Page 1

53-1001986-01
®
31 August 2010
BigIron RX Series
Configuration Guide
Supporting Multi-Service IronWare v02.7.03
Page 2
Copyright © 2010 Brocade Communications Systems, Inc. All Rights Reserved.
Brocade, the B-wing symbol, BigIron, DCX, Fabric OS, FastIron, IronPoint, IronShield, IronView, IronWare, JetCore, NetIron,
SecureIron, ServerIron, StorageX, and TurboIron are registered trademarks, and DCFM, Extraordinary Networks, and SAN Health
are trademarks of Brocade Communications Systems, Inc., in the United States and/or in other countries. All other brands,
products, or service names are or may be trademarks or service marks of, and are used to identify, products or services of their
respective owners.
Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning
any equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to
this document at any time, without notice, and assumes no responsibility for its use. This informational document describes
features that may not be currently available. Contact a Brocade sales office for information on feature and product availability.
Export of technical data contained in this document may require an export license from the United States government.
The authors and Brocade Communications Systems, Inc. shall have no liability or responsibility to any person or entity with
respect to any loss, cost, liability, or damages arising from the information contained in this book or the computer programs that
accompany it.
The product described by this document may contain “open source” software covered by the GNU General Public License or other
open source license agreements. To find-out which open source software is included in Brocade products, view the licensing
terms applicable to the open source software, and obtain a copy of the programming source code, please visit
http://www.brocade.com/support/oscd.
Brocade Communications Systems, Incorporated
Corporate and Latin American Headquarters
Brocade Communications Systems, Inc.
130 Holger Way
San Jose, CA 95134
Tel: 1-408-333-8000
Fax: 1-408-333-8101
E-mail: info@brocade.com
European Headquarters
Brocade Communications Switzerland Sàrl
Centre Swissair
Tour B - 4ème étage
29, Route de l'Aéroport
Case Postale 105
CH-1215 Genève 15
Switzerland
Tel: +41 22 799 5640
Fax: +41 22 799 5641
E-mail: emea-info@brocade.com
Asia-Pacific Headquarters
Brocade Communications Systems China HK, Ltd.
No. 1 Guanghua Road
Chao Yang District
Units 2718 and 2818
Beijing 100020, China
Tel: +8610 6588 8888
Fax: +8610 6588 9999
E-mail: china-info@brocade.com
Asia-Pacific Headquarters
Brocade Communications Systems Co., Ltd. (Shenzhen WFOE)
Citic Plaza
No. 233 Tian He Road North
Unit 1308 – 13th Floor
Guangzhou, China
Tel: +8620 3891 2000
Fax: +8620 3891 2111
E-mail: china-info@brocade.com
Document History
Title Publication number Summary of changes Date
BigIron RX Series Configuration Guide 53-1001986-01 Release 02.7.03 features Aug 2010
Page 3

Contents
About This Document
Audience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xli
Supported hardware and software . . . . . . . . . . . . . . . . . . . . . . . . . . xli
List of supported features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xli
Unsupported features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xliv
What’s new in this document. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xlv
Enhancements in release 02.7.03 . . . . . . . . . . . . . . . . . . . . . . . xlv
Enhancements in release 02.7.02 . . . . . . . . . . . . . . . . . . . . . . xlvi
Enhancements in release 02.7.00 . . . . . . . . . . . . . . . . . . . . . . xlvii
Enhancements in release 02.6.00. . . . . . . . . . . . . . . . . . . . . xlviii
Enhancements in patch release 02.5.00c . . . . . . . . . . . . . . . . . li
Enhancements in patch release 02.5.00b . . . . . . . . . . . . . . . . . li
Enhancements in release 02.5.00. . . . . . . . . . . . . . . . . . . . . . . . li
Enhancements in patch release 02.4.00c . . . . . . . . . . . . . . . . .lii
Enhancements in release 02.4.00. . . . . . . . . . . . . . . . . . . . . . . liii
Enhancements in patch release 02.3.00a . . . . . . . . . . . . . . . . lvii
Enhancements in release 02.3.00. . . . . . . . . . . . . . . . . . . . . . lviii
Enhancements in release 02.2.01 . . . . . . . . . . . . . . . . . . . . . . lxiii
Enhancements in release 02.2.00g. . . . . . . . . . . . . . . . . . . . . lxvii
Enhancements in release 02.2.00. . . . . . . . . . . . . . . . . . . . . lxviii
Document conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .lxix
Text formatting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . lxix
Command syntax conventions . . . . . . . . . . . . . . . . . . . . . . . . . lxix
Notes, cautions, and danger notices . . . . . . . . . . . . . . . . . . . . lxix
Notice to the reader . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . lxx
Related publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . lxx
Getting technical help or reporting errors . . . . . . . . . . . . . . . . . . . . . lxx
Web access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . lxxi
E-mail and telephone access . . . . . . . . . . . . . . . . . . . . . . . . . . lxxi
Chapter 1 Getting Started with the Command Line Interface
In this chapter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Logging on through the CLI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
On-line help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Command completion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Scroll control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Line editing commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
EXEC commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Global level. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
BigIron RX Series Configuration Guide iii
53-1001986-01
Page 4

CONFIG commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
Accessing the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Navigating among command levels . . . . . . . . . . . . . . . . . . . . . . . 8
CLI command structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Searching and filtering output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Allowable characters for LAG names . . . . . . . . . . . . . . . . . . . . .13
Syntax shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Saving configuration changes. . . . . . . . . . . . . . . . . . . . . . . . . . .14
Chapter 2 Getting Familiar With the BigIron RX Series Switch Management
Applications
How to manage BigIron RX Series switch . . . . . . . . . . . . . . . . . . . . .15
Logging on through the CLI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
On-line help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Command completion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Scroll control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Line editing commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Searching and filtering output from CLI commands . . . . . . . . . 17
Allowable characters for LAG names . . . . . . . . . . . . . . . . . . . . .21
Logging on through the Web Management Interface . . . . . . . . . . . . 22
Web Management Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Logging on through IronView Network Manager . . . . . . . . . . . . . . . . 24
Chapter 3 Using a Redundant Management Module
How management module redundancy works . . . . . . . . . . . . . . . . .25
Management module redundancy overview . . . . . . . . . . . . . . .25
Management module switchover . . . . . . . . . . . . . . . . . . . . . . . .26
Switchover implications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Management module redundancy configuration . . . . . . . . . . . . . . . 29
Changing the default active Chassis slot . . . . . . . . . . . . . . . . . .29
Managing management module redundancy. . . . . . . . . . . . . . . . . .29
File synchronization between the active and standby
management modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Manually switching over to the standby management
module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Rebooting the active and standby management
modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Monitoring management module redundancy . . . . . . . . . . . . . . . . .33
Determining management module status . . . . . . . . . . . . . . . . . 33
Displaying temperature information . . . . . . . . . . . . . . . . . . . . . .34
Displaying switchover information . . . . . . . . . . . . . . . . . . . . . . .34
iv BigIron RX Series Configuration Guide
53-1001986-01
Page 5

Flash memory and PCMCIA flash card file management
commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Management focus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
Flash memory file system . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
PCMCIA flash card file system. . . . . . . . . . . . . . . . . . . . . . . . . . .39
Wildcards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Formatting a flash card . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .40
Determining the current management focus. . . . . . . . . . . . . . . 41
Switching the management focus . . . . . . . . . . . . . . . . . . . . . . . 41
Displaying a directory of the files . . . . . . . . . . . . . . . . . . . . . . . . 42
Displaying the contents of a file . . . . . . . . . . . . . . . . . . . . . . . . .44
Displaying the hexadecimal output of a file. . . . . . . . . . . . . . . .45
Creating a subdirectory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Removing a subdirectory. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47
Renaming a file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
Changing the read-write attribute of a file . . . . . . . . . . . . . . . . .48
Deleting a file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Recovering (“undeleting”) a file . . . . . . . . . . . . . . . . . . . . . . . . .50
Appending a file to another file. . . . . . . . . . . . . . . . . . . . . . . . . .51
Copying files using the copy command . . . . . . . . . . . . . . . . . . . 51
Copying files using the cp command . . . . . . . . . . . . . . . . . . . . .55
Loading the software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
Saving configuration changes. . . . . . . . . . . . . . . . . . . . . . . . . . .58
File management messages. . . . . . . . . . . . . . . . . . . . . . . . . . . .59
System Monitoring Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
Chapter 4 Securing Access to Management Functions
Securing access methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Restricting remote access to management functions . . . . . . . . . . .65
Using ACLs to restrict remote access . . . . . . . . . . . . . . . . . . . .65
Restricting remote access to the device to specific
IP addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .68
Specifying the maximum number of login attempts for
Telnet access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Restricting remote access to the device to specific VLAN IDs . 69
Disabling specific access methods. . . . . . . . . . . . . . . . . . . . . . . 71
Setting passwords. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72
Setting a Telnet password . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72
Setting passwords for management privilege levels . . . . . . . . .73
Recovering from a lost password . . . . . . . . . . . . . . . . . . . . . . . .75
Displaying the SNMP community string . . . . . . . . . . . . . . . . . . .75
Disabling password encryption . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Specifying a minimum password length. . . . . . . . . . . . . . . . . . . 76
Setting up local user accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Configuring a local user account . . . . . . . . . . . . . . . . . . . . . . . .77
Username, password and login rules . . . . . . . . . . . . . . . . . . . . .79
Configuring the strict password feature . . . . . . . . . . . . . . . . . . .80
BigIron RX Series Configuration Guide v
53-1001986-01
Page 6

Configuring SSL security for the Web Management Interface. . . . .82
Enabling the SSL server on the device. . . . . . . . . . . . . . . . . . . .83
Importing digital certificates and RSA private key files. . . . . . .83
Generating an SSL certificate . . . . . . . . . . . . . . . . . . . . . . . . . . .84
Configuring TACACS and TACACS+ security . . . . . . . . . . . . . . . . . . . .84
How TACACS+ differs from TACACS . . . . . . . . . . . . . . . . . . . . . . .84
TACACS and TACACS+ authentication, authorization,
and accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
TACACS and TACACS+ configuration considerations . . . . . . . . . 88
Enabling SNMP to configure TACACS and TACACS. . . . . . . . . . . 89
Identifying the TACACS and TACACS+ servers . . . . . . . . . . . . . . 89
Specifying different servers for individual AAA functions . . . . . 90
Setting optional TACACS and TACACS+ parameters . . . . . . . . .90
Configuring authentication-method lists for TACACS
and TACACS+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .92
Configuring TACACS+ authorization . . . . . . . . . . . . . . . . . . . . . . 94
Configuring TACACS+ accounting . . . . . . . . . . . . . . . . . . . . . . . . 97
Configuring an interface as the source for all TACACS
and TACACS+ packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
Displaying TACACS and TACACS+ statistics and
configuration information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .98
Configuring RADIUS security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .100
RADIUS authentication, authorization, and accounting . . . . .100
RADIUS configuration considerations. . . . . . . . . . . . . . . . . . . .103
RADIUS configuration procedure . . . . . . . . . . . . . . . . . . . . . . .103
Configuring Brocade-specific attributes on the
RADIUS server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .104
Enabling SNMP to configure RADIUS . . . . . . . . . . . . . . . . . . . .105
Identifying the RADIUS server to the BigIron RX . . . . . . . . . . .105
Specifying different servers for individual AAA functions . . . .106
Setting RADIUS parameters . . . . . . . . . . . . . . . . . . . . . . . . . . .106
Configuring authentication-method lists for RADIUS. . . . . . . . 107
Configuring RADIUS authorization . . . . . . . . . . . . . . . . . . . . . .108
Configuring RADIUS accounting . . . . . . . . . . . . . . . . . . . . . . . .110
Configuring an interface as the source for all RADIUS
packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .111
Displaying RADIUS configuration information . . . . . . . . . . . . .112
Configuring authentication-method lists . . . . . . . . . . . . . . . . . . . . .113
Configuration considerations for authentication-
method lists . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .114
Examples of authentication-method lists. . . . . . . . . . . . . . . . .115
Chapter 5 Configuring Basic Parameters
Entering system administration information. . . . . . . . . . . . . . . . . .117
Configuring Simple Network Management Protocol traps . . . . . . .118
Specifying an SNMP trap receiver . . . . . . . . . . . . . . . . . . . . . .118
Specifying a Single trap source. . . . . . . . . . . . . . . . . . . . . . . . .119
Setting the SNMP Trap holddown time. . . . . . . . . . . . . . . . . . .119
Disabling SNMP traps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .120
Disabling Syslog messages and traps for CLI access . . . . . . .121
vi BigIron RX Series Configuration Guide
53-1001986-01
Page 7

Configuring an interface as source for all Telnet packets . . . . . . .122
Cancelling an outbound Telnet session . . . . . . . . . . . . . . . . . .123
Configuring an interface as the source for all TFTP packets . . . . .123
Configuring an interface as the source for Syslog packets . . . . . .123
Specifying a Simple Network Time Protocol (SNTP) server . . . . . .124
Setting the system clock. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .126
New Daylight Saving Time (DST) . . . . . . . . . . . . . . . . . . . . . . . .127
Configuring CLI banners . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .128
Setting a message of the day banner. . . . . . . . . . . . . . . . . . . .128
Setting a privileged EXEC CLI level banner . . . . . . . . . . . . . . .129
Displaying a message on the console when an incoming
Telnet session is detected. . . . . . . . . . . . . . . . . . . . . . . . . . . . .129
Configuring terminal display. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .130
Checking the length of terminal displays. . . . . . . . . . . . . . . . .130
Enabling or disabling routing protocols . . . . . . . . . . . . . . . . . . . . . .130
Displaying and modifying system parameter default settings . . . .131
Enabling or disabling Layer 2 switching . . . . . . . . . . . . . . . . . . . .133
CAM partitioning for the BigIron RX . . . . . . . . . . . . . . . . . . . . . . . . .134
Re-distributing CAM allocations . . . . . . . . . . . . . . . . . . . . . . . .134
Nexthop table. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .135
Changing the MAC age time. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Configuring static ARP entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Pinging an IPv4 address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Chapter 6 Configuring Interface Parameters
Assigning a port name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .139
Assigning an IP address to a port . . . . . . . . . . . . . . . . . . . . . . . . . .139
Speed/Duplex negotiation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .140
Disabling or re-enabling a port . . . . . . . . . . . . . . . . . . . . . . . . . . . .141
Changing the default Gigabit negotiation mode . . . . . . . . . . . . . . .141
Changing the negotiation mode . . . . . . . . . . . . . . . . . . . . . . . .142
Disabling or re-enabling flow control . . . . . . . . . . . . . . . . . . . . . . . .142
Specifying threshold values for flow control . . . . . . . . . . . . . .142
Locking a port to restrict addresses . . . . . . . . . . . . . . . . . . . . . . . .143
Wait for all cards feature . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .143
Port transition hold timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144
Port flap dampening . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144
Modifying port priority (QoS). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .145
Assigning a mirror port and monitor ports . . . . . . . . . . . . . . . . . . .146
Configuration guidelines for monitoring traffic . . . . . . . . . . . .146
Configuring port mirroring and monitoring. . . . . . . . . . . . . . . .146
BigIron RX Series Configuration Guide vii
53-1001986-01
Page 8

Monitoring an individual trunk port . . . . . . . . . . . . . . . . . . . . . . . . .147
Mirror ports for Policy-Based Routing (PBR) traffic. . . . . . . . . . . . .148
About hardware-based PBR . . . . . . . . . . . . . . . . . . . . . . . . . . .148
Configuring mirror ports for PBR traffic . . . . . . . . . . . . . . . . . .149
Displaying mirror and monitor port configuration. . . . . . . . . . . . . .149
Enabling WAN PHY mode support . . . . . . . . . . . . . . . . . . . . . . . . . .150
Chapter 7 Configuring IP
Overview of configuring IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .151
The IP packet flow. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .151
ARP cache table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
Static ARP table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
IP Route table. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .153
IP forwarding cache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .154
Basic IP parameters and defaults . . . . . . . . . . . . . . . . . . . . . . . . . .154
When parameter changes take effect . . . . . . . . . . . . . . . . . . .155
IP global parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .155
IP interface parameters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .158
Configuring IP parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .159
Configuring IP addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .159
Changing the network mask display to prefix format . . . . . . . 162
Configuring the default gateway . . . . . . . . . . . . . . . . . . . . . . . .162
GRE IP tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .163
IPv6 over IPv4 tunnels in hardware . . . . . . . . . . . . . . . . . . . . .168
Configuring Domain Name Server (DNS) resolver. . . . . . . . . .172
Adding host names to the DNS cache table . . . . . . . . . . . . . . 173
Configuring packet parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . .177
Changing the encapsulation type . . . . . . . . . . . . . . . . . . . . . . . 177
Setting maximum frame size per PPCR . . . . . . . . . . . . . . . . . .178
Changing the MTU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .179
Changing the router ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .180
Specifying a single source interface for Telnet, TACACS,
TACACS+, or RADIUS packets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .181
Configuring an interface as the source for Syslog packets . . . . . .183
IP fragmentation protection . . . . . . . . . . . . . . . . . . . . . . . . . . .184
IP option attack protection . . . . . . . . . . . . . . . . . . . . . . . . . . . .184
IP receive access list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .184
Configuring ARP parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .185
How ARP works. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .185
Rate limiting ARP packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . .186
Applying a rate limit to ARP packets on an interface. . . . . . . .187
Clearing the rate limit for ARP packets. . . . . . . . . . . . . . . . . . .188
Changing the ARP aging period. . . . . . . . . . . . . . . . . . . . . . . . .188
Creating a floating static ARP entry . . . . . . . . . . . . . . . . . . . . .190
Static route ARP validation check. . . . . . . . . . . . . . . . . . . . . . .191
viii BigIron RX Series Configuration Guide
53-1001986-01
Page 9

Configuring forwarding parameters. . . . . . . . . . . . . . . . . . . . . . . . .192
Disabling ICMP messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . .194
Disabling ICMP redirect messages . . . . . . . . . . . . . . . . . . . . . .196
Configuring static routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .197
Static route tagging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .201
Configuring a default network route . . . . . . . . . . . . . . . . . . . . .206
Configuring IP load sharing . . . . . . . . . . . . . . . . . . . . . . . . . . . .207
Default route ECMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .210
IP receive access list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .211
Configuring IRDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .212
Configuring UDP broadcast and IP helper parameters . . . . . .214
Configuring BootP/DHCP forwarding parameters . . . . . . . . . .216
Displaying IP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .218
Displaying IP interface information. . . . . . . . . . . . . . . . . . . . . .221
Displaying interface name in Syslog. . . . . . . . . . . . . . . . . . . . .222
Displaying ARP entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .222
Displaying the forwarding cache. . . . . . . . . . . . . . . . . . . . . . . .224
Displaying the IP route table . . . . . . . . . . . . . . . . . . . . . . . . . . .226
Clearing IP routes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .229
Displaying IP traffic statistics . . . . . . . . . . . . . . . . . . . . . . . . . .229
Displaying TCP traffic statistics. . . . . . . . . . . . . . . . . . . . . . . . .232
Chapter 8 Link Aggregation
Link aggregation overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .235
LAG formation rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .235
LAG load sharing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .238
Migration from a pre-02.6.00 trunk or LACP configuration . . . . . .239
Configuration of a LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .240
Creating a Link Aggregation Group (LAG) . . . . . . . . . . . . . . . .240
Deploying a LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .243
Commands available under LAG once it is deployed . . . . . . .244
Configuring ACL-based mirroring. . . . . . . . . . . . . . . . . . . . . . . .244
Disabling ports within a LAG . . . . . . . . . . . . . . . . . . . . . . . . . . .244
Enabling ports within a LAG . . . . . . . . . . . . . . . . . . . . . . . . . . .245
Monitoring an individual LAG port . . . . . . . . . . . . . . . . . . . . . .245
Assigning a name to a port within a LAG . . . . . . . . . . . . . . . . .246
Enabling sFlow forwarding on a port within a LAG. . . . . . . . . .246
Setting the sFlow sampling rate for a port within a LAG . . . . .246
Displaying LAG information . . . . . . . . . . . . . . . . . . . . . . . . . . . .247
Displaying LAG statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .250
Chapter 9 Configuring LLDP
Terms used in this chapter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .253
LLDP overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .253
Benefits of LLDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .254
BigIron RX Series Configuration Guide ix
53-1001986-01
Page 10

General operating principles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .255
Operating modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .255
LLDP packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .255
TLV support. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .256
MIB support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Syslog messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Configuring LLDP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .259
Configuration notes and considerations . . . . . . . . . . . . . . . . .260
Enabling and disabling LLDP. . . . . . . . . . . . . . . . . . . . . . . . . . .260
Changing a port’s LLDP operating mode . . . . . . . . . . . . . . . . .261
Specifying the maximum number of LLDP neighbors. . . . . . .262
Enabling LLDP SNMP notifications and Syslog messages . . .263
Specifying the minimum time between SNMP traps and
Syslog messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .263
Changing the minimum time between LLDP transmissions. .264
Changing the interval between regular LLDP transmissions .264
Changing the holdtime multiplier for transmit TTL . . . . . . . . .265
Changing the minimum time between port reinitializations. .265
LLDP TLVs advertised by the Brocade device . . . . . . . . . . . . .266
Displaying LLDP statistics and configuration settings. . . . . . .272
LLDP configuration summary . . . . . . . . . . . . . . . . . . . . . . . . . .272
LLDP statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .273
LLDP neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
LLDP neighbors detail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .275
LLDP configuration details . . . . . . . . . . . . . . . . . . . . . . . . . . . .277
Resetting LLDP statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .277
Chapter 10 Configuring Uni-Directional Link Detection (UDLD)
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .280
Configuring UDLD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .280
Changing the keepalive interval . . . . . . . . . . . . . . . . . . . . . . . .280
Changing the keepalive retries . . . . . . . . . . . . . . . . . . . . . . . . .280
Displaying UDLD information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .281
Displaying information for all ports. . . . . . . . . . . . . . . . . . . . . .281
Displaying link-keepalive information . . . . . . . . . . . . . . . . . . . .281
Displaying information for a single port . . . . . . . . . . . . . . . . . .282
Clearing UDLD statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .284
Chapter 11 VLANs
Overview of Virtual Local Area Networks (VLANs). . . . . . . . . . . . . .285
Tagged, untagged, and dual-mode ports . . . . . . . . . . . . . . . . .285
Protocol-based VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .287
x BigIron RX Series Configuration Guide
53-1001986-01
Page 11

VLAN configuration rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
VLAN ID range . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
Tagged VLANs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
VLAN hierarchy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
Multiple VLAN membership rules . . . . . . . . . . . . . . . . . . . . . . .288
Layer 2 control protocols on VLANs . . . . . . . . . . . . . . . . . . . . .289
Configuring port-based VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . .289
VLAN byte accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .290
Strictly or explicitly tagging a port . . . . . . . . . . . . . . . . . . . . . . .292
Assigning or changing a VLAN priority . . . . . . . . . . . . . . . . . . .292
Assigning a different ID to the default VLAN . . . . . . . . . . . . . .292
Configuring protocol-based VLANs. . . . . . . . . . . . . . . . . . . . . . . . . .293
Configuring an MSTP instance . . . . . . . . . . . . . . . . . . . . . . . . .294
Configuring virtual routing interfaces . . . . . . . . . . . . . . . . . . . . . . .294
Bridging and routing the same protocol simultaneously
on the same device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .295
Integrated Switch Routing (ISR) . . . . . . . . . . . . . . . . . . . . . . . .296
VLAN groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .297
Configuring a VLAN group . . . . . . . . . . . . . . . . . . . . . . . . . . . . .297
Configuring super aggregated VLANs . . . . . . . . . . . . . . . . . . . . . . .299
Configuring aggregated VLANs . . . . . . . . . . . . . . . . . . . . . . . . .301
Complete CLI examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .302
Configuring 802.1q-in-q tagging. . . . . . . . . . . . . . . . . . . . . . . . . . . .305
Configuration rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .306
Enabling 802.1Q-in-Q tagging. . . . . . . . . . . . . . . . . . . . . . . . . .307
Example configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .307
Configuring 802.1q tag-type translation . . . . . . . . . . . . . . . . . . . . .308
Configuration rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .310
Enabling 802.1q tag-type translation. . . . . . . . . . . . . . . . . . . .311
Private VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .312
Implementation notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .313
Configuration notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .313
Configuring a private VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . .314
Enabling broadcast, multicast or unknown unicast traffic to the
private VLAN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .316
CLI example for Figure 30 . . . . . . . . . . . . . . . . . . . . . . . . . . . . .316
Other VLAN features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
Allocating memory for more VLANs or virtual routing
interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .317
Hardware flooding for Layer 2 multicast and broadcast
packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
Unknown unicast flooding on VLAN ports . . . . . . . . . . . . . . . .318
Flow based MAC learning . . . . . . . . . . . . . . . . . . . . . . . . . . . . .318
Configuring uplink ports within a port-based VLAN . . . . . . . . .319
Configuring control protocols in VLANs . . . . . . . . . . . . . . . . . .319
Other configuration options . . . . . . . . . . . . . . . . . . . . . . . . . . .320
BigIron RX Series Configuration Guide xi
53-1001986-01
Page 12

