Chapter 6 LAN Setup
The following table describes the labels in this screen.
Table 28 DHCP Setup
LABEL DESCRIPTION
DHCP Setup
DHCP If set to Server, your ZyXEL Device can assign IP addresses, an IP default
gateway and DNS servers to Windows 95, Windows NT and other systems that
support the DHCP client.
If set to None, the DHCP server will be disabled.
If set to Relay, the ZyXEL Device acts as a surrogate DHCP server and relays
DHCP requests and responses between the remote server and the clients.
Enter the IP address of the actual, remote DHCP server in the Remote DHCP
Server field in this case.
When DHCP is used, the following items need to be set:
IP Pool Starting
Address
Pool Size This field specifies the size, or count of the IP address pool.
Remote DHCP
Server
DNS Server
DNS Servers
Assigned by DHCP
Server
Primary DNS Server
Secondary DNS
Server
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to begin configuring this screen afresh.
This field specifies the first of the contiguous addresses in the IP address pool.
If Relay is selected in the DHCP field above then enter the IP address of the
actual remote DHCP server here.
The ZyXEL Device passes a DNS (Domain Name System) server IP address to
the DHCP clients.
This field is not available when you set DHCP to Relay.
Enter the IP addresses of the DNS servers. The DNS servers are passed to the
DHCP clients along with the IP address and the subnet mask.
If the fields are left as 0.0.0.0, the ZyXEL Device acts as a DNS proxy and
forwards the DHCP client’s DNS query to the real DNS server learned through
IPCP and relays the response back to the computer.
6.5 LAN Client List
This table allows you to assign IP addresses on the LAN to specific individual computers
based on their MAC Addresses.
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC address
is assigned at the factory and consists of six pairs of hexadecimal characters, for example,
00:A0:C5:00:00:02.
To change your ZyXEL Device’s static DHCP settings, click Network > LAN > Client List.
The screen appears as shown.
P-660HW-Dx v2 User’s Guide
101

Chapter 6 LAN Setup
Figure 57 LAN Client List
The following table describes the labels in this screen.
Table 29 LAN Client List
LABEL DESCRIPTION
IP Address Enter the IP address that you want to assign to the computer on your LAN with
MAC Address Enter the MAC address of a computer on your LAN.
Add Click Add to add a static DHCP entry.
# This is the index number of the static IP table entry (row).
Status This field displays whether the client is connected to the ZyXEL Device.
Host Name This field displays the computer host name.
IP Address This field displays the IP address relative to the # field listed above.
MAC Address The MAC (Media Access Control) or Ethernet address on a LAN (Local Area
Reserve Select the check box(es) in each entry to have the ZyXEL Device always assign
Modify Click the modify icon to have the IP address field editable and change it.
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to begin configuring this screen afresh.
Refresh Click Refresh to reload the DHCP table.
the MAC address specified below.
The IP address should be within the range of IP addresses you specified in the
DHCP Setup for the DHCP client.
Network) is unique to your computer (six pairs of hexadecimal notation).
A network interface card such as an Ethernet adapter has a hardwired address
that is assigned at the factory. This address follows an industry standard that
ensures no other adapter has a similar address.
the selected entry(ies)’s IP address(es) to the corresponding MAC address(es)
(and host name(s)). You can select up to 32 entries in this table.
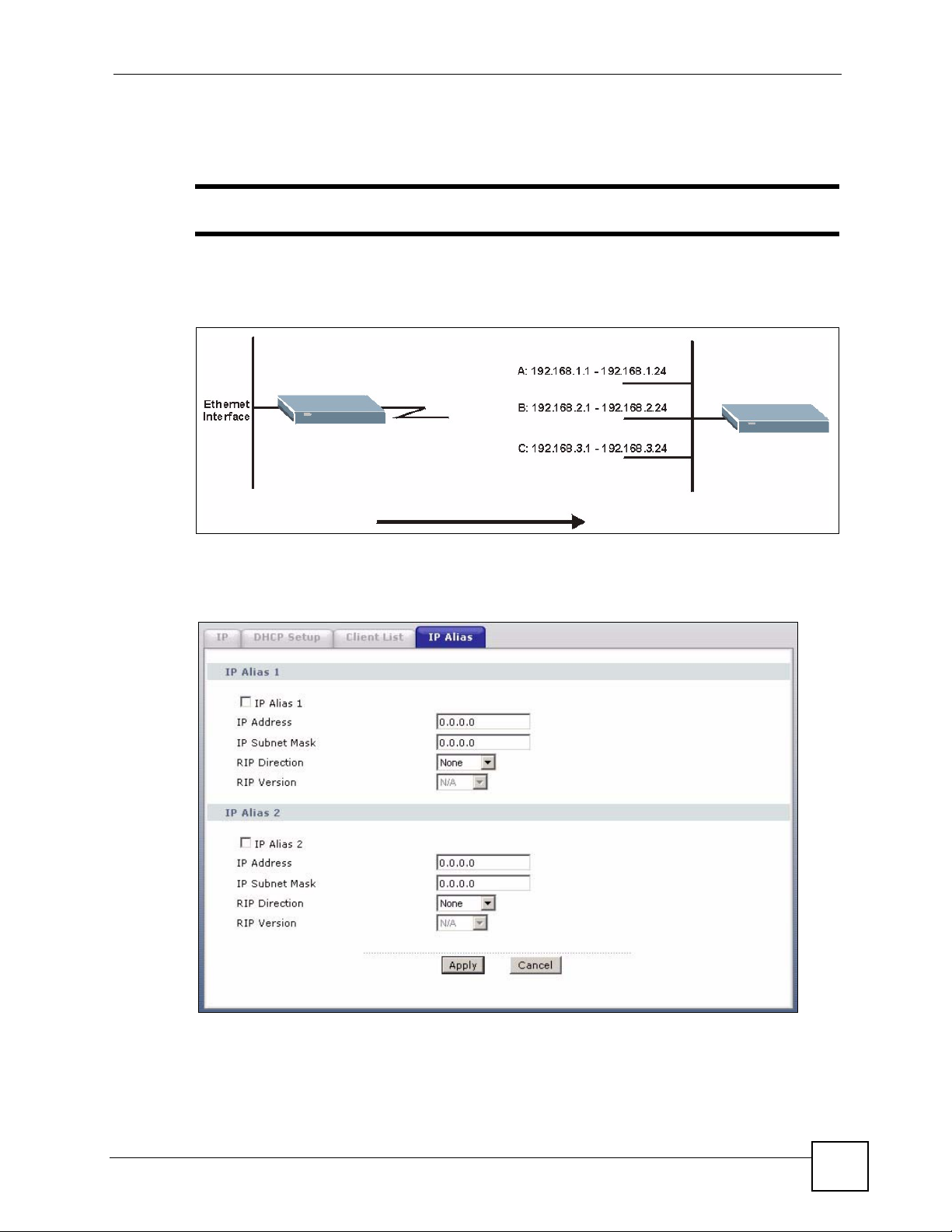
6.6 LAN IP Alias
IP alias allows you to partition a physical network into different logical networks over the
same Ethernet interface. The ZyXEL Device supports three logical LAN interfaces via its
single physical Ethernet interface with the ZyXEL Device itself as the gateway for each LAN
network.
102
P-660HW-Dx v2 User’s Guide
Chapter 6 LAN Setup
When you use IP alias, you can also configure firewall rules to control access between the
LAN's logical networks (subnets).
" Make sure that the subnets of the logical networks do not overlap.
The following figure shows a LAN divided into subnets A, B, and C.
Figure 58 Physical Network & Partitioned Logical Networks
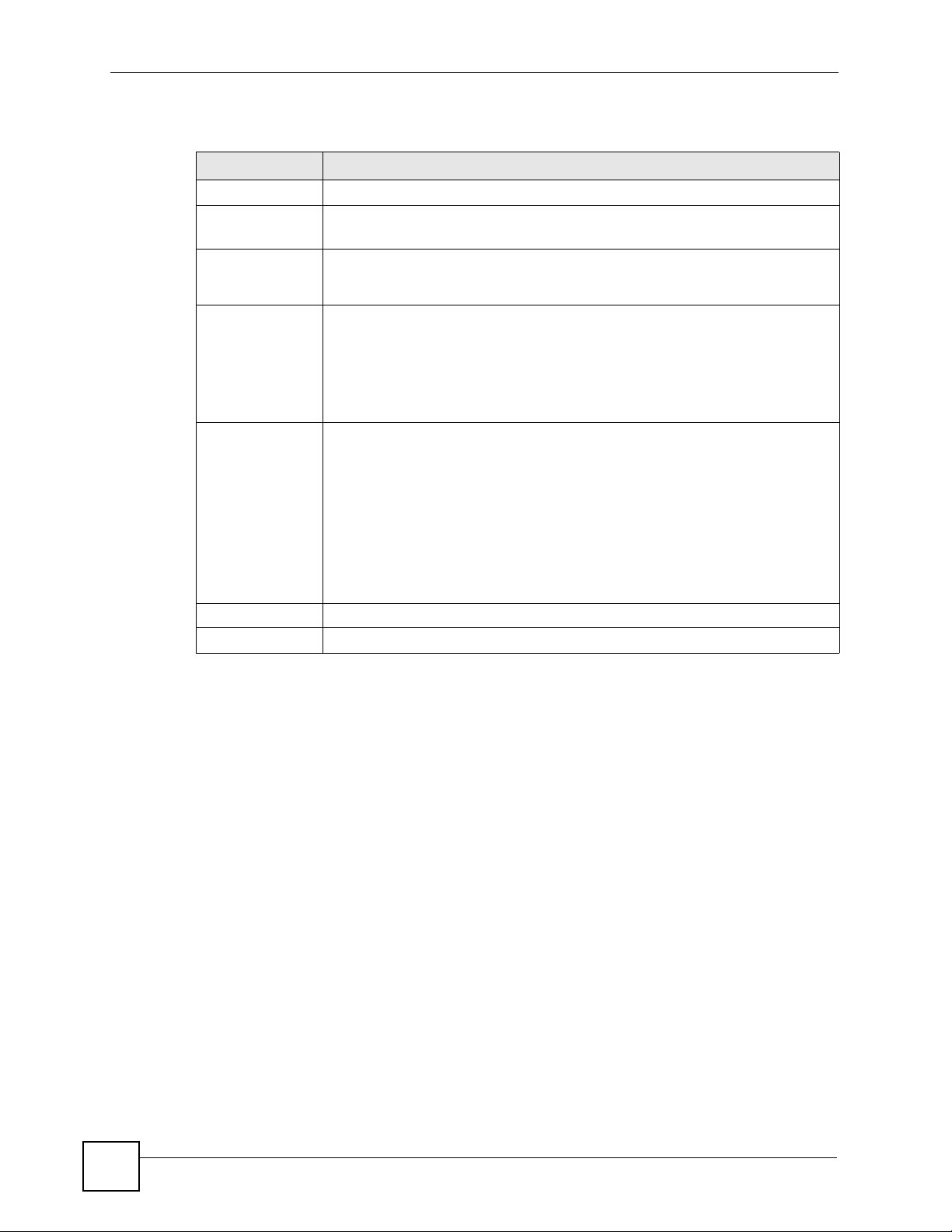
To change your ZyXEL Device’s IP alias settings, click Network > LAN > IP Alias. The
screen appears as shown.
Figure 59 LAN IP Alias
P-660HW-Dx v2 User’s Guide
103
Chapter 6 LAN Setup
The following table describes the labels in this screen.
Table 30 LAN IP Alias
LABEL DESCRIPTION
IP Alias 1, 2 Select the check box to configure another LAN network for the ZyXEL Device.
IP Address Enter the IP address of your ZyXEL Device in dotted decimal notation.
IP Subnet Mask Your ZyXEL Device will automatically calculate the subnet mask based on the IP
RIP Direction RIP (Routing Information Protocol, RFC 1058 and RFC 1389) allows a router to
RIP Version The RIP Version field controls the format and the broadcasting method of the RIP
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to begin configuring this screen afresh.
Alternatively, click the right mouse button to copy and/or paste the IP address.
address that you assign. Unless you are implementing subnetting, use the subnet
mask computed by the ZyXEL Device.
exchange routing information with other routers. The RIP Direction field controls
the sending and receiving of RIP packets. Select the RIP direction from None/
Both/In Only/Out Only. When set to Both or Out Only, the ZyXEL Device will
broadcast its routing table periodically. When set to Both or In Only, it will
incorporate the RIP information that it receives; when set to None, it will not send
any RIP packets and will ignore any RIP packets received.
packets that the ZyXEL Device sends (it recognizes both formats when receiving).
RIP-1 is universally supported but RIP-2 carries more information. RIP-1 is
probably adequate for most networks, unless you have an unusual network
topology. Both RIP-2B and RIP-2M sends the routing data in RIP-2 format; the
difference being that RIP-2B uses subnet broadcasting while RIP-2M uses
multicasting. Multicasting can reduce the load on non-router machines since they
generally do not listen to the RIP multicast address and so will not receive the RIP
packets. However, if one router uses multicasting, then all routers on your network
must use multicasting, also. By default, RIP direction is set to Both and the
Version set to RIP-1.
104
P-660HW-Dx v2 User’s Guide
CHAPTER 7
Wireless LAN
This chapter discusses how to configure the wireless network settings on your ZyXEL Device.
