Page 1

User Guide
Ruckus Wireless ZoneDirector
Release 3.0
Page 2

Legal Information
Copyright © 2007 Ruckus Wireless, Inc. All rights reserved.
Trademarks
Ruckus Wireless ZoneDirector, ZoneFlex, 2825, BeamFlex, MediaFlex, MediaFlex 2900 Multimedia Access Point, MediaFlex 2501
Multimedia Wireless Adapter, 2825 Wireless Multimedia Router,
2111 Wireless Multimedia Adapter, and 2211 Metro Broadband
Gateway are trademarks of Ruckus Wireless Web Interface
All other brands and product names are registered trademarks of
their respective holders.
Statement of Conditions
In the interest of improving internal design, operational function,
and/or reliability, Ruckus Wireless, Inc. reserves the right to make
changes to the products described in this document without
notice.
Ruckus Wireless, Inc. does not assume any liability that may
occur due to the use or application of the product(s) or circuit layout(s) described herein.
Federal Communications Commission (FCC) Compliance Notice:
Radio Frequency Notice
The device has met the FCC 15.247 requirement. In order to comply with the FCC RF exposure requirement, the user must keep
20cm away from the antenna.
This device has been tested and found to comply with the limits
for a Class B digital device, pursuant to part 15 of the FCC Rules.
These limits are designed to provide reasonable protection
against harmful interference in a residential installation. This
device generates, uses, and can radiate radio frequency energy
and, if not installed and used in accordance with the instructions,
may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this device does cause harmful interference
to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna.
Increase the separation between the equipment and receiver.
Connect the equipment into an outlet on a circuit different from
that to which the receiver is connected.
Consult the dealer or an experienced radio/TV technician for help.
Changes or modifications not expressly approved by the party
responsible for compliance could void the user’s authority to operate the equipment.
Information to the User
The user’s manual or instruction manual for an intentional or unintentional radiator shall caution the user that changes or modifications not expressly approved by the party responsible for
compliance could void the user’s authority to operate the equipment. In cases where the manual is provided only in a form other
than paper, such as on a computer disk or over the Internet, the
information required by this section may be included in the manual
in that alternative form, provided the user can reasonably be
expected to have the capability to access information in that form.
Part number: RKS1-ZDUG-12202007-001
EDITION: December 20, 2007 -- vABC
Contact Information
Ruckus Wireless
880 West Maude Ave, Suite 101
Sunnyvale, CA 94085
USA
Support
http://support.ruckuswireless.com
Web
http://www.ruckuswireless.com
ii
Page 3

Contents
Introducing ZoneDirector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1
ZoneDirector Device Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2
Overview of a Ruckus Wireless Network . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Using the WebUI Features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
About Ruckus WLAN Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Controlling Device Permissions: Blocking and ACLs . . . . . . . . . . . . . . . . . . . 7
System Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8
Changing the Network Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Changing the System Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Updating the Internal Clock. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Changing the System Log Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Setting up Email Alarm Notification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Customizing the Guest “Login” Page. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Upgrading ZoneDirector and ZoneFlex APs . . . . . . . . . . . . . . . . . . . . . . . . 15
Working with Backup Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Restoring the ZoneDirector to the Factory Default State. . . . . . . . . . . . . . . 17
Managing a Wireless Local Area Network . . . . . . . . . . . . . . . . . . . . . . . . 19
An Overview of Wireless Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Customizing Ruckus WLAN Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Setting Dynamic Pre-Shared Key Expiration . . . . . . . . . . . . . . . . . . . . . . . 24
Configuring Access Control Lists . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Creating a New WLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Creating a New WLAN for Workgroup Use . . . . . . . . . . . . . . . . . . . . . . . . . 30
Adding New Access Points to the WLAN . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Reviewing the Current Access Point Policies . . . . . . . . . . . . . . . . . . . . . . . 33
Editing Access Point Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Deploying ZoneDirector WLANs in a VLAN Environment . . . . . . . . . . . . . . . 34
Blocking Client Devices. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Optimizing Access Point Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Managing User and Guest Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Using an External Authentication Server . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Adding New User Accounts to ZoneDirector. . . . . . . . . . . . . . . . . . . . . . . . 42
Managing Current User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Creating New User Roles. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
iii
Page 4

Configuring System-Wide Guest Access Policy . . . . . . . . . . . . . . . . . . . . . . 45
Managing Guest Pass Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Activating Web Authentication of Users . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Managing Automatically Generated User Certificates and Keys . . . . . . . . . . 50
Monitoring Your Wireless Network. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Reviewing the ZoneDirector Monitoring Options. . . . . . . . . . . . . . . . . . . . . 52
Importing a Map View Floorplan Image. . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Using the Map View Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Reviewing Current Alarms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Reviewing Recent Network Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Clearing Recent Events/Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Reviewing Current User Activity. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Monitoring Access Point Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Detecting Rogue Access Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Evaluating and Optimizing Network Coverage . . . . . . . . . . . . . . . . . . . . . . 59
Customizing Background Radio Frequency Scans . . . . . . . . . . . . . . . . . . . . 60
Setting Administrator Preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Changing the ZoneDirector Administrator User Name and/or Password . . . . 63
Changing the Language Used in WebUI . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Upgrading the License . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Troubleshooting Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65
Troubleshooting Failed User Logins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Fixing User Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Diagnosing Poor Network Performance . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Starting a Radio Frequency Scan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Reviewing Self Healing and Intrusion Prevention Options . . . . . . . . . . . . . . 70
Generating a Debug File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Restarting an Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Restarting the Ruckus ZoneDirector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
iv
Page 5

CHAPTER 1
Introducing ZoneDirector
The Ruckus ZoneDirector serves as a central control system for Ruckus ZoneFlex access
points (also refered to as APs). The ZoneDirector provides simplified configuration and
updates, WLAN security control, RF management and automatic coordination of Ethernetconnected APs.
The ZoneDirector also integrates network, RF and location management within a single system. User authentication is accomplished with an integrated captive portal and internal
database, or forwarded to existing AAA servers such as RADIUS or ActiveDirectory. Once
users are authenticated, client traffic is not required to pass through the ZoneDirector
thereby eliminating potential bottlenecks as higher speed Wi-Fi technologies, such as
802.11n, emerge.
In addition, the ZoneDirector supports rogue AP detection and the ability to blacklist client
devices from the network—all of which are easily configured and enabled system-wide.
When multiple APs are in close proximity, the Ruckus ZoneDirector automatically controls
the power and the channel settings on each AP to provide the best possible total coverage
and resiliency.
This user guide provides complete instructions for use of the Ruckus Wireless WebUI, the
wireless network management toolbox for ZoneDirector. With WebUI, you can customize and
manage all aspects of ZoneDirector and the network. You’ll find all management tasks have
been organized as categories and topics in the Contents page.
1
Page 6

Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
ZoneDirector Device Features
The ZoneDirector device features the following:
• Power: Press button to turn on/off device.
• Status
• Two 10/100/1000 Ethernet Ports
• Console: DB-9 port
• Reset: Use to reset the ZoneDirector. This is a normal reset and does not set AP back to
factory defaults.
• (Not pictured) Power connection in rear
FIGURE 1-1
10/100/1000 LED Status
• If off
• If steady amber
• If flashing amber
• If steady green
• If flashing green
• Port is not connected.
• Ethernet port is connected to 10Mbs Layer 2 device.
• Ethernet port is passing traffic to a 10Mbs Layer 2 device.
• Ethernet port is connected to 100Mbs Layer 2 device.
• Ethernet port is passing traffic to a 100Mbs Layer 2 device.
2
Page 7

Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
Overview of a Ruckus Wireless Network
Your new Ruckus wireless network starts when you disperse a number of Ruckus Access
Points (APs) to efficiently cover your worksite. After connecting the APs to your Ruckus
ZoneDirector (through network hubs or switches), and completing the “zero IT” setup, you
have a secure wireless network for both registered users and guest users.
NOTE
After using WebUI to set up user accounts for staff and other authorized users, your WLAN
can be put to full use, enabling users to share files, print, check email, and more. And as a
bonus, guest workers, contractors and visitors can be granted controlled access to your
Ruckus WLAN with a minimum of setup.
You can now fine-tune and monitor your network through the WebUI, which assists you to
customize additional WLANs for authorized users, manage your users, monitor the network's
safety and performance, and even expand your radio coverage, if needed.
“Zero IT” refers to the ZoneDirector’s simple setup and ease-of-use features allowing end
users to configure wireless settings from a Windows XP/Vista client without aid of IT staff.
Using the WebUI Features
The ZoneDirector administrative application is divided into four components that you can
use to manage and monitor your Ruckus WLAN (including the ZoneDirector and all APs).
When you first log into your ZoneDirector with WebUI, the Dashboard appears, displaying a
number of widgets containing indicators and tables that summarize the network and its current status. Each indicator, gauge or table provides links to more focused, detailed views on
Dashboard
elements of the network.
Widgets
Tab s
Buttons
Workspace
[* = Except for the Dashboard.]
TIP: You can minimize (hide) any of the tables or indicators in the Dashboard, then reopen
them by means of the Widget options in the lower left corner.
Widgets are Dashboard components, each containing a separate indicator or table as part
of the active dashboard. Each widget can be added or removed to enhance your ZoneDirector Dashboard summary needs.
Click any of the four tabs (Dashboard, Configure, Monitor, and Admin) to take advantage of
related collections of features and options. When you click a tab, ZoneDirector displays a
collection of tab-specific buttons*. Each tab's buttons are a starting point for Ruckus Wireless network setup, management, and monitoring. Note: if you click any of the three tabs,
the Dashboard becomes available as a fourth tab.
The left-side column of buttons varies according to which tab has been clicked. The buttons
provide features that assist you in managing and monitoring your network. Click a button to
see related options in the workspace to the right.
The large area to the right of the buttons will display specific sets of features and options,
depending on which tab is open and which button was clicked.
3
Page 8

Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
Navigating the Dashboard
The Dashboard offers a number of self-contained indicators and tables that summarize the
network and its current status. Some indicators have values that link to more focused,
detailed views on elements of the network.
FIGURE 1-2
The following indicators are provided:
NOTE
• System Overview: ZoneDirector system information
• Devices Overview: Devices managed by the ZoneDirector, as well as clients connected to
those managed devices
• Usage Summary: Details on connected clients and transmission information
• Most Active Client Devices: Identification of most active clients by MAC address, IP
address, and user names. The usage is the total Rx and Tx byte counts by a user since first
connection.
• Most Recent User Activities: Audit log of activities performed by users on client
machines
• Most Recent System Activities: System activities related to ZoneDirector operation
• Most Frequently Used Access Points: Access points serving the most client requests
Some indicators may not be present upon initial view. The Add Widgets feature, located at
the bottom left of the screen, enables you to show or hide indicators. See “Using Indicator
Widgets” on page 5.
4
Page 9
Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
• Currently Active WLANs: Details of currently active ZoneDirector WLANs
• Currently Managed APs: Details of the access points currently managed by the ZoneDirector
• Support: Ruckus support information
Using Indicator Widgets
Dashboard widgets represent the indicators displayed as part of the active dashboard. Indicator widgets can be added or removed to enhance your ZoneDirector summary needs.
Adding a Widget
To add widgets, do the following:
1 Go to the Dashboard.
2 Click Add Widgets from the bottom left of the Dashboard page.
FIGURE 1-3
The Widgets pane opens to the left of the Dashboard.
3 Select any Widget icon and drag and drop it onto the Dashboard to add the widget. If
you have closed a widget, it appears in this pane.
5
Page 10
Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
4 Click Finish in the Widgets pane to close it.
FIGURE 1-4
Removing a Widget
To remove an indicator widget, click the red x icon for any of the indicator widgets presently open on the Dashboard.
About Ruckus WLAN Security
After your initial setup, your Ruckus wireless network connects all authorized users by
default to your internal WLAN. This WPA-based WLAN is configured to provide secure coverage for all authorized users. (A companion “guest” WLAN provides clear-text but controlled
access for guest users.) But Ruckus offers other security options that can be applied to the
internal WLAN through ZoneDirector. These options range from a less-secure WEP key-based
configuration, through the default WPA passphrase-based configuration to a higher-security,
certificate-based 802.1x EAP configuration. Your choice mostly depends on what kinds of client authentication your users' client devices support.
For example, some of your WLAN users may be limited to a WEP-based security system by
their client devices (computer or wireless network adapter). With WebUI, you do have
options: You can regress the existing internal configuration from WPA to the less-secure WEP,
or add a custom WLAN with WEP options for those users who require WEP, while retaining
the original, more secure internal WPA configuration for the rest of your users. Or, you can
replace the default WPA setup with a secure authentication/encryption methodology, 802.1x
EAP.
One drawback to 802.1x is the more labor-intensive setup, requiring (among other tasks) the
transfer of root certificate copies to your users, who must then import the certificates into
their client devices. This will prove disruptive if you have a large user audience already
using your network.
6
Page 11

Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
The ZoneDirector supports one or more WLANs, and if you need to add a WEP WLAN for
those users, in addition to your WPA internal WLAN, you can easily do so. User could utilize
the Zero-IT Activation to obtain the WEP key automatically or could manually enter the WEP
key in their client device wireless configuration.
If you like the security of the default configuration, you can take advantage of customizable
options that have no disruptive effect on your current users' connections.
All three basic options (WEP, WPA and 802.1x) are detailed in “Creating a New WLAN” on
page 26, and you can learn how to apply them to your Ruckus WLAN in the same section.
Controlling Device Permissions: Blocking and ACLs
The ZoneDirector features a block list as well as access control list (ACL) functionality to
control network permissions.
• Block List: When users log into a ZoneDirector network, their client devices (for example,
laptop computers and PCs) are recorded and tracked. If, for any reason, you need to
block a client device from network use, you can do via the ZoneDirector WebUI. For more
on configuring the block list, see “Blocking Client Devices” on page 36.
• ACLs: Access control lists establish which devices based on their MAC addresses are
allowed to associate to a ZoneDirector-managed AP. By using the Configuration > Access
Control options, you define Layer 2 ACLs, also known as MAC address ACLs, which can
then be applied to one or more ZoneDirector WLANs. ACLs are either allow-only or denyonly; that is, an ACL can be set up to allow only specified clients or to deny only specified
clients. For more on configuring ACLs, see “Configuring Access Control Lists” on page 24.
Note the following ZoneDirector rules:
• The block list is system-wide, and is applied to all WLAN’s in addition to the per-WLAN
ACL. If a MAC address is listed in the system-wide block list, it will be blocked even if it is
an allowed entry in an ACL. Thus, the block list take precedence over an ACL.
• MAC addresses that are in the deny list are blocked at the AP, not at the ZoneDirector.
7
Page 12

