Page 1

HP 9000 Networking
NetWare® 4.1/9000
NetWare Client for DOS
and MS Windows Technical Reference
HP Part No. J2771-90016
Printed in U.S.A. 12/96
hp
HEWLETT
PACKARD
Edition 1
Page 2
Notice
Notice
Hewlett-Packard makes no warranty of any kind with regard to this
material, including, but not limited to, the implied warranties of
merchantability and fitness for a particular purpose. Hewlett-Packard
shall not be liable for errors contained herein or for incidental or
consequential damages in connection with the furnishing, performance, or
use of this material. This product is based in whole or in part on technology
developed by Novell, Inc
Hewlett-Packard assumes no responsibility for the use or reliability of its
software on equipment that is not furnished by Hewlett-Packard
This document contains proprietary information, which is protected by
copyright. All rights are reserved. No part of this document may be
photocopied, reproduced, or translated into another language without the
prior written consent of Hewlett-Packard Company.The information
contained in this document is subject to change without notice.
UNIX is a registered trademark in the United States and other countries,
licensed exclusively through X/Open Company Limited.
Microsoft
a trademark of Microsoft Corporation.
NetWare, and Novell are registered trademarks of Novell, Inc.
®
, MS®, and MS-DOS® are registered trademarks, and Windows is
© Copyright 1996, Hewlett-Packard Company
Restricted Rights Legend
Use, duplication or disclosure by the U.S. Government is subject to
restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical
Data and Computer Software clause at DFARS 252.227-7013 for DoD
agencies, Computer Software Restricted Rights clause at FAR 52.227-19 for
other agencies.
Hewlett-Packard Co.
19420 Homestead Road
Cupertino, CA 95014 USA
ii
Page 3
Printing History
Printing History
The manual printing date and part number indicate its current edition. The
printing date will change when a new edition is printed. Minor changes may
be made at reprint without changing the printing date. The manual part
number will change when extensive changes are made.
Manual updates may be issued between editions to correct errors or document
product changes. To ensure that you receive the updated or new editions, you
should subscribe to the appropriate product support service. See your HP
sales representative for details.
First Edition: December, 1996
iii
Page 4
Preface
Preface
Introduction
NetWare Client for DOS and MS Windows Technical Reference provides you
with detailed information to configure the NetWare® DOS Requester™
software, modify the NetWare Client™ configuration file, and troubleshoot
client workstation error messages in order to manage client workstations on
a NetWare network.
This document is for supervisors responsible for managing NetWare client
workstations.
NetWare Client for DOS and MS Windows Technical Reference covers
concepts and procedures for configuring and using NetWare workstation
software on NetWare 2, NetWare 3™, and NetWare 4™ networks.
References are made to each version of NetWare. Ignore any references
which do not pertain to the version of NetWare you are connecting to.
Use NetWare Client for DOS and MS Windows User Guide for procedures
and information on installation and basic client workstation setup.
Contents Overview
To configure your NetWare Client software, use the chapters as described in
the following checklist.
• Use Chapter 1, “Optimizing the NetWare Client Software,” to learn how to
improve workstation performance by using Packet Burst™ and Large Internet
Packets (LIP) and to enhance security on client workstations by using NCP™
packet signatures.
• Use Chapter 2, “NET.CFG Options Reference,” to learn how to set up and
modify the NetWare Client (NET.CFG) configuration file and to reference
information for setting NET.CFG option parameters.
• Use Chapter 3, “Command Line Parameters Reference,” to learn how to
reference information for setting command line parameters.
• Use Chapter 4, “System Messages,” to receive an explanation of each client
workstation system message and a recommendation on a course of action for each
message.
iv
Page 5

Preface
Documentation Conventions
This manual uses the following Novell® conventions:
Asterisk ( * )
An asterisk denotes a trademarked name belonging to a third-party company.
Novell trademarks are denoted with specific trademark symbols (®, ™, etc.).
An ownership listing of all (Novell and third-party) trademarks cited in a
manual can be found either on the disclaimer page in the front or in a
“Trademarks” section at the back of printed manuals. A trademarks list is also
available in the DynaText* online documentation.
Commands
Boldface characters indicate items that you type, such as commands and
options. You can use any combination of uppercase and lowercase letters.
For example:
C:\A INSTALL
Delimiter Bar ( | )
In syntax examples, a delimiter bar separating two command options
indicates that you can choose one of the options.
For example:
–S | –R
Do not type the bar.
DOS Commands
DOS commands and command option letters are shown in uppercase letters.
For example: FTPD.
Because DOS is not case-sensitive, you can type DOS commands in
uppercase or lowercase letters.
DOS Filenames, Directory Names, and Pathnames
DOS filenames, directory names, and pathnames are shown in uppercase
letters. For example, AUTOEXEC.BAT.
Because DOS is not case-sensitive, you can type these names in uppercase or
v
Page 6
Preface
lowercase letters.
Ellipses
Ellipses in syntax examples indicate that parameters, options, or settings can
be repeated.
For example, in the command
LOGIN SERVER1/SUPERVISOR /option...
you could replace option with any number of available options.
Emphasis
Italic type also indicates emphasized text. For example:
Remember to load the driver before you install the application.
Key Names
Angle brackets surround the name of a key. For example, <Enter>
corresponds to the Enter key on your keyboard. <Ctrl>+<c> means hold
down the Ctrl key and simultaneously type the letter c (in lowercase, in this
case).
NET.CFG File Section Headings and Parameter Settings
NET.CFG section headings and parameter settings are shown in uppercase
when used as a reference item and lower case when used in syntax or working
examples.
For example:
[Begin example]
NETBIOS VERIFY TIMEOUT specifies how often in (ticks) NetBIOS
sends a keep-alive packet to the other side of a session to preserve the session.
If no packets are being exchanged on the NetBIOS session by the software
that established the session, NetBIOS sends packets at regular intervals to
make sure that the session is still valid.
Syntax
vi
netbios verify timeout
Replace number with a number of ticks.
number
Page 7
Preface
Default 54 (approximately 3 seconds)
Range 4 to 65,535
Example To make NetBIOS wait longer before sending a
request-for-acknowledgment packet, you could place the
following lines in your NET.CFG file:
netbios
netbios verify timeout 1350
[End example]
Because interpretation of this file is not case-sensitive, you can type its
contents in uppercase or lowercase letters.
Options
In syntax examples, braces indicate that you are required to choose one of the
enclosed options. For example, the following notation means that you must
include a 0 or a 1 in the command:
{0, 1}
Square Brackets
In syntax examples, boldface type enclosed in square brackets indicates
command options that you can type as needed. For example:
FTP [ –D ] [ –F ]
System Response
Monospace type shows system-generated responses that appear on your
workstation screen. For example:
TNVT220>
UNIX Commands
UNIX® commands are shown in boldface letters. For example, vi. Because
UNIX is case-sensitive, these commands are usually lowercase. Type UNIX
commands exactly as shown.
UNIX Filenames, Directory Names, and Pathnames
UNIX filenames, directory names, and pathnames are shown in italics. For
vii
Page 8

Preface
example, /etc/hosts.
Because UNIX is case-sensitive, these names usually are in lowercase letters.
Type UNIX filenames exactly as shown.
Variables
Italic type indicates variables—descriptive item names, such as command
parameters—that you replace with appropriate values.
For example, in the command
FTP –F remote_host
you type the name of a computer on your network in place of remote_host.
Supplemental Documentation
The following publications provide supplemental information specifically
related to the NetWare Client for DOS and MS Windows technology and
software:
• “The Functions and Operations of the NetWare DOS Requester 1.1,” Novell
Application Notes, May 94, Vol. 5, No. 5 (Novell part no. 164-000031-005)
• “Installing and Configuring Novell's Token-Ring Source Routing Drivers,”
NetWare Application Notes, Oct 91 (Novell part no. 164-000030-010)
• “Logging In to IBM LAN Server and NetWare from a DOS Workstation,”
NetWare Application Notes, Nov 91 (Novell part no. 164-000030-011)
• “Managing Memory in a DOS Workstation: Part 1,” NetWare Application Notes,
Aug 92 (Novell part no. 164-000031-008)
• “Managing Memory in a DOS Workstation: Part 2,” NetWare Application Notes,
Oct 92 (Novell part no. 164-000031-010)
• “Managing Memory in a DOS Workstation: Using Novell DOS 7,” NetWare
Application Notes, Oct 93 (Novell part no. 164-000032-010)
• “Migrating Ethernet Frame Types from 802.3 Raw to IEEE 802.2,” NetWare
Application Notes, Sep 93 (Novell part no. 164-000032-009)
• “Multilingual PC Setup with DR DOS,” NetWare Application Notes,
Sep 93 (Novell part no. 164-000032-009)
• “NET.CFG Parameters for the NetWare DOS Requester 1.1,” Novell Application
Notes, Jun 94, Vol. 5, No. 6 (Novell part no. 164-000036-006)
• “NetWare and LAN Server Client Interoperability via ODINSUP: Part 1,”
viii
Page 9

Preface
NetWare Application Notes, Sep 92 (Novell part no. 164-000031-009)
• “NetWare and LAN Server Client Interoperability via ODINSUP: Part 2,”
NetWare Application Notes, Nov 92 (Novell part no. 164-000031-011)
• “NetWare and Windows for Workgroups 3.1 Interoperability,” NetWare
Application Notes, Mar 93 (Novell part no. 164-000032-003)
• NetWare Client for DOS and MS Windows User Guide, Novell Publication
(Novell part no. 100-001623-002)
• “ODINSUP Interoperability Configurations for DOS Workstations,” NetWare
Application Notes, Feb 93 (Novell part no. 164-000032-002)
• “Using the DOS Requester with NetWare 4.0,” NetWare Application Notes, Apr
93 (Novell part no. 164-000032-004)
• “Understanding Token-Ring Source Routing,” NetWare Application Notes, May
91 (Novell part no. 164-000030-005)
• “Workstation Memory Management: Using QEMM386, 386 To The Max, and
MS-DOS 6,” NetWare Application Notes, Dec 93 (Novell part no.
164-000032-012)
ix
Page 10

Preface
x
Page 11

Contents
1 Optimizing the NetWare Client Software
Overview 1-2
Introduction 1-3
Increasing Speed 1-4
Using the Packet Burst Protocol 1-4
Requirement for Packet Burst 1-4
How Packet Burst Works 1-4
When to Use Packet Burst 1-5
Configuring for Packet Burst 1-5
Disabling Packet Burst 1-5
Using Large Internet Packet Functionality 1-5
How Large Internet Packet Works 1-6
When to Use Large Internet Packet 1-6
Configuring for Large Internet Packet 1-6
Disabling LIP 1-7
Improving Security 1-8
Using NCP Packet Signature to Improve Security 1-8
How NCP Packet Signature Works 1-8
When to Use NCP Packet Signature 1-9
NCP Packet Signature Options 1-9
Effective Packet Signature Levels 1-10
Examples of Using Packet Signature Levels 1-10
All Information on the Server Is Sensitive 1-10
Sensitive and Nonsensitive Information Reside on the Same Server 1-11
Client Workstation Users Often Change Locations 1-11
Client Workstation Is Publicly Accessible 1-11
Installing NCP Packet Signature 1-11
Workstation Setting 1-11
Server Setting 1-12
Disabling Packet Signature 1-12
xi
Page 12

Contents
Troubleshooting NCP Packet Signature 1-13
Client Workstations Are Not Signing Packets 1-13
Client Workstations Cannot Log In 1-13
The Error Message “Error Receiving from the Network” Appears 1-14
Third-Party NLM Programs Do Not Work 1-14
Insecure Client Workstations Log In to a Secure Server 1-14
Using Other Client Security Guidelines 1-15
Additional Information 1-16
2 NET.CFG Options Reference
Overview 2-2
Introduction 2-3
Creating and Modifying a NET.CFG File 2-4
Entering Options and Parameters into the NET.CFG File 2-4
Sample NET.CFG File 2-5
Using NET.CFG Options and Parameters 2-7
Using the NET.CFG Reference Pages 2-12
Desktop SNMP Option 2-13
Available Parameters and Values for the Desktop SNMP Option 2-13
DESKTOP SNMP 2-13
Asynchronous Timeout Connections 2-14
ASYNCHRONOUS TIMEOUT number 2-14
Community Types and Names 2-15
MONITOR COMMUNITY [“name | public | private”] 2-17
CONTROL COMMUNITY [“name | public | private”] 2-18
xii
Page 13

Contents
TRAP COMMUNITY [“name | public | private”] 2-18
Community Access Management 2-18
ENABLE MONITOR COMMUNITY [specified | any | off | omitted] 2-20
ENABLE CONTROL COMMUNITY [specified | any | off | omitted] 2-20
ENABLE TRAP COMMUNITY [specified | off | omitted] 2-20
MIB-II (Management Information Base) Support 2-22
System and SNMP Groups 2-22
SNMPENABLEAUTHENTRAP [on | off] 2-24
SYSCONTACT “contact” 2-24
SYSLOCATION “location” 2-25
SYSNAME “name” 2-25
Interface Group 2-25
TCP/IP Groups 2-26
Example of NET.CFG File Including Each Group Support 2-26
Link Driver Option 2-27
Available Parameters and Values for the Link Driver Option 2-27
LINK DRIVER driver_name 2-27
ALTERNATE 2-28
BUS ID name number 2-28
DMA [#1 | #2] channel_number 2-29
FRAME frame_type_name [addressing_mode] 2-30
Frame Types, Protocols, and LAN Drivers 2-31
Ethernet LAN Drivers 2-33
Token-Ring LAN Drivers 2-33
IRQ [#1 | #2] interrupt_request_number 2-34
MAX FRAME SIZE number 2-34
MEM [#1 | #2] hex_starting_address [hex_length] 2-35
NODE ADDRESS hex_address [mode] 2-36
LANSUP 2-37
PORT [#1 | #2] hex_starting_address [hex_number_of_ports] 2-38
PROTOCOL “name” hex_protocol_ID frame_type 2-39
Defined Protocols and Frame Types 2-39
SLOT number 2-40
xiii
Page 14

Contents
Listing of Commonly Used ODI LAN Drivers 2-41
Link Support Option 2-46
Available Parameters and Values for the Link Support Option 2-46
LINK SUPPORT 2-46
BUFFERS communication_number [buffer_size] 2-47
MAX BOARDS number 2-49
MAX STACKS number 2-50
MEMPOOL number [k] 2-50
NetWare DOS Requester Option 2-52
Current Core Virtual Loadable Module (VLM) Programs 2-52
Current Non-Core Virtual Loadable Module Programs 2-53
Compatibility with NetWare Shell Parameters 2-54
Managing the NetWare DOS Requester 2-56
Optimizing the NetWare DOS Requester 2-57
Best Performance 2-57
Best Conventional Memory Usage 2-59
Best Compromise 2-60
Available Parameters and Values for the NetWare DOS Requester Option 2-61
NETWARE DOS REQUESTER 2-63
AUTO LARGE TABLE=[on | off] 2-63
AUTO RECONNECT=[on | off] 2-64
AUTO RETRY=number 2-64
AVERAGE NAME LENGTH=number 2-65
BIND RECONNECT=[on | off] 2-66
BROADCAST RETRIES=number 2-66
BROADCAST SEND DELAY=number 2-67
BROADCAST TIMEOUT=number 2-67
CACHE BUFFER SIZE=number 2-68
CACHE BUFFERS=number 2-69
CACHE WRITES=[on | off] 2-69
CHECKSUM=number 2-70
CONFIRM CRITICAL ERROR ACTION=[on | off] 2-71
xiv
Page 15

