Page 1

HP BladeSystem Onboard Administrator
Command Line Interface
User Guide
Version 3.00
Part Number 416217-404
February 2010 (Thirteenth Edition)
Page 2

© Copyright 2006, 2010 Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express
warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP
shall not be liable for technical or editorial errors or omissions contained herein.
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212,
Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S.
Government under vendor’s standard commercial license.
Intended audience
This document is for the person who installs, administers, and troubleshoots servers and storage systems. HP assumes you are qualified in the
servicing of computer equipment and trained in recognizing hazards in products with hazardous energy levels.
Page 3

Contents
Accessing the command line interface ........................................................................................... 10
Remote access to the Onboard Administrator ................................................................................................ 10
Local access to the Onboard Administrator ................................................................................................... 10
Command line ............................................................................................................................ 12
Command line overview ............................................................................................................................. 12
Command line conventions ......................................................................................................................... 12
HP Integrity server blade restrictions ............................................................................................................. 13
Access level and privileges.......................................................................................................................... 13
Account authentication...................................................................................................................... 15
AutoLogin to iLO 2 ........................................................................................................................... 16
General commands ..................................................................................................................... 17
CLEAR SCREEN ......................................................................................................................................... 17
EXIT .......................................................................................................................................................... 17
HELP ......................................................................................................................................................... 17
LOGOUT ................................................................................................................................................... 17
QUIT ......................................................................................................................................................... 18
Rack commands ......................................................................................................................... 19
SET RACK NAME ....................................................................................................................................... 19
SHOW RACK NAME ................................................................................................................................. 19
SHOW TOPOLOGY ................................................................................................................................... 19
User account commands .............................................................................................................. 21
ADD USER ................................................................................................................................................. 21
ASSIGN .................................................................................................................................................... 21
ASSIGN OA .............................................................................................................................................. 22
DISABLE USER ........................................................................................................................................... 22
DISABLE STRONG PASSWORDS ................................................................................................................ 22
ENABLE STRONG PASSWORDS ................................................................................................................. 22
ENABLE USER ............................................................................................................................................ 23
HISTORY ................................................................................................................................................... 23
REMOVE USER .......................................................................................................................................... 23
SET MINIMUM PASSWORD LENGTH .......................................................................................................... 24
SET PASSWORD ........................................................................................................................................ 24
SET SESSION TIMEOUT ............................................................................................................................. 24
SET USER ACCESS ..................................................................................................................................... 25
SET USER CONTACT ................................................................................................................................. 25
SET USER FULLNAME ................................................................................................................................. 25
SET USER PASSWORD ............................................................................................................................... 26
SHOW PASSWORD SETTINGS .................................................................................................................. 26
SHOW SESSION TIMEOUT ........................................................................................................................ 27
SHOW USER ............................................................................................................................................. 27
SLEEP ........................................................................................................................................................ 28
UNASSIGN ............................................................................................................................................... 28
UNASSIGN OA
......................................................................................................................................... 28
Page 4

Two-Factor Authentication commands ............................................................................................ 29
DISABLE CRL .............................................................................................................................................. 29
DISABLE TWOFACTOR............................................................................................................................... 29
DOWNLOAD CA CERTIFICATE ................................................................................................................... 29
DOWNLOAD USER CERTIFICATE ................................................................................................................ 30
REMOVE CA CERTIFICATE .......................................................................................................................... 30
REMOVE USER CERTIFICATE ....................................................................................................................... 30
SHOW CA CERTIFICATES .......................................................................................................................... 30
SHOW TWOFACTOR INFO ....................................................................................................................... 31
Directory commands ................................................................................................................... 32
ADD LDAP CERTIFICATE ............................................................................................................................. 32
ADD LDAP GROUP..................................................................................................................................... 32
ASSIGN for LDAP ...................................................................................................................................... 32
ASSIGN OA LDAP GROUP ......................................................................................................................... 33
DISABLE LDAP............................................................................................................................................ 33
DOWNLOAD LDAP CERTIFICATE ................................................................................................................ 33
ENABLE LDAP ............................................................................................................................................ 34
REMOVE LDAP CERTIFICATE ....................................................................................................................... 34
REMOVE LDAP GROUP .............................................................................................................................. 34
SET LDAP GROUP ACCESS ......................................................................................................................... 35
SET LDAP GROUP DESCRIPTION ................................................................................................................. 35
SET LDAP NAME MAP ................................................................................................................................ 35
SET LDAP PORT .......................................................................................................................................... 36
SET LDAP SEARCH ..................................................................................................................................... 36
SET LDAP SERVER ...................................................................................................................................... 36
SHOW LDAP CERTIFICATE ......................................................................................................................... 36
SHOW LDAP GROUP ................................................................................................................................. 37
SHOW LDAP INFO .................................................................................................................................... 37
TEST LDAP ................................................................................................................................................. 38
UNASSIGN for LDAP ................................................................................................................................. 38
UNASSIGN OA LDAP GROUP .................................................................................................................... 38
HP SIM commands ...................................................................................................................... 40
ADD HPSIM CERTIFICATE ........................................................................................................................... 40
DOWNLOAD HPSIM CERTIFICATE .............................................................................................................. 40
REMOVE HPSIM CERTIFICATE ..................................................................................................................... 40
SET HPSIM TRUST MODE ........................................................................................................................... 41
SHOW HPSIM INFO .................................................................................................................................. 41
General management commands ................................................................................................. 42
DOWNLOAD OA CERTIFICATE .................................................................................................................. 42
FORCE TAKEOVER ..................................................................................................................................... 42
GENERATE CERTIFICATE ............................................................................................................................ 42
Generate certificate prompts ............................................................................................................. 43
PING ................................................................
SET DEVICE SERIAL_NUMBER BLADE ........................................................................................................... 45
SET FACTORY ........................................................................................................................................... 45
SET SCRIPT MODE ..................................................................................................................................... 45
SHOW ALL ................................................................................................................................................ 46
SHOW DEVICE SERIAL_NUMBER BLADE ..................................................................................................... 72
SHOW INTERCONNECT SESSIONS ........................................................................................................... 72
........................................................................................ 44
Enclosure Bay IP Addressing commands ........................................................................................ 74
ADD EBIPA ................................................................................................................................................ 74
Page 5

DISABLE EBIPA ........................................................................................................................................... 74
ENABLE EBIPA ........................................................................................................................................... 74
REMOVE EBIPA ......................................................................................................................................... 75
SET EBIPA ................................................................................................................................................. 75
SET EBIPA SERVER ........................................................................................................................... 76
SET EBIPA INTERCONNECT ............................................................................................................. 76
SHOW EBIPA ............................................................................................................................................ 76
Enclosure network configuration commands ................................................................................... 79
ADD OA ADDRESS IPV6 ............................................................................................................................ 79
ADD OA DNS ........................................................................................................................................... 79
ADD OA DNS IPV6 .................................................................................................................................... 79
ADD SNMP TRAPRECEIVER ......................................................................................................................... 80
ADD SSHKEY ............................................................................................................................................ 80
ADD TRUSTED HOST .................................................................................................................................. 81
CLEAR NTP ................................................................................................................................................ 81
CLEAR SSHKEY .......................................................................................................................................... 81
CLEAR VCMODE ....................................................................................................................................... 82
DISABLE ALERTMAIL ................................................................................................................................... 82
DISABLE DHCPV6 ...................................................................................................................................... 82
DISABLE ENCLOSURE_IP_MODE ................................................................................................................. 83
DISABLE HTTPS .......................................................................................................................................... 83
DISABLE IPV6 ............................................................................................................................................ 83
DISABLE NTP ............................................................................................................................................. 84
DISABLE ROUTER ADVERTISEMENTS ........................................................................................................... 84
DISABLE SECURESH ................................................................................................................................... 84
DISABLE SNMP .......................................................................................................................................... 84
DISABLE TELNET ........................................................................................................................................ 85
DISABLE TRUSTED HOST ............................................................................................................................ 85
DISABLE XMLREPLY..................................................................................................................................... 85
DOWNLOAD CONFIG .............................................................................................................................. 86
DOWNLOAD SSHKEY ............................................................................................................................... 86
ENABLE ALERTMAIL ................................................................................................................................... 86
ENABLE DHCPV6 ....................................................................................................................................... 87
ENABLE ENCLOSURE_IP_MODE ................................................................................................................. 87
ENABLE HTTPS .......................................................................................................................................... 87
ENABLE IPV6 ............................................................................................................................................. 88
ENABLE NTP ............................................................................................................................................. 88
ENABLE ROUTER ADVERTISEMENTS ........................................................................................................... 88
ENABLE SECURESH ................................................................................................................................... 88
ENABLE SNMP .......................................................................................................................................... 89
ENABLE TELNET ......................................................................................................................................... 89
ENABLE TRUSTED HOST ............................................................................................................................. 89
ENABLE XMLREPLY ..................................................................................................................................... 90
REMOVE OA ADDRESS IPV6 ...................................................................................................................... 90
REMOVE OA DNS ..................................................................................................................................... 90
REMOVE OA DNS IPV6 ............................................................................................................................. 91
REMOVE SNMP TRAPRECEIVER .................................................................................................................. 91
REMOVE TRUSTED HOST ........................................................................................................................... 91
SET ALERTMAIL MAILBOX ........................................................................................................................... 92
SET ALERTMAIL SENDERDOMAIN ............................................................................................................... 92
SET ALERTMAIL SMTPSERVER ...................................................................................................................... 92
SET ENCRYPTION ...................................................................................................................................... 93
SET OA GATEWAY ................................................................................................................................... 93
Page 6

SET OA NAME .......................................................................................................................................... 93
SET OA UID .............................................................................................................................................. 94
SET IPCONFIG .......................................................................................................................................... 94
SET NTP POLL ............................................................................................................................................ 94
SET NTP PRIMARY ...................................................................................................................................... 95
SET NTP SECONDARY ............................................................................................................................... 95
SET SNMP CONTACT ................................................................................................................................ 95
SET SNMP COMMUNITY ........................................................................................................................... 96
SET SNMP LOCATION ............................................................................................................................... 96
SHOW ENCRYPTION ................................................................................................................................ 96
SHOW NETWORK .................................................................................................................................... 97
SHOW SNMP ........................................................................................................................................... 98
SHOW SSHFINGERPRINT .......................................................................................................................... 99
SHOW SSHKEY ......................................................................................................................................... 99
TEST ALERTMAIL ........................................................................................................................................ 99
TEST SNMP ............................................................................................................................................. 100
Enclosure management commands ............................................................................................. 101
CLEAR SYSLOG ....................................................................................................................................... 101
DISABLE GUI_LOGIN_DETAIL .................................................................................................................... 101
DISABLE LLF ............................................................................................................................................. 101
ENABLE GUI_LOGIN_DETAIL .................................................................................................................... 102
ENABLE LLF ............................................................................................................................................. 102
RESTART OA ........................................................................................................................................... 102
SET DATE ................................................................................................................................................ 102
SET DISPLAY EVENTS ............................................................................................................................... 103
SET ENCLOSURE ASSET ........................................................................................................................... 103
SET ENCLOSURE NAME .......................................................................................................................... 104
SET ENCLOSURE PART_ NUMBER ............................................................................................................. 104
SET ENCLOSURE PDU_TYPE ..................................................................................................................... 104
SET ENCLOSURE SERIAL_NUMBER ........................................................................................................... 105
SET ENCLOSURE UID ............................................................................................................................... 105
SET LLF INTERVAL..................................................................................................................................... 105
SET OA USB ............................................................................................................................................ 106
SET POWER MODE ................................................................................................................................. 106
SET POWER LIMIT .................................................................................................................................... 106
SET POWER SAVINGS ............................................................................................................................. 107
SET TIMEZONE........................................................................................................................................ 107
SHOW CONFIG ..................................................................................................................................... 107
SHOW DATE........................................................................................................................................... 108
SHOW DISPLAY EVENTS .......................................................................................................................... 109
SHOW ENCLOSURE FAN ........................................................................................................................ 109
SHOW ENCLOSURE INFO ....................................................................................................................... 110
SHOW ENCLOSURE LCD
SHOW ENCLOSURE POWER_SUMMARY ................................................................................................. 111
SHOW ENCLOSURE POWERSUPPLY ........................................................................................................ 112
SHOW ENCLOSURE STATUS ................................................................................................................... 113
SHOW ENCLOSURE TEMP ....................................................................................................................... 113
SHOW FRU ............................................................................................................................................. 114
SHOW OA ............................................................................................................................................. 116
SHOW OA CERTIFICATE .......................................................................................................................... 116
SHOW OA INFO .................................................................................................................................... 117
SHOW OA NETWORK ............................................................................................................................ 117
SHOW OA STATUS ................................................................................................................................. 118
......................................................................................................................... 110
Page 7

SHOW OA USB ...................................................................................................................................... 119
SHOW POWER ....................................................................................................................................... 119
SHOW SYSLOG ...................................................................................................................................... 120
SHOW SYSLOG OA ................................................................................................................................ 120
SHOW VCMODE .................................................................................................................................... 121
UPDATE .................................................................................................................................................. 122
UPDATE ILO ............................................................................................................................................ 122
UPDATE IMAGE ....................................................................................................................................... 123
UPLOAD CONFIG ................................................................................................................................... 123
UPLOAD DEBUG ...................................................................................................................................... 124
Blade management commands ................................................................................................... 125
CONNECT SERVER .................................................................................................................................. 125
DISABLE URB ........................................................................................................................................... 125
ENABLE URB ........................................................................................................................................... 125
HPONCFG .............................................................................................................................................. 126
POWEROFF SERVER ................................................................................................................................ 126
POWERON SERVER ................................................................................................................................. 127
REBOOT SERVER ..................................................................................................................................... 127
SET NIC .................................................................................................................................................. 128
SET SERVER BOOT ................................................................................................................................... 128
SET SERVER BOOT ONCE ........................................................................................................................ 128
SET SERVER POWERDELAY ....................................................................................................................... 129
SET SERVER UID ....................................................................................................................................... 129
SET URB .................................................................................................................................................. 129
SHOW SERVER BOOT ............................................................................................................................. 130
SHOW SERVER INFO .............................................................................................................................. 131
SHOW SERVER LIST ................................................................................................................................. 132
SHOW SERVER NAMES ........................................................................................................................... 132
SHOW SERVER PORT MAP ....................................................................................................................... 133
SHOW SERVER POWERDELAY ................................................................................................................. 134
SHOW SERVER STATUS ........................................................................................................................... 135
SHOW SERVER TEMP .............................................................................................................................. 137
SHOW SYSLOG SERVER .......................................................................................................................... 138
UNASSIGN SERVER ................................................................................................................................. 139
Interconnect management commands .......................................................................................... 140
ASSIGN INTERCONNECT ........................................................................................................................ 140
CLEAR INTERCONNECT SESSION ............................................................................................................ 140
SHOW URB ............................................................................................................................................ 140
TEST URB ................................................................................................................................................ 141
CONNECT INTERCONNECT .................................................................................................................... 141
POWEROFF INTERCONNECT .................................................................................................................. 141
POWERON INTERCONNECT ................................................................
RESTART INTERCONNECT ....................................................................................................................... 142
SET INTERCONNECT POWERDELAY ......................................................................................................... 142
SET INTERCONNECT UID......................................................................................................................... 143
SHOW INTERCONNECT INFO ................................................................................................................ 143
SHOW INTERCONNECT LIST ................................................................................................................... 145
SHOW INTERCONNECT PORT MAP......................................................................................................... 145
SHOW INTERCONNECT POWERDELAY ................................................................................................... 146
SHOW INTERCONNECT STATUS ............................................................................................................. 146
Enclosure DVD commands ......................................................................................................... 148
................................................... 142
Page 8

SET SERVER DVD ..................................................................................................................................... 148
SHOW SERVER DVD ................................................................................................................................ 148
Remote syslog commands .......................................................................................................... 150
DISABLE SYSLOG REMOTE ....................................................................................................................... 150
ENABLE SYSLOG REMOTE ....................................................................................................................... 150
SET REMOTE SYSLOG PORT ..................................................................................................................... 150
SET REMOTE SYSLOG SERVER .................................................................................................................. 151
SHOW SYSLOG SETTINGS ...................................................................................................................... 151
TEST SYSLOG .......................................................................................................................................... 151
Remote syslog example ............................................................................................................................. 152
USB support commands ............................................................................................................. 153
DOWNLOAD CONFIG using USB key ...................................................................................................... 153
SET SERVER DVD for USB key ................................................................................................................... 153
SHOW USBKEY ....................................................................................................................................... 153
UPDATE IMAGE using USB key ................................................................................................................. 154
UPLOAD CONFIG using USB key .............................................................................................................. 155
VLAN commands ...................................................................................................................... 156
ADD VLAN .............................................................................................................................................. 156
DISABLE VLAN ......................................................................................................................................... 156
EDIT VLAN .............................................................................................................................................. 156
ENABLE VLAN ......................................................................................................................................... 157
REMOVE VLAN ....................................................................................................................................... 157
SAVE VLAN ............................................................................................................................................. 157
SET VLAN DEFAULT .................................................................................................................................. 157
SET VLAN FACTORY ................................................................................................................................ 158
SET VLAN INTERCONNECT ..................................................................................................................... 158
SET VLAN IPCONFIG ............................................................................................................................... 158
SET VLAN IPCONFIG DHCP ..................................................................................................................... 159
SET VLAN IPCONFIG SAVE ...................................................................................................................... 159
SET VLAN IPCONFIG STATIC .................................................................................................................... 159
SET VLAN OA ......................................................................................................................................... 160
SET VLAN REVERT .................................................................................................................................... 160
SET VLAN SERVER ................................................................................................................................... 160
SHOW VLAN .......................................................................................................................................... 161
Enclosure Dynamic Power Cap commands .................................................................................. 162
SET ENCLOSURE POWER_CAP ................................................................................................................. 162
SET ENCLOSURE POWER_CAP_BAYS_TO_EXCLUDE .................................................................................. 162
SHOW ENCLOSURE POWER_CAP ........................................................................................................... 163
SHOW ENCLOSURE POWER_CAP_BAYS_TO_EXCLUDE ............................................................................ 163
Event notifications ..................................................................................................................... 165
Enclosure event notifications ...................................................................................................................... 165
Command line event notifications............................................................................................................... 165
Technical support ...................................................................................................................... 168
Before you contact HP .............................................................................................................................. 168
HP contact information .............................................................................................................................. 168
Time zone settings .................................................................................................................... 169
Universal time zone settings ...................................................................................................................... 169
Africa time zone settings ........................................................................................................................... 169
Americas time zone settings ...................................................................................................................... 170
Page 9

