Page 1

Thecus N5200B
N5200BR
User’s Manual
Page 2

2
Copyright and Trademark Notice
Thecus and other names of Thecus products are registered trademarks of Thecus
Technology Corp. Microsoft, Windows, and the Windows logo are registered
trademarks of Microsoft Corporation. Apple, iTunes and Apple OS X are registered
trademarks of Apple Computers, Inc. All other trademarks and brand names are
the property of their respective owners. Specifications are subject to change
without notice.
Copyright © 2008 Thecus Technology Corporation. All rights reserved.
About This Manual
All information in this manual has been carefully verified t o ensure its correctness.
In case of an error, please provide us with your feedback. Thecus Technology
Corporation reserves the right to modify the contents of this manual without
notice.
Product name: Thecus N5200B/BR
Manual Version: 1.1
Release Date: March 2008
Limited Warranty
Thecus Technology Corporation guarantees all components of Thecus N5200 are
thoroughly tested before they leave the factory and should function normally
under general usage. In case of any system malfunctions, Thecus Technology
Corporation and its local representatives and dealers are responsible for repair
without cost to the customer if the product fails within the warranty period and
under normal usage. Thecus Technology Corporation is not responsible for any
damage or loss of data deemed to be caused by its products. It is highly
recommended that users conduct necessary back-up practices.
Page 3

3
Safety Warnings
For your safety, please read and follow the following safety warnings:
Read this manual thoroughly before attempting to set up your N5200.
Your N5200 is a complicated electronic device. DO NOT attempt to repair it
under any circumstances. In the case of malfunction, turn off the power
immediately and have it repaired at a qualified service center. Contact
your vendor for details.
DO NOT allow anything to rest on the power cord and DO NOT place the
power cord in an area where it can be stepped on. Carefully place
connecting cables to avoid stepping or tripping on them.
Your N5200 can operate normally under temperatures between 0°C and
40°C, with relative humidity of 20% – 85%. Using the N5200 under
extreme environmental conditions could damage the unit.
Ensure that the N5200 is provided with the correct supply voltage (AC
100V ~ 240V, 50/60 Hz, 3A). Plugging the N5200 to an incorrect power
source could damage the unit.
Do NOT expose the N5200 to dampness, dust, or corrosive liquids.
Do NOT place the N5200 on any uneven surfaces.
DO NOT place the N5200 in direct sunlight or expose it to other heat
sources.
DO NOT use chemicals or aerosols to clean the N5200. Unplug the power
cord and all connected cables before cleaning.
DO NOT place any objects on the N5200 or obstruct its ventilation slots to
avoid overheating the unit.
Keep packaging out of the reach of children.
If disposing of the device, please follow your local regulations for the safe
disposal of electronic products to protect the environment.
Page 4

4
Table of Contents
Copyright and Trademark Notice ................................................... 2
About This Manual.........................................................................2
Limited Warranty........................................................................... 2
Safety Warnings ............................................................................ 3
Table of Contents ..........................................................................4
Chapter 1: Introduction................................................................. 8
Overview...............................................................................................8
Product Highlights.................................................................................8
File Server ...........................................................................................8
FTP Server...........................................................................................8
Backup Server .....................................................................................8
Printer Server ......................................................................................8
Superior Power Management..................................................................8
Package Contents..................................................................................9
Front Panel..........................................................................................10
Hard Disk Trays...................................................................................11
Rear Panel (N5200B)...........................................................................11
Rear Panel (N5200BR) ........................................................................12
Chapter 2: Hardware Installation ................................................ 13
Overview.............................................................................................13
Before You Begin.................................................................................13
Hard Disk Installation .........................................................................13
Cable Connections ...............................................................................14
Checking System Status ......................................................................15
System Status Normal.........................................................................15
System Trouble.................................................................................. 15
Chapter 3: First Time Setup.........................................................16
Overview.............................................................................................16
Thecus Setup Wizard...........................................................................16
LCD Operation .....................................................................................18
LCD Controls......................................................................................18
Display Mode .....................................................................................18
USB Copy ................................................................................................. 19
Management Mode .............................................................................19
Typical Setup Procedure......................................................................19
Step 1: Network Setup........................................................................ 20
Step 2: RAID Creation......................................................................... 20
Step 3: Create Local Users or Setup Authentication.................................20
Step 4: Create Folders and Set Up ACLs ................................................20
Step 5: Start Services.........................................................................20
Chapter 4: System Management..................................................22
Overview.............................................................................................22
Web Administration Interface .............................................................22
Menu Bar ..........................................................................................22
Language Selection .............................................................................23
Status Menu ........................................................................................24
Product Information............................................................................ 24
System/Service Status........................................................................24
System Information............................................................................25
Printer Status.....................................................................................25
UPS Settings...................................................................................... 26
Wake-Up On Lan (WOL) ......................................................................27
Page 5

5
Power Management ............................................................................28
Storage Management ..........................................................................29
Disks Information...............................................................................29
S.M.A.R.T. Information............................................................................... 29
RAID Information ............................................................................... 30
RAID Configuration.............................................................................31
RAID Level ............................................................................................... 31
RAID Settings ...........................................................................................32
Creating a RAID ........................................................................................32
Expanding a RAID .....................................................................................33
Migrating a RAID....................................................................................... 34
Deleting a RAID ........................................................................................ 34
Space Allocation................................................................................. 35
Allocating Space for Target USB Volume .......................................................35
Folder Management ............................................................................ 36
Adding Folders..........................................................................................36
Editing Folders..........................................................................................37
Deleting Folders........................................................................................37
NFS Share................................................................................................ 38
Folder Access Control List (ACL) .................................................................. 39
File System Check .............................................................................. 40
Network Management .........................................................................42
WAN Configuration .............................................................................42
LAN Configuration...............................................................................43
DHCP Configuration ............................................................................ 43
WLAN Configuration............................................................................ 44
WAN LAN Exchange ............................................................................ 45
Web Services Configuration..................................................................45
AFP (Apple Network Setup).................................................................. 46
NFS Setup.........................................................................................46
User and Group Management ..............................................................47
Local User Configuration......................................................................47
Adding Users ............................................................................................ 47
Modifying Users.........................................................................................48
Deleting Users .......................................................................................... 48
Local Groups Configuration .................................................................. 48
Adding Groups ..........................................................................................48
Modifying Groups ...................................................................................... 49
Deleting Groups ........................................................................................49
Batch User and Group Creation.............................................................49
ADS/NT Configuration .........................................................................50
System Settings ..................................................................................52
System Notifications ........................................................................... 52
System Logs...................................................................................... 52
Time and Date Settings.......................................................................53
System Configuration Backup and Restore ............................................. 54
Module Management...........................................................................54
Reset to Factory Default Settings..........................................................55
Upgrading System Firmware ................................................................55
Change Administrator Password............................................................56
Reboot and Shutdown System..............................................................56
Logout ..............................................................................................56
Chapter 5: Additional Feature Setup............................................ 57
Overview.............................................................................................57
FTP Server...........................................................................................57
Media Server .......................................................................................58
Adding Media Share Folders .................................................................58
Connecting DMAs to the Media Server ...................................................58
Printer Server......................................................................................60
Page 6

6
Windows XP SP2.................................................................................60
Windows Vista....................................................................................61
Chapter 6: Using the N5200......................................................... 64
Overview.............................................................................................64
Login Page...........................................................................................64
Using WebDisk ....................................................................................64
Mapping a Client PC to the N5200 .......................................................65
Windows ........................................................................................... 65
Apple OS X........................................................................................65
File Backup..........................................................................................66
Nsync ............................................................................................... 66
Adding an Nsync Task................................................................................66
Setting Up an Nsync Target on an Nsync Device.............................................67
Setting Up an Nsync Target on Another Device ..............................................67
Designating N5200 as an Nsync Target.........................................................67
Thecus Backup Utility..........................................................................67
Windows XP Data Backup ....................................................................69
Apple OS X Backup Utilities..................................................................69
Chapter 7: Tips and Tricks........................................................... 70
USB and eSATA Storage Expansion......................................................70
Adding a Spare Disk ............................................................................70
Target USB ..........................................................................................70
Remote Administration........................................................................71
Part I - Setup a DynDNS Account.......................................................... 71
Part II - Enable DDNS on the Router .....................................................71
Part III - Setting up Virtual Servers (HTTPS) ..........................................71
Firewall Software Configuration..........................................................72
Replacing Damaged Hard Drives .........................................................72
Hard Drive Damage ............................................................................72
Replacing a Hard Drive........................................................................ 72
RAID Auto-Rebuild.............................................................................. 72
Chapter 8: Troubleshooting......................................................... 73
Forgot My Password............................................................................73
Forgot My Network IP Address............................................................73
Resetting NAS IP Address and Admin Password..................................73
Can't Map a Network Drive in Windows XP..........................................73
Restoring Factory Defaults..................................................................74
Problems with Time and Date Settings................................................74
Appendix A: Product Specifications ............................................. 75
Hardware Specifications......................................................................75
Software Specifications.......................................................................75
Appendix B: Customer Support.................................................... 77
Appendix C: RAID Basics ............................................................. 78
Overview.............................................................................................78
Benefits...............................................................................................78
Improved Performance........................................................................ 78
Data Security.....................................................................................78
RAID Levels.........................................................................................78
RAID 0..............................................................................................78
RAID 1..............................................................................................79
RAID 5..............................................................................................79
RAID 6..............................................................................................79
RAID 10............................................................................................79
JBOD................................................................................................79
Stripe Size...........................................................................................79
Disk Usage ..........................................................................................80
Appendix D: Active Directory Basics............................................81
Page 7

7
Overview.............................................................................................81
What is Active Directory? ....................................................................81
ADS Benefits........................................................................................81
Appendix E: UPS Compatibility List.............................................. 82
Appendix F: Licensing Information..............................................85
Overview.............................................................................................85
Source Code Availability......................................................................85
CGIC License Terms.................................................................................
GNU General Public License.................................................................86
Page 8

8
Chapter 1: Introduction
Overview
Thank you for choosing the Thecus N5200 IP Storage Server. The Thecus N5200
is an easy-to-use storage server that allows a dedicated approach to storing and
distributing data on a network. Data reliability is ensured with RAID features that
provide data security and recovery—over one Terabyte of storage is available
using RAID 5 and RAID 6. Gigabit Ethernet ports enhance network efficiency,
allowing the N5200 to take over file management functions, increase application
and data sharing and provide faster data response. The N5200 offers data
mobility with a disk roaming feature that lets you hot swap w o rking hard drives
for use in another N5200, securing the continuity of data in the event of hardware
failure. The N5200 allows data consolidation and sharing between Windows
(SMB/CIFS), UNIX/Linux, and Apple OS X environments. The N5200’s userfriendly GUI supports multiple languages.
Product Highlights
File Server
First and foremost, the N5200 allows you to store and share files over an IP
network. With a Network Attached Storage (NAS) device, you can centralize your
files and share them easily over your network. With the easy-to-use web-based
interface, users on your network can access these files in a snap.
To learn about the Web User Interface, go to Chapter 6: Using the N5200 >
Using WebDisk.
FTP Server
With the built-in FTP Server, friends, clients, and customers can upload and
download files to your N5200 over the Internet with their favorite FTP programs.
You can create user accounts so that only authorized users have access.
To set up the FTP Server, refer to Chapter 5: Additional Feature Setup > FTP
Server.
Backup Server
Don’t leave precious data to chance. With advanced backup capabilities, you can
easily upload mission critical files to the N5200, and even automate your backup
tasks for true peace-of-mind.
To find out how to backup your files with the N5200, refer to Chapter 6: Using
the N5200 > File Backup.
Printer Server
With the N5200’s Printer Server, you can easily share an IPP printer with other
PCs connected to your network.
To set up the Printer Server, refer to Chapter 5: Additional Feature Setup >
Printer Server.
Superior Power Management
N5200 supports schedule power on/off. With this feature, administrator can set at
what time to turn on or off the system. This feature is a big plus for people who
Page 9

9
want to conserve energy. Wake-On-LAN enables administrator to remotely turn
on the system without even leaving their own seat.
To schedule system on and off, refer to Chapter 4: System Management >
System Settings > Reboot and Shutdown System > Scheduled Power
On/Off.
Package Contents
Your N5200 package should contain the following items:
QIG
CD-Title
Ethernet Cable
USB 2.0 Cable Accessory
Screw Kit
Please check to see if your package is complete. If you find that some items are
missing, contact your dealer.
Page 10

Front Panel
The Thecus N5200’s front panel has the device’s controls, indicators, and hard
disk trays:
Front Panel
Item Description
1.DOM LED • Solid orange: system is being upgraded or system startup;
data currently inaccessible
2.WAN LED
• Solid green: network link
• Blinking green: network activity
3.LAN LED
• Solid green: network link
• Blinking green: network activi ty
4.USB Copy LED • Solid blue: files are bein g copied from a USB storage device
5.Busy LED • Blinking red: Raid volume in degrade mode or demage
6.USB Port
• USB 2.0 port for compatible USB devices, such as USB disks,
USB printers, and USB wireless dongles*
Note: For supported USB wireless dongles, please contact
http://esupport.thecus.com/support
7.Power Button • Power on/off N5200
• Solid blue: Device is powered on
• Blinking blue: eSATA hard disk is connected and active
8.Reset Button
• Resets the N5200
• Press for five seconds during boot process to reset IP address
and admin password
9.HDD Trays • Five 3.5” SATA HDD trays
• Locks are provided for added security
10.LCD Display • Displays current system status and warning messages
• Displays hostname, WAN/LAN IP address, RAID status, and
current time
11.Up Button ▲
• Push to scroll up when using the LCD displ ay
12.Down Button ▼
• Push to scroll down when using the LCD display
13.Enter Button ↵
• Push to confirm information entered into the LCD display
14.Escape Button
ESC
• Push to leave the current LCD menu
10
Page 11

Hard Disk Trays
Each of the N5200’s hard disk trays has a lock, a latch, and two LED indicators:
Hard Disk Trays
Item Description
Lock • Use the lock to physically secure the hard disk to the unit
Latch • Use to open and remove or close and secure the tray
HDD Power LED • Solid blue: hard disk is powered on
HDD Access/Error
LED
• Blinking green: system is accessing data on the hard disk
Rear Panel (N5200B)
The Thecus N5200B’s rear panel features ports and connectors.
N5200B Back Panel
Item Description
1.eSATA Port • eSATA port for hi gh-speed storage expansion
2.USB Port • USB 2.0 port for compatible USB devices, such as USB disks,
and USB printers
3.USB Port(target) • For connecting the N5200 to your PC as a mass storage device
4.LAN Port • LAN port that can be used for connection sharing
5.WAN Port • WAN port for connecting to an Ethernet network through a
switch or router
6.Power Switch • Switch for power supply
7.Power Connector • Connect the included power cords to these connectors
8.System Fan • System fan that exhausts heat from the unit
9.Serial Port • This port is for external UPS device
11
Page 12
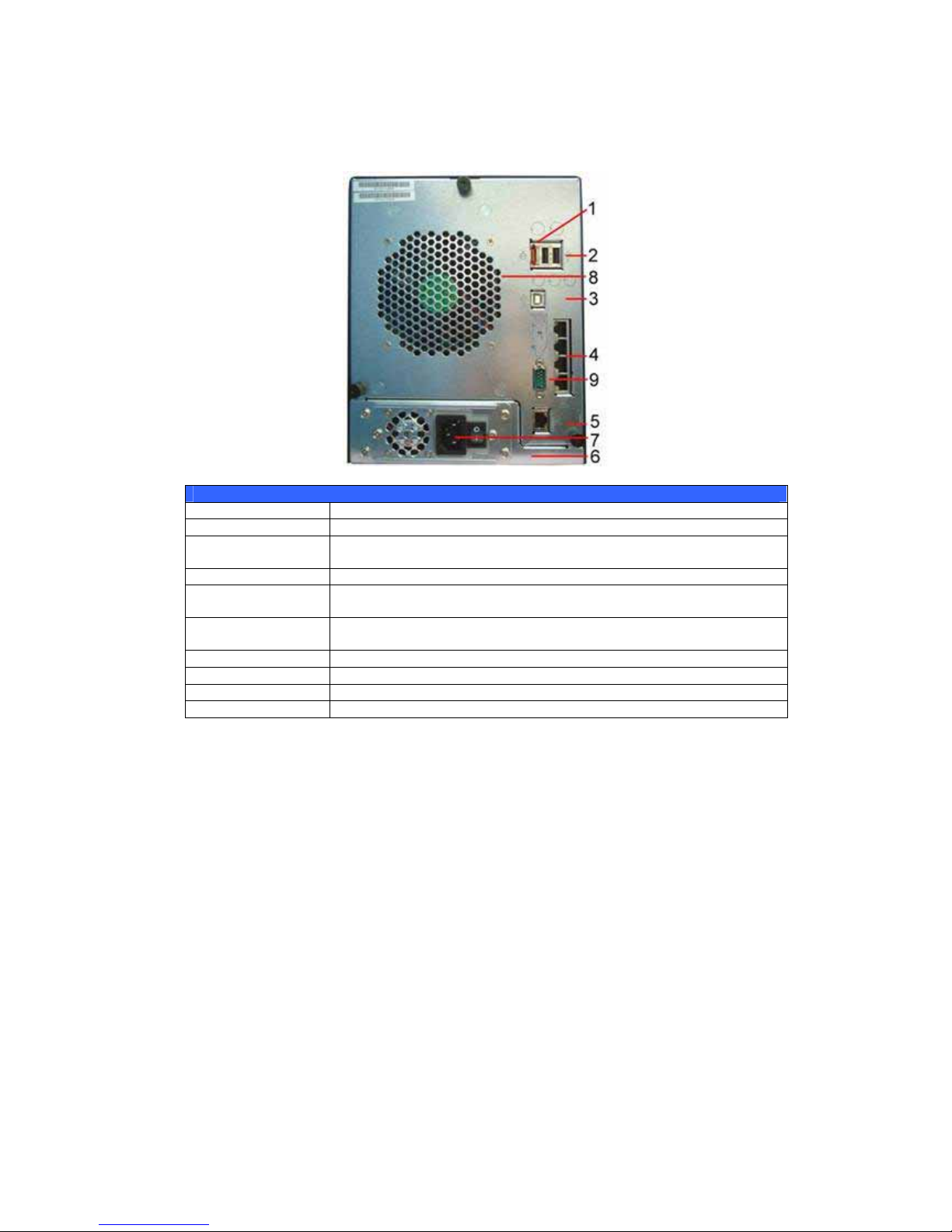
Rear Panel (N5200BR)
The Thecus N5200BR’s rear panel features ports and connectors.
N5200BR Back Panel
Item Description
1.eSATA Port • eSATA port for hi gh-speed storage expansion
2.USB Port • USB 2.0 port for compatible USB devices, such as USB disks,
and USB printers
3.USB Port(target) • For connecting the N5200 to your PC as a mass storage device
4.4-port Gigabit
Switch
• This 4 port switch can be used for connection sharing
5.WAN Port • WAN port for connecting to an Ethernet network through a
switch or router
6.Power Switch • Switch for power supply
7.Power Connector • Connect the included power cords to these connectors
8.System Fan • System fan that exhausts heat from the unit
9.Serial Port • This port is for external UPS device
12
Page 13
Chapter 2: Hardware Installation
Overview
Your N5200 is designed for easy installation. To help you get started, the
following chapter will help you quickly get your N5200 up and running. Please
read it carefully to prevent damaging your unit during installation.
Before You Begin
Before you begin, be sure to take the following precautions:
1. Read and understand the Safety Warnings outlined in the beginning of
the manual.
2. If possible, wear an anti-static wrist strap during installation to prevent
static discharge from damaging the sensitive electronic components on the
N5200.
3. Be careful not to use magnetized screwdrivers around the N5200’s
electronic components.
Hard Disk Installation
The N5200 supports five standard 3.5” Serial ATA (SATA) hard disks. To install a
hard disk into the N5200, follow the steps below:
1. Remove a hard disk tray from the N5200.
2. Slide the new SATA hard disk into the tray and fasten the screws.
3. Insert the hard disk and tray back into the N5200 until it snaps into place
and lock it with a key if desired.
4. The LED blinks green when the hard disk is accessed.
NOTE
If your HDD was part of a RAID 1 or RAID 5 array previously, it
automatically rebuilds. If you replace all the drives with higher capacity
drives, you will need to go to Administrator login and format the drives.
13
Page 14

