Page 1

System Security
Design Guidelines
Reference Manual
Original Instructions
Page 2

Publication Title Reference Manual
Important User Information
Read this document and the documents listed in the additional resources section about installation, configuration, and
operation of this equipment before you install, configure, operate, or maintain this product. Users are required to familiarize
themselves with installation and wiring instructions in addition to requirements of all applicable codes, laws, and standards.
Activities including installation, adjustments, putting into service, use, assembly, disassembly, and maintenance are required to
be carried out by suitably trained personnel in accordance with applicable code of practice.
If this equipment is used in a manner not specified by the manufacturer, the protection provided by the equipment may be
impaired.
In no event will Rockwell Automation, Inc. be responsible or liable for indirect or consequential damages resulting from the use
or application of this equipment.
The examples and diagrams in this manual are included solely for illustrative purposes. Because of the many variables and
requirements associated with any particular installation, Rockwell Automation, Inc. cannot assume responsibility or liability for
actual use based on the examples and diagrams.
No patent liability is assumed by Rockwell Automation, Inc. with respect to use of information, circuits, equipment, or software
described in this manual.
Reproduction of the contents of this manual, in whole or in part, without written permission of Rockwell Automation, Inc., is
prohibited.
Throughout this manual, when necessary, we use notes to make you aware of safety considerations.
WARNING: Identifies information about practices or circumstances that can cause an explosion in a hazardous environment, which may
lead to personal injury or death, property damage, or economic loss.
ATT EN TI ON : Identifies information about practices or circumstances that can lead to personal injury or death, property damage, or
economic loss. Attentions help you identify a hazard, avoid a hazard, and recognize the consequence.
IMPORTANT
Identifies information that is critical for successful application and understanding of the product.
Labels may also be on or inside the equipment to provide specific precautions.
SHOCK HAZARD: Labels may be on or inside the equipment, for example, a drive or motor, to alert people that dangerous voltage may
be present.
BURN HAZARD: Labels may be on or inside the equipment, for example, a drive or motor, to alert people that surfaces may reach
dangerous temperatures.
ARC FLASH HAZARD: Labels may be on or inside the equipment, for example, a motor control center, to alert people to potential Arc
Flash. Arc Flash will cause severe injury or death. Wear proper Personal Protective Equipment (PPE). Follow ALL Regulatory requirements
for safe work practices and for Personal Protective Equipment (PPE).
2 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 3

Table of Contents
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
How Can I Get Help To Manage My Security Risk? . . . . . . . . . . . . . . 5
Summary of Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Additional Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Chapter 1
Vulnerabilities How Rockwell Automation Handles Vulnerabilities . . . . . . . . . . . . . . 8
Report a Suspected Product Vulnerability . . . . . . . . . . . . . . . . . . . . 8
Public Vulnerability Disclosure. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Supply Chain Vulnerabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Threat Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Chapter 2
System Security Security Basics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Security Standards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Defense-in-Depth Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Notifications That Rockwell Automation Provides. . . . . . . . . . . 16
Security with Rockwell Automation Products . . . . . . . . . . . . . . . . . . . 16
Standard Security Components. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Secure Networks and
Communication
Chapter 3
Converged Plantwide Ethernet (CPwE). . . . . . . . . . . . . . . . . . . . . . . . . 19
Logical Zones . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Network Firewalls. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Deep Packet Inspection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Industrial Demilitarized Zone (IDMZ) . . . . . . . . . . . . . . . . . . . . . . . . . 23
Control Access to the Industrial Zone. . . . . . . . . . . . . . . . . . . . . . . 24
Remote Desktop Gateway. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Industrial Firewall Zones. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Stratix 5950 Security Appliance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Control Device Communication Ports . . . . . . . . . . . . . . . . . . . . . . 27
Switch and Routing Platforms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Stratix Managed Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Secure Communications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
CIP Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Wireless Connectivity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Additional Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 3
Page 4

Table of Contents
Chapter 4
Harden the Control System Patch Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Microsoft Patches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Product Change Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Hardware Series . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Software and Firmware Versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Workstation Hardening . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
FactoryTalk Directory Application . . . . . . . . . . . . . . . . . . . . . . . . . 34
Physical Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Device Hardening . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Digitally Signed Firmware and Software . . . . . . . . . . . . . . . . . . . . . 35
High Integrity Add-On Instructions . . . . . . . . . . . . . . . . . . . . . . . . 36
Additional Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Chapter 5
Manage User Access FactoryTalk Services Platform. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Control Data Access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
FactoryTalk Administration Console Software. . . . . . . . . . . . . . . 41
Studio 5000 Logix Designer Application . . . . . . . . . . . . . . . . . . . . 41
FactoryTalk Security Software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Policies and Actions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Centralized Security Authority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Security Authority Identifier (SAID). . . . . . . . . . . . . . . . . . . . . . . . 43
FactoryTalk View Site Edition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Protect Controller Logic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
License-based Source and Execution Protection . . . . . . . . . . . . . . 45
Additional Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Chapter 6
Monitor and Recover Audit and Change Management with FactoryTalk AssetCentre
Software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Backups via FactoryTalk AssetCentre Software . . . . . . . . . . . . . . . . . . 49
Component Change Detection and Logging for Controllers . . . . . . 50
Chapter 7
Disposal Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Appendix A
History of Changes SECURE-RM001D-EN-P, March 2020 . . . . . . . . . . . . . . . . . . . . . . . . 53
SECURE-RM001C-EN-P, December 2019 . . . . . . . . . . . . . . . . . . . . . 53
SECURE-RM001B-EN-P, April 2019 . . . . . . . . . . . . . . . . . . . . . . . . . . 53
4 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 5
Preface
This publication provides guidelines for how to use Rockwell Automation
products to improve the security of your industrial automation system.
For information on patch management options, security advisory details, and
general news and awareness on industrial security from the Rockwell
Automation Office of Product Safety and Security, see the Industrial
Cybersecurity capabilities web page.
How Can I Get Help To Manage My Security Risk?
Summary of Changes
The Knowledgebase Technote Industrial Security Advisory Index
specific product security alerts, advisories, and recommendations. Subscribe to
this index to receive notifications.
To address specific concerns, or to report issues, contact us
at secure@ra.rockwell.com
Block.
Rockwell Automation Network & Security Services consulting services are
available to assist customers assess and improve the state of security of
industrial control systems that use Rockwell Automation and other vendor
control products. We provide a holistic approach to manage your network
infrastructure and security throughout its lifecycle. For more information, see
Industrial Cybersecurity Services
This manual contains the following new information as indicated.
Top ic Pag e
New chapter on vulnerabilities, how to report suspected
vulnerabilities, and how Rockwell Automation responds
to reports.
Updates to patch management 31
Updates to version descriptions for software and
firmware
. Communicate securely via our PGP Public Key
.
7
33
points to
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 5
Page 6
Preface
Additional Resources
These documents contain additional information concerning related products
from Rockwell Automation.
Resource Description
Security Configuration User Manual, SECURE-UM001 Describes how to configure and use Rockwell Automation products to improve the security
CIP Secur ity with Rockwell Au tomation Products Application Technique,
SECURE-AT001
Converged Plantwide Ethernet (CPwE) Design and Implementation Guide,
publication ENET-TD001
Industrial Firewalls within a Converged Plantwide Ethernet Architecture White
Paper, publication ENET-WP011
Deploying Industrial Firewalls within a Converged Plantwide Ethernet Architecture
Design and Implementation Guide, publication ENET-TD002
Guidelines on Firewalls and Firewall Policy Recommendations of the National Institute of Standards and Technology
Industrial Automation Wiring and Grounding Guidelines, publication 1770-4.1
Product Certifications website,
http://www.rockwellautomation.com/global/certification/overview.page
of your industrial automation system.
Describes how to implement the Common Industrial Protocol (CIP™) Security standard in
your control system.
Provides guidelines for how to design, implement, and manage industrial Ethernet
networks.
Provides guidelines for how to implement industrial firewalls.
Outlines use cases for how to design, deploy, and manage industrial firewalls.
Provides general guidelines for how to install a Rockwell Automation industrial system.
Provides declarations of conformity, certificates, and other certification details.
You can view or download publications at
http://www.rockwellautomation.com/global/literature-library/overview.page
To order paper copies of technical documentation, contact your local
Allen-Bradley distributor or Rockwell Automation sales representative.
.
6 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 7
Chapter 1
Vulnerabilities
A vulnerability is a flaw or weakness in a product or system that can be
exploited to compromise product or system confidentiality, integrity, or
availability.
Risk and vulnerability assessments are the starting point for any security policy
implementation. Vulnerability assessments examine your situation from
technologies, policies, procedures, and behaviors. An assessment provides a
picture of your current security posture (current risk state) and what you need
(mitigation techniques) to get to a preferred state (acceptable risk state).
Rockwell Automation recommends the formation of a multi-discipline team of
operations, engineering, IT, and safety representatives to collaborate in the
development and deployment of your industrial security policy.
A vulnerability assessment provides, at a minimum:
• An inventory of existing devices and software.
• Detailed observation and documentation of intended system operation.
• Identification of possible vulnerabilities.
• Prioritization of each vulnerability based on the impact and exploitation
potential.
The Common Vulnerability Scoring System (CVSS) is a free, open industry
standard for assessing the severity of vulnerabilities. Rockwell Automation
includes CVSS-based scores in Product Security Advisory notices to help
customers assess their risk and exposure, including how prioritize responses
and resources according to a specific threat. For more information, see
Common Vulnerability Scoring System Specification Document
The outcome of a vulnerability assessment can include mitigation techniques
that bring an operation into an acceptable risk state.
Actions that are taken after a risk assessment can include the following:
• New firewall controls
• New switch ports to lock down
• Stronger password policies
• Removal of unused software programs
• Improved procedures for managing the connection of external devices,
such as USB devices
• New or patched versions of firmware or software
.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 7
Page 8
Chapter 1 Vulnerabilities
How Rockwell Automation Handles Vulnerabilities
Rockwell Automation recognizes the importance of security in industrial
control systems and is investing in its products, people, partnerships, and
integrated consulting services (Network & Security Services – NSS) to
enhance the security in our products and maintain productivity. Rockwell
Automation provides detailed and actionable information about security
vulnerabilities to help customers make informed decisions on what steps they
need to take to improve their security.
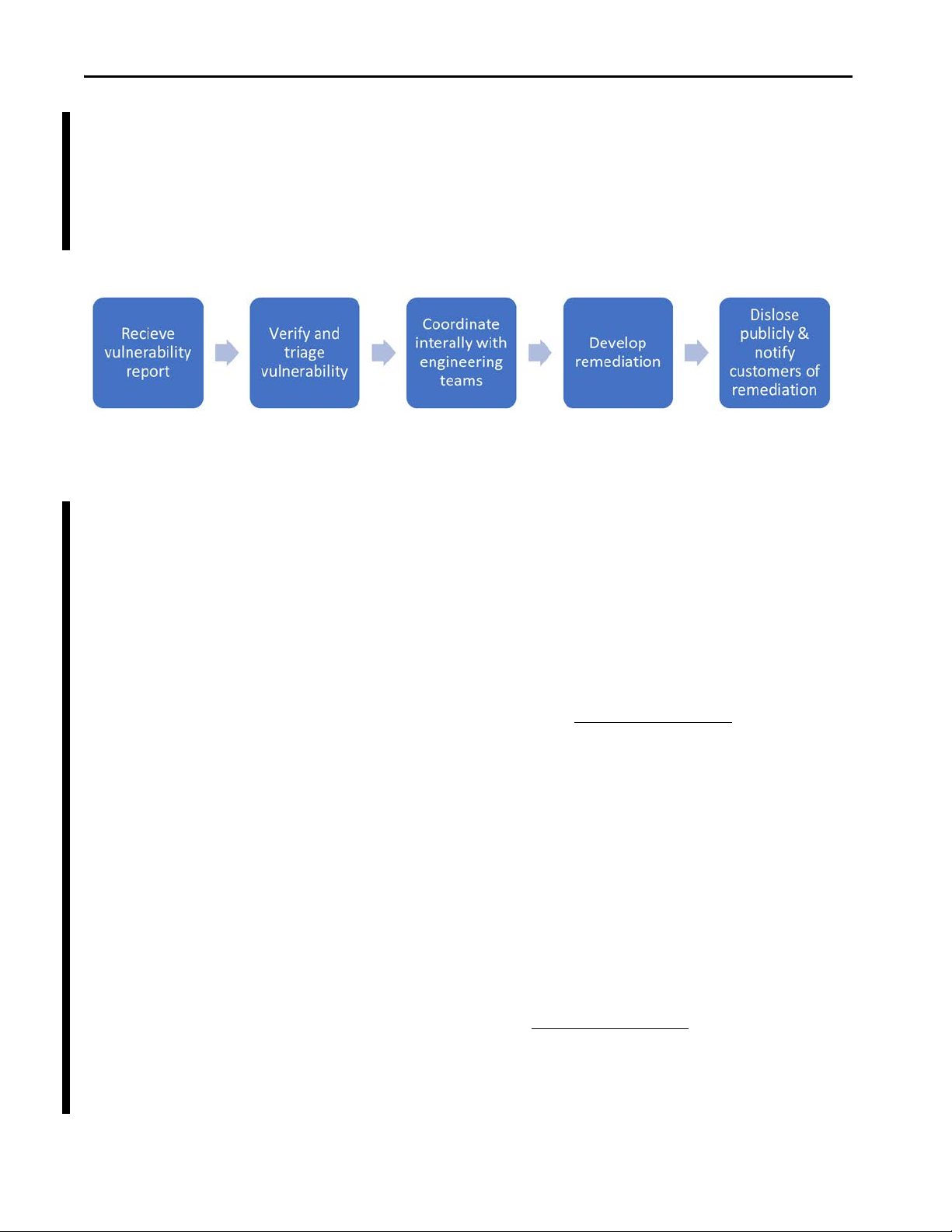
Report a Suspected Product Vulnerability
Rockwell Automation encourages submissions of suspected vulnerabilities as
soon as they are discovered. Rockwell Automation maintains a formalized
process to identify, assess, and remediate reported vulnerabilities for those
products that are in the Active or Active Mature state.
The Product Security Incident Response Team (PSIRT) at Rockwell
Automation responds to suspected vulnerabilities within Rockwell
Automation products. Reporters are strongly encouraged to file a vulnerability
report with the PSIRT via email at secure@ra.rockwell.com
The PSIRT works with reporters to understand and validate reports.
The PSIRT:
• Requests that the reporter keep any communication confidential
• Assigns a tracking ID to the vulnerability report
• Reviews and responds, usually within two business days
• Advises the reporter of significant changes in the status of any
vulnerability reported to the extent possible without revealing
information provided to us in confidence
• Works to remediate reported vulnerabilities in a timely manner.
The Rockwell Automation PSIRT encourages the encryption of sensitive
information prior to sharing over email. To request instructions on how to use
our public key, contact us at secure@ra.rockwell.com
The Rockwell Automation PSIRT may contact the reporter via email or an
another agreed upon communications mechanism throughout the disclosure
process.
.
.
8 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 9
Vulnerabilities Chapter 1
The PSIRT asks that reporters adhere to the following :
• Play by the rules. This includes following the guidelines, as well as any
other relevant agreements.
• Report any vulnerability discovered promptly.
• Avoid violating the privacy of others, disrupting our systems, destroying
data, or harming user experience.
• Use only our PSIRT email to discuss vulnerability information with us,
unless otherwise agreed upon with the PSIRT.
• Keep the details of any discovered vulnerabilities confidential until
Rockwell Automation identifies a resolution.
• If a vulnerability provides unintended access to data, limit the amount of
data you access to the minimum required to demonstrate the issue.
Cease testing and submit a report immediately if you encounter any user
data during testing, such as personally identifiable information (PII),
personal healthcare information (PHI), credit card data, or proprietary
information.
• Only interact with test accounts you own or with explicit permission
from the account holder.
• Do not engage in extortion.
• Comply with all applicable laws.
Public Vulnerability Disclosure
The PSIRT discloses vulnerability details, mitigations, and solutions via the
Knowledgebase Technote Industrial Security Advisory Index
You can find additional information on the Industrial Cybersecurity
capabilities web page.
Rockwell Automation recognizes the hard work of reporters and provides
recognition within the advisories, unless otherwise specified. We recognize
reporters if they are the first to report a unique vulnerability and the report
triggers a product change.
The Rockwell Automation Vulnerability Disclosure Policy draws on the
United States Core Terms compiled by disclose.io, the vulnerability disclosure
guidance set forth by the CERT Coordination Center (CERT/CC) at
Carnegie Mellon University, and ISO 29147 and ISO 30111, which define
standards for receiving and processing vulnerability reports. Rockwell
Automation defines a reporter as an individual or organization that notifies a
vendor or coordinator of a suspected product vulnerability. Coordinators, on
the other hand, are defined as an individual or organization that coordinates
vulnerability information to affected parties.
.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 9
Page 10

