Page 1

Voyager Reference Guide
Part No. N450820002 Rev A
Published December 2003
Page 2

COPYRIGHT
©2003 Nokia. All rights reserved.
Rights reserved under the copyright laws of the United States.
RESTRICTED RIGHTS LEGEND
Use, duplication, or disclosure by the United States Government is subject to restrictions as set
forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at
DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of,
this computer software, the rights of the United States Government regarding its use,
reproduction, and disclosure are as set forth in the Commercial Computer Software-Restricted
Rights clause at FAR 52.227-19.
IMPORTANT NOTE TO USERS
This software and hardware is provided by Nokia Inc. as is and any express or implied
warranties, including, but not limited to, implied warranties of merchantability and fitness for a
particular purpose are disclaimed. In no event shall Nokia, or its affiliates, subsidiaries or
suppliers be liable for any direct, indirect, incidental, special, exemplary, or consequential
damages (including, but not limited to, procurement of substitute goods or services; loss of use,
data, or profits; or business interruption) however caused and on any theory of liability, whether in
contract, strict liability, or tort (including negligence or otherwise) arising in any way out of the use
of this software, even if advised of the possibility of such damage.
Nokia reserves the right to make changes without further notice to any products herein.
TRADEMARKS
Nokia is a registered trademark of Nokia Corporation. Other products mentioned in this
document are trademarks or registered trademarks of their respective holders.
030114
2 Voyager Reference Guide
Page 3

Nokia Contact Information
Corporate Headquarters
Web Site http://www.nokia.com
Telephone 1-888-477-4566 or
1-650-625-2000
Fax 1-650-691-2170
Mail
Address
Regional Contact Information
Americas Nokia Inc.
Europe,
Middle East,
and Africa
Asia-Pacific 438B Alexandra Road
Nokia Customer Support
Web Site: https://support.nokia.com/
Email: tac.support@nokia.com
Nokia Inc.
313 Fairchild Drive
Mountain View, California
94043-2215 USA
313 Fairchild Drive
Mountain View, CA 94043-2215
USA
Nokia House, Summit Avenue
Southwood, Farnborough
Hampshire GU14 ONG UK
#07-00 Alexandra Technopark
Singapore 119968
Tel: 1-877-997-9199
Outside USA and Canada: +1 512-437-7089
email: ipsecurity.na@nokia.com
Tel: UK: +44 161 601 8908
Tel: France: +33 170 708 166
email: ipsecurity.emea@nokia.com
Tel: +65 6588 3364
email: ipsecurity.apac@nokia.com
Americas Europe
Voi ce: 1-888-361-5030 or
Fax: 1-613-271-8782 Fax: +44 (0) 125-286-5666
Asia-Pacific
Voi ce: +65-67232999
Fax: +65-67232897
Voyager Reference Guide 3
Voi ce: +44 (0) 125-286-8900
1-613-271-6721
031014
Page 4

4 Voyager Reference Guide
Page 5

Voyager Reference Guide 5
Contents
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
How to Use Voyager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
Command-Line Utility Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
Monitoring and Configuring System Resources . . . . . . . . . . . . . . . . . . .33
Dynamic Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .34
Static Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .48
Configuring Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65
Ethernet Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69
Gigabit Ethernet Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .75
Virtual LAN Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
FDDI Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .84
ISDN Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .89
Token Ring Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .121
Point-to-Point Link over ATM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .128
IP over ATM (IPoA) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .136
Serial (V.35 and X.21) Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .143
T1(with built-in CSU/DSU) Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
E1 (with built-in CSU/DSU) Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .164
HSSI Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .174
Unnumbered Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .180
Cisco HDLC Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .188
Point-to-Point Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .189
Frame Relay Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Loopback Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .197
GRE Tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .198
DVMRP Tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .209
ARP Table Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .214
Configuring ARP for the ATM Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .217
Page 6

6 Voyager Reference Guide
Configuring Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
OSPF (Open Shortest Path First) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
RIP (Routing Information Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Protocol-Independent Multicast (PIM) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
IGRP (Inter-Gateway Routing Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
DVMRP (Distance Vector Multicast Routing Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
IGMP (Internet Group Management Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Static Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Backup Static Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Route Aggregation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Route Rank . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
BGP (Border Gateway Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
Route Redistribution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
Configuring Traffic Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341
Configuring Clustering in IPSO . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 343
Configuring Access Control Lists (ACL) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 402
Configuring Access Control List Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 407
Configuring Aggregation Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
Configuring Queue Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 415
Configuring ATM QoS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 419
Configuring Common Open Policy Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 423
Configuring Transparent Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 435
Configuring Router Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .449
Bootp (Bootstrap Protocol) Relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 451
IP Broadcast Helper . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 453
Router Discovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 456
VRRP (Virtual Router Redundancy Protocol) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 459
NTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 486
Configuring System Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 491
DNS Hostname Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 493
Configuring Disk Mirroring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 494
Mail Relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 496
Failure Notification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 498
Time and Date Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 499
Static Host Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 499
System Logging Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 500
Hostname Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 504
Managing Configuration Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 505
Page 7

Voyager Reference Guide 7
Backing Up and Restoring Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .507
Scheduling Jobs Through the Crontab File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5 14
Managing IPSO Images . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .515
Installing New IPSO Images . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .517
Managing Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .520
Advanced System Tuning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .523
Configuring Security and Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .525
Password Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .528
Group Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .532
Network Access Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .533
Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .543
Secure Shell (SSH) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .545
Secure Socket Layer (SSL) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .555
Authentication, Authorization, and Accounting (AAA) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .560
Cryptographic Acceleration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .583
IPsec Tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .587
Voyager Session Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6 16
Configuring Fault Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .621
Fault Management Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .622
Configuring SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .627
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .628
Configuring SNMP v1 and v2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .634
Interpreting SNMP Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .643
SNMP v3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .647
Configuring Asset Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .651
Asset Management Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .651
Configuring IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .653
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .654
Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .656
IPv6 and IPv4 Compatibility . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .657
Routing Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .662
Router Discovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .665
Traffic Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .667
Security and Access Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .668
Page 8

8 Voyager Reference Guide
IPSO Process Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 671
IPSO Process Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 671
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 675
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 689
Page 9

1 Overview
Chapter Contents
! Software Overview
! Interface Overview
! Routing Overview
! Redistributing Routes Overview
Software Overview
This section gives you an overview of the Nokia software configured and
maintained by Nokia Voyager software.
Nokia firewalls function with the help of several software components:
! Operating System—Nokia firewalls run Nokia IPSO, a UNIX-like
operating system based on FreeBSD. IPSO is customized to support
Nokia’s enhanced routing capabilities and Check Point’s FireWall-1
firewall functionality, and to "harden" network security. Unnecessary
features have been removed to minimize the need for UNIX system
administration.
! Ipsilon Routing Daemon (IPSRD)—IPSRD is Nokia’s routing software.
The routing policy implemented by IPSRD resides in a database. Voyager
(see below) configures and maintains the routing software and database.
Voyager Reference Guide 9
Page 10

1 Overview
! Check Point Fir eW all-1—FireWall-1 consists of two major components:
(1) the Firewall module, which runs on the Nokia firewall and
implements the security policy, and (2) the Management module, which
runs either on the Nokia firewall or on another workstation. Use the
Management Module to define and maintain the security policy.
! Voyager—Voyager communicates with the routing software to configure
interfaces and routing protocols, to manage routing policy for the firewall,
and to monitor network traffic and protocol performance. Voyager also
provides online documentation. Voyager itself runs on a remote machine
as a client application of the Nokia routing software and is HTML based.
Interface Overview
This section describes how to configure network devices and assign IP
addresses to them using Voyager.
Interface Types
Nokia NAPs support the following interface types.
Note
Consult the appropriate hardware installation guide to find out what
interfaces your unit supports.
! Ethernet/Fast Ethernet
! FDDI
! ATM (RFC1483 PVCs only)
! Serial (V.35 and X.21) running PP P, point-to-point Frame Relay, or Cisco
HDLC
! T1/E1 running PPP, Frame Relay, or Cisco HDLC
! HSSI running PPP, point-to-point Frame Relay, or Cisco HDLC
! VPN Tunneling
10 Voyager Reference Guide
Page 11

! Token Ring
! Unnumbered Interface
! ISDN
You can configure these interfaces with IP addresses. You also can assign
additional IP addresses to the loopback, FDDI, and Ethernet interfaces. All
interface types support IP multicast.
Configuring Network Devices
Voyager displays network devices as physical interfaces. A physical interface
exists for each physical port on a network interface card (NIC) installed in the
unit. Physical interface names have the form:
<type>-s<slot>p<port>
where:
<type>
is a prefix indicating the device type. The interface-name prefixes for
each type are as follows:
Type Prefix
Ethernet
FDDI
ATM atm
Serial
T1/E1
HSSI
Token Ring tok
ISDN isdn
eth
fddi
ser
ser
ser
Voyager Reference Guide 11
Page 12

1 Overview
<slot>
<port>
is the number of the slot the device occupies in the unit.
is the port number of the card. The first port on a NIC is port one. Fo r
example, a two-port Ethernet NIC in slot 2 is represented by two physical
interfaces:
eth-s2p1
and
eth-s2p2
The loopback interface also has a physical interface named
Use Voyager to set the attributes of the device. For example, line speed and
duplex mode are attributes of an Ethernet physical interface. Each
communications port has exactly one physical interface.
Configuring IP Addresses
Logical interfaces are created for a device's physical interface. You assign an
IP address to logical interfaces and then route to the IP address. Ethernet,
FDDI, and Token Ring devices have one logical interface.
For ATM devices, you create a new logical interface each time you configure
an RFC1483 PVC for the device. Serial, T1/E1, and HSSI devices have one
logical interface when they are running PPP or Cisco HDLC. Serial, T1/E1
and HSSI devices running point-to-point Frame Relay have a logical interface
for each PVC configured on the port. You also have the option of configuring
an unnumbered interface for point-to-point interfaces. Tunnels, however,
cannot be configured as unnumbered interfaces.
.
loop0
.
Logical interfaces, by default, are named after the physical interface for which
they are created. If you wish, you can override this default name with a more
descriptive or familiar name. You can also associate a comment with the
logical interface as a further way to define its relationship in the network.
Default logical interface names have the form:
<type>-s<slot>p<port>c<chan>
where
<type>, <slot>
and
<port>
have the same values as the corresponding
physical interface
<chan>
is the channel number of the logical interface. For logical interfaces
created automatically, the channel number is always zero. For logical
12 Voyager Reference Guide
Page 13
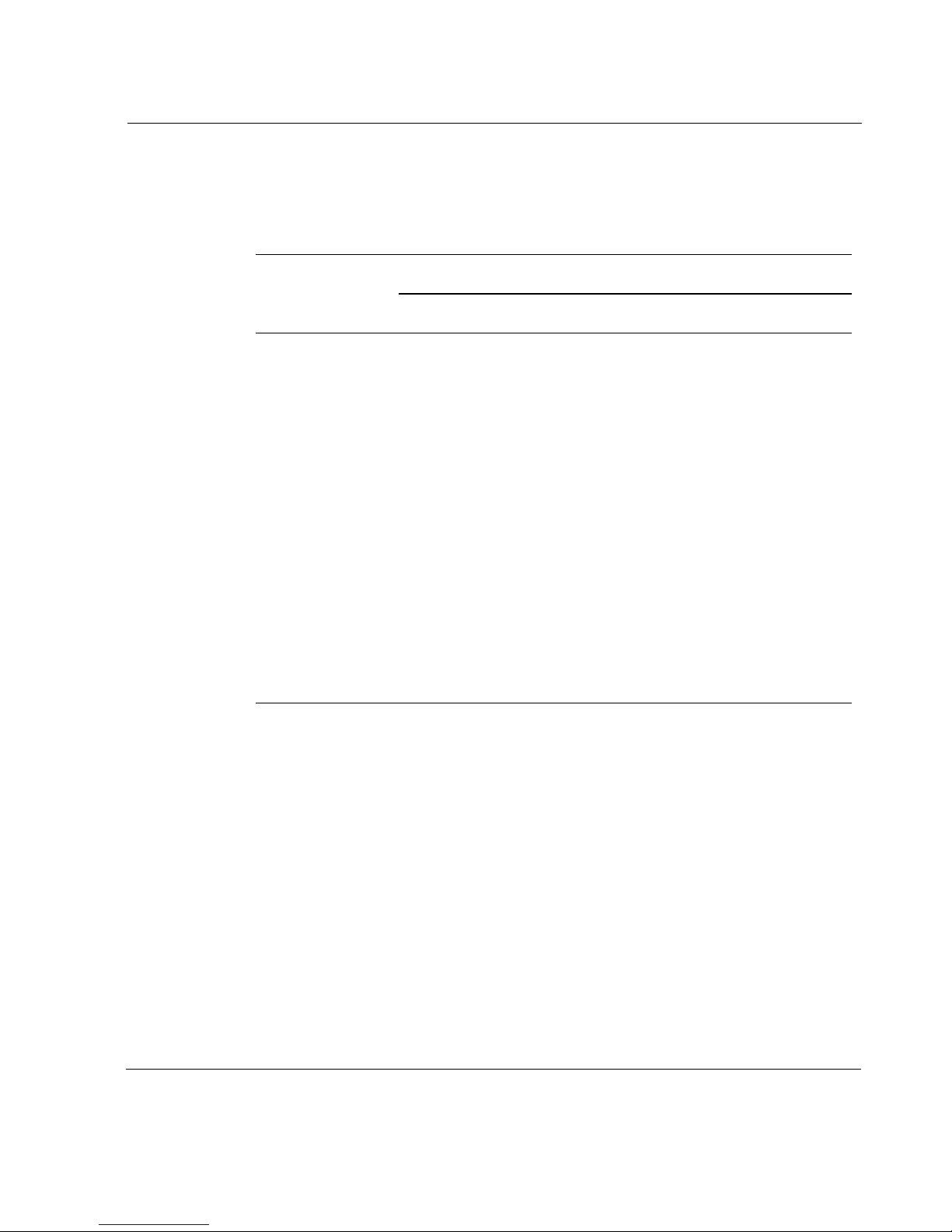
interfaces created manually, the channel number is the identifier of the virtual
circuit (VC) for which the interface is created (for example, the ATM VCI or
the Frame Relay DLCI).
Logical Interface
Physical
Interface
Ethernet One (
FDDI One (c0)
ATM One per VCI (
Serial
(X.21 or V.35)
T1/E1 One (
HSSI One (
Default Cisco HDLC PPP Frame Relay
c0
)
c#
)
c0
One (
) One (c0) One per DLCI
(c#)
c0
) One (c0) One per DLCI
(c#)
c0
) One (c0) One per DLCI
(c#)
Token Ring One (c0)
c#
ISDN One (
For example, the logical interface of a physical interface
eth-s2p1c0
slot 3 are called
. The logical interfaces for PVCs 17 and 24 on an ATM NIC in
atm-s3p1c17
and
atm-s3p1c24
respectively.
)
eth-s2p1
is called
Once a logical interface exists for a device, you can assign an IP address to it.
For Ethernet, FDDI, and T oken Ring, you must specify the interface's local IP
address and the length (in bits) of the subnet mask for the subnet to which the
device connects.
If you are running multiple subnets on the same physical network, you can
configure additional addresses and subnet masks on the single logical
Voyager Reference Guide 13
Page 14