Cable Connections
To connect the N5200 to your network, follow the steps below:
1. Connect an Ethernet cable from your
network to the WAN port on the back
panel of the N5200.
2. Connect the provided power cord
into the universal
power socket on
the back panel. Plug the other end of
the cord into a surge protector
socket. Press the power supply
switch to turn on the po
wer supply.
3. Press the power button on the Front
Panel to boot up the N5200.
14
Page 15

Checking System Status
After making connections on the N5200 and powering up, check whether the
system status is normal or has trouble by observing indicators on the front panel
and hard disk trays.
System Status Normal
The system status is normal if:
1. The WAN and LAN LEDs glow
green (assuming both are
connected).
2. The Power LED on the Front
Panel glows blue.
).
3. The HDD Power LED on each
HDD tray glows blue (assuming
all disks are installed
4. The default IP address of the
WAN port is 192.168.1.100.
System Trouble
The system has trouble if:
1. System Busy LED glows red.
If the system has trouble, please
refer to Chapter 8:
Troubleshooting.
WARNING
There are no user serviceable parts inside the N5200.
your distributor for service.
Please contact
15
Page 16

Chapter 3: First Time Setup
Overview
Once the hardware is installed, physically connected to your network, and
powered on, you can configure the N5200 so that it is accessible to your network
users. There are two ways to set up your N5200: using the Thecus Setup
Wizard or the LCD display. Follow the steps below for initial software setup.
Thecus Setup Wizard
The handy Thecus Setup Wizard makes configuring N5200 a snap. To configure
the N5200 using the Setup Wizard, perform the following steps:
1. Insert the installation CD into your CD-ROM drive (th e host PC must be
connected to the network).
2. The Setup Wizard should launch automatically. If not, please browse your
CD-ROM drive and double click on Setup.exe.
NOTE
For MAC OS X users, double click on Thecus Setup
Wizard 1.1.6.dmg
3. The Setup Wizard will start and automatically detect all Thecus storage
devices on your network. If none are found, please check your connection
and refer to Chapter 8: Troubleshooting for assistance.
4. Select the N5200 that you like to configure.
5. Login with the administrator account and password. The default account
and password are both “admin”.
16
Page 17

6. Name your N5200 and configure the network IP address. If your switch or
router is configured as a DHCP Server, configuring the N5200 to
automatically obtain an IP address is recommended. You may also use a
static IP address and enter the DNS Server address manually.
7. Change the default administrator password.
17
Page 18

8. Finished! Access the N5200 Web Administrator Interface by pressing the
Start Browser button. You can also configure another N5200 at this point
by clicking the Setup Other Device button. Press Exit to exit the wizard.
The Thecus Setup Wizard is designed for installati on on systems
running Windows XP/2000 or Mac OSX or later. Users with other
operating systems will need to install the Thecus Setup Wizard on a
host machine with one of these operating systems befor e using the
unit.
NOTE
LCD Operation
The N5200 is equipped with an LCD on the front for easy status display and setup.
There are four buttons on the front panel to control the LCD functions.
LCD Controls
Use the Up (▲), Down (▼), Enter (↵) and Escape (ESC) keys to select various
configuration settings and menu options for N5200 configuration.
The following table illustrates the keys on the front control panel:
LCD Controls
Icon Function Description
▲
Up Button Select the previous configuration settings option.
▼
Down Button Select the next configuration settings option.
↵
Enter Enter the selected menu option, sub-menu, or parameter setting.
ESC Escape Escape and return to the previous menu.
There are two modes of operation for the LCD: Display Mode and Management
Mode.
Display Mode
During normal operation, the LCD will be in Display Mode.
Display Mode
Item Description
Host Name Current host name of the system.
WAN Current WAN IP setting.
LAN Current LAN IP setting.
Link Aggregation Current Link Aggregation status (N5200B only)
Disk Info Current status of disk slot has been installed
18
Page 19

RAID Current RAID status.
System Fan Current system fan status.
CPU Fan Current CPU fan status
2006/06/16 12:00 Current system time.
The N5200 will rotate these messages every one-two seconds on the LCD display.
USB Copy
The USB Copy function enables you to copy files stored on USB devices such as
USB disks and digital cameras to the N5200 with a press of a button. To use USB
copy, follow the steps below:
1. Plug your USB device into an available USB port on the Front Panel.
2. In Display Mode, press the Down Button (▼).
3. The LCD will display “USB Copy?”
4. Press Enter (
↵) and the N5200 will start copying USB disks connected to
the front USB port.
5. All of data will be copied into system folder named “USBcopy”.
Management Mode
During setup and configuration, the LCD will be in Management Mode.
To enter into Management Mode, press Enter (
↵) and an “Enter Password”
prompt will show on the LCD.
At this time, the administrator has to enter the correct LCD password. System will
check whether the correct LCD password has been entered. The default LCD
password is “0000”. If correct password is entered, you will enter into the
Management Mode menu.
Management Mode
Item Description
WAN Setting IP address and netmask of your WAN ports.
LAN Setting IP address and netmask of your LAN ports.
Link Agg. Setting Select Load Balance or Failover. (N5200B only)
Change Admin Passwd Change administrator’s password for LCD operation.
Reset to Default Reset system to factory defaults.
Exit Exit Management Mode and return to Display Mode.
NOTE
You can also change your LCD password using the Web Administration
Interface by navigating to System > Administrator Password. For
more on the Web Administration Interface, see Chapter 4: System
Management.
Typical Setup Procedure
From the Web Administration Interface, you can begin to setup your N5200 for
use on your network. Setting up the N5200 typically follows the five steps
outlined below.
For more on how to use the Web Administration Interface, see Chapter 4:
System Management > Web Administration Interface.
19
Page 20

20
Step 1: Network Setup
From the Web Administration Interface, you can configure the network settings of
the N5200 for your network. You can access the Network menu from the menu
bar.
For details on how to configure your network settings, refer to Chapter 4:
System Management > Network Management.
Step 2: RAID Creation
Next, administrators can configure their preferred RAID setting and build their
RAID volume. You can access RAID settings from the menu bar of the Web
Administration Interface by navigating to Storage > RAID.
For more information on configuring RAID, see Chapter 4: System
Management > RAID Configuration.
Don’t know which RAID level to use? Find out more about the different RAID
levels from Appendix C: RAID Basics.
Step 3: Create Local Users or Setup Authentication
Once the RAID is ready, you can begin to create local users for the N5200, or
choose to setup authentication protocols such as Active Directory (AD).
For more on managing users, go to Chapter 4: System Management > User
and Group Management.
For more information on configuring Active Directory, see Chapter 4: System
Management > User and Group Management > ADS/NT Confi guration.
For information about the benefits of Active Directory, see Appendix D: Active
Directory Basics.
Step 4: Create Folders and Set Up ACLs
Once users are introduced into your network, you can begin to create various
folders on the N5200 and control user access to each using Folder Access Control
Lists.
More information on managing folders, see Chapter 4: System Management >
Folder Management.
To find out about configuring Folder Access Control Lists, see Chapter 4: System
Management > Folder Management > Folder Access Control List (ACL).
Step 5: Start Services
Finally, you can start to setup the different services of the N5200 for the users on
your network. You can find out more about each of these services by clicking
below:
SMB/CIFS
Apple File Protocol (AFP)
Network File System (NFS)
Page 21

21
File Transfer Protocol (FTP)
Media Server
Printer Server
Page 22

Chapter 4: System Management
Overview
The N5200 provides an easily accessible Web Administration Interface. With it,
you can configure and monitor the N5200 anywhere on the network.
Web Administration Interface
Make sure your network is connected to the Internet. To access the N5200 Web
Administration Interface:
1. Type the N5200’s IP address into your browser. (Default IP address is
http://192.168.1.100)
Your computer’s network IP address must be on the same subnet a s
the N5200. If the N5200 has default IP address of 192.168.1.100, your
managing PC IP address must be 192.168.1.x, where x is a number
between 1 and 254, but not 100.
NOTE
2. Login to the system using the administrator user name and password. The
factory defaults are:
User Name: admin
Password: admin
If you changed your password in the setup wizard, use the new password.
Once you are logged in as an administrator, you will see the Web
Administration Interface. From here, you can configure and monitor virtually
every aspect of the N5200 from anywhere on the network.
Menu Bar
The Menu Bar is where you will find all of the information screens and system
settings of the N5200. The various settings are placed in the following groups on
the menu bar:
Menu Bar
Item Description
Status Current system status of the N5200.
Storage Information and settings for storage devices installed into the
22
Page 23

N5200.
Network Information and settings for network connections, as well as
various services of the N5200.
Accounts Allows configuration of users and groups.
System Various N5200 system settings and information.
Language Choose your preferred language here.
Moving your cursor over any of these items will display the dropdown menu
selections for each group.
In the following sections, you will find detailed explanations of each function, and
how to configure your N5200.
Language Selection
The N5200 supports multiple languages,
including:
• English
• French
• German
• Italian
• Tradit iona l Ch in ese
• Simplified Chinese
• Japanese
• Korean
• Spanish
On the menu bar, click Language and the
Change Language screen appears. This
screen allows you to select preferred
language for the N5200. Press Apply to
confirm your selection.
23
Page 24

Status Menu
The Status Menu on the menu bar allows you to see various aspects of the
N5200. From here, you can discover the status of the N5200, and even find out
other details like firmware version and up time.
Product Information
Once you login, you will first see the basic
Product Information screen providing
Manufacturer, Product No., Firmware
Version, and Up Time information.
Product Information
Item Description
Manufacturer Displays the name of the system manufacturer.
Product No. Shows the model number of the system.
Firmware version Shows the current firmware version.
Up time Displays the total run time of the system.
To access this screen again, navigate to Status > About.
System/Service Status
From the Status menu, choose the System
item, and the System Status and Service
Status screens appear. These screens
provide basic system and service status
information.
System Status
Item Description
CPU Loading (%) Displays current CPU workload of the N5200.
CPU Fan Speed Displays current CPU fan status.
System Fan Speed Displays the current status of the system fan.
Up Time Shows how long the system has been running.
24
Page 25

Service Status
Item Description
AFP Status The status of the Apple Filing Protocol server.
NFS Status The status of the Network File Service Server.
SMB/CIFS Status The status of the SMB/CIFS server.
FTP Status The status of the FTP server.
Media Server The status of the Media Server
Nsync Status The status of the Nsync server.
UPnP Status The status of the UPnP service.
System Information
From Status menu, choose the Info
item, and the System Information
screen appears. You can change the
system information that appears on the
Login page by entering the new
information here and pressing Apply to
confirm.
System Information
Item Description
System Description Shows the system description that would also appear on the
Login page.
Printer Status
From the Status menu, choose the
Printer item, and the Printer
Information screen appears. This
screen provides the following
information about the USB printer
connected to the USB port.
25
Page 26

Printer Status
Item Description
Manufacturer Displays the name of the USB printer manufacturer.
Model Displays the model of the USB printer.
Status Displays the status of the USB printer.
Remove document
from Queue
Click to remove all documents from printer queue
Restart Printer service Click to restart printer service
If a corrupt print job is sent to a printer, printing may suddenly fail. If your print
jobs seem to be locked up, pressing the Remove All Documents button to clear
the print queue may resolve the issue.
For information on how to set up the Printer Server, refer to Chapter 5:
Additional Feature Setup > Printer Server.
UPS Settings
The N5200 can also support various
uninterruptible power supply units,
providing extra data security and
accessibility in the case of a power failure.
From the Status menu, choose the UPS
item and the UPS Setting screen appears.
Make any changes you wish, and press
Apply to confirm changes. See the
following table for a detailed description of
each item.
UPS Settings
Item Description
UPS Monitoring Enable or disable UPS monitoring.
Manufacturer Choose the UPS manufacturer and model number
from the dropdowns.
Battery Status Current status of the UPS battery
Power Current status of the power being supplied to the
UPS
Seconds between power failure and
first notification
Delay between power failure and first notification
in seconds.
Seconds between subsequent power
failure notifications
Delay between subsequent notifications in
seconds.
Shutdown the system when the
battery charge is less than
Amount of UPS battery remaining before system
should auto-shutdown.
Apply Press Apply to save your changes.
For a list of supported UPS units, see Appendix E: UPS Compatibility List.
26
Page 27

Wake-Up On Lan (WOL)
The N5200 has the ability to be awoken
from sleep mode via WAN port.
From the Status menu, choose the
WOL item, and the Wake-up On Lan
Configuration screen appears. From
here, you can Enable or Disable.
Wake-up On Lan Configuration
Item Description
WOL Servic Enable or Disable WOL service
Apply Click Apply to save changes.
27
Page 28
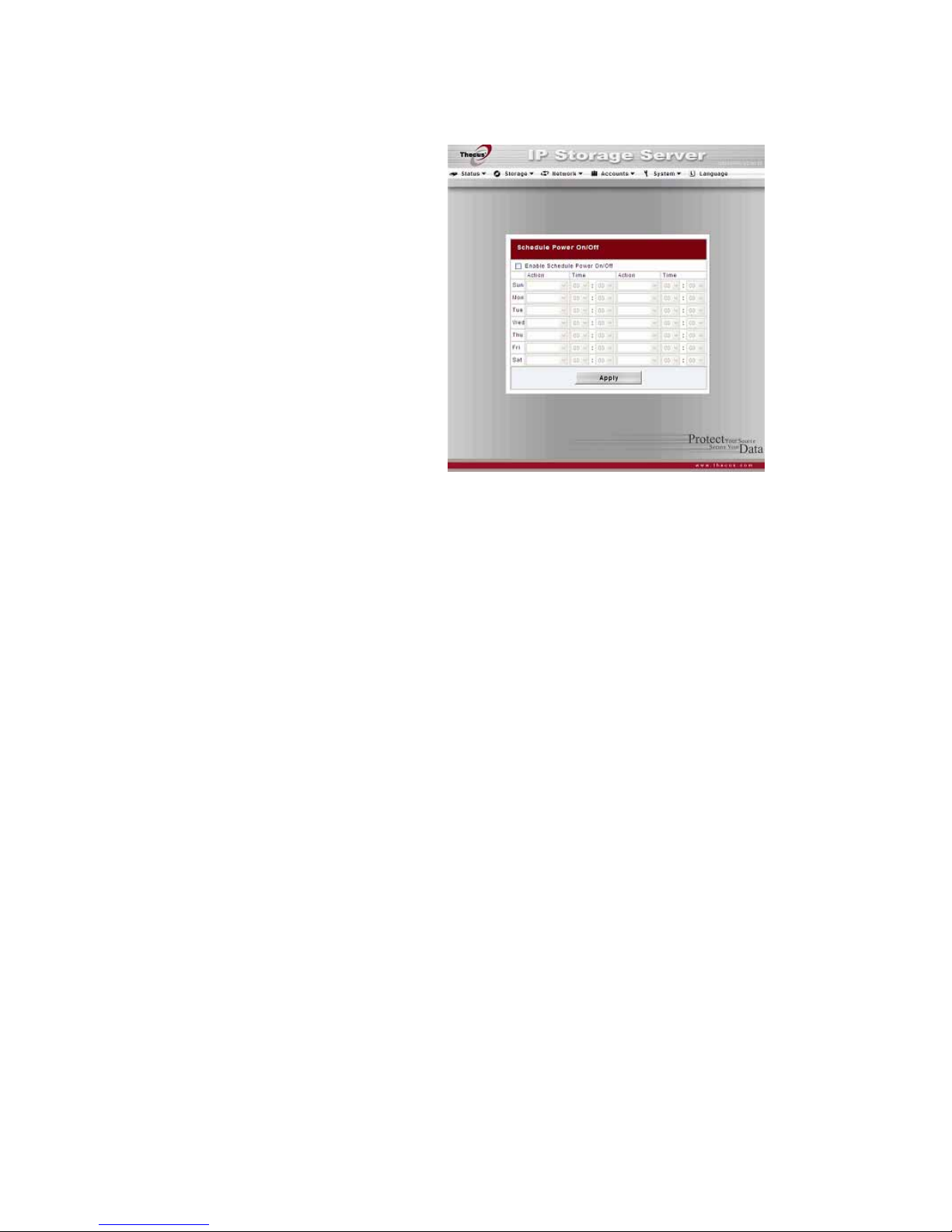
Power Management
Using the N5200’s Power
Management, you can save energy
and money by scheduling the
N5200 to turn itself on and off
during certain times of the day.
28
From the Status menu, choose the
Power Mgmt item and the
Schedule Power On/Off screen
appears.
To designate a schedule for the
N5200 to turn on and off, first
enable the feature by checking the
Enable Schedule Power On/Off
checkbox.
Then, simply choose an on and off
time for each day of the week that
you would like to designate a schedule by using the various dropdowns.
Finally, click Apply to save your changes.
Example - Monday: On: 8:00; Off: 16:00
System will turn on at 8:00 AM on Monday, and off at 16:00 on Monday. System
will turn on for the rest of the week.
If you choose an on time, but do not assign an off time, the system will turn on
and remain on until a scheduled off time is reached, or if the unit is shutdown
manually.
Example - Monday: On: 8:00
System will turn on at 8:00 AM on Monday, and will not shut down unless
powered down manually.
You may also choose two on times or two off times on a particular day, and the
system will act accordingly.
Example - Monday: Off: 8:00; Off: 16:00
System will turn off at 8:00 AM on Monday. System will turn off at 16:00 PM on
Monday, if it was on. If the system was already off at 16:00 PM on Monday,
system will stay off.
Page 29

