Page 1

Dell Networking W-Series
Instant Access Point
6.2.1.0-3.4
Syslog Messages
Reference Guide
Page 2

Copyright
© 2013 Aruba Networks, Inc. Aruba Networks trademarks include , Aruba Networks®, Aruba Wireless Networks®, the
registered Aruba the Mobile Edge Company logo, and Aruba Mobility Management System
PowerConnect™ are trademarks of Dell Inc.
All rights reserved. Specifications in this manual are subject to change without notice.
Originated in the USA. All other trademarks are the property of their respective owners.
®
. Dell™, the DELL™ logo, and
Open Source Code
Certain Aruba products include Open Source software code developed by third parties, including software code subject to the GNU
General Public License (GPL), GNU Lesser General Public License (LGPL), or other Open Source Licenses. Includes software from Litech
Systems Design. The IF-MAP client library copyright 2011 Infoblox, Inc. All rights reserved. This product includes software developed by
Lars Fenneberg, et al. The Open Source code used can be found at this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba Networks, Inc. switching platforms and software, by all individuals or corporations, to terminate other vendors’ VPN
client devices constitutes complete acceptance of liability by that individual or corporation for this action and indemnifies, in full, Aruba
Networks, Inc. from any and all legal actions that might be taken against it with respect to infringement of copyright on behalf of those
vendors.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide 0511439-01 | July 2013
Page 3

Contents
Contents ...................................................................................................3
Chapter 1 About the Guide ....................................................................................... 5
Document Organization......................................................................................... 5
Format of Messages..............................................................................................5
Severity Levels ................................................................................................ 6
Message Process Generation ...............................................................................6
Syslog Server.........................................................................................................7
Filtering Syslogs ....................................................................................................7
Related Documents ...............................................................................................8
Contacting Support ............................................................................................... 8
Chapter 2 Security Messages .................................................................................. 9
Critical Messages .................................................................................................. 9
Error Messages....................................................................................................10
Warning Messages ..............................................................................................22
Notice Messages .................................................................................................22
Information Messages ......................................................................................... 23
Debug Messages................................................................................................. 25
Chapter 3 System Messages.................................................................................. 27
Emergency Messages ......................................................................................... 27
Alert Messages ....................................................................................................27
Critical Messages ................................................................................................ 28
Error Messages....................................................................................................28
Warning Messages ..............................................................................................36
Notice Messages .................................................................................................43
Information Messages ......................................................................................... 46
Debug Messages................................................................................................. 52
Chapter 4 User Messages ......................................................................................57
Error Messages....................................................................................................57
Warning Messages ..............................................................................................59
Notice Messages .................................................................................................62
Information Messages ......................................................................................... 66
Debug Messages................................................................................................. 67
Chapter 5 Wireless Messages................................................................................ 79
Error Messages....................................................................................................79
Warning Messages ..............................................................................................79
Notice Messages .................................................................................................84
Information Messages ......................................................................................... 85
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide |3
Page 4

Debug Messages................................................................................................. 85
4 | Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 5
Chapter 1
About the Guide
This document covers syslog messages included in this Dell W-Instant release.
In this edition, message definition, recommended action and in some cases the cause that generated the syslog
message are included. Syslog messages were prioritized for definition; this edition includes definitions for
approximately 70% of Dell W-Instant syslog messages. For those messages yet to be defined, the phrase “No
description available” appears.
Document Organization
This document contains the complete listings of all syslog messages generated by Dell W-Instant. Each
chapter lists the syslogs for a single category as follows:
Security
System
User
Wireless
Each chapter contains the severity level syslog messages in table format (see Table 1 for the complete list of
severity levels). The syslog messages are the actual text displayed by Dell W-Instant when encountering the
syslog, and some further descriptive text, giving more information about the syslog. The entry may also
include recommended action when this syslog is encountered.
Format of Messages
Consider the following message as an example:
Jan 23 16:26:51 sapd[148]: <404003> <WARN> |AP 00:0b:86:cb:85:db@10.34.84.14 sapd| AM
00:0b:86:38:5d:b0: Interfering AP detected with SSID 06B408550367 and BSSID
00:12:0e:44:d4:2c
In this case, the message elements are:
<date and time stamp> = Jan 23 16:26:51
<error location>: = sapd[148]:
<error number> = <404003> (a unique number within the set of messages generated by Dell W-
Instant)
<severity> = <WARN> (Warning severity level)
|<process>| = |AP 00:0b:86:cb:85:db@10.34.84.14 sapd| (the Access Point Media Access
Control (MAC) device address, along with the IP address)
message text = the remaining part of the message.
The message text portion is frequently constructed from information returned with the syslog. For example,
the message text for the syslog above is constructed as:
(the specific module location where this syslog was generated)
AM <BSSID>: Interfering AP detected with SSID <SSID> and BSSID <BSSID>
Where:
<BSSID> = 00:0b:86:38:5d:b0
<SSID> = 06B408550367
<BSSID> = 00:12:0e:44:d4:2c
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide About the Guide | 5
Page 6

These substitutions generate message text as follows:
AM 00:0b:86:38:5d:b0: Interfering AP detected with SSID 06B408550367 and BSSID
00:12:0e:44:d4:2c
In the following chapters, messages are defined in generic terms with variables shown to indicate where
substitutions of actual data will occur.
Severity Levels
The severity levels defined for syslogs are outlined in Table 1, which orders the severity from most to least
severe. Note that the syslog messages with the lowest severity level, “Debug”, is listed in this manual. Also,
note that the severity level string (such as EMERG, or CRIT), as well as the numeric value associated with
that particular severity, is listed in the tables.
Table 1 Message Severity Levels
Level Value Meaning
Emergency <EMERG> 0 Panic condition that occurs when the system becomes unusable.
Alert <ALERT> 1 Any condition requiring immediate attention and correction.
Critical <CRIT> 2 Any critical conditions such as a hard drive error.
Error <ERR> 3 Error condition.
Warning <WARNING> 4 Warning message.
Notification <NOTICE> 5 Significant event of a non-critical and normal nature.
Informational <INFO> 6 Message of general interest to system users.
Debug <DEBUG> 7 Message containing information useful for debugging.
Message Process Generation
The process that generates syslog messages is detailed in Table 2.
Table 2 Process Generating Syslog Messages
Process Description Categories used by this component
802.1X Network Access Control authentication security, user
am Logging for AirMonitor security, system, wireless
meshd Logging for Mesh daemon system
radius Logging for RADIUS authentication security, system, user
sapd Logging for Access Point Manager (AP) system
stm Logging for Station Management system, user, wireless
vc Logging for Virtual Controller system
6 | About the Guide Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 7
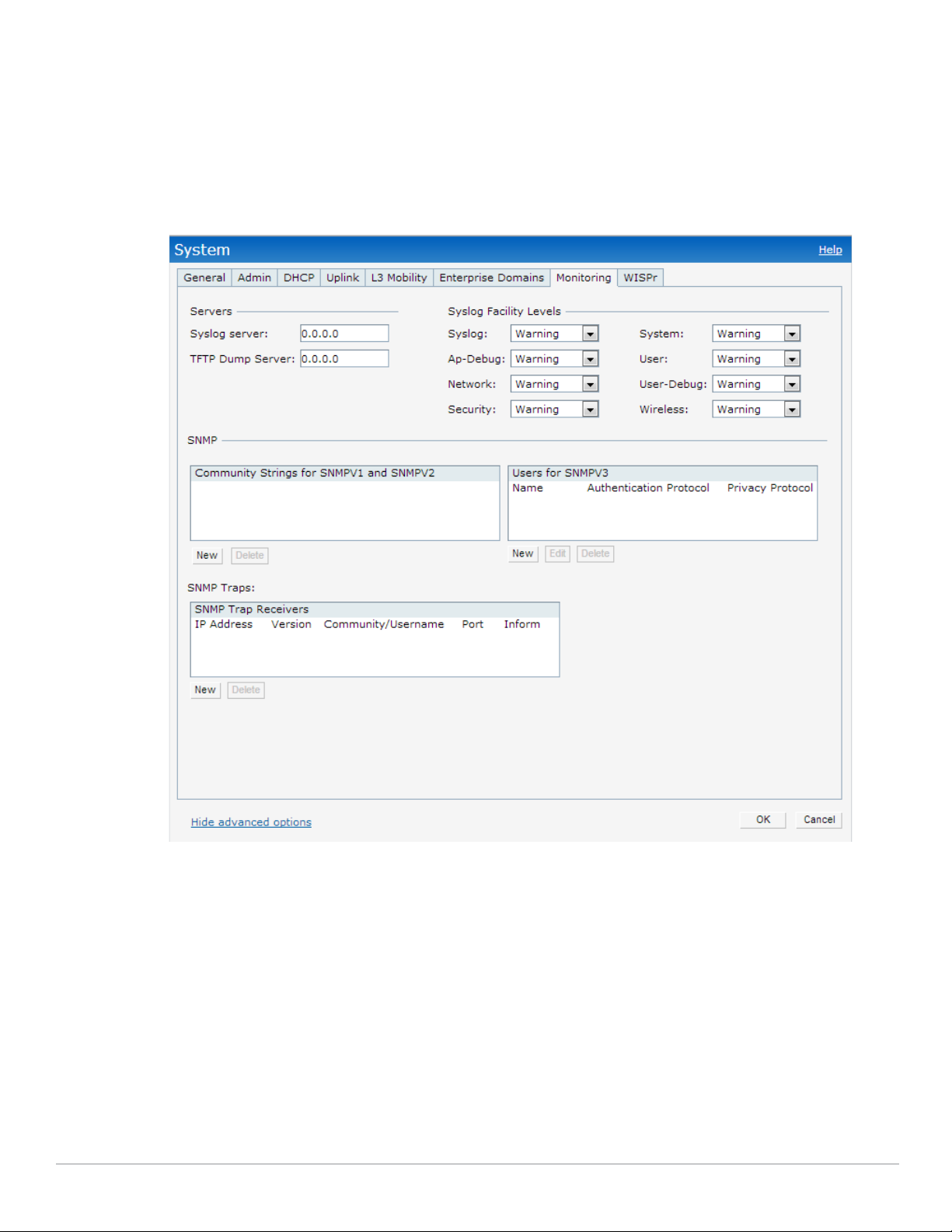
Syslog Server
To specify a Syslog Server for sending syslog messages to the external servers, navigate to System > Show
advanced options > Monitoring in the UI and update the following fields.
Syslog server— Enter the IP address of the server to send system logs.
Syslog level— For a global level configuration, select one of the logging levels from the standard list of
syslog levels. The default value is Notice.
Figure 1 Configuring Syslog Server Settings
You can also configure Syslog server details and logging levels by using the command-line Interface (CLI).
To configure a Syslog server:
(Instant Access Point)(config)# syslog-server <IP-address>
To configure logging levels:
(Instant Access Point)(config)# syslog-level <level>{apdebug|network|security|system|user|user-debug|wireless}
Filtering Syslogs
Searching through the logs for specific events, error categories, or other information, is often quite useful.
In addition, long term storage of data required for audits and other business requirements involving
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide About the Guide | 7
Page 8
information kept in the system logs is important. The capabilities required for handling logs should include
the following:
Efficient log management
Sophisticated analysis capabilities
Consistent report generation
Scalability
Security
Analyzing system logs, and extracting relevant information from them, requires an efficient pattern
matching engine, where the desired patterns can be created with standard pattern matching commands,
such as a regular expression engine.
Related Documents
In addition to this document, the Dell W-Instant product documentation includes the following:
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 Quick Start Guide
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 User Guide
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 Command Line Reference Guide
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 MIB Reference Guide
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 Release Notes
Contacting Support
Table 3 Contact Information
Web Site Support
Main Website dell.com
Support Website dell.com/support
Documentation Website dell.com/support/manuals
8 | About the Guide Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 9

Chapter 2
Security Messages
Critical Messages
Table 4 Security Critical Messages
Message ID Message and Description
132002 Enabling dot1x termination for AP [mac:%m] [auth_profile:%s] before cert download.
Description: Termination is being enabled before certificate is downloaded.
132011 Station [mac:%m] [name:%s] not found in AP’s [bssid:%m] station table.
Description: Station is not found in the specified AP’s station table.
132014 “AP [bssid:%m] [apname:%s] Incomplete AP configuration.Check if WEP Key, WEP
Transmit Key or WPA Passphrase is not configured.
Description: AP’s configuration is not complete. Either WEP key/WEP Transmit Key/
WPA Passphrase is not configured.
132135 Failed to create SSL_CTX.
Description: System failed to create SSL Context.
132136 Loading Certificate from [fname:%s] failed
Description: Failed to load the Certificate for 802.1x termination.
132137 Private key does not match cert
Description: Private key is not found in the certificate
132138 Failed to alloc BIO in.
Description: Failed to allocate BIO structure.
132139 Failed to alloc BIO out.
Description: Failed to allocate BIO out structure.
132140 Failed to set the cipher - ssl3_get_cipher_by_char.
Description: Failed to set the cipher using ssl3_get_cipher_by_char.
132141 Failed to create buf - BUF_MEM_new.
Description: Failed to create a buffer using BUF_MEM_new.
132142 ssl3_output_cert_chain returned error.
Description: Failed to output the certificate chain.
132143 Failed to download MODEXP for dot1x-termination.
Description: Failed to download MODEXP to datapath for 802.1x termination.
132144 Failed to download the cert for dot1x-termination.
Description: Failed to download the server certificate for dot1x termination.
132145 BIO_read failed len [ln:%d].
Description: BIO read failed.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 9
Page 10
Table 4 Security Critical Messages (Continued)
Message ID Message and Description
132146 ssl_get_server_send_cert faileds
Description: sl_get_server_send_cert failed
Error Messages
Table 5 Security Error Messages
Message ID Message and Description
121000 Failed to calculate the HMAC-MD5 digest
Description: Controller failed to calculate the HMAC-MD5 digest for RADIUS packet
due to an internal error.
Recommended Action: If the problem persists, contact Aruba support provider.
121001 Error [errno:%d],[errstr:%s] receiving packet [packet_len:%d], fd=[fd:%d]
Description: A socket error occurred while receiving RADIUS server response
Recommended Action: If the problem persists, contact your support provider.
121002 An error occurred while receiving RADIUS server response
Description: An error occurred while receiving RADIUS server response
Recommended Action: If the problem persists, contact your support provider.
121003 Discarding unknown response from server
Description: RADIUS Server has returned a response that does not match the request
or the packet could be corrupt
Recommended Action: Validate RADIUS server configuration. If the problem persists,
contact your support provider.
121005 An error occurred while receiving RADIUS server response on port 3799 (RFC 3576)
Description: An error occurred while receiving RADIUS server response on port 3799
(RFC 3576)
Recommended Action: If the problem persists, contact your support provider.
121008 RADIUS: Error [errno:%d],[errstr:%s] creating client socket
Description: Internal error occurred while initiating connection with the RADIUS server
Recommended Action: If the problem persists, contact your support provider.
121009 RADIUS: Error [errno:%d],[errstr:%s] in bind.
Description: Internal error occurred while connecting with the RADIUS server.
Recommended Action: If the problem persists, contact your support provider.
121010 Error [errno:%d],[errstr:%s] sending [data_len:%d] bytes on radius socket [sockfd:%d]
Description: Internal error occurred while sending data to the RADIUS server.
Recommended Action: If the problem persists, contact your support provider.
121011 Received RADIUS server response with invalid length [len:%d].
Description: The expected length of a RADIUS server response packet is between 20
and 4096 bytes.
Recommended Action: Check the length of response packet from the RADIUS server.
10 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 11

Table 5 Security Error Messages (Continued)
Message ID Message and Description
121012 Not enough buffer space to verify RADIUS server response packet with length
121013 Received non-matching ID in RADIUS server response [id:%d], expecting [seq_nbr:%d].
121014 Received invalid reply digest from RADIUS server.
121016 RADIUS server [server:%s],[fqdn:%s][ipaddr:%s] is out of sequence.
121018 Unknown RADIUS attribute ID [attrid:%d] in [func:%s]
[totallen:%d].
Description: The internal buffer is not big enough for the RADIUS response packet and
RADIUS secret.
Recommended Action: Check the length of the RADIUS response packet from the
RADIUS server and the length of RADIUS secret.
Description: Received a response from the RADIUS server, but the sequence number
doesn’t match the request.
Recommended Action: Check the RADIUS server is configured properly.
Description: The reply digest received from the RADIUS server doesn’t match the
calculated digest.
Recommended Action: Check the RADIUS server is configured properly and verify
shared secret configuration on the controller matches that on the RADIUS server.
Description: The PENDING request buffer to RADIUS server is already full (256).
Response from RADIUS server seems to be slower than the rate at which the users are
coming in.
Recommended Action: Check the RADIUS server is configured properly and the
connectivity between the controller and RADIUS server is good.
Description: The RADIUS attribute is not known.
Recommended Action: Use the show aaa radius-attributes command to check if the
attribute ID is supported.
121019 Received attribute with invalid length [attrlen:%d] in [func:%s]“
Description: Received RADIUS attribute with invalid length, while extracting the
attribute-value pairs
Recommended Action: Check the RADIUS server is configured properly and the
connectivity between controller and RADIUS server is good.
121021 RADIUS attribute [name:%s] has unknown type [type:%d] in [func:%s]“
Description: Received unknown RADIUS attribute type, while extracting the attributevalue pairs.
Recommended Action: Please check the supported RADIUS attribute type.
121022 Unknown RADIUS attribute name [name:%s] in [func:%s]“
Description: Received unknown RADIUS attribute name, while extracting the attributevalue pairs
Recommended Action: Please use the show aaa radius-attributes command to check
if the attribute name is supported.
121023 Unknown RADIUS attribute [attr_value:%s] in [func:%s]
Description: Controller received an unknown RADIUS attribute while extracting the
attribute-value pairs from Radius server response.
Recommended Action: Please use the show aaa radius-attributes command to check
if the attribute value is supported.
121025 Value pair is NULL or empty attribute [id:%d] in [func:%s].
Description: Internal error occurred while converting the attribute-value pairs received
in RADIUS response to strings.
Recommended Action: If the problem persists, contact your support provider.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 11
Page 12

Table 5 Security Error Messages (Continued)
Message ID Message and Description
121029 RADIUS: Error [errno:%d], [errstr:%s] creating rfc3576 socket.
Description: Internal error occurred while initiating connection with RADIUS server.
Recommended Action: If the problem persits, contact your support provider.
121030 RADIUS: Error [errno:%d], [errstr:%s] in rfc3576 bind.
Description: Error occurred while connecting to RADIUS server.
Recommended Action: If the problem persists, contact your support provider.
121033 “rc_pack_list: Attribute list exceeds 8192 bytes, dropping request
Description: rc_pack_list: Attribute list exceeds 8192 bytes, dropping request
121036 RADIUS: Error [errno:%d],[errstr:%s] setting client socket options.
Description: Internal error occurred while setting connection options with the RADIUS
server.
Recommended Action: Contact Aruba technical support if this problem persists.
121047 Failed to add user Port ID in the Radius Accounting Pkt [pkt:%s].
Description: This shows an internal debug message
121048 Unknown result type [resultType:%d].
Description: This shows an internal debug message
121049 Failed to add user Port ID in the Radius Accounting Start Pkt [portStr:%s].
Description: This shows an internal debug message
132003 xSec vlan not configured for [port:%s]
Description: xSec vlan is not configured for the specified port.
Recommended Action: Configure VLAN that supports XSEC on specified port..
132004 Unknown AP [mac:%m] [bssid:%m] [menc:%s] [vlan:%d].
Description: Authentication process has detected an unknown AP.
Recommended Action: Execute the show ap database command to determine if
system is aware of the Access Point. Power-cycle the unknown AP.
132005 AP [mac:%m] [apname:%s] is not enabled.
Description: Specified AP is not enabled.
Recommended Action: Configure AP with a valid virtual-AP or wired profile..
132006 Station Add failed [mac:%m] [bssid:%m] [apname:%s] [uenc:%s] [menc:%s]
Description: Station failed to complete the security association with authentication
process.
Recommended Action: Confirm that the SSID that the supplicant is associating to is
configured to support 802.1X authentication and is configured correctly..
132008 Station delete failed, does not exists in the station table.
Description: Failed to clear the station from the AP’s station table.
Recommended Action: Station does not exist in authentication process tables.
Confirm by running the show station command.
132009 Station’s dot1x context not initialized [name:%s] [mac:%m] [bssid:%m]
Description: Station’s internal context is not completely initialized.
Recommended Action: Internal error. Clear the station by running the aaa user delete
command and reconnect.
12 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 13

