Page 1

Catalyst 6500 Series Switch Cisco IOS
Software Configuration Guide—Release
12.1 E
Cisco IOS Release 12.1 E
Corporate Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 526-4100
Customer Order Number: DOC-7814099=
Text Part Number: 78-14099-04
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL
STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT
WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT
SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE
OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public
domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH
ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT
LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF
DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING,
WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
CCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, Cisco TelePresence, the Cisco logo, DCE, and Welcome to the Human Network are
trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are service marks; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You,
Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems,
Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing,
FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study, IronPort, the IronPort logo,
LightStream, Linksys, MediaTone, MeetingPlace, MeetingPlace Chime Sound, MGX, Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels,
ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The Fastest Way to Increase Your Internet Quotient, TransPath, WebEx, and the
WebEx logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (0807R)
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
Copyright © 2003 Cisco Systems, Inc. All rights reserved.
Page 3

Preface 21
Audience 21
Organization 21
Related Documentation 23
Conventions 24
CONTENTS
CHAPTER
CHAPTER
CHAPTER
1 Product Overview 1
Configuring Embedded CiscoView Support 2
Understanding Embedded CiscoView 2
Installing and Configuring Embedded CiscoView 2
Displaying Embedded CiscoView Information 3
2 Command-Line Interfaces 1
Accessing the CLI 1
Accessing the CLI through the EIA/TIA-232 Console Interface 1
Accessing the CLI through Telnet 2
Performing Command Line Processing 3
Performing History Substitution 3
Cisco IOS Command Modes 4
Displaying a List of Cisco IOS Commands and Syntax 5
ROM-Monitor Command-Line Interface 6
3 Configuring the Switch for the First Time 1
78-14099-04
Default Configuration 1
Configuring the Switch 2
Using the Setup Facility or the setup Command 2
Using Configuration Mode 10
Checking the Running Configuration Before Saving 10
Saving the Running Configuration Settings 11
Reviewing the Configuration 11
Configuring a Default Gateway 12
Configuring a Static Route 12
Configuring a BOOTP Server 14
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3
Page 4
Contents
Protecting Access to Privileged EXEC Commands 15
Setting or Changing a Static Enable Password 15
Using the enable password and enable secret Commands 15
Setting or Changing a Line Password 16
Setting TACACS+ Password Protection for Privileged EXEC Mode 16
Encrypting Passwords 17
Configuring Multiple Privilege Levels 17
Recovering a Lost Enable Password 19
Modifying the Supervisor Engine Startup Configuration 20
Understanding the Supervisor Engine Boot Configuration 20
Configuring the Software Configuration Register 21
Specifying the Startup System Image 24
Understanding Flash Memory 24
BOOTLDR Environment Variable 25
CONFIG_FILE Environment Variable 26
Controlling Environment Variables 26
CHAPTER
CHAPTER
4 Configuring EHSA Supervisor Engine Redundancy 1
Supervisor Engine Redundant Operation 1
Supervisor Engine Redundancy Requirements 2
Synchronizing the Supervisor Engine Configurations 3
Displaying the Supervisor Engine Redundancy 4
Copying Files to the Redundant Supervisor Engine 4
5 Configuring RPR and RPR+ Supervisor Engine Redundancy 1
Understanding Supervisor Engine Redundancy 1
Supervisor Engine Redundancy Overview 1
RPR Operation 2
RPR+ Operation 2
Supervisor Engine Synchronization 3
Supervisor Engine Redundancy Guidelines and Restrictions 4
RPR+ Guidelines and Restrictions 4
Hardware Configuration Guidelines and Restrictions 5
Restrictions 5
Configuration Mode Restrictions 6
Configuring Supervisor Engine Redundancy 6
Configuring RPR and RPR+ 6
Synchronizing the Supervisor Engine Configurations 7
Displaying the Redundancy States 8
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
4
78-14099-04
Page 5

Performing a Fast Software Upgrade 9
Copying Files to an MSFC 10
Contents
CHAPTER
6 Configuring Interfaces 1
Understanding Interface Configuration 1
Using the Interface Command 2
Configuring a Range of Interfaces 4
Defining and Using Interface-Range Macros 6
Configuring Optional Interface Features 7
Configuring Ethernet Interface Speed and Duplex Mode 7
Configuring Jumbo Frame Support 10
Configuring IEEE 802.3Z Flow Control 14
Configuring the Port Debounce Timer 15
Adding a Description for an Interface 16
Understanding Online Insertion and Removal 17
Monitoring and Maintaining Interfaces 17
Monitoring Interface Status 17
Clearing Counters on an Interface 18
Resetting an Interface 19
Shutting Down and Restarting an Interface 19
CHAPTER
CHAPTER
7 Configuring LAN Ports for Layer 2 Switching 1
Understanding How Layer 2 Switching Works 1
Understanding Layer 2 Ethernet Switching 1
Understanding VLAN Trunks 2
Layer 2 LAN Port Modes 4
Default Layer 2 LAN Interface Configuration 5
Layer 2 LAN Interface Configuration Guidelines and Restrictions 6
Restrictions 6
Guidelines 6
Configuring LAN Interfaces for Layer 2 Switching 7
Configuring a LAN Port for Layer 2 Switching 7
Configuring a Layer 2 Switching Port as a Trunk 8
Configuring a LAN Interface as a Layer 2 Access Port 14
Configuring a Custom IEEE 802.1Q EtherType Field Value 16
8 Configuring VTP 1
Understanding How VTP Works 1
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
5
Page 6

Contents
Understanding the VTP Domain 2
Understanding VTP Modes 2
Understanding VTP Advertisements 2
Understanding VTP Version 2 3
Understanding VTP Pruning 3
VTP Default Configuration 5
VTP Configuration Guidelines and Restrictions 5
Configuring VTP 6
Configuring VTP Global Parameters 6
Configuring the VTP Mode 8
Displaying VTP Statistics 10
CHAPTER
CHAPTER
9 Configuring VLANs 1
Understanding How VLANs Work 1
VLAN Overview 1
VLAN Ranges 2
Configurable VLAN Parameters 3
Understanding Token Ring VLANs 3
VLAN Default Configuration 6
VLAN Configuration Guidelines and Restrictions 8
Restrictions 8
Guidelines 8
Configuring VLANs 9
VLAN Configuration Options 9
Creating or Modifying an Ethernet VLAN 10
Assigning a Layer 2 LAN Interface to a VLAN 12
Configuring the Internal VLAN Allocation Policy 12
Mapping 802.1Q VLANs to ISL VLANs 12
10 Configuring Private VLANs 1
Understanding How Private VLANs Work 1
Private VLAN Configuration Restrictions and Guidelines 2
Configuring Private VLANs 5
Configuring a VLAN as a Private VLAN 5
Associating Secondary VLANs with a Primary VLAN 6
Mapping Secondary VLANs to the Layer 3 VLAN Interface of a Primary VLAN 7
Configuring a Layer 2 Interface as a Private VLAN Host Port 8
Configuring a Layer 2 Interface as a Private VLAN Promiscuous Port 9
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6
78-14099-04
Page 7

Contents
CHAPTER
CHAPTER
11 Configuring Cisco IP Phone Support 1
Understanding Cisco IP Phone Support 1
Cisco IP Phone Connections 1
Cisco IP Phone Voice Traffic 2
Cisco IP Phone Data Traffic 3
Cisco IP Phone Power Configurations 3
Default Cisco IP Phone Support Configuration 4
Cisco IP Phone Support Configuration Guidelines and Restrictions 4
Configuring Cisco IP Phone Support 5
Configuring Voice Traffic Support 5
Configuring Data Traffic Support 7
Configuring Inline Power Support 8
12 Configuring Layer 3 Interfaces 1
Configuring IP Routing and Addresses 2
Configuring IPX Routing and Network Numbers 6
Configuring AppleTalk Routing, Cable Ranges, and Zones 7
Configuring Other Protocols on Layer 3 Interfaces 8
CHAPTER
CHAPTER
13 Configuring EtherChannels 1
Understanding How EtherChannels Work 1
EtherChannel Feature Overview 2
Understanding How EtherChannels Are Configured 2
Understanding Port Channel Interfaces 5
Understanding Load Balancing 5
EtherChannel Feature Configuration Guidelines and Restrictions 5
Configuring EtherChannels 6
Configuring Port Channel Logical Interfaces for Layer 3 EtherChannels 7
Configuring Channel Groups 8
Configuring the LACP System Priority and System ID 10
Configuring EtherChannel Load Balancing 11
14 Configuring IEEE 802.1Q Tunneling and Layer 2 Protocol Tunneling 1
Understanding How 802.1Q Tunneling Works 1
802.1Q Tunneling Configuration Guidelines and Restrictions 4
Restrictions 4
Guidelines 4
78-14099-04
Configuring 802.1Q Tunneling 5
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
7
Page 8

Contents
Preconfiguration Tasks 6
Configuring 802.1Q Tunnel Ports 6
Configuring the Switch to Tag Native VLAN Traffic 7
Understanding How Layer 2 Protocol Tunneling Works 7
Configuring Support for Layer 2 Protocol Tunneling 8
CHAPTER
15 Configuring STP and IEEE 802.1s MST 1
Understanding How STP Works 2
STP Overview 2
Understanding the Bridge ID 3
Understanding Bridge Protocol Data Units 4
Election of the Root Bridge 4
STP Protocol Timers 5
Creating the Spanning Tree Topology 5
STP Port States 6
STP and IEEE 802.1Q Trunks 12
Understanding How IEEE 802.1w RSTP Works 13
IEEE 802.1w RSTP Overview 13
RSTP Port Roles 13
RSTP Port States 14
Rapid-PVST 14
Understanding How IEEE 802.1s MST Works 14
IEEE 802.1s MST Overview 15
MST-to-PVST Interoperability 16
Common Spanning Tree 18
MST Instances 18
MST Configuration Parameters 18
MST Regions 19
Message Age and Hop Count 20
Default STP Configuration 21
STP and MST Configuration Guidelines 21
Configuring STP 22
Enabling STP 23
Enabling the Extended System ID 24
Configuring the Root Bridge 25
Configuring a Secondary Root Bridge 26
Configuring STP Port Priority 27
Configuring STP Port Cost 29
Configuring the Bridge Priority of a VLAN 30
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
8
78-14099-04
Page 9

Configuring the Hello Time 32
Configuring the Forward-Delay Time for a VLAN 32
Configuring the Maximum Aging Time for a VLAN 33
Enabling Rapid-PVST 33
Configuring IEEE 802.1s MST 34
Enabling MST 34
Displaying MST Configurations 36
Configuring MST Instance Parameters 39
Configuring MST Instance Port Parameters 40
Restarting Protocol Migration 40
Contents
CHAPTER
16 Configuring Optional STP Features 1
Understanding How PortFast Works 2
Understanding How BPDU Guard Works 2
Understanding How PortFast BPDU Filtering Works 2
Understanding How UplinkFast Works 3
Understanding How BackboneFast Works 4
Understanding How EtherChannel Guard Works 6
Understanding How Root Guard Works 6
Understanding How Loop Guard Works 6
Enabling PortFast 8
Enabling PortFast BPDU Filtering 10
Enabling BPDU Guard 11
Enabling UplinkFast 12
Enabling BackboneFast 13
Enabling EtherChannel Guard 14
Enabling Root Guard 14
Enabling Loop Guard 15
CHAPTER
78-14099-04
17 Configuring IP Unicast Layer 3 Switching on Supervisor Engine 2 1
Understanding How Layer 3 Switching Works 1
Understanding Hardware Layer 3 Switching on PFC2 and DFCs 2
Understanding Layer 3-Switched Packet Rewrite 2
Default Hardware Layer 3 Switching Configuration 4
Layer 3 Switching Configuration Guidelines and Restrictions 4
Configuring Hardware Layer 3 Switching 5
Displaying Hardware Layer 3 Switching Statistics 6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
9
Page 10

Contents
CHAPTER
18 Configuring IP Multicast Layer 3 Switching 1
Understanding How IP Multicast Layer 3 Switching Works 1
IP Multicast Layer 3 Switching Overview 2
Multicast Layer 3 Switching Cache 2
IP Multicast Layer 3 Switching Flow Mask 3
Layer 3-Switched Multicast Packet Rewrite 3
Partially and Completely Switched Flows 4
Non-RPF Traffic Processing 5
Default IP Multicast Layer 3 Switching Configuration 7
IP Multicast Layer 3 Switching Configuration Guidelines and Restrictions 8
PFC2 with MSCF2 8
PFC1 with MSFC or MSCF2 8
PFC1 and PFC2 General Restrictions 9
Unsupported Features 9
Configuring IP Multicast Layer 3 Switching 9
Source Specific Multicast with IGMPv3, IGMP v3lite, and URD 10
Enabling IP Multicast Routing Globally 10
Enabling IP PIM on Layer 3 Interfaces 10
Enabling IP Multicast Layer 3 Switching on Layer 3 Interfaces 11
Configuring the Layer 3 Switching Global Threshold 11
Enabling Installation of Directly Connected Subnets 12
Enabling NetFlow-Based Rate Limiting of RPF Failures 12
Enabling CEF-Based Rate Limiting of RPF Failures 13
Enabling Shortcut-Consistency Checking 13
Configuring ACL-Based Filtering of RPF Failures 14
Displaying RPF Failure Rate-Limiting Information 14
Displaying IP Multicast Layer 3 Hardware Switching Summary 14
Displaying the IP Multicast Routing Table 16
Displaying IP Multicast Layer 3 Switching Statistics 17
Using Debug Commands 18
Clearing IP Multicast Layer 3 Switching Statistics 19
CHAPTER
10
19 Configuring IP Unicast Layer 3 Switching on Supervisor Engine 1 1
Understanding How IP MLS Works 2
IP MLS Overview 2
IP MLS Flows 2
Layer 3 MLS Cache 3
Flow Masks 3
Layer 3-Switched Packet Rewrite 4
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 11

IP MLS Operation 5
Default IP MLS Configuration 6
IP MLS Configuration Guidelines and Restrictions 6
Configuring IP MLS 6
Enabling IP MLS Globally 6
Disabling and Enabling IP MLS on a Layer 3 Interface 7
Displaying the Interface IP MLS Configuration 7
Configuring the MLS Aging-Time 8
Setting the Minimum IP MLS Flow Mask 8
Displaying IP MLS Cache Entries 9
Displaying IP MLS Information 9
Displaying IP MLS Cache Entries for a Specific Destination Address 10
Displaying Cache Entries for a Specific Source IP Address 10
Displaying Entries for a Specific IP Flow 11
Contents
CHAPTER
Clearing IP MLS Cache Entries 11
Displaying IP MLS Contention Table and Statistics 12
Troubleshooting IP MLS 14
20 Configuring IPX Unicast Layer 3 Switching on Supervisor Engine 1 1
Understanding How IPX MLS Works 2
IPX MLS Overview 2
IPX MLS Flows 2
Layer 3 MLS Cache 2
Flow Masks 3
Layer 3-Switched Packet Rewrite 3
IPX MLS Operation 4
Default IPX MLS Configuration 5
Configuration Guidelines and Restrictions 5
Configuring IPX MLS 6
Enabling IPX MLS Globally 6
Enabling IPX MLS on a Layer 3 Interface 6
Configuring the MLS Aging Time 7
Configuring the Minimum IPX MLS Flow Mask 8
78-14099-04
Displaying IPX MLS Information 8
Displaying IPX MLS Cache Entries 9
Displaying the IPX MLS Contention Table 11
Displaying IPX MLS VLAN Statistics 12
Clearing IPX MLS Cache Entries 13
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
11
Page 12

Contents
Troubleshooting IPX MLS 14
CHAPTER
21 Configuring IGMP Snooping 1
Understanding How IGMP Snooping Works 1
IGMP Snooping Overview 2
Joining a Multicast Group 2
Leaving a Multicast Group 4
Understanding IGMP Snooping Querier 5
Understanding IGMP Version 3 Support 6
Default IGMP Snooping Configuration 6
IGMP Snooping and IGMP Snooping Querier Configuration Guidelines and Restrictions 6
Guidelines 6
Restrictions 7
Enabling the IGMP Snooping Querier 7
Configuring IGMP Snooping 8
Enabling IGMP Snooping 9
Configuring IGMP Snooping Learning 10
Configuring a Multicast Router Port Statically 10
Configuring the IGMP Query Interval 11
Enabling IGMP Fast-Leave Processing 11
Configuring a Host Statically 12
Displaying IGMP Snooping Information 12
CHAPTER
CHAPTER
12
22 Configuring RGMP 1
Understanding How RGMP Works 1
Default RGMP Configuration 2
RGMP Configuration Guidelines and Restrictions 2
Enabling RGMP on Layer 3 Interfaces 3
23 Configuring Network Security 1
ACL Configuration Guidelines 1
Hardware and Software ACL Support 2
Guidelines and Restrictions for Using Layer 4 Operators in ACLs 3
Determining Layer 4 Operation Usage 3
Determining Logical Operation Unit Usage 4
Configuring the Cisco IOS Firewall Feature Set 5
Cisco IOS Firewall Feature Set Support Overview 5
Firewall Configuration Guidelines and Restrictions 6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 13

Configuring CBAC on Catalyst 6500 Series Switches 7
Configuring MAC Address-Based Traffic Blocking 8
Configuring VLAN ACLs 8
Understanding VACLs 8
Configuring VACLs 11
Configuring VACL Logging 17
Configuring TCP Intercept 18
Configuring Unicast Reverse Path Forwarding 19
Understanding Unicast RPF Support 19
Configuring Unicast RPF 19
Enabling Self-Pinging 19
Configuring the Unicast RPF Checking Mode 20
Configuring Unicast Flood Protection 21
Configuring MAC Move Notification 22
Contents
CHAPTER
CHAPTER
24 Configuring Denial of Service Protection 1
DoS Protection Overview 1
Configuring DoS Protection 2
Supervisor Engine DoS Protection 2
Security ACLs 2
QoS ACLs 4
Forwarding Information Base Rate-Limiting 5
ARP Throttling 5
Monitoring Packet Drop Statistics 6
25 Configuring IEEE 802.1X Port-Based Authentication 1
Understanding 802.1X Port-Based Authentication 1
Device Roles 2
Authentication Initiation and Message Exchange 3
Ports in Authorized and Unauthorized States 4
Supported Topologies 4
Default 802.1X Port-Based Authentication Configuration 5
802.1X Port-Based Authentication Guidelines and Restrictions 6
78-14099-04
Configuring 802.1X Port-Based Authentication 7
Enabling 802.1X Port-Based Authentication 7
Configuring Switch-to-RADIUS-Server Communication 8
Enabling Periodic Reauthentication 10
Manually Reauthenticating the Client Connected to a Port 11
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
13
Page 14

Contents
Initializing Authentication for the Client Connected to a Port 11
Changing the Quiet Period 11
Changing the Switch-to-Client Retransmission Time 12
Setting the Switch-to-Client Retransmission Time for EAP-Request Frames 13
Setting the Switch-to-Authentication-Server Retransmission Time for Layer 4 Packets 13
Setting the Switch-to-Client Frame Retransmission Number 14
Enabling Multiple Hosts 14
Resetting the 802.1X Configuration to the Default Values 15
Displaying 802.1X Status 15
CHAPTER
CHAPTER
CHAPTER
26 Configuring Port Security 1
Understanding Port Security 1
Default Port Security Configuration 2
Port Security Guidelines and Restrictions 2
Configuring Port Security 2
Configuring Port Security on an Interface 3
Configuring Port Security Aging 4
Displaying Port Security Settings 5
27 Configuring Layer 3 Protocol Filtering on Supervisor Engine 1 1
Understanding How Layer 3 Protocol Filtering Works 1
Configuring Layer 3 Protocol Filtering 2
Enabling Layer 3 Protocol Filtering 2
Configuring Layer 3 Protocol Filtering on a Layer 2 LAN Interface 3
Verifying Layer 3 Protocol Filtering Configuration 3
28 Configuring Traffic Storm Control 1
CHAPTER
14
Understanding Traffic Storm Control 1
Default Traffic Storm Control Configuration 2
Enabling Traffic Storm Control 2
Displaying Traffic Storm Control Settings 4
29 Configuring Broadcast Suppression 1
Understanding How Broadcast Suppression Works 1
Broadcast Suppression Configuration Guidelines and Restrictions 2
Enabling Broadcast Suppression 3
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 15

