Page 1
Configuring BaySecure Firewall-1
BayRS Version 13.00
Site Manager Software Version 7.00
Part No. 303515-A Rev 00
October 1998
Page 2

4401 Great America Parkway 8 Federal Street
Santa Clara, CA 95054 Billerica, MA 01821
Copyright © 1998 Bay Networks, Inc.
All rights reserved. Pr inted in the USA. October 1998.
The information in this document is subject to change without notice. The statements, configurations, technical data,
and recomm endations in this document are believed to be accurate and reliable, but are presented without express or
implied warranty. Users must take full responsibility for their appli cations of any products s pecified in this document.
The information in this document is proprietary to Bay Networks, Inc.
The software described in this document is furnished under a license agreement and may only be used in accordance
with the te rms of that license. A summary of the S oftware License is included in this document.
Trademarks
ACE, AFN, AN, BCN, BLN, BN, BNX, CN, FRE, LN, Optivity, PPX, Quick2Conf ig, and Bay Networks are
registered tradema rks and Advanced Remote Node, ANH, ARN, ASN, BayRS, BaySecure, BayStack, BayStream,
BCC, BCNX, BLNX, EZ Install, EZ Internetwork, EZ LAN, FN, IPAutoLearn, PathMan, RouterMan, SN, SPEX,
Switch Node, System 5000, and the Bay Netw orks logo are trademarks of Bay Networks, Inc.
Microsoft , MS, MS-DOS, Win32, Windows, and W indows NT are r egistered tr ademarks of Microsoft Corporation.
All other trademarks and registered trademarks are the property of their respective owners.
Restricted Rights Legend
Use, duplication, or disclosure b y the United States Government is subject to restrict ions as set forth in subparagraph
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement th at may pertain to, or accompany the delivery of, this com puter
software, the rights of the Unite d States Government regarding its use, reproduction, and disclosure are as set forth in
the Commercial Computer Software-Restricted Rights clause at FAR 52.227-19 .
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, Bay Networks, Inc. reserves the
right to make changes to the products described in this document with out notice.
Bay Networks, Inc. does not assume any liability that may occur due to the use or application of the product( s) or
circuit layout(s) described herein.
Portions of the code in this software product may be Copyright © 1988, Regents of the University of California. All
rights reserved. Red istribution and use in source and binary forms of such portions are permit ted, provided that the
above copyright notice and this paragraph are duplicated in all such forms and that any documentation, advertising
materials, and other materials related to such distribution and use acknowledge that such portions of the software were
deve loped by the Uni versity of California, Berkeley. The name of the University may not be used to endorse or
promote products derived from such portions of the software without specific prior written permission.
SUCH PORTIONS OF THE SOFTWARE ARE PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIE D WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
In additi on, the program and information contained herein are lice nsed only pursuant to a license agreement that
contains restrictions on use and discl osure (that may incorporate by reference certain limitations and notices imposed
by thir d pa rt ie s).
ii
303515-A Rev 00
Page 3

Bay Networks, Inc. Software License Agreement
NOTICE: Please carefully read this license agreement before copying or using the accompanying software or
instal ling the hardware unit w ith pre-enabled software (each of w hich is referred to as “Software” in this Agree m ent).
BY COPYING OR USING THE SOFTWARE, YOU ACCEPT ALL OF THE TERMS AND CONDITIONS OF
THIS LICENSE AGREEMENT. THE TERMS EXPRESSED IN THIS A GREEM ENT ARE THE ONLY TERMS
UNDER WHICH BAY NETWORKS WILL PERMIT YOU TO USE THE SOFTWARE. If you do not accept these
terms and conditions, return the product, unused and in the original shipping container, within 30 days of purchase to
obtain a credit for the full purchase price.
1. License Grant. Bay Networks, Inc. (“Bay Networ ks”) grants the end user of the Softwar e (“Licensee”) a personal,
nonexcl usive, nontransferab le license: a) t o use the Software either on a singl e com puter or, if applicable, on a single
authori zed de vi ce ide ntified by hos t ID, fo r whi ch it wa s ori gi nal ly acq uir ed ; b) to cop y th e Sof tw ar e so lely f or bac kup
purposes in support of author ized use of the Software; and c) to use and copy the associated user manual solely i n
support of authorized use of the Software by Licensee. This license applies to the Software only and does not extend
to Bay Networks Agent softw are or other Bay Networks softw are products. Bay Networks Agent software or other
Bay Networks software products are licensed for use under the terms of the applicable Bay Networks, Inc. Software
License Agreement that accompanies such software and upon payment by the end user of the applicable licen se fees
for such software.
2. Restrictions on use; reservation of rights. The Software and user manuals are protected under copyr ight laws.
Bay Networks and/or its licensors retai n all title and ownership in bot h the Software and user manuals, including any
revis ions made by Bay Networks or its li censors. The copyright noti ce m ust be reproduced and included with any
copy of any por tion of the Sof tw are or use r manua ls . Licens ee may not modif y, trans late , dec ompi le, di sas semb le, use
for any compe ti ti v e an al ysis, r e v erse e ngi ne er , dis tr ib ute , o r c rea te der i vativ e w ork s fro m th e Sof twa re or u se r man ual s
or any copy, in whole or in part. Except as expressly provided in this Agreement, Licensee may not copy or transfer
the Softw are or user manual s, in whole or in part. The Software and user manuals embody Bay Networks’ and its
licenso rs’ confident ial and proprietary intellectual property. Licensee shall not sublicense, assign, or other w ise
disclos e to any third pa rty the Software, or any information abou t the operation, design, performance, or
implementation of the Software and us er manuals that is confidential to Bay Networks and its li censors; how ever,
Licensee m ay grant permission to its consul tants, subcontractors , and agents to use the Software at License e’s facility,
provided they have agreed to use the Software only in accordance with the term s of this license.
3. Limited warranty. Bay Networks warrants each item of Softwa re, as delivered by Bay Networks and properly
installed and operated on Bay Networks har dw are or other equipment it is ori ginally licensed for, to function
substantially as descri bed in its accomp anying user manual during its warranty period, which begi ns on the date
Softwar e is fi r st shi pped to Licen see . If any it em of Soft war e fai ls to so func ti on du ring i ts warr anty pe ri od, as t he so le
remedy Bay Ne tworks will at its discretion provide a suitable fi x, patch, or workaround for the problem that may be
included in a future Software release. Bay Networks further warrants to Licensee that the media o n which the
Softwar e is provided will be free from defects in materials and workmans hip under norm al use for a period of 90 days
from the date Software is first shi pped to Licensee. B ay Networks will replace defectiv e media at no charge if it is
returned to Bay Networks during the warrant y period along with proof of the date of shipment. This w arranty d oes not
apply i f the media has been d amaged as a result of accident, misuse, or abuse. The Licens ee assumes all responsibility
for selection of the Software to achieve Licensee’s intended results and for the installation, use, and results obtained
from the Software. Bay Ne tworks does not warrant a) tha t the functions contained in the software will meet the
Licensee ’s requirements, b) that the Sof tware will operate in the hardware or software comb inations that the License e
may select, c) that the operation of the Software will b e uninterrupted or error free, or d) that all defects in the
operati on of the Softw are will be corrected. Bay Networks i s not obligated to remedy any Software defect that cannot
be repro duced with the latest Software release. These warranties do not apply to the Software if it has been (i) altered,
except by Bay Networks or in accordance with its instructions; (ii) used in conjunction with another vendor’s product,
resulting in the defect; or (iii) damaged by improper environment, abuse, mi suse, accident, or negligence. THE
FOREGOING WARRANTIES AND LIMITATIONS ARE EXCLUSIVE REMEDIES AND ARE IN LIEU OF ALL
OTHER WARRANTIES EXPRESS OR I MPLIED, INCLUDI NG WITHOUT LIMITATION ANY WARRANTY OF
MERCHANTABILITY OR FITNESS FOR A P ARTICULAR PURPOSE. Licensee is responsible for the security of
303515-A Rev 00
iii
Page 4

