Panasonic Nortel VPN Router User Manual

Version 7.00
Part No. NN46110-500
311642-M Rev 01
February 2007
Document status: Standard
600 Technology Park Drive
Billerica, MA 01821-4130
Nortel VPN Router
Configuration — Basic
Features

2
Copyright © 2007 Nortel Networks. All rights reserved.
The information in this document is subject to change without notice. The statements, configurations, technical data, and
recommendations in this document are believed to be accurate and reliable, but are presented without express or implied
warranty. Users must take full responsibility for their applications of any products specified in this document. The
information in this document is proprietary to Nortel Networks Inc.
The software described in this document is furnished under a license agreement and may be used only in accordance
with the terms of that license. The software license agreement is included in this document.
TrademarksNortel
Nortel Networks, the Nortel Networks logo, and Nortel VPN Router are trademarks of Nortel Networks.
Adobe and Acrobat Reader are trademarks of Adobe Systems Incorporated.
Java is a trademark of Sun Microsystems.
Microsoft, Windows, Windows NT, and MS-DOS are trademarks of Microsoft Corporation.
NETVIEW is a trademark of International Business Machines Corp (IBM).
OPENView is a trademark of Hewlett-Packard Company.
SPECTRUM is a trademark of Cabletron Systems, Inc.
All other trademarks and registered trademarks are the property of their respective owners.
Restricted rights legend
Use, duplication, or disclosure by the United States Government is subject to restrictions as set forth in subparagraph
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of, this computer software,
the rights of the United States Government regarding its use, reproduction, and disclosure are as set forth in the
Commercial Computer Software-Restricted Rights clause at FAR 52.227-19.
Statement of conditions
In the interest of improving internal design, operational function, and/or reliability, Nortel Networks Inc. reserves the
right to make changes to the products described in this document without notice.
Nortel Networks Inc. does not assume any liability that may occur due to the use or application of the product(s) or
circuit layout(s) described herein.
Portions of the code in this software product may be Copyright © 1988, Regents of the University of California. All
rights reserved. Redistribution and use in source and binary forms of such portions are permitted, provided that the above
copyright notice and this paragraph are duplicated in all such forms and that any documentation, advertising materials,
and other materials related to such distribution and use acknowledge that such portions of the software were developed
by the University of California, Berkeley. The name of the University may not be used to endorse or promote products
derived from such portions of the software without specific prior written permission.
SUCH PORTIONS OF THE SOFTWARE ARE PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
In addition, the program and information contained herein are licensed only pursuant to a license agreement that contains
restrictions on use and disclosure (that may incorporate by reference certain limitations and notices imposed by third
parties).
NN46110-500

Nortel Networks Inc. software license agreement
This Software License Agreement (“License Agreement”) is between you, the end-user (“Customer”) and Nortel
Networks Corporation and its subsidiaries and affiliates (“Nortel Networks”). PLEASE READ THE FOLLOWING
CAREFULLY. YOU MUST ACCEPT THESE LICENSE TERMS IN ORDER TO DOWNLOAD AND/OR USE THE
SOFTWARE. USE OF THE SOFTWARE CONSTITUTES YOUR ACCEPTANCE OF THIS LICENSE
AGREEMENT. If you do not accept these terms and conditions, return the Software, unused and in the original shipping
container, within 30 days of purchase to obtain a credit for the full purchase price.
“Software” is owned or licensed by Nortel Networks, its parent or one of its subsidiaries or affiliates, and is copyrighted
and licensed, not sold. Software consists of machine-readable instructions, its components, data, audio-visual content
(such as images, text, recordings or pictures) and related licensed materials including all whole or partial copies. Nortel
Networks grants you a license to use the Software only in the country where you acquired the Software. You obtain no
rights other than those granted to you under this License Agreement. You are responsible for the selection of the
Software and for the installation of, use of, and results obtained from the Software.
1. Licensed Use of Software. Nortel Networks grants Customer a nonexclusive license to use a copy of the Software on
only one machine at any one time or to the extent of the activation or authorized usage level, whichever is applicable. To
the extent Software is furnished for use with designated hardware or Customer furnished equipment (“CFE”), Customer
is granted a nonexclusive license to use Software only on such hardware or CFE, as applicable. Software contains trade
secrets and Customer agrees to treat Software as confidential information using the same care and discretion Customer
uses with its own similar information that it does not wish to disclose, publish or disseminate. Customer will ensure that
anyone who uses the Software does so only in compliance with the terms of this Agreement. Customer shall not a) use,
copy, modify, transfer or distribute the Software except as expressly authorized; b) reverse assemble, reverse compile,
reverse engineer or otherwise translate the Software; c) create derivative works or modifications unless expressly
authorized; or d) sublicense, rent or lease the Software. Licensors of intellectual property to Nortel Networks are
beneficiaries of this provision. Upon termination or breach of the license by Customer or in the event designated
hardware or CFE is no longer in use, Customer will promptly return the Software to Nortel Networks or certify its
destruction. Nortel Networks may audit by remote polling or other reasonable means to determine Customer’s Software
activation or usage levels. If suppliers of third party software included in Software require Nortel Networks to include
additional or different terms, Customer agrees to abide by such terms provided by Nortel Networks with respect to such
third party software.
2. Warranty. Except as may be otherwise expressly agreed to in writing between Nortel Networks and Customer,
Software is provided “AS IS” without any warranties (conditions) of any kind. NORTEL NETWORKS DISCLAIMS
ALL WARRANTIES (CONDITIONS) FOR THE SOFTWARE, EITHER EXPRESS OR IMPLIED, INCLUDING,
BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE AND ANY WARRANTY OF NON-INFRINGEMENT. Nortel Networks is not obligated to
provide support of any kind for the Software. Some jurisdictions do not allow exclusion of implied warranties, and, in
such event, the above exclusions may not apply.
3. Limitation of Remedies. IN NO EVENT SHALL NORTEL NETWORKS OR ITS AGENTS OR SUPPLIERS BE
LIABLE FOR ANY OF THE FOLLOWING: a) DAMAGES BASED ON ANY THIRD PARTY CLAIM; b) LOSS OF,
OR DAMAGE TO, CUSTOMER’S RECORDS, FILES OR DATA; OR c) DIRECT, INDIRECT, SPECIAL,
INCIDENTAL, PUNITIVE, OR CONSEQUENTIAL DAMAGES (INCLUDING LOST PROFITS OR SAVINGS),
WHETHER IN CONTRACT, TORT OR OTHERWISE (INCLUDING NEGLIGENCE) ARISING OUT OF YOUR
USE OF THE SOFTWARE, EVEN IF NORTEL NETWORKS, ITS AGENTS OR SUPPLIERS HAVE BEEN
ADVISED OF THEIR POSSIBILITY. The forgoing limitations of remedies also apply to any developer and/or supplier
of the Software. Such developer and/or supplier is an intended beneficiary of this Section. Some jurisdictions do not
allow these limitations or exclusions and, in such event, they may not apply.
4. General
a. If Customer is the United States Government, the following paragraph shall apply: All Nortel Networks
Software available under this License Agreement is commercial computer software and commercial computer
software documentation and, in the event Software is licensed for or on behalf of the United States
3
Nortel VPN Router Configuration — Basic Features