Storage Management
The Storage Menu displays the status of storage devices installed in the N5200,
and includes storage configuration options such as RAID and disk settings, folder
configuration, and Nsync settings.
Disks Information
From the Storage menu, choose the Disks
item and the Disks Information screen
appears. From here, you can see various
items about installed SATA hard disks. Blank
lines indicate that a SATA hard disk is not
currently installed in that particular disk slot.
Disks Information
Item Description
Disk No. Indicates disk location.
Capacity Shows the SATA hard disk capacity.
Model Displays the SATA hard disk model name.
Firmware Shows the SATA hard disk firmware version.
Status Indicates the status of the disk. Can read OK, Warning, or
Failed.
Total Capacity Shows the total SATA hard disk capacity.
Disk Power
Management
The administrator can set the disk to power down after a period
of inactivity.
NOTE
When the Status shows Warning, it usually means there a re bad sectors
on the hard disk. It is shown only as a precaution and you should
consider changing the drives.
S.M.A.R.T. Information
On the Disks Information screen, the status
of each disk will be displayed in the Status
column. Clicking on an OK or Warning link
will display the S.M.A.R.T Information
window for that particular disk.
29
Page 30
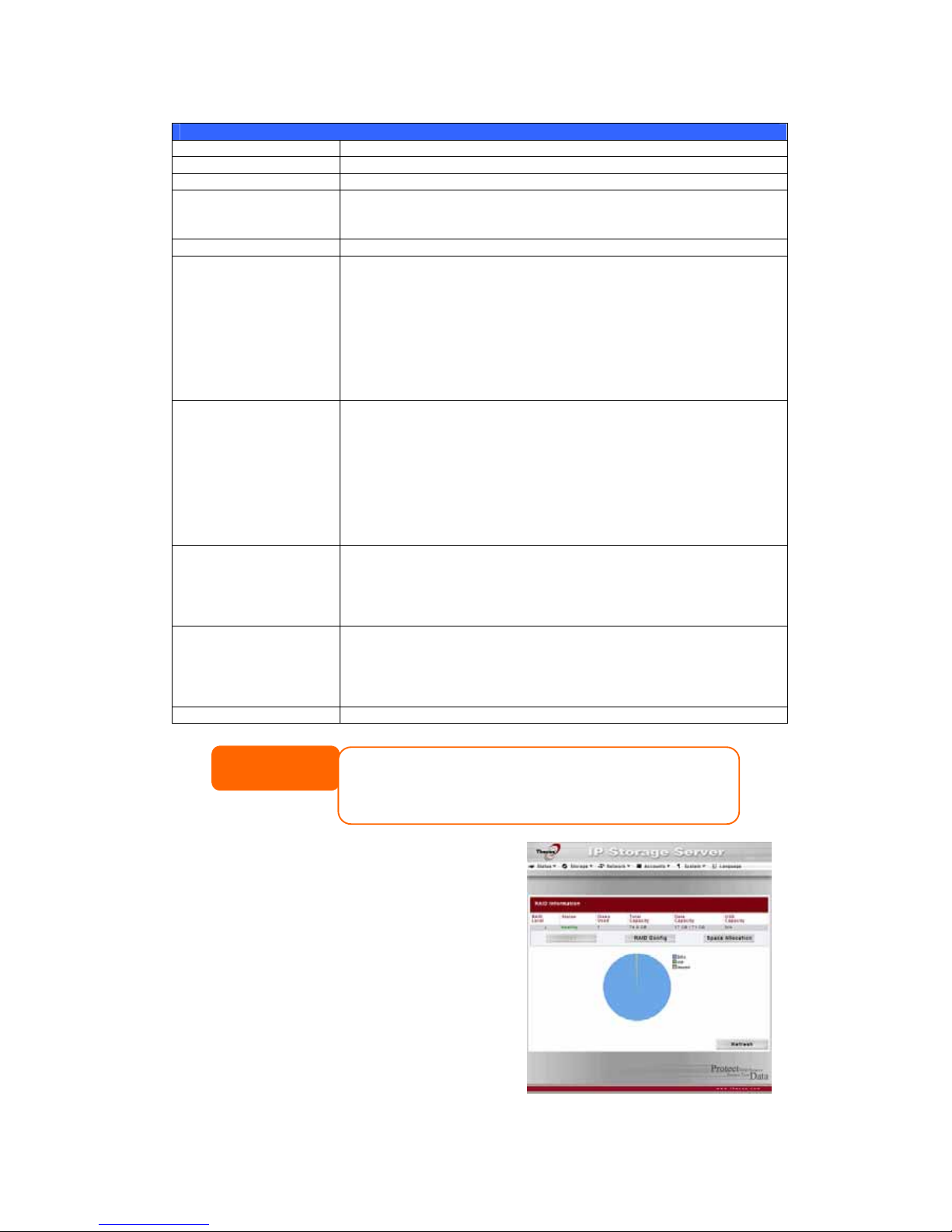
S.M.A.R.T. Information
Item Description
Tray Number Tray the hard disk is installed in.
Model Model name of the installed hard disk.
Power ON Hours Count of hours in power-on state. The raw value of this attribute
shows total count of hours (or minutes, or seconds, depending
on manufacturer) in power-on state.
Temperature Celsius The current temperature of the hard disk in degrees Celsius
Reallocated Sector
Count
Count of reallocated sectors. When the hard drive finds a
read/write/verification error, it marks this sector as "reallocated"
and transfers data to a special reserved area (spare area).
This process is also known as remapping and "reallocated"
sectors are called remaps. This is why, on a modern hard disks,
you can not see "bad blocks" while testing the surface - all bad
blocks are hidden in reallocated sectors. However, the more
sectors that are reallocated, the more a decrease (up to 10% or
more) can be noticed in disk read/write speeds.
Current Pending
Sector
Current count of unstable sectors (waiting for remapping). The
raw value of this attribute indicates the total number of sectors
waiting for remapping. Later, when some of these sectors are
read successfully, the value is decreased. If errors still occur
when reading sectors, the hard drive will try to restore the data,
transfer it to the reserved disk area (spare area), and mark this
sector as remapped. If this attribute value remains at zero, it
indicates that the quality of the corresponding surface area is
low.
Raw Read Error Rate This attribute value depends on read errors and disk surface
condition, and indicates the rate of hardware read errors that
occurred when reading data from a disk surface. Lower values
indicate that there is a problem with either the disk surface or
the read/write heads.
Seek Error Rate Rate of seek errors by the magnetic heads. If there is a failure
in the mechanical positioning system, servo damage or a
thermal widening of the hard disk, seek errors arise. More seek
errors indicates a worsening condition of a disk surface and the
disk mechanical subsystem.
Back Press Back to go back to the Disks Information screen.
NOTE
If the Reallocated Sector Count or Current Pending Sector of a hard
disk drive is not zero, the status of the disk will show “Warning”. This
warning is only used to alert the system administrator that there are
bad sectors on the disk, and they should replace those disks as soon as
possible.
RAID Information
From the Storage menu, choose the RAID
item and the RAID List screen appears.
This screen lists the RAID volumes currently
residing on the N5200. From this screen, you
can get information about the status of your
RAID volumes, as well as the capacities
allocated for data and USB target. There is
also a graph which represents how the RAID
volume is currently allocated.
To configure your RAID settings, press the
RAID Config button to go to the RAID
Configuration screen.
30
Page 31

RAID Information
Item Description
RAID Level Shows the current RAID configuration.
Status Indicates status of the RAID. Can read either Healthy,
Degraded, or Damaged.
Disks Used Hard disks used to form the current RAID volume.
Total Capacity Total capacity of the current RAID.
Data Capacity Indicates the used capacity and total capacity used by user
data.
USB Capacity Indicates the capacity allocated to USB target mode.
168BRAID Config Press this to configure RAID volumes.
Space Allocation Press this to adjust the space allocated for data and USB target
mode. .
RAID Configuration
On the RAID List screen, press the RAID
Config button to go to the RAID
Configuration screen. In addition to RAID
disk information and status, this screen lets
you make RAID configuration settings.
For more information on RAID, see Appendix
C: RAID Basics.
RAID Level
You can set the storage volume as JBOD, RAID 0, RAID 1, RAID 5, RAID 6 or
RAID 10. RAID configuration is usually required only when you first set up the
device. A brief description of each RAID setting follows:
RAID Levels
Level Description
JBOD The storage volume is a single HDD with no RAID support. JBOD
requires a minimum of 1 disk.
RAID 0 Provides data striping but no redundancy. Improves
performance but not data safety. RAID 0 requires a minimum of
2 disks.
RAID 1 Offers disk mirroring. Provides twice the read rate of single
disks, but same write rate. RAID 1 requires a minimum of 2
disks.
RAID 5 Data striping and stripe error correction information provided.
RAID 5 requires a minimum of 3 disks. RAID 5 can sustain one
failed disk.
RAID 6 Two independent parity computations must be used in order to
provide protection against double disk failure. Two different
algorithms are employed to achieve this purpose. RAID 6
requires a minimum of 4 disks. RAID 6 can sustain two failed
disks.
RAID 10 RAID 10 has high reliability and high performance. RAID 10 is
implemented as a striped array whose segments are RAID 1
arrays. It has the fault tolerance of RAID 1 and the performance
of RAID 0. RAID 10 requires 4 disks. RAID 10 can sustain two
31
Page 32

failed disks.
WARNING
If the administrator improperly removes a hard disk that should not be
removed when RAID status is Degraded, all data will be lost.
RAID Settings
Using RAID Settings, you can select stripe size, choose which disks are RAID
disks or the Spare Disk, as well as enter a name for each disk.
RAID Settings
Item Description
RAID Check the boxes of the hard drives you wish to add to the
storage volume.
Disk No. Number assigned to the instal led hard disks.
Capacity (MB) Capacity of the installed hard disks.
Model Model number of the installed hard disks.
Status Status of the installed hard disks.
Member If this is checked, current hard disk is a part of a RAID volume.
Spare If this is checked, current hard disk is designated as a spare for
a RAID volume.
Stripe Size This sets the stripe size to maximize performance of sequential
files in a storage volume. Keep the 64K setting unless you
require a special file storage layout in the storage volume. A
larger stripe size is better for large files.
Used Percentage The perc entage of the RAID volume that will be used to store
data.
Apply Press this button to configure a file system and create the RAID
storage volume.
Remove Click to remove the RAID volume. All user data, iSCSI, and
Target USB data will be removed.
Back Press this button to exit without saving changes.
Expand Press this button to configure a file system and create the RAID
storage volume.
Migration Press this button to migrate RAID level.
Creating a RAID
To create a RAID volume, follow the steps below:
1. On the RAID List screen, click New.
2. On the RAID Configuration screen, set the RAID storage space as JBOD,
RAID 0, RAID 1, RAID 5, RAID 6, or RAID 10 — see Appendix C:
RAID Basics for a detailed description of each.
3. Tick the checkboxes under the “member” heading of the hard disks you
wish to use to create a RAID.
4. Specify a stripe size — 64K is the default setting.
5. Specify the percentage allocated for user data. The remaining space will
be made available for target USB.
6. Press Apply to build the RAID storage volume.
32
Page 33
NOTE
Building a RAID storage space may take time, dep
hard drives and RAID mode.
ending on the size of
WARNING
Creating RAID destroys all data in the current RAID
volume. The data is
unrecoverable.
With a RAID 1, RAID 5, RAID 6, or RAID 10 volume, you can also add a spare
disk after the RAID is created. See Chapter 7: Tips and Tricks > Adding a
Spare Disk for details.
Expanding a RAID
To expand a RAID 1, RAID 5, RAID 6, or RAID 10 volume, follow the steps below:
1. Replace one of the hard drives in the RAID volume and allow it to
automatically rebuild.
2. Once rebuilt, you can continue to replace any remaining disks in the RAID
array.
3. When you are done replacing hard drives, log on to Web Management.
Navigate to Storage > RAID to open the RAID List screen.
4. On the RAID List screen, select the RAID volume by clicking on its radio
button, and click RAID Config to open the RAID Configuration screen.
5. On the RAID Configuration screen, click Expand.
33
Page 34

Migrating a RAID
Once a RAID volume has been created, you
may want to move it to other physical drives
or change the RAID array all together. To
migrate a RAID 0, RAID 1, or RAID 5
volume, follow the steps
below:
1. From the RAID Configuration screen,
click Migrate RAID.
2. A list of possible RAID migration
configurations will be listed. Select
the desired migration scheme and
click OK.
3. The system will begin migrating the RAID volume.
Migrating a RAID volume could take several hours to complete
NOTE
Below is a table listing of possible RAID migration schemes:
To
From
RAID 0 RAID 5
RAID 0
[RAID 0] HDDx2 to [RAID 0] HDDx3
[RAID 0] HDDx2 to [RAID 0] HDDx4
[RAID 0] HDDx2 to [RAID 0] HDDx5
[RAID 0] HDDx3 to [RAID 0] HDDx4
[RAID 0] HDDx3 to [RAID 0] HDDx5
[RAID 0] HDDx4 to [RAID 0] HDDx5
[RAID 0] HDDx2 to [RAID 5] HDDx3
[RAID 0] HDDx2 to [RAID 5] HDDx4
[RAID 0] HDDx2 to [RAID 5] HDDx5
[RAID 0] HDDx3 to [RAID 5] HDDx4
[RAID 0] HDDx3 to [RAID 5] HDDx5
[RAID 0] HDDx4 to [RAID 5] HDDx5
RAID 1
[RAID 1] HDDx2 to [RAID 0] HDDx2
[RAID 1] HDDx2 to [RAID 0] HDDx3
[RAID 1] HDDx2 to [RAID 0] HDDx4
[RAID 1] HDDx2 to [RAID 0] HDDx5
[RAID 1] HDDx2 to [RAID 5] HDDx3
[RAID 1] HDDx2 to [RAID 5] HDDx4
[RAID 1] HDDx2 to [RAID 5] HDDx5
RAID 5 X
[RAID 5] HDDx3 to [RAID 5] HDDx4
[RAID 5] HDDx3 to [RAID 5] HDDx5
[RAID 5] HDDx4 to [RAID 5] HDDx5
Deleting a RAID
To delete a RAID volume, follow the steps below:
1. On the RAID List screen, select the RAID volume by clicking on its radio
button, and click RAID Config to open the RAID Configuration screen.
2. On the RAID Configuration screen, click Remove RAID.
3. The confirmation screen appear, you will have to input “Yes” with exactly
wording case to complete “Remove RAID” operation
34
Removing RAID destroys all data in the current RAID volume. The data
is unrecoverable.
WARNING
Page 35

Space Allocation
You may specify the space allocated for Target USB volumes.
To do this, under the Storage menu, click RAID and the RAID List window
appears. Select the RAID volume you wish to reallocate by clicking on its radio
button, and click Space Allocation. The RAID Information and Volume
Allocation List windows will appear.
The Volume Allocation List displays the space allocated for Target USB volume
on the current RAID volume.
Volume Allocation List
Item Description
Modify Click this to modify the allocated space.
Del Click this to delete the allocated space.
Type Type of volume. Can be either USB or iSCSI.
Name Name assigned to the volume.
Capacity Capacity of the allocated space.
Target USB Click to allocate space to Target USB volume.
Allocating Space for Target USB Volume
To allocate space for a Target USB volume on the current RAID volume, follow
the steps below:
1. Under the Space Allocation , click
Target USB.
The Create Target USB Volume
screen appears.
Create Target USB Volume
Item Description
RAID ID ID of current RAID volume.
Unused Percentage and amount of unused space on current RAID
volume.
Allocation Percentage and amount of space allocated to Target USB
volume.
OK Click OK to save changes.
Back Click Back to exit without saving.
2. Designate the percentage that should be allocated to the Target USB
volume by selecting the appropriate percentage from the Allocation
dropdown.
3. Click OK to create the Target USB volume.
35
Page 36

Folder Management
From the Storage menu, choose Folder,
and the Folder screen appears. This screen
allows you to create and configure folders
on the N5200 volume.
Folder
Item Description
Folder name Displays the name of the folder.
Description Provides a description of the folder.
NFS Share Press NFS Share to configure which hosts on the network are
allowed to access this folder using NFS.
ACL Press ACL (Access Control List) to configure which users have
access to this folder.
Edit Press Edit to enter the Edit screen and modify the folder’s
name and description.
Del Press Del to delete the folder. A prompt appears asking to
confirm the deletion.
Add Press Add to enter the Add Folder screen.
Nsync folders will be created once the RAID is created. Nsync folder is
used by Nsync server. It will be used for files backed up by Nsync.
NOTE
Adding Folders
On the Folder screen, press the Add button
and the Add Folder screen appears. This
screen allows you to add a folder. After
entering the information, press Apply to
create new folder. Press Back to return to
the Folder screen.
36
Page 37

Add Folder
Item Description
Folder Name Enter the name of the folder.
Description Provide a description the folder.
Browseable Enable or disable users from browsing the folder contents. If
Yes is selected, then the share folder will be browseable.
Public Admit or deny public access to this folder. If Yes is selected,
then users do not need to have access permission to write to
this folder. When accessing a public folder via FTP, the behavior
is similar to anonymous FTP. Anonymous users can
upload/download a file to the folder, but they cannot delete a
file from the folder.
Share Folder Limit Enter the maximum size of the folder in Gigabytes (GB). The
folder cannot grow beyond this limit. You can enter a 0 to turn
off the share folder limit.
Apply Press Apply to create the folder.
Back Press Back to return to the Folder screen.
Folder names are limited to 60 characters. Systems running Windows
98 or earlier may not support file names longer than 15 characters.
NOTE
Editing Folders
On the Folder screen, press the Edit button and the Edit Folder screen appears.
This screen allows you to change folder information. After entering the
information, press Submit to apply the changes. Press Back to return to the
Folder screen.
Edit Folder
Item Description
Share Name Enter the name of the (Share) folder.
Comment Provide a description the folder.
Browseable Enable or disable users from browsing the folder contents. This
setting will only apply while access via SMB/CIFS and web disk.
Public Admit or deny public access to this folder.
Share Limit Enter the maximum size of the folder. The folder will not grow
beyond this limit. You can enter a 0 to turn off the share folder
limit.
Submit Press Submit to save your changes.
Back Press Back to return to the Folder screen.
Deleting Folders
To delete a folder, press the Del button from the specified folder row. The system
will confirm folder deletion. Press OK to delete the folder permanently or Cancel
to go back to the folder list.
All the data stored in the folder will be deleted once the folder is
deleted. The data will not be recoverable.
WARNING
37
Page 38

