
NWA-3160 Series
Models: NWA-3160, NWA-3163 & NWA-3166
Default Login Details
IP Address http://192.168.1.2
Password 1234
Firmware Version 3.70
Edition 3, 07/2009
www.zyxel.com
www.zyxel.com
Copyright © 2009
ZyXEL Communications Corporation


About This User's Guide
About This User's Guide
Intended Audience
This manual is intended for people who want to configure the NWA using the web
configurator.
Tips for Reading User’s Guides On-Screen
When reading a ZyXEL User’s Guide On-Screen, keep the following in mind:
• If you don’t already have the latest version of Adobe Reader, you can download
it from http://www.adobe.com.
• Use the PDF’s bookmarks to quickly navigate to the areas that interest you.
Adobe Reader’s bookmarks pane opens by default in all ZyXEL User’s Guide
PDFs.
• If you know the page number or know vaguely which page-range you want to
view, you can enter a number in the toolbar in Reader, then press [ENTER] to
jump directly to that page.
• Type [CTRL]+[F] to open the Adobe Reader search utility and enter a word or
phrase. This can help you quickly pinpoint the information you require. You can
also enter text directly into the toolbar in Reader.
• To quickly move around within a page, press the [SPACE] bar. This turns your
cursor into a “hand” with which you can grab the page and move it around
freely on your screen.
• Embedded hyperlinks are actually cross-references to related text. Click them to
jump to the corresponding section of the User’s Guide PDF.
Related Documentation
•Quick Start Guide
The Quick Start Guide is designed to help you get your NWA up and running
right away. It contains information on setting up your network and configuring
for Internet access.
• Web Configurator Online Help
The embedded Web Help contains descriptions of individual screens and
supplementary information.
• Command Reference Guide
The Command Reference Guide explains how to use the Command-Line
Interface (CLI) and CLI commands to configure the NWA.
Note: It is recommended you use the web configurator to configure the NWA.
NWA-3160 Series User’s Guide
3

About This User's Guide
• Support Disc
Refer to the included CD for support documents.
Documentation Feedback
Send your comments, questions or suggestions to: techwriters@zyxel.com.tw
Thank you!
The Technical Writing Team, ZyXEL Communications Corp.,
6 Innovation Road II, Science-Based Industrial Park, Hsinchu, 30099, Taiwan.
Need More Help?
More help is available at www.zyxel.com.
• Download Library
Search for the latest product updates and documentation from this link. Read
the Tech Doc Overview to find out how to efficiently use the User Guide, Quick
Start Guide and Command Line Interface Reference Guide in order to better
understand how to use your product.
• Knowledge Base
If you have a specific question about your product, the answer may be here.
This is a collection of answers to previously asked questions about ZyXEL
products.
•Forum
This contains discussions on ZyXEL products. Learn from others who use ZyXEL
products and share your experiences as well.
4
NWA-3160 Series User’s Guide

About This User's Guide
Customer Support
Should problems arise that cannot be solved by the methods listed above, you
should contact your vendor. If you cannot contact your vendor, then contact a
ZyXEL office for the region in which you bought the device.
See http://www.zyxel.com/web/contact_us.php for contact information. Please
have the following information ready when you contact an office.
• Product model and serial number.
• Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
NWA-3160 Series User’s Guide
5

Document Conventions
Warnings and Notes
These are how warnings and notes are shown in this User’s Guide.
Warnings tell you about things that could harm you or your NWA.
Note: Notes tell you other important information (for example, other things you may
need to configure or helpful tips) or recommendations.
Syntax Conventions
• The ZyWALL 1050 may be referred to as the “NWA”, the “device”, the “system”
or the “product” in this User’s Guide.
• Product labels, screen names, field labels and field choices are all in bold font.
Document Conventions
• A key stroke is denoted by square brackets and uppercase text, for example,
[ENTER] means the “enter” or “return” key on your keyboard.
• “Enter” means for you to type one or more characters and then press the
[ENTER] key. “Select” or “choose” means for you to use one of the predefined
choices.
• A right angle bracket ( > ) within a screen name denotes a mouse click. For
example, Maintenance > Log > Log Setting means you first click
Maintenance in the navigation panel, then the Log sub menu and finally the
Log Setting tab to get to that screen.
• Units of measurement may denote the “metric” value or the “scientific” value.
For example, “k” for kilo may denote “1000” or “1024”, “M” for mega may
denote “1000000” or “1048576” and so on.
• “e.g.,” is a shorthand for “for instance”, and “i.e.,” means “that is” or “in other
words”.
6
NWA-3160 Series User’s Guide

Document Conventions
Icons Used in Figures
Figures in this User’s Guide use the following generic icons. The NWA icon is not
an exact representation of your NWA.
Graphics in this book may differ slightly from the product due to differences in
operating systems, operating system versions, or if you installed updated
firmware/software for your device. Every effort has been made to ensure that the
information in this manual is accurate
NWA Computer Notebook computer
Server Printer Firewall
.
Telephone Switch Router
NWA-3160 Series User’s Guide
7

Safety Warnings
• Do NOT use this product near water, for example, in a wet basement or near a swimming
pool.
• Do NOT expose your device to dampness, dust or corrosive liquids.
• Do NOT store things on the device.
• Do NOT install, use, or service this device during a thunderstorm. There is a remote risk
of electric shock from lightning.
• Connect ONLY suitable accessories to the device.
• ONLY qualified service personnel should service or disassemble this device.
• Make sure to connect the cables to the correct ports.
• Place connecting cables carefully so that no one will step on them or stumble over them.
• Always disconnect all cables from this device before servicing or disassembling.
• Use ONLY an appropriate power adaptor or cord for your device.
• Connect the power adaptor or cord to the right supply voltage (for example, 110V AC in
North America or 230V AC in Europe).
• Do NOT allow anything to rest on the power adaptor or cord and do NOT place the
product where anyone can walk on the power adaptor or cord.
• Do NOT use the device if the power adaptor or cord is damaged as it might cause
electrocution.
• If the power adaptor or cord is damaged, remove it from the power outlet.
• Do NOT attempt to repair the power adaptor or cord. Contact your local vendor to order
a new one.
• Do not use the device outside, and make sure all the connections are indoors. There is a
remote risk of electric shock from lightning.
• Antenna Warning! This device meets ETSI and FCC certification requirements when using
the included antenna(s). Only use the included antenna(s).
• If you wall mount your device, make sure that no electrical lines, gas or water pipes will
be damaged.
• The PoE (Power over Ethernet) devices that supply or receive power and their connected
Ethernet cables must all be completely indoors.
Safety Warnings
8
Your product is marked with this symbol, which is known as the WEEE mark. WEEE
stands for Waste Electronics and Electrical Equipment. It means that used electrical
and electronic products should not be mixed with general waste. Used electrical and
electronic equipment should be treated separately.
NWA-3160 Series User’s Guide

