Cisco CSACSE-1111-K9 - Secure Access Control Server Solution Engine, Secure ACS Solution Engine 4.1 Installation Manual
Page 1

Installation Guide for Cisco Secure ACS
Solution Engine 4.1
Version 4.1
License and Warranty
April 2007
Corporate Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 526-4100
Text Part Number: OL-9969-03
Page 2

CCSP, the Cisco Square Bridge logo, Follow Me Browsing, and StackWise are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn, and iQuick
Study are service marks of Cisco Systems, Inc.; and Access Registrar, Aironet, ASIST, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, Cisco, the Cisco Certified
Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Empowering the Internet Generation,
Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, FormShare, GigaDrive, GigaStack, HomeLink, Internet Quotient, IOS, IP/TV, iQ Expertise, the iQ logo, iQ
Net Readiness Scorecard, LightStream, Linksys, MeetingPlace, MGX, the Networkers logo, Networking Academy, Network Registrar, Pac ket , PIX, Post-Routing, Pre-Routing,
ProConnect, RateMUX, ScriptShare, SlideCast, SMARTnet, StrataView Plus, SwitchProbe, TeleRouter, The Fastest Way to Increase Your Internet Quotient, TransPath, and VCO
are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (0501R)
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant
to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial
environment. This equipment generates, uses, and can radiate radio-frequency energy and, if not installed and used in accordance with the instruction manual, may cause
harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case users will be required
to correct the interference at their own expense.
The following information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it is not
installed in accordance with Cisco’s installation instructions, it may cause interference with radio and television reception. This equipment has been tested and found to
comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These specifications are designed to provide reasonable
protection against such interference in a residential installation. However, there is no guarantee that interference will not occur in a particular installation.
Modifying the equipment without Cisco’s written authorization may result in the equipment no longer complying with FCC requirements for Class A or Class B digital
devices. In that event, your right to use the equipment may be limited by FCC regulations, and you may be required to correct any interference to radio or television
communications at your own expense.
You can determine whether your equipment is causing interference by turning it off. If the interference stops, it was probably caused by the Cisco equipment or one of its
peripheral devices. If the equipment causes interference to radio or television reception, try to correct the interference by using one or more of the following measures:
• Turn the television or radio antenna until the interference stops.
• Move the equipment to one side or the other of the television or radio.
• Move the equipment farther away from the television or radio.
• Plug the equipment into an outlet that is on a different circuit from the television or radio. (That is, make certain the equipment and the television or radio are on circuits
controlled by different circuit breakers or fuses.)
Modifications to this product not authorized by Cisco Systems, Inc. could void the FCC approval and negate your authority to operate the product.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
IMPLIED, INCLUDING, WITHOUT
Installation Guide for Cisco Secure ACS Solution Engine 4.1
© 2003–2007 Cisco Systems, Inc. All rights reserved
Page 3

Preface ix
Audience ix
Organization ix
Conventions ix
Warning Definition x
Documentation Updates 1-xiv
Product Documentation xv
Related Documentation xvi
Obtaining Documentation xvi
Cisco.com xvi
Product Documentation DVD xvi
Ordering Documentation xvii
CONTENTS
CHAPTER
Documentation Feedback xvii
Cisco Product Security Overview xvii
Reporting Security Problems in Cisco Products xvii
Product Alerts and Field Notices xviii
Obtaining Technical Assistance xviii
Cisco Technical Support & Documentation Website xviii
Submitting a Service Request xix
Definitions of Service Request Severity xx
Obtaining Additional Publications and Information xx
Cisco 90-Day Limited Hardware Warranty Terms xxiii
1 Cisco Secure ACS Solution Engine Overview 1-1
System Description 1-1
ACS SE Hardware Description 1-2
Serial Port 1-2
Solution Engine Specifications for the Cisco 1113 1-3
Front Panel Features for the Cisco 1113 1-3
Back Panel Features for the Cisco 1113 1-5
Serial Port 1-6
Ethernet Connectors 1-7
Network Cable Requirements 1-7
78-xxxxx-xx
Book Title
iii
Page 4

Contents
CHAPTER
2 Preparing for Installation 2-1
Safety 2-1
Warnings and Cautions 2-1
General Precautions 2-4
Maintaining Safety with Electricity 2-4
Protecting Against Electrostatic Discharge 2-5
Preventing EMI 2-5
Preparing Your Site for Installation 2-6
Environmental 2-6
Choosing a Site for Installation 2-6
Grounding the System 2-6
Creating a Safe Environment 2-7
AC Power 2-7
Cabling 2-7
Precautions for Rack-Mounting 2-8
Precautions for Products with Modems, Telecommunications, or Local Area Network Options 2-8
Required Tools and Equipment 2-9
CHAPTER
CHAPTER
3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1 3-1
Installation Quick Reference 3-1
Installing the Cisco 1113 in a Rack 3-2
Attaching the Chassis Rail Mount 3-3
Attaching the Server Rail 3-6
Sliding Chassis On the Rack 3-8
Connecting to the AC Power Source 3-9
Connecting Cables 3-10
Initial Configuration 3-10
Establishing a Serial Console Connection 3-10
Configuring ACS SE 3-11
Verifying the Initial Configuration 3-15
Setting Up a GUI Administrator Account 3-16
Next Steps 3-17
4 Administering Cisco Secure ACS Solution Engine 4-1
Basic Command Line Administration Tasks 4-1
Logging In to the Solution Engine From a Serial Console 4-2
Shutting Down the Solution Engine From a Serial Console 4-2
Logging Off the Solution Engine From a Serial Console 4-3
Book Title
iv
78-xxxxx-xx
Page 5

Rebooting the Solution Engine From a Serial Console 4-3
Determining the Status of Solution Engine System and Services From a Serial Console 4-3
Tracing Routes 4-4
Stopping Solution Engine Services From a Serial Console 4-4
Starting Solution Engine Services From a Serial Console 4-5
Restarting Solution Engine Services From a Serial Console 4-6
Getting Command Help From the Serial Console 4-7
Working with System Data 4-8
Obtaining Support Logs From the Serial Console 4-9
Exporting Logs 4-10
Exporting a List of Groups 4-11
Exporting a List of Users 4-12
Backing Up ACS Data From the Serial Console 4-12
Restoring ACS Data From the Serial Console 4-14
Reconfiguring Solution Engine System Parameters 4-15
Resetting the Solution Engine Administrator Password 4-15
Resetting the Solution Engine CLI Administrator Name 4-16
Setting the GUI Administrator Logon and Password 4-17
Resetting the Solution Engine Database Password 4-18
Reconfiguring the Solution Engine IP Address 4-18
Setting the System Time and Date Manually 4-20
Setting the System Time and Date with NTP 4-20
Setting the System Timeout 4-21
Setting the Solution Engine System Domain 4-22
Setting the Solution Engine System Hostname 4-22
Contents
Patch Rollback 4-23
Removing Installed Patches 4-23
Understanding the CSAgent Patch 4-23
Recovery Management 4-24
Recovering from Loss of Administrator Credentials 4-24
Re-imaging the Solution Engine Hard Drive 4-25
CHAPTER
5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1 5-1
Upgrade Scenarios 5-1
Migration Scenarios 5-2
Upgrade Paths 5-2
Upgrade Procedure 5-4
Performing a Full Upgrade From ACS SE 4.0.1 to ACS SE 4.1 5-4
Performing a Full Upgrade from ACS SE 3.3.3 to ACS SE 4.1 5-8
78-xxxxx-xx
Book Title
v
Page 6

Contents
Migrating from ACS for Windows to ACS SE 5-13
Migrating ACS SE on the ACS 1111 or ACS 1112 Platform to ACS SE 4.1 on the Cisco 1113 Platform 5-15
APPENDIX
APPENDIX
APPENDIX
A Technical Specifications for the Cisco 1113 A-1
B Windows Service Advisement B-1
Services That are Run B-1
Services That Are Not Run B-2
C Command Reference C-1
CLI Conventions C-1
Command Privileges C-1
Checking Command Syntax C-2
System Help C-2
Command Description Conventions C-3
Commands C-3
add guiadmin C-3
backup C-3
download C-4
exit C-4
exportgroups C-5
exportlogs C-5
exportusers C-6
help C-6
ntpsync C-7
lock guiadmin C-7
ping C-7
reboot C-9
restart C-9
restore C-10
rollback C-11
set admin C-11
set dbpassword C-11
set domain C-12
set hostname C-12
set ip C-12
set password C-13
set time C-13
Book Title
vi
78-xxxxx-xx
Page 7

set timeout C-14
show C-14
shutdown C-14
start C-15
stop C-15
support C-16
tracert C-16
unlock guiadmin C-18
upgrade C-18
Contents
78-xxxxx-xx
Book Title
vii
Page 8

Contents
Book Title
viii
78-xxxxx-xx
Page 9

Audience
Preface
This guide describes how to install and initially configure the Cisco Secure ACS Solution Engine (ACS
SE), and includes upgrade and migration information for the Cisco 1111, Cisco 1112, and Cisco 1113
platforms. It also details administrative functions that you can perform from the command line interface.
This guide covers the CSACSE-1113-K9 hardware platform for the Cisco Secure ACS SE—also referred
to as the Cisco 1113 version.
This guide is intended for system administrators who install and configure internetworking equipment
and are familiar with Cisco IOS software.
Warning
Only trained and qualified personnel should install, replace, or service this equipment.
Organization
This guide contains:
• Preface
• Chapter 1, “Cisco Secure ACS Solution Engine Overview”
• Chapter 2, “Preparing for Installation”
• Chapter 3, “Installing and Configuring Cisco Secure ACS Solution Engine 4.1”
• Chapter 4, “Administering Cisco Secure ACS Solution Engine”
• Chapter 5, “Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1”
• Appendix A, “Technical Specifications for the Cisco 1113”
• Appendix B, “Windows Service Advisement”
• Appendix C, “Command Reference”
Conventions
This document uses the following conventions:
Item Convention
Commands and keywords boldface font
Variables for which you supply values italic font
Displayed session and system information
OL-9969-03
screen font
Installation Guide for Cisco Secure ACS Solution Engine 4.1
ix
Page 10

Contents
Item Convention
Information you enter
Variables you enter
Menu items and button names boldface font
Selecting a menu item Option > Network Preferences
Note Means reader take note. Notes contain helpful suggestions or references to material not covered in the
publication.
Caution Means reader be careful. In this situation, you might do something that could result in equipment
damage or loss of data.
Warning Definition
boldface screen font
italic screen font
Warning
Waarschuwing
IMPORTANT SAFETY INSTRUCTIONS
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you
work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar
with standard practices for preventing accidents. To see translations of the warnings that appear in
this publication, refer to the translated safety warnings that accompanied this device.
Note: SAVE THESE INSTRUCTIONS
Note: This documentation is to be used in conjunction with the specific product installation guide
that shipped with the product. Please refer to the Installation Guide, Configuration Guide, or other
enclosed additional documentation for further details.
BELANGRIJKE VEILIGHEIDSINSTRUCTIES
Dit waarschuwingssymbool betekent gevaar. U verkeert in een situatie die lichamelijk letsel kan
veroorzaken. Voordat u aan enige apparatuur gaat werken, dient u zich bewust te zijn van de bij
elektrische schakelingen betrokken risico's en dient u op de hoogte te zijn van de standaard
praktijken om ongelukken te voorkomen. Voor een vertaling van de waarschuwingen die in deze
publicatie verschijnen, dient u de vertaalde veiligheidswaarschuwingen te raadplegen die bij dit
apparaat worden geleverd.
Opmerking BEWAAR DEZE INSTRUCTIES.
Opmerking Deze documentatie dient gebruikt te worden in combinatie met de
installatiehandleiding voor het specifieke product die bij het product wordt geleverd. Raadpleeg de
installatiehandleiding, configuratiehandleiding of andere verdere ingesloten documentatie voor
meer informatie.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
x
OL-9969-03
Page 11

Contents
Varoitus
Attention
TÄRKEITÄ TURVALLISUUTEEN LIITTYVIÄ OHJEITA
Tämä varoitusmerkki merkitsee vaaraa. Olet tilanteessa, joka voi johtaa ruumiinvammaan. Ennen
kuin työskentelet minkään laitteiston parissa, ota selvää sähkökytkentöihin liittyvistä vaaroista ja
tavanomaisista onnettomuuksien ehkäisykeinoista. Tässä asiakirjassa esitettyjen varoitusten
käännökset löydät laitteen mukana toimitetuista ohjeista.
Huomautus SÄILYTÄ NÄMÄ OHJEET
Huomautus Tämä asiakirja on tarkoitettu käytettäväksi yhdessä tuotteen mukana tulleen
asennusoppaan kanssa. Katso lisätietoja asennusoppaasta, kokoonpano-oppaasta ja muista
mukana toimitetuista asiakirjoista.
IMPORTANTES INFORMATIONS DE SÉCURITÉ
Ce symbole d'avertissement indique un danger. Vous vous trouvez dans une situation pouvant causer
des blessures ou des dommages corporels. Avant de travailler sur un équipement, soyez conscient
des dangers posés par les circuits électriques et familiarisez-vous avec les procédures couramment
utilisées pour éviter les accidents. Pour prendre connaissance des traductions d'avertissements
figurant dans cette publication, consultez les consignes de sécurité traduites qui accompagnent cet
appareil.
Remarque CONSERVEZ CES INFORMATIONS
Remarque Cette documentation doit être utilisée avec le guide spécifique d'installation du produit
qui accompagne ce dernier. Veuillez vous reporter au Guide d'installation, au Guide de
configuration, ou à toute autre documentation jointe pour de plus amples renseignements.
Warnung
WICHTIGE SICHERHEITSANWEISUNGEN
Dieses Warnsymbol bedeutet Gefahr. Sie befinden sich in einer Situation, die zu einer
Körperverletzung führen könnte. Bevor Sie mit der Arbeit an irgendeinem Gerät beginnen, seien Sie
sich der mit elektrischen Stromkreisen verbundenen Gefahren und der Standardpraktiken zur
Vermeidung von Unfällen bewusst. Übersetzungen der in dieser Veröffentlichung enthaltenen
Warnhinweise sind im Lieferumfang des Geräts enthalten.
Hinweis BEWAHREN SIE DIESE SICHERHEITSANWEISUNGEN AUF
Hinweis Dieses Handbuch ist zum Gebrauch in Verbindung mit dem Installationshandbuch für Ihr
Gerät bestimmt, das dem Gerät beiliegt. Entnehmen Sie bitte alle weiteren Informationen dem
Handbuch (Installations- oder Konfigurationshandbuch o. Ä.) für Ihr spezifisches Gerät.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xi
Page 12

Contents
Avvertenza
Advarsel
IMPORTANTI ISTRUZIONI SULLA SICUREZZA
Questo simbolo di avvertenza indica un pericolo. La situazione potrebbe causare infortuni alle
persone. Prima di intervenire su qualsiasi apparecchiatura, occorre essere al corrente dei pericoli
relativi ai circuiti elettrici e conoscere le procedure standard per la prevenzione di incidenti. Per le
traduzioni delle avvertenze riportate in questo documento, vedere le avvertenze di sicurezza che
accompagnano questo dispositivo.
Nota CONSERVARE QUESTE ISTRUZIONI
Nota La presente documentazione va usata congiuntamente alla guida di installazione specifica
spedita con il prodotto. Per maggiori informazioni, consultare la Guida all'installazione, la Guida
alla configurazione o altra documentazione acclusa.
VIKTIGE SIKKERHETSINSTRUKSJONER
Dette varselssymbolet betyr fare. Du befinner deg i en situasjon som kan forårsake personskade.
Før du utfører arbeid med utstyret, bør du være oppmerksom på farene som er forbundet med
elektriske kretssystemer, og du bør være kjent med vanlig praksis for å unngå ulykker. For å se
oversettelser av advarslene i denne publikasjonen, se de oversatte sikkerhetsvarslene som følger
med denne enheten.
Merk TA VARE PÅ DISSE INSTRUKSJONENE
Merk Denne dokumentasjonen skal brukes i forbindelse med den spesifikke
installasjonsveiledningen som fulgte med produktet. Vennligst se installasjonsveiledningen,
konfigureringsveiledningen eller annen vedlagt tilleggsdokumentasjon for detaljer.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xii
OL-9969-03
Page 13

Contents
Aviso
¡Advertencia!
INSTRUÇÕES IMPORTANTES DE SEGURANÇA
Este símbolo de aviso significa perigo. O utilizador encontra-se numa situação que poderá ser
causadora de lesões corporais. Antes de iniciar a utilização de qualquer equipamento, tenha em
atenção os perigos envolvidos no manuseamento de circuitos eléctricos e familiarize-se com as
práticas habituais de prevenção de acidentes. Para ver traduções dos avisos incluídos nesta
publicação, consulte os avisos de segurança traduzidos que acompanham este dispositivo.
Nota GUARDE ESTAS INSTRUÇÕES
Nota Esta documentação destina-se a ser utilizada em conjunto com o manual de instalação
incluído com o produto específico. Consulte o manual de instalação, o manual de configuração ou
outra documentação adicional inclusa, para obter mais informações.
INSTRUCCIONES IMPORTANTES DE SEGURIDAD
Este símbolo de aviso indica peligro. Existe riesgo para su integridad física. Antes de manipular
cualquier equipo, considere los riesgos de la corriente eléctrica y familiarícese con los
procedimientos estándar de prevención de accidentes. Vea las traducciones de las advertencias
que acompañan a este dispositivo.
Nota GUARDE ESTAS INSTRUCCIONES
Nota Esta documentación está pensada para ser utilizada con la guía de instalación del producto
que lo acompaña. Si necesita más detalles, consulte la Guía de instalación, la Guía de
configuración o cualquier documentación adicional adjunta.
Varning!
VIKTIGA SÄKERHETSANVISNINGAR
Denna varningssignal signalerar fara. Du befinner dig i en situation som kan leda till personskada.
Innan du utför arbete på någon utrustning måste du vara medveten om farorna med elkretsar och
känna till vanliga förfaranden för att förebygga olyckor. Se översättningarna av de
varningsmeddelanden som finns i denna publikation, och se de översatta säkerhetsvarningarna som
medföljer denna anordning.
OBS! SPARA DESSA ANVISNINGAR
OBS! Denna dokumentation ska användas i samband med den specifika
produktinstallationshandbok som medföljde produkten. Se installationshandboken,
konfigurationshandboken eller annan bifogad ytterligare dokumentation för närmare detaljer.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xiii
Page 14

Contents
Documentation Updates
Ta b l e 1 Updates to Installation Guide for Cisco Secure ACS Solution Engine 4.1
Date Description
12/15/2009 • Updated Solution Engine Specifications for the Cisco 1113
• Updated the table ACS SE Technical Specifications for the Cisco 1113
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xiv
OL-9969-03
Page 15

