Grandstream Networks GXP21 Series, GXP16 Series Security Manual

Grandstream Networks, Inc.
GXP IP Phones
Security Guide

P a g e | 1
GXP Security Guide
Table of Contents
OVERVIEW ..................................................................................................................... 3
WEB UI/SSH ACCESS ................................................................................................... 4
Web UI Access ..................................................................................................................................... 4
Web UI Access Protocols ..................................................................................................................... 4
Admin Login .......................................................................................................................................... 5
User Management Levels .................................................................................................................... 6
SECURITY FOR SIP ACCOUNTS AND CALLS ............................................................ 7
Protocols and Ports .............................................................................................................................. 7
Anonymous/Unsolicited Calls Protection ............................................................................................. 8
SRTP .................................................................................................................................................. 10
SNMP ................................................................................................................................................. 10
SECURITY FOR GXP SERVICES ................................................................................ 11
Firmware Upgrade and Provisioning .................................................................................................. 11
TR-069 ................................................................................................................................................ 12
Syslog ................................................................................................................................................. 14
SECURITY GUIDELINES FOR GXP DEPLOYMENT .................................................. 15

P a g e | 2
GXP Security Guide
Table of Figures
Figure 1 : Web UI Access Settings................................................................................................................ 4
Figure 2 : Web UI Login ................................................................................................................................ 5
Figure 3 : Change Password on First Boot ................................................................................................... 5
Figure 4: Change Admin Level Password ..................................................................................................... 5
Figure 5 : Change User Level password ....................................................................................................... 6
Figure 6 : Configure TLS as SIP Transport ................................................................................................... 7
Figure 7 : SIP TLS Settings ........................................................................................................................... 7
Figure 8 : Additional SIP TLS Settings .......................................................................................................... 8
Figure 9 : Anonymous Call Rejection ............................................................................................................ 8
Figure 10 : Settings to Block Anonymous Call .............................................................................................. 9
Figure 11 : SRTP Settings ........................................................................................................................... 10
Figure 12 : SNMP Setting ........................................................................................................................... 10
Figure 13 : Upgrade and Provisioning ........................................................................................................ 11
Figure 14 : TR-069 Connection Settings ..................................................................................................... 13
Figure 15 : Syslog Protocol ......................................................................................................................... 14

P a g e | 3
GXP Security Guide
OVERVIEW
This document presents a summary of security measures, factors, and configurations that users are
recommended to consider when configuring and deploying our GXP series of IP Phones.
Note: We recommend using the latest firmware for latest security patches.
The following sections are covered in this document:
• Web UI/SSH Access
Web UI access is protected by username/password and login timeout. Three-level user management is
configurable. SSH access is supported for mainly troubleshooting purpose and it is recommended to disable
it in normal usage.
• Security for SIP Accounts and Calls
The SIP accounts use specific port for signaling and media stream transmission. It also offers configurable
options to block anonymous calls and unsolicited calls.
• Security for GXP Services
GXP supports service such as HTTP/HTTPS/TFTP/FTP/FTPS and TR-069 for provisioning. For better
security, we recommend using HTTPS/FTPS with username/password and using password-protected XML
file. We recommend disabling TR-069 (disabled by default) if not used to avoid potential port exposure.
• Deployment Guidelines for GXP
This section introduces protocols and ports used on the GXP and recommendations for routers/firewall
settings.
This document is subject to change without notice.
Reproduction or transmittal of the entire or any part, in any form or by any means, electronic or print, for
any purpose without the express written permission of Grandstream Networks, Inc. is not permitted.
P a g e | 4
GXP Security Guide
WEB UI/SSH ACCESS
Web UI Access
The GXP embedded web server responds to HTTP/HTTPS GET/POST requests. Embedded HTML pages
allow users to configure the device through a web browser such as Microsoft IE, Mozilla Firefox, Google
Chrome and etc. With this, administrators can access and configure all available GXP information and
settings. It is critical to understand the security risks involved when placing the IP Phones on public networks
and it’s recommended not to do so.