Asia time zone settings ............................................................................................................................. 171
Oceanic time zone settings ....................................................................................................................... 172
Europe time zone settings .......................................................................................................................... 173
Polar time zone settings ............................................................................................................................ 173
Acronyms and abbreviations ...................................................................................................... 174
Index ....................................................................................................................................... 177
Page 10
Accessing the command line interface
Remote access to the Onboard Administrator
The Onboard Administrator CLI can be accessed remotely through any Telnet or SSH session.
Telnet session
1. Open a command-line window from a network-connected client.
2. At the prompt, telnet to the IP address of the Onboard Administrator and press Enter.
For example, telnet 192.168.100.130, where the IP address is the address of your Onboard
Administrator.
3. Enter a valid user name and press Enter.
4. Enter a valid password and press Enter. The CLI command prompt displays.
5. Enter commands for the Onboard Administrator.
6. To terminate the remote access telnet session, enter Exit, Logout, or Quit at the CLI command
prompt.
SSH session
1. Start a SSH session to the Onboard Administrator using any SSH client application.
2. When prompted, enter the assigned IP address or DNS name of the Onboard Administrator and
press Enter.
3. Enter a valid user name and press Enter.
4. Enter a valid password and press Enter. The CLI command prompt displays.
5. Enter commands for the Onboard Administrator.
6. To terminate the remote access SSH session, close the communication software or enter Exit,
Logout, or Quit at the CLI command prompt.
Local access to the Onboard Administrator
The Onboard Administrator can be accessed locally through a serial port connector on the rear of the
Onboard Administrator module. Use a laptop or another computer as a serial console to communicate
with the Onboard Administrator. A laptop or PC connected to the Onboard Administrator serial port
requires a null-modem cable. The minimum connection to an external console is pins 2, 3, and 5.
1. Connect a serial cable between the serial port on the computer and the corresponding serial port on
the Onboard Administrator module. The following table is for the DB9 serial (RS232) port and shows
the pinout and signals for the RS232 connector. The signal direction is DTE (computer) relative to the
DCE (modem).
Pin Name Signal direction Description
1 CD <<-- Carrier detect
2 RXD <<-- Receive data
Accessing the command line interface 10
Page 11
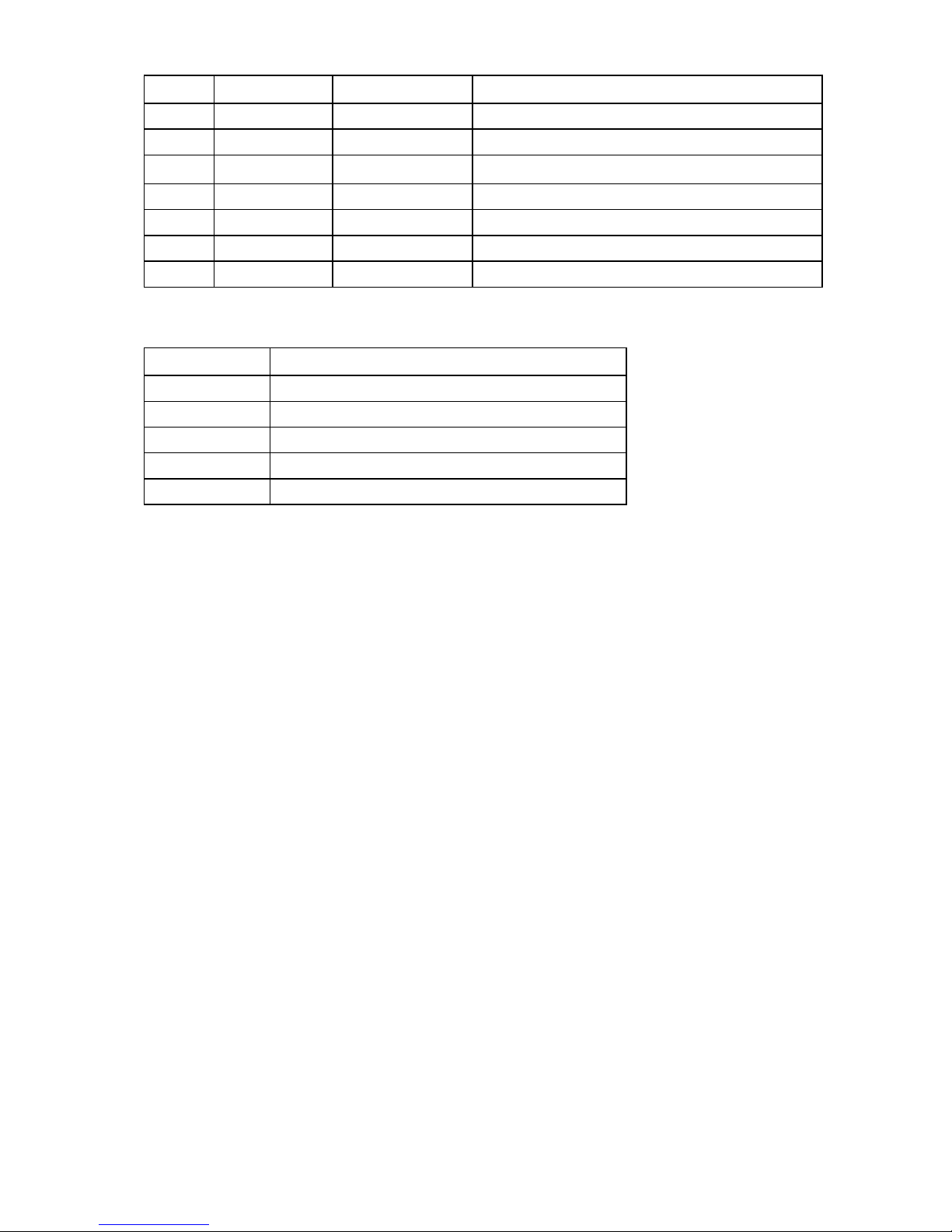
Pin Name Signal direction Description
3 TXD -->> Transmit data
4 DTR -->> Data terminal ready
5 GND
System ground
6 DSR <<-- Data set ready
7 RTS -->> Request to send
8 CTS <<-- Clear to send
9 RI <<-- Ring indicator
2. Use any standard communication software to launch a terminal emulation session with the following
parameters:
Parameter Value
Transmission rate 9600 bps
Data bits 8
Parity None
Stop bits 1
Protocol None
3. When prompted, enter a valid user name, and then press Enter.
4. Enter a valid password, and press Enter. The CLI command prompt appears.
5. Enter commands for the Onboard Administrator.
6. To terminate the terminal session, enter Exit at the prompt.
Accessing the command line interface 11
Page 12
Command line
•
•
SET ENCLOSURE UID OFF
Command line overview
The CLI can be used as an alternative method for managing the Onboard Administrator. Using the CLI
can be useful in the following scenarios:
• HP Management Applications (for example: Systems Insight Manager, Insight Control tools, and so
on) can query the Onboard Administrator for information these tools need to present a complete
management view of HP BladeSystem enclosures and the devices contained within. This interface is
also used by the Management tools to execute provisioning and configuration tasks to devices within
the enclosure.
• Users can develop tools that utilize Onboard Administrator functions for data collection and for
executing provisioning and configuration tasks.
• When no browser is available or you prefer to use a Linux command line interface to access
management data and perform configuration tasks.
Command line conventions
CLI input is case-insensitive except when otherwise noted. Commands are organized into a tree, with
approximately 30 base commands. Each of these commands can have any number of subcommands.
Subcommands can also have further subcommands.
Each command used in this guide follows the conventions listed in the following table.
Symbol Description
<lower case> Denotes the variable within the symbols that must be substituted with a value, such
as a user name. Symbols must be removed.
UPPER CASE
|
{ }
[ ]
" "
Denotes input to be entered as shown.
Unless noted, symbol is not case-sensitive.
Used to separate input options.
Denotes a list of mandatory choices that must be made.
For example, SET ENCLOSURE UID {ON | OFF} must be in the form of either
of the following:
SET ENCLOSURE UID ON
Denotes an optional argument or set of characters.
Used to enclose command arguments that contain spaces.
Command line 12
Page 13

HP Integrity server blade restrictions
HP Integrity server blades do not support all commands. See specific commands for restrictions on HP
Integrity server blades.
The following commands are not applicable to HP Integrity server blades
• Hponcfg
• Set Server Boot
• Set Server Boot Once
• Show Server Boot
• Show Syslog Server
• Update iLO
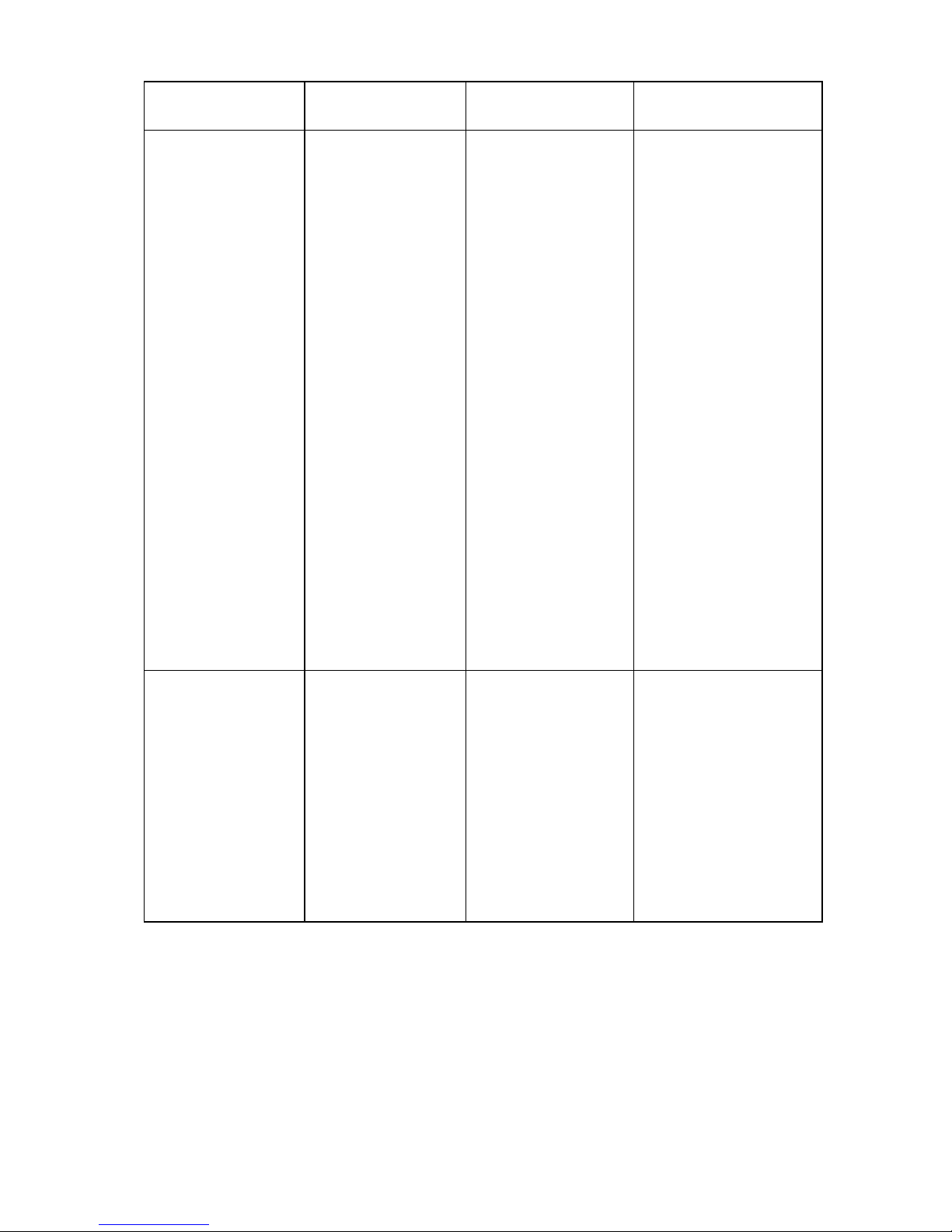
Access level and privileges
Onboard Administrator accounts and privileges
Onboard Administrator accounts are created with a username, password, privilege level, and permissions
to Device bays and Interconnect bays on the Onboard Administrator. You cannot delete or modify the
privileges of the default Administrator account, on the Onboard Administrator. You can only change the
password for the Administrator account. The following table indicates the capabilities of the user based
on their privileges and permitted bays.
Command line 13
Page 14
•
•
•
•
•
•
•
Account classification Capabilities
Administrator
All commands
Local account, not
LDAP
Account name /
Privilege level
Administrator /
administrator
Bays selected for this
account
All
Only account
remaining after a
reset Onboard
Administrator to
factory defaults
(account retains
configured
Administrator
password)
Administrator
account password
can be reset to
factory default
through the
Onboard
Administrator serial
port using "L" lost
password recovery
option
Can download,
add, and clear
SSHKey. This key
only works with the
Administrator
account.
OA administrator
All commands
Allows access to all
aspects of the HP
BladeSystem
Enclosure and
Onboard
Administrator
including
configuration,
firmware updates,
user management,
and resetting
default settings.
username /
administrator
OA bays (all bays
automatically selected)
Command line 14
Page 15
•
•
•
•
•
•
•
•
•
•
•
•
•
Account classification Capabilities
administrator
Can perform all
operations to
permitted device
bays and
interconnect bays
including virtual
power and console
access
Account name /
Privilege level
username /
administrator
Bays selected for this
account
No OA bays and only
selected device bays and
interconnect bays
administrator
permission on
device iLO2
OA operator
Set rack name
EBIPA
enable/disable
permitted bays
Change OA
network settings
username / operator
OA bays and can have
other bays selected, but the
capabilities for the other
bays are defined in
operator
Perform enclosure
management
commands
operator
Can perform all
operations to
permitted device
bays and
interconnect bays
including virtual
power and console
access
username / operator
Selected device bays and
interconnect bays
operator
permission on
device iLO2
user
Can view status
and information of
selected bays
username / user
No OA bays and some
device bays and
interconnect bays
Can view CLI
history
Can set password
for own account
Can set user
contact information
for own account
Can 'show' CLI
commands
Account authentication
Local users
Command line 15
Page 16
• This is the default setting. Local user accounts are directly authenticated against a password for each
account stored on the active Onboard Administrator.
• Account modifications are automatically synchronized between both Onboard Administrator
modules if two are present.
• Local users may be disabled if LDAP is enabled, leaving the Administrator account as the only local
account that cannot be disabled.
LDAP users
• The Enable/Disable LDAP is an optional setting. LDAP enabled can be used with local users enabled
or disabled.
• The Onboard Administrator will use configured LDAP server and search context to request account
authentication.
• Configuration of the LDAP group will determine the privileges instead of the username.
• If a user is configured for multiple groups with different privileges and bay permissions, then the user
will have the highest privileges and the combination of all permitted bays.
• In version 2.10 or higher, if the user logged into the Onboard Administrator is an LDAP user then the
Onboard Administrator enforces the iLO license and requires that the iLO have a Select license
before allowing the AutoLogin to iLO.
AutoLogin to iLO 2
The following table indicates Onboard Administrator account privileges mapped to iLO privileges when
using Onboard Administrator AutoLogin.
iLO privileges administrator operator user
Administer user accounts X
Remote console access X X
Virtual power and reset X X
Virtual media X X
Configure iLO settings X
Login to iLO X X X
Command line 16
Page 17

General commands
CLEAR SCREEN
• Command:
CLEAR SCREEN
• Description:
Clears the terminal screen
• Access level:
EXIT
• Command:
• Description:
• Access level:
HELP
• Command:
• Description:
Administrator, Operator, User
EXIT
Exits the command line interpreter
Administrator, Operator, User
HELP <command>
If you supply a command, the usage and help text for the command appears. If no argument is
given, all base commands appear.
• Access level:
Administrator, Operator, User
Example
OA-0018FE27577F> HELP
ADD | ASSIGN | CLEAR | CONNECT | DISABLE | DISCOVER | DOWNLOAD | EDIT | ENABLE | EXIT | FORCE
| GENERATE | HELP | HISTORY | HPONCFG | LOGOUT | PING | POWEROFF | POWERON | QUIT | REBOOT |
REMOVE | RESET | RESTART | SAVE | SET | SHOW | SLEEP | TEST | UNASSIGN | UPDATE | UPLOAD
LOGOUT
• Command:
General commands 17
Page 18

LOGOUT
• Description:
Exits the command line interpreter
• Access level:
QUIT
• Command:
• Description:
• Access level:
Administrator, Operator, User
QUIT
Exits the command line interpreter
Administrator, Operator, User
General commands 18
Page 19

Rack commands
SET RACK NAME
• Command:
SET RACK NAME <rack name>
• Description:
Sets the rack name
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The <rack name> must be a maximum of 32 characters long and includes all alphanumeric, the
dash, and the underscore characters.
UnnamedRack is the default rack name.
SHOW RACK NAME
• Command:
SHOW RACK NAME
• Description:
Displays the user defined rack name setting for the enclosure
• Access level/Bay level:
All
• Restrictions:
None
• Example:
OA-0018FE27577F> SHOW RACK NAME
Rack Name: UnnamedRack
SHOW TOPOLOGY
• Command:
SHOW TOPOLOGY
• Description:
o Displays the enclosures connected by the enclosure link
o Displays a table with the enclosure name, overall health of the enclosure, and the IP address
• Access level/Bay level
Rack commands 19
Page 20

All
• Restrictions:
None
Example
SHOW TOPOLOGY
Detecting linked enclosures ....
Rack Topology (top-down)
Rack UUID: 090987654321
Rack Name: UnnamedRack
Enclosure Name Status Local IP Address UUID
-------------------------------- -------- ----- --------------- ------------Shorty OK Yes 16.84.190.253 090987654321
OA-0018FE2F998B OK No 172.16.211.101 09USE644285C
Rack commands 20
Page 21