Contents Overview
Contents Overview
Introduction ............................................................................................................................21
Introduction ................................................................................................................................ 23
The Web Configurator ............................................................................................................... 35
Tutorials ..................................................................................................................................... 39
The Web Configurator ...........................................................................................................79
Status Screen ............................................................................................................................ 81
Management Mode .................................................................................................................... 87
AP Controller Mode ................................................................................................................... 93
System Screens ...................................................................................................................... 109
Wireless Screen ...................................................................................................................... 119
SSID Screen ............................................................................................................................ 149
Wireless Security Screen ........................................................................................................ 159
RADIUS Screen ....................................................................................................................... 173
Layer-2 Isolation Screen .......................................................................................................... 177
MAC Filter Screen ................................................................................................................... 183
IP Screen ................................................................................................................................. 187
Rogue AP Detection ........................................................................................................... 191
Remote Management Screens ................................................................................................ 199
Internal RADIUS Server .......................................................................................................... 213
Certificates ............................................................................................................................... 221
Log Screens ............................................................................................................................ 239
VLAN ....................................................................................................................................... 249
Load Balancing ........................................................................................................................ 269
Dynamic Channel Selection .................................................................................................... 275
Maintenance ............................................................................................................................ 279
Appendices and Index ......................................................................................................... 287
Troubleshooting ....................................................................................................................... 289
New Template User’s Guide
9

Contents Overview
10
New Template User’s Guide

Table of Contents
Table of Contents
About This User's Guide ..........................................................................................................3
Document Conventions............................................................................................................6
Safety Warnings........................................................................................................................8
Contents Overview ...................................................................................................................9
Table of Contents.................................................................................................................... 11
Part I: Introduction................................................................................. 21
Chapter 1
Introduction .............................................................................................................................23
1.1 Overview ............................................................................................................................. 23
1.2 Applications for the NWA ..................................................................................................... 24
1.2.1 Access Point .............................................................................................................. 24
1.2.2 Bridge / Repeater ....................................................................................................... 25
1.2.2.1 Bridge / Repeater Mode Example .................................................. 26
1.2.3 AP + Bridge ................................................................................................................ 28
1.2.4 MBSSID ..................................................................................................................... 28
1.2.5 Pre-Configured SSID Profiles .................................................................................... 30
1.3 CAPWAP ............................................................................................................................. 30
1.4 Ways to Manage the NWA .................................................................................................. 31
1.5 Good Habits for Managing the NWA ................................................................................... 31
1.6 Hardware Connections ........................................................................................................ 32
1.6.1 Antennas .................................................................................................................... 32
1.7 LEDs .................................................................................................................................... 33
Chapter 2
The Web Configurator ............................................................................................................35
2.1 Overview .............................................................................................................................. 35
2.2 Accessing the Web Configurator ......................................................................................... 35
2.3 Resetting the NWA .............................................................................................................. 36
2.3.1 Methods of Restoring Factory-Defaults ...................................................................... 36
2.4 Navigating the Web Configurator ........................................................................................ 37
Chapter 3
Tutorials...................................................................................................................................39
NWA-3160 Series User’s Guide
11

Table of Contents
3.1 Overview .............................................................................................................................. 39
3.2 How to Configure the Wireless LAN .................................................................................... 39
3.2.1 Choosing the Wireless Mode ..................................................................................... 39
3.2.2 Wireless LAN Configuration Overview ....................................................................... 40
3.2.3 Further Reading ......................................................................................................... 41
3.3 How to Configure Multiple Wireless Networks ..................................................................... 41
3.3.1 Change the Operating Mode ...................................................................................... 43
3.3.1.1 Access Point ................................................................................... 43
3.3.1.2 MBSSID .......................................................................................... 44
3.3.2 Configure the VoIP Network ....................................................................................... 45
3.3.2.1 Set Up Security for the VoIP Profile ............................................... 46
3.3.2.2 Activate the VoIP Profile ................................................................. 48
3.3.3 Configure the Guest Network ..................................................................................... 48
3.3.3.1 Set Up Security for the Guest Profile .............................................. 50
3.3.3.2 Set up Layer 2 Isolation .................................................................. 51
3.3.3.3 Activate the Guest Profile ............................................................... 52
3.3.4 Testing the Wireless Networks ................................................................................... 52
3.4 How to Set Up and Use Rogue AP Detection ..................................................................... 53
3.4.1 Set Up and Save a Friendly AP list ............................................................................ 55
3.4.2 Activate Periodic Rogue AP Detection ....................................................................... 58
3.4.3 Set Up E-mail Logs .................................................................................................... 59
3.4.4 Configure Your Other Access Points ......................................................................... 60
3.4.5 Test the Setup ............................................................................................................ 61
3.5 Using MAC Filters and L-2 Isolation Profiles ....................................................................... 61
3.5.1 Scenario ..................................................................................................................... 61
3.5.2 Your Requirements .................................................................................................... 62
3.5.3 Setup .......................................................................................................................... 62
3.5.4 Configure the SERVER_1 Network ............................................................................ 63
3.5.5 Configure the SERVER_2 Network ............................................................................ 66
3.5.6 Checking your Settings and Testing the Configuration .............................................. 67
3.5.6.1 Checking Settings ........................................................................... 67
3.5.6.2 Testing the Configuration ............................................................... 68
3.6 How to Configure Management Modes ............................................................................... 69
3.6.1 Scenario ..................................................................................................................... 69
3.6.2 Your Requirements .................................................................................................... 70
3.6.3 Setup .......................................................................................................................... 70
3.6.4 Configure Your NWA in Controller AP Mode ............................................................. 71
3.6.4.1 Secondary AP Controller ................................................................ 72
3.6.4.2 Primary AP Controller ..................................................................... 73
3.6.5 Setting Your NWA in Managed AP Mode .................................................................. 73
3.6.6 Configuring the Managed Access Points List ............................................................. 74
3.6.7 Checking your Settings and Testing the Configuration .............................................. 77
12
NWA-3160 Series User’s Guide