Chapter 1 Vulnerabilities
When conducting vulnerability research according to this policy, Rockwell
Automation considers the research to be:
• Authorized in accordance with the Computer Fraud and Abuse Act
(CFAA) (and/or similar state laws). Rockwell Automation will not
initiate or support legal action against you for accidental, good faith
violations of this policy.
• Exempt from the Digital Millennium Copyright Act (DMCA).
Rockwell Automation will not bring a claim against you for
circumvention of technology controls.
• Exempt from restrictions in our Terms & Conditions that would
interfere with conducting security research. Rockwell Automation
waives those restrictions on a limited basis for work done under this
policy.
• Lawful, helpful to the overall security of the Internet, and conducted in
good faith.
If at any time you have concerns or are uncertain whether your security
research is consistent with this policy, please email secure@ra.rockwell.com
before going any further.
.
Supply Chain Vulnerabilities
Threat Model
Rockwell Automation also prioritizes supply-chain vulnerabilities, especially if
a vulnerability affects more than one Rockwell Automation product. The
PSIRT accept reports regarding third-party components if the vulnerabilities
are disclosed in a multi-party, coordinated effort supported by a third-party
coordinator such as DHS CISA or the CERT/CC.
Threat modeling is a procedure to analyze network, application, and physical
security. A threat model identifies objectives and vulnerabilities, and then
defines countermeasures to mitigate the effects of threats to the system.
1. Describe the assets to protect.
Create classes of assets and information that you want to protect. For
example, a controller, the controller configuration, or recipe data in the
controller. Be as specific as possible. For example, include the following:
• serial number
•MAC ID
• IP address
•user access
• device dependencies
Prioritize the assets. Define the type of protection for each asset confidentiality, integrity, or availability.
10 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 11

Vulnerabilities Chapter 1
2. Describe the policies that govern the assets
The policies are typically control-based in that they define who can do
what to which asset. Other policies can define attributes such as asset
availability, version control, or confidentiality requirements.
Because policies are written in a general manner, they are supported with
procedures, standards, and guidelines to provide the details on how to
implement, enforce, and monitor the policy.
3. Characterize the assets and their supporting systems
Examine the assets in their information systems and identify
information flows that affect the assets. Characterize the systems and
software that are part of the information flow.
• How are the assets accessed?
• Who can copy, move, or modify them?
• What methods can be used to interact with them?
• Do they exist in multiple locations?
• How are multiple copies synchronized?
4. Identify threats to the assets
For each asset, identify how and where to enforce the policy that governs
the asset. Based on the type of protections for the asset, examine the
information flows, systems characterizations, and enforcement
mechanisms. Identify potential threats (such as threats to
confidentiality, threats to integrity, and threats to availability).
For example:
• ‘System goes off line’ is a threat to availability.
• ‘Database synchronization fails’ is a threat to integrity.
5. Characterize the threats
For each threat, enumerate the mechanisms (vulnerabilities) that can
cause the potential threat to become an actual threat. Keep the
vulnerabilities as broad as possible in scope.
6. Visualize
Use a network diagram and overlay system information, asset locations,
information flows, enforcement points, and vulnerabilities. Annotate
the diagram with available resources (people, money, equipment).
Use this visualization as a method to divide the system into manageable
pieces. This visualization also shows relationships and possible
consequences when you make changes.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 11
Page 12

Chapter 1 Vulnerabilities
7. Strategize
Use the visualization to find:
• Patterns that suggest enterprise-wide solutions rather than local or
point solutions.
• Interactions of resources and ease of affecting the network.
• Possibilities of vulnerabilities being exploited.
• Develop backup and restore procedures.
Group vulnerabilities and their locations. Identify methods to address as
many of the vulnerabilities as possible with one change or small set of
changes.
Remember that not all vulnerabilities need new technology to address
the issues. Proper configuration, privilege, and access control are key, and
can often be improved without harming production facilities.
8. Verify
• Map every proposed change directly to a threat to an asset.
• Make sure that the change does not introduce a new threat to another
asset.
Verify that no policy enforcement point can be circumvented.
12 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 13
Chapter 2
RESET
SERIAL
CON / AUX
GE WAN 0
5VDC
-4.QA
FE 1SLFE 0
SL
FE 3SLFE 2
SLSL
SYS
ACT
LAN
EIP Mod
EIP Net
Setup
GPS
TimeCD
3 1
4 2
Out
1 2
Speed
Duplex
PRP
DLR
PoE
Alarms PSU
12345 6789 1011122526
13
1458912
10/100/1000 PoE+
100/1000 SFP
100/1000 SFP+
GPS ANT. DIG.TimeCode ANA.TimeCode
Console Alarm
TOD
16 17 20 21 24
25
OUTINOUT
IN
28
2724212223201718191613 14 15 28
Express
Setup
Disp.
Mode
L
NHiL
N
Hi
Lo
100-240V-, 50-60Hz, 2A
100-250V , 2A
24-60V , 10A 24-60V , 10A
100-250V , 2A
100-240V-, 50-60Hz, 2A
Lo
PSU1 PSU2
Module
Status
Network
Activity
Network
Status
1734-AENT
Point Bus
Status
System
Power
Field
Power
Module
Status
Network
Activity
Network
Status
1734-AENT
Point Bus
Status
REDUNDANCY MODULE
OK
COMM
PRI
D+
D-
MBRK
SHLD
IN1
1
2
IN2
COM
W
V
U
+
-
Mod
Net
5500S2
32791M
Internet
Plant/Enterprise LAN
Firewall
Firewall
Firewall
Process LAN
Level 3
Levels 0… 2
Levels 4 and 5
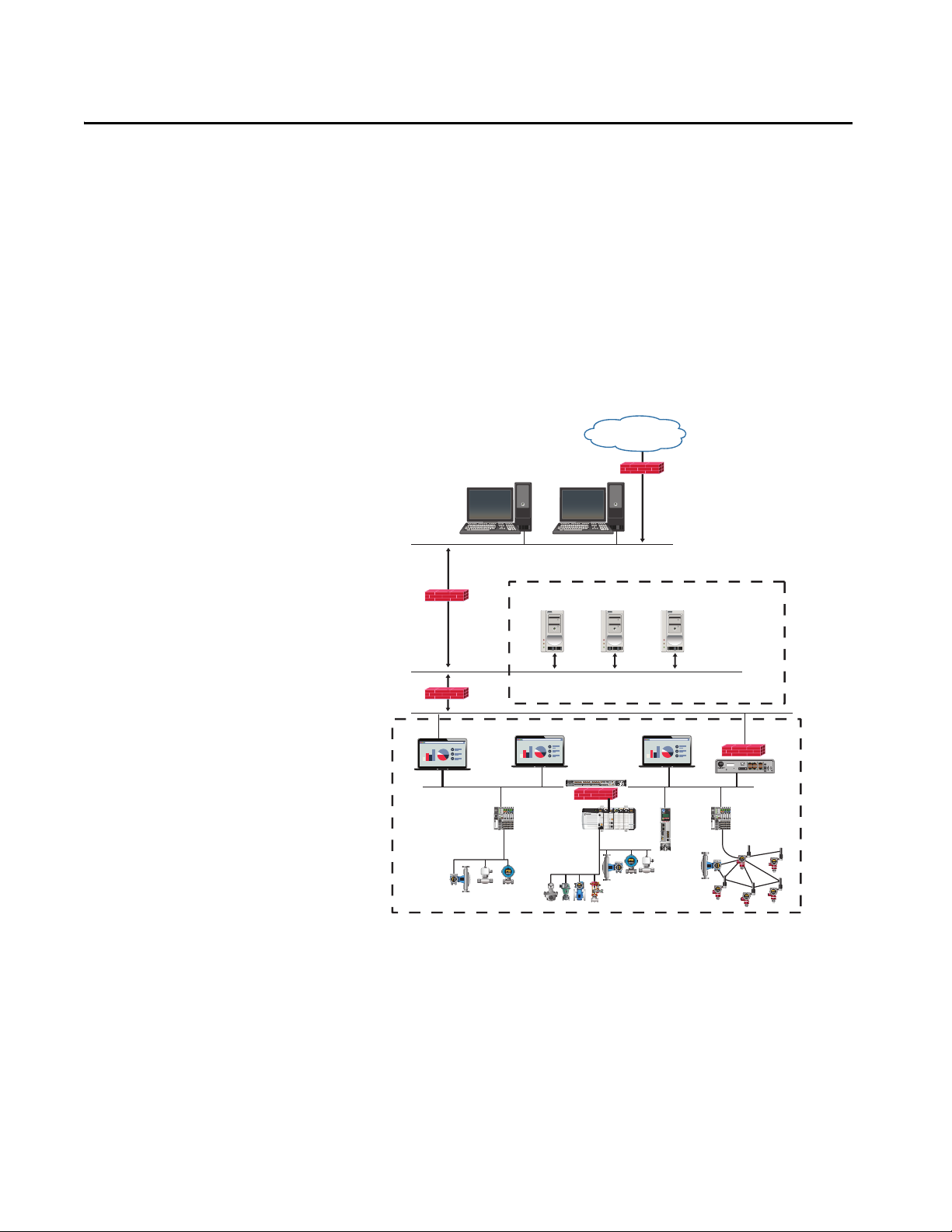
System Security
Just as the nature of manufacturing and industrial operations has changed, so
have the security risks. More connected operations can create more potential
entrance points for industrial security threats. Threats can come in many forms
– physical versus digital, internal versus external, or malicious versus
unintentional.
In the industrial automation and control system (IACS), follow common
industry standards, such as the Purdue Enterprise Reference Architecture
model, to define:
• Security zones - those assets that have the same security requirements
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 13
• Trusts within security zones - relationships between assets that support
identification, authentication, accountability, and availability.
Page 14