User account commands
ADD USER
• Command:
ADD USER "<user name>" ["<password>"]
• Description:
Adds a user to the system. If you do not provide a password, you are prompted for one. If SCRIPT
MODE is enabled and the password is not provided, the password is assigned an unmatched string.
This unmatched string requires an enclosure administrator to change the password to allow the new
user to access the system.
• Access level/Bay level:
OA administrator
• Restrictions:
o You can add a maximum of 30 users, including the reserved accounts.
o The <user name> is case sensitive and must be unique to all other user names and group names.
o The <user name> must begin with a letter.
o The <password> must be three to eight characters long for firmware 1.00 through 1.30 and 3 to
o Reserved user names are: ALL (case insensitive) ADMINISTRATOR (case insensitive), switch1,
ASSIGN
• Command:
ASSIGN {SERVER | INTERCONNECT} {<bay number> | ALL | <bay number>-<bay
number>} {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Assigns one or more bays to a user or group
• Access level/Bay level:
The <user name> must be 1 to 40 characters long and can include all alphanumeric characters,
the dash, and the underscore.
40 characters long for firmware 2.00 and later. The character set includes all printable
characters. If you do not enter a password, you are prompted to enter one.
switch2, switch3, switch4, switch5, switch6, switch7, switch8, ldapuser, nobody, vcmuser, and
root (for firmware 1.00 through 1.30).
OA administrator
• Restrictions:
The <user name> is case sensitive. If a bay is presently assigned to a user, you must unassign the
bay first.
User account commands 21
Page 22

ASSIGN OA
• Command:
ASSIGN OA {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Assigns the Onboard Administrators specified to an existing user or group
• Access level/Bay level:
OA administrator
• Restrictions:
The <user name> is case sensitive.
DISABLE USER
• Command:
DISABLE USER "<user name>"
• Description:
Disables a user account. The system immediately logs out the user and prevents the user from
logging in until the account is enabled. CLI sessions are terminated and all future SOAP web
accesses fail.
• Access level/Bay level:
OA administrator
• Restrictions:
o The <user name> is case sensitive.
o You cannot disable the built-in Administrator account
DISABLE STRONG PASSWORDS
• Command:
DISABLE STRONG PASSWORDS
• Description:
Removes strong password requirements for user passwords
• Access level/Bay level:
OA administrator
• Restrictions:
Only Administrators with Onboard Administrator permission are allowed to manage strong
passwords.
ENABLE STRONG PASSWORDS
• Command:
User account commands 22
Page 23

ENABLE STRONG PASSWORDS
• Description:
When enabled, this command requires that a user's password contain at least one character from
three of the four categories.
The four categories include:
o Uppercase
o Lowercase
o Numeric
o Nonalphanumeric
• Access level/Bay level:
OA administrator
• Restrictions:
Only Administrators with Onboard Administrator permission are allowed to manage strong
passwords
ENABLE USER
• Command:
ENABLE USER "<user name>"
• Description:
Enables a user account that was previously disabled by the DISABLE USER command
• Access level/Bay level:
OA administrator
• Restrictions:
The <user name> is case sensitive.
HISTORY
• Command:
HISTORY
• Description:
Shows the history of commands for the current session
• Access level/Bay level:
All
• Restrictions:
None
REMOVE USER
• Command:
User account commands 23
Page 24

REMOVE USER {ALL | "<user name>" | CERTIFICATE "<user name>"}
• Description:
Removes a user from the system and/or any certificate mapped to the user. If you specify ALL, then
the command is run for all users except the default system accounts.
• Access level/Bay level:
OA administrator
• Restrictions:
o The <user name> is case sensitive.
o You cannot remove the Administrator account.
SET MINIMUM PASSWORD LENGTH
• Command:
SET MINIMUM PASSWORD LENGTH <length>
• Description:
Sets a minimum length for passwords. When set, a user's password must contain at least the number
of characters specified.
• Access level/Bay level:
OA administrator
• Restrictions:
The minimum password length can be set between 3 and 40 characters.
SET PASSWORD
• Command:
SET PASSWORD ["<password>"]
• Description:
Sets the password of the user that executed the command. If you do not provide a password on the
command line, you are prompted for one.
• Access level/Bay level:
All
• Restrictions:
The <password> must be three to eight characters long for firmware 1.00 through 1.30 and 3 to 40
characters long for firmware 2.00 and later. The character set includes all printable characters.
SET SESSION TIMEOUT
• Command:
SET SESSION TIMEOUT <timeout>
• Description:
Sets the number of minutes before inactive sessions are removed. The default setting is 1440.
User account commands 24
Page 25

• Access level/ Bay level:
OA administrator
• Restriction:
Valid session timeout values range from 10 to 1440 minutes (24 hours).
SET USER ACCESS
• Command:
SET USER ACCESS "<user name>" {ADMINISTRATOR | OPERATOR | USER}
• Description:
Sets the user access level. Additionally, use the ASSIGN command to give the user access rights to
the Onboard Administrator, server bays, and interconnect bays.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET USER CONTACT
• Command:
SET USER CONTACT ["<user name>"] "<contact info>"
• Description:
Sets the contact information field for the user. If there is no <user name>, the command modifies the
contact information of the user who executed the command.
• Access level/Bay level:
o All users can modify their own contact information.
o The OA administrator can modify all users.
• Restrictions:
o The <user name> is case sensitive. The <contact info> must be a maximum of 20 characters long
and includes all alphanumeric characters, the dash, the underscore, and spaces.
o The default contact information is blank.
o You must use double quotes if the contact information contains any spaces.
SET USER FULLNAME
• Command:
SET USER FULLNAME ["<user name>"] "<full name>"
• Description:
Sets a user's full name. If you do not specify a <user name>, the command modifies the full name of
the user who is currently logged in.
• Access level/Bay level:
User account commands 25
Page 26

o
OA administrator, OA operator
o All users can modify their own full name.
• Restrictions:
o The <user name> is case sensitive. The <full name> must be a maximum of 20 characters long
and includes all alphanumeric, the dash, the underscore, and the space characters.
o The default full name is blank.
SET USER PASSWORD
• Command:
SET USER PASSWORD "<user name>" ["<new password>"]
• Description:
Sets a user's password. If you do not supply a password on the command line, you are prompted for
one.
• Access level/Bay level
OA administrator
OA operator and User access level users can change their own passwords.
• Restrictions:
o Only OA administrators can modify another user's password. Only the Administrator account
can modify the password of the Administrator account.
o The <user name> is case sensitive.
o The <new password> must be three to eight characters long for firmware 1.00 through 1.30 and
3 to 40 characters long for firmware 2.00 and higher.
o The character set includes all printable characters.
SHOW PASSWORD SETTINGS
• Command:
SHOW PASSWORD SETTINGS
• Description:
Displays the current minimum password length and strong password settings
• Access level/Bay level:
All users
• Restrictions:
None
Example
OA-0018FE27577F>SHOW PASSWORD SETTINGS
Strong Passwords: Disabled
Minimum Password Length: 3
User account commands 26
Page 27

SHOW SESSION TIMEOUT
• Command:
SHOW SESSION TIMEOUT
• Description:
Displays the current Onboard Administrator user session timeout. The session timeout is the number
of minutes before inactive sessions are removed.
• Access level/Bay level:
All
• Restriction:
None
Example
>SHOW SESSION TIMEOUT
Session Timeout: 1440 minutes
SHOW USER
• Command:
SHOW USER [LIST | "<user name>"]
• Description:
Displays the user's full name, contact information, whether the user has administrator rights, whether
the account is enabled, the access level, whether the user has access to the Onboard Administrator,
and the bays the user can access.
If you enter LIST and you are an OA administrator, the information for every user is listed. An
asterisk before a user name denotes the current user.
• Access level/Bay level:
All
• Restrictions:
o The <user name> is case sensitive.
o Users who do not have OA administrator access levels can only view their user information.
Example
OA-0018FE27577F> SHOW USER
Local User "Administrator" Information:
Full name: System Administrator
Contact Info:
User Rights: Admin
Account Status: Enabled
Server Bay Access List: 1 1A 1B 2 2A 2B 3 3A 3B 4 4A 4B 5 5A 5B 6 6A 6B
7 7A 7B 8 8A 8B
Interconnect Bay Access List: 1 2 3 4
OA Access: Yes
User account commands 27
Page 28

SLEEP
• Command:
• Description:
• Access level/Bay level:
• Restrictions:
SLEEP <seconds>
Pauses the sessions for a fixed period of time. This command is useful for adding delays to scripts.
After the pause has started, you cannot continue the session before time runs out. However, you can
terminate the session and start another session.
All
The <seconds> field must be a whole number from 1 to 86400.
UNASSIGN
• Command:
UNASSIGN {SERVER | INTERCONNECT} {<bay number> | ALL | <bay number>-<bay
number>} {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Removes a bay from the user
• Access level/Bay level:
OA administrator
• Restrictions:
The <user name> is case sensitive.
UNASSIGN OA
• Command:
UNASSIGN OA {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Removes the Onboard Administrator from the control of the user that it is currently assigned
• Access level/Bay level:
OA administrator
• Restrictions:
The <user name> is case sensitive.
User account commands 28
Page 29

Two-Factor Authentication commands
DISABLE CRL
• Command:
DISABLE CRL
• Description:
Disables certificate revocation checks
• Access level/Bay level:
OA administrator
• Restrictions:
None
DISABLE TWOFACTOR
• Command:
DISABLE TWOFACTOR
• Description:
Disables Two-Factor Authentication
• Access level/Bay level:
OA administrator
• Restrictions:
None
DOWNLOAD CA CERTIFICATE
• Command:
DOWNLOAD CA CERTIFICATE "<url>"
• Description:
Downloads a CA certificate to act as the trusted certification authority to validate user certificates
when using Two-Factor Authentication.
• Access level/Bay level:
OA administrator
• Restrictions:
Allows the download of up to five different certificates
Two-Factor Authentication commands 29
Page 30

DOWNLOAD USER CERTIFICATE
• Command:
DOWNLOAD USER CERTIFICATE "<user name>" <url>
• Description:
o Downloads an x.509 certificate for the user from <url>. The file at <url> must be a Base64 PEM
encoded file.
o Downloads a CA certificate used in Two-Factor Authentication
• Access level/Bay level:
OA administrator
• Restrictions:
None
REMOVE CA CERTIFICATE
• Command:
REMOVE CA CERTIFICATE "<certificate name>"
• Description:
• Removes the trust certificate corresponding to the SHA1 <certificate name>. Any users having their
certificates issued by this CA can no longer login if Two-Factor Authentication is enabled.
• Access level/Bay level:
OA administrator
• Restrictions:
None
REMOVE USER CERTIFICATE
• Command:
REMOVE USER CERTIFICATE "<user name>"
• Description:
Removes the user certificate. If Two-Factor Authentication is enabled, this user no longer has access
through HTTPS.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SHOW CA CERTIFICATES
• Command:
Two-Factor Authentication commands 30
Page 31

SHOW CA CERTIFICATES
• Description:
Displays a list of installed CA certificates
• Access level/Bay level:
OA Administrator
• Restrictions:
None
Example
OA-0016355E560A> SHOW CA CERTIFICATE
Details for ca certificate 1
certificateVersion = 3
issuerOrganization = ca.com
issuerOrganizationalUnit = IT Infrastructure
issuerCommonName = Hewlett-Packard Primary Class 2 Certification Authority
subjectOrganization = hp.com
subjectOrganizationalUnit = IT Infrastructure
subjectCommonName = Hewlett-Packard Primary Class 2 Certification Authority
validFrom = 1997-12-30T00:00:00Z
validTo = 2012-12-29T23:59:59Z
serialNumber =83:B7:1B:E9:27:AB:5C:61:F8:8F:90:30:E:0D:17:DE:C6
extensionCount = 7
md5Fingerprint = B6:22:5B:B8:43:CD:1A:66:64:19:33:B:3:C1:80:BF:B6
sha1Fingerprint = CF:5C:89:7B:84:7B:73:C4:C5:3E:3F:E:7:93:09:53:EB:C4:28:BE:CF
SHOW TWOFACTOR INFO
• Command:
SHOW TWOFACTOR INFO
• Description:
Displays the configuration details for Two-Factor Authentication
• Access level/Bay level:
All
• Restrictions:
None
Example
OA-0018FE27577F> SHOW TWOFACTOR INFO
Two Factor Authentication:
Enabled : Disabled
Certificate Revocation : Disabled
Certificate Owner Field : Subject
Two-Factor Authentication commands 31
Page 32

Directory commands
ADD LDAP CERTIFICATE
• Command:
ADD LDAP CERTIFICATE <end marker> <certificate> <end marker>
• Description:
Adds an LDAP certificate on the command line. To add the certificate:
1. Start with a string that does not appear within the certificate (the end marker)
2. Paste in the certificate
3. Terminate the command with the end marker
• Access level/Bay level:
OA administrator
• Restrictions:
The certificate text cannot exceed 3071 characters.
ADD LDAP GROUP
• Command:
ADD LDAP GROUP "<group name>"
• Description:
Adds an LDAP group to the group. This group must match a group in the directory server.
• Access level/Bay level:
OA administrator
• Restrictions:
o The maximum number of LDAP groups is 30.
o Group name must be 1 to 255 characters in length.
o Character set includes all printable characters, except quotation marks and new lines.
o The group name must start with an alpha character.
ASSIGN for LDAP
• Command:
ASSIGN {SERVER | INTERCONNECT} {<bay number> | ALL | <bay number>-<bay
number>} {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Directory commands 32
Page 33

Assigns the bay to a specified LDAP group, providing access to the bay at the access level of the
group
• Access level/Bay level:
OA administrator
• Restrictions:
None
ASSIGN OA LDAP GROUP
• Command:
ASSIGN OA {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Assigns access to the Onboard Administrator to the specified group
• Access level/Bay level:
OA administrator
• Restrictions:
None
DISABLE LDAP
NOTE: If LDAP is enabled, local accounts are disabled, and the LDAP server becomes
unavailable, you can recover by booting into Lost Password mode.
When booting in Lost Password mode, the local Administrator password will be reset, LDAP is
• Command:
disabled, and Local Logins are re-enabled
DISABLE LDAP
• Description:
• Disables directory authentication
• Access level/Bay level:
OA administrator
• Restrictions:
None
DOWNLOAD LDAP CERTIFICATE
• Command:
DOWNLOAD LDAP CERTIFICATE "<url>"
• Description:
Downloads an LDAP certificate to establish a trusted relationship with the LDAP server. Specify the
<url> where the certificate is located.
Directory commands 33
Page 34

• Access level/Bay level:
OA administrator
• Restrictions:
None
ENABLE LDAP
NOTE: If LDAP is enabled, local accounts are disabled, and the LDAP server becomes
unavailable, you can recover by booting into Lost Password mode.
When booting in Lost Password mode, the local Administrator password will be reset, LDAP is
disabled, and Local Logins are re-enabled
• Command:
ENABLE LDAP [NOLOCAL]
• Description:
Enables directory authentication. If you use the NOLOCAL option, local users are not enabled.
• Access level/Bay level:
OA administrator
• Restrictions:
Before you can enable LDAP, configuration must be complete.
REMOVE LDAP CERTIFICATE
• Command:
REMOVE LDAP CERTIFICATE "<certificate name>"
• Description:
o Removes the trust certificate corresponding to the MD5 <certificate name>.
o This command revokes trust in the LDAP server associated with the certificate.
• Access level/Bay level:
OA administrator
• Restrictions:
None
REMOVE LDAP GROUP
• Command:
REMOVE LDAP GROUP {ALL | "<group name>"}
• Description:
Removes the LDAP group from the system. If you specify ALL, then all LDAP groups are removed
from the system.
• Access level/Bay level:
Directory commands 34
Page 35

OA administrator
• Restrictions:
Before you can enable the LDAP group, configuration must be complete.
SET LDAP GROUP ACCESS
• Command
SET LDAP GROUP ACCESS "<group name>" {ADMINISTRATOR | OPERATOR | USER}
• Description:
o Sets the LDAP group access level.
o Additionally, use the ASSIGN OA command to give a user or group rights to the Onboard
Administrator.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET LDAP GROUP DESCRIPTION
• Command:
SET LDAP GROUP DESCRIPTION "<group name>" "<description>"
• Description:
Sets the LDAP group description field
• Access level/Bay level:
OA administrator
• Restrictions:
o Must be 0 to 58 characters in length.
o Valid characters are all alphanumeric, the underscore (_), the dash (-), and spaces.
o If the group name or description field contains spaces or zero characters, use double quotes.
SET LDAP NAME MAP
• Command:
SET LDAP NAME MAP {ON|OFF}
• Description:
Turns on NT name mapping to enable the user to enter their NT domain\username
• Access level/Bay level:
OA administrator
• Restrictions:
None
Directory commands 35
Page 36

SET LDAP PORT
• Command:
SET LDAP PORT <port number>
• Description:
Sets the TCP port number of the LDAP SSL service. Port 636 is the standard value.
• Access level/Bay level:
OA administrator
• Restrictions:
The valid port number range is 1 to 65535
SET LDAP SEARCH
• Command:
SET LDAP SEARCH {1-6 } "<search content>"
• Description:
Sets up to six search contexts in priority order
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET LDAP SERVER
• Command:
SET LDAP SERVER {<ip address> | <dns name>}
• Description:
Sets the <ip address> or the <dns name> of the directory server
• Access level/Bay level:
OA administrator
• Restrictions:
The <ip address> is in the form ###.###.###.###, where each ### is in the range 0 to 255.
SHOW LDAP CERTIFICATE
• Command:
SHOW LDAP CERTIFICATE
• Description:
Displays all LDAP certificates that are in effect on the Onboard Administrator
• Access level/Bay level:
Directory commands 36
Page 37