Contents
CHAPTER
CHAPTER
30 Configuring CDP 1
Understanding How CDP Works 1
Configuring CDP 1
Enabling CDP Globally 2
Displaying the CDP Global Configuration 2
Enabling CDP on a Port 2
Displaying the CDP Interface Configuration 3
Monitoring and Maintaining CDP 3
31 Configuring PFC QoS 1
Understanding How PFC QoS Works 1
Hardware Supported by PFC QoS 2
QoS Terminology 3
PFC QoS Feature Flowcharts 6
PFC QoS Feature Summary 11
Ingress LAN Port Features 12
PFC Marking and Policing 16
LAN Egress Port Features 21
PFC QoS Statistics Data Export 24
PFC QoS Default Configuration 25
PFC QoS Configuration Guidelines and Restrictions 31
Guidelines: 31
Restrictions 32
Configuring PFC QoS 33
Enabling PFC QoS Globally 33
Enabling Queueing-Only Mode 34
Creating Named Aggregate Policers 35
Configuring a PFC QoS Policy 37
Enabling or Disabling Microflow Policing 50
Enabling Microflow Policing of Bridged Traffic 50
Enabling or Disabling PFC Features on an Interface 51
Enabling VLAN-Based PFC QoS on Layer 2 LAN Ports 52
Configuring the Trust State of Ethernet LAN and OSM Ingress Ports 53
Configuring the Ingress LAN Port CoS Value 54
Configuring Standard-Queue Drop Threshold Percentages 54
Mapping CoS Values to Drop Thresholds 59
Allocating Bandwidth Between LAN-Port Transmit Queues 64
Setting the Receive-Queue Size Ratio on a 1p1q0t or 1p1q8t Ingress LAN Ports 64
Setting the LAN-Port Transmit-Queue Size Ratio 65
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
15
Page 16

Contents
Configuring DSCP Value Maps 66
Configuring PFC QoS Statistics Data Export 70
CHAPTER
CHAPTER
32 Configuring UDLD 1
Understanding How UDLD Works 1
UDLD Overview 1
UDLD Aggressive Mode 2
Default UDLD Configuration 3
Configuring UDLD 3
Enabling UDLD Globally 3
Enabling UDLD on Individual LAN Interfaces 4
Disabling UDLD on Fiber-Optic LAN Interfaces 5
Configuring the UDLD Probe Message Interval 5
Resetting Disabled LAN Interfaces 6
33 Configuring NDE 1
Understanding How NDE Works 1
NDE Overview 2
NDE from the MSFC 2
NDE from the PFC 2
Default NDE Configuration 7
CHAPTER
Configuring NDE 8
Configuring NDE on the PFC 8
Configuring NDE on the MSFC 13
Displaying the NDE Address and Port Configuration 14
Configuring NDE Flow Filters 15
Displaying the NDE Configuration 17
34 Configuring Local SPAN and RSPAN 1
Understanding How Local SPAN and RSPAN Work 1
Local SPAN and RSPAN Overview 1
Local SPAN and RSPAN Sessions 3
Monitored Traffic 4
SPAN Sources 4
Destination Ports 5
Local SPAN and RSPAN Configuration Guidelines and Restrictions 5
Local SPAN and RSPAN Session Limits 5
Local SPAN and RSPAN Source and Destination Limits 6
16
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 17

Local SPAN and RSPAN Guidelines and Restrictions 6
VSPAN Guidelines and Restrictions 7
RSPAN Guidelines and Restrictions 7
Configuring Local SPAN and RSPAN 8
Local SPAN and RSPAN Configuration Overview 8
Configuring RSPAN VLANs 9
Configuring Local or RSPAN Sources 9
Monitoring Specific Source VLANs on a Source Trunk Port 10
Configuring Local SPAN and RSPAN Destinations 10
Verifying the Configuration 12
Configuration Examples 13
Contents
CHAPTER
35 Configuring Web Cache Services Using WCCP 1
Understanding WCCP 2
WCCP Overview 2
Hardware Acceleration 2
Understanding WCCPv1 Configuration 3
Understanding WCCPv2 Configuration 4
WCCPv2 Features 5
Restrictions for WCCPv2 7
Configuring WCCP 7
Specifying a Version of WCCP 7
Configuring a Service Group Using WCCPv2 8
Excluding Traffic on a Specific Interface from Redirection 9
Registering a Router to a Multicast Address 10
Using Access Lists for a WCCP Service Group 10
Setting a Password for a Router and Cache Engines 11
Verifying and Monitoring WCCP Configuration Settings 12
WCCP Configuration Examples 12
Changing the Version of WCCP on a Router Example 13
Performing a General WCCPv2 Configuration Example 13
Running a Web Cache Service Example 13
Running a Reverse Proxy Service Example 14
Registering a Router to a Multicast Address Example 14
Using Access Lists Example 14
Setting a Password for a Router and Cache Engines Example 15
Verifying WCCP Settings Example 15
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
17
Page 18

Contents
CHAPTER
CHAPTER
36 Configuring SNMP IfIndex Persistence 1
Understanding SNMP IfIndex Persistence 1
Configuring SNMP IfIndex Persistence 1
Enabling and Disabling SNMP IfIndex Persistence Globally 2
Enabling and Disabling SNMP IfIndex Persistence on Specific Interfaces 2
Configuration Examples 3
37 Configuring the Switch Fabric Module 1
Understanding How the Switch Fabric Module Works 1
Switch Fabric Module Overview 1
Switch Fabric Module Slots 2
Switch Fabric Redundancy 2
Forwarding Decisions for Layer 3-Switched Traffic 2
Switching Modes 2
Configuring the Switch Fabric Module 3
Configuring the Switching Mode 3
Configuring Fabric-Required Mode 4
Configuring an LCD Message 5
CHAPTER
Monitoring the Switch Fabric Module 5
Displaying the Module Information 5
Displaying the Switch Fabric Module Redundancy Status 6
Displaying Fabric Channel Switching Modes 6
Displaying the Fabric Status 7
Displaying the Fabric Utilization 7
Displaying Fabric Errors 7
38 Power Management and Environmental Monitoring 1
Understanding How Power Management Works 1
Enabling or Disabling Power Redundancy 2
Using the CLI to Power Modules Off and On 3
Using the CLI to View System Power Status 3
Using the CLI to Power Cycle Modules 4
Determining System Power Requirements 4
Understanding How Environmental Monitoring Works 4
Using CLI Commands to Monitor System Environmental Status 4
Understanding LED Environmental Indications 4
18
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 19

Contents
APPENDIX
INDEX
A Acronyms 1
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
19
Page 20

Contents
20
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 21

Audience
Preface
This preface describes who should read the Catalyst 6500 Series Switch Cisco IOS Software
Configuration Guide, how it is organized, and its document conventions.
This guide is for experienced network administrators who are responsible for configuring and
maintaining Catalyst 6500 series switches.
Organization
This guide is organized as follows:
Chapter Title Description
Chapter 1 Product Overview Presents an overview of the Catalyst 6500 series
Chapter 2 Command-Line Interfaces Describes how to use the command-line interface
Chapter 3 Configuring the Switch for the
Chapter 4 Configuring EHSA Supervisor
Chapter 5 Configuring RPR and RPR+
Chapter 6 Configuring Interfaces Describes how to configure non-layer-specific
Chapter 7 Configuring LAN Ports for Layer
Chapter 8 Configuring VTP Describes how to configure the VLAN Trunking
Chapter 9 Configuring VLANs Describes how to configure VLANs.
Chapter 10 Configuring Private VLANs Describes how to configure private VLANs.
First Time
Engine Redundancy
Supervisor Engine Redundancy
2 Switching
switches.
(CLI).
Describes how to perform a baseline configuration.
Describes how to configure EHSA supervisor engine
redundancy.
Describes how to configure RPR and RPR+
supervisor engine redundancy.
features on LAN interfaces.
Describes how to configure LAN interfaces to
support Layer 2 features, including VLAN trunks.
Protocol (VTP).
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
21
Page 22
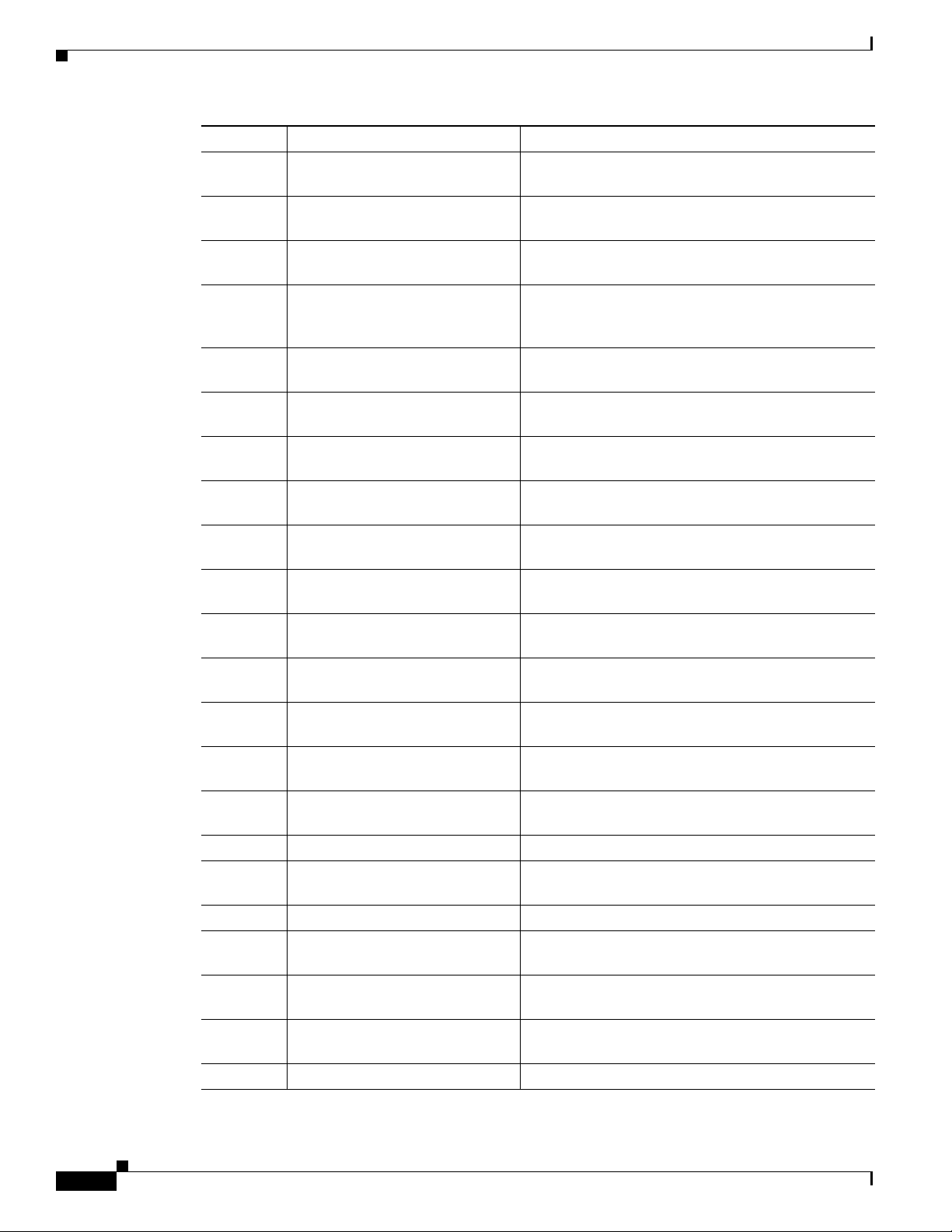
Organization
Preface
Chapter Title Description
Chapter 11 Configuring Cisco IP Phone
Support
Chapter 12 Configuring Layer 3 Interfaces Describes how to configure LAN interfaces to
Chapter 13 Configuring EtherChannels Describes how to configure Layer 2 and Layer 3
Chapter 14 Configuring IEEE 802.1Q
Tunneling and Layer 2 Protocol
Tunneling
Chapter 15 Configuring STP and IEEE 802.1s
MST
Chapter 16 Configuring Optional STP
Features
Chapter 17 Configuring IP Unicast Layer 3
Switching on Supervisor Engine 2
Chapter 18 Configuring IP Multicast Layer 3
Switching
Chapter 19 Configuring IP Unicast Layer 3
Switching on Supervisor Engine 1
Chapter 20 Configuring IPX Unicast Layer 3
Switching on Supervisor Engine 1
Chapter 21 Configuring IGMP Snooping Describes how to configure Internet Group
Chapter 22 Configuring RGMP Describes how to configure Router-Port Group
Chapter 23 Configuring Network Security Describes how to configure network security features
Chapter 24 Configuring Denial of Service
Protection
Chapter 25 Configuring IEEE 802.1X
Port-Based Authentication
Chapter 26 Configuring Port Security Describes how to configure port security.
Chapter 27 Configuring Layer 3 Protocol
Filtering on Supervisor Engine 1
Chapter 28 Configuring Traffic Storm Control Describes how to configure traffic storm control.
Chapter 29 Configuring Broadcast
Suppression
Chapter 30 Configuring CDP Describes how to configure Cisco Discovery Protocol
Chapter 32 Configuring UDLD Describes how to configure the UniDirectional Link
Chapter 31 Configuring PFC QoS Describes how to configure quality of service (QoS).
Describes how to configure Cisco IP Phone support.
support Layer 3 features.
EtherChannel port bundles.
Describes how to configure IEEE 802.1Q tunneling
and Layer 2 protocol tunneling.
Describes how to configure the Spanning Tree
Protocol (STP) and explains how STP works.
Describes how to configure the STP PortFast,
UplinkFast, and BackboneFast features.
Describes how to configure IP unicast Layer 3
switching for Supervisor Engine 2.
Describes how to configure IP Multicast Multilayer
Switching (MMLS).
Describes how to configure IP unicast Layer 3
switching for Supervisor Engine 1.
Describes how to configure IPX unicast Layer 3
switching for Supervisor Engine 1.
Management Protocol (IGMP) snooping.
Management Protocol (RGMP).
that are unique to the Catalyst 6500 series switches.
Describes how to configure denial of service
protection.
Describes how to configure IEEE 802.1X port-based
authentication.
Describes how to configure Layer 3 protocol filtering
on Supervisor Engine 1.
Describes how to configure broadcast suppression.
(CDP).
Detection (UDLD) protocol.
22
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 23
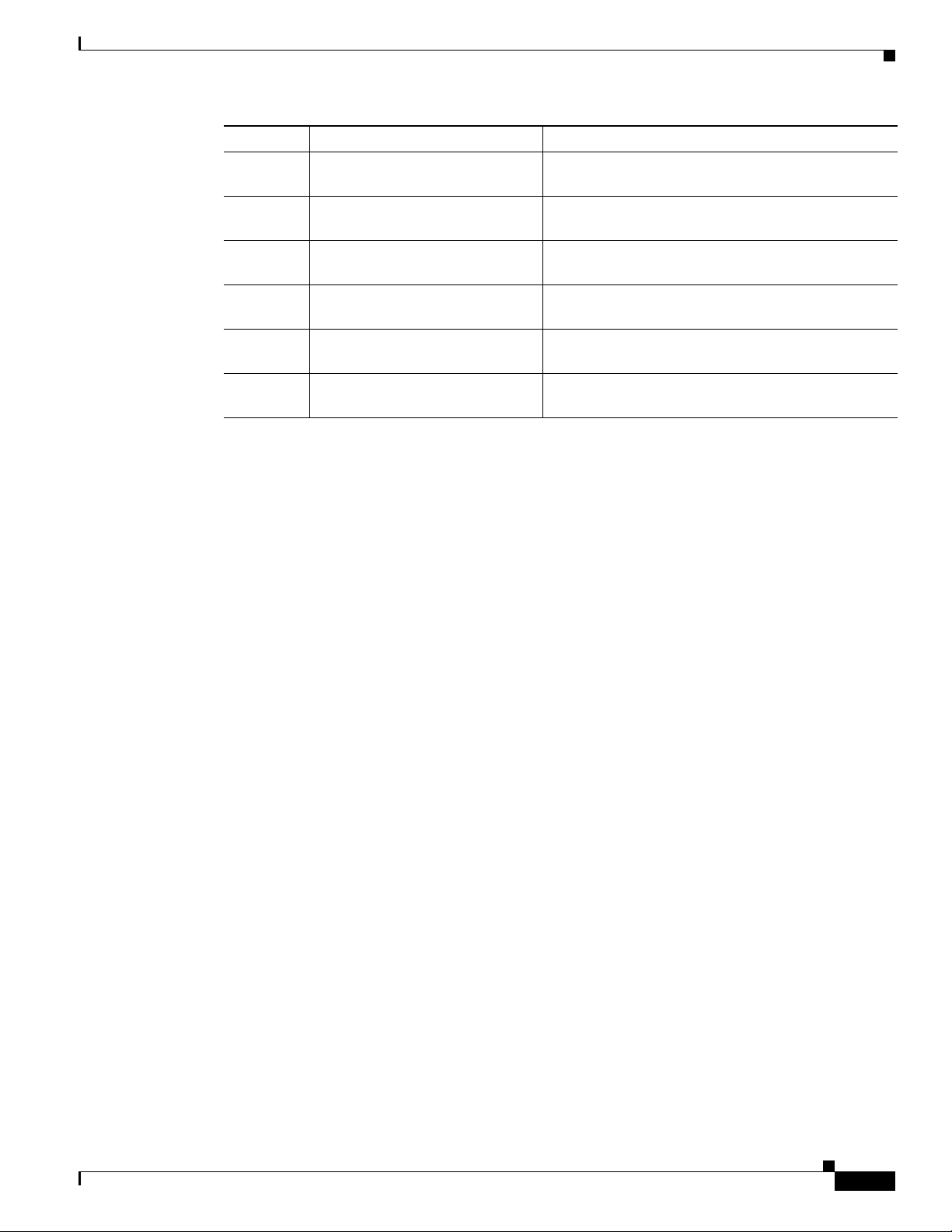
Preface
Chapter Title Description
Chapter 33 Configuring NDE Describes how to configure Neflow Data Export
Chapter 34 Configuring Local SPAN and
RSPAN
Chapter 35 Configuring Web Cache Services
Using WCCP
Chapter 36 Configuring SNMP IfIndex
Persistence
Chapter 37 Configuring the Switch Fabric
Module
Chapter 38 Power Management and
Environmental Monitoring
Related Documentation
Related Documentation
(NDE).
Describes how to configure the Switch Port Analyzer
(SPAN).
Describes how to configure web cache services using
WCCP.
Describes how to configure SNMP ifIndex
persistence.
Describes how to configure the Switch Fabric
Module.
Describes how to configure power management and
environmental monitoring features.
The following publications are available for the Catalyst 6500 series switches:
• Catalyst 6500 Series Switch Installation Guide
• Catalyst 6500 Series Switch Module Installation Guide
• Catalyst 6500 Series Switch Cisco IOS Command Reference
• Catalyst 6500 Series Switch Cisco IOS System Message Guide
• Release Notes for Cisco IOS Release 12.1 E on the Catalyst 6500 and Cisco 7600
Supervisor Engine and MSFC
• Cisco IOS Configuration Guides and Command References—Use these publications to help you
configure Cisco IOS software features not described in the Catalyst 6500 series switch publications:
–
Configuration Fundamentals Configuration Guide
–
Configuration Fundamentals Command Reference
–
Bridging and IBM Networking Configuration Guide
–
Bridging and IBM Networking Command Reference
–
Interface Configuration Guide
–
Interface Command Reference
–
Network Protocols Configuration Guide, Part 1, 2, and 3
–
Network Protocols Command Reference, Part 1, 2, and 3
–
Security Configuration Guide
–
Security Command Reference
–
Switching Services Configuration Guide
78-14099-04
–
Switching Services Command Reference
–
Voice, Video, and Home Applications Configuration Guide
–
Voice, Video, and Home Applications Command Reference
–
Software Command Summary
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
23
Page 24

Conventions
• For information about MIBs, go to this URL:
Conventions
This document uses the following conventions:
–
Software System Error Messages
–
Debug Command Reference
–
Internetwork Design Guide
–
Internetwork Troubleshooting Guide
–
Configuration Builder Getting Started Guide
The Cisco IOS Configuration Guides and Command References are located at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
Preface
Convention Description
boldface font Commands, command options, and keywords are in boldface.
italic font Arguments for which you supply values are in italics.
[ ] Elements in square brackets are optional.
{ x | y | z } Alternative keywords are grouped in braces and separated by vertical bars.
[ x | y | z ] Optional alternative keywords are grouped in brackets and separated by
vertical bars.
string A nonquoted set of characters. Do not use quotation marks around the
string or the string will include the quotation marks.
screen font Terminal sessions and information the system displays are in screen font.
boldface screen
Information you must enter is in boldface screen font.
font
italic screen font Arguments for which you supply values are in italic screen font.
This pointer highlights an important line of text in an example.
^ The symbol ^ represents the key labeled Control—for example, the key
combination ^D in a screen display means hold down the Control key
while you press the D key.
< > Nonprinting characters, such as passwords are in angle brackets.
Notes use the following conventions:
24
Note Means reader take note. Notes contain helpful suggestions or references to material not covered in the
publication.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 25

