Samsung WEA463E Users Manual

8.2.2.3 Manual configuration (Move)
Parameter
Description
MAC
MAC address of a detected AP
FROM
Previous classification of a MAC
TO
Classification to change
A user can change the classification of an unauthorized AP that is detected by the WI or
that is classified according to the rule configured by a user.
Configuration using CLI
1) Go to configure wi device configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# device
WEC8500/configure/wi/device#
By using the MAC of an unauthorized AP to change, execute the move command.
move [MAC] [FROM] [TO]
CHAPTER 8. Security
2) To check the changed configuration, use the following command.
show wi device ap list managed
show wi device ap list unmanaged
Configuration using Web UI
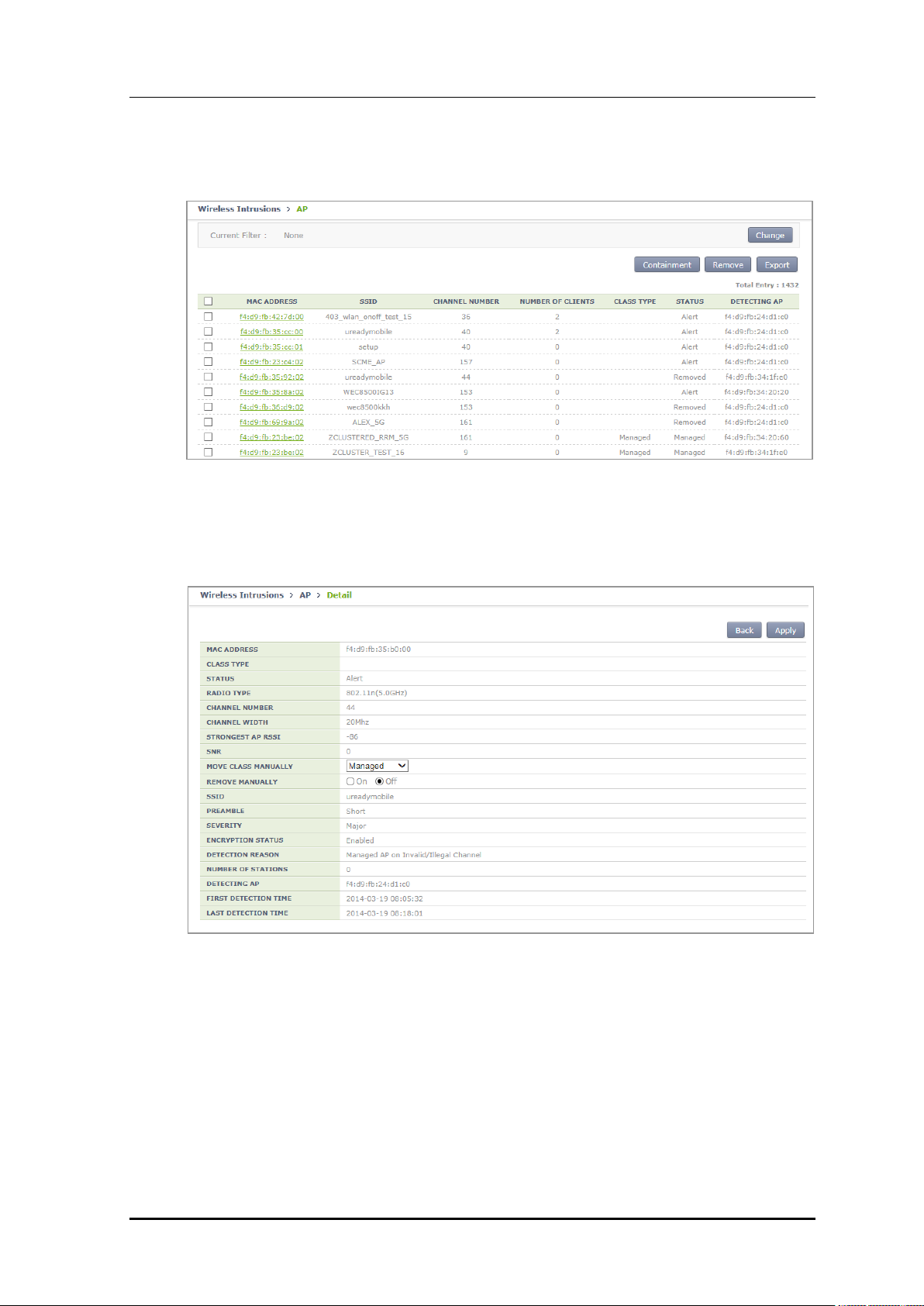
In the menu bar of <WEC Main window>, select <Monitor> and then select the
<Wireless Intrusion> <AP> menu in the sub-menus. And when the AP list is displayed,
select one out of the AP list to go to the detail view screen. In the detail view screen,
operator can manually change the classification of an AP by using the top down menu of
MOVE CLASSIFICATION MANUALLY.
© SAMSUNG Electronics Co., Ltd.
page 356 of 628
CHAPTER 8. Security
1) In the AP list screen, go to the detail view screen by clicking a MAC address.
Figure 165. List Window to Manually Change Classification
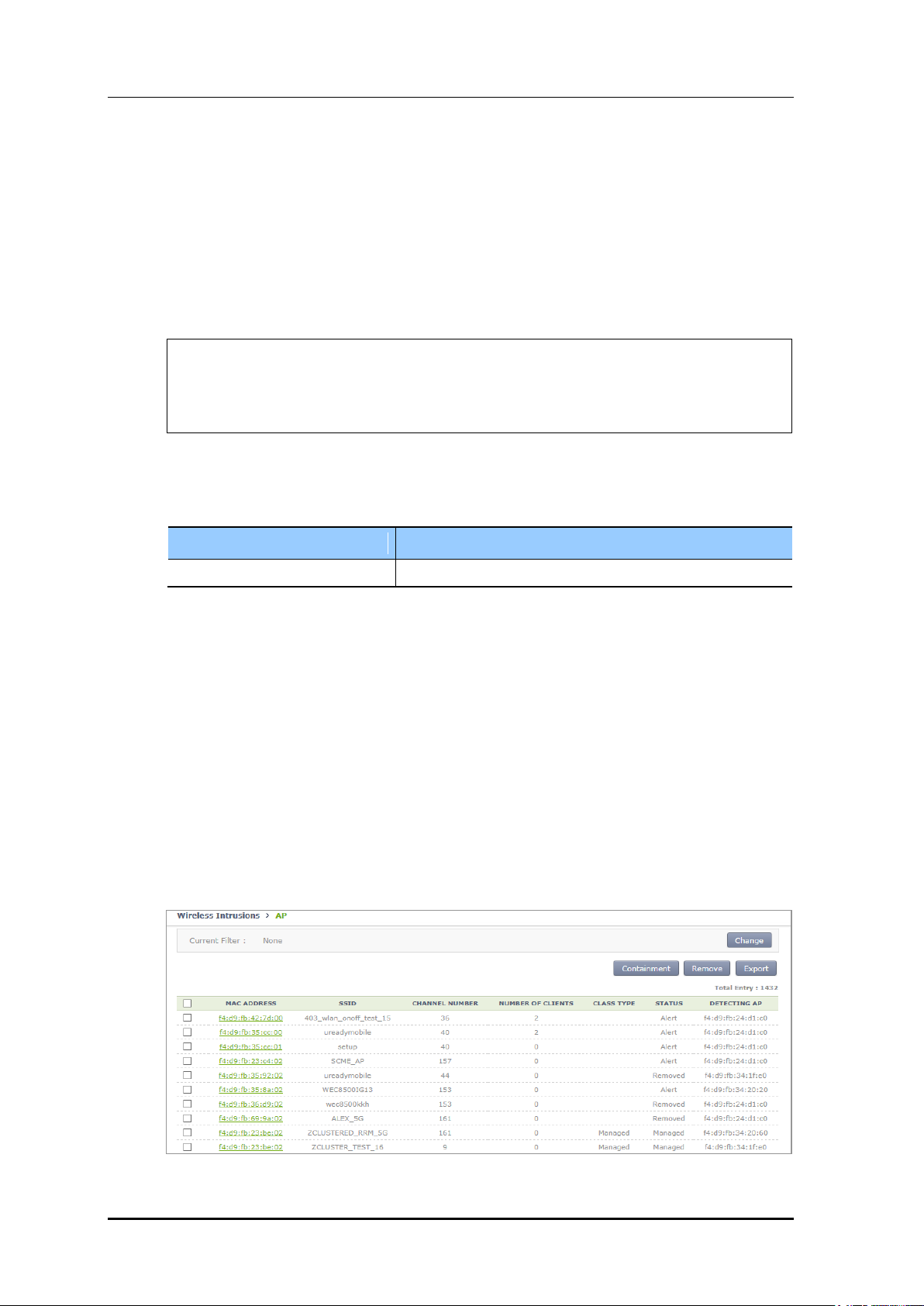
2) In the AP detail screen, change the classification and click Apply, then the
configuration is changed.
Figure 166. Classification Change Window in AP Detail Screen
© SAMSUNG Electronics Co., Ltd.
page 357 of 628
8.2.2.4 Manual configuration (Remove)
Parameter
Description
MAC
MAC address of an unauthorized AP
A user can manually change the status of an unauthorized AP to ‘Removed’, that is
detected by the WIDS or that is classified according to the rule configured by a user.
Configuration using CLI
1) Go to configure wi device configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# device
WEC8500/configure/wi/device#
2) By using the MAC of an unauthorized AP to change, execute the remove command.
remove [MAC]
CHAPTER 8. Security
3) To check the changed configuration, use the following command.
show wi device ap list removed
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Monitor> and then select the
<Wireless Intrusion> <AP> menu in the sub-menus. And when the AP list is displayed,
check a desired MAC in the list and click the <Remove> button to manually remove an AP.
In addition, after going into the detail view screen by selecting one out of the AP list,
operator can also remove an AP by changing the REMOVE MANUALLY option to On.
1) In the AP list screen, operator can change the status of several APs to ‘Removed’ by
clicking <Remove> button.
© SAMSUNG Electronics Co., Ltd.
Figure 167. List Window to Manually Remove
page 358 of 628
CHAPTER 8. Security
Parameter
Description
OPTION
Unauthorized AP detection option
NOTI_TYPE
Event save option
- notify: Notify the state with alarm
- detect: Save the state with sys log
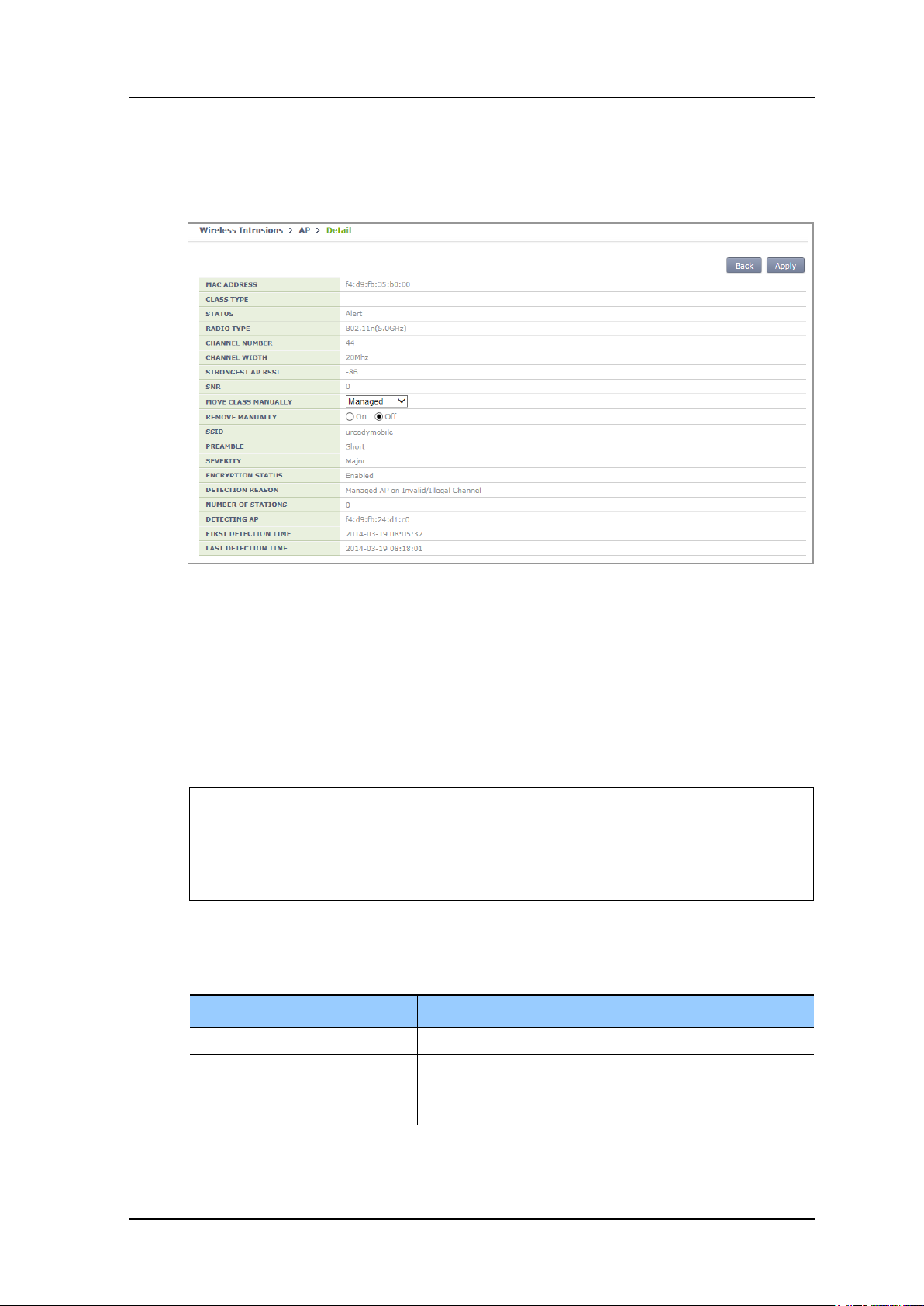
2) If you change the setting of REMOVE MANUALLY to ‘On’ in the AP detail screen
and click Apply, the AP status is changed to ‘Removed’.
