Page 1

HP P9000 Replication Manager Software
Application Agent CLI User Guide
Part number: TB584-96080
Ninth edition: October 2013
Page 2
Legal and notice information
© Copyright 2011, 2013 Hewlett-Packard Development Company, L.P.
Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211
and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items
are licensed to the U.S. Government under vendor's standard commercial license.
The information contained herein is subject to change without notice. The only warranties for HP products and services are set
forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as
constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Acknowledgments
Microsoft, Windows, and Windows XP are U.S. registered trademarks of Microsoft Corporation.
UNIX is a registered trademark of The Open Group.
Export Requirements
You may not export or re-export this document or any copy or adaptation in violation of export laws or regulations.
Without limiting the foregoing, this document may not be exported, re-exported, transferred or downloaded to or within (or to
a national resident of) countries under U.S. economic embargo, including Cuba, Iran, North Korea, Sudan, and Syria. This
list is subject to change.
This document may not be exported, re-exported, transferred, or downloaded to persons or entities listed on the U.S. Department
of Commerce Denied Persons List, Entity List of proliferation concern or on any U.S. Treasury Department Designated Nationals
exclusion list, or to parties directly or indirectly involved in the development or production of nuclear, chemical, biological
weapons, or in missile technology programs as specified in the U.S. Export Administration Regulations (15 CFR 744).
Hitachi and Universal Replicator are registered trademarks of Hitachi, Ltd. ShadowImage and TrueCopy are registered
trademarks of Hitachi, Ltd. and Hitachi Data Systems Corporation.
Revision history
DescriptionEditionVersionDate
First editionFirst7.1.0-00April 2011
Added information for new and changed features.Second7.1.1-00August 2011
Added information for new and changed features.Third7.2.0-00November 2011
Added information for new and changed features.Fourth7.2.1-00March 2012
Added information for new and changed features.Fifth7.3.1-00August 2012
Added information for new and changed features.Sixth7.4.0-00November 2012
Added information for new and changed features.Seventh7.4.1-00February 2013
Added information for new and changed features.Eighth7.5.0-00May 2013
Added information for new and changed features.Ninth7.6.0-00October 2013
Page 3

Contents
Preface .............................................................................................. 25
1 Overview of Application Agent .......................................................... 27
Application Agent features ........................................................................................................ 27
Application Agent functions ...................................................................................................... 28
Backing up data ............................................................................................................... 28
Restoring data .................................................................................................................. 29
Managing data by using dictionary map files ....................................................................... 29
Pair management using copy groups ................................................................................... 30
Cluster support .................................................................................................................. 30
Reducing workload by using commands ............................................................................... 31
Data management on another storage systems ...................................................................... 31
Managing generations ...................................................................................................... 32
2 Application Agent system configurations ............................................. 35
Basic configurations for backing up and restoring data .................................................................. 35
Configurations in which data is backed up and restored within a storage system ........................ 35
Configurations in which data can be backed up and restored between two storage systems ......... 36
Continuous Access Software or Continuous Access Journal configuration ............................. 36
Business Copy and Continuous Access Software multi-target configuration ........................... 37
Business Copy and Continuous Access Journal multi-target configuration ............................. 38
Continuous Access Software and Continuous Access Journal multi-target configuration .......... 39
Business Copy (multi-generation), Continuous Access Software, or Continuous Access Journal
configuration ............................................................................................................... 40
Precautions on backing up and restoring data between storage systems .................................... 41
Configurations using tape devices ........................................................................................ 42
Configurations for operation in cluster environments ...................................................................... 43
Operation-standby cluster configuration ................................................................................. 43
Mutual-standby cluster configuration ..................................................................................... 44
Configurations when VSS is used ................................................................................................ 45
Requirements and precautions for backing up file systems .............................................................. 46
System configurations for backing up SQL Server databases ........................................................... 47
Configurations for restoring an SQL Server database to a host that is not the original host ........... 47
Configurations for using the log-shipping functionality ............................................................. 48
Cascade configurations ...................................................................................................... 49
Multi-target configurations ................................................................................................... 50
Requirements and precautions for backing up SQL Server databases ............................................... 51
Allocating files that comprise a database .............................................................................. 54
Allocating multiple database configuration files to one volume ................................................. 55
Allocating metafiles ............................................................................................................ 55
Using a dynamic disk configuration ...................................................................................... 57
Using a cluster configuration ................................................................................................ 58
System configurations for backing up Exchange databases ............................................................. 58
Cascade configurations ...................................................................................................... 58
Application Agent CLI User Guide 3
Page 4

CCR configurations ............................................................................................................. 58
Configuration in which only the active server is used ........................................................ 59
Configuration in which only the standby server is used ...................................................... 59
Configuration in which different backup servers are used for the active and standby
servers ....................................................................................................................... 60
Configuration in which the same backup server is used for the active and standby servers ..... 60
SCR configurations ............................................................................................................. 61
DAG configurations ............................................................................................................ 62
Backing up and restoring active mailbox database copies ................................................. 63
Backing up and restoring passive mailbox database copies .............................................. 64
Backing up and restoring the active mailbox database copy and the passive mailbox database
copy by using different backup servers ........................................................................... 65
Backing up and restoring the active mailbox database copy and the passive mailbox database
copy by using the same backup server ........................................................................... 67
Comparison of DAG configurations ................................................................................ 68
Requirements and precautions for backing up Exchange databases ................................................. 69
Using VSS ......................................................................................................................... 70
Restoring backup data obtained using VSS in units of Information Stores ................................... 73
Using a dynamic disk configuration ...................................................................................... 75
Using a cluster configuration ................................................................................................ 75
Cascade configuration ........................................................................................................ 76
CCR configuration .............................................................................................................. 77
SCR configuration .............................................................................................................. 78
DAG configuration ............................................................................................................. 78
Requirements when using RAID Manager to configure a pair volume ............................................... 80
Volume configurations usable by Application Agent ...................................................................... 87
Examples of disk group configurations usable by Application Agent .......................................... 89
Requirements and precautions for volume configurations ................................................................ 91
Volume configuration requirements ....................................................................................... 91
Precautions when changing a volume configuration ................................................................ 92
Requirements and precautions when a disk group Is configured ................................................ 93
Using dynamic disks in Veritas Storage Foundation .......................................................... 93
Backing up and restoring dynamic disks by dynamically or statically recognizing secondary
volumes ...................................................................................................................... 94
Expanding dynamic volumes ......................................................................................... 94
Precautions for partition styles for disks ................................................................................. 94
3 Preparation for using Application Agent .............................................. 97
Setting up an environment for Application Agent ........................................................................... 97
Setting up RAID Manager ........................................................................................................ 100
Backing up one primary volume to multiple generations ........................................................ 101
Backing up multiple primary volumes to a single generation .................................................. 101
Backing up multiple primary volumes to multiple generations ................................................. 102
Backup or restore between storage systems .......................................................................... 103
Setting up a multi-target or cascade configuration ................................................................. 105
Setting up operation of Application Agent .................................................................................. 106
Specifying the retry count and interval for cluster resource status retry check ............................. 106
Specifying the retry count and interval for process status retry check ........................................ 108
Specifying the retry count and interval for command execution status retry check ...................... 109
Setting up the backup option for SQL Server database backup ............................................... 109
Setting up the dictionary map synchronization option for SQL Server database backup ............. 110
Setting up the recovery option for SQL Server database backup ............................................. 110
Setting up restoration while cluster resources are online ......................................................... 111
Setting up parallel execution of verification processes for Exchange database backup ............... 114
4
Page 5

Setting communication timeout periods for the Protection Manager service ............................... 114
Setting up Application Agent for linkage with RAID Manager ....................................................... 115
Specifying instance numbers .............................................................................................. 115
Specifying a retry count and interval for pair status retry checking .......................................... 118
Specifying a retry count and interval for RAID Manager command busy retry checking ............. 123
Specifying a retry count and interval appropriate to operation style ........................................ 123
Specifying track sizes used when copying data .................................................................... 125
Specifying volume pair creation ......................................................................................... 126
Settings for using secondary volume dynamic recognition ...................................................... 127
Setting up operation mode when automatically selecting copy groups ..................................... 128
Notes on starting and stopping RAID Manager .................................................................... 128
Specifying the installation path for RAID Manager ................................................................ 129
Specifying modification of pair status if a backup error occurs ................................................ 129
Creating dictionary map files ................................................................................................... 130
Creation in a non-cluster configuration or on a backup server ................................................ 130
Creation in an Active-Passive cluster configuration ................................................................. 131
Creation in an Active-Active cluster configuration .................................................................. 133
Creation in a cascade configuration for Exchange database backup ....................................... 135
Specifying cluster configuration settings and creating a definition file ............................................. 136
Settings related to shared disks and cluster groups ................................................................ 136
How to define a cluster group (when a backup target and shared disks are to be in the same
cluster group) ............................................................................................................ 137
How to Define Cluster Groups (When a Backup Target and Shared Disks Are to Be in Separate
Cluster Groups) ......................................................................................................... 138
Creating a cluster information configuration definition file when using Veritas cluster server ........ 139
Creating a database configuration definition file ......................................................................... 142
Creating a configuration definition file for SQL Server database backup .................................. 142
Specifying settings related to linkage with an SQL Server ............................................................. 144
Specifying settings for using VSS ............................................................................................... 147
Using VSS with P9000 RMXP Shadow Copy Provider version 01-02-03/03 or later .................. 149
Using VSS with P9000 RMXP Shadow Copy Provider version 01-02-03/02 or earlier ............... 150
Creating a cascade configuration definition file for Exchange database backup .............................. 151
Setting up linkage with a tape backup management software ....................................................... 155
Registering information for linkage with a tape backup management software .......................... 155
Creating a configuration definition file for tape backup ......................................................... 156
Configuration parameters ........................................................................................... 156
Configuration file examples ......................................................................................... 159
User-defined configuration definition file ....................................................................... 160
Creating a list file ................................................................................................................... 161
Creating a copy-group list file ............................................................................................ 161
Creating a database list file or mount point directory list file .................................................. 161
Commands that support a target definition file ............................................................... 162
File name of the list file ............................................................................................... 162
List file storage location .............................................................................................. 162
Contents of the list file ................................................................................................ 162
Creating a transaction log list file ....................................................................................... 163
File name of the transaction log list file ......................................................................... 163
Transaction log list file storage location ......................................................................... 163
Contents of the transaction log list file ........................................................................... 163
Creation of a transaction log list file ............................................................................. 164
Updating a dictionary map file ................................................................................................. 164
Specifying how to mount a secondary volume ............................................................................ 165
Making the OS dynamically recognize the secondary volume ................................................ 166
Making the OS statically recognize the secondary volume ..................................................... 174
Determining a mount point and mount target when mounting a secondary volume .................... 178
Application Agent CLI User Guide 5
Page 6

Determination of a mount point .................................................................................... 179
Determination of a mount target ................................................................................... 181
Preparations required before executing extended commands ........................................................ 181
Checking the prerequisite conditions ................................................................................... 182
Execution permissions for extended commands .............................................................. 183
Automatic execution of extended commands ................................................................. 183
Prerequisite VBScript version ........................................................................................ 183
Deletion of unnecessary files ....................................................................................... 183
Setting up an FTP service for backing up to tape .................................................................. 184
Specifying how to start the extended commands ................................................................... 184
Creating a host environment settings file .............................................................................. 185
Creating operation IDs ...................................................................................................... 186
Creating operation definition files for file system backup ........................................................ 187
Deployment of operation definition files ........................................................................ 187
Format of operation definition files ............................................................................... 188
Example of creating operation definition files (in a cluster configuration) ........................... 189
Creating operation definition files for SQL Server database backup ........................................ 191
Deployment of operation definition files ........................................................................ 192
Format of operation definition files ............................................................................... 192
Example of creating operation definition files ................................................................ 194
Creating operation definition files for Exchange database backup .......................................... 196
Deployment of operation definition files ........................................................................ 196
Format of operation definition files ............................................................................... 197
Example of creating operation definition files ................................................................ 199
Checking the temporary directory for extended commands .................................................... 201
Checking the copy-group list file ......................................................................................... 202
Checking the FTP service (if you are going to back up to tape) ............................................... 202
Creating a user script .............................................................................................................. 203
Overview of user scripts .................................................................................................... 203
Coding rules for user scripts ............................................................................................... 203
Coding rules for user scripts ........................................................................................ 203
Entries in user scripts .................................................................................................. 204
Script environment variables ........................................................................................ 210
Command execution permission ................................................................................... 210
Commands that can be specified in user pre-processing and user post-processing .............. 210
Examples of user script usage ............................................................................................ 212
Specifying settings for sending mail .......................................................................................... 212
Backing up the Application Agent operating environment ............................................................. 214
Files that need to be backed up ......................................................................................... 214
Application Agent environment setting files and log files ................................................. 214
Definition files created after the installation of Application Agent ...................................... 215
Application Agent backup information .......................................................................... 215
Recovering the operating environment ................................................................................. 217
Recovering operating environment (common among servers) ........................................... 217
Recovering backup information (file server) .................................................................... 218
Recovering backup information (database server) ........................................................... 218
Restoring backup information (backup server) ................................................................ 218
Creating the Exchange environment configuration file .................................................................. 219
4 Application Agent operations .......................................................... 221
Application Agent commands .................................................................................................. 221
Extended commands ........................................................................................................ 221
Basic commands .............................................................................................................. 222
Correspondence between extended commands and basic commands ........................................... 222
6
Page 7

Precautions on operations ........................................................................................................ 225
Precautions on operations ................................................................................................. 226
Precautions on backup and restoration ................................................................................ 226
Precautions on backup ...................................................................................................... 227
Precautions on restoration .................................................................................................. 229
Precautions when executing commands simultaneously .......................................................... 229
Precautions for executing commands in a cluster environment ................................................. 230
Precautions regarding backup servers ................................................................................. 230
Precautions when mounting ......................................................................................... 230
Precautions regarding the drive when mounting data to a backup server ........................... 231
Precautions when importing backup information ............................................................ 231
Command execution conditions ................................................................................... 231
Precautions when updating dictionary map files ................................................................... 231
Unavailable tools when executing commands ...................................................................... 232
Disk group configuration that does not allow backup (dynamic disk configuration) .................... 232
Notes on pair volume resynchronization in a cascade configuration ........................................ 233
Precautions when executing commands ..................................................................................... 233
Permissions required for users executing commands .............................................................. 233
Possibility of concurrent execution with other commands ........................................................ 237
Retry time when an error occurs ......................................................................................... 240
Stopping retry operations caused by a command that cannot execute concurrently with other
commands ...................................................................................................................... 240
Executing multiple drmmediabackup or drmmediarestore commands concurrently ..................... 241
Configurations that requires RAID Manager user authentication .............................................. 242
Starting and stopping the Protection Manager service ................................................................. 242
Starting the Protection Manager service .............................................................................. 242
Restarting the Protection Manager service ............................................................................ 243
Stopping the Protection Manager service ............................................................................. 243
5 Operation for file systems ................................................................ 245
Backing up and restoring a file system ....................................................................................... 245
Precautions when backing up a file system ........................................................................... 245
Precautions when restoring a file system .............................................................................. 245
Precautions when executing commands in a cluster environment ............................................. 246
Precautions on forced termination of commands ................................................................... 246
Backing up and restoring data between volumes ......................................................................... 246
System configuration ......................................................................................................... 246
Processing flow ................................................................................................................ 247
Backing up a file system to a secondary volume ................................................................... 248
Restoring a file system to a primary volume .......................................................................... 249
Backing up and restoring by using a tape device ........................................................................ 249
System configuration ......................................................................................................... 249
Flow of processing ........................................................................................................... 251
Backing up a file system to tape ......................................................................................... 253
Resynchronizing copy groups ...................................................................................... 253
Backing up a file system ............................................................................................. 253
Backup using VSS ...................................................................................................... 255
Restoring a file system from tape ......................................................................................... 256
Backing up a file system by using a user script ............................................................................ 258
System configuration ......................................................................................................... 258
Processing flow ................................................................................................................ 259
User script example .......................................................................................................... 260
Backup execution example ................................................................................................ 263
Backing up and restoring between local sites and remote sites ...................................................... 265
Application Agent CLI User Guide 7
Page 8

Backing up a file system to a remote site ............................................................................. 266
Operations at the local site ......................................................................................... 266
Operations at the remote site ...................................................................................... 267
Operations at the local site ......................................................................................... 268
Restoring a file system to the local site ................................................................................. 269
Operations at the remote site ...................................................................................... 269
Operations at the local site ......................................................................................... 270
Restoring a file system to a remote site ................................................................................ 271
Operations at the remote site ...................................................................................... 271
Recovering a file system from a remote site to the local site .................................................... 272
Operations at the local site ......................................................................................... 272
Operations at the remote site ...................................................................................... 272
Operations at the local site ......................................................................................... 272
Backing up and restoring a file system by using a tape backup management software that cannot link
with Application Agent ............................................................................................................ 272
Backing up and restoring a file system by using a file share .......................................................... 273
Preparing to back up or restore a file system by using a file share ........................................... 273
Example of backing up a file system by using a file share ...................................................... 274
Example of restoring a file system by using a file share .......................................................... 274
Deleting backup data .............................................................................................................. 275
6 Operation for SQL Server databases ................................................ 277
Backing up and restoring an SQL Server database ...................................................................... 277
Precautions when backing up and restoring a database ........................................................ 277
Precautions when restoring a database ............................................................................... 278
Precautions when recovering a database ............................................................................. 279
Precautions when backing up and restoring multiple databases .............................................. 279
When multiple databases are stored in the same volume ................................................ 279
When multiple databases are stored in multiple volumes ................................................. 280
Database status when restoring and recovering .................................................................... 281
Requirements for transaction log backup .............................................................................. 282
Precautions regarding backup of transaction logs ................................................................. 282
Precautions regarding sequences of transaction logs ............................................................. 283
Transaction log backups after roll-forward ..................................................................... 283
Precautions regarding application of transaction logs ............................................................ 285
Recovering the SQL Server database from the last backup data ....................................... 285
Recovering the SQL Server database from backup data existing prior to the last backup
data ......................................................................................................................... 286
SQL Server database requirements for executing commands .................................................. 286
Service status ............................................................................................................ 286
Database status ......................................................................................................... 287
Database type ........................................................................................................... 290
Backing up and restoring data between volumes ......................................................................... 291
System configuration ......................................................................................................... 291
Processing flow ................................................................................................................ 292
Backing up an SQL Server database to a secondary volume .................................................. 293
Restoring an SQL Server database to a primary volume ........................................................ 294
Restoring an SQL Server database ............................................................................... 294
Using the drmsqlrecover command to recover an SQL Server database ............................. 295
Using the drmsqlrecovertool dialog box to recover an SQL Server database ...................... 295
Backing up and restoring by using a tape device ........................................................................ 296
System configuration ......................................................................................................... 297
Processing flow ................................................................................................................ 298
Backing up an SQL Server database to tape ........................................................................ 300
8
Page 9

Resynchronizing copy groups ...................................................................................... 300
Backing up an SQL Server database ............................................................................ 301
Restoring an SQL Server database from tape ....................................................................... 303
Restoring an SQL Server database ............................................................................... 303
Recovering an SQL Server database with the drmsqlrecover command ............................. 305
Recovering an SQL Server database using the drmsqlrecovertool dialog box ..................... 305
Backing up an SQL Server database by using a user script .......................................................... 306
System configuration ......................................................................................................... 307
Processing flow ................................................................................................................ 307
User script example .......................................................................................................... 308
Backup execution example ................................................................................................ 310
Operation using SQL Server transaction logs .............................................................................. 311
System configuration ......................................................................................................... 311
Example of operation using a transaction log backup ........................................................... 312
Backing up an SQL Server database ................................................................................... 313
Resynchronizing copy groups ...................................................................................... 313
Backing up an SQL Server database ............................................................................ 314
Backing up transaction logs ............................................................................................... 314
Restoring SQL Server databases ......................................................................................... 315
Applying the drmsqlrecovertool dialog box to restore an SQL Server database ......................... 315
Using the drmsqlrecovertool dialog box to recover an SQL Server database ...................... 315
Using the drmsqlrecover command to recover an SQL Server database (using a transaction
log list file) ................................................................................................................ 316
Example of operation using transaction log backup .............................................................. 317
Backing up and restoring transaction log backup files .................................................................. 318
System configuration ......................................................................................................... 319
Backing up the transaction log backup file ........................................................................... 320
Restoring the transaction log backup file .............................................................................. 322
Backing up and restoring multiple generations by locking a copy group ......................................... 323
Example of operation using lock functionality and generation management ............................. 324
Locking a copy group ....................................................................................................... 324
Unlocking a copy group .................................................................................................... 326
Backing up and restoring between local sites and remote sites ...................................................... 327
Backing up an SQL Server database to a remote site ............................................................ 329
Operation at the local site .......................................................................................... 329
Operation at the remote site ........................................................................................ 330
Operation at the local site .......................................................................................... 331
Restoring an SQL Server database to the local site ................................................................ 331
Operation at the remote site ........................................................................................ 331
Operation at the local site .......................................................................................... 332
Restoring an SQL Server database to a remote site ............................................................... 333
Operation at the remote site ........................................................................................ 333
Recovering data from the remote site to the local site ............................................................ 334
Operation at the local site .......................................................................................... 335
Operation at the remote site ........................................................................................ 335
Operation at the local site .......................................................................................... 335
Backing up and restoring in a multi-target configuration ............................................................... 335
Example of backing up an SQL Server database .................................................................. 338
Example of restoring an SQL Server database ...................................................................... 339
Performing restoration and recovery on a host other than the backup host ...................................... 341
Using the SQL Server log-shipping function ................................................................................ 346
Before using the log-shipping function ................................................................................. 346
Setting a distribution target server as an operating server ...................................................... 350
Backing up and restoring in a cascade configuration or multi-target configuration ........................... 352
Application Agent CLI User Guide 9
Page 10