System Configuration
Chapter Contents
• “Changing the Network Addressing” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
• “Changing the System Name” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
• “Updating the Internal Clock” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
• “Changing the System Log Settings” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
• “Setting up Email Alarm Notification” . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
• “Customizing the Guest “Login” Page” . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
• “Upgrading ZoneDirector and ZoneFlex APs” . . . . . . . . . . . . . . . . . . . . . . . 15
CHAPTER 2
• “Working with Backup Files” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
• “Restoring the ZoneDirector to the Factory Default State” . . . . . . . . . . . . . 17
8
Page 13
Ruckus Wireless ZoneDirector User Guide | System Configuration
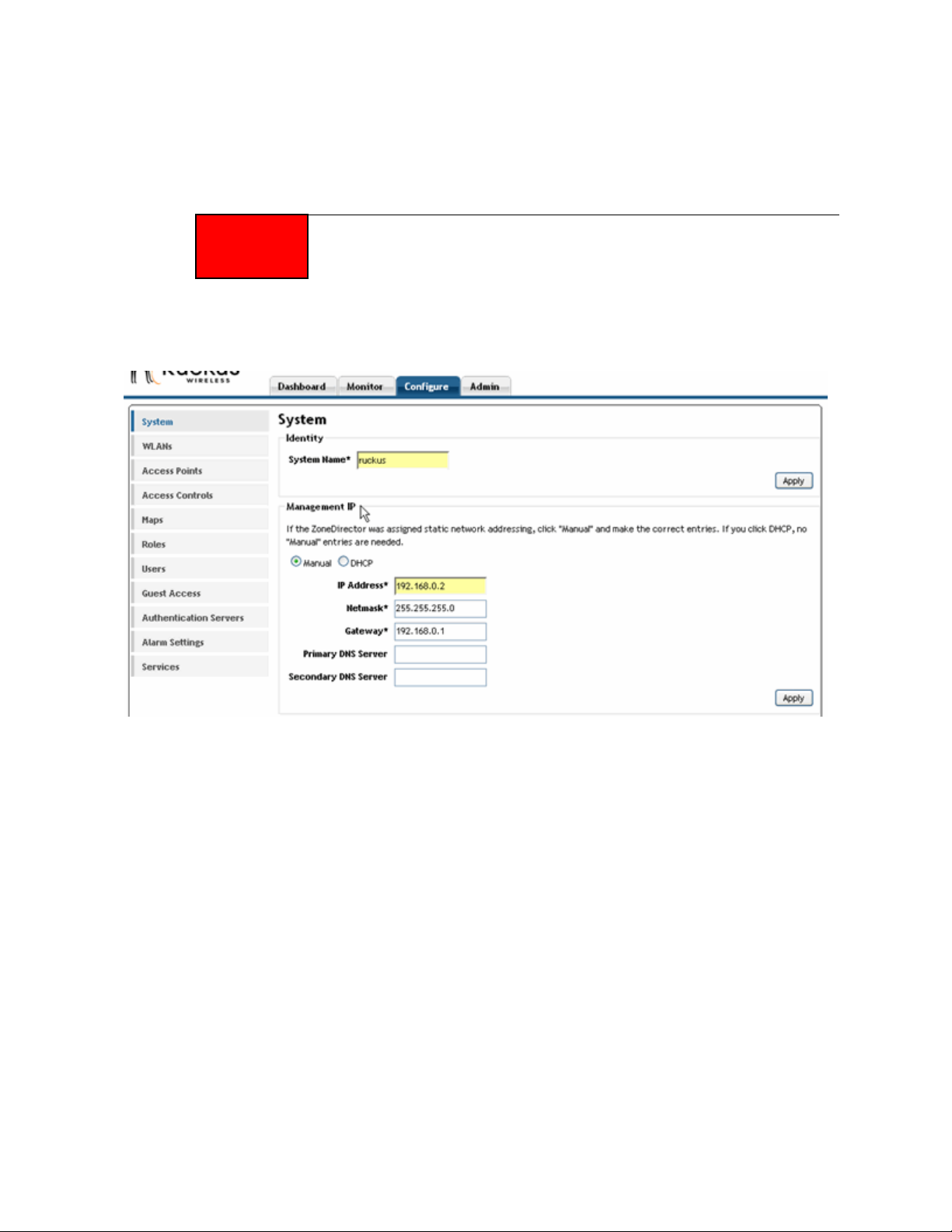
Changing the Network Addressing
If you need to replace or update the network settings for your Ruckus ZoneDirector, follow
these steps.
ALERT!
1 Go to Configure > System.
2 Review the Management IP options.
As soon as the IP address has been changed (applied), you will be disconnected from your
WebUI connection to the ZoneDirector. You can log in again with WebUI by using the new IP
address in your web browser.
FIGURE 2-1
3 Select one of the following:
• Manual: If you select Manual, enter the correct information in the now-active
fields (IP Address, Netmask, and Gateway are required).
• DHCP. If you select DHCP, no further information is required.
4 Click Apply to save your settings.
You will lose connection to the ZoneDirector.
5 To log back in to the WebUI, use the newly assigned IP address in your web browser or
use the UPnP application to re-discover the ZoneDirector.
9
Page 14
Ruckus Wireless ZoneDirector User Guide | System Configuration
Changing the System Name
When you first worked through the Setup Wizard, you were prompted for a network-recognizable system name for the Ruckus ZoneDirector. If needed, you can change that name by
following these steps:
1 Go to Configure > System.
2 In the Identity options, delete the text in the System Name field and type a new
name.
The name should be between 6 and 32 characters in length, using letters, numbers,
underscores (_) and hyphens (-). Do not use spaces or other special characters.
FIGURE 2-2
3 Click Apply to save your settings. The change goes into effect immediately.
Updating the Internal Clock
The internal clock in your Ruckus ZoneDirector is automatically synchronized with the clock
on your administration PC during the initial setup. You can use the WebUI to check the current time on the internal clock, which shows up as a static notation in the Configure tab
workspace. If this notation is incorrect, you can re-synchronize the internal clock to your PC
clock immediately.
Another option is to link your ZoneDirector to an NTP server (as detailed below), which provides continual updating with the latest time.
1 Go to Configure > System.
2 In the System Time features you have the following options:
• Refresh—Click this to update the ZoneDirector display (a static snapshot) from
the internal clock.
• Synch Time with your PC Now—If needed, click this to update the internal
clock with the current time settings from your administration PC.
• Use NTP... [Active by default]—Click this checkbox to deactivate this option.
10
Page 15

Ruckus Wireless ZoneDirector User Guide | System Configuration
3 Click Apply to save the results of any resynchronizations or NTP links.
Changing the System Log Settings
The Ruckus ZoneDirector maintains an internal log of current events and alarms. This file
has a fixed capacity; at a certain level, the ZoneDirector will start deleting the oldest
entries to make room for the newest. This log is volatile, and the contents will be deleted if
the ZoneDirector is powered down. If you want a permanent record of all logging activities,
you can set up your syslog server to receive log contents from the ZoneDirector, then use
the WebUI to direct all logging to the syslog server—as detailed in this topic.
FIGURE 2-3
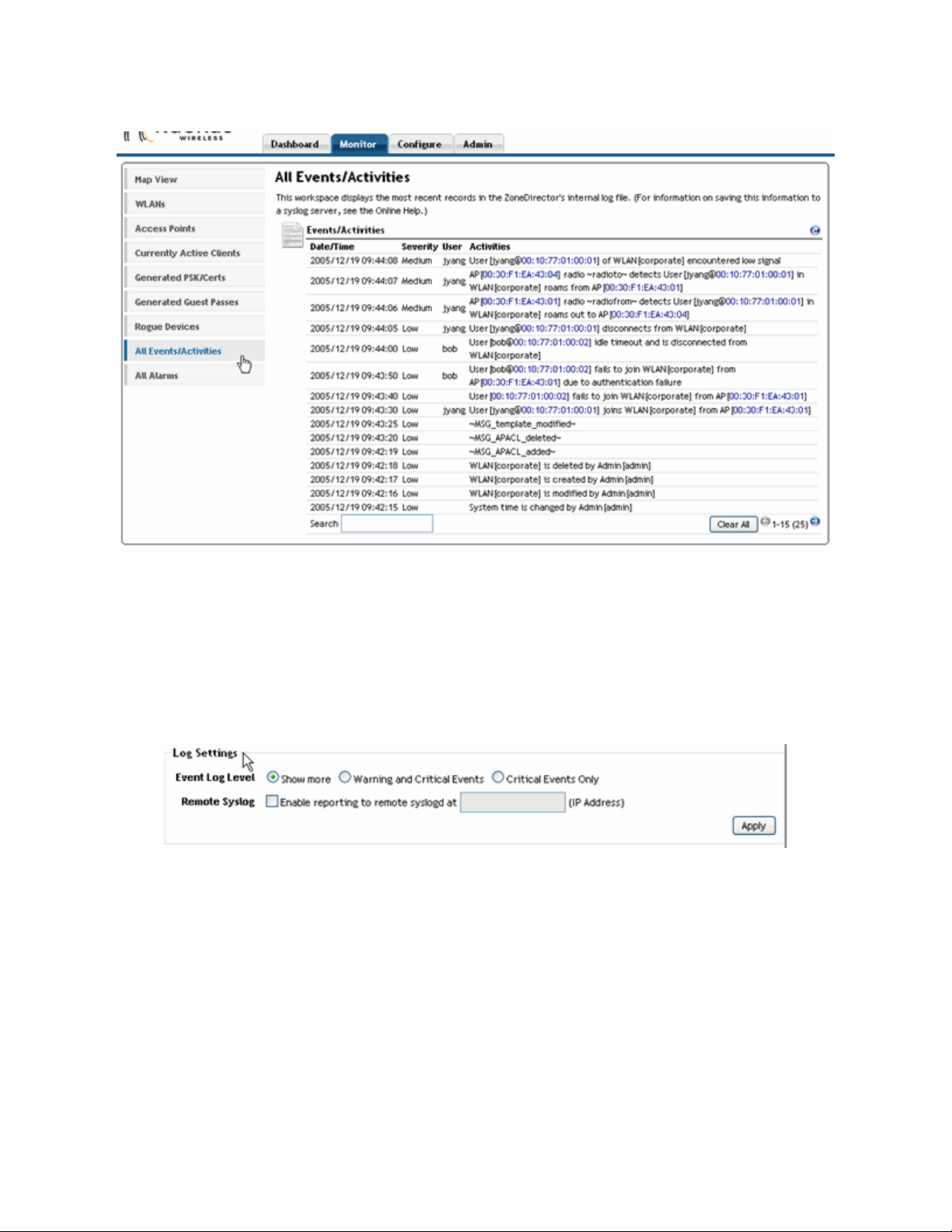
Reviewing the current log contents
1 Go to Monitor > All Events/Activities.
2 Review the events and alarms listed here. See “FIGURE 2-4” on page 12.
NOTE The entries are in reverse chronological order—latest at the top.
3 Click a column header to sort the contents by that category.
4 Click any column twice to switch chronological or alphanumeric sorting modes.
11
Page 16
Ruckus Wireless ZoneDirector User Guide | System Configuration
FIGURE 2-4
Checking the current log settings
You can review and customize the log settings by following these steps:
1 Go to Configure > System.
2 Scroll down to Log Settings.
3 Make your selections from these syslog server options:
Event Log Level Select one of the three logging levels— “Show more”, “Warning
and Critical Events”, or “Critical Events Only”.
Remote Syslog Click the checkbox by Enable reporting to remote syslogd at to
enable syslog logging.
Click in the text field and enter the IP address of the syslog
server.
FIGURE 2-5
4 Click Apply to save your settings. The changes go into effect immediately.
12
Page 17
Ruckus Wireless ZoneDirector User Guide | System Configuration
Setting up Email Alarm Notification
If an alarm condition is detected, the Ruckus ZoneDirector will record it in the event log. If
you prefer, an email notification can be sent to a configured email address of your choosing.
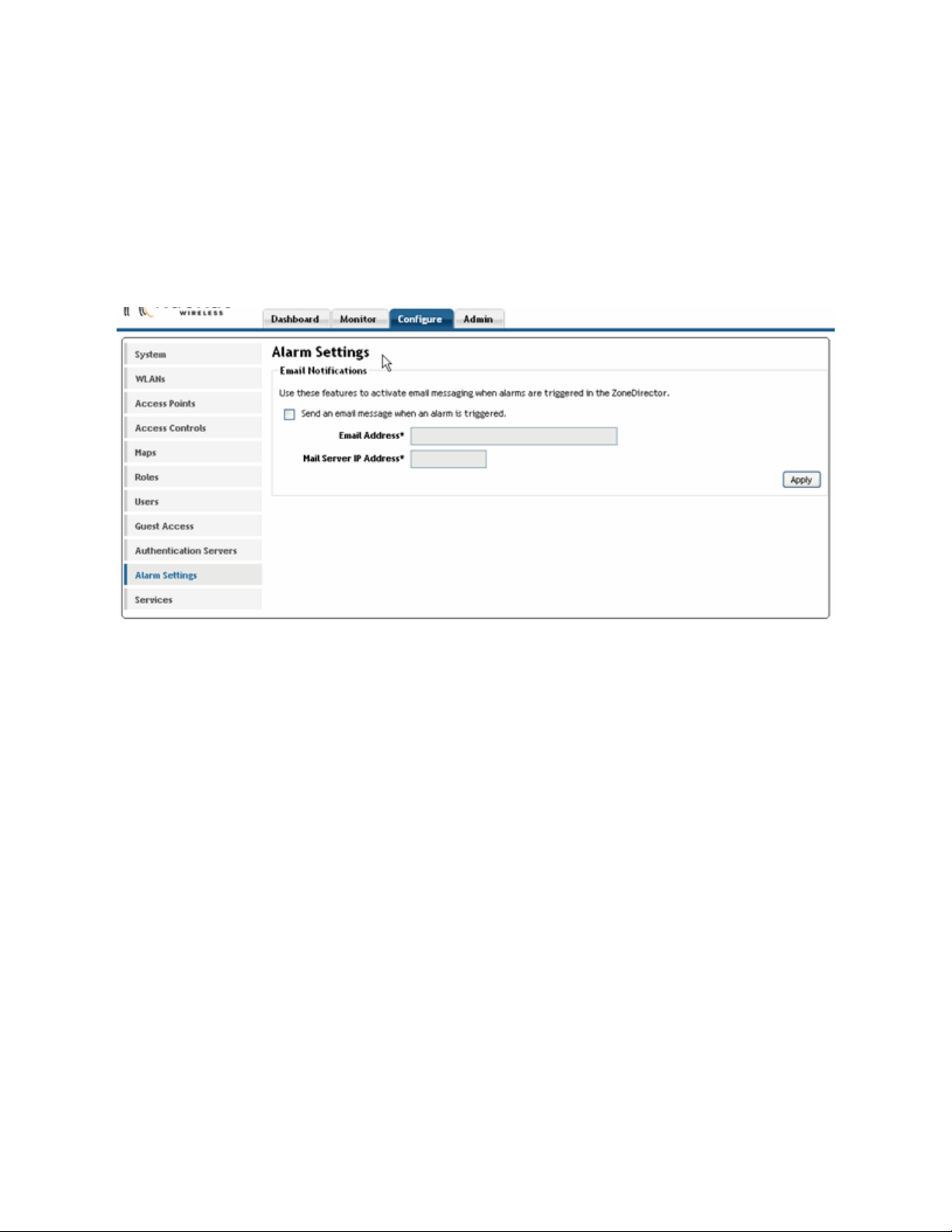
To activate this option, follow these steps:
1 Go to Configure > Alarm Settings.
When the Alarm Settings page appears, the Email Notifications features appear.
FIGURE 2-6
2 Click the Send an email message checkbox to activate this option.
3 Type the email address in the Email Address text field.
4 Enter the IP address of your mail server at Mail Server IP Address.
5 Click Apply. The email notification feature becomes active immediately.
13
Page 18
Ruckus Wireless ZoneDirector User Guide | System Configuration
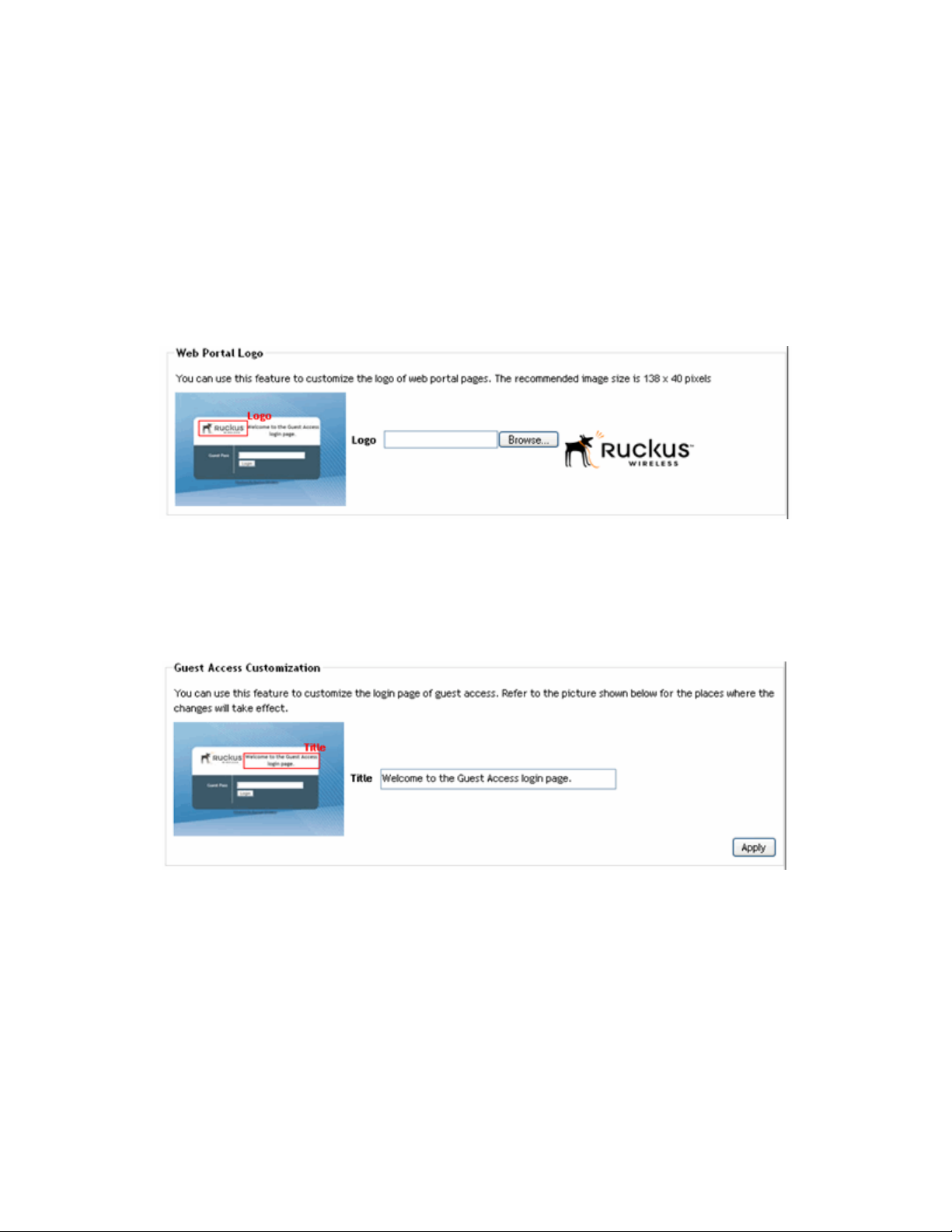
Customizing the Guest “Login” Page
You can customize the guest user login page, to display your corporate logo and to note
helpful instructions, along with a “Welcome” title. If you want to include a logo, you'll need
to prepare a web-ready graphic file, in one of three acceptable formats (.JPG, .GIF or
.PNG). Make sure the logo is no bigger than two inches long on any side, or larger than
200kB.
1 Go to Configure > Guest Access.
2 Locate the Web Portal Logo features.
FIGURE 2-7
3 If your logo is ready for use, click Browse to open a dialog box that you can use to
import the logo file. (ZoneDirector will notify you if the file is too large—height or
width).
4 Locate the Guest Access Customization features.
FIGURE 2-8
5 (Optional) Delete the text in the Title field and type a short descriptive title or “wel-
come” message.
6 Click Apply to save your settings. A “Setting applied!” confirmation message briefly
appears.
14
Page 19