OA administrator
• Restrictions:
None
Example
OA-0016355E560A> SHOW LDAP CERTIFICATE
1 Certificate name: 17D6A5ECBF51A1A47D44C1CDD29D19EE.pem
-----BEGIN CERTIFICATE----MIIHIzCCBgugAwIBAgIKFTKZbQAAAFx1EDANBgkqhkiG9w0BAQUFADB4MRMwEQYK
CZImiZPyLGQBGRYDbmV0MRcwFQYKCZImiZPyLGQBGRYHY3BxY29ycDEbMBkGCgmS
JomT8ixkARkWC2FzaWFwYWNpZmljMSswKQYDVQQDEyJIUFEgSXNzdWluZyBDQSBB
c2lhLVBhY2lmaWMgUmVnaW9uMB4XDTA3MTAyMDIyMzU0M1oXDTA5MTAxOTIyMzU0
M1owKTEnMCUGA1UEAxMeY2NlZ2NhbTAxLmFtZXJpY2FzLmhwcWNvcnAubmV0MIGf
MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDNYsB8T6rJhJQXbKvM5JLi6EXNAtFL
ayV11QVyrtjRtOjRGySwFCk9KNzRS7PIP/p9gH20Ic+ZvgX0fRPnnU/2imMeTGr2
raIYGRSFBJ4sCpAP87m/7Hzk0kiyZ+7KJq92Q61Pipkea...................
-----END CERTIFICATE-----
SHOW LDAP GROUP
• Command:
SHOW LDAP GROUP {LIST | "<group name>"}
• Description:
This command displays the LDAP group information. If you specify LIST, then a list of all the LDAP
groups appears.
• Access level/Bay level:
OA administrator, OA operator, OA user
• Restrictions:
None
Example
OA-0018FE27577F> SHOW LDAP GROUP LIST
Privilege LDAP Group /
Level Description
----------- --------------- Operator Widget.OPS.Team@hp.com
Widget operators
SHOW LDAP INFO
• Command:
SHOW LDAP INFO
• Description:
Displays the LDAP settings, including enabled or disabled status, LDAP server, LDAP port, search
contexts, and NT mapping state
• Access level/Bay level:
All
Directory commands 37
Page 38

• Restrictions:
None
Example
OA-0018FE27577F> show ldap info
Directory Services (LDAP)
Enabled : Disabled
Local Users Enabled : Enabled
NT Name Mapping : Disabled
Directory Server :
Directory Server SSL Port : 0
Search Context #1 :
Search Context #2 :
Search Context #3 :
Search Context #4 :
Search Context #5 :
Search Context #6 :
TEST LDAP
• Command:
TEST LDAP "<username>" "<password>"
• Description:
Run LDAP tests and optionally attempt to login to the LDAP server using the username and password.
• Access level/Bay level:
OA administrator
• Restrictions:
None
UNASSIGN for LDAP
• Command:
UNASSIGN {SERVER | INTERCONNECT} {<bay number> | ALL | <bay number>-<bay
number>} {"<user name>" | LDAP GROUP "<LDAP group name>"}
• Description:
Disables access to the bays for the group specified
• Access level/Bay level:
OA administrator
• Restrictions:
None
UNASSIGN OA LDAP GROUP
• Command:
UNASSIGN OA {"<user name>" | LDAP GROUP "<LDAP group name>"}
Directory commands 38
Page 39

• Description:
Disables access to the Onboard Administrator for the group specified
• Access level/Bay level:
OA administrator
• Restrictions:
None
Directory commands 39
Page 40

HP SIM commands
ADD HPSIM CERTIFICATE
• Command:
ADD HPSIM CERTIFICATE <end marker> <certificate> <end marker>
• Description:
Adds an HP SIM certificate on the command line.
1. Start with a string that does not appear within the certificate (the end marker).
2. Paste in the certificate.
3. Terminate the command with the end marker.
• Access level/Bay level:
OA administrator
• Restrictions:
o This command is only available in script mode.
o The certificate text cannot exceed 3071 characters.
DOWNLOAD HPSIM CERTIFICATE
• Command:
DOWNLOAD HPSIM CERTIFICATE { <host> }
• Description:
Downloads an HP SIM certificate from the specified IP address or fully-qualified DNS system name,
such as HP-SIM system. The <host> value can be an IPv4 address, an IPv6 address, or a DNS name.
• Access level/Bay level:
OA administrator
• Restrictions:
o The <IP address> must be in the form ###.###.###.###, where each ### ranges from 0 to
255.
o For IPv6 the <ip address> must be in the form ####:####:####:####:####:####:####:####
where each #### ranges from 0 to FFFF.
o IPv6 addresses must be informed without the network prefix length.
REMOVE HPSIM CERTIFICATE
• Command:
REMOVE HPSIM CERTIFICATE "<certificate name>"
HP SIM commands 40
Page 41

• Description:
Removes the trust certificate corresponding to the <certificate name>. Disables HP SIM SSO through
the application (for example HP SIM) that provided the certificate without disabling other HP SIM
applications.
The <certificate name> can be obtained using the SHOW HPSIM INFO command.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET HPSIM TRUST MODE
• Command:
SET HPSIM TRUST MODE {CERTIFICATE [ON] | DISABLED [OFF]}
• Description:
Enables or disables the HP SIM SSO mode. When enabled, the trusted applications can access the
Onboard Administrator GUI data without requiring additional authentication.
• Access level/Bay level:
OA administrator
• Restrictions:
The CERTIFICATE (On) mode trusts only applications with certificates that have been uploaded to the
Onboard Administrator.
SHOW HPSIM INFO
• Command:
SHOW HPSIM INFO
• Description:
Displays the current HP SIM SSO configuration for the Onboard Administrator.
The data includes the current HP SIM SSO Trust Mode (see SET HPSIM TRUST MODE) and a list of
names that the Onboard Administrator is configured to trust using a trust certificate.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
Example
OA-0018FE27577F> SHOW HPSIM INFO
HPSIM Trust Mode: Disabled
Trusted Server Certificates
No certificates were found.
HP SIM commands 41
Page 42

General management commands
DOWNLOAD OA CERTIFICATE
• Command:
DOWNLOAD OA CERTIFICATE [<bay number> | ACTIVE | STANDBY] <url>
• Description:
Downloads a CA supplied pkcs#7 file to replace the current security certificate on the system.
Supported protocols are HTTP, FTP, and TFTP. Format the URL as protocol://host/path/file. The URL
syntax for IPv6 addresses is protocol://[<ipv6 address>]/path/file.
• Access level/Bay level:
OA administrator
• Restrictions:
You must format the URL as protocol://host/path/file. If your FTP server does not support
anonymous connections, then you can specify a user name and password by replacing host in the
previous format with username:password@host.
FORCE TAKEOVER
• Command:
FORCE TAKEOVER
• Description:
Forces the redundant Onboard Administrator to become the active Onboard Administrator. The
active becomes the standby and the standby becomes the active.
• Access level/Bay level:
OA administrator
• Restrictions:
None
GENERATE CERTIFICATE
• Command:
GENERATE CERTIFICATE [REQUEST | SELFSIGNED]
• Description:
Generates a pkcs#10 certificate request or a self-signed certificate. You are prompted for the
following fields to generate a certificate:
o OA Host Name (CN)
o Organization Name (O)
General management commands 42
Page 43

o
City or Locality (L)
o State or Province (ST)
o Country (C)
o Organizational Unit
o Contact Person
o Email Address
o Surname
o Given Name
o Initials
o DN Qualifier
o Challenge Password
o Unstructured Name
• Access level/Bay level:
OA administrator
• Restrictions:
This command is not valid in SCRIPT MODE
Generate certificate prompts
Prompt Description Restrictions
OA Host Name (CN)
Organization Name (O)
City or Locality (L)
This is the most important
field. This is the Onboard
Administrator name that
appears in the browser web
address field. This certificate
attribute is generally referred
to as the common name.
The company or
organization that owns this
Onboard Administrator.
When this information is
used to generate a certificate
signing request, the issuing
certificate authority can verify
that the organization
requesting the certificate is
legally entitled to claim
ownership of the given
company name or
organization name.
The city or locality where the
Onboard Administrator is
located.
Must be 1 to 60 characters long. To prevent
security alerts, the value of this field must
match the host name exactly as it is known
by the web browser. The browser compares
the host name in the resolved web address to
the name that appears in the certificate. For
example, if the web address in the address
field is https://oa-001635.xyz.com, then the
value must be oa-001635.xyz.com
Must be 1 to 60 characters long
Must be 1 to 50 characters long
General management commands 43
Page 44

Prompt Description Restrictions
State or Province (ST)
Country (C)
Organizational Unit
Contact Person
Email Address
Surname
Given Name
Initials
DN Qualifier
Challenge Password
Unstructured Name
The state or province where
the Onboard Administrator is
located.
The two-character country
code that identifies the
country where the Onboard
Administrator is located.
The unit within the company
or organization that owns the
Onboard Administrator.
The person responsible for
the Onboard Administrator.
The email address of the
contact person responsible
for the Onboard
Administrator.
The surname of the person
responsible for the Onboard
Administrator.
The given name of the
person responsible for the
Onboard Administrator.
The initials of the person
responsible for the Onboard
Administrator.
The distinguished name
qualifier of the Onboard
Administrator.
The password to the
certificate-signing request.
This is for additional
information, for example, an
unstructured name that is
assigned to the Onboard
Administrator.
Must be 1 to 30 characters long
Must be a two-character country code
(Optional) Must be 0 to 60 characters long
(Optional) Must be 0 to 60 characters in
length
(Optional) Must be 0 to 60 characters long
(Optional) Must be 0 to 60 characters long
(Optional) Must be 0 to 60 characters long
(Optional) Must be 0 to 20 characters long
(Optional) Must be 0 to 60 characters long
(Optional) Must be 0 to 20 characters long
(Optional) Must be 0 to 60 characters long
PING
• Command:
PING [IPv6] [<number>] {ip address> | "<server name>"}
• Description:
Sends ICMP echo messages to a remote IP[v6] device. If <number> is omitted or between 9999 and
99999, then only four packets are sent. Packets are sent out at one-second intervals to prevent strain
on the network.
• Access level/Bay level:
All
General management commands 44
Page 45

• Restrictions:
o The <number> value cannot be greater than 99999 or negative.
o The <ip address> value must be in the form ###.###.###.###, where each ### ranges from 0
to 255.
o For IPv6 the <ip address> must be in the form ####:####:####:####:####:####:####:####
where each #### ranges from 0 to FFFF.
SET DEVICE SERIAL_NUMBER BLADE
• Command:
SET DEVICE SERIAL_NUMBER BLADE <bay number> "<serial number>"
• Description:
Sets the serial number of the specified Storage, Tape, or I/O expansion blade.
• Access level/Bay level:
OA administrator
• Restrictions:
o Length must be 10 characters. All printable characters are allowed.
o This operation cannot be performed on server blades.
SET FACTORY
• Command:
SET FACTORY
• Description:
o Restores the Onboard Administrator to its factory defaults. The Administrator account password
does not change.
o The Onboard Administrator restarts after all changes are made.
o All existing settings will be lost when this operation is run.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET SCRIPT MODE
• Command:
SET SCRIPT [MODE] {ON | OFF}
• Description:
o Ceases all prompting and verifying of entries when SCRIPT MODE is on.
o The ADD USER command must have a password argument if executed in SCRIPT MODE.
General management commands 45
Page 46

o
Default values are used for any parameters that would normally require user interaction.
• Access level/Bay level:
All
• Restrictions:
None
SHOW ALL
• Command:
SHOW ALL
• Description:
Executes all SHOW commands in succession
• Access level/Bay level:
All
• Restrictions:
o This command only displays the bays for which you have privileges.
o To save the output, you must configure your Telnet software to log the session to a file or increase
the history buffer size so that the output can be copied and pasted into another file.
Examples
OA-0018FE27577F> show all
>SHOW CONFIG
#Script Generated by Administrator
#Generated on: Wed Nov 11 06:22:18 2009
#Set Enclosure Time
SET TIMEZONE CST6CDT
#SET DATE MMDDhhmm{{CC}YY}
#Set Enclosure Information
SET ENCLOSURE ASSET TAG ""
SET ENCLOSURE NAME "OA-0018FE27577F"
SET RACK NAME "UnnamedRack"
SET POWER MODE REDUNDANT
SET POWER SAVINGS ON
#Power limit must be within the range of 950-8750
SET POWER LIMIT OFF
#Enclosure Dynamic Power Cap must be within the range of 1508-1508
#Derated Circuit Capacity must be within the range of 1508-1508
#Rated Circuit Capacity must be within the range of 1508-1508
SET ENCLOSURE POWER_CAP OFF
SET ENCLOSURE POWER_CAP_BAYS_TO_EXCLUDE None
#Set PowerDelay Information
SET INTERCONNECT POWERDELAY 1 0
SET INTERCONNECT POWERDELAY 2 0
SET INTERCONNECT POWERDELAY 3 0
SET INTERCONNECT POWERDELAY 4 0
SET SERVER POWERDELAY 1 0
SET SERVER POWERDELAY 2 0
General management commands 46
Page 47

SET SERVER POWERDELAY 3 0
SET SERVER POWERDELAY 4 0
SET SERVER POWERDELAY 5 0
SET SERVER POWERDELAY 6 0
SET SERVER POWERDELAY 7 0
SET SERVER POWERDELAY 8 0
SET SERVER POWERDELAY 1A 0
SET SERVER POWERDELAY 2A 0
SET SERVER POWERDELAY 3A 0
SET SERVER POWERDELAY 4A 0
SET SERVER POWERDELAY 5A 0
SET SERVER POWERDELAY 6A 0
SET SERVER POWERDELAY 7A 0
SET SERVER POWERDELAY 8A 0
SET SERVER POWERDELAY 1B 0
SET SERVER POWERDELAY 2B 0
SET SERVER POWERDELAY 3B 0
SET SERVER POWERDELAY 4B 0
SET SERVER POWERDELAY 5B 0
SET SERVER POWERDELAY 6B 0
SET SERVER POWERDELAY 7B 0
SET SERVER POWERDELAY 8B 0
# Set ENCRYPTION security mode to STRONG or NORMAL.
SET ENCRYPTION NORMAL
#Configure Protocols
ENABLE WEB
ENABLE SECURESH
ENABLE TELNET
ENABLE XMLREPLY
ENABLE GUI_LOGIN_DETAIL
#Configure Alertmail
SET ALERTMAIL SMTPSERVER
DISABLE ALERTMAIL
#Configure Trusted Hosts
#REMOVE TRUSTED HOST ALL
DISABLE TRUSTED HOST
#Configure NTP
SET NTP PRIMARY
SET NTP SECONDARY
SET NTP POLL 720
DISABLE NTP
#Set SNMP Information
SET SNMP CONTACT ""
SET SNMP LOCATION ""
SET SNMP COMMUNITY READ "public"
SET SNMP COMMUNITY WRITE ""
ENABLE SNMP
#Set Remote Syslog Information
SET REMOTE SYSLOG SERVER ""
SET REMOTE SYSLOG PORT 514
DISABLE SYSLOG REMOTE
#Set Enclosure Bay IP Addressing (EBIPA) Information
SET EBIPA SERVER NONE 1
SET EBIPA SERVER NONE 2
SET EBIPA SERVER NONE 3
SET EBIPA SERVER NONE 4
General management commands 47
Page 48

SET EBIPA SERVER NONE 5
SET EBIPA SERVER NONE 6
SET EBIPA SERVER NONE 7
SET EBIPA SERVER NONE 8
SET EBIPA SERVER NONE 1A
SET EBIPA SERVER NONE 2A
SET EBIPA SERVER NONE 3A
SET EBIPA SERVER NONE 4A
SET EBIPA SERVER NONE 5A
SET EBIPA SERVER NONE 6A
SET EBIPA SERVER NONE 7A
SET EBIPA SERVER NONE 8A
SET EBIPA SERVER NONE 1B
SET EBIPA SERVER NONE 2B
SET EBIPA SERVER NONE 3B
SET EBIPA SERVER NONE 4B
SET EBIPA SERVER NONE 5B
SET EBIPA SERVER NONE 6B
SET EBIPA SERVER NONE 7B
SET EBIPA SERVER NONE 8B
SET EBIPA SERVER NETMASK 0.0.0.0
SET EBIPA SERVER GATEWAY 0.0.0.0
SET EBIPA SERVER DOMAIN ""
DISABLE EBIPA SERVER 1,2,3,4,5,6,7,8,1A,2A,3A,4A,5A,6A,7A,8A,1B,2B,3B,4B,5B,6B,7B,8B
SET EBIPA INTERCONNECT NONE 1
SET EBIPA INTERCONNECT NONE 2
SET EBIPA INTERCONNECT NONE 3
SET EBIPA INTERCONNECT NONE 4
SET EBIPA INTERCONNECT NETMASK 0.0.0.0
SET EBIPA INTERCONNECT GATEWAY 0.0.0.0
SET EBIPA INTERCONNECT DOMAIN ""
SET EBIPA INTERCONNECT NTP PRIMARY 0.0.0.0
SET EBIPA INTERCONNECT NTP SECONDARY 0.0.0.0
DISABLE EBIPA INTERCONNECT 1,2,3,4
#Uncomment following line to remove all user accounts currently in the system
#REMOVE USERS ALL
#Create Users
ADD USER "Administrator"
SET USER CONTACT "Administrator" ""
SET USER FULLNAME "Administrator" "System Administrator"
SET USER ACCESS "Administrator" ADMINISTRATOR
ASSIGN SERVER 1,2,3,4,5,6,7,8,1A,2A,3A,4A,5A,6A,7A,8A,1B,2B,3B,4B,5B,6B,7B,8B "Administrator"
ASSIGN INTERCONNECT 1,2,3,4 "Administrator"
ASSIGN OA "Administrator"
ENABLE USER "Administrator"
ADD USER "Test"
SET USER CONTACT "Test" ""
SET USER FULLNAME "Test" ""
SET USER ACCESS "Test" USER
ASSIGN SERVER 1,2,1A,2A,1B,2B "Test"
ASSIGN OA "Test"
ENABLE USER "Test"
#Password Settings
DISABLE STRONG PASSWORDS
SET MINIMUM PASSWORD LENGTH 3
#Session Timeout Settings
SET SESSION TIMEOUT 1440
#Set LDAP Information
SET LDAP SERVER ""
SET LDAP PORT 0
General management commands 48
Page 49