its own data and inform ation and for mai ntaining adequate procedures apart from the Software t o reconstruct lost or
altered files, data, or programs.
4. Limitation of liability. IN NO EVENT WILL BAY NETWORKS OR ITS LICENSORS BE LIABLE FOR ANY
COST OF SUBSTITUTE PROCUREMENT; SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL
DAMAGES ; OR ANY DAMAGES RESULTING FROM INACCURATE OR LOST DATA OR LOSS OF USE OR
PROFITS ARISING OUT OF OR IN CONNECTION WITH THE PERFORMANCE OF THE SOFTWARE, EVEN
IF BAY NETWORKS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. IN NO EVENT
SHALL THE LIABILITY OF BAY NETWORKS RELATING TO THE SOFTWARE OR THIS AGREEMENT
EXCEED THE PRICE PAID TO BAY NETWORKS FOR THE SOFTWARE LICENSE.
5. Government L i c en s ees. This provision applies to all Software and documentation acquired directly or indirectly
by or on behalf of the United States Government. The Software and documentation are commercial products, licensed
on the open market at market p rices, and were developed ent irely at pri vate expense and without the use of any U.S.
Government funds. The license to the U. S. Governmen t is granted only with restricted rights, and use, duplica tion, or
disclos ure by the U.S. Go vernment is subject to the restrictions set forth in subparagraph (c)(1) of the Comm ercial
Computer So ftware––Restricted Rights clause of FAR 52.227-19 and the limitations set out in this license for c ivilian
agencies , and subparagra ph (c)(1)(ii) of the Rights in Technical Data a nd C om p uter Software clause of DFARS
252.227-7013, for agencies of the Department of Defen se or their successors, whichever is applicable.
6. Use of Software in the European Communit y. This pr ovision applies to all Software acquired for use within the
European Comm unity. If Licensee uses the Software within a country in the European Com mu n ity, t he Software
Directive enacted by the Council of European Communities Directive dated 14 May , 1991, will apply to the
examination of the Softw are to facili tate interoperability. Licensee agrees to notify Bay Networks of any such
intended examination of the Software and may procure support and assis tance from Bay Networks.
7. Term and termination. This license is effective until terminated; however, all of the restrictions with respect to
Bay Networks’ copyright in the Software and user manuals will cease being effective at the date of expiration of the
Bay Networks copyright; those restrictions relating to use and discl osure of Bay Networ ks’ confidential information
shall continue in effect. Licensee may terminate this license at any time. The license will automatically terminate if
Licensee fails to comply with any of the terms and conditions of the license. Upon termination for any reason,
Licensee will immediately destroy or return to Bay Networks the Software, user manuals, and all copies. Bay
Networks is not liable to Licensee for damages in any form so lely by reason of the terminati on of this license.
8. Export and Re-export. License e agrees not to export, directly or indirectly, the Software or related technical data
or information without first obtaining any required export licenses or other governmental approvals. Without limiting
the fore going, Licensee, on behalf of itself and its subsidiari es and affiliates, agrees that it wil l not, without first
obtaining all export licenses and appr ovals required by the U.S. Governmen t: (i) export, re-export, transfer, or divert
any such Sof tware or technical data, or an y direct product thereof, to any country to whi ch such exports or re-exports
are rest ricted or embargoed under United States ex port control laws and regu lations, or to any national or resident of
such rest ricted or embargoed countr ies; or (ii) provide the Software or related technical data or infor mation to any
military end user or for any m ilitary end use, including the design, development, or production of any chemical,
nuclear, or biological weapons.
9. General. If any provision of this Agreement is held to be invalid or unenforceable by a court of competent
jurisdiction, the remainder of the provisions of this Agreement shall remain in full force and effect. This Agreement
will be governed by the laws of the state of California.
Should you have any quest ions concerning this Agreement, contact Bay Networks, Inc., 4401 Great America
Parkway, P.O. Box 58185, Santa Clara, California 95054-8185.
LICENSEE ACKNOW LEDGES THAT LICENSEE HAS READ THIS AGREEMENT , UNDERSTANDS IT, AND
AGREES TO BE BOUND BY ITS TERMS AND CONDITIONS. LICENSEE FUR THER AGREES THAT THIS
AGREEMENT IS THE ENTIRE AND EXCLUSIVE AGREEMENT BETWEEN BAY NETWORKS AND
LICENSEE, WHICH SUPERSEDES ALL PRIOR ORAL AND WRITTEN AGREEMENTS AND
COMMUNICATIONS BETWEEN THE PARTIES PERTAINING TO THE SUBJECT MATTER OF THIS
AGREEMENT. NO DIFFERENT OR ADDITIONAL TERMS WILL BE ENFORCEABLE AGAINST BAY
NETWORKS UNLESS BAY NETWORKS GIVES ITS EXPRESS WRITTEN CONSENT, INCLUDING AN
EXPRESS WAIVER OF THE TERMS OF THIS AGREEMENT.
iv
303515-A Re v 00
Page 5

Contents
Preface
Before You Begin ..............................................................................................................ix
Text Convent io n s ..... ................................................ ........................................................ . .x
Acronyms .......................................................................................................................... x i
Bay Networks Technical Publications ...............................................................................xi
How to Get Help ...............................................................................................................xii
Chapter 1
BaySecure FireWall-1
Managing Firewall Operation .......................................................... ....... ..... ....... ....... ......1-1
How the Firewall Software Works ............................................................................1-2
Where You Should Go from Here ................................................................................... 1-2
Chapter 2
Installing FireWall-1 Management Software
Obtaining Software Licenses .......................................................................................... 2-1
Obtaining a FireWall-1 License for the Management Station ...................................2-2
Sample Response from Check Point .... .............................................................2-3
Obtaining a FireWall-1 License for the Router .........................................................2-4
Sample Response from Check Point .... .............................................................2-5
Installing and Running the FireWall-1 Management Software ........................................2-5
Installing on a Computer Running Windows NT ......................................................2-5
Sample Installation ............................................................................................2-6
Customizing the FireWall-1 Installation ...........................................................2 -12
Installing on a UNIX Platform ................................................................................. 2 -13
Before You Install .............................................................................................2-13
Mounting the CD and Extracting the Tar File ...................................................2-13
Installing the Check Point FireWall-1 Software ................................................ 2 -14
Installa tion Options ..........................................................................................2-14
Sample Installation .......................................................................................... 2 -14
303515-A Rev 00
v
Page 6

Customizing the FireWall-1 Installation ...........................................................2 -18
Installing a License on the Management Station .............................................2-19
Starting and Stopping the FireWall-1 Daemons . .............................................2-19
Synchronizing the Management Station and the Router Passwords ...............2-19
Starting FireWall-1 ...........................................................................................2-20
Chapter 3
Configuring a Firewall on a Router
Creating a Firewall on the Router ...................................................................................3-1
Before You Begin ...................................................................................................... 3-2
Using Site Manager ..................................................................................................3-2
Enabling or Disabling the Firewall on the Router ............................................................3-4
Setting Up Communications Between the Firewall Management Station
and the Router . ...............................................................................................................3-4
Establishing the Firewall Management Station ........................................................3-4
Establishing a Static Route ................................................................................3-5
Identifying the Router ...............................................................................................3-5
Enabling the Firewall on Router Interfaces .....................................................................3-6
Activating the Firewall .....................................................................................................3-9
Defining a Firewall Security Policy ................................................................................3-11
Installing the Security Policy on the Router and Its Interfaces ...................................... 3 -11
Deleting Firewall from the Router .................................................................................3-12
Deleting Firewall Locally or Remotely Using Site Manager ...................................3-12
Deleting Firewall Dynamically Using the Technician Interface ...............................3 -13
Troubleshooting Checklist ................................ .......... .. ....... .......... .. ....... ....... .......... .. ....3-14
Appendix A
Parameter Descriptions
FireWall Enable Parameter ........................................................................... .......... .. .....A-1
FireWall Par a mete r s ............ ............................................... ...........................................A-2
List FireWall Interfaces Parameters ...............................................................................A-3
Index
vi
303515-A Re v 00
Page 7