See the appendices for more detailed information about wireless networks.
7.1 Wireless Network Overview
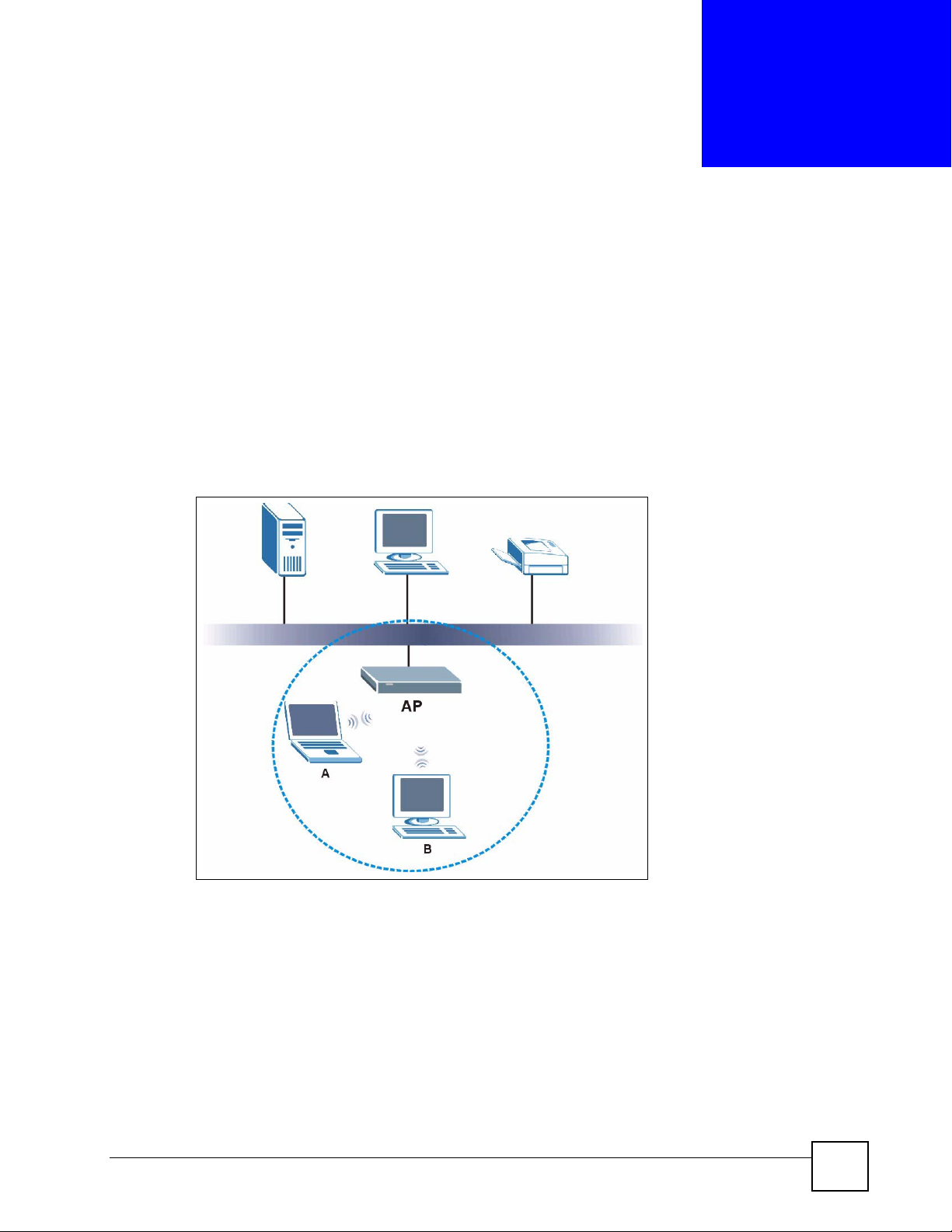
The following figure provides an example of a wireless network.
Figure 60 Example of a Wireless Network
The wireless network is the part in the blue circle. In this wireless network, devices A and B
are called wireless clients. The wireless clients use the access point (AP) to interact with other
devices (such as the printer) or with the Internet. Your ZyXEL Device is the AP.
Every wireless network must follow these basic guidelines.
• Every wireless client in the same wireless network must use the same SSID.
The SSID is the name of the wireless network. It stands for Service Set IDentity.
• If two wireless networks overlap, they should use different channels.
Like radio stations or television channels, each wireless network uses a specific channel,
or frequency, to send and receive information.
P-660HW-Dx v2 User’s Guide
105

Chapter 7 Wireless LAN
• Every wireless client in the same wireless network must use security compatible with the
AP.
Security stops unauthorized devices from using the wireless network. It can also protect
the information that is sent in the wireless network.
7.2 Wireless Security Overview
The following sections introduce different types of wireless security you can set up in the
wireless network.
7.2.1 SSID
Normally, the AP acts like a beacon and regularly broadcasts the SSID in the area. You can
hide the SSID instead, in which case the AP does not broadcast the SSID. In addition, you
should change the default SSID to something that is difficult to guess.
This type of security is fairly weak, however, because there are ways for unauthorized devices
to get the SSID. In addition, unauthorized devices can still see the information that is sent in
the wireless network.
7.2.2 MAC Address Filter
Every wireless client has a unique identification number, called a MAC address.1 A MAC
address is usually written using twelve hexadecimal characters
or 00:A0:C5:00:00:02. To get the MAC address for each wireless client, see the appropriate
User’s Guide or other documentation.
You can use the MAC address filter to tell the AP which wireless clients are allowed or not
allowed to use the wireless network. If a wireless client is allowed to use the wireless network,
it still has to have the correct settings (SSID, channel, and security). If a wireless client is not
allowed to use the wireless network, it does not matter if it has the correct settings.
This type of security does not protect the information that is sent in the wireless network.
Furthermore, there are ways for unauthorized devices to get the MAC address of an authorized
wireless client. Then, they can use that MAC address to use the wireless network.
7.2.3 User Authentication
Authentication is the process of verifying whether a wireless device is allowed to use the
wireless network. You can make every user log in to the wireless network before they can use
it. This is called user authentication. However, every wireless client in the wireless network
has to support IEEE 802.1x to do this.
For wireless networks, there are two typical places to store the user names and passwords for
each user.
2
; for example, 00A0C5000002
106
• In the AP: this feature is called a local user database or a local database.
1. Some wireless devices, such as scanners, can detect wireless networks but cannot use wireless networks.
These kinds of wireless devices might not have MAC addresses.
2. Hexadecimal characters are 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F.
P-660HW-Dx v2 User’s Guide
• In a RADIUS server: this is a server used in businesses more than in homes.
If your AP does not provide a local user database and if you do not have a RADIUS server,
you cannot set up user names and passwords for your users.
Unauthorized devices can still see the information that is sent in the wireless network, even if
they cannot use the wireless network. Furthermore, there are ways for unauthorized wireless
users to get a valid user name and password. Then, they can use that user name and password
to use the wireless network.
Local user databases also have an additional limitation that is explained in the next section.
7.2.4 Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
The types of encryption you can choose depend on the type of user authentication. (See
Section 7.2.3 on page 106 for information about this.)
Table 31 Types of Encryption for Each Type of Authentication
Weakest No Security WPA
Strongest WPA2-PSK WPA2
Chapter 7 Wireless LAN
NO AUTHENTICATION RADIUS SERVER
Static WEP
WPA-PSK
For example, if the wireless network has a RADIUS server, you can choose WPA or WPA2.
If users do not log in to the wireless network, you can choose no encryption, Static W EP,
WPA-PSK, or WPA2-PSK.
Usually, you should set up the strongest encryption that every wireless client in the wireless
network supports. For example, suppose the AP does not have a local user database, and you
do not have a RADIUS server. Therefore, there is no user authentication. Suppose the wireless
network has two wireless clients. Device A only supports WEP, and device B supports WEP
and WPA. Therefore, you should set up Static WEP in the wireless network.
" It is recommended that wireless networks use WPA-PSK, WPA, or stronger
encryption. IEEE 802.1x and WEP encryption are better than none at all, but it is
still possible for unauthorized devices to figure out the original information
pretty quickly.
It is not possible to use WPA-PSK, WPA or stronger encryption with a local
user database. In this case, it is better to set up stronger encryption with no
authentication than to set up weaker encryption with the local user database.
P-660HW-Dx v2 User’s Guide
107
Chapter 7 Wireless LAN
When you select WPA2 or WPA2-PSK in your ZyXEL Device, you can also select an option
(WPA compatible) to support WPA as well. In this case, if some wireless clients support
WPA and some support WPA2, you should set up WPA2-PSK or WPA2 (depending on the
type of wireless network login) and select the WPA compatible option in the ZyXEL Device.
Many types of encryption use a key to protect the information in the wireless network. The
longer the key, the stronger the encryption. Every wireless client in the wireless network must
have the same key.
7.2.5 One-Touch Intelligent Security Technology (OTIST)
With ZyXEL’s OTIST, you set up the SSID and WPA-PSK on the ZyXEL Device. Then, the
ZyXEL Device transfers them to the devices in the wireless networks. As a result, you do not
have to set up the SSID and encryption on every device in the wireless network.
The devices in the wireless network have to support OTIST, and they have to be in range of
the ZyXEL Device when you activate it. See Section 7.4 on page 117 for more details.
7.3 General Wireless LAN Screen
" If you are configuring the ZyXEL Device from a computer connected to the
wireless LAN and you change the ZyXEL Device’s SSID or WEP settings, you
will lose your wireless connection when you press Apply to confirm. You must
then change the wireless settings of your computer to match the ZyXEL
Device’s new settings.
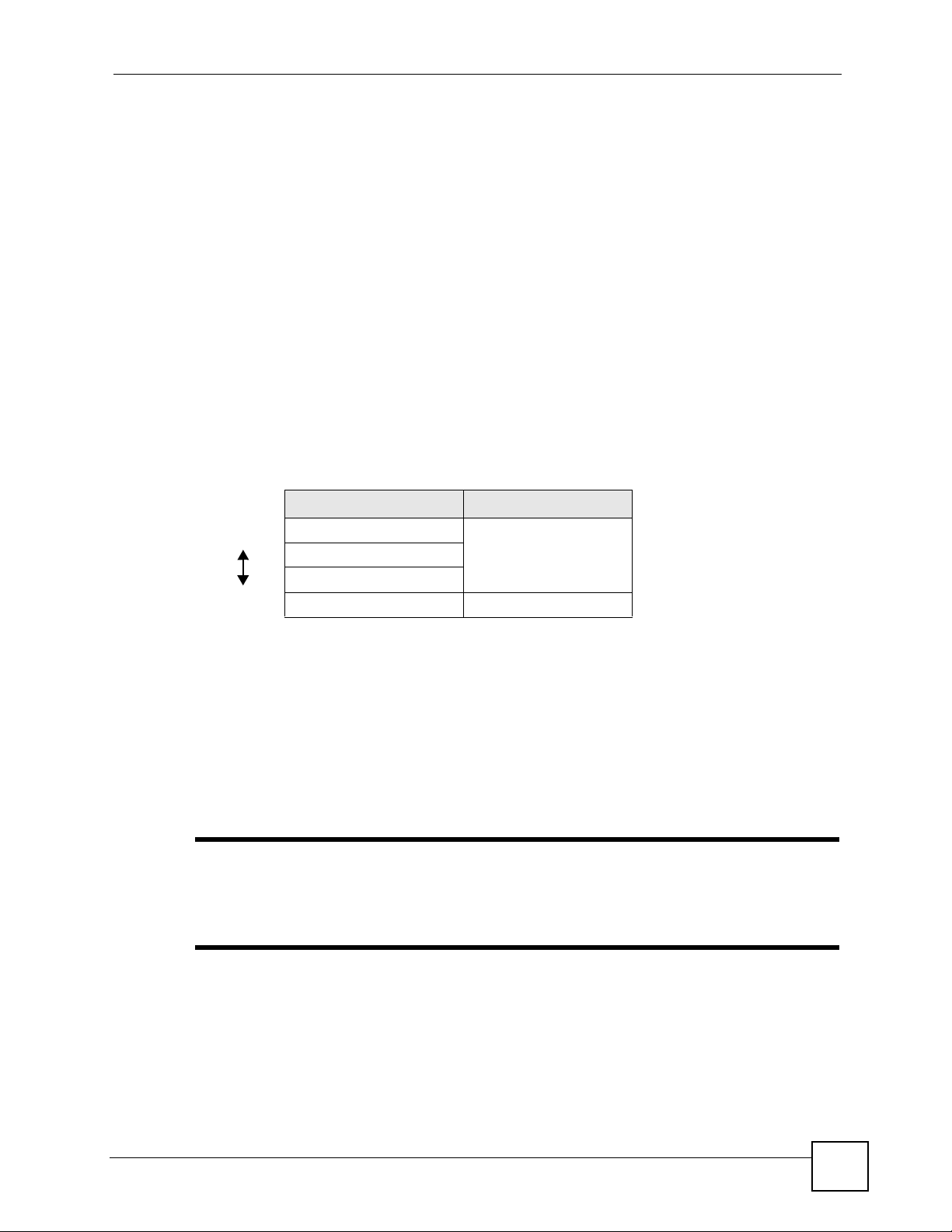
Click Network > Wireless LAN to open the General screen.