Product Documentation
Note We sometimes update the printed and electronic documentation after original publication. Therefore,
you should also review the documentation on Cisco.com for any updates.
Table 2 describes the product documentation that is available.
Ta b l e 2 Product Documentation
Document Title Available Formats
Documentation Guide for Cisco Secure ACS
Release 4.1
Release Notes for Cisco Secure ACS Release 4.1 On Cisco.com:
• Shipped with product.
• PDF on the product CD-ROM.
• On Cisco.com at:
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/products_documentation_roadmaps_list.html
Contents
User Guide for Cisco Secure Access Control
Server 4.1
Configuration Guide for Cisco Secure ACS
Release 4.1
Installation Guide for Cisco Secure ACS for
Windows Release 4.1
Installation Guide for Cisco Secure ACS Solution
Engine Release 4.1
Regulatory Compliance and Safety Information
for the Cisco Secure ACS Solution Engine
Release 4.1
Installation and Configuration Guide for Cisco
Secure ACS Remote Agents Release 4.1
Supported and Interoperable Devices and
Software Tables for Cisco Secure ACS Solution
Engine Release 4.1
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/prod_release_notes_list.html
On Cisco.com
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/products_user_guide_list.html
On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/ps2086/
products_installation_and_configuration_guides_list.html
On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/prod_installation_guides_list.html
On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/
ps5338/prod_installation_guides_list.html
• Shipped with product.
• PDF on the product CD-ROM.
• On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/
ps5338/prod_installation_guides_list.html
On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/
ps5338/prod_installation_guides_list.html
On Cisco.com:
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/products_device_support_tables_list.html
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xv
Page 16

Contents
Table 2 Product Documentation (continued)
Document Title Available Formats
Installation and User Guide for Cisco Secure
ACS User-Changeable Passwords
Online Documentation In the ACS HTML interface, click Online Documentation.
Online Help In the ACS HTML interface, online help appears in the right pane when
On Cisco.com at:
http://www.cisco.com/en/US/products/sw/secursw/
ps2086/prod_installation_guides_list.html.html
you are configuring a feature.
Related Documentation
Note We sometimes update the printed and electronic documentation after original publication. Therefore,
you should also review the documentation on Cisco.com for any updates.
A set of white papers about Cisco Secure ACS for Windows is available at:
http://www.cisco.com/en/US/partner/products/sw/secursw/ps2086/prod_white_papers_list.html
Much of the information in these papers is applicable to Cisco Secure ACS Solution Engine.
Obtaining Documentation
Cisco documentation and additional literature are available on Cisco.com. This section explains the
product documentation resources that Cisco offers.
Cisco.com
You can access the most current Cisco documentation at this URL:
http://www.cisco.com/techsupport
You can access the Cisco website at this URL:
http://www.cisco.com
You can access international Cisco websites at this URL:
http://www.cisco.com/public/countries_languages.shtml
Product Documentation DVD
The Product Documentation DVD is created and released regularly. DVDs are available singly or by
subscription. Registered Cisco.com
DOC-DOCDVD= or DOC-DOCDVD=SUB) from Cisco
Store at this URL:
http://www.cisco.com/go/marketplace/docstore
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xvi
users can order a Product Documentation DVD (product number
Marketplace at the Product Documentation
OL-9969-03
Page 17

Ordering Documentation
You must be a registered Cisco.com user to access Cisco Marketplace. Registered users may order
Cisco
documentation at the Product Documentation Store at this URL:
http://www.cisco.com/go/marketplace/docstore
If you do not have a user ID or password, you can register at this URL:
http://tools.cisco.com/RPF/register/register.do
Documentation Feedback
You can provide feedback about Cisco technical documentation on the Cisco Technical Support &
Documentation site area by entering your comments in the feedback form available in every online
document.
Cisco Product Security Overview
Contents
Cisco provides a free online Security Vulnerability Policy portal at this URL:
http://www.cisco.com/en/US/products/products_security_vulnerability_policy.html
From this site, you will find information about how to:
• Report security vulnerabilities in Cisco products
• Obtain assistance with security incidents that involve Cisco products
• Register to receive security information from Cisco
A current list of security advisories, security notices, and security responses for Cisco products is
available at this
http://www.cisco.com/go/psirt
To see security advisories, security notices, and security responses as they are updated in real time, you
can subscribe to the Product Security Incident Response Team Really Simple Syndication (PSIRT RSS)
feed. Information about how to subscribe to the PSIRT RSS feed is found at this
http://www.cisco.com/en/US/products/products_psirt_rss_feed.html
URL:
Reporting Security Problems in Cisco Products
Cisco is committed to delivering secure products. We test our products internally before we release them,
and we strive to correct all vulnerabilities quickly. If you think that you have identified a vulnerability
in a Cisco
product, contact PSIRT:
URL:
• For emergencies only — security-alert@cisco.com
An emergency is either a condition in which a system is under active attack or a condition for which
a severe and urgent security vulnerability should be reported. All other conditions are considered
nonemergencies.
• For nonemergencies — psirt@cisco.com
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xvii
Page 18

Contents
In an emergency, you can also reach PSIRT by telephone:
• 1 877 228-7302
• 1 408 525-6532
Tip We encourage you to use Pretty Good Privacy (PGP) or a compatible product (for example, GnuPG) to
encrypt any sensitive information that you send to Cisco. P SIRT ca n wor k with information that has been
encrypted with PGP versions
Never use a revoked encryption key or an expired encryption key. The correct public key to use in your
correspondence with PSIRT is the one linked in the Contact Summary section of the Security
Vulnerability Policy page at this
http://www.cisco.com/en/US/products/products_security_vulnerability_policy.html
The link on this page has the current PGP key ID in use.
If you do not have or use PGP, contact PSIRT to find other means of encrypting the data before sending
any sensitive material.
2.x through 9.x.
URL:
Product Alerts and Field Notices
Modifications to or updates about Cisco products are announced in Cisco Product Alerts and Cisco Field
Notices. You can receive Cisco Product Alerts and Cisco Field Notices by using the Product Alert Tool
on Cisco.com. This tool enables you to create a profile and choose those products for which you want to
receive information.
To access the Product Alert Tool, you must be a registered Cisco.com user. (To register as a Cisco.com
user, go to this URL:
tool at this URL: https://www.cisco.com/web/siteassets/account/index.html
http://tools.cisco.com/RPF/register/register.do) Registered users can access the
Obtaining Technical Assistance
Cisco Technical Support provides 24-hour-a-day award-winning technical assistance. The
Cisco
Technical Support & Documentation website on Cisco.com features extensive online support
resources. In addition, if you have a valid Cisco
(TAC) engineers provide telephone support. If you do not have a valid Cisco
your reseller.
Cisco Technical Support & Documentation Website
The Cisco Technical Support & Documentation website provides online documents and tools for
troubleshooting and resolving technical issues with Cisco
available 24
http://www.cisco.com/techsupport
hours a day at this URL:
service contract, Cisco Technical Assistance Center
products and technologies. The website is
service contract, contact
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xviii
OL-9969-03
Page 19
Contents
Access to all tools on the Cisco Technical Support & Documentation website requires a Cisco.com
user ID and password. If you have a valid service contract but do not have a user ID or password, you
can register at this
http://tools.cisco.com/RPF/register/register.do
Note Use the Cisco Product Identification Tool to locate your product serial number before submitting a
request for service online or by phone. You can access this tool from the Cisco
Documentation website by clicking the Tools & Resources link, clicking the All Tools (A-Z) tab, and
then choosing Cisco
options: by product ID or model name; by tree view; or, for certain products, by copying and pasting
show command output. Search results show an illustration of your product with the serial number label
location highlighted. Locate the serial number label on your product and record the information before
placing a service call.
Tip Displaying and Searching on Cisco.com
If you suspect that the browser is not refreshing a web page, force the browser to update the web page
by holding down the Ctrl key while pressing F5.
To find technical information, narrow your search to look in technical documentation, not the entire
Cisco.com website. On the Cisco.com home page, click the Advanced Search link under the Search box
and then click the Technical Support & Documentation radio button.
To provide feedback about the Cisco.com website or a particular technical document, click Contacts &
Feedback at the top of any Cisco.com web page.
URL:
Technical Support &
Product Identification Tool from the alphabetical list. This tool offers three search
Submitting a Service Request
Using the online TAC Service Request Tool is the fastest way to open S3 and S4 service requests. (S3 and
S4 service requests are those in which your network is minimally impaired or for which you require
product information.) After you describe your situation, the TAC
recommended solutions. If your issue is not resolved using the recommended resources, your service
request is assigned to a Cisco
http://www.cisco.com/techsupport/servicerequest
For S1 or S2 service requests, or if you do not have Internet access, contact the Cisco TAC by telephone.
(S1 or S2 service requests are those in which your production network is down or severely degraded.)
Cisco
engineers are assigned immediately to S1 and S2 service requests to help keep your business
operations running smoothly.
To open a service request by telephone, use one of the following numbers:
Asia-Pacific: +61 2 8446 7411
Australia: 1 800 805 227
EMEA: +32 2 704 55 55
USA: 1 800 553 2447
For a complete list of Cisco TAC contacts, go to this URL:
http://www.cisco.com/techsupport/contacts
OL-9969-03
Service Request Tool provides
engineer. The TAC Service Request Tool is located at this URL:
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xix
Page 20

Contents
Definitions of Service Request Severity
To ensure that all service requests are reported in a standard format, Cisco has established severity
definitions.
Severity 1 (S1)—An existing network is “down” or there is a critical impact to your business operations.
Yo u a nd C i sco
Severity 2 (S2)—Operation of an existing network is severely degraded, or significant aspects of your
business operations are negatively affected by inadequate performance of Cisco
Cisco
will commit full-time resources during normal business hours to resolve the situation.
Severity 3 (S3)—Operational performance of the network is impaired while most business operations
remain functional. You and Cisco
to satisfactory levels.
Severity 4 (S4)—You require information or assistance with Cisco product capabilities, installation, or
configuration. There is little or no effect on your business operations.
will commit all necessary resources around the clock to resolve the situation.
will commit resources during normal business hours to restore service
Obtaining Additional Publications and Information
products. You and
Information about Cisco products, technologies, and network solutions is available from various online
and printed sources.
• The Cisco Online Subscription Center is the website where you can sign up for a variety of
Cisco
e-mail newsletters and other communications. Create a profile and then select the
subscriptions that you would like to receive. To visit the Cisco Online Subscription Center,
go
to this URL:
http://www.cisco.com/offer/subscribe
• The Cisco Product Quick Reference Guide is a handy, compact reference tool that includes brief
product overviews, key features, sample part numbers, and abbreviated technical specifications for
many Cisco
the latest Cisco channel product offerings. To order and find out more about the Cisco
Reference Guide, go to this URL:
http://www.cisco.com/go/guide
• Cisco Marketplace provides a variety of Cisco books, reference guides, documentation, and logo
merchandise. Visit Cisco
http://www.cisco.com/go/marketplace/
• Cisco Press publishes a wide range of general networking, training, and certification titles. Both new
and experienced users will benefit from these publications. For current Cisco
information, go to Cisco
http://www.ciscopress.com
• Internet Protocol Journal is a quarterly journal published by Cisco Systems for engineering
professionals involved in designing, developing, and operating public and private internets and
intranets. You can access the Internet Protocol Journal at this
products that are sold through channel partners. It is updated twice a year and includes
Product Quick
Marketplace, the company store, at this URL:
Press titles and other
Press at this URL:
URL:
http://www.cisco.com/ipj
• Networking products offered by Cisco Systems, as well as customer support services, can be
obtained at this
http://www.cisco.com/en/US/products/index.html
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xx
URL:
OL-9969-03
Page 21

Contents
• Networking Professionals Connection is an interactive website where networking professionals
share questions, suggestions, and information about networking products and technologies with
Cisco
experts and other networking professionals. Join a discussion at this URL:
http://www.cisco.com/discuss/networking
• “What’s New in Cisco Documentation” is an online publication that provides information about the
latest documentation releases for Cisco products. Updated monthly, this online publication is
organized by product category to direct you quickly to the documentation for your products. You
can view the latest release of “What’s New in Cisco Documentation” at this URL:
http://www.cisco.com/univercd/cc/td/doc/abtunicd/136957.htm
• World-class networking training is available from Cisco. You can view current offerings at
this
URL:
http://www.cisco.com/en/US/learning/index.html
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xxi
Page 22

Contents
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xxii
OL-9969-03
Page 23

Cisco 90-Day Limited Hardware Warranty Terms
There are special terms applicable to your hardware warranty and various services that you can use
during the warranty period. Your formal Warranty Statement, including the warranties and license
agreements applicable to Cisco software, is available on Cisco.com. Follow these steps to access and
download the Cisco Information Packet and your warranty and license agreements from Cisco.com.
1. Launch your browser, and go to this URL:
http://www.cisco.com/univercd/cc/td/doc/es_inpck/cetrans.htm
The Warranties and License Agreements page appears.
2. To read t h e Cisco Information Packet, follow these steps:
a. Click the Information Packet Number field, and make sure that the part number
78-5235-03B0 is highlighted.
b. Select the language in which you would like to read the document.
c. Click Go.
The Cisco Limited Warranty and Software License page from the Information Packet appears.
d. Read the document online, or click the PDF icon to download and print the document in Adobe
Portable Document Format (PDF).
Note You must have Adobe Acrobat Reader to view and print PDF files. You can download
the reader from Adobe’s website: http://www.adobe.com
3. To read translated and localized warranty information about your product, follow these steps:
a. Enter this part number in the Warranty Document Number field:
78-5236-01C0
b. Select the language in which you would like to read the document.
c. Click Go.
The Cisco warranty page appears.
d. Review the document online, or click the PDF icon to download and print the document in
Adobe Portable Document Format (PDF).
You can also contact the Cisco service and support website for assistance:
http://www.cisco.com/public/Support_root.shtml.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xxiii
Page 24
Cisco 90-Day Limited Hardware Warranty Terms
Duration of Hardware Warranty
Ninety (90) days.
Replacement, Repair, or Refund Policy for Hardware
Cisco or its service center will use commercially reasonable efforts to ship a replacement part within ten
(10) working days after receipt of a Return Materials Authorization (RMA) request. Actual delivery
times can vary, depending on the customer location.
Cisco reserves the right to refund the purchase price as its exclusive warranty remedy.
To Receive a Return Materials Authorization (RMA) Number
Contact the company from whom you purchased the product. If you purchased the product directly from
Cisco, contact your Cisco Sales and Service Representative.
Complete the information below, and keep it for reference:
Company product purchased from
Company telephone number
Product model number
Product serial number
Maintenance contract number
Installation Guide for Cisco Secure ACS Solution Engine 4.1
xxiv
OL-9969-03
Page 25

Cisco Secure ACS Solution Engine Overview
System Description
Cisco Secure ACS Solution Engine (ACS SE) is a highly scalable, rack-mounted, dedicated platform that
serves as a high-performance access control server supporting centralized Remote Access Dial-In User
Service (RADIUS) and Terminal Access Controller Access Control System (TACACS+). ACS SE
controls the authentication, authorization, and accounting (AAA) of users accessing corporate resources
through the network.
You use ACS SE to control who can access the network, to authorize what types of network services are
available for particular users or groups of users, and to keep an accounting record of all user actions in
the network. The appliance supports access control and accounting for dial-up access servers, firewalls
and VPNs, Voice-over-IP solutions, content networking, and switched and wireless local area networks
(LANs and WLANs). In addition, you can use the same AAA framework, via TACACS+, to manage
administrative roles and groups and to control how network administrators change, access, and configure
the network internally.
ACS SE provides almost the same set of features and functions as in the Cisco Secure ACS for Windows
Server (the software product) in a dedicated, security hardened, application-specific, appliance
packaging. ACS SE includes additional features specific to operating and managing the ACS appliance.
See Release Notes for Cisco Secure ACS 4.1 for the new features in this release.
To ensure a highly secure posture, ACS SE:
CHAPTER
1
• Runs only the necessary services of the underlying hardened Windows operating system. (See
Appendix B, “Windows Service Advisement,” for details on the hardening.)
• Does not support a keyboard or monitor.
• Does not provide access to its file system.
• Does not allow you to run arbitrary applications on it.
• Allows TCP/IP connections only via the ports necessary for its own operations.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-1
Page 26
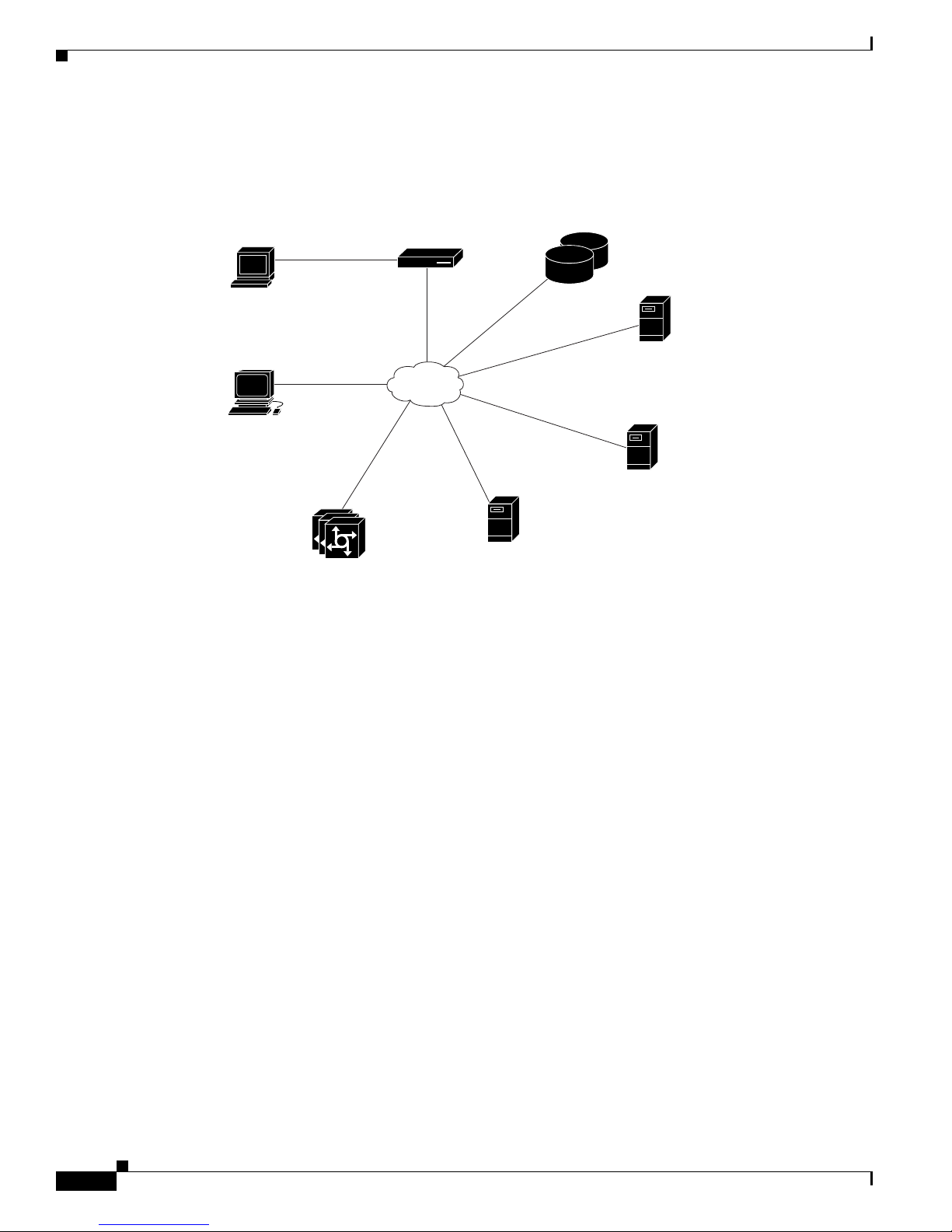
ACS SE Hardware Description
78230
Network
Cisco Secure
ACS Appliance
External User
Database(s)
Serial Port
Connection
HTTPS
Radius or
TACAS+
Encrypted
TCP
Encrypted
TCP
FTP
Administrative
Console
Administrative
HTML Interface
AAA clients
Solaris Server with
Solaris Remote Service
Windows Server with
Windows Remote Service
FTP Server
Figure 1-1 shows the ACS SE operating context.
Figure 1-1 ACS SE Context Diagram
Chapter 1 Cisco Secure ACS Solution Engine Overview
The administrative console in the context diagram represents any data terminal equipment (DTE)
capable of supporting administrative connection via a serial port connection and is generally referred to
as a console in this guide.
For more detailed information on ACS SE features and capabilities, see the User Guide for Cisco Secure
ACS Release 4.1 and the Release Notes for Cisco Secure ACS Solution Engine.
ACS SE Hardware Description
ACS SE is a rack-mountable 1U box. The sections below describe the Cisco 1113 device, which runs on
a Quanta S27 system.
Serial Port
Serial Port Connector
1-2
The integrated serial port on the back panel of the appliance uses a 9-pin, D-subminiature connector.
If you reconfigure your hardware, you may need information regarding the pin number and signal for
the serial port connector.
the pin assignments and interface signals for the serial port connector. (Pin numbering proceeds bottom
to top and right to left, as illustrated.)
Installation Guide for Cisco Secure ACS Solution Engine 4.1
Figure 1-4 illustrates the pin numbers for the serial port connector, and defines
OL-9969-03
Page 27

