Page 1

Image Controller IC-406
User’s Guide
[Network Scanner Operations]
[Copier Network Functions]
Page 2

Introduction
Introduction
Thank you for choosing this machine.
This User’s Guide contains descriptions of the network scanning functions
and operations that can be used from optional C352/C300 image controller
IC-406 and the network functions that can be used from the copier when the
IC-406 is installed. To ensure the best possible performance and most effective use of the machine, read this manual thoroughly. After reading this User’s Guide, store it in the designated holder for quick reference when
problems or questions arise during operation.
Views of the actual equipment may be slightly different from the illustrations
used in this manual.
IC-406 x-1
Page 3

Trademarks and Registered Trademarks
KONICA MINOLTA and the KONICA MINOLTA logo are trademarks of Konica Minolta Holdings, Inc.
PageScope is a registered trademark of Konica Minolta Business Technologies, Inc.
Apple and Macintosh are registered trademarks of Apple Computer, Inc.
Ethernet is a registered trademark of Xerox Corporation.
Microsoft, Windows and Windows NT are registered trademarks of Microsoft
Corporation.
PostScript is a registered trademark of Adobe Systems, Inc.
EFI, Fiery and the Fiery logo are registered trademarks of Electronics for Imaging, Inc. and are legally registered in the United States and other countries.
The Electronics for Imaging logo, Fiery Remote Scan, Fiery WebScan, and
Fiery WebTools are trademarks of Electronics for Imaging, Inc.
®
RC4
is a registered trademark or trademark of RSA Security Inc. in the Unit-
ed States and/or other countries.
RSA® is a registered trademark or trademark of RSA Security Inc. RSA
BSAFE® is a registered trademark or trademark of RSA Security Inc. in the
United States and/or other countries.
License information
This product includes RSA BSAFE Cryptographic software from RSA Security Inc.
Introduction
All other product names are either trademarks or registered trademarks of
their respective companies.
Copyright © 2006 KONICA MINOLTA BUSINESS TECHNOLOGIES, INC.
OpenSSL Statement
OpenSSL License
Copyright © 1998-2000 The OpenSSL Project. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
x-2 IC-406
Page 4

Introduction
2. Redistributions in binary form must reproduce the above copyright no-
3. All advertising materials mentioning features or use of this software must
4. The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used
5. Products derived from this software may not be called “OpenSSL” nor
6. Redistributions of any form whatsoever must retain the following ac-
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT “AS IS” AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@crypt-Soft.com). This product includes software written by Tim Hudson (tjh@cryptsoft.com).
Original SSLeay License
Copyright © 1995-1998 Eric Young (eay@cryptsoft.com) All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The following conditions apply to all code
found in this distribution, be it the RC4, RSA, Ihash, DES, etc., code; not just
the SSL code.
The SSL documentation included with this distribution is covered by the
tice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
display the following acknowledgment:
“This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit. (http://www.openssl.org/)”
to endorse or promote products derived from this software without prior
written permission. For written permission, please contact opensslcore@openssl.org.
may “OpenSSL” appear in their names without prior written permission
of the OpenSSL Project.
knowledgment:
“This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit (http://www.openssl.org/)”
IC-406 x-3
Page 5

Introduction
same copyright terms except that the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young’s, and as such any Copyright notices in the
code are not to be removed. If this package is used in a product, Eric Young
should be given attribution as the author of the parts of the library used. This
can be in the form of a textual message at program startup or in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list
of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgement:
“This product includes cryptographic software written by Eric Young
(eay@crypt-soft.com)”
The word ‘cryptographic’ can be left out if the rouines from the library being used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from
the apps directory (application code) you must include an acknowledgement:
“This product includes software written by Tin Hudson (tjh@cryptsoft.com)”
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
The licence and distribution terms for any publically available version or derivative of this code cannot be changed. i.e. this code cannot simply be copied and put under another distribution licence [including the GNU Public
Licence.]
In order to incorporate improvements in the product, the content of this manual is subject to change without notice.
x-4 IC-406
Page 6

Introduction
Contents
Introduction
Trademarks and Registered Trademarks ...................................... x-2
Contents ............................................................................................ x-5
About This Manual .......................................................................... x-14
Structure of the Manual ................................................................x-14
Notation .........................................................................................x-14
Explanation of Manual Conventions ............................................. x-16
1 Before Using the Scan Functions
1.1 Environment Required for Using the Scan Functions ................... 1-2
1.2 Available Scanning Functions ......................................................... 1-3
Sending the Scanned Data in an E-Mail Message ......................... 1-3
Sending the Scanned Data as Files (FTP) ...................................... 1-4
Sending the Scanned Data to a Computer on the Network
(SMB) ............................................................................................. 1-5
Saving Scanned Data in Boxes on the Image Controller Hard Disk
(Save in Mailbox of Image Controller) ............................................ 1-6
Copier Box Functions .................................................................... 1-7
1.3 Settings for Using Network/Scanning Functions .......................... 1-8
Specifying Network Settings .......................................................... 1-8
Registering Destinations and Specifying Their Settings ................ 1-8
1.4 Settings for Scanning ..................................................................... 1-10
Specifying the Scan Settings ....................................................... 1-10
Specifying the Destination ........................................................... 1-10
1.5 Connecting to the Network ........................................................... 1-11
Network Connection .................................................................... 1-11
Turning On the System ................................................................ 1-11
1.6 Flow Chart of Setup and Scanning Operations ........................... 1-13
1.7 Frequently Used Screens ............................................................... 1-15
To display the Scan screen .......................................................... 1-15
To display the User Setting screen .............................................. 1-16
To display the Administrator Setting screen ................................ 1-17
2 Scanning Documents
2.1 Control Panel .................................................................................... 2-2
2.2 Displaying the Scan Screen ............................................................. 2-5
IC-406 x-5
Page 7

Introduction
2.3 Sending Data in an E-Mail Message (Scan to E-Mail) ....................2-6
Scan to E-Mail ................................................................................2-6
Using Programs ..............................................................................2-6
Selecting Group Addresses ............................................................2-9
Selecting Destinations From the Address Book ...........................2-12
Performing an LDAP Search .........................................................2-15
Entering the Addresses Directly ...................................................2-16
2.4 Sending Data to a Server (Scan to FTP) ........................................2-19
Scan to FTP ..................................................................................2-19
Using Programs ............................................................................2-19
Selecting Group Addresses ..........................................................2-21
Selecting Destinations From the Address Book ...........................2-24
Entering the Addresses Directly ...................................................2-27
2.5 Sending Data to a PC on the Network (Scan to SMB) .................2-31
Scan to SMB .................................................................................2-31
Using Programs ............................................................................2-31
Selecting Group Addresses ..........................................................2-33
Selecting Destinations From the Address Book ...........................2-35
Entering the Addresses Directly ...................................................2-38
2.6 Saving Data on the Hard Disk
(Save in Mailbox of Image Controller) ...........................................2-41
Save in Mailbox .............................................................................2-41
Types of Mailboxes .......................................................................2-41
Using Programs ............................................................................2-42
Selecting Group Addresses ..........................................................2-44
Selecting Destinations From the Address Book ...........................2-46
To save data to the specified mailbox ..........................................2-49
2.7 Specifying the Scan Settings ..........................................................2-52
Available Settings .........................................................................2-52
File Type ........................................................................................2-54
To specify the File Type settings ..................................................2-55
Resolution .....................................................................................2-56
Simplex/Duplex .............................................................................2-57
To specify the Simplex/Duplex setting .........................................2-57
Color .............................................................................................2-58
To specify the Color setting ..........................................................2-59
Scan Size ......................................................................................2-60
To specify the Scan Size setting ...................................................2-60
Brightness .....................................................................................2-62
Background Removal ...................................................................2-63
Original Setting .............................................................................2-64
To specify the Original Settings ....................................................2-64
Book Scanning (Application) .........................................................2-66
To use the “Book Scan” function .................................................2-66
x-6 IC-406
Page 8

Introduction
Frame Erase (Application) ............................................................ 2-68
Separate Scan .............................................................................. 2-70
File Name ..................................................................................... 2-70
To change the file name ............................................................... 2-71
Despeckle .................................................................................... 2-72
2.8 Checking the Settings .................................................................... 2-73
Checking the Settings .................................................................. 2-73
To check a job .............................................................................. 2-74
Deleting Unneeded Destinations ................................................. 2-78
Changing the File Name and Other Settings ............................... 2-80
To change the e-mail settings ...................................................... 2-81
2.9 Checking the Scan Job List ........................................................... 2-82
Displaying the Job List for Scan to E-mail, Scan to FTP and
Scan to SMB Operations ............................................................. 2-82
Checking the Box Job List ........................................................... 2-83
3 Registering Destinations (Recipients) for Network
Scanning
3.1 Registering Abbreviated Destinations ............................................ 3-2
E-Mail Destinations ........................................................................ 3-2
FTP Destinations ............................................................................ 3-5
SMB Destinations .......................................................................... 3-9
Mailbox Destinations .................................................................... 3-13
3.2 Registering Group Destinations .................................................... 3-16
To register a group destination .................................................... 3-16
3.3 Registering Program Destinations ................................................ 3-18
To register a program destination ................................................ 3-18
4 Other Network Scanning Settings
4.1 Specifying E-Mail Settings ............................................................... 4-2
Subject ........................................................................................... 4-2
Text ................................................................................................ 4-4
4.2 Setting the Main Scan Mode Screen .............................................. 4-6
Default Tab ..................................................................................... 4-6
Program Default ............................................................................. 4-7
Address Book Default Index .......................................................... 4-8
Address Type Symbol Display ....................................................... 4-9
4.3 Setting the Save Format of the Data to Be Scanned .................. 4-10
JPEG Compression Level ............................................................ 4-10
To specify the compression level ................................................. 4-10
IC-406 x-7
Page 9

4.4 Prefix/Suffix Settings ......................................................................4-12
Prefix/Suffix Parameters ...............................................................4-12
To specify the prefix/suffix settings ..............................................4-12
Prefix/Suffix Setting ......................................................................4-14
4.5 Authentication Function ..................................................................4-16
User Authentication/Account Track and Scan Functions .............4-16
Authentication Method and Fiery Remote Scan Software ...........4-17
5 Specifying Network Scanning Settings
5.1 Available Settings ..............................................................................5-2
5.2 Entering the Image Controller Setup Screen ..................................5-4
Displaying the Setup Screen ..........................................................5-4
5.3 Specifying Settings for E-Mail Transmissions ................................5-5
Checking Copier E-Mail Transmission Settings .............................5-5
To check the e-mail transmission setting .......................................5-5
Checking TCP/IP Settings ..............................................................5-5
E-Mail Transmission Settings .........................................................5-5
URL Notification E-Mail Messages .................................................5-6
5.4 Specifying Settings for Save in Mailbox of Image Controller
Operations ..........................................................................................5-7
Checking the use of the copier’s network settings ........................5-7
Checking TCP/IP Settings ..............................................................5-7
Creating a Mailbox ..........................................................................5-8
Downloading the Image Data to the Computer ............................5-12
Creating a Mailbox 1 .....................................................................5-14
Creating a Mailbox 2 .....................................................................5-15
5.5 Specifying Settings for FTP File Transmissions ...........................5-17
Checking TCP/IP Settings ............................................................5-17
Enabling the FTP Transfer Function .............................................5-17
Proxy Settings ...............................................................................5-17
5.6 Specifying Settings for SMB Server Transmissions .....................5-18
Checking Copier SMB Settings ....................................................5-18
To check the SMB setting ............................................................5-18
Checking TCP/IP Settings ............................................................5-18
5.7 Setting the Error Notification Destination .....................................5-19
To set the error notification destination ........................................5-19
5.8 Setting the Sender (From) Address ...............................................5-20
To set the sender (from) address ..................................................5-20
5.9 Hold Period of the Image Data .......................................................5-21
To specify the hold period of the image data ...............................5-21
Introduction
x-8 IC-406
Page 10