Displaying VLAN information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .320
Displaying VLAN information. . . . . . . . . . . . . . . . . . . . . . . . . . .320
Displaying VLAN information for specific ports . . . . . . . . . . . .321
Displaying VLAN status and port types. . . . . . . . . . . . . . . . . . .321
Displaying VLAN group information . . . . . . . . . . . . . . . . . . . . .323
Transparent firewall mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .323
Enabling a transparent firewall . . . . . . . . . . . . . . . . . . . . . . . .323
Chapter 12 Configuring Spanning Tree Protocol
IEEE 802.1D Spanning Tree Protocol (STP) . . . . . . . . . . . . . . . . . .325
Enabling or disabling STP . . . . . . . . . . . . . . . . . . . . . . . . . . . . .325
Default STP bridge and port parameters . . . . . . . . . . . . . . . . .326
Changing STP bridge parameters . . . . . . . . . . . . . . . . . . . . . . .327
Changing STP port parameters. . . . . . . . . . . . . . . . . . . . . . . . .328
STP root guard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .328
Spanning Tree Protocol (STP) BPDU guard. . . . . . . . . . . . . . . .329
Displaying STP information . . . . . . . . . . . . . . . . . . . . . . . . . . . .330
IEEE Single Spanning Tree (SSTP) . . . . . . . . . . . . . . . . . . . . . . . . . .336
SSTP defaults. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .336
Enabling SSTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .337
Displaying SSTP information . . . . . . . . . . . . . . . . . . . . . . . . . . .338
PVST/PVST+ compatibility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .338
Overview of PVST and PVST+ . . . . . . . . . . . . . . . . . . . . . . . . . .339
VLAN tags and dual mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . .339
Enabling PVST+ support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .340
Displaying PVST+ support information. . . . . . . . . . . . . . . . . . .340
Configuration examples. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .341
SuperSpan™ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .343
Customer ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .344
BPDU forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .344
Configuring SuperSpan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .349
Chapter 13 Configuring Rapid Spanning Tree Protocol
Overview of Rapid Spanning Tree Protocol . . . . . . . . . . . . . . . . . . .353
Bridges and bridge port roles . . . . . . . . . . . . . . . . . . . . . . . . . .353
Assignment of port roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .354
Ports on Switch 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .355
Ports on Switch 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .355
Ports on Switch 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .355
Ports Switch 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .356
Edge ports and edge port roles . . . . . . . . . . . . . . . . . . . . . . . . . . . .356
Point-to-point ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .357
Bridge port states . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .357
Edge port and non-edge port states . . . . . . . . . . . . . . . . . . . . . . . .358
Changes to port roles and states. . . . . . . . . . . . . . . . . . . . . . . . . . .358
xii BigIron RX Series Configuration Guide
53-1001986-01
Page 13

State machines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .358
Handshake mechanisms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .359
Convergence in a simple topology . . . . . . . . . . . . . . . . . . . . . . . . . .369
Convergence at start up . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .370
Convergence after a link failure . . . . . . . . . . . . . . . . . . . . . . . .372
Convergence at link restoration . . . . . . . . . . . . . . . . . . . . . . . .373
Convergence in a complex RSTP topology. . . . . . . . . . . . . . . . . . . . 374
Propagation of topology change . . . . . . . . . . . . . . . . . . . . . . . .377
Compatibility of RSTP with 802.1D . . . . . . . . . . . . . . . . . . . . . . . . .380
Configuring RSTP parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . .381
Enabling or disabling RSTP in a port-based VLAN . . . . . . . . . .381
Enabling or disabling RSTP on a single spanning tree . . . . . .382
Disabling or enabling RSTP on a port. . . . . . . . . . . . . . . . . . . .382
Changing RSTP bridge parameters. . . . . . . . . . . . . . . . . . . . . .382
Changing port parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . .383
Fast port span . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .384
Fast uplink span. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .386
Displaying RSTP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .388
Chapter 14 Metro Ring Protocol (MRP) Phase 1 and 2
Metro Ring Protocol (MRP) phase 1. . . . . . . . . . . . . . . . . . . . . . . . .393
MRP rings without shared interfaces . . . . . . . . . . . . . . . . . . . . . . .394
Ring initialization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .395
How ring breaks are detected and healed . . . . . . . . . . . . . . . . . . .398
Master VLANs and customer VLANs in a topology group . . . . . . . .400
Configuring MRP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .402
Adding an MRP ring to a VLAN . . . . . . . . . . . . . . . . . . . . . . . . .403
Changing the hello and preforwarding times. . . . . . . . . . . . . .404
MRP phase 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .404
Ring initialization for shared interfaces. . . . . . . . . . . . . . . . . . . . . .406
How ring breaks are detected and healed between
shared interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .406
Selection of master node . . . . . . . . . . . . . . . . . . . . . . . . . . . . .407
RHP processing in rings with shared interfaces . . . . . . . . . . .407
Normal flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .408
Flow when a link breaks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .409
Configuring MRP with shared interfaces . . . . . . . . . . . . . . . . .409
Using MRP diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .410
Enabling MRP diagnostics. . . . . . . . . . . . . . . . . . . . . . . . . . . . .410
Displaying MRP diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . .411
Displaying MRP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 411
Displaying topology group information . . . . . . . . . . . . . . . . . . .411
Displaying ring information . . . . . . . . . . . . . . . . . . . . . . . . . . . .412
BigIron RX Series Configuration Guide xiii
53-1001986-01
Page 14

MRP CLI example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .413
Commands on switch A (master node). . . . . . . . . . . . . . . . . . .414
Commands on switch B. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .414
Commands on switch C. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .415
Commands on switch D. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 415
Chapter 15 Virtual Switch Redundancy Protocol (VSRP)
Overview of Virtual Switch Redundancy Protocol (VSRP). . . . . . . . 417
Layer 2 and Layer 3 redundancy . . . . . . . . . . . . . . . . . . . . . . .418
Master election and failover . . . . . . . . . . . . . . . . . . . . . . . . . . .418
Configuring basic VSRP parameters . . . . . . . . . . . . . . . . . . . . . . . .423
Enabling Layer 3 VSRP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .424
Configuring optional VSRP parameters . . . . . . . . . . . . . . . . . . . . . .424
Disabling VSRP on a VRID . . . . . . . . . . . . . . . . . . . . . . . . . . . . .424
Configuring authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . .424
Configuring a VRID IP address . . . . . . . . . . . . . . . . . . . . . . . . .425
VSRP fast start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .426
Changing the backup priority . . . . . . . . . . . . . . . . . . . . . . . . . .427
Saving the timer values received from the master . . . . . . . . .427
VSRP slow start . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .428
Changing the Time-To-Live (TTL) . . . . . . . . . . . . . . . . . . . . . . . .428
Changing the hello interval . . . . . . . . . . . . . . . . . . . . . . . . . . . .429
Changing the dead interval . . . . . . . . . . . . . . . . . . . . . . . . . . . .429
Changing the backup hello state and interval . . . . . . . . . . . . .429
Changing the hold-down interval . . . . . . . . . . . . . . . . . . . . . . .430
Changing the default track priority . . . . . . . . . . . . . . . . . . . . . .430
Specifying a track port. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .431
Disabling or re-enabling backup pre-emption . . . . . . . . . . . . .431
Port transition hold timer . . . . . . . . . . . . . . . . . . . . . . . . . . . . .431
Clearing VSRP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .432
VSRP and MRP signaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .432
Displaying VSRP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .434
Displaying VRID information . . . . . . . . . . . . . . . . . . . . . . . . . . .434
Displaying a summary of VSRP information. . . . . . . . . . . . . . .436
Displaying VSRP packet statistics for VSRP . . . . . . . . . . . . . . .437
Displaying the active interfaces for a VRID . . . . . . . . . . . . . . .438
Chapter 16 Topology Groups
Topology overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .439
Master VLAN and member VLANs . . . . . . . . . . . . . . . . . . . . . . . . . .439
Master VLANs and customer VLANs in MRP. . . . . . . . . . . . . . . . . .440
Control ports and free ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .440
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .440
Configuring a topology group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .441
xiv BigIron RX Series Configuration Guide
53-1001986-01
Page 15

Displaying topology group information . . . . . . . . . . . . . . . . . . . . . .441
Displaying topology group information . . . . . . . . . . . . . . . . . . .441
Chapter 17 Configuring VRRP and VRRPE
Overview of VRRP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .443
Standard VRRP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .443
Brocade enhancements of VRRP . . . . . . . . . . . . . . . . . . . . . . .445
Overview of VRRPE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .447
VRRP and VRRPE parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . .450
Configuring parameters specific to VRRP . . . . . . . . . . . . . . . . . . . .452
Configuring the owner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .452
Configuring basic VRRP parameters. . . . . . . . . . . . . . . . . . . . .452
Configuring the owner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .453
Configuring a backup. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .453
Configuration rules for VRRP. . . . . . . . . . . . . . . . . . . . . . . . . . .453
Configuring parameters specific to VRRPE . . . . . . . . . . . . . . . . . . .454
Configuration rules for VRRPE . . . . . . . . . . . . . . . . . . . . . . . . .454
Configuring additional VRRP and VRRPE parameters . . . . . . . . . .454
Authentication type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .455
Suppression of RIP advertisements on backup routers
for the backup up interface. . . . . . . . . . . . . . . . . . . . . . . . . . . .456
Hello interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .456
Dead interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .456
Backup hello message state and interval . . . . . . . . . . . . . . . .457
Track port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .457
Track priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .457
Backup preempt. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .458
Master router abdication and reinstatement. . . . . . . . . . . . . .458
Displaying VRRP and VRRPE information . . . . . . . . . . . . . . . . . . . .459
Displaying summary information . . . . . . . . . . . . . . . . . . . . . . .459
Displaying detailed information . . . . . . . . . . . . . . . . . . . . . . . .461
Displaying statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .464
Clearing VRRP or VRRPE statistics . . . . . . . . . . . . . . . . . . . . . .465
Configuration examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .465
VRRP example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .465
VRRPE example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .467
Chapter 18 Configuring Quality of Service
Overview of Quality of Service (QoS) . . . . . . . . . . . . . . . . . . . . . . . .469
Classification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .469
Processing of classified traffic . . . . . . . . . . . . . . . . . . . . . . . . .469
Marking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .472
Configuring DSCP classification by interface . . . . . . . . . . . . . .472
Configuring port, MAC, and VLAN-based classification . . . . . . 472
BigIron RX Series Configuration Guide xv
53-1001986-01
Page 16

Configuring ToS-based QoS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 474
Enabling ToS-based QoS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 474
Specifying trust level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 474
Enabling marking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 474
Configuring the QoS mappings. . . . . . . . . . . . . . . . . . . . . . . . . . . . .475
Changing the CoS –> DSCP mappings. . . . . . . . . . . . . . . . . . .475
Changing the DSCP –> DSCP mappings . . . . . . . . . . . . . . . . .475
Changing the DSCP –> internal forwarding priority
mappings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 476
Changing the CoS –> internal forwarding priority
mappings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 477
Displaying QoS configuration information. . . . . . . . . . . . . . . . . . . . 477
Determining packet drop priority using WRED . . . . . . . . . . . . . . . .479
How WRED Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .480
Calculating avg-q-size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .480
Calculating packets that are dropped . . . . . . . . . . . . . . . . . . .480
Using WRED with rate limiting. . . . . . . . . . . . . . . . . . . . . . . . . .481
Configuring packet drop priority using WRED . . . . . . . . . . . . . . . . .481
Enabling WRED . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .481
Setting the averaging-weight (Wq) parameter . . . . . . . . . . . . .481
Displaying the WRED configuration . . . . . . . . . . . . . . . . . . . . .485
Scheduling traffic for forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . .486
Configuring traffic scheduling . . . . . . . . . . . . . . . . . . . . . . . . . .486
Configuring multicast traffic engineering . . . . . . . . . . . . . . . . . . . .490
Displaying the multicast traffic engineering configuration . . .491
QoS for the oversubscribed 16 x 10GE modules . . . . . . . . . . . . . .492
Aggregation NP QOS modes . . . . . . . . . . . . . . . . . . . . . . . . . . .492
Port group assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .492
Setting the server and storage modes . . . . . . . . . . . . . . . . . . .492
Switching between server and storage modes . . . . . . . . . . . .493
Qos profiles. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .493
Setting the group port weights . . . . . . . . . . . . . . . . . . . . . . . . .494
Calculating the values for WFQ storage mode traffic
scheduling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .494
Egress port shaping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .495
Mirroring ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .495
Supported ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .495
Configuring QoS for the 16 x 10G module . . . . . . . . . . . . . . . .496
Chapter 19 Configuring Traffic Reduction
Traffic policing on the BigIron RX Series . . . . . . . . . . . . . . . . . . . . .499
Traffic reduction parameters and algorithm . . . . . . . . . . . . . . . . . .499
Requested rate. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .499
Maximum burst . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .500
Actual rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .500
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .501
xvi BigIron RX Series Configuration Guide
53-1001986-01
Page 17

Configuring rate limiting policies . . . . . . . . . . . . . . . . . . . . . . . . . . .502
Configuring a port-based rate limiting policy . . . . . . . . . . . . . .502
Configuring a port-and-priority-based rate limiting policy . . . .503
Configuring a port-and-VLAN-based rate limiting policy . . . . .503
Configuring a VLAN-group-based rate limiting policy. . . . . . . .504
Configuring a port-and-IPv6 ACL-based traffic reduction . . . .506
NP based multicast, broadcast, and unknown-unicast
rate limiting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .507
Displaying traffic reduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .507
Chapter 20 Layer 2 ACLs
Filtering based on ethertype . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .509
Configuration rules and notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . .509
Configuring Layer 2 ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .510
Creating a Layer 2 ACL table . . . . . . . . . . . . . . . . . . . . . . . . . . .510
Example Layer 2 ACL clauses . . . . . . . . . . . . . . . . . . . . . . . . . . 511
Inserting and deleting Layer 2 ACL clauses. . . . . . . . . . . . . . .512
Binding a Layer 2 ACL table to an interface . . . . . . . . . . . . . . .512
Increasing the maximum number of clauses per
Layer 2 ACL table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .512
Viewing Layer 2 ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .512
Example of Layer 2 ACL deny by MAC address . . . . . . . . . . . .513
Chapter 21 Access Control List
How the BigIron RX processes ACLs . . . . . . . . . . . . . . . . . . . . . . . .515
Disabling or re-enabling Access Control Lists (ACLs) . . . . . . . . . . .516
Default ACL action. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .516
Types of IP ACLs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .516
ACL IDs and entries. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 517
Enabling support for additional ACL statements . . . . . . . . . . . . . .517
ACL-based inbound mirroring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .518
Considerations when configuring ACL-based inbound
mirroring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .518
Configuring ACL-based inbound mirroring . . . . . . . . . . . . . . . .518
Creating an ACL with a mirroring clause . . . . . . . . . . . . . . . . .518
Applying the ACL to an interface . . . . . . . . . . . . . . . . . . . . . . . .519
Specifying the destination mirror port . . . . . . . . . . . . . . . . . . .519
Configuring ACL-based mirroring for ACLs bound to virtual
interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .521
Configuring numbered and named ACLs. . . . . . . . . . . . . . . . . . . . .521
Configuring standard numbered ACLs . . . . . . . . . . . . . . . . . . .521
Configuring extended numbered ACLs . . . . . . . . . . . . . . . . . . .523
Configuring standard or extended named ACLs . . . . . . . . . . .531
Configuring super ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .534
BigIron RX Series Configuration Guide xvii
53-1001986-01
Page 18

Displaying ACL definitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .536
Displaying of TCP/UDP numbers in ACLs . . . . . . . . . . . . . . . . .537
ACL logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .547
Enabling the new logging method. . . . . . . . . . . . . . . . . . . . . . .548
Specifying the wait time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .548
Modifying ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .548
Adding or deleting a comment . . . . . . . . . . . . . . . . . . . . . . . . .550
Deleting ACL entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .552
From numbered ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .552
From named ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .553
Applying ACLs to interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .554
Reapplying modified ACLs. . . . . . . . . . . . . . . . . . . . . . . . . . . . .554
ACL automatic rebind . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .554
Manually setting the ACL rebind. . . . . . . . . . . . . . . . . . . . . . . .554
Applying ACLs to a virtual routing interface . . . . . . . . . . . . . . .554
Configuring the Layer 4 session log timer . . . . . . . . . . . . . . . .555
Displaying ACL log entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . .555
QoS options for IP ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .556
Enabling ACL duplication check. . . . . . . . . . . . . . . . . . . . . . . . . . . .557
ACL accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .557
Displaying accounting statistics for all ACLs . . . . . . . . . . . . . .557
Displaying statistics for an interface . . . . . . . . . . . . . . . . . . . .558
Clearing the ACL statistics. . . . . . . . . . . . . . . . . . . . . . . . . . . . .559
Enabling ACL filtering of fragmented or non-fragmented
packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .560
ACL filtering for traffic switched within a virtual routing
interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .561
ICMP filtering for extended ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . .561
Troubleshooting ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .563
Chapter 22 Policy-Based Routing
Policy-Based Routing (PBR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .565
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .565
Configuring a PBR policy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .566
Configure the ACLs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .566
Configure the route map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .567
Enabling PBR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .568
Configuration examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .569
Basic example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .569
Setting the next hop. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .570
Setting the output interface to the null interface . . . . . . . . . . 571
Trunk formation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 571
xviii BigIron RX Series Configuration Guide
53-1001986-01
Page 19

Chapter 23 Configuring IP Multicast Protocols
Overview of IP multicasting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .573
Multicast terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .573
Changing global IP multicast parameters . . . . . . . . . . . . . . . . . . . . 574
Defining the maximum number of DVMRP cache entries. . . .574
Defining the maximum number of PIM cache entries. . . . . . . 574
IP multicast boundaries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 574
Configuring multicast boundaries. . . . . . . . . . . . . . . . . . . . . . .575
Displaying multicast boundaries. . . . . . . . . . . . . . . . . . . . . . . .575
Passive Multicast Route Insertion (PMRI) . . . . . . . . . . . . . . . . . . . .576
Configuring PMRI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 576
Displaying hardware-drop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 576
Changing IGMP V1 and V2 parameters. . . . . . . . . . . . . . . . . . . . . .577
Modifying IGMP (V1 and V2) query interval period . . . . . . . . .577
Modifying IGMP (V1 and V2) membership time. . . . . . . . . . . .577
Modifying IGMP (V1 and V2) maximum response time. . . . . .578
Adding an interface to a multicast group . . . . . . . . . . . . . . . . . . . .578
IGMP v3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .579
Default IGMP version. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .580
Compatibility with IGMP V1 and V2 . . . . . . . . . . . . . . . . . . . . .580
Enabling the IGMP version per interface setting. . . . . . . . . . .581
Enabling the IGMP version on a physical port within a
virtual routing interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .581
Setting the query interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . .583
Setting the group membership time. . . . . . . . . . . . . . . . . . . . .583
Setting the maximum response time . . . . . . . . . . . . . . . . . . . .583
Displaying IGMPv3 information. . . . . . . . . . . . . . . . . . . . . . . . .583
Clearing IGMP statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .587
IGMP V3 and source specific multicast protocols . . . . . . . . . .587
Configuring a static multicast route. . . . . . . . . . . . . . . . . . . . . . . . .587
Next hop validation check . . . . . . . . . . . . . . . . . . . . . . . . . . . . .589
PIM dense . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .589
Initiating PIM multicasts on a network . . . . . . . . . . . . . . . . . . .590
Pruning a multicast tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .590
Grafts to a multicast tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . .592
PIM DM versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .592
Configuring PIM DM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .593
Failover time in a multi-path topology . . . . . . . . . . . . . . . . . . .597
Modifying the TTL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .597
PIM Sparse . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .597
PIM Sparse router types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .598
RP paths and SPT paths . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .599
Configuring PIM Sparse. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .599
Route selection precedence for multicast. . . . . . . . . . . . . . . . . . . .604
Configuring the route precedence by specifying the route types604
Displaying the route selection . . . . . . . . . . . . . . . . . . . . . . . . . .605
BigIron RX Series Configuration Guide xix
53-1001986-01
Page 20

Changing the Shortest Path Tree (SPT) threshold . . . . . . . . . . . . .606
Changing the PIM join and prune message interval . . . . . . . .607
MLL optimization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .607
Displaying PIM Sparse configuration information and
statistics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .607
Displaying basic PIM Sparse configuration information . . . . .608
Displaying a list of multicast groups. . . . . . . . . . . . . . . . . . . . .609
Displaying BSR information. . . . . . . . . . . . . . . . . . . . . . . . . . . .610
Displaying candidate RP information . . . . . . . . . . . . . . . . . . . .611
Displaying RP-to-group mappings . . . . . . . . . . . . . . . . . . . . . . .612
Displaying RP information for a PIM Sparse group . . . . . . . . .612
Displaying the RP set list. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .613
Displaying multicast neighbor information. . . . . . . . . . . . . . . .613
Displaying information about an upstream neighbor device . 614
Displaying the PIM multicast cache . . . . . . . . . . . . . . . . . . . . .615
Displaying PIM traffic statistics. . . . . . . . . . . . . . . . . . . . . . . . . 617
PIM-SSMv4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 617
Enabling SSM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .618
Configuring Multicast Source Discovery Protocol (MSDP) . . . . . . .618
Peer Reverse Path Forwarding (RPF) flooding . . . . . . . . . . . . .620
Source active caching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .620
Configuring MSDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .620
Enabling MSDP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .621
Configuring MSDP peers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .621
Designating an interface’s IP address as the RP’s
IP address. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .622
Filtering MSDP source-group pairs . . . . . . . . . . . . . . . . . . . . . .622
Filtering incoming source-active messages . . . . . . . . . . . . . . .622
Filtering advertised source-active messages. . . . . . . . . . . . . .624
Displaying the differences before and after the source active
filters are applied. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .625
Configuring MSDP mesh groups . . . . . . . . . . . . . . . . . . . . . . . . . . .627
Configuring MSDP mesh group. . . . . . . . . . . . . . . . . . . . . . . . .628
Displaying summary information . . . . . . . . . . . . . . . . . . . . . . .634
Displaying peer information . . . . . . . . . . . . . . . . . . . . . . . . . . .635
Displaying source active cache information. . . . . . . . . . . . . . .638
Clearing MSDP information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .638
Clearing peer information . . . . . . . . . . . . . . . . . . . . . . . . . . . . .638
Clearing the source active cache . . . . . . . . . . . . . . . . . . . . . . .639
Clearing MSDP statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .639
DVMRP overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .639
Initiating DVMRP multicasts on a network. . . . . . . . . . . . . . . .640
Pruning a multicast tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .640
Grafts to a multicast tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . .642
xx BigIron RX Series Configuration Guide
53-1001986-01
Page 21

Configuring DVMRP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .643
Enabling DVMRP globally and on an interface. . . . . . . . . . . . .643
Modifying DVMRP global parameters. . . . . . . . . . . . . . . . . . . .643
Modifying DVMRP interface parameters . . . . . . . . . . . . . . . . .646
Displaying information about an upstream neighbor
device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .647
Configuring a static multicast route. . . . . . . . . . . . . . . . . . . . . . . . .647
Configuring IP multicast traffic reduction. . . . . . . . . . . . . . . . . . . .648
Enabling IP multicast traffic reduction . . . . . . . . . . . . . . . . . . .649
Layer 2 multicast filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .653
PIM SM traffic snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .654
Static IGMP membership. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .658
Chapter 24 Configuring RIP
Overview of Routing Information Protocol (RIP) . . . . . . . . . . . . . . .661
Configuring RIP parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .661
Enabling RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .661
Configuring metric parameters . . . . . . . . . . . . . . . . . . . . . . . . .662
Changing the administrative distance . . . . . . . . . . . . . . . . . . .662
Configuring redistribution . . . . . . . . . . . . . . . . . . . . . . . . . . . . .663
Configuring route learning and advertising parameters . . . . .664
Changing the route loop prevention method . . . . . . . . . . . . . .665
Suppressing RIP route advertisement on a VRRP or VRRPE
backup interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .666
Using prefix lists and route maps as route filters . . . . . . . . . .666
Setting RIP timers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .667
Displaying RIP filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .668
Clearing the RIP routes from the routing table . . . . . . . . . . . .669
Chapter 25 Configuring OSPF Version 2 (IPv4)
Overview of OSPF (Open Shortest Path First) . . . . . . . . . . . . . . . . . 671
Designated routers in multi-access networks . . . . . . . . . . . . .672
Designated router election in multi-access networks . . . . . . .672
OSPF RFC 1583 and 2328 compliance. . . . . . . . . . . . . . . . . .674
Reduction of equivalent AS external LSAs . . . . . . . . . . . . . . . . 674
Support for OSPF RFC 2328 appendix E . . . . . . . . . . . . . . . . .676
Dynamic OSPF activation and configuration . . . . . . . . . . . . . .677
BigIron RX Series Configuration Guide xxi
53-1001986-01
Page 22