Chapter 1 System Security
Industrial security must address a wide range of concerns, including:
• Safeguard intellectual property and other valuable information.
• Safeguard operations from intrusions that could impact productivity,
product quality, operator safety, or the environment.
• Maintain critical infrastructure systems, especially systems in regulated
areas like energy and water/waster-water management.
• Maintain high-availability traffic policies for networks.
• Enable and control remote access to industrial operations.
Security Basics
Industrial security must be comprehensive. Extend security policies from the
enterprise through the plant level and to end devices. Address risks across your
people, processes, and technologies. Involve collaboration between IT and OT
personnel for design, management, and regular communication on expected
system functional requirements and policy compliance.
A robust approach to security includes the development and implementation
of the appropriate activities to complete the following steps:
• Identify the cybersecurity risk to systems, assets, data, and capabilities.
• Protect critical infrastructure services.
• Detect cybersecurity events.
• Respond to a detected cybersecurity event.
• Recover from and restore any capabilities or services that were impaired
due to a cybersecurity event.
Cybersecurity is the collection of technologies, processes and practices that
help protect networked computer systems from unauthorized use or harm.
Cybersecurity addresses cyber- attacks, which are offensive in nature and
emphasize network penetration techniques, and cyber-defenses, which are
defensive in nature and emphasize counter-measures intended to help
eliminate or mitigate cyber- attacks.
The main goals of cybersecurity in an industrial setting:
• Availability: maintain and never give up control in a control system
• Confidentiality: protect proprietary information and only let
individuals with a need-to-know have access to the information
• Integrity: ensure that the information flowing through the system has
not been tampered with
14 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 15
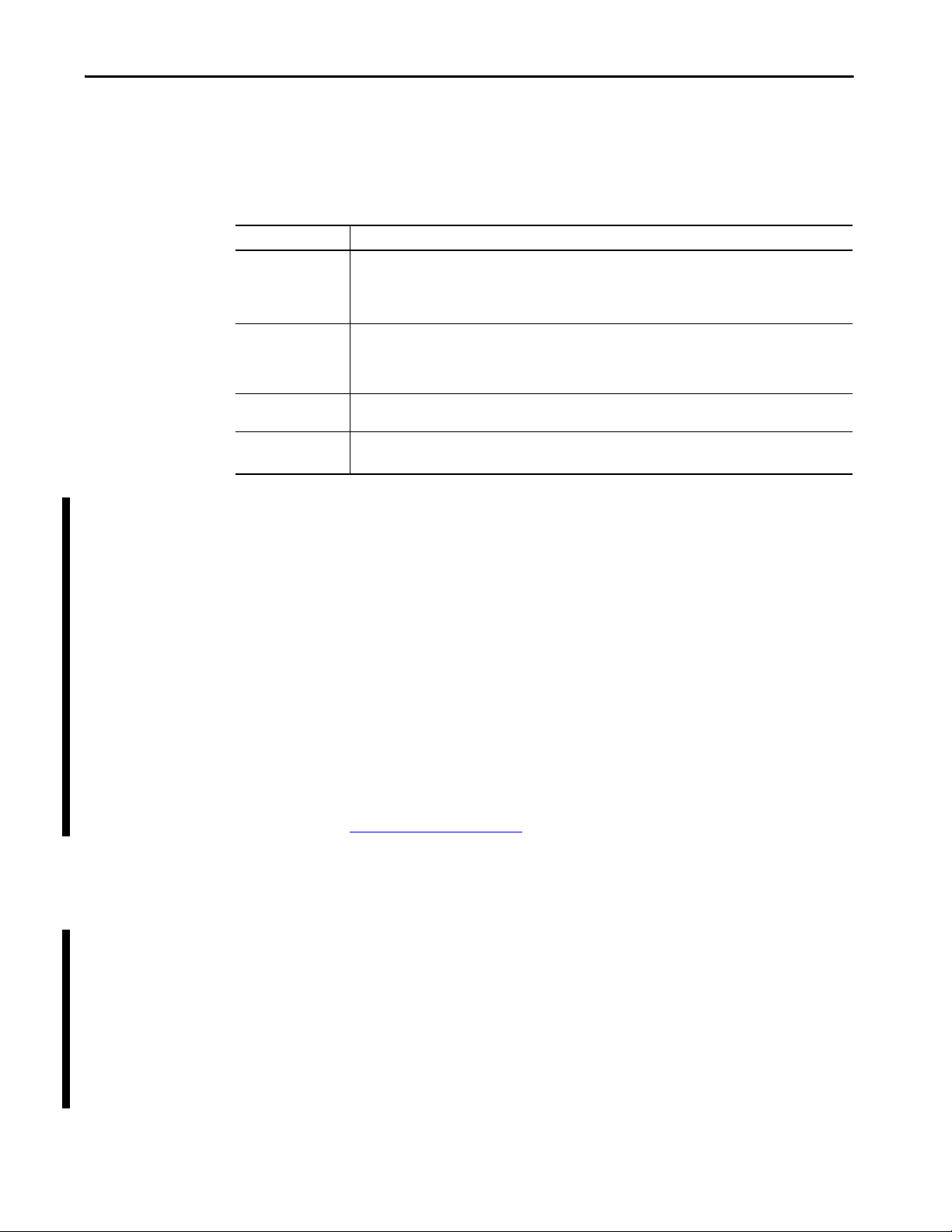
Security Standards
There are a number of resources that organizations can use as a basis to manage
security and risk within the IACS. These resources can help organizations
develop a security management program.
Resource Description
ISA/IEC 62443 Standard Industrial Automation and Control Systems (IACS) Security (formerly ISA-99)
This standard addresses network and system security and defines the provision of multiple security protections,
especially in layers, with the intent to delay, if not block, an attack.
This standard a lso recommends password structures.
NIST 800-82
Framework
NIST Cybersecurity
Framework
NCCIC Agency National Cybersecurity and Communications Integration Center
Guide to Industrial Control Systems (ICS) Security
This framework provides recommendations for securing an IACS. The standard covers the use of firewalls, the
creation of demilitarized zones and intrusion detection capabilities, along with effective security policies, training
programs, and incident response mechanisms.
This framework provides guidelines that help organizations align cybersecurity activities with business
requirements, risk tolerances, and resources.
This agency provides recommendations for secure architecture design.
The United States Department of Homeland Security (DHS) includes the
Cybersecurity & Infrastructure Security Agency (CISA). CISA manages a
repository of alerts, advisories, and reports (ICS-CERT) for industrial control
systems.
• Alerts: provide timely notification to critical infrastructure owners and
operators concerning threats to critical infrastructure networks.
• Advisories: provide timely information about current security issues,
vulnerabilities, and exploits.
• Reports: provide Technical Information Papers (TIPs), Annual Reports
(Year in Review), and 3rd-party products applicable to industrial control
system owners/operators.
• Newsletters: periodic publication of security news and information
applicable to industrial control system owners/operators.
System S ecurity Chapter 1
For more information, see Cybersecurity and Infrastructure Security Agency >
Industrial Control Systems
.
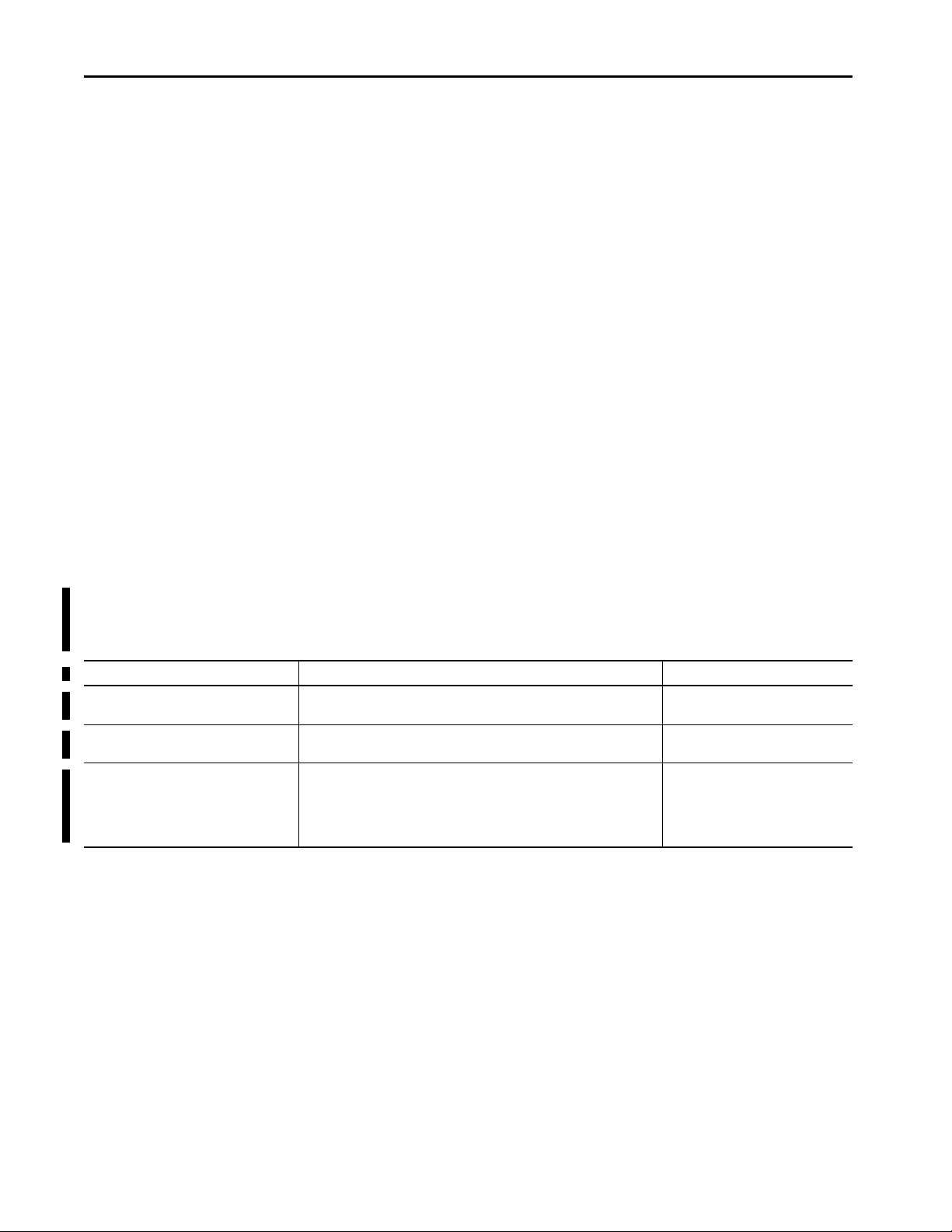
Defense-in-Depth Security
Industrial security is best implemented as a complete system across your
operations. Common to security standards is the concept of defense-in-depth
(DiD). DiD security establishes multiple layers of protection based on diverse
technologies through physical, electronic, and procedural safeguards. Just like a
bank uses multiple security measures – such as video cameras, a security guard,
and a vault – DiD helps make sure that threats encounter multiple lines of
defense. DiD also assumes the implementation of cybersecurity policies that
include operations planning, user training, and physical access security
measures.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 15
Page 16
Chapter 1 System Security
A defense-in-depth security approach consists of six main components:
• Policies and Procedures
•Physical
•Network
•Computer
•Application
•Device
Defense-in-depth employs a comprehensive approach to leverage multiple
methods to mitigate risks. To apply defense-in-depth, understand the
relationship of intruders (threats and threat actors) and vulnerabilities to the
controls (standards, detection methods, and countermeasures).
A threat actor, through intent, capability, or opportunity, poses a threat to the
IACS when the threat compromises operations, personnel, or technology and
exploits an existing weakness or vulnerability. Base countermeasures on best
practices, standards, and established company security policies.
Countermeasures protect critical assets through multiple layers of defense.
Organizations must constantly adjust and refine security countermeasures to
maintain protection against known and emerging threats.
Notifications That Rockwell Automation Provides
Rockwell Automation provides these types of product notices.
Notification Description Customer Action
Product Safety Advisory (PSA) Issued when a product failure may result in significant loss of capital equipment,
Product Notice (PN) Issued when a product failure may result in significant commercial loss or customer
Product Security Advisory Issued for security alerts and security recommendations where such risks stem
Security with Rockwell Automation Products
personal injury, or death.
dissatisfaction.
from cyber-attacks.
These advisories are intended to raise customer awareness of risks to affected
product operation or performance and also supply relevant recommendations for
how to reduce or remove the risk associated with a vulnerability.
Security is not a static end state, it is an interactive process. No single
product, methodology, or technology fully secures control networks. The
remaining chapters in this reference manual highlight Rockwell Automation
products that help manage:
• Identification, authentication, and user access
•Network segmentation and data flow
• Data confidentiality
• System integrity
• Resource availability and response to events
Required
Strongly Recommended
Strongly Recommended
16 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 17
System S ecurity Chapter 1
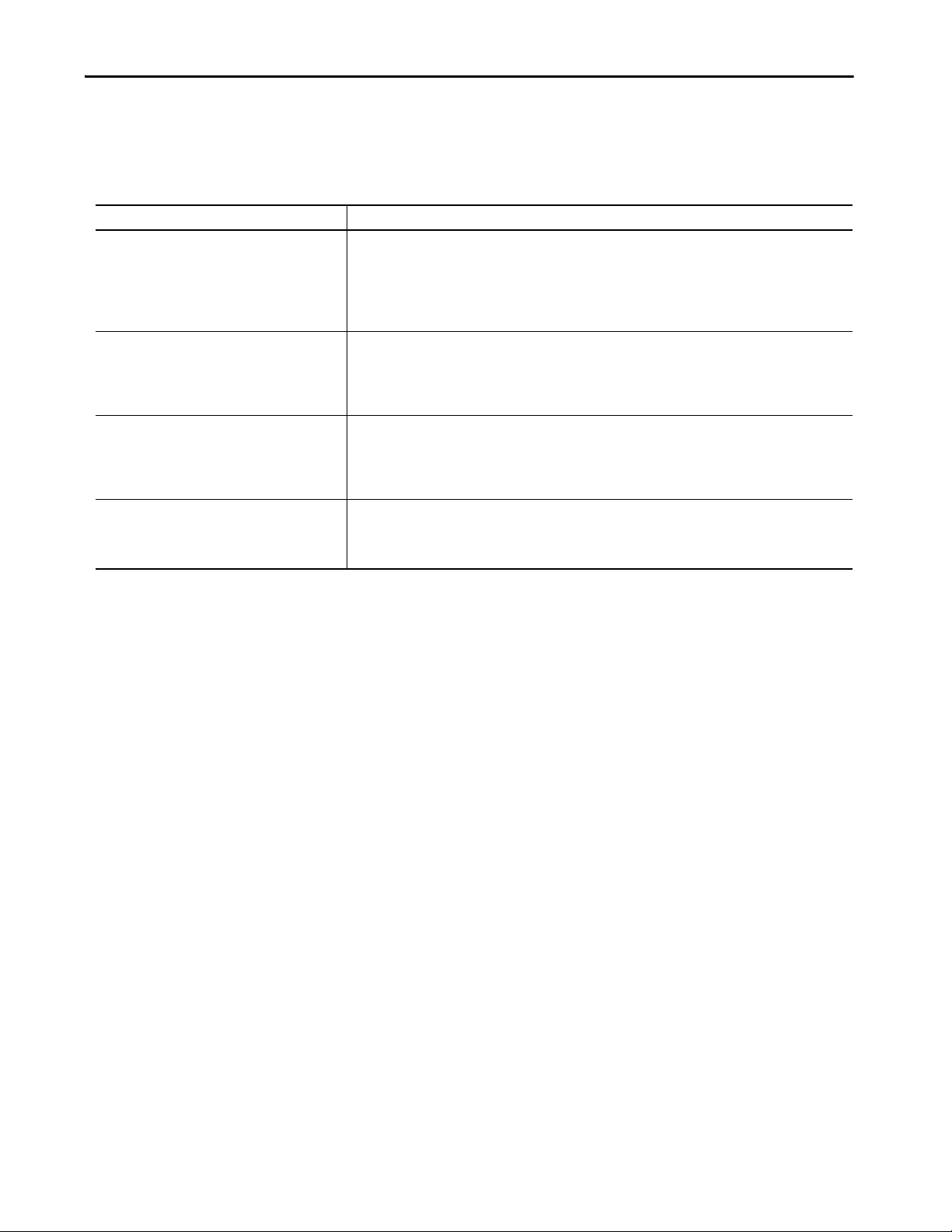
Standard Security Components
In addition to the Rockwell Automation products described in this
publication, there are also references to these additional technologies.
Component Description
Microsoft® Active Directory service Use Active Directory for authentication and authorization in a Windows domain.
Active Directory (AD) is a directory service that Microsoft developed for Windows domain networks. It is included in
most Windows Server operating systems as a set of processes and services.
A server that runs the Active Directory Domain S ervices (AD DS) is called a domain controller. The domain controller
authenticates and authorizes all users and computers in a Windows domain type network. The domain controller
assigns and enforces security policies for all computers and software updates.
RADIUS protocol You can use the Remote Authentication Dial-In User Service (RADIUS) protocol to manage access to the Internet or
Cisco® TACACS+ protocol You can use the Cisco Terminal Access Controller Access-Control System Plus (TAC ACS+) to manage remote
IEEE 802.1x authentication You can use 802.1x authentication to manage port-based access for devices that want to connect to a network.
internal networks, wireless networks, and integrated email services.
The RADIUS protocol is a network protocol that provides centralized authentication, authorization, and accounting
(AAA) management for users. The RADIUS protocol is often used by Internet service providers (ISPs) and enterprises
to manage access to the Internet or internal networks, wireless networks, and integrated email services.
authentication for networked access control through a centralized server.
The Cisco TACACS+ protocol manages authentication, authorization, and accounting (AAA) services. The TACACS+
protocol uses the Transmission Control Protocol (TCP). Since TCP is a connection-oriented protocol, TACACS+ does
not have to implement transmission control. TACACS+ encrypts the full content of each packet.
802.1x authentication secures communication between authenticated and authorized devices. You can connect this
access control to the Active Director y to create a central administration connection for both network mana gement
and network access. This access control is the preferred method to create a central network access layer.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 17
Page 18

