Page 1

IF
2
Network Reader
User Guide
Page 2

Disclaimer
Honeywell International Inc. (“HII”) reserves the right to make changes in specifications and other information contained in
this document without prior notice, and the reader should in all cases consult HII to determine whether any such changes
have been made. The information in this publication does not represent a commitment on the part of HII.
HII shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential
damages resulting from the furnishing, performance, or use of this material. HII disclaims all responsibility for the selection and use of software and/or hardware to achieve intended results.
This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated into another language without the prior written consent of HII.
Copyright 2011-2020 Honeywell International Inc. All rights reserved.
Web Address:
www.honeywellaidc.com
Trademarks
Other product names or marks mentioned in this document may be trademarks or registered trademarks of other companies and are the property of their respective owners.
The word Intermec, the Intermec logo, and Ready-to-Work are either trademarks or registered trademarks of Intermec by
Honeywell.
This product includes copyrighted software that is licensed under GPL v2 (www.gnu.org/licenses/old-licenses/gpl-
2.0.html) or LGPL v2.1 (www.gnu.org/licenses/lgpl-2.1.html). You may obtain the complete Corresponding Source code
from Honeywell (www.honeywell.com) for a period of three years after Honeywell’s last shipment of this product. This offer
is valid to anyone in receipt of this information
This product includes cryptographic software written by Eric Young (EAY@cryptsoft.com).
Part of the software embedded in this product is gSOAP software. Portions created by gSOAP are Copyright (C) 2001–
2004 Robert A. van Engelen, Genivia inc. All Rights Reserved.
In no event shall the author be liable for any direct, indirect, incidental, special, exemplary, or consequential damages
(including, but not limited to, procurement of substitute goods or services; loss of use, data, or profits; or business interruption) however caused and on any theory of liability, whether in contract, strict liability, or tort (including negligence or otherwise) arising in any way out of the use of this software, even if advised of the possibility of such damage.
ACE(TM), TAO(TM), CIAO(TM), and CoSMIC(TM) (henceforth referred to as “DOC software”) are copyrighted by Douglas C.
Schmidt and his research group at Washington University, University of California, Irvine, and Vanderbilt University, Copyright (c) 1993–2006, all rights reserved.
For patent information, refer to www.hsmpats.com.
Page 3

TABLE OF CONTENTS
Customer Support ....................................................................................................................... vii
Technical Assistance ............................................................................................................ vii
Product Service and Repair ............................................................................................... vii
Limited Warranty ................................................................................................................... vii
Chapter 1 - About the RFID Reader ............................................................... 1
About the IF2.................................................................................................................................... 1
About the LEDs......................................................................................................................... 2
About the Ready-to-Work Indicator ................................................................................. 3
About the Network and Power Ports ................................................................................ 3
About the Top Panel Ports.................................................................................................... 4
How to Communicate with the IF2.......................................................................................... 5
Assign an Initial IP Address .................................................................................................5
Use the Web Browser Interface ..........................................................................................7
Save Configuration Changes........................................................................................ 8
Disable Help in the Web Browser Interface ............................................................ 9
How to Install the IF2.................................................................................................................... 9
How to Ground the IF2 ..........................................................................................................9
How to Provide Adequate Heat Sinking....................................................................... 10
Install the IF2.......................................................................................................................... 10
Connect the IF2 to Your Network ................................................................................... 11
Set the Date and Time ............................................................................................................... 12
How to Use the IF2 Securely................................................................................................... 12
IF2 Network Reader User Guide i
Page 4

Chapter 2 - Configure Network Settings................................................... 13
Configure the Settings for Your Network ...........................................................................13
Configure Ethernet Settings.............................................................................................14
Configure Common Network Settings..........................................................................15
Configure Security ......................................................................................................................16
Control Access Services......................................................................................................17
Set Up Logins..........................................................................................................................18
Configure the IF2 to Use a Password Server .......................................................18
Change the Default Login...........................................................................................20
Disable Access Through the Serial Port .......................................................................21
Manage Certificates ...................................................................................................................21
View Certificates ....................................................................................................................21
Install and Uninstall Certificates ....................................................................................22
Chapter 3 - Develop and Use RFID Applications...................................... 25
About the IF2 Configurations .................................................................................................25
RFID Applications and the IF2................................................................................................26
Use the RFID Resource Kit.................................................................................................26
Create RFID Applications..........................................................................................................26
About RFID Services ...................................................................................................................26
Configure BRI Settings..............................................................................................................27
Change BRI Attribute Settings.........................................................................................27
About BRI Attribute Settings.............................................................................................27
Tag Types............................................................................................................................28
Read Tries...........................................................................................................................28
Write Tries ..........................................................................................................................28
Lock Tries ...........................................................................................................................28
Field Separator ................................................................................................................28
ID Report ............................................................................................................................28
No Tag Report...................................................................................................................29
Report Timeout ................................................................................................................29
Timeout Configuration Mode ....................................................................................29
Select Tries ........................................................................................................................29
ii IF2 Network Reader User Guide
Page 5

Unselect Tries ...................................................................................................................29
Session ................................................................................................................................30
Initial Q................................................................................................................................30
Initialization Tries............................................................................................................30
Schedule Option..............................................................................................................30
ID Tries.................................................................................................................................30
Antenna Tries ....................................................................................................................30
EPCC1G2 Advance Medium Access Mode ...........................................................30
Dense Reader Mode.......................................................................................................31
Antenna Field Strength 1 to 4....................................................................................31
Antenna Sequence: First through Eighth..............................................................31
Configure the BRI Server ....................................................................................................31
View the BRI Server Log ......................................................................................................32
Configure LLRP Settings ..........................................................................................................33
Chapter 4 - Install Applications on the IF2 with Expanded Memory
Option.................................................................................................................35
Create a Configuration File......................................................................................................35
Auto-Start Applications at Boot Time ..................................................................................36
About .NET Support ....................................................................................................................36
About Java Support.....................................................................................................................36
Execute Java Applications .................................................................................................37
Java Support for Microsoft SQL Server and Sybase.........................................37
Install RFID Applications...........................................................................................................38
Manage Applications ...........................................................................................................38
About the Edgeware Applications .........................................................................................39
Upgrade or Install Edgeware Applications..................................................................39
About the Developer Tools........................................................................................................39
Test the GPIO Interfaces.....................................................................................................40
Send BRI Commands and Running Scripts................................................................40
Load and Run a BRI Script.................................................................................................40
Use the Workbench...............................................................................................................41
IF2 Network Reader User Guide iii
Page 6

Chapter 5 - Manage, Troubleshoot, and Upgrade the IF2 ..................... 43
Manage the IF2 ............................................................................................................................43
Use the Device Configuration Web Service.......................................................................43
Open a Serial or USB Connection to the IF2.....................................................................44
Open a Serial Connection to the IF2 .............................................................................45
Open a USB Connection to the IF2 ................................................................................45
Maintain the IF2...........................................................................................................................47
View the System Log............................................................................................................47
View the About Screen.........................................................................................................48
Use the LEDs to Locate the IF2.......................................................................................49
Restore the IF2 to the Default Configuration ............................................................49
Restore Default Settings with the Web Browser ....................................................... 49
Restore Default Settings with the Reset Switch........................................................50
Restore Default Settings with a Serial Connection..................................................50
Reboot the IF2 ........................................................................................................................50
Troubleshoot the IF2 ..................................................................................................................51
Problems While Working with RFID ...............................................................................51
Connect Directly to the RFID Module ...........................................................................51
Problems With Connectivity .............................................................................................53
Call Customer Support ..............................................................................................................53
Upgrade Firmware.......................................................................................................................54
Chapter 6 - Use the IF2 GPIO Interfaces ................................................... 55
About the GPIO Interfaces .......................................................................................................55
Access the Interfaces .................................................................................................................55
Use the Input Interfaces ...........................................................................................................56
GPIO Input Signal Descriptions ......................................................................................56
IF2 Powered Input.................................................................................................................56
Isolated Input Interface ......................................................................................................56
Open Collector Input Interface ........................................................................................57
Use the Output Interfaces........................................................................................................57
GPIO Output Specifications..............................................................................................57
Switch the High Side with IF2 Power.............................................................................58
iv IF2 Network Reader User Guide
Page 7

Switch the Low Side with IF2 Power...............................................................................58
Switching the High Side With External Power ...........................................................59
Drive a DC Relay to Control an AC Load.......................................................................59
Use the Power Interface ............................................................................................................60
Appendix A - Specifications ..........................................................................61
IF2 Specifications ........................................................................................................................61
RFID Specifications.....................................................................................................................62
Port Pin Assignments.................................................................................................................62
GPIO Port..................................................................................................................................62
GPIO Port Pin Assignments........................................................................................62
Serial Ports (COM1)..............................................................................................................63
Serial Port Pin Assignments .......................................................................................63
Ethernet Port...........................................................................................................................64
Ethernet Port Pin Assignments.................................................................................64
IF2 Network Reader User Guide v
Page 8

vi IF2 Network Reader User Guide
Page 9

Customer Support
Technical Assistance
To search our knowledge base for a solution or to log in to the Technical Support
portal and report a problem, go to www.hsmcontactsupport.com.
For our latest contact information, see www.honeywellaidc.com/locations.
Product Service and Repair
Honeywell International Inc. provides service for all of its products through service
centers throughout the world. To obtain warranty or non-warranty service, return
your product to Honeywell (postage paid) with a copy of the dated purchase record.
To learn more, go to www.honeywellaidc.com and select Service & Repair at the
bottom of the page.
Limited Warranty
For warranty information, go to www.honeywellaidc.com and click Resources >
Product Warranty.
IF2 Network Reader User Guide vii
Page 10