Figures
Figure 2-1. Choose Destination Location Window ............................ ..... .. ..... ..... .. ..... .2-6
Figure 2-2. Selecting Product Type Window .......................................... ....... ....... ..... .2-7
Figure 2-3. Licenses Window ..................................................... ....... ....... ..... ....... ......2-8
Figure 2-4. Administrators Window ............................................................................2-9
Figure 2-5. Add Administrators Window . ....................................................................2-9
Figure 2-6. Key Hit Session Window ................ ..... ..... .... ..... ..... .. ..... .. ..... .. ..... ..... .. ....2-10
Figure 2-7. Choose Destination Location Window ............................ ..... .. ..... ..... .. ....2-11
Figure 2-8. Select Components Window ..................................................................2-12
Figure 3-1. Configuration Manager Window ...............................................................3-2
Figure 3-2. Create Firewall Dialog Box .......................................................................3-3
Figure 3-3. List Firewall Interfaces Window ......................... ....... ..... ....... ....... ....... ..... .3-7
Figure 3-4. Values Window ................ .. ..... .. ..... ..... .. ..... .. ..... ..... .. ..... ..... .... ..... ..... .. ..... .3-8
Figure 3-5. Boot Router Window ..............................................................................3-10
303515-A Rev 00
vii
Page 8

Page 9

This guide describes BaySecure™ FireWall-1, and the steps you need to take to
install, configure, and activate a firewall on a Bay Networks® router.
Before You Begin
Before using this guide, you must complete the following procedures. For a new
router:
• Install the router (refer to the installation guide that came with your router).
• Connect the router to the network a nd create a pilot configuration f ile (refer to
Quick-Starting Routers, Configuring BayStack Remote Access, or Connecting
ASN Routers to a Network).
Preface
303515-A Rev 00
Make sure that you are running the latest version of Bay Networks Site Manager
and router software . F or instructions, refer to the upgrade guide.
You will also need to consult the FireWall-1 document from Check Point
Technologies.
ix
Page 10

Configuring BaySecure FireWall-1
Text Conventions
This guide uses the following text conventions:
angle brackets (< >) Indicate that you choose the text to enter based on the
description inside the brackets. Do not type the
brackets when entering the command.
Example: If the command syntax is:
bold text
<ip_address>
ping
ping 192.32.10.12
Indicates text tha t you need to enter and command
, you enter:
names and options.
Example: Enter
Example: Use the
show ip {alerts | routes
command.
dinfo
}
italic text Indicates file and directory names, new terms, book
titles, and variables in command syntax descriptions.
Where a variable is two or more words, the words are
connected by an underscore.
Example: If the command syntax is:
<
show at
valid_route
valid_route>
is one va riable and you subs titu te one value
for it.
screen text Indicates system output , fo r exa mple, prompts and
system messages.
Example:
Set Ba y Netw orks Tr ap Mo nito r Fil ters
separator ( > ) Shows menu paths.
Example: Protocol s > IP identifie s the IP option on the
Protocols menu.
|
vertical line (
) Separates choices for command keywords and
arguments. Enter only one of the choices. Do not type
the vertical line when entering the command.
Example: If the command syntax is:
, you enter either:
show ip {alerts | rou tes
show ip alerts
x
or
}
show ip routes
, but not both.
303515-A Re v 00
Page 11

Acronyms
GUI graphical user interface
IP Internet Protocol
LAN local area networ k
MIB management information base
OSI Open Systems Interconnec tion
TCP/IP Tra nsmission Control Protocol/Internet Protocol
Bay Netwo rks Technical Publications
You can now print Bay Net wor ks technical manuals and release notes free,
directly from the Int ernet. Go to support.bayn etworks.com/libr ary/tpubs/. Fi nd the
Bay Networks product for which you need doc umenta tion. Then locate the
specific category and model or version for your hardware or software product.
Using Adobe Acrobat Reader, you can open the manuals and release note s, sear ch
for the sections you need, and print them on most standard printers. You can
download Acrobat Reader free from the Adobe Systems Web site,
www.adobe.com.
Preface
303515-A Rev 00
You can purchase Bay Networks documentation sets, CDs, and selected te ch nical
publications through the Bay Networks Collateral Catalog. The catalog is loc ated
on the World Wide Web at support.baynetworks.com/catalog.html and is divided
into sections arran ged alpha betically:
• The “CD ROMs” section lists available CDs.
• The “Guides/Books” section lists books on technical topics.
• The “Technical Manuals” section lists available printed documentation sets.
Make a note of the part numbers and prices of the items that you want to order.
Use the “Marketing Collateral Catalog description” link to place an order and to
print the order form.
xi
Page 12

Configuring BaySecure FireWall-1
How to Get Help
For product assista nce, support contracts, or informati on abou t educational
services, go to the following URL:
http://www.baynetworks.com/corporate/contacts/
Or telephone the Bay Networks Technical Solutions Center at:
800-2LANWAN
xii
303515-A Re v 00
Page 13

Chapter 1
BaySecure FireWall-1
BaySecure™ FireWall-1 builds firewall security features into Bay Networks router
software. It does this by integrating the statef ul inspection module from Version
2.1 of the Check Point Software Technologi es FireWall-1 software into the Bay
Networks router operating system of Bay Networks BN
routers. BaySecure FireWall-1 provides all of the security features from Version
2.1 of the Check Point Software Technologi es FireWall-1 software, except for
user authentication, address translation, statistics and encryption.
®
, ASN™ and ARN™
Managing Firewall Operation
A firewall is the hardware and/or software that limits the exposure of a computer
or network to an invasion from an external source. To control the operation of the
firewall on the router , you use the Check Point FireWa ll-1 management software.
You install this management software on either a computer runnin g
Windows NT or on a UNIX workstation to create a firewall management station.
From the management station, you can use the FireWall-1 management software
to define a security policy and download it to the router. The security policy
specifie s how the firewa ll operates. For instructions on how to install the
FireWall-1 management software, see Chapter 2
Management Software.” To learn how to configure a security polic y, see your
Check Point documentation .
303515-A Rev 00
, “Installing FireWall-1
1-1
Page 14
Configuring BaySecure FireWall-1
How the Firewall Software Works
The stateful inspect ion module in the Bay Networks router software inspects all
data packets traveling betwee n the data link a nd network la yers an d communica tes
the results to the management station. If the data packets meet the security
requirements specified in the security policy, the router forwards the data. If the
data packets violate the security policy, the route r drops the data packe ts, and logs
the information to the management station.
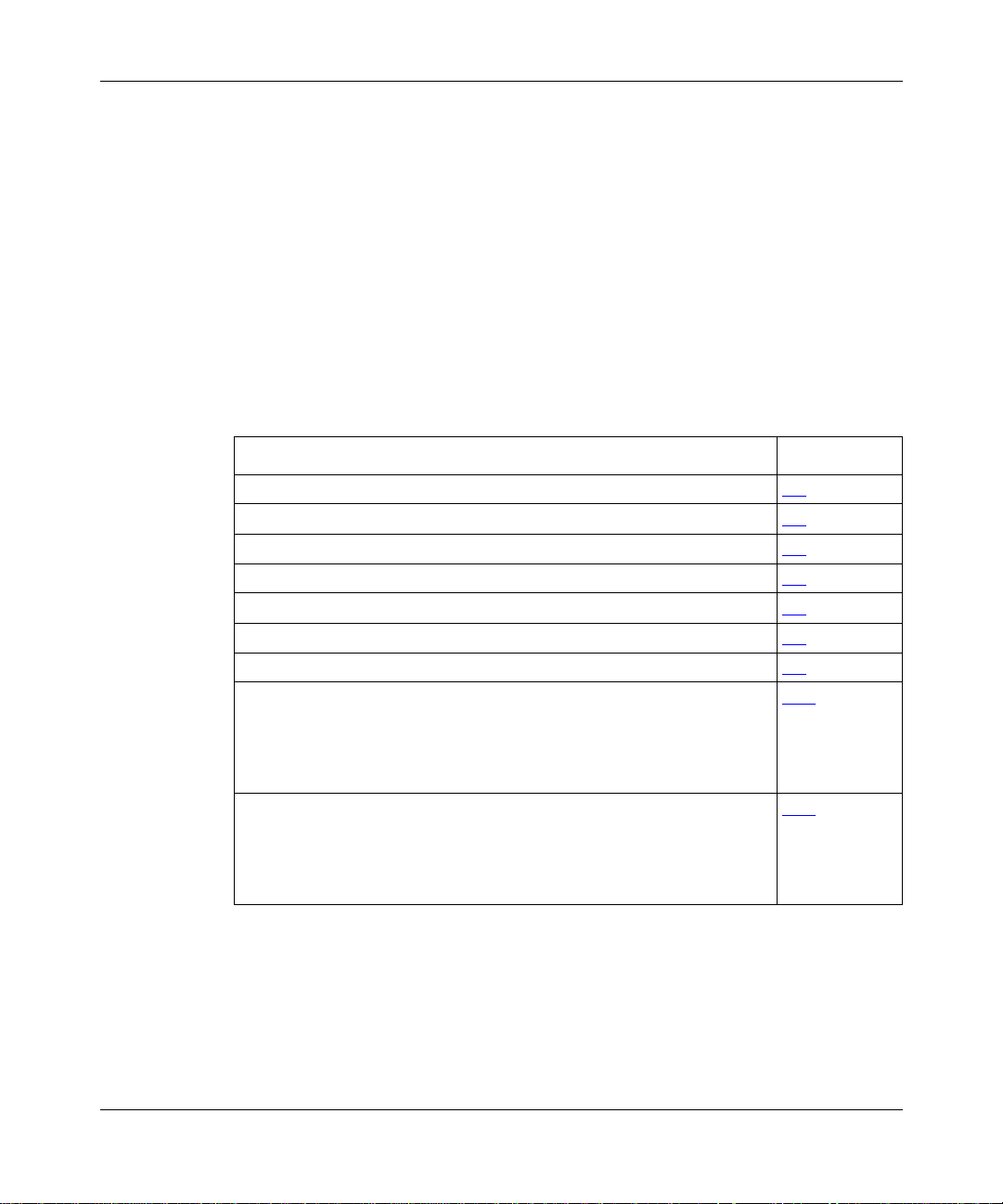
Where You Should Go from Here
To get a firewa ll up and running on your Bay Networks router:
For informati on on how to Go to page
Obtain licenses fro m Chec k Point 2-1
Install the Check Point Management software 2-5
Create a firewall 3-1
Enable the firewall on the router 3-4
Establish a relat ionship between the manageme nt st ation and the router 3-4
Enable the route r on specific interfaces 3-6
Activate the firewall 3-9
Configure a firewall security policy 3-11
Install the security policy on the router 3-11
and see your
Check Poin t
FireWall-1
documentation
and see your
Check Poin t
FireWall-1
documentation
1-2
303515-A Re v 00
Page 15