Chapter 1 System Security
Notes:
18 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 19

Chapter 3
DAPWAP
DAPWAP
DAPWAP
SMC-Flex
EscSel
Lang
1734-AENTR
Module
Status
Network
Activity
Network
Status
Link 1
Activity
Status
Link 2
Activity
Status
Point Bus
Status
System
Power
Field
Power
1734-AENTR
Module
Status
Network
Activity
Network
Status
Link 1
Activity
Status
Link 2
Activity
Status
Point Bus
Status
System
Power
Field
Power
Module
Status
Network
Activity
Network
Status
1734-AENT
Point Bus
Status
System
Power
PanelView Plus 1250PanelView Plus 1250
Mod
Net
5700
Mod
Net
5700
Mod
Net
5700
32792M
IFW
Enterprise Cloud
Site Operations
Level 3
Enterprise Zone
Levels 4 and 5
Industrial Demilitarized Zone (IDMZ)
Industrial Zone
Level 3
Cell/Area Zone
Levels 0, 1, and 2
Cell/Are a Zone
Levels 0, 1, and 2
Cell/A rea Zone
Levels 0, 1, and 2
Secure Networks and Communication
The continuing trend in networking is the convergence of technology,
operational technology (OT) with information technology (IT). Technologies
like the Ethernet and EtherNet/IP™ (Common Industrial Protocol over an
Ethernet network) protocols help enable network technology convergence.
Network technologies that filter, block, and control access help secure
networks. You can also select control products that offer security options.
Converged Plantwide Ethernet (CPwE)
Converged Plantwide Ethernet (CPwE) reference architectures, a Rockwell
Automation and Cisco® collaboration, use industry standards to model
characterized network architectures for use in an industrial network security
framework. This industrial network security framework establishes a
foundation for network segmentation for both traffic management and policy
enforcement. The industrial network security framework uses a
defense-in-depth approach and is aligned to industrial security standards.
For more information, see Converged Plantwide Ethernet (CPwE) Design and
Implementation Guide, ENET-TD001
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 19
Page 20

Chapter 2 Secure Networks and Communication
32796M
Level 5
Level 4
Level 3
Level 2
Level 1
Level 0
Enterprise Network
Email and Internet Site Business Planning and Logistics Network
Enterprise Security Zone
Levels 4 and 5
Remote Desktop
Gateway services
Industrial Security Zones
Level 3
Cell/A rea Zones
Levels 0, 1, and 2
Patch
Management
Email
Web
Application
Server
Web S ervi ces
Operations
Application
Server
Reverse
Proxy
Sensors Drives Actuators Robots
Fac tor yTal k
Client
Fact or yTalk
Client
Batch
Control
Discrete
Control
Drive
Control
Continuous
Process
Safety
Control
Operator
Interface
Engineering
Work stat ion
Operator
Interface
Fact oryTa lk
Application
Server
Fact or yTalk
Directory
Engineering
Work stat ion
Remote Access
Server
Industrial DMZ
Logical Zones
CPwE logical zones employ common industry standards to organize the plant
functions into levels, and the IEC-62443 (formerly ISA-99) standard to
organize the levels into functional and security zones. The goal is to define
smaller, more manageable areas, such as:
•connected LANs
•broadcast domains
•fault domains
•domains of trust
You can use physical or logical segmentation to define zones.
Infrastructure Benefits
Segmented physical: simplex, unidirectional A unidirectional network only lets data pass from one side of a network connection to another, and not the other
Segmented physical: duplex, bidirectional A bidirectional network lets data pass from both sides of a network connection.
Segmented logical: duplex, bidirectional CPwE industrial network security framework – IDMZ, VLANs, VRF, switch hierarchy (Layer 2 / 3)
20 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
direction.
The controlled interface that comprises the send and receive elements of a unidirectional network acts as a one-way
communication protocol break’ between the two network domains.
Connect, segment, encrypt, and cloak your critical assets and networks with crypto-IDs.
Page 21

Secure Networks and Communication Chapter 2
Outside
Interface
Inside
Interface
10.10.30.10 10.10.30.10
Firewall
Allow ICMP (ping) Traffic
To 10.10.30.20
Allow HTTPS Traffic
To 10.10.10.30
Block All Other Traffic
ACE
ACE
ACE
ACL
Network Firewalls
A firewall is a software or hardware device that separates zones. A firewall
permits or denies network traffic based on preconfigured policies or rules.
One type of preconfigured rule is an access control list (ACL). An ACL
contains permit and deny statements. Each permit or deny statement is an
access control entry (ACE).
This type of firewall control is stateful packet inspection (SPI) and operates by
tracking legitimate connections. SPI rejects attempted connections from
sources without a connection history. If you use a packet crafting tool in an
attempt to gain access, the firewall rejects packets with sequence numbers that
are out of range.
Firewall Guidelines
Firewalls are good security boundary appliances.
32793M
• Your firewall is only as good as your rules.
• If a rule permits traffic from a host on one side of the firewall to the
other side of the firewall, a compromised host is hard to detect.
• Use Network Address Translation (NAT) to isolate private network
addresses from public addresses.
• Inspect traffic for conformance with proper protocol behavior.
• Regularly monitor the firewall for rule updates, reports and metrics, and
firmware and software patches.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 21
Page 22

