Page 1
www.eaton.com
Network Shutdown Module V3
User Manual
Network Shutdown Module V3 – User Manual - 34 003 896 XU / AE
Page 2

www.eaton.com
Network Shutdown Module V3
User Manual
Table of Contents
1 Introduction to the EATON’s Network Solution................................................................... 3
1.1 Overview ...............................................................................................................................................3
1.2 Monitoring the UPSs over the network..................................................................................................4
1.3 Protecting the computers / servers .......................................................................................................5
1.4 Connecting the UPS..............................................................................................................................6
1.4.1 Connecting to the Network ............................................................................................................................6
1.4.2 Select Network Architecture..........................................................................................................................6
1.4.3 Network Performances..................................................................................................................................7
2 Installation............................................................................................................................... 8
2.1 Hardware Pre-requisites (Electrical and Network Connections)...........................................................8
2.2 Software Installation Pre-requisites.......................................................................................................9
2.2.1 On the System Hosting « Network Shutdown Module V3 » ..........................................................................9
2.2.1.1 Windows Compatibilities:........................................................................................................9
2.2.1.2 Linux Compatibilities:..............................................................................................................9
2.2.1.3 Mac Compatibilities:................................................................................................................9
2.2.1.4 Standby configuration (Windows):........................................................................................10
2.2.1.5 Broadcast Message configuration (Windows): .....................................................................10
2.2.1.6 Firewall configuration (Windows & Linux) and Gateway : ....................................................10
2.2.2 On the System that Displays Web-based Graphical User Interface............................................................10
2.3 Quick Start...........................................................................................................................................11
2.4 Software Installation Procedure ..........................................................................................................12
2.5 Application deployment and silent installation (advanced) .................................................................14
2.6 Uninstalling the Network Shutdown Module.......................................................................................14
3 Minimal configuration steps ................................................................................................ 15
3.1 Introduction..........................................................................................................................................15
3.2 The IP address of the UPS that powers your server...........................................................................15
3.3 Users accounts configuration..............................................................................................................17
4 Use ......................................................................................................................................... 18
4.1 Monitoring the server and the UPS(s).................................................................................................18
4.1.1 Local access ...............................................................................................................................................18
4.1.2 Remote access ...........................................................................................................................................18
4.2 System and UPS event log .................................................................................................................21
4.3 UPS Events list....................................................................................................................................21
4.4 Test the communication with the UPS ................................................................................................23
4.4.1 Simple Tests ...............................................................................................................................................23
4.4.2 Advanced tests............................................................................................................................................24
4.5 Start and stop the Shutdown Module (advanced)...............................................................................24
5 Other Configuration possibilities........................................................................................ 25
5.1 Introduction..........................................................................................................................................25
5.2 Configure system parameters .............................................................................................................25
5.3 Shutdown Configuration......................................................................................................................26
5.4 Checking for Upgrades........................................................................................................................28
5.5 Events and actions (advanced configuration) .....................................................................................28
6 Multi-UPS Systems...............................................................................................................30
6.1 Caution ................................................................................................................................................30
6.2 Presentation ........................................................................................................................................30
6.3 Create a multi-UPS configuration........................................................................................................33
7 Appendix ............................................................................................................................... 34
7.1 Single UPS Mode compatibility ...........................................................................................................34
7.1.1 Card/Proxy compatibility..............................................................................................................................34
7.1.2 UPSs compatibility ......................................................................................................................................34
7.2 Multi-UPS Mode Compatibility list .......................................................................................................34
7.2.1 Caution........................................................................................................................................................34
Network Shutdown Module V3 – User Manual - 34 003 896 XU / AE
Page 3

www.eaton.com
7.2.2 « simple » configurations.............................................................................................................................34
7.2.3 Simple associations of the previous configurations.....................................................................................36
7.2.4 Configurations NOT supported....................................................................................................................37
7.3 Examples of Multi UPS configurations ................................................................................................38
7.4 Multi-UPS Systems and Event Management......................................................................................38
7.5 Application deployment and silent installation.....................................................................................39
7.5.1 Introduction .................................................................................................................................................39
7.5.2 Customized installation package.................................................................................................................39
7.5.3 Install the Shutdown Module in silent mode ................................................................................................40
7.5.4 Advanced installation options......................................................................................................................41
7.6 Single UPS Shutdown Sequence........................................................................................................42
7.7 Multi UPS shutdown sequence (example with Static Transfer Switch) ..............................................45
7.8 Additional information on events and actions......................................................................................46
7.8.1 Action settings Tab......................................................................................................................................46
7.8.1.1 The different actions .............................................................................................................46
7.8.1.2 Add an action ........................................................................................................................47
7.8.1.3 «System Shutdown» Action..................................................................................................47
7.8.1.4 Execute Action ......................................................................................................................49
7.8.1.5 «Send email» Action............................................................................................................50
7.8.2 Events Tab ..................................................................................................................................................51
7.8.2.1 Notification alarms..............................................................................................................51
7.8.2.2 Protection alarms................................................................................................................52
7.8.2.3 Multi UPS Systems and Notification Alarms....................................................................52
7.8.2.4 Multi UPS Systems and Protection Alarms......................................................................52
7.8.3 Test tab .......................................................................................................................................................53
7.8.4 The action parameters (execute and send email) ......................................................................................54
7.8.5 Software utilities ..........................................................................................................................................54
7.8.5.1 Shutdown.bat (Windows Script)............................................................................................54
7.8.5.2 Shutdown.sh (Linux Script)...................................................................................................55
7.8.5.3 Wait (Windows).....................................................................................................................55
7.8.5.4 Windows RunAs command or legacy mgeRunAs software utility ....................................... 55
7.9 FAQ and Error messages....................................................................................................................57
8 Glossary ................................................................................................................................ 60
9 Acknowledgements.............................................................................................................. 61
9.1 SQLite..................................................................................................................................................61
9.2 Pi3Web................................................................................................................................................61
9.3 PHP .....................................................................................................................................................61
9.4 OpenSSL.............................................................................................................................................62
9.5 Lighttpd................................................................................................................................................64
9.6 WxWidget ............................................................................................................................................64
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 2/65
Page 4
www.eaton.com
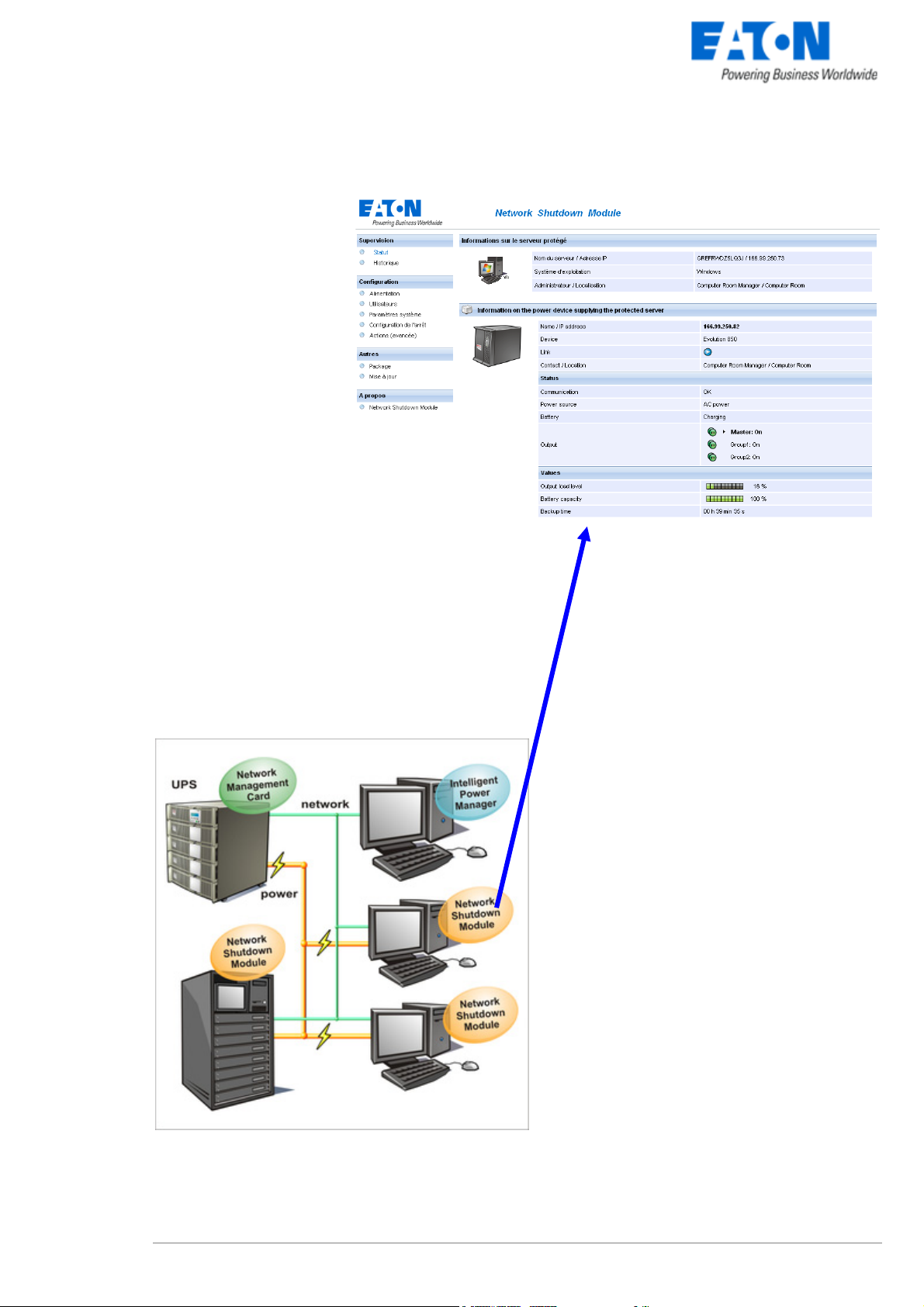
1 Introduction to the EATON’s Network Solution
1.1 Overview
EATON’s Network Solution:
z provides information on events concerning the supply of power to the computers connected to your
computer network,
z carries out automatic shutdown of computer systems,
z monitors and controls all the UPSs connected to the network.
As illustrated in the picture below, EATON Network Solution provides these 3 main functions:
z supervising the UPSs over the Network,
z protecting the computers,
z connecting the UPS to the Network.
The functions of EATON’s Network offering
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 3/65
Page 5
www.eaton.com
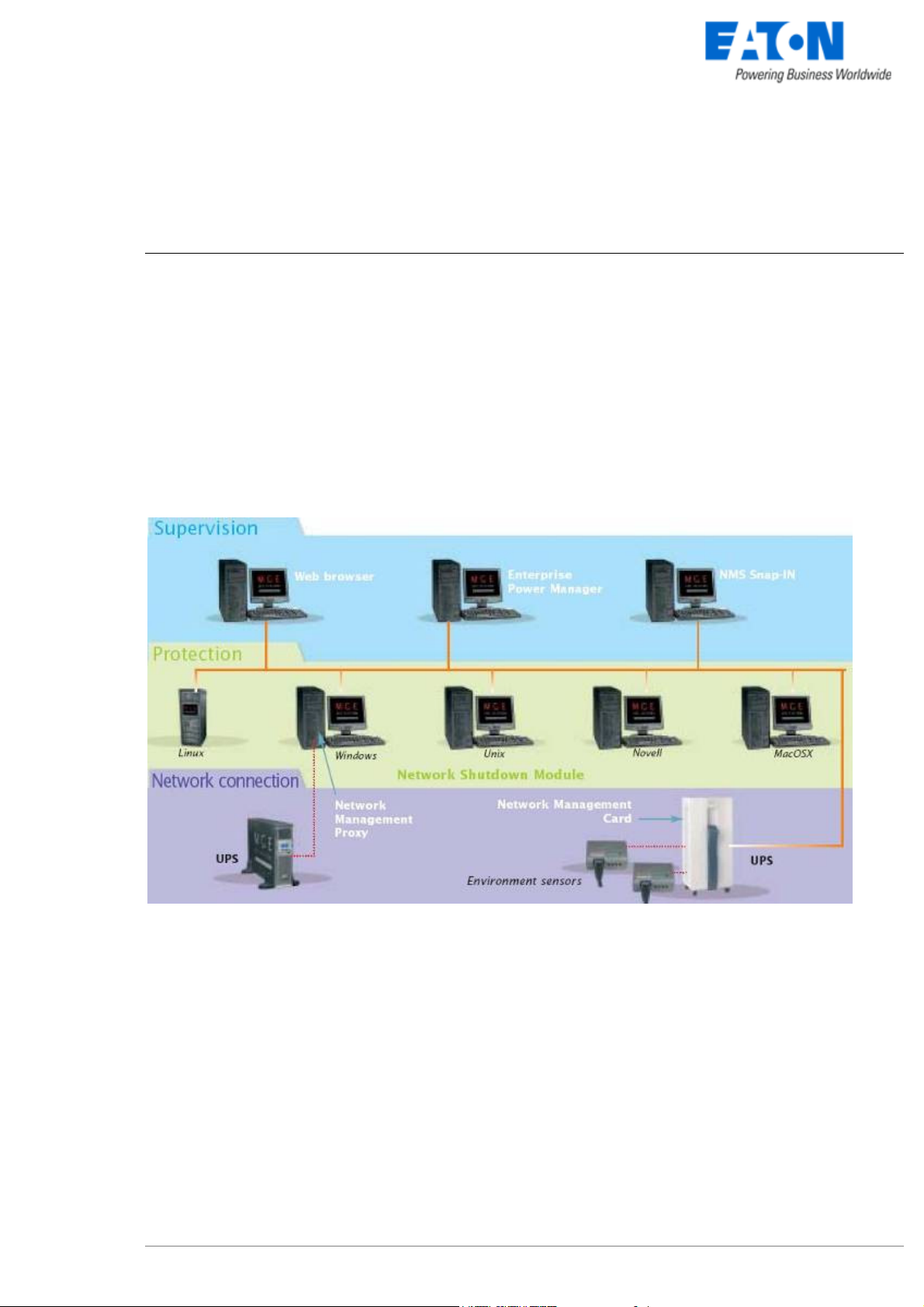
1.2 Monitoring the UPSs over the network
Depending on your needs, you can either use:
your Internet browser to monitor each UPS, as
Management Proxy, Management Card and
Shutdown Module include a Web server.
your company’s standard Network Management
System:
> HP-Openview,
> CA Unicenter,
> HP Insight Manager,
> IBM Tivoli Netview,
> …
To simplify integration of EATON UPSs with these
NMS, you can use one of the Network Management
System Kits for EATON devices. These kits are
available on Management Pac 2 CD-Rom (ref 66923).
the EATON supervisor "Intelligent Power Manager"
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 4/65
Page 6
www.eaton.com
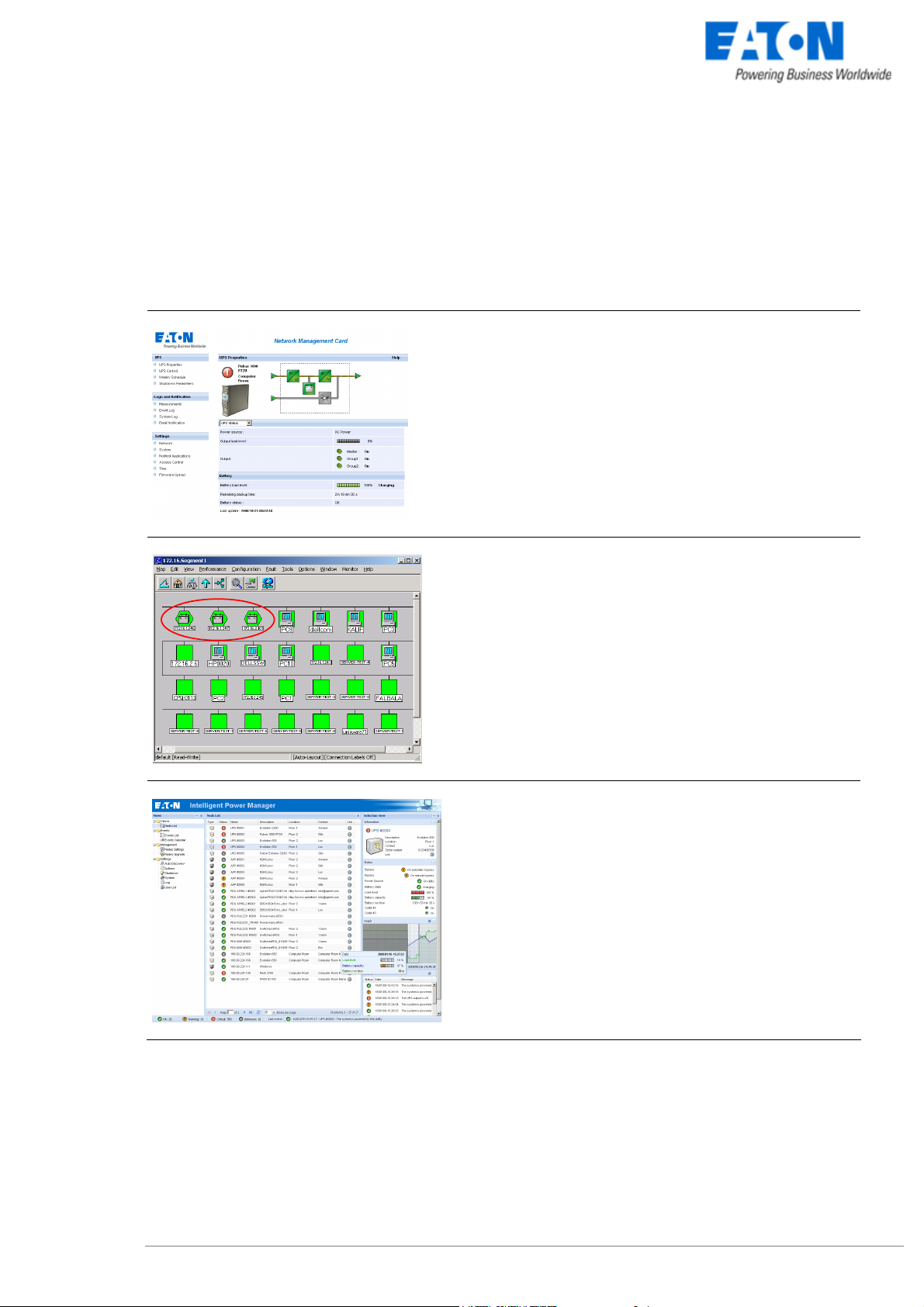
1.3 Protecting the computers / servers
The Network Shutdown Module installed on each of the servers to be protected performs this function. Note
that the Shutdown Module is available on several Operating Systems.
The Shutdown modules:
z continuously wait for information from the Mgt. Proxy or Mgt. Card connected to the EATON UPS.
z warns administrators and users if AC power fails and proceeds with graceful system shutdown before the
end of battery backup power is reached.
New functions:
The Network Shutdown Module V 3.20 offers the “mass configuration” advanced management feature
through Enterprise Power Manager 2.20.
The version V3 of the Network Shutdown Module:
z offers a remote supervision interface through any web browser (with a secured SSL/HTTPS connection
enabled by default),
z manages multi UPS redundant configurations (see “Multi-UPS systems” chapter )
z Several UPSs in parallel
> 2 UPSs in Hot standby (or serial) redundancy
> 2 redundant UPSs through Static Transfer Switch
> UPSs powering a server with multiple power supplies
UPSs powering servers with multiple power supplies
z manages switchable outlets
With this version you can trigger shutdown sequences with switchable outlets.
A UPS that powers servers with load-shedding function
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 5/65
Page 7

