This chapter discusses how to configure wireless settings and wireless security on your
ZyXEL Device.
6.1 Wireless LAN Overview
This section introduces the wireless LAN (WLAN) and some basic scenarios.
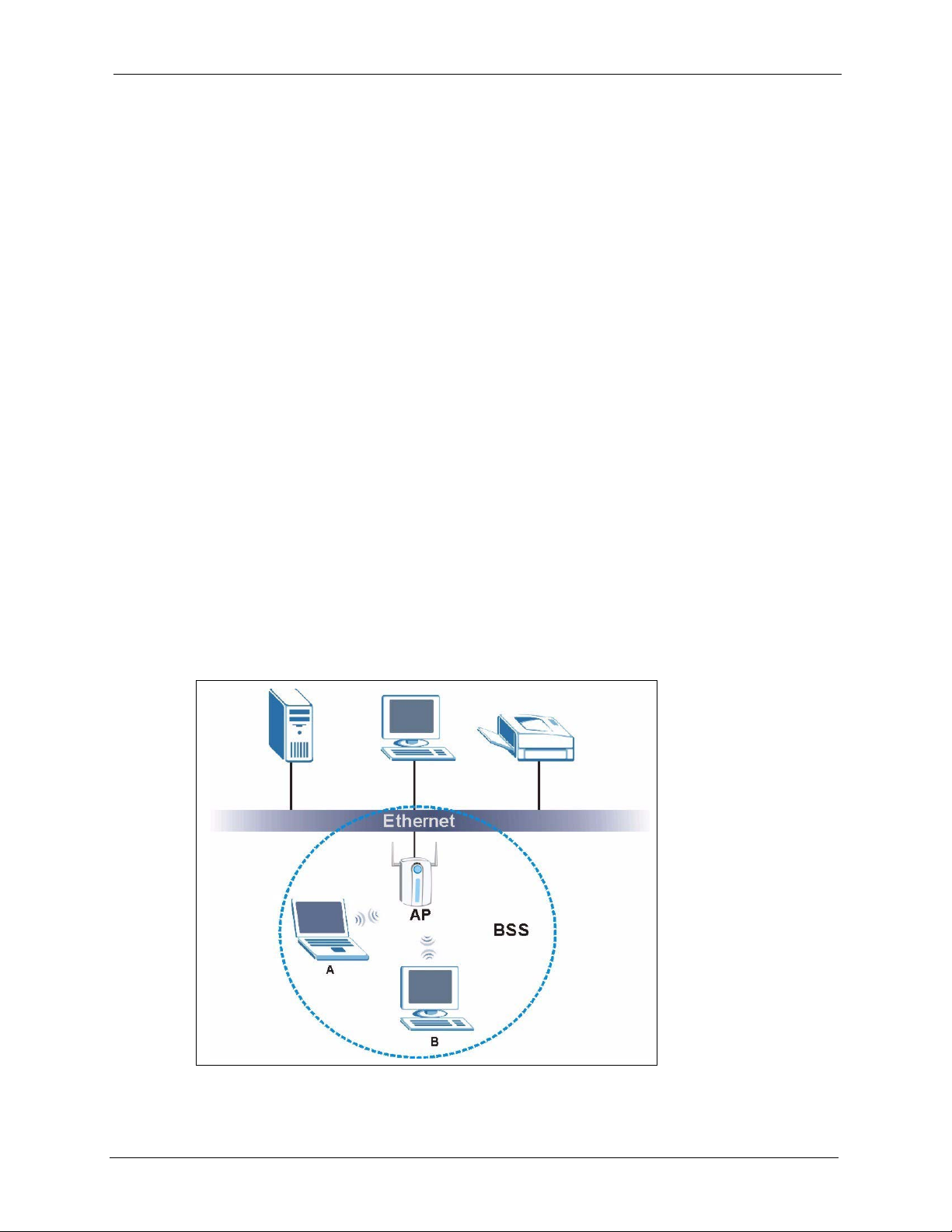
6.1.1 BSS (Infrastructure)
A Basic Service Set (BSS), also called an Infrastructure network, exists when all
communications between wireless stations or between a wireless station and a wired network
client go through one access point (AP).
G-470 User’s Guide
CHAPTER 6
Wireless Screens
Intra-BSS traffic is traffic between wireless stations in the BSS. When Intra-BSS is enabled,
wireless station A and B can access the wired network and communicate with each other.
When Intra-BSS is disabled, wireless station A and B can still access the wired network but
cannot communicate with each other.
Figure 26 Basic Service set
Chapter 6 Wireless Screens 55
G-470 User’s Guide
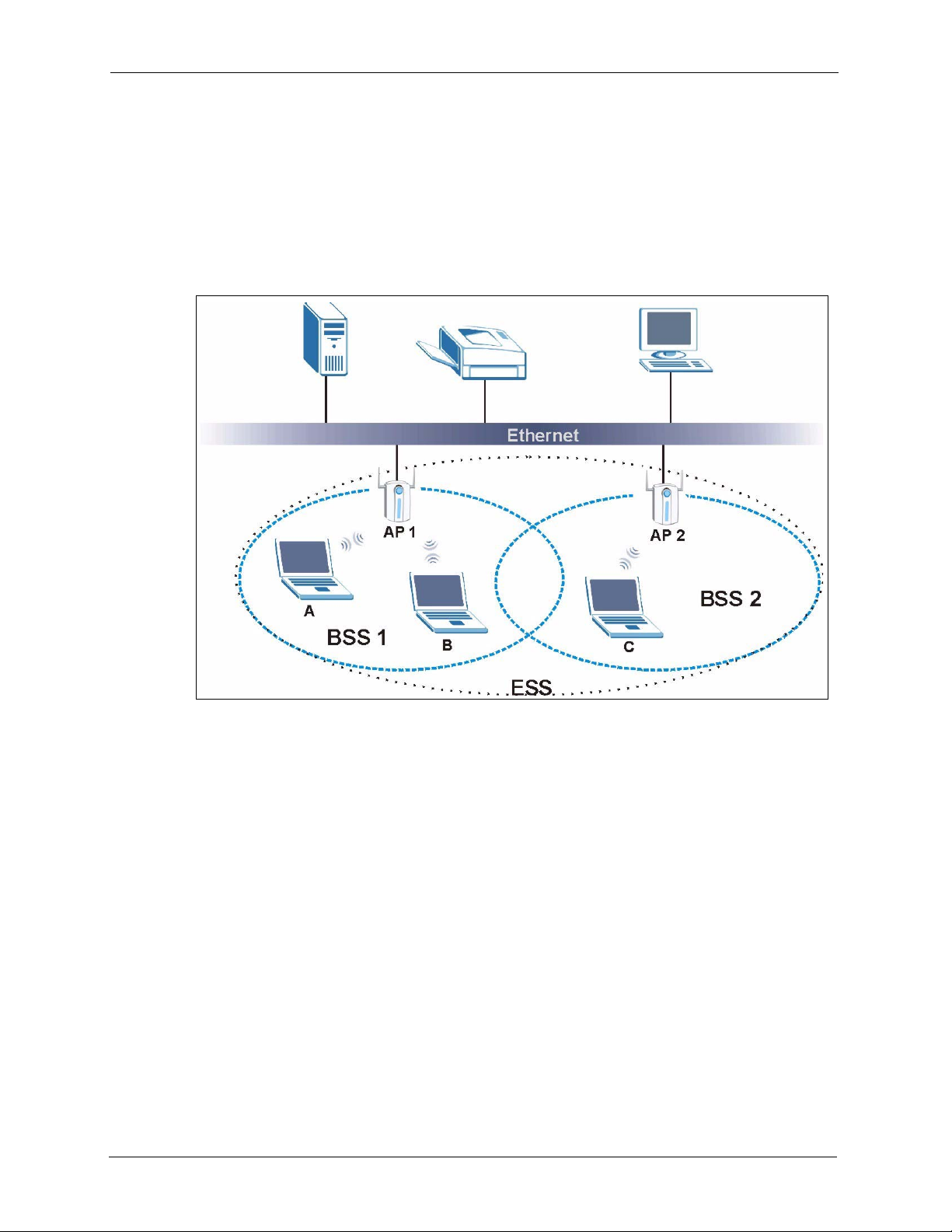
6.1.2 ESS
An Extended Service Set (ESS) consists of a series of overlapping BSSs, each containing an
access point, with each access point connected together by a wired network. This wired
connection between APs is called a Distribution System (DS). An ESSID (ESS IDentification)
uniquely identifies each ESS. All access points and their associated wireless stations within
the same ESS must have the same ESSID in order to communicate.
Figure 27 Extended Service Set
6.2 Wireless LAN Basics
This section describes the wireless LAN network terms.
6.2.1 Channel
A channel is the radio frequency or frequencies used by IEEE 802.11b wireless devices.