viii IF2 Network Reader User Guide
Page 11

CHAPTER
1
ABOUT THE RFID READER
This chapter introduces the IF2 Network Reader, explains the ports and LEDs, and
explains how the reader fits into your network. It contains these topics:
• About the IF2
• How to Communicate with the IF2
• How to Install the IF2
• Set the Date and Time
• How to Use the IF2 Securely
About the IF2
The IF2 Network Reader is an RFID reader that provides connectivity between tag
data and an enterprise system.
7
IF2 Network Reader
Note: The IF2 does not ship with RFID antennas. For more information on these
accessories, contact your sales representative.
IF2 Network Reader User Guide 1
Page 12
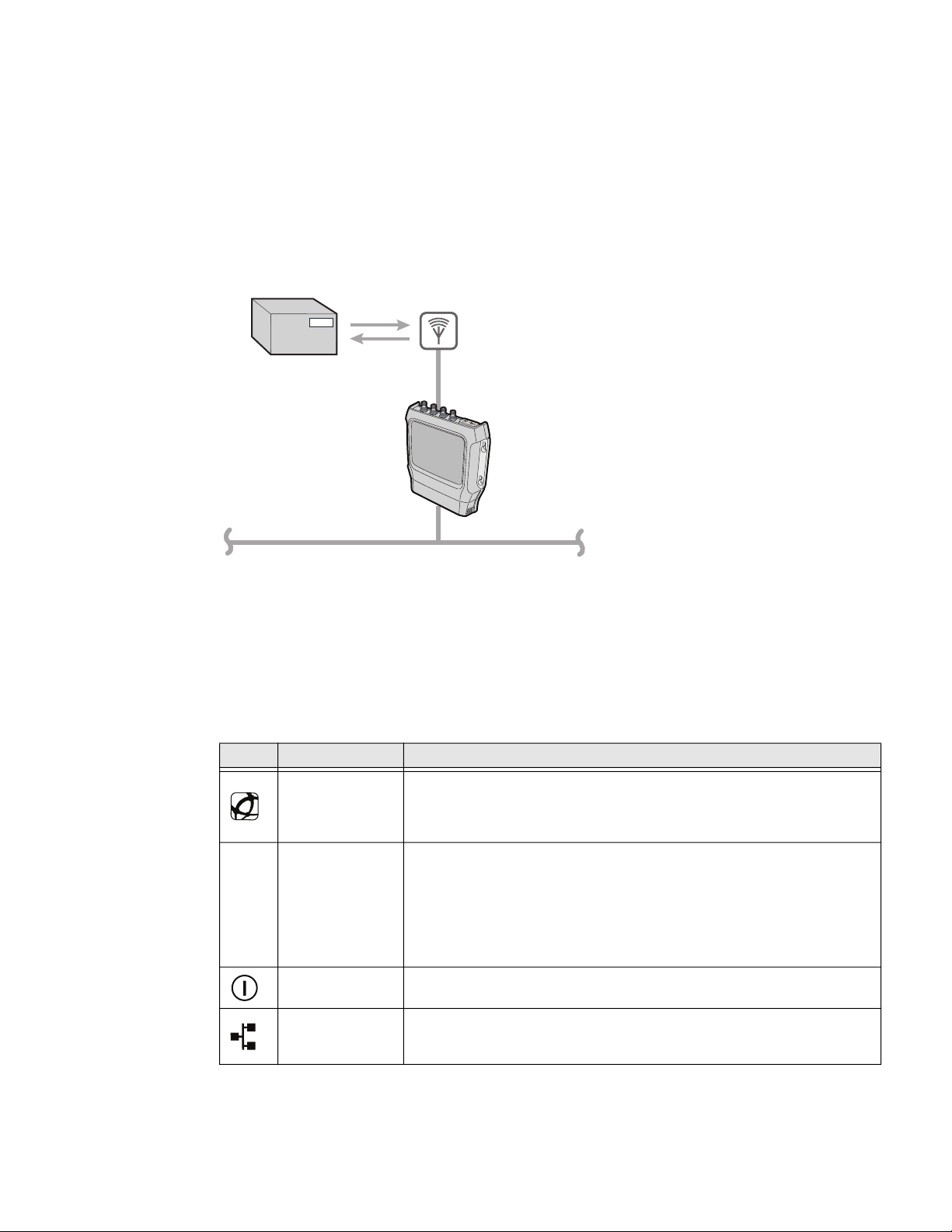
The IF2 comes in a standard configuration with no internal memory, or an
Container
with RFID tag
RFID
antenna
IF2
PoE
expanded memory option.
• For the standard IF2, the applications you develop reside on a remote server
which communicates with the reader, and all information processing is
processed through the server.
• For the IF2 with Expanded Memory Option, the applications you develop can be
hosted and run locally on the reader.
The reader forwards RFID tag data to the Ethernet network as shown in the next
illustration.
About the LEDs
IF2 in a Wired Ethernet Network
The IF2 has six LEDs that indicate the status of the reader during operation. Use
the next table to identify the LED icons on the front panel of the IF2.
IF2 LED Descriptions
Icon Name Description
• On when an application is communicating with the IF2 BRI server or
an LLRP client has connected.
• Blinks when no application is communicating with the IF2. For more
information, see "About the Ready-to-Work Indicator" on page 3.
• Green if Power Over Ethernet (POE) is enabled.
• Red if a fault condition is detected. For example, if the power
converter for POE does not provide enough power to the IF2, the
POE LED stays red indicating a fault condition.
• Red if the POE converter is not capable of meeting 802.3 AT
standards. If this is the case, the IF2 continues to run if it has
enough power.
• Off when there is no Ethernet connectivity.
• On when an Ethernet link is detected.
• Flashes when there is activity on the Ethernet network.
Intermec
Ready-toWork™ indicator
Power Over
Ethernet
Power On when the IF2 has power.
Wired LAN
2 IF2 Network Reader User Guide
Page 13
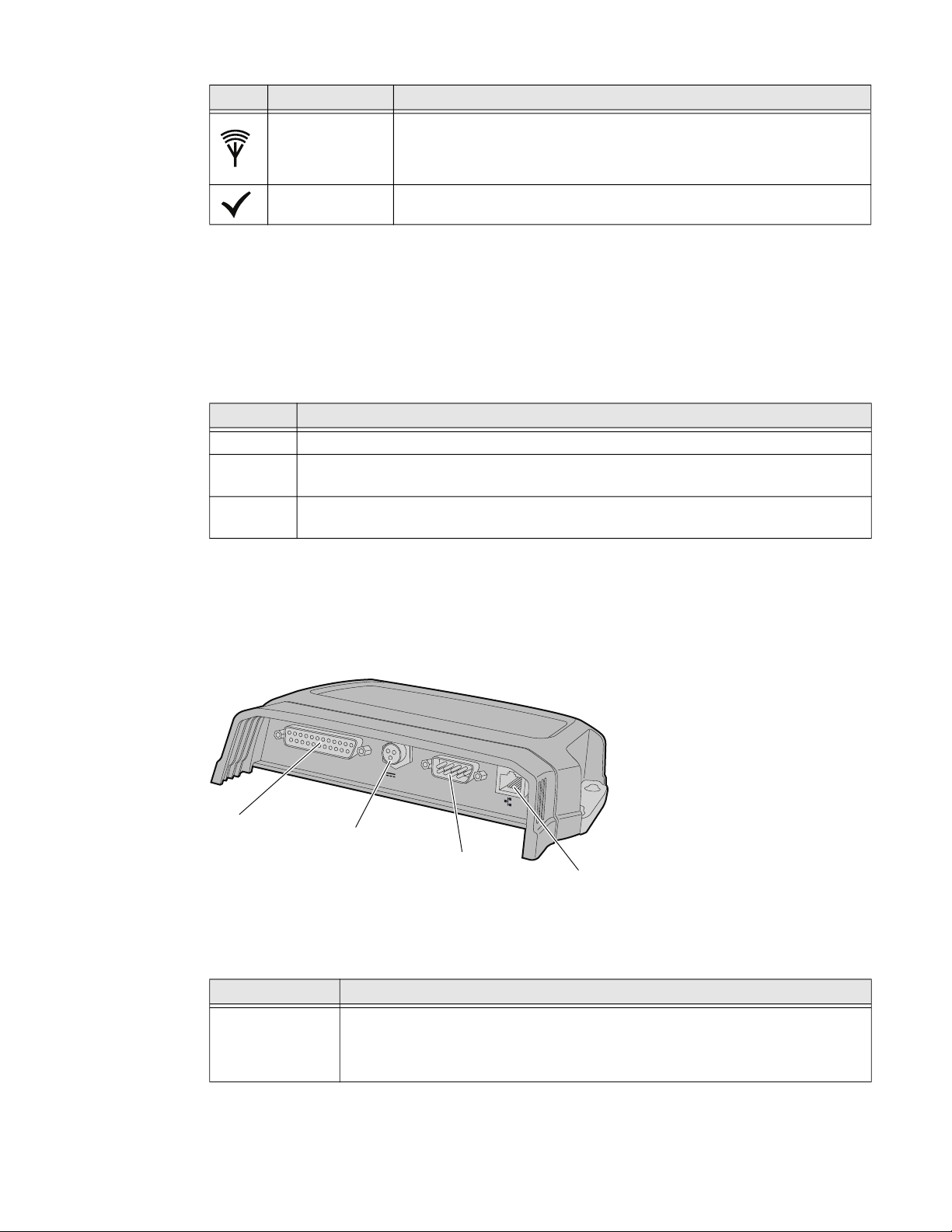
Icon Name Description
GPIO
IOIOI
GPIO port
DC power port
COM 1
Ethernet port
(high power POE)
RFID status
Tag ID Flashes when an RFID tag ID is successfully read or written to.
• Green if RF power is being transmitted.
• Red if an antenna fault is detected, or if the reader cannot output the
requested RF power level.
• Off if RF power is off.
About the Ready-to-Work Indicator
The blue Ready-to-Work indicator shows when an application is communicating
with the Basic Reader Interface (BRI) server or LLRP client on the IF2. The next
table explains the different states of the Ready-to-Work indicator.
Ready-to-Work Indicator Status Descriptions
Status Description
Off IF2 does not have power.
Blinking IF2 is initializing and not yet ready to use, or no application is currently communicating
with the IF2 BRI or LLRP server or LLRP server.
Steady An application is communicating with the BRI server or an LLRP client has connected
to the IF2.
For more information on the BRI server, see "Configure the BRI Server" on page 31.
About the Network and Power Ports
The IF2 network and power ports are located under the cable cover.
IF2 Network and Power Ports
IF2 Port Descriptions
Port Description
GPIO General purpose input/output (GPIO) port that connects the IF2 to industrial
controls such as relays or indicators.
For more information on the IF2 GPIO interfaces, see "About the GPIO
Interfaces" on page 55.
IF2 Network Reader User Guide 3
Page 14
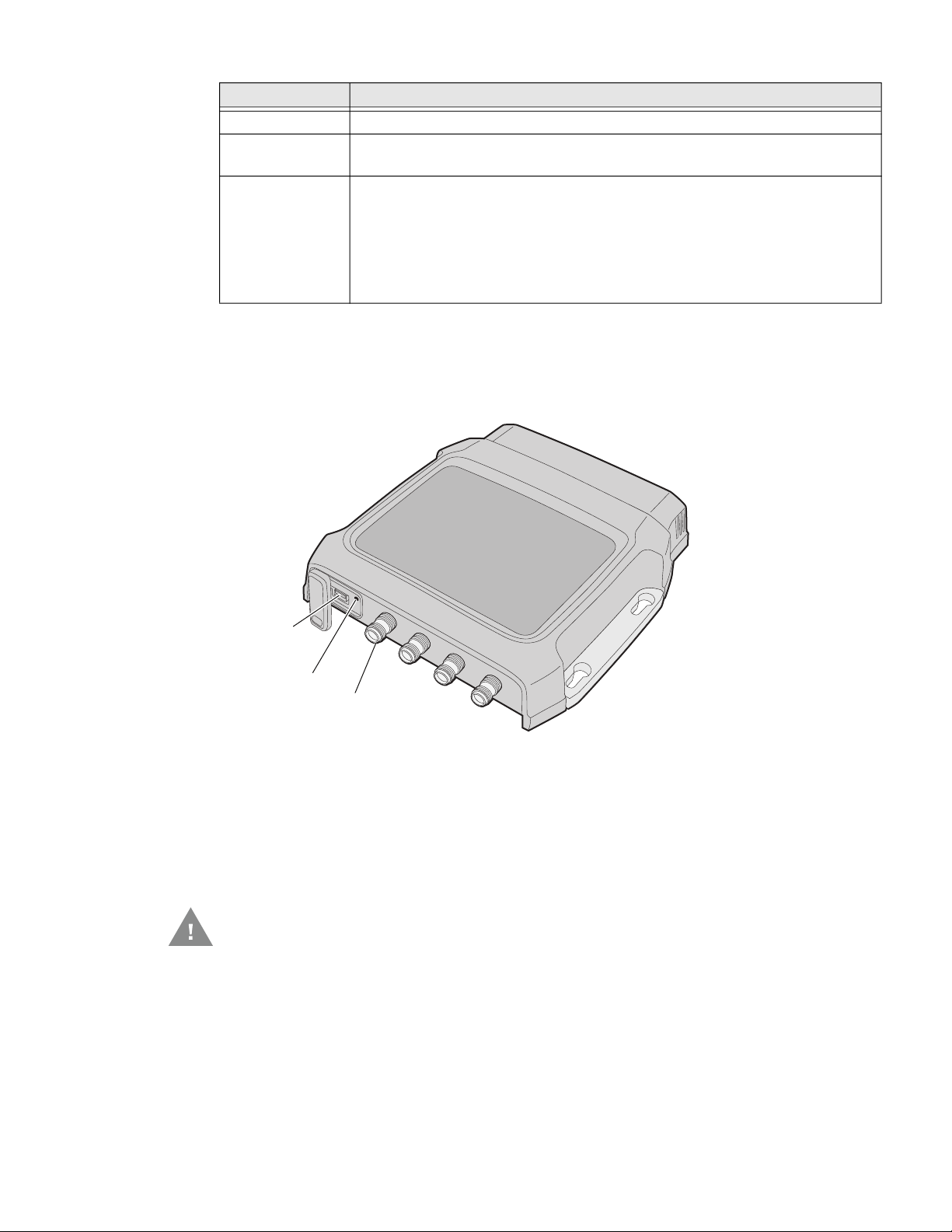
Port Description
Antenna port
(4 places)
Reset switch
USB service
port
DC power Connects the reader to a 12 volt DC power source.
COM1 Connects the IF2 to a desktop PC for configuration. Use an RS-232 null modem
cable (P/N 059167).
Ethernet 10BaseT/100BaseTx port that connects the reader to your Ethernet network.
The reader auto-negotiates with the server to set the best data rate. This port
uses MDI/MDI-X auto-switching so you can connect either a standard Ethernet
cable or a crossover cable.
The Ethernet port also supports POE. To use POE you need an 802.3at
compliant power converter. For more information, contact your sales
representative.
About the Top Panel Ports
The IF2 top panel ports consist of four antenna ports, a reset switch, and a USB
service port.
IF2 Top Panel Ports
The IF2 RFID antenna ports uses Reverse TNC connectors. Make sure you have
appropriate antennas and cables for your IF2. For help, contact your sales representative.
Note: USB is not supported on the IF2 with Expanded Memory Option.
Caution: Government regulatory agencies require that this RFID reader
uses only approved antennas. Therefore, this reader uses a
custom antenna connector. Do not use antennas not approved
for use with this reader.
4 IF2 Network Reader User Guide
Page 15

How to Communicate with the IF2
By default, the IF2 is configured to be a DHCP client and accepts offers from any
DHCP server. Therefore, the IF2 will work out of the box if you connect it to your
network and use a DHCP server to assign it an IP address. In this case, you configure the IF2 using the web browser interface from a desktop PC. For help, see "Use
the Web Browser Interface" on page 7.
However, if you are not using a DHCP server to assign an IP address, you use a
serial communications program such as HyperTerminal to assign a static IP
address. For help, see the next section, “Assigning an Initial IP Address.”
After the IF2 has been assigned an IP address, connect it to your network and then
complete the configuration by using a web browser interface from a desktop PC.
For help, see "Use the Web Browser Interface" on page 7.
Assign an Initial IP Address
Follow this procedure to assign an initial IP address to the IF2. After you assign the
IP address, connect the IF2 to your network and use the web browser interface to
complete the configuration.
1. Open a serial connection to the IF2. For help, see "Open a Serial or USB
Connection to the IF2" on page 44.
2. Type config and press Enter, and then type config again in the Password
field and press Enter. The IF2 Initial Configuration screen appears.
IF2 Network Reader User Guide 5
Page 16