Preface
Conventions
Cautions use the following conventions:
Caution Means reader be careful. In this situation, you might do something that could result in equipment
damage or loss of data.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional
information, see the monthly What’s New in Cisco Product Documentation, which also lists all new and
revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What’s New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed
and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free
service and Cisco currently supports RSS version 2.0.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
25
Page 26

Conventions
Preface
26
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 27

CHA PTER
1
Product Overview
The Cisco IOS on the Catalyst 6500 Series Switches product supports the following hardware and
software:
• Supervisor Engine 2, Policy Feature Card 2 (PFC2), and Multilayer Switch Feature Card 2
(MSFC2); and in Catalyst 6500 series switches:
–
Switch Fabric Module
–
Fabric-enabled switching modules
–
Fabric-enabled switching modules with a distributed forwarding card (DFC)
• Supervisor Engine 1, PFC, and MSFC or MSFC2
• All Layer 2 and Layer 3 configuration from the same user interface
• Except for VLANs, Layer 2 and Layer 3 configuration is stored in a standard IOS configuration file
Refer to the Release Notes for Cisco IOS Release 12.1 E on the Catalyst 6500 and Cisco 7600
Supervisor Engine and MSFC publication for complete information about the chassis, modules,
and software features supported by the Catalyst 6500 series switches:
http://www.cisco.com/univercd/cc/td/doc/product/lan/cat6000/12_1e/ol_2310.htm
The Cisco IOS on the Catalyst 6500 Series Switches product supports configuration using:
• CLI—See Chapter 2, “Command-Line Interfaces”
• SNMP—Refer to the IOS Configuration Fundamentals Configuration Guide and Command
Reference at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
• IOS web browser interface—Refer to “Using the Cisco Web Browser” in the IOS Configuration
Fundamentals Configuration Guide and Command Reference at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
• Embedded CiscoView—See the “Configuring Embedded CiscoView Support” section on page 1-2.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
1-1
Page 28
Configuring Embedded CiscoView Support
Configuring Embedded CiscoView Support
These sections describe the Embedded CiscoView support available with Release 12.1(20)E and later
releases:
• Understanding Embedded CiscoView, page 1-2
• Installing and Configuring Embedded CiscoView, page 1-2
• Displaying Embedded CiscoView Information, page 1-3
Understanding Embedded CiscoView
The Embedded CiscoView network management system is a web-based interface that uses HTTP and
SNMP to provide a graphical representation of the switch and to provide a GUI-based management and
configuration interface. You can download the Java Archive (JAR) files for Embedded CiscoView at
this URL:
http://www.cisco.com/kobayashi/sw-center/netmgmt/ciscoview/embed-cview-planner.shtml
Chapter 1 Product Overview
Installing and Configuring Embedded CiscoView
To install and configure Embedded CiscoView, perform the following steps:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
Step 7
Step 8
Step 9
Router# dir device_name
Router# delete device_name:cv/*
Router# squeeze device_name:
Router# archive tar /xtract tftp://
ip address of tftp server/ciscoview.tar
device_name:cv
Router# dir device_name:
Router# configure terminal
Router(config)# ip http server
Router(config)# snmp-server community string ro
Router(config)# snmp-server community string rw
Displays the contents of the device.
If you are installing Embedded CiscoView for the first
time, or if the CiscoView directory is empty, skip to
Step 4.
Removes existing files from the CiscoView directory.
Recovers the space in the file system.
Extracts the CiscoView files from the tar file on the TFTP
server to the CiscoView directory.
Displays the contents of the device.
In a redundant configuration, repeat Step 1 through
Step 5 for the file system on the redundant supervisor
engine.
Enters global configuration mode.
Enables the HTTP web server.
Configures the SNMP password for read-only operation.
Configures the SNMP password for read/write operation.
1-2
Note The default password for accessing the switch web page is the enable-level password of the switch.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 29

Chapter 1 Product Overview
For more information about web access to the switch, refer to “Using the Cisco Web Browser” in the
IOS Configuration Fundamentals Configuration Guide at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_c/fcprt1/fcd105.htm
Displaying Embedded CiscoView Information
To display the Embedded CiscoView information, enter the following EXEC commands:
Command Purpose
Router# show ciscoview package
Router# show ciscoview version
Displays information about the Embedded CiscoView files.
Displays the Embedded CiscoView version.
Configuring Embedded CiscoView Support
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
1-3
Page 30

Configuring Embedded CiscoView Support
Chapter 1 Product Overview
1-4
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 31

CHA PTER
Command-Line Interfaces
This chapter describes the command-line interfaces (CLIs) you use to configure the Catalyst 6500 series
switches.
Note For complete syntax and usage information for the commands used in this chapter, refer to the
Catalyst 6500 Series Switch Cisco IOS Command Reference publication and the Release 12.1
publications at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
This chapter consists of these sections:
• Accessing the CLI, page 2-1
• Performing Command Line Processing, page 2-3
• Performing History Substitution, page 2-3
2
• Cisco IOS Command Modes, page 2-4
• Displaying a List of Cisco IOS Commands and Syntax, page 2-5
• ROM-Monitor Command-Line Interface, page 2-6
Accessing the CLI
These sections describe accessing the CLI:
• Accessing the CLI through the EIA/TIA-232 Console Interface, page 2-1
• Accessing the CLI through Telnet, page 2-2
Accessing the CLI through the EIA/TIA-232 Console Interface
Note EIA/TIA-232 was known as recommended standard 232 (RS-232) before its acceptance as a standard by
the Electronic Industries Alliance (EIA) and Telecommunications Industry Association (TIA).
Perform initial configuration over a connection to the EIA/TIA-232 console interface. Refer to the
Catalyst 6500 Series Switch Module Installation Guide for console interface cable connection
procedures.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
2-1
Page 32

Accessing the CLI
To make a console connection, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Press Return. Brings up the prompt.
Router> enable
Password: password
Router#
Router# quit
After making a console connection, you see this display:
Press Return for Console prompt
Router> enable
Password:
Router#
Accessing the CLI through Telnet
Chapter 2 Command-Line Interfaces
Initiates enable mode enable.
Completes enable mode enable.
Exits the session when finished.
Step 1
Step 2
Step 3
Step 4
Step 5
Note Before you can make a Telnet connection to the switch, you must configure an IP address (see the
“Configuring IP Routing and Addresses” section on page 12-2).
The switch supports up to eight simultaneous Telnet sessions. Telnet sessions disconnect automatically
after remaining idle for the period specified with the exec-timeout command.
To make a Telnet connection to the switch, perform this task:
Command Purpose
telnet {hostname | ip_addr}
Makes a Telnet connection from the remote host, to the
switch you want to access.
Password: password
Router#
Initiates authentication.
Note If no password has been configured, press
Return.
Router> enable
Password: password
Router#
Router# quit
Initiates enable mode enable.
Completes enable mode enable.
Exits the session when finished.
2-2
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 33

Chapter 2 Command-Line Interfaces
This example shows how to open a Telnet session to the switch:
unix_host% telnet Router_1
Trying 172.20.52.40...
Connected to 172.20.52.40.
Escape character is '^]'.
User Access Verification
Password:
Router_1> enable
Password:
Router_1#
Performing Command Line Processing
Commands are not case sensitive. You can abbreviate commands and parameters if the abbreviations
contain enough letters to be different from any other currently available commands or parameters. You
can scroll through the last 20 commands stored in the history buffer, and enter or edit the command at
the prompt. Table 2- 1 lists the keyboard shortcuts for entering and editing commands.
Performing Command Line Processing
Table 2-1 Keyboard Shortcuts
Keystrokes Purpose
Press Ctrl-B or
press the left arrow key
Press Ctrl-F or
press the right arrow key
1
Moves the cursor back one character
Moves the cursor forward one character
1
Press Ctrl-A Moves the cursor to the beginning of the command line
Press Ctrl-E Moves the cursor to the end of the command line
Press Esc B Moves the cursor back one word
Press Esc F Moves the cursor forward one word
1. The arrow keys function only on ANSI-compatible terminals such as VT100s.
Performing History Substitution
The history buffer stores the last 20 commands you entered. History substitution allows you to access
these commands without retyping them, by using special abbreviated commands. Table 2-2 lists the
history substitution commands.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
2-3
Page 34

Cisco IOS Command Modes
Table 2-2 History Substitution Commands
Command Purpose
Ctrl-P or the up arrow key.
Ctrl-N or the down arrow key.
Router# show history
1. The arrow keys function only on ANSI-compatible terminals such as VT100s.
1
1
Cisco IOS Command Modes
Chapter 2 Command-Line Interfaces
Recalls commands in the history buffer, beginning
with the most recent command. Repeat the key
sequence to recall successively older commands.
Returns to more recent commands in the history
buffer after recalling commands with Ctrl-P or the
up arrow key. Repeat the key sequence to recall
successively more recent commands.
While in EXEC mode, lists the last several
commands you have just entered.
Note For complete information about Cisco IOS command modes, refer to the Cisco IOS Configuration
Fundamentals Configuration Guide and the Cisco IOS Configuration Fundamentals Command
Reference publication at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
The Cisco IOS user interface is divided into many different modes. The commands available to you
depend on which mode you are currently in. To get a list of the commands in a given mode, type a
question mark (?) at the system prompt. See the “Displaying a List of Cisco IOS Commands and Syntax”
section on page 2-5.
When you start a session on the switch, you begin in user mode, often called user EXEC mode. Only a
limited subset of the commands are available in EXEC mode. To have access to all commands, you must
enter privileged EXEC mode. Normally, you must type in a password to access privileged EXEC mode.
From privileged EXEC mode, you can type in any EXEC command or access global configuration mode.
The configuration modes allow you to make changes to the running configuration. If you later save the
configuration, these commands are stored across reboots. You must start at global configuration mode.
From global configuration mode, you can enter interface configuration mode, subinterface configuration
mode, and a variety of protocol-specific modes.
Note With Release 12.1(11b)E and later, when you are in configuration mode you can enter EXEC mode-level
commands by entering the do keyword before the EXEC mode-level command.
ROM-monitor mode is a separate mode used when the switch cannot boot properly. For example, the
switch might enter ROM-monitor mode if it does not find a valid system image when it is booting, or if
its configuration file is corrupted at startup. See the “ROM-Monitor Command-Line Interface” section
on page 2-6.
Table 2-3 lists and describes frequently used Cisco IOS modes.
2-4
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 35

Chapter 2 Command-Line Interfaces
Displaying a List of Cisco IOS Commands and Syntax
Table 2-3 Frequently Used Cisco IOS Command Modes
Mode Description of Use How to Access Prompt
User EXEC Connect to remote devices, change
terminal settings on a temporary
basis, perform basic tests, and
display system information.
Privileged EXEC (enable) Set operating parameters. The
privileged command set includes
the commands in user EXEC
mode, as well as the configure
command. Use this command to
access the other command modes.
Global configuration Configure features that affect the
system as a whole.
Interface configuration Many features are enabled for a
particular interface. Interface
commands enable or modify the
operation of an interface.
Console configuration From the directly connected
console or the virtual terminal
used with Telnet, use this
configuration mode to configure
the console interface.
Log in.
From the user EXEC mode, enter
the enable command and the
enable password.
From the privileged EXEC mode,
enter the configure terminal
command.
From global configuration mode,
enter the interface type slot/port
command.
From global configuration mode,
enter the line console 0 command.
Router>
Router#
Router(config)#
Router(config-if)#
Router(config-line)#
The Cisco IOS command interpreter, called the EXEC, interprets and executes the commands you enter.
You can abbreviate commands and keywords by entering just enough characters to make the command
unique from other commands. For example, you can abbreviate the show command to sh and the
configure terminal command to config t.
When you type exit, the switch backs out one level. To exit configuration mode completely and return
to privileged EXEC mode, press Ctrl-Z.
Displaying a List of Cisco IOS Commands and Syntax
In any command mode, you can display a list of available commands by entering a question mark (?).
Router> ?
To display a list of commands that begin with a particular character sequence, type in those characters
followed by the question mark (?). Do not include a space. This form of help is called word help because
it completes a word for you.
Router# co?
configure
To display keywords or arguments, enter a question mark in place of a keyword or argument. Include a
space before the question mark. This form of help is called command syntax help because it reminds you
which keywords or arguments are applicable based on the command, keywords, and arguments you have
already entered.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
2-5
Page 36

ROM-Monitor Command-Line Interface
For example:
Router# configure ?
memory Configure from NV memory
network Configure from a TFTP network host
overwrite-network Overwrite NV memory from TFTP network host
terminal Configure from the terminal
<cr>
To redisplay a command you previously entered, press the up arrow key or Ctrl-P. You can continue to
press the up arrow key to see the last 20 commands you entered.
Tip If you are having trouble entering a command, check the system prompt, and enter the question mark (?)
for a list of available commands. You might be in the wrong command mode or using incorrect syntax.
Enter exit to return to the previous mode. Press Ctrl-Z or enter the end command in any mode to
immediately return to privileged EXEC mode.
ROM-Monitor Command-Line Interface
Chapter 2 Command-Line Interfaces
The ROM-monitor is a ROM-based program that executes upon platform power-up, reset, or when a fatal
exception occurs. The switch enters ROM-monitor mode if it does not find a valid software image, if the
NVRAM configuration is corrupted, or if the configuration register is set to enter ROM-monitor mode.
From the ROM-monitor mode, you can load a software image manually from Flash memory, from a
network server file, or from bootflash.
You can also enter ROM-monitor mode by restarting and pressing the Break key during the first 60
seconds of startup.
Note The Break key is always enabled for 60 seconds after rebooting, regardless of whether the Break key is
configured to be off by configuration register settings.
To access the ROM-monitor mode through a terminal server, you can escape to the Telnet prompt and
enter the send break command for your terminal emulation program to break into ROM-monitor mode.
Once you are in ROM-monitor mode, the prompt changes to rommon 1>. Enter a question mark (?) to
see the available ROM-monitor commands.
For more information about the ROM-monitor commands, refer to the Catalyst 6500 Series Switch
Cisco IOS Command Reference publication.
2-6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 37

CHA PTER
Configuring the Switch for the First Time
This chapter contains information about how to initially configure the Catalyst 6500 series switch, which
supplements the administration information and procedures in these publications:
• Cisco IOS Configuration Fundamentals Configuration Guide, Release 12.1, at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_c/index.htm
• Cisco IOS Configuration Fundamentals Configuration Command Reference, Release 12.1, at
this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_r/index.htm
Note For complete syntax and usage information for the commands used in this chapter, refer to the
Catalyst 6500 Series Switch Cisco IOS Command Reference publication and the Release 12.1
publications at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
3
This chapter consists of these sections:
• Default Configuration, page 3-1
• Configuring the Switch, page 3-2
• Protecting Access to Privileged EXEC Commands, page 3-15
• Recovering a Lost Enable Password, page 3-19
• Modifying the Supervisor Engine Startup Configuration, page 3-20
Default Configuration
Table 3-1 shows the default configuration.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-1
Page 38

Configuring the Switch
Table 3-1 Default Configuration
Feature Default Value
Administrative connection Normal mode
Global information No value for the following:
System clock No value for system clock time
Passwords No passwords configured for normal mode or
Prompt
Configuring the Switch
Chapter 3 Configuring the Switch for the First Time
• System name
• System contact
• Location
enable mode (press the Return key)
Router>
These sections describe how to configure the switch:
• Using the Setup Facility or the setup Command, page 3-2
• Using Configuration Mode, page 3-10
• Checking the Running Configuration Before Saving, page 3-10
• Saving the Running Configuration Settings, page 3-11
• Reviewing the Configuration, page 3-11
• Configuring a Default Gateway, page 3-12
• Configuring a Static Route, page 3-12
• Configuring a BOOTP Server, page 3-14
Note With Release 12.1(11b)E and later, when you are in configuration mode you can enter EXEC mode-level
commands by entering the do keyword before the EXEC mode-level command.
Using the Setup Facility or the setup Command
These sections describe the setup facility and the setup command:
• Setup Overview, page 3-2
• Configuring the Global Parameters, page 3-3
Setup Overview
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-2
• Configuring Interfaces, page 3-8
At initial startup, the switch automatically defaults to the setup facility. (The setup command facility
functions exactly the same as a completely unconfigured system functions when you first boot it up.)
You can run the setup facility by entering the setup command at the enable prompt (#).
78-14099-04
Page 39

Chapter 3 Configuring the Switch for the First Time
When you enter the setup command, current system configuration defaults are displayed in square
brackets [ ] as you move through the setup command process and are queried by the system to make
changes.
For example, you will see this display when you use the setup facility:
Configuring interface FastEtherent3/1:
Is this interface in use?: yes
Configure IP on this interface?: yes
When you use the setup command, you see this display:
Configuring interface FastEthernet4/1:
Is this interface in use?[yes]: yes
Configure IP on this interface?[yes]: yes
Configuring the Global Parameters
When you first start the setup facility or enter the setup command, you are queried by the system to
configure the global parameters, which are used for controlling system-wide settings.
To boot the switch and enter the global parameters, follow these steps:
Configuring the Switch
Step 1 Connect a console terminal to the console interface on the supervisor engine, and then boot the system
to the user EXEC prompt (
Router>).
The following display appears after you boot the Catalyst 6500 series switch (depending on your
configuration, your display might not exactly match the example):
System Bootstrap, Version 6.1(2)
Copyright (c) 1994-2000 by cisco Systems, Inc.
c6k_sup2 processor with 131072 Kbytes of main memory
rommon 1 > boot slot0:c6sup22-jsv-mz.121-5c.EX.bin
Self decompressing the image : #################################################
################################################################################
################################################################################
################################################################################
################################################################################
[OK]
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
78-14099-04
Cisco Internetwork Operating System Software
IOS (tm) c6sup2_sp Software (c6sup2_sp-SPV-M), Version 12.1(5c)EX, EARLY DEPLOYM
ENT RELEASE SOFTWARE (fc1)
Synced to mainline version: 12.1(5c)
TAC:Home:Software:Ios General:CiscoIOSRoadmap:12.1
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-3
Page 40

Configuring the Switch
Chapter 3 Configuring the Switch for the First Time
Copyright (c) 1986-2001 by cisco Systems, Inc.
Compiled Wed 28-Mar-01 18:36 by hqluong
Image text-base: 0x30020980, data-base: 0x306B8000
Start as Primary processor
00:00:05: %SYS-3-LOGGER_FLUSHING: System pausing to ensure console debugging out
put.
00:00:03: Currently running ROMMON from S (Gold) region
00:00:05: %OIR-6-CONSOLE: Changing console ownership to route processor
System Bootstrap, Version 12.1(3r)E2, RELEASE SOFTWARE (fc1)
Copyright (c) 2000 by cisco Systems, Inc.
Cat6k-MSFC2 platform with 131072 Kbytes of main memory
rommon 1 > boot
Self decompressing the image : #################################################
################################################################################
## [OK]
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco Internetwork Operating System Software
IOS (tm) MSFC2 Software (C6MSFC2-BOOT-M), Version 12.1(3a)E4, EARLY DEPLOYMENT R
ELEASE SOFTWARE (fc1)
Copyright (c) 1986-2000 by cisco Systems, Inc.
Compiled Sat 14-Oct-00 05:33 by eaarmas
Image text-base: 0x30008980, data-base: 0x303B6000
cisco Cat6k-MSFC2 (R7000) processor with 114688K/16384K bytes of memory.
Processor board ID SAD04430J9K
R7000 CPU at 300Mhz, Implementation 39, Rev 2.1, 256KB L2, 1024KB L3 Cache
Last reset from power-on
X.25 software, Version 3.0.0.
509K bytes of non-volatile configuration memory.
16384K bytes of Flash internal SIMM (Sector size 512K).
3-4
Press RETURN to get started!
Note The first two sections of the configuration script (the banner and the installed hardware) appear
only at initial system startup. On subsequent uses of the setup command facility, the setup script
begins with the following System Configuration Dialog.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 41

Chapter 3 Configuring the Switch for the First Time
--- System Configuration Dialog ---
Continue with configuration dialog? [yes/no]: y
At any point you may enter a question mark '?' for help.
Use ctrl-c to abort configuration dialog at any prompt.
Default settings are in square brackets '[]'.
Basic management setup configures only enough connectivity
for management of the system, extended setup will ask you
to configure each interface on the system
Note The examples in this section are intended as examples only. Your configuration might look
differently depending on your system configuration.
Step 2 Enter yes or press Return when asked if you want to enter the configuration dialog and if you want to
see the current interface summary. Press Return to accept the default (yes):
Would you like to enter the initial configuration dialog? [yes]:
Configuring the Switch
First, would you like to see the current interface summary? [yes]:
This example of a yes response (displayed during the setup facility) shows a switch at first-time startup;
that is, nothing has been configured:
Current interface summary
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES TFTP administratively down down
GigabitEthernet1/1 unassigned YES TFTP administratively down down
GigabitEthernet1/2 unassigned YES TFTP administratively down down
GigabitEthernet3/1 unassigned YES TFTP administratively down down
GigabitEthernet3/2 unassigned YES TFTP administratively down down
GigabitEthernet3/3 unassigned YES TFTP administratively down down
GigabitEthernet3/4 unassigned YES TFTP administratively down down
GigabitEthernet3/5 unassigned YES TFTP administratively down down
GigabitEthernet3/6 unassigned YES TFTP administratively down down
GigabitEthernet3/7 unassigned YES TFTP administratively down down
GigabitEthernet3/8 unassigned YES TFTP administratively down down
78-14099-04
(Additional displayed text omitted from this example.)
This example of a yes response (displayed during the setup command facility) shows a switch with some
interfaces already configured:
Current interface summary
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES TFTP administratively down down
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-5
Page 42