Channels available depend on your geographical area. You may have a choice of channels (for
your region) so you should use a different channel from an adjacent AP (access point) to
reduce interference. Interference occurs when radio signals from different access points
overlap, causing signal disruption and degrading performance.
Adjacent channels partially overlap, however. To avoid interference due to overlap, your AP
should be on a channel at least five channels away from a channel that an adjacent AP is using.
For example, if your region has 11 channels and an adjacent AP is using channel 1, then you
need to select a channel between 6 or 11.
56 Chapter 6 Wireless Screens
6.2.2 SSID
The SSID (Service Set Identity) is a unique name shared among all wireless devices in a
wireless network. Wireless devices must have the same SSID to communicate with each other.
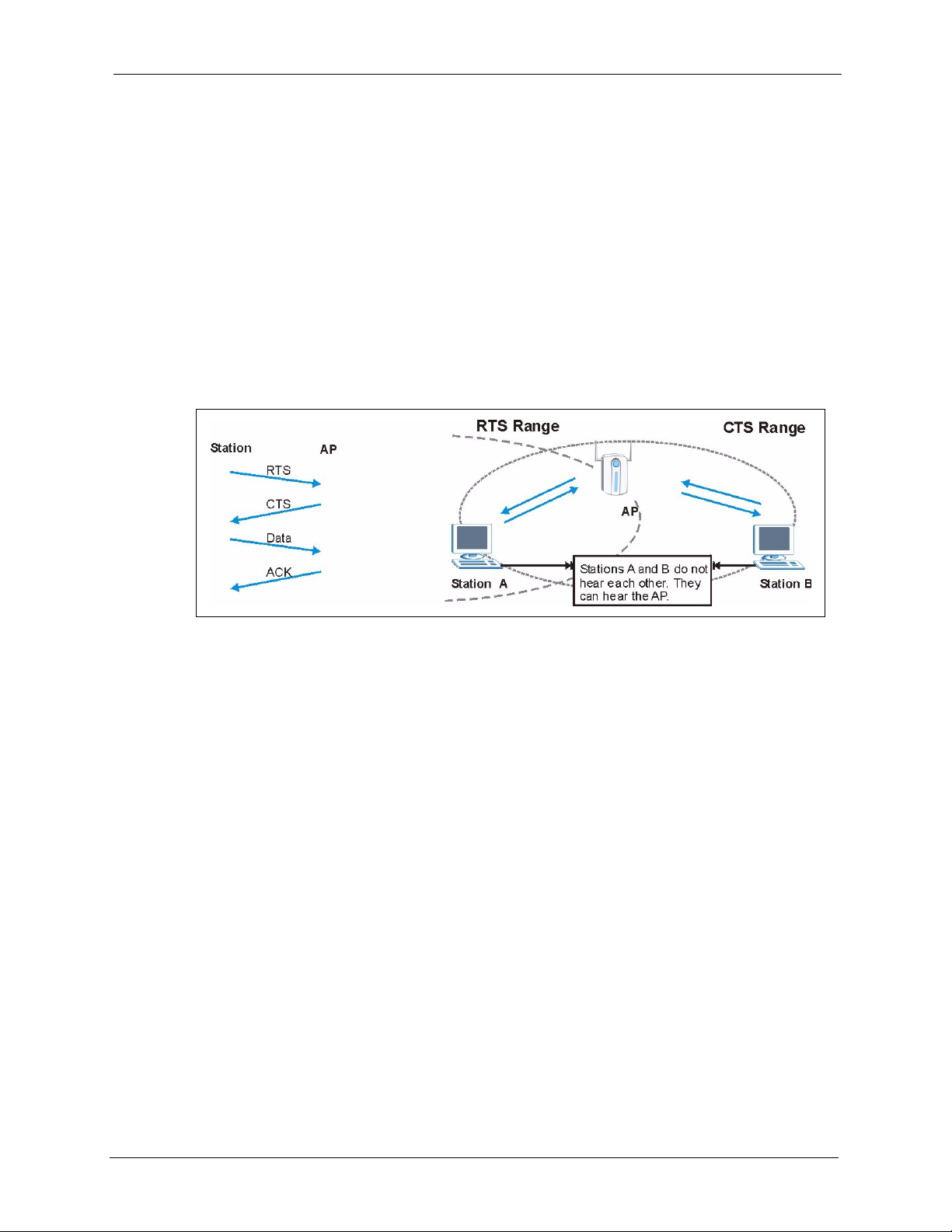
6.2.3 RTS/CTS
A hidden node occurs when two stations are within range of the same access point, but are not
within range of each other. The following figure illustrates a hidden node. Both stations are
within range of the access point (AP) or wireless gateway, but out of range of each other, so
they cannot “hear” each other; that is they do not know if the channel is currently being used.
Therefore, they are considered hidden from each other.
Figure 28 RTS/CTS
G-470 User’s Guide
When station A sends data to the AP, it might not know that the station B is already using the
channel. If these two stations send data at the same time, collisions may occur when both sets
of data arrive at the AP at the same time, resulting in a loss of messages for both stations.
RTS/CTS is designed to prevent collisions due to hidden nodes. An RTS/CTS defines the
biggest size data frame you can send before an RTS (Request To Send)/CTS (Clear to Send)
handshake is invoked.
When a data frame exceeds the RTS/CTS value you set (between 0 to 2432 bytes), the station
that wants to transmit this frame must first send an RTS (Request To Send) message to the AP
for permission to send it. The AP then responds with a CTS (Clear to Send) message to all
other stations within its range to notify them to defer their transmission. It also reserves and
confirms with the requesting station the time frame for the requested transmission.
Stations can send frames smaller than the specified RTS/CTS directly to the AP without the
RTS (Request To Send)/CTS (Clear to Send) handshake.
You should only configure RTS/CTS if the possibility of hidden nodes exists on your network
and the “cost” of resending large frames is more than the extra network overhead involved in
the RTS (Request To Send)/CTS (Clear to Send) handshake.
Chapter 6 Wireless Screens 57
G-470 User’s Guide
If the RTS/CTS value is greater than the Fragmentation Threshold value (see next), then the
RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as data frames will
be fragmented before they reach RTS/CTS size.
Note: Enabling the RTS Threshold causes redundant network overhead that could
negatively affect the throughput performance instead of providing a remedy.
6.2.4 Fragmentation Threshold
A Fragmentation Threshold is the maximum data fragment size (between 256 and 2432
bytes) that can be sent in the wireless network before the ZyXEL Device will fragment the
packet into smaller data frames.
A large Fragmentation Threshold is recommended for networks not prone to interference
while you should set a smaller threshold for busy networks or networks that are prone to
interference.
If the Fragmentation Threshold value is smaller than the RTS/CTS value (see previously)
you set then the RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as
data frames will be fragmented before they reach RTS/CTS size.
6.3 Configuring Wireless
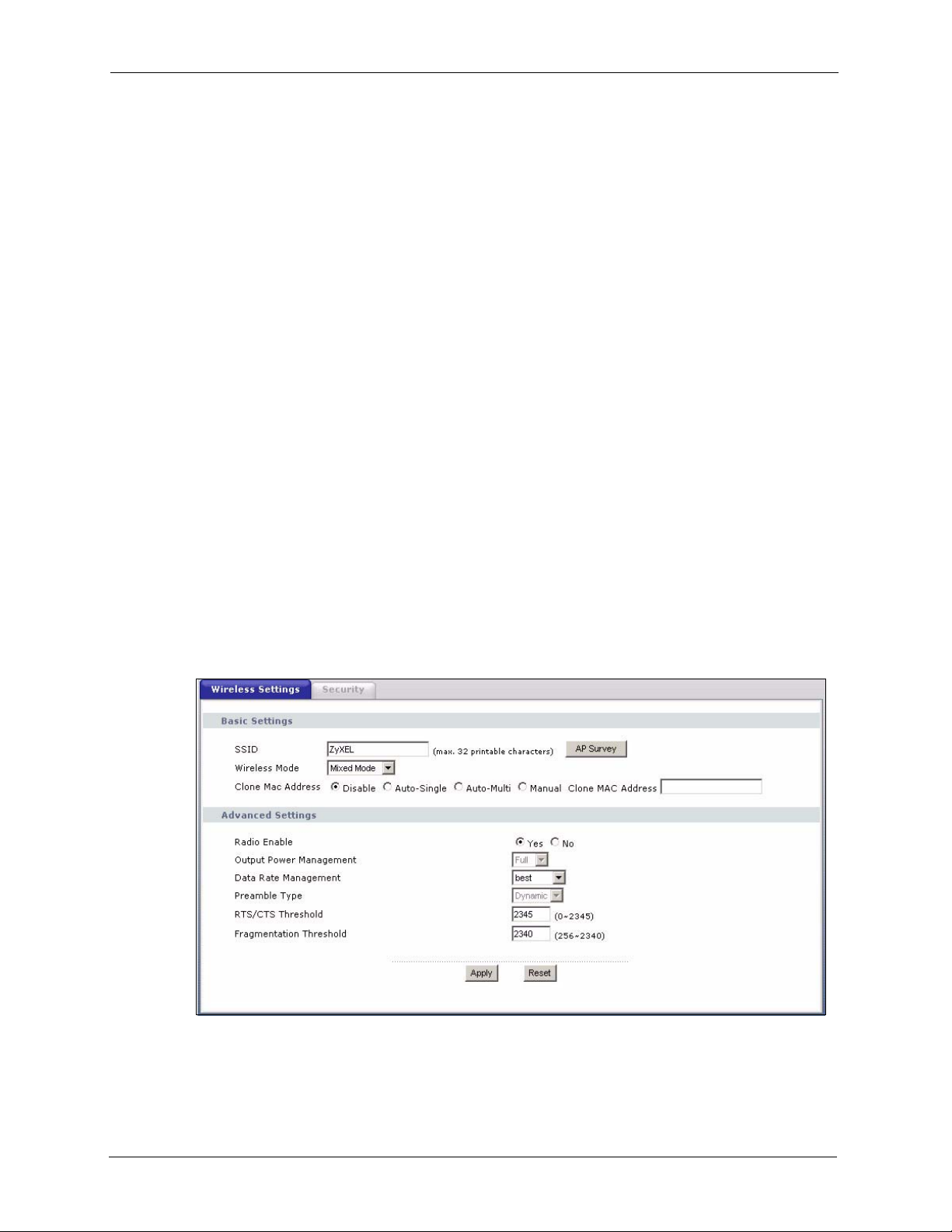
Click Wireless to display the Wireless Settings screen.