Ruckus Wireless ZoneDirector User Guide | System Configuration
Upgrading ZoneDirector and ZoneFlex APs
Check the Ruckus Wireless Support web site on a regular basis, for updates and upgrades
that can be applied to your Ruckus network devices—to ZoneDirector and all your Ruckus
ZoneFlex APs. After downloading any upgrade package to a convenient folder on your
administrative PC, you can complete the network upgrade (of both ZoneDirector and APs) by
following the steps detailed below.
NOTE
1 Go to Admin > Upgrade.
2 When the Software Upgrade features appear, click Browse.
3 When the Browse dialog box appears, use it to locate and open the upgrade package.
4 When the upgrade file name appears in the text field, the “Browse” button is trans-
formed into the “Upgrade” button.
Start this procedure at an off-peak time, to lessen the impact of network connection disruption.
FIGURE 2-9
5 Click Upgrade.
The ZoneDirector will automatically log you out of the WebUI, run the upgrade, then
restart itself.
6 When the Status LED on the device is steadily lit, you can log back in as Administrator
to the WebUI.
NOTE
The full network upgrade is successive in sequence. After the ZoneDirector is upgraded, it
will contact each active AP, upgrade it, then restore it to service.
15
Page 20
Ruckus Wireless ZoneDirector User Guide | System Configuration
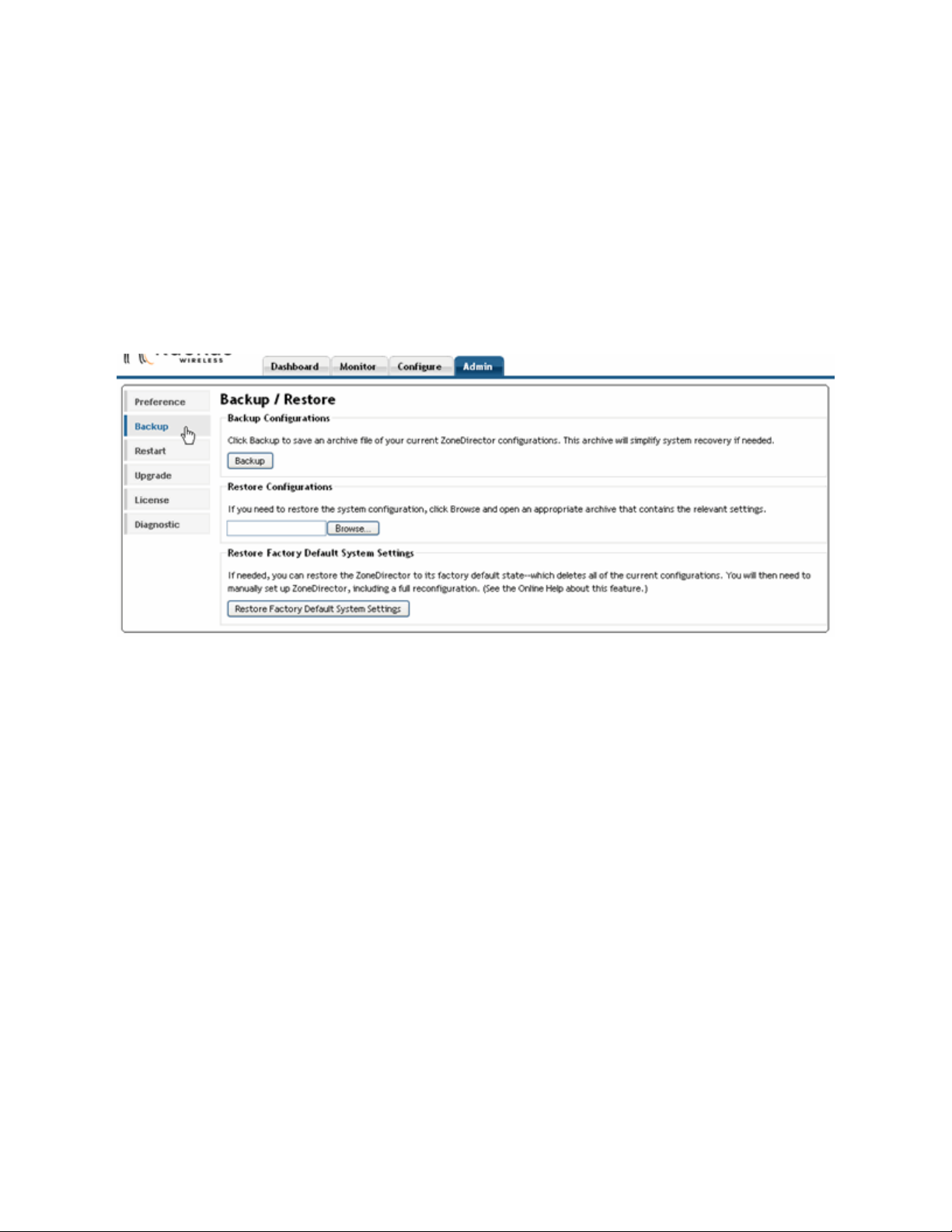
Working with Backup Files
After you have set up and configured your Ruckus wireless network, you may want to back
up the full configuration. The resulting archive can be used to restore your ZoneDirector and
network. And, whenever you make additions or changes to the setup, you can create new
backup files at that time, too.
Backing up a network configuration
1 Go to Admin > Backup.
FIGURE 2-10
2 In the Backup Configurations workspace, click Backup.
3 When the File Download dialog box appears, click Save.
4 When the Save As dialog box appears, enter a name for this archive file, pick a desti-
nation folder, then click Save.
5 Make sure the filename ends in a “.TGZ” extension.
6 When the Download Complete dialog box appears, click Close.
Restoring archived settings to the ZoneDirector
1 Go to Admin > Backup.
2 Review the Restore Configurations instructions, then click Browse. See “FIGURE 2-10”
on page 16.
3 Use the Browse dialog box to locate and open the appropriate backup archive file.
4 Click the Restore button.
While restoration is in progress, you will be logged out of the ZoneDirector.
When restoration to the archived configuration is complete, the ZoneDirector will be
automatically restarted and your network will be ready for use.
16
Page 21

Ruckus Wireless ZoneDirector User Guide | System Configuration
Restoring the ZoneDirector to the Factory Default State
In certain extreme conditions, you may want to reinitialize the Ruckus ZoneDirector, and
reset it to the "factory default" state. In such a state, the network is almost ready for use,
but all your user/guest/log and other records, accounts and configurations would all need to
be manually re-configured.
ALERT!
To reset your ZoneDirector to factory default settings, follow these steps:
1 Go to Admin > Backup.
When this procedure is complete, you will need to redo a complete setup. If the ZoneDirector
is on the live network, a new IP address may be assigned to the system. In this case, the
system can be discovered by an UPnP client application, such as Windows My Network
Places. If there is no DHCP server on the connected network, the system's default IP
address is “192.168.0.2” with subnet mask “255.255.255.0”. A complete set of instructions is
available in the Quick Start Guide (QSG). Before starting this “factory default settings” restoration, you should open and print out the QSG pages. You can follow those instructions to
set up the ZoneDirector after a factory-default state has been restored.
FIGURE 2-11
2 When the Backup/Restore page appears, look for Restore Factory Default System
Settings, and click the button.
3 Owing to the drastic effect of this operation, one or more confirmation dialog boxes
will appear. Click OK to confirm this operation.
When this process begins, you will be logged out of the WebUI.
When the reset is complete, the Status LED is a blinking red, then a blinking green,
indicating that the system is in the “factory default” state. After you complete the
Setup Wizard, the Status LED will be steady green.
17
Page 22
Ruckus Wireless ZoneDirector User Guide | System Configuration
Alternate factory default reset method
If you are unable to complete a software-based resetting of the Ruckus ZoneDirector, you
can do the following “hard” restoration:
NOTE Do not disconnect the ZoneDirector from any power source until this procedure is complete.
1 Look for a pinhole on the right side of the front panel of the ZoneDirector.
2 Insert a straightened paper clip in the hole and press for at least 5 seconds.
After the reset is complete, the Status LED is a blinking red, then a blinking green,
indicating that the system is in a “factory default” state.
After you complete the Setup Wizard, the Status LED will be steady green.
18
Page 23