3. If DHCP is enabled, press D. DHCP is disabled and the Ethernet Configuration
Options screen appears.
4. To set the IP address, press 1 and enter the static IP address in the entry field.
5. Press Enter. The static IP address is set. If you do not need to set the subnet
mask or IP router values, you can now continue to configure the IF2 through
the web browser interface. For help, see "Use the Web Browser Interface" on
page 7.
If you need to change the values for subnet mask or the IP router, continue with
the next step.
6. To set the subnet mask, press 2 and enter the subnet mask value in the entry
field. Press Enter to save the changes.
To set the IP router address, press 3 and enter the IP router address in the entry
field. Press Enter to save the changes.
7. (Optional) To change the Ethernet link speed, press L and choose a link speed
from the list of options:
Ethernet Link Speed Options
To choose this speed: Press:
Auto detect (default) A
100 Mbps - full duplex 1
100 Mbps - half-duplex 2
10 Mbps - full duplex 3
10 Mbps - half duplex 4
Keep the current selection and close this dialog box Q
8. Press Q to close the Initial Configuration screen.
9. Disconnect the null-modem cable from the IF2.
The IF2 is now ready to be connected to your network. See "Connect the IF2 to Your
Network" on page 11.
6 IF2 Network Reader User Guide
Page 17
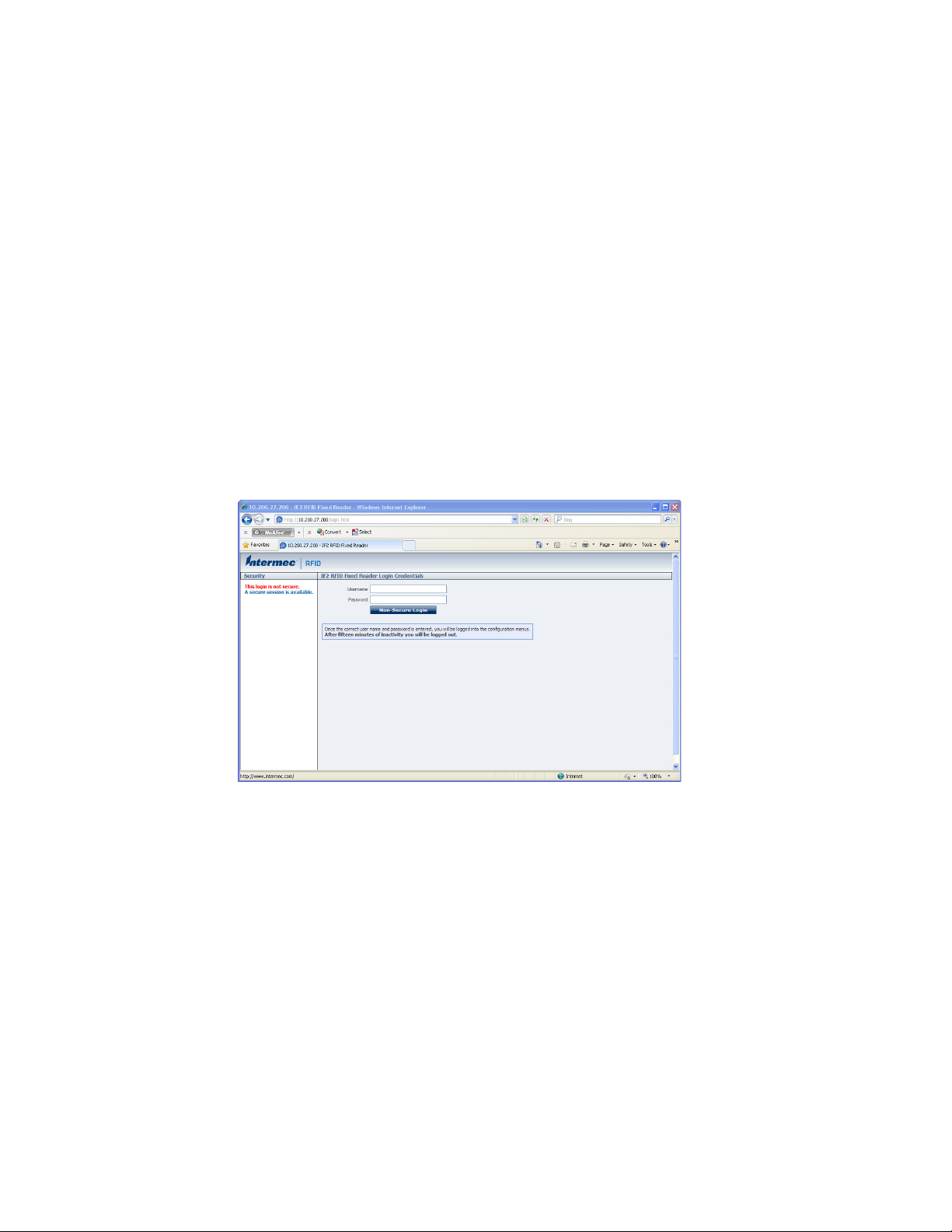
Use the Web Browser Interface
After the IF2 is assigned an IP address, configure the IF2 using the web browser
interface.
To use the web browser interface, the IF2 must be connected to your wired network.
For help, see "Connect the IF2 to Your Network" on page 11.
When using the web browser interface, remember that your session automatically
terminates if you do not use it for 15 minutes.
Note: If you access the Internet using a proxy server, add the IF2 IP address to your
Exceptions list. The Exceptions list contains the addresses that you do not want to
use with a proxy server.
1. Determine the IP address of the IF2. If a DHCP server assigned the IP address,
you need to get the IP address from that server.
2. Start the web browser.
3. In the browser address field, enter the IP address, and press Enter. The IF2 login
screen appears.
Or, for a secure session, click A secure session is available. The secure login
screen appears.
Note: If a security alert message appears:
• Click Yes to continue to the secure login screen.
• Click No to cancel.
• Click View certificate to see the security certificate before continuing.
IF2 Network Reader User Guide 7
Page 18
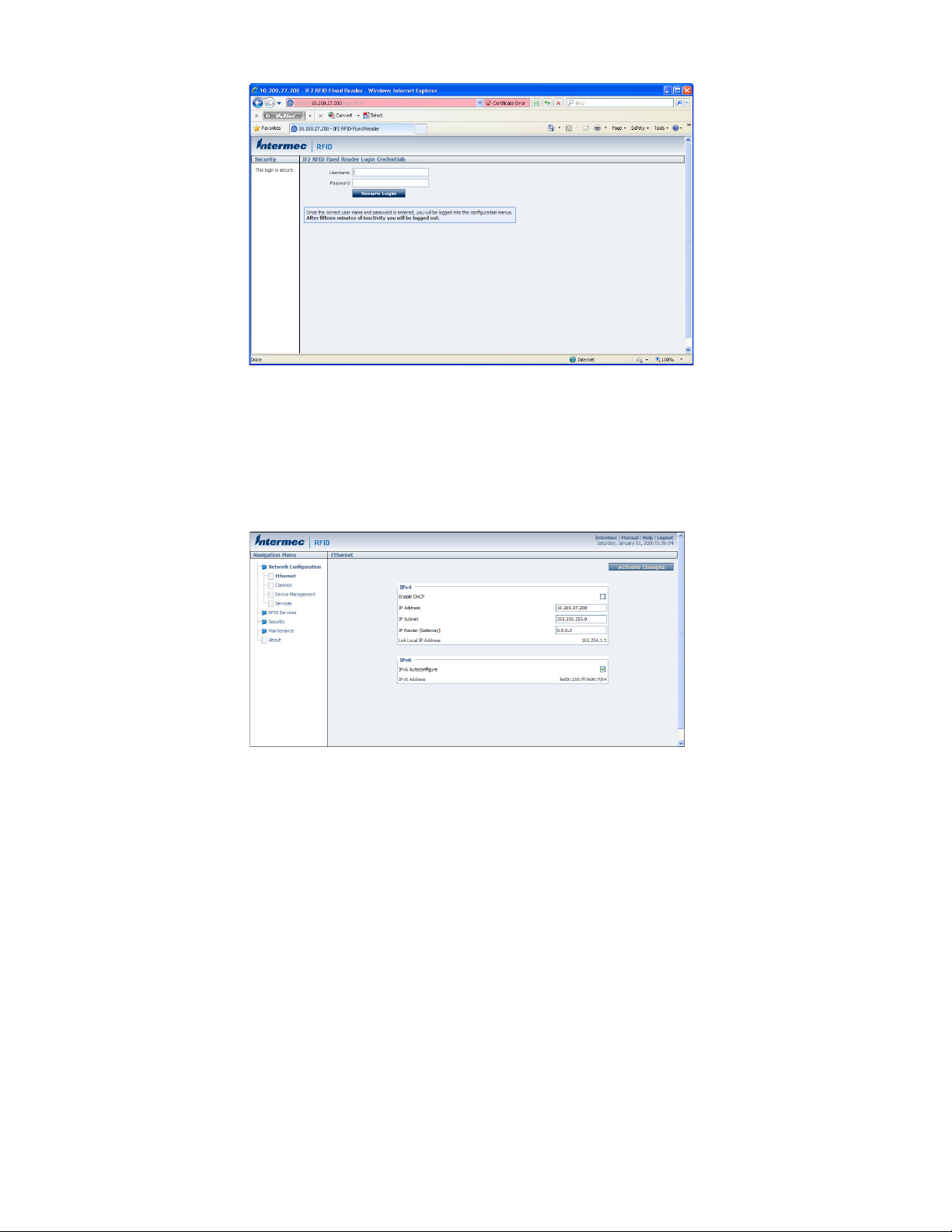
IF2 Secure Login Screen
4. If necessary, enter a user name and password. The default user name is
intermec and the default password is intermec. You can define the user name
and password. For help, see "Set Up Logins" on page 18.
5. Click Login (or Secure Login in the secure login screen). The Ethernet screen
appears and your web browser session is established.
For help with configuring network settings, see "Configure the Settings for Your
Network" on page 13.
For help with configuring RFID reader settings, see "Configure BRI Settings" on
page 27.
For more information on other methods for managing the IF2, see "Manage the
IF2" on page 43.
Save Configuration Changes
After you make configuration changes, click Activate Changes in the browser window to save your changes and immediately make the changes active.
Changes are discarded if you click another link in the browser window without
clicking Activate Changes first.
8 IF2 Network Reader User Guide
Page 19
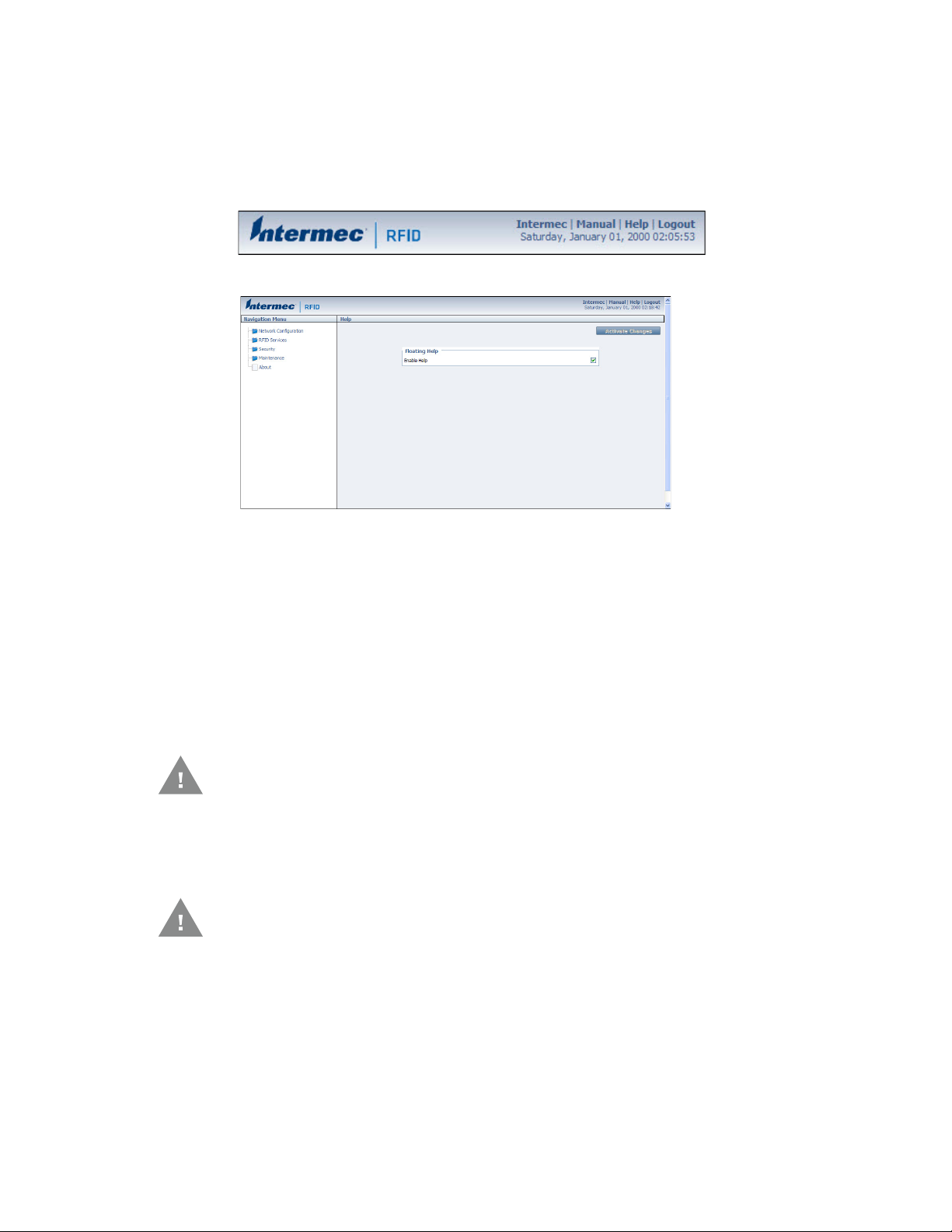
Disable Help in the Web Browser Interface
By default, the web browser interface shows help text as you move the cursor over
items in each screen. Follow the next procedure to disable the help text feature.
1. In the web browser interface, click Help in the upper right corner of the screen.
The Help screen appears.
2. Clear the Enable Help check box.
3. Click Activate Changes to save your changes and immediately make them
active. The Help text is disabled.
How to Install the IF2
This section explains how to properly install the IF2 reader and how to mount it to a
wall using the IF2 Network Reader Drilling Template Instructions that ship in the
box with the IF2.
Caution: The IF2 should be professionally installed. For more
information, contact your local Honeywell representative.
How to Ground the IF2
Caution: Make sure you properly ground the IF2 and all antennas. Proper
grounding of the IF2 and attached antennas will help mitigate
the buildup of static charge that may cause damage to the
reader.
Use these guidelines when grounding the IF2:
• Connect the IF2 case to earth ground.
• Connect each antenna rear ground plate to a good earth ground with a lowresistance wire or braid.
IF2 Network Reader User Guide 9
Page 20