Preparations for performing backup or restoration in a cascade configuration or multi-target
configuration ................................................................................................................... 353
Creating a user script to perform a backup in a cascade configuration .................................... 357
Outline of user script files ............................................................................................ 357
Coding rules for user script files ................................................................................... 358
Sample user script files ............................................................................................... 358
Backing up an SQL Server database in a cascade configuration ............................................ 367
Backing up transaction logs in a cascade configuration without a backup catalog .................... 371
Restoring an SQL Server database in a cascade configuration ............................................... 371
Backing up and restoring using a tape backup management software that cannot link with Application
Agent .................................................................................................................................... 376
Backing up and restoring an SQL Server database by using a file share ........................................ 377
Preparing to back up or restore by using a file share ............................................................. 378
Backing up an SQL Server database by using a file share ..................................................... 379
Example of restoring a database by using a file share ........................................................... 379
Restoring data to an SQL Server instance that is different from the backup source ............................ 380
System configuration ......................................................................................................... 380
Operation flow ................................................................................................................ 381
Preparations for restoration (recovery) ........................................................................... 381
Operations for restoration (recovery) ............................................................................ 382
Operation example .......................................................................................................... 382
Example of restoring an SQL Server database from tape and recovering on the secondary
volume ..................................................................................................................... 382
Example of restoring (recovering) an SQL Server database on the log distribution
destination ................................................................................................................ 383
Example of restoring (recovering) an SQL Server database on the primary volume ............. 383
Deleting backup data .............................................................................................................. 383
Making an SQL Server database backed up to a secondary volume available for use ..................... 384
System configuration ......................................................................................................... 384
User script example .......................................................................................................... 386
script1.txt (used for data mining) .................................................................................. 386
script2.txt (used for backup) ........................................................................................ 387
Example ......................................................................................................................... 388
Backing up and restoring when using an SQL Server replication configuration ................................ 388
System configuration ......................................................................................................... 388
Requirements for the publication database and the distribution database .......................... 389
Requirements for the subscription database ................................................................... 390
Example ......................................................................................................................... 390
Back up the databases ............................................................................................... 390
Back up the transaction logs of the publication database ................................................ 391
Prepare for database restoration .................................................................................. 391
Restore the databases ................................................................................................. 392
Perform database recovery .......................................................................................... 393
Prepare to restart operations ....................................................................................... 393
Setting and checking the 'sync with backup' option .............................................................. 393
How to set the 'sync with backup' option ...................................................................... 394
How to check the 'sync with backup' option .................................................................. 394
Backing up and restoring in an SQL Server AlwaysOn availability group configuration .................... 394
System configuration ......................................................................................................... 394
Backing up and restoring a user database to the active server ................................................ 395
Restoring a user database to the standby server from the active server ..................................... 396
Restoring a user database to the secondary-use server from the active server ............................ 398
7 Operation for Exchange databases .................................................. 401
10
Page 11

Backing up and restoring a storage group ................................................................................. 401
Precautions when backing up an Exchange database ........................................................... 401
Precautions when restoring an Exchange database ............................................................... 402
Precautions when restoring from a tape ......................................................................... 402
Note on performing a recovery using roll forward .......................................................... 402
Procedure for handing the message (KAVX1510-E) ........................................................ 402
Notes on restoring data obtained with a VSS backup ..................................................... 403
Procedure for when the Information Store cannot be mounted .......................................... 403
Precautions on recovery storage groups and recovery databases ............................................ 404
Precautions when configuring volumes ................................................................................ 404
Precautions on database verification ................................................................................... 404
Backing up and restoring data between volumes without using VSS ............................................... 404
System configuration ......................................................................................................... 404
Processing flow ................................................................................................................ 405
Backing up storage groups to a secondary volume ............................................................... 406
Restoring storage groups to a primary volume ...................................................................... 407
Backing up and restoring data between volumes by using VSS ..................................................... 407
System configuration ......................................................................................................... 407
Processing flow ................................................................................................................ 408
Backing up storage groups to a secondary volume ............................................................... 409
Restoring storage groups to a primary volume ...................................................................... 410
Backing up and restoring by using a tape device ........................................................................ 410
System configuration ......................................................................................................... 410
Processing flow ................................................................................................................ 412
Backing up storage groups to tape ..................................................................................... 414
Resynchronizing copy groups ...................................................................................... 414
Cold backup ............................................................................................................. 415
Online backup .......................................................................................................... 416
Backup using VSS ...................................................................................................... 417
Restoring storage groups from tape ..................................................................................... 419
Backing up a storage group by using a user script ...................................................................... 421
System configuration ......................................................................................................... 421
Processing flow ................................................................................................................ 421
User script example .......................................................................................................... 422
Backup execution example ................................................................................................ 423
Restoring by using transaction logs (Roll-forward) ........................................................................ 424
System configuration ......................................................................................................... 425
Rolling forward the transaction logs at the time of restoration ................................................. 426
Backing up and restoring between local sites and remote sites ...................................................... 427
Backing up storage groups to a remote site .......................................................................... 428
Operations at the local site ......................................................................................... 429
Operations at the remote site ...................................................................................... 430
Operations at the local site ......................................................................................... 431
Restoring a storage group to a local site .............................................................................. 431
Operations at the remote site ...................................................................................... 432
Operations at the local site ......................................................................................... 433
Backing up and restoring in a cascade configuration .................................................................. 434
Backing up concurrently at both local and remote sites .......................................................... 436
Operation at the local site .......................................................................................... 436
Operation at both the local and remote sites ................................................................. 438
Restoring data using the backup data at the local site ........................................................... 442
Restoring data using the backup data at the remote site ........................................................ 446
Backing up and restoring in a CCR configuration ........................................................................ 450
Using different backup servers for the active and standby servers ............................................ 452
Performing a backup on the active server ...................................................................... 453
Application Agent CLI User Guide 11
Page 12

Performing a backup on the standby server ................................................................... 457
Restoring data when using the automatic seed function ......................................................... 461
Restoring backup data acquired on the active server (when the automatic seed function is
used) ........................................................................................................................ 461
Restoring backup data acquired on the standby server (when the automatic seed function is
used) ........................................................................................................................ 465
Restoring data when not using the automatic seed function .................................................... 469
Restoring backup data acquired on the active server (when the automatic seed function is not
used) ........................................................................................................................ 469
Restoring backup data acquired on the standby server (when the automatic seed function is
not used) .................................................................................................................. 473
Backing up and restoring in SCR configurations .......................................................................... 477
System configuration ......................................................................................................... 477
Backing up in an SCR configuration .................................................................................... 478
Roll-forward recovery on backed up data acquired in an SCR configuration ............................. 482
Point-in-time restoration when not using the SCR seed function ................................................ 486
Point-in-time restoration when using the SCR seed function ..................................................... 489
Backing up and restoring in DAG configurations ......................................................................... 492
System Configuration ........................................................................................................ 492
Backing up active mailbox database copies ........................................................................ 494
Backing up passive mailbox database copies ...................................................................... 497
Restoring backup data of an active mailbox database copy ................................................... 500
Restoring backup data of a passive mailbox database copy .................................................. 503
Backing up and restoring storage groups using a tape backup management software that is unable to
link with Application Agent ...................................................................................................... 506
Backing up and restoring storage groups by using a file share ...................................................... 507
Preparing to use a file share for storage group backup and restore ......................................... 508
Example of using a file share for storage group backup ......................................................... 508
Example of using a file share for storage group restoration .................................................... 509
Deleting backup data .............................................................................................................. 509
8 Troubleshooting ............................................................................. 511
Troubleshooting procedure ....................................................................................................... 511
Troubleshooting extended commands ........................................................................................ 511
Data required for troubleshooting .............................................................................................. 512
Data required for troubleshooting ....................................................................................... 512
OS log information .................................................................................................... 512
Application Agent information ..................................................................................... 513
RAID Manager information ......................................................................................... 515
Database information (when the backup is of an SQL Server database or Exchange
database) ................................................................................................................. 516
Other information ...................................................................................................... 516
Operation details ....................................................................................................... 516
Log files output by extended commands .............................................................................. 516
Adjusting trace log settings ...................................................................................................... 519
Adjusting the output level for detailed trace log information ................................................... 519
Adjusting the number of log files for detailed trace log information ......................................... 519
Investigating collected data ...................................................................................................... 519
Investigating standard output logs ....................................................................................... 520
Investigating the trace logs for Application Agent-cooperative software .................................... 520
Investigating the detailed trace log ..................................................................................... 520
Troubleshooting dictionary map file errors .................................................................................. 522
Verifying dictionary map files ............................................................................................. 523
Restoring key definition files (.KDF) ..................................................................................... 524
12
Page 13

Restoring key files (.K01 or .Knn) ........................................................................................ 524
Restoring missing data files (.DRF or .DAT) ........................................................................... 525
When data file (.DRF or .DAT) backups exist ................................................................. 525
When data file (.DRF or .DAT) backups do not exist ....................................................... 525
Restoring incorrect data files (.DRF or .DAT) ......................................................................... 525
Displaying dictionary map file information or backup information ........................................... 526
Recreating dictionary map files .......................................................................................... 527
9 Support and other resources ............................................................ 529
Contacting HP ........................................................................................................................ 529
HP technical support ......................................................................................................... 529
Subscription service .......................................................................................................... 529
Documentation feedback ................................................................................................... 529
Related information ................................................................................................................. 529
Conventions ........................................................................................................................... 530
A Example of an Application Agent environment configuration ............... 533
System configuration ............................................................................................................... 533
Server configuration ......................................................................................................... 534
Storage system configuration ............................................................................................. 535
Example settings for the RAID Manager configuration definition file ............................................... 536
Example settings for the Application Agent configuration definition file (init.conf) ............................ 539
Example settings for the RAID Manager-linkage definition file (DEFAULT.dat) ................................... 540
Example of creating dictionary map files .................................................................................... 541
Example of registering SQL Server information ............................................................................ 541
Example settings for linkage to tape backup management software ............................................... 542
Example registering information for linkage to the tape backup management software .............. 543
Example of the configuration definition file for tape backup ................................................... 543
Example settings for the host environment settings file .................................................................. 544
Example settings for an operation definition file .......................................................................... 544
Example settings for a copy-group list file ................................................................................... 545
B List of files used in Application Agent ................................................ 547
List of files used in Application Agent ........................................................................................ 547
C Replacing primary and secondary volume disks while Application Agent
is running ........................................................................................ 553
Replacing primary and secondary volume disks while Application Agent is running ........................ 553
Procedure for replacing a primary volume disk ........................................................................... 553
Procedure for replacing a secondary volume disk ....................................................................... 556
D Restoring from a tape directly to a primary volume in a Fast Snap or
Snapshot configuration ...................................................................... 559
Example of Fast Snap or Snapshot configuration ......................................................................... 559
Procedure for backing up to tape on the backup server ................................................................ 559
Procedure for restoring from tape directly to the primary volume .................................................... 560
E Correspondence to Replication Manager GUI terms ............................ 561
Correspondence to Replication Manager GUI terms .................................................................... 561
Application Agent CLI User Guide 13
Page 14

Glossary .......................................................................................... 563
Index ............................................................................................... 567
14
Page 15

Figures
11
12
Overview of Application Agent ................................................................................. 281
Logical volume consisting of multiple copy groups ...................................................... 302
Data management at a remote site ........................................................................... 323
Backing up multiple generations .............................................................................. 334
Backing up multiple generations when a copy group is locked ..................................... 345
Example of a system configured to back up and restore data within a storage system ....... 366
Continuous Access Software or Continuous Access Journal system configuration .............. 377
Business Copy and Continuous Access Software multi-target configuration ...................... 388
Business Copy and Continuous Access Journal multi-target configuration ........................ 399
Continuous Access Software and Continuous Access Journal multi-target configuration ..... 4010
Business Copy (multi-generation), Continuous Access Software, or Continuous Access
Journal configuration ............................................................................................... 41
Example of configuration for concurrent backup from multiple primary volumes to multiple
secondary volumes (remote copy) ............................................................................. 42
Example of a system configured with a tape device ..................................................... 4313
Example of a cluster configuration of the operation standby type (Active-Passive) ............. 4414
Example of a cluster configuration of the mutual standby type (Active-Active) .................. 4515
Example of a system configured to use VSS to back up data ........................................ 4616
Example of a system configured to restore data on a host that differs from the host used
17
for backup ............................................................................................................. 48
Example of a system configuration for the log-shipping functionality ............................... 4918
Example of a cascade configuration (when the backup is of an SQL Server database) ..... 5019
Example of a multi-target configuration (when the backup is of an SQL Server
20
database) .............................................................................................................. 51
Allocation of database configuration files ................................................................... 5521
When multiple database configuration files are allocated to a volume ........................... 5522
Metafile allocation .................................................................................................. 5623
Metafile allocation (in the cluster configuration) ........................................................... 5724
Example of a cascade configuration (when backing up Exchange databases) ................. 5825
Example of a CCR configuration (only the active server is used) .................................... 5926
Example of a CCR configuration (only the standby server is used) ................................. 6027
Example of a CCR configuration (active and standby servers use different backup
28
servers) .................................................................................................................. 60
Application Agent CLI User Guide 15
Page 16

Example of a CCR configuration (active and standby servers use the same backup
29
server) ................................................................................................................... 61
Example of an SCR configuration .............................................................................. 6230
Configuration in which an active mailbox database copy Is backed up and restored ....... 6431
Configuration in which a passive mailbox database copy Is backed up and restored ....... 6532
Configuration in which an active mailbox database copy and a passive mailbox database
33
copy are backed up and restored by different backup servers ....................................... 66
Configuration in which an active mailbox database copy and a passive mailbox database
34
copy are backed up and restored by the same backup server ....................................... 67
Restoration in units of Information Stores (when the backup target is an Exchange
35
database) .............................................................................................................. 74
Configuration for managing the primary volume and secondary volume from the same
36
server (without using Application Agent) .................................................................... 80
System configuration (when the primary volume for Business Copy and the primary volume
37
for Continuous Access Software are the same LDEV) .................................................... 82
System configuration (when the secondary volume for Business Copy and the primary
38
volume for Continuous Access Software are the Same LDEV) ......................................... 83
System configuration (In a Business Copy cascade configuration, when the volume subject
39
to backup operates both as the primary volume and the secondary volume) ................... 84
In XP Continuous Access Asynchronous/Continuous Access Journal configuration: restoring
40
UserDB1 and UserDB2 together or separately ............................................................ 86
In XP Continuous Access Asynchronous/Continuous Access Journal configuration: restoring
41
UserDB1 and UserDB2 together ................................................................................ 86
Examples of a disk set configuration and of a relationship between a disk group and a
42
disk set .................................................................................................................. 88
Examples of disk group configurations usable by Application Agent .............................. 8943
Data backup and restoration in a system configuration where multiple disk groups exist
44
in a file system ........................................................................................................ 90
Configuration example of a mounted directory that becomes a backup target ................. 9245
Configuration example of a mounted directory that does not become a backup target ..... 9246
Volume configuration and configuration definition to back up one primary volume to
47
multiple generations .............................................................................................. 101
Volume configuration and configuration definition to back up multiple primary volumes
48
to a single generation ........................................................................................... 102
Volume configuration and configuration definition to back up multiple primary volumes
49
to multiple generations .......................................................................................... 103
Example of a configuration definition for backup or restore between storage systems ..... 10450
Configuration definition for a multi-target configuration and a cascade configuration ..... 10651
16
Example of specifying a RAID Manager instance number in the RAID Manager-linkage
52
definition file (DEFAULT.dat) .................................................................................... 118
Example of creating dictionary map files in an Active-Passive cluster configuration ......... 13153
Example of creating dictionary map files in an Active-Active cluster configuration .......... 13354
Page 17

Cluster group definition (when a backup target and shared disks are in the same cluster
55
group) ................................................................................................................. 138
Cluster Group Definition (When a Backup Target and Shared Disks are in Different Cluster
56
Groups) ............................................................................................................... 139
Example of deploying operation definition files (cluster configuration when the backup is
57
of a file system) ..................................................................................................... 187
Example of locations of operation definition files (when the backup is of an SQL Server
58
database) ............................................................................................................ 192
Example of locations of operation definition files (when the backup is of an Exchange
59
database) ............................................................................................................ 197
Protecting backup information for disk backups ......................................................... 21560
Protecting backup information for tape backups ........................................................ 21761
Correspondence of backup catalog and copy group ................................................. 22762
Disk group configuration that does not allow backup ................................................. 23363
System configuration for backing up and restoring data between volumes (when the backup
64
is of a file system) ................................................................................................. 247
Procedure for backing up a file system to the secondary volume .................................. 24865
Procedure for restoring a file system to the primary volume ......................................... 24866
System configuration for backing up a file system to tape and restoring it from tape ....... 25067
Procedure for backing up a file system to tape .......................................................... 25268
Procedure for restoring a file system from tape .......................................................... 25269
System configuration for backup of a file system to tape ............................................. 25970
Processing flow ..................................................................................................... 26071
System configuration for backing up and restoring a file system between a local site and
72
a remote site ........................................................................................................ 265
Backing up and restoring multiple databases (same volume configuration) .................... 28073
Backing up and restoring multiple databases (multiple volume configuration) ................ 28074
Tape restoring multiple databases (multiple volume configuration) ................................ 28175
Database statuses during restoration and recovery .................................................... 28276
Transaction log backups after roll-forward (1) ........................................................... 28477
Transaction log backups after roll-forward (2) ........................................................... 28478
Transaction log backup error after roll-forward .......................................................... 28579
Order of applying transaction log backups (1) .......................................................... 28580
Order of applying transaction log backups (2) .......................................................... 28681
System configuration for backing up and restoring data between volumes (when the backup
82
is of an SQL server database) ................................................................................. 292
Procedure for backing up an SQL Server database to the secondary volume ................ 29383
Procedure for restoring an SQL Server database to the primary volume ........................ 29384
System configuration for backing up an SQL Server database to tape and restoring it from
85
tape .................................................................................................................... 297
Application Agent CLI User Guide 17
Page 18

Procedure for restoring an SQL Server database to the primary volume ........................ 29986
Procedure for restoring an SQL Server database from its backup tape .......................... 30087
System configuration for backup of an SQL Server database to tape ............................ 30788
Processing flow ..................................................................................................... 30889
System configuration for operations using the SQL Server transaction log ..................... 31190
Operation using transaction log backups ................................................................. 31291
Operations using SQL Server transaction log backup (restoring a database to the state it
92
was immediately before failure) .............................................................................. 317
Backing up SQL Server transaction log backup files ................................................... 31993
Example of operation in which a particular copy group is locked ................................ 32494
System configuration for backing up and restoring an SQL Server database between a
95
local site and a remote site .................................................................................... 328
System configuration for backing up an SQL Server database to tape and restoring it from
96
tape in a multi-target configuration .......................................................................... 336
System configuration for restoring and recovering from a host not used for backup (when
97
backing up) ......................................................................................................... 342
System configuration for restoring and recovering from a host not used for backup (when
98
restoring) ............................................................................................................. 343
System configuration for log-shipping operations ....................................................... 34799
System configuration for setting a distribution target server to be an operating server ..... 351100
Sample configuration for backing up to a secondary volume at a remote site (cascade
101
configuration) ....................................................................................................... 352
Points in time at which a user script is executed ......................................................... 357102
Sample cascade configuration ................................................................................ 358103
Flow of script-specified operations performed when local backup is not involved ........... 360104
Flow of script-specified operations performed when local backup is involved ................. 364105
System configuration using file sharing to back up and restore an SQL Server
106
database ............................................................................................................. 378
System configuration for restoring data to an SQL Server instance different from the backup
107
source ................................................................................................................. 381
System configuration for restoring to an SQL Server instance that is different from the
108
backup source (using a user script) .......................................................................... 385
Configuration for using the SQL Server replication function ......................................... 389109
Configuration of backup server for the publisher/distributor server .............................. 390110
Operation when using Application Agent on an SQL Server in an AlwaysOn availability
111
group configuration ............................................................................................... 395
18
System configuration for backing up and restoring data between volumes without using
112
VSS (when an Exchange database is backed up) ...................................................... 405
Processing flow for backing up storage groups to a secondary volume ......................... 406113
Processing flow for restoring storage groups on the primary volume ............................. 406114
Page 19

