Page 1

DS-A80&81 Series Storage System
User Manual
UD.6L0205D1035A01
Page 2

DS-A80&81 Series Storage System User Manual
1
User Manual
COPYRIGHT © 2016 Hangzhou Hikvision Digital Technology Co., Ltd.
ALL RIGHTS RESERVED.
Any and all information, including, among others, wordings, pictures, graphs are the properties of Hangzhou
Hikvision Digital Technology Co., Ltd. or its subsidiaries (hereinafter referred to be “Hikvision”). This user manual
(hereinafter referred to be “the Manual”) cannot be reproduced, changed, translated, or distributed, partially or
wholly, by any means, without the prior written permission of Hikvision. Unless otherwise stipulated, Hikvision
does not make any warranties, guarantees or representations, express or implied, regarding to the Manual.
About this Manual
This Manual is applicable to DS-A80&81 Series Storage System.
The Manual includes instructions for using and managing the product. Pictures, charts, images and all other
information hereinafter are for description and explanation only. The information contained in the Manual is
subject to change, without notice, due to firmware updates or other reasons. Please find the latest version in the
company website (http://overseas.hikvision.com/en/).
Please use this user manual under the guidance of professionals.
Trademarks Acknowledgement
and other Hikvision’s trademarks and logos are the properties of Hikvision in various jurisdictions.
Other trademarks and logos mentioned below are the properties of their respective owners.
Legal Disclaimer
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, THE PRODUCT DESCRIBED, WITH ITS HARDWARE,
SOFTWARE AND FIRMWARE, IS PROVIDED “AS IS”, WITH ALL FAULTS AND ERRORS, AND HIKVISION MAKES NO
WARRANTIES, EXPRESS OR IMPLIED, INCLUDING WITHOUT LIMITATION, MERCHANTABILITY, SATISFACTORY
QUALITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT OF THIRD PARTY. IN NO EVENT WILL
HIKVISION, ITS DIRECTORS, OFFICERS, EMPLOYEES, OR AGENTS BE LIABLE TO YOU FOR ANY SPECIAL,
CONSEQUENTIAL, INCIDENTAL, OR INDIRECT DAMAGES, INCLUDING, AMONG OTHERS, DAMAGES FOR LOSS OF
BUSINESS PROFITS, BUSINESS INTERRUPTION, OR LOSS OF DATA OR DOCUMENTATION, IN CONNECTION WITH
THE USE OF THIS PRODUCT, EVEN IF HIKVISION HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
REGARDING TO THE PRODUCT WITH INTERNET ACCESS, THE USE OF PRODUCT SHALL BE WHOLLY AT YOUR OWN
RISKS. HIKVISION SHALL NOT TAKE ANY RESPONSIBILITES FOR ABNORMAL OPERATION, PRIVACY LEAKAGE OR
OTHER DAMAGES RESULTING FROM CYBER ATTACK, HACKER ATTACK, VIRUS INSPECTION, OR OTHER INTERNET
SECURITY RISKS; HOWEVER, HIKVISION WILL PROVIDE TIMELY TECHNICAL SUPPORT IF REQUIRED.
SURVEILLANCE LAWS VARY BY JURISDICTION. PLEASE CHECK ALL RELEVANT LAWS IN YOUR JURISDICTION
BEFORE USING THIS PRODUCT IN ORDER TO ENSURE THAT YOUR USE CONFORMS THE APPLICABLE LAW.
HIKVISION SHALL NOT BE LIABLE IN THE EVENT THAT THIS PRODUCT IS USED WITH ILLEGITIMATE PURPOSES.
IN THE EVENT OF ANY CONFLICTS BETWEEN THIS MANUAL AND THE APPLICABLE LAW, THE LATER PREVAILS.
Page 3
DS-A80&81 Series Storage System User Manual
2
Regulatory Information
FCC Information
FCC compliance: This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference when the equipment is operated in a commercial environment. This equipment generates, uses, and
can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may
cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to
cause harmful interference in which case the user will be required to correct the interference at his own expense.
FCC Conditions
This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions:
1. This device may not cause harmful interference.
2. This device must accept any interference received, including interference that may cause undesired operation.
EU Conformity Statement
This product and - if applicable - the supplied accessories too are marked with "CE" and comply
therefore with the applicable harmonized European standards listed under the EMC Directive
2004/108/EC, the RoHS Directive 2011/65/EU, the LVD Directive 2006/95/EC.
2012/19/EU (WEEE directive): Products marked with this symbol cannot be disposed of as unsorted
municipal waste in the European Union. For proper recycling, return this product to your local
supplier upon the purchase of equivalent new equipment, or dispose of it at designated collection
points. For more information see: www.recyclethis.info
2006/66/EC (battery directive): This product contains a battery that cannot be disposed of as
unsorted municipal waste in the European Union. See the product documentation for specific
battery information. The battery is marked with this symbol, which may include lettering to indicate
cadmium (Cd), lead (Pb), or mercury (Hg). For proper recycling, return the battery to your supplier or to a
designated collection point. For more information see: www.recyclethis.info
Industry Canada ICES-003 Compliance
This device meets the CAN ICES-3 (A)/NMB-3(A) standards requirements.
Page 4
DS-A80&81 Series Storage System User Manual
3
Safety Instruction
These instructions are intended to ensure that user can use the product correctly to avoid danger or property
loss.
The precaution measure is divided into “Warnings” and “Cautions”
Warnings: Serious injury or death may occur if any of the warnings are neglected.
Cautions: Injury or equipment damage may occur if any of the cautions are neglected.
Warnings
● Proper configuration of all passwords and other security settings is the responsibility of the installer and/or
end-user.
● In the use of the product, you must be in strict compliance with the electrical safety regulations of the nation
and region. Please refer to technical specifications for detailed information.
● Input voltage should meet both the SELV (Safety Extra Low Voltage) and the Limited Power Source with
100~240 VAC or 12 VDC according to the IEC60950-1 standard. Please refer to technical specifications for
detailed information.
● Do not connect several devices to one power adapter as adapter overload may cause over-heating or a fire
hazard.
● Please make sure that the plug is firmly connected to the power socket.
● If smoke, odor or noise rise from the device, turn off the power at once and unplug the power cable, and then
please contact the service center.
Warnings Follow these safeguards to
prevent serious injury or death.
Cautions Follow these precautions to
prevent potential injury or material
damage.
Page 5

DS-A80&81 Series Storage System User Manual
4
Table of Contents
Chapter 1 Overview ......................................................................................................................... 7
Chapter 2 Getting Started ................................................................................................................ 8
2.1 HDD Installation ............................................................................................................................... 9
2.2 Access by Web Browser ................................................................................................................. 10
2.3 Login .............................................................................................................................................. 11
Chapter 3 Maintenance .................................................................................................................. 12
3.1 System Monitor ............................................................................................................................. 13
3.2 Performance .................................................................................................................................. 13
3.3 Common ........................................................................................................................................ 15
3.3.1 Viewing Version Information ............................................................................................ 15
3.3.2 Resetting System ............................................................................................................... 16
3.3.3 Managing Maintenance Log.............................................................................................. 16
3.3.4 Application Service ........................................................................................................... 16
3.3.5 System Upgrade ................................................................................................................ 20
3.3.6 Strategy ............................................................................................................................. 20
3.4 Graphical Display ........................................................................................................................... 21
3.4.1 Front View ........................................................................................................................ 21
3.4.2 Pie Chart ........................................................................................................................... 22
3.5 Control Message ............................................................................................................................ 23
Chapter 4 Storage Management ..................................................................................................... 25
4.1 Managing Local Disk ...................................................................................................................... 26
4.1.1 Viewing Disk Status ........................................................................................................... 26
4.1.2 Rescanning Disk ................................................................................................................ 27
4.1.3 Positioning Disk ................................................................................................................. 27
4.1.4 Disk Initialization ............................................................................................................... 28
4.1.5 Disk Check ......................................................................................................................... 28
4.2 Array .............................................................................................................................................. 29
4.2.1 Creating Array ................................................................................................................... 29
4.2.2 Array Exception ................................................................................................................. 31
4.2.3 Rebuilding Array................................................................................................................ 31
4.2.4 Checking Array .................................................................................................................. 32
4.2.5 Repairing Array ................................................................................................................. 33
4.2.6 Renaming Array ................................................................................................................ 33
4.2.7 Deleting Array ................................................................................................................... 34
4.2.8 Adding Hot Spare .............................................................................................................. 34
4.2.9 Deleting Hot Spare ............................................................................................................ 35
4.3 Storage Pool ................................................................................................................................... 35
4.3.1 Adding Storage Pool .......................................................................................................... 36
4.3.2 Deleting Storage Pool ........................................................................................................ 37
4.3.3 Positioning Storage Pool ................................................................................................... 37
4.4 LUN (Logical Volume) ..................................................................................................................... 37
4.4.1 Creating LUN ..................................................................................................................... 37
Page 6

DS-A80&81 Series Storage System User Manual
5
4.4.2 Deleting LUN ..................................................................................................................... 38
4.4.3 Renaming LUN .................................................................................................................. 38
4.4.4 Enlarging LUN .................................................................................................................... 38
4.5 Settings .......................................................................................................................................... 39
4.5.1 Synchronization Speed and Type ...................................................................................... 39
4.5.2 Flashing Time .................................................................................................................... 40
Chapter 5 SAN ................................................................................................................................ 41
5.1 iSCSI ............................................................................................................................................... 42
5.1.1 Adding CHAP User ............................................................................................................. 42
5.1.2 Modifying CHAP User ........................................................................................................ 43
5.1.3 Enabling iSCSI .................................................................................................................... 43
5.1.4 Disabling iSCSI ................................................................................................................... 44
5.1.5 Modifying iSCSI Port.......................................................................................................... 44
5.2 FC (Optional) .................................................................................................................................. 45
5.2.1 Enabling FC ....................................................................................................................... 45
5.2.2 Disabling FC ....................................................................................................................... 46
Chapter 6 CVR ................................................................................................................................ 47
6.1 Quick-Setting CVR .......................................................................................................................... 48
6.2 CVR Configuration ......................................................................................................................... 49
6.2.1 Starting CVR ...................................................................................................................... 49
6.2.2 Resetting CVR .................................................................................................................... 51
6.2.3 Record Volume .................................................................................................................. 52
6.3 Backup and Restoring .................................................................................................................... 54
6.3.1 Viewing Private Volume Information ................................................................................ 54
6.3.2 Restoring ........................................................................................................................... 55
6.3.3 Backup .............................................................................................................................. 55
6.3.4 Recovering Video Data...................................................................................................... 56
6.4 N+1 Management .......................................................................................................................... 56
6.4.1 Adding Backup CVR ........................................................................................................... 57
6.4.2 Deleting Backup CVR ......................................................................................................... 58
6.4.3 Adding Master CVR ........................................................................................................... 58
Chapter 7 CVR Sub-System.............................................................................................................. 60
7.1 Access by Web Browser ................................................................................................................. 61
7.2 Information .................................................................................................................................... 61
7.3 Device Management...................................................................................................................... 62
7.3.1 Device ............................................................................................................................... 63
7.3.2 Tools .................................................................................................................................. 67
7.4 Live View and Record .................................................................................................................... 69
7.4.1 Live View ........................................................................................................................... 70
7.4.2 Manual Record .................................................................................................................. 70
7.5 Schedule and Alarm ....................................................................................................................... 71
7.5.1 Schedule ........................................................................................................................... 71
7.5.2 Record Upload................................................................................................................... 74
7.5.3 Alarm ................................................................................................................................ 76
Page 7

DS-A80&81 Series Storage System User Manual
6
7.6 Playing and Downloading .............................................................................................................. 77
7.6.1 Searching Video ................................................................................................................ 78
7.6.2 Archiving ........................................................................................................................... 78
7.6.3 Remote Backup ................................................................................................................. 80
7.6.4 Locking .............................................................................................................................. 80
7.6.5 Playback ............................................................................................................................ 81
7.6.6 Downloading ..................................................................................................................... 82
7.7 Archiving ........................................................................................................................................ 84
7.7.1 Archive Volume ................................................................................................................. 84
7.7.2 Archive Search .................................................................................................................. 85
7.8 User ............................................................................................................................................... 86
7.9 System Configuration..................................................................................................................... 86
7.9.1 System Alarm .................................................................................................................... 87
7.9.2 CVR Version ....................................................................................................................... 88
7.10 Log Management ........................................................................................................................... 89
7.10.1 Searching Log .................................................................................................................... 89
7.10.2 Exporting Log .................................................................................................................... 89
7.10.3 Clearing Log ...................................................................................................................... 90
Chapter 8 System ............................................................................................................................ 91
8.1 Network ......................................................................................................................................... 92
8.1.1 Modifying Data NIC ........................................................................................................... 92
8.1.2 NIC Bond ........................................................................................................................... 93
8.1.3 Adding Route .................................................................................................................... 94
8.1.4 MAC and IP Bonding ......................................................................................................... 95
8.1.5 Advanced Parameters ....................................................................................................... 96
8.2 Alarm ............................................................................................................................................. 98
8.2.1 Alarm Type ........................................................................................................................ 99
8.2.2 Adding E-Mail .................................................................................................................. 100
8.2.3 Testing E-Mail .................................................................................................................. 101
8.2.4 Adding SMTP Manager ................................................................................................... 101
8.2.5 Testing SMTP Manager ................................................................................................... 102
8.3 Time ............................................................................................................................................ 102
8.3.1 Adjusting System Time .................................................................................................... 103
8.3.2 Synchronizing Time ......................................................................................................... 103
8.4 Tool .............................................................................................................................................. 104
Chapter 9 Log ............................................................................................................................... 105
9.1 Operation Log .............................................................................................................................. 106
9.2 Performance Log.......................................................................................................................... 107
9.3 Update Log .................................................................................................................................. 107
Page 8
DS-A80&81 Series Storage System User Manual
7
Chapter 1 Overview
Purpose:
DS-A80&81 series storage system is a high-performance and highly reliable storage system. Designed with four
enterprise-class gigabyte network interfaces, it provides a bandwidth with 4 to 8G bps transmission capability and
a huge storage space. It is integrated with multiple advanced technologies, including a 64-bit hexa-core processors,
stable architecture, and the RAID 6 storage technology, thus to run reliably and protect user’s data security
effectively.
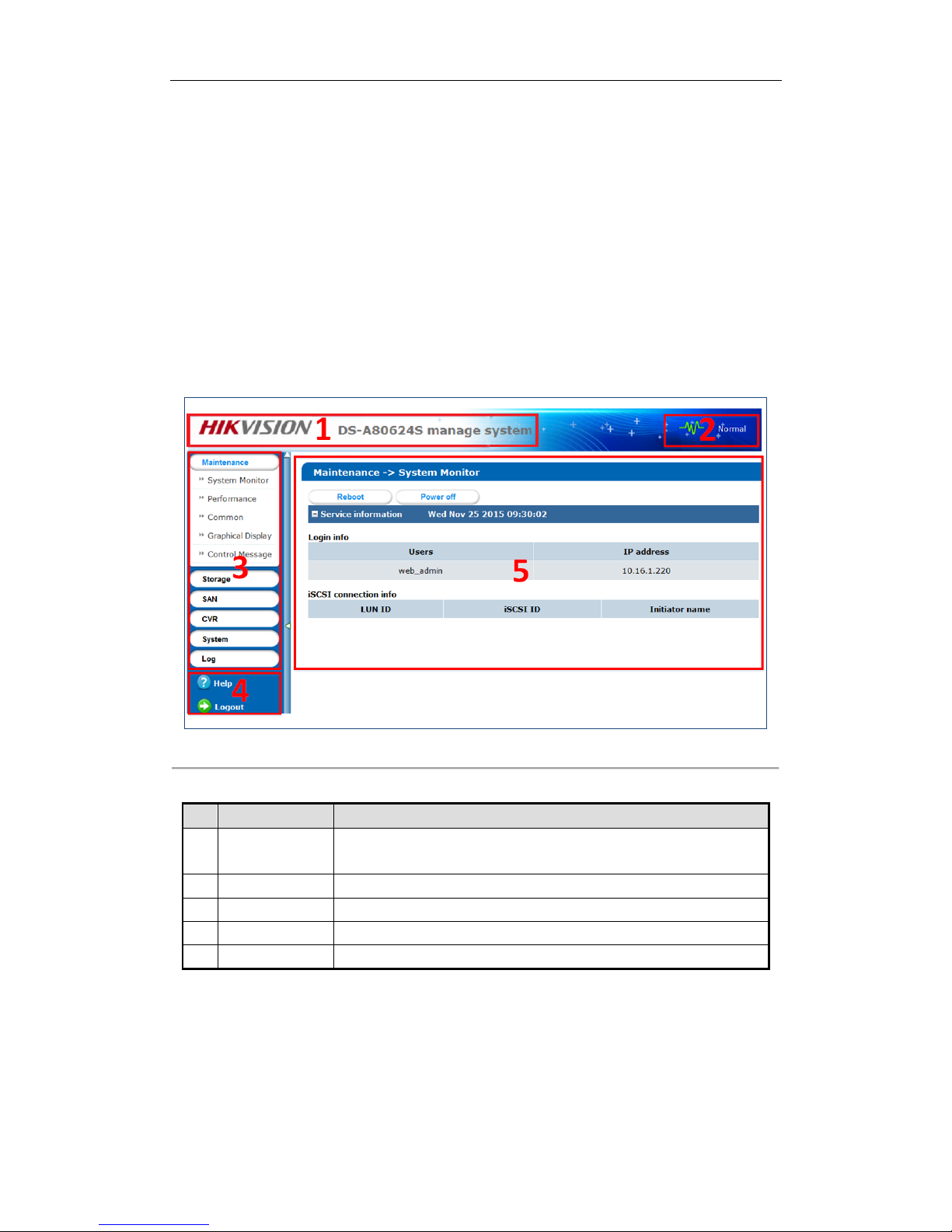
Figure 1. 1 GUI and Table 1. 1 GUI Introduction introduce the elements appear in the GUI (Graphical User
Interface) and clarify names for each element.
Figure 1. 1 GUI
Table 1. 1 GUI Introduction
No.
Name
Description
1
Banner and device
model
Shows the banner and device model.
2
Running status
A shortcut for obtaining the real-time running status.
3
Navigation Bar
Lists the storage system menu.
4
Help and logout
A shortcut for accessing user manuals, downloading software, and logout.
5
Operation window
Lists the parameters. You can configure parameters in the area.
Page 9
DS-A80&81 Series Storage System User Manual
8
Chapter 2 Getting Started
Purpose:
The chapter introduces HDD installation steps, web browser access steps, and login steps.
Table 2. 1 Module Description
Module
Description
HDD Installation
Describes the steps of HDD installation.
Web Browser Access
You can get access to the storage system via a server with the web browser
installed.
Login
Introduces login storage system steps.
Key Words:
HDD Installation, Web Browser Access, Login
Page 10
DS-A80&81 Series Storage System User Manual
9
2.1 HDD Installation
Before you start:
Prepare the following equipment and accessories.
A storage system
Hard disks
A pair of anti-static gloves
A screwdriver
Steps:
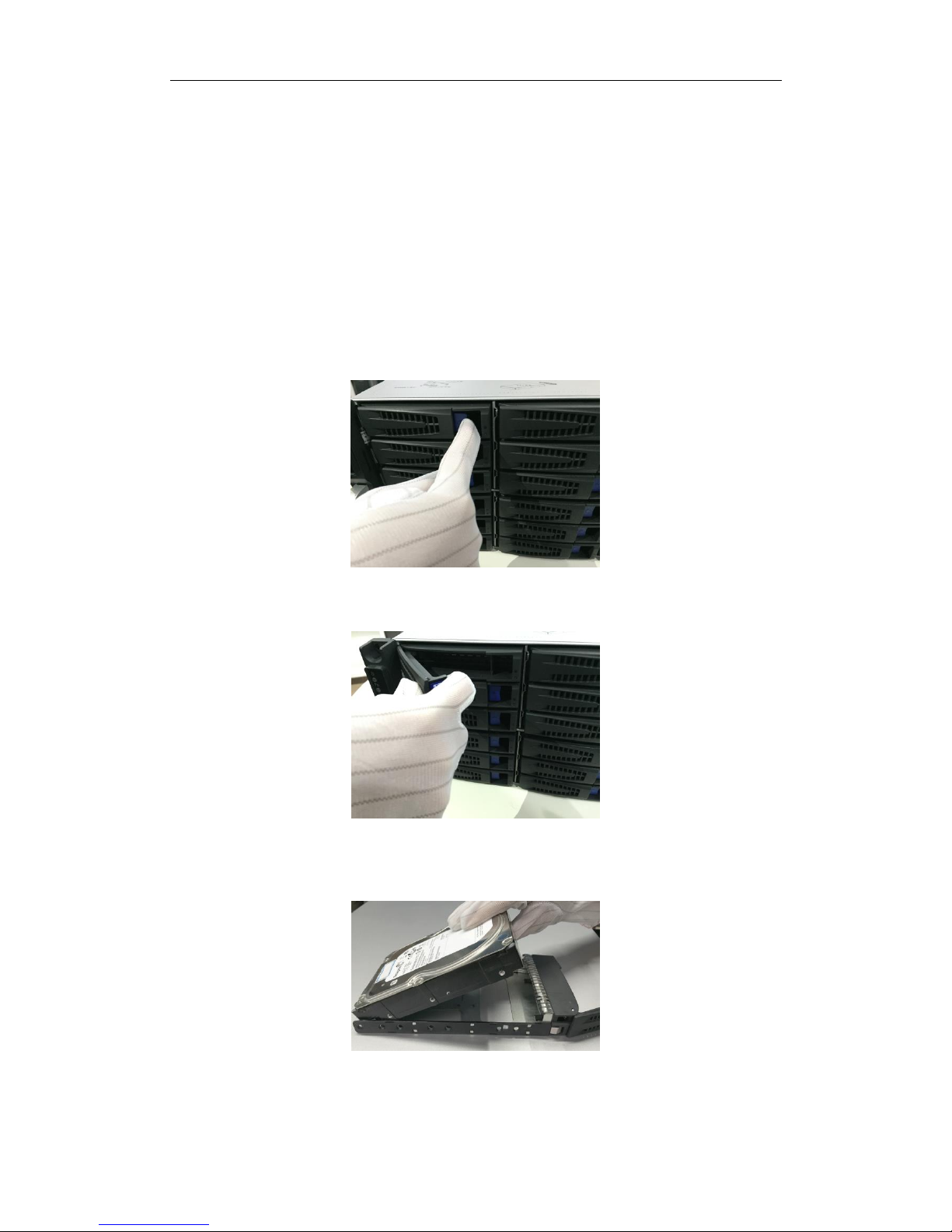
1. Press the blue button to pop up the hander.
Figure 2. 2 Press the Blue Button
2. Hold the hander and pull the hard disk box out of the slot.
Figure 2. 3 Pull out the Hard Disk Box
3. Use the screwdriver to uninstall the baffle in the bottom of hard disk slot.
4. Place a hard disk in the hard disk box. The SATA interface must face the hard disk box rear.
Figure 2. 4 Place Hard Disk
5. Adjust the hard disk position. Ensure the hard disk rear aligning with hard disk rear and the two screw holes
aiming at the holes that marked with red frame in Figure 2. 5 HDD Position.
Page 11