Establish the earth ground connection by attaching a ground wire or braid to one
of the mounting nuts next to the data interface connectors or to any antenna terminal. The base of the IF2 case is magnesium and this surface will NOT provide
adequate grounding.
How to Provide Adequate Heat Sinking
The IF2 contains thermal protection to prevent it from being damaged by operation
at high temperatures. This protection disables the transmitter if it gets too hot. The
IF2 will not overheat in most cases if the ambient temperature is cooler than 40
ºF).
(104
Adding a heat sink to the rear plate of the IF2 may provide adequate cooling to
allow continuous reading operation in high temperature environments, such as
what you might encounter inside of an unventilated enclosure. Periodic external
triggering of the IF2 to read tags will help keep the internal temperatures low
enough to operate without an additional heat sink.
Note: Make sure you provide adequate heat sinking in high temperature environments if
you intend to leave the IF2 reading tags continuously. If you externally trigger the IF2
to read a tag for two seconds every 30 seconds, it will not require additional heat
sinking.
ºC
Install the IF2
1. Choose a mounting location that meets these environmental requirements:
2. Provide an adequate heat sink if the reader will operate continually or is
3. Use the IF2 Network Reader Drilling Template Instructions to drill holes in the
4. Mount the IF2 using your parts and screws.
• Operating temperature between
• Storage temperature between -30 ºC (-22 ºF) and 70 ºC (158 ºF).
• Humidity (non-condensing) between 5% to 95%.
mounted outside or in an enclosure.
mounting location.
-20 ºC (-4 ºF) and 55 ºC (131ºF).
10 IF2 Network Reader User Guide
Page 21
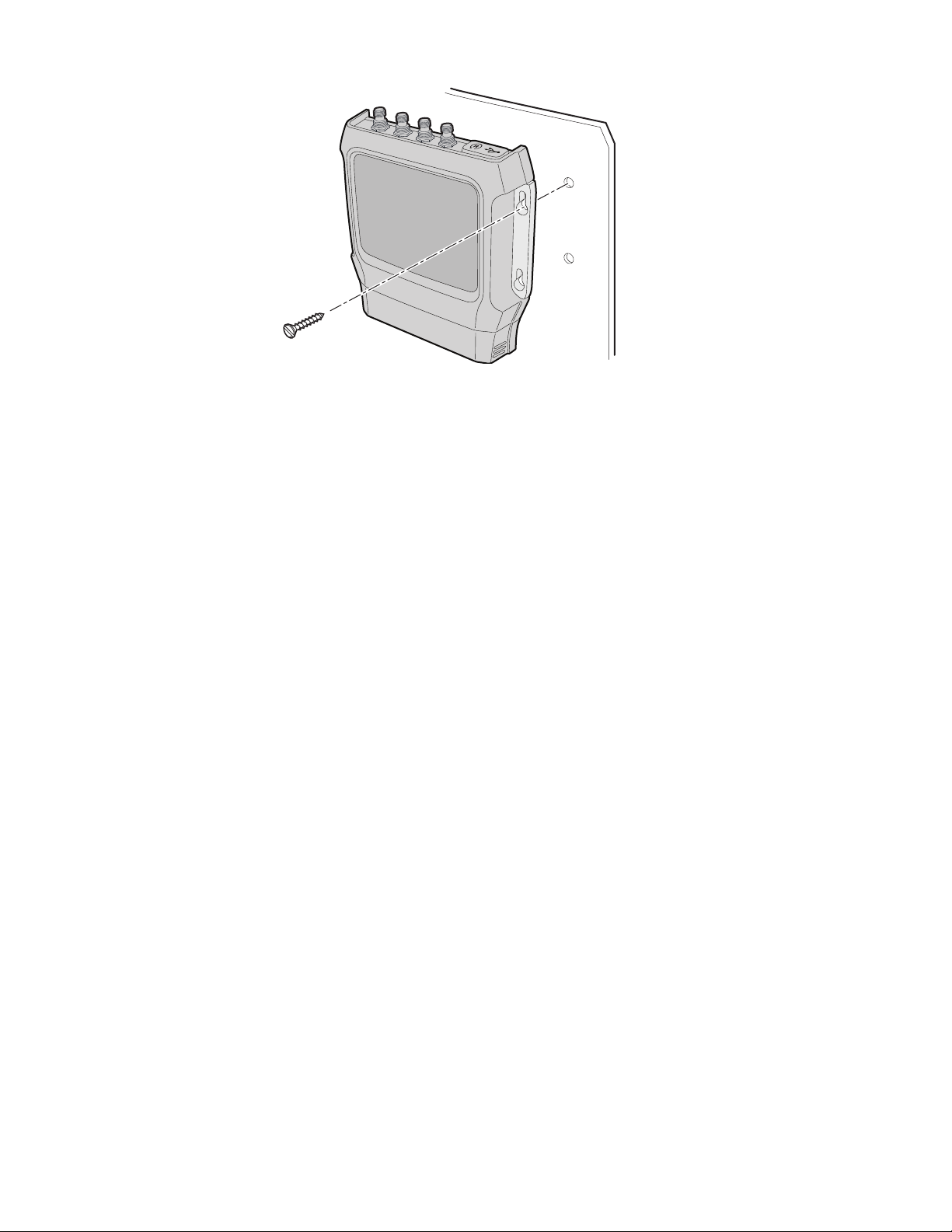
Note: The IF2 is certified to an IP53 environmental rating only when mounted as shown.
Mounting screw
(4 places)
5. Ground the IF2.
Connect the IF2 to Your Network
After you place the IF2 in its mounting location, you can connect it to your network.
1. Install the IF2 in its mounting location. For help, see "How to Install the IF2" on
page 9.
2. Attach one to four RFID antennas to the RFID antenna ports, starting with port
1. For help, see "About the Top Panel Ports" on page 4.
3. Connect an Ethernet cable to the IF2 Ethernet port.
4. Connect power to the IF2:
• If you are using DC power, connect the DC power cord to a power source and
to the power port on the IF2.
• If you are using Power Over Ethernet, connect the Ethernet cable to the
Ethernet port and use an 802.3at compliant power converter to power the
IF2.
When you apply power, the IF2 boots and the green Power LED turns on.
IF2 Network Reader User Guide 11
Note: If you are using a DHCP server, make sure the server is running before you connect
power to the IF2.
The IF2 is now ready to communicate with your network. Once the IF2 has been
assigned an IP address (either manually or from your DHCP server), you can use
the web browser interface to complete configuration. For help, see "Use the Web
Browser Interface" on page 7.
Page 22
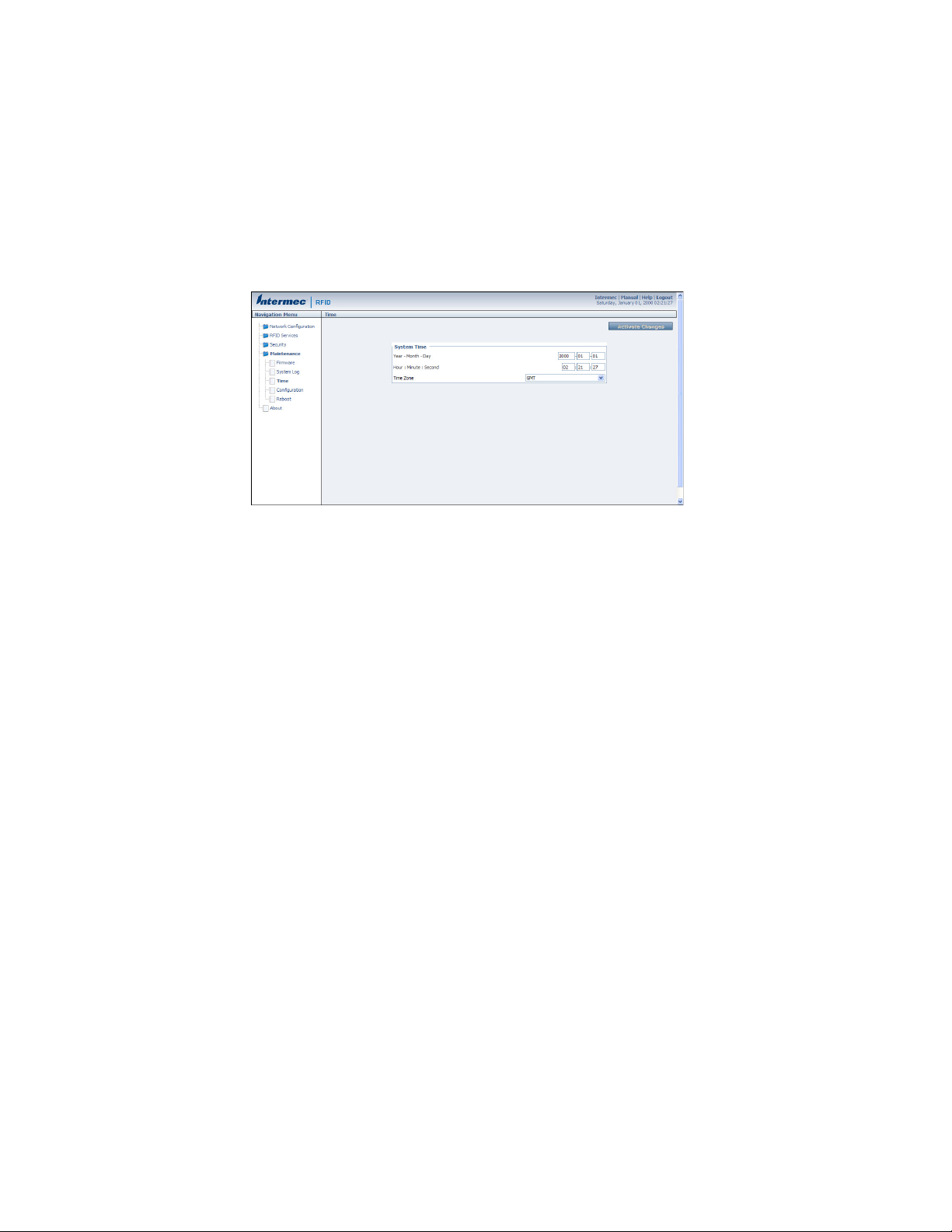
Set the Date and Time
After you have installed the IF2, you can set the date and time via the web browser
interface.
1. Connect to the IF2 via the web browser interface. For help, see "Use the Web
Browser Interface" on page 7.
2. In the web browser screen, click the date and time in the upper right corner. The
Time screen appears.
3. Choose your time zone from the drop-down list and then click Activate
Changes.
4. Enter the current month, day, and year in the entry fields.
5. Enter the current hour, minute, and second in the entry fields.
6. Click Activate Changes. The new time and date are set.
How to Use the IF2 Securely
To help protect the integrity and security of your data, the IF2 supports a variety of
secure access methods:
• You can use a secure web browser session (HTTPS) to access the IF2. For help,
see "Use the Web Browser Interface" on page 7.
• You can configure and use network security methods, or disable basic
configuration through the serial port. For help, see "Configure Security" on page
16.
12 IF2 Network Reader User Guide
Page 23

CHAPTER
2
CONFIGURE NETWORK SETTINGS
This chapter describes how to configure network settings for the IF2 and includes
these topics:
• Configure the Settings for Your Network
• Configure Security
• Manage Certificates
This chapter assumes that you are familiar with your network, networking terms,
and the type of security implemented by your network.
Configure the Settings for Your Network
You use the web browser interface to configure network settings. For more information on using the web browser, see "Use the Web Browser Interface" on page 7.
This chapter explains how to use the web browser interface to configure settings
for:
• wired Ethernet connections. For help, see the next section, “Configure Ethernet
Settings.”
• parameters common to the wired connections, such as DNS addresses and time
servers. For help, see "Configure Common Network Settings" on page 15.
• network security, such as passwords and access methods. For help, see
"Configure Security" on page 16.
• certificates. For help, see "Manage Certificates" on page 21.
From a device management standpoint, there are several other methods you can
use to configure network settings, including the web browsers and the Device Configuration web service. For more information on using these methods to configure
the IF2, see Chapter 5 “Manage, Troubleshoot, and Upgrade the IF2.”
IF2 Network Reader User Guide 13
Page 24

Configure Ethernet Settings
This section explains how to configure wired Ethernet settings using the web
browser interface.
If you are using a DHCP server, you may not need to configure Ethernet settings.
For more information, contact your network administrator.
1. From the menu, click Network Configuration or Ethernet in the left pane. The
Ethernet screen appears.
If DHCP is enabled, you see this screen:
If DHCP is disabled, the current values for IP address, subnet mask, and router
appear in entry fields:
2. Configure the Ethernet settings. For help, see the next table.
Note: Different settings appear in this screen depending on the current DHCP mode for the
IF2.
If you need to configure other network settings such as DNS addresses and
suffixes or a SYSLOG destination, see "Configure Common Network
Settings" on page 15.
3. Click Activate Changes to save your changes and immediately make them
active.
14 IF2 Network Reader User Guide
Page 25

Ethernet Settings Descriptions
Parameter Description
Enable DHCP Check this check box if you want the IF2 to get its IP address from a
DHCP server.
If this check box is not checked, you need to specify the IP address,
subnet mask, and IP router for your network.
IP Address IP address of the IF2. The IP address has the form x.x.x.x, where x is a
number from 0 to 255.
If DHCP is enabled, the currently assigned IP address appears in this
field.
If DHCP is disabled, specify the IP address in the entry field.
IP Subnet Subnet mask for this network. The subnet mask has the form x.x.x.x,
where x is a number from 0 to 255.
If DHCP is enabled, the currently assigned subnet mask appears in this
field.
If DHCP is disabled, you may need to specify the subnet mask for the
network.
IP Router (Gateway) IP address of the router. The IP address has the form x.x.x.x, where x is a
number from 0 to 255.
If DHCP is enabled, the currently assigned router address appears in
this field.
If DHCP is disabled, you may need to specify the router address for the
network.
Link Local IP Address IP address of the IF2 is only routable on the local IP subnet. The IF2
auto-negotiates with other devices on its Ethernet segment to obtain a
unique address, so no user configuration of the Link Local IP Address is
necessary. The IF2 will always have a Link Local IP Address, even if
another address is assigned through DHCP or statically via userconfiguration.
IPv6 Autoconfigure Enables IPv6 automatic configuration. Clear this check box to disable
IPv6 auto-configuration on the IF2.
Auto-configuration is enabled by default. If you disable autoconfiguration, you need to specify an IPv6 address, subnet mask, and
router.
IPv6 Address 128-bit IPv6 address for the IF2.
IPv6 Router 128-bit address for the IPv6 router.
Configure Common Network Settings
Common network settings are configuration items that apply to the IF2 network
interface. This section explains how to use the web browser interface to configure
these common network settings:
• Hostname
• Domain Name Server (DNS) addresses and suffixes
• Simple Network Time Protocol (SNTP) server addresses 1 and 2. For information
on public NTP servers, see http://support.ntp.org.
• Local time zone
• SYSLOG destination
IF2 Network Reader User Guide 15
Page 26

1. In the menu, click Network Configuration > Common. The Common screen
appears.
2. Configure settings. For help, see the next table.
3. Click Activate Changes to save your changes and immediately make them
active.
Common Network Settings Descriptions
Parameter Description
Hostname Name for this IF2. The default is “IF2<serial number of the IF2>”.
The hostname can be either a simple hostname, or a qualified domain
name (FQDN). If this IF2 obtains its IP address via DHCP, this
parameter is sent to the DHCP server. If the server supports it, this
field is used for dynamic DNS updates.
DNS Server 1 IP address of a domain name server that the IF2 uses to resolve DNS
names.
DNS Server 2 IP address of a second domain name server that the IF2 uses to
resolve DNS names.
DNS Suffix 1 Primary DNS suffix to be appended to unqualified names.
DNS Suffix 2 Secondary DNS suffix to be appended to unqualified names.
SNTP Server Name 1 DNS name or IP address of an SNTP or NTP server.
SNTP Server Name 2 DNS name or IP address of a second SNTP or NTP server.
Time Zone Time zone for this IF2. Choose the time zone from the drop-down list.
Default is GMT.
For more information, see "Set the Date and Time" on page 12.
SYSLOG Destination Domain name or IP address of the SYSLOG server.
Configure Security
Note: Before you configure security settings for this IF2, you should be familiar with the
type of security implemented for your network.
The IF2 supports a variety of security features to help maintain the integrity of your
secure network. You can:
• enable/disable access services.
16 IF2 Network Reader User Guide
Page 27