Contents
CONNECTIONS=number 2-72
DOS NAME=“name” 2-72
EOJ=[on | off] 2-73
EXCLUDE VLM=path_vlm 2-74
FIRST NETWORK DRIVE=drive_letter 2-74
FORCE FIRST NETWORK DRIVE=[on | off] 2-75
HANDLE NET ERRORS=[on | off] 2-75
LARGE INTERNET PACKETS=[on | off] 2-76
LIP START SIZE=number 2-77
LOAD CONN TABLE LOW=[on | off] 2-77
LOAD LOW CONN=[on | off] 2-78
LOAD LOW IPXNCP=[on | off] 2-79
LOAD LOW REDIR=[on | off] 2-79
LOCAL PRINTERS=number 2-80
LOCK DELAY=number 2-81
LOCK RETRIES=number 2-81
LONG MACHINE TYPE=“name” 2-82
MAX TASKS=number 2-83
MESSAGE LEVEL=number 2-83
MESSAGE TIMEOUT=number 2-84
MINIMUM TIME TO NET=number 2-85
NAME CONTEXT=“name_context” 2-85
NETWARE PROTOCOL=netware_protocol_list 2-86
NETWORK PRINTERS=number 2-87
PB BUFFERS=number 2-88
PBURST READ WINDOWS SIZE=number 2-88
PBURST WRITE WINDOWS SIZE=number 2-89
PREFERRED SERVER=“server_name” 2-89
PREFERRED TREE=“tree_name” 2-90
PREFERRED WORKGROUP=“workgroup_name” 2-91
PRINT BUFFER SIZE=number 2-91
PRINT HEADER=number 2-92
PRINT TAIL=number 2-92
READ ONLY COMPATIBILITY=[on | off] 2-93
xv
Page 16

Contents
RESPONDER=[on | off] 2-94
SEARCH MODE=number 2-94
SET STATION TIME=[on | off] 2-96
SHORT MACHINE TYPE=“name” 2-96
SHOW DOTS=[on | off] 2-97
SIGNATURE LEVEL=number 2-97
TRUE COMMIT=[on | off] 2-98
USE DEFAULTS=[on | off] 2-99
VLM=path_VLM 2-100
WORKGROUP NET=workgroup_net_address 2-101
Protocol IPX Option 2-103
Available Parameters and Values for the Protocol IPX Option 2-103
PROTOCOL IPX 2-103
BIND LAN_driver_name [#number] 2-104
INT64 [on | off] 2-104
INT7A [on | off] 2-105
IPATCH byte_offset, value 2-106
IPX PACKET SIZE LIMIT number 2-106
IPX RETRY COUNT number 2-107
IPX SOCKETS number 2-107
Protocol SPX Option 2-109
Available Parameters and Values for the Protocol SPX Option 2-109
PROTOCOL SPX 2-109
MINIMUM SPX RETRIES number 2-110
SPX ABORT TIMEOUT number 2-110
SPX CONNECTIONS number 2-111
SPX LISTEN TIMEOUT number 2-111
SPX VERIFY TIMEOUT number 2-112
Protocol TCPIP Option 2-114
Available Parameters and Values for the Protocol TCPIP Option 2-114
PROTOCOL TCPIP 2-115
xvi
Page 17

Contents
LAN Drivers 2-115
BIND odi_driver [number frame_type network_name] 2-116
IP Addresses 2-117
IP_ADDRESS ip_address [network_name] 2-118
IP_NETMASK net_mask_address [network_name] 2-119
IP_ROUTER ip_address [network_name] 2-120
Connection Sockets 2-120
Transmission Control Protocol (TCP) Sockets 2-121
TCP_SOCKETS number 2-121
User Datagram Protocol (UDP) Sockets 2-122
UDP_SOCKETS number 2-122
Raw Sockets 2-123
RAW_SOCKETS number 2-123
Additional Support 2-124
NO_BOOTP 2-124
PATH TCP_CFG [[ drive: ]path [ ; ... ]] 2-125
Transport Provider IPX | UDP Option 2-126
Available Parameters and Values for the Transport Provider IPX | UDP Option 2-126
TRANSPORT PROVIDER IPX | UDP 2-126
TRAP TARGET ipxaddress | ipaddress 2-127
3 Command Line Parameters Reference
Overview 3-2
Introduction 3-3
Core NetWare Client Software 3-4
IPXODI.COM 3-5
LSL.EXE 3-6
ODI LAN driver.COM 3-7
VLM.EXE 3-7
xvii
Page 18

Contents
DOSNP Software 3-10
4 System Messages
xviii
Page 19

1
Optimizing the NetWare Client
Software
1-1
Page 20
Optimizing the NetWare Client Software
Overview
Overview
This chapter explains how to optimize the NetWare® Client™ software for
increasing the speed of client workstations by using the Packet Burst™
protocol and Large Internet Packets (LIP). It also explains how to protect
information on client workstations.
The following topics are covered in this chapter.
Topic
Increasing Speed
Improving Security
Using Other Client Security Guidelines
1-2
Page 21
Optimizing the NetWare Client Software
Introduction
Introduction
You can increase the speed and improve the security of client workstations
by using the Packet Burst protocol and Large Internet Packets (LIPs), and by
implementing the NCP™ packet signature feature available in NetWare 4™
and 3.12 software.
1-3
Page 22
Optimizing the NetWare Client Software
Increasing Speed
Increasing Speed
NetWare 3.12 and 4 support the Packet Burst and Large Internet Packet
technologies which increase the access speed of network resources and
services for client workstations.
Using the Packet Burst Protocol
The Packet Burst protocol allows high-performance data transmission
between client workstations and servers.
Some network topologies, such as Ethernet and token ring, allow large
packets to be sent over the network. The LIP (Large Internet Packet)
capability enhances throughput over bridges or routers by increasing the
packet size.
The following sections provide you with information and procedures for
setting parameters used in the client workstation configuration file
(NET.CFG).
Packet Burst on the client workstation is enabled automatically in the
NetWare DOS Requester™ software.
Requirement for Packet Burst
The Packet Burst protocol code requires about 6 KB of memory. However,
as a default, the NetWare DOS Requester uses the Open Data-Link
Interface™ architecture for Packet Burst and doesn’t require additional
workstation memory.
How Packet Burst Works
At connection time, maximum burst sizes are negotiated with each server.
Since Packet Burst is established with each connection, it’s possible to
“burst” with one server but not with another.
Once you establish a Packet Burst connection between a client workstation
and a NetWare server, the client workstation automatically uses the Packet
Burst service whenever an application requests to write more than one
physical packet of data.
1-4
Page 23

Optimizing the NetWare Client Software
Increasing Speed
When to Use Packet Burst
Packet Burst is not required for every installation; however, disabling LIP
will results in noticeable speed degradation. Some network supervisors
might choose not to use Packet Burst because some of the servers that the
client workstations are connecting to do not support it.
Configuring for Packet Burst
Although Packet Burst is automatically enabled in the NetWare DOS
Requester, you can configure it for your needs.
See “PB BUFFERS=number” , “PBURST READ WINDOWS
SIZE=number” , and “PBURST WRITE WINDOWS SIZE=number” for
details on how to configure for Packet Burst.
Disabling Packet Burst
T o disable Packet Burst at client workstations, add this line to the NET.CFG
file under the “NetWare DOS Requester” option heading:
pb buffers = 0
For example, you would type
netware dos requester
pb buffers=0
Using Large Internet Packet Functionality
Large Internet Packet (LIP) functionality allows the packet size to be
increased from the default of 576 bytes. LIP is enabled automatically in the
NetWare DOS Requester software.
Previously, the size of packets that cross bridges or routers on NetWare
networks was limited to 576 total bytes. Some network architectures like
Ethernet and token ring allow larger packets to be sent over the network.
By allowing the packet size to be increased, LIP enhances the throughput
over bridges and routers if the routers aren’t limited to the smaller packet
size.
1-5
Page 24
Optimizing the NetWare Client Software
Increasing Speed
The following sections provide you with information and procedures for
setting parameters used in the client workstation configuration file
(NET.CFG).
The Large Internet Packet technology on the client workstation is enabled
automatically in the NetWare DOS Requester software.
NOTE: Some LAN drivers might not operate correctly using this parameter. If you
experience trouble, disable this parameter or update the version of your LAN driver.
How Large Internet Packet Works
In previous NetWare versions, the NetWare Client™ software initiated a
negotiation with the NetWare server to determine an acceptable packet size.
If the NetWare server software detected a router between it and the client
workstation, the server returned a maximum packet size of 576 bytes to the
NetWare Client software.
In the current NetWare version, the NetWare Client software still initiates
packet size negotiation. However, because of LIP, the NetWare server no
longer returns a packet size of 576 bytes when a router is detected.
Instead, the NetWare Client software negotiates with the NetWare server
software to agree on the largest packet size available.
When to Use Large Internet Packet
Large Internet Packet is not required for every installation; however,
disabling LIP results in noticeable speed degradation. Some network
supervisors might choose not to use Large Internet Packet because some of
the servers that the client workstations are connecting to do not support it,
such as NetWare 2 and NetWare 3.11 and earlier.
Configuring for Large Internet Packet
Although LIP is automatically enabled in the NetWare DOS Requester, you
can configure it for your needs.
See “LARGE INTERNET PACKETS=[on | off]” for details on how to
configure for Packet Burst.
1-6
Page 25

