Page 1
BayRS Version 15.1.0.0
Part No. 308644-15.1 Rev 00
October 2001
600 Technology Park Drive
Billerica, MA 01821-4130
Configuring SNMP, BootP,
and DHCP Services
Page 2

Copyright © 2001 Nortel Networks
All rights reserved. October 2001.
The information in this document is subject to change without notice. The statements, configurations, technical data,
and recommendations in this document are believed to be accurate and reliable, but are presented without express or
implied warranty. Users must take full responsibility for their applications of any products specified in this document.
The information in this document is proprietary to Nortel Networks NA Inc.
The software described in this document is furnished under a license agreement and may only be used in accordance
with the terms of that license. The software license agreement is included in this document.
Trademarks
Nortel Networks, the Nortel Networks logo, the Globemark, Unified Networks, ASN, BayRS, BCC, and System 5000
are trademarks of Nortel Networks.
Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation.
Adobe and Acrobat Reader are trademarks of Adobe Systems Incorporated.
UNIX is a trademark of X/Open Company Limited.
The asterisk after a name denotes a trademarked item.
Restricted Rights Legend
Use, duplication, or disclosure by the United States Government is subject to restrictions as set forth in subparagraph
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of, this computer
software, the rights of the United States Government regarding its use, reproduction, and disclosure are as set forth in
the Commercial Computer Software-Restricted Rights clause at FAR 52.227-19.
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, Nortel Networks Inc. reserves the
right to make changes to the products described in this document without notice.
Nortel Networks Inc. does not assume any liability that may occur due to the use or application of the product(s) or
circuit layout(s) described herein.
Portions of the code in this software product may be Copyright © 1988, Regents of the University of California. All
rights reserved. Redistribution and use in source and binary forms of such portions are permitted, provided that the
above copyright notice and this paragraph are duplicated in all such forms and that any documentation, advertising
materials, and other materials related to such distribution and use acknowledge that such portions of the software were
developed by the University of California, Berkeley. The name of the University may not be used to endorse or
promote products derived from such portions of the software without specific prior written permission.
SUCH PORTIONS OF THE SOFTWARE ARE PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
In addition, the program and information contained herein are licensed only pursuant to a license agreement that
contains restrictions on use and disclosure (that may incorporate by reference certain limitations and notices imposed
by third parties).
ii
308644-15.1 Rev 00
Page 3

Nortel Networks Inc. Software License Agreement
This Software License Agreement (“License Agreement”) is between you, the end-user (“Customer”) and Nortel
Networks Corporation and its subsidiaries and affiliates (“Nortel Networks”). PLEASE READ THE FOLLOWING
CAREFULLY. YOU MUST ACCEPT THESE LICENSE TERMS IN ORDER TO DOWNLOAD AND/OR USE
THE SOFTWARE. USE OF THE SOFTWARE CONSTITUTES YOUR ACCEPTANCE OF THIS LICENSE
AGREEMENT. If you do not accept these terms and conditions, return the Software, unused and in the original
shipping container, within 30 days of purchase to obtain a credit for the full purchase price.
“Software” is owned or licensed by Nortel Networks, its parent or one of its subsidiaries or affiliates, and is
copyrighted and licensed, not sold. Software consists of machine-readable instructions, its components, data,
audio-visual content (such as images, text, recordings or pictures) and related licensed materials including all whole or
partial copies. Nortel Networks grants you a license to use the Software only in the country where you acquired the
Software. You obtain no rights other than those granted to you under this License Agreement. You are responsible for
the selection of the Software and for the installation of, use of, and results obtained from the Software.
1. Licensed Use of Software. Nortel Networks grants Customer a nonexclusive license to use a copy of the
Software on only one machine at any one time or to the extent of the activation or authorized usage level, whichever is
applicable. To the extent Software is furnished for use with designated hardware or Customer furnished equipment
(“CFE”), Customer is granted a nonexclusive license to use Software only on such hardware or CFE, as applicable.
Software contains trade secrets and Customer agrees to treat Software as confidential information using the same care
and discretion Customer uses with its own similar information that it does not wish to disclose, publish or disseminate.
Customer will ensure that anyone who uses the Software does so only in compliance with the terms of this Agreement.
Customer shall not a) use, copy, modify, transfer or distribute the Software except as expressly authorized; b) reverse
assemble, reverse compile, reverse engineer or otherwise translate the Software; c) create derivative works or
modifications unless expressly authorized; or d) sublicense, rent or lease the Software. Licensors of intellectual
property to Nortel Networks are beneficiaries of this provision. Upon termination or breach of the license by
Customer or in the event designated hardware or CFE is no longer in use, Customer will promptly return the Software
to Nortel Networks or certify its destruction. Nortel Networks may audit by remote polling or other reasonable means
to determine Customer’s Software activation or usage levels. If suppliers of third party software included in Software
require Nortel Networks to include additional or different terms, Customer agrees to abide by such terms provided by
Nortel Networks with respect to such third party software.
2. Warranty. Except as may be otherwise expressly agreed to in writing between Nortel Networks and Customer,
Software is provided “AS IS” without any warranties (conditions) of any kind. NORTEL NETWORKS DISCLAIMS
ALL WARRANTIES (CONDITIONS) FOR THE SOFTWARE, EITHER EXPRESS OR IMPLIED, INCLUDING,
BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE AND ANY WARRANTY OF NON-INFRINGEMENT. Nortel Networks is not obligated
to provide support of any kind for the Software. Some jurisdictions do not allow exclusion of implied warranties, and,
in such event, the above exclusions may not apply.
3. Limitation of Remedies. IN NO EVENT SHALL NORTEL NETWORKS OR ITS AGENTS OR SUPPLIERS
BE LIABLE FOR ANY OF THE FOLLOWING: a) DAMAGES BASED ON ANY THIRD PARTY CLAIM; b)
LOSS OF, OR DAMAGE TO, CUSTOMER’S RECORDS, FILES OR DATA; OR c) DIRECT, INDIRECT,
SPECIAL, INCIDENTAL, PUNITIVE, OR CONSEQUENTIAL DAMAGES (INCLUDING LOST PROFITS OR
SAVINGS), WHETHER IN CONTRACT, TORT OR OTHERWISE (INCLUDING NEGLIGENCE) ARISING OUT
OF YOUR USE OF THE SOFTWARE, EVEN IF NORTEL NETWORKS, ITS AGENTS OR SUPPLIERS HAVE
BEEN ADVISED OF THEIR POSSIBILITY. The forgoing limitations of remedies also apply to any developer and/or
supplier of the Software. Such developer and/or supplier is an intended beneficiary of this Section. Some jurisdictions
do not allow these limitations or exclusions and, in such event, they may not apply.
308644-15.1 Rev 00
iii
Page 4

4. General
a. If Customer is the United States Government, the following paragraph shall apply: All Nortel Networks
Software available under this License Agreement is commercial computer software and commercial
computer software documentation and, in the event Software is licensed for or on behalf of the United States
Government, the respective rights to the software and software documentation are governed by Nortel
Networks standard commercial license in accordance with U.S. Federal Regulations at 48 C.F.R. Sections
12.212 (for non-DoD entities) and 48 C.F.R. 227.7202 (for DoD entities).
b. Customer may terminate the license at any time. Nortel Networks may terminate the license if Customer
fails to comply with the terms and conditions of this license. In either event, upon termination, Customer
must either return the Software to Nortel Networks or certify its destruction.
c. Customer is responsible for payment of any taxes, including personal property taxes, resulting from
Customer’s use of the Software. Customer agrees to comply with all applicable laws including all applicable
export and import laws and regulations.
d. Neither party may bring an action, regardless of form, more than two years after the cause of the action
arose.
e. The terms and conditions of this License Agreement form the complete and exclusive agreement between
Customer and Nortel Networks.
f. This License Agreement is governed by the laws of the country in which Customer acquires the Software. If
the Software is acquired in the United States, then this License Agreement is governed by the laws of the
state of New York.
iv
308644-15.1 Rev 00
Page 5

Contents
Preface
Before You Begin ............................................................................................................. xv
Text Conventions .............................................................................................................xvi
Acronyms ........................................................................................................................xvii
Hard-Copy Technical Manuals ....................................................................................... xviii
Chapter 1
Starting SNMP, BootP, and DHCP Services
Starting Configuration Tools ........................................................................................... 1-2
Configuring IP for Global Protocols ................................................................................1-2
Step 1: Configuring a Physical Interface ............................................................1-2
Step 2: Configuring an IP Interface ....................................................................1-3
Starting SNMP Services ................................................................................................. 1-5
Starting BootP Services .................................................................................................1-6
Starting BootP/DHCP Relay ...........................................................................................1-7
Starting a DHCP Server .................................................................................................1-9
Chapter 2
SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
SNMP Overview .............................................................................................................2-2
SNMP Messages .....................................................................................................2-2
SNMP Communities .................................................................................................2-4
SNMP Community Managers ............................................................................2-4
SNMP View-Based Access Control ...................................................................2-5
SNMP Implementation Notes ......................................................................................... 2-5
Internet Protocol .......................................................................................................2-5
Events and Traps ......................................................................................................2-5
Protocol Entities ................................................................................................. 2-6
Severity Levels ...................................................................................................2-6
SNMP Trap Format ............................................................................................2-7
308644-15.1 Rev 00
v
Page 6

Thresholds ...............................................................................................................2-7
Threshold Example .................................................................................................. 2-8
Event Message Format ......................................................................................2-9
State of a Threshold ..........................................................................................2-9
Memory Considerations ...................................................................................2-10
BootP Relay Agent Overview .......................................................................................2-10
DHCP Overview ...........................................................................................................2-14
Why Use DHCP? ...................................................................................................2-14
Dynamic IP Address Allocation ..............................................................................2-15
DHCP Components ................................................................................................2-16
DHCP Clients ..................................................................................................2-16
DHCP Server ...................................................................................................2-16
NetID Server Manager .....................................................................................2-16
BootP/DHCP Relay Implementation ......................................................................2-17
Acquiring an IP Address ..................................................................................2-18
Reacquiring the Same IP Address ..................................................................2-22
DHCP Server Implementation ................................................................................2-23
Acquiring an IP Address ..................................................................................2-24
Reacquiring the Same IP Address ..................................................................2-27
Chapter 3
Customizing SNMP
Configuring SNMP Using the BCC and Site Manager ....................................................3-2
Customizing SNMP Global Parameters ..........................................................................3-3
Disabling and Reenabling SNMP .............................................................................3-3
Enabling and Disabling the SNMP Lock Mechanism ............................................... 3-4
Specifying a Lock Address .......................................................................................3-6
Specifying a Lock Timeout Value .............................................................................3-6
Enabling and Disabling Authentication Failure Traps ...............................................3-7
Specifying the Type of Service for SNMP Packets ...................................................3-9
Adding SNMP Communities ........................................................................................... 3-9
Specifying an SNMP Community Name .................................................................. 3-9
Specifying Community Access Privileges ..............................................................3-10
Deleting an SNMP Community ..............................................................................3-12
Configuring SNMP Community Managers ....................................................................3-13
Adding a Manager ..................................................................................................3-13
vi
308644-15.1 Rev 00
Page 7

Configuring a Manager to Receive Traps ...............................................................3-14
Specifying the Trap Port ...................................................................................3-14
Specifying a Trap Type .....................................................................................3-16
Deleting a Manager ................................................................................................3-17
Configuring SNMP View-Based Access Control ..........................................................3-19
Configuring, Listing, and Deleting a View ..............................................................3-19
Configuring a View ..........................................................................................3-19
Listing All Views or the Contents of a View .....................................................3-21
Deleting a View or Its Contents .......................................................................3-22
Configuring Communities and Their View Associations .........................................3-22
Configuring a Community ................................................................................3-23
Associating a View with a Community .............................................................3-23
Listing Community Information ........................................................................3-23
Disassociating a View from a Community .......................................................3-24
Configuring Traps on the Router ...................................................................................3-25
Disabling a Trap Entity ............................................................................................3-27
Configuring Trap Exceptions ..................................................................................3-28
Deleting Trap Exceptions .......................................................................................3-30
Configuring Thresholds ................................................................................................3-31
Disabling and Reenabling Thresholds ...................................................................3-31
Setting the Threshold Polling Interval ..................................................................... 3-32
Adding a Threshold ................................................................................................3-33
Enabling and Disabling Thresholds for a Variable .................................................. 3-33
Specifying a Value for the Threshold Level ............................................................3-34
Specifying the Severity Level for Event Messages .................................................3-35
Specifying Threshold Units ....................................................................................3-36
Determining When to Record Threshold Events ....................................................3-37
Specifying the Maximum Number of Successive Alarms .......................................3-37
Specifying Polling Intervals for Held Variables .......................................................3-38
Specifying a Threshold Object Name .....................................................................3-39
Chapter 4
Customizing BootP
Customizing BootP Relay Agent Parameters .................................................................4-2
Disabling and Reenabling BootP ............................................................................. 4-2
Enabling ARP Cache Support ..................................................................................4-3
308644-15.1 Rev 00
vii
Page 8

Specifying the Buffer Limit for Unprocessed BootP/DHCP Packets .........................4-5
Specifying the Maximum Number of Hops from Client to Server .............................4-6
Specifying a Minimum Timeout Value ...................................................................... 4-7
Specifying the Pass Through Mode for Packet Forwarding ......................................4-9
Specifying the Interface Priority on a Multinetted Interface ....................................4-10
Setting the Routing Path from the BootP Server to the Router ....................................4-11
Enabling BootP on Router Interfaces ..................................................................... 4-12
Specifying Interfaces to Receive and Relay BOOTREQUEST Packets .................4-14
Creating a BootP Relay Agent Forwarding Table ...................................................4-14
Specifying the IP Interface Input/Output Address Pair .....................................4-14
Deleting an IP Interface Input/Output Address Pair .........................................4-16
Disabling BootP Route Forwarding ..................................................................4-17
Configuring an AN to Use EZ-Install over a Frame Relay PVC .................................... 4-19
Creating a BootP Client Interface Table .................................................................4-19
Specifying Servers for BootP Services .........................................................................4-21
Configuring BootP Preferred Servers .....................................................................4-21
Specifying the Target Server’s Host Name .............................................................4-23
Disabling the Forwarding Route ............................................................................. 4-24
Specifying the Pass Through Mode for Packet Forwarding ....................................4-26
Deleting the BootP Relay Agent from an IP Interface ...................................................4-27
Deleting BootP Globally ................................................................................................4-29
Chapter 5
Customizing BootP/DHCP Relay
Setting Up the Routing Path from the DHCP Server
to the Router ...................................................................................................................5-2
Specifying Interfaces to Receive and Forward DHCP Packets ................................5-2
Defining DHCP Servers ........................................................................................... 5-3
Deleting BootP/DHCP Relay from an IP Interface .......................................................... 5-5
Deleting BootP/DHCP Relay Globally ............................................................................5-6
Chapter 6
Customizing the DHCP Server
Modifying the DHCP Server Configuration .....................................................................6-2
Configuring the NetID Server Manager IP Address ................................................. 6-2
Specifying the DHCP Server IP Address .................................................................6-3
Specifying the DHCP Server TCP Port Number ...................................................... 6-4
viii
308644-15.1 Rev 00
Page 9