Managing a Wireless
LocalAreaNetwork
Chapter Contents
• “An Overview of Wireless Networks” . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
• “Customizing Ruckus WLAN Security” . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
• “Setting Dynamic Pre-Shared Key Expiration” . . . . . . . . . . . . . . . . . . . . . . 24
• “Configuring Access Control Lists” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
• “Creating a New WLAN” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
CHAPTER 3
• “Creating a New WLAN for Workgroup Use” . . . . . . . . . . . . . . . . . . . . . . . . 30
• “Adding New Access Points to the WLAN” . . . . . . . . . . . . . . . . . . . . . . . . . 31
• “Reviewing the Current Access Point Policies” . . . . . . . . . . . . . . . . . . . . . . 33
• “Reviewing the Current Access Point Policies” . . . . . . . . . . . . . . . . . . . . . . 33
• “Blocking Client Devices” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
• “Optimizing Access Point Performance” . . . . . . . . . . . . . . . . . . . . . . . . . . 37
19
Page 24

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
An Overview of Wireless Networks
When your Ruckus ZoneDirector setup is complete, you have a fully functional wireless network, based on two secure WLANs (“internal” and “guest”) with access for authorized users
and guests. The internal WLAN provides “zero IT” connectivity for “standard” client
devices, those computers running Windows XP/SP2 and utilizing WPA-ready NICs.
There are two scenarios in which you create additional WLANs, in addition to the internal
WLAN: (1) To limit certain WLANs to groups of qualified users, to enhance security and efficiency. For example, an “Engineering” WLAN with a closed roster of users.) Or, (2) to configure a specific WLAN with different security settings. For example, you may need a WLAN
that utilizes WEP encryption for wireless handheld devices that only support WEP-key encrytion.
In the first scenario, specific WLANs (esp. regarding authentication and encryption algorithm) can be set up that support specific groups of users. This requires a two-step process:
(1) create the custom WLAN and link it to qualified user accounts by “roles”, and (2) assist
all qualified users to prepare their client devices for custom WLAN connection.
As a result, you will have the default internal WLAN, plus the needed WLANs that fulfill different wireless security requirements.
Customizing Ruckus WLAN Security
The default security environment for your internal WLAN incorporates a WPA-based authentication passphrase and the TKIP encryption algorithm, and utilizes a dynamic pre-shared
key. To review the default WLAN configurations and the available options, review the following procedures.
Reviewing the initial security configuration
1 Go to Monitor > WLANs.
2 When the WLANs workspace appears, a WLANs table lists the two default WLANs cre-
ated in the setup process: corporate and guest. The internal WLAN, corporate, is the
one used by your authorized users, and you can review the details of its configuration
by clicking the WLAN name. See “FIGURE 3-1” on page 21.
3 You have three options with the internal WLAN: [1] continue using the current configu-
ration, [2] fine-tune the existing WPA-based mode, or [3] replace this mode entirely
with either a WEP-based mode or an 802.1x mode. The two WLAN-editing processes
are described separately, in the following sections.
20
Page 25

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
FIGURE 3-1
Fine-tuning the current security mode
1 In the internal WLAN (corporate) row, click Edit (if you haven't done so).
2 You can choose from the following options, which will enhance the default “zero IT”
protection without disrupting the user's connections.
WPA2 Switch to this encryption method if you prefer the IEEE 802.11i stan-
dard.
AES Switch to this algorithm for stronger encryption.
Passphrase Replace the current passphrase with a new one.
3 Click OK to apply any changes.
Switching to a different security mode
You also have the option of replacing the default internal WLANs’ WPA mode with one of
two other modes:
• The less-secure protection of a WEP key mode
• The more-secure protection of a 802.1x mode
Replacing your WPA configuration with 802.1x requires the users to make changes to their
Ruckus wireless connection configuration—including the importation of certificates.
1 Go to Configure > WLANs.
21
Page 26

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
2 When the WLANs workspace appears, you will want to review, then change the secu-
rity options for the internal network. To start, click Edit in the internal row.
3 When the Editing (corporate) features appear, look at the two main categories—
Authentication Options and Encryption Options.
4 If you click an Authentication Option Method such as Open, Shared, or 802.1x, differ-
ent sets of encryption options are displayed:
• Open allows you to configure a WPA- or WEP-based encryption, or “none” if you're
so inclined. After selecting a WPA or WEP, you can then enter a passphrase or key
text of your choosing.
• Shared limits you to WEP-key encryption.
• 802.1x EAP allows you to choose from all available encryptions, but you do not
need to create a key or passphrase.
5 Depending on your Authentication Option Method selection, review and reconfigure
the related Encryption Options.
6 Review the Advanced Options to change any settings as needed. (For example, if you
switch to 802.1x, you'll need to choose an authentication server from the menu.)
7 When you are finished, click OK to apply your changes.
Using the built-in EAP server
(Requires the selection of “Local Database” as the authentication server.) If you are re-con-
figuring your internal WLAN to use 802.1x/EAP authentication, you normally have to generate and install certificates for your wireless users. With the built-in EAP server and Zero-IT
Wireless Activation, certificates are automatically generated and installed on the end user's
computer. Users simply follow the instructions provided during the Zero-IT Wireless Activation process to complete this task. Once it is done, users can connect to the internal WLAN
using 802.1x/EAP authentication.
Authentication with an external RADIUS server
You could use an external RADIUS server for your wireless client 802.1x/EAP authentication.
An EAP-aware RADIUS server is required for this application. Also, you might need to deploy
your own certificates for wireless client devices and for the RADIUS server you are using. In
this case, the Ruckus ZoneDirector works as a bridge between your wireless clients and the
RADIUS server during the wireless authentication process. Ruckus ZoneDirector allows wireless clients to access the networks only after successful authentication of the wireless clients by the RADIUS server.
22
Page 27

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
If you change the internal WLAN to WEP or 802.1x
If you replace the default WPA configuration of the internal WLAN, your users must reconfigure the wireless LAN connection settings on their devices. This process is described in detail
and can be performed when logging into the WLAN as a new user.
If switching to WEP-based security:
1 Each user should be able to repeat the Zero-IT Wireless Activation process and install
the WEP key by executing the activation script.
2 Alternatively, they could manually enter the WEP key text into their wireless device
connection settings.
If switching to 802.1x-based security:
1 (Applies only to the use of the built-in EAP server.) Each user should be able to repeat
the Zero-IT Wireless Activation process and download the certificates and an activation script generated by the Ruckus ZoneDirector
2 Each user must first install certificates to his/her computer.
3 Each user must then execute the activation script, in order to configure the correct
wireless setting on his/her computer.
4 To manually configure 802.1x/EAP settings for non-Windows XP/SP2 client usage, use
the wireless setting generated by the Ruckus ZoneDirector to manually configure your
wireless devices as detailed in a separate Ruckus printed publication, Logging into the
WLAN as a New User. (An Acrobat edition is available for your use.)
23
Page 28

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Setting Dynamic Pre-Shared Key Expiration
When network users first activate their access to the WLAN with Dynamic PSK enabled, a
unique pre-shared key (PSK) is generated automatically for their authentication. (This was
activated by default in the WLAN Setup Wizard.) By default, all dynamic pre-shared keys
expire in two months. You can control when the PSK expires, at which time the users will be
prompted to re-activate their wireless access.
1 Go to Configure > WLANs.
2 In the Dynamic PSK features, open the drop-down list and pick the lifespan interval for
a new PSK.
FIGURE 3-2
3 Click Apply to save your settings. The new settings goes into effect immediately.
Configuring Access Control Lists
You can build access control lists to establish which devices based on their MAC addresses
are allowed to associate to ZoneDirector-managed APs. Using the Access Controls configuration options, you define Layer 2 ACLs, also known as MAC address ACLs, which can then be
applied to one or more WLANs (upon WLAN creation or edit). ACLs are either allow-only or
deny-only; that is, an ACL can be set up to allow only specified clients or to deny only specified clients.
MAC addresses that are in the ACL deny list are blocked at the AP, not at the ZoneDirector.
TIP
To configure an ACL, do the following:
ZoneDirector also has a system-wide block list that is applied to all WLAN’s in addition to the
per-WLAN ACL. The entries of the system-wide block list are added when the admin
chooses to block clients from the Monitor/Current Active Clients panel. The admin can
remove entries from the system-wide block list via Configure > Access Control > Block
Clients list. If a MAC address is listed in the system-wide block list, it will be blocked even if
it is an allowed entry in other ACL list.
1 Go to Configure > Access Control.
2 Under Access Control Policies, click Create New.
24
Page 29

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
FIGURE 3-3
3 Ty p e a Name for the ACL.
4 Ty p e a Description of the ACL.
5 Select the Restriction mode as either allow or deny.
6 Type a MAC address in the MAC Address text box, then click Create New to save the
address. The added address appears next to the Stations field.
7 Repeat Step 5 to add additional MAC addresses.
8 Click OK to save the ACL.
9 To apply the ACL, see the Advanced Options section in “Creating a New WLAN” on
page 26.
25
Page 30

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Creating a New WLAN
There are cases in which you might want to create additional WLANs. For example, you
might want to create a WLAN for WEP-only client devices. Or you might want to create a
WLAN that utilizes 802.1x/EAP and certificates. The following shows how to create such
WLANs that utilize different security settings.
Creating a WLAN
To create a custom wireless LAN, follow these steps:
1 Go to Configuration > WLAN.
2 Click Create New.
FIGURE 3-4
26
Page 31

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
The Create New workspace displays the following:
General Options
Name/ESSID Type a short name (2–31 characters/numbers) for this WLAN.
Description Enter a brief description of the qualifications/purpose for this
WLAN, e.g., “Engineering” or “Voice”.
Authentication Method Options
Method Open. [Default] No authentication mechanism is applied to
connections. If WPA or WPA2 encryption is used, this implies
WPA-PSK authentication.
Shared: If you click Shared, only WEP encryption will be available, and the WEP Key option appears. Uses a shared WEP key
for authentication. Requires creation of a WEP key, as detailed
below.
802.1x EAP: Uses 802.1x authentication mechanism. Requires
use of certificates.
Encryption Options
Method None: [Default] No encryption is applied; communications are
in clear text.
WPA / WPA2: (Not available to Shared authentication) Provides
a higher level of encryption and is more secure. WPA and WPA2
require selection of an encryption algorithm (as detailed
below).
WEP-64: Provides a lower level of encryption, and is less
secure, using 64-bit WEP encryption.
WEP-128: Provides a higher level of encryption, using a 128-bit
key for WEP encryption.
Algorithm (Only for WPA or WPA2 encryption methods)
TKIP: [Default] This algorithm is effective. It is set as the
default since some client devices do not support AES.
AES: This algorithm provides a high degree of security.
WEP Key WEP methods only. Click in the Hex field and type the required
key text. If the key is for WEP 64 encryption, the key text must
be up to 10 characters in length. If it is for WEP 128 encryption,
enter a key up to 26 characters in length.
Passphrase WPA/WP2 PSK methods only. Click in this field and type the text
of the passphrase used for authentication.
Options
Guest Usage If the WLAN being created is for Guest access, mark the This
WLAN is for Guest Access check box. When selected, the Wire-
27
Page 32

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
less Client Isolation option is automatically selected and cannot
be unchecked.
Guest WLANs are subject to guest access policies, such as redirection and subnet access restriction.
Web Authentication [Available only with "Open" or "Shared" authentication.] Click
the checkbox to require all WLAN users to complete a webbased login to this network each time they attempt to connect.
Authentication Server When "Web Authentication" is active, use this option to desig-
nate the server used to authenticate web-based user login.
When "802.1x" authentication is active, use this option to designate either "Local Database" or a configured RADIUS server as
the authentication source.
Wireless Client Isolation Wireless client isolation enables subnet restrictions for guests.
When wireless client isolation is enabled for a WLAN, any stations associated to this WLAN will not be able to access the local
LAN; rather, they can only access the Internet. Also, stations
associated to this WLAN cannot communicate with each other,
regardless of which APs they are associated to. The behavior of
stations will be exactly as the stations that associate to a guest
WLAN. The only difference between a WLAN with wireless client
isolation enabled and a guest WLAN is that a guest WLAN
requires users to enter a guest pass before they can access the
network. Same guest policy will be applied to guest WLAN as
well as WLAN’s with wireless client isolation enabled.
Zero IT Activation Leave this option active (the default state), as it activates the
Ruckus ZoneDirector's share in the automatic “new user” process, in which the new user's PC is efficiently (and speedily)
configured for WLAN use.
Advanced Options
See “FIGURE 3-5” on page 29.
Access Controls Toggle this drop-down list to select the ACL to apply to this
WLAN. An ACL must be created before being available here. See
“Configuring Access Control Lists” on page 24.
Rate Limiting Rate limiting controls fair access to the network. When
enabled, the network traffic throughput of each network device
(i.e., client) is limited to the rate specified in the traffic policy,
and that policy can be applied on either the uplink or downlink.
Toggle the Uplink and/or Downlink drop-down lists to limit the
rate at which WLAN clients upload/download data.
The "Disabled" state means rate limiting is disabled; thus, traffic
flows without prescribed limits.
VLAN Check this option to activate the VLAN function, then click in
the VLAN Tag field and type the relevant VLAN ID assigned to
28
Page 33