System configuration for backing up and restoring data between volumes by using VSS
115
(when an Exchange database is backed up) ............................................................. 408
Processing flow for backing up storage groups to a secondary volume ......................... 409116
Processing flow for restoring storage groups on the primary volume ............................. 409117
System configuration for backing up and restoring storage groups to and from tape ...... 411118
Processing flow for backing up storage groups to tape ............................................... 413119
Processing flow for restoring storage groups from tape ............................................... 414120
System configuration for backup of a storage group to tape ........................................ 421121
Processing flow ..................................................................................................... 422122
Flow of operation using transaction logs .................................................................. 424123
System configuration for restoring data in units of Information Stores by applying transaction
124
logs .................................................................................................................... 425
System configuration for backing up and restoring a storage group between a local site
125
and a remote site .................................................................................................. 427
Example of a system for backing up and restoring data in a cascade configuration ....... 435126
Example of a system for backing up and restoring data in a CCR configuration ............ 451127
System configuration for an SCR system ................................................................... 477128
System configuration for backing up and restoring data in a DAG configuration ............ 493129
System configuration (for the example Application Agent environment configuration) ...... 534130
Example of replacing a primary volume disk ............................................................ 554131
Example of replacing a secondary volume disk ......................................................... 556132
Application Agent CLI User Guide 19
Page 20

Tables
10
Types of data subject to backup in the SQL Server database ......................................... 511
Comparison of DAG configurations ........................................................................... 682
Types of data subject to backup in the Exchange database ........................................... 693
Approximate amount required to verify Exchange Server 2003 database for backup by
4
using VSS .............................................................................................................. 72
Approximate amount required to verify Exchange Server 2007 database for backup by
5
using VSS .............................................................................................................. 72
Approximate amount required to verify Exchange Server 2010 database for backup by
6
using VSS .............................................................................................................. 73
Conditions for allocating files when restoring backup data in units of Information
7
Stores .................................................................................................................... 74
Volume configurations that Application Agent can back up and restore .......................... 878
Application Agent environment setup tasks needed for each kind of server ..................... 979
Parameters in init.conf (to set the retry count and retry interval for checking the status of
cluster resources) ................................................................................................... 107
CLU_RETRY_WAIT value for each type of cluster software ........................................... 10711
Parameters in init.conf (to specify the retry count and retry interval for checking the status
12
of a process) ........................................................................................................ 108
Parameters in init.conf (to specifying a retry count and a retry interval for command
13
execution status retries checking) ............................................................................. 109
Parameter in init.conf (backup option) ...................................................................... 10914
Parameter in init.conf (dictionary map synchronization option) .................................... 11015
Parameter in init.conf (recovery option) .................................................................... 11016
Parameter in init.conf (setting up restoration when the cluster resources are in the online
17
state) ................................................................................................................... 111
Parameter in CLU_MSCS_RESTORE and cluster resource status (file system) ................... 11118
Parameter in CLU_MSCS_RESTORE and cluster resource status (SQL Server database
19
1) ....................................................................................................................... 112
Parameter in CLU_MSCS_RESTORE and cluster resource Status (SQL Server database
20
2) ....................................................................................................................... 113
Parameter in CLU_MSCS_RESTORE and cluster resource status (Exchange database) ...... 11321
Parameter in init.conf (setup of parallel execution of verification processes) ................... 11422
Parameter in init.conf (setting the communication timeout period for the Protection Manager
23
service) ................................................................................................................ 114
Parameters in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify an
24
instance number) .................................................................................................. 116
20
Page 21

Parameters in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify the retry
25
count and retry interval for checking the status of a pair) ............................................ 119
Values in the RETRY_WAIT parameter set for each storage system ................................ 11926
Parameters in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify the retry
27
count and interval for checking the pair status according to the purpose) ..................... 120
Parameters in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify a retry
28
count and a retry interval for RAID Manager command busy status retries checking) ...... 123
Parameter in copy parameter definition files ............................................................. 12429
Parameter in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify the track
30
size used when copying data) ................................................................................ 126
Parameter in the RAID Manager-linkage definition file (DEFAULT.dat) (to specify whether
31
to create a pair automatically) ................................................................................ 127
Parameters in the RAID Manager-linkage definition file (DEFAULT.dat) (settings for using
32
the secondary volume dynamic recognition functionality) ........................................... 127
Parameter in the RAID Manager-linkage definition file (DEFAULT.dat) (settings for operation
33
mode when automatically selecting copy groups) ...................................................... 128
Parameter in the RAID Manager-linkage definition file (DEFAULT.dat) (specifying the
34
installation path for RAID Manager) ........................................................................ 129
Parameter in the RAID Manager-linkage definition file (DEFAULT.dat) (specifying
35
modification of the pair status if an error occurs) ....................................................... 129
Directories that need to be created on a shared disk and locations of explanations on
36
how to create the directories ................................................................................... 137
Parameters for the cluster software ........................................................................... 14037
Relationship between SQL_AUTORECOVERY_TIME parameter and restored objects ....... 14438
Parameter defined in the sqlinit_instance-name.conf file (specification of SQL Server login
39
timeout option) ..................................................................................................... 146
Parameter defined in the sqlinit_instance-name.conf file (specification of SQL Server
40
automatic recovery time) ........................................................................................ 146
Default settings for Windows services related to P9000 RMXP Shadow Copy Provider .... 14741
vsscom.conf parameters ......................................................................................... 14842
System environment variables required to use VSS (file server or database server) .......... 14943
System environment variables required to use VSS (backupserver) ................................ 14944
System environment variables required to use VSS (file server or database server) .......... 15045
System environment variables required to use VSS (backup server) ............................... 15146
Parameters defined in the definition file for the cascade configuration .......................... 15247
How the -cascade option and the sections are evaluated ............................................ 15448
Parameters to be defined in the configuration definition file for tape backup (for
49
NetBackup) .......................................................................................................... 156
Parameters defined in the configuration file for tape backup (for Backup Exec) .............. 15850
How to determine a mount point when the command for mounting a secondary volume
51
is executed (with a backup id specified in the option) ................................................. 179
Application Agent CLI User Guide 21
Page 22

How to determine a mount point when the command for mounting a secondary volume
52
is executed (when a copy group is specified for an option) ......................................... 180
How to determine a mount target when the command for mounting a secondary volume
53
is executed ........................................................................................................... 181
Extended command execution preparation tasks needed for each kind of server ........... 18154
Value and maximum value length of each entry in a host environment settings file ......... 18555
Example: contents and maximum value length of each entry in an operation definition file
56
(when the backup is of a file system) ........................................................................ 188
Cluster Resources (In cluster configuration when the backup is of a file system) .............. 18957
Operation IDs for which an operation definition file is created (in cluster configuration
58
when the backup is of a file system) ......................................................................... 190
Contents and maximum value length of each entry in an operation definition file (when
59
the backup is of an SQL Server database) ................................................................ 193
Cluster resources (when the backup is of an SQL Server database) .............................. 19460
Example of VDI metafile storage directory ................................................................ 19561
Operation IDs for which to create operation definition files (when the backup is of an SQL
62
Server and in a cluster configuration) ....................................................................... 195
Contents and maximum value length of each entry in an operation definition file (when
63
the backup is of an Exchange database) .................................................................. 197
Cluster resources (when the backup is of an Exchange database) ................................ 19964
Operation IDs for which an operation definition file is created (when the backup is of an
65
Exchange database and in a cluster configuration) .................................................... 200
Naming conventions for the temporary directory for extended commands .................... 20166
Naming conventions for the temporary directory for extended commands .................... 20167
Directories used for inter-server FTP transmission and reception ................................... 20268
Directories used for inter-server FTP transmission and reception ................................... 20269
Coding rules for user scripts ................................................................................... 20370
Entries in user scripts ............................................................................................. 20471
Script environment variables ................................................................................... 21072
Commands that can be specified in user pre-processing and user post-processing ......... 21173
Examples of user script usage ................................................................................. 21274
mail.conf parameters ............................................................................................. 21275
Parameters in the Exchange environment configuration file .......................................... 21976
Correspondence between extended commands and basic commands (commands used
77
for backing up and restoring file systems) ................................................................. 222
Correspondence between extended commands and basic commands (Common
78
commands) .......................................................................................................... 222
22
Correspondence between extended commands and basic commands (Tape
79
commands) .......................................................................................................... 223
Correspondence between extended commands and basic commands (Utility
80
commands) .......................................................................................................... 224
Page 23

Correspondence between extended commands and basic commands (SQL server
81
database) ............................................................................................................ 224
Correspondence between extended commands and basic commands (Exchange
82
database) ............................................................................................................ 225
Required permissions for each command (commands used when backing up and restoring
83
a file system) ........................................................................................................ 234
Required permissions for each command (common system commands) ......................... 23484
Required permissions for each command (tape system commands) .............................. 23585
Required permissions for each command (utility commands) ....................................... 23686
Required permissions for each command (when the backup target is an SQL server
87
database) ............................................................................................................ 236
Required permissions for each command (when the backup target is an exchange
88
database) ............................................................................................................ 236
Possibility of concurrent execution with other commands (commands used when backing
89
up and restoring a file system) ................................................................................ 237
Possibility of concurrent execution with other commands (common commands) .............. 23890
Possibility of concurrent execution with other commands (tape-related commands) ......... 23891
Possibility of concurrent execution with other commands (utility commands) ................... 23992
Possibility of concurrent execution with other commands (when the backup is of an SQL
93
Server database) .................................................................................................. 239
Possibility of concurrent execution with other commands (when the backup is of an
94
Exchange database) ............................................................................................. 240
Functions that require that the Protection Manager service be running .......................... 24295
User script creation example ................................................................................... 26096
Relationship between the status of the SQL Server service and the executable
97
command ............................................................................................................ 286
SQL Server database status where a command can be executed (1) ............................ 28798
SQL Server database status where a command can be executed (2) ............................ 28999
Relationship between the type of the sql server database and executable commands ..... 290100
User script creation example ................................................................................... 308101
Sample script for when a local backup is not performed ............................................. 360102
Sample script for when a local backup is performed .................................................. 364103
User script creation example ................................................................................... 422104
OS log information .............................................................................................. 512105
Application Agent information ................................................................................ 513106
RAID Manager information .................................................................................... 515107
Database information (when the backup is of an SQL Server database or Exchange
108
database) ............................................................................................................ 516
Other information ................................................................................................. 516109
Items that are output to the log file for extended commands ........................................ 517110
Application Agent CLI User Guide 23
Page 24

Items output to the detailed trace log ....................................................................... 521111
Sources of messages (controlled objects) and corresponding message IDs .................... 521112
Commands for displaying dictionary map file information .......................................... 526113
Commands for displaying backup information .......................................................... 526114
Product reference conventions ................................................................................. 530115
Server configuration (for the example Application Agent environment configuration) ...... 534116
Storage system volume configuration (for the example Application Agent environment
117
configuration) ....................................................................................................... 535
Examples of shared directory usage (for the example Application Agent environment
118
configuration) ....................................................................................................... 536
List of files used in Application Agent ....................................................................... 547119
Correspondence of Replication Manager GUI and Application Agent command line
120
interface terms ...................................................................................................... 561
24
Page 25

Preface
This guide describes how to manage HP P9000 Replication Manager Software.
Application Agent CLI User Guide 25
Page 26

Preface26
Page 27

1 Overview of Application Agent
Application Agent is designed to reduce the workload on system administrators and to provide efficient
and reliable data protection. This chapter describes the features and functions of Application Agent.
The descriptions in this chapter apply to the Application Agent CLI.
Application Agent features
Application Agent is a software package that simplifies data maintenance operations, especially
those dealing with backup and restoration. Application Agent ensures the protection of important
data while minimizing the effect on other jobs that are being processed. In addition, Application
Agent reduces the workload on system administrators and the cost of data management.
Modern day information systems for enterprises must be able to protect important data without adversely
affecting any other jobs that are concurrently processing. These systems must also be able to quickly
restart any jobs that are being executed, if and when an error occurs. To meet these demands, all
storage systems are RAID-compliant (managed via the RAID Manager software) and include volume
replication functions. These replication functions are able to quickly create a replica of a logical
volume within a storage system without the use of a host. A system administrator who manages
backups can use these functions to then back up the replica (the secondary volume) of a logical volume
(the primary volume) to a tape device without having to disconnect the primary volume from the system.
This allows the primary volume to continue being used for any other jobs that are still being processed.
Until now, system administrators had to deal with the following issues when using volume replication
functions to back up a database during online operations (also referred to as an online backup):
Extensive expertise is required:
To use the volume replication functions included in storage systems, you needed to have extensive
expertise in databases, file systems, the logical volume manager, and RAID devices.
Backup operations are complex:
To back up a database object, many complex operations, some of which are susceptible to human
error, must be performed. In addition, since backup operations differ depending on the type of
database application or file system, learning how to perform all the necessary operations is difficult
and time-consuming.
Application Agent resolves these two issues while enabling high-speed, reliable backup operations
that allow the user to get the most out of the available storage system functions.
Application Agent internally manages the relationships between the objects to be backed up and
their associated logical units among the RAID devices, the relationships between the primary and
secondary volumes, and the backup history. This information is contained in dictionary map files.
Application Agent references the dictionary map files in order to automatically control the database
and RAID devices, thus reducing the workload on system administrators and the storage system's
TCO.
The following figure provides an overview of how Application Agent interacts with various storage
media.
Application Agent CLI User Guide 27
Page 28
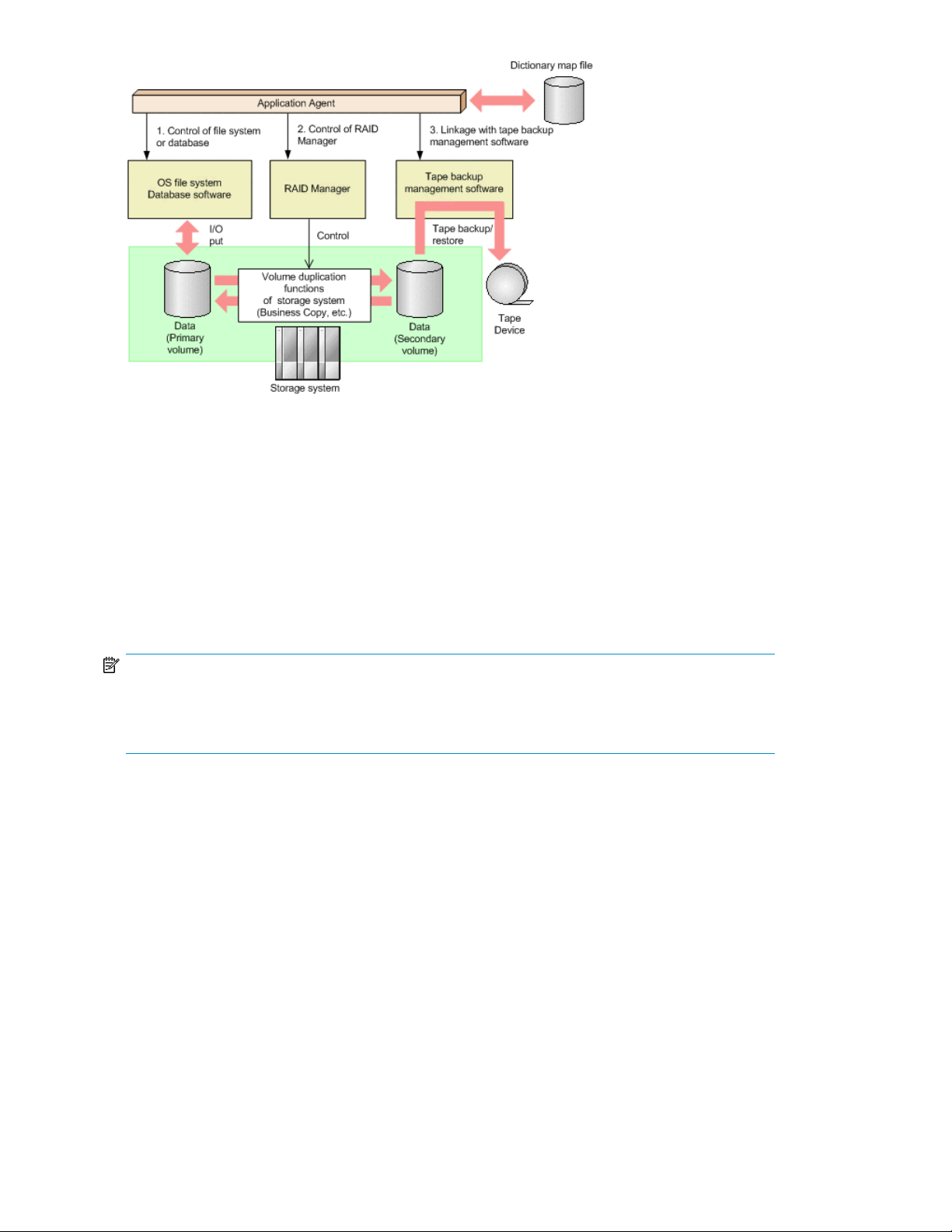
Figure 1 Overview of Application Agent
The following describes how Application Agent controls other software components. The numbers
below correspond to those in the figure above:
1. Application Agent quiesces (pauses) file systems or databases in storage systems in order to
ensure reliable backup operations.
2. By using RAID Manager, Application Agent backs up or restores volumes that have already been
operated on using the functions built into the storage systems.
3. Application Agent operates in conjunction with other tape backup management software to
perform tape backup or restore operations.
NOTE:
Application Agent utilizes a CLI to communicate with RAID Manager and other tape backup
management software. RAID Manager and one other tape backup management software must be
installed before using Application Agent.
Application Agent functions
This section describes the key functions provided by Application Agent and their benefits.
Backing up data
Application Agent provides two backup commands. One backup command uses the volume replication
function of the storage system to perform a high-speed disk copy operation. The other backup command
(in conjunction with another tape backup management software) backs up the data on the secondary
volume to a tape device. You can use whichever backup command most suits your specific needs.
Having two options for backups is useful because it decreases the amount of expertise required to
back up file systems or databases managed by DBMSs.
Overview of Application Agent28
Page 29

