Page 1

HP-UX Directory Server console guide
HP-UX Directory Server Version 8.1
HP Part Number: 5900-0314
Published: September 2009
Edition: 1
Page 2

© Copyright 2009 Hewlett-Packard Development Company, L.P.
Confidential computersoftware. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial
Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under
vendor's standard commercial license.
The informationcontained hereinis subject to change without notice. Theonly warranties for HPproducts andservices are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP
shall not be liable for technical or editorial errors or omissions contained herein.
Page 3

Table of Contents
1 Overview of the console................................................................................................5
1.1 How the Console, Directory Server, and Administration Server work together..............................5
1.2 Console menus..................................................................................................................................7
1.3 Console tabs......................................................................................................................................8
1.3.1 The Servers and Applications tab.............................................................................................8
1.3.2 The Users and Groups tab.........................................................................................................9
1.4 Server-specific consoles...................................................................................................................10
1.4.1 The Directory Server Console.................................................................................................10
1.4.2 The Administration Server console.........................................................................................11
2 Basic Console tasks.....................................................................................................13
2.1 Launching the Console....................................................................................................................13
2.2 Opening a directory or Administration Server window.................................................................14
2.3 Changing the Console appearance..................................................................................................14
2.3.1 Changing profile locations......................................................................................................15
2.3.2 Restoring default font settings................................................................................................16
2.3.3 Changing console fonts...........................................................................................................17
2.3.4 Reordering table columns.......................................................................................................19
2.3.5 Customizing the main window...............................................................................................22
2.3.6 Working with custom views...................................................................................................23
2.3.6.1 Creating custom views....................................................................................................23
2.3.6.2 Switching to a custom view............................................................................................25
2.3.6.3 Setting access permissions for a public view..................................................................25
3 Managing server instances.........................................................................................29
3.1 Editing domain, host, server group, and instance information......................................................29
3.2 Creating and removing admin domains.........................................................................................30
3.2.1 Creating and editing an admin domain..................................................................................30
3.2.2 Removing an admin domain...................................................................................................31
3.3 Creating a new Directory Server instance.......................................................................................32
3.4 Deleting a Directory Server instance...............................................................................................33
4 Managing Directory Server users and groups..........................................................35
4.1 Searching for users and groups.......................................................................................................35
4.2 Creating directory entries................................................................................................................37
4.2.1 Directory and administrative users.........................................................................................37
4.2.2 Groups.....................................................................................................................................40
4.2.3 Organizational units................................................................................................................43
4.3 Modifying directory entries............................................................................................................45
4.3.1 Editing entries.........................................................................................................................45
4.3.2 Allowing sync attributes for entries........................................................................................46
4.3.3 Changing administrator entries..............................................................................................47
4.3.3.1 Changing the configuration administrator and password.............................................48
4.3.3.2 Changing the admin password.......................................................................................49
4.3.3.3 Adding users to the configuration administrators group...............................................50
4.3.4 Removing an entry from the directory...................................................................................52
Table of Contents 3
Page 4

5 Setting access controls.................................................................................................53
5.1 Granting admin privileges to users for Directory Server and Administration Server...................53
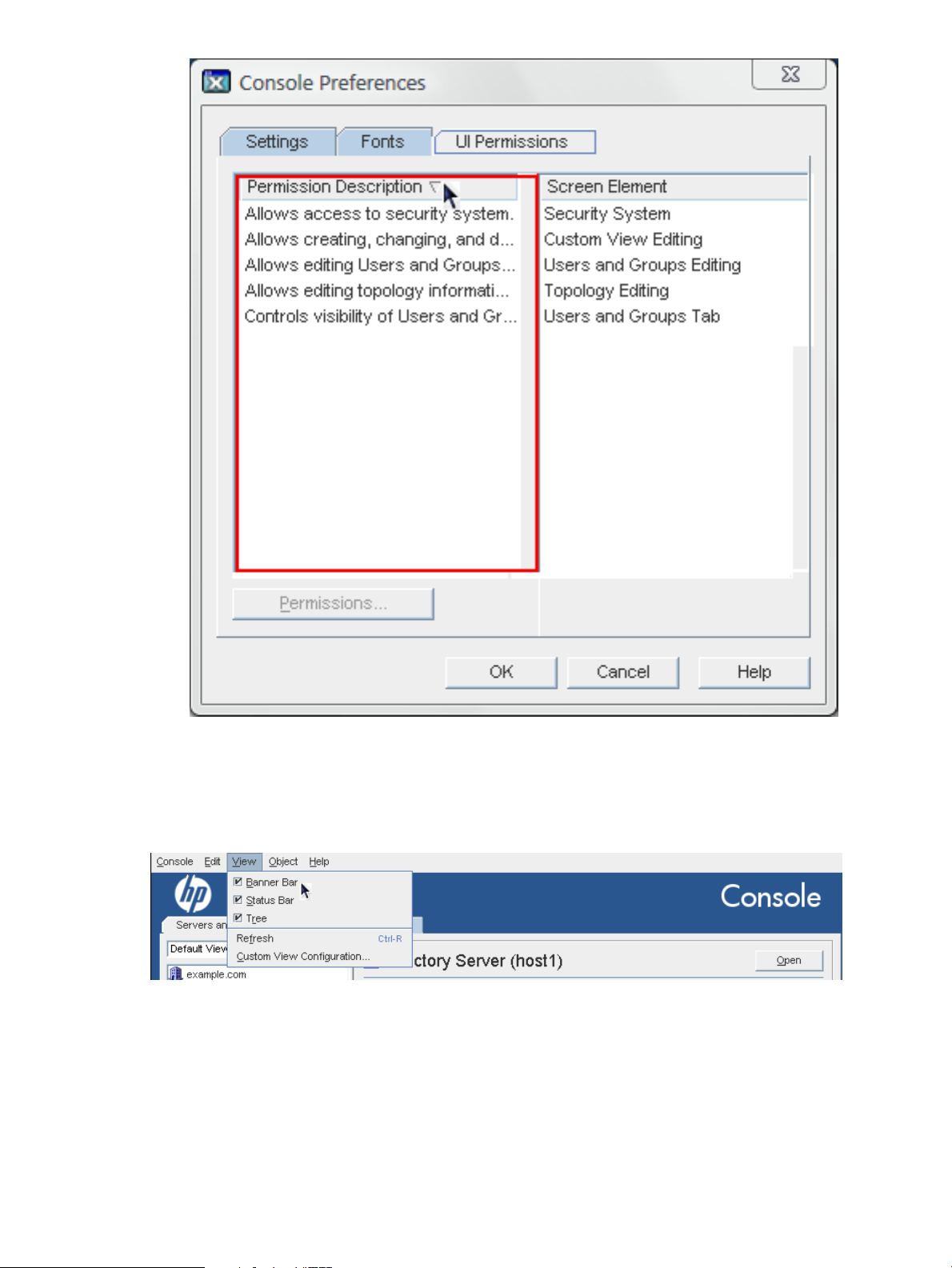
5.2 Setting access permissions on console elements.............................................................................55
6 Using SSL/TLS with the Console.................................................................................61
6.1 Overview of SSL/TLS......................................................................................................................61
6.2 Installing certificates........................................................................................................................62
6.2.1 Generating a certificate request...............................................................................................63
6.2.2 Installing the certificate...........................................................................................................65
6.2.3 Trusting a certificate authority or adding a certificate chain..................................................67
6.3 Enabling TLS/SSL............................................................................................................................71
6.4 Creating password files...................................................................................................................76
6.4.1 Creating a password file for the Directory Server..................................................................76
6.4.2 Creating a password file for the Administration Server.........................................................77
7 Support and other resources.......................................................................................79
7.1 Contacting HP.................................................................................................................................79
7.1.1 Information to collect before contacting HP...........................................................................79
7.1.2 How to contact HP technical support.....................................................................................79
7.1.3 HP authorized resellers...........................................................................................................79
7.1.4 Documentation feedback.........................................................................................................79
7.2 Related information.........................................................................................................................79
7.2.1 HP-UX Directory Server documentation set...........................................................................79
7.2.2 HP-UX documentation set......................................................................................................80
7.2.3 Troubleshooting resources......................................................................................................81
7.3 Typographic conventions................................................................................................................81
Glossary............................................................................................................................83
Index.................................................................................................................................93
4 Table of Contents
Page 5
1 Overview of the console
The DirectoryConsole is the user interface to manage HP-UX Directory Server and Administration
Server configuration and directory information. There is a single main Console window which
administers the servers (collected and identified in administration domains). The main
Console allows you to open server-specific Consoles to manage the settings and information in
individual instances.
This chapter provides an overview of how the Console interacts with the Directory Server and
Administration Server and walks through the Console windows and options.
1.1 How the Console, Directory Server, and Administration Server work together
The Directory Console is an independent Java application which works in conjunction with
instances of Directory Server and Administration Server. Most server management functions are
carried out in server-specific console windows for the Directory Server and Administration
Server. Console is part of a systemthat manages Directory Server instances andthe Administration
Server and, therefore, information in the directory. Although HP-UX Directory Server, the
Console, and Administration Server work tightly with one another, each plays a specific role in
managing servers, applications, and users.
The console is the front-end management application for HP-UX Directory Server. It finds all
servers and applications registered in the configuration directory, displays them in a graphical
interface, and can manage and configure them. The Main Console can also search for, create,
and edit user and group entries in the user directory.
Figure 1-1 The Console interface
When a user logs into Directory Console, the Console connects to the Administration Server over
Hypertext Transfer Protocol (HTTP). The Administration Server receives requests to administer
the different Directory Server instances and performs the changes to the configuration, such as
1.1 How the Console, Directory Server, and Administration Server work together 5
Page 6
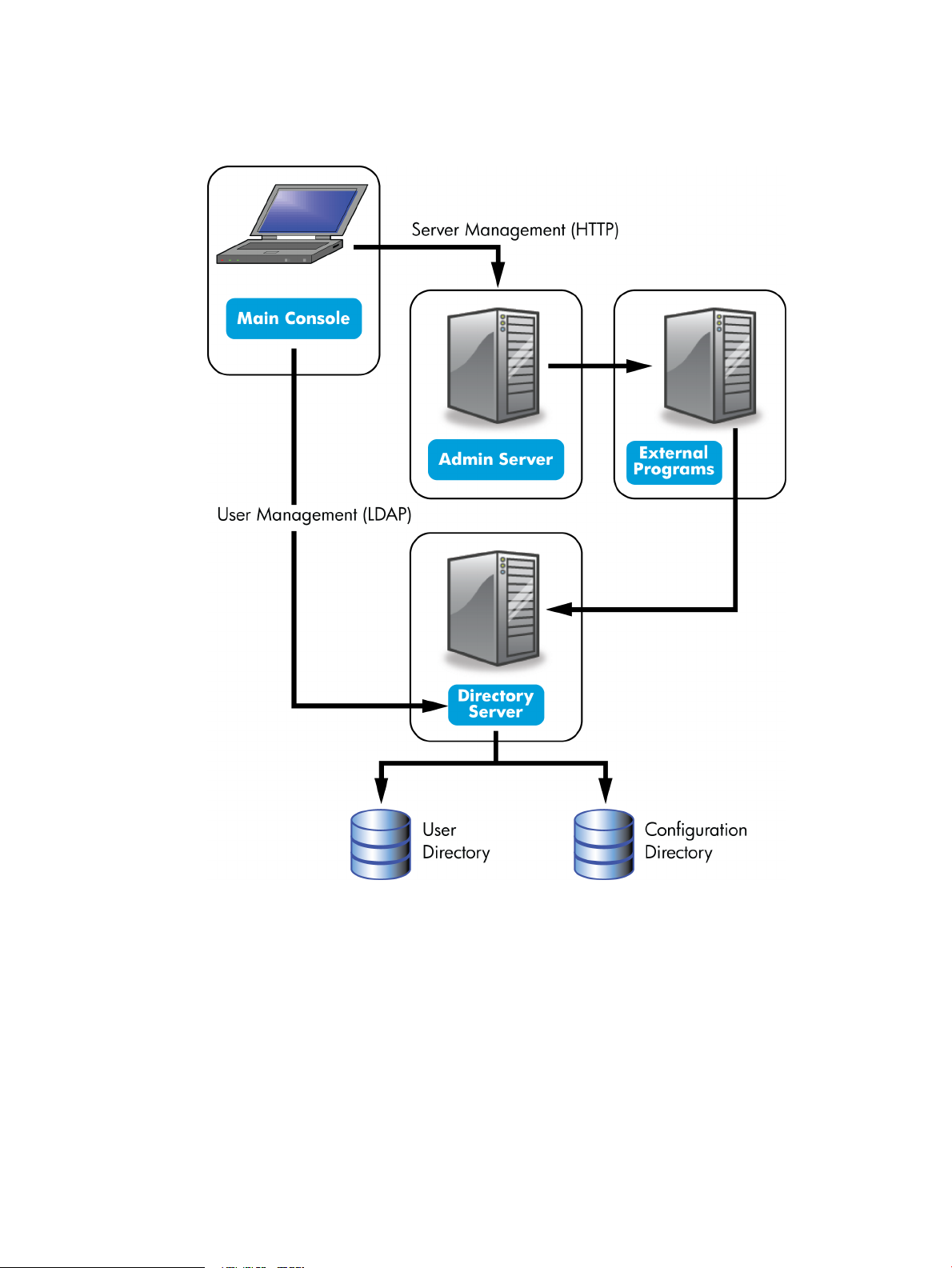
changing a port number. When a request is sent to the Directory Console to add or edit user
entries, the Console sends a Lightweight Directory Access Protocol (LDAP) message directly to
Directory Server to update the user directory.
Figure 1-2 Simple system using the Console
HP-UX Directory Server stores server and application configuration settings as well as user
information. Typically, application and server configuration information is stored in one subtree
of Directory Server while user and group entries are stored in another subtree. With a large
enterprise, however, configuration and user information can be stored in separate instances of
Directory Server (which can be on the same host machine or on two different host machines).
Figure 1-2 “Simple system using the Console” illustrates a relatively simple HP-UX Directory
Server system. As an enterprise grows and needs change, additional hosts and Directory and
Administration Servers can be added to the administration domain in the Console, so that a
single Console can manage multiple Directory and Admin Servers.
6 Overview of the console
Page 7
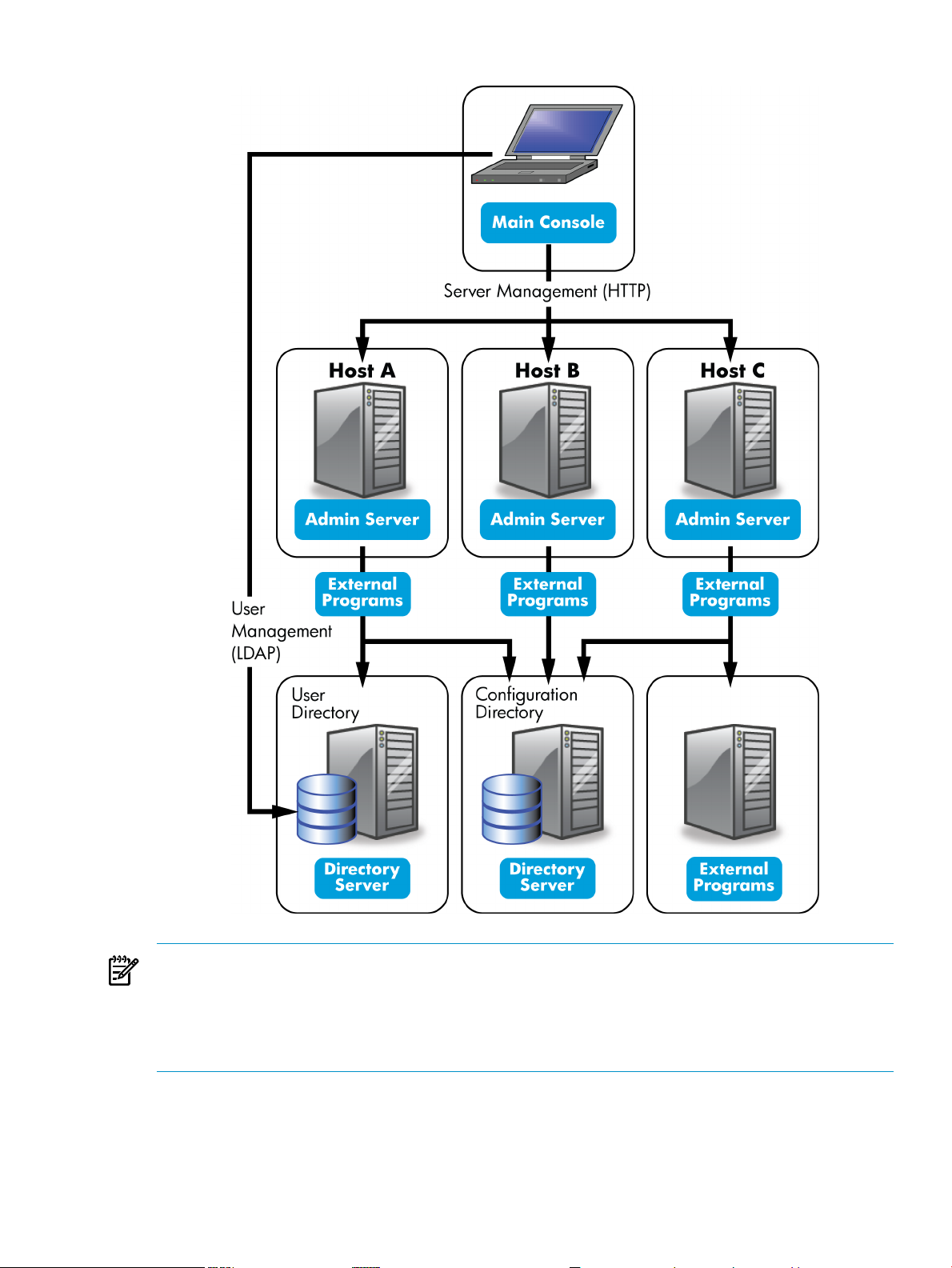
Figure 1-3 A more complex system
NOTE:
When the terms configuration directory and user directory are used in this guide, they refer to
where the configuration information and the user information is stored, regardless of whether
that is in the subtrees of a single instance of Directory Server or in two separate instances of
Directory Server.
1.2 Console menus
There are five menu items in the top menu the Console. The options for each of these menus
varies depending on the Console window open (the main Console, Directory Server Console, or
Administration Server Console) and the types of objects available in that server area.
1.2 Console menus 7
Page 8

Figure 1-4 Main Console menus
Table 1-1 Console menus
DescriptionMenu
Console
Edit
View
Object
Manages the Console session, such as closing the window or exiting the session entirely.
• For the main window, this menu also can be used to add and remove admin domain.
• For the Directory Server Console, this allows people to log in as a different user.
• For the AdministrationServer Console, it manages security issues, such as certificates andtokens.
Sets display preferences, for all three Consoles. For the Directory Server Console, this also provides
ways to copy, paste, and delete directory entries or text.
Sets whether to display certain parts of the Console window, such as the top banner, menus, and
side navigation panes. This also refreshes the current display. For the Directory Server Console, this
menu also sets what parts of the directory or which databases to view.
Provides available operations for the active object; this is the same as the right-click menu for the
active area or entry.
• For the main window, this menu simply opens or deletes a server instance.
• For the Directory Server Console, this provides all the configuration options for the directory
• For the Administration Server Console, this opens a configuration editor, starts, and stops the
Opens context-specific help for the current Console area.Help
1.3 Console tabs
There are two tabs in the main Console window:
• Servers and Applications, for managing the Directory Server and Administration Server
instances
• Users and Groups, for searching for and creating user and groupentries within the Directory
Server
entries, such as advanced property editors or creating new entries.
server.
1.3.1 The Servers and Applications tab
The Servers and Applications tab, by default, has a navigation tree on the left for viewing hosts
and Directory and Administration Servers and a center information panel. To access the Directory
Server instance, directory information, or Administration Server, open the server resource listed
in the navigation tree. The information for the server instance, such as the build number and
port number,
The navigation tree displays the HP-UX Directory Server topology, that is, a hierarchical
representation of all the resources (such as servers and hosts), that are registered in a configuration
directory.
8 Overview of the console
Page 9

Figure 1-5 The Servers and Applications tab
The top of the topology is the administration domain, a collection of host systems and servers
that share the same user directory. The server which hosts Directory Server or Administration
Server instances belongs to the administration domain; that is the host.
A server group consists of all Directory Servers that are managed by a common Administration
Server. A number of server groups can exist within an administration domain.
1.3.2 The Users and Groups tab
The Users and Groups tab can search for user and group entries in any Directory Server
administered by the Console. Any of the returned entries can be edited or deleted through this
tab, assuming that the users has the proper access permissions. New entries can also be created
through the Users and Groups tab.
1.3 Console tabs 9
Page 10

