Page 1

Encrypted Volume and File System v1.1 Administrator's Guide
HP-UX 11i v2 Update 2 and 11i v3
HP Part Number: 5992-4122
Published: May 2008
Page 2

© Copyright 2008 Hewlett-Packard Development Company, L.P
Confidential computersoftware. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standardcommercial license.The informationcontained hereinis subject to change without notice. The only warranties forHP products
and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. UNIX is a registered
trademark of The Open Group.
Trademark Notice
Oracle® is a registered US trademark of Oracle Corporation, Redwood City, California.
Page 3

Table of Contents
About This Document.......................................................................................................15
Intended Audience................................................................................................................................15
Document Organization.......................................................................................................................15
Typographic Conventions.....................................................................................................................15
Related Information..............................................................................................................................16
HP Encourages Your Comments..........................................................................................................16
1 EVFS Introduction.........................................................................................................17
Features and Benefits............................................................................................................................17
EVFS Architecture.................................................................................................................................19
EVFS Data Flow...............................................................................................................................20
Encryption Metadata (EMD)...........................................................................................................20
EVFS Encryption Keys.....................................................................................................................20
Volume Encryption Keys...........................................................................................................21
User Keys....................................................................................................................................21
Passphrases...........................................................................................................................21
Using HP-UX Trusted Computing Services with EVFS.............................................................21
How EVFS Uses Keys.................................................................................................................22
Creating an EVFS Volume....................................................................................................22
Enabling an EVFS Volume....................................................................................................22
Key Names and Key IDs..................................................................................................................23
User Key and Passphrase Storage...................................................................................................23
File Names..................................................................................................................................23
Alternate Storage Databases and Distributed Key Storage.......................................................23
User Key Privileges.........................................................................................................................24
User Privileges and Permissions................................................................................................24
EVFS Volume Owner Keys.........................................................................................................24
Recovery Keys............................................................................................................................24
Authorized User Keys................................................................................................................24
Summary of Key Type and Privileged User Capabilities................................................................24
EVFS Commands.............................................................................................................................25
Supported Software..............................................................................................................................26
Product Limitations and Precautions...................................................................................................27
Known Problems...................................................................................................................................29
Possible Device File Collision..........................................................................................................29
Symptoms...................................................................................................................................29
Workaround...............................................................................................................................29
Feedback and Enhancement Requests..................................................................................................30
2 Installation.....................................................................................................................31
Prerequisites..........................................................................................................................................32
Hardware Requirements.................................................................................................................32
Disk Space Requirements...........................................................................................................32
Operating System Requirements.....................................................................................................32
Patch Requirements and Recommendations...................................................................................32
Required Patches........................................................................................................................32
Recommended Patches...............................................................................................................32
System Reboot.................................................................................................................................32
Installing EVFS......................................................................................................................................33
Table of Contents 3
Page 4

Upgrading from EVFS v1.0 to EVFS v1.1.............................................................................................34
3 Preparing EVFS for Configuration..............................................................................35
Verifying for Preconfiguration..............................................................................................................35
Preparation Overview...........................................................................................................................36
Step 1: Configuring an Alternate EVFS Pseudo-User...........................................................................37
Step 1a: Setting the evfs_user Attribute..........................................................................................37
Example......................................................................................................................................37
Step 1b: Creating the User Group....................................................................................................37
Example......................................................................................................................................37
Step 1c: Creating the EVFS Pseudo-User Account..........................................................................37
Example......................................................................................................................................37
Step 2: (Optional) Configuring Alternate Key Database Directories...................................................39
Syntax for pub_key, priv_key, and pass_key Attribute Statements................................................39
Key Storage Directory Requirements..............................................................................................40
Default pub_key, priv_key and pass_key Attribute Statements.....................................................40
Example: Alternate Directory for Public Keys................................................................................41
Example: NFS Directory for Public and Private Keys.....................................................................41
Example: Fallback Directory for Nonprivileged Users...................................................................41
Step 3: (Optional) Modifying EVFS Global Parameters........................................................................42
Step 4: Starting the EVFS Subsystem....................................................................................................43
Example...........................................................................................................................................43
Step 5: Creating User Key Pairs............................................................................................................44
Guidelines for Creating User Keys..................................................................................................44
Creating Keys for EVFS Volume Owners........................................................................................44
Example......................................................................................................................................45
Creating Recovery Keys..................................................................................................................45
Storing the recovery user's Private Key.....................................................................................45
Examples....................................................................................................................................45
Creating Keys for authorized users.................................................................................................46
Examples....................................................................................................................................46
Examples...............................................................................................................................................47
User Session.....................................................................................................................................47
4 Configuring an EVFS Volume......................................................................................49
Configuration Overview.......................................................................................................................49
Option 1: Creating a New EVFS Volume..............................................................................................50
Step 1: Configuring an EVFS Volume..............................................................................................51
Step 1a: Creating an LVM or VxVM Volume for EVFS..............................................................51
Examples...............................................................................................................................51
Step 1b: Creating EVFS Volume Device Files.............................................................................51
Examples...............................................................................................................................52
Step 1c: Creating the EMD.........................................................................................................52
Example.................................................................................................................................53
Step 1d: (Optional) Adding Recovery Keys and authorized user Keys....................................53
Step 1e: Enabling the EVFS Volume...........................................................................................54
Example.................................................................................................................................55
Step 2: Creating and Mounting a File System on an EVFS Volume................................................56
Step 2a: Creating a New File System with newfs.......................................................................56
Example.................................................................................................................................56
Step 2b: (Optional) Using fsck to Check the File Volume..........................................................56
Example.................................................................................................................................56
Step 2c: Creating the Mount Point.............................................................................................57
4 Table of Contents
Page 5

Example.................................................................................................................................57
Step 2d: Mount the File System on the EVFS Volume...............................................................57
Example.................................................................................................................................57
Step 2e: (Optional) Adding an Entry to /etc/fstab......................................................................57
Example.................................................................................................................................58
Step 3: Verifying the Configuration.................................................................................................59
evfsadm stat -a............................................................................................................................59
evfsvol display evfs_volume_path.............................................................................................59
Verifying Data Encryption.........................................................................................................59
Example.................................................................................................................................60
Step 4: (Optional) Migrating Existing Data to an EVFS Volume.....................................................61
Example......................................................................................................................................61
Step 5: (Optional) Configuring the Autostart Feature.....................................................................62
Step 6: Backing Up Your Configuration..........................................................................................64
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption).............65
Step 1: Preparing the File System and Data....................................................................................66
Step 2: Performing Inline Encryption..............................................................................................67
iencrypt: Inline Encryption........................................................................................................67
Suspending an Ongoing Inline Encryption..........................................................................67
Re-starting a Suspended Inline Encryption..........................................................................67
Step 3: Verifying the Configuration.................................................................................................69
evfsadm stat -a............................................................................................................................69
evfsvol display evfs_volume_path.............................................................................................69
Verifying Data Encryption.........................................................................................................69
Example.................................................................................................................................70
Step 4: (Optional) Configuring the Autostart Feature.....................................................................72
Step 5: Backing Up Your Configuration..........................................................................................74
Examples...............................................................................................................................................75
Option 1...........................................................................................................................................75
Korn Shell Script for Creating an EVFS Volume and File System.............................................76
Option 2...........................................................................................................................................76
5 Administering EVFS......................................................................................................79
Starting and Stopping EVFS.................................................................................................................80
Starting the EVFS Subsystem..........................................................................................................80
Enabling Encryption and Decryption Access to EVFS Volumes.....................................................80
Disabling Encryption/Decryption Access to EVFS Volumes..........................................................81
Stopping the EVFS Subsystem........................................................................................................82
Opening Raw Access to EVFS Volumes..........................................................................................83
Closing Raw Access to EVFS Volumes............................................................................................83
Managing EVFS Keys and Users..........................................................................................................84
Displaying Key IDs for an EVFS Volume........................................................................................84
Syntax.........................................................................................................................................84
Example......................................................................................................................................84
Restoring User Keys........................................................................................................................84
Changing Owner Keys for an EVFS Volume...................................................................................86
Recovering from Problems with Owner Keys.................................................................................87
Removing Keys from an EVFS Volume...........................................................................................87
Removing User Keys or Stored Passphrase from the EVFS Key Database.....................................87
Changing the Passphrase for a Key.................................................................................................87
Creating or Changing a Stored Passphrase for an Existing Key.....................................................88
Recovering from EMD Corruption.......................................................................................................89
EMD Backup Directory...................................................................................................................89
Removing a Volume from the EVFS Subsystem...................................................................................90
Table of Contents 5
Page 6

Exporting and Importing EVFS Volumes.............................................................................................91
Exporting an EVFS Volume.............................................................................................................91
Importing an EVFS Volume.............................................................................................................93
6 Managing Data on EVFS Volumes.............................................................................95
Limitations and Known Problems When Using EVFS with Volume Managers and File Systems......96
Creating a New EVFS Volume Overwrites Existing Data...............................................................96
vxresize –F Might Cause Data Loss or Corruption.........................................................................96
Workaround...............................................................................................................................96
Renaming VxVM Volumes with EVFS Enabled Makes the Volume Unusable..............................96
Workaround...............................................................................................................................96
Resizing EVFS Volumes and File Systems............................................................................................97
LVM Example: Increasing Volume and File System Sizes..............................................................97
Correct........................................................................................................................................97
Incorrect......................................................................................................................................98
LVM Example: Reducing Volume and File System Sizes................................................................98
Correct........................................................................................................................................98
Incorrect......................................................................................................................................98
VxVM Example: Increasing Volume and File System Sizes............................................................99
Correct........................................................................................................................................99
Incorrect......................................................................................................................................99
VxVM Example: Reducing Volume and File System Sizes.............................................................99
Correct........................................................................................................................................99
Incorrect....................................................................................................................................100
7 Backing Up and Restoring Data on EVFS Volumes................................................101
Backing Up EVFS Volumes.................................................................................................................102
Backups Using LVM Mirrored Volumes.......................................................................................105
Creating Encrypted Backup Media on a Non-EVFS Device (LVM Mirrored Volumes) .........105
Example...............................................................................................................................106
Creating Encrypted Backup Media on a Second EVFS Volume Using a Block Device Utility
(LVM Mirrored Volumes).........................................................................................................107
Example...............................................................................................................................108
Creating Encrypted Backup Media on a Second EVFS Volume Using a File Utility (LVM
Mirrored Volumes)...................................................................................................................109
Example...............................................................................................................................110
Creating Cleartext Backup Media (LVM Mirrored Volumes)..................................................111
Example: Block Device Utility............................................................................................111
Example: File Utility............................................................................................................111
Backups Using VxVM Mirrored Volumes.....................................................................................112
Creating Encrypted Backup Media on a Non-EVFS Device (VxVM Mirrored Volumes).......112
Example...............................................................................................................................113
Creating Encrypted Backup Media on a Second EVFS Volume Using a Block Device Utility
(VxVM Mirrored Volumes)......................................................................................................115
Example...............................................................................................................................116
Creating Encrypted Backup Media on a Second EVFS Volume Using a File Utility (VxVM
Mirrored Volumes)...................................................................................................................117
Example...............................................................................................................................118
Creating Cleartext Backup Media (VxVM Mirrored Volumes)...............................................120
Example: Block Device Utility..................................................................................................120
Example: File Utility.................................................................................................................120
Backups Using Nonmirrored Volumes.........................................................................................121
Creating Encrypted Backup Media to a Non-EVFS Device (Nonmirrored Volumes).............121
6 Table of Contents
Page 7

Example...............................................................................................................................122
Creating Encrypted Backup Media on a Second EVFS Volume Using a Block Device Utility
(Nonmirrored Volumes)...........................................................................................................123
Example...............................................................................................................................123
Creating Encrypted Backup Media on a Second EVFS Volume Using a File Utility
(Nonmirrored Volumes)...........................................................................................................124
Example...............................................................................................................................124
Creating Cleartext Backup Media to a Non-EVFS Device (Nonmirrored Volumes)...............124
Restoring Backup Media.....................................................................................................................125
Restoring Encrypted Backup Media from a Non-EVFS Device to an EVFS Volume....................125
Example....................................................................................................................................126
Restoring Backup Data from an EVFS Volume to an EVFS Volume.............................................126
Example....................................................................................................................................127
8 Troubleshooting EVFS................................................................................................129
Troubleshooting Tools Overview........................................................................................................129
Displaying EVFS Volume Information...............................................................................................130
Displaying I/O and Encryption Statistics (evfsadm stat)..............................................................130
Syntax.......................................................................................................................................130
Examples..................................................................................................................................130
Displaying EVFS Volume Keys and Operating Parameters (evfsvol display)..............................131
Syntax.......................................................................................................................................131
Example....................................................................................................................................131
Verifying the EMD (evfsvol check).....................................................................................................133
Syntax.............................................................................................................................................133
Example.........................................................................................................................................133
Verifying User Keys (evfspkey lookup)..............................................................................................134
Syntax.............................................................................................................................................134
Example.........................................................................................................................................134
Problem Scenarios...............................................................................................................................135
evfspkey Cannot Generate Key Pairs............................................................................................135
Symptom..................................................................................................................................135
Description...............................................................................................................................135
Solution.....................................................................................................................................135
evfspkey Cannot Store Keys..........................................................................................................135
Symptom..................................................................................................................................135
Description...............................................................................................................................135
Solution.....................................................................................................................................135
evfsvol Cannot Retrieve Private Key.............................................................................................136
Symptom..................................................................................................................................136
Description...............................................................................................................................136
Solution.....................................................................................................................................136
evfsvol create Fails, EVFS Device File Not Found in evfstab File.................................................136
Symptom..................................................................................................................................136
Description...............................................................................................................................136
Solution.....................................................................................................................................136
evfsvol create Fails, Valid EMD Already Exists.............................................................................136
Symptom..................................................................................................................................136
Description...............................................................................................................................137
Solution.....................................................................................................................................137
evfsvol disable Fails, EVFS Volume Is Busy..................................................................................137
Symptom..................................................................................................................................137
Description...............................................................................................................................137
Solution.....................................................................................................................................137
Table of Contents 7
Page 8

evfsadm map Fails, Invalid Device................................................................................................137
Symptom..................................................................................................................................137
Description...............................................................................................................................137
Solution.....................................................................................................................................137
EMD Is Dirty..................................................................................................................................138
Symptom..................................................................................................................................138
Description...............................................................................................................................138
Solution.....................................................................................................................................138
Reporting Problems............................................................................................................................139
Collecting Data..............................................................................................................................139
A Product Specifications...............................................................................................141
User Files.............................................................................................................................................142
Commands and Tools.........................................................................................................................143
B EVFS Quick Reference...............................................................................................145
Preparing EVFS...................................................................................................................................146
Configuring EVFS...............................................................................................................................146
Option 1: Creating New EVFS Volume.........................................................................................147
Option 2: Converting an Existing Volume into an EVFS Volume (Inline Encryption).................148
EVFS Tasks and Commands...............................................................................................................149
C Using EVFS with Serviceguard.................................................................................153
EVFS and Serviceguard Overview......................................................................................................153
Requirements.................................................................................................................................153
Restrictions.....................................................................................................................................154
Configuration Overview.....................................................................................................................155
Step 1: Installing EVFS........................................................................................................................156
Step 2: Creating the Serviceguard Storage Infrastructure..................................................................157
Creating an LVM Serviceguard Storage Infrastructure.................................................................157
Configuration Node.................................................................................................................157
Adoptive Nodes.......................................................................................................................157
Creating a VxVM Serviceguard Storage Structure........................................................................157
Configuration Node.................................................................................................................157
Adoptive Nodes.......................................................................................................................158
Step 3: Configuring EVFS on the Configuration Node.......................................................................159
Step 3a: Creating a Cluster Key Pair..............................................................................................159
Step 3b: Adding the Cluster Keys to the EMD..............................................................................159
Step 3c: Modifying /etc/evfs/evfstab Entries.................................................................................159
Step 3d: Preparing EVFS Volumes for Adoptive Nodes...............................................................160
Step 4: Configuring EVFS Volumes on the Adoptive Nodes..............................................................161
Step 4a: Copying the EVFS Configuration Files and Keys............................................................161
Step 4b: Restoring the Cluster Key Pair Files................................................................................161
Step 4c: Creating a Local Passphrase File......................................................................................161
Step 4d: Activating the LVM Volume Group or VxVM Group on the Adoptive Node................161
LVM..........................................................................................................................................161
VxVM........................................................................................................................................161
Step 4e: Mapping the LVM or VxVM Volumes to EVFS...............................................................162
Step 4f: Modifying the /etc/evfs/evfstab File.................................................................................162
Step 4g: Verifying EVFS.................................................................................................................162
Step 4h: Deactivating the Volumes................................................................................................162
Step 4i: Configuring the Autostart Feature...................................................................................163
Step 5: Configuring Serviceguard using Modular packages..............................................................164
8 Table of Contents
Page 9

Step 5a: Halting an Existing Package.............................................................................................164
Step 5b: Installing the EVFS Attribute Definition File ..................................................................164
Step 5c: Copying the EVFS Control and Module Scripts .............................................................164
Step 5d: Creating a Modular Package Configuration File.............................................................165
Step 5e: Migrating a Legacy Package Configuration File .............................................................165
Step 5f: Adding the EVFS package to the Configuration File ......................................................165
Step 5g: Adding the EVFS Volumes to the Package Configuration File.......................................166
LVM and VxVM Modular package example...........................................................................166
LVM Example......................................................................................................................166
VxVM Example...................................................................................................................166
Step 5h: Verifying the Script..........................................................................................................166
Step 6: Configuring Serviceguard using Legacy packages.................................................................167
Step 6a: Halting an Existing Package.............................................................................................167
Step 6b: Creating the Package Configuration File.........................................................................167
Step 6c: Creating a Package Control Script....................................................................................167
Step 6d: Converting a Package Control Script...............................................................................167
Converting a Package Control Script.......................................................................................167
Modifying the Package Configuration File..............................................................................168
Step 6e: Adding the EVFS Volumes to the Package Control Script...............................................168
LVM and VxVM Legacy package example..............................................................................168
LVM Example......................................................................................................................168
VxVM Example...................................................................................................................168
Step 6f: Installing the EVFS Control Script....................................................................................168
Step 6g: Verifying the Script..........................................................................................................168
Glossary.........................................................................................................................169
Index...............................................................................................................................171
Table of Contents 9
Page 10

10
Page 11

List of Figures
1-1 EVFS Data Flow.............................................................................................................................20
1-2 Encryption Metadata (EMD) and Volume Encryption Keys........................................................21
1-3 Enabling an EVFS Volume............................................................................................................23
1-4 Software Types..............................................................................................................................26
11
Page 12

12
Page 13

List of Tables
1-1 Key Types and User Capabilities..................................................................................................25
7-1 Backup Types with LVM or VxVM Mirrored Volumes...............................................................103
7-2 Backup Types with Nonmirrored Volumes.................................................................................104
8-1 EVFS Troubleshooting Tasks and Commands............................................................................129
B-1 Starting and Stopping EVFS........................................................................................................149
B-2 Managing EVFS Volumes............................................................................................................149
B-3 Managing EVFS Keys and Users.................................................................................................150
B-4 Troubleshooting EVFS.................................................................................................................151
13
Page 14

14
Page 15
About This Document
This document describes how to install, configure, and troubleshoot the Encrypted Volume and
File System version 1.1 (EVFS v1.1) product.
You can find the latest version of this on line at http://docs.hp.com/en/internet.html.
Intended Audience
This document is intended for system and network administrators responsible for installing,
configuring, and managing EVFS. Administrators are expected to have knowledge of operating
system concepts, commands, and configuration.
It is helpful to have knowledge of HP-UX system administration, including disk and file system
administration.
This document is not a tutorial.
Document Organization
This document is organized as follows:
“EVFS Introduction” This chapter describes EVFS features, components, and
“Installation” This chapter explains how to install EVFS.
“Preparing EVFSfor Configuration” This chapter explains how to prepare for EVFS
“Configuring an EVFS Volume” This chapter explains how to configure an EVFS Volume.
“Administering EVFS” This chapter explains how to start and stop EVFS, manage
“Managing Data on EVFS Volumes” This chapter addresses limitations and workarounds when
“Backing Up and Restoring Data on
EVFS Volumes”
“Troubleshooting EVFS” This chapter describes EVFS troubleshooting tools, and
“Product Specifications” This appendix lists the user files and the commands
“EVFS Quick Reference” This appendix provides a quick reference guide of the EVFS
“Using EVFS with Serviceguard” This appendix describes how to configure EVFS volumes
product restrictions.
configuration.
EVFS keys and users, and perform other administrative
tasks.
using EVFS with volume managers and file systems.
This chapter describes how to back up and restore data on
EVFS volumes.
how to find solutions for common problems.
included with the EVFS product.
configuration procedure and EVFS tasks and commands.
in an HP Serviceguard cluster.
Typographic Conventions
This document uses the following typographical conventions:
%, $, or #
audit(5) A manpage. The manpage name is audit, and it is located in
Command
Computer output
A percent sign represents the C shell system prompt. A dollar
sign represents the system prompt for the Bourne, Korn, and
POSIX shells. A number sign represents the superuser prompt.
Section 5.
A command name or qualified command phrase.
Text displayed by the computer.
Intended Audience 15
Page 16

Ctrl+x A key sequence. A sequence such as Ctrl+x indicates that you
must hold down the key labeled Ctrl while you press another
key or mouse button.
ENVIRONMENT VARIABLE The name of an environment variable, for example, PATH.
[ERROR NAME]
Key The name of a keyboard key. Return and Enter both refer to the
Term The defined use of an important word or phrase.
User input
Variable
[] The contents are optional in syntax. If the contents are a list
{} The contents are required in syntax. If the contents are a list
... The preceding element can be repeated an arbitrary number of
Indicates the continuation of a code example.
| Separates items in a list of choices.
WARNING A warning calls attention to important information that if not
CAUTION A caution calls attention to important information that if not
IMPORTANT This alert provides essential information to explain a concept or
NOTE A note contains additional information to emphasize or
The name of an error, usually returned in the errno variable.
same key.
Commands and other text that you type.
The name of a placeholder in a command, function, or other
syntax display that you replace with an actual value.
separated by |, you must choose one of the items.
separated by |, you must choose one of the items.
times.
understood or followed will result in personal injury or
nonrecoverable system problems.
understood or followed will result in data loss, data corruption,
or damage to hardware or software.
to complete a task
supplement important points of the main text.
Related Information
The following documents contain useful and related information:
• Encrypted Volume and File System v1.1 (EVFS v1.1) Release Notes
• Managing Systems and Workgroups: A Guide for HP-UX System Administrators
• Managing Serviceguard
HP Encourages Your Comments
HP encourages your comments concerning this document. We are committed to providing
documentation that meets your needs.
Send comments to: netinfo_feedback@cup.hp.com
Include documenttitle, manufacturing part number, and anycomment, error found, or suggestion
for improvement you have concerning this document. Also, please include what we did right
so we can incorporate it into other documents.
16
Page 17

