Page 1

Dell Networking W-Series
Instant Access P oint
6.2.1.0-3.4
Command-Line
Interface
Reference Guide
Page 2

Copyright
© 2013 Aruba Networks, Inc. Aruba Networks trademarks include , Aruba Networks®, Aruba
Wireless Networks®, the registered Aruba the Mobile Edge Company logo, and Aruba Mobility Management
System®. Dell™, the DELL™ logo, and PowerConnect™ are trademarks of Dell Inc.
All rights reserved. Specifications in this manual are subject to change without notice.
Originated in the USA. All other trademarks are the property of their respective owners.
Open Source Code
Certain Aruba products include Open Source software code developed by third parties, including software code
subject to the GNU General Public License (GPL), GNU Lesser General Public License (LGPL), or other Open
Source Licenses. Includes software from Litech Systems Design. The IF-MAP client library copyright 2011 Infoblox,
Inc. All rights reserved. This product includes software developed by Lars Fenneberg, et al. The Open Source code
used can be found at this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba Networks, Inc. switching platforms and software, by all individuals or corporations, to terminate
other vendors’ VPN client devices constitutes complete acceptance of liability by that individual or corporation for
this action and indemnifies, in full, Aruba Networks, Inc. from any and all legal actions that might be taken against it
with respect to infringement of copyright on behalf of those vendors.
0511433-01 | July2013 Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 3

Chapter 1
About this Guide
This document describes the Dell W-Instant command syntax and provides the following information for each
command:
l Command Syntax—The complete syntax of the command.
l Description—A brief description of the command.
l Syntax—A description of the command parameters, the applicable ranges and default values, if any.
l Usage Guidelines—Information to help you use the command, including prerequisites, prohibitions, and related
commands.
l Example—An example of how to use the command.
l Command History—The version of Dell W-Instant in which the command was first introduced.
l Command Information—This table describes command modes and platforms for which this command is
applicable.
The commands are listed in alphabetical order.
Intended Audience
This guide is intended for customers who configure and use Dell W-Instant.
Related Documents
In addition to this document, the Dell W-Instant product documentation includes the following:
l Dell Networking W-Series Instant 6.2.1.0-3.4 Quick Start Guide
l Dell Networking W-Series Instant 6.2.1.0-3.4 User Guide
l Dell Networking W-Series Instant 6.2.1.0-3.4 MIB Reference Guide
l Dell Networking W-Series Instant 6.2.1.0-3.4 Syslog Messages Reference Guide
l Dell Networking W-Series Instant 6.2.1.0-3.4 Release Notes
Conventions
The following conventions are used throughout this document to emphasize important concepts:
Table 1:
Type Style Description
Italics
Typographical Conventions
This style is used for emphasizing important terms and to mark
the titles of books.
Boldface
Commands
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide About this Guide | 3
This style is used for command names and parameter options
when mentioned in the text.
This fixed-width font depicts command syntax and examples of
commands and command output.
Page 4

Type Style Description
<angle brackets> In the command syntax, text within angle brackets represents
items that you should replace with information appropriate to
your specific situation.
For example, ping <ipaddr>
In this example, you would type “ping” at the system prompt
exactly as shown, followed by the IP address of the system to
which ICMP echo packets are to be sent. Do not type the angle
brackets.
[square brackets] In the command syntax, items enclosed in brackets are
optional. Do not type the brackets.
{Item_A|Item_B} In the command examples, single items within curled braces
and separated by a vertical bar represent the available
choices. Enter only one choice. Do not type the braces or bars.
{ap-name <ap-name>}|{ipaddr <ip-addr>} Two items within curled braces indicate that both parameters
must be entered together. If two or more sets of curled braces
are separated by a vertical bar, like in the example to the left,
enter only one choice. Do not type the braces or bars.
The following informational icons are used throughout this guide:
Indicates helpful suggestions, pertinent information, and important things to remember.
Indicates a risk of damage to your hardware or loss of data.
Indicates a risk of personal injury or death.
Contacting Support
Web Site Support
Main Website
Support Website
Documentation Website
dell.com
dell.com/support
dell.com/support/manuals
4 | About this Guide Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 5
Chapter 2
Dell W-Instant CLI
In the current release, Dell W-Instant supports the use of Command Line Interface (CLI) for scripting purposes. You
can access the Instant CLI through a Secure Shell (SSH).
To enable the SSH access to the Instant CLI:
1. From the Dell W-Instant UI, navigate to System > Show advanced options.
2. Select Enabled from the Terminal access drop-down list.
3. Click OK.
Connecting to a CLI Session
On connecting to a CLI session, the system displays its host name followed by the login prompt. Use the
administrator credentials to start a CLI session. For example:
(Instant Access Point)
User: admin
Password: *****
If the login is successful, the privileged command mode is enabled and a command prompt is displayed. For
example:
(Instant Access Point)#
The privileged mode provides access to show, clear, ping, traceroute, and commit commands. The configuration
commands are available in the configuration (config) mode. To move from privileged mode to the configuration mode,
enter the following command at the command prompt:
(Instant Access Point)# configure terminal
The configure terminal command allows you to enter the basic configuration mode and the command prompt is
displayed as follows:
(Instant Access Point)(config)#
The Instant CLI allows CLI scripting in several other sub-command modes to allow the users to configure individual
interfaces, SSIDs, access rules, and security settings.
You can use the question mark (?) to view the commands available in a privileged mode, configuration mode, or submode.
Although automatic completion is supported for some commands such as configure terminal, the complete exit
and end commands must be entered at command prompt for successful execution.
Applying Configuration Changes
Each command processed by the Virtual Controller is applied on all the slaves W-IAPs in a cluster. When you make
configuration changes on a master W-IAP in the CLI, all associated W-IAPs in the cluster inherit these changes and
subsequently update their configurations. The changes configured in a CLI session are saved in the CLI context.
The CLI does not support the configuration data exceeding the 4K buffer size in a CLI session: therefore, it is
recommended that you configure fewer changes at a time and apply the changes at regular intervals.
To apply changes at regular intervals, use the following command in the privileged mode:
(Instant Access Point)# commit apply
To view the changes that are yet to be applied, use the following command in the privileged mode:
(Instant Access Point)# show uncommitted-config
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide Dell W-Instant CLI | 5
Page 6

To revert to the earlier configuration, use the following command in the privileged mode.
(Instant Access Point)# commit revert
Example:
(Instant Access Point)(config)# rf dot11a-radio-profile
(Instant Access Point)(RF dot11a Radio Profile)# beacon-interval 200
(Instant Access Point)(RF dot11a Radio Profile)# no legacy-mode
(Instant Access Point)(RF dot11a Radio Profile)# dot11h
(Instant Access Point)(RF dot11a Radio Profile)# interference-immunity 3
(Instant Access Point)(RF dot11a Radio Profile)# csa-count 2
(Instant Access Point)(RF dot11a Radio Profile)# spectrum-monitor
(Instant Access Point)(RF dot11a Radio Profile)# end
(Instant Access Point)# show uncommitted-config
rf dot11a-radio-profile
no legacy-mode
beacon-interval 200
no dot11h
interference-immunity 3
csa-count 1
no spectrum-monitor
Instant Access Point# commit apply
Configuration Sub-modes
Some commands in configuration mode allow you to enter into a sub-mode to configure the commands specific to
that mode. When you are in a configuration sub-mode, the command prompt changes to indicate the current submode.
You can exit a sub-command mode and return to the basic configuration mode or the privileged Exec (enable) mode
at any time by executing the exit or end command.
Deleting Configuration Settings
Use the no command to delete or negate previously-entered configurations or parameters.
l To view a list of no commands, type no at the prompt in the relevant mode or sub-mode followed by the question
mark. For example:
(Instant Access Point)(config) # no?
l To delete a configuration, use the no form of a configuration command. For example, the following command
removes a configured user role:
(Instant Access Point)(config) # no user <username>
l To negate a specific configured parameter, use the no parameter within the command. For example, the following
command deletes the PPPoE user configuration settings:
(Instant Access Point)(config) # pppoe-uplink-profile
(Instant Access Point)(pppoe_uplink_profile)# no pppoe-username
Using Sequence Sensitive Commands
The Instant CLI does not support positioning or precedence of sequence-sensitive commands. Therefore, it is
recommended that you remove the existing configuration before adding or modifying the configuration details for
sequence-sensitive commands. You can either delete an existing profile or remove a specific configuration by using
the no… commands.
The following table lists the sequence-sensitive commands and the corresponding no command to remove the
configuration.
6 | Dell W-Instant CLI Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 7

Table 2:
Sequence-Sensitive Commands
Sequence-Sensitive Command Corresponding no command
opendns <username <password> no opendns
rule <dest> <mask> <match> <protocol> <start-port>
<end-port> {permit |deny | src-nat | dst-nat {<IPaddress> <port>| <port>}}[<option1…option9>]
mgmt-auth-server <auth-profile-name>
set-role <attribute>{{equals| not-equals| startswith| ends-with| contains} <operator> <role>| valueof}
set-vlan <attribute>{{equals| not-equals| startswith| ends-with| contains} <operator> <VLAN-ID>|
value-of}
auth-server <name> no auth-server <name>
no rule <dest> <:mask> <match>
<protocol> <start-port> <end-port>
{permit | deny | src-nat | dst-nat}
no mgmt-auth-server <auth-profilename>
no set-role <attribute>{{equals|
not-equals| starts-with| ends-with|
contains} <operator>| value-of}
no set-role
no set-vlan <attribute>{{equals|
not-equals| starts-with| ends-with|
contains} <operator>| value-of}
no set-vlan
Saving Configuration Changes
The
running-config
To view the running-config of a W-IAP, use the following command:
holds the current W-IAP configuration, including all pending changes which are yet to be saved.
(Instant Access Point) # show running-config
When you make configuration changes through the CLI, the changes affect the current running configuration only. To
save your configuration changes, use the following command in the privileged Exec mode:
(Instant Access Point)# write memory
Commands that Reset the W-IAP
If you use the CLI to modify a currently provisioned radio profile, the changes take place immediately. A reboot of the
W-IAP is not required to apply the configuration changes. Certain commands, however, automatically force W-IAP
to reboot. Verify the current network loads and conditions before executing the commands that enforce a reboot of
the W-IAP, as they may cause a momentary disruption in service as the unit resets.
The reload command resets a W-IAP.
Command Line Editing
The system records your most recently entered commands. You can review the history of your actions, or reissue a
recent command easily, without having to retype it.
To view items in the command history, use theuparrow key to move back through the list and the
move forward. To reissue a specific command, press Enter when the command appears in the command history.
You can also use the command line editing feature to make changes to the command prior to entering it. The
command line editing feature allows you to make corrections or changes to a command without retyping. The
following table lists the editing controls. To use key shortcuts, press and hold the Ctrl button while you press a letter
key.
down
arrow key to
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide Dell W-Instant CLI | 7
Page 8
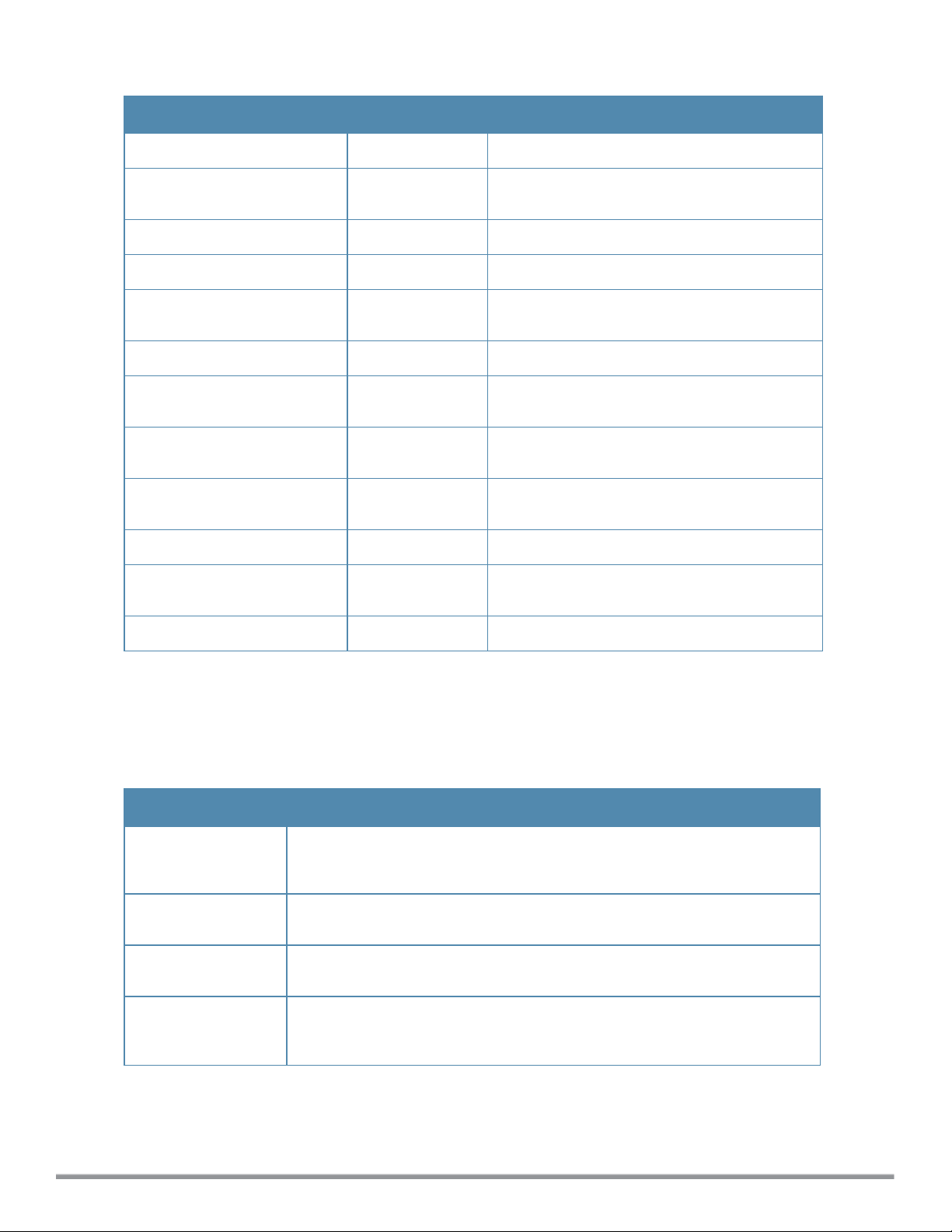
Table 3:
Line Editing Keys
Key Effect Description
Ctrl A Home Move the cursor to the beginning of the line.
Ctrl B or the
left arrow
Ctrl D Delete Right Delete the character to the right of the cursor.
Ctrl E End Move the cursor to the end of the line.
Ctrl F or the
right arrow
Ctrl K Delete Right Delete all characters to the right of the cursor.
Ctrl N or the
down arrow
Ctrl P or
up arrow
Ctrl T Transpose Swap the character to the left of the cursor with
Ctrl U Clear Clear the line.
Ctrl W Delete Word Delete the characters from the cursor up to and
Ctrl X Delete Left Delete all characters to the left of the cursor.
Back Move the cursor one character left.
Forward Move the cursor one character right.
Next Display the next command in the command
history.
Previous Display the previous command in the command
history.
the character to the right of the cursor.
including the first space encountered.
Specifying Addresses and Identifiers in Commands
This section describes addresses and other identifiers that you can reference in CLI commands.
Table 4:
Address/Identifier Description
IP address For any command that requires entry of an IP address to specify a network entity,
Netmask address For subnet addresses, specify a subnet mask in dotted decimal notation (for
Media Access Control
(MAC) address
Service Set Identifier
(SSID)
Addresses and Identifiers
use IPv4 network address format in the conventional dotted decimal notation (for
example, 192.0.2.1).
example, 255.255.255.0).
For any command that requires entry of a device’s hardware address, use the
hexadecimal format (for example, 00:05:4e:50:14:aa).
A unique character string (sometimes referred to as a network name), consisting
of no more than 32 characters. The SSID is case-sensitive (for example, WLAN-
01).
8 | Dell W-Instant CLI Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 9