Chapter 1 Cisco Secure ACS Solution Engine Overview
Solution Engine Specifications for the Cisco 1113
The ACS SE on the Cisco 1113 platform has the following specifications:
• Intel Pentium IV 3.4 GHz/800FSB/2M KB CPU
• Broadcom 5721J Ethernet network interface card
• 80-GB or more ATA hard drive
• QSI DVD-ROM drive
• Serial port
• 1 GB DDRII 667 unbuffered memory
• DVD-Combo drive
• 345 W power supply
Technical specifications are detailed in Appendix A, “Technical Specifications for the Cisco 1113.”
This section contains:
• Front Panel Features for the Cisco 1113, page 1-3
• Back Panel Features for the Cisco 1113, page 1-5
ACS SE Hardware Description
• Serial Port, page 1-2
• Ethernet Connectors, page 1-7
• Network Cable Requirements, page 1-7
Front Panel Features for the Cisco 1113
The Cisco 1113 front panel contains switches, indicators, and the CD-ROM drive. Figure 1-2 shows the
front panel switches and LED indicators. The functions of the switches and LED indicators are described
in the table below the illustration.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-3
Page 28
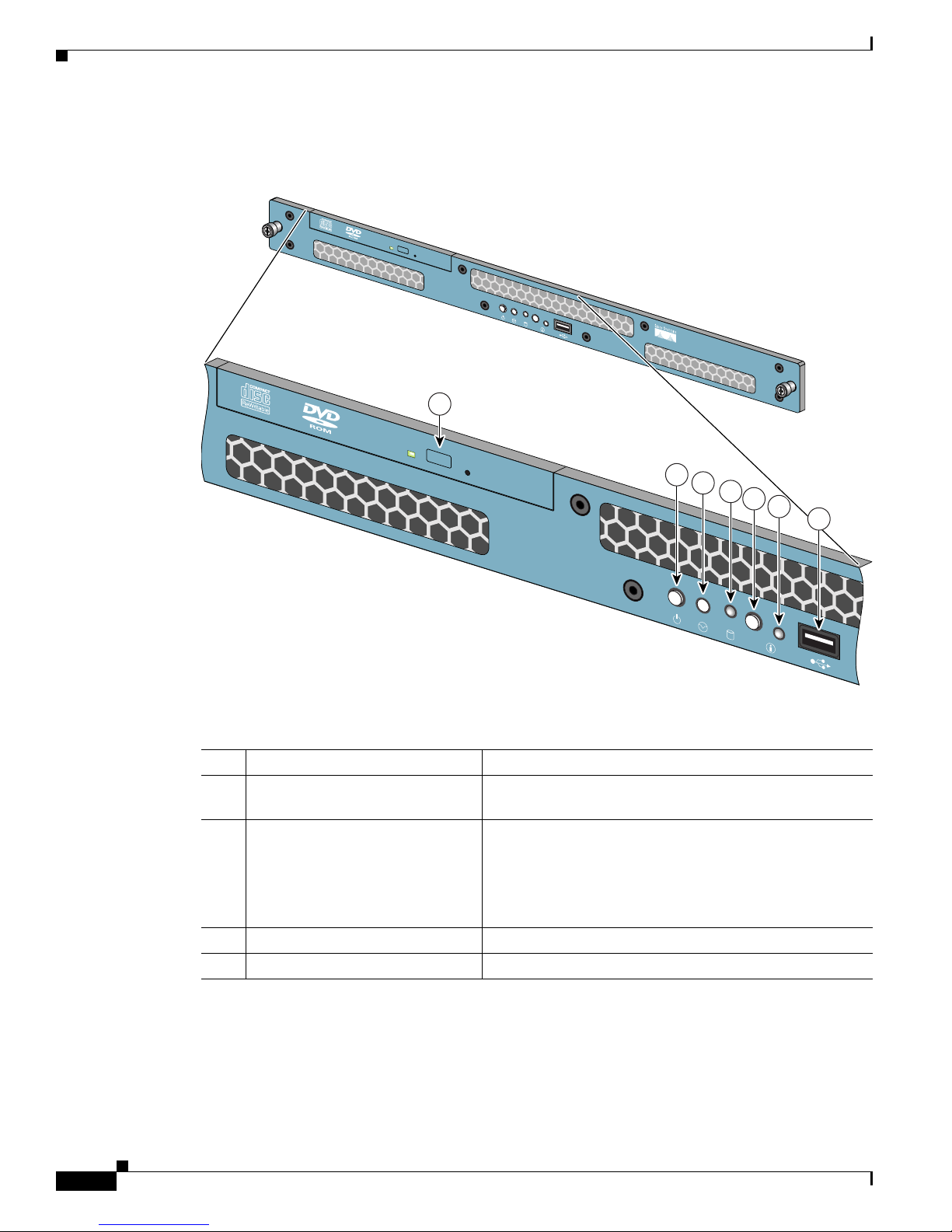
ACS SE Hardware Description
149998
1
2
3
4
5
6
CISC
O 1190
BUILDING BR
OADBA
ND SERVICE M
ANAG
ER
7
Figure 1-2 Front Panel Switches and Indicators for the Cisco 1113
Chapter 1 Cisco Secure ACS Solution Engine Overview
The following table describes the callouts in Figure 1-2.
No. Switch or LED Indicator Description
1 DVD-ROM drive activity LED On = Activity
Off = No Activity
2 Power On/Off button and LED Pushing the power button turns the unit on or off. The LED
in the center of the power On/Off button has three states:
Blinking Green = Power is connected but not on
Green = Power On
Off = Power Off
3 Unused button This button is not operational.
4 HDD LED Indicates that there is activity on the hard drive.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-4
OL-9969-03
Page 29
Chapter 1 Cisco Secure ACS Solution Engine Overview
No. Switch or LED Indicator Description
5 Unit Identification Button To enable the Unit Identification LED, push the Unit
6 Unit Identification LED The Unit Identification LED has the following states:
ACS SE Hardware Description
Identification Button.
When the Unit identification button is on, the Unit
Identification LEDs on the front and back panels flash
blue. This enables you to go behind the unit and look at the
flashing blue light on the back You can turn off the flashing
LED on the back of the unit off by pressing the Unit
Identification button on the back panel.
To turn off the Unit Identification LED, when the LED is
on, push the Unit Identification Button.
Off = System power is off, the system ID button has not
been pushed, and there is no fault assertion condition (the
system cover is on the device and there is no fault
condition).
Flashing Blue = When the system ID button is pushed, the
Unit Identification LED flashes blue if the system is in
either standby mode or system power is on.
Solid Blue = System power is on, the system cover is on the
device, and there is no fault assertion condition. The
system ID button has not been pushed.
7 USB port (not supported) Universal Serial Bus port. Do not use.
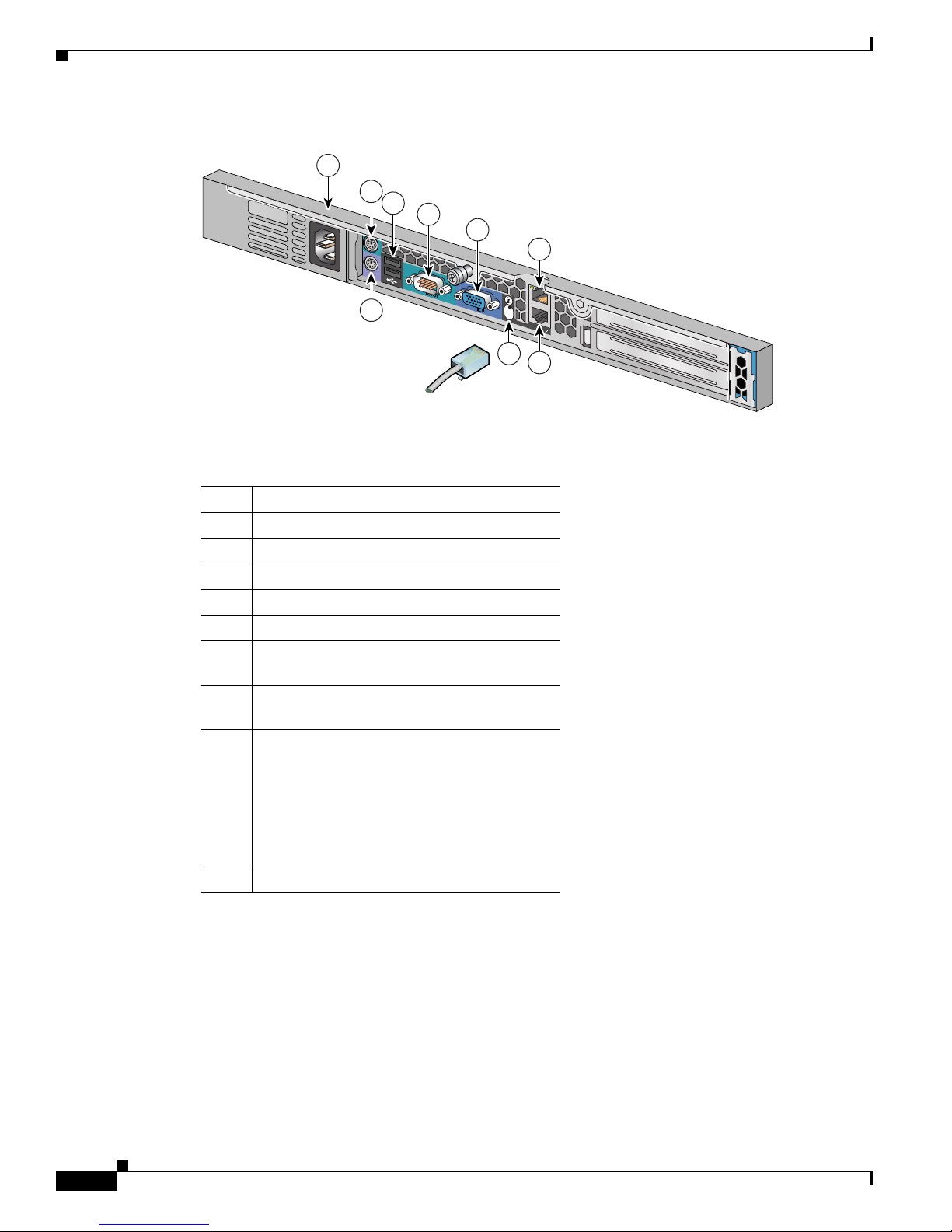
Back Panel Features for the Cisco 1113
The back panel for the Cisco 1113 contains the AC power receptacle, Ethernet connectors, indicator
LEDs, and a serial port.
Figure 1-3 shows the back-panel features.
Flashing Amber = The system is on standby power, there
is a fault assertion condition (for example, the cover has
been removed from the device), and the system ID button
has not been pushed.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-5
Page 30
ACS SE Hardware Description
149999
1
2
2
1
Gb
1
9
8
7
2
3
4
5
6
Figure 1-3 Back Panel Features for the Cisco 1113
The following table describes the callouts in Figure 1-3.
Chapter 1 Cisco Secure ACS Solution Engine Overview
Serial Port
No. Description
1 AC power receptacle
2 Mouse connector (not supported). Do not use.
3 USB connectors (not supported). Do not use.
4 Serial connector (see Figure 1-3)
5 Video connector (not supported). Do not use.
6 RJ-45 Fast Ethernet connector with
10/100/1000-Mbit/s operation for NIC 2
7 RJ-45 Fast Ethernet connector with
10/100/1000-Mbit/s operation for NIC 1
8 Unit Identification Button and LED. When the
Unit Identification Button on the front panel is
pressed, this causes the Unit Identification
Button on the back panel to flash blue. To turn
off the Unit Identification indicator on the
back panel, push the Unit Identification
button.
9 Keyboard connector
The integrated serial port on the back panel of the appliance uses a 9-pin, D-subminiature connector.
Serial Port Connector
If you reconfigure your hardware, you may need information regarding the pin number and signal for
the serial port connector.
the pin assignments and interface signals for the serial port connector. (Pin numbering proceeds bottom
to top and right to left, as illustrated.)
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-6
Figure 1-4 illustrates the pin numbers for the serial port connector, and defines
OL-9969-03
Page 31

Chapter 1 Cisco Secure ACS Solution Engine Overview
Serial
port
1
5
6
9
78229
Figure 1-4 Pin Numbers for the Serial Port Connector
Pin Signal I/O Definition
1 DCD I Data carrier detect
2 SIN I Serial input
3 SOUT O Serial output
4 DTR O Data terminal ready
5 GND N/A Signal ground
6 DSR I Data set ready
7 RTS O Request to send
8 CTS I Clear to send
9 RI I Ring indicator
Shell N/A N/A Chassis ground
ACS SE Hardware Description
Ethernet Connectors
Your Cisco 1113 system has two integrated 10/100/1000-megabit-per-second (Mbps) Ethernet
connectors. ACS SE supports the operation of either Ethernet connector, but not both connectors. Each
Ethernet connector provides all the functions of a network expansion card and supports the 10BASE-T,
100BASE-TX, and 1000BASE-TX Ethernet standards.
Each NIC is configured to automatically detect the speed and duplex mode of the network.
Network Cable Requirements
Warning
To avoid electric shock, do not connect safety extra-low voltage (SELV) circuits to
telephone-network voltage (TNV) circuits. LAN ports contain SELV circuits, and WAN ports contain
TNV circuits. Some LAN and WAN ports both use RJ-45 connectors. Use caution when connecting
cables.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-7
Page 32

ACS SE Hardware Description
The Ethernet connectors are designed for attaching an unshielded twisted pair (UTP) Ethernet cable
equipped with standard RJ-45 compatible plugs. Press one end of the UTP cable into the Ethernet
connector until the plug snaps securely into place. Connect the other end of the cable to an RJ-45 port
on a hub or other device, depending on your network configuration. Observe the following cabling
restrictions for 10BASE-T, 100BASE-TX, and 1000BASE-TX networks:
• For 10BASE-T networks, use Category 3 or greater wiring and connectors.
• For 100BASE-TX and 1000BASE-TX networks, use Category 5 or greater wiring and connectors.
• The maximum cable run length is 328 feet (ft) or 100 meters (m).
Chapter 1 Cisco Secure ACS Solution Engine Overview
Installation Guide for Cisco Secure ACS Solution Engine 4.1
1-8
OL-9969-03
Page 33

Safety
CHAPTER
2
Preparing for Installation
This chapter describes the safety instructions and site requirements for installing Cisco Secure ACS
Solution Engine (ACS SE) 4.1, and guides you through installation preparation. It contains:
• Safety, page 2-1
• Preparing Your Site for Installation, page 2-6
• Precautions for Rack-Mounting, page 2-8
• Required Tools and Equipment, page 2-9
This section provides safety information for installing this product.
Warnings and Cautions
Read the installation instructions in this document before you connect the system to its power source.
Failure to read and follow these guidelines could lead to an unsuccessful installation, and possibly
damage the system and components.
You should observe the following safety guidelines when working with any equipment that connects to
electrical power or telephone wiring. They can help you avoid injuring yourself or damaging the ACS
SE.
Note The English warnings in this document are followed by a statement number. To see the translations of a
warning into other languages, look up its statement number in the Regulatory Compliance and Safety
Information for the Cisco Secure ACS Solution Engine.
The following warnings and cautions are provided to help you prevent injury to yourself or damage to
the devices:
Warning
IMPORTANT SAFETY INSTRUCTIONS
This warning symbol means danger. You are in a situation that could cause bodily injury. Before you
work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar
with standard practices for preventing accidents. Use the statement number provided at the end of
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-1
Page 34