NFS Share
To allow NFS access to the share folder, enable the NFS Service, and then set up
hosts with access rights by clicking Add.
NFS Share
Item Description
Hostname Enter the name or IP address of the host
Privilege Host has either read only or writeable access to the folder.
Guest System Support There are two selections available:
• Unix / Linux System
• AIX (Allow source port > 1024)
Choose the one which best fits your needs.
IO Mapping There are three selections available:
• Guest system root account will have full access to this
share (root:root).
• Guest system root account will be mapped to
anonymous user (nobody:nogroup) on NAS.
• All user on guest system will be mapped to anonymous
user (nobody:nogroup) on NAS.
Choose the one which best fits your needs.
Apply Click to save your changes.
Back Click to abandon changes.
38
Page 39

Folder Access Control List (ACL)
On the Folder screen, press the ACL button,
and the Access Control List screen
appears. This screen allows you to configure
access to the specific folder for users and
groups. Select a user or a group from the
left hand column and then choose Deny,
Read Only, or Writable to configure their
access level. Press the Submit button to
confirm yo
ur settings.
Access Control List
Item Description
Deny Denies access to users or groups who are displayed in this
column.
Read Only Provides Read Only access to users or groups who are displayed
in this column.
Writable Provides Write access to users or groups who are displayed in
this column.
Remove Removes the selected user or group from the column in order to
reset their access privileges.
Sync AD account Press this button when there is no list from ADS/PDC or more
ADS user has been added but yet appear from list.
Submit Submits and confirms settings.
Reset Cancel your settings and return to the Folder screen.
To configure folder access, follow the steps below:
1. On the ACL screen, all network groups and users are listed in the left hand
column. Select a group or user from this list.
2. With the group or user selected, press one of the buttons from the three
access level columns at the top. The group or user then appears in that
column and has that level of access to the folder.
3. Continue selecting groups and users and assigning them access levels
using the column buttons.
4. To remove a group or user from an access level column, press the
Remove button in that column.
5. When you are finished, press Submit to submit and confirm your ACL
settings.
If one user has belonged to more than one group but different privilege
than the priority Deny > Read Only > Writable
NOTE
The ACL screen also allows you to search for a particular user. To do this, follow
the steps below:
1. In the blank, enter the name of the user
you would like to find.
39
Page 40

2. From the drop down select the group you would like to search for the user
in.
3. Click Search.
The system will list up to 1,000 users from the chosen category. To
narrow your search, enter a search term in the blank provided.
NOTE
File System Check
The File System Check allows you to perform a
check on the integrity of your disks’ file system.
Under the Storage menu, click Filesystm Check
and the File System Check prompt appears.
To perform a file system check, click Apply.
Once clicked, the following prompt will appear:
Click Yes to reboot the system.
Once the system has rebooted, you will be returned to the File System Check
prompt. There you will see the available RAID volumes to run the file system
check on. Check the desired RAID volumes and click Next to proceed with the file
system check. Click Reboot to reboot without running the check.
Once you click Next, you will see the following screen:
40
Page 41

Click Start to begin the file system check. Click Back to return to the previous
screen. Click Reboot to reboot the system.
When the file system check is run, the system will show 20 lines of information
until it is complete. Once complete, the results will be shown at the bottom.
The system must be rebooted before the N5200 can function normally.
NOTE
41
Page 42

Network Management
Use the Network menu to make network configuration settings as well as service
support settings.
WAN Configuration
From the Network menu, choose WAN,
and the WAN Configuration screen
appears. This screen displays the network
parameters of the WAN connection. You
may change any of these items and press
Apply to confirm your settings. See a
description of each item in the following
ble:
ta
WAN Configuration
Item Description
Host name Host name that identifies the N5200 on the network.
Domain name Specifies the domain name of the N5200.
MAC Address MA C address of the network interface.
Jumbo Frame Support ble Jumbo Frame Support of the WAN interface on Enable or disa
your N5200.
DHCP
c IP, disable this feature and
Enable or disable the N5200 from obtaining in IP address via
DHCP server. If you require a stati
input your network configuration.
IP IP address of the WAN interface.
Netmask
Network mask, which is generally: 255.255.255.0
Gateway Default Gateway IP address.
DNS Server Domain Name Service (DNS) server IP address.
IP Sharing Mode LAN port will be able to When enabled, PCs connected to the
access the WAN. Default is Enabled.
Link Aggregation
(N5200B only)
WAN and LAN ports will be aggregated and
Ethernet traffic will flow alternative between two
age two Ethernet ports in parallel to increase
throughput.
Specifies whether
act as one port.
Failover: When one port fails, the other one will take over.
Load Balance:
Ethernet ports.
802.3ad: Link
NOTE
•
TP
•
the other end of
Ethernet cable also supports 802.3ad protocol.
Only use Jumbo Frame settings when operating in a Gigabit
environment where all other clients have Jumbo Frame Setting
enabled.
Enabling DHCP au• tomatically turns on UPnP—see the Service
Support Screen.
If you are only using the WAN port, we suggest that • you disable IP
Sharing Mode. This wi ll re sult in higher throughput.
A correct D• NS setting is vital to networks services, such as SM
and NTP.
To use the Link Aggregation with “802.3ad selected” feature,
please make sure the networking equipment on
42
Page 43

Most Fast Ethernet (10/100) Switches/Routers do not support Jumbo
Frame and you will not be able to connect to your N5200 after Jumbo
Frame is turned on. If this happens, turn off the N5200. Then, power
on the N5200 and immediately press and hold the Reset button on the
back of the unit for 10 seconds. This will reset your network settings,
password, and turn off Jumbo Frame Support.
WARNING
LAN Configuration
The N5200 supports two Gigabit Ethernet
ports for higher service availability. To
configure these ports, choose LAN from the
Network menu, and the LAN
Configuration screen appears. Press Apply
to save your changes.
LAN Configuration
Item Description
MAC Address Displays the MAC address of the LAN interface.
IP Specifies the IP address of the LAN interface.
Netmask Specifies the Network Mask of the LAN interface.
Jumbo Frame Support Enable or disable Jumbo Frame Support on the LAN i n terface.
Before enabling Jumbo Frame Support, please make sure your network
equipment supports Jumbo Frame. If your equipment is incompatible,
you might not be able to connect to your N5200. In this case, you have
to reset the system back to default by the holding down front panel
reset button for 5 seconds during boot up process.
NOTE
DHCP Configuration
A DHCP server can be configured to assign IP addresses to devices connected to
the LAN port. To configure these ports, choose LAN from the Network menu.
DHCP Configuration
Item Description
DHCP Server Enable or disable the DHCP server to automatically assign IP
address to PCs connected to the LAN interface.
Start IP Specifies the starting IP address of the DHCP range.
End IP Specifies the ending IP address of the DHCP range.
DNS Server Displayed the DNS server IP address.
NOTE
The IP address of the LAN interface should not be in the range of the
Start IP address and End IP address.
WARNING
The IP Segment of WAN and LAN should not overlap.
43
Page 44

WLAN Configuration
When a compatible wireless USB dongle is
installed on the N5200, the N5200 will
become an access point, and the Network
dropdown menu will contain a WLAN menu
item. From the Network menu, choose
WLAN, and the WLAN Configuration
screen appears. This screen displays the
wireless network parameters of the system.
You can change any of these items and press
Apply to confirm your settings.
• Currently supported USB
wireless dongles are: 3Com
3CRUSB10075, Zyxel G220USB,
PCI GW-US54mini.
• USB dongles have to be
connected before N5200 is
powered up.
NOTE
WLAN Configuration
Item Description
MAC Address Displays the MAC Address of the USB wireless dongle.
IP Specifies the IP address of the network connection.
Netmask
Specifies the network mask, which is generally: 255.255.255.0
ESSID The ESSID (Extended Service Set Identification) is the
identifying name of a wireless network.
ESSID Broadcast Specifi es whether the ESSID will be broadcasted by the N5200.
This will prevent the Access Point from broadcasting the ESSID.
The N5200 will still respond to a wireless device that wants to
communicate if it sends a matching ESSID.
Channel The channel that the N5200 uses to communicate with client
devices.
Auth Mode Authentication mode used by the N5200.
Shared: Shared key authentication
Open: Open key authentication
WEP Enable Specifies whether to use encryption for transmission or not.
Key Length Key length specifies the level of encryption used by the N5200.
64 bit: 10 characters from 0 ~ 9 and A ~ F.
128 bit: 26 characters from 0 ~ 9 and A ~ F.
WEP KEY 1
WEP KEY 2
WEP KEY 3
WEP KEY 4
Input up to 4 WEP keys, and select the one you wish to use.
When connecting, be sure to enter the same key and select the
same index number on each client machine.
A DHCP server can be configured to assign IP addresses to devices connected to
LAN ports.
WLAN DHCP Configuration
Item Description
DHCP Server Select to enable or disable DHCP server.
Start IP Specifies the starting IP address of the DHCP range.
End IP Specifies the ending IP address of the DHCP range.
DNS Server Specifies the DNS server IP address.
44
Page 45

NOTE
The IP Segment of WLAN, WAN and LAN should no t overlap.
13 Europe (ETSI)
2 Spain
4 France
14 Japan
11 N. America
Users should obey the
international RF regulatory rules as they set up
the wireless RF channel on the N5200. The RF operating channels for
different regions have been specified as following. Thecus has no
responsibility for users attempting to violate the international RF
regulation.
NOTE
WAN LAN Exchange
The N5200 is equipped with both WAN and
LAN ports. The WAN LAN Exchange function
allows you to exchange the functionality of
these ports directly through the Web User
Interface.
From the Network menu, choose the WAN
LAN Exchange item, and the WAN LAN
Exchange Support screen appears. Choose
Enable or Disable, and click Apply to save
your changes. Click Cancel to exit without
saving.
Web Services Configuration
From the Network menu, choose the
Service item, and the Web Service screen
appears. This screen displays the service
support parameters of the system. You can
change any of these items and press Apply
to confirm your settings. A description of
each item follows:
• In some environments, due to
security concerns, you may
wish to disable SMB/CIFS as a
precaution against computer
viruses.
• Disable HTTP support and
Enable Secure HTTP support
to guarantee secure access.
NOTE
Web Service
Item Description
HTTP (WebDisk)
Support
Enable or disable WebDisk support. Enter the port number if this
option is enabled. The port number
HTTPs (Secure
WebDisk) Support
Enable or disable secure WebDisk support. Enter the port if this
option is enabled.
SMB/CIFS Enable or Disable SMB/CIFS protocol for Windows, Apple, Unix
drive mapping.
UPnP Enable or disabl e Universal Plug and Play protocol. UPnP helps to
45
Page 46

find the IP address of the N5200.
AFP (Apple Network Setup)
From the Network menu, choose the AFP
item, and the AFP Configuration screen
appears. This screen displays the
configuration items for the Apple Filing
Protocol. You can change any of these items
and press Apply to confirm your settings. A
description of each item follows:
Apple Network Configuration
Item Description
AFP Server Enable or disable Apple File Service to use the N5200 with MAC
OS-based systems.
Zone Specifies Zone for Applet Talk service.
If your AppleTalk network uses extended networks and is
assigned with multiple zones, assign a zone name to the N5200.
If you do not want to assign a network zone, enter an asterisk
(*) to use the default setting.
NFS Setup
From the Network menu, choose the NFS
item, and the NFS Server Setting screen
appears. The N5200 can act as an NFS
server, enabling users to download and
upload files with the favorite NFS clients.
Press Apply to confirm your settings. A
description of each item follows:
NFS Server Setting
Item Description
NFS Enable or Disable NFS support.
Apply Click Apply to save your changes.
Cancel Click Cancel to abandon your changes.
46
Page 47
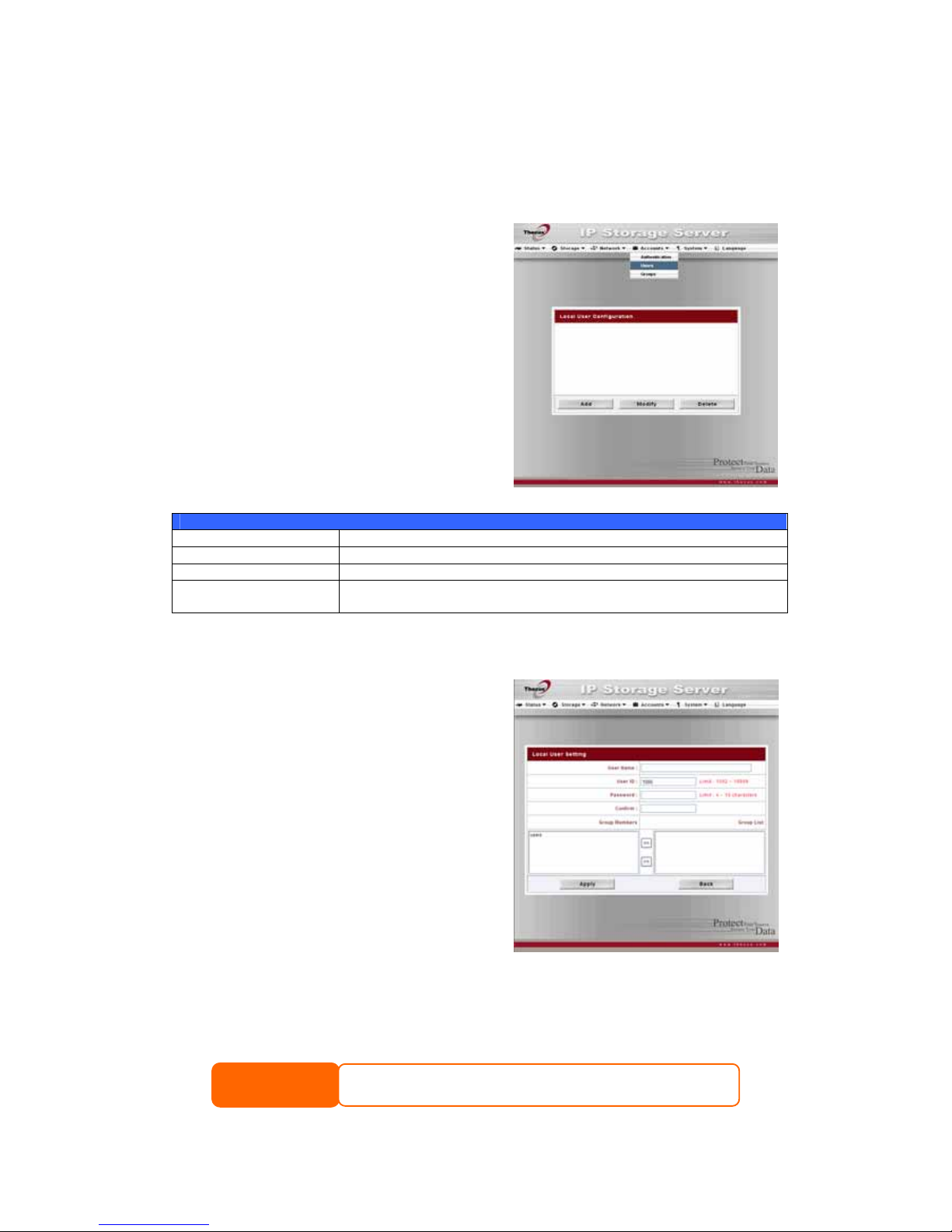
User and Group Management
The N5200 has built-in user database that allows administrators to manage user
access using different group policies. From the Accounts menu, you can create,
modify, and delete users, and assign them to groups that you designate.
Local User Configuration
From the Accounts menu, choose the
Users item, and the Local User
Configuration screen appears. This screen
allows you to Add, Modify, and Delete
local users.
Local User Configuration
Item Description
Add Press the Add button to add a user to the list of local users.
Modify Press the Modify button to modify a local user.
Delete Press the Delete button to delete a selected user from the
system.
Adding Users
1. Click on the Add button on Local
User Configuration screen, and
Local User Setting screen appears.
47
2. On the Local User Setting screen,
enter a name in the User Name box.
3. Enter a User ID number. If left
blank, the system will automatically
assign one.
4. Enter a password in the Password
box and re-enter the password in the
Confirm box.
5. Select which group the user will
belong to. Group Members is a list of groups this user belongs to. Group
List is a list of groups this user does not belong to. Use the << or >>
buttons to have this user join or leave a group.
6. Press the Apply button and the user is created.
All users are automatically assigned to the ‘users’ group.
NOTE
Page 48

Modifying Users
1. Select an existing user from the Local User Configuration screen.
2. Click on the Modify button, and Local User Setting screen appears.
3. From here, you can enter a new password and re-enter to confirm, or use
the << or >> buttons to have this user join or leave a group. Click the
Apply button to save your changes.
Deleting Users
1. Select an existing user from the Local User Configuration screen.
2. Click on Delete button and the user is deleted from the system.
Local Groups Configuration
From the Accounts menu, choose the
Groups item, and the Local Groups
Configuration screen appears. This screen
allows you to Add, Modify, and Delete
local groups.
Local Groups Configuration
Item Description
Add Press the Add button to add a user to the list of local groups.
Modify Press the Modify button to delete a selected group from the
system.
Delete Press the Delete button to delete a selected group from the
system.
Adding Groups
1. On the Local Group Configuration screen, click on the Add button.
2. The Local Group Setting screen appears.
3. Enter a Group Name.
4. Enter a Group ID number. If left blank, the system will automatically
assign one.
48
Page 49

5. Select users to be in this group from
the Users List by adding them to
the Members List using the <<
button.
6. Click the Apply button to save your
changes.
Modifying Groups
1. On the Local Group Configuration
screen, select a group name from
the list.
2. Press the Modify button to modify
the members in a group.
3. To add a user into a group, select
the user from the Users List, and
press the << button to move the user into the Members List.
4. To remove a user from a group, select the user from Members List, and
press the >> button.
5. Click the Apply button to save your changes.
Deleting Groups
1. On the Local Group Configuration screen, select a group name from the
list.
2. Press Delete to delete the group from the system.
Batch User and Group Creation
The N5200 can also add users and groups in
batch mode. This enables you to
conveniently add numerous users and
groups automatically by importing a simple
comma-separated plain text (*.txt) file.
From the Accounts menu, click Batch
Mgmt and the Batch Create Users and
Groups dialogue will appear. To import
your list of users and groups, follow these
steps:
1. Click Browse… to locate your
comma-separated text file.
The information in the text file
should follow this format:
[USERNAME], [PASSWORD], [GROUP]
2. Click Open.
3. Click Import to begin the user list import.
49
Page 50