SET LDAP NAME MAP OFF
SET LDAP SEARCH 1 ""
SET LDAP SEARCH 2 ""
SET LDAP SEARCH 3 ""
SET LDAP SEARCH 4 ""
SET LDAP SEARCH 5 ""
SET LDAP SEARCH 6 ""
#Uncomment following line to remove all LDAP accounts currently in the system
#REMOVE LDAP GROUP ALL
DISABLE LDAP
#Set SSO TRUST MODE
SET SSO TRUST Disabled
#Set Network Information
#NOTE: Setting your network information through a script while
# remotely accessing the server could drop your connection.
# If your connection is dropped this script may not execute to conclusion.
SET OA NAME 1 OA-0018FE27577F
SET IPCONFIG DHCP 1 DYNAMICDNS
SET NIC AUTO 1
#Set VLAN Information
SET VLAN FACTORY
SET VLAN DEFAULT 1
EDIT VLAN 1 "Default"
SET VLAN SERVER 1 1
SET VLAN SERVER 1 2
SET VLAN SERVER 1 3
SET VLAN SERVER 1 4
SET VLAN SERVER 1 5
SET VLAN SERVER 1 6
SET VLAN SERVER 1 7
SET VLAN SERVER 1 8
SET VLAN INTERCONNECT 1 1
SET VLAN INTERCONNECT 1 2
SET VLAN INTERCONNECT 1 3
SET VLAN INTERCONNECT 1 4
SET VLAN OA 1
DISABLE VLAN
SAVE VLAN
>SHOW DATE
Date: 2009-11-11T06:22:18-06:00
Time Zone: CST6CDT
>SHOW DISPLAY EVENT
Display Events is set to OFF.
>SHOW EBIPA
EBIPA Settings - Device Bay iLO Processors
Domain:
Subnet Mask: 0.0.0.0 Gateway: 0.0.0.0
DNS Server1: 0.0.0.0 Server2: 0.0.0.0
Server3: 0.0.0.0
Bay Enabled EBIPA Address Current Address Device Type
--- ------- --------------- --------------- ----------- 1 No 16.84.190.209 Server Blade
1A No N/A [Absent]
1B No N/A [Absent]
General management commands 49
Page 50

2 No 16.84.190.217 Server Blade
2A No N/A [Absent]
2B No N/A [Absent]
3 No N/A [Absent]
3A No N/A [Absent]
3B No N/A [Absent]
4 No 16.84.190.215 Server Blade
4A No N/A [Absent]
4B No N/A [Absent]
5 No N/A [Subsumed]
5A No N/A [Absent]
5B No N/A [Absent]
6 No N/A [Subsumed]
6A No N/A [Absent]
6B No N/A [Absent]
7 No N/A [Absent]
7A No N/A [Absent]
7B No N/A [Absent]
8 No N/A [Absent]
8A No N/A [Absent]
8B No N/A [Absent]
EBIPA Settings - Interconnect Management Ports
Domain:
Subnet Mask: 0.0.0.0 Gateway: 0.0.0.0
DNS Server1: 0.0.0.0 Server2: 0.0.0.0
Server3: 0.0.0.0
NTP Server1: 0.0.0.0 Server2: 0.0.0.0
Bay Enabled EBIPA Address Current Address Module Type
--- ------- --------------- --------------- ----------- 1 No 16.84.189.106 Ethernet
2 No 16.84.189.148 Ethernet
3 No N/A [Absent]
4 No N/A [Absent]
>SHOW ENCLOSURE FAN ALL
Fan #1 information:
Status: OK
Speed: 55 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 27
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
Diagnostic Status:
Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
Fan #2 information:
Status: OK
Speed: 43 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 20
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
General management commands 50
Page 51

Diagnostic Status:
Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
Fan #3 information:
Status: OK
Speed: 55 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 28
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
Diagnostic Status:
Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
Fan #4 information:
Status: OK
Speed: 55 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 28
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
Diagnostic Status:
Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
Fan #5 information:
Status: OK
Speed: 43 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 22
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
Diagnostic Status:
Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
Fan #6 information:
Status: OK
Speed: 55 percent of Maximum speed
Maximum speed: 18000
Minimum speed: 10
Power consumed: 28
Product Name: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Version: 2.7
Diagnostic Status:
General management commands 51
Page 52

Internal Data OK
Location OK
Device Failure OK
Device Degraded OK
Missing Device OK
>SHOW ENCLOSURE INFO
Enclosure Information:
Enclosure Name: OA-0018FE27577F
Enclosure Type: BladeSystem c3000 Enclosure
Part Number: 437506-B21
Serial Number: 0987654321
UUID: 090987654321
Asset Tag:
Midplane Spare Part Number: 441829-001
Power Distribution Unit:
[No PDU is present on c3000 enclosures]
Onboard Administrator Tray Information:
[No Tray Information is present on c3000 enclosures]
>SHOW ENCLOSURE LCD
Status : OK
Display : Blinking
Name : BladeSystem c3000 Insight Display
Spare Part# : 441831-001
Manufacturer: HP
Fw Version : 2.2.2
Diagnostic Status:
Internal Data OK
>SHOW ENCLOSURE POWER_CAP
Enclosure Dynamic Power Cap: Disabled
Derated Circuit Capacity: Disabled
Rated Circuit Capacity: Disabled
Allowable Enclosure Dynamic Power Cap: 1508 - 1508 Watts AC
Allowable Derated Circuit Capacity: 1508 - 1508 Watts AC
Allowable Rated Circuit Capacity: 1508 - 1508 Watts AC
>SHOW ENCLOSURE POWER_CAP_BAYS_TO_EXCLUDE
Bays opted out: None
>SHOW ENCLOSURE POWERSUPPLY ALL
Power Supply #1 Information:
Status: OK
AC Input Status: OK
Capacity: 1200 Watts
Current Power Output: 632 Watts
Serial Number: 531300ALL00233
Product Name: HP PROLIANT SERVER PS
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Product Ver:
Diagnostic Status:
Internal Data OK
Device Failure OK
Power Cord OK
Power Supply #2 Information:
Status: OK
AC Input Status: OK
Capacity: 1200 Watts
General management commands 52
Page 53

Current Power Output: 8 Watts
Serial Number: 531300ALL00014
Product Name: HP PROLIANT SERVER PS
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Product Ver:
Diagnostic Status:
Internal Data OK
Device Failure OK
Power Cord OK
Power Supply #3 Information:
Status: OK
AC Input Status: OK
Capacity: 1200 Watts
Current Power Output: 8 Watts
Serial Number: 531300ALL00399
Product Name: HP PROLIANT SERVER PS
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Product Ver:
Diagnostic Status:
Internal Data OK
Device Failure OK
Power Cord OK
Power Supply #4 Information:
Status: Power Supply Bay Empty
Power Supply #5 Information:
Status: Power Supply Bay Empty
Power Supply #6 Information:
Status: Power Supply Bay Empty
>SHOW ENCLOSURE POWER_SUMMARY
Enclosure Bay Output Allocation:
Bay Power Allocated (Watts DC)
------------- -------------------------Devices 776
Interconnects + 65
Fans + 480
------ = 1321
Enclosure Output Power Summary:
Enclosure Watts DC
---------------- -------Power Capacity 1321
Power Allocation - 1321
Power Available = 0
Enclosure Input Power Summary:
Enclosure Watts AC
----------------- -------Present Power 716
Max Input Power 1606
Dynamic Power Cap Not Set
Power Limit Not Set
Device Bay Power Summary:
Power Allocated
Bay Name (Watts DC)
--- -------------------- -------------- 1 RonChangedHostNameI 212
2 test45667 412
4 YOUR-EYZCGYAYBB 152
-------
General management commands 53
Page 54

= 776
Interconnect Bay Power Summary:
Bay Name Power Allocated (Watts DC)
--- -------------------------------- ------------------------- 1 GbE2c Ethernet Blade Switch 25
2 Cisco Catalyst Blade Switch 312 40
------ = 65
Fan Power Summary:
Total Fans Fan Rule Present Power Power Allocated
(Number of Fans) (Number of Fans) (Watts DC) (Watts DC)
---------------- ---------------- -------------- -------------- 6 6 153 480
>SHOW ENCLOSURE STATUS
Enclosure:
Status: Degraded
Unit Identification LED: On
Diagnostic Status:
Internal Data OK
Onboard Administrator:
Status: OK
Power Subsystem:
Status: Degraded
Power Mode: Redundant
Redundancy State: Redundancy Lost
Power Capacity: 1321 Watts DC
Present Power: 716 Watts AC
Cooling Subsystem:
Status: OK
Fans Good/Wanted/Needed: 6/6/5
Fan 1: 10010 RPM (56%)
Fan 2: 7810 RPM (43%)
Fan 3: 10012 RPM (56%)
Fan 4: 10013 RPM (56%)
Fan 5: 7814 RPM (43%)
Fan 6: 10002 RPM (56%)
>SHOW ENCLOSURE TEMP
Locale Bay # Temp Status Temp Caution Critical
---------------------- ----- ----------- -------- ------- -------Enclosure OK 23C/ 73F 40C 45C
Onboard Administrator 1 OK 25C/ 77F 75C 80C
Blade Bay 1 N/A 20C/ 68F 38C 43C
Blade Bay 2 N/A 23C/ 73F 40C 45C
Blade Bay 4 N/A 20C/ 68F 38C 43C
Interconnect Module 1 OK ---- --- --Interconnect Module 2 OK ---- --- -->SHOW ENCRYPTION
ENCRYPTION mode is NORMAL
>SHOW OA INFO
Onboard Administrator #1 information:
Product Name : BladeSystem c3000 Onboard Administrator
General management commands 54
Page 55

Part Number : 448589-B21
Spare Part No.: 441832-001
Serial Number : P30590A9VUQ04B
UUID : 18P30590A9VUQ04B
Manufacturer : HP
Firmware Ver. : 3.00 Nov 11 2009
Hw Board Type : 1
Hw Version : A0
>SHOW OA NETWORK
Onboard Administrator #1 Network Information:
Name: OA-0018FE27577F
- - - - - IPv4 Information - - - - DHCP: Enabled - Dynamic DNS
IPv4 Address: 16.84.189.60
Netmask: 255.255.252.0
Gateway Address: 16.84.188.1
- - - - - IPv6 Information - - - - IPv6: Disabled
Static Address: Not Set
DHCPv6: Disabled
Router Advertisement: Disabled
- - - - - General Information - - - - Primary DNS: 16.110.135.51
Secondary DNS: 16.110.135.52
Tertiary DNS: Not Set
MAC Address: 00:18:FE:27:57:7F
Link Settings: Auto-Negotiation, 100 Mbit, Full Duplex
Link Status: Active
Enclosure IP Mode: Not Supported
>SHOW OA STATUS
Onboard Administrator #1 Status:
Name: OA-0018FE27577F
Role: Active
UID: Off
Status: OK
>SHOW OA CERTIFICATE
Onboard Administrator #1 Certificate Information:
Issued by: OA-0018FE27577F
Valid from: 2009-11-03T14:12:11Z
Valid until: 2019-11-01T14:12:11Z
Serial Number: B9:F5:34:59:FF:C9:94:69
Version: 1
MD5 Fingerprint: 44:D2:51:CB:64:96:57:50:27:CB:64:2D:48:A3:13:34
SHA1 Fingerprint: 1F:16:54:A6:76:07:64:11:29:78:23:90:A3:62:CD:3A:4D:53:06:17
Subject:
Common Name (CN): OA-0018FE27577F
Country (C):
State or Province (ST):
City or Locality (L):
Organization Name (0): Hewlett-Packard
Organizational Unit: Onboard Administrator
General management commands 55
Page 56

>SHOW SYSLOG OA 1
bps - Full Duplex
Nov 9 10:21:11 OA: Time zone changed to CST+6
Nov 9 10:21:13 OA: LCD Status is: OK.
Nov 9 10:21:17 Enclosure-Link: Service started
Nov 9 10:21:20 OA: Onboard Administrator booted successfully
Nov 9 10:21:21 netreg: DDNS: Update refused by DNS server
Nov 9 10:21:24 OA: PS Subsystem N + N Redundancy - FAILED. Allocated Power: 480W DC,
Present Power: 662W AC.
Nov 9 10:21:24 OA: Enclosure Status changed from OK to Degraded.
Nov 9 10:21:26 OA: /dev/spi is busy
Nov 9 10:21:26 Enclosure-Link: Initial topology scan completed successfully
Nov 9 10:21:28 OA: /dev/spi is busy
Nov 9 10:21:29 OA: /dev/spi is busy
Nov 9 10:21:30 OA: /dev/spi is busy
Nov 9 10:21:30 OA: /dev/spi is busy
Nov 9 10:21:32 OA: /dev/spi is busy
Nov 9 10:21:35 OA: /dev/spi is busy
Nov 9 10:21:41 OA: /dev/spi is busy
Nov 9 10:21:43 OA: IO module in slot 2 temperature is normal
Nov 9 10:21:44 OA: Blade 1 is reporting nominal health status.
Nov 9 10:21:44 OA: Blade in bay #1 status changed to OK
Nov 9 10:21:45 OA: Blade in bay #1 status changed to OK
Nov 9 10:21:46 OA: Blade 2 is reporting nominal health status.
Nov 9 10:21:46 OA: Blade in bay #2 status changed to OK
Nov 9 10:21:47 OA: Blade in bay #2 status changed to OK
Nov 9 10:21:48 OA: Blade 4 is reporting nominal health status.
Nov 9 10:21:49 OA: Blade in bay #4 status changed to OK
Nov 9 10:21:49 OA: Blade in bay #4 status changed to OK
Nov 9 10:21:57 OA: VLAN is disabled
>SHOW NETWORK
Onboard Administrator Network Settings:
- - - - - IPv4 Information - - - - DHCP: Enabled - Dynamic DNS
IPv4 Address: 16.84.189.60
Netmask: 255.255.252.0
Gateway Address: 16.84.188.1
- - - - - IPv6 Information - - - - IPv6: Disabled
Static Address: Not Set
DHCPv6: Disabled
Router Advertisement: Disabled
- - - - - General Information - - - - Primary DNS: 16.110.135.51
Secondary DNS: 16.110.135.52
Tertiary DNS: Not Set
MAC Address: 00:18:FE:27:57:7F
Network Link Settings: Link Auto-negotiation
Onboard Administrator Protocol Status:
Web (HTTP/HTTPS): Enabled
SNMP: Enabled
SecureSH: Enabled
Encryption Mode: Normal
Trusted Hosts: Disabled
HPSIM Trust Mode: Disabled
Telnet: Enabled
General management commands 56
Page 57

AlertMail: Disabled
Mailbox: Not Set
SMTP Server: Not Set
Sender Domain: Not Set
XML Reply: Enabled
NTP: Disabled
Primary NTP server: Not Set
Secondary NTP server: Not Set
Server Poll-Interval: 720 seconds
Link Loss Failover: Not Supported
Link Loss Interval: Not Supported
Enclosure IP Mode: Not Supported
GUI Login Detail: Enabled
VLAN: Disabled
>SHOW POWER
Power Mode: Redundant
Dynamic Power: Enabled
Set Power Limit: Not Set
Power Capacity: 1321 Watts DC
Power Available: 0 Watts DC
Power Allocated: 1321 Watts DC
Present Power: 716 Watts AC
Power Limit: 1606 Watts AC
>SHOW RACK NAME
Rack Name: UnnamedRack
>SHOW SNMP
SNMP Configuration:
Status: Enabled
System Name: OA-0018FE27577F
System Location:
System Contact:
Read Community Name: public
Write Community Name:
No trap receivers specified.
>SHOW SSHFINGERPRINT
1024 26:8a:99:56:a3:c4:85:dc:b4:5f:c8:b5:36:37:69:9d /etc/ssh/id_dsa.pub (DSA)
>SHOW SSHKEY
There is no SSH key installed.
>SHOW HPSIM INFO
HPSIM Trust Mode: Disabled
Trusted Server Certificates
No certificates were found.
>SHOW INTERCONNECT INFO ALL
1. Ethernet
Product Name: GbE2c Ethernet Blade Switch
Width: Single
URL to Management interface:
In-Band IPv4 Address: 16.84.189.106
User Assigned Name:
Part Number: 410917-B21
Spare Part Number: 414037-001
General management commands 57
Page 58

Serial Number: MY36290EMT
Temperature Sensor: Present
JS2 Connector: Absent
Internal Ethernet Interface to OA: Present
Internal Ethernet Route to OA: Enabled
Internal Serial Interface to OA: Absent
Internal Serial Route to OA: Disabled
External Serial Port Interface: Present
External Ethernet Interface: Present
2. Ethernet
Product Name: Cisco Catalyst Blade Switch 3120X for HP w/ IP Base
Width: Single
URL to Management interface: http://16.84.189.148
In-Band IPv4 Address: 16.84.189.148
User Assigned Name: Switch
Part Number: WS-CBS3120X-S
Spare Part Number: 451357-001
Serial Number: FOC1129T0XE
Temperature Sensor: Absent
JS2 Connector: Absent
Internal Ethernet Interface to OA: Present
Internal Ethernet Route to OA: Enabled
Internal Serial Interface to OA: Absent
Internal Serial Route to OA: Disabled
External Serial Port Interface: Present
External Ethernet Interface: Absent
3. <absent>
4. <absent>
>SHOW INTERCONNECT LIST
Bay Interconnect Type Manufacturer Power Health UID Management IP
--- ----------------- -------------------- ------- --------- --- -------------- 1 Ethernet HP On OK Off 16.84.189.106
2 Ethernet Cisco Systems, Inc. On OK Off 16.84.189.148
3 [Absent]
4 [Absent]
Totals: 2 interconnect modules installed, 2 powered on.
>SHOW INTERCONNECT SESSION
Interconnect Bay User
------------------ --------------
No Interconnect remote console sessions were detected.
>SHOW INTERCONNECT STATUS ALL
Interconnect Module #1 Status:
Status : OK
Thermal: OK
CPU Fault: OK
Health LED: OK
UID: Off
Powered: On
Diagnostic Status:
Internal Data OK
Management Processor OK
Thermal Warning OK
Thermal Danger OK
I/O Configuration OK
Power OK
Device Failure OK
Device Degraded OK
General management commands 58
Page 59