Chapter 2 Secure Networks and Communication
32794M
Firewall
Outside Inside
DPI
Firewall
Poli cy
DPI
Inspection
1
2
3
Deep Packet Inspection
Another type of firewall control is deep packet inspection (DPI). DPI inspects
application-layer traffic and examines packets traversing the firewall. This
inspection examines IP address and port information, as well as the type of
traffic and the data (if unencrypted), to enforce rules.
DPI examines the contents of a particular packet, and then either records that
information for statistical purposes or performs an action on the packet. This
information can then be forwarded to intrusion detection systems (IDS) and
intrusion prevention systems (IPS).
• Intrusion detection systems (IDS) inspect traffic on a network but do
not affect traffic in any way; IDS only logs or alerts on malicious traffic.
• Intrusion prevention systems (IPS) inspect traffic on a network and can
block malicious traffic.
1. Traffic enters the firewall.
2. Firewall policies are applied.
3. If a DPI rule applies, the packet is sent to an IDS or IPS rules engine for
action.
22 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 23

Secure Networks and Communication Chapter 2
Level 5
Level 4
Level 3
Level 2
Level 1
Level 0
Enterprise Network
Email and Internet Site Business Planning and Logistics Network
Enterprise Security Zone
Levels 4 and 5
Remote Desktop
Gateway services
Industrial Security Zones
Level 3
Cell/A rea Zones
Levels 0, 1, and 2
Patch
Management
Email
Web
Application
Server
Web S ervi ces
Operations
Application
Server
Reverse
Proxy
Sensors Drives Actuators Robots
Fac tor yTal k
Client
Fact or yTalk
Client
Batch
Control
Discrete
Control
Drive
Control
Continuous
Process
Safety
Control
Operator
Interface
Engineering
Work stat ion
Operator
Interface
Fact oryTa lk
Application
Server
Fact or yTalk
Directory
Engineering
Work stat ion
Remote Access
Server
Industrial DMZ
Industrial Demilitarized Zone (IDMZ)
The industrial demilitarized zone (IDMZ) is a critical perimeter that acts as a
buffer zone. The IDMZ provides a barrier between the Industrial and
Enterprise Zones and lets the zones securely share data and services.
32796M
IDMZ Best Practices
Practice Consideration
Services Replicate critical services in the industrial zone, consider the following:
Availability Apply redundant network routers, switches, firewalls, and links to maintain overall network availability
Scalability At small sites, use combined core and distribution switches.
Routing Use link-state routing protocols or EIGRP for Layer 3 load balancing and convergence
• Domain Services, such as LDAP or Active Directory
• Naming services, such as DNS and WINS
• IP address services, such as DHCP
• Time services, such as NTP and PTP
Larger or growing sites separate core and distribution switches to avoid over-subscription on uplinks.
Use EIGRP to simplify configuration
If standard protocols are required, use OSPF
IDMZ Guidelines
• All network traffic from either side of the IDMZ terminates in the
IDMZ; no traffic directly traverses the IDMZ.
• The IDMZ is the only path between Industrial and Enterprise Zones.
• There are no common protocols in each logical firewall.
• EtherNet/IP control traffic does not traverse the IDMZ; it remains in
the Industrial Zone.
• The IDMZ does not store primary services.
• All data is transient; the IDMZ does not store data.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 23
Page 24

Chapter 2 Secure Networks and Communication
Enterprise Network Enterprise Network Enterprise Network
Plant Network Plant Network Plant Network
Router
(Zone-Based)
Firewall IDMZ
Silver
Gold
Platinum
• Use an application data mirror to move data in and out of the IDMZ.
• Limit outbound connections from the IDMZ.
• Be able to turn off access to the Industrial Zone via the firewall
• Set up functional subzones within the IDMZ to segment access to data
and services (IT, OT, trusted partner)
• The IDMZ is also a demarcation line for segmenting network policies
between the Enterprise and Industrial Zones.
• Segment network services such as Quality of Service (QoS), Virtual
LANS (VLANs), and multicast traffic. These services exist in both the
Enterprise and Industrial Zones and should be segmented.
Control Access to the Industrial Zone
Set up functional subzones in the IDMZ to segment access to data and services.
The IDMZ acts as the buffer between the Enterprise and Industrial Zones.
Most attacks attempt to pivot to other machines on the same network. Use the
firewall, intrusion detection, and intrusion prevention to stop the ‘pivot.’
24 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
32798M
Page 25

Secure Networks and Communication Chapter 2
HTTPS
Remote Desktop Clients
Enterprise Zone
RDP
Windows Server 2008 R2
Remote Desktop Gateway
Application Servers
Historian Server
Active Directory Server
IDMZ
Industrial Zone
Remote Desktop Gateway
The Remote Desktop Gateway is a server role in the Remote Desktop Services
function of Windows Server 2012 and later. The gateway enables authorized
remote users to connect to an internal corporate or private network.
32799M
Remote Desktop Gateway Guidelines
• Remote users connect to internal network resources by using an
encrypted connection, without virtual private network (VPN)
connections.
• The security configuration model lets you control access to specific
internal network resources (point-to-point connection).
• Remote users can connect to resources that are behind firewalls in
private networks and across network address translators (NATs).
• Configure authorization policies to define conditions for remote users
to connect to network resources. For example, specify:
– Who can connect to network resources (user group).
– What network resources (computer group) users can connect to.
– Whether client computers must be members of Active Directory
security groups.
– Whether device redirection is allowed.
– Whether clients need smart card authentication, password
authentication, or either.
• Configure clients to use Network Access Protection (NAP).
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 25
NAP is a health policy technology that lets administrators enforce
requirements, such as security updates, computer configurations, and
other settings.
Page 26

Chapter 2 Secure Networks and Communication
IFW
Default
Network A
Traffic
Network A
Traffic
IFW
Network A
Traffic
Network B
Traffic
Packe t
Packe t
Copy of
the Packet
Industrial Firewall Zones
Stratix 5950 Security Appliance
The Stratix® 5950 security appliance provides firewall, threat defense, and VPN
services. The appliance operates as an industrial DPI firewall with IDS and IPS
capabilities. The security appliance provides firewall, threat defense, and VPN
services. The Stratix 5950 security appliance can operate in the following
modes:
Architecture Mode Description
Inline Transparent Default mode
Use to segment a machine, skid, or unit
from the Cell/Area Zone network. This
mode supports different security
requirements between the larger control
network and the machine/skid or to restrict
ingress and egress traffic.
Inline Routed Use as a Layer 3 ingress and egress router
hop between a production line and a
machine/skid. Monitor or control traffic
firewall or DPI security policies.
Passive Monitor To avoid the possibility of the firewall affecting traffic,
configure a traffic-forwarding interface and connect that
interface to a SPAN por t on a switch.
Stratix 5950 Guidelines
• Use CIP™ (Common Industrial Protocol) Access Control Policy rules to
block specific CIP traffic
• Block CIP actions like CIP Reads, CIP Writes, CIP Administration
Firmware Update, and CIP Administration Download instead of permit
actions.
• CIP DPI rules include host addresses but are not granular enough to a
block specific users or tags.
For more information, see the Stratix 5950 Security Appliance User Manual,
publication 1783-UM010
.
IFW
26 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 27

Secure Networks and Communication Chapter 2
SMC-Flex
EscSel
Lang
Module
Status
Network
Activity
Network
Status
1734-AENT
Point Bus
Status
System
Power
Field
Power
PanelView Plus 1250PanelView Plus 1250
32800M
Com
IN2
IN1
Ref
Com
IN2
IN1
Ref
Com
IN2
IN1
Ref
IFW
Enterprise
Site Operations
Level 3
Industrial Demilitarized Zone
(IDMZ)
Controller - Level 1
Enterprise Zone
Levels 4 and 5
Area Supervisory Control
Level 2
Process - Level 0
Control Device Communication Ports
Customers using firewalls may want to configure communication ports on
devices so that routers forward only Transmission Control Protocol (UDP and
TCP) ports.
For more information, see Knowledgebase Technote TCP/UDP Ports Used by
rockwell Automation Products.
Switch and Routing
Stratix Managed Switches
Platforms
Configure Stratix managed switches to restrict access and segment your
network architecture.
Restriction Guidelines
Physical Restrict access to the control panel or zone enclosure to authorized personnel only.
Use Panduit block-outs for open access ports and lock-ins for copper and fiber media.
Electronic Configure layer 2 media access control address (MAC) security on access ports.
Configure layer 3 access control lists (ACLs).
Define virtual local area networks (VLANs) to segment the cell/area zone into smaller domains of trust.
Disable access ports from the controller and operator interface.
Configure traffic threshold settings to monitor denial-of-service (DOS) attacks.
Enable a cryptographic version of the switch operating system (SSH, HTTPS, SNMPv3).
Manage access to maintenance ports via authentication to the local HMI.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 27
Page 28

Chapter 2 Secure Networks and Communication
For more information, see the following publications.
Resource Description
Stratix Managed Switches User Manual, publication 1783-UM007 Covers :
Stratix 6000 Managed Switches User Manual, publication 1783-UM001 Covers Stratix 6000 switches.
Stratix 2500 Lightly Managed Switches User Manual, publication 1783-UM009 Covers Stratix 2500 switches.
• Stratix 5400 switches
• Stratix 5410 switches
• Stratix 5700 switches
• ArmorStratix™ 5700 switches
• Stratix 8000 and 8300 switches
Secure Communications
Secure communications between devices to support data integrity, data
confidentiality, and device authenticity.
CIP Security
CIP Security™ is a standard, communication method that helps to provide a
secure data transport across an EtherNet/IP network. The secure data
transport is used between certain connected devices to help protect the devices
from threats posed by unauthorized users with malicious intent.
Rockwell Automation uses the following products to implement CIP Security:
• FactoryTalk® Policy Manager
•FactoryTalk Linx
• Studio 5000® Design Environment
• CIP Security-enabled Allen-Bradley products
For more information on CIP Security, see the CIP Security Application
Te ch ni que , p u b l ica ti o n SECURE-AT001
This additional layer of security reinforces the depth-in-defense approach. The
CIP Security technology does not replace firewalls or other network
infrastructures.
.
28 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 29

Secure Networks and Communication Chapter 2
Wireless Connectivity
Option Description
WPA2-PSK (pre-shared key) authentication • One password for all clients, no user-based authentication
WPA2 Enterprise (802.1x) authentication • WPA2-Enterprise with EAP-TLS is the most secure method
Category Guidelines
Wireless node limitations • The number of wireless clients affects the performance
Latency and jitter • Make sure a channel load is below the limit and the proper wireless QoS policy
Packet loss and reliability • If a wireless frame is not received, it is retransmitted until the retry limit is
Unicast versus multicast • Multicast and broadcast traffic is much less reliable than unicast traffic
In a wireless architecture, always use Wi-Fi Protected Access II (WPA2)
security with Advanced Encryption Standard (AES) encryption.
• PSK is part of device configuration
• Does not provide fast roaming times
• Does not satisfy corporate security policy
• Uses individual user credentials and (optional) security certificates
Requires additional infrastructure and support
• Active Directory
•RADIUS server
• Certificate infrastructure
Wireless Guidelines
• Do not exceed 20 wireless nodes per access point
• Do not exceed 19 wired clients per workgroup bridge
• Keep the total number of Ethernet devices on a VLAN (wired or wireless) below
200 to restrict the amount of broadcast traffic
is applied
• A small percentage of packets is delayed significantly so the application should
handle delayed packets
• Low RPIs (faster than 5 ms) are not useful for wireless applic ations
• Overloading a channel leads to excessive latency and timeouts
• A larger number of wireless nodes increases latency
reached
• An application must tolerate occasional packet loss
• An excessive packet rate causes high packet loss and application timeouts
• A large number of wireless nodes increases the chance of timeouts
• Changes in the RF environment, interference, or unauthorized channel
transmissions can decrease reliability or disrupt wireless communication
• Multicast wireless frames are not acknowledged and not repeated if lost
• Use only unicast EtherNet/IP connections with I/O or produced/consumed tags
• Do not use a ControlLogix® redundancy system with wireless communication
• Configure IGMP snooping and querier in the network infrastructure
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 29
Page 30