Chapter 2
Installing FireWall-1 Management Software
To install the FireWall-1 software, see the following sections:
T opic Page
Obtaining Software Licenses
Installing and Runni ng the FireWall-1 Management Software 2-5
Obtaining Software Licenses
Before you ca n inst all the FireWall-1 software an d crea te a firewall on the router,
you must first obta in a permanent sof tware license from Check Point Software
Technologies for:
• The fire wall management station
You need one softwar e li cense for the firewall mana gement station, a PC or
UNIX workstation used to manage t he firewall software on the Bay Networks
router.
• The router
You need one software license for each Bay Netw orks router protected by the
firewall software.
2-1
303515-A Rev 00
2-1
Page 16

Configuring BaySecure FireWall-1
Obtaining a FireWall-1 License for the Management Station
To obtain a FireWall-1 license for the fir ewall management station, follow these
instructions :
You need one license for each FireWa ll-1 management station. To
Note:
obtain a license for each additional management station, you must repeat the
steps outlined in this section.
Locate your certificate key.
1.
A certificate key (serial number) is located on a sticker on the inside of the CD
folder containing the Check Point FireWall-1 management software media. If
you lose the certificate key bearing the FireW all-1 serial number, contact Bay
Networks.
Contact Check Point Software T e chnologies.
2.
To obtain a permanent license, you must contact Ch eck Poi nt with your
certif icate key information. You can reach Check Point in any of these ways:
• Via the World Wide Web at http://license.CheckPoint.com
2-2
• By sending mail to license@checkpoint.com
• By phoning Check Point:
800-429-4391 (North America)
+972-3-613-1833 (outside North America)
When requesting a license, you must also be prepared to provide the IP
address of the management station on which you plan to install the license.
303515-A Re v 00
Page 17

Installing FireWall-1 Management Software
Sample Response from Check Point
Your license request with the following details has been accepted.
Below you will find the corresponding license string.
We recommend printing this page and saving it in your files for future
reference.
Request Details
--------------Certificate Key: 5xxx 5xxx fxxx
Customer Name: Bay Networks
Product: CPFW-ESC-U
Version: 3.0
Host ID: 123.123.123.123
License(s) Issued
----------------Host ID: 123.123.123.123
Features: control
License String: 7xxxxxxx-8xxxxxxx-fxxxxxxx
License(s) Installation
----------------------run 'fw putlic 123.123.123.123 7xxxxxxx-8xxxxxxx-fxxxxxxx control '
303515-A Rev 00
Contact Information
------------------This Check Point product has been purchased through: Bay Networks
If you need to chang e the IP ad dres s of the Fire Wall-1 managem en t
Note:
station, contact Check Point at 800-429-4391 (North America) or
+972-3-613-1833 (locations outside of North America).
For information about how to install the license, refer to the section “Installing
and Running the FireWall-1 Management Software” on page 2-5 and the Check
Point FireWall-1 documentation.
2-3
Page 18

Configuring BaySecure FireWall-1
Obtaining a FireWall-1 License for the Router
To obtain a FireWall-1 license for a router you plan to prote ct with a firewall,
follow these instructions:
You need one license for each router that you plan to protect with a
Note:
firewall. To obtain a license for each additional r outer, you must repeat the
steps outlined in this section.
Locate your certificate key.
1.
A certificate key (serial number) is located on a sticker on the inside of the CD
folder containing the Check Point Fi reWall-1 software media. If you lose the
certif icate key bearing the FireWall-1 serial number, contact Bay Networks.
Contact Check Point Software T e chnologies.
2.
T o obt ai n a permanent lic ense, you must c ontact Chec k Point. To process your
request, Check Point requires your certificate key and the IP address of the
router you plan to protect with a firewall.
You can reach Check Point in any of these ways:
2-4
• Via the World Wide Web at http://license.CheckPoint.com
• By sending mail to license@checkpoint.com
• By phoning Check Point:
800-429-4391 (North America)
+972-3-613-1833 (outside North America)
To synchronize the FireWall-1 password on the router and the management
station, use the
fw putkey
command. See “Synchronizing the Management
Station and the Router Passwords” on page 2-19.
303515-A Re v 00
Page 19

Installing FireWall-1 Management Software
Sample Response from Check Point
The following license was generated:
We recommend printing this page and saving it in your files for future
reference.
Request Details
--------------Certificate Key: 7xxx dxxx 1xxx
Customer Name: Bay Networks
Product: BABN-IM-U
Version: 3.0
Host ID: 012.012.012.012
License Issued
-------------Host ID: 012.012.012.012
Features: embedul
License String: 7fff6161-408d3b21-a161c10f
License Installation
-------------------run 'fw putlic 012.012.012.012 7fff6161-408d3b21-a161c10f embedul '
Installing and Running the FireWall-1 Management Software
Once you obtain a FireWall-1 licens e from Check Point, you c an install the Check
Point FireWall-1 management software on a computer running either
Windows NT or UNIX.
Installing on a Computer Running Windows NT
Use the following sections as a guide to installing the FireWall-1 management
software on a computer running Windows NT. For more details, refer to your
Check Point FireWall-1 documentation.
303515-A Rev 00
2-5
Page 20