Configuring the Switch
Step 3 Choose which protocols to support on your interfaces. On IP installations only, you can accept the
Chapter 3 Configuring the Switch for the First Time
GigabitEthernet1/1 172.20.52.34 YES NVRAM up up
GigabitEthernet1/2 unassigned YES TFTP administratively down down
GigabitEthernet3/1 unassigned YES TFTP administratively down down
GigabitEthernet3/2 unassigned YES TFTP administratively down down
GigabitEthernet3/3 unassigned YES TFTP administratively down down
GigabitEthernet3/4 unassigned YES TFTP administratively down down
GigabitEthernet3/5 unassigned YES TFTP administratively down down
GigabitEthernet3/6 unassigned YES TFTP administratively down down
GigabitEthernet3/7 unassigned YES TFTP administratively down down
GigabitEthernet3/8 unassigned YES TFTP administratively down down
<...output truncated...>
default values for most of the questions.
A typical minimal configuration using IP follows and continues through Step 8:
Configuring global parameters:
Enter host name [Router]: Router
Step 4 Enter the enable secret password when the following is displayed (remember this password for future
reference):
The enable secret is a password used to protect access to
privileged EXEC and configuration modes. This password, after
entered, becomes encrypted in the configuration.
Enter enable secret: barney
Step 5 Enter the enable password when the following is displayed (remember this password for future
reference):
The enable password is used when you do not specify an
enable secret password, with some older software versions, and
some boot images.
Enter enable password: wilma
The commands available at the user EXEC level are a subset of those available at the privileged EXEC
level. Because many privileged EXEC commands are used to set operating parameters, you should
protect these commands with passwords to prevent unauthorized use.
You must enter the correct password to gain access to privileged EXEC commands. When you are
running from the boot ROM monitor, the enable password might be the correct one to use, depending on
your boot ROM level.
The enable and enable secret passwords need to be different for effective security. You can enter the same
password for both enable and enable secret during the setup script, but you receive a warning message
indicating that you should enter a different password.
3-6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 43

Chapter 3 Configuring the Switch for the First Time
Note An enable secret password can contain from 1 to 25 uppercase and lowercase alphanumeric
characters; an enable password can contain any number of uppercase and lowercase
alphanumeric characters. In both cases, a number cannot be the first character. Spaces are also
valid password characters; for example, “two words” is a valid password. Leading spaces are
ignored; trailing spaces are recognized.
Step 6 Enter the virtual terminal password when the following is displayed (remember this password for future
reference):
The virtual terminal password is used to protect
access to the router over a network interface.
Enter virtual terminal password: bambam
Step 7 In most cases you will use IP routing. If so, you must also select an interior routing protocol, for
example, the Enhanced Interior Gateway Routing Protocol (EIGRP).
Enter yes (the default) or press Return to configure IP, and then select EIGRP:
Configure IP? [yes]:
Configure EIGRP routing? [yes]:
Your IGRP autonomous system number [1]: 301
Configuring the Switch
Step 8 Enter yes or no to accept or refuse SNMP management:
Configure SNMP Network Management? [yes]:
Community string [public]:
For complete SNMP information and procedures, refer to these publications:
• Cisco IOS Configuration Fundamentals Configuration Guide, Release 12.1, “Cisco IOS System
Management,” “Configuring SNMP Support,” at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_c/fcprt3/fcd301.htm
• Cisco IOS Configuration Fundamentals Configuration Command Reference, Release 12.1, at
this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_r/index.htm
To provide a review of what you have done, a display similar to the following appears and lists all of the
configuration parameters you selected in Steps 3 through 8. These parameters and their defaults are
shown in the order in which they appeared on your console terminal:
The following configuration command script was created:
hostname router
enable secret 5 $1$S3Lx$uiTYg2UrFK1U0dgWdjvxw.
enable password lab
line vty 0 4
password lab
no snmp-server
!
ip routing eigrp 301
!
interface Vlan1
shutdown
no ip address
!
interface GigabitEthernet1/1
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-7
Page 44

Configuring the Switch
Chapter 3 Configuring the Switch for the First Time
shutdown
no ip address
!
interface GigabitEthernet1/2
shutdown
no ip address
!
.
<...output truncated...>
.!
end
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 2
% You can enter the setup, by typing setup at IOS command prompt
Router#
This completes the procedure on how to configure global parameters. The setup facility continues with
the process to configure interfaces in the next section “Configuring Interfaces.”
Configuring Interfaces
This section provides steps for configuring installed interfaces (using the setup facility or setup
command facility) to allow communication over your external networks. To configure the interface
parameters, you need your interface network addresses, subnet mask information, and which protocols
you want to configure. (For additional interface configuration information on each of the modules
available, refer to the individual configuration notes that shipped with your modules.)
Note The examples in this section are intended as examples only. Your configuration might look differently
depending on your system configuration.
To configure interfaces, follow these steps:
Step 1 At the prompt for the Gigabit Ethernet interface configuration, enter the appropriate responses for your
requirements, using your own address and subnet mask:
Do you want to configure GigabitEthernet1/1 interface? [no]: yes
Configure IP on this interface? [no]: yes
IP address for this interface: 172.20.52.34
Subnet mask for this interface [255.255.0.0] : 255.255.255.224
Class B network is 172.20.0.0, 27 subnet bits; mask is /27
Step 2 At the prompt for all other interface types, enter the appropriate responses for your requirements:
Do you want to configure FastEthernet5/1 interface? [no]: y
Configure IP on this interface? [no]: y
IP address for this interface: 172.20.52.98
Subnet mask for this interface [255.255.0.0] : 255.255.255.248
Class B network is 172.20.0.0, 29 subnet bits; mask is /29
3-8
Repeat this step for each interface you need to configure. Proceed to Step 3 to check and verify your
configuration parameters.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 45

Chapter 3 Configuring the Switch for the First Time
When you reach and respond to the configuration dialog for the last installed interface, your interface
configuration is complete.
Step 3 Check and verify the entire list of configuration parameters, which should display on your console
terminal and end with the following query:
Use this configuration? [yes/no]:
A no response places you back at the enable prompt (#). You will need to reenter the setup command to
reenter your configuration. A yes response saves the running configuration to NVRAM as follows:
Use this configuration? [yes/no]: yes
[OK]
Use the enabled mode ‘configure’ command to modify this configuration.
Press RETURN to get started!
After you press the Return key, this prompt appears:
Router>
This completes the procedures for configuring global parameters and interface parameters in your
system. Your interfaces are now available for limited use.
If you want to modify the currently saved configuration parameters after the initial configuration, enter
the setup command. To perform more complex configurations, enter configuration mode and use the
configure command. Check the current state of the switch using the show version command, which
displays the software version and the interfaces, as follows:
Router# show version
Cisco Internetwork Operating System Software
IOS (tm) c6sup2_rp Software (c6sup2_rp-JS-M), Version 12.1(13)E1, EARLY DEPLOYM)
TAC Support: http://www.cisco.com/tac
Copyright (c) 1986-2002 by cisco Systems, Inc.
Compiled Wed 06-Nov-02 13:57 by eaarmas
Image text-base: 0x40008C00, data-base: 0x41A72000
Configuring the Switch
78-14099-04
ROM: System Bootstrap, Version 12.1(11r)E1, RELEASE SOFTWARE (fc1)
BOOTLDR: c6sup2_rp Software (c6sup2_rp-JS-M), Version 12.1(13)E1, EARLY DEPLOYM)
Router uptime is 4 hours, 22 minutes
Time since Router switched to active is 4 hours, 22 minutes
System returned to ROM by power-on (SP by power-on)
System image file is "sup-bootflash:c6sup22-js-mz.121-13.E1"
cisco Catalyst 6000 (R7000) processor with 112640K/18432K bytes of memory.
Processor board ID SAD06210067
R7000 CPU at 300Mhz, Implementation 39, Rev 3.3, 256KB L2, 1024KB L3 Cache
Last reset from power-on
Bridging software.
X.25 software, Version 3.0.0.
SuperLAT software (copyright 1990 by Meridian Technology Corp).
TN3270 Emulation software.
4 Virtual Ethernet/IEEE 802.3 interface(s)
48 FastEthernet/IEEE 802.3 interface(s)
2 Gigabit Ethernet/IEEE 802.3 interface(s)
381K bytes of non-volatile configuration memory.
16384K bytes of Flash internal SIMM (Sector size 512K).
Configuration register is 0x2102
Router#
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-9
Page 46

Configuring the Switch
For detailed interface configuration information, refer to the Cisco IOS Interface Configuration Guide
at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/inter_c/index.htm
Using Configuration Mode
If you prefer not to use the setup facility, you can configure the switch from configuration mode as
follows:
Step 1 Connect a console terminal to the console interface of your supervisor engine.
Step 2 When you are asked if you want to enter the initial dialog, answer no to enter the normal operating mode
as follows:
Would you like to enter the initial dialog? [yes]: no
Step 3 After a few seconds you will see the user EXEC prompt (Router>). Type enable to enter enable mode:
Router> enable
Chapter 3 Configuring the Switch for the First Time
Note Configuration changes can only be made in enable mode.
The prompt will change to the privileged EXEC prompt (#) as follows:
Router#
Step 4 At the prompt (#), enter the configure terminal command to enter configuration mode as follows:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
At the prompt, enter the interface type slot/interface command to enter interface configuration mode as
follows:
Router(config)# interface fastethernet 5/1
Router(config-if)#
In either of these configuration modes, you can enter any changes to the configuration. Enter the end
command to exit configuration mode.
Step 5 Save your settings. (See the “Saving the Running Configuration Settings” section on page 3-11.)
Your switch is now minimally configured and can boot with the configuration you entered. To see a list
of the configuration commands, enter ? at the prompt or press the help key in configuration mode.
Checking the Running Configuration Before Saving
You can check the configuration settings you entered or changes you made by entering the show
running-config command at the privileged EXEC prompt (#) as follows:
Router# show running-config
Building configuration...
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-10
78-14099-04
Page 47

Chapter 3 Configuring the Switch for the First Time
Current configuration:
Current configuration : 3441 bytes
!
version 12.1
service timestamps debug datetime localtime
service timestamps log datetime localtime
no service password-encryption
!
hostname Router
!
boot buffersize 522200
boot system flash slot0:c6sup22-jsv-mz.121-5c.EX.bin
boot bootldr bootflash:c6msfc2-boot-mz.121-3a.E4
enable password lab
!
redundancy
main-cpu
auto-sync standard
ip subnet-zero
no ip finger
!
cns event-service server
!
<...output truncated...>
!
interface FastEthernet3/3
ip address 172.20.52.19 255.255.255.224
!
<...output truncated...>
!
line con 0
exec-timeout 0 0
transport input none
line vty 0 4
exec-timeout 0 0
password lab
login
transport input lat pad mop telnet rlogin udptn nasi
!
end
Router#
Configuring the Switch
Saving the Running Configuration Settings
To store the configuration or changes to your startup configuration in NVRAM, enter the copy
running-config startup-config command at the privileged EXEC prompt (#) as follows:
Router# copy running-config startup-config
This command saves the configuration settings that you created in configuration mode. If you fail to do
this step, your configuration will be lost the next time you reload the system.
Reviewing the Configuration
To display information stored in NVRAM, enter the show startup-config EXEC command. The display
should be similar to the display from the show running-config EXEC command.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
3-11
Page 48

Configuring the Switch
Configuring a Default Gateway
Note The switch uses the default gateway only when it is not configured with a routing protocol.
To send data to another subnet when the switch is not configured with a routing protocol, configure a
default gateway. The default gateway must be the IP address of an interface on a router in the same
subnet.
To configure a default gateway, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# ip default-gateway A.B.C.D
Router# show ip route
This example shows how to configure a default gateway and how to verify the configuration:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# ip default-gateway 172.20.52.35
Router(config)# end
3d17h: %SYS-5-CONFIG_I: Configured from console by console
Router# show ip route
Default gateway is 172.20.52.35
Chapter 3 Configuring the Switch for the First Time
Configures a default gateway.
Verifies that the default gateway appears correctly in the
IP routing table.
Host Gateway Last Use Total Uses Interface
ICMP redirect cache is empty
Router#
Configuring a Static Route
If your Telnet station or SNMP network management workstation is on a different network from your
switch and a routing protocol has not been configured, you might need to add a static routing table entry
for the network where your end station is located.
To configure a static route, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# ip route dest_IP_address mask
{forwarding_IP | vlan vlan_ID}
Router# show running-config
This example shows how to use the ip route command to configure a static route to a workstation at IP
address 171.10.5.10 on the switch with a subnet mask and IP address 172.20.3.35 of the forwarding
router:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# ip route 171.10.5.10 255.255.255.255 172.20.3.35
Router(config)# end
Router#
Configures a static route.
Verifies the static route configuration.
3-12
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 49

Chapter 3 Configuring the Switch for the First Time
This example shows how to use the show running-config command to confirm the configuration of the
previously configured static route:
Router# show running-config
Building configuration...
.
<...output truncated...>
.
ip default-gateway 172.20.52.35
ip classless
ip route 171.10.5.10 255.255.255.255 172.20.3.35
no ip http server
!
line con 0
transport input none
line vty 0 4
exec-timeout 0 0
password lab
login
transport input lat pad dsipcon mop telnet rlogin udptn nasi
!
end
Router#
Configuring the Switch
This example shows how to use the ip route command to configure a static route to a workstation at IP
address 171.20.5.3 on the switch with subnet mask and connected over VLAN 1:
Router# configure terminal
Router(config)# ip route 171.20.5.3 255.255.255.255 vlan 1
Router(config)# end
Router#
This example shows how to use the show running-config command to confirm the configuration of the
previously configured static route:
Router# show running-config
Building configuration...
.
<...output truncated...>
.
ip default-gateway 172.20.52.35
ip classless
ip route 171.20.52.3 255.255.255.255 Vlan1
no ip http server
!
!
x25 host z
!
line con 0
transport input none
line vty 0 4
exec-timeout 0 0
password lab
login
transport input lat pad dsipcon mop telnet rlogin udptn nasi
!
end
78-14099-04
Router#
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-13
Page 50

Configuring the Switch
Configuring a BOOTP Server
The Bootstrap Protocol (BOOTP) automatically assigns an IP address by adding the MAC and IP
addresses of the interface to the BOOTP server configuration file. When the switch boots, it
automatically retrieves the IP address from the BOOTP server.
The switch performs a BOOTP request only if the current IP address is set to 0.0.0.0. (This address is
the default address for a new switch or a switch that has had its startup-config file cleared using the erase
command.)
To allow your switch to retrieve its IP address from a BOOTP server, you must first determine the MAC
address of the switch and add that MAC address to the BOOTP configuration file on the BOOTP server.
To create a BOOTP server configuration file, follow these steps:
Step 1 Install the BOOTP server code on the workstation, if it is not already installed.
Step 2 Determine the MAC address from the label on the chassis.
Step 3 Add an entry in the BOOTP configuration file (usually /usr/etc/bootptab) for each switch. Press Return
after each entry to create a blank line between each entry. See the example BOOTP configuration file
that follows in Step 4.
Step 4 Enter the reload command to reboot and automatically request the IP address from the BOOTP server.
This example BOOTP configuration file shows the added entry:
# /etc/bootptab: database for bootp server (/etc/bootpd)
#
# Blank lines and lines beginning with '#' are ignored.
#
# Legend:
#
# first field -- hostname
# (may be full domain name and probably should be)
#
# hd -- home directory
# bf -- bootfile
# cs -- cookie servers
# ds -- domain name servers
# gw -- gateways
# ha -- hardware address
# ht -- hardware type
# im -- impress servers
# ip -- host IP address
# lg -- log servers
# lp -- LPR servers
# ns -- IEN-116 name servers
# rl -- resource location protocol servers
# sm -- subnet mask
# tc -- template host (points to similar host entry)
# to -- time offset (seconds)
# ts -- time servers
#
<information deleted>
#
#########################################################################
# Start of individual host entries
#########################################################################
Router: tc=netcisco0: ha=0000.0ca7.ce00: ip=172.31.7.97:
dross: tc=netcisco0: ha=00000c000139: ip=172.31.7.26:
<information deleted>
Chapter 3 Configuring the Switch for the First Time
3-14
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 51

Chapter 3 Configuring the Switch for the First Time
Protecting Access to Privileged EXEC Commands
Protecting Access to Privileged EXEC Commands
The following tasks provide a way to control access to the system configuration file and privileged
EXEC commands:
• Setting or Changing a Static Enable Password, page 3-15
• Using the enable password and enable secret Commands, page 3-15
• Setting or Changing a Line Password, page 3-16
• Setting TACACS+ Password Protection for Privileged EXEC Mode, page 3-16
• Encrypting Passwords, page 3-17
• Configuring Multiple Privilege Levels, page 3-17
Setting or Changing a Static Enable Password
To set or change a static password that controls access to the privileged EXEC mode, perform this task:
Command Purpose
Router(config)# enable password password
Sets a new password or changes an existing password for the
privileged EXEC mode.
This example shows how to configure an enable password as “lab” at the privileged EXEC mode:
Router# configure terminal
Router(config)# enable password lab
Router(config)#
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Using the enable password and enable secret Commands
To provide an additional layer of security, particularly for passwords that cross the network or that are
stored on a TFTP server, you can use either the enable password or enable secret commands. Both
commands configure an encrypted password that you must enter to access enable mode (the default) or
to access a specified privilege level. We recommend that you use the enable secret command.
If you configure the enable secret command, it takes precedence over the enable password command;
the two commands cannot be in effect simultaneously.
To configure the switch to require an enable password, perform either of these tasks:
Command Purpose
Router(config)# enable password [level level]
{password | encryption-type encrypted-password}
Router(config)# enable secret [level level] {password
| encryption-type encrypted-password}
Establishes a password for the privileged EXEC mode.
Specifies a secret password, saved using a nonreversible
encryption method. (If enable password and enable secret
commands are both set, users must enter the enable secret
password.)
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
3-15
Page 52

Protecting Access to Privileged EXEC Commands
Use either of these commands with the level option to define a password for a specific privilege level.
After you specify the level and set a password, give the password only to users who need to have access
at this level. Use the privilege level configuration command to specify commands accessible at various
levels.
If you enable the service password-encryption command, the password you enter is encrypted. When
you display it with the more system:running-config command, it displays in encrypted form.
If you specify an encryption type, you must provide an encrypted password that you copy from another
Catalyst 6500 series switch configuration.
Note You cannot recover a lost encrypted password. You must clear NVRAM and set a new password. See the
“Recovering a Lost Enable Password” section on page 3-19 if you lose or forget your password.
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Setting or Changing a Line Password
Chapter 3 Configuring the Switch for the First Time
To set or change a password on a line, perform this task:
Command Purpose
Router(config-line)# password password
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Sets a new password or change an existing password for the
privileged level.
Setting TACACS+ Password Protection for Privileged EXEC Mode
For complete information about TACACS+, refer to these publications:
• Cisco IOS Security Configuration Guide, Release 12.1, “Authentication, Authorization, and
Accounting (AAA),” at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/secur_c/scprt1/index.htm
• Cisco IOS Security Command Reference, Release 12.1, at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/secur_r/index.htm
To set the TACACS+ protocol to determine whether or not a user can access privileged EXEC mode,
perform this task:
Command Purpose
Router(config)# enable use-tacacs
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-16
Sets the TACACS-style user ID and password-checking
mechanism for the privileged EXEC mode.
78-14099-04
Page 53