1 Overview
interface connected to that network. You do not need to create additional
logical interfaces to run multiple subnets on a single physical network.
For point-to-point media, such as ATM, serial, or HSSI, you can either assign
IP addresses or configure an unnumbered interface. When assigning IP
addresses you must specify the IP address of the local interface and the IP
address of the remote system's point-to-point interface.
You can add only one local/destination IP address pair to a point-to-point
logical interface. To assign IP addresses to multiple VCs, you must create a
logical interface for each VC. IP subnets are not supported on point-to-point
interfaces.
Whenever an unnumbered interface generates a packet, it uses the address of
the interface that the user has specified as the source address of the IP packet.
Thus, for a router to have an unnumbered interface, it must have at least one
IP address assigned to it. The Nokia implementation of unnumbered
interfaces does not support virtual links.
Indicators and Interface Status
The configuration and status of removable-interface devices are displayed.
Interfaces can be changed while they are offline. The events, their effects, and
indications are:
! If you hot-insert a device (not power down the unit first), it appears in the
lists of interfaces immediately (after a page refresh) on the configuration
pages.
! If you hot-pull a device, and no configuration exists for it, it disappears
from the lists of interfaces immediately.
! If you hot-pull a device, and it had a configuration, its configuration
details continue to be displayed and can be changed even after a reboot.
! Hotswapped interfaces that are fully seated in a router’s chassis are
represented in the ifTable (MIB-II), ipsoCardTable (IP440-IPSO-SystemMIB), and the hrNetworkTable
(Host-Resources-MIB).
14 Voyager Reference Guide
Page 15

! Unwanted configurations of absent devices can be deleted, which
removes the physical and logical interfaces from all interface lists.
! None: If no color indication is displayed, the physical interface is
disabled. To enable the interface, click on the physical interface name to
go to its configuration page.
! Blue: The device corresponding to this physical interface has been
removed from the system, but its configuration remains. To delete its
configuration, click on the physical interface name to go to its
configuration page.
! Red: The physical interface is enabled, but the device does not detect a
connection to the network.
! Green: The physical interface is ready for use. It is enabled and
connected to the network.
Address Resolution Protocol (ARP)
ARP allows a host to find the physical address of a target host on the same
physical network using only the target’s IP address. ARP is a low-level
protocol that hides the underlying network physical addressing and permits
assignment of an arbitrary IP address to every machine.ARP is considered
part of the physical network system and not as part of the internet protocols.
Using the Loopback Interface
By default, the loopback interface has 127.0.0.1 configured as its IP address.
Locally originated packets sent to this interface are sent back to the
originating process.
You might want to assign an address to the loopback interface that is the same
as the OSPF firewall ID, or is the termination point of a BGP session. This
allows firewall adjacencies to stay up even if the outbound interface is down.
Do not specify an IP subnet mask length when you add addresses to the
loopback interface.
Voyager Reference Guide 15
Page 16

1 Overview
Configuring Tunnel Interfaces
Tunnel interfaces are used to encapsulate protocols inside IP packets. Use
tunneling to:
! send network protocols over IP networks that don’t support them
! encapsulate and encrypt private data to send over a public IP network.
Create a tunnel logical interface by specifying an encapsulation type. Use
Voyager to set the encapsulation type. Voyager supp orts two encapsulation
types, DVMRP and VPN.
The tunnel logical interface name has the form:
tun0c<chan>
where <chan> (channel number) is an instantiation identifier.
DVMRP (Distance Vector Multicast Routing
Protocol) Tunnels
DVMRP tunnels encapsulate multicast packets using IP-in-IP encapsulation.
The encapsulated packets appear as unicast IP packets. This technique allows
two multicast routers to exchange multicast packets even when they are
separated by routers that cannot forward multicast packets. For each DVMRP
tunnel you create, you must provide the IP address of the interface that forms
the local endpoint of the tunnel and the IP address of the multicast router that
is at the remote end of the tunnel forming the remote endpoint of the tunnel.
Note
The remote multicast router must support IP-in-IP encapsulation and
must be configured with a tunnel interface to the local router.
When you have created the DVMRP tunnel interface, set all other DVMRP
multicast configuration parameters from the DVMRP configuration page.
16 Voyager Reference Guide
Page 17

VPN (Virtual Private Networking) Tunnels
VPN tunnels encapsulate IP packets using Generic Routing Encapsulation
(GRE) without options. The encapsulated packets appear as unicast IP
packets. For each VPN tunnel you create, you must assign a local and remote
IP address. You also must provide the local and remote endpoint addresses of
the interface to which this tunnel is bound. VPN tunnels provide redundant
configuration between two sites for high availability. The remote router must
also support VPN encapsulation and must be configured with a tunnel
interface to the local router.
Routing Overview
This section discusses the following topics:
! Nokia Routing Subsystem
! Routing Protocols
Nokia Routing Subsystem
The Nokia routing subsystem, Ipsilon Routing Daemon (IPSRD), is an
essential part of your firewall. IPSRD’s role is to dynamically compute paths
or routes to remote networks. Routes are calculated by a routing protocol.
Besides providing routing protocols, IPSRD also allows routes to be
converted or redistributed between routing protocols. Finally, when there are
multiple protocols with a route to a given destination, IPSRD allows you to
specify a ranking of protocols. Based on this ranking, a single route is
installed in the forwarding table for each destination.
You can configure each of the supported routing protocols, route
redistribution, and other routing options via the Configuring Routing section
in Voyager.
Routing monitoring is available by following links from the individual
protocol pages or by clicking on the Monitor button in Voyager. Another
Voyager Reference Guide 17
Page 18

1 Overview
monitoring tool is ICLID. This tool provides interactive, text-based
monitoring of the routing subsystem.
Routing Protocols
Routing protocols compute the best route to each destination. Routing
protocols also exchange information with adjacent firewalls. The best route is
determined by the cost or metric values.
Routing protocols can be broken up into two major categories: exterior
gateway protocols (EGPs) and interior gateway protocols (IGPs). Inte rior
gateway protocols exchange routing information inside an autonomous
system (AS). An AS is a routing domain, such as inside an organization, that
contacts its own routing. An EGP exchanges routing information between
ASes and provides for specialized policy-bound filtering and configuration.
Interior Routing Protocols
IPSRD supports three IGPs: RIP (Routing Information Protocol), IGRP
(Interior Gateway Routing Protocol), and OSPF (Open Shortest Path First).
Static routes and aggregate routes are also supported.
RIP
RIP is a commonly used IGP. There are two versions of RIP: RIP version 1,
and RIP version 2. Both versions are supported by IPSRD.
RIP uses a simple distance vector algorithm called Bellman Ford to calculate
routes. In RIP, each destination has a cost or metric value, which is based
solely on the number of hops between the calculating firewall and the given
destination.
The maximum metric value is 15 hops, which means that RIP is not suited to
networks within a diameter greater than 15 firewalls. The advantage of RIP
version 2 over RIP version 1 is that it supports non-classful routes. Classful
routes are old-style class A, B, C routes. You should use RIP version 2 instead
of RIP version 1 whenever possible.
18 Voyager Reference Guide
Page 19
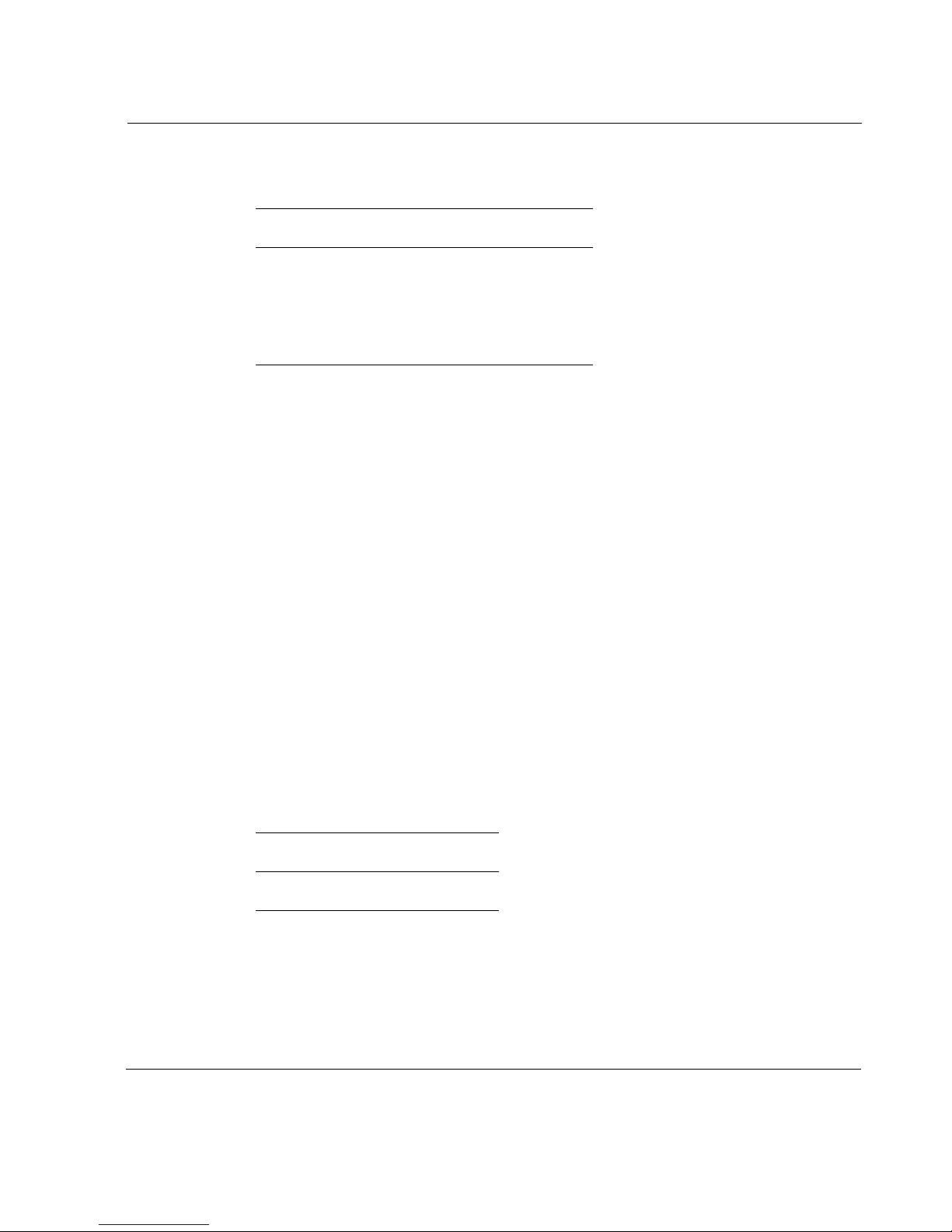
Nokia also supports RIPng, the version of RIP that supports IPv6 interfaces.
Protocol Described in RFC
RIP version 1 RFC1058
RIP version 2 RFC1723
RIPng
IGRP
IGRP (Interior Gateway Routing Protocol) is a distance v ector protocol. IGRP
has a number of metrics for each destination. These metrics include link delay,
bandwidth, reliability, load, MTU, and hop count. A single composite metric
is formed by combining metrics with a particular weight.
Like RIP version 1, IGRP does not fully support non-classful routing.
OSPF
OSPF (Open Shortest Path First) is a modern link-state routing protocol. It
fully supports non-classful networks. OSPF has a single, 24-bit metric for
each destination. You can configure this metric to any desired value.
OSPF allows the AS to be broken up into areas. Areas allow you to increase
overall network stability and scalability. At area boundaries, routes can be
aggregated to reduce the number of routes each firewall in the AS must know
about. If there are multiple paths to a single destination with the same
computed metric, OSPF can install them into the forwarding table.
Protocol Described in RFC
OSPF RFC2328
Voyager Reference Guide 19
Page 20