Figure 61 Wireless LAN: General
108
P-660HW-Dx v2 User’s Guide

Chapter 7 Wireless LAN
The following table describes the general wireless LAN labels in this screen.
Table 32 Wireless LAN: General
LABEL DESCRIPTION
Wireless Setup
Active Wireless
LAN
Network Name
(SSID)
Click the check box to activate wireless LAN.
(Service Set IDentity) The SSID identifies the Service Set with which a wireless client
is associated. Wireless clients associating to the access point (AP) must have the
same SSID. Enter a descriptive name (up to 32 printable 7-bit ASCII characters) for
the wireless LAN.
Note: If you are configuring the ZyXEL Device from a computer
connected to the wireless LAN and you change the ZyXEL
Device’s SSID or WEP settings, you will lose your wireless
connection when you press Apply to confirm. You must
then change the wireless settings of your computer to
match the ZyXEL Device’s new settings.
Hide SSID Select this check box to hide the SSID in the outgoing beacon frame so a station
Channel
Selection
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Advanced
Setup
cannot obtain the SSID through scanning using a site survey tool.
Set the operating frequency/channel depending on your particular region.
Select a channel from the drop-down list box.
Click Advanced Setup to display the Wireless Advanced Setup screen and edit
more details of your WLAN setup.
See the rest of this chapter for information on the other labels in this screen.
7.3.1 No Security
Select No Security to allow wireless clients to communicate with the access points without
any data encryption.
" If you do not enable any wireless security on your ZyXEL Device, your network
is accessible to any wireless networking device that is within range.
P-660HW-Dx v2 User’s Guide
109
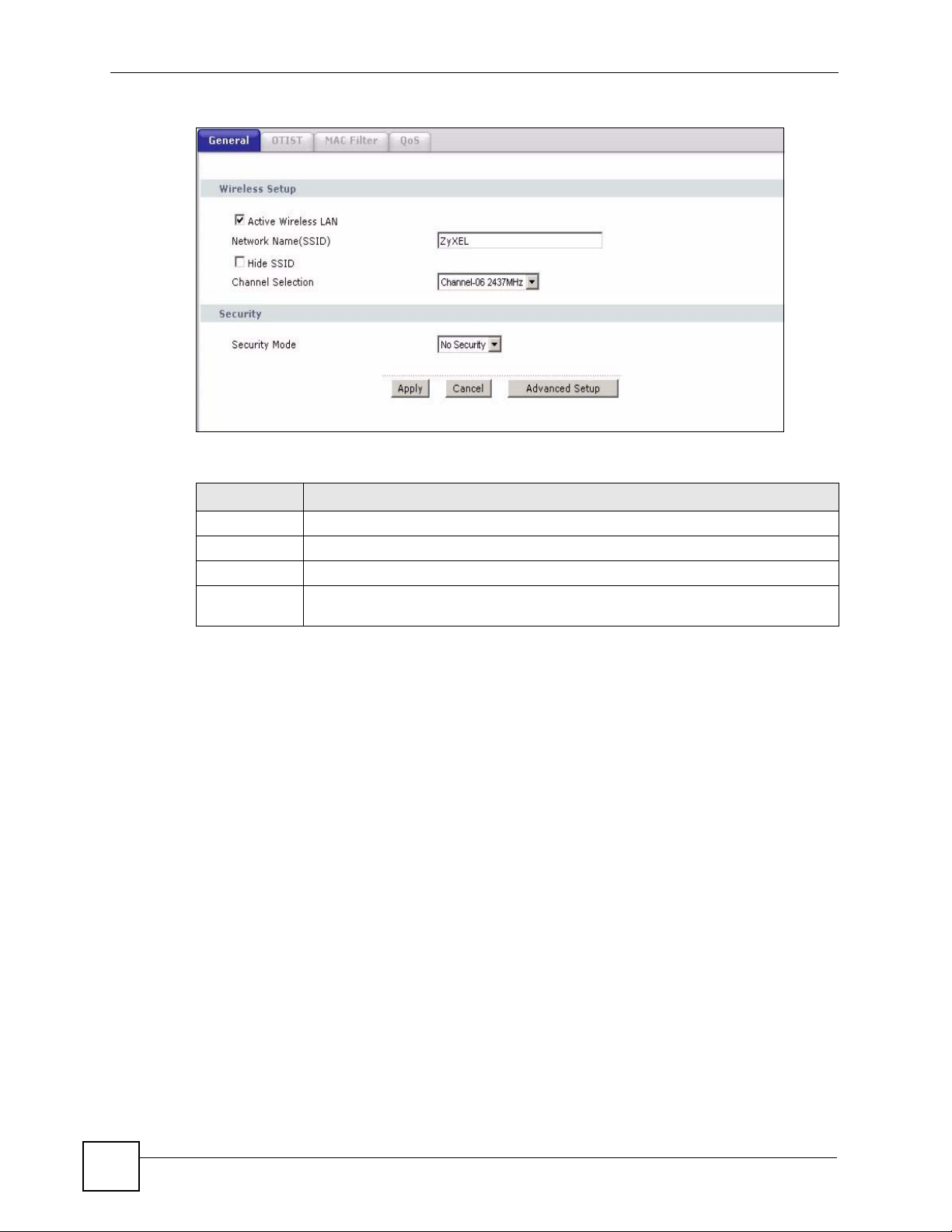
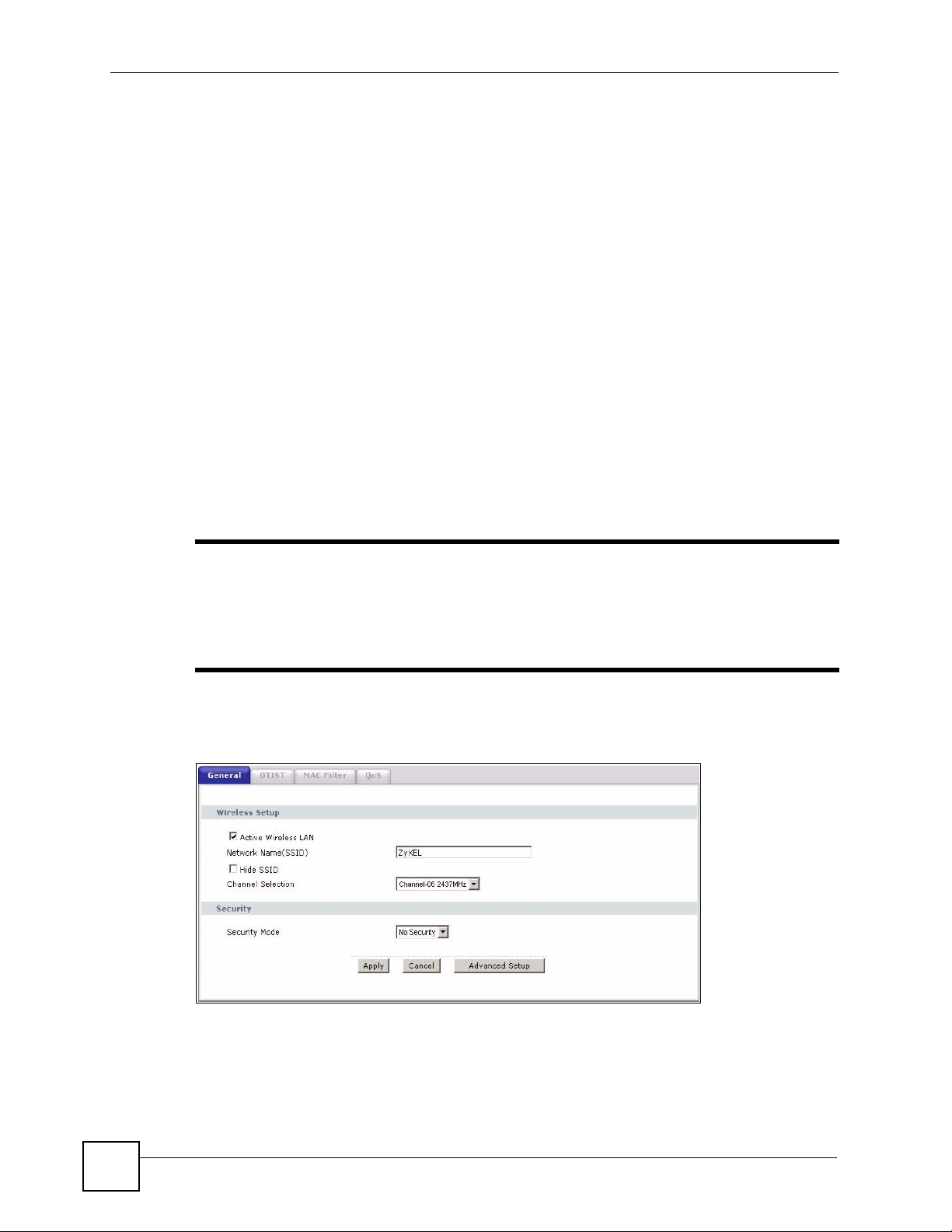
Chapter 7 Wireless LAN
Figure 62 Wireless: No Security
The following table describes the labels in this screen.
Table 33 Wireless No Security
LABEL DESCRIPTION
Security Mode Choose No Security from the drop-down list box.
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Advanced
Setup
Click Advanced Setup to display the Wireless Advanced Setup screen and edit
more details of your WLAN setup.
7.3.2 WEP Encryption
WEP encryption scrambles the data transmitted between the wireless clients and the access
points to keep network communications private. It encrypts unicast and multicast
communications in a network. Both the wireless clients and the access points must use the
same WEP key.
Your ZyXEL Device allows you to configure up to four 64-bit, 128-bit or 256-bit WEP keys
but only one key can be enabled at any one time.
In order to configure and enable WEP encryption; click Network > Wireless LAN to display
the General screen. Select Static WEP from the Security Mode list.
110
P-660HW-Dx v2 User’s Guide
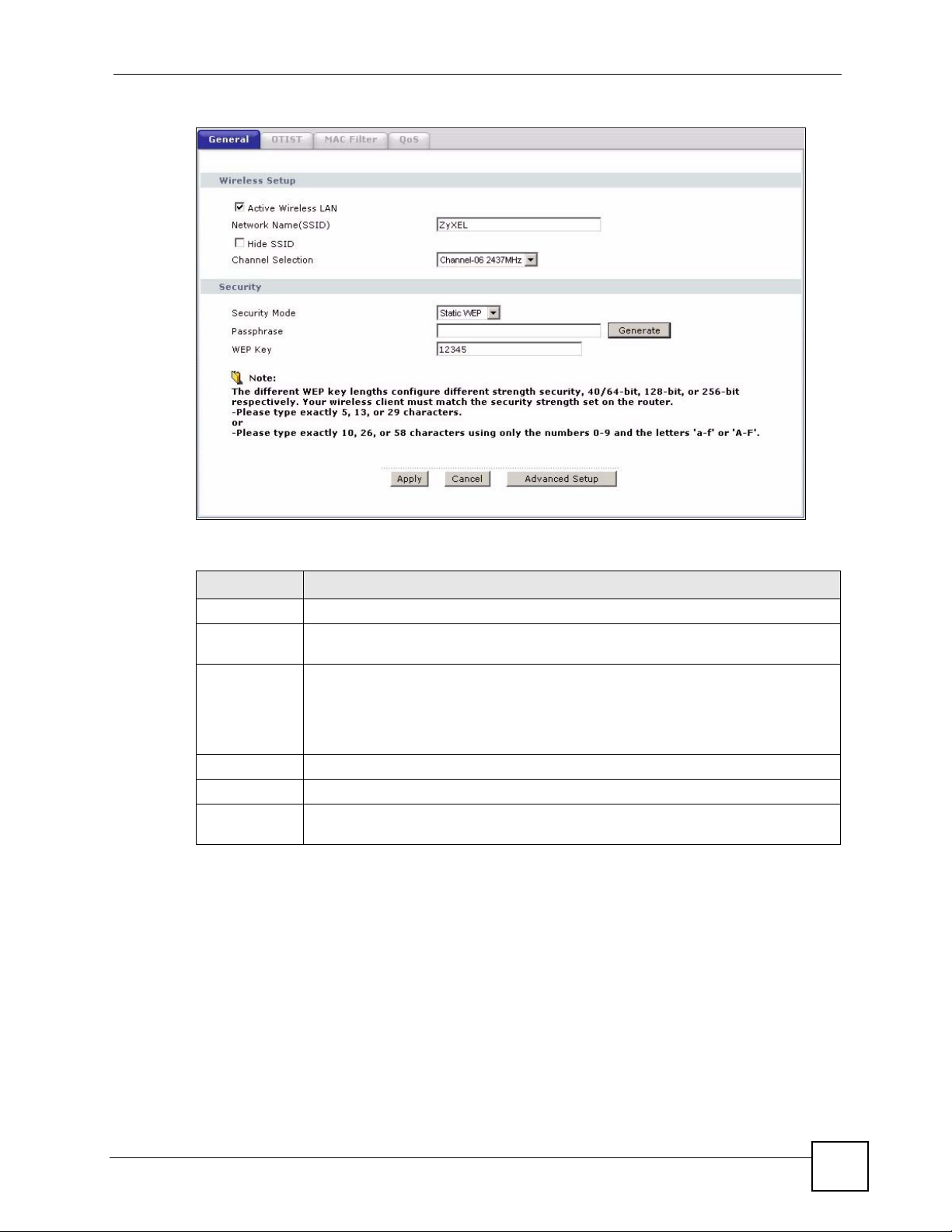
Figure 63 Wireless: Static WEP Encryption
Chapter 7 Wireless LAN
The following table describes the wireless LAN security labels in this screen.