Interconnect Module #2 Status:
Status : OK
Thermal: OK
CPU Fault: OK
Health LED: OK
UID: Off
Powered: On
Diagnostic Status:
Internal Data OK
Management Processor OK
Thermal Warning OK
Thermal Danger OK
Power OK
Device Failure OK
Device Degraded OK
Interconnect Module #3 Status:
Interconnect Module Type: No Interconnect Module Installed
Interconnect Module #4 Status:
Interconnect Module Type: No Interconnect Module Installed
>SHOW INTERCONNECT PORT MAP ALL
1: GbE2c Ethernet Blade Switch
Type: Ethernet
Width: Single
Status: OK
Port 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
Status OK OK OK OK OK OK OK OK OK OK
Blade 1 2 4 1 2 1 2 4 1 2
Mezz/Nic NI NI NI NI NI NI NI NI NI NI
Port 3 3 1 1 1 4 4 2 2 2
2: Cisco Catalyst Blade Switch 3120X for HP w/ IP Base
Type: Ethernet
Width: Single
Status: No Connection
3. <absent>
4. <absent>
>SHOW INTERCONNECT POWERDELAY ALL
Current PowerDelay Status: Not in Progress
Bay Device PowerDelay State Delay (seconds)
--- -------------------------------- ---------------- -------------- 1 GbE2c Ethernet Blade Switch Disabled 0
2 Cisco Catalyst Blade Switch 3120 Disabled 0
3 Absent Disabled 0
4 Absent Disabled 0
>SHOW SERVER LIST
Bay iLO Name iLO IP Address Status Power UID Partner
--- ----------------------------- --------------- -------- ------- --- ------ 1 ILOUSM64204B1 16.84.190.209 OK On Off
2 ILOUSM65103VJ 16.84.190.217 OK On Off
3 [Absent]
4 ILOUSM62401EP 16.84.190.215 OK On Off
General management commands 59
Page 60

5 [Subsumed]
6 [Subsumed]
7 [Absent]
8 [Absent]
Totals: 3 server blades installed, 3 powered on.
>SHOW SERVER NAMES
Bay Server Name Serial Number Status Power UID Partner
--- ----------------------------- --------------- -------- ------- --- ------ 1 RonChangedHostNameInILO USM64204B1 OK On Off
2 test45667 USM65103VJ OK On Off
3 [Absent]
4 YOUR-EYZCGYAYBB USM62401EP OK On Off
5 [Subsumed]
6 [Subsumed]
7 [Absent]
8 [Absent]
Totals: 3 server blades installed, 3 powered on.
>SHOW FRU
Enclosure
Model: BladeSystem c3000 Enclosure
Manufacturer: HP
Serial Number: 0987654321
Part Number: 437506-B21
Enclosure Midplane
Manufacturer: HP
Spare Part Number: 441829-001
Onboard Administrator 1
Model: BladeSystem c3000 Onboard Administrator
Manufacturer: HP
Serial Number: P30590A9VUQ04B
Part Number: 448589-B21
Spare Part Number: 441832-001
Firmware Version: 3.00
HwVersion: A0
Blade 1
Model: ProLiant BL480c G1
Manufacturer: HP
Serial Number: USM64204B1
Part Number: 416667-B21
Spare Part Number: 410293-001
Blade 2
Model: ProLiant BL480c G1
Manufacturer: HP
Serial Number: USM65103VJ
Part Number: 435460-B21
Spare Part Number: 438453-001
Blade 4
Model: ProLiant BL460c G1
Manufacturer: HP
Serial Number: USM62401EP
Part Number: 404664-B21
Spare Part Number: 410299-001
Interconnect 1
Model: GbE2c Ethernet Blade Switch
Manufacturer: HP
Serial Number: MY36290EMT
General management commands 60
Page 61

Part Number: 410917-B21
Spare Part Number: 414037-001
Interconnect 2
Model: Cisco Catalyst Blade Switch 3120X for HP w/ IP Base
Manufacturer: Cisco Systems, Inc.
Serial Number: FOC1129T0XE
Part Number: WS-CBS3120X-S
Spare Part Number: 451357-001
Fan 1
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Fan 2
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Fan 3
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Fan 4
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Fan 5
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Fan 6
Model: Active Cool 200 Fan
Part Number: 412140-B21
Spare Part Number: 413996-001
Power Supply 1
Model: HP PROLIANT SERVER PS
Serial Number: 531300ALL00233
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Power Supply 2
Model: HP PROLIANT SERVER PS
Serial Number: 531300ALL00014
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Power Supply 3
Model: HP PROLIANT SERVER PS
Serial Number: 531300ALL00399
Part Number: 438203-001
Spare Part Number: XXXXXX-001
Insight Display
Model: BladeSystem c3000 Insight Display
Manufacturer: HP
Spare Part Number: 441831-001
Firmware Version: 2.2.2
General management commands 61
Page 62

>SHOW SERVER INFO ALL
Server Blade #1 Information:
Type: Server Blade
Manufacturer: HP
Product Name: ProLiant BL480c G1
Part Number: 416667-B21
System Board Spare Part Number: 410293-001
Serial Number: USM64204B1
UUID: 36363134-3736-5355-4D36-343230344231
Server Name: RonChangedHostNameInILO
Asset Tag: [Unknown]
ROM Version: I14 06/21/2006
CPU 1: Dual-Core Intel Xeon 2333 MHz
CPU 2: Not present
Memory: 2048 MB
Embedded Ethernet
NIC 1 MAC Address: 00:18:FE:35:21:E0
NIC 2 MAC Address: 00:18:FE:35:21:DE
NIC 3 MAC Address: 00:18:FE:34:DB:9F
NIC 4 MAC Address: 00:18:FE:34:DB:A0
iSCSI 1 MAC Address: 00:18:FE:35:21:E1
iSCSI 2 MAC Address: 00:18:FE:35:21:DF
Management Processor Information:
Type: iLO2
Name: ILOUSM64204B1
Firmware Version: 2.00 Oct 13 2009
IP Address: 16.84.190.209
MAC Address: 00:18:FE:35:61:62
Power Management Controller Version: 0.5
Server Blade #2 Information:
Type: Server Blade
Manufacturer: HP
Product Name: ProLiant BL480c G1
Part Number: 435460-B21
System Board Spare Part Number: 438453-001
Serial Number: USM65103VJ
UUID: 34353334-3036-5355-4D36-35313033564A
Server Name: test45667
Asset Tag: [Unknown]
ROM Version: I14 11/03/2008
CPU 1: Quad-Core Intel Xeon 2666 MHz
CPU 2: Quad-Core Intel Xeon 2666 MHz
Memory: 2048 MB
Embedded Ethernet
NIC 1 MAC Address: 00:19:BB:34:A1:5A
NIC 2 MAC Address: 00:19:BB:34:91:FE
NIC 3 MAC Address: 00:19:BB:29:91:33
NIC 4 MAC Address: 00:19:BB:29:91:34
iSCSI 1 MAC Address: 00:19:BB:34:A1:5B
iSCSI 2 MAC Address: 00:19:BB:34:91:FF
Management Processor Information:
Type: iLO2
Name: ILOUSM65103VJ
Firmware Version: 2.00 Oct 13 2009
IP Address: 16.84.190.217
General management commands 62
Page 63

MAC Address: 00:19:BB:35:F6:42
Power Management Controller Version: 0.5
Server Blade #3 Information:
Server Blade Type: No Server Blade Installed
Server Blade #4 Information:
Type: Server Blade
Manufacturer: HP
Product Name: ProLiant BL460c G1
Part Number: 404664-B21
System Board Spare Part Number: 410299-001
Serial Number: USM62401EP
UUID: 36343034-3436-5355-4D36-323430314550
Server Name: YOUR-EYZCGYAYBB
Asset Tag: [Unknown]
ROM Version: I15 10/18/2007
CPU 1: Dual-Core Intel Xeon 2333 MHz
CPU 2: Not present
Memory: 2048 MB
Embedded Ethernet
NIC 1 MAC Address: 00:16:35:C5:EF:26
NIC 2 MAC Address: 00:16:35:C5:EF:3A
iSCSI 1 MAC Address: 00:16:35:C5:EF:27
iSCSI 2 MAC Address: 00:16:35:C5:EF:3B
Management Processor Information:
Type: iLO2
Name: ILOUSM62401EP
Firmware Version: 2.00 Oct 13 2009
IP Address: 16.84.190.215
MAC Address: 00:14:38:51:8E:26
Power Management Controller Version: 0.5
Server Blade #5 Information:
Server Blade Type: Bay Subsumed
Server Blade #6 Information:
Server Blade Type: Bay Subsumed
Server Blade #7 Information:
Server Blade Type: No Server Blade Installed
Server Blade #8 Information:
Server Blade Type: No Server Blade Installed
>SHOW SERVER PORT MAP ALL
Mezz
Mezz Mezz Device Port Interconnect Interconnect
Slot Device Port Status Bay Bay Port Device ID
---- ------ ------ ---------- ------------ ------------ ----------------
------------------------------- Blade 001 ------------------------------ 1 Not Present
2 Not Present
3 Not Present
Embedded Ethernet
Port 1 OK Bay 1 Port 5 00:18:FE:35:21:E0
iSCSI 1 OK Bay 1 Port 5 00:18:FE:35:21:E1
Port 2 OK Bay 1 Port 13 00:18:FE:35:21:DE
General management commands 63
Page 64

iSCSI 2 OK Bay 1 Port 13 00:18:FE:35:21:DF
Port 3 OK Bay 1 Port 1 00:18:FE:34:DB:9F
Port 4 OK Bay 1 Port 9 00:18:FE:34:DB:A0
------------------------------- Blade 002 ------------------------------ 1 Not Present
2 Not Present
3 Not Present
Embedded Ethernet
Port 1 OK Bay 1 Port 6 00:19:BB:34:A1:5A
iSCSI 1 OK Bay 1 Port 6 00:19:BB:34:A1:5B
Port 2 OK Bay 1 Port 14 00:19:BB:34:91:FE
iSCSI 2 OK Bay 1 Port 14 00:19:BB:34:91:FF
Port 3 OK Bay 1 Port 2 00:19:BB:29:91:33
Port 4 OK Bay 1 Port 10 00:19:BB:29:91:34
------------------------------- Blade 003 ------------------------------<absent>
------------------------------- Blade 004 ------------------------------ 1 Not Present
2 Not Present
Embedded Ethernet
Port 1 OK Bay 1 Port 4 00:16:35:C5:EF:26
iSCSI 1 OK Bay 1 Port 4 00:16:35:C5:EF:27
Port 2 OK Bay 1 Port 12 00:16:35:C5:EF:3A
iSCSI 2 OK Bay 1 Port 12 00:16:35:C5:EF:3B
------------------------------- Blade 005 ------------------------------<absent>
------------------------------- Blade 006 ------------------------------<absent>
------------------------------- Blade 007 ------------------------------<absent>
------------------------------- Blade 008 ------------------------------<absent>
>SHOW SERVER STATUS ALL
Blade #1 Status:
Power: On
Current Wattage used: 212
Health: OK
Unit Identification LED: Off
Diagnostic Status:
Internal Data OK
Management Processor OK
I/O Configuration OK
Power OK
Cooling OK
Location OK
Device Failure OK
Device Degraded OK
iLO Network OK
Blade #2 Status:
Power: On
Current Wattage used: 412
Health: OK
Unit Identification LED: Off
Diagnostic Status:
Internal Data OK
Management Processor OK
General management commands 64
Page 65

I/O Configuration OK
Power OK
Cooling OK
Location OK
Device Failure OK
Device Degraded OK
iLO Network OK
Blade #3 Status:
Power: No Server Blade Installed
Blade #4 Status:
Power: On
Current Wattage used: 152
Health: OK
Unit Identification LED: Off
Diagnostic Status:
Internal Data OK
Management Processor OK
I/O Configuration OK
Power OK
Cooling OK
Location OK
Device Failure OK
Device Degraded OK
iLO Network OK
Blade #5 Status:
Server Blade Type: Bay Subsumed
Blade #6 Status:
Server Blade Type: Bay Subsumed
Blade #7 Status:
Power: No Server Blade Installed
Blade #8 Status:
Power: No Server Blade Installed
>SHOW SERVER TEMP ALL
Device Bay #1 Temperature Information
Locale Status Temp Caution Critical
----------------------------------- ------ -------- ------- -------Memory Zone OK 36C/ 96F 81C 86C
CPU Zone OK 29C/ 84F 70C 75C
CPU 1 OK 30C/ 86F 127C 127C
CPU 1 OK 30C/ 86F 127C 127C
Ambient Zone OK 20C/ 68F 38C 43C
CPU 2 OK N/A
CPU 2 OK N/A
Device Bay #2 Temperature Information
Locale Status Temp Caution Critical
----------------------------------- ------ -------- ------- -------Memory Zone OK 43C/109F 81C 86C
CPU Zone OK 38C/100F 70C 75C
CPU 1 OK 57C/ 0F 95C 100C
CPU 1 OK 57C/ 0F 95C 100C
System Zone OK 24C/ 75F 40C 45C
CPU 2 OK 57C/ 0F 95C 100C
CPU 2 OK 57C/ 0F 95C 100C
Ambient Zone OK 24C/ 75F 40C 45C
Device Bay #3 Temperature Information
No Server Blade Installed
Device Bay #4 Temperature Information
Locale Status Temp Caution Critical
----------------------------------- ------ -------- ------- -------System Zone OK 38C/100F 80C 85C
General management commands 65
Page 66

CPU Zone OK 34C/ 93F 65C 70C
CPU 1 OK 52C/125F 95C 100C
CPU 1 OK 52C/125F 95C 100C
CPU Zone OK 33C/ 91F 70C 75C
CPU 2 OK N/A
CPU 2 OK N/A
Memory Zone OK 55C/ 0F 85C 100C
Ambient Zone OK 21C/ 69F 38C 43C
Device Bay #5 Temperature Information
Server Blade Type: Bay Subsumed
Device Bay #6 Temperature Information
Server Blade Type: Bay Subsumed
Device Bay #7 Temperature Information
No Server Blade Installed
Device Bay #8 Temperature Information
No Server Blade Installed
>SHOW SERVER DVD ALL
DVD Drive: Present
DVD Media: Absent
Server DVD connections:
Bay Connected Device or image URL
--- --------- ------------------------------------ 1 No
2 No
3 - [Bay empty]
4 No
5 - [Bay subsumed]
6 - [Bay subsumed]
7 - [Bay empty]
8 - [Bay empty]
>SHOW SERVER POWERDELAY ALL
Current PowerDelay Status: Not in Progress
Bay Device PowerDelay State Delay (seconds)
--- -------------------------------- ---------------- -------------- 1 ProLiant BL480c G1 Disabled 0
1A Absent Disabled 0
1B Absent Disabled 0
2 ProLiant BL480c G1 Disabled 0
2A Absent Disabled 0
2B Absent Disabled 0
3 Absent Disabled 0
3A Absent Disabled 0
3B Absent Disabled 0
4 ProLiant BL460c G1 Disabled 0
4A Absent Disabled 0
4B Absent Disabled 0
5 Subsumed Disabled 0
5A Absent Disabled 0
5B Absent Disabled 0
6 Subsumed Disabled 0
6A Absent Disabled 0
6B Absent Disabled 0
7 Absent Disabled 0
7A Absent Disabled 0
7B Absent Disabled 0
General management commands 66
Page 67

8 Absent Disabled 0
8A Absent Disabled 0
8B Absent Disabled 0
>SHOW SERVER BOOT ALL
Server Blade #1 Boot Information:
One time boot from: None
IPL Devices (Boot Order):
CD-ROM
Diskette Drive (A:)
USB
Hard Drive (C:)
Server Blade #2 Boot Information:
One time boot from: None
IPL Devices (Boot Order):
CD-ROM
Diskette Drive (A:)
USB
Hard Drive (C:)
PXE NIC 1
Server Blade #3 Boot Information:
The blade is not present.
Server Blade #4 Boot Information:
One time boot from: None
IPL Devices (Boot Order):
CD-ROM
Diskette Drive (A:)
USB
Hard Drive (C:)
Server Blade #5 Boot Information:
The blade is not present.
Server Blade #6 Boot Information:
The blade is not present.
Server Blade #7 Boot Information:
The blade is not present.
Server Blade #8 Boot Information:
The blade is not present.
>SHOW SYSLOG SERVER ALL
Retrieving Server syslog(s) ...
Server 1 Syslog:
<EVENT_LOG DESCRIPTION="Integrated Management Log">
<EVENT
SEVERITY="Informational"
CLASS="Maintenance"
LAST_UPDATE="07/09/2009 23:35"
INITIAL_UPDATE="07/09/2009 23:35"
COUNT="1"
DESCRIPTION="IML Cleared (iLO 2 user:OA Administrator)"
/>
<EVENT
General management commands 67
Page 68

SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="[NOT SET] "
INITIAL_UPDATE="[NOT SET] "
COUNT="1"
DESCRIPTION="Server Blade Enclosure Rack Name Changed (Enclosure Serial Number 0987654321)"
/>
<EVENT
SEVERITY="Critical"
CLASS="Rack Infrastructure"
LAST_UPDATE="[NOT SET] "
INITIAL_UPDATE="[NOT SET] "
COUNT="36"
DESCRIPTION="Server Blade Enclosure Inadequate Power To Power On: Not Enough Power
(Enclosure Address 0000, Slot 1)"
/>
<EVENT
SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="09/17/2009 21:18"
INITIAL_UPDATE="09/17/2009 21:18"
COUNT="1"
DESCRIPTION="Server Blade Enclosure LAN Settings Changed (Enclosure Serial Number
0987654321)"
/>
<EVENT
SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="09/22/2009 15:29"
INITIAL_UPDATE="09/22/2009 15:29"
COUNT="1"
DESCRIPTION="Server Blade Enclosure Rack Name Changed (Enclosure Serial Number 0987654321)"
/>
<EVENT
SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="[NOT SET] "
INITIAL_UPDATE="[NOT SET] "
COUNT="1"
DESCRIPTION="Server Blade Enclosure LAN Settings Changed (Enclosure Serial Number Unknown)"
/>
</EVENT_LOG>
Server 2 Syslog:
<EVENT_LOG DESCRIPTION="Integrated Management Log">
<EVENT
SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="06/03/2008 21:06"
INITIAL_UPDATE="06/03/2008 21:06"
COUNT="1"
DESCRIPTION="Server Blade Enclosure LAN Settings Changed (Enclosure Serial Number
USE644285C)"
/>
<EVENT
SEVERITY="Informational"
CLASS="Rack Infrastructure"
LAST_UPDATE="06/03/2008 21:18"
INITIAL_UPDATE="06/03/2008 21:18"
COUNT="1"
DESCRIPTION="Server Blade Enclosure Name Changed (Enclosure Serial Number USE644285C)"
/>
<EVENT
SEVERITY="Caution"
CLASS="POST Message"
General management commands 68
Page 69