1 EVFS Introduction
This chapter provides introductory information about the Encrypted Volume and File System
(EVFS) product. This chapter addresses the following topics:
• “Features and Benefits” (page 17)
• “EVFS Architecture” (page 19)
• “Supported Software” (page 26)
• “Product Limitations and Precautions” (page 27)
• “Known Problems” (page 29)
• “Feedback and Enhancement Requests” (page 30)
Features and Benefits
EVFS protects data by encrypting data volumes to protect data at rest – data on disks. You can
also use EVFS to create encrypted backup media. EVFS prevents anyone who gains unauthorized
physical access to storage media from reading or using the data.
EVFS creates EVFS volumes, which are pseudo-devices (or virtual devices) layered on Logical
Volume Manager (LVM), Veritas Volume Manager (VxVM), or physical volume devices. You
can use the newfs command to create a file system on an EVFS volume just as you would create
a file system on an LVM, VxVM, or physical volume. The EVFS subsystem encrypts data written
to an EVFS volume and decrypts data read from an EVFS volume as needed.
EVFS provides the following features:
• Data protection that is file-system independent.
EVFS supports all disk file system types that can be mounted on a LVM, VxVM, or physical
volume, including High Performance File System (HFS) and Veritas File System (VxFS, also
referred to as Journaled File System, or JFS).
• Application transparency.
EVFS volumes areimplemented as pseudo-devices below the HP-UX file system. Nochanges
to applications are necessary. EVFS is compatible with network file sharing utilities, such
as Network File System (NFS) and Common Internet File System (CIFS), and with network
file access utilities, such as File Transfer Protocol (FTP) and remote copy (rcp).
• High-performance bulk data encryption using symmetric keys.
EVFS encrypts volume data using a symmetric encryption key, referred to as the volume
encryption key. EVFS supports the following symmetric key algorithms for encrypting
volume data:
— 128-bit key Advanced Encryption Standard Cipher Block Chaining (AES CBC) mode
— 192-bit key AES CBC mode
— 256-bit key AES CBC mode
• Public/private keys for symmetric key storage.
EVFS uses public/private encryption key to store volume encryption keys. EVFS supports
the following public/private key encryption algorithms:
— 1024-bit key Rivest-Shamir-Adelman (RSA)
— 1536-bit key RSA
— 2048-bit key RSA
• Passphrase storage and retrieval for automatic start (autostart).
EVFS encrypts private keys with passphrases. In normal operation, EVFS prompts the user
for the passphrase to decrypt and retrieve the private key. To enable EVFS operation during
system startup without human intervention, EVFS provides a mechanism to store a user's
Features and Benefits 17
Page 18

passphrase in a file, encrypted with system-specific data. At system startup, EVFS can
automatically retrieve stored passphrases and use the passphrases to execute EVFS
commands.
CAUTION: Stored passphrases provide convenience, but they are security risks.
• DLKM Support
This version of EVFS is DLKM aware. The kernel module of EVFS can be loaded into the
running kernel without needing to rebuild or reboot. The kernel module can also be unloaded
on demand from the running kernel without needing to rebuild or reboot the system.
• In-line Encryption
This feature allows conversion of an existing volume with clear-text data into an EVFS
managed encrypted volume without doubling the amount of storage. Inline encryption is
handled offline, and the volume is not accessible during the process until the entire operation
is completed.
• Kernel Tracing
The evfsadm trace command traces and captures EVFS kernel code flow information in
order to facilitate debugging and analysis on a live system. This command is intended for
use by support personnel only. HP does not support this feature on Customer Environments.
• Large I/O Performance
EVFS performance for large I/O requests is increased by the implementation of simultaneous
data processing.
• LVM DLO Support
LVM version 2.0 with DLO is supported by this release of EVFS on 11i v3.
• Serviceguard A.11.18 Support
Serviceguard A.11.18 is supported by this release of EVFS on 11i v2 Update 2 and 11i v3.
• Maximum Number of Volumes Support
The maximum number of volumes which can be mapped to EVFS supported by this release
is 1023, an increase from 127.
18 EVFS Introduction
Page 19

EVFS Architecture
This section describes the following EVFS features:
• EVFS data flow
• Encryption metadata (EMD)
• EVFS encryption keys
• EVFS commands
EVFS Architecture 19
Page 20
EVFS Data Flow
(decrypts data read by upper layer )
(encrypts data written to lower layer )
File System
LVM
EVFS
DB or Direct-Access
Application
= Non -encrypted Data
= Encrypted Data
VxVM
Physical Disks
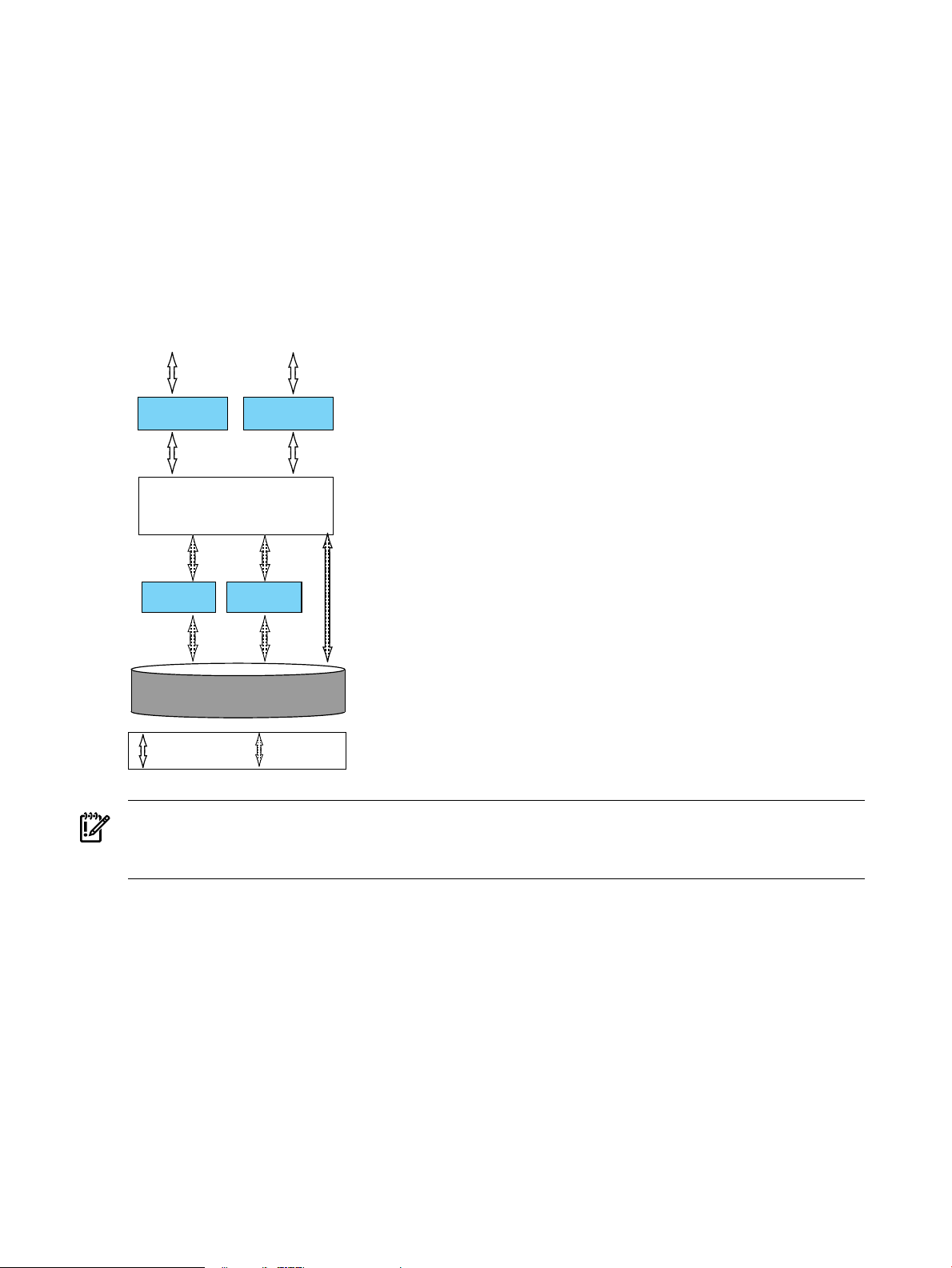
EVFS isimplemented using a pseudo-driver that operates on the EVFS volumes. An EVFS volume
is stacked between the underlying volume (a LVM, VxVM, or physical volume) and an upper
layer. The upper layer can be a file system or an application that reads data from and writes data
directly to the EVFS volume, such as a database application.
When the upper layer file writes data, the EVFS pseudo-driver encrypts the data before writing
it to the underlying volume. When the upper layer reads data, the pseudo-driver decrypts the
data from the underlying volume and provides the decrypted data to the upper layer. If the
upper layer caches data to the lower layer, such as a file system with buffer caching enabled, all
data in the buffer cache is in cleartext (it is not encrypted). Figure 1-1 shows a simplified EVFS
data flow.
Figure 1-1 EVFS Data Flow
IMPORTANT: After encryptionand decryption for an EVFS volume is enabled, all readoperations
performed on the EVFS volume output decrypted data. You must use normal HP-UX file system
permissions and access control to restrict access to the data.
Encryption Metadata (EMD)
Each EVFS volume has a set of encryption attributes, or encryption metadata (EMD) associated
with it. The EMD is stored as part of the EVFS volume. The data stored in the EMD includes
operating parameters for the EVFS volume, such as the data encryption algorithm, and copies
of the volume encryption key. The copies of the volume encryption key are encrypted ("wrapped")
by user keys, as described in the following section.
EVFS Encryption Keys
20 EVFS Introduction
EVFS uses two types of encryption keys:
• Symmetric keys to encrypt data, referred to as volume encryption keys
• Public/private key pairs to protect volume encryption keys, also referred to as user keys
EVFS also uses passphrases to protect private keys.
Page 21
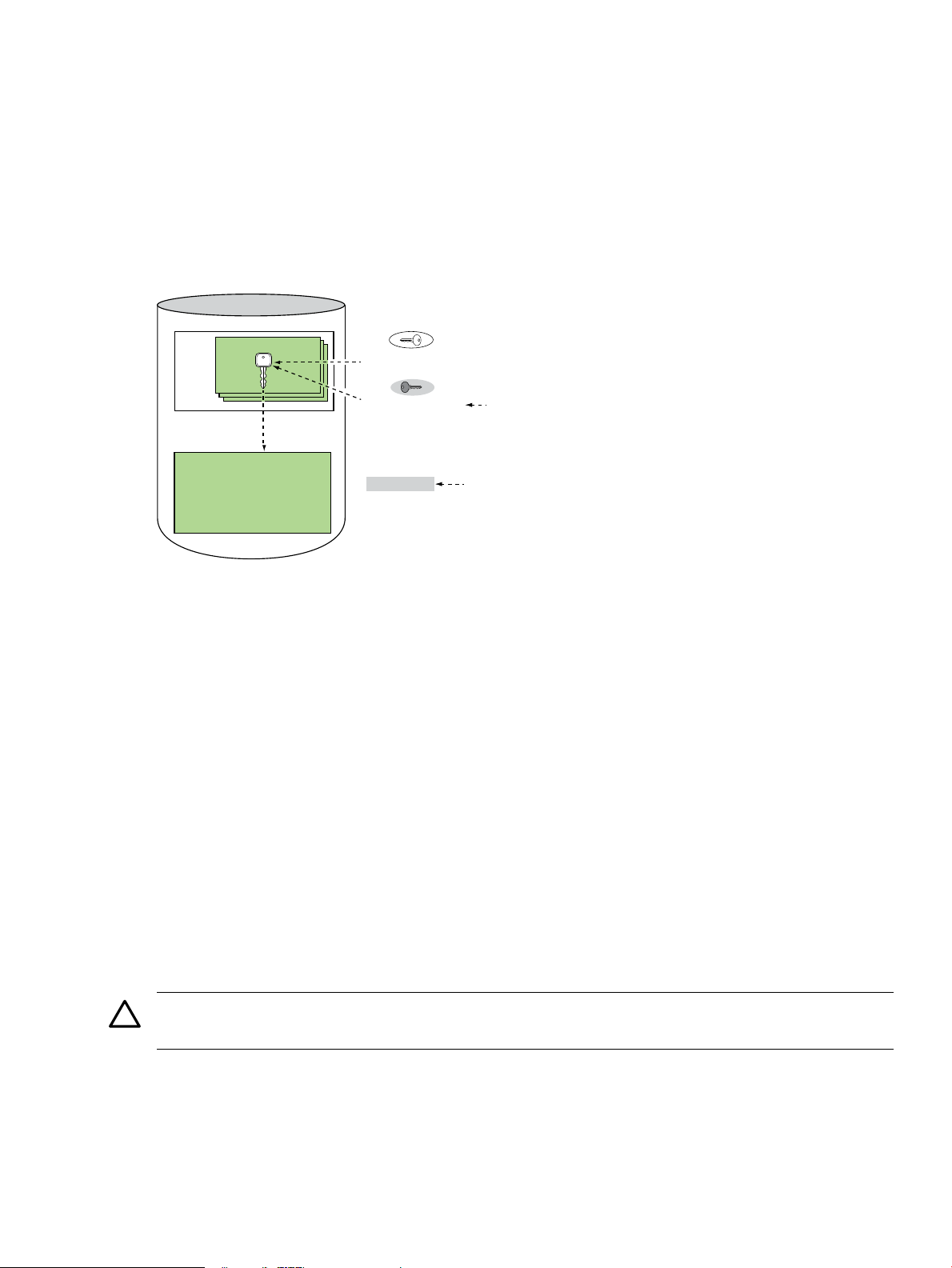
Volume Encryption Keys
Encryption Metadata (EMD)
Encrypted Data
EVFS Volume
Key
Records
Volume Encryption Key
User 1’s public key encrypts the
volume encryption key
User 1’s private key decrypts
the volume encryption key
Volume encryption
key encrypts/decrypts
the data
“my_passphrase”
encrypts private key
Stored Passphrase:
System-specific data
encrypts “my_passphrase”
“my_passphrase”
EVFS uses symmetric keys to encrypt data, referred to as volume encryption keys. In symmetric
key cryptography, the same key (bit string) is used to encrypt and decrypt the data. EVFS stores
the volume encryption keys in the EMD area of a volume, as part of key records. Each key record
contains the volume encryption key, encrypted with a user's public key. Because the volume
encryption key is encrypted with a public key, this data is also referred to as a “digital envelope.”
The digital envelope must be “opened,” or decrypted with the user's private key to retrieve the
volume encryption key. Figure 1-2 illustrates how EVFS uses and stores volume encryption kesy.
Figure 1-2 Encryption Metadata (EMD) and Volume Encryption Keys
User Keys
Using HP-UX Trusted Computing Services with EVFS
EVFS uses public/private encryption key pairs with passphrases to securely store volume
encryption keys. Each public/private key pair is owned by a user, and the key pairs are also
referred to as user keys.
Public/private key cryptography systems use pairs of related but different keys. The public and
private key pairs are mathematically related so that data encrypted with the public key requires
the private key to decrypt it. In public/private key systems, the public key does not have to be
kept secret.
Passphrases
For added protection, EVFS encrypts each private key with a passphrase before storing it. You
can specify the passphrase or have EVFS generate a passphrase for you.
Stored Passphrases
As an option, you can store a passphrase in a file. EVFS encrypts the passphrase with
system-specific information before storing it. Stored passphrases enable EVFS to retrieve a user's
private key without prompting for the passphrase. If you want to enable EVFS volumes at system
startup without manual intervention, you must use stored passphrases.
CAUTION: A stored passphrase enables you to use the EVFS autostart feature, but it is a security
risk.
On systems with HP-UX Trusted Computing Services (TCS), you can use TCS to secure EVFS
private keys. For more information, see the HP-UX TCS product documentation.
EVFS Architecture 21
Page 22

How EVFS Uses Keys
EVFS uses symmetric volume encryption keys to encrypt the volume data. EVFS also uses
public/private keys to encrypt the volume encryption keys, and it uses passphrases to encrypt
private keys, as follows:
• The volume encryption key is stored in key records, or digital envelopes, in the EMD area
of the EVFS volume. Each key record contains the volume encryption key, encrypted by a
user's public key.
• User's public keys are stored in a local database, unencrypted.
• User's private keys are stored in a local database. Each private key is encrypted with a
passphrase.
• As an option, a passphrase can be stored in a file, encrypted with system-specific data. A
stored passphraseis a security risk.However, it enables you to execute some EVFS commands
without entering a passphrase and to use the EVFS autostart feature.
Creating an EVFS Volume
When you create an EVFS volume and the EMD, the following sequence of events occurs:
1. The userenters the evfsvol create command and specifies a key pair name for the owner
key. The evfsvol utility prompts the user for the passphrase for the users's private key.
When creatinga new EVFS volume, evfsvol always prompts the user for passphrase. (Other
evfsvol subcommands, such as evfsvol enable, allow you to use stored passphrases.)
2. The evfsvol utility reads operating parameters from the /etc/evfs/evfs.conf file,
such as the data encryption algorithm for the volume, and writes them to the EMD.
3. The evfsvol utility generates the volume encryption key.
4. The evfsvol utility creates a key record for the owner by encrypting the volume encryption
key with the owner's public key (which creates a digital envelope). The evfsvol utility
writes this key record to the EMD.
Enabling an EVFS Volume
To enable encryption and decryption for an EVFS volume, the following sequence of events
occurs:
1. The user enters the evfsvol enable command. The evfsvol utility prompts the user
for the passphrase for the user's private key. The user enters the passphrase.
Alternatively, EVFS retrieves the user's passphrase from a file. In this case, the passphrase
is encrypted with system-specific data, and EVFS decrypts the passphrase before using it.
2. EVFS uses the passphrase to decrypt the user's private key.
3. EVFS uses the user's private key to decrypt the key record (EVFS “opens” the key record's
digital envelope) and extracts the volume encryption key from the key record.
4. EVFS uses the volume encryption key to encrypt and decrypt the EVFS volume data as
needed.
Figure 1-3 illustrates how EVFS uses keys to enable an EVFS volume.
22 EVFS Introduction
Page 23
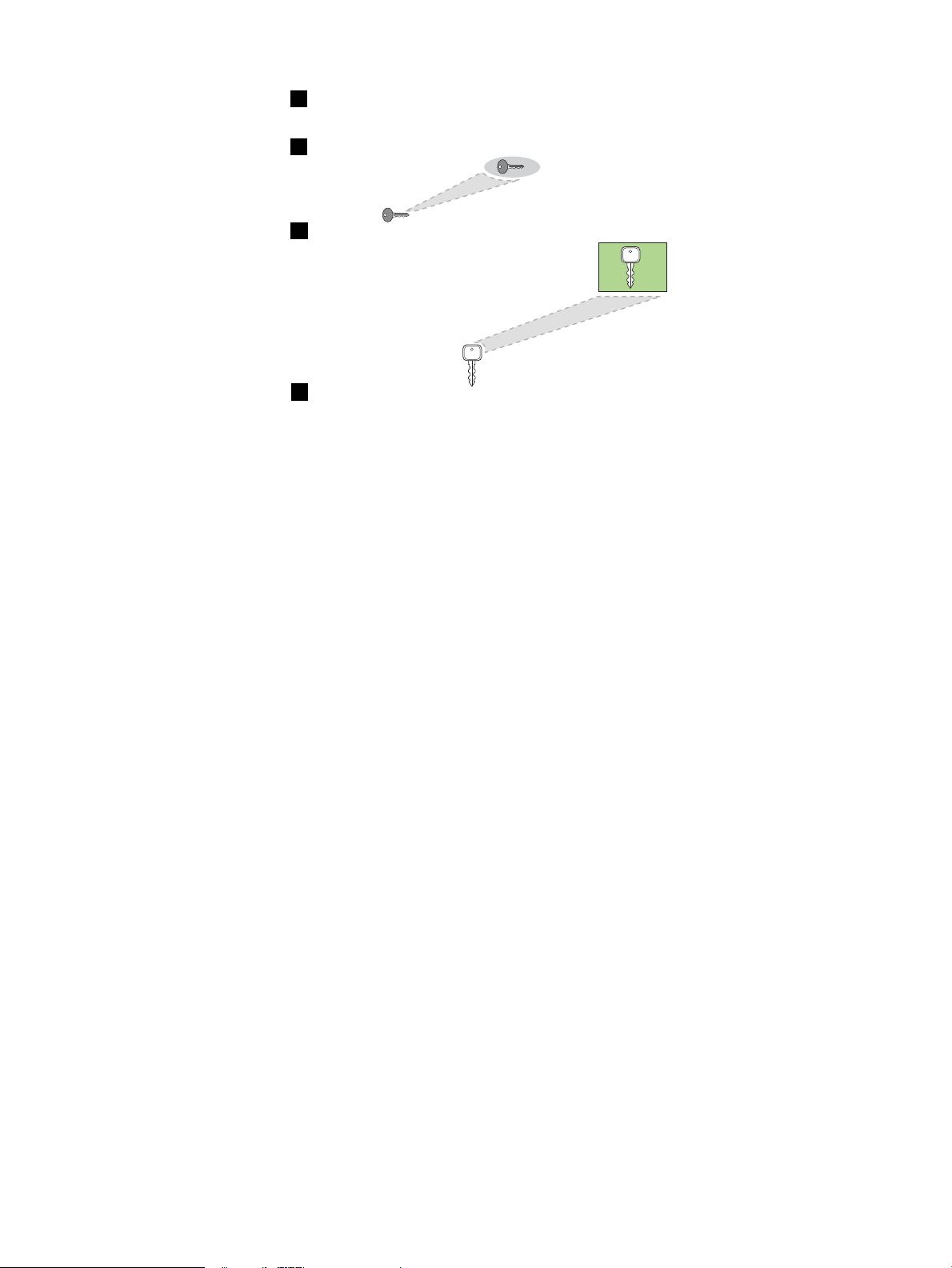
Figure 1-3 Enabling an EVFS Volume
1
evfsvol enable my_evol
Enter passphrase: my_passphrase
2
my_passphrase decrypts user 1’s private key
3
User 1’s private key decrypts the key record to extract the volume encryption key.
4
EVFS uses the volume encryption key to encrypt and decrypt the volume data as needed.
Key Names and Key IDs
Each public/private key pair has an owner and a key name. A user can have multiple
public/private key pairs. The default key name (the name EVFS uses if you do not specify a key
name) is the owner's user account name.
Public/private key pairs are also identified by a key ID formed by concatenating the owner's
user account name and the key name, separated by a period (.). For example, the user bob owns
the key pair named bobkey1. The key ID for this key pair is bob.bobkey1.
User Key and Passphrase Storage
By default, EVFS stores keys in a local database under the directory /etc/evfs/pkey. EVFS
creates a subdirectory for each user who owns EVFS user keys. The subdirectory name is the
user account name.
File Names
When using the default key storage directory, EVFS uses the following directory and file names
to store user keys:
Public Key
Private Key
Stored Passphrase
Alternate Storage Databases and Distributed Key Storage
You can configure EVFS to use different file directories for the user key database that contains
the public keys, private keys, and stored passphrases. The directories can be local directories or
remote directories that are NFS-mounted. You can also configure EVFS to use different database
directories according to the data type (key type or stored passphrase), and to use fallback
directories if attempts to store key data fail.
/etc/evfs/pkey/user_name/key_name.pub, where user_name
is the key owner's name and key_name is the key name.
/etc/evfs/pkey/user_name/key_name.priv, where
user_name is thekey owner's name and key_name is the key name.
/etc/evfs/pkey/user_name/key_name.pass.nnn, where
user_name is the key owner's name, key_name is the key name,
and nnn is a number based on system-specific data.
EVFS Architecture 23
Page 24