Table 34 Wireless: Static WEP Encryption
LABEL DESCRIPTION
Security Mode Choose Static WEP from the drop-down list box.
Passphrase Enter a Passphrase (up to 32 printable characters) and clicking Generate. The
ZyXEL Device automatically generates a WEP key.
WEP Key The WEP keys are used to encrypt data. Both the ZyXEL Device and the wireless
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Advanced
Setup
clients must use the same WEP key for data transmission.
If you want to manually set the WEP key, enter any 5, 13 or 29 characters (ASCII
string) or 10, 26 or 58 hexadecimal characters ("0-9", "A-F") for a 64-bit, 128-bit or
256-bit WEP key respectively.
Click Advanced Setup to display the Wireless Advanced Setup screen and edit
more details of your WLAN setup.
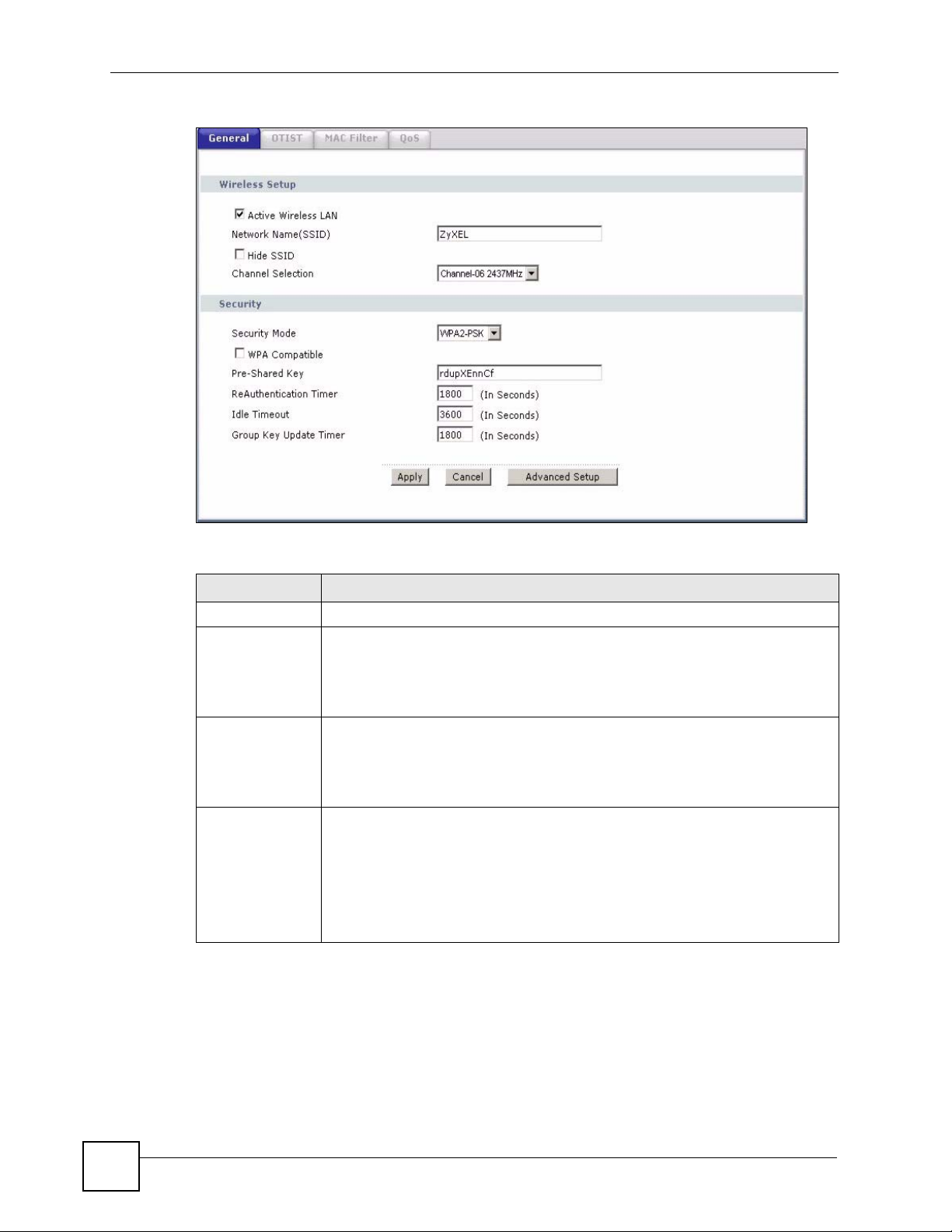
7.3.3 WPA-PSK/WPA2-PSK
In order to configure and enable WPA(2)-PSK authentication; click Network > Wireless
LAN to display the General screen. Select WPA-PSK or WPA2-PSK from the Security
Mode list.
P-660HW-Dx v2 User’s Guide
111
Chapter 7 Wireless LAN
Figure 64 Wireless: WPA-PSK/WPA2-PSK
The following table describes the wireless LAN security labels in this screen.
Table 35 Wireless: WPA-PSK/WPA2-PSK
LABEL DESCRIPTION
Security Mode Choose WPA-PSK or WPA2-PSK from the drop-down list box.
WPA Compatible This check box is available only when you select WPA2-PSK or WPA2 in the
Pre-Shared Key The encryption mechanisms used for WPA/WPA2 and WPA-PSK/WPA2-PSK
ReAuthentication
Timer (In
Seconds)
Security Mode field.
Select the check box to have both WPA2 and WPA wireless clients be able to
communicate with the ZyXEL Device even when the ZyXEL Device is using
WPA2-PSK or WPA2.
are the same. The only difference between the two is that WPA-PSK/WPA2-PSK
uses a simple common password, instead of user-specific credentials.
Type a pre-shared key from 8 to 63 case-sensitive ASCII characters (including
spaces and symbols).
Specify how often wireless clients have to resend usernames and passwords in
order to stay connected. Enter a time interval between 10 and 9999 seconds. The
default time interval is 1800 seconds (30 minutes).
Note: If wireless client authentication is done using a RADIUS
server, the reauthentication timer on the RADIUS server
has priority.
112
P-660HW-Dx v2 User’s Guide

Chapter 7 Wireless LAN
Table 35 Wireless: WPA-PSK/WPA2-PSK
LABEL DESCRIPTION
Idle Timeout (In
Seconds)
Group Key
Update Timer (In
Seconds)
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Advanced Setup Click Advanced Setup to display the Wireless Advanced Setup screen and edit
The ZyXEL Device automatically disconnects a wireless station from the wireless
network after a period of inactivity. The wireless station needs to send the
username and password again before it can use the wireless network again.
Some wireless clients may prompt users for a username and password; other
clients may use saved login credentials. In either case, there is usually a short
delay while the wireless client logs in to the wireless network again.
This value is usually smaller when the wireless network is keeping track of how
much time each wireless station is connected to the wireless network (for
example, using an authentication server). If the wireless network is not keeping
track of this information, you can usually set this value higher to reduce the
number of delays caused by logging in again.
The Group Key Update Timer is the rate at which the AP (if using WPA-PSK/
WPA2-PSK key management) or RADIUS server (if using WPA(2) key
management) sends a new group key out to all clients. The re-keying process is
the WPA(2) equivalent of automatically changing the WEP key for an AP and all
stations in a WLAN on a periodic basis. Setting of the Group Key Update Timer
is also supported in WPA-PSK/WPA2-PSK mode. The default is 1800 seconds
(30 minutes).
more details of your WLAN setup.
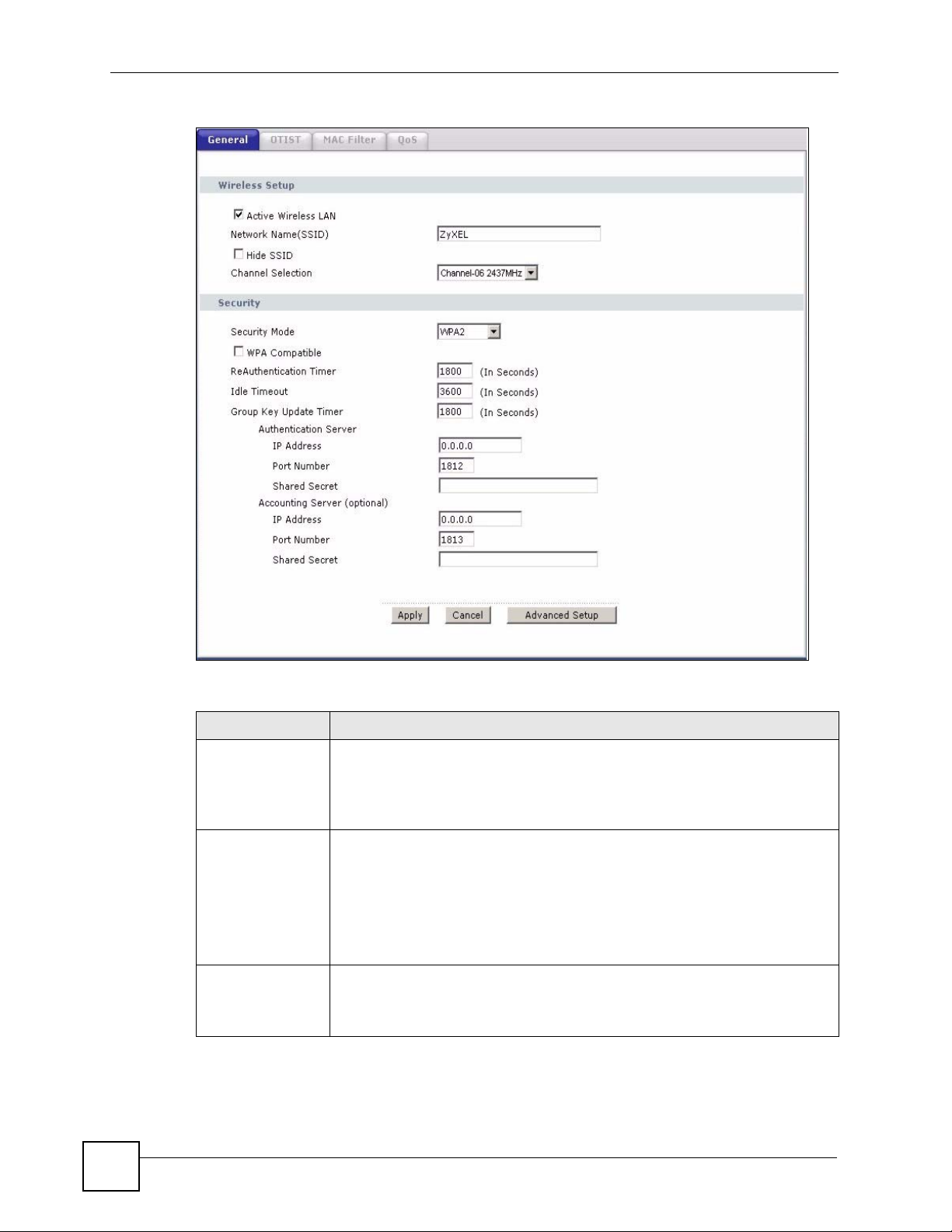
7.3.4 WPA/WPA2
In order to configure and enable WPA/WPA2; click the Wireless LAN link under Network to
display the General screen. Select WPA or WPA2 from the Security Mode list.
P-660HW-Dx v2 User’s Guide
113
Chapter 7 Wireless LAN
Figure 65 Wireless: WPA/WPA2
The following table describes the wireless LAN security labels in this screen.
Table 36 Wireless: WPA/WPA2
LABEL DESCRIPTION
WPA Compatible This check box is available only when you select WPA2-PSK or WPA2 in the
Security Mode field.
Select the check box to have both WPA2 and WPA wireless clients be able to
communicate with the ZyXEL Device even when the ZyXEL Device is using
WPA2-PSK or WPA2.
ReAuthentication
Timer (In Seconds)
Specify how often wireless clients have to resend usernames and passwords in
order to stay connected. Enter a time interval between 10 and 9999 seconds.
The default time interval is 1800 seconds (30 minutes).
Note: If wireless client authentication is done using a
RADIUS server, the reauthentication timer on the
RADIUS server has priority.
Idle Timeout (In
Seconds)
The ZyXEL Device automatically disconnects a wireless client from the wired
network after a period of inactivity. The wireless client needs to enter the
username and password again before access to the wired network is allowed.
The default time interval is 3600 seconds (or 1 hour).