• change the default user name and password. For help, see "Set Up Logins" on
page 18.
• use a password server to maintain a list of authorized users who can configure
and manage the IF2. For help, see "Set Up Logins" on page 18.
• disable serial port access to the IF2. For help, see "Disable Access Through the
Serial Port" on page 21.
For general information on securely using the IF2, see "How to Use the IF2
Securely" on page 12.
Control Access Services
Access services are the different ways that users can access and configure the IF2.
You can control how developers access the IF2 by enabling or disabling these services:
• Web browser interface (secure and non-secure)
• Discovering the IF2 via Bonjour or Universal Plug and Play™ (UPnP) service
advertisement (enabled by default)
1. From the menu, click Network Configuration > Services. The Services screen
appears.
2. Enable or disable developer access services by checking or clearing the check
boxes, or by choosing options from the drop-down list. For help, see the next
table.
3. Click Activate Changes to save your changes and immediately make them
active.
IF2 Network Reader User Guide 17
Page 28

Access Services Descriptions
Service Description
Enable Web Server Enables access to the IF2 via the web browser interface.
Enable Bonjour Service
Advertisement
Enable UPnP Discovery Enables the IF2 to be discovered by Universal Plug and Play protocols.
Set Up Logins
To ensure login security for configuring or maintaining the IF2, you should use a
password server or at least change the default user name and password.
Select Enable Web Server (Insecure) to allow users to log in using either
a nonsecure (HTTP via port 80) or secure (HTTPS via port 443) web
interface.
Select Enable Web Server (Secure) to allow only the secure web
interface through port 443.
If both web server services are disabled, you need to restore the IF2 to the
factory defaults. For more information, see "Restore the IF2 to the Default
Configuration" on page 49.
Enables the IF2 to advertise services and be discovered by Bonjour zeroconfiguration networking. Bonjour is enabled by default.
To prevent errors when using Bonjour, make sure the IF2 hostname does
not include spaces. To set the hostname, see "Configure Common
Network Settings" on page 15.
UPnP is enabled by default.
• A password server is typically an embedded authentication server (EAS) or other
RADIUS server. To use a password server, you must have a password server on
the network that contains the user name/password database. On the IF2, you
need to enable RADIUS for login authorization.
When you attempt to log in to the IF2, you must enter a user name and password. This login is sent to the RADIUS server, which compares the login to its
list of authorized logins. If a match is found, you can log in to the IF2 with read/
write privileges.
For help, see the next section, “Configuring the IF2 to Use a Password Server.”
• If you do not want to use a password server, you should change the default login
user name and password, and create a read-only password. For help, see
"Change the Default Login" on page 20.
Configure the IF2 to Use a Password Server
If you use a password server to manage users who log in to this IF2, you need to tell
the IF2 how to communicate with the password server and then you need to configure the password server.
Note: If errors occur and you cannot log in to the IF2, restore defaults via a serial connection
to reset all passwords to default values. For help, see "Restore the IF2 to the Default
Configuration" on page 49.
18 IF2 Network Reader User Guide
Page 29

1. From the menu, click Security > Passwords. The Passwords screen appears.
2. Check the Enable RADIUS check box. A list of RADIUS configuration items
appears.
3. Configure the settings. For help, see the next table.
4. Click Activate Changes.
5. Configure the password server database. For help, see the documentation that
came with your server.
RADIUS Server Information Descriptions
Type Description
Enable RADIUS Enables RADIUS authentication for this IF2.
Primary Radius Server IP address or DNS name of the RADIUS server. If this field is blank,
the RADIUS client does not use this entry.
Secret Secret key for this RADIUS server.
Port Port number of the primary RADIUS server. Default is 1812.
Secondary Radius Server IP address or DNS name of the RADIUS server to use if there is no
response from the primary RADIUS server.
Secret Secret key for this RADIUS server.
Port Port number of the secondary RADIUS server. Default is 1812.
Enable Serial Configuration Enable basic network configuration using the serial or USB port.
Note: USB is not supported on the IF2 with Expanded Memory Option.
IF2 Network Reader User Guide 19
Page 30

Change the Default Login
If you are not using a password server to authorize user logins, Honeywell recommends that you change the default user name and password and create a readonly password.
1. From the main menu, click Security > Passwords. The Passwords screen
appears.
2. Make sure the Enable RADIUS check box is not checked. Clear this check box if
necessary and then click Activate Changes.
3. Configure the parameters. For help, see the next table.
4. Click Activate Changes to save your changes and immediately make them
active.
Password Parameter Descriptions
Parameter Description
Username Enter the user name you need to use to log in to this IF2. The user name
can be from 1 to 32 characters long. You must always specify a user
name. Default is intermec.
Password Enter the password you need to use to log in to this IF2. This password
gives you read and write access to the IF2 configuration. The password
can be from 8 to 32 characters long. You must always specify a password.
Default is intermec.
Read-only Password Enter the password you need to use to log in to this IF2. This password
gives the user read-only access to the IF2. This user can view the
configuration and execute diagnostics but cannot perform any tasks that
affect IF2 operation, such as changing configuration options or
upgrading firmware. Default is readonly.
The read-only password cannot be deleted. To disallow read-only access,
you need to enable RADIUS authentication. For help, see "Configure
Security" on page 16.
20 IF2 Network Reader User Guide
Page 31

Disable Access Through the Serial Port
When serial port access is disabled, you also disable USB access. When you disable
access, you will not be able to configure the IF2 as described in "Assign an Initial IP
Address" on page 5. You must use a network application (such as a web browser,
SmartSystems Console, or Device Configuration Web Service application) for all
configuration.
Note: USB is not supported on the IF2 with Expanded Memory Option.
1. From the menu, click Security > Passwords. The Passwords screen appears.
2. Clear the Enable Serial Configuration check box.
3. Click Activate Changes to save your changes and immediately make them
active.
Manage Certificates
The default server certificate on the IF2 (ValidForHTTPSOnly) provides support for
secure network applications such as the secure web browser interface, secure
LLRP client connections, and secure web services. You can use a third-party certificate authority to issue unique client certificates and a root certificate.
Note: To install or uninstall certificates, you need to access the IF2 via a secure web browser.
For help, see "Use the Web Browser Interface" on page 7.
View Certificates
You can use the web browser interface to view the certificates loaded on the IF2.
• From the menu, click Security > Certificate Details. The Certificate Details
screen appears.
IF2 Network Reader User Guide 21
Page 32

The Server Certificate table lists the server certificate that is installed, and the CA
Certificate table lists the trusted CA certificate that is installed.
Install and Uninstall Certificates
Once you have determined that you need to install or uninstall a certificate, use
this procedure.
Note: If you follow the procedure to uninstall all certificates, you will lose the unique server
certificate and the trusted CA certificate. You will need to contact your local
representative to purchase new certificates.
Note: To install or uninstall certificates, you need to access the IF2 through a secure web
browser. For help, see “"Use the Web Browser Interface" on page 7.
1. From the main menu, click Security > Import Certificate. The Import Certifi-
cate screen appears.
2. Click Browse and follow the prompts to browse to the location of the certificate
you want to install. Or, enter the path to the certificate in the Enter or select the
name of the certificate file to import entry field.
Note: If you are not using a secure web browser, you will be prompted to log in again. Click
A secure session is available and log in to the IF2. If a Security Alert dialog box
appears, click Yes to proceed. Repeat Steps 1 and 2.
3. Click Server Certificate or Trusted CA Certificate.
22 IF2 Network Reader User Guide
Page 33

4. (Server Certificate only) In the Enter the associated passphrase for this
certificate field, carefully enter the passphrase for the certificate.
5. Click Import Certificate. If a Security Alert dialog box appears, click Yes to
proceed.
IF2 Network Reader User Guide 23
Page 34

24 IF2 Network Reader User Guide
Page 35

CHAPTER
DEVELOP AND USE RFID
3
APPLICATIONS
This chapter explains how you can develop and test RFID applications for the IF2
and IF2 with expanded memory option and includes these topics:
• About the IF2 Configurations
• RFID Applications and the IF2
• Create RFID Applications
• About RFID Services
• Configure BRI Settings
• Configure LLRP Settings
This chapter assumes you are familiar with developing applications and with your
RFID system.
About the IF2 Configurations
The IF2 comes in a standard configuration with no internal memory, or an
expanded memory option.
• For the IF2, the applications you develop resides on a remote server which
communicates with the reader, and all information is processed through the
server.
• For the IF2 with Expanded Memory Option, the applications you develop can be
hosted and run locally on the reader.
Note: This chapter applies to both the standard and expanded memory options of the IF2.
IF2 Network Reader User Guide 25
Page 36

RFID Applications and the IF2
Your application communicates with the IF2 through one of two RFID services:
• The Basic Reader Interface (BRI) server, which controls the reader by issuing BRI
commands. For more information on the BRI server, see "Configure the BRI
Server" on page 31.
For more information on using BRI, go to www.honeywellaidc.com to download
the Basic Reader Interface Programmer Reference Manual.
• The Low-Level Reader Protocol (LLRP), based on the EPCglobal standard. For
more information on LLRP settings, see "Configure LLRP Settings" on page 33.
For more information on LLRP, go to www.honeywellaidc.com to download the
LLRP Programmer’s Reference Guide.
For more information about creating an installation package or installing an application on the IF2 with Expanded Memory option, see Chapter 4, “Install
Applications on the IF2 with Expanded Memory Option.”
Use the RFID Resource Kit
The Intermec Developer Library RFID Resource Kit includes Java and C# tools you
can use to develop applications that enable control of the reader and data management.
The resource kit is available as part of the Intermec Developer Library (IDL). To
learn more about the RFID Resource Kit, go to hsmftp.honeywell.com and choose
Software>Software and Tools>Developer Library>SDKs for Windows>Intermec
Resource Kits>Developer Tools.
Create RFID Applications
An RFID application can communicate directly with the IF2 BRI Server using the
BRI protocol, or it can communicate with the IF2 using the Low-Level-Reader Protocol (LLRP).
Honeywell recommends that you write and test your application on a development
workstation (your desktop PC). The application can access the IF2 BRI interface via
TCP on port 2189.
About RFID Services
The RFID service sets the protocol your application uses to communicate with the
RFID module. The available services are:
• BRI (Basic Reader Interface) - Intermec proprietary protocol for controlling the
reader. To configure BRI settings, see the next section, “Configure BRI Settings.”
26 IF2 Network Reader User Guide
Page 37

• LLRP (Low-Level Reader Protocol) - EPCglobal standard for network interfaces
between the RFID reader and its controlling software. To configure LLRP
settings, see "Configure LLRP Settings" on page 33.
Configure BRI Settings
This section explains how to configure BRI settings that control reader operation
and communication with your application.
• To configure BRI attribute settings that control reader operation, such as read
and write tries, tag types, or antenna settings, see the next section, “Changing
BRI Attribute Settings.”
• To configure BRI server settings, which manage how your application
communicates with the reader, see "Configure the BRI Server" on page 31.
Change BRI Attribute Settings
BRI attribute settings control how the IF2 reader module reads tags. Follow the
next procedure to change attribute settings.
Note: The BRI attribute settings in the web interface define the default BRI attributes when
a client initially connects to the BRI. The settings do not change the attributes of any
current BRI sessions.
1. From the menu, click RFID Services > BRI > BRI Attributes. The BRI Attributes
screen appears.
2. Change RFID settings as needed. For help, see the next section.
3. Click Activate Changes to save your changes and immediately make them
active.
About BRI Attribute Settings
This section explains the BRI attribute settings that control how the reader
operates. For more information, go to www.honeywellaidc.com to download the
Basic Reader Interface Programmer Reference Manual.
IF2 Network Reader User Guide 27
Page 38

Tag Types
Read Tries
Write Tries
Check the appropriate check boxes to enable RFID operations for these kinds of
tags:
• EPC Class 1 Gen 2 (default)
• Phillips v1.19
• ISO6B/G1
• ISO6B/G2
This setting is equivalent to the TAGTYPE BRI attribute.
Sets the maximum number of times the read algorithm is executed before a
response is returned to a Read command.
In practice, this is the number of times an identified tag is read until the Read is
successful. Valid range is 1 to 254 (default is 3).
This setting is equivalent to the RDTRIES BRI attribute.
Lock Tries
Field Separator
ID Report
Sets the maximum number of times the write algorithm is executed before a
response is returned to a Write command.
In practice, this is the number of times an identified tag is written to until the Write
is successful. Valid range is 1 to 254 (default is 3).
This setting is equivalent to the WRTRIES BRI attribute.
Sets the maximum number of times the lock algorithm is executed before a
response is returned to a Lock command. Valid range is 1 to 254 (default is 3).
This setting is equivalent to the LOCKTRIES BRI attribute.
Sets the character to be used for separating fields in tag data. Choose from space
( ), comma (,), colon (:), semicolon (;), tab, caret (^), or tilde (~). Default is space.
This setting is equivalent to the FIELDSEP BRI attribute.
Enables or disables tag ID reporting after a Read, Write, or Lock command is executed:
• For ISO tags, the tag identifier corresponds to TAGID.
28 IF2 Network Reader User Guide
Page 39