DS-A80&81 Series Storage System User Manual
10
Figure 2. 5 HDD Position
6. Use a screwdriver to fasten the four screws into the screw holes that in both sides.
Figure 2. 6 Install Screws
7. Push the hard disk box back into the slot.
Figure 2. 7 Pull the HDD Box into Slot
2.2 Access by Web Browser
Purpose:
You can get access to the storage system via a server with a web browser installed, without needing to install any
other software. The recommended web browser includes Internet Explorer 8 and Internet Explorer 11.
Before you start:
1. Use a network cable to connect the server’s Ethernet port and the storage system’s Management NIC
(Network Interface Card).
2. Configure the server’s IP address. Ensure it is in the same network segment with the Management NIC (the
default IP address of Management NIC is 10.254.254.254.
Steps:
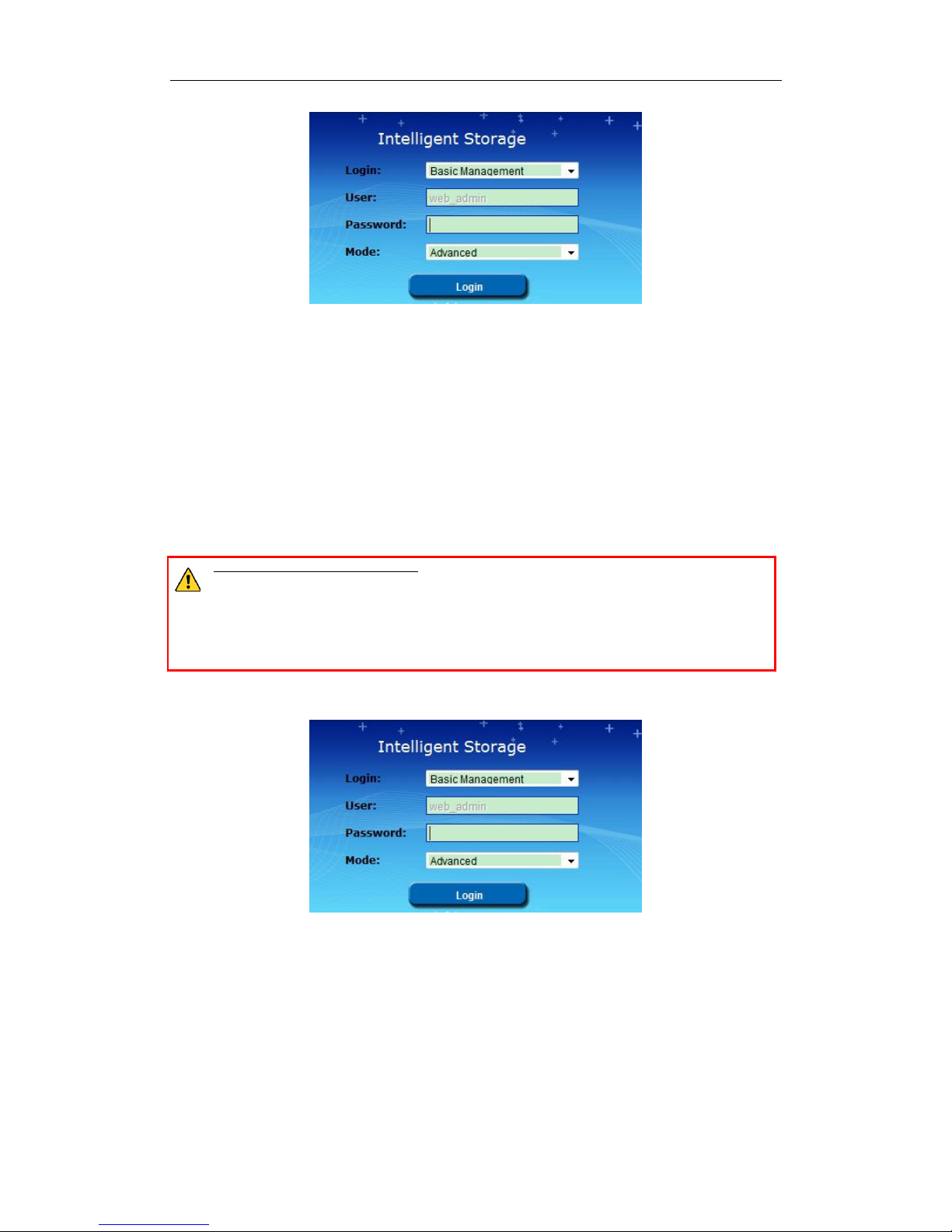
1. Open web browser.
2. Input the storage system’s IP address (https://10.254.254.254:2004) in Web browser address bar.
3. Press Enter. Then login interface appears.
Page 12
DS-A80&81 Series Storage System User Manual
11
Figure 2. 8 Login Interface
2.3 Login
Steps:
1. Select Login account as Basic Management or CVR Sub-system.
Basic Management: Used to configure basic parameters of storage system.
CVR Sub-system: Used to Log into CVR sub-system.
2. Select User name.
3. Enter Password. The default password is 123.
STRONG PASSWORD RECOMMENDED–We highly recommend you create a strong password of your own
choosing (Using a minimum of 8 characters, including at least three of the following categories: upper
case letters, lower case letters, numbers, and special characters.) in order to increase the security of your product.
And we recommend you reset your password regularly, especially in the high security system, resetting the
password monthly or weekly can better protect your product.
4. Mode is Advanced by default and is not selectable.
5. Click Login to log in system.
Figure 2. 9 Login
Page 13