4
Government, the respective rights to the software and software documentation are governed by Nortel
Networks standard commercial license in accordance with U.S. Federal Regulations at 48 C.F.R. Sections
12.212 (for non-DoD entities) and 48 C.F.R. 227.7202 (for DoD entities).
b. Customer may terminate the license at any time. Nortel Networks may terminate the license if Customer fails
to comply with the terms and conditions of this license. In either event, upon termination, Customer must
either return the Software to Nortel Networks or certify its destruction.
c. Customer is responsible for payment of any taxes, including personal property taxes, resulting from
Customer’s use of the Software. Customer agrees to comply with all applicable laws including all applicable
export and import laws and regulations.
d. Neither party may bring an action, regardless of form, more than two years after the cause of the action arose.
e. The terms and conditions of this License Agreement form the complete and exclusive agreement between
Customer and Nortel Networks.
f. This License Agreement is governed by the laws of the country in which Customer acquires the Software. If
the Software is acquired in the United States, then this License Agreement is governed by the laws of the state
of New York.
NN46110-500

Contents
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Before you begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Text conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Acronyms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Related publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Hard-copy technical manuals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
How to get Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Finding the latest updates on the Nortel Web site . . . . . . . . . . . . . . . . . . . . . . . . . 20
Getting help from the Nortel Web site . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Getting help over the phone from a Nortel Solutions Center . . . . . . . . . . . . . . . . . 21
Getting help from a specialist by using an Express Routing Code . . . . . . . . . . . . 21
Getting help through a Nortel distributor or reseller . . . . . . . . . . . . . . . . . . . . . . . . 21
New in this release. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
5
Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Network Time Protocol (NTP) support for Daylight Savings Time 2007 change
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Systemlog lifetime or disk size limit usage option . . . . . . . . . . . . . . . . . . . . . . 24
FTP server passive mode parameter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Source IPs access restriction to management . . . . . . . . . . . . . . . . . . . . . . . . 24
SSH server configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Chapter 1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Network deployment alternatives . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Virtual private networking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Licensing features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Command line interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Federal Information Processing Standard (FIPS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Nortel VPN Router Configuration — Basic Features

6 Contents
Chapter 2
Getting started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
IP addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Management virtual address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Multinetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
Changing the management IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Restricting source IPs access to management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Configuring the serial interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Using boot modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Managing through a Web browser . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Preparing for configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Welcome window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Configuring MVA with the serial menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Configuring Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Configuring ACL through the CLI: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Accessing ACL through the GUI: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Chapter 3
Setting up the Nortel VPN Router 1010, 1050, and 1100 . . . . . . . . . . . . . . 59
Default configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Branch office quick start utility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Enterprise environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Service provider environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Deployment procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Branch office quick start template . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Connecting for Internet access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Compact flash disk . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
NN46110-500
Before you begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Check that you received the following items . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Cable the VPN Router and turn the power on . . . . . . . . . . . . . . . . . . . . . . . . . 68
Make sure that your PCs can obtain IP addresses automatically . . . . . . . . . . 69
Test the VPN Router and start the quick-start tool . . . . . . . . . . . . . . . . . . . . . 69
DHCP instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
PPPoE instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Static IP instructions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71