www.eaton.com
1.4 Connecting the UPS
1.4.1 Connecting to the Network
This function can be performed either through network Cards inserted in the UPS (Network Management
Card) or through a software “agent” running on a nearby PC that is called the Network Management Proxy.
Note that the Network Management Proxy is available only on Windows.
The Network Management Card or Proxy:
z manages communication with the UPS (as well as local protection of the machine on which Proxy is
installed),
z periodically accesses the information concerning the UPS,
z makes this information available to the connected applications (Network Shutdown Modules, Web
Browser, Network Management Systems, Enterprise Power Manager)
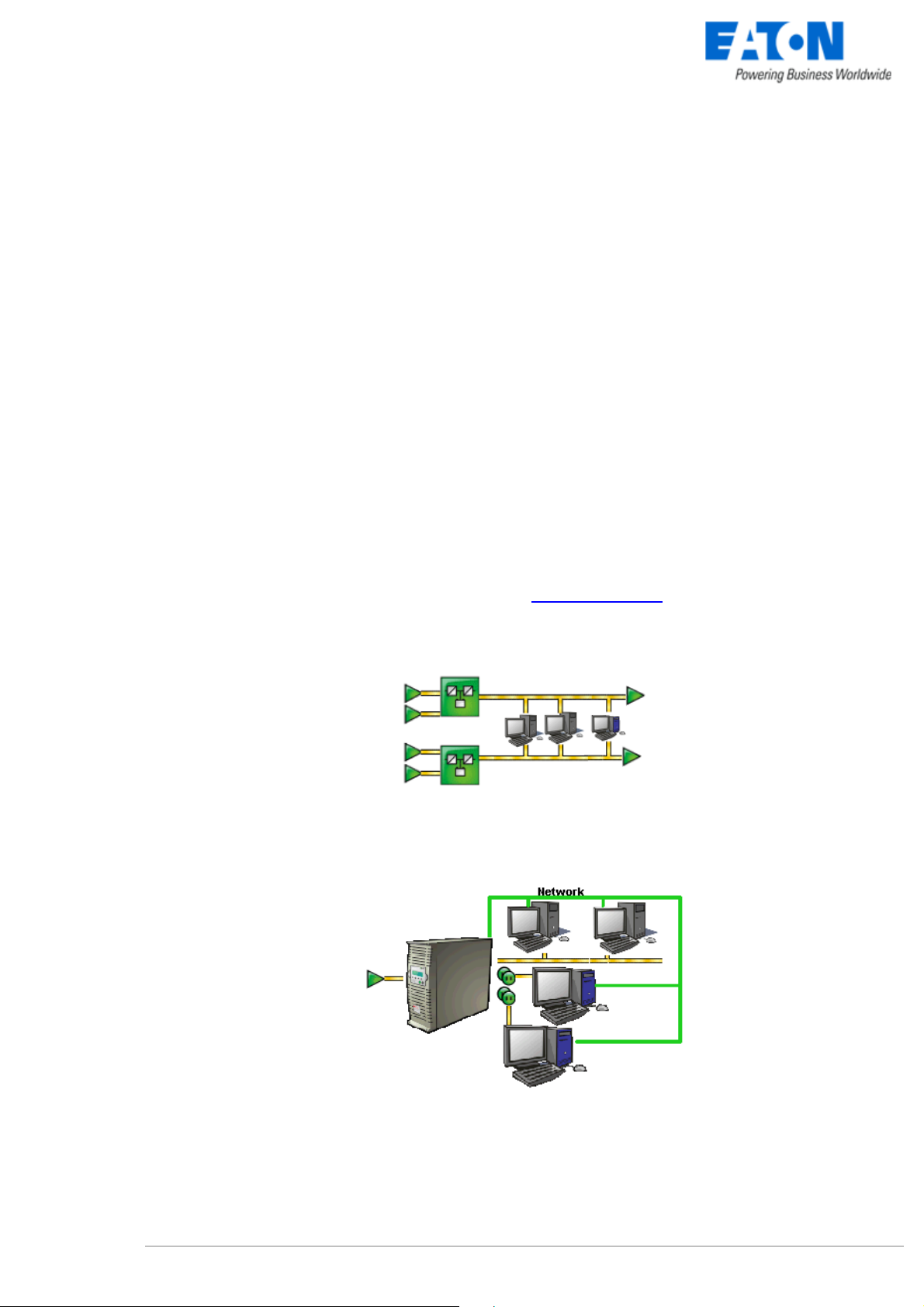
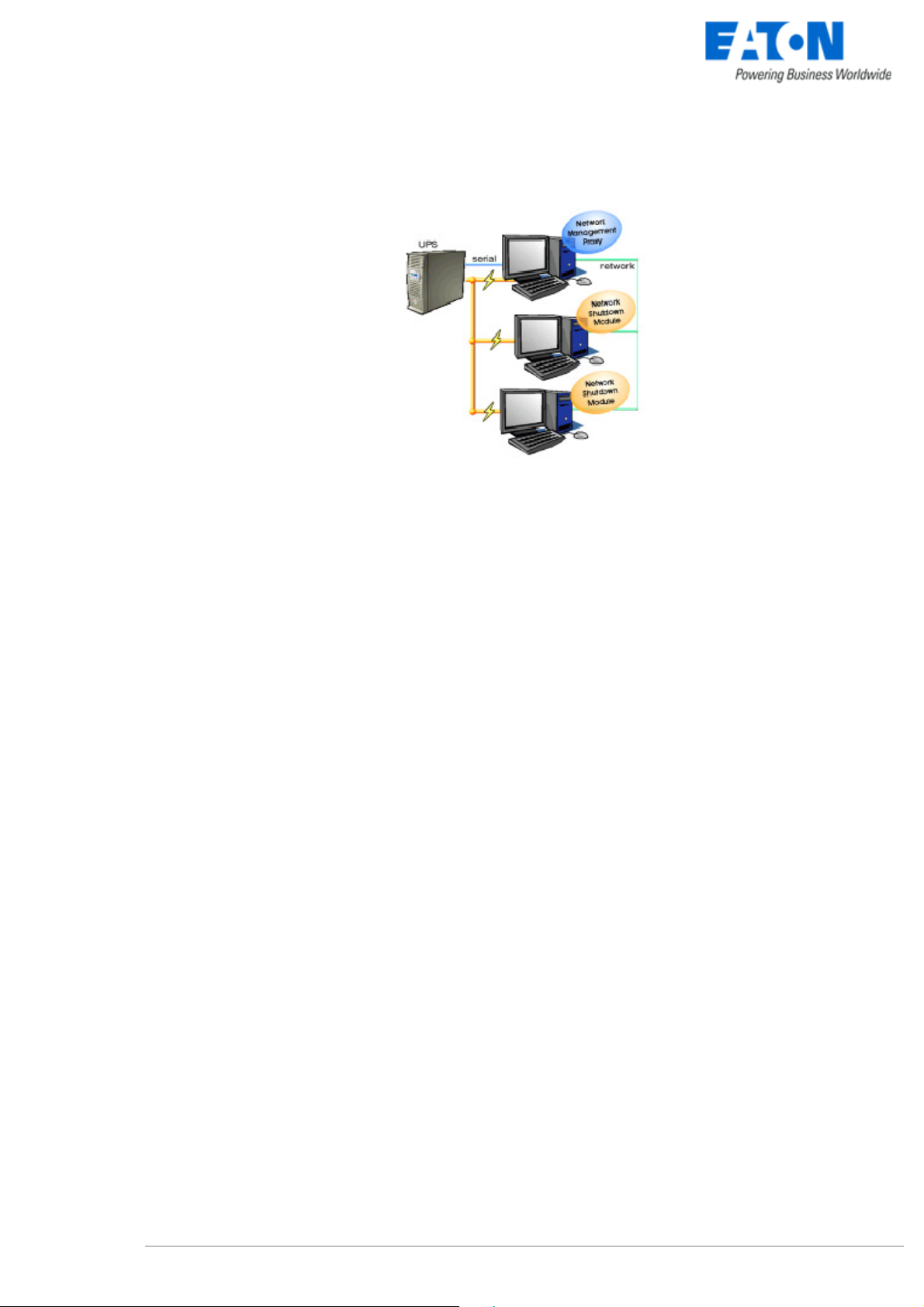
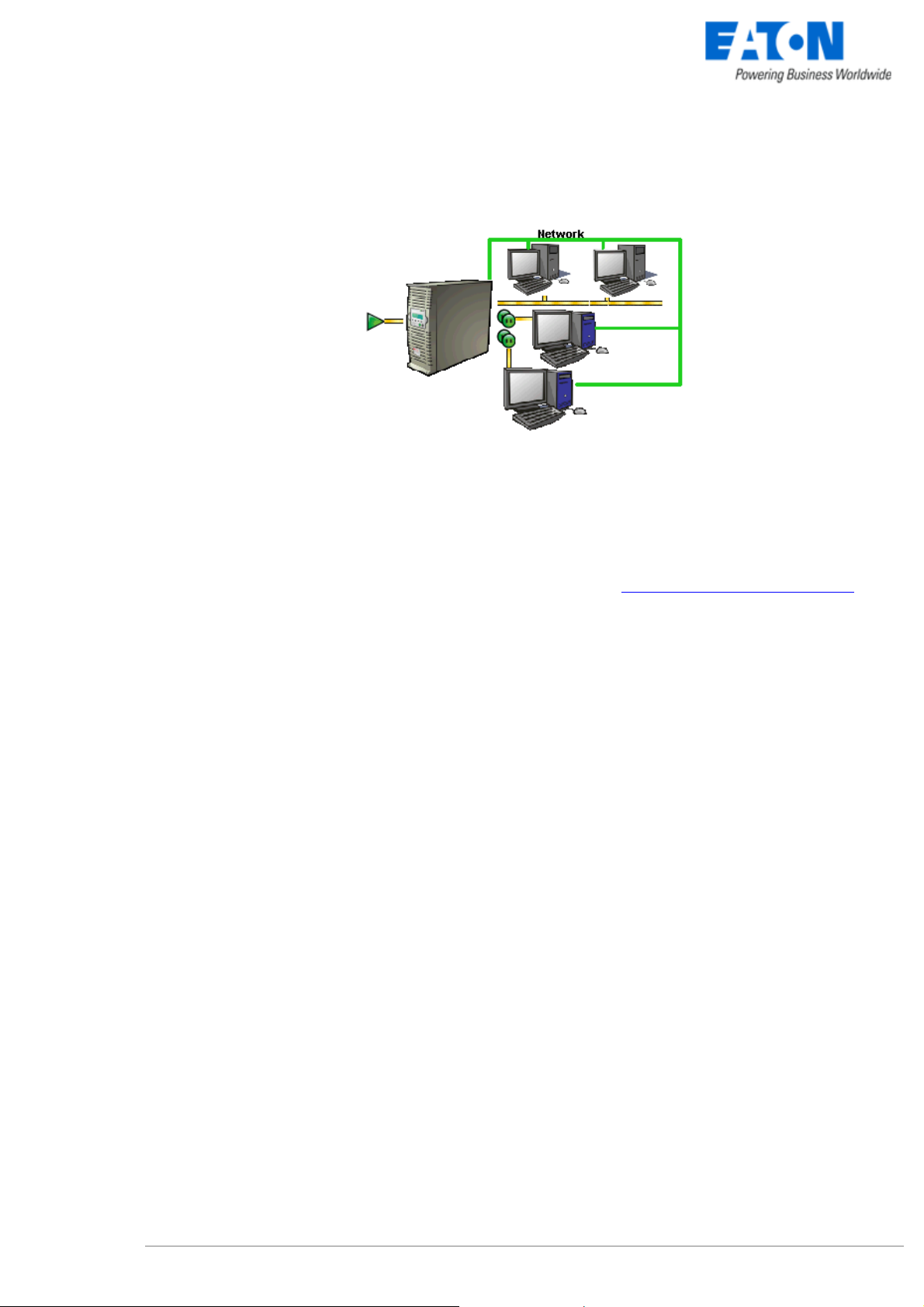
1.4.2 Select Network Architecture
Below are two software and hardware architectures showing how EATON UPSs can protect several
computers. These typical examples are intended to assist you in designing your own architecture.
Connection with Network Management Card
On the diagram above, the following two types of connections are required:
z the electrical power cables,
z the TCP/IP communication network.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 6/65
Page 8
www.eaton.com
Connection with Network Management Proxy
On the diagram above, three types of connections are required:
z a point-to-point link (serial or USB),
z the electrical power cables,
z the TCP/IP communication network.
1.4.3 Network Performances
The Network Management Card is designed to support a maximum of:
z 35 Network Shutdown Module connections in standard secure mode
z 100 connections with NSM 3.10 min. and NMC 66102/DA min. in UDP mode
Network Management Proxy, installed on a dedicated server, with at least 500 MB of Ram and a 1 GHz
CPU, is designed to support a maximum of:
z 250 Network Shutdown Module connections in standard secure mode.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 7/65
Page 9