Figure 168. Manual Remove Change Window in AP Detail Screen
8.2.2.5 Unauthorized AP detection option
Operator can enable or disable the AP detection option pre-defined in the system.
Configuration using CLI
1) Go to configure wi device ap configuration mode.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# device
WEC8500/configure/wi/device# ap
WEC8500/configure/wi/device/ap#
2) Using the following command, configure the unauthorized AP detection option.
[OPTION] [NOTI_TYPE]
© SAMSUNG Electronics Co., Ltd.
page 359 of 628
The description of OPTION parameter is as follows:
Parameter
Description
ap-blacklist-check
Allocates Rogue ID = 101 by checking a rogue included in the
black list.
managed_ssid_invalid_security
Allocates Rogue ID = 102 for an AP that uses a managed
SSID and its managed client is in the association status.
fakeap-beacon-on-invalid-channel
Allocates rogue ID = 103 for an AP whose UIC is invalid and
that uses a SSID that is not in the ssid white list among the
APs that use a managed MAC.
fakeap-beacon-without-ssid
Allocates Rogue ID = 104 for an AP whose UIC is invalid and
its SSID is hidden among the APs that use a managed MAC.
fakeap-managed-ssid
Allocates Rogue ID = 105 for an AP whose UIC is invalid and
its channel is not in the channel validation list among the APs
that use a managed MAC.
illegal-channel
Allocates Rogue ID = 106 if an AP uses a channel that is not
in the channel validation list among detected APs.
managedap-invalid-ssid
Allocates Rogue ID = 107 for an AP that uses a SSID that is
not in the ssid-whitelist among the APs that use a managed
MAC and its UIC is valid.
unknownap-managed-ssidwithauth-client
Allocates Rogue ID = 108 by checking the association status
between an unauthorized AP and a managed client.
CHAPTER 8. Security
3) To check the changed configuration, use the following command.
show wi device ap current-config
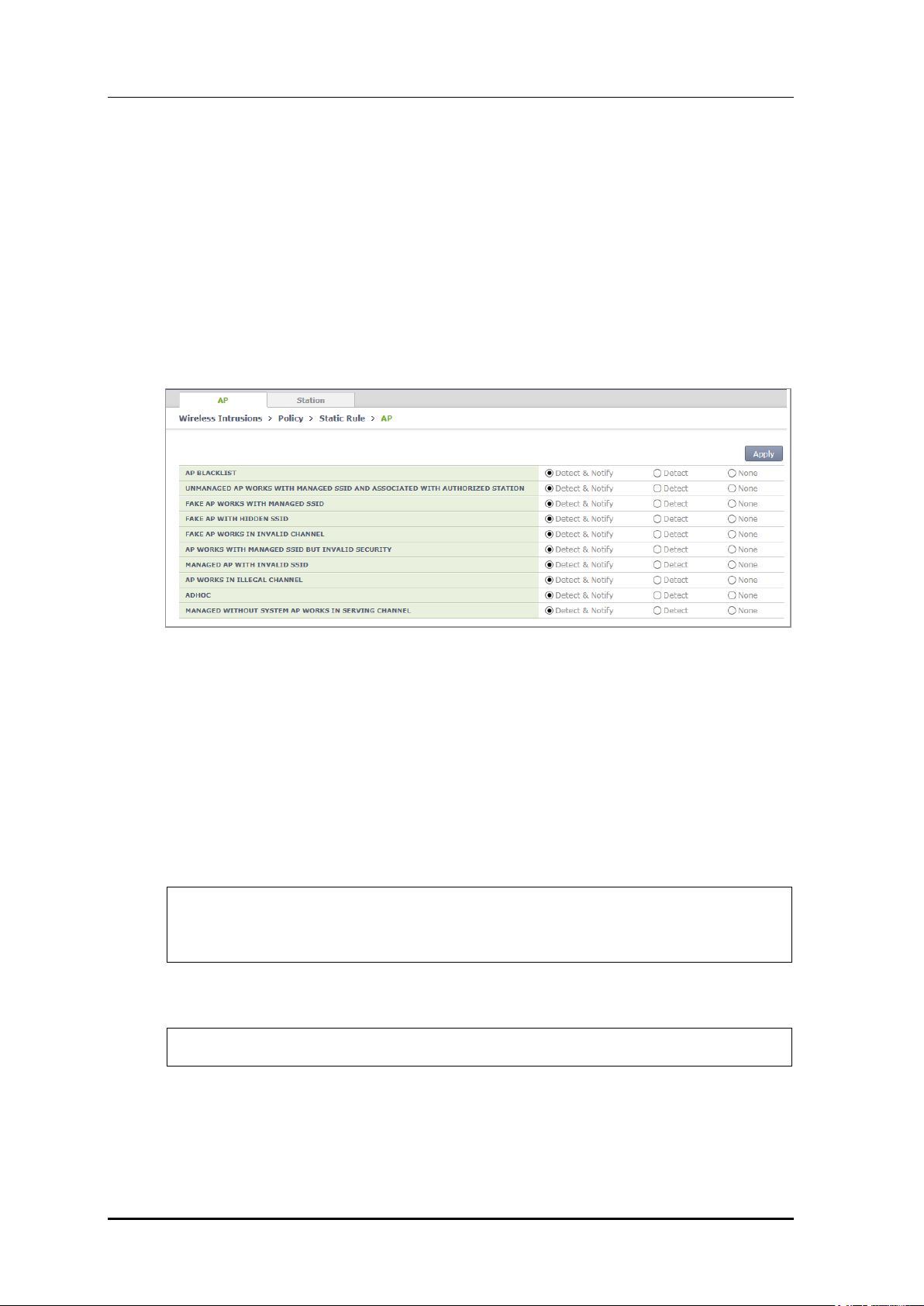
Configuration using Web UI
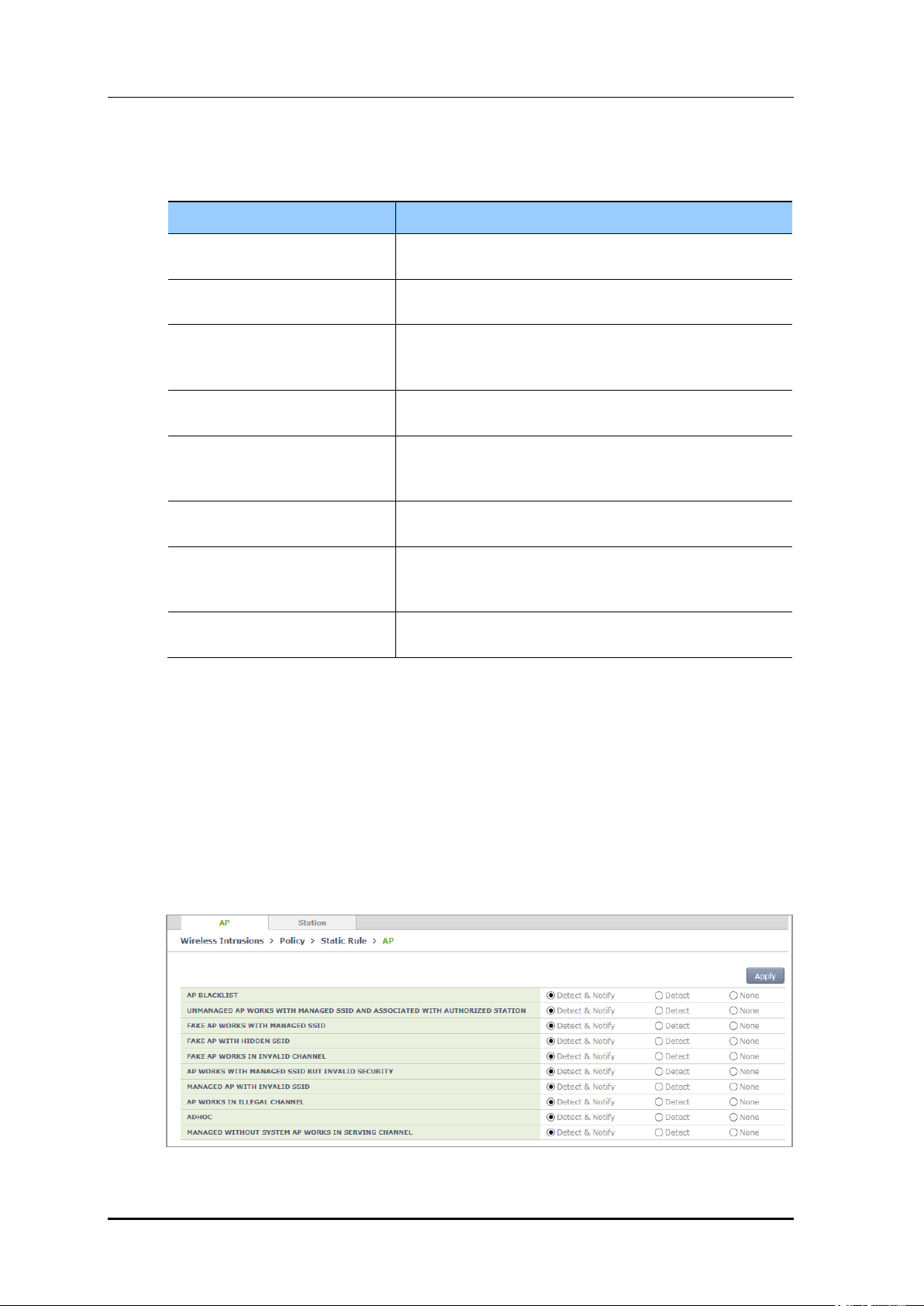
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<Wireless Intrusion> <Policy> <Static Rule> menu in the sub-menus. And then,
operator can change the setting by selecting <AP> at the upper tab and clicking Apply.
In the configuration screen, operator can check Option and click Apply for configuration.
Figure 169. Configuration Window for Unauthorized AP Detection Option
© SAMSUNG Electronics Co., Ltd.
page 360 of 628

8.2.2.6 Unauthorized client detection option
Parameter
Description
OPTION
Rogue Client detect option
NOTI_TYPE
Event save option
- notify: Notify the state with alarm
- detect: Save the state with sys log
Parameter
Description
assoc-fail-det
Classifies a client that exceeds the association fail threshold
as an unauthorized client.
auth-fail-det
Classifies a client that exceeds the authentication fail
threshold as an unauthorized client.
auth-request-det
Classifies a client that exceeds the authentication request
threshold as an unauthorized client.
deauth-request-det
Classifies a client that exceeds the de-authentication request
threshold as an unauthorized client.
exclusion-list-check
Classifies a MAC that does not exist in the client blacklist as
an unauthorized client.
oneXauth-fail-det
Classifies a client that exceeds the 802.1X authentication fail
threshold as an unauthorized client.
oui-list-check
Classifies an OUI that does not exist in the OUI list white list
as an unauthorized client.
probe-request-det
Classifies a client that exceeds the probe request threshold
as an unauthorized client.
webauth-fail-det
Classifies a client that exceeds the WEB authentication fail
threshold as an unauthorized client.
Operator can enable or disable the client detection option pre-defined in the system.
Configuration using CLI
1) Go to configure wi device client configuration mode.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# rogue
WEC8500/configure/wi/device# client
WEC8500/configure/wi/device /client#
2) Configure the unauthorized client detection option by using the following command.
[OPTION] [NOTI_TYPE]
CHAPTER 8. Security
The description of OPTION parameter is as follows:
© SAMSUNG Electronics Co., Ltd.
page 361 of 628
CHAPTER 8. Security
3) To check the changed configuration, use the following command.
show wi device client current-config
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<Wireless Intrusion> <Policy> <Static Rule> menu in the sub-menus. And then,
operator can change the setting by selecting <Station> at the upper tab and clicking Apply.
In the configuration screen, operator can check Option and click Apply for configuration.
Figure 170. Configuration Window for Unauthorized Station Detection Option
8.2.2.7 Unauthorized Channel Validation Configuration
The unauthorized channel validation function helps an operator detect an AP that uses an
unauthorized channel other than configured channels. The configuration procedure is as
follows:
Configuration using CLI
1) Go to configure wi channel-validation configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# channel-validation
2) Enable the unauthorized channel validation function.