Address/Identifier Description
Basic Service Set
Identifier (BSSID)
Extended Service Set
Identifier (ESSID)
This entry is the unique hard-wireless MAC address of the AP. A unique BSSID
applies to each frequency— 802.11a and 802.11g—used from the AP. Use the
same format as for a MAC address.
Typically the unique logical name of a wireless network. If the ESSID includes
spaces, enclose the name in quotation marks.
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide Dell W-Instant CLI | 9
Page 10
aaa test-server
aaa test-server <servername> <username>
Description
This command tests a configured authentication server.
Syntax
Parameter Description
<servername>
<username>
Allows you to specify the authentication server for which the authentication test
is run.
Allows you to specify the user name for which the authentication test is run.
Usage Guidelines
Use this command to view the CPU load for application and system processes. This command allows you to verify
a configured RADIUS authentication server or the internal database. You can use this command to check for an “out
of service” RADIUS server.
Example
The following example shows the output of the aaa test-server command:
Authentication is successful
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
10 | aaa test-server Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Privileged EXEC mode
Page 11
a-channel
a-channel <channel> <tx-power>
Description
This command configures 5 GHz radio channels for a specific W-IAP.
Syntax
Parameter Description Range
<channel>
<tx-power>
Configures the specified 5 GHz channel. The valid channels for a band
are determined by the AP
regulatory domain.
Configures the specified transmission
power values.
0-127 dBm
Usage Guidelines
Use this command to configure radio channels for the 5 GHz band for a specific W-IAP.
Example
The following example configures the 5 GHz radio channel:
(Instant Access Point)# a-channel 44 18
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide a-channel | 11
Privileged EXEC mode
Page 12
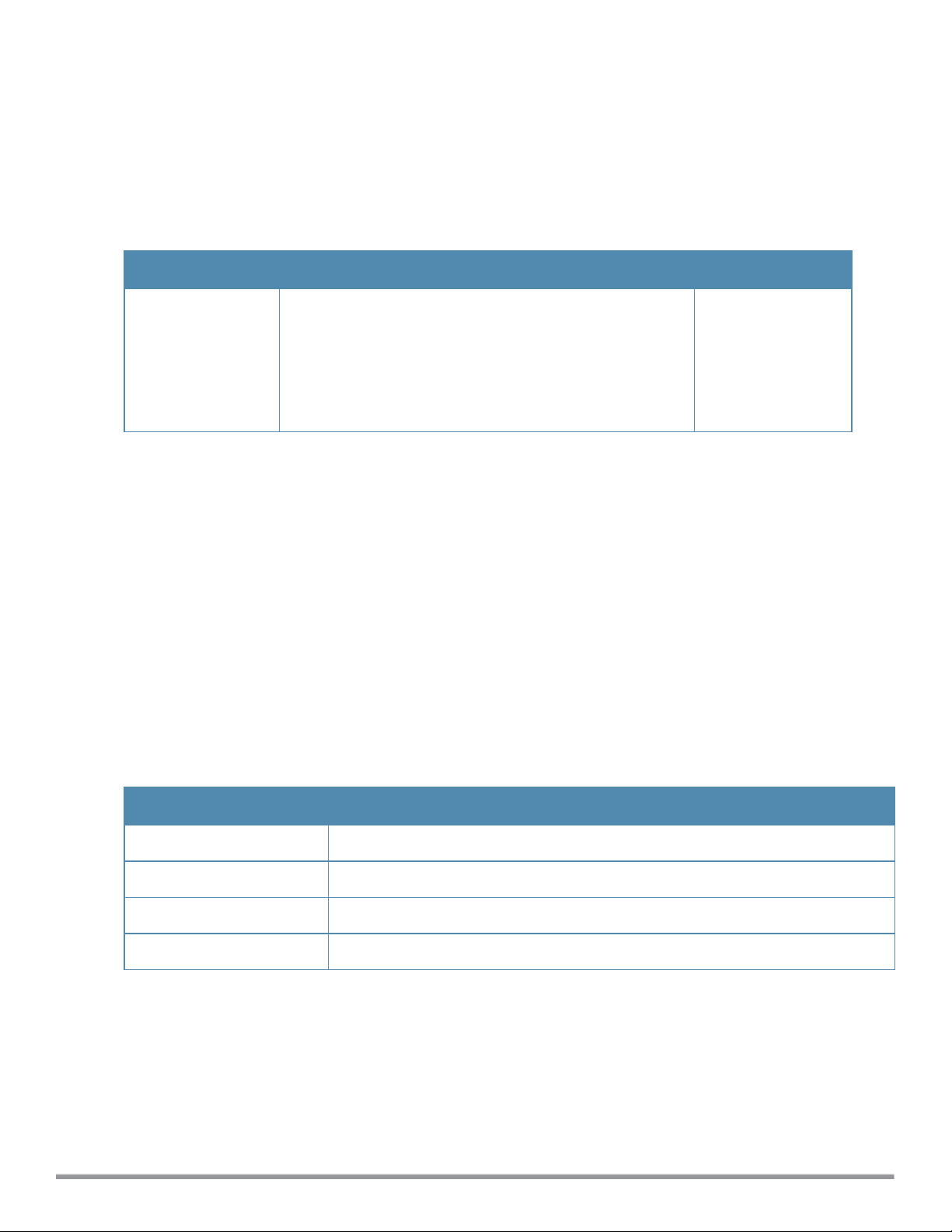
a-external-antenna
a-external-antenna <gain>
Description
This command configures external antenna connectors for a W-IAP.
Syntax
Parameter Description Range
<gain>
Configures the antenna gain. You can configure a gain value
in dBi for the following types of antenna:
l Dipole/Omni
l Panel
l Sector
Diploe/Omni - 6
Panel -14
Sector - 14
Usage Guidelines
If your W-IAP has external antenna connectors, you need to configure the transmit power of the system. The
configuration must ensure that the system’s Equivalent Isotropically Radiated Power (EIRP) is in compliance with
the limit specified by the regulatory authority of the country in which the W-IAP is deployed. You can also measure or
calculate additional attenuation between the device and antenna before configuring the antenna gain. To know if your
AP device supports external antenna connectors, see the
EIRP and Antenna Gain
The following formula can be used to calculate the EIRP limit related RF power based on selected antennas
(antenna gain) and feeder (Coaxial Cable loss):
EIRP = Tx RF Power (dBm)+GA (dB) - FL (dB)
The following table describes this formula:
Install Guide
that is shipped along with the AP device.
Table 5:
Formula Variable Definitions
Formula Element Description
EIRP Limit specific for each country of deployment
Tx RF Power RF power measured at RF connector of the unit
GA Antenna gain
FL Feeder loss
For information on antenna gain recommended by the manufacturer, see dell.com/support.
Example
The following example configures external antenna connectors for the W-IAP with the 5 GHz radio band.
(Instant Access Point)# a-external-antenna 14
12 | a-external-antenna Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 13

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide a-external-antenna | 13
Page 14
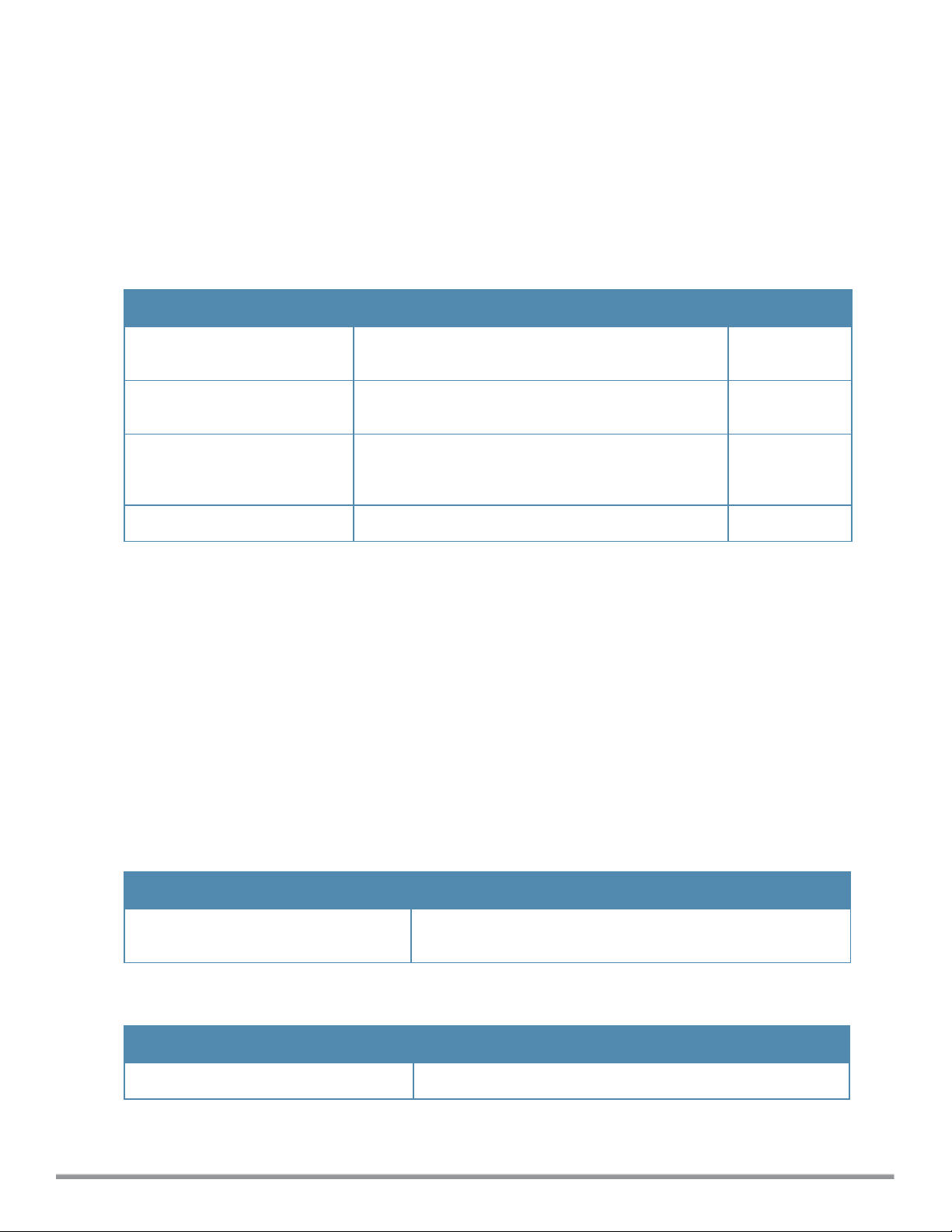
aeroscout-rtls
aeroscout-rtls <IP-address> <Port> [include-unassoc-sta]
no...
Description
This command configures the Aeroscout Real-Time Asset Location Server (RTLS) settings for Instant and sends the
Radio-frequency identification (RFID) tag information to an Aeroscout RTLS server.
Syntax
Command/Parameter Description Default
<IP-address>
<Port>
include-unassoc-stas
no
IP address of the Aeroscout RTLS server to which the
location reports are sent.
Port number of the Aeroscout RTLS server to which the
location reports are sent..
Includes the client stations not associated to any W-IAP
when mobile unit reports are sent to the Aeroscout
RTLS server.
Removes the Aeroscout RTLS configuration. —
—
—
Disabled
Usage Guidelines
This command allows you to integrate Aeroscout RTLS server with Instant by specifying the IP address and port
number of the Aeroscout RTLS server. When enabled, the RFID tag information for the stations associated with a
W-IAP are sent to the AeroScout RTLS. You can also send the RFID tag information for the stations that are not
associated with any W-IAP.
Example
The following example configures the Aeroscout RTLS server:
(Instant Access Point)(config)# aeroscout-rtls 192.0.2.2 3030 include-unassoc-sta
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
Command was introduced.
Command Information
W-IAP Platform Command Mode
All platforms
14 | aeroscout-rtls Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 15
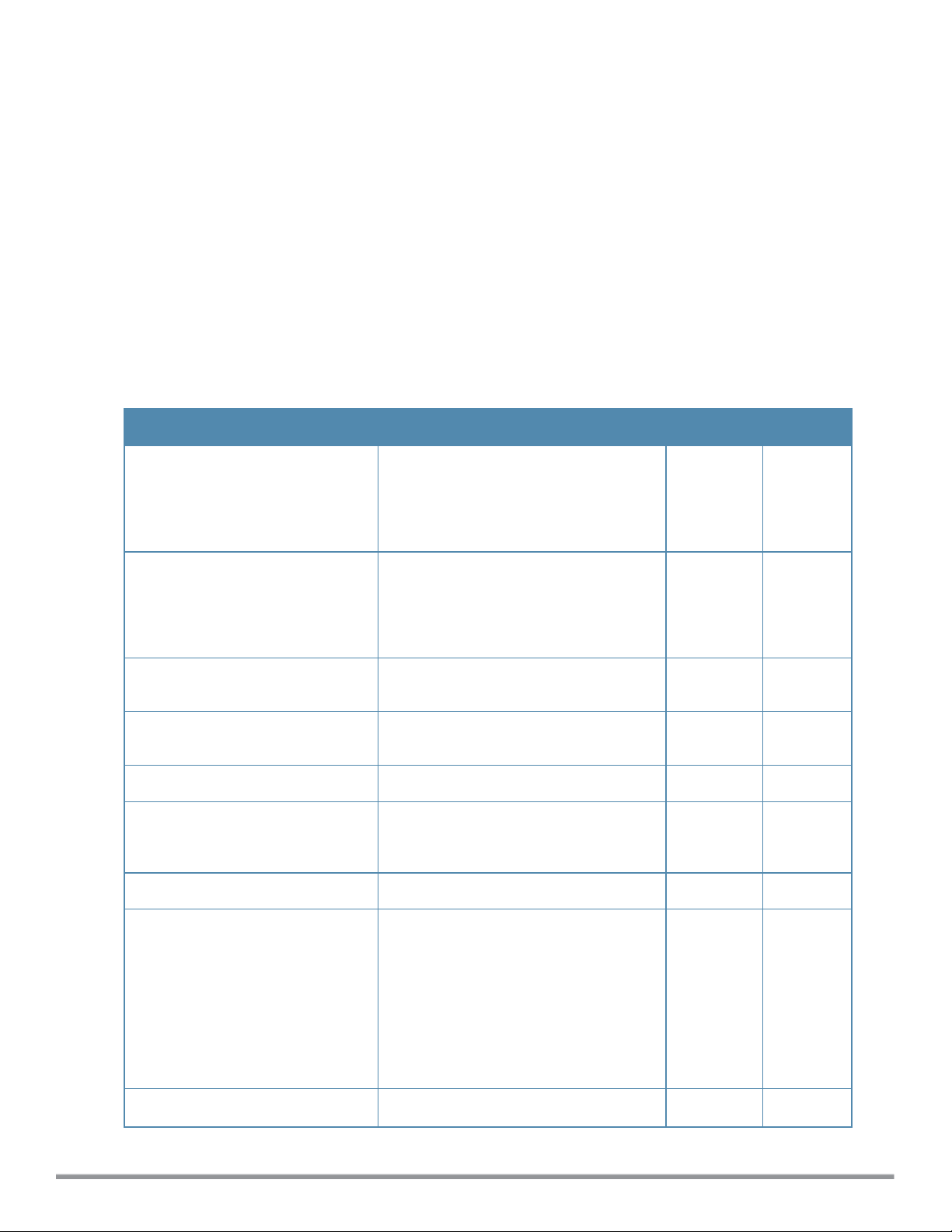
airgroup
airgroup
cppm enforce-registration
cppm-query-interval <interval>
cppm-server <server-name>
cppm-server-dead-time <interval>
disable
enable
enable-guest-multicast
multi-swarm
no…
Description
This command configures the AirGroup settings for Instant.
Syntax
Parameter Description Range Default
cppm enforce-registration
cppm-query-interval
<interval>
cppm-server <server-name>
cppm-server-dead-time
<interval>
disable
disallow-vlan
enable
Enforces the discovery of the CPPM
registered devices. When enabled, only
devices registered with CPPM will be
discovered by Bonjour® devices, based
on the CPPM policy configured.
Configures a time interval at which Instant
sends a query to ClearPass Policy
Manager for mapping the access
privileges of each device to the available
services.
Configures the ClearPass Policy Manager
server information for AirGroup policy.
Sets a dead time for the CPPM server. 0-60
Disables the AirGroup feature. — —
Excludes the VLANs, so that AirGroup
services such as AirPrint or AirPrint are
not discovered by all clients.
Enables the AirGroup feature. — —
— Enabled
1-60
minutes
— —
minutes
— Disabled
5
0
enable-guest-multicast
multi-swarm
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide airgroup | 15
Allows the users to use the Bonjour
services enabled in a guest VLAN. When
enabled, the Bonjour devices will be
visible only in the guest VLAN and
AirGroup will not discover or enforce
policies in guest VLAN.
Enables inter cluster or intra cluster — Disabled
— Enabled
Page 16
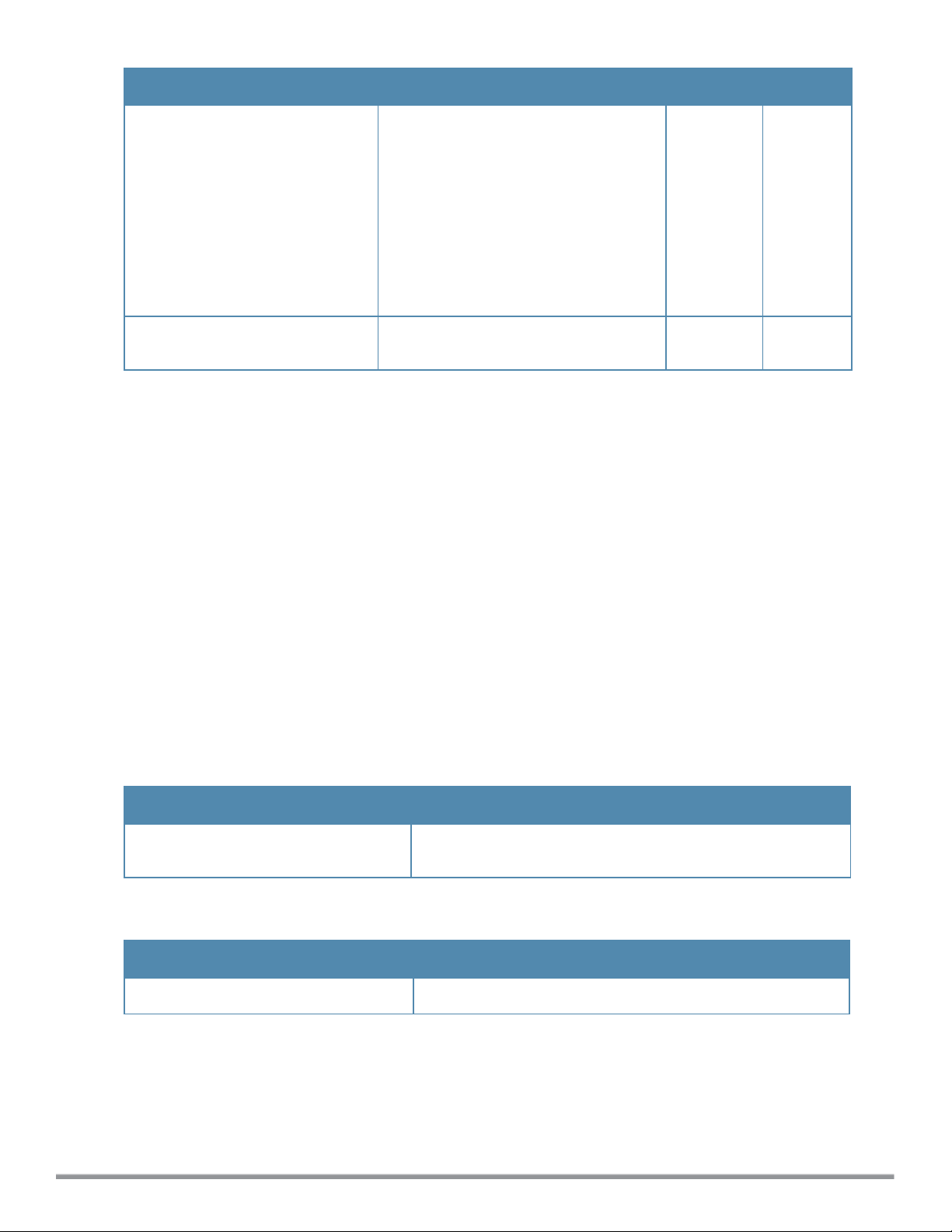
Parameter Description Range Default
mobility.
l In the Intra Cluster model, the W-IAP
does not share the Multicast DNS
(mDNS) database information with the
other clusters.
l In the Inter Cluster model, the W-IAP
shares the mDNS database
information with the other clusters. The
DNS records in the Virtual Controller
can be shared with the all the Virtual
Controllers specified for L3 Mobility.
no…
Removes the specified configuration
parameter.
— —
Usage Guidelines
Use this command to configure the AirGroup, the availability of the AirGroup services, and Dell Networking WClearPass Policy Manager (CPPM) servers.
Example
The following example configures an AirGroup profile:
(Instant Access Point)(config)# airgroup
(Instant Access Point)(airgroup)# cppm enforce-registration
(Instant Access Point)(airgroup)# cppm-server Test
(Instant Access Point)(airgroup)# cppm-server-dead-time 30
(Instant Access Point)(airgroup)# cppm-query-interval 10
(Instant Access Point)(airgroup)# disallow-vlan 200
(Instant Access Point)(airgroup)# enable-guest-multicast
(Instant Access Point)(airgroup)# multi-swarm
(Instant Access Point)(airgroup)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
16 | airgroup Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode and AirGroup configuration sub-mode.
Page 17