www.eaton.com
2 Installation
Note: This user manual only applies to Network Shutdown Module V3. For previous versions of Network
Shutdown Module V2.x, please read the HTML on line manual.
2.1 Hardware Pre-requisites (Electrical and Network Connections)
Connection steps
Before connecting the UPS, you must first decide on a software and hardware architecture
.
Before installing the EATON Network Solution, the UPS must be set up as indicated in the steps below.
z Shut down the computers to be protected by the UPS.
z Connect the UPS to a wall outlet. (For UPSs above 3kVA, please refer to the UPS installation manual).
z Connect the power cord of each computer to an outlet on the UPS. (For UPSs above 3kVA, please refer
to the UPS installation manual).
z How to connect UPS / proxy or card / network:
> If the Mgt. Proxy is used, connect the serial or USB port on the computer and on the UPS.
> If a Network Management Card is used, insert the optional card in the UPS and connect the UPS to
the computer network.
z Start the EATON UPS, then the computers.
z Setting up the protection
> If the Mgt. Proxy is used install it on the one machine directly connected to the UPS.
> If a Network Management Card is used, it must be set up (see the Mgt. Card's user manual).
z Install Network Shutdown Module on all the other machines that are to be protected by the UPS (supplied
with UPS battery backup power).
Note: The Mgt. Proxy manages protection of the machine on which it is installed.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 8/65
Page 10

www.eaton.com
2.2 Software Installation Pre-requisites
2.2.1 On the System Hosting « Network Shutdown Module V3 »
2.2.1.1 Windows Compatibilities:
Network Shutdown Module V3 Windows is compatible and has been tested with:
z Windows (x86) 2000 / XP (Home or Pro) / 2003 / Vista (Business or Ultimate) /
2008 (Web Server, Standard, Entreprise, Data Center) /
Windows 7
Server 2003 Appliance Edition (Tested on Iomega NAS Server)
z Windows (Xeon 64) Windows Server 2003 Standard x64 Edition
Windows Server 2008 Enterprise x64 Edition
Windows 7
Windows Vista Business x64
z Windows (AMD Opteron) IBM blade server AMD Opteron single processor for LS20 (type 8850)
Windows Server 2003
z Windows (Intel Xeon) IBM blade server Intel Xeon single processor for HS20 (type 8843)
Windows Server 2003
2.2.1.2 Linux Compatibilities:
Network Shutdown Module V3 Linux is compatible and has been tested with:
z Linux (x86/x86_64)
Debian GNU Linux: Etch, Lenny
SUSE/Novell: SLES 11, OpenSUSE 10.3, 11.2,
Redhat Enterprise Linux: RHEL 5.4, Fedore core 12
Ubuntu: 9.04, 9.10
VMWare: ESX3, 3.5, ESXi4 (NSM CLI installer)
Mandriva 2009, 2010
The Linux package is based on standard Linux mechanisms and therefore can be installed and used with
other Linux distributions. Feedbacks / test or bug reports are welcome at EATON Support.
The following list is not exhaustive. Network Shutdown Module V3 should be compatible with:
z Linux (x86/x86_64)
Debian GNU Linux: Testing,
SUSE/Novell: SLES 10, openSUSE 10.x, 11.x
Redhat Enterprise Linux: RHEL 4, 5 , Fedora core 10,11
Ubuntu: 7.10, 8.04, 8.04 LTS Server, 8.10
Others: IPCop, …
2.2.1.3 Mac Compatibilities:
Network Shutdown Module V3 Mac OSX is compatible and has been tested with:
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 9/65
Page 11
www.eaton.com
z Mac Intel Mac OS X 10.4, 10.5, 10.6
z Mac PowerPC Mac OS X 10.4, 10.5
2.2.1.4 Standby configuration (Windows):
In Configuration Panel -> Power Option properties:
z You must unselect the Standby configuration of your Operating System to be compliant with the
Network Shutdown Module. With the standby configuration checked your system is not protected.
z If you want to save energy, please prefer the hibernate feature.
2.2.1.5 Broadcast Message configuration (Windows):
If the “Broadcast administrator messages / Broadcast user messages ” function is activated, on Network
Shutdown Module, you have to check that the “Messenger” Service is started.
This service is mandatory to use the broadcast messages on Windows.
2.2.1.6 Firewall configuration (Windows & Linux) and Gateway :
(Optional) To enable a remote access for supervision and configuration you will have to open the following
UDP and TCP ports of the Windows Firewall:
z 4679 EATON Supervision
z 4680 EATON Management (access through SSL)
These ports are reserved for EATON at IANA (Internet Assigned Numbers Authority, http://www.iana.org/).
If you use Windows, the ports are automatically opened in the Windows Firewall.
If you use a Firewall with all ports closed by default:
To enable communication between Network Shutdown Module and Network Management Card:
z Port 80 must be opened as a destination port (for output) on the machine hosting Network Shutdown
Module.
If you use a Gateway without predefined routed port:
To enable communication between Network Shutdown Module and Network Management Card:
z Ensure to route 4679 and 4680 ports with the protocol «TCP»&«UDP».
2.2.2 On the System that Displays Web-based Graphical User Interface
Important:
The Network Shutdown Module graphical interface can be accessed remotely using a simple Web browser.
Access to this interface is secured through SSL connection (default configuration) and must also be secured
through Login & password.
The Network Shutdown Module graphical interface has been tested with:
z Mozilla Firefox (1.5, 2.0, 3.0) is recommended for better performance. (Firefox is mandatory for Linux)
z Microsoft Internet Explorer V6, V7, V8
z Safari
Note: For the Web browser, we advise you against the use of the highest security level. Some configuration
screens are not useable.
Javascript and Cookies must be authorized for the selected security level.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 10/65
Page 12
www.eaton.com
2.3 Quick Start
To install the Network Shutdown Module in 5 minutes, please perform the following steps on a machine
running Windows 2000 / XP / 2003 / 2008 / Vista / 7, Linux or Mac OSX:
z Step 1 (Pre-requisites)
Check that following connections are operational:
> the electrical connection between the UPS and the server to protect
> the network connection between the UPS and the Network Management Card (or Proxy).
z Step 2 (Optional)
To enable the configuration and supervision remote access, Network Shutdown Module needs the 4679
and 4680 ports (UDP/TCP) to be opened in the Firewall (Automatically opened in the Windows Firewall).
z Step 3 (Software Installation)
On a Windows 2000 / XP / 2003 / 2008 / Vista / 7, Linux or Mac OSX machine, execute the “Network
Shutdown Module” package under an administrator account.
z Step 4 (Configuration)
> In the Configuration->Power devices screen,
Enter the default Login «admin» and default Password «admin»
Then click on the Add button and
> Enter the IP (or the host name) of the Network Management Card (or Proxy)
or use the following new function:
New: With the Quick Scan … button, available with version 3.10 and later, you can discover
in a few seconds the cards connected to the network and then select a card from the list.
> Save your configuration
>In the Configuration->Users window configure your password
> For the multi-UPS configurations, please refer to chapter 6
z Step 5 (Operation)
(recommended)
You can now supervise the UPS state and the information concerning the protected server
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 11/65
Page 13

www.eaton.com
2.4 Software Installation Procedure
This section informs on how to install Network Shutdown Module to protect the computer system.
Before starting the installation:
z it is necessary first to install a Network Management Card in the UPS or the Mgt. Proxy on a server.
z make sure you have the necessary administrator rights to install Network Shutdown Module (for
Windows and Linux).
z it is assumed that you are aware of the installation prerequisites.
Follow these steps to install Network Shutdown Module in interactive (graphical) mode:
onnect to the EATON download area. Follow the instructions to download Network Shutdown Module
C
or insert the Solution-Pac 2 CD-ROM (/HF).
For Windows:
From CD ROM:
z At the firs
t navigator screen select "Network Solutions" and follow the instructions
From the Web:
For Lin
ux:
z Execute
From CD ROM:
z Mount your CD-ROM (ex: /mnt/cdrom)
z Open Default.htm from your internet bro
the downloaded package.
wser to discover the solutions and select
"Network Solutions".
z Follow the instruc
tions
From the web:
z Download a
z Authorize the execution right on the downloaded pa
nd save the file to your computer.
ckage (through graphical interface)
or execute the command : chmod 755 nsm_linux_xx_3_xx_xx.run
z To install execute the package (double click)
z If necessary enter the root password
z Follow the instructions
For Mac OSX
From the Web:
• Execute the
downloaded package.
Choose the installation language. The selected language will correspond to the one of the installed
z
product.
z Read and
z Choose the installation directory of the Network Shutdown Modu
> Windows default value is C:\Program Files\EATON\NetworkShutdownMod
accept the License Agreement for EATON Software.
le.
ule
> Linux default value is /usr/local/EATON/NetworkShutdownModule
> Mac OSX default value is /usr/local/EATON/NetworkShutdownModule
z Complete the installation.
After the installation,
> In the Configuratio
Enter the default Login «admin» and default Pas
n-> Power device screen,
sword «admin»
Then click on the Add button and
> Enter the IP (or the host name) of th
e Network Management Card (or Proxy)
or use the following new function:
New: With the Quick Scan … butto
n, available with version 3.10 and later, you can discover
in a few seconds the cards connected to the network and then select a card from the list.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 12/65
Page 14
www.eaton.com
Power device settings
> Save your configuration
z Configure your password (recommended)
z For multi-UPS systems, please refer to the chapter "Multi UPS systems" .
z The Network Shutdown Module is now configured by default. You can anyway customize the Network
Shutdown Module and for example configure your password (recommended).
z The installed components are automatically started.
z It is possible to test Network Shutdown Module.
z The protection function is now active on the computer and will be run automatically each time the
computer is started.
Follow these steps to install Network Shutdown Module in console mode:
z For Linux, if the server doesn’t have the graphical layer installed, you have to use the specific package
called nsm_linux-cli_xxx.run
z Login as root in a terminal
z Then install the Network Shutdown Module in silent mode
Note : You can configure the Network Shutdown Module either:
z through the silent mode parameters (e.g.)
./<FileName> -install –silent –agentName ‘172.17.1.2’
z through remote access
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 13/65
Page 15