Introduction
6 Copier Network Functions
6.1 Copier Network Settings .................................................................. 6-2
6.2 FTP Settings ...................................................................................... 6-5
FTP Parameters ............................................................................. 6-5
To specify FTP settings .................................................................. 6-5
6.3 SMB Settings ..................................................................................... 6-6
SMB Parameters ............................................................................ 6-6
To specify SMB settings ................................................................ 6-7
6.4 Enabling LDAP Settings ................................................................... 6-8
Enabling LDAP Parameters ............................................................ 6-8
To specify Enabling LDAP settings ................................................ 6-8
6.5 Setting Up LDAP Settings .............................................................. 6-10
LDAP Server Registration Parameters ......................................... 6-10
To specify Setting Up LDAP settings ........................................... 6-13
Initial Setting for Search Details ................................................... 6-17
6.6 Search Default Setting ................................................................... 6-19
To specify the detect default server settings ............................... 6-19
6.7 E-Mail TX (SMTP) Settings ............................................................. 6-20
E-Mail TX (SMTP) Parameters ...................................................... 6-20
To specify E-Mail TX (SMTP) settings .......................................... 6-22
SMTP Server Address .................................................................. 6-24
SMTP Detail ................................................................................. 6-25
SMTP Authentication ................................................................... 6-26
6.8 E-Mail RX (POP) Settings ............................................................... 6-28
E-Mail RX (POP) Parameters ........................................................ 6-28
To specify E-Mail RX (POP) settings ............................................ 6-29
POP Server Address .................................................................... 6-31
6.9 MAC Address .................................................................................. 6-33
Device Parameters ....................................................................... 6-33
To check the MAC address ......................................................... 6-33
6.10 Time Adjustment Settings ............................................................. 6-35
Time Adjustment Parameters ....................................................... 6-35
To specify time adjustment settings ............................................ 6-35
NTP Server Address ..................................................................... 6-36
6.11 Status Notification Settings ........................................................... 6-38
Status Notification Parameters .................................................... 6-38
To specify status notification settings ......................................... 6-38
Notification Item Setting .............................................................. 6-39
6.12 Total Counter Report Setting ........................................................ 6-40
To specify the total counter notification settings ......................... 6-40
IC-406 x-9
Page 11

Schedule Setting ...........................................................................6-41
To specify the notification schedule settings ................................6-43
Notification Address Setting .........................................................6-43
6.13 PING Confirmation ..........................................................................6-45
PING Confirmation Parameters ....................................................6-45
To specify PING confirmation settings .........................................6-45
PING TX Address ..........................................................................6-47
6.14 Job for the disable proof ................................................................6-49
To specify the Job for the disable proof settings .........................6-49
6.15 TCP Socket Setting .........................................................................6-51
To specify the TCP socket settings ..............................................6-51
6.16 OpenAPI Settings ............................................................................6-53
Access Setting ..............................................................................6-53
Port No. .........................................................................................6-54
SSL ...............................................................................................6-54
Authentication ...............................................................................6-56
6.17 NetWare Settings .............................................................................6-58
NetWare Parameters .....................................................................6-58
To display the NetWare Setting screen ........................................6-58
7 Using PageScope Web Connection
Introduction
7.1 System Requirements .......................................................................7-2
Computer ........................................................................................7-2
7.2 Accessing PageScope Web Connection .........................................7-3
To access PageScope Web Connection ........................................7-3
Page Structure ................................................................................7-4
7.3 Logging On and Logging Off ............................................................7-6
Logging Off .....................................................................................7-6
Logging On to User Mode (Public User) .........................................7-7
Logging On to User Mode (Registered User/Box Administrator) ...7-8
Administrator Modes ......................................................................7-9
Logging On to the Image Controller’s Administrator Mode ..........7-10
Logging On to the Copier’s Administrator Mode ..........................7-11
Changing the Administrator Password .........................................7-12
Changing the Image Controller’s Administrator Password ..........7-12
Changing the Copier’s Administrator Password ..........................7-12
7.4 System Tab (User Mode) .................................................................7-13
7.5 Job Tab (User Mode) .......................................................................7-14
7.6 Box Tab (User Mode) .......................................................................7-15
7.7 Print Tab (User Mode) .....................................................................7-16
x-10 IC-406
Page 12

Introduction
7.8 Address Book .................................................................................. 7-17
Registering New Destinations ...................................................... 7-17
To register new destinations in the address book ....................... 7-20
Editing abbreviated destinations .................................................. 7-21
Deleting the Address Book .......................................................... 7-21
7.9 Group Destination ........................................................................... 7-22
To register new destination .......................................................... 7-22
7.10 Program Registration ..................................................................... 7-24
To register new destinations ........................................................ 7-31
7.11 Temporary One-Touch Registration ............................................. 7-33
To register temporary destinations .............................................. 7-33
7.12 Subject Registration ....................................................................... 7-35
To register the subject ................................................................. 7-36
7.13 Text Registration ............................................................................ 7-37
To register text ............................................................................. 7-38
7.14 System Tab (Image Controller Administrator Mode) .................. 7-39
Device Information ....................................................................... 7-39
Online Assistance ......................................................................... 7-40
7.15 Box Tab (Image Controller Administrator Mode) ......................... 7-41
Mailbox ......................................................................................... 7-41
7.16 System Tab (Copier Administrator Mode) .................................... 7-43
7.17 Box tab (Copier Administrator Mode) ........................................... 7-44
7.18 Prefix/Suffix ..................................................................................... 7-45
To register prefixes and suffixes .................................................. 7-45
7.19 Import/Export .................................................................................. 7-47
Importing ...................................................................................... 7-47
Exporting ...................................................................................... 7-47
7.20 Other ................................................................................................ 7-48
7.21 NetWare ........................................................................................... 7-49
7.22 FTP ................................................................................................... 7-50
7.23 SMB .................................................................................................. 7-51
7.24 LDAP Setting ................................................................................... 7-52
LDAP Setting ................................................................................ 7-52
LDAP Server Registration ............................................................ 7-53
7.25 E-Mail Setting .................................................................................. 7-56
E-Mail Receive ............................................................................. 7-56
E-Mail Transmission ..................................................................... 7-57
IC-406 x-11
Page 13

7.26 SSL/TLS ............................................................................................7-60
SSL/TLS Setting ...........................................................................7-62
To create a certificate ...................................................................7-63
SSL/TLS Setting — Install a Certificate ........................................7-65
SSL/TLS Setting — Set a Encryption Strength ............................7-66
SSL/TLS Setting — Remove a Certificate ....................................7-67
SSL/TLS Setting — Set Mode using SSL .....................................7-68
Processing Method .......................................................................7-69
To specify the mode using SSL ....................................................7-69
7.27 Authentication ..................................................................................7-70
User Authentication/Account Track ..............................................7-70
To specify the user authentication and account track settings ....7-71
Auto Logout ..................................................................................7-72
7.28 OpenAPI ...........................................................................................7-73
7.29 TCP Socket Setting .........................................................................7-74
To specify the TCP socket settings ..............................................7-75
8 Print Job Management
8.1 Proof Print ..........................................................................................8-2
Setting procedure (for Windows) ....................................................8-2
Setting procedure (for Macintosh OS X) .........................................8-3
Recalling Jobs (Proof Print) ............................................................8-4
8.2 HDD Stored ........................................................................................8-6
Setting procedure (for Windows) ....................................................8-6
Setting procedure (for Macintosh OS X) .........................................8-7
8.3 Printing With This Machine When Account Track Settings Have
Been Applied ......................................................................................8-8
Setting procedure (for Windows) ....................................................8-9
Setting procedure (for Macintosh OS X) .......................................8-10
8.4 Lock Job ...........................................................................................8-11
Setting procedure (for Windows) ..................................................8-11
Setting procedure (for Macintosh OS X) .......................................8-12
8.5 Printing on Banner Paper ...............................................................8-13
Setting procedure .........................................................................8-14
Printing ..........................................................................................8-15
8.6 Printing to Suit the Paper Size .......................................................8-18
Introduction
x-12 IC-406
Page 14

Introduction
9 Appendix
9.1 Entering Text ..................................................................................... 9-2
To type text .................................................................................... 9-5
List of Available Characters ........................................................... 9-5
Number of Characters That Can Be Entered ................................. 9-6
9.2 Glossary ............................................................................................. 9-7
9.3 Index ................................................................................................ 9-12
IC-406 x-13
Page 15