DS-A80&81 Series Storage System User Manual
12
Chapter 3 Maintenance
Purpose:
Maintenance function enables you to view login and iSCSI information, monitor running status, restore default
settings, check and download logs, upgrade storage system, and so forth.
Table 3. 1 Module Description
Module
Description
System Monitor
It is a shortcut for reboot and shutdown and lists the login user’s information and
iSCSI connection information.
Performance
Shows you the real-time graph and data of system performance, including
bandwidth usage, memory usage, CPU usage, IO status, and Vmstatus.
Common
You can view system version, reset system, view logs, upgrade system, and add
check and repair strategy.
Graphical Display
Provides a graph to show the front view status and a pie chart to show the storage
information.
Control Message
Shows the fans’ information, modules’ temperature, fan control panel version, and
chassis power.
Key words:
System Monitor, Performance, Common, Graphical Display, Control Message
Figure 3. 2 Maintenance
Page 14
DS-A80&81 Series Storage System User Manual
13
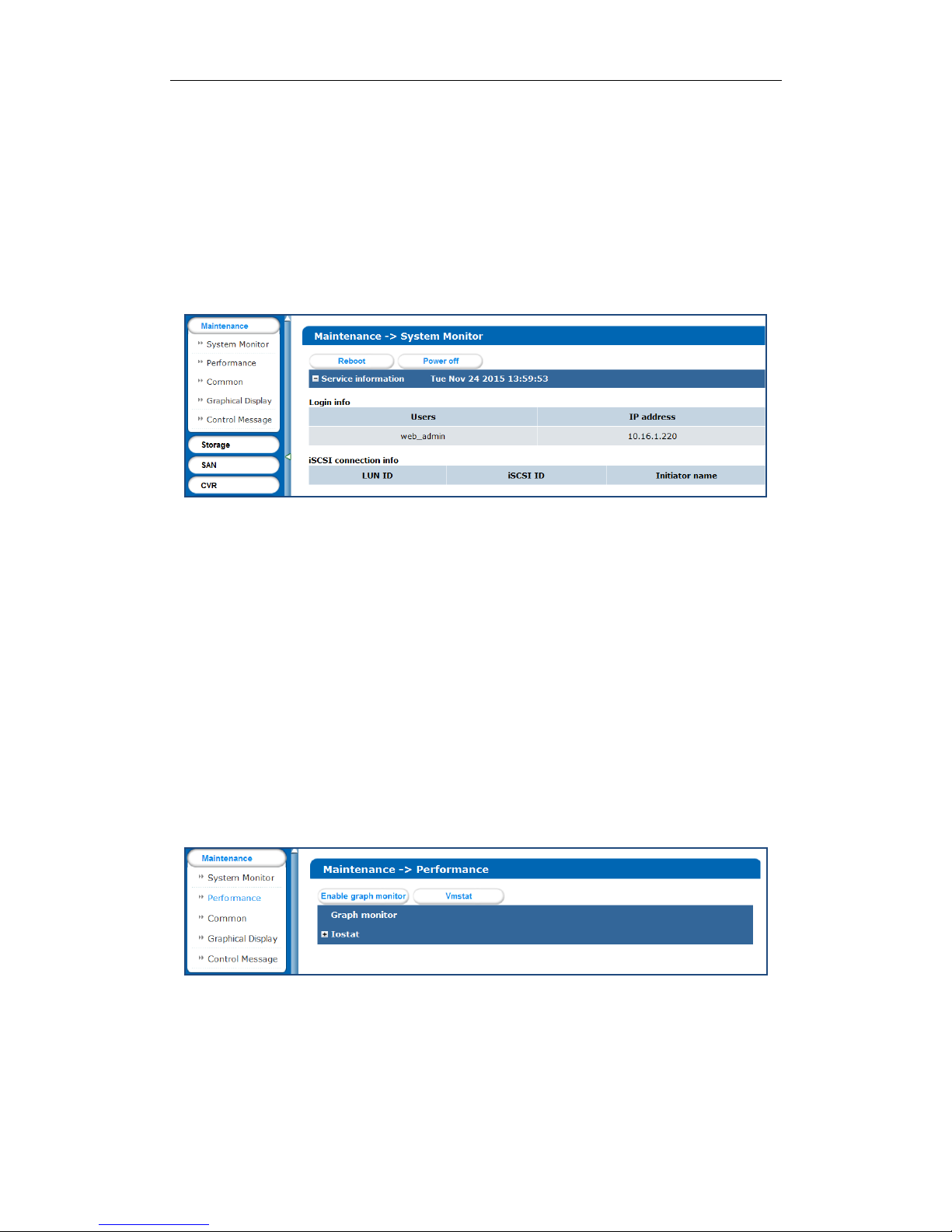
3.1 System Monitor
Purpose:
Once you log into the storage system, system monitor menu appears. System monitor menu is a shortcut for
reboot and shutdown and lists the login user’s information and iSCSI connection information.
Steps:
1. Click Maintenance in navigation bar and choose System Monitor to enter System Monitor interface.
Figure 3. 3 System Monitor
2. Reboot, power off, or view login information or iSCSI connection info.
Click Reboot or Power off to restart or shut down the storage system.
The logged in users’ names and IP addresses are listed in the Login info.
The LUN ID, iSCSI ID, and Initiator name are listed in iSCSI connection info, which shows which
devices are connecting iSCSI.
3.2 Performance
Purpose:
Performance menu shows you the real-time graph and data of system performance, including bandwidth usage,
memory usage, CPU usage, IO status, and Vmstatus.
Steps:
1. Click Maintenance in navigation bar and choose Performance to enter Performance interface.
Figure 3. 4 Performance
2. Click Enable Graph Monitor to show the real-time graphs of bandwidth usage, memory usage, and CPU
usage.
3. Optionally, click Disable Graph Monitor to fold the graphs.
Page 15
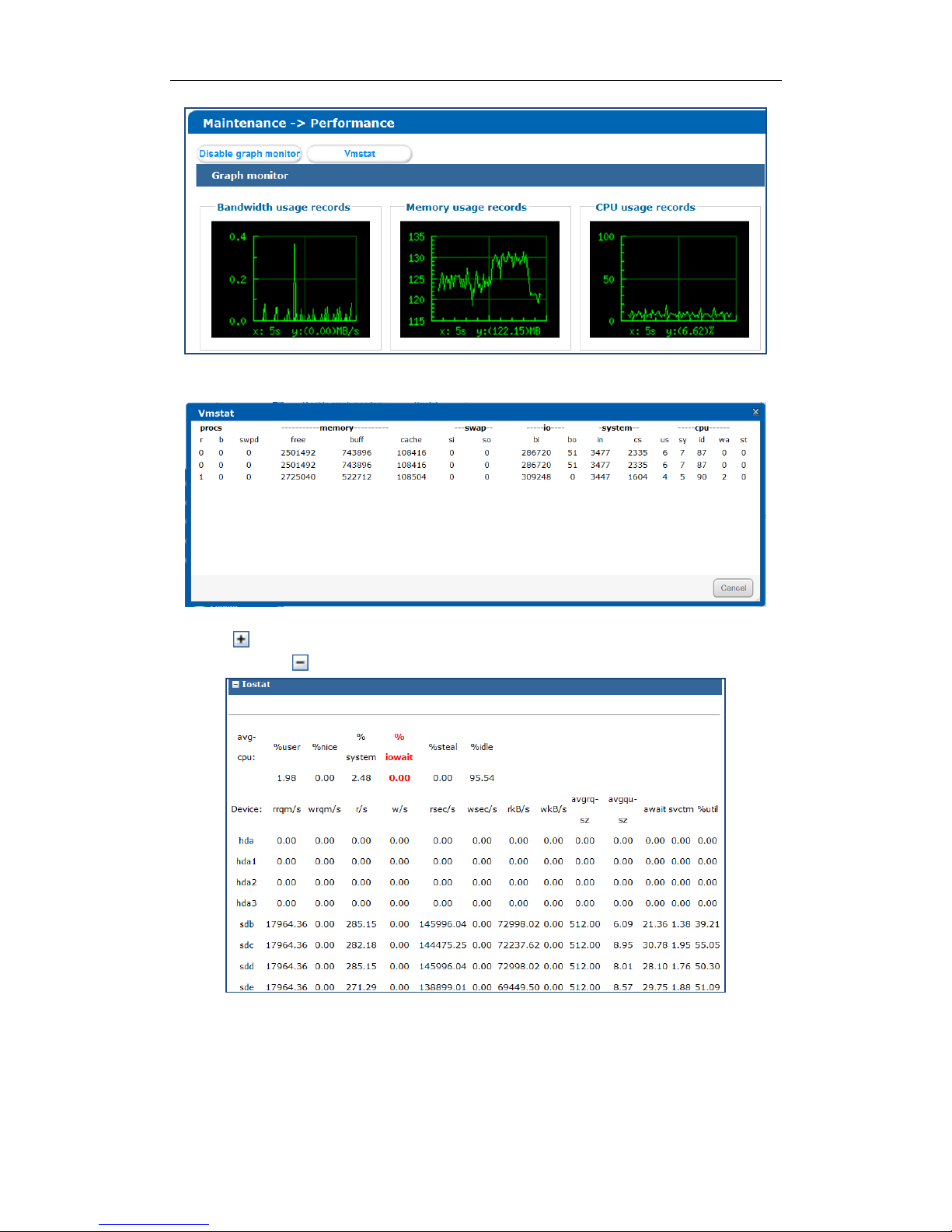
DS-A80&81 Series Storage System User Manual
14
Figure 3. 5 Graph Monitor
4. Click Vmstat to pop up Vmstat window. Vmstat updates per second.
Figure 3. 6 Vmstat
5. Click of Iostat to unfold input/output status.
6. Optionally, click of Iostat to fold input/output status.
Figure 3. 7 Iostat
Page 16
DS-A80&81 Series Storage System User Manual
15
3.3 Common
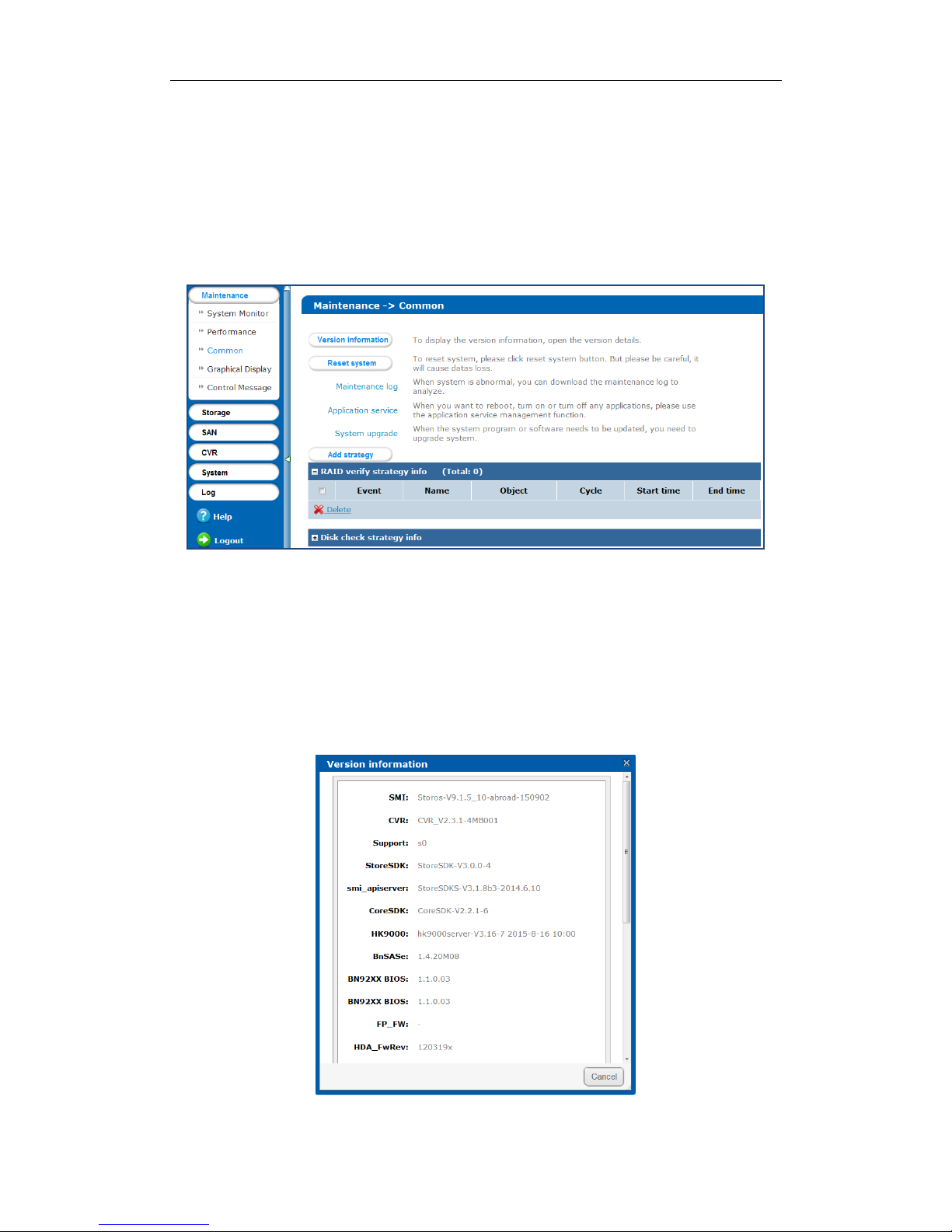
Purpose:
You can view system version, reset system, view logs, upgrade system, and add check and repair strategy.
Step:
Click Maintenance in navigation bar and choose Common to enter Common interface.
Figure 3. 8 Common
3.3.1 Viewing Version Information
Purpose:
Version information interface lists information including SMI, CVR, Support, and so on.
Steps:
1. Click Version information to pop up version information window.
2. Click Cancel to close the window.
Figure 3. 9 Version Information
Page 17
DS-A80&81 Series Storage System User Manual
16
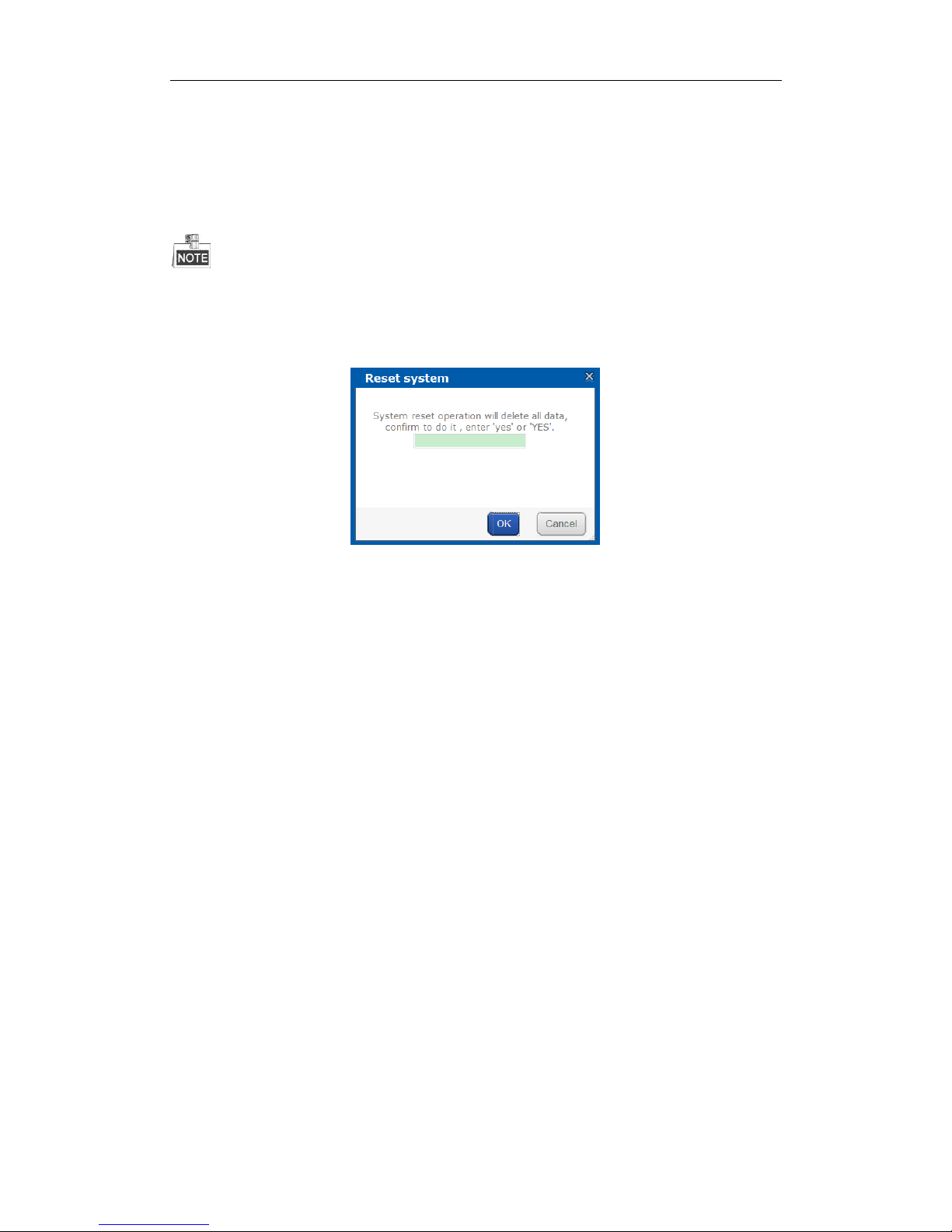
3.3.2 Resetting System
Purpose:
You can reset system to factory defaults when system is abnormal. You’re recommended to reset system under
the direction of professional technical support.
Resetting operation won’t restore administrator user name and password, RAID configuration, hot spot
configuration, and network parameters.
Steps:
1. Click Reset system to pop up reset system dialog.
Figure 3. 10 Reset System
2. Enter yes or YES in text field and click OK to reset.
3.3.3 Managing Maintenance Log
Purpose:
When system is abnormal, you can download the maintenance log to analyze problems.
Steps:
For details, refer to 9.1 Operation Log.
3.3.4 Application Service
Purpose:
When you want to reboot, turn on or turn off any applications, use the application service management function.
Step:
Click Application Service in Common menu to enter Application Service interface.
Page 18
DS-A80&81 Series Storage System User Manual
17
Figure 3. 11 Application Service
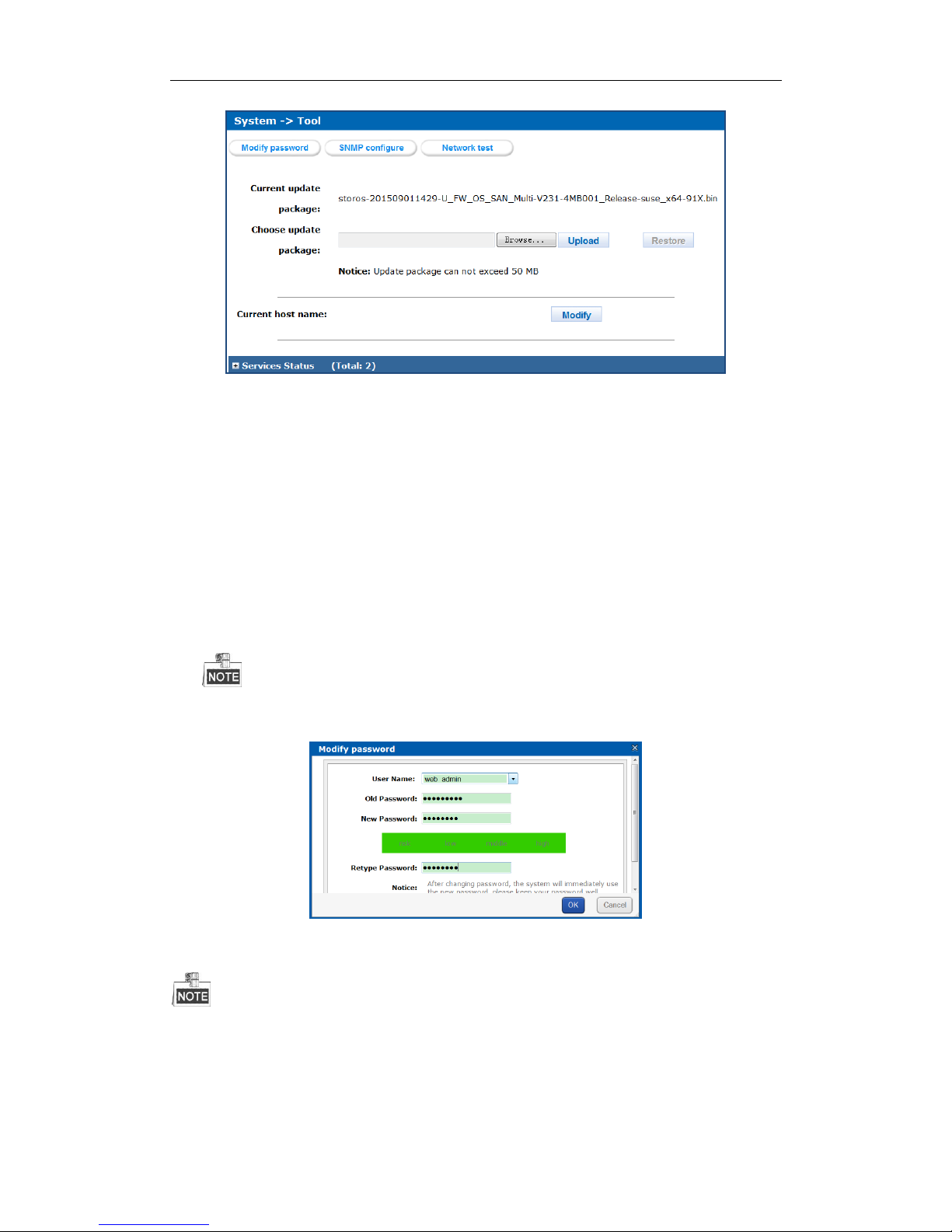
3.3.4.1 Modifying Password
Purpose:
You can modify password for basic management system and CVR sub-system user.
Steps:
1. Click Modify password button. And modify password window appears.
2. Select User Name as web_admin or nvr_admin.
web_admin: Basic management system user name.
nvr_admin: CVR sub-system user name.
3. Enter Old Password and the same password in New Password and Confirm Password.
The security level of modified password shouldn’t be lower than low security.
Password can only contain numbers, lowercase, uppercase, and underline for your password.
Figure 3. 12 Modify Password
4. Click OK and click OK in popup message dialog to save the new password.
Once password is modified, it jumps to login interface. You need to enter the new password to log in.
Another controller’s password changes with the current controller’s password.
Page 19
DS-A80&81 Series Storage System User Manual
18
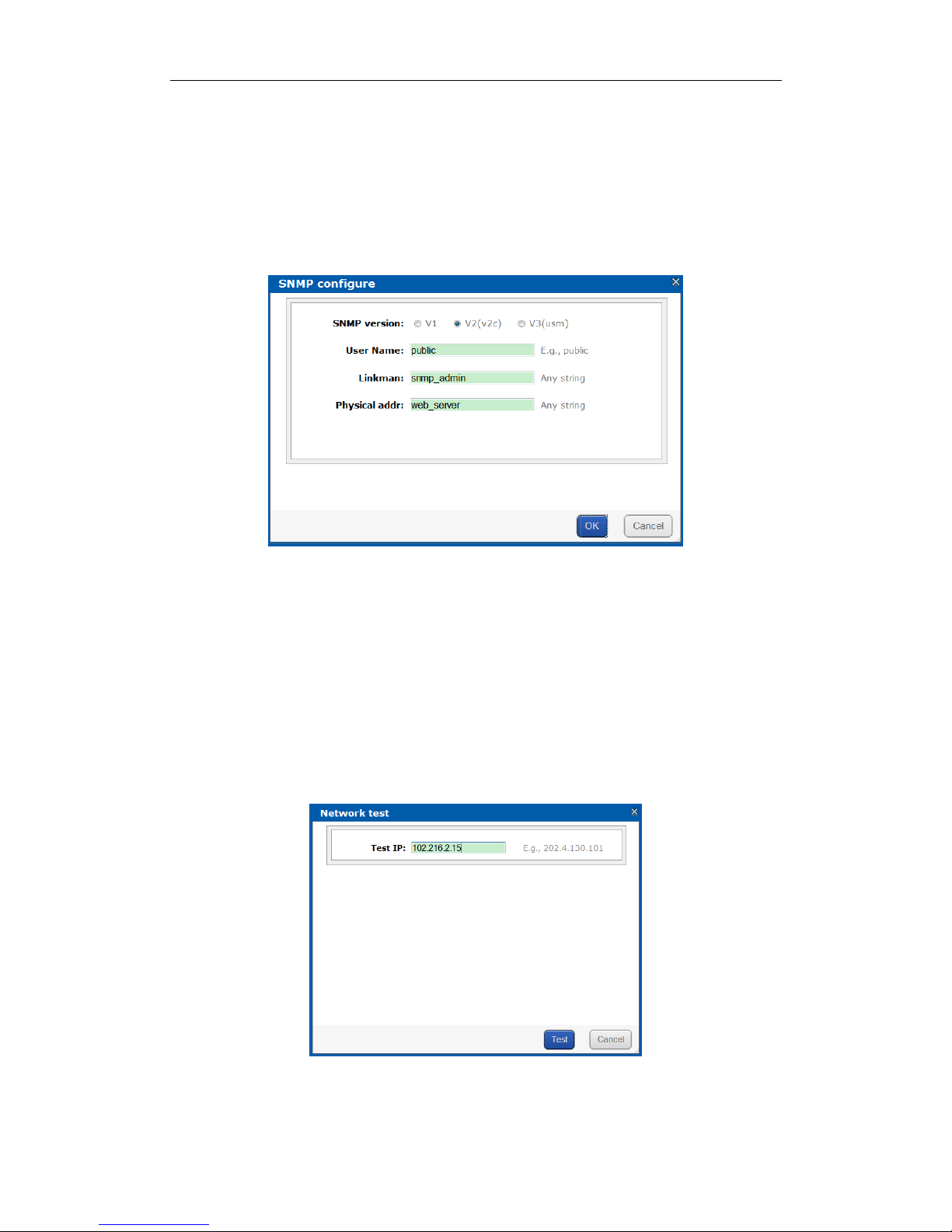
3.3.4.2 SNMP Configuration
Purpose:
By configuring SNMP parameters, you can log in PRTG Traffic Grapher tool to monitor the system status, including
exception information, CPU usage, and so forth.
Steps:
1. Click SNMP configure button. Then SNMP configure interface appears.
Figure 3. 13 SNMP Configuration
2. SNMP version is V2(v2c) by default and is not editable.
3. Enter User Name, Linkman, and Physical addr.
4. Click OK to save the settings. Then you can view system status by logging in PRTG Traffic Grapher Tool.
3.3.4.3 Network Test
Purpose:
You can test the network communication between the storage system with any other IP addresses.
Steps:
1. Click Network test to pop up Network test interface.
Figure 3. 14 Network Test
2. Input the IP address you want to test in Test IP text field.
Page 20
DS-A80&81 Series Storage System User Manual
19
3. Click Test to start testing. Test result would be listed in the current interface.
Figure 3. 15 Test Result
3.3.4.4 Modifying Host Name
Steps:
1. Click Modify and text field appears.
2. Enter host name in the text field.
3. Click Modify to activate the new host name.
Figure 3. 16 Modify Host Name
Only letters (a to z and A to Z), numbers (0 to 9), and underline (_) can be input.
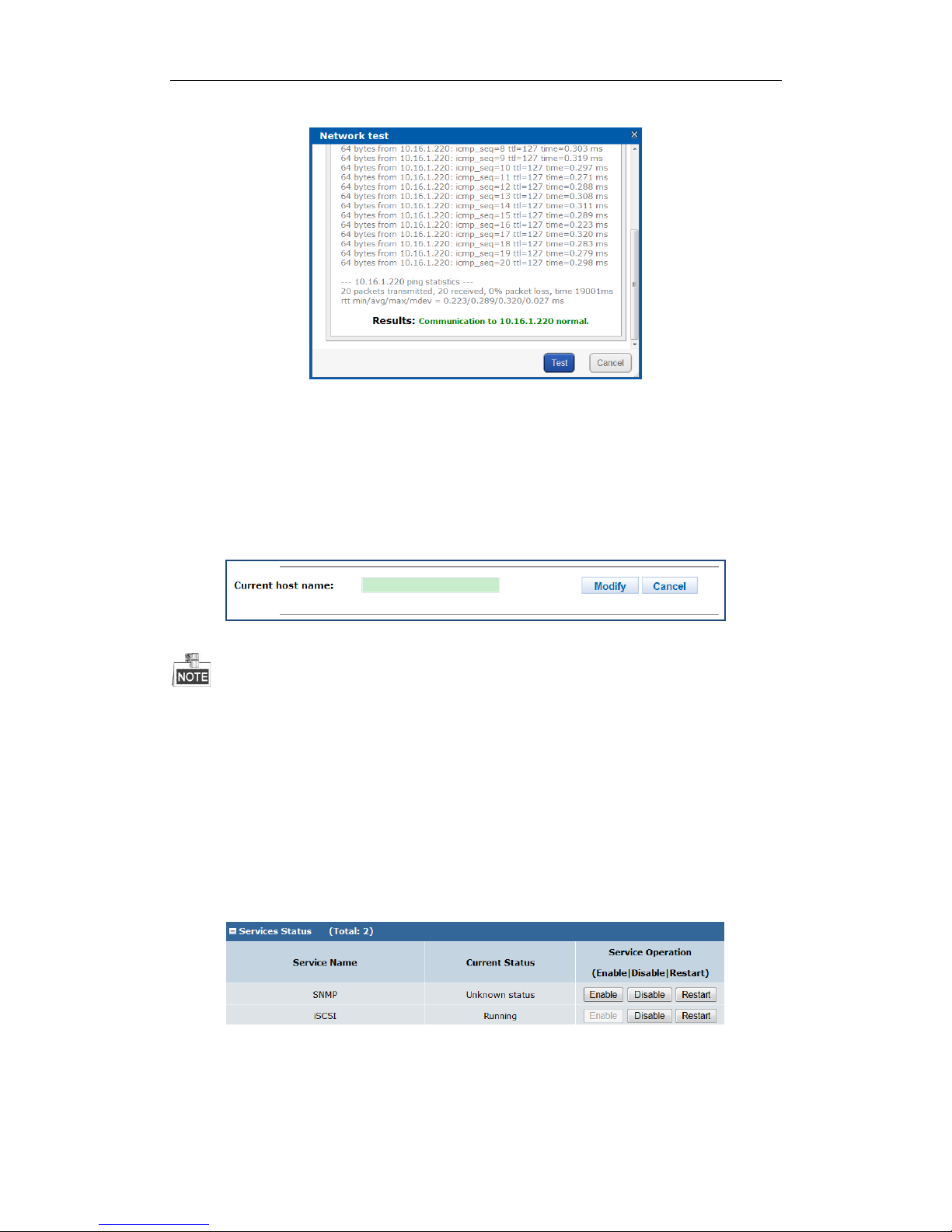
3.3.4.5 Viewing Service Status
Purpose:
Whether the services are running or not is listed. You can enable, disable, or restart the services.
Steps:
Click Enable to start the service isn’t running.
Click Disable to shut down the running service.
Click Restart to restart services.
Figure 3. 17 Service Status
Page 21
DS-A80&81 Series Storage System User Manual
20
3.3.5 System Upgrade
Purpose:
You’re recommended to upgrade system under the help of professional support.
Steps:
1. Click System upgrade in Common menu to enter Application Service interface.
Figure 3. 18 Application Service
2. Click Browser and choose the upgrade package.
3. Click Upload to upgrade. After upgrade succeeded, reboot the storage system to activate the new version.
4. Optionally, you can click Restore to restore to previous version.
You can only restore to the last upgraded version.
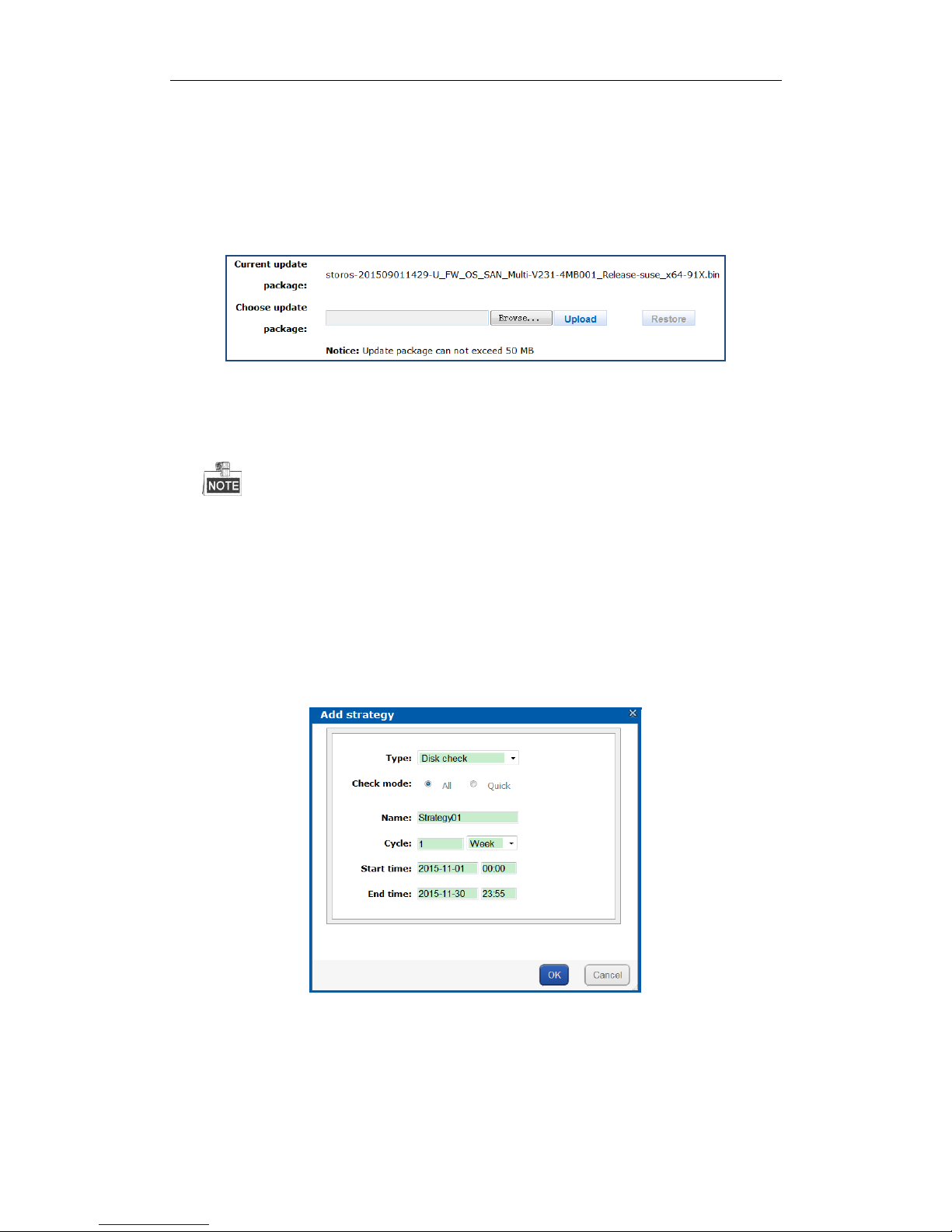
3.3.6 Strategy
Purpose:
By setting array and disk check strategy, the storage system automatically check array and disk according to
configuration.
Steps:
1. Select Add strategy in Common menu to pop up Add strategy interface.
Figure 3. 19 Add Strategy
2. Choose Type as RAID verification or Disk check.
Type is chosen as RAID verification.
1) Select Verify mode as Check or Require.
Check: Check whether the data bit and parity data in array match or not.
Page 22
DS-A80&81 Series Storage System User Manual
21
Require: Repair the data bit and parity data mismatch issue.
2) Select Array you want to verify.
Type is chosen as Disk check.
Select check mode as All or Check.
All: Check all disk blocks. It takes longer time than quick check.
Quick: Check parts of all disk blocks. It takes shorter time than all check.
3. Enter strategy Name in the text field.
Only letters (a to z and A to Z), numbers (0 to 9), and underline (_) are allowed.
4. Choose detection Cycle unit as Week, Year, Month, or Once in dropdown list and enter quantity in the text
field.
5. Choose Start time and End time.
6. Click OK to save the strategy. Added strategy is listed in the list.
3.4 Graphical Display
Purpose:
The storage system provides a graph to show the front view status and a pie chart to show the storage
information.
Step:
Click Maintenance in navigation bar and choose Graphical Display to enter Graphical Display interface.
Figure 3. 20 Graphical Display
3.4.1 Front View
Purpose:
Front view can show you the disk status.
Steps:
1. Click Front View in Graphical Display menu to show front view.
Page 23
DS-A80&81 Series Storage System User Manual
22
Table 3. 2 Indicator Status Description
Indicator
Color
Description
Top indicator
Unlit
Disk doesn’t exist.
Green
Disk is connected and recognized.
Bottom indicator
Green
Disk is normal.
Blue
Reading and writing normally.
Red
Disk is rebuilding.
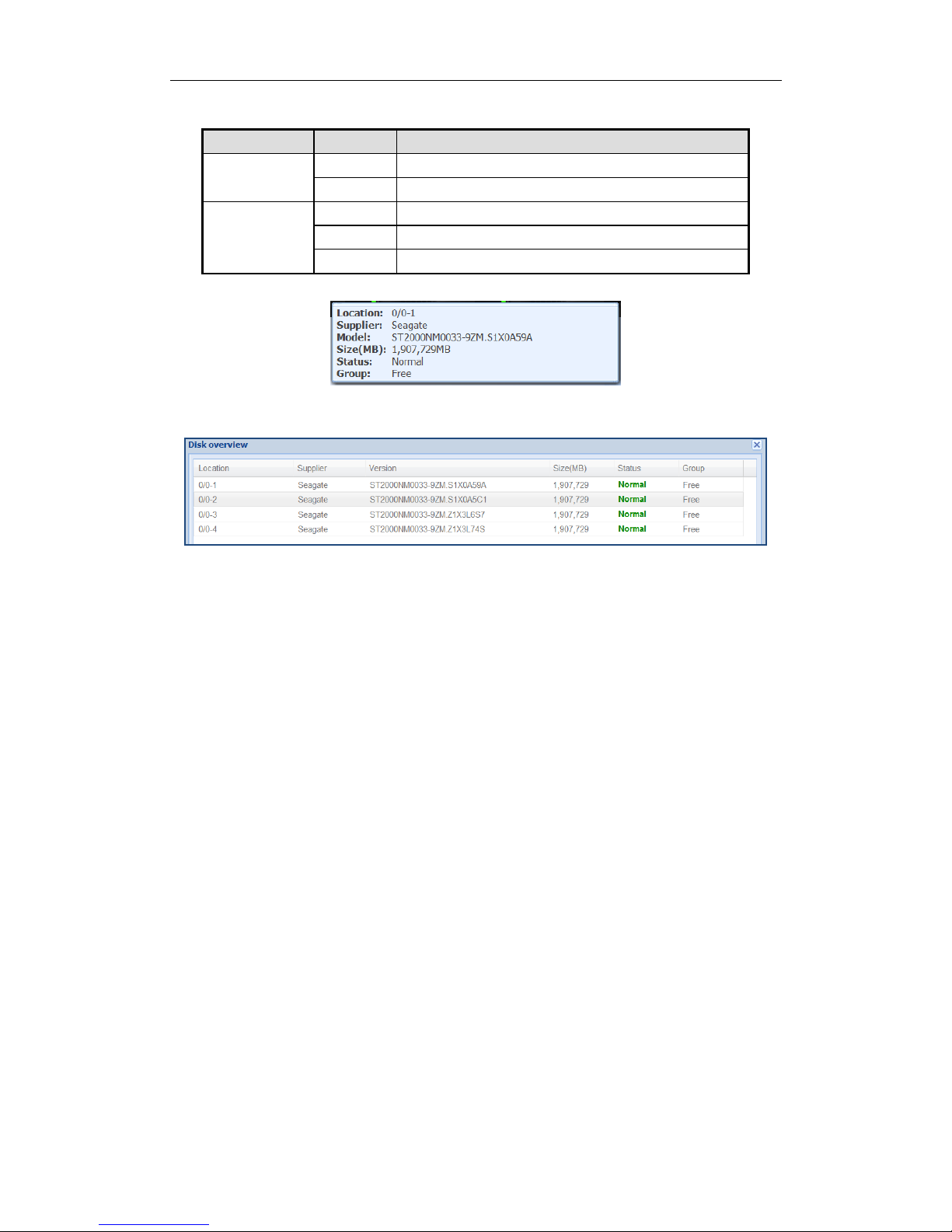
2. Positioning the pointer in a green indicator slot. Then the message dialog appears.
Figure 3. 21 Disk Information
3. Click Overview to view all disks’ information.
Figure 3. 22 Disk Overview
4. Optionally, click Refresh in top-right corner to update the front view.
3.4.2 Pie Chart
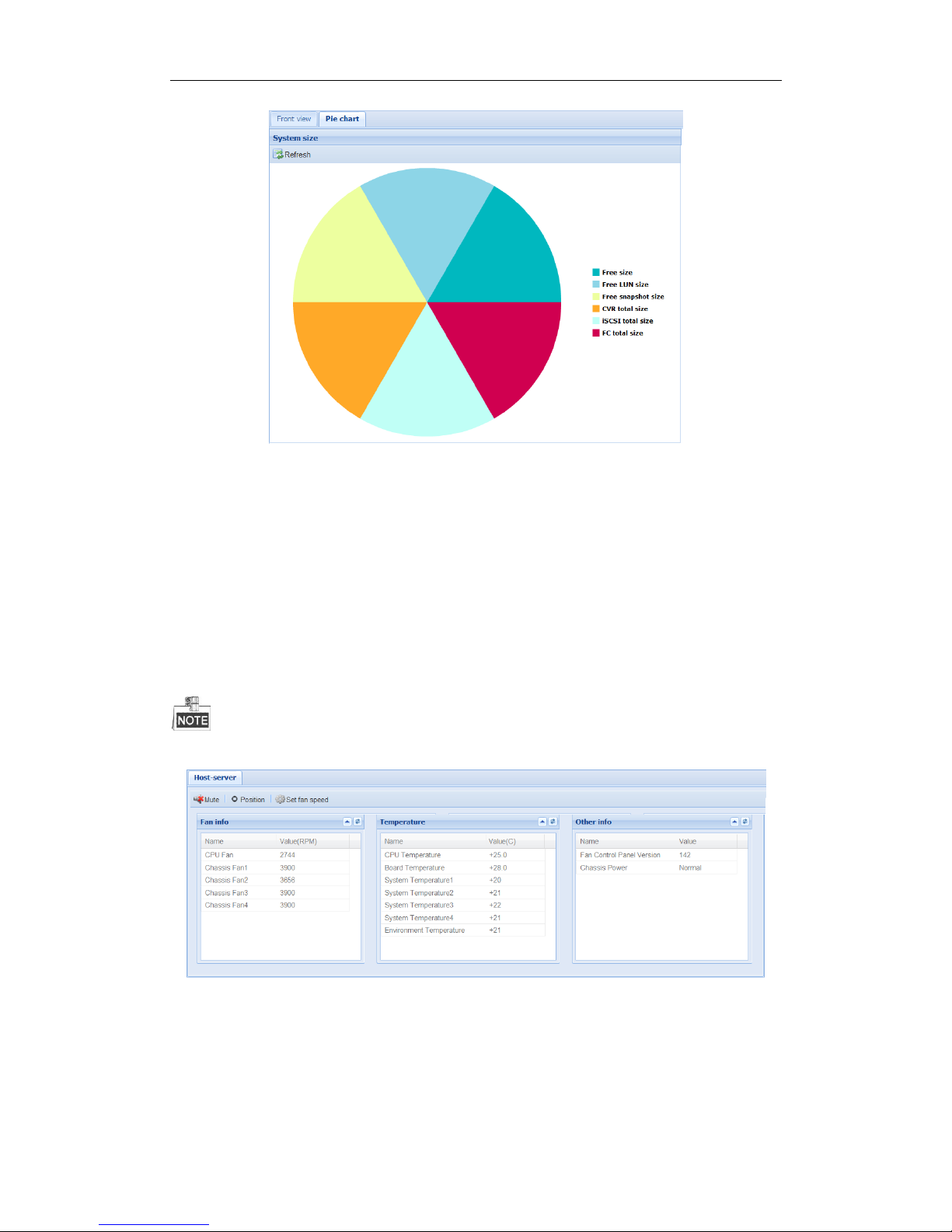
Purpose:
Pie chart shows the free size of all storage modules, including system, LUN, snapshot, CVR, iSCSI, and FC.
Steps:
1. Click Pie Chart in Graphical Display to enter Pie Chart interface.
2. Positioning the pointer in the part you want to view. Free size and free size Percentage appear in a dialog.
3. Optionally, click Refresh in top-right corner to update the information.
Page 24
DS-A80&81 Series Storage System User Manual
23
Figure 3. 23 Pie Chart
3.5 Control Message
Purpose:
Control Message shows the fans’ information, modules’ temperature, fan control panel version, and chassis
power.
Steps:
1. Click Maintenance in navigation bar and choose Control Message to enter Control Message interface. Fan
RPM (Revolutions per Minute), temperature, and other information are shown.
You can install or uninstall fans. Up to 6 fans’ formation can be connected.
Figure 3. 24 Host
2. Click Mute in top-right corner to turn off system audible warning.
3. To find out which controller is working, click Position in top-right corner and click OK in popup dialog. The
FN indicator of working controller would light up and flash for 10 minutes.
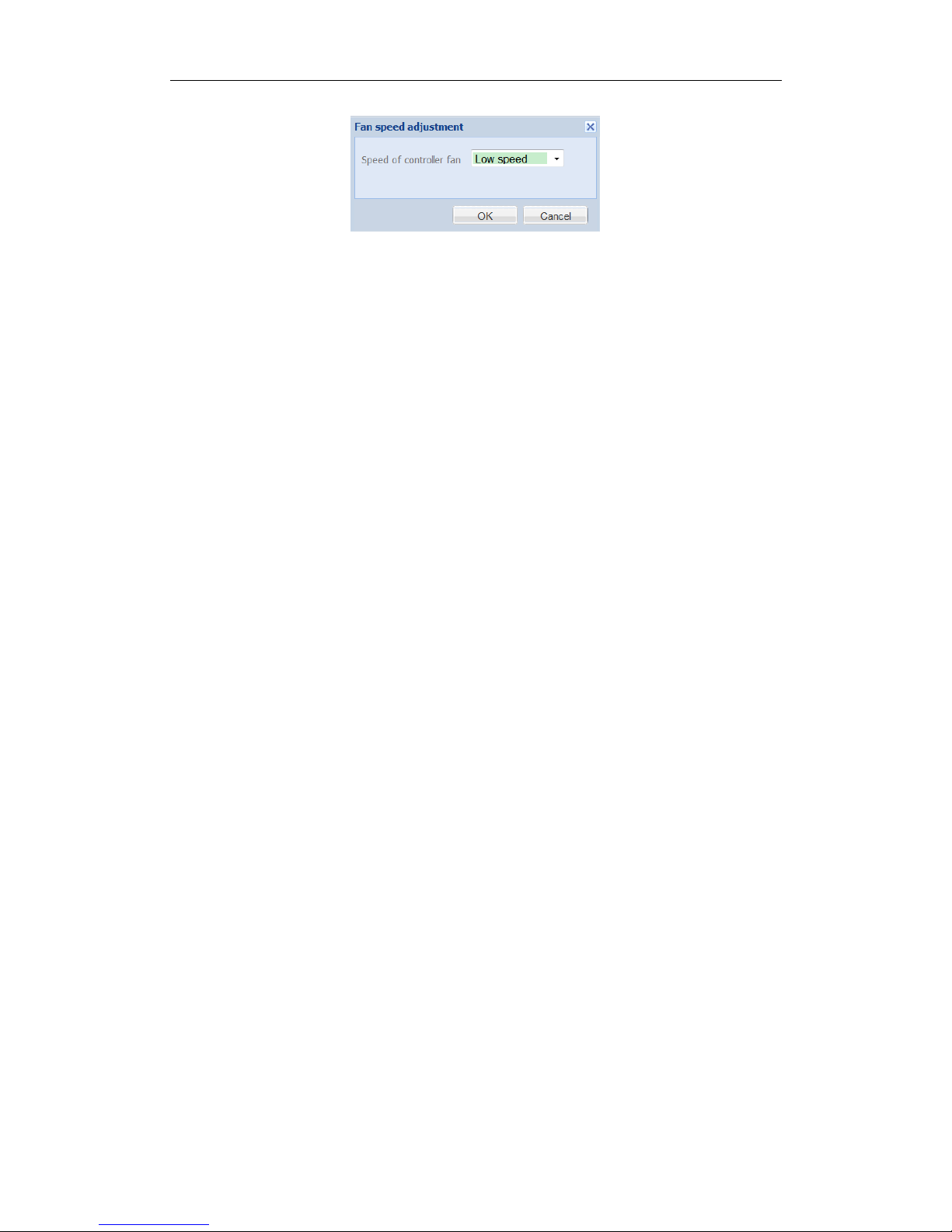
4. Set fan speed.
1) Click Set fan speed in top-right corner to pop up dialog box.
Page 25
DS-A80&81 Series Storage System User Manual
24
Figure 3. 25 Fan Speed
2) Choose speed as Low speed, Medium speed, or High speed in dropdown list.
3) Click OK to save the settings.
Page 26