• For EPC tags, the identifier corresponds to EPCID.
Check the check box to enable tag ID reporting. This setting is equivalent to the
IDREPORT BRI attribute, and is enabled by default.
No Tag Report
Enables or disables a NOTAG message, which is sent when no tags are found
during execution of a Read, Write, or Lock command. Check the check box to
enable the message. This setting is equivalent to the NOTAGRPT BRI attribute, and
is enabled by default.
Report Timeout
Sets the timeout (in ms) for delays in tag reporting when the IF2 is in continuous
read mode. Range is 0 (default) to 65534.
Timeout Configuration Mode
Enables a timeout mode. Instead of specifying the number of antenna or ID tries,
you specify an antenna or ID timeout value. If the IF2 does not find any tags after
an antenna or ID try, the reader waits this long before starting the next antenna or
ID try. If you enable timeout mode, you need to set the ID Timeout and Antenna
Timeout values.
Select Tries
Unselect Tries
This setting is equivalent to the TIMEOUTMODE BRI attribute, and is disabled by
default.
To enable Timeout Configuration mode:
1. Check the check box. The screen refreshes. The Antenna Tries setting is
replaced by Antenna Timeout, and the ID Tries setting is replaced by ID Timeout.
2. Specify the value (in ms) for the antenna or ID timeout in the entry fields and
then click Activate Changes.
For more information on ID Timeout and Antenna Timeout, see those topics later in
this section.
(Not supported by EPCglobal Class 1 Gen 2 tags) Sets the number of times a group
select is attempted. A group select is the command that starts the identity process.
Valid range is 1 (default) to 254.
This setting is equivalent to the SELTRIES BRI attribute.
(Not supported by EPCglobal Class 1 Gen 2 tags) Sets the number of times a group
unselect is attempted. Valid range is 1 (default) to 254.
IF2 Network Reader User Guide 29
Page 40

Session
(EPCglobal Class 1 Gen 2 tags only) Sets the command session parameter to the
corresponding EPCglobal Class 1 Gen 2 air protocol command (default is QueryAdjust).
This setting is equivalent to the SESSION BRI attribute. For more information on
this setting, see the EPCglobal Class 1 Gen 2 documentation.
Initial Q
(EPCglobal Class 1 Gen 2 tags only) Sets the initial Q parameter value used by the
Query command. Valid range is 0 to 15 (default is 4). If you know there is only one
tag in the field, set this attribute to 0 for best performance.
This setting is equivalent to the INITIALQ BRI attribute.
Initialization Tries
Sets the maximum number of times the reader attempts to initialize a tag. Valid
range is 1 (default) to 254.
This setting is equivalent to the INITTRIES BRI attribute.
Schedule Option
Determines how antennas are switched during the inventory process. This attribute controls the behavior of the inventory scheduling parameters.
This setting is equivalent to the SCHEDULOPT BRI attribute.
ID Tries
Sets the maximum number of times the reader executes the identify algorithm
before a response is returned to a Read or Write command.
In practice, this is the number of times a tag ID attempt is made for each antenna
being used. Valid range is 1 to 254 (default is 3).
This setting is equivalent to the IDTRIES BRI attribute.
Antenna Tries
Sets the maximum number of ID Tries that the reader executes per antenna. Valid
range is 1 to 254 (default is 3).
This setting is equivalent to the ANTTRIES BRI attribute.
EPCC1G2 Advance Medium Access Mode
Selects low-level protocol (such as tari and back-link frequency) settings. If you are
using CAEN tags, you must enable this mode before the tags can be read.
30 IF2 Network Reader User Guide
Page 41

This setting is equivalent to the EPCC1G2PARAMETERS or EPCC1G2PARMS BRI
attribute.
Dense Reader Mode
Allows the reader to hop between channels within a certain frequency spectrum to
prevent other readers in the area from interfering with one another.
This setting is equivalent to the DENSEREADERMODE or DRM BRI attribute.
Antenna Field Strength 1 to 4
Sets the RF power level (in dBm) for each of the 4 antenna ports. Valid range is 15
to 30. Default is 30. Note that the maximum power level is dependent on the region
that the IF2 is operating in.
Use this setting to attenuate the antenna field strength. In some situations, full
output power can cause unnecessary interference. For example, if the tag is close
to the antenna, full output power might overload the tag and cause unreliable
behavior.
This setting is equivalent to the FIELDSTRENGTH BRI attribute.
Antenna Sequence: First through Eighth
Sets the RFID antenna to be used for each of up to eight tag inventory operations.
Choose any one of the 16 available antennas from the drop-down list. If more than
one antenna is enabled, the antennas fire in this sequence.
This setting is equivalent to the ANTS BRI attribute.
Configure the BRI Server
The IF2 BRI server handles communication between your application and the RFID
module. When your application is communicating with the BRI server, the blue
Intermec Ready-To-Work Indicator on the IF2 front panel turns on and stays on.
For more information, see "About the Ready-to-Work Indicator" on page 3.
IF2 Network Reader User Guide 31
Page 42

1. From the menu, click RFID Services > BRI > BRI Server. The BRI Server screen
appears.
2. Change BRI server settings as needed. For help, see the next table.
3. Click Activate Changes to save your changes and immediately make them
active.
BRI Server Parameter Descriptions
Parameter Description
Enable External
BRI Connections
BRI TCP Port Specifies the TCP port used for incoming connections to the BRI server. This port
Enable Logging Enables/disables logging of BRI server events.
Enable BRI on
serial port
View the BRI Server Log
If you enable logging, you can see a list of BRI server events. You can save the logfile as a .txt file.
BRI Event Description
Event
Name
Time/Date Time and date of the event.
Connection Session ID of the client communicating with the BRI server.
Type Message type of the event, generally indicating which system sent the message:
Message Text of the message, including responses.
Description
1 = Command received by BRI server
2 = Response sent by BRI server
3 = BRI server connection message
Enables/disables external TCP connections to the BRI server. If this check box is
not checked, BRI applications will not be able to connect to the IF2.
must be unique for all TCP services running on the IF2. Valid range is 2189 to
65535. Default is 2189.
For more information on logging, see the next section.
Enables/disables sending BRI commands through the serial port.
32 IF2 Network Reader User Guide
Page 43

1. Enable BRI logging as described in the previous section, "Configure the BRI
Server" on page 31.
2. In the left navigation list, click RFID Services > BRI > BRI Log. The BRI Log
screen appears with a list of BRI events. For more information on server events,
see the “BRI Event Descriptions” table.
3. To save the log file, click Export log to text file and then choose File > Save As.
Follow the prompts to save the log file to your desktop PC.
Configure LLRP Settings
The IF2 supports version 1.0.1 of the EPCglobal Low-Level Reader Protocol
(LLRP), which establishes a specific interface method between a reader and its
corresponding client. Follow the next procedure to configure LLRP settings.
For information on LLRP, including standards, see
https://www.gs1.org/sites/default/files/docs/epc/llrp_1_1-standard-
20101013.pdf. An open source LLRP Toolkit can be downloaded at http://
sourceforge.net/projects/llrp-toolkit.
LLRP Settings Descriptions
Setting Description
Secure Server Enable Check this check box to allow connections to the secure LLRP server on
port 5085.
Unsecure Server
Enable
Download Intermec
Extension Definitions
Reader-Initiated
Connections
Check this check box to allow connections to the unsecure LLRP server on
port 5084.
Click the link to download the Intermec extension definitions xml file.
For reader-initiated TCP/IP connections to a remote LLRP client, enter this
information:
Client Address - IP address of the remote LLRP client.
TCP Port - Port number for the TCP/IP socket connection.
Enable Security (TLS) - Check this check box to enable Transport Layer
Security for this TCP/IP connection.
IF2 Network Reader User Guide 33
Page 44

1. From the menu, click RFID Services > LLRP. The LLRP screen appears.
2. Configure LLRP settings as needed. For help, see the “LLRP Settings
Descriptions” table.
• To disconnect an existing LLRP connection, click Terminate.
• To connect to a remote LLRP client, enter information in the Reader-Initiated
Connections section, and then click Initiate.
3. Click Activate Changes to save your changes and immediately make them
active.
34 IF2 Network Reader User Guide
Page 45

CHAPTER
INSTALL APPLICATIONS ON THE IF2
4
WITH EXPANDED MEMORY OPTION
This chapter explains how you can develop and install applications on the IF2 with
Expanded Memory option.
• Create a Configuration File
• Auto-Start Applications at Boot Time
• About .NET Support
• About Java Support
• Install RFID Applications
• About the Edgeware Applications
• About the Developer Tools
This chapter assumes you are familiar with developing applications and with your
RFID system.
Create a Configuration File
When you package your application for installation on the IF2, you need to include
a configuration file in the root directory of the archive. The file must be named
“userapp.conf” and must include this syntax:
AUTOSTART=true|false
RUNAFTERINSTALL=true|false
CMDLINE=<command line to start the application>
where:
AUTOSTART specifies whether or not the application should automatically be executed when the IF2 boots. When AUTOSTART=true, the Auto-Start check box for
this application on the Application Control screen will be checked.
Note: After you install the application on the IF2, you can enable or disable the auto-start
feature from the web browser interface. For help, see "Manage Applications" on
page 38.
IF2 Network Reader User Guide 35
Page 46

RUNAFTERINSTALL specifies whether or not the application should be started
immediately after installation.
CMDLINE specifies the application name and optional parameters it accepts. Specify command line parameters as if the application is being executed from inside
the directory containing the application.
Note: Do not use the $JAVA_HOME environment variable in the command line.
This example runs a C# application named “testapp.exe” using the Mono runtime:
CMDLINE=./testapp.exe
For Java applications, CMDLINE should specify the Java interpreter location, the
classpath, and the class containing the application’s entry point. This example
runs the class “HelloWorld”:
CMDLINE=/usr/java/bin/java -cp . HelloWorld
Note: The IF2 executes applications from their installation directories, so the userapp.conf
file does not need to include path information.
Auto-Start Applications at Boot Time
There are two ways to configure your application to auto-start when the IF2 boots:
• Specify AUTOSTART=true in the configuration file that you deliver with the
application. For more information, see "Create a Configuration File" on page 35.
• After you install the application on the IF2, you can use the web browser
interface to configure the application to auto-start at boot time. For help, see
"Use the Web Browser Interface" on page 7.
About .NET Support
The IF2 supports applications based on .NET Framework 1.0, 1.1, and 2.0. The IF2
uses Mono open source software to provide support for .NET applications
deployed on the IF2 Linux operating system.
Note: The IF2 does not support ASP.NET.
About Java Support
The IF2 comes with a JDBC driver you can use to create applications that write data
directly from the IF2 to a remote database. For more information, see "Java Support
for Microsoft SQL Server and Sybase" on page 37.
36 IF2 Network Reader User Guide
Page 47

For more sophisticated Java development, the IF2 supports the open standard
OSGi service-oriented architecture. This allows system administrators to install,
uninstall, enable, and disable system services (also known as bundles) without
having to reboot the IF2 each time. To use OSGi effectively, you need an OSGi
server. For more information, go to www.osgi.org.
Execute Java Applications
To execute a Java application on the IF2, use this command:
$JAVA_HOME/bin/java myJavaClass
To execute .jar files, use this command:
$JAVA_HOME/bin/java -jar myApplication.jar
Note: Your .jar files must have manifest files included within them, or the command will not
work:
• The manifest needs to include an attribute called “Main-Class” to specify the
application’s entry point (for example, Main-Class: MyJavaClass).
• If the executable .jar needs to reference other .jar files, specify the files in the
manifest file using the “Class-Path” attribute.
To enable the Java just-in-time (JIT) compiler for maximum performance, use this
command:
$JAVA_HOME/bin/java -jit java -jar MyJar.jar
where:
$JAVA_HOME is an environment variable that indicates the Java runtime installation path (/usr/java). Always use this variable for simplicity and to insure that the
correct runtime files are used.
java is the name of the Java runtime executable installed in the IF2.
If your application references third party Java libraries (such as components from
the Intermec RFID Resource Kit), you must use the “-cp” option to specify the class
path for the JVM to find the Java classes. Be sure to include the current path so
classes in the current directory can be found, as shown in this example:
$JAVA_HOME/bin/java -cp .:./BasicRFID.jar MyClass
Java Support for Microsoft SQL Server and Sybase
The IF2 jTDS driver (version 1.2) provides JDBC capabilities to Java applications
running on the IF2. You need to include the location of JDBC drivers in the class
path. Use the environment variable $JDBC_HOME as shown in this example:
$JAVA_HOME/bin/java -cp $JDBC_HOME/jtds-j2me-1.0.2.jar:. MyClass
The IF2 JDBC driver supports JDBC 1.0 and:
• Microsoft SQL Server versions 6.5, 7, 2000, and 2005.
• Sybase versions 10, 11,12, and 15.
IF2 Network Reader User Guide 37
Page 48

For more information on the jTDS driver, go to http://jtds.sourceforge.net.
Install RFID Applications
The IF2 provides up to 96 MB of storage for your applications. You use the web
browser interface to install applications on the IF2 as described in the next procedure.
Note: Before you install your application on the IF2, you must place the application into a
.zip, .tar, .tar/bz2, or .tar/gz file.
1. From the menu, click Edgeware Applications > Install User Application. The
Install User Application screen appears.
2. Click Browse and follow the prompts to navigate to the location of the
application file.
3. Click Upload. The application is uploaded to the IF2 and placed in the /home/
developer/edgeware/userapp0 directory. After the application is uploaded to
the reader, the application name appears in the Edgeware Applications list.
Manage Applications
To maximize IF2 resources, you can start, stop, or uninstall IF2 edgeware applications or your installed applications from the web browser interface. You can also
configure applications to auto-start at boot time. For more information, see the
next section.
1. From the menu, click Edgeware Applications > Application Control. The Appli-
cation Control screen appears.
The Edgeware Applications section lists all installed edgeware. The User Applications section lists all applications you have installed through the web
browser interface.
In this screen, you can:
• specify which applications automatically start when the IF2 boots.
• turn applications on and off in real time.
• uninstall applications (except for Developer Tools).
2. Choose an option:
• Check the Auto-Start check box if you want an application to automatically
launch when the IF2 boots.
• Click to stop a running application.
• Click to start an application.
• Click to uninstall an application.
38 IF2 Network Reader User Guide
Page 49

