Page 1

P-2602HWLNI Series
802.11g Wireless ADSL2+ 4-Port VoIP IAD
User’s Guide
Version 3.40
9/2007
Edition 2
DEFAULT LOGIN
IP Address http://192.168.1.1
Administrator Name admin
Administrator Password admin
User Name user
User Password 1234
www.zyxel.com
Page 2

Page 3
About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the ZyXEL Device using the web
configurator. You should have at least a basic knowledge of TCP/IP networking concepts and
topology.
Related Documentation
• Quick Start Guide
The Quick Start Guide is designed to help you get up and running right away. It contains
information on setting up your network and configuring for Internet access.
• Web Configurator Online Help
Embedded web help for descriptions of individual screens and supplementary
information.
" It is recommended you use the web configurator to configure the ZyXEL
Device.
• Supporting Disk
Refer to the included CD for support documents.
• ZyXEL Web Site
Please refer to www.zyxel.com
certifications.
User Guide Feedback
Help us help you. Send all User Guide-related comments, questions or suggestions for
improvement to the following address, or use e-mail instead. Thank you!
The Technical Writing Team,
ZyXEL Communications Corp.,
6 Innovation Road II,
Science-Based Industrial Park,
Hsinchu, 300, Taiwan.
E-mail: techwriters@zyxel.com.tw
for additional support documentation and product
P-2602HWLNI User’s Guide
3
Page 4
Document Conventions
Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
1 Warnings tell you about things that could harm you or your device.
" Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The P-2602HWLNI may be referred to as the “ZyXEL Device”, the “device”, the
“system” or the “product” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
• A key stroke is denoted by square brackets and uppercase text, for example, [ENTER]
means the “enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the [ENTER] key.
“Select” or “choose” means for you to use one of the predefined choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For example,
Maintenance > Log > Log Setting means you first click Maintenance in the navigation
panel, then the Log sub menu and finally the Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value. For
example, “k” for kilo may denote “1000” or “1024”, “M” for mega may denote “1000000”
or “1048576” and so on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other words”.
4
P-2602HWLNI User’s Guide
Page 5
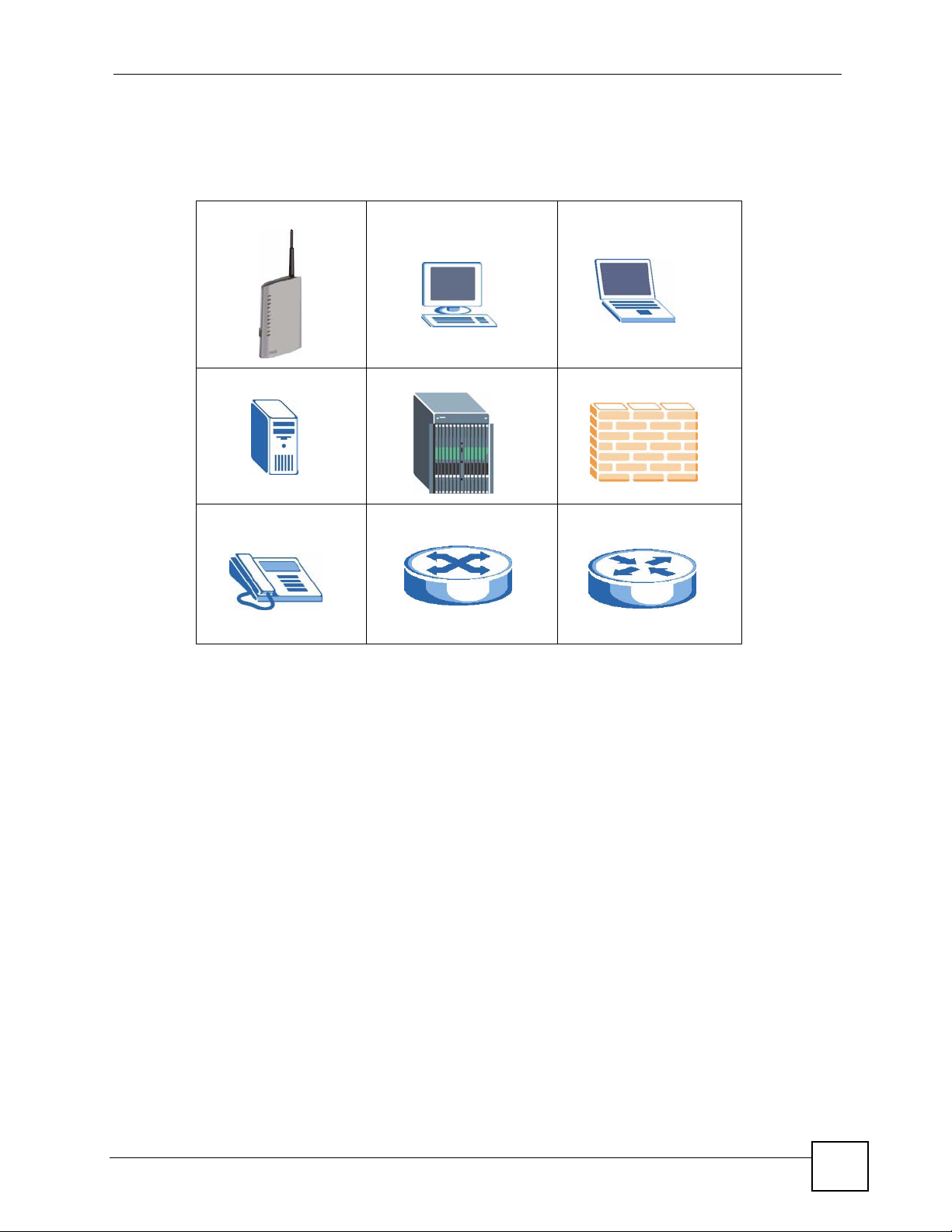
Document Conventions
Icons Used in Figures
Figures in this User’s Guide may use the following generic icons. The ZyXEL Device icon is
not an exact representation of your device.
ZyXEL Device Computer Notebook computer
Server DSLAM Firewall
Telephone Switch Router
P-2602HWLNI User’s Guide
5
Page 6

Safety Warnings
Safety Warnings
1 For your safety, be sure to read and follow all warning notices and instructions.
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• Do NOT open the device or unit. Opening or removing covers can expose you to
dangerous high voltage points or other risks. ONLY qualified service personnel should
service or disassemble this device. Please contact your vendor for further information.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in
North America or 230V AC in Europe).
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the device and the power source.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order a
new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• Do NOT obstruct the device ventilation slots, as insufficient airflow may harm your
device.
• Use only No. 26 AWG (American Wire Gauge) or larger telecommunication line cord.
• Antenna Warning! This device meets ETSI and FCC certification requirements when
using the included antenna(s). Only use the included antenna(s).
6
This product is recyclable. Dispose of it properly.
P-2602HWLNI User’s Guide
Page 7
Safety Warnings
P-2602HWLNI User’s Guide
7
Page 8

Safety Warnings
8
P-2602HWLNI User’s Guide
Page 9

Contents Overview
Contents Overview
Introduction ............................................................................................................................ 39
Introducing the ZyXEL Device ...................................................................................................41
Introducing the Web Configurator .............................................................................................. 49
Wizards and Status ................................................................................................................ 61
Internet and Wireless Setup Wizard .......................................................................................... 63
VoIP Wizard ............................................................................................................................... 77
Bandwidth Management Wizard ................................................................................................ 83
Status Screens .......................................................................................................................... 87
Network ................................................................................................................................... 99
WAN Setup .............................................................................................................................. 101
LAN Setup ................................................................................................................................117
Wireless LAN ........................................................................................................................... 129
Network Address Translation (NAT) Screens .......................................................................... 155
VoIP ....................................................................................................................................... 167
Voice ........................................................................................................................................ 169
VoIP Trunking ...........................................................................................................................211
Phone Usage ........................................................................................................................... 227
Security ................................................................................................................................. 231
Firewalls .................................................................................................................................. 233
Firewall Configuration .............................................................................................................. 245
Content Filtering ...................................................................................................................... 265
Introduction to IPSec ............................................................................................................... 269
VPN Screens ........................................................................................................................... 275
Certificates ............................................................................................................................... 301
Advanced .............................................................................................................................. 325
Static Route ............................................................................................................................. 327
Bandwidth Management .......................................................................................................... 331
Dynamic DNS Setup ................................................................................................................ 339
Remote Management Configuration ........................................................................................ 343
Universal Plug-and-Play (UPnP) ............................................................................................. 361
P-2602HWLNI User’s Guide
9
Page 10

Contents Overview
Maintenance and Troubleshooting ..................................................................................... 373
System ..................................................................................................................................... 375
Call History ............................................................................................................................. 381
Logs ........................................................................................................................................ 387
Troubleshooting ....................................................................................................................... 401
Tools ........................................................................................................................................ 407
Diagnostic ............................................................................................................................... 419
Product Specifications ............................................................................................................. 423
Appendices and Index ......................................................................................................... 433
10
P-2602HWLNI User’s Guide
Page 11

Table of Contents
Table of Contents
About This User's Guide ..........................................................................................................3
Document Conventions............................................................................................................4
Safety Warnings........................................................................................................................6
Contents Overview ...................................................................................................................9
Table of Contents.................................................................................................................... 11
List of Figures ......................................................................................................................... 25
List of Tables...........................................................................................................................33
Part I: Introduction................................................................................. 39
Chapter 1
Introducing the ZyXEL Device...............................................................................................41
1.1 Overview .............................................................................................................................. 41
1.2 Ways to Manage the ZyXEL Device .................................................................................... 42
1.3 Good Habits for Managing the ZyXEL Device ..................................................................... 42
1.4 Applications for the ZyXEL Device ...................................................................................... 43
1.4.1 Internet Access ..........................................................................................................43
1.4.2 Making Calls via Internet Telephony Service Provider ............................................... 43
1.4.3 Make Peer-to-peer Calls ............................................................................................ 44
1.4.4 Firewall for Secure Broadband Internet Access ......................................................... 44
1.4.5 LAN to LAN Application .............................................................................................. 45
1.5 LEDs .................................................................................................................................... 46
1.6 The RESET Button .............................................................................................................. 47
1.6.1 Using The Reset Button ............................................................................................. 47
Chapter 2
Introducing the Web Configurator ........................................................................................ 49
2.1 Web Configurator Overview ................................................................................................. 49
2.1.1 Accessing the Web Configurator ................................................................................ 49
2.2 Login Types ......................................................................................................................... 50
2.2.1 User Access ............................................................................................................... 50
2.2.2 Administrator Access ................................................................................................. 50
2.3 Web Configurator Main Screen ........................................................................................... 52
P-2602HWLNI User’s Guide
11
Page 12

Table of Contents
2.3.1 Title Bar ...................................................................................................................... 53
2.3.2 Navigation Panel ........................................................................................................ 53
2.3.3 Main Window ..............................................................................................................59
2.3.4 Status Bar ................................................................................................................... 59
Part II: Wizards and Status.................................................................... 61
Chapter 3
Internet and Wireless Setup Wizard...................................................................................... 63
3.1 Introduction .......................................................................................................................... 63
3.2 Internet Access Wizard Setup ............................................................................................. 63
3.2.1 Manual Configuration ................................................................................................. 66
3.3 Wireless Connection Wizard Setup ..................................................................................... 71
3.3.1 Manually Assign a WPA-PSK Key ............................................................................. 74
3.3.2 Manually Assign a WEP Key ...................................................................................... 74
Chapter 4
VoIP Wizard ............................................................................................................................. 77
4.1 Introduction .......................................................................................................................... 77
4.2 VoIP Wizard Setup .............................................................................................................. 77
Chapter 5
Bandwidth Management Wizard............................................................................................ 83
5.1 Introduction .......................................................................................................................... 83
5.2 Bandwidth Management Wizard Setup ............................................................................... 83
Chapter 6
Status Screens........................................................................................................................ 87
6.1 Status Screen ..................................................................................................................... 87
6.2 Any IP Table ........................................................................................................................ 91
6.3 WLAN Status ....................................................................................................................... 92
6.4 Packet Statistics .................................................................................................................. 92
6.5 VoIP Statistics ...................................................................................................................... 94
6.6 LED Status ........................................................................................................................... 96
Part III: Network...................................................................................... 99
Chapter 7
WAN Setup.............................................................................................................................101
7.1 WAN Overview .................................................................................................................. 101
12
P-2602HWLNI User’s Guide
Page 13

Table of Contents
7.1.1 Encapsulation ........................................................................................................... 101
7.1.2 Multiplexing .............................................................................................................. 102
7.1.3 VPI and VCI ............................................................................................................. 102
7.1.4 IP Address Assignment ............................................................................................ 102
7.1.5 Nailed-Up Connection (PPP) ................................................................................... 103
7.1.6 NAT .......................................................................................................................... 103
7.2 Metric ................................................................................................................................ 103
7.3 Traffic Shaping ................................................................................................................... 104
7.3.1 ATM Traffic Classes ................................................................................................. 105
7.4 Zero Configuration Internet Access ................................................................................... 105
7.5 Internet Access Setup ...................................................................................................... 106
7.5.1 Advanced Internet Access Setup ............................................................................. 108
7.6 WAN More Connections ................................................................................................... 109
7.7 More Connections Edit .......................................................................................................110
7.8 More Connections Edit Advanced .....................................................................................113
7.9 Traffic Redirect ...................................................................................................................114
7.10 WAN Backup Setup .........................................................................................................114
Chapter 8
LAN Setup.............................................................................................................................. 117
8.1 LAN Overview ....................................................................................................................117
8.1.1 LANs, WANs and the ZyXEL Device .........................................................................117
8.1.2 DHCP Setup ..............................................................................................................118
8.2 DNS Server Addresses ......................................................................................................118
8.3 LAN TCP/IP ........................................................................................................................118
8.3.1 IP Address and Subnet Mask ....................................................................................118
8.3.2 RIP Setup ................................................................................................................. 120
8.3.3 Multicast ................................................................................................................... 120
8.3.4 Any IP ....................................................................................................................... 121
8.4 Configuring LAN IP ............................................................................................................ 122
8.4.1 Configuring Advanced LAN Setup ........................................................................... 123
8.5 DHCP Setup ...................................................................................................................... 124
8.6 LAN Client List ................................................................................................................... 125
8.7 LAN IP Alias ...................................................................................................................... 126
Chapter 9
Wireless LAN.........................................................................................................................129
9.1 Wireless Network Overview ............................................................................................... 129
9.2 Wireless Security Overview ............................................................................................... 130
9.2.1 SSID ......................................................................................................................... 130
9.2.2 MAC Address Filter .................................................................................................. 130
9.2.3 User Authentication .................................................................................................. 130
9.2.4 Encryption ................................................................................................................ 131
P-2602HWLNI User’s Guide
13
Page 14

Table of Contents
9.2.5 One-Touch Intelligent Security Technology (OTIST) ................................................ 132
9.3 Wireless Performance Overview ....................................................................................... 132
9.3.1 Quality of Service (QoS) .......................................................................................... 132
9.3.2 Wireless Distribution System (WDS) ........................................................................ 132
9.4 Additional Wireless Terms ................................................................................................. 133
9.5 General WLAN Screen ...................................................................................................... 133
9.5.1 No Security ............................................................................................................... 134
9.5.2 WEP Encryption Screen ........................................................................................... 135
9.5.3 WPA(2)-PSK ............................................................................................................ 136
9.5.4 WPA(2) Authentication Screen ................................................................................. 138
9.5.5 Wireless LAN Advanced Setup ............................................................................... 139
9.6 OTIST Screen .................................................................................................................... 140
9.6.1 Notes on OTIST ....................................................................................................... 143
9.7 MAC Filter ..................................................................................................................... 143
9.8 Association List .................................................................................................................. 145
9.9 QoS Screen ....................................................................................................................... 145
9.9.1 Application Priority Configuration ............................................................................. 147
9.10 WDS Screen .................................................................................................................... 148
9.10.1 Static WEP ............................................................................................................. 149
9.10.2 WPA-PSK ............................................................................................................... 150
9.10.3 WPA2-PSK ............................................................................................................. 152
Chapter 10
Network Address Translation (NAT) Screens.....................................................................155
10.1 NAT General Overview ................................................................................................... 155
10.1.1 NAT Definitions ...................................................................................................... 155
10.1.2 What NAT Does ..................................................................................................... 156
10.1.3 How NAT Works ..................................................................................................... 156
10.1.4 NAT Application ...................................................................................................... 156
10.1.5 NAT Mapping Types ............................................................................................... 157
10.2 SUA (Single User Account) Versus NAT ......................................................................... 158
10.3 NAT General Setup .......................................................................................................... 158
10.4 Port Forwarding ............................................................................................................. 159
10.4.1 Default Server IP Address ...................................................................................... 160
10.4.2 Port Forwarding: Services and Port Numbers ........................................................ 160
10.4.3 Configuring Servers Behind Port Forwarding (Example) ....................................... 160
10.5 Configuring Port Forwarding ............................................................................................ 161
10.5.1 Port Forwarding Rule Edit ..................................................................................... 162
10.6 Address Mapping ............................................................................................................ 163
10.6.1 Address Mapping Rule Edit ................................................................................... 164
Part IV: VoIP.......................................................................................... 167
14
P-2602HWLNI User’s Guide
Page 15