114
P-660HW-Dx v2 User’s Guide
Chapter 7 Wireless LAN
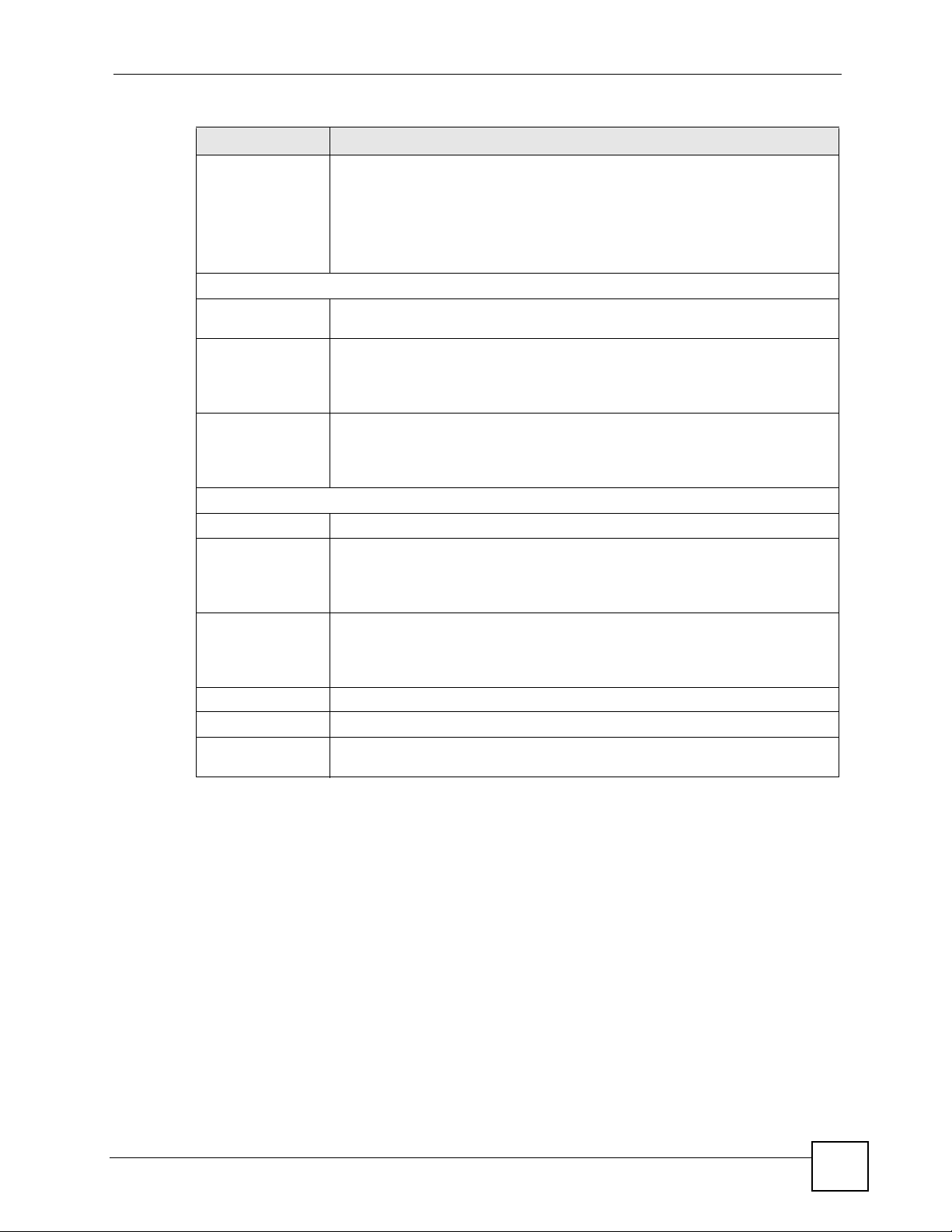
Table 36 Wireless: WPA/WPA2 (continued)
LABEL DESCRIPTION
Group Key Update
Timer (In Seconds)
Authentication Server
IP Address Enter the IP address of the external authentication server in dotted decimal
Port Number Enter the port number of the external authentication server. The default port
Shared Secret Enter a password (up to 31 alphanumeric characters) as the key to be shared
Accounting Server (optional)
IP Address Enter the IP address of the external accounting server in dotted decimal notation.
Port Number Enter the port number of the external accounting server. The default port number
Shared Secret Enter a password (up to 31 alphanumeric characters) as the key to be shared
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Advanced Setup Click Advanced Setup to display the Wireless Advanced Setup screen and
The Group Key Update Timer is the rate at which the AP (if using WPA-PSK/
WPA2-PSK key management) or RADIUS server (if using WPA(2) key
management) sends a new group key out to all clients. The re-keying process is
the WPA(2) equivalent of automatically changing the WEP key for an AP and all
stations in a WLAN on a periodic basis. Setting of the Group Key Update Timer
is also supported in WPA-PSK/WPA2-PSK mode. The default is 1800 seconds
(30 minutes).
notation.
number is 1812.
You need not change this value unless your network administrator instructs you
to do so with additional information.
between the external authentication server and the ZyXEL Device.
The key must be the same on the external authentication server and your ZyXEL
Device. The key is not sent over the network.
is 1813.
You need not change this value unless your network administrator instructs you
to do so with additional information.
between the external accounting server and the ZyXEL Device.
The key must be the same on the external accounting server and your ZyXEL
Device. The key is not sent over the network.
edit more details of your WLAN setup.
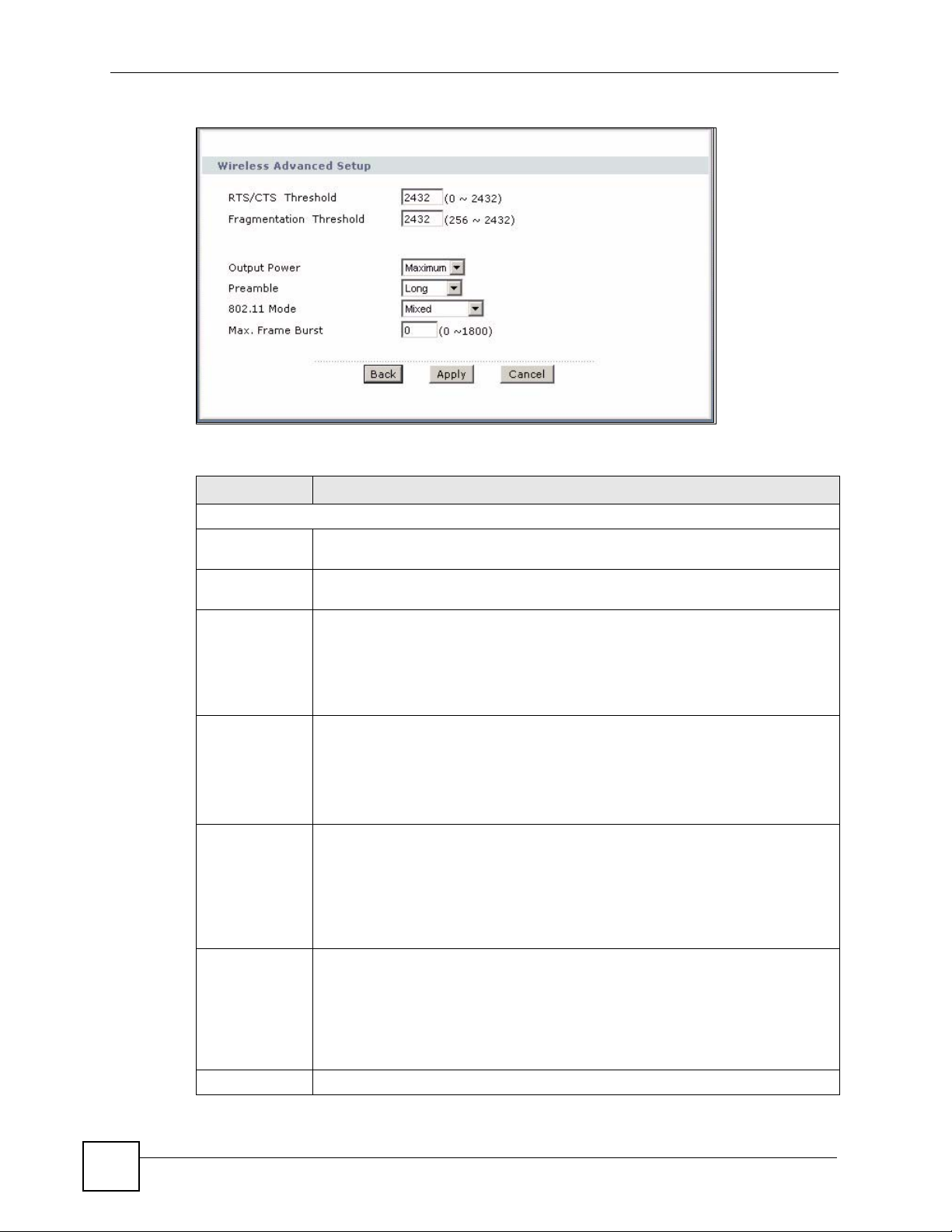
7.3.5 Wireless LAN Advanced Setup
To configure advanced wireless settings, click the Advanced Setup button in the General
screen. The screen appears as shown.
P-660HW-Dx v2 User’s Guide
115
Chapter 7 Wireless LAN
Figure 66 Advanced
The following table describes the labels in this screen.
Table 37 Wireless LAN: Advanced
LABEL DESCRIPTION
Wireless Advanced Setup
RTS/CTS
Threshold
Fragmentation
Threshold
Output Power Set the output power of the ZyXEL Device in this field. This control changes the
Preamble Select Long preamble if you are unsure what preamble mode the wireless adapters
802.11 Mode Select 802.11b Only to allow only IEEE 802.11b compliant WLAN devices to
Max. Frame
Burst
Back Click Back to return to the previous screen.
Enter a value between 0 and 2432.
This is the maximum data fragment size that can be sent. Enter a value between
256 and 2432.
strength of the ZyXEL Device's antenna gain or transmission power. Antenna gain
is the increase in coverage. Higher antenna gain improves the range of the signal
for better communications. If there is a high density of APs within an area, decrease
the output power of the ZyXEL Device to reduce interference with other APs.
The options are Maximum, Middle and Minimum.
support, and to provide more reliable communications in busy wireless networks.
Select Short preamble if you are sure the wireless adapters support it, and to
provide more efficient communications.
Select Dynamic to have the ZyXEL Device automatically use short preamble when
wireless adapters support it, otherwise the ZyXEL Device uses long preamble.
associate with the ZyXEL Device.
Select 802.11g Only to allow only IEEE 802.11g compliant WLAN devices to
associate with the ZyXEL Device.
Select Mixed to allow either IEEE802.11b or IEEE802.11g compliant WLAN
devices to associate with the ZyXEL Device. The transmission rate of your ZyXEL
Device might be reduced.
Enable Maximum Frame Burst to help eliminate collisions in mixed-mode
networks (networks with both IEEE 802.11g and IEEE 802.11b traffic) and enhance
the performance of both pure IEEE 802.11g and mixed IEEE 802.11b/g networks.
Maximum Frame Burst sets the maximum time, in micro-seconds, that the
ZZyXEL Device transmits IEEE 802.11g wireless traffic only.
Type the maximum frame burst between 0 and 1800 (650, 1000 or 1800
recommended). Enter 0 to disable this feature.
116
P-660HW-Dx v2 User’s Guide
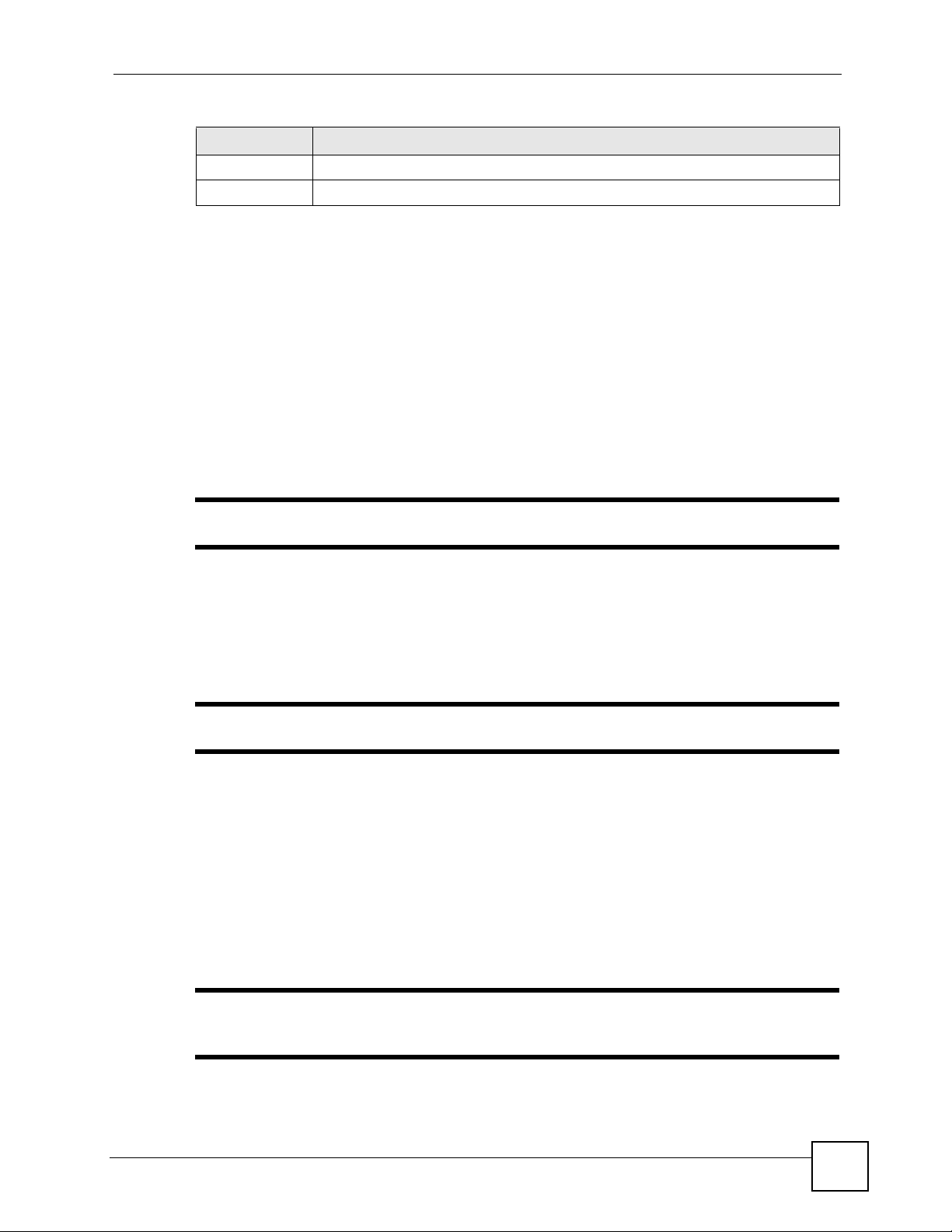
Table 37 Wireless LAN: Advanced (continued)
LABEL DESCRIPTION
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
7.4 OTIST
In a wireless network, the wireless clients must have the same SSID and security settings as
the access point (AP) or wireless router (we will refer to both as “AP” here) in order to
associate with it. Traditionally this meant that you had to configure the settings on the AP and
then manually configure the exact same settings on each wireless client.