www.eaton.com
2.5 Application deployment and silent installation (advanced)
After customizing the Network Shutdown Module configuration (name or IP address of Network Management
Card/Proxy, events and actions, etc.), you can build a Network Shutdown Module installation package that
contains your specific configuration.
You can then deploy this Network Shutdown Module configuration on other machines that have the same
operating system.
Network Shutdown Module application deployment
Refer to the appendix “Application deployment and silent installation
2.6 Uninstalling the Network Shutdown Module
Windows:
Linux:
Mac OSX:
z The shortcut EATON -> Network Shutdown Module->Uninstall is used to uninstall
Network Shutdown Module.
or
z In the Control panel, you can also run the Add/remove programs command and select
the Network Shutdown Module program.
z The KDE shortcut K:-> EATON -> Network Shutdown Module->Uninstall is used to
uninstall Network Shutdown Module.
z The Gnome shortcut Applications-> EATON -> Network Shutdown Module->Uninstall
is used to uninstall Network Shutdown Module.
z In console mode, you can execute <Installation directory>/packaging/nsmInstaller –
uninstall
<Installation directory> default value is /usr/local/EATON/NetworkShutdownModule/
z The shortcut Applications -> Utilities -> EATON -> Network Shutdown Module-
>Uninstall.command is used to uninstall Network Shutdown Module.
”
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 14/65
Page 16
www.eaton.com
3 Minimal configuration steps
3.1 Introduction
In this chapter we describe the basic and minimal configuration steps that must be performed before using the
Network Shutdown Module.
The other and optional configuration possibilities are described later
3.2 The IP address of the UPS that powers your server.
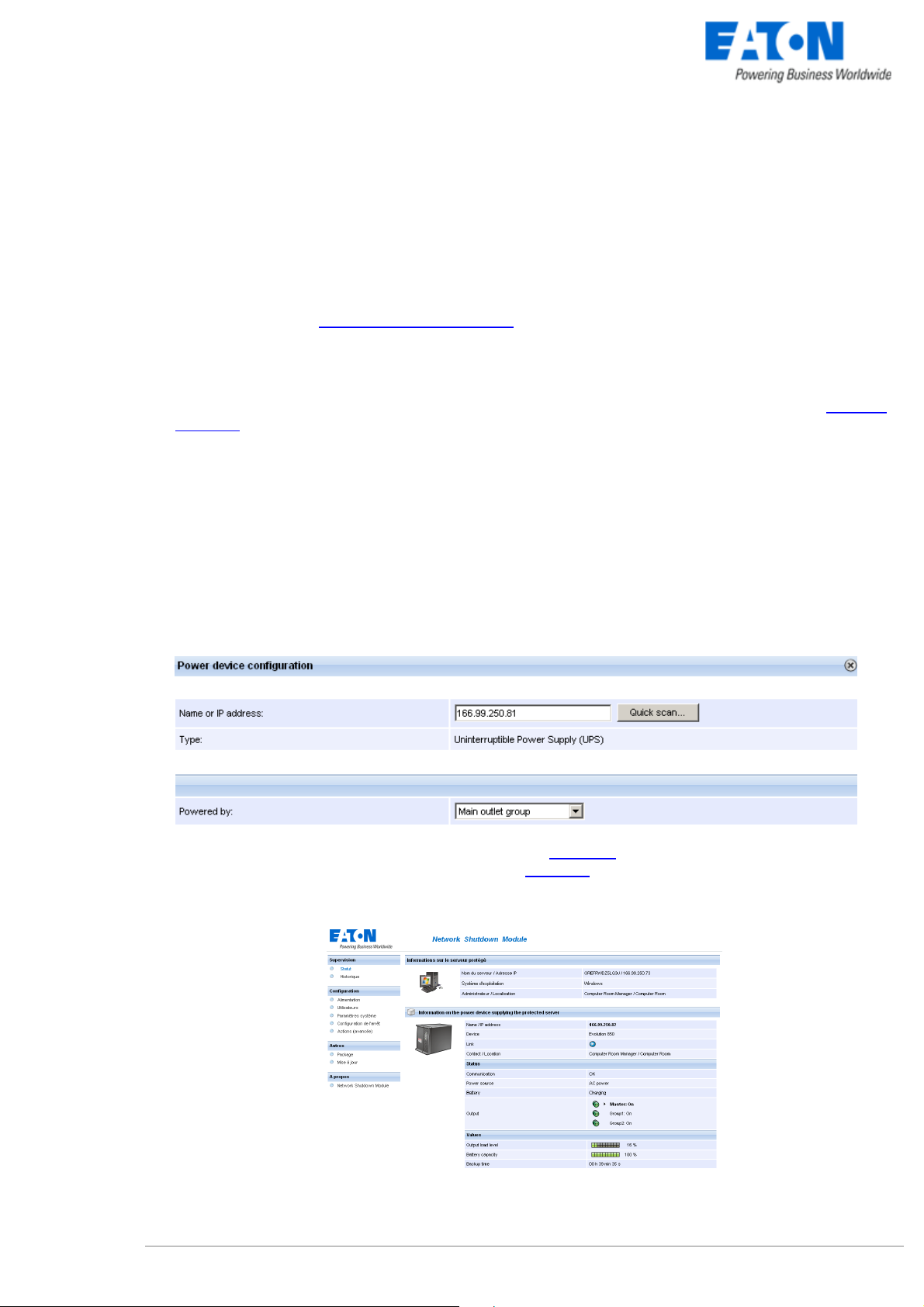
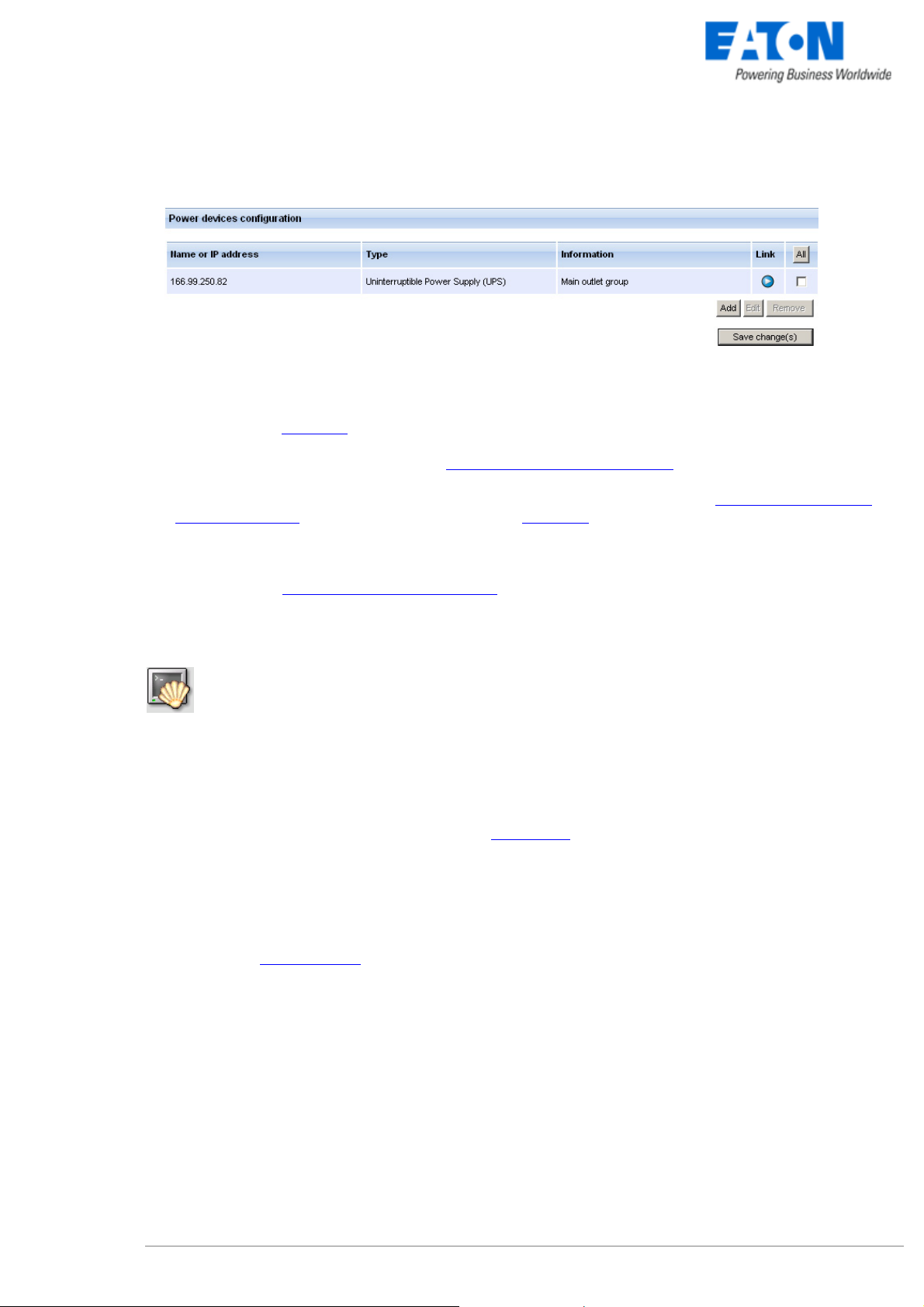
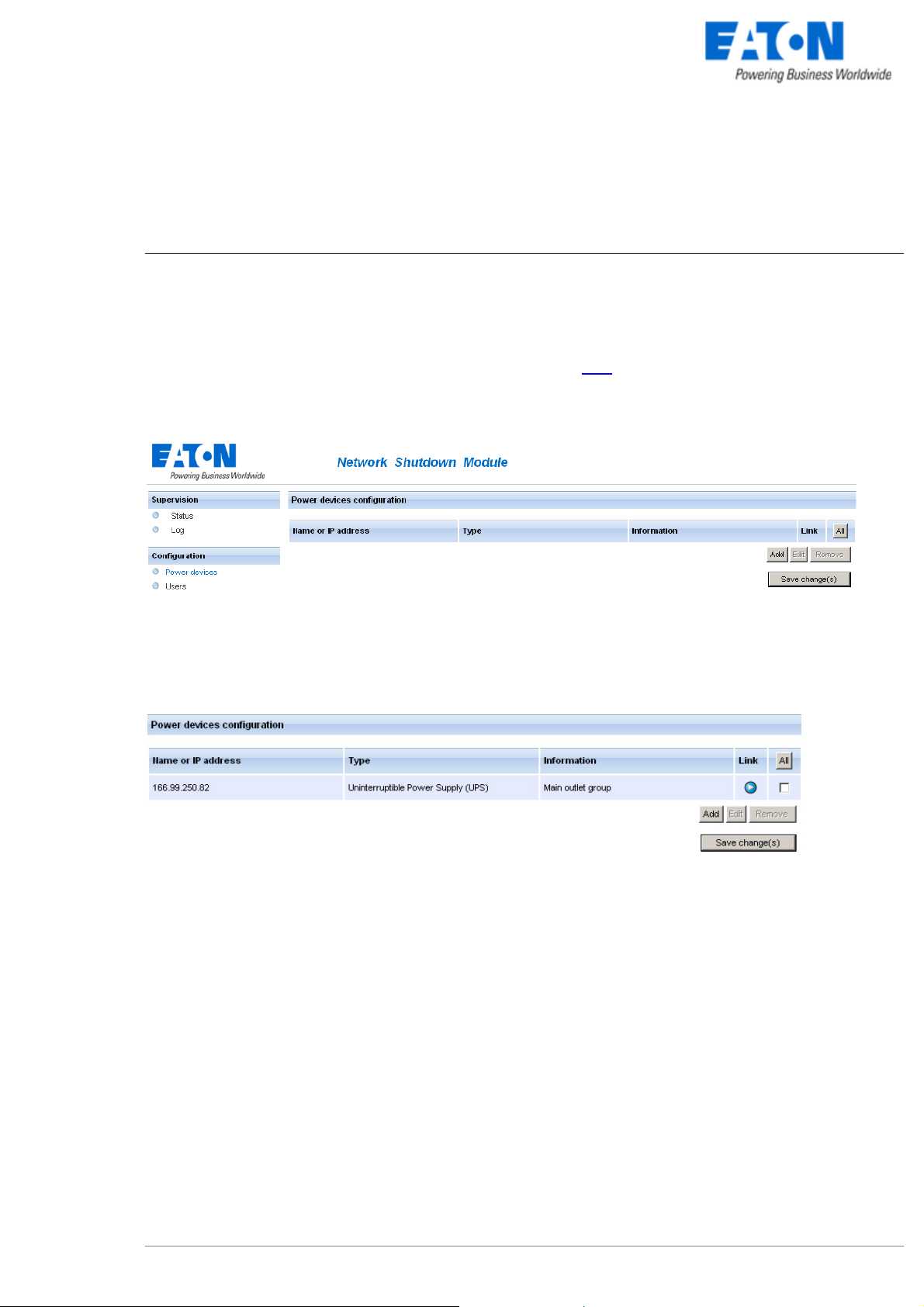
In the Configuration -> Power device screen, click on the Add button
.
Adding a power device
Then following screen appears:
> Enter the IP (or the host name) of the Network Management Card (or Proxy)
or use the following new function:
New: With the Quick Scan … button, available with version 3.10 and later, you can discover
in a few seconds the cards connected to the network and then select a card from the list.
Power device settings
From this screen, you can define the following parameters:
z Network Name or IP address of the Network Management Card / Proxy. This parameter must correspond
to the UPS that powers your machine.
z The UPS Outlet that powers the server
Powershare outlets and load shedding:
You have the possibility in this page to configure the electrical dependency between one of the UPS
switchable plugs and the server hosting Network Shutdown Module.
This function is useful for the servers that must be first shut down during the autonomy sequence.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 15/65
Page 17
www.eaton.com
Load shedding configuration on UPS powershare outlets
Remark:
This load shedding function is not available if the UPS doesn’t have any switchable outlet.
Note:
For multi-UPS configurations, you have the possibility to enter several names or IP addresses (using the
[Add] button). For these advanced configurations, please refer to the Chapter « Multi – UPS systems ».
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 16/65
Page 18
www.eaton.com
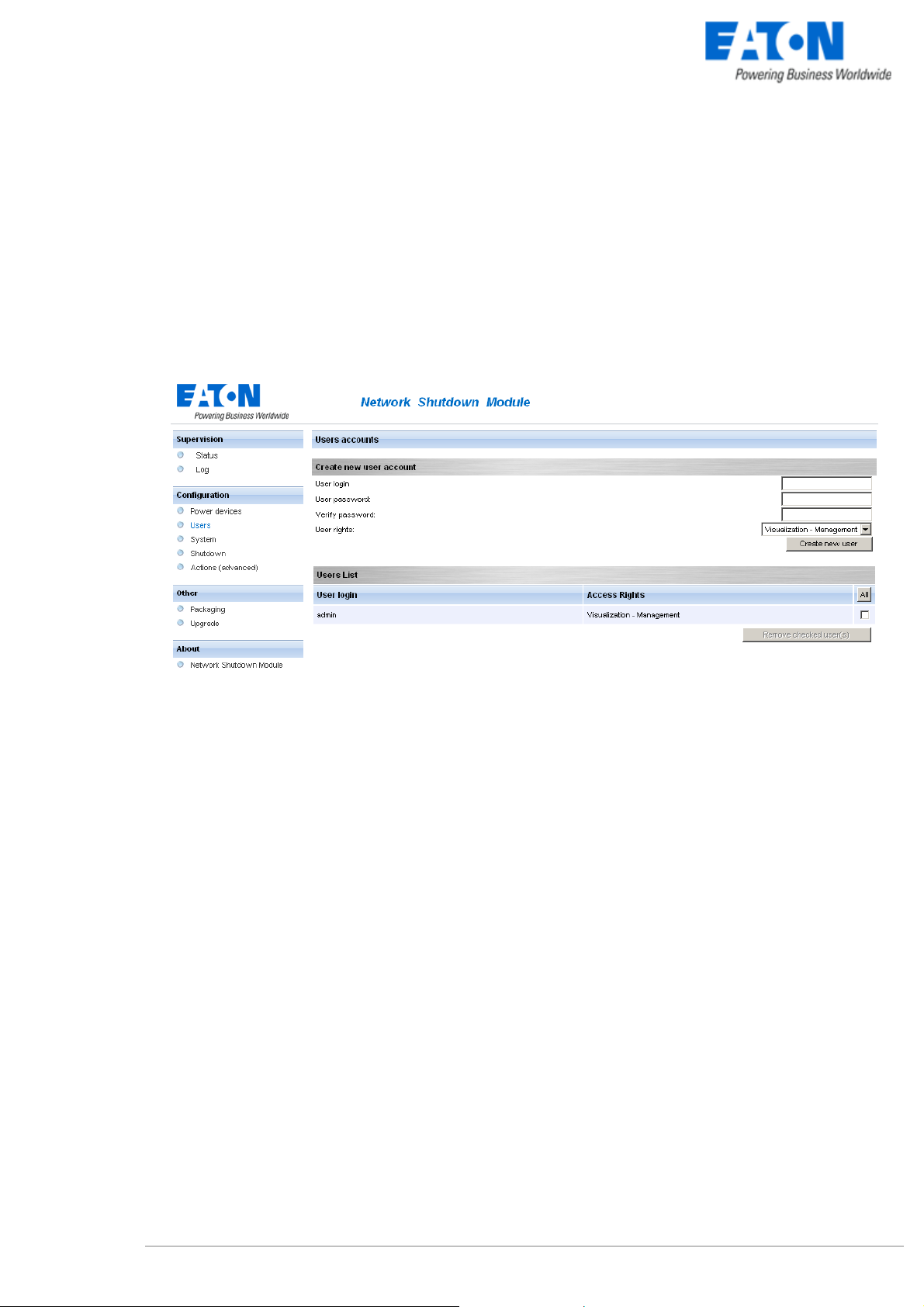
3.3 Users accounts configuration
Click on the Users item of the Configuration section on the left menu.
The default Login «admin» and default Password «admin» with Visualization – Management rights.
Note: For security reasons we advise you to remove this default login and to create a new login with
new access password.
User accounts configuration
You can configure several user accounts.
To add a user account:
z enter the User Login and the User password (twice),
z select the User’s Rights level. The following levels are available:
Visualization – Management (the user will be able to access all the sections)
Visualization (the user will only access to the Supervision (*) and the About sections)
z click on the Create new user button
(*) Remove logs function in UPS logs panel is only functional with Visualization – Management user's right.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 17/65
Page 19
www.eaton.com
4 Use
4.1 Monitoring the server and the UPS(s)
4.1.1 Local access
From the system where the Network Shutdown Module is installed,
z You can use the following shortcut:
For Windows: Start -> Programs -> EATON -> Network Shutdown Module -> Supervision
For Linux (KDE): K-> EATON -> Network Shutdown Module -> Supervision
For Linux (Gnome): Applications -> EATON -> Network Shutdown Module -> Supervision
For Mac OSX: Applications -> Utilities -> EATON -> Network Shutdown Module->Supervision.command
z You can also use the icon in the task bar:
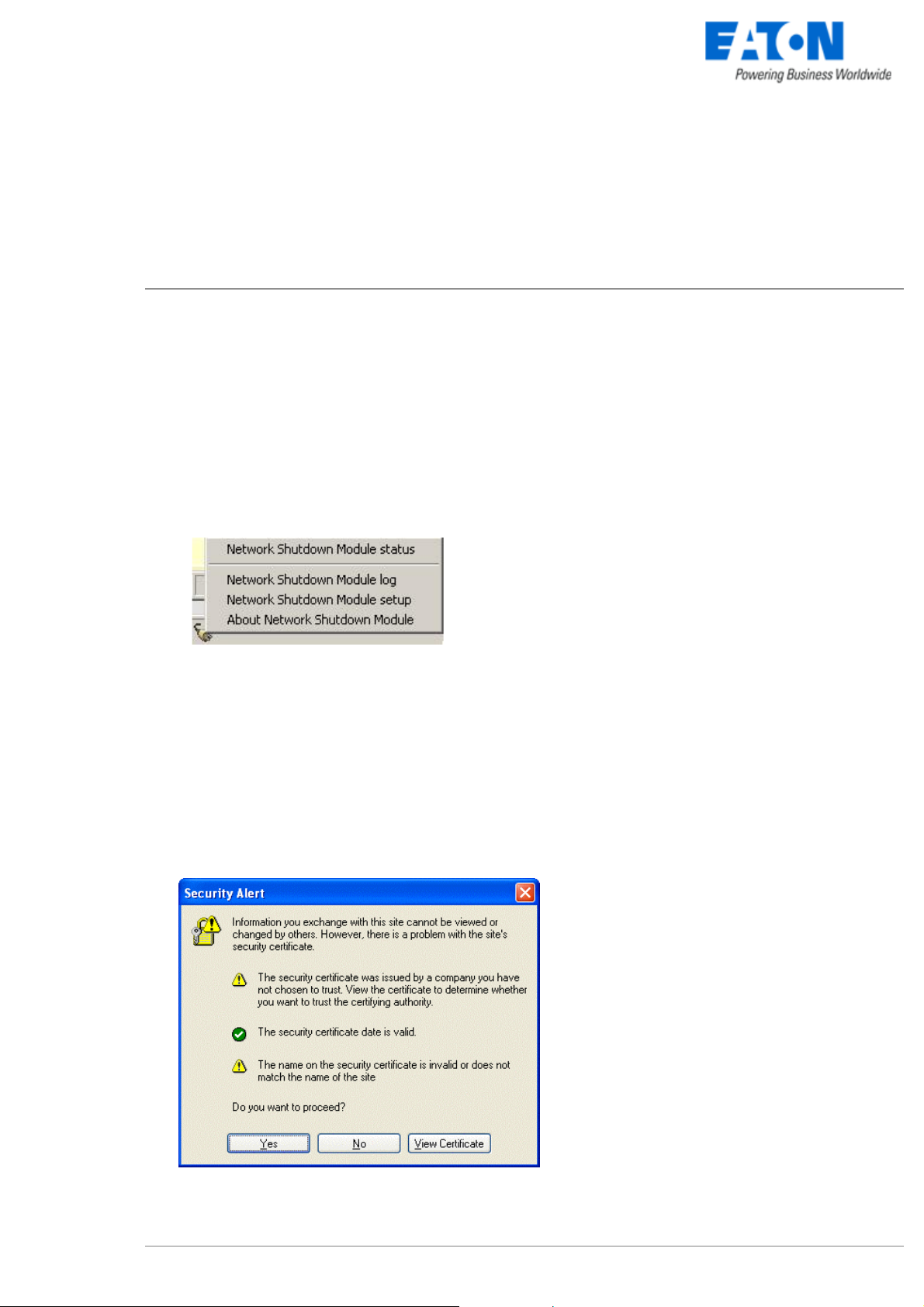
To access to this interface:
Z Double-click on the icon or
Z Right click the icon in the task bar to access to the item
“Network Shutdown module Status”
4.1.2 Remote access
z From a remote machine, you can type the following URL in a Web browser for
> secured SSL access:
https://< name or IP address of computer hosting NSM>:4680/
> or for non secured access:
http://< name or IP address of computer hosting NSM>:4679/
Note: The Web server is “case sensitive” for the URL.
z Accept the SSL Certificate (by clicking on Yes)
To install the certificate on IE7 for Vista, you need
to perform the following steps:
> Run IE as an administrator (Right-click the
desktop icon)
> Visit the NSM site.
> Click through the certificate error
> Click the "Certificate Error" button in the
address bar.
> Click View Certificate
> Click Install Certificate
Unlike on XP, you must click the “Place all
>
certificates in the following store” radio button,
and choose the “Trusted Root Certification
Authorities” store. If you don’t do this, the
Accepting the SSL Certificate
certificate goes in your personal store, and it
isn’t trusted by IE.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 18/65
Page 20
www.eaton.com
z Enter the Login and Password (optional)
z The following page appears:
Server and UPS supervision
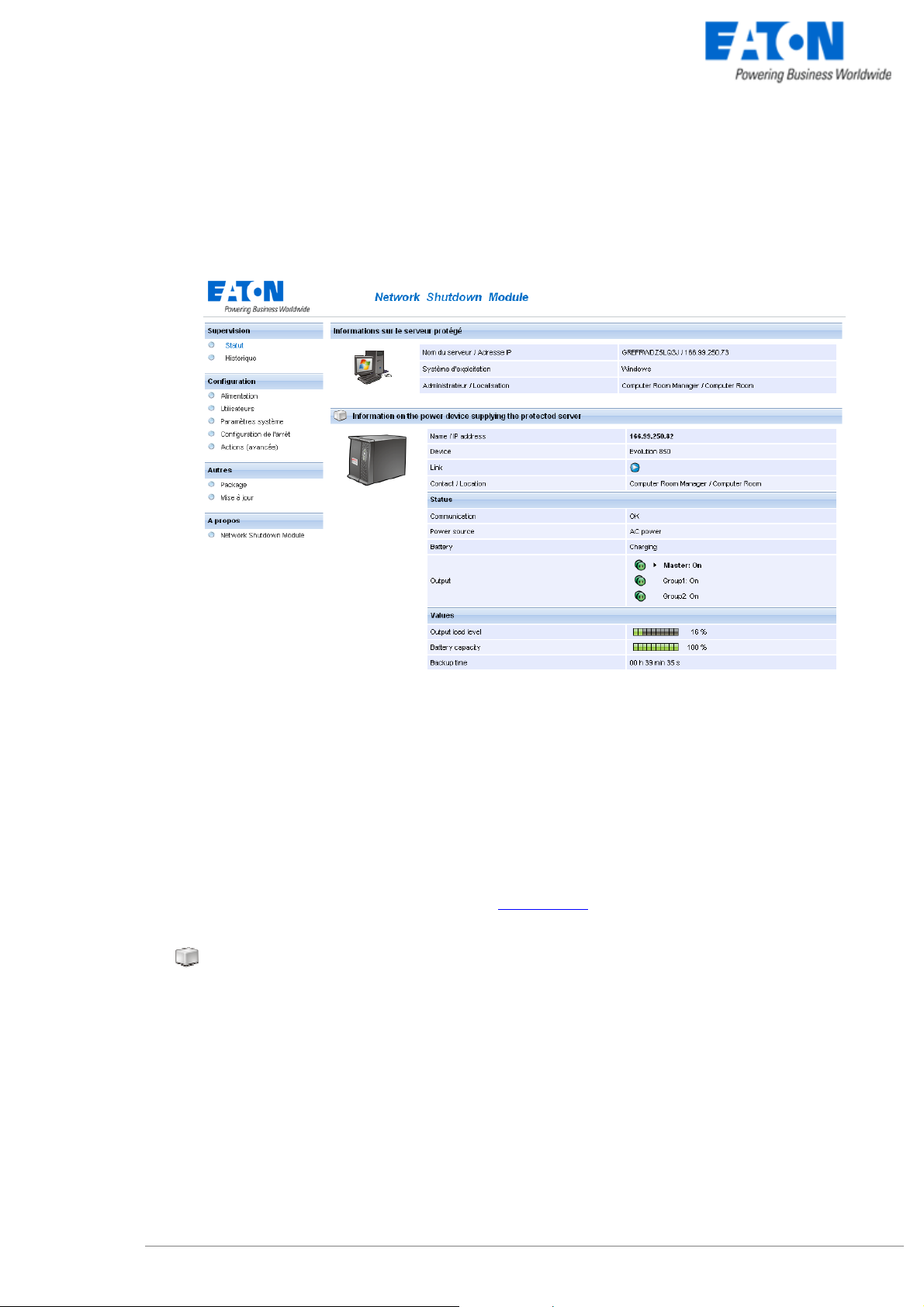
Section « Information on the protected server»
z Server name / IP address:
The Network name of the machine hosting the Network Shutdown Module and its IP address.
z Operating system:
The operating system of the machine hosting the Network Shutdown Module.
z Contact / Location:
The location of the machine hosting the Network Shutdown Module
the contact person for the machine hosting the Network Shutdown Module.
These values can be configured in the System page
.
Section concerning the UPS that powers the protected server
z This icon represents the status of the power device. It can have following
values: Critical/Alert/Normal
z Name/ IP address: The Network name (or IP address) of the device.
z Device: The commercial product name.
z Link: Link to the device Web site (if available).
z Contact / Location: The device contact. (value of syscontact object or can also be configured in the
Device page).
The device location. (value of syslocation object or can also be configured in the Device page).
Status
z Communication: Device communication status (OK / Network Communication Failure / device
Communication Failure).
z Power source: AC Power / Battery.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 19/65
Page 21