Optimizing the NetWare Client Software
Increasing Speed
Disabling LIP
To disable LIP functionality at the client workstation, add this line to the
NET.CFG file under the “NetWare DOS Requester” option heading:
large internet packets = off
For example, you would type
netware dos requester
large internet packets = off
1-7
Page 26
Optimizing the NetWare Client Software
Improving Security
Improving Security
You can increase the security of your network by using the NCP packet
signature feature available in NetWare 4 and 3.12.
The following sections provide you with information and procedures for
setting a parameter used in the client workstation configuration (NET.CFG)
file and the SET command used at each NetWare server.
Using NCP Packet Signature to Improve Security
NCP packet signature is an enhanced security feature that protects servers
and client workstations using the NetWare Core Protocol™ architecture by
preventing packet forgery.
The NCP packet signature is optional because the packet signature process
consumes CPU resources and slows performance, both for the client
workstation and the NetWare server.
Without the NCP packet signature installed, a knowledgeable network
operator can manipulate the client workstation software to send a forged
NCP request to a NetW are server . By for ging the proper NCP request packet,
an intruder can gain rights to access all network resources.
How NCP Packet Signature Works
NCP packet signature prevents forgery by requiring the server and the client
workstation to “sign” each NCP packet, using the RSA public and private
key encryption. The packet signature changes with every packet.
NCP packets with incorrect signatures are discarded without breaking the
client workstation’s connection with the server. However, an alert message
about the source of the invalid packet is sent to the error log, the affected
client workstation, and the NetWare server console.
If NCP packet signature is installed on the server and all of the network
client workstations, it is virtually impossible to forge an NCP packet that
would appear valid.
1-8
Page 27
Optimizing the NetWare Client Software
Improving Security
When to Use NCP Packet Signature
NCP packet signature is not required for every installation. Some network
supervisors might choose not to use it because they can tolerate certain
security risks.
Tolerable Security Risks The following are examples of network situations
that might not need NCP packet signature:
• Only executable programs reside on the server
• All client workstation users on the network are known and trusted by the network
supervisor
• Data on the NetWare server is not sensitive; access, loss, or corruption of this data
would not affect operations
Serious Security Risks NCP packet signature is recommended for security
risks such as these:
• Unauthorized client workstation users on the network
• Easy physical access to the network cabling system
• An unattended, publicly accessible client workstation within your network
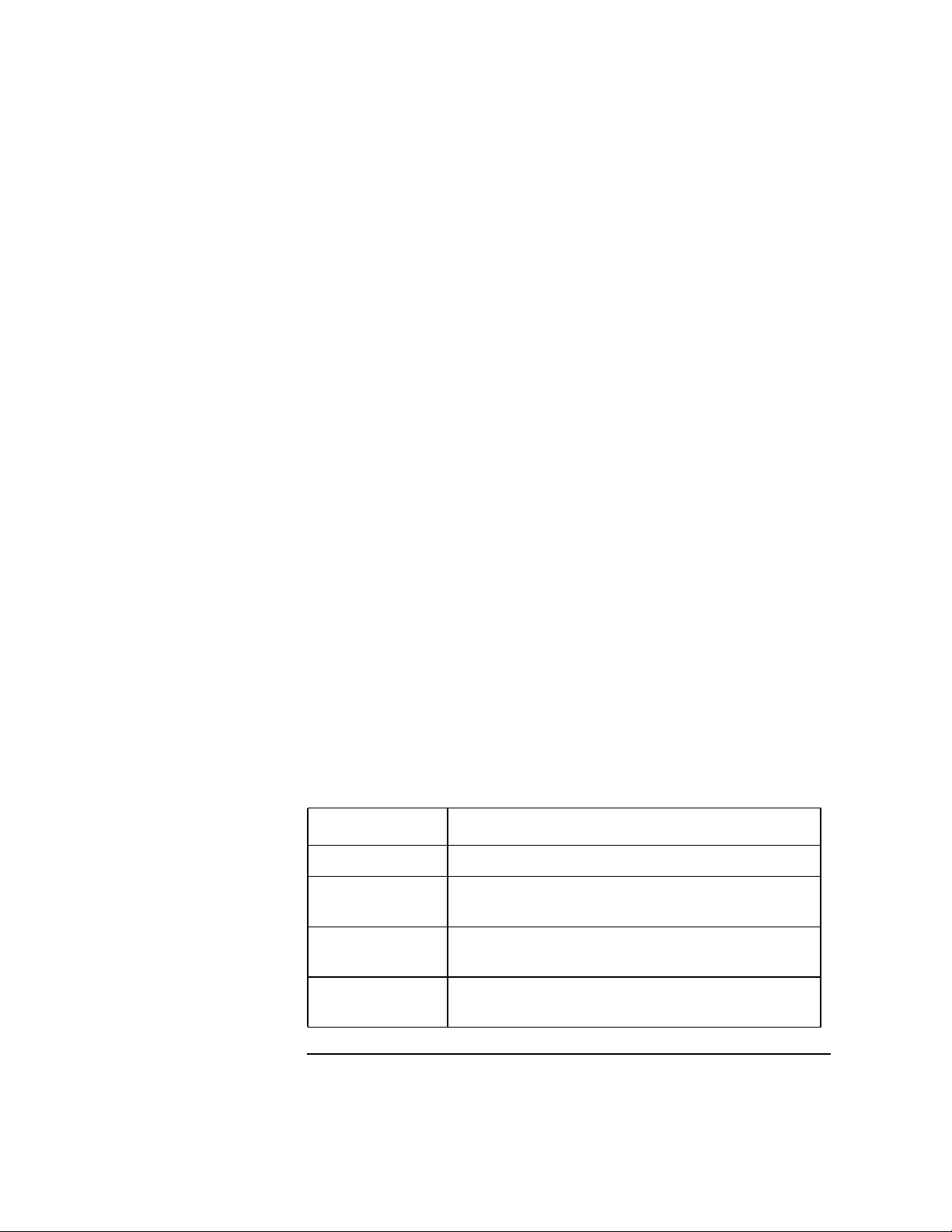
NCP Packet Signature Options
Several signature options are available, ranging from never signing NCP
packets to always signing NCP packets. NetWare servers and network client
workstations both have four signature levels, which are explained in the
following table.
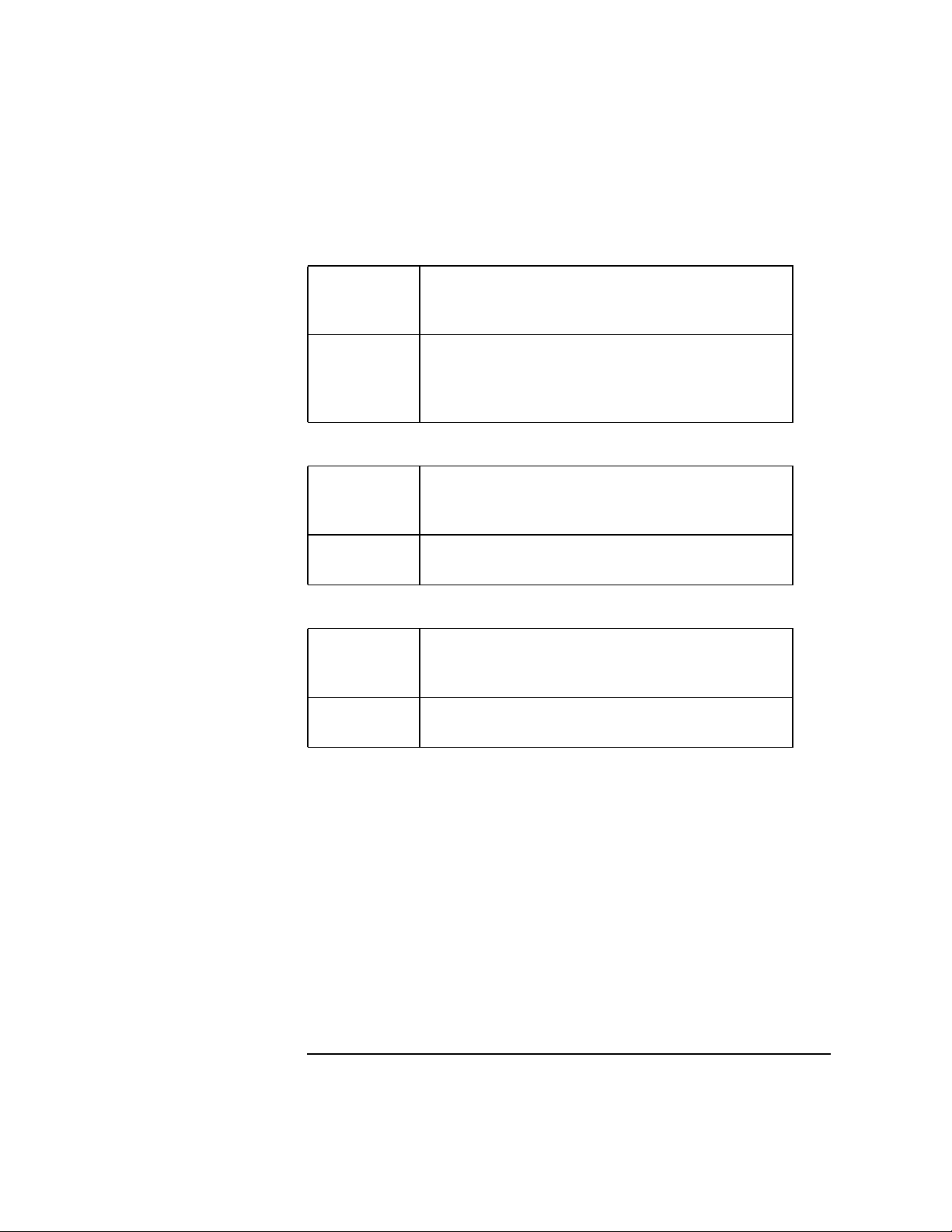
Table 1-1 NCP Packet Signature Levels
Level Number Explanation
0 Doesn’t sign packets.
1 Signs packets only if the server requests it (NetWare
server NCP option is 2 or higher).
2 Signs packets if the server is capable of signing
(NetWare server NCP option is 1 or higher).
3 Signs packets and requires the server to sign packets (or
logging in will fail).
1-9
Page 28
Optimizing the NetWare Client Software
Improving Security
Effective Packet Signature Levels
The signature levels for the server and the client workstations combine to
determine the overall level of NCP packet signature on the network called
the effective packet signature level.
Some combinations of server and client packet signature levels might slow
performance. However, low-CPU-demand systems might not show any
performance degradation.
You can choose the packet signature level that meets both their performance
needs and their security requirements.
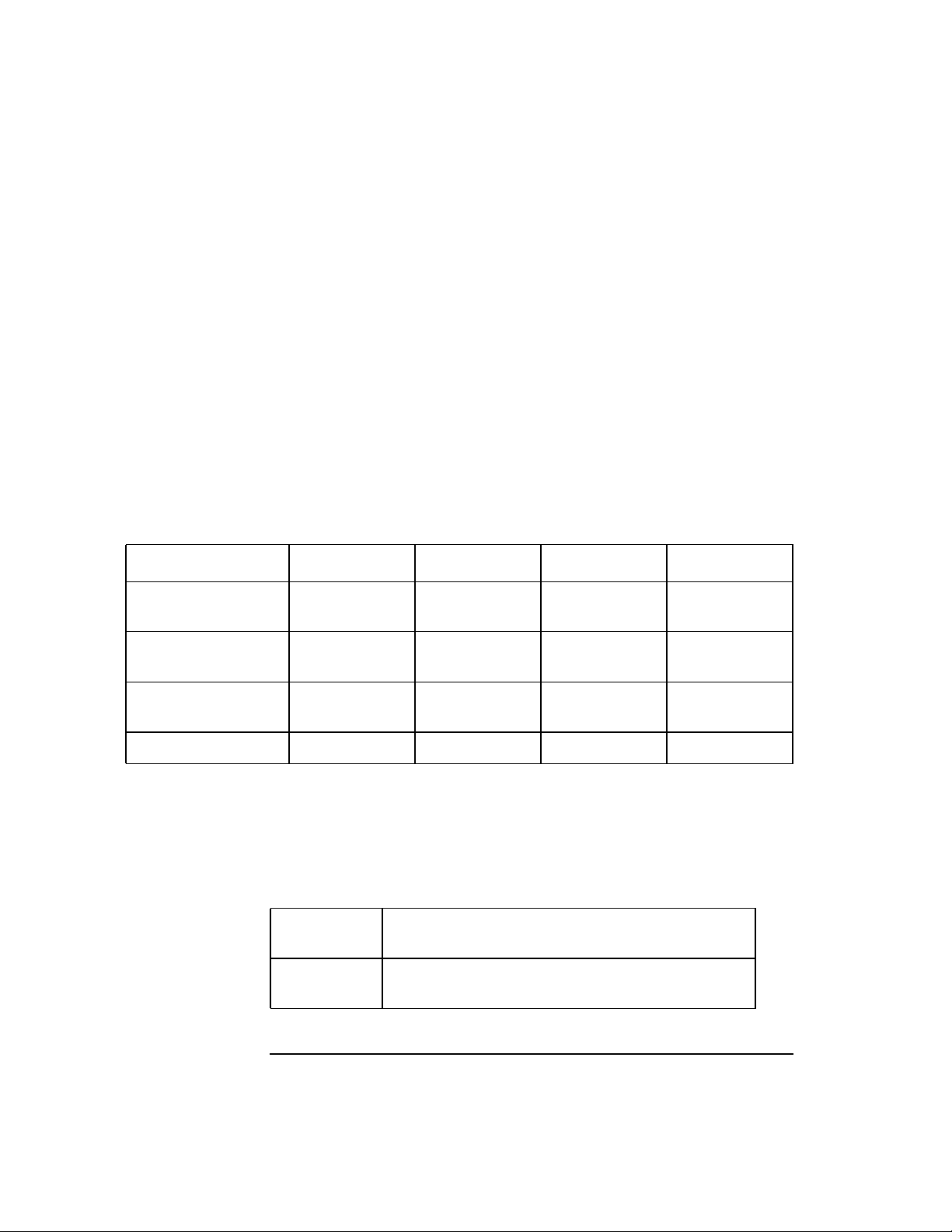
The following table shows the interactive relationship between the server
packet signature levels and the client workstation signature levels.
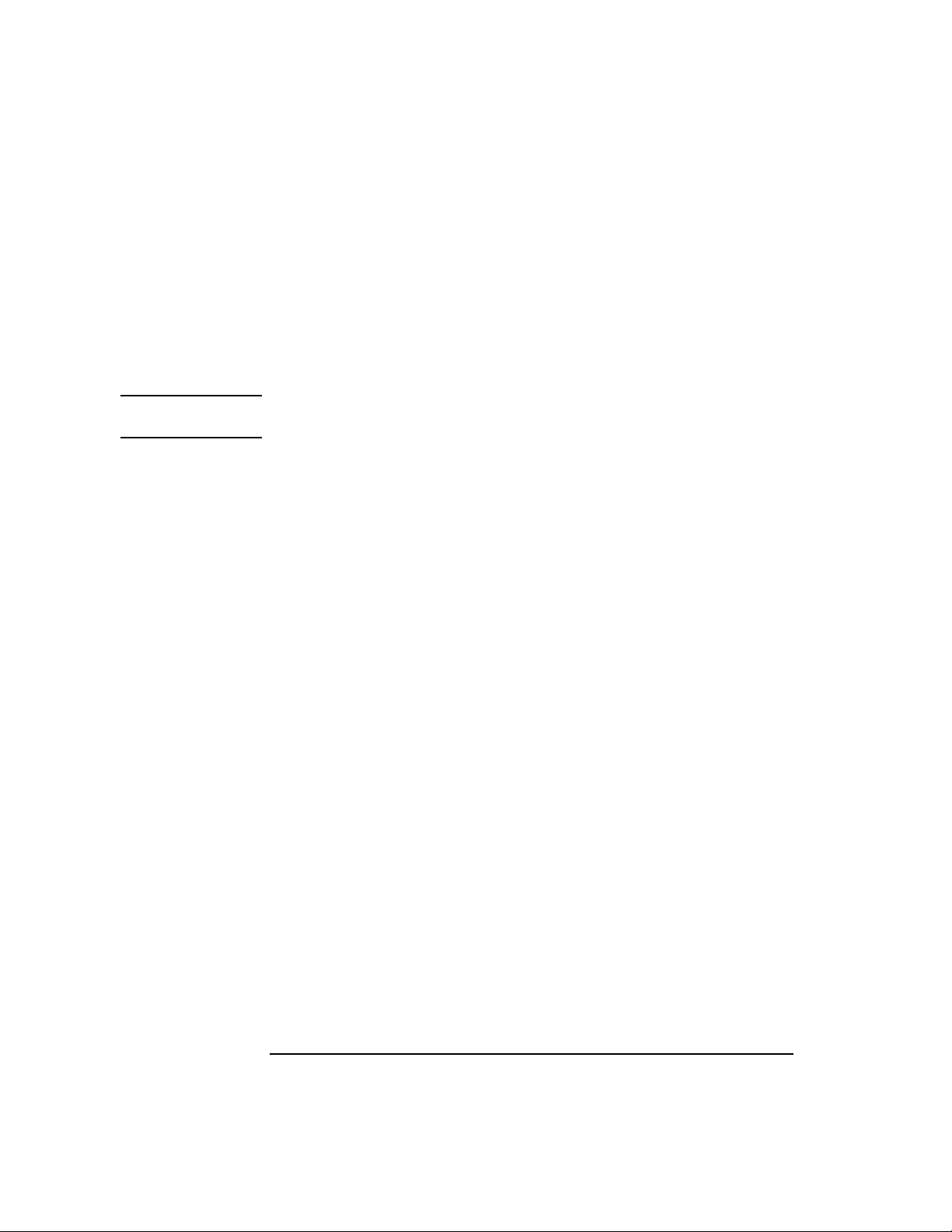
Table 1-2 Effective Packet Signature Combinations of Server and Client Workstations
IF Server = 0 Server = 1 Server = 2 Server = 3
Client Workstation = 0 No packet
signature
Client Workstation = 1 No packet
signature
Client Workstation = 2 No packet
signature
Client Workstation = 3 No logging in Packet signature Packet signature Packet signature
No packet
signature
No packet
signature
Packet signature Packet signature Packet signature
No packet
signature
Packet signature Packet signature
No logging in
Examples of Using Packet Signature Levels
This section includes some examples of when you would use different
signature levels.
All Information on the Server Is Sensitive
Example If an intruder gains access to any information on the
NetWare server, it could damage the company.
Solution The network supervisor sets the server to level 3 and all
client workstations to level 3 for maximum protection.
1-10
Page 29
Optimizing the NetWare Client Software
Improving Security
Sensitive and Nonsensitive Information Reside on the Same Server
Example The NetWare server has a directory for executable
programs and a separate directory for corporate finances
(such as accounts receivable).
Solution The network supervisor sets the server to level 2 and the
client workstations that need access to accounts
receivable to level 3. All other client workstations
remain at the default level 1.
Client Workstation Users Often Change Locations
Example The network supervisor is uncertain which employees
will be using which client workstations, and the NetW are
server contains some sensitive data.
Solution The network supervisor sets the server to level 3. Client
workstations remain at the default level 1.
Client Workstation Is Publicly Accessible
Example An unattended client workstation is set up for public
access to nonsensitive information, but another server on
the network contains sensitive information.
Solution The network supervisor sets the sensitive server to
level 3 and the unattended client workstation to level 0.
Installing NCP Packet Signature
To install the NCP packet signature support, you must set a parameter used
in the NET .CFG file on each client workstation and a SET command used at
each NetWare server.
Workstation Setting
To install NCP packet signature on a DOS or MS Windows client
workstation, add this line to the NET.CFG file under the NetWare DOS
Requester option:
signature level = number
For example, you would type
1-11
Page 30
Optimizing the NetWare Client Software
Improving Security
netware dos requester
signature level = 2
Replace number with 0, 1, 2, or 3. The default is level 1, which provides the
most flexibility while still offering protection from forged packets.
See “SIGNATURE LEVEL=number” for details on how to configure for
NCP packet signature support on the client workstation.
NOTE: Some LAN drivers might not operate correctly using this parameter. If you
experience trouble, disable this parameter or update the version of your LAN driver.
Server Setting
To ensure that the SET parameter “NCP PACKET SIGNATURE OPTION”
is added to the system at each server you want NCP packet signature support
on, type the following command at each server console:
SET NCP PACKET SIGNATURE OPTION = number <Enter>
Replace number with 0, 1, 2, or 3. The default is level 1, which provides the
most flexibility while still offering protection from forged packets.
See “Preventing Packet Forgery,” in Chapter 7 of Supervising the NetWork
for details on how to configure for NCP packet signature support on the
server.
Disabling Packet Signature
To disable NCP packet signature support at the client workstation, add this
line to the NET.CFG file under the “NetWare DOS Requester” option
heading:
signature level = 0
For example, you would type
netware dos requester
signature level = 0
For explanations of packet signature levels and their combined use, see
Table 1-1.
1-12
Page 31