About This Manual
This User’s Guide provides descriptions of the network scanning functions
available with IC-406 (the optional image controller for C352/C300). In addition, supplementary descriptions are provided in chapter 6 for the network
functions that can be used from the copier when IC-406 is installed.
This section introduces the structure of the manual and the notations used
for product names, etc.
This manual is intended for users who understand the basic operations of
computers and this machine. For operating procedures of the Windows or
Macintosh operating system and software applications, refer to the corresponding manuals.
Structure of the Manual
This manual consists of the following chapters.
Chapter 1 Before Using the Scan Functions
Chapter 2 Scanning Documents
Chapter 3 Registering Destinations (Recipients) for Network Scanning
Chapter 4 Other Network Scanning Settings
Chapter 5 Specifying Network Scanning Settings
Chapter 6 Copier Network Functions
Chapter 7 Using PageScope Web Connection
Chapter 8 Print Job Management
Chapter 9 Appendix
Lists the characters that can be entered from the control panel.
Introduction
Notation
Product Name Notation in the Manual
bizhub C352 Copier, C352
bizhub C300 Copier, C300
IC-406 Image Controller Image Controller
Microsoft Windows 98 Windows 98
Microsoft Windows Me Windows Me
Microsoft Windows NT 4.0 Windows NT 4.0
Microsoft Windows 2000 Windows 2000
Microsoft Windows XP Windows XP
x-14 IC-406
Page 16
Introduction
Product Name Notation in the Manual
Microsoft Windows Server 2003 Windows Server 2003
When the operating systems above are written
together
Windows 95/98/Me
Windows NT 4.0/2000/XP/Server 2003
Windows 95/98/Me/NT 4.0/2000/XP/Server
2003
IC-406 x-15
Page 17
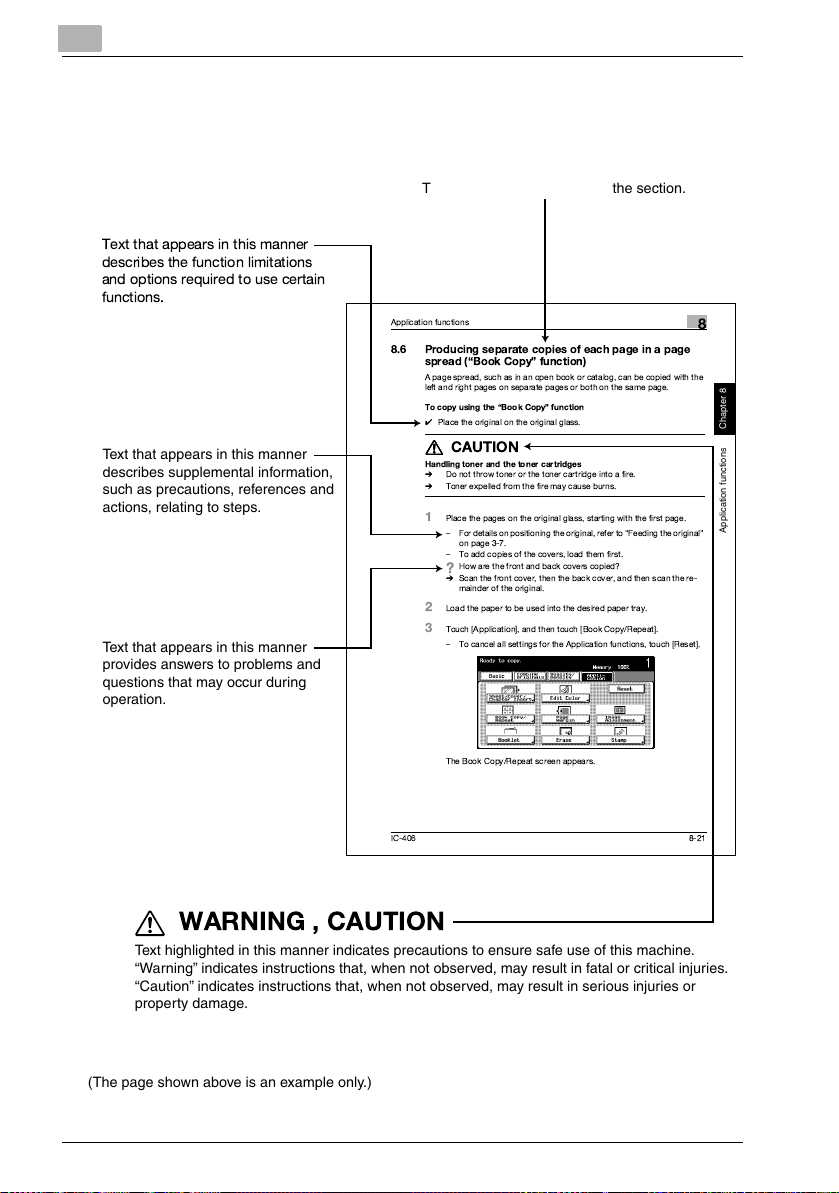
Explanation of Manual Conventions
Titles indicate the contents of the section.
Text that appears in this manner
describes the function limitations
and options required to use certain
functions.
Application functions
8.6 Producing separate copies of each page in a page
spread (Book Copy function)
A page spread, such asin an open book or catalog, can be copied with the
left and right pages on separate pages or both on the same page.
To copy using the Book Copy function
0
Place the original on the original glass.
Text that appears in this manner
describes supplemental information,
such as precautions, references and
actions, relating to steps.
Text that appears in this manner
provides answers to problems and
questions that may occur during
operation.
7777
Handling toner and the toner cartridges
%
Do not throw toner or the toner cartridge into a fire.
%
Toner expelled from the fire may cause burns.
1
Place the pages on the original glass, starting with the first page.
For details on positioning theoriginal, refer toFeeding the original
To add copies of the covers, load them first.
?
%
2
Load the paper to be used into the desired paper tray.
3
Touch [Application], and then touch [Book Copy/Repeat].
To cancel all settings for the Application functions, touch [Reset].
Introduction
CAUTION
on page 3-7.
How are the front and back covers copied?
Scan the front cover, then the back cover, and then scan the re-
mainder of the original.
8
Application functions Chapter 8
The Book Copy/Repeat screen appears.
IC-406 8-21
WARNING , CAUTION
7
Text highlighted in this manner indicates precautions to ensure safe use of this machine.
“Warning” indicates instructions that, when not observed, may result in fatal or critical injuries.
“Caution” indicates instructions that, when not observed, may result in serious injuries or
property damage.
(The page shown above is an example only.)
x-16 IC-406
Page 18
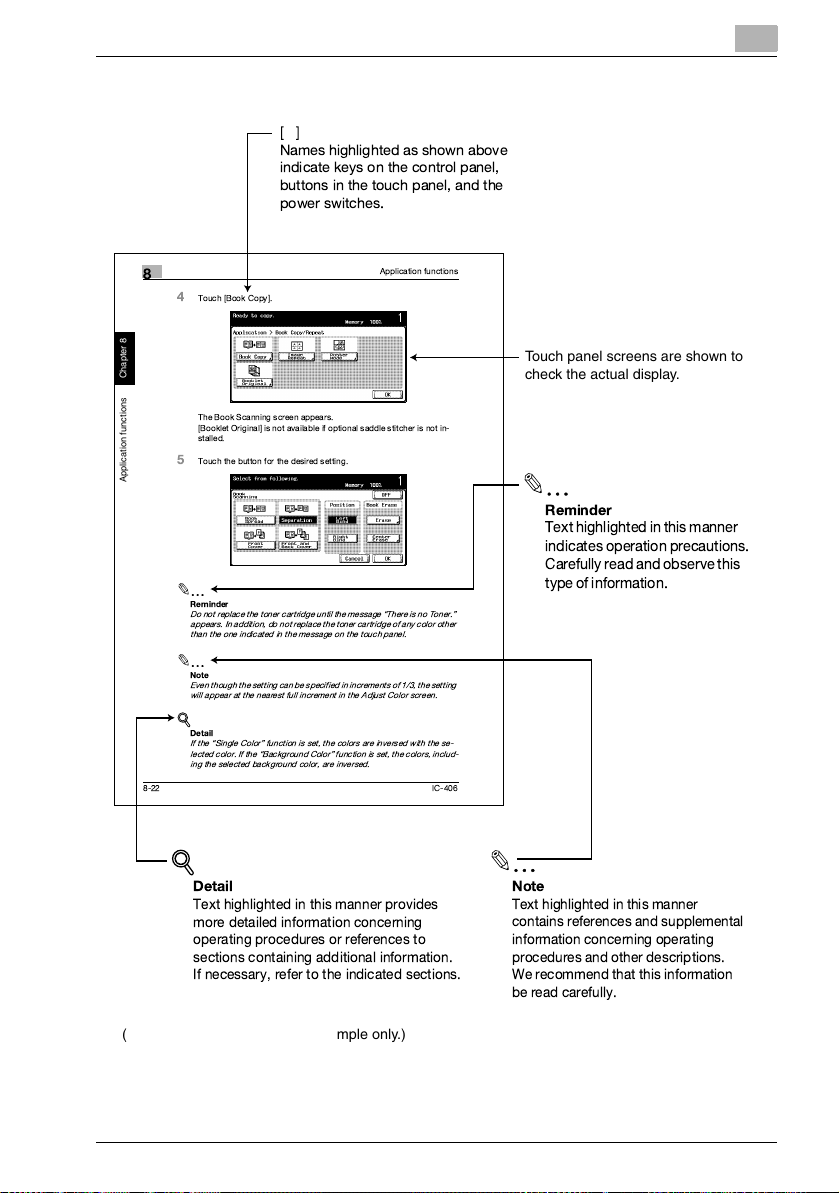
Introduction
[]
Names highlighted as shown above
indicate keys on the control panel,
buttons in the touch panel, and the
power switches.
8
Application functions Chapter 8
8-22
Application functions
4
Touch [Book Copy].
The Book Scanning screen appears.
[Booklet Original] is not available if optional saddle stitcher is not in-
stalled.
5
Touch the button for the desired setting.
2
Reminder
Do not replacethe toner cartridge until themessage There isno Toner.
appears. In addition,do not replace the tonercartridge ofany color other
than the one indicated in the message on the touch panel.
2
Note
Even though the setting can be specifiedin incrementsof 1/3, the setting
will appear at the nearest full increment in the Adjust Color screen.
!
Detail
If the Single Color function is set, the colors are inversed with the se-
lected color. If the Background Color function is set, the colors, includ-
ing the selected background color, are inversed.
Touch panel screens are shown to
check the actual display.
2
Reminder
Text highlightedin this manner
indicates operationprecautions.
Carefully readand observe this
type ofinformation.
IC-406
!
Detail
Text highlighted in this manner provides
more detailed information concerning
operating procedures or references to
sections containing additional information.
If necessary, refer to the indicated sections.
2
Note
Text highlighted in this manner
contains references and supplemental
information concerning operating
procedures and other descriptions.
We recommend that this information
be read carefully.
(The page shown above is an example only.)
IC-406 x-17
Page 19