User script files are used to perform a series of backup operations to copy data from a primary volume
to a secondary volume, and then from the secondary volume to a tape device. Using these scripts
allows system administrators to accomplish a series of commands in just one command.
Restoring data
Application Agent provides various commands that use volume replication functions to restore a
database or file system from a backup. You can use whichever restore command most suits your
specific needs. Having two options for restoring data is useful because it decreases the amount of
expertise required to restore file systems or databases managed by DBMSs.
Managing data by using dictionary map files
Application Agent can detect a variety of configuration definitions required for backup or restore
operations, such as information about file systems and databases, and disk management information
about RAID devices. Application Agent uses this information and creates a series of files called the
dictionary map files.
Application Agent refers to the dictionary map files for using RAID Manager, which helps reduce the
workload on system administrators.
The dictionary map files consist of the following files:
Application map file
This file stores information about the relationships between objects in the target database (such
as journal logs) and their associated files.
Core map file
This file stores information about the relationships between mount point directories for file systems
and disk numbers across RAID devices.
Copy group map file
This file stores information about the connections (mapping) between primary and secondary
volumes.
Backup catalog
The backup catalog stores the Application Agent backup history and the information pertaining
to generational backups. When a backup is performed, a new record that contains information
about the backup is created in the backup catalog. When Application Agent restores data from
a backup, Application Agent references the information in the backup catalog.
Information stored in the backup catalog includes the following:
• Backup ID
• Backup start date and time
• Backup source information
• Backup destination information
The backup ID is an ID used to uniquely differentiate sets of backup data. Application Agent
automatically assigns a 10-digit backup ID whenever data is backed up, and registers the ID in
the backup catalog.
When there are multiple sets of backup data, either because you are managing generations
(multiple secondary volumes that are associated with a single primary volume), or because you
have backed up data from secondary volumes to a tape device (after making a backup from the
primary volume to the secondary volume), you can restore the desired data by specifying the
backup ID. You can also specify a backup comment, if you want to be able to specify backup
data via a fixed character string instead of the normal 10-digit backup ID.
Application Agent CLI User Guide 29
Page 30
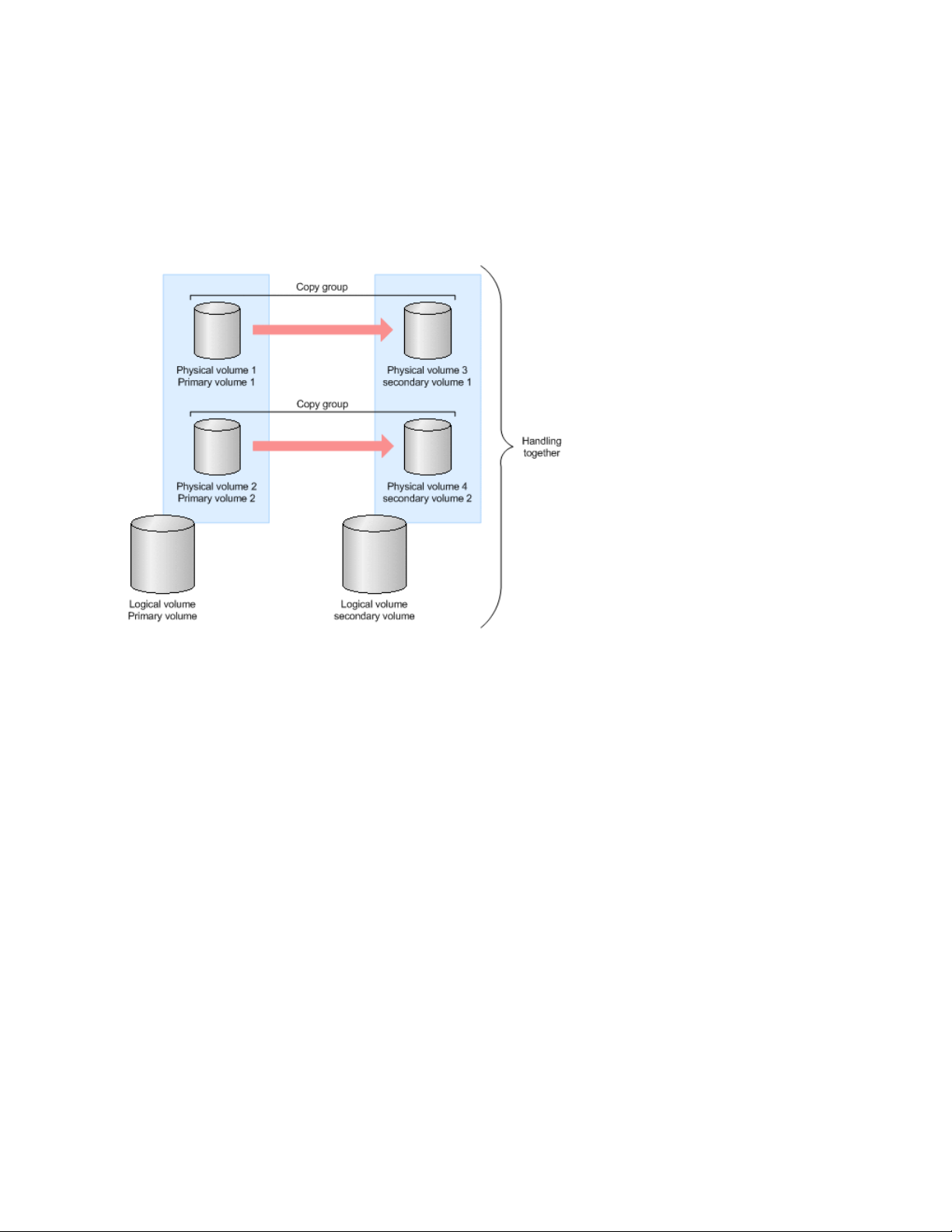
If you execute Application Agent commands in a cluster configuration, you must specify the location
of the dictionary map files to be used for each virtual server. For details on cluster configurations, see
“ Cluster support ” on page 30. For details on how to create the dictionary map files in a cluster
configuration, see “Creating dictionary map files” on page 130.
Pair management using copy groups
In Application Agent, a primary and secondary volume pair whose synchronization is started and
stopped by using volume replication or RAID Manager functions is referred to as a copy group (or
pair volume). The following figure shows a logical volume that consists of multiple copy groups.
Figure 2 Logical volume consisting of multiple copy groups
If the logical volume that contains the data you want to back up consists of more than one physical
volume, create a copy group (pair volume) for each of the primary and secondary physical volumes.
Application Agent can automatically manage multiple copy groups together in order to start and stop
the synchronization of the logical volume that you want to back up.
Copy group names consist of a RAID Manager group name (dev_group) and a RAID Manager pair
logical volume name (dev_name). For example, if a dev_group is VG01 and a dev_name is dev01,
the copy group name will become VG01,dev01.
Cluster support
Application Agent supports failover clustering, which is based on cluster software for a variety of
OSs. Applying the cluster configuration to file servers and database servers allows you to perform
backups without stopping the system, even if a failure occurs.
Application Agent comes with a function that can automatically control clusters, so that you can take
full advantage of the high-availability offered with cluster-based systems. In order to perform a cold
backup or restoration of a database, it must be taken offline. If a database is taken offline while the
cluster resources that are monitoring the DBMS are still online, a failover will occur. This usually results
in the need to control cluster resources manually. However, by utilizing the Application Agent function,
cluster resources that monitor the DBMS are automatically taken offline, and then put back online
whenever Application Agent is used to perform a cold backup or restore operation for data.
Overview of Application Agent30
Page 31

Application Agent supports mutual standby cluster configurations (Active-Active) as well as operational
standby cluster configurations (Active-Passive).
For details on cluster configurations see “Operation-standby cluster configuration” on page 43 or
“Mutual-standby cluster configuration” on page 44.
In a cluster environment using Microsoft Cluster Service or Windows Server Failover Clustering, you
can select whether to perform data restoration while cluster resources that monitor the DBMS are in
the online state or in the offline state. For a restore operation in which the cluster resources are in the
offline state, you need to take all the databases that are using the DBMS services offline. However,
for a restore operation in which the cluster resources are in the online state, you only need to take
offline the databases that are involved in the restore operation.
Depending on the storage system type and the functionality of the OS, you might not be able to
perform a restore operation while the cluster is online.
For details on how to perform a restore operation while the cluster resources are online, see “Setting
up restoration while cluster resources are online” on page 111.
Reducing workload by using commands
Application Agent provides two types of commands: basic and extended commands.
Basic commands are used to perform backups, restore operations, and other operations on backup
data, as well as for setting up Application Agent environments.
Execute basic commands in combination to perform Application Agent operations. For example, if
you want to perform a tape backup you must execute two commands in combination: a basic command
for mounting the primary volume to the secondary volume, and then another command for backing
up the data on the secondary volume to a tape device.
Application Agent provides scripts that can automatically execute a series of commands. These scripts
are called extended commands. Extended commands make it easier for you to perform backup tasks
that use multiple Application Agent commands.
Data management on another storage systems
Application Agent allows you to manage data that is on another storage system (hereafter referred
to as a remote site).
Application Agent allows you to back up and restore secondary volumes to and from a local site (the
storage system where the primary volume resides) and a remote site (a storage system different from
the one where the primary volume resides).
The figure below illustrates the relations between physical volumes and a local site or a remote site.
Application Agent CLI User Guide 31
Page 32

Figure 3 Data management at a remote site
Managing data at a remote site allows you have a secondary volume in a storage system that is
physically different from the storage system where the primary volume resides. Application Agent uses
the Continuous Access Software or Continuous Access Journal copy type to back up or restore volumes
to or from a remote site.
In this manual, using the volume copy function along with the Continuous Access Software or Continuous
Access Journal copy type to copy a volume to a remote site is generically referred to as copying a
volume between storage system (or the remote copy function). By backing up data to a remote site,
you can restore the data from the remote site should a problem occur in the storage system at the
local site. This improves the stability of data. Backing up data on a remote site is a great way to
ensure a fast and easy recovery, if and when a disaster occurs, damaging the data on the local site.
Application Agent can perform the following operations on a remote site:
• Back up and restore data
• Re-synchronize a copy group
• Display resource information
• Lock a copy group
• Back up to and restore data from a tape device
• Mount or unmount a secondary volume
Managing generations
Application Agent can manage multiple secondary volumes for a single primary volume. In these
cases, the secondary volumes are referred to as generations (or generational backups).
Overview of Application Agent32
Page 33

When selecting a secondary volume for a backup, you can either manually select the volume you
want to use or have Application Agent choose it for you. In order to have Application Agent choose
a secondary volume for you, you need to use the volume copy function. When manually selecting a
volume, specify the generation name unique to the desired volume. Application Agent creates
generation names using the following format:
local_MU# or remote_MU#
Each element used to create a unique generation name is described below:
local
Specify this when the secondary volume will be stored on the same storage system as the primary
volume.
remote
Specify this when the secondary volume will be stored on a different storage system than the
primary volume.
MU#
The MU number defined in the RAID Manager configuration definition file (horcmn.conf).
When you back up data to a Continuous Access Software secondary volume (on a remote site), the
assigned generation name is remote_0.
The following figure shows an example of what happens when backing up multiple generations. In
this example, because a maximum of only three generations can be made, after generations 1 to 3
are created, the fourth generation (generation 4) must write over one of the preexisting volumes. In
this case, the oldest volume (generation 1) is overwritten. Generations 5 and 6 follow the same pattern
of overwriting the oldest, existing generation.
Figure 4 Backing up multiple generations
Normally, Application Agent automatically determines which secondary volume to use for the backup
destination. However, if there are specific secondary volumes that you do not want to use for backup
purposes, you can use a Application Agent command to lock the contents of the secondary volumes.
The figure below illustrates the process of backing up multiple generations when a specific copy group
is locked. In this example, after generation 1 is obtained, the generation 1 copy group is locked in
order to prevent it from being overwritten. As a result, the remaining secondary volumes, 2 and 3,
are used as containers for any remaining generations.
Application Agent CLI User Guide 33
Page 34

Figure 5 Backing up multiple generations when a copy group is locked
The order in which secondary volumes are used for backups does not change regardless of which
generation you might decide to restore at some point in time.
The number of generations that Application Agent can manage, and the backup and restore operations
available are all dependent on the volume replication functions of the particular storage system.
Overview of Application Agent34
Page 35

2 Application Agent system configurations
This chapter describes the system configurations and volume configurations required for using
Application Agent as well as provides precautions applicable to those configurations. The descriptions
in this chapter apply to the Application Agent CLI.
Basic configurations for backing up and restoring data
This section describes the basic system configurations and provides precautions applicable to using
Application Agent to back up and restore data.
The following basic configurations can be used for backing up and restoring data with Application
Agent:
• Configurations in which data is backed up and restored within a storage system
• Configurations in which data can be backed up and restored between two storage systems
• Configurations in which data is backed up on tape devices
Configurations in which data is backed up and restored within a storage system
In order to use Application Agent to back up or restore data between a primary volume and a
secondary volume, connect a file server or a database server to the storage system.
Install Application Agent on the file server or the database server. You can now execute backup and
restore commands.
The following is an example of a system configured to back up and restore data within a storage
system. A file server or database server allows you to manage only the primary volume.
Application Agent CLI User Guide 35
Page 36

Figure 6 Example of a system configured to back up and restore data within a storage system
Configurations in which data can be backed up and restored between two storage systems
Application Agent supports the use of Continuous Access Software and Continuous Access Journal
for backing up and restoring data on the storage systems of remote sites, as a safeguard in the event
of storage system failure at a local site. This subsection describes the configurations in which data
can be backed up between two storage systems (local and remote sites).
Application Agent supports the following configurations as a system configuration for backing up and
restoring data between storage systems:
• Continuous Access Software and Continuous Access Journal configuration
• Business Copy and Continuous Access Software multi-target configuration
• Business Copy and Continuous Access Journal multi-target configuration
• Continuous Access Software and Continuous Access Journal multi-target configuration
• Business Copy (multi-generation), Continuous Access Software, or Continuous Access Journal
configuration
The following explains each of these configurations.
Continuous Access Software or Continuous Access Journal configuration
Application Agent supports the Continuous Access Software or Continuous Access Journal configuration
as the basic configuration for backing up and restoring data between storage systems.
The following figure shows a Continuous Access Software or Continuous Access Journal system
configuration diagram.
Application Agent system configurations36
Page 37

Figure 7 Continuous Access Software or Continuous Access Journal system configuration
Business Copy and Continuous Access Software multi-target configuration
Application Agent supports a multi-target configuration for Business Copy and Continuous Access
Software.
The following figure shows the Business Copy and Continuous Access Software multi-target configuration
diagram.
Application Agent CLI User Guide 37
Page 38

Figure 8 Business Copy and Continuous Access Software multi-target configuration
Business Copy and Continuous Access Journal multi-target configuration
Application Agent supports a multi-target configuration for Business Copy and Continuous Access
Journal.
The following figure shows the Business Copy and Continuous Access Journal multi-target configuration
diagram.
Application Agent system configurations38
Page 39

Figure 9 Business Copy and Continuous Access Journal multi-target configuration
Continuous Access Software and Continuous Access Journal multi-target configuration
Application Agent supports a multi-target configuration for Continuous Access Software and Continuous
Access Journal.
The following figure shows the Continuous Access Software and Continuous Access Journal multi-target
configuration diagram.
Application Agent CLI User Guide 39
Page 40

Figure 10 Continuous Access Software and Continuous Access Journal multi-target configuration
Business Copy (multi-generation), Continuous Access Software, or Continuous Access Journal configuration
Application Agent supports a system configuration for Business Copy (multi-generation), and Continuous
Access Software, or Continuous Access Journal.
The following figure shows the Business Copy (multi-generation) and Continuous Access Software, or
Continuous Access Journal configuration diagram.
Application Agent system configurations40
Page 41

Figure 11 Business Copy (multi-generation), Continuous Access Software, or Continuous Access Journal
configuration
Precautions on backing up and restoring data between storage systems
• Regarding pair creation of paired volumes between storage system
Application Agent does not automatically create paired volumes when it backs up data between
a local site and a remote site. Users must create a pair of paired volumes in advance.
• Regarding data backup from one primary volume to multiple volumes between storage system
Application Agent supports only data backup from one primary volume to one secondary volume.
It cannot back up data from one primary volume to multiple secondary volumes.
• Regarding data backup from multiple primary volumes to multiple secondary volumes between
storage system
Concurrent backup from multiple primary volumes to multiple secondary volumes requires that the
secondary volumes have the same generation number. To assign the same generation number to
multiple secondary volumes, specify the same number in MU#s defined in the RAID Manager
configuration definition file (horcmn.conf). For the system configuration, check the hardware
specifications.
The following figure shows a configuration diagram for concurrent backup from multiple primary
volumes to multiple secondary volumes.
Application Agent CLI User Guide 41
Page 42

Figure 12 Example of configuration for concurrent backup from multiple primary volumes to multiple
secondary volumes (remote copy)
• Regarding start of RAID Manager instances between storage systems
RAID Manager instances between a local site and a remote site are not automatically started.
Start the RAID Manager instances on the remote site in advance.
Configurations using tape devices
To store data backed up to tape by using Application Agent, the system needs two servers: a file
server or a database server that manages the primary volume, and a backup server connected to the
tape device.
When using this configuration, install Application Agent both in the file server or database server
and in the backup server, and then execute commands for the primary volume from the file server or
database server, and for the secondary volume from the backup server, respectively.
The following is an example of a system configured to store backed-up data to tape. A file server or
database server allows you to manage only the primary volume. A backup server allows you to
manage only the secondary volume.
Application Agent system configurations42
Page 43

Figure 13 Example of a system configured with a tape device
Configurations for operation in cluster environments
This section describes configurations for operation when a database server and a file server are used
in a cluster environment.
Application Agent supports the following configurations:
• Operation-standby cluster configurations
• Mutual-standby cluster configurations
Operation-standby cluster configuration
Application Agent can handle a two-node cluster configuration of the operation standby type
(Active-Passive) on a database server and file server.
The following is an example of a cluster configuration of the operation standby type (Active-Passive).
You can build a cluster configuration using file servers or database servers. You cannot allocate one
cluster server to a file server or database server and the other cluster server to a backup server.
Application Agent CLI User Guide 43
Page 44
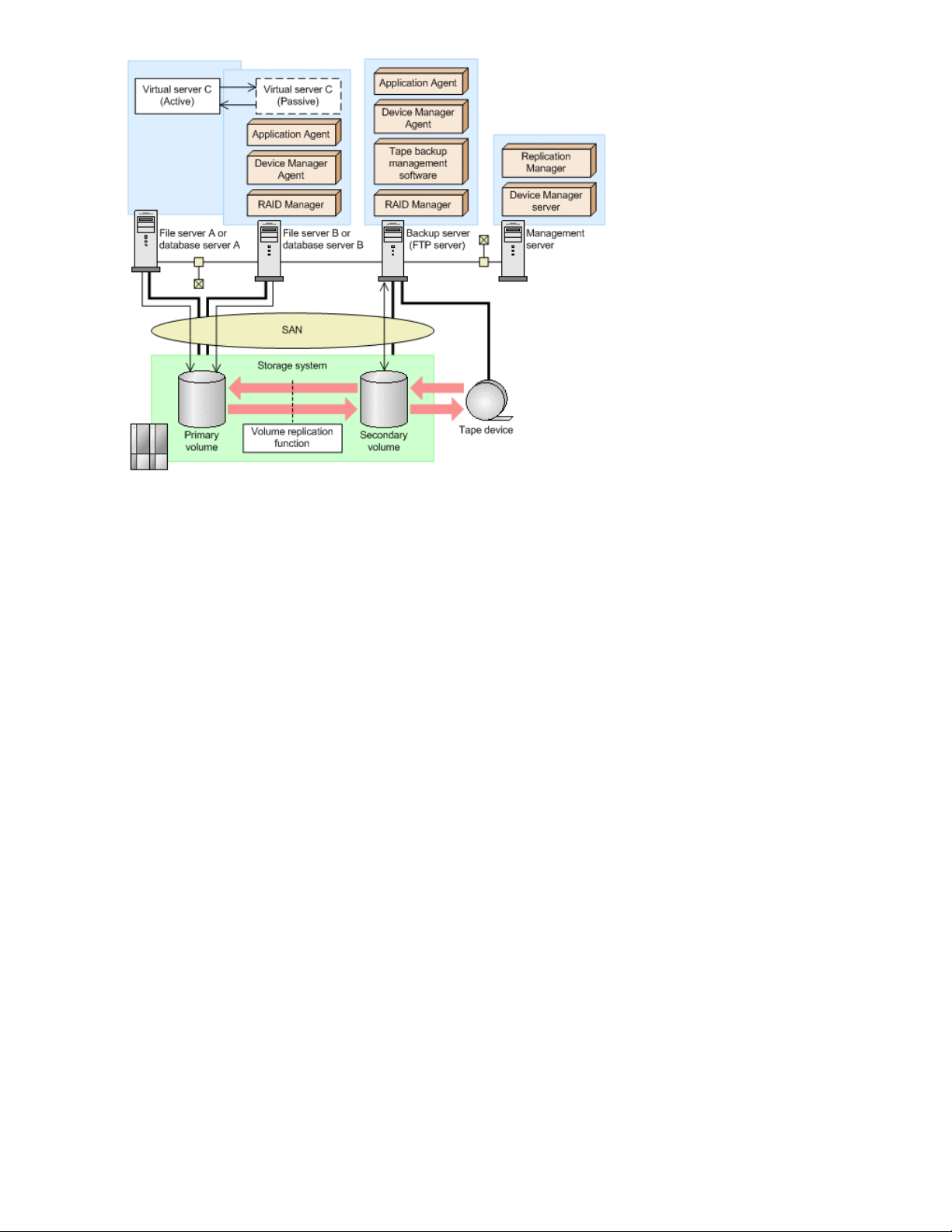
Figure 14 Example of a cluster configuration of the operation standby type (Active-Passive)
To execute Application Agent commands in a cluster configuration of the operation standby type
(Active-Passive), you need to assign a storage destination for the dictionary map files used by each
virtual server. For about the dictionary map files in a cluster configuration, see “Creation in an
Active-Passive cluster configuration” on page 131.
Mutual-standby cluster configuration
Application Agent can handle a cluster configuration of the mutual standby type (Active-Active) on a
database server and file server. A cluster configuration of the mutual standby type is a multiple structure
of operation standby type environments.
The following is an example of a cluster configuration of the mutual standby type (Active-Active). You
can build a cluster configuration using file servers or database servers. You cannot allocate one cluster
server to a file server or database server and the other cluster server to a backup server.
Application Agent system configurations44
Page 45

Figure 15 Example of a cluster configuration of the mutual standby type (Active-Active)
To execute Application Agent commands in a cluster configuration of the mutual standby type
(Active-Active), create a dictionary map files for each virtual server. Additionally, you need to assign
a storage destination for the dictionary map files used by each virtual server. For details about the
dictionary map files in a cluster configuration, see “Creation in an Active-Active cluster
configuration” on page 133.
Configurations when VSS is used
Application Agent can use VSS to back up data when the backup is of a file system or an Exchange
database.
Normally, when database data stored on a storage system volume is copied to another volume, access
from hosts (database applications) must be suspended and the database must be frozen. If VSS is
used, however, the OS functionality can control transactions for database applications and I/O
operations for a volume, and the database can be frozen without the previously mentioned suspensions.
This provides higher reliability for backup operations.
Application Agent requires two servers (one file server or database server and one backup server)
when it uses VSS to back up data. The file server and database server manage primary volumes. The
backup server imports VSS snapshots and verifies the Exchange database. The backup server can
also store backup results on a tape.
In this configuration, the user executes the backup and restore commands on the file server or on the
database server. On the backup server, the Protection Manager service imports VSS snapshots and
verifies the Exchange database via the backup and restore commands. For more information about
how to store data in a tape, see “Backing up a file system to tape” on page 253 or “Backing up storage
groups to tape” on page 414.
The following figure is an example of a system configuration where Application Agent uses VSS to
back up data.
Application Agent CLI User Guide 45
Page 46

