Page 1

Page 2

Yealink Configuration Encryption Tool User Guide
SOFTWARE LICENSE AGREEMENT
SOFTWARE LICENSE AGREEMENT FOR YEALINK CONFIGURATION CONVERSION TOOL IS
IMPORTANT. PLEASE READ THIS LICENSE AGREEMENT CAREFULLY BEFORE CONTINUING
WITH THIS PROGRAM: YEALINK NETWORK TECHNOLOGY CO., LTD Software License Agreement
(SLA) is a legal agreement between you (either an individual or a single entity) and Yealink Network
Technology CO., LTD. For the Yealink software product(s) identified above which may include
associated software components, media, printed materials, and “online” or electronic documentation
("SOFTWARE PRODUCT"). By installing, copying, or otherwise using the SOFTWARE PRODUCT, you
agree to be bound by the terms of this SLA. This license agreement represents the entire agreement
concerning the program between you and Yealink Network Technology CO., LTD., (referred to as
"licenser"), and it supersedes any prior proposal, representation, or understanding between the parties. If
you do not agree to the terms of this SLA, do not install or use the SOFTWARE PRODUCT.
The SOFTWARE PRODUCT is protected by copyright laws and international copyright treaties, as well
as other intellectual property laws and treaties. The SOFTWARE PRODUCT is licensed, not sold.
COPYRIGHT
All title, including but not limited to copyrights, in and to the SOFTWARE PRODUCT and any copies
thereof are owned by Yealink Network Technology CO., LTD. or its suppliers. All title and intellectual
property rights in and to the content which may be accessed through use of the SOFTWARE PRODUCT
is the property of the respective content owner and may be protected by applicable copyright or other
intellectual property laws and treaties. This EULA grants you no rights to use such content. All rights not
expressly granted are reserved by Yealink Network Technology CO., LTD.
WARRANTIES
THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS GUIDE ARE
SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND
RECOMMENDATIONS IN THIS GUIDE ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED
WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL
RESPONSIBILITY FOR THEIR APPLICATION OF PRODUCTS.
YEALINK NETWORK TECHNOLOGY CO., LTD. MAKES NO WARRANTY OF ANY KIND WITH
REGARD TO THIS GUIDE, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. Yealink Network Technology
CO., LTD. shall not be liable for errors contained herein nor for incidental or consequential damages in
connection with the furnishing, performance, or use of this guide.
Page 3