Configuring BaySecure FireWall-1
Sample Installation
The follo wing sample inst alla tion tak es the Check P oint FireWall-1 softw are from
a CD and installs it onto a PC running W indows NT. Use this sample installation
to familiariz e yourself with a basic FireWall-1 installation.
This sample installation shows only those screens necessary for a basic
Note:
installation.
Installing the Management Software
Insert the CD into the CD-ROM drive and run the Setup program,
1.
setup.exe
. To specify the name and location of the program to run, enter
(where D is the name of your CD-ROM drive):
D:
\windows\fw1\setup.exe
The Choose Destination Location window (Figure 2-1) opens.
2-6
Figure 2-1. Choose Destination Location Window
Choose a destination directory. You can either accept the default
2.
directory (Program Files) or make another selection.
Click on Next.
3.
303515-A Re v 00
Page 21

Installing FireWall-1 Management Software
The Selecting Product Type window (Figure 2-2) opens.
Figure 2-2. Selecting Prod uct Type Window
Choose the FireWall-1 component you want to install. To be compatible
4.
with BaySecure FireWall-1, choose FireWall-1 Enterprise Management
Console Product.
303515-A Rev 00
2-7
Page 22

Configuring BaySecure FireWall-1
Click on Next.
5.
The Licenses windo w (Figure 2-3)
Figure 2-3. Licenses Window
Enter the license information you obtained from Check Point.
6.
opens.
2-8
303515-A Re v 00
Page 23

Installing FireWall-1 Management Software
Click on Next.
7.
The Administrators window (Figure 2-4)
Figure 2-4. Administrato rs Wind ow
You must specify at least one administrator.
Click on Add.
8.
The Add Administrator window (Figure 2-5)
opens.
opens.
303515-A Rev 00
Figure 2-5. Add Administrat ors Window
Enter the administrator’s user name and password, which is limited to
9.
eight characters, and a password confirmation, and click on OK. You
return to the Admin istr a to rs win do w.
2-9
Page 24

Configuring BaySecure FireWall-1
Click on Next.
10.
The GUI Clients window opens. Do not enter any GUI clients at this time.
Click on Next.
11.
The Remote Modules window appears. Do not enter any remote modules at
this time.
Click on Next.
12.
The Key Hit Sessi on window (Figure 2-6)
Figure 2-6. Key Hit Session Window
Follo w the directions in the window and enter random characters, with a
13.
opens.
delay of a few seco nd s between them, unti l the ind i cato r bar is ful l .
2-10
Be sure not to type the same character twice in a row to vary the delay
between the characters.
303515-A Re v 00
Page 25

Installing FireWall-1 Management Software
Click on Next.
14.
The CA Key window ope ns.
Click on Generate to generate a new key .
15.
The host uses the RSA key to generat e a digita l signal for authenticating its
communications in its capacity as a Certificate Authority.
Generating the key may take several minutes.
Click on Finish.
16.
Installing the GUI Client
Insert the CD into the CD-ROM drive and run the
1.
setup.exe
file. To
specify the na me a nd l oca ti on of the progr a m to run, en ter (w h ere D is
the name of your CD-ROM drive):
\windows\gui_client\disk1\setup.exe
D:
The Choose Destination Location window (Figure 2-7) opens.
Choose a destination directory.
2.
303515-A Rev 00
Figure 2-7. Choose Destination Location Window
You can either accept the default directory (Program Files) or make anothe r
selection.
2-11
Page 26

Configuring BaySecure FireWall-1
Click on Next.
3.
The Select Components window (Figure 2-8)
Figure 2-8. Select Components Window
Install the S ecurit y P olicy, System Status, and Log V ie wer components b y
4.
opens.
clicking on ea ch item.
2-12
Customizing the FireWall-1 Installation
You can customize your Fire Wall-1 installation by running the FireWall-1
Configuration file.
To execute the f ile, enter:
\Start\Programs\FireWall-1\FireWall-1 Configuration
D:
Using the FireWall-1 Configuration file , you can add:
• A license
• Administrators
• GUI clients
• Remote modules
• CA keys
For more information, refer to your Check Point documentation.
303515-A Re v 00
Page 27

Installing on a UNIX Platform
Use the following sections as a guide to installing the FireWall-1 software on a
computer running UNIX. For more details, refer to your Check Point FireWall-1
documentation.
Before You Install
Before you attempt to install the Check Point FireWall-1 software, be sure that
you have completed these tasks:
• Obtain a FireWall-1 license for each firewall management station and router
that you plan to protect with a firewall.
• Add setenv FWDIR/etc/fw to your .cshrc file,
or add FWDIR=/etc/fw to your .cshrc file and, if using the korn shell, export FWDIR
to your .profile file; if using the c shell, setenv FWDIR to your .profile file.
• Add /etc/fw/bin to your path.
• Add /etc/fw/man to your MANP ATH envir onment.
Installing FireWall-1 Management Software
303515-A Rev 00
Mounting the CD and Extracting the Tar File
Check Point dist rib utes its FireWall-1 software on CD-R OM. You must supply the
UNIX commands to mount the CD drive and e xtr act the tar files.
The commands to mount a CD drive and extr act the tar fi les v ar y depe nding on the
device name of the CD drive, the operating system used, and other environmental
factors. Use the instructions that follow only as guidelines for mounting the CD
drive and extracting the tar files. The commands you need may differ.
For SunOS
lab#
lab#
lab#
mount -r -t hsfs /dev/sr0 /cdrom
cd /tmp
tar xvf /cdrom/sunos4/fw1/fw.sunos4.tar
For Solaris
lab#
lab#
lab#
mount - F hsfs -r /dev/sr0 / cdrom
cd /tmp
tar xvf /cdrom/solaris2/fw1/fw.solaris2.tar
2-13
Page 28

Configuring BaySecure FireWall-1
For HPUX
lab#
lab#
lab#
mount -r /dev/dsk/c1t2d0 (or your specific CD-ROM address) /cdrom
cd /tmp
tar xvf “/cdrom/HPUX/FW1/FW.HPUX.TAR;1”
Installing the Check Point FireWall-1 Software
Once you have extracted the Check Point FireWall-1 file s, you can install the
management softwa re. To install the sof tware, change director ies so that you’re in
the directory where you put the extracted files and then issue the
fwinstall
command.
For exa mple, if you e xtracte d the f il es into your /tmp d irector y, instal l the so ftwa re
by entering the following commands:
lab#
lab#
cd /tmp
./fwinstall
Installation Options
Note that during the ins ta llation , the script a sks y ou to se lect the Fir eWall-1 opti on
you want to install. To be compatible with BaySecure FireWall-1, enter selection
3, FireWall-1 Enterprise Management Console Product. A sample follows.
Which of the following FireWall-1 options do you wish to install?
(1) FireWall-1 Enterprise Product
(2) FireWall-1 Single Gateway Product
(3) FireWall-1 Enterprise Management Console Product
(4) FireWall-1 FireWall Module
(5) FireWall-1 Inspection Module
2-14
Enter yo ur se le ct ion (1-7/a) :
3
Sample Installation
The follo wing sample inst alla tion tak es the Check Point F ireWall-1 software from
a CD-ROM and installs it onto a SparcStation running SunOS. Use this sample
installation to familiariz e yourself with the FireWall-1 installation sc ri pt.
Note:
In the following sa mple installation, all user input is in
bold
.
303515-A Re v 00
Page 29