Introduction
x-18 IC-406
Page 20

1
Before Using the Scan
Functions
Before Using the Scan Functions Chapter 1
Page 21

1
Before Using the Scan Functions
1 Before Using the Scan Functions
1.1 Environment Required for Using the Scan Functions
The following conditions are required to use the network scanning functions.
- The machine is connected to the network.
The functions can be used over a TCP/IP network.
– For details on connecting the network cable, refer to “Connecting to the
Network” on page 1-11.
– In order to use this machine on a network, settings such as the IP address
of the image controller must be specified. For details, refer to “Settings
for Using Network/Scanning Functions” on page 1-8.
Before Using the Scan Functions Chapter 1
1-2 IC-406
Page 22
Before Using the Scan Functions
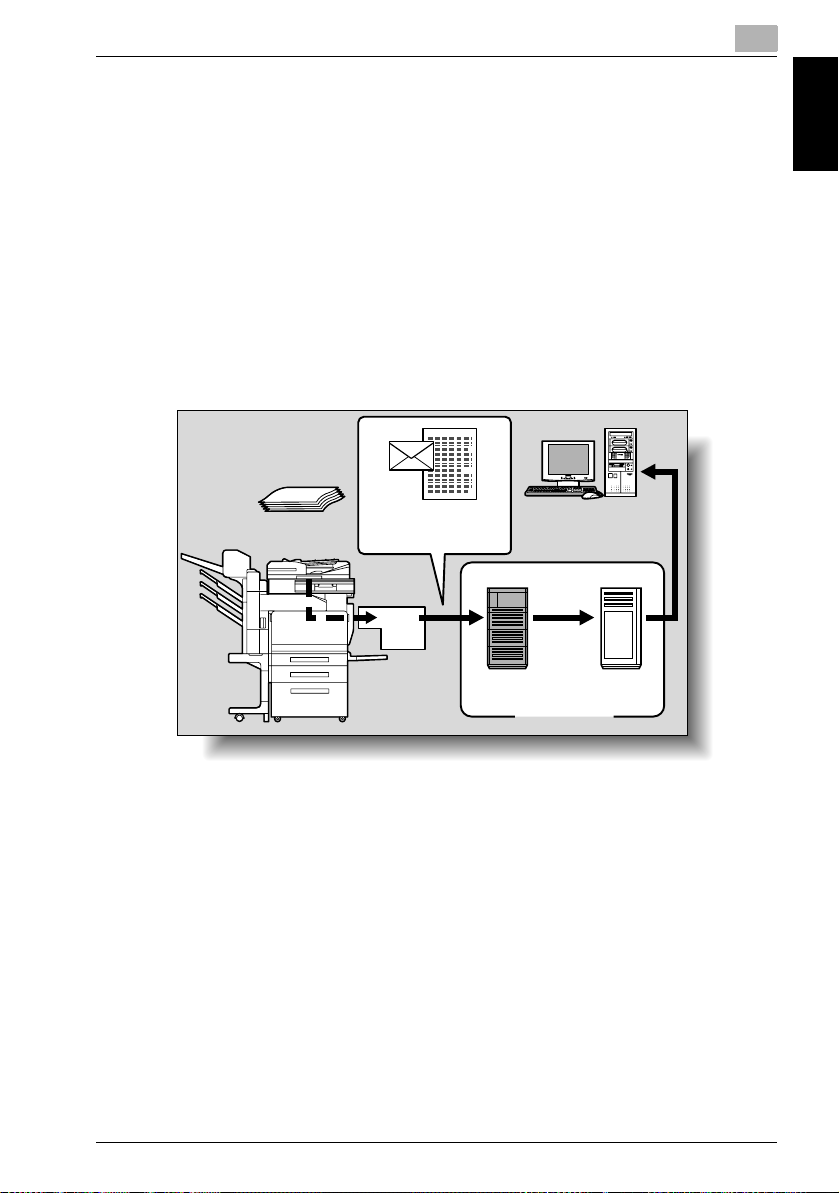
1.2 Available Scanning Functions
“Scanning” refers to the operation of reading the image of a document fed
through the automatic document feeder or placed on the original glass of the
copier. The scanning functions can be used to send scanned data in an email message over a network or upload the data to a file server.
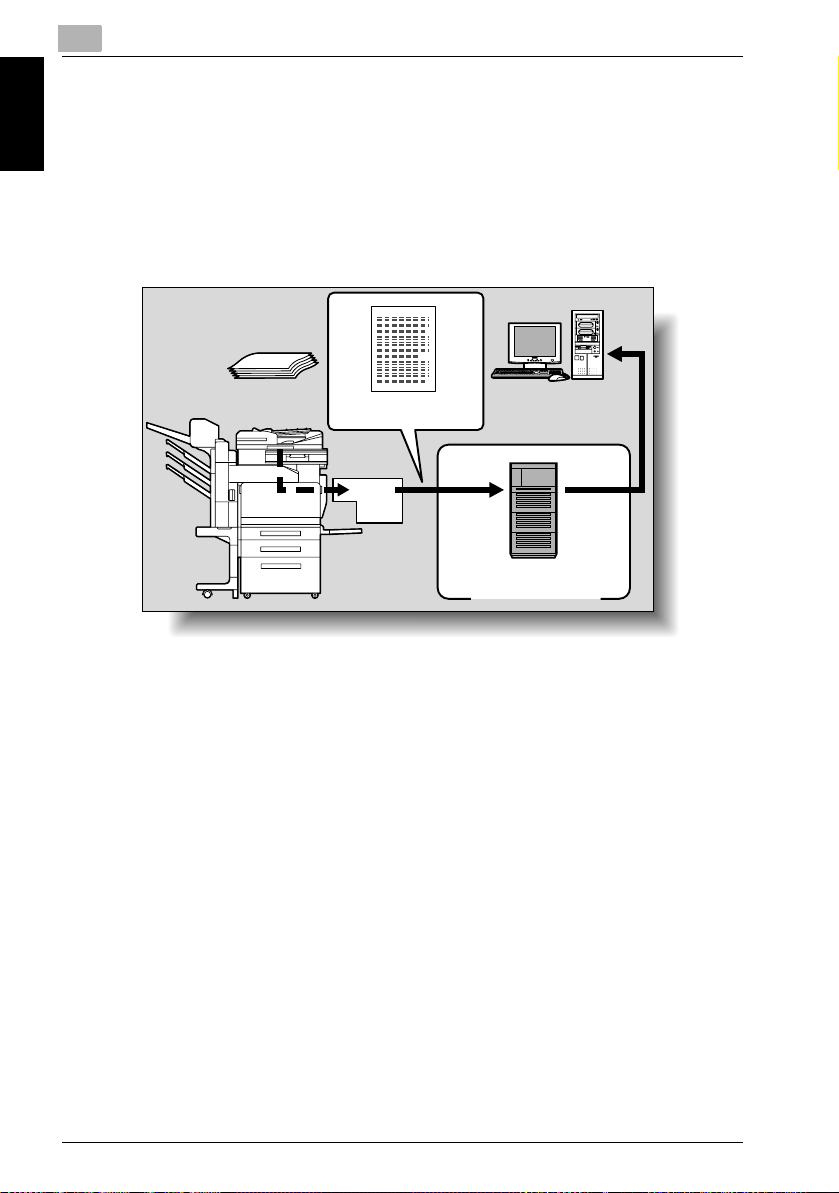
Sending the Scanned Data in an E-Mail Message
The scanned data can be sent to a specified e-mail address. The destination
is specified from the touch panel of this copier, and the scanned data is sent
as an e-mail attachment.
For details, refer to “Sending Data in an E-Mail Message (Scan to E-Mail)” on
page 2-6.
Original
E-mail and scan data
Copier
1
Before Using the Scan Functions Chapter 1
E-mail reception
Image controller
IC-406 1-3
SMTP server POP server
Internet
Page 23
1
Before Using the Scan Functions
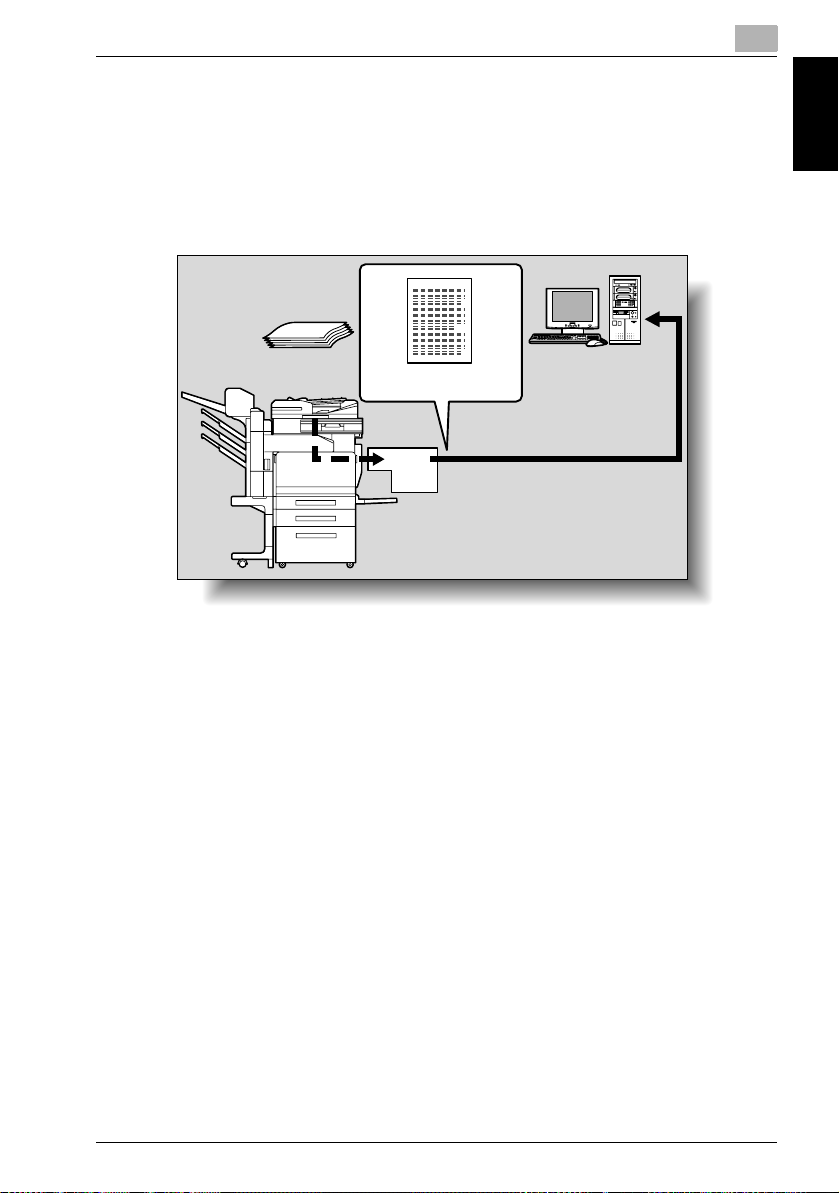
Sending the Scanned Data as Files (FTP)
The scanned data is uploaded to a specified FTP server. The FTP server address, login password, and other information are entered from the touch
panel of this copier.
The data files uploaded to the FTP server can be downloaded from a computer on the network.
For details, refer to “Sending Data to a Server (Scan to FTP)” on page 2-19.
Original
Before Using the Scan Functions Chapter 1
Copier
Scan data
Image controller
Download
FTP server
Internet
1-4 IC-406
Page 24
Before Using the Scan Functions
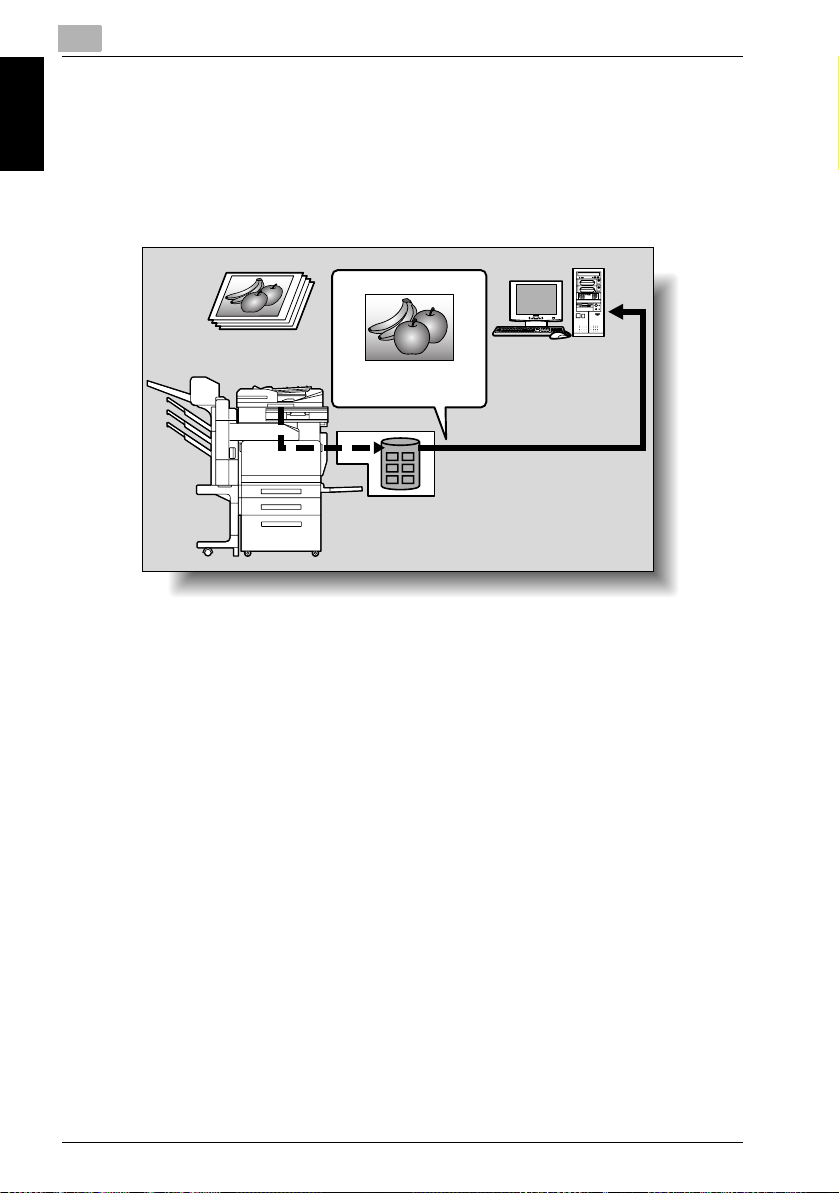
Sending the Scanned Data to a Computer on the Network (SMB)
The scanned data can be sent to a shared folder on a specified computer.
The name of the destination computer, login password, and other information are entered from the touch panel of this copier.
For details, refer to “Sending Data to a PC on the Network (Scan to SMB)”
on page 2-31.
Original
1
Copier
Scan data
Image controller
Save to a shared folder
Before Using the Scan Functions Chapter 1
IC-406 1-5
Page 25
1
Before Using the Scan Functions Chapter 1
Before Using the Scan Functions
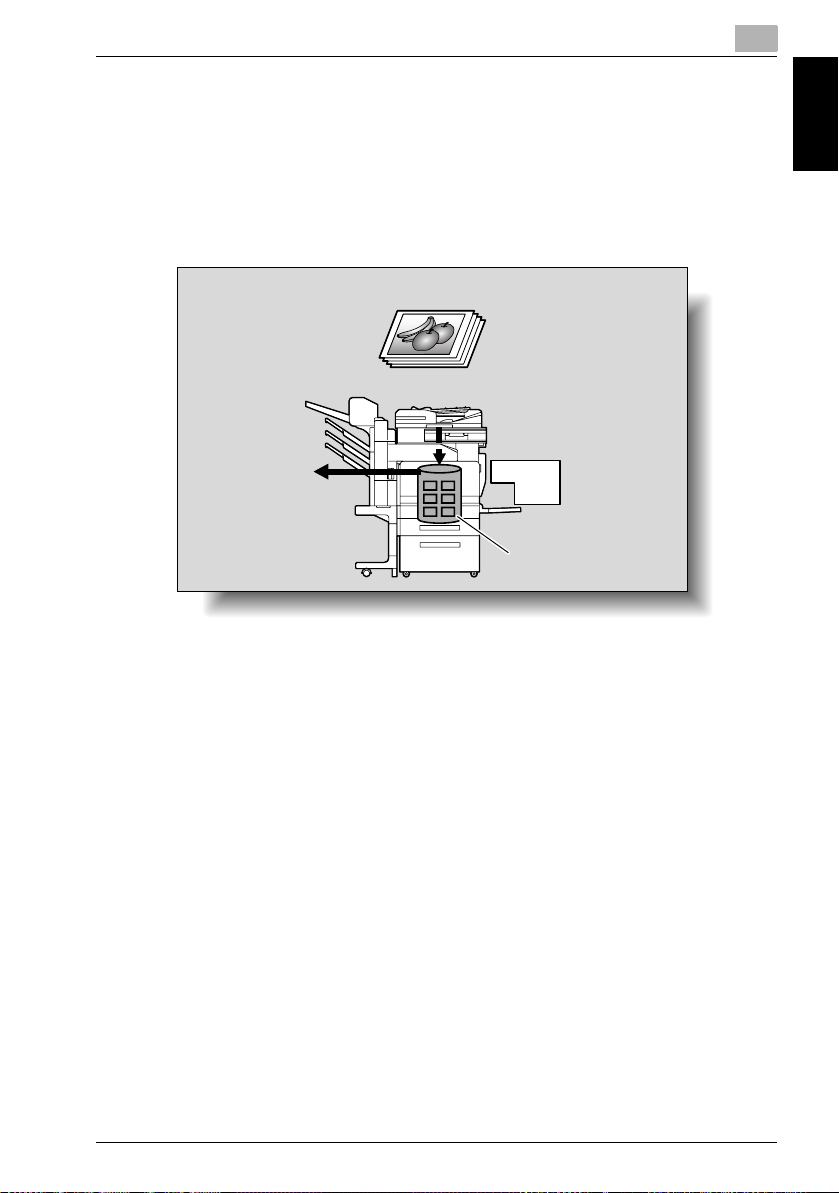
Saving Scanned Data in Boxes on the Image Controller Hard Disk (Save in Mailbox of Image Controller)
The scanned data can be saved in a mailbox created on the hard disk of the
image controller, and the saved data can be downloaded from a computer
on the network. For details, refer to “Saving Data on the Hard Disk (Save in
Mailbox of Image Controller)” on page 2-41.
Scan data
Image controller
1-6 IC-406
Page 26
Before Using the Scan Functions
Copier Box Functions
With the copier Box functions, documents can be saved on the hard disk installed in the copier or they can be outputted. These functions can also be
used with an image controller installed. This manual provides a description
of the Save in Mailbox operation using the hard disk installed in the image
controller. For details on the copier Box functions, refer to the User’s Guide
[Box Operations] included with the copier.
Output
1
Image controller
Before Using the Scan Functions Chapter 1
Hard disk
The User’s Guide [Box Operations] provides descriptions of functions that
can be used when the standard printer controller is installed. Some functions
that are described cannot be used when the image controller is installed.
Functions that cannot be used
- Functions for using scanning functions to save a document in a public
mailbox/personal mailbox on the copier and to route it
- Functions for using scanning functions to save a document in an annota-
tion user box and to route it
IC-406 1-7
Page 27
1
Before Using the Scan Functions
1.3 Settings for Using Network/Scanning Functions
It is recommended that the settings described below be specified before using the network scanning functions. The network settings described in
“Specifying Network Settings” must be specified first. Set other items as
necessary.
Specifying Network Settings
In order to use this machine on a network, the network settings for the image
controller must be specified.
Specify the network settings from the image controller screen, which appears in the control panel of the copier.
!
Detail
For details on specifying network settings and using the control panel of
Before Using the Scan Functions Chapter 1
the image controller, refer to “5 Specifying Network Scanning Settings”.
Registering Destinations and Specifying Their Settings
The destinations (recipients) of scanned data must be registered.
The following registration methods are available.
- Register from the touch panel of the copier.
- Use PageScope Web Connection from a PC on the network.
The three types of destinations described below can be registered.
Destination (Recipient) Characteristics
Abbreviated Destination The destination can be selected with one button. The registered
Group Multiple destinations can be registered in groups. E-mail, FTP,
Program The destination and scan settings can be registered together as a
destinations are displayed by press the [Scan] key, then touching
[Address Book].
SMB, and mailbox destinations can be registered together in a
single group. The registered destinations are displayed by press
the [Scan] key, then touching [Group].
single program. This is convenient for frequently scanning documents and sending data under the same conditions. The registered
destinations are displayed by press the [Scan] key, then touching
[Program].
1-8 IC-406
Page 28