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132010 Station [mac:%m] [name:%s] not associated with AP [bssid:%m]
Description: Station is not associated to the specified AP
132012 Station delete failed [name:%s] [mac:%m] [bssid:%m]
Description: Failed to delete the specified station
Recommended Action: Clear the station by running the aaa user delete command.
and reconnect. Manually clear the station by running the aaa user delete command.
132013 AP [bssid:%m] [apname:%s] Configuration not complete, No Transmit WEP Key set
Description: AP’s configuration is not complete. Check if the WEP transmit key is set
Recommended Action: Check of the WEP transmit key is set in the ssid-profile
132015 Failed to Deauthenticate the station [mac:%m] [name:%s]
Description: Failed to deauthenticate the specified station
Recommended Action: Internal error. Clear the station and reconnect.
132016 Local Database Server not available to cache the machine auth for user [name:%s]
[mac:%m]
Description: Internal server is not available for caching the machine authentication for
the specified User.
Recommended Action: Run the aaa test-server pap internal command to verify
connectivity to the local database server. If unavailability of local database server
persists and controller is a local-controller, verify connectivity to master-controller. If all
else fails, restart the udbserver process on the master-controller by executing the
process restart udbserver command and restart the AUTH process on the localcontroller by executing the process restart auth command.
132017 Failed to update Machine Auth status to local DB for Station [mac:%m] [name:%s]
Description: Failed to update the Machine authentication Status for the specified User
because udbserver process is not responding.
Recommended Action: Run the aaa test-server pap internal command to verify
connectivity to the local database server. If unavailability of local database server
persists and controller is a local-controller, verify connectivity to master-controller. If all
else fails, restart the udbserver process on the master-controller by executing the
process restart udbserver and restart the AUTH process on the local-controller by
executing process restart auth.
132018 Station [mac:%m] [bssid:%m] was deleted before the response from the local database
132023 802.1x authentication is disabled in profile [prof:%s] Station [mac:%m] [bssid:%m]
132024 Station [mac:%m] pre-authenticating with Unknown AP [bssid:%m] vlan [vl:%d]
server
Description: Station was deleted before receiving response from the Internal Server
due to high latency between local-controller’s AUTH process and master-controller’s
UDBSERVER process.
Recommended Action: Diagnose external IP-latency issues between mastercontroller and local-controller and have the client re-attempt their authenticationrequest.
Description: 802.1x authentication is disabled for the specified profile.
Recommended Action: Configure the specified aaa-profile to enable 802.1x
authentication.
Description: Station is trying to pre-authenticate with an AP that is not registered. This
log-message is generated when we detect a race-condition between STM, SOS and
AUTH. AUTH is receiving EAP packets from SOS before it received the New-AP
message from STM. Execute show ap database to determine if STM is aware of the
AP. If not, try rebooting the AP by executing apboot or powercycling the AP. If
symptoms persist, then AUTH is either not receiving or not processing New-AP
messages from STM. If all else fails, restart the AUTH process by executing process
restart auth or reload the controller.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 13
Page 14

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132025 Station [mac:%m] [bssid:%m] is not enabled for pre-auth.
Description: Preauthentication is always disabled
132026 Station [mac:%m] [bssid:%m] trying to pre-authenticate with AP that does not have
132027 Station [mac:%m] associating to Unknown AP [bssid:%m] [menc:%d] [vl:%d]
132029 Station [mac:%m] [bssid:%m] sent Unsupported EAPOL Type [type:%d]“
132030 Dropping EAPOL packet sent by Station [mac:%m] [bssid:%m]
132032 Invalid length in the [msg:%s] from Station [mac:%m] [bssid:%m] [len:%d]“
WPA2 enabled
Description: Station trying to preauhenticate with AP that is not WPA2 enabled.
Configure the ssid-profile to enable WPA2 and reload the AP.
Description: Station is trying to associate with AP that is not registered. This logmessage is generated when we detect a race-condition between STM, SOS and AUTH.
AUTH is receiving EAP packets from SOS before it received the New-AP message from
STM. If not, try rebooting the AP by executing apboot or powercycling the AP. If
symptoms persist, then AUTH is either not receiving or not processing New-AP
messages from STM. If all else fails, restart the AUTH process by executing process
restart auth or reload the controller.
Description: Station sent an unsupported EAPOL packet.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If the problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
Description: Dropping the EAPOL packet sent by the specified station.
Recommended Action: Check preceding log-messages to determine the reason the
EAPOL packet is being dropped.
Description: Station sent the specified packet with invalid length.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132033 Invalid WPA Key Description Version [ver:%d] Station [mac:%m]“
Description: Station sent a WPA key message with invalid version.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132035 Invalid WPA2 Key Description Version [ver:%d] Station [mac:%m]“
Description: Station sent a WPA key message with invalid version.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132036 Station [mac:%m] [bssid:%m] sent Unknown EAP-Request [eaptype:%d]“
Description: Station send an EAP packet that is invalid.
Recommended Action: Ensure the station is configured properly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132037 Station [mac:%m] [bssid:%m] sent username greater than [MAX_USERNAME_SIZE:%d]
Description: The user name sent by the station is larger than the maximum size
supported.
Recommended Action: Configure station to use a shorter username and attempt
authentication again.
14 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 15
Table 5 Security Error Messages (Continued)
Message ID Message and Description
132038 Station [mac:%m] [bssid:%m] sent Unsupported EAP type [eaptype:%d]]“
Description: Station sent an EAP packet that is not supported.
Recommended Action: Ensure the station is configured correctly to perform an EAP
authentication method that is supported by the controller. Ensure that the aa a-profile
associated with the authentication request matches the authentication-method the
client is sending to authenticate. If problem persists, check for packet-corruption by
capturing sniffer-traces between client, AP and controller.
132039 Station [mac:%m] [bssid:%m] sent Unsupported EAP Code [eapcode:%d]“
Description: Station send an EAP packet with unknown EAP code.
Recommended Action: Ensure the station is configured correctly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132042 Sending empty username for user [mac:%m] - WPS is not enabled on AP [bssid:%m]
[apname:%s]“
Description: Station sent no user name in the EAP Identity Request message.
Recommended Action: Ensure the station is configured correctly to perform EAP
authentication. If problem persists, check for packet-corruption by capturing sniffertraces between client, AP and controller.
132045 Error remove stateful dot1x ACL“
Description: Failed to remove the Acts configured for stateful dot1x authentication
from the stateful_role or logon_role.
Cause: This is because the stateful-dot1x ACL is not associated with the stateful_role
or logon_role.
Recommended Action: Since we are disabiling stateful-dot1x anyway, no further
action is required.
132049 “Received Invalid digest from Server [srvip:%p], AP [ip:%p]
Description: Received radius packet with invalid digest during stateful dot1x
authentication.
Cause: This error suggests a possible man-in-the-middle attack.
Recommended Action: Contact your administrator to check status of your Radius
server. Radius packet will be dropped.
132050 “No Stateful configuration found that could verify the stateful response. [nasip:%p],
132051 Failed to validate stateful radius response [nasip:%p] [srvip:%p] station [mac:%m]
132053 Dropping the radius packet for Station [mac:%m] [bssid:%m] doing 802.1x“
[srvip:%p]
Description: No server config entry was found for verifying the stateful dot1x response.
Recommended Action: Verify that the Radius server in question is configured in the
applicable server-group on the controller.
Description: Stateful dot1x authentication failed because validation failed.
Recommended Action: Refer to previous log-message. If CONFIG_NOTFOUND,
verify that the Radius server in question is configured in the applicable server-group on
the controller. Otherwise, this may be a potential man-in-the-middle attack.Contact
your administrator to validate the status of your Radius sever.”
Description: Radius packet for the specified station is dropped.
Cause: Either the station has disconnected, has already authenticated or it is busy.
Recommended Action: If reauthentication is required, the station will request
authentication again.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 15
Page 16

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132055 “[__FUNCTION__:%s]: missing configuration for dot1x profile \””[prof:%s]\””
Description: Specified Dot1x profile is not configured or has been deleted.
Recommended Action: Validate that the controller configuration contains the specified
dot1x profile.
132056 “[__FUNCTION__:%s]: missing server-group configuration for dot1x in aaa-profile
\””[prof:%s]\”” for Station [mac:%m] [bssid:%m]
Description: Specified server group for dot1x authentication in the aaa profile is not
configured or has been deleted.
Recommended Action: Validate that the controller configuration contains the specified
server-group profile.
132057 Failed to send the radius request for Station [mac:%m] [bssid:%m]
Description: Radius request for specified station is being dropped due to lack of
system resources.
Recommended Action: Free up system memory and other resources by throttling
user-authentication requests.
132059 Multicast Key type of the AP [bssid:%m] [apname:%s] is not static-wep or dynamic-wep
Description: Multicast key type is not static wep or dynamic wep for the specified AP.
Recommended Action: Confirm that the specified ssid-profile is configured for WEP
132060 Unknown Multicast Key-type [menc:%d] for AP [mac:%m] [apname:%s]
Description: The multicast key type for the specified AP is not known.
Recommended Action: Validate the SSID-profile associated with the AP and reboot
the AP.
132061 AP [bssid:%m] [apname:%s] configured with aaa profile [prof:%s] does not have an
132062 Wrong slot configured for AP [bssid:%m] [apname:%s]
132063 WPA Preshared Key not configured for AP [mac:%m]
132064 WPA Passphrase not configured for AP [bssid:%m] [apname:%s]
132065 AP [mac:%m] [apname:%s] configured with invalid static-wep key length [slot:%d]
associated dot1x profile
Description: No dot1x profile is configured for the specified aaa profile.
Recommended Action: Configure a dot1x profile in the specified aaa profile.
Description: Invalid key slot configured for the specified AP. This should never happen.
Recommended Action: If this happens, an internal error has occurred. Reboot your
controller.
Description: WPA Preshared Key is not configured for the specified AP.
Recommended Action: Configure a WPA Preshared Key for this AP.
Description: WPA passphrase not configured for the specified AP.
Recommended Action: Configure a WPA Passphrase for this AP.
[size:%d]
Description: AP is configured with invalid Static WEP key length. The valid key length is
40bits or 128bits.
Recommended Action: Configure the AP with either a 40bit or 128bit key.
132069 No Radius server configuration with [srvip:%p] available for creating Stateful AP
Configuration entry
Description: While automatically creating stateful dot1x configuration entry the radius
server specified was not found.
Recommended Action: Configure the specified radius server configuration and try
again.
16 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 17

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132073 Wrong WPA OUI Element [oui:%d] from Station [mac:%m] [bssid:%m] [apname:%s]
Description: Station sent WPA key message with invalid OUI element.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
132074 Version [stver:%d] does not match [apver:%d] in the [msg:%s] IE Elements from Station
[mac:%m] [bssid:%m] [apname:%s]
Description: Station sent WPA key message with invalid Version.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
132075 Multicast cipher from Station [mac:%m] [stmc:%X] does not match with AP [bssid:%m]
132076 Station [mac:%m] [bssid:%m] [apname:%s] sent invalid number of unicast ciphers
132077 Station’s [mac:%m] [stuc:%X] and AP’s [bssid:%m] [apuc:%X] [apname:%s] unicast
132078 Station [mac:%m] [bssid:%m] [apname:%s] sent invalid number of key management
132079 Station’s [mac:%m] [stkm:%X] and AP’s [bssid:%m] [apkm:%X] [apname:%s] key
132080 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the multicast cipher and the
[apmc:%X] [apname:%s]
Description: Mismatch in the multicast ciphers specified by the station and AP.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
[uc:%d]
Description: Station sent invalid number of unicast cipher in the WPA IE element.
Recommended Action: Identify the station and investigate why it is sending incorrect
data.
cipher suites does not match
Description: Mismatch in the unicast cipher specified by the station and the AP
suite [km:%d]
Description: Station sent invalid number of key management suite in the WPA IE
element
management suites does not match
Description: Mismatch in the key management suite specified by the station and the
AP
configured multicast cipher [mc:%X] did not match the default cipher TKIP
Description: Station did not specify any multicast cipher and the multicast cipher
specified by the is not TKIP
132081 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the unicast cipher and the
132082 Station [mac:%m] [bssid:%m] [apname:%s] did not specify the key management
132083 [Num:%d] TKIP Michael MIC failure was detected
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 17
configured unicast cipher [mc:%X] did not match the default cipher TKIP
Description: Station did not specify any unicast cipher and the multicast cipher
specified by the AP is not TKIP
selector and the configured key management [km:%X] did not match the default -
802.1x
Description: Station did not specify any key management selector and the configured
key management on the AP is not 802.1x
Description: Specified number of TKIP MIC failure was detected
Page 18
Table 5 Security Error Messages (Continued)
Message ID Message and Description
132084 Two TKIP Michael MIC Failures were detected within [last_scan_time:%d] seconds.AP
132085 Maximum number of %s Key exchanges attempted for station [name:%s] [mac:%m]
132088 “Invalid WPA [ver:%d] Key message from Station [mac:%m] [bssid:%m] [apname:%s],
132089 “Invalid WPA [ver:%d] Key message from Station [mac:%m] [bssid:%m]
132090 Received TKIP Michael MIC Failure Report from the Station [mac:%m] [bssid:%m]
132091 Wrong key type [kt:%d] in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
will be shutdown for next 60 seconds
Description: Two MIC failures was received from the station within 60 secs.
Recommended Action: The AP must be shutdown for 60 secs
[bssid:%m] [apname:%s]
Description: Maximum number of key exchanges was attempted for the station
reason:ACK bit set
Description: WPA key message with ACK bit set was received from the station. This is
invalid
[apname:%s],reason: Error flag without Request bit set
Description: WPA key message with error flag without request bit set was received
from the station. This is invalid
[apname:%s]
Description: Specified Station sent TKIP MIC failure report
Description: Station sent wrong key type in the WPA key message
132092 Request bit set in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
Description: Station sent WPA key message with request bit set
132093 [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s] did not match the replay
counter [stcnt1:%d][stcnt2:%d] vs [apcnt1:%d][apcnt2:%d]
Description: Station and AP’s replay counter does not match. The WPA key message
from the station has to be dropped
132099 [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s] has invalid datalen [ln:%d]
!= 0]
Description: Station sent WPA key message with invalid key length
132104 Invalid character in the passphrase [ch:%c]
Description: Invalid characters in the WPA passphrase
132105 Invalid password len [ln:%d]
Description: Invalid WPA passphrase length
132106 Invalid ssid len [ln:%d]
Description: Invalid SSID length
132113 Station’s [mac:%m] [strsn:%X] and AP’s [bssid:%m] [aprsn:%X] [apname:%s] RSN
Capability does not match
Description: Station and AP’s RSN capability does not match
132114 Failed to add xSec station [mac:%m] to AP [bssid:%m]
Description: Failed to add xSec station to AP’s station table
18 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 19

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132147 Invalid length [ln:%d] during inner EAP handling
Description: Station sent invalid length in the inner eap
132149 Station [mac:%m] [bssid:%m] lookup failed
Description: Specified station failed lookup
132150 Station [mac:%m] [bssid:%m] does not have 802.1x context
Description: Station [mac:%m] [bssid:%m] does not have 802.1x context
132152 “802.1x termination is disabled user [mac:%m], profile [dot1x_auth_profile:%s]
Description: 802.1x termination is disabled for the specified profile
132155 Station [mac:%m] [bssid:%m] sent inner EAP type [eaptype:%d] that is not supported
Description: Station sent inner eap type that is not supported
132156 Station [mac:%m] [bssid:%m] sent inner EAP Start
Description: Station sent inner EAP start packet. This is invalid
132157 Station [mac:%m] [bssid:%m] sent inner EAP packet with more-fragments bit set
Description: Station sent inner EAP packet with more fragment bit set. This is invalid
132158 Station [mac:%m] [bssid:%m] sent invalid EAP flag
Description: Station sent invalid flag in the inner EAP packet
132159 Station[mac:%m] [bssid:%m] sent invalid inner EAP Packet [eaplen:%d]
Description: Station sent invalid len in the inner EAP packet
132161 Station [mac:%m] [bssid:%m] sent Invalid TLS Record Layer Type [tlsrectype:%d]
Description: Station sent invalid TLS record layer type
132162 Station [mac:%m] [bssid:%m] sent with unsupported TLS client version [ver:%X]
Description: Station sent unsupported TLS client version
132165 Station[mac:%m] [bssid:%m] sent invalid MAC in the TLS Record layer
Description: Station send invalid MAC in the TLS record layer
132166 Station[mac:%m] [bssid:%m] sent more than one TLS Application Data Record Layer
Description: Station send more than one TLS application data record layer
132167 Verification of TLS Record Layer from Station [mac:%m] [bssid:%m] failed
Description: Verification of the TLS record layer from the station failed
132171 “Received EAP-NAK from Station [mac:%m] [bssid:%m], Station is configured with
[eaptype:%s]
Description: Station sent inner eap-nak
132177 Station [mac:%m] [bssid:%m] sent client finish is that is not 3DES encrypted
Description: Station send client finish that is not 3DES encrypted. This is not
supported
132179 Failed to decrypt the client finish message from Station [mac:%m] [bssid:%m]
Description: Station sent the client finish message that failed to decrypt
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 19
Page 20

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132180 Station [mac:%m] [bssid:%m] sent Unknown SSL type in the client finish header
132182 Verify data sent by the Station [mac:%m] [bssid:%m] is not valid
132185 Failed to send the server finish for Station [mac:%m] [bssid:%m]
132188 No user-name found in the inner EAP id response from Station [mac:%m] [bssid:%m]
132195 Invalid EAP code [code:%d] in the EAP-TLV/Phase2 response from Station [mac:%m]
132196 Invalid EAP TLV-Type [tlv_type:%d] in the EAP-TLV/Phase2 response from Station
132197 “Maximum number of retries was attempted for station [name:%s] [mac:%m]
[type:%d]
Description: Station sent unknown SSL type in the client finish header
Description: Verify data sent by the specified station in not valid
Description: Failed to send server finish for the specified station
Description: Station did not send any user name in the inner EAP id response
[bssid:%m]
Description: Station sent invalid EAP code in the TLV response
[mac:%m] [bssid:%m]
Description: Station sent invalid TLV type
[bssid:%m], deauthenticating the station
Description: Maximum number of retries was attempted for station to complete the
authentication phase.
Recommended Action: Deauthenticating the station
132198 Failed to load the CA List File [file:%s]
Description: Failed to load the specified CA List File for 802.1x termination
132199 Failed to set up SSL buffers
Description: Failed to set up SSL buffers
132200 Received TLS Client Finish but the client certificate [mac:%m][bssid:%m] is not verified
Description: Received TLS Client Finish but the client certificate is not verified
132201 Failed to cache EAP-GTC authentication info of Station [name:%s] [mac:%m]
132203 “Station [mac:%m][bssid:%m] sent a EAP-NAK, requesting unsupported inner-eap-type
132204 Inner eapid mismatched [id1:%d]:[id2:%d] for station [mac:%m] [bssid:%m]
132205 Invalid inner-eaptype configured [eaptype:%d]
132206 Multiple user name attributes in response packet.
[bssid:%m] in the Local Database Server
Description: Failed to cache EAP-GTC authentication information of the station in the
Internal server
[type:%d]
Description: Unsupported inner-eaptype requested by station
Description: Mismatch between the eapid station sent and what was expected
Description: Configured eaptype is not supported
Description: The RADIUS response packet is invalid because it contains multiple user
name attributes
20 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 21

Table 5 Security Error Messages (Continued)
Message ID Message and Description
132207 RADIUS reject for station [name:%s] [mac:%m] from server [server:%s].
Description: Radius packet for the specified station was rejected by the server.
132208 Station setup failed [mac:%m] [bssid:%m] [apname:%s] [uenc:%s] [menc:%s]
Description: Station failed to start the security association
132209 No unicast ciphers supported by AP [bssid:%m] [apname:%s]
Description: No unicast ciphers supported by AP with WPA2 opcode
132210 “Error in cb msg processing, message to
[ip:%s]:[port:%d]([app_name:%s]),[msg_code:%d], Msglen [len:%d], and Msgtype
[msg_type:%d] failed with Errno [errno:%d], Errstr [errstr:%s] “
Description: Error occurred during key propagation for a client in split/bridge/d-tunnel
mode for DWEP/AES/TKIP encryption.
Recommended Action: The msg is corrupted, retry the authentication to resolve the
issue.
132211 Station [mac:%m] [bssid:%m] sent a cert from which we couldn’t extract the public key
Description: Station sent a cert from which we couldn’t extract the public key
132212 Station [mac:%m] [bssid:%m] certificate signature verification failed“
Description: Station sent a cert, but the certificate signature verification failed
132217 Failed to convert cert into DER format before sending to certmgr
Description: Failed to convert cert into DER format before sending to certmgr
132221 Invalid EAP type [eaptype:%d] received for station[mac:%m][bssid:%m] configured in
termination mode
Description: Received invalid EAP type for station that is configured in termination
mode
132222 Received EAP packet on the wrong BSSID for station [mac:%m][bssid:%m]
Description: Received EAP packet on the wrong BSSID.
132224 Station [mac:%m] [bssid:%m] sent Unsupported EAP code [eapcode:%d]]
Description: Station sent an EAP packet that is not supported. Ensure the station is
configured correctly to perform an EAP authentication method that is supported by the
Aruba controller.
Recommended Action: Ensure that the aaa-profile associated with the authentication
request matches the authentication-method the client is sending to authenticate. If
problem persists, check for packet-corruption by capturing sniffer-traces between
client, AP and controller.
132225 MAC Authentication was not done for station [mac:%m] [bssid:%m]
Description: MAC Authentication was not done for the specific station
132226 MAC Authentication was not successful and l2-fail-thru is not enabled for station
[mac:%m] [bssid:%m]
Description: MAC Authentication was not successful and l2 fail thru knob was not
enabled for the specific station
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 21
Page 22