User Key Privileges
EVFS defines the following types of user keys and restricts the execution of EVFS commands
based on these keys and HP-UX user privileges:
• EVFS volume owner keys
• Recovery keys
• Authorized user keys
User Privileges and Permissions
Some EVFS commands do not require user keys. Only users with the appropriate privileges can
execute thesecommands. By default, the appropriate privilege required for these EVFS commands
is superuser privilege. See the privileges(5) manpage for more information about HP-UX privileges.
To performoperations on EVFS volumes and other volumes, users must also have the appropriate
file access permissions for the associated device files. In most installations, users who want to
perform operations on EVFS volumes must have superuser privileges.
NOTE: EVFS user keys restrict execution of EVFS commands only. Read, write and execute
access to data on EVFS volumes is still restricted by normal HP-UX file permissions and access
controls.
EVFS Volume Owner Keys
When you create an EVFS volume, you specify the volume owner key or owner key for the
volume. The user who owns the volume owner key (the volume owner) can use the key to
perform administrative operations on an EVFS volume, including enabling and disabling EVFS
for the volume. The owner can also add additional key records to the EMD.
Recovery Keys
A recovery key enables you to change a volume owner key if the owner's keys are not available.
Only the recovery key and the owner key can be used to change the owner key of an EVFS
volume. The only operation you can perform with a recovery key is to change the owner key for
an EVFS volume.
At installation, EVFS creates an EVFS pseudo-user account, evfs, if it does not already exist.
Recovery keys are owned by this pseudo-user.
HP recommends that you configure a recovery key for each volume, but configuring recovery
keys is not mandatory for normal EVFS operation. You can configure up to two recovery key
pairs per EVFS volume.
Authorized User Keys
A volume owner can configure additional user keys to use to perform administrative operations
on the EVFS volume. These user keys are authorized user keys for the volume.
A user with an authorized user key and the appropriate file system permissions for the volume
device files can perform the same EVFS operations that the holder of an owner key can perform,
except changing the EVFS volume owner, adding and deleting additional keys to a volume, and
destroying the EVFS volume by removing the EMD.
Summary of Key Type and Privileged User Capabilities
Table 1-1 summarizes the capabilities for the different key types and for users with superuser
privileges or the appropriate privileges.
24 EVFS Introduction
Page 25
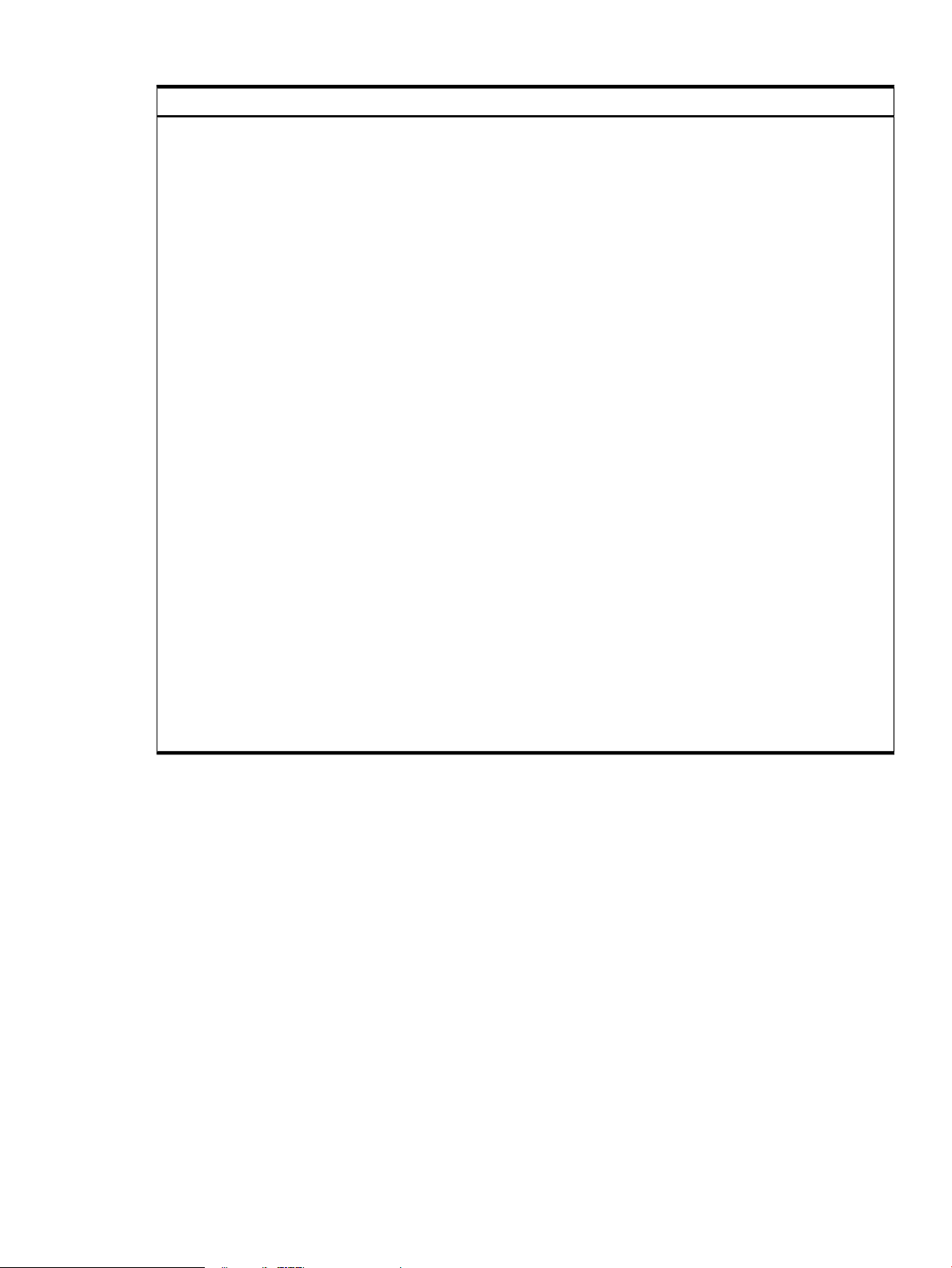
Table 1-1 Key Types and User Capabilities
CapabilitiesKey Type/User Type
Superuser or appropriate privileges and file permissions
for the device files
Owner Key
Recovery Key
Any user with superuser privileges or the appropriate
privileges and file permissions can perform thefollowing
tasks (no EVFS key is required):
• Start or stop the EVFS subsystem
• Map volumes to EVFS (create EVFS device files)
• Create EVFS volumes
• Create user keys for other users
• Display information about EVFS volumes
• Restore an EVFS volume's EMD
If a user has the owner key for an EVFS volume and the
appropriate file permissions for the device file, the user
can perform the following tasks:
• Enable and disable EVFS volumes
• Add and remove authorized user keys to EVFS
volumes
• Change the owner of an EVFS volume
• Destroy an EVFS volume (remove the EMD; the data
is irrecoverable)
The user can also perform tasks that do not require EVFS
keys, suchas displaying information about EVFS volumes.
If a user has the recovery key for an EVFS volume and
the appropriate file permissions for the device file, the
user can change the owner of an EVFS volume.
The user can also perform tasks that do not require EVFS
keys, suchas displaying information about EVFS volumes.
authorized user Key
EVFS Commands
EVFS provides the following commands to configure and manage EVFS:
• evfsadm
The evfsadm utility manages the EVFS subsystem and creates devicefiles for EVFS volumes.
• evfspkey
The evfspkey utility creates, stores, and manages EVFS user keys.
• evfsvol
The evfsvol utility configures and manages the EVFS volumes.
If a user has an authorized user key for an EVFS volume
and the appropriate file permissions for the device file,
the user can enable and disable EVFS volumes (note that
some backup procedures require the user to disable and
enable the volume).
The user can also perform tasks that do not require EVFS
keys, suchas displaying information about EVFS volumes.
EVFS Architecture 25
Page 26
Supported Software
Physical Disk
Type 1: User applications
Type 2: Kernel daemons that
interface with VFS
Type 3: Kernel
Modules that
interface with
physical disks and
implement file
system or volume
management
functions
System Calls
Kernel
Virtual File System (VFS)
File Systems (HFS, VxFS)
EVFS
Pseudo-Driver
Logical Volume Managers
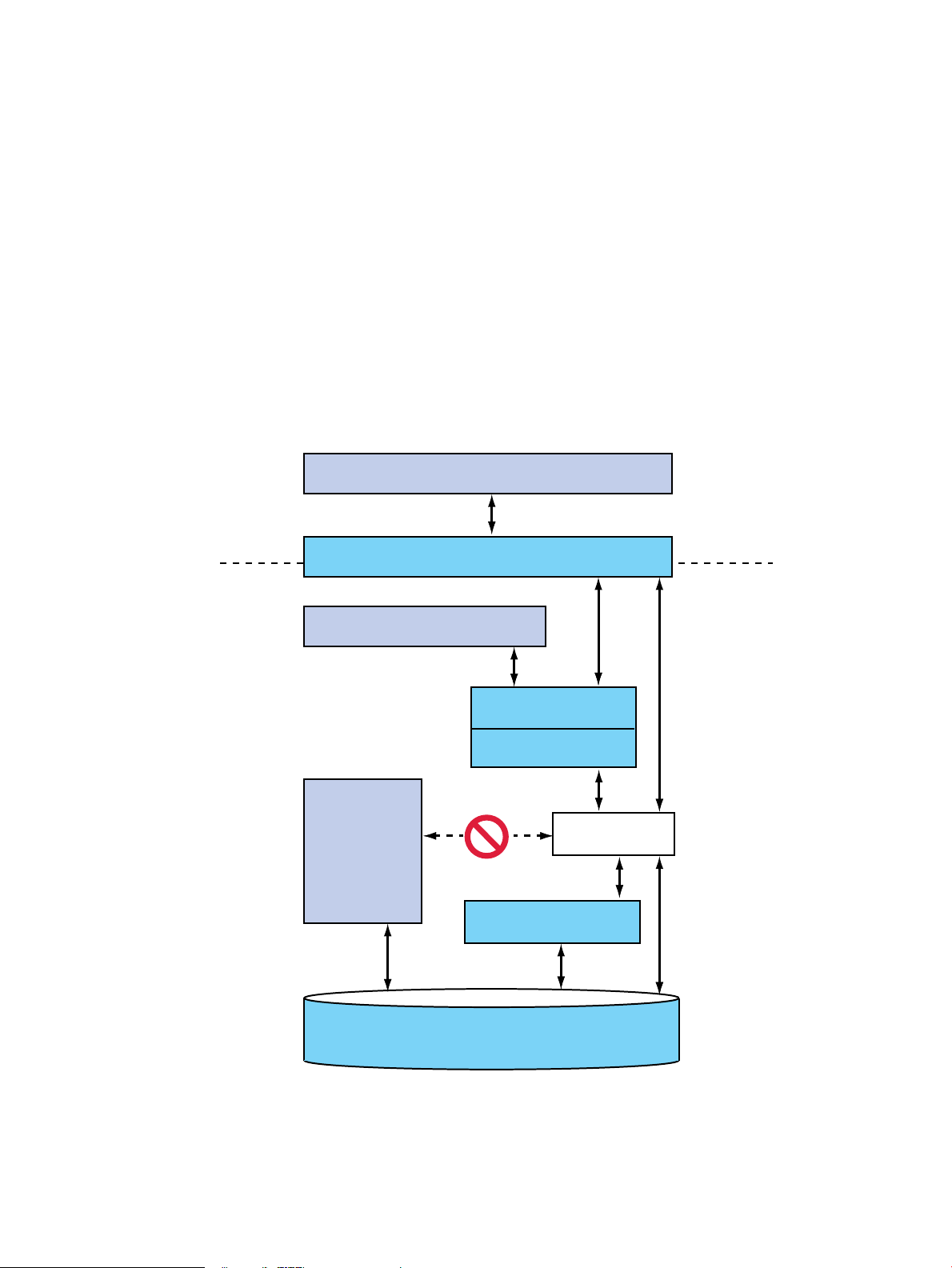
(LVM, VxVM)
Software used with EVFS can be categorized into three types:
• Type 1 Software: Applications without kernel components. EVFS supports Type 1 Software.
Examples of Type 1 software include FTP, rcp, CIFS Server, and Oracle® Database 10g.
(This list is not exhaustive and is included only to provide examples of Type 1 Software.)
• Type 2 Software: Software with kernel modules that access the file system (Virtual File
System, VFS, or HFS or VxFS). EVFS supports Type 2 Software. The NFS server daemon is
an example of Type 2 software.
• Type 3 Software: Software with kernel components that directly access physical volumes
and implement file system or volume management functionality. EVFS does not supprt
Type 3 Software. Examples of Type 3 software include OracleAutomatic Storage Management
(ASM), and file systems other than HFS and VxFS, such as Veritas Cluster File System (CFS)
and Clearcase Multiversion File System (MVFS). (This is not an exhaustive list and is included
only to provide examples of Type 3 Software.)
Figure 1-4 illustrates the data paths for the software types described in the preceding list.
Figure 1-4 Software Types
26 EVFS Introduction
Page 27

Product Limitations and Precautions
The EVFS product has the following limitations:
• EVFS operates with LVM, VxVM and physical volumes only. Each EVFS volume is mapped
to an underlying LVM, VxVM or physical volume.
• You enable EVFS encryption and decryption for an EVFS volume as a single unit. When
you enable EVFS encryption and decryption for a volume, EVFS encrypts and decrypts the
data blocks as the blocks are accessed, and all read operations through the EVFS volume
receive decrypted dataas output, and users can access individual files in cleartext. You must
use normal HP-UX file system permissions and access control to restrict access to the data.
• You cannot encrypt the following objects:
— Files or disk areas used during system boot. This includes the following objects:
◦ the root file system (/)
◦ the HP-UX kernel directory (/stand)
◦ the /usr directory
EVFS cannot decrypt the kernel or other data before the system boots.
CAUTION: Encrypting the boot disk can cause the boot disk to become unusable and
prevent you from booting the system.
— Dump devices.
— Swap space (swap devices or file swap space).
CAUTION: Encrypting swap space can cause the system to panic.
• EVFS does not automatically convert existing volume data to encrypted data. To encrypt
existing volume data, use the inline encryption feature. For more information, see “Step 4:
(Optional) Migrating Existing Data to an EVFS Volume” (page 61).
CAUTION: If you improperly configure EVFS on a volume that already contains data, the
existing data will be unusable.
IMPORTANT: To use inline encryption, 3 MB of spare disk space are required at the end
of the volume, and the minimum volume size must be 4 MB.
• To mount a file system on an EVFS volume, EVFS must be enabled and transferring data to
and from the file system in cleartext (unencrypted). Therefore, any executable that uses file
system utilities to read or write data can operate only on cleartext data.
Network file sharing utilities, such as NFS, CIFS, FTP, or rcp, will transmit files in cleartext,
even if the original files reside on an EVFS volume.
• If you want to use a backup utility that performs incremental backups or that backs up
individual files, EVFS must be enabled. The backup utility receives the data in cleartext,
even if the original files reside on an EVFS volume. If the target backup device is another
EVFS volume, the target EVFS volume re-encrypts the data.
If the target backup device is a tape device or other non-EVFS device:
— You must back up the volume as a volume device (as a single unit), not as a file system
or group of files, to create encrypted backup media. You can create encrypted backup
media using block device utilities, such as dd.
— You cannot create encrypted backup media using file-based utilities.
• If you use Ignite-UX to create boot or installation media, Ignite-UX will include system files
from the /var, /opt, and /usr directories in the media in addition to the kernel file.
Product Limitations and Precautions 27
Page 28

Ignite-UX will read these files in cleartext. If the output media is not an EVFS volume, such
as a tape, Ignite-UX will store these files in cleartext.
• EVFS supports alternate links when used with LVM or VxVM. EVFS does not support
alternate links when used with whole disk access.
• Executing the vxresize command with the -F option can cause lost or corrupted data.
For more information and a workaround, see “vxresize –F Might Cause Data Loss or
Corruption” (page 96).
• Renaming VxVM volumes with EVFS enabled makes the volume unusable. For more
information and a workaround, see “Renaming VxVM Volumes with EVFS Enabled Makes
the Volume Unusable” (page 96).
• EVFS is not supported by SAM or SMH.
• The evfsadm trace command is intended for use by support personnel only. HP does
not support this feature on customer environments.
• During inline encryption, the volume is not accessible until the entire operation is completed.
• The Multi Volume File System feature of Veritas, which is not supported by EVFS.
• EVFS is currently available in English only.
28 EVFS Introduction
Page 29
Known Problems
Possible Device File Collision
(SR 8606459127) Executing the newfs or mkfs command for an EVFS volume can fail on systems
with components that call alloc_fake_device(), such as systems that are NFS clients. This
problem is caused by a defect in the alloc_fake_device() routine.
Symptoms
The newfs or mkfs command fails with a message similar to the following:
vxfs mkfs: /dev/evfs/vg01/relvol1 is mounted, cannot mkfs
The output fromthe lsdev command shows that the charactermajor number used by the device
driver fake is the same as the block major number used by the device driver evfsevol. In the
example that follows, the common number is 2:
# lsdev
Character Block Driver Class
:
:
2 -1 fake pseudo
:
:
115 2 evfsevol pseudo
Workaround
The following workaround is only necessary and applicable to HP-UX 11i v2 Update 2.
Install patch PHKL_37146. You can download patches from the HP IT Resource Center at:
http://www2.itrc.hp.com/service/patch/mainPage.do
Known Problems 29
Page 30

Feedback and Enhancement Requests
HP is evaluating support for additional disk management and data storage products for
subsequent releases of EVFS. Contact your HP representative if you have specific requirements
or enhancement requests.
30 EVFS Introduction
Page 31

2 Installation
This chapter describes how to install EVFS, including prerequisites, installation steps, and
post-installation verification procedures. This chapter addresses the following topics:
• “Prerequisites” (page 32)
• “Installing EVFS” (page 33)
31
Page 32

Prerequisites
The following are the minimum requirements to install and use EVFS.
Hardware Requirements
• HP 9000 computers
• HP Integrity servers
Disk Space Requirements
The system must have at least 12 MB of disk space available.
Operating System Requirements
The operating system must be HP-UX 11i Version 2 Update 2 or HP-UX 11i Version 3.
Patch Requirements and Recommendations
Patch requirements and recommendations listed here are applicable to HP-UX 11i v2 Update 2
and HP-UX 11i v3 as indicated.
You can download patches from the HP IT Resource Center at:
http://www2.itrc.hp.com/service/patch/mainPage.do
NOTE: You do not need to install the superseding patches listed below if you have patches on
your system from a previous installation of EVFS.
Required Patches
For systems running 11i v2 Update 2, the following required patch applies:
On systems with PHCO_32488 and VxFS (the EnableVxFS bundle), you must install patch
PHCO_37228.
Recommended Patches
For systems running 11i v2 Update 2, HP recommends that you install the following patch:
PHKL_37146. HP strongly recommends that you install this patch, which fixes a defect that can
cause the newfs or mkfs command for an EVFS volume to fail on systems with components
that call alloc_fake_device(), such as systems that are NFS clients. See “Possible Device
File Collision” (page 29) for more information.
System Reboot
You do not need to reboot if there is no previous version of EVFS installed.
32 Installation
Page 33

