Page 1
Application Note
Configuring a Hub-and-Spoke VPN Using the NETGEAR
VPN Client
Summary
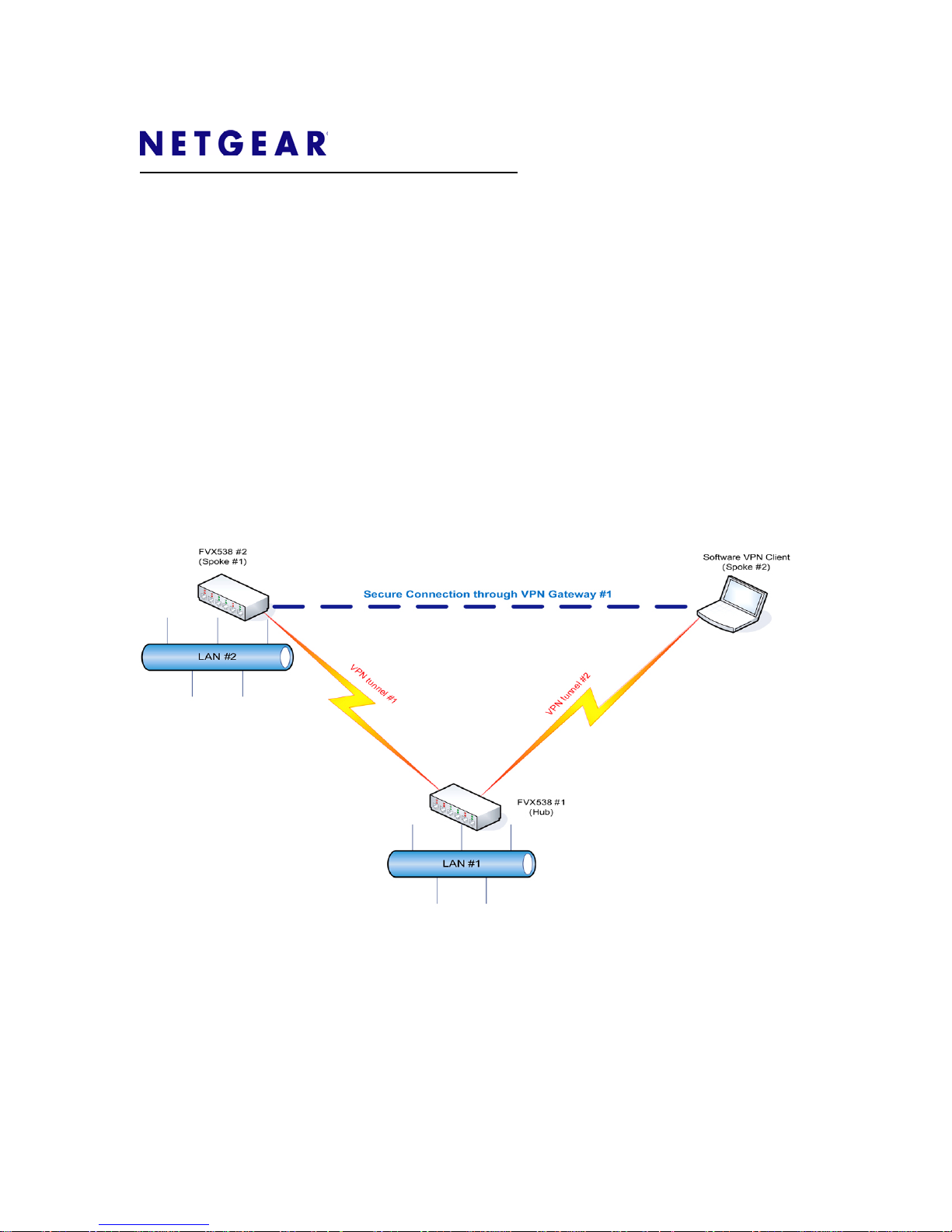
A Hub-and-Spoke VPN allows multiple sites to communicate through a central hub site.