OTIST (One-Touch Intelligent Security Technology) allows you to transfer your AP’s SSID
and WPA-PSK security settings to wireless clients that support OTIST and are within
transmission range. You can also choose to have OTIST generate a WPA-PSK key for you if
you didn’t configure one manually.
Chapter 7 Wireless LAN
" OTIST replaces the pre-configured wireless settings on the wireless clients.
7.4.1 Enabling OTIST
You must enable OTIST on both the AP and wireless client before you start transferring
settings.
" The AP and wireless client(s) MUST use the same Setup key.
7.4.1.1 AP
You can enable OTIST using the RESET button or the web configurator.
7.4.1.1.1 Reset button
If you use the RESET button, the default (01234567) or previous saved (through the web
configurator) Setup key is used to encrypt the settings that you want to transfer.
Hold in the RESET button for three to eight seconds.
" If you hold in the RESET button too long, the device will reset to the factory
defaults!
P-660HW-Dx v2 User’s Guide
117
Chapter 7 Wireless LAN
7.4.1.1.2 Web Configurator
Click the Network > Wireless LAN > OTIST. The following screen displays.
Figure 67 OTIST
The following table describes the labels in this screen.
Table 38 OTIST
LABEL DESCRIPTION
Setup Key Type an OTIST Setup Key of exactly eight ASCII characters in length.
The default OTIST setup key is "01234567".
Yes! If you want OTIST to automatically generate a WPA-PSK, you must:
Start Click Start to encrypt the wireless security data using the setup key and have
7.4.1.2 Wireless Client
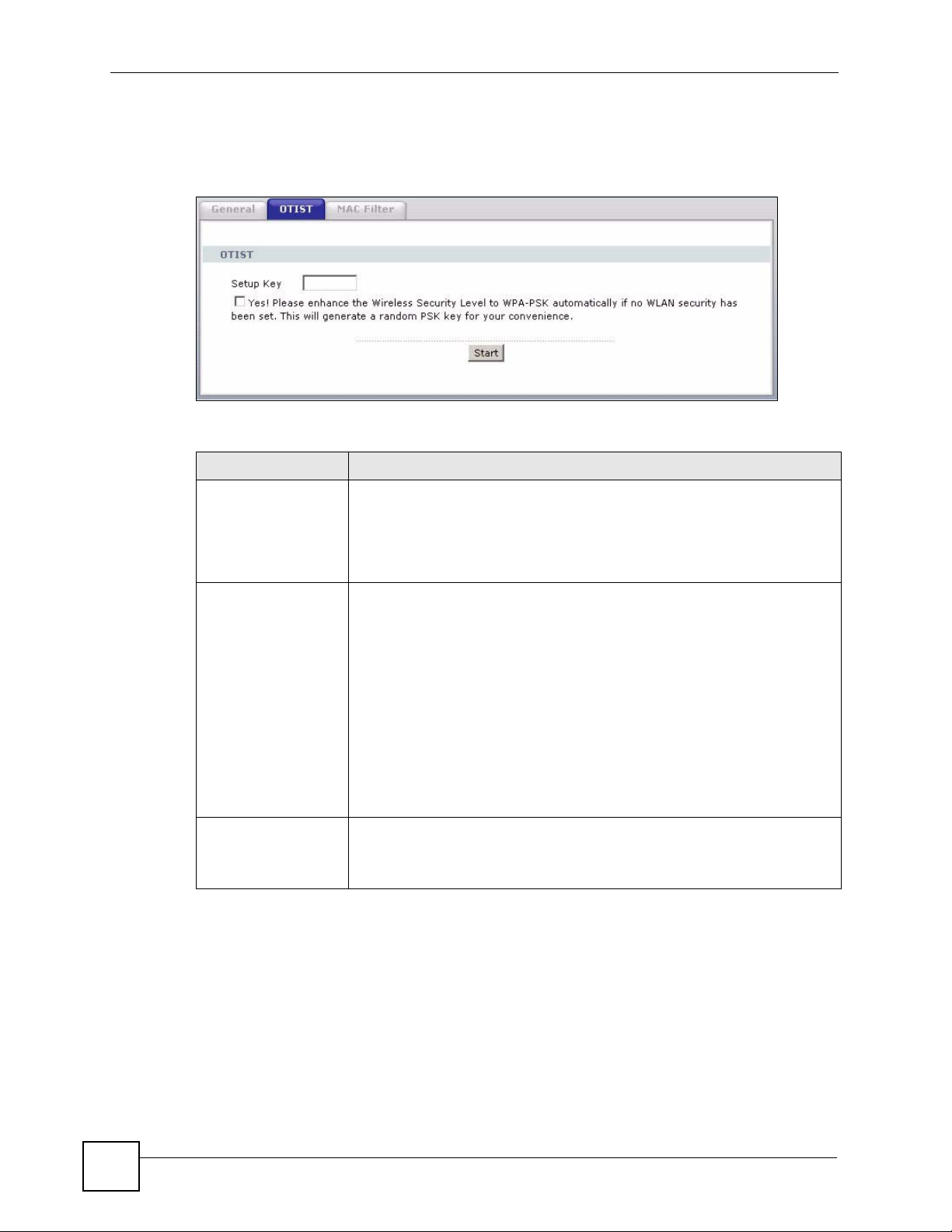
Start the ZyXEL utility and click the Adapter tab. Select the OTIST check box, enter the
same Setup Key as your AP’s and click Save.
Note: If you change the OTIST setup key here, you must
also make the same change on the wireless client(s).
• Change your security to any security other than WPA-PSK in the Wireless
LAN > General screen.
• Select the Yes ! checkbox in the OTIST screen and click Start.
• The wireless screen displays an auto generated WPA-PSK and is now in
WPA-PSK security mode.
The WPA-PSK security settings are assigned to the wireless client when you
start OTIST.
Note: If you already have a WPA-PSK configured in the
Wireless LAN > General screen, and you run OTIST
with Yes! selected, OTIST will use the existing WPAPSK.
the ZyXEL Device set the wireless client(s) to use the same wireless settings
as the ZyXEL Device. You must also activate and start OTIST on the wireless
client(s) all within three minutes.
118
P-660HW-Dx v2 User’s Guide
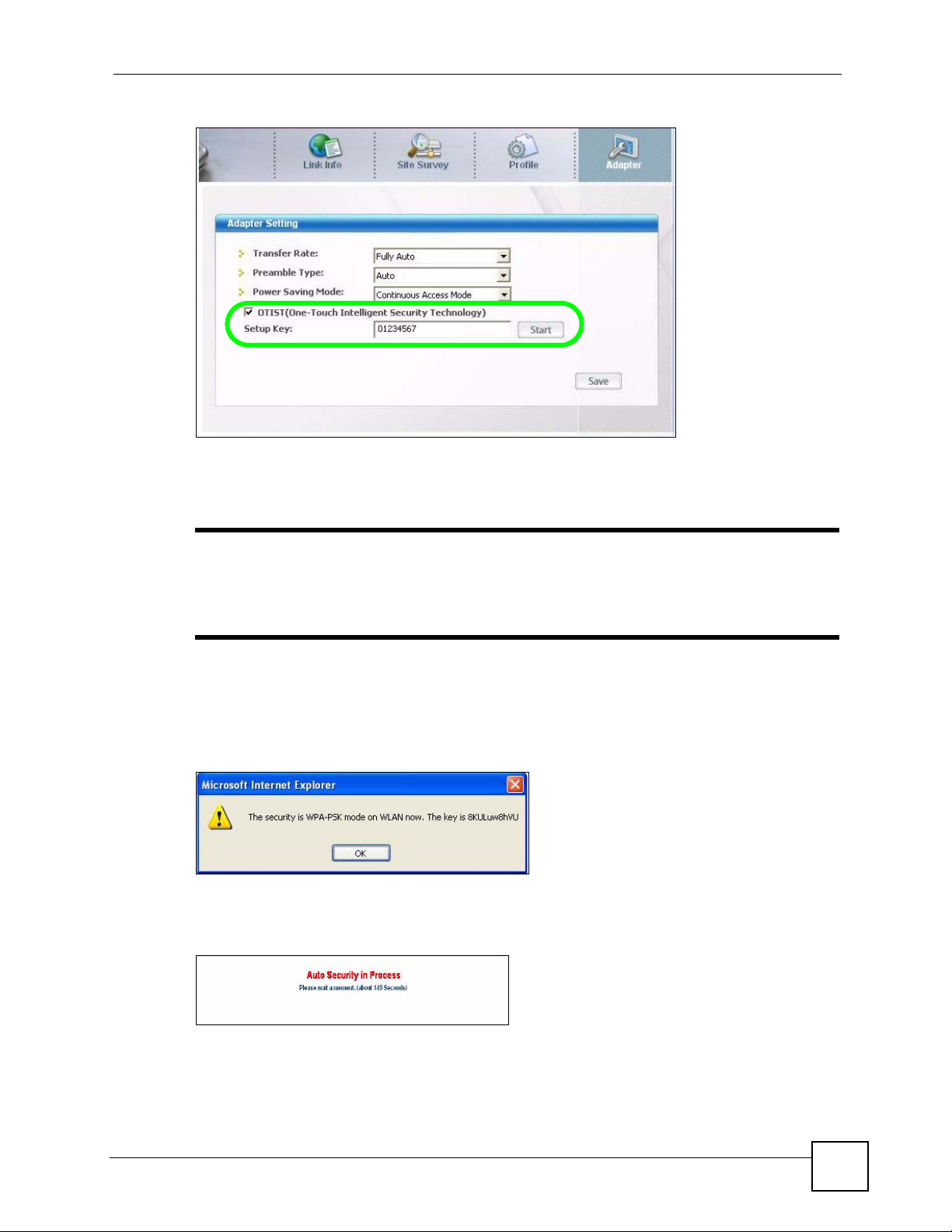
Figure 68 Example Wireless Client OTIST Screen
7.4.2 Starting OTIST
Chapter 7 Wireless LAN
" You must click Start in the AP OTIST web configurator screen and in the
wireless client(s) Adapter screen all within three minutes (at the time of writing).
You can start OTIST in the wireless clients and AP in any order but they must all
be within range and have OTIST enabled.
1 In the AP, a web configurator screen pops up showing you the security settings to
transfer. You can use the key in this screen to set up WPA-PSK encryption manually for
non-OTIST devices in the wireless network. After reviewing the settings, click OK.
Figure 69 Security Key
2 This screen appears while OTIST settings are being transferred. It closes when the
transfer is complete.
Figure 70 OTIST in Progress (AP)
P-660HW-Dx v2 User’s Guide
119
Chapter 7 Wireless LAN
Figure 71 OTIST in progress (Client)
In the wireless client, you see this screen if it can’t find an OTIST-enabled AP (with the same
Setup key). Click OK to go back to the ZyXEL utility main screen.
Figure 72 No AP with OTIST Found
• If there is more than one OTIST-enabled AP within range, you see a screen asking you to
select one AP to get settings from.
7.4.3 Notes on OTIST
1 If you enabled OTIST in the wireless client, you see this screen each time you start the
utility. Click Ye s for it to search for an OTIST-enabled AP.
Figure 73 Start OTIST?
2 If an OTIST-enabled wireless client loses its wireless connection for more than ten
seconds, it will search for an OTIST-enabled AP for up to one minute. (If you manually
have the wireless client search for an OTIST-enabled AP, there is no timeout; click
Cancel in the OTIST progress screen to stop the search.)
3 When the wireless client finds an OTIST-enabled AP, you must still click Start in the
AP OTIST web configurator screen or hold in the RESET button (for one to five
seconds) for the AP to transfer settings.
4 If you change the SSID or the keys on the AP after using OTIST, you need to run OTIST
again or enter them manually in the wireless client(s).