Figure 16 Example of a system configured to use VSS to back up data
Requirements and precautions for backing up file systems
This subsection explains requirements and precautions when using VSS to back up file systems.
• P9000 RMXP Shadow Copy Provider must be installed both in the file server and backup server
in advance. Note that, if P9000 RMXP Shadow Copy Provider has not been installed on those
servers when Application Agent is installed, P9000 RMXP Shadow Copy Provider will be installed
together with Application Agent.
• The backup server is required even if data is not backed up to tape, because the backup server
imports VSS snapshots.
• File system write processing is halted for a given length of time (within 10 seconds) during backup.
This processing is resumed after backup has been completed.
• Note on integrity of the backup data for a file system when VSS is used:
When VSS is used to back up a file system, Application Agent obtains a snapshot without using
VSS Writer. Although this ensures the integrity of the file system, the integrity of the data for an
application that was operating during the backup cannot be ensured.
• Set up the environment of Application Agent to use VSS. For details on environment settings required
to use VSS, see “Specifying settings for using VSS” on page 147.
• All the file systems subject to backup and restoration must be mounted in advance.
• Do not use LUN#0 as a secondary volume for the backup destination. If the LUN#0 disk is used
as a secondary volume for the backup destination, other disks might not be recognized.
Application Agent system configurations46
Page 47

• Do not mount another volume in a directory on the volume to be backed up. If another volume is
mounted, mounting and restoration for the secondary volume might fail.
• If you change the settings of the following files, use the Services pane in the Windows to restart
the Protection Manager service:
• Application Agent configuration definition file (init.conf)
• RAID Manager-linkage definition file (DEFAULT.dat)
• If Veritas Snapshot Provider is installed on the database server or backup server where a VSS
backup will be performed, make sure you use version Veritas Snapshot Provider 1.04 or later.
If a VSS backup is executed using version Veritas Snapshot Provider 1.03 or earlier, the volume
to be backed up might be left with Read-Only and Hidden attributes. If this happens, the drive
will not be allocated at system startup.
If this occurs, release these attributes as described in Microsoft Knowledge Base Article 840781.
• If a system failure or other problem causes a VSS backup to be interrupted, the volume that is the
target of the backup might be left with the Read-Only and Hidden attributes. If these attributes
remain, the drive will not be allocated at system startup. If this occurs, release the attributes as per
Microsoft Knowledge Base Article 840781.
• File systems on a dynamic disk cannot be backed up.
System configurations for backing up SQL Server databases
This section describes system configurations in which Application Agent is used to back up an SQL
Server database.
Configurations for restoring an SQL Server database to a host that is not the original host
When the backup is of an SQL Server database, data on a host that differs from the host used for
backup can be restored. To restore data by using Application Agent on a host that differs from the
host used for backup, the system needs two servers: database server 1 for backup, and database
server 2 for restoration. Operations are usually performed on database server 1, but when an error
occurs on database server 1, the operations are switched to database server 2.
In this configuration, install Application Agent both in database server 1 and in database server 2.
Execute backup commands on database server 1, and restoration commands on database server 2,
respectively.
The following is an example of a system configured to restore data on a host that differs from the host
used for backup.
Application Agent CLI User Guide 47
Page 48

Figure 17 Example of a system configured to restore data on a host that differs from the host used
for backup
Configurations for using the log-shipping functionality
You can use the log-shipping function to back up an SQL Server database. When you use this function,
the system needs two servers: a source server that distributes log files, and a destination server to
which the log files are distributed.
When using this configuration, install Application Agent both in the source server and in the destination
server.
The following is an example of a system configured to use SQL Server's log-shipping functionality.
Application Agent system configurations48
Page 49

Figure 18 Example of a system configuration for the log-shipping functionality
Cascade configurations
When the backup is of an SQL Server database, Application Agent can handle the backup to a
secondary volume at a remote destination. The backup configuration in this case is called a cascade
configuration because backup configuration has multiple hierarchies. For data backup and restoration
in a cascade configuration, use user scripts. However, in a cascade configuration consisting of Business
Copy volumes only, user script cannot be used.
The following is an example of a cascade configuration consisting of Business Copy volumes and
Continuous Access Software volumes when the backup is of an SQL Server database.
Application Agent CLI User Guide 49
Page 50

Figure 19 Example of a cascade configuration (when the backup is of an SQL Server database)
Multi-target configurations
When the backup is of an SQL Server database, Application Agent can handle a multi-target
configuration that backs up data to a remote destination and to a secondary volume with a local
environment at the same time. For data backup and restoration in multi-target configuration, use user
scripts.
The following is an example of a multi-target configuration when the backup is of an SQL Server
database.
Application Agent system configurations50
Page 51

Figure 20 Example of a multi-target configuration (when the backup is of an SQL Server database)
Requirements and precautions for backing up SQL Server databases
The table below describes the types of data subject to backup in the SQL Server database. Backed-up
databases differ depending on option specifications in the backup command (the drmsqlbackup
or EX_DRM_SQL_BACKUP command).
Table 1 Types of data subject to backup in the SQL Server database
Database subject
to backup
master
model
msdb
#1
Type of file subject to
backup
Data file
Transaction log file
Meta file
Data file
Transaction log file
Meta file
Data file
Transaction log file
#2
#2
Backup file name
Same as the backup source
file name
Same as the backup source
file name
Varies depending on the VDI metafile storage directory
specified with the -drmsqlinit command
Same as the backup source
file name
Same as the backup source
file name
Varies depending on the VDI metafile storage directory
specified with the -drmsqlinit command
Same as the backup source
file name
Same as the backup source
file name
Storage destination for
backup files
Secondary volume
Secondary volume
#3
Secondary volume
Secondary volume
#3
Secondary volume
Secondary volume
Meta file
#2
Varies depending on the VDI metafile storage directory
specified with the -drmsqlinit command
#3
Application Agent CLI User Guide 51
Page 52

Database subject
to backup
#1
Type of file subject to
backup
Backup file name
Storage destination for
backup files
User database
Distribution database
Data file
Transaction log file
Meta file
Data file
Transaction log file
Metafile
#2
#2
Same as the backup source
file name
Same as the backup source
file name
Varies depending on the VDI metafile storage directory
specified with the -drmsqlinit command
Same as the backup source
file name
Same as the backup source
file name
Depends on the VDI metafile storage directory specified
in the -drmsqlinit command
Secondary volume
Secondary volume
#3
Secondary volume
Secondary volume
#3
#1
When the -system option is not specified, only user databases are backed up.
#2
This file is created when the backup command executes.
#3
When a VDI metafile storage directory was registered by using the drmsqlinit command, the
metafile is stored in the registered directory. The file name is backup-ID_database-ID.dmp. When
a VDI metafile storage directory was not registered by using the drmsqlinit command, the
metafile is stored in the directory that contains the file whose management number (file_id)
for SQL Server in the database file is a minimum value. The file name is META_database-ID.dmp.
In Application Agent, data is backed up and restored in physical volumes units so the object
configuration of an SQL Server database requires the following:
• Configure the database configuration files that comprise one instance on one physical volume.
Do not store database configuration files that comprise multiple instances on one physical volume.
• Store the following directory and file on a physical volume that does not contain database config-
uration files (*.mdf, *.ndf, and *.ldf):
• Metafile storage directory (except when metafile setting is blank)
• Backup data of the transaction log
Roll-forward recovery processing can be performed if the above directory and file are placed on
separate volumes. This is because, even if a restoration is performed, the metadata and transaction
log file cannot return to the status they were in when the backup was performed.
Backup processing for Application Agent checks whether these requirements are satisfied. If they
are not satisfied, backup processing will terminate with an error.
• You can use the following characters when naming a database:
• ASCII characters
• Multi-byte characters (one character must be expressed by using 1 or 2 bytes)
However, do not use the following characters:
\ / : , ; * ? < > |
Application Agent system configurations52
Page 53

• Do not use the name META_database-ID (ten digits).dmp for a data file of a database or transaction
log file.
• Backed-up data cannot be restored or recovered by specifying the -undo option during execution
of the drmsqlinit command when there is no registered directory for storing the UNDO file.
• Backup for the transaction log cannot be executed during execution of the drmsqlinit command
when there is no registered directory for storing the transaction log backup file.
• If the system databases (master, model, and msdb) are to be backed up, specify, as the output
destination for SQL Server error log files, a volume different than the one that contains the system
databases.
• Store tempdb in a volume other than the user database to be backed up. If it is stored in the user
database subject to backup then, when the user database is restored, tempdb is overwritten by
the data restored from the secondary volume while it is online, and consequently the SQL Server
might go into an abnormal state. In this case, restart the SQL Server to recreate tempdb and restore
the server to a normal state. After restarting the SQL Server, specify a volume other than the user
database to be backed up, and then re-execute the restoration. Before re-executing restoration,
see “SQL Server database requirements for executing commands” on page 286 to check if the
database can properly be restored.
• The database cannot be restored to SQL Servers with the version different from the one at backup.
For example, a database backed up with SQL Server 2005 cannot be restored to SQL Server
2008.
• One execution of the drmsqlbackup command can back up a maximum of 64 databases. If
you want to back up 65 or more databases, execute the drmsqlbackup command more than
once.
The following points must be considered if you are using SQL Server:
• In Application Agent, a backup or restoration cannot be performed for database snapshots. If you
want to back up all the instances, delete the database snapshot. If you include the database
snapshot in the backup target, the backup will fail.
• The service broker becomes disabled for databases that are restored by using the drmsqlrestore
command. To enable the service broker, execute the following SQL statement after restoration:
ALTER DATABASE [database name database-name] SET ENABLE_BROKER
• If any of the following commands is executed on a database where the database mirroring function
is used, execute the command on the principal server:
drmsqlbackup, drmsqllogbackup, drmsqldisplay -refresh
• If a database that uses the database mirroring function is to be restored, release the database
mirroring setting before restoring the database.
• If the system databases (master, model, and msdb) are to be restored in addition to a database
that uses the database mirroring function, release the mirroring setting on the database that is to
be restored, restore the system databases, and then restore the database that uses the database
mirroring function.
• If you use any of the following commands to delete backup information, the VDI metafile that was
created when the backup was performed will also be deleted. Before deleting the backup information, back up the exported backup information and the VDI metafile.
• drmresync
• drmappcat -delete
• EX_DRM_RESYNC
• For SQL Server 2005, the database configuration files of the resource and master databases are
stored in the same location. Application Agent does not show information about freezing and
backup processing for the resource database. The database configuration file of the resource
Application Agent CLI User Guide 53
Page 54

database is backed up and restored along with the database configuration file of the master
database when the system database is backed up and restored.
• For SQL Server 2008, the data compression function is not supported.
• The following features of SQL Server 2008 and SQL Server 2012 are not supported:
• FILESTREAM Data
• Change Data Capture
• Change Tracking
• Backup Compression (Database and Transaction Log)
• SQL Server 2012 supports the following types of data compression:
• Row compression
• Page compression
• Columnstore indexes
• When SQL Server 2012 uses an AlwaysOn availability group configuration, operations for
backing up and restoring user databases on the active node are supported. The following operations
are not supported when using an AlwaysOn availability group configuration:
• An operation for backing up and restoring system databases
• An operation for backing up and restoring user databases on the passive node
• For SQL Server 2012, Server Core is not supported. Also, AlwaysOn failover cluster instance
operations using one of the following configurations are not supported:
• A database is stored in the shared folder for the network
• tempdb is stored on a local disk
• A cluster is configured across multiple subnets
Allocating files that comprise a database
Allocate the database file backed up by Application Agent to a volume separate from files not to be
backed up.
Application Agent can back up only the database configuration files (the *.mdf and *.ndf data
files and the *.ldf transaction log file) and metafiles. Metafiles are generated when the backup
command is executed.
For database configuration files that are not subject to backup and for general files, no freezing
processing is executed. Therefore, if the primary volume contains a file that is not subject to the freezing
processing, pair partitions will be duplicated during file writing, resulting in loss of database integrity.
Allocate only the database configuration files subject to the freezing processing in the primary volume.
Allocation of database configuration files is shown in the figure below.
Application Agent system configurations54
Page 55

Figure 21 Allocation of database configuration files
Allocating multiple database configuration files to one volume
When multiple database configuration files are allocated to a volume, all databases need to be
backed up or restored in a group.
The figure below shows how backup and restoration are performed in this case.
Figure 22 When multiple database configuration files are allocated to a volume
Allocating metafiles
A metafile is a file SQL Server outputs during backup processing. Metafiles store information about
database composition and are therefore used in restoration processing.
If you have specified a VDI metafile storage directory by using the drmsqlinit command, when
backup data of the secondary volume is backed up to tape, the metafile must also be backed up to
the tape (this is not necessary if the metafile is stored in the same directory as the database file).
When you back up to tape, you need to use FTP or a similar method to transfer the metafile created
in the metafile storage directory in the database server to the backup server. In this situation, transfer
the file in the directory using the same name as in the metafile storage directory in the backup server
and allocate the same drive characters.
Metafile allocation on the database server and the backup server is shown in the figure below.
Application Agent CLI User Guide 55
Page 56

Figure 23 Metafile allocation
Assume that you have a cluster system in which database servers are clustered using Microsoft Cluster
Service or Windows Server Failover Clustering, and one of the cluster servers has failed over to the
other server. In this case, if a metafile has been stored on a volume in the storage system, the primary
volume can be restored from the secondary volume.
HP recommends that you store metafiles in a volume belonging to the resource group of SQL Server
so that, even if the cluster resource of SQL Server fails over, you can use the files by having them fail
over at the same time.
Metafile allocation for cluster configuration of the operation standby type (Active-Passive) is shown
in the figure below.
Application Agent system configurations56
Page 57

Figure 24 Metafile allocation (in the cluster configuration)
Using a dynamic disk configuration
• Do not allocate a data file made up of multiple instances to a file system (drive) of a disk group
subject to backup and restoration.
• Allocate the following directories and files to a file system (drive) of a disk group different from
the one to which data files (*.mdf and *.ndf) are allocated. If these directories and files are
allocated to a file system (drive) of the same disk group, an error will occur when backup is executed.
• Metafile storage directory (only if a VDI metafile storage directory was specified with the
drmsqlinit command)
• Backup data of the transaction log
• To allocate a file that is made up of multiple databases to a file system (drive) of the same disk
group, you must collectively back up and restore all the databases. If these requirements are not
met when performing Application Agent backup, backup processing terminates with an error.
• To back up or restore databases individually, allocate database data files to a file system (drive)
of a different disk group.
• Store tempdb in a file system (drive) of a disk group different from the one to which a user database
subject to backup belongs.
When the user database is restored if tempdb is stored in a file system (drive) of the same disk
group, tempdb is overwritten by the data restored from the secondary volume in the online state.
Then, the SQL Server goes into an abnormal state. In this case, restart the SQL Server to recreate
tempdb and restore the server to a normal state. After restarting the SQL Server, specify a file
system (drive) different from the one to which a user database subject to backup belongs as a
destination in which tempdb is stored, and then re-execute restoration. Before re-executing restoration, see “SQL Server database requirements for executing commands” on page 286 to check if
the database can properly be restored.
Application Agent CLI User Guide 57
Page 58

Using a cluster configuration
• Do not register the service resources of multiple SQL Server instances into a cluster group.
• In a cluster environment, specify a user on each node for the owner of a database subject to
backup. Local users with the same user name and password on different nodes are not considered
to be the same user. Therefore, use a domain user account that is common to all nodes. If failover
is performed to a node where the database-owner user does not exist, backup fails because the
database owner is unknown.
• In a cluster environment, install an SQL Server instance as a failover cluster.
• In a cluster configuration using Veritas Cluster Server for Windows, the file system that contains
registry replication data should not be backed up by Application Agent. Make sure that you allocate
such a file system to a disk group or physical disk that is not subject to backup.
System configurations for backing up Exchange databases
This section describes system configurations in which Application Agent is used to back up Exchange
databases.
Cascade configurations
When you back up Exchange databases, Application Agent can back up data concurrently at both
the local and remote sites. This type of multi-level backup configuration is called a cascade
configuration.
To back up a volume in a cascade configuration, you need a database server and a backup server
at both the local site and the remote site.
The following figure shows an example of a cascade configuration when Application Agent is used
to back up Exchange databases.
Figure 25 Example of a cascade configuration (when backing up Exchange databases)
CCR configurations
Application Agent supports backup in a CCR configuration. CCR is a high availability function of
Exchange Server 2007, and includes the following features:
• Ability to ship logs (transaction log replication) between active and standby server volumes.
Application Agent system configurations58
Page 59

• When VSS backup is used with SCC, backups can be performed only at the active server. However,
when VSS backup is used with CCR, backups can also be performed at the standby server.
• Ability to reduce processing loads on the active server by performing backups on the standby
server.
In this manual, the function that performs seed processing automatically when restoring data is called
the automatic seed function. For details about seed processing, see the Exchange Server 2007 manual.
CCR can be configured for performing backups in any of the following four ways:
• Configuration in which only the active server is used
• Configuration in which only the standby server is used
• Configuration in which different backup servers are used for the active and standby servers
• Configuration in which the same backup server is used for the active and standby servers
Configuration in which only the active server is used
The following figure shows an example of a CCR configuration in which only the active server is used.
Figure 26 Example of a CCR configuration (only the active server is used)
Configuration in which only the standby server is used
The following figure shows an example of a CCR configuration in which only the standby server is
used.
Application Agent CLI User Guide 59
Page 60
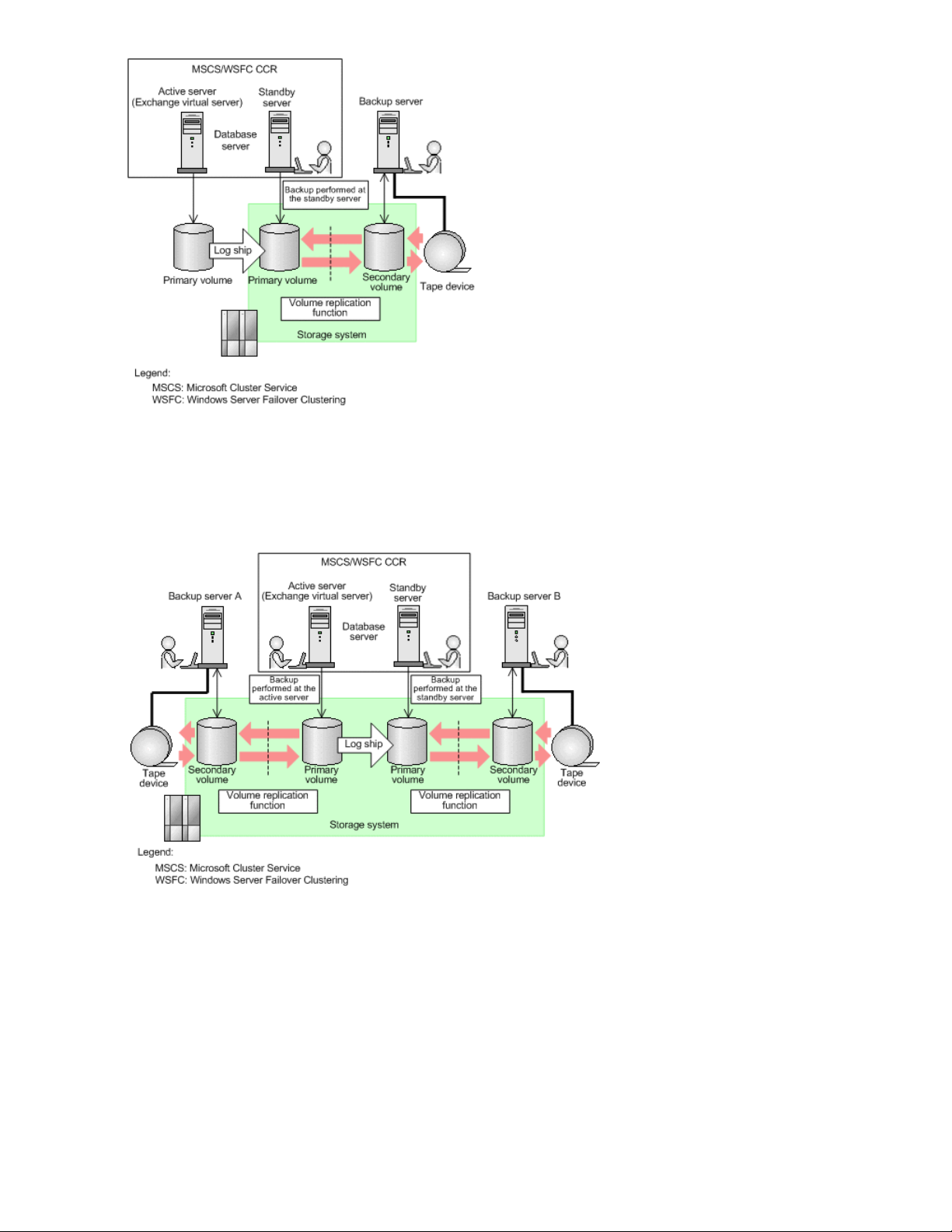
Figure 27 Example of a CCR configuration (only the standby server is used)
Configuration in which different backup servers are used for the active and standby servers
The following figure shows an example of a CCR configuration in which different backup servers are
used for the active and standby servers.
Figure 28 Example of a CCR configuration (active and standby servers use different backup servers)
Configuration in which the same backup server is used for the active and standby servers
The following figure shows an example of a CCR configuration in which the same backup server is
used for the active and standby servers.
Application Agent system configurations60
Page 61