ADS/NT Configuration
If you have a Windows Active Directory
Server (ADS) or Windows NT server to
handle the domain security in your network,
you can simply enable the ADS/NT support
feature; the N5200 will connect with the
ADS/NT server and get all the information
of the domain users and groups
automatically. From the Accounts menu,
choose Authentication item and the
ADS/NT Support screen appears. You can
to change any of these items and press
Apply to confirm your settings. A
description of each item follows:
ADS/NT Support
Item Description
WINS Server Specifies the WINS server if necessary.
Work Group / Domain
Name
Specifies the SMB/CIFS Work Group / ADS Domain Name (e.g.
N5200).
ADS/NT Support Select Disable to disable authentication through Windows Active
Directory Server or Windows NT.
Authentication Method Select ADS for Windows Active Directory Server, or select NT for
Windows NT
ADS/NT Server Name Specifies the ADS/NT server name (e.g. adservername).
ADS/NT Realm Specifies the ADS/NT realm (e.g. example.com).
Administrator ID Enter the administrators ID of Windows Active Directory or
Windows NT, which is required for N5200 to join domain.
Administrator
Password
Enter the ADS/NT Administrator password.
Confirm Password For re-entering password to confirm.
To join an AD domain, you can refer the figure and use the example below to
configure the N5200 for associated
filed input:
50
Page 51

AD Domain Example
Item Information
Work Group / Domain
Name
domain
ADS Support
Enable
ADS Server Name
Computer1
ADS/NT Realm
Domain.local
Administrator ID
Administrator
Administrator
Password
***********
Confirm Password
***********
• The Administrator Password field is for the password of ADS (Active
Directory Server) not N5200.
• The system time difference between N5200 and ADS should be less
than five minutes.
• The time zone setting between N5200 and ADS should be identical.
• The DNS server specified in the WAN configuration page should be
able to correctly resolve the ADS server name.
NOTE
51
Page 52

System Settings
The System menu gives you a wealth of settings that you can use to configure
your N5200’s system administration functions. You can set up system
notifications, view system logs, and even upgrade firmware from this menu.
System Notifications
From the System menu, choose the
Notification item, and the Notification
Configuration screen appears. This screen
lets you have the N5200 notify you in case
of any system malfunction. Press Apply to
confirm all settings. See following table for
a detailed description of each item.
Consult with your mail server
administrator for email server
information.
NOTE
Notification Configuration
Item Description
Beep Notification Enable or disable the system beeper that beeps when a problem
occurs.
Email Notification Enable or disable email notifications of system problems.
SMTP Server Specifies the hostname/IP address of the SMTP server.
Port Specifies the port to send outgoing notification emails.
Auth Type Select the SMTP Server account authentication type.
SMTP Account ID Set the SMTP Server Email account ID.
Account Password Enter a new password.
Confirm Account
Password
Confirm a new password.
Receiver’s E-mail
Address
Add one or more recipient’s email addresses to receive email
notifications.
Test E-Mail Click to send out a test e-mail to make sure the settings are
correct.
System Logs
From the System menu, choose the Logs
item and the System Logs screen appears.
This screen shows a history of system usage
and important events such as disk status,
network information, and system booting.
See the following table for a detailed
description of each item:
52
Page 53

System Logs
Item Description
Truncate All Log File Clear all log files.
|<< < > >>| Use the forward ( > >>| ) and backward ( |<< < ) buttons
to browse the log pages.
INFO Provides all log information including warning messages and
error messages.
WARN Shows all warning messages and error messages.
ERROR Shows only error messages.
GO Specify the number of lines per page and press Go.
Ascending Shows logs by date in ascending order.
Descending Shows logs by date in descending order.
Download All Log File Export all logs to an external file.
Time and Date Settings
From the System menu, choose the Time
item and the Time screen appears. Set the
desired Date, Time, and Time Zone. You
can also elect to synchronize the system
time on the N5200 with an NTP (Network
Time Protocol) Server. You can change
any of these items and press Apply to
confirm your settings.
See the following table for a detailed
description of each item:
Time
Item Description
Date Sets the system date.
Time Sets the system time.
Time Zone Sets the system time zone.
NTP Server Select Yes to allow the N5200 to synchronize with the NTP
server shown below.
Select Manually to allow the N5200 to synchronize with an NTP
server of your choice.
Select No to not have the N5200 to synchronize with an NTP
server.
If an NTP server is selected, please make sure your N5200’s network
has been setup to access the NTP server.
WARNING
53
Page 54

System Configuration Backup and Restore
From the System menu, choose the Config
Mgmt item and the System Configuration
Download/Upload screen appears. From
here, you can download or upload stored
system configurations. See the following
table for a detailed description of each item.
System Configuration Download/Upload
Item Description
Download Save and export the current system configuration.
Upload Import a saved configuration file to overwrite current system
configuration.
54
Module Management
NOTE
Backing up your system configuration is a great way to ensure that you
can revert to a working configuration when you are experimenting with
new system settings.
The system configuration you have backup can be only restore in same
firmware version. And the backup details have excluded user/group
From the System menu, choose the
Module Mgmt item and the Module
Management screen appears. From here,
you can install separate software modules
to extend the functionality of your N5200.
Module Management
Item Description
Name Displays the name of the module.
Version Displays the module version.
Description The description of the module.
Enable Displays whether the module has been enabled or not.
Status Displays the status of the module.
Uninstall Click to uninstall the module.
Enable/Disable Click to enable a module.
Page 55

Check Update Click to look for updates for the selected module.
Module File Location of the module file.
Browse Click to browse the folder of your PC to locate the module files.
Install Click to install the listed module into your N5200
Modules can potentially harm your system. Only install modules from
your vendor, or publishers you can trust.
NOTE
Reset to Factory Default Settings
From the System menu, choose the
Factory Default item and the Reset to
Factory Default screen appears. Press
Apply to reset the N5200 to factory default
settings. Press Cancel to go back to the
main menu.
Resetting to factory defaults will not erase the data stored in the hard
disks, but WILL revert all the settings to the factory default values.
WARNING
Upgrading System Firmware
From the System menu, choose the
Firmware Upgrade item and the
Firmware Upgrade screen appears.
Follow the steps below to upgrade your
firmware:
1. Use the Browse button to find the
firmware file.
2. Press Apply.
3. The beeper beeps and the Busy LED
blinks until the upgrade is complete.
• Check Thecus website for the latest firmware release and release
notes.
• The beeper only
beeps if it is enabled in th e Sy s t e m Not ification
menu.
NOTE
55
Do NOT turn off the system during the firmware upgrade process. This
will lead to a catastrophic result that may render the system inoperable.
WARNING
Page 56
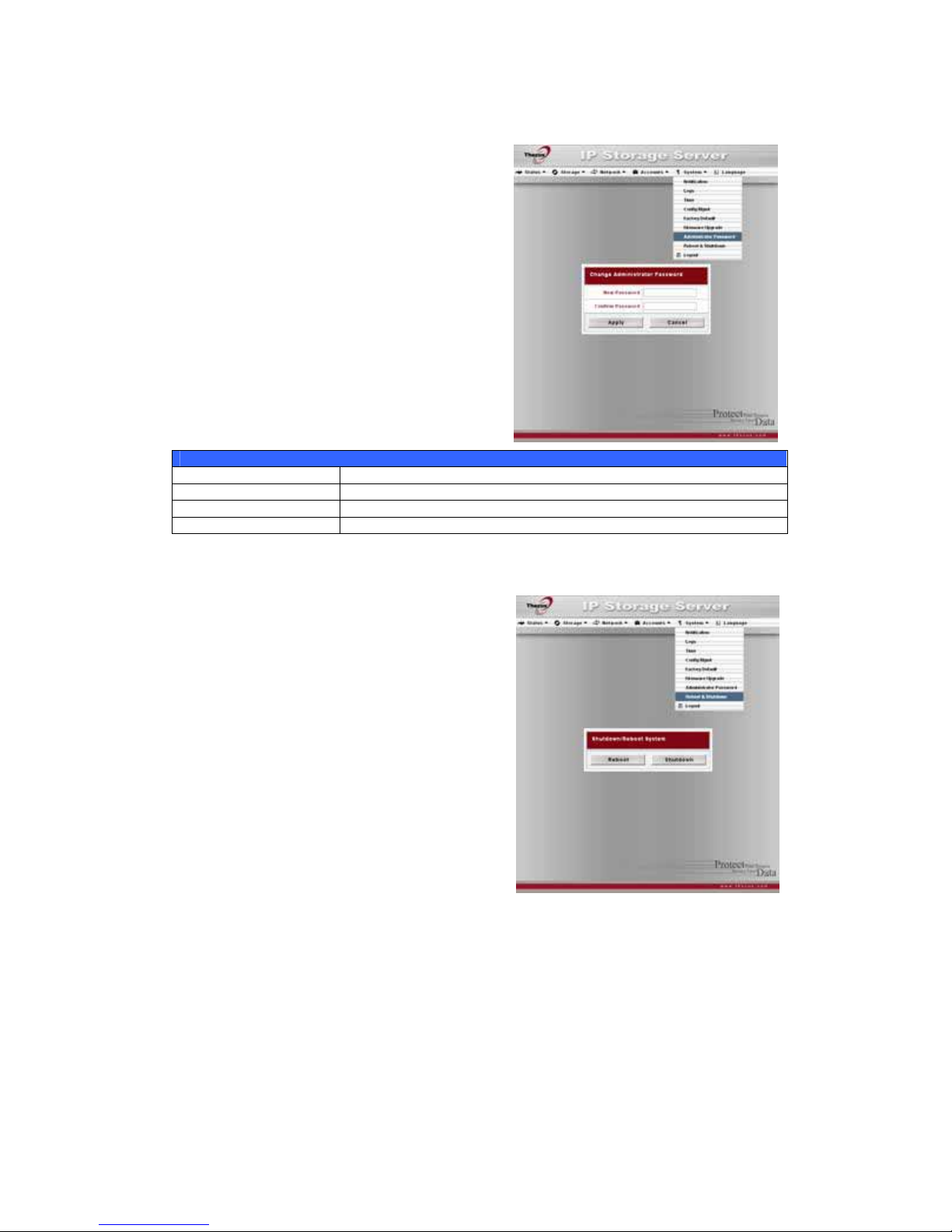
Change Administrator Password
From the System menu, choose the
Administrator Password item and the
Change Administrator Password screen
appears. Enter a new password in the New
Password box and confirm your new
password in the Confirm Password box.
Press Apply to confirm password changes.
See the following table for a detailed
description of each item.
Change Administrator Password
Item Description
New Password Type in a new administrator password.
Confirm Password Type the new password again to confirm.
Apply Press this to save your changes.
Reboot and Shutdown System
From the System menu, choose Reboot &
Shutdown item, and the
Shutdown/Reboot System screen
appears. Press Reboot to restart the
system or Shutdown to turn the syst
em off.
Logout
To logout of the Web Administration Interface, navigate to System > Logout.
56
Page 57

Chapter 5: Additional Feature Setup
Overview
The N5200 can also act as an FTP Server, allowing employees and clients to
transfer files using their favorite FTP programs. Th e integrated Print Server allows
you to share a single USB printer will all users on the network. The following
section shows you how.
FTP Server
N5200 can act as a FTP server, enabling
users to download and upload files with their
favorite FTP programs. From the Network
menu, choose the FTP item, and the FTP
screen appears. You can change any of
these items and press Apply to confirm
your settings. A description of each item
follows:
FTP
Item Description
FTP Enable FTP Service on the N5200.
FTP ENCODE If your FTP client or operating system does not support Unicode
(e.g. Windows® 95/98/ME or MAC OS9/8), select the same
encoding as your OS here in order to properly view the files and
directories on the server. Available options are BIG5, HZ,
GB2312, GB18030, ISO, EUC-JP, SHIFT-JIS and UTF-8.
To access the share folder on the N5200, use the appropriate user login and
password set up on the Users page (Accounts > Users). Access control to each
share folder is set up on the ACL page (Storage > Folder > ACL).
57
Page 58

Media Server
With the built-in Media Server capability,
the N5200 provides media streaming
service to stand-alone networked home
media adapters that support the UPnP AV
protocol or are Digital Living Network
Alliance (DLNA) standard compliant.
With the N5200’s built-in media server
capability, you can share digital media such
as music, pictures, and movies with any
compatible device throughout your entire
home.
To configure the media server, under the
Network menu, click Media Server and the
Media Manager Settings window will appear.
A description of each field follows:
Media Manager Settings
Item Description
Media Server Enable or disable the Media Server service.
Shared Media Folders Select the folder(s) that contains media files to be shared.
Rescan Click the Rescan button to have the N5200 for new contents in
the selected media folder.
Adding Media Share Folders
Once the Media Server software is installed, you can start adding folders that
contain the media that you would like to share. To create a media share folder,
follow the steps below:
1. Click on Network > Media Server in the menu bar.
2. From the Shared Media Folders window, select the folder that contains
your media files, and click its checkbox.
3. The contents in the folder will be scanned for the Media Server. The time
required for scanning depends on the size of the folder.
Connecting DMAs to the Media Server
Next, it’s time to connect your Digital Media Adapter (DMA) to the media server:
1. Connect your DMA to your Media Server
a. Configure your DMA to use a Dynamic IP address. The IP address
will be assigned by the router.
58
Page 59

59
b. Some DMAs are wireless enabled. You can connect the DMA to a
wireless router. For instructions on how to connect your DMA to a
wireless router, please refer to your DMA’s user manual.
2. Connect your DMA’s video output to video input of your TV set.
3. Turn on the TV and change the video signal input to DMA.
4. Setup the DMA (These steps will be different if you use a different DMA)
a. From the Server List screen, select “N5200:Mediabolic Server”
as the server.
b. Go to My Media
c. Click on the Up/Down Arrow buttons to select Music Jukebox,
Photo Albums, or Video Clips
d. Start enjoying the contents stored in your N5200.
Page 60
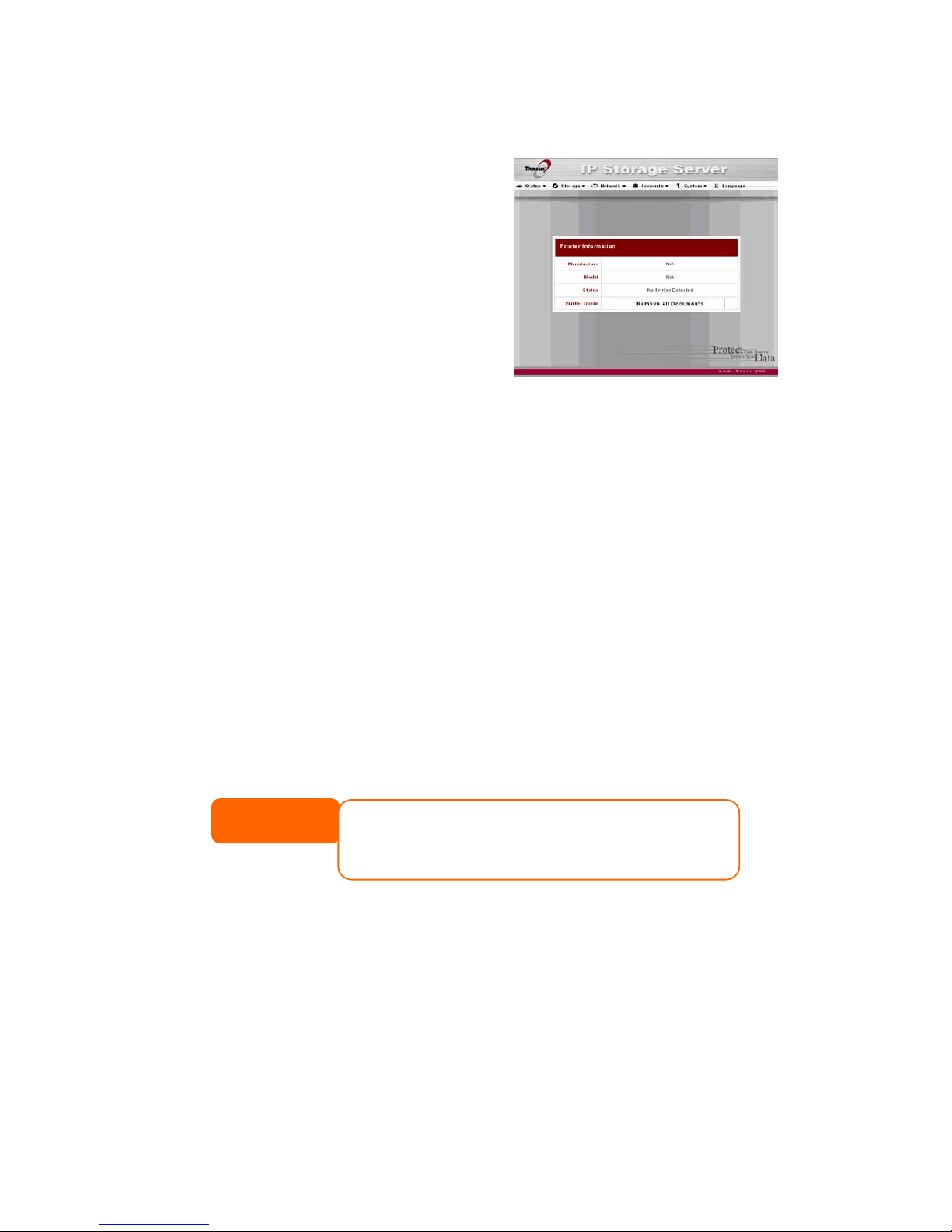
Printer Server
You can configure the N5200 to act as a
printer server. That way, all PCs connected
to the network can utilize the same printer.
Windows XP SP2
To set up the Printer Server in Windows XP
SP2, follow the steps below:
1. Connect the USB printer to one of
the USB ports (preferably the rear
USB ports; front USB ports can be
used for external HDD enclosures).
2. Go to Start > Printers and Faxes.
3. Click on File > Add Printer.
4. The Add Printer Wizard appears on your screen. Click Next.
5. Select the “A network printer, or a printer attached to another
computer” option.
6. Select “Connect to a printer on the Internet or on a home or office
network”, and enter “http://N5200_IP_ADDRESS:631/printers/usbprinter” into the URL field.
7. Your Windows system will ask you to install drivers for your prin ter. Select
correct driver for your printer.
8. Your Windows system will ask you if you want to set this printer as
“Default Printer”. Select Yes and all your print jobs will be submitted to
this printer by default. Click Next.
9. Click Finish.
• Note that if a multi-function (all-in-one) printer is attached to the
N5200, usually only the printing and fax functions will work. Other
features, such as scanning, will probably not function.
• Not all USB printers are supported. Please check Thecus website for
a list of supported printers.
NOTE
60
Page 61
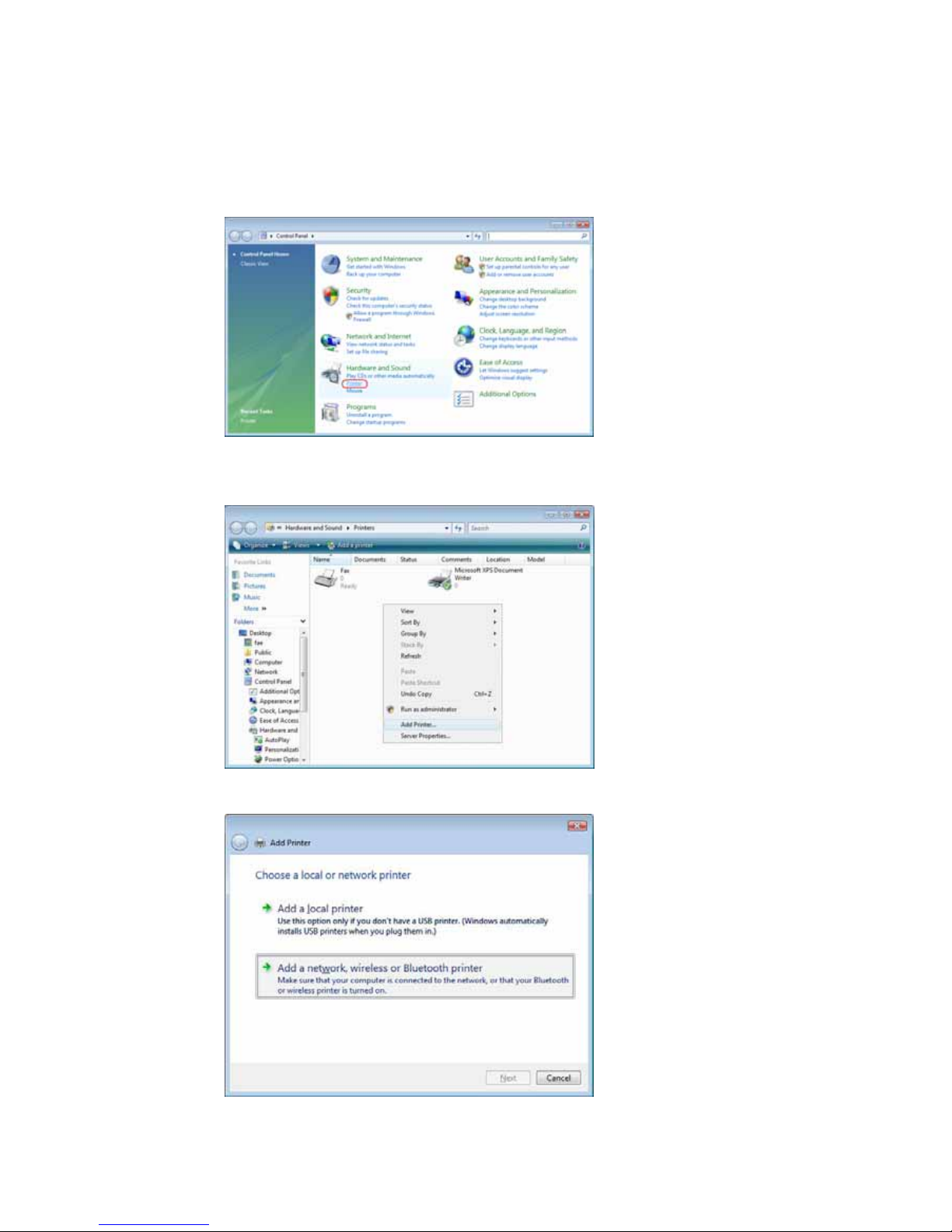
Windows Vista
To set up the Printer Server in Windows Vista, follow the steps below:
1. Open Printer Folder from the Control Panel.
2. Click the right mouse button in anywhere on the Printers folder and then
select Add Printer.
3. Select Add a network, wireless or Bluetooth printer.
61
Page 62