5 If you configure OTIST to generate a WPA-PSK key, this key changes each time you
run OTIST. Therefore, if a new wireless client joins your wireless network, you need to
run OTIST on the AP and ALL wireless clients again.
120
P-660HW-Dx v2 User’s Guide
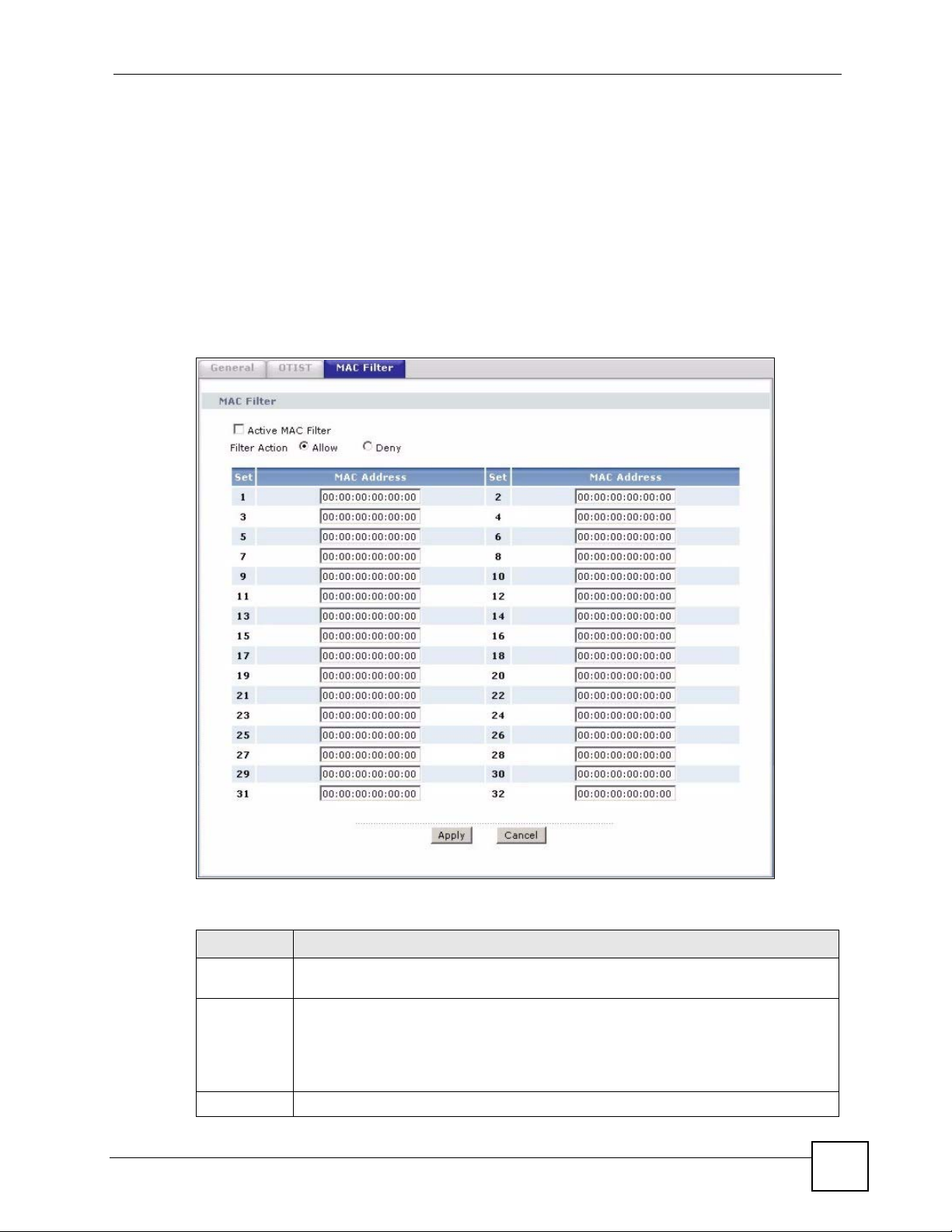
7.5 MAC Filter
The MAC filter screen allows you to configure the ZyXEL Device to give exclusive access to
up to 32 devices (Allow) or exclude up to 32 devices from accessing the ZyXEL Device
(Deny). Every Ethernet device has a unique MAC (Media Access Control) address. The MAC
address is assigned at the factory and consists of six pairs of hexadecimal characters, for
example, 00:A0:C5:00:00:02. You need to know the MAC address of the devices to configure
this screen.
To change your ZyXEL Device’s MAC filter settings, click Network > Wireless LAN >
MAC Filter. The screen appears as shown.
Figure 74 MAC Address Filter
Chapter 7 Wireless LAN
The following table describes the labels in this menu.
Table 39 MAC Address Filter
LABEL DESCRIPTION
Active MAC
Filter
Filter Action Define the filter action for the list of MAC addresses in the MAC Address table.
Set This is the index number of the MAC address.
P-660HW-Dx v2 User’s Guide
Select the check box to enable MAC address filtering.
Select Deny to block access to the ZyXEL Device, MAC addresses not listed will be
allowed to access the ZyXEL Device
Select Allow to permit access to the ZyXEL Device, MAC addresses not listed will be
denied access to the ZyXEL Device.
121
Chapter 7 Wireless LAN
Table 39 MAC Address Filter
LABEL DESCRIPTION
MAC
Address
Apply Click Apply to save your changes to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
Enter the MAC addresses of the wireless client that are allowed or denied access to
the ZyXEL Device in these address fields. Enter the MAC addresses in a valid MAC
address format, that is, six hexadecimal character pairs, for example,
12:34:56:78:9a:bc.
7.6 WMM QoS
WMM (Wi-Fi MultiMedia) QoS (Quality of Service) allows you to prioritize wireless traffic
according to the delivery requirements of individual services.
WMM is a part of the IEEE 802.11e QoS enhancement to certified Wi-Fi wireless networks.
7.6.1 WMM QoS Example
When WMM QoS is not enabled, all traffic streams are given the same access throughput to
the wireless network. If the introduction of another traffic stream creates a data transmission
demand that exceeds the current network capacity, then the new traffic stream reduces the
throughput of the other traffic streams.
When WMM QoS is enabled, the streams are prioritized according to the needs of the
application. You can assign different priorities to different applications. This prevents
reductions in data transmission for applications that are sensitive.
7.6.2 WMM QoS Priorities
The following table describes the priorities that you can apply to traffic that the ZyXEL
Device sends to the wireless network.
Table 40 WMM QoS Priorities
PRIORITY LEVELS:
Highest Typically used for voice traffic or video that is especially sensitive to jitter
High Typically used for video traffic which has some tolerance for jitter but needs to be
Mid Typically used for traffic from applications or devices that lack QoS capabilities.
Low This is typically used for non-critical “background” traffic such as bulk transfers
(variations in delay). Use the highest priority to reduce latency for improved voice
quality.
prioritized over other data traffic.
Use mid priority for traffic that is less sensitive to latency, but is affected by long
delays, such as Internet surfing.
and print jobs that are allowed but that should not affect other applications and
users. Use low priority for applications that do not have strict latency and
throughput requirements.
122
P-660HW-Dx v2 User’s Guide
7.6.3 Services
The commonly used services and port numbers are shown in the following table. Please refer
to RFC 1700 for further information about port numbers. Next to the name of the service, two
fields appear in brackets. The first field indicates the IP protocol type (TCP, UDP, or ICMP).
The second field indicates the IP port number that defines the service. (Note that there may be
more than one IP protocol type. For example, look at the DNS service. (UDP/TCP:53) means
UDP port 53 and TCP port 53.
Table 41 Commonly Used Services
SERVICE DESCRIPTION
AIM/New-ICQ(TCP:5190) AOL’s Internet Messenger service, used as a listening port by ICQ.
AUTH(TCP:113) Authentication protocol used by some servers.
BGP(TCP:179) Border Gateway Protocol.
BOOTP_CLIENT(UDP:68) DHCP Client.
BOOTP_SERVER(UDP:67) DHCP Server.
CU-SEEME(TCP/UDP:7648,
24032)
DNS(UDP/TCP:53) Domain Name Server, a service that matches web names (e.g.
FINGER(TCP:79) Finger is a UNIX or Internet related command that can be used to
FTP(TCP:20.21) File Transfer Program, a program to enable fast transfer of files,
H.323(TCP:1720) NetMeeting uses this protocol.
HTTP(TCP:80) Hyper Text Transfer Protocol - a client/server protocol for the world
HTTPS(TCP:443) HTTPS is a secured http session often used in e-commerce.
ICQ(UDP:4000) This is a popular Internet chat program.
IKE(UDP:500) The Internet Key Exchange algorithm is used for key distribution and
IPSEC_TUNNEL(AH:0) The IPSEC AH (Authentication Header) tunneling protocol uses this
IPSEC_TUNNEL(ESP:0) The IPSEC ESP (Encapsulation Security Protocol) tunneling protocol
IRC(TCP/UDP:6667) This is another popular Internet chat program.
MSN Messenger(TCP:1863) Microsoft Networks’ messenger service uses this protocol.
MULTICAST(IGMP:0) Internet Group Multicast Protocol is used when sending packets to a
NEW-ICQ(TCP:5190) An Internet chat program.
NEWS(TCP:144) A protocol for news groups.
NFS(UDP:2049) Network File System - NFS is a client/server distributed file service
NNTP(TCP:119) Network News Transport Protocol is the delivery mechanism for the
Chapter 7 Wireless LAN
A popular videoconferencing solution from White Pines Software.
www.zyxel.com
find out if a user is logged on.
including large files that may not be possible by e-mail.
wide web.
management.
service.
uses this service.
specific group of hosts.
that provides transparent file sharing for network environments.
USENET newsgroup service.
) to IP numbers.
P-660HW-Dx v2 User’s Guide
123

Chapter 7 Wireless LAN
Table 41 Commonly Used Services (continued)
SERVICE DESCRIPTION
PING(ICMP:0) Packet INternet Groper is a protocol that sends out ICMP echo
POP3(TCP:110) Post Office Protocol version 3 lets a client computer get e-mail from a
PPTP(TCP:1723) Point-to-Point Tunneling Protocol enables secure transfer of data
PPTP_TUNNEL(GRE:0) Point-to-Point Tunneling Protocol enables secure transfer of data
RCMD(TCP:512) Remote Command Service.
REAL_AUDIO(TCP:7070) A streaming audio service that enables real time sound over the web.
REXEC(TCP:514) Remote Execution Daemon.
RLOGIN(TCP:513) Remote Login.
RTELNET(TCP:107) Remote Telnet.
RTSP(TCP/UDP:554) The Real Time Streaming (media control) Protocol (RTSP) is a
SFTP(TCP:115) Simple File Transfer Protocol.
SMTP(TCP:25) Simple Mail Transfer Protocol is the message-exchange standard for
SNMP(TCP/UDP:161) Simple Network Management Program.
SNMP-TRAPS(TCP/UDP:162) Traps for use with the SNMP (RFC:1215).
SQL-NET(TCP:1521) Structured Query Language is an interface to access data on many
SSH(TCP/UDP:22) Secure Shell Remote Login Program.
STRM WORKS(UDP:1558) Stream Works Protocol.
SYSLOG(UDP:514) Syslog allows you to send system logs to a UNIX server.
TACACS(UDP:49) Login Host Protocol used for (Terminal Access Controller Access
TELNET(TCP:23) Telnet is the login and terminal emulation protocol common on the
TFTP(UDP:69) Trivial File Transfer Protocol is an Internet file transfer protocol
VDOLIVE(TCP:7000) Another videoconferencing solution.
requests to test whether or not a remote host is reachable.
POP3 server through a temporary connection (TCP/IP or other).
over public networks. This is the control channel.
over public networks. This is the data channel.
remote control for multimedia on the Internet.
the Internet. SMTP enables you to move messages from one e-mail
server to another.
different types of database systems, including mainframes, midrange
systems, UNIX systems and network servers.
Control System).
Internet and in UNIX environments. It operates over TCP/IP
networks. Its primary function is to allow users to log into remote host
systems.
similar to FTP, but uses the UDP (User Datagram Protocol) rather
than TCP (Transmission Control Protocol).
7.7 QoS Screen
The QoS screen by default allows you to automatically give a service a priority level
according to the ToS value in the IP header of the packets it sends.