Optimizing the NetWare Client Software
Improving Security
Troubleshooting NCP Packet Signature
This section describes some solutions to problems that might be associated
with using NCP packet signature.
Client Workstations Are Not Signing Packets
Problem Client workstations are not signing NCP packets.
Solution The SECURITY.VLM file is not loading. Ensure the signature
level on the client workstation is not set to 0.
SECURITY.VLM loads by default when the client signature
level is set to 1, 2 or 3.
Use the VLM /V4 command line parameter when
loading the VLM software to display load time
information.
Client Workstations Cannot Log In
Problem Client workstations cannot log in.
Solution Make sure the packet signature levels on the server and the
client workstation are correct. See “Effective Packet Signature
Levels”.
Note that the following situations do not allow logging in:
• Server packet signature = 3, client workstation signature = 0
• Server packet signature = 0, client workstation signature = 3
• The LOGIN utility is an older version that doesn’t support
packet signature
• The NetWare DOS Requester or the shell is an older version
that doesn’t support packet signature
1-13
Page 32

Optimizing the NetWare Client Software
Improving Security
The Error Message “Error Receiving from the Network” Appears
Problem The error message “Error receiving from the network”
appears.
Solution The client workstation is using a version of LOGIN.EXE file
that doesn’t include NCP packet signature. Make sure the new
LOGIN.EXE and other new utility files are installed on all
NetWare servers on the network.
Third-Party NLM Programs Do Not Work
Problem Third-party NetWare Loadable Module™ (NLM) programs
do not work.
Solution If the SET parameter “Allow Change to Client Rights” is set
to “OFF,” some third-party NLM™ programs might not
function. Set this parameter to “ON.”
Insecure Client Workstations Log In to a Secure Server
Problem Insecure client workstations log in to a secure server.
Solution
1-14
The client workstations are using an old LOGIN.EXE file that
does not include NCP packet signature. Make sure the new
LOGIN.EXE and other new utility files are installed on all
servers on the network.
Use the “Preferred Server” option in the NET.CFG file for all
client workstations that have access to secure servers (level
3). See “PREFERRED SERVER=“server_name” for details
on how to configure for this option.
Page 33

Optimizing the NetWare Client Software
Using Other Client Security Guidelines
Using Other Client Security Guidelines
In addition to installing NCP packet signature, you can use other NetWare
security features and protective measures to keep client workstations secure.
We suggest the following security guidelines for client workstations:
• Use only the most current versions of system software, NetWare Client software,
and patches.
• Check for viruses regularly.
• Use the SECURITY utility to detect vulnerable access points to the server.
• Enable intruder detection and lockout.
• Advise users to log out when their client workstations are unattended.
• Enable NCP packet signature level 3 on all unattended client workstations.
• Require passwords of at least five characters on all accounts.
• Force password changes at least every three months.
• Require unique passwords.
• Limit the number of grace logins.
• Limit the number of concurrent connections.
• Enforce login time restrictions and station restrictions.
1-15
Page 34

Optimizing the NetWare Client Software
Additional Information
Additional Information
Topic Reference
Setting up and modify your
NET.CFG file for Packet Burst,
LIP, and NCP packet signatures
Setting up Packet Burst support on
a NetWare server
Setting up Large Internet Packet
(LIP) support on a NetWare server
Setting up NCP packet signature
support on a NetWare server
Chapter 2, “NET.CFG Options
Reference”
Chapter 7, “Maintaining the NetWare
Server,” in Supervising the Network
Chapter 7, “Maintaining the NetWare
Server,” in Supervising the Network
Chapter 7, “Maintaining the NetWare
Server,” in Supervising the Network
1-16
Page 35

2
NET.CFG Options Reference
2-1
Page 36

NET.CFG Options Reference
Overview
Overview
This chapter explains how to create or modify a NET.CFG file and contains
an alphabetical listing and discussions of the currently available NET.CFG
file options.
The following topics are covered in this chapter.
Topic
Creating and Modifying a NET.CFG File
Using NET.CFG Options and Parameters
Using the NET.CFG Reference Pages
2-2
Page 37

NET.CFG Options Reference
Introduction
Introduction
NET.CFG is the configuration file that you use to specify nondefault value
settings for your NetWare Client™ software configuration options.
Use entries in the NET.CFG file to change the client workstation’s network
environment or configuration. For example, you might want to change the
configuration in these cases:
• You changed the default hardware settings on the network board
• You are using multiple protocols
• You are using the Novell® LAN Workplace® software
2-3
Page 38

NET.CFG Options Reference
Creating and Modifying a NET.CFG File
Creating and Modifying a NET.CFG File
1 Use a DOS text editor to type section headings and options in an existing
NET.CFG file or a NET.CFG file that you create to set up your client workstation
configuration.
The default location of the NET.CFG file is C:\NWCLIENT.
2 After a NET.CFG file is created or modified, copy or save the NET.CFG file to
the client workstation diskette or directory.
If all client workstations use the same NET.CFG file, you can save time by
copying the file onto a master client workstation diskette, then copying the
NET.CFG file to each client workstation. (The default location of the NET.CFG
file is C:\NWCLIENT.)
If each client workstation requires a unique NET.CFG file, you must copy a
unique file to each client workstation diskette or directory.
Entering Options and Parameters into the NET.CFG File
Use the following conventions when creating or modifying a NET.CFG file:
• Type one option or parameter per line.
Options and parameters are not case-sensitive unless used in quotation marks.
Blank lines are ignored, but they can be helpful in separating the options and
parameters to make the NET.CFG file easier to read.
• Enter options at the left margin of the file with no spaces before or after them.
Each option can have several parameters.
• Enter parameters, one per line, below the option that they apply to, and indent
each parameter line.
Use the Spacebar or T ab key to indent parameters. Parameters must be indented
at least one space.
• Place a hard return at the end of every line in the file, including the last line.
If you don’t put a return at the end of the last line, that line is ignored.
• Precede comment lines with a semicolon.
• User a semicolon (;) in front of a line to disable the option and parameter or write
a comment.
2-4
Page 39

NET.CFG Options Reference
Creating and Modifying a NET.CFG File
If a semicolon is placed in front of a NET .CFG option line, all of the parameters
listed below are disabled.
The following figure illustrates the NET.CFG file format.
Options typed flush
left, one per line.
link driver ne2000
int 4
port 360
frame ethernet_802.3
link driver ne1000
int 5
port 310
node address 02608c861759
link support
max stack 3
netware dos requester
preferred server=alpha
checksum=off
name context="o=sales"
first network drive=f
Figure 2-1 NET.CFG File Format
Settings indented
under option, one
setting per line.
Hard return and
line feed after all
lines, including the
last line.
Sample NET.CFG File
Following is a sample NET.CFG file that
• Changes the IRQ on the link driver to 4
• Changes the port to 340
• Sets up F: as the first network drive when logging in to the network
link driver ne2000
; Change the interrupt (IRQ) to 4
int #1 4
2-5
Page 40

NET.CFG Options Reference
Creating and Modifying a NET.CFG File
; Change the port to 340 (hex)
port #1 340
netware dos requester
; Set up F: as the first drive on network
first network drive = f
NOTE: Changing the value setting in the NET.CFG does not change the hardware setting for
the device you are using. Run the appropriate configuration utility or manually
change the appropriate jumper settings to correspond with value setting used in the
NET.CFG file.
2-6
Page 41

NET.CFG Options Reference
Using NET.CFG Options and Parameters
Using NET.CFG Options and Parameters
NetWare and Personal NetWare™ workstations support the following
configuration options in the NET.CFG file:
• Desktop SNMP Option
• Link Driver Option
• Link Support Option
• NetWare DOS Requester Option
• Protocol IPX Option
• Protocol SPX Option
• Protocol TCPIP Option
• Transport Provider IPX | UDP Option
NOTE: Because many products use the NET.CFG file for managing configuration
information, this might not be a comprehensive list of all the options used in your
NET.CFG file.
See the third-party manufacturer’s product documentation or the most current
README file provided with this NetWare Client for DOS and MS Windows kit for
information.
Table 2-1 shows the various parameters and values that you can use. Notice
the following markings in figure text:
* The default value is the maximum value for NetWare 2 and NetWare 3™
networks.
+This option is valid for NetWare 4™ networks only.
~ Defaults vary depending on your network setup. See the corresponding
option heading in this chapter for specific information.
2-7
Page 42

NET.CFG Options Reference
Using NET.CFG Options and Parameters
Table 2-1 NET.CFG Options
desktop snmp
asynchronous timeout number
control community [“name | public | private”]
enable control community [specified | any | off | omitted]
enable monitor community [specified | any | off | omitted]
enable trap community [specified | off | omitted]
monitor community [“name | public | private”]
snmpenableauthentrap [on | off]
syscontact “contact”
syslocation “location”
sysname “name”
trap community [“name | public | private”]
link driver driver_name
alternate
bus name number
dma [#1 | #2] channel_number
frame frame_type_name [addressing_mode]
irq [#1 | #2] interrupt_request_number
max frame size number
mem [#1 | #2] hex_starting_address [hex_length]
node address hex_address [mode]
port [#1 | #2] hex_starting_address [hex_number_of_ports]
protocol “name” hex_protocol_id frame_type
slot number
20 ticks
public
specified
specified
specified
public
off
(none)
(none)
(none)
public
(none)
(autodetect name), -1 (0FFh)
#1, 3
~
#1, 3
1024
#1, D000, ~
(none)
#1, 300, ~
(none)
1
link support
buffers communication_number [buffer_size]
max boards number
max stacks number
netware dos requester
auto large table=[on | off]
auto reconnect=[on | off]
auto retry=number
average name length=number
bind reconnect=[on | off]
broadcast retries=number
2-8
0, 1130
4
4
off
on
0
48
off
3
Page 43

Table 2-1 NET.CFG Options
NET.CFG Options Reference
Using NET.CFG Options and Parameters
broadcast send delay=number
broadcast timeout=number
cache buffer size=number
cache buffers=number
cache writes=[on | off]
checksum=number
confirm critical error action=[on | off]
connections=number*
dos name=”name”
eoj=[on | off]
exclude vim=path_vim
first network drive=drive_letter
force first network drive=[on | off]
handle net errors=[on | off]
large internet packets=[on | off]*
lip start size number
load conn table low=[on | off]
load low conn=[on | off]
local printers=number
lock delay=number
lock retries=number
long machine type=”name”
max tasks=number
message level=number
message timeout=number
minimum time to net=number
name context=”name_context”+
netware protocol=netware_protocol_list
network printers=number*
pb buffers=number
pburst read windows size=number
pburst write windows size=number
preferred server=”server_name”
preferred tree=”tree_name”+
preferred workgroup=”workgroup_name”
print buffer size=number*
print header=number*
print tail=number
read only compatibility=[on | off]
responder=[on | off]
0
2 ticks
(media maximum: 64 bytes)
5
on
1
on
8
msdos
on
(none)
(first available drive)
off
on
on
0
off
on
3
1 tick
1 tick
ibm-pc
31
1
0
0
root
nds bind pnw
3
3
16
10
(none)
(none)
(none)
64
64
16
off
on
2-9
Page 44

NET.CFG Options Reference
Using NET.CFG Options and Parameters
Table 2-1 NET.CFG Options
search mode=number
set station time=[on | off]
show dots=[on | off]
short machine type=”name’
signature level=number
true commit=[on | off]
use defaults=[on | off]
vim=path_vim
workgroup net=workgroup_net_address
protocol ipx
bind lan_driver_name [#number]
int64 [on | off]
int7a [on | off]
ipatch byte_offset, value
ipx packet size limit number
ipx retry count number
ipx sockets number
protocol spx
minimum spx retries number
spx abort timeout number
spx connections number
spx listen timeout number
spx verify timeout number
1
on
off
ibm
1
off
on
(none)
(none)
(none)
on
on
(none)
(lesser of either 4160 or size
specified by LAN driver)
20
20
20
540 (=30 seconds)
15
108 (=6 seconds)
54 (=3 seconds)
protocol tcpip
bind odi_driver [number frame_type network_name]
ip_address ip_address [network_name]
ip_netmask net_mask_address [network_name]
ip_router ip_address [network_name]
raw_sockets number
nb_adapter [0 | 1]
nb_brdcast [0 | 1]
nb_commands number
nb_domain domain_name
nb_sessions number
2-10
~
(none)
(none)
(none)
1
0
1
8
(none)
4
Page 45

Table 2-1 NET.CFG Options
NET.CFG Options Reference
Using NET.CFG Options and Parameters
no_bootp
path tcp_cfg [[ drive: ]path [; ...]]
tcp_sockets number
udp_sockets number
transport provider ipx | udp
trap target ipxaddress | ipaddress
(none)
c (drive) \net\tcp (path)
8
8
(none)
2-11
Page 46

Option name
Parameter name
Replace words in
italics with
specific values
What to type
Special
considerations
when using the
option
NET.CFG Options Reference
Using the NET.CFG Reference Pages
Using the NET.CFG Reference Pages
The following figure explains how to read the following NET .CFG reference
pages in this chapter.
Link Driver Option
Use this option to specify the hardware and software configurations
of the LAN drivers for each network board in your workstation.
The value settings you specify for each parameter with this option
should match the hardware and software settings for your network
board. This option also allows you to set up the proper frame type
and protocols for NetWare supported LAN drivers.
MEM [#1 | #2] hex_starting_address [hex_length]
Specifies a memory range to be used by the network board.
Syntax mem [#1 | #2] hex_starting_address [ hex_length ]
Replace hex_starting_address with the
hexadecimal physical (absolute) address of the
memory used by the network board.
Replace the hex_length with the memory address
range (in hexadecimal paragraphs, with one
paragraph of 16 bytes) used by the network
Default #1
Range When the node address on a network board is set
Example Therefore, for an NE2000 network board, you
Be sure you don't assign a range that is already used by other hardware. (VGA
Note
monitors commonly use a0000-C6FFF and XVGA monitors commonly use
a0000-CFFFF.)
board. Usually, the hex length is not needed.
from D0000 to D4000 (bytes), the starting address
is D0000 and the range is 400 hexadecimal
paragraphs.
would place the following lines in your NET.CFG
file:
link driver ne2000
mem d0000 400
Option
description
Parameter
description
Square brackets
mean the
value
is optional
Usage example
Figure 2-2 Format of NET.CFG Reference Pages
2-12
Page 47

NET.CFG Options Reference
Desktop SNMP Option
Desktop SNMP Option
Use this option to manage MIB-II support and communities for SNMP
desktops on NetWare and Personal NetWare networks.
Available Parameters and Values for the Desktop SNMP Option
This option has the following categories, parameters, and values.
Category Parameters and Values
Asynchronous
Timeout
Connections
Community
Types and
Names
Community
Access
Management
MIB-II
(Management
Information
Base) Support
ASYNCHRONOUS TIMEOUT number
MONITOR COMMUNITY [“name | public |
private”]
CONTROL COMMUNITY [“name | public |
private”]
TRAP COMMUNITY [“name | public | private”]
ENABLE MONITOR COMMUNITY [specified |
any | off | omitted]
ENABLE CONTROL COMMUNITY [specified |
any | off | omitted]
ENABLE TRAP COMMUNITY [specified | off |
omitted]
SNMPENABLEAUTHENTRAP [on | off]
SYSCONTACT “contact”
SYSLOCATION “location”
SYSNAME “name”
DESKTOP SNMP
Specifies the desktop SNMP option you are making configurations for.
2-13
Page 48