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
users/clients of your wireless network. (The ID should be a number between 1 and 4094).
Hide SSID Activate this option if you don't want the ID of this WLAN adver-
tised at any time. This will not affect the performance or force
the WLAN user to perform any unnecessary tasks.
FIGURE 3-5
3 When you are finished, click OK to save the entries. This WLAN is ready for use.
4 You can now select from these WLANs when assigning roles to users, as detailed in
“Creating New User Roles” on page 44.
Client authentication configuration
If your users are connecting with computers running Windows XP/SP2/Vista, an automatic
activation script is generated for them to install security settings of WLANs configured on
the Ruckus ZoneDirector. If your users are connecting with computers running early versions
of Windows, Mac OS X, Linux, or other operating systems, no activation script will be provided for them. Instead, a detailed page containing all necessary wireless settings is provided. Users must perform manual configuration on their computers based on these settings.
The following grid records the details.
Authentication Options Encryption Options Client Configurables
User must (1) manually enter the text of
the same WEP key in their wireless network configuration, or (2) must manually
enter the WPA passphrase.
Open
WPA
WPA-2
WEP-64
WEP-128
29
Page 34

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Authentication Options Encryption Options Client Configurables
User must manually enter the text of the
Shared
WEP-64
WEP-128
same WEP key stored in the Ruckus
ZoneDirector in their wireless network
configuration.
802.1x
WEP-64
WEP-128
WPA/WPA2
User must obtain and install certificates
generated on their computers. No key or
passphrase is required.
Creating a New WLAN for Workgroup Use
If you want to create an additional WLAN based on your existing internal WLAN and limit its
use to a select group of users (e.g, Marketing, Engineering), you can do so by following these
steps:
1 Make a list of the group of users (who ideally are using client devices running Windows
XP/SP2).
2 Go to Monitor > WLANs.
When the WLANs page appears, the default corporate and guest networks are listed in
the table (once you have created a WLAN, it will appear in this table).
3 If you have no need for custom authentication or encryption methodologies in this new
WLAN, locate the corporate WLAN record and click Clone.
A workspace appears, displaying the default settings of a new WLAN, using the same
zero-IT configuration settings as “Corporate”.
4 Type a descriptive name for this WLAN, then click OK. This new WLAN is ready for use
by selected users.
5 You can now assign access to this new WLAN to a limited set of “corporate” users, you
can do so as detailed in “Creating New User Roles” on page 44
30
Page 35

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Adding New Access Points to the WLAN
If your staffing or wireless coverage needs increase, you can add APs to your network easily
and efficiently. Depending on your network security preferences, the new APs can be automatically detected and activated, or new APs may require per-device manual approvals
before becoming active.
The “Auto-JOIN” automatic AP activation process is active by default. If you prefer, you can
deactivate Auto-JOIN. If this is your preference, the Ruckus ZoneDirector will detect new
APs, alert you to their presence, then wait for you to manually “approve” their activation—
as detailed in this guide.
Connecting the APs to the WLAN
1 Place the new APs in the appropriate locations.
2 Write down the MAC address (on the bottom of each device) and note the specific
location of each AP as you distribute them.
3 Connect the APs to the LAN with Ethernet cables.
4 Connect each AP to a power source.
NOTE
If the Ruckus APs you are using are POE-capable and power sources are not convenient,
they will draw power through the Ethernet cabling if connected to a POE-ready hub or
switch.
Verifying/Approving new APs
1 Go to Monitor > Access Points.
2 When the Access Points page appears, review the Currently Managed APs table. See
“FIGURE 3-6” on page 32.
•If the Configure > Access Points > Access Points Policies > Approval checkbox is
checked, all new APs should be listed in the table, and their Status should be “Connected”.
• If the Auto-JOIN option is deactivated, all new APs will be listed, but their status
will be “Approval Pending.”
3 Under the Action column, click Allow. After the status is changed from “Discon-
nected” to “Connected”, the new AP is activated and ready for use.
4 Click Apply to save your settings.
TIP!
Use “Map View” (in the Monitoring tab) to place the marker icons of any newly approved
APs. See “Evaluating and Optimizing Network Coverage” on page 59 for more information.
31
Page 36

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
FIGURE 3-6
32
Page 37

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Reviewing the Current Access Point Policies
The Access Point Policy options include how new APs are detected and approved for use in
WLAN coverage. To review and revise the general AP policy, follow these steps:
1 Go to Configure > Access Points.
2 Review the current settings in Access Point Policies. You can change the following:
Approval If you prefer, you can deactivate this option if you want to manually
review and approve the joining of new APs to the WLAN.
3 Click Apply to save your settings. This will affect only new/unapproved APs.
FIGURE 3-7
Editing Access Point Parameters
You can add a description, or change the channelization, channel, or transmit power settings of a managed access point by editing the APs parameters.
To edit the parameters of an access point, do the following:
1 Go to Configure > Access Points.
2 Find the AP to edit in the Access Points table, then click Edit under the Action column.
3 Edit any of the following:
Description Enter a description for the AP, such as the location.
Channelization (For 802.11n only) The “channel width” determines the manner
in which the spectrum is used during transmission.
Channel This is the channel used by the APs network.
33
Page 38

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
TX Power Specifies the maximum transmit power level relative to the cal-
ibrated power.
4 Click OK to save your settings.
FIGURE 3-8
Deploying ZoneDirector WLANs in a VLAN Environment
You can set up a ZoneDirector wireless LAN as an extension of a VLAN network environment,
but certain qualifications must be met due to the fact that management traffic between the
ZoneDirector and the APs is not VLAN-tagged. The WLAN-in-VLAN qualifications include the
following:
• Verifying that the VLAN switch supports native VLANs. A native VLAN is a VLAN that allows
the user to designate untagged frames going in/out of a port to a specific VLAN.
For example, if an 802.1Q port has VLANs 2, 3, and 4 assigned to it with VLAN 2 being the
Native VLAN, frames on VLAN 2 that egress (exit) the port are not
(i.e., they are plain Ethernet frames). Frames which ingress (enter) this port and have no
802.1Q header are put into VLAN 2. Behaviour of traffic relating to VLANs 3 and 4 is intuitive.
• Connecting the ZoneDirector and any Access Points (APs) to VLAN trunk ports in the VLAN
switch
given an 802.1Q header
34
Page 39

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
• Verifying that those trunk ports are on the same native VLAN
NOTE
Example configuration (“FIGURE 3-9” on page 35): VLAN ID 55 is used for management, and
wlan1 is tagged with VLAN ID 10.
All DNS, DHCP, ARP, HTTP traffic from an unauthenticated wireless client will be passed
onto the ZoneDirector from the AP via the management VLAN. If the client belongs to a particular VLAN, ZoneDirector will add the corresponding VLAN tag before passing traffic to the
corresponding wired network. After client authentication is performed, client traffic will
directly go to the wired network from the AP, which will add the corresponding VLAN tag.
This explains why it is necessary to configure tagged VLANs for all VLAN switch ports connecting to ZoneDirector and APs.
FIGURE 3-9
35
Page 40

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
Blocking Client Devices
When users log into a ZoneDirector network, their client devices (for example, laptop computers and PCs) are recorded and tracked. If, for any reason, you need to block a client
device from network use, you can do so with WebUI. The following subtopics detail various
tasks you can perform to monitor, block and track client devices.
Monitoring client devices
1 Go to the Dashboard, if it's not already in view.
2 Under Devices Overview, look at # of Client Devices.
FIGURE 3-10
3 Click the current number, which is also a link.
4 When the Currently Active Clients page under the Monitor tab appears, review the
Clients table.
To block any listed client devices, follow the next set of steps.
Temporarily disconnecting specific client devices
Follow these steps to temporarily disconnect a client device from your WLAN. (The user can
simply reconnect manually, if they prefer.) This is helpful as a troubleshooting tip for problematic network connections.
1 Look at the Status column to identify any “Unauthorized” users.
2 Click the Delete button in the Action column in a specific user row.
The entry is deleted from the Active/Current Client list, and the listed device are disconnected from your Ruckus WLAN.
NOTE
The user can reconnect at any time, which, if this proves to be a problem, may prompt you to
consider the following client option.
Permanently blocking specific client devices
Follow these steps to permanently block a client device from WLAN connections.
1 Look at the Status column to identify any unauthorized users.
2 Click the Block button in the Action column in a specific user row.
36
Page 41

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
The status is changed to “Blocked”. This will prevent the listed device (and its user)
from using your Ruckus WLAN.
Reviewing a list of previously blocked clients
1 Go to Configure > Access Controls.
2 Review the Blocked Clients table.
3 You can unblock any listed MAC address by clicking the Unblock button for that
address.
Optimizing Access Point Performance
ZoneDirector through the WebUI enables you to remotely monitor and adjust key hardware
settings on each of your network APs. After assessing AP performance in the context of network performance, you can reset channels and adjust transmission power, as needed.
Assessing current performance by using the Map View
REQUIREMENT: The importing of a floorplan and placement of APs are detailed in “Importing a Map View Floorplan Image” on page 52 and “Placing the access point markers” on
page 53.
1 Go to Monitor > Map View.
If Map View displays a floorplan with active device symbols, you can assess the performance of individual APs, in terms of coverage. (For detailed information on the Map
View, see “Using the Map View Tools” on page 54.)
2 In the Coverage options, click Yes .
3 When the “heat map” appears, look for the Signal % scale in the upper right corner of
the map.
4 Note the overall color range, especially colors that indicate low coverage.
5 Look at the floorplan and evaluate the current coverage. You can make adjustments as
detailed in the following procedure.
Improving AP RF coverage
1 Click and drag individual AP markers to new positions on the Map View floorplan until
your RF coverage coloration is optimized. There may be a need for additional APs to
fill in large coverage gaps.
2 When your adjustments are complete, note down the new locations of relocated AP
markers.
3 After physically relocating the actual APs in conformance to the Map View placements,
disconnect and reconnect the APs to a power source.
4 To refresh the ZoneDirector Map View, run a full-system RF Scan, as detailed in “Start-
ing a Radio Frequency Scan” on page 69.
37
Page 42

Ruckus Wireless ZoneDirector User Guide | Managing a Wireless Local Area Network
5 When the RF scan is complete and ZoneDirector has recalibrated the Map View, you
can assess your changes, and make further adjustments as needed.
Assessing current performance by using the Access Point table
1 Go to Monitor > Access Points.
2 When the Access Points page appears, review the Currently Active APs for specific AP
settings, especially the Channel and Clients columns.
3 If you want to make changes to individual AP settings, proceed to the next task.
Adjusting AP Settings
1 Go to Configure > Access Points.
2 Review the Access Points table and identify an AP that you want to adjust.
3 Click the Edit button in that AP row.
4 Review and adjust any of the following Editing (AP) options:
NOTE
MAC Address This information is taken from the AP. It cannot be modified in
Description Enter a short description of this device and its current location.
Radio B/G Channel Choose a specific channel for use by 802.11b/g devices from
TX Power Choose the amount of power allocated to this channel. The
5 Click OK. The adjusted AP will be automatically restarted, and when it is active, will
be ready for network connections.
Some options are read-only depending on the approval status.
ZoneDirector.
this drop-down list.
default setting is “Auto” and your options range from “Full” to
“1/8”.
38
Page 43

Managing User and
Guest Access
Chapter Contents
• “Using an External Authentication Server” . . . . . . . . . . . . . . . . . . . . . . . . 40
• “Adding New User Accounts to ZoneDirector” . . . . . . . . . . . . . . . . . . . . . . 42
• “Managing Current User Accounts”. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
• “Creating New User Roles” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
• “Configuring System-Wide Guest Access Policy” . . . . . . . . . . . . . . . . . . . . . 45
CHAPTER 4
• “Managing Guest Pass Access” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
• “Activating Web Authentication of Users” . . . . . . . . . . . . . . . . . . . . . . . . . 49
• “Managing Automatically Generated User Certificates and Keys” . . . . . . . . . 50
39
Page 44

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Using an External Authentication Server
Once your wireless network is set up, you can instruct the Ruckus ZoneDirector to authenticate wireless users using your existing Active Directory server, an existing RADIUS server, or
to create new user accounts in the internal user database. To use a RADIUS or Active Directory server as an authentication server, follow the steps:
1 Go to Configure > Authentication Servers.
2 When the Authentication Servers page appears, click the Create New link in the
Authentication Servers table.
FIGURE 4-1
40
Page 45

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
FIGURE 4-2
3 When the Create New form appears, make the following entries:
•Click in the Name field and type a descriptive name (e.g., “Active Directory”).
• Verify that “Active Directory” or “RADIUS” is selected as the Type .
• Enter the IP Address of the Active Directory server.
•Enter a Port number, if different from “389” for Active Directory or “1812” for
RADIUS.
• (For Active Directory only) Enter the Domain name of the Active Directory server,
for example, “domain.ruckuswireless.com”.
• (For RADIUS only) Enter the Shared Secret, and then re-enter that secret in Confirm
Secret.
4 Click OK to save this server entry.
TIP
Test your connection to the Active Directory server by entering an existing user ID and password in the Test Authentication Settings panel.
41
Page 46

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Adding New User Accounts to ZoneDirector
Once your wireless network is set up, you can instruct the Ruckus ZoneDirector to authenticate wireless users using an existing Active Directory server or RADIUS server, or to authenticate users by referring to accounts that are stored in the ZoneDirector's internal user
database. To use the internal user database as the default authentication source and to create new user accounts in the database, follow the steps:
1 Go to Configure > Users.
2 In the Internal User Database table, click Create New.
FIGURE 4-3
3 When the Create New options appear, fill in the text fields with the appropriate
entries:
Username Enter a name for this user, up to 32 characters in length, using
letters, numbers and the period (.) character. User names are
case-sensitive.
Full Name Enter the assigned user's first and last name.
Password Enter a unique password for this user, using a combination of
letters and numbers, between 4 and 32 characters in length. Do
not incorporate any letter spaces. Passwords are case-sensitive.
Confirm Password Re-enter the same password for this user.
4 If you've created roles that enable non-standard client logins or gather staff members
into workgroups, open the Role menu and choose the appropriate role for this user.
[For more information on roles and their application, see “Creating New User Roles”
on page 44.]
5 Click OK to save your settings. Be sure to communicate the user name and password to
the appropriate end user.
42
Page 47

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Managing Current User Accounts
The ZoneDirector allows you to review your current user roster in the internal user database, and to make needed changes to existing user accounts as needed.
Changing an Existing User Account
1 Go to Configure > Users.
2 When the Users features appear, locate the specific user account in the Internal User
Database panel, then click Edit.
3 When the Editing [user name] options appear, make the needed changes.
4 If a role must be replaced, open that menu and choose a new role for this user. [For
more information, see “Creating New User Roles” on page 44.]
5 Click OK to save your settings. Be sure to communicate the relevant changes to the
appropriate end user.
Deleting a User Record
1 Go to Configure > Users.
2 When the Users Authentication features appear, review the “Internal Users Data-
base”.
3 To delete one or more records, click the checkboxes by those account records.
4 Click the now-active Delete button.
5 When the Deletion Confirmation dialog box appears, click OK to save your settings.
The records are removed from the internal users database.
43
Page 48