Warning Messages
Table 6 Security Warning Messages
Message ID Message and Description
106010 “AM [bssid:%s]: Containment enabled on Suspect Rogue AP: BSSID [ap_bssid_str:%s],
121004 RADIUS server [name:%s]-[fqdn:%s]-[ipaddr:%s]-[sin_port:%u] timeout for
121006 RADIUS server [name:%s]-[fqdn:%s]-[ipaddr:%s]-[sin_port:%u] timeout for
121007 RADIUS (RFC 3576): Ignoring request from client [srv_ipaddr:%s] port([srv_port:%d])
132058 Vendor Id [vid:%d] not supported
SSID [ssid:%s], Conf-Level [conf_level:%d] “
Description: Containment has been enabled for a suspected rogue AP because the
confidence level for that AP equals or exceeds the configured value for that setting
client=[cbuf:%s] auth method [server:%s].
Description: RADIUS Server is unreachable. The server could be down or there is
connectivity problem.
Recommended Action: Check RADIUS server connectivity
client=[cbuf:%s] auth method [server:%s].
Description: RADIUS Server is unreachable. The server could be down or there is
connectivity problem.
Recommended Action: Check RADIUS server connectivity .
with unknown code [code:%d].
Description: A request was received on RADIUS port 3799 (RFC 3576) with unknown
code.
Recommended Action: Check RADIUS server and RFC 3799 client configuration.
Description: Vendor ID in the radius response is not supported. Radius packet will be
dropped.
132094 MIC failed in [msg:%s] from Station [mac:%m] [bssid:%m] [apname:%s]
Description: Station sent an WPA key message whose MIC verification failed
Notice Messages
Table 7 Security Notice Messages
Message ID Message and Description
106000 AM [bssid:%s]: Potentially rogue AP detected BSSID [bssid_str:%s] SSID [ssid:%s]
MATCH MAC [mac:%s]
Description: An AP has been detected with conditions that may cause it to be
classified as a rogue (unsecure) or suspected rogue
106001 AM [bssid:%s]: Potentially rogue AP detected BSSID [bssid_str:%s] SSID [ssid:%s]
Description: An AP has been detected with conditions that may cause it to be
classified as a rogue (unsecure) or suspected rogue
106005 AM: Wireless containment: Sending type [subtype:%s] to AP [bssid:%s] from STA
[mac:%s] channel [channel:%d]
Description: No description available.
106006 AM: Wireless containment: Sending type [subtype:%s] from AP [bssid:%s] to STA
[mac:%s] channel [channel:%d]
Description: No description available.
22 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 23
Table 7 Security Notice Messages
Message ID Message and Description
106012 AM: Wireless tarpit containment: Sending Probe-Response with fake channel from AP
106013 AM: Wireless tarpit containment: Sending Probe-Response with fake BSSID for frame
106014 AM: Wireless tarpit containment: Sending Auth reply for frame from AP [bssid:%m] to
106015 AM: Wireless tarpit containment: Sending Assoc-Response for frame from AP
106016 AM: Wireless tarpit containment: Client [mac:%m] is in tarpit for fake BSSID [bssid:%s]
106017 AM: Wireless tarpit containment: Client [mac:%m] is in tarpit for fake channel
[bssid:%m] to STA [mac:%m] on channel [channel:%d] with fake_channel [fc:%d]
Description: No description available.
from AP [bssid:%m] to STA [mac:%m] on channel [channel:%d] with fake_bssid
[fbssid:%m]
Description: No description available.
STA [mac:%m] on channel [channel:%d] with algorithm [alg:%d] transaction [xn:%d]
seq [seq:%d]
Description: No description available.
[bssid:%m] to STA [mac:%m] on channel [channel:%d] with aid [aid:%d] seq [seq:%d]
Description: No description available.
on channel [channel:%d]
Description: No description available.
[channel:%d] for BSSID [bssid:%m]
Description: No description available.
121015 “Purge Request: [packet_id:%d], [srv_ipaddr:%s], [fd:%d], [timer_id:%d]”
Description: A new config was received (write memory on master), hence purging all
the pending radius requests.
121017 Unknown vendor or attribute ID [vendor:%d]/[attrid:%d] in [func:%s].
Description: The RADIUS vendor or the attribute ID is not known.
Recommended Action: Use show aaa radius-attributes command to check if the
vendor or attribute ID is supported.
121032 “Purge Request: [packet_id:%d], [srv_ipaddr:%s], [fd:%d], [timer_id:%d]”
Description: Radius Client IP change, hence purging all the pending radius requests
Information Messages
Table 8 Security Information Messages
Message ID Message and Description
106009 AM: Wired Containment: MAC:[mac_addr:%s] IP:[ip:%s]
Description: No description available.
106011 AM: Wired Containment Tagged: MAC:[mac_addr:%s] IP:[ip:%s] VLAN:[vlanid:%d] GW-
MAC:[gw_mac:%s] GW-IP:[gw_ip:%s]
Description: No description available.
121034 RADIUS attribute not sent: [attribute:%s]
Description: Controller has a reference to a RADIUS attribute that will be dropped.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 23
Page 24

Table 8 Security Information Messages
Message ID Message and Description
121035 RADIUS type not sent: [type:%s]
Description: Controller has a reference to a RADIUS type that will be dropped.
132000 xSec is enabled wired usersx
Description: Sec is enabled for wired users
132001 xSec is disabled for wired usersx
Description: Sec is disabled for wired users
132019 Station [name:%s] [mac:%m] was Machine authenticated
Description: Station successfully authenticated the machine account
132020 Station [name:%s] [mac:%m] failed Machine authentication update role [rl:%s]
Description: Station failed to authenticate the machine account
132021 Station [mac:%m] [bssid:%m] entered Held state
Description: Authenticator is in the held state for the specified station. In this state no
response from the station is accepted till the end of quiet period. This is done to avoid
DOS attacks.
132028 Dropping EAPOL request from Station [mac:%m] reason:AP [bssid:%m] [apname:%s]
only is configured for Static-WEP
Description: Station is trying to send EAP packets to AP that is only configured with
Static-WEP.
Recommended Action: Either configure your client to support static-WEP
authentication or configure the ssid-profile on the controller to support an 802.1x
authentication method.
132044 Enabled Stateful Radius“
Description: Stateful Dot1x is enabled. Controller will start monitoring EAPOL frames
to track authentication status.
132048 Disabled Stateful Radius“Stateful Dot1x is disabled.
Description: Controller will stop monitoring EAPOL frames to track authentication
status.
132066 Station[mac:%m] [bssid:%m] [apname:%s] [vl:%d] [gretype:%d] VLAN has been
132067 Cleaning up the Stateful AP Configuration
132068 Removing all the Stateful config entries.
132070 Removing trusted AP [mac:%m]
132071 Added trusted AP [mac:%m]
updated
Description: Station VLAN has been changed.
Cause: This is because of VLAN derivation rules
Description: Clear all the stateful dot1x configuration entries
Description: Remove all stateful dot1 configuration entries.
Description: Remove the Trusted AP with the specified MAC address.
Description: Add the trusted AP with the specified MAC address.
132086 “WPA [ver:%d] Key exchange failed to complete, de-authenticating the station
24 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
[mac:%m] associated with AP [bssid:%m] [apname:%s] “
Description: WPA key exchange failed to complete, deauthenticating the station
Page 25
Table 8 Security Information Messages
Message ID Message and Description
132131 FIPS mode is enabled.
Description: FIPS mode is enabled.
132132 FIPS mode is disabled
Description: FIPS mode is disabled.
132133 WPA Countermeasure is enabled
Description: WPA Countermeasure is enabled
132134 WPA Countermeasure is disabled
Description: WPA Countermeasure is disabled
132202 Successfully downloaded the certs [rootcert:%s] [servercert:%s] for EAP termination
Description: Successfully downloaded the certificates for EAP termination
132218 Skipping certificate common name check for username=[user:%s] MAC=[mac:%s]
Description: Based on configuration settings, the check for the certificate common
name against a AAA server was skipped.
132219 MAC=[mac:%s] Local User DB lookup result for Machine auth=[r3:%s] Role=[r4:%s]
Description: Local user database lookup result for Machine authentication status.
Debug Messages
Table 9 Security Debug Messages
Message ID Message and Description
121031 \[[file:%s]:[line:%d]] [message:%s]
Description: aaa module’s debug message
121037 [func:%s]: sta_add_rad_class_attr failed.
Description: This shows an internal debug message
121038 Save Class in station for MAC [mac:%s].
Description: This shows an internal debug message
121039 [func:%s]: sta_update_last_authserver failed.
Description: This shows an internal debug message
121040 [func:%s]: last_authserver [authserver:%s].
Description: This shows an internal debug message
121041 User [user:%s] MAC=[mac:%s] not found.
Description: This shows an internal debug message
121042 [func:%s]: Server FQDN is '[server:%s]', IP Address is '[ipaddr:%s]'.
Description: This shows an internal debug message
121043 [func:%s]: Server FQDN '[fqdn:%s]' not found in hash.
Description: This shows an internal debug message
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Security Messages | 25
Page 26

Table 9 Security Debug Messages
Message ID Message and Description
121044 Radius authenticate user ([user:%s]) PAP query using server [server:%s].
Description: This shows an internal debug message
121045 [func:%s]: sta_update_last_srv_grp failed.
Description: This shows an internal debug message
121046 [func:%s]: last_srv_grp [last_srv_grp:%s].
Description: This shows an internal debug message
121050 [msg:%s]
Description: This is an internal RADIUS debug log
132007 Clearing Station state on AP [bssid:%m]
Description: Station is forced to be cleared from the AP’s stations table
132022 Station [mac:%m] [bssid:%m] sent 802.1x packet before association/l2 miss - dropping
packet
Description: Received an EAP packet from the station before receiving an association/
l2 miss message.
Cause: This log-message is generated when we detect a race-condition between STM,
SOS and AUTH. AUTH is receiving association-request messages from STM before it
received the L2-Miss message from SOS.
Recommended Action: If symptoms persist, then AUTH is either not receiving or not
processing L2-Miss messages from SOS. Restart the AUTH process by executing
“”process restart auth”” or reload the controller.
132047 Disabling Stateful 802.1x - removing all Stateful Config entries
Description: Removing all the stateful dot1x config entries that was created
132213 Failed to perform revocation check for client cert
Description: Auth failed to contact certmgr to perform revocation check for client cert
132214 Client certificate for mac [mac:%m] and bssid [bssid:%m] has been revoked
Description: Client certificate has been revoked
132215 Client certificate for mac [mac:%m] and bssid [bssid:%m] has NOT been revoked
Description: Client certificate has not been revoked
132216 Revocation check request for mac [mac:%m] and bssid [bssid:%m] sent to certmgr
Description: Auth sent a revocation check request to certmgr process
132220 Debug Log
Description: Debug Log
132223 EAP-ID mismatched [id1:%d]:[id2:%d] for station [mac:%m] [bssid:%m]
Description: Mismatch between the eapid station sent and what was expected.
132227 EAPOL-Logoff ignored for station [mac:%m] [bssid:%m]
Description: EAPOL-Logff ignored for the specific station.
26 | Security Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 27

Chapter 3
System Messages
Emergency Messages
Table 10 System Emergency Messages
Message ID Message and Description
330203 MESHD process initialization failed.
Cause: MESHD process initialization failed possibly because the mesh-node is not
correctly provisioned.
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
330204 MESHD process exiting. No MESH role was specified.
Cause: No MESH role was specified.
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
330205 MESHD process exiting. No MESH cluster profile was specified.
Cause: No MESH cluster profile was specified.
Recommended Action: Re-provision the AP. Contact Dell technical support if this
problem persists.
341008 [msg:%s]
Description: No description available.
Alert Messages
Table 11 System Alert Messages
Message ID Message and Description
341007 [msg:%s]
Description: No description available.
341091 [func:%s]: [line:%d]: out of memory.
Description: The AP is upgrading image from awc.
341276 Could not program ACL = [acl:%d] to datapath.
Description: Datapath ACL programming failed.
341279 Description: Managed mode: Could not download the configuration from the server.
Recommended Action: Could not download the configuration from the server.
341283 Managed mode: Could not download the configuration from server, retrying - [num:%d].
Description: Could not download the configuration from the server, retry in progress.
341284 Managed mode: Config download from server timed out.
Description: Config download from server timed out.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 27
Page 28
Table 11 System Alert Messages (Continued)
Message ID Message and Description
341285 Managed mode: Config file download retry count over.
Description: Config file download retry count over.
341286 Could not download the required file, reason [reason:%s].
Description: Could not download the required file
341287 Managed mode: Could not apply the config fetched from server [reason:%s], error code
[error_code:%d].
Description: Could not apply the configuration fetched from server.
Critical Messages
Table 12 Critical System Messages
Message ID Message and Description
341006 [msg:%s]
Description: No description available
341275 VPN tunnel switch to [tunnel:%s], reason:[reason:%s].
Description: VPN tunnel switch.
Error Messages
Table 13 Error System Messages
Message ID Message and Description
304000 Unexpected stm (Station management) runtime error at [func:%s], [line:%d].
Description: Unexpected condition occurred in the station manager (stm).
Recommended Action: Contact your support provider
304001 Unexpected stm (Station management) runtime error at [func:%s], [line:%d], [data:%s].
Description: Unexpected condition occurred in the station manager (stm).
Recommended Action: Contact your support provider
304035 PAPI_Send failed: [error:%d]; from [sport:%d] to [toaddr:%p]:[toport:%d] len [len:%d]
304039 VPOOL: Maximum capcity ([count:%d]) reached for Vlan Pool hash table
type [type:%d].
Description: Inter-process communication message failed to reach the target.
Recommended Action: Contact your support provider
304040 VPOOL: Vlan Pool hash table ([vap:%s]) collision at [entry:%d]. Not handled!
Recommended Action: Contact your support provider
304041 VPOOL: Error allocating VLAN from Virtual AP pool [name:%s]
Recommended Action: Contact your support provider
28 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 29

Table 13 Error System Messages (Continued)
Message ID Message and Description
304045 Connection to User DB failed
Description: The application was not able to connect to the user database.
304046 Creation of Client Blacklist tables in User DB failed
Description: The application was not able to create the Client Blacklist tables in the
user database.
304047 SQL Command [command:%s] failed on User DB. Reason: [reason:%s]
Description: This log indicates that an SQL command failed when it was executed on
the user database.
304049 Update to client blacklist database table failed.
Description: This log indicates that an update to the client blacklist database table
failed.
304054 Client blacklist is full and caused an entry to not be added. Limit: [limit: %d].
Description: This log indicates that the client blacklist table is full and an entry that
would have been added could not be added.
304055 Contact Aruba tech-support.“Unexpected stm (Station management) runtime error at
[func:%s], [line:%d], [data:%s]
Description: Unexpected condition occurred in the station manager (stm)
304058 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]; opcode [opcode:%d] action
304060 [func:%s], [line:%d]: Sibyte reply truncated; opcode [opcode:%d] action [action:%d]
304062 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]
304063 PAPI_Send failed, [func:%s], [line:%d]: [error:%s]
304064 PAPI_Send failed, [func:%s], [line:%d]: [error:%s], dstport [dst:%d], msgcode [code:%d]
304065 PAPI_Send failed, [func:%s], [line:%d]: [error:%s], dstport [dst:%d]
304067 PAPI_Send failed: [func:%s], [line:%d]: [error:%s]; from [sport:%d] to
311013 Image upgrade failed; details follow.
[action:%d]
Description: Aruba inter-process communication message failed to reach datapath.
Description: Datapath reply to PAPI message sent is truncated.
Description: Aruba inter-process communication message failed to reach auth
manager.
Description: Aruba inter-process communication message failed to reach air monitor.
Description: Aruba inter-process communication message failed to reach destination.
Description: Aruba inter-process communication message failed to reach destination.
[toaddr:%p]:[toport:%d] len [len:%d] type [type:%d]
Description: Inter-process communication message failed to reach the target.
Description: The AP was unable to upgrade its image. Message 311014 will
follow with details about the error.
311014 [line:%s]
Description: This message presents detailed information about an AP image
upgrade error.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 29
Page 30

Table 13 Error System Messages (Continued)
Message ID Message and Description
311016 Unable to create domain list file
Description: Internal error occured while accessing domain lists file.
311017 Error occured while resolving IP’s for domains
Description: Internal error occured while resolving the domain names
Recommended Action: Contact your support provider
311018 Unable to read domain results file
Description: Internal error occured while processing the domain results file
Recommended Action: Contact your support provider
311019 Unable to generate certificate signing request (CSR). AP will reboot.
Description: The access point was unable to generate a certificate signing
request (CSR).
Recommended Action: Contact your support provider
311020 An internal system error has occurred at file [file:%s] function [function:%s] line [line:%d]
error [error:%s].
Description: This log indicates that we encountered an internal system error.
Recommended Action: Contact your support provider
311021 An internal system error has occurred at file [file:%s] function [function:%s] line [line:%d]
311022 Error allocating memory at file [file:%s] function [function:%s] line [line:%d]. Allocating
311023 Error allocating memory at file [file:%s] function [function:%s] line [line:%d]. Allocating
326054 AM: read error - [recvlen:%d]
326055 AM: Received frame of size 0 from driver: Is-RX=[rx:%d] BufLen= [buf_len:%d]
326063 AM: INET not configured in this system
error [error:%s].
Description: This log indicates that we encountered an internal system error.
Recommended Action: Contact your support provider
[bytes:%d] bytes.
Description: System failed to allocate memory at the specified location
Recommended Action: Use the show memory and the show process commands to
monitor memory usage. If the problem persist, contact your support provider
[bytes:%d] bytes.
Description: System failed to allocate memory at the specified location
Recommended Action: Use the show memory and the show process commands to
monitor memory usage. If the problem persist, contact your support provider
Description: No description available.
Channel=[ch:%d]
Description: No description available.
Description: No description available.
326068 AM: Cannot retrieve ARP info
Description: No description available.
30 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 31

Table 13 Error System Messages (Continued)
Message ID Message and Description
326071 AM: System encountered an internal communication error. Error occurred when
326143 AM: Received incorrect number of Rate Threshold Profile instances: [np:%d]
326183 AM: Can’t get STA_INFO for [ifname:%s]:[rval:%d]
326267 An internal system error has occurred at file [file:%s] function [function:%s] line
326268 An internal system error has occurred at file [file:%s] function [function:%s] line [line:%d]
326269 AM: System encountered an internal communication error. Error occurred when
message was sent from source application [src:%s] destination application [dst:%s] at
file [file:%s] function [func:%s] line [line:%d] error [error:%s].
Description: This log indicates that application processes in the system encountered
an error when sending messages to each other.
Cause: This could be a transient condition and the problem may go away.
Recommended Action: If the problem persists, contact your support provider
Description: No description available.
Description: No description available.
[line:%d].
Description: This log indicates that we encountered an internal system error
Recommended Action: Contact your support provider
error [error:%s].
Description: This log indicates that we encountered an internal system error
Recommended Action: Contact your support provider
message is being sent from source application [src:%s] destination application [dst:%s]
at file [file:%s] function [func:%s] line [line:%d].“
Description: This log indicates that the application processes, in the system,
encountered an error while sending messages to each other. This may be a transient
condition and the problem might resolve itself.
Recommended Action: Contact your support provider
326270 AM: Error allocating memory at file [file:%s] function [function:%s] line [line:%d].
Allocating [bytes:%d] bytes.
Description: System failed to allocate memory at the specified location
Recommended Action: Execute the show memory and show process commands to
view and monitor memory usage. If the problem persists, contact your support provider.
326281 AM:SM: An internal system error has occurred at file [file:%s] function [function:%s] line
330201 System encountered an internal communication error. Error occured when message is
330208 [msg:%s]
[line:%d] error [error:%s].
Description: This log indicates that we encountered an internal system error
Recommended Action: Contact your support provider
being sent from source application [src:%s] destination application [dst:%s] at file
[file:%s] function [func:%s] line [line:%d] error [error:%s].
Description: This log indicates that application processes in the system encountered
an error sending messages to each other.
Cause: This could be a transient condition and the problem might go away.
Recommended Action: If he problem persists, contact your support provider
Description: This log indicates a general error other than internal/communications
errors. e.g. might point to a configuration problem.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 31
Page 32
Table 13 Error System Messages (Continued)
Message ID Message and Description
330209 An internal system error has occurred at file [file:%s] function [function:%s] line
330210 An internal system error has occurred at file [file:%s] function [function:%s] line [line:%d]
330211 Error allocating memory at file [file:%s] function [function:%s] line [line:%d]. Allocating
330212 System encountered an internal communication error. Error occurred when message is
341005 [msg:%s]
[line:%d].
Description: This log indicates that we encountered an internal system error.
Recommended Action: Contact your support provider
error [error:%s].
Description: This log indicates that we encountered an internal system error.
Recommended Action: Contact your support provider
[bytes:%d] bytes.
Description: System failed to allocate memory at the specified location
Recommended Action: Use the show memory and show process command to
monitor memory usage. If the problem persist, contact your support provider
being sent from source application [src:%s] destination application [dst:%s] at file
[file:%s] function [func:%s] line [line:%d].
Description: This log indicates that application processes in the system encountered
an error sending messages to each other. This could be a transient condition and the
problem might go away.
Recommended Action: IIf the problem persist, contact your support provider
Description: No description available.
341023 Error setting global LED mode at [node:%s].
Description: The AP is configuring LED mode.
341026 Fail to save configuration, error-[error:%s].
Description: The AP is saving configuration .
341027 Fail to initial configuration, error-[error:%s].
Description: The AP is initialing configuration .
341028 Image version format invalid: [version:%s].
Description: The AP is upgrading image.
341029 Compare image version fail, old version-[old_version:%s], current version-
[new_version:%s].
Description: The AP is upgrading image.
341030 Upgrade version fail, from version [old_version:%s] to [new_version:%s].
Description: The AP is upgrading image.
341031 Retrieve image fail, retry [time:%d].
Description: The AP is loading configuration.
341033 Read configuration fail, error-[error:%s].
Description: The AP is loading configuration.
341034 Save configuration fail, error-[error:%s].
Description: The AP is saving configuration.
32 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 33