Contents 7
Chapter 4
Configuring user tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Configuring group characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Setting up user tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Configuring inverse split tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Inverse split tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Using the 0.0.0.0/0 subnet wildcard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Configuring the subnet wildcard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Configuring tunneling modes using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Chapter 5
Configuring the system. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Configuring the system identity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Setting up LAN interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Edit LAN Interface window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Multinetting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .97
Configuring multinetting using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Adding an IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Deleting an IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Asynchronous data over TCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Configuring Network Time Protocol (NTP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Configuring system settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Using proxy ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Using the SSH server to allow secure sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Using the GUI for SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Enabling the SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Configuring the SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Using the CLI for SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Defining an SSH server (CLI) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Enabling or restarting the SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Displaying the current settings for the SSH server . . . . . . . . . . . . . . . . . . . . 116
Disabling the SSH server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Restricted product - export license requirement . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Nortel VPN Router Configuration — Basic Features

8 Contents
Chapter 6
Configuring branch office tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
PPTP nested tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
DNS for branch office tunnel endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Configuring a branch office . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Sample branch office configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Chapter 7
Configuring control tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
VPN DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 124
Round Robin DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Dynamic DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Adding a group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Adding a tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Configuring a tunnel connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Sample branch office procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Control tunnel types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Restricted mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Nailed-up control tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Creating control tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Adding a group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Adding a control tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Configuring a control tunnel connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Creating a user control tunnel from the serial interface . . . . . . . . . . . . . . . . . . . . . . . 146
Chapter 8
Configuring IPSec mobility and persistent mode. . . . . . . . . . . . . . . . . . . 147
IPSec mobility on Nortel VPN Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Roaming performance factors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Logging and status for clients and servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
IPSec mobility and NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Roaming from behind NAT to behind NAT . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Roaming from behind NAT to no NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Roaming from no NAT to behind NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
IPSec mobility in NAT environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
NN46110-500

Contents 9
Routing table changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Initial contact payload (ICP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Maximum roaming time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Persistent tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Session persistence time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Configuring IPSec mobility and persistence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Configuring IPSec mobility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Appendix A
Branch office quick start template . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Nortel VPN Router Configuration — Basic Features

10 Contents
NN46110-500

Figures
Figure 1 Typical PDN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 2 VPN service models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 3 Sample IP addressing scheme . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Figure 4 MVA on separate subnet from private physical interfaces . . . . . . . . . . . . 32
Figure 5 MVA on same subnet as private physical interface . . . . . . . . . . . . . . . . . 33
Figure 6 MVA managing from a remote PC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Figure 7 Deployment Scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Figure 8 Default configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Figure 9 Tunnel connection configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Figure 10 Inverse Split Tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Figure 11 Inverse Split Tunneling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Figure 12 Edit > IPsec page for wildcard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Figure 13 LAN-to-Nortel VPN Router connection . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Figure 14 LAN > Interfaces window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Figure 15 LAN Interfaces > Add IP Address window . . . . . . . . . . . . . . . . . . . . . . . . 99
Figure 16 Asynchronous data over TCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Figure 17 SSH Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Figure 18 Allowed Services window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Figure 19 Typical branch office environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Figure 20 Branch-to-branch with a firewall and a router . . . . . . . . . . . . . . . . . . . . . 121
Figure 21 Indirectly connected branch offices . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Figure 22 VPN DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Figure 23 Failover example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Figure 24 Load balancing example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Figure 25 Setting up a branch office configuration . . . . . . . . . . . . . . . . . . . . . . . . . 129
Figure 26 Sample branch office configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Figure 27 Branch office control tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Figure 28 Sample control tunnel environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Figure 29 Example configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
11
Nortel VPN Router Configuration — Basic Features

12 Figures
Figure 30 Roaming from behind NAT to behind NAT . . . . . . . . . . . . . . . . . . . . . . . 150
Figure 31 Roaming from behind NAT to no NAT . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Figure 32 Groups edit IPSec window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
NN46110-500

Tables
Table 1 Sample IP addressing associations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Table 2 Services supported on a multinetted interface . . . . . . . . . . . . . . . . . . . . . 39
Table 3 Web interface configuration options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Table 4 Configuration checklist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Table 5 Subnet assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Table 6 BOQS parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Table 7 Split tunneling mode options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Table 8 Adding/Deleting a secondary address . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Table 9 Configuring OSPF over a secondary address . . . . . . . . . . . . . . . . . . . . 101
Table 10 Configuring RIP over a secondary address . . . . . . . . . . . . . . . . . . . . . . 102
Table 11 Configuration considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
13
Nortel VPN Router Configuration — Basic Features

14 Tables
NN46110-500

Preface
This guide introduces the Nortel VPN Router. It also provides overview and basic
configuration information to help you initially set up your Nortel VPN Router.
Before you begin
This guide is for network managers who are responsible for setting up and
configuring the Nortel VPN Router. This guide assumes that you have experience
with windowing systems or graphical user interfaces (GUIs) and familiarity with
network management.
Text conventions
This guide uses the following text conventions:
15
angle brackets (< >) Indicate that you choose the text to enter based on the
description inside the brackets. Do not type the
brackets when entering the command.
Example: If the command syntax is
ping <ip_address>, you enter
ping 192.32.10.12
bold Courier text
Indicates command names and options and text that
you need to enter.
Example: Use the
Example: Enter
Nortel VPN Router Configuration — Basic Features
show health command.
terminal paging {off | on}.