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Creating New User Roles
The ZoneDirector provides a “Default” role that is automatically applied to all new user
accounts. This role links all users to the internal WLAN and permits any user to obtain guest
passes for on-site visitor use. As an alternative, you can create additional roles that you can
assign to selected wireless network users, to limit their access to certain WLANs, to allow
them to log in with non-standard client devices, or to grant permission to generate guest
passes. (You can then edit the “default” role to deactivate the guest-pass generation
option.)
1 Go to Configuration > Roles. The Roles and Policies page appears, displaying a
“Default” role in the Roles table.
2 Click Create New (below the Roles table).
FIGURE 4-4
3 Enter a Name and a short Description for this role.
4 Choose the options for this role from the following:
Group Attributes This field is only available if you choose Active Directory as your
authentication server. Enter the Active Directory User Group
names here. Active Directory users with the same group
attributes are automatically mapped to this user role.
Allow All WLANs You have two options: (1) Allow Access to all WLANs, or (2)
Specify WLAN Access. If you select the second option, you must
specify the WLANs by clicking the check box next to each one.
This option requires that you create WLANs prior to setting this
policy. See “Creating a New WLAN for Workgroup Use” on page
28.
44
Page 49

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Guest Pass If you want users with this role to have permission to generate
guest passes, activate this option.
5 When you are finished, click OK to save your settings. This role is ready for assignment
to authorized users.
6 If you want to create additional roles with different policies, repeat this procedure.
Configuring System-Wide Guest Access Policy
The Enable Guest Access (System-side) options enable the administrator to define the system-wide guest access policy. You can require guests to validate their guest pass, accept
terms of use, and be redirected to a URL you specify.
1 Go to Configure > Guest Access. The Guest Access page appears.
FIGURE 4-5
2 Under Enable Guest Access (System-side), select the Authentication to use:
• Use guest pass authentication: Redirect the user to a page requiring a valid guest
pass before allowing the user to use the guest WLAN.
• No authentication: Do not require redirection and guest pass validation.
3 Under Ter ms of Us e , mark the Show terms of use check box to compel the guest user
to read and accept your terms of use prior to use. Type (or cut and paste) your terms
of use into the large text box.
4 At Redirect, select one of the following radio buttons to use/not use redirection:
• Go to the original URL the user intended to: Allows the guest user to continue to
their destination without redirection.
• Redirect to the following URL: Redirect the user to a specified web page (entered
into the text box) prior to forwarding them to their destination. When guest users
45
Page 50

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
land on the redirected page(s), they are shown the expiration time for their guest
pass.
5 Click Apply to save your settings.
Managing Guest Pass Access
By default, all of your users are allowed to issue temporary “day use” guest passes for visitors and contractors. Such a guest pass allows its user to connect to the WLAN.
You must decide whether or not to permit all—or some—users to generate guest passes.
Additionally, you may also want to review the default settings and policies that control
guest-pass use of the network. There are options you can fine-tune to fit your work environment.
Activating guest pass access in ZoneDirector
1 Go to Configuration > Guest Access.
The Guest Access page appears.
2 Scroll down to Guest Access > Guest Pass Generation.
FIGURE 4-6
3 If you require a specific authentication server, toggle the Authentication Server drop-
down list to select the appropriate server.
4 Set the guest pass expiration parameters by selecting the radio button by either of the
following:
• Guest Pass will expire in the amount of time specified after it is issued: This
type of guest-pass is valid from the time it is first created to the specified expiration time, even if it is not being used by any end user.
• Guest Pass will expire in the amount of time specified after it is first used: This
type of guest pass is valid from the time the user uses it to authenticate to the
ZoneDirector until the specified expiration time. An additional parameter (A Guest
Pass will expire in X days) can be configured to specify when an unused guest pass
will expire regardless of use. The default is 7 days.
5 When you are finished, click Apply to save your settings and make this new policy
active.
46
Page 51

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Controlling guest pass generation privileges
To deactivate the “guest pass” generation privilege granted to all basic “default” role users,
follow these steps:
1 Go to Configure > Roles.
When the Roles and Policies page appears, a table lists all existing roles, including
“Default”.
2 Click Edit (in the “Default” role row).
3 In the Policies options, clear the checkbox by Allow Guest Pass Generation (if this
option is active).
4 Click OK to save your settings. Users with “default” roles no longer have guest-pass
generation privileges.
Creating a guest pass generation user role
To create a guest-pass generator role that can be assigned to authorized users, follow these
steps:
1 Go to Configuration > Roles.
2 In the Roles table, click Create New.
3 When the Create New features appear, make these entries:
Name Enter a name for this role.
Description Enter a short description of this role's application.
Group Attributes This field is only available if you choose Active Directory as your
authentication server. Enter the Active Directory User Group
names here. Active Directory users with the same group
attributes are automatically mapped to this user role.
Allow All WLANs You have two options: (1) allow all users with this role to con-
nect to all WLANs, or (2) limit this role's users to specific
WLANs, then pick the WLANs they can connect to.
Guest Pass If you want users with this role to have permission to generate
guest passes, check this option.
4 Click OK to save your settings. This new role is ready for application to authorized
users.
Assigning a Pass Generator role to a new user account
This procedure details the procedure for assigning a guest-pass generator role to a user
account.
1 Go to Configuration > User.
2 At the bottom of the Internal Users Database, click Create New.
3 When the Creating New User options appear, fill in the text fields with the appropriate
entries.
47
Page 52

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
4 Open the Role menu and choose the assigned role for this user.
NOTE You can edit an existing user account and reassign the pass-generator role, if you prefer.
5 Click OK to save your settings. Be sure to communicate the role, user name and pass-
word to the appropriate end user.
Monitoring generated guest passes
Once you have generated a pass for a guest, you can monitor and, if necessary, remove it.
1 Go to Monitor > Generated Guest Passes.
2 View generated guest passes.
3 To remove a guest pass, select the check box for the guest pass.
4 Click the Delete button.
Restricting guest subnet access
The Guest Pass > Restricted Subnet Access feature enables you to restrict guest access to
specified subnets. By default, guest pass users are automatically blocked from the ZoneDirector subnet (192.168.0.2/24).
You can configure up to 5 IP subnets to be blocked to guest access. This subnet access policy
is enforced both on the ZoneDirector side (for tunneled/redirect traffic) and the AP side (for
local-bridging traffic).
NOTE All guests share this same subnet access policy.
To specify a subnet which guests cannot access, do the following:
1 Go to Configure > Guest Access.
2 Under Restricted Subnet Access, type the IP address and subnet mask (format:
A.B.C.D/M) of the subnet in a provided text field. See “FIGURE 4-7” on page 48.
3 Repeat Step 2 to add additional subnets (up to five).
4 Click Apply to enforce your settings.
FIGURE 4-7
48
Page 53

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Activating Web Authentication of Users
Web authentication, when activated on an WLAN, compels all users to log in to a specific
WLAN every time they connect. This is helpful if you are managing an Internet hotzone.
After you activate web authentication on your hotzone/hotspot WLAN, you must then provide all users with a URL to your login page. Of course the users must be listed in an internal
or external authentication database. After they discover the WLAN on their wireless device
or laptop, they open their browser, connect to the Login page and enter the required login
information.
1 Go to Configure > WLANs.
2 When the WLANs page appears, click the Edit link in the row of the relevant WLAN
record.
3 When the Editing (WLAN_Name) options appear, locate the Web Authentication
option. See “FIGURE 4-8” on page 49.
4 Click the checkbox to enable portal/web authentication.
5 Select the preferred authentication server (for Web Authentication) from the Authen-
tication Server drop-down menu.
6 Click OK to save this entry.
7 Repeat this “enabling” process for each WLAN to which you want to apply web authen-
tication.
FIGURE 4-8
49
Page 54

Ruckus Wireless ZoneDirector User Guide | Managing User and Guest Access
Managing Automatically Generated User Certificates and Keys
With Ruckus Zero-IT wireless activation, a unique key or certificate is automatically generated for a user during the activation process. More precisely, for a WLAN configured with
WPA-PSK/WPA2-PSK and Dynamic PSK enabled, a unique and random key phrase is generated for each wireless user. Similarly, for a WLAN configured with 802.1X/EAP authentication, a unique certificate for each wireless user is created. When using the internal user
database, automatically generated user certificates and keys are deleted whenever the
associated user account is deleted from the user database. In the case of using Windows
Active Directory Server or a RADIUS server as an authentication server, you can delete the
generated user keys and certificates by following these steps:
1 Go to Monitor > Generated PSK/Certs.
2 When the Generated PSK/Certs page appears, click on the checkboxes next to the
PSKs and Certificates you like to delete.
3 Click Delete to delete the selected items.
The selected PSKs and Certificates are deleted from the system.
A user with a deleted PSK or a deleted certificate will not be able to connect to the
wireless network without obtaining a new key or a new certificate.
50
Page 55

Monitoring Your
Wireless Network
Chapter Contents
• “Reviewing the ZoneDirector Monitoring Options” . . . . . . . . . . . . . . . . . . . 52
• “Importing a Map View Floorplan Image” . . . . . . . . . . . . . . . . . . . . . . . . . 52
• “Using the Map View Tools” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
• “Reviewing Current Alarms” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
• “Reviewing Recent Network Events”. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
CHAPTER 5
• “Clearing Recent Events/Activities” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
• “Reviewing Current User Activity” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
• “Monitoring Access Point Status” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
• “Detecting Rogue Access Points” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
• “Evaluating and Optimizing Network Coverage” . . . . . . . . . . . . . . . . . . . . . 59
• “Customizing Background Radio Frequency Scans” . . . . . . . . . . . . . . . . . . . 60
51
Page 56

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Reviewing the ZoneDirector Monitoring Options
The following highlights key ZoneDirector tab options and what you can do with them.
Dashboard Every time you log in to the ZoneDirector via WebUI, this collection of status
surveys appears. Use it as your regular network-monitoring starting point.
Data are blue-colored links that you can use to further drill down to focus on
particular activities or devices.
Monitor The Map View provides a fast scan of key network factors: APs (legitimate,
neighboring and rogue), client devices, and radio frequency (RF) coverage.
You can see what devices are where in your floorplan, and visually evaluate
network coverage.
Other Monitor tab options incorporated in the left column's buttons provide
numeric data on WLAN performance and individual device activity. As with
Dashboard, some data entries are links that take you to more detailed information. And, finally, the All Events log displays the most recent actions by
users, devices and network, in chronological order.
Configure Use the options in this tab to assess the current state of WLAN users, any
restricted WLANs, along with the settings for guest access, user roles, etc.
You can also combine this tab's options with those in the Admin tab to perform system diagnostics and other preventive tasks.
Importing a Map View Floorplan Image
If your Ruckus ZoneDirector does not display a floorplan for your worksite when you open
the Monitor tab Map View, you can import a floorplan and place AP markers in relevant locations by following these steps.
There is no limit on the number of floor maps that can be imported. There is a limit on the
total size of all floor maps that are imported to the system: 2MB (an error message displays
if the total size of floor maps is more than 2MB).
Requirements
• A floorplan image in .GIF, .JPG or .PNG format
• The image should be monochrome or grayscale
• The file size should be no larger than 200Kb in size
• The floorplan image should be (ideally) no larger than 10 inches (720 pixels) per side.
52
Page 57

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Importing the floorplan image
1 Go to Configure > Maps.
FIGURE 5-1
2 Click Browse to open a dialog box that assists you in locating and “opening” an image.
If the import is successful, a thumbnail version of the floorplan will appear in the Cur-
rent Image area.
3 Go to Monitor > Map View to see this image.
You can now use the Map View to place the Access Point markers.
Placing the access point markers
After using the Configure > Maps options to import your floorplan image, you can use the
Monitor tab's Map View to distribute markers that represent the APs to the correct locations.
This will give you a powerful monitoring tool.
TIP
1 Have the list of APs handy, with MAC addresses and locations.
2 Go to Monitor > Map View (if it's not already in view).
3 Look in the upper left corner for AP marker icons. There should be one for each AP,
with a tiny red question mark at the top.
4 Look at the MAC address notation under the marker icon, to identify a marker.
If you have imported multiple floorplans representing multiple floors in your building(s), make
sure you place the access point markers on the correct floorplan.
5 Drag each marker icon from the upper left corner into its correct location on the floor-
plan.
When you are finished, you can make immediate use of the Map View to optimize your
wireless coverage, as detailed in “Optimizing Access Point Performance” on page 37.
53
Page 58

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Using the Map View Tools
If your worksite floorplan has been scanned in and mapped with APs, the Map View will display a graphical image of your physical Ruckus network AP distribution.
FIGURE 5-2
There are a number of helpful features built into the Map View, as noted here and marked in
the above illustration:
1 Map drop-down list: Select the floorplan to view from the Map drop-down list.
2 Coverage and Show Rogue APs box: For Coverage, selecting Yes enables a signal
strength view of your placed APs. This opens the Signal (%) legend on the right side of
the Map View. See item number 8 below for the description of the Signal %. For Show
Rogue APs, selecting Yes displays the detected rogue APs in the floorplan.
3 Unplaced APs area: As noted in Importing a Map View Floorplan Image, when you first
open the Map View, newly placed APs appear in this area. If they are approved for use
(see “Adding New Access Points to the WLAN” on page 31), you can drag them into the
correct location in the floorplan. Unplaced APs are available across all of the floorplans you upload. Thus, you can toggle between maps (see number 1) and place each
AP on the appropriate map. For the various AP icon types, see “AP icons” on page 55.
4 Access Points, Rogue APs, and Clients box: This lower left corner box displays the
number of active APs, any rogue (unapproved or illegitimate) APs, and all associated
clients.
54
Page 59