Table 13 Error System Messages (Continued)
Message ID Message and Description
341036 [func:%s]: invalid image name.
Description: The AP is upgrading image.
341037 Open image-[image:%s] fail.
Description: The AP is upgrading image.
341038 Read image-[image:%s] header fail.
Description: The AP is upgrading image.
341039 AP check image-[image:%s] version fail.
Description: The AP is upgrading image.
341040 AP verify image-[image:%s] fail.
Description: The AP is upgrading image.
341041 AP basic verify image-[image:%s] fail.
Description: The AP is upgrading image.
341042 AP check image-[image:%s] version for mesh fail.
Description: The AP is upgrading image.
341044 AP can't open MTD device-[device:%s].
Description: The AP is setuping image.
341047 AP regulatory domains don't match Master-[id1:%d], slave-[id2:%d].
Description: The AP is upgrading image.
341048 Controller doesn't allow new AP-[mac:%s], reboot it.
Description: The AP is upgrading image.
341049 [func:%s]: AP malloc sync list fail.
Description: The AP is upgrading image.
341050 AP setup image fail, ret-[ret:%d].
Description: The AP is setuping image.
341051 AP verdor name not match, Master-[name1:%s], Slave-[name2:%s].
Description: The AP is setuping image.
341052 [func:%s], [line:%d]: AP class not match, Master-[class:%d], Slave-[class2:%d].
Description: The AP is setuping image.
341054 [func:%s]: can't find right iurl for AP-[mac:%s], [ip:%s], class [class:%s].
Description: The AP is upgrading image.
341055 [func:%s]: find right iurl for AP-[mac:%s], url [url:%s].
Description: The AP is upgrading image.
341056 AP can't find image file-[file:%s].
Description: The AP is upgrading image.
341058 AP download image state-[state:%d] error.
Description: The AP is upgrading image.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 33
Page 34

Table 13 Error System Messages (Continued)
Message ID Message and Description
341063 Could not open socket for [dip:%x]/[mask:%x].
Description: The AP is setting kernal route.
341064 Could not add route for [dip:%x]/[mask:%x].
Description: The AP is setting kernal route.
341067 Open socket for corp fail [dip:%x]/[sip:%x]/[devname:%s].
Description: The AP is creating tunnel.
341068 Get ifindex for corp fail [dip:%x]/[sip:%x]/[devname:%s].
Description: The AP is creating tunnel.
341070 No space for corp tunnel [dip:%x]/[sip:%x]/[devname:%s].
Description: The AP is creating tunnel.
341072 AP could not find post auth role [name:%s].
Description: The AP is creating SSID.
341074 AP can't find essid-[name:%s].
Description: The AP is creating SSID.
341081 No space for acl-[name:%s].
Description: The AP is configuring ACL.
341082 ACL index-[index:%d] is invalid.
Description: The AP is configuring ACL.
341083 ACL index-[index:%d] is inuse.
Description: The AP is configuring ACL.
341085 [func:%s]: [line:%d]: payload empty.
Description: The AP is upgrading image.
341089 [func:%s]: [line:%d]: AWC login error.
Description: The AP is upgrading image from awc.
341090 [func:%s]: [line:%d]: could not save file.
Description: The AP is upgrading image from awc.
341092 [func:%s]: [line:%d]: Parse error in payload.
Description: The AP is upgrading image from awc.
341093 [func:%s]: [line:%d]: required class [class:%u] not found in payload.
Description: The AP is upgrading image.
341094 [func:%s]: no class in url.
Description: The AP is upgrading image.
341095 [func:%s]: url is NULL!.
Description: The AP is upgrading image.
341107 [func:%s]: [line:%d] Cannot get essid from datapath for client-[ip:%s] port-[port:%s].
Description: Handle papi message.
34 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 35

Table 13 Error System Messages (Continued)
Message ID Message and Description
341108 [func:%s]: [line:%d] invalid session client-[ip:%s] sid-[sid:%s].
341109 [func:%s]: save certificate fail-[error:%s].
Description: AP is setting cert.
341110 [func:%s]: delete certificate fail-[error:%s].
Description: AP is setting cert.
341111 [func:%s]: save cert key fail-[error:%s].
Description: AP is setting cert.
341113 [func:%s]: get gre host fail by [server:%s].
Description: AP is setting gre name.
341114 [func:%s]: set gre name-[name:%s] fail.
Description: AP is setting gre name.
341116 [func:%s]: clr gre name-[name:%s] fail.
Description: AP is setting gre name.
341118 [func:%s]: create session fail for ip-[ipaddr:%s].
Description: AP is creating session.
341119 [func:%s]: SID not match for IP-[ip:%s] sid-[sid:%s].
Description: Handle papi message.
341122 [func:%s]: Malloc fail [num:%d].
Description: Station sync.
341123 [func:%s]: [line:%d] parse token ret-[ret:%d].
Description: Station sync.
341130 [func:%s], [line:%d]: ioctl fail ipaddr-[ip:%d] mac-[mac:%s] add-[add:%d].
Description: AP is configuring arp entry.
341133 Find AP-[ip:%s] fail.
Description: AP is receiving stats sync.
341141 [func:%s], [line:%d]: bid is [bid:%d], max bid is [max_bid:%d].
Description: Invalid branch ID.
341143 [func:%s],[line:%d]: could not get class-[class:%s] in payload.
Description: AP receive upgrade message from airwave to update image.
341144 [func:%s],[line:%d]: could not find file-[file:%s].
Description: AP is executing "show support-commands".
341163 Fail to add ids radio [mac:%m].
Description: Fail to add ids radio.
341210 [func:%s]: ASAP to CLI socket open failed [errno:%d].
Description: ASAP to CLI socket open failed.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 35
Page 36

Table 13 Error System Messages (Continued)
Message ID Message and Description
341211 [func:%s]: ASAP to CLI socket ioctl failed [fd:%d] [errno:%d].
Description: ASAP to CLI socket ioctl failed.
341212 [func:%s]: ASAP to CLI socket bind failed [fd:%d] [errno:%d].
Description: ASAP to CLI socket bind failed.
341213 [func:%s]: ASAP to CLI socket recv failed [fd:%d] [errno:%d].
Description: ASAP to CLI socket recv failed.
341214 [func:%s]: L2 Roam failed at home network [mac:%s] [ssid:%s].
Description: L2 Roam failed at home network.
341224 [func: %s]: [nodename:%s], errno [errno:%s] info [info:%s].
Description: sysctl fw from cli error.
341230 Controller denys new AP when upgrading-[mac:%s].
Description: Controller denys new AP for upgrading image.
341232 Fail to retrieve ap config from flash after [retry:%d] retries.
Description: fail to retrieve ap config from flash
341235 Add [mac:%s] to subscription ap list failed.
Description: Add ap to subscription ap list failed.
341270 Set priority failed, failed to find type [type:%d], sub port [port:%d], priority [priority:%d].
Description: Set priority failed.
341271 Ethernet uplink [uplink_name:%s] link down.
Description: Ethernet uplink link down.
341272 Ethernet uplink [uplink_name:%s] link up.
Description: Ethernet uplink link up.
341289 Sending full configuration to slave ip = [ip:%s], ap config dirty = [dirty:%d] error cnt =
[cnt:%d].
Description: Sending full configuration from Master to slave APs.
Warning Messages
Table 14 Warning System Messages
Message ID Message and Description
304002 AP [name:%s]: No response from authmgr for BSSID [bssid:%m]
Description: Unexpected condition occurred in the station manager (stm).
Recommended Action: Contact your support provider
304004 “License Check failed, dropping request
Description: No description available.
304005 Ortronics AP support not licensed; dropping request
Description: No description available.
36 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 37

Table 14 Warning System Messages (Continued)
Message ID Message and Description
304009 enet_move_tunnel: Tunnel [id:%d] not found
Description: No description available.
304011 stop_signal - Why was I called ... exiting
Description: No description available.
304013 tunnel_timeout: Tunnel 0x[tunnel_id:%x] not found
Description: No description available.
304014 received frame of unknown type [type:%x] (subtype [stype:%x])
Description: No description available.
304015 handle_tunnel_info_request: Tunnel [tunnel_id:%d] not found
Description: No description available.
304016 IP [tunnel_ip:%p] MAC [mac:%m] ARP Query failed
Description: No description available.
304017 [func:%s]:[line:%d] Too many TCLAS. dropping...
Description: No description available.
304018 [func:%s]:[line:%d] Unknown EID - [eid:%d]
Description: No description available.
304019 Unknown Category in Action Frames: [category:%d]-[action:%d]... dropping
Description: No description available.
304020 Unknown WMM Action [action:%d] in [__func__:%s] dropping
Description: No description available.
304022 [func:%s]: dropped for license key enforcement
Description: No description available.
304023 [func:%s]: Response from Server for [mux_client_mac:%s]: Client has no state
Description: No description available.
304024 [func:%s]: Dropping Heartbeat from unknown mux [mac:%m]-[dest:%d]
Description: No description available.
304025 [func:%s]: Invalid S-[slot:%d] P-[port:%d]
Description: No description available.
304026 [func:%s]: New Id [new_id:%d] different than old [id:%d]
Description: No description available.
304027 VoIP Start/Stop received ... VoIP hash table not created yet
Description: No description available.
304028 [func:%s]: [ip:%p] message out of order
Description: No description available.
304029 [func:%s]: too many voip clients
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 37
Page 38

Table 14 Warning System Messages (Continued)
Message ID Message and Description
304033 Mesh AP support not licensed; dropping request
Description: No description available.
304044 Waiting for dbstart...
Description: The application is waiting for the database to be ready for access.
304048 User DB query issue in: [call: %s]. SQL command: [cmd: %s].
Description: This log indicates that there was an issue when a command was executed
on the user database.
304050 Client blacklist purged by Administrator.
Description: This log indicates that the client blacklist was purged by the administrator.
311000 Attempt to change LMS of remote AP ignored
Description: No description available.
311002 Rebooting: [reason:%s]
Description: No description available.
311003 AP flash image is invalid
Description: No description available.
311004 Missed [num:%d] heartbeats; rebootstrapping
Description: No description available.
311006 Broken tunnel to switch detected on radio [radio:%d] VAP [vap:%d];
rebootstrapping
Description: No description available.
311007 Broken tunnel to switch detected on wired AP interface [ifnum:%d];
311010 AP could not boot from flash -- bad checksum
311011 No Mesh Radio profile. Mesh role[role:%s] Band[band:%s] Radio[radio:%d].
311012 Enet [enetnum:%d]: Unsupported speed [rspeed:%s]; using [using:%s]
326004 AM: Error Adding STA [mac_addr:%s] to AP [bssid_str:%s] SSID [ssid:%s]
326070 AM: message too large:[len:%d]. Dropping!
rebootstrapping
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
326073 AM: [line:%d]: response too long [bl:%d]
Description: No description available.
326083 AM: Setting the communication path of state info to: Master switch
Description: No description available.
38 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 39

Table 14 Warning System Messages (Continued)
Message ID Message and Description
326084 AM: Setting the communication path of state and stats info to: Local switch
Description: No description available.
326085 AM: Setting collection of statistics to : [mode:%s]
Description: No description available.
326096 AM: message too long [bl:%d]
Description: No description available.
326157 AM: Too many Wi-Fi(s) interfaces = [wifi_index:%d]
Description: No description available.
326158 “AM: MAX_SIZE = [DET_STATS_READ:%d], actual size = [det_proc_stats_size:%d]
Description: No description available.
326159 AM: Name of WIFI_INT is invalid([proc_interface:%s])
Description: No description available.
326200 AM: Unable to find WIF for [bssid:%s]
Description: No description available.
326201 AM: Calibration already in progress for [bssid:%s]
Description: No description available.
326202 AM: Invalid Channel [channel:%d] for [bssid:%s]
Description: No description available.
326229 AM: Signature name too big: [name:%s]
Description: No description available.
326279 AM: Setting Learn Wired MACs at Controller to : [mode:%s]
Description: This log indicates that the configuration has changed for the feature Learn
Wired MACs at Controller.
341004 [msg:%s]
Description: No description available.
341011 AP image version mismatch [vcmodel:%s] [version:%s] [url:%s] [apmodel:%s]
Description: The image version on the AP is not the same as that on the virtual
controller. The AP will download a new image and reboot.
341012 AP downloading flash image [url:%s].
Description: The AP is downloading a new image to store in flash.
341013 [role:%s] AP upgrading flash image [cmd:%s].
Description: The AP is writing a new image in flash. When this process completes, the
AP will reboot.
341032 Read configuration successfully, retry [time:%d], image size [size:%d].
Description: The AP is loading configuration.
341098 [func:%s]: Convert AP url-[url:%s], mode-[mode:%d], master-[ip:%s].
Description: The AP is converting ap.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 39
Page 40

Table 14 Warning System Messages (Continued)
Message ID Message and Description
341102 Incorrect format for message
341103 Unknown version from [ipaddr:%s] in message type-[type:%d].
341104 Invalid version for message type-[type:%d] from [ipaddr:%s] (local [ver:%s] vs. master
341149 Sending upgrade url [url:%s] to [ap_ip:%s], mode [mode:%d], ip [ip:%s].
341159 Got AMP from dhcp ([org:%s]-[ip:%s]-[key:%s]) vs. mine ([org1:%s]-[ip1:%s]-
341164 send ap not allowed to [ip:%s].
341165 send image match to [ip:%s].
type[type:%d]:[msg_len:%d]:[recv_len:%d]:[bytes_read:%d]:[from_ip:%s]:[from_port:%
d].
Description: Handle papi message.
Description: Handle papi message.
[m_ver:%s]).
Description: Handle papi message.
Description: Master send upgrade url to slave.
[key1:%s]).
Description: Learning AMP info from DHCP.
Description: Send not allowed msg to an AP.
Description: Send image match msg to an AP.
341166 Get interface [ifname:%s] ip: [ip:%s]/[mask:%s].
Description: Print interface ip.
341167 Uplink [type:%s], state [old:%s]->[new:%s].
Description: Uplink state changed.
341169 Add uplink [type:%s] [pri:%d].
Description: Add new uplink.
341170 Del uplink [type:%s].
Description: Del uplink.
341171 Active 3g uplink, enable [yes: %d].
Description: Active 3g uplink.
341172 Find enet0 name [name: %s].
Description: Find enet0 uplink name.
341173 Current uplink set to [type:%s], state [state:%s].
Description: Print current uplink.
341174 No current uplink, pick the highest one - [type:%s].
Description: Pick the highest uplink.
341175 Connecting with current uplink - [type:%s].
Description: Connect with current uplink.
341176 Probing too long with current uplink - [type:%s].
Description: Probe too long.
40 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 41

Table 14 Warning System Messages (Continued)
Message ID Message and Description
341177 Try next uplink because current uplink is down - [type:%s].
Description: Try next uplink.
341181 Setup ip for uplink - [type:%s].
Description: Setup ip for uplink interface.
341182 Setup vpn for rap conversion - [ip:%s].
Description: Setup vpn for rap conversion.
341183 Downloading rap image via vpn - url [url:%s].
Description: Downloading rap image via vpn.
341184 Downloading rap image via vpn timeout - count [count:%d].
Description: Downloading rap image via vpn timeout.
341185 Retrieving ip address from [inf:%s], ip [ip:%s], mask [mask: %s].
Description: Retrieving ip address from an interface.
341194 Loading configuration, func [func:%s], line [line:%d].
Description: loading AP configuration.
341199 [func:%s]: send config to slave [ip:%s].
Description: Send ap config to slave.
341205 Applying enet config : port [name:%s].
Description: Apply enet config.
341206 Command syntax error: [cmd:%s].
Description: Command syntax error.
341207 AP support up to [num: %d] SSID.
Description: Max ssid support
341208 Activate SSID [SSID1: %s], remove SSID [SSID2:%s].
Description: Deactive SSID
341227 uplink detection: total_icmp_sent [sent:%d], total_icmp_lost [lost:%d],
continuous_icmp_lost [clost:%d].
Description: Uplink detetction statistics.
341228 uplink switchover internet since link threshold is reached [thld:%d].
Description: Uplink switchover internet.
341229 uplink switchover vpn since ipsec goes down for a while, cnt [cnt:%d] vs. threshold
[thld:%d].
Description: Uplink switchover vpn.
341233 Saveing AP config, reason [str:%s].
Description: Save ap config
341245 Not allowed ap [mac:%s] for invalid subscription status [status:%s] in
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 41
function[function:%s] [line:%d] .
Description: Not allowed ap for invalid subscription status.
Page 42

Table 14 Warning System Messages (Continued)
Message ID Message and Description
341250 VC record delta configuration, malloc error. len [len:%d] port [port:%d] flags [flags:%d]
341252 VC send delta configurations to ap error. ap [ap_ip:%s] ap_cfg_id [acid:%d]
341258 AP receive delta configuration id [acid:%d] current_cfg_id [cid:%d] from msg [msg:%s]
341260 VC rejects the [number:%d]th ap because IAP9x in the swarm.
341261 VC rejects the IAP9x becuase we have [number:%d] users in local DB.
341262 Switch to higher uplink [uplink_name:%s] by preemption.
341263 Enable uplink [uplink_name:%s].
341264 Disable uplink [uplink_name:%s].
seq [seq:%d] case [case:%s]
Description: VC record delta configuration, malloc error.
current_cfg_id [cid:%d] top_cfg_id [tid:%d] case [case:%s].
Description: VC send delta configuration to ap error.
is not correct.
Description: AP receive delta configuration id from msg is not correct.
Description: VC rejects slave for ap number.
Description: VC rejects slave for internal DB.
Description: Switch to highest uplink.
Description: Enable an uplink.
Description: Disable an uplink.
341265 Enable ethernet uplink [uplink_name:%s].
Description: Enable ethernet uplink.
341266 Uplink preempt to [uplink_name:%s].
Description: Uplink preempt.
341267 Add wired port [port_num:%d] to uplink table.
Description: Wired port add to uplink table.
341268 Del wired port [port_num:%d] from uplink table.
Description: Wired port delete from uplink table.
341269 Uplink [uplink_name:%s] is exist update it.
Description: Update uplink table because uplink is already exist.
341273 Config file length is [len:%d], allowed length is [len2:%d].
Description: Check configuration file before saving it.
341274 Update election ip from [inf:%s], election ip [elect_ip:%s]/[elect_mask:%s].
Description: Update election IP and mask.
42 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 43

Notice Messages
Table 15 Notice System Messages
Message ID Message and Description
304006 IGMP Drop Tx - [s_addr:%p]
Description: No description available.
304007 IGMP Join Tx - [s_addr:%p]
Description: No description available.
304031 PAPI message to [ip:%p] port [port:%d] timed out
Description: No description available.
304032 902il Compatibility mode [enadis:%s]
Description: NEC 902il compatibility mode was enabled or disabled
304056 Stm (Station management) notice at [func:%s], [line:%d], [data:%s]
Description: This log indicates the route point is an IP tunnel
311015 Wipe out AP flash.
Description: No description available.
311024 Attempting to transfer panic dump to server [server:%s]
Description: Transferring panic information file to server
Recommended Action: Contact your support provider
326009 AM: Wi-Fi Interface Reinit called for [bssid:%s]
Description: No description available.
326010 AM: calling remove_ap [bssid:%s].
Description: No description available.
326011 AM: calling remove_pot_sta [mac_addr:%s].
Description: No description available.
326012 AM: calling remove_pot_ap [bssid:%s]
Description: No description available.
326013 AM: SAPCP-Parse called
Description: No description available.
326014 AM: SAPCP-Parse dropped.
Description: No description available.
326067 AM: IP [newbury_ip:%s] Port [newbury_port:%d] Socket [newbury_sock:%d].
Description: No description available.
326077 AM: [function:%s]: length mismatch expected [bytes_read:%d], got [msg_len:%d]
Description: No description available.
326091 AM: Radio Stats: APs=[num_ap:%d] STAs=[num_assoc_sta:%d] Mon-
APs=[num_mon_ap:%d] Mon-STAs=[num_mon_sta:%d].
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 43
Page 44

