation lets you group up to eight consecutive ports into a single
dedicated connection. This feature can expand bandwidth to a device on the network. LACP operation requires full-duplex mode,
more detail information refer to the IEEE 802.3ad standard.
Port link aggregations can be used to increase the bandwidth of a network connection or to ensure fault recovery. Link
aggregation lets you group up to 4 consecutive ports into a single dedicated connection between any two the Switch or other
Layer 2 switches. However, before making any physical connections between devices, use the Link aggregation Configuration
menu to specify the link aggregation on the devices at both ends. When using a port link aggregation, note that:
• The ports used in a link aggregation must all be of the same media type (RJ-45, 100 Mbps fiber).
• The ports that can be assigned to the same link aggregation have certain other restrictions (see below).
• Ports can only be assigned to one link aggregation.
• The ports at both ends of a connection must be configured as link aggregation ports.
• None of the ports in a link aggregation can be configured as a mirror source port or a mirror target port.
• All of the ports in a link aggregation have to be treated as a whole when moved from/to, added or deleted from a VLAN.
• The Spanning Tree Protocol will treat all the ports in a link aggregation as a whole.
• Enable the link aggregation prior to connecting any cable between the switches to avoid creating a data loop.
• Disconnect all link aggregation port cables or disable the link aggregation ports before removing a port link aggregation to
avoid creating a data loop.
It allows a maximum of 10 ports to be aggregated at the same time. The Managed Switch support Gigabit Ethernet ports (up to 5
groups). If the group is defined as a LACP static link aggregationing group, then any extra ports selected are placed in a standby
mode for redundancy if one of the other ports fails. If the group is defined as a local static link aggregationing group, then the
number of ports must be the same as the group member ports.
The aggregation code ensures that frames belonging to the same frame flow (for example, a TCP connection) are always
forwarded on the same link aggregation member port. Reording of frames within a flow is therefore not possible. The
aggregation code is based on the following information:
• Source MAC
• Destination MAC
• Source and destination IPv4 address.
• Source and destination TCP/UDP ports for IPv4 packets
Normally, all 5 contributions to the aggregation code should be enabled to obtain the best traffic distribution among the link
aggregation member ports. Each link aggregation may consist of up to 10 member ports. Any quantity of link aggregation s may
be configured for the device (only limited by the quantity of ports on the device.) To configure a proper traffic distribution, the
ports within a link aggregation must use the same link speed.
Page 95

95
4.5.1 Static Aggregation
to enable the use of the IP Address, or uncheck to disable. By default, IP Address
This Page is used to configure the Aggregation hash mode and the aggregation group. The aggregation hash mode settings are
global, whereas the aggregation group relate to the currently selected stack unit, as reflected by the Page header.
Hash Code Contributors
The Stati c Aggeration screen in Figure 4-5-2 appears.
Figure 4-5-2 : Aggregation Mode Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Source MAC Address
• Destination MAC
Address
• IP Address
• TCP/UDP Port Number
Static Aggregation Group Configuration
The Aggregation Group Configuration screen in Figure 4-5-3 appears.
The Source MAC address can be used to calculate the destination port for the
frame. Check to enable the use of the Source MAC address, or uncheck to
disable. By default, Source MAC Address is enabled.
The Destination MAC Address can be used to calculate the destination port for
the frame. Check to enable the use of the Destination MAC Address, or uncheck
to disable. By default, Destination MAC Address is disabled.
The IP address can be used to calculate the destination port for the frame. Check
is enabled.
The TCP/UDP port number can be used to calculate the destination port for the
frame. Check to enable the use of the TCP/UDP Port Number, or uncheck to
disable. By default, TCP/UDP Port Number is enabled.
Page 96

96
Figure 4-5-3: Aggregation Group Configuration Page Screenshot
switch port is listed for each group ID. Select a radio button to include a port
The Page includes the following fields:
.Object Description
• Group ID
• Port Members
Buttons
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
Indicates the group ID for the settings contained in the same row. Group ID
"Normal" indicates there is no aggregation. Only one group ID is valid per port.
Each
in an aggregation, or clear the radio button to remove the port from the
aggregation. By default, no ports belong to any aggregation group.
Please note that PoE port can’t be set to link aggregation member port.
4.5.2 LACP Configuration
Link Aggregation Control Protocol (LACP) - LACP LAG negotiate Aggregated Port links with other LACP ports located on a
different device. LACP allows switches connected to each other to discover automatically whether any ports are member of the
same LAG.
Page 97