Figure 1-6 The Users and Groups tab
Switch the directory being searched or where the entries are added through the options in the
Users menu, as described in “Searching for users and groups”.
1.4 Server-specific consoles
The main Console can open into two server-specific windows to manage the Administration
Server and Directory Server. These windows are opened by clicking the server name in the
navigation area, then clicking the Open button in the resources area.
1.4.1 The Directory Server Console
The Directory Server Console manages the specific Directory Server instance configuration,
including the port number, SSL settings, and logging. The Directory Server Console also manages
the directory information (entries) and directory operations like importing and exporting
databases, creating suffixes, and extending the schema.
10 Overview of the console
Page 11
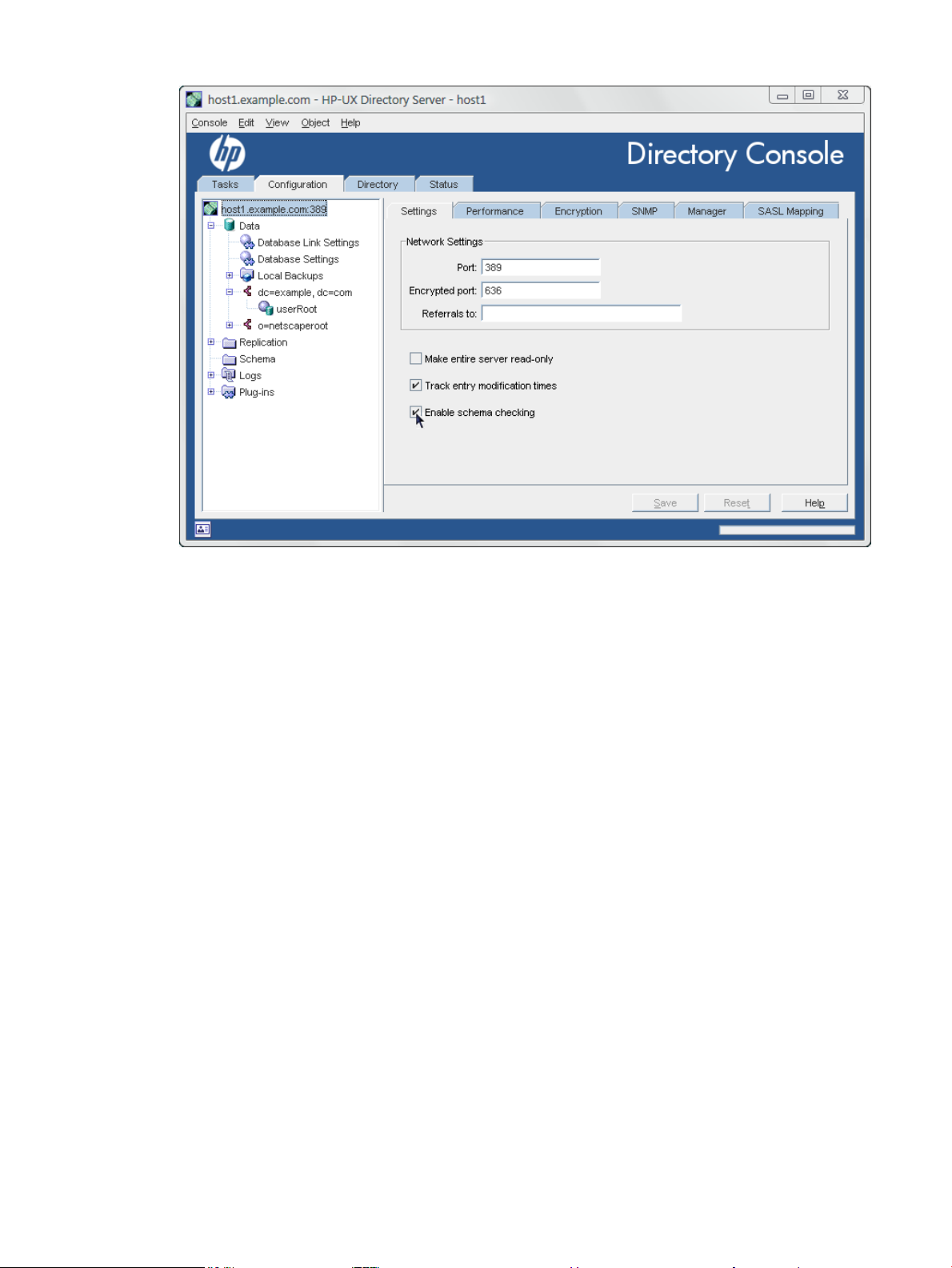
Figure 1-7 The Directory Server Console
There are four tabs in the Directory Server Console:
Tasks
Configuration
Directory
Status
Similar to the main Console, the Directory Server Console tabs have a navigation area on the left
and a center panel that displays information about the active setting, entry, or database.
The procedures for using the Directory Server Console to manage the Directory Server
configuration and directory entries is covered in the HP-UX Directory Server administrator guide.
This tab provides shortcuts to common server operations, including starting
and stopping the Directory Server instance, importing and exporting
databases, and managing SSL certificates
This tab defines all the server configuration settings, including SASL and
SSL authentication,port numbers, schema, replication and synchronization,
databases and suffixes, logging, and plug-ins
This tab accesses and manages the directory information, including user
entries and all group entries, including roles, classes of service, views, and
groups
This tab monitors the server performance and displays the different
monitoring and performance counters for the Directory Server and
databases
1.4.2 The Administration Server console
The Administration Server itself administers the configuration of other servers, especially the
configuration and user directories for the server group. The Administration Server Console
manages the Administration Server settings and the settings for these two Directory Server
directories; whenever the settings are changed in the Directory Server configuration, the
modifications must be carried into the Administration Server configuration for the server to
properly manage those servers.
1.4 Server-specific consoles 11
Page 12
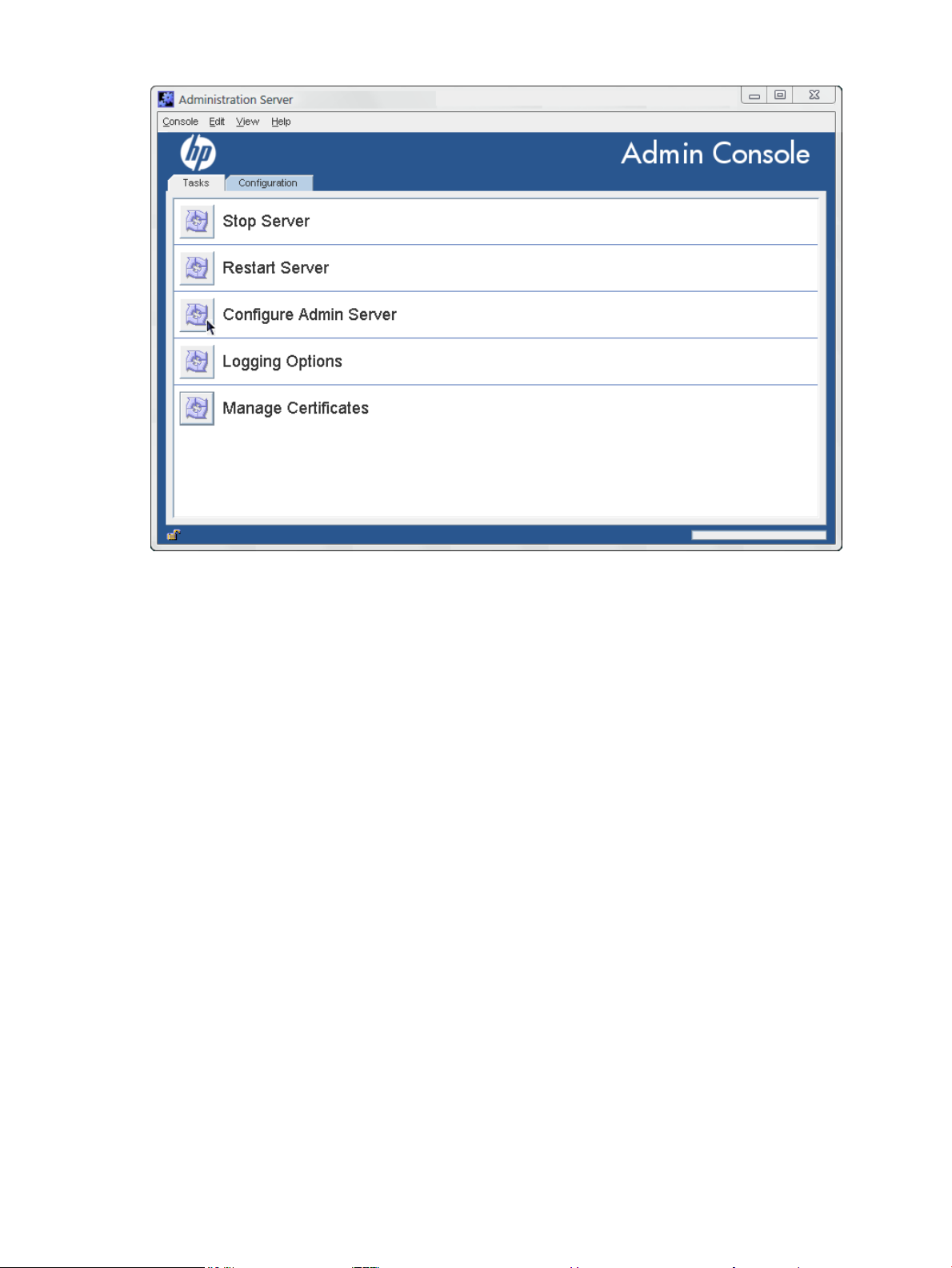
Figure 1-8 The Administration Server console
The Administration Server Console is simpler than the Directory Server Console, with only two
tabs:
Tasks
This tab has shortcuts to common server operations,including starting and
stopping the Administration Server instance, setting up logging, and
managing SSL certificates
Configuration
This tab defines all the Administration Server configuration settings,
including SSL authentication, port numbers, and logging, as well as the
Configuration Directory Server and User Directory Server settings which
the Administration Server uses to connect to the directory services
The procedures for using the Administration Server Console to manage the Administration
Server configuration and associated directory services is covered in the Using the Admin Server
guide.
12 Overview of the console
Page 13
2 Basic Console tasks
While most server management functions are carried out in server-specific console windows for
the HP-UX Directory Server and Administration Server, the main Console itself has some basic
management functions, such as creating server instances, searching the directory, setting some
access controls, and allowing some entry modifications.
This chapter covers basic tasks in the Console, including installing the Console, creating and
editing server instances, and configuring the Console appearance.
2.1 Launching the Console
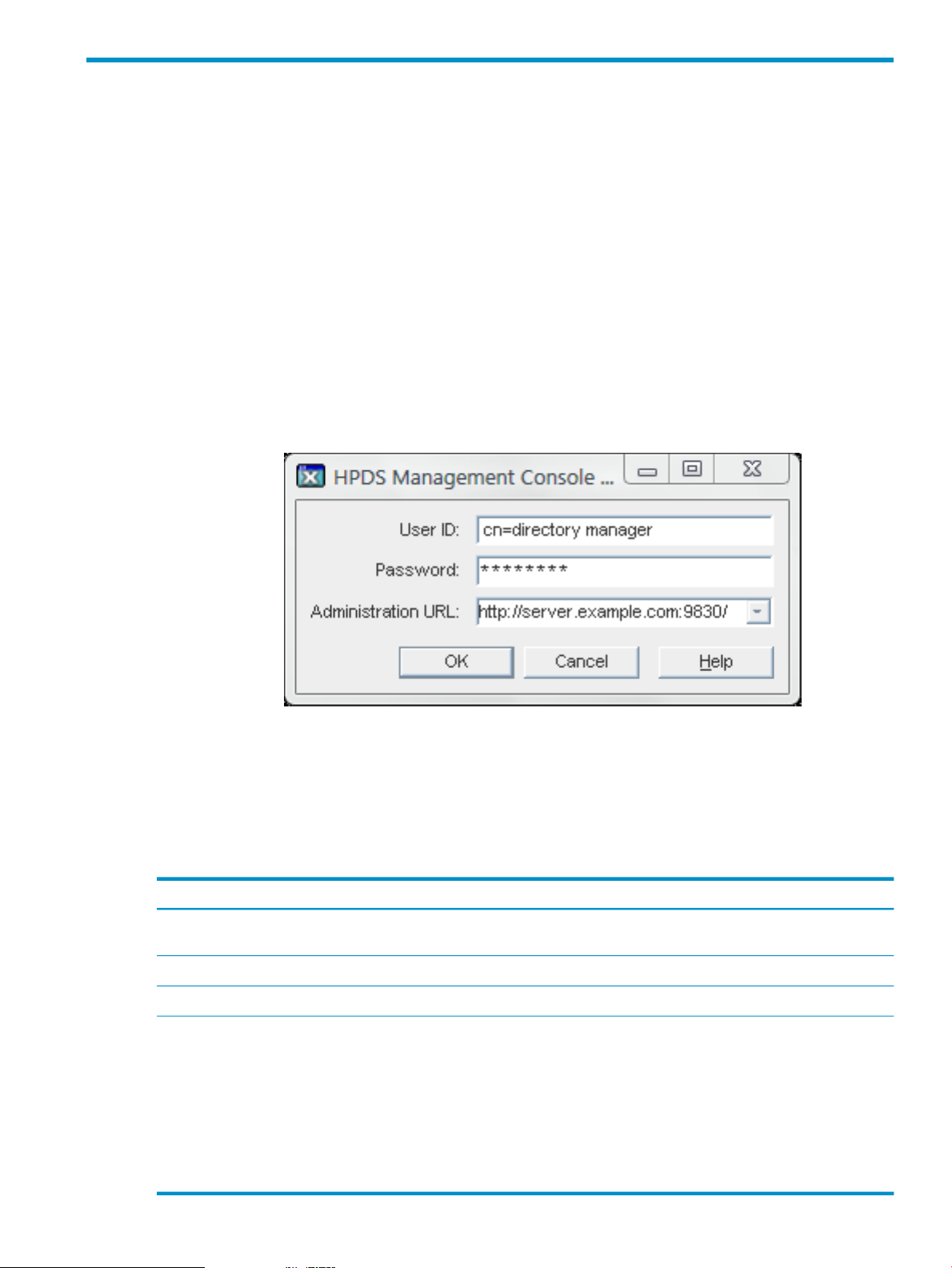
1. Run the hpds-idm-console command. For example:
hpds-idm-console -a http://server.example.com:9830
The different options for the hpds-idm-console command are listed in
Table 2-1 “Arguments for hpds-idm-console”.
2. Enter the user name and password.
Also, enter or select the URL for the instance of Administration Server, if one was not passed
with the command. The URL can be either the host name or the IP address of the
Administration Server host. The Administration Server port number must be given, as well.
The five most recent Administration Server URLs accessed are available as a drop-down
menu option.
Table 2-1 Arguments for hpds-idm-console
ExampleDescriptionArgument
-a adminURL
-h
-x options
Specifies a base URL for the instance of Administration
Server to log into.
Writes errors and system messages to fileName.-f fileName
Prints out the help message for hpds-idm-console.
extraOptions:
• nowinpos, which puts the Console window in the
upper left corner of the screen
• nologo, which prevents the splash screen from being
displayed and only opens the login dialog
• javalaf, which uses the Java look and feel for the
Console interface.
To use multiple options, separate them with a comma.
hpds-idm-console -a
http://eastcoast.example.com:987
hpds-idm-console -f system.out
hpds-idm-console -xnologo,nowinposSpecifies extra options. There are three values for
2.1 Launching the Console 13
Page 14
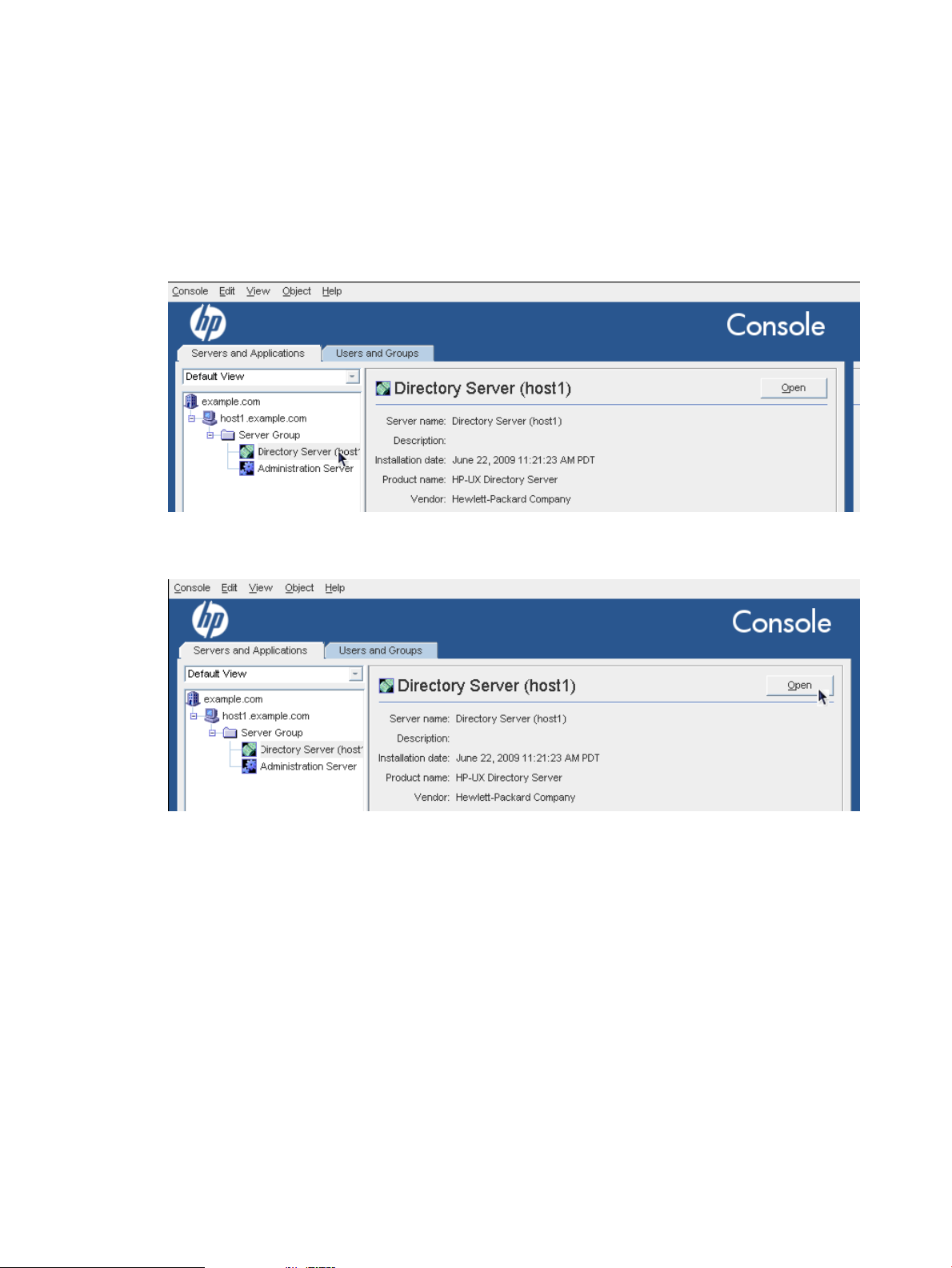
2.2 Opening a directory or Administration Server window
The Conosle is the avenue to access instance-specific management windows for the Directory
Server and Administration Server. To open a console window for a specific server instance:
1. Open the Console.
/opt/dirsrv/bin/hpds-idm-console
2. Click the Servers and Applications tab, which lists all the Directory Server and
Administration Server instances within the configured Directory Server domain.
3. In the navigation tree, click a server to select it.
4. In the right-hand panel, click Open.
Alternatively, double-click the server icon in the navigation tree.
2.3 Changing the Console appearance
The fonts used for different elements in the Console can be edited. The font settings and the
location where the font profiles are stored can be customized. The default font settings can be
restored easily.
This section also describes how to control other aspects of the appearance of the Console. For
example, table columns can be easily rearranged. It is also possible to control which server
instances are displayed (called a navigation view) which makes it easy to sort and find server
instances.
Access control instructions can be applied to user interface elements, which is discussed in
Chapter 5 “Setting access controls”.
• “Changing profile locations”
• “Restoring default font settings”
• “Changing console fonts”
14 Basic Console tasks
Page 15
• “Reordering table columns”
• “Customizing the main window”
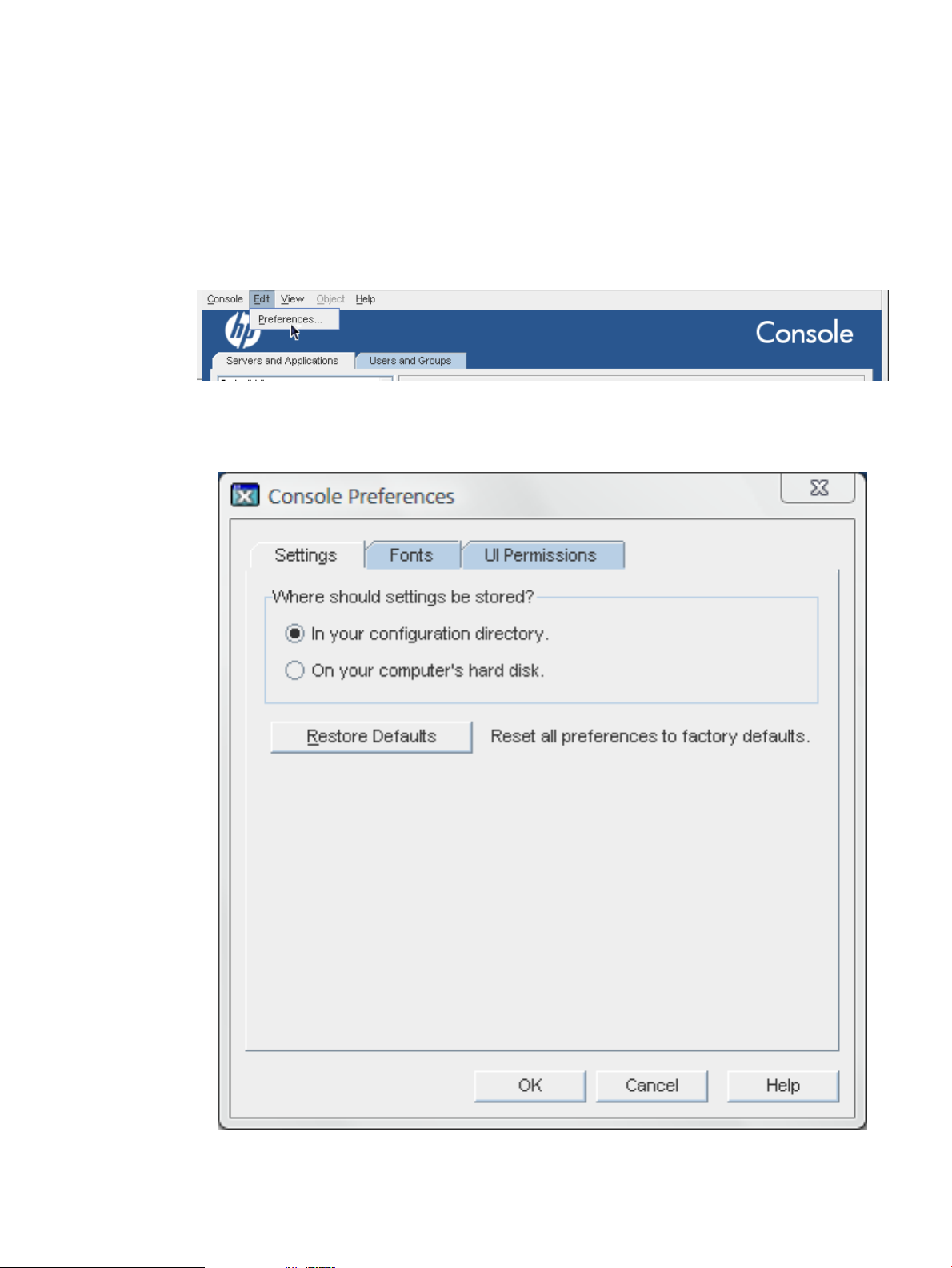
2.3.1 Changing profile locations
The Console formatting is stored in profiles. An entry's profiles can be stored locally, which
means that they are only available at a specific workstation, or can be stored in the configuration
directory, so they are accessible anywhere.
To set the profile location:
1. Click Edit in the top menu, and choose Preferences.
2. Click the Settings tab.
3. Select the radio button for the location to save the settings.
2.3 Changing the Console appearance 15
Page 16
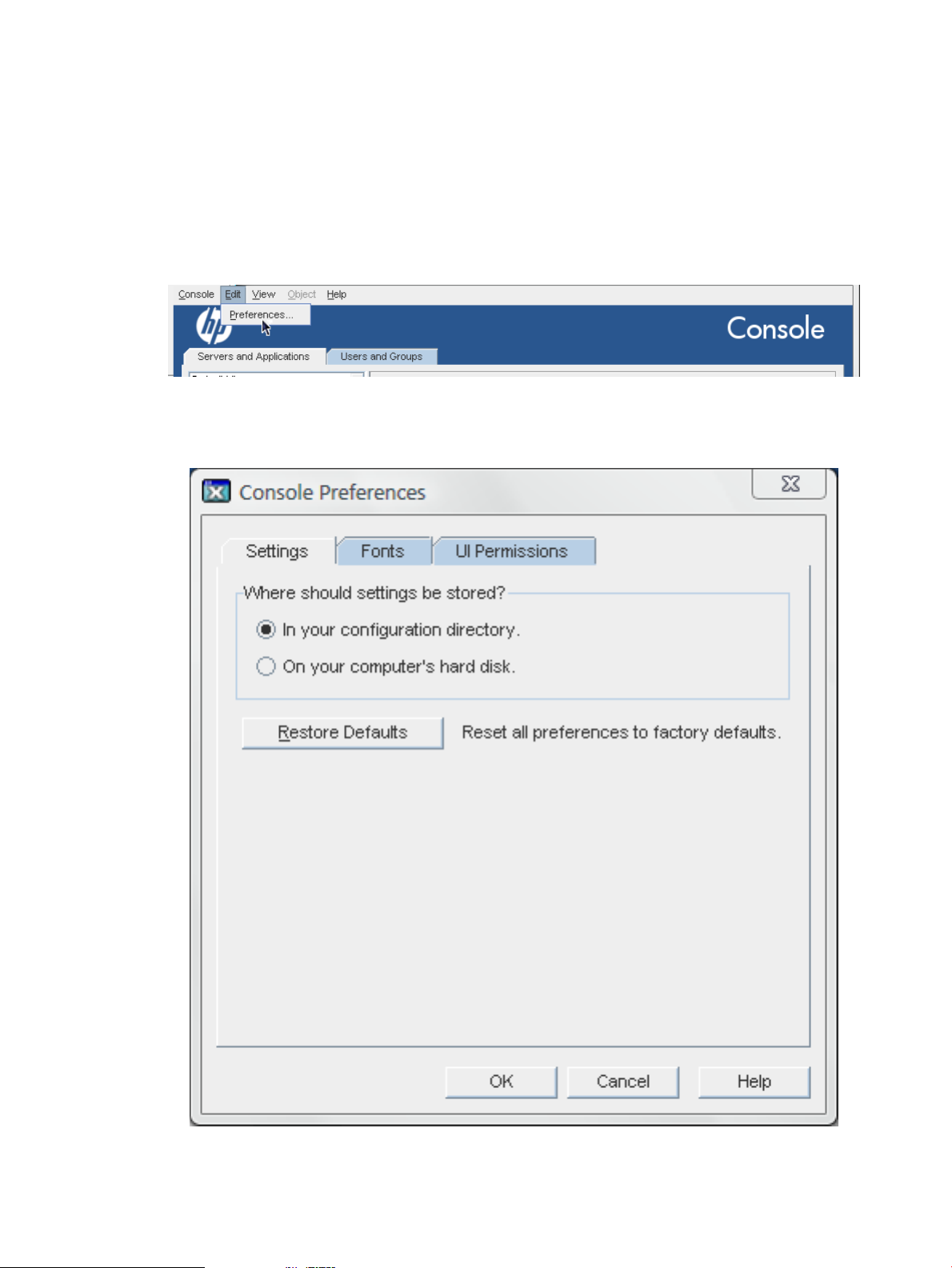
• In your configuration directory means that the settings are stored in the Directory
Server configuration, making them available no matter where you log into the Console.
• On your computer's hard disk stores the setting profiles locally. This is mainly useful
if you want specific, different settings used by default on different Consoles, such as a
workstation and a laptop.
4. Click OK.
2.3.2 Restoring default font settings
1. Click Edit in the top menu, and choose Preferences.
2. Click the Settings tab.
3. Click the Restore Defaults button to revert to the default display settings.
4. Click OK.
16 Basic Console tasks
Page 17
2.3.3 Changing console fonts
Different parts of the Console, such as table headings and regular text, have different font settings.
The font settings are stored in profiles, which define the font family, size, and formatting for
every text element. There can be multiple font profiles available, and the font profiles can be
private, such as settings for a specific user or group, or public, so that any user can access them.
The default profile can be edited without having to create new profiles.
To edit or create a font profile:
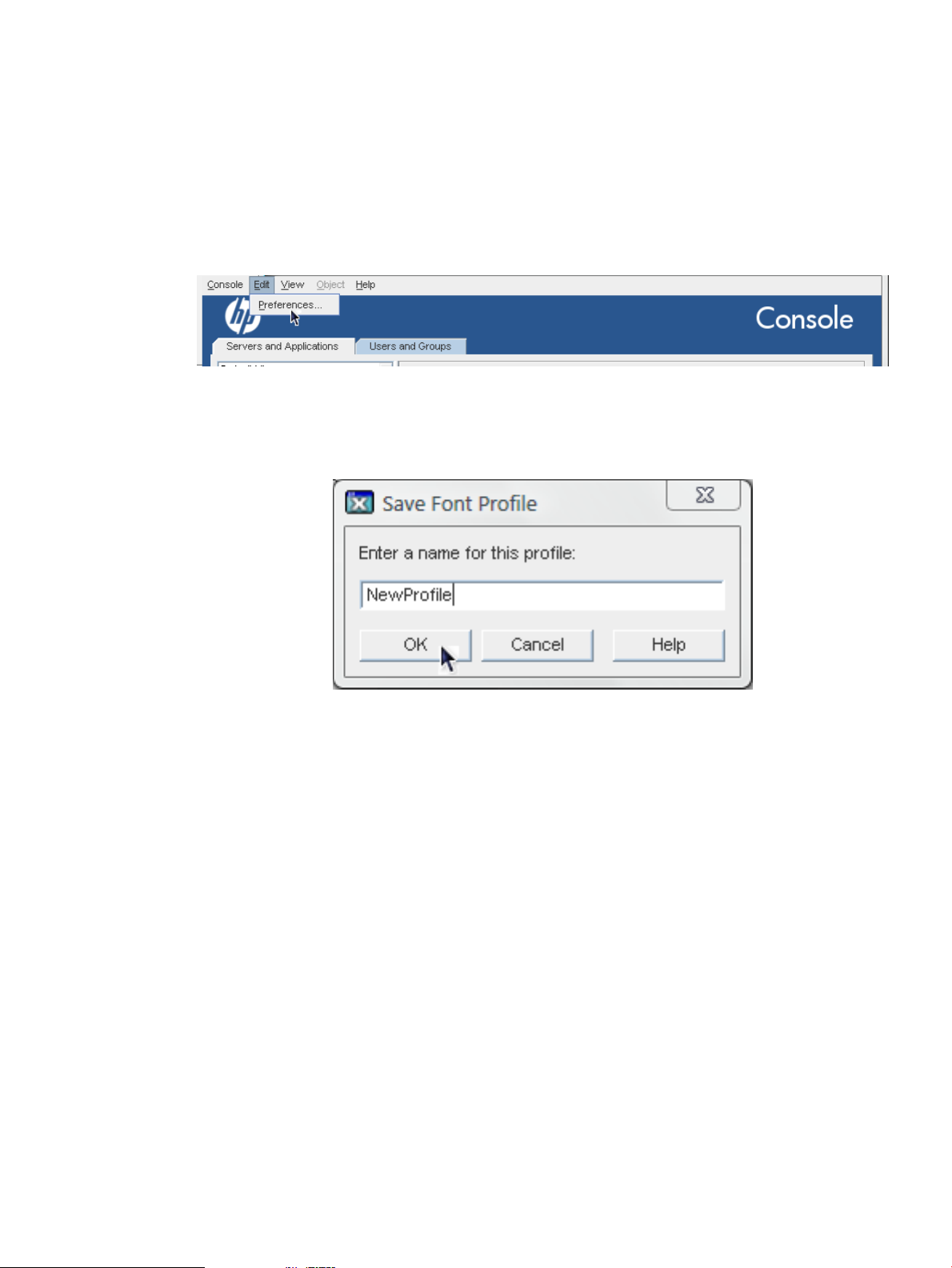
1. In the main Directory Console window, from the Edit menu, choose Preferences.
2. Click the Fonts tab.
3. To save the new settings as a new profile, click the Save As button, and fill in the profile
name.
To edit the default (or current) profile, simply begin editing the fonts.
4. In the Screen Element column, click a screen element to edit, then click the Change Font
button.
5. Edit the font for that specific element. There are three settings which can be changed: the
font family, the size, and the formatting (bold or italic).
2.3 Changing the Console appearance 17
Page 18