Table of Contents
Part II: The Web Configurator ............................................................... 79
Chapter 4
Status Screen..........................................................................................................................81
4.1 Overview .............................................................................................................................. 81
4.2 The Status Screen ............................................................................................................... 81
4.2.1 System Statistics Screen ........................................................................................... 84
Chapter 5
Management Mode.................................................................................................................. 87
5.1 Overview .............................................................................................................................. 87
5.2 About CAPWAP ................................................................................................................... 87
5.2.1 CAPWAP Discovery and Management ...................................................................... 88
5.2.2 CAPWAP and DHCP ................................................................................................. 88
5.2.3 CAPWAP and IP Subnets .......................................................................................... 88
5.2.4 Notes on CAPWAP .................................................................................................... 89
5.3 The Management Mode Screen .......................................................................................... 90
Chapter 6
AP Controller Mode ................................................................................................................93
6.1 Overview .............................................................................................................................. 93
6.1.1 What You Can Do in AP Controller Mode .................................................................. 93
6.1.2 What You Need to Know ............................................................................................ 93
6.1.3 Before You Begin ....................................................................................................... 94
6.2 Controller AP Navigation Menu ........................................................................................... 94
6.3 Controller AP Status Screen ................................................................................................95
6.4 AP Lists Screen ................................................................................................................... 97
6.4.1 The AP Lists Edit Screen ......................................................................................... 100
6.5 Configuration Screen ......................................................................................................... 101
6.6 Redundancy Screen ..........................................................................................................102
6.7 The Profile Edit Screens .................................................................................................... 103
6.7.1 The Radio Profile Screen ......................................................................................... 103
6.7.2 The Radio Profile Edit Screen .................................................................................. 104
Chapter 7
System Screens .................................................................................................................... 109
7.1 Overview ............................................................................................................................ 109
7.1.1 What You Can Do in the System Screens ............................................................... 109
7.1.2 What You Need To Know About the System Screens ............................................. 110
7.2 General Screen ................................................................................................................. 111
7.3 Password Screen .............................................................................................................. 113
7.4 Time Setting Screen ......................................................................................................... 115
7.5 Technical Reference .......................................................................................................... 117
NWA-3160 Series User’s Guide
13

Table of Contents
7.5.1 Administrator Authentication on RADIUS ................................................................. 117
7.5.2 Pre-defined NTP Time Servers List ......................................................................... 117
Chapter 8
Wireless Screen .................................................................................................................... 119
8.1 Overview ............................................................................................................................ 119
8.1.1 What You Can Do in the Wireless Screen ............................................................... 119
8.1.2 What You Need To Know About the Wireless Screen ............................................. 120
8.2 The Wireless Screen ......................................................................................................... 123
8.2.1 Access Point Mode .................................................................................................. 123
8.2.2 Bridge / Repeater Mode ........................................................................................... 127
8.2.3 AP + Bridge Mode .................................................................................................... 133
8.2.4 MBSSID Mode ......................................................................................................... 139
8.3 Technical Reference .......................................................................................................... 143
8.3.1 Spanning Tree Protocol (STP) ................................................................................. 144
8.3.1.1 Rapid STP .................................................................................... 144
8.3.1.2 STP Terminology .......................................................................... 144
8.3.1.3 How STP Works ........................................................................... 145
8.3.1.4 STP Port States ............................................................................ 145
8.3.2 DFS .......................................................................................................................... 145
8.3.3 Roaming ................................................................................................................... 146
8.3.3.1 Requirements for Roaming ........................................................... 147
Chapter 9
SSID Screen...........................................................................................................................149
9.1 Overview ............................................................................................................................ 149
9.1.1 What You Can Do in the SSID Screen ..................................................................... 149
9.1.2 What You Need To Know About SSID ..................................................................... 150
9.2 The SSID Screen ............................................................................................................... 151
9.2.1 Configuring SSID ..................................................................................................... 152
9.3 Technical Reference .......................................................................................................... 153
9.3.1 WMM QoS ................................................................................................................ 153
9.3.1.1 WMM QoS Priorities ..................................................................... 154
9.3.2 ATC .......................................................................................................................... 154
9.3.3 ATC+WMM .............................................................................................................. 155
9.3.3.1 ATC+WMM from LAN to WLAN ................................................... 156
9.3.3.2 ATC+WMM from WLAN to LAN ................................................... 156
9.3.4 Type Of Service (ToS) ............................................................................................. 156
9.3.4.1 DiffServ ......................................................................................... 156
9.3.4.2 DSCP and Per-Hop Behavior ....................................................... 157
9.3.4.3 ToS (Type of Service) and WMM QoS ......................................... 157
Chapter 10
Wireless Security Screen.....................................................................................................159
14
NWA-3160 Series User’s Guide