97
The Timeout controls the period between BPDU transmissions. Fast will transmit
This Page allows the user to inspect the current LACP port configurations, and possibly change them as well. The LACP port
settings relate to the currently selected stack unit, as reflected by the Page header. The LACP Configuration screen in Figure
4-5-4 appears.
Figure 4-5-4: LACP Port Configuration Page Screenshot
The Page includes the following fields:
Object Description
• Port
• LACP Enabled
• Key
• Role
The switch port number.
Controls whether LACP is enabled on this switch port. LACP will form an
aggregation when 2 or more ports are connected to the same partner.
Please note that PoE port can’t be set to link aggregation member port.
The Key value incurred by the port, range 1-65535 . The Auto setting will set the
key as appropriate by the physical link speed, 10Mb = 1, 100Mb = 2, 1Gb = 3.
Using the Specific setting, a user-defined value can be entered. Ports with the
same Key value can participate in the same aggregation group, while ports with
different keys cannot.
The default setting is “Auto”
The Role shows the LACP activity status. The Active will transmit LACP packets
each second, while Passive will wait for a LACP packet from a partner (speak if
spoken to).
• Timeout
LACP packets each second, while Slow will wait for 30 seconds before sending a
LACP packet.
• Priority
The Prio controls the priority of the port. If the LACP partner wants to form a
larger group than is supported by this device then this parameter will control
which ports will be active and which ports will be in a backup role. Lower number
Page 98

98
means greater priority.
Buttons
: Click to apply changes
: Click to undo any changes made locally and revert to previously saved values.
4.5.3 LACP System Status
This Page provides a status overview for all LACP instances. The LACP Status Page display the current LACP aggregation
Groups and LACP Port status. The LACP System Status screen in Figure 4-5-5 appears.
Figure 4-5-5: LACP System Status Page Screenshot
The Page includes the following fields:
Object Description
• Aggr ID
• Partner System ID
• Partner Key
• Partner Priority
• Last changed
• Local Ports
The Aggregation ID associated with this aggregation instance.
For LLAG the id is shown as 'isid:aggr-id' and for GLAGs as 'aggr-id'
The system ID (MAC address) of the aggregation partner.
The Key that the partner has assigned to this aggregation ID.
The priority of the aggregation partner.
The time since this aggregation changed.
Shows which ports are a part of this aggregation for this switch/stack.
The format is: "Switch ID:Port".
Buttons
: Click to refresh the Page immediately.
Auto-refresh
: Automatic refresh occurs every 3 seconds.
Page 99