Chapter 3 Configuring the Switch for the First Time
When you set TACACS password protection at the privileged EXEC mode, the enable EXEC command
prompts for both a new username and a password. This information is then sent to the TACACS+ server
for authentication. If you are using the extended TACACS+, it also sends any existing UNIX user
identification code to the TACACS+ server.
Caution If you enter the enable use-tacacs command, you must also enter tacacs-server authenticate enable,
or you are locked out of the privileged EXEC mode.
Note When used without extended TACACS, the enable use-tacacs command allows anyone with a valid
username and password to access the privileged EXEC mode, creating a potential security problem. This
problem occurs because the switch cannot tell the difference between a query resulting from entering the
enable command and an attempt to log in without extended TACACS.
Encrypting Passwords
Because protocol analyzers can examine packets (and read passwords), you can increase access security
by configuring the Cisco IOS software to encrypt passwords. Encryption prevents the password from
being readable in the configuration file.
Protecting Access to Privileged EXEC Commands
To configure the Cisco IOS software to encrypt passwords, perform this task:
Command Purpose
Router(config)# service password-encryption
Encryption occurs when the current configuration is written or when a password is configured. Password
encryption is applied to all passwords, including authentication key passwords, the privileged command
password, console and virtual terminal line access passwords, and Border Gateway Protocol (BGP)
neighbor passwords. The service password-encryption command keeps unauthorized individuals from
viewing your password in your configuration file.
Caution The service password-encryption command does not provide a high level of network security. If you
use this command, you should also take additional network security measures.
Although you cannot recover a lost encrypted password (that is, you cannot get the original password
back), you can regain control of the switch after you lose or forget the encrypted password. See the
“Recovering a Lost Enable Password” section on page 3-19 if you lose or forget your password.
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Encrypts a password.
Configuring Multiple Privilege Levels
By default, the Cisco IOS software has two modes of password security: user EXEC mode and privileged
EXEC mode. You can configure up to 16 hierarchical levels of commands for each mode. By configuring
multiple passwords, you can allow different sets of users to have access to specified commands.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
3-17
Page 54

Protecting Access to Privileged EXEC Commands
For example, if you want many users to have access to the clear line command, you can assign it level 2
security and distribute the level 2 password widely. If you want more restricted access to the configure
command, you can assign it level 3 security and distribute that password to more restricted users.
These tasks describe how to configure additional levels of security:
• Setting the Privilege Level for a Command, page 3-18
• Changing the Default Privilege Level for Lines, page 3-18
• Logging In to a Privilege Level, page 3-18
• Exiting a Privilege Level, page 3-19
• Displaying the Password, Access Level, and Privilege Level Configuration, page 3-19
Setting the Privilege Level for a Command
To set the privilege level for a command, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# privilege mode level level
command
Router(config)# enable password level level
[encryption-type] password
Chapter 3 Configuring the Switch for the First Time
Sets the privilege level for a command.
Specifies the enable password for a privilege level.
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Changing the Default Privilege Level for Lines
To change the default privilege level for a given line or a group of lines, perform this task:
Command Purpose
Router(config-line)# privilege level level
Changes the default privilege level for the line.
To display the password or access level configuration, see the “Displaying the Password, Access Level,
and Privilege Level Configuration” section on page 3-19.
Logging In to a Privilege Level
To log in at a specified privilege level, perform this task:
Command Purpose
Router# enable level
Logs into a specified privilege level.
3-18
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 55

Chapter 3 Configuring the Switch for the First Time
Exiting a Privilege Level
To exit to a specified privilege level, perform this task:
Command Purpose
Router# disable level
Exits to a specified privilege level.
Displaying the Password, Access Level, and Privilege Level Configuration
To display the password, access level, and privilege level configuration, perform this task:
Command Purpose
Step 1
Step 2
Router# show running-config
Router# show privilege
This example shows how to display the password and access level configuration:
Router# show running-config
<...output truncated...>
enable password lab
<...output truncated...>
Displays the password and the access level configuration.
Shows the privilege level configuration.
Recovering a Lost Enable Password
This example shows how to display the privilege level configuration:
Router# show privilege
Current privilege level is 15
Router#
Recovering a Lost Enable Password
To recover a lost enable password, follow these steps:
Step 1 Connect to the console interface.
Step 2 Configure the switch to boot up without reading the configuration memory (NVRAM).
Step 3 Reboot the system.
Step 4 Access enable mode (which can be done without a password when one is not configured).
Step 5 View or change the password, or erase the configuration.
Step 6 Reconfigure the switch to boot up and read the NVRAM as it normally does.
Step 7 Reboot the system.
78-14099-04
Note Password recovery requires the Break signal. You must be familiar with how your terminal or PC
terminal emulator issues this signal. For example, in ProComm, the Alt-B keys generate the Break
signal. In a Windows terminal session, you press the Break or Ctrl and Break keys simultaneously.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-19
Page 56

Chapter 3 Configuring the Switch for the First Time
Modifying the Supervisor Engine Startup Configuration
Modifying the Supervisor Engine Startup Configuration
These sections describe how the startup configuration on the supervisor engine works and how to modify
the configuration register and BOOT variable:
• Understanding the Supervisor Engine Boot Configuration, page 3-20
• Configuring the Software Configuration Register, page 3-21
• Specifying the Startup System Image, page 3-24
• Understanding Flash Memory, page 3-24
• BOOTLDR Environment Variable, page 3-25
• CONFIG_FILE Environment Variable, page 3-26
• Controlling Environment Variables, page 3-26
Understanding the Supervisor Engine Boot Configuration
These next sections describe how the boot configuration works on the supervisor engine.
Understanding the Supervisor Engine Boot Process
The supervisor engine boot process involves two software images: ROM monitor and supervisor engine
software. When the switch is powered up or reset, the ROM-monitor code is executed. Depending on the
NVRAM configuration, the supervisor engine either stays in ROM-monitor mode or loads the supervisor
engine software.
Two user-configurable parameters determine how the switch boots: the configuration register and the
BOOT environment variable. The configuration register is described in the “Modifying the Boot Field
and Using the boot Command” section on page 3-22. The BOOT environment variable is described in
the “Specifying the Startup System Image” section on page 3-24.
Understanding the ROM Monitor
The ROM monitor executes upon power-up, reset, or when a fatal exception occurs. The switch enters
ROM-monitor mode if the switch does not find a valid software image, if the NVRAM configuration is
corrupted, or if the configuration register is set to enter ROM-monitor mode. From ROM-monitor mode,
you can manually load a software image from bootflash or a Flash PC card.
Note For complete syntax and usage information for the ROM monitor commands, refer to the Catalyst 6500
Series Switch Cisco IOS Command Reference publication.
You can also enter ROM-monitor mode by restarting and then pressing the Break key during the first 60
seconds of startup. If you are connected through a terminal server, you can escape to the Telnet prompt
and enter the send break command to enter ROM-monitor mode.
3-20
Note The Break key is always enabled for 60 seconds after rebooting, regardless of whether the
configuration-register setting has the Break key disabled.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 57

Chapter 3 Configuring the Switch for the First Time
The ROM monitor has these features:
• Power-on confidence test
• Hardware initialization
• Boot capability (manual boot and autoboot)
• Debug utility and crash analysis
• Monitor call interface (EMT calls—the ROM monitor provides information and some functionality
to the running software images through EMT calls)
• File system (the ROM monitor knows the simple file system and supports the newly developed file
system through the dynamic linked file system library [MONLIB])
• Exception handling
Configuring the Software Configuration Register
The switch uses a 16-bit software configuration register, which allows you to set specific system
parameters. Settings for the software configuration register are written into NVRAM.
Modifying the Supervisor Engine Startup Configuration
Following are some reasons for changing the software configuration register settings:
• To select a boot source and default boot filename.
• To enable or disable the Break function.
• To control broadcast addresses.
• To set the console terminal baud rate.
• To load operating software from Flash memory.
• To recover a lost password.
• To allow you to manually boot the system using the boot command at the bootstrap program prompt.
• To force an automatic boot from the system bootstrap software (boot image) or from a default system
image in onboard Flash memory, and read any boot system commands that are stored in the
configuration file in NVRAM.
Table 3-2 lists the meaning of each of the software configuration memory bits, and Table 3-3 defines the
boot field.
Caution The recommended configuration register setting is 0x2102. If you configure a setting that leaves break
enabled and you send a break sequence over a console connection, the switch drops into ROMMON.
Table 3-2 Software Configuration Register Bit Meaning
78-14099-04
Bit Number1Hexadecimal Meaning
00 to 03 0x0000 to 0x000F Boot field (see Table 3-3)
06 0x0040 Causes system software to ignore NVRAM contents
07 0x0080 OEM
2
bit enabled
08 0x0100 Break disabled
09 0x0200 Use secondary bootstrap
10 0x0400 Internet Protocol (IP) broadcast with all zeros
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-21
Page 58

Modifying the Supervisor Engine Startup Configuration
Table 3-2 Software Configuration Register Bit Meaning (continued)
Bit Number1Hexadecimal Meaning
11 to 12 0x0800 to 0x1000 Console line speed (default is 9600 baud)
13 0x2000 Boot default Flash software if network boot fails
14 0x4000 IP broadcasts do not have network numbers
15 0x8000 Enable diagnostic messages and ignore NVRAM contents
1. The factory default value for the configuration register is 0x2102.
2. OEM = original equipment manufacturer.
Table 3-3 Explanation of Boot Field (Configuration Register Bits 00 to 03)
Boot Field Meaning
00 Stays at the system bootstrap prompt
01 Boots the first system image in onboard Flash memory
02 to 0F Specifies a default filename for booting over the network;
enables boot system commands that override the default filename
Chapter 3 Configuring the Switch for the First Time
Modifying the Boot Field and Using the boot Command
The configuration register boot field determines whether or not the switch loads an operating system
image, and if so, where it obtains this system image. The following sections describe using and setting
the configuration register boot field, and the tasks you must perform to modify the configuration register
boot field.
Bits 0 through 3 of the software configuration register form the boot field.
Note The factory default configuration register setting for systems and spares is 0x2102.
When the boot field is set to either 0 or 1 (0-0-0-0 or 0-0-0-1), the system ignores any boot instructions
in the system configuration file and the following occurs:
• When the boot field is set to 0, you must boot the operating system manually by entering the boot
command to the system bootstrap program or ROM monitor.
• When the boot field is set to 1, the system boots the first image in the onboard bootflash single
in-line memory module (SIMM).
• When the entire boot field equals a value between 0-0-1-0 and 1-1-1-1, the switch loads the system
image specified by boot system commands in the startup configuration file.
You can enter the boot command only, or enter the command and include additional boot instructions,
such as the name of a file stored in Flash memory, or a file that you specify for booting from a network
server. If you use the boot command without specifying a file or any other boot instructions, the system
boots from the default Flash image (the first image in onboard Flash memory). Otherwise, you can
instruct the system to boot from a specific Flash image (using the boot system flash filename command).
You can also use the boot command to boot images stored in the Flash PC cards located in Flash PC card
slot 0 or slot 1 on the supervisor engine. If you set the boot field to any bit pattern other than 0 or 1, the
system uses the resulting number to form a filename for booting over the network.
You must set the boot field for the boot functions you require.
3-22
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 59

Chapter 3 Configuring the Switch for the First Time
Modifying the Boot Field
You modify the boot field from the software configuration register. To modify the software configuration
register boot field, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Router# show version
Router# configure terminal
Router(config)# config-register value
Router(config)# end
Router# reload
To modify the configuration register while the switch is running Cisco IOS, follow these steps:
Modifying the Supervisor Engine Startup Configuration
Determines the current configuration register setting.
Enters configuration mode, selecting the terminal option.
Modifies the existing configuration register setting to
reflect the way in which you want the switch to load a
system image.
Exits configuration mode.
Reboots to make your changes take effect.
Step 1 Enter the enable command and your password to enter privileged level as follows:
Router> enable
Password:
Router#
Step 2 Enter the configure terminal command at the EXEC mode prompt (#) as follows:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
Step 3 Configure the configuration register to 0x2102 as follows:
Router(config)# config-register 0x2102
Set the contents of the configuration register by entering the config-register value configuration
command, where value is a hexadecimal number preceded by 0x (see Table 3-2 on page 3-21).
Step 4 Enter the end command to exit configuration mode. The new value settings are saved to memory;
however, the new settings do not take effect until the system software is reloaded by rebooting the
system.
Step 5 Enter the show version EXEC command to display the configuration register value currently in effect
and that will be used at the next reload. The value is displayed on the last line of the screen display, as
in this example:
Configuration register is 0x141 (will be 0x2102 at next reload)
Step 6 Save your settings. (See the “Saving the Running Configuration Settings” section on page 3-11.
However, note that configuration register changes take effect only after the system reloads, such as when
you enter a reload command from the console.)
78-14099-04
Step 7 Reboot the system. The new configuration register value takes effect with the next system boot.
This completes the procedure for making configuration register changes.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-23
Page 60

Modifying the Supervisor Engine Startup Configuration
Verifying the Configuration Register Setting
Enter the show version EXEC command to verify the current configuration register setting. In
ROM-monitor mode, enter the o command to verify the value of the configuration register boot field.
To verify the configuration register setting, perform this task:
Command Purpose
Router# show version | include Configuration register
In this example, the show version command indicates that the current configuration register is set so that
the switch does not automatically load an operating system image. Instead, it enters ROM-monitor mode
and waits for user-entered ROM monitor commands. The new setting instructs the switch to load a
system image from commands in the startup configuration file or from a default system image stored on
a network server.
Router1# show version | include Configuration register
Configuration register is 0x2102
Router#
Displays the configuration register setting.
Chapter 3 Configuring the Switch for the First Time
Specifying the Startup System Image
You can enter multiple boot commands in the startup configuration file or in the BOOT environment
variable to provide backup methods for loading a system image.
Note Store the system software image in the sup-bootflash: or slot0: device, not in the bootflash: device.
Store the boot loader image, if any, in the MSFC bootflash: device.
The BOOT environment variable is also described in the “Specify the Startup System Image in the
Configuration File” section in the “Loading and Maintaining System Images and Microcode” chapter of
the Cisco IOS Configuration Fundamentals Configuration Guide.
Understanding Flash Memory
The following sections describe Flash memory:
• Flash Memory Features, page 3-25
• Security Features, page 3-25
• Flash Memory Configuration Process, page 3-25
Note The descriptions in the following sections applies to both the bootflash device and to removable Flash
memory cards.
3-24
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 61

Chapter 3 Configuring the Switch for the First Time
Flash Memory Features
The Flash memory components allow you to do the following:
• Copy the system image to Flash memory using TFTP.
• Copy the system image to Flash memory using rcp.
• Boot the system from Flash memory either automatically or manually.
• Copy the Flash memory image to a network server using TFTP or rcp.
• Boot manually or automatically from a system software image stored in Flash memory.
Security Features
The Flash memory components support the following security features:
• Flash memory cards contain a write-protect switch that you can use to protect data. You must set the
switch to unprotected to write data to the Flash PC card.
• The system image stored in Flash memory can be changed only from privileged EXEC level on the
console terminal.
Modifying the Supervisor Engine Startup Configuration
Flash Memory Configuration Process
To configure your switch to boot from Flash memory, follow these steps:
Step 1 Copy a system image to Flash memory using TFTP or rcp (refer to the Cisco IOS Configuration
Fundamentals Configuration Guide, Release 12.1, “Cisco IOS File Management,” “Loading and
Maintaining System Images,” at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_c/fcprt2/fcd203.htm
Step 2 Configure the system to boot automatically from the file in Flash memory. You might need to change the
configuration register value. See the “Modifying the Boot Field and Using the boot Command” section
on page 3-22, for more information on modifying the configuration register.
Step 3 Save your configurations.
Step 4 Power cycle and reboot your system to ensure that all is working as expected.
BOOTLDR Environment Variable
The BOOTLDR environment specifies the Flash file system and filename containing the boot loader
image.
78-14099-04
Caution With a Supervisor Engine 1 and MSFC1, do not erase the boot loader image from the MSFC1 bootflash:
device. The boot loader must be present in the MSFC1 bootflash: device to boot a Supervisor Engine 1
and MSFC1 successfully.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-25
Page 62

Modifying the Supervisor Engine Startup Configuration
CONFIG_FILE Environment Variable
For Class A Flash file systems, the CONFIG_FILE environment variable specifies the file system and
filename of the configuration file to use for initialization (startup). Valid file systems can include
nvram:, slot0:, and sup-bootflash:.
For detailed file management configuration information, refer to the Cisco IOS Configuration
Fundamentals Configuration Guide at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/fun_c/index.htm
After you save the CONFIG_FILE environment variable to your startup configuration, the switch checks
the variable upon startup to determine the location and filename of the configuration file to use for
initialization.
The switch uses the NVRAM configuration during initialization when the CONFIG_FILE environment
variable does not exist or when it is null (such as at first-time startup). If the switch detects a problem
with NVRAM or a checksum error, the switch enters setup mode. See the “Using the Setup Facility or
the setup Command” section on page 3-2 for more information on the setup command facility.
Chapter 3 Configuring the Switch for the First Time
Controlling Environment Variables
Although the ROM monitor controls environment variables, you can create, modify, or view them with
certain commands. To create or modify the BOOT, BOOTLDR, and CONFIG_FILE environment
variables, use the boot system, boot bootldr, and boot config global configuration commands.
Refer to the “Specify the Startup System Image in the Configuration File” section in the “Loading and
Maintaining System Images and Microcode” chapter of the Configuration Fundamentals Configuration
Guide for details on setting the BOOT environment variable. Refer to the “Specify the Startup
Configuration File” section in the “Modifying, Downloading, and Maintaining Configuration Files”
chapter of the Configuration Fundamentals Configuration Guide for details on setting the
CONFIG_FILE variable.
Note When you use the boot system, boot bootldr, and boot config global configuration commands, you
affect only the running configuration. You must save the environment variable settings to your startup
configuration to place the information under ROM monitor control and for the environment variables to
function as expected. Enter the copy system:running-config nvram:startup-config command to save
the environment variables from your running configuration to your startup configuration.
You can view the contents of the BOOT, BOOTLDR, and the CONFIG_FILE environment variables
using the show bootvar command. This command displays the settings for these variables as they exist
in the startup configuration as well as in the running configuration if a running configuration setting
differs from a startup configuration setting.
This example shows how to check the BOOT, BOOTLDR, and the CONFIG_FILE environment
variables:
Router# show bootvar
BOOT variable = slot0:c6sup22-jsv-mz.121-5c.EX.bin,1;
CONFIG_FILE variable does not exist
BOOTLDR variable = bootflash:c6msfc2-boot-mz.121-3a.E4
Configuration register is 0x2
Router#
3-26
To display the contents of the configuration file pointed to by the CONFIG_FILE environment variable,
enter the more nvram:startup-config command.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 63

Chapter 3 Configuring the Switch for the First Time
Setting the BOOTLDR Environment Variable
To set the BOOTLDR environment variable, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
Router# dir bootflash:
Router# configure terminal
Router(config)# boot bootldr
bootflash:boot_loader
Router# end
Router# copy system:running-config
nvram:startup-config
Router# show bootvar
Modifying the Supervisor Engine Startup Configuration
Verifies that bootflash contains the boot loader image.
Enters the configuration mode from the terminal.
Sets the BOOTLDR environment variable to specify the
Flash device and filename of the boot loader image. This
step modifies the runtime BOOTLDR environment
variable.
Exits configuration mode.
Saves this runtime BOOTLDR environment variable to
your startup configuration.
(Optional) Verifies the contents of the BOOTLDR
environment variable.
This example shows how to set the BOOTLDR variable:
Router# dir bootflash:
Directory of bootflash:/
1 -rw- 1599488 Nov 29 1999 11:12:29 c6msfc-boot-mz.120-7.XE.bin
15990784 bytes total (14391168 bytes free)
Router# configure terminal
Router (config)# boot bootldr bootflash:c6msfc-boot-mz.120-7.XE.bin
Router (config)# end
Router# copy system:running-config nvram:startup-config
[ok]
Router# show bootvar
BOOT variable = sup-bootflash:c6sup-js-mz.120-7.XE.bin,1;
CONFIG_FILE variable does not exist
BOOTLDR variable = bootflash:c6msfc-boot-mz.120-7.XE.bin
Configuration register is 0x0
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
3-27
Page 64

Modifying the Supervisor Engine Startup Configuration
Chapter 3 Configuring the Switch for the First Time
3-28
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 65

CHA PTER
4
Configuring EHSA Supervisor Engine Redundancy
With 12.1 E releases earlier than Release 12.1(13)E, the Catalyst 6500 series switch supports dual
supervisor engines with EHSA.
Note EHSA is not supported in Release 12.1(13)E and later releases (see Chapter 5, “Configuring RPR and
RPR+ Supervisor Engine Redundancy,” for information about RPR or RPR+ redundancy in Release
12.1(13)E and later releases.
This chapter consists of these sections:
• Supervisor Engine Redundant Operation, page 4-1
• Supervisor Engine Redundancy Requirements, page 4-2
• Synchronizing the Supervisor Engine Configurations, page 4-3
• Displaying the Supervisor Engine Redundancy, page 4-4
• Copying Files to the Redundant Supervisor Engine, page 4-4
Note For complete syntax and usage information for the commands used in this chapter, refer to the
Catalyst 6500 Series Switch Cisco IOS Command Reference publication and the Release 12.1
publications at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
Supervisor Engine Redundant Operation
Catalyst 6500 series switches support fault resistance by allowing a redundant supervisor engine to take
over if the primary supervisor engine fails. The redundant supervisor engine runs in EHSA standby
mode.
Note The EHSA feature is not supervisor engine mirroring or load balancing. Network services are disrupted
until the redundant supervisor engine takes over and the switch recovers.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
4-1
Page 66