Table of Contents
10.1 Overview .......................................................................................................................... 159
10.1.1 What You Can Do in the Wireless Security Screen ............................................... 159
10.1.2 What You Need To Know About Wireless Security ............................................... 160
10.2 The Security Screen ........................................................................................................ 161
10.2.1 Security: WEP ........................................................................................................ 163
10.2.2 Security: 802.1x Only ............................................................................................. 165
10.2.3 Security: 802.1x Static 64-bit, 802.1x Static 128-bit ............................................... 166
10.2.4 Security: WPA ........................................................................................................ 167
10.2.5 Security: WPA2 or WPA2-MIX ............................................................................... 168
10.2.6 Security: WPA-PSK, WPA2-PSK, WPA2-PSK-MIX ............................................... 170
10.3 Technical Reference ........................................................................................................ 171
Chapter 11
RADIUS Screen .....................................................................................................................173
11.1 Overview .......................................................................................................................... 173
11.1.1 What You Can Do in the RADIUS Screen ............................................................. 174
11.1.2 What You Need To Know About RADIUS .............................................................. 174
11.2 The RADIUS Screen ....................................................................................................... 175
Chapter 12
Layer-2 Isolation Screen ......................................................................................................177
12.1 Overview .......................................................................................................................... 177
12.1.1 What You Can Do in the Layer-2 Isolation Screen ................................................ 178
12.1.2 What You Need To Know About Layer-2 Isolation ................................................. 178
12.2 The Layer-2 Isolation Screen .......................................................................................... 179
12.2.1 Configuring Layer-2 Isolation ................................................................................. 180
12.3 Technical Reference ........................................................................................................ 181
Chapter 13
MAC Filter Screen .................................................................................................................183
13.1 Overview .......................................................................................................................... 183
13.1.1 What You Can Do in the MAC Filter Screen .......................................................... 183
13.1.2 What You Should Know About MAC Filter ............................................................. 183
13.2 The MAC Filter Screen .................................................................................................... 184
13.2.1 Configuring the MAC Filter ..................................................................................... 185
Chapter 14
IP Screen................................................................................................................................ 187
14.1 Overview .......................................................................................................................... 187
14.1.1 What You Can Do in the IP Screen ........................................................................ 187
14.1.2 What You Need To Know About IP ........................................................................ 187
14.2 The IP Screen .................................................................................................................. 188
14.3 Technical Reference ........................................................................................................ 189
NWA-3160 Series User’s Guide
15

Table of Contents
14.3.1 WAN IP Address Assignment ................................................................................ 189
Chapter 15
Rogue AP Detection ........................................................................................................191
15.1 Overview .......................................................................................................................... 191
15.1.1 What You Can Do in the Rogue AP Screen ........................................................... 192
15.1.2 What You Need To Know About Rogue AP ........................................................... 192
15.2 Configuration Screen ....................................................................................................... 194
15.2.1 Friendly AP Screen ................................................................................................ 195
15.2.2 Rogue AP Screen .................................................................................................. 196
Chapter 16
Remote Management Screens............................................................................................. 199
16.1 Overview .......................................................................................................................... 199
16.1.1 What You Can Do in the Remote Management Screens ....................................... 200
16.1.2 What You Need To Know About Remote Management ......................................... 200
16.2 The Telnet Screen ........................................................................................................... 202
16.3 The FTP Screen .............................................................................................................. 203
16.4 The WWW Screen ........................................................................................................... 204
16.5 The SNMP Screen ...........................................................................................................207
16.5.1 SNMPv3 User Profile ............................................................................................ 209
16.6 Technical Reference ........................................................................................................ 210
16.6.1 MIB ......................................................................................................................... 210
16.6.2 Supported MIBs ..................................................................................................... 211
16.6.3 SNMP Traps ........................................................................................................... 211
Chapter 17
Internal RADIUS Server........................................................................................................213
17.1 Overview .......................................................................................................................... 213
17.1.1 What You Can Do in this Chapter .......................................................................... 214
17.1.2 What You Need To Know ....................................................................................... 214
17.2 Internal RADIUS Server Setting Screen .......................................................................... 214
17.3 The Trusted AP Screen ................................................................................................... 216
17.4 The Trusted Users Screen .............................................................................................. 217
17.5 Technical Reference ........................................................................................................ 218
Chapter 18
Certificates ............................................................................................................................221
18.1 Overview .......................................................................................................................... 221
18.1.1 What You Can Do in the Certificates Screen ......................................................... 221
18.1.2 What You Need To Know About Certificates ......................................................... 222
18.2 My Certificates Screen ....................................................................................................222
18.2.1 My Certificates Import Screen ................................................................................ 224
16
NWA-3160 Series User’s Guide

Table of Contents
18.2.2 My Certificates Create Screen ............................................................................... 226
18.2.3 My Certificates Details Screen ............................................................................... 229
18.3 Trusted CAs Screen ........................................................................................................232
18.3.1 Trusted CAs Import Screen .................................................................................... 233
18.3.2 Trusted CAs Details Screen ................................................................................... 234
18.4 Technical Reference ........................................................................................................ 237
18.4.1 Private-Public Certificates ...................................................................................... 237
18.4.2 Certification Authorities .......................................................................................... 237
18.4.3 Checking the Fingerprint of a Certificate ................................................................ 238
Chapter 19
Log Screens .......................................................................................................................... 239
19.1 Overview .......................................................................................................................... 239
19.1.1 What You Can Do in the Log Screens ................................................................... 239
19.1.2 What You Need To Know About Logs ................................................................... 240
19.2 The View Log Screen ...................................................................................................... 240
19.3 The Log Settings Screen ................................................................................................. 242
19.4 Technical Reference ........................................................................................................ 244
19.4.1 Example Log Messages ......................................................................................... 244
19.4.2 Log Commands ...................................................................................................... 246
19.4.3 Configuring What You Want the NWA to Log ........................................................ 246
19.4.4 Displaying Logs ...................................................................................................... 246
19.4.5 Log Command Example ......................................................................................... 247
Chapter 20
VLAN ...................................................................................................................................... 249
20.1 Overview .......................................................................................................................... 249
20.1.1 What You Can Do in the VLAN Screen .................................................................. 249
20.1.2 What You Need To Know About VLAN .................................................................. 250
20.2 Wireless VLAN Screen .................................................................................................... 251
20.2.1 RADIUS VLAN Screen ........................................................................................... 252
20.3 Technical Reference ........................................................................................................ 254
20.3.1 VLAN Tagging ........................................................................................................ 254
20.3.2 Configuring Management VLAN Example ............................................................. 254
20.3.3 Configuring Microsoft’s IAS Server Example ......................................................... 257
20.3.3.1 Configuring VLAN Groups .......................................................... 258
20.3.3.2 Configuring Remote Access Policies .......................................... 259
20.3.4 Second Rx VLAN ID Example ................................................................................ 267
20.3.4.1 Second Rx VLAN Setup Example .............................................. 267
Chapter 21
Load Balancing ..................................................................................................................... 269
21.1 Overview .......................................................................................................................... 269
NWA-3160 Series User’s Guide
17