Installing EVFS
Use the following procedure to install EVFS:
1. Review the “Prerequisites” (page 32).
2. Log on to the target system as the root user.
3. Download EVFS from the HP Software Depot at http://www.software.hp.com.
Save the EVFS depot as a local file on the target system, for example:
/tmp/<EVFS-depotname>.depot
4. Use the following command to verify the depot file on the target system:
swlist -d @ /tmp/<EVFS-depotname>.depot
If the EVFS depot file is correctly stored on the system, you will see the following message
after executing the command:
# swlist -d @ /tmp/EVFS.depot
# Initializing...
# Contacting target "my_host"...
#
# Target: my_host:/tmp/EVFS.depot
#
#
# Bundle(s):
#
EVFS A.01.01.00 HP-UX Encrypted Volume and File System (EVFS)
5. Install EVFSusing an interactive swinstall session or the following swinstall command:
# swinstall -x autoreboot=true -s /tmp/<EVFS-depotname>.depot EVFS
The swinstall utility will install the EVFS components.
6. Verify the installation using the swverify EVFS command . If EVFS is installed correctly
on the system, the swverify command will include the following text in the data it reports:
* Verification succeeded
NOTE: Encrypted Volume and File System (EVFS) is installed as a kernel-space component
and a user-space component. You do not need to reboot if there is no previous version of EVFS
installed.
Installing EVFS 33
Page 34

Upgrading from EVFS v1.0 to EVFS v1.1
Use the following procedure to upgrade from a previous version of EVFS:
1. Review the “Prerequisites” (page 32).
2. Log on to the target system as the root user.
3. Download EVFS from the HP Software Depot at http://www.software.hp.com.
Save the EVFS depot as a local file on the target system, for example:
/tmp/EVFS-depotname.depot
4. Stop the EVFS sub-system using the following command:
evfsadm stop
5. Use the following command to verify the depot file on the target system:
swlist -d @ /tmp/EVFS-depotname.depot
If the EVFS depot file is correctly stored on the system, you will see the following message
after executing the command:
# swlist -d @ /tmp/EVFS.depot
# Initializing...
# Contacting target "my_host"...
#
# Target: my_host:/tmp/EVFS.depot
#
#
# Bundle(s):
#
EVFS A.01.01.00 HP-UX Encrypted Volume and File System (EVFS)
6. Install using an interactive swinstall session or the following swinstall command:
# swinstall -x autoreboot=true -s /tmp/EVFS-depotname.depot EVFS
The swinstall utility will install the EVFS components.
NOTE: If your system does not automatically reboot, you must manually reboot to load
the DLKM module.
7. Verify the installation using the following swverify command:
#swverify EVFS
If EVFS is installed correctly on the system, the swverify command will include the
following text in the data it reports:
* Verification succeeded
34 Installation
Page 35

3 Preparing EVFS for Configuration
This chapter describes how to prepare the HP-UX Encrypted Volume and File System (EVFS)
product for configuration. This chapter addresses the following topics:
• “Verifying for Preconfiguration” (page 35)
• “Preparation Overview” (page 36)
• “Step 1: Configuring an Alternate EVFS Pseudo-User” (page 37)
• “Step 2: (Optional) Configuring Alternate Key Database Directories” (page 39)
• “Step 3: (Optional) Modifying EVFS Global Parameters” (page 42)
• “Step 4: Starting the EVFS Subsystem” (page 43)
• “Step 5: Creating User Key Pairs” (page 44)
• “Examples” (page 47)
Verifying for Preconfiguration
Before configuring EVFS, verify the following items:
• Verify that EVFS supports the applications that you want to use with EVFS. See “Supported
Software” (page 26) for more information.
• Verify that EVFS supports the directories you want to encrypt with EVFS. See “Product
Limitations and Precautions” (page 27) for more information.
• EVFS does not automatically convert existing volume data to encrypted data. To encrypt
existing volume data, use the inline encryption feature in this release of EVFS.
CAUTION: If you improperly configure EVFS on a volume that already contains data, the
existing data will be unusable.
IMPORTANT: To use inline encryption, 3 MB of spare disk space are required at the end
of the volume, and the minimum volume size must be 4 MB. If the entire volume is used,
extend the volume using lvextend for LVM, or vxassist for VXVM.
• Each EVFS volume requires approximately 1 MB for the encryption metadata (EMD). Verify
that the volumes you want to encrypt have sufficient space for the EMD.
• To create encrypted backup media to a tape or other non-EVFS device, you must back up
the volume as a volume device (as a single unit), not as a file system or group of files. You
can create encrypted backup media using block device utilities such as dd. Verify that the
size of the LVM, VxVM or physical volumes you are going to encrypt are appropriate for
the backup media you are using and for the time it will take to back up a whole volume.
Verifying for Preconfiguration 35
Page 36

Preparation Overview
Use the following procedure to prepare EVFS for configuration:
1. Configure an alternate EVFS pseudo-user account. You can skip this step if you can use
evfs as the user name and group name for the EVFS pseudo-user. See “Step 1: Configuring
an Alternate EVFS Pseudo-User” (page 37).
2. (Optional) Configure alternate directories for the key database. See “Step 2: (Optional)
Configuring Alternate Key Database Directories” (page 39).
3. (Optional) Modify EVFS global parameters. See “Step 3: (Optional) Modifying EVFS Global
Parameters” (page 42).
4. Start the EVFS subsystem. See “Step 4: Starting the EVFS Subsystem” (page 43).
5. Create user key pairs for EVFS volume owners and authorized users, and recovery key pairs.
See “Step 5: Creating User Key Pairs” (page 44).
36 Preparing EVFS for Configuration
Page 37

Step 1: Configuring an Alternate EVFS Pseudo-User
EVFS uses the pseudo-user evfs to own and control internal resources. When you install EVFS
for the first time, the installation script attempts to add the user account evfs and the group
evfs for the EVFS pseudo-user. If the evfs user account or evfs group already exists on the
system when you initially install EVFS, you must configure a different user account and group
for the EVFS pseudo-user.
TIP: Skip this step if you can use the name evfs as the user and group name for the EVFS
pseudo-user.
If you cannot use evfs as the user and group name for the EVFS pseudo-user, use the following
procedure to configure alternative names:
a. Set the evfs_user attribute in the /etc/evfs/evfs.conf file to an alternate user name.
b. Create an alternate user group for the EVFS pseudo-user.
c. Create the alternative user account for the EVFS pseudo-user.
Step 1a: Setting the evfs_user Attribute
Set the evfs_user attribute in the /etc/evfs/evfs.conf file to an alternative user name
for the EVFS pseudo-user.
Example
The following entry in the /etc/evfs/evfs.conf file sets the name of the EVFS pseudo-user
to my_evfs_user:
evfs_user = my_evfs_user
Step 1b: Creating the User Group
Create a user group reserved for the EVFS pseudo-user.
Example
The following groupadd command creates the user account my_evfs_group:
# groupadd my_evfs_group
Step 1c: Creating the EVFS Pseudo-User Account
Create the alternate EVFS pseudo-user account with the following characteristics:
• Name: This must match thevalue ofthe evfs_user attribute in the /etc/evfs/evfs.conf
file.
• Password: Do not specify a password, and do not enable the password. The entry in
/etc/passwd will contain an asterisk in the password field.
• User ID (UID): A unique ID greater than 100 so it does not conflict with UIDs reserved for
HP-UX system components. Do not use the superuser UID (0).
• Group ID: Any. HP recommends that you create a new groupreserved the EVFS pseudo-user.
• Gecos ID (comment field): Add a comment indicating that this account is used by EVFS.
• Initial Working Directory: Any directory, such as /tmp or /home/evfs.
• Shell: Non-interactive shell, such as /usr/bin/false or no shell.
Example
The following useradd command creates the user account my_evfs_user. The account name
my_evfs_user matches the value for the evfs_user account in the file
/etc/evfs/evfs.conf.
Step 1: Configuring an Alternate EVFS Pseudo-User 37
Page 38

# useradd -g my_evfs_group -c "EVFS pseudo-user" \
-d /tmp -s /usr/bin/false my_evfs_user
38 Preparing EVFS for Configuration
Page 39

Step 2: (Optional) Configuring Alternate Key Database Directories
EVFS stores user key data (public keys, private keys, and stored passphrases) in a key database.
By default, EVFS stores this database in subdirectories and files under the /etc/evfs/pkey
directory. You can modify the pub_key, priv_key, and pass_key attribute statements in the
/etc/evfs/evfs.conf file to configure EVFS to store the key database in alternate directories.
TIP: Configuring alternate key database directories is optional, and you can skip this step in
most topologies.
You can use alternate database directories as follows:
• Store public keys, private keys, and passphrase files in different directories according to
data type (key type or stored passphrase). For example, you can configure EVFS to store
public keys in a public directory because exposing public keys is not a security vulnerability.
• Store public and private keys in distributed file directories. For example, you can configure
EVFS to store public and private keys in an NFS directory so that administrators can access
and use the same keys on multiple systems. This topology is useful when using EVFS with
Serviceguard.
NOTE: It is not efficient to store passphrase files in distributed directories. EVFS encrypts
passphrases with system-specific data, so you must generate a passphrase file on each system
where you want to use the file.
• Use fallback directories to allow users without superuser privileges to create user keys. By
default, users must have superuser privileges to create EVFS keys because the default key
storage directory, /etc/evfs/pkey, is writable only by superusers . You can configure
EVFS to use a fallback storage directory if access to the /etc/evfs/pkey directory fails.
This enables EVFS to store keys created by users with superuser privileges in the protected
/etc/evfs/pkey directory and toallow userswithout superuserprivileges to create EVFS
keys in the fallback directory.
Syntax for pub_key, priv_key, and pass_key Attribute Statements
To configure EVFS to use alternate directories for the user keys and stored passphrases, you
modify the pub_key, priv_key, and pass_key attribute statements in the
/etc/evfs/evfs.conf file. The syntax for these attribute statements is as follows:
pub_key = library[pkeydir:key_directory,onfail:action]...
priv_key = library[pkeydir:key_directory,onfail:action]...
pass_key = library[pkeydir:key_directory,onfail:action]...
Each attribute statement must be on one input line, without line breaks or line continuation
characters. A statement can contain multiple library[specifications...]terms, separated
by spaces. A library[specifications] term cannot contain spaces.
The parameters have the following meanings:
pub_key
priv_key
pass_key
library
Indicates that the attribute statement specifies EVFS behavior for user public
keys.
Indicates that the attribute statement specifies EVFS behavior for user
private keys.
Indicates that the attribute statement specifies EVFS behavior for
passphrases that secure user private keys.
Specifies the fully qualified pathname of the encryption and storage library.
Valid values:
/usr/lib/evfs/hpux64/libevfs_pkey.so (HP Integrity servers)
Step 2: (Optional) Configuring Alternate Key Database Directories 39
Page 40

/usr/lib/evfs/pa20_64/libevfs_pkey.sl (HP 9000 servers)
[
key_directory
Literal left square bracket.
Specifies the fully qualified pathname of the base directory in which to
store key data, such as /etc/evfs/pkey. See “Key Storage Directory
Requirements” (page 40) for more information.
If you want to use the autostart feature, the autostart option you specify in
the /etc/evfs/evfstab file is determined by the location of the
key_directory. See “Step 5: (Optional) Configuring the Autostart
Feature” (page 62) for more information.
action
Specifies the EVFS action if attempts to write to or read from the
key_directory fail.
continue
stop
]
Literal right square bracket.
Key Storage Directory Requirements
• Directories used to store user keys and passphrases cannot be on EVFS volumes. EVFS
cannot access key files stored on an EVFS volume to enable the EVFS volume.
• If there are file systems on EVFS volumes in the /etc/fstab file that you want the system
to mount at system startup, the key database must reside on the local root file system (the
system must be able to access the keys early in the system startup procedure).
• If the private key directory is an NFS-mounted directory, the directory must be mounted
with read and write access so EVFS can re-encrypt the private key file as needed (the NFS
server must not export the directory with the ro flag).
• HP recommends that the base directory is writable by superusers or users with appropriate
privileges only. For example, the /etc/evfs/pkey directory is installed with the following
permissions, owner, and group:
drwxr-xr-x 4 bin bin 96 Mar 16 17:26 pkey
You can also create and configure a fallback directory to allow nonprivileged users to create
keys.
Causes EVFS to continue to the next
library[specifications...] term.
Causes EVFS to stop processing and return an error.
Default pub_key, priv_key and pass_key Attribute Statements
The /etc/evfs/evfs.conf file installed with the EVFS product on HP Integrity servers
contains the following pub_key, priv_key, and pass_key attribute statements:
pub_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
priv_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
pass_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
These statements configure EVFS to use the libevfs_pkey library to process all user key data
(public keys, private keys, and passphrase files), and to save all user key data in subdirectories
under the /etc/evfs/pkey directory. If EVFS cannot access key data in the directory
/etc/evfs/pkey, EVFS returns an error.
The /etc/evfs/evfs.conf file installed with the EVFS product on HP 9000 servers contains
equivalent statements, with the HP 9000 libevfs_pkey library,
/usr/lib/evfs/pa20_64/libevfs_pkey.sl.
40 Preparing EVFS for Configuration
Page 41

Example: Alternate Directory for Public Keys
The following attribute statements configure EVFS to store public keys in the user-created
directory /etc/evfs/mykeys and to store private keys and passphrase files in the directory
/etc/evfs/pkey:
pub_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/mykeys,onfail:stop]
priv_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
pass_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
Example: NFS Directory for Public and Private Keys
The following attribute statements configure EVFS to store public and private keys in the
NFS-mounted directory /nfs_server1/etc/evfs/pkey and to store passphrase files in the
local directory /etc/evfs/pkey:
pub_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/nfs_server1/etc/evfs/pkey,onfail:stop]
priv_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/nfs_server1/etc/evfs/pkey,onfail:stop]
pass_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:stop]
To use the autostart feature for volumes that have keys stored in NFS-mounted directories, you
must specify the boot_remote option in the /etc/evfs/evfstab file. See “Step 5:
(Optional) Configuring the Autostart Feature” (page 62) for more information.
Example: Fallback Directory for Nonprivileged Users
The following attribute statements configure EVFS to first attempt to store key data in the
protected directory /etc/evfs/pkey. If it fails, EVFS falls back to the user-created directory
/opt/evfskeys, which is writable by the appropriate users without superuser privileges. If
EVFS cannot access /opt/evfskeys, EVFS stops processing the request and return an error.
pub_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:
continue] /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/opt/evfskeys,onfail:stop]
priv_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:
continue] /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/opt/evfskeys,onfail:stop]
pass_key = /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/etc/evfs/pkey,onfail:
continue] /usr/lib/evfs/hpux64/libevfs_pkey.so[pkeydir:/opt/evfskeys,onfail:stop]
To use the autostart feature to enable an EVFS volume using keys stored on the root disk of the
local system, specify the boot_local option for the volume in the /etc/evfs/evfstab file.
To use the autostart feature to enable an EVFS volume using keys stored on a nonroot disk of
the local system, specify the boot_local2 option for the volume. In this example,
/opt/evfskeys is not on the root disk, so you must specify boot_local2 to use the autostart
feature for EVFS volumes enabled using keys stored in/opt/evfskeys. See “Step 5: (Optional)
Configuring the Autostart Feature” (page 62) for more information.
Step 2: (Optional) Configuring Alternate Key Database Directories 41
Page 42

Step 3: (Optional) Modifying EVFS Global Parameters
Edit the /etc/evfs/evfs.conf file to modify EVFS global parameters. This step is optional,
and you can use the default attribute values for most installations. Three attributes you might
want to modify are:
• data_cipher
The data_cipher attribute specifies the default data encryption algorithm (the algorithm
EVFS uses to encrypt volume data). You can also specify the data encryption when you enter
the evfsvol create command, as described in “Step 1: Configuring an EVFS Volume”
(page 51).
Valid values:
aes-128-cbc (128-bit AES CBC)
aes-192-cbc (192-bit AES CBC)
aes-256-cbc (256-bit AES CBC)
A longer key length provides more security, but slows data transfer rates.
Default: aes-128-cbc
• emd_backup
The emd_backup attribute specifies the directory EVFS uses to store backup images of EMD
data.
Default: /etc/evfs/emd
• pbe
The pbe attribute specifies the encryption library EVFS uses to secure EVFS private keys.
On systems with HP-UX Trusted Computing Services (TCS), you can modify this attribute
so that EVFS uses TCS to secure EVFS private keys.
For more information about using TCS with EVFS, see the HP-UX TCS product
documentation.
For a complete list of global parameters, see evfs.conf(4).
42 Preparing EVFS for Configuration
Page 43

Step 4: Starting the EVFS Subsystem
You must start the EVFS subsystem to create EVFS keys and volumes. Starting the EVFS
subsystem does not enable encryption of the EVFS volume. You must still create the EVFS
volumes and enable EVFS for each volume.
To start the EVFS subsystem, enter the following command:
evfsadm start [-n number_threads]
where:
-n number_threads
The evfsadm startcommand starts the EVFS subsystem by initializing the EVFS pseudo-driver
and starting the evfsevold process. The evfsevold process starts kernel threads for data
encryption and decryption. You must start the EVFS subsystem to generate EVFS user keys and
enable EVFS volumes. This command is automatically executed at system startup if EVFS is
enabled in the /etc/rc.config.d/evfs file. See “Step 5: (Optional) Configuring the Autostart
Feature” (page 62) for more information about enabling EVFS to automatically start at system
startup.
Specifies the number of threads to create for EVFS encryption and
decryption processing.
Range: On single-processor systems, 1 is the only valid value.
On multiprocessor systems, the maximum number of threads is the
number of processors in the system.
Default: On single-processor systems, the default is 1.
On multiprocessor systems, the default is the number of processors
in the system minus 1. Setting the number of threads to a lower value
can decrease EVFS throughput.
Example
# evfsadm start
EVFS subsystem started.
Step 4: Starting the EVFS Subsystem 43
Page 44

Step 5: Creating User Key Pairs
Each user key pair has a key name. The default key name is name of the user for whom the key
pair is created.
This section addresses the following topics:
• “Guidelines for Creating User Keys” (page 44)
• “Creating Keys for EVFS Volume Owners” (page 44)
• “Creating Recovery Keys” (page 45)
• “Creating Keys for authorized users” (page 46)
Guidelines for Creating User Keys
Use the following guidelines to determine the number and types of user keys to create. The user
key types and privileges are described in “User Key Privileges” (page 24).
• At a minimum, you must create one user key pair (public/private key pair) for the EVFS
volume owner.
• You can use one key pair for multiple EVFS volumes, but using a unique key pair for each
EVFS volume is more secure.
• HP recommends that you create at least one recovery key pair. You can use a recovery key
to assign a new owner to a volume if the owner key pair is lost or compromised. HP
recommends that you store the private recovery key off line.
• To use the autostart feature, you must create a passphrase file. Passphrase files are a security
risk. If you use a passphrase file, you can reduce the security risk by creating a user key pair
for an authorized user and creating the passphrase file for the authorized user key pair
instead of the owner key pair.
• To create encrypted backup media on a tape device, a user must have an authorized user
key pair for the volume. (The user must execute the evfsvol disable command as part
of the backup procedure, which requires an EVFS authorized user key or owner key pair.)
Creating and configuring an authorized user key pair will enable a non-owner to create
encrypted backup media.
• You can create multiple key pairs for each user. For example, if a user is the owner of multiple
EVFS volumes, you can create a unique key pair for each volume that the user owns.
Creating Keys for EVFS Volume Owners
Use the following evfspkey keygen command to create key pairs for EVFS volume owners:
evfspkey keygen [-p|-s] [-c cipher] [-u user] [-k keyname]
where:
-p Causes evfspkey to prompt for passphrase. The evfspkey utility prompts
you for a passphrase and store the passphrase in an encrypted file. The
passphrase must contain at least eight characters.
CAUTION: A stored passphrase enables you to use the EVFS autostart feature
but it is a security risk.
-s Causes evfspkey to generate a passphrase automatically. The evfspkey
utility generates a passphrase for you and stores the passphrase in an encrypted
file.
-c cipher
44 Preparing EVFS for Configuration
Specifies the type of public/private (cipher) keys to create.
Valid values:
rsa-1024 (RSA 1024-bit keys)
rsa-1536 (RSA 1536-bit keys)
Page 45

Example
rsa-2048 (RSA 2048-bit keys)
Default: rsa-1536
-u user Specifies the user name of the key owner. If you do not specify -u user,
evfspkey uses your user name as the key owner. You must have superuser
privileges or the appropriate privileges to create a key pair for another user.
-k keyname Specifies the key name. If you do not specify -k keyname, evfspkey uses the
user name as the key name.
Valid value: An ASCII string, 1 to 255 characters long.
NOTE: Do not use the -s option when creating a key pair for an EVFS volume owner. The -s
option does not prompt for a passphrase. It automatically generates the passphrase, so there is
no way for you to know the passphrase. You must know the owner key's passphrase when
creating an EVFS volume.
In the following example, the root user creates a key with the rootkey1 key name :
# evfspkey keygen -k rootkey1
Enter passphrase:(enter a passphrase)
Re-enter passphrase:(re-enter the passphrase to confirm it)
Public/Private key pair "root.rootkey1" has been successfully generated.
(The evfspkey utility shows the key ID, which is the owner name, root,
and the key name, rootkey1.)
Creating Recovery Keys
Creating recovery keys is optional, but HP recommends that you create at least one recovery
key pair.
Use the following evfspkey keygen command to create a public/private key pair for the
recovery user. The evfspkey utility will prompt you for a passphrase to secure the private key.
The passphrase must contain at least eight characters.
You must have superuser privileges or the appropriate privileges to create a key for the recovery
user.
evfspkey keygen -c rsa-2048 -r [-k keyname]
where:
-r
-k keyname Key name. If you do not specify -k keyname, evfspkey uses the EVFS
Storing the recovery user's Private Key
When you create the key pair for the recovery user, evfspkey saves the private key in the current
working directory with the file name key_name.priv, or evfs.priv by default. Store this
private key off line. Copy the private key to removable media, and delete the private key on the
local system.
Specifies that the key pair created is a recovery key pair.
pseudo-user name (evfs) as the key name.
Valid value: An ASCII string, 1 to 255 characters long.
Examples
In the following example, the user creates a recovery key. The evfspkey utility saves the private
key in the current directory with the file name evfs.priv. Store this file off line.
# evfspkey keygen -c rsa-2048 -r
Step 5: Creating User Key Pairs 45
Page 46