DS-A80&81 Series Storage System User Manual
25
Chapter 4 Storage Management
Purpose:
Storage management provides configuration including disk, array, storage pool, LUN (logical Volume), and storage
settings.
Table 4. 1 Module Description
Module
Description
Disk
You can:
View disks’ information and status.
Rescan, positioning, initialize, and check disks.
Array
You can:
Create arrays.
Add hot spare.
View array and hot spare information.
Delete array and hot spare.
Storage pool
You can:
Add, delete, and positioning storage pools.
Remove and positioning disks.
View system total and free capacity.
LUN (Logical volume)
You can
Add and delete LUNs.
Rename, expand, clone, and snapshot LUNs.
Settings
You can:
Set array synchronization speed.
Set array synchronization type.
Set flicking frequency for disk positioning indicator.
Key words:
Disk, Array, Storage Pool, LUN (Logical Volume), Settings
Figure 4. 2 Storage
Page 27
DS-A80&81 Series Storage System User Manual
26
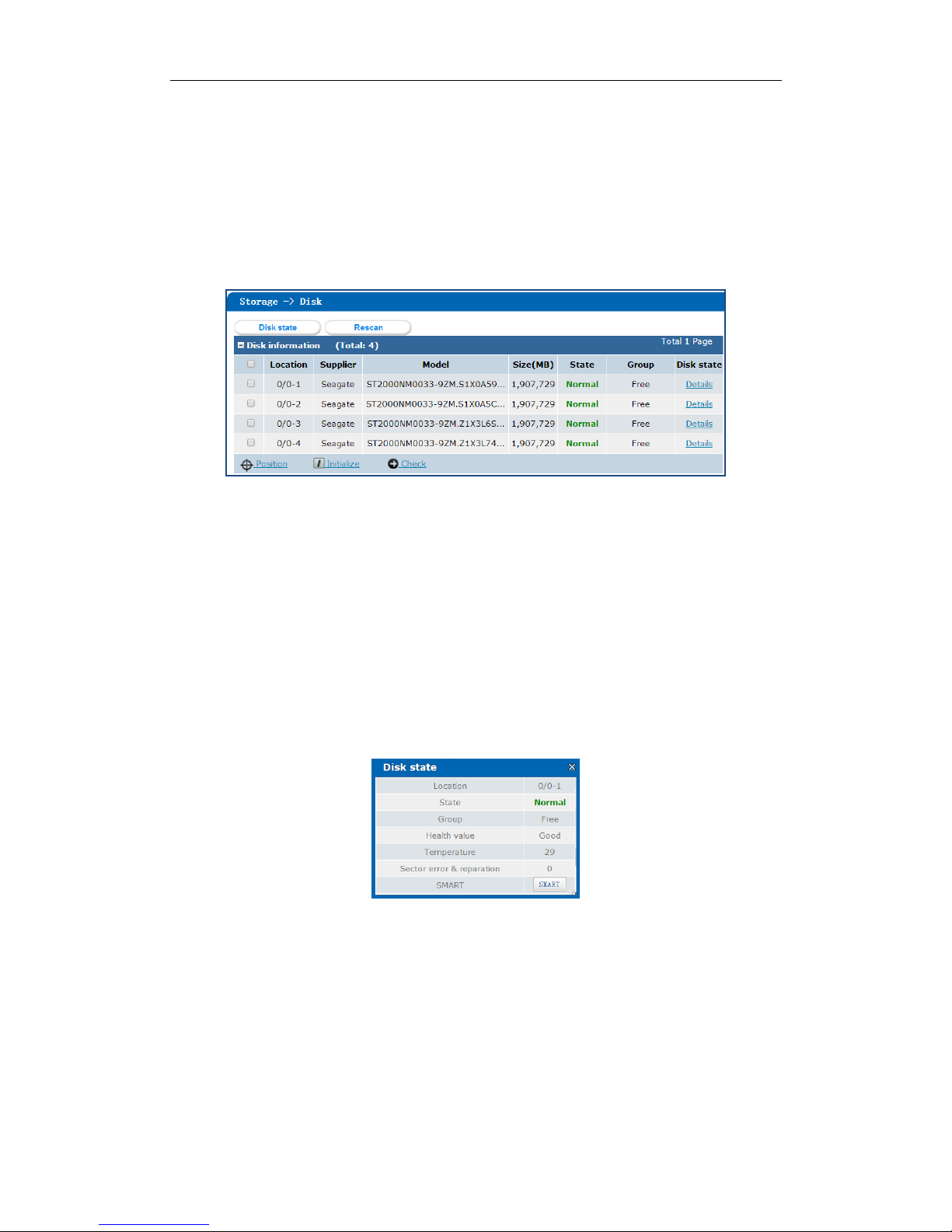
4.1 Managing Local Disk
Purpose:
You can view the disk information here, including disk location, supplier, model, size, status, and belonging group.
Step:
Click Storage in navigation bar and choose Disk to enter Disk interface.
Figure 4. 3 Disk
4.1.1 Viewing Disk Status
Purpose:
You can view status of one disk or all disks.
4.1.1.1 One Disk
Steps:
1. In the Disk information list, Click Details of a disk. Disk state dialog appears.
2. Click SMART to view the disk’s SMART detection information.
Figure 4. 4 Details
4.1.1.2 All Disks
Steps:
1. Click Disk state in the top-right corner. The following dialog appears.
2. Click SMART of a disk to view its SMART detection information.
Page 28