Configuring OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .677
Configuration rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .678
OSPF parameters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .678
Enable OSPF on the router . . . . . . . . . . . . . . . . . . . . . . . . . . . .679
Assign OSPF areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .679
Assigning an area range (optional) . . . . . . . . . . . . . . . . . . . . .683
Assigning interfaces to an area . . . . . . . . . . . . . . . . . . . . . . . .683
Modify interface defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . .683
Change the timer for OSPF authentication changes. . . . . . . .686
Block flooding of outbound LSAs on specific OSPF
interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .687
Assign virtual links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .687
Modify virtual link parameters . . . . . . . . . . . . . . . . . . . . . . . . .689
Configuring an OSPF non-broadcast interface. . . . . . . . . . . . .690
OSPF point-to-point links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .691
Changing the reference bandwidth for the cost on OSPF
interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .694
Define redistribution filters . . . . . . . . . . . . . . . . . . . . . . . . . . . .695
Modify default metric for redistribution . . . . . . . . . . . . . . . . . .696
Enable route redistribution . . . . . . . . . . . . . . . . . . . . . . . . . . . .697
Disable or re-enable load sharing. . . . . . . . . . . . . . . . . . . . . . .698
Configure external route summarization . . . . . . . . . . . . . . . . .700
Configure default route origination. . . . . . . . . . . . . . . . . . . . . .701
Configuring a default network route . . . . . . . . . . . . . . . . . . . . .702
Modify SPF timers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .703
Modify redistribution metric type . . . . . . . . . . . . . . . . . . . . . . .703
Modify administrative distance. . . . . . . . . . . . . . . . . . . . . . . . .704
Configure OSPF group Link State Advertisement pacing . . . .705
OSPF ABR type 3 LSA filtering. . . . . . . . . . . . . . . . . . . . . . . . . .705
Displaying the configured OSPF area prefix list. . . . . . . . . . . .708
Modifying OSPF traps generated . . . . . . . . . . . . . . . . . . . . . . .708
Modify OSPF standard compliance setting . . . . . . . . . . . . . . . 710
Modify exit overflow interval . . . . . . . . . . . . . . . . . . . . . . . . . . .711
Specify types of OSPF Syslog messages to log . . . . . . . . . . . .711
Displaying OSPF information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .712
Displaying general OSPF configuration information . . . . . . . .712
Displaying CPU utilization and other OSPF tasks. . . . . . . . . . .713
Displaying OSPF area information . . . . . . . . . . . . . . . . . . . . . .715
Displaying OSPF neighbor information. . . . . . . . . . . . . . . . . . . 716
Displaying OSPF interface information. . . . . . . . . . . . . . . . . . . 717
Displaying OSPF route information . . . . . . . . . . . . . . . . . . . . . . 719
Displaying OSPF external link state Information . . . . . . . . . . .721
Displaying OSPF database link state information . . . . . . . . . .722
Displaying OSPF ABR and ASBR information. . . . . . . . . . . . . .723
Displaying OSPF trap status . . . . . . . . . . . . . . . . . . . . . . . . . . .724
Displaying OSPF virtual neighbor and link information. . . . . .724
OSPF graceful restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .726
xxii BigIron RX Series Configuration Guide
53-1001986-01
Page 23

Chapter 26 Configuring BGP4 (IPv4 and IPv6)
Overview of BGP4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .731
Relationship between the BGP4 route table and the IP route
table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .732
How BGP4 selects a path for a route . . . . . . . . . . . . . . . . . . . .732
BGP4 message types. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .734
Brocade implementation of BGP4 . . . . . . . . . . . . . . . . . . . . . . . . . .736
Memory considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .736
Configuring BGP4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .737
When parameter changes take effect . . . . . . . . . . . . . . . . . . .739
Activating and disabling BGP4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 740
Note regarding disabling BGP4. . . . . . . . . . . . . . . . . . . . . . . . . 741
Entering and exiting the address family configuration level . . . . . 741
Filtering specific IP addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . .742
Defining an AS-path filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .743
Defining a community filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .744
Configuring a switch to allow routes with its own AS number . . . . 744
BGP Null0 routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .745
Aggregating routes advertised to BGP4 neighbors. . . . . . . . . . . . .749
Configuring the device to always compare MEDs . . . . . . . . . . . . . .749
Disabling or re-enabling comparison of the AS-path length . .750
Redistributing IBGP routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .750
Disabling or re-enabling client-to-client route reflection. . . . . . . . .751
Configuring a route reflector. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .751
Enabling or disabling comparison of the router IDs . . . . . . . . . . . .751
Configuring confederations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .752
Configuring route flap dampening . . . . . . . . . . . . . . . . . . . . . . . . . .755
Originating the default route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .755
Changing the default local preference . . . . . . . . . . . . . . . . . . . . . .756
Changing the default metric used for redistribution. . . . . . . . . . . .756
Changing administrative distances . . . . . . . . . . . . . . . . . . . . . . . . .757
Requiring the first AS to be the neighbor’s AS . . . . . . . . . . . . . . . .758
Neighbor local-AS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .758
Enabling fast external fallover . . . . . . . . . . . . . . . . . . . . . . . . . . . . .758
Setting the local AS number. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .759
Changing the maximum number of shared BGP4 paths . . . . . . . .759
Treating missing MEDs as the worst MEDs. . . . . . . . . . . . . . . . . . .760
Customizing BGP4 load sharing. . . . . . . . . . . . . . . . . . . . . . . . . . . . 760
BigIron RX Series Configuration Guide xxiii
53-1001986-01
Page 24

Configuring BGP4 neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .761
Removing route dampening from suppressed
neighbor routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .765
Encryption of BGP4 MD5 authentication keys. . . . . . . . . . . . . 766
Configuring a BGP4 peer group . . . . . . . . . . . . . . . . . . . . . . . . . . . .768
Peer group parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .768
Specifying a list of networks to advertise . . . . . . . . . . . . . . . . . . . . 771
Using the IP default route as a valid next hop for a BGP4 route . .772
Enabling next-hop recursion. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .773
Modifying redistribution parameters . . . . . . . . . . . . . . . . . . . . . . . .776
Using a table map to set the tag value . . . . . . . . . . . . . . . . . . . . . .779
Changing the keep alive time and hold time. . . . . . . . . . . . . . . . . .779
Changing the BGP4 next-hop update timer. . . . . . . . . . . . . . . . . . .780
Changing the router ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .780
Adding a loopback interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .781
Changing the maximum number of paths for BGP4 load sharing.781
Configuring route reflection parameters . . . . . . . . . . . . . . . . . . . . .782
Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .784
Filtering AS-paths. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .785
Filtering communities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .788
Defining and applying IP prefix lists . . . . . . . . . . . . . . . . . . . . .789
Defining neighbor distribute lists . . . . . . . . . . . . . . . . . . . . . . .790
Defining route maps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .791
Configuring cooperative BGP4 route filtering. . . . . . . . . . . . . .799
Configuring route flap dampening . . . . . . . . . . . . . . . . . . . . . .801
Generating traps for BGP . . . . . . . . . . . . . . . . . . . . . . . . . . . . .806
Updating route information and resetting a neighbor
session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .806
Clearing traffic counters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .812
Clearing route flap dampening statistics . . . . . . . . . . . . . . . . .813
Removing route flap dampening. . . . . . . . . . . . . . . . . . . . . . . .813
Clearing diagnostic buffers . . . . . . . . . . . . . . . . . . . . . . . . . . . . 814
Displaying BGP4 information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .814
Displaying summary BGP4 information . . . . . . . . . . . . . . . . . .815
Displaying the active BGP4 configuration . . . . . . . . . . . . . . . .817
Displaying summary neighbor information . . . . . . . . . . . . . . .817
Displaying BGP4 neighbor information. . . . . . . . . . . . . . . . . . .819
Displaying peer group information . . . . . . . . . . . . . . . . . . . . . .830
Displaying summary route information . . . . . . . . . . . . . . . . . .830
Displaying the BGP4 route table. . . . . . . . . . . . . . . . . . . . . . . .831
Displaying BGP4 route-attribute entries. . . . . . . . . . . . . . . . . .837
Displaying the routes BGP4 has placed in the IP route
table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .839
Displaying route flap dampening statistics . . . . . . . . . . . . . . .839
Displaying the active route map configuration . . . . . . . . . . . .840
Generalized TTL security mechanism support. . . . . . . . . . . . . . . .844
xxiv BigIron RX Series Configuration Guide
53-1001986-01
Page 25

Chapter 27 Configuring MBGP
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .848
Configuring MBGP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .848
Setting the maximum number of multicast routes
supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .848
Enabling MBGP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .849
Adding MBGP neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .849
Optional configuration tasks . . . . . . . . . . . . . . . . . . . . . . . . . . .850
Displaying MBGP information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .853
Displaying summary MBGP information. . . . . . . . . . . . . . . . . .853
Displaying the active MBGP configuration . . . . . . . . . . . . . . . .854
Displaying MBGP neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . .855
Displaying MBGP routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .856
Displaying the IP multicast route table. . . . . . . . . . . . . . . . . . .856
Chapter 28 Configuring IS-IS (IPv4)
Relationship to IP route table . . . . . . . . . . . . . . . . . . . . . . . . . .857
Intermediate systems and end systems. . . . . . . . . . . . . . . . . .858
Domain and areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .859
Level-1 routing and Level-2 routing . . . . . . . . . . . . . . . . . . . . .859
Neighbors and adjacencies. . . . . . . . . . . . . . . . . . . . . . . . . . . .859
Designated IS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .859
IS-IS CLI levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .861
Global configuration level . . . . . . . . . . . . . . . . . . . . . . . . . . . . .861
Address family configuration level . . . . . . . . . . . . . . . . . . . . . .862
Interface level. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .862
Configuring IPv4 IS-IS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .863
Enabling IS-IS globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .863
Globally configuring IS-IS on a device . . . . . . . . . . . . . . . . . . . . . . .864
Setting the overload bit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .864
Configuring authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . .865
Changing the IS-IS Level globally . . . . . . . . . . . . . . . . . . . . . . .866
Disabling or re-enabling display of hostname . . . . . . . . . . . . .866
Changing the sequence numbers PDU interval. . . . . . . . . . . .866
Changing the maximum LSP lifetime . . . . . . . . . . . . . . . . . . . .867
Changing the LSP refresh interval . . . . . . . . . . . . . . . . . . . . . .867
Changing the LSP generation interval . . . . . . . . . . . . . . . . . . .867
Changing the LSP interval and retransmit interval . . . . . . . . .868
Changing the SPF timer. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .868
Globally disabling or re-enabling hello padding. . . . . . . . . . . .868
Logging adjacency changes . . . . . . . . . . . . . . . . . . . . . . . . . . .869
Disabling partial SPF calculations . . . . . . . . . . . . . . . . . . . . . .869
BigIron RX Series Configuration Guide xxv
53-1001986-01
Page 26

Configuring IPv4 address family route parameters . . . . . . . . . . . .870
Changing the metric style . . . . . . . . . . . . . . . . . . . . . . . . . . . . .870
Changing the maximum number of load sharing paths . . . . .870
Enabling advertisement of a default route . . . . . . . . . . . . . . .870
Changing the administrative distance for IPv4 IS-IS . . . . . . . . 871
Configuring summary addresses . . . . . . . . . . . . . . . . . . . . . . .872
Redistributing routes into IPv4 IS-IS . . . . . . . . . . . . . . . . . . . . .873
Changing the default redistribution metric . . . . . . . . . . . . . . .873
Redistributing static IPv4 routes into IPv4 IS-IS. . . . . . . . . . . . 874
Redistributing directly connected routes into IPv4 IS-IS . . . . . 874
Redistributing RIP routes into IPv4 IS-IS . . . . . . . . . . . . . . . . .875
Redistributing OSPF routes into IPv4 IS-IS . . . . . . . . . . . . . . . .875
Redistributing BGP4+ routes into IPv4 IS-IS . . . . . . . . . . . . . .875
Redistributing IPv4 IS-IS routes within IPv4 IS-IS . . . . . . . . . .876
Configuring ISIS properties on an interface . . . . . . . . . . . . . . . . . .876
Disabling and enabling IS-IS on an interface. . . . . . . . . . . . . . 876
Disabling or re-enabling formation of adjacencies . . . . . . . . . 876
Setting the priority for designated IS election . . . . . . . . . . . . .877
Limiting access to adjacencies with a neighbor . . . . . . . . . . .877
Changing the IS-IS level on an interface . . . . . . . . . . . . . . . . .878
Disabling and enabling hello padding on an interface . . . . . .878
Changing the hello interval . . . . . . . . . . . . . . . . . . . . . . . . . . . .878
Changing the hello multiplier . . . . . . . . . . . . . . . . . . . . . . . . . .879
Changing the metric added to advertised routes . . . . . . . . . .879
Displaying IPv4 IS-IS information. . . . . . . . . . . . . . . . . . . . . . . . . . .880
Displaying the IS-IS configuration in the running-config . . . . .880
Displaying the name mappings. . . . . . . . . . . . . . . . . . . . . . . . .880
Displaying neighbor information. . . . . . . . . . . . . . . . . . . . . . . .881
Displaying IS-IS Syslog messages. . . . . . . . . . . . . . . . . . . . . . .882
Displaying interface information. . . . . . . . . . . . . . . . . . . . . . . .883
Displaying route information . . . . . . . . . . . . . . . . . . . . . . . . . . .886
Displaying LSP database entries . . . . . . . . . . . . . . . . . . . . . . .887
Displaying traffic statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . .890
Displaying error statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . .891
Clearing IS-IS information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .892
Chapter 29 BiDirectional Forwarding Detection (BFD)
Configuring BFD parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .896
Number of BFD sessions supported. . . . . . . . . . . . . . . . . . . . .896
Disabling BFD Syslog messages. . . . . . . . . . . . . . . . . . . . . . . .896
Displaying Bidirectional Forwarding Detection information . . . . . . 897
Displaying BFD information on a router . . . . . . . . . . . . . . . . . .897
Clearing BFD neighbor sessions . . . . . . . . . . . . . . . . . . . . . . . .901
Configuring BFD for the specified protocol . . . . . . . . . . . . . . . . . . .901
Configuring BFD for OSPFv2 . . . . . . . . . . . . . . . . . . . . . . . . . . .901
Configuring BFD for OSPFv3 . . . . . . . . . . . . . . . . . . . . . . . . . . .902
Configuring BFD for IS-IS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .902
xxvi BigIron RX Series Configuration Guide
53-1001986-01
Page 27

Chapter 30 Configuring Secure Shell
Overview of Secure Shell (SSH) . . . . . . . . . . . . . . . . . . . . . . . . . . . .905
SSH version 2 support. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .905
Supported features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .906
Configuring SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .906
Generating a host key pair . . . . . . . . . . . . . . . . . . . . . . . . . . . .907
Configuring DSA challenge-response authentication . . . . . . .908
Disabling 3-DES . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .913
Displaying SSH connection information . . . . . . . . . . . . . . . . . . . . .913
Using secure copy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .914
Chapter 31 Configuring Multi-Device Port Authentication
How multi-device port authentication works. . . . . . . . . . . . . . . . . .917
RADIUS authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 917
Authentication-failure actions . . . . . . . . . . . . . . . . . . . . . . . . . .918
Supported RADIUS attributes . . . . . . . . . . . . . . . . . . . . . . . . . .918
Dynamic VLAN and ACL assignments. . . . . . . . . . . . . . . . . . . .918
Support for authenticating multiple MAC addresses
on an interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .919
Support for multi-device port authentication and 802.1x
on the same interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .919
Configuring multi-device port authentication . . . . . . . . . . . . . . . . .919
Enabling multi-device port authentication . . . . . . . . . . . . . . . .919
Configuring an authentication method list for 802.1x . . . . . .920
Setting RADIUS parameters . . . . . . . . . . . . . . . . . . . . . . . . . . .920
Specifying the format of the MAC addresses sent to the
RADIUS server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .921
Specifying the authentication-failure action . . . . . . . . . . . . . .921
Defining MAC address filters. . . . . . . . . . . . . . . . . . . . . . . . . . .922
Configuring dynamic VLAN assignment . . . . . . . . . . . . . . . . . .922
Specifying to which VLAN a port is moved after its
RADIUS-specified VLAN assignment expires . . . . . . . . . . . . . .923
Saving dynamic VLAN assignments to the running
configuration file . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .924
Clearing authenticated MAC addresses. . . . . . . . . . . . . . . . . .924
Disabling aging for authenticated MAC addresses . . . . . . . . .925
Specifying the aging time for blocked MAC addresses . . . . . .925
Displaying multi-device port authentication information . . . . . . . .926
Displaying authenticated MAC address information . . . . . . . .926
Displaying multi-device port authentication configuration
information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .927
Displaying multi-device port authentication information for
a specific MAC address or port . . . . . . . . . . . . . . . . . . . . . . . . .929
Displaying the authenticated MAC addresses . . . . . . . . . . . . .930
Displaying the non-authenticated MAC addresses . . . . . . . . .930
BigIron RX Series Configuration Guide xxvii
53-1001986-01
Page 28

Chapter 32 Using the MAC Port Security Feature
and Transparent Port Flooding
MAC Port Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .931
Violation actions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .931
Local and global resources . . . . . . . . . . . . . . . . . . . . . . . . . . . .932
Configuring the MAC Port Security feature . . . . . . . . . . . . . . . . . . .932
Enabling the MAC Port Security feature . . . . . . . . . . . . . . . . . .932
Setting the maximum number of secure MAC addresses for
an interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .933
Specifying static secure MAC addresses . . . . . . . . . . . . . . . . .934
Enabling dynamic MAC address learning. . . . . . . . . . . . . . . . .934
Denying specific MAC addresses . . . . . . . . . . . . . . . . . . . . . . .934
Autosaving secure MAC addresses to the startup-config . . . .934
Setting the MAC Port Security age timer . . . . . . . . . . . . . . . . .935
Defining security violation actions . . . . . . . . . . . . . . . . . . . . . . . . . .935
Shutdown the interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .936
Restricting interface access . . . . . . . . . . . . . . . . . . . . . . . . . . .936
Denying a MAC address. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .938
Understanding the rules for violation action configuration . . . . . .938
Interaction between global and interface level violation
actions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .938
Changing the global violation action . . . . . . . . . . . . . . . . . . . .939
Changing the violation action for an interface. . . . . . . . . . . . .939
Re-enabling an interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .940
Interface shutdown time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .940
Manually re-enabling a interface . . . . . . . . . . . . . . . . . . . . . . .940
Displaying MAC Port Security information. . . . . . . . . . . . . . . . . . . .940
Displaying MAC Port Security settings . . . . . . . . . . . . . . . . . . .940
Displaying the secure MAC addresses list on the device . . . .941
Displaying MAC Port Security statistics . . . . . . . . . . . . . . . . . .942
Displaying a list of MAC addresses. . . . . . . . . . . . . . . . . . . . . .943
Displaying a list of secure and denied MAC addresses. . . . . .943
Displaying information when violation action is restrict . . . . .944
Displaying information when violation action is deny . . . . . . .944
Transparent port flooding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .945
Chapter 33 Configuring 802.1x Port Security
Overview of 802.1x port security . . . . . . . . . . . . . . . . . . . . . . . . . . .947
IETF RFC support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .947
How 802.1x port security works. . . . . . . . . . . . . . . . . . . . . . . . . . . .947
Device roles in an 802.1x configuration . . . . . . . . . . . . . . . . .947
Communication between the devices . . . . . . . . . . . . . . . . . . .948
Controlled and uncontrolled ports . . . . . . . . . . . . . . . . . . . . . .949
Message exchange during authentication. . . . . . . . . . . . . . . .950
Authenticating multiple clients connected to the same
port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .952
802.1x port security and sFlow . . . . . . . . . . . . . . . . . . . . . . . . . . . .954
xxviii BigIron RX Series Configuration Guide
53-1001986-01
Page 29

Configuring 802.1x port security . . . . . . . . . . . . . . . . . . . . . . . . . . .954
Configuring an authentication method list for 802.1x . . . . . .955
Setting RADIUS parameters . . . . . . . . . . . . . . . . . . . . . . . . . . .955
Configuring dynamic VLAN assignment for 802.1x ports . . . .956
Disabling and enabling strict security mode for dynamic
filter assignment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .957
Dynamically applying existing ACLs or MAC address filter . . .958
Configuring per-user IP ACLs or MAC address filters . . . . . . . .960
Enabling 802.1x port security. . . . . . . . . . . . . . . . . . . . . . . . . .960
Setting the port control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .961
Configuring periodic re-authentication . . . . . . . . . . . . . . . . . . .962
Re-authenticating a port manually . . . . . . . . . . . . . . . . . . . . . .962
Setting the quiet period. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .963
Setting the interval for retransmission of EAP-request/
identity frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .963
Specifying the number of EAP-request/identity frame
retransmissions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .963
Specifying a timeout for retransmission of messages
to the authentication server . . . . . . . . . . . . . . . . . . . . . . . . . . .964
Specifying a timeout for retransmission of
EAP-request frames to the client . . . . . . . . . . . . . . . . . . . . . . .964
Initializing 802.1x on a port . . . . . . . . . . . . . . . . . . . . . . . . . . .964
Allowing multiple 802.1x clients to authenticate. . . . . . . . . . .964
Displaying 802.1x information . . . . . . . . . . . . . . . . . . . . . . . . . . . . .966
Displaying 802.1x configuration information. . . . . . . . . . . . . .966
Displaying 802.1x statistics . . . . . . . . . . . . . . . . . . . . . . . . . . .968
Clearing 802.1x statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . .969
Displaying dynamically assigned VLAN information . . . . . . . .969
Displaying information on MAC address filters and IP ACLs on an
interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .970
Displaying information about the dot1x-mac-sessions on
each port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 971
Sample 802.1x configurations. . . . . . . . . . . . . . . . . . . . . . . . . . . . .973
Point-to-point configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . .973
Hub configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 974
Chapter 34 Protecting Against Denial of Service Attacks
Protecting against Smurf attacks. . . . . . . . . . . . . . . . . . . . . . . . . . .977
Avoiding being an intermediary in a Smurf attack. . . . . . . . . .978
ACL-based DOS-attack prevention . . . . . . . . . . . . . . . . . . . . . .978
Protecting against TCP SYN attacks. . . . . . . . . . . . . . . . . . . . . . . . .979
TCP security enhancement . . . . . . . . . . . . . . . . . . . . . . . . . . . .980
Displaying statistics due DoS attacks . . . . . . . . . . . . . . . . . . . . . . .981
Clear DoS attack statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .982
BigIron RX Series Configuration Guide xxix
53-1001986-01
Page 30

Chapter 35 Inspecting and Tracking DHCP Packets
Dynamic ARP inspection. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .983
ARP attacks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .983
How DAI works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .984
Limits and restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .985
Configuring DAI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .985
Displaying ARP inspection status and ports . . . . . . . . . . . . . .986
Displaying the ARP table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .987
DHCP snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .988
How DHCP snooping works . . . . . . . . . . . . . . . . . . . . . . . . . . . .988
System reboot and the binding database . . . . . . . . . . . . . . . .989
Configuring DHCP snooping . . . . . . . . . . . . . . . . . . . . . . . . . . .989
DHCP relay agent information (DHCP option 82) . . . . . . . . . . . . . .990
Disabling option 82 processing . . . . . . . . . . . . . . . . . . . . . . . .991
Displaying DHCP snooping status and ports . . . . . . . . . . . . . .991
DHCP snooping configuration example . . . . . . . . . . . . . . . . . .992
IP source guard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .992
Limits and restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .993
Enabling IP source guard. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .993
Chapter 36 Securing SNMP Access
Establishing SNMP community strings . . . . . . . . . . . . . . . . . . . . . .995
Encryption of SNMP community strings . . . . . . . . . . . . . . . . .995
Adding an SNMP community string . . . . . . . . . . . . . . . . . . . . .995
Displaying the SNMP community strings . . . . . . . . . . . . . . . . .996
Using the user-based security model. . . . . . . . . . . . . . . . . . . . . . . .997
Configuring your NMS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .997
Configuring SNMP version 3 on the BigIron RX . . . . . . . . . . . .997
Defining the engine ID. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .998
Defining an SNMP group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .998
Defining an SNMP user account. . . . . . . . . . . . . . . . . . . . . . . .999
Displaying the engine ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1001
Displaying SNMP groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1001
Displaying user information. . . . . . . . . . . . . . . . . . . . . . . . . . 1002
Interpreting varbinds in report packets . . . . . . . . . . . . . . . . 1002
Defining SNMP views . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1002
SNMP v3 configuration examples. . . . . . . . . . . . . . . . . . . . . 1003
Chapter 37 Enabling the Foundry Discovery Protocol (FDP) and Reading Cisco
Discovery Protocol (CDP) Packets
Using FDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1005
Configuring FDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1005
Displaying FDP information. . . . . . . . . . . . . . . . . . . . . . . . . . 1006
Clearing FDP and CDP information. . . . . . . . . . . . . . . . . . . . 1009
xxx BigIron RX Series Configuration Guide
53-1001986-01
Page 31