Configuring the Number of Pings and the Ping Timeout ..........................................6-6
Specifying the DHCP Server Operating Mode .........................................................6-8
Specifying the Maximum Number of Pending Leases .............................................. 6-9
Specifying the Debug Level ....................................................................................6-11
Disabling and Reenabling the DHCP Server ................................................................6-12
Deleting the DHCP Server from the Router ..................................................................6-14
Deleting DHCP Globally ...............................................................................................6-15
Appendix A
Site Manager Parameter Descriptions
SNMP Global Parameters ............................................................................................. A-3
SNMP Community Parameters ...................................................................................... A-5
SNMP Manager Parameters .......................................................................................... A-6
SNMP Trap Exception Parameters ................................................................................ A-7
SNMP Threshold Global Parameters ............................................................................ A-8
SNMP Threshold Interface Parameters ......................................................................... A-9
BootP and DHCP Parameters ..................................................................................... A-16
BootP Relay Agent Interface Parameters .............................................................. A-16
BootP Address Parameters ................................................................................... A-19
BootP Client Interface Address Parameters .......................................................... A-21
BootP Preferred Server Configuration Parameters ............................................... A-22
DHCP Server Global Parameters .......................................................................... A-24
Appendix B
SNMP and BootP/DHCP show Commands
show snmp community .................................................................................................. B-2
show snmp stats ............................................................................................................ B-3
show snmp trap-entity .................................................................................................... B-4
show snmp trap-event .................................................................................................... B-5
show bootp stats ............................................................................................................ B-5
show bootp config .......................................................................................................... B-6
show bootp relay-agent ................................................................................................. B-6
show bootp preferred-server .......................................................................................... B-7
show bootp client-intf ..................................................................................................... B-7
show dhcp-server summary .......................................................................................... B-7
show dhcp-server config ................................................................................................ B-8
308644-15.1 Rev 00
ix
Page 10

show dhcp-server lease-status ...................................................................................... B-8
show dhcp-server lease-id ............................................................................................. B-8
show dhcp-server packet-stats ...................................................................................... B-9
Index
x
308644-15.1 Rev 00
Page 11

Figures
Figure 2-1. Role of SNMP ..........................................................................................2-3
Figure 2-2. BootP Client and Server on the Same Physical Network ......................2-10
Figure 2-3. BootP Client and Server on Different Physical Networks .......................2-11
Figure 2-4. BOOTREQUEST and BOOTREPLY Fields ............................................ 2-12
Figure 2-5. BootP/DHCP Relay Implementation ......................................................2-17
Figure 2-6. Identifying DHCP Servers (BootP Relay Agent) ....................................2-18
Figure 2-7. Requesting and Receiving IP Information (BootP Relay Agent) ............2-21
Figure 2-8. DHCP Server Implementation ................................................................2-23
Figure 2-9. Identifying Routers Configured as DHCP Servers .................................2-24
Figure 2-10. Requesting and Receiving IP Information (DHCP Server) ....................2-26
Figure 4-1. Enabling BootP in a Sample Network ....................................................4-12
308644-15.1 Rev 00
xi
Page 12

Page 13

Tables
Table 2-1. Severity Levels .........................................................................................2-6
Table 2-2. Example of Threshold and Severity Settings ...........................................2-8
Table 2-3. IP Address Types Allocated by DHCP ...................................................2-15
Table 2-4. Fields in a DHCP Packet ........................................................................2-19
Table 3-1. SNMP Configuration Tasks ......................................................................3-2
Table 3-2. Trap Types Sent by the SNMP Agent .....................................................3-16
308644-15.1 Rev 00
xiii
Page 14

Page 15

This guide describes Simple Network Management Protocol (SNMP), Bootstrap
Protocol (BootP), BootP/Dynamic Host Configuration Protocol (DHCP) relay,
and DHCP server and what you need to do to start and customize them on a Nortel
Networks
*
You can use the Bay Command Console (BCC
these services on a router. In this guide, you will find instructions for using both
the BCC and Site Manager.
Before You Begin
router.
Preface
*
) or Site Manager to configure
Before using this guide, you must complete the following procedures. For a new
router:
• Install the router (see the installation guide that came with your router).
• Connect the router to the network and create a pilot configuration file (see
Make sure that you are running the latest version of Nortel Networks BayRS
Site Manager software. For information about upgrading BayRS and Site
Manager, see the upgrading guide for your version of BayRS.
308644-15.1 Rev 00
Quick-Starting Routers, Configuring Remote Access for AN and Passport
ARN Routers, or Connecting ASN Routers to a Network).
*
and
xv
Page 16

Configuring SNMP, BootP, and DHCP Services
Text Conventions
This guide uses the following text conventions:
angle brackets (< >) Indicate that you choose the text to enter based on the
description inside the brackets. Do not type the
brackets when entering the command.
Example: If the command syntax is:
ping
ping 192.32.10.12
<ip_address>
, you enter:
bold text
Indicates command names and options and text that
you need to enter.
Example: Enter
Example: Use the
show ip {alerts | routes
dinfo
command.
}.
braces ({}) Indicate required elements in syntax descriptions
where there is more than one option. You must choose
only one of the options. Do not type the braces when
entering the command.
Example: If the command syntax is:
show ip {alerts | routes
show ip alerts or show ip routes
}
, you must enter either:
, but not both.
brackets ([ ]) Indicate optional elements in syntax descriptions. Do
not type the brackets when entering the command.
Example: If the command syntax is:
show ip interfaces [-alerts
show ip interfaces
or
]
, you can enter either:
show ip interfaces -alerts
.
ellipsis points (. . . ) Indicate that you repeat the last element of the
command as needed.
xvi
Example: If the command syntax is:
ethernet/2/1
ethernet/2/1
[<parameter> <value>]
and as many parameter-value pairs as
needed.
. . .
, you enter
308644-15.1 Rev 00
Page 17

Preface
italic text Indicates file and directory names, new terms, book
titles, and variables in command syntax descriptions.
Where a variable is two or more words, the words are
connected by an underscore.
Example: If the command syntax is:
show at
valid_route
<valid_route>
is one variable and you substitute one value
for it.
screen text Indicates system output, for example, prompts and
system messages.
Acronyms
Example:
Set Trap Monitor Filters
separator ( > ) Shows menu paths.
Example: Protocols > IP identifies the IP option on the
Protocols menu.
vertical line (
) Separates choices for command keywords and
|
arguments. Enter only one of the choices. Do not type
the vertical line when entering the command.
Example: If the command syntax is:
show ip {alerts | routes
show ip alerts
or
}
show ip routes
This guide uses the following acronyms:
ARP Address Resolution Protocol
ASN.1 abstract syntax notation
BootP Bootstrap Protocol
, you enter either:
, but not both.
308644-15.1 Rev 00
DHCP Dynamic Host Configuration Protocol
ICMP Internet Control Message Protocol
IP Internet Protocol
MAC media access control
xvii
Page 18

Configuring SNMP, BootP, and DHCP Services
MIB management information base
PDU
protocol data unit
PPP Point-to-Point Protocol
RMON
remote monitoring
SNMP Simple Network Management Protocol
TCP Transmission Control Protocol
TFTP Trivial File Transfer Protocol
UDP
User Datagram Protocol
WAN wide area network
Hard-Copy Technical Manuals
You can print selected technical manuals and release notes free, directly from the
Internet. Go to the www.nortelnetworks.com/documentation URL. Find the
product for which you need documentation. Then locate the specific category and
model or version for your hardware or software product. Use Adobe* Acrobat
Reader* to open the manuals and release notes, search for the sections you need,
and print them on most standard printers. Go to Adobe Systems at the
www.adobe.com URL to download a free copy of the Adobe Acrobat Reader.
xviii
You can purchase selected documentation sets, CDs, and technical publications
through the Internet at the www1.fatbrain.com/documentation/nortel/ URL.
308644-15.1 Rev 00
Page 19

How to Get Help
If you purchased a service contract for your Nortel Networks product from a
distributor or authorized reseller, contact the technical support staff for that
distributor or reseller for assistance.
If you purchased a Nortel Networks service program, contact one of the following
Nortel Networks Technical Solutions Centers:
Technical Solutions Center Telephone
Europe, Middle East, and Africa (33) (4) 92-966-968
North America (800) 4NORTEL or (800) 466-7835
Asia Pacific (61) (2) 9927-8800
China (800) 810-5000
Additional information about the Nortel Networks Technical Solutions Centers is
available from the www.nortelnetworks.com/help/contact/global URL.
Preface
An Express Routing Code (ERC) is available for many Nortel Networks products
and services. When you use an ERC, your call is routed to a technical support
person who specializes in supporting that product or service.
your product or service, go to the
eserv/common/essContactUs.jsp
308644-15.1 Rev 00
To locate an ERC for
http://www130.nortelnetworks.com/cgi-bin/
URL.
xix
Page 20

Page 21

Chapter 1
Starting SNMP, BootP, and DHCP Services
This chapter describes how to create a basic SNMP, BootP, and BootP/DHCP
relay configuration by specifying values for required parameters only and
accepting default values for all other parameters of these services.
Topic Page
Starting Configuration Tools
Configuring IP for Global Protocols 1-2
Starting SNMP Services 1-5
Starting BootP Services 1-6
Starting BootP/DHCP Relay 1-7
Starting a DHCP Server 1-9
1-2
For background information about these protocols and how they work, see
Chapter 2, “
SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts.
308644-15.1 Rev 00
1-1
Page 22

Configuring SNMP, BootP, and DHCP Services
Starting Configuration Tools
Before configuring SNMP, BootP, and DHCP services, refer to the following user
guides for instructions on how to start and use the Nortel Networks configuration
tool of your choice.
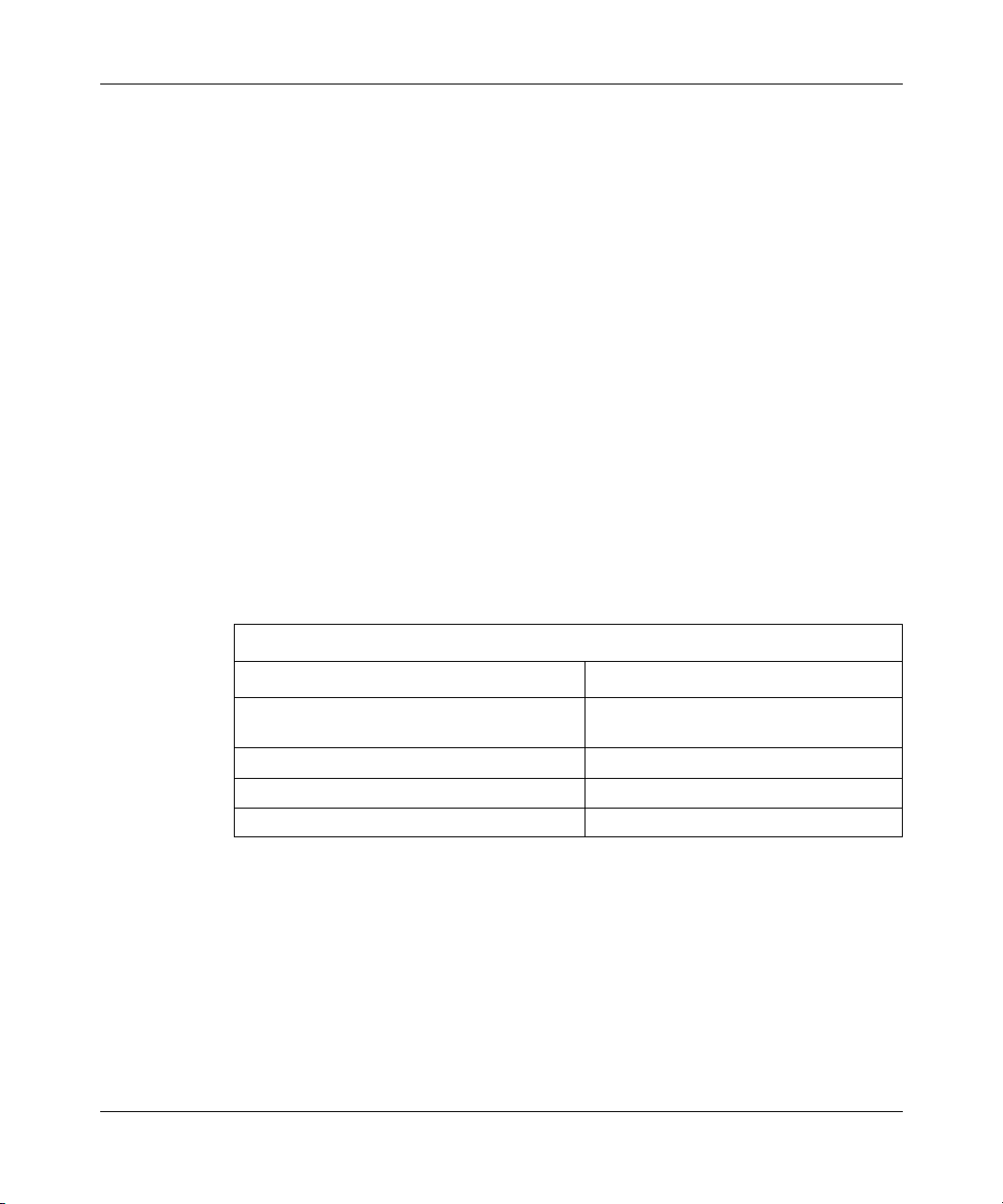
Configuration Tool User Guide
Bay Command Console (BCC) Using the Bay Command Console (BCC)
Site Manager Configuring and Managing Routers with Site Manager
These guides also describe generically how to create and modify a device
configuration.
Configuring IP for Global Protocols
SNMP, BootP, and DHCP services all use the Internet Protocol (IP) for message
transport. Before you configure SNMP, BootP, and DHCP services using the BCC
or Site Manager, you must first start IP on the router.
Using the BCC
1-2
To start IP on the router:
1.
Configure a physical interface on an available slot/connector.
2.
Configure an IP interface on the physical interface.
Step 1: Configuring a Physical Interface
To configure a physical interface on a slot and connector, navigate to the top-level
box or stack prompt and enter:
<interface_type>
<connector_number>
interface_type
•
slot_number
•
slot
is the name of a link or net module on the router.
is the number of the slot on which the link or net module is
<slot_number>
module
[
<module_number>
connector
]
located.
308644-15.1 Rev 00
Page 23