airgroupservice
airgroupservice <AirGroup-service-profile>
description <description>
disallow-role <role>
disallow-vlan <VLAN-ID>
enable
disable
id <AirGroupservice-ID>
no…
Description
This command configures the availability of AirGroup services such as AirPrint™ and AirPlay™ for a W-IAP.
Syntax
Parameter Description Default
<AirGroup-service>
<description>
disallow-role <role>
disallow-vlan <VLAN-ID>
enable
disable
id <AirGroupservice-ID>
no…
Assigns a name for the AirGroup service profile. —
Adds a description to the AirGroup Service profile. —
Restricts the user roles specified for role from
accessing the AirGroup service.
Restricts the users assigned to these VLANs from
accessing the AirGroup service.
Enables the AirGroup service for the profile. —
Disables AirGroup services for the profile. —
Indicates the AirGroup service ID, which is the name of
a Bonjour service offered by a Bonjour-enabled device
or application.
Removes the AirGroup service configuration. —
Disabled
Disabled
—
Usage Guidelines
Use this command to enforce AirGroup service policies and define the availability of a Bonjour services such as
Apple® AirPrint and AirPlay for an AirGroup profile. When configuring Bonjour service for an AirGroup profile, you
can also restrict specific user roles and VLANs from availing the AirGroup services.
Example
The following example configures AirGroup services:
(Instant Access Point)(config)# airgroupservice Example
(Instant Access Point)(airgroup-service)# id 23
(Instant Access Point)(airgroup-service)# description Example AirGroup Service
(Instant Access Point)(airgroup-service)# disallow-role guest
(Instant Access Point)(airgroup-service)# disallow-vlan 200
(Instant Access Point)(airgroup-service)# end
(Instant Access Point)# commit apply
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide airgroupservice | 17
Page 18