124
P-660HW-Dx v2 User’s Guide
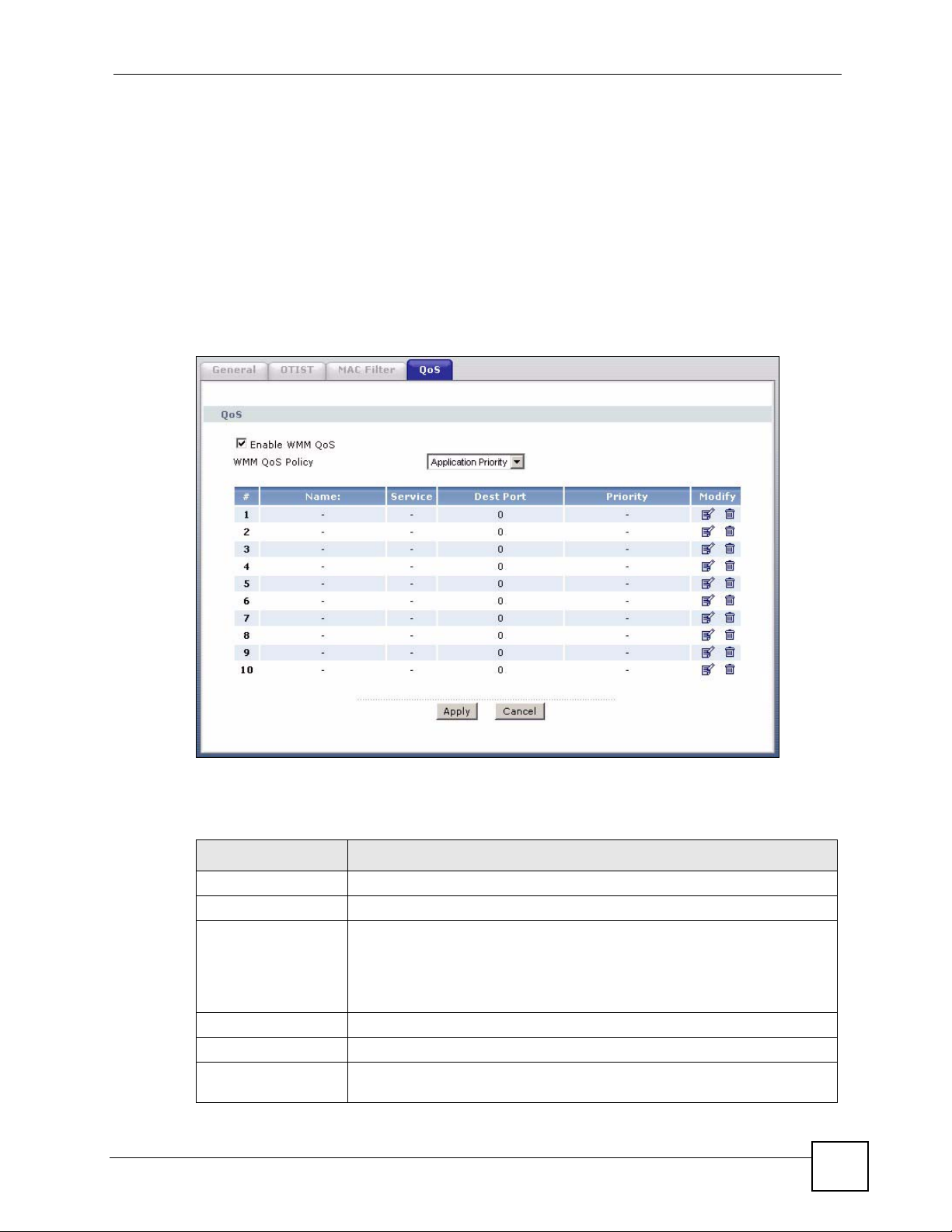
7.7.1 ToS (Type of Service) and WMM QoS
ToS defines the DS (Differentiated Service) field in the IP packet header. The ToS value of
outgoing packets is between 0 and 255. 0 is the lowest priority.
WMM QoS checks the ToS in the header of transmitted data packets. It gives the application a
priority according to this number. If the ToS is not specified, then transmitted data is treated as
normal or best-effort traffic.
Click Network > Wireless LAN > QoS. The following screen displays.
Figure 75 Wireless LAN: QoS
Chapter 7 Wireless LAN
The following table describes the fields in this screen.
Table 42 Wireless Lan: QoS
LABEL DESCRIPTION
QoS
Enable WMM QoS Select the check box to enable WMM QoS on the ZyXEL Device.
WMM QoS Policy Select Default to have the ZyXEL Device automatically give a service a
# This is the number of an individual application entry.
Name This field displays a description given to an application entry.
Service This field displays either FTP, WWW, E-mail or a User Defined service to
P-660HW-Dx v2 User’s Guide
priority level according to the ToS value in the IP header of packets it sends.
Select Application Priority from the drop-down list box to display a table of
application names, services, ports and priorities to which you want to apply
WMM QoS.
which you want to apply WMM QoS.
125

Chapter 7 Wireless LAN
Table 42 Wireless Lan: QoS (continued)
LABEL DESCRIPTION
Dest Port This field displays the destination port number to which the application sends
traffic.
Priority This field displays the WMM QoS priority for traffic bandwidth.
Modify Click the to open the Application Priority Configuration screen. Modify an
existing application entry or create a application entry in the Application
Priority Configuration screen.
Click the Remove icon to delete an application entry.
Apply Click Apply to save your changes back to the ZyXEL Device.
Cancel Click Cancel to reload the previous configuration for this screen.
7.7.2 Application Priority Configuration
To edit a WMM QoS application entry, click the edit icon ( ) under Modify. The following
screen displays.
Figure 76 Application Priority Configuration
126
The following table describes the fields in this screen.
Table 43 Application Priority Configuration
LABEL DESCRIPTION
Application Priority Configuration
Name Type a description of the application priority.
P-660HW-Dx v2 User’s Guide
Chapter 7 Wireless LAN
Table 43 Application Priority Configuration (continued)
LABEL DESCRIPTION
Service The following is a description of the applications you can prioritize with WMM
QoS. Select a service from the drop-down list box.
• FTP
File Transfer Program enables fast transfer of files, including large files that
may not be possible by e-mail. FTP uses port number 21.
• E-Mail
Electronic mail consists of messages sent through a computer network to
specific groups or individuals. Here are some default ports for e-mail:
POP3 - port 110
IMAP - port 143
SMTP - port 25
HTTP - port 80
•WWW
The World Wide Web is an Internet system to distribute graphical, hyper-linked
information, based on Hyper Text Transfer Protocol (HTTP) - a client/server
protocol for the World Wide Web. The Web is not synonymous with the
Internet; rather, it is just one service on the Internet. Other services on the
Internet include Internet Relay Chat and Newsgroups. The Web is accessed
through use of a browser.
• User-Defined
User-defined services are user specific services configured using known ports
and applications.
Dest Port This displays the port the selected service uses. Type a port number in the
field provided if you want to use a different port to the default port. See table
Table 41 on page 123 for information on port numbers.
Priority Select a priority from the drop-down list box.
Apply Click Apply to save your changes back to the ZyXEL Device.
Cancel Click Cancel to return to the previous screen without saving your changes.
P-660HW-Dx v2 User’s Guide
127

Chapter 7 Wireless LAN
128
P-660HW-Dx v2 User’s Guide

CHAPTER 8
Network Address Translation
(NAT) Screens
This chapter discusses how to configure NAT on the ZyXEL Device.
8.1 NAT Overview
NAT (Network Address Translation - NAT, RFC 1631) is the translation of the IP address of a
host in a packet, for example, the source address of an outgoing packet, used within one
network to a different IP address known within another network.
8.1.1 NAT Definitions
Inside/outside denotes where a host is located relative to the ZyXEL Device, for example, the
computers of your subscribers are the inside hosts, while the web servers on the Internet are
the outside hosts.
Global/local denotes the IP address of a host in a packet as the packet traverses a router, for
example, the local address refers to the IP address of a host when the packet is in the local
network, while the global address refers to the IP address of the host when the same packet is
traveling in the WAN side.
Note that inside/outside refers to the location of a host, while global/local refers to the IP
address of a host used in a packet. Thus, an inside local address (ILA) is the IP address of an
inside host in a packet when the packet is still in the local network, while an inside global
address (IGA) is the IP address of the same inside host when the packet is on the WAN side.
The following table summarizes this information.
Table 44 NAT Definitions
ITEM DESCRIPTION
Inside This refers to the host on the LAN.
Outside This refers to the host on the WAN.
Local This refers to the packet address (source or destination) as the packet travels on the
Global This refers to the packet address (source or destination) as the packet travels on the
LAN.
WAN.
NAT never changes the IP address (either local or global) of an outside host.
P-660HW-Dx v2 User’s Guide
129
Chapter 8 Network Address Translation (NAT) Screens
8.1.2 What NAT Does
In the simplest form, NAT changes the source IP address in a packet received from a
subscriber (the inside local address) to another (the inside global address) before forwarding
the packet to the WAN side. When the response comes back, NAT translates the destination
address (the inside global address) back to the inside local address before forwarding it to the
original inside host. Note that the IP address (either local or global) of an outside host is never
changed.
The global IP addresses for the inside hosts can be either static or dynamically assigned by the
ISP. In addition, you can designate servers, for example, a web server and a telnet server, on
your local network and make them accessible to the outside world. If you do not define any
servers (for Many-to-One and Many-to-Many Overload mapping – see Table 45 on page 132),
NAT offers the additional benefit of firewall protection. With no servers defined, your ZyXEL
Device filters out all incoming inquiries, thus preventing intruders from probing your network.
For more information on IP address translation, refer to RFC 1631, The IP Network Address
Translator (NAT).
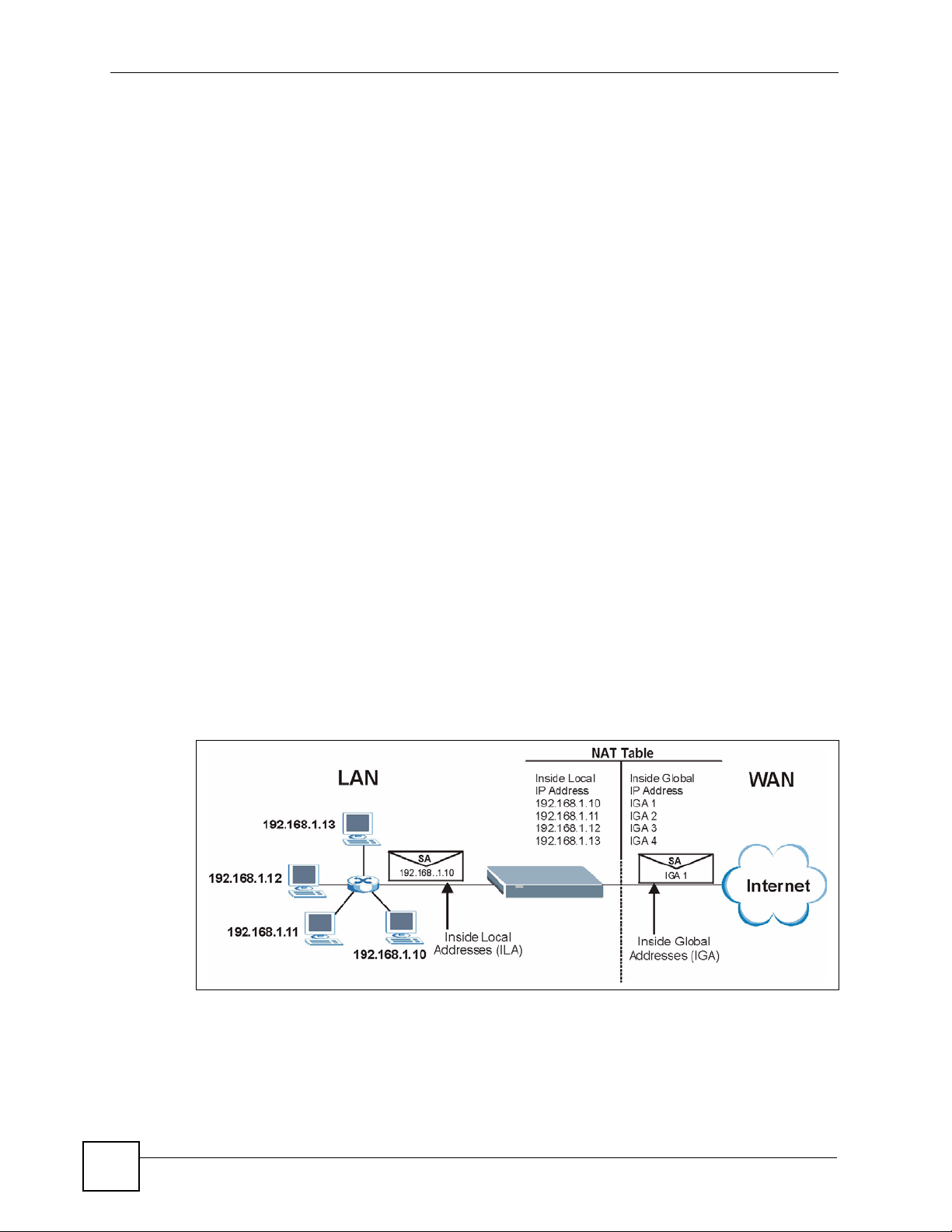
8.1.3 How NAT Works
Each packet has two addresses – a source address and a destination address. For outgoing
packets, the ILA (Inside Local Address) is the source address on the LAN, and the IGA (Inside
Global Address) is the source address on the WAN. For incoming packets, the ILA is the
destination address on the LAN, and the IGA is the destination address on the WAN. NAT
maps private (local) IP addresses to globally unique ones required for communication with
hosts on other networks. It replaces the original IP source address (and TCP or UDP source
port numbers for Many-to-One and Many-to-Many Overload NAT mapping) in each packet
and then forwards it to the Internet. The ZyXEL Device keeps track of the original addresses
and port numbers so incoming reply packets can have their original values restored. The
following figure illustrates this.
Figure 77 How NAT Works
8.1.4 NAT Application
The following figure illustrates a possible NAT application, where three inside LANs (logical
LANs using IP Alias) behind the ZyXEL Device can communicate with three distinct WAN
networks. More examples follow at the end of this chapter.
130
P-660HW-Dx v2 User’s Guide
 Loading...
Loading...