In the following example, the user creates a second recovery key. The evfspkey utility saves
the private key in the current directory with the file name evfs2.priv. Store this file off line.
# evfspkey keygen -c rsa-2048 -r -k evfs2
Creating Keys for authorized users
Creating keys for authorized users is optional. A user with an authorized user key can enable
and disable encryption and decryption access to an EVFS volume, but cannot change the EVFS
volume owner, destroy a volume, or add and delete keys to a volume.
Use the following evfspkey keygen command to create key pairs for authorized users:
evfspkey keygen [-p|-s] [-c cipher] [-u user] [-k keyname]
where:
-p Causes evfspkey to prompt for passphrase. The evfspkey utility will prompt
you for a passphrase and store the passphrase in an encrypted file. The
passphrase must contain at least eight characters.
CAUTION: A stored passphrase enables you to use the EVFS autostart feature
but it is a security risk.
-s Causes evfspkey to generate a passphrase automatically. The evfspkey
utility will generate a passphrase for you and store the passphrase in an
encrypted file.
-c cipher
Specifies the type of public/private (cipher) keys to create.
Valid values:
Examples
rsa-1024 (RSA 1024-bit keys)
rsa-1536 (RSA 1536-bit keys)
rsa-2048 (RSA 2048-bit keys)
Default: rsa-1536
-u user Specifies the user name of the key owner. If you do not specify -u user,
evfspkey uses your user name as the key owner. You must have superuser
capability or the appropriate privileges to create a key pair for another user.
-k keyname Specifies the key name. If you do not specify -k keyname, evfspkey uses the
user name as the key name.
Valid value: An ASCII string, 1 to 255 characters long.
In the following example, the root user creates a key for the user init with the key name
initkey. The key will be used for the autostart feature. The evfspkey utility generates a
passphrase and stores the passphrase.
# evfspkey keygen -s -u init -k initkey
Public/Private key pair "init.initkey" has been successfully generated.
In the following example, the root user creates a key for the user mittal-musa. The key name
is also mittal-musa.
# evfspkey keygen -u mittal-musa
Enter passphrase:(enter a passphrase)
Re-enter passphrase:(re-enter the passphrase to confirm it)
Public/Private key pair "mittal-musa.mittal-musa" has been
successfully generated.
46 Preparing EVFS for Configuration
Page 47

Examples
This section contains preparation examples.
User Session
The following example lists the commands entered by the root user to create an encrypted
volume. These commands correspond to steps 4 through 5 in this chapter. The user skips “Step
1: Configuring an Alternate EVFS Pseudo-User”, “Step 2: (Optional) Configuring Alternate Key
Database Directories”, and “Step 3: (Optional) Modifying EVFS Global Parameters”, and uses
the default EVFS pseudo-user and global parameters. The user must still configure the autostart
feature and back up the configuration.
Step 4: Start the EVFS subsystem.
# evfsadm start
Step 5: Create a key pair for the root user. The key name will be rootkey1. evfspkey will
prompt you for a passphrase.
# evfspkey keygen -u root -k rootkey1
Optional – Create a key pair for the recovery user. evfspkey will prompt you for a passphrase
and save the private key in the current working directory with the file name evfs.priv. Store
this key off line.
# evfspkey keygen -c rsa-2048 -r
Examples 47
Page 48

48
Page 49

4 Configuring an EVFS Volume
This chapter describes how to configure an EVFS Volume after preparing EVFS for configuration.
This chapter addresses the following topics:
• “Configuration Overview” (page 49)
• “Option 1: Creating a New EVFS Volume” (page 50)
• “Option 2: Converting a Volume with Existing Datato an EVFS Volume (Inline Encryption)”
(page 65)
• “Examples” (page 75)
Configuration Overview
There are two procedures to configure an EVFS Volume:
• Option 1: Creating a new EVFS volume
This procedure creates a new EVFS volume. Use this option to create an EVFS volume on
an unused LVM, VxVM or physical volume. After you have created the EVFS volume, you
can migrate existing data to the new EVFS volume.
CAUTION: You cannot create an LVM or VxVM volume above an EVFS volume.
You can create an EVFS volume on an existing LVM, VxVM, or physical volume, but any
existing data on the volume is rendered unusable.
• Option 2: Converting a volume with existing data into an EVFS volume (Inline Encryption)
This procedure converts a volume with existing data into an EVFS volume using the inline
encryption feature.
IMPORTANT: To use inline encryption, 3 MB of spare disk space are required at the end
of the volume, and the minimum volume size must be 4 MB. If the entire volume is used,
extend the volume using lvextend for LVM, or vxassist for VXVM.
NOTE: The inline encryption process takes approximately 1.2 minute per GB on 4-CPU
rx4640. Actual performance times vary depending on usage and configuration.
Configuration Overview 49
Page 50

Option 1: Creating a New EVFS Volume
This section describes how to create a new EVFS Volume. This section addresses the following
topics:
• “Step 1: Configuring an EVFS Volume” (page 51)
• “Step 2: Creating and Mounting a File System on an EVFS Volume” (page 56)
• “Step 3: Verifying the Configuration” (page 59)
• “Step 4: (Optional) Migrating Existing Data to an EVFS Volume” (page 61)
• “Step 5: (Optional) Configuring the Autostart Feature” (page 62)
• “Step 6: Backing Up Your Configuration” (page 64)
Before using this procedure, you must complete the tasks in Chapter 3 (page 35).
50 Configuring an EVFS Volume
Page 51

Step 1: Configuring an EVFS Volume
Use the following procedure to configure an EVFS volume.
a. Create an LVM or VxVM volume for the EVFS volume if you are not usingwhole diskaccess.
b. Create EVFS volume device files by mapping the LVM, VxVM, or physical volume to EVFS.
c. Create the EMD area on the EVFS volume.
d. (Optional) Add recovery keys and authorized user keys.
e. Enable the EVFS volume.
Step 1a: Creating an LVM or VxVM Volume for EVFS
Skip this step if you are not using LVM or VxVM (if you are directly accessing the whole
physical disk as a physical volume). You will create the EVFS volume directly above the physical
volume in the next step.
If you are using LVM or VxVM (you are not directly accessing the physical disk as a physical
volume), use the lvcreate or vxassist command to create a new LVM or VxVM volume to
use for the EVFS volume. Include 1 MB for the EVFS Encryption Metadata (EMD) area. See
lvcreate(1M) or vxassist(1M) for more information.
Mirrored Volumes To use an LVM or VxVM mirrored volume for the EVFS volume, create or
enable mirroring on the volume before configuring EVFS on the volume. Use the appropriate
LVM command (lvcreate -m or lvextend -m) or VxVM command (vxassist mirror or
vxplex att).
CAUTION: You cannot create an LVM or VxVM volume above an EVFS volume.
You can create an EVFS volume on an existing LVM, VxVM, or physical volume, but any existing
data on the volume is rendered unusable.
Examples
In the following example, the user creates a new LVM volume in the vg01 volume group:
# lvcreate -L 64 -n lvol5 vg01
Logical volume "/dev/vg01/lvol5" has been successfully created with
character device "/dev/vg01/rlvol5".
Volume Group configuration for /dev/vg01 has been saved in
/etc/lvmconf/vg01.conf
In the following example, the user creates a new VxVM volume in the rootdg disk group:
# vxassist -g rootdg make vol05 64m
Step 1b: Creating EVFS Volume Device Files
Use the evfsadm map command to create the EVFS volume device files by mapping the LVM,
VxVM, or physical volume to EVFS .
You cannot use EVFS with the following objects:
• Files or disk areas used during system boot. This includes the following objects:
— the root disk (/)
— the boot disk
— the HP-UX kernel directory (/stand)
— the /usr directory"
EVFS cannot decrypt the kernel or other data before the system boots.
Option 1: Creating a New EVFS Volume 51
Page 52

CAUTION: Encrypting the boot disk makes the boot disk unusable and prevents you from
booting the system.
• Swap space (swap devices or file swap space).
CAUTION: Encrypting swap space can cause the system to panic.
• Dump devices.
The syntax of the evfsadm map command is as follows:
evfsadm map volume_path
where:
volume_path
Specifies the absolute path of the block device file for the underlying LVM,
VxVM, or physical volume, such as /dev/vx/dsk/rootdg/vol01,
/dev/vg01/lvol5, or /dev/dsk/c2d0t0.
The evfsadm map command maps the underlying LVM, VxVM, or physical volume to an EVFS
volume. The command also creates a block and a character () device file for the EVFS volume
and adds them to the kernel registry. The evfsadm command stores the EVFS volume device
files using the same file names as the underlying volume block and character device files, but in
subdirectories under the /dev/evfs directory instead of the /dev directory.
NOTE: The maximum number of volumes that the system can map to EVFS is 1023.
Examples
In the following example, the user maps the LVM volume /dev/vg01/lvol5 to an EVFS
volume:
# evfsadm map /dev/vg01/lvol5
Logical volume "/dev/vg01/lvol5" has been successfully mapped
to encrypted volume "/dev/evfs/vg0l/lvol5".
The evfsadm utility creates the following EVFS volume device files:
/dev/evfs/vg01/lvol5
/dev/evfs/vg01/rlvol5
In the following example, the user maps the VxVM volume/dev/vx/dsk/rootdg/vol05 to
an EVFS volume:
# evfsadm map /dev/vx/dsk/rootdg/vol05
Logical volume "/dev/vx/dsk/rootdg/vol05" has been successfully mapped
to encrypted volume "/dev/evfs/vx/dsk/rootdg/vol05".
The evfsadm utility creates the following EVFS volume device files:
/dev/evfs/vx/dsk/rootdg/vol05
/dev/evfs/vx/rdsk/rootdg/vol05
In the following example, the user maps the physical volume /dev/dsk/c2t0d0 to an EVFS
volume:
# evfsadm map /dev/dsk/c2t0d0
Logical volume "/dev/dsk/c2t0d0" has been successfully mapped to
encrypted volume "/dev/evfs/dsk/c2t0d0".
The evfsadm utility creates the following EVFS volume device files:
/dev/evfs/dsk/c2t0d0
/dev/evfs/rdsk/c2t0d0
Step 1c: Creating the EMD
Use the evfsvol create command to create the EMD area on the EVFS volume and specify
the owner key pair for the volume:
52 Configuring an EVFS Volume
Page 53

evfsvol create -k keyname [-c cipher]evfs_volume_path
where:
-k keyname Specifies the keypair name. The evfsadm utility creates the EMD area
with the keyname as the owner key. For information about user keys,
see “Step 5: Creating User Key Pairs” (page 44).
-c cipher
Specifies the cipher (cryptography) algorithm EVFS uses to encrypt
the volume data.
Valid values:
aes-128-cbc (128-bit AES CBC)
aes-192-cbc (256-bit AES CBC)
aes-256-cbc (256-bit AES CBC)
A longer key length provides more security, but it slows data transfer
rates.
Default: The value of the data_cipher attribute in the
/etc/evfs/evfs.conf file. The default value for this attribute is
aes-128-cbc.
evfs_volume_path
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/rdsk/c2t0d1.
CAUTION: The evfsvol create command overwrites any existing data on the volume.
If you have existing data that you want to protect with EVFS, you must use one of the following
methods:
• Use option 1 to create an EVFS volume on an unused LVM, VxVM, or physical volume and
then copy the data to the EVFS volume.
• Use option 2 to convert an existing volume into an EVFS volume.
For more information, see “Configuration Overview” (page 49).
When the evfsvol utility creates the EMD, it:
• Reads operating parameters from the /etc/evfs/evfs.conf file, such as the data
encryption algorithm for the volume, and writes them to the EMD.
• Generates the volume encryption key (the symmetric key used to encrypt the volume data).
• Creates a key record for the owner by encrypting the volume encryption key using the
owner's public key. The evfsvol utility then writes this key record to the EMD.
Example
The root user enters the following evfsvol create command. EVFS creates the EMD and
overwrites any existing data on the volume. The owner key for the volume will be
root.rootkey1.
# evfsvol create -k rootkey1 /dev/evfs/vg01/lvol5
Enter owner passphrase:(Enter the passphrase for rootkey1.)
Encrypted volume "/dev/evfs/vg01/lvol5" has been successfully created.
Step 1d: (Optional) Adding Recovery Keys and authorized user Keys
Optionally, use the evfsvol add command to add recovery and authorized user key pairs to
the EVFS volume. HP recommends that you add a recovery key pair to each EVFS volume.
i. Use the following command to add a recovery key pair:
evfsvol add -r [-k keyname] evfs_volume_path
where:
Option 1: Creating a New EVFS Volume 53
Page 54

—r Specifies that the key pair is a recovery key pair.
-k keyname Specifies the name of the key pair to add. If you do not specify -k
keyname, evfsvol uses the EVFS pseudo-user (evfs)as the key
owner and key name. You can configure up to two recovery keys
per EVFS volume. For information about user keys, see “Step 5:
Creating User Key Pairs” (page 44).
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/rdsk/c2t0d1.
You must be the owner of the EVFS volume to add a recovery key. If you do not have a
stored passphrase for the owner key, evfsvol prompts you for the passphrase.
Example
The following command adds the default recovery key to the /dev/evfs/vg01/lvol5
volume. The default recovery key owner and key name is evfs.
# evfsvol add -r /dev/evfs/vg01/lvol5
Enter owner passphrase:
(Enter the passphrase for the recovery key evfs.)
Key "evfs.evfs" has been successfully added to encrypted volume
"/dev/evfs/vg01/lvol5".
ii. Use the following command to add authorized user key pairs for the EVFS volume.
Authorized users can perform all the operations on the EVFS volume that the owner can,
except changing the EVFS volume owner, adding keys to the volume, and destroying the
EMD.
evfsvol add -u user [-k keyname] evfs_volume_path
where:
-k keyname Specifies the name of the key to add. If you do not specify -k
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
You must be the owner of the EVFS volume to add an authorized user key. If you do not
have a stored passphrase for the owner's private key, evfsvol prompts you for the
passphrase.
Example
In the following example, the EVFS volume owner adds an authorized user key pair to the
EMD:
# evfsvol add -u init -k initkey /dev/evfs/vg01/lvol5
Enter owner passphrase:
(Enter the passphrase for the owner's key.)
Key ID "init.initkey" has been successfully added to encrypted volume
"/dev/evfs/vg01/lvol5"
Step 1e: Enabling the EVFS Volume
keyname, evfsvol uses your user name as the key name.
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/rdsk/c2t0d1.
Use the evfsvol enable command to enable encryption and decryption access for the EVFS
volume:
evfsvol enable [-p]|[-k keyname] evfs_volume_path
where:
54 Configuring an EVFS Volume
Page 55

-p
Specifies non-interactive mode. EVFS uses the key ID from the
/etc/evfs/evfstab file and uses a stored passphrase. To use this
option, you must add a key ID to the entry in the
/etc/evfs/evfstab file for this volume and have a stored
passphrase for the private key. If you do not specify this option,
evfsvol prompts you for the passphrase for the private key.
-k keyname
Specifies the name of the key pair to use. This must be the owner key
or the key of an authorized user for this EVFS volume. If you do not
specify -k keyname, evfsvol uses your user name as the key name.
evfs_volume_path
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/rdsk/c2t0d1.
To enable the EVFS volume, the evfsvol utility:
• Retrieves the passphrase for the owner or authorized user's private key by prompting the
user for the passphrase or by using system data to decrypt the stored passphrase.
• Uses the passphrase to decrypt the owner or authorized user's private key.
• Uses the private key to decrypt the volume encryption key in the appropriate key record.
EVFS can now use the volume encryption key to encrypt and decrypt the volume data.
Example
The root user enters the following command to enable the EVFS volume:
# evfsvol enable -k rootkey1 /dev/evfs/vg01/lvol5
Enter user passphrase:
(Enter the passphrase for the key rootkey1.)
Encrypted volume "/dev/evfs/vg01/lvol5" has been successfully enabled.
Option 1: Creating a New EVFS Volume 55
Page 56

Step 2: Creating and Mounting a File System on an EVFS Volume
Use the following procedure to createand mount a file system on an EVFS volume. This procedure
is the same as the one used to create and mount a file system on an LVM, VxVM, or physical
volume except that you specify the EVFS character (raw) and block volume device files instead
of the LVM, VxVM, or physical device files.
a. Use the newfs command to create a new file system on the character (raw) EVFS volume.
b. (Optional) Use the fsck command to check the integrity of the file volume.
c. Use the mkdir command to create a mount point for the new file system.
d. Mount the file system on the EVFS volume.
e. (Optional) Add an entry to the /etc/fstab file for the encrypted volume.
Step 2a: Creating a New File System with newfs
Use the newfs command to create a new file system on the character (raw) EVFS volume. For
example:
newfs [-F file_sys_type] raw_evfs_volume_path
where:
-F file_sys_type
raw_evfs_volume_path
Specifies the file system type. This must be a file system type
supported by the underlying LVM, VxVM, or physical volume,
such as hfs or vxfs.
Specifies the absolute pathname of the character (raw) EVFS
volume device file, such as /dev/evfs/vg01/rlvol5,
/dev/evfs/vx/rdsk/rootdg/vol05, or
/dev/evfs/rdsk/c2t0d1.
Example
The following example creates a new file system on the character (raw) EVFS volume
/dev/evfs/vg01/rlvol5 (the underlying volume is an LVM volume).
# newfs -F vxfs /dev/evfs/vg01/rlvol5
The following example creates a new file system on the character (raw) EVFS volume
/dev/evfs/vx/rdsk/rootdg/vol05 (the underlying volume is a VxVM volume).
# newfs -F vxfs /dev/evfs/vx/rdsk/rootdg/vol05
Step 2b: (Optional) Using fsck to Check the File Volume
Optionally, use the fsck command to check the integrity of the file volume:
fsck [-F file_sys_type] raw_evfs_volume_path
where:
-F file_sys_type
raw_evfs_volume_path
Specifies the file system type. This must be a file system type
supported by the underlying LVM, VxVM, or physical volume,
such as hfs or vxfs. If you do not specify this option,fsck uses
the file system type from the corresponding entry in the
/etc/fstab file. See fsck(1m) for more information.
Specifies the absolute pathname for the character (raw) EVFS
volume device file, such as /dev/evfs/vg01/rlvol5,
/dev/evfs/vx/rdsk/rootdg/vol05, or
/dev/evfs/rdsk/c2t0d1.
Example
The following example checks the integrity of the file system on the EVFS volume created in the
previous step:
56 Configuring an EVFS Volume
Page 57

# fsck /dev/evfs/vg01/rlvol5
Step 2c: Creating the Mount Point
Use the mkdir command to create the mount point. For example:
mkdir mount_point
where:
mount_point
Example
The following command creates the mount point /opt/encrypted_data:
# mkdir /opt/encrypted_data
Specifies the path for the mount point.
Step 2d: Mount the File System on the EVFS Volume
Mount the file system on the EVFS volume:
mount [-F file_sys_type] /dev/evfs/evfs_volume_path mount_point
where:
-F file_sys_type
evfs_volume_path
mount_point
Specifies the file system type. If you do not specify this option, the
mount command uses the file system type from the corresponding
entry in /etc/fstab. See mount(1m) for more information.
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/dsk/c2t0d1.
The path for the mount point.
Example
The following command mounts the EVFS-based file system on the mount point created in the
previous step:
# mount -F vxfs /dev/evfs/vg01/lvol5 /opt/encrypted_data
Step 2e: (Optional) Adding an Entry to /etc/fstab
Optionally, add an entry to the /etc/fstab file for the encrypted volume. The system can use
this entry for the mount -a command (mount all file systems in the /etc/fstab file) or to
automatically mount the file system at system startup. For file systems on EVFS volumes in the
/etc/fstab file that you want the system to mount at system startup, the key database must
reside on the local root file system (the system must be able access the keys early in the system
startup procedure).
The syntax for the entry is as follows:
evfs_volume_path mount_point file_sys_type [options]
where:
evfs_volume_path
mount_point
file_sys_type
options
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/dsk/c2t0d1.
The path for the mount point.
The file system type. This must be a file system type supported by the
underlying LVM, VxVM, or physical volume, such as hfs or vxfs.
Options for the entry. See fstab(4) for more information.
Option 1: Creating a New EVFS Volume 57
Page 58

Example
The administrator adds the following entry for the new file system in the /etc/fstab file:
/dev/evfs/vg01/lvol5 /opt/encrypted_data vxfs defaults 0 2
58 Configuring an EVFS Volume
Page 59