Supervisor Engine Redundant Operation
EHSA standby mode provides the following features:
• Auto-startup and bootvar synchronization between active and redundant supervisor engines
• Hardware signals that detect and decide the active or redundant status of supervisor engines
• Clock synchronization every 60 seconds from the active to the redundant supervisor engine
• A redundant supervisor engine that is booted but not all subsystems are up: if the active supervisor
engine fails, the redundant supervisor engine becomes fully operational
• An operational supervisor engine present in place of the failed unit becomes the redundant
supervisor engine
Note The two Gigabit Ethernet interfaces on the redundant supervisor engine are always active.
When the switch is powered on, EHSA runs between the two supervisor engines. The supervisor engine
that boots first, either in slot 1 or 2, becomes the EHSA active supervisor engine. The Multilayer Switch
Feature Card (MSFC or MSFC2) and Policy Feature Card (PFC or PFC2) become fully operational. The
MSFC and PFC on the redundant supervisor engine come out of reset but are not operational.
The following events cause an EHSA switchover:
• Clock synchronization failure between supervisor engines
• MSFC or PFC failure on the active supervisor engine
Chapter 4 Configuring EHSA Supervisor Engine Redundancy
In a switchover, the redundant supervisor engine becomes fully operational and the following occurs:
• All switching modules power up again
• Remaining subsystems on the MSFC (including Layer 2 and Layer 3 protocols) are brought up
• Access control lists (ACLs) are reprogrammed into supervisor engine hardware
Note In a switchover, there is a disruption of traffic because some address states are lost and then restored after
they are dynamically redetermined.
Supervisor Engine Redundancy Requirements
For redundant operation, the following requirements must be met:
• The active and redundant supervisor engines must be in slots 1 and 2.
• Each supervisor engine must have the resources to run the switch on its own, which means all
supervisor engine resources are duplicated. In other words, each supervisor engine has its own Flash
device and console port connections.
Note Make a separate console connection to each supervisor engine. Do not connect a “Y” cable
to the console ports.
4-2
• Both supervisor engines must have the same system image (see the “Copying Files to the Redundant
Supervisor Engine” section on page 4-4).
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 67

Chapter 4 Configuring EHSA Supervisor Engine Redundancy
Note If the redundant supervisor engine is running Catalyst operating system software, remove
the active supervisor engine and boot the switch with only the redundant supervisor engine
installed. Follow the procedures in the release notes to convert the redundant supervisor
engine from Catalyst operating system software.
• The configuration register in the startup-config must be set to autoboot (see the “Modifying the Boot
Field” section on page 3-23).
Note EHSA does not support booting from the network.
If these requirements are met, the switch functions in EHSA mode by default.
Synchronizing the Supervisor Engine Configurations
During normal operation, the startup-config and config-registers configuration are synchronized by
default between the two supervisor engines. In a switchover, the new active supervisor engine uses the
current configuration.
Supervisor Engine Redundant Operation
Step 1
Step 2
Step 3
Step 4
Step 5
Note The boot variables are not synchronized by default.
To manually synchronize the configurations used by the two supervisor engines, perform this task on the
active supervisor engine:
Command Purpose
Router(config)# redundancy
Router(config-r)# main-cpu
Router(config-r-mc)# auto-sync {startup-config |
config-register | bootvar | standard}
Router(config-r-mc)# end
Router# copy running-config startup-config
Enters redundancy configuration mode.
Enters main-cpu configuration submode.
Synchronizes the configuration elements.
Returns to privileged EXEC mode.
Forces a manual synchronization of the configuration
files in NVRAM.
Note This step is not required to synchronize the
running configuration file in DRAM.
Note The auto-sync standard command does not synchronize the boot variables.
This example shows how to reenable the default automatic synchronization feature using the auto-sync
standard command to synchronize the startup-config and config-register configuration of the active
supervisor engine with the redundant supervisor engine:
Router(config)# redundancy
Router(config-r)# main-cpu
Router(config-r-mc)# auto-sync standard
Router(config-r-mc)# auto-sync bootvar
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
4-3
Page 68

Supervisor Engine Redundant Operation
Router(config-r-mc)# end
Router# copy running-config startup-config
Note To manually synchronize only individual elements of the standard auto-sync configuration, disable the
default automatic synchronization feature.
This example shows how to disable default automatic synchronization and only allow automatic
synchronization of the config-registers of the active supervisor engine to the redundant supervisor
engine while disallowing synchronization of the startup configuration:
Router(config)# redundancy
Router(config-r)# main-cpu
Router(config-r-mc)# no auto-sync standard
Router(config-r-mc)# auto-sync config-register
Router(config-r-mc)# end
Router# copy running-config startup-config
Displaying the Supervisor Engine Redundancy
To display both supervisor engines, perform this task:
Chapter 4 Configuring EHSA Supervisor Engine Redundancy
Command Purpose
Router# show module all
Displays the redundancy configuration.
This example shows how to display the supervisor engine redundancy configuration:
Router# show module all
Mod Ports Card Type Model Serial No.
--- ----- -------------------------------------- ------------------ ---------- 1 2 Catalyst 6000 supervisor 2 (Active) WS-X6K-SUP2-2GE SAD0620046D
5 48 48 port 10/100 mb RJ-45 ethernet WS-X6248-RJ-45 SAD03181291
Mod MAC addresses Hw Fw Sw Status
--- ---------------------------------- ------ ------------ ------------ ------ 1 0001.c9db.3788 to 0001.c9db.3789 3.7 6.1(3) 7.5(0.6)HUB6 Ok
5 0050.f0ac.3054 to 0050.f0ac.3083 1.0 4.2(0.24)VAI 7.5(0.6)HUB6 Ok
Mod Sub-Module Model Serial Hw Status
--- --------------------------- --------------- --------------- ------- ------ 1 Policy Feature Card 2 WS-F6K-PFC2 SAD06200415 3.2 Ok
1 Cat6k MSFC 2 daughterboard WS-F6K-MSFC2 SAD06210067 2.3 Ok
Mod Online Diag Status
--- ------------------ 1 Pass
5 Pass
Router#
Copying Files to the Redundant Supervisor Engine
Use the following command to copy a file to the slot0: device on a redundant supervisor engine:
Router# copy source_device:source_filename slaveslot0:target_filename
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
4-4
78-14099-04
Page 69

Chapter 4 Configuring EHSA Supervisor Engine Redundancy
Use the following command to copy a file to the bootflash: device on a redundant supervisor engine:
Router# copy source_device:source_filename slavesup-bootflash:target_filename
Use the following command to copy a file to the bootflash: device on a redundant MSFC:
Router# copy source_device:source_filename slavebootflash:target_filename
Supervisor Engine Redundant Operation
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
4-5
Page 70

Supervisor Engine Redundant Operation
Chapter 4 Configuring EHSA Supervisor Engine Redundancy
4-6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 71

CHA PTER
5
Configuring RPR and RPR+ Supervisor Engine Redundancy
Release 12.1(13)E and later releases support supervisor engine redundancy with Route Processor
Redundancy (RPR) and Route Processor Redundancy Plus (RPR+). This chapter describes how to
configure supervisor engine redundancy with RPR and RPR+.
Note Enhanced high system availability (EHSA) is not supported in Release 12.1(13)E and later releases.
This chapter consists of these sections:
• Understanding Supervisor Engine Redundancy, page 5-1
• Supervisor Engine Redundancy Guidelines and Restrictions, page 5-4
• Configuring Supervisor Engine Redundancy, page 5-6
• Performing a Fast Software Upgrade, page 5-9
• Copying Files to an MSFC, page 5-10
Understanding Supervisor Engine Redundancy
These sections describe supervisor engine redundancy:
• Supervisor Engine Redundancy Overview, page 5-1
• RPR+ Operation, page 5-2
• Supervisor Engine Synchronization, page 5-3
Supervisor Engine Redundancy Overview
Catalyst 6500 series switches support fault resistance by allowing a redundant supervisor engine to take
over if the primary supervisor engine fails. RPR supports a switchover time of 2 to 4 minutes and RPR+
supports a switchover time of 30 to 60 seconds.
When RPR+ mode is used, the redundant supervisor engine is fully initialized and configured, which
shortens the switchover time. The active supervisor engine checks the image version of the redundant
supervisor engine when the redundant supervisor engine comes online. If the image on the redundant
supervisor engine does not match the image on the active supervisor engine, RPR redundancy mode is used.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
5-1
Page 72

Understanding Supervisor Engine Redundancy
RPR Operation
RPR supports the following features:
• Auto-startup and bootvar synchronization between active and redundant supervisor engines
• Hardware signals that detect and decide the active or redundant status of supervisor engines
• Clock synchronization every 60 seconds from the active to the redundant supervisor engine
• A redundant supervisor engine that is booted but not all subsystems are up: if the active supervisor
engine fails, the redundant supervisor engine become fully operational
• An operational supervisor engine present in place of the failed unit becomes the redundant
supervisor engine
• Support for fast software upgrade (FSU) (See the “Performing a Fast Software Upgrade” section on
page 5-9).
Note When a redundant supervisor engine is in standby mode, the two Gigabit Ethernet interfaces on the
redundant supervisor engine are always active.
Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
When the switch is powered on, RPR runs between the two supervisor engines. The supervisor engine
that boots first, either in slot 1 or 2, becomes the RPR active supervisor engine. The Multilayer Switch
Feature Card (MSFC or MSFC2) and Policy Feature Card (PFC or PFC2) become fully operational. The
MSFC and PFC on the redundant supervisor engine come out of reset but are not operational.
The following events cause an RPR switchover:
• Clock synchronization failure between supervisor engines
• MSFC or PFC failure on the active supervisor engine
• A manual switchover.
In a switchover, the redundant supervisor engine becomes fully operational and the following occurs:
• All switching modules power up again
• Remaining subsystems on the MSFC (including Layer 2 and Layer 3 protocols) are brought up
• Access control lists (ACLs) are reprogrammed into supervisor engine hardware
Note In a switchover, there is a disruption of traffic because some address states are lost and then restored after
they are dynamically redetermined.
RPR+ Operation
With RPR+, the redundant supervisor engine is fully initialized and configured, which shortens the
switchover time if the active supervisor engine fails or if a manual switchover is performed.
When the switch is powered on, RPR+ runs between the two supervisor engines. The supervisor engine
that boots first, either in slot 1 or 2, becomes the active supervisor engine. The Multilayer Switch Feature
Card (MSFC or MSFC2) and Policy Feature Card (PFC or PFC2) become fully operational. The MSFC
and PFC on the redundant supervisor engine come out of reset but are not operational.
5-2
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 73

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
RPR+ enhances RPR by providing the following additional benefits:
• Reduced switchover time
Depending on the configuration, the switchover time is in the range of 30 to 60 seconds.
• Installed modules are not reloaded
Because both the startup configuration and the running configuration are continually synchronized
from the active to the redundant supervisor engine, installed modules are not reloaded during a
switchover.
• Online insertion and removal (OIR) of the redundant supervisor engine
RPR+ allows OIR of the redundant supervisor engine for maintenance. When the redundant
supervisor engine is inserted, the active supervisor engine detects its presence and begins to
transition the redundant supervisor engine to fully initialized state.
• Synchronization of OIR events
• Manual user-initiated switchover using the redundancy force-switchover command
The following events cause an RPR+ switchover:
• Clock synchronization failure between supervisor engines
Understanding Supervisor Engine Redundancy
• MSFC or PFC failure on the active supervisor engine
Supervisor Engine Synchronization
During RPR mode operation, the startup-config and config-registers configuration are synchronized by
default between the two supervisor engines. In a switchover, the new active supervisor engine uses the
current configuration.
Note Unless auto-synchronization has been disabled, the boot variables are synchronized by default.
When a redundant supervisor engine configuration is running in RPR+ mode, the following operations
trigger synchronization:
• When a redundant supervisor engine first comes online, the configuration information is
synchronized in bulk from the active supervisor engine to the redundant supervisor engine. This
synchronization overwrites any existing startup configuration file on the redundant supervisor
engine.
• When configuration changes occur during normal operation, RPR+ performs an incremental
synchronization from the active supervisor engine to the redundant supervisor engine. RPR+
synchronizes user-entered CLI commands incrementally line-by-line from the active supervisor
engine to the redundant supervisor engine.
78-14099-04
Note • Even though the redundant supervisor engine is fully initialized, it only interacts with the active
supervisor engine to receive incremental changes to the configuration files as they occur. You cannot
enter CLI commands on the redundant supervisor engine.
• Synchronization of the startup configuration file is enabled by default in RPR+ mode.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
5-3
Page 74

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
Supervisor Engine Redundancy Guidelines and Restrictions
Supervisor Engine Redundancy Guidelines and Restrictions
These sections describe supervisor engine redundancy configuration guidelines and restrictions:
• RPR+ Guidelines and Restrictions, page 5-4
• Hardware Configuration Guidelines and Restrictions, page 5-5
• Configuration Mode Restrictions, page 5-6
RPR+ Guidelines and Restrictions
The following guidelines and restrictions apply to RPR+:
Restrictions
• RPR+ redundancy does not support configuration entered in VLAN database mode. Use global
configuration mode with RPR+ redundancy (see Chapter 9, “Configuring VLANs”).
• Configuration changes made through SNMP are not synchronized to the redundant supervisor
engine. Enter a copy running-config startup-config command to synchronize the configuration on
the redundant supervisor engine.
• Supervisor engine redundancy does not provide supervisor engine mirroring or supervisor engine
load balancing. Only one supervisor engine is active. Network services are disrupted until the
redundant supervisor engine takes over and the switch recovers.
• With RPR+, both supervisor engines must run the same version of Cisco IOS software. If the
supervisor engines are not running the same version of Cisco IOS software, the redundant supervisor
engine comes online in RPR mode.
• The Forwarding Information Base (FIB) tables are cleared on a switchover. As a result, routed traffic
is interrupted until route tables reconverge.
• Static IP routes are maintained across a switchover because they are configured from entries in the
configuration file.
• Information about dynamic states maintained on the active supervisor engine is not synchronized to
the redundant supervisor engine and is lost on switchover.
These are examples of dynamic state information that is lost at switchover:
–
Frame Relay switched virtual circuits (SVCs)
Note Frame Relay-switched DLCI information is maintained across a switchover because Frame
Relay-switched DLCI configuration is in the configuration file.
–
All terminated PPP sessions
–
All ATM SVC information
–
All terminated TCP and other connection-oriented Layer 3 and Layer 4 sessions
5-4
–
BGP sessions
–
All Automatic Protection System (APS) state information
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 75

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
Supervisor Engine Redundancy Guidelines and Restrictions
Guidelines
• The two Gigabit Ethernet interfaces on the redundant supervisor engine are always active.
• RPR+ switchover takes place after the failed supervisor engine completes a core dump. A core dump
can take up to 15 minutes. To get faster switchover time, disable core dump on the supervisor
engines.
Hardware Configuration Guidelines and Restrictions
For redundant operation, the following hardware configuration guidelines and restrictions apply:
Restrictions
• Supervisor engine redundancy does not support nondefault VLAN data file names or locations. Do
not enter the vtp file file_name command on a switch that has a redundant supervisor engine.
• Cisco IOS running on the supervisor engine and the MSFC supports redundant configurations where
the supervisor engines and MSFC routers are identical. If they are not identical, one will boot first
and become active and hold the other supervisor engine and MSFC in a reset condition.
• Each supervisor engine must have the resources to run the switch on its own, which means all
supervisor engine resources are duplicated. In other words, each supervisor engine has its own Flash
device and console port connections.
Guidelines
• Make separate console connections to each supervisor engine. Do not connect a Y cable to the
console ports.
• Both supervisor engines must have the same system image (see the “Copying Files to an MSFC”
section on page 5-10).
Note If the redundant supervisor engine is running Catalyst operating system software, remove
the active supervisor engine and boot the switch with only the redundant supervisor engine
installed. Follow the procedures in the current release notes to convert the redundant
supervisor engine from Catalyst software.
• The configuration register in the startup-config must be set to autoboot (see the “Modifying the Boot
Field” section on page 3-23).
• Before installing a redundant supervisor engine, enter the no vtp file command to return to the
default configuration.
Note There is no support for booting from the network.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
5-5
Page 76

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
Configuring Supervisor Engine Redundancy
Configuration Mode Restrictions
The following configuration restrictions apply during the startup synchronization process:
• You cannot perform configuration changes during the startup (bulk) synchronization. If you attempt
to make configuration changes during this process, the following message is generated:
Config mode locked out till standby initializes
• If configuration changes occur at the same time as a supervisor engine switchover, these
configuration changes are lost.
Configuring Supervisor Engine Redundancy
These sections describe how to configure supervisor engine redundancy:
• Configuring RPR and RPR+, page 5-6
• Synchronizing the Supervisor Engine Configurations, page 5-7
• Displaying the Redundancy States, page 5-8
Configuring RPR and RPR+
To configure RPR or RPR+, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Router(config)# redundancy
Router(config-red)# mode {rpr | rpr-plus}
Router# show running-config
Router# show redundancy states
This example shows how to configure the system for RPR+ and display the redundancy state:
Router> enable
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# redundancy
Router(config-red)# mode rpr-plus
Router(config-red)# ^Z
Router# show redundancy states
my state = 13 -ACTIVE
peer state = 1 -DISABLED
Mode = Simplex
Unit = Primary
Unit ID = 1
Enters redundancy configuration mode.
Configures RPR or RPR+. When this command is
entered, the redundant supervisor engine is reloaded and
begins to work in RPR or RPR+ mode.
Verifies that RPR or RPR+ is enabled.
Displays the operating redundancy mode.
5-6
Redundancy Mode (Operational) = Route Processor Redundancy Plus
Redundancy Mode (Configured) = Route Processor Redundancy Plus
Split Mode = Disabled
Manual Swact = Disabled Reason: Simplex mode
Communications = Down Reason: Simplex mode
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 77

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
client count = 11
client_notification_TMR = 30000 milliseconds
keep_alive TMR = 4000 milliseconds
keep_alive count = 0
keep_alive threshold = 7
RF debug mask = 0x0
Router#
Synchronizing the Supervisor Engine Configurations
During normal operation, the startup-config and config-registers configuration are synchronized by
default between the two supervisor engines. In a switchover, the new active supervisor engine uses the
current configuration.
To manually synchronize the configurations used by the two supervisor engines, perform this task on the
active supervisor engine:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Router(config)# redundancy
Router(config-red)# main-cpu
Router(config-r-mc)# auto-sync {startup-config |
config-register | bootvar | standard}
Router(config-r-mc)# end
Router# copy running-config startup-config
Enters redundancy configuration mode.
Enters main-cpu configuration submode.
Synchronizes the configuration elements.
Returns to privileged EXEC mode.
Forces a manual synchronization of the configuration
files in NVRAM.
Configuring Supervisor Engine Redundancy
Note This step is not required to synchronize the
running configuration file in DRAM.
Note The auto-sync standard command does not synchronize the boot variables.
This example shows how to reenable the default automatic synchronization feature using the auto-sync
standard command to synchronize the startup-config and config-register configuration of the active
supervisor engine with the redundant supervisor engine:
Router(config)# redundancy
Router(config-red)# main-cpu
Router(config-r-mc)# auto-sync standard
Router(config-r-mc)# auto-sync bootvar
Router(config-r-mc)# end
Router# copy running-config startup-config
Note To manually synchronize only individual elements of the standard auto-sync configuration, disable
the default automatic synchronization feature.
This example shows how to disable default automatic synchronization and only allow automatic
synchronization of the config-registers of the active supervisor engine to the redundant supervisor
engine while disallowing synchronization of the startup configuration:
Router(config)# redundancy
Router(config-red)# main-cpu
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
5-7
Page 78

Configuring Supervisor Engine Redundancy
Router(config-r-mc)# no auto-sync standard
Router(config-r-mc)# auto-sync config-register
Router(config-r-mc)# end
Router# copy running-config startup-config
Displaying the Redundancy States
To display the redundancy states, perform this task:
Command Purpose
Router# show redundancy states
This example shows how to display the redundancy states:
Router# show redundancy states
my state = 13 -ACTIVE
peer state = 8 -STANDBY HOT
Mode = Duplex
Unit = Primary
Unit ID = 1
Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
Displays the redundancy states.
Redundancy Mode (Operational) = Route Processor Redundancy Plus
Redundancy Mode (Configured) = Route Processor Redundancy Plus
Split Mode = Disabled
Manual Swact = Enabled
Communications = Up
client count = 11
client_notification_TMR = 30000 milliseconds
keep_alive TMR = 9000 milliseconds
keep_alive count = 0
keep_alive threshold = 18
RF debug mask = 0x0
Router#
my state = 13 -ACTIVE
peer state = 1 -DISABLED
Mode = Simplex
Unit = Primary
Unit ID = 1
Redundancy Mode (Operational) = Route Processor Redundancy Plus
Redundancy Mode (Configured) = Route Processor Redundancy Plus
Split Mode = Disabled
Manual Swact = Disabled Reason: Simplex mode
Communications = Down Reason: Simplex mode
client count = 11
client_notification_TMR = 30000 milliseconds
keep_alive TMR = 9000 milliseconds
keep_alive count = 0
keep_alive threshold = 18
RF debug mask = 0x0
5-8
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 79

Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
Performing a Fast Software Upgrade
The fast software upgrade (FSU) procedure supported by RPR allows you to upgrade the Cisco IOS
image on the supervisor engines without reloading the system.
Note If you are performing a first-time upgrade to RPR from EHSA, you must reload both supervisor engines.
FSU from EHSA is not supported.
To perform an FSU, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Step 5
Router# copy source_device:source_filename {disk0
| disk1}:target_filename
Or:
Router# copy source_device:source_filename
sup-bootflash:target_filename
Or:
Router# copy source_device:source_filename
{slavedisk0 | slavedisk1}:target_filename
Or:
Router# copy source_device:source_filename
slavesup-bootflash:target_filename
Router# config terminal
Router(config)# config-register 0x2102
Router(config)# boot system flash
device:file_name
Router# copy running-config start-config
Router# hw-module {module num} reset
Router# redundancy force-switchover
Copies the new Cisco IOS image to the disk0: device or
the disk1: device on the active supervisor engine.
Copies the new Cisco IOS image to the bootflash:
device on the active supervisor engine.
Copies the new Cisco IOS image to the disk0: device or
the disk1: device on the redundant supervisor engine.
Copies the new Cisco IOS image to the bootflash:
device on the redundant supervisor engine.
Configures the supervisor engines to boot the new image.
Saves the configuration.
Reloads the redundant supervisor engine and brings it
back online (running the new version of the Cisco IOS
software).
Note Before reloading the redundant supervisor
Conducts a manual switchover to the redundant
supervisor engine. The redundant supervisor engine
becomes the new active supervisor engine running the
new Cisco IOS image. The modules are reloaded and the
module software is downloaded from the new active
supervisor engine.
The old active supervisor engine reboots with the new
image and becomes the redundant supervisor engine.
Note To perform an EHSA to RPR FSU, use the reload
Performing a Fast Software Upgrade
engine, make sure you wait long enough to ensure
that all configuration synchronization changes
have completed.
command in Step 5.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
5-9
Page 80

Copying Files to an MSFC
This example shows how to perform an FSU:
Router# config terminal
Router(config)# config-register 0x2
Router(config)# boot system flash slot0: c6sup22-jsv-mz.121-11.E
Router# copy running-config start-config
Router# hw-module reset
Router# redundancy force-switchover
Router#
Copying Files to an MSFC
Use the following command to copy a file to the bootflash: device on an active MSFC:
Router# copy source_device:source_filename bootflash:target_filename
Use the following command to copy a file to the bootflash: device on a redundant MSFC:
Router# copy source_device:source_filename slavebootflash:target_filename
Chapter 5 Configuring RPR and RPR+ Supervisor Engine Redundancy
5-10
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 81

CHA PTER
Configuring Interfaces
This chapter describes how to configure interfaces on the Catalyst 6500 series switches. This chapter
consists of these sections:
• Understanding Interface Configuration, page 6-1
• Using the Interface Command, page 6-2
• Configuring a Range of Interfaces, page 6-4
• Defining and Using Interface-Range Macros, page 6-6
• Configuring Optional Interface Features, page 6-7
• Understanding Online Insertion and Removal, page 6-17
• Monitoring and Maintaining Interfaces, page 6-17
Note For complete syntax and usage information for the commands used in this chapter, refer to the
Catalyst 6500 Series Switch Cisco IOS Command Reference publication and the Release 12.1 publications
at this URL:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/index.htm
6
Understanding Interface Configuration
Many features in the software are enabled on a per-interface basis. When you enter the interface
command, you must specify the following information:
• Interface type:
–
Ethernet (use the ethernet keyword)
–
Fast Ethernet (use the fastethernet keyword)
–
Gigabit Ethernet (use the gigabitethernet keyword)
–
10-Gigabit Ethernet (use the tengigabitethernet keyword)
Note For WAN interfaces, refer to the configuration note for the WAN module.
• Slot number—The slot in which the module is installed. On the Catalyst 6500 series switch, slots
are numbered starting with 1, from top to bottom.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
6-1
Page 82

Using the Interface Command
• Port number—The physical port number on the module. On the Catalyst 6500 series switch, the port
numbers always begin with 1. When facing the rear of the switch, ports are numbered from the left
to the right.
You can identify ports from the physical location. You also can use show commands to display
information about a specific port, or all the ports.
Note With Release 12.1(11b)E and later releases, when you are in configuration mode you can enter EXEC
mode-level commands by entering the do keyword before the EXEC mode-level command.
Using the Interface Command
Note You use the commands described in this section to configure both physical ports and logical interfaces.
These procedures apply to all interface configuration processes. Begin the interface configuration
process in global configuration mode.
Chapter 6 Configuring Interfaces
Step 1 Enter the configure terminal command at the privileged EXEC prompt to enter global configuration
mode:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
Step 2 In the global configuration mode, enter the interfaces command. Identify the interface type and the
number of the connector or interface card.
The following example shows how to select Fast Ethernet, slot 5, interface 1:
Router(config)# interfaces fastethernet 5/1
Router(config-if)#
Step 3 Enter the show interfaces EXEC command to see a list of all interfaces that are installed. A report is
provided for each interface that the device supports, as shown in this display:
Router# show interfaces fastethernet 5/48
FastEthernet5/48 is up, line protocol is up
Hardware is C6k 100Mb 802.3, address is 0050.f0ac.3083 (bia 0050.f0ac.3083)
Internet address is 172.20.52.18/27
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Half-duplex, 100Mb/s
ARP type: ARPA, ARP Timeout 04:00:00
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 1000 bits/sec, 1 packets/sec
5 minute output rate 1000 bits/sec, 1 packets/sec
4834677 packets input, 329545368 bytes, 0 no buffer
Received 4796465 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 input packets with dribble condition detected
51926 packets output, 15070051 bytes, 0 underruns
0 output errors, 2 collisions, 2 interface resets
6-2
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 83

Chapter 6 Configuring Interfaces
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Router#
Step 4 Enter the show hardware EXEC command to see a list of the system software and hardware:
Router# show hardware
Cisco Internetwork Operating System Software
IOS (tm) c6sup2_rp Software (c6sup2_rp-JSV-M), Version 12.1(5c)EX, EARLY DEPLOY)
Synced to mainline version: 12.1(5c)
TAC:Home:Software:Ios General:CiscoIOSRoadmap:12.1
Copyright (c) 1986-2001 by cisco Systems, Inc.
Compiled Wed 28-Mar-01 17:52 by hqluong
Image text-base: 0x30008980, data-base: 0x315D0000
ROM: System Bootstrap, Version 12.1(3r)E2, RELEASE SOFTWARE (fc1)
BOOTFLASH: c6sup2_rp Software (c6sup2_rp-JSV-M), Version 12.1(5c)EX, EARLY DEPL)
Router uptime is 2 hours, 55 minutes
System returned to ROM by power-on (SP by power-on)
Running default software
cisco Catalyst 6000 (R7000) processor with 114688K/16384K bytes of memory.
Processor board ID SAD04430J9K
R7000 CPU at 300Mhz, Implementation 39, Rev 2.1, 256KB L2, 1024KB L3 Cache
Last reset from power-on
Bridging software.
X.25 software, Version 3.0.0.
SuperLAT software (copyright 1990 by Meridian Technology Corp).
TN3270 Emulation software.
1 Virtual Ethernet/IEEE 802.3 interface(s)
48 FastEthernet/IEEE 802.3 interface(s)
2 Gigabit Ethernet/IEEE 802.3 interface(s)
381K bytes of non-volatile configuration memory.
Using the Interface Command
16384K bytes of Flash internal SIMM (Sector size 512K).
Configuration register is 0x2
Router#
Step 5 To begin configuring Fast Ethernet port 5/5, enter the interface keyword, interface type, and slot
number/port number at the privileged EXEC prompt, as shown in the following example:
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# interface fastethernet 5/5
Router(config-if)#
Note You do not need to add a space between the interface type and interface number. For example,
in the preceding line you can specify either fastethernet 5/5 or fastethernet5/5.
Step 6 After each interface command, enter the interface configuration commands your particular interface
requires.
The commands you enter define the protocols and applications that will run on the interface. The
commands are collected and applied to the interface command until you enter another interface
command or press Ctrl-Z to get out of interface configuration mode and return to privileged EXEC
mode.
Step 7 After you configure an interface, check its status by using the EXEC show commands listed in
“Monitoring and Maintaining Interfaces” section on page 6-17.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-3
Page 84

Configuring a Range of Interfaces
Configuring a Range of Interfaces
The interface-range configuration mode allows you to configure multiple interfaces with the same
configuration parameters. After you enter the interface-range configuration mode, all command
parameters you enter are attributed to all interfaces within that range until you exit out of the
interface-range configuration mode.
To configure a range of interfaces with the same configuration, perform this task:
Command Purpose
Router(config)# interface range
{{vlan vlan_ID - vlan_ID [, vlan vlan_ID - vlan_ID]}
| {type slot/port - port [, type slot/port - port]} |
{macro_name [, macro_name]}}
Router(config)# no interface range
{{vlan vlan_ID - vlan_ID [, vlan vlan_ID - vlan_ID]}
| {macro_name [, macro_name]}}
When configuring a range of interfaces, note the following syntax information:
• For information about macros, see the “Defining and Using Interface-Range Macros” section on
page 6-6.
Selects the range of interfaces to be configured.
Selects the range of VLAN interfaces to remove.
Chapter 6 Configuring Interfaces
• You can enter up to five comma-separated ranges.
• You are not required to enter spaces before or after the comma.
• With releases earlier than Release 12.1(26)E, you must add a space between the interface numbers
and the dash when using the interface range command. For example, interface range fastethernet
1 - 5 is valid syntax; interface range fastethernet 1-5 is invalid.
• With Release 12.1(26)E and later releases, you do not need to add a space between the interface
numbers and the dash when using the interface range command.
• With releases earlier than Release 12.1(14)E, the interface range command supports these interface
keywords:
–
ethernet
–
fastethernet
–
gigabitethernet
–
tengigabitethernet
• With Release 12.1(14)E and later releases, the interface range command supports these additional
interface keywords:
–
pos
–
loopback
–
tunnel
• With Release 12.1(14)E and later releases, you can use the no interface range command to delete
VLAN interfaces.
• With releases earlier than Release 12.1(14)E, you cannot use the no keyword with the range
keyword to delete VLAN interfaces.
• With Release 12.1(14)E and later releases, you can use the interface range command to create
VLAN interfaces.
6-4
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 85

Chapter 6 Configuring Interfaces
• With releases earlier than Release 12.1(26)E, for VLAN interfaces, the interface range command
supports only those VLAN interfaces for which Layer 2 VLANs have been created with the
interface vlan command (the show running-configuration command displays the configured
VLAN interfaces). The interface range command does not support VLAN interfaces that are not
displayed by the show running-configuration command.
• With Release 12.1(26)E and later releases, the interface range command supports VLAN interfaces
for which Layer 2 VLANs have not been created with the interface vlan command.
• With releases earlier than Release 12.1(14)E, you cannot use the interface range command to create
VLAN interfaces: the interface range command is supported only to modify VLAN interfaces that
have been created with the interface vlan command. You can enter the show
running-configuration command to display the configured VLAN interfaces.
Note The link state messages (LINK-3-UPDOWN and LINEPROTO-5-UPDOWN) are disabled by default.
Enter the logging event link status command on each interface where you want the messages enabled.
This example shows how to reenable all Fast Ethernet ports 5/1 to 5/5:
Router(config)# interface range fastethernet 5/1 - 5
Router(config-if)# no shutdown
Router(config-if)#
*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet5/1, changed state to up
*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet5/2, changed state to up
*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet5/3, changed state to up
*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet5/4, changed state to up
*Oct 6 08:24:35: %LINK-3-UPDOWN: Interface FastEthernet5/5, changed state to up
*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
5, changed state to up
*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
3, changed state to up
*Oct 6 08:24:36: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
4, changed state to up
Router(config-if)#
Configuring a Range of Interfaces
78-14099-04
This example shows how to use a comma to add different interface type strings to the range to reenable
all Fast Ethernet ports in the range 5/1 to 5/5 and both Gigabit Ethernet ports (1/1 and 1/2):
Router(config-if)# interface range fastethernet 5/1 - 5, gigabitethernet 1/1 - 2
Router(config-if)# no shutdown
Router(config-if)#
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet5/1, changed state to up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet5/2, changed state to up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet5/3, changed state to up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet5/4, changed state to up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface FastEthernet5/5, changed state to up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface GigabitEthernet1/1, changed state to
up
*Oct 6 08:29:28: %LINK-3-UPDOWN: Interface GigabitEthernet1/2, changed state to
up
*Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
5, changed state to up
*Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
3, changed state to up
*Oct 6 08:29:29: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet5/
4, changed state to up
Router(config-if)#
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-5
Page 86

Defining and Using Interface-Range Macros
If you enter multiple configuration commands while you are in interface-range configuration mode, each
command is executed as it is entered (they are not batched together and executed after you exit
interface-range configuration mode).
If you exit interface-range configuration mode while the commands are being executed, some commands
may not be executed on all interfaces in the range. Wait until the command prompt reappears before
exiting interface-range configuration mode.
Defining and Using Interface-Range Macros
You can define an interface-range macro to automatically select a range of interfaces for configuration.
Before you can use the macro keyword in the interface range macro command string, you must define
the macro.
To define an interface-range macro, perform this task:
Command Purpose
Router(config)# define interface-range macro_name
{vlan vlan_ID - vlan_ID} | {type
[, {type
Router(config)# no define interface-range macro_name
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
1
slot/port - port}]
1
slot/port - port}
Defines the interface-range macro and save it in NVRAM.
Deletes a macro.
Chapter 6 Configuring Interfaces
This example shows how to define an interface-range macro named enet_list to select Fast Ethernet ports
5/1 through 5/4:
Router(config)# define interface-range enet_list fastethernet 5/1 - 4
To show the defined interface-range macro configuration, perform this task:
Command Purpose
Router# show running-config
Shows the defined interface-range macro configuration.
This example shows how to display the defined interface-range macro named enet_list:
Router# show running-config | include define
define interface-range enet_list FastEthernet5/1 - 4
Router#
To use an interface-range macro in the interface range command, perform this task:
Command Purpose
Router(config)# interface range macro macro_name
Selects the interface range to be configured using the values
saved in a named interface-range macro.
This example shows how to change to the interface-range configuration mode using the interface-range
macro enet_list:
Router(config)# interface range macro enet_list
Router(config-if)#
6-6
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 87

Chapter 6 Configuring Interfaces
Configuring Optional Interface Features
These sections describe optional interface features:
• Configuring Ethernet Interface Speed and Duplex Mode, page 6-7
• Configuring Jumbo Frame Support, page 6-10
• Configuring IEEE 802.3Z Flow Control, page 6-14
• Configuring the Port Debounce Timer, page 6-15
• Adding a Description for an Interface, page 6-16
Configuring Ethernet Interface Speed and Duplex Mode
These sections describe how to configure Ethernet port speed and duplex mode:
• Speed and Duplex Mode Configuration Guidelines, page 6-7
• Setting the Ethernet Interface Speed, page 6-8
• Setting the Interface Duplex Mode, page 6-8
Configuring Optional Interface Features
• Configuring Link Negotiation on Gigabit Ethernet Ports, page 6-8
• Displaying the Speed and Duplex Mode Configuration, page 6-9
Speed and Duplex Mode Configuration Guidelines
You usually configure Ethernet port speed and duplex mode parameters to auto and allow the
Catalyst 6500 series switch to negotiate the speed and duplex mode between ports. If you decide to
configure the port speed and duplex modes manually, consider the following information:
• If you set the Ethernet port speed to auto, the switch automatically sets the duplex mode to auto.
• If you enter the no speed command, the switch automatically configures both speed and duplex to
auto.
• If you configure an Ethernet port speed to a value other than auto (for example, 10, 100, or
1000 Mbps), configure the connecting port to match. Do not configure the connecting port to
negotiate the speed.
• If you manually configure the Ethernet port speed to either 10 or 100 Mbps, the switch prompts you
to also configure the duplex mode on the port.
Note Catalyst 6500 series switches cannot automatically negotiate Ethernet port speed and duplex mode if the
connecting port is configured to a value other than auto.
78-14099-04
Caution Changing the Ethernet port speed and duplex mode configuration might shut down and reenable the
interface during the reconfiguration.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-7
Page 88

Configuring Optional Interface Features
Setting the Ethernet Interface Speed
Note If you set the Ethernet port speed to auto on a 10/100-Mbps or 10/100/1000-Mbps Ethernet port, both
speed and duplex are autonegotiated.
To set the port speed for a 10/100 or a 10/100/1000-Mbps Ethernet port, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# interface fastethernet slot/port
Router(config-if)# speed {10 | 100 | 1000 | auto}
Router(config-if)# no speed
This example shows how to set the speed to 100 Mbps on the Fast Ethernet port 5/4:
Router(config)# interface fastethernet 5/4
Router(config-if)# speed 100
Chapter 6 Configuring Interfaces
Selects the Ethernet port to be configured.
Sets the speed of the Ethernet interface.
Reverts to the default configuration (speed auto).
Setting the Interface Duplex Mode
Note • 10-Gigabit Ethernet and Gigabit Ethernet are full duplex only. You cannot change the duplex mode
on 10-Gigabit Ethernet or Gigabit Ethernet ports or on a 10/100/1000-Mps port configured for
Gigabit Ethernet.
• If you set the port speed to auto on a 10/100-Mbps or a 10/100/1000-Mbps Ethernet port, both speed
and duplex are autonegotiated. You cannot change the duplex mode of autonegotiation ports.
To set the duplex mode of an Ethernet or Fast Ethernet port, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# interface fastethernet slot/port
Router(config-if)# duplex [auto | full | half]
Router(config-if)# no duplex
This example shows how to set the duplex mode to full on Fast Ethernet port 5/4:
Router(config)# interface fastethernet 5/4
Router(config-if)# duplex full
Selects the Ethernet port to be configured.
Sets the duplex mode of the Ethernet port.
Reverts to the default configuration (duplex auto).
Configuring Link Negotiation on Gigabit Ethernet Ports
Note Link negotiation does not negotiate port speed.
On Gigabit Ethernet ports, link negotiation exchanges flow-control parameters, remote fault
information, and duplex information. Link negotiation is enabled by default.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-8
78-14099-04
Page 89

Chapter 6 Configuring Interfaces
The ports on both ends of a link must have the same setting. The link will not come up if the ports at
each end of the link are set inconsistently (link negotiation enabled on one port and disabled on the other
port).
Table 6-1 shows the four possible link negotiation configurations and the resulting link status for each
configuration.
Table 6-1 Link Negotiation Configuration and Possible Link Status
Link Negotiation State Link Status
Local Port Remote Port Local Port Remote Port
Off Off Up Up
On On Up Up
OffOnUpDown
On Off Down Up
To configure link negotiation on a port, perform this task:
Configuring Optional Interface Features
Command Purpose
Step 1
Step 2
Router(config)# interface gigabitethernet
slot/port
Router(config-if)# speed nonegotiate
Router(config-if)# no speed nonegotiate
Selects the port to be configured.
Disables link negotiation.
Reverts to the default configuration (link negotiation
enabled).
This example shows how to enable link negotiation on Gigabit Ethernet port 5/4:
Router(config)# interface gigabitethernet 5/4
Router(config-if)# no speed nonegotiate
Displaying the Speed and Duplex Mode Configuration
To display the speed and duplex mode configuration for a port, perform this task:
Command Purpose
Router# show interfaces type1 slot/port
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
This example shows how to display the speed and duplex mode of Fast Ethernet port 5/4:
Router# show interfaces fastethernet 5/4
FastEthernet5/4 is up, line protocol is up
Hardware is Cat6K 100Mb Ethernet, address is 0050.f0ac.3058 (bia 0050.f0ac.3058)
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:33, output never, output hang never
Displays the speed and duplex mode configuration.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-9
Page 90