Web UI Access Protocols
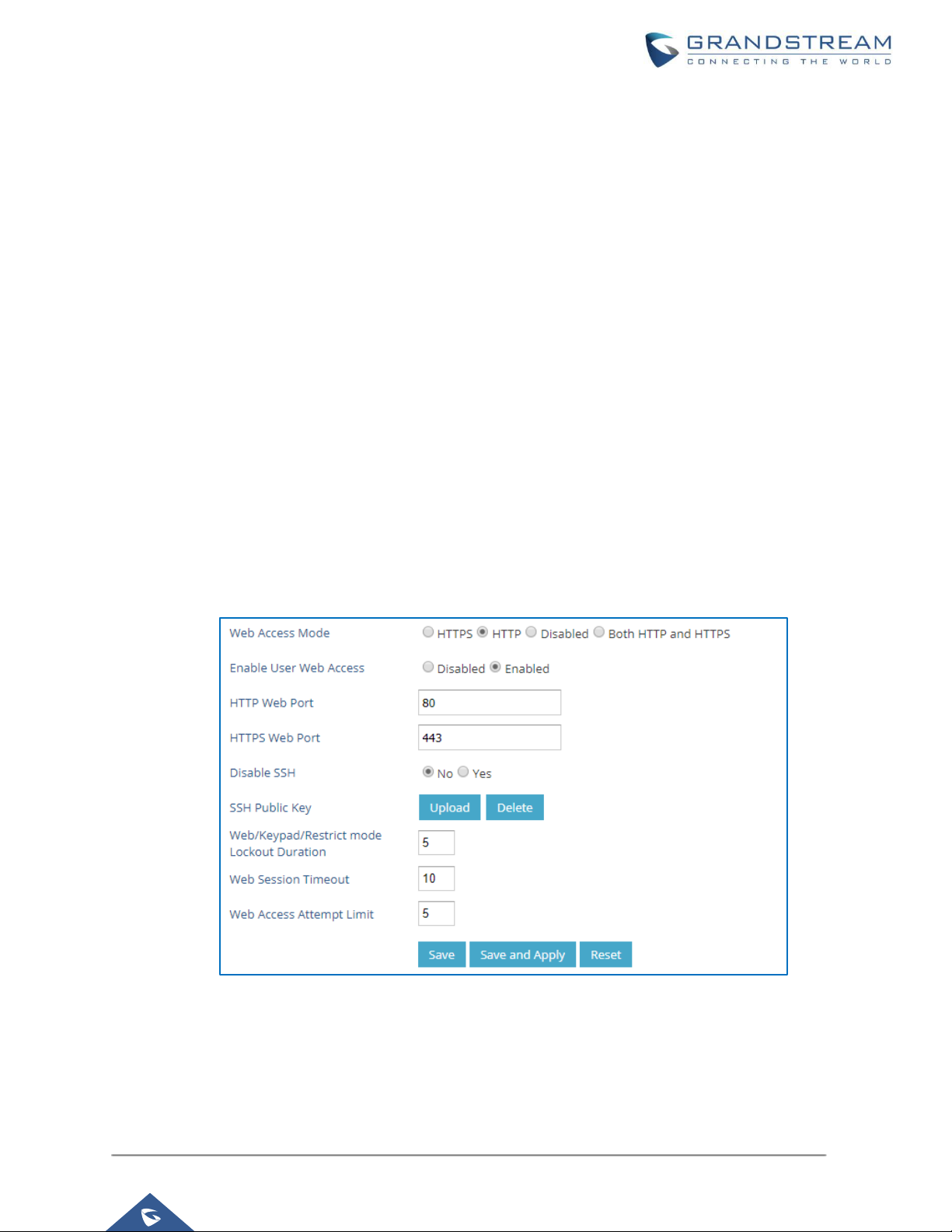
HTTP and HTTPS are supported to access the GXP’s web UI and can be configured under web UI →
Maintenance → Security settings → Security.
To secure transactions and prevent unauthorized access, it is highly recommended to:
1. Use HTTPS instead of HTTP.
2. Avoid using well known port numbers such as 80 and 443.
Figure 1 : Web UI Access Settings
3. The GXP allow access via SSH for advanced troubleshooting purpose. This is usually not needed
unless the administrator or Grandstream support needs it for troubleshooting purpose. SSH access
on the device is enabled by default with port 22 used. It’s recommended to disable it for daily normal
usage. If SSH access needs to be enabled, changing the port to a different port other than the well-
known port 22 is a good practice.