Table of Contents
21.1.1 What You Need to Know About Load Balancing .................................................... 269
21.2 The Load Balancing Screen ............................................................................................ 271
21.2.1 Disassociating and Delaying Connections ............................................................. 272
Chapter 22
Dynamic Channel Selection.................................................................................................275
22.1 Overview .......................................................................................................................... 275
22.2 The DCS Screen ............................................................................................................. 276
Chapter 23
Maintenance .......................................................................................................................... 279
23.1 Overview .......................................................................................................................... 279
23.1.1 What You Can Do in the Maintenance Screens ..................................................... 279
23.1.2 What You Need To Know ....................................................................................... 279
23.2 Association List Screen ...................................................................................................280
23.3 Channel Usage Screen ................................................................................................... 281
23.4 F/W Upload Screen .........................................................................................................282
23.5 Configuration Screen ....................................................................................................... 284
23.5.1 Backup Configuration ............................................................................................. 284
23.5.2 Restore Configuration ........................................................................................... 285
23.5.3 Back to Factory Defaults ........................................................................................ 286
23.6 Restart Screen ................................................................................................................. 286
Part III: Appendices and Index............................................................ 287
Chapter 24
Troubleshooting.................................................................................................................... 289
24.1 Overview .......................................................................................................................... 289
24.2 Power, Hardware Connections, and LEDs ...................................................................... 289
24.3 NWA Access and Login ................................................................................................... 290
24.4 AP Management Modes .................................................................................................. 292
24.5 Internet Access ................................................................................................................ 294
24.6 Wireless Router/AP Troubleshooting .............................................................................. 295
Chapter 25
Chapter 25 Product Specifications.....................................................................................297
25.1 Wall-Mounting Instructions .............................................................................................. 300
Appendix A Wireless LANs .................................................................................................. 303
Appendix B Pop-up Windows, JavaScripts and Java Permissions ......................................319
18
NWA-3160 Series User’s Guide

Table of Contents
Appendix C IP Addresses and Subnetting ...........................................................................327
Appendix D Text File Based Auto Configuration.................................................................. 349
Appendix E How to Access and Use the CLI .......................................................................357
Appendix F Legal Information ..............................................................................................363
Index....................................................................................................................................... 367
NWA-3160 Series User’s Guide
19

Table of Contents
20
NWA-3160 Series User’s Guide
PART I
Introduction
Introduction (23)
The Web Configurator (35)
Tutorials (39)
21

22

CHAPTER 1
Introduction
Note: This User’s Guide includes the NWA-3160, NWA-3163 and the NWA-3166.
Illustrations used throughout this book are based on the NWA-3160 (unless
otherwise stated). The Web Configuration screens are based on the NWA-3166
(unless otherwise stated).
1.1 Overview
Your NWA extends the range of your existing wired network without additional
wiring, providing easy network access to mobile users.
It is highly versatile as it supports up to eight Basic Service Set Identifiers
(BSSID) simultaneously. The Quality of Service (QoS) features allow you to
prioritize time-sensitive or highly important applications such as Voice over
Internet Protocol (VoIP).
Multiple security profiles allow you to easily assign different types of security to
groups of users. The NWA controls network access with Media Access Control
(MAC) address filtering, rogue Access Point (AP) detection, layer 2 isolation and an
internal authentication server. It also provides a high level of network traffic
security, supporting Institute of Electronic Engineers (IEEE) 802.1x, Wi-Fi
Protected Access (WPA), WPA2 and Wired Equivalent Privacy (WEP) data
encryption.
Your NWA is easy to install, configure and use. The embedded Web-based
configurator enables simple, straightforward management and maintenance.
See the Quick Start Guide for instructions on how to make hardware connections.
NWA-3160 Series User’s Guide
23