About This Guide
Configuration files contain sensitive information such as user accounts, login passwords or
registration information. To protect sensitive information from tampering, you must encrypt
configuration files. Yealink provides tools for encrypting configuration files on Windows
platform and Linux platform respectively. You can ask the distributor or the Yealink Field
Application Engineer for these tools, or you can download them online:
http://support.yealink.com/documentFront/forwardToDocumentFrontDisplayPage.
This guide provides detailed information on how to encrypt configuration files using
Yealink-supplied encryption tools, and how to deploy phones using these encrypted
configuration files. The information applies to MP58, MP58-WH, MP56, MP54, T58A, T56A,
T55A, T48S, T46S, T42S and T41S Skype for Business phones running firmware version 9
or later and CP960 Skype for Business phones running firmware version 8.
Introduction
Yealink Configuration Encryption Tool User Guide
The encryption tool encrypts plaintext <y0000000000xx>.cfg and <MAC>.cfg files (one by one
or in batch) using 16-character symmetric keys (the same or different keys for configuration
files) and generates encrypted configuration files with the same file name as before. This tool
also encrypts the plaintext 16-character symmetric keys using a fixed key, which is the same
as the one built in the phone, and generates new files named as <xx_Security>.enc (xx
indicates the name of the configuration file, for example, y000000000066_Security.enc for
y000000000066.cfg file). This tool generates another new file named as Aeskey.txt storing the
plaintext 16-character symmetric keys for each configuration file.
For the security reasons, administrator should upload encrypted configuration files,
<y0000000000xx_Security>.enc and/or <MAC_Security>.enc files to the root directory of the
provisioning server. During auto provisioning, the phone requests to download
<y0000000000xx>.cfg file first. If the downloaded configuration file is encrypted, the phone will
request to download <y0000000000xx_Security>.enc file (if enabled) and decrypt it into the
plaintext key (e.g., key2) using the built-in key (e.g., key1). Then the phone decrypts
<y0000000000xx>.cfg file using key2. After decryption, the phone resolves configuration files
and updates configuration settings onto the phone system. The way the phone processes the
<MAC>.cfg file is the same to that of the<y0000000000xx>.cfg file.
Configuration Encryption Tool on Windows Platform
This tool supports Microsoft Windows XP and Windows 7 (both 32-bit and 64-bit) system.
1
Page 4
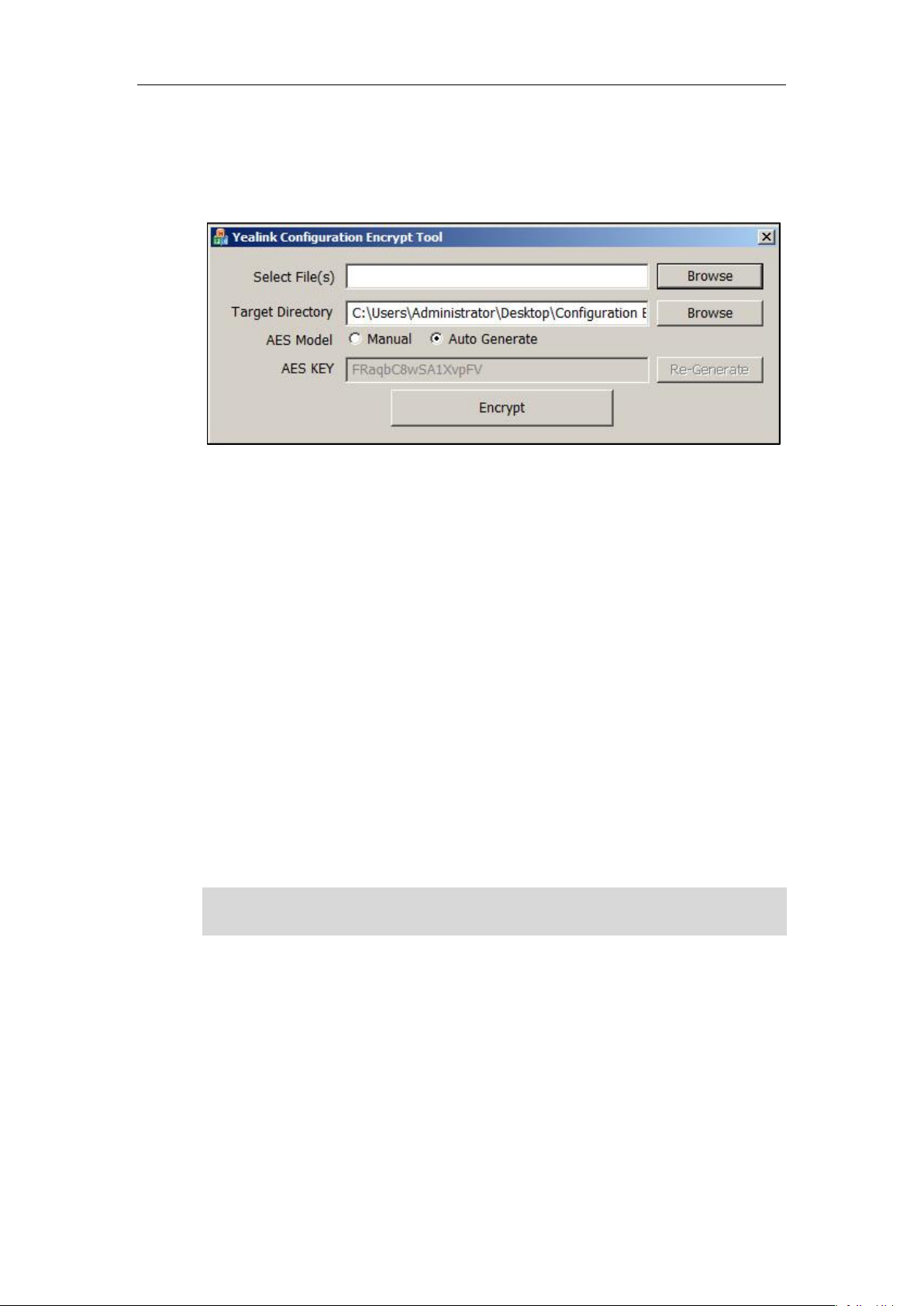
Yealink Configuration Encryption Tool User Guide
2
To encrypt configuration files:
1. Double click “Config_Encrypt_Tool.exe” to start the application tool.
The screenshot of the main page is shown as below:
When you start the application tool, a file folder named “Encrypted” is created
automatically in the directory where the application tool is located.
2. Click Browse to locate configuration file(s) (e.g., y000000000066.cfg) from your local
system in the Select File(s) field.
To select multiple configuration files, you can select the first file and then press and
hold the Ctrl key and select the next files.
3. (Optional.) Click Browse to locate a target directory from your local system in the Target
Directory field.
The tool uses the file folder “Encrypted” as the target directory by default.
4. (Optional.) Mark the desired radio box in the AES Model field.
If you mark the Manual radio box, you can enter an AES key in the AES KEY field or click
Re-Generate to generate an AES key in the AES KEY field. The configuration file(s) will
be encrypted using the AES key in the AES KEY field.
If you mark the Auto Generate radio box, the configuration file(s) will be encrypted using
random AES key. The AES keys of configuration files are different.
Note
AES keys must be 16 characters and the supported characters contain: 0 ~ 9, A ~ Z, a ~ z and the
following special characters are also supported: # $ % * + , - . : = ? @ [ ] ^ _ { } ~.
Page 5