Table of Contents
Chapter 11
Voice.......................................................................................................................................169
11.1 Introduction to VoIP .......................................................................................................... 169
11.2 SIP .................................................................................................................................. 169
11.2.1 SIP Identities ..........................................................................................................169
11.2.2 SIP Servers ............................................................................................................ 170
11.2.3 RTP ........................................................................................................................ 173
11.2.4 Pulse Code Modulation .......................................................................................... 173
11.2.5 SIP Call Progression .............................................................................................. 173
11.2.6 SIP Call Progression Through Proxies ................................................................... 173
11.2.7 Voice Coding .......................................................................................................... 175
11.2.8 PSTN Call Setup Signaling .................................................................................... 175
11.2.9 MWI (Message Waiting Indication) ......................................................................... 175
11.2.10 Custom Tones (IVR) ............................................................................................. 176
11.3 Quality of Service (QoS) ..................................................................................................176
11.3.1 Type Of Service (ToS) ............................................................................................ 177
11.3.2 DiffServ ................................................................................................................... 177
11.3.3 VLAN ...................................................................................................................... 177
11.4 SIP Settings Screen ......................................................................................................... 178
11.5 Advanced SIP Setup Screen .......................................................................................... 179
11.6 SIP QoS Screen .............................................................................................................. 182
11.7 Phone .............................................................................................................................. 183
11.7.1 PSTN Line .............................................................................................................. 183
11.7.2 ISDN Line ...............................................................................................................184
11.7.3 Voice Activity Detection/Silence Suppression ........................................................ 184
11.7.4 Comfort Noise Generation ...................................................................................... 184
11.7.5 Echo Cancellation .................................................................................................. 184
11.8 Analog Phone ................................................................................................................. 184
11.8.1 PHONE Port Call Types ......................................................................................... 184
11.8.2 Configuring the Analog Phone Screen ................................................................... 185
11.9 Advanced Analog Phone Setup Screen .......................................................................... 187
11.10 ISDN Phone .................................................................................................................. 189
11.10.1 ISDN Phone Port Call Types ................................................................................ 189
11.10.2 Configuring the ISDN Phone Screen .................................................................... 190
11.11 Common Phone Settings Screen .................................................................................. 191
11.12 Ext. Table ....................................................................................................................... 191
11.13 Advanced Ext. Table Setup Screen ............................................................................... 193
11.14 Phone Services Overview .............................................................................................. 194
11.14.1 The Flash Key ...................................................................................................... 195
11.14.2 Europe Type Supplementary Phone Services ...................................................... 195
11.14.3 USA Type Supplementary Services ..................................................................... 196
11.15 Phone Region Screen ................................................................................................... 198
11.16 Speed Dial .................................................................................................................... 198
P-2602HWLNI User’s Guide
15
Page 16

Table of Contents
11.17 Incoming Call Policy Screen ......................................................................................... 200
11.18 Distinctive Ring Screen ..................................................................................................202
11.19 SIP Prefix Screen ........................................................................................................... 204
11.20 PSTN Line ..................................................................................................................... 206
11.21 PSTN Line Screen .........................................................................................................206
11.22 ISDN Line Screen .......................................................................................................... 207
11.23 Fixed Line Numbers .......................................................................................................208
11.23.1 Multiple Subscriber Numbers ............................................................................... 208
11.23.2 Receiving Analog Calls With Digital Phones ........................................................ 209
11.23.3 Configuring the Fixed Line Numbers Screen ....................................................... 209
Chapter 12
VoIP Trunking........................................................................................................................ 211
12.1 VoIP Trunking Overview ..................................................................................................211
12.2 VoIP Trunking and Security ..............................................................................................211
12.2.1 Auto Attendant and Authentication ..........................................................................211
12.2.2 Peer Call Authentication ......................................................................................... 212
12.3 Call Rules ........................................................................................................................ 213
12.4 VoIP Trunking Scenarios ................................................................................................. 213
12.4.1 VoIP Phone To PSTN Phone ................................................................................. 213
12.4.2 PSTN Phone To VoIP Phone ................................................................................. 213
12.4.3 PSTN Phone To PSTN Phone via VoIP ................................................................. 214
12.5 Trunking General Screen ................................................................................................. 214
12.6 Trunking Peer Call Screen ............................................................................................... 215
12.7 Trunking Call Rule Screen ............................................................................................... 217
12.8 VoIP Trunking Example: VoIP to PSTN ........................................................................... 219
12.8.1 Background Information ......................................................................................... 219
12.8.2 Configuration Details: Outgoing ............................................................................. 219
12.8.3 Configuration Details: Incoming ............................................................................. 220
12.8.4 Call Progression ..................................................................................................... 221
12.9 VoIP Trunking Example: PSTN to PSTN via VoIP ........................................................... 221
12.9.1 Background Information ......................................................................................... 222
12.9.2 Configuration Details: Outgoing ............................................................................. 222
12.9.3 Configuration Details: Incoming ............................................................................. 224
12.9.4 Call Progression ..................................................................................................... 224
Chapter 13
Phone Usage ......................................................................................................................... 227
13.1 Dialing a Telephone Number ........................................................................................... 227
13.2 Using Speed Dial to Dial a Telephone Number ............................................................... 227
13.3 Internal Calls .................................................................................................................... 227
13.3.1 Phone Book ............................................................................................................ 228
13.3.2 Call Transfer ...........................................................................................................228
16
P-2602HWLNI User’s Guide
Page 17

Table of Contents
13.3.3 Call Forwarding ...................................................................................................... 228
13.3.4 Follow Me ...............................................................................................................228
13.3.5 Call Pickup .............................................................................................................229
13.4 Checking the Device’s IP Address ................................................................................... 229
13.5 Auto Firmware Upgrade .................................................................................................. 229
Part V: Security .................................................................................... 231
Chapter 14
Firewalls................................................................................................................................. 233
14.1 Firewall Overview ........................................................................................................... 233
14.2 Types of Firewalls ............................................................................................................ 233
14.2.1 Packet Filtering Firewalls ....................................................................................... 233
14.2.2 Application-level Firewalls ...................................................................................... 234
14.2.3 Stateful Inspection Firewalls .................................................................................. 234
14.3 Introduction to ZyXEL’s Firewall ...................................................................................... 234
14.3.1 Denial of Service Attacks ....................................................................................... 235
14.4 Denial of Service ............................................................................................................. 235
14.4.1 Basics ..................................................................................................................... 235
14.4.2 Types of DoS Attacks ............................................................................................. 236
14.5 Stateful Inspection ........................................................................................................... 238
14.5.1 Stateful Inspection Process .................................................................................... 239
14.5.2 Stateful Inspection on Your ZyXEL Device ............................................................. 240
14.5.3 TCP Security .......................................................................................................... 240
14.5.4 UDP/ICMP Security ................................................................................................ 241
14.5.5 Upper Layer Protocols ........................................................................................... 241
14.6 Guidelines for Enhancing Security with Your Firewall ..................................................... 242
14.6.1 Security In General ................................................................................................ 242
14.7 Packet Filtering Vs Firewall ............................................................................................. 243
14.7.1 Packet Filtering: ..................................................................................................... 243
14.7.2 Firewall ................................................................................................................... 243
Chapter 15
Firewall Configuration ..........................................................................................................245
15.1 Access Methods .............................................................................................................. 245
15.2 General Firewall Policy Overview ................................................................................... 245
15.3 Rule Logic Overview ....................................................................................................... 246
15.3.1 Rule Checklist ........................................................................................................ 246
15.3.2 Security Ramifications ............................................................................................ 246
15.3.3 Key Fields For Configuring Rules .......................................................................... 247
15.4 Connection Direction ....................................................................................................... 247
P-2602HWLNI User’s Guide
17
Page 18

Table of Contents
15.4.1 LAN to WAN Rules ................................................................................................. 248
15.4.2 Alerts ...................................................................................................................... 248
15.5 General Firewall Policy ................................................................................................... 248
15.6 Firewall Rules Summary ................................................................................................. 249
15.6.1 Configuring Firewall Rules ................................................................................... 251
15.6.2 Customized Services ............................................................................................ 254
15.6.3 Configuring a Customized Service ....................................................................... 254
15.7 Example Firewall Rule .....................................................................................................255
15.8 DoS Thresholds .............................................................................................................. 259
15.8.1 Threshold Values ................................................................................................... 259
15.8.2 Half-Open Sessions ............................................................................................... 260
15.8.3 Configuring Firewall Thresholds ............................................................................. 260
15.9 Firewall Commands .........................................................................................................262
Chapter 16
Content Filtering ................................................................................................................... 265
16.1 Content Filtering Overview ............................................................................................. 265
16.2 Configuring Keyword Blocking ........................................................................................ 265
16.3 Configuring the Schedule .............................................................................................. 266
16.4 Configuring Trusted Computers ..................................................................................... 267
Chapter 17
Introduction to IPSec............................................................................................................269
17.1 VPN Overview ............................................................................................................... 269
17.1.1 IPSec ...................................................................................................................... 269
17.1.2 Security Association ............................................................................................... 269
17.1.3 Other Terminology .................................................................................................. 269
17.1.4 VPN Applications ................................................................................................... 270
17.2 IPSec Architecture ........................................................................................................... 270
17.2.1 IPSec Algorithms .................................................................................................... 271
17.2.2 Key Management ................................................................................................... 271
17.3 Encapsulation .................................................................................................................. 271
17.3.1 Transport Mode ...................................................................................................... 272
17.3.2 Tunnel Mode ......................................................................................................... 272
17.4 IPSec and NAT ................................................................................................................ 272
Chapter 18
VPN Screens.......................................................................................................................... 275
18.1 VPN/IPSec Overview ....................................................................................................... 275
18.2 IPSec Algorithms ............................................................................................................. 275
18.2.1 AH (Authentication Header) Protocol ..................................................................... 275
18.2.2 ESP (Encapsulating Security Payload) Protocol .................................................... 275
18.3 My IP Address ................................................................................................................. 276
18
P-2602HWLNI User’s Guide
Page 19

Table of Contents
18.4 Secure Gateway Address ................................................................................................ 276
18.4.1 Dynamic Secure Gateway Address ....................................................................... 277
18.5 VPN Setup Screen ..........................................................................................................277
18.6 Keep Alive ....................................................................................................................... 279
18.7 VPN, NAT, and NAT Traversal ......................................................................................... 279
18.8 Remote DNS Server ........................................................................................................ 280
18.9 ID Type and Content ........................................................................................................ 281
18.9.1 ID Type and Content Examples ............................................................................. 282
18.10 Pre-Shared Key ............................................................................................................. 283
18.11 Editing VPN Policies ..................................................................................................... 283
18.12 IKE Phases ................................................................................................................... 288
18.12.1 Negotiation Mode ................................................................................................. 289
18.12.2 Diffie-Hellman (DH) Key Groups .......................................................................... 289
18.12.3 Perfect Forward Secrecy (PFS) .......................................................................... 289
18.13 Configuring Advanced IKE Settings ............................................................................. 289
18.14 Manual Key Setup .........................................................................................................292
18.14.1 Security Parameter Index (SPI) .......................................................................... 292
18.15 Configuring Manual Key ............................................................................................... 292
18.16 Viewing SA Monitor ......................................................................................................295
18.17 Configuring Global Setting ............................................................................................ 297
18.18 Telecommuter VPN/IPSec Examples ............................................................................ 297
18.18.1 Telecommuters Sharing One VPN Rule Example ................................................ 297
18.18.2 Telecommuters Using Unique VPN Rules Example ............................................. 298
18.19 VPN and Remote Management ..................................................................................... 300
Chapter 19
Certificates ............................................................................................................................301
19.1 Certificates Overview ...................................................................................................... 301
19.1.1 Advantages of Certificates ..................................................................................... 302
19.2 Self-signed Certificates .................................................................................................... 302
19.3 Configuration Summary ................................................................................................... 302
19.4 My Certificates ................................................................................................................. 303
19.5 My Certificate Import ...................................................................................................... 304
19.5.1 Certificate File Formats .......................................................................................... 305
19.6 My Certificate Create ...................................................................................................... 306
19.7 My Certificate Details ...................................................................................................... 308
19.8 Trusted CAs ....................................................................................................................311
19.9 Trusted CA Import ......................................................................................................... 313
19.10 Trusted CA Details ......................................................................................................... 314
19.11 Trusted Remote Hosts ................................................................................................. 316
19.12 Verifying a Trusted Remote Host’s Certificate ............................................................... 318
19.12.1 Trusted Remote Host Certificate Fingerprints ...................................................... 318
19.13 Trusted Remote Hosts Import ...................................................................................... 319
P-2602HWLNI User’s Guide
19
Page 20

Table of Contents
19.14 Trusted Remote Host Certificate Details ..................................................................... 319
19.15 Directory Servers ........................................................................................................... 322
19.16 Directory Server Add and Edit ...................................................................................... 323
Part VI: Advanced ................................................................................ 325
Chapter 20
Static Route ........................................................................................................................... 327
20.1 Static Route .................................................................................................................... 327
20.2 Configuring Static Route ..................................................................................................327
20.2.1 Static Route Edit ................................................................................................... 328
Chapter 21
Bandwidth Management.......................................................................................................331
21.1 Bandwidth Management Overview ................................................................................. 331
21.2 Application-based Bandwidth Management .................................................................... 331
21.3 Auto Classifier ................................................................................................................. 331
21.4 Subnet-based Bandwidth Management .......................................................................... 332
21.5 Application and Subnet-based Bandwidth Management ................................................. 333
21.5.1 Bandwidth Management Priorities ......................................................................... 333
21.6 Configuring Bandwidth Management (General) .............................................................. 333
21.7 Bandwidth Management Rule Setup ............................................................................. 334
21.7.1 Rule Configuration ................................................................................................. 335
21.8 Bandwidth Monitor ......................................................................................................... 337
Chapter 22
Dynamic DNS Setup ............................................................................................................. 339
22.1 Dynamic DNS Overview ................................................................................................ 339
22.1.1 DYNDNS Wildcard ................................................................................................. 339
22.2 Configuring Dynamic DNS ............................................................................................... 339
Chapter 23
Remote Management Configuration ...................................................................................343
23.1 Remote Management Overview ..................................................................................... 343
23.1.1 Remote Management Limitations .......................................................................... 344
23.1.2 Remote Management and NAT .............................................................................. 344
23.1.3 System Timeout .................................................................................................... 344
23.2 Introduction to HTTPS .....................................................................................................345
23.3 HTTP ............................................................................................................................... 346
23.4 Telnet ............................................................................................................................... 347
23.5 Configuring Telnet ............................................................................................................ 347
20
P-2602HWLNI User’s Guide
Page 21