Safety
Chapter 2 Preparing for Installation
each warning to locate its translation in the translated safety warnings that accompanied this device.
Statement 1071
SAVE THESE INSTRUCTIONS
Warning
Warning
Warning
Warning
Warning
Warning
Read the installation instructions before you connect the system to its power source.
The device is designed to work with TN power systems.
Statement 19
Statement 10
Before working on a chassis or working near power supplies, unplug the power cord on AC units.
Statement 246
Do not work on the system or connect or disconnect cables during periods of lightning activity.
Statement 1001
This product relies on the building’s installation for short-circuit (overcurrent) protection. Ensure that
the protective device is rated not greater than: 120 VAC, 15A (U.S./CAN); 240 VAC, 10A
(INTERNATIONAL)
Statement 1005
To prevent bodily injury when mounting or servicing this unit in a rack, you must take special
precautions to ensure that the system remains stable. The following guidelines are provided to
ensure your safety:
2-2
• This unit should be mounted at the bottom of the rack if it is the only unit in the rack.
• When mounting this unit in a partially filled rack, load the rack from the bottom to the top with the heaviest
component at the bottom of the rack.
• If the rack is provided with stabilizing devices, install the stabilizers before mounting or servicing the unit in
Warning
the rack.
There is the danger of explosion if the battery is replaced incorrectly. Replace the battery only with
Statement 1006
the same or equivalent type recommended by the manufacturer. Dispose of used batteries according
to the manufacturer’s instructions.
Warning
This unit is intended for installation in restricted access areas. A restricted access area can be
accessed only through the use of a special tool, lock and key, or other means of security.
Statement 1017
Installation Guide for Cisco Secure ACS Solution Engine 4.1
Statement 1015
OL-9969-03
Page 35

Chapter 2 Preparing for Installation
Safety
Warning
Warning
Warning
Warning
Warning
The plug-socket combination must be accessible at all times, because it serves as the main
disconnecting device.
Statement 1019
To avoid electric shock, do not connect safety extra-low voltage (SELV) circuits to telephone-network
voltage (TNV) circuits. LAN ports contain SELV circuits, and WAN ports contain TNV circuits. Some
LAN and WAN ports both use RJ-45 connectors. Use caution when connecting cables.
Statement 1021
This equipment must be grounded. Never defeat the ground conductor or operate the equipment in the
absence of a suitably installed ground conductor. Contact the appropriate electrical inspection
authority or an electrician if you are uncertain that suitable grounding is available.
Statement 1024
This unit might have more than one power supply connection. All connections must be removed to
de-energize the unit.
Statement 1028
Blank faceplates and cover panels serve three important functions: they prevent exposure to
hazardous voltages and currents inside the chassis; they contain electromagnetic interference (EMI)
that might disrupt other equipment; and they direct the flow of cooling air through the chassis. Do not
operate the system unless all cards, faceplates, front covers, and rear covers are in place.
Statement
1029
Warning
Warning
Warning
Only trained and qualified personnel should be allowed to install, replace, or service this equipment.
Statement 1030
Ultimate disposal of this product should be handled according to all national laws and regulations.
Statement 1040
Installation of the equipment must comply with local and national electrical codes.
Statement 1074
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-3
Page 36

Safety
General Precautions
Observe the following general precautions when using and working with your system:
• Keep your system components away from radiators and heat sources, and do not block cooling vents.
• Do not spill food or liquids on your system components, and never operate the product in a wet
environment. If the computer gets wet, see the appropriate chapter in your troubleshooting guide or
contact the Cisco Technical Assistance Center. For instructions on contacting the Technical
Assistance Center, see
• Do not push any objects into the openings of your system components. Doing so can cause fire or
electric shock by shorting out interior components.
• Position system cables and power cables carefully; route system cables and the power cable and plug
so that no one will step on or trip over them. Be certain that nothing rests on your system
components’ cables or power cable.
• Do not modify power cables or plugs. Consult a licensed electrician or your power company for site
modifications. Always follow your local and national wiring regulations.
• To help avoid possible damage to the system board, wait 5 seconds after turning off the system
before removing a component from the system board or disconnecting a peripheral device from the
computer.
Chapter 2 Preparing for Installation
Obtaining Technical Assistance, page xviii, in the Preface.
Maintaining Safety with Electricity
Follow these guidelines when working on equipment powered by electricity:
• If any of the following conditions occurs, contact the Cisco Technical Assistance Center:
–
The power cable or plug is damaged.
–
An object has fallen into the product.
–
The product has been exposed to water.
–
The product has been dropped or damaged.
–
The product does not operate correctly when you follow the operating instructions.
• Use the correct external power source. Operate the product only from the type of power source
indicated on the electrical ratings label. If you are not certain of the type of power source required,
consult the Cisco Technical Assistance Center or a local power company.
• Use only approved power cable(s). You have been provided with a power cable for your ACS SE
that is intended for your system (approved for use in your country, based on the shipping location).
Should you have to purchase a power cable, ensure that it is rated for the product and for the voltage
and current marked on the product’s electrical ratings label. The voltage and current rating of the
cable should be greater than the ratings marked on the product.
• To help prevent electric shock, plug the ACS SE, components, and peripheral power cables into
properly grounded electrical outlets. These cables are equipped with three-prong plugs to help
ensure proper grounding. Do not use adapter plugs or remove the grounding prong from a cable.
• Observe power strip ratings. Ensure that the total ampere rating of all products plugged into the
power strip does not exceed 80% of the rating.
• To help protect your system and components from sudden, transient increases and decreases in
electrical power, use a surge suppressor, line conditioner, or uninterruptable power supply (UPS).
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-4
OL-9969-03
Page 37

Chapter 2 Preparing for Installation
• Do not modify power cables or plugs. Consult a licensed electrician or your power company for site
modifications. Always follow your local and national wiring regulations.
Protecting Against Electrostatic Discharge
Static electricity can harm delicate components inside your computer. To prevent static damage,
discharge static electricity from your body before you touch any of your computer’s electronic
components, such as the microprocessor. You can do so by touching an unpainted metal surface on the
computer chassis.
As you continue to work inside the computer, periodically touch an unpainted metal surface to remove
any static charge that your body may have accumulated.
You can also take the following steps to prevent damage from electrostatic discharge (ESD):
• When unpacking a static-sensitive component from its shipping carton, do not remove the
component from the antistatic packing material until you are ready to install the component in your
computer. Just before unwrapping the antistatic packaging, ensure that you discharge static
electricity from your body.
• When transporting a sensitive component, first place it in an antistatic container or packaging.
Safety
• Handle all sensitive components in a static-safe area. If possible, use antistatic floor pads and
Preventing EMI
When you run wires for any significant distance in an electromagnetic field, electromagnetic
interference (EMI) can occur between the field and the signals on the wires.
Note Bad plant wiring can result in radio frequency interference (RFI).
Note Strong EMI, especially when it is caused by lightning or radio transmitters, can destroy the
To predict and remedy strong EMI, consult RFI experts.
workbench pads.
signal drivers and receivers in the system, and can even create an electrical hazard by conducting
power surges through lines and into the system.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-5
Page 38

Preparing Your Site for Installation
Preparing Your Site for Installation
This section describes the requirements that your site must meet for safe installation and operation of
your ACS SE. Ensure that your site is properly prepared before beginning installation.
Environmental
When planning your site layout and equipment locations, remember the precautions described in this
section to help avoid equipment failures and reduce the possibility of environmentally caused
shutdowns. If you are experiencing shutdowns or unusually high errors with your existing equipment,
these precautions will help you to isolate the cause of failures and prevent future problems.
Use the following precautions when planning the operating environment for your ACS SE:
• Always follow the ESD-prevention procedures described in Preventing EMI, page 2-5, to avoid
damage to equipment. Damage from static discharge can cause immediate or intermittent equipment
failure.
• Ensure that the chassis cover is secure. The chassis allows cooling air to flow effectively within it.
An open chassis allows air leaks, which could interrupt and redirect the flow of cooling air from
internal components.
• Electrical equipment generates heat. Ambient air temperature might not be adequate to cool
equipment to acceptable operating temperatures without adequate circulation. Ensure that the room
in which you operate has adequate air circulation.
Chapter 2 Preparing for Installation
Choosing a Site for Installation
Warning
This unit is intended for installation in restricted access areas. A restricted access area is where
access can only be gained by service personnel through the use of a special tool, lock and key, or
other means of security, and is controlled by the authority responsible for the location.
For optimal installation, choose a site:
• With a dry, clean, well-ventilated and air-conditioned area.
• That maintains an ambient temperature of 10° to 35°C (50° to 95°F).
Grounding the System
Warning
Never defeat the ground conductor or operate the equipment in the absence of a suitably installed
ground conductor. Contact the appropriate electrical inspection authority or an electrician if you are
uncertain that suitable grounding is available.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-6
OL-9969-03
Page 39

Chapter 2 Preparing for Installation
Creating a Safe Environment
Follow these guidelines to create a safe operating environment:
• Keep tools and chassis components off the floor and away from foot traffic.
• Clear the area of possible hazards, such as moist floors, ungrounded power extension cables, and
missing safety grounds.
• Keep the area around the chassis free from dust and foreign conductive material (such as metal
flakes from nearby construction activity).
AC Power
Ensure that the plug-socket combination is accessible at all times, because it serves as the main
disconnecting device. For the ACS SE power requirements, see
for the Cisco 1113.”
Preparing Your Site for Installation
Appendix A, “Technical Specifications
Cabling
Warning
This product requires short-circuit (overcurrent) protection to be provided as part of the building
installation. Install only in accordance with national and local wiring regulations.
Use the cables in the accessory kit to connect the ACS SE console port to a console or computer that is
running a console program. In addition to using the console cable, use the provided standard Ethernet
cable to connect the ACS SE to your network. For information detailing cable requirements, see
Back Panel Features for the Cisco 1113, page 1-5.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-7
Page 40

Precautions for Rack-Mounting
Precautions for Rack-Mounting
Chapter 2 Preparing for Installation
Warning
To prevent bodily injury when mounting or servicing this unit in a rack, you must take special
precautions to ensure that the system remains stable. The following guidelines are provided to
ensure your safety:
Observe the following precautions for rack stability and safety. Also refer to the rack installation
documentation accompanying the rack for specific warning and caution statements and procedures.
Note Component refers to any server, storage system, or appliance, and to various peripherals or
supporting hardware.
• Do not move large racks by yourself. Due to the height and weight of the rack, a minimum of two
people are needed to accomplish this task.
• Ensure that the rack is level and stable before extending a component from the rack.
• Do not overload the AC supply branch circuit that provides power to the rack. The total rack load
should not exceed 80% of the branch circuit rating.
• Ensure that proper airflow is provided to components in the rack.
• Do not step or stand on any system or component when servicing other systems and components
in a rack.
• This unit should be mounted at the bottom of the rack if it is the only unit in the rack.
• When mounting this unit in a partially filled rack, load the rack from the bottom to the top with the
heaviest component at the bottom of the rack.
• If the rack is provided with stabilizing devices, install the stabilizers before mounting or servicing
the unit in the rack.
Precautions for Products with Modems, Telecommunications,
or Local Area Network Options
When working with options:
• Do not connect or use a modem or telephone during a lighting storm. Electrical shock from lightning
can result.
• Never connect or use a modem or telephone in a wet environment.
• Do not plug a modem or telephone cable into the Ethernet connector.
• Disconnect the modem cable before opening a product enclosure, touching or installing internal
components, or touching an uninsulated modem cable or jack.
• Do not use a telephone line to report a gas leak while you are in the vicinity of the leak.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-8
OL-9969-03
Page 41

Chapter 2 Preparing for Installation
Required Tools and Equipment
You need the following tools and equipment to install the ACS SE:
• Number 2 Phillips-head screwdriver
• Tape measure and level
• Antistatic mat or antistatic foam
• ESD grounding strap
Required Tools and Equipment
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-9
Page 42

Required Tools and Equipment
Chapter 2 Preparing for Installation
Installation Guide for Cisco Secure ACS Solution Engine 4.1
2-10
OL-9969-03
Page 43

CHAPTER
3
Installing and Configuring Cisco Secure ACS
Solution Engine 4.1
This chapter describes how to install and initially configure Cisco Secure ACS Solution Engine (ACS
SE) 4.1. It contains:
• Installation Quick Reference, page 3-1
• Installing the Cisco 1113 in a Rack, page 3-2
• Connecting to the AC Power Source, page 3-9
• Connecting Cables, page 3-10
• Initial Configuration, page 3-10
• Verifying the Initial Configuration, page 3-15
• Next Steps, page 3-17
Note The details in this guide correspond to the CSACSE-1113-K9 platform only.
Installation Quick Reference
Table 3-1 provides a high-level overview of the installation and initial configuration process. Following
installation and initial configuration, see the User Guide for Cisco Secure ACS for information on how
to use a browser and the web interface to fully configure your ACS SE to provide the AAA services that
you want from this installation.
Ta b l e 3-1 Quick Reference
Task References
Use the rack mount kit to install the
ACS SE in a rack.
Connect the ACS SE to an AC power
source.
Connect network and console cables. Connecting Cables, page 3-10
Perform initial configuration of the
ACS SE
Installing the Cisco 1113 in a Rack,
page 3-2
Connecting to the AC Power Source,
page 3-9
Configuring ACS SE, page 3-11
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-1
Page 44

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Installing the Cisco 1113 in a Rack
Table 3-1 Quick Reference (continued)
Task References
Verify initial configuration Verifying the Initial Configuration,
page 3-15
Configure ACS SE to provide AAA
Next Steps, page 3-17
services
Installing the Cisco 1113 in a Rack
Before installing the Cisco 1113 in a rack, read Preparing Your Site for Installation, page 2-6 to
familiarize yourself with the proper site and environmental conditions. Failure to read and follow these
guidelines could lead to an unsuccessful installation and possible damage to the system and components.
Perform the steps below when installing and servicing the Cisco Secure ACS SE.
The rack must be properly secured to the floor, to the ceiling or upper wall, and where applicable, to
adjacent racks. The rack should be secured using floor and wall fasteners and bracing specified or
approved by the rack manufacturer or by industry standards.
Warning
When installing and servicing the ACS SE:
• Disconnect all power and external cables before installing the system.
• Install the system in compliance with your local and national electrical codes:
–
United States: National Fire Protection Association (NFPA) 70; United States National
Electrical Code.
–
Canada: Canadian Electrical Code, Part, I, CSA C22.1.
–
Other countries: If local and national electrical codes are not available, see IEC 364, Part 1
through Part 7.
• Do not work alone under potentially hazardous conditions.
• Do not perform any action that creates a potential hazard to people or makes the equipment unsafe.
• Do not attempt to install the ACS SE in a rack that has not been securely anchored in place. Damage
to the system and personal injury may result.
• Due to the size and weight of the computer system, never attempt to install the computer system by
yourself.
See Precautions for Rack-Mounting, page 2-8 for additional safety information on rack installation.
To prevent bodily injury when mounting or servicing this unit in a rack, you must take special
precautions to ensure that the system remains stable. The following guidelines are provided to
ensure your safety:
• This unit should be mounted at the bottom of the rack if it is the only unit in the rack.
• When mounting this unit in a partially filled rack, load the rack from the bottom to the top with the heaviest
component at the bottom of the rack.
• If the rack is provided with stabilizing devices, install the stabilizers before mounting or servicing the unit in
the rack.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-2
OL-9969-03
Page 45

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
1
2
3 4 5
The server can be installed in a system 1U rack. The rack rail components are as follows (numbers in
parentheses refer to
• 2 telescopic rails (1, 2)
• Bag containing:
–
8 Round head screws with washer (3)
–
2 Round head screws (4)
–
10 Cage nuts (5)
Figure 3-1 Rack Rail Components
Figure 3-1):
Installing the Cisco 1113 in a Rack
To install the Cisco 1113 in a rack:
1. Attach the chassis rail mount to the chassis (see Attaching the Chassis Rail Mount, page 3-3).
2. Attach the server rail to the rack assembly (see Attaching the Server Rail, page 3-6).
3. Slide the chassis on to the rack assembly (see Sliding Chassis On the Rack, page 3-8).
Attaching the Chassis Rail Mount
You must first remove the chassis rail mount section from the server rail and attach it to the chassis.
To attach the chassis rail mount:
Step 1 See Figure 3-2. Extend the server rail as far as it will go. When fully extended, the server rail locks into
the extended position.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-3
Page 46

Installing the Cisco 1113 in a Rack
1
2
3
154629
1
154625
Figure 3-2 Removing the Chassis Rail Mount
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Step 2 See Figure 3-3. Slide the white tab (1) in the direction of its arrow and slide out the chassis rail mount
part. (Set it aside for attaching to the chassis in the next step.)
Figure 3-3 Sliding the Chassis Rail Mount Release Tab
Step 3 Align the holes in the chassis rail mount to the pegs on the chassis (1 and 2 in Figure 3-4).
3-4
Installation Guide for Cisco Secure ACS Solution Engine 4.1
OL-9969-03
Page 47

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
1
2
154621
1
1
2
Figure 3-4 Positioning Chassis Rail Mount on Chassis
Step 4 See Figure 3-5. Align the holes (1) and then slide the rail until it locks into place (2).
Figure 3-5 Attaching Chassis Rail Mount to Chassis
Installing the Cisco 1113 in a Rack
Figure 3-6 shows the chassis rail mount locked into place.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-5
Page 48

Installing the Cisco 1113 in a Rack
2
154620
1
Figure 3-6 Chassis Rail Mount in Locked Position
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Attaching the Server Rail
Now that you have mounted the chassis rail mount, retract the server rail that you previously extended
and then attach it to the rack. If you have already retracted the server rail, go to step 2.
Procedure
Step 1 To retract the arm of the server rail, push the tab shown in Figure 3-7. Then slide the arm back in.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-6
OL-9969-03
Page 49

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
1
154617
Figure 3-7 Retracting the Server Rail
Installing the Cisco 1113 in a Rack
Step 2 Attach the server rail to the rack as shown in the figure that corresponds to your rack:
–
For a square-peg rack, see Figure 3-8.
–
For a circular-peg rack, see Figure 3-9.
Figure 3-8 Attaching Rail to a Square-Peg Rack
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-7
Page 50

Installing the Cisco 1113 in a Rack
Figure 3-9 Attaching Rail to a Circular-Peg Rack
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Step 3 Repeat this process with the other rail and rack assembly.
Note Leaving some play between the bracket and the rail until you install the rail into the rack will
make affixing the rail to the rack easier. After the rail is attached to the rack, you can tighten the
screws.
Sliding Chassis On the Rack
Step 1 See Figure 3-10. On the chassis rail mount, slide and hold the purple tab in the direction of the arrow.
This allows the chassis rail mount to slide on to the rail.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-8
OL-9969-03
Page 51