WEC8500/configure/wi/channel-validation# enable
3) Configure an authorized channel.
add [CHANNEL]
© SAMSUNG Electronics Co., Ltd.
page 362 of 628
CHAPTER 8. Security
Parameter
Description
CHANNEL
Authorized channel number (e.g. add 2, 3, 4)
4) To check the changed configuration, execute the following command.
show wi current-config
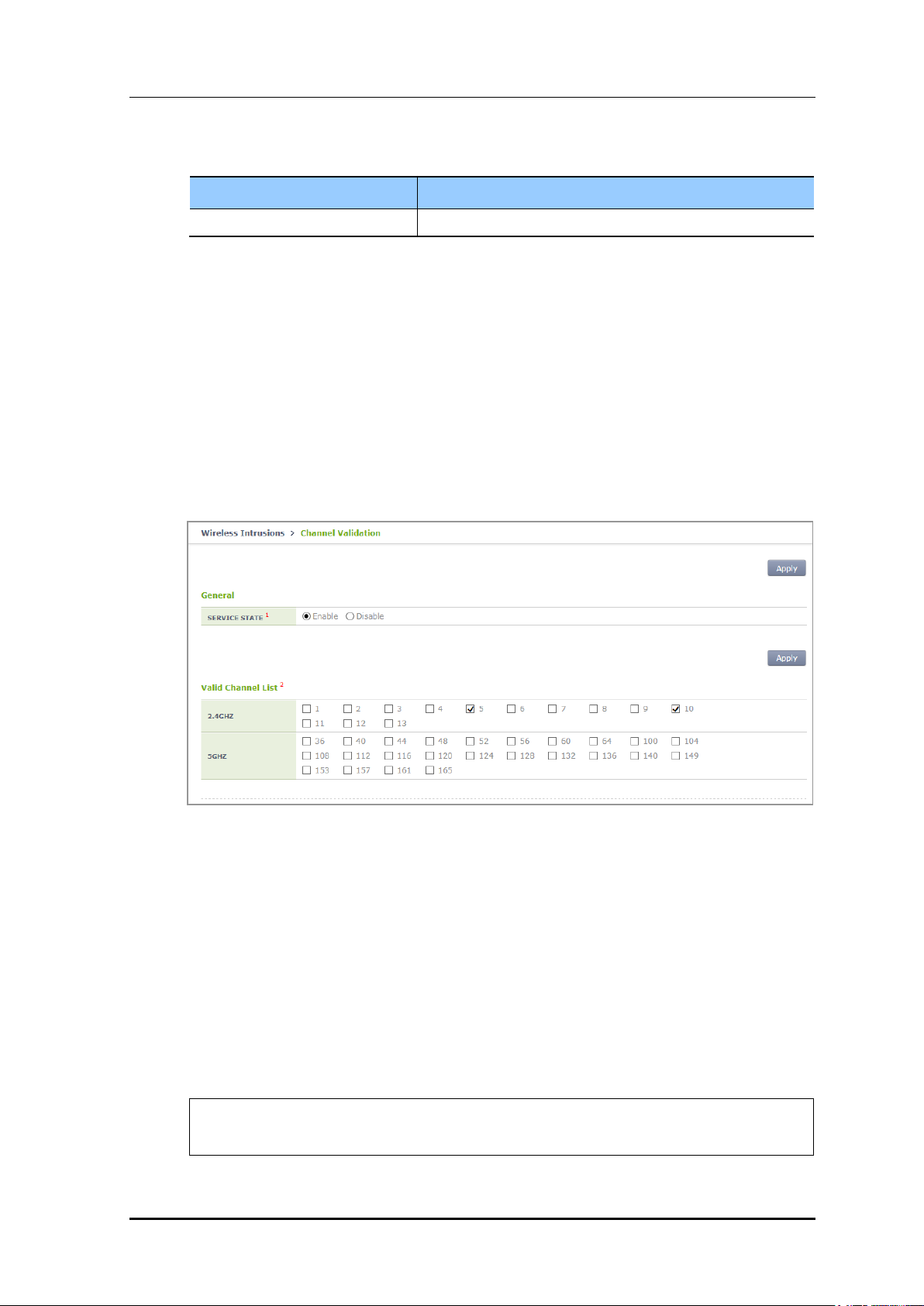
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<Wireless Intrusion> <Channel Validation> menu in the sub-menus. And then,
operator can configure the SERVICE STATE and Valid Channel List in the screen.
Operator can change configuration after changing the SERVICE STATE and Valid Channel
List and clicking Apply.
Figure 171. Configuration Window for Channel Validation
8.2.2.8 Configuring and Searching Black/White List
Operator can configure classification to distinguish authorized and unauthorized
APs/stations. The administrator configurable lists include <AP black-list, Station black-list,
Managed OUI, Managed/Neighbor AP>. The <Managed AP, Managed Station, Managed
SSID> are automatically configured and can be used only for search.
Configuration using CLI
1) Go to the configure wids configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wi
© SAMSUNG Electronics Co., Ltd.
page 363 of 628
2) Configure the AP black-list.
Parameter
Description
MAC
MAC address that will be used as AP black-list
Parameter
Description
MAC
MAC address that will be used as a black-list of the station
Parameter
Description
OUI
First 3 bytes of station MAC address
Parameter
Description
MAC
AP MAC address of Managed/Neighbor AP
TYPE
- Managed: Indicates that the address is located internally
during configuration
- Neighbor: Indicates that the address is located externally
during configuration
ap-blacklist [MAC]
3) Configure the station black-list.
client-black-list [MAC]
4) Configure the Managed Organizationally Unique Identifier (OUI).
oui-whitelist [OUI]
CHAPTER 8. Security
5) Configure the Managed/Neighbor AP.
Managed [MAC] [TYPE]
6) To check the changed configuration, execute the following command.
show wi lists managed-ap
show wi lists ap-blacklist
show wi lists managed-stat
show wi lists client-blacklist
show wi lists managed ssid
show wi lists oui-list
show wi lists neighbor-ap
© SAMSUNG Electronics Co., Ltd.
page 364 of 628
CHAPTER 8. Security
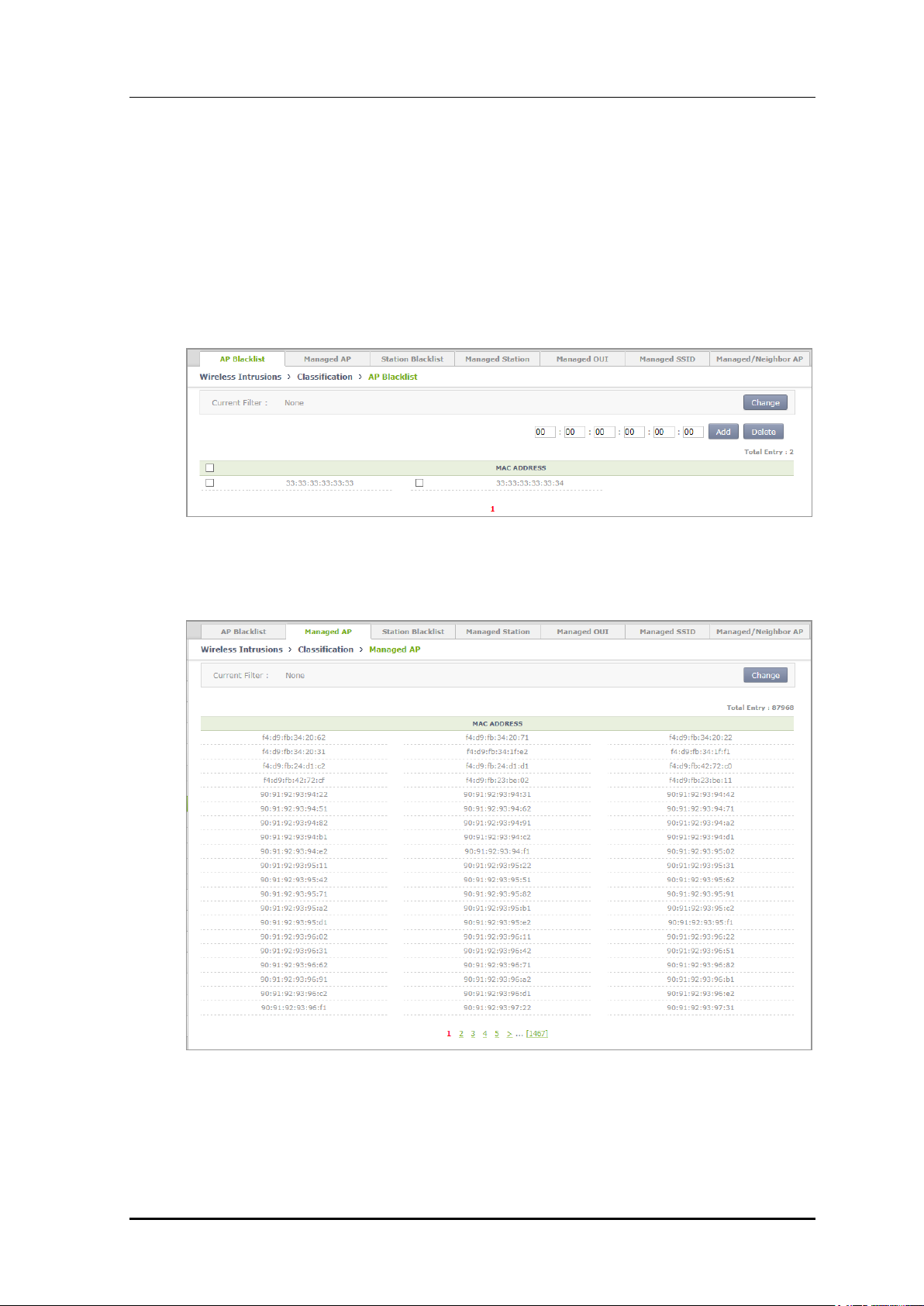
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<Wireless Intrusion> <Classifiation> menu in the sub-menus. And then, operator can
configure and search by using the upper tab in the screen.
1) In the [AP Blacklist] tab, operator can add an AP blacklist by entering a MAC and
click Add. Operator can also delete it by using Delete.
Figure 172. AP blacklist Configuration Window
2) In the [Managed AP] tab, operator can search for a Managed AP.
© SAMSUNG Electronics Co., Ltd.
Figure 173. Managed AP Window
page 365 of 628
CHAPTER 8. Security
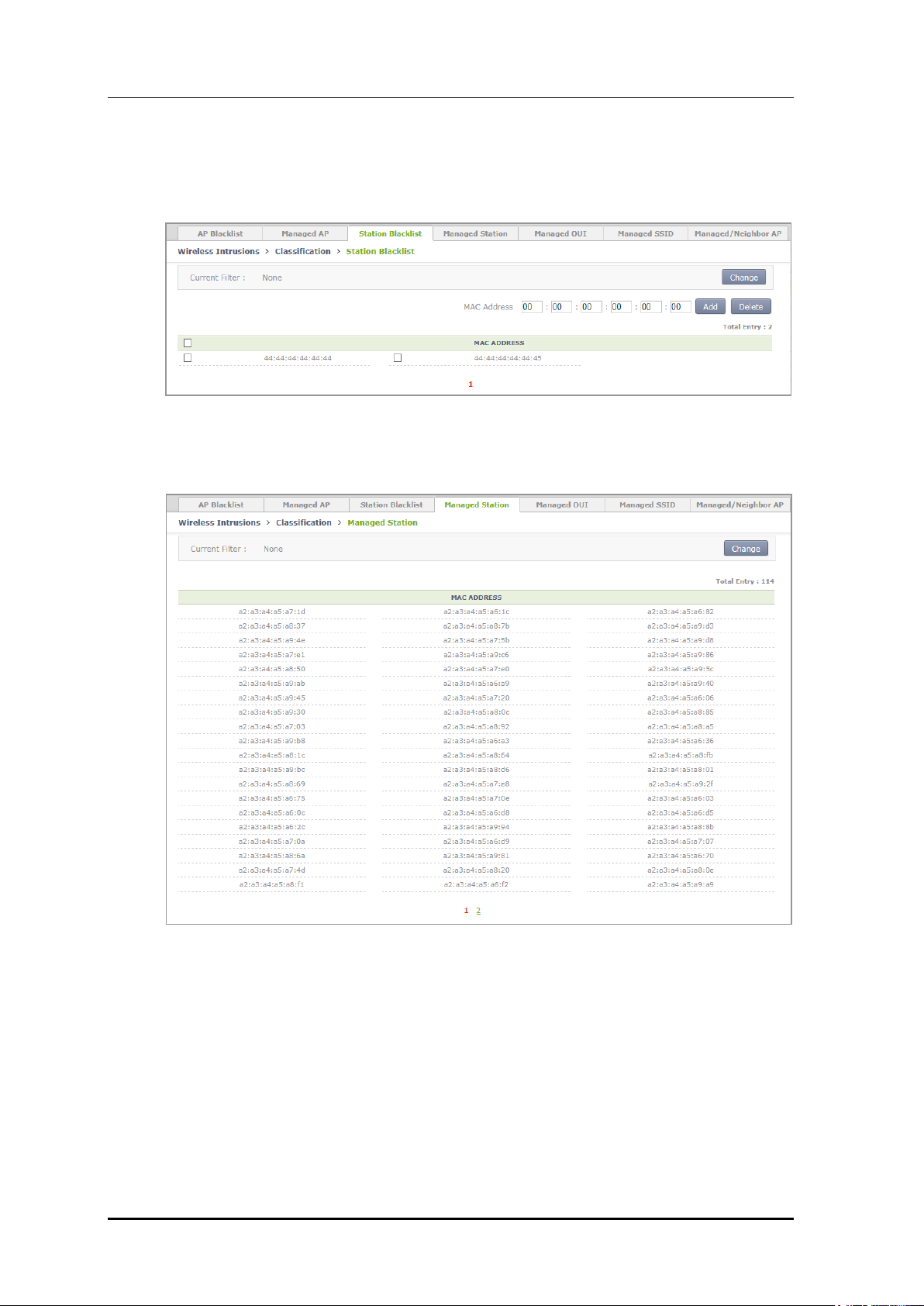
3) In the [Station Blacklist] tab, operator can add a station blacklist by entering a MAC
and click Add. Operator can also delete it by using Delete.
Figure 174. Station blacklist Search/Configuration Window
4) In the [Managed Station] tab, operator can search Managed Station.
© SAMSUNG Electronics Co., Ltd.