Figure 29 Example of a CCR configuration (active and standby servers use the same backup server)
SCR configurations
Application Agent provides VSS backup and restoration functionality for SCR configuration sources.
Limitations on the target configuration are the same as for Exchange Server 2007. For details about
the limitations for Exchange Server 2007, see the Exchange Server 2007 documentation.
The following shows an example of an SCR configuration.
Application Agent CLI User Guide 61
Page 62

Figure 30 Example of an SCR configuration
Application Agent's restore processing provides the SCR seed function that executes seed processing
(data resync) in an SCR configuration. The user can set whether the SCR seed function is to be used.
The SCR seed function is used in the following cases:
• When a point-in-time restore operation is performed.
• When data integrity between the source and target is known to have been lost when a roll-forward
restore operation was performed.
If at least one of the targets set for each storage group is running, you can perform the restore operation
using the seed function.
When the SCR seed function is not used in an SCR configuration, the user must perform seed processing
manually after restoration. The following describes seed processing in an SCR configuration:
1. Cancel replication.
2. Delete the Exchange database file, the transaction log file, and the checkpoint file from the target.
3. Resync data from the source to the target.
4. Restart replication.
DAG configurations
A DAG configuration is one type of high-availability functionality in Exchange Server 2010 or Exchange
Server 2013. A mailbox database used in a DAG configuration is called a mailbox database copy.
A replication-source mailbox database copy is called an active mailbox database copy, and a
replication-target mailbox database copy is called a passive mailbox database copy. In a DAG
configuration, you can group multiple Exchange databases, and back up mailbox databases within
Application Agent system configurations62
Page 63

a group. If an error occurs in an active mailbox database copy, you can use the data in a passive
mailbox database copy to continue operation.
Application Agent provides backup and restore functionalities for mailbox database copies in the
event of a logical error occurring due to issues such as incorrect email transmission and viruses. The
restore functionality performs seed processing, which resynchronizes data by copying the passive
mailbox database copy to the restored active mailbox database copy.
The DAG configuration manages only mailbox stores, but by using Application Agent, you can specify
both mailbox stores and public folder stores at the same time for backup or restore processing. This
availability is possible because Application Agent excludes public folder stores from processing related
to the DAG configuration, such as stopping replication or the seed function.
There are four types of DAG configurations that use Application Agent:
• Backing up and restoring active mailbox database copies
• Backing up and restoring passive mailbox database copies
• Backing up and restoring the active mailbox database copy and the passive mailbox database
copy by using different backup servers
• Backing up and restoring the active mailbox database copy and the passive mailbox database
copy by using the same backup server
Backing up and restoring active mailbox database copies
The following figure shows an example of a DAG configuration in which an active mailbox database
copy is backed up and restored.
Application Agent CLI User Guide 63
Page 64

Figure 31 Configuration in which an active mailbox database copy Is backed up and restored
Primary volume 1 is the active mailbox database copy, primary volume 2 is the passive mailbox
database copy, and the secondary volume is managed by the backup server. The active side manages
all the services and backup and restore operations, and the passive side temporarily takes over
execution of the active side's services if needed. The data synchronization between the active side
and the passive side is accomplished via log shipping. On the active side, data is backed up from
primary volume 1 to the secondary volume, and then the data on the secondary volume is stored on
a tape device.
If an error occurs on the active side, the passive side takes over the execution of services. You cannot
perform any backup or restore operations until the active side recovers from the error. After recovery,
seed processing is performed from the passive side, so that the data that was updated while the
passive side executing the services is applied to the active side.
If an error occurs on the passive side, seed processing is performed from the active side, so that the
data on the passive side is restored.
If logical errors, such as those caused by viruses, occur on both the active side and the passive side,
the data is restored from the tape device to the secondary volume, and then from the secondary
volume to primary volume 1. The restored data is then applied to primary volume 2 via seed processing.
Backing up and restoring passive mailbox database copies
The following figure shows an example of a DAG configuration in which a passive mailbox database
copy is backed up and restored.
Application Agent system configurations64
Page 65

Figure 32 Configuration in which a passive mailbox database copy Is backed up and restored
Primary volume 1 is the active mailbox database copy, primary volume 2 is the passive mailbox
database copy, and the secondary volume is managed by the backup server. The active side manages
services, and the passive side takes over execution of the active side's services if needed and also
performs backup and restore operations. The data synchronization between the active side and the
passive side is accomplished via log shipping. On the passive side, data is backed up from primary
volume 2 to the secondary volume, and then the data on the secondary volume is stored on a tape
device.
If an error occurs on the active side, the passive side takes over the execution of services. After the
active side recovers from the error, seed processing is performed from the passive side, so that the
data that was updated while the passive side was executing the services is applied to the active side.
If an error occurs on the passive side, seed processing is performed from the active side, so that the
data on the passive side is restored. You cannot perform any backup or restore operations until the
passive side has been recovered from the error.
If logical errors, such as those caused by viruses, occur on both the active side and the passive side,
the data is restored from the tape device to the secondary volume, and then from the secondary
volume to primary volume 2. The restored data is then applied to primary volume 1 via seed processing.
Backing up and restoring the active mailbox database copy and the passive mailbox database copy by using different backup servers
The following figure shows an example of a DAG configuration in which an active mailbox database
copy and a passive mailbox database copy are backed up and restored by different backup servers.
Application Agent CLI User Guide 65
Page 66

Figure 33 Configuration in which an active mailbox database copy and a passive mailbox database
copy are backed up and restored by different backup servers
Primary volume 1 is the active mailbox database copy, and primary volume 2 is the passive mailbox
database copy. Secondary volume 1 is managed by backup server 1, and secondary volume 2 is
managed by backup server 2. The data synchronization between the active side and the passive side
is accomplished via log shipping. Data is backed up on both the active side and the passive side,
and the data on each secondary volume is stored on a tape device.
If an error occurs on the active side, the passive side takes over the execution of services and also
performs backup and restore operations. If a logical error occurs on the passive side while the passive
side is executing the active side's services, the data is restored from the tape device to secondary
volume 2, and then from secondary volume 2 to primary volume 2. After the active side recovers from
the error, seed processing is performed from the primary volume 2, so that the data that was updated
while the passive side was executing the services is applied to primary volume 1.
If an error occurs on the passive side, seed processing is performed from the active side, so that the
data on the passive side is restored.
If logical errors, such as those caused by viruses, occur on both the active side and the passive side,
the data is restored from the tape device to secondary volume 1, and then from secondary volume 1
to primary volume 1. The restored data is then applied to primary volume 2 via seed processing.
Application Agent system configurations66
Page 67

Backing up and restoring the active mailbox database copy and the passive mailbox database copy by using the same backup server
The following figure shows an example of a DAG configuration in which an active mailbox database
copy and a passive mailbox database copy are backed up and restored by the same backup server.
Figure 34 Configuration in which an active mailbox database copy and a passive mailbox database
copy are backed up and restored by the same backup server
Primary volume 1 is the active mailbox database copy, and primary volume 2 is the passive mailbox
database copy. Secondary volume 1 and secondary volume 2 are managed by the backup server.
The data synchronization between the active side and the passive side is accomplished via log
shipping. Data is backed up on both the active side and the passive side, and the data on each
secondary volume is stored on a tape device.
If an error occurs on the active side, the passive side takes over the execution of services. After the
active side recovers from the error, seed processing is performed from the passive side, so that the
data that was updated while the passive side was executing the services is applied to the active side.
If an error occurs on the passive side, seed processing is performed from the active side, so that the
data on the passive side is restored.
Application Agent CLI User Guide 67
Page 68

If logical errors, such as those caused by viruses, occur on both the active side and the passive side,
the data is restored from the tape device to secondary volume 1, and then from secondary volume 1
to primary volume 1. The restored data is then applied to primary volume 2 via seed processing.
Comparison of DAG configurations
The following table compares the four types of DAG configurations that use Application Agent. Refer
to this table when setting up your system.
Table 2 Comparison of DAG configurations
Fault tolerance
If an error occurs on the backup server or the
backup volume, backup and restore operations
are not available.
Backup and restore
operations are still
available if an error
occurs on one
backup server or on
one backup volume.
Configuration 4Configuration 3Configuration 2Configuration 1Item
Backup and restore
operations are still
available if an error
occurs on one backup
volume. Backup and
restore operations are
not available if an error occurs on one
backup server.
More backup servers and backup volumes
are required than in Configuration 1 and
Configuration 2.
The verification time
is double that of the
other configurations
Verification time is
shorter than in Configuration 4, although
two backup volumes
are used, because
each backup volume
is managed by a different backup server.
because two backup
volumes are used and
only one backup
server manages these
volumes. However,
you can specify the
VERIFY_PARALLEL_COUNT paramet-
er to perform verification processing in
parallel to shorten the
time required.
Cost
Time required
for verification
Fewer backup servers and backup volumes
are required than in Configuration 3 and
Configuration 4.
Verification time is shorter than in Configuration 4 because only one backup volume is
used.
Legend:
Configuration 1: Configuration in which the active mailbox database copy is backed up and restored
Configuration 2: Configuration in which the passive mailbox database copy is backed up and
restored
Configuration 3: Configuration in which the active mailbox database copy and the passive
mailbox database copy are backed up and restored by different backup servers
Configuration 4: Configuration in which the active mailbox database copy and the passive
mailbox database copy are backed up and restored by the same backup server
Application Agent system configurations68
Page 69

Requirements and precautions for backing up Exchange databases
The following table describes the types of data subject to backup in the Exchange database.
Table 3 Types of data subject to backup in the Exchange database
ExtensionFiles subject to backupDatabase subject to backup
Data files (Exchange Server Information Store)
Exchange Server storage group
Data files
Exchange Server Information Store
#
Files with the .stm extension exist only in Exchange Server 2003.
In Application Agent, data is backed up and restored in physical volumes units so the object
configuration of an Exchange database requires the following:
• The files to be backed up must all be placed on a RAID volume defined as a pair.
• Deploy the storage group or Information Store by taking into consideration that the unit for backup
is physical volumes.
In Exchange Server 2003 or Exchange Server 2007:
• If you deploy multiple storage groups in the same physical volume, you need to back up or
restore these storage groups as one group. When backing up or restoring a storage group
separately, deploy the storage group on a separate physical volume.
In Exchange Server 2010 or Exchange Server 2013:
• If you deploy multiple Information Stores on the same physical volume, you need to back up
or restore these Information Stores as one group. When backing up or restoring an Information
Store separately, deploy the Information Store on a separate physical volume.
Transaction log files
Checkpoint files
*.edb
*.stm
*.logTransaction log files
*.chkCheckpoint files
*.edb
*.log
*.chk
#
• When you place an Exchange database that is subject to backup on the volume, note the following:
In Exchange Server 2003 or Exchange Server 2007:
• You cannot put the transaction log file (*.log) on a volume where a data file is placed.
• For online backup and VSS backup, data files (*.edb, *.stm) and checkpoint files (*.chk)
cannot be allocated to the same volume.
In Exchange Server 2010 or Exchange Server 2013:
• When you back up a database, you cannot put the transaction log file (*.log) on the same
volume that holds a data file (*.edb). Data is restored in physical volumes units so you will
not be able to perform a roll-forward restore operation if you put both the transaction log file
and the database file on the same physical volume. You must therefore put the transaction log
file and the database file on different physical volumes.
• When you set a name for a storage group or Information Store, note the following:
Application Agent CLI User Guide 69
Page 70

• Maximum length: 64 characters
• Characters that cannot be used = ; \ / ,
• The operations shown below change information pertaining to the Exchange Server on the Active
Directory, so if you perform any of these operations you will no longer be able to restore backup
data obtained before these operations (that is, you will no longer be able to use the drmex-
grestore or EX_DRM_EXG_RESTORE command):
• Modification of the paths of the Information Store, log, and system files.
• Addition or deletion of storage groups.
• Modification of the storage group name.
• Addition of an Information Store to a storage group.
• Deletion of an Information Store from a storage group.
If you have performed any of the above operations, you will need to back up the Active Directory
and the Exchange database again. To perform a backup for the Active Directory, follow the instructions given in documentation provided by Microsoft.
• Performing any of the operations shown below changes the database name, and you will no
longer be able to restore and recover backup data obtained before these operations (that is, you
will no longer be able to use the drmexgrestore or EX_DRM_EXG_RESTORE command with
the -recovery option specified):
• Repairing Information Store using the ESEUTIL utility (ESEUTIL /p).
• Defragmentation using the ESEUTIL utility (ESEUTIL /d).
If you have performed any of these operations, you will have to execute the drmexgbackup or
EX_DRM_EXG_BACKUP command, and then back up the Exchange database again.
• You can use a circular log only when using Exchange Server 2003 to perform a cold backup or
• The recovery storage groups for Exchange Server 2003 and Exchange Server 2007 cannot be
• The recovery database for Exchange Server 2010 and Exchange Server 2013 cannot be backed
• When using Fast Snap or Snapshot, you cannot perform a back up to tape by using Application
• When using Exchange Server 2003, you can use cold backup and online backup. When using
• Of the high-availability functions in Exchange Server 2007, only SCC, CCR, and SCR are suppor-
Using VSS
This section describes requirements and precautions used when VSS is used to back up an Exchange
database.
online backup. However, if you use a circular log, the oldest log among the existing log files is
deleted when a new log file is created. This means that some logs might disappear at roll-forward.
For this reason, when performing roll-forward recovery, do not use a circular log.
backed up. The files and folders that make up the recovery storage group must be placed on a
different file system from the storage groups to be backed up.
up. The files and folders that make up the recovery database must be placed on a different physical volume from that of the database to be backed up.
Agent. Therefore, use another backup product to make a tape backup of an Exchange database
that is on the primary volume.
Exchange Server 2007, Exchange Server 2010, or Exchange Server 2013, you can use only
VSS backup.
ted. LCR is not supported.
• P9000 RMXP Shadow Copy Provider must be installed in advance, on both the database server
and the backup server. If P9000 RMXP Shadow Copy Provider has not been installed on those
servers when Application Agent is installed, P9000 RMXP Shadow Copy Provider will be installed
together with Application Agent.
Application Agent system configurations70
Page 71

• The backup server is required even if data is not backed up to tape. This is because the backup
server imports VS snapshots and verifies the Exchange database.
• If Veritas Snapshot Provider is installed on the database server or backup server where a VSS
backup will be performed, make sure you use version Veritas Snapshot Provider 1.04 or later.
If a VSS backup is executed using version Veritas Snapshot Provider 1.03 or earlier, the volume
to be backed up might be left with Read-Only and Hidden attributes. If this happens, the drive
will not be allocated at system startup and Exchange Server will not operate normally. If this occurs,
release these attributes as described in Microsoft Knowledge Base Article 840781.
• If a system failure or other problem causes a VSS backup to be interrupted, the volume that is the
target of the backup might be left with the Read-Only and Hidden attributes. If these attributes
remain, the drive will not be allocated at system startup, and Exchange Server will not operate
normally. If this occurs, release the attributes as per Microsoft Knowledge Base Article 840781.
• If you want to perform a VSS backup, perform a restoration, or delete transaction logs while Ex-
change Server is operating, you must make sure that certain services are running. The services
that must be running differ depending on the version of Exchange Server.
For Exchange Server 2003, Exchange Server 2007, or Exchange Server 2010:
Microsoft Exchange Information Store Service must be running.
For Exchange Server 2013:
Microsoft Exchange Information Store Service and Microsoft Exchange Replication Service
must be running.
• During backup, the database write processing of Exchange Server shuts down for a certain period
(up to 10 seconds). During that period, the database write processing of Exchange Server (such
as sending mail) is suspended. After backup finishes, the database write processing of Exchange
Server is resumed.
• Since the number of log files might increase during backup operations by VSS, when you perform
backup by using VSS, the backup results might contain a log file that has not been recorded in
the catalog.
• Set the environment of Application Agent to use VSS. For details on environment settings required
to use VSS, see “Specifying settings for using VSS” on page 147.
• The Information Stores of the storage group that are to be backed up must all be mounted in ad-
vance.
• When Protection Manager version 4.4 or earlier is used to back up storage groups, the Information
Stores of storage groups to be restored must all be mounted in advance. When Protection Manager
version 5.5 is used, the Information Stores do not need to be mounted in advance in order to be
restored.
• If the name of the Exchange database has been changed, you must perform the following opera-
tions:
• For Exchange Server 2003 or Exchange Server 2007, unmount all of the Information Stores
in the relevant storage group and then remount them.
• For Exchange Server 2010 or Exchange Server 2013, unmount and then remount the Inform-
ation Stores.
• Do not use LUN#0 as a secondary volume for the backup destination. If the LUN#0 disk is used
as a secondary volume for the backup destination, other disks might not be recognized.
• When data is backed up, a folder named DRMVSSMETADATA_backup-ID is created in the root
directory of the secondary volume. Do not delete this folder, as a backup metadata file necessary
for restoration is stored in it. This folder is automatically deleted after data has been restored.
• Do not mount another volume in a directory on the volume to be backed up. If another volume is
mounted, mounting and restoration for the secondary volume might fail.
Application Agent CLI User Guide 71
Page 72

• It might take a long time to execute the backup command for VSS backup, because the VSS import
server verifies the backup result database. The time required to verify the database depends on
factors such as the database capacity, the backup server's machine performance, and disk performance. Also, an option can be specified in the drmexgbackup or EX_DRM_EXG_BACKUP
command used for completing the backup operation without verifying the database. If you omit
the verification, HP recommends that you use the drmexgverify or EX_DRM_EXG_VERIFY
command to verify the database before performing restoration or backing up data to tape.
Note that, although an option is provided for the drmexgbackup or EX_DRM_EXG_BACKUP
command to delete transaction logs after backup without verification, if this option is used when
the database is corrupted, roll-forward recovery might not be able to be performed.
• The following are the files verified during database verification when backup is performed by using
VSS:
• Data files in the Information Store (*.edb)
• Transaction log files that have not been committed (*.log)
• Note on approximate periods required for database verification when a backup is performed by
using VSS:
• For Exchange Server 2003, Application Agent uses the ESEUTIL utility to verify databases.
The table below lists the approximate amount of time required to verify a database. Note that
the approximate amount listed in the table only apply under certain conditions, and are not a
guarantee product performance.
Table 4 Approximate amount required to verify Exchange Server 2003 database for backup
by using VSS
Amount of time
required for
database verification
10 seconds2500 MB• CPU: Pentium 4 1.5 GHz
35 seconds22 GB
System configuration for the
database server
• Memory: 1 GB
• Storage system: XP128
Capacity of the
data file (*.edb)
Number of transaction log files
(*.log)
• The following table lists the approximate amount of time required to verify a database for Exchange Server 2007.
Table 5 Approximate amount required to verify Exchange Server 2007 database for backup
by using VSS
Amount of time
required for
database verification
3 hours5500 GB
System configuration for the
backup server
• CPU: 3.0 GHz x 2
• Memory: 6 GB
• Storage system: HP
XP24000
Capacity of the
data file (*.edb)
Number of transaction log files
(*.log)
Application Agent system configurations72
Page 73

• The following table lists the approximate amount of time required to verify a database for Exchange Server 2010.
Table 6 Approximate amount required to verify Exchange Server 2010 database for backup
by using VSS
Backup server system configuration
• CPU: 3.0 GHz x 2
• Memory: 4 GB
• Storage system: HP P9500
• If you change settings for the following files, restart the Protection Manager service:
• Application Agent configuration definition file (init.conf)
• RAID Manager-linkage definition file (DEFAULT.dat)
• For the storage groups subject to backup and restoration, do not enable circular logs. If a circular
log is enabled, you cannot perform backup and restoration by using VSS.
Data file capacity
(*.edb)
Number of
transaction log
files (*.log)
Amount of time
required for
database verification
30 minutes5100 GB
Restoring backup data obtained using VSS in units of Information Stores
When using Exchange Server 2003 and Exchange Server 2007, you can restore backup data
obtained using VSS in units of Information Stores (in units of *.edb and *.stm data files). Restoring
backup data in units of Information Stores makes it possible to quickly restore just the required data
files.
To restore backup data in units of Information Stores, you must partition the disk into units of data to
be restored. Therefore, take into account the unit of restoration when allocating data files.
Database configurations that allow restoration in units of Information Stores
• Configurations in which only the Information Store data files (*.edb and *.stm) to be restored
individually are stored on separate disks
• Configurations in which only Information Store data files (*.edb and *.stm) to be restored
individually are stored on the same disk
• Configurations in which multiple Information Store data files within the same storage group
are stored on the same disk
You can perform restoration of all Information Stores stored on the same disk provided that
you specify all the Information Stores. In this case, if you do not specify all Information Stores
stored on the same disk, the command will end with an error.
Database configurations that do not allow restoration in units of Information Stores
• When data files (*.edb and *.stm), transaction log files (*.log), and check point files
(*.chk) in different storage groups are located on the same disk, Information Stores below
a storage group that shares the disk cannot be restored individually.
Application Agent CLI User Guide 73
Page 74