This application note describes how to configure a Hub-and-Spoke VPN when one of the
spokes is the NETGEAR VPN client. It has been tested with the FVX538 router,
firmware version 2.x and NETGEAR ProSafe® VPN client, version 10.7.2 (Build 12).
Note: See
Hub-and-Spoke VPN for general instructions on configuration that does not
use the VPN Client.
In this configuration, there is a gateway-to-gateway VPN tunnel between FVX538 #1 and
FVX538 #2. By establishing a VPN connection to the FVX538#1, the software VPN
client gains access to Local Area Network #2 behind FVX538 #2 through FVX538 #1.
Procedure
This procedure was developed and tested using:
• NETGEAR FVX538 ProSafe VPN Firewall with version 2.x firmware
o WAN1 (10.1.1.2 ) IP address: 192.168.1.0
o WAN1 IP address subnet: 255.255.255.0
o WAN2 (10.1.2.2) IP address: 192.168.2.0
Page 2
o WAN2 IP address subnet: 255.255.255.0
• NETGEAR ProSafe VPN client, version 10.7.2 (Build 12)
o IP address: 192.168.1.100
IP Address Requirements
This configuration requires advanced IP address planning. The VPN client policy needs
to address both Local Area Network #1 and Local Area Network #2 in the same client
policy profile. Therefore, the two networks must be presentable as one subnet or one
address range.
Note: You can create the IKE and VPN policies using the VPN wizard, and then modify
them. You can also create the IKE and VPN policies manually.
Configuring the Hub-and-Spoke VPN
To configure the FVX538 #1 (the Hub):
1. Create an IKE policy for VPN to FVX538 #2.
2. Create a VPN policy using the IKE policy created in Step 1. The local IP subnet is
the LAN subnet behind FVX538 #1. The remote IP subnet is the LAN subnet behind
FVX 538 #2.
Page 3

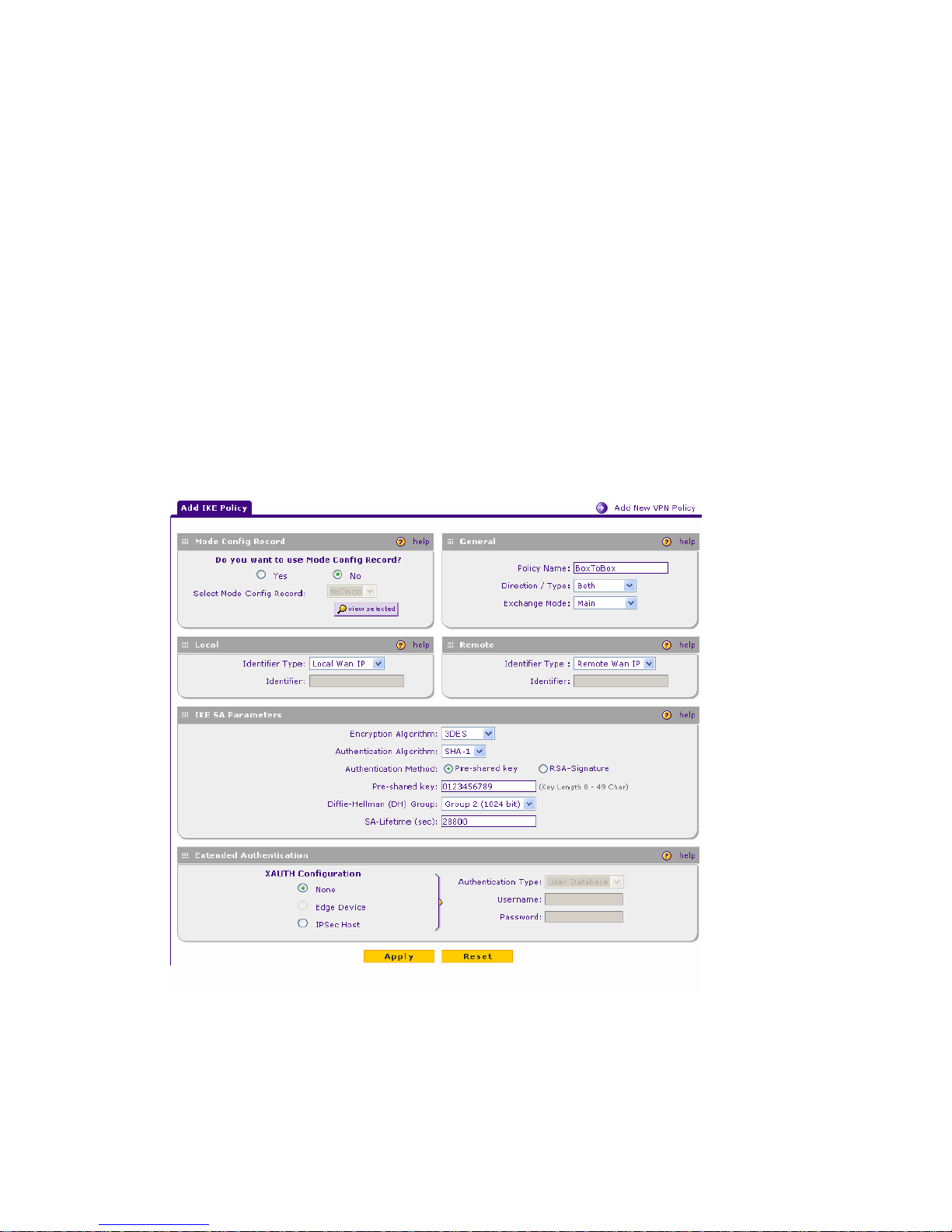
3. Create a VPN client policy. First create the IKE policy for the VPN client.
Page 4

4. Create a VPN policy using the IKE policy created in Step 3. The local subnet is Any.
The remote subnet is the internal IP address to be defined in the VPN client policy
profile. In this example, 192.168.4.100.
5. Create the VPN policy that will allow the VPN client to access the network behind
FVX538 #2. In the VPN policy, use the same IKE policy created in Step 1. For the