1 Overview
DVMRP
DVMRP (Distance Vector Multicast Routing Protocol) is a multicast routing
protocol (RIP, OSPF, and IGRP are unicast routing protocols). Multicasting is
typically used for real-time audio and video when there is a single source of
data and multiple receivers. DVMRP uses a hop-based metric and, like RIP, a
distance-vector route calculation.
BGP
BGP (Border Gateway Protocol) is an exterior gateway protocol that is used
to exchange network reachability information between BGP-speaking
systems running in each AS. BGP is unlike interior gateway protocols (IGRP
or OSPF), which periodically flood an intra-domain network with all the
known routing table entries and build their own reliability on top of a
datagram service. Instead, BGP uses TCP as its underlying transport
mechanism.
BGP is also a path-vector routing protocol, which limits the distribution of a
firewall’ s reachability information to its peer or neighbor firewalls. BGP uses
path attributes to provide more information about each route. BGP maintains
an AS path, which includes the number of each AS that the route has
transited. Path attributes may also be used to distinguish between groups of
routes to determine administrative preferences. This allows greater flexibility
in determining route preference and achieves a variety of administrative ends.
BGP supports two basic types of sessions between neighbors: internal (IBGP)
and external (EBGP). Internal sessions run between firewalls in the same
autonomous systems, while external sessions run between firewalls in
different autonomous systems.
Aggregate Routes
Route aggregation allows you to take many small routes and aggregate them
into one large route. This reduces the number of routes advertised for a given
protocol. These aggregate routes are then redistributed into other protocols.
The aggregates are activated by contributing routes. For example, if a firewall
has many stub interface routes subnetted from a class C and is running RIPv2
20 Voyager Reference Guide
Page 21

on another interface, the interface routes may be used to create an aggregate
route (of the class C) that can then be redistributed into RIP. This reduces the
number of routes advertised via RIP. Care must be taken when aggregating if
there are "holes" in the route that is aggregated.
Create an aggregate route by first specifying the network address and mask
length. Second, provide a set of contributing routes. A contributing route is
defined by specifying a source (for example, a routing protocol, a static route,
an interface route) and a route filter, which is a prefix. You can also choose to
contribute all of the routes. An aggregate route can have many contributing
routes, but at least one of the routes must be present to generate an aggregate.
Aggregate routes are not actually used for packet forwarding by the originator
of the aggregate route, only by the receiver (if it wishes). A firewall receiving
a packet which does not match one of the component routes that led to the
generation of an aggregate route should respond with an ICMP network
unreachable message. This message prevents packets for unknown
component routes from following a default route into another network where
they would be forwarded back to the border firewall, continually, until their
TTL expires.
Static Routes
Static routes are routes that you manually configure in the routing table. Static
routes cause packets moving between a source and a destination to take a
specified next hop. Static routes allow you to add routes to destinations that
are not described by dynamic routing protocols. This can be useful if dynamic
protocols cannot be used. It can also be useful in providing a default route.
Static routes consist of the following:
! Destination
! Type
! Next hop gateway
There are three types of static routes:
! Normal
! Black Hole
Voyager Reference Guide 21
Page 22

1 Overview
! Reject
A normal static route is used to forward packets for a given destination in the
direction indicated by the configured firewall.
A black hole static route uses the loopback address as the next hop. This route
discards packets that match the route for a given destination.
A reject static route uses the loopback as the next hop, discards packets that
match the route for a given destination and sends an ICMP unreachable
message back to the sender of the packet.
Redistributing Routes Overview
Route redistribution controls which routes are advertised by IPSRD to other
systems, as well as which routes are redistributed between the protocols run
on the firewall.
A metric is set for any redistributed route. This metric is sent to the peer by
certain protocols and may be used by the peer to choose a better route to a
given destination. Some routing protocols can associate a metric with a route
when announcing the route.
A route filter can be used to explicitly list all the redistributed routes.
Redistributing Routes with BGP
Redistributing to BGP is controlled by an AS. The same policy is applied to
all firewalls in the AS. BGP metrics are 16-bit, unsigned quantities; that is,
they range from 0 to 65535 inclusive, with zero being the most attractive.
While BGP version 4 supports 32-bit unsigned quantities, IPSRD does not.
Note
If you do not specify a redistribution policy, only routes to attached
interfaces are redistributed. If you specify any policy, the defaults are
22 Voyager Reference Guide
Page 23
overridden. You must explicitly specify everything that should be
redistributed.
Redistributing Routes with RIP and IGRP
Redistributing to RIP and IGRP is controlled by any one of three parameters:
! Protocol
! Interface
! Gateway
If more than one parameter is specified, they are processed from most general
(protocol) to most specific (gateway).
It is not possible to set metrics for redistributing RIP routes into RIP or for
redistributing IGRP routes into IGRP. Attempts to do this are silently ignored.
It is also not possible to set the metrics for redistributing routes into IGRP.
Note
If no redistribution policy is specified, RIP and interface routes are
redistributed into RIP and IGRP, and interface routes are redistributed into
IGRP. If any policy is specified, the defaults are overridden. You must
explicitly specify everything that should be redistributed.
RIP version 1 assumes that all subnets of the shared network have the same
subnet mask, so they are able to propagate only subnets of that network. RIP
version 2 removes that restriction and is capable of propagating all routes
when not sending version 1-compatible updates.
Redistributing Routes with OSPF
It is not possible to create OSPF intra-area or inter-area routes by
redistributing routes from the IPSRD routing table into OSPF. It is possible to
redistribute from the IPSRD routing table only into OSPF ASE routes. In
Voyager Reference Guide 23
Page 24

1 Overview
addition, it is not possible to control the propagation of OSPF routes within
the OSPF protocol.
There are two types of OSPF ASE routes:
! Type 1
! Type 2
See the OSPF protocol configuration for a detailed explanation of the two
types.
Route Redistribution Between Protocols
The redistribute_list specifies the source of a set of routes based on
parameters like the protocol from which the source has been learned. The
redistribute_list indirectly controls the redistribution of routes between
protocols.
The syntax varies slightly per source protocol. BGP routes may be specified
by source AS. RIP and IGRP routes may be redistributed by protocol, source
interface, and/or source gateway. Both OSPF and OSPF ASE routes may be
redistributed into other protocols. All routes may be redistributed by AS path.
When BGP is configured, all routes are assigned an AS path when they are
added to the routing table. For all interior routes, this AS path specifies IGP as
the origin and no ASes in the AS path. The current AS is added when the
route is redistributed. For BGP routes, the AS path is stored as learned from
BGP.
24 Voyager Reference Guide
Page 25

2 How to Use Voyager
Chapter Contents
! Navigating in Voyager
! Viewing Online Help
! Viewing Inline Help for the Page
! Viewing Inline Help for a Section or Field
! Voyager Help Conventions
! Opening a Second Window to View Help
Navigating in Voyager
The following table explains the functions of the large blue buttons in
Voyager. Other buttons are described in the inline help for each page.
Note
You can press buttons to produce a result when they ha ve a dark shadow
behind them. Buttons without shadows, such as those found in the
Voyager Online Help instructions, do not function; they are only for
display.
Voyager Reference Guide 25
Page 26

2 How to Use Voyager
Button Description
Apply Applies the settings on the current page (and any deferred applies
Config Takes you to the configuration page main menu.
Contents Takes you to the online help table of contents.
Doc Takes you to the online help table of contents.
Feedback Takes you to the documentation or Technical Assistance Center
Help Turns on contextual inline help for all elements of the page.
H Turns on contextual inline help for a specific element of the page.
from other pages) to the current (running) configuration file in
memory.
(TAC) feedback page.
Home Takes you to the home page.
Monitor Takes you to the monitor page main menu.
Reset Routing Restarts the routing daemon.
Save Saves the current (running) configuration file to disk.
Support Takes you to contact information for the Technical Assistance
Center (TAC).
Top Takes you to the top-level configuration page.
Up Takes you one level up from the current page.
Note
Avoid using your b rowser’s Back and Forward buttons while in Voyager.
The browser caches the HTML page information; therefore, using
and
FORWARD may not display the latest configuration and diagnostic
BACK
26 Voyager Reference Guide
Page 27
information as you move from page to page. Use the CONFIG, MONITOR,
HOME, TOP, and UP buttons to get the most current data.
If the pages seem to have outdated information, you can use the RELOAD
button on the browser to update it. You can also clear memory and disk cache
with the following procedure:
1. Select Network Preferences from the Options menu in Netscape.
2. Select Cache in the Preferences window.
3. Click the C
LEAR MEMORY CACHE NOW button, then click the OK
button.
4. Click the C
LEAR DISK CACHE NOW button, then click the OK button.
5. Click the OK button or close the Preferences window.
Viewing Online Help
Online help consists of procedures for common tasks you can perform with
Voyager.
Note
Buttons without shadows, such as those found in the V oyager on line help
instructions, do not function; they are there only for illustration.
1. Click the DOC button on the top of any Voyag er page.
The online contextual help displays information that relates to your
specific task.
If you can not find help that pertains to your interest, return to the home
page and click on the D
which you want to view online help.
Voyager Reference Guide 27
OC button. Click the topic link for the category for
Page 28

2 How to Use Voyager
Viewing Inline Help for the Page
If you want to view inline help for all of the fields and sections of a page :
1. Click the H
ELP button on any Voyager page.
Text-only definitions and related information on fields, buttons, and
sections appear in a separate window.
2. Click the Close button on the Help window to close inline help.
Viewing Inline Help for a Section or Field
If you want to view inline help for a section or field:
1. Click the H button next to a field or section.
Text-only definitions and related information related to that specific field
or section appear in a separate window.
2. Click the Close button on the Help window to close inline help.
Voyager Help Conventions
Inline and online help use the following text conventions.
This Type of Text Means This
italic text Introduces a word or phrase, highlights an important term,
phrase, or hypertext link, indicates a field name, system
message, or document title.
typewriter text Indicates a UNIX command, program, file name, or path
name.
bold typewriter text Indicates text to be entered verbatim by you.
Represents the name of a key on the keyboard, of a button
displayed on your screen, or of a button or switch on the
hardware. For example, press the R
28 Voyager Reference Guide
ETURN key.
Page 29

This Type of Text Means This
<bracketed> Indicates an argument that you or the software replaces with
an appropriate value. For example, the command rm
<filename> indicates that you should type rm follo wed by
the filename of the file to be removed.
LinkTe xt Indicates a hypertext link.
- OR - Indicates an exclusive choice between two items.
Opening a Second Window to View Help
You can preserve the current page content in your browser and start another
browser window to display the inline or online help text.
1. Using the right button (middle button in UNIX) of your mouse, click the
D
OC button.
2. Click O
PEN LINK IN NEW BROWSER WINDOW.
Displays the online help in a new window.
3. Using the right button (middle button in UNIX) of your mouse, click the
H
ELP ON button.
4. Click O
PEN LINK IN NEW BROWSER WINDOW.
Displays the inline (text-only) help in a new window.
Voyager Reference Guide 29
Page 30

2 How to Use Voyager
30 Voyager Reference Guide
Page 31

3 Command-Line Utility Files
Chapter Contents
! CAMCONTROL
! FTP
! ID
! MAIL
! MTRACE
! NETSTAT
! PCCARDD
! PING
! SCP
! SSH
! SSHD
! SSH-ADD
! SSH-AGENT
! SSH-KEYGEN
! TCPDUMP
! TELNET
! TFTPD
! TRACEROUTE
Voyager Reference Guide 31
Page 32

3 Command-Line Utility Files
32 Voyager Reference Guide
Page 33

4 Monitoring and Configuring
System Resources
Chapter Contents
! Dynamic Monitoring
! Dynamic and Static Monitoring Described
! Displaying System Utilization Statistics
! Configuring Data Collection Events
! Displaying Rate Shaping Bandwidth Report
! Displaying Historical Rate Shaping Bandwidth Statistics
! Displaying Interface Throughput Statistics
! Displaying Historical Interface Throughput Statistics
! Displaying Interface Linkstate Statistics
! Displaying Historical Interface Linkstate Statistics
! Displaying CPU Utilization Statistics
! Displaying Historical CPU Utilization Statistics
! Displaying Memory Utilization Statistics
! Displaying Historical Memory Utilization Statistics
! Monitoring System Health
! Monitoring System Logs
! Static Monitoring
Voyager Reference Guide 33
Page 34

4 Monitoring and Configuring System Resources
! Displaying Cluster Status and Members
! Displaying Routing Protocol Information
! Displaying Resource Settings
! Displaying the Kernel Forwarding Table
! Displaying Route Settings
! Displaying Interface Settings
! Displaying System Status
! Displaying Slot Statistics
! Displaying Cryptographic Acceleration States
! Displaying IPv6 Running States
! Displaying Routing Daemon Status (iclid)
! iclid Commands
! Resolving and Preventing Full Log Buffers and Related Console
Messages
Dynamic Monitoring
Dynamic and Static Monitoring Described
The monitoring features in Voyager give you the ability to better maintain
system performance and security . You can also customize certain types of data
collection to better help you manage and maintain system availability. The
following are some of the key features available to you:
! Displaying rate-sh aping bandwidth, throughput and linkstate data for each
interface
! Ability to monitor core values associated with different protocols
! Easy access to system logs, forwarding tables, and other interface
information
34 Voyager Reference Guide
Page 35

Displaying System Utilization Statistics
These pages display statistical information for the following:
! CPU and Memory
! Disk and Swap Space
! Processes
To display the statistical information, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Link under System Utilization for which you want to obtain
statistics.
Configuring Data Collection Events
To configure data collection events, follow these instructions:
1. Click M
2. Click Monitor Report Configuration link.
3. (Optional) Click the O
event. The default is set to on.
4. (Optional) Click the O
collection event.
5. (Optional) Enter the collection interval, in seconds, in the C
I
NTERVAL edit box for each data collection event. The default is 60
seconds.
6. Click A
ONITOR on the home page.
N radio button to enable a particular data collection
FF radio button to disable a particular data
PPLY .
OLLECTION
7. Click S
Voyager Reference Guide 35
AVE.
Page 36