99
4.5.4 LACP Port Status
'Yes' means that LACP is enabled and the port link is up. 'No' means that LACP is
This Page provides a status overview for LACP status for all ports. The LACP Port Status screen in Figure 4-5-6 appears.
Figure 4-5-6: LACP Status Page Screenshot
The Page includes the following fields:
Buttons
Object Description
• Port
• LACP
• Ke y
• Aggr ID
• Partner System ID
• Partner Port
• Partner Priority
: Click to refresh the Page immediately.
The switch port number.
not enabled or that the port link is down. 'Backup' means that the port could not
join the aggregation group but will join if other port leaves. Meanwhile it's LACP
status is disabled.
The key assigned to this port. Only ports with the same key can aggregate
together.
The Aggregation ID assigned to this aggregation group.
The partner’s System ID (MAC address).
The partner’s port number connected to this port.
The partner's port priority.
Auto-refresh
: Automatic refresh occurs every 3 seconds.
4.5.5 LACP Port Statistics
This Page provides an overview for LACP statistics for all ports. The LACP Port Statistics screen in Figure 4-5-7 appears.
Page 100
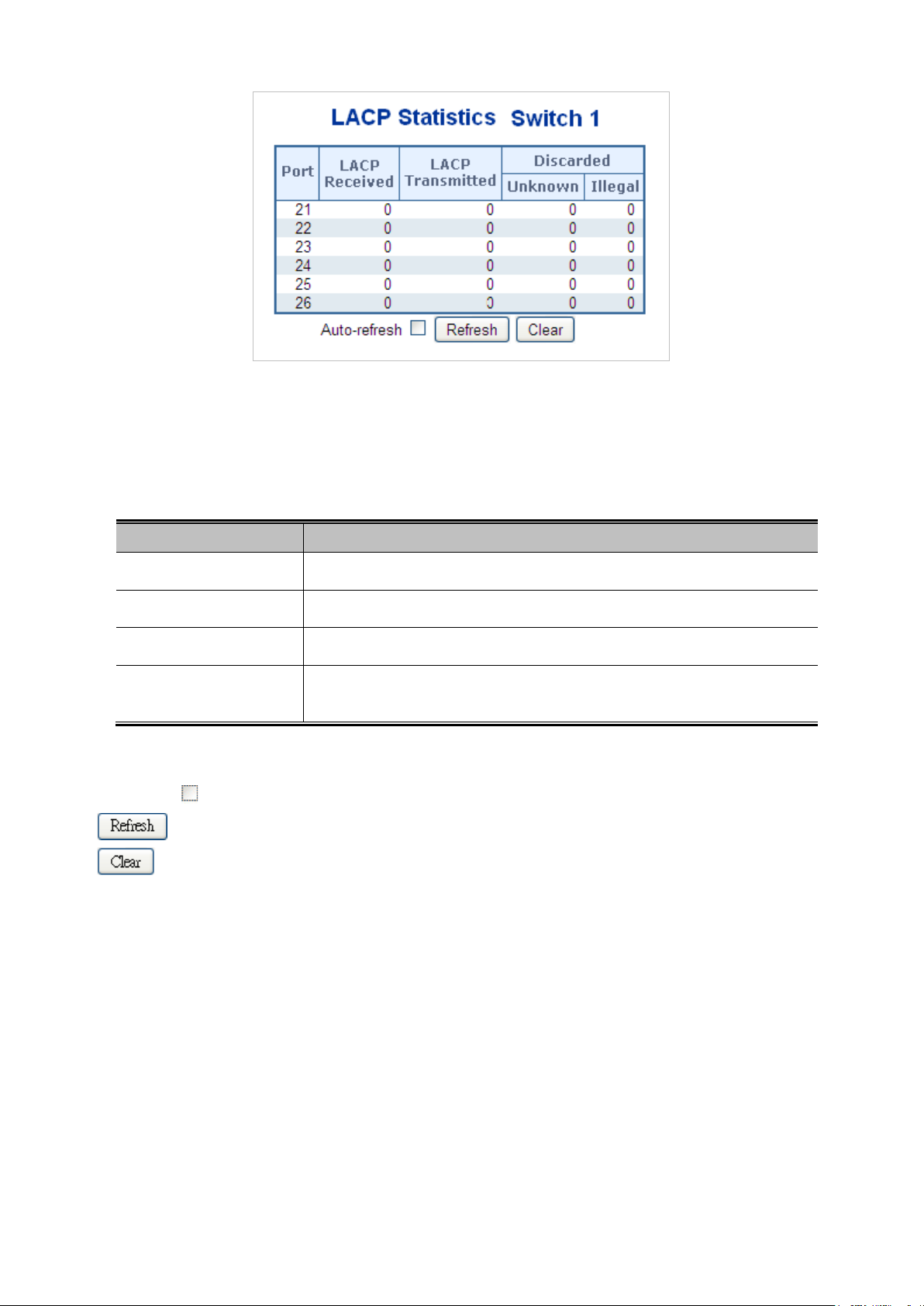
100
The Page includes the following fields:
Object Description
Figure 4-5-7: LACP Statistics Page Screenshot
• Port
• LACP Received
• LACP Transmitted
• Discarded
Buttons
Auto-refresh : Automatic refresh occurs every 3 seconds.
: Click to refresh the Page immediately.
: Clears the counters for all ports.
The switch port number.
Shows how many LACP frames have been sent from each port.
Shows how many LACP frames have been received at each port.
Shows how many unknown or illegal LACP frames have been discarded at each
port.
 Loading...
Loading...