Figure 175. Managed Station Search Window
page 366 of 628
CHAPTER 8. Security
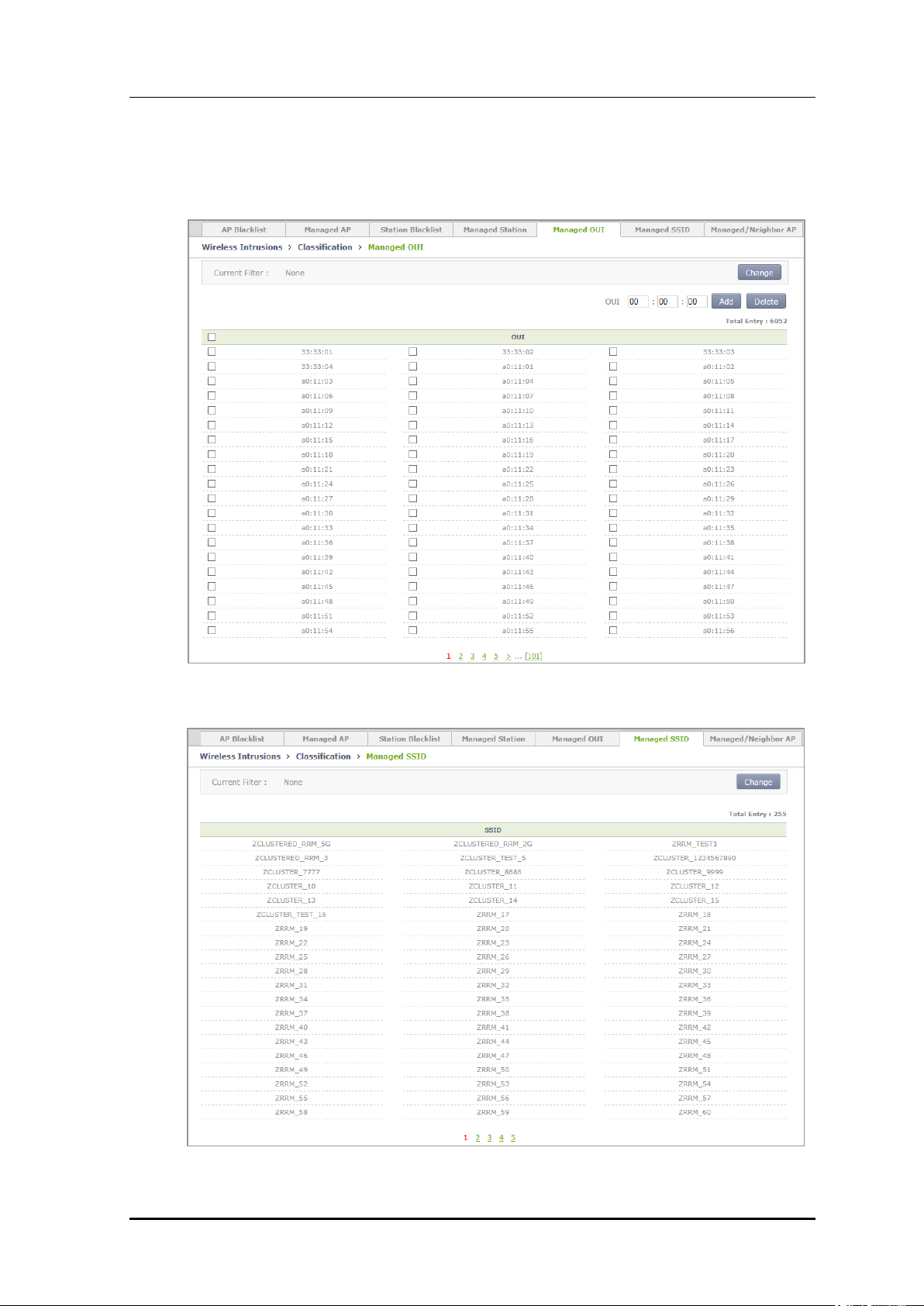
5) In the [Managed OUI] tab, operator can add a Managed OUI by entering an OUI and
click Add. Operator can also delete it by using Delete.
6) In the [Managed SSID] tab, you can check the SSID that the WLAN is using.
© SAMSUNG Electronics Co., Ltd.
Figure 176. Managed SSID Window
page 367 of 628
CHAPTER 8. Security
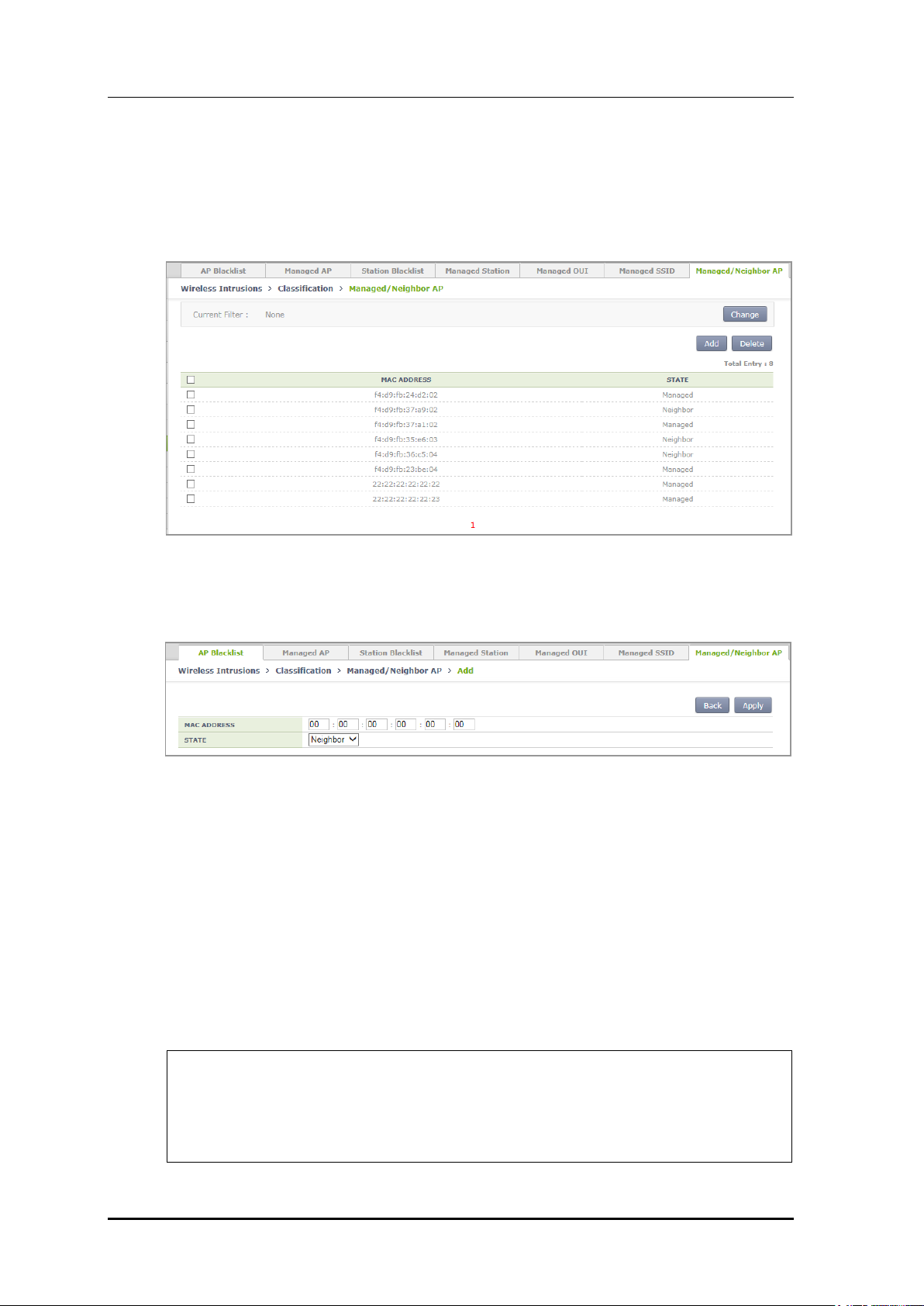
7) If you click Add in the [Managed/Neighbor AP] tab, operator can go to the Managed/
Neighbor AP list addition screen and can add a Managed/Neighbor AP list.
Operator can also delete it by using Delete.
[Managed/Neighbor AP] tab main screen
Figure 177. Managed/Neighbor AP Search/Configuration Window
Managed/Neighbor AP list addition screen
Figure 178. Managed/Neighbor AP List Addition Window
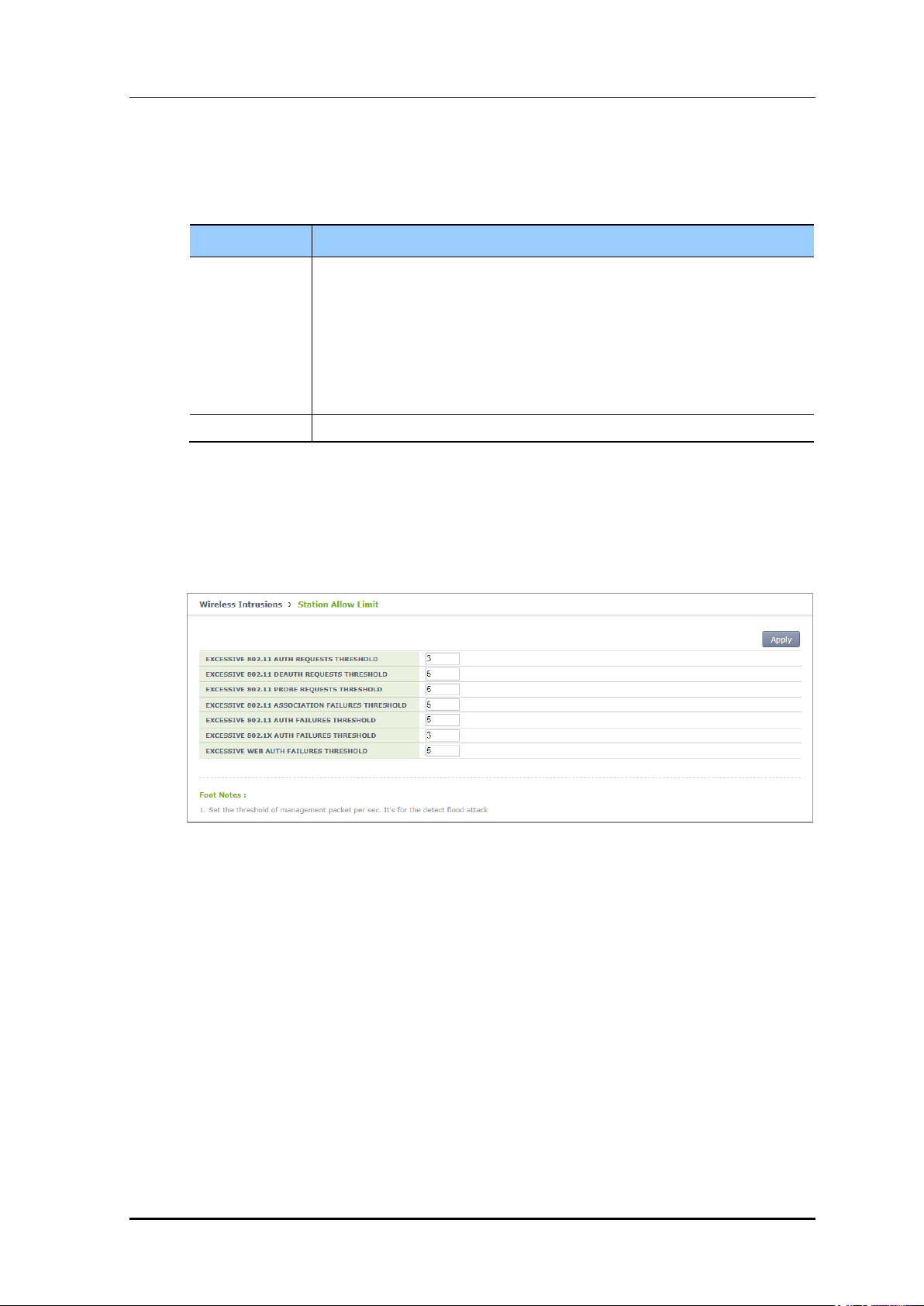
8.2.2.9 Station Allow Limit
The WIDS counts the number of frames and number of authentication failures to
distinguish a station that generates too many management frames in a network or that is
continuously failed for authentication. A threshold value is defined for the count and a
station is recognized as an unauthorized station if the count exceeds the threshold.
Configuration using CLI
1) Go to the configure wi device client configuration mode.
WEC8500# configure terminal
WEC8500/configure# wi
WEC8500/configure/wi# device
WEC8500/configure/wi/device# client
WEC8500/configure/wi/device/client#
© SAMSUNG Electronics Co., Ltd.
page 368 of 628
CHAPTER 8. Security
Parameter
Description
OPTION
- 80211-auth-req: Authentication requests threshold per second
- 80211-probe-req: Probe requests threshold per second
- 80211-deauth-req: De-authentication requests threshold per second
- 80211-assoc-fail: Association failures threshold per second
- 80211-auth-fail: Authentication failures threshold per second
- 8021x-auth-fail: 802.1x authentication failures threshold per WIDS interval
- web-auth-fail: Web authentication failures threshold that occurs continuously
COUNT
Threshold value of [OPTION] ranging from 3 to 20
2) Configure a threshold.
allowed-limit [OPTION] [COUNT]
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<Wireless Intrusion> <Station Allow Limit> menu in the sub-menus. And then, enter
a threshold value and click Apply to configure the value in the screen.
Figure 179. Station Allowed Limit Configuration Window
© SAMSUNG Electronics Co., Ltd.
page 369 of 628
8.2.3 Enabling Blocking Function
Blocking Method
Description
Manual blocking
The administrator performs blocking manually to APs or UEs.
Automatic blocking
APs or UEs are automatically blocked by the policy defined by the
administrator.
The setting of enabling the blocking function is as follows:
Configuration using CLI
1) Go to configure mode of CLI.
WEC8500# configure terminal
2) Enable the blocking function.