Figure 29 Wireless: Wireless Settings
58 Chapter 6 Wireless Screens
G-470 User’s Guide
The following table describes the labels in this screen.
Table 7 Wireless: Wireless Settings
LABEL DESCRIPTION
SSID Your ZyXEL Device must have the same SSID as the AP you want to connect to.
Enter a descriptive name (up to 32 printable characters) for the wireless LAN.
Spaces are allowed.
Note: If you are configuring the device from a computer connected
to the wireless LAN and you change the device's SSID,
channel or security settings, you will lose your wireless
connection when you press Apply to confirm. You must then
change the wireless settings of your computer to match the
device's new settings.
AP Survey Click this button to open the AP Survey window and select an access point.
Wireless Mode Select Mixed Mode to set the ZyXEL Device to operate in a wireless network with
both 802.11b and 802.11g wireless devices.
Select Pure B Mode to set the ZyXEL Device to operate in a wireless network with
only 802.11b wireless devices. If you select this, the ZyXEL Device may not
communicate with IEEE802.11g wireless devices
Select Pure G Mode to set the ZyXEL Device to operate in a wireless network with
only 802.11g wireless devices. If you select this, the ZyXEL Device may not
communicate with IEEE802.11b wireless devices
Clone MAC
Address
Advanced Settings
Radio Enable Select Yes to allow wireless communications between the device and other IEEE
Output Power
Management
Data Rate
Management
Every Ethernet-capable device is issued with a unique Media Access Control
(MAC) address at the factory. This address is used to identify the device across a
network.
Your ZyXEL Device is capable of “cloning”, or emulating, the MAC addresses of
one or more other devices.
Select Auto-Single to have the ZyXEL Device automatically use the MAC address
of a single Ethernet device connected to the ETHERNET port.
Select Auto-Multi to have the ZyXEL Device automatically use the MAC
addresses of multiple Ethernet devices connected to the ETHERNET port via a
hub.
Alternatively, enter a MAC address into the Clone MAC address field and select
Manual to have the ZyXEL Device use that address.
802.11b and IEEE 802.11g compliant wireless devices. Select No to stop wireless
communications between the device and other IEEE 802.11b and IEEE 802.11g
compliant wireless devices.
Set the output power of the device in this field. If there is a high density of APs
within an area, decrease the output power of the device to reduce interference with
other wireless LAN devices.
Use this field to select a maximum data rate for the wireless connection.
Chapter 6 Wireless Screens 59
G-470 User’s Guide
Table 7 Wireless: Wireless Settings (continued)
LABEL DESCRIPTION
Preamble Type Preamble is used to signal that data is coming to the receiver. Select the preamble
RTS/CTS
Threshold
Fragmentation
Threshold
Apply Click Apply to save your changes back to the device.
Reset Click Reset to begin configuring this screen afresh.
type that the AP uses.
Short and Long refer to the length of the
synchronization field in a packet.
Short Preamble increases performance as less time sending preamble means
more time for sending data. All IEEE 802.11b/g compliant wireless adapters
support Long Preamble, but not all support short preamble.
Select Auto to have the ZyXEL Device automatically use short preamble when all
access point or wireless stations support it; otherwise the ZyXEL Device uses long
preamble.
Note: The ZyXEL Device and the access point MUST use the same
preamble mode in order to communicate.
Enter a value between 0 and 2345. The default is 2345.
Enter a value between 256 and 2340. The default is 2340. It is the maximum data
fragment size that can be sent.
6.3.1 The AP Survey Window
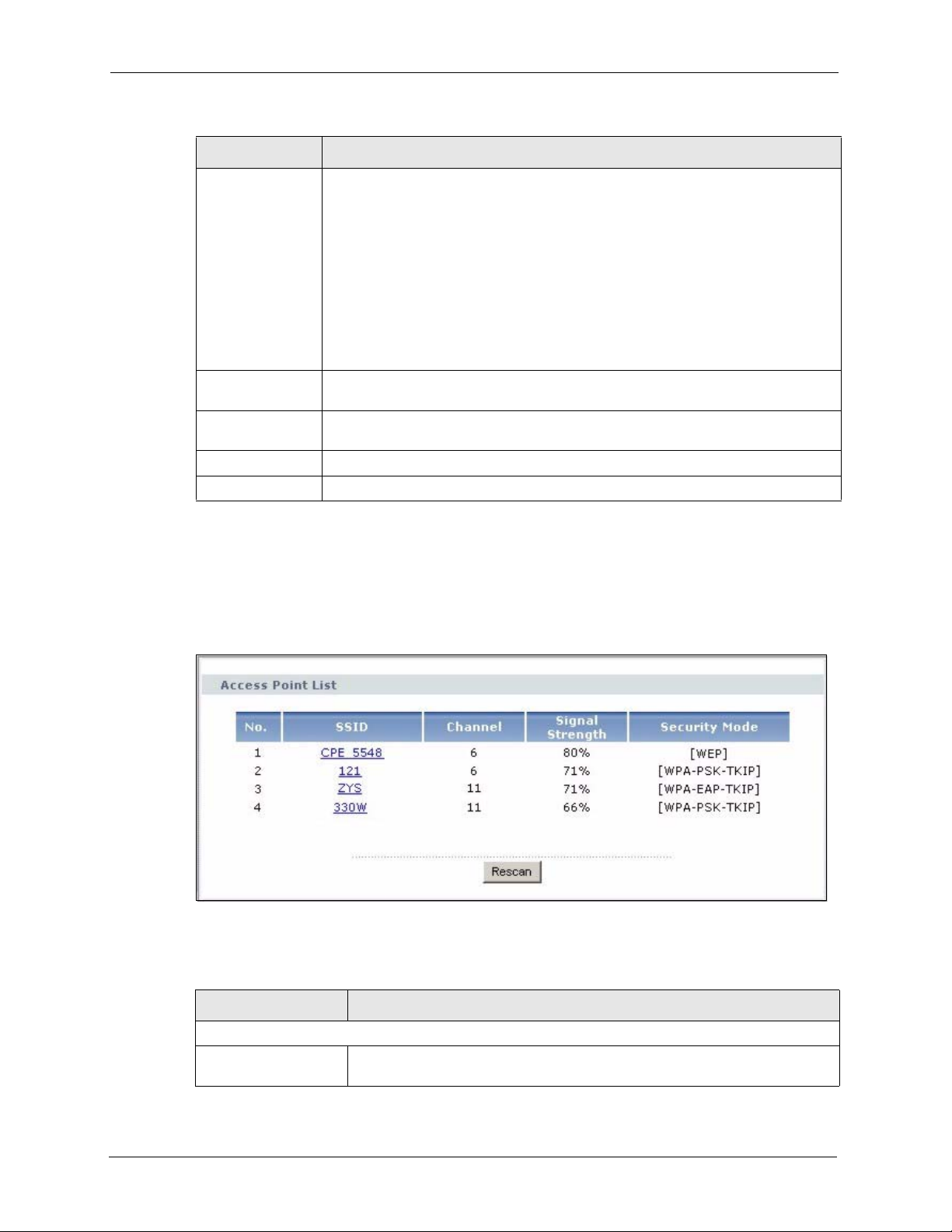
Click on Wireless > Wireless Settings > AP Survey to display the AP Survey screen. The
ZyXEL Device searches for available access points (APs).