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
1
154628
154624
Figure 3-10 Sliding the Chassis Rail Mount Extended Tab
Step 2 Insert the chassis in the rack. See Figure 3-11.
Figure 3-11 Sliding Chassis onto Rack
Connecting to the AC Power Source
Slide the chassis back and forth several times. Fasten with all the screws.
Warning
This product relies on the building’s installation for short-circuit (overcurrent)
you use a fuse or circuit breaker no larger than 120 VAC, 15A (U.S./CAN); 240 VAC, 10A (INTERNATIONAL).
Statement 1005
Connecting to the AC Power Source
Warning
OL-9969-03
This equipment must be grounded. Never defeat the ground conductor or
absence of a suitably installed ground conductor.
or an electrician if you are uncertain that suitable grounding is available.
Connect the AC power receptacle to the AC power source with the provided power cable.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
protection. Ensure that
operate the equipment in the
Contact the appropriate electrical inspection authority
Statement 1024
3-9
Page 52

Connecting Cables
Connecting Cables
Use unshielded twisted-pair (UTP,) copper-wire Ethernet cable, with standard RJ-45-compatible plugs,
to connect the ACS SE to the network.
To connect the cables:
Step 1 Plug the network connection into the Ethernet 0 port (NIC 1). See Figure 1-3 on page 1-6 for the location
of the Ethernet 0 port.
Step 2 Connect a console to the console or serial port using the supplied serial cable and, if necessary, the
DB-9-to-RJ-45 console adapter. See
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Figure 1-3 on page 1-6 for the location of the serial port.
Warning
Do not work on the system or connect or disconnect cables during periods of lightning activity.
Initial Configuration
The first three steps of the four steps required to configure the ACS are documented in this manual:
• Establishing a Serial Console Connection, page 3-10
• Configuring ACS SE, page 3-11
• Verifying the Initial Configuration, page 3-15
Note You perform the fourth and final part of the configuration, which includes providing AAA services by
establishing administrative and user accounts and configuring network connections, from the web
interface. See User Guide for Cisco Secure ACS for more information.
Establishing a Serial Console Connection
Before you can perform the initial configuration of ACS SE, you must establish a serial console
connection to it. This procedure requires a PC, two DB-9 to RJ-45 adapters (provided), an RJ-45 cable
(provided), and terminal emulation communication software (Hyper Terminal or equivalent).
To establish a serial console connection:
Note If you performed the procedure in Connecting Cables, page 3-10, you can skip to Step 2.
Step 1 Connect a console to the serial console port on the back panel:
a. Attach a DB-9 to RJ-45 adapter (provided) to the serial port of the console.
b. Attach a DB-9 to RJ-45 adapter (provided) to the serial port of the ACS SE. For the location of the
serial port, see
c. Use an RJ-45 cable (provided) to connect the console to the ACS SE.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-10
Figure 1-3 on page 1-6.
OL-9969-03
Page 53

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Tip You may also use a serial concentrator connection, if desired.
Step 2 Power on ACS SE and the console, and open your terminal emulation communication software on the
console.
Tip See Figure 1-2 on page 1-4 for the location of the power switch on the ACS SE.
Step 3 Set your terminal emulation communication software to operate with the following settings:
• Baud = 115200
• Databits = 8
• Parity = N
• Stops = 1
• Flow control = None
• Terminal emulation type = ANSI
Initial Configuration
Result: The login: prompt appears.
Configuring ACS SE
You must configure the ACS SE when you boot the system for the first time, and whenever you re-image
the system.
Before you begin to configure the solution engine, you should have the following information:
• Network hostname of the solution engine.
• DNS domain name.
• Administrator name and password.
• Database password.
• Whether you will enable DHCP (enabling DHCP is not recommended).
• IP, netmask, and gateway addresses you will assign to the ACS SE.
• Whether you will be using NTP synchronization and, if yes, the address of the NTP server.
To configure the ACS SE:
Step 1 Establish a serial console connection to the ACS SE; for details see Establishing a Serial Console
Connection, page 3-10.
Note If the ACS SE is not configured (that is, it is new or has been re-imaged) the system displays the
system information, including the software version.
Step 2 Confirm that the following information appears above the login: prompt:
Cisco Secure ACS: [version number]
Appliance Management Software: [version number]
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-11
Page 54

Initial Configuration
Note If this information does not appear and only the login prompt appears, you must reboot the appliance
Step 3 At the login: prompt, type Administrator and then press Enter.
Note When you boot the system for the first time, it is not configured. You must log in as CLI administrator
Step 4 At the password: prompt, type setup and press Enter.
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Appliance Base Image: [version number]
CSA build [version number]: (Patch: [version number])
Status: Appliance is functioning properly
The ACS Appliance has not been configured.
Logon as “Administrator” with password “setup” to configure appliance.
and then log in.
to configure the system.
Result: The system displays the password: prompt.
Note The password is case sensitive.
Result: The system displays the following message on the console:
Initialize Appliance.
Machine will be rebooted after initialization.
Entering Ctrl-C before setting appliance name will shutdown the appliance
Step 5 At the ACS Appliance name [deliverance1]: prompt, type the name that you intend to use for your
ACS SE, and then press Enter.
Tip The name can contain up to 15 letters and numbers, but no spaces.
Result: The system displays the following message on the console:
ACS Appliance name is set to xxx.
Step 6 At the DNS domain [ ]: prompt, type the domain name. Then press Enter.
Result: The system displays the following message on the console:
DNS name is set to xxx.com.
You need to set the administrator account name and password.
Step 7 At the Enter new account name: prompt, type the ACS SE administrator account name, and then press
Enter.
Tip There is only one ACS SE CLI administrator account at a given time. This account allows access
only through a serial cable and CLI commands. The account’s credentials can be changed. For
more information see Chapter 4, “Resetting the Solution Engine Administrator Password.”
Step 8 At the Enter new password: prompt, type the new ACS SE password and press Enter.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-12
OL-9969-03
Page 55

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Note The new password must contain a minimum of 6 characters, and include a mix of at least three
character types (uppercase letters, lowercase letters, digits, and special characters). Each of the
following examples is acceptable: 1PaSsWoRd, *password44, Pass*word. The password cannot
contain the account name.
Step 9 At the Enter new password again: prompt, type the new ACS SE password, and then press Enter.
Result: The system displays the following message on the console:
Password is set successfully.
Administrator name is set to xxx.
Step 10 The following prompt appears for the new database password:
Please enter the Encryption Password for the Configuration Store.
Please note this is different from the administrator account,
it is used to encrypt the Database.
Type the new database password and press Enter.
Initial Configuration
Note The new password must contain a minimum of 6 characters, and it must include a mix of at least
three character types (uppercase letters, lowercase letters, digits, and special characters). Each
of the following examples is acceptable: 1PaSsWoRd, *password44, Pass*word.
Step 11 At the Enter new password again: prompt, type the new database password, and then press Enter.
Result: The system displays the following message on the console:
Password is set successfully.
Step 12 At the Would you like to add GUI Administrator now?: prompt, type y for yes or n for no, and press
Enter.
Note If you do not enter y or n and press enter, the default value is (yes) is used.
Step 13 If you entered y, complete these steps:
a. When the Enter new GUI administrator name: prompt appears, enter the new GUI administrator
name.
The following prompt appears:
Enter new password:
b. Enter the new password.
Note The password can only contain a maximum of 32 characters and a minimum of 4 characters.
The following prompt appears:
Enter new password again:
c. Enter the new password again.
Result: The console displays:
GUI Administrator added successfully.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-13
Page 56

Initial Configuration
Step 14 At the Use Static IP Address [Yes]: prompt, type Y for yes or N for No, and then press Enter.
Step 15 The following prompts appear only if you set a static IP address manually. Otherwise the following
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
For more information on the GUI administrator account, see Setting Up a GUI Administrator Account,
page 3-16.
Note To set or change the IP address of your ACS SE, it must be connected to a working Ethernet
connection.
Note A static IP address must be assigned to your ACS SE. You can set the IP address directly by
answering Y to this step and performing the substeps detailed in
use a DHCP address if it assigns a single IP address that does not change.
message appears:
No change to the configuration.
Accept network setting [Yes]
a. To specify the ACS SE IP address, at the IP Address [xx.xx.xx.xx]: prompt, type the IP address,
and then press Enter.
b. At the Subnet Mask [xx.xx.xx.xx]: prompt, type the subnet mask value, and then press Enter.
c. At the Default Gateway [xx.xx.xx.xx]: prompt, type the default gateway value, and then press
Enter.
Step 15. Alternatively, you may
d. At the DNS Servers [xx.xx.xx.xx]: prompt, type the address of any DNS servers that you intend
to use (separate each by a single space), and then press Enter.
Note If you do not intend to use a DNS server, enter the IP address of the ACS SE at the DNS
Servers [xx.xx.xx.xx]:
prompt. If you do not configure the ACS SE to use a DNS server,
you must respond to all prompts for hostname or IP address only with an IP address.
Result: The system displays the new configuration information followed by this message:
IP Address is reconfigured.
e. At the prompt, Confirm the changes? [Yes]: type Y, and then press Enter.
Result: The system displays the following message:
New ip address is set.
Default gateway is set to xx.xx.xx.xx
DNS servers are set to: xx.xx.xx.xx xx.xx.xx.xx.
f. At the prompt, Test network connectivity [Yes]:, type y or Y, and then press Enter.
Tip This step is essentially executing a ping command to ensure the connectivity of the ACS SE.
g. At the prompt, Enter hostname or IP address:, type the IP address or hostname of a device
connected to the ACS SE, and then press Enter.
Result: If successful, the system displays the ping statistics. The system displays the prompt: Test
network connectivity [Yes]:.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-14
OL-9969-03
Page 57

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
h. If network connectivity is validated in the previous two steps, at the prompt, Test network
connectivity [Yes]:
Tip The system continues to provide you with the opportunity to test network connectivity until you
, type n or N, and then press Enter.
answer no. This means that you can correct network connections or retype the IP address.
Step 16 If the settings appear correctly, at the prompt, Accept network setting [Yes]:, type y or Y, and then
press Enter.
Result: The system displays the following message on the console:
Current Date Time Setting:
Time Zone: (GMT -xx:xx) XXX Time
Date and Time: mm/dd/yyyy
NTP Server(s): NTP Synchronization Disabled.
Step 17 To set the time and date of the ACS SE, at the Change Date & Time Setting [N]: prompt, type Y, and
then press Enter.
Result: The system displays a numbered list of time zones.
Step 18 At the Enter desired time zone index (0 for more choices): prompt, type the index number of
the time zone that you want, and then press Enter.
Result: The system displays the new time zone.
Step 19 At the Synchronize with NTP server? [N]: prompt, do one of the following:
Initial Configuration
• To set the time manually, type N, and then press Enter.
• To use an NTP server for setting time, type Y, and when prompted enter the IP address of the NTP
server that you want.
Tip Only if you select to use an NTP server can you subsequently use the ntpsync command.
Result: The system displays a confirmation message reflecting your choice.
Step 20 At the Enter date [mm/dd/yyyy]: prompt, type the date in the given format, and then press Enter.
Step 21 At the Enter time [hh:mm:ss]: prompt, type the current time in the given format, and then press Enter.
Result: The system displays the following message on the console:
Initial configuration is successful. Appliance will now reboot.
The system reboots.
Verifying the Initial Configuration
To verify that you have correctly completed the ACS SE initial configuration:
Before You Begin
Establish a serial console connection to the ACS SE. For details, see Establishing a Serial Console
Connection, page 3-10.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-15
Page 58

Initial Configuration
Step 1 Reboot the ACS SE. For more information, see Rebooting the Solution Engine From a Serial Console,
page 4-3.
Result: When the systems finish booting, a login: prompt appears on the console.
Step 2 At the login: prompt, type the new administrator name, and press Enter.
Result: The password prompt appears.
Step 3 At the password: prompt, enter the password you created during initial configuration.
Result: The system prompt appears.
Step 4 At the system prompt, type show, and then press Enter.
Result: The system displays status information.
Step 5 Verify the displayed information.
Setting Up a GUI Administrator Account
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
After initial installation or re-imaging, unless you specified a GUI administrator account during the
initial configuration using the setup script, only one administrator account exists: the CLI administrator
account. This account allows access only through a serial console log in and CLI commands.
If you specified a GUI administrator account when prompted for one by the setup script, a GUI
administrator account exists. However, before the designated GUI administrator user can use this
account, you must unlock it by entering the unlock guiadmin command.
You can also set up an additional GUI administrator account that can access the SE.
To set up an initial web GUI account:
Step 1 Log in as the CLI administrator.
Step 2 If a GUI administrator account was specified during initial configuration using the setup script, enter the
unlock guiadmin command to unlock the GUI administrator account:
unlock guiadmin <Admin> <Password>
where Admin is the name of the GUI administrator account and Password is the password for the account.
Step 3 If no GUI administrator account has been set up or you want to add additional GUI administrator
accounts, at the command prompt, enter:
add guiadmin
Result: The console displays:
Adding new GUI Administrator
Note! All ACS services will be restarted.
GUI Administrator password policy is:
Password must be at least 4 character(s) long.
Step 4 At the Enter new GUI administrator name: prompt, enter the new GUI administrator name, and
press
Enter.
Step 5 At the Enter new password: prompt, enter the new password, and press Enter.
Note The password can only contain a maximum of 32 characters and a minimum of 4 characters.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-16
OL-9969-03
Page 59

Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Step 6 At the Enter new password again: prompt, enter the new password again, and press Enter.
Result: The console displays:
GUI Administrator added successfully.
Note The new GUI administrator account is not usable until you unlock it by entering the unlock guiadmin
command.
Now, you can now use the GUI administrator account to remotely access the ACS GUI running on the
ACS SE.
Next Steps
After you have successfully performed the procedures in this guide, your ACS SE is installed and
initially configured. The next step is to log in using the GUI administrator account and use a browser
and the web interface to fully configure your ACS SE to provide the AAA services that you want from
this installation. The HTML address is in the following format: http://<ip address>:2002, where ip
address is the address that you assign during configuration.
For information on setting up user, group, network, and other parameters, see the User Guide for Cisco
Secure ACS.
Initial Configuration
Note The ACS Solution Engine automatically creates an entry called Self in the AAA Servers Table. This entry
identifies the Solution Engine machine.
However, in the Proxy Distribution Table and the AAA Server Table for RDMS synchronization, the
ACS Solution Engine creates an entry for the hostname of the device that is running the ACS Solution
Engine.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-17
Page 60

Initial Configuration
Chapter 3 Installing and Configuring Cisco Secure ACS Solution Engine 4.1
Installation Guide for Cisco Secure ACS Solution Engine 4.1
3-18
OL-9969-03
Page 61

CHAPTER
4
Administering Cisco Secure ACS Solution Engine
This section describes the major Cisco Secure ACS Solution Engine (ACS SE) system administration
tasks that you can perform by using the command line interface (CLI) in the serial console connection.
For all other ACS SE configuration and administration tasks, that is, those performed from the ACS web
interface, see the User Guide for Cisco Secure Access Control Server.
Serial console service starts automatically when the ACS SE boots and prompts the user to log in.
Successful login launches a command line application (shell) that operates the CLI.
This section contains:
• Basic Command Line Administration Tasks, page 4-1
• Working with System Data, page 4-8
• Reconfiguring Solution Engine System Parameters, page 4-15
• Patch Rollback, page 4-23
• Recovery Management, page 4-24
Basic Command Line Administration Tasks
This section details basic administrative tasks performed from a serial console connected to the ACS SE.
This section contains:
• Logging In to the Solution Engine From a Serial Console, page 4-2
• Shutting Down the Solution Engine From a Serial Console, page 4-2
• Logging Off the Solution Engine From a Serial Console, page 4-3
• Rebooting the Solution Engine From a Serial Console, page 4-3
• Determining the Status of Solution Engine System and Services From a Serial Console, page 4-3
• Tracing Routes, page 4-4
• Stopping Solution Engine Services From a Serial Console, page 4-4
• Starting Solution Engine Services From a Serial Console, page 4-5
• Restarting Solution Engine Services From a Serial Console, page 4-6
• Getting Command Help From the Serial Console, page 4-7
Installation Guide for Cisco Secure ACS Solution Engine 4.1
OL-9969-03
4-1
Page 62

Chapter 4 Administering Cisco Secure ACS Solution Engine
Basic Command Line Administration Tasks
Logging In to the Solution Engine From a Serial Console
To log in to the ACS SE from a serial console:
Step 1 Establish a serial console connection to the ACS SE. For details, see Establishing a Serial Console
Connection, page 3-10.
Step 2 At the login: prompt, enter the ACS SE administrator name.
Step 3 At the password: prompt, enter the ACS SE password.
Result: The system prompt appears:
ACS SE name
Note Only one set of ACS SE login credentials (administrator name and password) has the serial connection
privilege.
Shutting Down the Solution Engine From a Serial Console
You use the serial console to shut down the ACS SE.
Caution Powering off the ACS SE by using only the power switch may cause the loss or corruption of data.
To use the serial console to shut down the ACS SE:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type shutdown, and then press Enter.
Step 3 At the Are you sure you want to shut down? (Y/N) prompt, type Y for yes and then press Enter.
Result: The ACS SE displays the message:
It is now safe to turn off the computer
Step 4 Press the power switch and hold it down for 4 seconds to turn off the ACS SE. For the location of the
power switch see
Result: The ACS SE powers OFF.
Figure 1-1 on page 1-3.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-2
OL-9969-03
Page 63

Chapter 4 Administering Cisco Secure ACS Solution Engine
Logging Off the Solution Engine From a Serial Console
To log off the ACS SE from the serial console:
Step 1 At the system prompt, type exit.
Step 2 Press Enter.
Result: The serial console connection closes, and the login: prompt reappears.
Rebooting the Solution Engine From a Serial Console
To reboot the ACS SE from the serial console:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Basic Command Line Administration Tasks
Step 2 At the system prompt, enter reboot.
Result: The ACS SE displays the message:
Are you sure you want to reboot? (Y/N)
Step 3 Enter Y for yes.
Result: The ACS SE reboots. When the reboot is finished, the login: prompt reappears.
Determining the Status of Solution Engine System and Services From a Serial
Console
You can use the serial console connection to obtain system and service status information.
Note You typically perform status determination in the ACS SE web interface. For more information, see
“Determining the Status of Cisco Secure ACS Services” in the User Guide for Cisco Secure Access
Control Server.
To determine the status of the ACS SE and ACS Services:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type show, and then press Enter.
Result: The system displays the following status information:
ACS SE Name
ACS SE Version
Appliance Management Software Version
Appliance Base Image Version
CSA build XXXX: (Patch: x_x_x_xxx)
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-3
Page 64