WEC8500/configure# wids containment enable
3) To check the configuration information, execute the following command.
show wids containment current-config
CHAPTER 8. Security
Configuration using Web UI
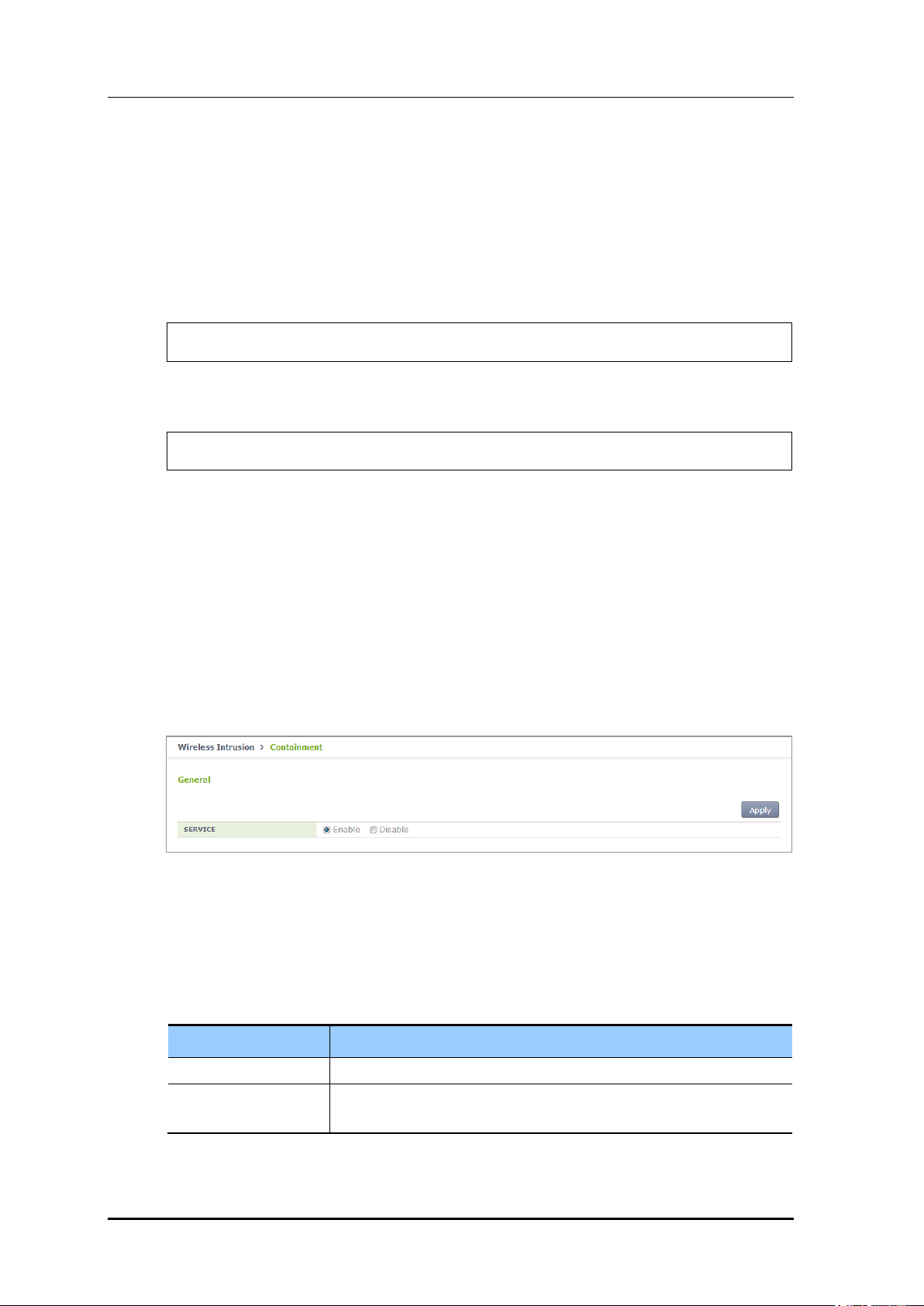
In the menu bar of <WEC Main window>, select <Configuration> and then select
<Wireless Intrusion> <Containment> <General> menus in the sub-menus.
Select Enable and Disable and press Apply to activate and deactivate the wireless intrusion
blocking policy.
Figure 180. Wireless Intrusion Containment General Configuration Window
8.2.4 Blocking
The W-EP WLAN system performs blocking to the detected AP and the wireless device.
The method for blocking is classified as follows:
© SAMSUNG Electronics Co., Ltd.
page 370 of 628
8.2.4.1 Configuring Manual Blocking
Parameter
Description
TARGET
Select either AP or station which is the target for manual blocking.
MAC
MAC address of the target for manual blocking
To configure manual blocking, execute the command as follows:
Configuration using CLI
1) Go to configure wids containment configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wids
WEC8500/configure/wids# containment
WEC8500/configure/wids/containment#
2) Configure manual blocking.
manual[TARGET] enable[MAC]
CHAPTER 8. Security
Configuration using Web UI
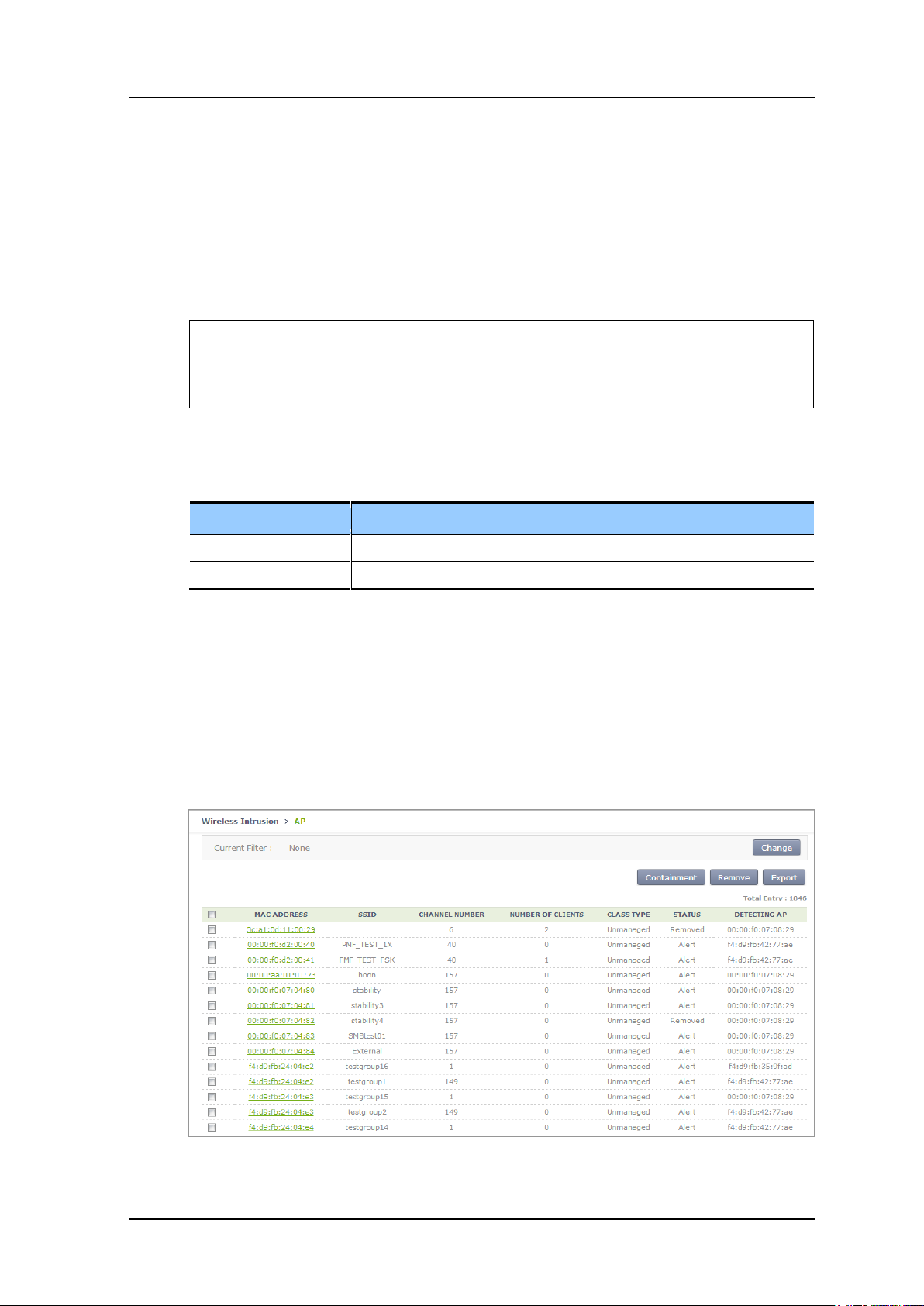
In the menu bar of <WEC Main window>, select <Monitor> and then select <Wireless
Intrusion> menu in the sub-menus.
Select the target and perform containment to perform manual blocking.
1) After selecting an AP in the AP list, possible to block by using the containment.
Figure 181. List Window for Blocking AP
© SAMSUNG Electronics Co., Ltd.
page 371 of 628
CHAPTER 8. Security
Parameter
Description
adhoc-connection
If adhoc is detected, it is automatically blocked.
managed-station-associated-withfriendly-external
If the managed station and the neighbor AP are connected, it
is automatically blocked.
rogue-ap-with-auth-station
If the managed station and the unmanaged AP are
connected, it is automatically blocked.
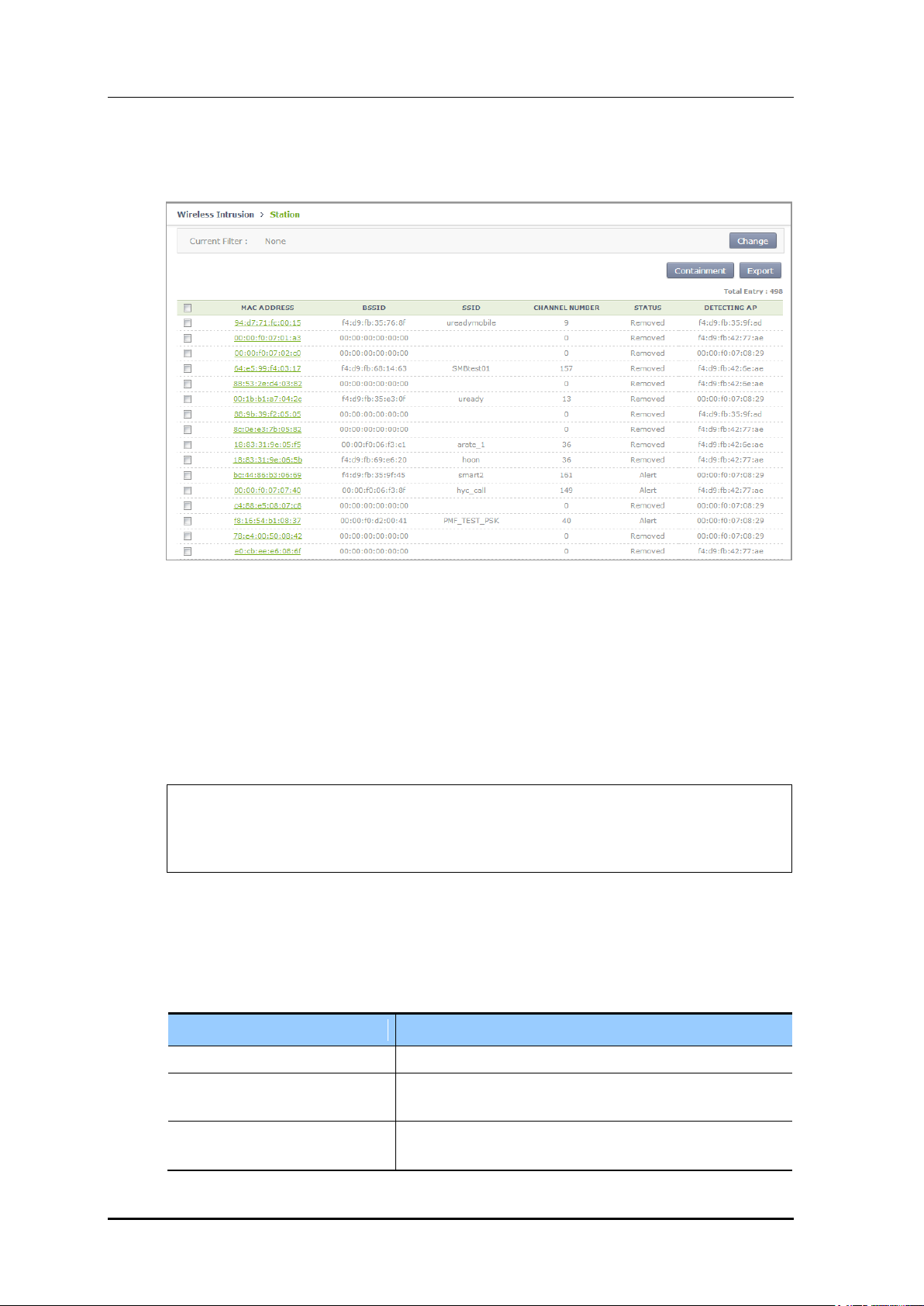
2) After selecting a station in the station list, possible to block by using the containment.
Figure 182. List Window for Blocking Station
8.2.4.2 Configuring Automatic Blocking
To configure automatic blocking, execute the command as follows:
Configuration using CLI
1) Go to configure wids containment configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wids
WEC8500/configure/wids# containment
WEC8500/configure/wids/containment#
2) Configure automatic blocking.
auto[OPTION]
The description of OPTION parameter is as follows:
© SAMSUNG Electronics Co., Ltd.
page 372 of 628
CHAPTER 8. Security
Parameter
Description
rogue-ap-with-managed-ssid
If the honeypot is detected, it is automatically blocked.
unmanaged-ap
If the unmanaged AP is detected, it is automatically blocked.
3) To check the configuration of automatic blocking, it is possible to use the following
command:
show wids containment current-config
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select
<Wireless Intrusion> <Containment> menus in the sub-menus.
Select the target and press Apply to configure automatic blocking.
Figure 183. Automatic Blocking Configuration Window
© SAMSUNG Electronics Co., Ltd.
page 373 of 628
8.3 Captive Portal
Parameter
Description
ID
Login ID of a user
PASSWD
Password
START_TIME
Start time (YYYY-MM-DD:HH:MM:SS format)
END_TIME
End time (YYYY-MM-DD:HH:MM:SS format)
Parameter
Description
ID
User ID
Parameter
Description
FLAG
Authentication method
- local-only: Uses internal authentication.
- radius-only: Uses the authentication of the RADIUS server.
- local-radius: Uses the authentication of the RADIUS if the
internal authentication is failed.
The W-EP WLAN system provides the Captive Portal function. A guest user can receive a
normal service after connected to a specific WLAN (SSID) and going through user
authentication.