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and AirGroup services configuration submode.
18 | airgroupservice Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 19
airwave-rtls
airwave-rtls <IP-address> <Port> <key> <frequency> [include-unassoc-sta]
no…
Description
This command integrates W-AirWave Real-Time Asset Location Server (RTLS) settings for Instant and sends the
Radio-frequency identification (RFID) tag information to an W-AirWave RTLS server with the RTLS feed to
accurately locate the wireless clients.
Syntax
Command/Parameter Description Default
<IP-address>
<Port>
<key>
<frequency>
include-unassoc-sta
no…
Configures the IP address of the W-AirWave RTLS
server.
Configures the port for the W-AirWave RTLS server. —
Configures key for service authorization. —
Configures the frequency at which packets are sent to
the RTLS server in seconds.
When enabled, this option sends mobile unit reports to
the W-AirWave RTLS server for the client stations that
are not associated to any W-IAP (unassociated
stations).
Removes the specified configuration parameter. —
—
5
Disabled
Usage Guidelines
Use this command to send the RFID tag information to W-AirWave RTLS. Specify the IP address and port number
of the W-AirWave server, to which the location reports must be sent. You can also send reports of the unassociated
clients to the RTLS server for tracking purposes.
Example
The following command enables AirWave RTLS:
(Instant Access Point)(config) # airwave-rtls ams-ip 192.0.2.3 3030 pass@1234 5 includeunassoc-sta
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide airwave-rtls | 19
Configuration mode
Page 20
alg
alg
sccp-disable
sip-disable
ua-disable
vocera-disable
no…
Description
This command allows you to modify the configuration settings for Application Layer Gateway (ALG) protocols
enabled on a W-IAP. An application-level gateway consists of a security component that augments a firewall or
NAT used in a network.
Syntax
Command/Parameter Description Default
sccp-disable
sip-disable
ua-disable
vocera-disable
no…
Disables the Skinny Call Control Protocol (SCCP). Enabled
Disables the Session Initiation Protocol (SIP) for VOIP
and other text and multimedia sessions.
Disables the Alcatel-Lucent NOE protocol. Enabled
Disables the VOCERA protocol. Enabled
Removes the specified configuration parameter. —
Usage Guidelines
Use this command to functions such as SIP, Vocera, and Cisco Skinny protocols for ALG.
Example
The following example configures the ALG protocols:
(Instant Access Point)(config)# alg
(Instant Access Point)(ALG)# sccp-disable
(Instant Access Point)(ALG)# no sip-disable
(Instant Access Point)(ALG)# no ua-disable
(Instant Access Point)(ALG)# no vocera-disable
(Instant Access Point)(ALG)# end
(Instant Access Point)# commit apply
Enabled
Command History
Version Description
Dell Networking W-Series Instant Access Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
20 | alg Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode and ALG configuration sub-mode.
Page 21
allow-new-aps
allow-new-aps
no…
Description
This command allows the new access points to join the W-IAP cluster.
Syntax
Command/Parameter Description
allow-new-aps
no
Allows new access points in the domain.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to allow the new access points to join the W-IAP cluster.
Example
The following command allows the new W-IAPs to join the cluster.
(Instant Access Point)(config)# allow-new-aps
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide allow-new-aps | 21
Configuration mode
Page 22
allowed-ap
allowed-ap <MAC-address>
no…
Description
This command allows an AP to join the W-IAP cluster.
Syntax
Command/Parameter Description
allowed-ap <MAC-address>
no…
Specifies the MACaddress of the W-IAP that is allowed to join the
cluster.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to allow a W-IAP to join the cluster.
Example
The following command configures an allowed W-IAP:
(Instant Access Point)(config)# allowed-ap 01:23:45:67:89:AB
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
22 | allowed-ap Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 23
ams-backup-ip
ams-backup-ip <IP-address>
no…
Description
This command adds the IP address of the backup W-AirWave Management Server.
Syntax
Parameter Description
<IP-address>
no…
Configures the IP address of the secondary W-AirWave Management
Server.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to add the IP address of the backup W-AirWave Management Server. The backup server
provides connectivity when the W-AirWave primary server is down. If the W-IAP cannot send data to the primary
server, the Virtual Controller switches to the backup server automatically.
Example
The following command configures an W-AirWave backup server.
(Instant Access Point)(config)# ams-backup-ip 192.0.2.1
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide ams-backup-ip | 23
Configuration mode
Page 24
ams-identity
ams-identity <Name>
Description
This command uniquely identifies the group of W-IAPs managed or monitored by the W-AirWave Management
console. The name can be a location, vendor, department, or any other identifier.
Syntax
Parameter Description
ams-identity <Name>
Configures a name that uniquely identifies the W-IAP on the WAirWave Management server. The name defined for this command
will be displayed under the Groups tab in the W-AirWave user
interface.
Usage Guidelines
Use this command to assign an identity for the W-IAPs monitored or managed by the W-AirWave Management
Server.
Example
The following command configures an W-AirWave identifier:
(Instant Access Point)(config)# ams-identity dell
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
24 | ams-identity Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 25
ams-ip
ams-ip <IP-address>
no…
Description
This command configures the IP address of the W-AirWave Management console for a W-IAP.
Syntax
Parameter Description
<IP-address>
Configures the IP address of an W-AirWave Management server for
a W-IAP.
Usage Guidelines
Use this command to configure the IP address of the AMS console for a W-IAP.
Example
The following command configures the W-AirWave Server.
(Instant Access Point)(config)# ams-ip 192.0.1.2
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide ams-ip | 25
Configuration mode
Page 26
ams-key
ams-key <key>
no…
Description
This command assigns a shared key for service authorization.
Syntax
Parameter Description
<key>
no…
Authorizes the first Virtual Controller to communicate with the W-AirWave
server.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to assign a shared key for service authorization. This shared key is used for configuring the first
AP in the Instant network.
Example
The following command configures the shared key for the W-AirWave server.
(Instant Access Point)(config)# ams-key key@789
Command History
Version Description
Dell Networking W-Series Instant Access Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
26 | ams-key Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 27
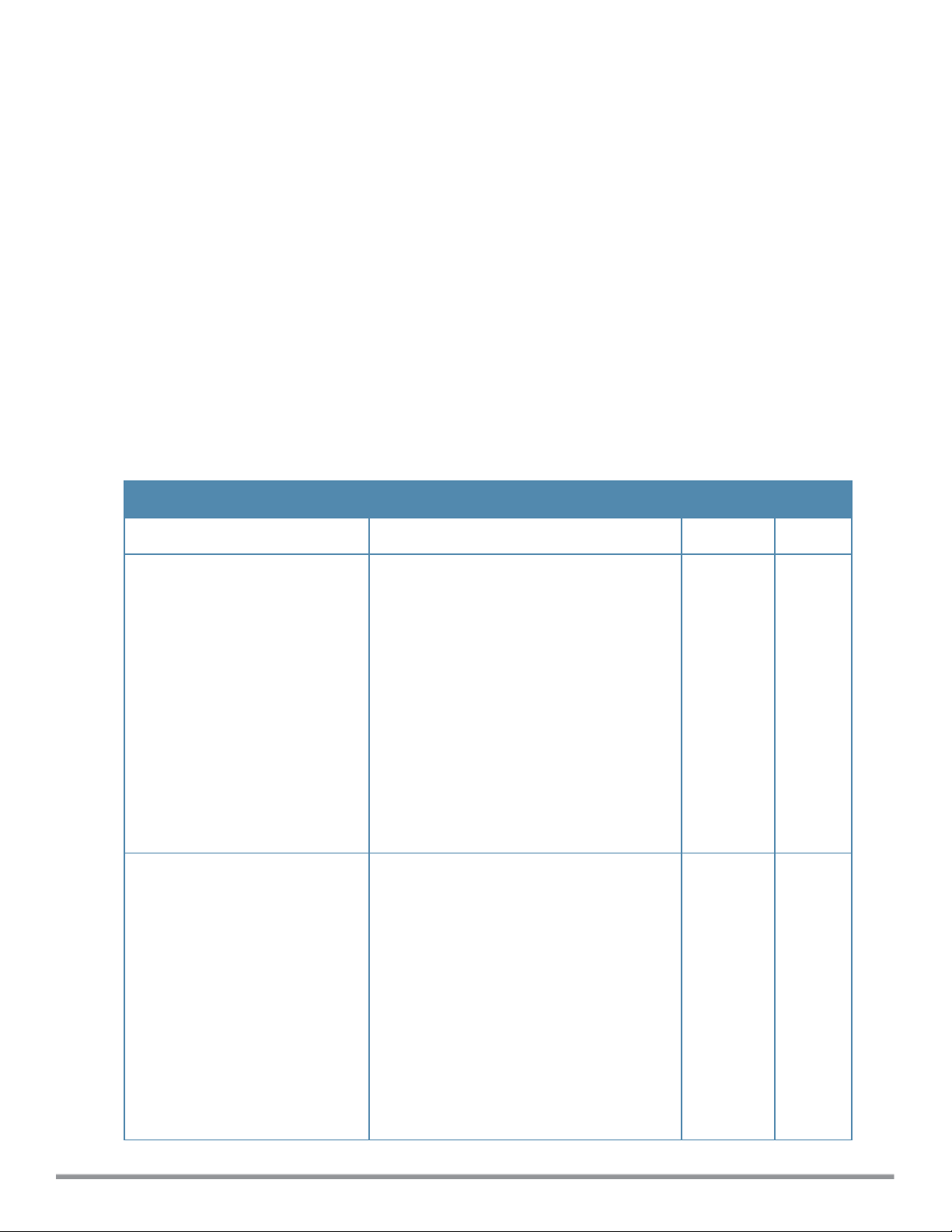
arm
arm
a-channels <a-channel>
air-time-fairness-mode {<default-access>| <fair-access>| <preferred-access>}
band-steering-mode {balance-bands|prefer-5ghz| force-5ghz| disable}
client-aware
g-channels <g-channel>
min-tx-power <power>
max-tx-power <power>
scanning
spectrum-load-balancing [calc-interval <Seconds> |calc-threshold <threshold> | nb-matching
<Percentage>]
wide-bands {<none>| <all>| <2.4>| <5>}
no…
Description
This command assigns an Adaptive Radio Management (ARM) profile for a W-IAP and configures ARM features
such as band steering, spectrum load balancing, airtime fairness mode, and access control features.
Syntax
Command/Parameter Description Range Default
a-channels <a-channel>
air-time-fairness-mode
{<default-access>| <fairaccess>| <preferredaccess>}
band-steering-mode
{<balance-bands>|<prefer5ghz>| <force-5ghz>|
<disable>}
Configures 5 GHz channels. — —
Allows equal access to all clients on the
wireless medium, regardless of client type,
capability, or operating system and prevents
the clients from monopolizing resources. You
can configure any of the following modes:
l default-access — To provide access based
on client requests. When this mode is
configured, the per user and per SSID
bandwidth limits are not enforced.
l fair-access — To allocate Airtime evenly
across all the clients.
l preferred-access — To set a preference
where 11n clients are assigned more
airtime than 11a/11g. The 11a/11g clients
get more airtime than 11b. The ratio is
16:4:1.
Assigns the dual-band capable clients to the 5
GHz band on dual-band. It reduces cochannel interference and increases available
bandwidth for dual-band clients, because
there are more channels on the 5 GHz band
than on the 2.4 GHz band. You can configure
any of the following band-steering modes:
default-
access,fair-
access,
preferred-
access
balance-
bands,
prefer-
5ghz,
force-5ghz,
disable
default-
access
balance-
bands
l prefer-5ghz — To allow the W-IAP to steer
the client to 5 GHz band (if the client is 5
GHz capable). However, the W-IAP allows
the client connection on the 2.4 GHz band
if the client persistently attempts for 2.4
GHz association.
l force-5ghz — To enforce 5 GHz band
steering mode on the W-IAPs, so that the 5
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide arm | 27
Page 28
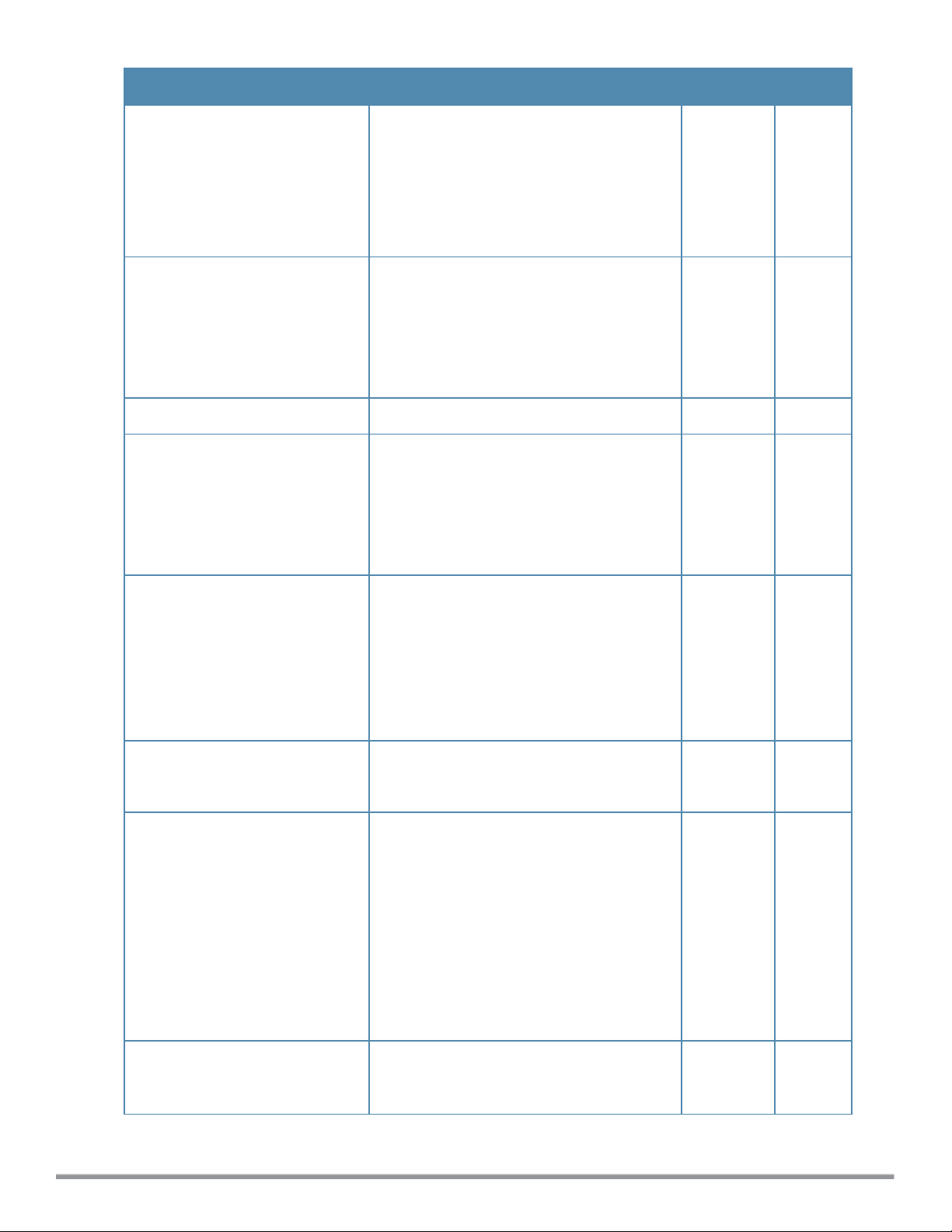
Command/Parameter Description Range Default
GHz capable clients are allowed to use
only the 5GHz channels.
l balance-bands — To allow the W-IAP to
balance the clients across the two 2.4 GHz
and 5 GHz radio and to utilize the
available bandwidth.
l disable — To allow the clients to select the
bands.
client-aware
g-channels <g-channel>
min-tx-power <power>
max-tx-power <power>
Enables the client aware feature. When
— Enabled
enabled, the W-IAP will not change channels
for the Access Points when clients are active,
except for high priority events such as radar or
excessive noise. The client aware feature
must be enabled in most deployments for a
stable WLAN.
Configures 2.4 GHz channels. — —
Sets the minimum transmission power. This
0-127 dBm 18
indicates the minimum Effective Isotropic
Radiated Power (EIRP). If the minimum
transmission EIRP setting configured on an
AP is not supported by the AP model, this
value is reduced to the highest supported
power setting.
Sets the highest transmit power levels for the
0-127 dBm 127
AP. If the maximum transmission EIRP
configured on an AP is not supported by the
AP model, the value is reduced to the highest
supported power setting.
NOTE: Higher power level settings may be
constrained by local regulatory requirements
and AP capabilities.
scanning
Allows the W-IAPs to scan other channels for
— Disabled
RF Management and Wireless Intrusion
Protection System enforcement.
spectrum-load-balancing
Enables spectrum load balancing on W-IAPs
so that clients are assigned to less loaded
Enable,
Disable
Enabled
channels. When enabled, The W-IAPs create
virtual RF neighborhoods amongst access
points for efficient client association
management. The Virtual Controller compares
whether a W-IAP has more clients than its
neighboring W-IAPs on other channels. When
the client load for a W-IAP reaches or
exceeds the threshold specified for SLB
threshold, load balancing is enabled on the
W-IAP.
spectrum-load-balancing
calc-interval <Seconds>
Determines how often spectrum load
balancing must be calculated. The W-IAPs
10–600
seconds
30
scan all valid channels in the regulatory
28 | arm Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 29
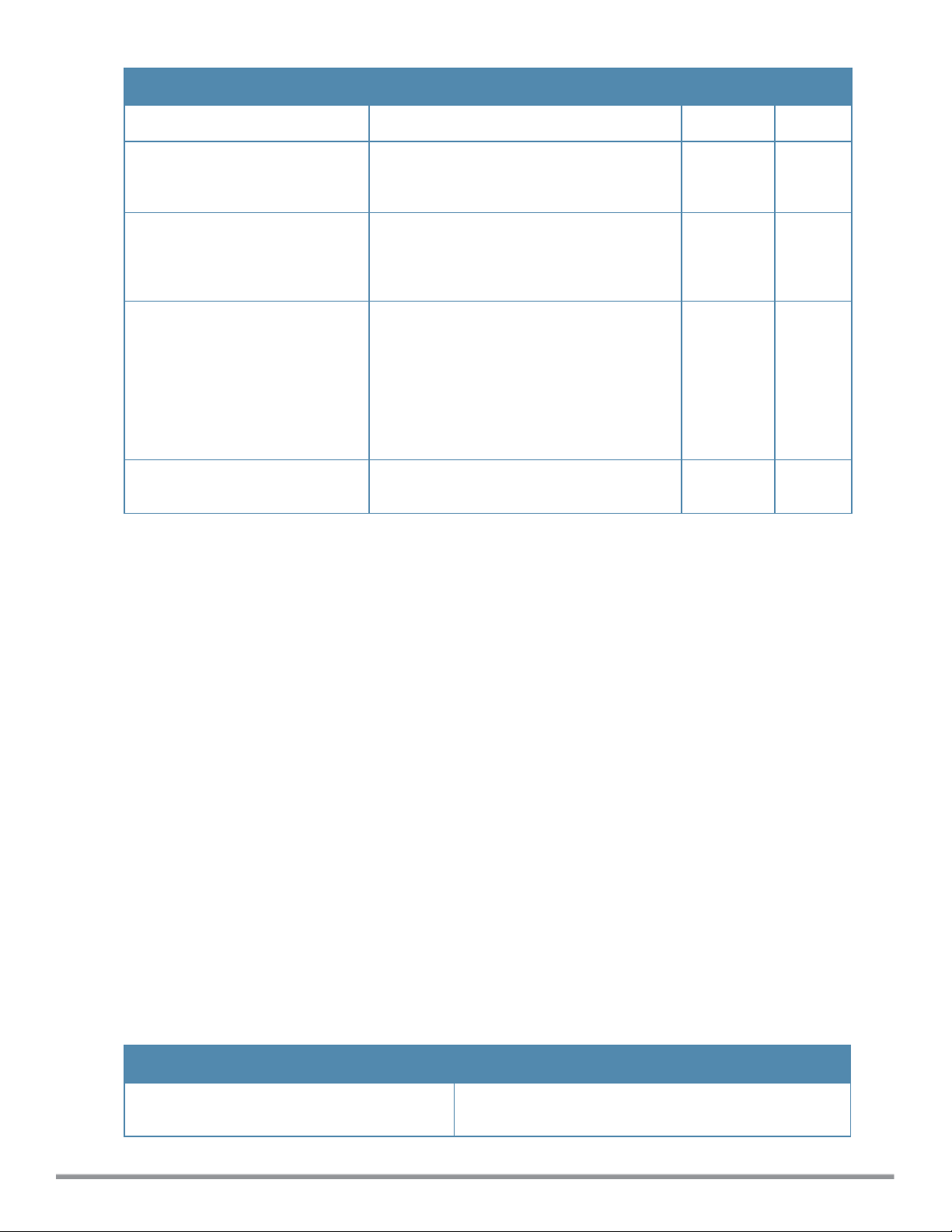
Command/Parameter Description Range Default
domain at the interval specified on this field.
spectrum-load-balancing nbmatching <Percentage>
spectrum-load-balancing
calc-threshold <threshold>
wide-bands {<none>| <all>|
<2.4>| <5>}
no…
Indicates the percentage for comparing client
density of W-IAP neighbors to determine the
client load on a specific AP channel.
Indicates the number of clients on a channel.
When the client load for a W-IAP reaches or
exceeds the specified threshold, load
balancing is enabled on the AP.
Allows administrators to configure 40 MHz.
channels in the 2.4 GHz and 5.0 GHz bands.
40 MHz channels are two 20 MHz adjacent
channels that are bonded together. The 40
MHz channels double the frequency
bandwidth available for data transmission. For
high performance, enter 5GHz. If the AP
density is low, enter 2.4GHz.
Removes the current value for that parameter
and return it to its default setting
20-100 75%
1-20 2
none, all,
2.4, and 5
— —
5
Usage Guidelines
Use this command to configure ARM features on a W-IAP. ARM ensures low-latency roaming, consistently high
performance, and maximum client compatibility in a multi-channel environment. By ensuring the fair distribution of
available Wi-Fi bandwidth to mobile devices, ARM ensures that data, voice, and video applications have sufficient
network resources at all times. ARM allows mixed 802.11a, b, g, and n client types to inter operate at the highest
performance levels.
Example
The following example configures an ARM profile:
(Instant Access Point)(config)# arm
(Instant Access Point)(ARM)# a-channels 44
(Instant Access Point)(ARM)# min-tx-power 18
(Instant Access Point)(ARM)# max-tx-power 127
(Instant Access Point)(ARM)# band-steering-mode prefer-5ghz
(Instant Access Point)(ARM)# air-time-fairness-mode fair-access
(Instant Access Point)(ARM)# wide-bands 5
(Instant Access Point)(ARM)# spectrum-load-balancing
(Instant Access Point)(ARM)# spectrum-load-balancing calc-interval 60
(Instant Access Point)(ARM)# spectrum-load-balancing nb-matching 60
(Instant Access Point)(ARM)# spectrum-load-balancing calc-threshold 2
(Instant Access Point)(ARM)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide arm | 29
Page 30

Command Information
W-IAP Platform Command Mode
All platforms
Configuration and ARM configuration sub-mode.
30 | arm Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 31

attack
attack
drop-bad-arp-enable
fix-dhcp-enable
no…
poison-check-enable
Description
This command enables firewall settings to protect the network against wired attacks, such as ARP attacks or
malformed DHCP packets, and notify the administrator when these attacks are detected.
Syntax
Command/Parameter Description
drop-bad-arp-enable
fix-dhcp-enable
poison-check-enable
no…
Enables the W-IAP to block the bad ARP request.
Enables the W-IAP to fix the malformed DHCP packets.
Enables the W-IAP to trigger an alert notifying the user about the
ARP poisoning that may have been caused by the rogue APs.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to block ARP attacks and to fix malformed DHCP packets.
Example
The following example configures firewall settings to protect the network from Wired attacks:
(Instant Access Point)(config)# attack
(Instant Access Point)(ATTACK)# drop-bad-arp-enable
(Instant Access Point)(ATTACK)# fix-dhcp-enable
(Instant Access Point)(ATTACK)# poison-check-enable
(Instant Access Point)(ATTACK)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide attack | 31
Configuration and Attack configuration sub-mode
Page 32

auth-failure-blacklist-time
auth-failure-blacklist-time <seconds>
Description
This command allows the W-IAPs to dynamically blacklist the clients when they exceed the authentication failure
threshold.
Syntax
Parameter Description Default
auth-failure-blacklisttime <seconds>
Configures the duration in seconds for which the clients
that exceed the maximum authentication failure
threshold are blacklisted.
3600
Usage Guidelines
Use this command to dynamically blacklist the clients that exceed the authentication failure threshold configured for
a network profile.
Example
The following example blacklists the clients dynamically:
(Instant Access Point)(config)# auth-failure-blacklist-time 60
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
32 | auth-failure-blacklist-time Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 33

auth-survivability cache-time-out
auth-survivability cache-time-out <time-out>
Description
This command configures an interval after which the authenticated credentials of the clients stored in the cache
expire. When the cache expires, the clients are required to authenticate again.
Syntax
Parameter Description Range Default
auth-survivability
cache-time-out
Indicates the duration after which the
authenticated credentials in the cache expire.
1-99 hours 24 hours
Usage Guidelines
Use this command when the authentication survivability is enabled on a network profile, to set a duration after which
the authentication credentials stored in the cache expires. To enable the authentication survivability feature, use the
auth-survivability in WLAN SSID profile sub-mode.
Example
(Instant Access Point) (config)# auth-survivability cache-time-out 60
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide auth-survivabilitycache-time-out | 33
Configuration mode
Page 34

blacklist-client
blacklist-client <MAC-address>
no…
Description
This command allows you to manually blacklist the clients by using MAC addresses of the clients.
Syntax
Parameter Description
blacklist-client <MAC-address>
no…
Adds the MAC address of the client to the blacklist.
Removes the specified configuration parameter.
Usage Guidelines
Use this command to blacklist the MAC addresses of clients.
Example
The following command blacklists a W-IAP client:
(Instant Access Point)(config)# blacklist-client 01:23:45:67:89:AB
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
34 | blacklist-client Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 35