Configuring Optional Interface Features
Last clearing of "show interface" counters never
Queueing strategy: fifo
Output queue 0/40, 0 drops; input queue 0/75, 0 drops
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
1238 packets input, 273598 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 input packets with dribble condition detected
1380 packets output, 514382 bytes, 0 underruns
0 output errors, 0 collisions, 2 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Router#
Configuring Jumbo Frame Support
These sections describe jumbo frame support:
• Understanding Jumbo Frame Support, page 6-10
Chapter 6 Configuring Interfaces
• Configuring MTU Sizes, page 6-13
Caution The following switching modules support a maximum ingress frame size of 8092 bytes:
• WS-X6516-GE-TX when operating at 100 Mbps
• WS-X6148-RJ-45 and WS-X6148-RJ-45V
• WS-X6148-RJ21 and WS-X6148-RJ21V
• WS-X6248-RJ-45
• WS-X6248-TEL
• WS-X6248A-RJ-45
• WS-X6248A-TEL
• WS-X6348-RJ-45 and WS-X6348-RJ45V
• WS-X6348-RJ-21 and WX-X6348-RJ21V
When jumbo frame support is configured, these modules drop ingress frames larger than 8092 bytes.
Note The WS-X6548-GE-TX, WS-X6548V-GE-TX, WS-X6148-GE-TX, and WS-X6148V-GE-TX do not
support jumbo frames.
Understanding Jumbo Frame Support
6-10
These sections describe jumbo frame support:
• Jumbo Frame Support Overview, page 6-11
• Ethernet Ports, page 6-12
• VLAN Interfaces, page 6-13
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 91

Chapter 6 Configuring Interfaces
Jumbo Frame Support Overview
A jumbo frame is a frame larger than the default Ethernet frame size. You enable jumbo frame support
by configuring a larger-than-default maximum transmission unit (MTU) size on a port or VLAN
interface and, with Release 12.1(13)E and later releases, configuring the global LAN port MTU size.
Note • Jumbo frame support fragments routed traffic in software on the MSFC.
• Jumbo frame support does not fragment bridged traffic.
These sections provide an overview of jumbo frame support:
• Bridged and Routed Traffic Size Check at Ingress 10, 10/100, and 100 Mbps Ethernet and 10 Gigabit
Ethernet Ports, page 6-11
• Bridged and Routed Traffic Size Check at Ingress Gigabit Ethernet Ports, page 6-11
• Routed Traffic Size Check on the PFC, page 6-11
• Bridged and Routed Traffic Size Check at Egress 10, 10/100, and 100 Mbps Ethernet Ports, page
6-11
Configuring Optional Interface Features
• Bridged and Routed Traffic Size Check at Egress Gigabit Ethernet and 10 Gigabit Ethernet Ports,
page 6-12
Bridged and Routed Traffic Size Check at Ingress 10, 10/100, and 100 Mbps Ethernet and 10 Gigabit Ethernet Ports
Jumbo frame support compares ingress traffic size with the global LAN port MTU size at ingress 10,
10/100, and 100 Mbps Ethernet and 10 Gigabit Ethernet LAN ports that have a nondefault MTU size
configured. The port drops traffic that is oversized.
With Release 12.1(13)E and later releases, you can configure the global LAN port MTU size (see the
“Configuring the Global LAN Port MTU Size” section on page 6-14). With earlier releases, the global
LAN port MTU size is 9216 bytes and 9216 bytes is the only configurable nondefault MTU size for
Layer 2 LAN ports.
Bridged and Routed Traffic Size Check at Ingress Gigabit Ethernet Ports
Gigabit Ethernet LAN ports configured with a nondefault MTU size accept frames containing packets
of any size larger than 64 bytes. With a nondefault MTU size configured, Gigabit Ethernet LAN ports
do not check for oversize ingress frames.
Routed Traffic Size Check on the PFC
For traffic that needs to be routed Jumbo frame support on the PFC compares traffic sizes to the
configured MTU sizes and provides Layer 3 switching for jumbo traffic between interfaces configured
with MTU sizes large enough to accommodate the traffic. Between interfaces that are not configured
with large enough MTU sizes, if the “do not fragment bit” is not set, the PFC sends the traffic to the
MSFC to be fragmented and routed in software. If the “do not fragment bit” is set, the PFC drops the
traffic.
78-14099-04
Bridged and Routed Traffic Size Check at Egress 10, 10/100, and 100 Mbps Ethernet Ports
10, 10/100, and 100 Mbps Ethernet LAN ports configured with a nondefault MTU size transmit frames
containing packets of any size larger than 64 bytes. With a nondefault MTU size configured, 10, 10/100,
and 100 Mbps Ethernet LAN ports do not check for oversize egress frames.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-11
Page 92

Configuring Optional Interface Features
Bridged and Routed Traffic Size Check at Egress Gigabit Ethernet and 10 Gigabit Ethernet Ports
Jumbo frame support compares egress traffic size with the global egress LAN port MTU size at egress
Gigabit Ethernet and 10 Gigabit Ethernet LAN ports that have a nondefault MTU size configured. The
port drops traffic that is oversized.
With Release 12.1(13)E and later releases, you can configure the global LAN port MTU size (see the
“Configuring the Global LAN Port MTU Size” section on page 6-14). With earlier releases, the LAN
port MTU size is 9216 bytes and 9216 bytes is the only configurable nondefault MTU size for Layer 2
LAN ports.
Ethernet Ports
These sections describe configuring nondefault MTU sizes on Ethernet ports:
• Ethernet Port Overview, page 6-12
• Layer 3 Ethernet Ports, page 6-12
• Layer 2 Ethernet Ports, page 6-12
Ethernet Port Overview
Configuring a nondefault MTU size on a 10, 10/100, or 100 Mbps Ethernet port limits ingress packets
to the global LAN port MTU size and permits egress traffic of any size larger than 64 bytes.
Configuring a nondefault MTU size on a Gigabit Ethernet port permits ingress packets of any size larger
than 64 bytes and limits egress traffic to the global LAN port MTU size.
Chapter 6 Configuring Interfaces
Configuring a nondefault MTU size on a 10 Gigabit Ethernet port limits ingress and egress packets to
the global LAN port MTU size.
Configuring a nondefault MTU size on an Ethernet port limits routed traffic to the configured MTU size.
With Release 12.1(11b)E and later releases, you can configure the MTU size on any Ethernet port.
With earlier releases, you can configure the MTU size only on Gigabit Ethernet and 10-Gigabit Ethernet
ports.
Layer 3 Ethernet Ports
On a Layer 3 port, you can configure an MTU size that is different than the global LAN port MTU size.
With Release 12.1(13)E and later releases, you can configure a different MTU size on each Layer 3
Ethernet port.
With earlier releases, you can configure only a single larger-than-default MTU size on the switch for
Layer 3 Ethernet ports. When you configure a Layer 3 Ethernet port with a nondefault MTU size, the
switch automatically configures all other Layer 3 Ethernet ports and Layer 3 EtherChannels with
nondefault MTU sizes to the newly configured size. Layer 3 Ethernet ports and EtherChannels that have
not been changed from the default are not affected.
Note Traffic through a Layer 3 Ethernet LAN port that is configured with a nondefault MTU size is also
subject to the global LAN port MTU size (see the “Configuring the Global LAN Port MTU Size” section
on page 6-14).
6-12
Layer 2 Ethernet Ports
On a Layer 2 port, you can only configure an MTU size that matches the global LAN port MTU size (see
the “Configuring the Global LAN Port MTU Size” section on page 6-14).
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 93

Chapter 6 Configuring Interfaces
Release 12.1(13)E and later releases support nondefault MTU sizes between 1,500 and 9,216 bytes for
Layer 2 Ethernet ports, configured per-port with the mtu command and globally with the
system jumbomtu command.
With earlier releases, 9216 bytes is the only supported nondefault MTU size for Layer 2 Ethernet ports,
configured per-port with the mtu command.
VLAN Interfaces
You can configure a different MTU size on each Layer 3 VLAN interface. Configuring a nondefault
MTU size on a VLAN interface limits traffic to the nondefault MTU size.
You can configure the MTU size on VLAN interfaces to support jumbo frames with the following
hardware and software:
• Supervisor Engine 1 and Release 12.1(7)E or later
• Supervisor Engine 2 and Release 12.1(8a)E or later
Configuring MTU Sizes
These sections describe how to configure MTU sizes:
Configuring Optional Interface Features
• Configuring MTU Sizes, page 6-13
• Configuring the Global LAN Port MTU Size, page 6-14
Configuring the MTU Size
To configure the MTU size, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Step 4
Router(config)# interface {{vlan vlan_ID} |
1
{{type
port_channel_number} slot/port}}
Router(config-if)# mtu mtu_size
Router(config-if)# no mtu
Router(config-if)# end
Router# show running-config interface
[{gigabitethernet | tengigabitethernet}
slot/port]
slot/port} | {port-channel
1. type = ethernet, fastethernet, gigabitethernet, tengigabitethernet, or ge-wan
When configuring the MTU size, note the following syntax information:
• For VLAN interfaces and Layer 3 Ethernet ports, supported MTU values are from 64 to 9216 bytes.
• For Layer 2 Ethernet ports with Release 12.1(13)E and later releases, you can configure only the
• For Layer 2 Ethernet ports with earlier releases, the only supported MTU size is 9216 bytes.
Selects the interface to configure.
Configures the MTU size.
Reverts to the default MTU size (1500 bytes).
Exits configuration mode.
Displays the running configuration.
global egress LAN port MTU size (see the “Configuring the Global LAN Port MTU Size” section
on page 6-14).
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-13
Page 94

Configuring Optional Interface Features
This example shows how to configure the MTU size on Gigabit Ethernet port 1/2:
Router# configure terminal
Router(config)# interface gigabitethernet 1/2
Router(config-if)# mtu 9216
Router(config-if)# end
This example shows how to verify the configuration:
Router# show interface gigabitethernet 1/2
GigabitEthernet1/2 is administratively down, line protocol is down
Hardware is C6k 1000Mb 802.3, address is 0030.9629.9f88 (bia 0030.9629.9f88)
MTU 9216 bytes, BW 1000000 Kbit, DLY 10 usec,
<...Output Truncated...>
Router#
Configuring the Global LAN Port MTU Size
To configure the global LAN port MTU size, perform this task:
Command Purpose
Step 1
Step 2
Router(config)# system jumbomtu mtu_size
Router(config)# no system jumbomtu
Router(config)# end
Chapter 6 Configuring Interfaces
Configures the global LAN port MTU size.
Reverts to the default global LAN port MTU size (9216
bytes).
Exits configuration mode.
Configuring IEEE 802.3Z Flow Control
Gigabit Ethernet and 10-Gigabit Ethernet ports on the Catalyst 6500 series switches use flow control to
stop the transmission of frames to the port for a specified time; other Ethernet ports use flow control to
respond to flow-control requests.
If a Gigabit Ethernet or 10-Gigabit Ethernet port receive buffer becomes full, the port transmits an
IEEE 802.3Z pause frame that requests remote ports to delay sending frames for a specified time. All
Ethernet ports (10 Gbps, 1 Gbps, 100 Mbps, and 10 Mbps) can receive and respond to IEEE 802.3Z
pause frames from other devices.
To configure flow control on an Ethernet port, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Router(config)# interface type1 slot/port
Router(config-if)# flowcontrol {receive | send}
{desired | off | on}
Router(config-if)# no flowcontrol {receive |
send}
Router# show interfaces [type1 slot/port]
flowcontrol
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
Selects the port to configure.
Configures a port to send or respond to pause frames.
Reverts to the default flow control settings.
Displays the flow-control configuration for all ports.
6-14
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 95

Chapter 6 Configuring Interfaces
When configuring flow control, note the following syntax information:
• 10-Gigabit Ethernet ports are permanently configured to respond to pause frames.
• When the configuration of the remote ports is unknown, use the receive desired keywords to
configure a Gigabit Ethernet port to respond to received pause frames.
• Use the receive on keywords to configure a Gigabit Ethernet port to respond to received pause
frames.
• Use the receive off keywords to configure a Gigabit Ethernet port to ignore received pause frames.
• When configuring transmission of pause frames, note the following information:
–
–
–
This example shows how to turn on receive flow control and how to verify the flow-control
configuration:
Router# configure terminal
Router(config)# interface gigabitethernet 1/2
Router(config-if)# flowcontrol receive on
Router(config-if)# end
Router# show interfaces flowcontrol
Configuring Optional Interface Features
When the configuration of the remote ports is unknown, use the send desired keywords to
configure a port to send pause frames.
Use the send on keywords to configure a port to send pause frames.
Use the send off keywords to configure a port not to send pause frames.
Interface Send Receive
Gi1/1 Desired OFF
Gi1/2 Desired ON
Fa5/1 Not capable OFF
<output truncated>
Configuring the Port Debounce Timer
The port debounce timer delays notification of a link change, which can decrease traffic loss due to
network reconfiguration. Release 12.1(13)E and later releases support the port debounce timer on all
LAN ports. You can configure the port debounce timer separately on each LAN port.
Caution Enabling the port debounce timer causes link up and link down detections to be delayed, resulting in loss
of traffic during the debouncing period. This situation might affect the convergence and reconvergence
of some Layer 2 and Layer 3 protocols.
Table 6-2 lists the time delay that occurs before notification of a link change.
Table 6-2 Port Debounce Timer Delay Time
Port Type Debounce Timer Disabled Debounce Timer Enabled
10BASE-FL ports 300 milliseconds 3100 milliseconds
10/100BASE-TX ports 300 milliseconds 3100 milliseconds
100BASE-FX ports 300 milliseconds 3100 milliseconds
10/100/1000BASE-TX ports 300 milliseconds 3100 milliseconds
1000BASE-TX ports 300 milliseconds 3100 milliseconds
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-15
Page 96

Configuring Optional Interface Features
Table 6-2 Port Debounce Timer Delay Time (continued)
Port Type Debounce Timer Disabled Debounce Timer Enabled
Fiber Gigabit ports 10 milliseconds 100 through 5000 milliseconds
10-Gigabit ports
To configure the debounce timer on a port, perform this task:
Command Purpose
Step 1
Step 2
Step 3
Router(config)# interface type1 slot/port
Router(config-if)# link debounce
[time debounce_time]
Router(config-if)# no link debounce
Router# show interfaces debounce
1. type = ethernet, fastethernet, or gigabitethernet
Chapter 6 Configuring Interfaces
Note With Release 12.1(13)E and later releases, you can
configure the port debounce timer on 10 Gigabit Ethernet
ports, but it has no effect. With Release 12.1(19)E and later
releases, you cannot configure the port debounce timer on
10 Gigabit Ethernet ports.
Selects the port to configure.
Configures the debounce timer.
Note The time keyword is supported only on fiber
Gigabit Ethernet ports.
Reverts to the default setting.
Verifies the configuration.
On fiber Gigabit Ethernet ports, you can increase the port debounce timer value in increments of
100 milliseconds up to 5000 milliseconds.
This example shows how to enable the port debounce timer on Fast Ethernet port 5/12:
Router(config)# interface fastethernet 5/12
Router(config-if)# link debounce
Router(config-if)# end
This example shows how to display the port debounce timer settings:
Router# show interfaces debounce | include enable
Fa5/12 enable 3100
Adding a Description for an Interface
You can add a description about an interface to help you remember its function. The description appears
in the output of the following commands: show configuration
interfaces.
To add a description for an interface, perform this task:
Command Purpose
Router(config-if)# description string
Router(config-if)# no description
Adds a description for an interface.
Deletes a description from an interface.
, show running-config, and show
6-16
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 97

Chapter 6 Configuring Interfaces
Understanding Online Insertion and Removal
This example shows how to add a description on Fast Ethernet port 5/5:
Router(config)# interface fastethernet 5/5
Router(config-if)# description Channel-group to "Marketing"
Understanding Online Insertion and Removal
The online insertion and removal (OIR) feature supported on the Catalyst 6500 series switches allows
you to remove and replace modules while the system is online. You can shut down the modules before
removal and restart it after insertion without causing other software or interfaces to shut down.
Note Do not remove or install more than one module at a time. After you remove or install a module, check
the LEDs before continuing. For module LED descriptions, refer to the Catalyst 6500 Series Switch
Installation Guide.
When a module has been removed or installed, the Catalyst 6500 series switch stops processing traffic
for the module and scans the system for a configuration change. Each interface type is verified against
the system configuration, and then the system runs diagnostics on the new module. There is no disruption
to normal operation during module insertion or removal.
The switch can bring only an identical replacement module online. If the replacement module is different
from the removed module, you must configure it before the switch can bring it online.
Layer 2 MAC addresses are stored in an EEPROM, which allows modules to be replaced online without
requiring the system to update switching tables and data structures. Regardless of the types of modules
installed, the Layer 2 MAC addresses do not change unless you replace the supervisor engine. If you do
replace the supervisor engine, the Layer 2 MAC addresses of all ports change to those specified in the
address allocator on the new supervisor engine.
Monitoring and Maintaining Interfaces
You can perform the tasks in the following sections to monitor and maintain interfaces:
• Monitoring Interface Status, page 6-17
• Clearing Counters on an Interface, page 6-18
• Resetting an Interface, page 6-19
• Shutting Down and Restarting an Interface, page 6-19
Monitoring Interface Status
The software contains commands that you can enter at the EXEC prompt to display information about
the interface including the version of the software and the hardware and statistics about interfaces. The
following table lists some of the interface monitoring commands. (You can display the complete list of
show commands by using the show ? command at the EXEC prompt.) These commands are described
in the Cisco IOS Interface Command Reference publication.
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
6-17
Page 98

Monitoring and Maintaining Interfaces
To display information about the interface, perform these tasks:
Command Purpose
Router# show ibc
Router# show eobc
Router# show interfaces [type slot/port]
Router# show running-config
Router# show rif
Router# show protocols [type slot/port]
Router# show version
This example shows how to display the status of Fast Ethernet port 5/5:
Router# show protocols fastethernet 5/5
FastEthernet5/5 is up, line protocol is up
Router#
Displays current internal status information.
Displays current internal out-of-band information.
Displays the status and configuration of all or a specific
interface.
Displays the currently running configuration.
Displays the current contents of the routing information field
(RIF) cache.
Displays the global (system-wide) and interface-specific
status of any configured protocol.
Displays the hardware configuration, software version, the
names and sources of configuration files, and the boot images.
Chapter 6 Configuring Interfaces
Clearing Counters on an Interface
To clear the interface counters shown with the show interfaces command, perform this task:
Command Purpose
Router# clear counters {{vlan vlan_ID} |
1
{type
slot/port} | {port-channel channel_ID}}
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
This example shows how to clear and reset the counters on Fast Ethernet port 5/5:
Router# clear counters fastethernet 5/5
Clear "show interface" counters on this interface [confirm] y
Router#
*Sep 30 08:42:55: %CLEAR-5-COUNTERS: Clear counter on interface FastEthernet5/5
The clear counters command clears all the current counters from the interface unless the optional
arguments specify a specific interface.
Note The clear counters command clears counters displayed with the EXEC show interfaces command, not
counters retrieved using SNMP.
Clears interface counters.
6-18
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
Page 99

Chapter 6 Configuring Interfaces
Resetting an Interface
To reset an interface, perform this task:
Command Purpose
Router# clear interface type1 slot/port
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
Resets an interface.
This example shows how to reset Fast Ethernet port 5/5:
Router# clear interface fastethernet 5/5
Router#
Shutting Down and Restarting an Interface
You can shut down an interface, which disables all functions on the specified interface and shows the
interface as unavailable on all monitoring command displays. This information is communicated to other
network servers through all dynamic routing protocols. The interface is not included in any routing
updates.
Monitoring and Maintaining Interfaces
Step 1
Step 2
Step 3
To shut down an interface and then restart it, perform this task:
Command Purpose
Router(config)# interface {{vlan vlan_ID} |
1
{type
slot/port} | {port-channel channel_ID}}
Router(config-if)# shutdown
Router(config-if)# no shutdown
1. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
Selects the interface to be configured.
Shuts down the interface.
Reenables the interface.
This example shows how to shut down Fast Ethernet port 5/5:
Router(config)# interface fastethernet 5/5
Router(config-if)# shutdown
Router(config-if)#
*Sep 30 08:33:47: %LINK-5-CHANGED: Interface FastEthernet5/5, changed state to
administratively down
This example shows how to reenable Fast Ethernet port 5/5:
Router(config-if)# no shutdown
Router(config-if)#
*Sep 30 08:36:00: %LINK-3-UPDOWN: Interface FastEthernet5/5, changed state to up
To check if an interface is disabled, enter the EXEC show interfaces command. An interface that has
been shut down is shown as administratively down in the show interfaces command display.
78-14099-04
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
6-19
Page 100

Monitoring and Maintaining Interfaces
Chapter 6 Configuring Interfaces
6-20
Catalyst 6500 Series Switch Cisco IOS Software Configuration Guide—Release 12.1 E
78-14099-04
 Loading...
Loading...