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
5 Search text box: Enter a string, such as part of an AP's name or MAC address, and the
map is filtered to show only the matching results. Clearing the search value returns
the map to its unfiltered view.
6 Floorplan area: The floorplan displays in this main area. You can manipulate the size
and angle of the floorplan by using the tools on this screen.
7 Note the following icons:
Click this icon and then click an AP from the floorplan to remove that
AP.
Click this icon to rotate the floorplan. When clicked, rotation crosshairs
appear in the center of the map; click and hold these crosshairs and
move your cursor to rotate the view.
Refresh the floorplan.
8 Signal (%): This colored legend displays the signal strength coverage when you
selected "Yes" for Coverage (see #2 above). See “Evaluating and Optimizing Network
Coverage” on page 59 for more information.
9 Upper Slider: The upper slider is a zoom slider, allowing you to zoom in and out of the
floorplan. This is helpful in exact AP marker placement, and in assessing whether physical obstructions that affect RF coverage are in place.
10 Lower slider: The bottom slider is the image contrast slider, allowing you to dim or
enhance the presence of the floorplan. If you have trouble seeing the floorplan, move
the slider until you achieve a satisfactory balance between markers and floorplan
details.
11 Scale legend: To properly assess the distances in a floorplan, a scaler has been pro-
vided so that you can place APs in the most precise location. The scale works best
when the floorplan view has not been zoomed in or out. The scale offers both feet and
meters as units of meaure. Use a physical object as a reference to the scale in order to
judge distances on your floorplan. For example, cut a piece of paper to the lenght of
the scale, and then use that piece of paper on the floorplan to measure off distance
increments.
12 Open Space Office drop-down list: Open Office Space refers to the methodology used
to compute RF coverage/signal % (i.e., heat map) based on the current environment.
AP icons
Each AP marker has variable features that help indicate identity and status:
A normal AP marker displays this devices' Ethernet MAC address below the icon.
Above the icon is the “Users” count that shows the number of currently active client
connections through this AP.
55
Page 60

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
An unapproved AP marker displays a “?” (question mark) above the antenna.
A rogue AP displays a smaller red icon imprinted with a “bug”.
A disconnected AP displays a red “X” above the antennae.
Reviewing Current Alarms
If an alarm condition is detected, the Ruckus ZoneDirector will record it in the events log,
which, if configured, will send an email warning. To review the current alarms and clear all
resolved alarm records, follow these steps:
1 Go to Monitor > All Alarms.
2 When the All Alarms page appears, the Alarms table lists the unresolved alarms, the
most recent at the top.
FIGURE 5-3
3 Review the contents of this table. The Activities column is especially informative.
4 If a listed alarm condition has been resolved, click the now-active Clear link to the
right. You also have the option of clicking Clear All to resolve all alarms at one time.
56
Page 61

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Reviewing Recent Network Events
You have two options for reviewing events in your network: [1] open a complete list of all
events, or [2] look at specific lists of events in each Monitor tab workspace, such as the
WLANs workspace “Events/Activities” table.
1 Open the ZoneDirector Dashboard and look at the Most Recent User Activities table
and Most Recent System Activities table for summaries of activity in the network.
2 Go to the Monitor tab.
3 Click any of the specific options, such as WLANs, Access Points, or Currently Active
Clients.
4 Look for an All Events table that specifically focuses on the selected WLAN category.
5 Under the Monitor tab, click either All Alarms button or All Events/Activities button
to see a complete list, with all categories represented in chronological order.
Clearing Recent Events/Activities
To review the current events and, if appropriate, clear all resolved events, follow these
steps:
1 Go to Monitor > All Events/Activities.
2 When the All Events/Activities page appears, the Events/Activities table lists the
unresolved events, the most recent at the top.
3 Review the contents of this table. The Activities column is especially informative.
4 You can click Clear All at the bottom of the table to resolve and clear all events in the
view.
Reviewing Current User Activity
You can monitor current users of the network on a per-client-device basis by doing the following:
1 Go to Monitor > Currently Active Clients.
2 When the Currently Active Clients page appears, review the table for a general sur-
vey.
3 Click any client device MAC address link to monitor that client in more detail.
4 To review blocked clients, go to Configuration > Blocked Clients.
57
Page 62

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Monitoring Access Point Status
There are several ZoneDirector features you can take advantage of, to monitor the performance and status of your Ruckus wireless APs:
1 Open the Dashboard for a snapshot view of the most active APs. Click the MAC
address link of any AP record to see more details.
2 Go to Monitor > Map View and click a radio frequency to see a heat-map rendering of
the current RF coverage.
3 Go to Monitor > Access Points and review the usage and coverage of your APs. Click
the MAC address link of any listed APs to see more details.
4 Click the System Info link to retrieve the support.txt file from an AP.
Detecting Rogue Access Points
As contrasted with “neighboring” access points (APs) that are parts of a neighboring WLAN,
“rogue” (unauthorized) APs pose problems for a wireless network. Usually, a rogue AP
appears in the following way: an employee obtains another manufacturer's AP and connects
it to the LAN, to gain wireless access to other LAN resources. This would potentially allow
even more unauthorized users to access your corporate LAN posing a security risk. Rogue APs
also interfere with nearby Ruckus APs, thus degrading overall wireless network coverage.
Your ZoneDirector rogue detection options include identifying the presence of a rogue AP,
and locating it on your worksite floorplan prior to its removal. You can also mark rogue APs
as “Known” if they are located in a neighboring network—outside your worksite—and pose no
threat. To detect a rogue AP, follow these steps:
1 Click the Dashboard tab (or go to Monitor > Rogue Devices).
2 Look under Devices Overview for “# of Rogue Devices”.
FIGURE 5-4
3 If there are “1” or more tallied in this row, click the number for more details.
4 When the Monitor > Rogue Devices page appears, two tables are listed:
•the Currently Active Rogue Devices table
•the Known/Recognized Rogue Devices table.
5 Review the Currently Active Rogue Devices table. The types of Rogue APs recognized
by Zone Director are (an alarm is generated if ZoneDirector detects one of the these
rogue APs):
58
Page 63

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
• AP: An access point unknown to the ZoneDirector.
• AP (SSID-spoof): A rogue AP that uses the same SSID as ZoneDirector’s AP, also
known as Evil-twin AP.
• AP (MAC-spoof): A rogue AP that has the same BSSID (MAC) of one of the virtual APs
managed by the ZoneDirector.
The Encryption column indicates if a rogue device is encrypted or is open.
6 If a listed AP is part of another, nearby neighbor network, click Mark as Known. This
identifies the AP as posing no threat, while copying the record to the Known/Recog-
nized Rogue Devices table.
7 To locate rogue APs that do pose a threat to your internal WLAN, click the MAC
Address of a device to open the Map View.
8 If your worksite floorplan is imported into the Map View window and your APs are posi-
tioned on the map, rogue APs can be generally identified with relative accuracy.
9 Open the Map View, and look for rogue APs that appear as shown here:
This provides a clue as to their location.
10 You can now find the rogue APs and disconnect them. Or, if a rogue AP is actually a
component in a neighboring network, you can mark it as “known”.
TIP
If your office/worksite is on a single floor in a multistory building, your upper- and lower-floor
neighbors' wireless access points may show up on the Map View, but seemingly in your site.
As Ruckus cannot locate them in vertical space, you may need to do a bit more research to
determine where the AP is located and if it should be marked as “Known”.
Evaluating and Optimizing Network Coverage
If there are gaps or dead spots in your worksite WLAN coverage, you can use ZoneDirector to
assess network RF coverage and then reposition APs to enhance coverage. Remember that a
Ruckus AP can cover an area with a radius of 30 to 50 feet using average broadcasting power
settings on any frequency. Local structural obstructions may limit coverage.
1 Go to Monitor > Map View.
2 If Map View displays a floorplan with active device symbols, you can assess the perfor-
mance of individual APs, in terms of coverage. (See “Importing a Map View Floorplan
Image” on page 52 for information on setting up the Map View.)
3 For the Coverage option, click Ye s .
4 When the “heat map” appears, look for a Signal% scale in the upper right corner of the
map.
5 Note the color range, especially colors that indicate low coverage.
6 Look at the floorplan and evaluate the current coverage.
59
Page 64

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
Moving the APs into more efficient positions
You can now move the APs into more efficient positions.
1 To do so, click and drag individual AP markers on the Map View floorplan until your RF
coverage coloration is optimized. (You may need to acquire additional APs to fill in
large coverage gaps.)
2 To turn off the heat map and restore the floorplan to view, click No (in the Coverage
options).
3 Note down the new physical locations of relocated AP markers.
4 After physically relocating the actual APs in accordance with Map View repositioning,
disconnect and reconnect each AP to a power source.
5 When ZoneDirector has recalibrated the Map View after each AP restart, you can
assess your changes, and make further adjustments as needed.
Customizing Background Radio Frequency Scans
As a key element of your network monitoring, the Ruckus ZoneDirector regularly samples
the activity in all Access Points to assess radio frequency (RF) usage. The scans sample one
channel at a time in each AP, and do not interfere with network use. This information is
then applied in Map View and other ZoneDirector monitoring features.
1 Go to Configure > Services.
FIGURE 5-5
2 Check the Background Scanning settings. The default interval is 20 seconds.
60
Page 65

Ruckus Wireless ZoneDirector User Guide | Monitoring Your Wireless Network
3 You can disable this feature by unchecking the check box, which results in a minor
increase in AP performance, but removes the detection of rogue APs from ZoneDirector monitoring.
4 You can also decrease the scan frequency, as less frequent scanning improves overall
AP performance.
5 Click Apply to save your settings and apply them to your network immediately.
61
Page 66

Setting Administrator
Preferences
Chapter Contents
• “Changing the ZoneDirector Administrator User Name and/or Password” . . . . 63
• “Changing the Language Used in WebUI” . . . . . . . . . . . . . . . . . . . . . . . . . . 63
• “Upgrading the License”. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
CHAPTER 6
62
Page 67

Ruckus Wireless ZoneDirector User Guide | Setting Administrator Preferences
Changing the ZoneDirector Administrator User Name and/or Password
You should change your ZoneDirector administrator login password on a monthly basis, but
the administrator user name should be changed only if necessary. To edit or replace the current name or password, follow these steps:
1 Go to Admin > Preferences.
FIGURE 6-1
2 When the Preference page appear, you have the following options under Administra-
tor Name/Password:
Admin Name Delete the text in this field and type the new adminis-
trator account name (used solely to log into ZoneDirector with WebUI.)
Password/Confirm Password Delete the texts in both fields and type the same text
for a new password.
3 Click Apply to save your settings. The changes go into effect immediately.
NOTE
The ZoneDirector allows only one “administrator” user to log in with WebUI to perform management and maintenance. Additional accounts cannot be created, but ZoneDirector and
the Ruckus WLAN don't require more than one “admin” account.
Changing the Language Used in WebUI
Depending on your preferences, you can change the language in which WebUI is displayed in
your web browser. The default is “English”.
This change only affects how WebUI appears, and does not modify either OS/system or
browser settings (which are managed through other processes).
1 Go to Admin > Preferences.
63
Page 68

Ruckus Wireless ZoneDirector User Guide | Setting Administrator Preferences
2 When the Preferences page appear, open the Language menu and choose the pre-
ferred language. See “FIGURE 6-1” on page 63.
ALERT!
3 Click Apply to save your settings. The changes go into effect immediately.
This only affects how WebUI appears, and does not modify either system (OS) or browser
settings.
Upgrading the License
Depending on the number of Ruckus APs you need to manage with your ZoneDirector, you
may need to upgrade your license. Once you load the license via the WebUI, it takes effect
immediately.
Current license information (description, PO number, status, etc) is displayed in the WebUI.
NOTE The system does not reboot or reset after a license is imported.
To import a new license, do the following:
1 Go to Admin > License.
FIGURE 6-2
2 Click Browse to find your license. Once you find your license and closed the Browse
window, the ZoneDirector immediately attempts to validate and install the license.
64
Page 69

Troubleshooting Tips
Chapter Contents
• “Troubleshooting Failed User Logins” . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
• “Fixing User Connections” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
• “Diagnosing Poor Network Performance”. . . . . . . . . . . . . . . . . . . . . . . . . . 68
• “Starting a Radio Frequency Scan” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
• “Reviewing Self Healing and Intrusion Prevention Options” . . . . . . . . . . . . . 70
• “Generating a Debug File” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
• “Restarting an Access Point” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
CHAPTER 7
• “Restarting the Ruckus ZoneDirector” . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
65
Page 70

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
Troubleshooting Failed User Logins
SUMMARY: This “troubleshooting” topic addresses the problems that network users might
have with configuring their client devices and logging into your Ruckus WLAN.
At the end of the setup wizard, your Ruckus ZoneDirector automatically activates a default
internal WLAN for authorized users. A key benefit of the internal WLAN is the “zero IT” configuration, which extends to new users, to make their device configuration and initial login
as easy as it can be. “Zero IT” client device configuration requires the client be running
Windows XP SP 2/Vista, and using a wireless network adapter that implements WPA.
If you and your WLAN users run into initial connection failures when using the “zero IT” configuration and login, almost all of the problems have two key causes:
• Your users' client devices are running another OS, or running a version of Windows pre-XP/
SP2. (This includes XP/SP1.)
• Your users' client devices are using wireless network adapters without a WPA implementation.
The following list of options may be applicable based on your client system’s qualifications:
Option 1 If Windows XP SP2/Vista is on the client machine, check the wireless network
adapter to verify the implementation of WPA.
Option 2 Upgrade to Windows XP SP2/Vista, and if needed, acquire a wireless network
adapter with WPA support. Once these changes are made, your users can
attempt a “zero IT” login.
Option 3 If an older version of Windows is in use, or if another OS is being used, the user
must manually enter the Ruckus WPA passphrase in their network configuration.
Option 4 Assumes that the client OS cannot be upgraded and the wireless network
adapter is limited to WEP. This requires two phases:
Ruckus Administration— [1] You, the network manager, create a supplemental
WLAN for the non-standard client connections, then [2] create a Role that refers
to this WLAN, and [3] assign that role to the affected user account.
User Configuration— Enter the needed WEP key in the network configuration.
In most solutions, you will need to open a Windows control panel and enter a WPA passphrase which you provide, or a WEP key (if you switch internal WLAN to WEP, which means
you must provide the user with a copy of the key.) Once the passphrase or key is stored in
Windows on their client, they can log into the WLAN.
66
Page 71