8.3.1 Configuring Guest Authentication
Configuration using CLI
To configure guest authentication, go to the Configure mode and execute the command.
1) Go to configure security captive-portal configuration mode of CLI.
APC# configure terminal
APC/configure# security
APC/configure/security# captive-portal
APC/configure/security/captive-portal#
CHAPTER 8. Security
2) The command to add a guest user is as follows:
guest add [ID][PASSWD][START_TIME][END_TIME]
3) The command to add a guest user is as follows:
guest delete [ID]
4) To select the authentication method for a guest service, execute the command as follows:
auth-type[FLAG]
© SAMSUNG Electronics Co., Ltd.
page 374 of 628
CHAPTER 8. Security
Parameter
Description
- radius-local: Uses the internal authentication if the RADIUS
server authentication is failed.
Parameter
Description
PROFILE_ID
Profile ID
5) For RADIUS authentication, the operator can configure the primary and secondary
servers by using a profile ID.
radius-primary [PROFILE_ID]
radius-secondary [PROFILE_ID]
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select
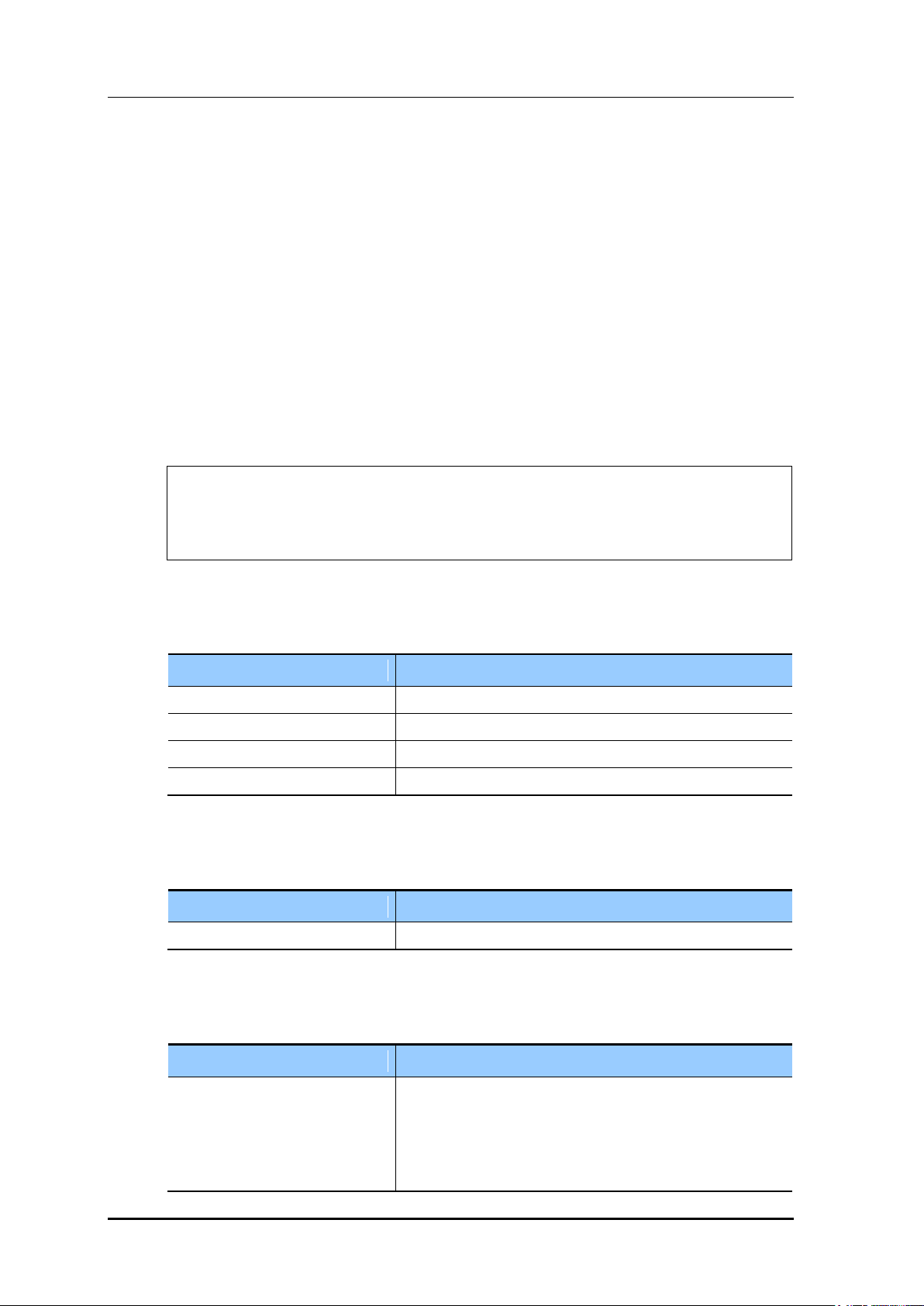
<Security> <CaptivePortal> <Guest Users> menus in the sub-menus.
Figure 184. Guest User Configuration Window
© SAMSUNG Electronics Co., Ltd.
page 375 of 628
CHAPTER 8. Security
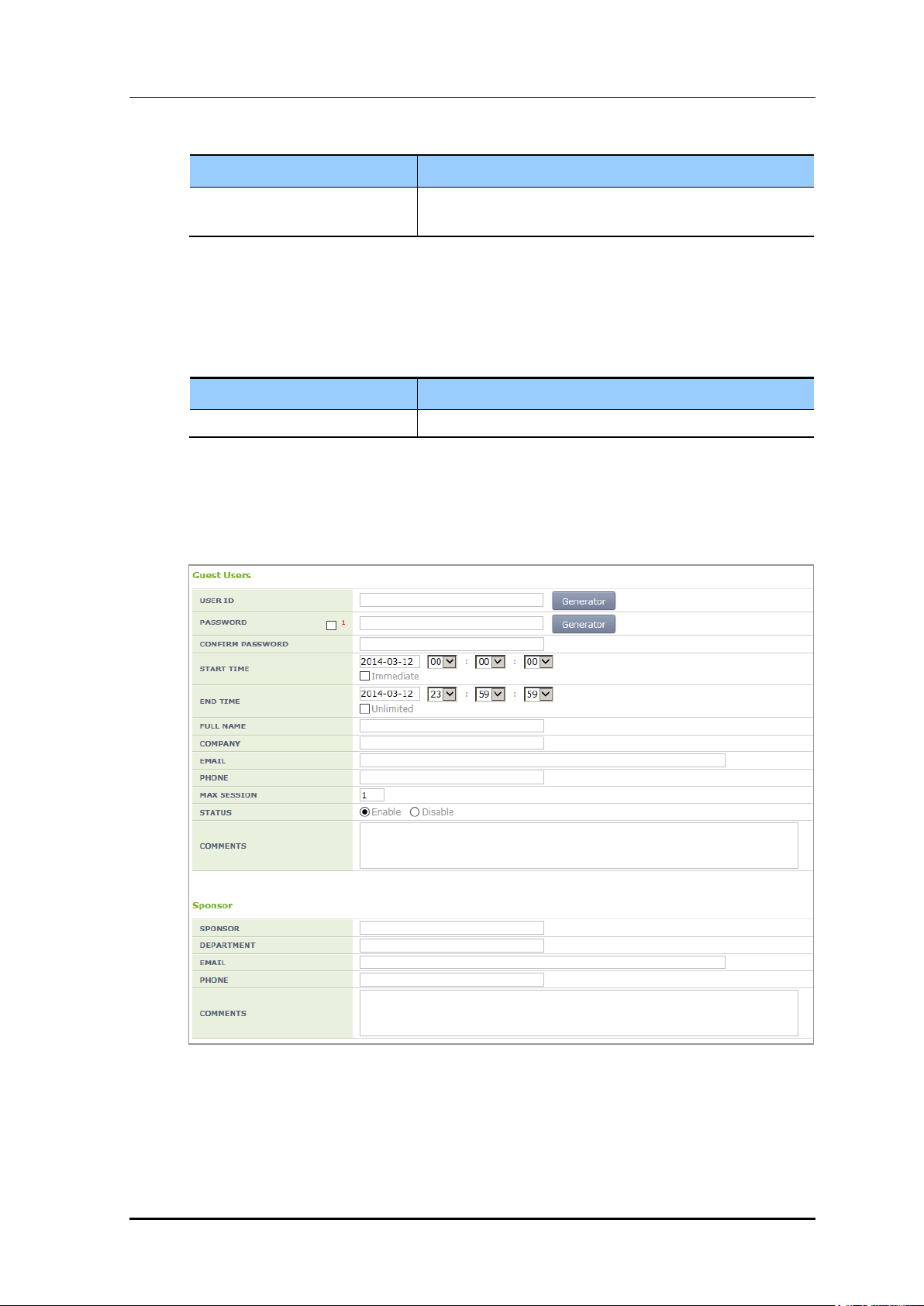
The operator can check and delete a guest created in the <Guest Users> menu.
Figure 185. Guest User List Window
In the <Guest Users> menu, the operator can select Auth Type and also PRIMARY
RADIUS and SECONDARY RADIUS servers.
Figure 186. Guest Auth Configuration Window
8.3.2 Configuring Guest ACL
To operate the captive portal services, redirection must be basically performed and if a drop
occurs by the Pre-Auth ACL of the WLAN, the redirection is performed.
Accordingly, the proper configuration of the ACL for guests is necessary depending on
types of captive portal services.
For the guest ACL, the DNS permit rule, and the permit rule for the web service address
used by the captive portal are basically necessary and the permit rule of the address of the
external web server is additionally necessary if the external web server is used.
Configuration using CLI
To configure the guest ACL, execute the following command:
1) Go to configure fqm-mode configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# fqm-mode
2) Configure an access list.
WEC8500/configure/fqm-mode#
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 1 udp
any eq * any eq 53 os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 2 tcp
192.168.20.10 255.255.255.255 eq 80 any eq * os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 3 tcp
any eq * 192.168.20.10 255.255.255.255 eq 80 os-aware *
© SAMSUNG Electronics Co., Ltd.
page 376 of 628

CHAPTER 8. Security
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 4 tcp
90.90.100.120 255.255.255.255 eq 80 any eq * os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 5 tcp
any eq * 90.90.100.120 255.255.255.255 eq 80 os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 6 udp
any eq * any eq * os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 7 tcp
192.168.10.10 255.255.255.255 eq 80 any eq * os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 8 tcp
any eq * 192.168.10.10 255.255.255.255 eq 80 os-aware *
WEC8500/configure/fqm-mode# access-list ip guest_acl permit seq 10 tcp
192.168.0.0 255.255.0.0 eq * any eq 443 os-aware *
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<IP ACL> menu in the <Access Control Lists> sub-menu of <Security> in the sub-
menus.
Select Add on the <IP ACL> screen and then configure the ACL.
Figure 187. Access List Addition Window
Figure 188. Access List Entry Addition Window
© SAMSUNG Electronics Co., Ltd.
page 377 of 628
8.3.3 Configuring Web Authentication
Parameter
Description
ACL
ACL applied before the guest is authenticated
To provide the web authentication service, the security L3 item of the WLAN and the web
authentication of the captive portal must be configured.
Configuration using CLI
[WLAN Configuration]
To configure web authentication in the WLAN, execute the command as follows:
1) Go to configure WLAN configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wlan 1
2) Configure a guest flag (default: disabled).
guest-flag
CHAPTER 8. Security
WEC8500/configure/wlan 1# guest-flag
3) Go to configure WLAN security layer 3 configuration mode of CLI.
WEC8500/configure/wlan 1# security
WEC8500/configure/wlan 1/security# layer3
WEC8500/configure/wlan 1/security/layer3#
4) Enable the WEB authentication (default: disabled).
web-policy authentication
WEC8500/configure/wlan 1/security/layer3# web-policy authentication
5) Configure the Pre-Authentication ACL.
pre-auth-acl [ACL]
6) To change the redirection of the basic captive portal configuration to another address,
configure an overriding URL.
redirect-URL-override [URL]
© SAMSUNG Electronics Co., Ltd.
page 378 of 628
CHAPTER 8. Security
Parameter
Description
URL
URL to which the guest is redirected
Parameter
Description
FLAG
Web Authentication Method
- internal: Uses the internal authentication page.
- external: Uses the authentication page of an external web
server.
- downloaded: Uses the authentication page downloaded
from the system.
- customized: Uses the authentication page created through
configuration.
URL
Address of an external authentication server
Parameter
Description
FLAG
Operation after authentication
- redirect: Redirect to a specified URL
- request: Redirect to a requested URL
URL
URL specified as the operation after authentication
7) To check the configuration, use the ‘show wlan security detail’ command.
WEC8500# show wlan security detail 1
[Captive Portal Configuration]
1) Go to configure security captive-portal configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# security
WEC8500/configure/security# captive-portal
WEC8500/configure/security/captive-portal#
2) To configure the web authentication method of web authentication in the captive
portal, execute the command as follows:
web-auth web-type [FLAG]
web-auth external-url [URL]
3) To configure the operation after authentication, execute the command as follows:
web-auth after-auth [FLAG]
web-auth redirect-url [URL]
© SAMSUNG Electronics Co., Ltd.
page 379 of 628
CHAPTER 8. Security
4) To check the configuration, use the ‘show security captive-portal web-auth’ command.