Table of Contents
23.6 Configuring FTP ............................................................................................................. 348
23.7 SNMP .............................................................................................................................. 349
23.7.1 Supported MIBs ..................................................................................................... 350
23.7.2 SNMP Traps ........................................................................................................... 351
23.7.3 Configuring SNMP ................................................................................................. 351
23.8 Configuring DNS ............................................................................................................ 352
23.9 Configuring ICMP ............................................................................................................ 353
23.10 SSH ............................................................................................................................. 354
23.11 How SSH Works ............................................................................................................355
23.12 SSH Implementation on the ZyXEL Device ................................................................... 356
23.12.1 Requirements for Using SSH ............................................................................... 356
23.13 Configuring SSH ............................................................................................................ 356
23.14 Secure Telnet Using SSH Examples ............................................................................. 357
23.14.1 Example 1: Microsoft Windows ............................................................................ 357
23.14.2 Example 2: Linux .................................................................................................. 357
23.15 Secure FTP Using SSH Example .................................................................................. 358
Chapter 24
Universal Plug-and-Play (UPnP).......................................................................................... 361
24.1 Introducing Universal Plug and Play ............................................................................... 361
24.1.1 How do I know if I'm using UPnP? ......................................................................... 361
24.1.2 NAT Traversal ........................................................................................................ 361
24.1.3 Cautions with UPnP ............................................................................................... 361
24.2 UPnP and ZyXEL ............................................................................................................362
24.2.1 Configuring UPnP .................................................................................................. 362
24.3 Installing UPnP in Windows Example .............................................................................. 363
24.4 Using UPnP in Windows XP Example ............................................................................. 366
Part VII: Maintenance and Troubleshooting ...................................... 373
Chapter 25
System ................................................................................................................................... 375
25.1 General Setup and System Name ................................................................................... 375
25.1.1 General Setup ....................................................................................................... 375
25.2 Time Setting .................................................................................................................... 377
Chapter 26
Call History ........................................................................................................................... 381
26.1 Call History Overview ..................................................................................................... 381
26.2 Viewing the Call History Summary .................................................................................. 381
26.3 Viewing Call History ......................................................................................................... 382
P-2602HWLNI User’s Guide
21
Page 22

Table of Contents
26.4 Configuring Call History Settings .................................................................................... 384
Chapter 27
Logs ...................................................................................................................................... 387
27.1 Logs Overview ................................................................................................................ 387
27.1.1 Alerts and Logs ...................................................................................................... 387
27.2 Viewing the Logs ............................................................................................................. 387
27.3 Configuring Log Settings ................................................................................................ 388
27.4 SMTP Error Messages .................................................................................................... 390
27.4.1 Example E-mail Log ............................................................................................... 391
27.5 Log Descriptions .............................................................................................................. 392
Chapter 28
Troubleshooting.................................................................................................................... 401
28.1 Power, Hardware Connections, and LEDs ...................................................................... 401
28.2 ZyXEL Device Access and Login .................................................................................... 402
28.3 Internet Access ................................................................................................................ 404
28.4 Phone Calls and VoIP ......................................................................................................405
Chapter 29
Tools.......................................................................................................................................407
29.1 Introduction ...................................................................................................................... 407
29.2 Filename Conventions ..................................................................................................... 407
29.3 File Maintenance Over WAN ........................................................................................... 408
29.4 Firmware Upgrade Screen ............................................................................................ 409
29.5 Backup and Restore .......................................................................................................410
29.5.1 Backup Configuration .............................................................................................411
29.5.2 Restore Configuration ............................................................................................411
29.5.3 Reset to Factory Defaults ...................................................................................... 412
29.6 Restart ............................................................................................................................. 413
29.7 Using FTP or TFTP to Back Up Configuration ................................................................ 413
29.7.1 Using the FTP Commands to Back Up Configuration ............................................ 413
29.7.2 FTP Command Configuration Backup Example ................................................... 414
29.7.3 Configuration Backup Using GUI-based FTP Clients ............................................ 414
29.7.4 Backup Configuration Using TFTP ......................................................................... 414
29.7.5 TFTP Command Configuration Backup Example .................................................. 415
29.7.6 Configuration Backup Using GUI-based TFTP Clients .......................................... 415
29.8 Using FTP or TFTP to Restore Configuration ............................................................... 416
29.8.1 Restore Using FTP Session Example .................................................................... 416
29.9 FTP and TFTP Firmware and Configuration File Uploads .............................................. 416
29.9.1 FTP File Upload Command from the DOS Prompt Example ................................. 417
29.9.2 FTP Session Example of Firmware File Upload .................................................... 417
29.9.3 TFTP File Upload ................................................................................................... 417
22
P-2602HWLNI User’s Guide
Page 23

Table of Contents
29.9.4 TFTP Upload Command Example ......................................................................... 418
Chapter 30
Diagnostic ............................................................................................................................. 419
30.1 General Diagnostic ......................................................................................................... 419
30.2 DSL Line Diagnostic ...................................................................................................... 419
Chapter 31
Product Specifications.........................................................................................................423
31.1 Hardware Specifications .................................................................................................. 423
31.2 Firmware Specifications ...................................................................................................423
31.3 Voice Specifications ......................................................................................................... 427
31.4 Wireless Features (Wireless Devices Only) .................................................................... 429
31.4.1 IEEE 802.11g Wireless LAN .................................................................................. 430
31.5 Power Adaptor Specifications .......................................................................................... 431
Part VIII: Appendices and Index ......................................................... 433
Appendix A Setting up Your Computer’s IP Address............................................................ 435
Appendix B Pop-up Windows, JavaScripts and Java Permissions ...................................... 447
Appendix C IP Addresses and Subnetting ........................................................................... 453
Appendix D Wireless LANs .................................................................................................. 461
Appendix E Services ............................................................................................................ 475
Appendix F Legal Information ..............................................................................................479
Appendix G Customer Support ............................................................................................483
Index....................................................................................................................................... 489
P-2602HWLNI User’s Guide
23
Page 24

Table of Contents
24
P-2602HWLNI User’s Guide
Page 25

List of Figures
List of Figures
Figure 1 Internet Access Application ...................................................................................................... 43
Figure 2 Internet Telephony Service Provider Application ...................................................................... 44
Figure 3 Peer-to-peer Calling ................................................................................................................. 44
Figure 4 Firewall Application .................................................................................................................. 45
Figure 5 LAN-to-LAN Application ........................................................................................................... 45
Figure 6 LEDs ......................................................................................................................................... 46
Figure 7 Password Screen ..................................................................................................................... 50
Figure 8 Change Password Screen ........................................................................................................ 51
Figure 9 Replace Certificate Screen ....................................................................................................... 51
Figure 10 Wizard or Advanced Screen .................................................................................................. 52
Figure 11 Main Screen ........................................................................................................................... 52
Figure 12 Select a Mode ........................................................................................................................ 64
Figure 13 Wizard Welcome .................................................................................................................... 64
Figure 14 Auto Detection: No DSL Connection ...................................................................................... 65
Figure 15 Auto-Detection: PPPoE .......................................................................................................... 65
Figure 16 Auto Detection: Failed ............................................................................................................ 66
Figure 17 Internet Access Wizard Setup: ISP Parameters ..................................................................... 67
Figure 18 Internet Connection with PPPoE ............................................................................................ 68
Figure 19 Internet Connection with RFC 1483 ...................................................................................... 68
Figure 20 Internet Connection with ENET ENCAP ................................................................................. 69
Figure 21 Internet Connection with PPPoA ............................................................................................ 70
Figure 22 Connection Test Failed-1 ........................................................................................................ 71
Figure 23 Connection Test Failed-2. ....................................................................................................... 71
Figure 24 Connection Test Successful ................................................................................................... 72
Figure 25 Wireless LAN Setup Wizard 1 ................................................................................................ 72
Figure 26 Wireless LAN ......................................................................................................................... 73
Figure 27 Manually Assign a WPA-PSK Key .......................................................................................... 74
Figure 28 Manually Assign a WEP Key .................................................................................................. 74
Figure 29 Wireless LAN Setup 3 ............................................................................................................ 75
Figure 30 Internet Access and WLAN Wizard Setup Complete ............................................................. 76
Figure 31 VoIP Phone Calls ................................................................................................................... 77
Figure 32 Select a Mode ........................................................................................................................ 78
Figure 33 Wizard: Welcome ................................................................................................................... 79
Figure 34 SIP Server Profile Selection ................................................................................................... 79
Figure 35 VoIP Wizard Configuration ..................................................................................................... 80
Figure 36 SIP Registration Test .............................................................................................................. 81
Figure 37 VoIP Wizard Fail ..................................................................................................................... 81
Figure 38 VoIP Wizard Finish ................................................................................................................ 81
P-2602HWLNI User’s Guide
25
Page 26

List of Figures
Figure 39 Select a Mode ........................................................................................................................ 83
Figure 40 Wizard: Welcome ................................................................................................................... 84
Figure 41 Bandwidth Management Wizard: General Information ........................................................... 84
Figure 42 Bandwidth Management Wizard: Complete ........................................................................... 85
Figure 43 Status Screen ......................................................................................................................... 88
Figure 44 Any IP Table ........................................................................................................................... 91
Figure 45 WLAN Status .......................................................................................................................... 92
Figure 46 Packet Statistics ..................................................................................................................... 93
Figure 47 VoIP Statistics ......................................................................................................................... 94
Figure 48 LED Status ............................................................................................................................. 96
Figure 49 Example of Traffic Shaping .................................................................................................. 104
Figure 50 Internet Access Setup (PPPoE) ........................................................................................... 106
Figure 51 Advanced Internet Access Setup ......................................................................................... 108
Figure 52 WAN More Connections ........................................................................................................110
Figure 53 More Connections Edit ..........................................................................................................111
Figure 54 More Connections Edit Advanced .........................................................................................113
Figure 55 Traffic Redirect Example .......................................................................................................114
Figure 56 Traffic Redirect LAN Setup ....................................................................................................114
Figure 57 WAN Backup Setup ...............................................................................................................115
Figure 58 LAN and WAN IP Addresses .................................................................................................117
Figure 59 Any IP Example .................................................................................................................... 121
Figure 60 LAN IP .................................................................................................................................. 122
Figure 61 Advanced LAN Setup ........................................................................................................... 123
Figure 62 DHCP Setup ......................................................................................................................... 124
Figure 63 LAN Client List ...................................................................................................................... 126
Figure 64 Physical Network & Partitioned Logical Networks ................................................................ 127
Figure 65 LAN IP Alias ......................................................................................................................... 127
Figure 66 Example of a Wireless Network ........................................................................................... 129
Figure 67 Example of a WDS Link ....................................................................................................... 132
Figure 68 Wireless LAN: General ........................................................................................................ 134
Figure 69 Wireless: No Security ........................................................................................................... 135
Figure 70 Wireless: Static WEP Encryption .......................................................................................... 136
Figure 71 Wireless: WPA(2)-PSK ......................................................................................................... 137
Figure 72 Wireless: WPA(2) ................................................................................................................. 138
Figure 73 Wireless LAN: Advanced ...................................................................................................... 139
Figure 74 Network > Wireless LAN > OTIST ........................................................................................ 141
Figure 75 Example: Wireless Client OTIST Screen ............................................................................. 142
Figure 76 OTIST: Settings .................................................................................................................... 142
Figure 77 OTIST: In Progress on the ZyXEL Device ............................................................................ 142
Figure 78 OTIST: In Progress on the Wireless Device ......................................................................... 143
Figure 79 Start OTIST? ........................................................................................................................ 143
Figure 80 MAC Address Filter .............................................................................................................. 144
Figure 81 Wireless LAN: Association List ............................................................................................. 145
26
P-2602HWLNI User’s Guide
Page 27

List of Figures
Figure 82 Wireless LAN: QoS .............................................................................................................. 146
Figure 83 Application Priority Configuration ......................................................................................... 147
Figure 84 Wireless LAN > WDS ........................................................................................................... 149
Figure 85 Wireless LAN > WDS > Static WEP ..................................................................................... 150
Figure 86 Example: WDS Link using WPA-PSK with TKIP .................................................................. 151
Figure 87 Wireless LAN > WDS > WPA-PSK ....................................................................................... 151
Figure 88 Wireless LAN > WDS > WPA2-PSK .................................................................................... 152
Figure 89 How NAT Works ................................................................................................................... 156
Figure 90 NAT Application With IP Alias .............................................................................................. 157
Figure 91 NAT General ......................................................................................................................... 159
Figure 92 Multiple Servers Behind NAT Example ................................................................................ 160
Figure 93 Port Forwarding .................................................................................................................... 161
Figure 94 Port Forwarding Rule Setup ............................................................................................... 162
Figure 95 Address Mapping Rules ....................................................................................................... 163
Figure 96 Edit Address Mapping Rule ................................................................................................ 165
Figure 97 SIP User Agent ..................................................................................................................... 170
Figure 98 SIP Proxy Server .................................................................................................................. 171
Figure 99 SIP Redirect Server .............................................................................................................. 172
Figure 100 SIP Call Through Proxy Servers ........................................................................................ 174
Figure 101 DiffServ: Differentiated Service Field .................................................................................. 177
Figure 102 SIP > SIP Settings .............................................................................................................. 178
Figure 103 VoIP > SIP Settings > Advanced ........................................................................................ 180
Figure 104 SIP > QoS .......................................................................................................................... 183
Figure 105 Phone > Analog Phone ...................................................................................................... 186
Figure 106 Phone > Analog Phone > Advanced .................................................................................. 188
Figure 107 Phone > ISDN Phone ......................................................................................................... 190
Figure 108 Phone > Common .............................................................................................................. 191
Figure 109 VoIP > Phone > Ext. Table ................................................................................................. 192
Figure 110 VoIP > Phone > Ext. Table > Advanced .............................................................................. 194
Figure 111 VoIP > Phone > Region ...................................................................................................... 198
Figure 112 Phone Book > Speed Dial ................................................................................................... 199
Figure 113 Phone Book > Incoming Call Policy .................................................................................... 200
Figure 114 Phone Book > Distinctive Ring ........................................................................................... 203
Figure 115 Phone Book > SIP Prefix .................................................................................................... 205
Figure 116 PSTN Line > General ......................................................................................................... 206
Figure 117 ISDN Line > General .......................................................................................................... 207
Figure 118 VoIP > Fixed Line Numbers Screen ................................................................................... 210
Figure 119 Peer Devices Connecting ................................................................................................... 212
Figure 120 VoIP Phone To PSTN Phone .............................................................................................. 213
Figure 121 PSTN Phone To VoIP Phone .............................................................................................. 214
Figure 122 PSTN Phone To PSTN Phone via VoIP ............................................................................. 214
Figure 123 VoIP > Trunking > General ................................................................................................. 214
Figure 124 VoIP > Trunking > Peer Call .............................................................................................. 216
P-2602HWLNI User’s Guide
27
Page 28

List of Figures
Figure 125 VoIP > Trunking > Call Rule ............................................................................................... 218
Figure 126 VoIP to PSTN Example ...................................................................................................... 219
Figure 127 VoIP to PSTN Example - Speed Dial Screen ..................................................................... 220
Figure 128 VoIP to PSTN Example - Outgoing Authentication ............................................................. 220
Figure 129 VoIP to PSTN Example - Incoming Authentication ............................................................. 221
Figure 130 PSTN to PSTN Example .................................................................................................... 222
Figure 131 PSTN to PSTN Example: General Configuration ............................................................... 223
Figure 132 PSTN to PSTN Example - Outgoing Authentication ........................................................... 223
Figure 133 PSTN to PSTN Example - Call Rule .................................................................................. 224
Figure 134 PSTN to PSTN Example - Incoming Authentication ........................................................... 224
Figure 135 Firewall Application ............................................................................................................ 235
Figure 136 Three-Way Handshake ....................................................................................................... 236
Figure 137 SYN Flood .......................................................................................................................... 237
Figure 138 Smurf Attack ....................................................................................................................... 237
Figure 139 Stateful Inspection .............................................................................................................. 239
Figure 140 Firewall: General ................................................................................................................ 248
Figure 141 Firewall Rules .................................................................................................................... 250
Figure 142 Firewall: Edit Rule .............................................................................................................. 252
Figure 143 Firewall: Customized Services ........................................................................................... 254
Figure 144 Firewall: Configure Customized Services ........................................................................... 255
Figure 145 Firewall Example: Rules ..................................................................................................... 256
Figure 146 Edit Custom Port Example ................................................................................................. 256
Figure 147 Firewall Example: Edit Rule: Destination Address ............................................................ 257
Figure 148 Firewall Example: Edit Rule: Select Customized Services ................................................. 258
Figure 149 Firewall Example: Rules: MyService .................................................................................259
Figure 150 Firewall: Threshold ............................................................................................................. 261
Figure 151 Content Filter: Keyword ...................................................................................................... 265
Figure 152 Content Filter: Schedule ..................................................................................................... 266
Figure 153 Content Filter: Trusted ........................................................................................................ 267
Figure 154 Encryption and Decryption ................................................................................................. 270
Figure 155 IPSec Architecture .............................................................................................................. 271
Figure 156 Transport and Tunnel Mode IPSec Encapsulation ............................................................. 272
Figure 157 IPSec Summary Fields ....................................................................................................... 277
Figure 158 VPN Setup .......................................................................................................................... 278
Figure 159 NAT Router Between IPSec Routers ................................................................................. 280
Figure 160 VPN Host using Intranet DNS Server Example .................................................................. 281
Figure 161 Edit VPN Policies .............................................................................................................. 284
Figure 162 Two Phases to Set Up the IPSec SA ................................................................................. 288
Figure 163 Advanced VPN Policies ...................................................................................................... 290
Figure 164 VPN: Manual Key ............................................................................................................... 293
Figure 165 VPN: SA Monitor ................................................................................................................ 296
Figure 166 VPN: Global Setting ........................................................................................................... 297
Figure 167 Telecommuters Sharing One VPN Rule Example .............................................................. 298
28
P-2602HWLNI User’s Guide
Page 29