4 Monitoring and Configuring System Resources
Displaying Rate Shaping Bandwidth Report
To display rate shaping bandwidth statistics, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Rate Shaping Bandwidth link.
3. In the S
D
AILY, WEEKLY, or MONTHLY.
4. In the S
class for which you want to display a report or click on A
ELECT REPORT TYPE field, click the button next to HOURLY,
ELECT AGGREGATES field, click on the name of the Aggregation
LL AGGREGATES
to display data for all configured aggregation classes.
Note
You must configure an aggregation class and asso ciate it with an access
control list for the name to appear as a choice in the Aggregation Class
list. See Traffic Mana gement, "Creating an Aggregation Class" and
"Creating an Access Control List" in Voyager.
5. In the TYPE OF RATESHAPING DATA field, click the check box either
next to P
6. To select a format type for displaying the report, in the S
field, click the button next to G
you select D
and select either S
ACKETS DELAYED or BYTES DELAYED.
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
Note
The Graphical View displays information at the bottom of the page in a
table. Delimited Text format displays the report in a new page from which
you can download the information.
7. Click VIEW REPORT or APPLY to view current rate shaping bandwidth
data.
36 Voyager Reference Guide
Page 37

Displaying Historical Rate Shaping Bandwidth
Statistics
To Display Rate Shaping Bandwidth for a specific period of time, follow
these instructions:
1. Click M
ONITOR On The Home Page.
2. Click The Rate Shaping Bandwidth link.
3. In the S
EARCH.
S
4. Enter a value for the date and time in the S
ELECT REPORT TYPE field, click the button next to DETAILED
TART DATE Edit Box. The date
defaults to the current date and time minus 10 minutes.
5. Enter a value for the date and time in the E
ND DATE Edit Box. The date
defaults to the current date and time.
Note
Data for the previous 7 days is available.
6. In the SELECT AGGREGATES field, click on the name of the Aggregation
class for which you want to display a report or click on A
LL AGGREGATES
to display data for all configured aggregation classes.
Note
You Must Configure An Aggregation Class And Associate It With An
Access List For The Name To Appear As A Choice In The Aggregation
Class Drop-down Menu. See Traffic Management, "Creating an
Aggregation Class" And "Creating an Access Control List" In Voyager.
7. In the TYPE OF RATESHAPING DATA field, click the check box either
next to P
8. To select a format type for displaying the report, in the S
field, click the button next to G
Voyager Reference Guide 37
ACKETS DELAYED or BYTES DELAYED.
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
Page 38

4 Monitoring and Configuring System Resources
you select DELIMITED TEXT, click on the Delimiter drop-down window
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table. Delimited Text format displays the report in a new page from which
you can download the information.
EMI-COLON(;) COMMA(,) or TAB.
9. Click VIEW REPORT or APPLY to view rate shaping bandwidth data for
the period of time selected.
Displaying Interface Throughput Statistics
To display interface throughput statistics, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Interface Throughput link.
3. In the S
AILY, WEEKLY, or MONTHLY. The default is set to Daily.
D
4. Select an interface name from the S
OGICAL to display throughput data for all logical interfaces.
L
ELECT REPORT TYPE field, click the button next to HOURLY,
ELECT INTERFACE list or select ALL
5. In the Type of Throughput field, click the check box next to P
T
HROUGHPUT, BYTE THROUGHPUT, BROADCAST THROUGHPUT, or
ULTICAST THROUGHPUT to select the type of throughput data you want
M
to view.
6. To select a format type for displaying the report, in the S
field, click the button next to G
you select D
and select either S
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
RAPHICAL VIEW or DELIMTED TEXT. If
ELECT FORMAT
ACKET
38 Voyager Reference Guide
Page 39

Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
7. Click VIEW REPORT or APPLY to view current interface throughput data.
Displaying Historical Interface Throughput Statistics
To display interface throughput statistics for a specific period of time, follow
these instructions:
1. Click M
ONITOR on the home page.
2. Click the Interface Throughput link.
3. In the S
S
EARCH.
4. Enter a value for the date and time in the S
ELECT REPORT TYPE field, click the button next to DETAILED
TART DATE Edit Box. The date
defaults to the current date and time minus 10 minutes.
5. Enter a value for the date and time in the E
ND DATE Edit Box. The date
defaults to the current date and time.
Note
Data for the previous 7 days is available.
6. Select an interface name from the SELECT INTERFACE list or select ALL
L
OGICAL to display throughput data for all logical interfaces.
7. In the Type of Throughput field, click the check box next to P
T
HROUGHPUT, BYTE THROUGHPUT, BROADCAST THROUGHPUT, or
ULTICAST THROUGHPUT to select the type of throughput data you want
M
ACKET
to view.
Voyager Reference Guide 39
Page 40

4 Monitoring and Configuring System Resources
8. To select a format type for displaying the report, in the SELECT FORMAT
field, click the button next to G
you select D
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
RAPHICAL VIEW or DELIMTED TEXT. If
9. Click VIEW REPORT or APPLY to view interface throughput data for the
period of time selected.
Displaying Interface Linkstate Statistics
To display interface linkstate statistics, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Interface Linkstate link.
3. In the S
D
AILY, WEEKLY, or MONTHLY. The default is set to Daily.
4. Select an interface name from the S
or select A
5. To select a format type for displaying the report, in the S
field, click the button next to G
you select D
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table. Delimited Text format displays the report as text in a new page from
which you can download the information.
ELECT REPORT TYPE field, click the button next to HOURLY,
ELECT INTERFACES FOR QUERY list
LL LOGICAL to display linkstate data for all logical interfaces.
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
40 Voyager Reference Guide
Page 41

6. Click VIEW REPORT or APPLY to view current interface linkstate data
Displaying Historical Interface Linkstate Statistics
To display interface linkstate statistics for a specific period of time, follow
these instructions:
1. Click M
ONITOR on the home page.
2. Click the Interface Linkstate link.
3. In the S
S
EARCH.
4. Enter a value for the date and time in the S
ELECT REPORT TYPE field, click the button next to DETAILED
TART DATE Edit Box. The date
defaults to the current date and time minus 10 minutes.
5. Enter a value for the date and time in the E
ND DATE Edit Box. The date
defaults to the current date and time.
Note
Data for the previous 7 days is available.
6. Select an interface name from the SELECT INTERFACES FOR QUERY list
or select A
7. To select a format type for displaying the report, in the S
field, click the button next to G
you select D
and select either S
LL LOGICAL to display linkstate data for all logical interfaces.
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
Note
The Graphical View displays information at the bottom of the page in a
table. Delimited Text format displays the report as text in a new page from
which you can download the information.
Voyager Reference Guide 41
Page 42

4 Monitoring and Configuring System Resources
8. Click VIEW REPORT or APPLY to view interface linkstate data for the
period of time selected.
Displaying CPU Utilization Statistics
To display CPU Utilization statistics, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the CPU Utilization link.
3. In the S
D
AILY, WEEKLY, or MONTHLY. The default is set to Hourly.
4. To select a format type for displaying the report, in the S
field, click the button next to G
you select D
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
ELECT REPORT TYPE field, click the button next to HOURLY,
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
5. Click VIEW REPORT or APPLY to view current CPU utilization data.
Displaying Historical CPU Utilization Statistics
To display cpu utilization statistics for a specific period of time, follow these
instructions:
1. Click M
ONITOR on the home page.
2. Click the CPU Utilization link.
3. In the S
S
EARCH.
42 Voyager Reference Guide
ELECT REPORT TYPE field, click the button next to DETAILED
Page 43

4. Enter a value for the date and time in the START DATE Edit Box. The date
defaults to the current date and time minus 10 minutes.
5. Enter a value for the date and time in the E
ND DATE Edit Box. The date
defaults to the current date and time.
Note
Data for the previous 7 days is available.
6. To select a format type for displaying the report, in the SELECT FORMAT
field, click the button next to G
you select D
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
RAPHICAL VIEW or DELIMTED TEXT. If
7. Click VIEW REPORT or APPLY to view interface throughput data for the
period of time selected.
Displaying Memory Utilization Statistics
To display memory utilization statistics, follow these instructions:
1. Click M
2. Click the Memory Utilization link.
3. In the S
AILY, WEEKLY, or MONTHLY. The default is set to Hourly.
D
4. To select a format type for displaying the report, in the S
field, click the button next to G
Voyager Reference Guide 43
ONITOR on the home page.
ELECT REPORT TYPE field, click the button next to HOURLY,
ELECT FORMAT
RAPHICAL VIEW or DELIMTED TEXT. If
Page 44

4 Monitoring and Configuring System Resources
you select DELIMITED TEXT, click on the Delimiter drop-down window
and select either S
Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
EMI-COLON(;) COMMA(,) or TAB.
5. Click VIEW REPORT or APPLY to view current memory utilization data.
Displaying Historical Memory Utilization Statistics
To display memory utilization statistics for a specific period of time, follow
these instructions:
1. Click M
ONITOR on the home page.
2. Click the Memory Utilization link.
3. In the S
EARCH.
S
4. Enter a value for the date and time in the S
ELECT REPORT TYPE field, click the button next to DETAILED
TART DATE Edit Box. The date
defaults to the current date and time minus 10 minutes.
5. Enter a value for the date and time in the E
ND DATE Edit Box. The date
defaults to the current date and time.
Note
Data for the previous 7 days is available.
6. To select a format type for displaying the report, in the SELECT FORMAT
field, click the button next to G
you select D
and select either S
ELIMITED TEXT, click on the Delimiter drop-down window
EMI-COLON(;) COMMA(,) or TAB.
RAPHICAL VIEW or DELIMTED TEXT. If
44 Voyager Reference Guide
Page 45

Note
The Graphical View displays information at the bottom of the page in a
table and graph. Delimited Text format displays the report as text in a new
page from which you can download the information.
7. Click VIEW REPORT or APPLY to view memory utilization data for the
period of time selected.
Monitoring System Health
The following pages allow you to display statistics to help you monitor the
health of your system.
! Useful System Statistics
! Interface Traffic Statistics
! Interface Queue Statistics
! VRRP Service Statistics
To display the statistical information, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Link under System Health for which you want to obtain
statistics.
Monitoring System Logs
The following pages allow you to display updated system logs:
! System Message Log
! Web Server access Log
! Web Server error Log
! User Login/Logout Activity
Voyager Reference Guide 45
Page 46

4 Monitoring and Configuring System Resources
! Management Activity Log
To display the statistical information, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Link under System Logs for which you want to obtain log
activity.
Note
You do not need to configure the Web Server Access log or the Web
Server Error log. For more information on configuring the System
Message Log, User Login/Logout Activity, and Management Activity Log,
see the appropriate section be low.
To refresh the information in a log, reload the web page.
System Message log
The system message log lets you view the message log file either in its
entirety or to select search criteria to view specific system log activity.
To view a particular type or types of log activity, click one or more items in
the Log Type list. On a management console running the Windows OS, hold
down the
messages. The default is to display all types of system messages.
Crtl key while selecting multiple items. Click APPLY to view
To select a a month for which display messages, click on the Select Month
drop-down list and select a particular month. Click A
display all messages available.
To select a particular date for which to display messages, click on the Select
Date drop-down list and select a particular date. You must also select a month
form the Select Month drop-down list to activate this option. Click A
You can also display system messages based on a keyword. Enter a keyword
to search for in the system messages in the Keyword edit box. To make the
46 Voyager Reference Guide
PPLY . The default is
PPLY.
Page 47

keyword search case-sensitive, click the Case Sensitive check box. Click
A
PPLY.
You can also include certain zipped files in your search. Click the appropriate
check box in the Include Zipped Files in Search section. Click A
PPLY .
The system log also displys messages generated by the Voyager AuditLog.
For more information on how to configure the Voyager AuditLog, see Setting
the Voyager AuditLog.
User Login/Logout Activity
The user login/logout activity log lets you view login and logout activity for
users. The default is to display activity for all users. To view activity for a
particular user only, click the L
OGIN/LOGOUT INFO FOR USER drop-down
window and select the user for whom you want to view login and logout
activity. Click A
PPLY .
Management Activity Log
The management activity log lets you view configuration changes. The log
includes a timestamp, which provides the date and time when a configuration
change occurred; the hostname or IP address from which the user logged in;
and the config entry, which displays the entry changed in the configuration
database.
To activate the management activity log feature, click the System Logging
link in the S
YSTEM CONFIGURATION section. For more information see
“Setting the System Configuration Auditlog.”
Voyager Reference Guide 47
Page 48

4 Monitoring and Configuring System Resources
Static Monitoring
Displaying Cluster Status and Members
This page provides information about a configured IPSO cluster, including
information about cluster status and load sharing among members of the
cluster. This page retrieves an information summary every 30 seconds.
The Cluster Status table contains the following information:
! Cluster ID: ID number of the cluster.
! Cluster Uptime: Ti me since the cluster was formed.
! Number of Members: Current number of members in the cluster.
! Number Of Interfaces: Number of interfaces on which clustering is
enabled.
! Network: Networks on which clustering is enabled.
! Cluster IP Address: Cluster IP Address on each network.
The Cluster Member table contains the following information:
! Member Id: Node ID in the cluster.
! IP Addr: Primary IP address of the member.
! Hostname: Hostname of the node.
! Platform: Type of platform.
! OS Release: Operating system version node is running.
! Rating: Node performance rating.
! Time since join: Time since node joined the cluster.
! Work Assigned(%): Percentage of work load assigned to this node.
To display the information, follow these instructions:
1. Click M
ONITOR on the home page.
2. Click the Cluster Monitor link to view cluster information.
48 Voyager Reference Guide
Page 49

Note
If your cluster is not initialized, the Cluster Monitor page co ntains a link to
the Cluster Configuration page, which enables you to configure cluster
parameters for this node.
Displaying Routing Protocol Information
This page displays statistical information on the following routing protocols:
! OSPF
! BGP
! RIP
! IGRP
! VRRP
! PIM
! DVMRP
! IGMP
It also presents the routing daemon’s information regarding the routing table
(via the Route link) and interfaces (via the Interfaces link).
To display routing information, follow these instructions.
1. Click M
ONITOR on the home page.
2. Click the Routing Protocol link for which you want to obtain statistics.
Displaying Resource Settings
This page displays system resource statistics.
1. Click M
2. Click the Resource Statistics link to display system resource statistics.
Voyager Reference Guide 49
ONITOR on the home page.
Page 50