Chapter 2 Secure Networks and Communication
Additional Resources
The following publications provide details related to secure network
connections.
Resource Description
Design and Implementation
Deploying Industrial Firewalls within a Converged Plantwide Ethernet Architecture
Design and Implementation Guide, publication ENET-TD002
Site-to-Site VPN to a Converged Plantwide Ethernet Architecture Design an
Implementation Guide, publication ENET-TD012
Deploying Identity Services within a Converged Plantwide Ethernet Architecture
Design and Implementation Guide, publication ENET-TD008
Securely Traversing IACS Data across the Industrial Demilitarized Zone Design and
Implementation Guide, publication ENET-TD009
Deploying 802.11 Wireless LAN Technology within a Converged Plantwide
Ethernet Architecture, publication ENET-TD006
Application
Industrial Firewalls within a Converged Plantwide Ethernet Architecture White
Paper, publication ENET-WP011
Deploying Identity Services within a Converged Plantwide Ethernet Architecture
White Paper, publication ENET-WP037
Securely Traversing IACS Data Across the Industrial Demilitarized Zone White Paper,
publication ENET-WP038
Design Considerations for Securing Industrial Automation and Networks White
Pape r, ENET-WP031
Use cases for designing, deploying, and managing industrial firewalls throughout an IACS
network infrastructure.
Use cases for connecting remote IACS assets to a plant-wi de network architecture. This guide
highlights the key application requirements, technology, and suppor ting design
considerations.
The requirements and design considerations to deploy the Cisco Identity Services Engine
(Cisco ISE) within an IACS architecture.
The requirements and design considerations to deploy an industrial demilitarized zone
(IDMZ) within an IACS architecture.
Wireless LAN network capabilities, with emphasis on equipment connectivity.
Guidelines for designing, deploying, and managing industrial firewalls throughout an IACS.
Guidelines for designing, deploying, and managing identity services throughout an IACS.
Guidelines for designing, deploying, and managing industrialized demilitarized zones
throughout an IACS.
Guidelines for designing, deploying, and managing secure networks throughout an IACS.
30 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 31

Chapter 4
Harden the Control System
For guidelines on system hardening, see Knowledgebase Technote Rockwell
Automation Customer Hardening Guidelines.
Patch Management
Keep security updates (patches) for both operating system and IACS software
up-to-date. Patches can be critical to mitigate risk.
Verify any update to Rockwell Automation products or third-party products
before implementation. Verify that configuration settings are still correct.
Microsoft Patches
Microsoft® releases a range of security updates for operating systems and other
software products. Rockwell Automation qualifies certain Microsoft updates
that impact Rockwell Automation software products.
It is recommended that you implement a controlled system suitable for your
application and environment. Follow the guidance for Microsoft Patch
Qualifications at:
http://www.rakb-patchtests.com/data/MS_Patch_Qualification/start.htm
Before implementing any Fully Qualified Microsoft updates, verify them on a
non-production system, or when the facility is non-active, to ensure that there
are no unexpected results or side effects.
Microsoft regularly releases security updates. If your system is not connected to
the Internet, you will not automatically receive these updates.
Rockwell Automaton has a MS Patch Qualification team (PQUAL) to qualify
Microsoft security updates against the most popular set of products available
from Rockwell Automation. Results are posted on the Patch Qualification
Portal. For more information, see the Knowledgebase Technote Microsoft Patch
Qualifications.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 31
Page 32

Chapter 3 Harden the Control System
Product Change Management
Keep your Rockwell Automation systems current to help you achieve improved
security in your systems. Rockwell Automation uses product and version status
policies to help you plan how to keep your system current.
Rockwell Automation assigns the status of a product based on the product
catalog number.
Status Definition
Active Most current offering within a product category.
Active Mature Product is fully supported, but a newer product or family exists. Gain value by migrating.
End of Life Discontinued date announced - actively execute migrations and last time buys. Product generally orderable until the
Discontinued New product no longer manufactured or procured. Repair/exchange services may be available.
discontinued date.
To check the lifecycle status of a product, see the Product Lifecycle Status
website.
Rockwell Automation further classifies product changes to catalog numbers
(versions and revisions) to help customers manage their system.
Change Type Description
Series Change A series change indicates that there was a backward compatible hardware modification or non-field upgradeable
Direct Replacement A direct replacement is any new product that emulates an earlier product. Form, fit, and function are backward
Functional Replacement A functional replacement is any new product with minor form, fit, and function differences. It is not a direct
Engineered Replacement An engineered replacement is any new product with major form, fit, and function differences.
firmware modification to a product.
A series for product with firmware increments the major firmware revision number.
compatible.
No user application changes are needed.
replacement and it does not emulate the earlier product.
Minor application changes are required.
Major application changes are required.
Hardware Series
An alphabetical designator at the end of the product catalog number indicates
the series of the product. The series indicator increments when there is a
hardware change related to form, fit, or function.
• If a product has firmware, a series changes also requires a firmware
revision. However, a firmware revision does not necessitate a series
change.
• A series change can also require a new device profile. The new device
profile is backward compatible to older series of the product.
• An older series product cannot replace a newer series product.
32 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 33

Harden the Control System Chapter 3
Software and Firmware Versions
To further understand the state of your system and help you keep the system
current, Rockwell Automation assigns a lifecycle state to each individual
version of a product.
Version State Description
Preferred Versions to adopt to stay current.
Managed Versions to adopt when you cannot use Preferred, typically for following reasons:
Limited Versions that are available for download, but that are not the recommended versions to use. In general, these versions
Retired Versions that are no longer available for download because of security or safety concerns, or lack of suppor t viability.
• Major release versions of Active and Active Mature products remain in the Preferred state for 3 years following release
• The latest version of an Active or Active Mature product is always preferred
When a new minor or sub-minor version is released, the new minor or sub-minor release inherits the major version
lifecycle state and the previous minor or sub-minor version transitions to be a Limited or Retired version.
• Maintain compatibility between non- discontinued hardware and software
• Customer IT/OT lifecycle planning requires extended security coverage through Rockwell Automation patch updates.
Major release versions of select Active and Active Mature products remain in the Managed state for 2 years following the
Preferred state period.
remain available to support customers who have chosen not to stay current.
For more information see the Knowledgebase Technote What is the Rockwell
Automation Software and Firmware version lifecycle policy?.
To check the lifecycle state of a product version, see the product’s entry in the
Product Compatibility and Download Center
website.
Rockwell Automation designs, develops, maintains, and supports Preferred
and Managed versions in accordance with the ISA/IEC 62443-4-1 certified
secure, product development lifecycle.
For Preferred and Managed versions, Rockwell Automation:
• Notifies you of security-related issues in our products, and maintains a
way for you to report back if you encounter security-related issues with
our products.
• Notifies you if security patches for other products used in conjunction
with our products (such as operating systems or anti virus programs)
interfere with the correct operation of our products.
• Makes sure that qualified engineers and cybersecurity experts assess
security-related issues for risk to our products and customers.
• Issues security updates accordingly and updates documentation with the
latest information for how to secure our products.
• Makes software and firmware updates available through our support
website and other support channels.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 33
Page 34

Chapter 3 Harden the Control System
Managed Ethernet Switch
Fac tor yTalk
Directory Server
Engineering
Work stat ion
Managed Ethernet Switch
Domain
Controller
Workstation Hardening
Many IACS solutions use computers and servers to run applications. Consider
these workstations and their operating systems in the overall security plan.
• Use Microsoft Active Directory for authentication and authorization.
• Secure Group security policies.
• Join all workstations to the domain.
• Dedicate workstations to operator and engineering functions, and
remove all other unnecessary applications, services, and ports.
• Install endpoint protection, such as anti virus and anti-malware
software, and keep the definition files up-to-date.
• Minimize users with access to administrative rights.
• Secure USB, CD, and DVD drives so they are available only for
authorized purposes.
• Regularly restart workstations to prevent against memory-only
infections.
• Implement a validated backup and restore process for important data
and systems.
FactoryTalk Directory Application
The FactoryTalk® Directory application is a common service that is used by
FactoryTalk View Site Edition and other Rockwell Automation software
products. The FactoryTalk Directory server hosts a common address lookup of
shared resources among FactoryTalk-enabled products.
REDUNDANCY MODULE
OK
COMM
PRI
REDUNDANCY MODULE
OK
COMM
PRI
REDUNDANCY MODULE
OK
COMM
PRI
D
D
D
D
D
D
D
00 10 00 10
01 11 01 11
C
1
02 12 02 12
O
0
03 13 03 13
U
04 14 04 14
TO
05 15 05 15
T
3
06 16 06 16
P
0
07 17 07 17
U
BATT
V
PROG
FUSE
T
PROC
R
E
M
2
FORCE
RUN
4
COMM
AAB
6
8
10
12
1
14
2
16
1
18
B
2
20
CH 2
22
CH 0
AAB
24
2A
26
28
2B
30
1
32
1A
2
34
1
36
B
1B
2
38
CH 1
40
SEE PROD LITERATURE
FOR BATT REPLACEMENT
INFORMATION
BATTERY INSTALLED
DMY
PLC-5/80
PROGRAMMABLE
CONTROLLER
D
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
C
C
C
C
C
C
C
1
1
1
1
1
1
1
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
O
O
O
O
O
O
O
0
0
0
0
0
0
0
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
U
U
U
U
U
U
U
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
TO
TO
TO
TO
TO
TO
TO
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
T
T
T
T
T
T
T
3
3
3
3
3
3
3
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
P
P
P
P
P
P
P
0
0
0
0
0
0
0
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
U
U
U
U
U
U
U
BATT
V
V
V
V
V
V
V
PROG
FUSE
FUSE
FUSE
FUSE
FUSE
FUSE
FUSE
T
T
T
T
T
T
T
PROC
R
E
1
1
1
1
1
1
1
1
M
2
2
2
2
2
2
2
FORCE
3
3
3
3
3
3
3
3
RUN
4
4
4
4
4
4
4
COMM
5
5
5
5
5
5
5
5
AAB
6
6
6
6
6
6
6
7
7
7
7
7
7
7
7
8
8
8
8
8
8
8
9
9
9
9
9
9
9
9
10
10
10
10
10
10
10
11
11
11
11
11
11
11
11
12
12
12
12
12
12
12
1
13
13
13
13
13
13
13
13
14
14
14
14
14
14
14
15
15
15
15
15
15
15
15
2
16
16
16
16
16
16
16
1
17
17
17
17
17
17
17
17
18
18
18
18
18
18
18
B
19
19
19
19
19
19
19
19
2
20
20
20
20
20
20
20
CH 2
21
21
21
21
21
21
21
21
22
22
22
22
22
22
22
CH 0
23
23
23
23
23
23
23
23
AAB
24
24
24
24
24
24
24
2A
25
25
25
25
25
25
25
25
26
26
26
26
26
26
26
27
27
27
27
27
27
27
27
28
28
28
28
28
28
28
2B
29
29
29
29
29
29
29
29
30
30
30
30
30
30
30
31
31
31
31
31
31
31
31
1
32
32
32
32
32
32
32
1A
33
33
33
33
33
33
33
33
2
34
34
34
34
34
34
34
35
35
35
35
35
35
35
35
1
36
36
36
36
36
36
36
B
1B
37
37
37
37
37
37
37
37
2
38
38
38
38
38
38
38
39
39
39
39
39
39
39
39
CH 1
40
40
40
40
40
40
40
SEE PROD LITERATURE
FOR BATT REPLACEMENT
INFORMATION
BATTERY INSTALLED
DMY
PLC-5/80
PROGRAMMABLE
CONTROLLER
32802M
34 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 35