List of Figures
Figure 168 Telecommuters Using Unique VPN Rules Example ........................................................... 299
Figure 169 Certificate Configuration Overview ..................................................................................... 302
Figure 170 My Certificates ................................................................................................................... 303
Figure 171 My Certificate Import .......................................................................................................... 305
Figure 172 My Certificate Create .......................................................................................................... 306
Figure 173 My Certificate Details ......................................................................................................... 309
Figure 174 Trusted CAs ........................................................................................................................ 312
Figure 175 Trusted CA Import .............................................................................................................. 313
Figure 176 Trusted CA Details ............................................................................................................. 314
Figure 177 Trusted Remote Hosts ........................................................................................................ 317
Figure 178 Remote Host Certificates ................................................................................................... 318
Figure 179 Certificate Details .............................................................................................................. 318
Figure 180 Trusted Remote Host Import .............................................................................................. 319
Figure 181 Trusted Remote Host Details ............................................................................................. 320
Figure 182 Directory Servers ................................................................................................................ 323
Figure 183 Directory Server Add and Edit ............................................................................................ 324
Figure 184 Example of Static Routing Topology ................................................................................... 327
Figure 185 Static Route ........................................................................................................................ 328
Figure 186 Static Route Edit ................................................................................................................. 329
Figure 187 Subnet-based Bandwidth Management Example .............................................................. 332
Figure 188 Bandwidth Management: General ...................................................................................... 333
Figure 189 Bandwidth Management: Rule Setup ................................................................................. 334
Figure 190 Bandwidth Management Rule Configuration ...................................................................... 335
Figure 191 Bandwidth Management: Monitor ......................................................................................337
Figure 192 Dynamic DNS ..................................................................................................................... 340
Figure 193 Secure and Insecure Remote Management From the WAN .............................................. 343
Figure 194 HTTPS Implementation ...................................................................................................... 345
Figure 195 Remote Management: HTTP .............................................................................................346
Figure 196 Telnet Configuration on a TCP/IP Network ......................................................................... 347
Figure 197 Remote Management: Telnet ............................................................................................. 348
Figure 198 Remote Management: FTP ................................................................................................ 349
Figure 199 SNMP Management Model ................................................................................................ 350
Figure 200 Remote Management: SNMP ............................................................................................ 351
Figure 201 Remote Management: DNS ............................................................................................... 353
Figure 202 Remote Management: ICMP .............................................................................................. 354
Figure 203 SSH Communication Over the WAN Example .................................................................. 355
Figure 204 How SSH Works ................................................................................................................. 355
Figure 205 ADVANCED > REMOTE MGMT > SSH ............................................................................. 356
Figure 206 SSH Example 1: Store Host Key ........................................................................................ 357
Figure 207 SSH Example 2: Test ........................................................................................................ 358
Figure 208 SSH Example 2: Log in ...................................................................................................... 358
Figure 209 Secure FTP: Firmware Upload Example ............................................................................ 359
Figure 210 Configuring UPnP ............................................................................................................... 362
P-2602HWLNI User’s Guide
29
Page 30

List of Figures
Figure 211 Add/Remove Programs: Windows Setup: Communication ................................................ 363
Figure 212 Add/Remove Programs: Windows Setup: Communication: Components .......................... 364
Figure 213 Network Connections ......................................................................................................... 364
Figure 214 Windows Optional Networking Components Wizard .......................................................... 365
Figure 215 Networking Services ........................................................................................................... 365
Figure 216 Network Connections ......................................................................................................... 366
Figure 217 Internet Connection Properties .......................................................................................... 367
Figure 218 Internet Connection Properties: Advanced Settings ........................................................... 368
Figure 219 Internet Connection Properties: Advanced Settings: Add .................................................. 368
Figure 220 System Tray Icon ................................................................................................................ 369
Figure 221 Internet Connection Status ................................................................................................. 369
Figure 222 Network Connections ......................................................................................................... 370
Figure 223 Network Connections: My Network Places ........................................................................ 371
Figure 224 Network Connections: My Network Places: Properties: Example ...................................... 371
Figure 225 System General Setup ....................................................................................................... 376
Figure 226 System Time Setting .......................................................................................................... 377
Figure 227 Call History > Summary ...................................................................................................... 382
Figure 228 Call History > Call History ................................................................................................... 383
Figure 229 Call History > Call History Settings ..................................................................................... 384
Figure 230 View Log ............................................................................................................................. 388
Figure 231 Log Settings ....................................................................................................................... 389
Figure 232 E-mail Log Example ........................................................................................................... 391
Figure 233 Firmware Upgrade .............................................................................................................. 409
Figure 234 Firmware Upload In Progress ............................................................................................. 410
Figure 235 Network Temporarily Disconnected ....................................................................................410
Figure 236 Error Message .................................................................................................................... 410
Figure 237 Configuration .......................................................................................................................411
Figure 238 Configuration Upload Successful ....................................................................................... 412
Figure 239 Network Temporarily Disconnected ....................................................................................412
Figure 240 Configuration Upload Error ................................................................................................. 412
Figure 241 Reset Warning Message .................................................................................................... 412
Figure 242 Reset In Process Message ................................................................................................ 413
Figure 243 Restart Screen ................................................................................................................... 413
Figure 244 FTP Session Example ........................................................................................................ 414
Figure 245 Restore Using FTP Session Example ................................................................................ 416
Figure 246 FTP Session Example of Firmware File Upload ................................................................. 417
Figure 247 Diagnostic: General ............................................................................................................ 419
Figure 248 Diagnostic: DSL Line .......................................................................................................... 420
Figure 249 WIndows 95/98/Me: Network: Configuration ...................................................................... 436
Figure 250 Windows 95/98/Me: TCP/IP Properties: IP Address .......................................................... 437
Figure 251 Windows 95/98/Me: TCP/IP Properties: DNS Configuration .............................................. 438
Figure 252 Windows XP: Start Menu .................................................................................................... 439
Figure 253 Windows XP: Control Panel ............................................................................................... 439
30
P-2602HWLNI User’s Guide
Page 31

List of Figures
Figure 254 Windows XP: Control Panel: Network Connections: Properties ......................................... 440
Figure 255 Windows XP: Local Area Connection Properties ............................................................... 440
Figure 256 Windows XP: Advanced TCP/IP Settings .......................................................................... 441
Figure 257 Windows XP: Internet Protocol (TCP/IP) Properties .......................................................... 442
Figure 258 Macintosh OS 8/9: Apple Menu .......................................................................................... 443
Figure 259 Macintosh OS 8/9: TCP/IP ................................................................................................. 443
Figure 260 Macintosh OS X: Apple Menu ............................................................................................ 444
Figure 261 Macintosh OS X: Network .................................................................................................. 445
Figure 262 Pop-up Blocker ................................................................................................................... 447
Figure 263 Internet Options: Privacy .................................................................................................... 448
Figure 264 Internet Options: Privacy .................................................................................................... 449
Figure 265 Pop-up Blocker Settings ..................................................................................................... 449
Figure 266 Internet Options: Security ................................................................................................... 450
Figure 267 Security Settings - Java Scripting ....................................................................................... 451
Figure 268 Security Settings - Java ...................................................................................................... 451
Figure 269 Java (Sun) .......................................................................................................................... 452
Figure 270 Network Number and Host ID ............................................................................................ 454
Figure 271 Subnetting Example: Before Subnetting ............................................................................ 456
Figure 272 Subnetting Example: After Subnetting ............................................................................... 457
Figure 273 Peer-to-Peer Communication in an Ad-hoc Network ......................................................... 461
Figure 274 Basic Service Set ............................................................................................................... 462
Figure 275 Infrastructure WLAN ........................................................................................................... 463
Figure 276 RTS/CTS ........................................................................................................................... 464
Figure 277 WPA(2) with RADIUS Application Example ....................................................................... 471
Figure 278 WPA(2)-PSK Authentication ............................................................................................... 472
P-2602HWLNI User’s Guide
31
Page 32

List of Figures
32
P-2602HWLNI User’s Guide
Page 33

List of Tables
List of Tables
Table 1 Models Covered ........................................................................................................................ 41
Table 2 LEDs ......................................................................................................................................... 46
Table 3 Web Configurator Icons in the Title Bar .................................................................................... 53
Table 4 Navigation Panel Summary ...................................................................................................... 53
Table 5 Available Features .................................................................................................................... 57
Table 6 Internet Access Wizard Setup: ISP Parameters ....................................................................... 67
Table 7 Internet Connection with PPPoE .............................................................................................. 68
Table 8 Internet Connection with RFC 1483 .......................................................................................... 69
Table 9 Internet Connection with ENET ENCAP ...................................................................................69
Table 10 Internet Connection with PPPoA ............................................................................................. 70
Table 11 Wireless LAN Setup Wizard 1 ................................................................................................. 72
Table 12 Wireless LAN Setup Wizard 2 ................................................................................................. 73
Table 13 Manually Assign a WPA key ................................................................................................... 74
Table 14 Manually Assign a WEP key ................................................................................................... 75
Table 15 VoIP Wizard Configuration ...................................................................................................... 80
Table 16 Bandwidth Management Wizard: General Information ........................................................... 84
Table 17 Status Screen .......................................................................................................................... 88
Table 18 Any IP Table ............................................................................................................................ 91
Table 19 WLAN Status ........................................................................................................................... 92
Table 20 Packet Statistics ...................................................................................................................... 93
Table 21 VoIP Statistics ......................................................................................................................... 94
Table 22 LED Status .............................................................................................................................. 96
Table 23 Internet Access Setup ........................................................................................................... 106
Table 24 Advanced Internet Access Setup .......................................................................................... 108
Table 25 Advanced Internet Access Setup ...........................................................................................110
Table 26 More Connections Edit ...........................................................................................................111
Table 27 More Connections Edit Advanced ..........................................................................................113
Table 28 WAN Backup Setup ...............................................................................................................115
Table 29 LAN IP ................................................................................................................................... 122
Table 30 Advanced LAN Setup ............................................................................................................ 123
Table 31 DHCP Setup ......................................................................................................................... 124
Table 32 LAN Client List ...................................................................................................................... 126
Table 33 LAN IP Alias .......................................................................................................................... 128
Table 34 Types of Encryption for Each Type of Authentication ........................................................... 131
Table 35 Additional Wireless Terms ..................................................................................................... 133
Table 36 Wireless LAN: General ......................................................................................................... 134
Table 37 Wireless No Security ............................................................................................................. 135
Table 38 Wireless: Static WEP Encryption .......................................................................................... 136
P-2602HWLNI User’s Guide
33
Page 34

List of Tables
Table 39 Wireless: WPA(2)-PSK ......................................................................................................... 137
Table 40 Wireless: WPA(2) .................................................................................................................. 138
Table 41 Wireless LAN: Advanced ...................................................................................................... 140
Table 42 Network > Wireless LAN > OTIST ........................................................................................ 141
Table 43 MAC Address Filter ............................................................................................................... 144
Table 44 Wireless LAN: Association List ............................................................................................. 145
Table 45 Wireless LAN: QoS ............................................................................................................... 146
Table 46 Application Priority Configuration .......................................................................................... 147
Table 47 Wireless LAN > WDS ............................................................................................................ 149
Table 48 Wireless LAN > WDS > Static WEP ......................................................................................150
Table 49 Wireless LAN > WDS > WPA-PSK ...................................................................................... 152
Table 50 Wireless LAN > WDS > WPA2-PSK ..................................................................................... 153
Table 51 NAT Definitions ..................................................................................................................... 155
Table 52 NAT Mapping Types .............................................................................................................. 158
Table 53 NAT General ......................................................................................................................... 159
Table 54 Port Forwarding .................................................................................................................... 161
Table 55 Port Forwarding Rule Setup .................................................................................................. 162
Table 56 Address Mapping Rules ........................................................................................................ 163
Table 57 Edit Address Mapping Rule .................................................................................................. 165
Table 58 SIP Call Progression ............................................................................................................. 173
Table 59 SIP Call Progression ............................................................................................................. 174
Table 60 Custom Tones Details ........................................................................................................... 176
Table 61 SIP > SIP Settings ................................................................................................................ 178
Table 62 VoIP > SIP Settings > Advanced .......................................................................................... 180
Table 63 SIP > QoS ............................................................................................................................. 183
Table 64 Phone > Analog Phone ......................................................................................................... 186
Table 65 Phone > Analog Phone > Advanced ..................................................................................... 188
Table 66 Phone > ISDN Phone ........................................................................................................... 190
Table 67 Phone > Common ................................................................................................................. 191
Table 68 VoIP > Phone > Ext. Table .................................................................................................... 193
Table 69 VoIP > Phone > Ext. Table > Advanced ................................................................................ 194
Table 70 European Flash Key Commands ..........................................................................................195
Table 71 USA Flash Key Commands .................................................................................................. 197
Table 72 VoIP > Phone > Region ........................................................................................................ 198
Table 73 Phone Book > Speed Dial ..................................................................................................... 199
Table 74 Phone Book > Incoming Call Policy ...................................................................................... 201
Table 75 Phone Book > Distinctive Ring .............................................................................................. 203
Table 76 Phone Book > SIP Prefix ...................................................................................................... 205
Table 77 PSTN Line > General ............................................................................................................ 207
Table 78 ISDN Line > General ............................................................................................................. 207
Table 79 VoIP > Fixed Line Numbers Screen ...................................................................................... 210
Table 80 Matching Incoming and Outgoing Authentication ................................................................. 212
Table 81 Call Rules .............................................................................................................................. 213
34
P-2602HWLNI User’s Guide
Page 35

List of Tables
Table 82 VoIP > Trunking > General .................................................................................................... 215
Table 83 VoIP > Trunking > Peer Call .................................................................................................. 216
Table 84 VoIP > Trunking > Call Rule .................................................................................................. 218
Table 85 VoIP Trunking Call Progression ............................................................................................ 221
Table 86 PSTN to PSTN: VoIP Trunking Call Progression .................................................................. 225
Table 87 Common IP Ports .................................................................................................................. 235
Table 88 ICMP Commands That Trigger Alerts ................................................................................... 238
Table 89 Legal NetBIOS Commands ................................................................................................... 238
Table 90 Legal SMTP Commands ...................................................................................................... 238
Table 91 Firewall: General ................................................................................................................... 249
Table 92 Firewall Rules ....................................................................................................................... 250
Table 93 Firewall: Edit Rule ................................................................................................................. 252
Table 94 Customized Services ............................................................................................................ 254
Table 95 Firewall: Configure Customized Services ............................................................................. 255
Table 96 Firewall: Threshold ................................................................................................................ 261
Table 97 Sys Firewall Commands ....................................................................................................... 262
Table 98 Content Filter: Keyword ........................................................................................................ 266
Table 99 Content Filter: Schedule ....................................................................................................... 267
Table 100 Content Filter: Trusted ........................................................................................................ 267
Table 101 VPN and NAT ...................................................................................................................... 273
Table 102 AH and ESP ........................................................................................................................ 276
Table 103 VPN Setup .......................................................................................................................... 278
Table 104 VPN and NAT ...................................................................................................................... 280
Table 105 Local ID Type and Content Fields ....................................................................................... 282
Table 106 Peer ID Type and Content Fields ........................................................................................ 282
Table 107 Matching ID Type and Content Configuration Example ...................................................... 282
Table 108 Mismatching ID Type and Content Configuration Example ................................................ 283
Table 109 Edit VPN Policies ................................................................................................................ 284
Table 110 Advanced VPN Policies ...................................................................................................... 290
Table 111 VPN: Manual Key ................................................................................................................ 293
Table 112 VPN: SA Monitor ................................................................................................................. 296
Table 113 VPN: Global Setting ............................................................................................................ 297
Table 114 Telecommuters Sharing One VPN Rule Example ............................................................... 298
Table 115 Telecommuters Using Unique VPN Rules Example ............................................................ 299
Table 116 My Certificates .................................................................................................................... 303
Table 117 My Certificate Import ........................................................................................................... 305
Table 118 My Certificate Create .......................................................................................................... 306
Table 119 My Certificate Details .......................................................................................................... 310
Table 120 Trusted CAs ........................................................................................................................ 312
Table 121 Trusted CA Import ............................................................................................................... 313
Table 122 Trusted CA Details .............................................................................................................. 315
Table 123 Trusted Remote Hosts ........................................................................................................ 317
Table 124 Trusted Remote Host Import ............................................................................................... 319
P-2602HWLNI User’s Guide
35
Page 36