4 Monitoring and Configuring System Resources
Displaying the Kernel Forwarding Table
This page displays the information contained in the kernel forwarding table.
1. Click M
2. Click the Forwarding Table link.
This displays the IP forwarding table that the kernel is using to make its
forwarding decisions.
ONITOR on the home page.
Displaying Route Settings
This page displays interface statistics.
1. Click M
Click the Route Settings link for the interface for which you want to obtain
statistics.
ONITOR on the home page.
Displaying Interface Settings
This page displays interface statistics.
1. Click M
2. Click the Interface Settings link for the interface for which you want to
obtain statistics.
ONITOR on the home page.
Displaying System Status
To display system status information, follow these instructions:
1. Click M
2. Click the System Status link.
50 Voyager Reference Guide
ONITOR on the home page.
Page 51

Displaying Slot Statistics
To display the statistical information, follow these instructions:
1. Click M
2. Click the Slot Status link.
ONITOR on the home page.
Displaying Cryptographic Acceleration States
Use this procedure to monitor the Nokia Cryptographic Acceleration Card.
1. Click M
2. Click the Cryptographic Accelerator Statistics link in the Hardware
Monitoring section.
ONITOR on the home page.
Displaying IPv6 Running States
Use this page to monitor the IPv6 running state.
1. Click Monitor on the home page.
2. Click the IPv6 Monitor link to display IPv6 running state.
Displaying Routing Daemon Status (iclid)
Obtain routing diagnostic information by creating a telnet session on the
network application platform (NAP) and running iclid (IPSRD CommandLine Interface Daemon).
To display routing daemon status using iclid, follow these instructions.
1. Create a telnet session and log into the firewall.
2. Type
The prompt will change (to <node-name>) to indicate that you can now enter
iclid commands.
Voyager Reference Guide 51
iclid
Page 52

4 Monitoring and Configuring System Resources
iclid Commands
Command Description
? or <tab> Shows all possible command completions.
help
quit or exit Quits iclid.
show
Displays help information.
Shows formatted, categorized system
information.
Some commands might produce more output than can fit on a single screen;
iclid will page the output of such commands for you, that is, stop the
output after one screen and indicate that there is more output with a MORE...
prompt. You can see the next screenful of output by selecting any key except
the
q key; you can abort the command and any further output by typing q at
the MORE... prompt. If you do not enter anything within about 30 seconds,
the system will automatically page to the next screenful of information. You
can temporarily defeat this automatic paging by typing ctl-S, although when
you resume scrolling (by selecting any key) you may lose a page of
information.
At any point in iclid, you can type
? to display possible command
completions. You can also abbreviate commands when there is no ambiguity.
The
help command takes as arguments iclid commands and top-level
iclid categories; it displays a brief summary of what the specified
command will display.
The
quit command returns control to the firewall shell. The exit command
is the same as the
The
show command provides many kinds of information, displayed in useful
quit command.
formats. The following table shows examples of the top-level iclid element
that may be displayed by the
52 Voyager Reference Guide
show command as applied to each parameter,
Page 53

along with any selected categories and subcategories, and a description of the
information the command will display.
Element Category Subcategory Description
bgp Provides a BGP summary.
errors A table of BGP errors.
groups A table of parameters and
data for each BGP group.
detailed Detailed statistics on BGP
groups.
summary A summary of statistics on
BGP groups.
memory Lists BGP memory
parameters and statistics.
neighbor <peerid> advertise Shows BGP neighbor
statistics.
detailed Provides detailed
information about BGP
neighbors and is organized
by neighbor address. In the
event of an excessively
long list, type q.
paths List of BGP paths; in the
event of an excessively
long list, type q.
peers Summary information
about peer firewalls.
Voyager Reference Guide 53
Page 54

4 Monitoring and Configuring System Resources
redistribution to AS <as number> Shows detailed
detailed Detailed information about
each peer firewall; in the
event of an excessively
long list, type q.
summary Summary table about peer
firewalls.
redistribution data from
BGP to the designated AS.
to AS <as number>
from <proto>
statistics A table of peer parameters
summary BGP summary.
bootpgw interface BOOTP relay state of
<interface> BOOTP relay state of
stats Summary of BOOTP relay
rec Summary of BOOTP relay
Shows detailed
redistribution data to the
designated AS from the
specified protocol.
and statistics.
interfaces enabled for
BOOT protocols.
specified interface.
requests, and replies
received and made.
requests received.
54 Voyager Reference Guide
req Summary of BOOTP relay
requests made.
rep Summary of BOOTP relay
replies made.
Page 55

dvmrp Summary of DVMRP state.
interface Interface-specific state of
DVMRP for each DVMRPenabled interface.
neighbor-routes State of DVMRP Neighbor
Route.
neighbors Interface state of DVMRP
neighbor parameters.
route Shows state of DVMRP
route parameters.
stats Statistical information
about DVMRP packets
sent and received,
including an error
summary.
receive A summary of statistical
information about received
DVMRP packets.
transmit A summary of statistical
information about
transmitted DVMRP
packets.
error A summary of DVMRP
packets with errors.
igmp State of IGMP.
groups State of the IGMP groups
maintained for each
network interface.
Voyager Reference Guide 55
Page 56

4 Monitoring and Configuring System Resources
if-stats Summary of information
interface IGMP settings for each
stats Statistical information
inbound-filter Lists inbound filters and
interface Status and addresses of all
about IGMP interface
packets transmitted and
received for each network
interface.
network interface.
about IGMP packets sent
and received as well as an
error summary.
data for all protocols.
configured interfaces.
krt Displays IPSRD core
information.
memory Total memory usage in
kbytes.
detailed Total memory usage as
well as memory usage by
each routing protocol.
ospf border-ro uters Lists OSPF border routers
and associated codes.
database area Provides statistical data on
OSPF database area.
database-summary A database summary of the
OSPF firewall.
56 Voyager Reference Guide
Page 57

router Statistical data on firewall
link states as well as link
connections.
asbr-summary A summary of the OSPF
firewall.
external Information on the OSPF
external database.
summary Summary of OSPF
database.
checksum Statistical data on the
OSPF checksum database.
network Data on OSPF database
network.
type Data on the state of firewall
link parameters.
errors brief Provides basic data on
OSPF errors.
dd OSPF dd errors.
hello OSPF hello errors.
ip OSPF interface protocol
errors.
lsack OSPF ls acknowledge
errors.
lsr OSPF lsr errors.
lsu A list of OSPF lsu errors.
proto OSPF protocol errors.
Voyager Reference Guide 57
Page 58

4 Monitoring and Configuring System Resources
events OSPF events and event
interface detail A comprehensive
neighbor Lists OSPF neighbors and
packets Lists received and
<proto> inbound-filter Lists inbound filter data for
redistribution Lists redistributions from all
occurrences.
presentation of detailed
OSPF interface data.
stats A comprehensive list of
OSPF interface statistics.
associated parameters.
transmitted OSPF packets.
the specified protocol.
sources to the designated
protocol.
redistribution
from <proto>
redistribution Shows a comprehensive
resource A comprehensive listing of
rip A summary of information
errors A list of various RIP errors.
Lists redistributions from a
specified protocol to
another specified protocol.
list of redistributions to
various protocols and
autonomous systems, and
includes detailed
distribution data.
resource statistics.
on the RIP routing process.
58 Voyager Reference Guide
Page 59

packets Statistics on various RIP
transmitted and received
packets.
route Lists data on static and
directly connected routes.
aggregate Data on aggregate routes
by code letter.
all List of all routes and status
data. In the event of a long
list, abort by typing q.
aggregate Data on all aggregate
routes by code letter.
bgp Data on BGP routes.
direct Data on direct routes.
igrp Data on IGRP routes.
ospf Data on OSPF routes.
rip Data on RIP routes.
static Dat a on st atic routes.
bgp Statistics on BGP routes.
aspath List of parameters and
status of BGP AS path.
communities Status of BGP
communities.
detailed Details of BGP routes.
metrics Status of BGP metrics.
Voyager Reference Guide 59
Page 60

4 Monitoring and Configuring System Resources
direct Directly connected routes
igrp Displays IGRP routes.
inactive Inactive routes.
suppressed List and status of
suppressed bgp routes.
and their status.
aggregate Inactive aggregate routes.
bgp Inactive BGP routes.
direct Inactive direct routes.
igrp Inactive IGRP routes.
ospf Inactive OSPF routes.
rip Inactive RIP routes.
static Inactive static routes.
ospf OSPF route data.
rip RIP route data.
static Static route data.
summary Dis plays the number of
routes for each protocol.
version Operating system version
information.
vrrp VRRP state information.
60 Voyager Reference Guide
Page 61

interface VRRP interfaces and
associated information.
stats VRRP transmission and
reception statistics.
The following table shows examples of the iclid show command.
iclid Show Command Results
show ospf
show ospf neighbor (s o n)
show route
show route bgp 127
show b?
Shows OSPF summary information.
Shows OSPF neighbor information.
Shows all routes.
Shows only BGP routes that start with 127.
Shows all possible command completions
show b.
for
Resolving and Preventing Full Log Buffers and
Related Console Messages
When a significant amount of your traffic is using fast path for delay-critical,
real-time routing through the firewall, the console might display one of the
following error messages:
[LOG-CRIT] kernel: FW-1: Log Buffer is full
[LOG-CRIT] kernel: FW-1: lost 500 log/trap messages
The kernel module maintains a buffer of waiting log messages that it forwards
through
logging volumes can cause buffer entries to be overwritten before they are
Voyager Reference Guide 61
fwd
to the management module. The buffer is circular, so that high
Page 62

4 Monitoring and Configuring System Resources
sent to
fwd
. When this happens, the system log displays the following
message:
log records lost
The lost records are those that should have been recorded in the FW-1 log
message file (typically located in the $FWDIR/log directory).
You can use one or both of the following solutions to resolve this issue:
! Reduce the number of rules that are logged by:
! Disa bling as many accounting rules as possible
! Changing as many long logging rules to short logging as possible
! Eliminating logging entirely if it is practical to do so
! Increase the size of the kernel module buffer
Note
To perform the following procedures, use the zap or modzap utility
(which you can obtain from the Nokia Technical Assistance Center
(TAC); refer to Resolution 1261).
If you are using FireWall-1 4.1, do the following:
1. Set the execute permissions by issuing an
fwstop command.
2. To confirm that you have sufficient resources to increase the buffer
size, issue the following command:
# ./modzap -n _fw_logalloc $FWDIR/boot/modules/
fwmod.o 0x20000
where
causes
0x20000
modzap
indicates a buffer size of 2MB, and the -n option
to check the value at the symbol reported.
3. A console message is displayed confirming the change that will take
place when you issue the modzap command in the next step. You can
safely ignore this message.
62 Voyager Reference Guide
Page 63

Note
If the message indicates there are insufficient resources to
accommodate a larger buffer size, take appro priate actions and try
this procedure again. For further information, cont act Nokia Technical
Assistance Center (TAC).
4. After you verify that the change is appropriate, issue the same
-n
command without the
# ./modzap _fw_logalloc $FWDIR/boot/modules/fwmod.o
0x20000
option:
A confirmation message is displayed, which you can safely ignore.
5. Reboot the system.
If you are using FireWall-1 NG, do the following:
1. Set the execute permissions by issuing a
cpstop command.
2. To confirm that you have sufficient resources to increase the buffer
size, issue the following command:
modzap -n _fw_log_bufsize $FWDIR/boot/modules/
fwmod.o 0x200000
where
causes
0x20000
modzap
indicates a buffer size of 2MB, and the -n option
to check the value at the symbol reported.
3. A console message is displayed confirming the change that will take
place when you issue the modzap command in the next step. You can
safely ignore this message.
Note
If the message indicates there are insufficient resources to
accommodate a larger buffer size, take appro priate actions and try
this procedure again. For further information, cont act Nokia Technical
Assistance Center (TAC).
Voyager Reference Guide 63
Page 64

4 Monitoring and Configuring System Resources
4. After verifying that the change is appropriate, issue the same
command without the
modzap _fw_log_bufsize $FWDIR/boot/modules/fwmod.o
0x200000
A confirmation message is displayed, which you can safely ignore.
5. Reboot the system.
Because these console messages are also written to the FW-1 log message
file, Nokia recommends that you do the following to prevent depleting the
disk space allocated for the FW-1 log message file:
1. Move your log file(s) from the system hard drive to a server.
2. Configure the relocated files using the Check Point management client
GUI (Smart Dashboard) as follows:
a. Select the Check Point gateway object you are configuring.
b. Under Gateway Object Configuration, select the Logs and
Masters.section and do the following:
-n
option:
! Spe cify the amount of free disk space required for local logging.
! Specify to stop logging when the free disk space drops below
x MBytes and to start logging to a new file.
Once a new file is being used, the previously used log files are deleted
until the required free disk space is restored.
64 Voyager Reference Guide
Page 65

5 Configuring Interfaces
Chapter Contents
! Ethernet Interfaces
! Configuring an Ethernet Interface
! Changing the Speed of an Ethernet Interface
! Changing the Duplex Setting of an Ethernet Interface
! Changing the Autoadvertise Setting of an Ethernet Interface
! Changing the IP Address of an Ethernet Interface
! Ethernet Example
! Gigabit Ethernet Interfaces
! Configuring a Gigabit Ethernet Interface
! Changing the IP Address of a Gigabit Ethernet Interface
! Gigabit Ethernet Example
! Virtual LAN Interface
! Virtual LAN Description
! Configuring a VLAN Interface
! Defining the Maximum number of VLANs
! VLAN Example Topology
! FDDI Interfaces
! Configuring an FDDI Interface
! Changing the Duplex Setting of an FDDI Interface
Voyager Reference Guide 65
Page 66