Basic Command Line Administration Tasks
Session Timeout (in minutes)
Last Reboot Time
Current Date & Time
Time Zone
NTP Server(s)
CPU Load (percentage)
Free Disk (amount of hard drive space available)
Free Physical Memory
Appliance IP Configuration
DHCP Enabled (Yes/No)
IP Address
Subnet Mask
Default Gateway
DNS Servers
ACS Services (running/stopped)
CSAdmin
CSAgent
CSAuth
CSDbSync
CSLog
CSMon
CSRadius
CSTacacs
Chapter 4 Administering Cisco Secure ACS Solution Engine
Tracing Routes
If you are unfamiliar with the trace route command or want information on the command’s optional
arguments, see the Command Reference entry
tracert, page C-16.
To trace the network route that the ACS SE takes to a given destination:
Step 1 At the system prompt, type tracert, followed by zero (0) or more optional arguments, and then the IP
address of the target destination.
Step 2 Press Enter.
Result: The system displays the route tracing information followed by the message:
Trace complete
Stopping Solution Engine Services From a Serial Console
Note You typically stop solution engine services in the web interface.
You can stop any of the ACS SE services from the serial console. The ACS SE services include:
• CSAdmin
• CSAgent
• CSAuth
• CSDbSync
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-4
OL-9969-03
Page 65

Chapter 4 Administering Cisco Secure ACS Solution Engine
• CSLog
• CSMon
• CSRadius
• CSTacacs
Tip To list the services and their status, you can use the show command. For more information, see
Determining the Status of Solution Engine System and Services From a Serial Console,
page 4-3.
Note When you stop the CSAgent service, that service remains disabled until you explicitly start it again. That
is, if you stop the CSAgent service it does not automatically restart when the system is rebooted.
To stop a service on the ACS SE:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Basic Command Line Administration Tasks
Step 2 Type stop followed by a single space and the name of the ACS service that you want to stop.
Tip You can list more than one service to stop; type a single space between each.
Step 3 Press Enter.
Result: The system immediately displays the message:
[service name] is stopping. . .
Followed by the message:
[service name] is not running
Starting Solution Engine Services From a Serial Console
Note You typically start solution engine services in the web interface.
You can start any of the ACS services from the serial console. The ACS SE services include:
• CSAdmin
• CSAgent
• CSAuth
• CSDbSync
• CSLog
• CSMon
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-5
Page 66

Basic Command Line Administration Tasks
• CSRadius
• CSTacacs
Tip To list the services and their status, you can use the show command. For more information, see
Determining the Status of Solution Engine System and Services From a Serial Console,
page 4-3.
To start an ACS service:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type start followed by a single space and the name of the ACS service that you want to start.
Tip You can list more than one service to start; type a single space between each.
Step 3 Press Enter.
Chapter 4 Administering Cisco Secure ACS Solution Engine
Result: The system immediately displays the message:
[service name] is starting. . .
Followed by the message:
[service name] is running
Restarting Solution Engine Services From a Serial Console
Note You typically restart solution engine services in the web interface.
You can restart any ACS SE service from the serial console. ACS SE services include:
• CSAdmin
• CSAgent
• CSAuth
• CSDbSync
• CSLog
• CSMon
• CSRadius
• CSTacacs
Tip To list the services and their status, you can use the show command. For more information, see
Determining the Status of Solution Engine System and Services From a Serial Console,
page 4-3.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-6
OL-9969-03
Page 67

Chapter 4 Administering Cisco Secure ACS Solution Engine
To restart an ACS service:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type restart followed by a single space and the name of the ACS service that you want to restart.
Tip You can list more than one service to restart; type a single space between each.
Step 3 Press Enter.
Result: The system immediately displays the message:
service name is stopping. . .
Followed by the messages:
service name is not running
service name is starting
service name is running
Basic Command Line Administration Tasks
Getting Command Help From the Serial Console
To obtain a list and description of commands on the ACS SE from the serial console:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type help, and then press Enter.
Tip Press Enter again to scroll through the list of commands, as necessary.
Result: The ACS SE displays the list of commands and their descriptions, as shown in Table 4-1.
Ta b l e 4-1 ACS SE Commands
Command Description
? List commands
add-guiadmin Adds a GUI account that allows access to the SE
using the ACS web GUI.
backup Backup Appliance
download Download ACS Install Package
exit Log off
exportgroups Export group information to an FTP server
exportlogs Export appliance diagnostic logs to FTP server
exportusers Export user information to an FTP server
help List commands
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-7
Page 68

Working with System Data
Table 4-1 ACS SE Commands (continued)
Chapter 4 Administering Cisco Secure ACS Solution Engine
Command Description
ntpsync Perform Network Time Protocol synchronization
ping Verify connections to remote computers
reboot Soft reboot appliance
restart Restart ACS services
restore Restore Appliance
rollback Rollback patched package
set admin Set administrator's name
set dbpassword Set database password
set domain Set DNS domain
set hostname Set appliance's hostname
set ip Set IP configuration
set password Set administrator's password
set time Set timezone, enable NTP synch, or set date and
time
set timeout Set the timeout for serial console with no activity
show Show appliance status
shutdown Shut down appliance
start Start ACS services
stop Stop ACS services
support Collect logs, registry, and other useful
information
tracert Determine the route take to a destination
upgrade Upgrade appliance (stage II)
For more information on ACS SE commands, see Appendix C, “Command Reference.”
Working with System Data
This section explains basic data-manipulation tasks performed from a serial console connected to the
ACS SE:
• Obtaining Support Logs From the Serial Console, page 4-9
• Exporting Logs, page 4-10
• Exporting a List of Groups, page 4-11
• Exporting a List of Users, page 4-12
• Backing Up ACS Data From the Serial Console, page 4-12
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-8
OL-9969-03
Page 69

Chapter 4 Administering Cisco Secure ACS Solution Engine
• Restoring ACS Data From the Serial Console, page 4-14
Obtaining Support Logs From the Serial Console
This section details the procedure for running the support tool. The support tool first collects logs,
system Registry information, and other ancillary data, and then compresses the collected information
into a single file with the extension .cab. This file can then be sent to support personnel for analysis.
Caution Performing this procedure stops and restarts all services, and will interrupt use of the ACS SE.
Note You typically perform this procedure in the ACS SE web interface.
This procedure uses the support command. For more information on this command, see support,
page C-16. The arguments for the support command include:
Working with System Data
Argument Description
-d n Collect the previous n days logs
-u Collect user database information
server Hostname for the FTP server to which the file is to be sent
filepath Location under the FTP root for the server into which the
package.cab is to be sent
username Account used to authenticate the FTP session
To generate a .cab file of log and system registry information:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type support and the arguments necessary to your purpose.
Step 3 Press Enter.
Step 4 To collect user database information, at the Collect User Data? prompt, type Y and then press Enter.
Step 5 At the Enter FTP Server directory prompt, enter the pathname to the location on your FTP server to
which you want to send the file and then press Enter.
Step 6 At the Collect Previous days logs? prompt, type the number of days for which you want to collect
information (from 1 to 9999) and press Enter.
Step 7 At the Enter FTP Server Hostname or IP address prompt, enter your FTP server hostname or IP
address and press Enter.
Step 8 At the Enter FTP Server Username prompt, enter your FTP server user account name and press Enter.
Caution Performing this next step begins the procedure that stops and restarts all services, and will interrupt use
of the ACS SE.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-9
Page 70

Working with System Data
Step 9 At the Enter FTP Server Password prompt, enter your FTP server password and press Enter.
Step 10 Press Enter.
Exporting Logs
Chapter 4 Administering Cisco Secure ACS Solution Engine
Result: The ACS SE displays a series of messages detailing the writing and dumping of the files, and
the stopping and starting of services. At file transfer conclusion the system displays the following
messages:
Transferring ‘Package.cab’ completed
Press any key to finish.
This message indicates the ACS SE has packaged and transferred the .cab file as specified and restarts
services.
Result: The system returns to the system prompt.
This section details the procedure for exporting ACS SE log files to an FTP server for further
examination and processing. Using the exportlogs command, you can enter the name of the log or logs
to export, or select log names from a list.
Before You Begin
You must have the FTP server address and pathname, as well as the proper credentials for writing to the
FTP server (username and password).
Caution Performing this procedure stops and restarts all services, and will interrupt use of the ACS SE.
To export log files to an FTP server:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type exportlogs logname, where logname is the name of the log you want to export.
Tip You can enter more than one log name and separate each with a space. If you enter no log name,
after you press Enter, the system displays the names of the log files available for export.
Caution Performing this procedure stops and restarts all services, and will interrupt use of the ACS SE.
Step 3 Press Enter.
Step 4 At the prompt, enter the IP address or hostname of the FTP server and press Enter.
Step 5 At the prompt, enter your FTP server username and press Enter.
Step 6 At the prompt, enter your FTP server password and press Enter.
Step 7 At the prompt, enter the FTP server directory pathname and press Enter.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-10
OL-9969-03
Page 71

Chapter 4 Administering Cisco Secure ACS Solution Engine
Result: The ACS SE exports the specified files to the specified location.
Exporting a List of Groups
This section details the procedure for exporting a list of ACS SE user groups to an FTP server for further
examination and processing.
Before You Begin
You must have the FTP server address and pathname, as well as the proper credentials for writing to the
FTP server (username and password).
Caution Performing this procedure stops and restarts the CSAuth service, and will interrupt use of the ACS SE.
To export a user group list to an FTP server:
Working with System Data
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type exportgroups.
Tip You can enter the following parameters after the command or in response to subsequent prompts:
[server] [username] [filepath]
Step 3 Press Enter.
Result: The system displays the message:
Command with restart CSAuth. Are you sure you want to continue?
Caution Performing this procedure stops and restarts the CSAuth service, and will interrupt use of the ACS SE.
Step 4 To proceed, type Y and press Enter.
Step 5 At the Enter FTP Server Hostname or IP Address prompt, enter the FTP server IP address or
hostname and press Enter.
Step 6 At the Directory: prompt, enter the FTP server pathname and press Enter.
Step 7 At the Username: prompt, enter your FTP server username and press Enter.
Step 8 At the Password: prompt, enter your FTP server password and press Enter.
Result: The ACS SE exports the group list file to the specified location. When done the system displays
the message:
Transferring ‘groups.txt’ completed
The system prompt returns.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-11
Page 72

Working with System Data
Exporting a List of Users
This section details the procedure for exporting a list of ACS SE users to an FTP server for further
examination and processing.
Before You Begin
You must have the FTP server address and pathname, as well as the proper credentials for writing to the
FTP server (username and password).
Caution Performing this procedure stops and restarts the CSAuth service, and will interrupt use of the ACS SE.
To export a list of users to an FTP server:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type exportusers.
Chapter 4 Administering Cisco Secure ACS Solution Engine
Tip You can enter the following parameters after the command or in response to subsequent prompts:
[server] [username] [filepath]
Step 3 Press Enter.
Result: The system displays the message:
Command with restart CSAuth. Are you sure you want to continue?
Caution Performing this procedure stops and restarts the CSAuth service, and will interrupt use of the ACS SE.
Step 4 To proceed, type Y and press Enter.
Step 5 At the Enter FTP Server Hostname or IP Address prompt, enter the FTP server IP address or
hostname and press Enter.
Step 6 At the Directory: prompt, enter the FTP server pathname and press Enter.
Step 7 At the Username: prompt, enter your FTP server username and press Enter.
Step 8 At the Password: prompt, enter your FTP server password and press Enter.
Result: ACS SE exports the file of the list of users to the specified location, and then displays the
message:
Transferring ‘users.txt’ completed
The system prompt reappears.
Backing Up ACS Data From the Serial Console
This section details how to use the serial console to back up ACS SE data to an FTP server.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-12
OL-9969-03
Page 73

Chapter 4 Administering Cisco Secure ACS Solution Engine
Note You typically perform this procedure in the web interface.
During backup, AAA services are interrupted, and ACS SE data is packaged and sent in a file to an FTP
server. You may choose to encrypt this file package. For information on how to restore the backup data
to the system, see
Restoring ACS Data From the Serial Console, page 4-14.
Before You Begin
You must have the FTP server address and pathname, as well as the proper credentials for writing to the
FTP server (username and password).
Caution This procedure interrupts the use of the ACS SE for AAA services.
To export ACS SE data to an FTP server:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Working with System Data
Step 2 Type backup.
Tip You can enter the following parameters after the command or in response to subsequent prompts:
[server] [username] [filepath]
Step 3 Press Enter.
Step 4 At the Enter FTP Server Hostname or IP Address: prompt, enter the FTP server IP address or
hostname and press Enter.
Step 5 At the Enter FTP Server Directory: prompt, enter the FTP server pathname and press Enter.
Step 6 At the Enter FTP Server Username: prompt, enter your FTP server username and press Enter.
Step 7 At the Enter FTP Server Password: prompt, enter your FTP server password and press Enter.
Step 8 At the File: prompt, enter the name that you want to give the backup file and then press Enter.
Step 9 At the Encrypt Backup File? (Y or N) prompt, type Y to encrypt the backup file or N not to encrypt
it, and then press Enter.
Caution This procedure interrupts the use of the ACS SE for AAA services.
Step 10 If you previously chose to encrypt the backup file, at the Encryption Enter FTP Server Password:
prompt, type a password and then press Enter.
Result: The ACS SE displays the messages:
Backing up now . . .
All running services will be stopped and restarted automatically.
Are you sure you want to proceed? (y/Y = proceed)
Step 11 To proceed, type Y and press Enter.
Result: The ACS SE exports the backup file to the specified location and displays messages regarding
the progress of the backup.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-13
Page 74

Working with System Data
The following message signifies the completion of the backup process:
Transferring xxx completed.
The system prompt reappears.
Restoring ACS Data From the Serial Console
This section details how to use the serial console to restore ACS SE data from an FTP server after you
perform a backup. For more information on backing up ACS SE data, see
the Serial Console, page 4-12.
Note You typically perform this procedure in the web interface.
Before You Begin
You must have the FTP server address and pathname, as well as the proper credentials for writing to the
FTP server (username and password). You also need the name of the backup file and, if the backup was
encrypted, the decryption password.
Chapter 4 Administering Cisco Secure ACS Solution Engine
Backing Up ACS Data From
Caution This procedure interrupts the use of the ACS SE for AAA services.
Caution This procedure overwrites current system data and replaces it with the backup data.
To restore ACS SE data from an FTP server:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type restore.
Tip You can enter the following parameters after the command or in response to subsequent prompts:
[server] [username] [filepath]
Step 3 Press Enter.
Step 4 At the Enter FTP Server Hostname or IP Address: prompt, enter the FTP server IP address or
hostname and press Enter.
Step 5 At the Enter FTP Server Directory: prompt, enter the FTP server pathname and press Enter.
Step 6 At the Enter FTP Server Username: prompt, enter your FTP server username and press Enter.
Step 7 At the Enter FTP Server Password: prompt, enter your FTP server password and press Enter.
Step 8 At the File: prompt, enter the name of the backup file and then press Enter.
Step 9 At the Select Components to Restore: User and Group Database: prompt, to restore the user and
group database type Y and then press Enter.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-14
OL-9969-03
Page 75

Chapter 4 Administering Cisco Secure ACS Solution Engine
Step 10 At the CiscoSecure ACS System Configuration: (Y or N) prompt, to restore the system configuration
data type Y and then press Enter.
Step 11 At the Decrypt Backup file? (Y or N) prompt, if you previously encrypted the backup file, type Y
and then press Enter.
Step 12 If you previously chose to decrypt the backup file, at the Encryption Password: prompt, type the FTP
password, and then press Enter.
Note The system displays a warning message:
Reloading a system backup will overwrite ALL current configuration information. All
services will be stopped and started automatically
Step 13 At the Are you sure you want to proceed? (Y or N) prompt, type Y and then press Enter.
Result: The ACS SE receives the backup file from the specified location and displays messages
regarding the restoration. You may see warnings about components not included in the backup file. For
example, if ACS SE has no shared profile components configured, you see a message about DCS (device
command sets) not on the backup, which is normal.
When completed the system displays the message:
Done
Reconfiguring Solution Engine System Parameters
Reconfiguring Solution Engine System Parameters
This section details basic reconfiguration tasks performed from a serial console connected the ACS SE.
This section contains:
• Resetting the Solution Engine Administrator Password, page 4-15
• Resetting the Solution Engine CLI Administrator Name, page 4-16
• Resetting the Solution Engine Database Password, page 4-18
• Reconfiguring the Solution Engine IP Address, page 4-18
• Setting the System Time and Date Manually, page 4-20
• Setting the System Time and Date with NTP, page 4-20
• Setting the System Timeout, page 4-21
• Setting the Solution Engine System Domain, page 4-22
• Setting the Solution Engine System Hostname, page 4-22
Resetting the Solution Engine Administrator Password
There is always a single ACS SE administrator username and password that consists of the administrator
name and password. Unlike other ACS administrative accounts, this unique administrative account is
granted all privileges, cannot be deleted, and is not listed in the Administrators table of the
Administrative Control page in the ACS web interface. This account is called the CLI administrator
account and allows access to the SE only through a serial console.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-15
Page 76

Reconfiguring Solution Engine System Parameters
You can reset the ACS SE CLI administrator name, the administrator password, or both. This procedure
details how to reset the password after you log in with the existing credentials. To reset the CLI
administrator name see
If you do not have the existing ACS SE CLI administrator login credentials, you must have the recovery
CD-ROM to reset these credentials. For information on resetting the administrator login and password
without first logging in, see
To reset the ACS SE administrator login credentials:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set password and then press Enter.
Result: The ACS SE displays the prompt:
Enter old password:
Step 3 Type the password, and then press Enter.
Result: The ACS SE displays the prompt:
Enter new account name:
Chapter 4 Administering Cisco Secure ACS Solution Engine
Resetting the Solution Engine CLI Administrator Name, page 4-16.
Recovering from Loss of Administrator Credentials, page 4-24.
Step 4 Type the new account name, and then press Enter.
Result: The ACS SE displays the prompt:
Enter new password
Step 5 Type the new password, and then press Enter.
Note The new password must not contain the administrator account name, must contain a minimum
of 6 characters, and it must include a mix of at least 3 character types (numerals, special
characters, uppercase letters, and lowercase letters). Each of the following examples is
acceptable: 1PaSsWoRd, *password44, Pass*word.
Result: The ACS SE displays the prompt:
Reenter new password
Step 6 Type the new password again, and then press Enter.
Result: The ACS SE displays the prompt:
Password is set successfully.
Administrator account name is set to _____
Resetting the Solution Engine CLI Administrator Name
There is always a single set of ACS SE CLI administrator credentials that consists of the administrator
name and password. Unlike other ACS administrative accounts, this unique administrative account is
granted all privileges, cannot be deleted, and is not listed in the Administrators table of the
Administrative Control page in the ACS web interface.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-16
OL-9969-03
Page 77