List of Tables
Table 125 Trusted Remote Host Details .............................................................................................. 321
Table 126 Directory Servers ................................................................................................................ 323
Table 127 Directory Server Add and Edit ............................................................................................ 324
Table 128 Static Route ......................................................................................................................... 328
Table 129 Static Route Edit ................................................................................................................. 329
Table 130 Typical Packet Sizes ........................................................................................................... 332
Table 131 Automatic Traffic Classifier Priorities .................................................................................. 332
Table 132 Application and Subnet-based Bandwidth Management Example ..................................... 333
Table 133 Bandwidth Management Priorities ...................................................................................... 333
Table 134 Bandwidth Management: General ...................................................................................... 334
Table 135 Bandwidth Management: Rule Setup ................................................................................. 334
Table 136 Bandwidth Management Rule Configuration ...................................................................... 336
Table 137 Dynamic DNS ..................................................................................................................... 340
Table 138 Remote Management: HTTP .............................................................................................. 346
Table 139 Remote Management: Telnet .............................................................................................. 348
Table 140 Remote Management: FTP ................................................................................................. 349
Table 141 SNMP Traps ........................................................................................................................ 351
Table 142 Remote Management: SNMP .............................................................................................352
Table 143 Remote Management: DNS ................................................................................................ 353
Table 144 Remote Management: ICMP .............................................................................................. 354
Table 145 ADVANCED > REMOTE MGMT > SSH ............................................................................. 356
Table 146 Configuring UPnP ............................................................................................................... 362
Table 147 System General Setup ........................................................................................................ 376
Table 148 System Time Setting ........................................................................................................... 377
Table 149 Call History > Summary ...................................................................................................... 382
Table 150 Call History > Call History ................................................................................................... 383
Table 151 Call History > Call History Settings ..................................................................................... 385
Table 152 View Log ............................................................................................................................. 388
Table 153 Log Settings ........................................................................................................................ 389
Table 154 SMTP Error Messages ........................................................................................................ 391
Table 155 System Maintenance Logs .................................................................................................. 392
Table 156 System Error Logs .............................................................................................................. 393
Table 157 Access Control Logs ........................................................................................................... 393
Table 158 TCP Reset Logs .................................................................................................................. 393
Table 159 Packet Filter Logs ............................................................................................................... 394
Table 160 ICMP Logs .......................................................................................................................... 394
Table 161 CDR Logs ........................................................................................................................... 394
Table 162 PPP Logs ............................................................................................................................ 395
Table 163 UPnP Logs .......................................................................................................................... 395
Table 164 Content Filtering Logs ......................................................................................................... 395
Table 165 Attack Logs ......................................................................................................................... 395
Table 166 802.1X Logs ........................................................................................................................ 396
Table 167 ACL Setting Notes .............................................................................................................. 397
36
P-2602HWLNI User’s Guide
Page 37

List of Tables
Table 168 ICMP Notes ......................................................................................................................... 397
Table 169 Syslog Logs ........................................................................................................................ 398
Table 170 SIP Logs ............................................................................................................................. 398
Table 171 RTP Logs ............................................................................................................................ 399
Table 172 FSM Logs: Caller Side ........................................................................................................ 399
Table 173 FSM Logs: Callee Side ....................................................................................................... 399
Table 174 PSTN Logs .......................................................................................................................... 399
Table 175 RFC-2408 ISAKMP Payload Types .................................................................................... 400
Table 176 Filename Conventions ........................................................................................................ 408
Table 177 Firmware Upgrade .............................................................................................................. 409
Table 178 Restore Configuration ..........................................................................................................411
Table 179 General Commands for GUI-based FTP Clients ................................................................ 414
Table 180 General Commands for GUI-based TFTP Clients .............................................................. 415
Table 181 Diagnostic: General ............................................................................................................ 419
Table 182 Diagnostic: DSL Line .......................................................................................................... 420
Table 183 Hardware Specifications ..................................................................................................... 423
Table 184 Firmware Specifications ...................................................................................................... 423
Table 185 Voice Features .................................................................................................................... 427
Table 186 Wireless Features ............................................................................................................... 429
Table 187 IEEE 802.11g ...................................................................................................................... 430
Table 188 P-2602HWL Series Power Adaptor Specifications ............................................................. 431
Table 189 Subnet Masks ..................................................................................................................... 454
Table 190 Subnet Masks ..................................................................................................................... 455
Table 191 Maximum Host Numbers .................................................................................................... 455
Table 192 Alternative Subnet Mask Notation ....................................................................................... 455
Table 193 Subnet 1 .............................................................................................................................. 457
Table 194 Subnet 2 .............................................................................................................................. 458
Table 195 Subnet 3 .............................................................................................................................. 458
Table 196 Subnet 4 .............................................................................................................................. 458
Table 197 Eight Subnets ...................................................................................................................... 458
Table 198 24-bit Network Number Subnet Planning ............................................................................ 459
Table 199 16-bit Network Number Subnet Planning ............................................................................ 459
Table 200 IEEE 802.11g ...................................................................................................................... 465
Table 201 Wireless Security Levels ..................................................................................................... 466
Table 202 Comparison of EAP Authentication Types .......................................................................... 469
Table 203 Wireless Security Relational Matrix .................................................................................... 472
Table 204 Examples of Services ......................................................................................................... 475
P-2602HWLNI User’s Guide
37
Page 38

List of Tables
38
P-2602HWLNI User’s Guide
Page 39

PART I
Introduction
Introducing the ZyXEL Device (41)
Introducing the Web Configurator (49)
39
Page 40

40
Page 41

CHAPTER 1
Introducing the ZyXEL Device
This chapter introduces the main applications and features of the ZyXEL Device. It also
introduces the ways you can manage the ZyXEL Device.
1.1 Overview
The ZyXEL Device is an Integrated Access Device (IAD) that combines an ADSL2+ router
with Voice over IP (VoIP) communication capabilities to allow you to use a traditional analog
or ISDN telephone to make Internet calls. By integrating DSL and NAT, you are provided with
ease of installation and high-speed, shared Internet access. The ZyXEL Device is also a
complete security solution with a robust firewall and content filtering.
At the time of writing, this guide covers the following models.
Table 1 Models Covered
P-2602HWNLI-D3A
P-2602HWNLI-D7A
• In the ZyXEL Device product name, “H” denotes an integrated 4-port switch (hub).
• “W” denotes wireless functionality. There is an embedded mini-PCI module for IEEE
802.11g wireless LAN connectivity.
• “N” denotes the ability to connect an ISDN (Integrated Services Digital Network)
telephone to the device.
• “L” denotes the PSTN (Public Switched Telephone Network) line feature.
" When the ZyXEL Device does not have power, only the phone connected to
the PHONE 1 port can be used for making calls. Ensure you know which
phone this is, so that in case of emergency you can make outgoing calls.
• “I” denotes the ISDN (Integrated Services Digital Network) line feature.
1
1. A device that includes both “L” and “I” in the model name can support either a PSTN line or a ISDN
line, but not both at the same time.
P-2602HWLNI User’s Guide
41
Page 42

Chapter 1 Introducing the ZyXEL Device
The P-2602HWNLI-D3A works over ISDN (Integrated Services Digital Network).
The P-2602HWNLI-D7A works over T-ISDN (UR-2).
" Only use firmware for your ZyXEL Device’s specific model. Refer to the label
on the bottom of your ZyXEL Device.
The web browser-based Graphical User Interface (GUI) provides easy management.See the
appendix on Product Specifications for a full list of features.
1.2 Ways to Manage the ZyXEL Device
Use any of the following methods to manage the ZyXEL Device.
• Web Configurator. This is recommended for everyday management of the ZyXEL Device
using a (supported) web browser.
• Command Line Interface. Line commands are mostly used for troubleshooting by service
engineers.
• FTP for firmware upgrades and configuration backup/restore.
• SNMP. The device can be monitored by an SNMP manager. See the SNMP chapter in this
User’s Guide.
• SPTGEN. SPTGEN is a text configuration file that allows you to configure the device by
uploading an SPTGEN file. This is especially convenient if you need to configure many
devices of the same type.
• Vantage CNM (Centralized Network Management). The device can be remotely managed
using a Vantage CNM server.
• TR-069. This is an auto-configuration server used to remotely configure your device.
1.3 Good Habits for Managing the ZyXEL Device
Do the following things regularly to make the ZyXEL Device more secure and to manage the
ZyXEL Device more effectively.
• Change the password. Use a password that’s not easy to guess and that consists of
different types of characters, such as numbers and letters.
• Write down the password and put it in a safe place.
• Back up the configuration (and make sure you know how to restore it). Restoring an
earlier working configuration may be useful if the device becomes unstable or even
crashes. If you forget your password, you will have to reset the ZyXEL Device to its
factory default settings. If you backed up an earlier configuration file, you would not have
to totally re-configure the ZyXEL Device. You could simply restore your last
configuration.
42
P-2602HWLNI User’s Guide
Page 43

1.4 Applications for the ZyXEL Device
Here are some example uses for which the ZyXEL Device is well suited.
1.4.1 Internet Access
Your device is the ideal high-speed Internet access solution. It supports the TCP/IP protocol,
which the Internet uses exclusively. It is compatible with all major ADSL DSLAM (Digital
Subscriber Line Access Multiplexer) providers. A DSLAM is a rack of ADSL line cards with
data multiplexed into a backbone network interface/connection (for example, T1, OC3, DS3,
ATM or Frame Relay). Think of it as the equivalent of a modem rack for ADSL. In addition,
your device allows wireless clients access to your network resources and the Internet. A
typical Internet access application is shown below.
Figure 1 Internet Access Application
Chapter 1 Introducing the ZyXEL Device
1.4.1.1 Internet Single User Account
For a SOHO (Small Office/Home Office) environment, your device offers the Single User
Account (SUA) feature that allows multiple users on the LAN (Local Area Network) to access
the Internet concurrently for the cost of a single IP address
1.4.2 Making Calls via Internet Telephony Service Provider
In a home or small office environment, you can use your device to make and receive VoIP
telephone calls through an Internet Telephony Service Provider (ITSP).
The following figure shows a basic example of how you would make a VoIP call through an
ITSP. You use your analog phone (A in the figure) and your device (B) changes the call into
VoIP. Your device then sends your call to the Internet and the ITSP’s SIP server (C). The VoIP
call server forwards calls to PSTN phones (E) through a trunking gateway (D) to the PSTN
network. The VoIP call server forwards calls to IP phones (F) through the Internet.
P-2602HWLNI User’s Guide
43
Page 44

Chapter 1 Introducing the ZyXEL Device
Figure 2 Internet Telephony Service Provider Application
1.4.3 Make Peer-to-peer Calls
You can call directly to someone’s IP address without using a SIP proxy server. Peer-to-peer
calls are also called “Point to Point” or “IP-to-IP” calls. You must know the peer’s IP address
in order to do this.
The following figure shows a basic example of how you would make a peer-to-peer VoIP call.
You use your analog phone (A in the figure) and your device (B) changes the call into VoIP.
and sends the call through the Internet to the peer VoIP device (C).
Figure 3 Peer-to-peer Calling
1.4.4 Firewall for Secure Broadband Internet Access
Your device provides protection from attacks by Internet hackers. By default, the firewall
blocks all incoming traffic from the WAN. The firewall supports TCP/UDP inspection and
DoS (Denial of Services) detection and prevention, as well as real time alerts, reports and logs.
44
P-2602HWLNI User’s Guide
Page 45

Figure 4 Firewall Application
1.4.5 LAN to LAN Application
You can use your device to connect two geographically dispersed networks over the ADSL
line. A typical LAN-to-LAN application is shown as follows.
Chapter 1 Introducing the ZyXEL Device
Figure 5 LAN-to-LAN Application
P-2602HWLNI User’s Guide
45
Page 46

Chapter 1 Introducing the ZyXEL Device
1.5 LEDs
Figure 6 LEDs
46
The following table describes your device’s LEDs.
Table 2 LEDs
LED COLOR STATUS DESCRIPTION
POWER Green On Your device is receiving power and functioning properly.
Blinking Your device is rebooting and performing a self-test.
Red On Your device is not ready or there is a malfunction.
None Off Your device is not turned on.
ETHERNET
1-4
WLAN Green On Your device is ready, but is not sending/receiving data
Green On Your device has a successful Ethernet connection.
Blinking The ZyXEL Device is sending/receiving data.
None Off The Ethernet port is not connected.
through the wireless LAN.
Blinking Your device is sending/receiving data through the wireless
LAN.
None Off The wireless LAN is not ready or has failed.
P-2602HWLNI User’s Guide
Page 47

Chapter 1 Introducing the ZyXEL Device
Table 2 LEDs (continued)
LED COLOR STATUS DESCRIPTION
DSL Green On Your device has a DSL connection.
Blinking Your device is initializing the DSL line.
None Off The DSL link is down.
INTERNET Green On Your device has an IP connection but no traffic.
Your device has a WAN IP address (either static or assigned
by a DHCP server), PPP negotiation was successfully
completed (if used) and the DSL connection is up.
Blinking Your device is sending or receiving IP traffic.
Red On Your device attempted to make an IP connection but failed.
Possible causes are no response from a DHCP server, no
PPPoE response, PPPoE authentication failed).
None Off Your device does not have an IP connection
PHONE 1, 2 Green On A SIP account is registered for the phone port.
Blinking A telephone connected to the phone port has its receiver off
of the hook or there is an incoming call.
ISDN
PHONE
Orange On A SIP account is registered for the phone port and there is a
Blinking A telephone connected to the phone port has its receiver off
None Off The phone port does not have a SIP account registered.
Green On A SIP account is registered for the phone port.
Blinking A telephone connected to the phone port has its receiver off
None Off The phone port does not have a SIP account registered.
voice message in the corresponding SIP account.
of the hook and there is a voice message in the
corresponding SIP account.
of the hook or there is an incoming call.
Refer to the Quick Start Guide for information on hardware connections.
1.6 The RESET Button
You can use the RESET button at the back of the device to turn the wireless LAN off or on.
You can also use it to activate OTIST in order to assign your wireless security settings to
wireless clients. If you forget your password or cannot access the web configurator, you will
need to use the RESET button to reload the factory-default configuration file. This means that
you will lose all configurations that you had previously and the password will be reset to
“1234”. You can also use the
1.6.1 Using The Reset Button
1 Make sure the POWER LED is on (not blinking).
2 Do one of the following.
To turn the wireless LAN off or on, press the RESET button for one second and release
it. The WLAN LED should change from on to off or vice versa. (“W” models only)
P-2602HWLNI User’s Guide
47
Page 48

Chapter 1 Introducing the ZyXEL Device
To activate OTIST in order to assign your wireless security settings to wireless clients,
press the RESET button for five seconds and release it. The WLAN LED should flash
while the device uses OTIST to send wireless settings to OTIST clients.(“W” models
only)
To set the device back to the factory default settings, press the RESET button for ten
seconds or until the POWER LED begins to blink and then release it. When the
POWER LED begins to blink, the defaults have been restored and the device restarts.
48
P-2602HWLNI User’s Guide
Page 49

CHAPTER 2
Introducing the Web
Configurator
This chapter describes how to access and navigate the web configurator.
2.1 Web Configurator Overview
The web configurator is an HTML-based management interface that allows easy device setup
and management via Internet browser. Use Internet Explorer 6.0 and later or Netscape
Navigator 7.0 and later versions. The recommended screen resolution is 1024 by 768 pixels.
In order to use the web configurator you need to allow:
• Web browser pop-up windows from your device. Web pop-up blocking is enabled by
default in Windows XP SP (Service Pack) 2.
• JavaScripts (enabled by default).
• Java permissions (enabled by default).
See Appendix B on page 447 if you need to make sure these functions are allowed in Internet
Explorer.
2.1.1 Accessing the Web Configurator
1 Make sure your ZyXEL Device hardware is properly connected (refer to the Quick Start
Guide).
2 Launch your web browser.
3 Type "192.168.1.1" as the URL.
4 A password screen displays.
P-2602HWLNI User’s Guide
49
Page 50