Yealink Configuration Encryption Tool User Guide
3
5. Click Encrypt to encrypt the configuration file(s).
6. Click OK.
The target directory will be automatically opened. You can find the encrypted CFG file(s),
encrypted key file(s) and an Aeskey.txt file storing plaintext AES key(s).
Configuration Encryption Tool on Linux Platform
To encrypt configuration files:
1. Place the encryption tool “yealinkencrypt” and configuration files in the same directory.
2. Open a terminal window.
3. Execute the cd command to locate the directory where the encryption tool is stored. For
example, execute cd /tmp to locate the /tmp directory.
Page 6

Yealink Configuration Encryption Tool User Guide
4
4. Execute one of the following commands according to your requirements:
- If you want to encrypt one or multiple specified configuration files, you need to
execute the following command:
./yealinkencrypt -f file1.cfg [file2.cfg ...] [-p DESTPATH(Default as 'Encrypted')] [-k
AESKEY(Default as random)]
Example:
[root@localhost tmp]#./yealinkencrypt -f y000000000066.cfg -p /home/test -k
0123456789123456
AES Key: 0123456789123456
Generate Security Key File...
Generate Encrypt Config File...
Write file to /home/test/Aeskey.txt!
Write file to /home/test/y000000000066_Security.enc!
Read file y000000000066.cfg!
Write file to /home/test/y000000000066.cfg!
This tool will encrypt the y000000000066.cfg file using the AES key
0123456789123456. You can find the encrypted y000000000066.cfg file,
y000000000066_Security.enc file and an Aeskey.txt file storing the plaintext AES
key 0123456789123456 in the specified directory.
- If you want to encrypt configuration files in batch using a random AES key, you need
to execute the following command:
./yealinkencrypt –f *.cfg [-p DESTPATH(Default as 'Encrypted')] -m
Example:
[root@localhost tmp]#./yealinkencrypt -f *.cfg -p /home/test -m
Generate AES Key...
Write file to /home/test/Aeskey.txt!
Write file to /home/test/0015652ac1cc_Security.enc!
Page 7

Yealink Configuration Encryption Tool User Guide
5
Read file 0015652ac1cc.cfg!
Write file to /home/test/0015652ac1cc.cfg!
Write file to /home/test/Aeskey.txt!
Write file to /home/test/y000000000066_Security.enc!
Read file y000000000066.cfg!
Write file to /home/test/y000000000066.cfg!
This tool will encrypt all CFG files using random AES keys (each CFG file
corresponds to a random AES key). You can find the encrypted CFG files, encrypted
key files and an Aeskey.txt file storing the plaintext AES keys in the specified
directory.
- If you want to encrypt configuration files in batch using a specified AES key, you
need to execute the following command:
./yealinkencrypt –f *.cfg [-p DESTPATH(Default as 'Encrypted')] -k
0123456789123456
Example:
[root@localhost tmp]#./yealinkencrypt -f *.cfg -p /home/test -k 0123456789123456
AES Key: 0123456789123456
Generate Security Key File...
Generate Encrypt Config File...
Write file to /home/test/Aeskey.txt!
Write file to /home/test/0015652ac1cc_Security.enc!
Read file 0015652ac1cc.cfg!
Write file to /home/test/0015652ac1cc.cfg!
Write file to /home/test/Aeskey.txt!
Write file to /home/test/y000000000066_Security.enc!
Read file y000000000066.cfg!
Write file to /home/test/y000000000066.cfg!
Page 8