www.eaton.com
z Battery: Charging / Discharging / Battery fault.
z Output: Main output status (ON/OFF/Internal Failure/On Automatic
Bypass/Manual By Pass/Overload).
Or output outlet status (ON/OFF).
The outlet group that powers the device is highlighted in bold
Values
z Output Load Level: The output load level of the device.
z Battery capacity: Battery capacity of the device.
z Backup time: The device remaining backup time.
Note that this view is impacted when any device status is affected.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 20/65
Page 22

www.eaton.com
4.2 System and UPS event log
In the Supervision section, Select the Log item, and the following page appears:
Network Shutdown Module event Log
Use the filter in the top right to choose the data to display:
z All: Displays all the logs.
z UPS logs: Only displays the UPS events.
z System logs: Only displays the System events.
z Use the Export … button to record the displayed data into a CSV file.
z Use the Clear… button to clear the displayed data.
4.3 UPS Events list
The icons in the Status view represent the event severity.
Icon Event status
Normal. With this event, the device is coming back to a normal status.
Event list:
z Communication with "Management Card / Proxy" is restored.
z The system is powered by the utility.
z The UPS output is on.
z Communication restored with UPS.
z Battery OK.
z UPS returns to normal load.
z UPS OK.
z Bypass: Return on UPS.
z End of low battery alarm.
z Outlet group 1 is on.
z Outlet group 2 is on.
z Protection lost
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 21/65
Page 23

www.eaton.com
z Redundancy lost (for multi-UPS systems)
Warning. A problem has occurred on the device. Your application is still powered.
Event list:
z The system is powered by the UPS battery.
z Output on automatic bypass.
z Output on manual bypass.
z Protection lost
z Redundancy lost (for multi-UPS systems)
Critical. A serious problem has occurred on the device. This problem requires an urgent action.
Your application might NOT BE powered anymore.
Event list:
z UPS output is off.
z Battery fault.
z UPS overload.
z UPS fault.
z Low battery alarm.
z System shutdown in progress...
z Outlet group 1 is off.
z Outlet group 2 is off.
Communication lost between the Card/Proxy agent and the Network Shutdown Module.
Or communication lost between the device and the Card/Proxy.
Event list:
z Communication with "Management Card / Proxy" has failed (Warning).
z Communication failure with UPS (Warning).
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 22/65
Page 24

www.eaton.com
4.4 Test the communication with the UPS
After the installation, it is important to check that Network Shutdown Module communicates with the agent
(Mgt. Proxy or the Network Management Card).
4.4.1 Simple Tests
Test 1:
When Network Shutdown Module starts, an icon is displayed by default in the task bar, if you’re running
Windows or Linux (Gnome or KDE). It can indicate one of the following status conditions:
Icon Description Meaning
AC power
Utility failure /
load on battery
Communication
failure
The Acquisition
Engine is
stopped
Battery fault
Remark:
When your mouse is over the icon in the taskbar a summary status is displayed:
The installation is in correct running order.
Check the power cable for the UPS. Note that this is the normal
display if the AC-input power has failed.
Wait an instant, then check the communication parameters
between
the computer and the Cards/Proxy.
Check in the services list that the service is started
.
Contact the EATON support department or your dealer to check
battery connections or replace worn batteries.
Test 2:
z You can view the Network Shutdown Module HTML supervision interface and then check that the UPS
has been recognized and that the communication status is OK.
To access to this interface:
Z Double-click on the icon or
Z Right click the icon in the task bar to access to access to the
item “Network Shutdown module Status”
Test 3:
Where possible, another procedure is to generate an event such as a loss of AC power (by disconnecting the
UPS from the wall outlet) to obtain the message below.
Do not forget to reconnect the UPS to the wall outlet.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 23/65
Page 25

www.eaton.com
4.4.2 Advanced tests
For test purpose, it is also possible to display the messages in verbose mode and check the content.
Messages in verbose mode:
z Event log:
It is possible to consult the Event log
z Advanced trace:
We warn you against the use of disk space for this Trace mode.
To validate verbose mode :
> in the bin/dae and bin/netsystray directory of the application, rename the file called debugMode.off
into debugMode.on,
> restart the EATON Network Shutdown Module - Acquisition engine as explained hereafter,
> view the trace in the file called traceDebug.txt in the same directory.
To stop verbose mode :
> in the bin directory of the application, rename the file called debugMode.off into debugMode.on,
> restart the EATON Network Shutdown Module - Acquisition engine as explained hereafter.
.
4.5 Start and stop the Shutdown Module (advanced)
(Warning, if you stop, your computer is not protected anymore).
Windows:
Linux:
Mac OSX: z In console mode, as root, you can also run the following commands:
From the Windows services panel you can start and stop the 2 services that are created:
z EATON Network Shutdown Module - Acquisition engine
z EATON Network Shutdown Module - Web server
z In graphical mode, from your services panel you can start and stop the eaton-nsm
service that is created.
z In console mode, as root, you can also run the following commands:
/etc/init.d/eaton-nsm start
/etc/init.d/eaton-nsm stop
/etc/init.d/eaton-nsm restart
/System/Library/StartupItems/NetworkShutdownModule/NetworkShutdownModule start
/System/Library/StartupItems/NetworkShutdownModule/NetworkShutdownModule stop
/System/Library/StartupItems/NetworkShutdownModule/NetworkShutdownModule restart
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 24/65
Page 26