4. Select The printer that I want isn’t listed.
You can press The printer that I want isn’t listed to go into next page
without waiting for Searching for available printers to finish.
5. Click Select a shared printer by name.
Type http://<Thecus_NAS>:631/printers/usb-printer in the box,
where <Thecus_NAS_IP> is the IP address of the N5200. Click Next.
6. Select or install a printer and then press OK.
62
Page 63

If your printer model is not listed, please contact your printer
manufacturer for help.
7. Windows will attempt to connect to the printer.
8. You can choose to set this printer as the default printer by checking the
Set as the default printer box. Click Next to continue.
9. Done! Click Finish.
63
Page 64

Chapter 6: Using the N5200
Overview
Once the N5200 is setup and operating, users on the network may manage all
varieties of digital music, photos, or files by simply using their web browsers. To
manage your personal files or access public files on the N5200, just enter its IP
address into your browser (default IP address is http://192.168.1.100), and
you will be taken to the N5200 Login page.
Before proceeding, make sure that WebDisk Support or Secure
WebDisk Support is enabled in the Service Support screen in the
system’s Network menu. See Service Support in Chapter 4: System
Management > Network Management > Web Services Configuration.
NOTE
Login Page
To login to the system, enter your user name and password, and click Login to
log into the system. You will be taken to the WebDisk interface.
Using WebDisk
The N5200 provides a WebDisk function that allows you to access the system
over the Internet from any browser.
1. In the Login page, type in the User ID and password that were previously
set for you in the Accounts menu. See Chapter 4: System Management
> User and Group Management > Local User Configuration.
2. The WebDisk page appears showing folders made currently available to
you via the Access Control List (ACL).
3. Click on a folder name to enter the folder.
4. The folder’s page appears displaying files and folders. Click on a file to
download the file.
Folder Page
Item Description
Name Displays the names of folders and files.
Size Shows the size of folders and files.
Type Displays the type of folders and files.
Modified Date Shows the time of most recent modification of folders and files.
5. Buttons on the folder page allow you to create a new folder, upload files
and delete files in the folder.
Folder Page Buttons
Button Description
Up Goes to the previous folder level.
New folder Creates a new folder.
New file (upload) Uploads a file from your computer to the current folder.
Delete Selected Items Deletes selected files and folders.
6. To create a new folder within the current folder, press the New folder
button. When the screen appears enter a name for the folder. Press OK to
create the folder.
64
Page 65

65
7. To upload a file from your computer to the current folder, press the New
file (upload) button. When the screen appears, press Browse and locate
the file to upload. Press OK and the file is uploaded to the current folder.
8. To delete a file or folder, select the file or folder’s check box. Press the
Delete selected items button. You can also check the check box as the red
circle indicates to select all files and folders in this folder.
To access folders with access control, you must first login with a local user
account.
For more information on how to setup user rights to the folders, please check
Chapter 4: System Management > Folder Management > Folder Access
Control List (ACL).
Mapping a Client PC to the N5200
You can map share folders on the N5200 so that you can access them as if they
were drives on your computer. You can connect to the shared network folders on
the N5200 as follows:
Windows
1. Go to the My Computer folder in Windows.
2. In the menu bar, select Tools and then Map Network Drive…
3. The Map Network Drive window appears.
4. Assign a drive letter for the share folder.
5. Click the Browse button to find the folder over your network. Alternatively,
you may enter the folder name you wish to connect to or enter its IP
address. (i.e. \\192.168.1.100\share)
6. Click Finish. When the Connect As… window appears, enter your user
name and password.
7. Click OK. The share folder appears as the drive you assigned. You can now
access this folder as though it were a drive on your computer.
Apple OS X
On an Apple computer, you can connect to shared computers and servers using a
network address.
1. Choose Go > Connect to Server…
2. Enter the network address for the server in the Server Address text box.
When connecting using SMB/CIFS protocol, type:
smb://192.168.1.100/Folder1
When connecting using AFP protocol, type:
afp://192.168.1.100/Folder1
Click Connect.
3. When MAC OS X is trying to connect N5200, it will ask for a User Name
and Password which has access to the folder.
Page 66

66
4. When MAC OS X has connected to the N5200 successfully, an icon
representing the folder will appear on the MAC OS X desktop. You can
access the folder by double clicking on the icon.
File Backup
There are a number of ways to back up data with the N5200.
Nsync
You can backup a share folder to another N5200 (Nsync Target) or any FTP
server for safe keeping as long as you have appropriate access right on that
target. When using Nsync between two N5200s, you have the option to transmit
files securely between two N5200s.
If the files on your N5200 are lost for any reason, you can restore those files from
the target N5200. To backup files regularly, you can set up a scheduled task to
run only once, daily, weekly, or monthly. You can also limit the bandwidth of your
Nsync tasks, so other users on the network can share the bandwidth equally.
Under the Storage menu, click Nsync and the Nsync window appears. Below is
a description of each field:
Nsync
Item Description
Task name The name of your Nsync task.
Server The IP address of your target server
Share folder The share folder you would want to backup.
Last Time The time when the last Nsync task was executed.
Last Status The status of your last Nsync task.
Action Administrator can run or stop an Nsync task by pressing the
action button.
Bandwidth Setting Bandwidth control on Nsync tasks.
Add Click to add a Nsync task
Modify Click to modify an Nsync task.
Restore Restore share folder from an Nsync target.
Delete Click to delete an Nsync task. Backup files on Nsync target is
also deleted.
Adding an Nsync Task
From the Nsync Information screen, click Add to display the Add Nsync Task
screen.
Add Nsync Task
Item Description
Task Name The name of your Nsync task.
Manufacturer Select whether the target is a Thecus Product (e.g. N5200) or
FTP server.
Target Server IP
Address
The IP address of your target server.
Source Folder The share folder you want to backup.
Nsync Task Name The name of your Nsync task.
Authorized Username
on Target Server
The account name on the target server.
Password on Target
Server
The password for the username on the target server.
Test Connection Click to check the connection to the Target Server.
Schedule Schedule backup of your share folders.
Page 67

Time The time when the Nsync task will run.
Type Select whether to run the Nsync task daily, weekly, or monthly.
Daily: input the time of day to execute Nsync task.
Weekly: input which day of the week to execute the task.
Monthly: decide which day of the month to execute the task.
Apply Click to submit the task.
Before starting an Nsync Task, make sure the target server’s Nsync
Server (or FTP Server) is enabled.
NOTE
Setting Up an Nsync Target on an Nsync Device
On the Nsync target server, the administrator of that server has to set up a user
account with a folder named “nsync” and grant write access.
1. On the Nsync server, add a user for Nsync source (ex. nsyncsource1). For
instructions on how to add a user on the N5200, see Chapter 4: System
Management > User and Groups Management > Local User
Configuration > Adding Users.
2. On the Nsync server, grant that user (ex. nsyncsource1) write access to
the nsync folder. For instructions on how to set up a folder’s ACL, see
Chapter 4: System Management > Folder Management > Folder
Access Control List (ACL).
3. Once this is done, the target server will start accepting Nsync tasks from
server using that ID and password.
Setting Up an Nsync Target on Another Device
If you selected “Other Device” when setting up your Nsync task, the N5200 will
use the FTP protocol to back up the share folder. On the external storage device,
make sure there is a folder named “nsync”, and the Auth ID has writable
permission in that folder.
Designating N5200 as an Nsync Target
The N5200 can act as an Nsync server, enabling another Nsync-equipped Thecus
NAS at a remote location backup their files to this N5200. From the Network
menu, choose the Nsync Target item, and the Nsync Target Server Setting
screen appears.
Nsync Target Server Setting
Item Description
Nsync Target Server Enable or Disable Nsync Target support.
To enable Nsync task to go thru firewall, you have to open port
TCP/1194 on your firewall in both directions.
NOTE
Thecus Backup Utility
The Thecus Backup Utility is on your Installation CD. When you click on the CD,
the Backup Utility will be installed under Program Groups > Thecus > Thecus
Backup Utility. If it is not installed, you can copy the file (Thecus Backup
Utility.exe) to a convenient location on your hard disk and double click to
execute it.
67
Page 68
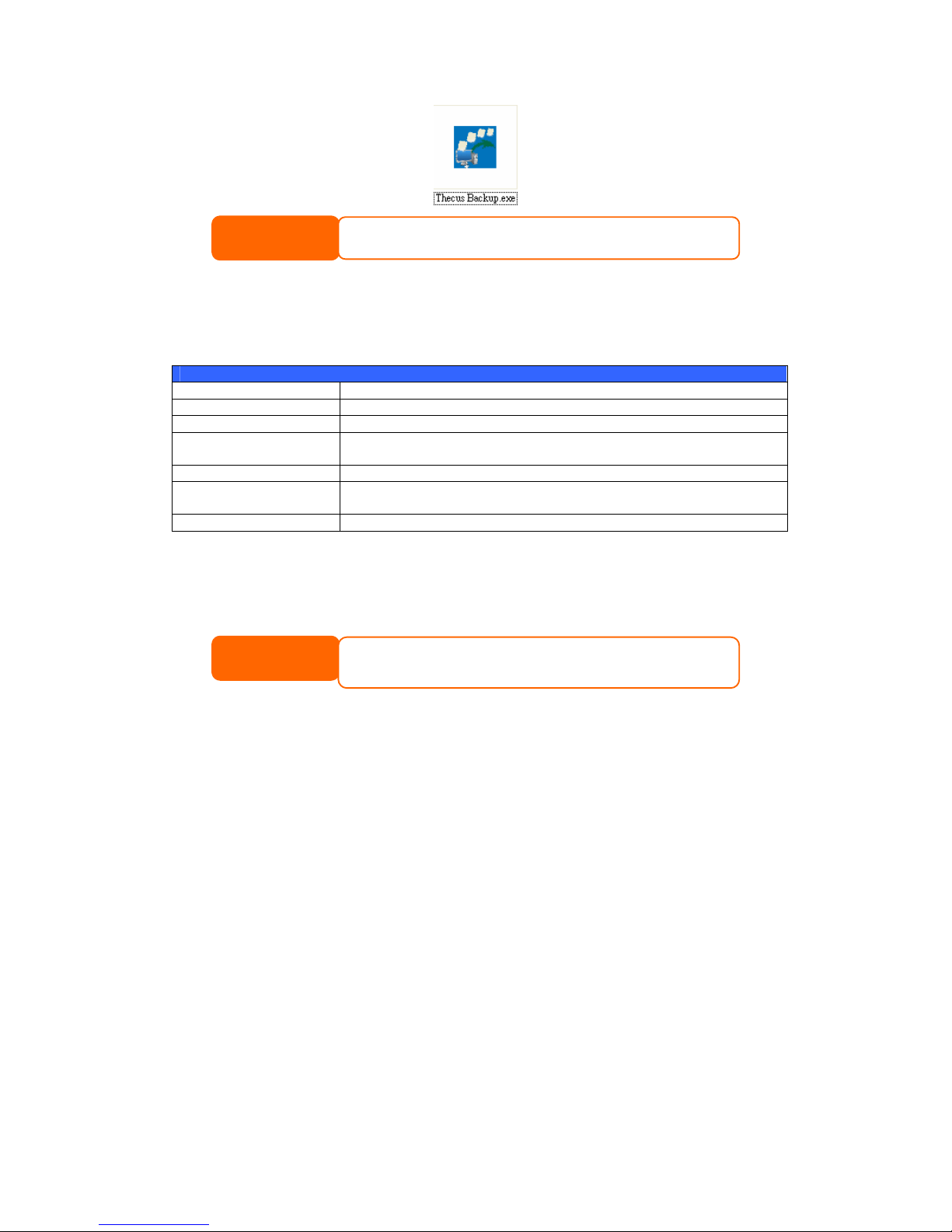
If you can not find Thecus Backup Utility on your CD, please download it
from the Thecus website (http://www.thecus.com).
NOTE
When you execute this utility for the first time, it will ask you whether to create a
DB file. Click Yes.
1. Click Add to create a Backup task. The Add New Task dialog box appears.
Add New Task
Item Description
Task Specifies a name for the current task.
Source Click to specify the source folder/file location.
Incremental Click to specify whether the backup will be incremental.
If unchecked, the backup will be a full backup.
Destination Click to specify the destination folder/file location.
Excluded extensions Files with these file name extensions will be skipped and not
back up to the destination.
Comments If you wish, enter comments here for your records.
2. To schedule the task to run at regular intervals, click on the Schedule
icon for that task. You can schedule the task to run Monthly or Weekly.
3. To check the log for that task, click on the Log icon for that task.
Thecus Backup Utility also supports MAC OS X. Just copy the Thecus
Backup Utility.dmg to your MAC OS X machine and double click to
execute it.
NOTE
68
Page 69

69
Windows XP Data Backup
If you use Windows XP Professional, you can also use the Wind ows Backup Utility
(Ntbackup.exe) to backup your files.
If you use Windows XP Home Edition, follow these steps to install t he utility:
1. Insert the Windows XP CD into a drive and double-click the CD icon in My
Computer.
2. When the Welcome to Microsoft Windows XP screen appears, click
Perform Additional Tasks.
3. Click Browse this CD.
4. In Windows Explorer, navigate to ValueAdd > Msft > Ntbackup.
5. Double-click Ntbackup.msi to install the backup utilit y.
Once installed, you can use the Windows Backup Utility by follow in g the steps
below:
1. Click Start, and point to All Programs > Accessories > System Tools
> Backup to start the wizard.
2. Click Next to skip past the opening page. Choose Backup files and
settings from the second page, and then click Next.
3. Select which option you want to back up.
4. Click Next and in the Backup Type, Destination, and Name page, specify a
back up location using the Browse button.
5. Find and select the drive that specifies your N5200 as your backup
destination and click Next.
6. Click Next to display the wizard’s final page and click Finish to start
backing up.
Apple OS X Backup Utilities
Mac OS X does not include any backup software. However, there are a number of
backup solutions available for the Mac OS X, including: iBackup, Psyncx, iMSafe,
Rsyncx, Folder Synchronizer X, Tri-BACKUP, Impression, Intego Personal Backup,
SilverKeeper, and Apple's dotMac Backup utility to name just a few. To find even
more freeware and shareware backup utilities to choose from, go to
VersionTracker or MacUpdate and search on "backup".
Page 70