Reading CDP packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1010
Enabling interception of CDP packets globally . . . . . . . . . . .1010
Enabling interception of CDP packets on an interface . . . . .1010
Displaying CDP information. . . . . . . . . . . . . . . . . . . . . . . . . . .1010
Clearing CDP information . . . . . . . . . . . . . . . . . . . . . . . . . . . .1012
Chapter 38 Remote Network Monitoring
Basic management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1015
Viewing system information . . . . . . . . . . . . . . . . . . . . . . . . . .1015
Viewing configuration information . . . . . . . . . . . . . . . . . . . . .1015
Viewing port statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1015
Viewing STP statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1015
Clearing statistics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1016
RMON support. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1016
Statistics (RMON group 1) . . . . . . . . . . . . . . . . . . . . . . . . . . . .1016
History (RMON group 2). . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1019
Alarm (RMON group 3). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1019
Event (RMON group 9). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1019
Chapter 39 Configuring sFlow
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . .1021
Configuring and enabling sFlow . . . . . . . . . . . . . . . . . . . . . . 1022
ACL-based inbound sFlow . . . . . . . . . . . . . . . . . . . . . . . . . . . 1026
Displaying sFlow information . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1029
Display sFlow configuration and statistics. . . . . . . . . . . . . . 1029
Displaying sFlow counters. . . . . . . . . . . . . . . . . . . . . . . . . . . 1030
Clearing sFlow statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1030
Chapter 40 Multiple Spanning Tree Protocol (MSTP) 802.1s
802.1s Multiple Spanning Tree Protocol . . . . . . . . . . . . . . . . . . . 1033
Multiple spanning-tree regions . . . . . . . . . . . . . . . . . . . . . . . 1033
Configuring MSTP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1035
Setting the MSTP name. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1035
Setting the MSTP revision number . . . . . . . . . . . . . . . . . . . . 1035
Configuring an MSTP instance . . . . . . . . . . . . . . . . . . . . . . . 1036
Configuring port priority and port path cost. . . . . . . . . . . . . 1036
Configuring bridge priority for an MSTP instance . . . . . . . . 1036
Setting the MSTP global parameters . . . . . . . . . . . . . . . . . . .1037
Setting ports to be operational edge ports . . . . . . . . . . . . . .1037
Setting point-to-point link . . . . . . . . . . . . . . . . . . . . . . . . . . . .1037
Disabling MSTP on a port . . . . . . . . . . . . . . . . . . . . . . . . . . . 1038
Forcing ports to transmit an MSTP BPDU. . . . . . . . . . . . . . . 1038
Enabling MSTP on a switch . . . . . . . . . . . . . . . . . . . . . . . . . . 1038
Displaying MSTP statistics. . . . . . . . . . . . . . . . . . . . . . . . . . . .1041
Displaying MSTP information for a specified instance . . . . 1042
Displaying MSTP information for CIST instance 0 . . . . . . . . 1043
BigIron RX Series Configuration Guide xxxi
53-1001986-01
Page 32

Chapter 41 Configuring IP Multicast Traffic Reduction
Enabling IP multicast traffic reduction . . . . . . . . . . . . . . . . . . . . 1046
Changing the IGMP mode . . . . . . . . . . . . . . . . . . . . . . . . . . . .1047
Modifying the query interval . . . . . . . . . . . . . . . . . . . . . . . . . 1048
Modifying the age interval. . . . . . . . . . . . . . . . . . . . . . . . . . . 1048
Filtering multicast groups . . . . . . . . . . . . . . . . . . . . . . . . . . . 1048
Static IGMP membership. . . . . . . . . . . . . . . . . . . . . . . . . . . . 1049
PIM SM traffic snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1051
Application examples. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1052
Configuration requirements . . . . . . . . . . . . . . . . . . . . . . . . . 1053
Enabling PIM SM traffic snooping. . . . . . . . . . . . . . . . . . . . . 1054
Multicast traffic reduction per VLAN. . . . . . . . . . . . . . . . . . . 1055
Displaying IP multicast information . . . . . . . . . . . . . . . . . . . . . . . 1055
Displaying multicast information . . . . . . . . . . . . . . . . . . . . . 1055
Displaying IP multicast statistics . . . . . . . . . . . . . . . . . . . . . 1056
Clearing IP multicast statistics . . . . . . . . . . . . . . . . . . . . . . . .1057
Clearing IGMP group flows . . . . . . . . . . . . . . . . . . . . . . . . . . .1057
Chapter 42 IPv6 Addressing
IPv6 addressing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1059
IPv6 address types. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1060
IPv6 stateless autoconfiguration . . . . . . . . . . . . . . . . . . . . . . . . . 1062
Chapter 43 Configuring Basic IPv6 Connectivity
Enabling IPv6 routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1063
Configuring IPv6 on each router interface. . . . . . . . . . . . . . . . . . 1063
Configuring a global or site-local IPv6 address . . . . . . . . . . 1064
Configuring a link-local IPv6 address . . . . . . . . . . . . . . . . . . 1065
Configuring IPv6 anycast addresses . . . . . . . . . . . . . . . . . . 1066
Configuring the management port for an IPv6 automatic
address configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1066
IPv6 host support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1066
Restricting SNMP access to an IPv6 node. . . . . . . . . . . . . . 1066
Specifying an IPv6 SNMP trap receiver . . . . . . . . . . . . . . . . 1067
Restricting web management access to an IPv6 host by
specifying an IPv6 ACL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1067
Restricting web management access to an IPv6 host . . . . 1067
Configuring an IPv6 Syslog server . . . . . . . . . . . . . . . . . . . . 1067
xxxii BigIron RX Series Configuration Guide
53-1001986-01
Page 33

Configuring an IPv6 host address for a BigIron RX running a switch image
1068
Configuring a global or site-local IPv6 address with a
manually configured interface ID as the switch’s
system-wide address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1068
Configuring a global or site-local IPv6 address with an
automatically computed EUI-64 interface ID as the
switch’s system-wide address. . . . . . . . . . . . . . . . . . . . . . . . 1069
Configuring a link-local IPv6 address as the switch’s system-wide
address. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1069
Configuring IPv4 and IPv6 protocol stacks . . . . . . . . . . . . . . . . . .1070
Configuring IPv6 Domain Name Server (DNS) resolver . . . . . . . .1071
Defining a DNS entry . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1071
ECMP load sharing for IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1072
Disabling or re-enabling ECMP load sharing for IPv6 . . . . . .1072
Changing the maximum number of load sharing paths for
IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1073
Changing the ECMP load-sharing method for IPv6 . . . . . . . .1073
DHCP relay agent for IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1073
Configuring DHCP for IPv6 relay agent. . . . . . . . . . . . . . . . . . 1074
Displaying DHCP relay information . . . . . . . . . . . . . . . . . . . . .1074
Enabling support for network-based ECMP load sharing for
IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1074
Displaying ECMP load-sharing information for IPv6 . . . . . . .1074
Configuring IPv6 ICMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1075
Configuring ICMP rate limiting . . . . . . . . . . . . . . . . . . . . . . . .1075
Disabling or reenabling ICMP redirect messages . . . . . . . . .1076
Configuring IPv6 neighbor discovery . . . . . . . . . . . . . . . . . . . . . . .1076
Neighbor solicitation and advertisement messages . . . . . . .1077
Router advertisement and solicitation messages. . . . . . . . .1078
Neighbor redirect messages . . . . . . . . . . . . . . . . . . . . . . . . . .1078
Setting neighbor solicitation parameters for duplicate
address detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1078
Setting IPv6 router advertisement parameters . . . . . . . . . . .1079
Controlling prefixes advertised in IPv6 router advertisement
messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1080
Setting flags in IPv6 router advertisement messages. . . . . .1081
Enabling and disabling IPv6 router advertisements . . . . . . .1081
Configuring reachable time for remote IPv6 nodes. . . . . . . 1082
Changing the IPv6 MTU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1082
Configuring static neighbor entries . . . . . . . . . . . . . . . . . . . . . . . 1083
Limiting the number of hops an IPv6 packet can traverse . . . . 1083
QoS for IPv6 traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1084
BigIron RX Series Configuration Guide xxxiii
53-1001986-01
Page 34

Clearing global IPv6 information . . . . . . . . . . . . . . . . . . . . . . . . . 1084
Clearing the IPv6 cache. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1084
Clearing IPv6 neighbor information . . . . . . . . . . . . . . . . . . . 1085
Clearing IPv6 routes from the IPv6 route table . . . . . . . . . . 1085
Clearing IPv6 traffic statistics . . . . . . . . . . . . . . . . . . . . . . . . 1086
Deleting IPv6 session flows. . . . . . . . . . . . . . . . . . . . . . . . . . 1086
Displaying global IPv6 information. . . . . . . . . . . . . . . . . . . . . . . . 1086
Displaying IPv6 cache information . . . . . . . . . . . . . . . . . . . . 1086
Displaying IPv6 interface information. . . . . . . . . . . . . . . . . . .1087
Displaying IPv6 neighbor information. . . . . . . . . . . . . . . . . . 1089
Displaying the IPv6 route table . . . . . . . . . . . . . . . . . . . . . . . .1091
Displaying local IPv6 routers. . . . . . . . . . . . . . . . . . . . . . . . . 1092
Displaying IPv6 TCP information . . . . . . . . . . . . . . . . . . . . . . 1093
Displaying IPv6 traffic statistics . . . . . . . . . . . . . . . . . . . . . . 1096
Chapter 44 Configuring RIPng
Configuring RIPng . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1101
Enabling RIPng . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1101
Configuring RIPng timers. . . . . . . . . . . . . . . . . . . . . . . . . . . . 1102
Configuring route learning and advertising parameters . . . 1103
Redistributing routes into RIPng . . . . . . . . . . . . . . . . . . . . . . 1105
Controlling distribution of routes through RIPng . . . . . . . . . 1105
Configuring poison reverse parameters. . . . . . . . . . . . . . . . 1106
Clearing RIPng routes from IPv6 route table. . . . . . . . . . . . . . . . 1106
Displaying RIPng information . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1106
Displaying RIPng configuration . . . . . . . . . . . . . . . . . . . . . . . .1107
Displaying RIPng routing table . . . . . . . . . . . . . . . . . . . . . . . .1107
Chapter 45 Configuring BGP4+
Address family configuration level. . . . . . . . . . . . . . . . . . . . . . . . 1109
Configuring BGP4+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1110
Enabling BGP4+. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1110
Configuring BGP4+ neighbors using global or site-local
IPv6 addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1111
Adding BGP4+ neighbors using link-local addresses . . . . . 1112
Configuring a BGP4+ peer group . . . . . . . . . . . . . . . . . . . . . 1113
Advertising the default BGP4+ route . . . . . . . . . . . . . . . . . . 1115
Importing routes into BGP4+ . . . . . . . . . . . . . . . . . . . . . . . . 1115
Redistributing prefixes into BGP4+ . . . . . . . . . . . . . . . . . . . .1116
Aggregating routes advertised to BGP4 neighbors . . . . . . . .1117
Using route maps. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1117
xxxiv BigIron RX Series Configuration Guide
53-1001986-01
Page 35

Clearing BGP4+ information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1118
Removing route flap dampening. . . . . . . . . . . . . . . . . . . . . . 1118
Clearing route flap dampening statistics . . . . . . . . . . . . . . . 1118
Clearing BGP4+ local route information. . . . . . . . . . . . . . . . 1119
Clearing BGP4+ neighbor information . . . . . . . . . . . . . . . . . 1119
Clearing and resetting BGP4+ routes in the IPv6 route
table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1122
Clearing traffic counters for all BGP4+ neighbors. . . . . . . . 1122
Displaying BGP4+ information . . . . . . . . . . . . . . . . . . . . . . . . . . . 1122
Displaying the BGP4+ route table. . . . . . . . . . . . . . . . . . . . . 1123
Displaying BGP4+ route information . . . . . . . . . . . . . . . . . . 1129
Displaying BGP4+ route-attribute entries. . . . . . . . . . . . . . . 1130
Displaying the BGP4+ running configuration. . . . . . . . . . . . 1132
Displaying dampened BGP4+ paths. . . . . . . . . . . . . . . . . . . 1132
Displaying filtered-out BGP4+ routes . . . . . . . . . . . . . . . . . . 1133
Displaying route flap dampening statistics . . . . . . . . . . . . . .1137
Displaying BGP4+ neighbor information . . . . . . . . . . . . . . . 1139
Displaying BGP4+ peer group configuration information . . 1162
Displaying BGP4+ summary . . . . . . . . . . . . . . . . . . . . . . . . . 1163
Chapter 46 Configuring IPv6 MBGP
Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1167
Configuring IPv6 MBGP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1167
Setting the maximum number of multicast routes
supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1168
Enabling IPv6 MBGP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1168
Adding IPv6 MBGP neighbors . . . . . . . . . . . . . . . . . . . . . . . . 1168
Optional configuration tasks . . . . . . . . . . . . . . . . . . . . . . . . . 1169
Aggregating routes advertised to IPv6 BGP neighbors . . . . .1172
Displaying IPv6 MBGP information . . . . . . . . . . . . . . . . . . . . . . . .1172
Displaying summary MBGP information. . . . . . . . . . . . . . . . .1173
Displaying the Active MBGP Configuration. . . . . . . . . . . . . . .1173
Displaying MBGP neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . 1174
Displaying MBGP routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1175
Displaying the IPv6 multicast route table. . . . . . . . . . . . . . . .1176
Chapter 47 IPv6 Access Control Lists (ACLs)
IPv6 ACLs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1177
Using IPv6 ACLs as input to other features . . . . . . . . . . . . . . . . . .1178
Configuring an IPv6 ACL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1178
Example configurations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1178
Default and implicit IPv6 ACL action. . . . . . . . . . . . . . . . . . . 1180
ACL syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1181
Applying an IPv6 ACL to an interface . . . . . . . . . . . . . . . . . . . . . . 1186
Adding TCP flags to an IPv6 ACL entry . . . . . . . . . . . . . . . . . . . . . 1186
Adding a comment to an IPv6 ACL entry . . . . . . . . . . . . . . . . . . . .1187
Displaying ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1188
BigIron RX Series Configuration Guide xxxv
53-1001986-01
Page 36

Chapter 48 Configuring OSPF Version 3
OSPF version 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1189
Link state advertisement types for OSPFv3 . . . . . . . . . . . . . . . . 1189
Configuring OSPFv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1190
Enabling OSPFv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1190
Assigning OSPFv3 areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1191
Configuring virtual links. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1193
Changing the reference bandwidth for the cost on OSPFv3
interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1195
Redistributing routes into OSPFv3 . . . . . . . . . . . . . . . . . . . . 1196
Filtering OSPFv3 routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1200
Configuring default route origination . . . . . . . . . . . . . . . . . . 1202
Modifying shortest path first timers . . . . . . . . . . . . . . . . . . . 1203
Modifying administrative distance . . . . . . . . . . . . . . . . . . . . 1204
Configuring the OSPFv3 LSA pacing interval . . . . . . . . . . . . 1205
Modifying exit overflow interval. . . . . . . . . . . . . . . . . . . . . . . 1205
Modifying external link state database limit . . . . . . . . . . . . 1205
Modifying OSPFv3 interface defaults . . . . . . . . . . . . . . . . . . 1206
Disabling or reenabling event logging . . . . . . . . . . . . . . . . . 1207
Displaying OSPFv3 information . . . . . . . . . . . . . . . . . . . . . . . . . . 1207
Displaying OSPFv3 area information . . . . . . . . . . . . . . . . . . 1207
Displaying OSPFv3 database Information . . . . . . . . . . . . . . 1208
Displaying OSPFv3 interface information. . . . . . . . . . . . . . . .1214
Displaying OSPFv3 memory usage . . . . . . . . . . . . . . . . . . . . .1217
Displaying OSPFv3 neighbor information. . . . . . . . . . . . . . . 1218
Displaying routes redistributed into OSPFv3 . . . . . . . . . . . . 1220
Displaying OSPFv3 route information . . . . . . . . . . . . . . . . . . 1221
Displaying OSPFv3 SPF information . . . . . . . . . . . . . . . . . . . 1223
Displaying IPv6 OSPF virtual link information . . . . . . . . . . . 1226
Displaying OSPFv3 virtual neighbor information . . . . . . . . . 1226
Chapter 49 Configuring IPv6 Multicast Features
IPv6 PIM sparse . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1229
PIM sparse router types. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1229
RP paths and SPT paths . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1230
Configuring PIM sparse . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1230
IPv6 PIM-sparse mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1231
Configuring IPv6 PIM-SM on a virtual routing interface . . . 1231
Passive Multicast Route Insertion (PMRI) . . . . . . . . . . . . . . 1238
Displaying PIM sparse configuration information and
statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1239
xxxvi BigIron RX Series Configuration Guide
53-1001986-01
Page 37

Multicast Listener Discovery and source specific multicast
protocols (MLDv2). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1247
MLD version distinctions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1248
Enabling MLDv2. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1249
Enabling source specific multicast . . . . . . . . . . . . . . . . . . . . 1249
Setting the query interval . . . . . . . . . . . . . . . . . . . . . . . . . . . 1249
Setting the maximum response time . . . . . . . . . . . . . . . . . . 1250
Setting the last listener query count. . . . . . . . . . . . . . . . . . . 1250
Setting the last listener query interval . . . . . . . . . . . . . . . . . 1250
Setting the robustness . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1250
Setting the version. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1250
Specifying a port version . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1251
Specifying a static group . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1251
Setting the interface MLD version . . . . . . . . . . . . . . . . . . . . 1251
Displaying MLD information . . . . . . . . . . . . . . . . . . . . . . . . . 1251
Displaying MLD group information . . . . . . . . . . . . . . . . . . . . 1251
Displaying MLD definitions for an interface . . . . . . . . . . . . . 1252
Displaying MLD traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1253
Clearing IPv6 MLD traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . 1254
Embedded Rendezvous Point (RP). . . . . . . . . . . . . . . . . . . . 1254
Chapter 50 Configuring IPv6 Routes
Configuring a static IPv6 route. . . . . . . . . . . . . . . . . . . . . . . . . . . 1257
Configuring a IPv6 multicast route. . . . . . . . . . . . . . . . . . . . . . . . 1259
Appendix A Using Syslog
Displaying Syslog messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1261
Configuring the Syslog service . . . . . . . . . . . . . . . . . . . . . . . . . . . 1263
Displaying the Syslog configuration . . . . . . . . . . . . . . . . . . . 1263
Disabling or re-enabling Syslog. . . . . . . . . . . . . . . . . . . . . . . 1267
Specifying a Syslog server. . . . . . . . . . . . . . . . . . . . . . . . . . . 1267
Specifying an additional Syslog server. . . . . . . . . . . . . . . . . 1267
Disabling logging of a message level . . . . . . . . . . . . . . . . . . 1268
Logging all CLI commands to Syslog . . . . . . . . . . . . . . . . . . 1268
Changing the number of entries the local buffer can hold. 1269
Changing the log facility . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1269
Displaying the interface name in Syslog messages . . . . . . 1270
Displaying TCP/UDP port numbers in Syslog messages . . 1270
Syslog messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1271
Appendix B Software Specifications
IEEE compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1291
BigIron RX Series Configuration Guide xxxvii
53-1001986-01
Page 38

RFC compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1291
RFC compliance - BGPv4. . . . . . . . . . . . . . . . . . . . . . . . . . . . 1291
RFC compliance - OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1292
RFC compliance - IS-IS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1292
RFC compliance - RIP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1292
RFC compliance - IP Multicast . . . . . . . . . . . . . . . . . . . . . . . 1292
RFC compliance - general protocols. . . . . . . . . . . . . . . . . . . 1293
RFC compliance - management . . . . . . . . . . . . . . . . . . . . . . 1294
RFC compliance - IPv6 core. . . . . . . . . . . . . . . . . . . . . . . . . . 1294
RFC compliance - IPv6 routing . . . . . . . . . . . . . . . . . . . . . . . 1295
RFC compliance - IPv6 multicast . . . . . . . . . . . . . . . . . . . . . 1295
RFC compliance - IPv6 transitioning. . . . . . . . . . . . . . . . . . . 1295
RFC compliance - IPv6 management . . . . . . . . . . . . . . . . . . 1295
Internet drafts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1295
Appendix C NIAP-CCEVS Certification
NIAP-CCEVS certified Brocade equipment and
Ironware releases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1297
Web management access to NIAP-CCEVS certified
equipment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1297
Local user password changes . . . . . . . . . . . . . . . . . . . . . . . . . . . 1298
Appendix D Commands That Require a Reload
Appendix E Index to the CLI Commands
ACLs (IP). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1301
Numbered ACL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1301
Named ACL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1302
Other ACL commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1302
ACLs (L2) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1303
BGP4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1303
FDP/CDP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1309
IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1309
Metro Ring protocol. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1312
IPv6 BGP4+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1313
IPv6 ACL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1315
IPv6 basic connectivity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1316
IPv6 multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1318
IPv6 RIPng . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1319
IPv6 OSPFv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1320
IS-IS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1321
Metro Ring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1324
MSTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1324
xxxviii BigIron RX Series Configuration Guide
53-1001986-01
Page 39

Multicast (IP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1325
Multicast (L2) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1327
OSPF version 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1327
Port parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1329
Port-based routing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1330
Quality of Service (QoS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1330
Rate limiting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1332
RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1332
RMON. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1333
RSTP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1334
Security/Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1334
802.1x Port Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1334
Access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1335
Authentication method list . . . . . . . . . . . . . . . . . . . . . . . . . . 1336
Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1336
Privilege level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1336
RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1336
SNMP access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1337
SSH access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1337
SSL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1337
TACACS and TACACS+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1338
Telnet access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1338
TFTP access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1339
User account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1339
Web management access. . . . . . . . . . . . . . . . . . . . . . . . . . . 1339
DoS Protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1339
MAC authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1340
MAC port security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1341
Redundant management module . . . . . . . . . . . . . . . . . . . . . . . . 1342
SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1344
SSH. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1344
sFlow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1345
STP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1346
SysLog messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1346
System parameters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1347
Topology. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1348
LAG. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1349
UDLD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1349
VLAN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1350
VRRP/VRRPE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1351
VSRP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1352
BigIron RX Series Configuration Guide xxxix
53-1001986-01
Page 40

xl BigIron RX Series Configuration Guide
53-1001986-01
Page 41

About This Document
Audience
This document is designed for system administrators with a working knowledge of Layer 2 and
Layer 3 switching and routing.
If you are using a Brocade Layer 3 Switch, you should be familiar with the following protocols if
applicable to your network – IP, RIP, OSPF, BGP, ISIS, IGMP, PIM, DVMRP, and VRRP.
Supported hardware and software
Although many different software and hardware configurations are tested and supported by
Brocade Communications Systems, Inc., documenting all possible configurations and scenarios is
beyond the scope of this document.
The following hardware platforms are supported by this release of this guide:
• Software release version 02.7.03
List of supported features
Features or options not listed in the Supported features table or documented in this guide are not
supported.
TABLE 1 Supported features
Category Feature description
System level features
Cisco Discovery Protocol (CDP) Allows you to configure a Brocade device to intercept and display the
contents of CDP packets. This feature is useful for learning device
and interface information for Cisco devices in the network.
CLI Logging
Denial of Service (DoS) protection Protection from SYN attacks
Protection from Smurf attacks
Foundry Discovery Protocol (FDP) Enables Brocade devices to advertise themselves to other Brocade
devices on the network.
High Availability OS Layer 2 Hitless Software Upgrade
BigIron RX Series Configuration Guide xli
53-1001986-01
Page 42

TABLE 1 Supported features (Continued)
Category Feature description
Management Options Serial and Telnet access to industry-standard Command Line
Interface (CLI)
SSHv2
TFTP
Web-based GUI
SNMP versions 1, 2, and 3
IronView Network Manager .
Security AAA Authentication
Local passwords
RADIUS
Secure Shell (SSH) version 2
Secure Copy (SCP)
TACACS and TACACS+
User accounts
802.1x: All EAP types, including MD5, TLS, TTLS, and PEAP
Multi-device port authentication
AES for SNMPv3, SSHv2, SCP, and HTTPS
Note:Telnet, SSH, Web and SNMP servers are disabled by default,
and can be enabled selectively.
CPU protection There are no CLI commands for CPU protection. The device forwards
unknown unicast, broadcast and multicast packets in hardware;
therefore, the CPU is automatically 'protected' from having to handle
too many packets.
SysLogD Server Logging Multiple SysLogD server logging
sFlow sFLow version 5
Uni-directional Link Detection (UDLD) Monitors a link between two Brocade devices and brings the ports on
both ends of the link down if the link goes down at any point between
the two devices.
Layer 2 features
802.1d Spanning Tree Protocol (STP)
and
Single Spanning Tree Protocol (SSTP)
802.1p Quality of Service (QoS) queue mapping
802.1q See VLANs, below
802.1s Multiple Spanning Tree Protocol (MSTP)
802.1w Rapid Spanning Tree Protocol (RSTP)
802.3ad Dynamic Link Aggregation on tagged and untagged trunks
Jumbo packets Layer 2 jumbo packet support
Layer 2 Hitless failover
Layer 2 IGMP Snooping
L2 ACL Filtering based on MAC layer-2 parameters.
MAC Filtering MAC filtering and address-lock filters to enhance network security
MRP Metro Ring Protocol (MRP) Phase 1 and 2
PVST / PVST+ Per-VLAN Spanning Tree (PVST)
xlii BigIron RX Series Configuration Guide
53-1001986-01
Page 43

TABLE 1 Supported features (Continued)
Category Feature description
Rate Limiting Port-based, port-and-priority based, port-and-vlan-based, and
port-and-ACL-based rate limiting on inbound ports are supported.
SuperSpan A Brocade STP enhancement that allows Service Providers (SPs) to
use STP in both SP networks and customer networks.
Topology Groups A named set of VLANs that share a Layer 2 topology. You can use
topology groups with the following Layer 2 protocols:
• STP
• Brocade MRP
• VSRP
• 802.1W
Trunk Groups and LAG Allows you to manually configure multiple high-speed load-sharing
links between two Brocade devices or between a Brocade device and
a server.
VLANs 802.1Q tagging
Port-based VLANs
Super Aggregated VLANs (SAV)
Dual-mode VLAN ports
Transparent Port Flooding
VLAN ID to MSTP Instance Pre-assignment
Private VLANs
VSRP Layer 2 Virtual Switch Redundancy Protocol (VSRP)
Layer 3 Virtual Switch Redundancy Protocol (VSRP)
VSRP and MRP Signaling
Layer 2 ACLs Replaces MAC filters
Layer 2 PIM Snooping
Layer 3 features
ACLs Standard, Extended and Super
Inbound
ACL logging
ACL editing
BGP BGP routes
BGP peers
BGP dampening
Graceful Restart
FDR Foundry Direct Routing
IP Forwarding IPv4 Routing
IPv6 Routing
IP Static entries Routes
ARPs
Virtual interfaces
Secondary addresses
IS-IS
BigIron RX Series Configuration Guide xliii
53-1001986-01
Page 44