LAST_UPDATE="10/25/2008 00:53"
INITIAL_UPDATE="10/25/2008 00:53"
COUNT="1"
DESCRIPTION="POST Error: 1726-Drive Array - Array Accelerator Memory Size Change Detected"
/>
<EVENT
SEVERITY="Caution"
CLASS="POST Message"
LAST_UPDATE="10/25/2008 00:53"
INITIAL_UPDATE="10/25/2008 00:53"
COUNT="1"
DESCRIPTION="POST Error: 1724-Drive Array - Physical Drive Position Change(s) Detected"
/>
<EVENT
SEVERITY="Caution"
CLASS="POST Message"
LAST_UPDATE="10/25/2008 00:53"
INITIAL_UPDATE="10/25/2008 00:53"
COUNT="1"
DESCRIPTION="POST Error: 1727-Drive Array - New Logical Drive(s) Attachment Detected"
/>
<EVENT
SEVERITY="Caution"
CLASS="POST Message"
LAST_UPDATE="10/25/2008 00:55"
INITIAL_UPDATE="10/25/2008 00:55"
COUNT="1"
DESCRIPTION="POST Error: 1785-Drive Array not Configured"
/>
<EVENT
SEVERITY="Critical"
CLASS="Rack Infrastructure"
LAST_UPDATE="[NOT SET] "
INITIAL_UPDATE="[NOT SET] "
COUNT="6"
DESCRIPTION="Server Blade Enclosure Inadequate Power To Power On: Not Enough Power
(Enclosure Address 0000, Slot 1)"
/>
<EVENT
SEVERITY="Caution"
CLASS="Maintenance"
LAST_UPDATE="03/29/2009 10:50"
INITIAL_UPDATE="03/29/2009 10:50"
COUNT="1"
DESCRIPTION="No communication from group power manager - reverting to manual power cap
control."
/>
<EVENT
SEVERITY="Caution"
CLASS="Maintenance"
LAST_UPDATE="06/01/2009 21:00"
INITIAL_UPDATE="06/01/2009 21:00"
COUNT="1"
DESCRIPTION="CPU(s) operating at reduced performance level
due to an enclosure power event."
/>
</EVENT_LOG>
Server 3 Syslog:
The blade is not present.
</EVENT_LOG>
Server 5 Syslog:
General management commands 69
Page 70

Server Blade Type: Bay Subsumed
>SHOW TOPOLOGY
Detecting linked enclosures ........
Rack Topology (top-down)
Rack UUID: 090987654321
Rack Name: UnnamedRack
Enclosure Name Status Local IP Address UUID
-------------------------------- -------- ----- --------------- -------------OA-0018FE27577F Degraded Yes 16.84.189.60 090987654321
USE644285C OK No 172.16.211.101 09USE644285C
OA-0018FE273799 Degraded No 172.16.210.1 091234567890
1Z34AB7890 Degraded No 0.0.0.0 091Z34AB7890
>SHOW USBKEY
No USB keys detected in this Onboard Administrator. Note: USB keys can only be used in the
Active Onboard Administrator.
>SHOW USER (current user)
Local User "Administrator" Information:
Full name: System Administrator
Contact Info:
User Rights: Admin
Account Status: Enabled
Server Bay Access List: 1 1A 1B 2 2A 2B 3 3A 3B 4 4A 4B 5 5A 5B 6 6A 6B 7 7A 7B 8 8A
8B
Interconnect Bay Access List: 1 2 3 4
OA Access: Yes
>SHOW USER LIST
* denotes current user
Privilege Acct.
User Name Full Name Level Status
---------------------------- -------------------- ---------- -------- * Administrator System Administrator Admin Enabled
Test User Enabled
>SHOW LDAP INFO
Directory Services (LDAP)
Enabled : Disabled
Local Users Enabled : Enabled
NT Name Mapping : Disabled
Directory Server :
Directory Server SSL Port : 0
Search Context #1 :
Search Context #2 :
Search Context #3 :
Search Context #4 :
Search Context #5 :
Search Context #6 :
>SHOW LDAP CERTIFICATE
No certificates were found.
>SHOW LDAP GROUP LIST
General management commands 70
Page 71

No LDAP groups were detected.
>SHOW CA CERTIFICATE INFO
No CA certificates are imported.
>SHOW TWOFACTOR INFO
Two Factor Authentication:
Enabled : Disabled
Certificate Revocation : Disabled
Certificate Owner Field : Subject
>SHOW PASSWORD SETTINGS
Strong Passwords: Disabled
Minimum Password Length: 3
>SHOW UPDATE
Device Name Location Version NewVersion
----------------------------------------------------------------------------------TRAY | BladeSystem c3000 Onboard Administrator | - | 2.9 | 2.9
LCD | BladeSystem c3000 Insight Display | - | 2.2.2 | 2.2.2
FAN | Active Cool 200 Fan | 1 | 2.7.4 | 2.7.4
FAN | Active Cool 200 Fan | 2 | 2.7.4 | 2.7.4
FAN | Active Cool 200 Fan | 3 | 2.7.4 | 2.7.4
FAN | Active Cool 200 Fan | 4 | 2.7.4 | 2.7.4
FAN | Active Cool 200 Fan | 5 | 2.7.4 | 2.7.4
FAN | Active Cool 200 Fan | 6 | 2.7.4 | 2.7.4
>SHOW SYSLOG SETTINGS
Remote log: Disabled
Address:
Port: 514
>SHOW VCMODE
Virtual Connect Mode: Disabled
>SHOW SESSION TIMEOUT
Session Timeout: 1440 minutes
>SHOW VLAN
VLAN is disabled. OA VLAN ID = 1. Default VLAN ID (untagged) = 1.
VLAN VLAN NAME
---- --------1 Default
Device Settings
BAY VLAN
--- ---1 1
2 1
3 1
4 1
5 1
6 1
7 1
8 1
General management commands 71
Page 72

Interconnect Settings
BAY VLAN
--- ---1 1
2 1
3 1
4 1
>SHOW URB
URB Reporting: Enabled
URB Endpoint URL: http://urburl.hp.com/urb_receiver
URB Proxy URL: http://proxy.mycompany.com:8080
URB Interval: Hourly at minute 30
Last Attempt: Failed on Thu Jan 21 13:23:00 2010
SHOW DEVICE SERIAL_NUMBER BLADE
• Command:
SHOW DEVICE SERIAL_NUMBER BLADE <bay number>
• Description:
Shows the specified direct attached blade device serial number
• Access level/Bay level:
o All
o Bay specific
• Restrictions:
Dependent on bay privileges
Example
OA-0016355E560A> SHOW DEVICE SERIAL_NUMBER BLADE
Blade 1 serial number: USM81500RP
SHOW INTERCONNECT SESSIONS
• Command:
SHOW INTERCONNECT SESSIONS
• Description:
Displays which users have serial console sessions in progress for each interconnect
• Access level/Bay level:
o OA administrator, OA operator
o Bay specific
• Restrictions:
You must have access to the specified bay.
Example
OA-0018FE27577F> SHOW INTERCONNECT SESSION
General management commands 72
Page 73

Interconnect Bay User
------------------ -------------No Interconnect remote console sessions were detected.
General management commands 73
Page 74

Enclosure Bay IP Addressing commands
ADD EBIPA
• Command:
ADD EBIPA {SERVER | INTERCONNECT} DNS <ip address>
• Description:
Adds a DNS server IP address to the list of DNS servers for either SERVER bays or INTERCONNECT
bays
• Access Level/Bay level:
Administrator, Operator
• Restrictions:
o A maximum of three DNS servers can be added for EBIPA.
o The <ip address> must be in the form ###.###.###.###, where each ### ranges from 0 to
255.
DISABLE EBIPA
CAUTION: : This command cycles power to the interconnect and causes a loss of
• Command:
• Description:
• Access level/Bay level:
connectivity.
DISABLE EBIPA {SERVER|INTERCONNECT} [ALL | <bay number> [{ , | - } <bay
number>]]
Disables the ability of the Onboard Administrator to give devices in the bays IP addresses using
DHCP.
If no bay numbers are specified, then EBIPA is disabled for all bays. Devices in bays receive IP
addresses from an external server.
This causes a reset of the iLO, which causes it to attempt to get an IP address from an external DHCP
server. The interconnect is power-cycled.
Administrator, Operator
• Restrictions:
None
ENABLE EBIPA
Enclosure Bay IP Addressing commands 74
Page 75

CAUTION: This command cycles power to the interconnect and causes a loss of connectivity.
• Command:
ENABLE EBIPA {SERVER|INTERCONNECT} [ALL | <bay number> [{ , | - } <bay
number>]]
• Description:
Enables the Onboard Administrator to provide IP addresses to the devices in the bays using DHCP.
If you do not specify any bay numbers, then EBIPA is enabled for all bays.
DHCP traffic from iLO and the switch modules can no longer go outside the enclosure.
This causes a reset of the iLO, which causes it to attempt to get an IP address. The interconnect is
power-cycled.
• Access level/Bay level:
Administrator, Operator
• Restrictions:
Before using this command you must set up the EBIPA settings. This includes setting the initial IP
address, the netmask, and the default gateway.
REMOVE EBIPA
• Command:
REMOVE EBIPA {SERVER|INTERCONNECT} DNS <ip address>
• Description:
Removes the DNS server specified by the <ip address> from the list of DNS servers for either SERVER
bays or INTERCONNECT bays
• Access level/Bay level:
Administrator, Operator
• Restrictions:
The <ip address> and must be in the form ###.###.###.###, where each ### ranges from 0 to
255.
SET EBIPA
• Command:
SET EBIPA { SERVER | INTERCONNECT }
• Description:
Sets EBIPA settings for device or interconnect bays.
• Access level/Bay level:
Administrator, Operator
• Restrictions:
Enclosure Bay IP Addressing commands 75
Page 76

o
The <IP address> and <netmask> must be in the form ###.###.###.###, where each ###
ranges from 0 to 255.
o The <domain name> is a string containing letters (a–z, A–Z), digits (0–9), or a dash (-).
SET EBIPA SERVER
• Command:
SET EBIPA SERVER { <IP address> <netmask> } | { NETMASK <netmask> } | {
GATEWAY <gateway> } | { DOMAIN <domain> } [ ALL | <bay number> [{- | ,}
<bay number>]
• Description:
Sets EBIPA settings for device (server) bays. If the bay number parameter is not specified, the settings
will be applied to all device bays. The NONE keyword may be used to clear the IP address and
netmask values.
• Access level/Bay level:
Administrator, Operator
• Restrictions:
o The <IP address> and <netmask> must be in the form ###.###.###.###, where each ###
ranges from 0 to 255.
o The <domain name> is a string containing letters (a–z, A–Z), digits (0–9), or a dash (-).
SET EBIPA INTERCONNECT
• Command:
SET EBIPA INTERCONNECT { <IP address> <netmask> } | { NETMASK <netmask>
} | { GATEWAY <gateway> } | { DOMAIN <domain> } | { NTP PRIMARY |
SECONDARY <IP address> } [ ALL | <bay number> [{- | ,} <bay number>]
• Description:
Sets EBIPA settings for interconnect bays. If the bay number parameter is not specified, the settings
are applied to all interconnect bays. The NONE keyword can be used to clear the IP address and
netmask values.
• Access level/Bay level:
Administrator, Operator
• Restrictions:
o The <IP address> and <netmask> must be in the form ###.###.###.###, where each ###
ranges from 0 to 255.
o The <domain name> is a string containing letters (a–z, A–Z), digits (0–9), or a dash (-).
SHOW EBIPA
• Command:
SHOW EBIPA
• Description:
Enclosure Bay IP Addressing commands 76
Page 77

Displays EBIPA information
• Access level/Bay level:
Administrator, Operator, user
• Restrictions:
None
Example
OA-0018FE27577F> SHOW EBIPA
EBIPA Device Server Settings
Bay Enabled EBIPA/Current Netmask Gateway DNS Domain
--- ------- --------------- --------------- --------------- --------------- ----- 1 Yes 172.16.211.111 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.211.111 172.16.0.2
172.16.0.3
1A Yes 172.16.211.119 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
1B Yes 172.16.211.127 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
2 Yes 172.16.211.112 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.211.112 172.16.0.2
172.16.0.3
2A Yes 172.16.211.120 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
2B Yes 172.16.211.128 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
3 Yes 172.16.211.113 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
3A Yes 172.16.211.121 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
3B Yes 172.16.211.129 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
4 Yes 172.16.211.114 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.211.114 172.16.0.2
172.16.0.3
4A Yes 172.16.211.122 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
4B Yes 172.16.211.130 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
5 Yes 172.16.211.115 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
5A Yes 172.16.211.123 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
5B Yes 172.16.211.131 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
6 Yes 172.16.211.116 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
6A Yes 172.16.211.124 255.255.0.0 172.16.0.1 172.16.0.1 test.com
Enclosure Bay IP Addressing commands 77
Page 78

172.16.0.2
172.16.0.3
6B Yes 172.16.211.132 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
7 Yes 172.16.211.117 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
7A Yes 172.16.211.125 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
7B Yes 172.16.211.133 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
8 Yes 172.16.211.118 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
8A Yes 172.16.211.126 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
8B Yes 172.16.211.134 255.255.0.0 172.16.0.1 172.16.0.1 test.com
172.16.0.2
172.16.0.3
EBIPA Device Interconnect Settings
Bay Enabled EBIPA/Current Netmask Gateway DNS NTP
Domain
--- ------- --------------- --------------- --------------- --------------- --------------- -
---- 1 Yes 172.16.211.183 255.255.0.0 172.16.0.1 172.16.0.1 2.3.4.5
testIO.com
0.0.0.0
2 Yes 172.16.211.184 255.255.0.0 172.16.0.1 172.16.0.1 2.3.4.5
testIO.com
0.0.0.0
3 Yes 172.16.211.185 255.255.0.0 172.16.0.1 172.16.0.1 2.3.4.5
testIO.com
4 Yes 172.16.211.186 255.255.0.0 172.16.0.1 172.16.0.1 2.3.4.5
testIO.com
Enclosure Bay IP Addressing commands 78
Page 79

Enclosure network configuration commands
ADD OA ADDRESS IPV6
• Command:
ADD OA ADDRESS IPV6 {<bay number>} <ipv6 address/prefix length>
• Description:
Adds an IPv6 static address for the Onboard Administrator. If IPv6 is enabled, this setting takes
effect immediately. If no Onboard Administrator number is provided, the command defaults to the
active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o The prefix length is mandatory.
o The <ip address> must be in the form ####:####:####:####:####:####:####:####/###,
where each #### ranges from 0 to FFFF and the prefix /### ranges from 0 to 128.
ADD OA DNS
• Command:
ADD OA DNS [<bay number>] <ip address>
• Description:
Adds an IP address of a DNS server to the list. DNS servers are used if the system is configured to
use a static IP address.
If a bay number is not specified, the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
A maximum of two DNS servers can be added.
The <ip address> must be in the form ###.###.###.###, where each ### ranges from 0 to 255.
ADD OA DNS IPV6
• Command:
ADD OA DNS IPV6 {<bay number>} <ipv6 address{/prefix length}>
• Description:
Adds an IPv6 address to the list of DNS servers. If a bay number is not specified, then the command
defaults to the active Onboard Administrator. The network prefix length is optional.
Enclosure network configuration commands 79
Page 80

• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o A maximum of two DNS servers can be added.
o The <ip address> must be in the form ####:####:####:####:####:####:####:#### or
####:####:####:####:####:####:####:####/### (with a prefix), where each ####
ranges from 0 to FFFF and the prefix /### ranges from 0 to 128.
ADD SNMP TRAPRECEIVER
• Command:
ADD SNMP TRAPRECEIVER <host> ["<community name>"]
• Description:
Adds a new trap receiver address to the SNMP configuration. Defaults for the traps are version v1
and port 162. The SNMP Trap community string is set to public or the optional "<community
name>". The "<community name>" string, if specified, must be 1 to 20 characters in length.
Acceptable characters include any printable character excluding quotes and newlines.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o A maximum of eight IP addresses can be added to receive SNMP traps.
o Only v1 traps are supported.
o The <host> value can be an IPv4 address, an IPv6 address, or a DNS name (maximum of 64
characters).
o IPv6 addresses must be typed without the network prefix length.
ADD SSHKEY
• Command:
ADD SSHKEY <end marker> <certificate> <end marker>
• Description:
Adds an SSH key or keys to the Administrator local account. Multiple SSHKEYs can be concatenated
in the string.
a. Locate a string that does not appear in the key, to use as the end marker.
b. Paste in the SSHKEY string.
c. Finish the command with the end marker.
Failure to give a proper end marker before and after the certificate might cause the interface to wait
for the appropriate end marker indefinitely.
• Access level/Bay level:
Administrator
• Restrictions:
Enclosure network configuration commands 80
Page 81

o
SSHKEY is only available for the Administrator local account
o SSHKEY works only in script mode
o SSHKEY string is limited to 4KB on Onboard Administrator versions prior to 2.30
o SSHKEY string is limited to 8KB on Onboard Administrator version 2.30 and later
o This command is only valid in script mode.
ADD TRUSTED HOST
• Command:
ADD TRUSTED HOST <ip address>
• Description:
Adds a new IPv4 or IPv6 address to the list of addresses being handled by the IP Security feature.
• Access level /Bay level:
OA administrator, OA operator
• Restrictions:
You can add a maximum of five IP addresses to the IP Manager.
CLEAR NTP
• Command:
CLEAR NTP {PRIMARY | SECONDARY}
• Description:
Disables access to the Primary or Secondary NTP server
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
Clearing the Primary NTP server disables NTP.
CLEAR SSHKEY
• Command:
CLEAR SSHKEY
• Description:
Removes the authorized key file used for SSH login
• Access level/Bay level:
Administrator
• Restrictions:
None
Enclosure network configuration commands 81
Page 82