Chapter 1 Introduction
1.2 Applications for the NWA
The NWA can be configured to use the following WLAN operating modes
• Access Point
•Bridge / Repeater
•AP + Bridge
•MBSSID
Applications for each operating mode are shown below.
1.2.1 Access Point
The NWA is an ideal access solution for wireless Internet connection. A typical
Internet access application for your NWA is shown as follows. Stations A, B and C
can access the wired network through the NWAs.
Figure 1 Access Point Application
AP1
A
BSS1
AP2
B
C
BSS2
24
NWA-3160 Series User’s Guide
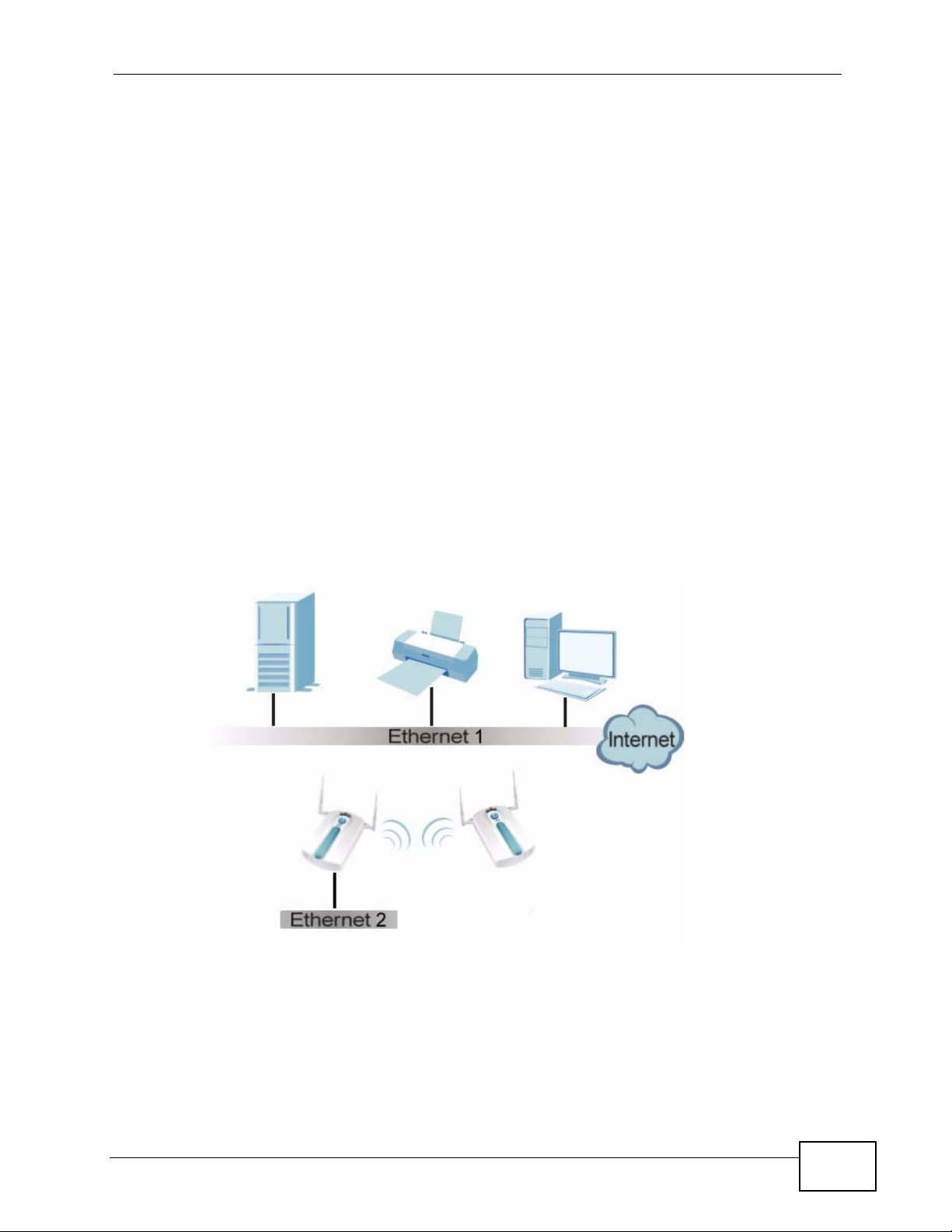
1.2.2 Bridge / Repeater
The NWA can act as a wireless network bridge and establish wireless links with
other APs. In the figure below, the two NWAs (A and B) are connected to
independent wired networks and have a bridge connection (A can communicate
with B) at the same time. A NWA in repeater mode (C in Figure 3) has no Ethernet
connection. When the NWA is in bridge mode, you should enable Spanning Tree
Protocol (STP) to prevent bridge loops.
When the NWA is in Bridge / Repeater mode, security between APs (the Wireless
Distribution System or WDS) is independent of the security between the wireless
stations and the AP. If you do not enable WDS security, traffic between APs is not
encrypted. When WDS security is enabled, both APs must use the same preshared key. See Section 8.2.2 on page 127 for more details.
Once the security settings of peer sides match one another, the connection
between devices is made.
At the time of writing, WDS security is compatible with other ZyXEL access points
only. Refer to your other access point’s documentation for details.
Chapter 1 Introduction
Figure 2 Bridge Application
A
B
NWA-3160 Series User’s Guide
25
Chapter 1 Introduction
Figure 3 Repeater Application
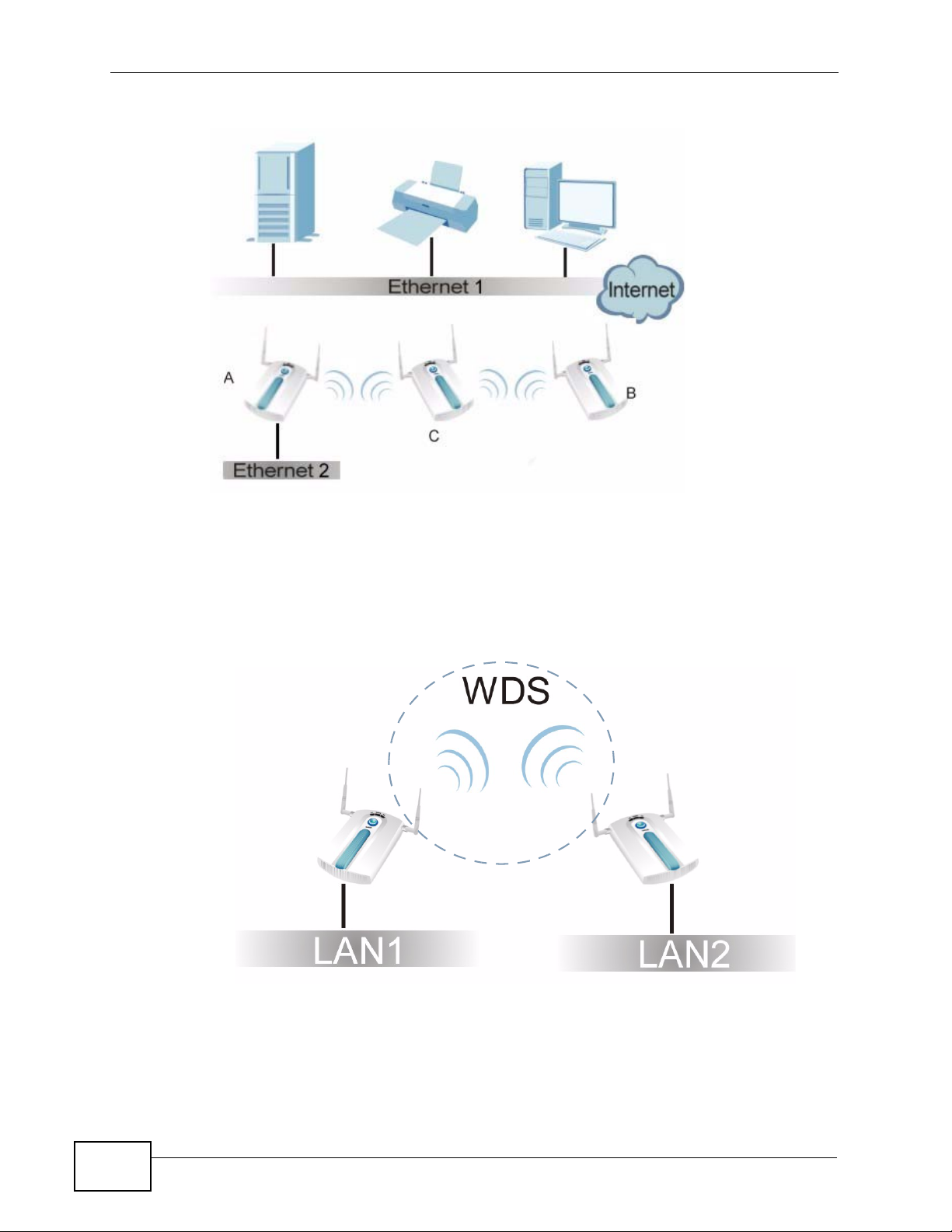
1.2.2.1 Bridge / Repeater Mode Example
In the example below, when both NWAs are in Bridge / Repeater mode, they form
a WDS (Wireless Distribution System) allowing the computers in LAN 1 to connect
to the computers in LAN 2.
Figure 4 Bridging Example
26
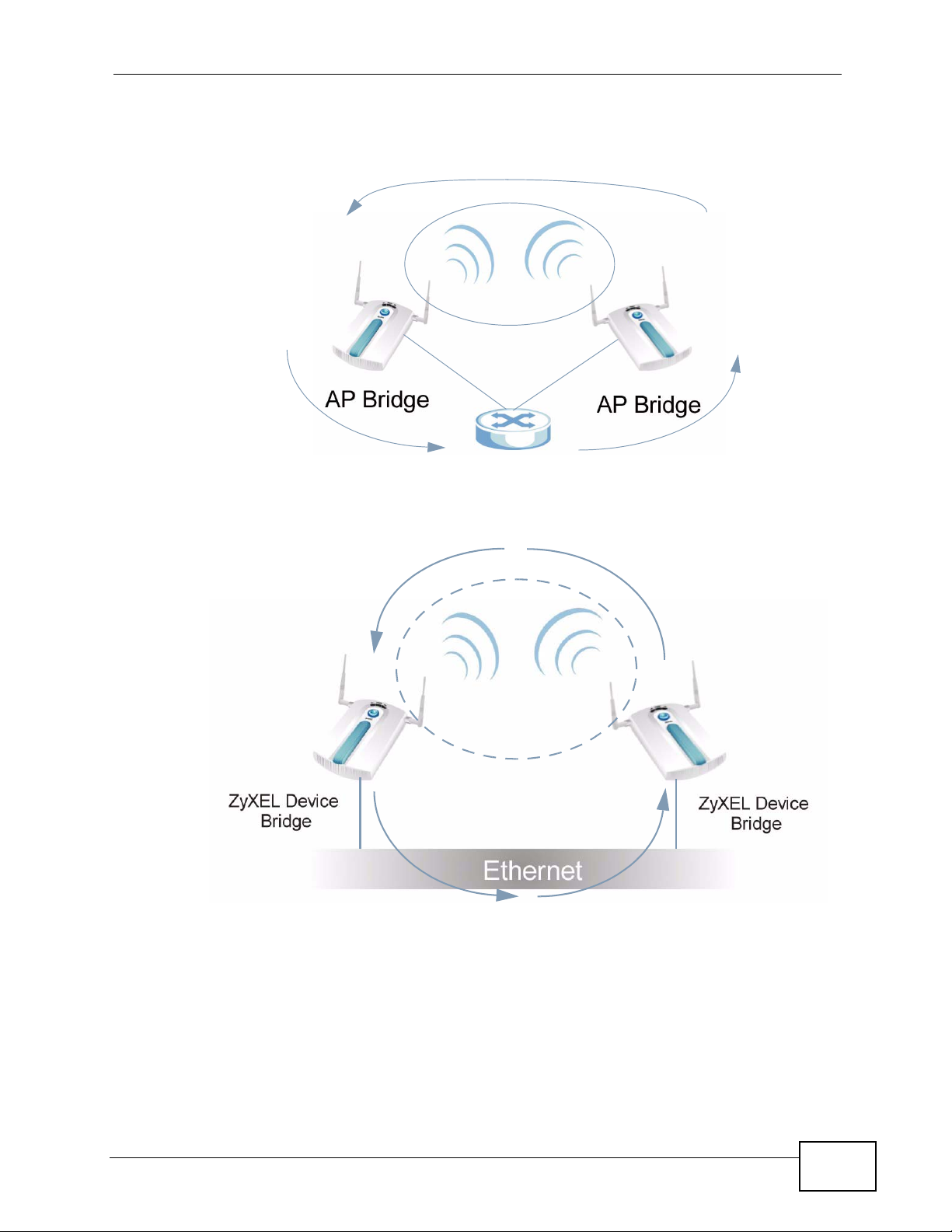
Be careful to avoid bridge loops when you enable bridging in the NWA. Bridge
loops cause broadcast traffic to circle the network endlessly, resulting in possible
throughput degradation and disruption of communications. The following
examples show two network topologies that can lead to this problem:
NWA-3160 Series User’s Guide
Chapter 1 Introduction
• If two or more NWAs (in bridge mode) are connected to the same hub.
Figure 5 Bridge Loop: Two Bridges Connected to Hub
• If your NWA (in bridge mode) is connected to a wired LAN while communicating
with another wireless bridge that is also connected to the same wired LAN.
Figure 6 Bridge Loop: Bridge Connected to Wired LAN
To prevent bridge loops, ensure that you enable Spanning Tree Protocol (STP) in
the Wireless screen or your NWA is not set to bridge mode while connected to
both wired and wireless segments of the same LAN.
NWA-3160 Series User’s Guide
27