Step 3: Verifying the Configuration
Use the following commands to verify your EVFS configuration:
• evfsadm stat -a
• evfsvol display evfs_volume_path
evfsadm stat -a
After you access data or mount a file system on an EVFS volume that is correctly configured, the
output for the evfsadm stat -a command shows nonzero values for the number of blocks
read (bpr), written (bpw), decrypted (bpd), and encrypted (bpe). The output is similar to the
following:
# evfadm stat -a
----- EVFS statistics -----
Total EVFS Volumes: 1
EVFS Subsystem Status: up
Active Encryption Threads: 2
---- EVFS Volume Name ----|--- State ---|---------------- Queues -------------|
orr owr odr oer
/dev/evfs/vg01/lvol5 enabled 0 0 0 0
---- EVFS Volume Name ----|--- State ---|-------------- Counters -------------|
bpr bpw bpd bpe
/dev/evfs/vg01/lvol5 enabled 2074 52441 362 52345
---- EVFS Volume Name ----|--- State ---|---------------- Rates --------------|
kbpsr kbpsw dkbps ekbps
/dev/evfs/vg01/lvol5 enabled 25 3 362 34
For descriptions of the output fields, see “Displaying I/O and Encryption Statistics (evfsadm
stat)” (page 130) .
evfsvol display evfs_volume_path
The evfsvol display evfs_volume_path command displays information about the EVFS
volume, including the name of the underlying LVM, VxVM, or physical volume device file, and
the names of the keys configured for the EVFS volume. The output for the evfsvol display
evfs_volume_path is similar to the following:
# evfsvol display /dev/evfs/vg01/lvol5
EVFS Volume Name: /dev/evfs/vg01/lvol5
Mapped Volume Name: /dev/vg01/lvol5
EVFS Volume State: enabled
EMD Size (Kbytes): 520
Max User Envelopes: 1024
Data Encryption Cipher: aes-128-cbc
Digest: sha1
Owner Key ID: root.rootkey1
Recovery Agent Key IDs: evfs.evfs
Total Recovery Agent Keys: 1
User Key IDs: init.initkey
Total User Keys: 1
See “Displaying EVFS Volume Keys and Operating Parameters (evfsvol display)” (page 131) for
more information.
Verifying Data Encryption
You can use the following procedure to verify that EVFS is encrypting data before it is written
to the underlying LVM, VxVM, or physical volume:
1. Write text (a character string) to a file on an enabled EVFS volume.
2. Use the strings utility to search the EVFS volume device file. The text is stored in the
underlying LVM, VxVM or physical volume as encrypted data, but the strings utility is
Option 1: Creating a New EVFS Volume 59
Page 60

reading from the EVFS volume. The EVFS subsystem will provide decrypted data to the
strings utility, and strings will find and display the text string you wrote.
3. Verify that applications that bypass EVFS receive encrypted data. To do this, you must
disable EVFS on the volume. Use the following procedure to disable EVFS on the volume:
a. For data consistency, stop all applications accessing the EVFS volume. You can use the
fuser -cu command to determine the processes accessing files and the fuser -cku
command to terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See
shutdown(1M) for more information.
b. Use the umount command to unmount the file system. See umount( (1M)) for more
information.
c. Use the following commandto disable encryption and decryption access to the volume:
evfsvol disable [-k keyname] evfs_volume_path
See “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81) for more
information.
4. Use the following command to open the EVFS volume for raw access:
evfsvol raw evfs_volume_path
See “Opening Raw Access to EVFS Volumes” (page 83) and the evfsvol( (1M)) manpage for
more information.
CAUTION: After you open the volume for raw access, any entity reading data from the
EVFS volume receives encrypted data. Any entity writing data to the EVFS volume writes
directly to the underlying disk; EVFS does not encrypt the text. HP recommends that you
use the evfsvol raw command only when creating encrypted backup media or restoring
encrypted backup media.
5. Use the strings utility and try to find the text. The strings utility will not find the text
because it receives data from the EVFS volume in encrypted form.
6. Return the EVFS volume to a working state. Close raw access using the following command:
evfsvol close evfs_volume_path
Enable the volume using the following command:
evfsvol enable –k keyname evfs_volume_path
Remount the file system using the mount command.
Example
In the following example, the administrator writes the string TOP SECRET TOP SECRET to the
EVFS volume. When the administrator uses the strings command to search the EVFS volume
for this string, the search is successful. When the administrator searches the underlying LVM
volume for the same string, the search is unsuccessful.
# echo "TOP SECRET TOP SECRET" > /opt/encrypted_data/my_evfs_test
# strings /dev/evfs/vg01/lvol5 | grep "TOP SECRET"
(The strings command finds the string "TOP SECRET" on the EVFS volume.)
TOP SECRET TOP SECRET
(Disable EVFS so we open raw access to the file)
# fuser -cku /opt/encrypted_data
# umount /opt/encrypted_data
# evfsvol disable /dev/evfs/vg01/lvol5
Enter user passphrase: (enter the passphrase)
# evfsvol raw /dev/evfs/vg01/lvol5 (EVFS will print a warning and ask
if you want to continue)
60 Configuring an EVFS Volume
Page 61

# strings /dev/vg01/lvol5 | grep "TOP SECRET"
(The strings command does not find the string "TOP SECRET")
# evfsvol close /dev/evfs/vg01/lvol5
# evfsvol enable /dev/evfs/vg01/lvol5
Enter user passphrase: (enter the passphrase)
# mount -F vxfs /dev/evfs/vg01/lvol5 /opt/encrypted_data
Step 4: (Optional) Migrating Existing Data to an EVFS Volume
Use the following procedure to migrate an existing directory of data to the EVFS volume:
a. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
b. (Optional) Create a backup of the existing data.
c. Use the cp command or other utility to copy the data from the existing files to an EVFS
volume.
d. (Optional) Remove the old files or directories. If you migrated all the data from a file system,
you can unmount the old file system. See umount(1M) for more information.
e. (Optional) If you unmounted a file system in the previous step, remove the entry for the file
system from the /etc/fstab file.
f. (Optional) Use the ln command to create a symbolic link from the old directory to the
appropriate directory on the encrypted volume. See ln(4) for more information.
g. Restart applications that use the data as needed.
Example
In the following example, the /opt/encrypted_data directory is located on an EVFS volume
has already been created and enabled.
# fuser -cu /opt/my_data
# fuser -cku /opt/my_data
# cp -R /opt/my_data/* /opt/encrypted_data
# rm -r /opt/mydata
(If /opt/mydata was a file system, you would unmount it instead and remove the corresponding
entry from the /etc/fstab file.)
# ln -s /opt/encrypted_data /opt/my_data
Option 1: Creating a New EVFS Volume 61
Page 62

Step 5: (Optional) Configuring the Autostart Feature
The EVFS autostart feature allows you to enable and mount EVFS volumes automatically at
system startupwithout manual intervention. You must use the autostart feature for EVFS volumes
that have file systems mounted at system startup (file systems with entries in the /etc/fstab
file).
CAUTION: Using the autostart feature requires you to store passphrases, and stored passphrases
are security risks.
Use the following procedure to configure the autostart feature:
a. Enable EVFS in the /etc/rc.config.d/evfs file. Change the value for EVFS_ENABLED
to 1 as follows:
EVFS_ENABLED = 1
b. Modify the entries in the /etc/evfs/evfstab file for the EVFS volumes that you want
enabled at system startup. You must add a key ID and the boot_local or boot_remote
option. The syntax for each entry is as follows:
v volume_path evfs_volume_path user_name.key_name options
where:
v Specifies that the entry is for an EVFS volume. The EVFS
subsystem automatically adds this field to the
/etc/evfs/evfstab file when you create the EVFS volume
device files.
volume_path The path for the underlying LVM, VxVM, or physical volume
block device file, such as /dev/vg01/lvol5,
/dev/vx/dsk/rootdg/vol05, or /dev/dsk/c2t0d1. The
EVFS subsystem automatically adds this field to the
/etc/evfs/evfstab file when you create the EVFS volume
device files.
evfs_volume_path Specifies the absolute pathname for the EVFS volume block
device file, such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1. The EVFSsubsystem automatically
adds this field to the /etc/evfs/evfstab file when you
create the EVFS volume device file.
user_name.key_name A valid key ID (user name and key pair name) for this EVFS
volume. The key pair must have a stored passphrase.
EVFS uses the stored passphrase to decrypt the private key,
then uses the private key to enable the EVFS volume.
options Following are the valid options for the autostart feature:
62 Configuring an EVFS Volume
boot_local Causes EVFS to enable the EVFS volume
before local file systems in /etc/fstab are
mounted and before NFS and other
networking subsystems are started. Use this
flag if the private key and stored passphrase
used to enable the volume are located on the
root disk of the local system.
boot_local2 Enable the EVFS volume after local file
systems in /etc/fstab are mounted and
before NFS and other networking
subsystems are started. Use this flag if the
private key and stored passphrase used to
Page 63

enable the volume are located on a nonroot
disk of the local system.
If you specify the boot_local2 option, the
system will be unable to automatically
mount a file system on the EVFS volume as
part of the system startup procedure and
you must manually mount the file system.
boot_remote Enable the EVFSvolume after NFS and other
networking subsystems are started. Use this
flag if the private key or stored passphrase
used to enable the volume is located on a
remote system, such as an NFS directory.
If you specify the boot_remote option, the
system will be unable to automatically
mount a file system on the EVFS volume as
part of the system startup procedure and
you must manually mount the file system.
See evfstab(4) for more information.
Example
The following entry in the /etc/evfs/evfstab file configures the autostart feature and
uses the init user's key initkey, which was created with a stored passphrase:
v /dev/vg01/lvol5 /dev/evfs/vg01/lvol5 init.initkey boot_local
c. Verify that a stored passphrase exists for the key IDs specified in the /etc/evfs/evfstab
entries. If you did not store the passphrase when you created the key pair, use the evfspkey
passgen command to create a passphrase. See “Creating or Changing a Stored Passphrase
for an Existing Key” (page 88).
Option 1: Creating a New EVFS Volume 63
Page 64

Step 6: Backing Up Your Configuration
After you have completed your configuration, back up the files and subdirectories under the
/etc/evfs directory.
You must back up the user key database. You cannot re-create lost or corrupt user keys or
passphrases. Determine the directories used for the key database by checking the pkey attribute
statement in the /etc/evfs/evfs.conf file. By default, EVFS stores the user key database in
subdirectories below the /etc/evfs/pkey directory.
64 Configuring an EVFS Volume
Page 65

Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption)
This section describes how to convert existing data on a volume into an EVFS Volume. This
section addresses the following topics:
• “Step 1: Preparing the File System and Data” (page 66)
• “Step 2: Performing Inline Encryption” (page 67)
• “Step 3: Verifying the Configuration” (page 69)
• “Step 4: (Optional) Configuring the Autostart Feature” (page 72)
• “Step 5: Backing Up Your Configuration” (page 74)
Before using this procedure, you must complete the tasks in Chapter 3 (page 35).
IMPORTANT: To use inline encryption, 3 MB of spare disk space are required at the end of the
volume, and the minimum volume size must be 4 MB. If the entire volume is used, extend the
volume using lvextend for LVM, or vxassist for VXVM.
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption) 65
Page 66

Step 1: Preparing the File System and Data
a. Verify the file systems or volumes you want to secure with EVFS are suitable for encryption.
You cannot use EVFS with the following objects:
• Files or disk areas used during system boot. This includes the following objects:
— the root disk (/)
— the boot disk
— the HP-UX kernel directory (/stand)
— the /usr directory"
EVFS cannot decrypt the kernel or other data before the system boots.
CAUTION: Encrypting the boot disk makes the boot disk unusable and prevents you
from booting the system.
• Swap space (swap devices or file swap space).
CAUTION: Encrypting swap space can cause the system to panic.
• Dump devices.
b. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
c. Back up the data on the volume. This ensures data recovery is possible if an unexpected
event occurs before completion of the operation.
d. Unmount the file system:
# umount file_system
e. Extend the volume if there is no spare disk space at the end of the volume. 3 MB of spare
disk space are required at the end of the volume. Extend the volume by using the lvextend
command on an LVM volume, or the vxassist command on a VXVM volume. If you do
not know if there is spare disk space at the end of the volume, you can check if there is still
space available for you to extend the volume by using the vgdisplay command on a LVM
volume group, or the vxdg command on a VXVM disk group that the volume belongs to.
f. Map the regular volume to an EVFS volume:
# evfsadm map volume_name
66 Configuring an EVFS Volume
Page 67

Step 2: Performing Inline Encryption
a. Start inline encryption:
# evfsvol iencrypt [-f] [-k keyname] [-c cipher] evfs_volume_path
For more information about the evfsvol iencrypt command, see “iencrypt: Inline
Encryption” (page 67).
b. Enable the EVFS volume:
# evfsvol enable evfs_volume_path
c. Mount the file system to the EVFS volume:
# mount evfs_volume_path file_system
For more information about mounting file systems, see “Step 2: Creating and Mounting a
File System on an EVFS Volume” (page 56)
iencrypt: Inline Encryption
When the EVFS Volume state is “iencrypt in progress” or “iencrypt suspended”, the volume is
not accessible.
When the EVFS Volume state is “iencrypt suspended”, only the following commands can be
applied to the EVFS volume:
evfsvol iencrypt Use this command to resume the inline encryption operation.
evfsvol display Use this command to display the status of the volume.
CAUTION: The following two operations render the volume data irrecoverable.
evfsvol create –f Use this command to recreate the EMD on the volume.
evfsvol destroy Use this command to remove the EMD header from the volume.
The percentage of progress is reported after every 1 MB of data is processed. When the entire
volume is converted successfully, a message is displayed.
If the option -f is specified, we force the operation without prompting.
Suspending an Ongoing Inline Encryption
HP does not recommend suspending an ongoing inline encryption. However, inline encryption
can be a long operation which can take many hours for a large volume. The following common
signals used to stop a process are handled by evfsvol iencrypt:
• SIGTERM
• SIGHUP
• SIGQUIT
• SIGABRT
• SIGINT
When one of these signals is received by evfsvol iencrypt, the user is shown the followng
prompt:
Are you sure you want to abort inline-encrypting "/dev/evfs/vg00/lvolxx"? Interrupting this operation is not
recommended! Answer [yes/no]:
NOTE: Do not use the SIGKILL signal to terminate an evfsvol iencrypt process (do not
use the command kill -KILL evfsvol-iencrypt-pid).
Re-starting a Suspended Inline Encryption
To resume a previously stopped inline encryption, use the following command:
# evfsvol iencrypt [-k keyname] evfs_volume_path
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption) 67
Page 68

The –f and –c options are not valid for a resumed inline encryption. The volume owner key is
needed to resume an operation, and you will be prompted for a passphrase.
68 Configuring an EVFS Volume
Page 69

Step 3: Verifying the Configuration
Use the following commands to verify your EVFS configuration:
• evfsadm stat -a
• evfsvol display evfs_volume_path
evfsadm stat -a
After you access data or mount a file system on an EVFS volume that is correctly configured, the
output for the evfsadm stat -a command shows nonzero values for the number of blocks
read (bpr), written (bpw), decrypted (bpd), and encrypted (bpe). The output is similar to the
following:
# evfadm stat -a
----- EVFS statistics -----
Total EVFS Volumes: 1
EVFS Subsystem Status: up
Active Encryption Threads: 2
---- EVFS Volume Name ----|--- State ---|---------------- Queues -------------|
orr owr odr oer
/dev/evfs/vg01/lvol5 enabled 0 0 0 0
---- EVFS Volume Name ----|--- State ---|-------------- Counters -------------|
bpr bpw bpd bpe
/dev/evfs/vg01/lvol5 enabled 2074 52441 362 52345
---- EVFS Volume Name ----|--- State ---|---------------- Rates --------------|
kbpsr kbpsw dkbps ekbps
/dev/evfs/vg01/lvol5 enabled 25 3 362 34
For descriptions of the output fields, see “Displaying I/O and Encryption Statistics (evfsadm
stat)” (page 130) .
evfsvol display evfs_volume_path
The evfsvol display evfs_volume_path command displays information about the EVFS
volume, including the name of the underlying LVM, VxVM, or physical volume device file, and
the names of the keys configured for the EVFS volume. The output for the evfsvol display
evfs_volume_path is similar to the following:
# evfsvol display /dev/evfs/vg01/lvol5
EVFS Volume Name: /dev/evfs/vg01/lvol5
Mapped Volume Name: /dev/vg01/lvol5
EVFS Volume State: enabled
EMD Size (Kbytes): 520
Max User Envelopes: 1024
Data Encryption Cipher: aes-128-cbc
Digest: sha1
Owner Key ID: root.rootkey1
Recovery Agent Key IDs: evfs.evfs
Total Recovery Agent Keys: 1
User Key IDs: init.initkey
Total User Keys: 1
See “Displaying EVFS Volume Keys and Operating Parameters (evfsvol display)” (page 131) for
more information.
Verifying Data Encryption
You can use the following procedure to verify that EVFS is encrypting data before it is written
to the underlying LVM, VxVM, or physical volume:
1. Write text (a character string) to a file on an enabled EVFS volume.
2. Use the strings utility to search the EVFS volume device file. The text is stored in the
underlying LVM, VxVM or physical volume as encrypted data, but the strings utility is
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption) 69
Page 70

reading from the EVFS volume. The EVFS subsystem will provide decrypted data to the
strings utility, and strings will find and display the text string you wrote.
3. Verify that applications that bypass EVFS receive encrypted data. To do this, you must
disable EVFS on the volume. Use the following procedure to disable EVFS on the volume:
a. For data consistency, stop all applications accessing the EVFS volume. You can use the
fuser -cu command to determine the processes accessing files and the fuser -cku
command to terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See
shutdown(1M) for more information.
b. Use the umount command to unmount the file system. See umount( (1M)) for more
information.
c. Use the following commandto disable encryption and decryption access to the volume:
evfsvol disable [-k keyname] evfs_volume_path
See “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81) for more
information.
4. Use the following command to open the EVFS volume for raw access:
evfsvol raw evfs_volume_path
See “Opening Raw Access to EVFS Volumes” (page 83) and the evfsvol( (1M)) manpage for
more information.
CAUTION: After you open the volume for raw access, any entity reading data from the
EVFS volume receives encrypted data. Any entity writing data to the EVFS volume writes
directly to the underlying disk; EVFS does not encrypt the text. HP recommends that you
use the evfsvol raw command only when creating encrypted backup media or restoring
encrypted backup media.
5. Use the strings utility and try to find the text. The strings utility will not find the text
because it receives data from the EVFS volume in encrypted form.
6. Return the EVFS volume to a working state. Close raw access using the following command:
evfsvol close evfs_volume_path
Enable the volume using the following command:
evfsvol enable –k keyname evfs_volume_path
Remount the file system using the mount command.
Example
In the following example, the administrator writes the string TOP SECRET TOP SECRET to the
EVFS volume. When the administrator uses the strings command to search the EVFS volume
for this string, the search is successful. When the administrator searches the underlying LVM
volume for the same string, the search is unsuccessful.
# echo "TOP SECRET TOP SECRET" > /opt/encrypted_data/my_evfs_test
# strings /dev/evfs/vg01/lvol5 | grep "TOP SECRET"
(The strings command finds the string "TOP SECRET" on the EVFS volume.)
TOP SECRET TOP SECRET
(Disable EVFS so we open raw access to the file)
# fuser -cku /opt/encrypted_data
# umount /opt/encrypted_data
# evfsvol disable /dev/evfs/vg01/lvol5
Enter user passphrase: (enter the passphrase)
# evfsvol raw /dev/evfs/vg01/lvol5 (EVFS will print a warning and ask
if you want to continue)
70 Configuring an EVFS Volume
Page 71

# strings /dev/vg01/lvol5 | grep "TOP SECRET"
(The strings command does not find the string "TOP SECRET")
# evfsvol close /dev/evfs/vg01/lvol5
# evfsvol enable /dev/evfs/vg01/lvol5
Enter user passphrase: (enter the passphrase)
# mount -F vxfs /dev/evfs/vg01/lvol5 /opt/encrypted_data
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption) 71
Page 72

Step 4: (Optional) Configuring the Autostart Feature
The EVFS autostart feature allows you to enable and mount EVFS volumes automatically at
system startupwithout manual intervention. You must use the autostart feature for EVFS volumes
that have file systems mounted at system startup (file systems with entries in the /etc/fstab
file).
CAUTION: Using the autostart feature requires you to store passphrases, and stored passphrases
are security risks.
Use the following procedure to configure the autostart feature:
a. Enable EVFS in the /etc/rc.config.d/evfs file. Change the value for EVFS_ENABLED
to 1 as follows:
EVFS_ENABLED = 1
b. Modify the entries in the /etc/evfs/evfstab file for the EVFS volumes that you want
enabled at system startup. You must add a key ID and the boot_local or boot_remote
option. The syntax for each entry is as follows:
v volume_path evfs_volume_path user_name.key_name options
where:
v Specifies that the entry is for an EVFS volume. The EVFS
subsystem automatically adds this field to the
/etc/evfs/evfstab file when you create the EVFS volume
device files.
volume_path The path for the underlying LVM, VxVM, or physical volume
block device file, such as /dev/vg01/lvol5,
/dev/vx/dsk/rootdg/vol05, or /dev/dsk/c2t0d1. The
EVFS subsystem automatically adds this field to the
/etc/evfs/evfstab file when you create the EVFS volume
device files.
evfs_volume_path Specifies the absolute pathname for the EVFS volume block
device file, such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1. The EVFSsubsystem automatically
adds this field to the /etc/evfs/evfstab file when you
create the EVFS volume device file.
user_name.key_name A valid key ID (user name and key pair name) for this EVFS
volume. The key pair must have a stored passphrase.
EVFS uses the stored passphrase to decrypt the private key,
then uses the private key to enable the EVFS volume.
options Following are the valid options for the autostart feature:
72 Configuring an EVFS Volume
boot_local Causes EVFS to enable the EVFS volume
before local file systems in /etc/fstab are
mounted and before NFS and other
networking subsystems are started. Use this
flag if the private key and stored passphrase
used to enable the volume are located on the
root disk of the local system.
boot_local2 Enable the EVFS volume after local file
systems in /etc/fstab are mounted and
before NFS and other networking
subsystems are started. Use this flag if the
private key and stored passphrase used to
Page 73

enable the volume are located on a nonroot
disk of the local system.
If you specify the boot_local2 option, the
system will be unable to automatically
mount a file system on the EVFS volume as
part of the system startup procedure and
you must manually mount the file system.
boot_remote Enable the EVFSvolume after NFS and other
networking subsystems are started. Use this
flag if the private key or stored passphrase
used to enable the volume is located on a
remote system, such as an NFS directory.
If you specify the boot_remote option, the
system will be unable to automatically
mount a file system on the EVFS volume as
part of the system startup procedure and
you must manually mount the file system.
See evfstab(4) for more information.
Example
The following entry in the /etc/evfs/evfstab file configures the autostart feature and
uses the init user's key initkey, which was created with a stored passphrase:
v /dev/vg01/lvol5 /dev/evfs/vg01/lvol5 init.initkey boot_local
c. Verify that a stored passphrase exists for the key IDs specified in the /etc/evfs/evfstab
entries. If you did not store the passphrase when you created the key pair, use the evfspkey
passgen command to create a passphrase. See “Creating or Changing a Stored Passphrase
for an Existing Key” (page 88).
Option 2: Converting a Volume with Existing Data to an EVFS Volume (Inline Encryption) 73
Page 74

Step 5: Backing Up Your Configuration
After you have completed your configuration, back up the files and subdirectories under the
/etc/evfs directory.
You must back up the user key database. You cannot re-create lost or corrupt user keys or
passphrases. Determine the directories used for the key database by checking the pkey attribute
statement in the /etc/evfs/evfs.conf file. By default, EVFS stores the user key database in
subdirectories below the /etc/evfs/pkey directory.
74 Configuring an EVFS Volume
Page 75