Table 15 Notice System Messages (Continued)
Message ID Message and Description
326101 AM: length mismatch for message [msg_type:%d], expected [bytes_read:%d], got
326102 AM: unable to find AP [bssid:%s].
326106 AM: unable to find STA [bssid:%s] PHY [phy_type:%d].
326107 AM: RSTA Type set to [rap_type:%d] for STA [bssid:%s]
326148 AM: set_mode called for [bssid:%s] type [probe_type:%d] active [active:%d].
326205 AM: Adding new Gateway MAC: [mac:%s].
326215 AM: Adding new tagged Gateway MAC: VLAN:[vlanid:%d] MAC:[mac:%s] IP: [ip:%s].
326206 AM: Adding new Router MAC: [mac:%s].
[msg_len:%d].
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
326218 AM: [mac:%s]
Description: No description available.
326219 AM: Setting Gateway MAC to: [mac:%s]
Description: No description available.
326220 AM: Sending ARP Request for Gateway IP: [ip:%s]
Description: No description available.
326266 AM: MAC OUI: Range Entries = [ids_mac_oui_range_size:%d] Hash Entries =
326271 AM: New Node Detected Node = [addr:%s] SSID = [ssid:%s] BSSID [bssid_str:%s]
326272 AM: New AP Detected Channel = [channel:%d] SSID = [ssid:%s] BSSID = [bssid:%s]
326273 AM: SSID Change #2: BSS [bssid:%s] Old SSID [from_ssid:%s] New SSID [ssid:%s]
326274 AM: Inactive Node Detected = [mac_addr:%s] SSID = [ssid:%s] BSSID [bssid_str:%s].
[IdsMacOuiHash:%d]
Description: No description available.
Description: No description available.
Description: No description available.
Channel [channel:%d].
Description: No description available.
Description: No description available.
326275 AM: Inactive IBSS Detected SSID = [ssid:%s] BSSID = [bssid_str:%s].
Description: No description available.
44 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 45

Table 15 Notice System Messages (Continued)
Message ID Message and Description
326276 AM: Inactive AP Detected SSID = [ssid:%s] BSSID = [bssid_str:%s].
Description: No description available.
326277 AM: Setting RAP Type for AP [bssid_str:%s] to: [rap_str:%s].
Description: No description available.
326278 AM: STA [mac_addr:%s] Authenticated with AP [bssid_str:%s].
Description: No description available.
341003 [msg:%s
Description: No description available.
341043 AP check image-[image:%s] successfully.
Description: The AP is upgrading image.
341045 Receive image upgrade successful for [ipaddr:%s].
Description: The AP is upgrading image.
341046 Receive download image successful for [ipaddr:%s].
Description: The AP is upgrading image.
341053 AP try version [version:%s] [number:%d] times.
Description: The AP is setuping image.
341057 [func:%s]: upgrade image file [file:%s], url [url:%s].
Description: The AP is upgrading image.
341097 [func:%s]: mac-[mac:%s], version-[version:%s], ccode_idx-[id:%d].
Description: The AP is upgrading image.
341147 Upimage: [msg:%s]
Description: Upimage related messages.
341148 Checking slave [ap_ip:%s] [state:%s]
Description: Master check image upgrade for a slave.
341150 Local AP-[ipaddr:%s] start upgrade image.
Description: The AP starts to upgrade image.
341151 Local AP-[ipaddr:%s] start download image.
Description: The AP starts to download image.
341152 Receive image err [state:%s] for [ap_ip:%s].
Description: Set AP image err state.
341153 Sending upgrade write flash to [ap_ip:%s].
Description: Master send upgrade write flash to slave.
341154 Sending upgrade success to [ap_ip:%s].
Description: Send upgrade success to Master.
341155 Sending download success to [ap_ip:%s].
Description: Send download success to Master.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 45
Page 46

Table 15 Notice System Messages (Continued)
Message ID Message and Description
341156 Sending image err [state:%s] to [ap_ip:%s].
Description: Send image err state to Master.
341157 AP reaches count [count:%d]-[msg:%s].
Description: AP image upgrade timeout.
341158 [func:%s],[line:%d]: Setup image with code [ret:%d].
Description: AP image upgrade timeout.
341201 AP [name:%s] reports a spectrum alert: non-wifi device(ID: [id:%d],type: [type:%s]).
Description: Non-wifi device is detected.
341202 AP [name:%s] removes a spectrum alert: non-wifi device(ID: [id:%d],type: [type:%s]).
Description: Non-wifi device is removed.
341288 Managed mode: Insufficient configuration to start this mode.
Description: Because of insufficient configuration, the managed mode did not start.
341290 [msg:%s]
Description: Per ap settings are applied.
Information Messages
Table 16 Information System Messages
Message ID Message and Description
304037 VPOOL: Initialized VLAN pool for virtual AP ‘[name:%s]’ (size=[size:%d], VLAN-
304038 VPOOL: VLAN Pool already initialized for VLAN-MAP [addr:%x], refcnt [cnt:%d]”
304042 VPOOL: Adding VLAN [vid:%d] to hash table
304043 VPOOL: Free VLAN Pool for VLAN-MAP [addr:%x], refcnt [cnt:%d]
304057 [msg:%s] AP Heartbeat Tunnel Timeout indication from Datapath
304068 [func:%s], [line:%d]: STM restarts and notifies AUTH to clean up users STM restarts and
MAP=[addr:%x], Refcnt=[cnt:%d])
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
notifies AUTH to clean up users.
Description: No description available.
311001 LMS changed from [old_ip:%p] to [new_ip:%p]
Description: No description available.
326000 AM initialized.
Description: Air Monitor is starting
46 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 47

Table 16 Information System Messages (Continued)
Message ID Message and Description
326075 AM: Dropping PROBE_POLL_REQUEST from Switch IP [wms_ip:%s]
Description: No description available.
326088 AM: Marking Switch [ip:%s] as Down
Description: No description available.
326097 AM [bssid:%s]: Received a PROBE_POLL_REQUEST from [ip:%s]
Description: No description available.
326098 AM: PAPI_Send failed. [msg:%s]
Description: PAPI Send failed
326129 AM: Setting PPP IP to [ip:%s] for interface [iface:%s]
Description: No description available.
326130 AM: Applying [type:%s] profile config
Description: No description available.
326140 AM: Max number of Valid OUIs reached.
Description: No description available.
326141 AM: Applying IDS Rate Thresholds profile config for frametype: [frametype:%d]
Description: No description available.
326145 AM: Applying IDS Signature profile config. Group: [group_num:%d] Number of
Instances: [num_sign:%d]
Description: No description available.
330206 Getting out of recovery mode after [time:%d] minutes to scan.
Description: Exiting recovery mode to try and find potential parents matching
provisioned clusters.
330207 Received association request from an already associated child [mac:%s] - clearing old
341002 [msg:%s]
341009 AP [name:%s] is down T
341010 AP [name:%s] is up
341014 AP rebooting [reason:%s].
state.
Description: Received association request from an already associated child. Clearing
old state before processing the new association request.
Description: No description available.
Description: he virtual controller has lost contact with the access point.
Description: The AP has registered with the virtual controller.
Description: The AP is rebooting.
341015 AP is operating in regulatory [domain:%s] [code:%d].
Description: The AP is in specified regulatory domain.
341016 AP is operating in creating auth server-[name:%s], add-[flag:%d].
Description: The AP is configuring auth server.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 47
Page 48

Table 16 Information System Messages (Continued)
Message ID Message and Description
341017 AP is adding auth server-[ipaddr:%s], as_port-[as_port:%d], acctport-[acctport:%d].
Description: The AP is configuring auth server.
341018 Auth server NAS ip-[ipaddr:%s].
Description: The AP is configuring auth server.
341019 Auth server source ip-[ipaddr:%s].
Description: The AP is configuring auth server.
341020 Add termination server-[ipaddr:%s].
Description: The AP is configuring termination server.
341021 Add LDAP server-[ipaddr:%s], add-[flag:%d].
Description: The AP is configuring LDAP server.
341035 Set boot partition for AP: convert_ap-[convert_ap:%d], partition id-[part_id:%d].
Description: The AP is setting boot partition id.
341059 [func:%s]: can't find index for role-[name:%s].
Description: The AP is setting acl.
341060 [func:%s]: unknown client subnet type-[type:%d] for [ip:%x]/[mask:%x].
Description: The AP is setting acl.
341061 No SSID for vlan-[vlan:%d] for [ip:%x]/[mask:%x].
Description: The AP is setting acl.
341062 No space for vlan-[vlan:%d] for [ip:%x]/[mask:%x].
Description: The AP is setting acl.
341065 Activated tunnel route [desk:%x]/[mask:%x] to [dip:%x]/[ifindex:%x] usecnt-[cnt:%d].
Description: The AP is setting kernal route.
341066 Activated tunnel route [desk:%x]/[mask:%x] to [dip:%x]/[ifindex:%x] usecnt-[cnt:%d].
The AP is setting kernal route.
341069 Corp tunnel [sip:%x] to [dip:%x]/[eip:%x]/[ifindex:%d] is up.
Description: The AP is creating tunnel.
341071 Corp tunnel [sip:%x] to [dip:%x]/[eip:%x]/[ifindex:%d] is down.
Description: The AP is creating tunnel.
341073 AP derived acl for post auth role-[name:%s], idx-[idx:%u], acl-[acl:%u].
Description: The AP is creating SSID.
341075 [func:%s] AP can't find default post auth acl for SSID-[name:%s].
Description: The AP is creating SSID.
341076 Using default acl-[acl:%d] for SSID-[name:%s].
Description: The AP is creating SSID.
341077 AP add new acl-[name:%s], idx-[id:%d], vlan-[vid:%d], caleaOn-[on:%d].
Description: The AP is configuring ACL.
48 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 49

Table 16 Information System Messages (Continued)
Message ID Message and Description
341078 AP remove acl-[name:%s].
Description: The AP is configuring ACL.
341079 AP flush acl-[name:%s].
Description: The AP is configuring ACL.
341080 [func:%s]: can't find acl-[name:%s].
Description: The AP is configuring ACL.
341084 Reset index of access rule profile [file:%s] from [old_id:%u] to [id:%u].
Description: The AP is configuring ACL.
341086 [func:%s]: [line:%d]: version=[version:%s], image_url=[image:%s].
Description: The AP is upgrading image.
341087 [func:%s]: [line:%d]: response payload=[payload:%s].
Description: The AP is upgrading image.
341088 [func:%s]: [line:%d]: Html message=[msg:%s].
Description: The AP is upgrading image.
341096 [func:%s]: url is [url:%s]!.
Description: The AP is upgrading image.
341099 [func:%s]: user-[user:%s] [type:%s] use local DB.
Description: User authenticate.
341100 [func:%s]: corp subnet [ipaddr:%x]/[mask:%x] updated for vlan-[vid:%d].
Description: Corp configuration.
341101 Execute command-[cli:%s].
Description: Cli command.
341105 [func:%s]: [line:%d] rip-[rip:%s], eip-[eip:%s], backup-[backup:%d],lip-[lip:%s],
dev_name-[name:%s].
Description: Handle papi message.
341106 [func:%s]: [line:%d] rip-[rip:%s], eip-[eip:%s], backup-[backup:%d],lip-[lip:%s],
341112 [func:%s]: cert key is [psk:%s].
341115 [func:%s]: set gre [ipaddr:%s] successfully.
dev_name-[name:%s].
Description: Handle papi message.
Description: AP is setting cert.
Description: AP is setting gre name.
341117 [func:%s]: clear gre successfully.
Description: AP is setting gre name.
341120 SNMP get next mac-[mac:%s], index-[index:%d].
Description: SNMP action.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 49
Page 50

Table 16 Information System Messages (Continued)
Message ID Message and Description
341121 SNMP return [mac:%s]:[num:%d].
Description: SNMP action.
341128 [func:%s], [line:%d]: index-[idx:%d] is [type:%s].
Description: AP is setting SSID.
341129 [func:%s], [line:%d]: index-[idx:%d] of ssid-[ssid:%s]is set to [new_idx:%d].
Description: AP is setting SSID.
341134 AP will remove alerts of client-[mac:%s].
Description: AP is removing alerts.
341135 Master Changed - new [new_ip:%s] old [old_ip:%s] current swarm state [state:%d].
Master in network changed.
341136 Perform image checking with master [master_ip:%s].
Description: Slave check image with master.
341139 SNMP get mac-[mac:%s], index-[index:%d].
Description: SNMP action.
341140 [func:%s], [line:%d]: payload is [payload:%s].
Description: Airwave upgrade image.
341145 Cert type is [type:%s], format is [format:%s].
Description: AP upload certificate for radius server.
341146 [func:%s]: result for CLI_EXECUTE_CERT_UPLOAD [result:%s].
Description: AP upload certificate for radius server.
341160 Send reboot cmd to AP [ap:%s], reason [reason:%s].
Description: Send reboot cmd.
341161 Send reboot ack to AP [ap:%s].
Description: Send reboot ack cmd.
341162 Receive reboot ack from AP [ap:%s].
Description: Receive reboot ack.
341168 [func:%s],[line:%d]: uplink type [type:%s], state [state:%s].
Description: Print the uplink info.
341178 [func:%s],[line:%d]: send message to awc [type:%d], [username:%s], [password:%s],
[device_key:%s], [label:%s].
Description: clid send papi message to awc.
341179 [func:%s],[line:%d]: receive message from awc [key:%s], [state:%d], [value:%s].
Description: clid receives message from awc.
341180 [func:%s],[line:%d]: send mesh cfg.
Description: Send mesh cfg.
341186 Find uplink fail, type [type:%d].
Description: Find uplink fail.
50 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 51

Table 16 Information System Messages (Continued)
Message ID Message and Description
341187 Add [mac:%m] to ap whitelist.
Description: Add an ap to the whitelist.
341188 Del [mac:%m] from ap whitelist.
Description: Del an ap from the whitelist.
341189 [func:%s]: discover client [mac:%s] [fapip:%s] [vlan:%d].
Description: Discover client request.
341190 [func:%s]: found client [mac:%s] [vlan:%d] [hapip:%s] [oldapip:%s] [vcip:%s].
Description: Found client response.
341191 [func:%s]: hap req for [mac:%s] [fapip:%s] [vcip:%s] [oldapip:%s] [rtid:%d] [vlan:%d]
[vapvlan:%d].
Description: HAP request.
341192 [func:%s]: hap ack for [mac:%s] [rtid:%d].
Description: HAP Ack.
341193 [func:%s]: foreign client info [mac:%s] [type:%s] [vapvlan:%d] [vlan:%d] [ssid:%s]
341195 [func:%s]: clt del req for [mac:%s] [rehome:%d] [fapip:%s].
341196 [func:%s]: clt del notification for [mac:%s] [hapip:%s].
341197 Send [msg:%s] to vc [ip:%s].
341198 [func:%s]: receive register/heartbeat from [mac:%m], [ip:%s].
341203 [func:%s]: foreign client rehome [mac:%s].
341204 [func:%s]: client subnet info [mac:%s] [subnet:%s].
341209 [func:%s]: mip tunnel down [tid:%d].
[vcip:%s] [hapip:%s].
Description: Foreign client info.
Description: Client Delete Request.
Description: Client Delete Notification.
Description: Send register/heartbeat msg to vc.
Description: Receive register/heartbeat msg from slave.
Description: Foreign Client re-home.
Description: Foreign Client re-home.
Description: MIP tunnel down.
341215 [func:%s]: L3 Subnet Update [cmd:%d] [subnet:%s] [mask:%s] [vlan:%d] [vcip:%s]
[flag:%x].
Description: L3 Subnet Update.
341216 [func:%s]: awc logout from [ip:%s].
Description: Awc logout.
341217 [func:%s]: awc connect to [ip:%s] successfully.
Description: Awc connect successfully.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 51
Page 52
Table 16 Information System Messages (Continued)
Message ID Message and Description
341218 [func:%s]: awc login to [ip:%s] successfully.
Description: Awc login successfully.
341219 [func:%s]: awc identify [ip:%s] successfully.
Description: Awc identify successfully.
341220 [func:%s]: L2 Roam session requested for client [mac:%s] [ssid:%s].
Description: L2 Roam session requested.
341221 [func:%s]: Foreign sta info for [mac:%s] from [vcip:%s].
Description: Foreign sta info.
341222 [func:%s]: Remote sta info for [mac:%s] from [vcip:%s].
Description: Remote sta info.
341223 [func:%s]: L3 VC Update [cmd:%d] [vcip:%s] [flags:%d].
Description: L3 VC Update.
341225 [func:%s]: VC Auto Discover.
Description: VC Auto Discover.
341226 [func:%s]: VC IP changed [oip:%s] [nip:%s].
Description: L3 VC Update.
341231 [func:%s]: Sta ACL changed for [mac:%s] [ssid:%s] [role:%s].
Description: L3 Sta ACL changed.
Debug Messages
Table 17 Debug System Messages
Message ID Message and Description
304003 [msg:%s]
Description: System related debugging messages logged in the station manager (stm).
304008 [msg:%s]
Description: No description available.
304021 [func:%s]:[line:%d] Flow [flow_id:%d] not found
Description: No description available.
304030 License key - [f:%s] - [mode:%s]
Description: This message indicates whether the specified licensed feature is enabled
or disabled
304034 handle_enet_message_response: MAC [mac:%m] nothing outstanding
Description: No description available.
304036 handle_enet_message_response: MAC [mac:%m] not found
Description: No description available.
52 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 53

Table 17 Debug System Messages (Continued)
Message ID Message and Description
304051 In-memory client blacklist table cleared.
Description: This log indicates that the in-memory client blacklist was cleared.
304052 Client blacklist database table cleared.
Description: This log indicates that the client blacklist database table was cleared.
304053 Client blacklist repopulated from database.
Description: This log indicates that the in-memory client blacklist was repopulated
from the database.
304059 [func:%s], [line:%d]: sap_ip: [sapip:%s], tunnel_ip: [tunnelip:%s], tunnel id:
[tunnelid:%x]
Description: This debugging log indicates the tunnel id returned from datapath.
304061 [func:%s], [line:%d]: add [add:%d] mcast_group [group:%x] dest_idx: [dest:%x]
Description: This debugging log indicates the multicast group and destination index.
304066 [func:%s]: [line:%d]: vlan [id:%d] has [user:%d] users
Description: Count user number from a specified vlan.
311008 [msg:%s]
Description: No description available.
311009 [msg:%s]
Description: No description available.
326001 AM: [msg:%s]
Description: No description available.
326076 AM: Sending Probe Poll Response V2: NumAPs=[num_aps:%d]
326081 AM: Processing WMS_MODE message
326086 AM: Sending Probe Register Message to : [ip:%s]
326087 AM: Sending Probe UnRegister Message to : [ip:%s]
326090 AM: message len [node_bl:%d]
326092 AM: [line:%d]: Sending PROBE_STATS_UPDATE_MESSAGE for STAs of length [bl:%d]
NumSTAs=[num_sta:%d] Len=[bl:%d]
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
326093 AM: [line:%d]: Sending STM_AP_STATS_UPDATE for STAs of length [bl:%d]
Description: No description available.
326094 AM:SM: Sending Spectrum Register Message for radio [r:%d] band [band:%s] to
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 53
[ip:%s]
Description: This log indicates that spectrum radio is registering with the controller.
Page 54

Table 17 Debug System Messages (Continued)
Message ID Message and Description
326095 AM:SM: Sending Spectrum Unregister Message for radio [r:%d] band [band:%s] to
326099 AM:SM: Received Spectrum Unknown Radio Message for [bssid:%s]
326213 AM: MAC [mac:%s] matched with offset [match:%s]
326216 AM: MAC [mac:%s] matched in [config_eth:%s] wired mac table
326280 AM:SM: [msg:%s]
330200 [msg:%s]
341001 [msg:%s]
341022 AP can't retrieve data from datapath for session [ipaddr:%s] - [dipaddr:%s].
[ip:%s]
Description: This log indicates that spectrum radio is un-registering with the controller.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: The AP is configuring ACL.
341024 Setting global LED mode [mode:%d].
Description: The AP is configuring LED mode.
341025 Setting virtual controller key [key:%s].
Description: The AP is configuring VC key.
341124 [func:%s]: mac auth token client number-[num:%d].
Description: Station update.
341125 [func:%s]: add reauth ctx client-[num:%d].
Description: Station update.
341126 User: [user:%s] login by [type:%s] [result:%s].
Description: User login.
341127 [func:%s], [line:%d]: flushing ACL rule-[profile:%s].
Description: AP is setting SSID.
341131 AP sends meshd parameters [cs_key:%s]-[key:%s]-[country_code:%d].
Description: AP is sending mesh parameters.
341132 Check sum error for AP-[ip:%s], slave [s_sum:%u] vs master [m_sum:%u].
Description: AP is checking configuration.
341137 Client [mac:%s] was removed.
Description: AP remove client when timeout.
341138 Master received alerts message from AP [ap_ip:%s].
Description: AP receive user alert.
54 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 55