DS-A80&81 Series Storage System User Manual
27
Figure 4. 5 Disk Status
There are totally 6 kinds of status for a disk.
Table 4. 2 Disk Status Description
Status
Description
Normal
Disk works normally.
Undetected
Disk hasn’t gone through disk check in a storage system.
Lost
Disk is unrecognized.
Risky
Exception occurs during disk detection. But it can still work.
Bad
Disk is kicked out by an array.
Warning
Disk read and writing speed is higher than 10 MB/S during pressure test.
4.1.2 Rescanning Disk
Step:
If detecting a newly installed disk failed, click Rescan to find the disk.
If a disk is uninstalled from the storage system, click Rescan to remove it from the Disk interface.
Rescanning disks may resulted in disk’s status appearing as Unknown. Fresh the interface or click Rescan again to
solve the problem.
4.1.3 Positioning Disk
Purpose:
Disk bottom indicator flickers after enabling the function. It enables you to find a certain disk more easily.
Before you start:
Set the flashing time first. For details, refer to 4.5.2 Flashing Time.
Steps:
1. Check the checkbox of disk you want to find.
2. Click Position and click OK in popup dialog box. Then disk indicator keeps flickering in red for the set
flashing time.
Page 29
DS-A80&81 Series Storage System User Manual
28
4.1.4 Disk Initialization
Purpose:
To recover a disk when its status is uninitialized or when it is kicked out by an array, you can initialize it.
Steps:
1. Check the checkbox of disk you want to initialize.
2. Click Initialize and click OK in popup dialog box to start initializing.
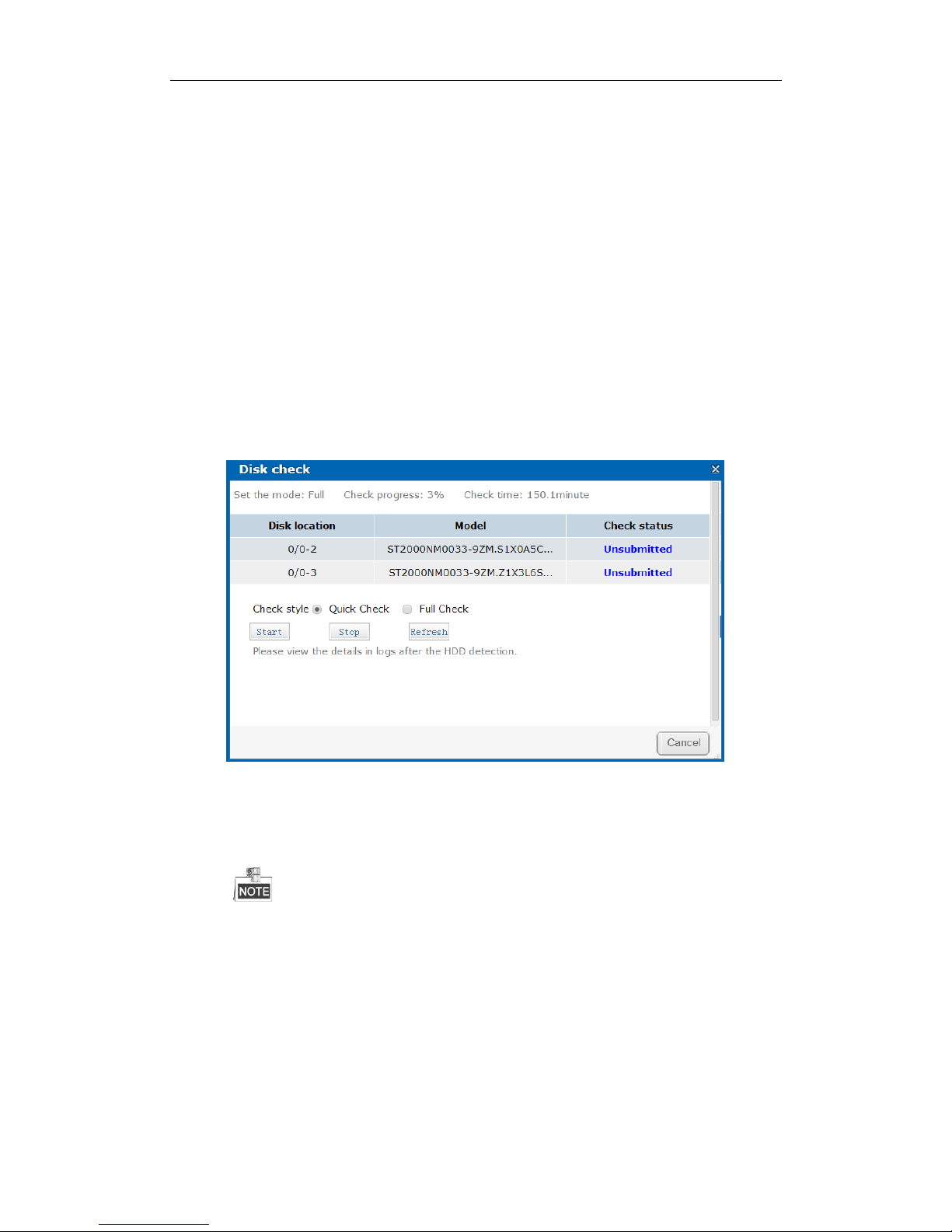
4.1.5 Disk Check
Purpose:
To recognize a disk which is added to a storage system for the first time, check it.
Steps:
1. Check the checkboxes of disks you want to check.
2. Click Check to pop up Disk check interface.
Figure 4. 6 Disk Check
3. Select the Check style as Quick Check or Full Check.
Quick Check: Check parts of all disk blocks. It takes shorter time than Full Check.
Full Check: Check all disk blocks. It takes longer time than Quick Check.
It is recommended to operate full check when system is under low pressure.
You are recommended to operate full check for the first use disk.
To keep data safe, check a disk every 3 months.
4. Click Start to start checking. The selected check type, check progress, and checked time are listed in the top
part of the interface.
5. Optionally, click Refresh to update the check status, check process and checked time.
Or you can click Stop to end all disks’ check.
Page 30

DS-A80&81 Series Storage System User Manual
29
There are 3 kinds of check status: Unsubmitted, Checking, and Completed.
Table 4. 3 Check Status Description
Check Status
Description
Unsubmitted
Disk check hasn’t been submitted.
Checking
Disk is being checked.
Waiting
Another disk is being checked. You need to wait till the check is finished.
4.2 Array
Purpose:
You can create and manage array.
Step:
Click Storage in navigation bar and choose Array to enter Array interface.
Figure 4. 7 Array
4.2.1 Creating Array
Purpose:
You can use available disks to create array.
Steps:
1. Click Create to enter Create array interface.
Page 31

DS-A80&81 Series Storage System User Manual
30
Figure 4. 8 Create Array
2. Input Array name in text field.
3. Select RAID level in dropdown list. Up to 8 kinds of RAID are provided, including RAID 0, RAID 1, RAID 3,
RAID 5, RAID 6, RAID 10, and RAID 50.
Figure 4. 9 Required Disk Quantity
RAID Level
Required Disk Quantity
RAID 0
At least 2 disks.
RAID 1
At least 2 disks.
RAID 3
At least 3 disks.
RAID 5
Valid range: [3, 12].
RAID 6
At least 4 disks.
RAID 10
RAID is made of RAID 0 and RAID 1 which requires
at least 4 even disks.
RAID 50
RAID is made of RAID 0 and RAID 5 which requires
at least 6 even disks.
4. Select Block size(KB) in dropdown list.
5. Select I/O priority as Performance priority, Protection priority, Balance, or Intelligent.
Performance priority: To guarantee external IO task’s performance, internal IO task is totally stopped.
Protection priority: To guarantee internal IO task’s performance, external IO task would only take the
rest channel.
Balance: When both internal and external IO task exist, Balance ensures internal IO task occupy
certain channel without influencing external IO task.
Page 32

DS-A80&81 Series Storage System User Manual
31
Intelligent: W ithout external IO task, array is initialized in the highest speed. Or array is initialized in
the lowest speed.
If RAID level is RAID 0, I/O priority isn’t available.
6. Select the Available disks to create RAID.
Or select Available arrays to create RAID.
Or select the combination of Available disks and Available arrays.
Only enterprised disks are listed in Auailable disks list.
In order to increase the performance of created RAID, it is recommended to use disks of the same
model and capacity when creating a RAID.
7. Click OK to create array. The successfully created array lists in Array information list. Once created, the array
starts initializing.
4.2.2 Array Exception
Purpose:
When certain quantity’s disks in an array fail, array degrades. When more disks fail, array fails. Degraded array can
keep working. However, failed array can’t work. Notification area will notify you once array degraded or failed.
Refer to following table for array degraded and failed condition.
Table 4. 4 Array Degraded Condition
RAID Level
Degraded Condition
Failed Condition
RAID 0
RAID 0 won’t degrade.
One disk fails.
RAID 1
N-1 disks fail.
All disks fail.
RAID 3
One disk fails.
Two disks fail.
RAID 5
RAID 6
N-1 disks fail.
More than three disks fail.
RAID 10
One disk fails.
Two disks fail in either contained RAID.
RAID 50
If array in storage pool degrades, physical volume degrades.
If array in storage pool fails, physical volume fails.
4.2.3 Rebuilding Array
Purpose:
Rebuilding refers to the process of using a normal disk or array to virtually replace a failed disk in a degraded array.
The normal disk can be hot spare disk, newly inserted disk, and so forth.
During rebuilding process, if the rebuilding disk fails, the array stays degraded.
Page 33

DS-A80&81 Series Storage System User Manual
32
During rebuilding process, if a normal disk in array fails, the array becomes failed.
During rebuilding process, if I/O error occurs to the rebuilding disk, you need to change rebuilding disk.
4.2.3.1 Rebuilding with Hot Spare
Before you start:
Add global, area, or local hot spare disk or array for array.
Step:
Once the array degraded, hot spare disk or hot spare array automatically rebuilds the array.
When the degraded array possesses both global and local hot spare, it rebuilds with local hot spare preferentially.
4.2.3.2 Rebuilding with Available Disk
Before you start:
Ensure there is at least one available disk which isn’t included in any array or storage pool.
Steps:
1. Click Maintain of a degraded array in Array information list.
2. Click Rebuild to pop up Array rebuild interface.
3. Select an Available disk or Available array.
4. Click OK to start rebuilding.
4.2.4 Checking Array
Purpose:
You can check whether the data bit and parity data in an array match or not.
If array in storage pool starts checking, physical volume’s status is checking.
4.2.4.1 Auto Check
Steps:
Refer to 3.3.6 Strategy to start auto check.
Select Type as RAID verification and select Verify mode as Check.
4.2.4.2 Manual Check
Steps:
1. Click Maintain of a degraded array in Array information list.
2. Click Check to start checking.
Page 34

DS-A80&81 Series Storage System User Manual
33
4.2.5 Repairing Array
Purpose:
You can repair the data bit and parity data mismatch issue.
If array in storage pool starts repairing, physical volume’s status is repairing.
4.2.5.1 Auto Repair
Steps:
Refer to 3.3.6 Strategy to start auto repair.
Select Type as RAID verification and select Verify mode as Repair.
4.2.5.2 Manual Repair
Steps:
1. Click Maintain of a degraded array in Array information list.
2. Click Repair to start repairing.
4.2.6 Renaming Array
Steps:
1. Click Maintain of an array in Array information list.
2. Click Rename.
3. Enter a new name.
4. Click OK to save the new name.
4.2.6.1 Modify I/O Priority
Steps:
1. Click Maintain of an array in Array information list.
2. Click Modify.
3. Select I/O priority in dropdown list.
4. Click OK to save.
4.2.6.2 Pause Initialization/Rebuilding/Check/Repair
Purpose:
When the array is initializing, rebuilding, checking, or repairing, you can pause.
Steps:
1. Click Maintain of an array in Array information list.
2. Click Pause to pause current process.
Page 35

DS-A80&81 Series Storage System User Manual
34
3. You can click Keep to resume.
4.2.7 Deleting Array
Steps:
1. Check the checkbox of array you want to delete.
2. Click button to delete.
If the array has been added to a storage pool, you need to remove it from storage pool first, or it can’t be deleted.
4.2.8 Adding Hot Spare
Purpose:
The hot spare disk can replace failed disk in the degraded array. In order to protect data from damage in case of
disks in array fail, it is recommended to add hot spare disks for a created array.
RAID 0 won’t degrade. So you needn’t add local hot spare disk for it.
Steps:
1. Click Create hot spare to enter Add hot spare interface.
2. Select Group as Global, Area, or Local.
Global: Global hot spare disks can replace failed disks in any degraded arrays of storage devices in the
same system.
Area: Area hot spare disks replace failed disks in any degraded arrays of one storage system.
Local: Local hot spare disks replace failed disks in designated array.
Priority of hot spare: Local hot spare › area hot spare › global hot spare
3. If Group is Area, select available array in Area dropdown list.
If Group is Local, select array in Array dropdown list.
4. Select at least one Available disk.
Or select at least one Available array.
Or select the combination of Available disk or Available array.
5. Click OK to create hot spare.
Page 36