blacklist-time
blacklist-time <seconds>
Description
This command sets the duration in seconds for which the clients can be blacklisted due to an ACL rule trigger.
Syntax
Parameter Description Default
blacklist-time <seconds>
Sets the duration in seconds for blacklisting clients due
to an ACL rule trigger.
3600
Usage Guidelines
Use this command to configure the duration in seconds for which the clients can be blacklisted when the blacklisting
rule is triggered.
Examples
The following command configures the duration for blacklisting clients:
(Instant Access Point) (config) # blacklist-time 30
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide blacklist-time | 35
Configuration mode
Page 36
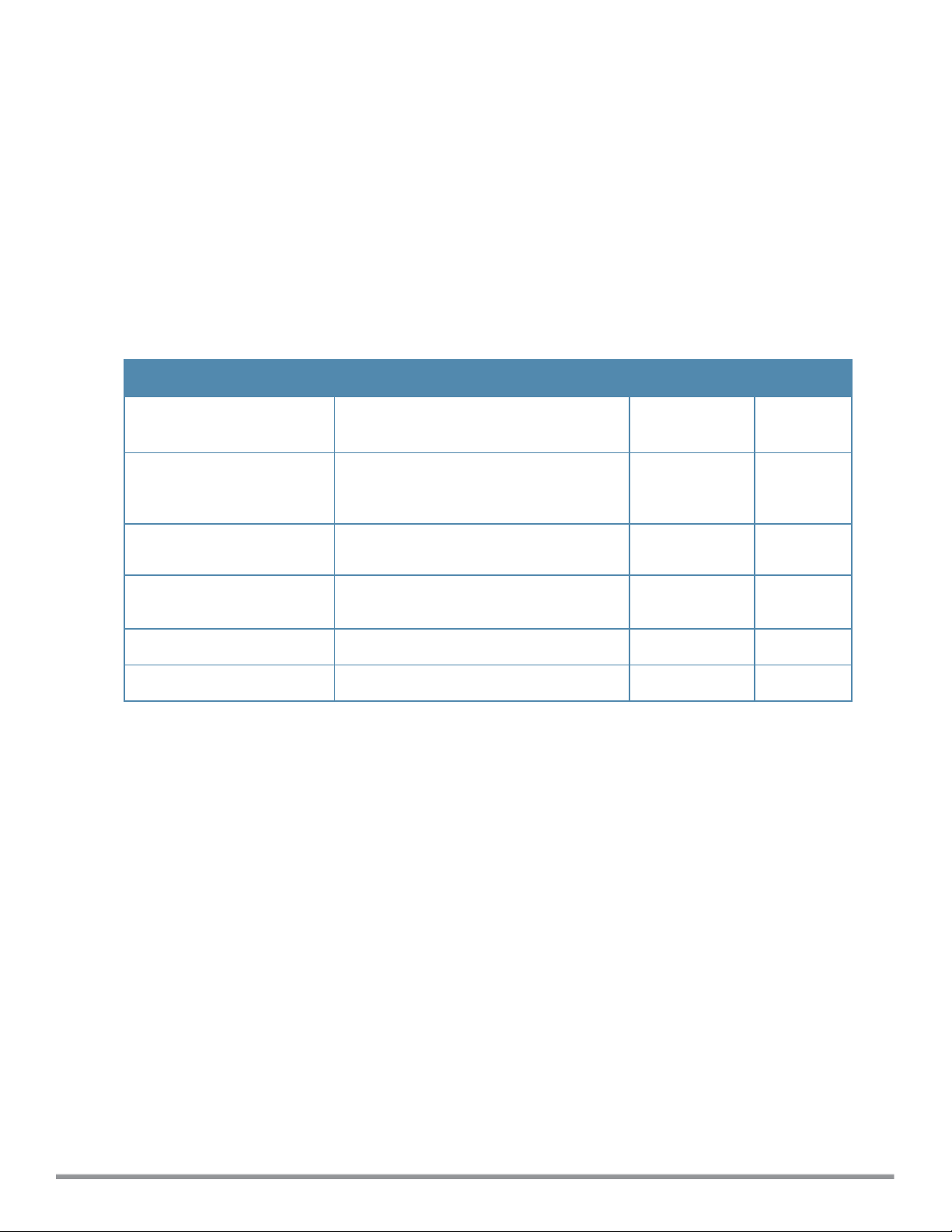
calea
calea
encapsulation-type <gre>
ip <IP-address>
ip mtu <size>
gre-type <type>
no...
Description
This command creates a Communications Assistance for Law Enforcement Act (CALEA) profile to enable W-IAPs
for Lawful Intercept (LI) compliance and CALEA integration.
Syntax
Command/Parameter Description Range Default
calea
encapsulation-type
<gre>
ip <IP-address>
ip mtu <size>
gre-type
no…
Enables
CALEA profile configuration.
Specifies the encapsulation type for
Generic Routing Encapsulation (GRE)
packets.
Configures the IP address of the CALEA
server on a W-IAP.
Configures the Maximum Transmission
Unit size to use.
Specifies GRE type. — 25944
Removes the configuration — —
configuration sub-mode for
calea
— —
GRE GRE
— —
68—1500 1500
Usage Guidelines
Use this command to configure a W-IAP to support Lawful Intercept (LI). LI allows the Law Enforcement Agencies
(LEA) to conduct an authorized electronic surveillance. Depending on the country of operation, the service providers
(SPs) are required to support LI in their respective networks.
In the United States, SPs are required to ensure LI compliance based on CALEA specifications. LI compliance in the
United States is specified by the CALEA.
For more information on configuring W-IAPs for CALEA integration, see
3.4 User Guide
.
Dell Networking W-Series Instant 6.2.1.0-
Example
The following example configures a CALEA profile:
(Instant Access Point)(config)# calea
(Instant Access Point)(calea)# ip 192.0.8.29
(Instant Access Point)(calea)# ip mtu 1500
(Instant Access Point)(calea)# encapsulation-type gre
(Instant Access Point)(calea)# gre-type 25944
(Instant Access Point)(calea)# end
(Instant Access Point)# commit apply
36 | calea Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 37

Command History
Version Description
Dell Networking W-Series Instant 6.2.1.0-
3.4
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and access rule configuration sub-mode.
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide calea | 37
Page 38
cellular-uplink-profile
cellular-uplink-profile <profile>
4g-usb-type <4G-usb-type>
modem-isp <modem_isp>
modem-country <modem-country>
usb-auth-type <usb_authentication_type>
usb-dev <usb-dev>
usb-dial <usb-dial>
usb-init <usb-init>
usb-modeswitch <usb-modeswitch>
usb-passwd <usb-passwd>
usb-tty <usb-tty>
usb-type <usb-type>
usb-user <usb-user>
modem-isp <modem_isp>
modem-country <modem-country>
no…
Description
This command provisions the cellular (3G/4G) uplink profiles on a W-IAP. Contact your IT administrator or the
manufacturer of your modem to obtain the parameter details for command execution.
Syntax
Parameter Description Range Default
cellular-uplink-profile
<profile>
4g-usb-type <4G-usb-type>
modem-isp <modem_isp>
modem-country <modem-country>
usb-auth-type <usb_
authentication_type>
usb-dev <usb-dev>
usb-dial <usb-dial>
usb-init <usb-init>
Configures a 3G or 4G cellular
profile for a W-IAP.
Configures the driver type for
the 4G modem.
Specifies the name of the ISP
to connect.
Specifies the country for the
deployment.
Specifies the authentication
type for USB.
Specifies the device ID of the
USB modem.
Specifies the parameter to dial
the cell tower.
Specifies the parameter name
to initialize the modem.
— —
ether-lte,
pantech-lte,
none
— —
— —
PAP, CHAP PAP
— —
— —
— —
—
usb-passwd <usb-passwd>
38 | cellular-uplink-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Specifies the password for the
account associated with the
subscriber of the selected ISP.
— —
Page 39

Parameter Description Range Default
usb-modeswitch <usbmodeswitch>
usb-type <usb-type>
usb-tty <usb-tty>
usb-user <usb-user>
no…
Specifies the parameter used
to switch modem from storage
mode to modem mode.
Configures the driver type for
the 3G modem.
Specifies the modem tty port. — —
Specifies the username of
subscriber of the selected ISP.
Removes the specified
configuration parameter.
— —
acm,
airprime, hso,
option,
pantech-3g,
sierra-evdo,
sierra-gsm,
none
— —
— —
—
Usage Guidelines
Use this command to configure a cellular uplink profile on a W-IAP and modem parameters 3G /4G uplink
provisioning. Dell W-Instant supports the use of 3G/4G USB modems to provide Internet backhaul to an Dell WInstant network. The 3G/4G USB modems can be used to extend client connectivity to places where an Ethernet
uplink cannot be configured. This enables the W-IAPs to automatically choose the available network in a specific
region.
The3G and 4G LTE USB modems can be provisioned on , , and .
Types of Modems
Dell W-Instant supports the following three types of 3G modems:
l True Auto Detect— Modems of this type can be used only in one country and for a specific ISP. The parameters
are configured automatically and hence no configuration is necessary.
l Auto-detect + ISP/country— Modems of this type require the user to specify the Country and ISP. The same
modem is used for different ISPs with different parameters configured for each of them.
l No Auto-detect— Modems of this type are used only if they share the same Device-ID, Country, and ISP details.
You need to configure different parameters for each of them. These modems work with Dell W-Instant when the
appropriate parameters are configured.
The following table lists the types of supported 3G modems:
Table 6:
Modem Type Supported 3G Modems
True Auto Detect l USBConnect 881 (Sierra 881U)
List of Supported 3G Modems
l Quicksilver (Globetrotter ICON 322)
l UM100C (UTstarcom)
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide cellular-uplink-profile | 39
Page 40

Table 6:
List of Supported 3G Modems
Modem Type Supported 3G Modems
l Icon 452
l Aircard 250U (Sierra)
l USB 598 (Sierra)
l U300 (Franklin wireless)
l U301 (Franklin wireless)
l USB U760 for Virgin (Novatel)
l USB U720 (Novatel/Qualcomm)
l UM175 (Pantech)
l UM150 (Pantech)
l UMW190(Pantech)
l SXC-1080 (Qualcomm)
l Globetrotter ICON 225
l UMG181
l NTT DoCoMo L-05A (LG FOMA L05A)
l NTT DoCoMo L-02A
l ZTE WCDMA Technologies MSM (MF668?)
l Fivespot (ZTE)
l c-motech CNU-600
l ZTE AC2736
l SEC-8089 (EpiValley)
l Nokia CS-10
l NTT DoCoMo L-08C (LG)
l NTT DoCoMo L-02C (LG)
l Novatel MC545
l Huawei E220 for Movistar in Spain
l Huawei E180 for Movistar in Spain
l ZTE-MF820
l Huawei E173s-1
l Sierra 320
l Longcheer WM72
l U600 (3G mode)
Auto-detect + ISP/country
l Sierra USB-306 (HK CLS/1010 (HK))
l Sierra 306/308 (Telstra (Aus))
l Sierra 503 PCIe (Telstra (Aus))
l Sierra 312 (Telstra (Aus))
l Aircard USB 308 (AT&T's Shockwave)
l Compass 597(Sierra) (Sprint)
l U597 (Sierra) (Verizon)
l Tstick C597(Sierra) (Telecom(NZ))
l Ovation U727 (Novatel) (Sprint)
l USB U727 (Novatel) (Verizon)
l USB U760 (Novatel) (Sprint)
l USB U760 (Novatel) (Verizon)
l Novatel MiFi 2200 (Verizon Mifi 2200)
l Huawei E272, E170, E220 (ATT)
l Huawei E169, E180,E220,E272 (Vodafone/SmarTone (HK))
l Huawei E160 (O2(UK))
l Huawei E160 (SFR (France))
l Huawei E220 (NZ and JP)
l Huawei E176G (Telstra (Aus))
l Huawei E1553, E176 (3/HUTCH (Aus))
l Huawei K4505 (Vodafone/SmarTone (HK))
l Huawei K4505 (Vodafone (UK))
l ZTE MF656 (Netcom (norway))
40 | cellular-uplink-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 41

Table 6:
List of Supported 3G Modems
Modem Type Supported 3G Modems
l ZTE MF636 (HK CSL/1010)
l ZTE MF633/MF636 (Telstra (Aus))
l ZTE MF637 (Orange in Israel)
l Huawei E180, E1692,E1762 (Optus (Aus))
l Huawei E1731 (Airtel-3G (India))
l Huawei E3765 (Vodafone (Aus))
l Huawei E3765 (T-Mobile (Germany)
l Huawei E1552 (SingTel)
l Huawei E1750 (T-Mobile (Germany))
l UGM 1831 (TMobile)
l Huawei D33HW (EMOBILE(Japan))
l Huawei GD01 (EMOBILE(Japan))
l Huawei EC150 (Reliance NetConnect+ (India))
l KDDI DATA07(Huawei) (KDDI (Japan))
l Huawei E353 (China Unicom)
l Huawei EC167 (China Telecom)
l Huawei E367 (Vodafone (UK))
l Huawei E352s-5 (T-Mobile (Germany))
No auto-detect l Huawei D41HW
l ZTE AC2726
Table 7:
4G Supported Modem
Modem Type Supported 4G Modem
True Auto Detect l Pantech UML290
l Ether-lte
When UML290 runs in auto detect mode, the modem can switch from 4G network to 3G network or vice-versa
based on the signal strength. To configure the UML290 for the 3G network only, manually set the USB type to
pantech-3g. To configure the UML290 for the 4G network only, manually set the 4G USB type to pantech-lte.
Example
The following example configures a cellular uplink profile:
(Instant Access Point)(config) # cellular-uplink-profile
(Instant Access Point)(cellular-uplink-profile)# 4g-usb-type pantech-lte
(Instant Access Point)(cellular-uplink-profile)# modem-country India
(Instant Access Point)(cellular-uplink-profile)# modem-isp example
(Instant Access Point)(cellular-uplink-profile)# usb-auth-type PAP
(Instant Access Point)(cellular-uplink-profile)# usb-user user1
(Instant Access Point)(cellular-uplink-profile)# usb-passwd user123
(Instant Access Point)(cellular-uplink-profile)# modem-country India
(Instant Access Point)(cellular-uplink-profile)# end
(Instant Access Point)# commit apply
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide cellular-uplink-profile | 41
Page 42

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and cellular uplink profile configuration submode
42 | cellular-uplink-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 43

clear
clear
ap <ip-address>
arp <ip-address>
client <mac>
datapath {session-all| statistics}
trace airgroup module {all|coa|cppm|db-sync|host|master|papi|query|records|slave|update}
trace-filter airgroup client
Description
This command clears various user-configured values from the running configuration on a W-IAP.
Syntax
Parameter Description
ap <ip-address>
arp <ip-address>
client <mac>
datapath datapath {session-all|
statistics}
trace airgoup module
trace-filter airgroup client
Clears all W-IAP related information.
Clears all ARP table information for a W-IAP.
Clears all information pertaining to a W-IAP client.
Clears all configuration information and statistics for datapath
modules and user sessions.
Clears all AirGroupconfiguration information or clears data for the
following individual AirGroup module information:
coa
cppm
db-sync
host
master
papi
query
records
slave
update
Clears all trace-filters for the AirGroup clients.
Usage Guidelines
Use the clear command to clear the current information stored in the running configuration of a W-IAP.
Example
The following command clears all information related to a W-IAP:
(Instant Access Point)# clear ap 192.0.2.3
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide clear | 43
This command is introduced.
Page 44

Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
44 | clear Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 45

clear airgroup state statistics
clear airgroup state statistics
Description
This command removes the AirGroup statistics.
Usage Guidelines
Use this command to remove AirGroup details from the W-IAP database.
Example
The following command clears AirGroup statistics:
(Instant Access Point)(config)# clear airgroup state statistics
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide clear airgroup state statistics | 45
Page 46
clear-cert
clear-cert {ca| server}
Description
This command clears client and server certificates from the W-IAP database.
Syntax
Parameter Description
ca
server
Clears all certificates uploaded for the client system.
Clears all Server certificates.
Usage Guidelines
Use this command to clear the certificates from the W-IAP database.
Example
The following command shows an example for clearing server certificates:
(Instant Access Point)# clear-cert server
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
46 | clear-cert Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Privileged EXEC mode
Page 47
clock set
clock set <year> <month> <day> <time>
Description
This command sets the date and time on the W-IAP system clock.
Syntax
Parameter Description Range
<year>
<month>
<day>
<time>
Sets the year. Requires all 4 digits. Numeric
Sets the month. 1-12
Sets the day. 1-31
Sets the time. Specify hours, minutes, and
seconds separated by spaces.
Numeric
Usage Guidelines
You can configure the year, month, day, and time. Specify the time using a 24-hour clock with hours, minutes and
seconds separated by spaces.
Example
The following example sets the clock to 21 May 2013, 1:03:52 AM:
(Instant Access Point) (config) #clock set 2013 5 21 1 3 52
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide clock set | 47
Privileged EXEC mode
Page 48

clock summer-time
clock summer-time <timezone> recurring <start-week> <start-day> <start-month> <start-hour>
<eweek> <eday> <emonth> <ehour>
no…
Description
This command configures daylight saving for the time zones that support daylight saving time.
Syntax
Parameter Description Range
clock summer-time
<timezone>
recurring
<start-week>
<start-day>
<start-month>
<start-hour>
<eweek>
<eday>
<emonth>
Configures Daylight Saving time. Timezones
that support
daylight
saving
configuration
Indicates the recurrences. —
Indicates the week from which the daylight saving configuration is
effective.
Indicates the day from which the daylight saving configuration
applies.
Indicates the month from which the daylight saving configuration
applies.
Indicates the hour from which the daylight saving configuration
applies.
Indicates the week in which the daylight saving configuration ends. —
Indicates the day on which daylight saving configuration ends. —
Indicates the month in which daylight saving configuration ends. —
—
—
—
1-24
<ehour>
no…
Indicates the hour at which daylight saving configuration ends. 1-24
Removes the configuration —
Usage Guidelines
Use this command to configure daylight saving for the timezones that support daylight saving. When enabled, the
daylight saving time ensures that the W-IAPs reflect the seasonal time changes in the region they serve.
Example
The following example configures daylight saving for a timezone:
(Instant Access Point)(config)# clock summer-time PST recurring 7 10 March 9PM 38 10 October
9PM
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
48 | clock summer-time DellNetworking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 49