5 Configuring Interfaces
! Changing the IP Address of an FDDI Interface
! FDDI Example
! ISDN Interfaces
! Features
! Configuring a Physical Interface
! Creating a Logical Interface
! Dial-on-Demand Routing Lists
! ISDN Network Configuration Example
! ISDN Troubleshooting
! Token Ring Interfaces
! Configuring a Token Ring Interface
! Deactivating a Token Ring Interface
! Changing a Token Ring Interface
! Token Ring Example
! Point-to-Point Link over ATM
! Configuring an ATM Interface
! Changing the VPI/VCI of an ATM Interface
! Changing the IP Address of an ATM Interface
! Changing the IP MTU of an ATM Interface
! Removing an ATM Interface
! ATM Example
! Logical IP Subnets (LIS) over ATM
! Configuring an ATM Logical IP Subnet (LIS) Interface
! Changing the VPI/VCIs of an ATM LIS Interface
! Changing the IP Address of an ATM LIS Interface
! Changing the IP MTU of an ATM Interface
! Removing an ATM Interface
! Serial (V.35 and X.21) Interfaces
! Configuring a Serial Interface for Cisco HDLC
66 Voyager Reference Guide
Page 67

! Configuring a Serial Interface for PPP
! Configuring a Serial Interface for Frame Relay
! Serial Inte rface Example
! T1 (with built-in CSU/DSU) Interfaces
! Configuring a T1 Interface for Cisco HDLC
! Configuring a T1 Interface for PPP
! Configuring a T1 Interface for Frame Relay
! T1 Interface Example
! E1 (with built-in CSU/DSU) Interfaces
! Configuring an E1 Interface for Cisco HDLC
! Configuring an E1 Interface for PPP
! Configuring an E1 Interface for Frame Relay
! HSSI Interfaces
! Configuring an HSSI Interface for Cisco HDLC
! Configuring an HSSI Interface for PPP
! Configuring an HSSI Interface for Frame Relay
! Unnumbered Interfaces
! Unnumbered Interfa ces Description
! Configuring an Unnumbered Interface
! Changing an Unnumbered Interfac e to a Numbered Interface
! Configuring a Static Route over an Unnumbered Interface
! Configuring OSPF over an Unnumbered Interface
! Configuring OSPF over an Unnumbered Interface Using Virtual Links
! Cisco HDLC Protocol
! Changing the Keepalive Interval for Cisco HDLC
! Changing the IP Address in Cisco HDLC
! Point-to-Point Protocol
! Changing the Keepalive Interval in PPP
! Changing the Keepalive Maximum Failures in PPP
Voyager Reference Guide 67
Page 68

5 Configuring Interfaces
! Changing the IP Address in PPP
! Frame Relay Protocol
! Changing the Keepalive Interval in Frame Relay
! Changing the DLCI in Frame Relay
! Changing the LMI Parameters in Frame Relay
! Changing the Interface Type in Frame Relay
! Changing the Active Status Monitor Setting in Frame Relay
! Changing the IP Address in Frame Relay
! Removing a Frame Relay Interface
! Loopback Interfaces
! Adding an IP Address to a Loopback Interface
! Changing the IP Address of a Loopback Interface
! GRE Tunnels
! Creating a GRE Tunnel
! Changing the Local and/or Remote Address or Local/Remote
Endpoint of a GRE Tunnel
! Changing IP TOS Value of a GRE Tunnel
! Rem ov ing a GRE Tunnel
! GRE Tunnel Example
! HA GRE Tunnels Description
! HA GRE Tunnel Example
! DVMRP Tunnels
! Creating a DVMRP Tunnel
! Changing the Local or Remote Addresses of a DVMRP Tunnel
! Removing a DVMRP Tunnel
! DVMRP Tunnel Example
! ARP Table Entries
! Changing ARP Global Parameters
! Adding a Static ARP Entry
68 Voyager Reference Guide
Page 69

! Adding a Proxy ARP Entry
! Deleting a Static ARP Entry
! Viewing Dynamic ARP Entries
! Deleting Dynamic ARP Entries
! Flushing All Dynamic ARP Entries
! Configuring ARP for the ATM Interface
! Changing Global Parameters
! Adding a Static ATM ARP Entry
! Deleting a Static ATM ARP Entry
! Viewing and Deleting Dynamic ATM ARP Entries
Ethernet Interfaces
Configuring an Ethernet Interface
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
HYSICAL
column.
Example—
eth-s2p1
4. Click the 10 MBIT/SEC or the 100 MBIT/SEC radio button in the
P
HYSICAL CONFIGURATION table LINK SPEED field to select the link
speed.
Note
This setting must be the same for all hosts on the network to which the
device connects.
Voyager Reference Guide 69
Page 70

5 Configuring Interfaces
5. Click the FULL or HALF radio button in the PHYSICAL CONFIGURATION
table DUPLEX field to select the duplex mode. Click APPLY.
Note
This setting must be the same for all hosts on the network to which the
device connects.
6. (Optional) Click ON or OFF radio button in the PHYSICAL
CONFIGURATION table AUTOADVERTISE field to enable or disable the
autoadvertise feature. If turned on, the device will advertise its
configuration speed and duplex status using Ethe rnet negotiation. Click
A
PPLY.
7. Click the logical interface name in the I
OGICAL INTERFACES table to go to the Interface page.
L
8. Enter the IP address for the device in the N
9. Enter the IP subnet mask length in the N
Click A
Each time you click A
PPLY .
PPLY, the configured IP address and mask length
NTERFACE column of the
EW IP ADDRESS edit box.
EW MASK LENGTH edit box.
are added to the table. The entry fields remain blank to allow you to add
more IP addresses.
To enter another IP address and IP subnet mask length, repeat steps 8-9.
10. (Optional) Change the interface’s logical name to a more meaningful one
by typing the preferred name in the L
A
PPLY.
OGICAL NAME edit box. Click
11. (Optional) Add a comment to further define the logical interfaces function
in the C
12. Click the U
13. Click the O
have configured, Click A
OMMENTS edit box. Click APPLY.
P button to go to the Interface Configuration page.
N radio button that corresponds to the logical interface you
PPLY.
The Ethernet interface is now available for IP traffic and routing.
To make your changes permanent, click S
70 Voyager Reference Guide
AVE.
Page 71

Changing the Speed of an Ethernet Interface
If the link speed of an Ethernet interface is incorrect, it will not send or
receive data. The following steps describe how to change the speed of an
Ethernet interface.
1. Click C
ONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to change in the P
HYSICAL
column.
Example—
eth-s2p1
4. Click the 10 MBIT/SEC or the 100 MBIT/SEC radio button in the
HYSICAL CONFIGURATION table LINK SPEED field. Click APPLY.
P
Note
This setting must be the same for all hosts on the network to which the
device connects.
To make your changes permanent, click SAVE.
Changing the Duplex Setting of an Ethernet Interface
Note
If the duplex setting of an Ethernet interface is incorrect, it may not
receive data, or it may receive duplicates of the data it sends.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to change in the P
column.
Voyager Reference Guide 71
HYSICAL
Page 72

5 Configuring Interfaces
Example—
eth-s2p1
4. Click the FULL or HALF radio button in the PHYSICAL CONFIGURATION
table D
Note
This setting must be the same for all hosts on the network to which the
device connects.
UPLEX field. Click APPLY.
To make your changes permanent, click SAVE.
Changing the Autoadvertise Setting of an Ethernet
Interface
When Autoadvertise is enabled on an Ethernet interface, the device advertises
its configured speed and duplex setting using Ethernet negotiation.
1. Click C
ONFIG on the Voyager home page.
2. Click the Interfaces link.
3. Click the Physical interface that you want to change in the Physical
column.
Example—
eth-s2p1
4. Click the O
A
UTOADVERTISE field to enable or disable the autoadvertise feature.
Click
To make your changes permanent, click S
N or OFF radio button in the PHYSICAL CONFIGURATION table
APPLY.
AVE.
72 Voyager Reference Guide
Page 73

Changing the IP Address of an Ethernet Interface
Note
Do not change the IP address you use in your browser to access
Voyager. If you do, you can no longer access the network application
platform (unit) with your browser.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the logical interface link for which you want to change the IP
address in the L
Example—
eth-s2p1c0
4. To remove the old IP address, click the DELETE check box that
corresponds to the address you want to delete, then click A
OGICAL column.
PPLY.
5. T o add the new IP address, enter the IP address for the device in the N
ADDRESS edit box.
IP
6. Enter the IP subnet mask length in the N
Click A
PPLY .
Each time you click A
length are added to the table. The entry fields remain blank to allow you
to add more IP addresses.
To make your changes permanent, click S
Ethernet Example
This section describes how you might configure the interfaces of your
network application platform (unit) in an example network, using Voyager.
Before you can configure the unit using Voyager, you must configure an IP
address on one of the interfaces. You can do this through the unit console port
EW
EW MASK LENGTH edit box.
PPLY , the newly configured IP address and mask
AVE.
Voyager Reference Guide 73
Page 74

5 Configuring Interfaces
during installation or by using the Lynx browser. This allows a graphical
browser such as Microsoft Internet Explorer or Netscape Navigator to access
the unit through that interface. You can use any graphical web browse r to
configure the other interfaces on the unit by entering the IP address of the unit
in the location field of the browser.
The figure below shows the network configuration for this example.
Provider
(192.168.2.93)
ser-s1p1c0 (192.168.2.1)
Nokia Platform A
atm-s2p1c93 (192.168.3.2)
ATM
Switch
atm-s1p1c52 (192.168.3.1)
Nokia Platform B
eth-s2p1c0 (192.168.4.1/24)
192.168.4.xxx
00037
Server
FDDI
192.168.1.xxx
fddi-s3p1c0
(192.168.1.1/24)
Server Server
In a company's main office, Nokia Platform A terminates a serial line to an
Internet service provider, running PPP with a keepalive value of 10.
Nokia Platform A also provides internet access for a FDDI ring and a remote
branch office connec te d via ATM PVC 93.
74 Voyager Reference Guide
Page 75

The branch office contains Nokia Platform B, which routes traffic between a
local Fast Ethernet network and ATM PVC 52. It provides access to the main
office and the Internet. We are configuring the Ethernet interface on Nokia
Platform B.
1. Click C
ONFIG on the home page.
2. Click the Interfaces link.
3. Click
4. Click the 100 M
5. Click A
6. Click
eth-s2p1 in the PHYSICAL column of the table.
BIT/SEC radio button.
PPLY .
eth-s2p1c0 in the LOGICAL INTERFACES table to go to the Interface
page.
7. Enter 192.168.4.1 in the N
8. Enter 24 in the N
9. Click A
10. Click the U
11. Click the O
12. Click A
13. Click S
PPLY .
P button to go the Interfaces page.
N radio button for eth-s2p1c0.
PPLY .
AVE.
EW MASK LENGTH edit box.
EW IP ADDRESS edit box.
Gigabit Ethernet Interfaces
Configuring a Gigabit Ethernet Interface
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
column of the Interface Configuration page.
Voyager Reference Guide 75
HYSICAL
Page 76

5 Configuring Interfaces
Example—
eth-s5p1
Note
The link speed appears in the PHYSICAL CONFIGURATION table in the
LINK SPEED field. The speed is fixed.
Note
The duplex mode, in the PHYSICAL CONFIGURATION table, is set to full at
all times.
4. (Optional) Click the ON or OFF radio button in the PHYSICAL
CONFIGURATION table’s FLOW CONTROL field to select the appropriate
choice. The default value is OFF. Click A
PPLY.
Click the logical interface name in the I
L
OGICAL INTERFACES table to go to the Interface page.
5. Enter the IP address for the device in the N
6. Enter the IP subnet mask length in the N
Click A
7. Each time you click A
PPLY .
PPLY, the configured IP address and mask length
NTERFACE column of the
EW IP ADDRESS edit box.
EW MASK LENGTH edit box.
are added to the table. The entry fields remain blank to allow you to add
more IP addresses.
To enter another IP address and IP subnet mask length, repeat steps 5-6.
8. (Optional) Change the interface’s logical name to a more meaningful one
by typing the preferred name in the L
PPLY.
A
OGICAL NAME edit box. Click
9. (Optional) Add a comment to further define the logical interfaces function
in the C
10. Click the U
OMMENTS edit box. Click APPLY.
P button to go to the Interface Configuration page.
76 Voyager Reference Guide
Page 77

11. Click the ON radio button that corresponds to the logical interface you
have configured. Click A
PPLY.
The Gigabit Ethernet interface is now available for IP traffic and routing.
To make your changes permanent, click S
AVE.
Changing the IP Address of a Gigabit Ethernet
Interface
Note
Do not change the IP address you use in your browser to access
Voyager. If you do, you can no longer access the network application
platform (unit) with your browser.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the logical interface link for which you want to change the IP
address in the L
Example—
eth-s5p1c0
OGICAL column of the Interface Configuration page.
4. To remove the old IP address, click the DELETE check box that
corresponds to the address you want to delete; then click A
5. T o add the new IP address, enter the IP address for the device in the N
ADDRESS edit box.
IP
6. Enter the IP subnet mask length in the N
Click A
Each time you click A
PPLY .
PPLY , the newly configured IP address and mask
EW MASK LENGTH edit box.
PPLY .
EW
length are added to the table. The entry fields remain blank to allow you
to add more IP addresses.
To make your changes permanent, click S
Voyager Reference Guide 77
AVE.
Page 78