Before Using the Scan Functions
2
Note
The destination can also be entered from the copier’s control panel before scanning, even if no destination has been registered in advance.
The destination can also be entered before scanning. This is called “direct input”. For details, refer to “Entering the Addresses Directly” on
page 2-16.
!
Detail
For details on registering destinations and specifying settings, refer to the
sections listed below.
“Registering Abbreviated Destinations” on page 3-2
“Registering Group Destinations” on page 3-16
“Registering Program Destinations” on page 3-18
1
Before Using the Scan Functions Chapter 1
IC-406 1-9
Page 29
1
1.4 Settings for Scanning
Specifying the Scan Settings
The following scan settings can be specifying when scanning a document.
These settings are specified from the touch panel of the copier.
Item Description
File Type Sets the file type to be saved.
Resolution Sets the scan resolution.
Simplex/Duplex Selects whether to scan one side of the document or both sides.
Color Sets the color of the scanned document.
Scan Size Sets the size to be scanned.
Brightness Adjusts the brightness of the document.
Background Removal Adjusts the density of the background (blank areas) of the docu-
Before Using the Scan Functions Chapter 1
Original Setting Specifies the type and characteristics of the loaded document.
Application Provides functions for adjusting the print image, for example, for
Separate Scan The scan operation can be divided into several sessions when all
File Name Changes the file name to be saved.
Despeckle Removes the speckles from the slit glass and scans the document
Before Using the Scan Functions
ment.
scanning books and for erasing the surrounding area.
pages of a document cannot be loaded into the automatic document feeder or when placing the document on the original glass. In
addition, the documents can be scanned separately according to
their type, such as when single-sided documents are mixed with
double-sided documents.
that is loaded in the ADF.
!
Detail
For details on the scan settings, refer to “Specifying the Scan Settings”
on page 2-52.
An annotation user box cannot be selected, when the image controller is
installed. For details on the Box functions, refer to “Copier Box Functions” on page 1-7.
Specifying the Destination
Specify the destination (recipient) for the scan data. If the destination has
been registered in advance, select a destination from those that are already
registered. If the destination has not been registered, specify the destination
through direct input.
1-10 IC-406
Page 30
Before Using the Scan Functions
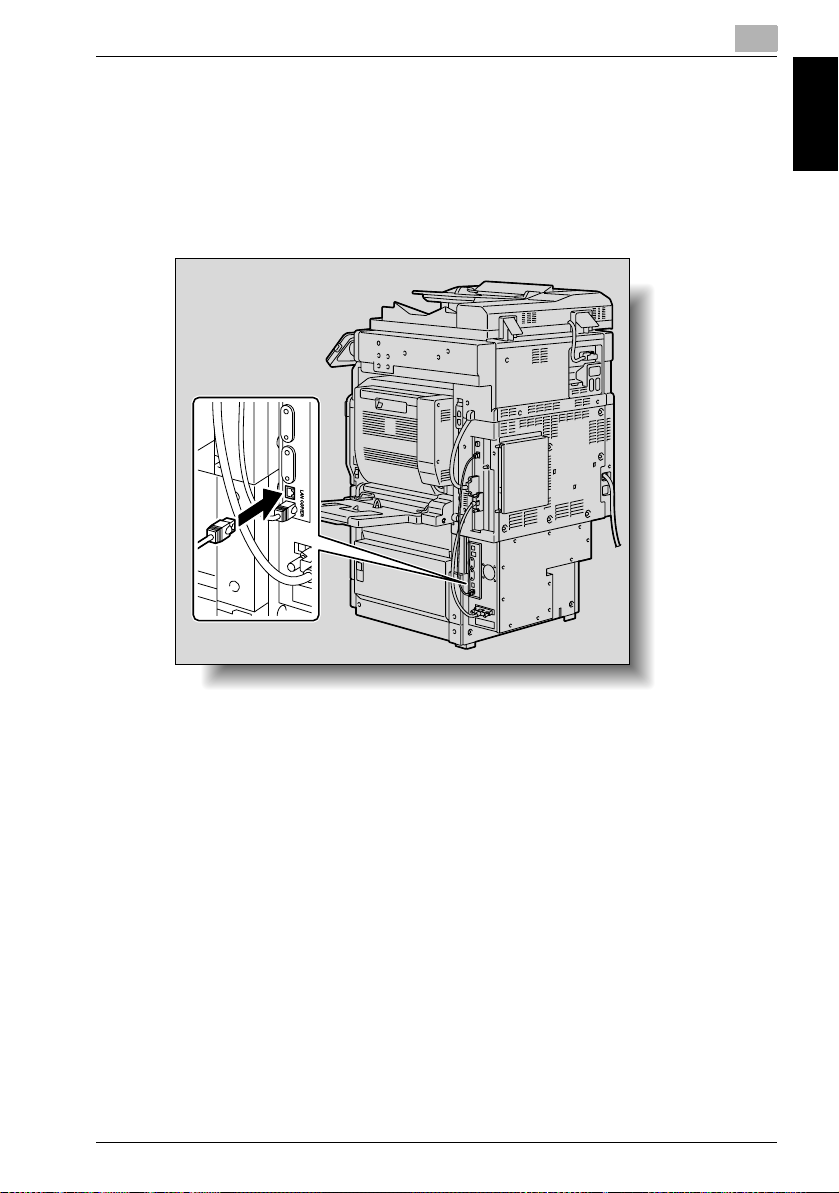
1.5 Connecting to the Network
The image controller can be connected to the network.
Network Connection
Connect a UTP cable (category 5E or more) from the network to the Ethernet
connector on the image controller.
1
Before Using the Scan Functions Chapter 1
Turning On the System
Follow the procedure described below to turn on the system.
1 Turn on the image controller.
2 Wait a little while and turn on the copier.
– If the network functions of the copier are operating correctly, turn
the copier off, then on.
!
Detail
If the copier is turned on before the image controller has finished starting
up and is ready to be used, the copier’s network functions may not operate correctly. Therefore, before turning on the copier, be sure to wait a
little while after turning on the image controller.
IC-406 1-11
Page 31

1
Before Using the Scan Functions Chapter 1
Before Using the Scan Functions
2
Reminder
When the copier is turned off, then on again, turn off the auxiliary power
button before turning off the main power switch. In addition, wait at least
10 seconds to turn the machine on after turning it off; otherwise, the machine may not function normally.
1-12 IC-406
Page 32

Before Using the Scan Functions
1.6 Flow Chart of Setup and Scanning Operations
The sequence from the setup operations required to use the scanning functions to the scanning operation is shown below.
Specify network settings.
* Specify settings in order to use the network scanning operations (refer to “Available Settings”
on page 5-2, “Specifying Settings for E-Mail Transmissions” on page 5-5, “Specifying Settings
for FTP File Transmissions” on page 5-17, “Specifying Settings for SMB Server Transmissions”
on page 5-18).
Create mailboxes for saving documents.
*Specify settings for saving documents in mailboxes (refer to “Specifying Settings for Save in
Mailbox of Image Controller Operations” on
page 5-7).
Register destinations.
* Register destinations (e-mail addresses, ftp servers, computer names and mailbox names).
(refer to “Registering Abbreviated Destinations” on page 3-2, “Registering Group Destinations”
on page 3-16, “Registering Program Destinations” on page 3-18).
1
Before Using the Scan Functions Chapter 1
Load the document.
Specify the destination.
Specify the scan settings (refer to page 2-52).
Press the [Start] key in the control panel.
The document is scanned, and the data is transmitted.
IC-406 1-13
Page 33

1
Before Using the Scan Functions Chapter 1
Before Using the Scan Functions
!
Detail
Scanning can also be performed without creating a mailbox. For details,
refer to “Creating a Mailbox 2” on page 5-15.
The destination can also be entered from the copier’s control panel before scanning, even if no destination has been registered in advance. This
is called “direct input”. For details, refer to “Entering the Addresses Directly” on page 2-16.
1-14 IC-406
Page 34

Before Using the Scan Functions
1.7 Frequently Used Screens
This section describes the copier’s control panel screens that are frequently
used for specifying network scanning settings.
To display the Scan screen
1 Press the [Utility/Counter] key.
Utility/
Counter
2 Touch [1 One-Touch Registration].
1
Before Using the Scan Functions Chapter 1
3 Touch [1 Scan].
IC-406 1-15
Page 35

1
Before Using the Scan Functions
The Scan screen appears.
To display the User Setting screen
1 Press the [Utility/Counter] key.
Before Using the Scan Functions Chapter 1
Utility/
Counter
2 Touch [2 User Setting].
1-16 IC-406
Page 36