Examples
This section contains configuration examples for “Option 1” (page 75) and “Option 2” (page 76).
Option 1
Step 1a: Create an EVFS volume. If you are using LVM or VxVM, create a new LVM or VxVM
volume to use as the underlying volume. If you reuse an existing LVM or VxVM volume as the
underlying volume, you will lose all existing data. You can skip this step if you are using whole
disk access.
# lvcreate -L 64 -n lvol5 /dev/vg01
Step 1b: Map the new LVM or VxVM volume or physical volume to an EVFS volume.
# evfsadm map /dev/vg01/lvol5
Step 1c: Create the EMD on the new EVFS volume. The root user (the owner of the key named
rootkey1) will be the volume owner. evfsvol prompts for the passphrase to the owner's
private key.
# evfsvol create -k rootkey1 /dev/evfs/vg01/lvol5
Step 1d: Optional – Add a recovery user key. evfsvol prompts for the passphrase to theowner's
private key.
# evfsvol add -r /dev/evfs/vg01/lvol5
Step 1e: Enable the EVFS volume. evfsvol prompts for the passphrase for your key named
rootkey1.
# evfsvol enable -k rootkey1 /dev/evfs/vg01/lvol5
Step 2a: Create a new file system on the character/raw EVFS volume.
# newfs -F vxfs /dev/evfs/vg01/rlvol5
Step 2b: Verify the file system.
# fsck /dev/evfs/vg01/rlvol5
Step 2c: Create the directory for the new mount point.
# mkdir /opt/my_secure_dir
Step 2d: Mount the new file system.
# mount -F vxfs /dev/evfs/vg01/lvol5 /opt/my_secure_dir
Step 2e: Optional—Add an entry to /etc/fstab. In this example, the administrator used the
echo command, but you can also use an editor to do this
# echo "/dev/evfs/vg01/lvol5 /opt/my_secure_dir vxfs defaults 0 2" >>
/etc/fstab
Step 3: Verify the EVFS configuration.
# evfsadm stat –a
# evfsvol display /dev/evfs/vg01/lvol5
Step 4: Migrate any existing data.
To migrate an existing directory of data to the new EVFS volume, follow these steps:
Step 4b: Stop all applications accessing the existing data.
# fuser –cu /opt/my_data
# fuser –cku /opt/my_data
Step 4d: Copy the existing data to the new EVFS directory.
# cp –R /opt/my_data /opt/my_secure_dir
Clean up the old data and create a symbolic link to the EVFS data.
Examples 75
Page 76

Optionally, configure the autostart feature, as described in “Step 5: (Optional) Configuring the
Autostart Feature” (page 62). Finally, backup your EVFS configuration and user keys, as described
in “Step 6: Backing Up Your Configuration” (page 64).
Korn Shell Script for Creating an EVFS Volume and File System
The following Korn shell (ksh) script configures an EVFS volume and creates and mounts a file
system on the volume. This script is a basic script, and HP recommends that you enhance it to
perform error checking. The script does not use file locking when editing /etc/evfs/evfstab
or /etc/fstab. This script assumes the administrator has already performed the following
tasks:
• Created an alternate recovery user account, if necessary.
• Created EVFS owner and recovery key pairs for the EVFS volume using the evfspkey
keygen command.
• Created a new LVM or VxVM volume for the EVFS volume using the lvcreate or
vxassist command or SAM.
The script takes the following four arguments as input:
1. Block volume device file name.
2. Character (raw) volume device file name.
3. Name of the owner key pair for the EVFS volume.
4. Mount point for the new file system.
#! /bin/ksh
block_volume=$1
raw_volume=$2
owner_key=$3
mount_point=$4
evolume=/dev/evfs/${block_volume#/dev/}
raw_evolume=/dev/evfs/${raw_volume#/dev/}
# Create the EVFS volume
evfsadm map $block_volume
evfsvol create -k $owner_key $evolume
# Add the recovery key
evfsvol add -r $evolume
# Enable the volume
evfsvol enable $evolume
# create and mount the file system
newfs -F vxfs $raw_evolume
mkdir $mount_point
mount -F vxfs $evolume $mount_point
echo "$evolume $mount_point vxfs defaults 0 2" >> /etc/fstab
Option 2
In the following example, there is existing data on a 96 MB LVM volume (e.g. /dev/vg00/lvol10)
with a file system (e.g. /home) configured on it:
# umount /home
# vgdisplay /dev/vg00
# lvextend -L 100 /dev/vg00/lvol10
(The existing size is 96 MB; we now extend it by 4 MB, to 100 MB)
# evfsadm map /dev/vg00/lvol10
# evfsvol iencrypt /dev/evfs/vg00/lvol10
# evfsvol enable /dev/evfs/vg00/lvol10
# mount /dev/evfs/vg00/lvol10 /home
# evfsadm stat –a
# evfsvol display /dev/evfs/vg00/lvol10
In the following example, there is existing data on a 96 MB VXVM volume (e.g.
/dev/vx/dsk/rootdg/lvol10) with a file system (e.g. /home) configured on it:
76 Configuring an EVFS Volume
Page 77

# umount /home
# vxdg -g rootdg free
# vxassist -g rootdg growby vol10 4m
(The existing size is 96 MB; we now extend it by 4 MB, to 100 MB)
# evfsadm map /dev/vx/dsk/rootdg/vol10
# evfsvol iencrypt /dev/evfs/vx/dsk/rootdg/vol10
# evfsvol enable /dev/evfs/vx/dsk/rootdg/vol10
# mount /dev/evfs/vx/dsk/rootdg/vol10 /home
# evfsadm stat –a
# evfsvol display /dev/evfs/vx/dsk/rootdg/vol10
Optionally, configure the autostart feature, as described in “Step 4: (Optional) Configuring the
Autostart Feature” (page 72). Finally, backup your EVFS configuration and user keys, as described
in “Step 5: Backing Up Your Configuration” (page 74).
Examples 77
Page 78

78
Page 79

5 Administering EVFS
This chapter describes how to perform the following EVFS administrative tasks:
• Starting and stopping EVFS components. This includes the tasks described in the following
sections:
— “Starting the EVFS Subsystem” (page 80)
— “Enabling Encryption and Decryption Access to EVFS Volumes” (page 80)
— “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81)
— “Stopping the EVFS Subsystem” (page 82)
— “Opening Raw Access to EVFS Volumes” (page 83)
— “Closing Raw Access to EVFS Volumes” (page 83)
• Managing EVFS keys and users. This includes the tasks described in the following sections:
— “Displaying Key IDs for an EVFS Volume” (page 84)
— “Restoring User Keys” (page 84)
— “Changing Owner Keys for an EVFS Volume” (page 86)
— “Recovering from Problems with Owner Keys” (page 87)
— “Removing Keys from an EVFS Volume” (page 87)
— “Removing User Keys or Stored Passphrase from the EVFS Key Database” (page 87)
— “Changing the Passphrase for a Key” (page 87)
— “Creating or Changing a Stored Passphrase for an Existing Key” (page 88)
• Recovering from encryption metadata (EMD)corruption. This task is described in the section
“Recovering from EMD Corruption” (page 89).
• Removing a volume from theEVFS subsystem. This task is described in “Removing a Volume
from the EVFS Subsystem” (page 90).
• Exporting and importing EVFS volumes. This includes the tasks described in the following
sections:
— “Exporting an EVFS Volume” (page 91)
— “Importing an EVFS Volume” (page 93)
79
Page 80

Starting and Stopping EVFS
This section describes the following procedures for enabling and disabling EVFS components:
• “Starting the EVFS Subsystem” (page 80)
• “Enabling Encryption and Decryption Access to EVFS Volumes” (page 80)
• “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81)
• “Stopping the EVFS Subsystem” (page 82)
• “Opening Raw Access to EVFS Volumes” (page 83)
• “Closing Raw Access to EVFS Volumes” (page 83)
Starting the EVFS Subsystem
The following evfsadm start command starts the EVFS subsystem by initializing the EVFS
pseudo-driver and startingthe evfsevold process. The evfsevold process starts kernel threads
for data encryption and decryption. You must start the EVFS subsystem to generate user keys
and enable EVFS volumes. This command is executed automatically at system startup if EVFS
is enabled in the /etc/rc.config.d/evfs file, as described in “Step 5: (Optional) Configuring
the Autostart Feature” (page 62).
evfsadm start [-n number]
where:
-n number
Specifies the number of threads to create for EVFS encryption and decryption
processing.
Range: On single-processor systems, 1 is the only valid value.
On multiprocessor systems, the maximum number of threads is the number of
processors in the system.
Default: On single-processor systems, the default is 1.
On multiprocessor systems, the default is the number of processors in the system
minus 1. Setting the number of threads to a lower value can decrease EVFS
throughput.
Enabling Encryption and Decryption Access to EVFS Volumes
The following evfsvol enable commands enable EVFS encryption and decryption access to
EVFS volumes. The EVFS volumes must already be configured, as described in “Preparing EVFS
for Configuration” (page 35). You can use the evfsvol enable command in the following
ways:
• To enable a single EVFS volume without a stored passphrase:
evfsvol enable [-k keyname] evfs_volume_path
You must be the volume owner or an authorized user for the volume to execute this
command.
• To enable a single EVFS volume with a stored passphrase and an entry in the
/etc/evfs/evfstab file:
evfsvol enable -p evfs_volume_path
• To enable EVFS encryption and decryption for all volumes in the file /etc/evfs/evfstab
that include a key ID field:
evfsvol enable -a
where:
-a
80 Administering EVFS
Causes EVFS to enable encryption and decryption for all volumes in
the /etc/evfs/evfstab file.
Page 81

-p
-k keyname Specifies the key name. If you do not specify -k keyname, evfspkey
Causes EVFS to use a stored passphrase to enable encryption and
decryption for the named EVFS volume. The /etc/evfs/evfstab
file must contain an entry for this volume with a key ID field.
uses the user name as the key name.
Valid value: An ASCII string, 1 to 255 characters long.
evfs_volume_path
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/dsk/c2t0d1.
Disabling Encryption/Decryption Access to EVFS Volumes
The evfsvol disable command disables encryption and decryption access to EVFS volumes.
The evfsvol disable command fails if a file system is mounted on the EVFS volume or if the
EVFS volume device file is opened by any process.
Use the following procedure to disable encryption and decryption access to a volume:
1. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See the
shutdown(1M) manpage for more information.
2. If you have a file system mounted on the EVFS volume, use the umount command to
unmount the file system. See umount(1M) for more information.
Starting and Stopping EVFS 81
Page 82

3. Use the evfsvol disable command to disable EVFS operation for the volume as follows:
• To disable a single EVFS volume without a stored passphrase:
evfsvol disable [-k keyname] evfs_volume_path
You must be the volume owner or an authorized user for the volume to execute this
command.
• To disable a single EVFS volume with a stored passphrase and an entry in the
/etc/evfs/evfstab file:
evfsvol disable -p evfs_volume_path
• To disable EVFS encryption and decryption for all volumes in the /etc/evfs/evfstab
file that include a key ID field:
evfsvol disable -a
where:
-a Causes EVFS to disable encryption and decryption for all volumes
in the file /etc/evfs/evfstab.
-p Causes EVFS to use a stored passphrase to disable encryption and
decryption for the specified EVFS volume. The
/etc/evfs/evfstab file must contain an entry for this volume
with a key ID field.
-k keyname Specifies the key name. If you do not specify -k keyname,
evfspkey uses the user name as the key name.
Valid value: An ASCII string, 1 - 255 characters long.
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
Stopping the EVFS Subsystem
The evfsadm stop command stopsthe EVFS subsystem and terminatesall kernel EVFS threads.
Use the following procedure to stop the EVFS subsystem:
1. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See the fuser(1M) manpage for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
2. If you have a file system mounted on the EVFS volume, use the umount command to
unmount the file system. See the umount(1M) manpage for more information.
3. Disable all the EVFS volumes using the evfsvol disable command, as described in
“Disabling Encryption/Decryption Access to EVFS Volumes” (page 81). You must be the
volume owner or an authorized user for the volume to disable the volume.
4. Enter the following evfsadm stop command:
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
evfsadm stop
82 Administering EVFS
Page 83

Opening Raw Access to EVFS Volumes
Use the following evfsvol raw command to open an EVFS volume for raw access. When an
EVFS volume is open for raw access, EVFS does not decrypt data read from the volume and does
not encrypt data written to the volume. Entities reading data from the EVFS volume receive
encrypted data. Entities writing data to the EVFS volume write directly to the underlying disk;
EVFS does not encrypt the text.
CAUTION: Writing data to or reading data from an EVFS volume when it is opened for raw
access can cause data corruption. HP recommends that you use this operation only when creating
encrypted backup media or restoring encrypted backup media, as described in “Backing Up
EVFS Volumes” (page 102).
Use the following procedure to open raw access to an EVFS volume:
1. Disable encrypted and decrypted access to the EVFS volume using the evfsvol disable
command, as described in “Disabling Encryption/Decryption Access to EVFS Volumes”
(page 81). You must be the volume owner or an authorized user for the volume to disable
the volume.
2. Enter the evfsvol raw command. The syntax is as follows:
evfsvol raw evfs_volume_path
where:
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
Closing Raw Access to EVFS Volumes
Use the following evfsvol close command to close raw access to a volume. After you close
raw access, you can enable encrypted and decrypted access to the volume using the evfsvol
enable command.
You must be the volume owner or an authorized user for the volume to execute the evfsvol
close command.
evfsvol close evfs_volume_path
where:
evfs_volume_path
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/dsk/c2t0d1.
Starting and Stopping EVFS 83
Page 84

Managing EVFS Keys and Users
This section describes the following procedures for managing EVFS keys and users:
• “Displaying Key IDs for an EVFS Volume” (page 84)
• “Restoring User Keys” (page 84)
• “Changing Owner Keys for an EVFS Volume” (page 86)
• “Recovering from Problems with Owner Keys” (page 87)
• “Removing Keys from an EVFS Volume” (page 87)
• “Removing User Keys or Stored Passphrase from the EVFS Key Database” (page 87)
• “Changing the Passphrase for a Key” (page 87)
• “Creating or Changing a Stored Passphrase for an Existing Key” (page 88)
Displaying Key IDs for an EVFS Volume
Use the following evfsvol display command to display EMD information for EVFS volumes,
including the owner key ID, recovery key IDs, and authorized user key IDs. The evfsvol
display command also displays operating parameters for the EVFS volume, including the
volume encryption algorithm and the underlying LVM, VxVM, or physical volume device file
name.
Syntax
evfsvol display [-a|evfs_volume_path]
where:
-a
-evfs_volume_path
Displays the EMD information for all configured EVFS volumes.
Specifies the absolute pathname for the EVFS volume device file,
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1. The evfsvol utility displays the EMD
information for the volume.
Example
The output for the evfsvol display evfs_volume_path is similar to the following:
# evfsvol display /dev/evfs/vg01/lvol5
EVFS Volume Name: /dev/evfs/vg01/lvol5
Mapped Volume Name: /dev/vg01/lvol5
EVFS Volume State: enabled
EMD Size (Kbytes): 520
Max User Envelopes: 1024
Data Encryption Cipher: aes-128-cbc
Digest: sha1
Owner Key ID: root.rootkey1
Recovery Agent Key IDs: evfs.evfs
Total Recovery Agent Keys: 1
User Key IDs: root.admink
Total User Keys: 1
The Owner Key ID, Recovery Agent Key IDs, and User Key IDs fields show the key
IDs configured for the volume.
Restoring User Keys
Use the following procedure to restore user key files from backup media:
84 Administering EVFS
Page 85

1. Verify the directory structure for the key database, and re-create it if necessary. By default,
EVFS stores the user key database in subdirectories below the /etc/evfs/pkey directory,
with a subdirectory for each user. The administrator can configure alternate database
directory or directories using the pkey attribute in the /etc/evfs/evfs.conf file.
HP recommends that the primary directory is writable only by superusers. For example,
the /etc/evfs/pkey directory is installed with the following permissions, owner, and
group:
drwxr-xr-x 4 bin bin 96 Mar 16 17:26 pkey
If you configure a fallback directory to allow users without superuser privileges to create
keys, the fallback directory must allow the appropriate users to read, write, and execute the
contents.
2. Create the appropriate directory for each user, such as /etc/evfs/pkey/root. Each
directory must have the following permissions, owner, and group:
drwxr-xr-x 2 user sys 96 Mar 16 17:27 user
3. Create a directory to store the recovery keys. If you are using the default name for the EVFS
pseudo-user account and the default key storage directory, create the
/etc/evfs/pkey/evfs directory (or a subdirectory under the key storage directory using
the EVFS pseudo-user name) with the following permissions, owner, and group:
drwxr-xr-x 2 bin bin 96 Mar 16 17:27 evfs
Managing EVFS Keys and Users 85
Page 86

4. Restore the public and private key files and any passphrase files with the following name,
owner, group, and permissions:
• Public Key
— File name: key_storage_directory/user_name/key_name.pub
(/etc/evfs/pkey/user_name/key_name.pub if youare using the default key
storage directory)
— Owner: the user name for the owner
— Group: sys
— Permissions: Readable andwritable by the owner, readable by group, and readable
by everyone else (644, or -rw-r--r--)
• Private Key:
— File name: key_storage_directory/user_name/key_name.priv
(/etc/evfs/pkey/user_name/key_name.priv if you are using the default
key storage directory)
— Owner: the user name for the owner
— Group: sys
— Permissions: Readable and writable by only the owner (600, or -rw-------)
• Passphrase File:
— File name: key_storage_directory/user_name/key_name.pass.nnn
(/etc/evfs/pkey/user_name/key_name.pass.nnn if you are using the
default key storage directory), where nnn is a number based on system-specific
data
— Owner: the user name for the owner
— Group: sys
— Permissions: Readable and writable only by the owner (600, or -rw-------)
After you restore these files, a listing of the files shows output similar to the following:
# ll /etc/evfs/pkey/root
total 32
-rw------- 1 root sys 634 Mar 16 17:26 rootkey2.priv
-rw-r--r-- 1 root sys 344 Mar 16 17:26 rootkey2.pub
-rw-r--r-- 1 root sys 272 Mar 16 17:26 rootkey2.pass.08
192003-6e81-11d9-8b9e-b8f2666e6f49
Changing Owner Keys for an EVFS Volume
Use the following evfsvol assign command to change the owner or owner key of an EVFS
volume. To execute this command, you must be the current owner of the EVFS volume or have
the private key file for the volume recovery key. (The procedure for creating a recovery key is
described in “Creating Recovery Keys” (page 45). The procedure for adding a recovery key to
an EVFS volume is described in “Step 1d: (Optional) Adding Recovery Keys and authorized user
Keys” (page 53).)
evfsvol assign -u newowner [-r recoveryprivkeyfile] [-k keyname]
evfs_volume_path
where:
-u newowner
-r recoveryprivkeyfile
Specifies the name of the new owner for the EVFS volume.
Specifies the name of the file containing private key that
corresponds to a recovery user's key in the EMD. If you do
not specify this option, you must be the EVFS volume owner
to execute this command; evfsvol prompts you for the
passphrase for the owner's key.
86 Administering EVFS
Page 87

-k keyname
evfs_volume_path
Specifies the key pair name for the new owner. If you do not
specify this option or the -r option, evfsvol uses the owner's
user name as the key pair name.
Specifies the absolute pathname for the EVFS volume device
file, such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
Recovering from Problems with Owner Keys
If the keys for an owner of an EVFS volume cannot be restored or are compromised, or if the
owner forgets the passphrase for the private key, you must use the recovery user's private key
to assign a new owner for the EVFS volume. For more information, see the section “Changing
Owner Keys for an EVFS Volume” (page 86).
Removing Keys from an EVFS Volume
Use the following evfsvol delete command to remove a key record pair from an EVFS
volume. You must be the owner of the EVFS volume to execute this command.
evfsvol delete [-u username|-r] [-k keyname] evfs_volume_path
where:
-u username
-r
-k keyname
evfs_volume_path
Specifies the user name for the keys you want to delete from the
volume. If you do not specify this argument or the -r option, evfsvol
uses your user name.
Specifies that you want to delete recovery user keys.
Specifies the name of the key pair you want to delete. If you do not
specify this option, evfsvol uses the user name as the key name.
Specifies the absolute pathname for the EVFS volume device file, such
as /dev/evfs/vg01/lvol5, /dev/evfs/vx/dsk/rootdg/vol05,
or /dev/evfs/dsk/c2t0d1.
Removing User Keys or Stored Passphrase from the EVFS Key Database
Use the evfspkey delete command to remove a user key pair from the EVFS key database
or to remove the passphrase for a private key. You must have superuser privileges to delete a
key pair or passphrase that you do not own.
evfspkey delete [-u username|-r] [-p] [-k keyname]
where:
-u username
-r
-p
-k keyname
Specifies the user name for the keys you want to delete from the database. If
you do not specify this argument or the -r option, evfsvol uses your user
name.
Specifies that you want to delete recovery user keys.
Specifies that you only want to delete the stored passphrase for the private
key.
Specifies the name of the key pair you want to delete. If you do not specify
this option, evfsvol uses the user name as the key name.
Changing the Passphrase for a Key
Use the evfspkey passgen command to change the passphrase for an existing private key.
You must have superuser privileges to change the passphrase for a key that you do not own. If
a stored passphrase does not exist for the current passphrase, evfspkey prompts you for the
current passphrase.
Managing EVFS Keys and Users 87
Page 88

The syntax for changing the passphrase for a volume owner or authorized user key is as follows:
evfspkey passgen [-u username] [-k keyname]
The syntax for changing the passphrase for a recovery key is as follows:
evfspkey passgen -r recovkey_file
where:
-u username
-k keyname
-r recovkey_file
Specifies the name of the user for the passphrase you want to delete.
If you do not specify this argument, evfsvol uses your user name.
Specifies the name of the key pair that corresponds to the passphrase
you want to change. If you do not specify this option, evfsvol uses
the user name as the key name.
Specifies the name of the file that contains the recovery user's private
key, for example, /tmp/recovery.priv. HP recommends that you
store the recovery user's private key off line and restore only when
needed.
Creating or Changing a Stored Passphrase for an Existing Key
Use the evfspkey passgen command to create or change a stored passphrase for an existing
private key. You must have superuser privileges to create a stored passphrase for a key that you
do not own. If the current passphrase has not been previously stored, the evfspkey command
prompts you for the current passphrase.
EVFS encrypts stored passphrases with system-specific information. A stored passphrase is
usable only on the system on which it was created.
CAUTION: A stored passphrase enables you to use the EVFS autostart feature, but it is a security
risk.
evfspkey passgen –f|–p|–s [-u username] [-k keyname]
where:
-f Causes evfspkeyto create a stored passphrase.The evfspkey utility prompts
you for the current passphrase and stores the passphrase in an encrypted file.
-p Causes evfspkey to change the current passphrase and create a stored
passphrase. If the current passphrase is not stored, evfspkey prompts you
for the current passphrase. The evfspkey utility prompts you for a new
passphrase, thenstores the new passphrasein an encrypted file.The passphrase
must be at least eight characters.
-s Causes evfspkey to to generate a new passphrase and store it. If the current
passphrase is not stored, evfspkey prompts you for the current passphrase.
The evfspkey utility generates a passphrase for you and stores the passphrase
in an encrypted file.
-u username
-k keyname
Specifies the name of the user for the key pair that corresponds to the
passphrase you want to modify. If you do not specify this argument, evfsvol
uses your user name. You must have superuser or appropriate privileges to
specify a different user.
Specifies the name of the key pair that corresponds to the passphrase you
want to modify. If you do not specify this option, evfsvol uses the user name
as the key name.
88 Administering EVFS
Page 89