Harden the Control System Chapter 3
Network FactoryTalk Directory Guidelines
• Host the role of the Network server on a dedicated computer. Do not
co-locate a FactoryTalk Directory server or any other FactoryTalk
software on a domain controller.
• The FactoryTalk Directory server can host other system components:
– FactoryTalk Activation software
– FactoryTalk Alarms and Events software
– Centralized FactoryTalk
FactoryTalk AssetCentre software
–FactoryTalk Historian software
• Use a server operating system that is optimized to service network
requests. Do not use a domain controller.
• Install the FactoryTalk Directory server on a Microsoft Windows Server
operating system (as opposed to a workstation or desktop operating
system).
• Use caching instead of redundancy.
• FactoryTalk Directory servers do not communicate with each other.
®
Diagnostics server in the absence of
Device Hardening
Physical Access
To secure physical access to the system, consider these options:
• Subscribe to the Rockwell Automation Security Advisory Index to
access information about security matters that affect Rockwell
Automation products.
• Limit physical access to authorized personnel: control room, cells/areas,
control panels, and devices.
• Provide training and communication to personnel to raise awareness of
threats.
• Implement physical barriers, such as locked cabinets.
Individual devices have their own capabilities that can be enabled or disabled.
A common best practice is to disable the capabilities that your application does
not use. See individual product documentation for guidance.
Digitally Signed Firmware and Software
Digitally signed firmware and software helps to make sure that users download
and use authentic Rockwell Automation content.
Only download firmware and software from the Rockwell Automation official
download portal at:
https://compatibility.rockwellautomation.com/Pages/home.aspx
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 35
Page 36

Chapter 3 Harden the Control System
Do not download firmware or software from non-Rockwell Automation sites.
To verify whether a file is a signed image, you can use the Microsoft SignTool
utility. This utility is a command-line tool that digitally signs files, verifies
signatures in files, or time stamps files. The tool is installed in the \Bin folder of
the Microsoft Windows Software Development Kit (SDK) installation path.
Additionally, when you update the firmware in a device, use the
ControlFLASH™ or ControlFLASH Plus™ utility.
For more information on how to configure and use ControlFLASH software,
see the ControlFLASH online help and ControlFLASH Firmware Upgrade
Kit User Manual, publication 1756-UM105
Start Guide, publication CFP-QS001
or ControlFLASH Plus Quick
.
High Integrity Add-On Instructions
Generate a signature on an Add-On Instruction to determine whether the
Add-On Instruction is ever modified. The signature is required when an
Add-On Instruction is used in SIL 3 safety-related functions, and can be
required for regulated industries. Use the signature when your application calls
for a higher level of integrity.
Once generated, the instruction signature seals the Add-On Instruction,
including rung comments, tag descriptions, and any instruction
documentation.
When an instruction is sealed, you can perform only these actions without
affecting the signature:
• Copy the instruction signature
• Create or copy a signature history entry
• Create instances of the Add-On Instruction
• Download the instruction
• Remove the instruction signature
• Print reports
Edits to a sealed Add-On Instruction invalidate the signature. These changes
include:
• Add, delete, or move parameters, local tags, or members in referenced
User-define d Data Types.
• Change the name, data type, or display style of parameters, local tags, or
members in referenced User-defined Data Types.
For more information how to secure Add-On Instructions, see Logix 5000
Controllers Add-On Instructions Programming Manual, publication
1756-PM010
.
36 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 37

Harden the Control System Chapter 3
Additional Resources
The following publications provide details that are related to hardening the
IACS.
Resource Description
Add-On Instructions Programming Manual, publication 1756-PM001 Generate a sign ature to identify Add-On Instructions.
Computer System Security Updates White Paper, publication SECUR-WP002
Knowledgebase Technote Rockwell Automation Customer Hardening Guidelines Best practices to harden computers and servers.
Knowledgebase Technote Industrial Security Advisory Index Current security matters that affect Rockwell Automation products.
Best practices for a patch management process.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 37
Page 38

Chapter 3 Harden the Control System
Notes:
38 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 39

Chapter 5
Manage User Access
Comprehensive security depends on identification and ‘AAA’:
• Authentication (you are who you say you are)
• Authorization (you can do only what you have been authorized to do)
• Accounting (I keep track of what you do)
Give users only the privileges that they need (this is known as least privilege
access). Passwords must meet current industry-standards and best practices for
password strength. Grant a limited set of privileges to reduce the possibility of
foreign software accessing privileges to perform a malicious act – a common
technique that is used by malware.
Avoid local passwords (user name/password combinations that are stored
locally on a device) to reduce the overhead required to manage the system.
Instead you must manage users and passwords in a central system (FactoryTalk®
Security or Microsoft® Active Directory applications). In the event an
employee leaves or you make changes to user authorities, you can manage access
from a central location rather than on each separate device.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 39
Page 40

Chapter 4 Manage User Access
32805M
Common software license
management for all
FactoryTalk products
Common address lookup of
resources that are shared
among FactoryTalk-enabled
products
Common security authority for
all FactoryTalk components in
the system
Common diagnostic
messaging subsystem across
all FactoryTalk products
Comprehensive record of
changes made to the
manufacturing system
Enterprise-wide access to
real-time, manufacturing data
Enterprise-wide notification to
real-time alarms and events
that require action
Activation Directory DiagnosticsSecurity
Audit Live Data Alarms and Events
FactoryTalk Services Platform
The FactoryTalk Services Platform software combines software components
and services that are used by multiple products. These shared software services
form a services-oriented architecture (SOA) that enable applications to share
definitions, administration settings, and data.
FactoryTalk Services Guidelines
• FactoryTalk Services Platform CPR9 versions are compatible between
all Service Releases (SRs). For example: CPR9 SR6 hosts can co-exist
with CPR9 SR5 hosts.
• Where possible, maintain the same FactoryTalk Services Platform
version and patch level across all hosts.
• Upgrade the FactoryTalk Directory server to the highest FactoryTalk
Services Platform version currently installed.
• Do not co-locate a FactoryTalk Services Platform instance on a domain
controller.
40 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 41

Manage User Access Chapter 4
Control Data Access
Centralize security to better control data access.
FactoryTalk Administration Console Software
The FactoryTalk Administration Console software provides the interface to
configure centralized application security.
Security Component Description
Product and system policies System-wide rules that govern how security is implemented
Computer accounts Which computers can access your system
Networks and devices Secure access to control hardware
User accounts Who can access your system
For more information on how to create and manage permission sets, see the
online help in the FactoryTalk Administration Console software or Logix 5000
Controllers Security Programming Manual, publication 1756-PM016
.
Studio 5000 Logix Designer Application
Configure access to controller logic within the controller project.
Security Component Description
Match the project to a controller Match the project file to a controller serial number to minimize
Secure tags Restrict tag write access by user, group, or permission set.
inadvertent downloads. You see a prompt if there is a mismatch between
serial numbers during a download.
The Studio 5000 Logix Designer® application has two tag attributes that
control access to tag data. The External Access attribute controls how external
applications can access tags. The Constant attribute value determines if
controller logic can change a tag.
The External Access attribute sets read/write access to tags from external
CIP™-capable devices, such as HMIs and other controllers. Grant the minimal
read/write permissions needed for a tag and set External Access to None by
default. Set the External Access attribute on the Edit Tags tab in Controller
Ta gs ed it or.
The Constant tag attribute denies write access to both internal and external
modification. An attempt to mark a tag as Constant that has External Access
set to read/write results in an error.
For more information on how to configure these tag attributes to manage data
access, see the online help in the Logix Designer application or Logix 5000
Controllers I/O and Tag Data Programming Manual, publication
1756-PM004
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 41
.
Page 42

Chapter 4 Manage User Access
FactoryTalk Security Software
FactoryTalk Security software acts as a centralized authority to manage user
authentication and authorization. FactoryTalk Security software grants or
denies user requests to perform actions on resources within the system.
Policies and Actions
Policies and actions can apply to all users and all computers or to specific users
on specific computers.
Policy or Action Description
System Policy Policies that affect all software
System policies affect the behavior of the software that is integrated with the
FactoryTalk Directory application
For example, password length, complexity, and expiration
Product Policy Sets of securable features for the individual products in your FactoryTalk system
Product policies affect specific products.
For example, in the Logix Designer application, set a policy on who can create projects.
This policy does not affect other software products
Securable Action Allow or deny functionality to resources
• Apply to all products that use that action
• Apply to a resource or resources within a specific context, such a FactoryTalk
Directory, application, or area)
• Grant or deny permission to perform action by users and computers
• Can inherit security settings from a parent context
For example, Tag > Write Value controls whether a user or group can write to tags that
are on a data server. This action applies to all software products that attempt to write
to the tag on that data server.
For more information on how to configure and manage access controls for
users and groups, see the online help in the FactoryTalk Security software or
Logix 5000 Controllers Security Programming Manual, publication
1756-PM016
.
FactoryTalk Security Guidelines
• Secure a project file with a permission set to use the same policies for
many controllers
• Apply permission sets to routines, Add-On Instructions, and tags to
have different policies for different components
42 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 43

Manage User Access Chapter 4
Work stati on 1
Work stati on 2
FactoryTalk Application
Security
Admini stration
FactoryTalk Application
Security Authority
Central Director y
Fac tor yTalk
Services
Centralized Security Authority
Every workstation shares a common authority. Each client workstation has a
copy of the common authority.
Logix5585E
NET
LINK
REM
RUN PROG
32804M
Security Authority Identifier (SAID)
The security authority identifier (SAID) is a unique identifier for each
FactoryTalk Directory instance. Use the SAID with FactoryTalk Security
services to require that all users authenticate from a specific FactoryTalk
Directory instance before they access the controller. The SAID is stored in the
controller project (project binding) to secure the offline file.
This binding reduces the attack surface for security server spoofing because the
client software and the security software determine the identity of the security
authority responsible for controlling access.
For more information on how to configure and manage access controls for
users and groups, see the online help in the FactoryTalk Directory software or
Logix 5000 Controllers Security Programming Manual, publication
1756-PM016
.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 43
Page 44

Chapter 4 Manage User Access
SAID Guidelines
• Both the ACD file and downloaded project are secured
– Can only be opened by authorized users
– Authorization can only be provided by a specific FactoryTalk
Directory instance
• Maintain a backup of the SAID
– If a FactoryTalk Directory instance is lost, you must be able to restore
the SAID or you lose access to secured projects
– A backup can be encrypted with a passphrase or password
– A backup lets you duplicate and distribute multiple FactoryTalk
Directory instances with the same SAID
• Requires a Network FactoryTalk Directory implementation
FactoryTalk View Site Edition
HMI applications support additional configuration options that secure user
actions based on roles, such as maintenance or operator. The HMI displays can
show different resources based on these roles.
FactoryTalk View SE applications use FactoryTalk Security services to
authenticate and authorize application users. In a FactoryTalk View Studio
project, create user and group accounts. Then determine which accounts have
access to which resources, such as the local directory or the application.
FactoryTalk Security services use FactoryTalk View SE settings to provide two
services:
• User authentication verifies a user identity, and whether a request for
service that is actually originated with that user.
• User authorization verifies a user request to access a software resource,
based on the access rights and privileges defined for that user.
Perform the following tasks to secure access to system resources:
• Remove ALL USERS from the FactoryTalk Local or Network
Directory list.
• Create FactoryTalk accounts for the users, groups, and computers you
want to secure.
• Assign security permissions to FactoryTalk user and group accounts.
• Configure system-wide security and product policies.
44 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 45

Manage User Access Chapter 4
Web portal manages licenses
Source licenses on
USB/SD card
Execution licenses
on SD card
Developers
End user retains access to
unprotected code
Application s ource code
manager
Maintenance engineer
Protect Controller Logic
The following solutions can be used individually or together to protect
intellectual property in controller applications.
Scenario Solution Requirements
I want flexible, manageable policies for who can access my controller content
• Many users with different permissions
FactoryTalk Security software • Central server, similar to Microsoft Windows
domain functionality
• Restrict users not part of FactoryTalk Security.
I want the most secure protection possible for my intellectual property. Concern over
external and internal theft of IP.
License-based source and execution protection
•Activated secure device
• Subscription to License Portal
• Customers with highly sensitive IP
• Heavily regulated industries where theft or modification of controller content is a
concern
For more information on license-based protection, see Logix 5000 Controllers
Security Programming Manual, publication 1756-PM016
License-based Source and Execution Protection
You can implement license-based protection on a routine or Add-On
Instruction .
Logix5585E
NET
LINK
REM
RUN PROG
.
Additional Resources
Resource Description
FactoryTalk Security System Configuration Guide, publication FTSEC-QS001
FactoryTalk View Site Edition User Manual, publication VIEWSE-UM006
Logix 5000 Controllers Security Programming Manual, publication 1756-PM016
SensaGuard
™
PanelView Plus 1000PanelView Plus 1000
CAUTION
Hot surface
Do not touch
32806M
The following publications provide details that are related to manage user
access.
Guidelines on how to integrate, configure, and optimize FactoryTalk Security settings.
How to develop and implement HMI applications that involve multiple users and servers,
which are distributed over a network.
How to configure security options for Logix Designer projects.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 45
Page 46