Figure 30 Wireless: the AP Survey Screen
The following table describes the labels in this screen.
Table 8 Wireless: the AP Survey Screen
LABEL DESCRIPTION
Access Point List
No. This field displays the number of the access point. The access points are
ranked by signal strength.
60 Chapter 6 Wireless Screens
Table 8 Wireless: the AP Survey Screen
LABEL DESCRIPTION
SSID This field displays the SSID (Service Set IDentifier) of each access point. Click
on an SSID to select that wireless device.
Channel This field displays the channel number used by each access point.
Signal Strength This field displays the signal strength of each access point.
Security Mode This field displays details of the access point’s security and data encryption
settings.
Rescan Click Rescan to have the ZyXEL Device search again for available access
points.
6.4 Wireless Security Overview
Wireless security is vital to your network to protect wireless communication between wireless
stations, access points and the wired network.
The figure below shows the possible wireless security levels on your ZyXEL Device. EAP
(Extensible Authentication Protocol) is used for authentication and utilizes dynamic WEP key
exchange. It requires interaction with a RADIUS (Remote Authentication Dial-In User
Service) server either on the WAN or your LAN to provide authentication service for wireless
stations.
G-470 User’s Guide
Table 9 Wireless Security Levels
SECURITY LEVEL SECURITY TYPE
L e a s t S e c u r e
Most Secure
Unique SSID (Default)
Unique SSID with Hide SSID Enabled
MAC Address Filtering
WEP Encryption
IEEE802.1x EAP with RADIUS Server Authentication
Wi-Fi Protected Access (WPA)
WPA2
If you do not enable any wireless security on your ZyXEL Device, your network is accessible
to any wireless networking device that is within range.
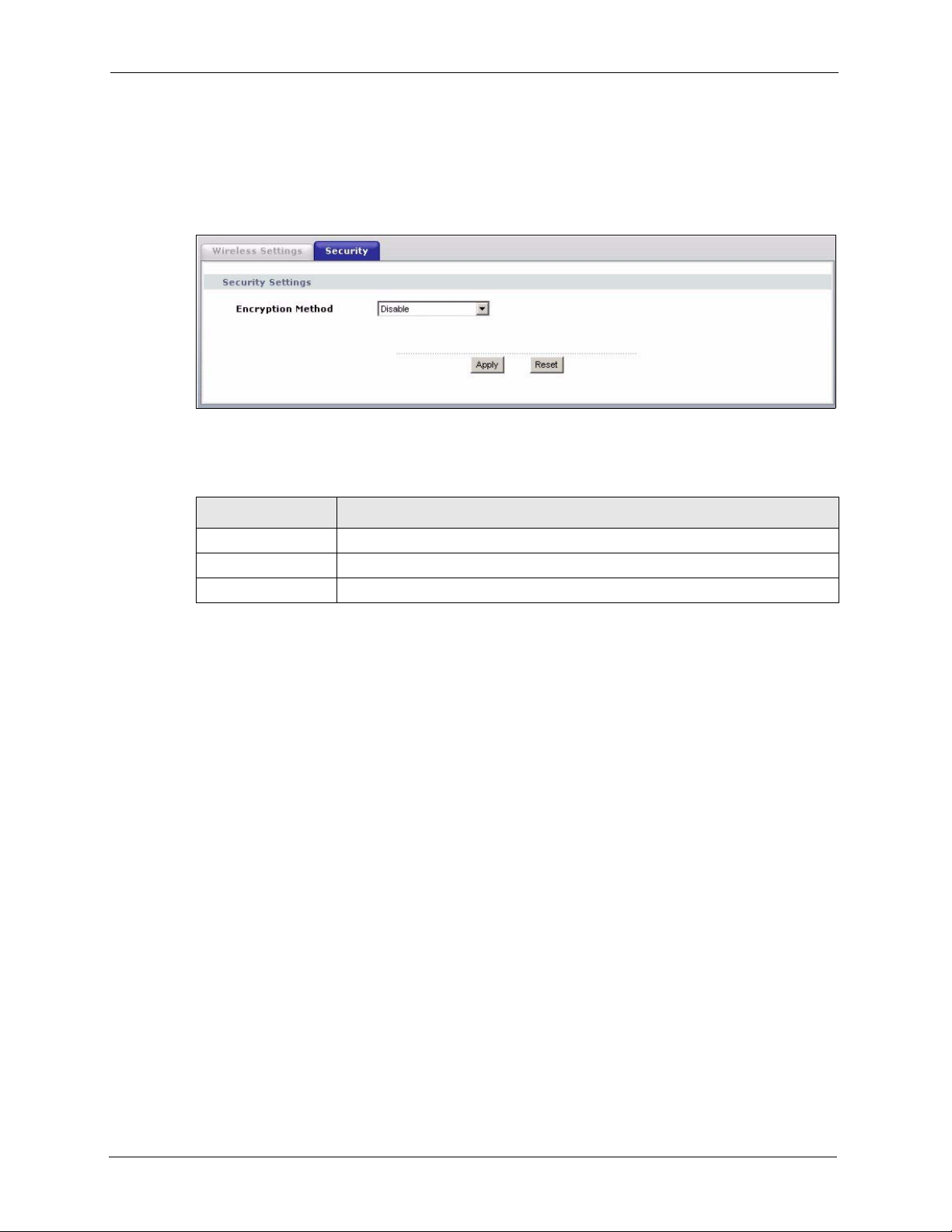
6.5 Configuring Wireless Security
In order to configure and enable wireless security; click Wireless > Security to display the
Security screen. This screen varies according to the encryption method you select.
Chapter 6 Wireless Screens 61
G-470 User’s Guide
6.5.1 Wireless Security: Disable
If you do not enable any wireless security on your device, your network is accessible to any
wireless networking device that is within range.
Figure 31 Wireless Security: Disable
The following table describes the labels in this screen.
Table 10 Wireless Security: Disable
LABEL DESCRIPTION
Encryption Method Select Disable to have no wireless LAN security configured.
Apply Click Apply to save your changes back to the device.
Reset Click Reset to begin configuring this screen afresh.
6.5.2 Wireless Security: WEP
WEP provides a mechanism for encrypting data using encryption keys. Both the AP and the
wireless stations must use the same WEP key to encrypt and decrypt data. You can configure
up to four 64-bit or 128-bit WEP keys, but only one key can be used at any one time.
62 Chapter 6 Wireless Screens
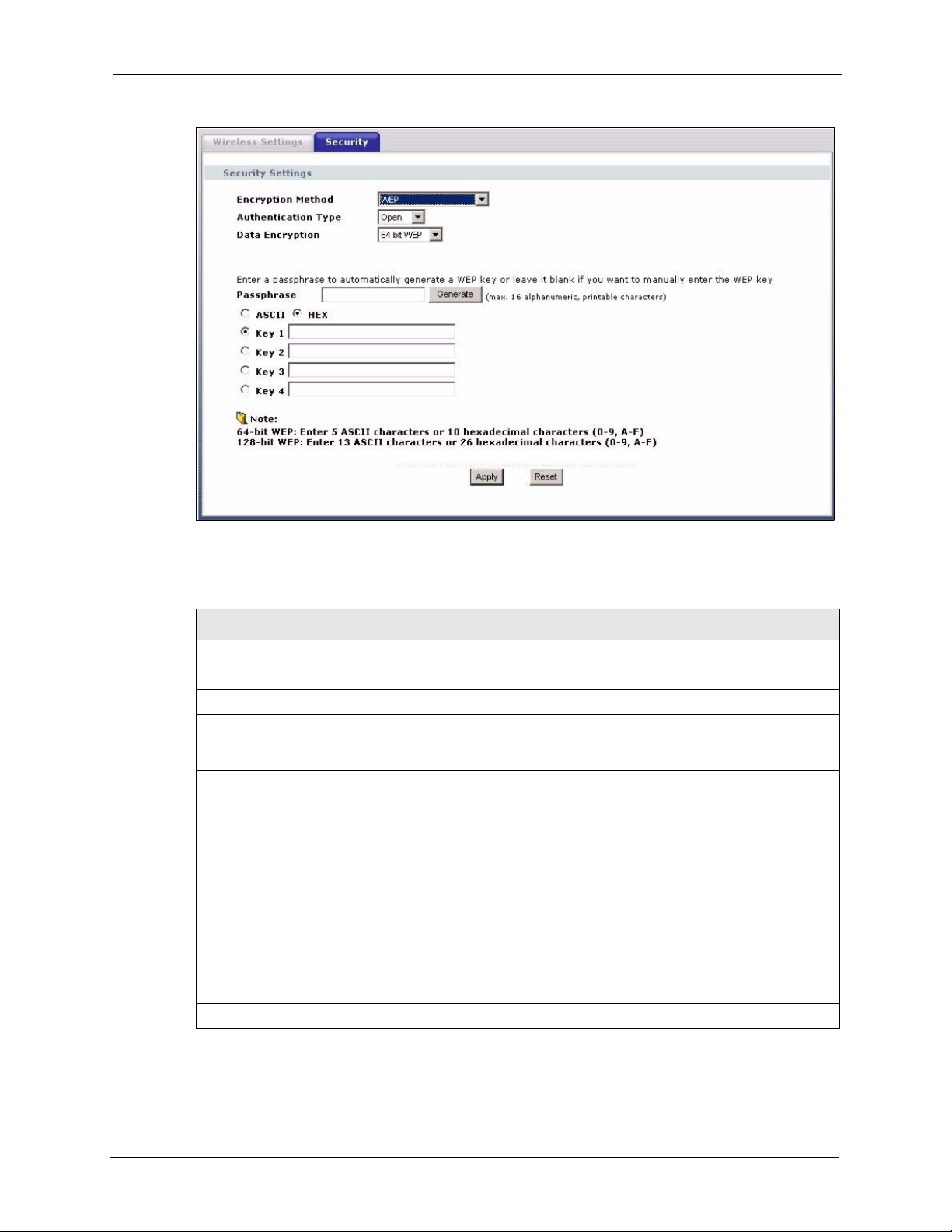
Figure 32 Wireless Security: WEP
G-470 User’s Guide
The following table describes the labels in this screen.