local network, use the VPN client network defined in Step 4, 192.168.4.0, subnet
mask 255.255.255.0. For the remote network, use the network behind FVX538 #2,
192.168.2.0, subnet mask 255.255.255.
Page 5

Configuring the FVX538 #2
To configure the FVX538 #2:
1. Create an IKE policy to FVX538 #1.
2. Create a VPN policy using the IKE policy created in Step 1. For the local subnet, use
the LAN subnet behind FVX538 #2. For the remote subnet, use the LAN subnet
behind FVX538 #1.
3. Create the second VPN policy to allow the VPN client to access the network behind
FVX538 #2. Use the same IKE policy that you created in Step 1. For the remote
network, enter the network address being used by the VPN client, which is
192.168.4.0, subnet mask 255.255.255.0.
Configuring the VPN Client Software
To configure the VPN client software:
1. To create a new connection, under Remote Party Identity and Addressing, define an
object to cover both LANs behind FVX538 #1 and FVX538 #2. In this case, select
IP Address Range as the ID Type and enter an IP address range of 192.168.1.1 to
Page 6

192.168.2.254. This will cover both 192.168.1.0, subnet mask 255.255.255.0 and
192.168.2.0, subnet mask 255.255.255.0.
2. Click on My Identity For Internal Network IP Address, enter the same address used
in the client VPN policy on the FVX538 #1, which is 192.168.4.100. The rest of the
configurations are the same as a standard VPN client configuration.
3. Configure the Security Policy.
4. Configure the Authentication/Proposal 1.
5. Configure the Key Exchange/Proposal 1.
Testing the Connection
To test the connection:
1. Right-click the VPN client icon on the system tray.
2. Select Connect and choose the client policy that you just created. A pop-up window
appears showing an “attempting to connect” message. Eventually the message will
show that there is a successful connection to the FVX538.
3. From the command prompt, ping both the subnets behind FVX538 #1 and
FVX538 #2.
Conclusion
If user wants to configure two remote locations so their traffic goes through a central
location instead of directly between them, please refer to this document.
November 27, 2006
Copyright © 2006 NETGEAR®
 Loading...
Loading...