Chapter 2 Introducing the Web Configurator
Figure 7 Password Screen
2.2 Login Types
There are two login types; “user” and “administrator”. When you choose user access, you can
make basic configuration changes only. Advanced features are not available. When you
choose administrator access, all features are available. See Chapter 2 on page 57 for more
information.
2.2.1 User Access
1 For user access, type the default user name user and default user password 1234 in the
password screen to enter the user mode.
2 If you haven’t changed the password yet, you can just click Login. Click Cancel to
revert to the default password in the password field. If you have changed the password,
enter your password and click Login.
3 Follow steps (from step 3) in Section 2.2.2 on page 50.
" The default user name and password are case-sensitive.
2.2.2 Administrator Access
1 For administrator access, type the default user name admin and the default admin
password admin in the password screen to configure the advanced features.
2 Click Login to proceed to a screen asking you to change your password or click Cancel
to revert to the default password.
3 The following screen displays if you have not yet changed your password. It is strongly
recommended you change the default password. Enter a new password, retype it to
confirm and click Apply; alternatively click Ignore to proceed to the main menu if you
do not want to change the password now.
50
P-2602HWLNI User’s Guide
Page 51

Chapter 2 Introducing the Web Configurator
" If you do not change the password, the following screen appears every time
you log in with the default password.
Figure 8 Change Password Screen
4 Click Apply in the Replace Certificate screen to create a certificate using your ZyXEL
Device’s MAC address that will be specific to this device. This screen displays only
when you log in as an administrator.
Figure 9 Replace Certificate Screen
5 A screen displays to let you choose whether to go to the wizard or the advanced screens.
• Click Go to Wizard setup if you are logging in for the first time or if you want to make
basic changes. The wizard selection screen appears after you click Apply. See Chapter 3
on page 63 for more information.
• Click Go to Advanced setup if you want to configure features that are not available in the
wizards. Select the check box if you always want to go directly to the advanced screens.
The main screen appears after you click Apply. See Section 2.3 on page 52 for more
information.
• Click Exit if you want to log out.
P-2602HWLNI User’s Guide
51
Page 52

Chapter 2 Introducing the Web Configurator
" For security reasons, the ZyXEL Device automatically logs you out if you do
not use the web configurator for five minutes (default). If this happens, log in
again.
Figure 10 Wizard or Advanced Screen
2.3 Web Configurator Main Screen
Figure 11 Main Screen
B
C
A
52
D
As illustrated above, the main screen is divided into these parts:
P-2602HWLNI User’s Guide
Page 53

• A - title bar
• B - navigation panel
• C - main window
• D - status bar
2.3.1 Title Bar
The title bar allows you to change the language and provides some icons in the upper right
corner.
The icons provide the following functions.
Table 3 Web Configurator Icons in the Title Bar
ICON DESCRIPTION
Chapter 2 Introducing the Web Configurator
Help: Click this icon to open up help screens.
Wizards: Click this icon to go to the configuration wizards. See Chapter 3 on page
63 for more information.
Logout: Click this icon to log out of the web configurator.
2.3.2 Navigation Panel
Use the menu items on the navigation panel to configure ZyXEL Device features. When a user
logs in, only basic menu items display. When an administrator logins in, all menu items
display for configuration. See Chapter 2 on page 57 for more information.
The following tables describe each menu item.
Table 4 Navigation Panel Summary
LINK TAB FUNCTION
Status This screen contains administrative and system-related information.
Network
WAN Internet Access
Setup
More
Connections
WAN Backup
Setup
LAN IP Use this screen to configure LAN TCP/IP settings, enable Any IP and other
DHCP Setup Use this screen to configure LAN DHCP settings.
Client List Use this screen to view current DHCP client information and to always
IP Alias Use this screen to partition your LAN interface into subnets.
Use this screen to configure ISP parameters, WAN IP address assignment,
DNS servers and other advanced properties.
Use this screen to configure additional WAN connections.
Use this screen to configure a backup gateway.
advanced properties.
assign specific IP addresses to individual MAC addresses (and host
names).
P-2602HWLNI User’s Guide
53
Page 54

Chapter 2 Introducing the Web Configurator
Table 4 Navigation Panel Summary
LINK TAB FUNCTION
Wireless LAN General Use this screen to configure the wireless LAN settings and WLAN
authentication/security settings.
OTIST Use this screen to assign your wireless security settings to wireless clients.
MAC Filter Use this screen to configure the ZyXEL Device to give exclusive access to
specific wireless clients or exclude specific wireless clients from accessing
the ZyXEL Device.
Association List Use this screen to view the wireless stations that are currently associated
with the ZyXEL Device. You can also block the individual wireless station
from accessing the ZyXEL Device.
QoS WMM QoS allows you to prioritize wireless traffic according to the delivery
requirements of individual services.
WDS Use this screen to set up your WDS (Wireless Distribution System) links
NAT General Use this screen to enable NAT.
Port Forwarding Use this screen to make your local servers visible to the outside world.
VoIP
SIP SIP Settings Use this screen to configure your ZyXEL Device’s Voice over IP settings.
QoS Use this screen to configure your ZyXEL Device’s Quality of Service
Phone Analog Phone Use this screen to set which Phone 1 and Phone 2 port settings.
ISDN Phone Use this screen to configure the ISDN phone port settings.
Common Use this screen to configure general phone port settings.
Ext. Table Use this screen to configure extension numbers of the phone ports.
Region Use this screen to select your location and call service mode.
Phone Book Speed Dial Use this screen to configure speed dial for SIP phone numbers that you call
Incoming Call
Policy
Distinctive Ring Use this screen to configure ring tone behavior based on the origin of
SIP Prefix Use this screen to set up numbers you dial to select a SIP account for
PSTN Line General Use this screen to configure your ZyXEL Device’s settings for PSTN calls.
ISDN Line General Use this screen to configure your ZyXEL Device’s settings for ISDN calls.
Fixed Line
Numbers
Trunking General Use this screen to enable trunking on your ZyXEL Device.
Security
Fixed Line
Numbers
Peer Call Use this screen to configure peer device authentication for trunking calls.
Call Rule Use this screen to configure forwarding rules on your ZyXEL Device for
between the ZyXEL Device and other wireless APs.
settings for VoIP.
often.
Use this screen to configure call-forwarding.
incoming calls.
outgoing calls.
Use this screen to allow your ISDN phone to receive PSTN calls.
You can also use this screen to allow your analog phone(s) to make and
receive calls over the ISDN line using Multiple Subscriber Numbers
(MSNs).
trunking calls.
54
P-2602HWLNI User’s Guide
Page 55

Chapter 2 Introducing the Web Configurator
Table 4 Navigation Panel Summary
LINK TAB FUNCTION
Firewall General Use this screen to activate/deactivate the firewall and the default action to
take on network traffic going in specific directions.
Rules This screen shows a summary of the firewall rules, and allows you to edit/
add a firewall rule.
Threshold Use this screen to configure the thresholds for determining when to drop
sessions that do not become fully established.
Content Filter Keyword Use this screen to block access to web sites containing certain keywords in
the URL.
Schedule Use this screen to set the days and times for your device to perform content
Trusted Use this screen to exclude a range of users on the LAN from content
VPN Setup Use this screen to configure each VPN tunnel.
Monitor Use this screen to look at the current status of each VPN tunnel.
VPN Global
Setting
Certificates My Certificates Use this screen to generate and export self-signed certificates or
Trusted CAs Use this screen to save CA certificates to the ZyXEL Device.
Trusted Remote
Hosts
Directory
Servers
Advanced
Static Route Static Route Use this screen to configure IP static routes to tell your device about
Bandwidth
MGMT
Dynamic DNS Dynamic DNS This screen allows you to use a static hostname alias for a dynamic IP
General Use this screen to configure bandwidth management on an interface.
Rule Setup Use this screen to define a bandwidth rule.
Monitor Use this screen to view the ZyXEL Device’s bandwidth usage and
filtering.
filtering.
Use this screen to allow NetBIOS traffic through VPN tunnels.
certification requests and import the ZyXEL Device’s CA-signed certificates.
Use this screen to import self-signed certificates.
Use this screen to configure a list of addresses of directory servers (that
contain lists of valid and revoked certificates).
networks beyond the directly connected remote nodes.
allotments.
address.
P-2602HWLNI User’s Guide
55
Page 56

Chapter 2 Introducing the Web Configurator
Table 4 Navigation Panel Summary
LINK TAB FUNCTION
Remote MGMT HTTP Use this screen to configure through which interface(s) and from which IP
address(es) users can use HTTP and HTTPS to manage the ZyXEL
Device.
Telnet Use this screen to configure through which interface(s) and from which IP
address(es) users can use Telnet to manage the ZyXEL Device.
FTP Use this screen to configure through which interface(s) and from which IP
SNMP Use this screen to configure your ZyXEL Device’s settings for Simple
DNS Use this screen to configure through which interface(s) and from which IP
ICMP Use this screen to set whether or not your ZyXEL Device will respond to
SSH Use this screen to configure through which interface(s) and from which IP
UPnP General Use this screen to turn UPnP on or off.
Maintenance
System General Use this screen to configure your device’s name, domain name,
Time Setting Use this screen to change your ZyXEL Device’s time and date.
Logs View Log Use this screen to display your device’s logs.
Log Settings Use this screen to select which logs and/or immediate alerts your device is
Call History Summary Use this screen to display duration and packet statistics about calls made
Call History Use this screen to display information about individual incoming and
Call History
Settings
Tools Firmware Use this screen to upload firmware to your device.
Configuration Use this screen to backup and restore your device’s configuration (settings)
Restart This screen allows you to reboot the ZyXEL Device without turning the
Diagnostic General Use this screen to test the connections to other devices.
DSL Line These screen displays information to help you identify problems with the
address(es) users can use FTP to access the ZyXEL Device.
Network Management Protocol management.
address(es) users can send DNS queries to the ZyXEL Device.
pings and probes for services that you have not made available.
address(es) users can use Secure Shell to manage the ZyXEL Device.
management inactivity timeout and password.
to record. You can also set it to e-mail the logs to you.
and received on the ZyXEL Device.
outgoing calls.
Use this screen to configure to where the ZyXEL Device is to send call
history records and the schedule for when the ZyXEL Device is to save and
send the records.
or reset the factory default settings.
power off.
DSL connection.
56
P-2602HWLNI User’s Guide
Page 57

2.3.2.1 Available Features for User and Administrator
The following table lists the features respectively available for user and administrator access.
An “O” indicates that a feature is available in this mode.
Table 5 Available Features
LINK FEATURE USER ADMINISTRATOR
Internet/Wireless
Setup Wizard
VoIP Setup Wizard O O
Bandwidth
Management Wizard
System Statistics O O
Network
WAN Internet Access Setup O O
More Connections O
WAN Backup Setup O
LAN IP O
DHCP Setup O
Client List O
IP Alias O
Wireless LAN General O O
OTIST O O
MAC Filter O
Association List O
QoS O
WDS O
NAT General O
Port Forwarding O O
VoI P
SIP SIP Settings O O
QoS O
Phone Analog Phone O O
ISDN Phone O
Common O O
Ext. Table O O
Region O O
Phone Book Speed Dial O O
Incoming Call Policy O
Distinctive Ring O
SIP Prefix O O
PSTN Line General O O
ISDN Line General O O
OO
OO
Chapter 2 Introducing the Web Configurator
P-2602HWLNI User’s Guide
57
Page 58

Chapter 2 Introducing the Web Configurator
Table 5 Available Features
LINK FEATURE USER ADMINISTRATOR
Fixed Line
Numbers
Trunking General O
Security
Firewall General O O
Content Filter Keyword O
VPN Setup O
Certificates My Certificates O
Advanced
Static Route Static Route O
Bandwidth MGMT General O O
Dynamic DNS Dynamic DNS O
Remote MGMT HTTP O
UPnP General O O
Maintenance O
System General O O
Logs View Log O O
Fixed Line Numbers O O
Peer Call O
Call Rule O
Rules O
Threshold O
Schedule O
Trusted O
Monitor O
VPN Global Setting O
Trusted CAs O
Trusted Remote Hosts O
Directory Servers O
Rule Setup O
Monitor O O
Te ln e t O
FTP O
SNMP O
DNS O
ICMP O
SSH O
Time Setting O O
Log Settings O O
58
P-2602HWLNI User’s Guide
Page 59

Table 5 Available Features
LINK FEATURE USER ADMINISTRATOR
Call History Summary O
Tools Firmware O O
Diagnostic General O
2.3.3 Main Window
The main window displays information and configuration fields. It is discussed in the rest of
this document.
Right after you log in, the Status screen is displayed. See Chapter 6 on page 87 for more
information about the Status screen.
Chapter 2 Introducing the Web Configurator
Call History O
Call History Settings O
Configuration O O
Restart O O
DSL Line O
2.3.4 Status Bar
Check the status bar when you click Apply or OK to verify that the configuration has been
updated.
P-2602HWLNI User’s Guide
59
Page 60

Chapter 2 Introducing the Web Configurator
60
P-2602HWLNI User’s Guide
Page 61

PART II
Wizards and Status
Internet and Wireless Setup Wizard (63)
VoIP Wizard (77)
Bandwidth Management Wizard (83)
Status Screens (87)
61
Page 62

62
Page 63

CHAPTER 3
Internet and Wireless Setup
Wizard
This chapter provides information on the Wizard Setup screens for Internet access in the web
configurator.
3.1 Introduction
Use the wizard setup screens to configure your system for Internet access with the information
given to you by your ISP.
" See the advanced menu chapters for background information on these fields.
3.2 Internet Access Wizard Setup
1 After you enter the password to access the web configurator, select Go to Wizard setup
and click Apply. Otherwise, click the wizard icon ( ) in the top right corner of the
web configurator to go to the wizards.
P-2602HWLNI User’s Guide
63
Page 64

Chapter 3 Internet and Wireless Setup Wizard
Figure 12 Select a Mode
2 Click INTERNET/WIRELESS SETUP to configure the system for Internet access and
wireless connection.
Figure 13 Wizard Welcome
3 Your ZyXEL device attempts to detect your DSL connection and your connection type.
3a The following screen appears if a connection is not detected. Check your hardware
connections and click Restart the Internet/Wireless Setup Wizard to return to the
wizard welcome screen. If you still cannot connect, click Manually configure your
Internet connection. Follow the directions in the wizard and enter your Internet
setup information as provided to you by your ISP. See Section 3.2.1 on page 66 for
more details.
If you would like to skip your Internet setup and configure the wireless LAN
settings, leave Ye s selected and click Next.
64
P-2602HWLNI User’s Guide
Page 65

Chapter 3 Internet and Wireless Setup Wizard
Figure 14 Auto Detection: No DSL Connection
3b The following screen displays if a PPPoE or PPPoA connection is detected. Enter
your Internet account information (username, password and/or service name)
exactly as provided by your ISP. Then click Next and see Section 3.3 on page 71 for
wireless connection wizard setup.
Figure 15 Auto-Detection: PPPoE
3c The following screen appears if the ZyXEL device detects a connection but not the
connection type. Click Next and refer to Section 3.2.1 on page 66 on how to
manually configure the ZyXEL Device for Internet access.
P-2602HWLNI User’s Guide
65
Page 66

Chapter 3 Internet and Wireless Setup Wizard
Figure 16 Auto Detection: Failed
3.2.1 Manual Configuration
1 If the ZyXEL Device fails to detect your DSL connection type but the physical line is
connected, enter your Internet access information in the wizard screen exactly as your
service provider gave it to you. Leave the defaults in any fields for which you were not
given information.
66
P-2602HWLNI User’s Guide
Page 67