16 Preface
braces ({}) Indicate required elements in syntax descriptions where
there is more than one option. You must choose only
one of the options. Do not type the braces when
entering the command.
Example: If the command syntax is
source {external | internal}
ldap-server source external or
either
ldap-server source internal
ldap-server
, you must enter
, but not both.
brackets ([ ]) Indicate optional elements in syntax descriptions. Do
not type the brackets when entering the command.
Example: If the command syntax is
show ntp [associations], you can enter
show ntp or show ntp associations.
either
Example: If the command syntax is default rsvp
[token-bucket
default rsvp, default rsvp token-bucket
depth, or default rsvp token-bucket rate.
{depth | rate}], you can enter
ellipsis points (. . . ) Indicate that you repeat the last element of the
command as needed.
Example: If the command syntax is
more diskn:<directory>/...<file_name>,
you enter
more and the fully qualified name of the file.
NN46110-500
italic text Indicates new terms, book titles, and variables in
command syntax descriptions. Where a variable is two
or more words, the words are connected by an
underscore.
Example: If the command syntax is
ping <ip_address>, ip_address is one variable
and you substitute one value for it.
plain Courier
text
Indicates system output, for example, prompts and
system messages.
Example:
File not found.

Preface 17
separator ( > ) Shows menu paths.
Example: Choose Status > Health Check.
Acronyms
vertical line (
This guide uses the following acronyms:
ACK acknowledgement
CA certificate authority
CHAP Challenge Handshake Authentication protocol
CRL certificate revocation list
DN distinguished name
DNS domain name system
FIPS Federal Information Processing Standards
| ) Separates choices for command keywords and
arguments. Enter only one of the choices. Do not type
the vertical line when entering the command.
Example: If the command syntax is
terminal paging {off | on}, you enter either
terminal paging off or terminal paging on,
but not both.
FTP File Transfer Protocol
IP Internet Protocol
IKE IPsec Key Exchange
ISAKMP Internet Security Association and Key Management
Protocol
ISP Internet service provider
L2TP Layer2 Tunneling Protocol
LDAP Lightweight Directory Access Protocol
LAN local area network
MAC media access control address
Nortel VPN Router Configuration — Basic Features

18 Preface
NAT network address translation
NOC network operations center
NTP Network Time Protocol
NVR Nortel VPN Router
OSPF Open Shortest Path First
OSS operations support systems
PAP Password Authentication Protocol
PDN public data networks
POP point-of-presence
PPP Point-to-Point Protocol
PPTP Point-to-Point Tunneling Protocol
RSVP Resource Reservation Protocol
RIP Routing Information Protocol
SNMP Simple Network Management Protocol
NN46110-500
UDP User Datagram Protocol
URL uniform resource locator
VPN virtual private network
VRRP Virtual Router Redundancy Protocol
WAN wide area network

Related publications
For more information about the Nortel VPN Router, refer to the following
publications:
• Release notes provide the latest information, including brief descriptions of
the new features, problems fixed in this release, and known problems and
workarounds.
• Nortel VPN Router Configuration — SSL VPN Services provides instructions
for configuring services on the Nortel SSL VPN Module 1000, including
authentication, networks, user groups, and portal links.
• Nortel VPN Router Security — Servers, Authentication, and Certificates
provides instructions for configuring authentication services and digital
certificates.
• Nortel VPN Router Security — Firewalls, Filters, NAT, and QoS provides
instructions for configuring the Nortel VPN Router Stateful Firewall and
Nortel VPN Router interface and tunnel filters.
• Nortel VPN Router Configuration — Advanced Features provides instructions
for configuring advanced LAN and WAN settings, PPP, frame relay, PPPoE,
ADSL and ATM, T1CSU/DSU, dial services and BIS, DLSw, IPX, and SSL
VPN.
• Nortel VPN Router Security — Tunneling Protocols configuration information
for the tunneling protocols IPsec, L2TP, PPTP, and L2F.
• Nortel VPN Router Configuration — Routing provides instructions for
configuring RIP, OSPF, and VRRP, as well as instructions for configuring
ECMP, routing policy services, and client address redistribution (CAR).
• Nortel VPN Router Troubleshooting provides information about system
administrator tasks such as backup and recovery, file management, and
upgrading software, and instructions for monitoring VPN Router status and
performance. Also, provides troubleshooting information and inter operability
considerations.
• Nortel VPN Router Using the Command Line Interface provides syntax,
descriptions, and examples for the commands that you can use from the
command line interface.
• Nortel VPN Router Configuration —TunnelGuard provides information about
configuring and using the TunnelGuard feature.
Preface 19
Nortel VPN Router Configuration — Basic Features

20 Preface
Hard-copy technical manuals
You can print selected technical manuals and release notes free, directly from the
Internet. Go to the www.nortel.com/support URL. Find the product for which you
need documentation. Then locate the specific category and model or version for
your hardware or software product. Use Adobe* Acrobat Reader* to open the
manuals and release notes, search for the sections you need, and print them on
most standard printers. Go to Adobe Systems at the www.adobe.com URL to
download a free copy of the Adobe Acrobat Reader.
How to get Help
This section explains how to get help for Nortel products and services.
Finding the latest updates on the Nortel Web site
The content of this documentation was current at the time the product was
released. To check for updates to the latest documentation and software for Nortel
VPN Router, click one of the following links:
Link to Takes you directly to the
Latest software Nortel page for Nortel VPN Router software.
Latest documentation Nortel page for Nortel VPN Router documentation.
Getting help from the Nortel Web site
The best way to get technical support for Nortel products is from the Nortel
Technical Support Web site:
www.nortel.com/support
This site provides quick access to software, documentation, bulletins, and tools to
address issues with Nortel products. From this site, you can:
• download software, documentation, and product bulletins
NN46110-500