NET.CFG Options Reference
Desktop SNMP Option
Syntax
Example To identify the name of the system administrator for MIB
NOTE: For transport providers used with SNMP desktops, see “Transport Provider
IPX | UDP Option”.
desktop snmp
parameter_name value
Replace parameter_name with the name of the
parameter you want to use.
Replace value with the number or setting which
corresponds with the parameter name.
II, you would place these lines in your NET.CFG file:
desktop snmp
sysname “Suzanne Morley x893”
Asynchronous Timeout Connections
Use this parameter and value to manage the timeout for asynchronous
connections.
Parameter and Value
ASYNCHRONOUS TIMEOUT number
Desktop SNMP provides a way to monitor and control asynchronous
connections for managing Desktop SNMP and other SNMP entities over
asynchronous lines.
ASYNCHRONOUS TIMEOUT number
Monitors and controls your SNMP connections.
When an SNMP manager requests information from a managed object, the
desktop SNMP waits a set amount of time before attempting to cancel
requests it has made against managed objects.
2-14
Page 49

NET.CFG Options Reference
Desktop SNMP Option
Syntax
Default 20
Example For example, to have Desktop SNMP wait 35 system ticks
NOTE: The timeout number is in ticks (18.21 ticks per second on IBM* PCs and
compatibles).
asynchronous timeout number
(approximately 2 seconds) before attempting to cancel a
request, you would place the following lines in your
NET.CFG file:
desktop snmp
asynchronous timeout 35
Community Types and Names
Use these parameters and values to identify types and names of access
control groups.
Parameters and Values
MONITOR COMMUNITY [“name | public | private”]
CONTROL COMMUNITY [“name | public | private”]
TRAP COMMUNITY [“name | public | private”]
Desktop SNMP provides default community names for the monitor (readonly) and control (read/write) communities, as well as a default community
types used for traps. Desktop SNMP and other SNMP entities use these
types and names for access control.
The community name contained in a request message from an SNMP
management station must match the name expected by Desktop SNMP.
For examples of complete files, see “Example of NET.CFG Files Using the
Community Name and Types.”
2-15
Page 50

NET.CFG Options Reference
Desktop SNMP Option
NOTE: If Desktop SNMP receives a request protocol data unit (PDU) whose community
name is not authorized, it does not respond to the request.
For example, suppose the control community name is “secret,” and Desktop SNMP
receives a SETRequest PDU with a community name of “public.” Desktop SNMP
discards the SETRequest UDP and does not respond to the UDP. However, Desktop
SNMP does send an authentication trap to the trap targets if
SNMPENABLEAUTHENTRAPS ON.
A community name can be any arbitrary, case-sensitive ASCII string up to
32 characters in length. It can include any characters except space, tab, open
square bracket ( [ ), equal sign ( = ), colon ( : ), semicolon ( ; ), single
quotation mark ( “ ), or number sign ( # ).
Community name strings are case-sensitive. Therefore, always enclose the
community name string in double quotation marks.
In the Desktop SNMP section of the NET.CFG file, you can define three
communities, as described in the following table:
2-16
Page 51

NET.CFG Options Reference
Table 2-2 Desktop SNMP Option Parameters for Community Names
Parameter Explanation
control community Describes the read/write community (the
community that is allowed to do SET operations).
Any community name established for read/write
access is also valid for read-only access. The
default value is “public.” When the control
community is disabled, all write access is
disabled.
monitor community Describes the read-only community (the
community that is allowed to do GET and GET
NEXT operations). The default value is “public.”
When the monitor community is disabled, all
read access is disabled.
trap community Describes the community name used for traps.
The default value is “public.” When the trap
community name is disabled, Desktop SNMP
does not send traps.
Desktop SNMP Option
MONITOR COMMUNITY [“name | public | private”]
Specifies the monitor community name.
Syntax monitor community [“name | public | private”]
Default public
Example To specify the monitor community as “private,” you would
place the following lines in your NET.CFG file:
desktop snmp
monitor community “private”
2-17
Page 52

NET.CFG Options Reference
Desktop SNMP Option
CONTROL COMMUNITY [“name | public | private”]
Specifies the control community name.
Syntax control community [“name | public | private”]
Default public
Example To specify the control community as “secret,” you would
place the following lines in your NET.CFG file:
desktop snmp
control community “secret”
TRAP COMMUNITY [“name | public | private”]
Specifies the trap community name.
Syntax trap community [“name | public | private”]
Default public
Example To specify the trap community as “agenttrap,” you would
place the following lines in your NET.CFG file:
desktop snmp
trap community “agenttrap”
Community Access Management
Use these parameters and values to manage access control of SNMP agents
and resources.
Parameters and Values
ENABLE MONITOR COMMUNITY [specified | any | off | omitted]
ENABLE CONTROL COMMUNITY [specified | any | off | omitted]
ENABLE TRAP COMMUNITY [specified | off | omitted]
Community types can also be disabled. When a community type is disabled,
no management entity can access information for that community that you
named.
2-18
Page 53

NET.CFG Options Reference
Desktop SNMP Option
For example, if you disable the control community, no one can use Desktop
SNMP to do SET operations against the data it manages.
For examples of complete files, see “Example of NET.CFG Files Using the
Community Name and Types.”
Desktop SNMP reads the community name definition as follows, depending
on the enable community_type community line:
Table 2-3 Desktop SNMP Option Values for Community Type Parameters
Value Explanation
Any
Off If enable community_type community is set to
Omitted If enable community_type community is set to
Specified If enable community_type community is set to
If enable community_type community is set to
“any” for a community type, any community
string can be used to gain access. The line defining
the community name can be omitted. If it is
present, Desktop SNMP ignores it.
For trap community strings, the “any” option is not
applicable. If you specify enable trap community
any, Desktop SNMP interprets the line as if the
community type were specified.
“off” for a community type, access for that
community type is disabled. The line defining the
community name can be omitted. If the line is
present, Desktop SNMP ignores it.
“omitted” for a specific community type, Desktop
SNMP defaults to “specified” for that community
type and looks for a line defining a community
name for the community type. If no community
name is specified, Desktop SNMP defaults to
“public.”
“specified” for a community type, Desktop SNMP
uses only the specified community name for that
community type. If none is specified, Desktop
SNMP defaults to “public.”
2-19
Page 54

NET.CFG Options Reference
Desktop SNMP Option
ENABLE MONITOR COMMUNITY [specified | any | off | omitted]
Enables the value settings for the monitor community.
Syntax enable monitor community [specified | any | off | omitted]
Default specified
Example To enable the monitor community as “private” only, you
would place the following lines in your NET.CFG file:
desktop snmp
enable monitor community specified
ENABLE CONTROL COMMUNITY [specified | any | off | omitted]
Enables the value settings for the control community.
Syntax enable control community [specified | any | off | omitted]
Default specified
Example To enable full access to the control community “secret,”
you would place the following lines in your NET .CFG file:
desktop snmp
enable control community any
ENABLE TRAP COMMUNITY [specified | off | omitted]
Enables the value settings for the trap community.
Syntax enable trap community [specified |
off | omitted]
Default specified
Example To disable the trap community name “agenttrap,” you
would place the following lines in your NET.CFG file:
desktop snmp
enable trap community off
2-20
Page 55

NET.CFG Options Reference
Desktop SNMP Option
Example of NET.CFG Files Using the Community Name and Types
To use the default trap community, allow any community name to be used
for read access, but set the read/write community name to “secret,” you
would place the following lines in your NET.CFG file:
desktop snmp
enable monitor community any
enable control community specified
control community “secret”
To disable all traps and use the default values for the monitor and control
communities, you would place the following lines in your NET.CFG file:
desktop snmp
enable trap community off
To specify a NULL string for the control community and use the default
values for the monitor and trap communities, you would place the following
lines in your NET.CFG file:
desktop snmp
enable control community specified
control community “”
Setting a NULL string is the same as setting the enable community_type
community line to “off.”
To allow only the “private” community to have access and set the
community name for traps to “agenttrap,” you would place the following
lines in your NET.CFG file:
desktop snmp
enable monitor community specified
monitor community “private”
enable control community specified
control community “private”
enable trap community specified
trap community “agenttrap”
To temporarily allow any community name to have read-only access in the
previous example, you would modify the lines in your NET.CFG file as
follows:
2-21
Page 56

NET.CFG Options Reference
Desktop SNMP Option
desktop snmp
enable monitor community any
monitor community “private”
enable control community specified
control community “private”
enable trap community specified
trap community “agenttrap”
Desktop SNMP ignores the monitor community “private” line until you
reset the enable monitor community line to “specified.” This allows you to
temporarily change the value to “any” or “off” without deleting the specific
community name.
MIB-II (Management Information Base) Support
Desktop SNMP automatically supports three MIB-II groups:
• System and SNMP groups
• Interface group
• TCP/IP groups (all groups except interface, system, and SNMP, which are
supported by other VLM™ files, and EGP and transmission, which are not
supported)
System and SNMP Groups
Use these parameters and values to define information that can be retrieved
by SNMP management stations or reported in SNMP traps, which are
discussed on the indicated pages:
Parameters and Values
SNMPENABLEAUTHENTRAP [on | off]
SYSCONTACT “contact”
SYSLOCATION “location”
SYSNAME “name”
Desktop SNMP automatically supports two MIB-II groups, system and
SNMP. These groups provide SNMP management stations with information
about your workstation and about Desktop SNMP.
2-22
Page 57

You can define some parameters for your workstation environment in the
NET.CFG file (or other defined configuration file). The following table
explains these parameters.
Table 2-4 Desktop SNMP Option Parameters for MIB-II Support
Parameter Explanation
snmpenableauthentrap The snmpenableauthentraps parameter defaults to
“off.” When set to “on,” it instructs Desktop
SNMP to send a trap message if someone without
proper access tries to use SNMP to get or change
information that Desktop SNMP manages.
syscontact Use the real name of the person who should be
contacted if your workstation needs maintenance.
syslocation Use the physical location of your workstation.
sysname Use your user or login name—or your
TCP/IP host name, if one is assigned.
NET.CFG Options Reference
Desktop SNMP Option
Each of these parameters is optional and can be used in groups or separately .
The first parameter enables the workstation to notify a network supervisor
that an unauthorized user is trying to access the workstation without proper
authority.
The last three parameters define information that can be retrieved by SNMP
management stations or reported in SNMP traps.
Following is an example of a NET.CFG entry that notifies Suzanne Morley
that an unauthorized user is tying to access the network:
desktop snmp
sysname “Suzanne Morley x893”
syslocation “Building 2”
syscontact “suzanne@acompany.com”
snmpenableauthentraps on
2-23
Page 58

NET.CFG Options Reference
Desktop SNMP Option
NOTE: Always enclose the name, location, or contact information in quotation marks.
SNMPENABLEAUTHENTRAP [on | off]
Instructs the Desktop SNMP to send a trap message if someone without
proper access tries to use SNMP to get or change information that Desktop
SNMP manages.
Syntax snmpenableauthentrap [on | off]
Default off
Example To increase security on your workstation, you would
enable the Desktop SNMP to send a trap message to the
manager by placing the following lines in your NET.CFG
file:
desktop snmp
snmpenableauthentrap on
SYSCONTACT “contact”
Informs the SNMP manager of your workstation’s system administrator.
Syntax syscontact “contact”
Default None
Example To notify the SNMP manager that the name of your
workstation’s system administrator is “Bob Jones” at
“x324,” you would place the following lines in your
NET.CFG file:
desktop snmp
syscontact “Bob Jones x324”
2-24
Page 59

NET.CFG Options Reference
Desktop SNMP Option
SYSLOCATION “location”
Informs the SNMP manager of the physical location of your workstation.
Syntax syslocation “location”
Default None
Example To notify the SNMP manager that your workstation is in
“Building 2,” you would place the following lines in your
NET.CFG file:
desktop snmp
syslocation “Building 2”
SYSNAME “name”
Informs the SNMP manager of your username.
Syntax sysname “name”
Default None
Example To notify the SNMP manager of your username
“Suzanne,” you would place the following lines in your
NET.CFG file:
desktop snmp
sysname “Suzanne”
Interface Group
Desktop SNMP provides a separate VLM file, MIB2IF.VLM, that supports
the interface group. This group provides information about your network
connection, such as the number of packets transmitted and received and
whether it is Ethernet or token ring.
Add the following lines to the NET.CFG file:
netware dos requester
vlm=mib2if.vlm
2-25
Page 60

NET.CFG Options Reference
Desktop SNMP Option
NOTE: Always place the vlm=mib2if.vlm line after the lines that load the Desktop SNMP
VLM suite of files.
TCP/IP Groups
Desktop SNMP also provides a separate VLM file, MIB2PROT.VLM, that
supports the TCP/IP groups (all groups except interface, system, and SNMP,
which are supported by other VLM files, and EGP and transmission, which
are not supported).
Load this VLM when you are using the TCP/IP stack from LAN
WorkPlace® software.
Add the following lines to the NET.CFG file:
netware dos requester
vlm=mib2prot.vlm
NOTE: Always place the vlm=mib2prot.vlm line after the lines that load the Desktop SNMP
VLM suite of files.
Example of NET.CFG File Including Each Group Support
On a workstation where the NetWare DOS Requester™ and comprehensive
MIB-II support are both loaded, the entire Netware DOS Requester and
Desktop SNMP sections of your NET.CFG file might read as follows:
netware dos requester
vlm=wssnmp.vlm
vlm=wstrap.vlm
vlm=wsreg.vlm
vlm=wsasn1.vlm
vlm=mib2if.vlm
vlm=mib2prot.vlm
desktop snmp
sysname “Suzanne Morley x893”
syslocation “Building 2”
syscontact “Suzanne@acompany.com”
snmpenableauthentraps on
2-26
Page 61

NET.CFG Options Reference
Link Driver Option
Link Driver Option
Use this option to specify the hardware and software configurations of the
LAN drivers for each network board in your workstation.
The value settings you specify for each parameter with this option should
match the hardware and software settings for your network board.
This option also allows you to set up the proper frame type and protocols for
NetWare supported LAN drivers.
Available Parameters and Values for the Link Driver Option
This option has the following parameters and values.
Parameters and Values
ALTERNATE
BUS ID name number
DMA [#1 | #2] channel_number
FRAME frame_type_name [addressing_mode]
IRQ [#1 | #2] interrupt_request_number
MAX FRAME SIZE number
MEM [#1 | #2] hex_starting_address [hex_length]
NODE ADDRESS hex_address [mode]
PORT [#1 | #2] hex_starting_address [hex_number_of_ports]
PROTOCOL “name” hex_protocol_ID frame_type
SAPS number
SLOT number
LINK DRIVER driver_name
Specifies the LAN driver you are making configurations for.
2-27
Page 62