Before Using the Scan Functions
The User Setting screen appears.
To display the Administrator Setting screen
1 Press the [Utility/Counter] key.
1
Utility/
Counter
2 Touch [3 Administrator Setting].
Before Using the Scan Functions Chapter 1
IC-406 1-17
Page 37

1
Before Using the Scan Functions Chapter 1
Before Using the Scan Functions
3 Type in the password, and then touch [OK].
The Administrator Setting screen appears.
1-18 IC-406
Page 38

2
Scanning Documents
Scanning Documents Chapter 2
Page 39

2
er Sa
Bo
Access
ABC
DEF
JKL
GHI
MNO
TUV
PQRS
WXYZ
Mode Memor
Mode Chec
Utility/
Counter
ax
Scan
Cop
Reset
Interr
upt
er
Stop
Proof Cop
Star
Data
Main P
Help
Accessibility
Enlarge Displa
Contr
ast
2 Scanning Documents
2.1 Control Panel
1234 5 6 7
Scanning Documents
Fax
x
24
23
22
Power Sa
ve
Help
Accessibility
Enlarge Displa
ast
Contr
Bo
Access
Mode Memor
y
y
Utility/
Counter
Mode Chec
k
Cop
y
Scan
ABC
DEF
JKL
GHI
MNO
Proof Cop
TUV
PQRS
WXYZ
Star
t
Data
Main P
Scanning Documents Chapter 2
17192021
No. Part Name Description
1 [Power Save] key Press to enter Power Save mode. While the
machine is in Power Save mode, the indicator on
the [Power Save] key lights up in green and the
touch panel goes off. To cancel Power Save mode,
press the [Power Save] key again.
2 Touch panel Displays various screens and messages.
Specify the various settings by directly touching the
panel.
3 [Access] key If user authentication or account track settings
have been applied, press this key after entering the
user name and password (for user authentication)
or the account name and password (for account
track) in order to use the copier.
This key is also used to log off.
4 [Box] key Press to enter Box mode.
5 [Fax] key Switches to the fax functions if the optional fax kit
While the machine is in Box mode, the indicator on
the [Box] key lights up in green. For details, refer to
“Copier Box Functions” on page 1-7 and the User’s
Guide [Box Operations] included with the copier.
has been installed.
While the machine is in Fax mode, the indicator on
the [Fax] key lights up in green.
For details, refer to the User’s Guide [Facsimile
Operations] included with the copier.
2-2 IC-406
13
15141618
Interr
y
Reset
Power
ower
Stop
8
upt
9
10
11
12
Page 40

Scanning Documents
No. Part Name Description
6 [Scan] key Press to enter Scan mode. While the machine is in
7 [Copy] key Press to enter Copy mode. (As a default, the
8 [Reset] key Press to clear all settings (except programmed
9 [Interrupt] key Press to enter Interrupt mode. While the machine is
10 Auxiliary power button Press to turn on/off machine operations, for exam-
11 [Stop] key Press the [Stop] key during scanning to stop the
12 [Start] key Press to start scanning. When the copier is ready to
13 Main Power indicator Lights up in green when the copier is turned on with
14 Data indicator Flashes in green while a print job is being received.
15 [Proof Copy] key Press to print a single proof copy to be checked
16 Keypad Use to type in the number of copies to be
17 [C] (clear) key Press to erase a value (such as the number of
18 [Mode Check] key Press to display screens showing the specified
19 [Utility/Counter] key Press to display the Utility screen and Meter Count
20 [Mode Memory] key Press to register the desired copy settings as a pro-
21 Contrast dial Use to adjust the contrast of the touch panel.
Scan mode, the indicator on the [Scan] key lights
up in green.
For details, refer to this manual.
machine is in Copy mode.) While the machine is in
Copy mode, the indicator on the [Copy] key lights
up in green.
For details, refer to the User’s Guide [Copy Operations].
settings) entered in the control panel and touch
panel.
in Interrupt mode, the indicator on the [Interrupt]
key lights up in green and the message “Now in
Interrupt mode.” appears on the touch panel. To
cancel Interrupt mode, press the [Interrupt] key
again.
ple, for copying, printing or scanning. When turned
off, the copier enters a state where it conserves energy.
scan operation.
begin scanning, the indicator on the [Start] key
lights up in green. If the indicator on the [Start] key
lights up in orange, scanning cannot begin.
Press to restart a stopped job.
the auxiliary power button
Lights up in green when data is being printed.
before printing a large number of copies.
produced.
Use to type in the zoom ratio.
Use to type in the various settings.
copies, a zoom ratio, or a size) entered using the
keypad.
settings.
screen.
gram or to recall a registered copy program.
2
Scanning Documents Chapter 2
IC-406 2-3
Page 41

2
Scanning Documents
No. Part Name Description
22 [Enlarge Display] key Press to enter Enlarge Display mode.
23 [Accessibility] key Press to display the screen for specifying user
24 [Help] key Press to display the Help Main Menu screen, where
7
7 CAUTION
7 7
To prevent damage to the touch panel, do not push down on the touch
panel with force.
% Also, do not push down on the touch panel using hard or sharp objects.
accessibility functions.
descriptions of the various functions and details of
operations can be displayed.
2
Scanning Documents Chapter 2
Reminder
When the copier is turned off, then on again, turn off the auxiliary power
button before turning off the main power switch. In addition, wait at least
10 seconds to turn the machine on after turning it off; otherwise, the machine may not function normally.
2-4 IC-406
Page 42

Scanning Documents
2.2 Displaying the Scan Screen
Display the Scan mode screen in order to perform scanning operations.
Turn the machine on. When the machine is ready to make copies, the Basic
screen appears.
Press the [Scan] key in the control panel to display the Scan mode screen.
The displayed functions and modes can be selected by gently touching the
buttons that are displayed in the screen.
2
2 4 5 6 7 8 10
93
1
No Name Description
1 Sub display area This area displays destinations, etc.
2 [Job List] button Displays jobs being performed and jobs being stored.
3 Date/Time display area Displays the current date/time.
4 Message display area Displays the copier status and details on operations that
5 [Program] button Displays destinations that are registered in programs.
6 [Group] button Displays destinations that are registered in groups.
7 [Address Book] button Used to search for abbreviated destinations that are
8 [Direct Input] button Used to type in the destination when performing Scan to
9 Available memory display Shows the amount of space available on the copier’s
10 Address number display
area
11 [Scan Settings] button Used to specify scan settings.
Various commands for checking and managing jobs are
available.
must be performed.
registered.
E-mail, Scan to FTP, or Scan to SMB operations or to select the mailbox where the job is to be stored.
This button does not appear if the [Manual Destination Input] on the Security Details screen (displayed by touching
[9 Security Setting] on the Administrator Setting screen)
is set to “Restrict”.
built-in memory.
Shows the number of specified addresses.
11
Scanning Documents Chapter 2
IC-406 2-5
Page 43

2
Scanning Documents
2.3 Sending Data in an E-Mail Message (Scan to E-Mail)
Scan to E-Mail
The Scan to E-mail operation is used to send images scanned on this machine to an e-mail address as an attachment.
The methods described below are available for specifying the destination.
The methods can also be combined, for example, by selecting a group destination, then adding other destinations through direct input.
Using Programs
“Program” refers to a set of destination addresses and scan settings that are
registered together. This feature is convenient for frequently scanning documents and sending data under the same conditions. The following procedure
describes how to send data by selecting a program that has been registered
in advance.
For details on registering programs, refer to “Registering Program Destina-
Scanning Documents Chapter 2
tions” on page 3-18.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2-6 IC-406
Page 44

Scanning Documents
2 Touch [Program].
The selected destinations are listed under “Broadcast Destinations”.
Only the destinations that can be specified are displayed. For example,
fax destinations are not displayed.
3 Touch [Scan Settings] to check the specified scan settings. The set-
tings that appear in the main Scan mode screen can be specified in advance for each program. For details, refer to “Registering Program
Destinations” on page 3-18.
2
Scanning Documents Chapter 2
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
IC-406 2-7
Page 45

2
Scanning Documents
4 After checking the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group], [Address Book] or [Direct Input] to specify or add other
destinations.
5 Load the document into the automatic document feeder or position it
on the original glass of the copier.
Scanning Documents Chapter 2
6 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-8 IC-406
Page 46

Scanning Documents
Selecting Group Addresses
“Group” refers to multiple destinations that are registered collectively. The
following procedure describes how to send data by selecting a group that
has been registered in advance.
For details on registering groups, refer to “Registering Group Destinations”
on page 3-16.
1 Press the [Scan] key on the control panel.
The Scan mode screen appears.
2
Scan
Scanning Documents Chapter 2
2 Touch [Group].
Touching the button for a group displays the list of members registered
in the group.
IC-406 2-9
Page 47

2
Scanning Documents Chapter 2
Scanning Documents
3 Select the desired destinations, and then touch [OK].
The selected destinations are listed under “Broadcast Destinations”.
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Address Book] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
2-10 IC-406
Page 48

Scanning Documents
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2
Scanning Documents Chapter 2
IC-406 2-11
Page 49

2
Scanning Documents Chapter 2
Scanning Documents
Selecting Destinations From the Address Book
“Address book” refers to the collection of abbreviated destinations that have
been registered in advance and appear so that the desired destination can
be selected. The following procedure describes how to send data by selecting destinations from the address book. Multiple addresses can be specified
simultaneously from the address book.
For details on registering addresses in the address book, refer to “Registering Abbreviated Destinations” on page 3-2.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Address Book].
When the address book appears, touch an index button to display the
buttons for the abbreviated destinations registered in the selected index. The index for the abbreviated destinations can be specified when
the abbreviated destination is registered.
2-12 IC-406
Page 50

Scanning Documents
– Touch [Detail Search], and then type in the name of the destination
or part of the address to search for the corresponding address.
– Touch [LDAP Search] to search the addresses registered on the
LDAP server for the address that corresponds to the specified conditions.
Why is [LDAP Search] not displayed on the Address Book tab?
?
% If the [Manual Destination Input] on the Security Details screen (dis-
played by touching [9 Security Setting] on the Administrator Setting
screen) is set to [Restrict], [LDAP Search] does not appear on the
Address Book tab. For details on LDAP searches, refer to “Performing an LDAP Search” on page 2-15.
To perform LDAP searches, what settings are required?
?
% Administrator settings such as the LDAP sever setting are required.
For details, refer to “Performing an LDAP Search” on page 2-15.
2
Scanning Documents Chapter 2
3 Touch the button for a destination to select it.
The selected buttons are highlighted, and the selected destinations are
listed under “Broadcast Destinations”. Other destination addresses
can be added through direct input.
IC-406 2-13
Page 51

2
Scanning Documents Chapter 2
Scanning Documents
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-14 IC-406
Page 52

Scanning Documents
Performing an LDAP Search
Searches the address that meets the conditions from the addresses registered on the LDAP server.
A “Basic Search” in which a keyword is entered and a “Advanced Search” in
which multiple conditions are used to narrow down the search are available.
!
Detail
To perform LDAP searches, the LDAP server settings that are specified
in Administrator Setting are required. For details, refer to “Enabling LDAP
Settings” on page 6-8.
Basic Search
2
Scanning Documents Chapter 2
Advanced Search
IC-406 2-15
Page 53

2
Scanning Documents Chapter 2
Scanning Documents
Entering the Addresses Directly
“Direct input” refers to the operation of directly entering the destination address from the copier’s control panel.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Direct Input], then [Scan to E-Mail].
A screen for entering the destination address appears.
Why is the Direct Input tab not displayed?
?
% If the [Manual Destination Input] on the Security Details screen (dis-
played by touching [9 Security Setting] on the Administrator Setting
screen) is set to [Restrict], the Direct Input tab does not appear.
2-16 IC-406
Page 54

Scanning Documents
3 Enter the destination address, and then touch [OK].
– To specify an additional address, touch [Next Dest.], and then
specify the address.
– Frequently entered user names and domain names can be regis-
tered to be recalled and used again. First, prefixes and suffixes
must be registered.
The addresses that were entered are listed under “Broadcast Destinations”.
2
Scanning Documents Chapter 2
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
IC-406 2-17
Page 55

2
Scanning Documents
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Address Book] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
Scanning Documents Chapter 2
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-18 IC-406
Page 56