6. Click OK to save the profile.
7. Restart the Console to apply the changes.
# /opt/dirsrv/bin/hpds-idm-console
To load and use a saved font profile, open the Font tab in the Preference dialog, and simply
select the font profile to use and click OK.
18 Basic Console tasks
Page 19
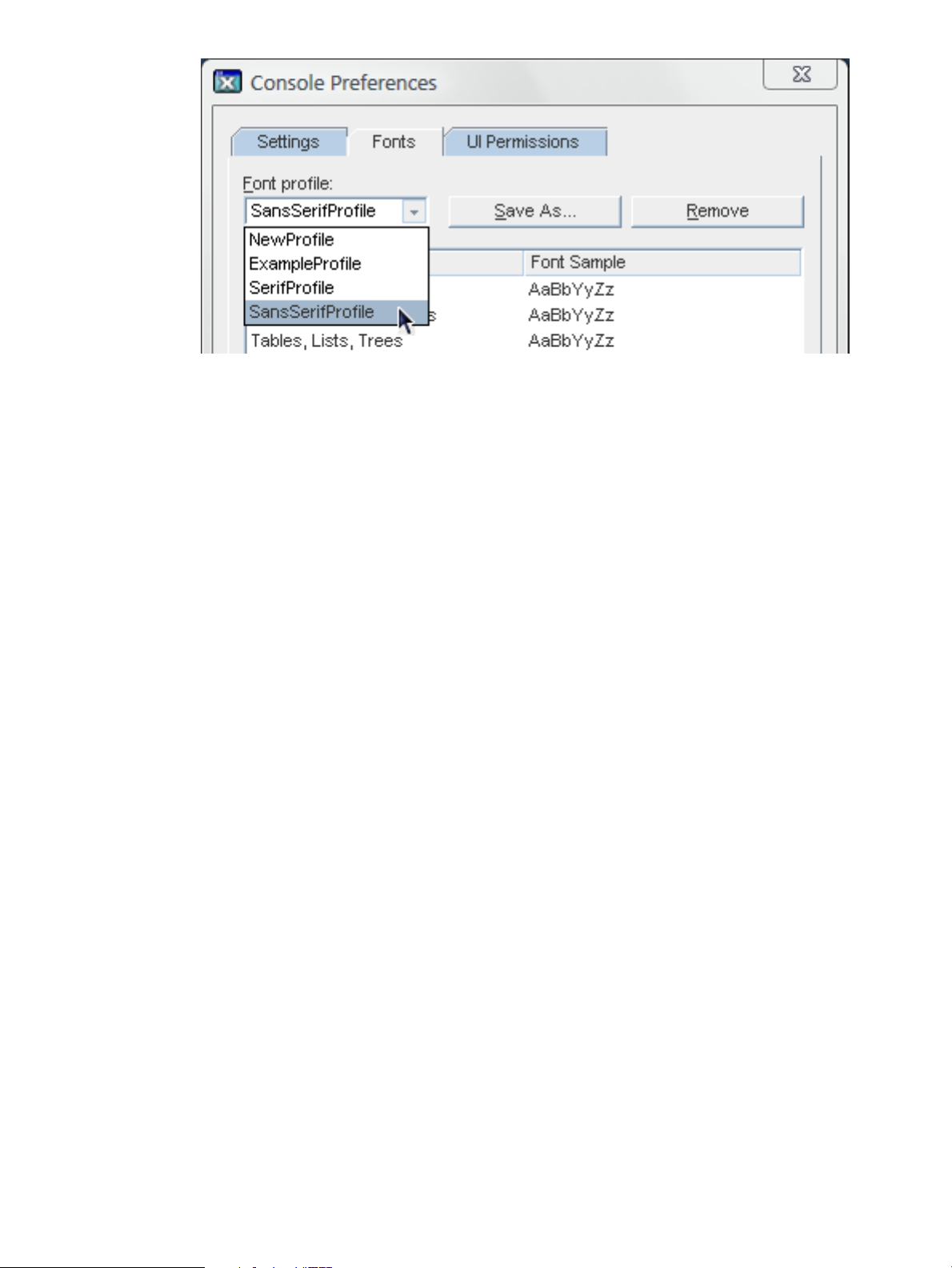
To delete a font profile, simply make sure that it is selected from the drop-down menu in the
Fonts tab, and click the Remove button.
2.3.4 Reordering table columns
The columns in a table can be rearranged by dragging them into a new position.
1. Click in the table heading.
2.3 Changing the Console appearance 19
Page 20

2. Still holding down the left mouse button, drag the column to its new location. The other
table columns will automatically shift down to their new positions.
20 Basic Console tasks
Page 21
3. When you release the mouse button, the column snaps into its new position.
2.3 Changing the Console appearance 21
Page 22
2.3.5 Customizing the main window
Different elements of the main Directory Console window can be displayed or hidden; this is
set by check boxes in the View menu.
There are three parts of the Console which can be hidden: the navigation tree (the smaller panel
on the left of the Console window); the decorative background and banner at the top of the
Console window; and the status bar at the bottom of the Console.
22 Basic Console tasks
Page 23

2.3.6 Working with custom views
The Console allows different views to be created to show different server and domain entries in
the Directory Console window. Views show only a defined set of server entries; this makes it
easier to maintain large numbers of instances or to have a quick way to perform specific tasks.
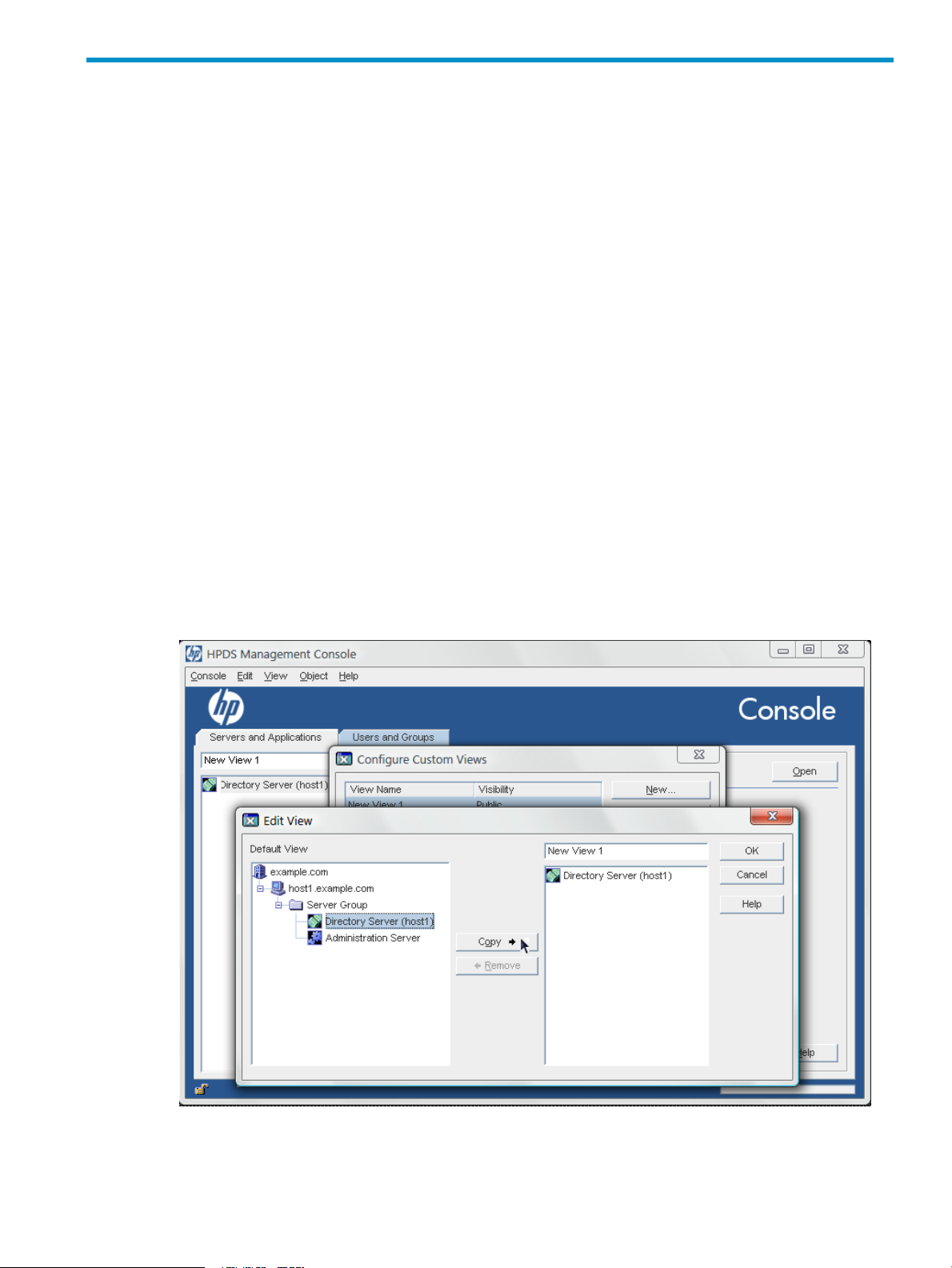
2.3.6.1 Creating custom views
Custom views show different, defined server instances. Views are either public or private. A
public view is visible to any user, while a private view is visible only to the person who created
it.
1. In the View menu, choose Custom View Configuration.
2. Click New.
2.3 Changing the Console appearance 23
Page 24
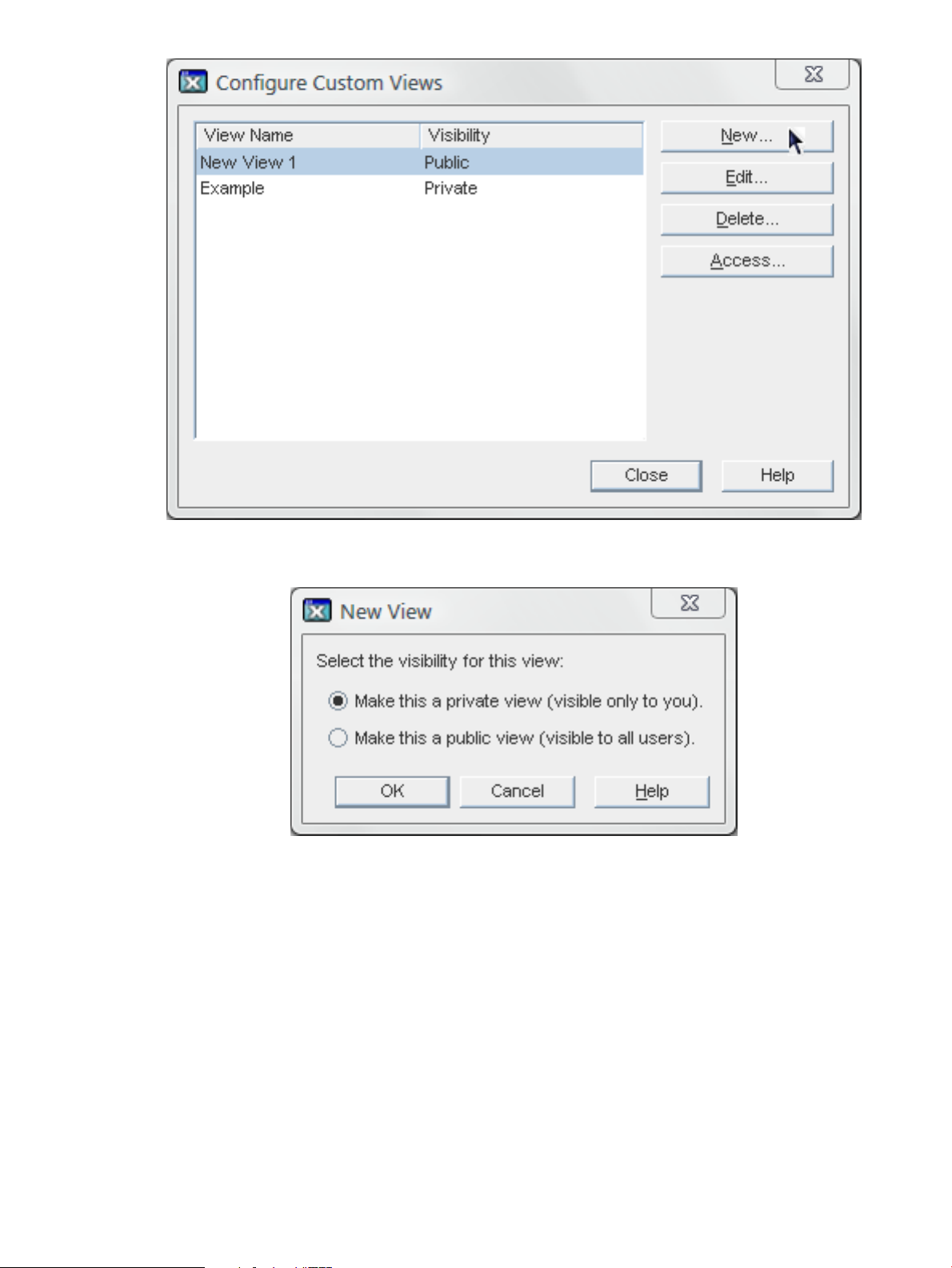
3. Choose whether the new view will be public or private, then click OK.
• A public view is visible to all Console users by default, but access control instructions
(ACIs) can be set to restrict access. For more information, see “Setting access permissions
for a public view”.
• A private view is only visible to the user who sets it, and ACIs cannot be set to change
the access to it.
4. In the Edit View window, enter a descriptive name for this view.
5. Select a resource from the Default View navigation tree on the left. Click Copy to list it in
the panel on the right and include it in the view.
24 Basic Console tasks
Page 25