The table below lists the conditions for allocating files when restoring backup data in units of Information
Stores.
Table 7 Conditions for allocating files when restoring backup data in units of Information Stores
Files on the same disk
Restoration
target
No other
files
Information Store that
is a restoration target
Information Stores in
the same storage group
Information Stores in
different storage
groups
*.stm*.edb*.stm*.edb*.stm*.edb
*.edb
I
NNAAI--
NNAA--I*.stm
Legend:
I: Can be restored individually.
A: Can be restored provided all Information Stores on the same disk are specified.
N: Cannot be restored individually.
--: Not applicable
The figure below shows a database configuration that allows restoration in units of Information Stores.
Figure 35 Restoration in units of Information Stores (when the backup target is an Exchange database)
In the above example, Information Stores from IS11 to IS14 belong to the storage group SG1. In this
case, you can restore backup data in the following units:
• Restore only IS11 individually
Application Agent system configurations74
Page 75

• Restore only IS12 individually
• Restore IS13 and IS14 at the same time (you cannot restore just one)
NOTE:
When restoring backup data in units of Information Stores, you must apply (roll forward) the transaction
log at the time of restoration. For details on precautions relating to executing commands at restoration,
see the description for the drmexgrestore command in the manual
Software Application Agent CLI Reference Guide
Using a dynamic disk configuration
• Dynamic disks are supported only by Exchange Server 2003.
• If multiple storage groups are allocated to a file system (drive or mount point directory) of the same
disk group, you must collectively backup or restore these storage groups.
• To back up or restore storage groups individually, allocate them to a file system (drive or mount
point directory) of a different disk group.
• When allocating an Exchange database subject to backup to a file system (drive or mount point
directory), note the following points:
• You cannot allocate the transaction log file (*.log) to a file system (drive or mount point dir-
ectory) of the same disk group to which data files are allocated.
• For online backup, you cannot allocate the data files (*.edb, *.stm) and checkpoint file
(*.chk) to a file system (drive or mount point directory) of the same disk group.
HP P9000 Replication Manager
.
• The recovery storage groups for Exchange Server 2003 cannot be backed up. Allocate files and
folders that comprise a recovery storage group to a file system (drive or mount point directory) of
a disk group different from a storage group subject to backup.
Using a cluster configuration
• Do not register the instances of multiple Exchange resources into a cluster group.
• In a cluster environment, when restoring data in a physical node different from that used during
backup, an Exchange virtual server that uses the same shared disk as that used during backup
must be running. Application Agent cannot restore data for an Exchange virtual server, such as
one at a remote site, that uses a disk different from the one used during backup.
Using the Veritas Cluster Server for Windows
• The status of the cluster resource groups must be online during backup. If it is not online, the backup
command (drmexgbackup or EX_DRM_EXG_BACKUP) will end in error.
• The file system that stores registry replication data should not be backed up via Application Agent.
Make sure that you allocate such a file system to a disk group or physical disk that is not subject
to backup.
• Application Agent uses Veritas Cluster Server Enterprise Agent for Microsoft Exchange to manage
the Exchange services and Exchange protocol services. Do not change the default name for the
resource type ExchService and ExchProtocol provided by Veritas Cluster Server Enterprise
Agent for Microsoft Exchange. Veritas Cluster Server Enterprise Agent for Microsoft Exchange is
bundled with Veritas Storage Foundation.
Application Agent CLI User Guide 75
Page 76

Using Microsoft Cluster Service or Windows Server Failover Clustering
If you are using Exchange Server 2003 or Exchange Server 2007, note the following points:
• Among the cluster resource groups, the Exchange System Attendant resource and the Exchange
Information Store resource must be online during backup. If they are not online, the backup command (drmexgbackup or EX_DRM_EXG_BACKUP) will result in an error.
• When using VSS, the following conditions must be satisfied regarding the relationship between
the cluster resource and the Exchange Information Store resource to be operated:
For Exchange Server 2003:
Except for the relationship between the cluster resource and the Exchange System Attendant
resource to be operated, do not set the Exchange Information Store resource to go offline
when a cluster resource goes offline.
For Exchange Server 2007:
Do not set the Exchange Information Store resource to go offline when the cluster resource to
be operated goes offline.
Cascade configuration
• Backups in an SCC environment are supported.
• Backups must be executed on the active server of a cluster.
• A disk with Remote Copy defined must be registered as a disk resource of the cluster.
• The primary volume of Remote Copy must be connected to the active server.
• The secondary volume of Remote Copy must be connected to the standby server.
• When you concurrently back up at both the local and remote sites, different backup servers must
be used at each site.
• The Protection Manager service must be running at both the local and remote sites.
• When you back up by using VSS, the VSXPHORCMINST_REMOTE system environment variable
must be set for the backup server at the remote site.
• You must create a definition file for the cascade configuration. For details about creating a
definition file for the cascade configuration, see “Creating a cascade configuration definition file
for Exchange database backup” on page 151.
• You must store the dictionary map files and backup catalog on different disks at both the local
and remote sites. These disks must be accessible regardless of whether the virtual server is online
or offline.
• The dictionary map files at both the local and remote sites must be updated with the most recent
information.
• The RAID Manager instance for managing Remote Copy must be active.
• If the RAID Manager instance used for managing Remote Copy is the same as the RAID Manager
instance managed by Application Agent (the RAID Manager instance specified for the HORCMINST
parameter in the RAID Manager-linkage definition file), after you update the dictionary map files,
you must use the drmcgctl command at both the local and remote sites to lock the Remote Copy
copy groups.
• Before you back up, you must use the RAID Manager command to set the Remote Copy pair status
to PAIR.
• Before you back up, you must conceal the secondary volume of the local copy at both the local
and remote sites.
• When you back up, you must set the Exchange virtual server name to the DRM_HOSTNAME envir-
onment variable.
Application Agent system configurations76
Page 77

• If an error occurs after backup of the local site is complete but before backup of the remote site
is complete, you cannot restore using the data backed up at the local site.
• Before you restore, you must use the RAID Manager command to set the Remote Copy pair status
to PSUS (SSUS).
• You can only restore backup data obtained at the site that is being restored. You cannot restore
backup data that was obtained at a different site.
CCR configuration
• With a CCR configuration, you must manage dictionary map files and backup catalogs separately
for the active and standby servers. The dictionary map files and backup catalogs acquired by
each of the servers are used by the respective database servers and by the backup servers used
by these database servers.
• If the active and standby servers use the same backup server, the active and standby servers must
use different copy group names for the disk to which the backups are saved.
• The active and backup servers cannot back up the same storage group concurrently. Wait until
execution of the backup command is finished on the first server before you begin backup on the
other server.
• With VSS backup, the active and backup servers can back up different storage groups concurrently.
• If a transaction log is deleted, roll-forward cannot be performed using backup data that was ac-
quired earlier than the deleted transaction log.
• Backup data can be restored only to the node on which the backup was performed. The backup
data acquired at the active server cannot be restored to the standby server, and the backup data
acquired at the standby server cannot be restored to the active server.
• To restore a backup acquired at the standby server, you must perform a fail-over operation on the
active server so that the standby server is switched to the active server.
• In a CCR environment, the replication function must be stopped before you perform a point-in-time
restore operation.
• If data on the active server becomes corrupted or if the database is restored, you must perform
seed processing (data resync).
If you use the automatic seed function, all seed processing is performed automatically during res-
toration. If you do not use this function, you must manually perform seed processing for each
storage group. If an error occurs during restoration using the automatic seed function, you must
manually perform seed processing on the storage group that resulted in the seed processing error.
The following describes how to perform manual seed processing:
• Stop the replication function.
• Delete the Exchange database file, the transaction log file, and the checkpoint file on the
standby server.
• Resynchronize the standby server with the active server data.
• Restart the replication function.
• If you use the automatic seed function, the EXG_CCR_SEED parameter value must be ON in the
Exchange environment configuration file that is specified in the -ef option of the restore command.
For details about the Exchange environment configuration file, see “Creating the Exchange envir-
onment configuration file” on page 219.
• If you use the automatic seed function, the Protection Manager service must be active on the
standby server.
• If you use the automatic seed function, the same version of Application Agent must be installed
on both the active and standby servers.
To use the automatic seed function, the same version of Application Agent must be installed on
both the active and standby servers.
Application Agent CLI User Guide 77
Page 78

• The following is a guideline for determining the time required for seed processing:
Seed processing time per storage group (seconds) = capacity-of-database-subject-to-seed-processing
(MB)/25 (MB/second)
For the above formula to be applicable, the following conditions must be satisfied:
• The network used for seed processing is a Gigabit Ethernet.
• The server used for seed processing has sufficient performance (such as CPU and disk perform-
ance) to adequately run the installed applications (such as Application Agent, Exchange
Server, and tape backup management softwares).
SCR configuration
• If you use the SCR seed function, the same version of Application Agent as the source must be
installed on all targets.
• If you use the SCR seed function, the EXG_SCR_SEED parameter value must be set to ON in the
Exchange environment configuration file that is specified in the -ef option of the restore command.
• If you use the SCR seed function, the Protection Manager service must be active on all targets.
• SCR is not supported in a cascade configuration.
• If you perform a point-in-time restore without using the SCR seed function, the replication function
to be restored will be stopped, but seeding or replication will not be restarted. After the restoration,
manually perform seed processing.
• To perform a backup for a database in an SCR configuration, the following conditions must be
satisfied:
• The source Microsoft Exchange Replication Service must be running.
• For storage groups in which SCR is enabled, replication statuses of all targets are Healthy.
• A storage group that has been specified as the source can be backed up or restored by using
VSS.
• The guideline for determining the time required for SCR seed processing is described below.
For the formula shown below to be applicable, the following conditions must be satisfied:
• Gigabit Ethernet is employed for the network that is used for seed processing.
• The CPU and disks have sufficient performance.
Note that depending on CPU or disk performance, the actual processing time might be shorter
than the result calculated by the following formula. The calculation result should be used for
estimation, and it does not guarantee the product performance.
Seed processing time per storage group (seconds) = capacity-of-database-subject-to-seed-pro-
cessing (MB) * the-number-of-targets / 25 (MB/second)
DAG configuration
The following conditions must be satisfied when backing up the database in a DAG configuration:
• To back up the active mailbox database copy, see “Using VSS” on page 70.
• To back up the passive mailbox database copy, the conditions below must be satisfied in addition
to the conditions in “Using VSS” on page 70. If any of the conditions are not satisfied, a message
indicating an error is displayed and you cannot perform backup.
• The active mailbox database copy must be mounted for the passive mailbox database copy
that is to be backed up.
• Microsoft Replication Service must be running on the Exchange Server that performs the backup.
Application Agent system configurations78
Page 79

• For Information Stores for which DAGs are enabled, the replication status of each passive
mailbox database copy to be backed up must be Healthy.
• For a mailbox database copy, you cannot back up both the active mailbox database copy and
the passive mailbox database copy at the same time. Wait until the backup command executed
for one mailbox database copy is finished before executing the backup command for the other
mailbox database copy.
• To restore the backup data, the mailbox database copy to be restored must be in the active status.
If it is not in the active status, a message indicating an error is displayed.
• Backup data can be restored only by the Exchange Server that backed up the data. An Exchange
Server cannot restore backup data that was obtained by a different Exchange Server.
• Correct execution of the replication function after restoration requires seed processing. If you do
not perform seed processing, the replication function will not return to normal.
• If you use the seed function in a DAG configuration, for the -ef option, you need to specify an
Exchange environment configuration file in which the EXG_DAG_SEED parameter value is set to
ON. If the Exchange environment configuration file does not have this setting (for example, the first
priority is finishing a restoration or deferring seed processing), seed processing will not be executed.
• If you perform a restore operation without using the seed function in a DAG configuration, the
replication function for the object to be restored stops, and seed processing is not executed. After
the restore operation finishes, you will need to manually start seed processing and the replication
function.
• If you want to perform a roll-forward restore operation in a configuration in which mailbox database
copies on both the active side and the passive side are backed up, specify the option for deleting
transaction logs only for the active side or only for the passive side. This is because if an option
for deleting transaction logs is executed, the transaction log information for other mailbox database
copies will be also deleted. HP recommends that you specify the option for deleting transaction
logs only for the active side or only for the passive side to prevent all of the transaction logs from
being deleted and to improve redundancy.
• When you perform a restore operation, the Microsoft Exchange Replication Service must be running
on an Exchange Server that is operating as the primary active manager.
• Even when you execute seed processing after performing a point-in-time restore operation, the
copy queue length might not be 0. To switch over mailbox database copies in this state, use Exchange Management Shell.
• Example command: Move-ActiveMailboxDatabase database-name -ActivateOn-
Server switchover-target-server-name -SkipLagChecks:$True -MountDialOverride:Besteffort
• You cannot perform a backup operation in an environment in which both an active mailbox
database copy and a passive mailbox database copy exist.
• When you perform a point-in-time restore of the passive mailbox database copy backup, the active
mailbox database copy might be restored to a status it was in before the execution of the backup
command. To avoid this problem, perform the following procedure:
1. Stop the database copy.
2. Reseed the database.
3. Back up the passive mailbox database copy.
• Automatic reseed cannot be used with Exchange Server 2013.
• For Exchange Server 2013, before performing the restore, you must stop the Microsoft Exchange
Search Host Controller Service on the database server.
The following problems might occur when you stop the Microsoft Exchange Search Host Controller
Service:
Application Agent CLI User Guide 79
Page 80

• Users cannot search items with Outlook Web App or Outlook (online mode). However, users
can search items with Outlook in cache mode.
• When you execute the Get-MailboxDatabaseCopyStatus command, Failed appears for
ContentIndexState.
• After you restart the Microsoft Exchange Search Host Controller Service, the index processing
starts again. At this time, ContentIndexState changes from Failed to Healthy, and the processing
required before you can resume email searches on Outlook Web App might take some time.
Requirements when using RAID Manager to configure a pair volume
Application Agent uses the pair volumes defined by RAID Manager to back up or restore a file system
or database object. When you create a pair volume by using RAID Manager, abide by the following
rules:
• You cannot configure a paired volume so that the same server manages both the primary volume
and secondary volume as physical disks.
Figure 36 Configuration for managing the primary volume and secondary volume from the same
server (without using Application Agent)
• A copy group must consist of pair volumes for the same application. When a copy group consists
of more than one pair volume and there are pair volumes for different applications in the copy
group, an unexpected backup or restoration might be performed.
• When using Business Copy, configure the pair volume in the storage system. When using Continu-
ous Access Software, configure the pair volume between the storage systems.
Application Agent system configurations80
Page 81

• Application Agent operates the pair volumes for Business Copy, Fast Snap, Snapshot, Continuous
Access Software or Continuous Access Journal.
• Application Agent cannot back up or restore volumes paired by Flex Copy or Auto LUN.
• Depending on the version of RAID Manager, the model of the storage system, and the version of
the microcode, the functionality for acquiring the copy type of the pair volume (copy group) might
not be supported. Because of this, Application Agent might not be able to correctly recognize
whether the copy type of a pair volume (copy group) is supported, since the copy type cannot be
retrieved. Thus, if you configure a system in which Flex Copy pair volumes and Business Copy,
Fast Snap, or Snapshot pair volumes co-exist, since the Flex Copy pair volumes (copy groups) are
not supported, make sure that they are disregarded as backup or restoration targets, by locking
them with the drmcgctl command.
• When using Continuous Access Software, do not enter an MU number in the MU# setting in the
RAID Manager configuration definition file (horcmn.conf). If 0 is defined for the MU# setting,
volume information for the Continuous Access Software pair will not be stored in the dictionary
map when you execute a drmXXdisplay# command with the -refresh option specified.
Therefore, the volume information cannot be displayed by the Application Agent command, and
the pair volume cannot be backed up.
#
drmXXdisplay indicates the drmfsdisplay, drmsqldisplay, or drmexgdisplay
command.
• When using Continuous Access Journal, define h0 (h and a generation number) for the MU#
setting in the RAID Manager configuration definition file (horcmn.conf). If 0 is defined for MU#,
the Continuous Access Journal information will not be stored in the dictionary map when you execute
a drmXXdisplay command with the -refresh option specified. Therefore, volume information
cannot be displayed by the Application Agent command, and the pair volume cannot be backed
up.
• When using Continuous Access Software or Continuous Access Journal, make sure that you start
the RAID Manager instance that manages the secondary volume (the RAID Manager instance that
manages the primary volume when you are executing the command in a backup server) in advance.
• The RAID Manager configuration definition file (horcmn.conf) of a RAID Manager instance that
links with Application Agent must satisfy the following conditions:
• The RAID Manager configuration definition file (horcmn.conf) must be in the Windows dir-
ectory (%windir%).
The environment variable HORCM_CONF cannot be used to change the location of the RAID
Manager configuration definition file (horcmn.conf).
• The instance number (n) in the RAID Manager configuration definition file name (horcmn.conf)
must include only numeric characters. Also, note that 0 must not be placed before numeric
characters.
Examples of valid file names: horcm1.conf, horcm120.conf
Examples of invalid file names: horcm001.conf, horcmA20.conf
• When using Continuous Access Software or Continuous Access Journal, make sure that you create
a pair before executing a Application Agent command. If you do not, the pair volume cannot be
backed up.
• When performing a backup or restoration on a database server, make sure that you unmount the
secondary volume in advance. If you do not, unexpected backup or restoration might be performed.
• When you want to mix the pair volumes for Business Copy and Continuous Access Software, the
following system configurations can be used:
Application Agent CLI User Guide 81
Page 82

Figure 37 System configuration (when the primary volume for Business Copy and the primary
volume for Continuous Access Software are the same LDEV)
When using the configuration shown in Figure 37 to restore the paired volume for Business Copy
by using Application Agent, set the status of the paired volume for Continuous Access Software
to SMPL or PSUS (SSUS). When you restore the pair volume for Business Copy with the status of
a pair volume for Continuous Access Software PAIR, an error message indicating that the status
of the copy group is invalid is output and the restore operation fails.
Application Agent system configurations82
Page 83

Figure 38 System configuration (when the secondary volume for Business Copy and the primary
volume for Continuous Access Software are the Same LDEV)
When using the configuration shown in Figure 38 to back up or restore the paired volume for
Business Copy using Application Agent, set the status of the paired volume for Continuous Access
Software to SMPL or PSUS (SSUS). When you back up or restore a pair volume for Business Copy
with the status of a pair volume for Continuous Access Software PAIR, an error message indicating
that the status of the copy group is invalid is output and the backup or restore operation fails.
Application Agent CLI User Guide 83
Page 84

Figure 39 System configuration (In a Business Copy cascade configuration, when the volume subject
to backup operates both as the primary volume and the secondary volume)
In a Business Copy cascade configuration, Application Agent only supports backup and restore
operations for the pair volumes of the primary volumes used in the database or the file system.
When using a Business Copy cascade configuration as shown in Figure 39 and the volume subject
to backup serves both as the primary volume and secondary volume, set the paired volume status
on the secondary volume to SMPL and SSUS. Similarly, for restoration, set the status to SMPL.
• For the consistency group definitions It is necessary to consider how Application Agent backup
and restore operations are performed when defining consistency groups. Perform a backup or
restore operation after defining consistency groups as described below:
• Define consistency groups while considering the operations for restoring the databases. Pay
extra attention to the definitions if partial restoration of databases backed up at the same time
will be performed.
• For SQL Server databases
If restoring individual databases separately:
Define one consistency group to one database to make each database in a separate consistency
group.
If restoring multiple databases together:
It is possible to define consistency groups to make databases that are always restored together
in a same consistency group.
• For Exchange databases
If restoring individual Information Stores separately:
Define consistency groups to make each Information Store of data files (*.edb, *.stm) in a
same consistency group. In addition, define consistency groups to make the transaction log
files and checkpoint files (*.log, *.chk) of each storage group in a same consistency group.
If restoring multiple Information Stores together:
It is possible to define consistency groups so that the data files (*.edb, *.stm) of Information
Stores that are always restored together are in one consistency group. In addition, define
consistency groups to make the transaction log files and checkpoint files (*.log, *.chk) of
each storage group in a same consistency group.
If restoring individual storage groups separately:
Define consistency groups to make each file type of each storage group in a separate consist-
ency group. However, if rolling forward is not performed when restore and recovery operations
are performed, it is possible to define consistency groups to make all files of each storage
group are in a same consistency group.
If restoring multiple storage groups together:
Application Agent system configurations84
Page 85

If not using VSS:
It is possible to define consistency groups to make files of the same file types of multiple storage
groups that are always restored together are in a same consistency group. However, if rolling
forward is not performed when restore and recovery operations are performed, it is possible
to define consistency groups to make all files of the storage groups that are always restored
together are in a same consistency group.
If using VSS:
Define consistency groups to make files of each file type of each storage group in a separate
consistency group. However, if rolling forward is not performed when restore and recovery
operations are performed, it is possible to define consistency groups to make all files of each
storage group are in a same consistency group.
• Define consistency groups to make each consistency group correspond to one RAID Manager
configuration definition file group (dev_group) so that the same copy groups are in each consistency group and RAID Manager configuration definition file.
The figures below show the relationships between databases, volumes, consistency groups, and
RAID Manager groups.
Application Agent CLI User Guide 85
Page 86