WEC8500# show security captive-portal web-auth
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<WLANs> menu in the sub-menus. In the WLANs screen, select WLAN ID and enable
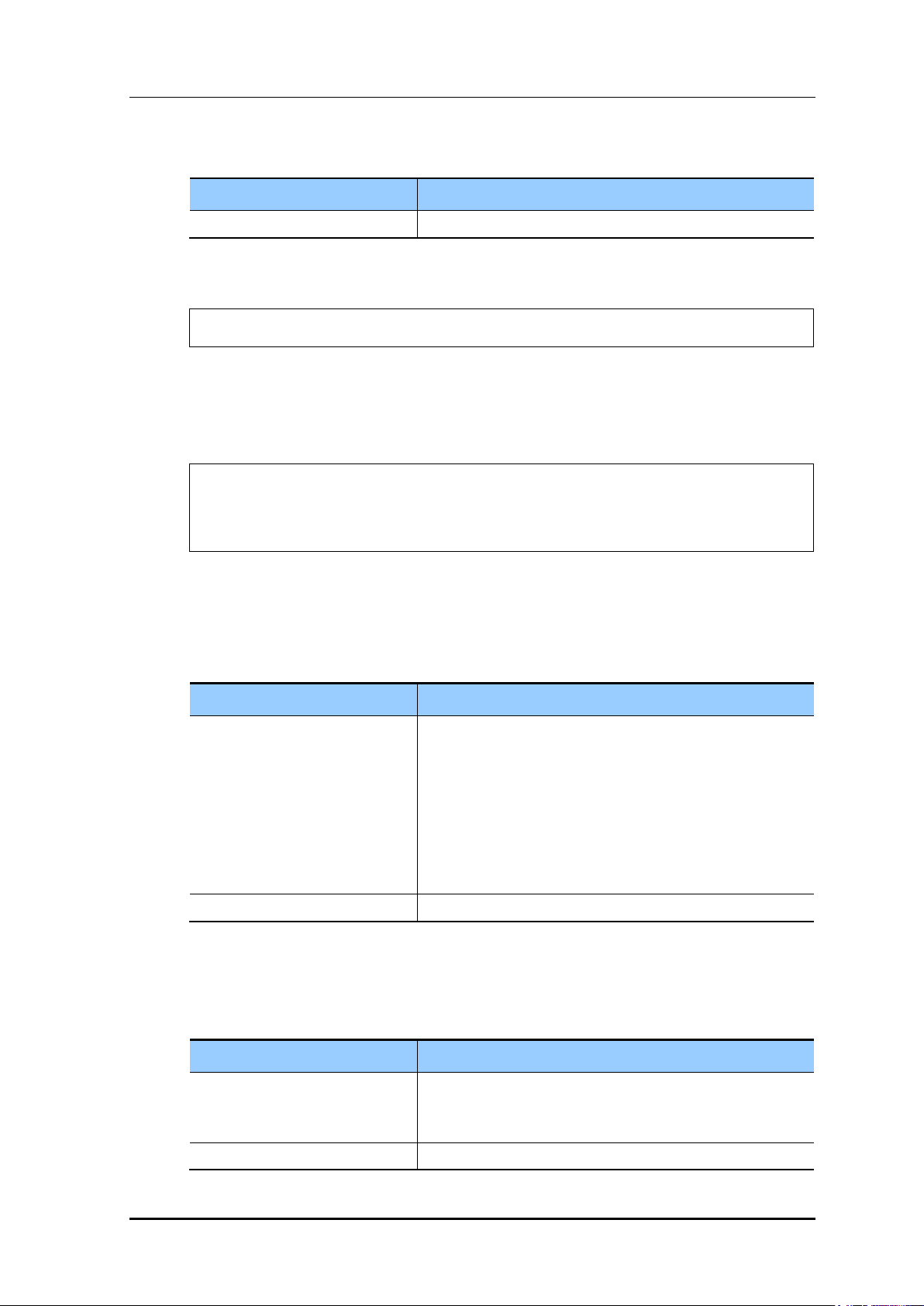
the <GUEST SERVICE> option.
Figure 189. WLAN Guest Configuration Window
Go to the <L3> of the <Security> tab.
Enable <WEB POLICY> and select the Web Authentication item and then designate the
ACL set in the guest ACL to <PRE-AUTHENTICATION ACL>.
To change a URL, enable <OVERRIDING REDIRECT ACL> and configure <URL>.
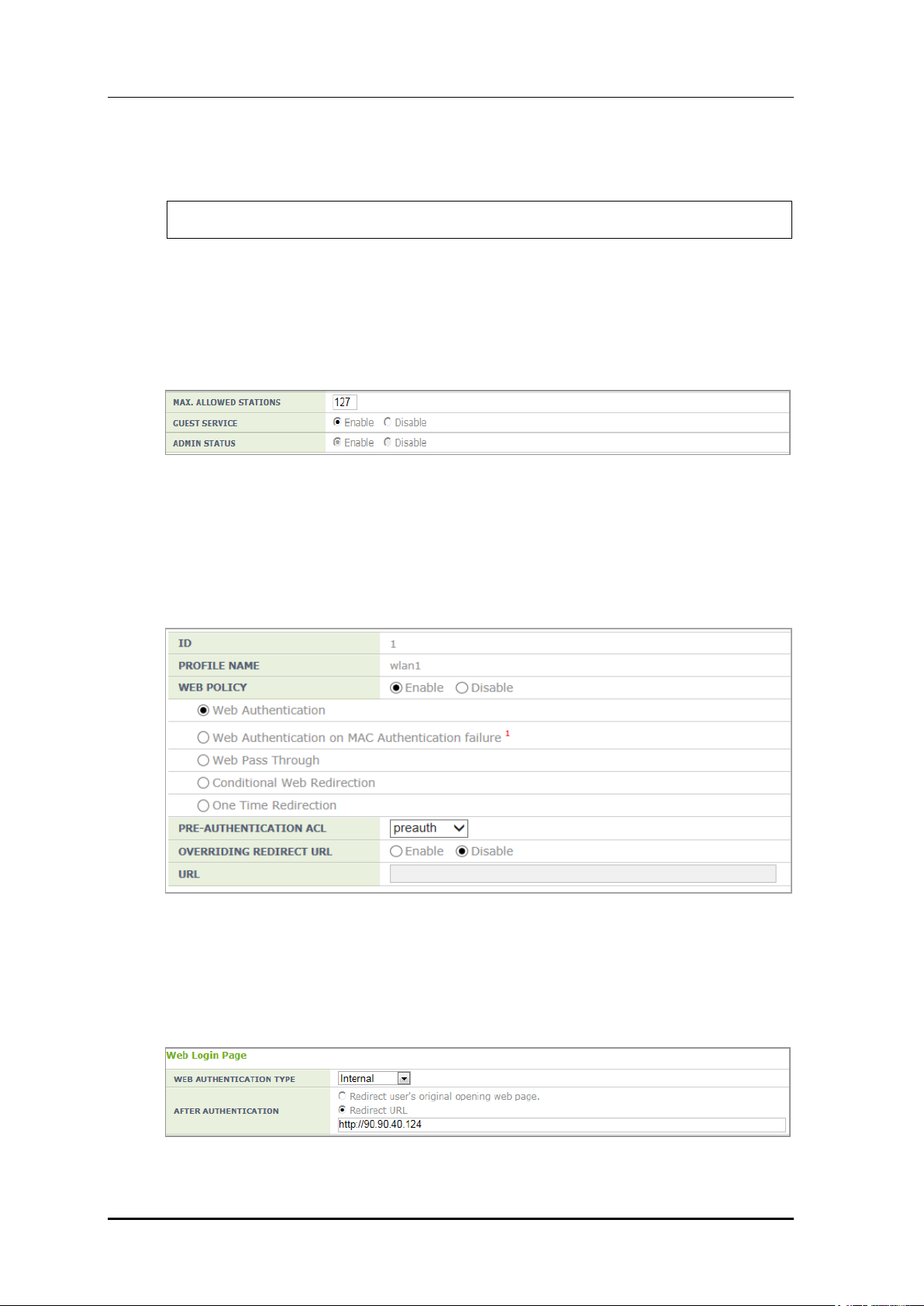
In the <CaptivePortal> <Web Authentication> menu, the operator can select web
authentication method. The operator can also configure Redirect as the operation after
authentication.
© SAMSUNG Electronics Co., Ltd.
Figure 190. WLAN Web Policy Configuration Window
Figure 191. Web Auth Configuration Window
page 380 of 628

CHAPTER 8. Security
Parameter
Description
ACL
ACL applied before the guest is authenticated
8.3.4 Configuring Web Authentication on MAC Authentication
Failure
To provide the service of Web Authentication on MAC Authentication Failure, the MAC
Authentication of security L2 of the WLAN must be enabled and the web policy of L3 and
the web authentication of the captive portal must be configured.
Configuration using CLI
[WLAN Configuration]
To configure Web Authentication on MAC Authentication Failure in the WLAN, execute
the command as follows:
1) Go to configure WLAN configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wlan 1
2) Configure a guest flag (default: disabled).
guest-flag
WEC8500/configure/wlan 1# guest-flag
3) Go to configure WLAN security layer 3 configuration mode of CLI.
WEC8500/configure/wlan 1# security
WEC8500/configure/wlan 1/security# layer3
WEC8500/configure/wlan 1/security/layer3#
4) Enable the WEB authentication (default: disabled).
web-policy authentication
WEC8500/configure/wlan 1/security/layer3# web-policy macAuthFailure
5) Configure the Pre-Authentication ACL.
pre-auth-acl [ACL]
© SAMSUNG Electronics Co., Ltd.
page 381 of 628
CHAPTER 8. Security
Parameter
Description
URL
URL to which the guest is redirected
Parameter
Description
FLAG
Web Authentication Method
- internal: Uses the internal authentication page.
- external: Uses the authentication page of an external web
server.
- downloaded: Uses the authentication page downloaded
from the system.
- customized: Uses the authentication page created through
configuration.
URL
Address of an external authentication server
6) To change the redirection of the basic captive portal configuration to another address,
configure an overriding URL.
redirect-URL-override [URL]
7) To check the configuration, use the ‘show wlan security detail’ command.
WEC8500# show wlan security detail 1
[Captive Portal Configuration]
1) Go to configure security captive-portal configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# security
WEC8500/configure/security# captive-portal
WEC8500/configure/security/captive-portal#
2) To configure the web authentication method of web authentication in the captive
portal, execute the command as follows:
web-auth web-type [FLAG]
web-auth external-url [URL]
3) To configure the operation after authentication, execute the command as follows:
web-auth after-auth [FLAG]
web-auth redirect-url [URL]
© SAMSUNG Electronics Co., Ltd.
page 382 of 628
CHAPTER 8. Security
Parameter
Description
FLAG
Operation after authentication
- redirect: Redirect to a specified URL
- request: Redirect to a requested URL
URL
URL specified as the operation after authentication
4) To check the configuration, use the ‘show security captive-portal web-auth’ command.
WEC8500# show security captive-portal web-auth
Configuration using Web UI
In the menu bar of <WEC Main window>, select <Configuration> and then select the
<WLANs> menu in the sub-menus. In the WLANs screen, select WLAN ID and enable
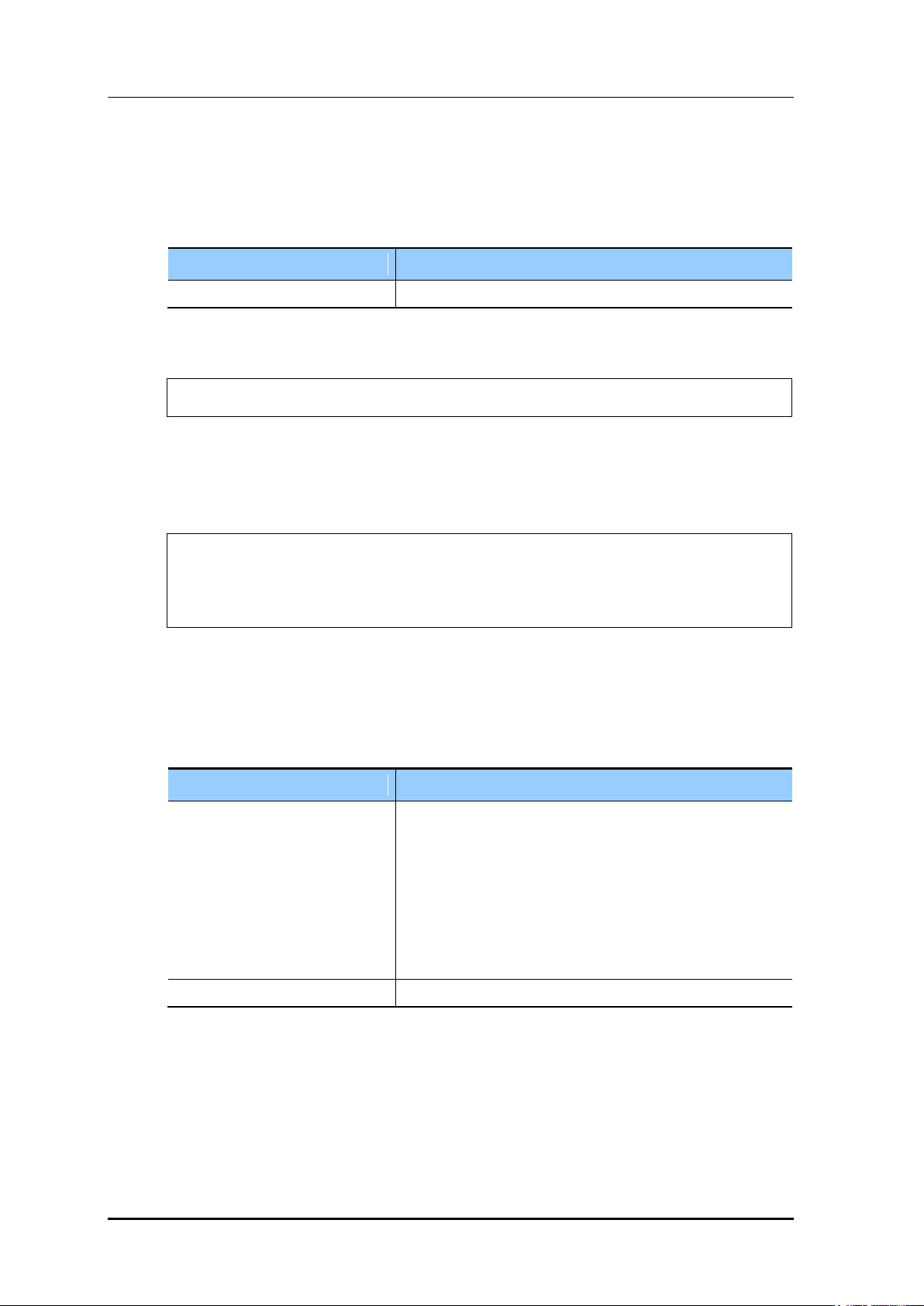
the <GUEST SERVICE> option.