Yealink Configuration Encryption Tool User Guide
6
This tool will encrypt all CFG files using a specified AES key. You can find the
encrypted CFG files, encrypted key files and an Aeskey.txt file storing the plaintext
AES key in the specified directory.
Note
Configuring Yealink Skype for Business Phones
You can configure the phones to decrypt the encrypted configuration files during auto
provisioning using the encrypted AES key files or the AES keys configured on the phones.
Before deploying phones using the encrypted configuration files, you need to configure the
following parameters for the phones using the configuration files first.
1. Add/Edit the following parameters in configuration files.
Parameters
Permitted Values
Default
static.auto_provision.aes_key_in_file
0 or 1
0
Description:
Enables or disables the phone to decrypt configuration files using the encrypted AES keys.
0-Disabled
1-Enabled
If it is set to 0 (Disabled), the phone will decrypt the encrypted configuration files using
plaintext AES keys configured on the phone.
If it is set to 1 (Enabled), the phone will download <y0000000000xx_Security>.enc and
<MAC_Security>.enc files during auto provisioning, and then decrypt these files into the
plaintext keys (e.g., key2, key3) respectively using the phone built-in key (e.g., key1). The
phone then decrypts the encrypted configuration files using corresponding key (e.g., key2,
key3).
AES keys must be 16 characters and the supported characters contain: 0 ~ 9, A ~ Z, a ~ z and the
following special characters are also supported: # $ % * + , - . : = ? @ [ ] ^ _ { } ~.
Page 9

Yealink Configuration Encryption Tool User Guide
7
Parameters
Permitted Values
Default
Web User Interface:
None
Phone User Interface:
None
2. Upload configuration files to the root directory of the provisioning server and trigger
phones to perform an auto provisioning for configuration update.
For more information on auto provisioning, refer to
Yealink Skype for Business HD IP
Phones Auto Provisioning Guide
.
Deploying Phones Using Encrypted Configuration
Files and AES keys
This section shows a scenario on how to deploy Yealink phones using encrypted configuration
files and AES keys.
Scenario: Encrypt configuration files and ensure no plaintext configurations and keys
are transmitted across the network
Scenario Conditions:
The administrator wants to encrypt configuration files to protect sensitive information in
configuration files from tampering.
T46S Skype for Business phone, MAC address: 0015651137F6.
static.auto_provision.aes_key_in_file =1 (Enable the phone to download
y000000000066_Security.enc and 0015651137f6_Security.enc files during auto
provisioning)
Scenario Operations:
1. The administrator encrypts y000000000066.cfg and 0015651137f6.cfg files and then
uploads y000000000066_Security.enc, 0015651137f6_Security.enc, y000000000066.cfg
(encrypted) and 0015651137f6.cfg (encrypted) files to the root directory of the
provisioning server.
For more information on encrypting configuration files, refer to Configuration Encryption
Tool on Windows Platform on page 1 or Configuration Encryption Tool on Linux Platform
on page 3.
2. Reboot the phone to trigger auto provisioning process. For more information, refer to
Yealink Skype for Business HD IP Phones Auto Provisioning Guide
.
During auto provisioning, the phone requests to download y000000000066.cfg file first.
Because the downloaded configuration file is encrypted, the phone requests to download
Page 10

Yealink Configuration Encryption Tool User Guide
8
y000000000066_Security.enc file and then decrypts it into the plaintext key (e.g., key2) using
the built-in key (e.g., key1). The phone then decrypts the configuration file y000000000066.cfg
using the key2. After decryption, the phone resolves configuration files and updates
configuration settings onto the phone system.
The way the phones process the <MAC>.cfg file is the same as the <y000000000066>.cfg file.
For more information, refer to Appendix Auto Provisioning Flowchart on page 9.
Page 11

Yealink Configuration Encryption Tool User Guide
9
Appendix Auto Provisioning Flowchart
The following shows the flowchart for provisioning Yealink phones using the encrypted
configuration file (taking the Common CFG file as an example). The way the phone processes
the MAC-Oriented CFG file is the same as that of the Common CFG file.
 Loading...
Loading...