Chapter 4 Administering Cisco Secure ACS Solution Engine
You can reset the ACS SE CLI administrator name, the administrator password, or both. This procedure
details how to reset the administrator name after you log in with the existing credentials. To reset the
password, see
Note The CLI administrator logon does not provide access to the ACS SE using the ACS web GUI. You must
Resetting the Solution Engine Administrator Password, page 4-15.
set up an initial web GUI password using the add-guiadmin command. For information on setting up
an initial web GUI account, see Setting the GUI Administrator Logon and Password, page 4-17.
If you do not have the existing ACS SE CLI administrator login credentials, you must have the recovery
CD-ROM to reset these credentials. For information on resetting the administrator login and password
without first logging on, see
To reset the ACS SE CLI administrator name:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, enter:
set admin
Result: The ACS SE displays the Set administrator’s name prompt.
Step 3 Type the new administrator name, and then press Enter.
Reconfiguring Solution Engine System Parameters
Recovering from Loss of Administrator Credentials, page 4-24.
Step 4 At the Set administrator name again prompt, type the administrator name again and then press
Enter.
Result: The system displays the message:
Administrator name is set successfully.
Setting the GUI Administrator Logon and Password
After initial installation of the ACS SE, the only password that exists is the CLI administrator password.
This password allows access only through a serial console logon and CLI commands.
To enable an initial administrator account that can access the ACS SE through the ACS web GUI, you
must set up a GUI administration account using the add-guiadmin command.
To set up an initial web GUI account:
Step 1 Log in as the CLI administrator.
Step 2 At the command prompt, issue the following command:
add-guiadmin <admin> <password>
where admin is the name of the GUI administrator account and password is the password is the password
for the GUI administrator.
There is now a GUI administrator account that a remote user can use to access the ACS GUI running on
the ACS SE.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-17
Page 78

Chapter 4 Administering Cisco Secure ACS Solution Engine
Reconfiguring Solution Engine System Parameters
Resetting the Solution Engine Database Password
You should change the ACS SE database password from time to time, to ensure database security. This
procedure details how to reset the password after you have logged on with the existing credentials.
To reset the ACS SE database password:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set dbpassword and then press Enter.
Result: The ACS SE displays the prompt:
Enter old password:
Step 3 Type the password, and then press Enter.
Result: The ACS SE displays the prompt:
Enter new password
Step 4 Type the new password, and then press Enter.
Note The new password must not contain the administrator account name, must contain a minimum
of 6 characters, and it must include a mix of at least 3 character types (numerals, special
characters, uppercase letters, and lowercase letters). Each of the following examples is
acceptable: 1PaSsWoRd, *password44, Pass*word.
Result: The ACS SE displays the prompt:
Reenter new password
Step 5 Type the new password again, and then press Enter.
Result: The ACS SE displays the prompt:
Password is set successfully.
Reconfiguring the Solution Engine IP Address
Typically, you configure the IP address only once, during initial configuration. See Configuring ACS SE,
page 3-11.
Caution Reconfiguring the IP address may cause other network devices to fail to recognize the ACS SE.
Caution Reconfiguring the IP address causes services to restart. AAA services to users will be interrupted.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-18
OL-9969-03
Page 79

Chapter 4 Administering Cisco Secure ACS Solution Engine
Note To set or change the IP address of your ACS SE, ACS SE must be connected to a working Ethernet
connection.
To reconfigure the IP address:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 Type set ip, and then press Enter.
Step 3 At the Use Static IP Address [Y]: prompt, type Y for yes or N for No, and then press Enter.
Step 4 If you answered No to using a static IP address, the system displays a confirmation of DHCP and the
message
IP Address is reconfigured. Continue the procedure with Step 5.
If you responded Yes in the previous step to use a static IP address:
a. To specify the ACS SE IP address, at the IP Address [xx.xx.xx.xx]: prompt, type the IP address,
and then press Enter.
b. At the Subnet Mask [xx.xx.xx.xx]: prompt, type the subnet mask, and then press Enter.
Reconfiguring Solution Engine System Parameters
c. At the Default Gateway [xx.xx.xx.xx]: prompt, type the default gateway, and then press Enter.
d. At the DNS Servers [xx.xx.xx.xx]: prompt, type the address of any DNS servers you intend to
use (separate each by a single space), and then press Enter.
Result: The system displays the new configuration information and the message:
IP Address is reconfigured.
Step 5 Review the information presented and, at the Confirm the changes? [Y]: prompt, press Enter.
Result: The ACS SE restarts. The system displays the message:
New ip address is set.
Step 6 At the prompt, Test network connectivity [Yes]:, type Y, and then press Enter.
Tip This step executes a ping command to ensure the connectivity of the ACS SE.
Step 7 At the prompt, Enter hostname or IP address:, type the IP address or hostname of a device connected
to the ACS SE and then press Enter.
Result: If successful, the system displays the ping statistics. Once again the system displays the Test
network connectivity [Yes]:
Step 8 If network connectivity is proven okay in the previous two steps, at the prompt, Test network
connectivity [Yes]:
, type N, and then press Enter.
prompt.
Tip The system will continue to provide you with the opportunity to test network connectivity until
you answer N. This procedure gives you an opportunity, if required, to correct network
connections or retype the IP address.
Result: The ACS SE restarts services, and displays the system prompt.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-19
Page 80

Reconfiguring Solution Engine System Parameters
Setting the System Time and Date Manually
You can set and maintain the system date and time by using one of two methods:
• Set the time and date manually.
• Assign a network time protocol (NTP) server with which the system synchronizes its date and time.
To set the ACS SE system time and date by using an NTP, see Setting the System Time and Date with
NTP, page 4-20.
To set the ACS SE system time and date manually:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set time, and then press Enter.
Result: The system displays the message:
Current Date Time Setting:
Time Zone: (GMT -xx:xx) XXX Time
Date and Time: mm/dd/yyyy hh/mm/ss
Chapter 4 Administering Cisco Secure ACS Solution Engine
NTP Servers: (“Ntp Synchronization Disabled” - or -a list of NTP servers)
Change Date & Time Setting? [N]
Step 3 To set the time zone, time, or date type Y, and then press Enter.
Result: The system displays a list of indexed time zones and the message:
[xx] (GMT -xx:xx) XXX Time.
Enter desired time zone index (0 for more choices) [x]:
Step 4 Enter the desired time zone index number from the time zone setting list, and then press Enter.
Tip You can also type 0 (zero) and press Enter to see more time zone index numbers.
Result: The system displays the new time zone.
Step 5 At the Synchronize with NTP Server? prompt, type N, and then press Enter.
Step 6 At the Enter date [mm/dd/yyyy]: prompt, type the date, and then press Enter.
Step 7 At the Enter time [hh:mm:ss]: prompt, type the current time, and then press Enter.
Result: The system time is reset.
Setting the System Time and Date with NTP
You can set and maintain the system date and time by using one of two methods:
• Set the time and date manually.
• Assign a network time protocol (NTP) server with which the system synchronizes its date and time.
(You can configure backup NTP servers if you desire.)
To set the ACS SE system time and date manually, see Setting the System Time and Date Manually,
page 4-20.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-20
OL-9969-03
Page 81

Chapter 4 Administering Cisco Secure ACS Solution Engine
To set the ACS SE system time and date with NTP:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set time, and then press Enter.
Result: The system displays the message:
Current Date Time Setting:
Time Zone: (GMT -xx:xx) XXX Time
Date and Time: mm/dd/yyyy hh/mm/ss
NTP Servers: (“Ntp Synchronization Disabled” - or - List of NTP servers)
Change Date & Time Setting? [N]
Step 3 To set the time zone, time, or date type Y, and then press Enter.
Result: The system displays indexed time zones and the message:
[xx] (GMT -xx:xx) XXX Time.
Enter desired time zone index (0 for more choices) [x]:
Step 4 Enter the desired time zone index number from the time zone setting list, and then press Enter.
Reconfiguring Solution Engine System Parameters
Tip You can also type 0 (zero) and press Enter to see more time zone index numbers; or simply press
Enter to accept the existing time zone.
Result: The system displays the time zone setting.
Step 5 At the Synchronize with NTP Server? prompt, type Y, and then press Enter.
Step 6 At the Enter NTP Server IP Address(es): prompt, enter the IP address of the NTP server that you
want to use, and then press Enter.
Tip If you want to configure multiple NTP servers, at the Enter NTP Server IP Address: prompt,
enter multiple IP addresses, each separated by a space.
Result: The system displays the message:
Successfully synchronized with NTP server
Current Date/Time Setting:
Time Zone: XXX
Date & Time:
NTP servers:
Setting the System Timeout
You can set a system timeout. This is the number of minutes that can pass with no activity on the serial
console before the console login times out.
To set the ACS SE system timeout:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-21
Page 82

Reconfiguring Solution Engine System Parameters
Step 2 At the system prompt, type set timeout followed by a single space and the timeout period in minutes.
Step 3 Press Enter.
Result: The system sets the new timeout period.
Setting the Solution Engine System Domain
You can set the system DNS domain from the serial console. To set the ACS SE system domain:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set domain followed by a single space and the domain name.
Step 3 Press Enter.
Result: The system displays the confirmation message:
You should reboot appliance for the change to take effect.
Chapter 4 Administering Cisco Secure ACS Solution Engine
Setting the Solution Engine System Hostname
Caution Performing this procedure stops and restarts all services, and will interrupt use of the ACS SE.
You can set the system hostname. To set the ACS SE system hostname:
Step 1 Log in to the ACS SE. For more information, see Logging In to the Solution Engine From a Serial
Console, page 4-2.
Step 2 At the system prompt, type set hostname followed by a single space and the hostname.
Tip You can use up to 15 letters and numbers; but no spaces.
Step 3 Press Enter.
Result: The system restarts all services, and the hostname is reset. The system then displays the
confirmation message:
You should reboot appliance for the change to take effect.
(The hostname is then reset after system reboot.)
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-22
OL-9969-03
Page 83

Chapter 4 Administering Cisco Secure ACS Solution Engine
Patch Rollback
This section contains:
• Removing Installed Patches, page 4-23
• Understanding the CSAgent Patch, page 4-23
Removing Installed Patches
Use this procedure to uninstall one or more patches and to roll back the ACS SE to the version that
existed before the patch installation.
To roll back a ACS SE system patch:
Step 1 Connect a console to the ACS SE console port. For the location of the console port, see Figure 1-2 on
page 1-5.
Step 2 Type rollback and the name of the patch application that you want rolled back. Then press Enter.
Patch Rollback
Tip If you do not include the specific patch application name as a parameter following the rollback
command, the system displays the list of patches that can be rolled back. Use this list to identify
the patch application name, type rollback followed by the patch application name, and then
press Enter.
Result: The system displays the confirmation message:
Are you sure you want to rollback [patch name]?)(Y/N):
Step 3 Type Y to continue.
Result: The system displays a series of messages that include:
Rolling patch back
Rollback process initiated successfully
Successfully rolled back ‘[patch name]’ to 0.
Tip To obtain system information, including the current version, see Determining the Status of
Solution Engine System and Services From a Serial Console, page 4-3.
Understanding the CSAgent Patch
In ACS SE the CSAgent service is implemented as a pre-installed patch. You must stop CSAgent before
you can install any patch or upgrade. Although, as a patch, the CSAgent can be rolled back, the preferred
method for disabling this service is simply to stop it. Once stopped, the CSAgent service does not restart
when the system is restarted; you must explicitly restart the service for it to operate. For more
information, see the User Guide for Cisco Secure Access Control Server.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-23
Page 84

Chapter 4 Administering Cisco Secure ACS Solution Engine
Recovery Management
Recovery Management
ACS SE functionality includes two procedures that the administrator can perform by using the ACS SE
Recovery CD-ROM:
• Recovering from Loss of Administrator Credentials, page 4-24
• Re-imaging the Solution Engine Hard Drive, page 4-25
Recovering from Loss of Administrator Credentials
If you cannot log in to the system because you have lost the account name or password for the ACS SE
administrator account, perform this procedure. In this procedure you use the ACS SE Recovery
CD-ROM to access the system from the serial console and reset the administrator login credentials.
You should understand the following regarding the ACS SE administrator login credentials:
• Only one set of administrator login credentials exists at one time.
• Administrator login credentials are set (that is, changed from the default) during initial
configuration.
• Administrator login credentials may be reset. For more information, see Resetting the Solution
Engine Administrator Password, page 4-15.
• This recovery procedure entails replacing the administrator login credentials with a new account
name and password.
To reset the administrator login credentials:
Step 1 Connect a console to the ACS SE console port. For the location of the console port, see Figure 1-2 on
page 1-5.
Step 2 Power on the console.
Step 3 Insert the ACS SE Recovery CD-ROM into the solution engine CD-ROM drive.
Step 4 Power on the ACS SE. (Or if already running, reboot the solution engine. For more information, see
Rebooting the Solution Engine From a Serial Console, page 4-3.)
Result: The system displays the message:
ACS Appliance Recovery Options
[1] Reset administrator account
[2] Restore hard disk image from CD
[3] Exit and reboot
Enter menu item number: [ ]
Step 5 Type 1.
Result: The system displays the prompt:
Hit the Return key to log in.
Step 6 Type Y.
Result: The system displays the prompt:
Please remove this recovery CD from the drive,
then hit RETURN to restart the system:
Step 7 Remove the recovery CD from the drive, and then press Enter.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-24
OL-9969-03
Page 85

Chapter 4 Administering Cisco Secure ACS Solution Engine
Result: The system reboots, and then displays the system version information followed by:
Status: The appliance is functioning properly
Login:
Step 8 Type Administrator, and then press Enter.
The password is case sensitive.
Step 9 At the password prompt, type setup, and then press Enter.
Result: The system displays the system prompt.
Step 10 At the Enter new account name: prompt, type the name of the ACS SE administrator. and then press
Enter.
Step 11 At the Enter new password: prompt, enter the new ACS SE password. Press Enter.
Note The new password must contain a minimum of 6 characters, and it must include a mix of at least
3 character types (numerals, special characters, uppercase letters, and lowercase letters). Each
of the following examples is acceptable: 1PaSsWoRd, *password44, Pass*word.
Step 12 At the Enter new password again: prompt, type the new ACS SE password, and then press Enter.
Result: The system displays the message:
Password is set successfully.
Recovery Management
Re-imaging the Solution Engine Hard Drive
Use the ACS SE Recovery CD-ROM to re-image the ACS SE if necessary.
Caution Performing this procedure destroys all data stored on the ACS SE.
To re-image your ACS SE:
Step 1 Connect a console to the ACS SE console port. For the location of the console port, see Figure 1-2 on
page 1-5.
Step 2 Put the Recovery CD in the ACS SE CD-ROM drive. See Figure 1-2 on page 1-5.
Step 3 Power on the ACS SE. (Or, if the solution engine is already running, reboot it.) For more information,
see
Rebooting the Solution Engine From a Serial Console, page 4-3.
Result: The ACS SE displays the message:
ACS Appliance Recovery Options
[1] Reset administrator account
[2] Restore hard disk image from CD
[3] Exit and reboot
Enter menu item number: [ ]
Step 4 Type 2, and then press Enter.
Result: The ACS SE displays the message:
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-25
Page 86

Recovery Management
Caution The next step erases the ACS SE hard drive. You will permanently lose all system data that you have not
Step 5 Type Y.
Step 6 Remove the Recovery CD from the ACS SE.
Step 7 Press Enter to restart the ACS SE.
Chapter 4 Administering Cisco Secure ACS Solution Engine
This operation will completely erase the hard drive. Press ‘Y’ to confirm, any other key
to cancel: __
backed up.
Result: The ACS SE processes the new image (this may take more than 2 minutes) while displaying odd
characters and then displays the message:
The system has been reimaged successfully. Please remove this recovery CD from the drive,
then hit RETURN to restart the system:
Result: The ACS SE reboots, performs some configurations, and reboots again. The configurations that
occur after the first reboot take a significant amount of time, during which there is no feedback, which
is normal system behavior.
Note After re-imaging the solution engine hard drive, you must once again perform initial configuration of the
ACS SE. For detailed instructions, see Configuring ACS SE, page 3-11.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
4-26
OL-9969-03
Page 87

CHAPTER
5
Upgrading and Migrating to Cisco Secure ACS
Solution Engine 4.1
This chapter describes how to:
• Upgrade to Cisco Secure ACS Solution Engine (ACS SE) 4.1.
• Migrate from an ACS for Windows server to ACS SE.
• Migrate ACS SE from an earlier hardware platform to the Cisco 1113 platform.
This chapter contains:
• Upgrade Scenarios, page 5-1
• Migration Scenarios, page 5-2
• Upgrade Paths, page 5-2
• Upgrade Procedure, page 5-4
• Migrating from ACS for Windows to ACS SE, page 5-13
• Migrating ACS SE on the ACS 1111 or ACS 1112 Platform to ACS SE 4.1 on the Cisco 1113
Platform, page 5-15
Upgrade Scenarios
Cisco Secure ACS Solution Engine 4.1 supports the following upgrade scenarios:
• ACS 3.x to ACS 4.1—You can upgrade ACS 3.2.x or 3.3.x (ACS 3.2.1, 3.2.2, 3.2.3, 3.3.1, 3.3.2, or
3.3.4) to ACS 4.1 on all ACS SE hardware platforms (The Cisco 1111 SE appliance, the Cisco 1112
SE appliance, and the Cisco 1113 SE appliance).
• ACS 4.0.1 to ACS 4.1—You can upgrade ACS 4.0.1 to ACS 4.1 on all ACS SE hardware platforms.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-1
Page 88

Migration Scenarios
Migration Scenarios
• ACS for Windows to ACS SE Migration— You can migrate data from an ACS for Windows server
to the ACS SE 4.1.
• Hardware to Hardware Migration—You can migrate data from earlier versions of the ACS SE
(the Cisco 1111 or the Cisco 1112 platform) to the Cisco 1113 platform.
Upgrade Paths
Depending on the ACS version you are upgrading from, there are different paths for upgrading to ACS
SE 4.1. You can upgrade to ACS 4.1 from ACS version 3.2.x, 3.3.x, 3.3.3 or 4.0.1:
1. ACS 3.2.x or 3.3.x (ACS 3.2.1, 3.2.2, 3.2.3, 3.3.1, or 3.3.2) to 4.1.
The ACS 3.2.x or 3.3.x upgrade package contains three CDs:
–
ACS 3.3.3 Upgrade CD. Use this CD to upgrade from ACS 3.2.x or 3.3.x to ACS 3.3.3.
–
ACS 4.1 Upgrade CD. After upgrading to ACS 3.3.3, use this CD to upgrade to ACS 4.1.
–
ACS 1113 Recovery CD for 1113. To restore the ACS 1113 system software, use the ACS SE
4.1 Recovery CD for 1113.
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Note If you are upgrading on an ACS 1111 or 1112 device and need to restore the ACS 1111
or 1112 system software, obtain the required recovery CD from the Cisco Technical
Assistance Center (TAC). For information on contacting the Cisco TAC, see
Technical Assistance, page xviii.
2. ACS SE 3.3.3 to 4.1.
The ACS SE 3.3.3 to 4.1 upgrade package includes:
–
ACS SE 4.1 Upgrade CD. Use this CD to upgrade an existing ACS SE 3.3.3 installation to ACS
4.1.
–
ACS 4.1 Recovery CD for 1113. Use this CD to restore the Cisco 1113 system software if the
system fails.
Note If you are upgrading on an ACS 1111 or 1112 device and need to restore the ACS 1111
or 1112 system software, obtain the required recovery CD from the Cisco Technical
Assistance Center (TAC). For information on contacting the Cisco TAC, see
Technical Assistance, page xviii.
3. ACS SE 4.0.1 to 4.1.
The ACS SE 4.0 to 4.1 upgrade package includes two CDs:
–
ACS SE 4.1 Upgrade CD. Use this CD to upgrade an existing ACS SE 4.0.1 installation to ACS
4.1.
Obtaining
Obtaining
–
ACS 4.1 Recovery CD for 1113. Use this CD to restore the Cisco 1113 system software if the
system fails.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-2
OL-9969-03
Page 89