TABLE 1 Supported features (Continued)
Category Feature description
Multicast Routing Multicast cache
L2 IGMP table
DVMRP routes
PIM-DM
PIM-SM
PIM-SSM
PIM Snooping
OSPF OSPF routes
OSPF adjacencies - Dynamic
OFPF LSAs
OSPF filtering of advertised routes
PBR Policy Based Routing (Release 02.2.01 and later)
RIP versions 1 and 2 RIP routes
VRRP and VRRPE Virtual Router Redundancy Protocol (VRRP)
and
VRRP Extended (VRRPE)
IPv6 features
IPv6 ACLs Extended ACLs
IPv6 Routing Protocols RIPng
OSPFv3
BGP4+
IPv6 Multicast PIM-SM
MLD
Unsupported features
The following features are not supported in software release 02.7.03
• AppleTalk
• IPX
• Mirroring across VLANs
• MPLS
• NAT
• RARP
• VLAN translation
• Subnet VLANs
• Source IP Port Security
xliv BigIron RX Series Configuration Guide
53-1001986-01
Page 45

What’s new in this document
The following tables provide brief descriptions of the enhancements added in each BigIron RX
software release and a reference to the specific chapter, and section in the BigIron RX
Configuration Guide or the Brocade BigIron RX Series Installation Guide that contain a detailed
description and operational details for the enhancement.
Enhancements in release 02.7.03
TABLE 2 Summary of enhancements in release 02.7.03
Enhancement Description See page
System Monitoring
Service (SYSMON)
clear ipv6 ospf
command
switchover command When you enter the switchover command, the
Support for active cable
for 16-po rt 10 Gigabit
Ethernet module
Monitoring I2C failure on
a management module
Rebranded show version
command output
Rebranded RADIUS Vendor specific attributes for RADIUS have
This feature was introduced in the 02.6.00c
patch release. It monitors the hardware in the
system to detect, report, and in some cases
isolate and recover hardware errors in the
system. When an error or event occurs,
SYSMON generates Syslog messages, which
must be reported to Brocade Technical Support
This enhancement was introduced in Patch
Release 02.7.02a and has been added to this
issue of the BigIron RX Series Configuration
Guide.
The clear ipv6 ospf CLI command has been
deprecated
This enhancement was introduced in Patch
Release 02.7.02c and has been added to this
issue of the BigIron RX Series Configuration
Guide.
CLI asks you to confirm your request. Enter Y to
continue or N to cancel your request.
This enhancement was introduced in Patch
Release 02.7.02c and has been added to this
issue of the BigIron RX Series Configuration
Guide.
10 Gbps Direct Attached Small Form-Factor
Pluggable (SFP+) copper cable (1m, 3m, 5m) is
available for the 16-port 10 Gigabit Ethernet
module
The show logging command can be use to
monitor I2C failures.
The output of the show version command now
shows "Brocade Communications"
been renamed to "brocade-command-string",
"brocade-privilege-level", and
"brocade-command-exception-flag"
Book: BigIron RX Series
Configuration Guide
Chapter: “Using a Redundant
Management Module”
Section: “System Monitoring
Service”
N/A
Book: BigIron RX Series
Configuration Guide
Chapter: “Using a Redundant
Management Module”
Section: “Manually switching over to
the standby management module”
Book: Brocade BigIron RX Series
Installation Guide
Book: Brocade BigIron RX Series
Installation Guide
Book: Brocade BigIron RX Series
Installation Guide
Book: BigIron RX Configuration
Giuide
Chapter: “Securing Access to
Management Functions”
Section: “Configuring RADIUS
security” on page 100
BigIron RX Series Configuration Guide xlv
53-1001986-01
Page 46

TABLE 2 Summary of enhancements in release 02.7.03
Enhancement Description See page
MAC Port Security The MAC Port Security feature has been
updated for the 02.7.03 release.
Syslog update The System Log has been updated as follows:
• Separate buffers for static and dynamic
logs
• Entries in the static log buffer are cleared
at reset or reload, while entries in the
dynamic log are preserved
Book: BigIron RX Configuration
Giuide
Chapter: “Using the MAC Port
Security Feature and Transparent
Port Flooding” on page 931
Book: BigIron RX Configuration
Giuide
Chapter: “Using Syslog” on
page 1261
• Log buffer size cannot be changed. the log
buffer size is set at 3800 lines
• A show logging command is now available
at the monitor level for Active and Standby
Management Processors
Enhancements in release 02.7.02
TABLE 3 Summary of enhancements in release 02.7.02
Enhancement Description See page
System features
Enhanced spreed-duplex
command
The speed-duplex command has been
enhanced to support 24F and 24HF modules.
The auto (Autonegotiation mode) option has
also been added to allow the user to set the
speed on E1MG-TX media.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring Interface
Parameters”
Section: “Speed/Duplex
negotiation”
Enhancements in release 02.7.01
TABLE 4 Summary of enhancements in release 02.7.01
Enhancement Description See page
System features
New 16x10G module.iew The new 16 port 10GE oversubscribed module
provides 4:1 over-subscription on the network
ports. The new module is compatible with all
previous modules on the BigIron RX.
xlvi BigIron RX Series Configuration Guide
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Product Overview
Section: 16-port 10 Gigabit
Ethernet Oversubscribed
Module
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Quality of Service”
Section: “QoS for the
oversubscribed 16 x 10GE
modules”
53-1001986-01
Page 47

Enhancements in release 02.7.01
TABLE 4 Summary of enhancements in release 02.7.01 (Continued)
Enhancement Description See page
Network management
128-bit AES encryption
support for SNMP V3
AES Encryption for SSH v2,
Secure Copy (SCP), and
Secure HTTPS (HTTPS)
The Advanced Encryption Standard (AES) provides
one of the most advanced encryption capabilities
available today. This release adds AES for SNMPv3
as specified in RFC 3826.
To enable AES encryption, specify the aes
encryption type when defining an SNMP user
account.
SSH v2, SCP, and HTTPS now supports a very strong
AES encryption algorithm in the following modes:
aes256-cbc, aes192-cbc, and aes128-cbc.
Book: BigIron RX Series
Configuration Guide
Chapter: “Securing SNMP
Access”
Section: “Defining an
SNMP user account”
Book: BigIron RX Series
Configuration Guide
Chapter: “Securing SNMP
Access”
Section:
Enhancements in release 02.7.00
TABLE 5 Summary of enhancements in release 02.7.00
Enhancement Description See page
Layer 1 features
New Optics Support The SFP-compliant E1MG-TX fiber-optic module now
supports speeds of 10/100/1000.
UDLD Start-up Mode In this release, after UDLD is enabled on a port,
UDLD can be configured to be kept in a newly
created suspended state until it receives its first
keep-alive message from the other end.
Multicast, Broadcast, and
Unknown Unicast Rate
Limiting per Module
Link Layer Discovery Protocol
(LLDP)
CLI Change To globally enable MAC port security, the
This release introduces a new hardware (module)
based Multicast/Broadcast/Unknown Unicast
Rate-Limiting for both CPU based flooding and
Hardware based flooding.
Beginning with release 02.7.00, Link Layer
Discovery Protocol (LLDP) is supported. This
protocol enables a station to advertise its
capabilities to, and to discover other LLDP-enabled
stations in the same 802.1AB LAN segments.
global-port-security command has been added. The
port security command is now only used when
configuring MAC port security on specific interfaces.
Book: Brocade BigIron RX
Series Installation Guide
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Uni-Directional Link
Detection (UDLD)”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Traffic Reduction”
Section: “NP based
multicast, broadcast, and
unknown-unicast rate
limiting”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
LLDP”
Book: BigIron RX Series
Configuration Guide
Chapter: “Using the MAC
Port Security Feature and
Transparent Port Flooding”
Section: “Enabling the MAC
Port Security feature”
BigIron RX Series Configuration Guide xlvii
53-1001986-01
Page 48

TABLE 5 Summary of enhancements in release 02.7.00 (Continued)
Enhancement Description See page
Network management
DHCP Relay Enhancement Beginning with this release, the IP subnet
configured on the port which is directly connected
to the device sending a BootP/DHCP request, does
not have to match the subnet of the IP address
given by the DHCP server.
SNMP MIBs for Layer 2 ACLs
and Filters
The following MIB tables have been added to this
release:
• Textu al Convent io ns
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Configuring
BootP/DHCP forwarding
parameters”
Book: MIB Reference
Chapter: Filtering Traffic
Section: Layer 2 ACLs
• Layer 2 ACL Next Clause Table
• Layer 2 ACL Configuration Table
• Layer 2 ACL Binding Configuration Table
Enhancements in release 02.6.00
TABLE 6 Summary of enhancements in release 02.6.00
Enhancement Description See page
Layer 1 features
Digital Optical Monitoring Beginning with release 0 2.6.00, Digital Optical
Monitoring will only support newly qualified
1Gigabit optics. Digital Optical Monitoring for
previous 1Gigabit optics that do not include "OM"
after the model numbers will not be able to use this
feature.
BFD for IS-IS, OSPFv2 and
OSPF v3
LACP Continous Fast Timer In a dynamic or keep-alive LAG, a port's timeout can
Rate Limiting ARP Packets This new feature allows you to rate-limit ARP traffic
Layer 2 features
BigIron RX provides support for Bidirectional
Forwarding Detection (BFD) in Version 02.6.00 of
the Multi-Service IronWare software.
be configured as short or long
that is destined for CPU of the BigIron RX router.
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Connecting a
BigIron RX Series Switch
to a Network Device
Section:Digital Optical
Monitoring
Book: BigIron RX Series
Configuration Guide
Chapter: “BiDirectional
Forwarding Detection
(BFD)”
Book: BigIron RX Series
Configuration Guide
Chapter: “Link
Aggregation”
Section: “Configuring an
LACP timeout”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section:“Apply in g a rate
limit to ARP packets on an
interface”
xlviii BigIron RX Series Configuration Guide
53-1001986-01
Page 49

TABLE 6 Summary of enhancements in release 02.6.00 (Continued)
Enhancement Description See page
VSRP Fast Start Non-Brocade or non-VSRP aware devices
connected to a VSRP master can now quickly switch
over to the new master when a VSRP failover
occurs.
LACP Enhancements Beginning with release 02.6.00 of the Multi-Service
IronWare software, all trunking and link aggegation
configuration has been revamped and placed under
a single interface. This new interface allows you to
configure either of the previously supported LAG
types: Static LAGs and Dynamic LAGs as well as the
new “Keep Alive” LAGs.
The new LAG configuration procedures supersede
the previous configurations procedures for Trunks
and Dynamic Link Aggregation.
Multicast Layer 2 Filter Beginning with release 02.6.00, you can define
multicast boundaries on a per VLAN basis.
Layer 3 features
IPv6 PIM-SM In Release 02.6.00 of the Multi-Service IronWare
software, the BigIron RX supports IPv6 Protocol
Independent Multicast (PIM) Sparse. IPv6 PIM
Sparse provides multicasting that is especially
suitable for widely distributed multicast
environments
IPv6 Embedded RP This release supports Embedded RP which allows
the switch to learn RP information using the
multicast group destination address instead of the
statically configured RP.
IPv4 PIM Snooping PIM SM traffic snooping eliminates the superfluous
traffic by configuring the device to forward IP
multicast group traffic only on the ports that are
attached to receivers for the group
Multicast Listening Discovery
(MLD)
Release 02.6.00 adds support for MLD Snooping
(MLDv1 and MLDv2) on Brocade BigIron RXdevices
running IPv6.
Book: BigIron RX Series
Configuration Guide
Chapter: “Virtual Switch
Redundancy Protocol
(VSRP)”
Section: “VSRP fast start”
Book: BigIron RX Series
Configuration Guide
Chapter: “Link
Aggregation”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “Layer 2 multicast
filters”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IPv6
Multicast Features”
Section: “IPv6 PIM-sparse
mode”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IPv6
Multicast Features”
Section: “Embedded
Rendezvous Point (RP)”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “PIM SM traffic
snooping”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IPv6
Multicast Features”
Section: “Multicast
Listener Discovery and
source specific multicast
protocols (MLDv2)”
BigIron RX Series Configuration Guide xlix
53-1001986-01
Page 50

TABLE 6 Summary of enhancements in release 02.6.00 (Continued)
Enhancement Description See page
IGMPv3 and IGMP Snooping In Release 02.6.00 of the Multi-Service IronWare
software, creating an IGMP static-group allows the
BigIron RX switch having L2 interfaces configured
with snooping to pull traffic from upstream sources
using IGMP joins. When using the uplink option, you
avoid burning a dedicated port. This is supported
for IGMP v2 and v3.
IGMP v3 Static Client In Release 02.6.00 of the Multi-Service IronWare
software, creating an IGMP static-group allows the
BigIron RXswitch having L2 interfaces configured
with snooping to pull traffic from upstream sources
using IGMP joins. When using the uplink option, you
avoid burning a dedicated port. This is supported
for IGMP v2 and v3.
IGMP v3 Fast Leave and
Tra ckin g
Static Route ARP Validate
Next Hop
IGMP Proxy per VLAN or
instance
Layer 4 features
Automatic ACL Rebind Beginning wirh release 02.6.00, the ACL automatic
Network management
Support for BFD MIB and
SNMP Traps
In Release 02.6.00 of the Multi-Service IronWare
software, you can configure a device running IGMP
Snooping to immediately remove a VLAN from the IP
multicast group when it detects a fast leave
message on a specified VLAN.
Beginning with release 02.6.00, you can configure
the BigIron RX to perform multicast validation
checks on the destination MAC address, the sender
and target IP addresses, and the source MAC
address.
Introduced in version 02.6.00 of the Multi-Service
IronWare software, multicast traffic can be reduced
by configuring an BigIron RX switch to issue IGMP
host messages on behalf of hosts that the
configured router discovers through standard PIM
interfaces. The router is then able to act as a proxy
for the discovered hosts and perform IGMP tasks
upstream of the discovered hosts. Where there are
multiple IGMP hosts downstream, this removes the
need to send multiple messages.
rebind feature allows the newly changed ACL filter
definitions to be automatically applied to the ports
where the ACL was bound.
Support for BFD IETF draft mib version 3
(draft-ietf-bfdmib-03.mib) with this release as
described in the Management Information Base
Reference.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “IGMP v3”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “Creating a static
IGMP group”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section:“Enabling
membership tracking and
fast leave”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “Next hop
validation check”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Traffic
Reduction”
Section: “Multicast traffic
reduction per VLAN”
Book: BigIron RX Series
Configuration Guide
Chapter: “Access Control
List”
Section: “ACL automatic
rebind”
Book: MIB Reference
Chapter:
Forwarding
Bidirectional
l BigIron RX Series Configuration Guide
53-1001986-01
Page 51

Enhancements in patch release 02.5.00c
TABLE 7 Summary of enhancements in release 02.5.00c
Enhancement Description See page
Super ACLs With this patch release, the Multi-Service IronWare
software supports Super ACLs that can match on
fields in a Layer 2 or Layer 4 packet header.
Book: BigIron RX Series
Configuration Guide
Chapter: “Access Control
List”
Section: “Configuring
super ACLs”
Enhancements in patch release 02.5.00b
TABLE 8 Summary of enhancements in release 02.5.00b
Enhancement Description See page
ACL-based Inbound sFlow With this patch release, the Multi-Service IronWare
software supports using an IPv4 ACL to select
packets that should be collected as special sFlow
samples, in addition to the regular statistical
sampling of sFlow.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
sFlow”
Section: “ACL-ba sed
inbound sFlow”
Enhancements in release 02.5.00
TABLE 9 Summary of enhancements in release 02.5.00
Enhancement Description See page
BigIron RX-32
Chassis
New Process for Upgrading
Multi-Service IronWare
Software
SDS Over Telnet Beginning with release 02.5.00 of the Multi-Service
Enhancement on Static ARP In Release 02.5.00 of the Multi-Service IronWare
Release 02.5.00 introduces the BigIron RX-32
chassis which runs the same Multi-Service
IronWare software as other chassis in the BigIron
RX series.
The new BigIron RX-32 chassis provide support for
up to 32 interface modules.
The software images required for operating the
BigIron RX switch remain the same however,
beginning with version 02.5.00 of the Multi-Service
IronWare software, the upgrading procedures have
been changed. The new procedure is described in
the Release Notes for BigIron RX – Multi-Service
IronWare Software Release 02.5.00.
IronWare software, remote SDS is supported. This
feature will dramatically improve the ability to
troubleshoot issues on the line-card without the
need of a serial cable.
software, static ARP has been enhanced to support
the ability to create a static ARP entry without an
outgoing interface.
Book: Brocade BigIron RX
Series Installation Guide
Book: Release Notes for
BigIron RX – Multi-Service
IronWare Software Release
02.5.00.
N/A
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Creating a
floating static ARP entry”
BigIron RX Series Configuration Guide li
53-1001986-01
Page 52

TABLE 9 Summary of enhancements in release 02.5.00 (Continued)
Enhancement Description See page
Static Route ARP Validate Next
Hop
Multicast Mll Sharing In Release 02.5.00, the multicast hardware device
Multicast Starting release 02.5.00, low priority multicast
Changes to the copy tftp
Image command
New MIB Objects The following MIB objects have been added to the
Beginning with release 02.5.00, you can configure
the BigIron RX to perform validation checks on the
destination MAC address, the sender and target IP
addresses, and the source MAC address.
drivers have been enhanced to optimize utilization
and improve overall performance.
traffic is rate-limited to 1.8 Gbps per packet
processor.
In Release 02.5.00 of the Multi-Service IronWare
software, new option have been added to the copy
tftp image command to enable the user to upgrade
the boot, monitor, and MBRIDGE only when
needed.
snIfStpTable:
• snIfStpPortRole
• snIfStpBPDUTransmitted
• snIfStpBPDUReceived
• snIfRstpConfigBPDUReceived
• snIfRstpTCNBPDUReceived
• snIfRstpConfigBPDUTransmitted
• snIfRstpTCNBPDUTransmitted
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Static route ARP
validation check”
N/A
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Quality of Service”
Section: “Configuring
multicast traffic
engineering”
Book: Release Notes for
BigIron RX – Multi-Service
IronWare Software Release
02.5.00.
Book: MIB Reference
Chapter: Interfaces
Section: Port STP
Configuration Groups
Enhancements in patch release 02.4.00c
TABLE 10 Summary of enhancements in release 02.4.00c
Enhancement Description See page
ACL Based RP assignment The rp-address command has been enhanced to
allow multiple static RP configurations.
Route Selection Precedence
for Multicast
lii BigIron RX Series Configuration Guide
In patch 02.4.00c, the route-precedence command
allows the user to specify a precedence table that
dictates how routes are selected for multicast.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “ACL based RP
assignment”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section:“Route selection
precedence for multicast”
53-1001986-01
Page 53

Enhancements in release 02.4.00
TABLE 11 Summary of enhancements in release 02.4.00
Enhancement Description See page
US Daylight Saving Time
scheme
New show boot-image
command
New show image_checksum
command
Private VLAN A private VLAN is a VLAN that has the properties of
MRP Phase 2 In Metro Ring Protocol (MRP) Phase 2, the same
Outbound Rate Limiting Outbound rate limiting support has been added to
Increase Global Static ARP
Entries
OSPF ABR Type 3 LSA Filtering The OSPF ABR Type 3 LSA Filtering feature extends
The new Daylight Saving Time (DST) change that
went into effect on March 11th, 2007 affects only
networks following the US time zones. However, to
trigger the device to the correct time, the device
must be configured to the US time zone, not the
GMT offset.
Using the show boot-image command displays
which image the device will use for the next reboot
or reload.
The image_checksum command will allow the user
to verify the checksum of a image.
standard Layer 2 port-based VLANs but also
provides additional control over flooding packets on
a VLAN.
physical interface can be shared by multiple rings
belonging to the same VLAN.
this release.
The system max value for ip-static-arp can be
configured to values up to 16,384 beginning with
version 02.4.00 of the BigIron RX Multi-Service
IronWare software.
the ability of an ABR that is running the OSPF
protocol to filter type 3 link-state advertisements
(LSAs) that are sent between different OSPF areas.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Basic Parameters”
Section: “New Daylight
Saving Time (DST)”
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Upgrading
Software Images and
Configuration Files
Section: Displaying the
Next Boot Image
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Upgrading
Software Images and
Configuration Files
Section: Verifying the
Checksum of an Image
Book: BigIron RX Series
Configuration Guide
Chapter:“VLANs”
Section: “Private VLANs”
Book: BigIron RX Series
Configuration Guide
Chapter: “Metro Ring
Protocol (MRP) Phase 1
and 2”
Section: “MRP phase 2”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Traffic Reduction”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Changing the
maximum transmission
unit on an individual
interface”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
OSPF Version 2 (IPv4)”
Section: “OSPF ABR type 3
LSA filtering”
BigIron RX Series Configuration Guide liii
53-1001986-01
Page 54

TABLE 11 Summary of enhancements in release 02.4.00 (Continued)
Enhancement Description See page
New show OSPF neighbor by
area command
Track IP route time in show
command
Compare MED for internal BGP
route with empty as-path
OSPF Default Network Route This feature enables the BigIron RX to use default
IPv6 Default Route ECMP This feature allows for load distribution of traffic
IPv6 Tunneling in Hardware Manual configuration of IPv6 to IPv4 tunnels is now
IPv6 Load Sharing over ECMP
and Trunks
Directly Attached Host
Resource Allocation
This feature allows OSPF to display the OSPF
neighbors existing in a particular area.
The show ip route command has been enhanced to
include the elapse time since an IP route was
installed.
This new BGP command directs iBGP to take the
MED value into consideration even if the route has
an empty as-path path attribute.
route (0.0.0.0/0) to a resolve static OSPF route.
Note:This differs from the default behavior in
previous versions of Multi-Service IronWare
software.
among the available IPv6 default route next-hops.
supported in this release. These tunnels will be
installed into the hardware route table and tunnel
encapsulation and decapsulation is done in
hardware.
When the device receives traffic for a destination,
and the IPv6 route table contains multiple,
equal-cost paths to that destination, the packets
are load balanced between multiple next-hops
including member ports of a trunk.
The CAM allocations can be re-distributed using the
cam-partition next-hop command.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
OSPF Version 2 (IPv4)”
Section: “Displaying OSPF
neighbor information”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Displaying the IP
route table”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
BGP4 (IPv4 and IPv6)”
Section: “Configuring the
device to always compare
MEDs”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
OSPF Version 2 (IPv4)”
Section: “Configuring a
default network route”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Basic IPv6 Connectivity”
Section: “ECMP load
sharing for IPv6”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section:“IPv6 over IPv4
tunnels in hardware”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Basic IPv6 Connectivity”
Section: “ECMP load
sharing for IPv6”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Basic Parameters”
Section: “Re-distributing
CAM allocations”
liv BigIron RX Series Configuration Guide
53-1001986-01
Page 55

TABLE 11 Summary of enhancements in release 02.4.00 (Continued)
Enhancement Description See page
Multicast Boundaries The Multicast Boundary feature is designed to
selectively allow or disallow multicast flows to
configured interfaces.
MBGP for IPv6 This release supports the Multi-protocol Border
Gateway Protocol (MBGP) for IPv6.
IPv6 mroute This release supports multicast route table ipv6
multicast display and management.
Passive Multicast Route
Insertion (PMRI)
IP Source Guard IP source guard is used on client ports to prevent IP
Dynamic ARP Inspection Dynamic ARP Inspection (DAI) is a security feature
DHCP Snooping with Option 82 This feature allows the device to snoop DHCP
DoS Protection This feature allows for monitoring the hit rate of the
This new feature prevents unwanted multicast
traffic from being sent the CPU by conditionally
dropping unwanted multicast traffic in hardware.
source address spoofing.
that can prevent Man-in-the-Middle (MiM) or ARP
spoofing/poisoning attacks.
packets for Dynamic ARP inspection and allows for
the insertion of DHCP Option 82 attributes into the
DHCP packet prior to relaying to the DHCP server.
ACL and drops matching traffic above a selected
rate and locking the port if the rate exceeds a
maximum allowed amount.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “IP multicast
boundaries”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IPv6
MBGP”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IPv6
Routes”
Section: “Configuring a
IPv6 multicast route”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP
Multicast Protocols”
Section: “Passive Multicast
Route Insertion (PMRI)”
Book: BigIron RX Series
Configuration Guide
Chapter: “Inspecting and
Tra cki ng D HCP Pac ke ts. ”
Section: “IP source guard”
Book: BigIron RX Series
Configuration Guide
Chapter: “Inspecting and
Tra cki ng D HCP Pac ke ts”
Section: “Dynamic ARP
inspection”
Book: BigIron RX Series
Configuration Guide
Chapter: “Inspecting and
Tra cki ng D HCP Pac ke ts”
Section: “DHCP relay agent
information (DHCP option
82)”
Book: BigIron RX Series
Configuration Guide
Chapter: “Protecting
Against Denial of Service
Attacks”
Section:“ACL-based
DOS-attack prevention”
BigIron RX Series Configuration Guide lv
53-1001986-01
Page 56