Table 11 Wireless Security: WEP
LABEL DESCRIPTION
Encryption Method Select WEP if you want to configure WEP encryption parameters.
Authentication Type Select Open or Shared from the drop-down list box.
Data Encryption Select 64 bit WEP or 128 bit WEP to enable data encryption.
Passphrase With 64-bit or 128-bit WEP, you can enter a “passphrase” (password phrase) of
up to 32 case-sensitive printable characters and click Generate to have the
device create four different WEP keys.
Generate After you enter the passphrase, click Generate to have the device generate
four different WEP keys automatically.
Key 1 to Key 4 If you want to manually set the WEP keys, enter the WEP key in the field
provided.
Select a WEP key to use for data encryption.
The WEP keys are used to encrypt data. Both the device and the wireless
stations must use the same WEP key for data transmission.
If you chose 64 bit WEP, then enter any 5 ASCII characters or 10 hexadecimal
characters ("0-9", "A-F").
If you chose 128 bit WEP, then enter 13 ASCII characters or 26 hexadecimal
characters ("0-9", "A-F").
Apply Click Apply to save your changes back to the device.
Reset Click Reset to begin configuring this screen afresh.
Chapter 6 Wireless Screens 63
G-470 User’s Guide
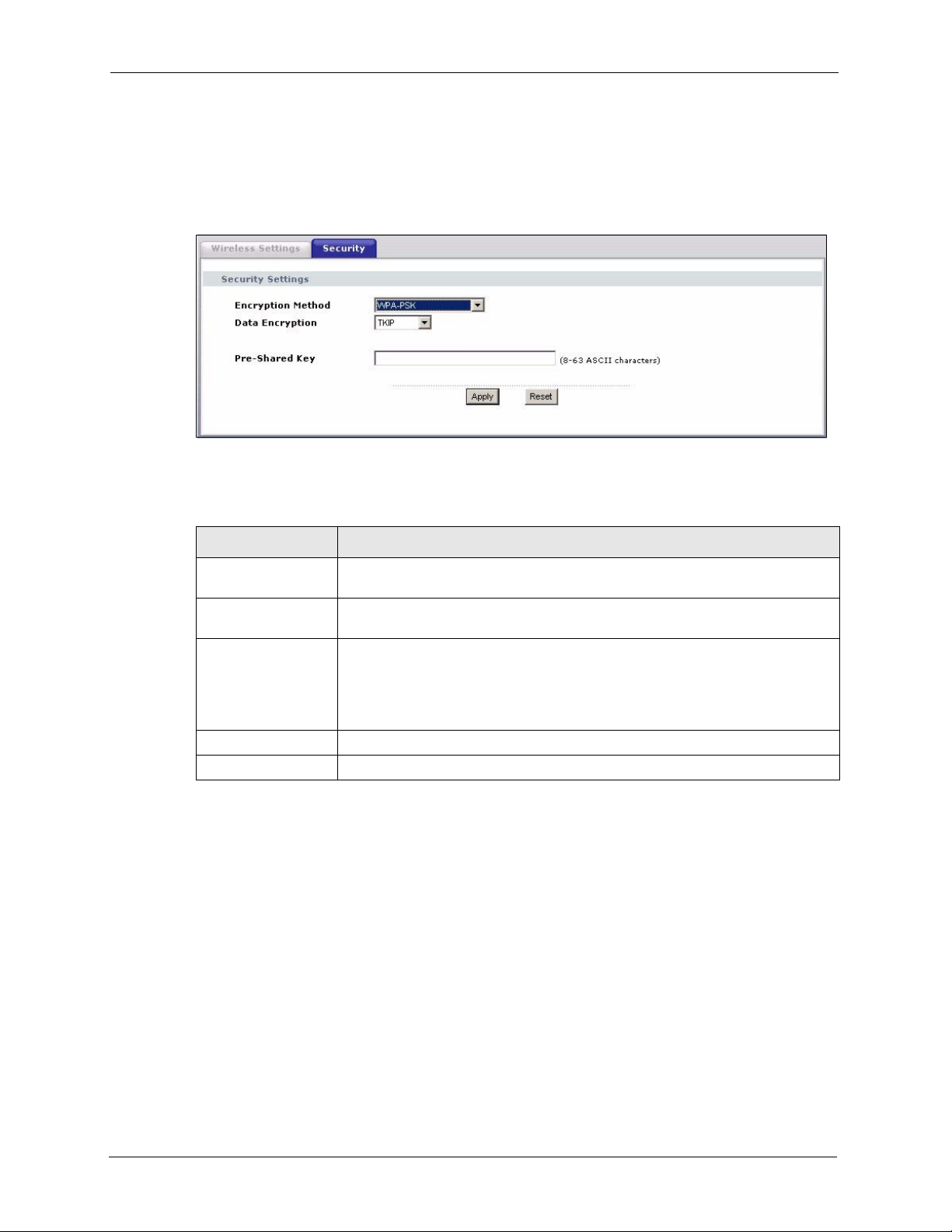
6.5.3 Wireless Security: WPA(2)-PSK
Select WPA-PSK, WPA2-PSK or WPA-PSK & WPA2-PSK in the Encryption Method
drop down list-box to display the next screen.
Figure 33 Wireless Security: WPA(2)-PSK
The following table describes the labels in this screen.
Table 12 Wireless Security: WPA-PSK
LABEL DESCRIPTION
Encryption Method Select WPA-PSK, WPA2-PSK or WPA-PSK & WPA2-PSK if you want to
configure a pre-shared key. Choose this option only if your AP supports it.
Data Encryption Select TKIP, AES or TKIP + AES to enable data encryption. For more
information, see the Wireless Security appendix.
Pre-Shared Key The encryption mechanisms used for WPA and WPA-PSK are the same. The
Apply Click Apply to save your changes to the device.
Reset Click Reset to begin configuring this screen afresh.
only difference between the two is that WPA-PSK uses a simple common
password, instead of user-specific credentials.
Type a pre-shared key from 8 to 63 ASCII characters (including spaces and
symbols). This field is case-sensitive.
6.5.4 Wireless Security: WPA(2)
WPA (Wi-Fi Protected Access) is a subset of the IEEE 802.11i standard. WPA2 (IEEE
802.11i) is a wireless security standard that defines stronger encryption, authentication and
key management than WPA. Key differences between WPA(2) and WEP are user
authentication and improved data encryption.