Starting SNMP, BootP, and DHCP Services
module_number
•
is the net module number (ASN* and System 5000* routers
only).
connector_number
•
is the number of a connector on the link or net module.
For example, the following command configures an Ethernet interface on slot 1,
connector 2:
box#
ethernet slot 1 connector 2
ethernet/1/2#
Step 2: Configuring an IP Interface
To configure an IP interface on a physical interface, navigate to the prompt for the
physical interface and enter:
ip address
address
and
address>
<
mask
mask
are a valid IP address and its associated subnet mask, expressed
mask>
<
in either dotted-decimal notation or in bit notation.
For example, the following command configures IP interface 2.2.2.2/255.0.0.0 on
an Ethernet physical interface on slot 1, connector 2:
ethernet/1/2#
ip/2.2.2.2/255.0.0.0#
ip address 2.2.2.2 mask 255.0.0.0
An IP interface is now configured on the Ethernet interface with default values for
all interface parameters. When you configure an IP interface, the BCC also
configures IP globally on the router with default values for all IP global
parameters.
You can customize IP by modifying IP global and interface parameters as
described in Configuring IP, ARP, RARP, RIP, and OSPF Services.
308644-15.1 Rev 00
1-3
Page 24
Configuring SNMP, BootP, and DHCP Services
Using Site Manager
Before you can select a protocol to run on the router, you must configure a circuit
that the protocol can use as an interface to an attached network. For information
and instructions, see Configuring WAN Line Services and Configuring Ethernet,
FDDI, and Token Ring Services.
When you have successfully configured the circuit, the Select Protocols window
opens. Proceed as follows:
Site Manager Procedure
You do this System responds
1. In the Select Protocols window, select IP.
Then click on OK.
If you plan to add BootP or DHCP
services, you can also select BootP.
2. Set the following parameters:
•
IP Address
•
Subnet Mask
•
Transmit Bcast Addr
•
UnNumbered Assoc Address
Click on
RARP, RIP, and OSPF Services
parameter descriptions.
3. Click on OK. Site Manager displays a window asking
4. Click on
click on No.
or see
Help
to enable TFTP. Otherwise,
Yes
Configuring IP, ARP,
for
The IP Configuration window opens.
whether you want to enable TFTP on the
router.
You return to the Configuration Manager
window.
1-4
308644-15.1 Rev 00
Page 25

Starting SNMP Services
You can use the BCC command-line interface or the Site Manager graphical user
interface to start SNMP on the router, accepting default values for all parameters.
SNMP is globally enabled on the router by default when you install BayRS
software. By default, the Quick-Start installation script (install.bat) creates a
read/write SNMP community named “public” with a wildcard manager (0.0.0.0)
that allows universal read/write access. You should restrict read-write access to the
router as soon as possible by reconfiguring the security of this SNMP community.
When you add SNMP with the BCC, access is defined by default as read-only.
If you decide to change some or all of the default values, refer to the instructions
in Chapter 3
Before you begin, verify that IP is configured on an interface, as described in
“Configuring IP for Global Protocols
Using the BCC
To configure SNMP on the router with default settings, begin in configuration
mode at the box or stack prompt:
, “Customizing SNMP.”
Starting SNMP, BootP, and DHCP Services
” on page 1-2.
1.
2.
308644-15.1 Rev 00
Configure SNMP.
snmp
box#
Display SNMP default settings.
snmp#
info
lock enabled
lock-address 0.0.0.0
lock-timeout 2
authentication-traps enabled
type-of-service reliability
state enabled
1-5
Page 26
Configuring SNMP, BootP, and DHCP Services
Using Site Manager
To start SNMP, complete the following tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
Protocols.
2. Choose
3. Choose
4. Choose
5. Click on OK. You return to the Configuration Manager
IP.
SNMP.
Global.
Starting BootP Services
You can start BootP using default values for all parameters. If you decide to
change some or all of the default values, see Chapter Chapter 4, “
BootP.”
Before you begin, verify that IP is configured on an interface, as described in
“Configuring IP for Global Protocols
BootP on an interface simultaneously.
You can use the BCC or Site Manager to enable BootP on an interface.
Using the BCC
The Protocols menu opens.
The IP menu opens.
The SNMP menu opens.
The Edit SNMP Global Parameters
window opens.
window.
Customizing
” on page 1-2. You can also enable IP and
1-6
To enable BootP on an interface, go to the IP interface prompt (for example,
eth 2/2; ip/2.2.2.2/255.255.0.0
bootp
) and enter:
For example, the following command enables BootP on IP interface 2.2.2.2.
ip/2.2.2.2/255.255.0.0#
bootp/2.2.2.2#
bootp
308644-15.1 Rev 00
box;
Page 27
Using Site Manager
To enable BootP on an interface, complete the following tasks:
You do this System responds
Starting SNMP, BootP, and DHCP Services
Site Manager Procedure
1. In the Configuration Manager window,
click on the link or net module connector.
2. Choose
3. Choose
4. Choose
5. Choose
6. Choose
7. Choose
Edit Circuit
Protocols
Add/Delete
BOOTP
. The File menu opens.
File
. You return to the Configuration Manager
Exit
. The Circuit Definition window opens.
. The Protocols menu opens.
. The Select Protocols window opens.
and click on OK.
Starting BootP/DHCP Relay
You can start BootP/DHCP relay using default values for all parameters. If you
decide to change some or all of the default values, see Chapter Chapter 5,
“Customizing BootP/DHCP Relay.”
Before you begin, you must verify that IP is configured on an interface, as
described in “Configuring IP for Global Protocols
enable IP, BootP, and BootP/DHCP on the router simultaneously.
Note:
BootP and DHCP will not operate properly if the Broadcast Storms
feature is enabled. See Configuring Ethernet, FDDI, and Token Ring Services
for procedures to disable this feature, as necessary.
The Edit Connector window opens.
window.
” on page 1-2. You can also
You can use the BCC or Site Manager to enable BootP/DHCP relay on an
interface.
308644-15.1 Rev 00
1-7
Page 28

Configuring SNMP, BootP, and DHCP Services
Using the BCC
To enable BootP/DHCP relay on an interface, go to the BootP prompt (for
example,
pass-thru-mode bootp-dhcp
or
pass-thru-mode dhcp
box; eth 2/2; ip/2.2.2.2/255.255.0.0; bootp
For example, the following command sets the pass through mode to bootp-dhcp,
which enables the BootP relay agent on the router to transmit both BootP and
DHCP packets to the server.
) and enter either:
bootp/2.2.2.2#
bootp/2.2.2.2#
Using Site Manager
To enable BootP/DHCP relay on an interface, complete the following tasks:
You do this System responds
1. Enable BootP on the interface.
2. Choose
3. Choose IP. The IP menu opens.
4. Choose
5. Choose
6. Set the
7. Click on
8. Edit the parameters in this window.
pass-thru-mode bootp-dhcp
Site Manager Procedure
For instructions, see “Starting BootP
Services” on page 1-7.
Protocols.
. The BOOTP menu opens.
BOOTP
Relay Agent Interface Table
Pass Through Mode
or to
DHCP
For instructions, see “
Relay Agent Parameters” on page 4-2.
BootP/DHCP
.
Apply
parameter to
.
Customizing BootP
The Protocols menu opens.
. The BootP Relay Agent Interface Table
window opens.
You return to the Configuration Manager
window.
1-8
308644-15.1 Rev 00
Page 29

Starting a DHCP Server
You can use either the BCC or Site Manager to start a DHCP server.
Before you begin, you must do the following:
1.
Verify that IP is configured on an interface, as described in “Configuring IP
for Global Protocols” on page 1-2.
2.
Configure TCP on the router. For instructions on how to configure TCP on a
router, see Configuring IP Utilities.
3.
Configure the NetID* Server Manager to communicate with the DHCP server.
For the DHCP server to operate, you must first install the NetID Server
Manager on a Microsoft
it to communicate with the DHCP server. Typically, you install the NetID
Server Manager on the same workstation as the one that contains the NetID
database.
Because the DHCP server uses the information in the NetID database to
assign IP addresses and host configuration information, you need to set up
your network configuration using the NetID Management Console before the
DHCP server can operate correctly.
Starting SNMP, BootP, and DHCP Services
*
Windows NT* or UNIX* workstation and configure
You can use the BCC or Site Manager to create and enable the DHCP server on
the router. You must then must enable the DHCP server on an IP interface.
Using the BCC
To create and enable the DHCP server on the router, go to the global IP prompt for
example,
dhcp
For example, the following command creates and enables the DHCP server on the
router.
ip#
dhcp#
308644-15.1 Rev 00
Using the NetID Management Console, you configure a DHCP server and
make IP addresses available for dynamic allocation. For more information
about installing the NetID Server Manager and setting your network
configuration using the NetID Management Console, see the NetID System
Administrator’s Guide.
box; ip
dhcp
) and enter:
1-9
Page 30
Configuring SNMP, BootP, and DHCP Services
After you create and enable the DHCP server on the router, you must enable the
DHCP server on an IP interface. By default, the DHCP server is disabled on an IP
interface.
To enable the DHCP server on an IP interface, go to the BootP prompt (for
example,
dhcp-svr-state <state>
state
enabled
disabled
box; eth 2/2; ip/2.2.2.2/255.255.0.0; bootp
is one of the following:
(default)
For example, the following command enables DHCP server on IP interface
2.2.2.2:
) and enter:
bootp/2.2.2.2#
bootp/2.2.2.2#
Using Site Manager
To create and enable the DHCP server on the router, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
2. Choose
3. Choose
4. Choose
choose
dhcp-server-state enabled
Site Manager Procedure
The Protocols menu opens.
Protocols
Global Protocols
DHCP
Create DHCP
.
. The Global Protocols menu opens.
. The DHCP menu opens.
.
1-10
308644-15.1 Rev 00
Page 31

Starting SNMP, BootP, and DHCP Services
After you create and enable the DHCP server on the router, you must enable the
DHCP server on an IP interface. By default, the DHCP server is disabled on an IP
interface. To enable the DHCP server on an IP interface, complete the following
tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Set the
to
parameter description on page A-18
6. Click on
7. Click on
Protocols
BOOTP
Relay Agent Interface Table
DHCP Server Enable
Enable.
Apply
Done
.
. The BOOTP menu opens.
parameter
Click on
.
. You return to the Configuration Manager
Help
or see the
.
The Protocols menu opens.
. The BOOTP Relay Agent Interface Table
window opens.
window.
For information about modifying DHCP server parameters, see Chapter 6
“Customizing the DHCP Server
.”
,
308644-15.1 Rev 00
1-11
Page 32

Page 33

Chapter 2
SNMP, BootP, BootP/DHCP Relay,
and DHCP Server Concepts
This chapter describes the concepts behind SNMP, BootP, BootP/DHCP relay,
and DHCP server services and how Nortel Networks routers implement them.
You can use this information to decide how to customize SNMP, BootP,
BootP/DHCP relay, and DHCP server parameters for your system.
Topic Page
308644-15.1 Rev 00
SNMP Overview
SNMP Implementation Notes 2-5
BootP Relay Agent Overview 2-10
DHCP Overview 2-14
2-2
2-1
Page 34

Configuring SNMP, BootP, and DHCP Services
SNMP Overview
SNMP is a simple request/response protocol that communicates management
information between two types of SNMP software entities: SNMP applications
(also called SNMP managers) and SNMP agents.
SNMP applications contain manager software that runs on a network management
station (also known as an SNMP client), such as a PC or a workstation. The
manager software implements the protocols used to exchange data with SNMP
agents. SNMP applications issue queries to gather information about the status,
configuration, and performance of external network devices, called network
elements in SNMP terminology. Network elements contain an agent and perform
the network management function that the network management stations request.
The Nortel Networks Site Manager software is an example of a network
management station, and the Nortel Networks Backbone Node (BN
example of a network element.
The SNMP agent is a software entity that responds to information and action
request messages (SNMP get and set requests) sent by a network management
station (your Site Manager workstation). The messages exchanged between
manager and router SNMP agents enable you to access and manage objects in an
active or inactive (stored) management information base (MIB) on a router.
*
) router is an
The agents also send unsolicited reports (called traps) back to the network
management station when certain network activity occurs. An example of a trap is
an overload condition as defined by the packet load’s crossing some threshold.
You use the management station to configure, monitor, and receive trap messages
from other network devices configured as SNMP agents. The management station
can get and set objects in the agents and can receive traps from the agents. The
management station, therefore, has the capability to “manage” a number of
agents.
SNMP Messages
SNMP managers and network elements communicate with each other by sending
SNMP messages (Figure 2-1
2-2
).
308644-15.1 Rev 00
Page 35

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
The management station issues three types of SNMP messages to retrieve single
or multiple object variables:
• GetRequest messages
• GetNextRequest messages
• SetRequest messages
The agent acknowledges all three types of messages by passing a GetResponse
message to the management application. In addition, an agent may issue a trap to
the network management station to identify a condition, such as a threshold that
exceeds a predefined value.
SNMP management station SNMP agent
Management application
Application
manages objects
SNMP managed objects
Managed resources
GetRequest
Network-dependent protocols
SetRequest
GetNextRequest
SNMP manager
UDP
IP
Tr ap
GetResponse
Figure 2-1. Role of SNMP
308644-15.1 Rev 00
SNMP messages
Network or
internetwork
GetRequest
Network-dependent protocols
SetRequest
GetNextRequest
SNMP agent
UDP
IP
Tr ap
GetResponse
SNM00012A
2-3
Page 36

Configuring SNMP, BootP, and DHCP Services
SNMP Communities
For security reasons, the SNMP agent validates each request from an SNMP
manager before responding to the request, by verifying that the manager belongs
to a valid SNMP community. An SNMP community is a logical relationship
between an SNMP agent and one or more SNMP managers (the manager software
implements the protocols used to exchange data with SNMP agents). You define
communities locally at the agent.
The agent establishes one community for each combination of authentication and
access control characteristics that you choose. You assign each community a
unique name (within the agent), and all members of a community have the same
access privileges, either read-only or read-write:
• Read-only: members can view configuration and performance information.
• Read-write: members can view configuration and performance information,
and also change the configuration.
By defining a community, an agent limits access to its MIB to a selected set of
management stations. By using more than one community, the agent can provide
different levels of MIB access to different management stations.
2-4
SNMP Community Managers
All SNMP message exchanges consist of a community name and a data field,
which contains the SNMP operation and its associated operands. You can
configure the SNMP agent to receive requests and send responses only from
managers that are members of a known community.
If the agent knows the community name in the SNMP message and knows that the
manager generating the request is a member of that community, it considers the
message to be authentic and gives it the access allowed for members of that
community. In this way, the SNMP community prevents unauthorized managers
from viewing or changing the configuration of a router.
For information about configuring SNMP managers see “Configuring SNMP
Community Managers” on page 3-13.
308644-15.1 Rev 00
Page 37

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
SNMP View-Based Access Control
SNMP view-based access control allows you to filter the information from an
SNMP agent, thereby letting you control the view of the network. For example, a
service provider can create a unique view for two different customers, so that each
customer sees only the statistics and configuration information that the service
provider wants each to see. The customer can view these statistics remotely using
Site Manager.
To configure view-based access control, you must use either the BCC or the
Technician Interface. You enable an SNMP agent view by associating a view with
a community. A community can have only one agent view associated with it;
however, the view itself can contain many different MIB subtree inclusions and
exclusions.
For information about how to configure, list, or delete a view or its contents, see
“Configuring SNMP View-Based Access Control
SNMP Implementation Notes
” on page 3-19.
This section contains information about features specific to the Nortel Networks
implementation of SNMP.
Internet Protocol
SNMP uses the User Datagram Protocol (UDP) to transport its messages. You
must enable the Internet Protocol (IP) to use UDP and SNMP.
Events and Traps
An event is a change in the operating status of a router. The router stores the event
as a single entry in a memory-resident log.
An event log message provides a brief description of an event, along with the
event code associated with that event.
A trap is an event that the router transmits to the network management station.
308644-15.1 Rev 00
2-5
Page 38