Chapter 1 Introduction
1.2.3 AP + Bridge
In AP + Bridge mode, the NWA supports both AP and bridge connection at the
same time.
In the figure below, A and B use X as an AP to access the wired network, while X
and Y communicate in bridge mode.
When the NWA is in AP + Bridge mode, security between APs (WDS) is
independent of the security between the wireless stations and the AP. If you do
not enable WDS security, traffic between APs is not encrypted. When WDS
security is enabled, both APs must use the same pre-shared key.
Unless specified, the term “security settings” refers to the traffic between the
wireless stations and the NWA.
Figure 7 AP + Bridge Application
A
1.2.4 MBSSID
A Basic Service Set (BSS) is the set of devices forming a single wireless network
(usually an access point and one or more wireless clients). The Service Set
IDentifier (SSID) is the name of a BSS. In Multiple BSS (MBSSID) mode, the NWA
28
B
X
Y
NWA-3160 Series User’s Guide
Chapter 1 Introduction
provides multiple virtual APs, each forming its own BSS and using its own
individual SSID profile.
You can configure up to sixteen SSID profiles, and have up to eight active at any
one time.
You can assign different wireless and security settings to each SSID profile. This
allows you to compartmentalize groups of users, set varying access privileges,
and prioritize network traffic to and from certain BSSs.
To the wireless clients in the network, each SSID appears to be a different access
point. As in any wireless network, clients can associate only with the SSIDs for
which they have the correct security settings.
For example, you might want to set up a wireless network in your office where
Internet telephony (VoIP) users have priority. You also want a regular wireless
network for standard users, as well as a ‘guest’ wireless network for visitors. In
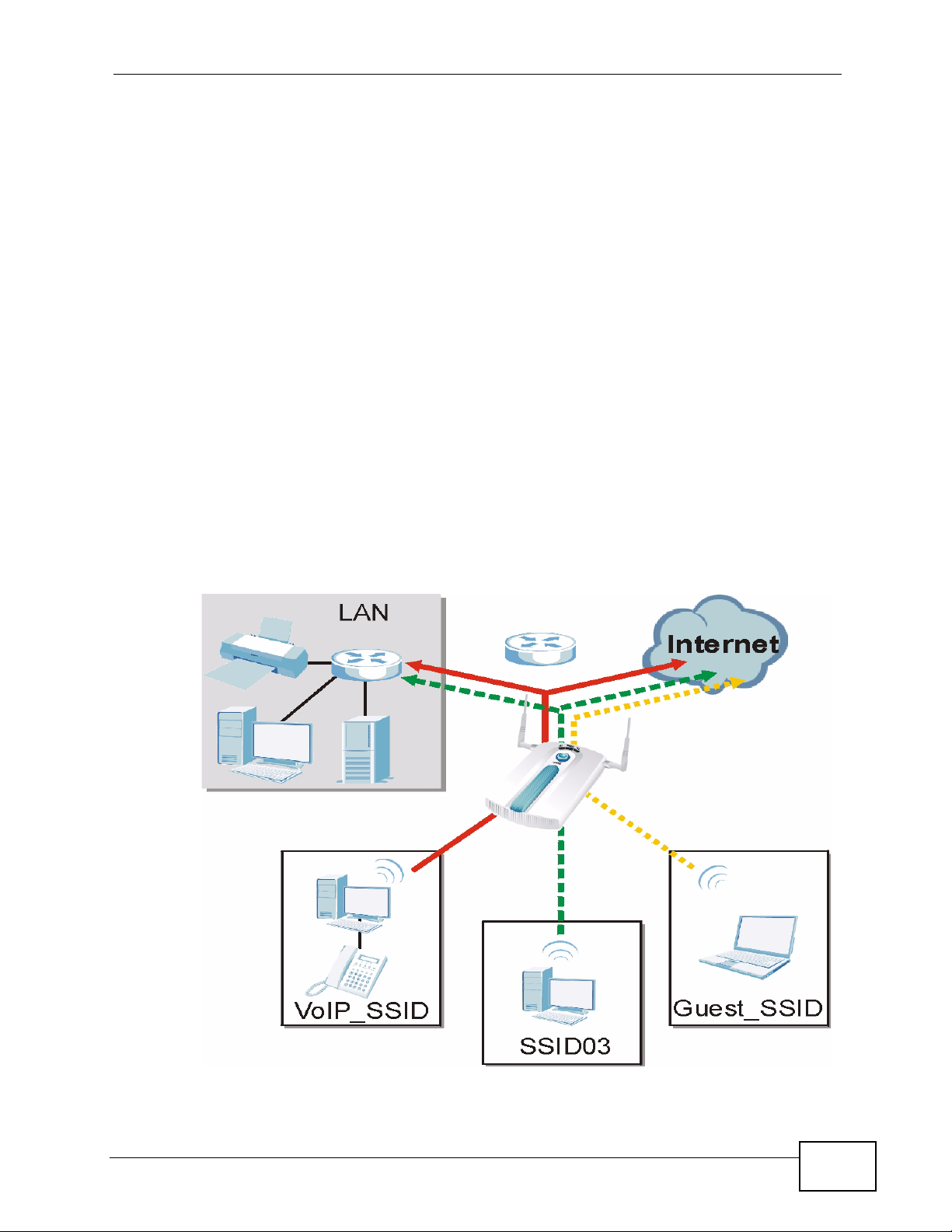
the following figure, VoIP_SSID users have QoS priority, SSID03 is the wireless
network for standard users, and Guest_SSID is the wireless network for guest
users. In this example, the guest user is forbidden access to the wired Land Area
Network (LAN) behind the AP and can access only the Internet.
Figure 8 Multiple BSSs
NWA-3160 Series User’s Guide
29