3. Click Activate Changes to save your changes and immediately make them
active.
Note: If you change the date or time on the IF2, stop and restart any running applications
(or reboot the IF2) for the date and time changes to be made effective.
About the Edgeware Applications
Edgeware applications are supplied by Honeywell and its partner developers, and
provide immediate functionality for your RFID system. The IF2 includes these
edgeware applications:
• The Developer Tools. Use the Developer Tools to test your RFID systems and
settings. For more information, see "About the Developer Tools" on page 39.
• The SAP device controller. Enable this edgeware so the controller communicates
with the SAP backend module on your server. For more information on SAP
implementation on the IF2, see the SAP Device Controller User’s Guide.
You can uninstall any edgeware application other than the Developer Tools, Java
Runtime Environment, and Mono Runtime Environment. For help, see the previous
section, “Manage Applications.”
There are many upgrades for existing edgeware applications, as well as additional
edgeware applications you can install. For help with locating IF2 upgrades, see
"Upgrade Firmware" on page 54. To install or upgrade edgeware applications, see
the next section.
Upgrade or Install Edgeware Applications
You use the web browser interface to install or upgrade IF2 edgeware applications,
such as the SAP device controller.
Note: Use only .bin files provided by . To install your own applications in .zip, .tar, .tar/bz2, or
.tar/gz formats, see "Install RFID Applications" on page 38.
1. From the menu, click Edgeware Applications > Install Edgeware. The Install
Edgeware screen appears.
2. Click Browse and follow the prompts to navigate to the location of the .bin file.
3. Click Upload. The application file is installed on the IF2. When the installation
is complete, the reader reboots.
About the Developer Tools
Use the Developer Tools for basic testing of your RFID system. The Developer Tools
support these features:
IF2 Network Reader User Guide 39
Page 50

• General purpose input/output (GPIO) testing. For help, see the next section,
“Test the GPIO Interfaces.”
• Sending BRI commands or BRI script files to the IF2 from an interactive browser
interface. For help, see "Send BRI Commands and Running Scripts" on page 40.
• Editing and testing JavaScript files. For help, see "Use the Workbench" on
page 41.
Note: To use the Developer Tools, you need to enable them. For help, see "About the
Edgeware Applications" on page 39.
Test the GPIO Interfaces
If you have external GPIO controls such as motion sensors or indicator lamps connected to the IF2, you can use the Diagnostics tool to test the interfaces and verify
that the controls behave as expected. Leave the controls connected to the IF2
GPIO port when using the Diagnostics tool.
1. From the menu, click Edgeware Applications > Developer Tools > GPIO. The
GPIO screen appears.
2. Check the check box for each of the GPIO interfaces you want to test. When you
check the check box, that GPIO output will be turned on, and its associated
GPIO input is turned on.
3. Click Read and Write GPIO. The GPIO interface state is changed.
Send BRI Commands and Running Scripts
You can send BRI commands to the IF2 through the web browser interface.
1. From the menu, click Edgeware Applications > Developer Tools > BRI Com-
mands. The BRI Commands screen appears.
2. Enter the BRI command in the Command entry field.
3. Click Run. The command is executed and return values appear onscreen. For
example, if you sent the ATTRIB command, the reader attributes appear in the
list.
Load and Run a BRI Script
You can load and run a BRI script through the web browser interface.
1. From the menu, click Edgeware Applications > Developer Tools > BRI Com-
mands. The BRI Commands screen appears.
2. Click Browse and browse to the location of the BRI script.
3. Double-click the name of the file. The script filename appears in the Script
name field.
40 IF2 Network Reader User Guide
Page 51

4. Click Load. The script is loaded and run, and return values appear onscreen.
Use the Workbench
You can create and edit a JavaScript file, load the file on the IF2, and run the file
from the Workbench.
Note: These instructions assume you understand how to create and edit JavaScript files.
1. From the menu, click Edgeware Applications > Developer Tools > Workbench.
The Workbench screen appears.
2. Click in the JavaScript Code box to enter code. You can also paste text copied
from Notepad or another application. Copy the text from the other application
and choose Edit > Paste in the browser menu.
3. To save your JavaScript code to the IF2 work buffer, click Save As and enter a
new file name in the entry field. Click OK.
If you previously saved your JavaScript, click on the drop-down menu and
select the file name to reload it in the JavaScript Code box.
4. Click Run. The IF2 runs the JavaScript. Responses from the reader appear in
the output pane. For example, if your script instructed the reader to read tags,
the tag IDs appear in the Output Pane.
IF2 Network Reader User Guide 41
Page 52

42 IF2 Network Reader User Guide
Page 53

5
MANAGE, TROUBLESHOOT, AND
UPGRADE THE IF2
This chapter includes information on managing the IF2 and includes these topics:
• Manage the IF2
• Use the Device Configuration Web Service
• Open a Serial or USB Connection to the IF2
• Maintain the IF2
• Troubleshoot the IF2
• Call Customer Support
• Upgrade Firmware
Manage the IF2
There are two methods you can use to manage the IF2. You can use:
• a web browser. For help, see "Use the Web Browser Interface" on page 7. This
manual assumes you are using this method for all procedures.
• the Device Configuration web service. For help, see the next section.
Use the Device Configuration Web Service
The Device Configuration web service provides a way to programmatically configure the IF2 over your network. This SOAP-based service provides a configuration
API that allows you to specify a variety of network, RFID, and system settings via
XML-encoded messages.
Follow the next procedure to enable the web service or to download the Device
Configuration web service description language (WSDL) document.
IF2 Network Reader User Guide 43
Page 54

1. From the menu, click Network Configuration > Device Management. The
Device Management screen appears.
By default, Device Configuration web services are enabled for either secure or
insecure connections.
2. To disable web services over a secure connection, clear the Enable Device Web
Services (Secure) check box, and then click Activate Changes.
To disable web services over an insecure connection, uncheck the Enable
Device Web Services (Insecure) check box, and then click Activate Changes.
To download the device configuration WSDL document, click DeviceConfigu-
ration.wsdl. The document opens in the browser window.
Open a Serial or USB Connection to the IF2
You can connect the IF2 to your desktop PC via the serial or USB port to perform
these tasks:
• Assign the IF2 an initial IP address.
• Restore default settings.
• Establish a BRI session.
44 IF2 Network Reader User Guide
Page 55

Open a Serial Connection to the IF2
If you are opening a serial connection to the IF2, you need:
• a null-modem cable (P/N 059167).
• a communications program such as HyperTerminal.
Note: If you have Microsoft ActiveSync running on your desktop PC, disable ActiveSync to
make the serial port available.
1. Connect the null-modem cable from the serial port on the IF2 to a serial port on
your PC.
2. Start the communications program and configure the serial port
communications parameters to:
• Bits per second: 115200
• Data bits: 8
• Parity: None
• Stop bit: 1
• Flow control: None
3. Connect the IF2 to power. The IF2 boots as soon as you apply power. In about a
minute, the message “Loading System” appears as the IF2 initializes, and in
another minute or two the login message appears.
The serial connection is established. From here you can do these tasks:
• You can assign an initial IP address to the IF2 for configuration. For help, see
"Assign an Initial IP Address" on page 5.
• You can restore default settings. For help, see "Restore Default Settings with
a Serial Connection" on page 50.
• You can open a BRI session.
Open a USB Connection to the IF2
If you are connecting the IF2 using a USB connection, you need:
• a USB cable.
• to create a folder with a gserial.inf and a usbser.sys file.
Note: USB is not supported on the IF2 with Expanded Memory Option.
IF2 Network Reader User Guide 45
Page 56

1. Create a folder to place the gserial.inf and usb.sys file in.
2. Click Start > Programs > Accessories > Notepad.
3. In Notepad, copy and paste the following text:
[Version]
Signature="$Windows NT$"
Class=Ports
ClassGuid={4D36E978-E325-11CE-BFC1-08002BE10318}
Provider=%LINUX%
DriverVer=08/17/2004,0.0.2.0
; Copyright(C)2004 Al Borchers (alborchers@steinerpoint.com)
[Manufacturer]
%LINUX%=GSerialDeviceList
[GSerialDeviceList]
%GSERIAL%=GSerialInstall, USB\VID_0525&PID_A4A7
[DestinationDirs]
DefaultDestDir=10,System32\Drivers
[GSerialInstall]
CopyFiles=GSerialCopyFiles
AddReg=GSerialAddReg
[GSerialCopyFiles]
usbser.sys
[GSerialAddReg]
HKR,,DevLoader,,*ntkern
HKR,,NTMPDriver,,usbser.sys
HKR,,EnumPropPages32,,"MsPorts.dll,SerialPortPropPageProvider"
[GSerialInstall.Services]
AddService = usbser,0x0002,GSerialService
[GSerialService]
DisplayName = %GSERIAL_DISPLAY_NAME%
ServiceType = 1 ; SERVICE_KERNEL_DRIVER
StartType = 3 ; SERVICE_DEMAND_START
ErrorControl = 1 ; SERVICE_ERROR_NORMAL
ServiceBinary = %10%\System32\Drivers\usbser.sys
LoadOrderGroup = Base
[Strings]
LINUX = "Linux"
46 IF2 Network Reader User Guide
Page 57

GSERIAL = "Gadget Serial"
GSERIAL_DISPLAY_NAME = "USB Gadget Serial Driver"
4. Click File > Save As.
5. Browse to the folder that you created in Step 1.
6. In the File name: text box, type gserial.inf, and click Save.
7. Browse to the c:\Windows\Driver Cache\i386 directory and locate the
driver.cab file.
8. Open the driver.cab file with a .cab extraction tool and find the usb.sys file.
9. Copy the usb.sys file to the folder you created in Step 1.
10. Connect the IF2 to your PC using a USB cable. The Found New Hardware
Wizard appears.
11. Select Install from a list or specific location (Advanced), and click Next.
12. Select Include this location in the search, and enter browse to the folder you
created in Step 1.
13. Click Continue Anyway when the Windows Logo Testing screen appears. The
IF2 is connected by a USB connection. From here you can do these tasks:
• You can assign an initial IP address to the IF2 for configuration. For help, see
"Assign an Initial IP Address" on page 5.
• You can restore default settings. For help, see "Restore Default Settings with
a Serial Connection" on page 50.
• You can open a BRI session.
Maintain the IF2
The Maintenance menu lets you view IF2 parameters and statistics, including a list
of logged events. You may need this information if you need to call Honeywell
Product Support.
View the System Log
The System Log screen shows events that have been logged by the IF2.
IF2 Network Reader User Guide 47
Page 58

1. From the menu, click Maintenance > System Log. The System Log screen
appears. This screen is read-only.
2. To save the list, click Export log to text file. The log is saved as Syslog.log and
appears in the browser window.
3. Choose File > Save As and follow the prompts to save the log file to your
desktop PC.
View the About Screen
The About screen lists installed software versions, serial numbers, and other IF2specific information.
• From the menu, click About. The About screen appears. This screen is read-only.
The About screen includes this information:
• Device information: IF2 firmware version, hardware configuration string, and
serial number.
• System information: Available memory, number of running processes, and
amount of time the IF2 has been running.
• RFID Module firmware: Firmware version installed.
• Network interface information.
• Installed subsystems: versions of all currently loaded IF2 subsystems, including
Linux.
48 IF2 Network Reader User Guide
Page 59

Use the LEDs to Locate the IF2
You can use the LEDs to help locate a specific IF2 in your location.
• In the About This IF2 RFID Reader screen, click Find This Device. All of the LEDs
except the Power and Wired LAN LEDs flash. Click Finished Finding This
Device to turn off the LEDs.
Restore the IF2 to the Default Configuration
Note: Restoring default settings as described in this section does not affect security
certificates you have installed.
There are four ways to restore the default configuration on the IF2:
• You can restore default settings from the web browser interface. For help, see
the next section.
• You can restore default settings by pressing the reset switch located on the top
of the IF2.
• You can restore default settings through a serial connection. For help, see
"Restore Default Settings with a Serial Connection" on page 50.
• You can restore default settings using the Device Configuration Web Services.
For help, see the Device Configuration Web Services Command Reference
Manual.
Restore Default Settings with the Web Browser
If you are having problems with the IF2, you can use the web browser interface to
restore the default settings to the IF2.
1. From the menu, click Maintenance > Configuration. The Configuration screen
appears and displays all configuration changes from the factory default settings.
2. Click Restore Defaults. A confirmation message appears.
IF2 Network Reader User Guide 49
Page 60

3. Click OK. The IF2 reboots and restores the default configuration.
Reset switch
Or, click Cancel to close the confirmation message without restoring defaults.
Restore Default Settings with the Reset Switch
If you are having problems with the IF2, you can press the reset switch to restore
the default settings to the IF2.
1. Make sure the IF2 is powered on.
2. Using a paper clip, push and hold the reset switch for three seconds. The LEDs
on the IF2 flashes.
3. Release the reset switch. The IF2 reboots and restores the default
configuration.
Restore Default Settings with a Serial Connection
If you are having problems with the IF2, you can use a serial connection to restore
the default settings to the IF2.
1. Open a serial connection to the IF2. For help, see "Open a Serial or USB
Connection to the IF2" on page 44.
2. In the login field, type restore_defaults and then press Enter.
3. In the Password field, press Enter. The IF2 reboots and the default settings are
restored.
Reboot the IF2
You can reboot the IF2 from the web browser interface as described in the next procedure. For example, you may need to reboot the IF2 to enable changes in an application.
50 IF2 Network Reader User Guide
Page 61

1. From the menu, click Maintenance > Reboot. The Reboot screen appears.
2. Click Reboot to reboot the IF2. You need to log in again after the IF2 reboots.
Troubleshoot the IF2
This section includes lists of problems and possible solutions.
Problems While Working with RFID
Many problems you may encounter when working with your RFID system can be
solved by carefully checking the RFID settings and changing them accordingly. For
help, see "About RFID Services" on page 26.
RFID Problems and Solutions
Problem Solution
The IF2 is unable to read
RFID tags, or seems to read
tags slowly or inconsistently.
The IF2 does not respond to
your RFID application.
Check these conditions:
• Your RFID antennas must be connected correctly to the IF2 and
mounted in optimum locations. Make sure all antenna
connections are tight and that the cables are in good condition.
For help, contact your Honeywell RFID system consultant.
• To maximize IF2 performance, make sure you have chosen the
correct tag types for your application. For help, see "Configure
BRI Settings" on page 27.
Your application may not be communicating with the IF2 BRI server.
You may need to change BRI server settings to communicate with
your application. For example, if your application is running on a
desktop PC, you need to enable external BRI connections to the IF2.
For help, see "Configure the BRI Server" on page 31.
Connect Directly to the RFID Module
If your application does not appear to be communicating with the IF2 RFID module, you can use a communications program to verify that the RFID module is
working properly.
IF2 Network Reader User Guide 51
Page 62