Configuring SNMP, BootP, and DHCP Services
SNMP allows you to configure which event log messages are sent to the network
management station as traps. You select these traps based on slot, protocol entity,
and severity level. You can also specify up to 50 exceptions, which are traps that
the agent always sends, or never sends, regardless of slot and regardless of how
you configure the trap parameters.
For information about how to specify which traps the agent sends, see
“Configuring Traps on the Router
Protocol Entities
Events are always associated with a particular protocol entity. An entity is the
software that generates a message. Entities include Nortel Networks software
dedicated to the operation of a software service, such as Trivial File Transfer
Protocol (TFTP) and IP, and the GAME operating system.
Both events and entities are assigned numeric codes. Together, this pair uniquely
identifies a Nortel Networks router platform event. To access the event message
database, look on the documentation CD that comes with BayRS or look on the
Web a t http://www25.nortelnetworks.com/library/tpubs/events/.
” on page 3-25.
2-6
Severity Levels
Event and trap messages are always associated with a severity level. Tab le 2- 1
describes the severity levels and gives the code that corresponds to each one. This
guide does not cover Debug messages, because they are for Nortel Networks
internal use only.
Table 2-1. Severity Levels
Severity Description Code
Information Indicates routine events that usually require no action. 2
Warning Indicates that a service acted in an unexpected manner. 4
Fault Indicates a major service disruption, usually caused by a
configuration, network, or hardware problem. The entities
involved keep restarting until the problem is resolved.
Trace Indicates information about each packet that traversed the
network. Nortel Networks recommends viewing this type of trap
message only when diagnosing network problems.
Debug Indicates information that Nortel Networks Customer Support
uses. These messages are not documented.
308644-15.1 Rev 00
8
10
1
Page 39

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
SNMP Trap Format
Some third-party network management applications, such as NetExpert,
OpenView, and SunNet, let you trigger an operation when a specific SNMP trap is
received. This section describes the SNMP trap format.
The router platform transmits a Nortel Networks event log trap as a 32-bit value as
follows:
• Octets 1 and 2 (the most significant 16 bits) of the specific trap ID contain
values of 1 and 0, respectively, to identify a Nortel Networks event log trap.
• Octet 3 of the specific trap ID contains a code that identifies the software
entity that generated the trap.
• Octet 4 of the specific ID contains the event code that, in conjunction with the
entity code, uniquely identifies the event.
Each 32-bit value is accompanied by three variable bindings that convey the event
string that describes the trap condition, the slot that hosts the entity that generated
the trap, and the trap severity (see Tab le 2- 1
).
Thresholds
SNMP uses a management information base (MIB) to manage the router. The
MIB includes an extensive collection of statistics (MIB variables) that track the
router’s performance and provide early warnings of abnormal operating
conditions.
With the Site Manager threshold feature, you can configure the agent to
automatically notify you when specific statistics (or instances of the variable)
reach certain levels.
You can set a threshold for any integer, counter, gauge, or time-tick variable in the
MIB. Using the threshold parameters, you:
• Select the polling interval, which specifies how often the agent checks the
• Set three threshold values (high, medium, and low).
• Specify the threshold action as Lessthan or Greaterthan.
For information about setting thresholds, see “
page 3-31
308644-15.1 Rev 00
statistic to see whether its value has reached the threshold.
Configuring Thresholds” on
.
2-7
Page 40

Configuring SNMP, BootP, and DHCP Services
When the statistic reaches the threshold, the agent generates an event. You specify
the severity level at which you want the manager to log the event. Ta bl e 2- 1
the available severity levels and their suggested meanings. Depending on how you
configure the SNMP trap parameters (see “
page 3-25
), the agent may also send the threshold exception as an SNMP trap.
The Site Manager threshold feature is functionally similar to the remote
monitoring (RMON) Alarm and Event facility, with some minor differences. The
Site Manager threshold feature provides three-tiered thresholds and defines a
user-definable hysteresis mechanism. The RMON Alarm and Event facility
provides a two-tiered proprietary threshold system. For information about RMON,
RMON 2, and RMON alarms and events, see Configuring RMON and RMON2.
Threshold Example
Suppose you want SNMP to warn you if the number of high-priority (Priority
Level 1) packets queued for transmission is approaching the maximum number
supported by an interface. This maximum value is specified by the
wfCctOptsCngcCfgQp1Threshold MIB object. Using the threshold parameters,
you set a threshold for wfCctOptsCngcCfgQp1Threshold equal to 205.
shows
Configuring Traps on the Router” on
2-8
You also set the polling interval to 20 seconds to indicate that, every 20 seconds,
the agent should check variables for which you have configured thresholds. You
set the threshold action to Greaterthan and set the threshold levels and severity of
events to the values shown in Ta bl e 2 -2
Table 2-2. Example of Threshold and Severity Settings
Threshold Level Low Medium High
Depth of Priority 1
transmit queue
Severity of event INFO INFO WARNING
102
(40% of capacity)
.
153
(60% of capacity)
205
(80% of capacity)
When you add this threshold to the MIB, the agent polls the variable
wfCctOptsCngcCfgQp1Threshold every 20 seconds and responds as follows:
• If its value is greater than 102, but less than or equal to 153, the manager logs
an informational event indicating that the queue depth exceeded the low
threshold.
308644-15.1 Rev 00
Page 41

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
• If its value is greater than 153 but less than or equal to 205, the manager logs
an informational event indicating that the queue depth exceeded the medium
threshold.
• If its value is greater than 205, the manager logs a warning event indicating
that the queue depth exceeded the high threshold.
Event Message Format
By default, the threshold event messages include the MIB object identifier (OID)
of the variable that exceeded the threshold, the value of the variable, and the
threshold level exceeded.
For example, if the wfCctOptsCngcCfgQp1Threshold variable has a value of 120,
the agent generates an event message similar to the following:
#1:08/27/99 10:53:20.802 INFO SLOT 2 STA CODE: 6
Object 1.3.6.1.4.1.18.3.5.1.4.10.1.24 with value = 120 units/ hour
is > low threshold.
You can, however, identify objects more easily by configuring the software to
report the object name rather than the OID in the event message. To configure the
software to report the object name in the event message, use the Threshold Label
parameter (see “
Specifying a Threshold Object Name” on page 3-39).
For example, if you set the Threshold Label parameter to
wfCctOptsCngcCfgQp1Threshold
to the following:
#1:08/27/99 10:53:20.802 INFO SLOT 2 STA CODE: 6
Object wfCctOptsCngcCfgQp1Threshold with value = 120 units/ hour is
> low threshold.
State of a Threshold
If the collision rate stays above a threshold for an extended period of time, the
agent continues to generate a new event every 5 seconds. You can specify the
maximum number of event messages that you want the agent to generate before it
changes the threshold’s state to held.
When the threshold is in a held state, the agent does not generate new events
unless the statistic exceeds the threshold at a different level. If the statistic does
not exceed any threshold for a specified number of polling periods, the agent no
longer considers the threshold held.
308644-15.1 Rev 00
, the agent generates an event message similar
2-9
Page 42

Configuring SNMP, BootP, and DHCP Services
Memory Considerations
Polling statistics to determine whether they have reached a threshold and reporting
events when variables exceed thresholds require router processing capacity. When
you set many thresholds and use shorter polling intervals, the router performance
will probably decline.
BootP Relay Agent Overview
BootP is built on the client-server model and allows a diskless client to boot
remotely from a server on the same network or on a different physical network.
The client broadcasts a request to boot from a remote server. When a suitable
server receives the BOOTREQUEST packet, it responds to the client by issuing a
BOOTREPLY packet, which includes the client’s IP address, the address of the
gateway, and the address of a server. The server then transmits the boot file to the
client via a transfer protocol, such as Trivial File Transfer Protocol (TFTP).
Figure 2-2
illustrates how BootP works when the client and the server are on the
same network. The client transmits a BOOTREQUEST packet to the IP broadcast
address (255.255.255.255). The server sends a BOOTREPLY packet to the client.
Depending on the server’s implementation, the server addresses the packet to
either the broadcast address or the client’s IP address.
Client broadcasts a request
to boot from a remote server
(BOOTREQUEST).
Server sends acknowledgment
to the client (BOOTREPLY).
Client Server
Figure 2-2. BootP Client and Server on the Same Physical Network
SNM0002A
2-10
308644-15.1 Rev 00
Page 43

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
If, however, the client and the server are on different physical networks, a BootP
relay agent (also known as a BootP gateway) must forward BootP packets to their
correct destinations. When you configure a Nortel Networks router for BootP
services, the router acts as a BootP relay agent. Figure 2-3
illustrates how BootP
works when the client and the server are on different physical networks.
Server
Client
1. Client broadcasts
a request to boot from a
remote server
(BOOTREQUEST).
4. BootP relay
agent transmits
BOOTREPLY
packet to client.
Router
(BootP relay agent)
2. BootP relay
agent transmits
BOOTREQUEST
packet to servers
on other networks.
3. Server transmits
BOOTREPLY
packet to BootP
relay agent.
Figure 2-3. BootP Client and Server on Different Physical Networks
The client transmits a BOOTREQUEST packet to the IP broadcast address
(255.255.255.255). The router receives the BOOTREQUEST packet at an
interface that you configured to receive BOOTREQUEST packets (an input
interface). If the BOOTREQUEST packet has an address other than
255.255.255.255, the router drops the packet.
SNM0003A
Figure 2-4
308644-15.1 Rev 00
shows the fields in the BOOTREQUEST and BOOTREPLY packets.
2-11
Page 44

Configuring SNMP, BootP, and DHCP Services
Operation (1)*
Hardware type (1)
Hardware address
length (1) Hops (1)
Transaction ID (4)
Seconds (2)
Client IP address (4)
Your IP address (4)
Server IP address (4)
Gateway IP address (16)
Client hardware address (16)
Server name (64)
File name (128)
Vendor-specific area (64)
*The number in parentheses indicates the number of octets in each field.
Flags (2)
SNM0001A
Figure 2-4. BOOTREQUEST and BOOTREPLY Fields
The packet relay process uses these fields as follows:
1. When a router interface receives a BOOTREQUEST packet, the router
examines the seconds and hops fields in the packet and compares these values
to BootP parameters that you configured on that interface.
2-12
The seconds field contains the minimum number of seconds that the router
waits before forwarding a BOOTREQUEST packet. If the value in the
seconds field of the packet is less than the value of the Timeout Secs.
parameter configured on the interface, the router drops the packet.
The hops field contains the maximum number of hops that a packet can take
between the source and destination devices. If the packet has traversed more
hops than the value of the hops parameter specified for that interface, the
router drops the packet.
308644-15.1 Rev 00
Page 45

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
2. If the router accepts the packet, it alters the packet by:
• Incrementing the hops field by 1
• Writing the IP address of the input interface to the gateway IP address
field
3. The router then determines which networks should receive this packet and
broadcasts it to other networks through a forwarding route that you specify
when you configure the router for BootP services.
If the BootP packet has to travel to a network through another router, you must
specify the forwarding route using one of the following methods:
• Configure the second router for BootP services.
In this case, the second router inspects the packet in the same way as the
first router, and increments the hops field by 1. The second router will not,
however, replace the address in the gateway IP address field, because
servers will reply to the first router that received the BOOTREQUEST
packet.
• Configure the first router to forward the BOOTREQUEST packet to a
specific server.
4. Servers on other networks receive the BOOTREQUEST packet and respond
5. When the router that first received the BOOTREQUEST packet receives the
6. If the router accepts the packet, it examines the flags field and forwards the
308644-15.1 Rev 00
In this case, the router will unicast the BOOTREQUEST packet to the
server through normal IP services.
with a BOOTREPLY packet. Those servers transmit the BOOTREPLY
packets through normal IP services to the address of the first interface that
received the BOOTREQUEST packet. That address appears in the gateway IP
address field in the BOOTREQUEST packet.
BOOTREPLY packet, it examines the gateway IP address field to check that
the value in this field is the same as the IP destination address that the server
used for the packet. If the addresses differ, the router discards the
BOOTREPLY packet.
packet to the client as follows:
• If the flags field contains the value 1, the client does not know its own IP
address. The router broadcasts the BOOTREPLY packets to the IP
broadcast address (255.255.255.255).
2-13
Page 46

Configuring SNMP, BootP, and DHCP Services
• If the flags field contains the value 0, the client knows its own IP address,
which appears in the client IP address field of the BOOTREPLY packet.
The router sends the BOOTREPLY packet to that IP address and the
link-layer address that appears in the client hardware address field.
DHCP Overview
DHCP, described in RFC 1541, is an extension of BootP and is built on the
client-server mode. DHCP allows designated DHCP servers to automatically
assign IP addresses and host names to dynamically configured DHCP clients for a
predefined period of time.
The DHCP packet format is based on a BootP packet. As a result, DHCP uses the
BootP relay agent to forward DHCP packets. This scheme provides
interoperability between the existing BootP clients and DHCP servers. The BootP
relay agent uses the same criteria and methods for forwarding both DHCP and
BootP packets. For information about the packet relay process, see “BootP Relay
Agent Overview” on page 2-10.
Why Use DHCP?
2-14
Each DCHP client on the network requires its own IP address and configuration
information. The DHCP client’s IP address is the identifier that other network
devices use to recognize the client on the network. The client’s configuration
information includes the network domain name, the address of the network
servers and gateways, and the subnet mask.
Without DHCP, each time that you add a client to its network, you must manually
assign an IP address and configuration information to the client. When clients
change offices or users, or leave the network altogether, the configuration
information changes as well.
DHCP facilitates network management by automating and centralizing IP address
administration and by providing IP configuration information automatically to
each network device when it is needed.
308644-15.1 Rev 00
Page 47

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
DHCP can allocate three types of IP addresses to DHCP clients: static DHCP
addresses, dynamic DHCP addresses, and static BootP addresses. Tab le 2 -3
describes these types of IP addresses.
Table 2-3. IP Address Types Allocated by DHCP
IP Address Type Description
Static DHCP address An address that the DHCP server fixes to a client by a
unique key, typically the MAC address.
Dynamic DHCP address An address that the DHCP server allocates to a client for
fixed periods of time, called
The client can extend the lease so that it continues to use
the same dynamic address. When the client leaves the
network, the client typically releases the address, and the
DHCP server can assign it to another client.
Static BootP address An address that a DHCP server allocates dynamically with
no fixed time period.
Unlike a dynamic DHCP address, a static BootP address
has an infinite lease time. When the client leaves the
network, it must send a message to the DHCP server to
release the address. The address is then available for the
DHCP server to reassign.
lease times
.
Dynamic IP Address Allocation
If you have only a limited number of IP addresses in a TCP/IP network, DHCP
enables you to efficiently use and reuse IP addresses by implementing a concept
called IP address leasing. A DHCP client can lease an IP address from a DHCP
server for a fixed, configurable period of time. The lease period can range from 1
minute to 99 years. If you have more clients than IP addresses, using shorter
leases can prevent you from running out of addresses. If you have more addresses
than clients, you can use permanent addresses or you can assign fixed addresses to
specific clients.
When a lease expires, the DHCP client can contact the DHCP server to renew the
lease. Typically, the client attempts to renew the lease halfway through the lease
period. For example, if the client is granted an address with a lease time of 1 hour,
it asks to renew the address approximately 30 minutes after the client has started
to use it.
308644-15.1 Rev 00
2-15
Page 48