Preface 21
• search the Technical Support Web site and the Nortel Knowledge Base for
answers to technical issues
• sign up for automatic notification of new software and documentation for
Nortel equipment
• open and manage technical support cases
Getting help over the phone from a Nortel Solutions Center
If you do not find the information you require on the Nortel Technical Support
Web site, and you have a Nortel support contract, you can also get help over the
phone from a Nortel Solutions Center.
In North America, call 1-800-4NORTEL (1-800-466-7835).
Outside North America, go to the following web site to obtain the phone number
for your region:
www.nortel.com/callus
Getting help from a specialist by using an Express Routing Code
To access some Nortel Technical Solutions Centers, you can use an Express
Routing Code (ERC) to quickly route your call to a specialist in your Nortel
product or service. To locate the ERC for your product or service, go to:
www.nortel.com/erc
Getting help through a Nortel distributor or reseller
If you purchased a service contract for your Nortel product from a distributor or
authorized reseller, contact the technical support staff for that distributor or
reseller.
Nortel VPN Router Configuration — Basic Features

22 Preface
NN46110-500

New in this release
The following sections details what is new in Nortel VPN Router Configuration —
Basic Features for Release 7.0.
Network Time Protocol (NTP) support for Daylight Savings Time 2007 change
Systemlog lifetime or disk size limit usage option
FTP server passive mode parameter
Source IPs access restriction to management
SSH server configurations
Features
23
See the following sections for information about feature changes:
Network Time Protocol (NTP) support for Daylight Savings
Time 2007 change
NTP supports the 2007 Daylight Savings Time change in the United States and
various Canadian provinces. In 2007, Daylight Savings Time begins at 2 a.m. on
the second Sunday in March and ends at 2 a.m. on the first Sunday in November.
For more information about NTP support for Daylight Savings Time, see
“Configuring Network Time Protocol (NTP)” on page 106.
Nortel VPN Router Configuration — Basic Features

24 New in this release
Systemlog lifetime or disk size limit usage option
VPN Router allows you to choose between setting a log file disk size limit or a log
file lifetime for the Systemlog. Previous versions of the VPN Router only allowed
the Systemlog to have a lifetime specified (default 60 days).
For more information about the Systemlog lifetime and disk size limit option, see
Step 5 in “Configuring system settings” on page 108.
FTP server passive mode parameter
There is a new check box called disk size limitfound in System > Settings in the
Router Settings section.
By enabling this parameter, you allow passive FTP connections to connect to the
unit, perform directory listings, and upload and download files. If this check box
is not enabled, you can still use passive FTP connections to connect to the unit, but
you cannot perform directory listings or upload and download files.
For more information about the FTP server passive mode parameter, see Step 7 in
“Configuring system settings” on page 108.
Source IPs access restriction to management
This release enables an administrator to have more control over management
services by restricting source IPs connections for management purposes through
Access Lists (ACL). For more information about Source IPs access restriction to
management, see “Restricting source IPs access to management” on page 44.
SSH server configurations
You can now enable an SSH server to allow secure CLI sessions, such as telnet, to
the NVR. You can enable the private and public interface filters, set the port for
the SSH server, and restart the server. You can use either the NVR GUI or CLI to
configure the SSH server. For more information about SSH server configurations,
see “Using the SSH server to allow secure sessions” on page 112.
NN46110-500