TABLE 11 Summary of enhancements in release 02.4.00 (Continued)
Enhancement Description See page
ACL-Based Mirroring With this release, the Multi-Service IronWare
software supports using an ACL to select traffic for
mirroring from one port to another.
ip dns domain-list command This feature is designed to define a list od domain
names that are used in order to resolve a host.
CLI Logging This feature provides the logging of all valid CLI
commands from each user session into the system
log.
Syslog Source Interface You can configure the BigIron RX to use the
lowest-numbered IP or IPv6 address configured on
a loopback interface, virtual interface, or Ethernet
port as the source for all Syslog packets from the
device.
UDLD Traps and Syslogs UDLD state changes will now be logged by default. Book: MIB Reference
New Brocade MIB objects The following MIBs have been depreciated by
snAgentCpuUtilTable:
• snAgGblCpuUtil1SecAvg
• snAgGblCpuUtil5SecAvg
• snAgGblCpuUtil1MinAvg
Book: BigIron RX Series
Configuration Guide
Chapter:“Access Control
List”
Section: “AC L-b ased
inbound mirroring”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section: “Defining a DNS
entry”
Book: BigIron RX Series
Configuration Guide
Chapter: “Using Syslog”
Section:“Logging all CLI
commands to Syslog”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section:“Configuring an
interface as the source for
Syslog packets”
Chapter: Traps and Objects
to Enable Traps
Section: UDLD Traps
Book: MIB Reference
Chapter: Monitoring and
Logging
Section: Usage Notes on
CPU Utilization and System
CPU Utility Table
lvi BigIron RX Series Configuration Guide
53-1001986-01
Page 57

Enhancements in patch release 02.3.00a
TABLE 12 Summary of enhancements in patch release 02.3.00a
Enhancement Description See...
Transparent Port Flooding When the Transparent Port Flooding feature in
enabled for a port, all MAC learning will be disabled
for that port. This will result in all Layer 2 traffic to
be flooded to all other ports within the VLAN.
Starting with release 02.3.00a.
VLAN ID to MSTP Instance
Pre-assignment
This feature will allow the user to assign a VLAN ID
to a Common Spanning Tree (CIST), or Multiple
Spanning Tree Instance (MSTI) even though a VLAN
has not been created yet. Starting with release
02.3.00a.
Book: BigIron RX Series
Configuration Guide
Chapter: “Using the MAC
Port Security Feature
and Transparent Port
Flooding”
Section:“Transparent
port flooding”
Book: BigIron RX Series
Configuration Guide
Chapter: “Multiple
Spanning Tree Protocol
(MSTP) 802.1s” and
“VLANs”
Section:“Configuring an
MSTP instance”
BigIron RX Series Configuration Guide lvii
53-1001986-01
Page 58

Enhancements in release 02.3.00
System enhancements
TABLE 13 System enhancements
Enhancement Description See...
New Hardware
Support
The following new hardware is supported with the 02.3.00
software release for the BigIron RX:
1 10G-XFP-CX4 - part number 10G-XFP-CX4 , A new XFP
Module is available for use in the BigIron RX Series and
10G Interface Modules with the following capabilities:
Book: Brocade BigIron RX
Series Installation Guide
• 10GBASE-CX4 compliant per 802.1ak
• CX4 connector
• Up to 15 meter reach when using CX4 grade copper
cables
• Restriction of Hazardous Substances (RoHS) 5/6
compliant
• Hot pluggable
• Compatible with industry-standard MDI socket for
CX4
• Supports 4 channel full-duplex copper cable
2 10GBase-ZR – part number 10G-XFP-ZR supports 1550
nm wavelength with a maximum distance of up to 80 km
over single mode fiber (SMF).
3 10GBase-ZRD – part number 10G-XFP-ZRD supports 40
different wavelengths at 1550 nm.
4 48-port 1 Gbps Copper Ethernet interface module
Hitless OS Upgrade
for Layer 2
Logging of packets
denied by ACLs.
Modifying ACLs You can modify ACL entries anywhere in an ACL. Book: BigIron RX Series
SFM FE Monitoring In this release, the Switch Fabric Module monitoring has been
Version 02.5.00 of the Multi-Service IronWare software
supports hitless upgrade of the operating system on a BigIron
RX switch. Using this feature, you can upgrade the
Multi-Service IronWare software without a loss or disruption of
service as described.
You can restrict the number of times a message is logged in
the Syslog due to packets that matches a deny ACL condition.
enhanced. If the SFM fails, it generates a syslog that includes
the status of individual fabric elements on the SFM modules.
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Upgrading
Software Images and
Configuration Files
Section:Layer 2 Hitless OS
Upgrade
Book: BigIron RX Series
Configuration Guide
Chapter: “Access Control
List”
Section: “Enabling the
new logging method”
Configuration Guide
Chapter: “Access Control
List”
Section: “Enabling the
new logging method”
Book: Brocade BigIron RX
Series Installation Guide
lviii BigIron RX Series Configuration Guide
53-1001986-01
Page 59

TABLE 13 System enhancements (Continued)
Enhancement Description See...
Enhanced Digital
Optical Monitoring
Re-distributing CAM
Allocations
Enhanced SFM
(power-off)
command
Enhanced
speed-duplex
command
You can configure the BigIron RX to monitor XFPs and SFPs in
the system either globally or by specified port.
In releases prior to 02.3.00, CAM partitioning was not
configurable. Starting in BigIron RX software release 02.3.00,
you can specify the CAM assigned to each of the CAM entry
types globally.
You can disable power to a specified switch fabric module and
then reenable it.
In this release, the speed-duplex command has been
enhanced to include the master and slave parameters.
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Connecting a
BigIron RX Series Switch
to a Network Device
Section: Enhanced Digital
Optical Monitoring
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Basic Parameters”
Section: “Re-distributing
CAM allocations”
Book: Brocade BigIron RX
Series Installation Guide
Chapter: Managing the
BigIron RX Series Chassis
and Modules
Section: Disabling and
Reenabling Power to the
Switch Fabric Modules
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Interface Parameters”
Section:“Speed/Duplex
negotiation”
Layer 2 enhancements
TABLE 14 Layer 2 enhancements
Enhancement Description See...
Flow based MAC Learning In this release, the cpu-flooding unknown-unicast
command that disables hardware flooding of
unknown unicast on every VLAN has been added.
This will allow MAC learning only where necessary
and at a system level to allow more than 16k MACs.
VSRP Slow-Start This feature allows for a hold down time before the
backup returns ownership to the master after the
link is seen.
802.1s Multiple Spanning Tree
Protocol (MSTP)
With this release, you can configure multiple STP
instances using MSTP protocol, as defined in IEEE
802.1s
Book: BigIron RX Series
Configuration Guide
Chapter: “VLANs”
Section: “Flow based
MAC learning”
Book: BigIron RX Series
Configuration Guide
Chapter: “Virtual Switch
Redundancy Protocol
(VSRP)”
Section:“VSRP slow
start”
Book: BigIron RX Series
Configuration Guide
Chapter: “Multiple
Spanning Tree Protocol
(MSTP) 802.1s”
BigIron RX Series Configuration Guide lix
53-1001986-01
Page 60

Layer 3 enhancements
TABLE 15 Layer 3 enhancements
Enhancement Description See...
OSPF NBMA You can configure an interface to send OSPF
unicast packets rather than broadcast packets to
its neighbor by configuring non-broadcast
multi-access (NBMA) networks.
Layer 3 VSRP VSRP redundancy and sub-second failover for
Layer 3 topologies is available in this release.
VSRP Delay Link Events This is a new VSRP command that will delay the
sending of port "up"/"down" events.
IPv6 Hardware Forwarding Forwarding for Layer 3 IP switching technology for
the forwarding of IPv6 packets.See the
"Configuring Basic IPv6 Connectivity" chapter of
the BigIron RX Series Configuration Guide.
OSPF v3 IPv6 supports OSPF version 3 (OSPFv3), which
functions similarly to OSPF version 2.
BGP+ Brocade’s implementation of IPv6 supports multi
protocol BGP (MBGP) extensions, which allow
IPv6 BGP (known as BGP4+) to distribute routing
information for protocols such as IPv4 BGP.
RIPng IPv6 RIP, known as Routing Information Protocol
Next Generation or RIPng, functions similarly to
IPv4 RIP version 2. RIPng supports IPv6
addresses and prefixes.
ACL Duplication Check The acl-duplication-check command has been
changed to acl-duplication-check-disable. With
this command, software checking for duplicate
ACL entries will be disabled after an upgrade.
IPv6 ACLs In this release you can use an IPv6 ACL to provide
input to other features such as route maps and
distribution lists.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
OSPF Version 2 (IPv4)”
Section:“Configuring an
OSPF non-broadcast
interface”
Book: BigIron RX Series
Configuration Guide
Chapter: “Virtual Switch
Redundancy Protocol
(VSRP)”
Section:“Enabling Layer 3
VSRP”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
Interface Parameters”
Section:“Port transition
hold timer”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Basic IPv6 Connectivity”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
OSPF Version 3”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
BGP4+”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
RIPng”
Book: BigIron RX Series
Configuration Guide
Chapter: “Access Control
List”
Section:“Enabling ACL
duplication check”
Book: BigIron RX Series
Configuration Guide
Chapter: “IPv6 Access
Control Lists (ACLs)”
lx BigIron RX Series Configuration Guide
53-1001986-01
Page 61

TABLE 15 Layer 3 enhancements (Continued)
Enhancement Description See...
Default Originate Route for BGP In this release, if a default route is not present in
the IP routing table, the user can configure a
major route to be used for forwarding packets to
all unknown destination. Starting with release
02.3.00a.
Changes to BGP4 Path Selection
for a Route
BGP allowas-in command The allowas-in command has been added to this
Default Route ECMP This feature allows for load distribution of traffic
Transparent Firewall Mode The Transparent Firewall mode feature allows
With this release of Multi-Service IronWare, the
process by which BGP selects a path has
changed. The following procedure replaces the
procedure described in the BigIron RX Series
Configuration Guide.
release to allow you to set a parameter that
disables the BGP AS_PATH check function for
routes learned from a specified location.
among the available default route next-hops.
users to insert a Firewall in front of their existing
network without changing the statically defined
IP addresses of their network-connected devices.
This will allow the users to permit selected
devices from a subnet to cross the firewall while
access to other devices on the same subnet are
denied.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
BGP4 (IPv4 and IPv6)”
Section:“Originating the
default route”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
BGP4 (IPv4 and IPv6)”
Section:“How BGP4
selects a path for a route”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
BGP4 (IPv4 and IPv6)”
Section:“Configuring a
switch to allow routes with
its own AS number”
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring IP”
Section:“Default route
ECMP”
Book: BigIron RX Series
Configuration Guide
Chapter: “VLANs”
Section:“Transparent
firewall mode”
IP multicast enhancements
TABLE 16 IP multicast enhancements
Enhancement Description See...
MBGP Multiprotocol BGP allows for the inclusion of
information other than IPv4 routes via BGP
packets is available in this release.
Multicast Source Discover Protocol
(MSDP)
BigIron RX Series Configuration Guide lxi
53-1001986-01
This release supports the Multicast Source
Discovery Protocol (MSDP). It is used by
Protocol Independent Multicast (PIM) Sparse
routers to exchange routing information for
PIM Sparse multicast groups across PIM
Sparse domains.
Book: BigIron RX Series
Configuration Guide
Chapter: “Configuring
MBGP”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Protocols”
Section:“Configuring
Multicast Source Discovery
Protocol (MSDP)”
Page 62

TABLE 16 IP multicast enhancements (Continued)
Enhancement Description See...
MSDP Mesh Groups This release supports Multicast Source
Discovery Protocol (MSDP) Mesh Groups. This
feature allows you to connect several RPs to
each other which reduces the forwarding of
SA messages within a domain.
IGMP v3 IGMP v3 provides selective filtering of traffic
based on traffic source.
PIM-SSM v4 PIM-SSM is a routing protocol used for source
specific multicast groups and is used in
conjunction with IGMPv3
IGMP v2/v3 Fast Leave IGMP Fast leave allows clients to leave groups
without the three second waiting period, if
certain conditions are met.
MLDv1/v2 MLDv2 supports source filtering, and the
ability of a node to send reports on traffic that
is from a specific address source or from all
multicast addresses except the specified
address sources.
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Protocols”
Section:“Configuring MSDP
mesh group”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Protocols”
Section:“IGMP v3”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Protocols”
Section:“PIM-SSMv4”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Protocols”
Section:“Enabling
membership tracking and
fast leave”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IPv6
Multicast Features”
Section:“MLD version
distinctions”
IP service, security, and Layer 4 enhancements
TABLE 17 IP service, security, and Layer 4 enhancements
Enhancement Description See...
Root Guard This is a security feature that allows a port to
run STP but not allow the connected device to
become the Root.
BPDU Guard BPDU Guard is an extension to the port fast
feature. If a port is in port fast mode of
operation and a BDPU is received, the port is
put into the disabled mode.
lxii BigIron RX Series Configuration Guide
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Spanning Tree Protocol”
Section:“STP root guard”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Spanning Tree Protocol”
Section:“Spanning Tree
Protocol (STP) BPDU guard”
53-1001986-01
Page 63

TABLE 17 IP service, security, and Layer 4 enhancements (Continued)
Enhancement Description See...
Port Security MAC Violation Limit This feature provides protection against
physical link instability. It allows a user to
configure it to keep a port in a down state in
cases where the port has experienced some
number of state transitions within a configured
amount of time.
IPv6 DHCP Gateway You can allow a DHCP client to send a message
to a DHCP server by using a DHCP relay agent.
Book: BigIron RX Series
Configuration Guide
Chapter:“Using the MAC Port
Security Feature and
Transparent Port Flooding”
Section:“Restricting
interface access”
Book: BigIron RX Series
Configuration Guide
Chapter:“Inspecting and
Tra cki ng D HCP Pac kets”
Section:“DHCP relay agent
information (DHCP option
82)”
Network management
TABLE 18 Network management
Enhancement Description See...
IPv6 Management TFTP, SSH,
Telnet, AAA, and WEB
You can perform system management tasks for
the BigIron RX using the TFTP, telnet, AAA, and
Secure Shell (SSH).
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring Basic
IPv6 Connectivity”
Enhancements in release 02.2.01
Hardware enhancements
TABLE 19 Hardware enhancements
Enhancement Description See page
New Hardware Support The following new hardware is supported with the
02.2.01 software release for the BigIron RX:
• Management module with 2 GB of memory
• 24-port 100/1000 Mbps SFP Ethernet interface
module
• 48-port 1 Gbps Copper Ethernet interface module
• DC Power Supply
• New fan controller
Book: Brocade BigIron RX
Series Installation Guide
BigIron RX Series Configuration Guide lxiii
53-1001986-01
Page 64

Layer 2 enhancements
TABLE 20 Layer 2 enhancements
Enhancement Description See page
VLAN Byte Accounting With this release, you can configure a VLAN to account
for the number of bytes received by all the member
ports.
Super Aggregated VLANs
(SAV)
Enhancement to the lacp
system-priority command
Multiple VLANs can be aggregated within another VLAN
to allow you to construct Layer 2 paths and channels.
The lacp system-priority command has been moved
from the interface configuration level to the global
configuration level.
Book: BigIron RX Series
Configuration Guide
Chapter:“VLANs”
Section:“VLAN byte
accounting”
Book: BigIron RX Series
Configuration Guide
Chapter:“VLANs”
Section:“Configuring
super aggregated VLANs”
Book: BigIron RX Series
Configuration Guide
Chapter: See the
Dynamic Link
Aggregation chapter in
the BigIron RX Series
Configuration Guide Versions 02.5.00 and
earlier.
Section:Configuring Link
Aggregation Parameters
Layer 3 enhancements
TABLE 21 Layer 3 enhancements
Enhancement Description See page
Graceful Restart With this release, you can enable Graceful Restart
for OSPF and BGP
BGP Null0 Routing With this release, BGP can use null0 to resolve the
next hop and install null0 BGP routes to the routing
table
GRE IP Tunneling This release supports creation of a GRE tunnel
across an IP network.
lxiv BigIron RX Series Configuration Guide
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
OSPF Version 2 (IPv4)”
and “Configuring BGP4
(IPv4 and IPv6)”
Section: “OSPF graceful
restart” and “Graceful
restart in BGP”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
BGP4 (IPv4 and IPv6)”
Section:“BGP Null0
routing”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP”
Section:“GRE IP tunnel”
53-1001986-01
Page 65

TABLE 21 Layer 3 enhancements (Continued)
Enhancement Description See page
OSPF point-to-point OSPF point-to-point eliminates the need for
Designated and Backup Designated routers,
allowing for faster convergence of the network.
Neighbor Local AS Neighbor Local Autonomous System (AS) feature
allows a router that is a member of one AS to appear
to be a member of another AS.
Full AS Path information in
sFlow
Policy Based Routing Policy-Based Routing (PBR) allows you to use ACLs
In this release, sFlow packets now contain full AP
Path information.
and route maps to selectively modify and route IP
packets in hardware. The ACLs classify the traffic.
Route maps that match on the ACLs set routing
attributes for the traffic.
Multicast enhancement
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
OSPF Version 2 (IPv4)”
Section: “OSPF
point-to-point links”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
BGP4 (IPv4 and IPv6)”
Section:“Neighbor
local-AS”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
sFlow”
Section: “Extended
gateway information”
Book: BigIron RX Series
Configuration Guide
Chapter:“Policy-Based
Routing”
TABLE 22 Multicast enhancement
Enhancement Description See page
IGMP Snooping The BigIron RX supports IGMP snooping. Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP
Multicast Traffic Reduction”
Section: “Enabling IP
multicast traffic reduction”
Security enhancements
TABLE 23 Security enhancements
Enhancement Description See page
Multi-device Port
Authentication
802.1x Port Security This release allows you to enable 802.1X port
Multi-device port authentication is now supported on
the BigIron RX.
security and multi-device port authentication on the
same interface.
Book: BigIron RX Series
Configuration Guide
Chapter:“Using the MAC
Port Security Feature and
Transparent Port Flooding”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
802.1x Port Security”
BigIron RX Series Configuration Guide lxv
53-1001986-01
Page 66

TABLE 23 Security enhancements (Continued)
Enhancement Description See page
Port Security MAC Deny With this release, you can configure deny mac
addresses on a global level or on a per port level.
IP Fragmentation Protection Fragmented IP packets with undersized fragments
and overlapping fragments are dropped.
IP Option Attack Prevention Packets with IP options in their header are
automatically dropped. Enabling the ip
ip-option-process command allows the device to
process packets that use IP options.
IP Receive ACLs You can use IPv4 ACLs to filter the packets intended
for the management processor to protect the
management module from being overloaded with
heavy traffic that was sent to one of the Layer 3
Switch IP interfaces.
Static Route Tagging Static routes can be configured with tag values. Book: BigIron RX Series
MTU enhancements for IPv4 In this release, you can configure IPv4 MTU to be
greater than 1500 bytes.
Enhancements to passwords The following have been implemented to enhance the
password features in the BigIron RX:
Book: BigIron RX Series
Configuration Guide
Chapter:“Using the MAC
Port Security Feature and
Transparent Port Flooding”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP”
Section:“IP fragmentation
protection”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring IP”
Section:“IP option attack
protection”
Book: BigIron RX Series
Configuration Guide
Chapter:“Access Control
List”
Section:“Specifying the
destination mirror port for
IP receive ACLs”
Configuration Guide
Chapter:“Configuring IP”
Section:“Static route
tagging”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Quality of Service”
Section:“Changing the
MTU”
Book: Brocade BigIron RX
Series Installation Guide
• New rules for enable and user passwords
• Users are now required to accept the message
of the day
• Users are locked out if they reach the maximum
number of login attempts and have not logged in
successfully.
• Previous passwords used are now stored in the
CLI. When users change their password, they
must select a password that has not been
stored in the CLI.
• A password can now be set to expire
lxvi BigIron RX Series Configuration Guide
53-1001986-01
Page 67

TABLE 23 Security enhancements (Continued)
Enhancement Description See page
Port Security Enhancements You can specify how many packets from denied MAC
addresses can be received on a port in a one-second
interval before the BigIron RX shuts the port down.
Larger SSHv2 Crypto Key The size of the SSH v2 crypto key in this release is
larger than crypto key in previous releases.
Therefore, after upgrading to this release, you must
clear the existing crypto key, then regenerate a new
one.
Book: BigIron RX Series
Configuration Guide
Chapter:“Using the MAC
Port Security Feature and
Transparent Port Flooding”
Section:“Defining security
violation actions”
Book: Brocade BigIron RX
Series Installation Guide
System enhancements
TABLE 24 System enhancements
Enhancement Description See page
Unified software image for
software upgrades
Change to the SNMP MIB
objects for trunking
Once the BigIron RX software has been upgraded to
Release 02.2.01, you can use the unified software
image to upgrade the device’s software.
The snMSTrunkTable has been replaced by
snMSTrunkIfTable
Book: Brocade BigIron RX
Series Installation Guide
Book: MIB Reference
Enhancements in release 02.2.00g
TABLE 25 Summary of enhancements in 02.2.00g
Enhancement Description See page
New Hardware Support The following new hardware is supported with the 02.2.01
software release for the BigIron RX:
• 2-port 10 Gigabit Ethernet port module
• DC Power Supply
Book: Brocade BigIron RX
Series Installation Guide
BigIron RX Series Configuration Guide lxvii
53-1001986-01
Page 68

Enhancements in release 02.2.00
TABLE 26 Summary of emhancements in 02.2.00
Enhancement Description See page
Quality of Service (QoS)
Support
Rate-limiting Support Rate-limiting can be performed based on ACL matching of
QoS support on the BigIron RX is different than for the
BigIron MG8.
flows and L2/L3 priority. It operates as on the BigIron
MG8 except:
• Only Inbound rate limiting is supported.
• 802.1p packet priority is used by default
• Rate limit accounting is available if WRED is not
enabled.
CLI changes required for these differences are described
in the page referenced on the next column.
Hardware Forwarding of
Packets
Switching and Routing
Packets
No Support for Core
Device to Copy the QoS
Priority
Trunk Support On the BigIron RX, the switch, server, and per-packet
Multicast Entry Limit 1542 multicast entries are limited to IPv4 1542 entries
WAN PHY Mode Support This release supports WAN PHY Mode per 10 GB Ethernet
Default behavior on BigIron RX is hardware unknown
unicast and multicast flooding.
Operation of packet switching and routing have changed
with the BigIron RX. Details are described in the page
referenced on the next column.
This feature is not supported on BigIron RX. N/A
options for trunking are not supported.
provided every group has only one destination.
port.
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Quality of Service”
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Traffic Reduction”
Book: BigIron RX Series
Configuration Guide
Chapter:“VLANs”
Section:“Hardware
flooding for Layer 2
multicast and broadcast
packets”
Book: BigIron RX Series
Configuration Guide
Chapter:“VLANs”
Section:“Unknown
unicast flooding on VLAN
ports”
N/A
N/A
Book: BigIron RX Series
Configuration Guide
Chapter:“Configuring
Interface Parameters”
Section:“Enabling WAN
PHY mode support”
For further information about new features and documentation updates for this release, refer to
the Knowledge Portal at kp.foundrynet.com.
lxviii BigIron RX Series Configuration Guide
53-1001986-01
Page 69

Document conventions
NOTE
This section describes text formatting conventions and important notice formats used in this
document.
Text formatting
The narrative-text formatting conventions that are used are as follows:
bold text Identifies command names
italic text Provides emphasis
code text Identifies CLI output
For readability, command names in the narrative portions of this guide are presented in bold: for
example, show version.
Identifies the names of user-manipulated GUI elements
Identifies keywords
Identifies text to enter at the GUI or CLI
Identifies variables
Identifies document titles
Command syntax conventions
Command syntax in this manual follows these conventions:
command and
parameters
[ ] Optional parameter.
variable Variables are printed in italics enclosed in angled brackets < >.
... Repeat the previous element, for example “member[;member...]”
| Choose from one of the parameters.
Commands and parameters are printed in bold.
Notes, cautions, and danger notices
The following notices and statements are used in this manual. They are listed below in order of
increasing severity of potential hazards.
A note provides a tip, guidance or advice, emphasizes important information, or provides a reference
to related information.
BigIron RX Series Configuration Guide lxix
53-1001986-01
Page 70

CAUTION
A Caution statement alerts you to situations that can be potentially hazardous to you or cause
DANGER
NOTE
damage to hardware, firmware, software, or data.
A Danger statement indicates conditions or situations that can be potentially lethal or extremely
hazardous to you. Safety labels are also attached directly to products to warn of these conditions
or situations.
Notice to the reader
This document may contain references to the trademarks of the following corporations. These
trademarks are the properties of their respective companies and corporations.
These references are made for informational purposes only.
Corporation Referenced Trademarks and Products
HP H P Top Too ls
Related publications
The following Brocade documents supplement the information in this guide:
• Brocade BigIron RX Series Installation Guide.
• IronWare MIB Reference.
For the latest edition of these documents, which contain the most up-to-date information, go to
my.Brocade.com, click the Product Documentation tab, then click on the link to the Knowledge
Portal (KP)
Getting technical help or reporting errors
Brocade is committed to ensuring that your investment in our products remains cost-effective. If
you need assistance or find errors in the manuals, contact Brocade using one of the following
options.
lxx BigIron RX Series Configuration Guide
53-1001986-01
Page 71