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Note If you are upgrading on an ACS 1111 or 1112 device and need to restore the ACS 1111 or 1112
system software, obtain the required recovery CD from the Cisco Technical Assistance Center
(TAC). For information on contacting the Cisco TAC, see
page xviii.
You can upgrade your exiting ACS appliance with the latest ACS software and appliance management
software.
Table 5-1 describes various upgrade use cases that you can use to decide the appropriate upgrade path
to follow.
Note Before you begin any upgrade procedure, we recommend that you back up your existing data and
configuration.
Note If you use ACS Remote Agents, after any type of upgrade to ACS SE 4.1, you must uninstall your old
version of ACS Remote Agents, and install Remote Agents for ACS SE 4.1.
Upgrade Paths
Obtaining Technical Assistance,
Ta b l e 5-1 Upgrade Use Cases
From Version Upgrade Path Results
3.2.x or 3.3.x to
4.1
Full Upgrade
To perform a full upgrade with data restore:
1. Use the ACS SE 3.3.3 Upgrade CD.
For instructions on upgrading to ACS 3.3.3, see Release
Notes for Cisco Secure Access Control Server Solution
Engine 3.3 at:
http://www.cisco.com/en/US/docs/net_mgmt/cisco_secure
• Base image upgraded including SNMP
support, and installation of Cisco
Security Agent (Cisco Security Agent).
• Appliance management software
upgraded.
• ACS software upgraded.
• Data restored.
_access_control_server_for_solution_engine/3.3/release/no
tes/RNsol331.html.
2. Use the ACS SE 4.1 Upgrade CD.
3.3.3 to 4.1
4.0.1 to 4.1
Full Upgrade
To perform a full upgrade with data restore, use the ACS SE 4.1
Upgrade CD:
For a complete list of steps, see Performing a Full Upgrade from
ACS SE 3.3.3 to ACS SE 4.1, page 5-8.
Full Upgrade
To perform a full upgrade with data restore, use the ACS SE 4.1
Upgrade CD.
• Base image upgraded including
additional Microsoft hotfixes.
• Appliance management software
upgraded.
• ACS software upgraded.
• Data restored.
• ACS SE 4.0.1 is upgraded to ACS SE
4.1.
• Data restored.
For a complete list of steps, see Performing a Full Upgrade From
ACS SE 4.0.1 to ACS SE 4.1, page 5-4.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-3
Page 90

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Upgrade Procedure
Upgrade Procedure
You can perform a full upgrade from:
• ACS SE 4.0.1 to ACS SE 4.1.
• ACS SE 3.3.3 to ACS SE 4.1
Performing a Full Upgrade From ACS SE 4.0.1 to ACS SE 4.1
This section describes the procedure for performing a full upgrade from ACS SE 4.0.1 to ACS SE 4.1.
Before You Begin
Make a backup of your existing data and configuration.
To upgrade ACS SE 4.0.1 to ACS SE 4.1:
Step 1 Obtain the ACS 4.0 to 4.1 upgrade package.
Step 2 If the ACS SE is running Cisco Security Agent, you must disable the CSAgent service before upgrading.
You can do so at the console or in the web interface (ACS GUI). Using the:
• Console, enter show. If the CSAgent service is running, enter stop csagent.
• Web interface, choose System Configuration > Appliance Configuration and verify that the CSA
Enabled check box is not checked. If it is checked, uncheck the CSA Enabled check box and click
Submit.
Step 3 If you do not already have a GUI administrator account on the ACS SE, create a new GUI administrator
account from the web interface:
a. Start the web interface.
b. Click Administration Control.
The Administration Control page opens.
c. Click Add Administrator.
The Add Administrator page opens.
d. Add a new administrator and grant all administrative privileges to the administrator.
Note When you create a GUI administrator account, you will have two administrator accounts for the
ACS SE: one each for a GUI and CLI.
Warning
If you do not have a GUI administrator account; then, after the upgrade is complete, you will
not be able to log in to the ACS SE from the web interface.
Step 4 Insert the ACS SE 4.1 Upgrade CD into the CD-ROM drive on the distribution server (the server from
which you are performing the upgrade).
Step 5 Download the ACS Management Upgrade package:
a. Open the upgrade CD.
b. Go to the /Upgrade Appliance management ACS 4.1 folder.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-4
OL-9969-03
Page 91

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
c. Double-click the autorun.bat icon.
The download utility starts. You are prompted to enter the hostname or IP address of the appliance,
as shown in
Figure 5-1 Appliance Prompt
d. Enter the hostname or the IP address of the distribution server and then click Install.
Figure 5-1.
The web interface starts.
e. Log in to the web interface.
f. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-2.
Upgrade Procedure
Figure 5-2 Appliance Upgrade Page
g. Click Download.
The Appliance Upgrade Form page opens, as shown in Figure 5-3. On this page you enter the IP
address of the distribution server.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-5
Page 92

Upgrade Procedure
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Figure 5-3 Appliance Upgrade Form with Text Box for the Distribution Server
h. Enter the IP address of the distribution server and then click Connect.
The Appliance Upgrade Form page opens, as shown in Figure 5-4. This page lists the current
appliance-management software version number.
Figure 5-4 Appliance Upgrade Form
i. Click Download Now.
The upgrade utility downloads the upgrade image.
The Appliance Upgrade page opens, as shown in Figure 5-5. The Appliance Versions table provides
information about the software version.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-6
OL-9969-03
Page 93

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Figure 5-5 Appliance Upgrade Page
Upgrade Procedure
j. Click Apply Upgrade.
The upgrade utility applies the management software upgrade.
Note This process takes several minutes. The system reboots several times.
Step 6 Download and apply the ACS Software Upgrade package.
a. Go to the /Upgrade package software for appliance ACS 4.1 folder on the upgrade CD.
b. Double-click the autorun.bat icon.
The download utility starts. You are prompted to enter the hostname of IP address of the appliance,
as shown in
c. Enter the hostname or the IP address of the distribution server and then click Install.
Figure 5-1.
The ACS web interface starts.
d. Log in to the web interface.
e. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-2.
f. Download and install the software upgrade.
The steps for downloading and installing the software upgrade package are the same as the steps for
installing the management software as described in
Step 5.
Note If you complete the upgrade and the ACS console displays the message Appliance upgrade in
progress
If this condition occurs, start an ACS console session and enter the command download
[hostAddress]
console from the upgrade process.
OL-9969-03
, this indicates that the upgrade progress is hanging.
, where hostAddress can be any IP address. This action releases the ACS
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-7
Page 94

Upgrade Procedure
Step 7 Download and install the MS Hotfixes package.
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
a. Go to the /Upgrade package MS Hotfixes for ACS 4.0 to 4.1 folder on the upgrade CD.
b. Double-click the autorun.bat icon.
The download utility starts. You are prompted to enter the hostname of IP address of the appliance,
as shown in
c. Enter the hostname or the IP address of the distribution server and then click Install.
The ACS web interface starts.
d. Log in to the web interface.
e. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-2.
f. Download and install the MS Hotfixes.
The steps for downloading and installing the MS Hotfixes package are the same as the steps for
installing the management software as described in
g. Follow the prompts that the upgrade program displays to install the upgrade.
Figure 5-1.
Step 5.
Performing a Full Upgrade from ACS SE 3.3.3 to ACS SE 4.1
This section describes the procedure for performing a full upgrade from ACS SE 3.3.3 to ACS SE 4.1.
Before You Begin
Make a backup of your existing data and configuration. The first backup is for ensuring that you have
the 3.3.3 original data backed up.
Caution Back up and restore are supported and tested only when done on the same version. For example, backup
on 4.1 and restore on 4.1 is supported; not backup on 3.3.3 and restore on 4.1.
To upgrade ACS SE 3.3.3 to ACS SE 4.1:
Step 1 Obtain the ACS SE 4.1 upgrade CD.
Step 2 If the ACS SE is running Cisco Security Agent, you must disable the CSAgent service before upgrading.
You can do so at the console or in the web interface (ACS GUI). Using the:
• Console, enter show. If the CSAgent service is running, enter stop csagent.
• Web interface, choose System Configuration > Appliance Configuration and verify that the CSA
Enabled check box is not checked. If it is checked, uncheck the CSA Enabled check box and click
Submit.
Step 3 If you do not already have a GUI administrator account on the ACS SE, create a new GUI administrator
account from the web interface:
a. Start the web interface.
b. Click Administration Control.
The Administration Control page opens.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-8
OL-9969-03
Page 95

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
c. Click Add Administrator.
The Add Administrator page opens.
d. Add a new administrator and grant all administrative privileges to the administrator.
Note When you create a GUI administrator account, you will have two administrator accounts for the
ACS SE: one each for a GUI and CLI.
Upgrade Procedure
Warning
If you do not have a GUI administrator account; then, after the upgrade is complete, you will
not be able to log in to the ACS SE from the web interface.
Step 4 Insert the ACS SE 4.1 Upgrade CD into the CD-ROM drive on the distribution server (the server from
which you are performing the upgrade).
Step 5 Download the ACS Management Upgrade package:
a. Open the upgrade CD.
b. Go to the /Upgrade Appliance management ACS 4.1 folder.
c. Double-click the autorun.bat icon.
The download utility starts. You are prompted to enter the hostname or IP address of the appliance,
as shown in
Figure 5-6 Appliance Prompt
d. Enter the hostname or the IP address of the distribution server and then click Install.
Figure 5-6.
The web interface starts.
e. Log in to the web interface.
f. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-7.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-9
Page 96

Upgrade Procedure
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Figure 5-7 Appliance Upgrade Page
g. Click Download.
The Appliance Upgrade Form page opens, as shown in Figure 5-8. On this page, you enter the IP
address of the distribution server.
Figure 5-8 Appliance Upgrade Form with Text Box for the Distribution Server
h. Enter the IP address of the distribution server and then click Connect.
The Appliance Upgrade Form page opens, as shown in Figure 5-9. This page lists the current version
number of the appliance-management software.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-10
OL-9969-03
Page 97

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Figure 5-9 Appliance Upgrade Form
i. Click Download Now.
The upgrade utility downloads the upgrade image.
The Appliance Upgrade page opens, as shown in Figure 5-10. The Appliance Versions table
provides information about the software version.
Upgrade Procedure
Figure 5-10 Appliance Upgrade Page
j. Click Apply Upgrade.
The upgrade utility applies the management software upgrade.
Note This process takes several minutes. The system reboots several times.
Step 6 Download and apply the ACS Software Upgrade package.
a. Go to the /Upgrade package software for appliance ACS 4.1 folder on the upgrade CD.
b. Double-click the autorun.bat icon.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-11
Page 98

Upgrade Procedure
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
The download utility starts. You are prompted to enter the hostname of IP address of the appliance,
as shown in
c. Enter the hostname or the IP address of the distribution server and then click Install.
The ACS web interface starts.
d. Log in to the web interface.
e. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-7.
f. Download and install the software upgrade.
The steps for downloading and installing the software upgrade package are the same as the steps for
installing the management software as described in
Note If you complete the upgrade and the ACS console displays the message Appliance upgrade in
progress
If this condition occurs, start an ACS console session and enter the command download
[hostAddress]
console from the upgrade process.
Figure 5-6.
Step 5.
, this indicates that the upgrade progress is hanging.
, where hostAddress can be any IP address. This action releases the ACS
Step 7 Download and install the MS Hotfixes package.
a. Go to the /Upgrade package MS Hotfixes for ACS 4.0 to 4.1 folder on the upgrade CD. (verify folder
b. Double-click the autorun.bat icon.
The download utility starts. You are prompted to enter the hostname of IP address of the appliance,
as shown in
c. Enter the hostname or the IP address of the distribution server and then click Install.
Figure 5-1.
The ACS web interface starts.
d. Log in to the web interface.
e. Choose System Configuration > Appliance Upgrade Status.
The Appliance Upgrade page opens, as shown in Figure 5-7.
f. Download and install the MS Hotfixes.
The steps for downloading and installing the MS Hotfixes package are the same as the steps for
installing the management software as described in
g. Follow the prompts that the upgrade program displays to install the upgrade.
Step 8 Back up the upgraded ACS SE data and configuration.
To upgrade the ACS SE appliance to the latest Microsoft hotfixes, you must reimage the ACS SE device.
Because reimaging destroys all of the existing data on the device, you must first back up your existing
data and then restore it by using one of the following features:
• ACS Backup, which is available in the System Configuration section of the web interface. For more
information, see the User Guide for Cisco Secure ACS 4.1.
• The CLI backup command, which you enter from the serial console. For more information, see
Backing Up ACS Data From the Serial Console, page 4-12.
Step 5.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-12
OL-9969-03
Page 99

Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
Note Use this backup to restore the data after you recover the 4.1 base image.
Step 9 Use the Recovery package for your ACS SE hardware version. If your ACS SE is a:
• Cisco 1113 device, use the ACS SE 4.1 Recovery CD for 1113 (provided with your upgrade
package) to update the ACS database on the appliance.
• Cisco 1111 or Cisco 1112 device, obtain a Recovery CD image from Cisco.com. To obtain the
image, contact the Cisco TAC.
For information on contacting the Cisco TAC, see Obtaining Technical Assistance, page xviii.
Note The recovery procedure destroys all previous data and installs a new image. Ensure that you have the
correct version for your hardware.
For more information about reimaging the hard drive, see Re-imaging the Solution Engine Hard Drive,
page 4-25.
Step 10 Perform an initial configuration of the ACS SE. For more information, see Configuring ACS SE,
page 3-11.
Migrating from ACS for Windows to ACS SE
Step 11 Restore the data that you previously backed up in Step 8 by using one of the following features:
• ACS Restore, which is available in the System Configuration section of the web interface. For more
information, see the User Guide for Cisco Secure ACS 4.1.
• The restore command, which you enter from the serial console. For more information, see Restoring
ACS Data From the Serial Console, page 4-14.
Step 12 Verify that Cisco Security Agent is enabled by using one of the following features:
• At the console, enter show. If the CSAgent service is not running, enter start csagent.
• In the web interface, choose System Configuration > Appliance Configuration and verify that the
CSA Enabled check box is checked. If not, check it and click Submit.
Migrating from ACS for Windows to ACS SE
Migrating from Cisco Secure ACS for Windows Server (ACS for Windows) to ACS SE uses the backup
and restore features of ACS. Backup files produced by ACS for Windows are compatible with ACS SE,
provided that both are using the same version of ACS software.
Before You Begin
Before upgrading or transferring data, back up your original ACS database and configuration, and save
the backup file in a location on a drive that is not local to the computer on which ACS is running.
Note If ACS runs on Windows NT 4.0, the following procedure will advise you when it is necessary to upgrade
to Windows 2000 Server. Because the use of the backup and restore features is only supported between
ACSs of the same version, you must use ACS for Windows 4.1, to transfer data from ACS for Windows
to ACS SE. ACS for Windows 4.1 supports Windows 2000 Server and Windows Server 2003, not
Windows NT 4.0. See the following procedure for more details.
OL-9969-03
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-13
Page 100

Migrating from ACS for Windows to ACS SE
To migrate from a Windows version of ACS to ACS SE:
Step 1 Set up the appliance, following the steps in Chapter 3, “Installing and Configuring Cisco Secure ACS
Solution Engine 4.1.”
Step 2 On the ACS server, upgrade ACS for Windows to version 4.1. If you do not have a license for version 4.1,
you can use the trial version, available at http://www.cisco.com/cgi-bin/tablebuild.pl/acs-win-3des.
Note If you are running ACS 2.0 on Windows NT 4.0, upgrade to ACS 3.0, and then migrate to
Windows 2000 Server before upgrading to ACS
on Windows NT. For information about upgrading to ACS 3.0 or about migrating to Windows
2000 Server, see Installing Cisco Secure ACS 3.0 for Windows 2000/NT Servers. You can acquire
the trial version of ACS 3.0 at http://www.cisco.com/cgi-bin/tablebuild.pl/acs-win-3des.
Step 3 In the web interface of ACS for Windows 4.1, use the ACS Backup feature to back up the database. For
more information about the ACS Backup feature, see the User Guide for Cisco
Windows
Step 4 Copy the backup file from the computer that is running ACS for Windows 4.1 to a directory on an FTP
Server.
server. The directory must be accessible from the FTP root directory. ACS SE must be able to contact
the FTP server. Any gateway devices must permit FTP communication between the appliance and the
FTP server.
Chapter 5 Upgrading and Migrating to Cisco Secure ACS Solution Engine 4.1
4.1. Only ACS 3.0 and previous releases can run
Secure ACS for
Step 5 In the web interface for ACS 4.1, use the ACS Restore feature to restore the database. For more
information about restoring databases, see the User Guide for Cisco Secure ACS 4.1.
The ACS SE contains the original configuration of the ACS for Windows version from which you
migrated.
Step 6 Continuing in the web interface, verify that the settings for the (Default) entry in the Proxy Distribution
Table are correct. To do so, choose Network Configuration
> (Default) and ensure that the Forward To
list contains the entry for the appliance.
Step 7 To replace the computer that is running ACS for Windows with ACS SE, you must change the IP address
of the appliance to that used by the computer that is running ACS for Windows:
a. Record the IP address of the computer that is running ACS for Windows.
b. Change the IP address of the computer that is running ACS for Windows to a different IP address.
c. Change the IP address of the ACS SE to the IP address used previously by the computer that is
running ACS for Windows. This is the IP address that you recorded in Step
a. For detailed steps, see
Reconfiguring the Solution Engine IP Address, page 4-18.
Note If you do not change the IP address of the ACS SE to the address of the computer that is running
ACS for Windows, you must reconfigure all AAA clients to use the IP address of the ACS SE.
Installation Guide for Cisco Secure ACS Solution Engine 4.1
5-14
OL-9969-03
 Loading...
Loading...