P a g e | 5
GXP Security Guide
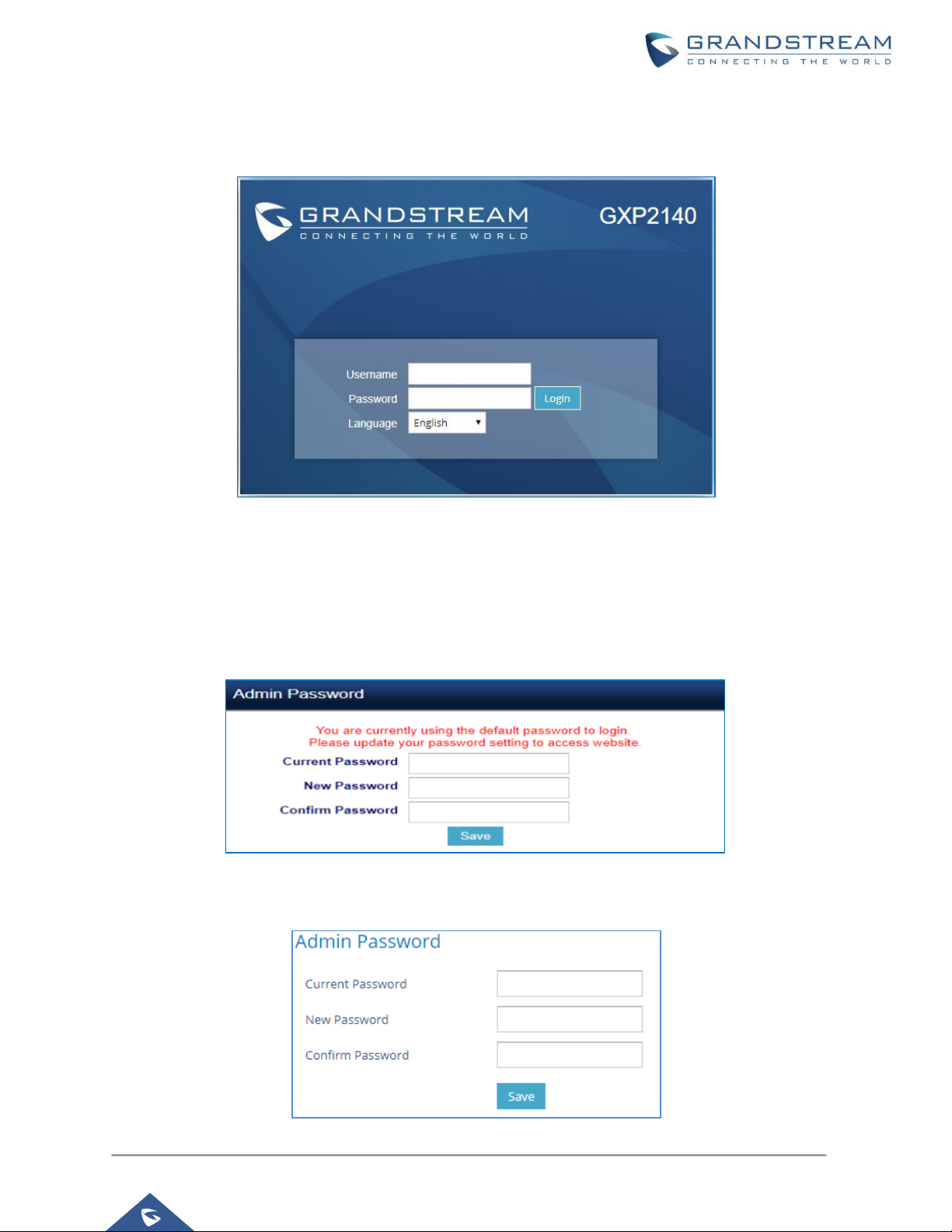
Admin Login
Username and password are required to log in the GXP’s web UI.
Figure 2 : Web UI Login
The factory default username for administrator level is “admin” and the default password is “admin”.
Changing the default password at first time login is highly recommended.
When accessing the GXP phones for the first time or after factory reset, users will be asked to change the
default administrator password before accessing GXP Web interface.
To change the password for default user "admin", navigate to Web GUI → Maintenance →Web Access
Figure 4: Change Admin Level Password
Figure 3 : Change Password on First Boot
 Loading...
Loading...