Installing FireWall-1 Management Software
**************** FireWall-1 v3.0 Installation ****************
Reading fwinstall configuration. This might take a while.
Please wait.
Configuratio n loaded. Running FireWall-1 Setup.
Checking available options. Please wait.....................
Which of the following FireWall-1 options do you wish to install/
configure ?
------------------------------------------------------------------
-----
(1) FireWall-1 Enterprise Product
(2) FireWall-1 Single Gateway Product
(3) FireWall-1 Enterprise Management Console Product
(4) FireWall-1 FireWall Module
(5) FireWall-1 Inspection Module
Enter yo ur se le ct ion (1-5/a) :
Installing/Configuring FireWall-1 Enterprise Management Console
Product.
Please wait...
Selecting wher e to install FireWall-1
---------------------------------------
FireWall-1 requires approximately 9017 KB of free disk space.
Additional space is recommended for logging information.
Enter destination directory [/etc/fw]):
Checking disk space availability...
Installing FW under /etc/fw (50836 KB free)
Are you sur e (y /n ) [y ] ?
Software distribution extraction
--------------------------------
Extracting software distribution. Please wait ...
Software Distribution Extracted to /etc/fw
Instal li ng li ce nse
------ -- --- -- -----
Reading pre-installed license file fw.LICENSE... done.
3
<RETURN>
y
303515-A Rev 00
2-15
Page 30

Configuring BaySecure FireWall-1
The following evaluation License key is provided with this
FireWa ll -1 di st ribution
Eval 15Mar97 3.x pfmx controlx routers connect motif
Do you want to use this evaluation FW-1 license (y/n) [y]?
Do you wish to start FireWall-1 automatically from /etc/rc.local
(y/n) [y] ?
Welcome to FireWall-1 Configuration Program
===========================================
This program will guide you through several steps where you
will define your FireWall-1 configuration. In any later time,
you can reconfigure these parameters by running fwconfig
Configuring Licenses...
=======================
The following licenses are installed on this host:
Eval 15Mar97 3.x pfmx controlx routers connect motif
n
n
Do you want to add licenses (y/n) [n] ?
Configuring Administrators...
=============================
No FireWall-1 Administrators are currently defined for this
Manage me nt St at ion.
Do you want to add users (y/n) [y] ?
Configuring GU I clients...
==========================
GUI clients are trusted hosts from which FireWall-1 Administrators
are
allowed to log on to this Management Station using Windows/X-Motif
GUI.
Do you want to add GUI clients (y/n) [y] ?
Configuring Remote Modules...
=============================
Remote Modules are FireWall or Inspection Modules that are going
to be controlled by this Management Station.
Do you want to add Remote Modules (y/n) [y] ?
n
n
n
n
2-16
303515-A Re v 00
Page 31

Installing FireWall-1 Management Software
Configuring Groups...
=====================
FireWall-1 access and execution permissions
-------------------------------------------
Usually, FireWall-1 is given group permission for access and
execution.
You may now name such a group or instruct the installation
procedure
to give no group permissions to FireWall-1. In the latter case,
only the
Super-User will be able to access and execute FireWall-1.
Please specify group name [<RET> for no group permissions]:
No group permissions will be granted. Is this ok (y/n) [y] ?
Configuring Random Pool...
==========================
You are now asked to perform a short random keystroke session.
The random data collected in this session will be used for
generating Certificate Authority RSA keys.
Please enter random text containing at least six different
characters. You will see the '*' symbol after keystrokes that
are too fast or too similar to preceding keystrokes. These
keystrokes will be ignored.
Please keep typing until you hear the beep and the bar is full.
[ ] *
Thank yo u.
Configuring CA Keys...
======================
fw: no license for 'ca'
The installation procedure is now creating an FWZ Certificate
Authority Key
for this host. This can take several minutes. Please wait...
fw: no license for 'ca'
y
303515-A Rev 00
Configuration ended successfully
**************** FireWall-1 is now installed. ****************
Do you wish to start FW-1 now (y/n) [y] ?
******************************************************************
*
n
2-17
Page 32

Configuring BaySecure FireWall-1
Configuration ended successfully
**************** FireWall-1 is now installed. ****************
Do you wish to start FW-1 now (y/n) [y] ?
******************************************************************
*
DO NOT FORGET TO:
1. add the line: setenv FWDIR /etc/fw to .cshrc
or FWDIR=/etc/fw; export FWDIR to .profile
2. add /etc/fw/bin to path
3. add /etc/fw/man to MANPATH environment
******************************************************************
*
You may configure FireWall-1 anytime, by running fwconfig.
****** ** *** ** *** Instal la tio n complete d suc ce ss fully
****** ** *** ** ***
n
Customizing the FireWall-1 Installation
You can use the
fwconfig
Using
fwconfig
, you can add or remove:
command to customize your FireWall-1 installation.
• A license
• Administrators
• Groups
2-18
• GUI clients
• Remote modules
• CA keys
Note:
To add an administrator, you must first add a grou p to which the user is
a member . If you do not add a group, then you can run the GUI using only the
fwui
command if you are logged in as root.
For further deta ils, refer to your Check Point FireWall-1 documentation.
303515-A Re v 00
Page 33

Installing FireWall-1 Management Software
Installing a License on the Management Station
To install a license on the firewall management station, use the following
command:
fw putlic
The
The
<hostid> <lic_stri ng>
<hostid>
<lic_string>
is the host ID of the management station.
is a string of alphanumeric characters that Check Point provides
pfmx cont rolx route rs mo t if em bedded
with your FireWall-1 license.
Starting and Stopping the FireWall-1 Daemons
To start the FireWall-1 daemons, use the
fwstart
command. For example, at the
system prompt, enter:
lab#
fwstart
To stop the FireWall-1 daemons, use the
fwstart
command. For example, at the
system prompt, enter:
lab#
fwstop
Synchronizing the Management Station and the Router Passwords
Once you have inst al led licenses on the firewa ll management station and the
router, you must synchronize your password on the two systems. To synchronize
the router and the management station passwords, enter the following commands:
303515-A Rev 00
• On the firewall management station:
fw putkey -p
<password> <ip_address_fwall_router>
• On the router:
fwputkey
where is
<password>
<ip_address_fw all_rou ter>
<ip_address_mgm t_station>
<password> <ip_address_mgmt_stat ion>
A s tring of alph anumeric char acters tha t specifies y our
password
The IP address of your firewalled router
The IP address of your FireWall-1 GUI management
station
2-19
Page 34

Configuring BaySecure FireWall-1
Starting FireWall-1
To start Fir eWall-1, enter the
command. For e xample, at the sys tem p rompt,
fwui&
enter:
lab#
fwui&
Optionally, you can use the FireWall-1 XMotif GUI. For instructions on how to
install and start the XMoti f GUI, see you Check Point documentation.
2-20
303515-A Re v 00
Page 35

Chapter 3
Configuring a Firewall on a Router
To configure a f ir ewall on the router, see the following topics:
T opic Page
Creating a Firewall on the Router
Enabling or Disabling the Firewall on the Rout er 3-4
Setting Up Communications Between the Firewall Management Station and
the R o uter
Enabling the Firewall on Router Interfaces 3-6
Activating the Firewall 3-9
Defining a Firewall Security Pol icy 3-11
Installing the Sec urit y Policy on the Router and Its Interfaces 3-11
Deleting Firewall from the Router 3-12
Troubleshooting Checklist 3-14
Creating a Firewall on the Router
This section expla ins how to cre ate a fir e wall on a Bay Networ ks router using Si te
Manager .
3-1
3-4
303515-A Rev 00
3-1
Page 36

Configuring BaySecure FireWall-1
You can also use the Technician Interface, whic h lets you modify parameters by
issuing
set
and
commit
is equivalent to modifying parameters using Site Manager. For more information
about using the Technicia n In terface to access the MIB, refer to Using Technician
Interface Software.
commands that specify the MIB object ID. This process
Caution:
that the value you enter for a parameter is valid. Entering an invalid value can
corrupt your conf iguration.
Before You Begin
Before you begi n, you must first configure and enable IP on the router a nd enable
TCP on all slots on the router. For instructions , se e Quick-Starting Routers.
Using Site Manager
Begin by start ing Site Manager. Then follow these steps:
Select Configu ra tion Manager in either local, remote, or dynamic mode
1.
from the Tools menu.
The Configuration Manager window opens (Figure 3-1)
Unlike using Site Mana ger, the Technician Interface does not verify
.
3-2
Figure 3-1. Configurati on Manager Window
303515-A Re v 00
Page 37