Figure 192. WLAN Guest Configuration Window
Go to the <L2> of the <Security> tab.
Enable <MAC AUTHENTICATION>.
Figure 193. WLAN Layer 2 Security Configuration Window
Go to the <L3> of the <Security> tab.
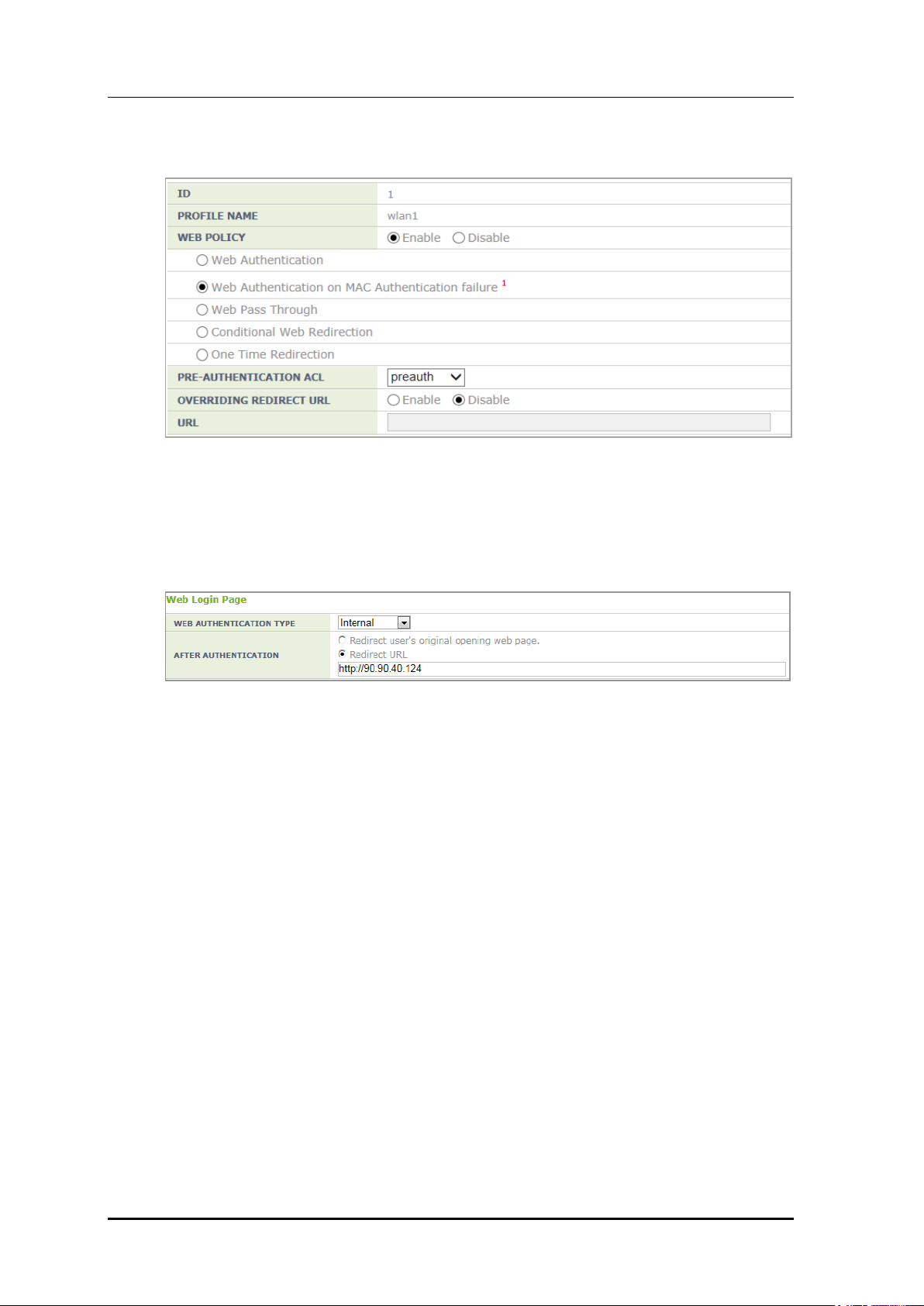
Enable <WEB POLICY> and select the Web Authentication on MAC Authentication
Failure item and then designate the ACL set in the guest ACL to <PRE-
AUTHENTICATION ACL>.
To change a URL, enable <OVERRIDING REDIRECT ACL> and configure <URL>.
© SAMSUNG Electronics Co., Ltd.
page 383 of 628
CHAPTER 8. Security
Figure 194. WLAN Web Policy Configuration Window
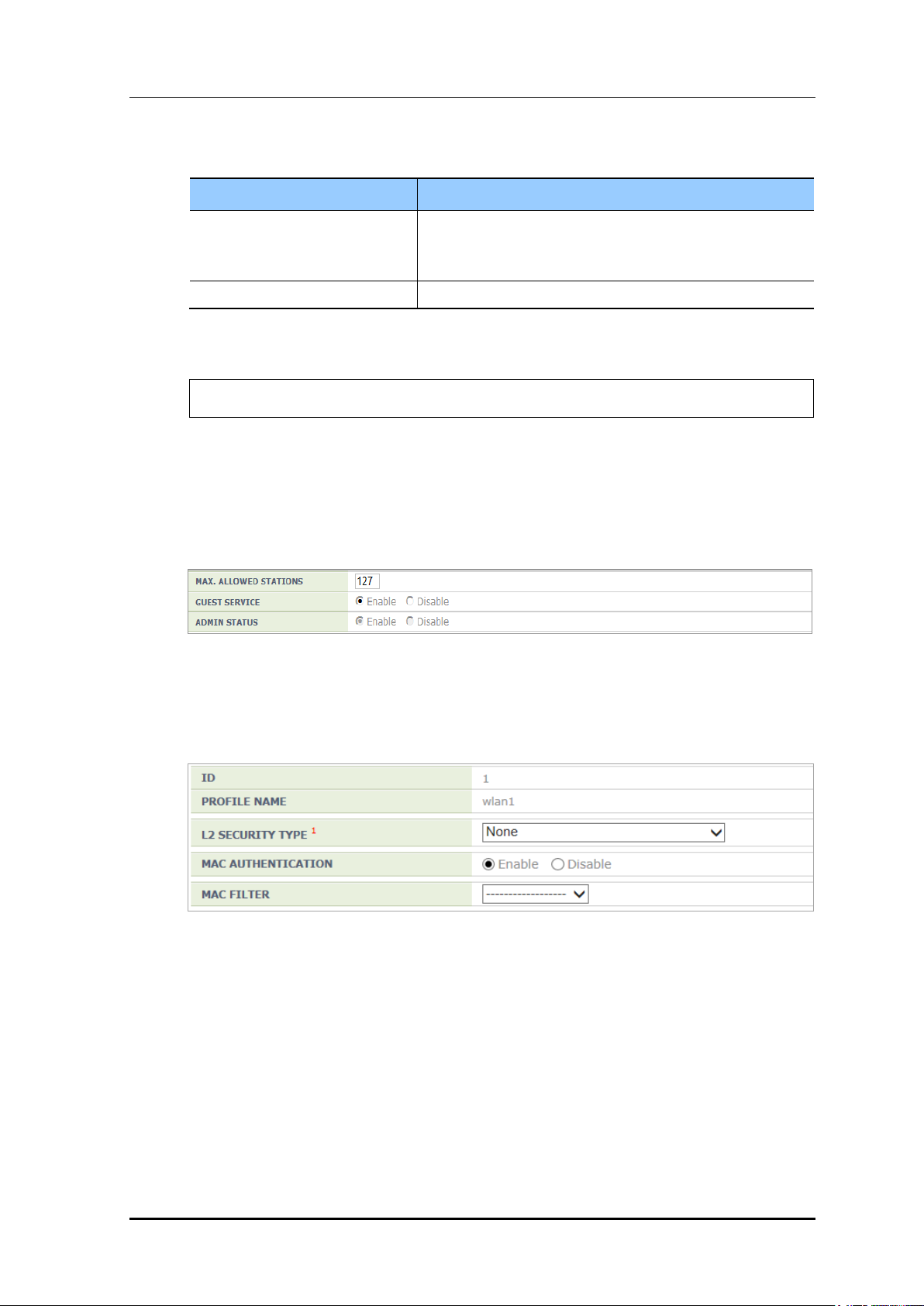
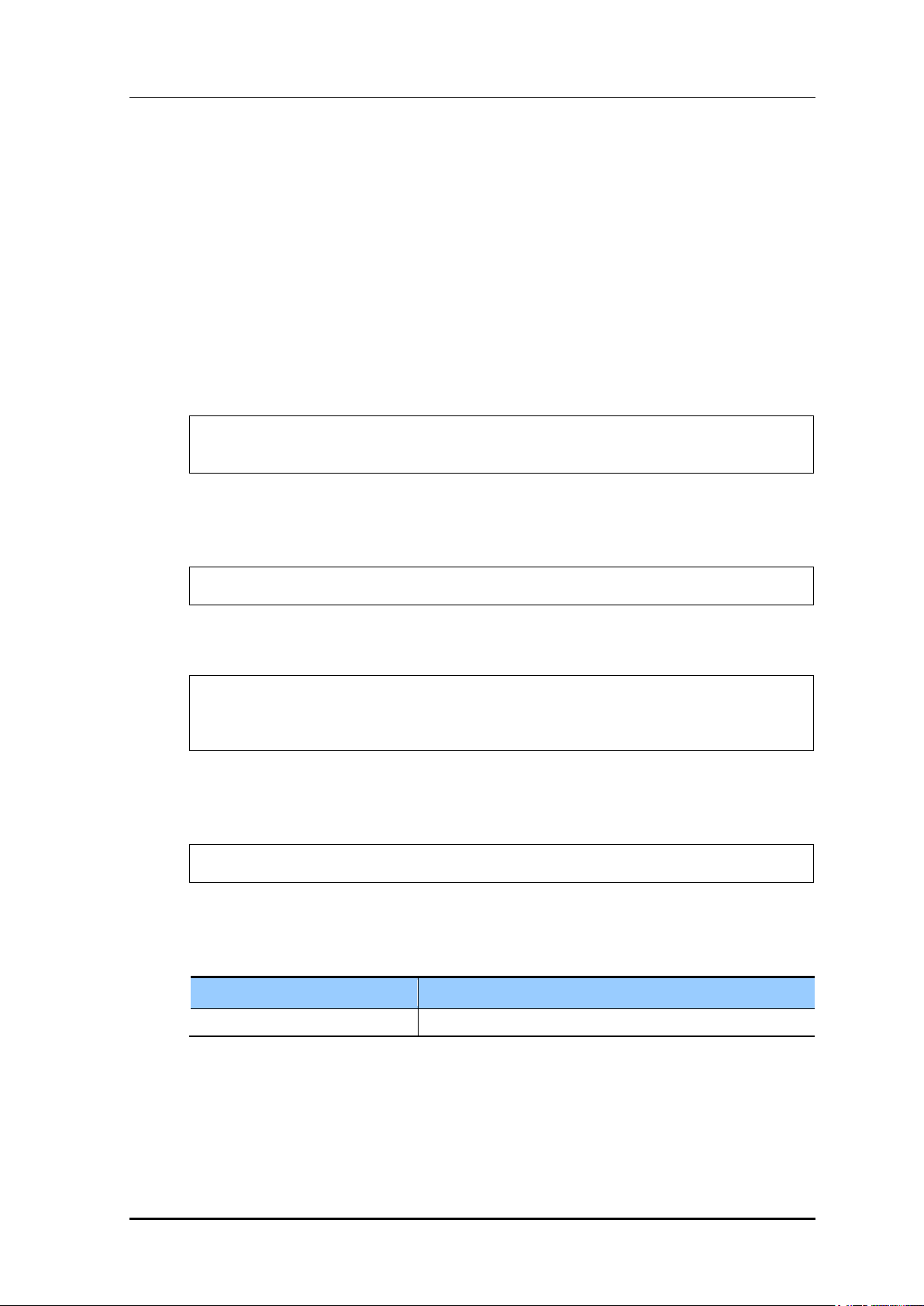
In the <CaptivePortal> <Web Authentication> menu, the operator can select web
authentication method. The operator can also configure Redirect as the operation after
authentication.
Figure 195. Web Auth Configuration Window
© SAMSUNG Electronics Co., Ltd.
page 384 of 628
8.3.5 Configuring Web Pass-through
Parameter
Description
ACL
ACL for occurrence of redirection
The APC provides the web pass-through function to move to a specific address all the time
when the user uses the web.
Configuration using CLI
[WLAN Configuration]
To configure web pass-through in the WLAN, execute the command as follows:
1) Go to configure WLAN configuration mode of CLI.
WEC8500# configure terminal
WEC8500/configure# wlan 1
2) Configure a guest flag (default: disabled).
guest-flag
CHAPTER 8. Security
WEC8500/configure/wlan 1# guest-flag
3) Go to configure WLAN security layer 3 configuration mode of CLI.
WEC8500/configure/wlan 1# security
WEC8500/configure/wlan 1/security# layer3
WEC8500/configure/wlan 1/security/layer3#
4) Enable the WEB authentication (default: disabled).
web-policy pass-through
WEC8500/configure/wlan 1/security/layer3# web-policy pass-through
5) Configure the Pre-Authentication ACL.
pre-auth-acl [ACL]
6) To change the redirection of the basic captive portal configuration to another address,
configure an overriding URL.
redirect-URL-override [URL]
© SAMSUNG Electronics Co., Ltd.
page 385 of 628
 Loading...
Loading...