DS-A80&81 Series Storage System User Manual
35
Figure 4. 10 Add Hot Spare
4.2.9 Deleting Hot Spare
Steps:
1. Select arrays you want to delete.
2. Click button to delete.
4.3 Storage Pool
Purpose:
Storage pool, which is made of physical volumes and contains arrays and disks, is designed for central
management of storage capacity.
Step:
Click Storage in navigation bar and choose Storage Pool to enter Storage Pool interface.
Figure 4. 11 Storage Pool
Page 37

DS-A80&81 Series Storage System User Manual
36
Table 4. 5 Interface Description
Area
Name
Description
1
Information Area
Lists the storage pool’s total size, free size, LUN size, snapshot size, CVR
size, iSCSI size, and FC size.
2
Configuration Area
You can add, delete, and positioning created physical volume here.
4.3.1 Adding Storage Pool
Purpose:
You need to create physical volumes to build storage pool.
Before you start:
Ensure available array or disk exists in the storage system.
Steps:
1. Click Add to enter Add storage pool interface.
Figure 4. 12 Add Storage Pool
2. Select at least one array or disk iSCSI as storage pool.
Or select the combination of array or disk.
3. Input Physical volume name in text field.
4. Click OK to add the storage pool.
Figure 4. 13 Storage Pool
Page 38

DS-A80&81 Series Storage System User Manual
37
4.3.2 Deleting Storage Pool
Purpose:
You can delete storage pool by deleting the added physical volumes.
Steps:
1. Check the checkboxes of physical volumes you want to delete.
2. Click or button to delete them.
Idle physical volumes can be deleted except the first created physical volume.
4.3.3 Positioning Storage Pool
Before you start:
Set the flashing time first. For details, refer to 4.5.2 Flashing Time.
Steps:
1. Check the checkbox of physical volume you want to positioning.
2. Click button. Then the disk bottom indicator keeps flickering in green for the set flashing time.
4.4 LUN (Logical Volume)
Purpose:
LUN is the virtual disk which is made of physical disk.
Step:
Click Storage in navigation bar and choose LUN to enter LUN interface.
Figure 4. 14 LUN
4.4.1 Creating LUN
Purpose:
You can create LUN by using available physical volumes.
Steps:
1. Click Create to enter Create LUN interface.
Page 39

DS-A80&81 Series Storage System User Manual
38
Figure 4. 15 Create LUN
2. Enter LUN name.
3. Enter LUN size (MB).
4. Select Block size (Byte) from dropdown list.
5. Choose Available PV.
6. Click OK to create LUN. Created LUN is listed in LUN information list.
4.4.2 Deleting LUN
Steps:
1. Select the LUN you want to delete.
2. Click button to delete them.
The working LUN can be deleted. Only free LUN can be deleted.
4.4.3 Renaming LUN
You can only rename the free LUNs.
Steps:
1. Click button of the LUN you want to rename.
2. Enter a new name.
3. Click OK to save the new name.
4.4.4 Enlarging LUN
Purpose:
You can enlarge the size of created LUN.
You can only enlarge the free LUNs.
Page 40

DS-A80&81 Series Storage System User Manual
39
Steps:
1. Click button of the LUN you want to extend.
Figure 4. 16 Extend LUN
2. Enter New size (MB).
3. Select Available PV used to extend.
4. Click OK to extend.
4.5 Settings
Purpose:
You can set the array synchronization speed type and flashing time of positioning indicator.
Step:
Click Storage in navigation bar and choose Settings to enter Settings interface.
Figure 4. 17 Settings
4.5.1 Synchronization Speed and Type
Purpose:
Array synchronization speed and synchronization type is editable.
Steps:
1. Click Modify of Sync speed.
2. Select Sync speed as High, Medium, Low, or Zero.
Page 41

DS-A80&81 Series Storage System User Manual
40
The faster the speed is, the highest the internel IO percentage is.
3. Click OK to save.
4. Click Modify of Sync type.
5. Select Sync type as Sync Signal Drive or Sync Multiple Drives Concurrently.
6. Click OK to save.
Figure 4. 18 Synchronization Speed and Type
4.5.2 Flashing Time
Purpose:
When positioning a disk, the disk bottom indicator keeps flickering for the set time.
Steps:
1. Enter a number as flashing time in Flashing time of positioning a disk (s).
Valid flashing time ranges from 5 to 300 and the unit is second.
2. Click Modify to save.
Page 42

DS-A80&81 Series Storage System User Manual
41
Chapter 5 SAN
Purpose:
You can add iSCSI disks and FC (Fiber Channel) disks in your computer.
Table 5. 1 Module Description
Module
Description
iSCSI
You can add iSCSI disks in your computer.
FC
You can add FC disks in your computer.
Keywords:
iSCSI, FC
Figure 5. 2 SAN
Page 43

DS-A80&81 Series Storage System User Manual
42
5.1 iSCSI
Purpose:
You can add iSCSI disks in your computer.
Step:
Click SAN in navigation bar and choose iSCSI to enter iSCSI interface.
Figure 5. 3 iSCSI
5.1.1 Adding CHAP User
Purpose:
When enabling iSCSI, you can select an added CHAP user as a way to verify your computer permission.
Steps:
1. Click button to enter Add CHAP User interface.
Figure 5. 4 Add CHAP User
2. Enter CHAP username, Password, and Retype password.
CHAP username: Only letters, numbers, and underline are allowed.
Password: Only 12 to 16 characters, including letters, numbers, and underline, are allowed.
Retype password: It must be the same as Password.
3. Click OK and click OK in confirmation dialog box to add the CHAP user.
Page 44

DS-A80&81 Series Storage System User Manual
43
5.1.2 Modifying CHAP User
Purpose:
You can modify the password of added users.
Before you start:
If the CHAP going to be modified is linked to one or more iSCSIs and these iSCSIs are connecting with computers,
you need to disconnect them from computer first.
Steps:
1. Click button to enter Modify CHAP User Interface.
2. Enter the CHAP username you want to modify in the text field.
3. Enter a new Password and Retype password.
4. Click OK and click OK in confirmation dialog box to modify the CHAP user.
5.1.3 Enabling iSCSI
Purpose:
Enabling iSCSI in storage system makes it possible for you to add iSCSI disks in computer.
Steps:
1. Click button to pop up Enable iSCSI interface.
Figure 5. 5 Enable iSCSI
2. Enter Client IP and iSCSI ID.
Client IP: To turn on iSCSI for a specified client (computer), enter the client’s IP address. To turn on
iSCSI for multiple clients, enter 0.0.0.0 in the text field.
iSCSI ID: It is used to distinguish iSCSI from each other. Specify an integer between 1 and 1024. It is
recommended to specify a dedicated ID for each iSCSI.
3. Select the identity authentication method in the dropdown list of CHAP authentication.
No CHAP: There is no limit for client access.
Other CHAP user: Correct CHAP user name and password are needed for client to get access to LUN.
Page 45

DS-A80&81 Series Storage System User Manual
44
4. Select the LUN Access mode as R/W, SR/W, RO, or IRO.
R/W: Read and writing permission.
IRO (Intelligent Read Only): Even though writing operation succeeded, data wouldn’t be written into
LUN. It is mainly used to test storage system’s performance.
RO: Read only
SR/W (Synchronous Read/Write): It writes the data into disks directly without writing into disk buffer.
A low writing speed makes the data complete.
5. Choose an Available LUN.
6. Click OK to enable the iSCSI.
When multiple iSCSIs share the same LUN, only one iSCSI server’s access mode can be R/W and other servers
should be RO or IRO, or file system may be damaged or data may lose.
5.1.4 Disabling iSCSI
Purpose:
For the unnecessary iSCSIs, you can disable them, thus to keep storage system safe and stable.
Before you start:
Disconnect the storage system from the clients for which you want to disable iSCSI.
Steps:
1. Check the checkbox of iSCSI you want to disable.
2. Click and click OK in confirmation dialog box.
5.1.5 Modifying iSCSI Port
Purpose:
iSCSI port is needed when accessing via computer. It can be edited.
Before you start:
Disconnect all iSCSIs first, or iSCSI enabled under pervious iSCSI port couldn’t be deleted.
Steps:
1. Click SAN in navigation bar and choose Setting to enter Setting interface.
Figure 5. 6 Setting
2. Enter a number between 3000 and 65534 except 7402 in Current target port text field.
3. Click Modify, click OK in confirmation dialog box, and click OK in second popup dialog box.
Page 46

DS-A80&81 Series Storage System User Manual
45
5.2 FC (Optional)
Purpose:
You can add FC disks in your computer.
Before you start:
1. Install fiber Ethernet adapter and fiber Ethernet adapter drive in both storage system and client server.
2. Connect storage system and client server to fiber channel switch with fiber.
Step:
Click SAN in navigation bar and choose FC to enter FC interface.
Figure 5. 7 iSCSI
5.2.1 Enabling FC
Purpose:
Enabling FC in storage system makes it possible for you to add FC disks in computer. To visit FC disk via computer,
storage system and computer should locate in an optical fiber network. You can enable FC service for:
A specified fiber channel.
All available fiber channels.
A specified FC port.
All available FC ports.
Before you start:
Install optical fiber card first.
Create at least one LUN first. For detailed steps, refer to 4.4 LUN (Logical Volume).
Steps:
1. Click Enable FC to enter Enable FC interface.
Figure 5. 8 Enable FC
2. According to actual connection, select Fiber Channel as Fiber Channel0, Fiber Channel1, Fiber Channel2, or
Page 47

DS-A80&81 Series Storage System User Manual
46
Fiber Channel3. If you are not sure about selecting which one, select Available channels. Storage system
can automatically connect storage system and client with an available channel.
Fiber Channel 0 refers to fiber port 1 in real panel. Fiber Channel 1 refers to fiber port 2 in rear panel. And
so on.
3. To specify a client, enter Client WWPN of 16 numbers.
Client WWPN: The client’s fiber Ethernet adapter WWPN. You can use a fiber client to obtain WWPN. If no
client is available, enter 0000000000000000. The storage system connects all available clients WWPN and
share FC with all connected clients.
4. Select available LUN in the dropdown list of LUN name.
5. Choose Logical LUN ID as Auto or Manual.
Auto: Storage system automatically specifies a free LUN ID.
Manual: It is recommended to choose Manual. The logical LUN ID which is the first manual one must
be 0.
6. Select LUN access mode as R/W, SR/W, RO, or IRO.
R/W: Read and writing permission.
IRO (Intelligent Read Only): Even though writing operation succeeded, data wouldn’t be written into
LUN. It is mainly used to test storage system’s performance.
RO: Read only
SR/W (Synchronous Read/Write): It writes the data into disks directly without writing into disk buffer.
A low writing speed makes the data complete.
7. Click OK and click OK in confirmation dialog box to enable FC.
5.2.2 Disabling FC
Purpose:
You can disable FC service for:
A specified fiber channel.
All available fiber channels.
A specified FC port
All available FC ports.
Steps:
1. Check the checkbox of FC you want to disable.
2. Click and click OK in confirmation dialog box.
Page 48

DS-A80&81 Series Storage System User Manual
47
Chapter 6 CVR
Purpose:
You can configure CVR and N+1 parameters.
Table 6. 1 Module Description
Module
Description
CVR
You can:
Configure private volume, CVR configuration, create record volume, and extend
record volume.
CVR one-key configuration.
Manage N+1.
Log in CVR sub-system to add encoders, add strategy, search video, and so forth.
N+1
A storage system whose CVR service has started can serve as a backup CVR for other
CVRs.
Keywords:
CVR, N+1
Figure 6. 2 CVR
Page 49

DS-A80&81 Series Storage System User Manual
48
6.1 Quick-Setting CVR
Purpose:
Quick-setting creating helps you to create CVR quickly.
Before you start:
Ensure there is neither storage pool nor array in storage system.
Steps:
1. Click button in top-right corner to start quick settings.
2. Click OK to confirm. Quick-setting takes 3 to 15 minutes. During the quick-settings, following operations are
performed automatically.
1) Add disks to storage pool. Or create RAIDs and add them to storage pool.
The whole disks are added to storage pool with no more free capacity. You can view the storage pool
usage in Storage › Storage Pool.
2) Create private volume, reserved volume, and record volume. If more than 3 LUNs are created, one
archive volume is created.
Figure 6. 3 CVR Settings Interface
Bad disk, risky disk, and warning disk would not be added to storage pool.
Non-enterprise disk is added to storage pool by single-disk mode.
Quick-setting takes longer if any unchecked disk exists.
If disks in storage system are less than 6, they are added to storage pool by single-disk mode.
If disks in storage system are not less than 6 and disks in storage enclosure is less than 6, the storage
system disks are added by array mode and the storage enclosure disks won’t be added.
If disks in storage system and disks in storage enclosure are both not less than 6, they are both added to
Page 50

DS-A80&81 Series Storage System User Manual
49
storage pool by array mode.
If only one disk exists, no reserved volume is created. In single-disk mode, no reserved volume is
created in the last disk of storage system. In array mode, two reserved volumes are created in each
RAID.
By default, a 50 GB size’s private volume and a 50 GB size’s reserved volume should be created.
6.2 CVR Configuration
Purpose:
You can start and reset CVR and create record volume.
Step:
Click button in upper-right corner to enter CVR configuration interface.
Figure 6. 4 CVR
6.2.1 Starting CVR
Purpose:
You can start CVR after private volumes are created.
Before you start:
1. To create storage pool, do one of the following:
Single-disk mode: Add disks to storage pool.
Array mode: Create arrays and add them to storage pool.
2. Create at least 5 LUNs. Ensure at least 4 of them are larger than 20 GB. The four LUNs are used to create
private volume, reserved volume. Other LUNs are used to create record volume.
If record volume’s size is fewer than 120T, then private volume 1 and private volume 2’s size should
both larger 50G.
If record volume’s size ranges from 120T to 180T, then private volume 1 and private volume 2’s size
should both larger 60G.
If record volume enlarges by 60T, record volume 1 and record volume 2 should both enlarge by 10G.
Page 51

DS-A80&81 Series Storage System User Manual
50
Steps:
1. Click Set private volume menu to enter Set private volume interface.
Figure 6. 5 CVR Configuration
2. Check the checkbox of Start CVR after setting.
3. Optionally, check the checkbox of Config spare LUN for private LUN and Use spare LUN of Private LUN.
Spare LUN for private LUN: Create a spare volume for private volume. The spare volume works as a backup
volume. When error occurs to the two private volumes, the two spare LUNs would replace them.
It’s no recommended to use a spare volume in the same physical volume with the private volume.
4. To add private volume 1, choose a Free LUN and click button.
5. To add private volume 2, choose a Free LUN and click button.
CVR configuration information is saved in private volume 1 and private volume 2.
It’s not recommended to use the LUN created by the disk first added to storage pool to create private
volume 1.
The chosen LUNs’ capacity should meet the demand shown in red frames in Figure 6. 5 CVR
Configuration.
If Config spare LUN for private LUN and Use spare LUN of Private LUN are selected, storage system
automatically select two free LUN as the spare volumes.
6. Click OK to start creating the two private volumes. After private volumes are created, CVR starts running.
Page 52

DS-A80&81 Series Storage System User Manual
51
Figure 6. 6 Created Prviate Volume
Figure 6. 7 CVR Starts Running
Table 6. 2 CVR Status Description
Status
Description
Not configured or incomplete
CVR is not configured.
Running
CVR is correctly started.
Stopped
Click Stop CVR to stop CVR service. Once CVR is stopped, you are not able
to view encoder information and videos. You can click Start CVR to recover
to Running status.
Running and Recovering
Indicators CVR is working normally and in automatic recovery process.
Stopped and Recovering
Indicators CVR is stopped and in automatic recovery process.
6.2.2 Resetting CVR
Purpose:
You can delete CVR videos, encoders, and other configurations by resetting CVR. After reset, CVR status restores
to not configured or incomplete.
Steps:
1. Click CVR config menu and click Reset CVR.
2. Enter yes or YES in text field to start reset.
Figure 6. 8 Reset CVR
Page 53

DS-A80&81 Series Storage System User Manual
52
6.2.3 Record Volume
Purpose:
Record volume is the logical volume stores videos.
6.2.3.1 Creating Record Volume
Steps:
1. Click Create record volume menu.
Figure 6. 9 Create Record Volume
2. Enter the Name in text field.
3. Select Data overlay as Cycle cover or No cover.
Cycle cover: Once the record volume is full, videos can still write into it by covering the earliest videos.
No cover: Once the record volume is full, videos can’t write in it
4. Select record volume Usage as Video Storage or Picture Storage.
5. If you want to create record volume based on local disk or array, select LUN source as Local. If you want to
create it based on IP SAN, select LUN source as IP SAN.
6. Select one or more Free LUN.
If the capacity of private volume 1 and private volume 2 are both larger than 50 GB, maximum capacity of
each LUN of record volume is 8 TB.
7. Click OK to create the record volume. The created record volumes are listed in Record Volume list.
Figure 6. 10 Record Volume List
Page 54

DS-A80&81 Series Storage System User Manual
53
6.2.3.2 Clearing, Modifying, and Deleting Record Volume
Purpose:
The created record volumes are listed in Record Volume list. You can clear videos saved in it, modify its
configuration, and delete it.
Table 6. 3 Icon Description
Icon
Name
Description
Clear data
You can clear videos saved in the record volume.
Modify
You can modify record volume name, usage, and data overlay strategy.
Delete
You can delete the record volume. Data saved in it is removed.
Don’t delete record volume when linked encoder is recording.
If a record volume consists of two or more LUNs, you can delete one of them according to following steps:
Steps
1. Click the record volume name.
Figure 6. 11 LUNs
2. Click of the LUN you want to delete.
3. Enter yes or YES in text field to delete it. After it is deleted, data saved in the LUN is deleted and the LUN’s
status is Free.
6.2.3.3 Extending
Purpose:
When the record volume’s capacity is insufficient, you can use the free LUNs to extend it.
Steps:
1. Click Extend record volume menu.
Page 55

DS-A80&81 Series Storage System User Manual
54
Figure 6. 12 Extend Record Volume
2. Select the record volume you want to extend in Name dropdown list.
3. Select the Free LUN used to extend.
4. Click OK to start extending.
6.3 Backup and Restoring
Purpose:
The chapter introduces the video backup and CVR restoring steps.
Step:
Click button in top-right corner to enter Backup and Restoring interface.
Figure 6. 13 Back and Restoring
6.3.1 Viewing Private Volume Information
Step:
Click Private volume information menu to enter Private Volume information interface. LUNs making up private
volume 1 and private volume 2 are listed.
Page 56

DS-A80&81 Series Storage System User Manual
55
6.3.2 Restoring
Purpose:
When error occurs to CVR, restoring CVR can recover it. Restoring may cause data loss, so you need to contact us
for professional help. We are not responsible for error caused by unprofessional operation.
Step:
Click Restore menu to enter Restore interface.
Figure 6. 14 Restore
6.3.3 Backup
Purpose:
Storage system backs up all videos’ index every hour. You can manually back up all videos’ index according to
following steps. The backed up index is saved in database.
The function backs up videos’ index instead of videos.
Steps:
1. Click Backup menu to enter Backup interface.
2. Click OK to start backing up.
Page 57

DS-A80&81 Series Storage System User Manual
56
Figure 6. 15 Backup
6.3.4 Recovering Video Data
Purpose:
If you reset CVR, deleted record volume, or cleared record volume by mistake, you can contact us for professional
help, we would help you to recover these data. We are not responsible for error caused by unprofessional
operation.
Step:
Click Record Data Recovery menu to enter Record Data Recovery interface.
Figure 6. 16 Record Data Recovery
6.4 N+1 Management
Purpose:
A storage system whose CVR service has started can serve as a backup CVR for other CVRs. When one or more
Page 58