You need to know the IF2 IP address to connect directly to the RFID module. To verify that the RFID reader is reading tags, you need a known good RFID antenna and
at least one good RFID tag.
1. Make sure the RFID antenna is connected properly to the IF2.
2. Apply power to the IF2.
3. Use a communications program (such as HyperTerminal) to open a TCP/IP
connection to the IF2 with these parameters:
Parameter Value
IP Address IP address of the IF2
Port 2189
Configure the communications program to echo typed characters locally and
to send line feeds with line ends.
4. Press Enter. The BRI prompt (OK>) appears.
If the prompt does not appear, there may be a problem with the RFID module or
your connection to the module.
5. Type ATTRIB and press Enter. A list of the current settings for the RFID module
appears, indicating that the module is receiving commands.
If the list does not appear, there may be a problem with the RFID module.
6. (Optional) To verify that the RFID module is reading tags:
• Place a known good RFID tag within range of the antenna.
• Type READ and press Enter. The tag ID appears, indicating that the module
is reading tags.
If the tag ID does not appear, there may be a problem with the RFID module or
antenna system.
52 IF2 Network Reader User Guide
Page 63

Problems With Connectivity
When troubleshooting problems with connectivity, make sure you know and understand these network-specific items:
• TCP/IP settings
• COM port settings for serial connections
You should also make sure all physical network connectors and cables are in good
working order.
Connectivity Problems and Solutions
Problem Solution
You cannot connect to the IF2
using the serial port.
You cannot connect to the IF2
using a web browser.
You cannot load a security
certificate.
You have assigned a static IP
address to the IF2 but cannot
connect to the IF2 over your
network.
1 Verify that you are using a null-modem cable to connect
to the desktop PC.
2 Verify that you are communicating through the correct
serial port.
3 Verify that your PC is set to 115200, N, 8, 1, no flow
control.
1 Verify that you have the correct IP address for the IF2.
2 If you access the Internet through a proxy server, be sure
you have added the IP address of the IF2 to the
Exceptions list.
You must use a secure web browser connection to load
certificates. For help, see "Use the Web Browser Interface" on
page 7.
Make sure that DHCP is disabled and that your TCP/IP
parameters are set correctly. For help, see "How to
Communicate with the IF2" on page 5.
Call Customer Support
You may need to call support if you have problems operating the IF2. Before calling, be sure you can answer the following questions:
• What kind of network are you using?
• What were you doing when the error occurred?
• What error message did you see?
• What is your RFID reader’s serial number?
• Can you reproduce the problem?
• What versions of IF2 and RFID software are you using? For help, see "View the
About Screen" on page 48.
When you have gathered this information, call customer support. To find the correct telephone number, go to www.honeywellaidc.com/locations.
IF2 Network Reader User Guide 53
Page 64

Upgrade Firmware
This section explains how to configure and install firmware upgrades on the IF2.
Note: To upgrade the firmware, use only .bin files provided by Honeywell. Be sure to contact
your RFID system consultant before upgrading.
Caution: Make sure the IF2 is connected to a reliable power source
before you upgrade the firmware. If power is lost during the
upgrade, the IF2 may require factory repair.
1. Download the Intermec IF2 OS Upgrade Package utility from the Honeywell
downloads page hsmftp.honeywell.com. (See Software > RFID > RFID Fixed
Readers > IF2 > Current > OS Firmware Drivers.)
2. Run the Upgrade Package utility (.exe file) to configure the firmware upgrade
file (.bin file).
3. Using the IF2 web browser interface (Username = intermec / Password =
intermec), from the menu, click Maintenance > Firmware. The Firmware screen
appears.
4. Click Browse to browse to the location of the upgrade file, and then doubleclick the filename. The name of the file appears in the Enter or select the name
of the firmware upgrade file entry field.
5. Click Upgrade IF2 RFID Fixed Reader. The upgrade process begins and the
firmware is transferred to the IF2. During the upgrade, the web browser
interface screen does not auto-refresh. Click Refresh in the web browser to
check the progress of the upgrade. When the login screen appears, the upgrade
is complete and the IF2 has already rebooted.
54 IF2 Network Reader User Guide
Page 65

6
USE THE IF2 GPIO INTERFACES
This chapter explains how to access the IF2 general purpose input/output (GPIO)
interfaces and how to connect industrial controls such as motion sensors or indicator lamps to the IF2. This chapter includes the following topics:
• About the GPIO Interfaces
• Access the Interfaces
• Use the Input Interfaces
• Use the Output Interfaces
• Use the Power Interface
About the GPIO Interfaces
The IF2 has four general purpose input and output (GPIO) interfaces. You connect
external controls such as motion sensors or indicator lamps to the GPIO interfaces,
which can then trigger IF2 operations.
Each interface is electrically isolated from the IF2 and designed for low voltage DC
loads. The IF2 can also supply 12 VDC at 0.5 A to external devices.
How the inputs and outputs are used depends on the RFID application software
being used in the system. You need to coordinate input and output control wiring
with the software developer.
If your application uses the IF2 GPIO interfaces to control external devices such as
indicator lamps, running the application on the IF2 may decrease response time
for those devices. For more information, see Chapter 4, “Install Applications on the
IF2 with Expanded Memory Option.”
Access the Interfaces
You can access the GPIO interfaces through the IF2 GPIO port. The port uses a
standard 25-pin serial cable. For port pin assignments, see "Port Pin
Assignments" on page 62.
IF2 Network Reader User Guide 55
Page 66

Use the Input Interfaces
External
input
switch
+Input
+12 V
Ground
- Input
Each of the four inputs is compatible with input signals of 10 to 36 VDC. Both the
high and low signal contacts are exposed and isolated to 1500 V. Input impedance
is 1.8 K ohms minimum.
GPIO Input Signal Descriptions
Signal Description Min. Typical Max.
Vin (High) High input voltage 10 V 24 V 36 V
(Low) Low input voltage -1 V 0 V 1 V
V
in
In a typical application, the IF2 senses input from an external control like a switch
and then starts a tag read operation.
There are three basic ways to connect input controls to the IF2 input interfaces:
• Supply the input interface with power from the IF2.
• Isolate the IF2 from the input power source.
• Use an open collector solid state drive from a remote device to control the
inputs.
For more information, see the next examples.
IF2 Powered Input
This is the simplest way to connect a control to an IF2 input interface. If the external control device is a switch, you can connect one side of the switch to an IF2
+Input pin, and the other side of the switch to one of the +12 VDC sources. Ground
the corresponding -Input pin as shown in the next illustration.
IF2 Powered Input
Isolated Input Interface
Use this method to minimize noise induced by distance or grounding characteristics. The isolated input avoids induced noise by referencing a remote input to chassis return of the IF2. The next illustration shows how this method is wired.
56 IF2 Network Reader User Guide
Page 67

External
+Input
+12 V
Ground
- Input
input
switch
+Input
-Input
Twisted
pair
Isolated Input Interface
-
10-48 VDC
Open Collector Input Interface
The input can be connected to an open collector interface of an external device.
This typically implies that the grounds are tied together for the two systems. The
common ground can be a source of input noise, so you should follow good grounding practices for both the IF2 and the input device.
In this situation, the IF2 provides power to the pull-up resistor for the open collector. Connect the +Input pin to the +12 VDC source as shown in the next illustration.
+
Open Collector Input Interface
Use the Output Interfaces
Each IF2 output interface is optically isolated from the IF2, polarized, and rated for
5 to 48 VDC at 0.25 A. All IF2 outputs include internal thermal fuses that trip if the
load exceeds 0.25 A, and the fuses are self-recovering once the excessive load is
removed. The high and low contacts are exposed and isolated from ground. Transient suppression limits output voltage spikes to 65 VDC.
GPIO Output Specifications
Signal Description Min. Typical Max.
Leakage current (High) Switch output, high leakage current 0 mA 1 mA 10 mA
(Low) Switch output on, saturation voltage
V
sat
with 0.25A load
0V 1V 1.5V
IF2 Network Reader User Guide 57
Page 68

Since the outputs are optically isolated, you can configure each one to switch the
External
indicator lamp
0.25 A maximum
+Output
+12 V
Ground
- Output
high side or the low side of the load. You can power the load directly from the IF2 or
from an external power supply.
In a typical application, the outputs control indicator lamps that signal good reads
or errors. The basic methods for connecting external devices to the GPIO outputs
include:
• Switching the high side, with the load powered by the IF2
• Switching the low side, with the load powered by the IF2
• Switching the high side, with the load powered externally
• Driving a DC relay that controls an AC load
These methods are shown in the next examples.
Switch the High Side with IF2 Power
In this example, an external indicator lamp (0.25 A maximum current) is connected
to the -Output and Ground pins, and the corresponding +Output pin is connected
to the +12 VDC source.
Switching the High Side
Switch the Low Side with IF2 Power
For low side switching applications, the lamp power is routed to all the lamps in
common and the low side of the load is routed to the switch.
In this method, connect the external indicator lamp to the +Output and +12 VDC
pins, and short the corresponding -Output pin to ground as shown.
58 IF2 Network Reader User Guide
Page 69

Switching the Low Side of the Output Load
External
indicator lamp
0.25 A maximum
Ground
- Output
+Output
+12 V
External
indicator
lamp
External
power
5-48 VDC
+
-
Ground
+Output
- Output
Switching the High Side With External Power
To use external power (5 to 48 VDC) to switch the high side, connect the Ground pin
to the ground system of the external power supply, and connect the positive side of
the external supply to the +Output pin. The external indicator lamp is connected to
the corresponding Output and Ground pins as shown in the next illustration.
Switching the High Side With External Power
Drive a DC Relay to Control an AC Load
While the IF2 outputs are designed to switch DC loads, they can drive relays that
control AC loads. The next illustration shows how to connect such a system to an
IF2 output.
IF2 Network Reader User Guide 59
Page 70

+ 12 V
+ Output
AC motor
- Output
Ground
External
relay
Driving a DC Relay: The external relay provides dry contacts for controlling the AC motor.
Note: In many installations, the relay and AC wiring must be placed in an enclosure that
meets local fire code regulations.
Use the Power Interface
The IF2 GPIO interface provides 12 VDC at 0.5 A for powering external inputs and
loads, eliminating the need for an external DC supply and simplifying the system
installation.
The GPIO interface power has an internal thermal fuse that trips if the load exceeds
0.5 A. The fuse is self-recovering once the excessive load is removed.
The total load on the GPIO interface power must stay within the 0.5 A limit. When
you design a system that uses the GPIO interface power, be sure to complete a
power budget assessment to ensure that the supply is adequate for the system.
120-230
VAC
If your system needs more than +12 VDC at 0.5 A, you can connect an external
power supply to the +12 V and Ground pins. The external supply powers the external loads, and that power will be available at all +12 V pins on the GPIO port.
60 IF2 Network Reader User Guide
Page 71

APPENDIX
SPECIFICATIONS
A
This appendix includes physical and electrical specifications for the IF2 and information about the port pin assignments.
IF2 Specifications
Specifications Values
Height 19.9 cm (7.87 in)
Length 18.8 cm (7.42 in)
Width 4.3 cm (1.7 in)
Weight 1 kg (2.2 lb)
DC electrical rating 12 V +/- 5%, 30 W
Operating temperature -20 ºC to +55 ºC (-4ºF to +131 ºF)
Storage temperature -30 ºC to +70 ºC (-22 ºF to +158 ºF)
Humidity
(non-condensing)
Ethernet interfaces 10BaseT/100BaseTx (twisted-pair) with
Ethernet compatibility Ethernet frame types and Ethernet
Ethernet data rate 10 Mbps/100 Mbps
Serial port maximum
data rate
IF2 with Expanded Memory
Option
(55 V, 30 W for High Power Over
Ethernet)
5% to 95% non-condensing
802.3 at High Power Over Ethernet (POE)
addressing
115,200 bps
96 MB of flash application memory
96 MB of flash data storage
64 MB RAM
IF2 Network Reader User Guide 61
Page 72

RFID Specifications
Pin 1
Pin 13
Pin 25
Pin 14
Specifications Values
Protocols Supported EPCglobal Class 1 Gen 2
Frequency Range 865.6 - 867.6 MHz, or 902 - 928 MHz
Frequency Range Malaysia
Output power
865-867 MHz, 900
MHz
Occupied frequency
bandwidth
Tag data rate 32 kbps/320 kbps
Dispatch rates > 200 tags per second
Transmitter type 90% amplitude modulation index
Frequency stability <±100 ppm from -25 °C to +55 °C
Number of antennas Up to 4, electronically switched
Antenna port isolation 22 dB
Antenna connectors Reverse TNC
ISO 18000-6B Generation 1
ISO 18000-6B Generation 2
ATA
919 - 923 MHz
Minimum: 1 dBm
Maximum: 30.0 dBm
<250 KHz
(-13°F to 131°F)
Port Pin Assignments
GPIO Port
GPIO Port Pin Assignments
62 IF2 Network Reader User Guide
Pin Description Active Polarity
1 -Input 1 Low-RTN
2 -Input 2 Low-RTN
3 -Input 3 Low-RTN
4 -Input 4 Low-RTN
5 Ground
6 Ground
7 +Output 1 High (10-48 V)
Page 73

Pin Description Active Polarity
8 Ground
9 +Output 2 High (10-48 V)
10 Ground
11 +Output 3 High (10-48 V)
12 Ground
13 +Output 4 High (10-48 V)
14 +Input 1 High (10-48 V)
15 +Input 2 High (10-48 V)
16 +Input 3 High (10-48 V)
17 +Input 4 High (10-48 V)
18 12VDC
19 -Output 1 Low-RTN
20 12VDC
21 -Output 2 Low-RTN
22 12VDC
23 -Output 3 Low-RTN
24 12 VDC
25 -Output 4 Low-RTN
Serial Ports (COM1)
Pin 9
Serial Port Pin Assignments
Pin Description Active Polarity
1 NC
2 Receive data (RXD)
3 Transmit data (TXD)
4 NC
5 Signal ground
6 NC
7 Request to send (RTS) Low
8 Clear to send (CTS) Low
9 NC
Pin 1
IF2 Network Reader User Guide 63
Page 74

Ethernet Port
Pin 1
Ethernet Port Pin Assignments
Pin Description
1 Ethernet TX+/Spare POE return
2 Ethernet TX-/Spare POE return
3 Ethernet RX+/Spare POE 48 VDC
4 Not used/POE 48 VDC
5 Not used/POE 48 VDC
6 Ethernet RX-/Spare POE 48 VDC
7 Not used/POE return
8 Not used/POE return
64 IF2 Network Reader User Guide
Page 75

Page 76

Honeywell
9680 Old Bailes Road
Fort Mill, SC 29707
www.honeywellaidc.com
™
935-040-005 Rev A
04/20
 Loading...
Loading...