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide clock summer-time | 49
Page 50

clock timezone
clock timezone <name> <hour-offset> <minute-offset>
no…
Description
This command sets the timezone on a W-IAP.
Syntax
Parameter Description Range
clock timezone
<name>
<hour-offset>
<minute-offset>
no…
Configures the required timezone. All supported
Specifies the hours offset from the Universal Time Clock
(UTC).
Specifies the hours offset from the Universal Time Clock
(UTC).
Removes the timezone configuration. —
Usage Guidelines
Use this command to set the timezone on a W-IAP.
Example
The following example configures the PST timezone:
(Instant Access Point) (config)# clock timezone PST -8 0
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
timezones
—
—
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
50 | clock timezone Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 51
commit
commit {apply| revert}
Description
This command allows you to commit configuration changes performed during a user session. You can also revert the
changes that are already committed.
Syntax
Parameter Description
apply
revert
Applies the required changes to the W-IAP configuration.
Reverts the changes committed to the current configuration of a W-IAP.
Usage Guidelines
Each command processed by the Virtual Controller is applied on all the slaves W-IAPs in a cluster. The changes
configured in a CLI session are saved in the CLI context. The CLI does not support the configuration data exceeding
the 4K buffer size in a CLI session: therefore, Dell recommends that you configure fewer changes at a time and
apply the changes at regular intervals.
Example
The following command allows you to commit the configuration changes:
(Instant Access Point) # commit apply
The following command reverts the already committed changes.
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide commit | 51
Privileged EXEC mode.
Page 52

configure terminal
configure terminal
Description
This command allows you to enter configuration commands.
Syntax
No parameters.
Usage Guidelines
Upon entering this command, the enable mode prompt changes to:
(Instant Access Point)(config)#
To return to EXEC mode, enter Ctrl-Z, end or exit.
Example
The following command allows you to enter configuration commands:
(Instant Access Point) # configure terminal
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode.
52 | configure terminal Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 53

content-filtering
content-filtering
no…
Description
This command enables content filtering feature. When content filtering is enabled on an SSID, all DNS requests to
non-corporate domains on this wireless network are sent to OpenDNS.
Syntax
Command/Parameter Description
content-filtering
no
Enables content filtering.
Removes the configuration.
Usage Guidelines
Use this command to enable content filter. With content filter feature enabled, you can:
l Prevent known malware hosts from accessing your wireless network.
l Improve employee productivity by limiting access to certain Websites.
l Reduce bandwidth consumption significantly.
You can enable content filtering on an SSID. When enabled, all DNS requests to non-corporate domains on this
SSID are sent to the open DNS server.
Example
The following example enables content filtering:
(Instant Access Point)# content-filtering
(Instant Access Point)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide content-filtering | 53
Configuration mode.
Page 54
convert-aos-ap
convert-aos-ap <mode> <controller-IP>
Description
This command allows you to provision a W-IAP as a Campus AP or Remote AP in a controller-based network, or as
a standalone AP.
Syntax
Parameter Description Range
<mode>
<controller-IP>
Provisions the W-IAP as remote AP or campus AP in a
controller-based network or as a standalone AP.
Allows you to specify the IP address of the Controller to which
the Remote AP or Campus AP will be connected.
RAP, CAP,
StandaloneAP
—
Usage Guidelines
Before converting a W-IAP, ensure that both the W-IAP and controller are configured to operate in the same
regulatory domain. A W-IAP can be converted to a Campus AP and Remote AP only if the controller is running
ArubaOS 6.1.4 or later.
Example
The following command allows you to convert a W-IAP to a remote AP:
(Instant Access Point)# convert-aos-ap RAP 192.0.2.5
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
54 | convert-aos-ap Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Privileged EXEC mode.
Page 55

copy
copy {config tftp <ip-address> <filename>|core-file tftp <ip-address> <filename>|flash tftp
<ip-address> <filename>| tftp <ip-address> <filename> system {1xca [format {der|pem}]|1xcert
<passsword>[format {p12|pem}]|config|flash}}
Description
This command copies files to and from the W-IAP.
Syntax
Parameter Description
config Copies a configuration file to the TFTP server.
core-file Copies a core file to the TFTP server.
flash Copies a file from flash to the TFTP server or to flash from a TFTP server.
tftp Copies files and certificates to the W-IAP database from a TFTP server.
<ip-address> Copies files to the specified TFTP server IP address.
<file-name> Indicates the name of the file to be copied.
system Copies the file to the system partition.
1xca Copies the CA certificate used for 802.1X authentication from the TFTP server.
der
pem
1xcert Copies the server certificate used for 802.1X authentication from the TFTP
<passsword> Indicates the password for certificate authentication.
p12
pem
Indicates the system partition file extensions.
server.
Indicates the certificate file extensions.
Usage Guidelines
Use this command to save backup copies of the configuration file to a TFTP server, or to load a saved file from a
TFTP server to W-IAP.
Example
The following example copies a configuration file to the TFTP server:
(Instant Access Point)# copy config tftp 10.0.0.1 filename.cfg
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide copy | 55
This command is introduced.
Page 56

Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
56 | copy Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 57
deny-inter-user-bridging
deny-inter-user-bridging
no…
Description
This command disables bridging traffic between two clients of a W-IAP on the same VLAN. Bridging traffic between
the clients will be sent to the upstream device to make the forwarding decision.
Syntax
Parameter Description
deny-inter-user-bridging
no…
Prevents the inter-user bridging.
Removes the configuration.
Usage Guidelines
Use this command if you have security and traffic management policies defined for upstream devices.
Example
The following command disables inter-user bridging:
(Instant Access Point)(config)# deny-inter-user-bridging
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide deny-inter-user-bridging | 57
Configuration mode
Page 58

deny-local-routing
deny-local-routing
no…
Description
This command disables routing traffic between two clients of a W-IAP on different VLANs. Routing traffic between
the clients will be sent to the upstream device to make the forwarding decision.
Syntax
Parameter Description
deny-local-routing
no…
Disables local routing of traffic.
Removes the configuration.
Usage Guidelines
Use this command to prevent the local routing of traffic if you have security and traffic management policies defined
for upstream devices.
Example
The following command disables local routing:
(Instant Access Point)(config)# deny-local-routing
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
58 | deny-local-routing Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 59

device-id
device-id <device>
Description
This command assigns an ID for the AP device.
Syntax
Parameter Description
device-id <device>
Configures an ID for the W-IAP device.
Usage Guidelines
Use this command to configure a device identification.
Example
The following example configures a device ID:
(Instant Access Point)(config)# device-ID Device1
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide device-id | 59
Configuration mode
Page 60
disconnect-user
disconnect-user
Description
This command disconnects the clients from a W-IAP.
Example
The following example shows the output of disconnect-user command:
(Instant Access Point)# disconnect-user
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
60 | disconnect-user Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 61
download-cert
download-cert {ca| server} <URL>
Description
This command allows you to download the client and server certificates from an FTP or TFTP server, or by using an
HTTP URL.
Syntax
Parameter Description
ca
server
<url>
Downloads client certificates.
Downloads Server certificates.
Allows you to specify the FTP, TFTP, or HTTP URL.
Usage Guidelines
Use this command to download certificates.
Example
The following command shows an example for downloading CAclient certificates:
(Instant Access Point)# download-cert ca ftp://192.0.2.7
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide download-cert | 61
Privileged EXEC mode
Page 62

dynamic-cpu-mgmt
dynamic-cpu-mgmt {auto| disable| enable}
Description
This command enables or disables the dynamic CPU management feature, to manage resources across different
functions performed by a W-IAP.
Syntax
Parameter Description
auto
disable
enable
Configures the W-IAP to automatically enable or disable CPU management feature
during run-time. When configured, the W-IAP determines the need for enabling or
disabling CPU management, based on the real-time load calculations taking into
account all different functions that the CPU needs to perform.
The aut o option is the default and recommended setting.
Disables CPU management on all APs, typically for small networks. This setting
protects the user experience.
Enables the CPU management feature. When configured, the client and network
management functions are protected. This setting helps in large networks with a
high client density.
Usage Guidelines
Use this command to enable or disable resource management across different functions performed by a W-IAP.
Example
The following example enables the automatic enabling or disabling of CPU management:
(Instant Access Point)(config)# dynamic-cpu-mgmt auto
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant 6.2.1.0-
3.4
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
62 | dynamic-cpu-mgmt Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 63
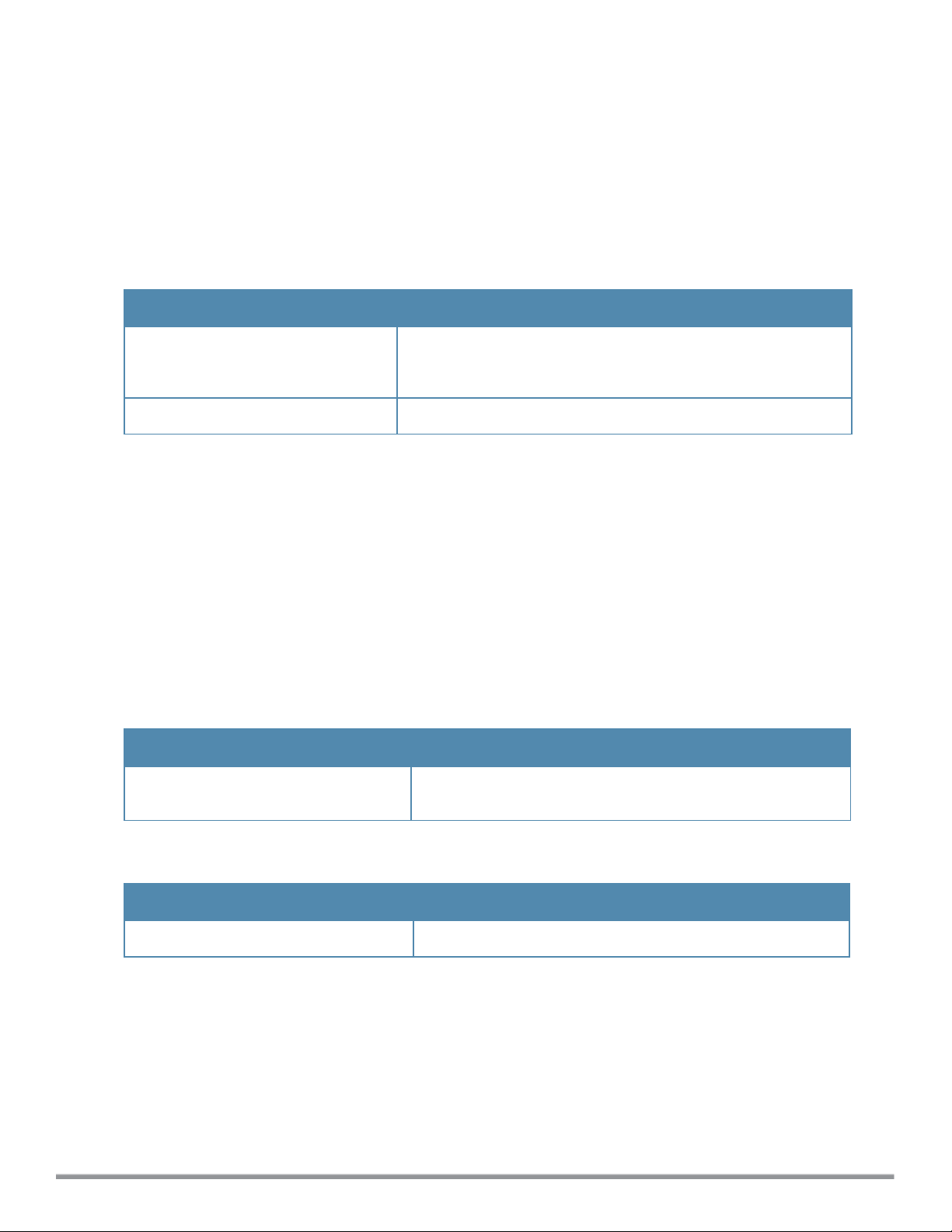
dynamic-radius-proxy
dynamic-radius-proxy
no…
Description
This command enables the use of IP Address of the Virtual Controller for communication with external RADIUS
servers.
Syntax
Command/Parameter Description
dynamic-radius-proxy
no…
Enables dynamic RADIUS proxy feature to allow the Virtual
Controller network to use the IPaddress of the Virtual Controller
when communicating with the external RADIUS servers.
Removes the configuration.
Usage Guidelines
Ensure that you set the Virtual Controller IP address as a NAS client in the RADIUS server when Dynamic RADIUS
proxy is enabled.
Example
The following example enables the dynamic RADIUS proxy feature:
(Instant Access Point)(config)# dynamic-radius-proxy
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide dynamic-radius-proxy | 63
Configuration mode
Page 64

enet-vlan
enet-vlan <vlan-ID>
no…
Description
This command configures a VLAN for Ethernet connections.
Syntax
Parameter Description Range
enet-vlan <vlan-ID>
no…
Configures VLAN for Ethernet ports and wired profiles 0–4093
Removes the configuration —
Usage Guidelines
Use this command to configure VLAN for the Ethernet connections.
Example
The following example configures VLAN for the Ethernet ports:
(Instant Access Point)(config)# enet-vlan 200
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
64 | enet-vlan DellNetwor king W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 65

enet0-bridging
enet0-bridging
Description
This command allows you to use all ports on the APs as downlink ports.
Usage Guidelines
Use this command for W-IAP models that have only one Ethernet port enabled. When Eth0 bridging is configured,
ensure that the uplink for each W-IAP is mesh link, Wi-Fi, or 3G/4G.
Example
The following command enables Eth0 bridging:
(Instant Access Point)# enet0-bridging
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide enet0-bridging | 65
Page 66

enet0-port-profile
enet0-port-profile <profile>
Description
This command assigns a wired profile to the Ethernet 0 port on a W-IAP.
Syntax
Parameter Description
enet0-port-profile <profile>
Assigns a wired profile to the Ethernet 0 interface port.
Usage Guidelines
Use this command to assign a wired profile to the Ethernet 0 port to activate the wired profile.
Example
The following command assigns a wired profile to the Ethernet 0 port:
(Instant Access Point)(config)# enet0-port-profile <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
66 | enet0-port-profile DellNetworking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 67

enet1-port-profile
enet1-port-profile <profile>
Description
This command assigns a wired profile to the Ethernet 1 port on a W-IAP.
Syntax
Parameter Description
enet1-port-profile <profile>
Assigns a wired profile to the Ethernet 1 interface port.
Usage Guidelines
Use this command to assign a wired profile to the Ethernet 1 port to activate the wired profile.
Example
The following command assigns a wired profile to the Ethernet 1 port:
(Instant Access Point)(config)# enet1-port-profile <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide enet1-port-profile | 67
Configuration mode
Page 68

enet2-port-profile
enet2-port-profile <profile>
Description
This command assigns a wired profile to the Ethernet 2 port on a W-IAP.
Syntax
Parameter Description
enet2-port-profile <profile>
Assigns a wired profile to the Ethernet 2 interface port.
Usage Guidelines
Use this command to assign a wired profile to the Ethernet 2 port to activate the wired profile.
Example
The following command assigns a wired profile to the Ethernet 2 port:
(Instant Access Point)(config)# enet2-port-profile <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
68 | enet2-port-profile DellNetworking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 69

enet3-port-profile
enet3-port-profile <profile>
Description
This command assigns a wired profile to the Ethernet 3 port on a W-IAP.
Syntax
Parameter Description
enet3-port-profile <profile>
Assigns a wired profile to the Ethernet 3 interface port.
Usage Guidelines
Use this command to assign a wired profile to the Ethernet 3 port to activate the wired profile.
Example
The following command assigns a wired profile to the Ethernet 3 port:
(Instant Access Point)(config)# enet3-port-profile <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide enet3-port-profile | 69
Configuration mode
Page 70

enet4-port-profile
enet4-port-profile <profile>
Description
This command assigns a wired profile to the Ethernet 4 port on a W-IAP.
Syntax
Parameter Description
enet4-port-profile <profile>
Assigns a wired profile to the Ethernet 4 interface port.
Usage Guidelines
Use this command to assign a wired profile to the Ethernet 4 port to activate the wired profile.
Example
The following command assigns a wired profile to the Ethernet 4 port:
(Instant Access Point)(config)# enet4-port-profile <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
70 | enet4-port-profile DellNetworking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 71