To select a range of resources, click the SHIFT key and select the first and last entries; select
multiple, separate resouces by holding down the CRTL key and selecting the entries.
To edit a custom view, select it from the list, click the Edit button, and make the changes to the
name or resources.
To delete a custom view, select it from the list, and click the Remove button.
2.3.6.2 Switching to a custom view
Choose the desired custom view from the drop-down list on the Servers and Applications tab.
To return to the default view, choose Default View from the drop-down list.
2.3.6.3 Setting access permissions for a public view
1. From the View menu, choose Custom View Configuration.
2. Choose a public Custom View from the list and click Access.
2.3 Changing the Console appearance 25
Page 26
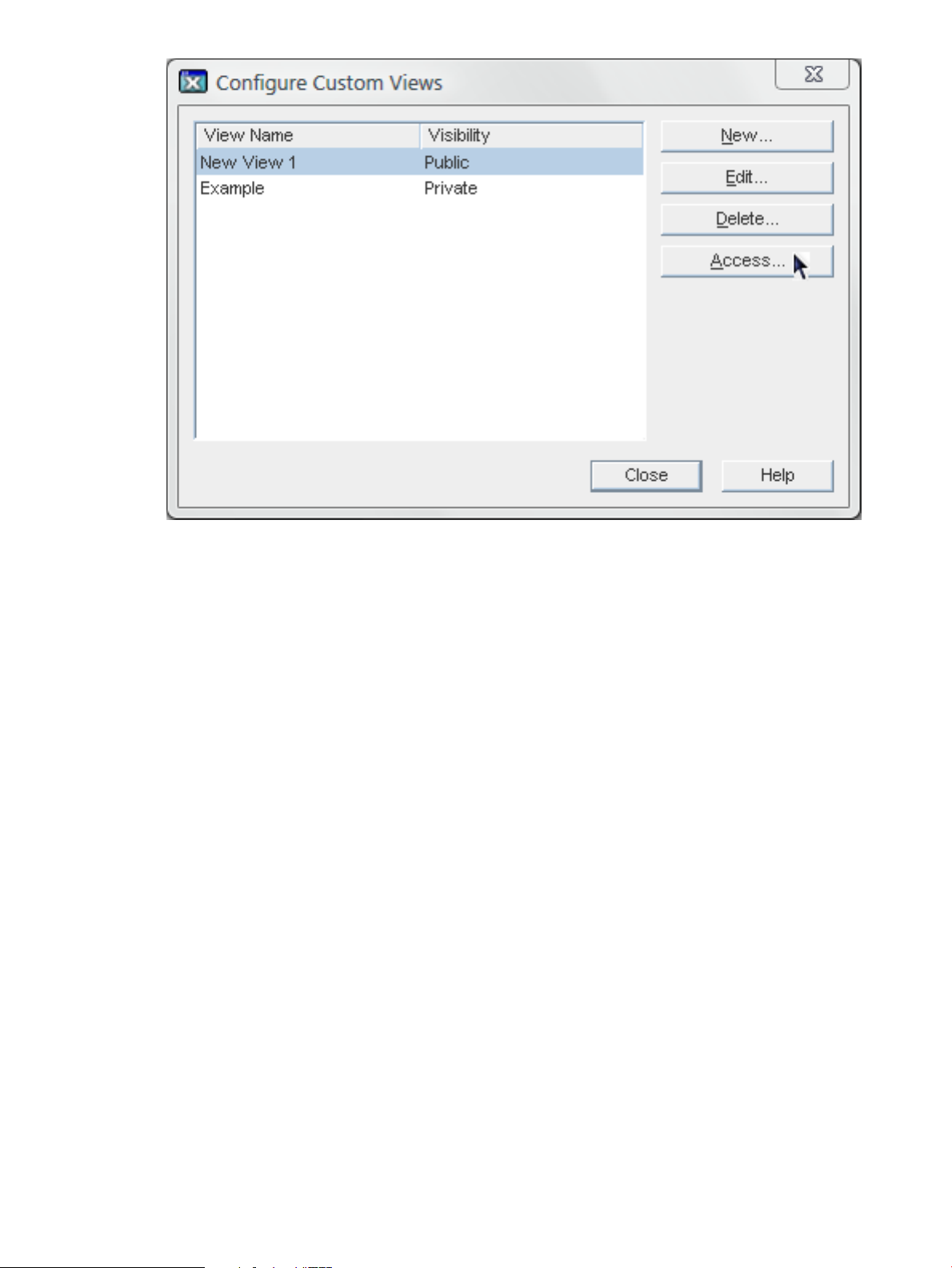
3. Set the access control instructions.
26 Basic Console tasks
Page 27
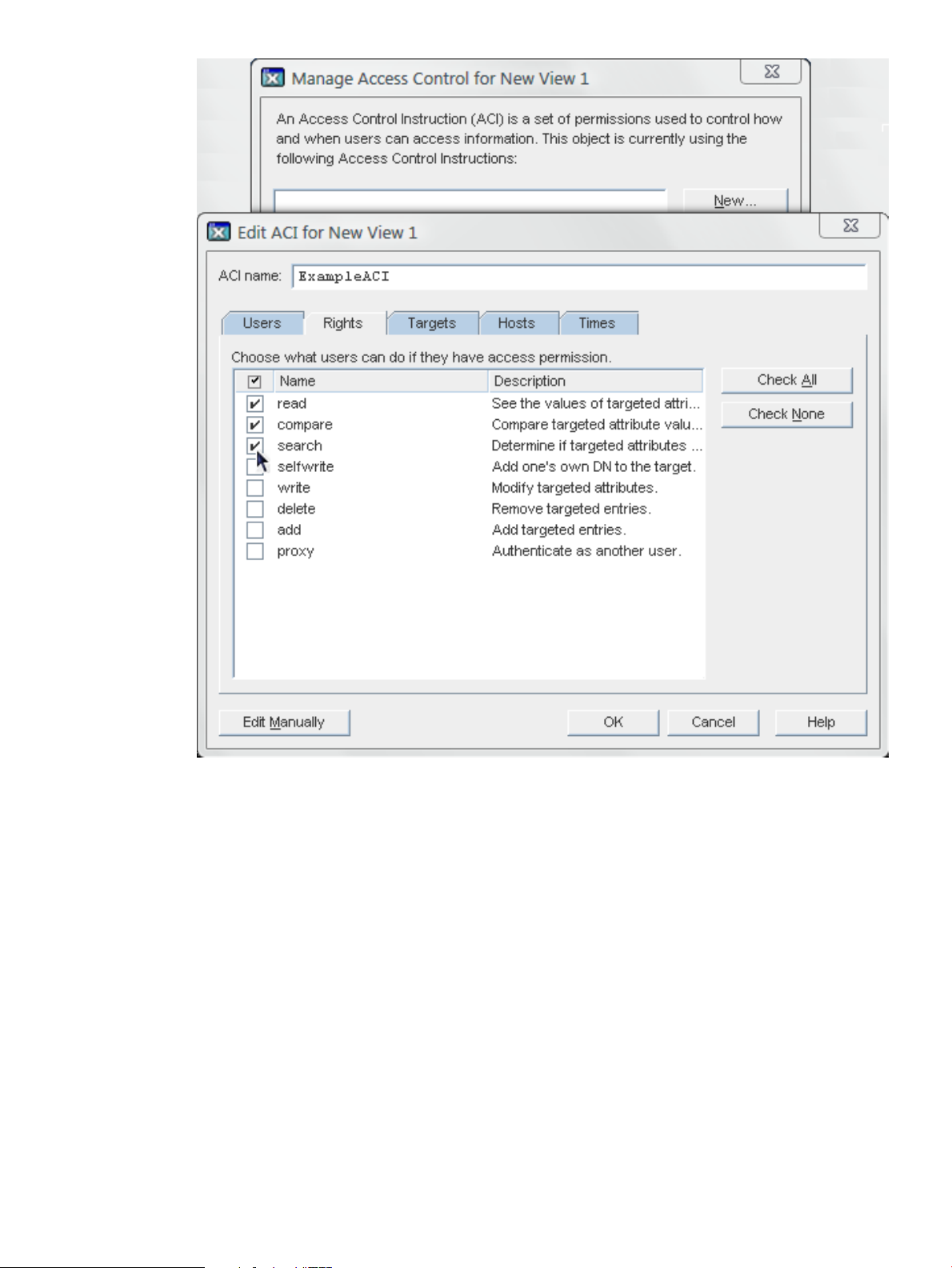
4. Click OK to save the ACI.
For more information on setting access permissions and creating access control instructions, see
Chapter 5 “Setting access controls”.
2.3 Changing the Console appearance 27
Page 28

28
Page 29
3 Managing server instances
The server instances managed by the Directory Console are arranged in a hierarchy. At the top
is the admin domain. Within the domain are hosts, representing different server machines. Each
host has server groups, which identifies an inter-related group of Directory Servers using the
same Administration Server instance. The individual Directory Server instances and a single
Administration Server instance belong withing a server group. There can only be one
Administration Server instance per server group.
These high level entries can be created and managed in the Directory Console.
3.1 Editing domain, host, server group, and instance information
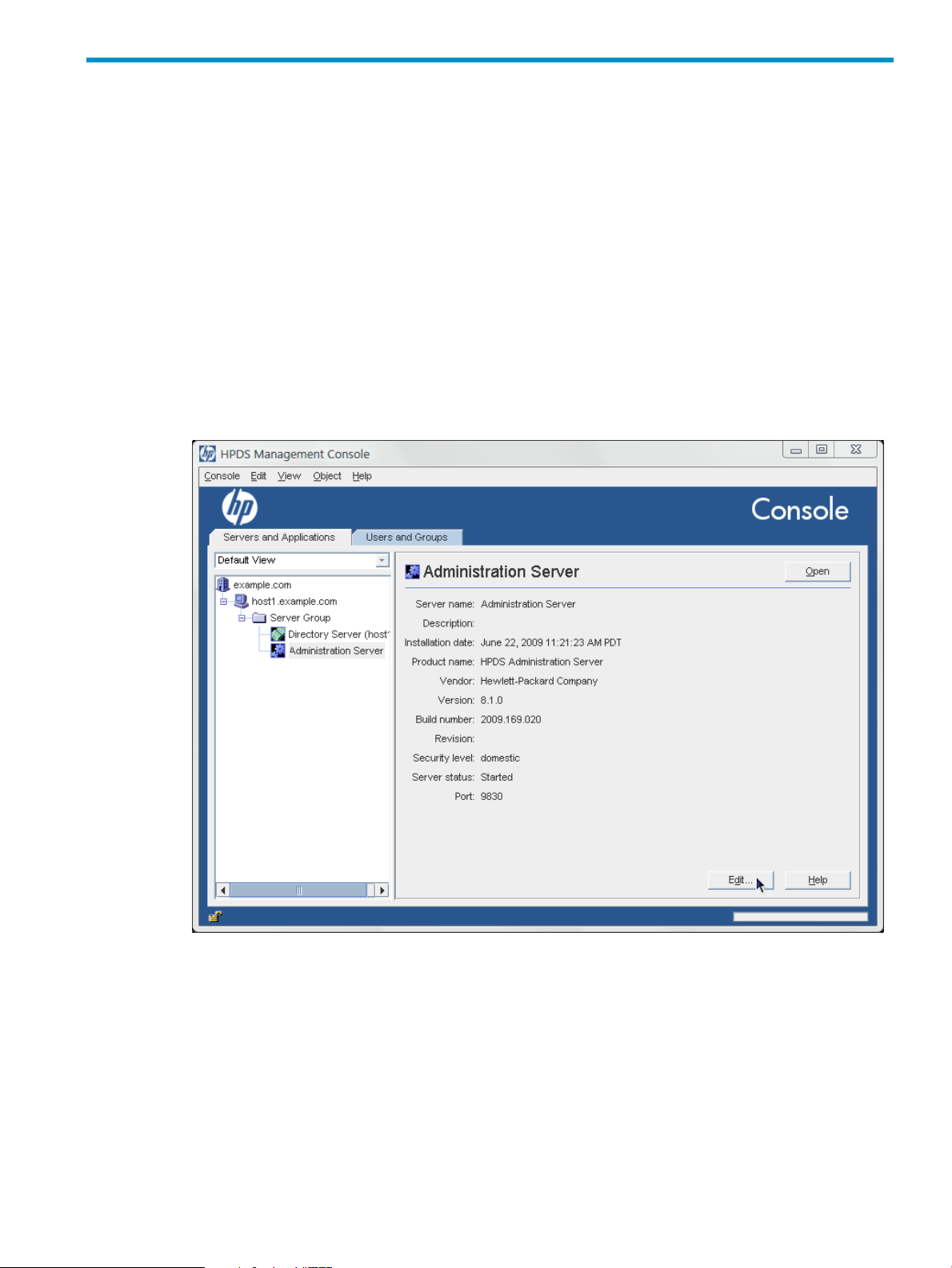
The Console displays some information about every admin domain, host, group, and server
instances. Most of this information, such as the installation date and build number, cannot be
edited, but some information can.
1. In the Servers and Applications tab, select the entry to modify.
2. Click Edit.
3. Edit the instance's information. Every entryhas the option to change its name and description.
The host, which is the physical machine on which the instances are installed, also has the
option of changing the location.
3.1 Editing domain, host, server group, and instance information 29
Page 30
4. Click OK.
3.2 Creating and removing admin domains
An admin domain is a container entry for server groups (and each server groupcontains Directory
Server instances which are configured to work with the same Configuration Directory Server
and the same Administration Server, which is also in the server group).
3.2.1 Creating and editing an admin domain
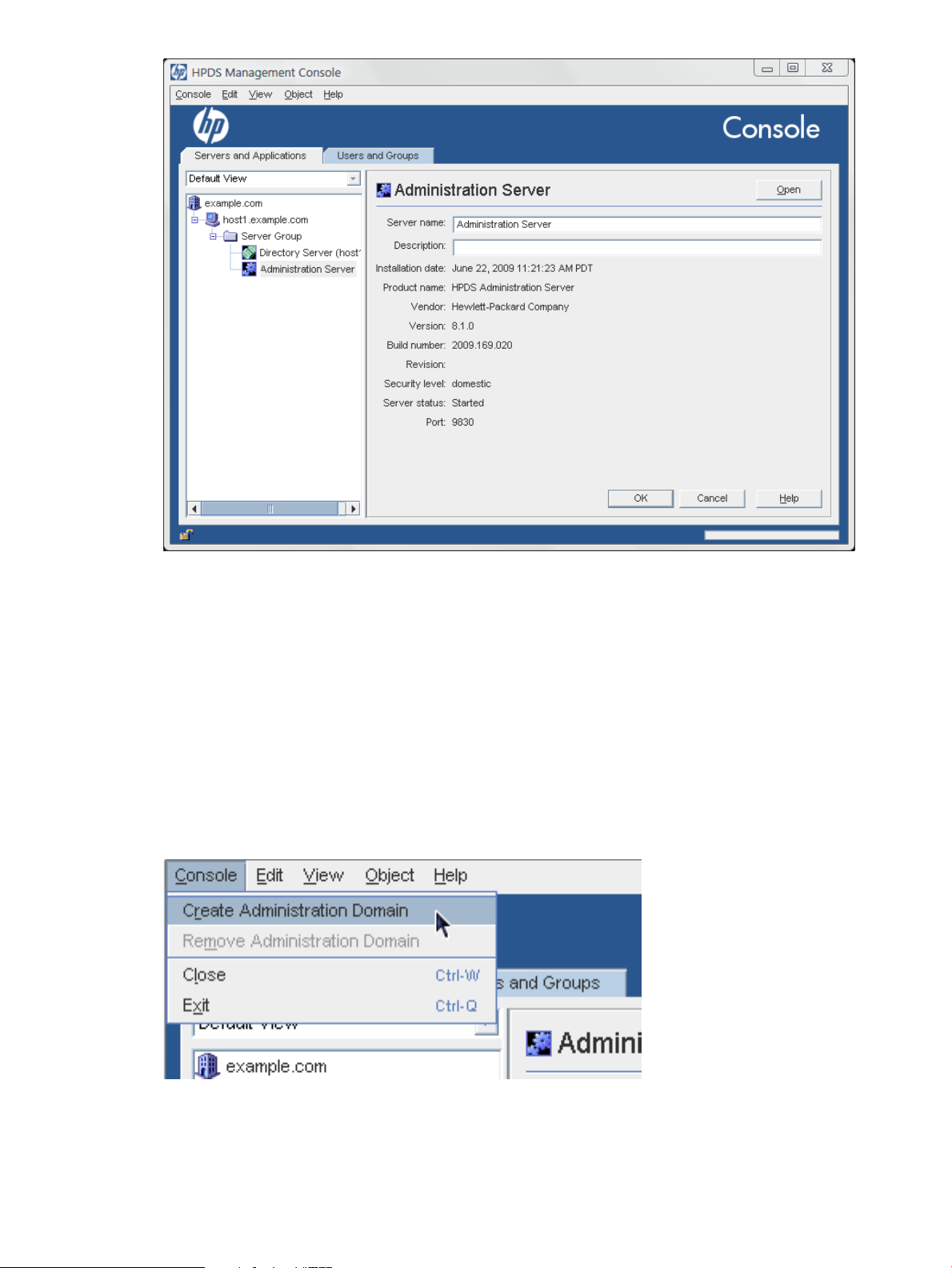
To create a new admin domain:
1. In the top menu, click the Console menu item.
2. Select Create New Admininistration Domain.
3. Fill in the admin domain's information, including information for a new Directory Server
instance.
30 Managing server instances
Page 31
4. Click OK.
To edit an admin domain, select the entry in the server window and click the Edit button.
CAUTION:
The admin domain settings affect all servers within the domain. Making any changes to the
admin domain settings means that all servers in the domain must be restarted.
3.2.2 Removing an admin domain
To remove an admin domain:
1. Highlight the admin domain to remove in the navigation tree.
2. In the top menu, click the Console menu item.
3. Select Remove Admininistration Domain.
4. Click Yes.
3.2 Creating and removing admin domains 31
Page 32

NOTE:
Any server group and servers within the domain must be removed before the domain can be
deleted.
3.3 Creating a new Directory Server instance
After the default Directory Server and Administration Server instances are installed and
configured, additional Directory Server instances can be created using the same schema and
configuration and in the same installation directory, /opt/dirsrv. Having multiple instances
on the same host makes it easier to maintain divisions between directories while simplifying
administering multiple directories.
1. In Directory Console, select the server group that will contain the new server instance.
2. Right-click on the server group entry, and select Create Instance Of, then select HP-UX
Directory Server.
Alternatively, click Object in the top menu bar, and select Create Instance Of.
3. Fill in the information for the new instance of Directory Server, including the base DN,
Directory Manager, and port.
32 Managing server instances
Page 33

4. Click OK.
3.4 Deleting a Directory Server instance
1. In the Directory Console, select the instance to delete.
2. Right-click the server instance, and select Remove Server.
3. Click Yes to confirm the deletion.
3.4 Deleting a Directory Server instance 33
Page 34

34
Page 35

4 Managing Directory Server users and groups
Users for both multiple Directory Server instances and Administration Server can be created,
edited, and searched for in the Directory Console. The main Console window can also be used
to create organizational units and groups and to add entries to the new ous and groups.
Chapter 5 “Setting access controls” describes how to work with user and group information
when setting access privileges and other security information.
4.1 Searching for users and groups
The Users and Groups searches for directory entries; by default, it looks in the default user
directory configured for the Administration Server, but the directory can be changed to any
Directory Server instance.
To search the directory:
1. Click the Users and Groups tab.
2. Enter the search criteria, and click Search.
• For a simple search, enter all or part of an entry name in the text box. To return all
entries, leave the search field blank or enter an asterisk (*).
• For a more complex or focused search, click the Advanced button, and enter the
attributes to search (such as cn, givenName, or ou), the kind of search, and the search
term. To add or remove search criteria, click the More and Fewer buttons.
4.1 Searching for users and groups 35
Page 36

3. Click Search. Results are displayed in the list box.
To change the search directory:
1. Click the Users and Groups tab.
2. In the top menu, select the User menu item, and choose Change Directory.
3. Fill in the user directory information.
36 Managing Directory Server users and groups
Page 37

• User Directory Host.
The fully qualified host name for the Directory Server instance.
• User Directory Port and Secure Connection.
The port number for the connection and whether this is an SSL (LDAPS).
• User Directory Subtree.
The DN of the subtree to search in the directory; for example, dc=example,dc=com
for the base DN or ou=Marketing, dc=example,dc=com for a subtree.
• Bind DN and Bind Password.
The credentials to use to authenticate to the directory.
4. Click OK.
4.2 Creating directory entries
The Directory Console can be used to add, edit, and delete users, groups, and organization units
in the Users and Groups tab. The different kinds of entries and options for creating entries is
explained in more detail in the HP-UX Directory Server administrator guide.
4.2.1 Directory and administrative users
NOTE:
A user can be added to the Directory Server user database through the Console or a user can be
added as an Administration Server administrator. The process is almost identical, with two
exceptions:
• A Directory Server user is added by clicking the Create button, then select the Users option,
while an administrator is created by selecting the Administrator option.
• An administrator does not require selecting an organization unit, while the Directory Server
user does, because the administrator is automatically added to
ou=Groups,ou=Topology,o=NetscapeRoot.
1. Click the Users and Groups tab.
2. Click the Create button, and choose User.
4.2 Creating directory entries 37
Page 38

Alternatively, open the User option in the top menu, and choose Create > User.
3. Select the directory subtree where you want to create the new entry.
NOTE:
When creating an administrator, there is no option to select the ou to which to add the user
as there is with a regular Directory Server user. This is because the administrator is added
to ou=Groups,ou=Topology,o=NetscapeRoot, with the admin users.
The entry can be added to an ou or a view, if views have been added to the directory.
38 Managing Directory Server users and groups
Page 39