5 Configuring Interfaces
Gigabit Ethernet Example
This section describes how you might configure the interfaces of your
network application platform (unit) in an example network, using Voyager.
Before you can configure the unit using Voyager, you must configure an IP
address on one of the interfaces. You can do this through the unit’s console
port during installation or by using the Lynx browser. This allows a graphical
browser such as Microsoft Internet Explorer or Netscape Navigator to access
the unit through that interface. You can use any graphical web browse r to
configure the other interfaces on the unit by entering the IP address of the unit
in the location field of the browser.
78 Voyager Reference Guide
Page 79

The figure below shows the network configuration for this example.
Provider
(192.168.2.93)
ser-s1p1c0 (192.168.2.1)
Nokia Platform A
atm-s2p1c93 (192.168.3.2)
ATM
Switch
atm-s1p1c52 (192.168.3.1)
Nokia Platform B
eth-s2p1c0 (192.168.4.1/24)
192.168.4.xxx
00037
Server
FDDI
192.168.1.xxx
fddi-s3p1c0
(192.168.1.1/24)
Server Server
In a company's main office, Nokia Platform A terminates a serial line to an
Internet service provider.
Nokia Platform A also provides internet access for a FDDI ring and a remote
branch office connec ted via ATM.
The branch office contains Nokia Platform B, which routes traffic between a
local Gigabit Ethernet network and ATM. It provides access to the main office
Voyager Reference Guide 79
Page 80

5 Configuring Interfaces
and the Internet. We are configuring the Gigabit Ethernet interface on Nokia
Platform B.
1. Click C
ONFIG on the home page.
2. Click the Interfaces link.
3. Click
4. Click the
P
5. Click A
6. Click
eth-s2p1 in the PHYSICAL column of the table.
ON or OFF radio button in the FLOW CONTROL field of the
HYSICAL CONFIGURATION table.
PPLY .
eth-s2p1c0 in the LOGICAL INTERFACES table to go to the Interface
page.
7. Enter 192.168.4.1 in the N
8. Enter 24 in the N
9. Click A
10. Click the U
11. Click the O
12. Click A
13. Click S
PPLY .
P button to go the Interface Configuration page.
N radio button for eth-s5p1c0.
PPLY .
AVE.
EW MASK LENGTH edit box.
EW IP ADDRESS edit box.
Virtual LAN Interfaces
Virtual LAN Description
Nokia supports Virtual LAN (VLAN) interfaces on all supported ethernet
interfaces. The use of VLAN interfaces lets you configure subnets with a
secure private link to Check Point FW-1/VPN-1 with the existing topology.
The use of VLAN enables the multiplexing of ethernet traffic into channels on
a single cable.
80 Voyager Reference Guide
Page 81

The Nokia implementation supports adding a logical interface with a VLAN
ID to a physical interface. In a VLAN packet, the OSI layer-two header, or
MAC header, contains four more bytes than the typical ethernet header for a
total of 18 bytes. When traffic arrives at the physical interface, the system
examines it for the VLAN layer-two header and accepts and forwards the
traffic if a VLAN logical interface is configured. If the traffic that arrives at
the physical interface does not have a VLAN header, it is directed to the
channel 0, or untagged, interface. In the Nokia implementation the untagged
channel 0 interface drops VLAN packets sent to the subnets on that interface.
Outgoing traffic from a VLAN interface is tagged with the VLAN header . The
Nokia appliance can receive and generate fully conformant IEEE 802.1Q
tags. The IEEE802.1Q standard defines the technology for virtual bridged
networks. The Nokia implementation is completely interoperable as a router,
not as a switch.
Configuring a VLAN Interface
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the link to the physical ethernet interface for which you want to
enable a VLAN interface in the P
HYSICAL field. This action takes you to
the physical interface page for that interface.
4. Enter a value to identify the VLAN interface in the C
VLAN I
D edit box. The range is 2 to 4094. The values 0 and 4095 are
REATE A NEW
reserved by the IEEE standard. VLAN ID 1 is reserved by convention.
There is no default. Click A
5. The new logical interface for the VLAN appears in the L
I
NTERFACES field with the name eth-sXpYcZ, where X is the slot
PPLY.
OGICAL
number, Y is the physical port number and Z is the channel number. The
channel numbers increment starting with 1 with each VLAN ID that you
create.
6. Click S
Voyager Reference Guide 81
AVE to make your changes permanent.
Page 82

5 Configuring Interfaces
7. Repeat steps 4 through 6 for each VLAN interface you want to create.
8. To assign an IP address to the new logical VLAN interface, click the link
for the logical interface in the I
I
NTERFACES table. Enter the IP address in the NEW IP ADDRESS edit
box. Enter the mask length in the N
A
PPLY.
NTERFACE field of the LOGICAL
EW MASK LENGTH edit box. Click
9. Click S
AVE to make your changes permanent.
The new logical interface appears as active on the interface configuration
page. Click the U
P button to view that page.
(Optional) To disable the interface, click the
field in the row for the logical interface. Click A
S
AVE to make your change permanent.
Note
You can assign multiple IP addresses to each logical VLAN interface.
Repeat steps 8 and 9 for each IP address you want to assign to the same
VLAN logical interface.
Deleting a VLAN Interface
1. Click CONFIG on the home page.
2. Click the I
3. Click the link for the physical interface for which you want to delete a
VLAN interface in the P
physical interface page for the interface.
NTERFACES link.
OFF button in the ACTIVE
PPLY , and then click
HYSICAL field. This action takes you to the
4. In the L
OGICAL INTERFACE table, click the DELETE box in the row for the
logical VLAN interface you want to delete.
5. Click A
PPLY , and then click SAVE to make your change permanent.
The entry for the logical VLAN interface disappears from the L
NTERFACES table.
I
82 Voyager Reference Guide
OGICAL
Page 83

Defining the Maximum number of VLANs
1. Click CONFIG on the home page.
2. Click the I
NTERFACES link.
3. Enter a number in the M
The maximum value is 1015.
4. Click A
PPLY , and then click SAVE to make your change permanent.
VLAN Example Topology
The topology below represents a fully-redundant firewall with load sharing
and VLAN. Each Nokia appliance running Check Point FW-1 is configured
with the V irtual Router Redundancy Protocol (VRRP). This protocol provides
dynamic fail-over of IP addresses from one router to another in the event of
failure. See VRRP Description for more information. Each appliance is
configured with Gigabit Ethernet and supports multiple VLANs on a single
cable. The appliances receive and forward VLAN-tagged traffic to subnets
AXIMUM NUMBER OF VLANS ALLOWED edit-box.
Voyager Reference Guide 83
Page 84

5 Configuring Interfaces
configured for VLAN, creating a secure private network. In addition, the
appliances are configured to create VLAN-tagged messages for output.
Multiple VLANs on
single cable
GSR
GS
FDDI Interfaces
gigabit
switch
switch
Un tagged VLAN tagged Un tagged
Ethernet
gigabit
Ethernet
VRRP
pair
NOK/CP
FW-1
FW-1
sync
NOK/CP
FW-1
VRRP
pair
gigabit
Ethernet
gigabit
Ethernet
VLAN
switch
VLAN
switch
00203
Configuring an FDDI Interface
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
column.
84 Voyager Reference Guide
HYSICAL
Page 85

Example—
fddi-s2p1
4. Click the FULL or HALF radio button in the PHYSICAL CONFIGURATION
table D
Note
A device attached to a ring topology should be set to half duplex. If the
device is running in point-to-point mode, the du ple x set tin g sh ou ld be set
to full. This setting must be the same for all hosts on the network to which
the device connects.
UPLEX field, then click APPLY.
5. Click the logical interface name in the INTERFACE column of the
OGICAL INTERFACES table to go to the Interface page.
L
6. Enter the IP address for the device in the N
7. Enter the subnet mask length in the N
click A
Each time you click A
PPLY.
PPLY , the configured IP address and mask length
EW IP ADDRESS edit box.
EW MASK LENGTH edit box, then
are added to the table. The entry fields remain blank to allow you to add
more IP addresses.
To enter another IP address and IP subnet mask length, repeat steps 6-7.
8. (Optional) Change the interface’s logical name to a more meaningful one
by typing the preferred name in the L
PPLY.
A
OGICAL NAME edit box, then click
9. (Optional) Add a comment to further define the logical interfaces function
in the C
10. Click the U
11. Click the O
have configured, then click A
OMMENTS edit box. Click APPLY.
P button to go the Interface Configuration page.
N radio button that corresponds to the logical interface you
PPLY.
The FDDI interface is now available for IP traffic and routing.
To make your changes permanent, click S
AVE.
Voyager Reference Guide 85
Page 86

5 Configuring Interfaces
Changing the Duplex Setting of an FDDI Interface
Note
If the duplex setting of an FDDI interface is incorrect, it may not receive
data, or it may receive duplicates of the data it sends.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to change in the P
HYSICAL
column.
Example—
fddi-s2p1
4. Click the FULL or HALF radio button in the PHYSICAL CONFIGURATION
table D
Note
A device attached to a ring topology should be set to half duplex. If the
device is running in point-to-point mode, the du ple x set tin g sh ou ld be set
to full. This setting must be the same for all hosts on the network to which
the device connects.
UPLEX field, then click APPLY.
To make your changes permanent, click SAVE.
86 Voyager Reference Guide
Page 87

Changing the IP Address of an FDDI Interface
Note
Do not change the IP address you use in your browser to access
Voyager. If you do, you can no longer access the network application
platform (unit) with your browser.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the logical interface link for which you want to change the IP
address in the L
Example—
fddi-s2p1c0
4. To remove the old IP address, click the DELETE check box that
corresponds to the address you want to delete,
OGICAL column.
then click APPLY.
5. T o add the new IP address, enter the IP address for the device in the N
IP
6. Enter the subnet mask length in the N
click A
Each time you click A
added to the table. The entry fields remain blank to allow you to add more
IP addresses.
To make your changes permanent, click S
FDDI Example
This section describes how you might configure the interfaces of your
network application platform (unit) in an example network, using Voyager.
Before you can configure the unit using Voyager, you must configure an IP
address on one of the interfaces. You can do this through the unit console port
EW
ADDRESS edit box.
EW MASK LENGTH edit box, then
PPLY.
PPLY , the new IP address and mask length are
AVE.
Voyager Reference Guide 87
Page 88

5 Configuring Interfaces
during installation or by using the Lynx browser. This allows a graphical
browser such as Internet Explorer or Netscape Navigator to access the unit
through that interface. You can use any graphical web browser to configure
the other interfaces on the unit by entering the IP address of the unit in the
location field of the browser.
The figure below shows the network configuration for this example.
Provider
(192.168.2.93)
ser-s1p1c0 (192.168.2.1)
Nokia Platform A
atm-s2p1c93 (192.168.3.2)
ATM
Switch
atm-s1p1c52 (192.168.3.1)
Nokia Platform B
eth-s2p1c0 (192.168.4.1/24)
192.168.4.xxx
00037
Server
FDDI
192.168.1.xxx
fddi-s3p1c0
(192.168.1.1/24)
Server Server
In a company's main office, Nokia Platform A terminates a serial line to an
Internet service provider, running PPP with a keepalive value of 10.
Nokia Platform A also provides internet access for a FDDI ring and a remote
branch office connec te d via ATM PVC 93.
88 Voyager Reference Guide
Page 89

The branch office contains Nokia Platform B, which routes traffic between a
local Fast Ethernet network and ATM PVC 52. It provides access to the main
office and the Internet. We are configuring the FDDI interface on Nokia
Platform A.
1. Click C
ONFIG on the home page.
2. Click the Interfaces link.
3. Click
4. Click the H
5. Click A
6. Click
fddi-s3p1 in the PHYSICAL column of the table.
ALF radio button to select the duplex setting.
PPLY .
fddi-s3p1c0 in the LOGICAL INTERFACES table to go to the
Interface page.
7. Enter
8. Enter 24 in the N
9. Click A
10. Click the U
11. Click the O
12. Click A
13. Click S
192.168.1.1 in the NEW IP ADDRESS edit box.
EW MASK LENGTH edit box.
PPLY .
P button to go the Interfaces page.
N radio button for fddi-s3p1c0.
PPLY .
AVE.
ISDN Interfaces
Integrated Services Digital Network is a system of digital phone connections
that allows voice, digital network services, and video data to be transmitted
simultaneously using end-to-end digital connectivity.
Nokia’s Network Application Platform (Nokia PlatformNokia Platform)
offers support for an ISDN Basic Rate Interface (BRI) physical interface. The
ISDN BRI comprises one 16 Kbps D-channel for signalling and control, and
two 64 Kbps B-channels for information transfer . Nokia’ s physical interface is
Voyager Reference Guide 89
Page 90

5 Configuring Interfaces
certified to conform to the European Telecommunications Standards Institute
(ETSI) ISDN standard.
The physical interface is the manageable representation of the physical
connection to ISDN. One physical interface will be visible in Voyager for
every ISDN BRI card in the Nokia Platform chassis. The physical interface
enables management of the parameters specific to each ISDN connection. It
permits enabling or disabling of the ISDN connection and is the entity under
which logical interfaces are created.
The logical interface is the logical communication end-point. It contains all
information used to set up and maintain the ISDN call. The logical interface
comprises:
! Data link encapsulation and addressing
! Call connection information such as call direction, data rate, and the
number to call
! Authentication information such as names, passwords, and authentication
method
Features
! Bandwidth allocation for Multilink PPP
After configuring the physical interface, then creating and configuring the
logical interfaces, the Nokia Platform will be ready to make and accept ISDN
calls. Detailed information on how to create and configure ISDN interfaces
begins in “Configuring a Physical Interface.”
The features supported by the ISDN interface are summarized below:
! Port—ISDN Basic Rate S/T interface with RJ45 connector
! ISDN signaling—ETSI EURO-ISDN (ETS 300 102)
! B-channel protocols—IETF PPP (RFC 1661 and 1662); IETF Multilink
PPP (RFC 1990)
! Security—PAP (RFC 1334), CHAP (RFC 1994), and ISDN Caller ID
90 Voyager Reference Guide
Page 91