extended-ssid
extended-ssid
no…
Description
This command enables the configuration of additional WLAN SSIDs.
Syntax
Command/Parameter Description
extended-ssid
no…
Enables the users to configure additional SSIDs.
Removes the configuration.
Usage Guidelines
Use this command to create additional SSIDs. By default, you can create up to six WLAN SSIDs. With the
Extended SSID option enabled, you can create up to 16 WLANs. The following W-IAPs support 16 WLANs:
l W-IAP3WN/3WNP
l IAP-93
l IAP-134
l IAP-135
The number of SSIDs that become active on each W-IAP depends on the W-IAP platform.
Example
The following example enables the configuration of extended SSIDs:
(Instant Access Point)(config)# extended-ssid
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide extended-ssid | 71
Configuration mode
Page 72

factory-ssid-enable
factory-ssid-enable
Description
This command resets the W-IAP to use the factory configuration.
Syntax
Parameter Description
factory-ssid-enable
Enables factory SSID configuration.
Usage Guidelines
Use this command to reset a W-IAP to use the factory default SSID.
Example
The following example enables factory default configuration:
(Instant Access Point)(config)# factory-ssid-enable
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
72 | factory-ssid-enable Dell Networking W-Ser ies Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 73
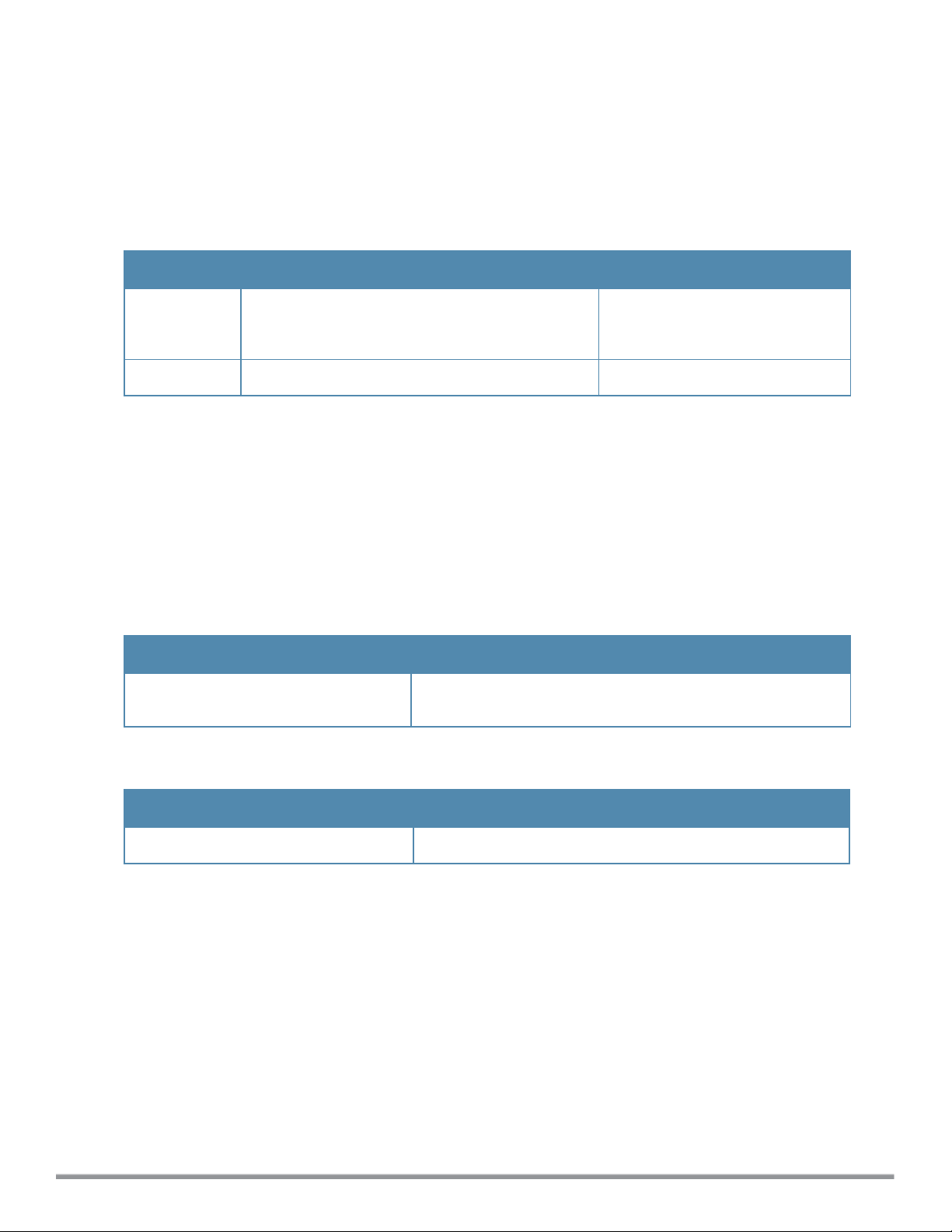
g-channel
g-channel <channel> <tx-power>
Description
This command configures 2.4 GHz radio channels for a specific W-IAP.
Syntax
Parameter Description Range
<channel>
<tx-power>
Configures the specified 2.4 GHz channel. The valid channels for a band are
determined by the AP regulatory
domain.
Configures the specified transmission power values.
0-127 dBm
Usage Guidelines
Use this command to configure radio channels for the 2.4 GHz band for a specific W-IAP.
Example
The following example configures the 2.4 GHz radio channel:
(Instant Access Point)# g-channel 11 18
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide g-channel | 73
Privileged EXEC mode
Page 74

g-external-antenna
g-external-antenna <gain>
Description
This command configures external antenna connectors for a W-IAP.
Syntax
Parameter Description Range Default
<gain>
Configures the antenna gain. You can configure gain
value in dBi for the following types of antenna:
l Dipole/Omni
l Panel
l Sector
Diploe/Omni - 6
Panel -12
Sector - 12
—
Usage Guidelines
If your W-IAP has external antenna connectors, you need to configure the transmit power of the system. The
configuration must ensure that the system’s Equivalent Isotropically Radiated Power (EIRP) is in compliance with
the limit specified by the regulatory authority of the country in which the W-IAP is deployed. You can also measure or
calculate additional attenuation between the device and antenna before configuring the antenna gain. To know if your
AP device supports external antenna connectors, see the
EIRP and Antenna Gain
The following formula can be used to calculate the EIRP limit related RF power based on selected antennas
(antenna gain) and feeder (Coaxial Cable loss):
EIRP = Tx RF Power (dBm)+GA (dB) - FL (dB)
The following table describes this formula:
Install Guide
that is shipped along with the AP device.
Table 8:
Formula Variable Definitions
Formula Element Description
EIRP Limit specific for each country of deployment
Tx RF Power RF power measured at RF connector of the unit
GA Antenna gain
FL Feeder loss
For information on antenna gain recommended by the manufacturer, see dell.com/support.
Example
The following example configures external antenna connectors for the W-IAP with the 2.4 GHz radio band.
(Instant Access Point)# g-external-antenna 12
74 | g-external-antenna Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 75

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode.
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide g-external-antenna | 75
Page 76
gre per-ap-tunnel
gre per-ap-tunnel
no…
Description
This command configures a generic routing encapsulation (GRE) tunnel from each W-IAP to the VPN/GRE Endpoint
rather than the tunnels created just from the Virtual Controller.
Syntax
Parameter Description
gre per-ap-tunnel
no…
Creates a GRE tunnel from the W-IAP to the VPN/GRE endpoint.
Removes the configuration.
Usage Guidelines
Use this command to allow the traffic to be sent to the corporate network through a Layer-2 GRE tunnel from the WIAP itself. When a GRE tunnel per W-IAP is created, the traffic need not be forwarded through the Virtual Controller.
Example
The following example creates a GRE tunnel for the W-IAP:
(Instant Access Point)(config)# gre per-ap-tunnel
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
76 | gre per-ap-tunnel Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 77

gre primary
gre primary <name>
no…
Description
This command configures a host for the primary VPN/GRE endpoint.
Syntax
Parameter Description
gre primary <name>
no…
Specifies the fully qualified domain name (FQDN) of the primary
host.
Removes the configuration.
Usage Guidelines
Use this command to configure the primary VPN/GRE host.
Example
The following example configures a GRE primary host:
(Instant Access Point)(config)# gre primary <name>
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide gre primary | 77
Configuration mode
Page 78
gre type
gre type <type>
Description
This command configures a GREprotocol number as GRE type.
Syntax
Parameter Description Range Default
gre type <type>
Configures the protocol number or IP address for
GRE type
16-bit
protocol
number
0
Usage Guidelines
Use this command to specify GRE type. The 16-bit protocol number uniquely identifies a Layer-2 tunnel. The WIAPs or controllers at both endpoints of the tunnel must be configured with the same protocol number.
Example
The following example configures the GRE type:
(Instant Access Point)(config)# gre type 0
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
78 | gre type Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode
Page 79
help
help
Description
This command displays help for the CLI.
Usage Guidelines
This command displays keyboard editing commands that allow you to make corrections or changes to the command
without retyping.
You can also enter the question mark (?) to get various types of command help:
l When typed at the beginning of a line, the question mark lists all commands available in the current mode.
l When typed at the end of a command or abbreviation, the question mark lists possible commands that match.
l When typed in place of a parameter, the question mark lists available options.
Example
The following example shows the output of the help command.
HELP:
Special keys:
BS .... delete previous character
Ctrl-A .... go to beginning of line
Ctrl-E .... go to end of line
Ctrl-F .... go forward one character
Ctrl-B .... go backward one character
Ctrl-D .... delete current character
Ctrl-U, X .. delete to beginning of line
Ctrl-K .... delete to end of line
Ctrl-W .... delete previous word
Ctrl-T .... transpose previous character
Ctrl-P .... go to previous line in history buffer
Ctrl-N .... go to next line in history buffer
Ctrl-Z .... return to root command prompt
Tab .... command-line completion
exit .... go to next lower command prompt
? .... list choices
Help may be requested at any point in a command by entering
a question mark '?'. If nothing matches, the help list will
be empty and you must back up until entering a '?' shows the
available options.
Two styles of help are provided:
1. Full help is available when you are ready to enter a
command argument (e.g. 'show ?') and describes each possible
argument.
2. Partial help is provided when an abbreviated argument is entered
and you want to know what arguments match the input
(e.g. 'show w?'.)
Command History
Version Description
Dell Networking W-Series Instant Access Point
6.2.1.0-3.3
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide help | 79
This command is introduced.
Page 80

Command Information
W-IAP Platform Command Mode
All platforms
Privileged EXEC mode
80 | help Dell NetworkingW-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 81

hostname
hostname <name>
Description
This command changes the hostname of the Virtual Controller.
Syntax
Parameter Description
<name>
Configures a hostname for the Virtual Controller.
Usage Guidelines
The hostname is used as the default prompt. You can use any alphanumeric character, punctuation, or symbol
characters. When spaces, plus symbols (+), question marks (?), or asterisks (*) are used, enclose the text in quotes.
Example
The following example configures host name for a W-IAP.
(Instant Access Point)# hostname IAP1
Command History
Version Description
Dell Networking W-Series Instant Access Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hostname | 81
Privileged EXEC mode
Page 82
hotspot anqp-3gpp-profile
hotspot anqp-3gpp-profile <profile-name>
3gpp-plmn1…3gpp-plmn6 <PLMN-ID>
enable
no…
Description
This command configures a 3rd Generation Partnership Project (3GPP) Cellular Network for hotspots that have
roaming relationships with cellular operators.
Syntax
Parameter Description
hotspot anqp-3gpp-profile
<profile-name>
3gpp-plmn1…3gpp-plmn6 <PLMN-ID>
enable
no…
Creates a 3GPP profile.
Configures the Public Land Mobile Networks (PLMN) value of the
network. The PLMN value can be specified for first, second, third,
fourth, fifth, and sixth highest priority network.
The PLMN ID consists of a 12-bit Mobile Country Code (MCC) and
the 12-bit Mobile Network Code (MNC).
Activates the configuration profile.
Removes the configuration
Usage Guidelines
Use this command to configure a 3GPP Cellular Network hotspot profile that defines the ANQP information element
(IE) for 3G Cellular Network for hotspots. The IE defined in this profile will be sent in a Generic Advertisement
Service (GAS) query response from a W-IAP in a cellular network hotspot. The 3GPP Mobile Country Code (MCC)
and the 12-bit Mobile Network Code data in the IE can help the client select a 3GPP network when associated with a
hotspot profile and enabled on a WLAN SSID profile.
Example
The following command configures a 3GPP profile:
(Instant Access Point)(config)# hotspot anqp-3gpp-profile cellcorp1
(Instant Access Point)(3gpp "cellcorp1")# 3gpp-plmn1 310026
(Instant Access Point)(3gpp "cellcorp1")# 3gpp_plmn2 208000
(Instant Access Point)(3gpp "cellcorp1")# 3gpp_plmn3 208001
(Instant Access Point)(3gpp "cellcorp1")# enable
(Instant Access Point)(3gpp "cellcorp1")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
82 | hotspot anqp-3gpp-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
This command is introduced.
Page 83

Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the 3GPP hotspot profile configuration
sub-mode
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-3gpp-pr ofile | 83
Page 84
hotspot anqp-domain-name-profile
hotspot anqp-domain-name-profile <profile-name>
domain-name <domain-name>
enable
no…
Description
This command defines the domain name to be sent in an Access Network Query Protocol (ANQP) information
element in a Generic Advertisement Service (GAS) query response.
Syntax
Parameter Description
hotspot anqp-domain-name-profile
<profile-name>
domain-name <domain-name>
enable
no…
Creates a domain profile.
Configures a domain name of the hotspot operator.
Enables the configuration profile.
Removes the existing configuration
Usage Guidelines
Use this command to configure a domain name in the ANQP Domain Name profile. If a client uses the Generic
Advertisement Service (GAS) to post an ANQP query to a W-IAP, the W-IAP will return an ANQP Information
Element with the domain name when this profile is associated with a hotspot profile and enabled on a WLAN SSID
profile.
Example
The following command defines a domain name for the ANQP domain name profile:
(Instant Access Point)(config)# hotspot anqp-domain-name-profile domain1
(Instant Access Point)(domain-name "domain1")# domain-name example.com
(Instant Access Point)(domain-name "domain1")# enable
(Instant Access Point)(domain-name "domain1")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
84 | hotspot anqp-domain-name-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configuration mode and the ANQP domain profile configuration
sub-mode
Page 85
hotspot anqp-ip-addr-avail-profile
hotspot anqp-ip-addr-avail-profile <profile-name>
enable
ipv4-addr-avail
ipv6-addr-avail
no…
Description
This command defines the available IP address types to be sent in an Access network Query Protocol (ANQP)
information element in a Generic Advertisement Service (GAS) query response.
Syntax
Parameter Description
hotspot anqp-ip-addr-avail-profile <profilename>
enable
ipv4-addr-avail
ipv6-addr-avail
no…
Creates an ANQP IP Address availability
profile.
Enables the IP address availability profile.
Indicates the availability of an IPv4 network.
Indicates the availability of an IPv6 network.
Removes the existing configuration.
Usage Guidelines
Use this command to configure the IP Address availability information and IP address types which could be
allocated to the clients after they associate to the hotspot W-IAP.
Example
The following command configures an AP using this profile to advertise a public IPv4 network.
(Instant Access Point)(config)# hotspot anqp-ip-addr-avail-profile default
(Instant Access Point)(IP-addr-avail "default")# ipv4-addr-avail
(Instant Access Point)(IP-addr-avail "default")# ipv6-addr-avail
(Instant Access Point)(IP-addr-avail "default")# enable
(Instant Access Point)(IP-addr-avail "default")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-ip-addr-avail-profile | 85
Configuration mode and the ANQP IP address availability profile
configuration sub-mode
Page 86