NET.CFG Options Reference
Link Driver Option
Syntax
Default None
Example To configure an NE2000™ driver, you could type
ALTERNATE
link driver driver_name
parameter_name, value
Replace driver_name with the name of the LAN driver.
Replace parameter_name with the name of the parameter you
want to use.
Replace value with the value setting which corresponds with the
parameter name.
(See Table 2-6 “List of ODI LANB Driver Names and
Supported Network Boards” for more information.)
link driver ne2000
int 5
port 360
frame ethernet_802.2
Specifies an alternate network board. Normally , the LANSUP and NTR2000
drivers use the primary board.
Syntax alternate
Default None
Example To specify the LANSUP.COM driver to use an alternate
network board, you would place the following lines in
your NET.CFG file:
link driver lansup
alternate
BUS ID name number
Specifies the bus that the network board is inserted into. Use this parameter
with LAN drivers that support multiple bus types.
The currently defined bus ID types and numbers are as follows:
2-28
Page 63

NET.CFG Options Reference
Link Driver Option
Bus Type Identification Number
ISA 0
MCA 1
EISA 2
PCMCIA 3
PCI 4
VL (VESA Local Bus) 5
NOTE: This is not a conclusive list of bus types. You can obtain an updated list of identifiers
from the Novell Labs™ facility.
The default value indicates that the LAN driver should search each of the machine’s
buses for a supported network board. The LAN driver should then initialize the first
supported network board it finds. The LAN driver determines the order that the buses
are searched in.
Syntax
Default -1 0FFh
Example To specify the bus type for an ISA adapter, you would
DMA [#1 | #2] channel_number
bus id
Replace name with the name of the bus type you want
to use.
Replace number with the identification number
that corresponds with the bus type that you want
to use.
place the following lines in your NET.CFG file:
link driver ntr2000
name number
bus id isa 0
Specifies the hardware setting of the network board used in the workstation.
It allows DMA channels to be configured..
2-29
Page 64

NET.CFG Options Reference
Link Driver Option
Syntax
Default #1
Example
FRAME frame_type_name [addressing_mode]
dma [#1 | #2]
Enter the channel number to be used. You can specify
two DMA values.
If the first configurable DMA channel on your NE2100
network board uses DMA channel 3 and the second
configurable channel uses channel 4, you would place the
following lines in your NET.CFG file:
link driver ne2100
dma #1 3
dma #2 4
channel_number
TM
Enables the frame types used by the LAN driver.
When the LAN driver initializes the network board, it creates a logical board
for the frame type name that is specified. You can create multiple frame
types concurrently on each client workstation.
This parameter also allows for configuration of the addressing mode for
some LAN drivers on the basis of frame types. The following keywords
determine the address mode:
• LSB canonical addressing mode
• MSB non-canonical addressing mode
For example, the frame type Token-Ring can be used in LSB.
Syntax
2-30
frame
Replace frame_type_name with the supported frame type of
the network you are connecting to.
Replace addressing_mode with the address mode for your
frame type.
frame_type_name [addressing_mod]
Page 65

NET.CFG Options Reference
Link Driver Option
Default
Example To enable the Token-Ring frame type for an NTR2000 LAN
NOTE: The NetWare Client binds to the first frame type listed under the LINK DRIVER
heading.
Ethernet LAN drivers: Ethernet_802.2
Token-ring LAN drivers: Token-Ring
TCP/IP LAN driver SLIP_PPP: SLIP
See Table 2-4 “List of Frame Types, Protocols, and LAN
Drivers” for more information.
driver, you would place the following lines in your NET.CFG
file:
link driver ntr2000
token-ring lsb
T o enable the Ethernet_II and Ethernet 802.2 frame type for an
NE2000 LAN driver, you would place the following lines in
your NET.CFG file (for two logical networks):
link driver ne2000
frame ethernet_ii
frame ethernet_802.2
Frame Types, Protocols, and LAN Drivers
The following table shows the frame types currently defined by Novell and
their respective protocols. Included is a list of the supporting LAN drivers
for each frame type that currently ship with the NetWare Client Kit for DOS
and MS Windows.
2-31
Page 66

NET.CFG Options Reference
Link Driver Option
Table 2-5 List of Frame Types, Protocols, and LAN Drivers
Frame Type and Description Protocols LAN Drivers
ETHERNET_802.2
Ethernet (802.3) using an 802.2
envelope
ETHERNET_802.3
IPX 802.3 raw encapsulation
IPX/SPX 3C1100, 3C501, 3C501, 3C503, 3C505,
3C523, 3C5X9, CEODI, E20ODI,
E2HODI, E30ODI, E31ODI, ES3210,
EXP16ODI, HPMCAODI, IBMFDDIO,
IBMODISH, ILANAT, INTEL593,
INTEL595, INTEL596, LANSUP,
NCRWL05, NE1000, NE1500T, NE2,
NE2_32, NE2000, NE2100, NE3200,
NI5210, NI6510, NI9210, ODINSUP,
PCMDM, PE2ODI, SMC8000, TCE16A TW ,
TCE16MCW, TCE32MCW, TCNSW,
UBODI
IPX/SPX 3C1100, 3C501, 3C501, 3C503, 3C505,
3C523, 3C5X9, CEODI, E20ODI,
E2HODI, E30ODI, E31ODI, ES3210,
EXP16ODI, HPMCAODI, IBMFDDIO,
IBMODISH, ILANAT, INTEL593,
INTEL595, INTEL596, NCRWL05,
NE1000, NE1500T , NE2, NE2_32, NE2000,
NE2100, NE3200, NI5210, NI6510,
NI9210, ODINSUP, PCMDM, PE2ODI,
SMC8000, TCE16ATW, TCE16MCW,
TCE32MCW, TCNSW, UBODI
ETHERNET_II
Ethernet using a DEC Ethernet II
envelope
2-32
IP
IPX/SPX
3C1100, 3C501, 3C501, 3C503, 3C505,
3C523, 3C5X9, CEODI, E20ODI,
E2HODI, E30ODI, E31ODI, ES3210,
EXOS, EXP16ODI, HPMCAODI,
IBMFDDIO, IBMODISH, ILANAT,
INTEL593, INTEL595, INTEL596,
NCRWL05, NE1000, NE1500T, NE2,
NE2_32, NE2000, NE2100, NE3200,
NI5210, NI6510, NI9210, ODINSUP,
PCMDM, PE2ODI, SMC8000, TCE16A TW ,
TCE16MCW, TCE32MCW, TCNSW,
UBODI
Page 67

Table 2-5 List of Frame Types, Protocols, and LAN Drivers
Frame Type and Description Protocols LAN Drivers
NET.CFG Options Reference
Link Driver Option
FDDI_802.2
FDDI using an 802.2 envelope
IP
IP Tunnel frame envelope
Token-Ring
Token ring (802.5) using an 802.2
envelope
NOTE: † Currently, no LAN drivers supporting this frame type are available in the NetWare
Client for DOS and MS Windows Client kit. Contact third-party vendors for details.
IPX/SPX †
IP
IPX/SPX
IPX/SPX
RPL
SNA
NetBIOS
†
LANSUP, MADGEODI, NTR2000,
ODINSUP, OSH391R, OSH392R,
OSH89XR, OSH990R, SMC8100, T20ODI,
T30ODI, TCTOKSH, NTR2000
You can specify more than one frame type statement for a single driver.
For example, you can specify that an Ethernet NE2000 board can use both
Ethernet_802.2 and Ethernet_802.3 frame types.
802.2 is the type of communications sent on one network, and 802.3 is the
type of communication sent on the other network.
Ethernet LAN Drivers
For Ethernet, enable Ethernet_802.3, Ethernet_II, and Ethernet_802.2 frame
types.
You can use up to four frame types for a single Ethernet cable segment.
You can use either four network boards each with one frame type defined, or
you can use one network board with four frames defined, or any similar
combination.
Token-Ring LAN Drivers
For token ring, enable token ring frame types.
2-33
Page 68

NET.CFG Options Reference
Link Driver Option
IRQ [#1 | #2] interrupt_request_number
Specifies which interrupt (IRQ) the network board is set to use.
Syntax irq [#1 | #2] interrupt_request_number
Use the same interrupt request number that is set
on the network board.
Default #1
See your LAN driver documentation for the
specific IRQ default values.
Example To specify interrupt 5 on an NE2100 network board, you
would place the following lines in your NET.CFG file:
link driver ne2100
irq 5
To specify more than one interrupt request number,
you could place the following lines in your NET .CFG
file:
link driver ne2100
irq #1 5
irq #2 3
NOTE: The syntax for this parameter has changed from INT to IRQ. The INT syntax is still
supported, but it is recommended that you update client workstations to use IRQ.
Before changing the value of the interrupt request number for your network
board, be sure you know what interrupt value settings are used on other
hardware (such as monitors) that you are using.
For example, interrupts 2 and 9 through 15 are usually reserved, so don’t use
those numbers (especially 2) for your network board.
We recommend using 3, 5, or 7 for most network boards.
MAX FRAME SIZE number
Sets the maximum number of bytes that can be put on the network by the
NTR2000.COM and LANSUP.COM LAN drivers.
2-34
Page 69

NET.CFG Options Reference
Link Driver Option
Syntax max frame size number
If the line speed is 16 Mbps, the value for number
must be between 638 and 17,954. If the line speed is 4
Mbps, the value must be between 638 and 4464.
The value must include the number of bytes for the
data packet (usually 1, 2, 4, or 8KB), and for the
largest possible header (currently, 52 bytes LAN
header + 74 bytes protocol header = 126 bytes).
For example, to use 2KB data packets, you would
calculate the value for number as
2048 + 52 + 74 = 2174
Default The NTR2000.COM driver’s default size is 4222 bytes. But if
your network board has 8 KB of shared RAM available, the
default size is 2174 bytes.
The LANSUP .COM driver’s default is 1150 bytes. But
if you’re using the IBM LAN Support Program with
an Ethernet network board driver , the maximum size
is 1496 bytes.
Example To specify the maximum frame size of an NTR2000 LAN
driver, you would place the following line in your NET.CFG
file:
link driver ntr2000
max frame size 2174
If you are running MS Windows in enhanced mode, the VIPX.386 device
driver requires the maximum frame size to be less than 8000 bytes. If the
frame size exceeds 8000 bytes, network communication fails.
MEM [#1 | #2] hex_starting_address [hex_length]
Specifies a memory range to be used by the network board.
Syntax
mem [#1 | #2] hex_starting_address [hex_length]
2-35
Page 70

NET.CFG Options Reference
Link Driver Option
Replace hex_starting_address with the
hexadecimal physical (absolute) address of the
memory used by the network board.
Replace the hex_length with the memory address
range (in hexadecimal paragraphs, with each
paragraph being 16 bytes) used by the network
board. Usually, the hex length is not needed.
Default #1
Example When the node address on a network board is set from
D0000 to D4000 (bytes), the starting address is D0000 and
the range is 400 hexadecimal paragraphs.
Therefore, for an NE2000 network board, you
would place the following lines in your NET .CFG
file:
link driver ne2000
mem d0000 400
Assign each board a unique memory range.
Be sure you don’t assign a range that is already used by other hardware.
(VGA monitors commonly use A0000-C6FFF and XVGA monitors
commonly use A0000-CFFFF.)
NODE ADDRESS hex_address [mode]
Overrides the hard-coded node address in the LAN driver, if the hardware
allows it. The new address is used to program the network board.
Changing the node address for a network board can create conflicts with
other LAN drivers. Use the hard-coded node address whenever possible.
You can use either the canonical or non-canonical mode. Use the following
keywords to determine the mode:
• LSB (canonical addressing mode)
• MSB (non-canonical addressing mode)
2-36
Page 71

NET.CFG Options Reference
Link Driver Option
For example, node addresses for both modes could appear as follows:
• node address 0800005A656BL (canonical LSB)
• node address 1000005AA6D6M (non-canonical MSB)
NOTE: If the “M” or “L” is not specified, the default mode for the node address is the
physical layer form of the address.
Syntax node address hex_address [mode]
Default None
Example To change the node address of an NTR2000 LAN driver to
“1000005aa6d6” for non-canonical mode, you would
place the following lines in your NET.CFG file:
link driver ntr2000
node address 1000005aa6d6m
NOTE: Even though FDDI is a non-canonical topology at the physical layer, all address are
sent and received in canonical (LSB) mode.
A node labeled with an “M” for non-canonical mode address supports media setup
for canonical mode, because the LAN driver simply swaps the provided address to
obtain the appropriate canonical (LSB) address.
LANSUP
This parameter allows the LANSUP.COM file set to the frame size for a
token-ring driver.
Syntax open
Default None
Example
To allow the RPL protocol to increase the frame size
for a remote boot workstation running the LANSUP
software above 1 KB, you would place the following
lines in your NET.CFG file:
link driver lansup
open
2-37
Page 72

NET.CFG Options Reference
Link Driver Option
If the IBM LAN Support driver’s DXMT0MOD.SYS file is to load in the
CONFIG.SYS file, one of two actions must be performed:
1 Set “o=n” on the command line for loading the DXMT0MOD.SYS file in the
CONFIG.SYS file and use this parameter in the NET.CFG file.
2 Set “o=y” on the command line to load the DXMT0MOD.SYS file and set the
frame size for the NDIS driver. Do not use this parameter in the NET.CFG file.
PORT [#1 | #2] hex_starting_address [hex_number_of_ports]
Specifies the starting port (hex_starting_address) and number of ports in the
range (hex_number_of_ports).
Syntax port [#1 | #2] hex_starting_address
[hex_number_of_ports]
All values must be written in hexadecimal
notation.
Default #1
Example If the starting I/O port on an NE2100 LAN driver is 300
and 16 ports are in the first range, you would place the
following lines in your NET.CFG file:
link driver ne2100
port 300 16
T o specify two ranges with 32 ports in each range, you
could place the following lines in your NET.CFG file:
link driver ne2100
port #1 300 32
port #2 340 32
2-38
Page 73

NET.CFG Options Reference
Link Driver Option
PROTOCOL “name” hex_protocol_ID frame_type
Allows existing LAN drivers to handle new network protocols.
Syntax
Default None
Example To use a new protocol named “XYZ” with an
protocol name hex_protocol_ID frame_type
Replace name with the name of the new protocol.
Replace hex_protocol_ID with the assigned
hexadecimal protocol ID that the protocol is
assigned.
Replace frame_type with the frame type that the
new protocol ID applies to.Table 5-6 for more
information.
NE/2-32™ LAN driver using the Ethernet_II frame type,
you would place the following lines in your NET .CFG file:
link driver ne2_32
frame ethernet_II
protocol xyz 904a ethernet_II
Defined Protocols and Frame Types
The following table lists the protocols and frame types currently defined
within the industry and their corresponding protocol ID and frame ID
numbers.
2-39
Page 74