Chapter 1 Introduction
1.2.5 Pre-Configured SSID Profiles
The NWA has two pre-configured SSID profiles.
• VoIP_SSID. This profile is intended for use by wireless clients requiring the
highest QoS level for VoIP telephony and other applications requiring low
latency. The QoS level of this profile is not user-configurable.
• Guest_SSID. This profile is intended for use by visitors and others who require
access to certain resources on the network (an Internet gateway or a network
printer, for example) but must not have access to the rest of the network. Layer
2 isolation is enabled (see Section on page 178), and QoS is set to NONE.
Intra-BSS traffic blocking is also enabled (see Section 8.1.2 on page 120).
These fields are all user-configurable.
1.3 CAPWAP
The NWA supports Control And Provisioning of Wireless Access Points (CAPWAP).
This is ZyXEL’s implementation of the Internet Engineering Task Force’s (IETF)
CAPWAP protocol.
ZyXEL’s CAPWAP allows a single access point to manage up to eight other access
points. The managed APs receive all their configuration information from the
controller AP. The CAPWAP dataflow is protected by Datagram Transport Layer
Security (DTLS).
The following ZyXEL AP models can be CAPWAP managed APs:
• NWA-3160
• NWA-3163
• NWA-3500
• NWA-3550
• NWA-3166
30
NWA-3160 Series User’s Guide
 Loading...
Loading...