Chapter 4 Manage User Access
Notes:
46 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 47

Chapter 6
Monitor and Recover
Monitor the system for suspicious activity.
• Examine logs from workstations, firewalls, switches, and devices for
evidence of foreign activity.
• Inspect network traffic and controller memory use for anomalies.
Management, audit, measurement, and detection technologies, such as the
following, monitor the IACS:
• Log audit utilities
• Virus and malicious code detection systems
• Intrusion detection systems (IDS)
•Vulnerability scanners
• Forensics and analysis tools (FAT)
• Host configuration management tools (HCM)
• Automated software management tools (ASM)
•Syslog aggregate tools
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 47
Page 48

Chapter 5 Monitor and Recover
Managed Ethernet Switch
Fac tor yTalk
Directory Server
Redundant
HMI/Data Server
Smart Devices
and Tablets
Engineering
Workstation
Managed Ethernet Switch
Fac tor yTalk
Historian Server
Domain
Control ler
Fac tor yTalk
AssetCentre Server
Engineering
Work stat ion
Fac tor yTalk
Clients
Audit and Change Management with FactoryTalk AssetCentre Software
Feature Description
Audit The audit feature gathers information about user interactions with FactoryTalk-enabled applications. Audits are
Security FactoryTalk AssetCentre software internally leverages the security that is provided by the FactoryTalk Services
Tamper Detection Factor yTalk AssetCentre software continuously monitors controllers for changes. The software detects changes, logs
The FactoryTalk® AssetCentre server centrally tracks and manages
configuration changes and restricts who can make changes. This server
functionality assists with diagnostics and troubleshooting and reduces
maintenance time for production assets.
captured while connected or even disconnected from the network.
The audit trail includes Logged Time, Occurred Time, Source, Location, Resource, Username, and Message.
platform. This security model minimizes efforts to administer users and passwords on workstations. Security rights
are even enforced while computers hosting FactoryTalk applications are disconnected from the network.
activities, and creates a report. For example, the software logs and reports if a contractor walks up to a panel,
connects a laptop to a controller, goes online, and modifies logic.
REDUNDANCY MODULE
OK
COMM
PRI
REDUNDANCY MODULE
OK
COMM
PRI
REDUNDANCY MODULE
OK
COMM
PRI
REDUNDANCY MODULE
OK
COMM
PRI
D
D
D
D
D
D
D
00 10 00 10
01 11 01 11
C
1
02 12 02 12
O
0
03 13 03 13
U
04 14 04 14
TO
05 15 05 15
T
3
06 16 06 16
P
0
07 17 07 17
U
BATT
V
PROG
FUSE
T
PROC
R
E
1
M
2
FORCE
3
RUN
4
COMM
5
AAB
6
7
8
9
10
11
12
1
13
14
15
2
16
1
17
18
B
19
2
20
CH 2
21
22
CH 0
23
AAB
24
2A
25
26
27
28
2B
29
30
31
1
32
1A
33
2
34
35
1
36
B
1B
37
2
38
39
CH 1
40
SEE PROD LITERATURE
FOR BATT REPLACEMENT
INFORMATION
BATTERY INSTALLED
DMY
PLC-5/80
PROGRAMMABLE
CONTROLLER
D
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
00 10 00 10
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
01 11 01 11
C
C
C
C
C
C
C
1
1
1
1
1
1
1
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
02 12 02 12
O
O
O
O
O
O
O
0
0
0
0
0
0
0
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
03 13 03 13
U
U
U
U
U
U
U
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
04 14 04 14
TO
TO
TO
TO
TO
TO
TO
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
05 15 05 15
T
T
T
T
T
T
T
3
3
3
3
3
3
3
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
06 16 06 16
P
P
P
P
P
P
P
0
0
0
0
0
0
0
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
07 17 07 17
U
U
U
U
U
U
U
BATT
V
V
V
V
V
V
V
PROG
FUSE
FUSE
FUSE
FUSE
FUSE
FUSE
FUSE
T
T
T
T
T
T
T
PROC
R
E
1
1
1
1
1
1
1
M
2
2
2
2
2
2
2
FORCE
3
3
3
3
3
3
3
RUN
4
4
4
4
4
4
4
COMM
5
5
5
5
5
5
5
AAB
6
6
6
6
6
6
6
7
7
7
7
7
7
7
8
8
8
8
8
8
8
9
9
9
9
9
9
10
12
14
16
18
20
22
24
26
28
30
32
34
36
38
40
9
10
10
10
10
10
10
11
11
11
11
11
11
11
12
12
12
12
12
12
1
13
13
13
13
13
13
13
14
14
14
14
14
14
15
15
15
15
15
15
15
2
16
16
16
16
16
16
1
17
17
17
17
17
17
17
18
18
18
18
18
18
B
19
19
19
19
19
19
19
2
20
20
20
20
20
20
CH 2
21
21
21
21
21
21
21
22
22
22
22
22
22
CH 0
23
23
23
23
23
23
23
AAB
24
24
24
24
24
24
2A
25
25
25
25
25
25
25
26
26
26
26
26
26
27
27
27
27
27
27
27
28
28
28
28
28
28
2B
29
29
29
29
29
29
29
30
30
30
30
30
30
31
31
31
31
31
31
31
1
32
32
32
32
32
32
1A
33
33
33
33
33
33
33
2
34
34
34
34
34
34
35
35
35
35
35
35
35
1
36
36
36
36
36
36
B
1B
37
37
37
37
37
37
37
2
38
38
38
38
38
38
39
39
39
39
39
39
39
CH 1
40
40
40
40
40
40
SEE PROD LITERATURE
FOR BATT REPLACEMENT
INFORMATION
BATTERY INSTALLED
DMY
PLC-5/80
PROGRAMMABLE
CONTROLLER
Route individual product events to the FactoryTalk AssetCentre system log.
Individual products with rolling audit logs can overwrite event data before you
48 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
have a chance to react. Configure the log in FactoryTalk AssetCentre software
to make sure that the log is large enough to record all events. Also, monitor the
log to make sure the log does not overflow.
32801M
Page 49

Monitor and Recover Chapter 5
A typical FactoryTalk AssetCentre system has the following components
(roles).
Role Quantity
Network FactoryTalk Directory server 1
Microsoft® SQL server 1
FactoryTalk AssetCentre server 1
FactoryTalk AssetCentre agent (required for all
configurations)
FactoryTalk AssetCentre client
One of the following required for audit functionality:
• Studio 5000 Logix Designer
•FactoryTalk View Studio
• FactoryTalk View SE clie nt
ProCalV5 server (for calibration management) 0 or 1
ProCalV5 client (for calibration management) 0 or 1+
1+
Maximum 10 agent groups
Single agent services ~100 assets/12 hrs
1+
Maximum 50 concurrent
Maximum 50 concurrent
Backups via FactoryTalk AssetCentre Software
FactoryTalk AssetCentre Guidelines
• Link a FactoryTalk AssetCentre server with only one FactoryTalk
Network Directory server.
• Each FactoryTalk
(MSSQL) application, which can be co-located with the server
component.
• There is only one agent per host. The agent component can be
co-located with the server component.
• Do not use agent hosts as engineering workstations due to resource use.
• Audits and events are not collected automatically. You must install a
client on the host to send the diagnostic information to the server.
System-level backup is done via FactoryTalk AssetCentre software. You can:
• Centrally manage versions of programs, files, and folders.
• Automate the backup of automation assets.
• Generate detailed difference-detection reports of assets.
ControlLogix® Disaster Recovery supports the automated backup and
comparison of program files running in ControlLogix controllers. Once a
ControlLogix device is configured as an asset in the FactoryTalk AssetCentre
asset tree, it can be added to a Disaster Recovery schedule. The results of the
Disaster Recovery schedule are added to the FactoryTalk AssetCentre Event
Log, and can also be configured to be emailed.
AssetCentre system can use one Microsoft SQL
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 49
Page 50

Chapter 5 Monitor and Recover
Component Change Detection and Logging for Controllers
The Logix Designer application, revision 30 and later, supports component
change detection. This detection determines whether changes are made to a
program offline.
• The tracking group setting tracks changes on tags, I/O modules, and
routines within a program
• In the event that changes are made to components within a tracked
group, the group signature changes:
– The tracked state value can be accessed from the Security tab in
Controller Properties
– The list of items tracked is on the View Components page
50 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 51

Chapter 7
Disposal Guidelines
Devices contain various types of memory that store device and network
settings, information from embedded solutions, and user data. The types of
memory—along with the types of data in each—are described as follows.
• Volatile memory—Some devices use random access memory (RAM) to
buffer user data temporarily.
• Nonvolatile memory—Some devices use EEPROM or NAND
nonvolatile memory to store the operating system, device settings, and
network information.
• SD card memory—Some devices support the use of an SD card to store
user data.
To dispose of this data:
• If there is a battery, remove the battery and wait for residual power to
dissipate.
• Reset the device to the default, factory settings.
See the user documentation for your device for instructions.
In high-security environments, you might need additional steps to verify that
confidential data on the controller cannot be accessed once the controller is
removed from your premises. Consider one or more of the following actions
before disposing of a controller:
• Degaussing—Flushes the device with a magnetic field that erases stored
data
• Crush—Physically compresses the device to break component parts and
render them unreadable
• Mill—Physically shreds the device into small metal bits
To guarantee that all data is completely erased, physically destroy each memory
device on which data was stored.
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 51
Page 52

Chapter 6 Disposal Guidelines
Notes:
52 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 53

Appendix A
History of Changes
This appendix contains the new or updated information for each revision of
this publication. These lists include substantive updates only and are not
intended to reflect all changes. Translated versions are not always available for
each revision.
SECURE-RM001D-EN-P, March 2020
SECURE-RM001C-EN-P, December 2019
SECURE-RM001B-EN-P, April 2019
This revision updated the section on Product Change Management to add
more information about product series indicators
This revision added a section on Product Change Management.
This revision:
• Added a section on Control Device Communication Ports
• Added a section on CIP Security for secure communication
• Updated Workstation Hardening
• Added FactoryTalk Administration Console and Studio 5000 Logix
Designer features to Control Data Access.
• Renamed Monitor the Control System to Monitor and Recover
• Added a section on Backups via FactoryTalk AssetCentre Software
Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 53
Page 54

Appendix 1 History of Changes
Notes:
54 Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021
Page 55

Rockwell Automation Publication SECURE-RM001E-EN-P - March 2021 55
Page 56

Rockwell Automation Support
Use these resources to access support information.
Technical Support Center Find help with how-to videos, FAQs, chat, user forums, and product notification updates. rok.auto/support
Knowledgebase Access Knowledgebase articles. rok.auto/knowledgebase
Local Technical Support Phone Numbers Locate the telephone number for your country. rok.auto/phonesupport
Literature Library Find installation instructions, manuals, brochures, and technical data publications. rok.auto/literature
Product Compatibility and Download Center
(PCDC)
Get help determining how products interact, check features and capabilities, and find
associated firmware.
rok.auto/pcdc
Documentation Feedback
Your comments help us serve your documentation needs better. If you have any suggestions on how to improve our content, complete the
form at rok.auto/docfeedback
Rockwell Automation maintains current product environmental information on its website at rok.auto/pec.
.
Allen-Bradley, ArmorStratix, ControlFLASH, ControlFLASH Plus, ControlLogix, expanding human possibility, FactoryTalk, Logix 5000, Rockwell Automation, Rockwell Software, SensaGuard, Stratix,
and Studio 5000 are trademarks of Rockwell Automation, Inc.are trademarks of Rockwell Automation, Inc.
Cisco is a trademark of Cisco Systems, Inc.
CIP, CIP Security, and EtherNet/IP are trademarks of ODVA, Inc.
Microsoft is a trademark of Microsoft Corporation.
Trademarks not belonging to Rockwell Automation are property of their respective companies.
Rockwell Otomasyon Ticaret A.Ş. Kar Plaza İş Merkezi E Blok Kat:6 34752, İçerenkÖy, İstanbul, Tel: +90 (216) 5698400 EEE YÖnetmeliğine Uygundur
Publication SECURE-RM001E-EN-P - March 2021
Supersedes Publication SECURE-RM001D-EN-P - March 2020 Copyright © 2021 Rockwell Automation, Inc. All rights reserved. Printed in the U.S.A.
Supersedes Publication SECUR-LM003A-EN-P - S eptember 2016
 Loading...
Loading...