Configuring SNMP, BootP, and DHCP Services
If the client does not receive an answer from the DHCP server (perhaps because
the server is down), it can attempt to reacquire configuration parameters and an IP
address from another server, or let the lease lapse, returning the IP address to a
client pool. The client pool is a group of one or more client IDs or MAC addresses
maintained by a DHCP server.
DHCP Components
The Nortel Networks implementation of DHCP consists of the following
components:
• DHCP clients
• DHCP server
• NetID Server Manager
The sections that follow describe these components.
DHCP Clients
A DHCP client is a host that uses DHCP to obtain configuration information, such
as an IP address, from a DHCP server.
2-16
DHCP Server
A DHCP server is a host that provides IP addresses and configuration parameters
to DHCP clients.
NetID Server Manager
The NetID Server Manager operates as an interface for the DHCP server (see
Figure 2-8
). The NetID Server Manager manages and maintains IP addresses and
configuration information, and allocates IP addresses to the DHCP server. The
NetID Server Manager polls the database periodically and sends configuration
changes to the appropriate DHCP servers. The DHCP servers send updated
information to the NetID Server Manager, and the Server Manager stores this
information in its database.
308644-15.1 Rev 00
Page 49

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
For example, when the DHCP server starts up, it connects to the NetID Server
Manager and requests its configuration. When the DHCP server assigns an IP
address to a client, it sends the client’s host name and IP address to the NetID
Server Manager. The NetID Server Manager then sends this information to the
database.
The NetID Server Manager reduces the load on the database, because each DHCP
server is not polling for configuration changes and does not require an active
(resource-consuming) connection to the database. It also reduces the load on the
network, because it is the only component that polls the database for configuration
changes.
BootP/DHCP Relay Implementation
The BootP/DHCP relay implementation allows you to configure a router to act as
a BootP relay agent. The BootP relay agent forwards DHCPREQUEST packets to
DHCP servers on other subnets and forwards DHCPREPLY packets back to
DHCP clients.
You must enable the BootP relay agent on the interface to the subnet to be served
and configure it with the IP address of the DHCP server. For more information
about configuring a BootP relay agent, see “Specifying Interfaces to Receive and
Forward DHCP Packets” on page 5-2.
Figure 2-5
DHCP
DHCP
Figure 2-5. BootP/DHCP Relay Implementation
308644-15.1 Rev 00
client
client
illustrates a BootP/DHCP relay implementation.
Router
BootP
(relay agent)
IP network
DHCP server
DC0005A
2-17
Page 50

Configuring SNMP, BootP, and DHCP Services
Acquiring an IP Address
A client acquires its IP address from a router configured as a BootP relay agent as
follows:
1.
Identify DHCP servers.
2.
Request and receive IP information.
3.
Accept or decline IP information.
The following sections describe each of these stages in detail.
Identifying DHCP Servers
Figure 2-6
shows the first stage of the process of acquiring a new IP address from
a router configured as a BootP relay agent.
DHCP
client
DHCP
client
4. BootP relay
1. Client broadcasts
a DHCPDISCOVER
packet.
agent transmits
DHCPOFFER
packets to client.
Router (BootP
relay agent)
Figure 2-6. Identifying DHCP Servers (BootP Relay Agent)
2. BootP relay agent
transmits the
DHCPDISCOVER
packet to servers
on other networks.
3. Servers transmit
DHCPOFFER
packets to BootP
relay agent.
DHCP
server
SNM0005A
2-18
308644-15.1 Rev 00
Page 51

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
To locate DHCP servers on the network, the DHCP client broadcasts a
DHCPDISCOVER packet. Tab le 2 -4
Table 2-4. Fields in a DHCP Packet
Field Octets Description
Operation 1 Message operation code or message type.
Hardware type 1 Hardware address type, for example:
Hardware address length 1 Hardware address length, for example:
Hops 1 DHCP client sets to 0.
Transaction ID 4 A random number chosen by the client. The DHCP
Seconds 2 The number of seconds that elapsed since a client
Flags 2 If the flags field contains the value 1, the client
describes the fields in a DHCP packet.
• 1= BOOTREQUEST
• 2= BOOTREPLY
1= 10 Mb Ethernet
“6” for 10 Mb Ethernet
client and the DHCP server use this number to
associate messages and responses exchanged
between them.
started trying to boot. The client fills in this number.
does not know its own IP address. The router
broadcasts the DHCPREPLY packets to the IP
broadcast address (255.255.255.255).
308644-15.1 Rev 00
If the flags field contains the value 0, the client
knows its own IP address, which appears in the
client IP address field of the DHCPREPLY packet.
The router sends the DHCPREPLY packet to that
IP address and to the link-layer address that
appears in the client hardware address field.
Client IP address 4 The DHCP client IP address. This field is filled in
only if the DHCP client is in BOUND, RENEW, or
REBINDING state and can respond to ARP
requests.
Your IP address 4 DHCP client IP address
Gateway IP address 16 IP address of the DHCP server to use in the next
step of the client’s bootstrap process. The DHCP
server returns this address when it sends
DHCPOFFER and DHCPACK messages to the
client.
(continued)
2-19
Page 52

Configuring SNMP, BootP, and DHCP Services
Table 2-4. Fields in a DHCP Packet
Field Octets Description
Client hardware address 16 The hardware address of the client
Server name 64 Optional DHCP server host name, represented as
a null terminated string
File name 128 A boot file name. Represented as a null terminated
string in a DHCPDISCOVER message, and a fully
qualified directory path name in a DHCPOFFER
message.
Options 312 Variable length optional parameters field
(continued)
The packet relay process uses these fields as follows:
1.
The BootP relay agent receives the packet and, if it accepts the packet,
transmits it to DHCP servers on other networks.
2.
DHCP servers on the local segment see the broadcast packet and respond with
a DHCPOFFER packet that includes an available IP address and other
configuration information. Before offering the IP address, the DHCP servers
may generate an ARP or ICMP echo request on the network to determine
whether the IP address is already in use by another device.
3.
When a DHCP server offers an IP address, that address is temporarily
unavailable to other clients. If the client does not accept or reject the address
within a certain period of time, the server reclaims it. The address is then
available for other clients.
2-20
4.
The BootP relay agent receives the DHCPOFFER packet and examines the
packet. If the BootP relay agent accepts the packet, it forwards it to the client.
5.
If a client does not receive a DHCPOFFER packet within a specified amount
of time after broadcasting a DHCPDISCOVER packet, it sends the packet
again. The client may rebroadcast the packet a number of times. However,
clients operating on systems running Windows
*
95 broadcast four
DHCPDISCOVER packets, each 2 seconds apart.
6.
The client may receive DHCPOFFER packets from several potential servers.
If you configure the client to wait for multiple responses, it compares
configuration parameters in the DHCPOFFER packets to decide which server
to target.
308644-15.1 Rev 00
Page 53

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
Requesting and Receiving IP Information
Figure 2-7
shows the next stage of the process for acquiring a new IP address from
a router configured as a BootP relay agent:
1. Client broadcasts
DHCP
client
a DHCPREQUEST
packet.
4. BootP relay agent
transmits DHCPACK
or DHCPNAK
packet to client.
Router (BootP
relay agent)
Figure 2-7. Requesting and Receiving IP Information (BootP Relay Agent)
1.
When the client has chosen a target server, it broadcasts a DHCPREQUEST
2. BootP relay agent
transmits DHCPREQUEST
packet to all servers
that supplied a
DHCPOFFER packet.
3. Target server transmits
DHCPACK or DHCPNAK
packet to BootP relay
agent.
packet. The DHCPREQUEST packet contains the address of the target server
in the server IP address field and the lease offer that it prefers.
DHCP
server
SNM0006A
2.
3.
Accepting or Declining IP Information
In a network configuration in which a router is configured as a BootP/DHCP relay
agent, the target server recognizes its IP address in the server IP address field, and
responds to the DHCPREQUEST packet as follows:
• If the target server can supply the requested configuration parameters, it sends
308644-15.1 Rev 00
The router configured as a BootP relay agent receives the packet and forwards
it to all servers.
Those servers examine the packet, and if their IP addresses differ from the
value in the server IP address field, they reclaim the IP addresses that they
supplied in the DHCPOFFER packets. These addresses are now available for
other clients.
a DHCPACK packet to the client through the BootP relay agent. The
DHCPACK packet contains the committed IP address.
2-21
Page 54

Configuring SNMP, BootP, and DHCP Services
The client examines the configuration parameters in the DHCPACK packet
and records the duration of the lease period. If the client detects a problem
with the configuration parameters, it sends a DHCPDECLINE packet to the
server and issues a new DHCPDISCOVER packet. Otherwise, the client
accepts the configuration parameters.
• If the target server cannot supply the requested configuration parameters, it
sends a DHCPNAK packet to the client through the BootP relay agent.
When the client receives the DHCPNAK packet, it broadcasts a new
DHCPDISCOVER packet and the process begins again.
A client may choose to relinquish its IP address before the lease period expires by
sending a DHCPRELEASE packet to the server. This packet contains the
relinquished IP address in the client IP address field and the client’s MAC address
in the client hardware address field.
Reacquiring the Same IP Address
A client may want to reuse an IP address that a server allocated earlier using a
BootP relay agent. In this case, the interchange between client and server omits
some of the steps described in the previous sections.
2-22
The client can acquire the same IP address again using a BootP relay agent by
following these steps:
1.
The client starts the interchange by broadcasting a DHCPREQUEST packet
that contains its previous IP address in the client IP address field.
2.
The BootP relay agent receives the packet and forwards it to DHCP servers on
other networks.
3.
DHCP servers examine the client’s configuration parameters in the options
field of the DHCPREQUEST packet.
4.
The server that originally supplied the configuration parameters recognizes
them and responds with a DHCPACK packet.
5.
When a client receives a DHCPACK packet, it accepts or declines the
parameters, as it would when receiving a new IP address.
If a client’s request is invalid (for example, if the client has moved to a new
network), servers respond with a DHCPNAK packet. If a client receives only
DHCPNAK packets, it must request a new IP address by broadcasting a
DHCPDISCOVER packet.
308644-15.1 Rev 00
Page 55

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
DHCP Server Implementation
The DHCP server implementation allows you to configure a router to act as a
DHCP server. In this scenario, the DHCP server, acting in proxy fashion, uses the
NetID Server Manager to manage and maintain IP addresses and configuration
information stored in its database (Figure 2-8
The DHCP server uses the information in the database to assign IP addresses and
host configuration information to DHCP clients. For more information about
configuring a DHCP server, see “Modifying the DHCP Server Configuration
page 6-2
.
).
” on
Figure 2-8
DHCP
client
DHCP
client
illustrates a DHCP server implementation.
Router (DHCP server)
IP network
Figure 2-8. DHCP Server Implementation
NetID
Server
Manager
DC0004A
308644-15.1 Rev 00
2-23
Page 56

Configuring SNMP, BootP, and DHCP Services
Acquiring an IP Address
A client acquires its IP address from a router configured as a DHCP server as
follows:
1.
Identify DHCP servers.
2.
Request and receive IP information.
3.
Accept or decline IP information.
The following sections describe each of these stages in detail.
Identifying DHCP Servers
Figure 2-9
shows the first stage of the process of acquiring a new IP address from
a DHCP server.
1. Client broadcasts
DHCP
client
4. DHCP server
a DHCPDISCOVER
packet.
DHCP
client
transmits
DHCPOFFER
packet to client.
Router (DHCP server)
Figure 2-9. Identifying Routers Configured as DHCP Servers
2. DHCP server sends
ICMP echo request to
prospective IP address.
The ICMP echo
3.
request times out,
indicating that
request can be sent to client.
NetID
Server
Manager
DC0003A
To identify routers configured as DHCP servers, the DHCP client broadcasts a
DHCPDISCOVER packet on its local physical subnet. Tab le 2 -4
on page 2-19
describes the fields in the DHCP packet. The packet release process uses these
fields as follows:
2-24
308644-15.1 Rev 00
Page 57

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
1.
The router configured as a DHCP server receives the packet and finds an
available IP address to assign to the client.
2.
The DHCP server sends an ICMP echo request to the prospective IP address
to determine whether the address is available. If the DHCP server receives a
response, the address is unavailable because it is being used by another host
on the network. The DHCP server selects another IP address to offer and
sends another ICMP echo request.
3.
If there is no response to the ICMP echo request, the DHCP server sends a
DHCPOFFER packet that includes an available IP address to the target DHCP
client.
4.
If a client does not receive a DHCPOFFER packet within a specified amount
of time after broadcasting a DHCPDISCOVER packet, it sends the packet
again. The client may rebroadcast the packet a number of times. However,
clients operating on systems running Windows 95 broadcast four
DHCPDISCOVER packets, each 2 seconds apart.
5.
The client may receive DHCPOFFER packets from several potential servers.
If you configure the client to wait for multiple responses, it compares
configuration parameters in the DHCPOFFER packets to decide which server
to target.
Requesting and Receiving IP Information
Figure 2-10
from a DHCP server.
308644-15.1 Rev 00
shows the next stage of the process of acquiring a new IP address
2-25
Page 58

Configuring SNMP, BootP, and DHCP Services
DHCP
client
4. DHCP server
transmits DHCPACK
or DHCPNAK
packet to client.
1. Client broadcasts
a DHCPREQUEST
packet.
DHCP
client
Router (DHCP server)
2. DHCP server transmits
information from
the DHCPREQUEST
packet to NetID Server
Manager.
3. NetID Server Manager updates
NetID database for IP address and
configuration parameters and sends
committed update message to DHCP server.
NetID
Server
Manager
Figure 2-10. Requesting and Receiving IP Information (DHCP Server)
1.
When the client has chosen a target DHCP server, it broadcasts a
DHCPREQUEST packet to the server. The DHCPREQUEST packet contains
the address of the target server in the server IP address field.
2.
The router configured as a DHCP server examines the packet, and if its IP
address differs from the value in the server IP address field, it reclaims the IP
address it supplied in the DHCPOFFER packet. This address is now available
for other clients.
DC0002A
2-26
3.
If the DHCPREQUEST packet is valid, the DHCP server forwards the request
information to the NetID Server Manager.
4.
After the NetID Server Manager updates the NetID database with the new
request information, the NetID Server Manager sends a committed update
message back to the DHCP server.
Accepting or Declining IP Information
In a network configuration in which the router is configured as a DHCP server, the
target server recognizes its IP address in the server IP address field, and responds
to the DHCPREQUEST packet as follows:
308644-15.1 Rev 00
Page 59