DS-A80&81 Series Storage System User Manual
57
master CVRs fail, the backup CVR would record the videos from encoders. Master CVR error includes network
error, private volumes damaged, database error, and CVR service error. After the master CVRs recovers to normal,
backup CVR would upload videos back to master CVRs.
Before you start:
Start CVR service in both master CVR and backup CVR.
Step:
Click N+1 in navigation bar and choose N+1 to enter CVR interface.
Figure 6. 17 N+1 Management
Log into master CVR and add backup CVR for master CVR first. And then Log into backup CVR and add
master CVR for backup CVR.
A storage system can be either backup CVR or master CVR.
Ensure the system time of backup CVR and master CVR are the same. For detailed steps of modifying system
time, refer to Chapter 8.3 Time.
Once master CVR can only link to one backup CVR
It is not recommended that encoding devices added in backup CVR have duplicate name.
6.4.1 Adding Backup CVR
Purpose:
Add backup CVR in master CVR first.
Before you start:
Log into master CVR and enter N+1 Management interface.
Steps:
1. Click button.
Figure 6. 18 Add Backup CVR
2. Enter the backup CVR’s IP address.
3. Click OK to add. The added backup CVR is listed in CVR servant list.
4. Optionally, you can check the checkboxes of Enable data fetch and Delete the data of working device
remained on the backup device and click Modify to enable them.
Page 59

DS-A80&81 Series Storage System User Manual
58
Enable data fetch: Once master CVR recovers to normal, backup CVR uploads the videos back to
master CVR.
Delete the data of working device remained on the backup device: Delete the videos in backup CVR
once they are uploaded to master CVR.
Figure 6. 19 Backup CVR
6.4.2 Deleting Backup CVR
Steps:
1. Check the checkbox of backup CVR you want to delete.
2. Click button and click OK in confirmation dialog box.
6.4.3 Adding Master CVR
Before you start:
1. Log into backup CVR and enter N+1 Management interface.
2. Add the same encoding devices in backup CVR, which have been added in master CVR. For details, refer to
chapter 7.3.1.1 Adding Encoding Device. Ensure the name of encoding devices from different backup CVRs
varies from each other.
3. Delete the added encoding devices in step 2.
4. Add schedule for encoding devices in backup CVR the same as schedule in master CVR. For details, refer to
chapter 7.5.1 Schedule.
Steps:
1. Click button.
Figure 6. 20 Add Master CVR
2. Enter master CVR’s IP address.
3. Click OK to add. The added master CVR is listed in CVR master list
4. Enter the max. taken-over number and click Modify. If maximum taken-over master CVR is 4 and 7 master
CVRs are added, when 5 master CVRs are abnormal, the backup CVR would take over the first added 4
master CVRs. After one or more of the 4 CVRs recovers, other master CVRs would be taken over.
The max. taken-over number can’t be more than 10. If input 0 or input nothing, system regards it as 10.
Page 60

DS-A80&81 Series Storage System User Manual
59
Table 6. 4 Backup CVR Status
Backup CVR Status
Description
Standby
When master CVR is normal, backup CVR is standby.
Working
When master CVR is abnormal, backup CVR takes over the tasks. Now backup CVR’s
status is working and master CVR’s status is taken-over. When master CVR recovers,
backup CVR recovers to standby.
Page 61

DS-A80&81 Series Storage System User Manual
60
Chapter 7 CVR Sub-System
Purpose:
You can configure the parameters for CVR sub-system.
Table 7. 1 Module Description
Module
Description
Information
Encoding device, record schedule, and record volume information are listed.
Device Management
You can add and manage encoding devices, adjust CVR sub-system time, count remaining
recoding capacity, and analyze video loss.
Live View & Record
You can view encoding devices’ status and live view image, and start and stop manual
record of one or more encoding devices.
Schedule & Alarm
You can configure recording schedule, create uploading task and schedule, and configure
alarm parameter.
Play & Download
You can search, archive, backup, lock, play, and download recorded videos.
Archive
For the purpose of saving significant videos, you can save them in archive volumes.
User
You can switch system language and edit display rows in each page.
System Config
You can configure system alarms and view CVR version.
Log Management
Log helps you figure out CVR history actions. You can search, export, and clear logs.
Key Words:
Information, Device & Management, Live View & Record, Schedule & Alarm, Play & Download, Archive, User,
System Config, Log Management
Figure 7. 2 CVR Sub-System
Page 62

DS-A80&81 Series Storage System User Manual
61
7.1 Access by Web Browser
Steps:
1. Open web browser.
2. Input the storage system’s IP address (https://10.254.254.254:2004) in Web browser address bar.
3. Press Enter. Then login interface appears.
4. Enter Password of CVR sub-system and click Login to log in. The default password is 123.
STRONG PASSWORD RECOMMENDED–We highly recommend you create a strong password of your own
choosing (Using a minimum of 8 characters, including at least three of the following categories: upper
case letters, lower case letters, numbers, and special characters.) in order to increase the security of your product.
And we recommend you reset your password regularly, especially in the high security system, resetting the
password monthly or weekly can better protect your product.
Figure 7. 3 CVR Sub-System
7.2 Information
Purpose:
Encoding device, record schedule, and record volume information are listed.
Step:
Click Information in navigation bar.
Page 63

DS-A80&81 Series Storage System User Manual
62
Figure 7. 4 Information
Table 7. 2 Status Description
State
Description
Free
Connection is normal and it is recording.
No video input
It appears when encoding device amount reaches the limit or CVR is
rebooting.
Recording
Encoding device is recording.
Password or user name error
Incorrect user name or password for encoding device.
Not load
When CVR starts, loading encoding device failed.
Unknown
CVR is error.
Not connected
Failed to get stream for encoding device.
Recording… Archiving…
Encoding device is recording and archiving.
Recording… Uploading…
Encoding device is recording and receiving videos from front-end
devices.
Archiving
Encoding device isn’t recording, but is archiving.
Uploading
Encoding device isn’t recording, but is receiving videos from cameras.
7.3 Device Management
Purpose:
You can add and manage encoding devices, adjust CVR sub-system time, count remaining recoding capacity, and
analyze video loss.
Step:
Click Device Management in navigation bar.
Page 64

DS-A80&81 Series Storage System User Manual
63
Figure 7. 5 Device Management
7.3.1 Device
Purpose:
You can add and edit encoding devices and add and edit groups.
Step:
Click Device Management in navigation bar and choose Device to enter Device Management interface.
7.3.1.1 Adding Encoding Device
Steps:
1. Click button to enter Add encoding device interface.
2. Enter Name according to your
3. According to encoding device’s acutal parameters, select protocol Type in dropdown list, enter IP/Host, Port,
Channel, Login user, and Password.
4. Optionally, you can enable stream media server by checking the checkbox of Whether to use Stream Media,
inputting IP address:port (e.g., 192.168.0.2:554) in Steam Media Server, and select URL mark and
Transmission mode.
5. Optionally, you can select Options according to your needs.
Getting stream on demand: Storage system releases occupied bandwidth, when no stream
requirement for the encoding device. If selected, the encoding device Attribute marks as P.
Enable Automatic Network Replenishment: When storage system disconnects with the encoding
device, the encoding device records video and stores in its own storage device, like SD card. Once
connection recovers, encoding device sends the video to storage system. If selected, the encoding
device Attribute marks as T.
Enable sub-stream: If selected, when you preview and record via sub-stream, it takes lower
bandwidth. But sub-stream’s video quality and bitrate is lower than main stream. And the encoding
device Attribute would mark as S. If record strategy exists, CVR gets stream according to strategy.
Enable arming: If selected, when alarm occurs to encoding device, CVR can trigger alarm record. And
the encoding device Attribute would mark as A.
Enable backup: Before enabling backup, add an archive volume first. If selected, videos save in record
volume as well as in archive volume. And the Attribute would mark as B.
6. Select Related to record volume.
7. Click OK and click OK in confirmation dialog box to add the encoding device.
Page 65

DS-A80&81 Series Storage System User Manual
64
Figure 7. 6 Add Encoding Device
Repeat above steps to add more encoding devices. Up to 1024 encoding devices can be added.
If the encoding device you add isn’t in the List of Compatible of Encoding Device, the Attribute would mark
as B. You can ask technical support for the List of Compatible of Encoding Device.
7.3.1.2 Modifying and Deleting
Steps:
To delete encoding devices, do following steps:
1. Check the checkbox of encoding device you want to delete.
2. Click button to delete.
To modify encoding device’s parameters, do following steps:
1. Click button of encoding device you want to modify.
2. Edit the parameters you want to modify.
3. Click OK and click OK in confirmation dialog box to save the settings.
To modify linked record volume, do following steps:
1. Check the checkbox encoding device you want to modify.
2. Select the target record volume in the dropdown list.
Figure 7. 7 Encoding Device List
Page 66

DS-A80&81 Series Storage System User Manual
65
7.3.1.3 Exporting and Importing Encoding Device
Purpose:
For the purpose of modifying a large number of encoding device in batch, you can export them, modify their
parameters, and import them back to CVR sub-system.
Steps:
To export encoding devices, do following steps:
1. Click button and click OK in confirmation dialog box.
Figure 7. 8 Export
2. Select file saving path and click OK to save it.
The exported file is a .csv file. You can view and edit it via Microsoft Excel. The content of exported file is shown in
Figure 7. 9 Exported File.
Figure 7. 9 Exported File
To import encoding devices, do following steps:
1. Click button.
2. Click Browse and select the target file.
3. Optionally, you can select the Operation options.
Update duplicate equipment: When the contents of HOST and CHANNEL column of several encoding
devices are the same, CVR judges them as duplicate encoding device. If it is selected, CVR would add
all of the duplicate encoding devices and update the previous encoding devices’ parameters. Or
duplicated wouldn’t be added.
Update encoding device with the same name: If selected, when encoding devices in CVR sub-system
and importing file share the same name, once imported, the encoding devices in importing file would
replace the one in CVR sub-system.
Assign record volume automatically: If selected, when encoding devices in importing file have no
linked record volume, once imported they would link to the first record volume in CVR sub-system.
Rename automatically: If selected, when duplicated name exists during add and modifying, the name
of added encoding devices would be renamed as “previous name _1”.
4. Click OK and click OK in confirmation dialog box to import. The encoding device list would be updated
according to imported file.
Page 67

DS-A80&81 Series Storage System User Manual
66
Figure 7. 10 Import
7.3.1.4 Adding Group
Purpose:
Group helps you to manage encoding devices.
Steps:
1. Click button.
Figure 7. 11 Add Group
2. Enter Name and Note.
3. Click button, select Type, IP address and Name, and click OK to add.
Page 68

DS-A80&81 Series Storage System User Manual
67
Figure 7. 12 Select & Add
Or select encoding device you want to contain in dropdown list of Add encoding device.
4. Click OK and click OK in confirmation dialog box to add the group.
7.3.1.5 Exporting and Importing Group
Purpose:
For the purpose of managing group in batch, you can export and import groups.
Step:
The steps are the same as chapter 7.3.1.3 Exporting and Importing Encoding Device.
7.3.2 Tools
Purpose:
You can adjust CVR sub-system time, count remaining recoding capacity, and analyze video loss.
Step:
Click Device Management in navigation bar and choose Tools to enter Tools interface.
Figure 7. 13 Tools
7.3.2.2 Time Synchronization
Purpose:
Time synchronization is used to synchronize encoding devices’ time with CVR.
Page 69

DS-A80&81 Series Storage System User Manual
68
If iVMS-5200 has started time synchronization with encoding devices, it isn’t recommended to start time
synchronization in storage system.
Step:
Click and click OK in confirmation dialog box. CVR modify connected encoding devices’ time
once it is started. And then synchronize time every 5 minutes.
Figure 7. 14 Time Synchronization
7.3.2.3 Record Volume Calculator
Purpose:
You can calculate the remaining record time of a certain record volume.
Steps:
1. Click button.
2. Select Record Volume to view in the dropdown list.
3. Enter Record stream of each device(Kbit/s), Number of recording devices, and Duration hours in each day.
And then the Available days appears.
Figure 7. 15 Record Volume Calculator
7.3.2.4 Detecting Video
Purpose:
You can detect whether frame loss exists in specified videos.
Steps:
Page 70

DS-A80&81 Series Storage System User Manual
69
1. Click button.
2. Select encoding devices in the list.
Or enter encoding device’s name in text field and click OK.
Detecting takes a long time, so it isn’t recommended to select more than 10 encoding devices.
Figure 7. 16 Select Encoding Device.
3. Select Detection start time and Detection end time.
Ensure videos exist between start time and end time.
The duration can’t longer than 10 minutes.
4. Click Start to start detecting.
5. After detection finishes, click View to view detection result. You can also click Export to save detection
result in local path.
7.4 Live View and Record
Purpose:
You can view encoding devices’ status and live view image, and start and stop manual record of one or more
encoding devices.
Step:
Click Live View & Record in navigation bar to enter Live View & Record interface.
Figure 7. 17 Live View and Record
Page 71

DS-A80&81 Series Storage System User Manual
70
7.4.1 Live View
Purpose:
Preview the real-time image of connected encoding device.
Before you start:
To add IP address of CVR to web browser trusted sites and enable all of ActiveX controls and plug-ins, do following
steps:
1. Enter Trusted Sites menu.
Tools › Internet Options › Security › Trusted Sites
Figure 7. 18 Trusted Sites
2. Click button, enter https://IP address of CVR, click Add, and click Close to go back to
upper menu.
3. Click button, enable all of ActiveX controls and plug-ins, click OK to save and go back to
upper menu.
4. Click OK to save the settings.
Steps:
1. Check the checkboxes of encoding devices you want to view.
2. Click button to start live view. Up to 16 encoding devices can be viewed at the same time.
7.4.2 Manual Record
Purpose:
Page 72

DS-A80&81 Series Storage System User Manual
71
To start or stop recording manually, do following steps.
Steps:
To start or stop manual recording for specified encoding devices, do following steps:
1. Check the checkboxes of encoding devices you want to start manual record.
2. Click button to start recording. And you can click button to stop
recording.
To start or stop manual recording for all encoding devices, do following step:
Click button to start recording for all. And you can click button to stop recording for
all.
If the encoding device is recording according to record schedule, click Stop recording or All stop wouldn’t stop
recording, for record schedule would start recording again. For schedule details, refer to 7.5 Schedule and Alarm.
7.5 Schedule and Alarm
Purpose:
You can configure recording schedule, create uploading task and schedule, and configure alarm parameter.
Step:
Click Schedule & Alarm in navigation bar to enter Schedule & Alarm interface.
Figure 7. 19 Schedule & Alarm
7.5.1 Schedule
Purpose:
Set the record schedule, and then the encoding devices automatically starts and stops recording according to the
configured schedule.
Step:
Click Schedule & Alarm in navigation bar to enter Schedule interface.
Figure 7. 20 Schedule
Page 73

DS-A80&81 Series Storage System User Manual
72
It is recommended to configure either basic schedule or advanced schedule.
7.5.1.2 Basic Schedule
Purpose:
Set the basic record schedule, and then the specified encoding devices automatically start/stop recording
according to the configured schedule.
Steps:
1. Click button to pop up Make plan interface.
2. Enter in the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 21 Select Encoding Devices
3. Select the Date on which you want to set schedule.
Figure 7. 22 Date
4. In Record mode, to schedule an all-day recording, check the checkbox of Full-Day.
Or you can select the one or more time segments to set start time and end time.
Up to 8 periods can be configured for each day. And the time periods can’t be overlapped with each other.
Figure 7. 23 Record
5. Optionally, you can select one or more Schedule options.
Page 74

DS-A80&81 Series Storage System User Manual
73
Dead status at initial state: If selected, schedule state is Stopped. And encoding device wouldn’t start
recording. Other Schedule options wouldn’t take effective.
Deactivate the record schedule: If selected, encoding device wouldn’t start recording. Other Schedule
options wouldn’t take effective.
Pulling back data from encoding device: If selected and uploading schedule exists, the camera’s video
would upload to CVR. For details of configuring uploading schedule, refer to chapter 7.5.2.3 Adding
Uploading Schedule.
Deactivate schedule of alarm pre-record: Pre-record refers to the time you set to record before the
scheduled time or event. If selected, pre-record is turned off.
Deactivate alarm arm: If selected, when encoding device is error, CVR wouldn’t alarm.
Locking: If selected, you need to set locking time as a specified duration or keep locking. During locking time,
videos wouldn’t be overlapped. Locking time must be longer than duration time.
Sub-stream: If selected, encoding device records via sub-stream instead of main stream.
Figure 7. 24 Schedule Options
7.5.1.3 Advanced Schedule
Purpose:
By setting advanced schedule, you can specify the start recording time and recording duration for designated.
Steps:
1. Click button to pop up Add advanced schedule interface.
2. Enter in the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 25 Select Encoding Devices
3. Select Start time by Record now or User-defined.
Start time: Starts recording once schedule is added.
User-defined: Starts recording at the set time.
4. Select Duration time unit as Week, day, hour, minute, or second and enter number.
Duration time: Keeps recording during duration time.
Figure 7. 26 Start Time and Duration Time
Page 75

DS-A80&81 Series Storage System User Manual
74
5. Optionally, you can select one or more Schedule options. For details, refer to step 5 of 7.5.1.2 Basic
Schedule.
6. Select Schedule and set the End time.
If Schedule is set as hour, minute, or customized, locking in schedule options is not selectable.
7. Click OK to save the schedule. Then before the end time, the selected encoding devices would repeatedly
start recording at set start time and stop recording till the duration time.
7.5.1.4 Exporting and Importing Advanced Schedule
Purpose:
For the purpose of managing advanced schedules in batch, you can export them, modify their parameters, and
import them back to CVR sub-system.
Step:
For detailed steps, you can refer to chapter 7.3.1.3 Exporting and Importing Encoding Device.
7.5.2 Record Upload
Purpose:
When videos in CVR lost, and the lost videos exist in encoding devices. You can upload the videos back to CVR.
Step:
Click Schedule & Alarm in navigation bar and choose Record Upload to enter Record Upload interface.
Figure 7. 27 Schedule
7.5.2.1 Basic Settings
Steps:
1. Click button.
2. Enter Detection Start Time, Detection End Time, Max. Camera Number, and Max. Uploading Camera for
One DVR.
Detection Start Time: Start time of detecting uploading.
Detection End Time: End time of detecting uploading. V ideos ranges from detection start time to end
time would be uploaded.
Max. Camera Number: The maximum cameras that could upload simultaneously.
Max. Uploading Camera for One DVR: The maximum cameras in a DVR that could upload
Page 76

DS-A80&81 Series Storage System User Manual
75
simultaneously.
Figure 7. 28 Basic Settings
7.5.2.2 Adding Uploading Tasks
Purpose:
When videos in CVR lost, and the lost videos exist in encoding devices. You can upload the videos back to CVR by
adding uploading tasks.
Steps:
1. Click the button.
2. Enter the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 29 Select Encoding Devices
3. Set the Start time and End time of video you want to upload.
Figure 7. 30 Add Uploading Tasks
4. Click OK to add the task. Then if encoding device contains the video, it starts uploading the video to CVR.
Page 77