4. In the Create User window,enter user information. The Common Name and User ID fields
are automatically filled in with the combined values the First Name and Last Name fields.
These first, last, and common name fields are required; a password is also required for the
user to be able to log into the Directory Server and the Console, but is not a required attribute.
5. Optionally, click the Languages link on the left, select an alternate language and fill in
internationalized values for common attributes.
This option allows international users to select a language other than English and to represent
their names in their preferred language. The pronunciation attribute allows for phonetic
searching against the international name attributes.
4.2 Creating directory entries 39
Page 40

6. Click OK.
4.2.2 Groups
A group consists of users who share a common attribute or are part of a list. Directory Server
supports three types of groups: static, dynamic, and certificate. Each group differs by the way
in which users, or members, are added to it:
static group A static group has members who are manually added to it, so it is
dynamic group A dynamic group automatically includes users based on one or more
certificate group A certificate group includes all users who have a specific
To create a group:
static because the members do not change unless an administrator
manually adds or removes users.
attributes in their entries; the attributes and values are determined
using LDAP URLs. For example, a dynamic group can use an LDAP
filter which searches for entries which contain the attributes and
values st=California and department=sales. As entries are
added to the directory with those two attributes, the users are
automatically added as members to the dynamic group. If those
attributes are removed from the entry, the entry is removed from the
group.
attribute-value pair in the subject name of the certificate. For example,
the certificate group could be based on having the string
st=California,ou=Sales,ou=West in the subject name. If a
user logs onto a server using a certificate with those attributes in his
certificate, the user is automatically added to the group and is granted
all the access privileges of that group.
40 Managing Directory Server users and groups
Page 41

1. Click the Users and Groups tab.
2. Click the Create button, and choose Group.
Alternatively, open the User option in the top menu, and choose Create > Group.
3. Select the directory tree under which the entry is created.
4.2 Creating directory entries 41
Page 42
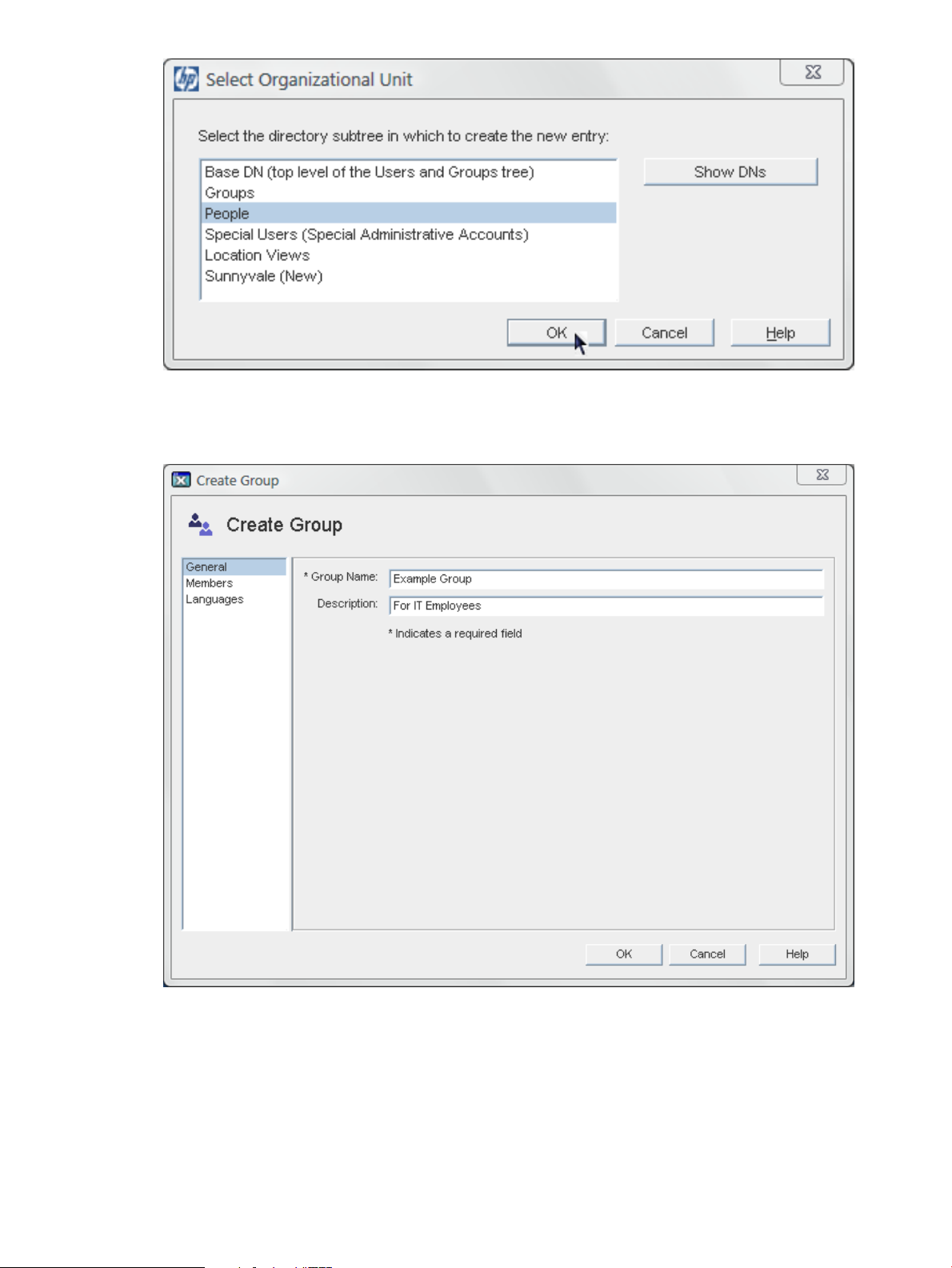
The subtree entry can be an ou or a view, if views have been added to the directory.
4. Enter the group's name and description.
It is possible to save the new group entry at this point, without adding members. Click OK.
5. Click the Members link to add members to the group, and click the tab of the type of group
membership, Static, Dynamic, or Certificate.
6. Configure the members. For static groups, manually search for and add users; for dynamic
groups, construct the LDAP URL to use to find entries; and for certificate groups, enter the
values to search for in user certificate subject names.
42 Managing Directory Server users and groups
Page 43
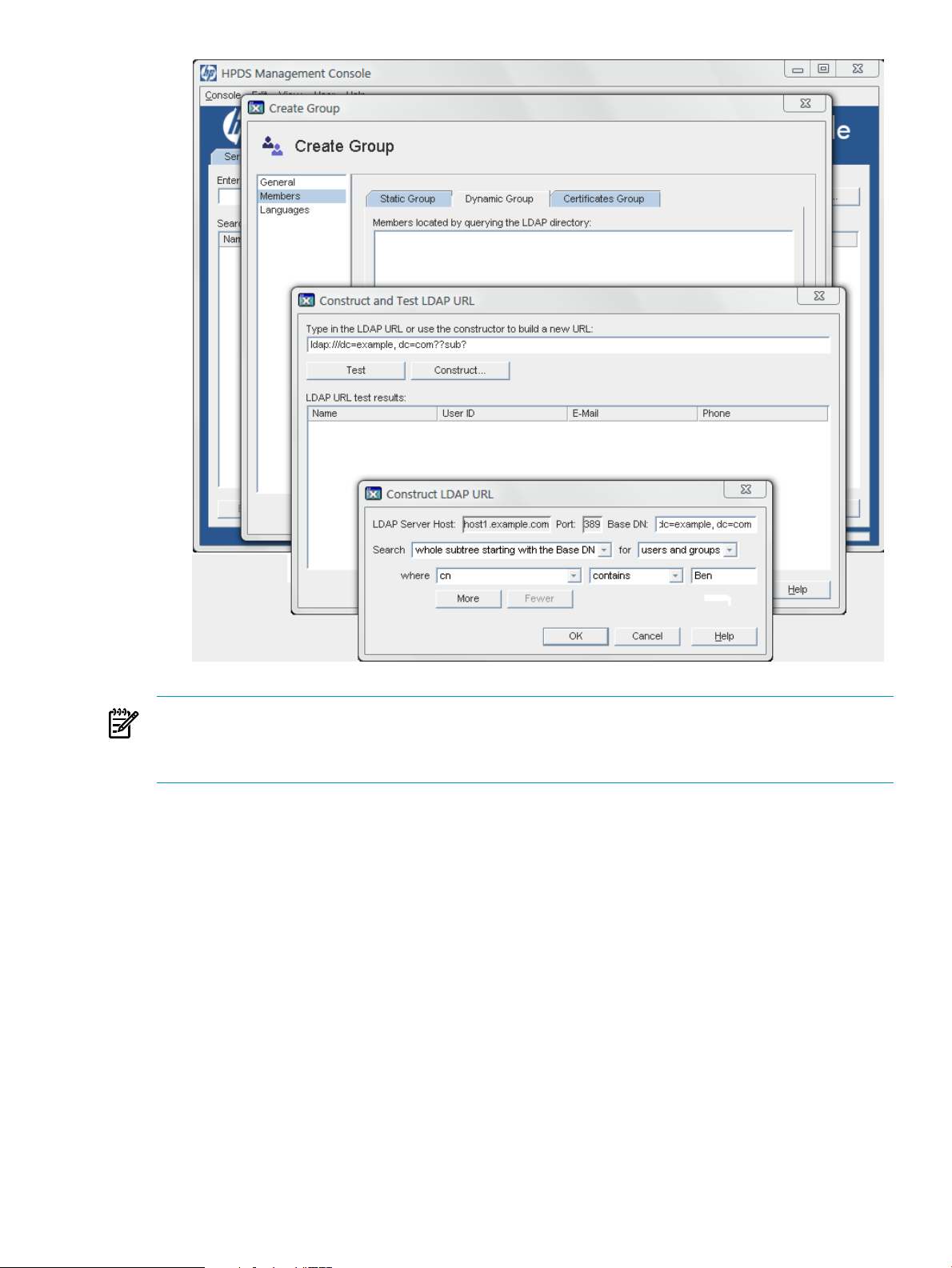
NOTE:
The different kinds of groups and how to configure their members are explained in more detail
in the HP-UX Directory Server administrator guide.
4.2.3 Organizational units
An organizational unit can include a number of groups and users. An org unit usually represents
a distinct, logical division in an organization, such as different departments or geographical
locations. Each organizationalUnitName (ou) is a new subtree branch in the directory tree.
This is reflected in the relative distinguished name of the ou, such as
ou=People,dc=example,dc=com, which becomes part of the distinguished names of its
sub-entries.
1. Click the Users and Groups tab.
4.2 Creating directory entries 43
Page 44

2. Click the Create button, and choose Organizational Unit.
Alternatively, open the User option in the top menu, and choose Create > Organizational
Unit.
3. Select the directory subtree under which to locate the new organizational unit.
4. Fill in the organizational unit information. The Alias offers an alternative name for the
organizational unit that can be used instead of the full name.
44 Managing Directory Server users and groups
Page 45

5. Click OK.
4.3 Modifying directory entries
4.3.1 Editing entries
1. Search for the entry to edit.
See “Searching for users and groups” for more information on searching for entries.
2. Select the entry, and click Edit.
4.3 Modifying directory entries 45
Page 46

3. Edit the entry information, and click OK to save the changes.
4.3.2 Allowing sync attributes for entries
Directory Server and Active Directory synchronization unify some Unix and Windows-specific
directory attributes; to carry over a Directory Server entry to Active Directory, the entry must
have ntUser attributes. (Likewise, Windows entries must have posixAccount attributes.)
Windows (NT) attributes must an be enabled on entries. By default, these attributes are added
manually to individual entries. The user edit windows have links on the left for NT User to allow
Directory Server entries to contain Windows-specific attributes for synchronization.
It is also possible to configure the server so that all new entries will automatically possess the
ntUser object class; this is described in the Directory Server—Active Directory synchronization
chapter of the HP-UX Directory Server administrator guide.
NOTE:
Any Directory Server entry must have the ntUser object class and required attributes added in
order to be synchronized to Active Directory.
To enable synchronization:
1. Select or create a user, and click the NT User link.
2. Enable the NT account, and check how the entry will be synchronized (meaning, whether
a new entry will be created and whether that entry should be deleted on Active Directory
if it is delete on Directory Server).
46 Managing Directory Server users and groups
Page 47
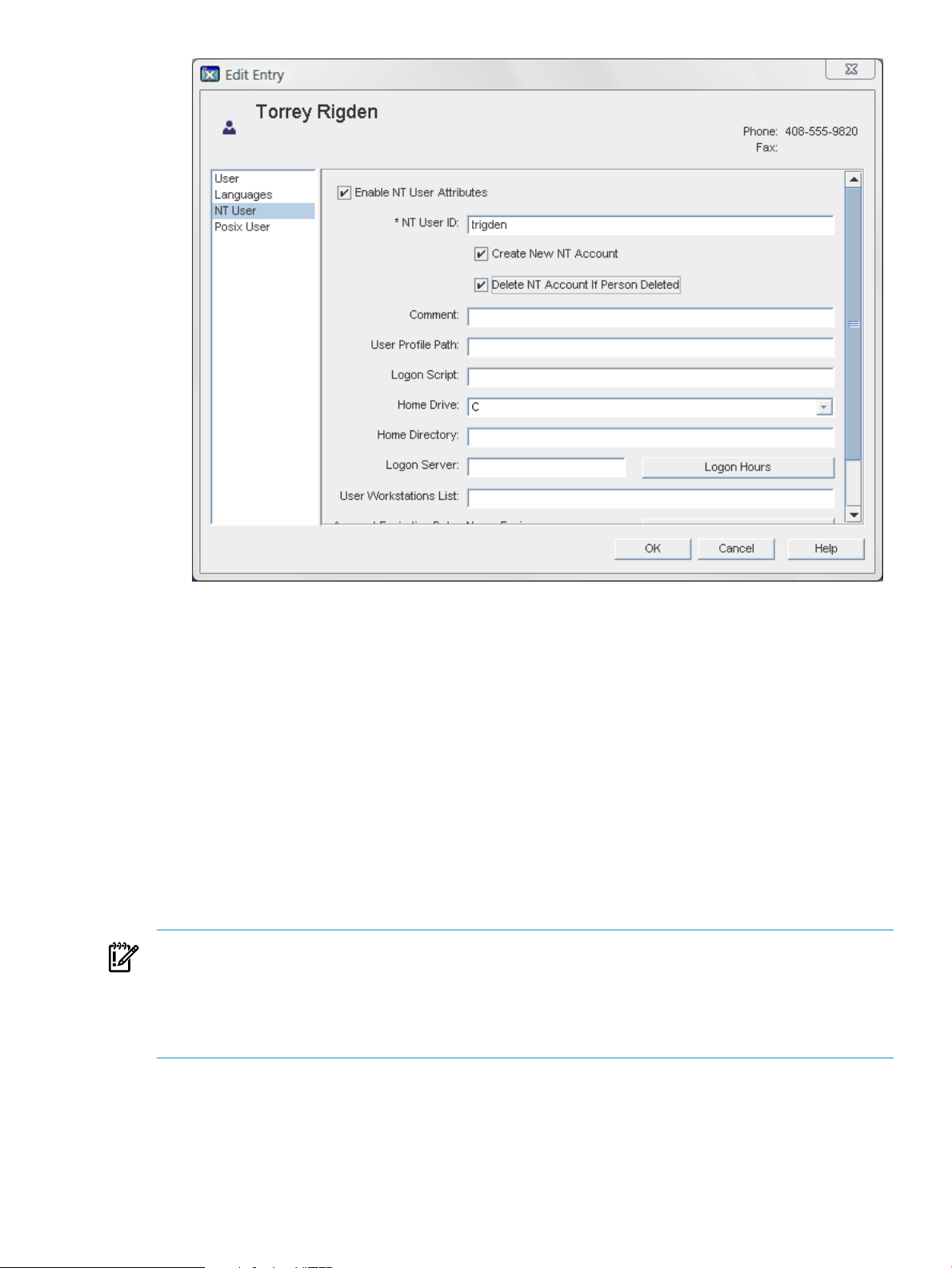
3. Click OK.
4.3.3 Changing administrator entries
When the Administration Server is installed, two entries are created with administrator access
in the Console. The main entry is the Configuration Administrator, who is authorized to access
and modify the entire configuration directory (o=NetscapeRoot). The Configuration
Administrator entry is stored in the uid=username,
ou=Administrators,ou=TopologyManagement,o=NetscapeRoot entry.
The Configuration Administrator's username and password are automatically used to create the
Administration Server Administrator, who can perform a limited number of tasks, such as
starting, stopping, and restarting servers. The Administration Server Administrator is created
so that a user can log into the Directory Console when the Directory Server is not running. The
Administration Server Administrator does not have an LDAP entry; it exists in the Administration
Server's configuration file, /etc/opt/dirsrv/admin-serv/admpw.
IMPORTANT:
Even though they are created at the same time during installation, and are identical at that time,
the Configuration Administrator and Administration Server Administrator are two separate
entities. If the username or password is changed for one, Directory Console doesnot automatically
make the same changes for the other.
• “Changing the configuration administrator and password”
• “Changing the admin password”
• “Adding users to the configuration administrators group”
4.3 Modifying directory entries 47
Page 48

4.3.3.1 Changing the configuration administrator and password
1. In the Users and Groups, click Advanced.
2. Search for the Configuration Administrator. Select the Administrators object, and enter the
administrator's username, Configuration Administrator by default.
3. Select the Configuration Administrator from the list of search results, then click Edit.
4. Change the administrator's uid and password. The uid is the naming attribute used to log
into the Console and run commands.
48 Managing Directory Server users and groups
Page 49

5. Click OK.
NOTE:
If you are logged into the Console as the Configuration Administrator when you edited the
Configuration Administrator entry, update the login information for the directory.
1. In the Users and Groups tab, click the User menu in the top menu and select Change
Directory.
2. Update the Bind DN and Bind Password fields with the new information for the
Configuration Administrator, and click OK.
4.3.3.2 Changing the admin password
1. Select the Administration Server in the Servers and Applications tab, and click Open.
2. Click the Configuration tab, and open the Access tab.
3. Set the new password.
4.3 Modifying directory entries 49
Page 50

CAUTION:
Do not change the admin username.
4. Click Save.
5. Restart the Administration Server.
/opt/dirsrv/sbin/restart-ds-admin
4.3.3.3 Adding users to the configuration administrators group
1. In the Users and Groups tab, click the User menu in the top menu and select Change
Directory.
2. Change to the o=NetscapeRoot subtree, which contains the configuration information
and the Configuration Administrators group.
50 Managing Directory Server users and groups
Page 51

3. Search for the Configuration Administrators group, and click Edit.
4. Click the Members link in the left of the edit window.
5. Click Add, and search for the user to add to the group.
4.3 Modifying directory entries 51
Page 52

NOTE:
Only users in the o=NetscapeRoot database can be added to the Configuration
Administrators group. This means that the entry must be created as an administrator, not
a regular user, when added through the Console. See “Directory and administrative users”.
4.3.4 Removing an entry from the directory
1. Search for the entry to deleted.
See “Searching for users and groups” for more information on searching for entries.
NOTE:
All entries must be removed from under an organization unit before it can be deleted.
2. Select the entry in the results list, and click Delete. Click OK to confirm the deletion.
52 Managing Directory Server users and groups
Page 53

5 Setting access controls
Access control instructions (ACIs) can be set in the Directory Console to set limits on what users
can see and what operations they can performa on Directory Server and Administration Server
instances managed in the Console.
ACIs define what operations users can do with a specific instance of Directory Server or
Administration Server. ACIs set rules on areas of the subtree which can be accessed or modified,
what operations are allowed, even what hosts can be used to access the server and what times
of day access is allowed.
For Directory Console, access controls can be used to grant administrative privileges very easily
to specific users and to set restrictions on different aspects of the main Console, such as searcing
the directory, adding and editing users and groups, and editing server or Console settings.
ACIs and access control lists (ACLs) are described in much more detail in the HP-UX Directory
Server administrator guide.
5.1 Granting admin privileges to users for Directory Server and Administration Server
Users can be granted administrative privileges, the same as the admin user for the Administration
Server and similar to the cn=Directory Manager user in Directory Server (though not exactly
the same as the Directory Manager, which is a special user).
1. Highlight a server in the Console navigation tree.
2. Select the Object menu, and choose Set Access Permissions.
Alternatively, right-click the entry, and choose Set Access Permissions.
3. Click Add to add a new user to the list of administrators for the server. The default users,
Directory Manager for the Directory Server and admin for the Administration Server,
are not listed in the Set Permissions Dialog box.
5.1 Granting admin privileges to users for Directory Server and Administration Server 53
Page 54

4. Search for the users to add as an administrators. In the results, highlight the selected users,
and click Add to add them to the administrators list.
54 Setting access controls
Page 55