Chapter 7: Tips and Tricks
USB and eSATA Storage Expansion
The N5200 supports external USB hard disks through its three USB ports. Once a
USB hard disk has successfully mounted, the entire volume will be copied
automatically to the default USB HDD folder. The N5200 supports up to 6 USB
external storage devices. All file names on the USB disk volume are case sensitive.
The N5200 also supports eSATA hard disks with its eSATA port.
Before attaching an eSATA or USB disk drive to N5200, you have to partition and
format it on a desktop computer or a notebook first. The attached device will be
located at \\192.168.1.100\usbhdd\sdf1 where 192.168.1.100 means the IP
address of N5200 and sdf1 stands for the first partition on disk #6, the eSATA or
USB disk drive. If it is an NTFS partition, NAS users can open or copy files from
\\192.168.1.100\usbhdd\sdf1 but cannot add new files or modify existing files.
If you want to write to an USB storage device, the file system must be
FAT32.
USB Storage FAT32 Partition
NOTE
70
NTFS Partition
Read OK OK
Write OK -
Adding a Spare Disk
With a RAID 1, RAID 5, RAID 6, or RAID 10 volume, you can add a spare disk
after the initial RAID is setup. To add a spare disk, follow the steps below:
1. On the RAID Configuration Screen, tick the checkbox of the hard disk
you wish to designate as a spare disk.
2. Click Add Spare. The disk will be configured as a spare disk. The system
automatically rebuilds the spare disk when one of the disks in the RAID set
fails.
Target USB
N5200 can operate in dual mode. When connecting to a regular USB disk or
thumb drive, N5200 is acting as USB host. When connecting to a PC thru its USB
Type B connector on the back panel, N5200 can act as a USB disk. This feature
allows user to transfer files without using network connection.
When you create RAID, you can assign a portion of space on the RAID to be used
as USB disk. When connecting N5200 to a PC using the supplied USB A to B cable,
the PC will recognize this space as an unformatted disk. At th is point, the PC can
format this portion of disk and create file system on it. Since this disk is created
on the RAID, it will be protected by the RAID level you select.
When RAID is removed or damaged, all the data on the Target USB
device will be deleted.
WARNING
Page 71
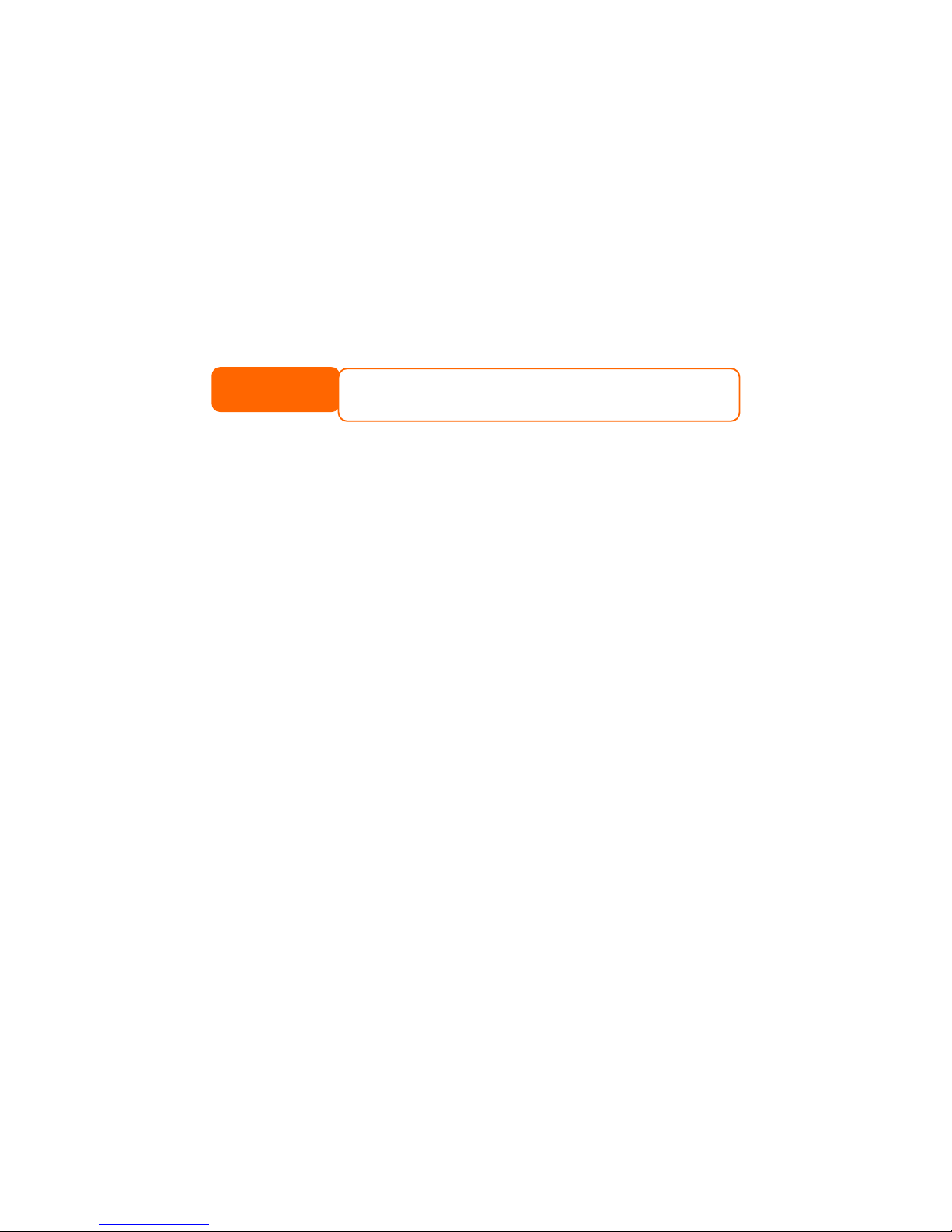
Remote Administration
You can set up your N5200 for remote administration. With remote administration,
you can access your N5200 over the Internet, even if your N5200 is behind a
router. This is especially useful if you are traveling and suddenly need a file from
your N5200.
Setting up remote administration is a three-part process, and will require the
following equipment:
• Thecus N5200 NAS device
• Cable/DSL Router with Dynamic DNS support
• Home PC
• Internet Connecti on
NOTE
Router setup will differ slightly depending on router used. For this
example, we will use the Asus WL500g because it has support for
Dynamic DNS. Contact your router hardware vendor for setup help.
Part I - Setup a DynDNS Account
1. Go to http://www.dyndns.org from your home PC.
2. Click on the Sign Up Now link.
3. Check the Check boxes, select a user name (i.e.: N5200), enter your
email address (i.e.: xxx@example.com), check Enable Wildcard, and
create a password (i.e.: xxxx).
4. Wait for an email from www.dyndns.org.
5. Open the email and click on the link to activate your account
Part II - Enable DDNS on the Router
1. Go to the router setup screen and select IP Config > Miscellaneous
DDNS Setting from your Home PC.
2. Click on Yes for Enable the DDNS Client?
3. Select www.dyndns.org.
4. Go to router setup screen, and enter the following information:
a. User Name or E-mail Address: xxx@example.com
b. Password or DDNS Key: xxxx
c. Host Name: www.N5200.dyndns.org
d. Enable wildcard? Select Yes
e. Update Manually: Click Update
Part III - Setting up Virtual Servers (HTTPS)
1. Navigate to NAT Setting > Virtual Server.
2. For Enable Virtual Server?, select Yes
3. Setup the HTTPS Server
a. Well-Known Applications: Select User Defined
b. Local IP: Enter 192.168.1.100
c. Port Range: 443 (the default HTTPS port setting on the N5200)
d. Protocol: select TCP
e. Click Add.
f. Click Apply.
4. Test the HTTPS connection from another computer on the Internet
a. From a remote computer, open your browser and enter
https://www.N5200.dyndns.org
71
Page 72

72
b. You should see the login page of N5200.
Firewall Software Configuration
If you are using a software firewall (i.e. Norton Internet Security) and are having
trouble connecting to the N5200, you can try the following steps:
1. Double click the NIS icon on system tray, and then configure the
Personal Firewall.
2. On the Programs page, find the SetupWizard.exe and change its
permission to "Permit All". If it's not in the program list, use the Add or
Program Scan buttons to find it.
3. On the Networking page, manually add N5200 IP address (i.e.
192.168.1.100) to the Trusted list.
Replacing Damaged Hard Drives
If you are using RAID 1, RAID 5, RAID 6, or RAID 10, you can easily replace a
damaged hard drive in the Thecus N5200 while keeping your data secure with the
system’s automatic data recovery.
Hard Drive Damage
When a hard drive is damaged and data in the RAID volume, the system LCD will
display warning message also the system beeps.
Replacing a Hard Drive
To replace a hard disk drive in the N5200:
1. Remove the tray with the damaged hard disk.
2. Unscrew the damaged hard disk and remove it from the tray.
3. Slide a new hard disk into the tray and fasten the screws.
4. Insert the hard disk tray back into the N5200 until it snaps into place. You
can also lock it with a key if desired.
5. The LED blinks green when the HDD is accessed.
RAID Auto-Rebuild
When using RAID 1, 5, 6, or 10 on the N5200, you can use the auto-rebuild
function when an error is detected.
1. When a hard disk fails the system beeps and/or an email notification is
sent to specified receivers.
2. Check the LCD to see which disk has failed.
3. Follow the steps mentioned above to replace the failed hard disk.
4. The system automatically recognizes the new hard disk and starts the
auto-rebuild sequence to resume its status before the hard disk crash.
Page 73

73
Chapter 8: Troubleshooting
Forgot My Password
If you forget your password, you can reset the unit to use the defaul t password.
To do this, press the reset button on the front panel after system is booted, and
N5200 will be reset. WAN IP address will become 192.168.1.100 and admin
password will be admin.
Forgot My Network IP Address
If you forget your network IP address and have no physical access to the system,
you can find out the IP address by either looking directly onto the N5200’s LCD
panel, or by using the setup wizard to retrieve the IP of your N5200.
1. Start the Setup Wizard, and it will automatically detect all Thecus IP
storage products on your network.
2. You should be able to find the IP address of the N5200 which you have
forgotten in the Device Discovery screen.
Resetting NAS IP Address and Admin Password
In case you changed the N5200 IP address and then forgot it, or forgot the
administration password, follow the steps below to reset to default settings:
1. Power on the N5200 till system ready and press the Reset button while
buzzer with long beeping approximately 3-5 seconds. (The reset button is
right below power button)
2. This resets the N5200 to its default IP address and password settings.
Default IP: 192.168.1.100 for WAN and 192.168.2.100 for LAN
Default admin password: admin
Jumbo Frame support: disabled
HTTP Port: 80, HTTPs:443
Can't Map a Network Drive in Windows XP
You may have problems mapping a network drive under the following conditions:
1. The network folder is currently mapped using a different user name and
password. To connect using a different user name and password, first
disconnect any existing mappings to this network share.
2. The mapped network drive could not be created because the following
error has occurred: Multiple connections to a server or shared
resource by the same user, using more than one user name, are
not allowed. Disconnect all previous connections to the server or shared
resource and try again.
To check out existing network connections, type net use under the DOS prompt.
You may refer the URL below for more network mapping information.
http://esupport.thecus.com/support/index.php?_m=downloads&_a=viewdownload&downloaditemid=5
7&nav=0
Page 74

Restoring Factory Defaults
From the System menu, choose the Factory Default item and the Reset to
Factory Default screen appears. Press Apply to reset the N5200 to factory
default settings.
WARNING
Resetting to factory defaults will not erase the data
disks, but WILL revert all the settings to the factor
stored in the hard
y default values.
Problems with Time and Date Settings
The administrator is able to select an NTP Server to keep the N5200’s time
synchronized. However, if the N5200 can not access the Internet, you may
encounter a problem when setting the Time and Time Zone. If this happens:
1. Login to the Web Administration Interface.
2. Navigate to System > Time.
3. Under NTP Server, select No.
4. Set the Date, Time, and Time Zone.
5. Click Apply.
In addition, if the N5200 is able to access the Internet and you want to keep the
NTP Server clock.isc.org by default, please make sure the DNS Server is correctly
entered, thereby allowing the NTP Server name to correctly resolve. (See
Network > WAN > DNS Server)
74
Page 75

75
Appendix A: Product Specifications
Hardware Specifications
Product Model N5200B N5200BR
Core Processors / Memory
Processor Intel® 600MHz Celeron® M
Memory 512MB DDR
Network Interfaces
WAN Gigabit RJ-45 connector Gigabit RJ-45 connector
LAN Gigabit RJ-45 connector 4 Port Gigabit switch
Storage
HDD Bays 5 x 3.5” SATA II HDD, hot-swappable
HDD Support SATA II HDDs up to 1000GB
eSATA 1 x eSATA connector for capacity expansion
I/O Interfaces
USB Ports 3 x USB type A ports (Host mode)
1 x USB type B ports (Client mode)
System Information
LCD Control Panel For basic configurations and status display
System LED Display 5 x LED (DOM, Network Activity x 2, USB Copy,
System Busy)
Physical
Height 230 mm
Width 190 mm
Depth 230 mm
Power Supply Server-rated AC power supply
100/220V AC, 50/60Hz, Auto-detect
Security Lockable disk trays
Environment
Temperature 0 ~ 40°C
Humidity 20 ~ 85% relative humidity (non-condensing)
Certifications CE, FCC, BSMI, C-Tick, RoHS Compliant
Software Specifications
Network File Protocols Microsoft Networks (CIFS/SMB)
Apple Filing Protocol (AFP 3.1)
Network File System (NFS v3)
File Transfer Protocol (FTP)
Hyper Text Transfer Protocol (HTTP)
Secure Hyper Text Transfer Protocol (HTTPs)
Authentication Local User Account
Microsoft NT Domain Controller (PDC)*
Microsoft Active Directory Authentication (AD)*
Network Client Type Microsoft Windows NT/2000/XP/2003/Vista
Unix/Linux/BSD
MAC OS X/9/8.6
Network Configuration Fixed IP address
Dynamic IP address
802.3ad based failover and link aggregation*
Page 76

76
(*N5200B only)
Disk Management Disk status monitoring (S.M.A.R.T.)
Disk idle spin-down
RAID RAID 0, 1, 5, 6, 10, and JBOD
Auto rebuild
Hot swappable
Hot spare
Disk roaming
RAID level migration
RAID expansion
Folder Management Share folder level permission
File level permission
Public folder
Quota Management Share folder quota control
Backup Thecus Backup Utility (Windows XP/2000 and MAC
OS X)
Thecus Nsync
System Management Web GUI
Multilingual support (English, French, German,
Italian, Traditional Chinese, Simplified Chin ese,
Japanese, Korean, and Spanish)
NTP support
Wake-on-LAN
Scheduled Power On/Off
Event Notification Email notification
Buzzer notification
LCD
UPS Support UPS monitoring via RS-232 and system shutdown
on low battery
Printer Server USB Printer (IPP support)
Supported USB Devices USB Printer
External HDD/flash disk
USB IEEE 802.11 b/g dongle w/AP mode support**
Setup Utility Windows 2000/XP/2003
MAC OS X
*PDC/AD support: Works as a client member in a Microsoft NT 4.0 domain/Active
Directory domain, allowing the N5200 to utilize the domain users and groups
setting for authentication to the system and authorization to the share folders.
**For supported USB dongles, please contact sales@thecus.com
Page 77

Appendix B: Customer Support
If your N5200 is not working properly, we encourage you to check out Chapter 8:
Troubleshooting, located in this manual. You can also try to ensure that you are
using the latest firmware version for your N5200. Thecus is committed to
providing free firmware upgrades to our customers. Our newest firmware is
available on our Download Center:
http://www.thecus.com/download.php
If you are still experiencing problems with your N5200, or require a Return
Merchandise Authorization (RMA), feel free to contact technical support via our
Technical Support Website:
http://www.thecus.com/support_tech.php
Customers in the US should send all technical support enquiries to t his email
address:
support-us@thecus.com
For Sales Information you can e-mail us at:
sales@thecus.com
Thank you for choosing
Thecus!
77
Page 78

78
Appendix C: RAID Basics
Overview
A Redundant Array of Independent Disks (RAID) is an array of several hard disks
that provide data security and high performance. A RAID system accesses several
hard disks simultaneously, which improves I/O performance over a single hard
disk. Data security is enhanced by a RAID, since data loss due to a hard disk
failure is minimized by regenerating redundant data from the other RAID hard
disks.
Benefits
RAID improves I/O performance, and increases data security through fault
tolerance and redundant data storage.
Improved Performance
RAID provides access to several hard disk drives simultaneously, which greatly
increases I/O performance.
Data Security
Hard disk drive failure unfortunately is a common occurrence. A RAID helps
prevent against the loss of data due to hard disk failure. A RAID offers additional
hard disk drives that can avert data loss from a hard disk drive failure. If a hard
drive fails, the RAID volume can regenerate data from the data and parity stored
on its other hard disk drives.
RAID Levels
The Thecus N5200 supports standard RAID levels 0, 1, 5, 6, 10, and JBOD. You
choose a RAID level when you create a system volume. The factors for selecting a
RAID level are:
• Your requirements for performance
• Your need for data security
• Number of hard disk drives in the system, capacity of hard disk drives in
the system
The following is a description of each RAID level:
RAID 0
RAID 0 is best suited for applications that need high bandwidth but do not require
a high level of data security. The RAID 0 level provides the best performance of
all the RAID levels, but it does not provide data redundancy.
RAID 0 uses disk striping and breaking up data into blocks to write across all hard
drives in the volume. The system can then use multiple h ard drives for faster
read and write. The stripe size parameter that was set when the RAID was
created determines the size of each block. No parity calculations complicate the
write operation.
Page 79