Scanning Documents
2.4 Sending Data to a Server (Scan to FTP)
Scan to FTP
The Scan to FTP operation can be used in a network environment with an
FTP server. The scanned data is sent to a specified folder in an FTP server
on the network.
This function is suitable for sending data of a large size such as high-resolution images.
The methods described below are available for specifying the destination.
The methods can also be combined, for example, by selecting a group destination, then adding other destinations through direct input.
Transmission may not be possible if the destination server has placed limitations on the document name. Because the document name becomes the file
name at the time of transmission, consult your network administrator when
specifying the document name.
2
2
Note
If a mail server is available on the network, the e-mail notification function
can be used to send an e-mail message containing notification of the
storage location of the scan data. For details on the e-mail notification
function, refer to “Checking the Settings” on page 2-73.
Using Programs
“Program” refers to a set of destination FTP servers and scan settings that
are registered together. The following procedure describes how to send data
by selecting a program that has been registered in advance.
If a proxy server is available on the network, FTP servers on the Internet can
be accessed via a proxy server. For details on the proxy settings, refer to
“Specifying Settings for FTP File Transmissions” on page 5-17.
For details on registering programs, refer to “Registering Program Destinations” on page 3-18.
Scanning Documents Chapter 2
IC-406 2-19
Page 57

2
Scanning Documents Chapter 2
Scanning Documents
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Program].
The selected destinations are listed under “Broadcast Destinations”.
Only the destinations that can be specified are displayed. For example,
fax destinations are not displayed.
3 Touch [Scan Settings] to check the specified scan settings. The set-
tings that appear in the main Scan mode screen can be specified in advance for each program. For details, refer to “Registering Program
Destinations” on page 3-18.
2-20 IC-406
Page 58

Scanning Documents
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
4 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group], [Address Book] or [Direct Input] to specify or add other
destinations.
2
5 Load the document into the automatic document feeder or position it
on the original glass of the copier.
6 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
Selecting Group Addresses
“Group” refers to multiple destinations that are registered collectively. The
following procedure describes how to send data by selecting a group that
has been registered in advance.
For details on registering groups, refer to “Registering Group Destinations”
on page 3-16.
Scanning Documents Chapter 2
IC-406 2-21
Page 59

2
Scanning Documents
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
Scanning Documents Chapter 2
2 Touch [Group].
Touching the button for a group displays the list of members registered
in the group. Other destination addresses can be added using the address book or through direct input.
3 Select the desired destination, and then touch [OK].
The selected destinations are listed under “Broadcast Destinations”.
2-22 IC-406
Page 60

Scanning Documents
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Address Book] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
2
Scanning Documents Chapter 2
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
IC-406 2-23
Page 61

2
Scanning Documents Chapter 2
Scanning Documents
Selecting Destinations From the Address Book
“Address book” refers to the collection of abbreviated destinations that have
been registered in advance and appear so that the desired destination can
be selected. The following procedure describes how to send data by selecting destinations from the address book. Multiple addresses can be specified
simultaneously from the address book.
For details on registering addresses in the address book, refer to “Registering Abbreviated Destinations” on page 3-2.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2-24 IC-406
Page 62

Scanning Documents
2 Touch [Address Book].
When the address book appears, touch an index button to display the
buttons for the abbreviated destinations registered in the selected index. The index for the abbreviated destinations can be specified when
the abbreviated destination is registered.
How can the address book be searched for the desired address?
?
% Touch [Detail Search] to search for addresses. The address book
can be searched for names or addresses.
2
Scanning Documents Chapter 2
3 Touch the button for a destination to select it.
The buttons are highlighted, and the selected destinations are listed
under “Broadcast Destinations”. Other destinations can be added
through direct input.
IC-406 2-25
Page 63

2
Scanning Documents Chapter 2
Scanning Documents
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-26 IC-406
Page 64

Scanning Documents
Entering the Addresses Directly
“Direct input” refers to the operation of directly inputting the destination address from the copier’s control panel.
The following procedure describes how to directly specify an address.
1 Press the [Scan] key on the control panel.
The Scan mode screen appears.
2 Touch [Direct Input], then [Scan to FTP].
2
Scan
Scanning Documents Chapter 2
A screen for entering the destination host name, destination folder, and
other information appears.
Why is the Direct Input tab not displayed?
?
% If the [Manual Destination Input] on the Security Details screen (dis-
played by touching [9 Security Setting] on the Administrator Setting
screen) is set to [Restrict], the Direct Input tab does not appear.
IC-406 2-27
Page 65

2
Scanning Documents Chapter 2
Scanning Documents
3 Enter the host name, destination folder, user name, and password.
– Host Name: Use the keyboard that appears in the touch panel to
specify the destination host name or IP address, and then touch
[OK].
– In order to specify an FTP destination as a host name, the DNS set-
ting must have been specified in the image controller’s setup
screen. In the setup screen for the image controller, select [Network
Setup] – [Protocol Setup] – [IPv4 Setup] – [DNS Setup] to specify
the setting. For details on displaying the image controller’s setup
screen, refer to “Displaying the Setup Screen” on page 5-4.
– Destination Folder: Use the keyboard that appears in the touch
panel to specify the path to the destination folder, and then touch
[OK].
– User Name: Use the keyboard that appears in the touch panel to
specify the login user name, and then touch [OK].
– Password: Use the keyboard that appears in the touch panel to
specify the password, and then touch [OK].
4 Touch [Detail Setting], and then specify detailed FTP settings.
– Port Number: Check the port number.
– PASV mode: Select whether the PASV (passive) mode is used.
Touch [Yes] or [No].
– Proxy: Select whether a proxy server is used. Touch [Yes] or [No].
5 Touch [OK].
2-28 IC-406
Page 66

Scanning Documents
6 Enter the destination Information, and then touch [OK].
– To specify an additional address, touch [Next Dest.], and then
specify the address.
The addresses that were entered are listed under “Broadcast Destinations”.
2
Scanning Documents Chapter 2
7 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
IC-406 2-29
Page 67

2
Scanning Documents
8 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Address Book] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
Scanning Documents Chapter 2
9 Load the document into the automatic document feeder or position it
on the original glass of the copier.
10 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-30 IC-406
Page 68

Scanning Documents
2.5 Sending Data to a PC on the Network (Scan to SMB)
Scan to SMB
The Scan to SMB operation can be used to directly send the scanned data
to a specific computer on the network.
To use the Scan to File (SMB) function, specify the Windows shared file setting on the PC that is to receive the data in advance.
2
Reminder
To send to a Windows shared folder, enter the host name and folder
name using capital letters when registering the destination.
2
Note
For the SMB transmission procedure, refer to “Sending the Scanned
Data to a Computer on the Network (SMB)” on page 1-5.
Using Programs
“Program” refers to a set of destination computers and scan settings that are
registered together. The following procedure describes how to send data by
selecting a program that has been registered in advance.
For details on registering programs, refer to “Registering Program Destinations” on page 3-18.
2
Scanning Documents Chapter 2
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
IC-406 2-31
Page 69

2
Scanning Documents Chapter 2
Scanning Documents
2 Touch [Program].
The selected destinations are listed under “Broadcast Destinations”.
Only the destinations that can be specified are displayed. For example,
fax destinations are not displayed.
3 Touch [Scan Settings] to check the specified scan settings. The set-
tings that appear in the main Scan mode screen can be specified in advance for each program. For details, refer to “Registering Program
Destinations” on page 3-18.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
4 After checking the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group], [Address Book] or [Direct Input] to specify or add other
destinations.
2-32 IC-406
Page 70

Scanning Documents
5 Load the document into the automatic document feeder or position it
on the original glass of the copier.
6 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
Selecting Group Addresses
“Group” refers to multiple destinations that are registered collectively. The
following procedure describes how to send data by selecting a group that
has been registered in advance.
For details on registering groups, refer to “Registering Group Destinations”
on page 3-16.
1 Press the [Scan] key on the control panel.
2
Scan
The Scan mode screen appears.
2 Touch [Group].
Touching the button for a group displays the list of members registered
in the group. Other destination addresses can be added using the address book or through direct input.
Scanning Documents Chapter 2
IC-406 2-33
Page 71

2
Scanning Documents Chapter 2
Scanning Documents
3 Select the desired destinations, and then touch [OK].
The selected destinations are listed under “Broadcast Destinations”.
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Address Book] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
2-34 IC-406
Page 72

Scanning Documents
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
Selecting Destinations From the Address Book
“Address book” refers to the collection of abbreviated destinations that have
been registered in advance and appear so that the desired destination can
be selected. The following procedure describes how to send data by selecting destinations from the address book. Multiple addresses can be specified
simultaneously from the address book.
For details on registering addresses in the address book, refer to “Registering Abbreviated Destinations” on page 3-2.
1 Press the [Scan] key on the control panel.
2
Scanning Documents Chapter 2
Scan
The Scan mode screen appears.
IC-406 2-35
Page 73

2
Scanning Documents Chapter 2
Scanning Documents
2 Touch [Address Book].
When the address book appears, touch an index button to display the
buttons for the abbreviated destinations registered in the selected index. The index for the abbreviated destinations can be specified when
the abbreviated destination is registered.
How can the address book be searched for the desired address?
?
% Touch [Detail Search] to search for addresses. The address book
can be searched for names or addresses.
3 Touch the button for a destination to select it.
The selected buttons are highlighted, and the selected destinations are
listed under “Broadcast Destinations”. Other destinations can be added through direct input.
2-36 IC-406
Page 74

Scanning Documents
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Direct Input] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
2
Scanning Documents Chapter 2
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
IC-406 2-37
Page 75

2
Scanning Documents Chapter 2
Scanning Documents
Entering the Addresses Directly
“Direct input” refers to the operation of directly inputting the destination address from the copier’s control panel.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Direct Input], then [Scan to SMB].
A screen for entering the destination host name, destination folder, and
other information appears.
Why is the Direct Input tab not displayed?
?
% If the [Manual Destination Input] on the Security Details screen (dis-
played by touching [9 Security Setting] on the Administrator Setting
screen) is set to [Restrict], the Direct Input tab does not appear.
2-38 IC-406
Page 76

Scanning Documents
3 Enter the destination information.
– Host Name: Specify the destination host name (enter using capital
letters) or the IP address. Type in the destination name using the
keyboard, and then touch [OK].
– Destination Folder: Enter the path to the destination folder using
capital letters.
– User Name: Use the keyboard that appears in the touch panel to
specify the login user name, and then touch [OK].
– Password: Use the keyboard that appears in the touch panel to
specify the password, and then touch [OK].
– In order to send scan data to a folder that can only be accessed by
user accounts belonging to the domain, the user ID must be entered in either of the following formats.
1 user_ID>@<domain_name>
2 <domain_name>\<user_ID>
(Note: In format 2, use the backslash (\). If the slash (/) is used, the
data will not be sent correctly.)
– To specify an additional address, touch [Next Dest.], and then
specify the address.
2
Scanning Documents Chapter 2
4 Touch [OK].
The specified addresses are listed under “Broadcast Destinations”.
IC-406 2-39
Page 77

2
Scanning Documents Chapter 2
Scanning Documents
5 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
6 After specifying the settings, touch [OK].
– To send the data to another destination at the same time, touch
[Group] or [Address Book] to specify or add other destinations.
– If a destination registered in a program is added, the scan settings
registered in the program are given priority, and the scan data is
sent with the scan settings registered in the program.
7 Load the document into the automatic document feeder or position it
on the original glass of the copier.
8 Press the [Start] key on the control panel.
The document is scanned, and the data is sent.
2-40 IC-406
Page 78

Scanning Documents
2.6 Saving Data on the Hard Disk (Save in Mailbox of Image Controller)
Save in Mailbox
The Save in Mailbox operation can be used to save document data on the
hard disk of the image controller. The saved data can be imported from a
computer.
Types of Mailboxes
Default mailboxes
As a default, three mailboxes (“admin”, “operator”, and “guest”) have been
created. The image controller administrator password is required to access
the “admin” mailbox. However, the “operator” and “guest” mailboxes do not
require a password for access.
Added mailboxes
Mailboxes can be added by the user. Personal mailboxes can be protected
with a password. If a password has been specified, access to the mailbox is
permitted only if the correct password is entered.
2
Scanning Documents Chapter 2
IC-406 2-41
Page 79