DS-A80&81 Series Storage System User Manual
76
7.5.2.3 Adding Uploading Schedule
Purpose:
Uploading schedule can judge whether video loss happens during record schedule. Configure the uploading
schedule to upload the videos saved in encoding devices back to CVR.
Before you start:
Ensure pulling back data from encoding device in schedule options is selected when configuring basic or advanced
schedule. For detailed steps, refer to chapter 7.5.1.2 Basic Schedule and chapter 7.5.1.3 Advanced Schedule.
Steps:
1. Click button.
2. Enter the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 31 Select Encoding Devices
6. Select the Date on which you want to set schedule.
7. In Uploading mode, to schedule an all-day uploading, check the checkbox of All-day Uploading.
Or you can select the one or more time segments to set start time and end time.
Up to 8 periods can be configured for each day. And the time periods can’t be overlapped with each other.
8. Click OK to add the schedule. Then selected encoding devices only upload videos during the set data and
time segments.
During uploading process, you can pause uploading by clicking button in
Live view & Record interface.
7.5.3 Alarm
Purpose:
You can set the recording time for alarm events.
Before you start:
Enable alarm events you want to pay attention in encoding devices first. For details, refer to user manual of
encoding device.
Steps:
1. Click Schedule & Alarm in navigation bar and choose Alarm to enter Alarm interface.
Page 78

DS-A80&81 Series Storage System User Manual
77
Figure 7. 32 Alarm
2. Click button to pop up Add alarm configuration interface.
3. Enter the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 33 Select Encoding Devices
4. Enter Duration for alarm types you want to pay attention. Valid Duration ranges from 5 to 9999. Then when
an alarm occurs, CVR starts recording for the set Duration.
The supported alarm types include Signal Source, Motion Detection, V ideo Tampering, Border Cross, Wrong
Direction, Unattended Baggage, and Object Loss.
5. Optionally, you can check the checkbox of Archive of alarm types. Then the alarm videos can be viewed in
Archive Search interface.
Figure 7. 34 Other Configurations
6. Click OK to save the settings.
7.6 Playing and Downloading
Purpose:
You can search, archive, backup, lock, play, and download recorded videos.
Page 79

DS-A80&81 Series Storage System User Manual
78
Step:
Click Play & Download in navigation bar to enter Play & Download interface.
Figure 7. 35 Schedule & Alarm
7.6.1 Searching Video
Steps:
1. Click button to enter Search record interface.
2. Enter the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Figure 7. 36 Select Encoding Devices
3. Specify the search conditions including Start time, End time, Record Type, Search Type, and Show lock
time (whether it’s a locked video).
4. Click OK to start search. And the videos meet the search conditions would be listed.
Figure 7. 37 Search Result
7.6.2 Archiving
Purpose:
For the purpose of saving significant videos, you can save them in archive volumes.
Before you start:
Specify archive volume first. For detailed steps, refer to chapter 7.7.1 Archive Volume.
Search videos first.
Page 80

DS-A80&81 Series Storage System User Manual
79
7.6.2.1 Archiving a Single Video
Steps:
1. Click button and click Archive in popup window.
2. Enter Level and Note.
Level: Type in your custom level.
3. Select the Start time and Duration to archive.
4. Click OK to start archiving. You can check logs for archiving process.
Figure 7. 38 Archive
7.6.2.2 Archiving Videos in Batch
Steps:
1. Check the checkboxes of videos you want to archive and click button.
2. Enter Level and Note.
Level: Enter your custom level.
3. Click OK to start archiving. You can check logs for archiving process.
Page 81

DS-A80&81 Series Storage System User Manual
80
Figure 7. 39 Archive
7.6.3 Remote Backup
Purpose:
Remote backup refers to back up the videos saved in current CVR to the archive volume of another storage
system.
Before you start:
Search videos first.
Prepare a storage system with an archive volume.
Steps:
1. Check the checkboxes of videos you want to back up.
2. Click button to enter Remote backup interface.
3. Enter the target storage system’s IP address in Set IP for B PC.
4. If the corresponding encoding device of the backup video doesn’t exist in target storage system, check the
checkbox of Add encoding device. Or clear the checkbox.
5. Click OK to start backing up. Check the event log for backup process.
Figure 7. 40 Remote Backup
6. During the backup process, you can break it. For details, refer to chapter 7.7.1.3 Break Remote Backup.
7.6.4 Locking
Purpose:
The locked videos wouldn’t be overlapped by other videos.
Page 82

DS-A80&81 Series Storage System User Manual
81
Before you start:
Search videos first.
Steps:
1. Check the checkboxes of videos you want to lock. Not more than 100 videos can be selected.
2. Click button.
3. Select lock mode as Unlock, Lock last, or Lock time.
Unlock: If selected, the locked video would be unlocked.
Lock last: If selected, the video is locked permanently.
Lock time: If selected, you need to set the locking time. Then the video would be locked from the
video start time for the set time.
Figure 7. 41 Lock Mode
7.6.5 Playback
Purpose:
Play back videos to view the history image.
Before you start:
Search videos first.
Add IP address of CVR to web browser trusted sites and enable all of ActiveX controls and plug-ins. For detailed
steps, refer to Before you start of 7.4.1 Live View.
7.6.5.1 Whole Video Playback
Purpose:
Play the original video.
Steps:
1. Check the checkboxes of videos you want to play. Not more than 16 videos can be selected.
2. Click button. And another window pops up. You can view the playback image.
Page 83

DS-A80&81 Series Storage System User Manual
82
Figure 7. 42 Playback Window
3. You can play all selected videos by clicking button in upper-right corner.
7.6.5.2 Segment Playback
Purpose:
Divide original videos into several segments to play.
Steps:
1. Click button.
2. Enter the segment number in Block text field and click Segment file. Then the segment videos are listed.
3. Select videos and click button to start playback.
Figure 7. 43 Segment Playback
7.6.6 Downloading
Purpose:
Save the videos to computer by downloading them.
Page 84

DS-A80&81 Series Storage System User Manual
83
Before you start:
Search videos first.
7.6.6.1 One-Key Downloading
Step:
Click button and select the saving path to save a single video.
7.6.6.2 Block Downloading
Steps:
Click button and click Integrated Download to download.
Figure 7. 44 Segment Downloading
7.6.6.3 Batch Dowloading
Steps:
1. Check the checkboxes of videos you want to download.
2. Click button to pop up batch downloading interface.
3. Click button to select saving path.
4. Select downloading mode as By signle-task or By multi-task.
By single-task: Download one video at a time.
By multi-task: Download several videos simultaneously. The maximum downloading video
amount is Max. number of tasks whose valid range is from 1 to 5.
5. Click Start to start downloading. You can click Stop to stop downloading.
Page 85

DS-A80&81 Series Storage System User Manual
84
Figure 7. 45 Batch Downloading
7.7 Archiving
Purpose:
For the purpose of saving significant videos, you can save them in archive volumes.
Step:
Click Archive in navigation bar to enter Archive interface.
Figure 7. 46 Archive
7.7.1 Archive Volume
Step:
Click Archive in navigation bar and choose Archive volume to enter Archive volume interface.
Page 86

DS-A80&81 Series Storage System User Manual
85
Figure 7. 47 Archive Volume
7.7.1.2 Specify Archive Volume
Step:
Select archive volume from dropdown list and click Modify to save the settings.
7.7.1.3 Break Remote Backup
Step:
Click button and click OK in popup confirmation dialog box to stop remote
backup.
7.7.2 Archive Search
Purpose:
You can search the archived videos.
Steps:
1. Click Archive in navigation bar and choose Archive Search to enter Archive Search interface.
Figure 7. 48 Archive Volume
2. Click button to enter Search archive interface.
3. Enter the encoding device name and click OK to select the encoding device. Repeat the step to add more.
Or select encoding devices or groups in the list.
Page 87

DS-A80&81 Series Storage System User Manual
86
Figure 7. 49 Select Encoding Devices
4. Set the search conditions including video start time, end time, Record type, Level, Archive start time,
Archive end time, and Comment.
5. Click OK to start search. The matched archive files would be listed.
7.8 User
Purpose:
You can switch system language and edit display rows in each page.
Steps:
1. Click User in navigation bar to enter User interface.
2. To modify Display language, select language in the dropdown list.
3. To modify the display rows in each page, select number in the dropdown list of Rows per table page.
4. Click Update prefs to save the changes.
Figure 7. 50 User
7.9 System Configuration
Purpose:
You can configure system alarms and view CVR version.
Step:
Click System in navigation bar to enter System interface.
Page 88

DS-A80&81 Series Storage System User Manual
87
Figure 7. 51 System
7.9.1 System Alarm
Purpose:
You can set linkage actions for alarm type, specify alarm type for alarm events, and turn on or turn off status
alarm.
Steps:
1. Click System in navigation bar and choose System Alarm to enter System Alarm interface.
2. Alarm type includes Info (Information), Warning, Error, and Fatal. Specify 3 linkage actions for the 4 alarm
types.
Figure 7. 52 Alarm Setting
3. Specify alarm type for alarm events.
Page 89

DS-A80&81 Series Storage System User Manual
88
Figure 7. 53 Alarm Events
4. Turn on or turn off status alarm.
Figure 7. 54 Status Alarm
5. Click to save the settings.
7.9.2 CVR Version
Purpose:
You can view CVR version, CVR library version, and CVR other version.
Step:
Click System in navigation bar and choose CVR Version to enter CVR Version interface.
Figure 7. 55 CVR Version
Page 90

DS-A80&81 Series Storage System User Manual
89
7.10 Log Management
Purpose:
Log helps you figure out CVR history actions. You can search, export, and clear logs.
Step:
Click Log Management in navigation bar to enter Log Management interface.
Figure 7. 56 Log Management
7.10.1 Searching Log
Steps:
1. Click button to pop up Log Search interface.
2. Specify the search condition including Log type, Start time, End time, and Keyword.
3. Click OK to start search. The matched logs would be listed.
Figure 7. 57 Log Search
7.10.2 Exporting Log
Purpose:
You can export the listed logs to local disk.
Before you start:
Search the logs you want to export.
Step:
Click button and choose the saving path to save it.
The exported logs are integrated in a .csv file.
Page 91

DS-A80&81 Series Storage System User Manual
90
7.10.3 Clearing Log
Step:
Click button and click OK in popup confirmation dialog box to clear all logs saved in CVR sub-system.
Page 92

DS-A80&81 Series Storage System User Manual
91
Chapter 8 System
Purpose:
You can configure network parameters, alarm triggered action, system time, modify system password, and so
forth.
Table 8. 1 Module Description
Module
Description
Network
You can:
Modify the configuration of management NIC and data NICs.
Bond data NICs.
Remotely access storage system via a specified gateway.
Edit DNS server’s IP address, bond mode, and network work speed.
Alarm
You can:
Send storage system’s alarm to client via e-mail or SNMP manager.
Time
You can:
Manually or automatically adjust system time.
Tool
You can:
Modify user’s password.
Configure SMTP parameters.
Test network communication between storage system and a specified IP address.
Update storage system.
View services’ status.
Keywords:
Network, Alarm, Time, Tool
Figure 8. 2 System
Page 93

DS-A80&81 Series Storage System User Manual
92
8.1 Network
Purpose:
Storage system provides one Management NIC (Network Interface Card) and two Data NICs. The Management
NIC is designed for configuring the Data NIC and device maintenance. The Data NICs are used to transmit data.
Step:
Click System in navigation bar and choose Network to enter Network interface.
Figure 8. 3 Network
8.1.1 Modifying Data NIC
Steps:
1. Check the checkbox of data NIC to modify in NIC Information list.
2. Click in NIC Information list.
3. Enter the new IP Address and Subnet Mask and select MTU in dropdown list.
MTU (Maximum Transmission Unit): Select MTU as larger than 1500 byte for the purpose of improving
transmission performance.
4. Click OK to save the settings.
Page 94

DS-A80&81 Series Storage System User Manual
93
Figure 8. 4 Modify NIC Information
8.1.2 NIC Bond
Purpose:
When transmitting data via a single data NIC, once the data NIC fails, data transmission stops. By bonding
multiple data NICs into one, they can share one IP address, thus to balance network load and create redundant
links. When transmitting data via a bonded NIC, once a data NIC fails, other data NICs take over the transmission
task.
The management NIC doesn’t support bond.
The IP addresss of bonded NIC is the same as the first data NIC.
Before you start:
Connect all data NICs to network via network cables.
8.1.2.1 Creating Bond
Steps:
1. Check the checkboxes of Data NICs in NIC Information list.
Figure 8. 5 NIC Information
2. Click and click OK in confirmation dialog box. The bonded NIC is listed in Bonded NIC
Information list.
Page 95

DS-A80&81 Series Storage System User Manual
94
Figure 8. 6 Bonded NIC Information
8.1.2.2 Deleting Bond
Steps:
1. Check the bonded NIC checkbox.
2. Click and click OK in confirmation dialog box. Then the bonded NIC is recovered to several data
NICs.
Figure 8. 7 Confirmation Dialog Box
8.1.2.3 Modifying Bond Mode
For detailed information and steps, refer to section 8.1.5.2 Bond Mode.
8.1.3 Adding Route
Purpose:
By default, the route is empty, clients in different network segment access storage system via the default gateway.
If you want to access storage system via a specified gateway, add route here.
Steps:
1. Click in Custom Route Information list.
Page 96

DS-A80&81 Series Storage System User Manual
95
Figure 8. 8 Add Route
2. Input Route IP, Subnet Mask, and Default Gateway.
The client server within Route IP address can access storage system via the Default Gateway.
3. Select Bonded Data NIC in the dropdown list.
4. Click OK to add the route. Thus the client server within 10.128.50.1 to 10.128.50.55 can access storage
system via the bonded NIC 1 whose the gateway is 192.168.0.2.
8.1.4 MAC and IP Bonding
Purpose:
Only client with the specified MAC address and IP address is allowed to get access to iSCSI disk.
Steps:
1. Click to pop up IP and MAC bonding interface.
Figure 8. 9 Add Route
2. Input target Client IP and MAC Address.
Ensure the client IP is in the same network segment with the storage system.
3. Click OK and click OK in pop up confirmation box to create bond.
Page 97

DS-A80&81 Series Storage System User Manual
96
8.1.5 Advanced Parameters
Purpose:
You can configure DNS server, bond mode, and network work speed parameters.
8.1.5.1 DNS Server
Purpose:
You are required to add DNS server IP address if you need to access external network.
Steps:
1. Click Modify of Preferred DNS Server.
2. Enter IP address in text field.
3. Click OK and click OK in confirmation dialog box to save the settings.
Figure 8. 10 DNS Server
8.1.5.2 Bond Mode
Purpose:
The selection of bond mode is related to actual application and network situation. Up to seven types of bond
modes are provided. For details, refer to Table 8. 2 Bond Mode Description.
Steps:
1. Click Modify of Current NIC Bond Mode.
2. Select bond mode in dropdown list. Up to 7 bond modes are selectable.
3. Click OK and click OK in confirmation dialog box to save the settings.
Figure 8. 11 Current NIC Bond Mode
Table 8. 2 Bond Mode Description
Bond Mode
Description
Balance-rr
Definition:
All data NICs sends and receives data in turn.
When using the mode, it is recommended to apply protocols except
TCP/IP.
Advantage:
Load balance.
All data NICs are fully used.
There is no requirement about hardware like network switch.
Disadvantage:
Page 98

DS-A80&81 Series Storage System User Manual
97
Bond Mode
Description
The order of received data is uncertain.
Low network throughput.
Active-Backup
Definition: The default bond mode. Transmits data via a specified data NIC,
other data NICs are standby. Only when the specified data NIC fails, another
standby data NIC takes over transmission task.
Advantage:
There is no requirement about hardware like network switch.
Redundant network links.
Disadvantage:
Load balance isn’t supported.
Uses only one data NIC at a time. Other data NICs aren’t fully used.
Balance-xor
Definition:
The storage system can figure out the relationship between each data NIC
and clients’ MAC addresses. According to the relationship, storage system
transmits data to clients with corresponding data NIC. If the working data
NIC fails, another data NIC takes over the task.
It is recommended to use this mode in a local area network. However, if
data is transmitted via network gateway, don’t use the mode.
Advantage:
There is no requirement to hardware like network switch.
Balance the load in the local area network within a network switch.
Disadvantage: Load balance isn’t supported in different local area network.
Broadcast
Definition: All the data NICs transmit the same data.
Advantage:
There is no requirement about hardware like network switch.
Redundant network links.
Data NICs are fully used.
Disadvantage:
Load balance isn’t supported.
Low data NIC usage.
802.3ad
Definition: The storage system figures out the relationship between each data
NIC and clients’ MAC addresses according to Hash Algorithm. Storage system
transmits data to client via corresponding data NIC.
Advantage:
Based on IEEE standard, devices in system can work efficiently if they are
all 802.3ad mode.
Load balance.
Data NICs are fully used.
Disadvantage: Storage system, network switch, and client server are all required
to support 802.3ad mode.
Balance-tlb
Definition: Storage system allocates output traffic to each data NICs, according
to current load. And transmits data to clients via different data NICs. If the
working data NIC fails, another data NIC takes over the task.
Page 99

DS-A80&81 Series Storage System User Manual
98
Bond Mode
Description
Advantage:
Data NICs are fully used.
Load balance when sending data.
Disadvantage: Load balance isn’t supported when receiving data.
Balance-alb
Definition:
Storage system allocates input and output traffic to each data NICs,
according to current load.
It is recommended to use the mode when sending and receiving data to
multiple clients.
Advantage:
Data NICs are fully used.
Load balance in both sending and receiving data.
8.1.5.3 Network Work Speed
Purpose:
It is the speed of all data NICs. The default network work speed is 100 Mb/s. It is recommended to set network
work speed according to actual network situation.
Steps:
1. Click Modify of Network Word Speed.
2. Select Network Work Speed as 1000 Mb/s or 100 Mb/s.
3. Click OK and click OK in confirmation dialog box to save the settings.
8.2 Alarm
Purpose:
Storage system supports notifying you about the occurring alarms via e-mail and SMTP manager.
Steps:
Click System in navigation bar and choose Alarm to enter Network interface.
Figure 8. 12 Alarm
Page 100

DS-A80&81 Series Storage System User Manual
99
8.2.1 Alarm Type
Purpose:
The Table 8. 3 Alarm Type Description describes the supported alarm types and corresponding event level. E-mail
and SNMP manager support notifying you about the alarm types in Table 8. 3.
Table 8. 3 Alarm Type Description
Module
Alarm Type
Event Level
Power supply
Controller’s power supply error
Serious
Storage enclosure’s power supply error
Serious
Temperature
Temperature is too high
Warning
Temperature is high
Serious
Temperature is too low
Serious
Fan
Fan speed is too low
Warning
Fan speed error
Serious
Fan damaged or poor connection
Serious
Memory
Memory is used too much.
Warning
DOM card
Insufficient capacity
Serious
Disk
Disk loss
Serious
Disk warning
Warning
Bad disk
Serious
Risky disk
Serious
Drive kicked a disk
Serious
Array kicked a disk
Serious
Array
Not available
Serious
Degraded
Warning
Rebuilding
Warning
Storage system
Physical disk loss
Serious
Unknown physical disk loss
Serious
Storage pool unmounted
Serious
All storage pool lost
Serious
NAS
SAMBA error
Serious
NFS error
Serious
FTP error
Serious
AFP error
Serious
HTTP error
Serious
RSYNC error
Serious
iSCSI
iSCSI configurations mismatch
Serious
I/O error
Serious
Network
Data NIC %d unconnected
Serious
Network speed of Data NIC %d is 100M Ethernet.
Serious
Single data NIC %d unconnected
Serious
Cluster
Cluster heartbeat communication error: network
Serious
 Loading...
Loading...