Web access
The Knowledge Portal (KP) contains the latest version of this guide and other user guides for the
product. You can also report errors on the KP.
Log in to my.Brocade.com, click the Product Documentation tab, then click on the link to the
Knowledge Portal (KP). Then click on Cases > Create a New Ticket to report an error. Make sure you
specify the document title in the ticket description.
E-mail and telephone access
Go to http://www.brocade.com/services-support/index.page for the latest e-mail and telephone
contact information.
BigIron RX Series Configuration Guide lxxi
53-1001986-01
Page 72

lxxii BigIron RX Series Configuration Guide
53-1001986-01
Page 73

Chapter
NOTE
NOTE
Getting Started with the Command Line Interface
In this chapter
•Logging on through the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
•EXEC commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
•CONFIG commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
•Accessing the CLI. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
•Searching and filtering output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Logging on through the CLI
This user guide assumes that an IP address and default gateway have been assigned to the BigIron
RX when it was installed. If you need to assign an IP address or default gateway to the device, refer
to the Brocade BigIron RX Series Installation Guide.
1
Once an IP address is assigned to the device’s management port, you can access the CLI through a
PC or terminal attached to the management module’s serial (Console) port or
10BaseT/100BaseTX Ethernet (management) port, or from a Telnet or SSH connection to the PC or
terminal.
You can initiate a local Telnet, SSH or SNMP connection by specifying the management port’s IP
address.
The commands in the CLI are organized into the following levels:
• User EXEC – Lets you display information and perform basic tasks such as pings and
traceroutes.
• Privileged EXEC – Lets you use the same commands as those at the User EXEC level plus
configuration commands that do not require saving the changes to the system-config file.
• CONFIG – Lets you make configuration changes to the device. To save the changes across
software reloads and system resets, you need to save them to the system-config file. The
CONFIG level contains sub-levels for individual ports, for VLANs, for routing protocols, and other
configuration areas.
By default, any user who can open a direct or Telnet connection to a BigIron RX Switch can access
all these CLI levels. To secure access, you can configure Enable passwords or local user accounts,
or you can configure the device to use a RADIUS or TACACS o rTACACS+ server for authentication.
Refer to the Security Guide.
BigIron RX Series Configuration Guide 1
53-1001986-01
Page 74

Logging on through the CLI
1
On-line help
To display a list of available commands or command options, enter “?” or press Tab. If you have not
entered part of a command at the command prompt, all the commands supported at the current
CLI level are listed. If you enter part of a command, then enter “?” or press Tab, the CLI lists the
options you can enter at this point in the command string.
If you enter an invalid command followed by ?, a message appears indicating the command was
unrecognized.
BigIron RX(config)# rooter ip
Unrecognized command
Command completion
The CLI supports command completion, so you do not need to enter the entire name of a command
or option. As long as you enter enough characters of the command or option name to avoid
ambiguity with other commands or options, the CLI understands what you are typing.
Scroll control
By default, the CLI uses a page mode to paginate displays that are longer than the number of rows
in your terminal emulation window. For example, if you display a list of all the commands at the
global CONFIG level but your terminal emulation window does not have enough rows to display
them all at once, the page mode stops the display and lists your choices for continuing the display.
aaa
access-list
all-client
arp
banner
base-mac-addr
boot
some lines omitted for brevity...
default-vlan-id
enable
enable-acl-counter
end
exit
--More--, next page: Space, next line: Return key, quit: Control-c
The software provides the following scrolling options:
• Press the Space bar to display the next page (one screen at time).
• Press the Return or Enter key to display the next line (one line at a time).
• Press Ctrl-C cancel the display.
2 BigIron RX Series Configuration Guide
53-1001986-01
Page 75

EXEC commands
1
Line editing commands
The CLI supports the following line editing commands. To enter a line-editing command, use the
CTRL-key combination for the command by pressing and holding the CTRL key, then pressing the
letter associated with the command.
TABLE 27 CLI line-editing commands
Ctrl-key combination Description
Ctrl-A Moves to the first character on the command line.
Ctrl-B Moves the cursor back one character.
Ctrl-C Escapes and terminates command prompts and ongoing tasks (such as
lengthy displays), and displays a fresh command prompt.
Ctrl-D Deletes the character at the cursor.
Ctrl-E Moves to the end of the current command line.
Ctrl-F Moves the cursor forward one character.
Ctrl-K Deletes all characters from the cursor to the end of the command line.
Ctrl-L; Ctrl-R Repeats the current command line on a new line.
Ctrl-N Enters the next command line in the history buffer.
Ctrl-P Enters the previous command line in the history buffer.
Ctrl-U; Ctrl-X Deletes all characters from the cursor to the beginning of the command
line.
Ctrl-W Deletes the last word you typed.
Ctrl-Z Moves from any CONFIG level of the CLI to the Privileged EXEC level; at the
Privileged EXEC level, moves to the User EXEC level.
EXEC commands
There are two different levels of EXEC commands, the User Level and the Privileged Level.
User level
The User level commands are at the top of the CLI hierarchy. These are the first commands that you
have access to when connected to the device through the CLI. For example, when you first connect
to the device, you may see the following prompt.
BigIron RX>
The “BigIron RX“part of the prompt is configurable. Your system may display a different string.
At this level, you can view basic system information and verify connectivity but cannot make any
changes to the device configuration. To make changes to the configuration, you must move to
other levels of the CLI hierarchy. such as the Privileged EXEC level.
Privileged EXEC level
Commands at the Privileged EXEC level enable you to transfer and store software images and
configuration files between the network and the system, and review the configuration.
BigIron RX Series Configuration Guide 3
53-1001986-01
Page 76

CONFIG commands
1
You reach this level by entering the enable [<password>] or enable <username> <password> at
the User EXEC level.
BigIron RX>enable
or
BigIron RX>enable user1 mypassword
After entering the enable command, you see the following prompt.
BigIron RX>#.
The prompt indicates that you are at the Privilege EXEC level.
When you are at the Privilege EXEC level, you can enter commands that are available at that level.
It is also at this level where you enter the configure terminal command to Global Configuration
level.
Global level
The global CONFIG level allows you to globally apply or modify parameters for ports on the device.
You reach this level by entering configure terminal at the privileged EXEC level.
BigIron RX>enable
BigIron RX>#configuration terminal
The prompt changes to the Global Configuration level.
BigIron RX(config)#
CONFIG commands
CONFIG commands modify the configuration of a device. Once you are at the Global Configuration
level, you can enter commands to configure the features in the device. This section describes the
following CONFIG CLI levels.
Redundancy level
This redundancy level allows you to configure redundancy parameters for redundant management
modules. You reach this level by entering the redundancy command at the global CONFIG level.
Interface level
The interface level allows you to assign or modify specific port parameters on a port-by-port basis.
You reach this level by entering the following at the global CONFIG level:
• interface ethernet <slot/port>
• interface loopback <num>
• interface management <portnum>
• interface ve <num>
• interface tunnel <tunnel_id>
• interface group-ve <vlan_group_id>
4 BigIron RX Series Configuration Guide
53-1001986-01
Page 77

CONFIG commands
1
Trunk level
The trunk level allows you to change parameters for statically-configured trunk groups. You reach
this level by entering a trunk command with the appropriate port parameters.
Router RIP level
The RIP level allows you to configure parameters for the RIP routing protocol. You reach this level by
entering the router rip command at the global CONFIG level.
Router OSPF level
The OSPF level allows you to configure parameters for the OSPF routing protocol. You reach this
level by entering the router ospf command at the global CONFIG level.
BGP level
The BGP level allows you to configure Border Gateway Protocol version 4 (BGP4) features. You
reach this level by entering the router bgp command at the global CONFIG level.
Global BGP and BGP4 Unicast address family level
The global BGP and BGP4 unicast address family levels are present only on Brocade devices that
support IPv6. The global BGP level allows you to configure the BGP routing protocol. The BGP4
unicast address family level allows you to configure a BGP4 unicast route. For backward
compatibility, you can currently access BGP4 unicast address family commands at both global BGP
configuration and BGP4 unicast address family configuration levels. Therefore, the global BGP and
BGP4 unicast address family commands are documented together.
You reach the global BGP level by entering the router bgp command at the global CONFIG level. You
reach the BGP4 unicast address family level by entering the address-family ipv4 unicast command
at the global BGP level.
BGP4 multicast address family level
The BGP4 multicast address family level allows you to configure BGP4 multicast routes. You reach
this level by entering the address-family ipv4 multicast command at the global BGP, BGP4 unicast
address family, or IPv6 BGP unicast address family levels.
Router DVMRP level
The DVMRP level allows you to configure details for the DVMRP multicast protocol. You reach this
level by entering the router dvmrp command at the global CONFIG level.
Router PIM level
The PIM level allows you to configure parameters for the Protocol Independent Multicast (PIM)
routing protocol. You reach this level by entering the router pim command at the global CONFIG
level.
BigIron RX Series Configuration Guide 5
53-1001986-01
Page 78

CONFIG commands
1
Route Map level
The Route Map level allows you to configure parameters for a BGP4 route map. You reach this level
by entering the route-map <name> command at the global CONFIG level.
Router VRRP level
The VRRP level allows you to configure parameters for the Virtual Router Redundancy Protocol
(VRRP). You reach this level by entering the router vrrp command at the global CONFIG level, then
entering the ip vrrp vrid <num> command at the interface configuration level.
Router VRRPE level
The VRRPE level allows you to configure parameters for VRRP Extended. You reach this level by
entering the router vrrp-extended command at the global CONFIG level, then entering the ip
vrrp-extended vrid <num> command at the interface configuration level.
VLAN level
Policy-based VLANs allow you to assign VLANs to a protocol, port, or 802.1q tags.
You reach this level by entering the vlan <vlan-id> command at the Global CONFIG Level.
Metro ring level
Metro rings provide Layer 2 connectivity and fast failover in ring topologies.
You reach this level by entering the metro-ring <ring-id> command at the Global CONFIG Level.
VSRP level
The VSRP level allows you to configure parameters for the Virtual Switch Redundancy Protocol
(VSRP). You reach this level by entering the vsrp vrid <num> command at the VLAN configuration
level, then entering the vsrp vrid <num> command at the VLAN configuration level.
Topology group level
A topology group enables you to control the Layer 2 protocol configuration and Layer 2 state of a set
of ports in multiple VLANs based on the configuration and states of those ports in a single master
VLAN. One instance of the Layer 2 protocol controls all the VLANs.
You reach this level by entering the topology-group <group-id> command at the Global CONFIG
Level.
802.1x port security level
The 802.1x port security level allows you to configure the 802.1x port security. You reach this level
by entering the dot1x-enable command at the at the Global level.
6 BigIron RX Series Configuration Guide
53-1001986-01
Page 79
MAC port security level
NOTE
The MAC port security level allows you to configure the port security feature. You reach this level by
entering the global-port-security command at the at the Global or Interface levels.
Accessing the CLI
The CLI can be accessed through both serial and Telnet connections. For initial log on, you must
use a serial connection. Once an IP address is assigned, you can access the CLI through Telnet.
Once connectivity to the device is established, you will see the following prompt.
BigIron RX>
When accessing the CLI through Telnet, you maybe prompted for a password. By default, the
password required is the password you enter for general access at initial setup. You also have the
option of assigning a separate password for Telnet access with the enable telnet password
<password> command, found at the Global Level.
At initial log on, all you need to do is type enable at the prompt, then press Return. You only need to
enter a password after a permanent password is entered at the Global CONFIG Level of the CLI.
Accessing the CLI
1
If you install switch code on a router, the command prompt begins with "SW-" to indicate the software
change. This is true even if you change the system name.
To reach the Global CONFIG Level, the uppermost level of the CONFIG commands, enter the
following commands:
• BigIron RX> enable
• BigIron RX# configure terminal
• BigIron RX(config)#
You can then reach all other levels of the CONFIG command structure from this point.
The CLI prompt will change at each level of the CONFIG command structure to easily identify the
current level.
User Level commands
Privileged Level-EXEC commands
Global Level-CONFIG commands
BigIron RX Series Configuration Guide 7
53-1001986-01
Page 80

Accessing the CLI
NOTE
NOTE
BigIron RX> User Level EXEC Command
BigIron RX# Privileged Level EXEC Command
BigIron RX(config)#Global Level CONFIG Command
BigIron RX(config-if-e10000-5/1)#Interface Level CONFIG Command
BigIron RX(config-lbif-1)#Loopback Interface CONFIG Command
BigIron RX(config-ve-1)#Virtual Interface CONFIG Command
BigIron RX(config-trunk-4/1-4/8)#Trunk group CONFIG Command
BigIron RX(config-if-e10000-tunnel)#IP Tunnel Level CONFIG Command
BigIron RX(config-bgp-router)#BGP Level CONFIG Command
BigIron RX(config-dvmrp-router)#DVMRP Level CONFIG Command
BigIron RX(config-ospf-router)#OSPF Level CONFIG Command
BigIron RX(config-isis-router)#IS-IS Level CONFIG Command
BigIron RX(config-pim-router)#PIM Level CONFIG Command
BigIron RX(config-redundancy)#Redundant Management Module CONFIG Command
BigIron RX(config-rip-router)#RIP Level CONFIG Command
BigIron RX(config-port-80)#Application Port CONFIG Command
BigIron RX(config-bgp-routemap Map_Name)#Route Map Level CONFIG Command
BigIron RX(config-vlan-1)#VLAN Port-based Level CONFIG Command
BigIron RX(config-vlan-atalk-proto)#VLAN Protocol Level CONFIG Command
1
The CLI prompt at the interface level includes the port speed. The speed is one of the following.
BigIron RX(config-if–e100-5/1)# – The interface is a 10/100 port.
BigIron RX(config-if–e1000-5/1)# – The interface is a Gigabit port.
For simplicity, the port speeds sometimes are not shown in example Interface level prompts in this
manual.
Navigating among command levels
To reach other CLI command levels, you need to enter certain commands. At each level there is a
launch command that allows you to move either up or down to the next level.
CLI command structure
Many CLI commands may require textual or numeral input as part of the command.
Required or optional fields
8 BigIron RX Series Configuration Guide
These fields are either required or optional depending on how the information is bracketed. For
clarity, a few CLI command examples are explained below.
Syntax: [no] deny redistribute <value> all | bgp | rip | static address <ip-addr> <ip-mask>
[match-metric <value> | set-metric <value>]
When an item is bracketed with “< >” symbols, the information requested is a variable and
required.
When an item is not enclosed by “< >” or “[ ]” symbols, the item is a required keyword.
When an item is bracketed with “[ ]” symbols, the information requested is optional.
53-1001986-01
Page 81

Searching and filtering output
1
Optional fields
When two or more options are separated by a vertical bar, “| “, you must enter one of the options
as part of the command.
Syntax: priority normal | high
For example, the "normal | high" entry in the Syntax above means that priority can be either priority
normal or priority high. The command in the syntax above requires that you enter either normal or
high as part of the command.
List of available options
To get a quick display of available options at a CLI level or for the next option in a command string,
enter a question mark (?) at the prompt or press TAB.
To view all available commands at the user EXEC level, enter the following or press TAB at the User
EXEC CLI level.
BigIron RX> ? <return>
enable
exit
fastboot
ping
show
stop-trace-route
traceroute
You also can use the question mark (?) with an individual command, to see all available options or
to check context.
To view possible copy command options, enter the following.
BigIron RX# copy ?
flash
running-config
startup-config
tftp
BigIron RX# copy flash ?
tftp
Searching and filtering output
You can filter CLI output from show commands and at the --More-- prompt. You can search for
individual characters, strings, or construct complex regular expressions to filter the output.
Searching and filtering output from show commands
You can filter output from show commands to display lines containing a specified string, lines that
do not contain a specified string, or output starting with a line containing a specified string. The
search string is a regular expression consisting of a single character or string of characters. You can
use special characters to construct complex regular expressions. Refer to “Using special characters
in regular expressions” on page 12 for information on special characters used with regular
expressions.
BigIron RX Series Configuration Guide 9
53-1001986-01
Page 82

Searching and filtering output
NOTE
1
Displaying lines containing a specified string
The following command filters the output of the show interface command for port 3/11 so it
displays only lines containing the word “Internet”. This command can be used to display the IP
address of the interface.
BigIron RX# show interface e 3/11 | include Internet
Internet address is 192.168.1.11/24, MTU 1518 bytes, encapsulation ethernet
Syntax: <show-command> | include <regular-expression>
The vertical bar ( | ) is part of the command.
Note that the regular expression specified as the search string is case sensitive. In the example
above, a search string of “Internet” would match the line containing the IP address.
Displaying lines that do not contain a specified string
The following command filters the output of the show who command so it displays only lines that
do not contain the word “closed”. This command can be used to display open connections to the
Brocade device.
BigIron RX# show who | exclude closed
Console connections:
established
you are connecting to this session
2 seconds in idle
Telnet connections (inbound):
1 established, client ip address 192.168.9.37
27 seconds in idle
Telnet connection (outbound):
SSH connections:
Syntax: <show-command> | exclude <regular-expression>
Displaying lines starting with a specified string
The following command filters the output of the show who command so it displays output starting
with the first line that contains the word “SSH”. This command can be used to display information
about SSH connections to the device.
BigIron RX# show who | begin SSH
SSH connections:
1 established, client ip address 192.168.9.210
7 seconds in idle
2 closed
3 closed
4 closed
5 closed
Syntax: <show-command> | begin <regular-expression>
Searching and filtering output at the --More-- prompt
The --More-- prompt is displayed when output extends beyond a single page. From this prompt, you
can press the Space bar to display the next page, the Return or Enter key to display the next line, or
Ctrl-C or Q to cancel the display. You can also search and filter output from this prompt.
10 BigIron RX Series Configuration Guide
53-1001986-01
Page 83

Searching and filtering output
BigIron RX# ?
append Append one file to another
attrib Change file attribute
boot Boot system from bootp/tftp server/flash image
cd Change current working directory
chdir Change current working directory
clear Clear table/statistics/keys
clock Set clock
configure Enter configuration mode
copy Copy between flash, tftp, config/code
cp Copy file commands
debug Enable debugging functions (see also 'undebug')
delete Delete file on flash
dir List files
dm test commands
dot1x 802.1x
erase Erase image/configuration files from flash
exit Exit Privileged mode
fastboot Select fast-reload option
force-sync-standby Sync active flash (pri/sec/mon/startup config/lp images)
to standby
format Format PCMCIA card
hd Hex dump
ipc IPC commands
--More--, next page: Space, next line: Return key, quit: Control-c
--More--, next page: Space, next line: Return key, quit: Control-c
/telnet
searching...
telnet Telnet by name or IP address
terminal Change terminal settings
traceroute TraceRoute to IP node
undelete Recover deleted file
whois WHOIS lookup
write Write running configuration to flash or terminal
--More--, next page: Space, next line: Return key, quit: Control-c
+telnet
filtering...
telnet Telnet by name or IP address
1
At the --More-- prompt, you can press the forward slash key ( / ) and then enter a search string. The
Brocade device displays output starting from the first line that contains the search string, similar to
the begin option for show commands.
The results of the search are displayed.
BigIron RX Series Configuration Guide 11
53-1001986-01
To display lines containing only a specified search string (similar to the include option for show
commands) press the plus sign key ( + ) at the --More-- prompt and then enter the search string.
The filtered results are displayed.
To display lines that do not contain a specified search string (similar to the exclude option for show
commands) press the minus sign key ( - ) at the --More-- prompt and then enter the search string.
Page 84

Searching and filtering output
--More--, next page: Space, next line: Return key, quit: Control-c
-telnet
filtering...
sync-standby Sync active flash (pri/sec/mon/startup config/lp images)
to standby if different
terminal Change terminal settings
traceroute TraceRoute to IP node
undelete Recover deleted file
whois WHOIS lookup
write Write running configuration to flash or terminal
1
The filtered results are displayed.
As with the commands for filtering output from show commands, the search string is a regular
expression consisting of a single character or string of characters. You can use special characters
to construct complex regular expressions. Refer to “Using special characters in regular
expressions” on page 12 for information on special characters used with regular expressions.
Using special characters in regular expressions
You use a regular expression to specify a single character or multiple characters as a search string.
In addition, you can include special characters that influence the way the software matches the
output against the search string. These special characters are listed in the following table.
TABLE 28 Special characters for regular expressions
Character Operation
. The period matches on any single character, including a blank space.
For example, the following regular expression matches “aaz”, “abz”, “acz”, and so on, but not just
“az”:
a.z
* The asterisk matches on zero or more sequential instances of a pattern.
For example, the following regular expression matches output that contains the string “abc”,
followed by zero or more Xs:
abcX*
+ The plus sign matches on one or more sequential instances of a pattern.
For example, the following regular expression matches output that contains "de", followed by a
sequence of “g”s, such as “deg”, “degg”, “deggg”, and so on:
deg+
? The question mark matches on zero occurrences or one occurrence of a pattern.
For example, the following regular expression matches output that contains "dg" or "deg":
de?g
NOTE: Normally when you type a question mark, the CLI lists the commands or options at that CLI
level that begin with the character or string you entered. However, if you enter Ctrl-V and
then type a question mark, the question mark is inserted into the command line, allowing
you to use it as part of a regular expression.
^ A caret (when not used within brackets) matches on the beginning of an input string.
For example, the following regular expression matches output that begins with “deg”:
^deg
12 BigIron RX Series Configuration Guide
53-1001986-01
Page 85

Searching and filtering output
TABLE 28 Special characters for regular expressions (Continued)
Character Operation
$ A dollar sign matches on the end of an input string.
For example, the following regular expression matches output that ends with “deg”:
deg$
_ An underscore matches on one or more of the following:
• , (comma)
• { (left curly brace)
• } (right curly brace)
• ( (left parenthesis)
• ) (right parenthesis)
• The beginning of the input string
• The end of the input string
• A blank space
For example, the following regular expression matches on “100” but not on “1002”, “2100”, and
so on.
[ ] Square brackets enclose a range of single-character patterns.
For example, the following regular expression matches output that contains “1”, “2”, “3”, “4”, or
“5”:
[1-5]
You can use the following expression symbols within the brackets. These symbols are allowed
only inside the brackets.
• ^ – The caret matches on any characters except the ones in the brackets. For example, the
following regular expression matches output that does not contain “1”, “2”, “3”, “4”, or “5”:
[^1-5
• - The hyphen separates the beginning and ending of a range of characters. A match occurs if
any of the characters within the range is present. See the example above.
| A vertical bar separates two alternative values or sets of values. The output can match one or the
other value.
For example, the following regular expression matches output that contains either “abc” or “defg”:
abc|defg
( ) Parentheses allow you to create complex expressions.
For example, the following complex expression matches on “abc”, “abcabc”, or “defg”, but not on
“abcdefgdefg”:
((abc)+)|((defg)?)
1
If you want to filter for a special character instead of using the special character as described in the
table above, enter “\” (backslash) in front of the character. For example, to filter on output
containing an asterisk, enter the asterisk portion of the regular expression as “\*”.
BigIron RX# show ip route bgp | include \*
Allowable characters for LAG names
When creating a LAG name, you can use spaces in a file or subdirectory name if you enclose the
name in double quotes. For example, to specify a subdirectory name that contains spaces, enter a
string such as the following: “a long subdirectory name”. The maximum length for a string is 64
characters.
The following characters are valid in file names:
• All upper and lowercase letters
BigIron RX Series Configuration Guide 13
53-1001986-01
Page 86

Searching and filtering output
NOTE
1
Any of the following special characters are valid:
• All digits
• $
• %
• '
• -
• _
• @
• ~
• `
• !
• (
• )
• {
• }
• ^
• #
• &
Syntax shortcuts
A command or parameter can be abbreviated as long as enough text is entered to distinguish it
from other commands at that level. For example, given the possible commands copy tftp… and
config tftp…, possible shortcuts are cop tftp and con tftp respectively. In this case, co does not
properly distinguish the two commands.
Saving configuration changes
You can make configuration changes while the device is running. The type of configuration change
determines whether or not it becomes effective immediately or requires a save to flash (write
memory) and reset of the system (reload), before it becomes active.
This approach in adopting configuration changes:
• Allows you to make configuration changes to the operating or running configuration of the
device to address a short-term requirement or validate a configuration without overwriting the
permanent configuration file, the startup configuration, that is saved in the system flash, and;
• Ensures that dependent or related configuration changes are all cut in at the same time.
In all cases, if you want to make the changes permanent, you need to save the changes to flash
using the write memory command. When you save the configuration changes to flash, this will
become the configuration that is initiated and run at system boot.
Most configuration changes are dynamic and thus do not require a software reload. If a command
requires a software reload to take effect, the documentation states this.
14 BigIron RX Series Configuration Guide
53-1001986-01
Page 87