2
Scanning Documents Chapter 2
Scanning Documents
Using Programs
“Program” refers to a destination mailbox and scan settings that are registered together. The following procedure describes how to save data by selecting a program that has been registered in advance.
For details on registering programs, refer to “Registering Program Destinations” on page 3-18.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Program].
The selected destinations are listed under “Broadcast Destinations”.
Only the destinations that can be specified are displayed. For example,
fax destinations are not displayed.
2-42 IC-406
Page 80

Scanning Documents
3 Touch [Scan Settings] to check the specified scan settings. The set-
tings that appear in the main Scan mode screen can be specified in advance for each program. For details, refer to “Registering Program
Destinations” on page 3-18.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
2
4 After checking the settings, touch [OK].
5 Load the document into the automatic document feeder or position it
on the original glass of the copier.
6 Press the [Start] key on the control panel.
The document is scanned, and the document data is saved in the mailbox.
Scanning Documents Chapter 2
IC-406 2-43
Page 81

2
Scanning Documents Chapter 2
Scanning Documents
Selecting Group Addresses
“Group” refers to multiple destinations that are registered collectively. The
following procedure describes how to save data by selecting a destination
from a group that has been registered in advance.
For details on registering groups, refer to “Registering Group Destinations”
on page 3-16.
1 Press the [Scan] key on the control panel.
Scan
The Scan mode screen appears.
2 Touch [Group].
Touching the button for a group displays the list of members registered
in the group.
2-44 IC-406
Page 82

Scanning Documents
3 Select the desired destination, and then touch [OK].
The selected destinations are listed under “Broadcast Destinations”.
4 Touch [Scan Settings], and then specify the scan settings.
2
Scanning Documents Chapter 2
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
5 After specifying the settings, touch [OK].
6 Load the document into the automatic document feeder or position it
on the original glass of the copier.
7 Press the [Start] key on the control panel.
The document is scanned, and the document data is saved in the mailbox.
IC-406 2-45
Page 83

2
Scanning Documents Chapter 2
Scanning Documents
Selecting Destinations From the Address Book
“Address book” refers to the collection of abbreviated destinations that have
been registered in advance and appear so that the desired destination can
be selected. The following procedure describes how to save data by selecting destinations from the address book. Multiple addresses can be specified
simultaneously from the address book.
For details on registering addresses in the address book, refer to “Registering Abbreviated Destinations” on page 3-2.
1 Press the [Scan] key in the control panel.
Scan
The Scan mode screen appears.
2 Touch [Address Book].
When the address book appears, touch an index button to display the
buttons for the abbreviated destinations registered in the selected index. The index for the abbreviated destinations can be specified when
the abbreviated destination is registered.
2-46 IC-406
Page 84

Scanning Documents
How can the address book be searched for the desired address?
?
% Touch [Detail Search] to search for addresses. The address book
can be searched for names or addresses.
3 Touch the button for the mailbox where the data is to be saved.
The selected destinations are listed under “Broadcast Destinations”.
2
Scanning Documents Chapter 2
4 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
IC-406 2-47
Page 85

2
Scanning Documents Chapter 2
Scanning Documents
5 After specifying the settings, touch [OK].
6 Load the document into the reverse automatic document feeder or
place it on the original glass of the copier.
7 Press the [Start] key in the control panel.
The document is scanned and the document data is saved.
2-48 IC-406
Page 86

Scanning Documents
To save data to the specified mailbox
Specifying the mailbox where the data is to be saved directly from the copier’s control panel is called “direct input”.
1 Press the [Scan] key in the control panel.
The Scan mode screen appears.
2 Touch [Direct Input], then [Save in User Box].
2
Scan
Scanning Documents Chapter 2
A screen appears, allowing you to enter the mailbox name.
Why is the Direct Input tab not displayed?
?
% If the “Manual Destination Input” parameter on the Security Details
screen (displayed by touching [9 Security Setting] on the Administrator Setting screen) is set to “Restrict”, the Direct Input tab does
not appear.
Why does [Save in User Box] not appear?
?
% If “3 Network Function Setting” (displayed by touching [9 Security
Setting] on the Administrator Setting screen, then [7 Management
Function Setting]) is set to “Disable”, [Save in User Box] does not
appear.
IC-406 2-49
Page 87

2
Scanning Documents Chapter 2
Scanning Documents
3 Type in the name of the mailbox where the data is to be saved.
4 Touch [OK].
The selected destinations are listed under “Broadcast Destinations”.
5 Touch [Scan Settings], and then specify the scan settings.
– For details on the scan settings, refer to “Specifying the Scan Set-
tings” on page 2-52.
2-50 IC-406
Page 88

Scanning Documents
6 After specifying the settings, touch [OK].
7 Load the document into the reverse automatic document feeder or
place it on the original glass of the copier.
8 Press the [Start] key in the control panel.
The document is scanned, and the document data is saved in the mailbox.
!
Detail
For details on the scan settings, refer to “Specifying the Scan Settings”
on page 2-52.
2
Scanning Documents Chapter 2
For the procedure to enter characters, refer to “Entering Text” on
page 9-2.
For details on specifying the settings of the main Scan mode screen in
advance, refer to “Setting the Main Scan Mode Screen” on page 4-6.
IC-406 2-51
Page 89

2
2.7 Specifying the Scan Settings
Available Settings
Detailed scan settings can be specified by touching [Scan Settings] in the
Scan mode screen.
The settings that can be specified are as follows:
Scanning Documents
Scanning Documents Chapter 2
Item Description Reference
File Type Selects the file type for saving the
Resolution Selects the scan resolution. “Resolution” on page 2-56
Simplex/Duplex Selects whether to scan one side of
Color Sets whether to scan in color or
Scan Size Sets the paper size to be scanned. “Scan Size” on page 2-60
Brightness Adjusts the brightness of the docu-
Background
Removal
Original Setting Specifies the type of document that
Application Provides functions for adjusting the
Despeckle Removes the speckles from the slit
scanned data.
the document or both sides.
black and white.
ment.
Adjusts the density of the
background (blank areas) of the
document.
is loaded, for example, if it contains
mixed sizes or is a thick document.
print image, for example, for
scanning books and for erasing the
surrounding area.
glass and scans the document that
is loaded in the ADF.
“File Type” on page 2-54
“Simplex/Duplex” on page 2-57
“Color” on page 2-58
“Brightness” on page 2-62
“Background Removal” on
page 2-63
“Original Setting” on page 2-64
“Book Scanning (Application)” on
page 2-66
“Frame Erase (Application)” on
page 2-68
“Despeckle” on page 2-72
2-52 IC-406
Page 90

Scanning Documents
Item Description Reference
Separate Scan The scan operation can be divided
File Name Changes the file name to be saved. “File Name” on page 2-70
into several sessions when all pages
of a document cannot be loaded
into the automatic document feeder
or when placing the document on
the original glass. In addition, the
documents can be scanned separately according to their type, such
as when single-sided documents
are mixed with double-sided documents.
2
“Separate Scan” on page 2-70
Scanning Documents Chapter 2
IC-406 2-53
Page 91

2
Scanning Documents Chapter 2
Scanning Documents
File Type
Select the file type for saving the scanned data. The following three file types
are available.
File type
Item Description
PDF Saves to the PDF format.
TIFF Saves to the TIFF format.
JPEG Saves to the JPEG format.
Some file types may not be available depending on the selected Color setting. The possible combinations of the File Type and Color settings are
shown below.
!
Detail
For details on the Color settings, refer to “Color” on page 2-58.
Auto Full Color Gray
Scale
PDF Yes Yes Yes Yes
TIFF No No No Yes
JPEG Yes Yes Yes No
Black
Also, grouping of the saved data can be specified.
Scan Setting
Item Description
Single Page A file is created for each page of the document. When a
Multi Page The entire scanned document is saved to a single file. This
double-sided document is scanned, a file is created from
every two pages that are scanned. This setting is not
selectable when [File Type] is PDF.
setting is not selectable when [File Type] is JPEG.
2-54 IC-406
Page 92

Scanning Documents
To specify the File Type settings
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [File Type].
3 Select the file type.
2
Scanning Documents Chapter 2
4 Select the scan setting.
5 Touch [OK], and then touch [OK] in the next screen that appears.
IC-406 2-55
Page 93

2
Scanning Documents
Resolution
Set the scanning resolution to 200 dpi, 300 dpi, 400 dpi, or 600 dpi.
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Resolution].
Scanning Documents Chapter 2
3 Select the resolution.
4 Touch [OK], and then touch [OK] in the next screen that appears.
2-56 IC-406
Page 94

Scanning Documents
Simplex/Duplex
Select whether to scan one side of the document or both sides.
Item Description
1-Sided Scans one side of the document.
2-Sided Scans both sides of the document.
Cover + 2-Sided Scans the first page of the document as the cover page only
To specify the Simplex/Duplex setting
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Simplex/Duplex].
2
on one side and scans the remaining pages on both sides.
Scanning Documents Chapter 2
3 Select the scan type.
4 Touch [OK], and then touch [OK] in the next screen that appears.
IC-406 2-57
Page 95

2
Scanning Documents
Color
Set whether to scan in color or black and white. Select from the following four
types.
Item Description
Auto Automatically detects the color of the document and scans
Full Color Scans at full color.
Gray Scale Select this setting when the document is full of halftone colors
Black Select this setting when the white and black boundaries are
accordingly.
such as in a black-and-white photo.
distinct such as in a line drawing.
Some color settings may not be available depending on the selected File
Type setting. The possible combinations of the File Type and Color settings
are shown below.
Scanning Documents Chapter 2
!
Detail
For details on the File Type settings, refer to “File Type” on page 2-54.
Auto Full Color Gray
PDF Yes Yes Yes Yes
TIFF No No No Yes
JPEG Yes Yes Yes No
Scale
Black
2-58 IC-406
Page 96

Scanning Documents
To specify the Color setting
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Color].
3 Select the color type.
2
Scanning Documents Chapter 2
4 Touch [OK], and then touch [OK] in the next screen that appears.
IC-406 2-59
Page 97

2
Scanning Documents
Scan Size
Set the paper size to be scanned.
The available scan sizes are as follows:
Item Description
Auto Detects the size of the first page of the loaded document.
Standard sizes Select a standard size and direction.
Custom Size Use to enter the dimensions of a custom size not available as
Photo Size Use to select the photo size.
To specify the Scan Size setting
a standard size.
The lengths in the X and Y directions can be set within the
ranges of 2 in. to 17 in. (30 mm - 432 mm) and 2 in. to 11-11/
16 in. (30 mm - 297 mm), respectively.
Scanning Documents Chapter 2
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Scan Size].
3 Select the size and direction.
2-60 IC-406
Page 98

Scanning Documents
– Select the size and direction of the paper to be scanned.
– Touch [Custom Size] to display a screen for specifying the size.
Use the keypad or touch [-] and [+] to specify the size. Touch [⇔]
to switch between the integer and the fraction. The integer can be
specified in increments of 1 inch, and the fraction can be specified
in increments of 1/16 in. (0.1 mm). Touch [OK].
2
Scanning Documents Chapter 2
– Touch [Photo Size] to display a screen for specifying the size. Se-
lect the size and direction of the photo to be Scanned, and then
touch [OK].
4 Touch [OK], and then touch [OK] in the next screen that appears.
IC-406 2-61
Page 99

2
Scanning Documents
Brightness
Adjust the brightness of the document during scanning.
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Brightness].
Scanning Documents Chapter 2
3 Specify the adjustment amount.
4 Touch [OK], and then touch [OK] in the next screen that appears.
2-62 IC-406
Page 100

Scanning Documents
Background Removal
Adjust the background density of the document during scanning. When
scanning a document on colored paper, the background may be dark in the
scan. In such cases, the background density can be adjusted.
1 Touch [Scan Settings] in the Scan mode screen.
2 Touch [Background Removal].
– Touch [Auto] to adjust the background density automatically.
– To select a specific density, touch [Light] or [Dark].
– Touch [Std.] to select the default setting.
2
Scanning Documents Chapter 2
3 Touch [OK], and then touch [OK] in the next screen that appears.
IC-406 2-63
 Loading...
Loading...