For more information on searching for users and groups, see “Searching for users and
groups”.
5. Click OK to add the names to the Set Permissions Dialog list, then click OK again to save
the changes and close the dialog.
NOTE:
Granting a user the right to administer a server does not automatically allow that user to give
others the same right. To allow a user to grant administrative rights to other users, add that user
to the Configuration Administrators group, as described in “Adding users to the configuration
administrators group”.
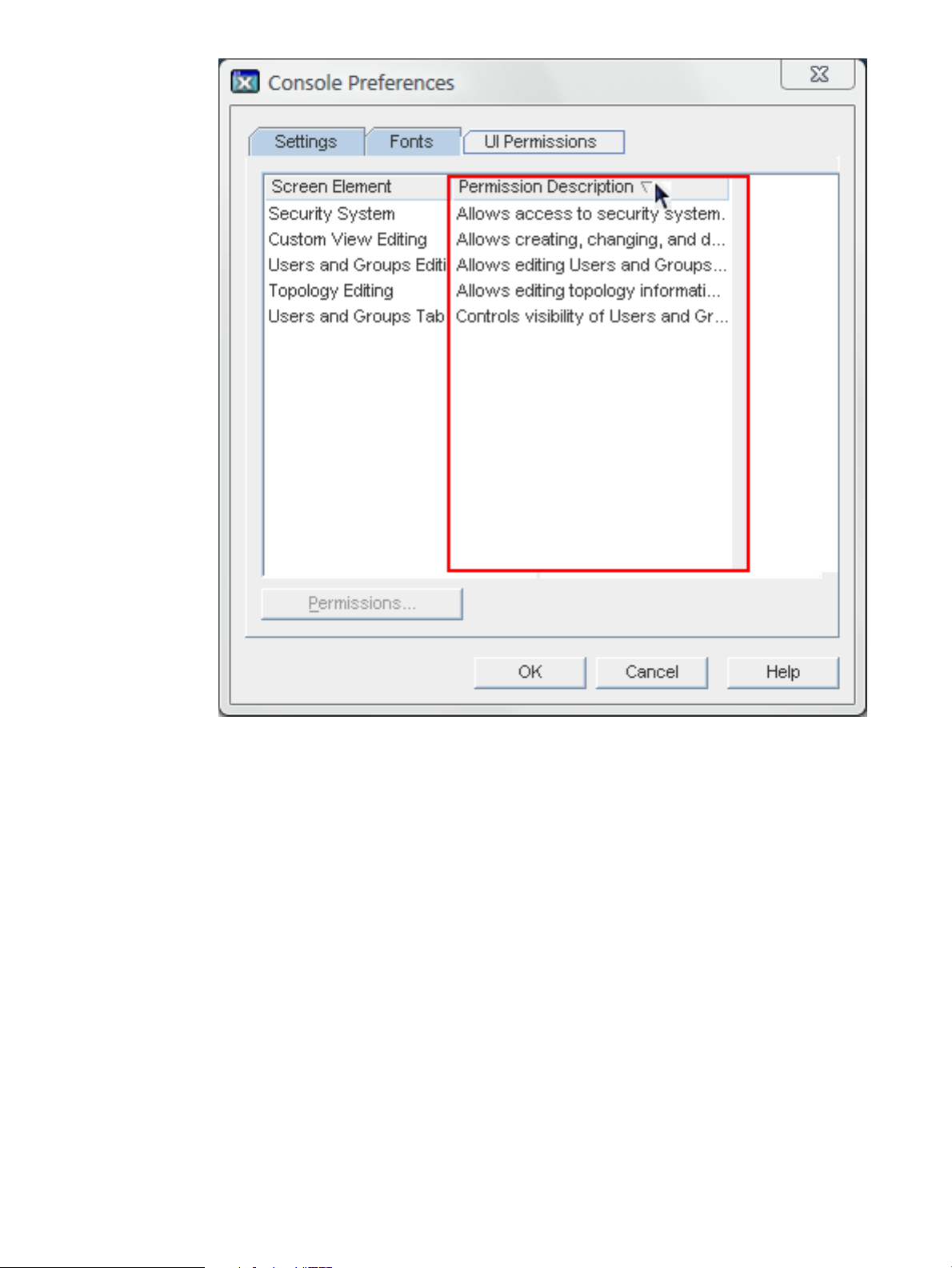
5.2 Setting access permissions on console elements
There are five elements defined in the Console for access control rules:
• User and Groups Tab (viewing)
• User and Groups Tab (editing)
• Topology Tab (editing)
• Custom View Tab (editing)
• Server Security (editing)
By default, each of these Console elements has five inherited ACIs:
• Enabling anonymous access
• Default anonymous access
• Configuration administrator's modifications
• Enabling group expansions
• SIE (host) group permissions
These inherited ACIs cannot be edited, but new ACIs can be added for each Console element in
addition to these defaults. Additional ACIs can limit anonymous access, for example, and change
other permissions within the Directory Console, which, in turn, affects access to the Directory
Server and Administration Server instances.
To create new ACIs:
1. In the top menu, select Edit then select Preferences.
2. Select the Console element from the list, and click the Permissions button.
5.2 Setting access permissions on console elements 55
Page 56

3. In the ACI Manager window, click the New button.
56 Setting access controls
Page 57

The five inherited ACIs are not displayed by default; to see them listed, click the Show
inherited ACIs checkbox.
4. Configure the ACI by setting, at a minimum, the users to which it applies and the rights
which are allowed. To configure the ACI in the wizard (visually):
a. Enter a name for the ACI in the ACI Name field.
b. In the Users/Groups tab, click the Add button to open the search window. Search for
and add the users to which apply the ACI.
5.2 Setting access permissions on console elements 57
Page 58
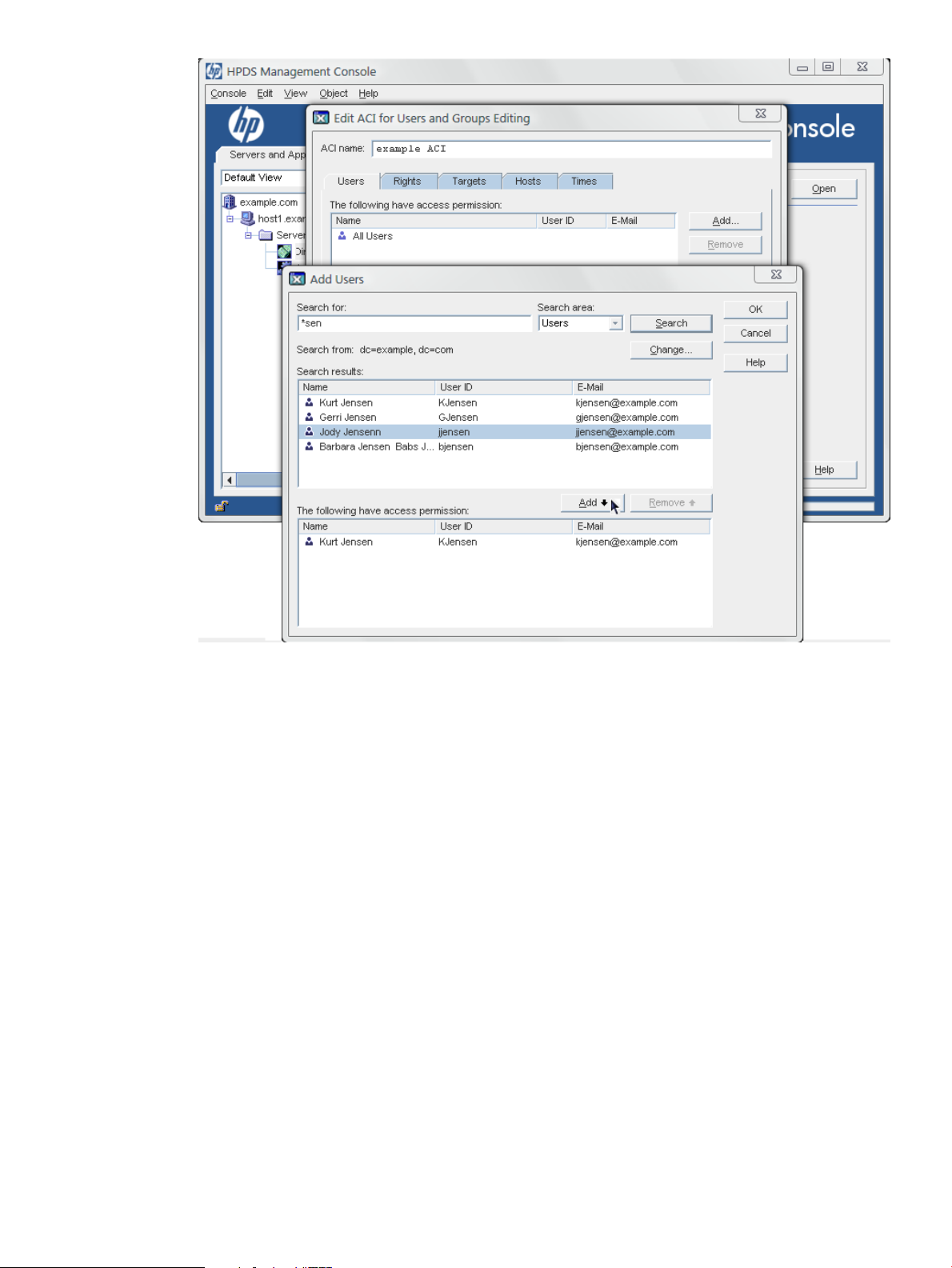
Select the users from the results list and click the Add button to include them. Click OK
to save the list.
c. In the Rights tab, specify which operations are permitted as part of this ACI.
58 Setting access controls
Page 59
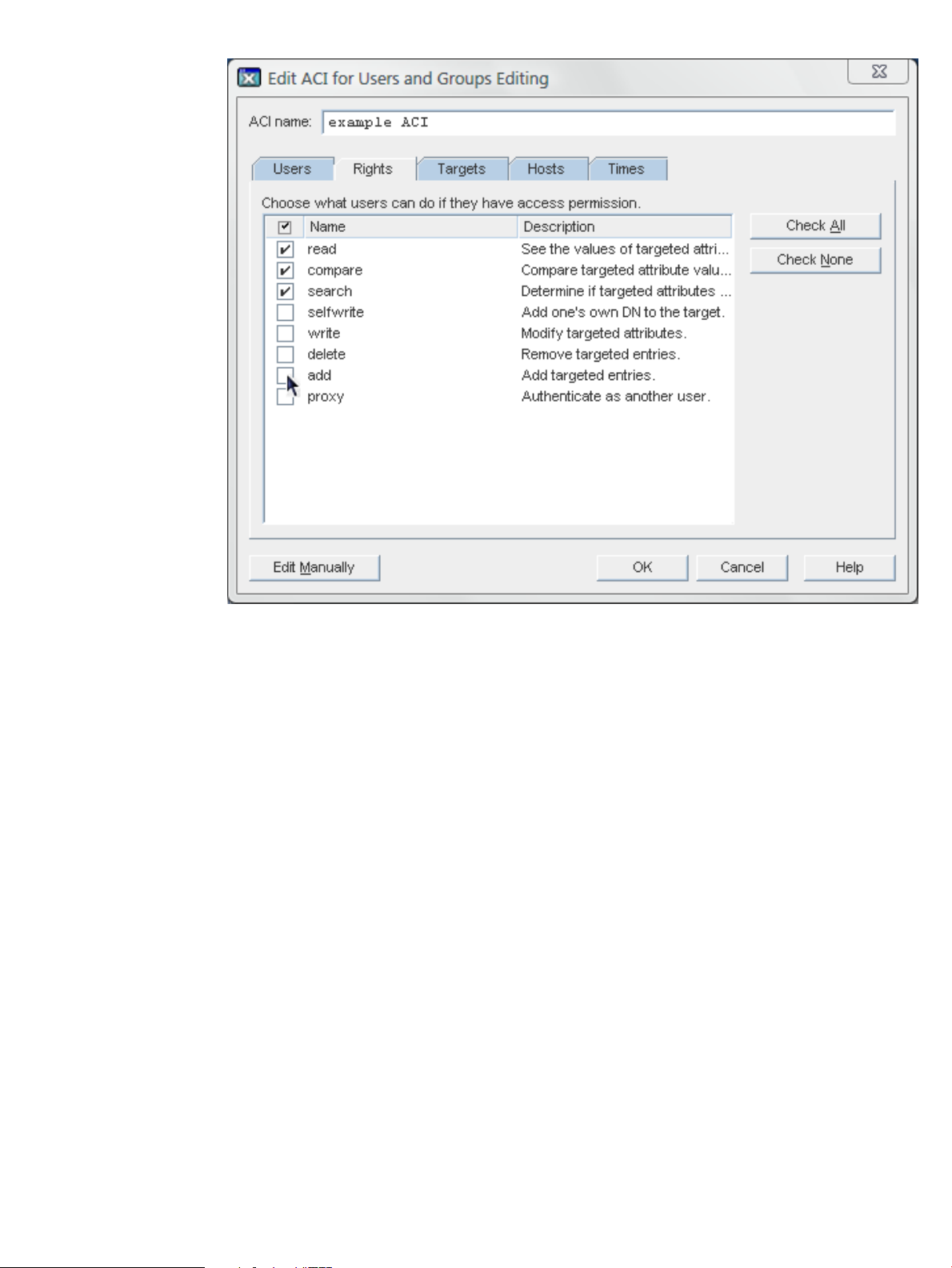
To hide a Console element entirely from the selected users, groups, and hosts, click
Check None to block any access.
d. Optionally, set the target entry in the subtree, host names, or times of day where the
ACI is in effect.
More complex ACIs may not be able to be edited visually; in those cases, click the Edit
Manually button, and configure the ACI entry directly.
5.2 Setting access permissions on console elements 59
Page 60

Use the Check syntax button to validate the ACI.
5. Click OK to save the ACI.
6. Restart Directory Console to apply the new ACI.
60 Setting access controls
Page 61

6 Using SSL/TLS with the Console
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols which set up secure,
encrypted communication between an SSL/TLS server and a client which connects to it. In
Directory Server, the Directory Server can be configured to communicate with LDAP over SSL,
LDAPS. Likewise, the Administration Server can be configured to run over secure HTTP (HTTPS)
rather than standard HTTP. Both the Directory Server and Administration Server are SSL servers.
The Console can be configured as an SSL client, which connects to the servers over SSL, and can
be configured so that all Console operations are over SSL.
6.1 Overview of SSL/TLS
Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL) set rules that
govern authentication (identity verification) between two entities and set up encrypted
communication between servers and clients. For Directory Server and Administration Server,
TLS/SSL means that directory operations run over LDAPS (secure LDAP) and HTTPS (secure
HTTP), respectively.
Secure communication depends on the ability to hide and uncover information by disguising it
with complex codes. Both the TLS server (the application which is being contacted) and the TLS
client (the user or application which contacts the server) have to be able to understand the encoded
information.
Cryptography encrypts and protects information using recognized algorithms and ciphers, or
mathematical equations which can scramble information; sets of related algorithms and ciphers
are called cipher suites. The equations are also used to unscramble the information as long as a
server has the right information to decode the data; the decoder information is called a key. Keys
come in two halves:
• The private key is held by only one entity and encrypts (wraps) the information.
• The public key matches the private key and can be used to decrypt information wrapped
by the private key.
A certificate contains a public key that can be used to decrypt information, algorithms used for
a digital signature (similar to a fingerprint), and identity information for the server or user.
In server authentication (the TLS method allowed by the Directory Console), the server presents
a certificate (containing a public key, algorithms used for the digital signature, and server identity
information) to the client. The client may be validated (authenticated) to the server through
simple authentication, such as a username and password, or no authentication. With client
authentication, both the server and client present certificates proving their identity.
TLS/SSL communication has two major parts: the SSL/TLS handshake (where the server and
client authenticate their identities) and secure communication (the encrypted session between
the client and server). Authentication and encryption are performed using secure materials,
called certificates and keys.
The TLS handshake is when the server and client negotiate the parameters of the connection and
generate the keys which will be used for secure communication:
1. The TLS client initiates contact with the TLS server. The client sends information about its
TLS configuration to help the server negotiate the connection parameters:
• The TLS/SSL version the client is using (all TLS/SSL versions are backward compatible)
• A list of acceptable cipher suites
1
1. For HP-UX Directory Server, the Directory Server and Administration Server are the TLS servers, and the Directory
Console or a user through LDAP tools or browsers are the TLS client.
6.1 Overview of SSL/TLS 61
Page 62

• A list of acceptable compression methods
• A randomly-generated number
2. The server responds to the client:
• The chosen TLS/SSL version (this is the highest version in common with both the server
and client)
• The selected cipher suite (the most secure version the server and client have in common)
• The selected compression method (the most secure version the server and client have
in common)
• A randomly-generated number of its own
3. The server then sends its certificate. The server and client will use the public key in the
certificate to decrypt messages once the handshake ends and the secure session is established.
4. The client verifies the identity of the server using the information in the server certificate:
• The validity period (the expiration date of the server certificate)
• Whether the client possesses a copy of the CA certificate for the authority which issued
the server's certificate (whether the certificate was issued by a trusted CA)
• Verifying the digital signature of the issuing CA for the server certificate
• Whether the domain name for the server in the certificate subject name matches the
actual domain name of the server
5. Depending on the cipher suite being used, the client sends the server key material to use to
generate session keys to encrypt data. This key material can be public key or a master key
secret, which is used to derive the encryption keys.
6. Using the key material sent by the client, the randomly-generated numbers from the client
and server, and the selected cipher, the server and client independently derive the same
encryption keys.
7. The client sends a notification to the server that all subsequent messages from it will be
encrypted. It also sends a hash and a message authentication key, which are wrapped in the
client's encryption key.
8. The server successfully decrypts the client's message using its derived encryption keys.
9. The server then sends a hash and a MAC key to the client, wrapped in the server's encryption
key.
10. The client successfully decrypts the server's message using its derived encryption keys.
11. The TLS handshake closes, and the secure channel opens between the server and the client.
The Directory Console can be configured to be encrypted by SSL/TLS by configuring the Directory
Server to enable SSL in the Console.
6.2 Installing certificates
Before the Directory Server can be set to run in TLS/SSL, server and CA certificates must be
properly installed in the servers.
Obtaining and installing certificates consists of the following steps:
1. Generate a certificate request.
2. Send the certificate request to a certificate authority.
3. Install the server certificate.
4. Set the Directory Server to trust the certificate authority.
The Directory Server Console has two wizards to make it easier to request and install certificates.
62 Using SSL/TLS with the Console
Page 63
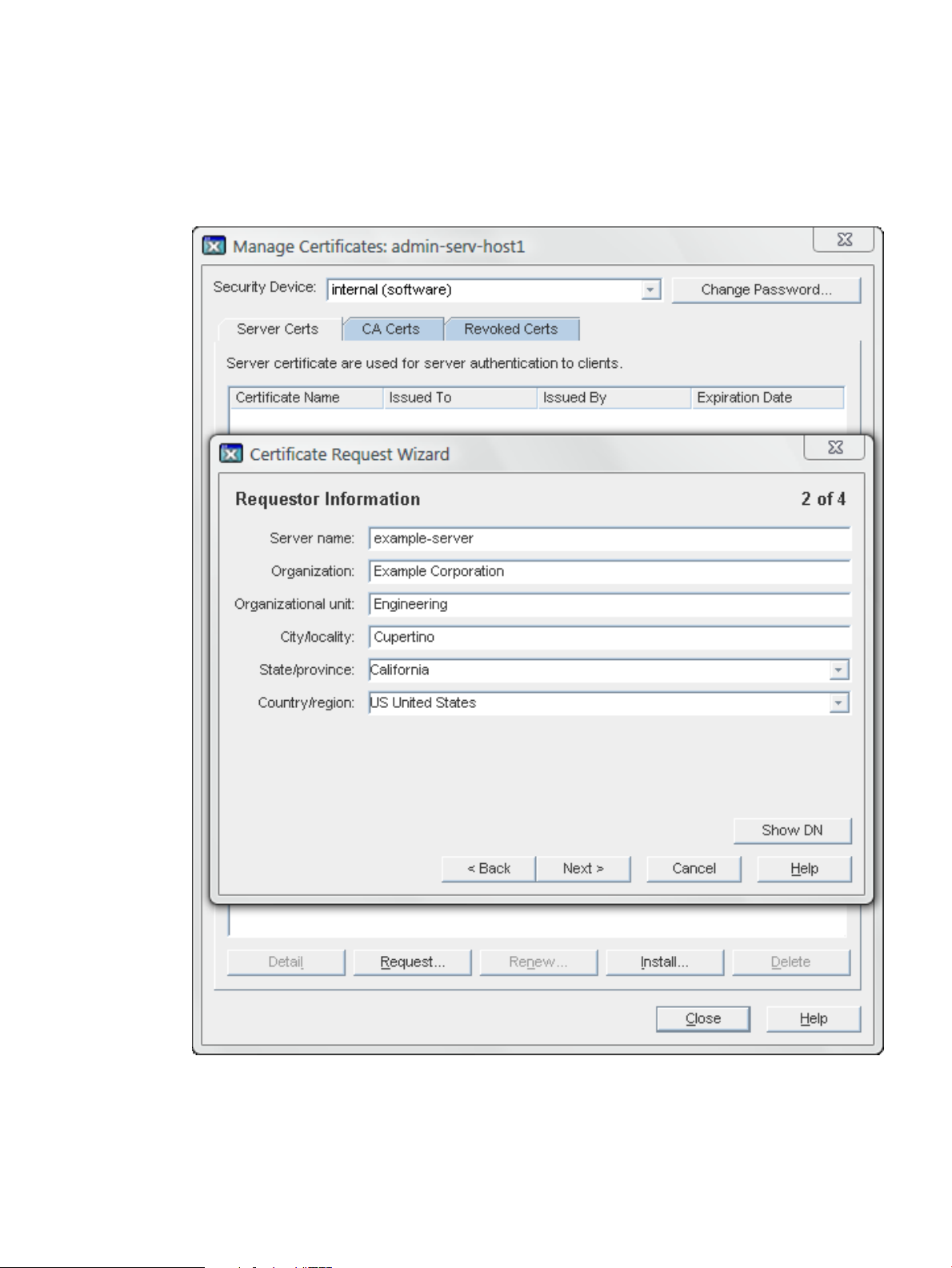
6.2.1 Generating a certificate request
1. In the Directory Server Console, select the Tasks tab, and click Manage Certificates.
2. Select the Server Certs tab, and click the Request button. This opens the Certificate Request
Wizard.
3. Click Next.
4. Enter the Requester Information in the blank text fields, then click Next.
• Server Name
Enter the fully qualified host name of the Directory Server as it is used in DNS and
reverse DNS lookups; for example, dir.example.com. The server name is critical for
client-side validation to work, which prevents man-in-the-middle attacks.
6.2 Installing certificates 63
Page 64

IMPORTANT:
This must be a valid host name that can be resolved correctly by all server clients, or
TLS/SSL will not work.
• Organization
Enter the legal name of the company or institution. Most CAs require this information
to be verified with legal documents such as a copy of a business license.
• Organizational Unit (optional)
Enter a descriptive name for the organization within the company.
• locality (optional)
Enter the company's city name.
• State/Province
Enter the full name of the company's state or province (no abbreviations).
• Country/region
Select the two-character abbreviation for the country's name (ISO format). The country
code for the United States is US.
5. Enter the password that will be used to protect the private key, and click Next.
The Next button is grayed out until a password is supplied.
6. The Request Submission dialog box provides two ways to submit a request: directly to
the CA (if there is one internally) or manually. To submit the request manually, select Copy
to Clipboard or Save to File to save the certificate request which will be submitted to the
CA.
64 Using SSL/TLS with the Console
Page 65

7. Click Done to dismiss the Certificate Request Wizard.
After generating the certificate request, send it to the CA, and wait for the CA to issue the server
certificate.
When the CA issues the certificate, save it to a text file that is local to the Directory Server. The
certificate must be available to install in the Directory Server. This file can also be used as a
backup to re-install the certificate in the server in case the certificate is ever lost.
6.2.2 Installing the certificate
1. In the Directory Server Console, select the Tasks tab, and click Manage Certificates.
6.2 Installing certificates 65
Page 66

2. Select the Server Certs tab, and click Install.
3. Give the certificate location or paste the certificate text in the text box, then click Next.
• In this local file.
Enter the absolute path to the certificate in this field.
• In the following encoded text block.
Copy the text from the CA's email or from the created text file, and paste it in this field.
66 Using SSL/TLS with the Console
Page 67