Configuring a Firewall on a Router
If local or remote mode is selected, open a configuration file .
2.
Create a firewall:
3.
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Platform
2. Choose
3. Choose
4. Click on
.
FireWall
Create
OK
. The FireWall menu opens.
. A dialog box opens. See Figure 3-2
The Platform menu opens.
.
You return to the Configuration Manager
window.
By default, the firewall is automatically enabled on the router. To change this
status, see “Enabling or Disabling the Firewall on the Router
” on page 3-4.
create_war ning
Figure 3-2. Create Firewall Dialog Box
303515-A Rev 00
3-3
Page 38

Configuring BaySecure FireWall-1
Enabling or Disabling the Firewall on the Router
When you first create a firewall, it is enabled by default.
Note:
To enable or disable the firewall on the router:
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Platform.
2. Choose
3. Choose
4. Set the
or see the parameter des cription on
page A-1
5. Click on OK. You return to the Configuration Manager
FireWall
Global.
Enable
.
. The FireWall menu opens.
parameter. Click on
Help
The Platform menu opens.
The FireWall Enable window opens .
window.
Setting Up Communications Between the Firewall Management Station and the Router
The fire wall cannot protect your router until you set up communications between
the fire wall management station and the router.
T o e stabli sh thi s relati onship , you must use the same IP addr ess you used to obta in
FireWall-1 licenses for the firewall management station and the router.
Establishing the Firewall Management Station
3-4
The fire wall management station is the PC or UNIX workstation where you
installed the Fire Wall-1 software. You use the firewall management station to
enforce the firewall security policy that you created for the router. The
management station also logs all attempted violations of the security policy. (To
define a security policy, see “Defining a Firewall Security Policy
” on page 3-11.
You will also need to consult your Check Point FireWall-1 documentation.)
303515-A Re v 00
Page 39

Configuring a Firewall on a Router
To identify the management stati on to the route r:
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Platform
2. Choose
3. Choose
4. Set the
Click on
description on page A-2
5. Click on OK. You return to the Configuration Manager
.
FireWal
FireWall Parameters
Log Host IP Address
Help
Establishing a Static Route
You may need to establish a static route between the router and the management
station before you configure the parameters. By default, FireWall-1 filters
in-bound routing protoc ol packets from RIP or OSPF . Therefore, if your router
and firewall managem en t stat ion are o n different subnets, you will need to
establish a static ro ute on the router, pointing to the management station's subnet;
otherwise, your management station will be unable to communicate with the
router. For information about creating a static route, see Configuring IP Services.
Identifying the Router
The Platform menu opens.
l. The FireWall menu opens.
.
parameter.
or see the parameter
.
window.
303515-A Rev 00
To identify the router prote cted by the firewal l:
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Platform
2. Choose
3. Choose
.
FireWall
FireWall Parameters
. The FireWall menu opens.
. The FireWall Parameters window opens.
The Platform menu opens.
(continued)
3-5
Page 40

Configuring BaySecure FireWall-1
Site Manager Procedur e
You do this System responds
4. Set the
parameter. Click on
parameter descri pti on on pageA-2
5. Click on OK. You return to the Configuration Manager
Local Interface IP Address
Help
or see the
.
(continued)
window.
Enabling the Firewall on Router Interfaces
After you have created a fi rewall on the ro uter, you can enab l e it on on e or more
interfaces.
To enable a firewall on router interfaces:
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Protocols
2. Choose
3. Choose
4. Click on
5. Click on
or choose a
router inter faces by connection type.
6. Click on
interf aces, or highlight indiv idual
interfaces.
7. Click on OK. Site Manager retu rns you to the List
8. Set the FireWall
highlighted interface. Click on
the parameter description on page A- 3
.
IP .
FIREWALL
Add
All
to display all router interface s
connection button
Check All
. The List FireWall Int erfaces window
. The Values window opens. See
to display
to highlight all li sted
Name
parameter for the
Help
or see
The Protocols menu opens.
The IP menu opens.
opens. See Figure 3-3
Figure 3-4
Site Manager lists the interfaces at the
top of the screen.
FireWall Interfaces window. See
Figure 3-3
.
.
.
.
(continued)
3-6
303515-A Re v 00
Page 41

Configuring a Firewall on a Router
Site Manager Procedur e
You do this System responds
9. Set the
or see the parameter des cription on
page A-3
10.Click on Done. You return to the Configuration Manager
Disable
.
parameter. Click on
Help
(continued)
window.
303515-A Rev 00
Figure 3-3. List Firewall Interfaces Window
3-7
Page 42

Configuring BaySecure FireWall-1
Note:
Once the fire wall is prote cting your ro uter , if you put f ire w all pro tection
on a new interface, the new interface will use the default security policy
supplied by Check Point, which prevents the ne w interface from
communicating with the route r.
You can download your customized security policy to the new interface using
the Check Point FireWall-1 command line. You can also use the Check Point
FireWall-1 graphical user interface (GUI) download the security policy. The
GUI, howe v er, downloads the sa me secur ity polic y to all i nterf aces. For furthe r
information and instr uct ions, see your Check Point documentation.
3-8
Figure 3-4. Values Window
303515-A Re v 00
Page 43

Configuring a Firewall on a Router
Once you enable the firew all on an interface and reboot the router, you will not be
able to communicate with the router through Site Manager until you change the
FireWall-1 defau lt securi ty polic y. For more infor matio n, see “Defi ning a Fire wall
Security Policy” on page 3-11.
Caution:
If your fire wall management station and router are on different
subnets, you will not be able to communicat e with the router from the
management station unles s you establish a static route from the management
station to the router before you activate the fi rew a l l . For info rmatio n a bout
creating a static route, see Configuring IP Services.
Activating the Firewall
Before the FireWall-1 security policy can take effect on the rout er, you must first
activate the fire wall by booting the rout er using Site Manager on the management
station. Booting a router warm-starts every processor module in the router.
Pressing the Reset button on the front panel of the router performs the same
procedure.
When you activate the firewall, the default security poli c y prevents all
Note:
interface s supported b y the f ire wa ll fr om communicating with th e route r. If the
firewalled router and management station are on different subnets, you must
establish a static ro ute to enable communication between the router and the
management station befor e you activate the f irewall. For information about
configuring a static route, see Confi guring IP Services.
303515-A Rev 00
3-9
Page 44

Configuring BaySecure FireWall-1
To reboot the router using Site Manager:
From the main Site Manager window, choose Administration > Boot
1.
Router .
The Boot Router window opens (Figure 3-5
Figure 3-5. Boot Router Window
Specify the corre ct volume and boot image.
2.
Select the correct router volume and configuration file. Then click on
3.
).
Boot.
A confirmation window appears.
Click on OK in the confirmation window and wait a few minutes to give
4.
the router time to reboot.
Choose View > Refresh Display from the main Site Manager window to
5.
verify that the router booted correctly.
3-10
If the router booted correctly, system information appears in the main Site
Manager window.
If the router did not boot correctly, system information does not appear. In this
case, make sure that you followed the procedures described in this section.
If you have any questions, refer to Configuring and Managing Route rs with Site
Manager or call your local Bay Networks Technical Solutions Center.
303515-A Re v 00
Page 45

Configuring a Firewall on a Router
Defining a Firewall Security Policy
A security policy is a collection of rules that define the way the firewall operates.
The default FireWall-1 security policy drops all attempts at communication with
the router. This secur ity policy goes into effect when you first activate the firewall
on the router.
You must establish a securi ty policy that explicitly defines acceptable
communication to the router , based on the source addr ess, destination addres s, and
type of service. For details about how to configure a security policy, see your
Check Point FireWall-1 documentation.
Installing the Security Policy on th e Router and Its Interfaces
Once you have defined a security policy, you must install it on the router.
Installing a securi ty policy means downloading it to the f ir ewalled objects that
will enforce it.
When you download the security policy, the FireWall-1 software:
303515-A Rev 00
• Verifies that the rule base is logical and consistent
• Generates an inspection script from the rule base
• Compiles the inspectio n script to generate inspection code for the router
• Downloads the inspection code to the router
Once the fire wall is prote cting your ro uter , if you put f ire w all pro tection
Note:
on a new interface, the new interface will use the default security policy
supplied by Check Point, which prevents the ne w interface from
communicating with the route r.
You can download your customized security policy to the new interface using
either the Check Point FireWall-1 command line or the Check Point
FireWall-1 graphical user interface (GUI). The GUI, however, downloads the
same securi ty poli cy to all interfaces.
For instruct ions on how to install the security policy, see your Check Point
FireWall-1 documentation.
3-11
Page 46