www.eaton.com
5 Other Configuration possibilities
5.1 Introduction
Basic configuration steps are described before (refer to Power devices and Users).
In this chapter we describe other configuration possibilities.
5.2 Configure system parameters
Click on the System item of the Configuration section on the left menu
System parameters configuration
This page lets you enter the system parameters for the application.
It contains:
z The system administrator name.
z The system localisation.
Note:
This information is visible in the Supervision -> Status page
Alarm reception mode
In this area, you can:
z Authorize UDP and TCP modes (default value)
The Network Shutdown Module will thus determine automatically which mode is supported by the
card and will give UDP mode priority because this can be used to support a greater number of
Network Shutdown Modules per card.
z Authorize TCP mode only (selection of this option limits the maximum number of nodes connected).
This configuration is useful if a piece of equipment likely to filter UDP broadcast network frames is
present between the Network Shutdown Module and the card (for example, a router or a manageable
switch configured specifically for filtering UDP frames)
Note:
With Mac OSX Power PC, you will have to restart the machine (or the services) to change the Alarm
reception mode configuration
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 25/65
Page 27

www.eaton.com
5.3 Shutdown Configuration
Shutdown Configuration page
From this screen, you can define the following parameters:
z Use central configuration provided by Management Card/Proxy:
With this function, all the Network Shutdown Modules will obtain their configuration from the card (or
proxy).
In multi-UPS context, you can select the IP of the card/proxy from which you obtain the configuration
If you unselect this option, you can modify for your computer the following parameters:
z Shutdown duration:
This is the time in seconds required by the system to go through its shutdown procedure.
The Network Shutdown Modules transmit their own shutdown duration to the Card/proxy.
The role of this parameter is illustrated by the example of shutdown sequence.
> Possible values : 0 to 9999
> Default value : 120
> Unit : Second
It is on the basis of these values (shutdown duration of all the systems) that the Card/proxy sends the
delayed shutdown order to the UPS.
z Shutdown timer (Shutdown when timer reaches)
After AC power failure before initiating the system shutdown procedure, this is the time in seconds
that the system waits.
> Possible values : 0 to 999999
> Default value : this criterion for system shutdown is not enabled by default
> Unit : Second
This value must be selected to provide users with enough time to close their applications and
disconnect, but within the battery backup time provided by the UPS.
See the UPS manual for information on the backup time.
If another criterion occurs before the end of the shutdown timer, the shutdown procedure is
immediately run.
The role of this parameter is illustrated by the example of shutdown sequence
.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 26/65
Page 28

www.eaton.com
Remark:
If the shutdown timer on a client is the criterion that trips the shutdown procedure, automatic restart of
the client is not guaranteed (the case where AC power returns and only the client station is shut
down).
z Message broadcast to the administrator
A message is sent over the network to administrators connected to the server protected by Network
Shutdown Module.
Check following Windows pre-requisite
> Default value : activated
z Message broadcast to users
A message is sent over the network to users connected to the server protected by Network Shutdown
Module.
Check following Windows pre-requisite
> Default value : activated
z Access to Network Management Cards
If you customize the « Shutdown duration » on your computer, the update mechanism in UDP
broadcast mode for this value requires write access for the card. The « Manager login » and
« Password » are thus required.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 27/65
Page 29

www.eaton.com
5.4 Checking for Upgrades
This function gives you access to EATON software updates.
Your Enterprise Power Manager will always be up to date if you select the Check automatically option.
When a new software version is detected, just follow the wizard instructions.
Note: This operation will preserve your database information.
Check for upgrade window
5.5 Events and actions (advanced configuration)
Basic principles:
Network Shutdown Module receives events (e.g. Utility Failure) from the UPS and in reply to these events
executes actions (e.g. notification, e-mail, etc.).
The above interface allows links between events and actions to be configured, as well as customizing
protection for the machine hosting Network Shutdown Module.
events / actions
This very powerful tool enables the Network Shutdown Module behaviour to be modified intuitively.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 28/65
Page 30

www.eaton.com
Modifying events and actions is only necessary if you require your protection module to operate in a particular
way. The default configuration ensures optimal protection of your installation. Modifying parameters must
therefore be done with care as it could compromise the protection of your installation.
This advanced settings is described in appendix
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 29/65
Page 31

www.eaton.com
6 Multi-UPS Systems
6.1 Caution
Please check complete list of UPSs compatible with our Redundancy/Parallel mode service:
Caution:
We strongly recommend you contact trained EATON personnel for setup, in order to guarantee the integrity of
your high-availability system.
Recommendations:
z For the UPS Models it is better to Enable "Communication Shutoff orders" so that the UPS accepts
Network Management Card off commands.
Exception for 2 UPSs in Hot standby (Sequential redundancy)
z The Network Management Cards MUST have the same shutdown criteria parameters.
You can use default settings (or duplicate configuration using specific tools like Mupgrade or …)
z For 3 phase UPS systems it is mandatory to check battery parameters before installing Network
Shutdown Module.
.
6.2 Presentation
With the latest version V3 the Network Shutdown Module manages multi UPS redundant configurations.
The Network Shutdown Module V3 makes it possible
z to supervise an installation made up of several UPSs. It provides the user with an overall view of the
installation by concentrating the information acquired from the individual UPSs. The data acquisition is
performed through the IP network.
z to trigger the shutdown of the machine on which it is installed, taking into account the consolidated
« global » view of the electrical installation.
The Network Shutdown Module V3 manages following electrical configurations:
z Several UPSs in parallel:
z 2 UPSs in Hot standby (Sequential redundancy):
Note: For the UPS Model that is close to the load you have to
disable "Communication Shutoff orders" so that the UPS
transfers to bypass and doesn't accept Network Management
Card off commands.
(You can use the UPS display or the UPS Configuration tool)
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 30/65
Page 32

www.eaton.com
z 2 UPSs in serial redundancy:
z 2 unitary UPSs through Static Transfer Switch:
z UPSs powering a server with multiple power supplies:
z Some simple combinations of these electrical associations are also supported by Network Shutdown
module.
Important: To know the list of multi-UPS configurations that are supported by the Network Shutdown
Module, please refer to the appendix List of tested multi-UPS configurations
.
The Network Shutdown module doesn’t take into account the real electrical drawing. It computes dynamically
the minimal number of UPSs below which the system has to be shut down.
This minimal number of UPSs is recomputed permanently according to the following parameters:
z the nominal load of each UPS
z the output load level of each UPS
z the UPS remaining backup time of each UPS
When several UPSs electrically power the computer hosting Network Shutdown Module, the main interface is
as follows:
Server and multi-UPS supervision
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 31/65
Page 33

www.eaton.com
Following information is displayed:
Information on the protected server section
z Server name / IP address:
the Network name of the machine hosting the Network Shutdown Module and its IP address.
z Operating system:
the Operating System name of the machine hosting the Network Shutdown Module.
z Contact / Location:
the location of the machine hosting the Network Shutdown Module
the contact person for the machine hosting the Network Shutdown Module.
These values can be configured in the System page
.
Multi-sources Information section:
z Power devices: x + y redundant(s)
> the first value x is the minimal number of UPSs that is necessary
to power the load.
> the second value y is the number of UPSs in redundancy.
> the addition of these 2 values is the total number of available UPSs.
z Global estimated load level: the output load level for the global installation.
z Global estimated battery capacity: the battery capacity for the global installation.
z Global estimated backup time: the remaining backup time for the global installation. This value takes
into account UPS load balancing anticipation.
Power devices List section:
In this section you will find the information, concerning the UPSs that power the server hosting Network
Shutdown Module:
The following UPS information is displayed in this page:
z Status this icon represents the severity of the monitored device;
z Name the Network name (if available) or the IP address
z Device name the EATON product name
z Output Load Level the output level of the device
z Battery Capacity the battery capacity of the device
z Backup Time the remaining backup time of the device
z Link link to the device Web site (if available)
Notes:
z You can sort out your device list by clicking on the column titles (Status / Name / Device Name / Load
Level / …).
A second click will reverse the sorting order.
z Detailed view access: Select one of the device in the left menu and the following detailed view page
appears.
z The following icons of the detailed view offer these functions:
Previous device Back to list view Next device
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 32/65
Page 34

www.eaton.com
6.3 Create a multi-UPS configuration
For the multi-UPS configurations, you have to enter the IP address of each UPS that electrically powers the
machine hosting the Network Shutdown Module.
From the, Configuration->Communication page, please proceed as follows:
Multi-UPS configuration
z Click on the Add button
z Key in the first IP address
z Key in the next IP addresses (Click on the Add button).
z Select the Redundancy type of your installation (Parallel, STS, Sequential, Serial, Server with multiple
power supplies) according to your electrical configuration.
Note: For the Hot Standby/Sequential UPS Model refer to the specific UPS configuration
z (optional) key in the Minimal number of redundant UPSs powering your system:
The default value is 0.
If you set this parameter to a higher level you will receive the Redundancy Lost alarm when you don’t
have enough redundant UPSs.
Note: We warn you against the consequences of this settings, but you also have the possibility to trigger
the shutdown action on “Redundancy Lost“ alarm in the actions settings.
z Click on the Save button
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 33/65
Page 35

www.eaton.com
7 Appendix
7.1 Single UPS Mode compatibility
7.1.1 Card/Proxy compatibility
In single UPS Mode, Network Shutdown Module V3 is compatible with following cards/Proxy:
z Network Management Card Minislot 66102 (BA is the Minimum firmware revision)
z Industrial Network Management Card Minislot 66103
z Network Management Card Transverse 66074
z Network Management Card Minislot – 66244
z Network Management Proxy V5
7.1.2 UPSs compatibility
In Single UPS Mode, the following UPSs are compatible through the Cards/Proxy:
z Pulsar, Pulsar M, EX
z Pulsar Extreme C
z Pulsar & Comet EXtreme
z Evolution & Pulsar Evolution
z Pulsar MX, MX
z Pulsar EX RT, Comet EX RT, EXRT
In Multi-UPS mode you also have to check the following Multi-ups mode compatibility list.
7.2 Multi-UPS Mode Compatibility list
7.2.1 Caution
We strongly recommend you contact trained EATON personnel for setup, in order to guarantee the integrity of
your high-availability system.
7.2.2 « simple » configurations
z UPSs in parallel:
Single Phase Pulsar MX 1+1 (2 Max)
MX 1+1 (2 Max)
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 34/65
Page 36

www.eaton.com
Note: The status of the Normal Secours box is not yet supervised by Network Shutdown Module V3
z 2 UPSs in Hot-Standby:
Single Phase Comet EXRT, EXRT
Note: Specific configuration for 2 UPSs in Hot standby (Sequential redundancy).
z 2 UPSs in serial redundancy:
Single Phase Pulsar, Pulsar M, EX
Pulsar Extreme C
Evolution
z 2 UPSs through Static Transfer Switch:
Single Phase Pulsar, Pulsar M, EX
Comet EXRT
Pulsar Extreme C
STS 16A (without synchro)
Note: The status of the STS Upsilon box is not yet supervised by the Network Shutdown Module V3
z 2 UPSs powering a server with redundant
power supplies:
Single Phase (without
synchro)
Pulsar M, EX
Pulsar Extreme C
Evolution
Pulsar MX, MX
Comet EXRT, EXRT
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 35/65
Page 37

www.eaton.com
7.2.3 Simple associations of the previous configurations
z Servers with single power supply (and Multiple
STS):
Single Phase (without
synchro)
Pulsar Extreme C
Pulsar M, EX
STS 16A (without synchro)
Notes:
z This configuration has also been tested with 3 STSs
z The Network Shutdown Module V3 is NOT compatible with a configuration where UPS1 and UPS2
are replaced by 2 groups of UPSs.
z Servers with triple power supplies:
Single Phase (without
synchro)
Pulsar, Pulsar M, EX
Pulsar MX, MX
If your configuration is not listed, please contact EATON
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 36/65
Page 38

www.eaton.com
7.2.4 Configurations NOT supported
z This configuration with STS in cascade is NOT
supported by NSM V3
z This configuration with a load derived between the 2
UPSs in serial redundancy is NOT supported by
NSM V3
z This configuration with a mix of “Parallel” and “STS”
is NOT supported by NSM V3
z The following configuration is NOT supported,
because it is NOT symmetrical on both STS inputs
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 37/65
Page 39

www.eaton.com
7.3 Examples of Multi UPS configurations
Electrical drawing Description " Minimal number
of necessary
UPSs"
2 UPSs of 1000 VA in parallel through a Static Transfer
Switch
1 UPS loaded at 75 %
1 UPS loaded at 0%
2 UPSs of 1500 VA and a server with redundant power
supply
Each UPS loaded at 25 %
2 UPSs of 1500 VA and a server with redundant power
supply
Each UPS loaded at 60 %
2 UPSs of 3000 VA in hot standby configuration
1 UPS loaded at 33 %
1 UPS loaded at 0%
2 UPSs 30 KVA parallel/ redundant mode
Each UPS loaded at 40 %
2 UPSs 30 KVA parallel/power extension mode
Each UPS loaded at 60 %
4 UPSs 100 KVA parallel
(3 power extension + 1 redundant mode)
Each UPS loaded at 70 %
8 UPSs 400 KVA parallel
(7 power extension + 1 r redundant mode)
Each UPS loaded at 80 %
1
1
2
1
1
2
3
7
7.4 Multi-UPS Systems and Event Management
Please refer to the Events and Actions section
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 38/65
Page 40

www.eaton.com
7.5 Application deployment and silent installation
7.5.1 Introduction
Network Shutdown Module offers powerful features to easily deploy the application on several computers:
z Silent Installation
z Providing some command line parameters to the installer
z Re-packaging of a customized application
According to your needs you have several possibilities:
First example:
Your computers are powered by a single UPS and you are using the Network Shutdown Module default
configuration.
z Step 1: Copy the Network Shutdown Module package on the different computers (according to Operating
System)
z Step 2: Execute the installation in silent mode and provide the card IP address as a parameter in the
command line
Second example:
Your computers are powered by a Multi UPS system or you don’t use Network Shutdown Module default
configuration.
z Step 1: Install Network Shutdown Module on a computer (interactive or silent mode)
z Step 2: Configure Network Shutdown Module
z Step 3: Create a customized package (containing your configuration)
z Step 4: Copy this package on the different computers (according to the Operating System)
z Step 5: Execute the installation in silent (or possibly in interactive mode)
7.5.2 Customized installation package
After having customized the Network Shutdown Module
Management Card/Proxy, events and actions, etc.), you can build a Network Shutdown Module installation
package which contains your specific configuration.
You can then deploy this Network Shutdown Module configuration on other machines which have the same
operating system.
Note: Specific configuration include the UPS(s) IP address(es), the event and action, … but not the install
path or install mode.
Please proceed as follows to build the customized package (Windows or Linux):
configuration (name or IP address of Network
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 39/65
Page 41