Chapter 1
Overview
This chapter introduces the Nortel VPN Router. The Nortel VPN Router is a
family of products that deliver security and IP services in a single integrated
platform. With IP routing, Virtual Private Networking (VPN), stateful firewall,
policy management and QoS services, a single Nortel VPN Router device offers
the IP services that normally require multiple purpose devices. Designed for
enterprise networks, the Nortel VPN Router leverages the cost advantages of the
Internet while providing secure communications across the public IP
infrastructure.
As a highly scalable device, the Nortel VPN Router can address the security and
IP services needs of the smallest branch site or largest headquarters environment.
A Nortel VPN Router can be installed as an IP access router or stateful packet
firewall.
25
The Nortel VPN Router incorporates Nortel’s Secure Routing Technology (SRT).
SRT is a software framework that provides a security structure through all Nortel
VPN Router operational components, including IP routing, VPN, firewall, and
policy services. This allows for management consistency and scalable
performance even when running multiple IP services in the same device. SRT also
provides dynamic routing (RIP/OSPF) over secure IPsec tunnels, uniform security
policies across VPN, routing, and firewall services and a flexible software
licensing scheme.
Network deployment alternatives
With its combination of secure, manageable, and scalable features, you can shift
information technology resources from solving the current remote user access
problems to other, more proactive administrative and management areas. And you
can eliminate modem-management pool problems from your organization and
shift them to your Nortel VPN Router provider.
Nortel VPN Router Configuration — Basic Features
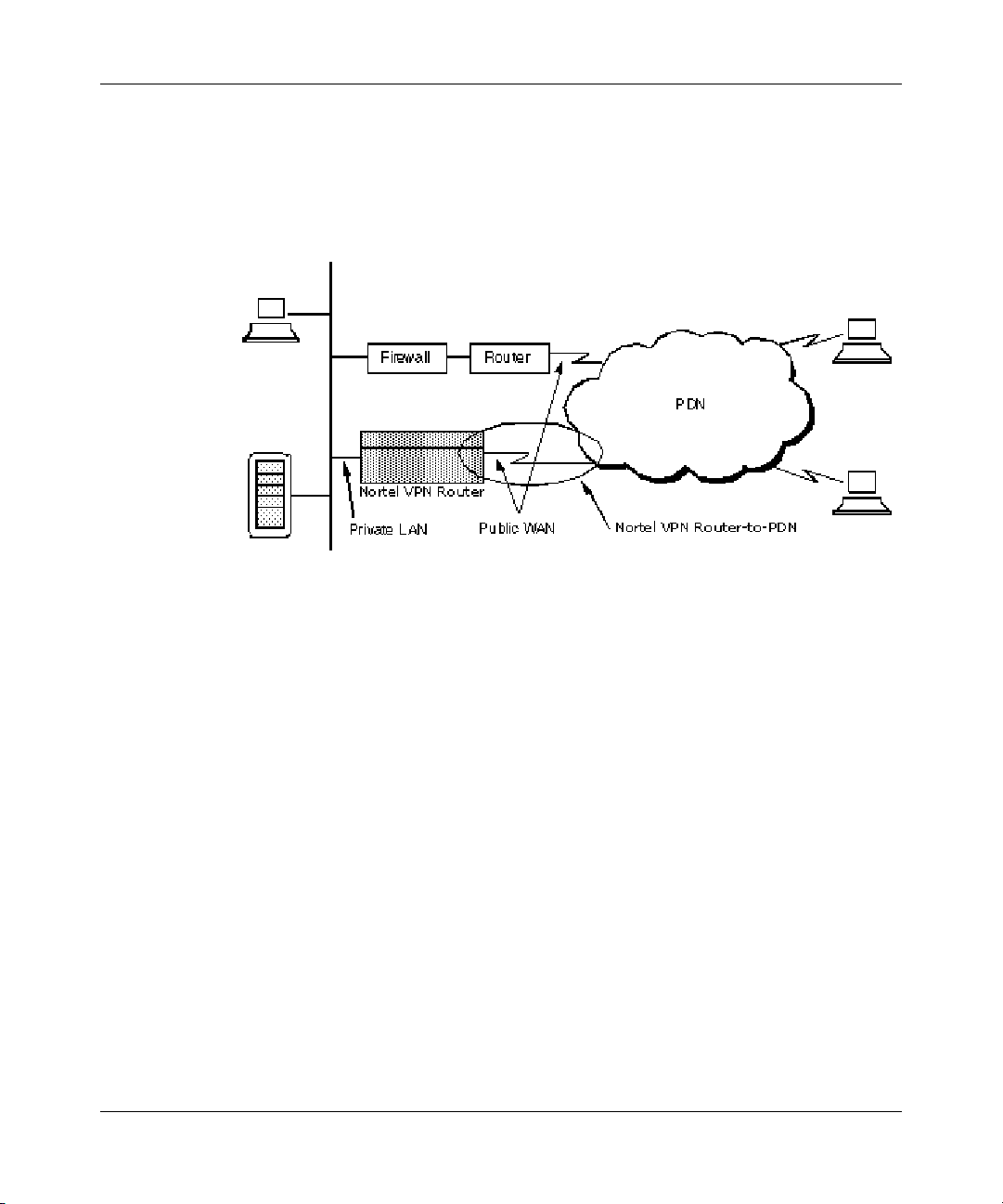
26 Chapter 1 Overview
Nortel VPN Router access allows remote users to dial in to an Internet Service
Provider (ISP) anywhere and reach corporate headquarters or branch offices. The
Nortel VPN Router provides remote users access to corporate databases, mail
servers, and file servers. Figure 1 shows a typical packet data network (PDN).
Figure 1 Ty p i c a l P D N
The Nortel VPN Router allows ISPs to take over the role of point-of-presence
(POP) providers of modem access. It improves performance while lowering
overhead, which translates to significant corporate savings.
Virtual private networking
A VPN is a private data communication channel that uses a public IP network as
the basic transport for connecting corporate data centers, remote offices, mobile