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
Fixing User Connections
If any of your users report problematic connections to the WLAN, here is one debugging
technique that may prove helpful. Basically, you will be deleting that user's client from the
Active Clients table in the Ruckus ZoneDirector, and when their client connection automatically renews itself, any previous problems will hopefully be bypassed.
To debug an active user connection, follow these steps:
1 Go to Monitor > Currently Active Clients.
2 When the Currently Active Clients page appears, locate the buggy client connection
in the Clients table.
3 Click Delete.
That client will be automatically logged out of the ZoneDirector.
After a minute or two, when the client has automatically re-logged into the WLAN, the
Client table will re-display the client and the user will have fewer or no problems.
FIGURE 7-1
67
Page 72

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
If WLAN connection problems persist
If the previous technique fails to resolve the user's client mis-connections, you may need to
guide them through a full re-setting of their WLAN configuration. This requires your deleting
the user record, then creating a new user record, at which time the user must repeat the
“new user connection” process, with the two-part login and the downloading and installing
of a new WLAN configuration.
1 Have the user log out of the WLAN until they receive notification from you.
2 Go to Configure > Users.
3 When the User Authentication features appear, locate and delete this user record
from the Internal Users Database table.
4 Add a new user account for this user, and send notification to that user, with instruc-
tions on how to re-configure their client and log into the WLAN again.
At the end of this process, the user should be reconnected. If problems persist, they
may originate in Windows or in the wireless network adapter.
Diagnosing Poor Network Performance
You can try the following diagnostic and troubleshooting techniques to resolve poor network
performance.
1 Go to Monitor > Map View.
2 Look on the map for rogue APs. If there is a large number, and they belong to neigh-
boring networks, proceed to the next task.
3 Go to Configure > Access Points.
4 Edit each AP record, to assign each device a channel that will not interfere with other
APs.
5 For example, if you have three Ruckus APs, open the Radio B/G Channel drop-down
list in each AP record and choose “1”, “6” and “11” in each of the three. However
many APs you have, make sure that each AP has a fixed channel number not too close
to the number of a nearby Ruckus AP.
68
Page 73

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
Starting a Radio Frequency Scan
This task complements the automatic RF scanning feature that is built into the Ruckus ZoneDirector. That automatic scan assesses one radio frequency at a time, every 20 seconds or
so. To manually start a complete radio frequency scan that assesses all possible frequencies
in all devices at one time, follow these steps:
1 Go to Admin > Diagnostic.
FIGURE 7-2
2 When the Diagnostic page appears, look for the Manual Scan options and click Scan.
ALERT! This operation will interrupt active network connections for all current users.
3 Open the Dashboard or go to Monitor > Map View to review the scanning results. This
will include rogue device detection, and an updated coverage evaluation.
69
Page 74

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
Reviewing Self Healing and Intrusion Prevention Options
This Ruckus network feature adds automatic network adjustments to the existing monitoring
functions, so that the Ruckus ZoneDirector can efficiently shift AP-specific settings and
resources to improve coverage.
1 Go to Configure > Services.
2 Review and change the following self-healing options (which are all active by default):
Adjust AP radio power If this capability is activated (default) and the tx power
of a radio is auto (default), the Ruckus APs automatically reduce or maximize the transmit power to provide
the best wireless service.
Adjust AP channel If interference of any kind is detected in an AP, the
radio frequency will automatically be switched.
3 Review and change the following intrusion prevention options (which are all active by
default):
Excessive wireless requests If this capability is activated (default), excessive 802.11
probe request frames and management frames launched
by malicious attackers will be discarded.
Repeat Authentication Failure If this capability is activated, any clients that repeat-
4 Click Apply to save your settings. The new settings go into effect immediately.
Generating a Debug File
ALERT! Do not start this procedure unless asked to do so by technical support staff.
If requested to generate and save a debug file, follow these steps:
1 Go to Admin > Diagnostic.
2 Review the settings in the Debug Log options, and make the request adjustments with
the three Levels drop-down lists. (If no settings were specified, ignore this step.)
APD For information between Ruckus AP and Ruckus ZoneDirector
ACD For information on wireless clients activities
EMF For information regarding WebUI operations
edly fail in attempting authentication will be temporarily blocked for a period of time. Default is 30
seconds.
3 If you did change the Levels settings, click Apply to save your settings.
4 In the Save Debug Info options, click Save Debug Info.
5 When the File Download dialog box appears, click Save.
70
Page 75

Ruckus Wireless ZoneDirector User Guide | Troubleshooting Tips
6 When the Save As dialog box appears, pick a convenient destination folder, type a
name for the file, and click Save.
7 When the Download Complete dialog box appears, click Close.
After the file is saved, you can email it to the technical support representative.
Restarting an Access Point
One helpful fix for network coverage issues is to restart individual APs. To do so, follow
these steps:
1 Go to Monitor > Access Points.
2 When the Access Points page appears, look in the AP Summary table for the particular
Access Point record.
The Status column should display “Connected.”
3 Click Restart.
The Status column now displays “Disconnected”.
After restart is complete and the Ruckus ZoneDirector detects the active AP, the status will be returned to “Connected.”
Restarting the Ruckus ZoneDirector
There are three “restart” options: [1] to disconnect and then reconnect the Ruckus ZoneDirector from the power source, [2] to follow this procedure which simultaneously shuts down
the ZoneDirector and all APs, then restarts all devices, and [3] a restart of individual APs
(detailed in Restarting an Access Point.)
To restart the ZoneDirector (and all currently active APs), follow these steps:
1 Go to Admin > Restart.
2 When the Restart/Shutdown features appear, click Restart.
You will be automatically logged out of the ZoneDirector. After a minute, when the
ZoneDirector Status LED is steadily lit, you can log back in with ZoneDirector.
FIGURE 7-3
71
Page 76

Index
Symbols
.TGZ file extension
backup files 16
Numerics
802.1x
Client Authentication option 30
user requirements 23
WLAN security 23
802.1x EAP
Authentication options 22
option values 27
Windows OS requirements 23
802.1x mode 21
A
Access Point Policy options 33
Access Point status
monitoring 58
Access Points
see also “APs”
Access Points Policy approval 31
Activating Guest Pass Access 46
Active Directory server 40
Adding new access points 31
Adjust AP channel 70
Adjust AP radio power 70
Adjusting AP Settings
Map View 38
Administrator
changing the admin password 63
AES 21
option values 27
Alarms
activating email notification 13
Algorithm
New WLAN creation 27
All Events/Activities (Logs) 11
AP markers
overview 55
APs
Access Points 31
detecting rogue devices 58
placing markers on a floorplan map 53
restarting 71
see also “Access Points”
verifying new APs 31
Archived ZoneDirector settings
restoring 16
Assigning a Pass Generator role to a user 47
Authentication Options 22
Authentication options
Active Directory 40
RADIUS 40
Authentication Servers
internal user database 42
Auto-JOIN automatic AP activation process 31
Auto-JOIN option 31
Automatically Generated User Certificates and
Keys
managing 50
B
Backing up ZoneDirector settings 16
Backup Files 16
Blocked clients
reviewing a list 37
Blocking specific client devices 36
Buttons (WebUI)
explained 3
C
changing 12
Changing an Existing User Account 43
Changing the Administrator password 63
Changing the event log level 12
Channel
Map View options 38
Client Authentication configuration 29
72
Page 77

Ruckus Wireless ZoneDirector User Guide | Index
Client devices
monitoring 36
permanently blocking WLAN access 36
reviewing a list of blocked clients 37
temporarily disconnecting 36
Configure 52
Configuring client authentication 29
Controlling Guest Pass Generation Privileges
47
Create New options
Authentication Servers 41
Create New options (Authentication server)
Confirm Password 42
Full Name 42
Password/s 42
Username 42
Creating a Guest Pass Generation User role 47
Creating a new WLAN
Algorithm 27
Description 27
Hide SSID 29
Method 27
Name/ESSID 27
Passphrase 27
VLAN 28
WEP key 27
Zero IT Activation 28
creating additional WLANs 26, 30
Current Alarms
reviewing 56
Current User accounts
managing 43
Current user activity
reviewing 57
customizing 14
Customizing network security 20
Customizing RF scans 60
D
Dashboard
overview 52
Dashboard (WebUI)
explained 3
Debug file
generating 70
Deleting a User Record 43
Description
Map View options 38
New WLAN creation 27
option values 27
Detecting rogue Access Points 58
DHCP
network address option 9
Diagnostics
generating a debug file 70
Disconnecting specific client devices 36
disconnecting users from the WLAN 66
Dynamic PSK
WLAN security option 24
E
EAP
using the built-in server 22
Email alarm notification
activation 13
Encryption Options 22
Event Log Level 12
Excessive wireless requests 70
F
Factory default state
restoring ZoneDirector 17
failed user connections 66
Floorplan
Adding to Map View 37
G
graphic file formats
guest user login page 14
graphic file specifications
guest user login page 14
Guest Access Customization 14
Guest Pass Access
managing 46
guest user login page
adding a graphic 14
editing the welcome text 14
guest users
login page customization 14
H
Hide SSID
New WLAN creation 29
I
Importing the floorplan image 53
Improving AP RF coverage 37
Internal clock
73
Page 78

Ruckus Wireless ZoneDirector User Guide | Index
synchronizing 10
updating/refreshing current settings 10
using NTP 10
Internal user database
using for authentication 42
Intrusion prevention options 70
Excessive wireless requests 70
Repeat Authentication Failure 70
L
Language
changing the WebUI language 63
Log settings
changing 11
overview 11
Login failures 66
Login page
guest use 14
Logs
sorting contents 11
M
MAC Address
Map View options 38
Managing current user accounts 43
Map View
Adding a floorplan 37
Adjusting AP positions and settings 38
importing a floorplan 52
placing AP markers on a floorplan 53
Requirements (graphics) 52
Tools 54
Maps
importing a floorplan image 53
Method
New WLAN creation 27
Microsoft Windows
EAP requirements 23
Monitor
overview 52
Monitoring AP status 58
Monitoring Client Devices 36
Monitoring ZoneDirector
overview 52
N
Name/ESSID
New WLAN creation 27
option values 27
Network addressing
changing 9
network performance
diagnosing 68
New User Accounts
adding new accounts 42
New User Roles
Creating 44
NTP
using with system clock 10
O
Open
Authentication options 22
Client Authentication option 29
Optimizing network coverage 59
overview 52
P
Passphrase
New WLAN creation 27
WLAN security setup 21
passwords
changing the Administrator password 63
Placing the Access Point markers 53
Policies
Access Point-specific 33
Poor network performance
diagnosis 68
Preference tab
use 63
Pre-shared key (PSK) 24
PSK
Setting key expiration 24
PSK lifetime settings 24
R
Radio Frequency scans
customizing the settings 60
Radio frequency scans
starting a scan 69
RADIUS
using an external server 22
using for authentication 40
Recent events
overview 57
Repeat Authentication Failure 70
Replacing a WPA configuration with 802.1x
21
74
Page 79

Ruckus Wireless ZoneDirector User Guide | Index
restarting a ZoneDirector 71
Restarting an Access Point 71
Restoring archived settings 16
reviewing AP policies 33
Reviewing current alarms 56
RF
see also 'Radio frequencies'
RF background scans
customizing 60
Rogue APs
detecting 58
Roles options
Allow all WLANs 44
Description 44
Group attributes 44
Guest Pass 44
Name 44
S
scanning radio frequencies 69
Security
overview 6, 20
Security configuration
reviewing 20
Self healing options 70
Adjust AP channel 70
Adjust AP radio power 70
Setting Dynamic Pre-Shared Key expiration 24
Shared
Authentication options 22
Client Authentication option 30
Shared WEP key
option values 27
Switching to a different security mode 21
System name
changing 10
parameters 10
T
Tabs (WebUI)
explained 3
TKIP
option values 27
Tools
Map View 54
Troubleshooting
diagnosing poor network performance 68
diagnosing poor WLAN performance 68
generating a debug file 70
manually scanning radio frequencies 69
problems with user connections 66
restarting the ZoneDirector 71
reviewing current activity 57
reviewing current alarms 56
reviewing recent events 57
users cannot connect to WLAN 66
TX Power
Map View options 38
U
Upgrading
ZoneDirector software 15
ZoneFlex APs 15
Username 42
Users
Activating guest pass access 46
adding new accounts 42
creating new roles 44
disconnecting a user from the WLAN 66
failed WLAN logins 66
managing accounts 43
reviewing current activity 57
switching to 802.1x-based security 23
switching to WEP-based security 23
troubleshooting connection problems 66
Using Active Directory 40
Using an external RADIUS server 22
Using Map View to assess network performance 37
Using the built-in EAP server 22
Using the Map View 54
V
Verifying/Approving New APs 31
VLAN
New WLAN creation 28
VLANs
deploying a ZoneDirector WLAN 34
W
Web Authentication
activating 49
Web Portal Logo 14
WebUI
changing the language 63
features 3
Generated PSK/Certs page 50
75
Page 80

Ruckus Wireless ZoneDirector User Guide | Index
Roles and Policies 44
WebUI buttons
explained 3
WebUI Dashboard
explained 3
WebUI tabs
explained 3
WebUI workspaces
explained 3
WEP
WLAN Security 23
WEP Key
New WLAN creation 27
WEP key mode 21
WEP-128
option values 27
WEP-64
option values 27
WEP-based security
user requirements 23
Windows XP/SP2
EAP requirements 23
Wireless networks
overview 3, 20
WLAN
adding new access points 31
diagnosing poor performance 68
optimizing coverage 59
Recent events (reviewing) 57
WLAN network security
customizing 20
WLAN performance
using Map View 37
WLAN security
client authentication 29
overview 6
switching modes 21
WLAN-in-VLAN qualifications 34
WLANs
blocking client devices 36
creating additional networks 26, 30
failed user logins 66
Workspaces (WebUI)
explained 3
WPA and WPA2
option values 27
WPA2 21
Z
Zero IT Activation
New WLAN creation 28
ZoneDirector
backing up settings 16
changing network addressing 9
changing system name 10
features 1
Monitoring options overview 52
overview 1
restarting the device 71
restoring backup file contents 16
restoring to a factory default state 17
upgrading software 15
WLAN security explained 6
ZoneDirector wireless LAN
deploying in a VLAN environment 34
ZoneFlex APs
upgrading software 15
76
 Loading...
Loading...