www.eaton.com
Build customized package
z In the Package section, click on the Build customized package button to build a customized package.
z From the dialog box, then click on "OK".
z A confirmation message is displayed when the package is built. You will find in this message the path and
the name of the new package.
z Copy this package to the other machines in your chosen directory.
Note that the Customized installation package will be installed in default installation directory.
> Windows default value is C:\Program Files\EATON\NetworkShutdownModule
> Linux default value is /usr/local/EATON/NetworkShutdownModule
> Mac OSX default value is /usr/local/EATON/NetworkShutdownModule
z Execute the package (standard installation or Silent installation).
Important:
z For Repackaging function, If you are running Debian Sarge, Redhat 3,4, Mandriva 2010, SLES 11 ,
please read the FAQ first.
z If you install a “customized package” on a computer where a “previous version” of Network Shutdown
Module is running:
=> The software version will be upgraded but the configuration of the “previous version” will be kept.
In order to replace a previous installation, you must first uninstall it.
7.5.3 Install the Shutdown Module in silent mode
In addition to Network Shutdown Module installation in standard mode where the user configures the
parameters during the installation, it is possible to install Network Shutdown Module in silent mode i.e. with no
user interaction.
Follow these steps to install Network Shutdown Module in silent mode:
z Make sure you have administrator rights.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 40/65
Page 42

www.eaton.com
z Build a customized package with specific parameters (ex: The Network Management Card IP address,
the events and actions …).
z Copy this package to the “target” machine in your chosen directory.
z (Linux) If necessary execute the command: chmod 755 nsm_linux_xx_3_xx_xx.run
z To start the installation procedure, run the command:
<Filename> -install -silent to validate silent mode for Windows.
./<Filename> -install -silent to validate silent mode for (Linux and Mac
OSX).
Or to provide the card IP address as parameter to the installer run the command:
<Filename> -install -silent –agentName 192.12.13.14 (Windows)
./<Filename> -install –silent –agentName 192.12.13.14 (Linux and Mac OSX)
Note: for the other options refer to the next paragraph
z The installed software is automatically started (except on Mandriva 2010 where you have to start mgedae
process). It is possible to test Network Shutdown Module
.
Example of secured deployment script for Linux:
We use ssh to copy the package on several machines and then execute it.
The script iterates on the machine names.
#!/bin/sh
# Notes :
# - Actions to be performed under root account
# - The target.list file contains the target machine names (1 per line)
# - All theses machines must accept automatic ssh connection.
# - It must be authorized with a key generation on the master
# (machine that executes the script) using "ssh-keygen -t rsa2",
# - Then copy the file ~/.ssh/id_rsa.pub to the target machines
# - and add its content into the file ~/.ssh/known_hosts, ie
# "cat id_rsa.pub >> ~/.ssh/known_hosts"
for i in `cat target.list`
do
echo "Network Shutdown Module Installation on machine $i"
scp nsmlinuxv3xxx.run $i:/tmp
ssh $i /tmp/nsmlinuxv3xxx.run –install -silent
done
7.5.4 Advanced installation options
z The installer is started with following default options:
-install -installPath <InstallPath>
By default for Windows <InstallPath> =
Files\EATON\NetworkShutdownModule
By default for Linux <InstallPath> =
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 41/65
"C:\Program
"
"/usr/local/EATON/NetworkShutdownModule"
Page 43

www.eaton.com
z The following exclusive options define the installation / uninstallation mode :
-install (with additional options if necessary)
-uninstall (with additional options if necessary)
z Additional options :
-silent Runs the installer without user interactions
-installPath <InstallPath> Provides the installation path as parameter
-debug Starts installer in debug mode
-agentName Provides the Card/proxy IP name as parameter
-help For the complete list of options
7.6 Single UPS Shutdown Sequence
Typical example of the backup time provided by a UPS connected to Network Management Card:
As soon as it detects the loss of AC power, the Mgt. Card notifies the Network
1
Shutdown Modules that the system is running on battery power.
The Mgt. Card then continuously monitors the criteria set to trip the shutdown
2
procedure. The procedure is launched if:
1. the shutdown time delay (*) (in seconds), started when the loss of AC power
occurred, expires.
2. the UPS battery level drops below (*) a threshold expressed in %.
3. the UPS backup time drops below (*) a threshold expressed in seconds.
4. the UPS backup time reaches the maximum value of the "shutdown duration"
parameters
6
The Mgt. card centralizes the "shutdown duration" parameters for all the protected
computers (machines hosting Network Shutdown Module).
This fourth tripping criterion is implicit.
The Mgt. Card launches the shutdown procedure:
3
The Mgt. Card sends to all the Network Shutdown Modules the system shutdown order.
As a result, each Network Shutdown Module proceeds with shutdown of its system.
Once all the computers have been shut down, the UPS shuts off (interrupts the supply
4
of power to the loads) to protect the battery.
Note. This function is not authorized on some UPSs.
Once the utility is restored, the UPS restarts all computers (if shut off the UPS output is
5
a function available).
The diagrams below present the sequence.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 42/65
Page 44

e
y
t
n
www.eaton.com
Utilit
Outpu
Network
Management
Card Sequence
Utility failur
1
Shutdown condition
3
2
Maxim um
shutdown duration
Shutdow
4 5
6
Utility restored
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 43/65
Page 45

y
y
www.eaton.com
Example
A UPS protects 3 machines hosting a Network Shutdown Module. Machine 3 is programmed to shut down
before the others to take some of the load off the UPS.
Shutdown timer None None
Shutdown duration 120 sec
Machine 1 Machine 2 Machine 3
100 sec
180 sec
60 sec
The main output shutdown duration is equal to 180 sec. It is the shutdown duration of the machine 2
(maximum of all the shutdown duration).
Utilit
UPS output
Autonom
Machine 1 on
main outlet group
Machine 2 on
main outlet group
Machine 3 on
main outlet group
30%
Utility Failure
Shutdown
timer
Shutdown criteria reached
Maximum shutdown
duration
Shutdown duration 1
Shutdown
duration 2
Shutdown
duration 3
UPS Shut Off
Utility restored
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 44/65
Page 46

www.eaton.com
7.7 Multi UPS shutdown sequence (example with Static Transfer Switch)
Typical example of the backup time provided by 2 UPSs in redundancy through Static Transfer Switch.
z The Output load level of the first UPS is less than 50 %.
z The Output load level of the second UPS is 0 %.
As soon as they detect the loss of AC power, the Mgt. Cards notify the Network
1
Shutdown Modules that the system is running on battery power.
The Network Shutdown Modules continuously compute the “minimum number of
2
necessary UPSs”.
The diagrams below present the sequence.
Utility
UPS1 Output
UPS2 Output
In this case we suppose that the minimal number is 1.
When the first UPS stops its output, the Static Transfer Switch balances the load on the
second UPS. Then we are in a typical « single UPS sequence »
z The Mgt. Card launches the shutdown procedure for UPS 2.
3
z As a result, each Network Shutdown Module proceeds with the shutdown of its
system.
Once all the computers have been shut down, the UPS shuts off (interrupts the supply of
4
power to the loads) to protect the battery.
Note: This function is not authorized on some UPSs.
Once the utility is restored, the UPS restarts all computers (if the shutting off the UPS
5
output function available).
Utility Failure
1
Shutdown
criteria on
UPS1
UPS1
Shutoff
Shutdown
criteria on
UPS2
UPS 2
Shutoff
3 4 5
Utility Restored
2
Shutdown Mod
powered by STS
System Shutdown
Duration
Load powered
by UPS1
Load
powered by
UPS2
6
Load
unpowered
Load powered
by UPS1
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 45/65
Page 47

www.eaton.com
7.8 Additional information on events and actions
7.8.1 Action settings Tab
In the Action settings tab you can configure the actions that are executed by the Network Shutdown Module.
Action settings tab
Select an action in the Action List (eg. User Notification) then you have the possibility to select the different
tabs for the considered action:
z In the “Settings” tab, you can configure the selected action that is executed by the Network Shutdown
Module.
z In the "Events" tab, you can associate the selected action with the event(s) that will be able to trigger the
action.
z In the "Test" tab, you can execute the action (by simulating the event occurrence).
z The Restore to default button takes you back to the initial configuration.
z The Save Change(s) button saves your configuration.
Possible operations on actions
z Add ...: Adds a new action in the Action list, all the parameters must be entered
z Duplic.: Duplicates the selected action, with all its parameters (see Add ...)
z Del: Deletes the selected action
7.8.1.1 The different actions
There are several actions classified into two categories:
z Standard actions
By default, Network Shutdown Module only uses these actions to ensure the machine's protection and to
inform users.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 46/65
Page 48

www.eaton.com
z Customized actions
These user-customized actions give access to additional functions.
Action name Role
User notification
A message is displayed on the screen of the protected machine, its importance is
indicated by a colored symbol:
- Green: Information message.
- Yellow: Alarm message.
- Red: Critical alarm message.
- Grey: Communication Lost.
Message broadcast
to the administrator
A message is sent over the network to administrators connected to the server
protected by Network Shutdown Module.
Note: This action only occurs if the "Administrator notification" box is checked on the
Configuration Network Shutdown Module
screen.
Message broadcast
to users
A message is sent over the network to users connected to the server protected by
Network Shutdown Module.
Note: This action only occurs if the "Administrator notification" box is checked on the
Configuration Network Shutdown Module
screen.
System shutdown System and UPS shutdown according to the configured parameters.
Execute a program Execution of an application (.exe file) or script (.bat, .cmd, .sh … file).
Send an E-mail Send an alarm message by e-mail using the SMTP network server.
7.8.1.2 Add an action
Follow these steps to add a new action:
1. Click on the Add button
2. Enter the name of the new action (unique action identifier)
3. Select the type of action to be added
Execute
Send an e-mail
7.8.1.3 «System Shutdown» Action
When personalizing the action System shutdown in the action configuration page, you can choose the type
of shutdown:
z For Windows, there is a choice of shutdown depending on your system and your requirements.
Click on the Parameter button, to read the help on the shutdown type:
z For Linux, only the shutdown option is currently supported.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 47/65
Page 49

www.eaton.com
Shutdown parameters
z Shutdown (-shutdown: default selection). This option shuts down your applications and the system,
but does not de-energize the computer. The system offers the user the choice to de-energize the
computer, in which case it is the UPS that cuts power.
On most NT, 2000 and XP systems, this configuration is necessary if you want the server to restart as
soon as mains power returns.
z Hibernate (-standby). If your system has the hibernation function (available with Windows 2000), it is
better to use it because there are a number of advantages. If the system is shut down, all work in
progress and system information are automatically saved to the disk. The computer itself is also deenergized. When mains power returns, all the applications re-open exactly as they were and the user
finds himself back in his work environment.
The hibernate function must first have been activated in the operating system. In the power options on the
Windows control panel, check that the hibernate option is activated on the Hibernate tab sheet.
Note: If you select hibernate, but your computer does not in fact have this function, Network Shutdown
Module nonetheless protects the installation by carrying out the normal (default) shutdown.
z No force shutdown (-noforce). Shuts the system down without closing the opened applications
e.g. Microsoft Word with an unsaved file. (Warning, the system shutdown is not guaranteed)
z Power off ( -poweroff: system de-energized). This option shuts down your applications and the system,
but does not de-energize the computer. This configuration is advised if you wish to be on hand when the
system re-starts. (or for load shedding)
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 48/65
Page 50

www.eaton.com
7.8.1.4 Execute Action
Follow these steps to create an action « Execute a program »:
Action settings tab
z Click on the Add button
z Name: Enter the name of the new action (unique action identifier)
z Type: Select Execute
z Command line: Fill in the command line (the Browse… button will help you find the path of the
program to be executed).
The following utilities are supplied to help you customize your Execute actions:
- Shutdown.bat (Windows script ) or shutdown.sh (Linux or Mac OSX script)
- EatonRunAs (Windows utility program)
(Windows utility program)
- Wait
z The Parameter… button lets you include the variables in the program.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 49/65
Page 51

www.eaton.com
7.8.1.5 «Send email» Action
Follow these steps to create a Send email action:
Configure the send email action
z Click on the Add button
z Name: Enter the name of the new action (unique action identifier)
z Type: Select "Send email"
z Server: Enter the name of the relay SMTP server (e.g. mail.server.com)
z Recipient: Enter the e-mail address. To send the message to several recipients, separate their
addresses by a comma or semi colon.
z The Sender, Subject and Message fields can be customized as above.
Notes:
1) The "Send an e-mail" action is already pre-configured as above in the installation default. You can use
the Duplicate function to create new actions configured in the same way.
2) Some SMTP servers require an email address in the Sender field (and sometimes a valid email
address)
z The ... buttons let you include the variables in the program.
z Click on the Save Changes button.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 50/65
Page 52

www.eaton.com
7.8.2 Events Tab
In this tab you can associate the action with the event(s) that will trigger the action :
Events Tab
z Select the action from the left hand side of the above screen
=> The list of events already associated with this event appear (checked boxes)
z Check (or uncheck) the events you wish to associate with this action
z Save your configuration using Save change(s) button.
For each event, an on-line help is displayed when the mouse pointer is positioned over it.
Following events can trig the actions. They are classed by category:
7.8.2.1 Notification alarms
These alarms are mainly dedicated to trigger user notification actions:
z Utility failure The system is now powered by the UPS battery
or [by the utility]
z 'Run time to shutdown' alarm Alarm to indicate the remaining time before system shutdown
z UPS fault (internal fault or battery fault) Internal UPS fault or battery fault was detected
or [end of Internal/Battery fault]
z UPS overload The output is over loaded
or [the output load is correct]
z Output on bypass UPS has switched to automatic or manual bypass mode
or [end of bypass alarm]
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 51/65
Page 53

www.eaton.com
z Communication failure Communication between Network Management Card/Proxy and UPS (or
NSM) has failed
or [Communication between Network Management Card/Proxy and UPS is restored]
7.8.2.2 Protection alarms
These alarms are mainly dedicated to trigger operating system shutdown actions:
z Shutdown criteria is reached One of the criteria for which the system should be shutdown has
been reached
z Redundancy lost The installation has no redundancy source available anymore
or [The installation has one or several redundancy source available]
z Protection lost The number of sources ensuring your installation protection is not sufficient
or [The number of sources ensuring your installation protection is sufficient]
7.8.2.3 Multi UPS Systems and Notification Alarms
With default configuration, the Network Shutdown Module considers that the “Notification Alarms” don’t trigger
the shutdown. (only the notification action is performed).
Anyway it is possible to configure a “Shutdown action” when a “Notification Alarm” event is received.
In this case:
z The first alarm reception (from one of the UPSs) will trigger the system shutdown.
7.8.2.4 Multi UPS Systems and Protection Alarms
z Shutdown criteria is reached.
With default configuration, the Network Shutdown Module triggers the shutdown when this event is
received.
Anyway it is possible to configure a “Shutdown” action when the following events are received.
z Redundancy lost alarm
If the user configures a “Shutdown action” when a “Redundancy lost” event is received, the shutdown will
occur when the installation has no redundant source available anymore.
The redundancy Level is configured in Configuration-> Power Devices screen
Following Alarms are taken into account for this alarm :
> UPS fault (internal fault or battery fault)
> Communication failure,
> Output on bypass,
> UPS Stopped.
z Protection Lost Alarm
If the user configures a “Shutdown action” when a “Protection Lost” event is received, the shutdown will
occur when the number of sources ensuring your installation protection is not sufficient.
> Only following UPS faults are taken into account (internal fault or battery fault).
> The By-Pass events (Automatic or Manual) for maintenance reasons are not taken into account.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 52/65
Page 54

www.eaton.com
7.8.3 Test tab
In the "Test" tab you can execute the action (by simulating the event occurrence).
You can select the event.
Warning! This action will be really executed. Check that you're ready to perform this test.
Some actions can trigger the shutdown !!
Test Tab
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 53/65
Page 55