Table 17 Debug System Messages (Continued)
Message ID Message and Description
341142 [func:%s], [line:%d]: html msg is [msg:%s].
Description: AP receives HTML message from controller.
341200 Check session id fail: client_ip [ip:%s], string [sid:%s].
Description: Checking session id fail
341234 Receive stats publish from [ip:%s].
Description: Receive stats publish msg.
341236 Add [mac:%s] [status:%s] to subscription ap list.
Description: Add ap to subscription ap list
341237 Del [mac:%s] [status:%s] from subscription ap list.
Description: Del ap from subscription ap list
341238 Update [mac:%s] [status:%s] - [newstatus:%s] in subscription ap list.
Description: Update ap status in subscription ap list
341239 Del [mac:%s] [status:%s] from subscription ap list in timer.
Description: Del ap from subscription ap list in timer
341240 Del [mac:%s] from whitelist ap for not in subscription ap list.
Description: Del ap from whitelist ap for not in subscription ap list
341241 Del [mac:%s] from whitelist ap in case of [status:%s].
Description: Del ap from whitelist ap in case of invalid status
341242 Ap [mac:%s] has invalid subscription status [status:%d] in function[function:%s]
[line:%d] .
Description: ap has invalid subscription status
341243 Reboot ap [mac:%s] for not in subscription ap list.
Description: Reboot ap for not in subscription ap list
341244 Reboot ap [mac:%s] for invalid subscription status [status:%s] in function[function:%s]
341246 VC set delta configuration current_cfg_id [cid:%d] top_cfg_id [tid:%d].
341247 VC need shrink delta configuration entrys. current_cfg_id [cid:%d] top_cfg_id [tid:%d]
341248 VC delta configuration entry list is empty.
[line:%d] .
Description: Reboot ap for invalid subscription status
Description: New master set its own celta cfg id
max [mid:%d].
Description: VC need shrink delta configuration entrys
Description: VC delta configuration entry list is empty.
341249 VC delete delta configuration cfg_id [cid:%d] in shrink operation. current_cfg_id
[ccid:%d] top_cfg_id [tid:%d].
Description: VC delete delta configuration entry in shrink operation
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide System Messages | 55
Page 56

Table 17 Debug System Messages (Continued)
Message ID Message and Description
341251 VC record new delta configuration entry. cfg_id [cid:%d] current [c:%d] top [t:%d] len
341253 VC send delta configurations to ap. ap [ap_ip:%s] ap_cfg_id [acid:%d] delta_cfg_id
341254 VC add delta configuration id [id:%d] to msg [msg:%s].
341255 VC need send delta configurations to ap [ap_ip:%s]. ap_cg_id [acid:%d] current_cfg_id
341256 AP receive delta configuration id [acid:%d] current_cfg_id [cid:%d] from msg [msg:%s] .
341257 VC delete delta configuration cfg_id [cid:%d] in timer operation. current_cfg_id
341259 Forming the Register Request message [Func:%s] - [Register:%s] .
[len:%d] port [port:%d] flags [flags:%d] seq [seq:%d].
Description: VC record new delta configuration entry.
[did:%d] current_cfg_id [cid:%d] top_cfg_id [tid:%d].
Description: VC send delta configuration to ap.
Description: VC add delta configuration to msg.
[cid:%d] top_cfg_id [tid:%d].
Description: VC need send delta configurations to ap.
Description: AP receive delta configuration id from msg.
[ccid:%d] top_cfg_id [tid:%d] timestamp [t:%u] current_time [ct:%u].
Description: AP receive delta configuration id from msg.
Description: Register Request Message.
341277 Managed mode: Starts fetching configuration from the server
Description: Starts fetching configuration from the server.
341278 Managed mode: Config download done. File hash before [csum1:%s], after [csum2:%s]
Description: Config file downloaded from server.
341280 Managed mode: Config on AP and server matches.
Description: Configuration on AP matches with the configuration on the server.
341281 Managed mode: AP and server configuration differs.
Description: AP and server configuration differs.
341282 Managed mode: Applied the latest config from server.
Description: : Applied the latest configuration from the server.
341291 [msg:%s]
Description: No per ap setting is present.
56 | System Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 57

Chapter 4
User Messages
Error Messages
Table 18 User Error Messages
Message ID Message and Description
524005 Invalid action :[file:%s],[func:%s],[line:%d],[action:%d]
Description: This shows internal debug messages.
524006 [file:%s], [func:%s],[line:%d],cur=0x[cur:%x],end=0x[end:%x]
Description: This shows internal debug messages.
524007 [file:%s], [func:%s],[line:%d], realloc size invalid, tot=:[tot:%d],certlen=:[len:%d]
Description: This shows internal debug messages.
524008 [file:%s], [func:%s],[line:%d], offset should be zero but is =[offset:%d]
Description: This shows internal debug messages.
524009 [file:%s], [func:%s],[line:%d] Sanity check for first/Only cert chunk failed. Ignoring cert
chunk.
Description: This shows internal debug messages.
524010 [file:%s], [func:%s],[line:%d] malloc size:=[total:%d] failed
Description: This shows internal debug messages.
524019 Invalid MPPE recv-key length:[len:%d]
Description: This shows internal debug messages.
524020 Unknown protocol/Opcode [proto:%2X] [opcode:%2X] from the Datapath
Description: This shows internal debug messages.
524021 [string:%s]
Description: This shows internal debug messages.
524022 Radius Shared secret is NULL, NASIP = [nasip:%s], Radius Server [srvip:%s]
Description: This shows internal debug messages.
524023 Error decoding LEAP key (code=[code:%d])
Description: This shows internal debug messages.
524024 Error decoding MPPE recv-key (code = [code:%d])
Description: This shows internal debug messages.
524025 Could not create the stateful config entry, dropping the request.
NASIP=:[nasip:%s],[srvip:%s]
Description: This shows internal debug messages.
524026 Dropping the radius request to=:[srvip:%s]
Description: This shows internal debug messages.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 57
Page 58

Table 18 User Error Messages
Message ID Message and Description
524027 Error decoding MPPE send-key (code = [code:%d])
Description: This shows internal debug messages.
524028 Invalid MPPE send-key length:[len:%d]
Description: This shows internal debug messages.
524030 Invalid Radius Code [radcode:%d]
Description: This shows internal debug messages.
524043 [string:%s]: FT mic=[string1:%s]
Description: This shows internal debug messages.
524044 AES-GCM key size should be either [key1:%d] or [key2:%d]
Description: This shows internal debug messages.
524046 Station UP failed for station [str:%s] [str1:%s]
Description: This shows internal debug messages.
524056 Invalid radius code
Description: This shows internal debug messages.
524057 Dropping the radius packet for stateful dot1x processing
Description: This shows internal debug messages.
524058 No Valid NAS IP dropping the request
Description: This shows internal debug messages.
524059 NAS IP address didn't match the NASIP attribute
Description: This shows internal debug messages.
524060 No Valid Calling Station ID dropping the request
Description: This shows internal debug messages.
524061 Could not create a new user entry
Description: This shows internal debug messages.
524062 Failed to add to the radius request list
Description: This shows internal debug messages.
524063 Dropping radius response to AP
Description: This shows internal debug messages.
524064 No matching request fot the response..dropping the pkt
Description: This shows internal debug messages.
524065 User was deleted before the response came in
Description: This shows internal debug messages.
524066 No dot1xctx for this response
Description: This shows internal debug messages.
524067 Failed to process EAP packet from backend
Description: This shows internal debug messages.
58 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 59

Table 18 User Error Messages
Message ID Message and Description
524068 AES-GCM key setting is allowed only for Tunnel mode VAP's
Description: This shows internal debug messages.
541012 [func:%s]: [line:%d]: find client-[mac:%m] fail.
Description: Station sync.
541017 [func:%s]: parse tlv ret-[ret:%d] mac-[mac:%m] fail.
Description: Station sync.
541018 [func:%s],[line:%d]: could not find client-[mac:%m].
Description: AP is looking up station.
541021 sta [mac:%m] - fail to find wlan profile for ssid-[ssid:%s].
Description: Station sync.
541028 [func:%s],[line:%d]: could not get stm ip for client-[client:%m], essid-[essid:%s].
Description: AP send portal auth acl to STM.
541046 [func:%s]: Unexpected sta-[mac:%m] lkup resp from [ip:%s].
Description: Unexpected station lkup response.
Warning Messages
Table 19 User Warning Messages
Message ID Message and Description
501026 Station [sta:%m]: too many vlan ([num:%d]) trying to associate to BSSID [bss:%m] on
501027 “Station [sta:%m]: authentication payload shorter than min, length [len:%d], expected
501030 “Station [sta:%m]: Packet too short, length [len:%d], expected [elen:%d] trying to
501040 “Station [sta:%m]: Packet too short, length [len:%d], expected [elen:%d] trying to de-
501060 Station [sta:%m]: Ignored Association response to BSSID [bss:%m] on AP [name:%s]
AP [name:%s]
Description: No description available.
[elen:%d] trying to associate to BSSID [bss:%m] on AP [name:%s]
Description: No description available.
disassociate to BSSID [bss:%m] on AP [name:%s]
Description: An 802.11 Disassociation frame was received that was too short.
Recommended Action: It will be ignored.
authenticate to BSSID [bss:%m] on AP [name:%s]
Description: No description available.
Description: No description available.
501061 Station [sta:%m]: Ignored Re-Association response to BSSID [bss:%m] on AP
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 59
[name:%s]
Description: No description available.
Page 60

Table 19 User Warning Messages
Message ID Message and Description
501062 Station [sta:%m]: Ignored ATIM to BSSID [bss:%m] on AP [name:%s]
Description: No description available.
501064 Station [sta:%m]: Ignored unknown management frame subtype [stype:%x]h to BSSID
501067 Source: [sa:%m] Failed AP [ip:%p]-[bssid:%m]-[name:%s] Rates Mismatch STA
501068 Source: [sa:%m] Failed AP [ip:%p]-[bssid:%m]-[name:%s] Multicast Encryption
501069 Source: [sa:%m] Failed AP [ip:%p]-[bssid:%m]-[name:%s] Unicast Encryption
501070 STA [mac:%m] not found in sta_hash_table
501071 wifi_update_sta_vlan: STA [mac:%m] not found
501072 wifi_update_sta_vlan: STA [mac:%m] not associated with SAP [bssid:%m]
[bss:%m] on AP [name:%s]
Description: No description available.
0x[rates:%x] AP 0x[tx_rates:%x]
Description: No description available.
Mismatch
Description: No description available.
Mismatch
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
501073 STA [mac:%m] not found in sta_hash_table
Description: No description available.
501074 “wifi_deauth_sta: bad data, dropping. mac: [mac:%m] bssid: [bssid:%m]
Description: No description available.
501075 wifi_counter_measures_enable: STA [mac:%m] not found
Description: No description available.
501076 wifi_bss_counter_measures_enable: STA [mac:%m] not found
Description: No description available.
501077 wifi_update_sta_vlan: AP [bssid:%m] STA [mac:%m]: VAP Not found. ageout
Description: No description available.
501078 wifi_update_sta_vlan: AP [bssid:%m] STA [mac:%m]: VLAN [vlan_id:%d] not found.
501079 handle_sta_stat_req: Unknown STA [mac:%m]
501083 Probe request: [mac:%m]: Invalid Station MAC address from AP [ip:%P]-[bssid:%m]-
ageout
Description: No description available.
Description: No description available.
[name:%s]
Description: No description available.
60 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 61

Table 19 User Warning Messages
Message ID Message and Description
501086 Probe request: [mac:%m]: Invalid Station MAC address from AP [ip:%P]-[bssid:%m]-
501091 Auth request: [mac:%m]: Invalid Station MAC address from AP [ip:%P]-[bssid:%m]-
501092 Auth request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for STA DoS
501096 Assoc request: [mac:%m]: Invalid Station MAC address from AP [ip:%P]-[bssid:%m]-
501097 Assoc request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for STA DoS
501103 Blacklist add: [mac:%m]: Reason: [reason:%s]
501104 Disassoc from sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Disassoc Flood DoS
[name:%s] SSID [essid:%s]
Description: No description available.
[name:%s]
Description: No description available.
protection
Description: No description available.
[name:%s]
protection
Description: No description available.
Description: No description available.
Attack Detected
Description: No description available.
501115 Blacklist del: [mac:%m]: by administrator
Description: No description available.
501116 Blacklist del: [mac:%m]: timeout
Description: No description available.
501118 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. STA Not Found
Description: No description available.
501119 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. STA Not Associated
Description: No description available.
501120 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. SIP client not on-call
Description: No description available.
501121 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. Invalid TCLAS count/
type ([num_tclas:%d]/[type:%d])
Description: No description available.
501122 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. TCLAS/SDP
mismatch ([tbuf:%s]/[sdpbuf:%s])
Description: No description available.
501123 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. TSPEC does’t match
codec characteristics ([rv:%d])
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 61
Page 62

Table 19 User Warning Messages
Message ID Message and Description
501124 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. Voice Capacities
501125 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] refused. Flow Setup Failed
501127 Delts: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] STA Not found
501128 Delts: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] STA Not Associated
501130 Delts: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Flow Not Found
501131 [func:%s]:[line:%d] STA [mac:%m] not found.
501135 Source: [sa:%m] Failed AP [ip:%P]-[bssid:%m]-[name:%s] WEP and TKIP encryption
501141 Blacklist client: [mac:%m] removed during repopulation from db. Reason: [reason:%s]
Reached
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
not valid with high throughput
Description: No description available.
Description: This log indicates that a client blacklist entry was removed during
repopulation from db.
541003 Client [mac:%s] is failed to authenticate, failure count is [count:%d].
Description: Client authentication failure.
541004 [func:%s]: receive station msg, mac-[mac:%m] bssid-[bssid:%m] ssid-[ssid:%s].
Description: AP receive station online/offline.
541013 [func:%s],[line:%d]: add client [mac:%m], client count [num:%d].
Description: Add a new client.
541023 [func:%s],[line:%d]: del client [mac:%m], client count [num:%d].
Description: Put a client to remove list.
541026 [func:%s]: send disconnect user, AP ip: [ap_ip:%s], client ip [clent_ip:%s].
Description: AP disconnect client.
Notice Messages
Table 20 User Notice Messages
Message ID Message and Description
501001 Station [sta:%m]: Trying to associate to BSSID [bss:%m] on AP [name:%s] before
authentication
Description: No description available.
62 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 63

Table 20 User Notice Messages
Message ID Message and Description
501002 “Station [sta:%m]: ESSID length error trying to associate to BSSID [bss:%m] on AP
501003 “Station [sta:%m]: Supported rates length trying to associate to BSSID [bss:%m] on AP
501004 Station [sta:%m]: WPA too Many Ucast ([num:%d]) trying to associate to BSSID
501005 Station [sta:%m]: WPA2 too Many Ucast ([num:%d]) trying to associate to BSSID
501010 Station [sta:%m]: Ucast ([ucast:%d]) cannot be non WPA trying to associate to BSSID
501011 Station [sta:%m]: Ucast ([ucast:%d]) cannot be non AES trying to associate to BSSID
501020 Station [sta:%m]: WPA too Many auth ([num:%d]) trying to associate to BSSID [bss:%m]
[name:%s], length [len:%d]
Description: No description available.
[name:%s], length [len:%d], actual [alen:%d]
Description: No description available.
[bss:%m] on AP [name:%s]
Description: No description available.
[bss:%m] on AP [name:%s]
Description: No description available.
[bss:%m] on AP [name:%s]
Description: No description available.
[bss:%m] on AP [name:%s]
Description: No description available.
on AP [name:%s]
Description: No description available.
501021 Station [sta:%m]: WPA2 too Many auth ([num:%d]) trying to associate to BSSID
501025 Station [sta:%m]: WPA2 too Many PMKID ([num:%d]) trying to associate to BSSID
501037 Station [sta:%m]: no association found trying to disassociate to BSSID [bss:%m] on AP
501044 Station [sta:%m]: No authentication found trying to de-authenticate to BSSID [bss:%m]
501080 Deauth to sta: [mac:%m]: Ageout AP [ip:%P]-[bssid:%m]-[name:%s] [reason:%s]
501081 Deauth to sta: [mac:%m]: Ageout AP [ip:%P]-[bssid:%m]-[name:%s] [reason:%d]
501084 Probe request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for STA DoS
[bss:%m] on AP [name:%s]
Description: No description available.
[bss:%m] on AP [name:%s]
Description: No description available.
[name:%s]
Description: No description available.
on AP [name:%s]
Description: No description available.
Description: No description available.
Description: No description available.
protection
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 63
Page 64

Table 20 User Notice Messages
Message ID Message and Description
501087 Probe request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for STA DoS
501088 Probe request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for Rates
501089 Probe request: [mac:%m]: Dropped AP [ip:%P]-[bssid:%m]-[name:%s] for Load
501093 Auth success: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s]
501094 Auth failure: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%s]
501095 Assoc request @ [tstr:%s]: [mac:%m] (SN [sn:%d]): AP [ip:%P]-[bssid:%m]-[name:%s]
501098 Deauth to sta: [mac:%m]: Moved out from AP [ip:%P]-[bssid:%m]-[name:%s] to new AP
501099 Deauth to sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%s]
protection SSID [essid:%s]
Description: No description available.
Mismatch STA 0x[rates:%x] AP 0x[tx_rates:%x] SSID [essid:%s]
Description: No description available.
Balancing SSID [essid:%s]
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
501100 Assoc success @ [tstr:%s]: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s]
Description: No description available.
501101 Assoc failure: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%s]
Description: No description available.
501102 Disassoc from sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason
[reason_code:%s]
Description: No description available.
501105 Deauth from sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason
501106 Deauth to sta: [mac:%m]: Ageout AP [ip:%P]-[bssid:%m]-[name:%s] [func:%s]
501107 Deauth to sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] AP going down
501108 Deauth to sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Configuration Change
501109 Auth request: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] auth_alg [auth_alg:%d]
[reason_code:%s]
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
64 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 65

Table 20 User Notice Messages
Message ID Message and Description
501110 Auth failure: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%d]
Description: No description available.
501111 Deauth to sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%d]
Description: No description available.
501112 Assoc failure: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason [resp:%d]
501113 Disassoc from sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason
[reason_code:%d]
Description: No description available.
501114 Deauth from sta: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Reason
[reason_code:%d]
Description: No description available.
501117 Addts req: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s]
Description: No description available.
501126 Addts resp: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] accept flow - [flow:%s]
Description: No description available.
501129 Delts: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] Flow - [flow:%s]
Description: No description available.
501132 [ip:%p]:[mac:%m] - kick off idle VoIP STA
Description: No description available.
501133 [func:%s]:[line:%d] Extra call admitted [mac:%m]-[ip:%p]
Description: No description available.
501134 STA [mac:%m]: HT Capabilities element too short ([len:%d]); ignoring
Description: No description available.
501136 Source: [sa:%m] Failed AP [ip:%P]-[bssid:%m]-[name:%s] Legacy stations not allowed.
Description: No description available.
501153 STA [mac:%m]: required MFP but SSID [bssid:%s] not capable; ignoring
Description: No description available.
501154 STA [mac:%m]: not MFP capable but SSID [bssid:%s] requires MFP; reject
Description: No description available.
501155 STA [mac:%m]: sent illegal MFP params [bssid:%s] ; reject
Description: No description available.
501156 STA [mac:%m]: MFPC 0 but MFPR 1 [bssid:%s] ; reject
Description: No description available.
501165 User authenticated, mac-[mac:%m], username-[name:%s], IP-[ip:%p], method-
[method:%d], role-[role:%s]
Description: This log indicates that a user has been authenticated.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 65
Page 66
Table 20 User Notice Messages
Message ID Message and Description
501167 [func:%s][line:%d]: mac-[mac:%m], role-[role:%s], caleaOn-[on:%d].
Description: This log indicates that a user has been caleaOn
Information Messages
Table 21 User Information Messages
Message ID Message and Description
501035 Station [sta:%m]: DA [da:%m] not found trying to disassociate to BSSID [bss:%m] on
501137 Source: [sa:%m] Disabled aggregation on AP [ip:%P]-[bssid:%m]-[name:%s]; WEP or
501138 Description: “VPOOL: [sa:%m] Assign Vlan [vlan:%d] on BSSID [bssid:%s]
501139 Description: “VPOOL: [sa:%m] Release Vlan [vlan:%d] for BSSID [bssid:%s]
541001 Add client [mac:%s] to blacklist, reason is [reason:%s].
541002 Remove client [mac:%s] from blacklist, reason is [reason:%s].
541031 Learning client username: mac-[mac:%m] usr-[username:%s] acct-[acctname:%s].
AP [name:%s]
Description: No description available.
TKIP encryption in use
Description: No description available.
(remain=[remain:%d], reason=[res:%s])”
Recommended Action: This message indicates that a VLAN was assigned to a client
from the Pool
(remain=[remain:%d], reason=[res:%s])
Recommended Action: This message indicates that a VLAN was released to VLAN
pool for future reuse
Description: add a client to blacklist.
Description: remove a client from blacklist.
Description: learning client usrname.
541032 [func: %s]: allocate accounting session id, user-[mac:%m] id-[id:%u].
Description: learning client usrname.
541034 func: %s]: set user idle timeout, user-[mac:%m] timeout-[to:%u].
Description: Set user idle timeout.
541035 Set user agent str for [mac:%m] detail-[us:%s].
Description: Set user agent info.
541036 [func:%s]: send idle timeout, sta [mac:%m] , idle time-[time:%d].
Description: Station update.
541047 Recv sta l2 roam msg for sta-[mac:%m], pap-[ip:%s], essid-[ssid:%s]
Description: Receive sta l2 roam.
541048 Send move req to [pap:%s], for sta-[mac:%m], essid-[essid:%s]
Description: Send station move request.
66 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 67
Table 21 User Information Messages
Message ID Message and Description
541049 Receive move req for sta-[mac:%m], essid-[essid:%s], from-[ap:%s]
Description: Send station move request.
541050 Send move response for sta-[mac:%m], to ap-[ip:%s],
Description: Send sta move resp.
541051 Recv sta move resp for sta-[mac:%m], from [ip:%s],
Description: Receive sta move resp.
541052 Sta [mac:%s] move timeout, retry cnt [retry:%d]
Description: Station move timeout.
Debug Messages
Table 22 User Debug Messages
Message ID Message and Description
501000 Station [mac:%m]: Clearing state
Description: No description available.
501042 Station [sta:%m]: DA [da:%m] not found trying to de-authenticate to BSSID [bss:%m]
501050 “Station [sta:%m]: No bssid found for management frame type [type:%d], subtype
501052 “Station [sta:%m]: Dropping management frame type [type:%d], subtype [stype:%d],
501065 [msg:%s]
501066 Source: [sa:%m] Failed AP [ip:%P]-[bssid:%m]-[name:%s] SSID Mismatch
501082 Probe request: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s]
501085 Probe request: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] SSID [essid:%s]
501090 Probe response: [mac:%m]: AP [ip:%P]-[bssid:%m]-[name:%s] SSID [essid:%s]
on AP [name:%s]
Description: No description available.
[stype:%d] to BSSID [bss:%m]”
Description: No description available.
bss [bss:%m]
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
Description: No description available.
501140 Blacklist client added from db: [mac:%m]. Reason: [reason:%s]
Description: This log indicates that a client blacklist entry was added from the
database at startup.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 67
Page 68