CLEAR VCMODE
• Command:
CLEAR VCMODE
• Description:
Clears Virtual Connect Mode settings.
• Access level/Bay level:
OA Administrator
OA Bays
• Restrictions:
o All servers in the enclosure should be powered off before clearing the VCMODE.
o The enclosure will no longer be managed by Virtual Connect, and servers will revert to default
Ethernet MAC and Fibre Channel WWN assignments. Virtual Connect might disconnect the
servers from Ethernet networks and Fibre Channel fabrics.
DISABLE ALERTMAIL
• Command:
DISABLE ALERTMAIL
• Description:
Disables the sending of emails when events occur
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE DHCPV6
• Command:
DISABLE DHCPV6 {<bay number>}
• Description:
Disable DHCPv6 mode of the OA external interface. With DHCPv6 disabled, the IPv6 and DNS
addresses are not obtained from the DHCPv6 Server. This setting takes effect immediately.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
Enclosure network configuration commands 82
Page 83

DISABLE ENCLOSURE_IP_MODE
• Command:
DISABLE ENCLOSURE_IP_MODE
• Description:
Disables Enclosure IP Mode.
Active and Standby Onboard Administrators retain their current IP addresses.
After disabling Enclosure IP Mode and a takeover occurs, there will no longer be a single IP address
for the enclosure.
• Access level/Bay level:
OA administrator, Operator
• Restrictions:
None
DISABLE HTTPS
• Command:
DISABLE HTTPS
• Description:
Disables HTTPS access to the Onboard Administrator, which prevents access to the web-based user
interface
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE IPV6
• Command:
DISABLE IPV6 {<bay number>}
• Description:
Disables IPv6 protocol of the Onboard Administrator external interface. If a bay number is not
specified, then the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
Enclosure network configuration commands 83
Page 84

DISABLE NTP
• Command:
DISABLE NTP
• Description:
Disables the synchronizing of time and date with a remote server using the NTP protocol. Does not
clear any NTP servers that have been configured.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE ROUTER ADVERTISEMENTS
• Command:
DISABLE ROUTER ADVERTISEMENTS {<bay number>}
• Description:
Disables auto-configuration of IPv6 addresses from Router Advertisement messages. If a bay number
is not specified, then the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE SECURESH
• Command:
DISABLE SECURESH
• Description:
Disables SSH access to the Onboard Administrator.
Disabling SSH prevents access to the web-based user interface and the SSH terminal interface until a
terminal session re-enables the SSH protocol.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE SNMP
• Command:
Enclosure network configuration commands 84
Page 85

DISABLE SNMP
• Description:
Disables SNMP support for the Onboard Administrator.
Does not clear the SNMP trap receivers that have been configured.
SNMP trap receivers can still be added and removed.
If you disable SNMP, then Insight Manager Agents do not work properly.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE TELNET
• Command:
DISABLE TELNET
• Description:
Disables telnet access to the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DISABLE TRUSTED HOST
• Command:
DISABLE TRUSTED HOST
• Description:
Disables the host-based access to the Onboard Administrator. Disabling TRUSTED HOSTS allows all
hosts to connect to the Onboard Administrator.
• Access level/Bay level:
OA administrator, Operator
• Restrictions:
None
DISABLE XMLREPLY
• Command:
DISABLE XMLREPLY
• Description:
Disables XML reply data return over the HTTP port
Enclosure network configuration commands 85
Page 86

• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
DOWNLOAD CONFIG
• Command:
DOWNLOAD CONFIG <url>
• Description:
Downloads a previously saved configuration script file from a specific IP host, and then executes it.
Supported protocols are HTTP, FTP, TFTP, and USB. Format the <URL> as protocol://host/path/file.
The URL syntax for IPv6 addresses is protocol://[<ipv6_address>]/path/file. If your FTP server does
not support anonymous connections, then specify a user name and password by replacing the host
part in the above format with username:password@host.
• Access level/Bay level:
OA administrator
• Restrictions:
o The file cannot change the Administrator account password.
o The user password is not saved or restored by the DOWNLOAD CONFIG command.
DOWNLOAD SSHKEY
• Command:
DOWNLOAD SSHKEY <url>
• Description:
Downloads an authorized key file to use for SSH logins. The file contains the public keys for users.
Supported protocols are HTTP, FTP, and TFTP.
Format the <url> as protocol://host/path/file.
• Access level/Bay level:
Administrator
• Restrictions:
None
ENABLE ALERTMAIL
• Command:
ENABLE ALERTMAIL
• Description:
Enables the sending of alert emails when an event occurs
• Access level/Bay level:
Enclosure network configuration commands 86
Page 87

OA administrator, OA operator
• Restrictions:
You can only issue this command if the configuration has been set up.
ENABLE DHCPV6
• Command:
ENABLE DHCPV6 {<bay number>}
• Description:
Enables DHCPv6 mode to the Onboard Administrator. In DHCPv6 mode, IPv6 and DNS addresses
are obtained from the DHCPv6 Server. This setting takes effect immediately.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE ENCLOSURE_IP_MODE
• Command:
ENABLE ENCLOSURE_IP_MODE
• Description:
Enables Enclosure IP Mode
• Access level/Bay level:
OA administrator, Operator
• Restrictions:
When using enclosure IP mode only replace the standby OA module while the enclosure is powered
on to ensure persistence of Enclosure IP Mode settings.
ENABLE HTTPS
• Command:
ENABLE HTTPS
• Description:
Enables HTTPS access to the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
Enclosure network configuration commands 87
Page 88

ENABLE IPV6
• Command:
ENABLE IPV6 {<bay number>}
• Description:
Enables IPv6 protocol for the Onboard Administrator external interface. If bay number is not
specified, then the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE NTP
• Command:
ENABLE NTP
• Description:
Enables NTP support for the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE ROUTER ADVERTISEMENTS
• Command:
ENABLE ROUTER ADVERTISEMENTS {<bay number>}
• Description:
Enables auto-configuration of IPv6 addresses from Router Advertisement messages. If a bay number
is not specified, then the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE SECURESH
• Command:
ENABLE SECURESH
• Description:
Enclosure network configuration commands 88
Page 89

Enables SSH support for the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE SNMP
• Command:
ENABLE SNMP
• Description:
Enables SNMP Trap support for the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE TELNET
• Command:
ENABLE TELNET
• Description:
Enables telnet access to the Onboard Administrator
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
ENABLE TRUSTED HOST
• Command:
ENABLE TRUSTED HOST
• Description:
Enables IP security for the Onboard Administrator
• Access level/Bay level:
OA administrator
• Restrictions:
None
Enclosure network configuration commands 89
Page 90

ENABLE XMLREPLY
• Command:
ENABLE XMLREPLY
• Description:
Enables XML reply data over an HTTP connection
• Access Level/Bay Level:
OA administrator, OA operator
• Restrictions:
None
REMOVE OA ADDRESS IPV6
• Command:
REMOVE OA ADDRESS IPV6 {<bay number>} <ipv6 address/prefix length>
• Description:
Removes the IPv6 static address for the Onboard Administrator. If IPv6 is enabled, then this
command takes effect immediately. If no Onboard Administrator number is provided, the command
defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o The prefix length is mandatory.
o The <ip address> value must be in the form
####:####:####:####:####:####:####:####/###, where each #### ranges from 0 to
FFFF and the prefix /### ranges from 0 to 128.
REMOVE OA DNS
• Command:
REMOVE OA DNS [<OA bay number>] <ip address>
• Description:
Removes the IP address of a DNS server from the list for the specified Onboard Administrator.
The DNS servers are used only if the system is configured to use a static IP address.
If no bay number is provided, the command default to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The <ip address> must be in the form ###.###.###.###, where each ### ranges from 0 to 255.
Enclosure network configuration commands 90
Page 91

REMOVE OA DNS IPV6
• Command:
REMOVE OA DNS IPV6 {<OA bay number>} <ipv6 address{/prefix length}>
• Description:
Removes the specified DNS IPv6 address from the list of DNS addresses for the specified Onboard
Administrator. If a bay number is not specified, then the command defaults to the active Onboard
Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o A maximum of two DNS servers can be added.
o The <ip address> must be in the form ####:####:####:####:####:####:####:#### or
####:####:####:####:####:####:####:####/### (with a prefix), where each ####
ranges from 0 to FFFF and the prefix /### ranges from 0 to 128.
REMOVE SNMP TRAPRECEIVER
• Command:
REMOVE SNMP TRAPRECEIVER <host> {"<community name>"}
• Description:
o Removes an IP address from the list of systems that receive SNMP traps. If the same IP address is
listed multiple times with different communities, all instances of the IP address disappear unless
<community> specifies which one is to be removed.
o Removes an existing trap receiver from the SNMP configuration. If the same <host> is listed
multiple times with different communities, all instances of the <host> disappears unless
<community name> specifies which one is to be removed.
o The <host> value can be either an IPv4 address, an IPv6 address, or a DNS name.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
IPv6 addresses cannot specify the network prefix length.
REMOVE TRUSTED HOST
• Command:
REMOVE TRUSTED HOST <ip address>
• Description:
Removes an IPv4 or IPv6 address from the list of addresses being handled by the IP Security feature.
• Access level/Bay level:
OA administrator, OA operator
Enclosure network configuration commands 91
Page 92

• Restrictions:
None
SET ALERTMAIL MAILBOX
• Command:
SET ALERTMAIL MAILBOX "<email address>"
• Description:
Sets the email address where events are sent
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
SET ALERTMAIL SENDERDOMAIN
• Command:
SET ALERTMAIL SENDERDOMAIN "<domain>"
• Description:
Sets the AlertMail domain. This is the DNS domain where the Onboard Administrator is located (for
example, AB.com).
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
SET ALERTMAIL SMTPSERVER
• Command:
SET ALERTMAIL SMTPSERVER [ <host> ]
• Description:
Sets the SMTP server. This is the mail server where the Onboard Administrator delivers its e-mail
based events.
The <host> value can be either an IPv4 address, an IPv6 address, or a DNS name.
• Access level/Bay level
Administrator, OA operator
• Restrictions:
IPv6 addresses cannot specify the network prefix length.
Enclosure network configuration commands 92
Page 93

SET ENCRYPTION
• Command:
SET ENCRYPTION { NORMAL | STRONG }
• Description:
Using STRONG encryption enforces use of only FIPS 140-2 approved algorithms including AES,
3DES, and SHA. Setting this option to NORMAL also enables other SSLv3 algorithms such as RSA,
RC4, and MD5.
• Access level/Bay level:
OA administrator
• Restrictions:
None
SET OA GATEWAY
• Command:
SET OA GATEWAY [<bay number>] <ip address>
• Description:
o Sets the network default gateway.
o This command is used if the system is configured to use a static IP address.
o If you do not specify a bay number, the command defaults to the active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The <ip address> must be in the form ###.###.###.###, where each ### ranges from 0 to 255.
SET OA NAME
• Command:
SET OA NAME [<bay number>] "<OA name>"
• Description:
Sets the Onboard Administrator name. If a bay number is not specified, the command defaults to the
active Onboard Administrator.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The Onboard Administrator name is 1 to 32 characters long including all alphanumeric characters
and the dash (-).
Enclosure network configuration commands 93
Page 94

SET OA UID
• Command:
SET OA UID [<bay number>] {ON | OFF}
• Description:
Sets the Onboard Administrator UID on or off.
If you do not specify a bay number, the command defaults to the active Onboard Administrator.
• Access level/Bay level:
All
• Restrictions:
None
SET IPCONFIG
• Command:
SET IPCONFIG {DHCP | STATIC} [<OA bay number>] [DYNAMICDNS] <ip address>
<netmask> [<gateway> [<DNS1address> [<DNS2 address>]]]
• Description:
o Configures IP settings for the Onboard Administrator to DHCP mode or static mode.
o In STATIC mode, the IP address and Netmask are set to <ip address> and <netmask>
respectively. These settings take affect immediately. If the Gateway address and/or DNS
addresses are cleared, they are omitted. The Gateway and DNS address can also be set by
using the SET OA GATEWAY and ADD OA DNS commands.
o SET IPCONFIG STATIC [<OA bay number>] <ip address> <netmask>
[<gateway> [<DNS1 address> [<DNS2 address>]]]
o In DHCP mode, the IP address, Netmask, Gateway address, and DNS addresses are obtained
from the DHCP. This setting immediately takes affect. If DYNAMICDNS is specified, then the
DNS server is notified of the new IP address of the system when it is received from the DHCP
server.
o SET IPCONFIG DHCP [<OA bay number>] [DYNAMICDNS]
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
SET NTP POLL
• Command:
SET NTP POLL <seconds>
• Description:
Sets the polling interval of the NTP servers
Enclosure network configuration commands 94
Page 95

• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
Poll time should be between 60 and 86,400 seconds.
SET NTP PRIMARY
• Command:
SET NTP PRIMARY <host>
• Description:
Sets the primary server used for synchronizing time and date using the NTP. The <host> value can
be an IPv4 address, an IPv6 address, or a DNS name.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
IPv6 addresses cannot specify the network prefix length.
SET NTP SECONDARY
• Command:
SET NTP SECONDARY <host>
• Description:
Sets the secondary server used for synchronizing time and date using the NTP. The <host> value can
be either an IPv4 address, an IPv6 address, or a DNS name.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
IPv6 addresses cannot specify the network prefix length.
SET SNMP CONTACT
• Command:
SET SNMP CONTACT "<contact>"
• Description:
Configures the name of the system contact. The default contact is blank.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The <contact> must be no more than 20 characters long. Valid characters are all alphanumeric, the
underscore (_), the dash (-), and spaces.
Enclosure network configuration commands 95
Page 96

SET SNMP COMMUNITY
• Command:
SET SNMP COMMUNITY {READ | WRITE} "<community name>"
• Description:
Sets the community name for the read or write SNMP community. If a blank write community name is
given, then SNMP set commands are disabled until a non-empty community name is given.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
o The write <community name> must be no more than 20 characters long, and the read
<community name> must be 1 to 20 characters long.
o All printable characters are valid.
o The default read community name is public.
o The default write community name is public.
SET SNMP LOCATION
• Command:
SET SNMP LOCATION "<location>"
• Description:
Configures the SNMP location of the enclosure. The default location is blank.
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
The <location> must be no more than 20 characters long. Valid characters are all alphanumeric, the
underscore (_), the dash (-), and spaces.
SHOW ENCRYPTION
• Command:
SHOW ENCRYPTION
• Description:
Displays the ENCRYPTION setting.
• Access level/Bay level:
OA administrator, OA user
• Restrictions:
In STRONG mode, only FIPS 140-2 approved algorithms including AES, 3DES, and SHA are
permitted.
Enclosure network configuration commands 96
Page 97

SHOW NETWORK
• Command:
SHOW NETWORK
• Description:
Displays:
o Enclosure
o IPv4 information
o IPv6 information
o DHCP state
o Dynamic DNS state
o IP address subnet mask
o Gateway address
o Primary and secondary DNS addresses
o MAC address
o HTTP and HTTPS server status
o SNMP status
o SSH status
o Telnet status
o NTP status
o Trusted Host status
• Access level/Bay level:
All
• Restrictions:
VLAN ID information displays only when VLAN is enabled.
Example
OA-0018FE27577F> show network
Onboard Administrator Network Settings:
- - - - - IPv4 Information - - - - DHCP: Enabled - Dynamic DNS
IPv4 Address: 16.84.189.190
Netmask: 255.255.252.0
Gateway Address: 16.84.188.1
- - - - - IPv6 Information - - - - IPv6: Enabled
Link-local Address: fe80::218:feff:fe27:577f/64
Static Address [1]: 2001::10/64
DHCPv6: Disabled
Router Advertisement: Disabled
- - - - - General Information - - - - Primary DNS: 16.110.135.51
Secondary DNS: 16.110.135.52
Tertiary DNS: Not Set
VLAN ID: 1
MAC Address: 00:18:FE:27:57:7F
Network Link Settings: Link Auto-negotiation
Enclosure network configuration commands 97
Page 98

Onboard Administrator Protocol Status:
Web (HTTP/HTTPS): Enabled
SNMP: Disabled
SecureSH: Enabled
Encryption Mode: Normal
Trusted Hosts: Disabled
HPSIM Trust Mode: Disabled
Telnet: Enabled
AlertMail: Disabled
Mailbox: michael.slama@hp.com
SMTP Server: 16.84.189.199
Sender Domain: Not Set
XML Reply: Enabled
NTP: Enabled
Primary NTP server: 2001::11
Secondary NTP server: 16.84.190.248
Server Poll-Interval: 60 seconds
Last Update: 13 Jun 04:52:23 from 16.84.190.248
Link Loss Failover: Not Supported
Link Loss Interval: Not Supported
Enclosure IP Mode: Not Supported
GUI Login Detail: Enabled
VLAN: Enabled
SHOW SNMP
• Command:
SHOW SNMP
• Description:
Displays:
o SNMP system name
o Location
o Contact
o Read community name
o Write community name
o List of the trap destinations
• Access level/Bay level:
OA administrator, OA operator
• Restrictions:
None
Example
OA-0018FE27577F> SHOW SNMP
SNMP Configuration:
Status: Disabled
System Name: Shorty
System Location:
System Contact:
Read Community Name: public
Write Community Name:
No trap receivers specified.
Enclosure network configuration commands 98
Page 99

SHOW SSHFINGERPRINT
• Command:
SHOW SSHFINGERPRINT
• Description:
Displays the key fingerprint of the Onboard Administrator host public key
• Access level/Bay level:
OA administrator, OA operator, user
• Restrictions:
None
Example
OA-0018FE27577F> SHOW SSHFINGERPRINT
1024 3f:5c:33:0a:a1:2e:9b:2c:da:eb:fe:90:87:34:13:b7 /etc/ssh/id_dsa.pub
SHOW SSHKEY
• Command:
SHOW SSHKEY
• Description:
Displays the contents of the existing SSH authorized key files
• Access level/Bay level:
Administrator
• Restrictions:
None
Example
Firmware Version: 2.20
Built: 04/14/2008 @ 14:04
OA Bay Number: 1
OA Role: Active
Authenticating with public key "rsa-key-123456789"
TEST ALERTMAIL
• Command:
TEST ALERTMAIL
• Description:
Sends a test AlertMail message to the configured email address
• Access level/Bay level:
Administrator, operator
Restrictions:
Enclosure network configuration commands 99
Page 100

You must have OA permission to perform this command.
TEST SNMP
• Command:
TEST SNMP
• Description:
Sends a test SNMP trap to all of the configured trap destinations
• Access level/Bay level:
OA administrator
• Restrictions:
You must enable SNMP to use this function
Enclosure network configuration commands 100
 Loading...
Loading...