Chapter 3 Internet and Wireless Setup Wizard
Figure 17 Internet Access Wizard Setup: ISP Parameters
The following table describes the fields in this screen.
Table 6 Internet Access Wizard Setup: ISP Parameters
LABEL DESCRIPTION
Mode From the Mode drop-down list box, select Routing (default) if your ISP allows
multiple computers to share an Internet account. Otherwise select Bridge.
Encapsulation Select the encapsulation type your ISP uses from the Encapsulation drop-down list
box. Choices vary depending on what you select in the Mode field.
If you select Bridge in the Mode field, select either PPPoA or RFC 1483.
If you select Routing in the Mode field, select PPPoA, RFC 1483, ENET ENCAP or
PPPoE.
Multiplexing Select the multiplexing method used by your ISP from the Multiplex drop-down list
box either VC-based or LLC-based.
Virtual Circuit IDVPI (Virtual Path Identifier) and VCI (Virtual Channel Identifier) define a virtual circuit.
Refer to the appendix for more information.
VPI Enter the VPI assigned to you. This field may already be configured.
VCI Enter the VCI assigned to you. This field may already be configured.
Back Click Back to go back to the previous screen.
Next Click Next to continue to the next wizard screen. The next wizard screen you see
depends on what protocol you chose above.
Exit Click Exit to close the wizard screen without saving your changes.
2 The next wizard screen varies depending on what mode and encapsulation type you use.
All screens shown are with routing mode. Configure the fields and click Next to
continue. See Section 3.3 on page 71 for wireless connection wizard setup
P-2602HWLNI User’s Guide
67
Page 68

Chapter 3 Internet and Wireless Setup Wizard
Figure 18 Internet Connection with PPPoE
The following table describes the fields in this screen.
Table 7 Internet Connection with PPPoE
LABEL DESCRIPTION
User Name Enter the user name exactly as your ISP assigned. If assigned a name in the form
user@domain where domain identifies a service name, then enter both components
exactly as given.
Password Enter the password associated with the user name above.
Service Name Type the name of your PPPoE service here.
Back Click Back to go back to the previous wizard screen.
Apply Click Apply to save your changes back to the ZyXEL Device.
Exit Click Exit to close the wizard screen without saving your changes.
68
Figure 19 Internet Connection with RFC 1483
P-2602HWLNI User’s Guide
Page 69

Chapter 3 Internet and Wireless Setup Wizard
The following table describes the fields in this screen.
Table 8 Internet Connection with RFC 1483
LABEL DESCRIPTION
IP Address This field is available if you select Routing in the Mode field.
Type your ISP assigned IP address in this field.
Back Click Back to go back to the previous wizard screen.
Next Click Next to continue to the next wizard screen.
Exit Click Exit to close the wizard screen without saving your changes.
Figure 20 Internet Connection with ENET ENCAP
The following table describes the fields in this screen.
Table 9 Internet Connection with ENET ENCAP
LABEL DESCRIPTION
Obtain an IP
Address
Automatically
Static IP
Address
IP Address Enter your ISP assigned IP address.
Subnet Mask Enter a subnet mask in dotted decimal notation.
Gateway IP
address
First DNS
Server
Second DNS
Server
Back Click Back to go back to the previous wizard screen.
P-2602HWLNI User’s Guide
A static IP address is a fixed IP that your ISP gives you. A dynamic IP address is not
fixed; the ISP assigns you a different one each time you connect to the Internet.
Select Obtain an IP Address Automatically if you have a dynamic IP address.
Select Static IP Address if your ISP gave you an IP address to use.
Refer to the appendix to calculate a subnet mask If you are implementing subnetting.
You must specify a gateway IP address (supplied by your ISP) when you use ENET
ENCAP in the Encapsulation field in the previous screen.
Enter the IP addresses of the DNS servers. The DNS servers are passed to the DHCP
clients along with the IP address and the subnet mask.
As above.
69
Page 70

Chapter 3 Internet and Wireless Setup Wizard
Table 9 Internet Connection with ENET ENCAP (continued)
LABEL DESCRIPTION
Apply Click Apply to save your changes back to the ZyXEL Device.
Exit Click Exit to close the wizard screen without saving your changes.
Figure 21 Internet Connection with PPPoA
The following table describes the fields in this screen.
Table 10 Internet Connection with PPPoA
LABEL DESCRIPTION
User Name Enter the login name that your ISP gives you.
Password Enter the password associated with the user name above.
Back Click Back to go back to the previous wizard screen.
Apply Click Apply to save your changes back to the ZyXEL Device.
Exit Click Exit to close the wizard screen without saving your changes.
• If the user name and/or password you entered for PPPoE or PPPoA connection are not
correct, the screen displays as shown next. Click Back to Username and Password setup
to go back to the screen where you can modify them.
70
P-2602HWLNI User’s Guide
Page 71

Chapter 3 Internet and Wireless Setup Wizard
Figure 22 Connection Test Failed-1
• If the following screen displays, check if your account is activated or click Restart the
Internet/Wireless Setup Wizard to verify your Internet access settings.
Figure 23 Connection Test Failed-2.
3.3 Wireless Connection Wizard Setup
After you configure the Internet access information, use the following screens to set up your
wireless LAN.
1 Select Yes and click Next to configure wireless settings. Otherwise, select No and skip to
Step 6.
P-2602HWLNI User’s Guide
71
Page 72

Chapter 3 Internet and Wireless Setup Wizard
Figure 24 Connection Test Successful
2 Use this screen to activate the wireless LAN and OTIST. Click Next to continue.
Figure 25 Wireless LAN Setup Wizard 1
72
The following table describes the labels in this screen.
Tabl e 11 Wireless LAN Setup Wizard 1
LABEL DESCRIPTION
Active Select the check box to turn on the wireless LAN.
Enable OTIST Select the check box to enable OTIST if you want to transfer your ZyXEL
Device’s SSID and WEP or WPA-PSK security settings to wireless clients that
support OTIST and are within transmission range.
You must also activate and start OTIST on the wireless client at the same time.
The process takes three minutes to complete.
Setup Key Type an OTIST Setup Key of up to eight ASCII characters in length. Be sure to
use the same OTIST Setup Key on the ZyXEL Device and wireless clients.
Back
Next
Exit Click Exit to close the wizard screen without saving.
Click Back to display the previous screen.
Click Next to proceed to the next screen.
P-2602HWLNI User’s Guide
Page 73

Chapter 3 Internet and Wireless Setup Wizard
3 Configure your wireless settings in this screen. Click Next.
Figure 26 Wireless LAN
The following table describes the labels in this screen.
Table 12 Wireless LAN Setup Wizard 2
LABEL DESCRIPTION
Network
Name(SSID)
Channel
Selection
Security Select Automatically assign a WPA key (Recommended) to have the ZyXEL
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
Enter a descriptive name (up to 32 printable 7-bit ASCII characters) for the wireless
LAN.
If you change this field on the ZyXEL Device, make sure all wireless stations use the
same SSID in order to access the network.
The range of radio frequencies used by IEEE 802.11b/g wireless devices is called a
channel. Select a channel ID that is not already in use by a neighboring device.
Device create a pre-shared key (WPA-PSK) automatically only if your wireless clients
support WPA and OTIST. This option is available only when you enable OTIST in the
previous wizard screen.
Select Manually assign a WPA-PSK key to configure a Pre-Shared Key (WPA-PSK).
Choose this option only if your wireless clients support WPA. See Section 3.3.1 on
page 74 for more information.
Select Manually assign a WEP key to configure a WEP Key. See Section 3.3.2 on
page 74 for more information.
Select Disable wireless security to have no wireless LAN security configured. Your
network is accessible to any wireless networking device that is within range.
" The wireless stations and ZyXEL Device must use the same SSID, channel ID
and WEP encryption key (if WEP is enabled), WPA-PSK (if WPA-PSK is
enabled) for wireless communication.
4 This screen varies depending on the security mode you selected in the previous screen.
Fill in the field (if available) and click Next.
P-2602HWLNI User’s Guide
73
Page 74

Chapter 3 Internet and Wireless Setup Wizard
3.3.1 Manually Assign a WPA-PSK Key
Choose Manually assign a WPA-PSK key in the Wireless LAN setup screen to set up a PreShared Key.
Figure 27 Manually Assign a WPA-PSK Key
The following table describes the labels in this screen.
Table 13 Manually Assign a WPA key
LABEL DESCRIPTION
Pre-Shared
Key
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
Type from 8 to 63 case-sensitive ASCII characters. You can set up the most secure
wireless connection by configuring WPA in the wireless LAN screens. You need to
configure an authentication server to do this.
3.3.2 Manually Assign a WEP Key
Choose Manually assign a WEP key to setup WEP Encryption parameters.
Figure 28 Manually Assign a WEP Key
74
P-2602HWLNI User’s Guide
Page 75

Chapter 3 Internet and Wireless Setup Wizard
The following table describes the labels in this screen.
Table 14 Manually Assign a WEP key
LABEL DESCRIPTION
Key The WEP keys are used to encrypt data. Both the ZyXEL Device and the wireless
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
5 Click Apply to complete your wireless LAN settings.
Figure 29 Wireless LAN Setup 3
stations must use the same WEP key for data transmission.
Enter any 5, 13 or 29 ASCII characters or 10, 26 or 58 hexadecimal characters ("0-9",
"A-F") for a 64-bit, 128-bit or 256-bit WEP key respectively.
6 Use the read-only summary table to check whether what you have configured is correct.
Click Finish to complete and save the wizard setup.
" No wireless LAN settings display if you chose not to configure wireless LAN
settings.
P-2602HWLNI User’s Guide
75
Page 76

Chapter 3 Internet and Wireless Setup Wizard
Figure 30 Internet Access and WLAN Wizard Setup Complete
7 Launch your web browser and navigate to www.zyxel.com. Internet access is just the
beginning. Refer to the rest of this guide for more detailed information on the complete
range of ZyXEL Device features. If you cannot access the Internet, open the web
configurator again to confirm that the Internet settings you configured in the wizard
setup are correct.
76
P-2602HWLNI User’s Guide
Page 77

CHAPTER 4
VoIP Wizard
This chapter shows you how to configure and register your SIP account(s).
4.1 Introduction
The ZyXEL Device has Voice over IP (VoIP) communication capabilities that allow you to use
a traditional analog or ISDN telephone to make Internet calls. This section describes how you
can set up your ZyXEL Device to call someone who is also using a VoIP device. You can
configure the ZyXEL Device to use up to two SIP-based VoIP accounts.
" The ZyXEL Device provides ten SIP accounts although you can configure only
2 via the VoIP wizard. See Chapter 11 on page 178 to configure the others.
In the following figure, A represents your phone and B represents the phone of the person you
would like to call.
Figure 31 VoIP Phone Calls
In order to make VoIP calls you need to register at least one SIP account on your ZyXEL
Device. You can register your SIP account in the VoIP Setup Wizard.
4.2 VoIP Wizard Setup
Use the wizard setup screens to set up your SIP account with the information given to you by
your ISP and register your SIP account.
P-2602HWLNI User’s Guide
77
Page 78

Chapter 4 VoIP Wizard
" Make sure you have a successful Internet connection before you run the VoIP
wizard. To test your Internet connection, you can open your web browser and
go to any web page (for example, http://www.zyxel.com).
" You must have a SIP account before you setup the VoIP wizard.
1 After you enter the password to access the web configurator, select Go to Wizard setup
and click Apply. Otherwise, click the wizard icon ( ) in the top right corner of the
web configurator to display the wizard main screen.
Figure 32 Select a Mode
78
2 Click VOICE OVER INTERNET SETUP to configure your SIP settings.
P-2602HWLNI User’s Guide
Page 79

Chapter 4 VoIP Wizard
Figure 33 Wizard: Welcome
3 Select the SIP server profile of your VoIP service provider, either SIP Profile 1 or SIP
Profile 2, and click Apply. If your VoIP service provider is not in the list, select None
and click Apply.
Figure 34 SIP Server Profile Selection
4 Fill in the fields with the information provided by your VoIP service provider. When you
are finished, click Apply. Contact your VoIP service provider if you do not have this
information.
" If your selected a preconfigured SIP profile, just enter your SIP number, user
name and password. Leave the remaining fields at default.
P-2602HWLNI User’s Guide
79
Page 80

Chapter 4 VoIP Wizard
Figure 35 VoIP Wizard Configuration
The following table describes the labels in this screen.
Table 15 VoIP Wizard Configuration
LABEL DESCRIPTION
SIP Number Enter your SIP number in this field. Use the number or text that comes
SIP Server Address Type the IP address or domain name of the SIP server in this field in
SIP Service Domain Enter the SIP service domain name in this field (the domain name that
User Name This is the username you use to login to your SIP account and to register
Password Type the password associated with the user name above. You can use up
Check here to set up
SIP2 settings.
before the @ symbol in a SIP account. If your SIP account is
11223344@SIPA-Account.com, your SIP number is “11223344”. You can
use up to 127 ASCII characters.
dotted decimal notation (for example 192.168.3.1). It doesn’t matter
whether the SIP server is a proxy, redirect or register server. You can use
up to 95 ASCII characters.
comes after the @ symbol in a SIP account like 11223344@SIPA-
Account.com). You can use up to 127 ASCII Extended set characters.
this SIP account with the SIP register server. Type the user name exactly
as it was given to you. You can use up to 95 ASCII characters.
to 95 ASCII Extended set characters.
This screen configures SIP account 1. Select the check box if you have
a second SIP account that you want to use. You will need to configure
the same fields for the second SIP account.
80
Note: If you configure more than one SIP account, you need
to configure Analog Phone settings to distinguish
between the two accounts when you make and
receive phone calls.
Back Click Back to return to the previous screen.
Apply Click Apply to complete the wizard setup and save your configuration.
Exit Click Exit to close the wizard without saving your settings.
5 When the SIP registration test screen displays, your ZyXEL Device attempts to register
your SIP account with your VoIP service provider. Wait until it finishes.
P-2602HWLNI User’s Guide
Page 81

Chapter 4 VoIP Wizard
Figure 36 SIP Registration Test
6 The following screen displays if SIP account registration fails. Check whether you can
access the Internet. If you have a successful Internet connection, click Register Again.
Or click Back and check the information you entered in SIP account settings is correct.
If you do not have a successful Internet connection, see Chapter 28 on page 401 for
troubleshooting.
Figure 37 VoIP Wizard Fail
7 The congratulations screen displays if your SIP account registration was successful. You
are ready to make and receive VoIP phone calls. Click Return to Wizard Main Page if
you want to use another configuration wizard. Click Go to Advanced Setup page or
Finish to close the wizard and go to the main web configurator screens.
Figure 38 VoIP Wizard Finish
8 To call other VoIP users, you need to have their SIP numbers and ensure that their SIP
accounts are registered and active. You can use your VoIP service provider’s dialing plan
to call SIP numbers.
P-2602HWLNI User’s Guide
81
Page 82

Chapter 4 VoIP Wizard
You can also use your VoIP service provider’s dialing plan to call regular phone
numbers. You dial a prefix number, provided to you by your VoIP service provider,
followed by a regular phone number.
" To find out more information about configuring your VoIP features and making
non-VoIP calls see Chapter 11 on page 169.
82
P-2602HWLNI User’s Guide
Page 83

CHAPTER 5
Bandwidth Management Wizard
This chapter shows you how to configure basic bandwidth management using the wizard
screens.
5.1 Introduction
Bandwidth management allows you to control the amount of bandwidth going out through the
ZyXEL Device’s WAN port and prioritize the distribution of the bandwidth according to
service bandwidth requirements. This helps keep one service from using all of the available
bandwidth and shutting out other users.
5.2 Bandwidth Management Wizard Setup
1 After you enter the password to access the web configurator, select Go to Wizard setup
and click Apply. Otherwise, click the wizard icon ( ) in the top right corner of the
web configurator to display the wizard main screen.
Figure 39 Select a Mode
2 Click BANDWIDTH MANAGEMENT SETUP.
P-2602HWLNI User’s Guide
83
Page 84

Chapter 5 Bandwidth Management Wizard
Figure 40 Wizard: Welcome
3 Select Active to allocate bandwidth to packets based on the packet size.
Figure 41 Bandwidth Management Wizard: General Information
The following fields describe the label in this screen.
Table 16 Bandwidth Management Wizard: General Information
LABEL DESCRIPTION
Active Select the Active check box to have the ZyXEL Device apply bandwidth
management to traffic going out through the ZyXEL Device’s WAN, LAN or WLAN
port based on the packet size.
Back Click Back to display the previous screen.
Next Click Next to proceed to the next screen.
Exit Click Exit to close the wizard screen without saving.
4 Follow the on-screen instructions and click Finish to complete the wizard setup and save
your configuration.
84
P-2602HWLNI User’s Guide
Page 85

Chapter 5 Bandwidth Management Wizard
Figure 42 Bandwidth Management Wizard: Complete
P-2602HWLNI User’s Guide
85
Page 86