Configuring BaySecure FireWall-1
Deleting Firewall from the Router
You can use Site Manager to delete a firewall from the router. To dynamically
delete a firewall from the router, you must use t he Technician Interface.
Deleting Firewall Locally or Remotely Using Site Manager
Site Manager allows you to delete a firewall from the entire router in local and
remote modes only.
To delete a firewall:
Site Manager Procedure
You do this System responds
1. From Configuration Manager, choose
Platform
2. Choose
3. Choose
4. Click on
Warning:
.
FireWall
Delete
OK
. The FireWall menu opens.
. A dia log bo x opens , asking if y ou are su re
Deleting a firewall using Site Manager deletes the firewall
The Platform menu opens.
that you want to delete the firewall.
You return to the Configuration Manager
window.
management information base (MIB). This action disables firewall
functionality on the router, but it does not affect internal resources tha t were
originally alloc ated for the FireWall-1 application.
After you delete a firewall using Site Manager, you should save the
configura tion file and reboot the router to free internal resources. You can then
reconfigure FireWall dynamically.
3-12
303515-A Re v 00
Page 47

Configuring a Firewall on a Router
Deleting Firewall Dynamically Using the Technician Interface
To delete a firewall dynamically, you must use the T e chnician Interface. The
T echnic ian I nterface allows you to delete a firewall on a slot/port basis, or f rom all
ports on the router.
firewall delete
<slot> <port>
_all
Warning:
The
[
<slot > <port>
Deletes a firewall from a specific slot/port combination.
Deletes a firewall from the router entirely.
firewall delete all
| _
]
all
command deletes the MIB. This action
disables the FireWall functionality on the router, but it does not affect internal
resources that were ori gina lly allocated for the FireWall-1 applicati on.
After using the
firewall delete all
command, you should save the
configura tion file and reboot the router to free internal resources. You can then
reconfigure FireWall dynamically.
303515-A Rev 00
3-13
Page 48

Configuring BaySecure FireWall-1
Troubleshooting Checklist
If you experience proble ms with FireWall-1, ve rify that you hav e perfo rmed these
steps:
• Enabled IP on the router
• Enabled TCP on all slots on the router
• Created a firewall using Site Manager
• Created a static route if the router and firewall management stations are on
different subnets
• Synchronized the route r and management sta tion passwords by exec uting the
fwputkey
• Defined a security policy and added a network object for the router using the
FireWall-1 GUI
• Saved the configuration and booted the router
• Installed the security policy on the router
If you have performed these steps and are still having system problems, contact
your Bay Networks Technical Solutions Center.
command on both the router and the firewall management station
3-14
303515-A Re v 00
Page 49

This appendix contains parameter descriptions for BaySecure FireWall-1
parameters.
FireWall Enable Parameter
Parameter: Enable
Appendix A
Parameter Descriptions
Path: Platform > FireWall > Global
Default: Enable
|
Options: Enable
Function: Enables or disables the f ir ewall on the entire router.
Instructions: Choose Enable to a llo w the f ire wa ll t o be active on the router. Choose Disabl e to
disable the firewall on the router.
303515-A Rev 00
Disable
A-1
Page 50

Configuring BaySecure FireWall-1
FireWall Parameters
Parameter: Log Host IP Address
Path: Platform > FireWall > FireWall Parameters
Default: 0.0.0.0
Options: Any valid IP address.
Function: Identifies the IP address of the primary firewall management station.
Instructions: Enter the IP address of the PC or UNIX worksta tion where you installed the
Check Point FireWall-1 management sof tware. If you have installed FireW all-1
management software on more than one PC or UNIX workstation, enter in the
IP address of the workstation you plan to use as your primar y FireWall-1
management station.
If the IP address of the management station and the IP address of the route r are
on different subne ts, then you must configure a static route to the route r to
enable communication between the router and the management station.
Configuring IP Services provide s info rmation about configuring a static rou te.
Parameter: Local Interface IP Address
Path: Platform > FireWall > FireWall Parameters
Default: 0.0.0.0
Options: Any valid IP address.
Function: Identifies the IP address of the router to be protected by the firewall.
Instructions: Enter the IP address of the router you intend to have protected by the firewall.
If the IP address of the firewall management station and the IP address of the
router are on different subnets, then you must configure a static route to the
local host IP address to enable communication between the router and the
firewall management station. Configuring IP Serv ices provides information
about configuri ng a static route.
A-2
303515-A Re v 00
Page 51

Parameter Descriptions
List FireWall Inte rfaces Parameters
Parameter: Name
Path: Protoc ols > IP > FIREWALL
Default: None
Options: Any string of alphanumeric characters.
Function: Identifies an interface by name.
Instructions: Enter a meaningful name in alphanumeric characters.
Parameter: Disable
Path: Protoc ols > IP > FIREWALL
Default: Disable
|
Options: Enable
Function: Enables or disables the firewall on one or more interfaces.
Instructions: Highli ght one or more interfaces and choose Enable to allow the firewall to be
active on the interfaces. Choose Disable to deactivate the firewall on the
interfaces.
Disable
303515-A Rev 00
A-3
Page 52

Page 53

Index
A
acrony m s , xi
acti vating FireWa ll-1, 3-9
adding
administrato rs , 2- 18
groups, 2-18
GUI clients, 2-1 2, 2-18
license, 2-12, 2-18
remote modules, 2-12, 2-18
B
bootin g the router, 3-9
C
Check Point, contacting, 2-2, 2-4
commands
commit, 3-2
fw putlic, 2-19
fwconf ig, 2-18
fwinstall, 2-14
fwput ke y, 2-19
fwstart, 2-19
fwstop, 2-19
fwui&, 2- 20
set, 3-2
Configuration Manager, 3-2
configuring a firewall, 3- 1
conventions, text, x
creat ing a firewall, 3-1
D
daemons, 2-19
E
educational services, xii
enabli ng the firewall
on an interface, 3-6
on the router, 3-4
extracting tar files, 2-13
F
FireWall-1 License
for the Management station, obtaining, 2-1
for the router, obtaining, 2-1
fw putlic command, 2-19
fwconfig command, 2-18
fwinstall command, 2-14
fwputkey command, 2-19
fwstart command, 2-19
fwstop command, 2-19
fwui& comma nd, 2-20
G
groups, adding, 2-18
GUI clients, adding, 2-12, 2-18
I
inspec tion code, 3-11
installation
options, 2-14
sample, 2-6, 2-14
installing management software, 2-14
303515-A Rev 00
Index-1
Page 54

L
T
license
adding, 2-12, 2-18
installing on management station, 2-19
M
management station, 3- 4
primary, 3-5
modules
firewall stateful inspection, 1-2
mounting a CD drive, 2-13
P
product support, xii
publications, Bay Networks, xi
R
refreshing the display, 3-10
remote modules, adding, 2-12, 2-18
Reset button, 3-9
rule bas e, verifying, 3-11
tar files, extr ac ti ng, 2-13
technical publications, xi
technical support, xii
Technician I nterface, 3-2
text conventions, x
S
security policy
configuring, 3-11
downl oading, 3-11
security rules, 3-11
serial num ber, obtaining, 2-2, 2-4
starting the daemons, 2-19
stateful inspection module, 1-2
static route, configuring, 3-9
support, Bay Networks, xii
synchro nizing the router and managemen t station, 2-19
Index-2
303515-A Re v 00
 Loading...
Loading...