64 Chapter 6 Wireless Screens
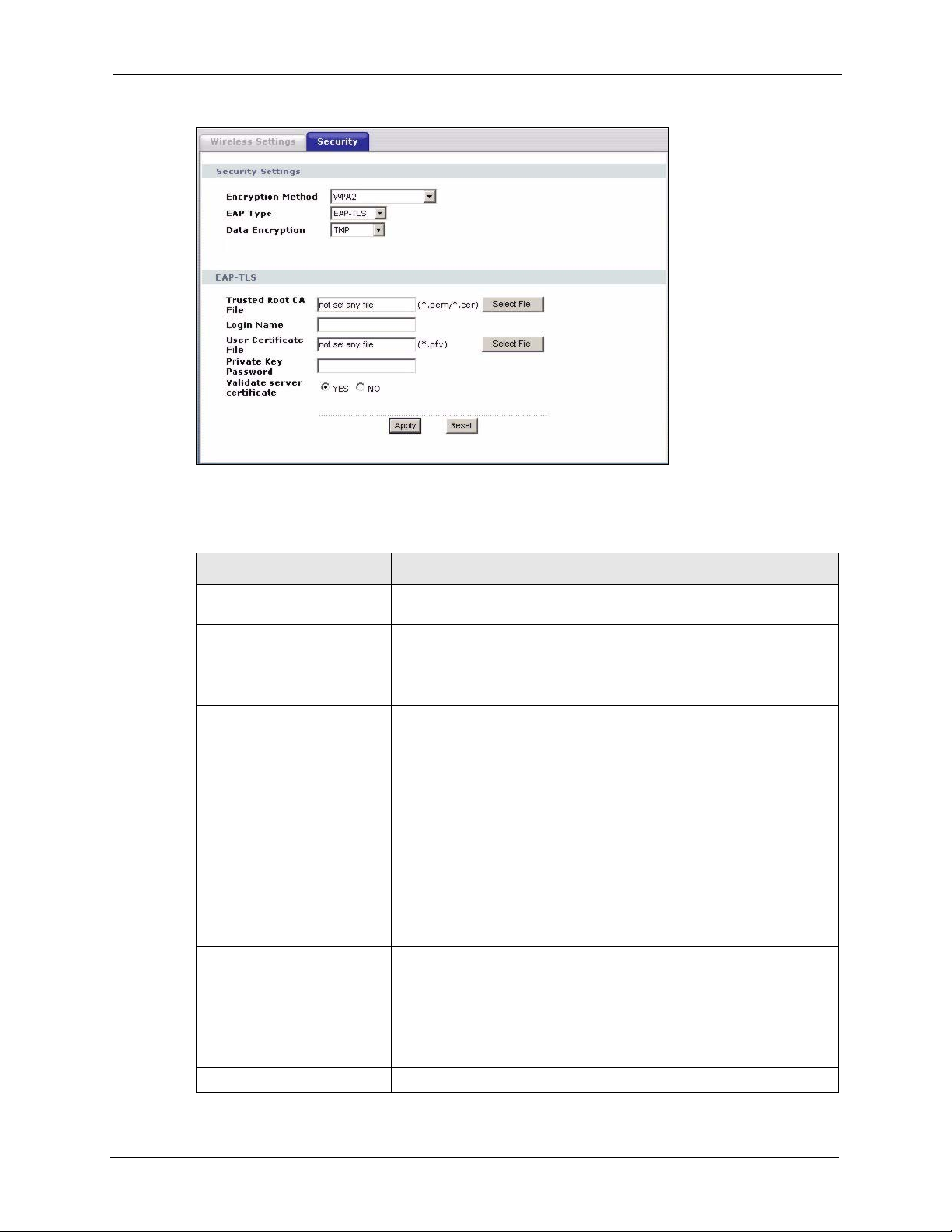
Figure 34 Wireless Security: WPA(2)
The following table describes the labels in this screen.
G-470 User’s Guide
Table 13 Wireless Security: WPA(2)
LABEL DESCRIPTION
Encryption Method Select WPA, WPA2 or WPA & WPA2 to configure user authentication
and improved data encryption.
EAP Type Select EAP-TLS, EAP-TTLS, EAP-LEAP or EAP-PEAP from the drop-
down box. See the Wireless Security appendix for more information.
Data Encryption Select TKIP, AES or TKIP + AES to enable data encryption. For more
Trusted Root CA File
(EAP-TLS, EAP-TTLS and
EAP-PEAP only)
Select File Click here to choose a certificate.
information, see the Wireless Security appendix.
This is the name of the certificate issued by the certificate authority
(CA).
Select a certificate from the list box and click Select to activate it. Click
Delete if you want to remove a certificate from the list.
Alternatively, click Browse to locate a certificate. Click Upload to add it
to the list.
The certificate file must have a .pem or .cer ending.
Note: You must first have a wired connection to a network
and obtain the certificate(s) from a certificate
authority (CA).
Login Name Enter a user name.
This is the user name that you or an administrator set up on a RADIUS
server.
Password
(EAP-TTLS, EAL-LEAP and
EAP-PEAP only)
User Certificate File This is your encrypted private key file.
Enter the password associated with the login name above.
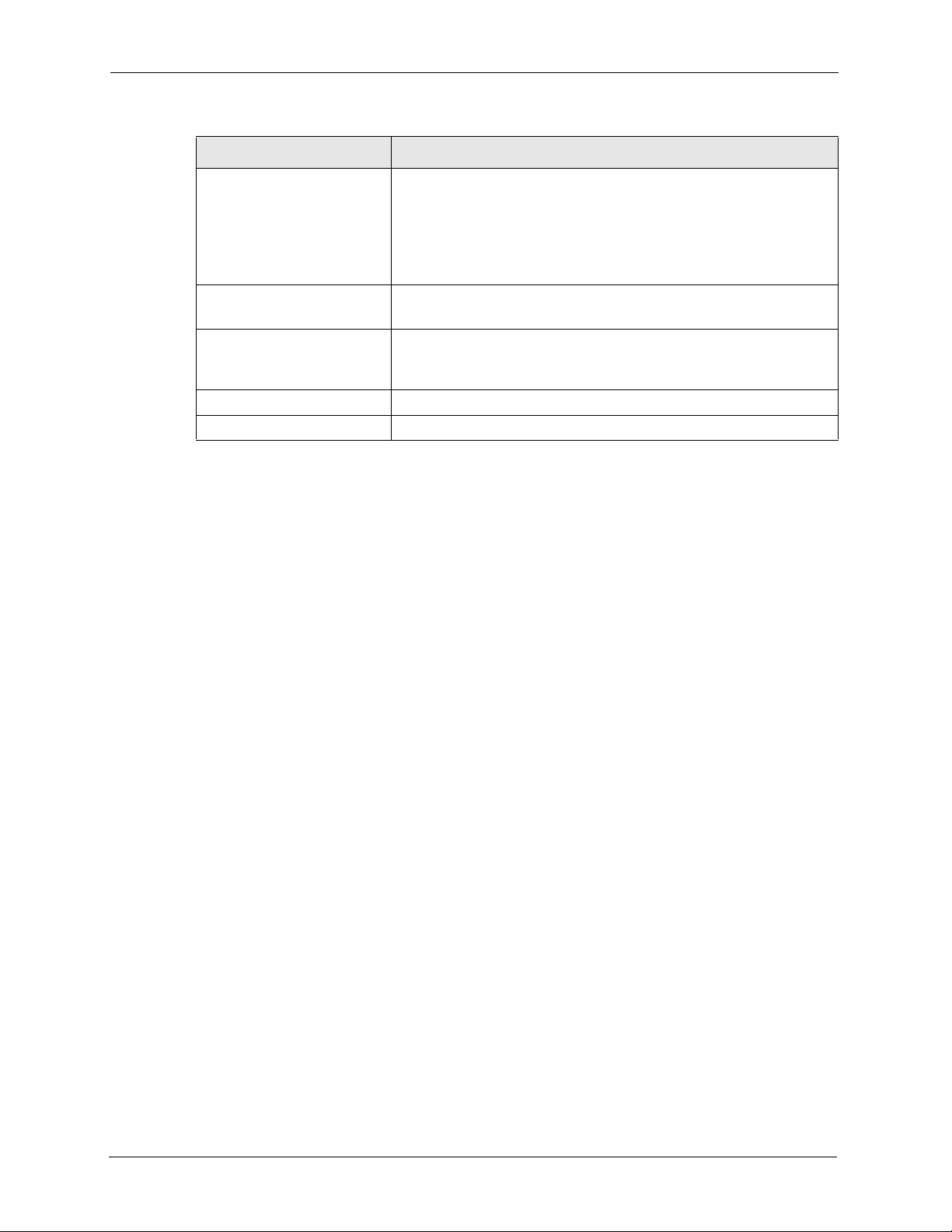
Chapter 6 Wireless Screens 65
G-470 User’s Guide
Table 13 Wireless Security: WPA(2) (continued)
LABEL DESCRIPTION
Select File Click here to choose a private key.
Select a private key from the list box and click Select to activate it.
Click Delete if you want to remove a private key from the list.
Alternatively, click Browse to locate a private key. Click Upload to add
it to the list.
The private key file must have a .pfx ending.
Private Key Password
(EAP-TLS only)
Validate Server Certificate
(EAP-TLS, EAP-TTLS and
EAP-PEAP only)
Apply Click Apply to save your changes to the device.
Reset Click Reset to begin configuring this screen afresh.