NET.CFG Options Reference
Link Driver Option
Table 2-6 List and Description of Protocols and Frame Types with Their Identification
Numbers
Frame
ID
2 ETHERNET_II IPX/SPX 8137h Ethernet using a DEC* Ethernet II
2 ETHERNET_II IP 800h Ethernet using a DEC Ethernet II
3 ETHERNET_802.2 IPX/SPX E0h Ethernet (802.3) using an 802.2
4 Token-Ring IPX/SPX E0h Token ring (802.5) using an 802.2
5 ETHERNET_802.3 IPX/SPX 00h IPX 802.3 raw encapsulation
19 IP IPX/SPX N/A IP Tunnel frame envelope
20 FDDI_802.2 IPX/SPX E0h FDDI using an 802.2 envelope
Frame Type Protocol
SLOT number
Protocol
ID
Number
Description
envelope
envelope
envelope
envelope
In slot-based machines, the LAN driver usually locates the network board by
scanning through the slots in order from lowest to highest.
This option directs the driver to locate the network board in the specified
slot, instead of scanning for it.
Syntax slot number
Use the number of the slot you inserted the
network board into. The slot number is usually
found on the back of the computer.
Default None
2-40
Page 75

NET.CFG Options Reference
Link Driver Option
Example If you were using two NE/2™ boards in the same
workstation and you inserted one network board into slot 1
and the other into slot 2, you would place the following
lines in your NET.CFG file:
link driver NE2
slot 1
link driver NE2
slot 2
Listing of Commonly Used ODI LAN Drivers
The following table lists some of the common ODI™ LAN drivers used
with NetWare Client™ software for DOS and MS Windows.
This is not a comprehensive list of all LAN drivers certified by Novell. See
the documentation included with your network board for information
concerning the appropriate LAN driver to use with the NetWare operating
system.
The table also includes a list of ODI LAN driver names and supported
network boards. for information on the available parameters for each driver,
see the .INS file accompanying each LAN driver.
Driver Name
(.COM)
3C501
3C501
3C503 3Com 3C503 EtherLink II*
3C505 3Com 3C505 EtherLink Plus*
3C523 3Com EtherLink/MC
3C5X9 3Com EtherLink III* Parallel Tasking Family
3Com* 3C1100 3Station* Ethernet
3Com 3C501 EtherLink*
3Com 3C503 EtherLink II TP
3Com 3C503 EtherLink II/163C
3Com 3C503 EtherLink II/16 TP
3Com EtherLink/MC TP
Network Board
2-41
Page 76

NET.CFG Options Reference
Link Driver Option
Driver Name
(.COM)
CEODI Xircom Credit Card Ethernet Adapter
E20ODI Cabletron Systems Ethernet E20
E2HODI Cabletron Systems Ethernet E2HUB
E30ODI Cabletron Systems Ethernet E3010
Cabletron Systems Ethernet E3010-X
Cabletron Systems Ethernet E3020
Cabletron Systems Ethernet E3020-X
Cabletron Systems Ethernet E3030
Cabletron Systems Ethernet E3030-X
Cabletron Systems Ethernet E3040E
Cabletron Systems Ethernet E3040-X
E31ODI Cabletron Systems Ethernet E31
Cabletron Systems Ethernet E31-X
ES3210 Racal-Datacom* ES3210
EXP16ODI Intel EtherExpress* ISA Family
Intel EtherExpress MCA Family
HPMCAODI Hewlett-Packard* MC Adapter 16
Network Board
HPISAODI.COM Hewlett-Packard PC Adapter 8/16/16+
HP32ODI.COM HP* Ethertwist LAN Adapter/32
AM2100.COM HP PC LAN Adapter NC/16 TP
IBMFDDIO IBM FDDI
IBMODISH IBM PS/2 Ethernet Adapter
ILANAT Racal-Datacom InterLan AT/XT
INTEL593 Intel 593 Based Adapter
Zenith Data Systems Z-NOTE
INTEL595 Intel 82595 Based Adapter
INTEL596 Intel 596 Based Adapter
2-42
Page 77

NET.CFG Options Reference
Link Driver Option
Driver Name
(.COM)
LANSUP ODI Module for the IBM LAN Support Program
MADGEODI
NCRWL05 NCR* WaveLAN*
NE1000 Novell Ethernet NE1000
NE1500T Novell Ethernet NE1500TN
NE2 Novell Ethernet NE/2
NE2_32 Novell Ethernet NE2-32
NE2000 Novell Ethernet NE2000
NE2100 Novell Ethernet NE2100
NE3200 Novell Ethernet NE3200
Madge Smart 16/4 PC Ringnode
Madge Smart 16/4 AT Ringnode
Madge Smart 16/4 MC Ringnode
Madge Smart 16/4 MC32 Ringnode
Madge Smart 16/4 EISA Ringnode
Madge Smart 16/4 EISA Mk II Ringnode
National Semiconductor NE2000 InfoMover
Network Board
NE3300.COM Microdyne NE3300 Ethernet
NI5210 Racal-Datacom NI5210
NI6510 Racal-Datacom NI6510
NI9210
NTR2000
Racal-Datacom NI9210
Novell NTR2000 Token-Ring Adapter
IBM Token-Ring Network Adapter II
IBM Token-Ring Network 16/4 Adapter
IBM Token-Ring Network Adapter /A
IBM Token-Ring Network 16/4 Adapter /A
IBM Token-Ring 16/4 Credit Card Adapter compatible
2-43
Page 78

NET.CFG Options Reference
Link Driver Option
Driver Name
(.COM)
NULLDRV This is not a working LAN driver. The NetWare client
installation program copies this file to the client
directory during installation for dedicated (not ODI)
IPX drivers.
Contact the network board manufacturer for copies of
the latest ODI drivers.
This LAN driver can also be used to support the
Personal NetW are™ client and server software running
on a workstation without a network board installed.
OC32TR16.COM Olicom EISA 32 Token-Ring 16/4 Adapter
OCTOK16.COM Olicom Token-Ring MC 16/4 Adapter
OSH391R Proteon p1391 RapiDriver
OSH89XR Proteon p189X RapiDriver
OSH990R Proteon p1990 RapiDriver
ODINSUP ODI Module for the NDIS protocol stack
PCMDM NSC Ethernet PCMCIA Card
Network Board
PE2ODI Xircom Credit Card Ethernet Adapter
SLIP_PPP Novell LAN WorkPlace® Asynchronous SLIP & PPP
Driver
This driver runs on workstations serial hardware with
either PPP or SLIP frame types. It supports both direct-
connection line and indirect modem connections.
SMC8000 SMC* EtherCard* PLUS* Family Adapter
SMC8100 SMC Token Ring Elite Family Adapter
SMC9000.COM Standard Microsystems Corporation SMC9000
2-44
Page 79

NET.CFG Options Reference
Link Driver Option
Driver Name
(.COM)
SMCARCWS SMC PC130/130E/270E
SMC PC500WS/550WS (short or long card)
SMC PC600WS/650WS
SMC PS110//210/310 PS/2
T20ODI Cabletron Systems Token-Ring T20
T30ODI Cabletron Systems Token-Ring T30
TCCARC Thomas-Conrad TC6x42 ARCnet 8-bit Adapter
Thomas-Conrad TC6x45 ARCnet 16-bit Adapter
Thomas-Conrad TC6x46 ARCnet MC Adapter
TCE16ATW Thomas-Conrad TC5045 Ethernet Adapter
TCE16MCW Thomas-Conrad TC5046 Ethernet Adapter - 16 bit
TCE32MCW Thomas-Conrad TC5046 Ethernet Adapter - 32 bit
TCNSW Thomas-Conrad TC3042 TCNS 8-bit Adapter
Thomas-Conrad TC3045 TCNS 16-bit Adapter
Thomas-Conrad TC3046 TCNS MC Adapter
Thomas-Conrad TC3047 TCNS EISA Adapter
Network Board
TCTOKSH Thomas-Conrad TC4035/TC4045 Adapter
Thomas-Conrad TC4046 Adapter
TRXNET Novell RX-Net & RX-Net II®
Novell RX-Net/2T™
UBODI Ungermann-Bass* NIUpc/EOTP
Ungermann-Bass NIUps
Ungermann-Bass NIUpc
Ungermann-Bass Personal NIU/ex
Ungermann-Bass Personal NIU
2-45
Page 80

NET.CFG Options Reference
Link Support Option
Link Support Option
Use this option of the NET.CFG file to configure the number and size of the
receive buffers, the size of the memory pool buffers, and the number of
boards and stacks used by the Link Support Layer™ (LSL).
Available Parameters and Values for the Link Support Option
This option has the following parameters and values, which are discussed on
the following pages.
Parameters and Values
BUFFERS communication_number [buffer_size]
MAX BOARDS number
MAX STACKS number
MEMPOOL number [k]
LINK SUPPORT
Determines the number and size of the receive buffers, the size of the
memory pool buffers, and the number of boards and stacks used by the
LSL™ program.
Syntax
Example To configure for four network boards, you would place the
2-46
link support
parameter_name value
Replace parameter_name with the name of the
parameter you want to use.
Replace value with the value setting which
corresponds with the parameter name.
following lines in your NET.CFG file:
link support
max boards 4
Page 81

NET.CFG Options Reference
Link Support Option
BUFFERS communication_number [buffer_size]
Configures the number and size of receive buffers that the Link Support
Layer (LSL) manages.
Communication Number The number of communication buffers must be
large enough to hold all protocol headers and the maximum data size. If you
make many connections, you should increase the number of buffers to
increase performance.
If the protocol you are using builds the media header (MAC) for the LAN
driver, then you need to set the buffer size large enough to manage the
header also.
For example, IPX requires 512 bytes (LAN header) + 74 bytes (protocol
header) + 52 bytes (MAC) = 638 bytes.
See the manufacturer’s specifications for possible parameters and values
required for third-party protocol stacks.
Buffer Size The total buffer size must share a 64KB segment with the
mempool and resident program code from the LSL.COM file when loaded
into memory (approximately 5 KB).
This means that the communication number multiplied by the buffer size
(plus the code size and mempool) cannot be greater than 65,536 bytes.
For example, 20 communication buffers multiplied by a buffer size of 1514
bytes equals 30,280 bytes.
Syntax buffers communication_number [buffer_size]
Replace communication_number with a number of
buffers greater than 1.
Replace buffer_size with a number of bytes greater
than 638.
The buffer size is optional.
2-47
Page 82

NET.CFG Options Reference
Link Support Option
Default For IPX:
communication_number: The IPX protocol utilizes its
own buffers and does not require the Link Support
Layer software to provide buffers for it.
buffer_size: 1500 bytes
For TCP/IP:
communication_number: 8 buffers
buffer_size: 1500 bytes
TCP/IP requires only 1500 bytes, because the LAN
driver places the 14 bytes of media header on the
frame, prior to transmission.
For LSL:
buffer_size: 1514 bytes
This accommodates any protocol that utilizes raw
sends on Ethernet.
Example To ensure that the communication buffers are large enough
to hold all media headers, you could place the following
lines in your NET.CFG file:
[For an Ethernet configuration]
link support
buffers 8 1514
[For a token-ring configuration]
link support
buffers 8 4222
2-48
Page 83

NET.CFG Options Reference
Link Support Option
NOTE: For the most efficient communication, your link support buffer size should be the
same size as the packets that your workstation receives over the network. You might
want to set the link support buffer size equal to the largest buffer size that the network
boards in your workstation supports.
MAX BOARDS number
Configures the maximum number of logical boards that the LSL.COM file
can manage.
Each LAN driver can use more than one board resources.
If a LAN driver fails to load because of an out-of-resource condition,
increase the value for this option.
The amount of resident memory the LSL.COM file consumes increases with
larger MAX BOARD values and decreases with smaller values. Thus, you
can conserve some memory by reducing the value to the actual number of
boards used by a particular system.
For example, if you had the NE2000.COM file configured to load all
possible Ethernet frame types (ETHERNET_II, ETHERNET_802.3,
ETHERNET_802.2, and ETHERNET_SNAP), four network board
resources would be used. Therefore, to load all four frame types, MAX
BOARDS must be set to a value of 4 or higher.
Syntax
Default 4
Range 1 to 16
Example T o specify that two boards can be loaded, you would place
max boards number
the following lines in your NET.CFG file:
link support
max boards 2
2-49
Page 84

NET.CFG Options Reference
Link Support Option
NOTE: Each LAN driver resource or frame type requires approximately 200 bytes of
memory.
MAX STACKS number
Configures the maximum number of logical protocol stack IDs the
LSL.COM file can manage.
Each protocol stack can use more than one stack ID resources.
If a protocol stack fails to load because of an out-of-resource condition,
increase the value for this option.
The amount of resident memory the LSL.COM file consumes increases with
larger MAX STACKS values and decreases with smaller values. Thus, you
can conserve some memory by reducing the value to the actual number of
stack IDs used by a particular system.
Syntax
Default 4
Range 1 to 16
Example To specify that three logical protocol stack IDs can be
MEMPOOL number [k]
max stacks number
loaded, you would place the following lines in your
NET.CFG file:
link support
max stacks 3
Configures the size of the memory pool that the LSL program maintains for
allocating buffers for some protocols.
Thus, the notation means to multiply by 1024.
2-50
Page 85

NET.CFG Options Reference
Syntax mempool number [k]
Default 0
Example T o configure the size of the memory pool, you could place
the following lines in your NET.CFG file:
link support
mempool 1024
NOTE: The IPXODI protocol stack does not use memory pool buffers.
Link Support Option
2-51
Page 86

NET.CFG Options Reference
NetWare DOS Requester Option
NetWare DOS Requester Option
Use this option of the NET.CFG file to configure the NetWare Client
software for various types of networking support and connectivity.
The NetWare DOS Requester software provides networking support for
DOS and Microsoft (MS) Windows client workstations.
The NetWare DOS Requester is built on an architecture of Virtual Loadable
Module (VLM) software. The VLM.EXE (VLM manager) file is responsible
for loading the required modules.
Previous versions of the NetWare DOS and MS Windows client software
relied on the single shell file NETX.EXE to provide networking support.
NOTE: The NetWare DOS Requester is not compatible with the NETX.COM or NETX.EXE
file. Use the NETX.VLM file for compatibility with shell calls.
The following topics are covered in this section.
Topic
Current Core Virtual Loadable Module (VLM) Programs
Current Non-Core Virtual Loadable Module Programs
Compatibility with NetWare Shell Parameters
Managing the NetWare DOS Requester
Optimizing the NetWare DOS Requester
Available Parameters and Values for the NetWare DOS
Requester Option
Current Core Virtual Loadable Module (VLM) Programs
The following table lists the current core VLM programs in their default
load order.
2-52
Page 87

NET.CFG Options Reference
NetWare DOS Requester Option
The table also includes descriptions and flags indicating whether the module
is required (R) or optional (O) for NetWare Directory Services™ (NDS)
support, bindery services (BIND), and Personal NetWare™ (PNW) services.
Table 2-7 List of Current Core VLM Programs and the Respective Load Order
Module Name Description NDS BIND PNW
BIND.VLM NetWare protocol implementation using
the bindery
CONN.VLM Connection table manager R R R
FIO.VLM File Input/Output R R R
GENERAL.VLM Miscellaneous functions for the
NETX.VLM and REDIR.VLM files
IPXNCP.VLM Transport protocol implementation using
IPX
NDS.VLM NetWare protocol implementation using
NDS™ support
NETX.VLM NetWare shell compatibility O O O
NWP.VLM NetWare protocol multiplexor R R R
PNW.VLM NetWare protocol implementation using
Personal NetWare
PRINT.VLM Printer redirector O O O
REDIR.VLM DOS redirector R R R
SECURITY.VLM NetWare enhanced security O O O
ORO
RRR
RRR
ROO
OOR
TRAN.VLM Transport protocol multiplexor R R R
Current Non-Core Virtual Loadable Module Programs
The following table lists the current non-core VLM programs. Non-core
VLM programs do not automatically load by default.
Use the VLM path_vlm parameter and value to load any non-core modules.
for details on how to use this parameter and value.
2-53
Page 88