SNMP, BootP, BootP/DHCP Relay, and DHCP Server Concepts
• If the DHCP server can supply the requested configuration parameters, it
sends a DHCPACK packet to the client through the DHCP server.
The client examines the configuration parameters in the DHCPACK packet
and records the duration of the lease period. If the client detects a problem
with the configuration parameters, it sends a DHCPDECLINE packet to the
server and issues a new DHCPDISCOVER packet. Otherwise, the client
accepts the configuration parameters.
• If the target server cannot supply the requested configuration parameters, it
sends a DHCPNAK packet to the client through the DHCP server.
When the client receives the DHCPNAK packet, it broadcasts a new
DHCPDISCOVER packet and the process begins again.
Reacquiring the Same IP Address
A client may want to reuse an IP address that a server allocated earlier using
DHCP. In this case, the interchange between client and server omits some of the
steps described in the previous sections.
The client can acquire the same IP address again using a DHCP server by
following these steps:
1.
2.
3.
4.
5.
If a client’s request is invalid (for example, if the client has moved to a new
network), servers respond with a DHCPNAK packet. If a client receives only
DHCPNAK packets, it must request a new IP address by broadcasting a
DHCPDISCOVER packet.
308644-15.1 Rev 00
The client starts the interchange by broadcasting a DHCPREQUEST packet
that contains its previous IP address in the client IP address field.
The DHCP server receives the packet, examines the client’s configuration
parameters in the options field of the DHCPREQUEST packet, and forwards
the client request information to the NetID Server Manager.
The NetID Server Manager updates its database and sends a committed
update message back to the DHCP server.
The DHCP server that originally supplied the configuration parameters
recognizes them and responds with a DHCPACK packet.
When a client receives a DHCPACK packet from the DHCP server, it accepts
or declines the parameters, as it would when receiving a new IP address.
2-27
Page 60

Page 61

Chapter 3
Customizing SNMP
This chapter describes how to customize SNMP services. It assumes that you
configured an IP interface using the default parameters, as described in Chapter 1,
“Starting SNMP, BootP, and DHCP Services,” and that you understand the SNMP
concepts in Chapter 2, “
Concepts.”
Topic Page
SNMP, BootP, BootP/DHCP Relay, and DHCP Server
Configuring SNMP Using the BCC and Site Manager
Customizing SNMP Global Parameters 3-3
Adding SNMP Communities 3-9
Configuring SNMP Community Managers 3-13
Configuring SNMP View-Based Access Control 3-19
Configuring Traps on the Router 3-25
Configuring Thresholds 3-31
3-2
308644-15.1 Rev 00
3-1
Page 62

Configuring SNMP, BootP, and DHCP Services
Configuring SNMP Using the BCC and Site Manager
Tabl e 3 -1 lists the SNMP configuration tasks described in this chapter and
indicates whether you can use the BCC or Site Manager to perform each task.
Table 3-1. SNMP Configuration Tasks
Task BCC Site Manager
Disabling and Reenabling SNMP
Enabling and Disabling the SNMP Lock Mechanism
Specifying a Lock Address
Specifying a Lock Timeout Value
Enabling and Disabling Authentication Failure Traps
Specifying the Type of Service for SNMP Packets
Specifying an SNMP Community Name
Specifying Community Access Privileges
Deleting an SNMP Community
Adding a Manager
Configuring a Manager to Receive Traps
Deleting a Manager
Configuring, Listing, and Deleting a View
Configuring Communities and Their View Associations
Configuring Traps on the Router
Disabling a Trap Entity
Configuring Trap Exceptions
Deleting Trap Exceptions
Disabling and Reenabling Thresholds
Setting the Threshold Polling Interval
Adding a Threshold
Enabling and Disabling Thresholds for a Variable
Specifying a Value for the Threshold Level
Specifying the Severity Level for Event Messages
Specifying Threshold Units
✓✓
✓✓
✓
✓✓
✓✓
✓
✓✓
✓✓
✓✓
✓✓
✓✓
✓✓
✓
✓
✓✓
✓✓
✓✓
✓✓
✓
✓
✓
✓
✓
✓
✓
(continued)
3-2
308644-15.1 Rev 00
Page 63

Customizing SNMP
Table 3-1. SNMP Configuration Tasks
Task BCC Site Manager
Determining When to Record Threshold Events
Specifying the Maximum Number of Successive
Alarms
Specifying Polling Intervals for Held Variables
Specifying a Threshold Object Name
Customizing SNMP Global Parameters
You can enable SNMP services most easily by accepting all the default parameter
values. However, you may want to change these values, depending on your
network requirements.
Disabling and Reenabling SNMP
When you enable IP on an interface, SNMP access is automatically enabled
through that interface. You can disable and reenable SNMP on the router.
Using the BCC
(continued)
✓
✓
✓
✓
To disable SNMP, navigate to the SNMP prompt (for example,
enter:
disable
For example, the following command disables SNMP:
snmp#
To reenable SNMP, navigate to the SNMP prompt and enter:
enable
For example, the following commands reenable SNMP and display its default
values:
snmp#
snmp#
308644-15.1 Rev 00
disable
enable
info
lock enabled
lock-address 0.0.0.0
lock-timeout 2
box; snmp
) and
3-3
Page 64

Configuring SNMP, BootP, and DHCP Services
authentication-traps enabled
type-of-service reliability
state enabled
snmp#
Using Site Manager
To disable or reenable SNMP, complete the following tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Set the
Click on
description on page A-3
6. Click on OK. You return to the Configuration Manager
Caution:
Protocols
SNMP
Globa
Enable
Help
When you disable the SNMP agent in dynamic mode, you
.
. The SNMP menu opens.
l. The Edit SNMP Global Parameters
parameter.
or see the parameter
.
The Protocols menu opens.
window opens.
window.
immediately prohibit Site Manager from communicating with the router and
disconnect your Site Manager session.
Enabling and Disabling the SNMP Lock Mechanism
The SNMP lock mechanism prohibits the SNMP agent from responding to
multiple network management stations issuing simultaneous SNMP
commands to the router. The SNMP lock mechanism is enabled by default.
set
3-4
If this lock is enabled, the SNMP agent identifies the station from which it
set
receives the next SNMP
SNMP
set
commands from that station. If the agent receives an SNMP
command and, for a specified time, responds only to
set
command from another network management station during this time, it issues an
SNMP genErr GetResponse PDU, which that station logs as an SNMP Set Error
message.
308644-15.1 Rev 00
Page 65

Customizing SNMP
To allow the SNMP agent to respond to simultaneous SNMP
multiple network management stations, disable the SNMP lock mechanism.
Using the BCC
To disable the lock mechanism, navigate to the SNMP prompt (for example,
snmp
lock disabled
To reenable the lock, navigate to the SNMP prompt and enter:
lock enabled
Using Site Manager
To enable or disable the SNMP lock mechanism, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Set the
Click on
description on page A-3
6. Click on OK. You return to the Configuration Manager
) and enter:
Protocols
SNMP
Global
Use Lock
Help
commands from
set
Site Manager Procedure
The Protocols menu opens.
.
. The SNMP menu opens.
. The Edit SNMP Global Parameters
window opens.
parameter.
or see the parameter
.
window.
box;
308644-15.1 Rev 00
3-5
Page 66

Configuring SNMP, BootP, and DHCP Services
Specifying a Lock Address
The default lock address is 0.0.0.0. Using the BCC, you can specify a different
lock address by navigating to the SNMP prompt (for example,
entering:
box; snmp
) and
lock-address
address
<address>
is an IP address in dotted-decimal notation.
For example, the following command sets the lock address to 192.32.15.55:
snmp#
snmp#
lock-address 192.32.15.55
Specifying a Lock Timeout Value
If the SNMP lock mechanism is enabled, you can customize the lock timeout
period. The lock timeout period is the maximum number of minutes that the
SNMP agent allows an idle network management station to hold a lock on it.
During this time, the SNMP agent locks out SNMP
network management stations. The lock timer is reset each time the locking
manager issues an SNMP
By default, the SNMP agent allows an idle network management station to hold a
lock on it for 2 minutes. To change the default lock timeout period, specify a value
from 1 through 60 minutes.
Using the BCC
set
command.
set
commands from other
3-6
To reset the lock timeout value, navigate to the SNMP prompt (for example,
snmp
) and enter:
lock-timeout
integer
is the number of minutes.
integer>
<
box;
For example, the following command sets the lock timeout period to 3 minutes:
snmp#
snmp#
lock-timeout 3
308644-15.1 Rev 00
Page 67

Using Site Manager
To reset the lock timeout value, complete the following tasks:
You do this System responds
Customizing SNMP
Site Manager Procedure
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Set the
Click on
description on page A-4
6. Click on OK. You return to the Configuration Manager
Protocols
SNMP
Globa
Lock Time
Help
.
. The SNMP menu opens.
l. The Edit SNMP Global Parameters
parameter.
Out
or see the parameter
.
The Protocols menu opens.
window opens.
window.
Enabling and Disabling Authentication Failure Traps
The router generates an authentication failure trap when it receives an SNMP
message from an SNMP manager falsely claiming to be in a particular community
or specifying an unknown community.
When you enable the authentication failure traps feature on the router, you must
configure an SNMP community manager to receive the trap (see “Configuring
SNMP Community Managers” on page 3-13).
You can prohibit the router from generating authentication failure traps by
disabling the authentication failure trap feature.
Using the BCC
By default, SNMP sends an authentication failure trap for sets from a false
manager or community. To disable authentication traps, navigate to the SNMP
prompt (for example,
authentication-traps disabled
308644-15.1 Rev 00
box; snmp
) and enter:
3-7
Page 68

Configuring SNMP, BootP, and DHCP Services
For example, the following command prohibits SNMP from sending
authentication failure traps from a false manager or community:
snmp#
authentication-traps disabled
snmp#
To reenable authentication failure traps, navigate to the SNMP prompt and enter:
authentication-traps enabled
For example, the following command causes SNMP to generate authentication
failure traps from a false manager or community:
snmp#
snmp#
Using Site Manager
To enable or disable authentication failure traps, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Set the
parameter. Click on
parameter description on page A-4.
6. Click on OK. You return to the Configuration Manager
authentication-traps enabled
Site Manager Procedure
Protocols
SNMP
Globa
Authentication Failure Traps
.
. The SNMP menu opens.
l. The Edit SNMP Global Parameters
or see the
Help
The Protocols menu opens.
window opens.
window.
3-8
308644-15.1 Rev 00
Page 69

Specifying the Type of Service for SNMP Packets
Using the BCC, you can specify the type of service in which SNMP packets will
be generated by setting the type of service to either reliability or normal. For
SNMP, high-reliability type of service is important.
By default, the type of service is set to reliability. To specify the type of service,
navigate to the SNMP prompt (for example,
box; snmp
Customizing SNMP
) and enter:
type-of-service {reliability
normal
|
For example, the following command causes SNMP to generate packets with a
type of service of reliability:
type-of-service reliability
snmp#
snmp#
Adding SNMP Communities
An SNMP community is a logical relationship between an SNMP agent and one or
more SNMP managers. The community has a name, and all members of a
community have the same access privileges: either read-only (members can view
configuration and performance information) or read-write (members can view
configuration performance information, and also change the configuration).
This section describes how to add and delete the SNMP communities to which the
SNMP agent responds or sends traps.
Specifying an SNMP Community Name
You can add SNMP communities by specifying the name of the community. The
community name can consist of up to 63 characters, including embedded spaces.
}
Using the BCC
To create a community name, navigate to the SNMP prompt (for example,
snmp
community
name
including embedded spaces.
308644-15.1 Rev 00
box;
) and enter:
<name>
is any string of printable ASCII characters, up to 63 characters in length,
3-9
Page 70

Configuring SNMP, BootP, and DHCP Services
For example, the following commands create a community named “router1” and
display its default values:
snmp#
community router1
community/router1#
label router1
access read-only
scope-type {}
info
Using Site Manager
To specify the name of a community, complete the following tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Choose
6. Choose
7. Set the
Click on
description on page A-5.
8. Click on OK. You return to the SNMP Community List
Protocols
SNMP
Communities
Community
Add Community
Community Name
Help
.
. The SNMP menu opens.
. The SNMP Community List window
. The Community menu opens.
. The Add SNMP Community window
parameter.
or see the parameter
Specifying Community Access Privileges
After you specify the name of the community, you must assign access privileges
to all members of the community. You can specify one of two types of access
privileges to each community that you define: read-only or read-write.
The Protocols menu opens.
opens.
opens.
window.
3-10
308644-15.1 Rev 00
Page 71

Using the BCC
Customizing SNMP
By default, the router grants read-only access privileges to all members of an
SNMP community. Read-only access allows members of a community to view
configuration and performance information. Set this parameter to read-write to
allow members of a community to view configuration and performance
information, and also to change the configuration of a router.
By default, the community has read-only access. To specify the type of access,
navigate to the community-specific prompt (for example,
community/router1
access {read-write | read-only}
) and enter:
box; snmp;
For example, the following command allows read-write access to the community
“router1”:
community/router1#
community/router1#
Using Site Manager
To specify the access privilege for a community, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Choose
6. Choose
7. Set the
Click on
description on page A-5.
8. Click on OK. You return to the SNMP Community List
access read-write
Site Manager Procedure
The Protocols menu opens.
Protocols
SNMP
Communities
Community
Edit Community
Access
Help
.
. The SNMP menu opens.
. The SNMP Community List window
opens.
. The Community menu opens.
. The Edit SNMP Community window
opens.
parameter.
or see the parameter
window.
308644-15.1 Rev 00
3-11
Page 72

Configuring SNMP, BootP, and DHCP Services
Deleting an SNMP Community
You can delete an SNMP community to which the agent responds or sends traps.
Using the BCC
To delete an SNMP community, navigate to the community-specific prompt (for
example,
delete
For example, the following command deletes the community “router1”:
box; snmp; community/router1
) and enter:
community/router1#
snmp#
Using Site Manager
To delete an SNMP community, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Select the community that you want to
delete.
6. Choose
7. Choose
8. Verify that the correct community name
appears in the window. Click on
you do not want to delete the selected
community.
9. Click on
delete
Site Manager Procedure
The Protocols menu opens.
Protocols
SNMP
Communities
Community
Delete Community
Delete
.
. The SNMP menu opens.
. The SNMP Community List window
opens.
. The Community menu opens.
. The Delete SNMP Community window
opens.
if
Cancel
. The Configuration Manager removes the
community from the list.
3-12
308644-15.1 Rev 00
Page 73

Configuring SNMP Community Managers
This section describes how to add and delete SNMP community members
(managers). It also describes how to configure managers to receive traps from the
SNMP agent.
Adding a Manager
After you add a community name on the router and assign access privileges to it,
you can add one or more community members (called managers). By default, the
IP address 0.0.0.0 is a manager in the public community.
Note:
When you add the first IP interface, Site Manager automatically creates
a read-write public community with a wildcard manager (0.0.0.0). For security
reasons, you should replace the public community and wildcard manager with
a unique community specifying a limited list of managers.
Using the BCC
Customizing SNMP
To add a manager to a community, navigate to the community prompt (for
example,
manager address
For example, the following command creates a manager with an IP address of
2.2.2.2 and assigns it to the community router1:
community/router1#
manager/router1/2.2.2.2#
Using Site Manager
To add a manager to a particular community, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
308644-15.1 Rev 00
box; snmp; community/router1
<ip_address>
manager address 2.2.2.2
Site Manager Procedure
Protocols
.
) and enter:
The Protocols menu opens.
(continued)
3-13
Page 74