Enter the password associated with the private key above.
Select the check box to verify the certificate of the authentication
server.
6.5.5 Wireless Security: IEEE 802.1x
The IEEE 802.1x standard outlines enhanced security methods for both the authentication of
wireless stations and encryption key management.
Note: Once you enable user authentication, you need to specify an external RADIUS
server on the device for authentication.
66 Chapter 6 Wireless Screens
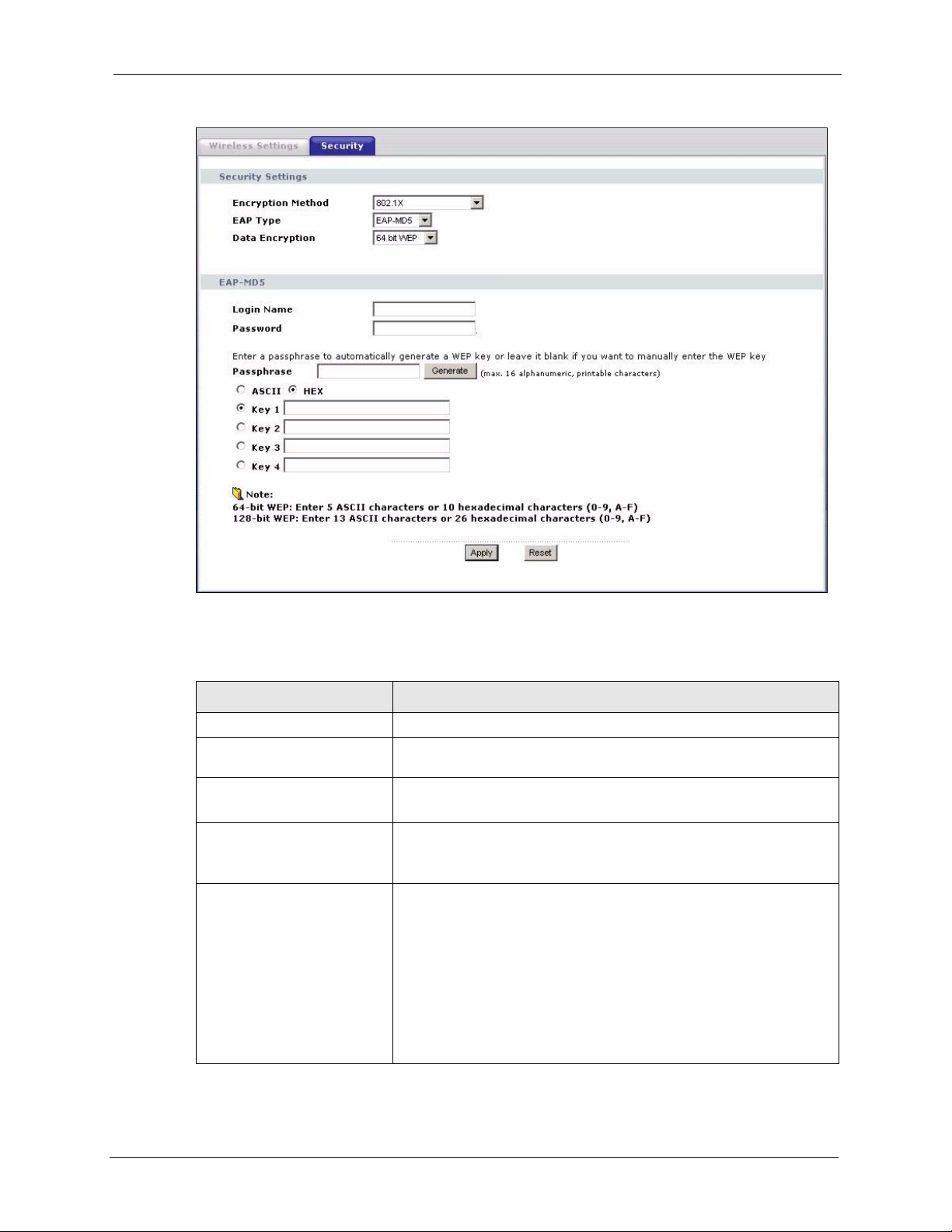
Figure 35 Wireless Security: 802.1x
G-470 User’s Guide
The following table describes the labels in this screen.
Table 14 Wireless Security: 802.1x
LABEL DESCRIPTION
Encryption Method Select 802.1X to configure encryption key management.
EAP Type Select EAP-TLS, EAP-TTLS, EAP-LEAP or EAP-PEAP from the drop-
Data Encryption
(EAP-MD5 only)
Trusted Root CA File
(EAP-TLS, EAP-TTLS and
EAP-PEAP only)
Select File
(EAP-TLS, EAP-TTLS and
EAP-PEAP only)
down box. See the Wireless Security appendix for more information.
Select 64 bit WEP or 128 bit WEP to enable data encryption.
This is the name of the certificate issued by the certificate authority
(CA).
Click here to choose a certificate.
Select a certificate from the list box and click Select to activate it. Click
Delete if you want to remove a certificate from the list.
Alternatively, click Browse to locate a certificate. Click Upload to add it
to the list.
The certificate file must have a .pem or .cer ending.
Note: You must first have a wired connection to a network
and obtain the certificate(s) from a certificate
authority (CA).
Chapter 6 Wireless Screens 67
G-470 User’s Guide
Table 14 Wireless Security: 802.1x
LABEL DESCRIPTION
Login Name Enter a user name.
Password
(EAP-TTLS, EAL-LEAP and
EAP-PEAP only)
User Certificate File
(EAP-TLS only)
Select File
(EAP-TLS only)
Private Key Password
(EAP-TLS only)
Validate Server Certificate
(EAP-TLS, EAP-TTLS and
EAP-PEAP only)
Passphrase
(EAP-MD5 only)
Generate
(EAP-MD5 only)
Key 1 to Key 4
(EAP-MD5 only)
Apply Click Apply to save your changes to the device.
Reset Click Reset to begin configuring this screen afresh.
This is the user name that you or an administrator set up on a RADIUS
server.
Enter the password associated with the login name above.
This is your encrypted private key file.
Click here to choose a private key.
Select a private key from the list box and click Select to activate it.
Click Delete if you want to remove a private key from the list.
Alternatively, click Browse to locate a private key. Click Upload to add
it to the list.
The private key file must have a .pfx ending.
Enter the password associated with the private key above.
Select the check box to verify the certificate of the authentication
server.
With 64-bit or 128-bit WEP, you can enter a “passphrase” (password
phrase) of up to 32 case-sensitive printable characters and click
Generate to have the device create four different WEP keys.
After you enter the passphrase, click Generate to have the device
generate four different WEP keys automatically.
If you want to manually set the WEP keys, enter the WEP key in the
field provided.
Select a WEP key to use for data encryption.
The WEP keys are used to encrypt data. Both the device and the
wireless stations must use the same WEP key for data transmission.
If you chose 64 bit WEP, then enter any 5 ASCII characters or 10
hexadecimal characters ("0-9", "A-F").
If you chose 128 bit WEP, then enter 13 ASCII characters or 26
hexadecimal characters ("0-9", "A-F").
68 Chapter 6 Wireless Screens
Management Screens
This chapter describes the Management screens.
7.1 Management Overview
Use these management screens to change the password, back up or restore the configuration
files and upgrade your ZyXEL Device’s firmware.