Table 22 User Debug Messages
Message ID Message and Description
501142 Derive user vlan: [mac:%m] Derive user Vlan [vlan:%d] from [reason:%s]
Description: This log indicates that user vlan derivation information .
501143 Derive user vlan: [mac:%m] Can't derive user Vlan from [vlan1:%d] to [vlan2:%d]
501144 stm_user_dhcp_role_msg: [reason:%s]
501145 DHCP option signature: DHCP option [option:%d] signature [reason:%s]
501146 Derive user role: [mac:%m] Match user role [role:%s] acl [acl:%d] rule_index [index:%x]
501147 Update user role: [mac:%m] Update user role [role:%d] rule_index [index:%x] from
501148 Receive portal auth acl: [mac:%m] ip str [ip:%s] port [port:%s] essid [essid:%s] user
501149 Send radius auth info: authtime [time:%s] timeouts [to:%u], authdone [true:%u]
501150 Derive user role: [mac:%m] Derive user role [role:%s] acl [acl:%d] rule_index [index:%x]
through [reason:%s]
Description: This log indicates that user vlan derivation error information .
Description: This log indicates dhcp role debug information .
Description: This log indicates dhcp option signature information .
Description: This log indicates that matched user role information.
master msg
Description: This log indicates that update user role information from master.
[usr:%s]
Description: This log indicates that we received portal auth acl msg from cli0.
Description: This log indicates that we are sending radius auth info to cli0.
Description: This log indicates that derive user role information.
501151 user-agent signature: signature [reason:%s]
Description: This log indicates user-agent signature information .
501152 Dot1x-auth-type signature: signature [reason:%s]
Description: This log indicates dot1x-auth-type signature information .
501157 Station [sta:%m]: Unexpected SA-Query Response bss [bss:%m]
Description: No description available.
501158 Station [sta:%m]: SA-Query Request from non-MFP STA to bss [bss:%m]
Description: No description available.
501159 Derive user role from dhcp-option: [mac:%m] Match user role [role:%s] acl [acl:%d]
rule_index [index:%x].
Description: This log indicates that matched user role information using DHCP-option.
501160 Derive user role from dhcp-option(applied): [mac:%m] Match user role [role:%s] acl
[acl:%d] rule_index [index:%x].
Description: This log indicates that matched user role information using DHCP-option.
501161 Update dhcp-opt: [mac:%m] Update dhcp-opt [vlan:%d] [vlanhow:%s] [role:%d]
rule_index [index:%x] essid [essid:%s] from master msg.
Description: This log indicates that update user DHCP-option information from master.
68 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 69

Table 22 User Debug Messages
Message ID Message and Description
501162 Update dhcp-opt: [mac:%m] Update dhcp-opt [vlan:%d] [vlanhow:%s] [role:%d]
501163 Send user role info: mac-[mac:%m], acl-[acl:%d].
501164 Receive disconnect user, mac-[mac:%m], bssid-[bssid:%m], logout-[logout:%d],
520001 \[[file:%s]:[line:%d]] [message:%s]
501166 Rap bridge user msg, flags-[flags:%d] action-[action:%d] aclnum-[aclnum:%d] ip-
501168 Receive user acct req, mac-[mac:%m], bssid-[bssid:%m], acctreq-[acctreq:%d], term-
501169 Receive user accounting info: mac-[mac:%m], status-[status:%d], inocts-[inocts:%d],
rule_index [index:%x] essid [essid:%s] to cli0 msg.
Description: This log indicates that update user dhcp-opt information to CLI.
Description: No description available.
deauth-[deauth:%d], term-[trem:%d].
Description: This log indicates that we are receiving disconnect user message from
CLI0.
Description: aaa module’s debug message
[ip:%p] mac-[mac:%m],bssid-[bssid:%m] vlan-[vlan:%d] wired-[wired:%d].
Description: This log indicates that stm received ASAP_STM_BRIDGE_USER message
[trem:%d].
Description: This log indicates that we are receiving user acct req msg from cli0.
outocts-[outocts:%d], inpkts-[inpkts:%d], outpkts-[outpkts:%d], sesstim-[sesstim:%d],
sessid-[sessid:%s], multisessid-[multisessid:%s].
Description: This log indicates that we are sending user acct info to cli0.
501170 Send user accounting info: mac-[mac:%m], status-[status:%d], inocts-[inocts:%d],
outocts-[outocts:%d], inpkts-[inpkts:%d], outpkts-[outpkts:%d], sesstim-[sesstim:%d],
sessid-[sessid:%s], multisessid-[multisessid:%s].
Description: This log indicates that we are sending user acct info to cli0.
524000 Skipping disable operation, opcode:0x[address:%x] not registered.
Description: This shows an internal user debug message.
524001 cert id [certid:%d] tun id [tuneid:%d].
Description: This shows an internal user debug message.
524002 Download was skipped
Description: This shows an internal user debug message.
524003 Dot1x- Default profile cert id:[certid:%d].
Description: This shows an internal user debug message.
524004 Dot1x- Download time ID :[certid:%d],[certname:%s],[caname:%s]
Description: This shows an internal user debug message
524011 Src ip:[src:%s],Dst ip:[dst:%s],offset= [offset:%d] flags:=[flags:%d] Fragmented Packet
Description: This shows an internal user debug message
524012 Fragment Length [fraglen:%d]
Description: This shows an internal user debug message
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 69
Page 70

Table 22 User Debug Messages
Message ID Message and Description
524013 Forwarding the Radius packet after stateful dot1x processing code=:[code:%d],
524014 radius request timeout, unauthenticating station name:[name:%s], mac=:[mac:%s]
524015 Forwarding the Radius Response to AP:[ipstr:%s],[len:%d]
524016 radius response timeout, unauthenticating station name=:[name:%s],mac=:[mac:%s]
524017 User name:[name:%s] ,has moved from SAP mac:[mac:%s] to SAPmac:[smac:%s]
524018 Forwarding to the Radius Server[srvip:%s],len:[len:%d]
524029 FT([string:%s]): sap=[string1:%s] mdie=[mdie:%d], ft_cap=0x[ft_cap:%x] ucast
524031 Continuing show at [i:%d] [instance:%d]
smac=:[smac:%s],sport=:[sport:%d],dport[dport:%d]
Description: This shows an internal user debug message
Description: This shows an internal user debug message
Description: This shows an internal user debug message
Description: This shows an internal user debug message
Description: This shows an internal user debug message
Description: This shows an internal user debug message
0x[ucast:%x]
Description: This shows an internal user debug message
Description: This shows an internal user debug message
524032 For kcache table [i:%x], got pcache [pcache:%d] for mac [mac:%s] bssid [mac1:%s]
Description: This shows an internal user debug message
524033 Breaking the show at [i:%d] [pcache:%x] ie for mac [mac:%s] bssid [bssid:%s]
Description: This shows an internal user debug message
524034 [string:%s]: begins=>
Description: This shows an internal user debug message
524035 [i:%2x] [j:%2x] [k:%2x] [l:%2x] [m:%2x] [n:%2x] [o:%2x] [p:%2x]
Description: This shows an internal user debug message
524036 [string:%s]: ends=>
Description: This shows an internal user debug message
524037 [string:%s]: sending key1 11r ([ft:%d]) xsec([xsec:%d])
Description: This shows an internal user debug message
524038 [string:%s]: FT sending key1
Description: This shows an internal user debug message
524039 [string:%s]: MFP sending Key Desc Ver 3 in key1
Description: This shows an internal user debug message
524040 [string:%s]: rsn len ([len:%d])
Description: This shows an internal user debug message
70 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 71

Table 22 User Debug Messages
Message ID Message and Description
524041 [string:%s] :FT mesg3 copied gtk, len=[len:%d] data len=[len1:%d]
Description: This shows an internal user debug message
524042 [string:%s]: FT mic=[string1:%s]
Description: This shows an internal user debug message
524045 FT ([func:%s]): sap=[bssid:%s] mdie=[mdie:%d] ft_cap=0x[cap:%x] ucast=0x[ucast:%x]
mcast 0x[mcast:%x]
Description: This shows an internal user debug message
524047 USERNAME
Description: This shows an internal user debug message
524048 NAP_IP_ADDRESS
Description: This shows an internal user debug message
524049 CALLING_STATION_ID
Description: This shows an internal user debug message
524050 CALLED_STATION_ID
Description: This shows an internal user debug message
524051 EAP MESSAGE
Description: This shows an internal user debug message
524052 NAS_IDENTIFIER_ID
Description: This shows an internal user debug message
524053 NAS_IDENTIFIER_ID
Description: This shows an internal user debug message
524054 NAS_IP is set to 0.0.0.0, Using source ip as the NAS_IP
Description: This shows an internal user debug message
524055 Received Valid Radius Response
Description: This shows an internal user debug message
524069 FT [str:%s] input: pmk_r0=[str1:%s], pmk_r0_name=[str2:%s] r1kh_id=[id:%s]
Description: This shows an internal user debug message
524071 FT [str:%s] Derived pmk_r1=[str1:%s], pmk_r1_name=[str2:%s]
Description: This shows an internal user debug message
524072 FT ([str:%s]): bssid=[bssid:%s]
Description: This shows an internal user debug message
524073 FT ([str:%s]): input pmk_r1 =[str1:%s]
Description: This shows an internal user debug message
524074 FT ([str:%s]): input pmk_r1_name =[str1:%s]
Description: This shows an internal user debug message
524075 FT ([str:%s]): snonce=[str1:%s]
Description: This shows an internal user debug message
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 71
Page 72

Table 22 User Debug Messages
Message ID Message and Description
524076 FT ([str:%s]): anonce=[str1:%s]
Description: This shows an internal user debug message
524077 FT ([str:%s]): Derived ptk [ptk:%s]
Description: This shows an internal user debug message
524078 FT ([str:%s]): Derived ptk_name [ptk:%s]
Description: This shows an internal user debug message
524079 FT ([str:%s]): essid:[essid:%s], bssid:[bssid:%s] ukey:0[ukey:%x], mkey:[mkey:%x],
psk:[psk:%s],tkip:[tkip:%s]
Description: This shows an internal user debug message
524080 FT: cannot allocate FT key info entry
Description: This shows an internal user debug message
524081 [str:%s]: kcache [cache:%p] for sta [sta:%s] added
Description: This shows an internal user debug message
524082 [str:%s]: Error adding pcache
Description: This shows an internal user debug message
524083 [str:%s]: pcache [pcahe:%x] for sta [sta:%s] added.
Description: This shows an internal user debug message
524084 FT: xxxkey([xxx:%d])=[str:%s], mdid=[mdid:%d], ssid=[ssid:%s], r0kh_id=[id:%s]
Description: This shows an internal user debug message
524085 FT[str:%s]: pmk_r0:[pmk:%s], pmk_r0_name [name:%s]
Description: This shows an internal user debug message
524086 FT[str:%s]: ptk[ptk:%s]
Description: This shows an internal user debug message
524087 FT[str:%s]: input: sta [sta:%s], sap_mac[sap:%s]
Description: This shows an internal user debug message
524088 [str:%s]: kcache [cache:%p] found for sta [sta:%s]
Description: This shows an internal user debug message
524089 [str:%s]: Error adding kcache and r0_data
Description: This shows an internal user debug message
524090 [str:%s]: Copy new pmk_r1 = [pmk:%s], pmk_r1_name = [str1:%s]
Description: This shows an internal user debug message
524091 [str:%s]: Missing kcache entry!
Description: This shows an internal user debug message
524092 [str:%s]: kcache found
Description: This shows an internal user debug message
524093 FT([str:%s]) r0kh:[r0kh:%s], r0_name:[str1:%s]
Description: This shows an internal user debug message
72 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 73

Table 22 User Debug Messages
Message ID Message and Description
524095 Missing kcachThis shows an internal user debug message e entry!
Description:
524096 PMKR0-Name mismatch! cached=[str:%s]
Description: This shows an internal user debug message
524097 Generated anonce:[str:%s]
Description: This shows an internal user debug message
524098 [str:%s]: Derived gtk=[str1:%s]
Description: This shows an internal user debug message
524099 [str:%s]: Encrypted gtk=[str1:%s]
Description: This shows an internal user debug message
524100 FT([str:%s]): Calculating MIC
Description: This shows an internal user debug message
524101 MIC buf(60)=[str:%s], mic_buf_len [len:%d]
Description: This shows an internal user debug message
524102 MIC buf([mic:%d])=[str:%s], mic_buf_len [len:%d]
Description: This shows an internal user debug message
524103 MIC =[str:%s]
Description: This shows an internal user debug message
524104 FT:Failed to calculate MIC
Description: This shows an internal user debug message
524105 FT([str:%s]): buf_len ([len:%d]) = 2*ETH_ALEN + 1 + mdie_len ([mdie:%d]) +
ftie_len([ftie:%d]) + rsnie_len([rsnie:%d]) + ric_len([ric:%d]), buf [buf:%x]
Description: This shows an internal user debug message
524106 FT association request
Description: This shows an internal user debug message
524108 [str:%s]: Error adding kcache
Description: This shows an internal user debug message
524109 [str:%s]: missing sap entry for bssid [bssid:%s], encr 0x[encr:%x]
Description: This shows an internal user debug message
524110 Mismatch PMKR1-Name!
Description: This shows an internal user debug message
524111 [str:%s]: missing sap entry for bssid [bssid:%s]
Description: This shows an internal user debug message
524112 [func:%s]: kcache essid ([kcacheessid:%s]), essid ([essid:%s])
Description: This shows an internal user debug message
524113 auth done called from ncfg_dot1x_validatepmkid_enabled
Description: This shows an internal user debug message
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 73
Page 74

Table 22 User Debug Messages
Message ID Message and Description
524114 MAC auth failed, skipping dot1x.
Description: This shows an internal user debug message
524115 Auth done called from Authenticated state.
Description: This shows an internal user debug message
524116 DHCP UDR defined vlan. Got response from STM VLAN UPDATED.
Description: This shows an internal user debug message
524117 Auth done called from Key Challenge.
Description: This shows an internal user debug message
524118 [func:%s] cached entry [buf:%s].
Description: This shows an internal user debug message
524119 [func:%s] Failed to lookup user/dot1xctx.
Description: This shows an internal user debug message
524120 [func:%s] Failed to lookup user.
Description: This shows an internal user debug message
524121 Derived VLAN for the user is [vlan:%d].
Description: This shows an internal user debug message
524122 ACL/Key propagation failed, Msgtype:[msgtype:%d], keytype:[keytype:%d],
mac:[mac:%s], bssid:[bssid:%s], error:[errstr:%s]([errid:%d]), station doesnt exist
currently.
Description: This shows an internal user debug message
524123 ACL/Key propagation failed, Msgtype:[msgtype:%d], keytype:[keytype:%d],
mac:[mac:%s], bssid:[bssid:%s], error:[errstr:%s]([errid:%d]), sending deauth to station.
Description: This shows an internal user debug message
541005 [func:%s]: accounting session, client mac-[mac:%m], time-[time:%u].
Description: AP update client from STM.
541006 [func:%s]: auth state, Station [mac:%m] essid [essid:%s] authenticated [true:%d].
Description: Station authenticated state.
541007 [func:%s]: persist client mac-[mac:%m], bssid-[bssid:%m], essid-[essid:%s].
Description: AP sync persist client to STM.
541008 [func:%s]: client mac-[mac:%m], bssid-[bssid:%m], essid-[essid:%s], session-
[name:%s] [time:%u].
Description: AP sync client to STM.
541009 [func:%s]: machine auth token, mac-[mac:%m], bssid-[bssid:%m], ssid-[ssid:%s].
Description: AP configure machine auth.
541010 [func:%s]: apip-[ap_ip:%s], clientip-[client_ip:%s], mac-[mac:%m], bssid-
[bssid:%m].
Description: AP sent reauth.
74 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 75

Table 22 User Debug Messages
Message ID Message and Description
541011 [func:%s]: sta look up req to apip-[ap_ip:%s], mac-[mac:%m].
Description: AP sent/receive station request.
541014 [func:%s]: sta lkup response to apip-[ap_ip:%s], mac-[mac:%m].
Description: AP sent/receive station response.
541015 [func:%s]: Add mac auth token for sta-[sta:%m].
Description: Station update.
541016 [func:%s]: add reauth ctx for client-[mac:%m].
Description: Station update.
541019 [func:%s]: session timeout, sta [mac:%m] , reauth-[session_time:%d], current-
[current:%d].
Description: Station update.
541020 [func:%s]: sta [mac:%m] reauth disable in ssid-[ssid:%s].
Description: Station update.
541022 [func:%s]: send sta-[mac:%m] update to master-[master:%s], ssid-[ssid:%s].
Description: Station update.
541024 [func:%s],[line:%d]:get sync message for client [mac:%m], from [from_ap:%s]
Description: station ip updated.
541025 [func:%s]: check client [mac:%m] [ip:%s] on AP [ap_ip:%s], timeout [timeout:%d] auth
541026 [func:%s]: send disconnect user, AP ip: [ap_ip:%s], client ip [clent_ip:%s].
541027 Locate client response for [mac:%m], AP-ip: [ap_ip:%s].
541029 Receive stat publish for client - [mac:%m], from ap [ip:%s].
541030 [func:%s]: User role, Station [mac:%m] essid [essid:%s] role [num:%d] rule_index
541033 [func: %s]: L3 mobility updates user [mac:%m] [action:%s] [type:%s] with [peerip:%s]
541036 [func:%s]: idle timeout, sta [mac:%m] , idle time-[time:%d].
time [time:%d].
Description: Debug client reauth info.
Description: AP disconnect client.
Description: AP locate client.
Description: Receive stat publish msg.
[index:%x].
Description: Station user role update.
[vcip:%s].
Description: Marking or clearing the client as foreign or remote.
Description: Station update.
541037 [func:%s]: set accounting interval, sta [mac:%m] , account interval-[time:%d].
Description: Station update.
541038 [func:%s]: set class attribute, sta [mac:%m] , class attribute-[class:%s].
Description: Station update.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 75
Page 76