employees, telecommuters, customers, suppliers, and business partners.
Physically discontiguous networks are made to appear logically connected and
contiguous.
A remote access VPN service requires the creation and operation of a secure
tunnel between client software on a remote device, such as a PC, and host
software on a Nortel VPN Router.
Figure 2 on page 27 shows examples of VPN services.
NN46110-500
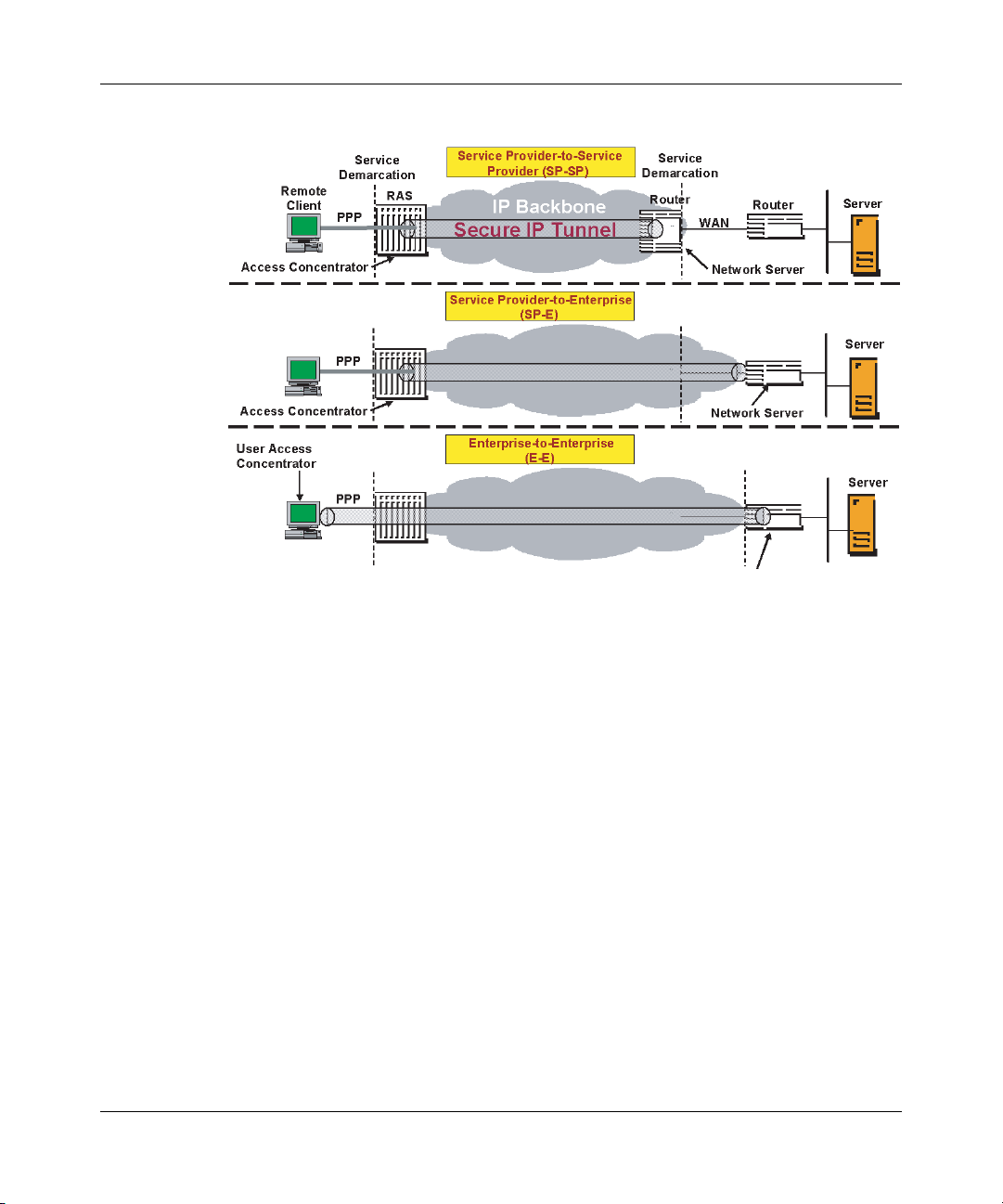
Chapter 1 Overview 27
Figure 2 VPN service models
The Nortel VPN Router uses a combination of authorization, authentication,
privacy, and access control for each user.
Licensing features
Licence keys can be obtained through Nortel’s customer support. The Nortel VPN
Router provides several license key options:
• Advanced Routing
• Nortel VPN Router Stateful Firewall
• VPN Tunnels
•Premium
•DSLw
•BGP only
The Advanced Routing License key must be installed to enable OSPF on the
Nortel VPN Router. (The Firewall License Key is required only when the
redistribution capabilities of RIP and OSPF are necessary).
Nortel VPN Router Configuration — Basic Features
28 Chapter 1 Overview
The Nortel VPN Router Stateful Firewall License key must be installed to enable
the Nortel VPN Router Stateful firewall.
Tunnel keys are specific to the Nortel VPN Router hardware model that you are
using. Nortel VPN Router switches are manufactured to allow either access to the
maximum number of tunnels (VPN bundle) or support for 5 tunnels (Base Unit).
This feature offers reduced cost for users who want fewer tunnels. The existing
VPN bundle does not add a cost increase nor a need for a tunnel license key.
Note: It is only necessary to install a key once on each Nortel VPN
Router. To enter the license key, go to the Admin > Install screen. You
must reboot the Nortel VPN Router to gain access to the new tunnel
limit.
Command line interface
The command line interface allows you to make configuration changes to the
Nortel VPN Router via Telnet. You can access the command line interface by
initiating a Telnet session to the Nortel VPN Router management IP address. For
further information, see Nortel VPN Router Using the Command Line Interface .
Federal Information Processing Standard (FIPS)
You must separately order, purchase, and implement a FIPS kit to be FIPS
compliant. This kit contains detailed documentation concerning setting up,
operating, and configuring the Nortel VPN Router to be FIPS compliant. The
FIPS kit also includes tamper-resistant labels to be put on the hardware as
instructed in the FIPS kit documentation.
NN46110-500