Configuring SNMP, BootP, and DHCP Services
Site Manager Procedure
You do this System responds
3. Choose
4. Choose
5. Choose
6. Choose
7. Choose
8. Choose
9. Enter the IP address of the SNMP
manager that you want to add.
10. Click on OK. The Configuration Manager adds the
. The SNMP menu opens.
SNMP
Communities
Community
Managers
Manager
Add Manager
. The SNMP Community List window
. The Community menu opens.
. The SNMP Manager List window for that
. The Manager menu opens.
. The Add SNMP Manager window opens.
Configuring a Manager to Receive Traps
After you add a manager to a community, you can configure the manager to
receive traps by specifying its UDP port number and the types of traps that the
agent sends to that manager.
(continued)
opens.
community opens.
manager to the community.
3-14
When you configure a manager to receive specific traps or all traps (see Tab le 3 -2
on page 3-16
), the router sends this manager all enabled event traps. There is no
MIB correspondence between a specific SNMP manager and a trap entity. Rather,
all SNMP managers that you configure to receive specific traps receive all traps
that you configure.
Specifying the Trap Port
By default, the standard port number on the managing station to which the SNMP
agent transmits traps is 162. To use a different UDP port number, specify a value
from 1 through 9999. Do not specify a port that another application uses.
308644-15.1 Rev 00
Page 75

Using the BCC
Customizing SNMP
To specify the UDP port number on the managing station to which the SNMP
agent sends traps, navigate to the manager-specific prompt (for example,
snmp; community/router1; manager/router1/2.2.2.2
trap-port <integer>
) and enter:
box;
integer
For example, the following command causes the SNMP agent to send traps to
manager 2.2.2.2 on port number 150:
manager/router1/2.2.2.2#
manager/router1/2.2.2.2#
Using Site Manager
To specify the UDP port number on the managing station to which the SNMP
agent sends traps, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Choose
6. Choose
7. Select the manager that you want to edit.
8. Choose
9. Choose
10. Set the
Click on
description on page A-6.
11. Click on OK. You return to the SNMP Manager List
is a number from 1 through 9999.
trap-port 150
Site Manager Procedure
Protocols
SNMP
Communities
Community
Managers
Manager
Edit Manager
Trap Po rt
Help
.
. The SNMP menu opens.
. The SNMP Community List window
. The Community menu opens.
. The SNMP Manager List window for that
. The Manager menu opens.
. The SNMP Manager window opens.
parameter.
or see the parameter
The Protocols menu opens.
opens.
community opens.
window.
308644-15.1 Rev 00
3-15
Page 76

Configuring SNMP, BootP, and DHCP Services
Specifying a Trap Type
You can specify one of four types of traps that the SNMP agent can send to the
manager: generic, specific, all, or none. Tabl e 3- 2
Table 3-2. Trap Types Sent by the SNMP Agent
Trap Type Description
Generic This is the default trap type. It sends the well-defined SNMP traps
(cold-start, warm-start, and authentication failure traps) to the manager.
The cold-start and warm-start traps are automatically active in the SNMP
agent; however, you must enable the Authentication Failure Traps global
parameter for the agent to send such traps to a specified manager.
Specific Allows you to configure the agent software to send all enabled log event
traps to a specified manager
All Allows you to send cold-start and warm-start traps, and all enabled log
event traps, to a specified manager
None Prohibits the SNMP agent from sending traps to a specified manager
Using the BCC
describes these trap options.
3-16
By default, the SNMP agent sends generic traps to the manager. To specify a
different type of trap, navigate to the manager-specific prompt (for example,
snmp; community/router1; manager/router1/2.2.2.2
<trap_type>
traps
trap_type
is one of the following:
generic
specific
all
none
) and enter:
box;
For example, the following command causes the SNMP agent to send specific
traps to manager 2.2.2.2:
manager/router1/2.2.2.2#
manager/router1/2.2.2.2#
traps specific
308644-15.1 Rev 00
Page 77

Using Site Manager
To specify a trap type, complete the following tasks:
You do this System responds
Customizing SNMP
Site Manager Procedure
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Choose
6. Choose
7. Select the manager that you want to edit.
8. Choose
9. Choose
10. Set the
Click on
description on page A-6.
11. Click on OK. You return to the SNMP Manager List
Deleting a Manager
You can delete a manager from its associated community by deleting the
manager’s IP address from the list of SNMP managers.
The Protocols menu opens.
Protocols
SNMP
Communities
Community
Managers
Manager
Edit Manager
Trap Ty p es
Help
.
. The SNMP menu opens.
. The SNMP Community List window
opens.
. The Community menu opens.
. The SNMP Manager List window for that
community opens.
. The Manager menu opens.
. The SNMP Manager window opens.
parameter.
or see the parameter
window.
Using the BCC
To delete a manager, navigate to the manager-specific prompt (for example,
snmp; community/router1; manager/router1/2.2.2.2
delete
308644-15.1 Rev 00
box;
) and enter:
3-17
Page 78

Configuring SNMP, BootP, and DHCP Services
For example, the following command deletes the manager 2.2.2.2 from the
community router1:
manager/router1/2.2.2.2#
community/router1#
Using Site Manager
To delete a manager, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Select the community from which you want
to delete the manager.
6. Choose
7. Choose
8. Select the manager that you want to
delete.
9. Choose
10. Choose
11. Make sure that the correct manager IP
address appears.
12. Click on
delete
Site Manager Procedure
The Protocols menu opens.
Protocols
SNMP
Communities
Community
Managers
Manager
Delete Manager
Delete
.
. The SNMP menu opens.
. The SNMP Community List window
opens.
. The Community menu opens.
. The SNMP Manager List window for that
community opens.
. The Manager menu opens.
. The Delete SNMP Manager window
opens.
. The Configuration Manager removes the
manager from the community.
3-18
308644-15.1 Rev 00
Page 79

Configuring SNMP View-Based Access Control
The SNMP view-based access control feature allows you to modify what can or
cannot be seen of a router’s MIB tree. You can include or exclude from a view any
MIB object, attribute, or instance in the router’s MIB. You can also include or
exclude access to a MIB subtree for traps, and to the SNMP operations
get-next
, and
set
.
Customizing SNMP
get
,
Note:
Because of the way that SNMP works, the SNMP
does not allow you to exclude an attribute and include subsequent attributes.
When you exclude an attribute, all subsequent attributes are also excluded. For
example, if you have six attributes, and you exclude the second attribute, you
are really excluding attributes 2 through 6; you will not be able to view
attributes 2 through 6.
When you configure a view, you specify view subtrees -- that is, instructions for
what MIB information the agent will allow to be seen and not seen by managers in
the specified community.
This feature also lets you manage overlapping private address spaces. For
example, if two routers use the same IP address, you can create a view that
excludes the MIB of one address. Then, when the management station queries the
MIB for information, it receives information only from the router whose view you
did not exclude.
You can configure SNMP view-based access control using the BCC or the
Technician Interface.
Configuring, Listing, and Deleting a View
To configure, list, or delete a view and its contents, use the
command. You can enter this command at the BCC or Technician Interface
prompt.
get-next
function
snmpserver view
Configuring a View
When you configure a view, you control access to a MIB subtree. To configure a
view, enter the following command:
308644-15.1 Rev 00
3-19
Page 80

Configuring SNMP, BootP, and DHCP Services
<view_name>} {<oid_tree>
snmpserver view
view_name
•
{
is the name that you assign to this particular view.
} {
included
|
excluded
}
oid_tree
•
•
included
• excluded
If you specify the
use wildcards. You can use one wildcard with any portion of the
second wildcard at the end of the
specifies the portions of the MIB that you want to include or exclude.
specifies that
specifies that
oid_tree
oid_tree
oid_tree
is to be included in this view.
is to be excluded from this view.
argument in the
oid_tree
snmpserver view
command, you can
oid_tree
, and a
. The first wildcard affects the attribute
portion of the subtree, and the second wildcard affects the instance portion of the
subtree. A match on an incoming SNMP OID is made on the longest matching
MIB subtree.
The following examples illustrate the use of wildcards.
Entering this Value for <oid_tree> Includes or Excludes in the View
wfIpIntfCfgEntry.*.192.32.140.1.1
wfIpIntfCfgEntry.*
or
wfIpIntfCfgEntry
wfIpIntfCfgEntry.1.*
wfIpIntfCfgEntry.1.192.32.*
wfIpIntfCfgEntry.*.192.32.*
All attributes of wfIpIntfCfgEntry
All instances of wfIpIntfCfgEntry
All instances of wfIpIntfCfgEntry with an
attribute ID of 1
All instances of wfIpIntfCfgEntry with an
attribute of 1 that have an instance ID that
begins with 192.32.
All attributes of wfIpIntfCfgEntry that have an
instance ID that begins with 192.32.
3-20
For example, the following command creates a view named “block,” which will
exclude any attributes of wfIpIntfCfgEntry for the IP address 192.32.140.1.1:
snmpserver view block wfIpIntfCfgEntry.*.192.32.140.1.1 excluded
When multiple view subtrees are configured within a view, an incoming SNMP
OID will match on the longest matching subtree in the view. For example, in
looking for a match against the
oid_tree
value wfIpIntfCfgEntry.1.192.32.140.1.1,
SNMP will bypass the subtree that is excluded, and then match on all values in the
included
oid_tree
for subtree 2.
308644-15.1 Rev 00
Page 81

Customizing SNMP
oid_tree
oid_tree
value for subtree 1:
value for subtree 2:
wfIPIntfCfgEntry excluded
wfIPIntfCfgEntry.*.192.32.140.1.1 included
Listing All Views or the Contents of a View
To list all configured views or the contents (MIB subtrees) of a particular view,
enter:
<view_name>] list
snmpserver view
view_name
•
subtrees. If you do not specify the argument
[
is the name of the view for which you want to display MIB
view_name
, the command
displays the names of all configured views.
•
displays all MIB subtrees that belong to a view, or the names of all
list
configured views, depending on whether you specify
view_name.
For example, to display all subtrees that belong to a view named “block,” enter:
snmpserver view block list
This command displays the following subtree information for that view:
View Subtree View Type Subtree Index
To display the names of all configured views, enter:
snmpserver view list
The command displays the following:
308644-15.1 Rev 00
wfIpIntfCfgEntry.*.192.32.140.1.1 Excluded 1.1
View Index View Name
1 block
3-21
Page 82

Configuring SNMP, BootP, and DHCP Services
Deleting a View or Its Contents
To delete a view or the contents (MIB subtrees) belonging to a particular view,
enter:
<view_name>} [<oid_tree>]
snmpserver view
view_name
•
{
is the name of the view that you want to delete, or from which you
want to delete MIB subtrees.
delete
oid_tree
•
you do not specify
specifies the MIB subtree that you want to delete from
oid_tree
, then this command will delete the view itself,
including all subtree associations.
•
deletes a view, or deletes a MIB subtree from a view, depending on
delete
whether you specify
oid_tree
.
For example, to delete the entire view named “block,” enter:
snmpserver view block delete
By specifying
oid_tree
to delete a particular MIB subtree from a view, you also
delete the “include” or “exclude” action associated with the subtree that you
specified when you configured the view.
For example, to delete the
oid_tree
identified by
wfIpIntfCfgEntry.*.192.32.140.1.1 and its associated include or exclude action
from the view named “block,” enter:
snmpserver view block wfIpIntfCfgEntry.*.192.32.140.1.1 delete
Configuring Communities and Their View Associations
To configure a community, associate and disassociate a view with the community,
list community information, or to delete a community, you use the
community
Interface prompt. The
communities that you may have already created.
command. You can enter this command at the BCC or Technician
snmpserver community
commands also work with any
view_name
snmpserver
. If
3-22
An SNMP community is a logical relationship between an SNMP agent and one or
more SNMP community managers. The agent establishes one community for each
combination of authentication and access control characteristics that you choose.
308644-15.1 Rev 00
Page 83

Customizing SNMP
Configuring a Community
To configure a community, enter the following command:
snmpserver community
community_name
•
•
•
specifies read-only access to the viewable MIBs for this community.
RO
specifies read-write access to the viewable MIBs for this community.
RW
is the name that you give to this community.
<community_name>}
{
{
RO
}
RW
|
For example, to create a community named “pubnet” that is configured to allow
read-write access, enter:
snmpserver community pubnet RW
Associating a View with a Community
Although a view can be associated with multiple communities, each community
can be associated with only one view. To associate a view with a community, enter
the following command:
snmpserver community
•
community_name
associate the view
•
view_name
community
is the name of the community with which you want to
.
is the name of the view that you are associating with the
.
community_name>}
{<
{<view_name>
view
}
For example, to associate the view named “block” with the community name
“pubnet” allowing read-write community access, enter:
snmpserver community pubnet view block
Listing Community Information
To list information (index, name, associated view, and access rights) for a specific
community, or for all configured communities, enter:
snmpserver community
•
308644-15.1 Rev 00
<community_name>]
community_name
display
this information. If you do not specify the
[
is the name of the community for which you want to
list
community_name
argument, the command displays information for all configured communities.
3-23
Page 84

Configuring SNMP, BootP, and DHCP Services
•
displays information for a particular community or for all communities,
list
depending on whether you specify the
community_name
argument.
For example, to list information for a community named “pubnet,” enter:
snmpserver community pubnet list
The command displays the following:
Community
Index
2 pubnet block read-write
Community
Name
Associated
View Access
To see a complete list of all configured communities, enter the following
command. Note that a community named public is always configured by default.
snmpserver community list
The command displays the following:
Community
Index
1 public none read-write
2 pubnet block read-write
3 private secret read-only
Community
Name Associated View Access
3-24
Disassociating a View from a Community
You can disassociate a view from a community or delete a community record,
which automatically removes the view association. To disassociate a view from a
community, enter:
snmpserver community
community_name
•
is the name of the community from which you want to
<community_name>}
{
[
view <view_name>
delete
]
disassociate a view.
view_name
•
community. If you do not specify
specified community
is the name of the view that you want to disassociate from the
entirely
view_name
.
, then the command deletes the
308644-15.1 Rev 00
Page 85

Customizing SNMP
•
disassociates a view from a community or deletes the community,
delete
depending on whether you specify
For example, to disassociate the view named “block” from the community
“pubnet,” enter:
snmpserver community pubnet view block delete
To delete the community named “pubnet,” and thereby the view association with
“pubnet,” enter:
snmpserver community pubnet delete
Configuring Traps on the Router
A trap is an event that the router sends to some external network device, such as a
network management station. You can specify which log events the SNMP agent
sends to the network management station as traps, based on the following:
• Slot number: the number of the slot on which the trap will be received
• Entity number: the code assigned to the entity issuing the event that uniquely
identifies a router event
• Severity level: indicates whether the trap is a fault, warning, information,
trace, or debug message
view_name
.
A router never broadcasts traps on the network. Rather, it sends traps to specific IP
addresses, which you configure on the router as managers of a community. Traps
are always sent to specific managers. For more information about traps, see
“
Using the BCC
To specify a trap entity based on slot and protocol entity, enter the following
command at the SNMP prompt:
trap-entity entity <entity_name> slot <slot_number>
entity_name
enter
slot_number
308644-15.1 Rev 00
Events and Traps” on page 2-5.
is the name of the entity issuing the event. For a list of all entities,
help trap-entity entity
at the SNMP prompt.
is the number of the slot on which the trap will be received.
3-25
Page 86