79
RAID 1
RAID 1 mirrors all data from one hard disk drive to a second one hard disk drive,
thus providing complete data redundancy. However, the cost of data storage
capacity is doubled.
This is excellent for complete data security.
RAID 5
RAID 5 offers data security and it is best suited for networks that perform many
small I/O transactions at the same time, as well as applications that require data
security such as office automation and online customer service. Use it also for
applications with high read requests but low write requests.
RAID 5 includes disk striping at the byte level and parity information is written to
several hard disk drives. If a hard disk fails the system uses parity stored on each
of the other hard disks to recreate all missing information.
RAID 6
RAID 6 is essentially an extension of RAID level 5 which allows for additional fault
tolerance by using a second independent distributed parity scheme (dual parity)
Data is striped on a block level across a set of drives, just like in RAID 5, and a
second set of parity is calculated and written across all the drives; RAID 6
provides for an extremely high data fault tolerance and can sustain two
simultaneous drive failures.
This is a perfect solution for mission critical applications.
RAID 10
RAID 10 is implemented as a striped array whose segments are RAID 1 arrays.
RAID 10 has the same fault tolerance as RAID level 1.
RAID 10 has the same overhead for fault-tolerance as mirroring alone. High I/O
rates are achieved by striping RAID 1 segments.
Under certain circumstances, RAID 10 array can sustain up to 2 simultaneous
drive failures
Excellent solution for applications that would have ot herwise gone with RAID 1
but need an additional performance boost.
JBOD
Although a concatenation of disks (also called JBOD, or "Just a Bunch of Disks") is
not one of the numbered RAID levels, it is a popular method for combining
multiple physical disk drives into a single virtual one. As the name implies, disks
are merely concatenated together, end to beginning, so they appear to be a
single large disk.
As the data on JBOD is not protected, one drive failure could result tot al data loss.
Stripe Size
The length of the data segments being written across multiple hard disks. Data is
written in stripes across the multiple hard disks of a RAID. Since multiple disks
are accessed at the same time, disk striping enhances performance. The stripes
can vary in size.
Page 80

Disk Usage
When all 5 disks are of the same size, and used in RAID, N5200 disk usage
percentage is listed below:
RAID Level Percentage Used
RAID 0 100%
RAID 1 20%
RAID 5 80%
RAID 6 60%
RAID 10 50%
JBOD 100%
NOTE
RAID 10 allows only 4 disks and one as spare disk.
80
Page 81

81
Appendix D: Active Directory Basics
Overview
With Windows 2000, Microsoft introduced Active Directory (ADS), which is a large
database/information store. Prior to Active Directory the Windows OS could not
store additional information in its domain database. Active Directory also solved
the problem of locating resources; which previously relied on Network
Neighborhood, and was slow. Managing users and groups were among other
issues Active Directory solved.
What is Active Directory?
Active Directory was built as a scalable, extensible directory service that was
designed to meet corporate needs. A repository for storing user information,
accounts, passwords, printers, computers, network information and other data,
Microsoft calls Active Directory a "namespace" where names can be resolved.
ADS Benefits
ADS lets the N5200 integrate itself with the existing ADS in an office environment.
This means the N5200 is able to recognize your office users and passwords on the
ADS server. Other major benefits ADS support provides include:
1. Easy integration of the N5200 into the existing office IT infrastructure
The N5200 acts as a member of the ADS. This feature significantly lowers
the overhead of the system administrator. For example, corporate security
policies and user privileges on an ADS server can be enforced
automatically on the N5200.
2. Centralized user/password database
The N5200 does not maintain its own copy of the user/password database.
This avoids data inconsistency between the N5200 and other servers. For
example, without ADS support, an administrator might need to remove a
specific user privilege on the N5200 and each individual server. With ADS
support, the change on an ADS server is known to all of its ADS members.
Page 82

82
Appendix E: UPS Compatibility List
Brand Series Model Notes
Ablerex MS-RT
ActivePower 1400VA
AEC
MiniGuard UPS 700 M2501
cable
Back-UPS Pro
Matrix-UPS
Smart-UPS
Back-UPS 940-0095A/C cables, 940-0020B/C cables, 940-0023A cable
Back-UPS Office 940-0119A cable
Masterswitch Not a UPS - 9400020 cable
APC
Back-UPS RS 500 custom nonUSB cable
Regulator Pro serial
Resource
Home Office F6H350-SER, F6H500-SER, F6H650-SER
Belkin
Universal UPS F6C800-UNV, F6C120-UNV, F6C1100-UNV, F6H500ukUNV
Fortress (newer)
Fortress Telecom
Axxium Rackmount
Patriot Pro
Patriot Pro II
Patriot INT51 cable
Micro-Ferrups
Best Power
Fortress/Ferrups f-command
support
Centralion Blazer
Clary ST-800
Compaq T1500h
Cyber Power
Systems
320AVR, 500AVR, 650AVR, 700AVR, 800AVR
850AVR, 900AVR, 1250AVR,. 1500AVR, Power99
550SL, 725SL, CPS825VA, 1100AVR, 1500AVR-HO
Deltec PowerRite Pro II
Dynex 975AVR
Effekta MI/MT/MH 2502 cable
Energy Sistem (various)
ETA mini+UPS WinNT/Upsoft cable
ETA
mini+UPS PRO UPS Explorer
cable
NET *-DPC
Ever UPS
AP *-PRO
Ever-Power 625/1000
Exide NetUPS SE
PowerPal P-series
PowerPal L-series
PowerOn
Fenton
Technologies
PowerPure
Fairstone L525/L625/L750
Ares 700 and larger
Fideltronik
Other Ares models
Page 83
83
Brand Series Model Notes
PowerRite MAX
Fiskars
PowerServer 10, 30
All models with alarm interface
MP110/210
MS-T
MS
Gamatronic
µPS3/1
Gemini UPS625/UPS1000
R3000 XR
HP
R5500 XR
INELT Monolith 1000LT
Infosec iPEL 350, 500, 750, 1000
Ippon (various)
Liebert
UPStation GXT2 contact-closure
cable
Masterguard (various)
HF Line 1..4 boards, /2 5..8 boards
HF Millennium 810, 820
HF TOP Line 910, 920, 930, 940, 950, 960, 970, 980
ECO Network
750, M1000, M1050, M1500, M1800
M2000, M2100, M2500, M3000
ECO 305, 308, 311, 511, 516, 519, 522
ally HF 800, 1000, 1250, 1600, 2000, 2500
Meta System
Megaline 1250, 2500, 3750, 5000, 6250, 7500, 8750, 10000
NOVA AVR 600 Serial
NOVA AVR 1100 Serial
Pulsar Ellipse USBS Serial cable, S, Premium USBS Serial cable, Premium S
Ellipse Office
600 Serial cable, 750 Serial cable, 1000 Serial cable, 1500 Serial
cable
Pulsar EXtreme C / EX RT
Comet EX RT Serial port, 3:1 Serial port
Pulsar Esprit
Evolution S 1250, 1750, 2500, 3000 Serial Port
Pulsar M 2200, 3000, 3000 XL Serial Port
700, 1000, 1500, 1000 RT2U, 1500 RT2U, MX 4000 RT, MX 5000
RT
Pulsar
Evolution, EXtreme C, ES+, ESV+, SV, ESV, EX, EXL, PSX, SX,
Extreme
Serial Port
Comet EXtreme
MGE UPS
SYSTEMS
Comet / Galaxy (Serial) Utalk Serial Card (ref 66060), HID COM Serial Card (ref 66066)
MicroDowell B.Box BP 500, 750, 1000, 1500
Solis 1.0 1000VA, 1.5 1500VA, 2.0 2000VA, 3.0 3000VA
Microsol
Rhino 6.0 6000VA, 7.5 7500VA, 10.0 10000VA, 20.0 20000VA
Various
Mustek
Powermust
400VA Plus, 600VA Plus, 800VA Pro
1000VA Plus, 1400VA Plus, 2000VA USB
Nitram Elite 500, 2002
Oneac
EG/ON Series advanced
interface
Online P-Series
OnLite AQUA 50
Orvaldi various not 400 or 600
SMK-800A
Powercom
ULT-1000
Page 84

Brand Series Model Notes
TrustTrust 425/625
BNT-1000AP
Advice Partner/King Pr750
Powercom
BNT-2000AP
PowerGuard PG-600
PowerKinetics 9001
PowerTech Comp1000 DTR cable power
Power Walker Line-Interactive VI1000
Powerware
3110, 3115, 5119, 5125, 5119 RM, PW5115
PW5125PW9120, PW9125, 9120, 9150, 9305
Powerwell
PM525A/-625A/-800A/-1000A/1250A
RPF525/625/800/1000
RPT-800A
Repotec
RPT-162A
SMS (Brazil) Manager III
SOLA 325, 520, 610, 620, 330
SOLA/BASIC
Mexico
various ISBMEX protocol
Socomec
Sicon
Egys 420 VA
Soltec Winmate 525/625/800/1000
Soyntec Sekury C 500, 800
SquareOne
Power
QP1000
SuperPower HP360, Hope-550
500/1000 smart - shipped with
SafeNet
500/1000 contact closure shipped with UPSmart
Sweex
BC100060 800VA
Sysgration UPGUARDS Pro650
Tecnoware Easy Power 1200
SmartUPS
SmartOnline
Tripp-Lite
(various) Lan 2.2 interface black 73-0844 cable
Trust
UPS 1000 Management PW4105
UNITEK Alpha 500 IC, 1000is, 500 ipE
LAN Saver 600
UPSonic
Power Guardian
(various)
Victron/IMV
Lite crack cable
• The UPSes marked Blue have been tested and work well
• If your UPS is not in the support list, be sure that the UPS supports
one of following protocols:
o SEC protocol
o Generic RUPS model
o Generic RUPS 2000 (Megatec M2501 cable)
o PhoenixTec protocol
o Safenet software
NOTE
84
Page 85

85
Appendix F: Licensing Information
Overview
This product included copyrighted third-party software licensed under the terms
of GNU General Public License. Please see THE GNU General Public License for
extra terms and conditions of this license.
Source Code Availability
Thecus Technology Corp. has exposed the full source code of the GPL licensed
software. For more information on how you can obtain our source code, please
visit our web site, http://www.thecus.com.
Copyrights
• This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com).
• This product includes software developed by Mark Murray.
• This product includes software developed by Eric Young
(eay@cryptsoft.com).
• This product includes software developed by the OpenSSL Project for use in
the OpenSSL Toolkit (http://www.openssl.org/).
• This product includes PHP, freely available from (http://www.php.net/).
• This product includes software developed by the Univ ersity of California,
Berkeley and its contributors.
• This product includes software developed by Winning Strategies, Inc.
• This product includes software developed by the Apache Group for use in
the Apache HTTP server project (http://www.apache.org/).
• This product includes software developed by Softweyr LLC, the University
of California, Berkeley, and its contributors.
• This product includes software developed by Bodo Moeller.
• This product includes software developed by Greg Roelofs and contributors
for the book, "PNG: The Definitive Guide," published by O'Reilly and
Associates.
• This product includes software developed by the NetBSD Foundation, Inc.
and its contributors.
• This product includes software developed by Yen Yen Lim and North Dakota
State University.
• This product includes software developed by the Computer Systems
Engineering Group at Lawrence Berkeley Laboratory.
• This product includes software developed by the Kungliga Tekniska
Högskolan and its contributors.
• This product includes software developed by the Nick Simicich.
• This product includes software written by Tim Hudson (tjh@cryptsoft.com).
• This product includes software developed by Christopher G. Demetriou for
the NetBSD Project.
Page 86

86
CGIC License Terms
Basic License
CGIC, copyright 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004 by
Thomas Boutell and Boutell.Com, Inc.
Permission is granted to use CGIC in any application, commercial or
noncommercial, at no cost. HOWEVER, this copyright paragraph must appear on
a "credits" page accessible in the public online and offline docu mentation of the
program. Modified versions of the CGIC library should not be distributed without
the attachment of a clear statement regarding the author of the modifications,
and this notice may in no case be removed. Modifications may also be submitted
to the author for inclusion in the main CGIC distribu tion.
GNU General Public License
Version 2, June 1991
Copyright © 1989, 1991 Free Software Foundation, Inc.
51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies of this license
document, but changing it is not allowed.
PREAMBLE
The licenses for most software are designed to take away your freedom to share
and change it. By contrast, the GNU General Public License is intended to
guarantee your freedom to share and change free software--to make sure the
software is free for all its users. This General Public License applies to most of
the Free Software
Foundation's software and to any other program whose authors commit to using
it. (Some other Free Software Foundation software is covered by the GNU Library
General Public License instead.) You can apply it to your programs, t oo.
When we speak of free software, we are referring to freedom, not price. Our
General Public Licenses are designed to make sure that you have the freedom to
distribute copies of free software (and charge for this service if you wish), that
you receive source code or can get it if you want it, that you can change the
software or use pieces of it in new free programs; and that you know you can do
these things.
To protect your rights, we need to make restrictions that forbid anyone to deny
you these rights or to ask you to surrender the rights. These restrictions translate
to certain responsibilities for you if you distribute copies of the software, or if you
modify it.
For example, if you distribute copies of such a program, whether gratis or for a
fee, you must give the recipients all the rights that you have. You must make
sure that they, too, receive or can get the source code. And you must show them
these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer
you this license which gives you legal permission to copy, distribute and/or
modify the software.
Page 87

87
Also, for each author's protection and ours, we want to make certain that
everyone understands that there is no warranty for this free software. If the
software is modified by someone else and passed on, we want its recipients to
know that what they have is not the original, so that any problems introduced by
others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish
to avoid the danger that redistributors of a free program will individually obtain
patent licenses, in effect making the program proprietary. To prevent this, we
have made it clear that any patent must be licensed for everyone's free use or
not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice
placed by the copyright holder saying it may be distributed under the terms of
this General Public License. The "Program", below, refers to any such
program or work, and a "work based on the Program" means either the
Program or any derivative work under copyright law: that is to say, a work
containing the Program or a portion of it, either verbatim or with modifications
and/or translated into another language. (Hereinafter, translation is included
without limitation in the term "modification" .) Each licensee is addressed as
"you".
Activities other than copying, distribution and modification are not covered by
this License; they are outside its scope. The act of running the Program is not
restricted, and the output from the Program is covered only if its contents
constitute a work based on the Program (independent of having been made
by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as
you receive it, in any medium, provided that you conspicuously and
appropriately publish on each copy an appropriate copyright notice and
disclaimer of warranty; keep intact all the notices that refer to this License
and to the absence of any warranty; and give any other recipients of the
Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may
at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus
forming a work based on the Program, and copy and distribute such
modifications or work under the terms of Section 1 above, provided that you
also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that
you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in
part contains or is derived from the Program or any part thereof, to be
licensed as a whole at no charge to all third parties under the terms of this
License.
Page 88

88
c) If the modified program normally reads commands interactively when run,
you must cause it, when started running for such interactive use in the
most ordinary way, to print or display an announcement including an
appropriate copyright notice and a notice that there is no warranty (or else,
saying that you provide a warranty) and that users may redistribute the
program under these conditions, and telling the user how to view a copy of
this License. (Exception: if the Program itself is interactive but does not
normally print such an announcement, your work based on the Program is
not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable
sections of that work are not derived from the Program, and can be
reasonably considered independent and separate works in themselves, then
this License, and its terms, do not apply to those sections when you distribute
them as separate works. But when you distribute the same sections as part
of a whole which is a work based on the Program, the distribution of the whole
must be on the terms of this License, whose permissions for other licensees
extend to the entire whole, and thus to each and every part regardless of who
wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to
work written entirely by you; rather, the intent is to exercise the right to
control the distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with
the Program (or with a work based on the Program) on a volume of a storage
or distribution medium does not bring the other work under the scope of this
License.
3. You may copy and distribute the Program (or a work based on it, under
Section 2) in object code or executable form under the terms of Sections 1
and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable sour ce
code, which must be distributed under the terms of Sections 1 and 2 above on
a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give
any third party, for a charge no more than your cost of physically performing
source distribution, a complete machine-readable copy of the corresponding
source code, to be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to
distribute corresponding source code. (This alternative is allowed only for
noncommercial distribution and only if you received th e program in object
code or executable form with such an offer, in accord with Subsection b
above.)
The source code for a work means the preferred form of the work for making
modifications to it. For an executable work, complete source code means all
the source code for all modules it contains, plus any associated interface
definition files, plus the scripts used to control compilation an d installation of
the executable. However, as a special exception, the source code distributed
need not include anything that is normally distributed (in either source or
binary form) with the major components (compiler, kernel, and so on) of the
Page 89

89
operating system on which the executable runs, unless that component itself
accompanies the executable.
If distribution of executable or object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the source
code from the same place counts as distribution of the source code, even
though third parties are not compelled to copy the source along with the
object code.
4. You may not copy, modify, sublicense, or distribute the Program except as
expressly provided under this License. Any attempt otherwise to copy, modify,
sublicense or distribute the Program is void, and will automatically terminate
your rights under this License. However, parties who have received copies, or
rights, from you under this License will not have their lice nses terminated so
long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it.
However, nothing else grants you permission to modify or distribute the
Program or its derivative works. These actions are prohibited by law if you do
not accept this License. Therefore, by modifying or distributing the Program
(or any work based on the Program), you indicate your acceptance of this
License to do so, and all its terms and conditions for copying, distributing or
modifying the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the Program),
the recipient automatically receives a license from the original licensor to copy,
distribute or modify the Program subject to these terms and conditions. You
may not impose any further restrictions on the recipients' exercise of the
rights granted herein. You are not responsible for enforcing compliance by
third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement
or for any other reason (not limited to patent issues), conditions are imposed
on you (whether by court order, agreement or otherwise) that contradict the
conditions of this License, they do not excuse you from the cond itions of this
License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a
consequence you may not distribute the Program at all. For example, if a
patent license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then the only
way you could satisfy both it and this License would be to refrain entirely from
distribution of the Program.
If any portion of this section is held invalid or unenforceable u nder any
particular circumstance, the balance of the section is intended to apply and
the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or
other property right claims or to contest validity of any such claims; this
section has the sole purpose of protecting the integrity of the free software
distribution system, which is implemented by public license practices. Many
people have made generous contributions to the wide range of software
distributed through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing to
distribute software through any other system and a licensee cannot impose
that choice.
Page 90

90
This section is intended to make thoroughly clear what is believed t o be a
consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries
either by patents or by copyrighted interfaces, the original copyright holder
who places the Program under this License may add an explicit geographical
distribution limitation excluding those countries, so that distribution is
permitted only in or among countries not thus excluded. In such case, this
License incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the
General Public License from time to time. Such new versions will be similar in
spirit to the present version, but may differ in detail to address new problems
or concerns.
Each version is given a distinguishing version number. If the Program
specifies a version number of this License which applies to it and "any later
version", you have the option of following the terms and conditions either of
that version or of any later version published by the Free Software Foun dation.
If the Program does not specify a version number of this License, you may
choose any version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs
whose distribution conditions are different, write to the author to ask for
permission. For software which is copyrighted by the Free Software
Foundation, write to the Free Software Foundation; we sometimes make
exceptions for this. Our decision will be guided by the two goals of preserving
the free status of all derivatives of our free software and of promoting the
sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE
LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT
HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE
RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH
YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF
ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY
MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE
LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL,
INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR
INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS
OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED
BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE
WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY
HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
 Loading...
Loading...