4. Check that the certificate information displayed is correct, and click Next.
5. Give a name to the certificate, and click Next.
6. Provide the password that protects the private key. This password is the same as the one
provided in step 5 in “Generating a certificate request”.
After installing the server certificate, it is listed in the Certificates tab.
If necessary, configure the Directory Server to trust the CA which issued the server's certificate.
6.2.3 Trusting a certificate authority or adding a certificate chain
Configuring the Directory Server to trust the certificate authority consists of obtaining the CA's
certificate (a process which varies, depending on the CA) and installing it in the server's certificate
database. Instead of a single CA certificate, some sites have a certificate chain, which is several
CA certificates in a single certificate blob. Certificate chains are treated the same as CA certificates.
1. In the Directory Server Console, select the Tasks tab, and click Manage Certificates.
6.2 Installing certificates 67
Page 68

2. Go to the CA Certs tab, and click Install.
68 Using SSL/TLS with the Console
Page 69

3. If the CA's certificate is saved to a file, enter the path in the field provided. Alternatively,
copy and paste the certificate, including the headers, into the text box. Click Next.
6.2 Installing certificates 69
Page 70

4. Check that the certificate information that opens is correct, and click Next.
5. Name the certificate, and click Next.
6. Select the purpose of trusting this certificate authority; it is possible to select both options:
70 Using SSL/TLS with the Console
Page 71

• Accepting connections from clients (Client Authentication)
The server checks that the client's certificate has been issued by a trusted certificate
authority.
• Making connections to other servers (Server Authentication)
This server checks that the directory to which it is making a connection (for replication
updates, for example) has a certificate that has been issued by a trusted certificate
authority.
7. Click Done.
After installing the CA certificate, it is listed in the CA Certificates tab.
NOTE:
If a CA certificate is incorrectly generated, it is listed in the Server Certificates tab in the Console
rather than the CA Certificates tab. The certificate still works as a CA certificate, even though
it is listed in the wrong tab.
Still, request certificates from a real certificate authority to minimize the risk of using an incorrectly
generated certificate and breaking SSL/TLS in the Administration Server.
6.3 Enabling TLS/SSL
In order to run the Directory Console over TLS/SSL, the Administration Server and Directory
Server must also be configured to run in TLS/SSL.
This configures server authentication for the Directory Console and the Directory Server and
Administration Server.
1. Obtain server certificates and CA certs, and install them on the Directory Server. This is
described in “Installing certificates”.
2. Obtain and install server and CA certificates on the Administration Server. This is a similar
process as for the Directory Server.
6.3 Enabling TLS/SSL 71
Page 72

NOTE:
It is important that the Administration Server and Directory Server have a CA certificate in
common so that they can trust the other's certificates.
3. If the default port number of 636 is not used, change the secure port setting.
a. Change the secure port number in the Configuration>Settings tab of the Directory
Server Console, and save.
b. Restart the Directory Server. It restarts over the regular port.
/opt/dirsrv/slapd-example/restart-slapd
4. In the Configuration tab of the Directory Server Console, highlight the server name at the
top of the table, and select the Encryption tab.
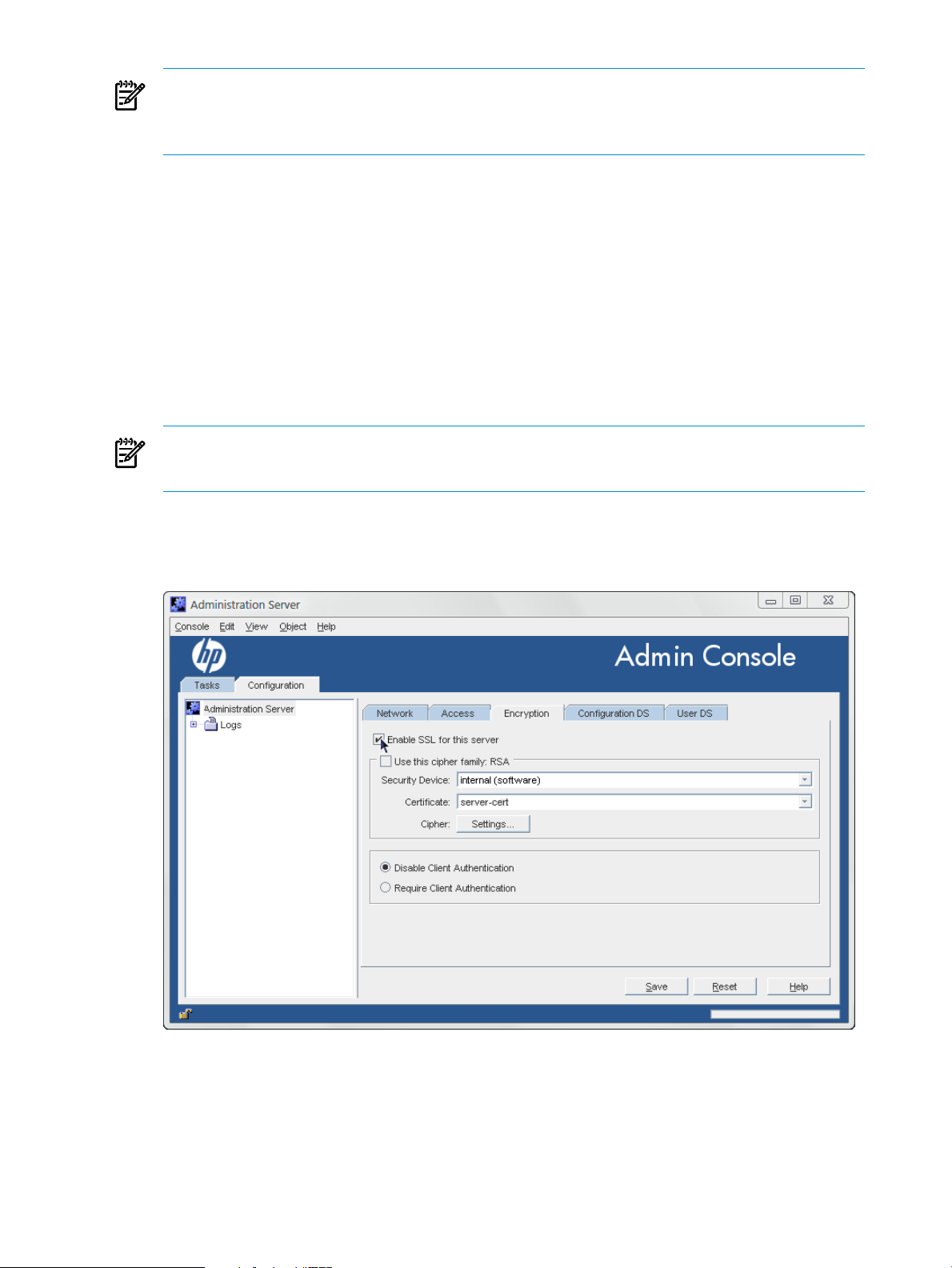
5. Select the Enable SSL checkbox.
6. Check the Use this Cipher Family checkbox.
7. Select the certificate to use from the drop-down menu.
8. Click Cipher Settings. By default, all ciphers are selected.
72 Using SSL/TLS with the Console
Page 73

9. Set the preferences for client authentication.
• Do not allow client authentication.
With this option, the server ignores the client's certificate. This does not mean that the
bind will fail.
• Allow client authentication
This is the default setting. With this option, authentication is performed on the client's
request.
• Require client authentication.
With this option, the server requests authentication from the client. With this option,
all clients must use a certificate to authenticate to the server, and no simple authentication
(username/password) is allowed.
6.3 Enabling TLS/SSL 73
Page 74
NOTE:
To use client certificate-based authentication with replication, configure the consumer server
either to allow or to require client authentication.
10. To verify the authenticity of requests, select the Check hostname against name in
certificate for outbound SSL connections option. The server does this verification by
matching the host name against the value assigned to the common name (cn) attribute of
the subject name in the being presented for authentication. The host name that is checked
in the certificate is the same one set in the server name field in the request in “Generating a
certificate request”.
By default, this feature is disabled. If it is enabled and if the host name does not match the
cn attribute of the certificate, appropriate error and audit messages are logged. HP
recommends enabling this option to protect Directory Server's outbound TLS/SSL connections
against a man-in-the-middle (MITM) attack.
11. Check the Use SSL in the Console box.
NOTE:
This is the only option which sets whether the Directory Console will run over SSL.
12. Click Save.
13. In the Administration Server Console, select the Configuration tab. Select the Encryption
tab, check the Enable SSL checkbox, and fill in the appropriate certificate information.
After TLS/SSL is enabled, the Administration Server can only be connected to using HTTPS.
All the previous HTTP (standard) URLs for connecting to the Administration Server and its
services no longer work. This is true whether connecting to the Administration Server using
the Console or using a web browser.
74 Using SSL/TLS with the Console
Page 75
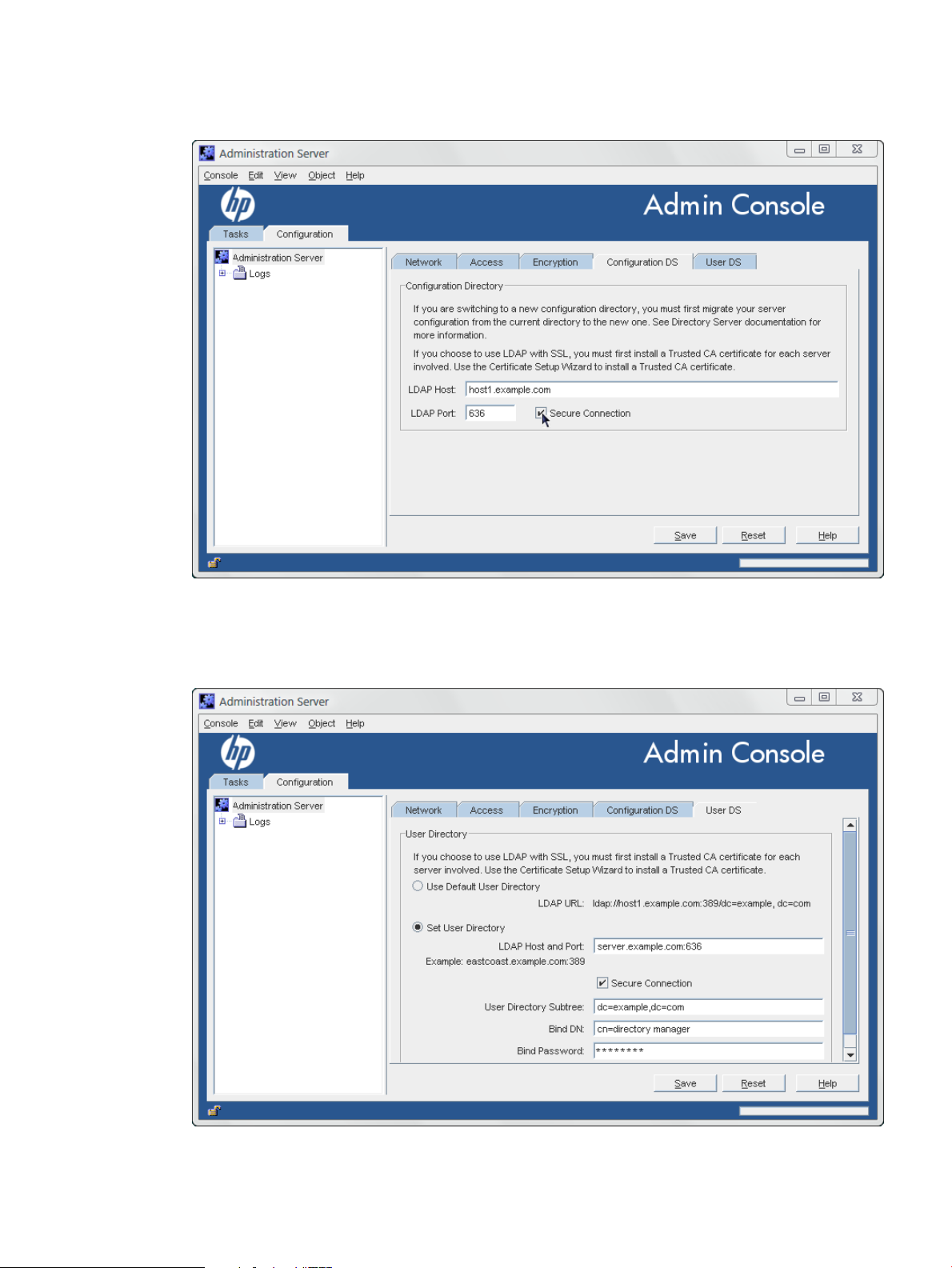
14. In the Configuration DS tab, change the port number to the new Directory Server secure
port information, even if the default port of 636 is used. Check the Secure Connection
checkbox.
15. In the User DS tab, select the Set User Directory radio button, and fill in the Directory
Server secure port information, the LDAP URL, and the user database information. Check
the Secure Connection checkbox.
16. Save the new TLS/SSL settings and Configuration DS and User DS information in the
Administration Server Console.
6.3 Enabling TLS/SSL 75
Page 76

17. Restart the Directory Server. The server must be restarted from the command line.
/opt/dirsrv/slapd-example/restart-slapd
When the server restarts, it prompts for the PIN or password to unlock the key database.
This is the same password used when the server certificate and key were imported into the
database.
Using a pin.txt file to store the token database passwords allows the Directory Server to
restart without prompting for the password. This is covered in “Creating a password file
for the Directory Server”.
18. Restart the Administration Server. The server must be restarted from the command line.
/opt/dirsrv/sbin/restart-ds-admin
When the server restarts, it prompts for the PIN or password to unlock the key database.
This is the same password used when the server certificate and key were imported into the
database.
Using a password.conf file to store the token database passwords allows the
Administration Server to restart without prompting for the password. This is covered in
“Creating a password file for the Administration Server”.
NOTE:
After configuring SSL/TLS for the Administration Server, be certain that the address reads https
when next logging into the Administration Server or Directory Console. With SSL/TLS, all
connections to the Administration Server must be over HTTPS. Otherwise, the operation will
time out, unable to find the server since it is running on a secure connection. After successfully
connecting, a dialog box appears to acceptthe certificate. Click OK to accept the certificate (either
only for that current session or permanently).
6.4 Creating password files
If SSL/TLS is enabled for the Directory Server or Administration Server, the server prompts for
a password to access the certificate and key databases every time the server is restarted. The
servers can restart silently if that password is supplied in a password file which the start scripts
can access.
6.4.1 Creating a password file for the Directory Server
It is possible to store the certificate password in a password file. By placing the certificate database
password in a file, the server can be started from the Directory Server Console and also restarted
automatically when running unattended.
CAUTION:
This password is stored in clear text within the password file, so its usage represents a significant
security risk. Do not use a password file if the server is running in an unsecured environment.
The password file must be in the same directory where the other key and certificate databases
for Directory Server are stored. This is usually the main configuration directory,
/etc/opt/dirsrv/slapd-instance_name. The file should be named pin.txt.
Include the token name and password in the file. For example:
Internal (Software) Token:secret
For the NSS software crypto module (the default software database), the token is always called
internal.
The PIN file should be owned by the Directory Server user and set to read-only by the Directory
Server user, with no access to anyone other user (mode 0400).
76 Using SSL/TLS with the Console
Page 77

6.4.2 Creating a password file for the Administration Server
Like the Directory Server, the Administration Server can use a password file during login when
TLS/SSL is enabled.
CAUTION:
This password is stored in clear text within the password file, so its usage represents a significant
security risk. Do not use a password file if the server is running in an unsecured environment.
1. Open the Administration Server configuration directory,/etc/opt/dirsrv/admin-serv.
2. Create a password file named password.conf. The file should include a line with the
token name and password, in the form token:password. For example:
internal:secret
For the NSS software crypto module (the default software database), the token is always
called internal.
The password file should be owned by the Administration Server user and set to read-only
by the Administration Server user, with no access to any other user (mode 0400).
NOTE:
To find out what the Administration Server user ID is, run grep in the Administration
Server configuration directory:
cd /etc/opt/dirsrv/admin-serv
grep \^User console.conf
3. In the /etc/opt/dirsrv/admin-serv directory, edit the nss.conf file to point to the
location of the new password file.
# Pass Phrase Dialog:
# Configure the pass phrase gathering process.
# The filtering dialog program (`builtin' is a internal
# terminal dialog) has to provide the pass phrase on stdout.
NSSPassPhraseDialog file://etc/opt/dirsrv/admin-serv/password.conf
4. Restart the Administration Server.
/opt/dirsrv/sbin/restart-ds-admin
6.4 Creating password files 77
Page 78

78
Page 79

7 Support and other resources
7.1 Contacting HP
7.1.1 Information to collect before contacting HP
Be sure to have the following information available before you call contact HP:
• Software product name
• Hardware product model number
• Operating system type and version
• Applicable error message
• Third-party hardware or software
• Technical support registration number (if applicable)
7.1.2 How to contact HP technical support
Use the following methods to contact HP technical support:
• In the United States, see the CustomerService / Contact HP United States website for contact
options:
http://welcome.hp.com/country/us/en/contact_us.html
• In other locations, see the Contact HP Worldwide website for contact options:
http://welcome.hp.com/country/us/en/wwcontact.html
7.1.3 HP authorized resellers
For the name of the nearest HP authorized reseller, see the following sources:
• In the United States, see the HP U.S. service locator website at:
http://www.hp.com/service_locator
• In other locations, see the Contact HP worldwide website at:
http://welcome.hp.com/country/us/en/wwcontact.html
7.1.4 Documentation feedback
HP welcomes your feedback. To make comments and suggestions about product documentation,
send a message to:
docsfeedback@hp.com
Include the document title and manufacturing part number in your message. All submissions
become the property of HP.
7.2 Related information
7.2.1 HP-UX Directory Server documentation set
• HP-UX Directory Server release notes
The release notes contain important information on new features, fixed bugs, known issues
and workarounds, and other important information for this specific version of the HP-UX
Directory Server.
• HP-UX Directory Server administrator guide
This guide contains information and procedures you need to perform to maintain your
Directory Server.
7.1 Contacting HP 79
Page 80

• HP-UX Directory Server administration server guide
The Administration Server is a support server that drives access to the Directory Server
Console , provides a web server for Directory Server web applications, and stores some
Directory Server configuration. This guide covers how to manage the Administration Server
through the Console, through the command line, and through the web services. It also covers
basic Administration Server concepts.
• HP-UX Directory Server configuration, command, and file reference
This document provides reference information on the command line scripts, configuration
attributes, and log files shipped with the Directory Server.
• HP-UX Directory Server console guide
This guide covers the basic structure of the Console for both the Directory Server and the
Administration Server and provides an overview of how to use the main Console to manage
users and access within the Console.
• HP-UX Directory Server deployment guide
This guide covers the basic considerations that should be addressed before deploying the
Directory Server. The decisions made during this phase can have a significant and lasting
affect on the effectiveness, efficiency, and scalability of your Directory Server. You should
have a good understanding of your Directory Server requirements before moving on to the
installation phase.
• HP-UX Directory Server installation guide
This manual contains information and procedures for installing your Directory Serveras
well as procedures for migrating from Netscape Directory Server 6.21 or Red Hat Directory
Server 7.1.
• HP-UX Directory Server plug-in reference
This reference document describes server plug-ins, as well as how to write server plug-ins
in order to customize and to extend the capabilities of the HP-UX Directory Server.
• HP-UX Directory Server schema reference
This reference provides an overview of some of the basic concepts of the directory schema,
including lists and descriptions of default schema files, and descriptions of object classes,
attributes, object identifiers (OIDs), schema checking, and extending server schema.
For the latest information about HP-UX Directory Server, including currentrelease notes, complete
product documentation, technical notes, and white papers, as well as other HP Internet and
Security products, see the HP-UX Directory Server documentation site at:
http://docs.hp.com/en/internet.html.
7.2.2 HP-UX documentation set
For the latest information about the HP-UX operating system, including current release notes,
complete product documentation, technical notes, and white papers, see the HP-UX Operating
Environments documentation sites for the version of HP-UX you use:
• HP-UX 11i v3 Operating Environments: http://docs.hp.com/en/oshpux11iv3.html
• HP-UX 11i v2 Operating Environments: http://docs.hp.com/en/oshpux11iv2.html
80 Support and other resources
Page 81

7.2.3 Troubleshooting resources
• You can search a technical knowledge database available on the HP IT Resource Center
(ITRC) website at:
http://itrc.hp.com/
• To seek solutions to problems, you can post messages on the ITRC Forums page at the
following website (select the HP-UX area in the Areas of peer problem solving section):
http://forums.itrc.hp.com/
7.3 Typographic conventions
This document uses the following typographical conventions:
Book title The title of a book. On the web, this can be a hyperlink to the
Command A command name or command phrase, for example ls -a.
Computer output
Ctrl+x or Ctrl-x
ENVIRONMENT VARIABLE The name of an environment variable, for example, PATH.
Key The name of a keyboard key. Return and Enter both refer to the
Term A term or phrase that is defined in the body text of the document,
User input
Replaceable
[ ] In commandsyntax statements, these characters enclose optional
{ } In commandsyntax statements, these charactersenclose required
| The character that separates items in a linear list of choices.
... Indicates that the preceding element can be repeated one or more
WARNING An alert that calls attention to important information that, if not
CAUTION An alert that calls attention to important information that, if not
IMPORTANT An alert that calls attention to essential information.
NOTE An alert that contains additional or supplementary information.
TIP An alert that provides helpful information.
book itself.
Information displayed by the computer.
A key sequence that indicates you must hold down the keyboard
key labeled Ctrl while you press the letter x.
same key.
not in a glossary.
Indicates commands and text that you type exactly as shown.
The name of a placeholder that you replace with an actual value.
content.
content.
times.
understood or followed, results in personal injury.
understood or followed, results in data loss, data corruption, or
damage to hardware or software.
7.3 Typographic conventions 81
Page 82