Chapter 5 Bandwidth Management Wizard
86
P-2602HWLNI User’s Guide
Page 87

CHAPTER 6
Status Screens
Use the Status screens to look at the current status of the device, system resources, interfaces
(LAN and WAN), and SIP accounts. You can also register and unregister SIP accounts. The
Status screen also provides detailed information from Any IP and DHCP and statistics from
VoIP, bandwidth management, and traffic.
6.1 Status Screen
Click Status to open this screen.
P-2602HWLNI User’s Guide
87
Page 88

Chapter 6 Status Screens
Figure 43 Status Screen
88
Each field is described in the following table.
Table 17 Status Screen
LABEL DESCRIPTION
Refresh Interval Enter how often you want the ZyXEL Device to update this screen.
Apply Click this to update this screen immediately.
Device
Information
Host Name This field displays the ZyXEL Device system name. It is used for identification. You
can change this in the Maintenance > System > General screen’s System Name
field.
Model
Number
This is the model name of your device.
P-2602HWLNI User’s Guide
Page 89

Chapter 6 Status Screens
Table 17 Status Screen
LABEL DESCRIPTION
MAC Address This is the MAC (Media Access Control) or Ethernet address unique to your
ZyXEL Device.
ZyNOS
Firmware
Ver si on
DSL Firmware
Ver si on
WAN Information
DSL Mode This is the DSL standard that your ZyXEL Device is using.
IP Address This field displays the current IP address of the ZyXEL Device in the WAN. Click
IP Subnet
Mask
Default
Gateway
VPI/VCI This is the Virtual Path Identifier and Virtual Channel Identifier that you entered in
LAN Information
IP Address This field displays the current IP address of the ZyXEL Device in the LAN. Click
IP Subnet
Mask
DHCP This field displays what DHCP services the ZyXEL Device is providing to the LAN.
WLAN
Information
SSID This is the descriptive name used to identify the ZyXEL Device in the wireless
Channel This is the channel number used by the ZyXEL Device now.
Security This displays the type of security mode the ZyXEL Device is using in the wireless
Security
Firewall This displays whether or not the ZyXEL Device’s firewall is activated. Click this to
Content Filter This displays whether or not the ZyXEL Device’s content filtering is activated. Click
System Status
System
Uptime
This field displays the current version of the firmware inside the device. It also
shows the date the firmware version was created. Click this to go to the screen
where you can change it.
This field displays the current version of the device’s DSL modem code.
this to go to the screen where you can change it.
This field displays the current subnet mask in the WAN.
This is the IP address of the default gateway, if applicable.
the wizard or WAN screen.
this to go to the screen where you can change it.
This field displays the current subnet mask in the LAN.
Choices are:
Server - The ZyXEL Device is a DHCP server in the LAN. It assigns IP addresses
to other computers in the LAN.
Relay - The ZyXEL Device acts as a surrogate DHCP server and relays DHCP
requests and responses between the remote server and the clients.
None - The ZyXEL Device is not providing any DHCP services to the LAN.
Click this to go to the screen where you can change it.
(“W” models only)
LAN. Click this to go to the screen where you can change it.
LAN.
go to the screen where you can change it.
this to go to the screen where you can change it.
This field displays how long the ZyXEL Device has been running since it last
started up. The ZyXEL Device starts up when you plug it in, when you restart it
(Maintenance > Tools > Restart), or when you reset it (see Section 1.6 on page
47).
P-2602HWLNI User’s Guide
89
Page 90

Chapter 6 Status Screens
Table 17 Status Screen
LABEL DESCRIPTION
Current Date/
Time
System Mode This displays whether the ZyXEL Device is functioning as a router or a bridge.
CPU Usage This field displays what percentage of the ZyXEL Device’s processing ability is
Memory
Usage
Interface Status
Interface This column displays each interface the ZyXEL Device has.
Status This field indicates whether or not the ZyXEL Device is using the interface.
Rate For the LAN interface, this displays the port speed and duplex setting.
Summary
Client List Click this link to view current DHCP client information. See Section 8.6 on page
AnyIP Table Click this link to view a list of IP addresses and MAC addresses of computers,
WLAN Status Click this link to display the MAC address(es) of the wireless stations that are
Bandwidth
Status
VPN Status Click this link to view the ZyXEL Device’s current VPN connections. See Section
Packet
Statistics
VoIP Statistics Click this link to view statistics about your VoIP usage. See Section 6.5 on page
LED Status Click this link to view the ZyXEL Device’s port status. See Section 6.5 on page 94.
VoIP Status
Account This column displays each SIP account in the ZyXEL Device.
This field displays the current date and time in the ZyXEL Device. You can change
this in Maintenance > System > Time Setting.
currently used. When this percentage is close to 100%, the ZyXEL Device is
running at full load, and the throughput is not going to improve anymore. If you
want some applications to have more throughput, you should turn off other
applications (for example, using bandwidth management; see Chapter 21 on page
331).
This field displays what percentage of the ZyXEL Device’s memory is currently
used. Usually, this percentage should not increase much. If memory usage does
get close to 100%, the ZyXEL Device is probably becoming unstable, and you
should restart the device. See Section 29.6 on page 413, or turn off the device
(unplug the power) for a few seconds.
For the DSL interface, this field displays Down (line is down), Up (line is up or
connected) if you're using Ethernet encapsulation and Down (line is down), Up
(line is up or connected), Idle (line (ppp) idle), Dial (starting to trigger a call) and
Drop (dropping a call) if you're using PPPoE encapsulation.
For the LAN interface, this field displays Up when the ZyXEL Device is using the
interface and Down when the ZyXEL Device is not using the interface.
For the WLAN interface, it displays Active when WLAN is enabled or Inactive
when WLAN is disabled.
For the DSL interface, it displays the downstream and upstream transmission rate.
For the WLAN interface, it displays the transmission rate when WLAN is enabled
or N/A when WLAN is disabled.
125.
which are not in the same subnet as the ZyXEL Device. See Section 6.2 on page
91.
currently associating with the ZyXEL Device. See Section 6.3 on page 92.
Click this link to view the ZyXEL Device’s bandwidth usage and allotments. See
Section 21.8 on page 337.
18.16 on page 295.
Click this link to view port status and packet specific statistics. See Section 6.4 on
page 92.
94.
90
P-2602HWLNI User’s Guide
Page 91

Chapter 6 Status Screens
Table 17 Status Screen
LABEL DESCRIPTION
Registration This field displays the current registration status of the SIP account. You have to
register SIP accounts with a SIP server to use VoIP.
If the SIP account is already registered with the SIP server,
• Click Unregister to delete the SIP account’s registration in the SIP server. This
does not cancel your SIP account, but it deletes the mapping between your
SIP identity and your IP address or domain name.
• The second field displays Registered.
If the SIP account is not registered with the SIP server,
• Click Register to have the ZyXEL Device attempt to register the SIP account
with the SIP server.
• The second field displays the reason the account is not registered.
Inactive - The SIP account is not active. You can activate it in VoIP > SIP > SIP
Settings.
Register Fail - The last time the ZyXEL Device tried to register the SIP account
with the SIP server, the attempt failed. The ZyXEL Device automatically tries to
register the SIP account when you turn on the ZyXEL Device or when you activate
it.
URI This field displays the account number and service domain of the SIP account.
You can change these in VoIP > SIP > SIP Settings.
6.2 Any IP Table
Click Status > AnyIP Table to access this screen. Use this screen to view the IP address and
MAC address of each computer that is using the ZyXEL Device but is in a different subnet
than the ZyXEL Device.
Figure 44 Any IP Table
Each field is described in the following table.
Table 18 Any IP Table
LABEL DESCRIPTION
# This field is a sequential value. It is not associated with a specific entry.
IP Address
MAC Address
Refresh
This field displays the IP address of each computer that is using the ZyXEL Device
but is in a different subnet than the ZyXEL Device.
This field displays the MAC address of the computer that is using the ZyXEL
Device but is in a different subnet than the ZyXEL Device.
Click this to update this screen.
P-2602HWLNI User’s Guide
91
Page 92

Chapter 6 Status Screens
6.3 WLAN Status
Click Status > WLAN Status to access this screen. Use this screen to view the wireless
stations that are currently associated to the ZyXEL Device.
Figure 45 WLAN Status
The following table describes the labels in this screen.
Table 19 WLAN Status
LABEL DESCRIPTION
# This is the index number of an associated wireless station.
MAC Address This field displays the MAC (Media Access Control) address of an associated
Association
TIme
Refresh Click Refresh to reload this screen.
wireless station.
This field displays the time a wireless station first associated with the ZyXEL Device.
6.4 Packet Statistics
Click Status > Packet Statistics to access this screen. Read-only information here includes
port status and packet specific statistics. Also provided are "system up time" and "poll
interval(s)". The Poll Interval(s) field is configurable.
92
P-2602HWLNI User’s Guide
Page 93

Figure 46 Packet Statistics
Chapter 6 Status Screens
The following table describes the fields in this screen.
Table 20 Packet Statistics
LABEL DESCRIPTION
System Monitor
System up Time This is the elapsed time the system has been up.
Current Date/Time This field displays your ZyXEL Device’s present date and time.
CPU Usage This field specifies the percentage of CPU utilization.
Memory Usage This field specifies the percentage of memory utilization.
WAN Port Statistics
Link Status This is the status of your WAN link.
WAN IP Address This is the IP address of the ZyXEL Device’s WAN port.
Upstream Speed This is the upstream speed of your ZyXEL Device.
Downstream Speed This is the downstream speed of your ZyXEL Device.
Node-Link This field displays the remote node index number and link type. Link types are
Status This field displays Down (line is down), Up (line is up or connected) if you're
TxPkts This field displays the number of packets transmitted on this port.
RxPkts This field displays the number of packets received on this port.
Errors This field displays the number of error packets on this port.
Tx B/s This field displays the number of bytes transmitted in the last second.
Rx B/s This field displays the number of bytes received in the last second.
Up Time This field displays the elapsed time this port has been up.
LAN Port Statistics
PPPoA, ENET, RFC 1483 and PPPoE.
using Ethernet encapsulation and Down (line is down), Up (line is up or
connected), Idle (line (ppp) idle), Dial (starting to trigger a call) and Drop
(dropping a call) if you're using PPPoE encapsulation.
P-2602HWLNI User’s Guide
93
Page 94

Chapter 6 Status Screens
Table 20 Packet Statistics (continued)
LABEL DESCRIPTION
Interface This field displays either Ethernet (LAN ports) or Wireless (WLAN port).
Status For the LAN ports, this field displays Down (line is down) or Up (line is up or
TxPkts This field displays the number of packets transmitted on this interface.
RxPkts This field displays the number of packets received on this interface.
Collisions This is the number of collisions on this interfaces.
Poll Interval(s) Type the time interval for the browser to refresh system statistics.
Set Interval Click this to apply the new poll interval you entered in the Poll Interval field
Stop Click this button to halt the refreshing of the system statistics.
6.5 VoIP Statistics
connected).
For the WLAN port, it displays the transmission rate when WLAN is enabled or
N/A when WLAN is disabled.
above.
Click Status > VoIP Statistic s to access this screen.
Figure 47 VoIP Statistics
94
Each field is described in the following table.
Table 21 VoIP Statistics
LABEL DESCRIPTION
SIP Status
Account This column displays each SIP account in the ZyXEL Device.
P-2602HWLNI User’s Guide
Page 95

Chapter 6 Status Screens
Table 21 VoIP Statistics
LABEL DESCRIPTION
Registration This field displays the current registration status of the SIP account. You can
change this in the Status screen.
Registered - The SIP account is registered with a SIP server.
Register Fail - The last time the ZyXEL Device tried to register the SIP account
with the SIP server, the attempt failed. The ZyXEL Device automatically tries to
register the SIP account when you turn on the ZyXEL Device or when you activate
it.
Inactive - The SIP account is not active. You can activate it in VoIP > SIP > SIP
Settings.
Last Registration This field displays the last time you successfully registered the SIP account. It
displays N/A if you never successfully registered this account.
URI This field displays the account number and service domain of the SIP account.
Protocol This field displays the transport protocol the SIP account uses. SIP accounts
Message Waiting This field indicates whether or not there are any messages waiting for the SIP
Last Incoming
Number
Last Outgoing
Number
Call Statistics
Phone This field displays each phone port in the ZyXEL Device.
Hook This field indicates whether the phone is on the hook or off the hook.
Status This field displays the current state of the phone call.
Codec This field displays what voice codec is being used for a current VoIP call through a
Peer Number This field displays the SIP number of the party that is currently engaged in a VoIP
Duration This field displays how long the current call has lasted.
Tx Pkts This field displays the number of packets the ZyXEL Device has transmitted in the
Rx Pkts This field displays the number of packets the ZyXEL Device has received in the
Tx B/s This field displays how quickly the ZyXEL Device has transmitted packets in the
Rx B/s This field displays how quickly the ZyXEL Device has received packets in the
You can change these in VoIP > SIP > SIP Settings.
always use UDP.
account.
This field displays the last number that called the SIP account. It displays N/A if no
number has ever dialed the SIP account.
This field displays the last number the SIP account called. It displays N/A if the
SIP account has never dialed a number.
On - The phone is hanging up or already hung up.
Off - The phone is dialing, calling, or connected.
N/A - There are no current VoIP calls, incoming calls or outgoing calls being
made.
DIAL - The callee’s phone is ringing.
RING - The phone is ringing for an incoming VoIP call.
Process - There is a VoIP call in progress.
DISC - The callee’s line is busy, the callee hung up or your phone was left off the
hook.
phone port.
call through a phone port.
current call.
current call.
current call. The rate is the average number of bytes transmitted per second.
current call. The rate is the average number of bytes transmitted per second.
P-2602HWLNI User’s Guide
95
Page 96

Chapter 6 Status Screens
Table 21 VoIP Statistics
LABEL DESCRIPTION
Poll Interval(s) Enter how often you want the ZyXEL Device to update this screen, and click Set
Set Interval Click this to make the ZyXEL Device update the screen based on the amount of
Stop Click this to make the ZyXEL Device stop updating the screen.
6.6 LED Status
Use this screen to view the current status of each of the ZyXEL Device’a ports. Click Status >
LED Status to access this screen.
Figure 48 LED Status
Interval.
time you specified in Poll Interval.
96
Each field is described in the following table.
Table 22 LED Status
LABEL STATUS DESCRIPTION
Connection
DSL Green The DSL port has a successful connection. The current
downstream and upstream transmission rates display.
Off When the DSL port does not have a successful connection, it
displays Down.
WLAN Green The wireless LAN is enabled. Your ZyXEL Device’s SSID
(Service Set IDentity) displays.
Off When the wireless LAN is disabled, it displays Inactive.
LAN 1~4 Green The corresponding LAN port has a successful Ethernet
connection.
Off The corresponding LAN port does not have a successful Ethernet
connection.
Internet and
Telephone
P-2602HWLNI User’s Guide
Page 97

Chapter 6 Status Screens
Table 22 LED Status
LABEL STATUS DESCRIPTION
Internet Green The ZyXEL Device has a successful Internet connection. This
field displays the current IP address of the ZyXEL Device in the
WAN.
Off The ZyXEL Device does not have a successful Internet
connection. This field displays the default IP address of the
ZyXEL Device in the WAN.
Phone 1
Phone 2
Poll Interval (s) Enter how often you want the ZyXEL Device to update this
Set Interval Click this to make the ZyXEL Device update the screen based on
Stop Click this to make the ZyXEL Device stop updating the screen.
Green This phone port has a successful SIP account registration. This
field displays the number of the SIP account used to make
outgoing calls on the corresponding phone port. This field also
displays the current SIP registration status of the phone port.
On Register - The phone port has a successful SIP account
registration, and the phone connecting to this phone port is ready
to make outgoing VoIP calls.
Off This phone port does not have a successful SIP account
registration. This field displays the number of the SIP account
used to make outgoing calls on the corresponding phone port.
This field also displays the current SIP registration status.
Not Register - The phone port has not registered a SIP account
yet.
Register Fail - The phone port tried to register a SIP account
and the registration failed.
Inactive - The phone port does not have a SIP account enabled.
If you did not change the SIP account settings from the defaults,
ChangeMe displays instead of the SIP account number.
screen, and click Set Interval.
the amount of time you specified in Poll Interval.
P-2602HWLNI User’s Guide
97
Page 98

Chapter 6 Status Screens
98
P-2602HWLNI User’s Guide
Page 99

PART III
Network
WA N S e t u p ( 1 0 1 )
LAN Setup (117)
Wireless LAN (129)
Network Address Translation (NAT) Screens (155)
99
Page 100

100
 Loading...
Loading...