Chapter
NOTE
Getting Familiar With the BigIron RX Series Switch Management Applications
How to manage BigIron RX Series switch
This chapter describes the different applications you can use to manage the BigIron RX Series
Switch. The BigIron RX Series Switch supports the same management applications as other
Brocade devices.
As with other Brocade devices, you can manage a BigIron RX Series Switch using any of the
following applications:
• Command Line Interface (CLI) – a text-based interface accessible directly from a PC or terminal
attached to the management module’s serial (Console) port or 10BaseT/100BaseTX Ethernet
(management) port, or from a Telnet connection to the PC or terminal.
• Web management interface – A GUI-based management interface accessible through an HTTP
(web browser) connection.
• IronView Network Manager – An optional SNMP-based standalone GUI application.
The following section describes how to log on to these applications.
2
Logging on through the CLI
Once an IP address is assigned to the BigIron RX Series Switch’s management port, you can access
the CLI through a PC or terminal attached to the management module’s serial (Console) port or
10BaseT/100BaseTX Ethernet (management) port, or from a Telnet or SSH connection to the PC or
terminal.
You can initiate a local Telnet, SSH or SNMP connection by specifying the management port’s IP
address.
The commands in the CLI are organized into the following levels:
• User EXEC – Lets you display information and perform basic tasks such as pings and
traceroutes.
• Privileged EXEC – Lets you use the same commands as those at the User EXEC level plus
configuration commands that do not require saving the changes to the system-config file.
• CONFIG – Lets you make configuration changes to the device. To save the changes across
software reloads and system resets, you need to save them to the system-config file. The
CONFIG level contains sub-levels for individual ports, for VLANs, for routing protocols, and other
configuration areas.
By default, any user who can open a direct or Telnet connection to a BigIron RX Series Switch can
access all these CLI levels. To secure access, you can configure Enable passwords or local user
accounts, or you can configure the device to use a RADIUS or TACACS and TACACS+ server for
authentication. Refer to the Security Guide.
BigIron RX Series Configuration Guide 15
53-1001986-01
Page 88

Logging on through the CLI
2
On-line help
To display a list of available commands or command options, enter “?” or press Tab. If you have not
entered part of a command at the command prompt, all the commands supported at the current
CLI level are listed. If you enter part of a command, then enter “?” or press Tab, the CLI lists the
options you can enter at this point in the command string.
If you enter an invalid command followed by ?, a message appears indicating the command was
unrecognized.
BigIron RX(config)# rooter ip
Unrecognized command
Command completion
The CLI supports command completion, so you do not need to enter the entire name of a command
or option. As long as you enter enough characters of the command or option name to avoid
ambiguity with other commands or options, the CLI understands what you are typing.
Scroll control
By default, the CLI uses a page mode to paginate displays that are longer than the number of rows
in your terminal emulation window. For example, if you display a list of all the commands at the
global CONFIG level but your terminal emulation window does not have enough rows to display
them all at once, the page mode stops the display and lists your choices for continuing the display.
aaa
access-list
all-client
arp
banner
base-mac-addr
boot
some lines omitted for brevity...
default-vlan-id
enable
enable-acl-counter
end
exit
--More--, next page: Space, next line: Return key, quit: Control-c
The software provides the following scrolling options:
• Press the Space bar to display the next page (one screen at time).
• Press the Return or Enter key to display the next line (one line at a time).
• Press Ctrl-C cancel the display.
Line editing commands
The CLI supports the following line editing commands. To enter a line-editing command, use the
CTRL-key combination for the command by pressing and holding the CTRL key, then pressing the
letter associated with the command.
16 BigIron RX Series Configuration Guide
53-1001986-01
Page 89

Logging on through the CLI
NOTE
TABLE 29 CLI line editing commands
Ctrl-key combination Description
Ctrl-A Moves to the first character on the command line.
Ctrl-B Moves the cursor back one character.
Ctrl-C Escapes and terminates command prompts and ongoing tasks (such as
lengthy displays), and displays a fresh command prompt.
Ctrl-D Deletes the character at the cursor.
Ctrl-E Moves to the end of the current command line.
Ctrl-F Moves the cursor forward one character.
Ctrl-K Deletes all characters from the cursor to the end of the command line.
Ctrl-L; Ctrl-R Repeats the current command line on a new line.
Ctrl-N Enters the next command line in the history buffer.
Ctrl-P Enters the previous command line in the history buffer.
Ctrl-U; Ctrl-X Deletes all characters from the cursor to the beginning of the command
line.
Ctrl-W Deletes the last word you typed.
Ctrl-Z Moves from any CONFIG level of the CLI to the Privileged EXEC level; at
the Privileged EXEC level, moves to the User EXEC level.
2
For a complete list of CLI commands and syntax information for each command, refer to the Switch
and Router Command Line Interface Reference.
Searching and filtering output from CLI commands
You can filter CLI output from show commands and at the --More-- prompt. You can search for
individual characters, strings, or construct complex regular expressions to filter the output.
You can also filter output from show commands to display lines containing a specified string, lines
that do not contain a specified string, or output starting with a line containing a specified string.
The search string is a regular expression consisting of a single character or string of characters.
You can use special characters to construct complex regular expressions. Refer to “Using special
characters in regular expressions” on page 20 for information on special characters used with
regular expressions.
Displaying lines containing a specified string
The following command filters the output of the show interface command for port 3/1 so it displays
only lines containing the word “Internet”. This command can be used to display the IP address of
the interface.
BigIron RX# show interface e 3/1 | include Internet
Internet address is 192.168.1.11/24, MTU 1518 bytes, encapsulation ethernet
Syntax: <show-command> | include <regular-expression>
The vertical bar ( | ) is part of the command.
BigIron RX Series Configuration Guide 17
53-1001986-01
Page 90

Logging on through the CLI
NOTE
BigIron RX# show who | exclude closed
Console connections:
established
you are connecting to this session
2 seconds in idle
Telnet connections (inbound):
1 established, client ip address 192.168.9.37
27 seconds in idle
Telnet connection (outbound):
SSH connections:
BigIron RX# show who | begin SSH
SSH connections:
1 established, client ip address 192.168.9.210
7 seconds in idle
2 closed
3 closed
4 closed
5 closed
2
The regular expression specified as the search string is case sensitive. In the example above, a
search string of “Internet” would match the line containing the IP address, but a search string of
“internet” would not.
Displaying lines that do not contain a specified string
The following command filters the output of the show who command so it displays only lines that
do not contain the word “closed”. This command can be used to display open connections to a
BigIron RX Series Switch.
Syntax: <show-command> | exclude <regular-expression>
Displaying lines starting with a specified string
The following command filters the output of the show who command so it displays output starting
with the first line that contains the word “SSH”. This command can be used to display information
about SSH connections to the BigIron RX Series Switch.
Syntax: <show-command> | begin <regular-expression>
Searching and filtering output at the --More-- prompt
The --More-- prompt displays when output extends beyond a single page. From this prompt, you can
press the Space bar to display the next page, the Return or Enter key to display the next line, or
Ctrl-C to cancel the display. In addition, you can search and filter output from this prompt.
18 BigIron RX Series Configuration Guide
53-1001986-01
Page 91

Logging on through the CLI
BigIron RX# ?
append Append one file to another
attrib Change file attribute
boot Boot system from bootp/tftp server/flash image
cd Change current working directory
chdir Change current working directory
clear Clear table/statistics/keys
clock Set clock
configure Enter configuration mode
copy Copy between flash, tftp, config/code
cp Copy file commands
debug Enable debugging functions (see also 'undebug')
delete Delete file on flash
dir List files
dm test commands
dot1x 802.1x
erase Erase image/configuration files from flash
exit Exit Privileged mode
fastboot Select fast-reload option
force-sync-standby Sync active flash (pri/sec/mon/startup config/lp images)
to standby
format Format PCMCIA card
hd Hex dump
ipc IPC commands
--More--, next page: Space, next line: Return key, quit: Control-c
--More--, next page: Space, next line: Return key, quit: Control-c
/telnet
The results of the search are displayed:
searching...
telnet Telnet by name or IP address
terminal Change terminal settings
traceroute TraceRoute to IP node
undelete Recover deleted file
whois WHOIS lookup
write Write running configuration to flash or terminal
--More--, next page: Space, next line: Return key, quit: Control-c
+telnet
filtering...
telnet Telnet by name or IP address
2
At the --More-- prompt, you can press the forward slash key ( / ) and then enter a search string. The
device displays output starting from the first line that contains the search string, similar to the
begin option for show commands. For example:
BigIron RX Series Configuration Guide 19
53-1001986-01
To display lines containing only a specified search string (similar to the include option for show
commands) press the plus sign key ( + ) at the --More-- prompt and then enter the search string.
The filtered results are displayed:
To display lines that do not contain a specified search string (similar to the exclude option for show
commands) press the minus sign key ( - ) at the --More-- prompt and then enter the search string.
Page 92

Logging on through the CLI
--More--, next page: Space, next line: Return key, quit: Control-c
-telnet
filtering...
sync-standby Sync active flash (pri/sec/mon/startup config/lp images)
to standby if different
terminal Change terminal settings
traceroute TraceRoute to IP node
undelete Recover deleted file
whois WHOIS lookup
write Write running configuration to flash or terminal
2
The filtered results are displayed:
As with the commands for filtering output from show commands, the search string is a regular
expression consisting of a single character or string of characters. You can use special characters
to construct complex regular expressions. See the next section for information on special
characters used with regular expressions.
Using special characters in regular expressions
You use a regular expression to specify a single character or multiple characters as a search string.
In addition, you can include special characters that influence the way the software matches the
output against the search string. These special characters are listed in the following table.
TABLE 30 Special characters for regular expressions
Character Operation
. The period matches on any single character, including a blank space.
For example, the following regular expression matches “aaz”, “abz”, “acz”, and so on, but not just
“az”:
a.z
* The asterisk matches on zero or more sequential instances of a pattern.
For example, the following regular expression matches output that contains the string “abc”,
followed by zero or more Xs:
abcX*
+ The plus sign matches on one or more sequential instances of a pattern.
For example, the following regular expression matches output that contains "de", followed by a
sequence of “g”s, such as “deg”, “degg”, “deggg”, and so on:
deg+
? The question mark matches on zero occurrences or one occurrence of a pattern.
For example, the following regular expression matches output that contains "dg" or "deg":
de?g
NOTE: Normally when you type a question mark, the CLI lists the commands or options at that CLI
level that begin with the character or string you entered. However, if you enter Ctrl-V and then
type a question mark, the question mark is inserted into the command line, allowing you to
use it as part of a regular expression.
^ A caret (when not used within brackets) matches on the beginning of an input string.
For example, the following regular expression matches output that begins with “deg”:
^deg
$ A dollar sign matches on the end of an input string.
20 BigIron RX Series Configuration Guide
For example, the following regular expression matches output that ends with “deg”:
deg$
53-1001986-01
Page 93

Logging on through the CLI
TABLE 30 Special characters for regular expressions (Continued)
Character Operation
_ An underscore matches on one or more of the following:
• , (comma)
• { (left curly brace)
• } (right curly brace)
• ( (left parenthesis)
• ) (right parenthesis)
• The beginning of the input string
• The end of the input string
• A blank space
For example, the following regular expression matches on “100” but not on “1002”, “2100”, and so
on:
_100_
[ ] Square brackets enclose a range of single-character patterns.
For example, the following regular expression matches output that contains “1”, “2”, “3”, “4”, or “5”:
[1-5]
You can use the following expression symbols within the brackets. These symbols are allowed only
inside the brackets.
• ^ – The caret matches on any characters except the ones in the brackets. For example, the
following regular expression matches output that does not contain “1”, “2”, “3”, “4”, or “5”:
[^1-5]
• - The hyphen separates the beginning and ending of a range of characters. A matchoccurs if
any of the characters within the range is present. See the example above.
| A vertical bar separates two alternative values or sets of values. The output can match one or the
other value.
For example, the following regular expression matches output that contains either “abc” or “defg”:
abc|defg
( ) Parentheses allow you to create complex expressions.
For example, the following complex expression matches on “abc”, “abcabc”, or “defg”, but not on
“abcdefgdefg”:
((abc)+)|((defg)?)
2
If you want to filter for a special character instead of using the special character as described in the
table above, enter “\” (backslash) in front of the character. For example, to filter on output
containing an asterisk, enter the asterisk portion of the regular expression as “\*”.
BigIron RX# show ip route bgp | include \*
Allowable characters for LAG names
When creating a LAG name, you can use spaces in a file or subdirectory name if you enclose the
name in double quotes. For example, to specify a subdirectory name that contains spaces, enter a
string such as the following: “a long subdirectory name”. The maximum length for a string is 64
characters.
The following characters are valid in file names:
• All upper and lowercase letters
• All digits
Any of the following special characters are valid:
• $
BigIron RX Series Configuration Guide 21
53-1001986-01
Page 94
Logging on through the Web Management Interface
NOTE
2
• %
• '
• -
• _
• @
• ~
• `
• !
• (
• )
• {
• }
• ^
• #
• &
Logging on through the Web Management Interface
To use the Web Management Interface, open a Web browser and enter the IP address of a BigIron
RX Series Switch’s management port in the Location or Address field. The Web browser contacts
the device and displays the login panel for the BigIron RX Series Switch, as shown in Figure 1.
FIGURE 1 Web Management Interface login panel
If you are unable to connect with the device through a Web browser due to a proxy problem, it may
be necessary to set your Web browser to direct Internet access instead of using a proxy. For
information on how to change a proxy setting, refer to the on-line help provided with your Web
browser.
To log in, click on the Login link. Figure 2 shows the dialog box that displays.
22 BigIron RX Series Configuration Guide
53-1001986-01
Page 95
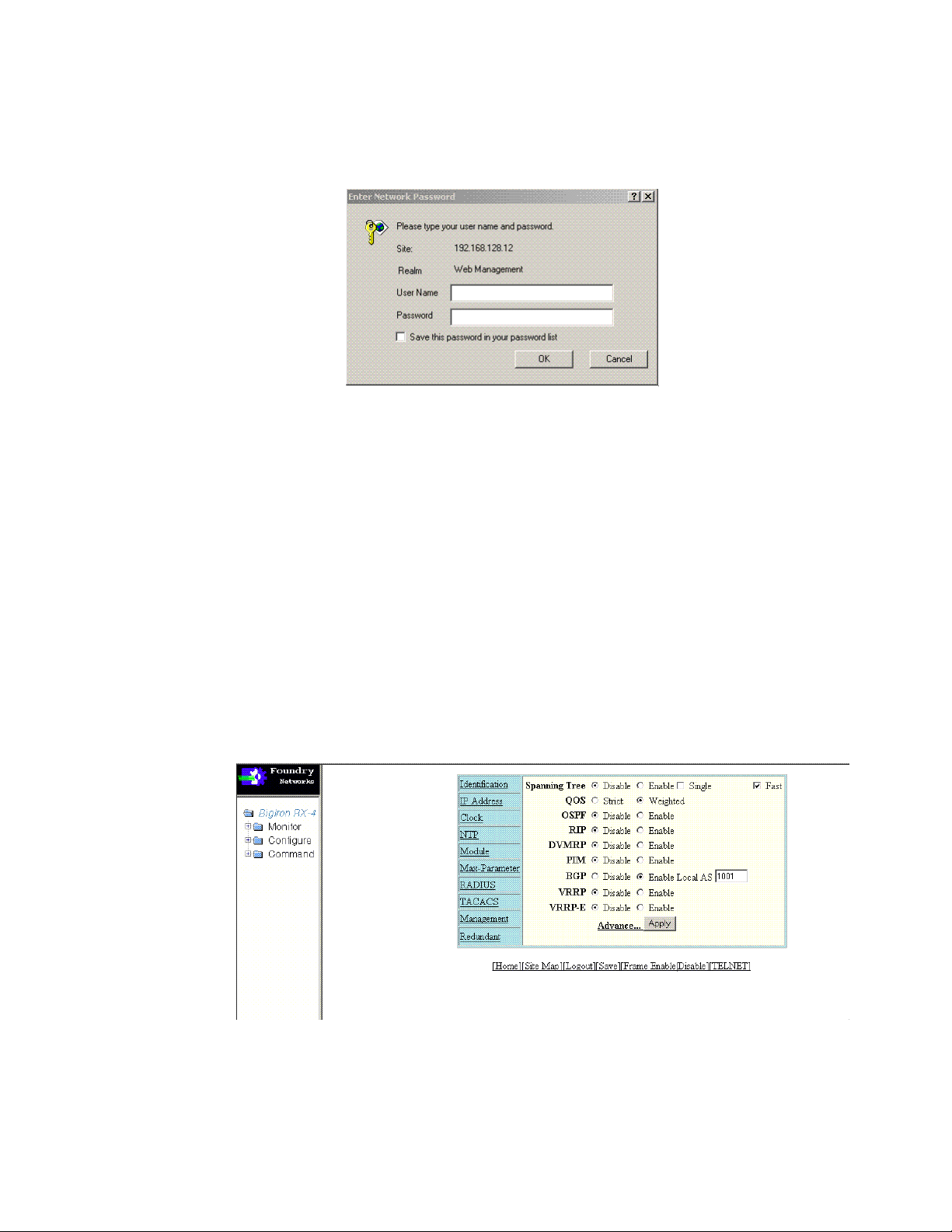
Logging on through the Web Management Interface
2
FIGURE 2 Web Management Interface login dialog box
The login username and password you enter depends on whether your device is configured with
AAA authentication for SNMP. If AAA authentication for SNMP is not configured, you can use the
user name “get” and the default read-only password “public” for read-only access. However, for
read-write access, you must enter “set” for the user name, and enter a read-write community string
you have configured on the device for the password. There is no default read-write community
string. You must add one using the CLI. Refer to the Security Guide.
Web Management Interface
When you log into a device, the System configuration panel is displayed. This panel allows you to
enable or disable major system features. You can return to this panel from any other panel by
selecting the Home link.
The Site Map link gives you a view of all available options on a single screen.
Figure 3 displays the Web Management Interface panel for Layer 3 Switch features. This panel
allows you to configure the features supported by the Layer 3 Switch software.
FIGURE 3 Panel for Layer 3 Switch features
The left pane of the Web Management Interface window contains a “tree view,” similar to the one
found in Windows Explorer. Configuration options are grouped into folders in the tree view. These
folders, when expanded, reveal additional options. To expand a folder, click on the plus sign to the
left of the folder icon.
BigIron RX Series Configuration Guide 23
53-1001986-01
Page 96

Logging on through IronView Network Manager
2
Logging on through
Refer to the IronView Network Management User’s Guide for information about using IronView
Network Manager.
IronView Network Manager
24 BigIron RX Series Configuration Guide
53-1001986-01
Page 97

Chapter
Using a Redundant Management Module
How management module redundancy works
You can install a redundant management module in slot M1 or M2 of the BigIron RX Series chassis.
By default, the system considers the module installed in slot M1 to be the active management
module and the module installed in slot M2 to be the redundant or standby module. If the active
module becomes unavailable, the standby module automatically takes over management of the
system.
This chapter describes the redundant management module, how it works with the active module,
and how to configure and manage it.
This section explains the following:
• How management module redundancy works under normal operating conditions.
• Events that cause a standby management module to assume the role of the active module and
how the switchover occurs as a result of each event.
• Implications that you should be aware of if a switchover occurs.
3
Management module redundancy overview
When you power on or reload a BigIron RX Series chassis with two management modules installed,
by default, the management module installed in slot M1 becomes the active module and the
module installed in slot M2 becomes the standby module. (You can change the default active slot
from M1 to M2 using the active-management command. For information about performing this
task, refer to “Changing the default active Chassis slot” on page 29.)
After the active and standby modules are determined, both modules boot from the source specified
for the active module. The active management module can boot from the following sources:
• The active management module’s flash memory.
• A PCMCIA flash card inserted in one of the PCMCIA slots in the active management module’s
front panel.
After the modules boot, the active module compares the standby module’s flash code and
system-config file to its own. If differences exist, the active module synchronizes the standby
module’s flash code and system-config file with its own.
During normal operation, the active module handles tasks such as obtaining network topology and
reachability information and determining the best paths to known destinations. The active module
also monitors the standby module.
The standby module functions in an active standby mode. Configuration changes made from the
CLI to the active management module are also written to the standby management module even if
they are not written to flash memory. Keeping the system-config and running-config files on both
modules synchronized allows the standby module to assume the role of active module seamlessly
if necessary.
BigIron RX Series Configuration Guide 25
53-1001986-01
Page 98

How management module redundancy works
3
The interface modules are not reset, as they are with the previous cold-restart redundancy feature.
The interface modules continue to forward traffic while the standby management module takes
over operation of the system. The new now-active management module receives updates from the
interface modules and sends verification information to the interface modules to ensure that they
are synchronized. If the new active management module becomes out-of-sync with an interface
module, information on the interface module can be overwritten in some cases which can cause an
interruption of traffic forwarding.
Management module switchover
The events cause the standby management module to become the active module, which is called a
switchover. Those events are as follows:
• The active module becomes unavailable.
• You perform a manual switchover.
• You remove and replace the active management module.
The following sections explain how the switchover occurs for each event.
Unavailable active module
The following events cause an active module to become unavailable and a switchover to occur:
• An active module experiences a problem significant enough to cause a reset of the module.
• The active module loses power.
Before a switchover occurs, the active module resets itself and sends an interrupt signal to the
standby module. The standby module then becomes the active module and the interface modules
continue to forward traffic.
The new active module begins to manage the system. When the original active module becomes
available again or is replaced, it assumes the role of standby module.
Manual switchover
In some situations, you may want to manually switch the role of active management module from
the currently active module to the standby module. For example, if the module in slot M2 is the
active module and the module in slot M1 is the standby module and you want the module in M1 to
be the active module and the module in M2 to be the standby module, you can perform a manual
switchover using the switchover command. For information about performing this task, refer to
“Manually switching over to the standby management module” on page 32.
When the switchover occurs, the standby module becomes the active module.
This section explains how management module redundancy is affected when you remove and
replace an active or standby management module.
Removal and replacement of an active management module
If you remove the active management module, the standby module automatically assumes the role
of the active module. After you insert a replacement module in the slot from which the original
active module was removed, the replacement module becomes the standby module. The module
boots from the source specified for the active module. The active management module can boot
from the following sources:
26 BigIron RX Series Configuration Guide
53-1001986-01
Page 99

How management module redundancy works
3
• The active management module’s flash memory.
• A PCMCIA flash card inserted in one of the PCMCIA slots in the active management module’s
front panel.
After the replacement module boots, the active module compares the standby module’s flash code
and system-config file to its own. If differences exist, the active module synchronizes the standby
module’s flash code and system-config file with its own.
Removal and replacement of a standby management module
You can remove a standby management module without causing a switchover to occur. The active
module continues to function as is. Communication between the active module and the removed
module stops until the new module is installed in the BigIron RX Series chassis. After the new
module is installed, it assumes the role of standby module. The module boots from the source
specified for the active module. The active management modules can boot from the following
sources:
• The active management module’s flash memory.
• A PCMCIA flash card inserted in one of the PCMCIA slots in the active management module’s
front panel.
After the module boots, the active module compares the standby module’s flash code and
system-config file to its own. If differences exist, the active module synchronizes the standby
module’s flash code and system-config file with its own.
Switchover implications
After the role of the active management module switches from one module to another, you must be
aware of implications that affect the following areas:
• Management sessions
• Syslog and SNMP traps
• MAC addresses
The following sections explain the implications for these areas.
Management sessions
You can establish management sessions with the active management module’s management port.
If a switchover occurs, the management port on the original active module shuts down and all open
CLI, Web management interface, and IronView Network Manager sessions with that port close. You
can open new sessions with the new active module, provided that the new active module has the
same management port connections. (For example, if you were accessing the Web management
interface through a PC connected to the original active module’s management port, you can open a
new session if a PC is connected to the new active module’s management port.)
In the scenario described above, you can open a new session using the same IP address you were
using before the switchover. (You configure an IP address for the active module only; if a switchover
occurs, the IP address is used by the new active module.)
BigIron RX Series Configuration Guide 27
53-1001986-01
Page 100

How management module redundancy works
NOTE
3
Syslog and SNMP traps
When a switchover occurs, the BigIron RX system sends a Syslog message to the local Syslog buffer
and also to the Syslog server, if you have configured the system to use one. In addition, if you have
configured an SNMP trap receiver, the system sends an SNMP trap to the receiver.
When the system is powered on or otherwise reset normally, the system sends a cold start
message and trap. However, if the system is reset as the result of switchover to the standby
management module, the system instead sends a warm start message and trap.
MAC address changes
The MAC addresses in theBigIron RX Series system are based on the MAC address of the BigIron
RX Series chassis. During switchover, the system's MAC addresses change and the system sends
out gratuitous ARP requests to flush the old MAC addresses from the ARP caches on attached IP
devices, and update the caches with the system’s new MAC addresses.
Layer 2 Hitless Failover
The Layer 2 Hitless Failover feature provides automatic failover from the active management
module to the standby management module without interrupting operation of any interface
modules in the chassis. Configuration changes made from the CLI to the active management
module are also written to the standby management module even if they are not written to flash
memory.
Since both the standby and active management modules run the same code, a command that
brings down the active management module will most likely bring down the standby management
module. Because all configuration commands are synchronized from active to standby
management module in real time, both management modules will crash at almost the same time.
This in turn causes the system to reset all interface modules (similar to the behavior when the
'reboot' command is executed) and causes packet loss associated with a system reboot.
Once booted, the redundant management module keeps up-to-date copies of the active module's
running configuration. Layer 2 protocols such as STP, RSTP, MRP, and VSRP are run concurrently on
both the active and standby management modules. Upon the failover of the active management
module, the standby module takes over as the active management module and picks up where the
active module left off, without interrupting any Layer 2 traffic.
The interface modules are not reset, as they are with the previous cold-restart redundancy feature.
The interface modules continue to forward traffic while the standby management module takes
over operation of the system. The new now-active management module receives updates from the
interface modules and sends verification information to the interface modules to ensure that they
are synchronized.
If the new active management module becomes out-of-sync with an interface module, information
on the interface module can be overwritten in some cases which can cause an interruption of
traffic forwarding. Layer 3 hitless failover is not supported in this release. Consequently, a failover
will result in a re-synchronization of Layer 3 data structures
28 BigIron RX Series Configuration Guide
53-1001986-01
 Loading...
Loading...