Configuring SNMP, BootP, and DHCP Services
For example, the following command causes the SNMP agent to send to a network
management station a trap for the IP protocol on slot 2:
snmp#
trap-entity entity ip slot 2
trap-entity/ip/2#
By default, the attribute for all severity levels is set to
any severity level, navigate to the trap entity-specific prompt (for example,
snmp; trap-entity/ip/2
fault-log on
warning-log on
information-log on
trace-log on
debug-log on
For example, to send warning and fault traps to the network management station,
enter the following commands:
trap-entity/ip/2#
Using Site Manager
To specify a trap entity, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. Choose
6. Select the slot for which you want to
configure traps by clicking on the bar in the
Slot box.
7. Select an entity for which you want to
configure traps. If you want to configure
traps for all entities running on the slot,
choose
column.
) and enter one or more of the following commands:
warning-log on; fault-log on
Site Manager Procedure
The Protocols menu opens.
Protocols
SNMP
Trap Configuration
Interfaces
All Entities
.
. The SNMP menu opens.
. The Trap Configuration menu opens.
. The Trap Configuration window opens.
The entity names appear in the Available
Entities column, a comprehensive list of
all protocols available, regardless of the
from the top of the
platform or software that you are using.
. To turn on logging for
off
(continued)
box;
3-26
308644-15.1 Rev 00
Page 87

Customizing SNMP
You do this System responds
8. Select the severity level at which you want
to receive traps by clicking on the Events
box at the bottom of the window.
For a description of severity levels, see
Severity Levels” on page 2-6.
“
9. Click on
10. Repeat steps 6 through 9 for other slots
that you want to configure.
11. Click on
Update
Save
Disabling a Trap Entity
Site Manager Procedure
. The entity name moves to the Current
. You return to the Configuration Manager
(continued)
Entities column, indicating that you want
to receive traps for this entity at the
severity level that you specified.
(To move an entity from the column,
select the entity name and then click on
Remove
window.
.)
You can prevent the SMNP agent from sending a specific trap entity to a network
management station regardless of slot by disabling the trap entity.
Using the BCC
Trap entities are enabled by default. To prevent the SMNP agent from sending a
specific trap entity to a network management station regardless of slot, navigate to
the trap entity-specific prompt (for example,
enter the following command:
disable
For example, the following command prevents the SNMP manager from sending
traps for the IP entity on slot 2:
trap-entity/ip/2#
trap-entity/ip/2#
308644-15.1 Rev 00
disable
box; snmp; trap_entity/ip/2
) and
3-27
Page 88

Configuring SNMP, BootP, and DHCP Services
Using Site Manager
To disable a trap entity, complete the following tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
4. Choose
5. In the Current Entities column, select the
entity name that you want to delete.
6. Click on
7. Click on
Protocols
SNMP
Trap Configuration
Remove
Save
.
. The SNMP menu opens.
. The entity name is removed from the
. Site Manager saves the changes that you
Configuring Trap Exceptions
You can configure up to 50 trap exceptions, which specify that the SNMP agent
always sends or never sends traps to the network management station, regardless
of the trap configuration settings and regardless of the slot that you specified.
You configure a trap exception by specifying the following:
• Entity code for the event for which you want to configure an exception
• Code of the event for which you want to configure an exception
The Protocols menu opens.
. The Trap Configuration menu opens.
The entity name that you selected is
highlighted.
Current Entities column.
made.
3-28
• Whether the SNMP agent always sends or never sends a trap to the network
management station (Site Manager only)
To access the event message database, look on the documentation CD
that comes with BayRS or look on the Web at the following URL:
http://www25.nortelnetworks.com/library/tpubs/events/
308644-15.1 Rev 00
Page 89

Using the BCC
Customizing SNMP
To specify a trap exception based on protocol entity and event code, enter the
following command at the SNMP prompt:
trap-event entity <entity_name> event <event_code>
entity_name
enter
event_code
For example, the following command causes the SNMP agent to send to a network
management station a trap for the IP protocol generating messages for interfaces
that transition to the down state (event code 3):
snmp#
trap-event/ip/3#
snmp#
Using Site Manager
To configure a trap exception, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu open.
3. Choose
4. Choose
5. Choose
6. Click on
is the name of the entity issuing the message. For a list of all entities,
help trap-event entity
is the numerical value assigned to the event message.
trap-event entity ip event 3
info
entity ip
event 3
state enabled
Protocols
SNMP
Trap Configuration
Exceptions
Add
.
. The SNMP menu opens.
. The Trap Exceptions List window opens.
. The Add Trap window opens.
at the SNMP prompt.
Site Manager Procedure
The Protocols menu opens.
. The Trap Configuration menu opens.
(continued)
308644-15.1 Rev 00
3-29
Page 90

Configuring SNMP, BootP, and DHCP Services
You do this System responds
7. Set the following parameters:
• Entity Code
• Event Code
• Always/Never Trap
Click on
descriptions beginning on page A-7
8. Click on OK. You return to the Trap Exceptions List
or see the parameter
Help
Deleting Trap Exceptions
You can delete a trap exception by specifying the entity name and the event code
for the trap event.
Using the BCC
To delete a trap exception, navigate to the trap-exception prompt (for example,
box; snmp; trap-event/ip/3
delete
Site Manager Procedure
.
window.
) and enter:
(continued)
For example, the following command deletes the trap exception for IP protocol
event code 3:
trap-event/ip/3#
snmp#
Using Site Manager
To delete a trap exception, complete the following tasks:
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose IP. The IP menu opens.
3. Choose
3-30
delete
Site Manager Procedure
The Protocols menu opens.
Protocols
SNMP
.
. The SNMP menu opens.
(continued)
308644-15.1 Rev 00
Page 91

Customizing SNMP
Site Manager Procedure (continued)
You do this System responds
4. Choose
5. Choose
6. Select the trap exception that you want to
delete.
7. Click on
8. Click on
Trap Configuration
Exceptions
Delete
Done
. The Trap Exceptions List window opens.
.
. You return to the Configuration Manager
. The Trap Configuration menu opens.
Configuring Thresholds
Using Site Manager, you can configure thresholds for any integer, counter, gauge,
or time-tick variable in the MIB. For more information about using thresholds, see
“
Thresholds” on page 2-7.
To configure a threshold, you must have a good understanding of the MIB and be
able to identify the instances of MIB objects to which you want to apply a
threshold. For complete information about identifying a MIB object or an instance
identifier, see the statistics chapter of Configuring and Managing Routers with
Site Manager.
Disabling and Reenabling Thresholds
window.
By default, the thresholds feature is enabled on all interfaces on which IP is
configured.
To disable and reenable thresholds, complete the following tasks:
308644-15.1 Rev 00
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
Protocols
Global Protocols
Thresholds
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
The Protocols menu opens.
(continued)
3-31
Page 92

Configuring SNMP, BootP, and DHCP Services
Site Manager Procedure
You do this System responds
4. Choose
5. Set the
Click on
description on page A-8
6. Click on OK. You return to the Configuration Manager
Enable/Disable
. The Edit Thresholds Global Parameters
Global
parameter.
or see the parameter
Help
.
Setting the Threshold Polling Interval
The threshold polling interval sets the time interval at which the agent polls the
variable to determine whether that variable has reached a threshold. You must set a
minimum polling interval of 5 seconds; there is no maximum value. The default
polling interval is 60 seconds.
When setting a polling interval, remember that the more often the agent polls the
variable, the more memory it needs to manage the thresholds for this statistic.
To set the threshold polling interval, complete the following tasks:
(continued)
window opens.
window.
3-32
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Click on
description on page A-9
6. Click on OK. You return to the Configuration Manager
Protocols
Global Protocols
Thresholds
Global
Polling Interval
Help
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Edit Thresholds Global Parameters
parameter.
or see the parameter
.
The Protocols menu opens.
window opens.
window.
308644-15.1 Rev 00
Page 93

Adding a Threshold
To add a threshold, complete the following tasks:
You do this System responds
Customizing SNMP
Site Manager Procedure
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Click on
6. Select the object to which you want to
apply a threshold.
7. Enter the instance identifier in the Instance
field.
8. Click on
9. Click on
10. Repeat steps 5 through 9 to add other
thresholds.
11. Click on
adding thresholds.
Protocols
Global Protocols
Thresholds
Thresholds
Add
Save
Apply
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
. The Threshold Configuration window
. You return to the Threshold Interface Lists
.
when you have finished
The Protocols menu opens.
opens.
opens, displaying a list of all MIB objects
that the agent supports.
The object appears in the Object field.
window.
You return to the Configuration Manager
window.
Enabling and Disabling Thresholds for a Variable
You can decide whether to turn the threshold for a specific variable on or off by
setting the Threshold Enable parameter.
To tell the agent to apply the threshold to a variable, specify Enable. To tell the
agent to ignore the threshold for a variable, specify Disable.
308644-15.1 Rev 00
3-33
Page 94

Configuring SNMP, BootP, and DHCP Services
To enable or disable thresholds for a variable, complete the following tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Click on
description on page A-9.
6. Click on
Protocols
Global Protocols
Thresholds
Thresholds
Threshold Enable
Help
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
parameter.
or see the parameter
. You return to the Configuration Manager
Specifying a Value for the Threshold Level
You can specify an integer value that determines the level (low, medium, or high)
at which you want the agent to generate a threshold exception event for a variable.
To specify a value for the threshold level, complete the following tasks:
Site Manager Procedure
You do this System responds
The Protocols menu opens.
opens.
window.
3-34
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
Protocols
Global Protocols
Thresholds
Thresholds
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
The Protocols menu opens.
opens.
(continued)
308644-15.1 Rev 00
Page 95

Customizing SNMP
Site Manager Procedure
You do this System responds
5. Set the following parameters:
• Threshold Low Value
• Threshold Medium Value
• Threshold High Value
Click on
descriptions beginning on page A-10
6. Click on
or see the parameter
Help
.
. You return to the Configuration Manager
Done
(continued)
window.
Specifying the Severity Level for Event Messages
You can specify the severity level of the event message that the agent generates
when a variable exceeds a low, medium, or high threshold level.
You can specify one of these severity levels:
• Information: allows low, medium, or high threshold exceptions to generate
routine events that require no action.
• Warning: allows low, medium, or high threshold exceptions to generate events
that indicate that an unexpected situation occurred.
• Debug: allows low, medium, or high threshold exceptions to generate events
To specify the severity level for event messages, complete the following tasks:
308644-15.1 Rev 00
that you can use to solve network problems.
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
Protocols
Global Protocols
Thresholds
Thresholds
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
The Protocols menu opens.
opens.
(continued)
3-35
Page 96

Configuring SNMP, BootP, and DHCP Services
You do this System responds
5. Set the following parameters:
• Threshold Low Event Level
• Threshold Medium Event Level
• Threshold High Event Level
Click on
descriptions beginning on page A-10
6. Click on
or see the parameter
Help
. You return to the Configuration Manager
Done
Specifying Threshold Units
You can specify the units used to determine whether a variable has exceeded a
threshold.
• To generate a threshold event when the variable’s rate of change per second
reaches a threshold, set the Threshold Units parameter to Persecond.
• To generate a threshold event when the value of the variable reaches a
threshold, set the Threshold Units parameter to Absolute.
To specify threshold units, complete the following tasks:
Site Manager Procedure
.
window.
(continued)
3-36
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Click on
description on page A-13
6. Click on
Protocols
Global Protocols
Thresholds
Thresholds
hreshold Units
T
Help
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
parameter.
or see the parameter
.
. You return to the Configuration Manager
The Protocols menu opens.
opens.
window.
308644-15.1 Rev 00
Page 97

Determining When to Record Threshold Events
You can determine when the agent generates a threshold event by setting the
Threshold Action parameter.
By default, the agent generates a threshold event when the value of the variable
you specify is greater than the threshold that you specify. If you want the agent to
generate threshold events when the value of the variable is less than the threshold
that you specify, set the Threshold Action parameter to Lessthan.
To determine when to record threshold events, complete the following tasks:
Site Manager Procedure
You do this System responds
Customizing SNMP
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Click on
description on page A-13.
6. Click on
Protocols
Global Protocols
Thresholds
Thresholds
hreshold Action
T
Help
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
parameter.
or see the parameter
. You return to the Configuration Manager
The Protocols menu opens.
opens.
window.
Specifying the Maximum Number of Successive Alarms
Successive alarms represent two or more polling periods when the agent generates
an alarm as a result of an exception at the same threshold level. By default, the
maximum number of successive alarms is set to 5.
You can specify the maximum number of successive alarms that the agent
generates for a variable. When the agent exceeds the maximum number of alarms,
it marks the threshold as held. The agent generates no more alarms until the
variable either crosses the threshold at a different level or crosses no threshold for
the number of polling intervals equal to the value of the Threshold HoldDown
Intervals parameter.
308644-15.1 Rev 00
3-37
Page 98

Configuring SNMP, BootP, and DHCP Services
To specify the maximum number of successive alarms, complete the following
tasks:
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Alarms
the parameter description on page A-14
6. Click on
Protocols
Global Protocols
Thresholds
Thresholds
T
hreshold Max Successive
parameter. Click on
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
or see
Help
. You return to the Configuration Manager
The Protocols menu opens.
opens.
.
window.
Specifying Polling Intervals for Held Variables
You can specify the number of exception-free polling intervals through which a
variable in a held state must pass before the variable is no longer considered held.
The lower the number that you specify, the more likely the agent is to generate
repetitive event messages for a variable that is intermittently exceeding thresholds.
To specify the number of exception-free polling intervals through which a variable
in a held state must pass before the variable is no longer considered held, complete
the following tasks:
3-38
Site Manager Procedure
You do this System responds
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
Protocols
Global Protocols
Thresholds
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
The Protocols menu opens.
(continued)
308644-15.1 Rev 00
Page 99

Customizing SNMP
Site Manager Procedure
You do this System responds
4. Choose
5. Set the
parameter. Click on
parameter description on page A-14
6. Click on
Thresholds
Threshold HoldDown Intervals
Done
. The Thresholds Interface Lists window
or see the
Help
. You return to the Configuration Manager
Specifying a Threshold Object Name
By default, the ASN.1 object identifier is the object name that appears in the
threshold event message. You can replace the ASN.1 object identifier by
specifying a name for the object in string format. The string that you enter appears
in the log file, making it easier to identify the object that is the subject of the trap.
To specify a threshold object name, complete the following tasks:
Site Manager Procedure
You do this System responds
(continued)
opens.
.
window.
308644-15.1 Rev 00
1. In the Configuration Manager window,
choose
2. Choose
3. Choose
4. Choose
5. Set the
Click on
description on page A-15
6. Click on
Protocols
Global Protocols
Thresholds
Thresholds
hreshold Label
T
Help
Done
.
. The Global Protocols menu opens.
. The Thresholds menu opens.
. The Thresholds Interface Lists window
parameter.
or see the parameter
.
. You return to the Configuration Manager
The Protocols menu opens.
opens.
window.
3-39
Page 100

 Loading...
Loading...