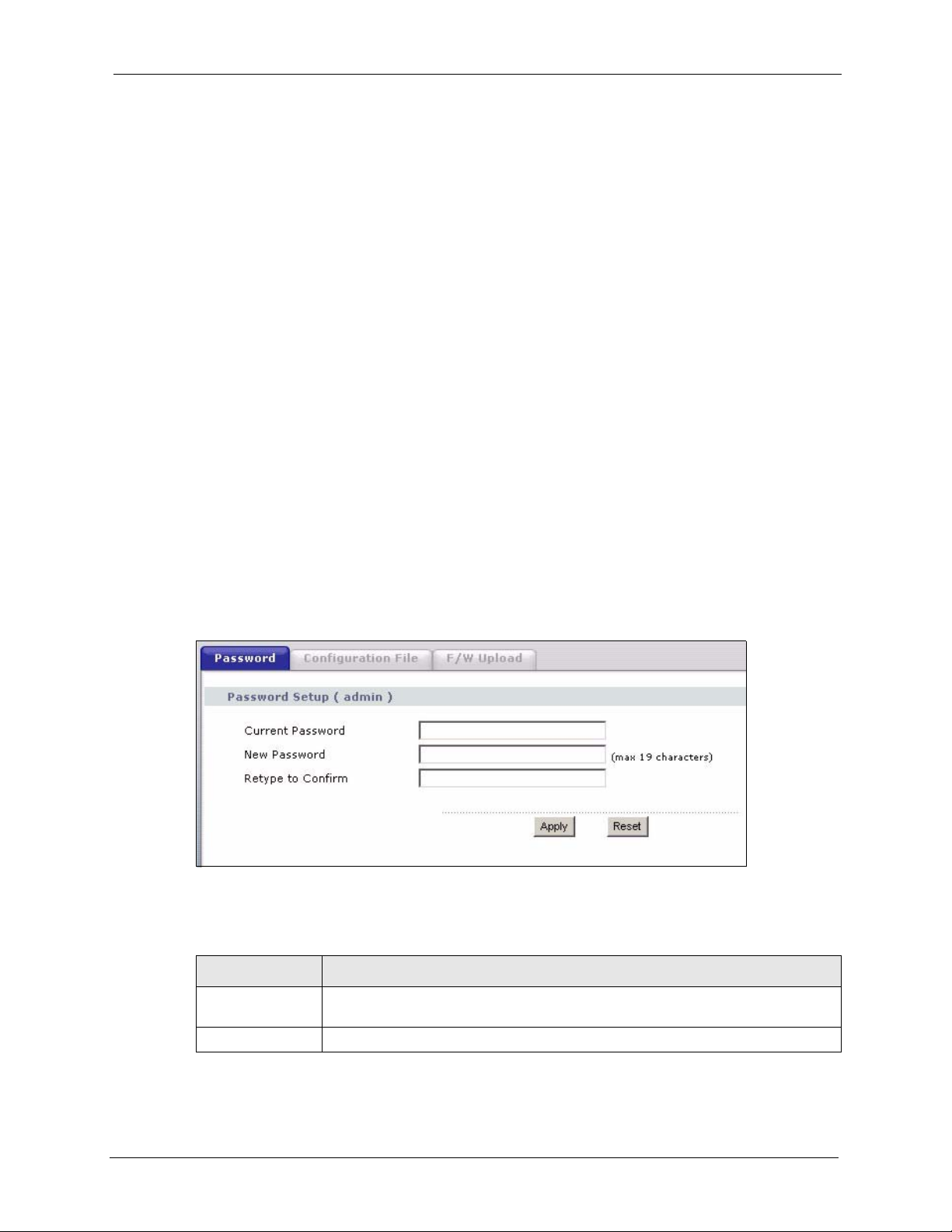
7.2 Password
To change your device's password (recommended), click Management. The screen appears as
shown. This screen allows you to change the device's password.
G-470 User’s Guide
CHAPTER 7
If you forget your password (or the device IP address), you will need to reset the device. See
Section 4.3 on page 41 for details.
Figure 36 Management: Password
The following table describes the labels in this screen.
Table 15 Management: Password
LABEL DESCRIPTION
Password Setup
(admin)
Current Password Type in your existing system password (1234 is the default password).
Use this section to change the password details for the admin username.
Chapter 7 Management Screens 69
G-470 User’s Guide
Table 15 Management: Password (continued)
LABEL DESCRIPTION
New Password Type your new system password (up to 19 printable characters). Spaces are not
allowed.
As you type a password, the screen displays an asterisk (*) for each character you
type.
Retype to Confirm Retype your new system password for confirmation.
Apply Save your changes back to the device.
Reset Reload the previous configuration for this screen.
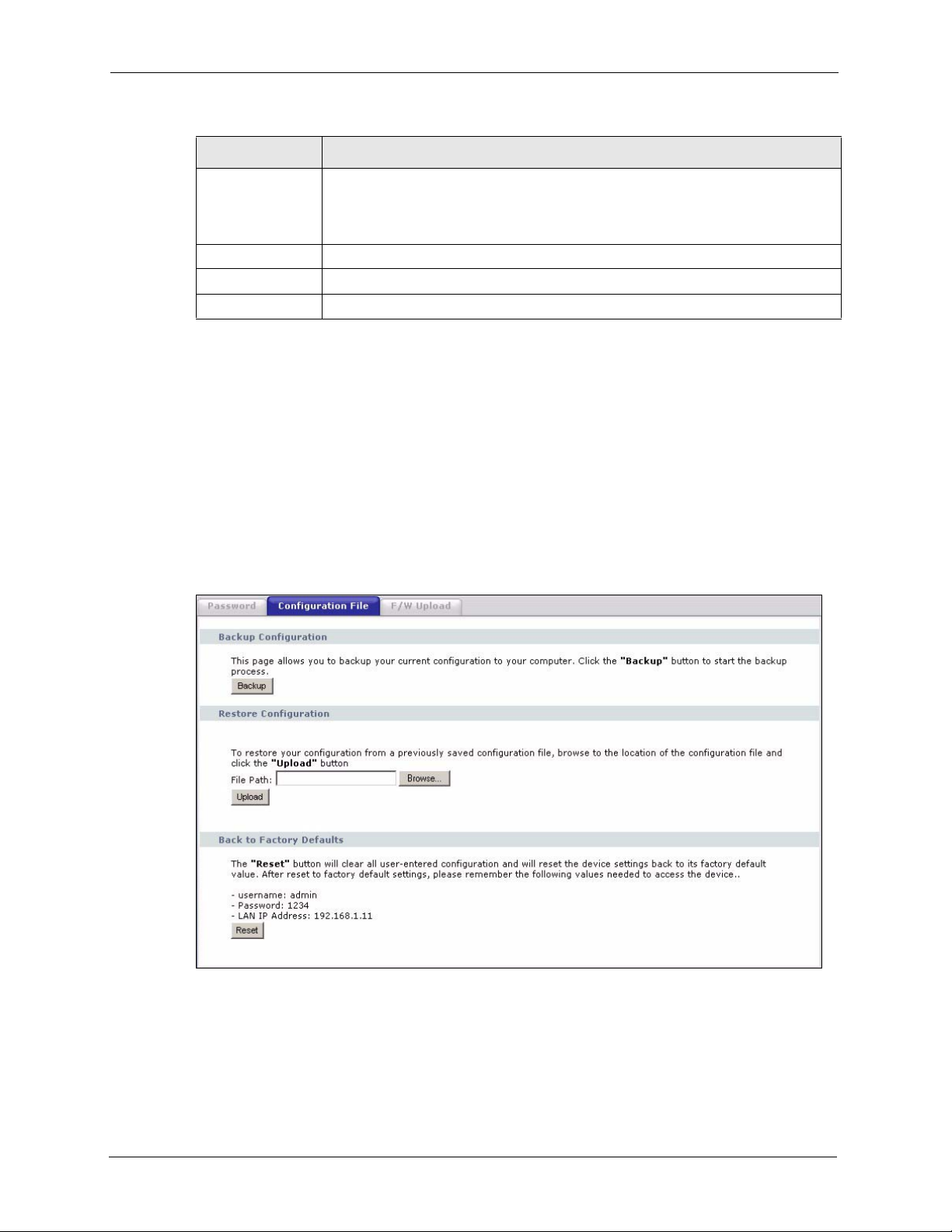
7.3 Configuration File
The configuration file (often called the romfile or rom-0) contains the factory default settings
such as password and TCP/IP Setup, etc. It arrives from ZyXEL with a .rom filename
extension. Once you have customized the device's settings, they can be saved back to your
computer under a filename of your choosing.
Click Management > Configuration File. Information related to factory defaults, backup
configuration, and restoring configuration appears as shown next.
Figure 37 Management: Configuration File
70 Chapter 7 Management Screens
7.3.1 Backup Configuration
Backup configuration allows you to back up (save) the device's current configuration to a file
on your computer. Once your device is configured and functioning properly, it is strongly
recommended that you back up your configuration file before making configuration changes.
The backup configuration file will be useful in case you need to return to your previous
settings.
Click Backup to save the device's current configuration to your computer.
7.3.2 Restore Configuration
Restore configuration allows you to upload a new or previously saved configuration file from
your computer to your device.
Table 16 Management: Configuration File: Restore Configuration
LABEL DESCRIPTION
File Path Type in the location of the file you want to upload in this field or click Browse ... to
find it.
Browse... Click Browse... to find the file you want to upload. Remember that you must
decompress compressed (.zip) files before you can upload them.
Upload Click Upload to begin the upload process.
G-470 User’s Guide
Warning: Do not turn off the device while configuration file upload is in progress.
The following screen displays in the Status bar at the bottom of the configurator screen.
Figure 38 Management: Configuration Upload Successful
If you uploaded the default configuration file you may need to change the IP address of your
computer to be in the same subnet as that of the default device IP address (192.168.1.12 to
1.192.168.1.254).
7.3.3 Back to Factory Defaults
Clicking the RESET button in this section clears all user-entered configuration information
and returns the device to its factory defaults. The following warning screen will appear.
Figure 39 Management: Reset Warning Message
Chapter 7 Management Screens 71
 Loading...
Loading...