Recovering from EMD Corruption
EVFS stores one backup image of the EMD for each EVFS volume. When you change the owner
of an EVFS volume, or add or delete user keys for a volume, EVFS updates the EMD. Before
EVFS updates the EMD, it stores a backup copy of the current EMD. The evfsvol restore
command restores the backup copy of the EMD for an EVFS volume.
Use the following procedure to restore a backup copy of an EMD:
1. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
2. (Optional) Create a cleartext backup copy of the data, or copy the cleartext data from the
EVFS volume to another disk device using a utility such as fbackup, cp, or tar.
3. If you have a file system mounted on the EVFS volume, use the umount command to
unmount the file system. See umount(1M) for more information.
4. Use the following command to disable encryption and decryption on the target volume:
evfsvol disable [-k keyname] evfs_volume_path
See “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81) for more
information.
5. Use the following evfsvol restore command to restore the EMD:
evfsvol restore evfs_volume_path
where:
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
6. Use the following command to enable EVFS operation for the volume:
evfsvol enable [-k keyname] evfs_volume_path
See “Enabling Encryption and Decryption Access to EVFS Volumes” (page 80) for more
information.
7. If you had a file system mounted on the EVFS volume, use the mount command to remount
the file system. See mount(1M) for more information.
8. restart applications, as necessary.
EMD Backup Directory
By default, EVFS stores EMD backup images in the directory /etc/evfs/emd. See “Step 3:
(Optional) Modifying EVFS Global Parameters” (page 42) information about changing this
directory path. Ensure there is enough space in this directory to store all the system's backup
EMDs fromthe encrypted volumes. The storage requirement is approximately 1 MB per encrypted
volume.
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
Recovering from EMD Corruption 89
Page 90

Removing a Volume from the EVFS Subsystem
Use the following procedure to deconfigure EVFS on a volume and remove it from the EVFS
subsystem.
1. For data consistency, suspend or stop all applications accessing the data. You can use the
fuser -cu command to determine the processes accessing files and the fuser -cku
command to terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
2. Create a cleartext backup copy of the data, or copy the cleartext data from the EVFS volume
to another disk device using a utility such as fbackup, cp or tar.
3. If you have a file system mounted on the EVFS volume, use the umount command to
unmount the file system. See umount(1M) for more information.
4. Use the following command to disable encryption and decryption access to the volume:
evfsvol disable [-k keyname] evfs_volume_path
See “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81) for more
information.
5. Use the following evfsvol command to destroy the EMD for the volume:
evfsvol destroy [-f] evfs_volume_path
The -f option forcibly destroys the EMD, even if the EMD is corrupt. You must be the
volume owner to execute this command.
CAUTION: Destroying the EMD is irreversible. You cannot recover data from the EVFS
volume after you destroy the EMD.
Example
# evfsvol destroy /dev/evfs/vg01/lvol5
Enter owner passphrase:(enter the passphrase for the owner's private key)
Are you sure you want to destroy "/dev/evfs/vg01/lvol5"? Continuing with this
operation will make your data permanently irrecoverable!
Answer [yes/no]: yes
6. Use the following evfsadm unmap command to remove the EVFS volume device files and
delete the device entries in kernel registry:
evfsadm unmap evfs_volume_path
where:
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
7. You can now create a new file system on the underlying device (LVM, VxVM, or physical
volume device), mount the file system, and add an entry for the underlying device in
/etc/fstab. You can also restore the cleartext data stored in step 2.
90 Administering EVFS
Page 91

Exporting and Importing EVFS Volumes
This section describes procedures for exporting and importing EVFS volumes. You can use these
procedures to remove EVFS data from a system when moving (exporting) a volume and disk in
from one system and installing (importing) the volume and disk on another system. This section
describes the following procedures:
• “Exporting an EVFS Volume” (page 91)
• “Importing an EVFS Volume” (page 93)
NOTE: Do not use the procedures in this section to configure EVFS volumes for use in an HP
Serviceguard cluster. See “Using EVFS with Serviceguard” (page 153) for more information.
Exporting an EVFS Volume
Use the following procedure to export an EVFS volume. You can use this procedure to remove
EVFS volume information from a system before moving the volume and disk to another system.
If you are using LVM, repeat the following procedure for each volume in the group before you
execute the vgexport command.
Exporting and Importing EVFS Volumes 91
Page 92

1. If you are moving the volume to another system, add an authorized user key pair for the
administrator on the destination system. You will use this key pair on the destination system.
a. Create a new key pair for the administrator on the destination system using the following
criteria:
• The user account for the key owner must exist on the destination system.
• The key name must be unique for the owner on the destination system.
• You must know the passphrase for the private key, so do not specify the -s option
for the evfspkey command. When you use the -s option, EVFS generates and
stores the passphrase for you, and you cannot retrieve the passphrase. Stored
passphrase files are encrypted with system-specific information, so a stored
passphrase created on one system is unusable on any other system.
Use the following evfspkey keygen command syntax:
evfspkey keygen [-c cipher] [-u user] [-k keyname]
where:
-c cipher Specifies the type of public/private keys to create.
Valid values:
rsa-1024 (RSA 1024-bit keys)
rsa-1536 (RSA 1536-bit keys)
rsa-2048 (RSA 2048-bit keys)
Default: rsa-1536
-u user Specifies the user name of the key owner. This must be a valid user
name on the destination system. If you do not specify -u user,
evfspkey uses your user name as the key owner. You must have
superuser or the appropriate privileges to create a key pair for another
user.
-k keyname Specifies the key name. Specify a key name that does not already exist
for the key owner on the destination system. If you do not specify -k
keyname, evfspkey uses the user name as the key name.
Valid value: An ASCII string, 1 to 255 characters long.
The evfspkey utility prompts you for a passphrase to protect the private key.
IMPORTANT: Make a note of this passphrase, because you must specify it when you
administer the EVFS volume on the target system.
b. Use the following command to add the key to the EVFS volume:
evfsvol add -u user [-k keyname] evfs_volume_path
where:
-k keyname Specifies the name of the key to add. If you do not specify -k
keyname, evfsvol uses your user name as the key name.
evfs_volume_path Specifies the absolute pathname for the EVFS volume device
file, such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
2. Copy the owner's public and private keys files to removable media. You must restore these
files on the destination system.
By default, EVFS stores the user key database in subdirectories below /etc/evfs/pkey,
with a subdirectory for each user. The administrator can configure alternate database
directories using the pub_key, priv_key, and pass_key attributes in the
92 Administering EVFS
Page 93

/etc/evfs/evfs.conf file. Using the default key storage directory, the key file names
are:
Public Key /etc/evfs/pkey/user_name/key_name.pub, where user_name is
the key owner's name and key_name is the key name.
Private Key /etc/evfs/pkey/user_name/key_name.priv, where user_name
is the key owner's name and key_name is the key name.
3. For data consistency, stop all applications accessing the data. You can use the fuser -cu
command to determine the processes accessing files, and the fuser -cku command to
terminate the processes. See fuser(1M) for more information.
If the data is used by system processes, you might need to terminate the processes by
changing the system runlevel to single-user level with the shutdown utility. See shutdown(1M)
for more information.
4. Create a cleartext backup copy of the data or copy the cleartext data from the EVFS volume
to another disk device using a utility such as fbackup, cp or tar.
5. If you have a file system mounted on the EVFS volume, use the umount command to
unmount the file system. See umount(1M) for more information.
6. Use the following command to disable encryption and decryption access to the volume:
evfsvol disable [-k keyname] evfs_volume_path
See “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81) for more
information.
7. Use the following evfsvol export command to remove the EVFS volume device files
and delete the device entries in kernel registry:
evfsvol export evfs_volume_path
where:
evfs_volume_path Specifies the absolute pathname for the EVFS volume device file,
Importing an EVFS Volume
Use the following procedure to import an EVFS volume. If you are using LVM, use this procedure
after importing the volume group using vgimport, and repeat the procedure for each volume
in the group.
1. Copy the key files saved from the source system to the target system. Use the procedure
described in “Restoring User Keys” (page 84) to install the key files from the source system
on the target system.
2. Use the following evfsvol import command to create the EVFS volume device files and
add the entries in kernel registry:
evfsvol import volume_path
where:
such as /dev/evfs/vg01/lvol5,
/dev/evfs/vx/dsk/rootdg/vol05, or
/dev/evfs/dsk/c2t0d1.
volume_path Specifies the path for the underlying LVM, VxVM, or physical volume
device file, suchas /dev/vx/dsk/rootdg/vol01, /dev/vg01/lvol5,
or /dev/dsk/c0d0t2.
3. Use the evfsvol enable command to enable the encrypted volume:
evfsvol enable [-p] [-k keyname] evfs_volume_path
See “Step 1: Configuring an EVFS Volume” (page 51) or evfsvol(1m) for more information.
Exporting and Importing EVFS Volumes 93
Page 94

4. If the EVFS volume had a file system, use the mount command to mount the file system to
a mount point. Add an entry to the /etc/fstab file.
See “Step 2: Creating and Mounting a File System on an EVFS Volume” (page 56) for more
information.
94 Administering EVFS
Page 95

6 Managing Data on EVFS Volumes
This chapter contains information about managing volumes and files on systems with EVFS
configured.
This chapter addresses the following topics:
• “Limitations and Known Problems When Using EVFS with Volume Managers and File
Systems” (page 96)
• “Resizing EVFS Volumes and File Systems” (page 97)
95
Page 96

Limitations and Known Problems When Using EVFS with Volume Managers and File Systems
The following limitations and known problems exist when using EVFS with volume managers
(LVM and VxVM)and file systems. For a complete list of product limitations and known problems,
see “Product Limitations and Precautions” (page 27) and “Known Problems” (page 29).
Creating a New EVFS Volume Overwrites Existing Data
EVFS does not automatically convert existing volume data to encrypted data. To encrypt existing
volume data, see “Step 4: (Optional) Migrating Existing Data to an EVFS Volume” (page 61).
CAUTION: If you configure EVFS on a volume that already contains data without following
“Step 4: (Optional) Migrating Existing Data to an EVFS Volume” (page 61), the existing data is
rendered unusable.
vxresize –F Might Cause Data Loss or Corruption
The vxresize –F command resizes a VxVM volume and the file system mounted on the
volume. The vxresize command has no knowledge of EVFS, so if you configure EVFS on a
VxVM volume and then execute the vxresize –F command, vxresize will not allocate space
for the EVFS data structure (the EMD) on the volume. The vxresize -F command will
complete, but file operations might fail; data might be lost or corrupted.
Workaround
Resize the VxVM volume and file system in separate operations. Use the vxassist command
to increase or decrease the VxVM volume size (or the vxresize command without the –F
option). Use the extendfs or fsadm command to resize the file system. See “Resizing EVFS
Volumes and File Systems” (page 97) for more information.
Renaming VxVM Volumes with EVFS Enabled Makes the Volume Unusable
The vxedit rename command renames a VxVM volume. The vxedit rename command
has no knowledge of EVFS, so if you have a VxVM volume with EVFS enabled and then rename
the volume, the mapping between the VxVM volume becomes unusable. The vxedit rename
command will complete, but EVFS operations will fail.
Workaround
Disable and unmap the EVFS volume before renaming the underlying VxVM volume, as described
in “Disabling Encryption/Decryption Access to EVFS Volumes” (page 81). After you rename the
VxVM volume, use the following procedure to access the EVFS volume again:
1. Map the new VxVM volume name to EVFS using the evfsadm map volume_path
command.
2. Enable the EVFS volume using the evfsvol enable evfs_volume_path command.
NOTE: Do not use the evfsvol create command to create a new encryption metadata
(EMD) area on the volume. The EMD area already exists on the volume.
96 Managing Data on EVFS Volumes
Page 97

Resizing EVFS Volumes and File Systems
If you resize EVFS volumes and file systems created on EVFS volumes, HP recommends that
you create a backup copy of the data before resizing an EVFS volume or file system above an
EVFS volume. In addition, you must:
• Allow 1 MB on the EVFS volume for the encryption metadata (EMD). Subtract 1 MB from
the size of the underlying LVM, VxVM, or physical volume when calculating the number
of bytes available for the file system. The size of the EMD depends on the configured
maximum number of user records, as specified by the emd_envelopes attribute in the
/etc/evfs/evfs.conf file. The actual size of the EMD might be less than 1 MB, but HP
recommends that you allow 1 MB for the EMD.
CAUTION: If you do not allocate sufficient space for the EVFS EMD when reducing the
size of a file system and underlying volume, the file system is rendered unusable.
• Resize an EVFS volume by resizing the underlying LVM or VxVM volume. Use the
appropriate LVM or VxVM command and specify the LVM or VxVM device file. For example:
# lvextend -L 112 /dev/vg01/lvol5
• If you have a file system on the EVFS volume, you must resize the file system as a separate
operation using the extendfs or fsadm utilities.
CAUTION: Do not use the vxresize -F fstype command to resize the VxVM and the
file system in one operation. The vxresize command does not allocate space on the VxVM
volume for the EMD.
LVM Example: Increasing Volume and File System Sizes
In the following sessions, the VxFS file system size is 65016 Kbytes, created on a 64-Mbyte
(65536-Kbyte) LVM volume (520 Kbytes is used for the EMD). The user increases the size of the
LVM volume to 112 Mbytes and wants to increase the corresponding file system size.
Correct
The user increases the LVM volume size to 112 Mbytes (114688 Kbytes). When calculating the
number of Kbytes available for the file system, the user reserves 1 Mbyte for the EVFS EMD:
(112 –1) * 1024 = 113664 Kbytes. The existing file system size is 65016 Kbytes, so the user increases
the file system size by 48648 Kbytes (113664 – 65016 = 48648).
# lvdisplay /dev/vg01/lvol5
--- Logical volumes ---
LV Name /dev/vg01/lvol5
VG Name /dev/vg01
LV Permission read/write
:
:
LV Size (Mbytes) 64
:
:
# bdf /test5
Filesystem kbytes used avail %used Mounted on
/dev/evfs/vg01/lvol5
65016 1125 59905 2% /test5
# umount /test5
# lvextend -L 112 /dev/vg01/lvol5
Logical volume "/dev/vg01/lvol5" has been successfully extended.
Volume Group configuration for /dev/vg01 has been saved in
/etc/lvmconf/vg01.conf
Resizing EVFS Volumes and File Systems 97
Page 98

# lvdisplay /dev/vg01/lvol5
--- Logical volumes --LV Name /dev/vg01/lvol5
VG Name /dev/vg01
:
:
LV Size (Mbytes) 112
:
:
# extendfs -F vxfs -s 48648 /dev/evfs/vg01/rlvol5
# mount -F vxfs /dev/evfs/vg01/lvol5 /test5
# bdf /test5
Filesystem kbytes used avail %used Mounted on
/dev/evfs/vg01/lvol5
113664 1141 105498 1% /test5
Incorrect
When calculating the number of Kbytes available for the file system, the user does not reserve
space for the EVFS EMD. The LVM is 112 Mbytes = 114688 Kbytes. The user attempts to increase
the current file system size, 65016 Kbytes, by 49672 Kbytes to use all available space on the LVM
for the file system (114688 – 65016 = 49672).
# extendfs -F vxfs -s 49672 /dev/evfs/vg01/rlvol5
# vxfs extendfs: New size (114688 blocks) beyond device capacity (114168 blocks).
LVM Example: Reducing Volume and File System Sizes
Correct
Incorrect
In the following sessions, the LVM volume is 112 Mbytes and the file system size is 113664 Kbytes.
The administrator wants to decrease the size of the LVM volume to 64 Mbytes.
When calculating the number of Kbytes available for file system on a 64-Mbtye LVM volume,
the user reserves 1 Mbyte for the EMD: 64 – 1 Mbytes = 63 * 1024 = 64512 Kbytes for the file
system. The user reduces the size of the file system to 64512 Kbytes, then reduces the size of the
LVM volume to 64 Mbytes.
# fsadm -F vxfs -b 64512 /test1
vxfs fsadm: /dev/evfs/vg01/rlvol5 is currently 113664 sectors - size will be
reduced
# lvreduce -L 64 /dev/vg01/lvol5
When a logical volume is reduced useful data might get lost;
do you really want the command to proceed (y/n) : y
Logical volume "/dev/vg01/lvol5" has been successfully reduced.
Volume Group configuration for /dev/vg00 has been saved in /etc/lvmconf
# cd /test1
# pwd
/test1
The user does not reserve space for the EMD when calculating the number of Kbytes available
for a file system on a 64-Mbyte LVM volume. The user reduces the size of the file system to 65536
Kbytes, (64 *1024 Mbytes = 65536 Kbytes), then reducesthe size of the LVM volume to 64 Mbytes.
Subsequent operations on the file system might fail. Data might be lost or corrupted.
# fsadm -F vxfs -b 65536 /test1
vxfs fsadm: /dev/evfs/vg01/rlvol5 is currently 113664 sectors - size will be
reduced
# lvreduce -L 64 /dev/vg01/lvol5
When a logical volume is reduced useful data might get lost;
do you really want the command to proceed (y/n) : y
Logical volume "/dev/vg01/lvol5" has been successfully reduced.
Volume Group configuration for /dev/vg00 has been saved in /etc/lvmconf
# cd /test1
ksh: /test1: bad directory
98 Managing Data on EVFS Volumes
Page 99

# bdf /test1
bdf: /test1: I/O error
VxVM Example: Increasing Volume and File System Sizes
In the following sessions, the VxFS file system size is 66040 Kbytes, created on a 65-Mbyte (66560
Kbyte) VxVM volume (520 Kbytes is used for the EMD). The user increases the size of the VxVM
volume to 112 Mbytes and wants to increase the corresponding file system size.
Correct
The user increases the VxVM volume size to 112 Mbytes (114688 Kbytes). When calculating the
number of Kbytes available for the file system, the user reserves 1 Mbyte for the EVFS EMD:
(112 –1) * 1024 = 113664 Kbytes. The existing file system size is 66040 Kbytes, so the user increases
the file system size by 47624 Kbytes (113664 – 66040 = 47624).
# vxprint -g rootdg vol05
TY NAME ASSOC KSTATE LENGTH PLOFFS STATE TUTIL0 PUTIL0
v vol05 fsgen ENABLED 66560 - ACTIVE - pl vol05-01 vol05 ENABLED 66560 - ACTIVE - sd c3t0d0-01 vol05-01 ENABLED 66560 0 - - -
# bdf /test5
Filesystem kbytes used avail %used Mounted on
/dev/evfs/vx/dsk/rootdgelvol05
66040 1133 60858 2% /test5
# umount /test5
# vxassist -g rootdg growto vol05 112m
# vxprint -g rootdg vol05
TY NAME ASSOC KSTATE LENGTH PLOFFS STATE TUTIL0 PUTIL0
v vol05 fsgen ENABLED 114688 - ACTIVE - pl vol05-01 vol05 ENABLED 114688 - ACTIVE - sd c3t0d0-01 vol05-01 ENABLED 114688 0 - - # extendfs -F vxfs -s 47624 /dev/evfs/vx/dsk/rootdg/vol05
# mount -F vxfs /dev/evfs/vx/dsk/rootdg/evol05 /test5
# bdf /test5
Filesystem kbytes used avail %used Mounted on
/dev/evfs/vx/dsk/rootdg/evol05
113664 1141 105850 1% /test5
Incorrect
When calculating the number of Kbytes available for the file system, the user does not reserve
space for the EVFS EMD. The VxVM is 112 Mbytes = 114688 Kbytes. Theuser attempts to increase
the current file system size, 66040 Kbytes, by48648 Kbytes to use all available space on the VxVM
for the file system (114688 – 66040 = 48648).
# extendfs -F vxfs -s 48648 /dev/evfs/vg01/rlvol5
# vxfs extendfs: New size (114688 blocks) beyond device capacity (114168 blocks).
VxVM Example: Reducing Volume and File System Sizes
In the following sessions, the VxVM volume is 112 Mbytes and the file system size is 113664
Kbytes. The administrator wants to decrease the size of the VxVM volume to 64 Mbytes.
Correct
When calculating the number of Kbytes available for file system on a 64-Mbtye VxVM volume,
the user reserves 1 Mbyte for the EMD: 64 – 1 Mbytes = 63 * 1024 = 64512 Kbytes for the file
system. The user reduces the size of the file system to 64512 Kbytes, then reduces the size of the
VxVM volume to 64 Mbytes.
# fsadm -F vxfs -b 64512 /test5
vxfs fsadm: /dev/evfs/vx/rdsk/rootdg/evol05 is currently 114040 sectors - size will be reduced
# vxassist -g rootdg -f shrinkto vol05 64m
Resizing EVFS Volumes and File Systems 99
Page 100

Incorrect
The user does not reserve space for the EMD when calculating the number of Kbytes available
for a file system on a 64-Mbyte VxVM volume. The user reduces the size of the file system to
65536 Kbytes, (64 * 1024 Mbytes = 65536 Kbytes), then reduces the size of the VxVM volume to
64 Mbytes. Although no file system error is returned, data might be lost corrupted.
# fsadm -F vxfs -b 65536 /test5
vxfs fsadm: /dev/evfs/vx/rdsk/rootdg/evol05 is currently 114040 sectors - size will be reduced
# vxassist -g rootdg -f shrinkto vol05 64m
# cd /test5 (no immediate error, but data may be lost or corrupt)
100 Managing Data on EVFS Volumes
 Loading...
Loading...