82
Page 83

Glossary
A
access control
instruction
access control list See ACL.
access rights In the context of access control, specify the level of access granted or denied. Access rights are
account
inactivation
ACI An instruction that grants or denies permissions to entries in the directory.
ACL The mechanism for controlling access to your directory.
All IDs Threshold Replaced with the ID list scan limit in Directory Server version 7.1. A size limit which is globally
All IDs token A mechanism which causes the server to assume that all directory entries match the index key.
anonymous
access
approximate
index
attribute Holds descriptive information about an entry. Attributes have a label and a value. Each attribute
attribute list A list of required and optional attributes for a given entry type or object class.
authenticating
directory server
authentication (1) Process of proving the identity of the client user to the Directory Server. Users must provide
See ACI.
related to the type of operation that can be performed on the directory. The following rights
can be granted or denied: read, write, add, delete, search, compare, selfwrite, proxy and all.
Disables a user account, group of accounts, or an entire domain so that all authentication
attempts are automatically rejected.
See also access control instruction.
See also access control list.
applied to every index key managed by the server. When the size of an individual ID list reaches
this limit, the server replaces that ID list with an All IDs token.
See also ID list scan limit.
In effect, the All IDs token causes the server to behave as if no index was available for the search
request.
When granted, allows anyone to access directory information without providing credentials,
and regardless of the conditions of the bind.
Allows for efficient approximate or "sounds-like" searches.
also follows a standard syntax for the type of information that can be stored as the attribute
value.
In pass-through authentication (PTA), the authenticating Directory Server is the Directory
Server that contains the authentication credentials of the requesting client. The PTA-enabled
host sends PTA requests it receives from clients to the host.
a bind DN and either the corresponding password or certificate in order to be granted access
to the directory. Directory Server allows the user to perform functions or access files and
directories based on the permissions granted to that user by the directory administrator.
(2) Allows a client to make sure they are connected to a secure server, preventing another
computer from impersonating the server or attempting to appear secure when it is not.
authentication
certificate
B
base
distinguished
name
base DN Base distinguished name. A search operation is performed on the base DN, the DN of the entry
Digital file that is nottransferable and not forgeable and is issued bya third party. Authentication
certificates are sent from server to client or client to server in order to verify and authenticate
the other party.
See base DN.
and all entries below it in the directory tree.
83
Page 84

bind
See bind DN.
distinguished
name
bind DN Distinguished name used to authenticate to Directory Server when performing an operation.
bind rule In the context of access control, the bind rule specifies the credentials and conditions that a
particular user or client must satisfy in order to get access to directory information.
branch entry An entry that represents the top of a subtree in the directory.
browser Software, such as Mozilla Firefox, used to request and view World Wide Web material stored
as HTML files. The browser uses the HTTP protocol to communicate with the host server.
browsing index Speeds up the display of entries in the Directory Server Console. Browsing indexes can be
created on any branch point in the directory tree to improve display performance.
See also virtual list view index .
C
CA See Certificate Authority.
cascading
replication
In a cascading replication scenario, one server, often called the hub supplier, acts both as a
consumer and a supplier for a particular replica. It holds a read-only replica and maintains a
changelog. It receives updates from the supplier server that holds the master copy of the data
and in turn supplies those updates to the consumer.
certificate A collection of data that associates the public keys of a network user with their DN in the
directory. The certificate is stored in the directory as user object attributes.
Certificate
Authority
Company or organization that sells and issues authentication certificates. You may purchase
an authentication certificate from a Certification Authority that you trust. Also known as a CA.
CGI CommonGateway Interface.An interface for external programs to communicate with the HTTP
server. Programs written to use CGI are called CGI programs or CGI scripts and can be written
in many of the common programming languages. CGI programs handle forms or perform
output parsing that is not done by the server itself.
chaining A method for relaying requests to another server. Results for the request are collected, compiled,
then returned to the client.
changelog A changelog is a record that describes the modifications that have occurred on a replica. The
supplier server then replays these modifications on the replicas stored on replica servers or on
other masters, in the case of multi-master replication.
character type Distinguishes alphabetic characters from numeric or other characters and the mapping of
upper-case to lower-case letters.
ciphertext Encrypted information that cannot be read by anyone without the proper key to decrypt the
information.
class definition Specifies the information needed to create an instance of a particular object and determines
how the object works in relation to other objects in the directory.
class of service See CoS.
classic CoS A classic CoS identifies the template entry by both its DN and the value of one of the target
entry's attributes.
client See LDAP client.
code page An internal table used by a locale in the context of the internationalization plug-in that the
operating system uses to relate keyboard keys to character font screen displays.
collation order Provides language and cultural-specific information about how the characters of a given
language are to be sorted. This information might include the sequence of letters in the alphabet
or how to compare letters with accents to letters without accents.
consumer Server containing replicated directory trees or subtrees from a supplier server.
consumer server In the context of replication, a server that holds a replica that is copied from a different server
is called a consumer for that replica.
CoS A method for sharing attributes between entries in a way that is invisible to applications.
84 Glossary
Page 85

CoS definition
entry
CoS template
entry
Identifies the type of CoS you are using. It is stored as an LDAP subentry below the branch it
affects.
Contains a list of the shared attribute values.
See also template entry.
D
daemon A background process on a Unix machine that is responsible for a particular system task.
Daemon processes do not need human intervention to continue functioning.
DAP Directory Access Protocol. The ISO X.500 standard protocol that provides client access to the
directory.
data master The server that is the master source of a particular piece of data.
database link An implementationof chaining. The database link behaves like a databasebut has no persistent
storage. Instead, it points to data stored remotely.
default index One of a set of default indexes created per database instance. Default indexes can be modified,
although care should be taken before removing them, as certain plug-ins may depend on them.
definition entry See CoS definition entry.
Directory Access
See DAP.
Protocol
Directory
Manager
The privileged database administrator, comparable to the root user in UNIX. Access control
does not apply to the Directory Manager.
directory service A database application designed to manage descriptive, attribute-based information about
people and resources within an organization.
directory tree The logical representation of the information stored in the directory. It mirrors the tree model
used by most filesystems, with the tree's root point appearing at the top of the hierarchy. Also
known as DIT.
distinguished
String representation of an entry's name and location in an LDAP directory.
name
DIT See directory tree.
DM See Directory Manager.
DN See distinguished name.
DNS Domain Name System. The system used by machines on a network to associate standard IP
addresses (such as 198.93.93.10) with host names (such as www.example.com). Machines
normally get the IP address for a host name from a DNS server, or they look it up in tables
maintained on their systems.
DNS alias A DNS alias is a host name that the DNS server knows points to a different host specifically
a DNS CNAME record. Machines always have one real name, but they can have one or more
aliases. For example, an alias such as www.yourdomain.domain might point to a real machine
called realthing.yourdomain.domain where the server currently exists.
E
entry A group of lines in the LDIF file that contains information about an object.
entry distribution Method of distributing directory entriesacross more than one server in order to scale to support
large numbers of entries.
entry ID list Each index that the directory uses is composed of a table of index keys and matching entry ID
lists. The entry ID list is used by the directory to build a list of candidate entries that may match
the client application's search request.
equality index Allows you to search efficiently for entries containing a specific attribute value.
F
file extension The section of a file name after the period or dot (.) that typically defines the type of file (for
example, .GIF and .HTML). In the file name index.html the file extension is html.
85
Page 86

file type The format of a given file. For example, graphics files are often saved in GIF format, while a
text file is usually saved as ASCII text format. File types are usually identified by the file
extension (for example, .GIF or .HTML).
filter A constraint applied to a directory query that restricts the information returned.
filtered role Allows you to assign entries to the role depending upon the attribute contained by each entry.
You do this by specifying an LDAP filter. Entries that match the filter are said to possess the
role.
G
general access When granted, indicates that all authenticated users can access directory information.
GSS-API Generic Security Services. The generic access protocol that is the native way for UNIX-based
systems to access and authenticate Kerberos services; also supports session encryption.
H
host name A name for amachine in the form machine.domain.dom, which is translated into an IP address.
For example, www.example.com is the machine www in the subdomain example and com
domain.
HTML Hypertext Markup Language. Theformatting languageused fordocuments onthe World Wide
Web.HTML files are plain text files with formatting codes that tell browsers such as theMozilla
Firefox how to display text, position graphics, and form items and to display links to other
pages.
HTTP Hypertext Transfer Protocol. The method for exchanging information between HTTP servers
and clients.
HTTPD An abbreviation for the HTTP daemon or service, a program that serves information using the
HTTP protocol. The daemon or service is often called an httpd.
HTTPS A secure version of HTTP, implemented using the Secure Sockets Layer, SSL.
hub In the context of replication, a server that holds a replica that is copied from a different server,
and, in turn, replicates it to a third server.
See also cascading replication.
I
ID list scan limit A size limit which is globally applied to any indexed search operation. When the size of an
individual ID list reaches this limit, the server replaces that ID list with an all IDs token.
index key Each index that the directory uses is composed of a table of index keys and matching entry ID
lists.
indirect CoS An indirect CoS identifies the template entry using the value of one of the target entry's attributes.
international
Speeds up searches for information in international directories.
index
International
See ISO.
Standards
Organization
IP address Also Internet Protocol address. A set of numbers, separated by dots, that specifies the actual
location of a machine on the Internet (for example, 198.93.93.10).
ISO International Standards Organization.
K
knowledge
Pointers to directory information stored in different databases.
reference
86 Glossary
Page 87

L
LDAP Lightweight Directory Access Protocol. Directory service protocol designed to run over TCP/IP
and across multiple platforms.
LDAP client Software used to request and view LDAP entries from an LDAP Directory Server.
See also browser.
LDAP Data
See LDAP Data Interchange Format.
Interchange
Format
LDAP URL Provides the means of locating Directory Servers using DNS,then completing the query through
LDAP. A sample LDAP URL is ldap://ldap.example.com.
LDAPv3 Version 3 of the LDAP protocol, upon which Directory Server bases its schema format.
LDBM database A high-performance, disk-based database consisting of a set of large files that contain all the
data assigned to it. The primary data store in Directory Server.
LDIF LDAP DataInterchange Format. Format used to represent Directory Server entries in text form.
leaf entry An entry under which there are no other entries. A leaf entry cannot be a branch point in a
directory tree.
Lightweight
See LDAP.
Directory Access
Protocol
locale Identifies the collation order, character type, monetary format and time / date format used to
present data for users of a specific region, culture, and/or custom. This includes information
on how data of a given language is interpreted, stored, or collated. The locale also indicates
which code page should be used to represent a given language.
M
managed object A standard value which the SNMP agent can access and send to the NMS. Each managed object
is identified with an official name and a numeric identifier expressed in dot-notation.
managed role Allows creation of an explicit enumerated list of members.
management
See MIB.
information base
mapping tree A data structure that associates the names of suffixes (subtrees) with databases.
master See supplier.
master agent See SNMP master agent.
matching rule Provides guidelines for how the server compares strings during a search operation. In an
international search, the matching rule tells the server what collation order and operator to use.
MD5 A message digest algorithm by RSA Data Security, Inc., which can be used to produce a short
digest of data that is unique with high probability and is mathematically extremely hard to
produce; a piece of data that will produce the same message digest.
MD5 signature A message digest produced by the MD5 algorithm.
MIB Management Information Base. All data, or any portion thereof, associated with the SNMP
network. We can think of the MIB as a database which contains the definitions of all SNMP
managed objects. The MIB has a tree-like hierarchy, where the top level contains the most
general information about the network and lower levels deal with specific, separate network
areas.
MIB namespace Management Information Base namespace. The means for directory data to be named and
referenced. Also called the directory tree.
monetary format Specifies the monetary symbol used by specific region, whether the symbol goes before or after
its value, and how monetary units are represented.
multi-master
replication
An advanced replication scenario in which two servers each hold a copy of the same read-write
replica. Each server maintains a changelog for the replica. Modifications made on one server
87
Page 88

are automatically replicated to the other server. In case of conflict, a time stamp is used to
determine which server holds the most recent version.
multiplexor The server containing the database link that communicates with the remote server.
N
n + 1 directory
problem
The problem of managing multiple instances of the same information in different directories,
resulting in increased hardware and personnel costs.
name collisions Multiple entries with the same distinguished name.
nested role Allows the creation of roles that contain other roles.
network
management
application
network
Network Management Station component that graphically displays information about SNMP
managed devices,such as which device is up or down and which and how many error messages
were received.
See NMS.
management
station
NIS Network Information Service. A system of programs and data files that Unix machines use to
collect, collate, and share specific information about machines, users, filesystems, and network
parameters throughout a network of computers.
NMS Powerful workstation with one or more network management applications installed. Also
network management station.
ns-slapd LDAP Directory Server daemon or service that is responsible for all actions of the Directory
Server.
See also slapd.
O
object class Defines an entry type in the directory by defining which attributes are contained in the entry.
object identifier A string, usually of decimal numbers, that uniquely identifies a schema element, such as an
object class or an attribute, in an object-oriented system. Object identifiers are assignedby ANSI,
IETF or similar organizations.
See also OID.
OID See object identifier.
operational
attribute
Contains information used internally by the directory to keep track of modifications and subtree
properties. Operational attributes are not returned in response to a search unless explicitly
requested.
P
parent access When granted, indicates that users have access to entries below their own in the directory tree
if the bind DN is the parent of the targeted entry.
pass-through
See PTA.
authentication
pass-through
subtree
In pass-through authentication, the PTA directory server will pass through bind requests to
the authenticating directory server from all clients whose DN is contained in this subtree.
password file A file on Unix machines that stores Unix user login names, passwords, and user ID numbers.
It is also known as /etc/passwd because of where it is kept.
password policy A set of rules that governs how passwords are used in a given directory.
PDU Encoded messageswhich form the basis of data exchanges between SNMP devices. Also protocol
data unit.
permission In the context of access control, permission states whether access to the directory information
is granted or denied and the level of access that is granted or denied.
See also access rights.
pointer CoS A pointer CoS identifies the template entry using the template DN only.
88 Glossary
Page 89

presence index Allows searches for entries that contain a specific indexed attribute.
protocol A set of rules that describes how devices on a network exchange information.
protocol data unit See PDU.
proxy
authentication
A special formof authentication where the user requesting access to thedirectory does not bind
with its own DN but with a proxy DN.
proxy DN Used with proxied authorization. The proxy DN is the DN of an entry that has access permissions
to the target on which the client-application is attempting to perform an operation.
PTA Mechanism by which one Directory Server consults another to check bind credentials. Also
pass-through authentication.
PTA directory
server
In pass-through authentication (PTA), the PTA Directory Server is the server that sends (passes
through) bind requests it receives to the authenticating directory server.
PTA LDAP URL In pass-through authentication, the URL that defines the authenticating directory server,
pass-through subtree(s), and optional parameters.
R
RAM Random access memory. The physical semiconductor-based memory in acomputer. Information
stored in RAM is lost when the computer is shut down.
RDN The name of the actual entry itself, before the entry's ancestors have been appended to the string
to form the full distinguished name. Also relative distinguished name.
read-only replica A replica that refers all update operations to read-write replicas. A server can hold any number
of read-only replicas.
read-write replica A replica that contains a master copy of directory information and can be updated. A server
can hold any number of read-write replicas.
referential
integrity
Mechanism that ensures that relationships between related entries are maintained within the
directory.
referral (1) When a server receives a search or update request from an LDAP client that it cannot process,
it usually sends back to the client a pointer to the LDAP sever that can process the request.
(2) In the context of replication, when a read-only replica receives an update request, it forwards
it to the server that holds the corresponding read-write replica. This forwarding process is
called a referral.
relative
See RDN.
distinguished
name
replica A database that participates in replication.
replica-initiated
replication
Replication configuration where replica servers, either hub or consumer servers, pull directory
data from supplier servers. This method is available only for legacy replication.
replication Act of copying directory trees or subtrees from supplier servers to replica servers.
replication
agreement
Set of configuration parameters that are stored on the supplier server and identify the databases
to replicate, the replica servers to which the data is pushed, the times during which replication
can occur, the DN and credentials used by the supplier to bind to the consumer, and how the
connection is secured.
RFC Request for Comments. Procedures or standards documents submitted to the Internet
community. People can send comments on the technologies before they become accepted
standards.
role An entry grouping mechanism. Each role has members, which are the entries that possess the
role.
role-based
attributes
Attributes that appear on an entry because it possesses a particular role within an associated
CoS template.
root The most privileged user available on Unix machines. The root user has complete access
privileges to all files on the machine.
root suffix The parent of one or more sub suffixes. A directory tree can contain more than one root suffix.
89
Page 90

S
SASL An authentication framework for clients as they attempt to bind to a directory. Also Simple
Authentication and Security Layer .
schema Definitions describing what types of information can be stored as entries in the directory. When
information that does not match the schema is stored in the directory, clients attempting to
access the directory may be unable to display the proper results.
schema checking Ensures that entries added or modified in thedirectory conform to the defined schema. Schema
checking is on by default, and users will receive an error if they try to save an entry that does
not conform to the schema.
Secure Sockets
See SSL.
Layer
self access When granted, indicates that users have access to their own entries if the bind DN matches the
targeted entry.
Server Console Java-based application that allowsyou to perform administrative management of your Directory
Server from a GUI.
server daemon The server daemon is a process that, once running, listens for and accepts requests from clients.
Server Selector Interface that allows you select and configure servers using a browser.
server service A process on Windows that, once running, listens for and accepts requests from clients. It is
the SMB server on Windows NT.
service A background process on a Windows machine that is responsible for a particular system task.
Service processes do not need human intervention to continue functioning.
SIE Server Instance Entry. The ID assigned to an instance of Directory Server during installation.
Simple
See SASL.
Authentication
and Security
Layer
Simple Network
See SNMP.
Management
Protocol
single-master
replication
The most basic replication scenario in which multiple servers, up to four, each hold a copy of
the same read-write replicas to replica servers. In a single-master replication scenario, the
supplier server maintains a changelog.
SIR See supplier-initiated replication.
slapd LDAP Directory Server daemon or service that is responsible for most functions of a directory
except replication.
See also ns-slapd.
SNMP Used to monitor and manage application processes running on the servers by exchanging data
about network activity. Also Simple Network Management Protocol.
SNMP master
Software that exchanges information between the various subagents and the NMS.
agent
SNMP subagent Software that gathers information about the managed device and passes the information to the
master agent. Also called a subagent.
SSL A software library establishing a secure connection between two parties (client and server)
used to implement HTTPS, the secure version of HTTP. Also called Secure Sockets Layer.
standard index index maintained by default.
sub suffix A branch underneath a root suffix.
subagent See SNMP subagent.
substring index Allows for efficient searching against substrings within entries. Substring indexes are limited
to a minimum of two characters for each entry.
suffix The name of the entry at the top of the directory tree, below which data is stored. Multiple
suffixes are possible within the same directory. Each database only has one suffix.
90 Glossary
Page 91

superuser The most privileged user available on Unix machines. The superuser has complete access
privileges to all files on the machine. Also called root.
supplier Server containing the master copy of directory trees or subtrees that are replicated to replica
servers.
supplier server In the context of replication, a server that holds a replica that is copied to a different server is
called a supplier for that replica.
supplier-initiated
Replication configuration wheresupplier servers replicate directory data to any replicaservers.
replication
symmetric
encryption
Encryption that uses the same key for both encrypting and decrypting. DES is an example of
a symmetric encryption algorithm.
system index Cannot be deleted or modified as it is essential to Directory Server operations.
T
target In the context of access control, the target identifies the directory information to which a
particular ACI applies.
target entry The entries within the scope of a CoS.
TCP/IP Transmission Control Protocol/Internet Protocol. The main network protocol for the Internet
and for enterprise (company) networks.
template entry See CoS template entry.
time/date format Indicates the customary formatting for times and dates in a specific region.
TLS The new standard for secure socket layers; a public key based protocol. Also Transport Layer
Security.
topology The way a directory tree is divided among physical servers and how these servers link with
one another.
Transport Layer
See TLS.
Security
U
uid A unique number associated with each user on a Unix system.
URL Uniform Resource Locater. The addressing system used by the server and the client to request
documents. It is often called a location. The format of a URL is
protocol://machine:port/document. The port number is necessary only on selected
servers, and it is often assigned by the server, freeing the user of having to place it in the URL.
V
virtual list view
index
Speeds up the display of entries in the Directory Server Console. Virtual list view indexes can
be created on any branch point in the directory tree to improve display performance.
See also browsing index.
X
X.500 standard The set of ISO/ITU-T documents outlining the recommended information model, object classes
and attributes used by directory server implementation.
91
Page 92

92
Page 93

Index
A
Access Control
to navigation tree, 53
admin domain
creating, 30, 31
administration domain
defined, 8
removing, 31
Administration Server
defined, 5
Administration Server Administrator
changing user name or password for, 49
defined, 47
administrators, overview of, 47
Directory Server Console
overview of, 5
documentation
providing feedback, 79
reporting errors in, 79
dynamic group, 40
E
encryption, 61
F
feedback
email address for documentation, 79
fonts
changing, 17
C
certificate
password, 76
certificate group, 40
Configuration Administrator
changing user name or password for, 47
defined, 47
Configuration Administrators group
adding users to, 50
configuration directory
defined, 5
custom views, 14
changing to, 25
creating, 23
editing, 25
removing, 25
setting ACIs on, 25
using, 23
D
deleting
Directory Server instance, 33
digital signatures, 61
directory
changing the search directory, 36
Directory Console
defined, 5
information panel, 8
logging into, 13
menus, 7
tabs, 8
directory entries
creating, 37
removing, 52
searching for, 35
Directory Server
configuration subtree, 5
deleting instance, 33
role in managing resources and users, 5
user subtree, 5
G
groups
creating, 40
editing, 45
locating, 35
removing, 52
types, 40
H
host information, modifying, 29
HP authorized resellers, 79
HP technical support, 79
L
logging into Console
logging in, 13
M
management window
opening for Directory or Administration Server, 14
menus, in Directory Console, 7
N
navigation tree
overview, 8
setting access permissions to, 53
O
organizational units
creating, 43
removing, 52
P
password
changing for a user or administrator, 46
password file
Administration Server, 77
SSL certificate, 76
passwords
certificate, 76
93
Page 94

preferences, 14
font, 17
UI permissions, 14
R
reporting documentation errors
email address, 79
S
searching
changing the search directory, 36
for directory entries, 35
server
defined, 8
opening a management window for, 14
server group
defined, 8
modifying information for, 29
server instance
creating, 32
modifying information for, 29
SSL, 61
Administration Server password file, 77
certificate password, 76
static group, 40
synchronization options
enabling, 46
overview, 46
T
tables
changing column position in, 19
tabs, in Directory Console, 8
TLS, 61
topology
defined, 8
typographic conventions, 81
U
user entries
changing passwords for, 46
creating, 37
editing, 45
locating, 35
removing, 52
Users and Groups tab, changing the search directory for,
36
W
websites
HP authorized resellers, 79
HP technical support, 79
94 Index
Page 95

95
Page 96

 Loading...
Loading...