NET.CFG Options Reference
NetWare DOS Requester Option
The table also includes descriptions and flags indicating whether the module
is used (U) or not used (N) for NetWare Directory Services (NDS), bindery
services (BIND), and Personal NetWare (PNW) services.
Table 2-8 List of Current Non-Core VLM Programs
Module name Description NDS BIND PNW
AUTO.VLM Auto-reconnect/auto-retry U U U
MIB2IF.VLM MIB-II interface groups support U U U
MIB2PROT.VLM MIB-II support for the TCP/IP groups U U U
NMR.VLM NetWare management responder U U U
RSA.VLM RSA encryption for NetWare Directory
Services re-authentication
WSASN1.VLM SNMP ASN.1 translation U U U
WSDRVPRN.VLM The print information collection file for
gathering information about print
mappings and captured printers
WSREG.VLM SNMP MIB registration U U U
WSSNMP.VLM Desktop SNMP module, which includes
support for MIB-II System and SNMP
groups
WSTRAP.VLM SNMP trap U U U
UUU
UUU
UUU
Compatibility with NetWare Shell Parameters
† Parameter is supported under the NetWare DOS Requester heading in the
NET.CFG file. See specific reference to the parameter for more information.
¤ No longer supported. The functionality of this parameter was either
developed into the NetWare DOS Requester software or is no longer
required because of the NetW are DOS Requester architecture. Existing lines
in your NET.CFG file for these parameters will be ignored.
2-54
Page 89

NET.CFG Options Reference
NetWare DOS Requester Option
Parameters and Values Status
all servers=[on | off] ¤
cache buffers=number †
checksum=[on | off]
(Now requires a number value from 0 to 3.)
dos name=name †
entry stack size=number ¤
environment pad=number ¤
eojs=[on | off] †
file handles=number
(Functionality is provided by the FILES parameter setting in
the CONFIG.SYS file.)
get local target stacks=number ¤
hold=[on | off] ¤
lipackets=[on | off]
(Functionality is provided by LARGE INTERNET
PACKETS.)
local printers=number †
lock delay=number †
¤
¤
¤
lock retries=number †
long machine type=name †
max cur dir length=number
(Because of a limitation in DOS, the maximum character
length is hard set to a value of 63 characters.)
max path length=number ¤
max tasks=number †
¤
2-55
Page 90

NET.CFG Options Reference
NetWare DOS Requester Option
Parameters and Values Status
patch=byte_offset_value ¤
pb buffers=number †
preferred server=server_name †
print header=number †
print tail=number †
read only compatibilitys=[on | off] †
search mode=number †
set station times=[on | off] †
share=[on | off] ¤
short machine type=name †
show dots=[on | off] †
sign 386 mode ¤
signature level=number †
special uppercases=[on | off] ¤
task mode=number ¤
Managing the NetWare DOS Requester
Use the following information to manage loading and using the VLM.EXE
file and its modules under specific conditions.
Condition Explanation
Loading the VLM.EXE file from a
directory other than your current
directory
2-56
The current directory is used for VLM software. To load the
VLM software from another directory, use the “VLM =”
command in the NET.CFG file.
For example:
VLM=C:\NWCLIENT\CONN.VLM
Page 91

NetWare DOS Requester Option
Condition Explanation
NET.CFG Options Reference
Specifying a NET.CFG file outside
the current directory
Loading the NetWare DOS
Requester memory managers under
MS Windows 3.0
Avoid Loading VLM software in
expanded memory with MS
Windows
Disabling the VLM software The following are the preferred ways to disable specific VLM
At the command line, enter a command similar to the
following (or add the command to the AUTOEXEC.BAT
file):
VLM /C=C:\NWCLIENT\NET.CFG
If you are running MS Windows 3.0, ensure that the
VLM.EXE file is loaded after any upper- or high-memory
managers are loaded.
Don’t use the expanded memory option (/ME). Run MS
Windows with the NetWare DOS Requester only if you use
the extended memory option (/MX, preferred) or the
conventional memory option (/MC).
software:
• Rename the module with an extension other than .VLM
• Use the parameter and value. See “USE DEFAULTS=[on
| off]” on page 165
• Use the parameter and value. See “EXCLUDE
VLM=path_vlm”
Optimizing the NetWare DOS Requester
You can optimize the NetWare DOS Requester software for the following
three conditions:
• Best Performance
• Best Conventional Memory Usage
• Best Compromise
Best Performance
For the best performance, use the following parameters under the NetWare
DOS Requester option in the NET.CFG file.
2-57
Page 92

NET.CFG Options Reference
NetWare DOS Requester Option
AUTO LARGE TABLE=[on | off] LOAD LOW CONN=[on | off]
AUTO RECONNECT=[on | off] LOAD LOW IPXNCP=[on | off]
AVERAGE NAME LENGTH=number MINIMUM TIME TO NET=number
CACHE BUFFER SIZE=number NETWARE PROTOCOL=netware_protocol_list
CACHE BUFFERS=number PB BUFFERS=number
CACHE WRITES=[on | off] PRINT BUFFER SIZE=number
CHECKSUM=number SIGNATURE LEVEL=number
LARGE INTERNET PACKETS=[on | off] TRUE COMMIT=[on | off]
NOTE: Use the /MC command line parameter when loading the VLM.EXE file. /MC loads
all of the VLM programs into conventional memory.
Loading the NetWare DOS Requester into conventional memory requires
approximately 100 KB of memory.
Following is a sample NET.CFG file entry for a client workstation:
netware dos requester
cache buffers=64
cache buffer size=1540
cache writes=on
checksum=0
exclude=nds.vlm
large internet packet=on
load low conn=on
load low ipxncp=on
minimum time to net=0
netware protocol=bind,nds,pnw
pb buffers=3
print buffer size=256
signature level=0
true commit=off
2-58
Page 93

NET.CFG Options Reference
NetWare DOS Requester Option
This entry indicates the following:
• The CACHE BUFFER SIZE is set for an Ethernet network board
• The “DOS FILES=” command in the CONFIG.SYS file is set above 64 files
• The servers are running NetWare 3.12
Best Conventional Memory Usage
For the best memory usage, use the following parameters under the NetW are
DOS Requester option in the NET.CFG file.
Table 2-9 Parameters and Values Used to Configure for Best Memory Usage
AUTO LARGE TABLE=[on | off] LOAD LOW CONN=[on | off]
AUTO RECONNECT=[on | off] LOAD LOW IPXNCP=[on | off]
AVERAGE NAME LENGTH=number NETWORK PRINTERS=number
CACHE BUFFERS=number PB BUFFERS=number
CONNECTIONS=number PRINT HEADER=number
EXCLUDE VLM=path_vlm PRINT TAIL=number
LARGE INTERNET PACKETS=[on | off] SIGNATURE LEVEL=number
NOTE: Configuring for the smallest conventional memory usage will result in some
performance degradation.
Following is a sample NET.CFG file entry for a client workstation:
netware dos requester
auto large table=off
auto reconnect=off
average name length=7
cache buffers=0
connections=4
exclude=pnw.vlm
exclude=netx.vlm
load low conn=off
load low ipxncp=off
2-59
Page 94

NET.CFG Options Reference
NetWare DOS Requester Option
network printers=0
pb buffers=0
print header=0
print tail=0
signature level=0
This entry indicates the following:
• The sum of character length of server names attached to is 24
• You are not running any NETX applications
• You print to a local printer only
• The servers are running NetWare 4 only (no bindery or Personal NetWare
connections)
Best Compromise
The default settings for the NetWare DOS Requester provide the best
compromise between performance and memory usage.
You should use the default settings until you can determine the optimal
configuration for your particular network and client workstations.
Following is a sample working NET.CFG file for a client workstation.
Wherever feasible, default settings are used. Otherwise, example variable
replacements are used (for example, the preferred server name):
link driver ne2000
port 300
int 3
frame ethernet_802.2
netware dos requester
netware protocol=nds,bind
first network drive=f
preferred server=sales
auto retry=10
bind reconnect=on
cache buffers=40
checksum=0
connections=16
2-60
Page 95

NET.CFG Options Reference
NetWare DOS Requester Option
large internet packet=on
load low conn=on
load low ipxncp=on
message timeout=183
pb buffers=8
signature level=0
pburst read window size=64
pburst write window size=64
Available Parameters and Values for the NetWare DOS Requester
Option
Parameters and Values
AUTO LARGE TABLE=[on | off]
AUTO RECONNECT=[on | off]
AUTO RETRY=number
AVERAGE NAME LENGTH=number
BIND RECONNECT=[on | off]
BROADCAST RETRIES=number
BROADCAST SEND DELAY=number
BROADCAST TIMEOUT=number
CACHE BUFFER SIZE=number
CACHE BUFFERS=number
CACHE WRITES=[on | off]
CHECKSUM=number
CONFIRM CRITICAL ERROR ACTION=[on | off]
CONNECTIONS=number
DOS NAME=”name”
EOJ=[on | off]
EXCLUDE VLM=path_vim
FIRST NETWORK DRIVE=drive_letter
FORCE FIRST NETWORK DRIVE=[on | off]
HANDLE NET ERRORS=[on | off]
LARGE INTERNET PACKETS=[on | off]
LIP START SIZE=number
LOAD CONN TABLE LOW=[on | off]
LOAD LOW CONN=[on | off]
LOAD LOW IPXNCP=[on | off]
2-61
Page 96

NET.CFG Options Reference
NetWare DOS Requester Option
Parameters and Values
LOAD LOW REDIR=[on | off]
LOCAL PRINTERS=number
LOCK DELAY=number
LOCK RETRIES=number
LONG MACHINE TYPE=“name”
MAX TASKS=number
MESSAGE LEVEL=number
MESSAGE TIMEOUT=number
MINIMUM TIME TO NET=number
NAME CONTEXT=“name_context”
NETWARE PROTOCOL=netware_protocol_list
NETWORK PRINTERS=number
PB BUFFERS=number
PBURST READ WINDOWS SIZE=number
PBURST WRITE WINDOWS SIZE=number
PREFERRED SERVER=“server_name”
PREFERRED TREE=“tree_name”
PREFERRED WORKGROUP=“workgroup_name”
PRINT BUFFER SIZE=number
PRINT HEADER=number
PRINT TAIL=number
READ ONLY COMPATIBILITY=[on | off]
RESPONDER=[on | off]
SEARCH MODE=number
SET STATION TIME=[on | off]
SHORT MACHINE TYPE=“name”
SHOW DOTS=[on | off]
SIGNATURE LEVEL=number
TRUE COMMIT=[on | off]
USE DEFAULTS=[on | off]
VLM=path_VLM
WORKGROUP NET=workgroup_net_address
This option has the following parameters and values, which are discussed on
the indicated pages:
2-62
Page 97

NET.CFG Options Reference
NetWare DOS Requester Option
NETWARE DOS REQUESTER
Controls network requests from your client workstation to a NetWare server
or network.
Syntax netware dos requester
parameter_name=value
Replace parameter_name with the name of the
parameter you want to use.
Replace value with the value setting which
corresponds with the parameter name.
Example To configure for four server connections, you would place
these lines in your NET.CFG file:
netware dos requester
connections=4
AUTO LARGE TABLE=[on | off]
Allocates a small table of 34 bytes per connection for bindery reconnects.
When the parameter is enabled, the AUTO.VLM program allocates a large
connection table of 178 bytes per connection for bindery reconnects.
Change the default value to “on” if the length of your username and
password combined is more than 16 characters.
Syntax auto large table=[on | off]
Default off
Modules AUTO.VLM
Example To use a username and password longer than 16 characters
combined, you would place the following lines in your
NET.CFG file:
netware dos requester
auto large table=on
2-63
Page 98

NET.CFG Options Reference
NetWare DOS Requester Option
Use this parameter for binder connections if your username and password
total more than 32 characters. For this parameter to work, also set BIND
RECONNECT=ON.
AUTO RECONNECT=[on | off]
When this parameter is set to “on,” the AUTO.VLM program reconnects a
client workstation to a NetWare server and rebuilds the workstation’s
environment (excluding file-specific items) prior to connection loss.
When this parameter is set to “off,” the AUTO.VLM program load fails at
pre-initialization time.
Syntax auto reconnect=[on | off]
Default on
Modules AUTO.VLM, NDS.VLM
Example To make reconnecting to a NetWare server the user’s
responsibility, you would place the following lines in your
NET.CFG file:
netware dos requester
auto reconnect=off
To enable the VLM.EXE program to load the AUTO.VLM file, you must
include the VLM=AUTO.VLM parameter and value. You must also load
RSA.VLM if you are re-establishing a NetWare Directory Services (NDS)
connection, by using the VLM=RSA.VLM parameter.
AUTO RETRY=number
Sets the number of seconds the AUTO.VLM program waits before
attempting a retry after receiving a network critical error.
Syntax
Default 0
Range 0 to 3640
Modules AUTO.VLM
2-64
auto retry=number
Page 99

NET.CFG Options Reference
NetWare DOS Requester Option
Example To make the AUTO.VLM program wait for one minute
before retrying a connection, you would place the
following lines in your NET.CFG file:
netware dos requester
auto retry=60
To enable the VLM.EXE program to load the AUTO.VLM file, you must
include the VLM=AUTO.VLM parameter and value. You must also load
RSA.VLM if you are re-establishing a NetWare Directory Services (NDS)
connection, by using the VLM=RSA.VLM parameter.
NOTE: When the value for this parameter is set to 0, the AUTO.VLM program makes no
retry attempts.
AVERAGE NAME LENGTH=number
Allows the NetWare DOS Requester to set aside space for a table of
NetWare server names based on the values set for the AVERAGE NAME
LENGTH and CONNECTIONS parameters.
For shorter NetWare server names, you can save some memory by setting
the average length to a lower number.
Syntax
Default 48
Range 2 to 48
Modules CONN.VLM
average name length=
Replace number with the sum of the average character
length of your network server names, divided by the
number set in the CONNECTIONS parameter plus 1.
number
2-65
Page 100

NET.CFG Options Reference
NetWare DOS Requester Option
Example To save memory by shortening the average name length
allowed to eight characters, you would place the following
lines in your NET.CFG file:
netware dos requester
average name length=9
BIND RECONNECT=[on | off]
Automatically rebuilds bindery connections and restores drive mappings and
printer connections.
Syntax bind reconnect=[on | off]
Default off
Modules AUTO.VLM, BIND.VLM
Example To make reconnecting to bindery services automatic, you
would place the following lines in your NET.CFG file:
netware dos requester
bind reconnect=on
To enable the VLM.EXE program to load the AUTO.VLM file, you must
include the VLM=AUTO.VLM parameter and value.
For this parameter to work, also set AUTO RECONNECT=ON.
BROADCAST RETRIES=number
Sets the number of times the NetWare DOS Requester software broadcasts a
request.
Set this to a higher number if you are not seeing some resources in various
utility lists.
NOTE: Increasing this number decreases the response time of some utilities.
2-66
 Loading...
Loading...