hotspot anqp-nai-realm-profile
hotspot anqp-nai-realm-profile <profile-name>
enable
nai-home-realm
nai-realm-auth-id-1 <auth-ID>
nai-realm-auth-id-2 <auth-ID>
nai-realm-auth-value-1 <auth-value>
nai-realm-auth-value-2 <auth-value>
nai-realm-eap-method <eap-method>
nai-realm-encoding <encoding>
nai-realm-name <name>
no…
Description
This command defines a Network Access Identifier (NAI) realm information that can be sent as an Access network
Query Protocol (ANQP) information element in a Generic Advertisement Service (GAS) query response.
Syntax
Parameter Description Range
hotspot anqp-nairealm-profile
<profile-name>
enable
nai-home-realm
nai-realm-auth-id-1
nai-realm-auth-id-2
<auth-id>
Configures a NAI relam hotspot profile. —
Enables the NAI realm profile.
Sets the realm in this profile as the NAI Home Realm. —
Configures the NAI realm authentication ID.
Use the nai-realm-auth-id-1 command to send the one of the
following authentication methods for the primary NAI realm ID.
Use the nai-realm-auth-id-2 command to send the one of the
following authentication methods for the secondary NAI realm
ID.
Configures any of the following types of authentication ID:
l credential— Uses credential authentication.
l eap-inner-auth—Uses EAP inner authentication type.
l exp-inner-eap— Uses the expanded inner EAP
authentication method.
l expanded-eap—Uses the expanded EAP authentication
method.
l non-eap-inner-auth—Uses non-EAP inner authentication
type.
l reserved—Uses the reserved authentication method.
—
—
credential,
eap-innerauth, expinner-auth,
expandedeap, non-eapinner-auth,
reserved,
nai-realm-auth-value1
nai-realm-auth-value2
86 | hotspot anqp-nai-r ealm-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Configures a value for NAI relam authentication. Use the nairealm-auth-value-1 command to select an authentication
value for the authentication method specified by nai-realmauth-id-1. Use thenai-realm-auth-value-2 command to select
the authentication value for the authentication method
specified bynai-realm-auth-id-2.
—
Page 87
Parameter Description Range
<auth-value>
Configures any of following types of authentication values for
the specified <auth-id>:
l For credential <auth-ID>, specify the following values:
l sim
l usim
l nfc-secure
l hw-token
l softoken
l certificate
l uname-passward
l none
l reserved
l vendor-specific
l For eap-inner-auth <aut- ID>, specify the following values:
l reserved
l pap
l chap
l mschap
l mschapv2
l For exp-inner-eap <auth-ID>, specify exp-inner-eap as the
authentication value.
l For expanded-eap<auth-ID>, specify expanded-eap as the
authentication value
l For non-eap-inner-auth<auth-ID> specify any of the
following values:
sim, usim. nfcsecure, hwtoken,
softoken,
certificate,
unamepassward,
none,
reserved,
vendorspecific
reserved, pap
chap, mschap,
mschapv2,
exp-inner-eap,
expandedeap, reserved
nai-realm-eap-method
<eap-method>
l reserved
l pap
l chap
l mschap
l mschapv2
l For reserved auth-ID> use reserved as the authentication
value.
Configures an EAP method for NAI relam.
Configures any of the following EAP methods:
l crypto-card— Crypto card authentication
l eap-aka—EAP for UMTS Authentication and Key
Agreement
l eap-sim—EAP for GSM Subscriber Identity Modules
l eap-tls—EAP-Transport Layer Security
l eap-ttls—EAP-Tunneled Transport Layer Security
l generic-token-card—EAP Generic Token Card (EAP-GTC)
l identity— EAP Identity type
l notification—The hotspot realm uses EAP Notification
messages for authentication.
l one-time-password—Authentication with a single-use
password
l peap—Protected Extensible Authentication Protocol
l peapmschapv2— Protected Extensible Authentication
Protocol with Microsoft Challenge Handshake
Authentication Protocol version 2
crypto-card,
eap-aka, eapsim, eap-tls,
eap-ttls,
generic-tokencard, identity
notification,
one-timepassword,
peap,
peapmschapv2
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-nai-realm-pr ofile | 87
Page 88
Parameter Description Range
nai-realm-encoding
<encoding>
nai-realm-name
<nai-realm-name>
no…
Configures a UTF-8 or rfc4282 formatted character string for
NAI realm encoding.
Configures a name for the NAI realm. The realm name is often
the domain name of the service provider.
Removes any existing configuration.
rfc4282,
utf8
—
—
Usage Guidelines
Use this command to configure an NAI Realm profile that identifies and describes a NAI realm accessible to the WIAP, and the method used for NAI realm authentication. The settings configured in this profile determine the NAI
realm elements that are included as part of a GAS Response frame.
Example
The following example creates an NAI realm profile:
(Instant Access Point)(config)# hotspot anqp-nai-realm-profile home
(Instant Access Point)(nai-realm "home")# nai-realm-name home-hotspot.com
(Instant Access Point)(nai-realm "home")# nai-realm-encoding utf8
(Instant Access Point)(nai-realm "home")# nai-realm-eap-method eap-sim
(Instant Access Point)(nai-realm "home")# nai-realm-auth-id-1 non-eap-inner-auth
(Instant Access Point)(nai-realm "home")# nai-realm-auth-value-1 mschapv2
(Instant Access Point)(nai-realm "home")# nai-home-realm
(Instant Access Point)(nai-realm "home")# enable
(Instant Access Point)(nai-realm "home")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the NAI realm profile configuration submode
88 | hotspot anqp-nai-r ealm-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 89

hotspot anqp-nwk-auth-profile
hotspot anqp-nwk-auth-profile <profile-name>
enable
nwk-auth-type <auth-type>
url <url>
no…
Description
This command configures an ANQP network authentication profile to define authentication type being used by the
hotspot network.
Syntax
Parameter Description Range
hotspot anqp-nwk-auth-profile
<profile-name>
enable
nwk-auth-type
<auth-type>
Configures an ANQP network authentication
profile.
Enables the network authentication profile. —
Defines the network Authentication type being
used by the hotspot network.
Allows you to specify any of the following values:
l accept-term-and-cond—When configured, the
network requires the user to accept terms and
conditions.
NOTE: This option requires you to specify a
redirection URL string as an IP address, FQDN
or URL.
l online-enrollment—When configured, the
network supports the online enrollment.
l http-redirect—When configured, additional
information on the network is provided
through HTTP/HTTPS redirection.
l dns-redirect—When configured, additional
information on the network is provided
through DNS redirection.
NOTE: This option requires you to specify a
redirection URL string as an IP address, FQDN
or URL.
—
—
accept-termand-cond,
onlineenrollment,
http-redirect,
dns-redirect
url
no…
Configures URL, IP address, or FQDN used by
the hotspot network for the accept-term-andcond or dns-redirect network authentication
types.
Removes any existing configuration.
—
—
Usage Guidelines
When the asra option is enabled in the hotspot profile associated with a WLANSSID, the settings configured for the
network authentication profile are sent in the GAS response to the client.
Example
The following command configures a network authentication profile for DNS redirection.
(Instant Access Point)(config)# hotspot anqp-nwk-auth-profile default
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-nwk-auth-profile | 89
Page 90

(Instant Access Point)(network-auth"default")# nwk-auth-type dns-redirection
(Instant Access Point)(network-auth"default")# url http://www.example.com
(Instant Access Point)(network-auth"default")# enable
(Instant Access Point)(network-auth"default")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the ANQP network authentication profile
configuration sub-mode
90 | hotspot anqp-nwk-auth-profile Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Page 91

hotspot anqp-roam-cons-profile
hotspot anqp-roam-cons-profile <profile-name>
enable
roam-cons-oi <roam-cons-oi>
roam-cons-oi-len <roam-cons-oi-len>
no…
Description
This command configures the Roaming Consortium Organization Identifier (OI) information to be sent in an Access
network Query Protocol (ANQP) information element in a Generic Advertisement Service (GAS) query response.
Syntax
Parameter Description Range
hotspot anqp-roam-cons-profile
<profile-name>
enable
roam-cons-oi
<roam-cons-oi>
roam-cons-oi-len
<roam-cons-oi-len>
Creates roaming consortium profile.
Enables the roaming consortium profile. —
Sends the specified roaming consortium OI in
a GAS query response. The OI must be a
hexadecimal number 3-5 octets in length.
Indicates the length of the OI. The value of the
roam-cons-oi-len parameter must equal
upon the number of octets of the roam-cons-
—
Hexadecimal
number 3-5
octets in length
—
oi field.
l 0: 0 Octets in the OI (Null)
l 3: OI length is 24-bit (3 Octets)
l 5: OI length is 36-bit (5 Octets)
no…
Removes any existing configuration.
—
Usage Guidelines
Use this command to configure the roaming consortium OIs assigned to service providers when they register with
the IEEE registration authority. The Roaming Consortium Information Elements (IEs) contain information about the
network and service provider, whose security credentials can be used to authenticate with the W-IAP transmitting
this IE.
Example
The following command defines the roaming consortium OI and OI length in the ANQP roaming consortium profile:
(Instant Access Point)(config)# hotspot anqp-roam-cons-profile profile1
(Instant Access Point)(roaming-consortium "profile1")# roam-cons-oi 506F9A
(Instant Access Point)(roaming-consortium "profile1")# roam-cons-oi-len 3
(Instant Access Point)(roaming-consortium "profile1")# enable
(Instant Access Point)(roaming-consortium "profile1")# end
(Instant Access Point)# commit apply
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-roam-cons-profile | 91
Page 92

Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the ANQP roaming consortium profile
configuration sub-mode
92 | hotspot anqp-roam-cons-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 93
hotspot anqp-venue-name-profile
hotspot anqp-venue-name-profile <profile-name>
enable
venue-group <group>
venue-lang-code <language>
venue-name <name>
venue-type <type>
no…
Description
This command defines venue information be sent in an Access network Query Protocol (ANQP) information element
in a Generic Advertisement Service (GAS) query response.
Syntax
Parameter Description Range Default
hotspot anqp-venue-name-profile
<profile-name>
enable
venue-group <group>
Creates a ANQP venue
name profile.
Enables the ANQP venue
name profile.
Configures one of the
following venue groups to
be advertised in the IEs
from APs associated with
this hotspot profile.
l assembly
l business
l educational
l factory-and-industrial
l institutional
l mercantile
l outdoor
l residential
l storage
l utility-and-misc
l vehicular
NOTE: This parameter
only defines the venue
group advertised in the IEs
from hotspot APs. To
define the venue group to
be included in ANQP
responses, use anqpvenue-name-profile
<profile-name> command.
— —
— —
assembly, business,
educational,
factory-and-industrial,
institutional,
mercantile,
outdoor,
residential,
storage,
unspecified,
utility-and-misc,
vehicular
unspecified
venue-lang-code <language>
Configures an ISO 639
— —
language code that
identifies the language
used in the Venue Name
field.
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-venue-name-profile | 93
Page 94

Parameter Description Range Default
venue-name <name>
Configures the venue
— —
name to be advertised in
the ANQP IEs. If the venue
name includes spaces, the
name must be enclosed in
quotation marks, e.g.
“Midtown Shopping
Center”.
venue-type <type>
Specifies the venue type to
be advertised in the IEs.
The complete list of
supported venue types
unspecified
is described in hotspot
anqp-venue-name-
profile on page 93.
no…
Removes any existing
— —
configuration.
Usage Guidelines
Use this command to configure the venue group and venue type in an ANQP Venue Name profile. If a client uses the
Generic Advertisement Service (GAS) to post an ANQP query to an Access Point, the W-IAP will return ANQP
Information Elements with the values configured in this profile.
Venue Types
The following list describes the different venue types for each venue group:
Venue Group Associated Venue Type Value
assembly
business
l arena
l stadium
l passenger-terminal
l amphitheater
l amusement-park
l place-of-worship
l convention-center
l library
l museum
l restaurant
l theater
l bar
l coffee-shop
l zoo-or-aquarium
l emegency-cord-center
l unspecified
l doctor
l bank
l fire-station
l police-station
l post-office
l professional-office
l research-and-dev-facility
l attorney-office
l unspecified
94 | hotspot anqp-venue-name-profile Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Page 95

Venue Group Associated Venue Type Value
educational
factory-and-industrial
institutional
mercantile
outdoor
l school-primary
l school-secondary
l univ-or-college
l unspecified
l factory
l unspecified
l hospital
l long-term-care
l alc-drug-rehab
l group-home
l prison-or-jail
l unspecified
l retail-store
l grocery-market
l auto-service-station
l shopping-mall
l gas-station
l unspecified
l muni-mesh-network
l city-park
l rest-area
l traffic-control
l bus-stop
l kisok
l unspecified
residential
storage
utility-and-misc
vehicular
l private-residence
l hotel
l dormitory
l boarding-house
l unspecified
unspecified
unspecified
l unspecified
l automobile-or-truck
l airplane
l bus
l ferry
l ship
l train
l motor-bike
Example
The following command defines an ANQP Venue Name profile for a shopping mall:
(Instant Access Point)(config)# hotspot anqp-venue-name-profile Mall1
(Instant Access Point)(venue-name <name>)# venue-name ShoppingCenter1
(Instant Access Point)(venue-name <name>)# venue-group mercantile
(Instant Access Point)(venue-name <name>)# venue-type shopping-mall
(Instant Access Point)(venue-name <name>)# venue-lang-code EN
(Instant Access Point)(venue-name <name>)# enable
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot anqp-venue-name-profile | 95
Page 96

(Instant Access Point)(venue-name <name>)# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the ANQP venue name profile
configuration sub-mode
96 | hotspot anqp-venue-name-profile Dell Networking W-SeriesInstant 6.2.1.0-3.4 | CLI Reference Guide
Page 97
hotspot h2qp-conn-cap-profile
hotspot h2qp-conn-cap-profile <profile-name>
enable
esp-port
icmp
tcp-ftp
tcp-http
tcp-pptp-vpn
tcp-ssh
tcp-tls-vpn
tcp-voip
udp-ike2
udp-ipsec-vpn
udp-voip
no…
Description
This command configures a Hotspot 2.0 Query Protocol (H2QP) profile that advertises hotspot protocol and port
capabilities.
Syntax
Parameter Description
hotspot h2qp-conn-capprofile<profile-name>
enable
esp-port
icmp
tcp-ftp
tcp-http
tcp-pptp-vpn
tcp-ssh
tcp-tls-vpn
tcp-voip
udp-ike2
udp-ipsec-vpn
Creates a connection capability profile.
Enables the connection capability H2QP profile.
Enables the Encapsulating Security Payload (ESP) port used by IPSec
VPNs. (port 0)
Indicates that the ICMP port is enabled and available. (port 0)
Enables the FTP port. (port 20)
Enables the HTTP port. (port 80)
Enables the PPTP port used by IPSec VPNs. (port 1723)
Enables the SSH port. (port 22)
Enables the TCP TLS port used by VPNs. (port 80)
Enables the TCP VoIP port. (port 5060)
Enables the IKEv2 port.
Enables the IPsec VPN port. (ports 500, 4500 and 0)
udp-voip
no…
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot h2qp-conn-cap-profile | 97
Enables the UDP VoIP port. (port 5060)
Removes any existing configuration.
Page 98

Usage Guidelines
Use this command to configure the values to be sent in an ANQP IE to provide information about the IP protocols
and associated port numbers that are available and open for communication.
Example
The following example allows the H2QP connection capability profile to advertise the availability of ICMP and HTTP
ports.
(Instant Access Point)(config) # hotspot h2qp-conn-cap-profile Wan1
(Instant Access Point)(connection-capabilities"Wan1")# icmp
(Instant Access Point)(connection-capabilities"Wan1")# tcp-http
(Instant Access Point)(connection-capabilities"Wan1")# enable
(Instant Access Point)(connection-capabilities"Wan1")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
This command is introduced.
Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the H2QP connection capability profile
configuration sub-mode
98 | hotspot h2qp-conn-cap-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
Page 99

hotspot h2qp-oper-name-profile
hotspot h2qp-oper-name-profile <profile>
enable
op-fr-name <name>
op-lang-code <language>
no…
Description
This command configures a Hotspot 2.0 Query Protocol (H2QP) operator-friendly name profile.
Syntax
Parameter Description Range Default
hotspot h2qp-oper-nameprofile <profile>
enable
op-fr-name
<name>
op-lang-code <language>
no…
Creates an operator-friendly name profile. — —
Enables the operator-friendly name profile.
Configures an operator-friendly name to be sent by
devices using this profile. If the name includes
quotation marks (“), include a backslash character (\)
before each quotation mark. (e.g. \"example\")
Configures an ISO 639 language code that identifies
the language used in the op-fr-name command.
Removes any existing configuration.
— —
1-64
alphanumeric
characters
— —
— —
—
Usage Guidelines
Use this command to configure an operator-friendly name that can identify the operator and also provides information
about the location.
Example
The following example configures an operator friendly profile:
(Instant Access Point)(config)# hotspot h2qp-oper-name-profile Profile1
(Instant Access Point)(operator-friendly-name "Profile1")# op-fr-name hotspot1
(Instant Access Point)(operator-friendly-name "Profile1")# op-lang-code EN
(Instant Access Point)(operator-friendly-name "Profile1")# enable
(Instant Access Point)(operator-friendly-name "Profile1")# end
(Instant Access Point)# commit apply
Command History
Version Description
Dell Networking W-Series Instant Access
Point 6.2.1.0-3.3
Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide hotspot h2qp-oper -name-profile | 99
This command is introduced.
Page 100

Command Information
W-IAP Platform Command Mode
All platforms
Configuration mode and the H2QP operator friendly name profile
configuration sub-mode
100 | hotspot h2qp-oper-name-profile Dell Networking W-Series Instant 6.2.1.0-3.4 | CLI Reference Guide
 Loading...
Loading...