! Dial-on-demand routing—The ISDN interface can be configured so that
only certain types of traffic establish and maintain an ISDN connection.
Circuits are automatically torn down if they are not required.
! Dynamic bandwidth allocation—The ISDN interface can be configured to
add or remove additional bandwidth as the traffic requires it.
! Multiple destination support—An ISDN interface can be configured to
connect to two different destinations simultaneously.
! Dial-in support—The ISDN interface can be configured to accept
incoming calls from remote sites.
Configuring a Physical Interface
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
HYSICAL
column.
Example—
isdn-s2p1
4. From the pull-down menu in the SWITCH TYPE field in the PHYSICAL
C
ONFIGURATION table, select the service provider-switch type that
corresponds to the interface's network connection.
5. In the L
click the P
INE TOPOLOGY field in the PHYSICAL CONFIGURATION table,
OINT-TO-POINT or MULTIPOINT radio button to describe the
connection type of the interface.
6. Click the A
(terminal-endpoint identifier) field in the P
UTOMATIC or MANUAL radio button in the TEI OPTION
HYSICAL CONFIGURATION
table.
Generally, automatic TEIs are used with multipoint connections, while
fixed TEIs are used in point-to-point configurations.
7. Click A
PPLY .
Voyager Reference Guide 91
Page 92

5 Configuring Interfaces
8. (Optional) If you selected MANUAL as the TEI Option, enter the TEI
assigned to the ISDN interface in the TEI field.
9. In the P
P
OWERUP radio button in the TEI ASSIGN field to specify when you
HYSICAL CONFIGURATION table, click the FIRST-CALL or
want the ISDN Layer 2 (TEI) negotiation to occur.
! First-Call—ISDN TEI negotiation should occur when the first ISDN call
is placed or received.
The first-call option is mainly used in European ISDN switch types (for
example, ETSI).
! PowerUp—ISDN TEI negotiation should occur when the router is
powered on.
10. Click A
PPLY .
11. To make your changes permanent, click S
Creating a Logical Interface
To Configure an ISDN Logical Interface to Place
Calls
AVE.
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. In the P
HYSICAL column, click on the ISDN physical-name, interface link
you want to configure.
Example—
isdn-s2p1
4. Using the ENCAPSULATION edit box in the CREATE NEW LOGICAL
I
NTERFACE table, select whether to run PPP or multilink PPP on the
interface; then click A
A newly created logical interface appears in the I
L
OGICAL INTERFACES table.
92 Voyager Reference Guide
PPLY.
NTERFACE column of the
Page 93

5. Click the logical interface name in the INTERFACE column of the
L
OGICAL INTERFACES table to go to the Interface page.
6. If the interface should be unnumbered, perform steps a and b. If the
interface should be numbered, skip to step 7.
In unnumbered mode the interface does not have its own unique IP
address—the address of another interface is used.
a. Click Y
b. Use the P
ES next to UNNUMBERED INTERFACE, then click APPLY.
ROXY INTERFACE pull-down menu to select the logical
interface from which the address for this interface is taken.
7. Enter the IP address for the local end of the connection in the L
ADDRESS edit box in the INTERFACE INFORMATION table.
OCAL
You must enter a valid IP address. IPSO does not support dynamically
assigned IP addresses for ISDN interfaces. Do not enter 0.0.0.0.
8. Enter the IP address of the remote end of the connection in the R
ADDRESS edit box in the INTERFACE INFORMATION table.
9. (Optional) Enter a string comment in the D
ONNECTION INFORMATION table to describe the purpose of the logical
C
ESCRIPTION edit box in the
interface, for example, Connection to Sales Office.
10. Click the O
NFORMATION table.
I
11. (Optional) Enter the value for the idle time-out in the I
in the C
UTGOING Direction radio button in the CONNECTION
DLE TIME edit box
ONNECTION INFORMATION table.
This time entry defines the time in seconds that an active B-channel can
be idle before it is disconnected. A value of zero indicates that the active
B-channel will never disconnect. The range is 0-99999. The default value
is 120.
EMOTE
12. (Optional) Enter the value for the minimum call time in the M
C
ALL TIME edit box in the CONNECTION INFORMATION table.
This entry defines the minimum number of seconds a call must be
connected before it can be disconnected by an idle timeout. A value of 0
indicates that the call can be disconnected immediately upon expiration of
Voyager Reference Guide 93
INIMUM
Page 94

5 Configuring Interfaces
the idle timer . If the service provider has a minimum charge for each call,
it is recommended the minimum call time be set to this value. The range
is 0-99999. The default value is 120.
13. Click the 64 K
ONNECTION INFORMATION table to set the data rate for outgoing calls.
C
14. Enter values for a remote number and subaddress in the R
N
UMBER and (optional) REMOTE SUB NUMBER edit boxes in the
C
ONNECTION INFORMATION table.
BPS or 56 KBPS radio button in the RATE field in the
EMOTE
15. (Optional) Enter values for a calling number and subaddress in the
C
ALLING NUMBER and CALLING SUB NUMBER edit boxes in the
ONNECTION INFORMATION table.
C
The calling number and subaddress are inserted in a SETUP message
when an outgoing call is made.
Note
The AUTHENTICATION table entries, which follow, allow the user to
manage the parameters used to authenticate both ends of the
communication link.
16. In the TO REMOTE HOST section of the AUTHENTICATION table, in the
AME edit box, enter the name that needs to be returned to a remote host
N
when it attempts to authenticate this host.
17. In the T
P
ASSWORD edit box, enter the password to be returned to the remote host
O REMOTE HOST section of the AUTHENTICATION table, in the
for PAP authentication, or the secret used to generate the challenge
response for CHAP authentication.
Note
The TO REMOTE HOST information must be the same as the FROM
EMOTE HOST information (or its equivalent) at the remote end of the
R
link.
94 Voyager Reference Guide
Page 95

18. In the FROM REMOTE HOST section of the AUTHENTICATION table select
the authentication method used to authenticate the remote host.
19. In the F
N
ROM REMOTE HOST section of the AUTHENTICATION table, in the
AME edit box, enter the name that will be returned from the remote host
when this host attempts to authenticate the remote host.
20. In the F
P
ASSWORD edit box, enter a password to be returned by the remote host
ROM REMOTE HOST section of the AUTHENTICATION table, in the
for PAP authentication, or the secret used to validate the challenge
response for CHAP authentication.
Note
The FROM REMOTE HOST information must be the same as the TO
REMOTE HOST information (or its equivalent) at the remote end of the
link.
Note
The BANDWIDTH ALLOCATION table entries that follow allow the network
administrator to manage the p arameters th at are used to determine when
to add or remove an additional B-channel only when using Multilink PPP.
21. In the BANDWIDTH ALLOCATION table, in the UTILIZATION LEVEL edit
box, enter a percentage bandwidth utilization level at which the additional
B-channel will be added or removed. When the measured utilization of an
outgoing B-channel exceeds the utilization level threshold for a period of
time greater than the utilization period, the second B-channel will be
brought into operation. When the outgoing B-channel utilization falls
below the utilization level for a period of time greater than the value of
the utilization period, the second B-channel will be removed from
operation.
A utilization level of zero means that the second B-channel is never
brought into operation. To bring the second B-channel into operation
quickly, set the utilization level to a low number, such as one.
Voyager Reference Guide 95
Page 96

5 Configuring Interfaces
22. In the BANDWIDTH ALLOCATION table, in the UTILIZATION PERIOD edit
box, enter the utilization period. This value specifies the number of
seconds the outgoing B-channel utilization must remain above the
utilization level before a second channel is brought into operation. Once a
second B-channel has been added, this value specifies the nu mber of
seconds that the utilization of the outgoing B-channel must be below the
utilization level before the second B-channel is removed from operation.
A utilization period set to zero will cause the second B-channel to be
brought into operation immediately; the utilization level has been
exceeded. It will also cause the second B-channel to be removed from
operation; immediately the measured utilization drops below the
utilization level.
23. Click A
24. To make your changes permanent, click S
PPLY .
AVE.
For troubleshooting information, see “ISDN Troubl esho oting.”
To Configure an Interface to Receive Calls
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
column.
Example—
isdn-s2p1
4. Select whether to run PPP or multilink PPP on the interface from the
E
NCAPSULATION edit box in the CREATE NEW LOGICAL INTERFACE
table; then click A
A new logical interface appears in the I
OGICAL INTERFACES table.
L
PPLY .
NTERFACE column of the
HYSICAL
5. Click the logical interface name in the I
L
OGICAL INTERFACES table to go to the Interface page.
96 Voyager Reference Guide
NTERFACE column of the
Page 97

6. Enter the IP address for the local end of the connection in the LOCAL
ADDRESS edit box in the INTERFACE INFORMATION table.
7. Enter the IP address of the remote end of the connection in the R
ADDRESS edit box in the INTERFACE INFORMATION table.
8. Click the I
NFORMATION table.
I
9. Click A
NCOMING Direction radio button in the CONNECTION
PPLY .
EMOTE
10. To configure the list of incoming numbers with permission to call into this
interface, click the Incoming Numbers link.
Note
If no incoming call numbers are configured, all incoming calls will be
accepted.
11. In the TO REMOTE HOST section of the AUTHENTICATION table, in the
N
AME edit box, enter the name that needs to be returned to a remote host
when it attempts to authenticate this host.
12. In the T
ASSWORD edit box, enter the password to be returned to the remote host
P
O REMOTE HOST section of the AUTHENTICATION table, in the
for PAP authentication, or the secret used to generate the challenge
response for CHAP authentication.
Note
The TO REMOTE HOST information must be the same as the FROM
EMOTE HOST information (or its equivalent) at the remote end of the
R
link.
13. In the FROM REMOTE HOST section of the AUTHENTICATION table select
the authentication method used to authenticate the remote host.
14. In the F
N
ROM REMOTE HOST section of the AUTHENTICATION table, in the
AME edit box, enter the name that will be returned from the remote host
when this host attempts to authenticate the remote host.
Voyager Reference Guide 97
Page 98

5 Configuring Interfaces
15. In the FROM REMOTE HOST section of the AUTHENTICATION table, in the
P
ASSWORD edit box, enter a password to be returned by the remote host
for PAP authentication, or the secret used to validate the challenge
response for CHAP authentication.
Note
The FROM REMOTE HOST information must be the same as the TO
REMOTE HOST information (or its equivalent) at the remote end of the
link.
16. To make your changes permanent, click SAVE
For troubleshooting information, see “ISDN Troubl esho oting.”
To configure Calling Line-Identification Screening
Incoming calls to the Nokia Platform can be filtered using the calling number
in the received SETUP message. Calling Line Identification (CLID) must be
supported by the network to filter calls using the calling number.
When an incoming call is received, the calling number in the received SETUP
message is checked against the incoming numbers configured on each logical
interface. The calling number is compared with each incoming call using the
“right-most-digits” algorithm. A number matches if the shortest string
between the received calling number and the incoming number is the same.
For example, if the calling number received was 345 and the logical interface
has an incoming number of 12345, then this is deemed a match.
The call is answered on the interface that is configured with the incoming
number with the highest number of matching digits. If no matching incoming
number is found, the call is rejected.
If no incoming numbers are configured on an interface then any incoming call
is deemed a match.
Information on how to add and delete incoming numbers to the logical
interface is detailed below.
98 Voyager Reference Guide
Page 99

To Add an Incoming Number
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link in the P
HYSICAL column.
Example—
isdn-s2p1
4. Click the logical interface link in the LOGICAL INTERFACES table.
5. Click the Incoming Numbers link.
6. In the N
to accept incoming calls; click A
An
7. Click the Y
UMBER edit box, enter the telephone number on which you want
PPLY.
x is used to represent a wild-card character.
ES radio button in the CALLBACK field if you want the
incoming call to be disconnected, and an outgoing call attempted;
otherwise, click the N
O radio button to have the incoming call answered.
If Callback is set to Yes, the Nokia Platform uses the number in the
R
EMOTE NUMBER field on the logical interface to make the outgoing call.
8. If Callback has been set to Yes, enter the value for the timeout in the
TIMEOUT field.
This is the amount of time (in seconds) the Nokia Platform will wait
before placing a call back to the remote system. The range is 0-999. The
default is 15.
9. Click A
10. To record your changes, click S
For troubleshooting information, see “ISDN Troubl esho oting.”
To Remove an Incoming Number
1. Click CONFIG on the home page.
2. Click the Interfaces link.
Voyager Reference Guide 99
PPLY .
AVE.
Page 100

5 Configuring Interfaces
3. Click the physical interface link in the PHYSICAL column.
Example—
isdn-s2p1
4. Click the logical interface link in the LOGICAL INTERFACES table.
5. Click the Incoming Numbers link.
6. Find the incoming number you want to remove in the N
click its corresponding D
7. To record your changes, click S
ELETE button, and then click APPLY.
AVE.
UMBERS table,
To Configure an Interface to Place and Receive
Calls
1. Click CONFIG on the home page.
2. Click the Interfaces link.
3. Click the physical interface link you want to configure in the P
column.
Example—
isdn-s2p1
4. Select whether to run PPP or multilink PPP on the interface from the
NCAPSULATION edit bo x in the Create New Logical Interface section;
E
then click A
A new logical interface appears in the I
PPLY.
NTERFACE column.
HYSICAL
5. Click the logical interface name in the I
L
OGICAL INTERFACES table to go to the Interface page.
6. Enter the IP address for the local end of the connection in the L
ADDRESS edit box.
7. Enter the IP address of the remote end of the connection in the R
ADDRESS edit box.
8. Click the B
100 Voyager Reference Guide
NTERFACE column of the
OCAL
EMOTE
OTH Direction radio button.
 Loading...
Loading...