www.eaton.com
7.8.4 The action parameters (execute and send email)
The Parameter... buttons let you access following screen:
The action parameters (execute and send email)
The following parameters can be transmitted to actions:
Parameter Description
/object
/value
/message
/date
/ldate
/card_proxy
/hostname
Send object name as a parameter
Send object value as a parameter
Send formatted message as a parameter (refer to label file)
Send date in YYYY/MM/DD - HH:MN:SS format
Send date in the local format of Network Shutdown Module host
Send Network Management Card / Proxy name or IP address
Send Network Shutdown Module host name or IP address
7.8.5 Software utilities
The following utilities are supplied to help you to customize your "Execute" actions:
7.8.5.1 Shutdown.bat (Windows Script)
The "shutdown.bat" script lets you customize the system shutdown.
It allows:
z synchronous (which block whilst running) or asynchronous programs to be run before shutting the system
down.
z programs to be time delayed. The "wait.exe" synchronous utility, distributed by EATON in the Network
Shutdown Module default installation directory (<Program Files\EATON\NetworkShutdownModule), is
used.
z programs with specific rights to be run. Using eatonRunAs.exe (Windows NT/2000/2003/XP).
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 54/65
Page 56

www.eaton.com
z your own system shutdown solution to be used.
z For further information refer to the "shutdown.bat" file in the Network Shutdown Module installation
directory. <Program Files\EATON\NetworkShutdownModule\bin\tools>.
7.8.5.2 Shutdown.sh (Linux Script)
The "shutdown.sh" script lets you customize the system shutdown.
z For further information refer to the "shutdown.sh" file in the Network Shutdown Module installation
directory. <install_path>/bin/tools.
7.8.5.3 Wait (Windows)
z Presentation:
"Wait.exe" is a utility used to set up a time delay in a command file (.bat or .cmd file). It can be used in the
shutdown.bat file to wait until the end of an asynchronous task (non blocking).
z Location:
The program is located in the installation directory <Program
Files\EATON\NetworkShutdownModule\bin\tools>.
z Use:
The parameter for the program is the time delay expressed in milliseconds.
z Example:
Wait.exe 2000 <- The system will wait for two seconds.
7.8.5.4 Windows RunAs command or legacy mgeRunAs software utility
z Presentation:
Network Shutdown Module action is carried out in the security context of the user's account. It may be
necessary to modify the context before certain actions may be run.
EatonRunAs.exe is the means for a user to run specific tools and programs with permissions that are
different from those assigned to the user's account.
z Microsoft recently introduced in Windows RunAs Command the possibility to
save password (Windows XP Service Pac 2 and more recent versions)
We advise you to use following Microsoft command
runas /profile /user:<my login> /savecred <my_prgram.exe>
On first execution a password is required. Then it is saved for the next
executions.
z On previous Windows versions, you can use mgerunas.exe
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 55/65
Page 57

www.eaton.com
z Localisation: The executable may be found in the Network Shutdown Module installation directory (by
default <Program Files\EATON\NetworkShutdownModule\bin\tools>).
z Instructions for use:
1. Fill in the domain name as well as the user's name and password.
2. Indicate the program or command to be run using the specified account.
3. Click the Generate button.
4. Copy the command line and paste it in your application. This line may be used as it is in a Network
Shutdown Module Run action or in a script file.
5. The Open console option opens a DOS emulation console during execution.
z Remark. The information on the user profile is encrypted in the command line. Encryption also depends
on the executable and the parameters mentioned. If the name of the executable or one of the parameters
is changed, the command line must be generated (encrypted) again.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 56/65
Page 58

www.eaton.com
7.9 FAQ and Error messages
During Installation:
(Linux) I’m running Debian Sarge (or some other distribution), and the NSM installer doesn't display the
text properly.
Some older systems are not configured to support UTF-8 by default.
z The first solution is to switch your system to be UTF-8 compliant, but which may cause you some
problem.
To switch a Debian system to UTF-8, simply call the following command as root:
$ dpkg-reconfigure locales
And select UTF-8 (or one of its subsets) as your system's default.
z The second solution is to install Network Shutdown Module in English
(Linux) I’m running Debian (Etch or Sarge) at the end of installation, the Web browser is not automatically
started
z You can use the systray icon to start the Web browser.
(Linux) I’m running Debian (Sarge) at the end of installation, a temporary file “eatonInstall.xml” is not
removed.
z This file is created in the directory where you execute the installer.
Solution: At the end of installation you can remove manually the file.
During use:
(Linux) Mandriva 2010 / SLES 11
The NSM can not connect to NMC through UDP mode or the communication is lost after some time.
Solution: use the TCP Mode and configure the firewall as indicated in the pre-requisite
(Linux) How to use Network Shutdown Module system tray with Gnome?
The NSM systray isn’t displayed in Gnome. Some older versions of Gnome do not allow to automate
NSM Systray launch minimized to the tray on login on Gnome. To do so manually :
z Open up your GNOME menu,
z Select Preferences followed by Sessions. Switch to the Startup programs tab,
z Click Add and enter “<Installation directory>/bin/netsystray/eatonNetSystray” as
the startup command,
z Click OK and you're done.
To stop NSM Systray from loading upon login, simply remove its entry from the startup programs listing.
(Linux) I’m running WindowMaker or XFCE. Can I use the NSM system tray?
Yes, you can use the systray icon, using:
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 57/65
Page 59

www.eaton.com
z wmsystray (http://freshmeat.net/projects/wmsystray/) for WindowMaker,
z xfce4-systray for XFCE.
(Linux) The menu or the systray are missing
Some desktop or windows manager do not provide a way to register menus with sub menu
z Solution 1:
copy the NSM menu files to your desktop
$ cp <installpath>/desktop/*.menu ~/Desktop
z Solution 2:
Bookmark the NSM Supervision Page in your favorite Internet Browser,
> https://< name or IP address of computer hosting NSM>:4680/
> or http://< name or IP address of computer hosting NSM>:4679/
and call the uninstall from the command line using
<Installation directory>/packaging/nsmInstaller –uninstall
z Solution 3:
Add the menu entries using your favorite menu editor
Entry 1: name : Supervision
: cmd : <Installation directory>/packaging/nsmInstaller –openURL <URL>
with <URL>
> https://< name or IP address of computer hosting NSM>:4680/
> or http://< name or IP address of computer hosting NSM>:4679/
Entry 2: name : Uninstall
: cmd : <Installation directory>/packaging/nsmInstaller –uninstall
(Linux) Repackaging function on Redhat 3, 4 and Debian Sarge, SLES 11
On these platforms, just after Installation and configuration, the NSM has sufficient user rights to build the
customized package.
After a computer reboot, the NSM doesn’t have sufficient user rights to build the customized package.
Solutions to build a customized package after reboot:
z Execute the command /etc/init.d/mge-nsm restart
z Or you can install again the NSM on your computer, your configuration is not modified.
Then you have sufficient user rights to build the customized package.
z Or you can use the command line installation parameters to deploy a customised software
z Or you can use Intelligent Power Manager “Mass configuration” feature
(Linux) Repackaging function on Mandriva 2010
On these platforms, just after Installation and configuration, the NSM has sufficient user rights to build the
customized package.
After a computer reboot, the NSM doesn’t have sufficient user rights to build the customized package.
Solutions to build a customized package after reboot:
z You can install again the NSM on your computer, your configuration is not modified.
Then you have sufficient user rights to build the customized package.
z Or you can use the command line installation parameters to deploy a customised software
z Or you can use Intelligent Power Manager “Mass configuration” feature
In the HTML pages.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 58/65
Page 60

www.eaton.com
In the page “Configuration -> Power Device”, when I click on the “Add” button the expected page is not
displayed
Solution: Check if an anti popup filter is activated on your web browser and configure this filter to accept
the page.
Check you don’t have the highest security level on IE
Cannot display the UPS properties page. HTTP 404 error with IE.
Solution: Check the URL entered.
> https://< name or IP address of computer hosting NSM>:4680/
> or http://< name or IP address of computer hosting NSM>:4679/
When you attempt to view the properties or configuration pages, the browser requests a user name and
password.
Solution: The system administrator has protected access to the pages. You must request a user name
and password from your administrator.
No UPS information is available.
Solution:
Check that communication between the UPS and the computer is OK.
Check also that following requirement is met
Port 80 must be opened as a destination port (for output) on the machine hosting Network Shutdown
Module.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 59/65
Page 61

www.eaton.com
8 Glossary
IP address / name
When TCP/IP is installed on a computer, an address and a name are assigned to the system. Each address
or name are unique and the address is made up of four numbers, each between 0 and 256 (e.g.
168.8.156.210).
Network Management Proxy
Network Management Proxy is used to control a UPS and connect it to the TCP/IP network.
NMS (Network Management System)
The NMS supervises SNMP devices connected to the TCP-IP Network.
Network Shutdown Module
The Network Shutdown Module is a software module that uses the information transmitted by the Network
Management Card/Proxy to inform computer users on the current status of the electrical power supplied to
the computer.
If the supply of the electrical power from the EATON UPS is at risk, the Network Shutdown Module initiates an
orderly shutdown of the computer under the most secure conditions possible.
Shutdown Duration
Shutdown Timer
SSL (Secure Socket Layer, created by Netscape)
A solution for securing transactions over the internet. SSL is a communication protocol that authenticates the
data exchanged, as well as ensuring its confidentiality and integrity. The protocol uses a recognized
encryption method, the RSA algorithm with a public key (where RSA means Rivest, Shamir and Adleman,
the inventors). An RSA key is the result of operations involving prime numbers. SSL is built into the Internet
browsers on the market. The padlock in the bottom of your browser screen is automatically displayed if the
server sending information uses SSL.
TCP/IP (Transmission Control Protocol / Internet Protocol)
Family of protocols for the transport and network
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 60/65
Page 62

www.eaton.com
9 Acknowledgements
9.1 SQLite
Huge thanks from the EATON software development team to the SQLite Project http://www.sqlite.org/.
Their generous donation of the source code to the public domain helped us for this project.
9.2 Pi3Web
Huge thanks from the EATON software development team to the Pi3Web Project. http://pi3web.sourceforge.net/
License
Copyright (c) 1997-2003 Pi3 Development Group. All rights reserved.
These sources, libraries and applications are FREE FOR COMMERCIAL AND NON-COMMERCIAL USE as long as the following
conditions are adhered to.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are
met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. The name of the author may not be used to endorse or promote products derived from this software without specific prior written
permission.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO
EVENT SHALL THE AUTHORS OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN
ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
All trademarks and copyrights are property of their respective owners.
Copyright © 1998-2000, 2001 Holger Zimmermann, John Roy.
9.3 PHP
Huge thanks from the EATON software development team to the PHP Project.
--------------------------------------------------------------------
The PHP License, version 3.0
Copyright (c) 1999 - 2002 The PHP Group. All rights reserved.
--------------------------------------------------------------------
Redistribution and use in source and binary forms, with or without
modification, is permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the
distribution.
3. The name "PHP" must not be used to endorse or promote products
derived from this software without prior written permission. For
written permission, please contact group@php.net.
4. Products derived from this software may not be called "PHP", nor
may "PHP" appear in their name, without prior written permission
from group@php.net. You may indicate that your software works in
conjunction with PHP by saying "Foo for PHP" instead of calling
it "PHP Foo" or "phpfoo"
5. The PHP Group may publish revised and/or new versions of the
license from time to time. Each version will be given a
distinguishing version number.
Once covered code has been published under a particular version
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 61/65
Page 63

www.eaton.com
of the license, you may always continue to use it under the terms
of that version. You may also choose to use such covered code
under the terms of any subsequent version of the license
published by the PHP Group. No one other than the PHP Group has
the right to modify the terms applicable to covered code created
under this License.
6. Redistributions of any form whatsoever must retain the following
acknowledgment:
"This product includes PHP, freely available from
<http://www.php.net/>".
THIS SOFTWARE IS PROVIDED BY THE PHP DEVELOPMENT TEAM ``AS IS'' AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE PHP
DEVELOPMENT TEAM OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE POSSIBILITY OF SUCH DAMAGE.
--------------------------------------------------------------------
This software consists of voluntary contributions made by many
individuals on behalf of the PHP Group.
The PHP Group can be contacted via Email at group@php.net.
For more information on the PHP Group and the PHP project,
please see <http://www.php.net>.
This product includes the Zend Engine, freely available at
<http://www.zend.com>.
9.4 OpenSSL
Huge thanks from the EATON software development team to the OpenSSL Project.
OpenSSL License
--------------/* ====================================================================
* Copyright (c) 1998-2006 The OpenSSL Project. All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)"
* 4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
* 5. Products derived from this software may not be called "OpenSSL"
* nor may "OpenSSL" appear in their names without prior written
* permission of the OpenSSL Project.
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:
* "This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)"
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 62/65
Page 64

www.eaton.com
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
* ====================================================================
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
----------------------/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
* Copyright remains Eric Young's, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modification, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* "This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)"
* The word 'cryptographic' can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specific code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* "This product includes software written by Tim Hudson (tjh@cryptsoft.com)"
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 63/65
Page 65

www.eaton.com
9.5 Lighttpd
Huge thanks from the EATON software development team to the Lighttpd Project.
Copyright (c) 2004, Jan Kneschke, incremental
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
- Neither the name of the 'incremental' nor the names of its contributors may
be used to endorse or promote products derived from this software without
specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
THE POSSIBILITY OF SUCH DAMAGE.
9.6 WxWidget
Huge thanks from the EATON software development team to the WxWidget Project.
wxWindows Library Licence, Version 3.1
======================================
Copyright (C) 1998-2005 Julian Smart, Robert Roebling et al
Everyone is permitted to copy and distribute verbatim copies
of this licence document, but changing it is not allowed.
WXWINDOWS LIBRARY LICENCE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
This library is free software; you can redistribute it and/or modify it
under the terms of the GNU Library General Public Licence as published by
the Free Software Foundation; either version 2 of the Licence, or (at
your option) any later version.
This library is distributed in the hope that it will be useful, but
WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Library
General Public Licence for more details.
You should have received a copy of the GNU Library General Public Licence
along with this software, usually in a file named COPYING.LIB. If not,
write to the Free Software Foundation, Inc., 59 Temple Place, Suite 330,
Boston, MA 02111-1307 USA.
EXCEPTION NOTICE
1. As a special exception, the copyright holders of this library give permission for additional
uses of the text contained in this release of the library as licenced under the wxWindows
Library Licence, applying either version 3.1 of the Licence, or (at your option) any later
version of the Licence as published by the copyright holders of version 3.1 of the Licence
document.
2. The exception is that you may use, copy, link, modify and distribute under your own terms,
binary object code versions of works based on the Library.
3. If you copy code from files distributed under the terms of the GNU General Public Licence or the
GNU Library General Public Licence into a copy of this library, as this licence permits, the
exception does not apply to the code that you add in this way. To avoid misleading anyone as to
the status of such modified files, you must delete this exception notice from such code and/or
adjust the licensing conditions notice accordingly.
4. If you write modifications of your own for this library, it is your choice whether to permit
this exception to apply to your modifications. If you do not wish that, you must delete the
exception notice from such code and/or adjust the licensing conditions notice accordingly.
Network Shutdown Module V3 – User Manual - 34 003 934 XU / AE Page 64/65
 Loading...
Loading...