Figure 40 In XP Continuous Access Asynchronous/Continuous Access Journal configuration: restoring
UserDB1 and UserDB2 together or separately
Figure 41 In XP Continuous Access Asynchronous/Continuous Access Journal configuration: restoring
UserDB1 and UserDB2 together
• For information about precautions to take when changing a volume configuration, see “Precautions
when changing a volume configuration” on page 92.
• Even if there are pair volumes created in the storage system, you cannot use them unless they have
RAID Manager configurations defined on the host.
• For an environment that uses virtual command device as a command device, start the RAID Manager
instances on the virtual command device server before executing Application Agent CLI so that
the virtual command device is in a state that can be used. Since Application Agent CLI itself does
not activate nor stop the RAID Manager instances on the virtual command device server, when
Application Agent CLI is executed but the virtual command device is in a state that cannot be used,
an error will occur.
If an error occurs, check the log file for RAID Manager on the server where Application Agent CLI
was executed and confirm that the cause of the error is the virtual command device (\\.\IP-
Application Agent system configurations86
Page 87

CMD-IP-address-PORT-number), take measures based on the confirmed information, and
then start Application Agent CLI operation once again.
Volume configurations usable by Application Agent
The table below describes volume configurations that Application Agent can back up and restore.
Table 8 Volume configurations that Application Agent can back up and restore
Logical volume
manager
LDM
Veritas Storage
Foundation
#2
Disk management method
Basic disk
#1
Volume-configuration unit that
Application Agent can back up
and restore
Location where a database or
file to be backed up and restored is stored
File system on a disk partitionPhysical disk
File system on a logical volumePhysical diskBasic disk
File system on a logical volumeDisk groupDynamic disk
Legend:
--: Not applicable
#1
GPT disks are supported.
#2
VSS cannot be used.
When using a Windows dynamic disk , you can use the logical volume manager to group one or
more physical volumes and use the group as one or more logical volumes. Specifying a logical volume
enables users to back up and restore data without needing to consider any physical volume.
The unit for grouping physical volumes and logical volumes is called a disk group.
In Application Agent dynamic disk configuration, a group of one or more dynamic disks and one or
more logical volume groups allocated to a dynamic disk is called a disk set. In Figure 42, part of the
physical volume A is allocated to the logical volume A, and the rest of the physical volume A and
part of the physical volume B are allocated to the logical volume B. Likewise, the rest of the physical
volume B and part of the physical volume C are allocated to the logical volume C, and the rest of the
physical volume C is allocated to the logical volume D. In this case, a group of the four logical volumes
to which the contents of the three physical volumes are allocated is one disk set (disk set 1). Also, if
you allocate all the contents of one physical volume to one logical volume, you can make a one-to-one
relationship disk set (disk set 2).
In the Veritas Storage Foundation environment, when configured, a disk group is recognized as one
or more disk sets. In this environment, Application Agent backs up and restores data using a disk
group as the minimum unit.
The following figure shows examples of a disk set configuration and of a relationship between a disk
group and a disk set.
Application Agent CLI User Guide 87
Page 88

Figure 42 Examples of a disk set configuration and of a relationship between a disk group and a disk
set
In this manual, unless it is necessary to distinguish between Veritas Storage Foundation and LVM disk
groups, both groups are generically referred to as a disk group.
Application Agent can also simultaneously back up a basic disk and a disk group.
When a dynamic disk is being used, Application Agent supports both of the following configurations:
• One disk group is used as one logical volume.
• One disk group is divided into multiple logical volumes.
When a basic disk is being used, Application Agent supports only a configuration where one physical
disk is used as one logical volume (partition).
NOTE:
For Windows, before using Application Agent, make sure that Automatic mounting of new
volume is disabled on the database server or backup server.
Perform the following procedure to check the current status, and if Automatic mounting of
new volume is enabled, disable it:
1. Execute the diskpart command in the command prompt.
2. Enter automount to display the current status.
3. If Automatic mounting of new volumes enabled. is displayed, enter automount
disable to disable the setting.
4. Type exit to end the diskpart command execution.
Application Agent system configurations88
Page 89

Examples of disk group configurations usable by Application Agent
If you configure a disk group with logical volume manager, Application Agent can be used only when
one or more physical volumes constitute one disk group. You cannot divide one physical group into
multiple disk groups.
The following figure shows examples of disk group configurations usable by Application Agent.
Figure 43 Examples of disk group configurations usable by Application Agent
In the Windows dynamic disk configuration, when multiple disk groups exist in a file system, Application
Agent collectively backs up and restores all the mount points in disk groups. It cannot back up only
some drives in a disk group.
The following figure shows data backup and restoration in a system configuration where multiple disk
groups exist in a file system.
Application Agent CLI User Guide 89
Page 90

Figure 44 Data backup and restoration in a system configuration where multiple disk groups exist in
a file system
In this figure, disk groups DG01 and DG02 each of which consists of two physical volumes are
configured. Three logical volumes are created on DG01 and one logical volume is created on DG02.
Mount points D:, E:, and F:, are assigned to DG01 and mount point G: assigned to DG02.
In this case, specifying a mount point directory batch definition file in the drmfsbackup command
enables Application Agent to back up data. In this mount point directory batch definition file, the
mount points of all the file systems defined in the disk groups are written.
Example:
In this example, the command uses the mount point directory batch definition file mp_dg01.dat
to specify the mount points D:, E:, and F: of DG01, and the mount point G:of DG02:
PROMPT> drmfsbackup mp_dg01.dat -mode cold
KAVX0001-I The drmfsbackup command will now start.
KAVX0019-I Copying file(s) now...
KAVX0040-I The backup ID has been assigned as follows:
Backup ID = 0000000001
KAVX0002-I The drmfsbackup command will now end.
PROMPT>
For example, specifying DG02 file system (G:) following the -target option of the drmfsrestore
command enables Application Agent to restore only DG02. Executing the drmfsrestore command
without -target option restores both DG01 and DG02 file systems.
Application Agent system configurations90
Page 91

Example:
Restore only the file system created in disk group DG02 after backing up disk groups DG01 and
DG02.
PROMPT> drmfsrestore 0000000001 -resync -target G:
KAVX0001-I The drmfsrestore command will now start.
KAVX0019-I Copying file(s) now...
KAVX0002-I The drmfsrestore command will now end.
PROMPT>
Requirements and precautions for volume configurations
This section describes the requirements and precautions for volume configurations when Application
Agent is used.
Volume configuration requirements
• You cannot use Application Agent in a configuration where a physical volume is divided into
multiple disk groups using logical volume manager.
• Do not use any functions for expanding or reducing the capacity of a logical volume. If you use
such functions, Application Agent will not perform backup and restoration correctly. This is because
the number of physical volumes that make up the logical volume changes according to the change
in capacity of the logical volume. Application Agent checks whether the configuration of logical
volumes has been changed and, if changed, restoration terminates with an error.
• If the volumes to be processed by Application Agent contain an LDEV for which a mode other
than the normal mode is specified for the access level by using Data Retention Utility, neither a
backup nor a restoration can be performed.
• When executing backup and restoration of file systems and databases, Application Agent mounts
and unmounts the volume subject to processing. In this situation, set the mount point directory
name as follows:
Maximum number of characters: The specifiable path length depends on the limitation for the
RAID Manager mount or unmount functionality:
- When performing a disk backup:
The path length limitation described above applies to the length of the path where the volume for
which cold backup operations are to be performed has been mounted.
- When backing up to tape:
The path length limitation described above applies to the length of the path where the volume for
which disk backup operations are to be performed has been mounted. This limitation also applies
to the length of the path where the secondary volume for which tape backup operations are to be
performed is mounted.
Usable characters: Characters that can be used for a folder name in Windows (you cannot use
a null character).
• One mount point can be specified for each logical volume.
• Allocate database files and file systems that are not subject to backup and restoration so that they
are not included in the same disk configuration unit as those that are subject to backup and restoration.
• Allocate database files and file systems that are backed up simultaneously but can be restored
separately so that they are not included in the same disk configuration unit as those that are subject
to backup and restoration.
Application Agent CLI User Guide 91
Page 92

• If one disk group contains multiple physical volumes, Application Agent performs volume duplication
operation for backup only by the number of physical volumes.
• Do not define the following as copy groups, and do not specify them as backup targets: directories
at a directory mount point, or volumes mounted to a drive. Also, configure directory mount points
that are backup targets so that they are on the same directory level.
The following shows a configuration example of a mounted directory that can become a backup
target. In the figure below, data files and log files are mounted to a directory and specified as
backup targets.
Figure 45 Configuration example of a mounted directory that becomes a backup target
The following shows a configuration example of a mounted directory that does not become a
backup target. When the configuration places a mount point directory on a directory below a
volume, higher-level volumes that contain a volume that was mounted to a directory cannot be
specified as a backup target.
Figure 46 Configuration example of a mounted directory that does not become a backup target
Precautions when changing a volume configuration
• If the following operations or changes are performed on a logical volume manager that is a backup
operation target, or on a file system or RAID Manager configuration definition file (horcmn.conf),
then update the dictionary map files before executing backup. Note that if you execute backup
without updating the dictionary map files, a system inconsistency might occur. To update the dictionary map files, use the drmfsdisplay, drmsqldisplay, or drmexgdisplay command.
For details about how to use these commands, see the HP P9000 Replication Manager Software
Application Agent CLI Reference Guide.
• A new file system was mounted on a directory under the file system.
• A file system was unmounted.
• A file system was moved to another directory and mounted.
Application Agent system configurations92
Page 93

• A disk group was deleted or disabled.
• A logical volume allocated to a disk group was added or deleted.
• A physical volume belonging to a disk group is added, deleted, or replaced.
• A change was made in the RAID Manager configuration definition file (horcmn.conf), such
as the adding or deleting of a pair volume.
• If you made changes to a configuration involving an update of the dictionary map files, to restore
the data backed up before the change to a file server or database server, first restore the configuration for the logical volume manager and file system to the state that was in place at the time
the backup was created, and then perform restoration. Note that if you perform restoration incorrectly, a system inconsistency might occur. To review the configuration that was in place at the
time the backup was created, use the drmfscat, drmsqlcat, or drmexgcat command. For
details about how to use these commands, see the HP P9000 Replication Manager Software Ap-
plication Agent CLI Reference Guide. For details about restoration when a physical volume is replaced, see Appendix C on page 553.
Requirements and precautions when a disk group Is configured
When you operate Application Agent in a disk group configuration managed by Veritas Storage
Foundation, the following prerequisites apply:
• The same OS, version revision, and service pack are installed on all the Windows servers subject
to backup and restoration by Application Agent.
• The physical disk subject to backup and restoration does not include a system (OS startup) disk.
• All the physical disks subject to backup and restoration are LUs of a storage system device and
for which a pair volume is defined.
• The dynamic volume is a concatenated volume (simple volume or spanned volume).
• HP recommends that one disk group consist of one concatenated volume.
• Striped volumes, mirrored volumes, and RAID5 volumes are not supported.
• You must dynamically recognize the secondary volume when backing up secondary volumes
(dynamic disk backup destinations) of multiple generations to tape.
Using dynamic disks in Veritas Storage Foundation
Prerequisites for the Veritas Storage Foundation environment and disk groups are as follows:
• Veritas Storage Foundation with the same version revision and service pack is installed on all the
Windows servers subject to backup and restoration by Application Agent.
• Do not back up and restore data with Veritas Storage Foundation functions because the disk group
configurations managed by Application Agent might be changed.
• Disk group names must be unique in all the systems that back up and restore data. If multiple file
servers or database servers are sharing one backup server, the disk group names used by the file
server and database server might be duplicated in the backup server. If this occurs, Application
Agent is unable to uniquely recognize the disk groups in which data to be backed up to tape is
stored.
• Application Agent cannot back up and restore primary disk groups.
• Installing Veritas Storage Foundation enables you to use Veritas Enterprise Administrator instead
of Windows disk management. Do not use Veritas Enterprise Administrator during execution of
Application Agent.
Application Agent CLI User Guide 93
Page 94

Backing up and restoring dynamic disks by dynamically or statically recognizing secondary volumes
Dynamically recognizing secondary volumes:
• When Application Agent dynamically recognizes the secondary volume, the Demount Device
Warning message is output to the Windows event log.
Statically recognizing secondary volumes:
• Do not rescan disk information with disk management, Veritas Enterprise Administrator, or the
diskpart or vxassist command. A Foreign disk, Failed volume, or Missing disk appears,
making it impossible for Application Agent to recognize the disk configuration correctly. If there
is an application that is using the appropriate disk, an unexpected write error might occur.
If Application Agent is unable to recognize the disk configuration correctly, restore the disk configuration in the following procedures. However, restoration of application data being executed
when disk information is being rescanned is not guaranteed.
1. Execute Import Foreign Disk Format for the Foreign disk with Disk Management.
2. Execute Reactivate Volume for the Failed volume. This mounts the file system and restores the
original configuration. HP recommends that you execute CHKDSK (disk check) for the restored
file system.
• If you change a disk configuration on a physical disk (e.g., by volume expansion), update the
dictionary map files on the file server or database server, back up the files to a volume once as
in initial construction, and then restart the backup server. This enables the server to recognize the
secondary volume disk configuration correctly.
Expanding dynamic volumes
• If you expand a dynamic volume, update the dictionary map files.
• When you expand a dynamic volume, HP recommends that you do not expand it to a new phys-
ical disk that does not belong to the disk set. This expansion will cause multiple disk sets to join.
If you change a volume configuration such that multiple disk sets are joined, when restoring prejoin data, you must return the dynamic disks to the basic disks, restore the disk set configuration
to the pre-join configuration, and then restore all pre-join disk sets.
• Once you have expanded a dynamic volume, you cannot restore data backed up before the ex-
pansion. If you want to restore data backed up before expanding the dynamic volume, return the
volume configuration to the configuration that existed before the expansion and then update the
dictionary map files.
Precautions for partition styles for disks
• After performing a backup, disk partition styles cannot be modified.
When replacing a disk, the same partition style that was in use at the time the backup was performed must be applied to the disk.
• If the partition style was changed after the backup was performed, and you execute the restore
command (drmfsrestore, drmsqlrestore, or drmexgrestore), or you execute the drmdevctl command by specifying either the -sigview or -sigset option, the operation might
end with an error. In this case, change the partition style to the one that was in use when the
backup was performed.
• When the backup target is being managed in a cluster configuration, the disk signatures for the
primary volume and secondary volume must be the same signatures when the backup was per-
Application Agent system configurations94
Page 95

formed. To view the backup signatures that were created when the backup was performed, execute
the drmdevctl command by specifying the backup ID and the -sigview option.
Application Agent CLI User Guide 95
Page 96

Application Agent system configurations96
Page 97

3 Preparation for using Application Agent
This chapter explains the flow of environment setup required for using Application Agent, and gives
details on each step in the environment setup. The descriptions in this chapter apply to the Application
Agent CLI.
Setting up an environment for Application Agent
Table 4-1 shows the procedures for setting up an environment for Application Agent and the tasks
required for each server. To set up the environment, refer to the tasks marked "Needed" for each type
of server in the table.
Sometimes Application Agent commands need to be executed during environment setup. Administrator
permissions are required to execute Application Agent commands. For details on user permissions
for executing commands, see “Permissions required for users executing commands” on page 233.
NOTE:
If you omit specifying the parameters for setting up an environment or specify an invalid value (a
value that cannot be set), the default values will be used.
Table 9 Application Agent environment setup tasks needed for each kind of server
File serv-
Environment setup task
er
or
database
Backup
server
File name
server
Set up the
Set up the environment for
prerequisite
products.
#1
volume replication functionality of
the storage
system.
Set up RAID
Manager
Set up the
tape backup
management
software
Not
needed
Not
needed
#2
Not
needed
NeededNeeded
#2
RAID Manager configuration
definition file (horcmn.conf)
--
--Needed
Sections and
documents for
reference
Documentation
for the storage
system
Setting up RAID
Manager, page 100
Documentation
for the tape
backup management software
Application Agent CLI User Guide 97
Page 98

Environment setup task
Set up Application Agent
operations.
Specify settings for linkage
with RAID Manager.
Create a cluster information
configuration definition file.
File server
or
database
server
Backup
server
NeededNeeded
NeededNeeded
Not neededNeeded
File name
Application Agent configuration
definition file (init.conf)
RAID Manager-linkage definition
file (DEFAULT.dat)
--NeededNeededCreate dictionary map files.
Cluster information configuration
definition file (cluster-name.dat)
Sections and
documents for
reference
Setting up operation of Application
Agent, page 106
Setting up Application Agent
for linkage with
RAID Manager, page 115
Creating dictionary map
files, page 130
Specifying
cluster configuration settings
and creating a
definition
file, page 136
Create a database configuration definition file (when the
backup is of an SQL Server
database).
Specify the
SQL Server
Specify settings related
to linkage
with an SQL
#3
server
Specify settings for using VSS
(when the backup is of a file
system or an Exchange
database).
Create a definition file for the
cascade configuration (when
backing up an Exchange
database)
login timeout
option
Specify the
SQL Server
automatic
recovery
time
Creating a
Not neededNeeded
Not neededNeeded
NeededNeeded
Not neededNeeded
Database configuration definition
file (instance-name.dat)
sqlinit_instance-name.conf
VSS definition file
(vsscom.conf)
Definition file for the cascade
configuration (Exchange-virtual-
server-name.dat)
database configuration
definition
file, page 142
Specifying settings related to
linkage with an
SQL Server, page 144
Specifying settings for using
VSS, page 147
Creating a cascade configuration definition
file for Exchange database
backup, page 151
Preparation for using Application Agent98
Page 99

Environment setup task
File server
or
database
server
Backup
server
File name
Sections and
documents for
reference
Set up linkage with a tape
backup management software.
Specify settings for batch
operations.
Update the dictionary map
files.
Perform preparation for executing extended commands.
Specify settings for sending
mail.
Not
needed
Needed
Needed
Needed
Not neededNeeded
Configuration definition file for
linkage with a tape backup management software (DE-
FAULT.dat)
Configuration definition file for
tape backup
Any fileNeededNeeded
#4
User script file (any file name)Not neededNeededCreate a user script.
Mail send definition file
(mail.conf)
--
--NeededNeeded
Setting up linkage with a
tape backup
management
software, page 155
Creating a list
file, page 161
Updating a
dictionary map
file, page 164
Preparations
required before
executing extended commands, page 181
Creating a user
script, page 203
Specifying settings for sending
mail, page 212
Back up the operating environment of Application Agent.
Create an Exchange environment settings file.
Exchange environment settings
Not neededNeeded
file (Exchange-environment-
settings-file-name.conf)
--NeededNeeded
Legend:
Needed: This setup task is needed.
Not needed: This setup task is not needed.
--: File setting is not required.
#1
To use SQL Server's log-shipping functionality, the source server and distribution-destination
servers must have the same environment settings as the database server.
#2
In each storage system, set up the volume replication functionality of the storage system.
#3
Backing up the
Application
Agent operating environment, page 214
Creating the
Exchange environment configuration
file, page 219
Application Agent CLI User Guide 99
Page 100

Specify these settings when a command has ended with an error (with the error message
KAVX1008-E).
#4
This is not required for a backup server.
When a primary volume exists in the backup server, the dictionary map files must be updated.
When the primary volume does not exist in the backup server, updating of the dictionary map
files is not necessary.
Setting up RAID Manager
To back up data by using Application Agent, you need to create a RAID Manager configuration
definition file (horcmn.conf, when n is the instance number) for each instance, to match the intended
usage.
The location of the RAID Manager configuration definition file (horcmn.conf) is as follows:
system-drive\Windows
NOTE:
• Do not specify a path to the configuration definition file in the HORCM_CONF environment variable.
• When using the Device Manager agent on the same host as Application Agent, do not set the
server.agent.rm.pairDefinitionForm property in the server.properties file. For
details about the server.agent.rm.pairDefinitionForm property, see the
Command View Advanced Edition Suite Software Administrator Guide
HP P9000
.
In Application Agent, a pair of a primary volume and secondary volume is managed as a copy group.
A copy group is defined by a combination of dev_group and dev_name specified in a RAID
Manager configuration definition file.
Application Agent does not allow duplication of copy group names on the same server. If more than
one RAID Manager instance is activated, make sure that the combination of dev_group and
dev_name is unique among all the RAID Manager configuration definition files.
If the system contains both a copy group that is subject to Application Agent backup operation and
a copy group that is not subject to Application Agent backup operation, the conditions below must
be met. If an Application Agent command is executed when the conditions below are not met, pair
volumes that are not subject to backup operation will enter an unexpected state.
• A copy group that is subject to Application Agent backup operation and a copy group that is not
subject to Application Agent backup operation must be defined with different dev_group names.
• The primary volumes of all copy groups defined with the same dev_group name as a copy group
that is subject to Application Agent backup operation must be connected to a database server or
file server.
In addition, HP recommends that you define pair volumes that are not subject to Application Agent
backup operation in the RAID Manager configuration definition file (horcm.conf) of a RAID Manager
instance that is different from the one used by Application Agent.
Application Agent supports the HORCM_LDEV section of the RAID Manager configuration definition
file (horcmn.conf) if the RAID Manager version is 01-18-03/06 or later. Application Agent supports
the HORCM_ALLOW_INST and HORCM_LDEVG sections in configuration definition files (horcmn.conf)
if the RAID Manager version is 01-24-03/12 or later.
Preparation for using Application Agent100
 Loading...
Loading...