Chapter 2
Getting started
This chapter describes methods for configuring and managing the Nortel VPN
Router .
Note: If you are setting up a Nortel VPN Router 1010, 1050 or 1100,
see Chapter 3, “Setting up the Nortel VPN Router 1010, 1050, and
1100.” These VPN Routers have unique set up and configuration
considerations.
Full details on hardware installation, including adding local area network (LAN)
or wide area network (WAN) cards, are in the Getting Started or installation guide
that came with the Nortel VPN Router. You should complete the hardware
installation before starting this chapter.
29
IP addressing
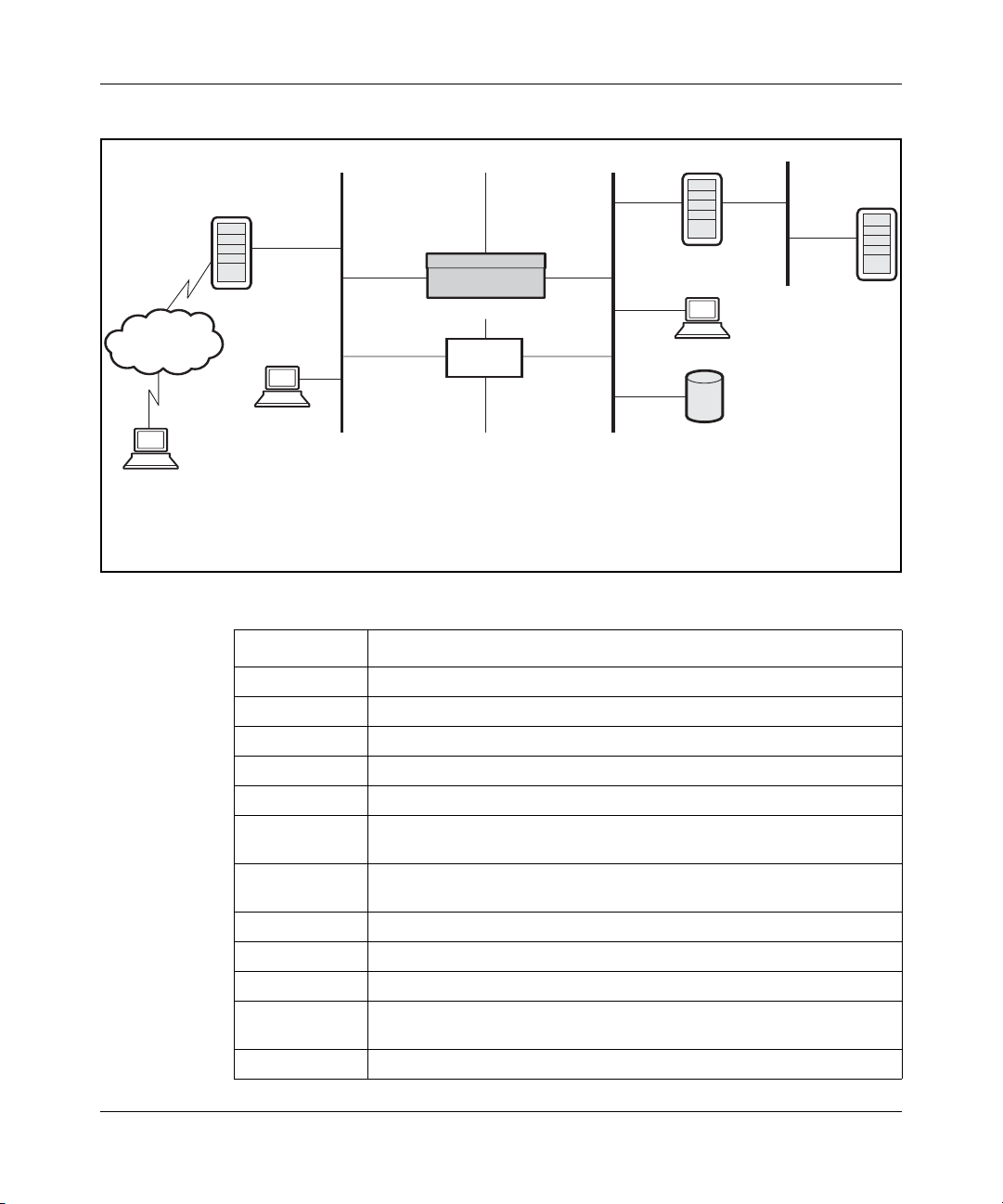
Figure 3 on page 30 shows sample IP address assignments in a network using a
Nortel VPN Router. Refer to Table 1 on page 30 to see the IP address associations.
Nortel VPN Router Configuration — Basic Features
30 Chapter 2 Getting started
Figure 3 Sample IP addressing scheme
Public Private
Existing Public Default
Public
Data Network
192.168.43.6
Remote User
172.19.2.30
And
10.2.1.23
-or-
10.8.4.6
10.2.4.56
Gateway Router
192.19.2.30
192.19.2.33
10.2.3.2
Nortel VPN Router
192.19.2.31
Web Server
192.19.2.32
Class C
Subnetworks
255.255.255.0
Existing
Firewall
Table 1 Sample IP addressing associations
IP address Description (when applicable, where configured)
192.168.43.6 Dial-up networking to ISP (Internet access, ISP assigned)
192.19.2.30 Public default Internet VPN Router
192.19.2.33 Public LAN port IP address (remote user destination address)
192.19.2.32 Firewall public network address
10.2.3.2 Nortel VPN Router management IP address: System > Identity
10.2.3.3 Nortel VPN Router private LAN interface IP address: System > LAN
Edit IP address
10.2.3.4 Private network default VPN Router: System > Routing Add/Edit
Default Route
10.2.3.6 Sample partners FTP server for inventory and price list
10.2.3.7 Firewall private network address
10.2.3.8 DHCP server IP address
10.2.1.1 to
10.2.1.254
172.19.2.30 ISP-assigned address
Private Network Addresses Assigned to Remote Tunnel Sessions:
DHCP pool: Servers > User IP Addr
10.2.3.3
10.2.3.7
Class A
Subnetworks
255.0.0.0
10.2.1.1
-To-
10.2.1.254
10.10.0.1
10.2.3.4
Existing Private Default
Gateway Router
10.2.3.6
10.2.3.8
DHCP Server
10.10.0.5
NN46110-500
 Loading...
Loading...