Table 22 User Debug Messages
Message ID Message and Description
541039 [func:%s]: Set dhcp-opt, Station [mac:%m] essid [essid:%s] role [num:%d] rule_index
541040 [func:%s]: Set os string, client [mac:%m], os [os:%s].
541041 [func:%s]: update vc for client [mac:%m].
541042 [func:%s]: set accounting interval, sta [mac:%m] , account interval-[time:%d].
541043 [func:%s]: set class attribute, sta [mac:%m] , class attribute-[class:%s].
541044 [func:%s]: set reauth ctx for client-[mac:%m], timeout-[to:%d].
541045 [func:%s]: Send accounting session, client mac-[mac:%m].
541053 [func:%s]: Send os string, client [mac:%m], os [os:%s].
[index:%x] vlan [vlan:%d] vlanhow[vlanhow:%s].
Description: Station dhcp-option update.
Description: Station os update.
Description: Station update to vc.
Description: Station update.
Description: Station update.
Description: No description available.
Description: No description available.
Description: Station OS update.
541054 [func:%s]: Send user role, Station [mac:%m] essid [essid:%s] role [num:%d] rule_index
541055 [func:%s]: Send dhcp-opt, Station [mac:%m] essid [essid:%s] role [num:%d] rule_index
541056 [func:%s]: Add auth state, Station [mac:%m], authenticated [true:%d].
541057 [func:%s]: Station [mac:%m], essid [ssid:%s], cp-enable [yes:%d].
541058 [func:%s]: Add calea state, Station [mac:%m], caleaOn [yes:%d].
541059 [func:%s]: Set calea state, Station [mac:%m], caleaOn [yes:%d].
541060 [func:%s]: Send accounting ctx, client mac-[mac:%m], status-[status:%u], inocts-
[index:%x].
Description: Station user role update.
[index:%x] vlan [vlan:%d] vlanhow[vlanhow:%s].
Description: Station DHCP-option update.
Description: Station authenticated state.
Description: Print CP user.
Description: Print calea state add.
Description: Print calea state add.
[inocts:%u], outocts-[outocts:%u], inpkts-[inpkts:%u], outpkts-[outpkts:%u],
sessid-[sessid:%s].
Description: AP update client from STM.
541061 [func:%s]: Set accounting ctx, client mac-[mac:%m], status-[status:%u], inocts-
76 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
[inocts:%u], outocts-[outocts:%u], inpkts-[inpkts:%u], outpkts-[outpkts:%u],
sessid-[sessid:%s].
Description: AP update client in CLI.
Page 77

Table 22 User Debug Messages
Message ID Message and Description
541062 [func:%s]: Send accounting request, client mac-[mac:%m], status-[status:%u].
Description: Send sta accouting request to STM.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide User Messages | 77
Page 78

78 | User Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 79

Chapter 5
Wireless Messages
Error Messages
Table 23 Wireless Error Messages
Message ID Message and Description
400143 AP [name:%s]: ESSID mismatch index [ndx:%d]. expected [e1:%s] got [e2:%s]
Description: An internal error has occurred.
Recommended Action: Contact your support provider.
400144 AP [name:%s]: Station [sta:%m] not found while clearing association
Description: An internal error has occurred.
Recommended Action: Contact Aruba Technical Support.
Warning Messages
Table 24 Wireless Warning Messages
Message ID Message and Description
400130 “AP [name:%s]: SAPCP payload shorter than minimum bssid [bss:%m]; minimuum
length [len:%d], actual [alen:%d]
Description: No description available.
400135 AP [name:%s]: SAPCP: Unknown frame type [type:%d]
Description: No description available.
400140 AP [name:%s]: No virtual AP defined
Description: No description available.
400141 AP [name:%s]: VLAN [vlan:%d] not found
Description: No description available.
400142 AP [name:%s]: Remote AP support not licensed; dropping request
Description: No description available.
400146 AP [name:%s]: number of VLANs limit exceeded [nvlan:%d]
Description: No description available.
400150 AP [name:%s]: GRE tunnel setup failed for bssid [bss:%m]
Description: No description available.
400165 AP [name:%s]: Too many virtual APs [nvap:%d] configured.
Description: No description available.
400167 wifi_mgmt_del_sap: sap_list for [bssid:%m]-[ip:%P] not found
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide Wireless Messages | 79
Page 80

Table 24 Wireless Warning Messages
Message ID Message and Description
400169 “AP - [bssid:%m], max_clients [max_clients:%d] too big
Description: No description available.
400171 wifi_sap_down:unknown SAP IP [ip:%P] BSS [bssid:%m]
Description: No description available.
400172 wifi_load_balance:unknown SAP IP [ip:%P] BSS [bssid:%m]
Description: No description available.
400173 wifi_update_sta_vlan: AP [bssid:%m] not found
Description: No description available.
400174 wifi_update_sta_vlan: Too Many VLANs on [bssid:%m]
Description: No description available.
400176 wifi_bss_counter_measures_enable: AP [bssid:%m] not found
Description: No description available.
400177 wifi_handle_vlan_message: AP [bssid:%m]: Too Many VLANs
Description: No description available.
400178 Association Flood DoS attack detected - AP [bssid:%m]
Description: No description available.
400179 handle_ap_message_response: BSS [bssid:%m] not found
Description: No description available.
400180 handle_ap_message_response: BSS [bssid:%m] nothing outstanding
Description: No description available.
400181 handle_clear_ap_state: Unknown AP [bssid:%m]
Description: No description available.
400182 stat_update: IP Addr Mismatch SAP [bssid:%m] Wrong IP [ip:%P]
Description: No description available.
400183 [func:%s]:Unknown SAP [bssid:%m]
Description: No description available.
400184 [func:%s]:Unknown SAP [bssid:%m] Mode [fw_mode:%d]
Description: No description available.
400194 Dropping association request from [sta:%m]: too many STM_STA_MESSAGE
outstanding
Description: No description available.
404021 AM [bssid:%s]: Unexpected channel [channel:%d] change by AM for RFprotect Sensor
radio
Description: No description available.
404046 AM [bssid:%s]: Low RSSI [rssi:%d] detected for STA [mac_str:%s] BSS [bssid_str:%s]
80 | Wireless Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
ESS [essid:%s] Deauthing STA
Description: No description available.
Page 81

Table 24 Wireless Warning Messages
Message ID Message and Description
404050 AM [bssid:%s]: ARM C [channel:%d] PER [per:%d] MER [mer:%d] FRR [frr:%d]
404052 AM [bssid:%s]: [message:%s]
404061 AM [bssid:%s]: ARM Band Request - GC [g_covered_channels:%d] AC
404062 AM [bssid:%s]: ARM Band Request - AC [a_covered_channels:%d] GC
404063 AM [bssid:%s]: ARM Channel Band Trigger new [channel:%d]-[arm_ii_arm_ccii:%d]/
404064 AM [bssid:%s]: ARM Radar Detected Trigger Current Channel [ap_amc_channel:%d]
404065 AM [bssid:%s]: ARM Error Threshold Trigger Current Channel [ap_amc_channel:%d]
[arm_error_rate_threshold:%d]-[arm_error_rate_wait_time:%d]
Description: No description available.
Description: No description available.
[a_covered_channels:%d]
Description: No description available.
[g_covered_channels:%d]
Description: No description available.
[arm_nii_arm_nccii:%d] old [ap_amc_channel:%d]-[arm_ccii_arm_ii:%d]/
[arm_nccii_arm_nii:%d] new_rra [min_amc_channel:%d]/[new_tx_power:%d]
Description: No description available.
new_rra [min_amc_channel:%d]/[new_tx_power:%d]
Description: No description available.
new_rra [min_amc_channel:%d]/[new_tx_power:%d]
Description: No description available.
404066 AM [bssid:%s]: ARM Invalid Channel Trigger Current Channel [ap_amc_channel:%d]
404067 AM [bssid:%s]: ARM Active Rogue Trigger new [rogue_channel:%d] old
404068 AM [bssid:%s]: ARM Noise Threshold Trigger Current Channel [ap_channel:%d] new_rra
404069 AM [bssid:%s]: ARM Channel Interference Trigger new [min_amc_channel:%d]-
404070 AM [bssid:%s]: ARM Empty Channel Trigger new [empty_amc_channel:%d]-
404071 AM [bssid:%s]: ARM Empty Co Channel Trigger new [empty_amc_channel:%d]-
new_rra [min_amc_channel:%d]/[new_tx_power:%d]
Description: No description available.
[ap_channel:%d] new_rra [channel:%d]/[new_tx_power:%d] TCI [arm_tci:%d]
Description: No description available.
[zero_ci_channel:%d]/[new_tx_power:%d]
Description: No description available.
[arm_nii_arm_nccii:%d] old [ap_amc_channel:%d]-[arm_nccii_arm_nii:%d] new_rra
[channel:%d]/[new_tx_power:%d] TCI [arm_tci:%d]
Description: No description available.
[empty_amc_arm_ii:%d]/[empty_amc_arm_nii:%d] old [ap_amc_channel:%d][ap_amc_arm_ii:%d]/[ap_amc_arm_nii:%d] new_rra [channel:%d]/[new_tx_power:%d]
Description: No description available.
[empty_amc_arm_ii:%d]/[empty_amc_arm_nii:%d] old [ap_amc_channel:%d][ap_amc_arm_ii:%d]/[ap_amc_arm_nii:%d] new_rra [channel:%d]/[new_tx_power:%d]
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Reference Guide Wireless Messages | 81
Page 82

Table 24 Wireless Warning Messages
Message ID Message and Description
404072 AM [bssid:%s]: ARM - too much power decreasing... cov-index [arm_ci:%d]/
404073 AM [bssid:%s]: ARM - too little power increasing... cov-index [arm_ci:%d]/[arm_nci:%d]
404074 AM [bssid:%s]: ARM - increasing power cov-index [arm_ci:%d]/[arm_nci:%d] tx-power
404075 AM [bssid:%s]: ARM - decreasing power cov-index [arm_ci:%d]/[arm_nci:%d] tx-power
404076 “AM [bssid:%s]: Radar detected on interface [interface:%s], channel [channel:%d],
404077 AM [bssid:%s]: ARM Channel Quality Threshold Trigger Current Channel
[arm_nci:%d] tx-power [current_tx_power:%d] new_rra [current_channel:%d]/
[arm_max_tx_power:%d]
Description: No description available.
tx-power [current_tx_power:%d] new_rra [current_channel:%d]/
[arm_min_tx_power:%d]
Description: No description available.
[current_tx_power:%d] new_rra [current_channel:%d]/[current_tx_power_1:%d]
Description: No description available.
[current_tx_power:%d] new_rra [current_channel:%d]/[current_tx_power_2:%d]
Description: No description available.
typeid [typeid:%d]”
Description: No description available.
[ap_channel:%d] new_rra [zero_ci_channel:%d]/[new_tx_power:%d] T
Description: No description available.
404085 AM [bssid:%s]: ARM HT Channel Interference Trigger new [min_amc_channel:%d]-
[min_amc_channel_sec:%d]/[arm_pii:%d] old [ap_amc_channel:%d]/
[ap_amc_channel_sec:%d]-[old_arm_pii:%d] new_rra [channel:%d]/[secondary:%d][new_tx_power:%d] TCI [arm_tci:%d]
Description: No description available.
404086 AM [bssid:%s]: ARM HT Noise Threshold Trigger Current Channel [ap_channel:%d]-
[ap_sec_channel:%d] new_rra [zero_ci_channel:%d]-[zero_ci_channel_sec:%d]/
[new_tx_power:%d]
Description: No description available.
404087 AM [bssid:%s]: ARM Invalid HT Channel Trigger Current Channel old
404088 AM [bssid:%s]: ARM HT Radar Detected Trigger Current Channel old
404089 AM [bssid:%s]: ARM HT Error Threshold Trigger Current Channel old
[ap_amc_channel:%d]-[ap_amc_sec_channel:%d] new [min_amc_channel:%d][min_sec_channel:%d]/[new_tx_power:%d]
Description: No description available.
[ap_amc_channel:%d]-[ap_amc_sec_channel:%d] new [min_amc_channel:%d][min_sec_channel:%d]/[new_tx_power:%d]
Description: No description available.
[ap_amc_channel:%d]-[ap_amc_sec_channel:%d] new [min_amc_channel:%d][min_sec_channel:%d]/[new_tx_power:%d]
Description: No description available.
404090 Description: AM [bssid:%s]: ARM HT Channel Quality Threshold Trigger Current
82 | Wireless Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Channel [ap_channel:%d]-[ap_sec_channel:%d] new_rra [zero_ci_channel:%d][zero_ci_channel_sec:%d]/[new_tx_power:%d]
Description: No description available.
Page 83

Table 24 Wireless Warning Messages
Message ID Message and Description
404092 AM [bssid:%s]: ARM HT Channel Band Trigger new [channel:%d]-[sec_channel:%d]-
404093 AM [bssid:%s]: ARM HT Empty Channel Trigger new [empty_amc_channel:%d]-
404094 AM [bssid:%s]: ARM HT Empty Co Channel Trigger new [empty_amc_channel:%d]-
404095 AM [bssid:%s]: ARM - HT too much power decreasing... cov-index [arm_ci:%d]/
404096 AM [bssid:%s]: ARM - HT too little power increasing... cov-index [arm_ci:%d]/
[arm_ii_arm_ccii:%d]/[arm_nii_arm_nccii:%d] old [ap_amc_channel:%d][ap_amc_channel_sec:%d]-[arm_ccii_arm_ii:%d]/[arm_nccii_arm_nii:%d] new_rra
[min_amc_channel_pri:%d]-[min_amc_channel_sec:%d]/[new_tx_power:%d]
Description: No description available.
[empty_amc_channel_sec:%d]/[empty_amc_arm_ii:%d]/[empty_amc_arm_nii:%d] old
[ap_amc_channel:%d]-[ap_amc_channel_sec:%d]/[ap_amc_arm_ii:%d]/
[ap_amc_arm_nii:%d] new_rra [channel:%d]-[channel_sec:%d]/[new_tx_power:%d]
Description: No description available.
[empty_amc_channel_sec:%d]/[empty_amc_arm_ii:%d]/[empty_amc_arm_nii:%d] old
[ap_amc_channel:%d]-[ap_amc_channel_sec:%d]/[ap_amc_arm_ii:%d]/
[ap_amc_arm_nii:%d] new_rra [channel:%d]-[channel_sec:%d]/[new_tx_power:%d]
Description: No description available.
[arm_nci:%d] tx-power [current_tx_power:%d] new_rra [current_channel:%d][sec_channel:%d]/[arm_max_tx_power:%d]
Description: No description available.
[arm_nci:%d] tx-power [current_tx_power:%d] new_rra [current_channel:%d][sec_channel:%d]/[arm_min_tx_power:%d]
Description: No description available.
404097 AM [bssid:%s]: ARM - HT increasing power cov-index [arm_ci:%d]/[arm_nci:%d] tx-
404098 AM [bssid:%s]: ARM - HT decreasing power cov-index [arm_ci:%d]/[arm_nci:%d] tx-
404099 AM [bssid:%s]: Tx Hang: Driver reset radio to 20 MHz mode [current_channel:%d]-
404100 AM [bssid:%s]: Tx Hang cleared: Set radio back to 40 MHz mode [current_channel:%d]-
404102 AM [bssid:%s]: ARM - Radar event cleared on channel [radar_channel:%d]
404404 AM [bssid:%s]: AP to APM : Too much coverage on channel [channel:%d] coverage
404405 AM [bssid:%s]: Coverage hole: APM converting to AP on channel [channel:%d]
power [current_tx_power:%d] new_rra [current_channel:%d]-[sec_channel:%d]/
[current_tx_power_1:%d]
Description: No description available.
power [current_tx_power:%d] new_rra [current_channel:%d]-[sec_channel:%d]/
[current_tx_power_2:%d]
Description: No description available.
[current_sec_channel:%d]
Description: No description available.
[current_sec_channel:%d]
Description: No description available.
Description: No description available.
[arm_ci:%d] tx-power [current_tx_power:%d]
Description: No description available.
coverage [amc_coverage:%d] [tx_power:%d]
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Reference Guide Wireless Messages | 83
Page 84

Table 24 Wireless Warning Messages
Message ID Message and Description
404406 AM [bssid:%s]:SM: Unexpected channel [channel:%d] change by AM for Spectrum
Monitor radio
Description: No description available.
Notice Messages
Table 25 Wireless Notice Message
Message ID Message and Description
400102 AP [name:%s]: probe request: dropped entry in ip table for [ip:%P]
Description: No description available.
400160 AP [name:%s]: Starting to configure AP at [ap:%p]
Description: No description available.
400161 “AP [name:%s]: Registering AP: IP [apip:%p], BSS [bss:%m], [phy:%s] band, [T:%s]
mode, max clients [MC:%d], [CV:%d%] virtual APs
Description: No description available.
400168 Added AP [bssid:%m]-[name:%s]
Description: No description available.
400175 AP Radio Attributes Changed - BSSID [bssid:%m] Name [name:%s] IP [ip:%P] Channel
[channel:%d] Tx Power [tx_power:%s]
Description: No description available.
400185 [func:%s]:[bssid:%m] High Capacity Threshold Enabled
Description: No description available.
400186 [func:%s]:[bssid:%m] High Capacity Threshold Disabled
Description: No description available.
400187 [func:%s]:[bssid:%m] Call Handoff Reservation Enabled
Description: No description available.
400188 [func:%s]:[bssid:%m] Call Handoff Reservation Disabled
Description: No description available.
400189 Station EDCA parameters configured: AC=[ac:%s] params=[af:%d] [cmin:%d]
400190 AP EDCA parameters configured: AC=[ac:%s] params=[af:%d] [cmin:%d] [cmax:%d]
400192 STA [mac: %m] at AP [ip:%P]-[bssid:%m]-[name: %s] 5GHz capable.
[cmax:%d] [t:%d] [acm:%d]
Description: No description available.
[t:%d] [acm:%d]
Description: No description available.
Description: No description available.
404083 “AM: Tag ([MAC:%s]) detected on channel [channel:%d], battery = [battery:%d], tx-
power = [tx_pwr:%d] and notification is sent to [to:%s]
Description: Tag chirp packet is detected and sent to rtls servers.
84 | Wireless Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
Page 85

Table 25 Wireless Notice Message
Message ID Message and Description
404400 AM:SM: Spectrum: new Wi-Fi device found = [addr:%s] SSID = [ssid:%s] BSSID
404401 AM:SM: Spectrum: deleting Wi-Fi device = [addr:%s] SSID = [ssid:%s] BSSID
404402 AM:SM: Spectrum: new non-Wi-Fi device found = DEVICE ID [did:%u] Type [dytpe:%s]
404403 AM:SM: Spectrum: deleting non-Wi-Fi device = DEVICE ID [did:%d] Type [dtype:%s]
[bssid_str:%s] DEVICE ID [did:%d]
Description: This log indicates a new Wi-Fi device is detected by the spectrum radio.
[bssid_str:%s] DEVICE ID [did:%d].
Description: This log indicates a previously detected Wi-Fi device is being deleted due
to inactivity.
Signal [sig:%u] Freq [freq:%u]KHz Bandwidth [bw:%u]KHz
Description: This log indicates a new non-Wi-Fi device is detected by the spectrum
radio.
Description: This log indicates a previously detected non-Wi-Fi device is being deleted
due to inactivity.
Information Messages
Table 26 Wireless Information Messages
Message ID Message and Description
400189 Station EDCA parameters configured: AC=[ac:%s] params=[af:%d] [cmin:%d]
400193 VPOOL: STA [mac:%m] at AP [ip:%P]-[bssid:%m]-[name: %s] assigned vlan [vid:%d].
[cmax:%d] [t:%d] [acm:%d].
Description: No description available.
Description: This message indicates VLAN assigned to a new station
Debug Messages
Table 27 Wireless Debug Messages
Message ID Message and Description
400100 AP [name:%s]: LED state [state:%x]
Description: No description available.
400101 AP [name:%s]: Unidentified rate [val1:%x] [val2:%x]
Description: No description available.
400110 AP [name:%s]: Delete AP state for bssid [bss:%m]; Deauth [deauth:%d] Clear [clear:%d]
Description: No description available.
400131 AP [name:%s]: SAPCP Received SAPCP Probe - [band:%s]- [bssis:%m]
Description: No description available.
400132 AP [name:%s]: SAPCP Sending SAPCP Probe Response
Description: No description available.
Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Reference Guide Wireless Messages | 85
Page 86

Table 27 Wireless Debug Messages
Message ID Message and Description
400133 “AP [name:%s]: SAPCP Probe from unknown bssid [bss:%m], dropping
Description: No description available.
400134 AP [name:%s]: SAPCP: Unknown sap
Description: No description available.
400162 “AP [name:%s]: Registering AP, new virtual ap for ESSID [ess:%s], deny broadcast
[db:%d]
Description: No description available.
400166 [msg:%s]
Description: No description available.
400191 BSSID [bssid:%m]: STA [sta:%m] AID [aid:%d]: Duplicate AID on STA [osta:%m]
Description: No description available.
404014 AM: [msg:%s]
Description: No description available.
404051 AM: ARM Channel [channel:%d] Current Noise Level [noise:%d] ARM Noise threshold
404053 AM: ARM Channel [channel:%d] Current Channel Quality Level [ch_quality:%d] ARM
[arm_noise_threshold:%d] ARM Noise wait time [arm_noise_wait_time:%d]
Description: No description available.
Channel Quality threshold [arm_channel_quality_threshold:%d] ARM Channel Quality
wait time [arm_channel_quality_wait_time:%d] T
Description: No description available.
86 | Wireless Messages Dell Networking W-Series Instant Access Point 6.2.1.0-3.4 | Syslog Messages Reference Guide
 Loading...
Loading...